-
 @ ee11a5df:b76c4e49
2024-07-11 23:57:53
@ ee11a5df:b76c4e49
2024-07-11 23:57:53What Can We Get by Breaking NOSTR?
"What if we just started over? What if we took everything we have learned while building nostr and did it all again, but did it right this time?"
That is a question I've heard quite a number of times, and it is a question I have pondered quite a lot myself.
My conclusion (so far) is that I believe that we can fix all the important things without starting over. There are different levels of breakage, starting over is the most extreme of them. In this post I will describe these levels of breakage and what each one could buy us.
Cryptography
Your key-pair is the most fundamental part of nostr. That is your portable identity.
If the cryptography changed from secp256k1 to ed25519, all current nostr identities would not be usable.
This would be a complete start over.
Every other break listed in this post could be done as well to no additional detriment (save for reuse of some existing code) because we would be starting over.
Why would anyone suggest making such a break? What does this buy us?
- Curve25519 is a safe curve meaning a bunch of specific cryptography things that us mortals do not understand but we are assured that it is somehow better.
- Ed25519 is more modern, said to be faster, and has more widespread code/library support than secp256k1.
- Nostr keys could be used as TLS server certificates. TLS 1.3 using RFC 7250 Raw Public Keys allows raw public keys as certificates. No DNS or certification authorities required, removing several points of failure. These ed25519 keys could be used in TLS, whereas secp256k1 keys cannot as no TLS algorithm utilizes them AFAIK. Since relays currently don't have assigned nostr identities but are instead referenced by a websocket URL, this doesn't buy us much, but it is interesting. This idea is explored further below (keep reading) under a lesser level of breakage.
Besides breaking everything, another downside is that people would not be able to manage nostr keys with bitcoin hardware.
I am fairly strongly against breaking things this far. I don't think it is worth it.
Signature Scheme and Event Structure
Event structure is the next most fundamental part of nostr. Although events can be represented in many ways (clients and relays usually parse the JSON into data structures and/or database columns), the nature of the content of an event is well defined as seven particular fields. If we changed those, that would be a hard fork.
This break is quite severe. All current nostr events wouldn't work in this hard fork. We would be preserving identities, but all content would be starting over.
It would be difficult to bridge between this fork and current nostr because the bridge couldn't create the different signature required (not having anybody's private key) and current nostr wouldn't be generating the new kind of signature. Therefore any bridge would have to do identity mapping just like bridges to entirely different protocols do (e.g. mostr to mastodon).
What could we gain by breaking things this far?
- We could have a faster event hash and id verification: the current signature scheme of nostr requires lining up 5 JSON fields into a JSON array and using that as hash input. There is a performance cost to copying this data in order to hash it.
- We could introduce a subkey field, and sign events via that subkey, while preserving the pubkey as the author everybody knows and searches by. Note however that we can already get a remarkably similar thing using something like NIP-26 where the actual author is in a tag, and the pubkey field is the signing subkey.
- We could refactor the kind integer into composable bitflags (that could apply to any application) and an application kind (that specifies the application).
- Surely there are other things I haven't thought of.
I am currently against this kind of break. I don't think the benefits even come close to outweighing the cost. But if I learned about other things that we could "fix" by restructuring the events, I could possibly change my mind.
Replacing Relay URLs
Nostr is defined by relays that are addressed by websocket URLs. If that changed, that would be a significant break. Many (maybe even most) current event kinds would need superseding.
The most reasonable change is to define relays with nostr identities, specifying their pubkey instead of their URL.
What could we gain by this?
- We could ditch reliance on DNS. Relays could publish events under their nostr identity that advertise their current IP address(es).
- We could ditch certificates because relays could generate ed25519 keypairs for themselves (or indeed just self-signed certificates which might be much more broadly supported) and publish their public ed25519 key in the same replaceable event where they advertise their current IP address(es).
This is a gigantic break. Almost all event kinds need redefining and pretty much all nostr software will need fairly major upgrades. But it also gives us a kind of Internet liberty that many of us have dreamt of our entire lives.
I am ambivalent about this idea.
Protocol Messaging and Transport
The protocol messages of nostr are the next level of breakage. We could preserve keypair identities, all current events, and current relay URL references, but just break the protocol of how clients and relay communicate this data.
This would not necessarily break relay and client implementations at all, so long as the new protocol were opt-in.
What could we get?
- The new protocol could transmit events in binary form for increased performance (no more JSON parsing with it's typical many small memory allocations and string escaping nightmares). I think event throughput could double (wild guess).
- It could have clear expectations of who talks first, and when and how AUTH happens, avoiding a lot of current miscommunication between clients and relays.
- We could introduce bitflags for feature support so that new features could be added later and clients would not bother trying them (and getting an error or timing out) on relays that didn't signal support. This could replace much of NIP-11.
- We could then introduce something like negentropy or negative filters (but not that... probably something else solving that same problem) without it being a breaking change.
- The new protocol could just be a few websocket-binary messages enhancing the current protocol, continuing to leverage the existing websocket-text messages we currently have, meaning newer relays would still support all the older stuff.
The downsides are just that if you want this new stuff you have to build it. It makes the protocol less simple, having now multiple protocols, multiple ways of doing the same thing.
Nonetheless, this I am in favor of. I think the trade-offs are worth it. I will be pushing a draft PR for this soon.
The path forward
I propose then the following path forward:
- A new nostr protocol over websockets binary (draft PR to be shared soon)
- Subkeys brought into nostr via NIP-26 (but let's use a single letter tag instead, OK?) via a big push to get all the clients to support it (the transition will be painful - most major clients will need to support this before anybody can start using it).
- Some kind of solution to the negative-filter-negentropy need added to the new protocol as its first optional feature.
- We seriously consider replacing Relay URLs with nostr pubkeys assigned to the relay, and then have relays publish their IP address and TLS key or certificate.
We sacrifice these:
- Faster event hash/verification
- Composable event bitflags
- Safer faster more well-supported crypto curve
- Nostr keys themselves as TLS 1.3 RawPublicKey certificates
-
 @ 42342239:1d80db24
2024-07-06 15:26:39
@ 42342239:1d80db24
2024-07-06 15:26:39Claims that we need greater centralisation, more EU, or more globalisation are prevalent across the usual media channels. The climate crisis, environmental destruction, pandemics, the AI-threat, yes, everything will apparently be solved if a little more global coordination, governance and leadership can be brought about.
But, is this actually true? One of the best arguments for this conclusion stems implicitly from the futurist Eliezer Yudkowsky, who once proposed a new Moore's Law, though this time not for computer processors but instead for mad science: "every 18 months, the minimum IQ necessary to destroy the world drops by one point".
Perhaps we simply have to tolerate more centralisation, globalisation, control, surveillance, and so on, to prevent all kinds of fools from destroying the world?
Note: a Swedish version of this text is avalable at Affärsvärlden.
At the same time, more centralisation, globalisation, etc. is also what we have experienced. Power has been shifting from the local, and from the majorities, to central-planning bureaucrats working in remote places. This has been going on for several decades. The EU's subsidiarity principle, i.e. the idea that decisions should be made at the lowest expedient level, and which came to everyone's attention ahead of Sweden's EU vote in 1994, is today swept under the rug as untimely and outdated, perhaps even retarded.
At the same time, there are many crises, more than usual it would seem. If it is not a crisis of criminality, a logistics/supply chain crisis or a water crisis, then it is an energy crisis, a financial crisis, a refugee crisis or a climate crisis. It is almost as if one starts to suspect that all this centralisation may be leading us down the wrong path. Perhaps centralisation is part of the problem, rather than the capital S solution?
Why centralisation may cause rather than prevent problems
There are several reasons why centralisation, etc, may actually be a problem. And though few seem to be interested in such questions today (or perhaps they are too timid to mention their concerns?), it has not always been this way. In this short essay we'll note four reasons (though there are several others):
- Political failures (Buchanan et al)
- Local communities & skin in the game (Ostrom and Taleb)
- The local knowledge problem (von Hayek)
- Governance by sociopaths (Hare)
James Buchanan who was given the so-called Nobel price in economics in the eighties once said that: "politicians and bureaucrats are no different from the rest of us. They will maximise their incentives just like everybody else.".
Buchanan was prominent in research on rent-seeking and political failures, i.e. when political "solutions" to so-called market failures make everything worse. Rent-seeking is when a company spends resources (e.g. lobbying) to get legislators or other decision makers to pass laws or create regulations that benefit the company instead of it having to engage in productive activities. The result is regulatory capture. The more centralised decision-making is, the greater the negative consequences from such rent-seeking will be for society at large. This is known.
Another economist, Elinor Ostrom, was given the same prize in the great financial crisis year of 2009. In her research, she had found that local communities where people had influence over rules and regulations, as well as how violations there-of were handled, were much better suited to look after common resources than centralised bodies. To borrow a term from the combative Nassim Nicholas Taleb: everything was better handled when decision makers had "skin in the game".
A third economist, Friedrich von Hayek, was given this prize as early as 1974, partly because he showed that central planning could not possibly take into account all relevant information. The information needed in economic planning is by its very nature distributed, and will never be available to a central planning committee, or even to an AI.
Moreover, human systems are complex and not just complicated. When you realise this, you also understand why the forecasts made by central planners often end up wildly off the mark - and at times in a catastrophic way. (This in itself is an argument for relying more on factors outside of the models in the decision-making process.)
From Buchanan's, Ostrom's, Taleb's or von Hayek's perspectives, it also becomes difficult to believe that today's bureaucrats are the most suited to manage and price e.g. climate risks. One can compare with the insurance industry, which has both a long habit of pricing risks as well as "skin in the game" - two things sorely missing in today's planning bodies.
Instead of preventing fools, we may be enabling madmen
An even more troubling conclusion is that centralisation tends to transfer power to people who perhaps shouldn't have more of that good. "Not all psychopaths are in prison - some are in the boardroom," psychologist Robert Hare once said during a lecture. Most people have probably known for a long time that those with sharp elbows and who don't hesitate to stab a colleague in the back can climb quickly in organisations. In recent years, this fact seems to have become increasingly well known even in academia.
You will thus tend to encounter an increased prevalance of individuals with narcissistic and sociopathic traits the higher up you get in the the status hierarchy. And if working in large organisations (such as the European Union or Congress) or in large corporations, is perceived as higher status - which is generally the case, then it follows that the more we centralise, the more we will be governed by people with less flattering Dark Triad traits.
By their fruits ye shall know them
Perhaps it is thus not a coincidence that we have so many crises. Perhaps centralisation, globalisation, etc. cause crises. Perhaps the "elites" and their planning bureaucrats are, in fact, not the salt of the earth and the light of the world. Perhaps President Trump even had a point when he said "they are not sending their best".
https://www.youtube.com/watch?v=w4b8xgaiuj0
The opposite of centralisation is decentralisation. And while most people may still be aware that decentralisation can be a superpower within the business world, it's time we remind ourselves that this also applies to the economy - and society - at large, and preferably before the next Great Leap Forward is fully thrust upon us.
-
 @ 3bf0c63f:aefa459d
2024-03-23 08:57:08
@ 3bf0c63f:aefa459d
2024-03-23 08:57:08Nostr is not decentralized nor censorship-resistant
Peter Todd has been saying this for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right.
Nostr today is indeed centralized.
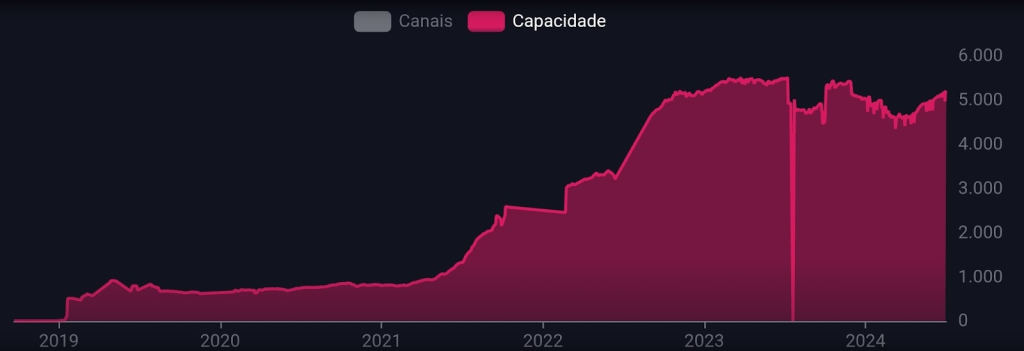
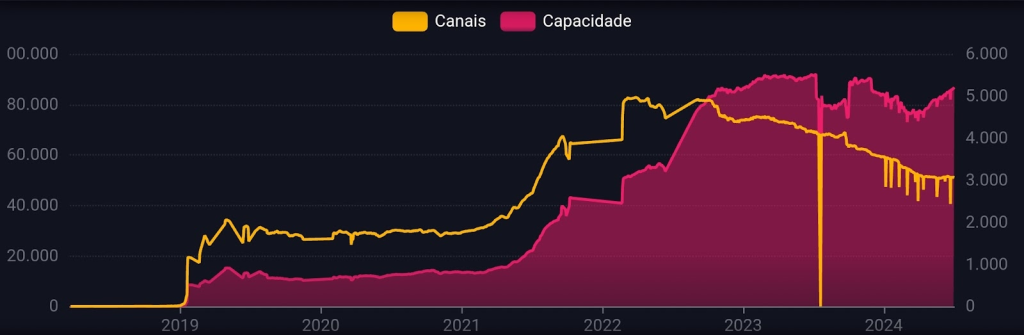
Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:
The top one was published to
wss://nostr.wine,wss://nos.lol,wss://pyramid.fiatjaf.com. The second was published to the relay where I generally publish all my notes to,wss://pyramid.fiatjaf.com, and that is announced on my NIP-05 file and on my NIP-65 relay list.A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:
These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains.
What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all.
Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant.
What happens is that most people who engaged with the note are following me, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on
wss://pyramid.fiatjaf.com.If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before.
Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today.
Peter Todd is wrong that Nostr is inherently centralized or that it needs a protocol change to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we drive in the right direction we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary.
See also:
-
 @ b12b632c:d9e1ff79
2024-05-29 12:10:18
@ b12b632c:d9e1ff79
2024-05-29 12:10:18One other day on Nostr, one other app!
Today I'll present you a new self-hosted Nostr blog web application recently released on github by dtonon, Oracolo:
https://github.com/dtonon/oracolo
Oracolo is a minimalist blog powered by Nostr, that consists of a single html file, weighing only ~140Kb. You can use whatever Nostr client that supports long format (habla.news, yakihonne, highlighter.com, etc ) to write your posts, and your personal blog is automatically updated.
It works also without a web server; for example you can send it via email as a business card.Oracolo fetches Nostr data, builds the page, execute the JavaScript code and displays article on clean and sobr blog (a Dark theme would be awesome 👀).
Blog articles are nostr events you published or will publish on Nostr relays through long notes applications like the ones quoted above.
Don't forget to use a NIP07 web browser extensions to login on those websites. Old time where we were forced to fill our nsec key is nearly over!
For the hurry ones of you, you can find here the Oracolo demo with my Nostr long notes article. It will include this one when I'll publish it on Nostr!
https://oracolo.fractalized.net/
How to self-host Oracolo?
You can build the application locally or use a docker compose stack to run it (or any other method). I just build a docker compose stack with Traefik and an Oracolo docker image to let you quickly run it.
The oracolo-docker github repo is available here:
https://github.com/PastaGringo/oracolo-docker
PS: don't freak out about the commits number, oracolo has been the lucky one to let me practrice docker image CI/CD build/push with Forgejo, that went well but it took me a while before finding how to make Forgejo runner dood work 😆). Please ping me on Nostr if you are interested by an article on this topic!
This repo is a mirror from my new Forgejo git instance where the code has been originaly published and will be updated if needed (I think it will):
https://git.fractalized.net/PastaGringo/oracolo-docker
Here is how to do it.
1) First, you need to create an A DNS record into your domain.tld zone. You can create a A with "oracolo" .domain.tld or "*" .domain.tld. The second one will allow traefik to generate all the future subdomain.domain.tld without having to create them in advance. You can verify DNS records with the website https://dnschecker.org.
2) Clone the oracolo-docker repository:
bash git clone https://git.fractalized.net/PastaGringo/oracolo-docker.git cd oracolo-docker3) Rename the .env.example file:
bash mv .env.example .env4) Modify and update your .env file with your own infos:
```bash
Let's Encrypt email used to generate the SSL certificate
LETSENCRYPT_EMAIL=
domain for oracolo. Ex: oracolo.fractalized.net
ORACOLO_DOMAIN=
Npub author at "npub" format, not HEX.
NPUB=
Relays where Oracolo will retrieve the Nostr events.
Ex: "wss://nostr.fractalized.net, wss://rnostr.fractalized.net"
RELAYS=
Number of blog article with an thumbnail. Ex: 4
TOP_NOTES_NB= ```
5) Compose Oracolo:
bash docker compose up -d && docker compose logs -f oracolo traefikbash [+] Running 2/0 ✔ Container traefik Running 0.0s ✔ Container oracolo Running 0.0s WARN[0000] /home/pastadmin/DEV/FORGEJO/PLAY/oracolo-docker/docker-compose.yml: `version` is obsolete traefik | 2024-05-28T19:24:18Z INF Traefik version 3.0.0 built on 2024-04-29T14:25:59Z version=3.0.0 oracolo | oracolo | ___ ____ ____ __ ___ _ ___ oracolo | / \ | \ / | / ] / \ | | / \ oracolo | | || D )| o | / / | || | | | oracolo | | O || / | |/ / | O || |___ | O | oracolo | | || \ | _ / \_ | || || | oracolo | | || . \| | \ || || || | oracolo | \___/ |__|\_||__|__|\____| \___/ |_____| \___/ oracolo | oracolo | Oracolo dtonon's repo: https://github.com/dtonon/oracolo oracolo | oracolo | ╭────────────────────────────╮ oracolo | │ Docker Compose Env Vars ⤵️ │ oracolo | ╰────────────────────────────╯ oracolo | oracolo | NPUB : npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2 oracolo | RELAYS : wss://nostr.fractalized.net, wss://rnostr.fractalized.net oracolo | TOP_NOTES_NB : 4 oracolo | oracolo | ╭───────────────────────────╮ oracolo | │ Configuring Oracolo... ⤵️ │ oracolo | ╰───────────────────────────╯ oracolo | oracolo | > Updating npub key with npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2... ✅ oracolo | > Updating nostr relays with wss://nostr.fractalized.net, wss://rnostr.fractalized.net... ✅ oracolo | > Updating TOP_NOTE with value 4... ✅ oracolo | oracolo | ╭───────────────────────╮ oracolo | │ Installing Oracolo ⤵️ │ oracolo | ╰───────────────────────╯ oracolo | oracolo | added 122 packages, and audited 123 packages in 8s oracolo | oracolo | 20 packages are looking for funding oracolo | run `npm fund` for details oracolo | oracolo | found 0 vulnerabilities oracolo | npm notice oracolo | npm notice New minor version of npm available! 10.7.0 -> 10.8.0 oracolo | npm notice Changelog: https://github.com/npm/cli/releases/tag/v10.8.0 oracolo | npm notice To update run: npm install -g npm@10.8.0 oracolo | npm notice oracolo | oracolo | >>> done ✅ oracolo | oracolo | ╭─────────────────────╮ oracolo | │ Building Oracolo ⤵️ │ oracolo | ╰─────────────────────╯ oracolo | oracolo | > oracolo@0.0.0 build oracolo | > vite build oracolo | oracolo | 7:32:49 PM [vite-plugin-svelte] WARNING: The following packages have a svelte field in their package.json but no exports condition for svelte. oracolo | oracolo | @splidejs/svelte-splide@0.2.9 oracolo | @splidejs/splide@4.1.4 oracolo | oracolo | Please see https://github.com/sveltejs/vite-plugin-svelte/blob/main/docs/faq.md#missing-exports-condition for details. oracolo | vite v5.2.11 building for production... oracolo | transforming... oracolo | ✓ 84 modules transformed. oracolo | rendering chunks... oracolo | oracolo | oracolo | Inlining: index-C6McxHm7.js oracolo | Inlining: style-DubfL5gy.css oracolo | computing gzip size... oracolo | dist/index.html 233.15 kB │ gzip: 82.41 kB oracolo | ✓ built in 7.08s oracolo | oracolo | >>> done ✅ oracolo | oracolo | > Copying Oracolo built index.html to nginx usr/share/nginx/html... ✅ oracolo | oracolo | ╭────────────────────────╮ oracolo | │ Configuring Nginx... ⤵️ │ oracolo | ╰────────────────────────╯ oracolo | oracolo | > Copying default nginx.conf file... ✅ oracolo | oracolo | ╭──────────────────────╮ oracolo | │ Starting Nginx... 🚀 │ oracolo | ╰──────────────────────╯ oracolo |If you don't have any issue with the Traefik container, Oracolo should be live! 🔥
You can now access it by going to the ORACOLO_DOMAIN URL configured into the .env file.
Have a good day!
Don't hesisate to follow dtonon on Nostr to follow-up the future updates ⚡🔥
See you soon in another Fractalized story!
PastaGringo 🤖⚡ -
 @ 4523be58:ba1facd0
2024-05-28 11:05:17
@ 4523be58:ba1facd0
2024-05-28 11:05:17NIP-116
Event paths
Description
Event kind
30079denotes an event defined by its event path rather than its event kind.The event directory path is included in the event path, specified in the event's
dtag. For example, an event path might beuser/profile/name, whereuser/profileis the directory path.Relays should parse the event directory from the event path
dtag and index the event by it. Relays should support "directory listing" of kind30079events using the#ffilter, such as{"#f": ["user/profile"]}.For backward compatibility, the event directory should also be saved in the event's
ftag (for "folder"), which is already indexed by some relay implementations, and can be queried using the#ffilter.Event content should be a JSON-encoded value. An empty object
{}signifies that the entry at the event path is itself a directory. For example, when savinguser/profile/name:Bob, you should also saveuser/profile:{}so the subdirectory can be listed underuser.In directory names, slashes should be escaped with a double slash.
Example
Event
json { "tags": [ ["d", "user/profile/name"], ["f", "user/profile"] ], "content": "\"Bob\"", "kind": 30079, ... }Query
json { "#f": ["user/profile"], "authors": ["[pubkey]"] }Motivation
To make Nostr an "everything app," we need a sustainable way to support new kinds of applications. Browsing Nostr data by human-readable nested directories and paths rather than obscure event kind numbers makes the data more manageable.
Numeric event kinds are not sustainable for the infinite number of potential applications. With numeric event kinds, developers need to find an unused number for each new application and announce it somewhere, which is cumbersome and not scalable.
Directories can also replace monolithic list events like follow lists or profile details. You can update a single directory entry such as
user/profile/nameorgroups/follows/[pubkey]without causing an overwrite of the whole profile or follow list when your client is out-of-sync with the most recent list version, as often happens on Nostr.Using
d-tagged replaceable events for reactions, such as{tags: [["d", "reactions/[eventId]"]], content: "\"👍\"", kind: 30079, ...}would make un-reacting trivial: just publish a new event with the samedtag and an empty content. Toggling a reaction on and off would not cause a flurry of new reaction & delete events that all need to be persisted.Implementations
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
f) already support this feature. - IrisDB client side library: treelike data structure with subscribable nodes.
https://github.com/nostr-protocol/nips/pull/1266
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
-
 @ b12b632c:d9e1ff79
2024-04-24 20:21:27
@ b12b632c:d9e1ff79
2024-04-24 20:21:27What's Blossom?
Blossom offers a bunch of HTTP endpoints that let Nostr users stash and fetch binary data on public servers using the SHA256 hash as a universal ID.
You can find more -precise- information about Blossom on the Nostr article published today by hzrd149, the developper behind it:
nostr:naddr1qqxkymr0wdek7mfdv3exjan9qgszv6q4uryjzr06xfxxew34wwc5hmjfmfpqn229d72gfegsdn2q3fgrqsqqqa28e4v8zy
You find the Blossom github repo here:
GitHub - hzrd149/blossom: Blobs stored simply on mediaservers https://github.com/hzrd149/blossom
Meet Blobs
Blobs are files with SHA256 hashes as IDs, making them unique and secure. You can compute these IDs from the files themselves using the sha256 hashing algorithm (when you run
sha256sum bitcoin.pdf).Meet Drives
Drives are like organized events on Nostr, mapping blobs to filenames and extra info. It's like setting up a roadmap for your data.
How do Servers Work?
Blossom servers have four endpoints for users to upload and handle blobs:
GET /<sha256>: Get blobs by their SHA256 hash, maybe with a file extension. PUT /upload: Chuck your blobs onto the server, verified with signed Nostr events. GET /list/<pubkey>: Peek at a list of blobs tied to a specific public key for smooth management. DELETE /<sha256>: Trash blobs from the server when needed, keeping things tidy.Yon can find detailed information about the Blossom Server Implementation here..
https://github.com/hzrd149/blossom/blob/master/Server.md
..and the Blossom-server source code is here:
https://github.com/hzrd149/blossom-server
What's Blossom Drive?
Think of Blossom Drive as the "Front-End" (or a public cloud drive) of Blossom servers, letting you upload, manage, share your files/folders blobs.
Source code is available here:
https://github.com/hzrd149/blossom-drive
Developpers
If you want to add Blossom into your Nostr client/app, the blossom-client-sdk explaining how it works (with few examples 🙏) is published here:
https://github.com/hzrd149/blossom-client-sdk
How to self-host Blossom server & Blossom Drive
We'll use docker compose to setup Blossom server & drive. I included Nginx Proxy Manager because it's the Web Proxy I use for all the Fractalized self-hosted services :
Create a new docker-compose file:
~$ nano docker-compose.ymlInsert this content into the file:
``` version: '3.8' services:
blossom-drive: container_name: blossom-drive image: pastagringo/blossom-drive-docker
ports:
- '80:80'
blossom-server: container_name: blossom-server image: 'ghcr.io/hzrd149/blossom-server:master'
ports:
- '3000:3000'
volumes: - './blossom-server/config.yml:/app/config.yml' - 'blossom_data:/app/data'nginxproxymanager: container_name: nginxproxymanager image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: - '80:80' - '81:81' - '443:443' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt - ./nginxproxymanager/_hsts_map.conf:/app/templates/_hsts_map.conf
volumes: blossom_data: ```
You now need to personalize the blossom-server config.yml:
bash ~$ mkdir blossom-server ~$ nano blossom-server/config.ymlInsert this content to the file (CTRL+X & Y to save/exit):
```yaml
Used when listing blobs
publicDomain: https://blossom.fractalized.net
databasePath: data/sqlite.db
discovery: # find files by querying nostr relays nostr: enabled: true relays: - wss://nostrue.com - wss://relay.damus.io - wss://nostr.wine - wss://nos.lol - wss://nostr-pub.wellorder.net - wss://nostr.fractalized.net # find files by asking upstream CDNs upstream: enabled: true domains: - https://cdn.satellite.earth # don't set your blossom server here!
storage: # local or s3 backend: local local: dir: ./data # s3: # endpoint: https://s3.endpoint.com # bucket: blossom # accessKey: xxxxxxxx # secretKey: xxxxxxxxx # If this is set the server will redirect clients when loading blobs # publicURL: https://s3.region.example.com/
# rules are checked in descending order. if a blob matches a rule it is kept # "type" (required) the type of the blob, "" can be used to match any type # "expiration" (required) time passed since last accessed # "pubkeys" (optional) a list of owners # any blobs not matching the rules will be removed rules: # mime type of blob - type: text/ # time since last accessed expiration: 1 month - type: "image/" expiration: 1 week - type: "video/" expiration: 5 days - type: "model/" expiration: 1 week - type: "" expiration: 2 days
upload: # enable / disable uploads enabled: true # require auth to upload requireAuth: true # only check rules that include "pubkeys" requirePubkeyInRule: false
list: requireAuth: false allowListOthers: true
tor: enabled: false proxy: "" ```
You need to update few values with your own:
- Your own Blossom server public domain :
publicDomain: https://YourBlossomServer.YourDomain.tldand upstream domains where Nostr clients will also verify if the Blossom server own the file blob: :
upstream: enabled: true domains: - https://cdn.satellite.earth # don't set your blossom server here!- The Nostr relays where you want to publish your Blossom events (I added my own Nostr relay):
yaml discovery: # find files by querying nostr relays nostr: enabled: true relays: - wss://nostrue.com - wss://relay.damus.io - wss://nostr.wine - wss://nos.lol - wss://nostr-pub.wellorder.net - wss://nostr.fractalized.netEverything is setup! You can now compose your docker-compose file:
~$ docker compose up -dI will let your check this article to know how to configure and use Nginx Proxy Manager.
You can check both Blossom containers logs with this command:
~$ docker compose logs -f blossom-drive blossom-serverRegarding the Nginx Proxy Manager settings for Blossom, here is the configuration I used:
PS: it seems the naming convention for the kind of web service like Blossom is named "CDN" (for: "content delivery network"). It's not impossible in a near future I rename my subdomain blossom.fractalized.net to cdn.blossom.fractalized.net and blossom-drive.fractalized.net to blossom.fractalized.net 😅
Do what you prefer!
After having configured everything, you can now access Blossom server by going to your Blossom server subdomain. You should see a homepage as below:
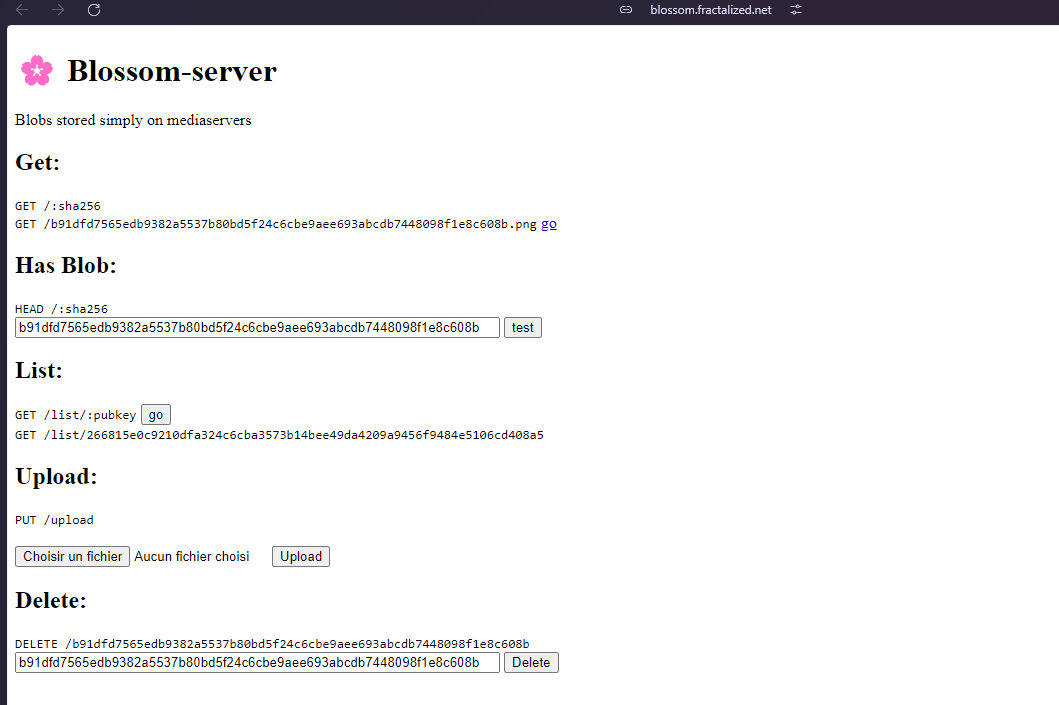
Same thing for the Blossom Drive, you should see this homepage:
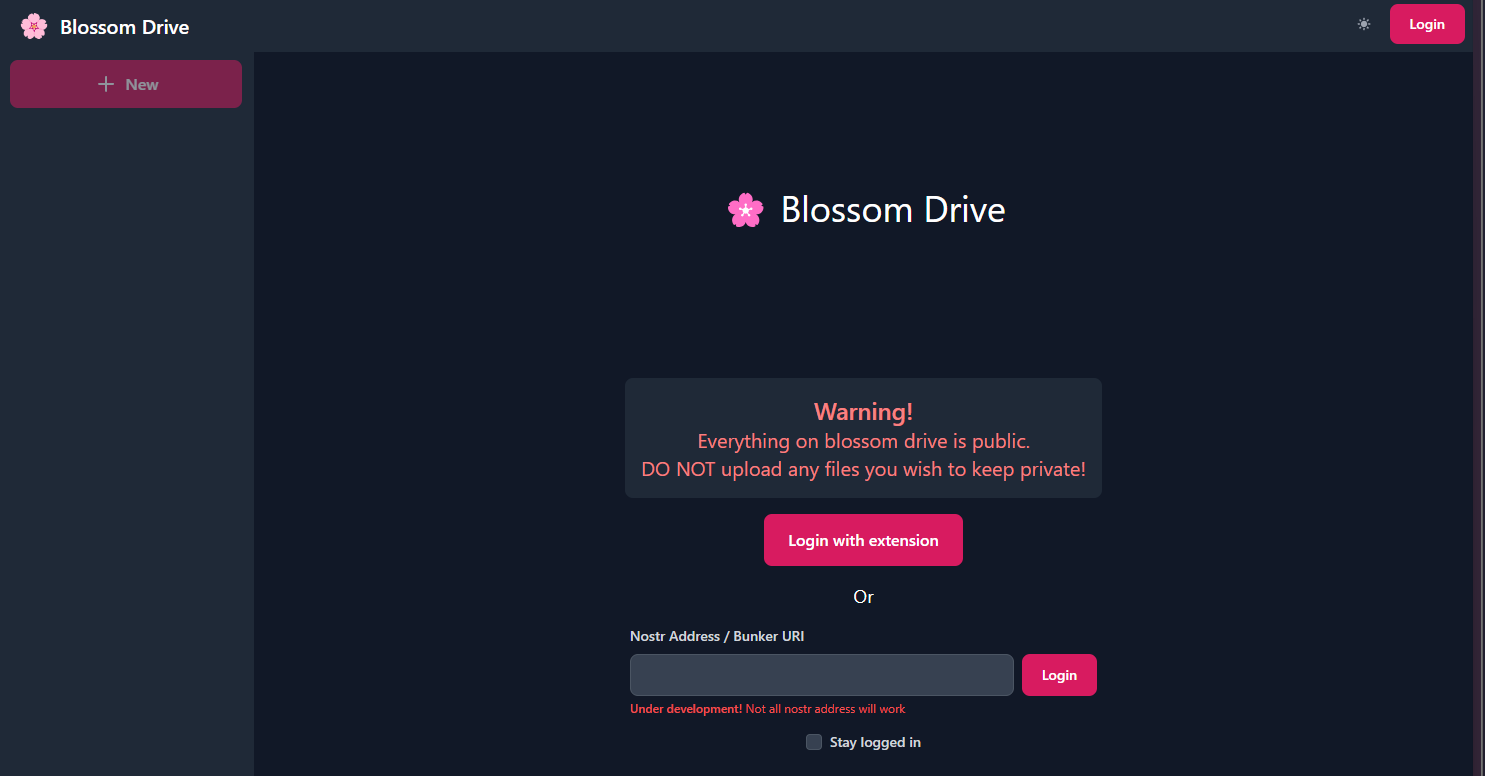
You can now login with your prefered method. In my case, I login on Blossom Drive with my NIP-07 Chrome extension.
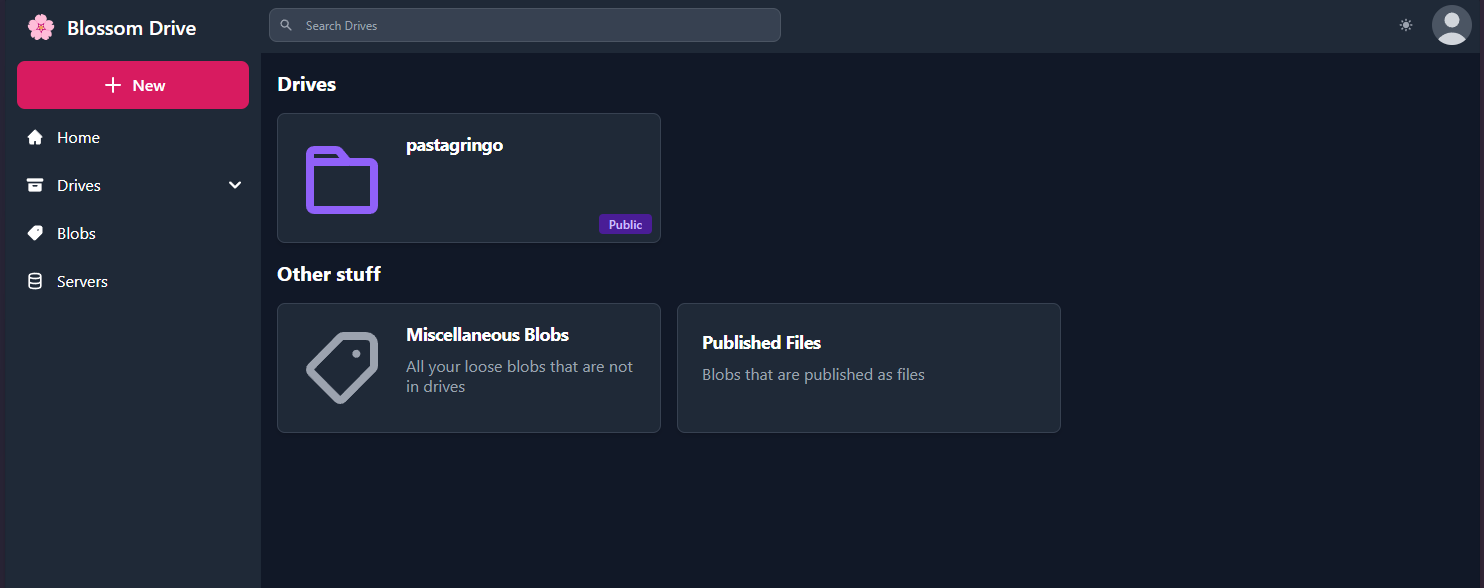
You now need to go the "Servers" tab to add some Blossom servers, including the fresh one you just installed.
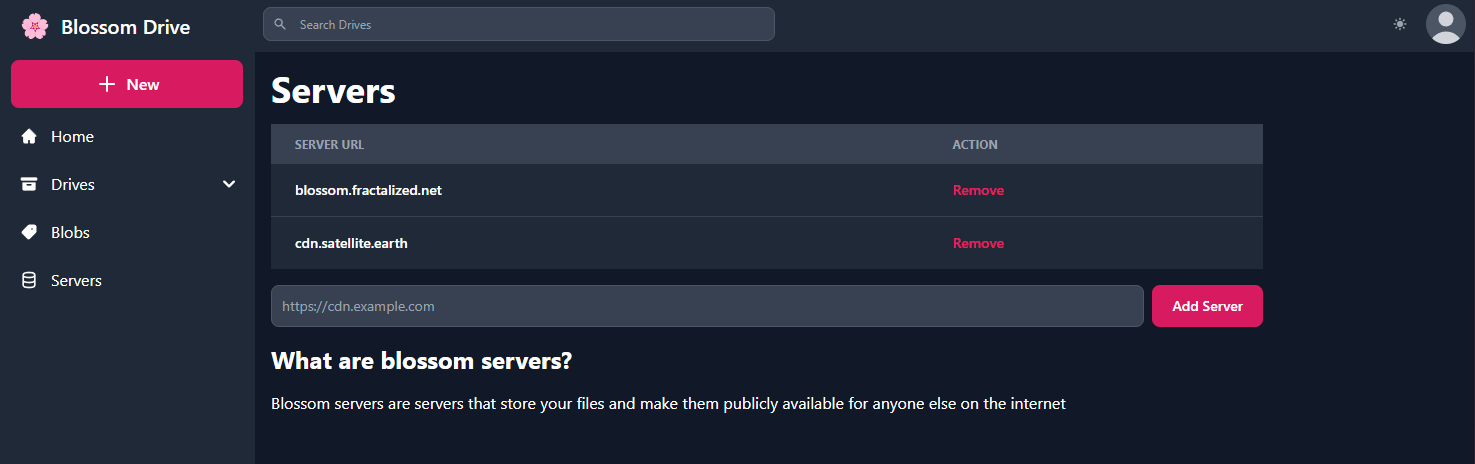
You can now create your first Blossom Drive by clicking on "+ New" > "Drive" on the top left button:
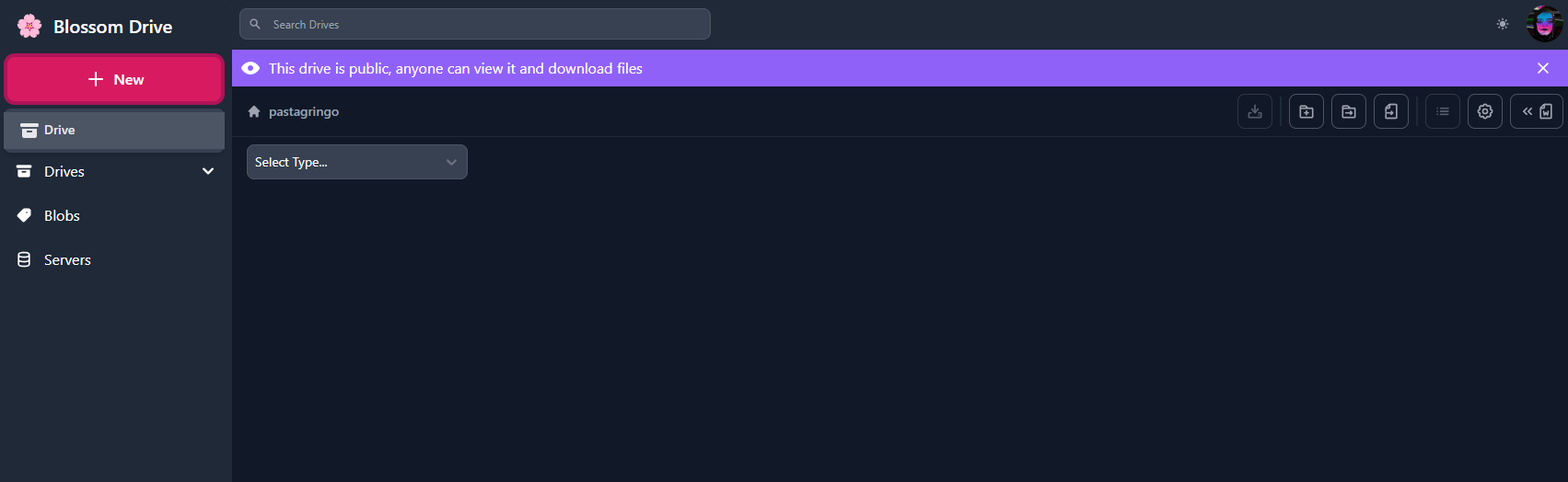
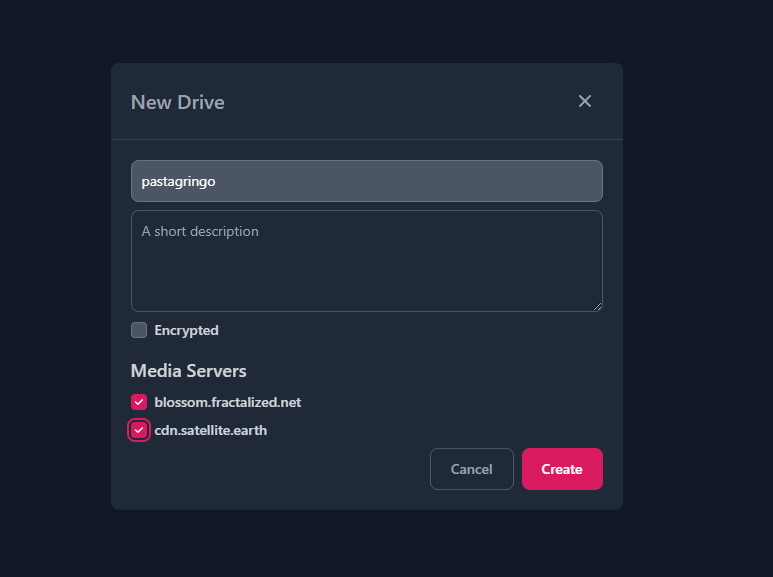
Fill your desired blossom drive name and select the media servers where you want to host your files and click on "Create":
PS: you can enable "Encrypted" option but as hzrd149 said on his Nostr note about Blossom:
"There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify"
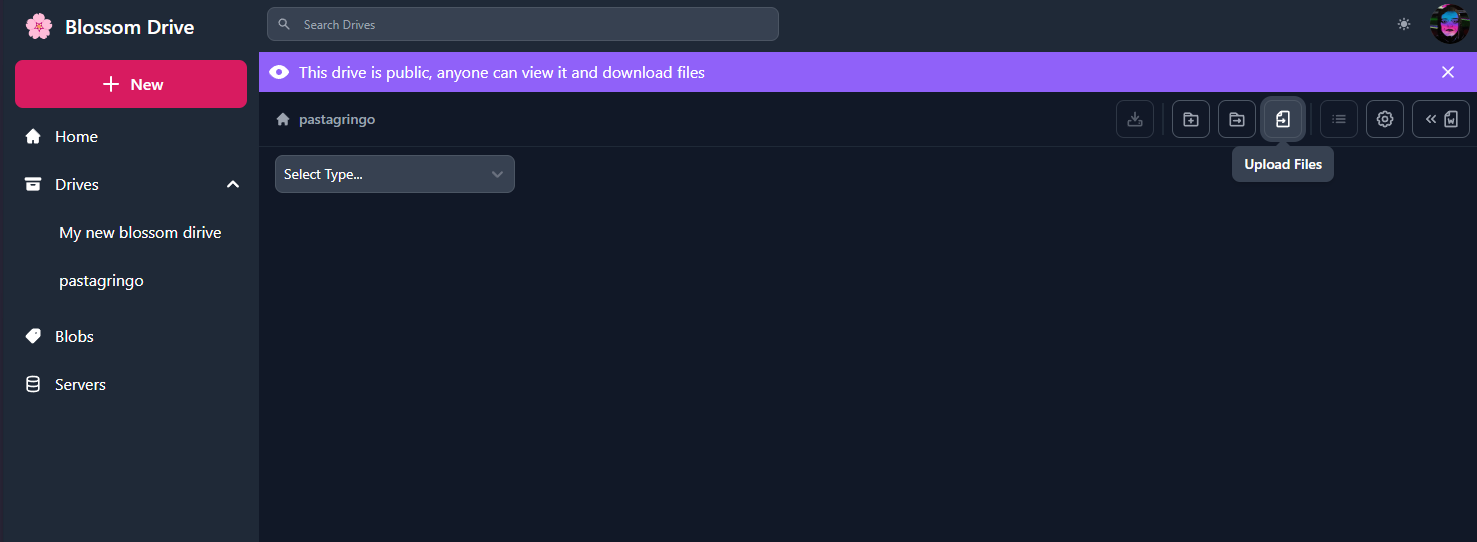
You are now able to upload some files (a picture for instance):
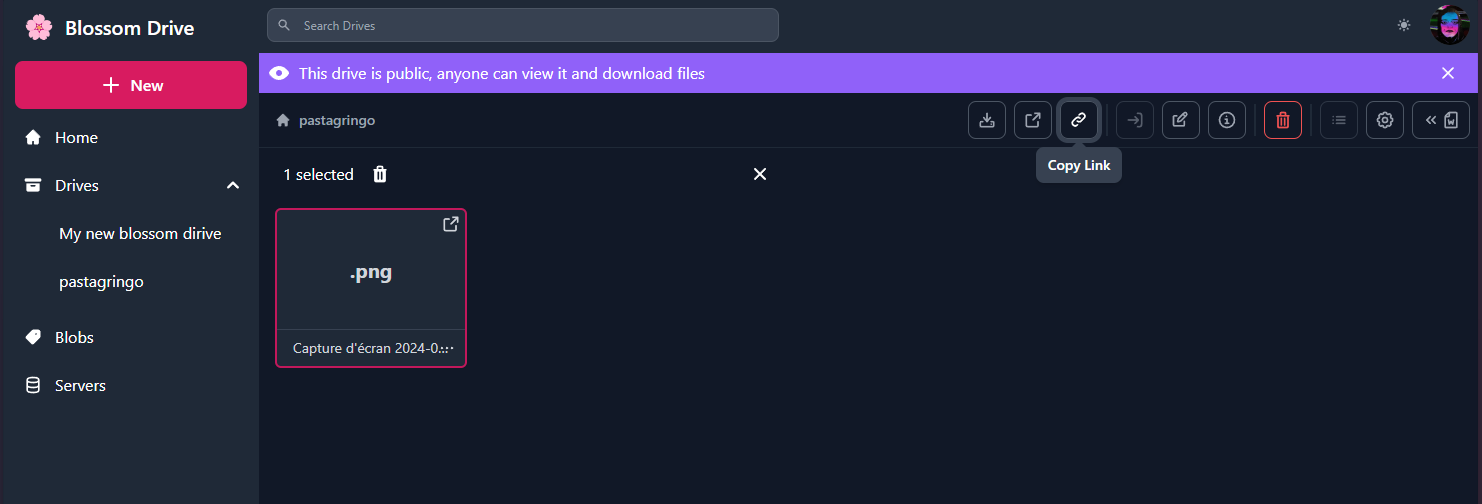
And obtain the HTTP direct link by clicking on the "Copy Link" button:
If you check URL image below, you'll see that it is served by Blossom:

It's done ! ✅
You can now upload your files to Blossom accross several Blossom servers to let them survive the future internet apocalypse.
Blossom has just been released few days ago, many news and features will come!
Don't hesisate to follow hzrd149 on Nostr to follow-up the future updates ⚡🔥
See you soon in another Fractalized story!
PastaGringo 🤖⚡ -
 @ 42342239:1d80db24
2024-04-05 08:21:50
@ 42342239:1d80db24
2024-04-05 08:21:50Trust is a topic increasingly being discussed. Whether it is trust in each other, in the media, or in our authorities, trust is generally seen as a cornerstone of a strong and well-functioning society. The topic was also the theme of the World Economic Forum at its annual meeting in Davos earlier this year. Even among central bank economists, the subject is becoming more prevalent. Last year, Agustín Carstens, head of the BIS ("the central bank of central banks"), said that "[w]ith trust, the public will be more willing to accept actions that involve short-term costs in exchange for long-term benefits" and that "trust is vital for policy effectiveness".
It is therefore interesting when central banks or others pretend as if nothing has happened even when trust has been shattered.
Just as in Sweden and in hundreds of other countries, Canada is planning to introduce a central bank digital currency (CBDC), a new form of money where the central bank or its intermediaries (the banks) will have complete insight into citizens' transactions. Payments or money could also be made programmable. Everything from transferring ownership of a car automatically after a successful payment to the seller, to payments being denied if you have traveled too far from home.
"If Canadians decide a digital dollar is necessary, our obligation is to be ready" says Carolyn Rogers, Deputy Head of Bank of Canada, in a statement shared in an article.
So, what do the citizens want? According to a report from the Bank of Canada, a whopping 88% of those surveyed believe that the central bank should refrain from developing such a currency. About the same number (87%) believe that authorities should guarantee the opportunity to pay with cash instead. And nearly four out of five people (78%) do not believe that the central bank will care about people's opinions. What about trust again?
Canadians' likely remember the Trudeau government's actions against the "Freedom Convoy". The Freedom Convoy consisted of, among others, truck drivers protesting the country's strict pandemic policies, blocking roads in the capital Ottawa at the beginning of 2022. The government invoked never-before-used emergency measures to, among other things, "freeze" people's bank accounts. Suddenly, truck drivers and those with a "connection" to the protests were unable to pay their electricity bills or insurances, for instance. Superficially, this may not sound so serious, but ultimately, it could mean that their families end up in cold houses (due to electricity being cut off) and that they lose the ability to work (driving uninsured vehicles is not taken lightly). And this applied not only to the truck drivers but also to those with a "connection" to the protests. No court rulings were required.
Without the freedom to pay for goods and services, i.e. the freedom to transact, one has no real freedom at all, as several participants in the protests experienced.
In January of this year, a federal judge concluded that the government's actions two years ago were unlawful when it invoked the emergency measures. The use did not display "features of rationality - motivation, transparency, and intelligibility - and was not justified in relation to the relevant factual and legal limitations that had to be considered". He also argued that the use was not in line with the constitution. There are also reports alleging that the government fabricated evidence to go after the demonstrators. The case is set to continue to the highest court. Prime Minister Justin Trudeau and Finance Minister Chrystia Freeland have also recently been sued for the government's actions.
The Trudeau government's use of emergency measures two years ago sadly only provides a glimpse of what the future may hold if CBDCs or similar systems replace the current monetary system with commercial bank money and cash. In Canada, citizens do not want the central bank to proceed with the development of a CBDC. In canada, citizens in Canada want to strengthen the role of cash. In Canada, citizens suspect that the central bank will not listen to them. All while the central bank feverishly continues working on the new system...
"Trust is vital", said Agustín Carstens. But if policy-makers do not pause for a thoughtful reflection even when trust has been utterly shattered as is the case in Canada, are we then not merely dealing with lip service?
And how much trust do these policy-makers then deserve?
-
 @ 42342239:1d80db24
2024-03-31 11:23:36
@ 42342239:1d80db24
2024-03-31 11:23:36Biologist Stuart Kauffman introduced the concept of the "adjacent possible" in evolutionary biology in 1996. A bacterium cannot suddenly transform into a flamingo; rather, it must rely on small exploratory changes (of the "adjacent possible") if it is ever to become a beautiful pink flying creature. The same principle applies to human societies, all of which exemplify complex systems. It is indeed challenging to transform shivering cave-dwellers into a space travelers without numerous intermediate steps.
Imagine a water wheel – in itself, perhaps not such a remarkable invention. Yet the water wheel transformed the hard-to-use energy of water into easily exploitable rotational energy. A little of the "adjacent possible" had now been explored: water mills, hammer forges, sawmills, and textile factories soon emerged. People who had previously ground by hand or threshed with the help of oxen could now spend their time on other things. The principles of the water wheel also formed the basis for wind power. Yes, a multitude of possibilities arose – reminiscent of the rapid development during the Cambrian explosion. When the inventors of bygone times constructed humanity's first water wheel, they thus expanded the "adjacent possible". Surely, the experts of old likely sought swift prohibitions. Not long ago, our expert class claimed that the internet was going to be a passing fad, or that it would only have the same modest impact on the economy as the fax machine. For what it's worth, there were even attempts to ban the number zero back in the days.
The pseudonymous creator of Bitcoin, Satoshi Nakamoto, wrote in Bitcoin's whitepaper that "[w]e have proposed a system for electronic transactions without relying on trust." The Bitcoin system enables participants to agree on what is true without needing to trust each other, something that has never been possible before. In light of this, it is worth noting that trust in the federal government in the USA is among the lowest levels measured in almost 70 years. Trust in media is at record lows. Moreover, in countries like the USA, the proportion of people who believe that one can trust "most people" has decreased significantly. "Rebuilding trust" was even the theme of the World Economic Forum at its annual meeting. It is evident, even in the international context, that trust between countries is not at its peak.
Over a fifteen-year period, Bitcoin has enabled electronic transactions without its participants needing to rely on a central authority, or even on each other. This may not sound like a particularly remarkable invention in itself. But like the water wheel, one must acknowledge that new potential seems to have been put in place, potential that is just beginning to be explored. Kauffman's "adjacent possible" has expanded. And despite dogmatic statements to the contrary, no one can know for sure where this might lead.
The discussion of Bitcoin or crypto currencies would benefit from greater humility and openness, not only from employees or CEOs of money laundering banks but also from forecast-failing central bank officials. When for instance Chinese Premier Zhou Enlai in the 1970s was asked about the effects of the French Revolution, he responded that it was "too early to say" - a far wiser answer than the categorical response of the bureaucratic class. Isn't exploring systems not based on trust is exactly what we need at this juncture?
-
 @ b12b632c:d9e1ff79
2024-03-23 16:42:49
@ b12b632c:d9e1ff79
2024-03-23 16:42:49CASHU AND ECASH ARE EXPERIMENTAL PROJECTS. BY THE OWN NATURE OF CASHU ECASH, IT'S REALLY EASY TO LOSE YOUR SATS BY LACKING OF KNOWLEDGE OF THE SYSTEM MECHANICS. PLEASE, FOR YOUR OWN GOOD, ALWAYS USE FEW SATS AMOUNT IN THE BEGINNING TO FULLY UNDERSTAND HOW WORKS THE SYSTEM. ECASH IS BASED ON A TRUST RELATIONSHIP BETWEEN YOU AND THE MINT OWNER, PLEASE DONT TRUST ECASH MINT YOU DONT KNOW. IT IS POSSIBLE TO GENERATE UNLIMITED ECASH TOKENS FROM A MINT, THE ONLY WAY TO VALIDATE THE REAL EXISTENCE OF THE ECASH TOKENS IS TO DO A MULTIMINT SWAP (BETWEEN MINTS). PLEASE, ALWAYS DO A MULTISWAP MINT IF YOU RECEIVE SOME ECASH FROM SOMEONE YOU DON'T KNOW/TRUST. NEVER TRUST A MINT YOU DONT KNOW!
IF YOU WANT TO RUN AN ECASH MINT WITH A BTC LIGHTNING NODE IN BACK-END, PLEASE DEDICATE THIS LN NODE TO YOUR ECASH MINT. A BAD MANAGEMENT OF YOUR LN NODE COULD LET PEOPLE TO LOOSE THEIR SATS BECAUSE THEY HAD ONCE TRUSTED YOUR MINT AND YOU DID NOT MANAGE THE THINGS RIGHT.

What's ecash/Cashu ?
I recently listened a passionnating interview from calle 👁️⚡👁 invited by the podcast channel What Bitcoin Did about the new (not so much now) Cashu protocol.
Cashu is a a free and open-source Chaumian ecash project built for Bitcoin protocol, recently created in order to let users send/receive Ecash over BTC Lightning network. The main Cashu ecash goal is to finally give you a "by-design" privacy mechanism to allow us to do anonymous Bitcoin transactions.
Ecash for your privacy.\ A Cashu mint does not know who you are, what your balance is, or who you're transacting with. Users of a mint can exchange ecash privately without anyone being able to know who the involved parties are. Bitcoin payments are executed without anyone able to censor specific users.
Here are some useful links to begin with Cashu ecash :
Github repo: https://github.com/cashubtc
Documentation: https://docs.cashu.space
To support the project: https://docs.cashu.space/contribute
A Proof of Liabilities Scheme for Ecash Mints: https://gist.github.com/callebtc/ed5228d1d8cbaade0104db5d1cf63939
Like NOSTR and its own NIPS, here is the list of the Cashu ecash NUTs (Notation, Usage, and Terminology): https://github.com/cashubtc/nuts?tab=readme-ov-file
I won't explain you at lot more on what's Casu ecash, you need to figured out by yourself. It's really important in order to avoid any mistakes you could do with your sats (that you'll probably regret).
If you don't have so much time, you can check their FAQ right here: https://docs.cashu.space/faq
I strongly advise you to listen Calle's interviews @whatbbitcoindid to "fully" understand the concept and the Cashu ecash mechanism before using it:
Scaling Bitcoin Privacy with Calle
In the meantime I'm writing this article, Calle did another really interesting interview with ODELL from CitadelDispatch:
CD120: BITCOIN POWERED CHAUMIAN ECASH WITH CALLE
Which ecash apps?
There are several ways to send/receive some Ecash tokens, you can do it by using mobile applications like eNuts, Minibits or by using Web applications like Cashu.me, Nustrache or even npub.cash. On these topics, BTC Session Youtube channel offers high quality contents and very easy to understand key knowledge on how to use these applications :
Minibits BTC Wallet: Near Perfect Privacy and Low Fees - FULL TUTORIAL
Cashu Tutorial - Chaumian Ecash On Bitcoin
Unlock Perfect Privacy with eNuts: Instant, Free Bitcoin Transactions Tutorial
Cashu ecash is a very large and complex topic for beginners. I'm still learning everyday how it works and the project moves really fast due to its commited developpers community. Don't forget to follow their updates on Nostr to know more about the project but also to have a better undertanding of the Cashu ecash technical and political implications.
There is also a Matrix chat available if you want to participate to the project:
https://matrix.to/#/#cashu:matrix.org
How to self-host your ecash mint with Nutshell
Cashu Nutshell is a Chaumian Ecash wallet and mint for Bitcoin Lightning. Cashu Nutshell is the reference implementation in Python.
Github repo:
https://github.com/cashubtc/nutshell
Today, Nutshell is the most advanced mint in town to self-host your ecash mint. The installation is relatively straightforward with Docker because a docker-compose file is available from the github repo.
Nutshell is not the only cashu ecash mint server available, you can check other server mint here :
https://docs.cashu.space/mints
The only "external" requirement is to have a funding source. One back-end funding source where ecash will mint your ecash from your Sats and initiate BTC Lightning Netwok transactions between ecash mints and BTC Ligtning nodes during a multimint swap. Current backend sources supported are: FakeWallet*, LndRestWallet, CoreLightningRestWallet, BlinkWallet, LNbitsWallet, StrikeUSDWallet.
*FakeWallet is able to generate unlimited ecash tokens. Please use it carefully, ecash tokens issued by the FakeWallet can be sent and accepted as legit ecash tokens to other people ecash wallets if they trust your mint. In the other way, if someone send you 2,3M ecash tokens, please don't trust the mint in the first place. You need to force a multimint swap with a BTC LN transaction. If that fails, someone has maybe tried to fool you.
I used a Voltage.cloud BTC LN node instance to back-end my Nutshell ecash mint:
SPOILER: my nutshell mint is working but I have an error message "insufficient balance" when I ask a multiswap mint from wallet.cashu.me or the eNuts application. In order to make it work, I need to add some Sats liquidity (I can't right now) to the node and open few channels with good balance capacity. If you don't have an ecash mint capable of doig multiswap mint, you'll only be able to mint ecash into your ecash mint and send ecash tokens to people trusting your mint. It's working, yes, but you need to be able to do some mutiminit swap if you/everyone want to fully profit of the ecash system.
Once you created your account and you got your node, you need to git clone the Nutshell github repo:
git clone https://github.com/cashubtc/nutshell.gitYou next need to update the docker compose file with your own settings. You can comment the wallet container if you don't need it.
To generate a private key for your node, you can use this openssl command
openssl rand -hex 32 054de2a00a1d8e3038b30e96d26979761315cf48395aa45d866aeef358c91dd1The CLI Cashu wallet is not needed right now but I'll show you how to use it in the end of this article. Feel free to comment it or not.
``` version: "3" services: mint: build: context: . dockerfile: Dockerfile container_name: mint
ports:
- "3338:3338"
environment:- DEBUG=TRUE
- LOG_LEVEL=DEBUG
- MINT_URL=https://YourMintURL - MINT_HOST=YourMintDomain.tld - MINT_LISTEN_HOST=0.0.0.0 - MINT_LISTEN_PORT=3338 - MINT_PRIVATE_KEY=YourPrivateKeyFromOpenSSL - MINT_INFO_NAME=YourMintInfoName - MINT_INFO_DESCRIPTION=YourShortInfoDesc - MINT_INFO_DESCRIPTION_LONG=YourLongInfoDesc - MINT_LIGHTNING_BACKEND=LndRestWallet #- MINT_LIGHTNING_BACKEND=FakeWallet - MINT_INFO_CONTACT=[["email","YourConctact@email"], ["twitter","@YourTwitter"], ["nostr", "YourNPUB"]] - MINT_INFO_MOTD=Thanks for using my mint! - MINT_LND_REST_ENDPOINT=https://YourVoltageNodeDomain:8080 - MINT_LND_REST_MACAROON=YourDefaultAdminMacaroonBase64 - MINT_MAX_PEG_IN=100000 - MINT_MAX_PEG_OUT=100000 - MINT_PEG_OUT_ONLY=FALSE command: ["poetry", "run", "mint"]wallet-voltage: build: context: . dockerfile: Dockerfile container_name: wallet-voltage
ports:
- "4448:4448"
depends_on: - nutshell-voltage environment:- DEBUG=TRUE
- MINT_URL=http://nutshell-voltage:3338
- API_HOST=0.0.0.0 command: ["poetry", "run", "cashu", "-d"]```
To build, run and see the container logs:
docker compose up -d && docker logs -f mint0.15.1 2024-03-22 14:45:45.490 | WARNING | cashu.lightning.lndrest:__init__:49 - no certificate for lndrest provided, this only works if you have a publicly issued certificate 2024-03-22 14:45:45.557 | INFO | cashu.core.db:__init__:135 - Creating database directory: data/mint 2024-03-22 14:45:45.68 | INFO | Started server process [1] 2024-03-22 14:45:45.69 | INFO | Waiting for application startup. 2024-03-22 14:45:46.12 | INFO | Loaded 0 keysets from database. 2024-03-22 14:45:46.37 | INFO | Current keyset: 003dba9e589023f1 2024-03-22 14:45:46.37 | INFO | Using LndRestWallet backend for method: 'bolt11' and unit: 'sat' 2024-03-22 14:45:46.97 | INFO | Backend balance: 1825000 sat 2024-03-22 14:45:46.97 | INFO | Data dir: /root/.cashu 2024-03-22 14:45:46.97 | INFO | Mint started. 2024-03-22 14:45:46.97 | INFO | Application startup complete. 2024-03-22 14:45:46.98 | INFO | Uvicorn running on http://0.0.0.0:3338 (Press CTRL+C to quit) 2024-03-22 14:45:47.27 | INFO | 172.19.0.22:48528 - "GET /v1/keys HTTP/1.1" 200 2024-03-22 14:45:47.34 | INFO | 172.19.0.22:48544 - "GET /v1/keysets HTTP/1.1" 200 2024-03-22 14:45:47.38 | INFO | 172.19.0.22:48552 - "GET /v1/info HTTP/1.1" 200If you see the line :
Uvicorn running on http://0.0.0.0:3338 (Press CTRL+C to quit)Nutshell is well started.
I won't explain here how to create a reverse proxy to Nutshell, you can find how to do it into my previous article. Here is the reverse proxy config into Nginx Proxy Manager:
If everything is well configured and if you go on your mint url (https://yourminturl) you shoud see this:
It's not helping a lot because at first glance it seems to be not working but it is. You can also check these URL path to confirm :
- https://yourminturl/keys and https://yourminturl/keysets
or
- https://yourminturl/v1/keys and https://yourminturl/v1/keysets
Depending of the moment when you read this article, the first URLs path might have been migrated to V1. Here is why:
https://github.com/cashubtc/nuts/pull/55
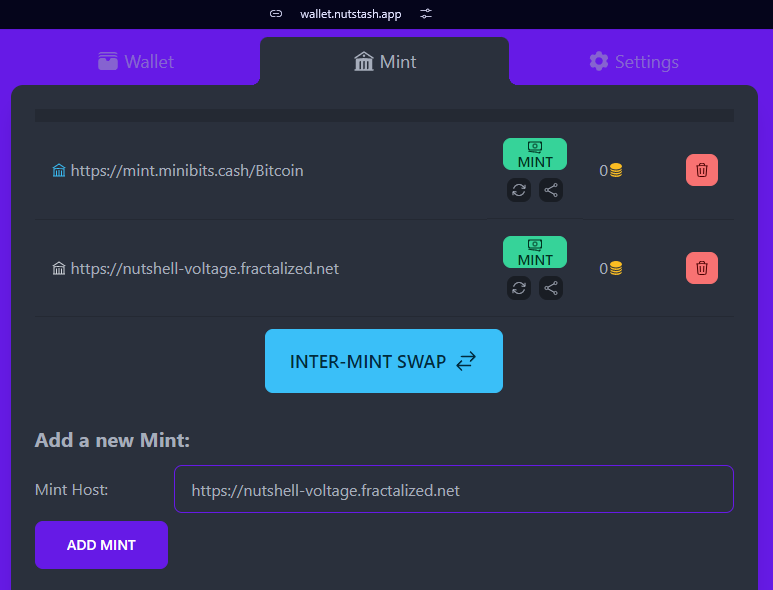
The final test is to add your mint to your prefered ecash wallets.
SPOILER: AT THIS POINT, YOU SHOUD KNOW THAT IF YOU RESET YOUR LOCAL BROWSER INTERNET CACHE FILE, YOU'LL LOSE YOUR MINTED ECASH TOKENS. IF NOT, PLEASE READ THE DOCUMENTATION AGAIN.
For instace, if we use wallet.cashu.me:
You can go into the "Settings" tab and add your mint :
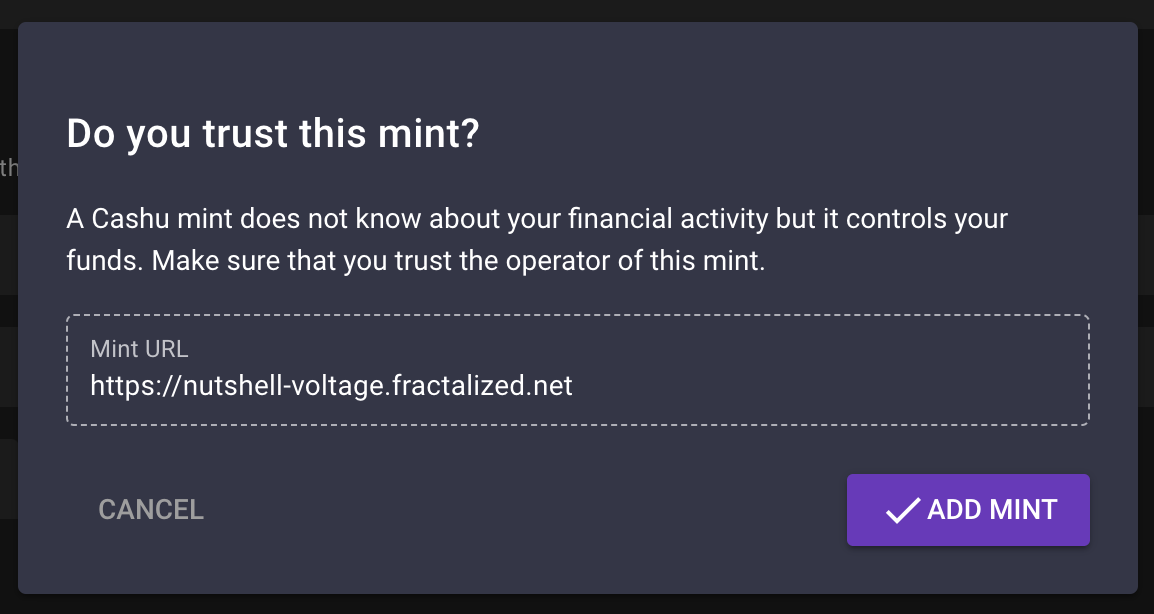
If everything went find, you shoud see this :
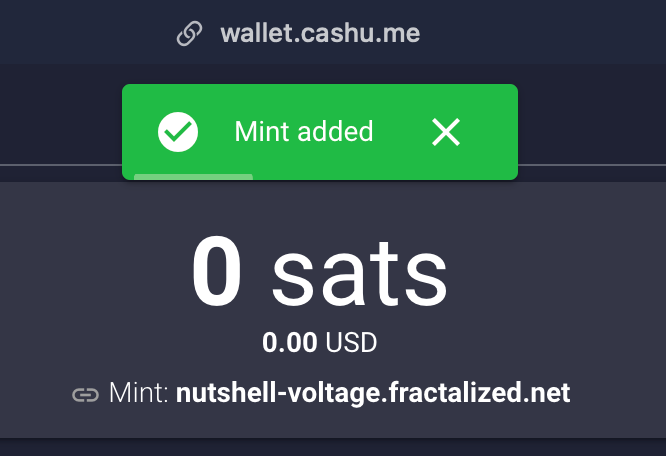
You can now mint some ecash from your mint creating a sats invoice :
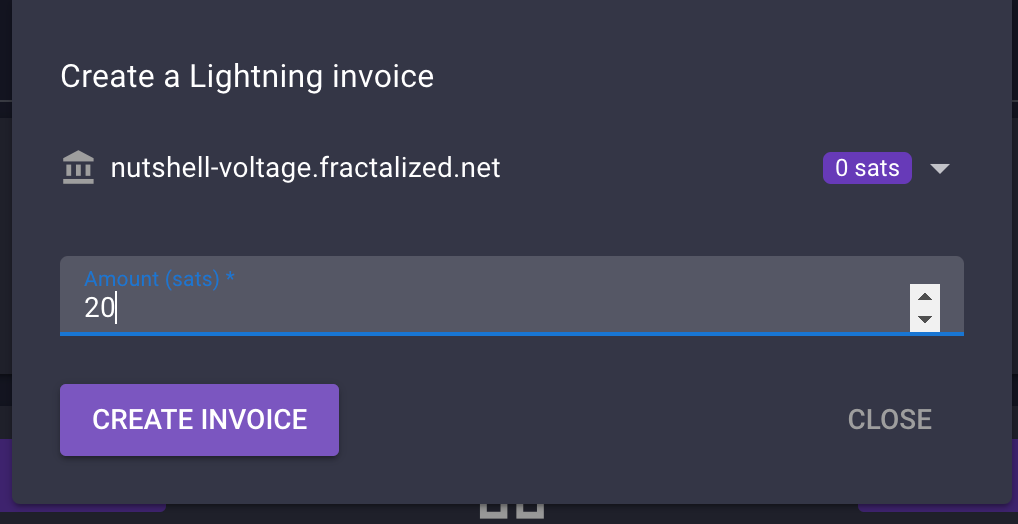
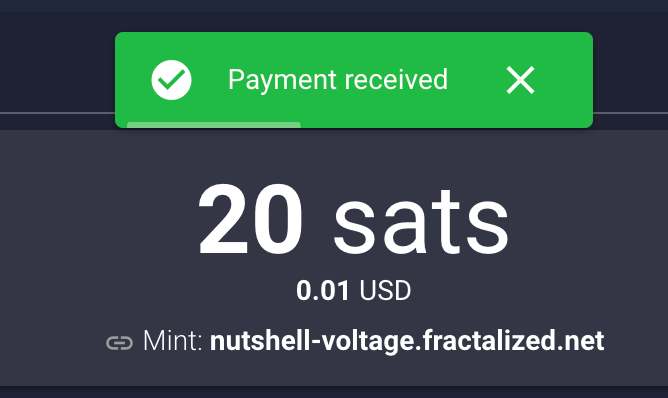
You can now scan the QR diplayed with your prefered BTC LN wallet. If everything is OK, you should receive the funds:
It may happen that some error popup sometimes. If you are curious and you want to know what happened, Cashu wallet has a debug console you can activate by clicking on the "Settings" page and "OPEN DEBUG TERMINAL". A little gear icon will be displayed in the bottom of the screen. You can click on it, go to settings and enable "Auto Display If Error Occurs" and "Display Extra Information". After enabling this setting, you can close the popup windows and let the gear icon enabled. If any error comes, this windows will open again and show you thé error:
Now that you have some sats in your balance, you can try to send some ecash. Open in a new windows another ecash wallet like Nutstach for instance.
Add your mint again :
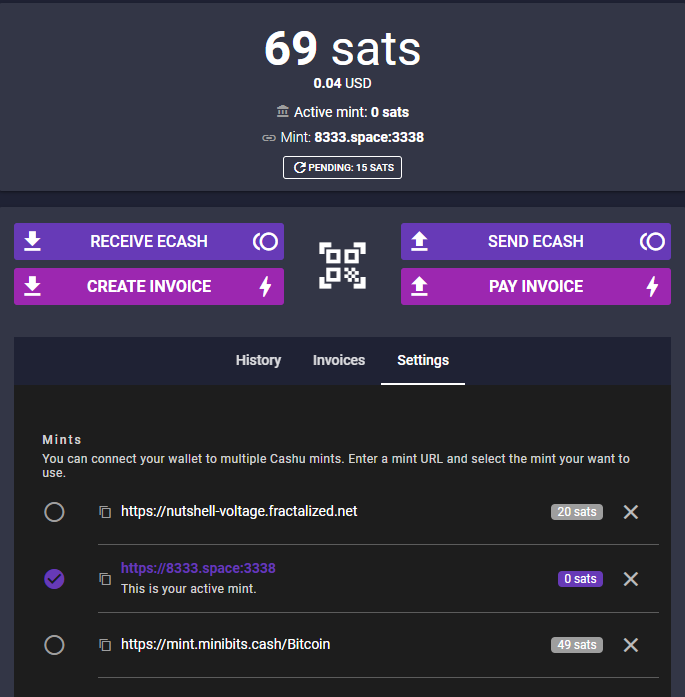
Return on Cashu wallet. The ecash token amount you see on the Cashu wallet home page is a total of all the ecash tokens you have on all mint connected.
Next, click on "Send ecach". Insert the amout of ecash you want to transfer to your other wallet. You can select the wallet where you want to extract the funds by click on the little arrow near the sats funds you currenly selected :


Click now on "SEND TOKENS". That will open you a popup with a QR code and a code CONTAINING YOUR ECASH TOKENS (really).

You can now return on nutstach, click on the "Receive" button and paste the code you get from Cashu wallet:
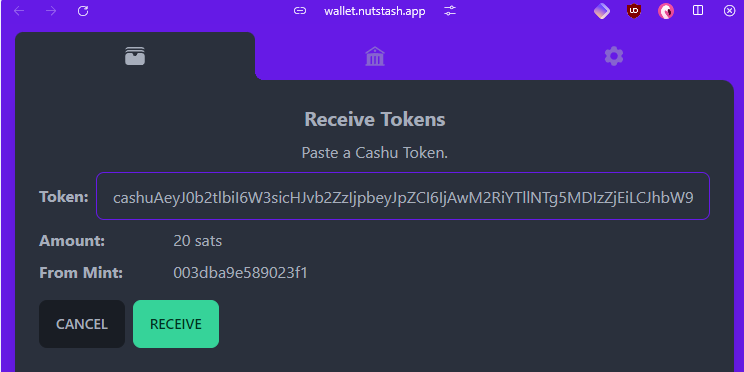
Click on "RECEIVE" again:
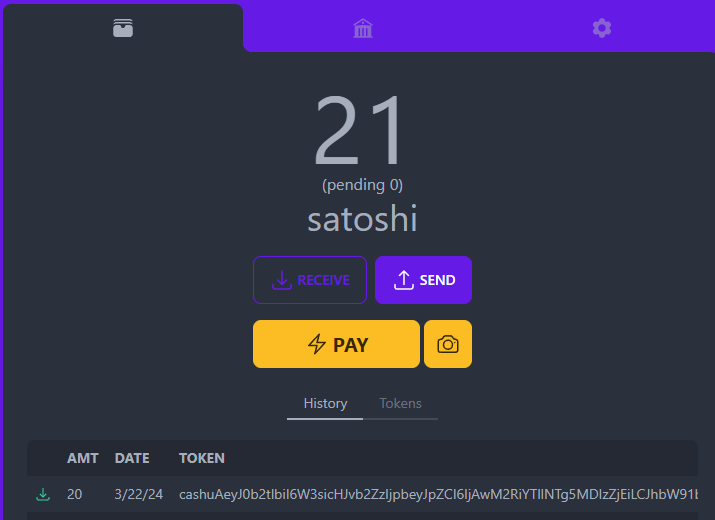
Congrats, you transfered your first ecash tokens to yourself ! 🥜⚡
You may need some time to transfer your ecash tokens between your wallets and your mint, there is a functionality existing for that called "Multimint swaps".
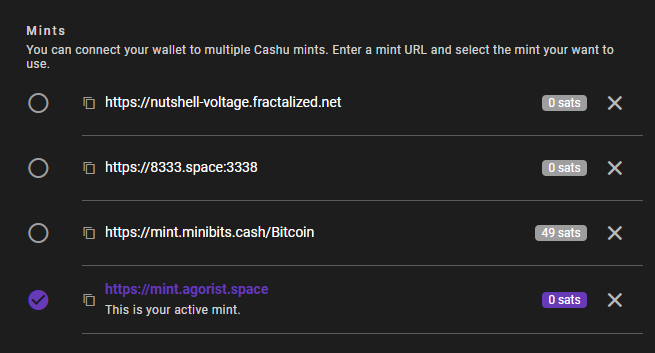
Before that, if you need new mints, you can check the very new website Bitcoinmints.com that let you see the existing ecash mints and rating :
Don't forget, choose your mint carefuly because you don't know who's behind.
Let's take a mint and add it to our Cashu wallet:
If you want to transfer let's say 20 sats from minibits mint to bitcointxoko mint, go just bottom into the "Multimint swap" section. Select the mint into "Swap from mint", the mint into "Swap to mint" and click on "SWAP" :
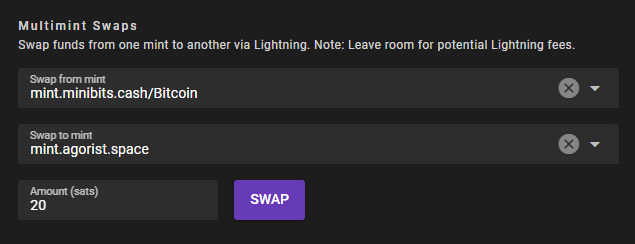
A popup window will appear and will request the ecash tokens from the source mint. It will automatically request the ecash amount via a Lightning node transaction and add the fund to your other wallet in the target mint. As it's a Lightning Network transaction, you can expect some little fees.
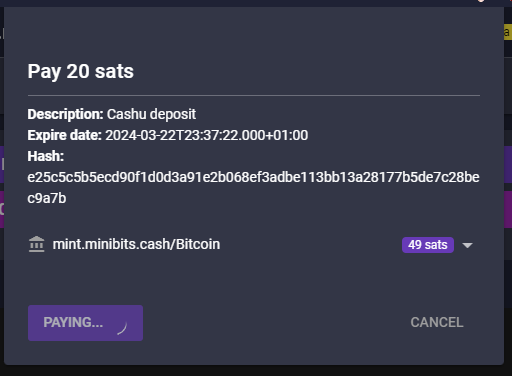
If everything is OK with the mints, the swap will be successful and the ecash received.
You can now see that the previous sats has been transfered (minus 2 fee sats).
Well done, you did your first multimint swap ! 🥜⚡
One last thing interresting is you can also use CLI ecash wallet. If you created the wallet contained in the docker compose, the container should be running.
Here are some commands you can do.
To verify which mint is currently connected :
``` docker exec -it wallet-voltage poetry run cashu info
2024-03-22 21:57:24.91 | DEBUG | cashu.wallet.wallet:init:738 | Wallet initialized 2024-03-22 21:57:24.91 | DEBUG | cashu.wallet.wallet:init:739 | Mint URL: https://nutshell-voltage.fractalized.net 2024-03-22 21:57:24.91 | DEBUG | cashu.wallet.wallet:init:740 | Database: /root/.cashu/wallet 2024-03-22 21:57:24.91 | DEBUG | cashu.wallet.wallet:init:741 | Unit: sat 2024-03-22 21:57:24.92 | DEBUG | cashu.wallet.wallet:init:738 | Wallet initialized 2024-03-22 21:57:24.92 | DEBUG | cashu.wallet.wallet:init:739 | Mint URL: https://nutshell-voltage.fractalized.net 2024-03-22 21:57:24.92 | DEBUG | cashu.wallet.wallet:init:740 | Database: /root/.cashu/wallet 2024-03-22 21:57:24.92 | DEBUG | cashu.wallet.wallet:init:741 | Unit: sat Version: 0.15.1 Wallet: wallet Debug: True Cashu dir: /root/.cashu Mints: - https://nutshell-voltage.fractalized.net ```
To verify your balance :
``` docker exec -it wallet-voltage poetry run cashu balance
2024-03-22 21:59:26.67 | DEBUG | cashu.wallet.wallet:init:738 | Wallet initialized 2024-03-22 21:59:26.67 | DEBUG | cashu.wallet.wallet:init:739 | Mint URL: https://nutshell-voltage.fractalized.net 2024-03-22 21:59:26.67 | DEBUG | cashu.wallet.wallet:init:740 | Database: /root/.cashu/wallet 2024-03-22 21:59:26.67 | DEBUG | cashu.wallet.wallet:init:741 | Unit: sat 2024-03-22 21:59:26.68 | DEBUG | cashu.wallet.wallet:init:738 | Wallet initialized 2024-03-22 21:59:26.68 | DEBUG | cashu.wallet.wallet:init:739 | Mint URL: https://nutshell-voltage.fractalized.net 2024-03-22 21:59:26.68 | DEBUG | cashu.wallet.wallet:init:740 | Database: /root/.cashu/wallet 2024-03-22 21:59:26.68 | DEBUG | cashu.wallet.wallet:init:741 | Unit: sat Balance: 0 sat ```
To create an sats invoice to have ecash :
``` docker exec -it wallet-voltage poetry run cashu invoice 20
2024-03-22 22:00:59.12 | DEBUG | cashu.wallet.wallet:_load_mint_info:275 | Mint info: name='nutshell.fractalized.net' pubkey='02008469922e985cbc5368ce16adb6ed1aaea0f9ecb21639db4ded2e2ae014a326' version='Nutshell/0.15.1' description='Official Fractalized Mint' description_long='TRUST THE MINT' contact=[['email', 'pastagringo@fractalized.net'], ['twitter', '@pastagringo'], ['nostr', 'npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2']] motd='Thanks for using official ecash fractalized mint!' nuts={4: {'methods': [['bolt11', 'sat']], 'disabled': False}, 5: {'methods': [['bolt11', 'sat']], 'disabled': False}, 7: {'supported': True}, 8: {'supported': True}, 9: {'supported': True}, 10: {'supported': True}, 11: {'supported': True}, 12: {'supported': True}} Balance: 0 sat
Pay invoice to mint 20 sat:
Invoice: lnbc200n1pjlmlumpp5qh68cqlr2afukv9z2zpna3cwa3a0nvla7yuakq7jjqyu7g6y69uqdqqcqzzsxqyz5vqsp5zymmllsqwd40xhmpu76v4r9qq3wcdth93xthrrvt4z5ct3cf69vs9qyyssqcqppurrt5uqap4nggu5tvmrlmqs5guzpy7jgzz8szckx9tug4kr58t4avv4a6437g7542084c6vkvul0ln4uus7yj87rr79qztqldggq0cdfpy
You can use this command to check the invoice: cashu invoice 20 --id 2uVWELhnpFcNeFZj6fWzHjZuIipqyj5R8kM7ZJ9_
Checking invoice .................2024-03-22 22:03:25.27 | DEBUG | cashu.wallet.wallet:verify_proofs_dleq:1103 | Verified incoming DLEQ proofs. Invoice paid.
Balance: 20 sat ```
To pay an invoice by pasting the invoice you received by your or other people :
``` docker exec -it wallet-voltage poetry run cashu pay lnbc150n1pjluqzhpp5rjezkdtt8rjth4vqsvm50xwxtelxjvkq90lf9tu2thsv2kcqe6vqdq2f38xy6t5wvcqzzsxqrpcgsp58q9sqkpu0c6s8hq5pey8ls863xmjykkumxnd8hff3q4fvxzyh0ys9qyyssq26ytxay6up54useezjgqm3cxxljvqw5vq2e94ru7ytqc0al74hr4nt5cwpuysgyq8u25xx5la43mx4ralf3mq2425xmvhjzvwzqp54gp0e3t8e
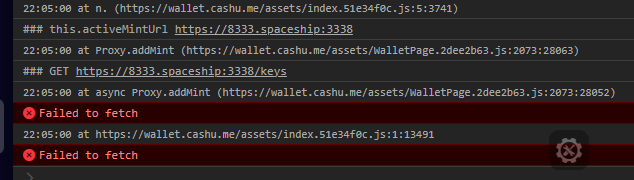
2024-03-22 22:04:37.23 | DEBUG | cashu.wallet.wallet:_load_mint_info:275 | Mint info: name='nutshell.fractalized.net' pubkey='02008469922e985cbc5368ce16adb6ed1aaea0f9ecb21639db4ded2e2ae014a326' version='Nutshell/0.15.1' description='Official Fractalized Mint' description_long='TRUST THE MINT' contact=[['email', 'pastagringo@fractalized.net'], ['twitter', '@pastagringo'], ['nostr', 'npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2']] motd='Thanks for using official ecash fractalized mint!' nuts={4: {'methods': [['bolt11', 'sat']], 'disabled': False}, 5: {'methods': [['bolt11', 'sat']], 'disabled': False}, 7: {'supported': True}, 8: {'supported': True}, 9: {'supported': True}, 10: {'supported': True}, 11: {'supported': True}, 12: {'supported': True}} Balance: 20 sat 2024-03-22 22:04:37.45 | DEBUG | cashu.wallet.wallet:get_pay_amount_with_fees:1529 | Mint wants 0 sat as fee reserve. 2024-03-22 22:04:37.45 | DEBUG | cashu.wallet.cli.cli:pay:189 | Quote: quote='YpNkb5f6WVT_5ivfQN1OnPDwdHwa_VhfbeKKbBAB' amount=15 fee_reserve=0 paid=False expiry=1711146847 Pay 15 sat? [Y/n]: y Paying Lightning invoice ...2024-03-22 22:04:41.13 | DEBUG | cashu.wallet.wallet:split:613 | Calling split. POST /v1/swap 2024-03-22 22:04:41.21 | DEBUG | cashu.wallet.wallet:verify_proofs_dleq:1103 | Verified incoming DLEQ proofs. Error paying invoice: Mint Error: Lightning payment unsuccessful. insufficient_balance (Code: 20000) ```
It didn't work, yes. That's the thing I told you earlier but it would work with a well configured and balanced Lightning Node.
That's all ! You should now be able to use ecash as you want! 🥜⚡
See you on NOSTR! 🤖⚡\ PastaGringo
-
 @ ee11a5df:b76c4e49
2024-03-22 23:49:09
@ ee11a5df:b76c4e49
2024-03-22 23:49:09Implementing The Gossip Model
version 2 (2024-03-23)
Introduction
History
The gossip model is a general concept that allows clients to dynamically follow the content of people, without specifying which relay. The clients have to figure out where each person puts their content.
Before NIP-65, the gossip client did this in multiple ways:
- Checking kind-3 contents, which had relay lists for configuring some clients (originally Astral and Damus), and recognizing that wherever they were writing our client could read from.
- NIP-05 specifying a list of relays in the
nostr.jsonfile. I added this to NIP-35 which got merged down into NIP-05. - Recommended relay URLs that are found in 'p' tags
- Users manually making the association
- History of where events happen to have been found. Whenever an event came in, we associated the author with the relay.
Each of these associations were given a score (recommended relay urls are 3rd party info so they got a low score).
Later, NIP-65 made a new kind of relay list where someone could advertise to others which relays they use. The flag "write" is now called an OUTBOX, and the flag "read" is now called an INBOX.
The idea of inboxes came about during the development of NIP-65. They are a way to send an event to a person to make sure they get it... because putting it on your own OUTBOX doesn't guarantee they will read it -- they may not follow you.
The outbox model is the use of NIP-65. It is a subset of the gossip model which uses every other resource at it's disposal.
Rationale
The gossip model keeps nostr decentralized. If all the (major) clients were using it, people could spin up small relays for both INBOX and OUTBOX and still be fully connected, have their posts read, and get replies and DMs. This is not to say that many people should spin up small relays. But the task of being decentralized necessitates that people must be able to spin up their own relay in case everybody else is censoring them. We must make it possible. In reality, congregating around 30 or so popular relays as we do today is not a problem. Not until somebody becomes very unpopular with bitcoiners (it will probably be a shitcoiner), and then that person is going to need to leave those popular relays and that person shouldn't lose their followers or connectivity in any way when they do.
A lot more rationale has been discussed elsewhere and right now I want to move on to implementation advice.
Implementation Advice
Read NIP-65
NIP-65 will contain great advice on which relays to consult for which purposes. This post does not supersede NIP-65. NIP-65 may be getting some smallish changes, mostly the addition of a private inbox for DMs, but also changes to whether you should read or write to just some or all of a set of relays.
How often to fetch kind-10002 relay lists for someone
This is up to you. Refreshing them every hour seems reasonable to me. Keeping track of when you last checked so you can check again every hour is a good idea.
Where to fetch events from
If your user follows another user (call them jack), then you should fetch jack's events from jack's OUTBOX relays. I think it's a good idea to use 2 of those relays. If one of those choices fails (errors), then keep trying until you get 2 of them that worked. This gives some redundancy in case one of them is censoring. You can bump that number up to 3 or 4, but more than that is probably just wasting bandwidth.
To find events tagging your user, look in your user's INBOX relays for those. In this case, look into all of them because some clients will only write to some of them (even though that is no longer advised).
Picking relays dynamically
Since your user follows many other users, it is very useful to find a small subset of all of their OUTBOX relays that cover everybody followed. I wrote some code to do this as (it is used by gossip) that you can look at for an example.
Where to post events to
Post all events (except DMs) to all of your users OUTBOX relays. Also post the events to all the INBOX relays of anybody that was tagged or mentioned in the contents in a nostr bech32 link (if desired). That way all these mentioned people are aware of the reply (or quote or repost).
DMs should be posted only to INBOX relays (in the future, to PRIVATE INBOX relays). You should post it to your own INBOX relays also, because you'll want a record of the conversation. In this way, you can see all your DMs inbound and outbound at your INBOX relay.
Where to publish your user's kind-10002 event to
This event was designed to be small and not require moderation, plus it is replaceable so there is only one per user. For this reason, at the moment, just spread it around to lots of relays especially the most popular relays.
For example, the gossip client automatically determines which relays to publish to based on whether they seem to be working (several hundred) and does so in batches of 10.
How to find replies
If all clients used the gossip model, you could find all the replies to any post in the author's INBOX relays for any event with an 'e' tag tagging the event you want replies to... because gossip model clients will publish them there.
But given the non-gossip-model clients, you should also look where the event was seen and look on those relays too.
Clobbering issues
Please read your users kind 10002 event before clobbering it. You should look many places to make sure you didn't miss the newest one.
If the old relay list had tags you don't understand (e.g. neither "read" nor "write"), then preserve them.
How users should pick relays
Today, nostr relays are not uniform. They have all kinds of different rule-sets and purposes. We severely lack a way to advice non-technical users as to which relays make good OUTBOX relays and which ones make good INBOX relays. But you are a dev, you can figure that out pretty well. For example, INBOX relays must accept notes from anyone meaning they can't be paid-subscription relays.
Bandwidth isn't a big issue
The outbox model doesn't require excessive bandwidth when done right. You shouldn't be downloading the same note many times... only 2-4 times depending on the level of redundancy your user wants.
Downloading 1000 events from 100 relays is in theory the same amount of data as downloading 1000 events from 1 relay.
But in practice, due to redundancy concerns, you will end up downloading 2000-3000 events from those 100 relays instead of just the 1000 you would in a single relay situation. Remember, per person followed, you will only ask for their events from 2-4 relays, not from all 100 relays!!!
Also in practice, the cost of opening and maintaining 100 network connections is more than the cost of opening and maintaining just 1. But this isn't usually a big deal unless...
Crypto overhead on Low-Power Clients
Verifying Schnorr signatures in the secp256k1 cryptosystem is not cheap. Setting up SSL key exchange is not cheap either. But most clients will do a lot more event signature validations than they will SSL setups.
For this reason, connecting to 50-100 relays is NOT hugely expensive for clients that are already verifying event signatures, as the number of events far surpasses the number of relay connections.
But for low-power clients that can't do event signature verification, there is a case for them not doing a lot of SSL setups either. Those clients would benefit from a different architecture, where half of the client was on a more powerful machine acting as a proxy for the low-power half of the client. These halves need to trust each other, so perhaps this isn't a good architecture for a business relationship, but I don't know what else to say about the low-power client situation.
Unsafe relays
Some people complain that the outbox model directs their client to relays that their user has not approved. I don't think it is a big deal, as such users can use VPNs or Tor if they need privacy. But for such users that still have concerns, they may wish to use clients that give them control over this. As a client developer you can choose whether to offer this feature or not.
The gossip client allows users to require whitelisting for connecting to new relays and for AUTHing to relays.
See Also
-
 @ 42342239:1d80db24
2024-03-21 09:49:01
@ 42342239:1d80db24
2024-03-21 09:49:01It has become increasingly evident that our financial system has started undermine our constitutionally guaranteed freedoms and rights. Payment giants like PayPal, Mastercard, and Visa sometimes block the ability to donate money. Individuals, companies, and associations lose bank accounts — or struggle to open new ones. In bank offices, people nowadays risk undergoing something resembling being cross-examined. The regulations are becoming so cumbersome that their mere presence risks tarnishing the banks' reputation.
The rules are so complex that even within the same bank, different compliance officers can provide different answers to the same question! There are even departments where some of the compliance officers are reluctant to provide written responses and prefer to answer questions over an unrecorded phone call. Last year's corporate lawyer in Sweden recently complained about troublesome bureaucracy, and that's from a the perspective of a very large corporation. We may not even fathom how smaller businesses — the keys to a nation's prosperity — experience it.
Where do all these rules come?
Where do all these rules come from, and how well do they work? Today's regulations on money laundering (AML) and customer due diligence (KYC - know your customer) primarily originate from a G7 meeting in the summer of 1989. (The G7 comprises the seven advanced economies: the USA, Canada, the UK, Germany, France, Italy, and Japan, along with the EU.) During that meeting, the intergovernmental organization FATF (Financial Action Task Force) was established with the aim of combating organized crime, especially drug trafficking. Since then, its mandate has expanded to include fighting money laundering, terrorist financing, and the financing of the proliferation of weapons of mass destruction(!). One might envisage the rules soon being aimed against proliferation of GPUs (Graphics Processing Units used for AI/ML). FATF, dominated by the USA, provides frameworks and recommendations for countries to follow. Despite its influence, the organization often goes unnoticed. Had you heard of it?
FATF offered countries "a deal they couldn't refuse"
On the advice of the USA and G7 countries, the organization decided to begin grading countries in "blacklists" and "grey lists" in 2000, naming countries that did not comply with its recommendations. The purpose was to apply "pressure" to these countries if they wanted to "retain their position in the global economy." The countries were offered a deal they couldn't refuse, and the number of member countries rapidly increased. Threatening with financial sanctions in this manner has even been referred to as "extraterritorial bullying." Some at the time even argued that the process violated international law.
If your local Financial Supervisory Authority (FSA) were to fail in enforcing compliance with FATF's many checklists among financial institutions, the risk of your country and its banks being barred from the US-dominated financial markets would loom large. This could have disastrous consequences.
A cost-benefit analysis of AML and KYC regulations
Economists use cost-benefit analysis to determine whether an action or a policy is successful. Let's see what such an analysis reveals.
What are the benefits (or revenues) after almost 35 years of more and more rules and regulations? The United Nations Office on Drugs and Crime estimated that only 0.2% of criminal proceeds are confiscated. Other estimates suggest a success rate from such anti-money laundering rules of 0.07% — a rounding error for organized crime. Europol expects to recover 1.2 billion euros annually, equivalent to about 1% of the revenue generated in the European drug market (110 billion euros). However, the percentage may be considerably lower, as the size of the drug market is likely underestimated. Moreover, there are many more "criminal industries" than just the drug trade; human trafficking is one example - there are many more. In other words, criminal organizations retain at least 99%, perhaps even 99.93%, of their profits, despite all cumbersome rules regarding money laundering and customer due diligence.
What constitutes the total cost of this bureaurcratic activity, costs that eventually burden taxpayers and households via higher fees? Within Europe, private financial firms are estimated to spend approximately 144 billion euros on compliance. According to some estimates, the global cost is twice as high, perhaps even eight times as much.
For Europe, the cost may thus be about 120 times (144/1.2) higher than the revenues from these measures. These "compliance costs" bizarrely exceed the total profits from the drug market, as one researcher put it. Even though the calculations are uncertain, it is challenging — perhaps impossible — to legitimize these regulations from a cost-benefit perspective.
But it doesn't end there, unfortunately. The cost of maintaining this compliance circus, with around 80 international organizations, thousands of authorities, far more employees, and all this across hundreds of countries, remains a mystery. But it's unlikely to be cheap.
The purpose of a system is what it does
In Economic Possibilities for our Grandchildren (1930), John Maynard Keynes foresaw that thanks to technological development, we could have had a 15-hour workweek by now. This has clearly not happened. Perhaps jobs have been created that are entirely meaningless? Anthropologist David Graeber argued precisely this in Bullshit Jobs in 2018. In that case, a significant number of people spend their entire working lives performing tasks they suspect deep down don't need to be done.
"The purpose of a system is what it does" is a heuristic coined by Stafford Beer. He observed there is "no point in claiming that the purpose of a system is to do what it constantly fails to do. What the current regulatory regime fails to do is combat criminal organizations. Nor does it seem to prevent banks from laundering money as never before, or from providing banking services to sex-offending traffickers
What the current regulatory regime does do, is: i) create armies of meaningless jobs, ii) thereby undermining mental health as well as economic prosperity, while iii) undermining our freedom and rights.
What does this say about the purpose of the system?
-
 @ 862fda7e:02a8268b
2024-07-15 06:48:28
@ 862fda7e:02a8268b
2024-07-15 06:48:28As of April 27, 2024, I will make the conscious effort to no longer refer nor use the imperial system for measurments. This will be a difficult change for me to make, as I have been accostumed to the imperial measurment system for the past 25 years of my life. However, I find the system of measurment very flawed and inconvenient, especially as most of the world opts for the more accurate metric system.
I have decided to finally make this change after learning about the ridiculous naming system of CMD ceramic capacitor casings. The CMD ceramic capacitor casings are named after their measurments, which I find convenient and straight forward. However, they are based off of imperial measurments. When we know that CMD ceramic capacitors are notociously small; you would think it's foolish to name their casings after the imerial system, as we know the smallest measurment in the imerial system is inches. Most Americans do not bother using centimeters nor millimeters.
Well, this is where our problem is. The CMD ceramic capacitor casings are MILLIMETERS small. They cannot measure an inch, not even half an inch. A common CMD cermaic capacitor measures 0.08 inches by 0.06 inches. The casing is named a 0806 casing, meaning it's 0.08 inches by 0.06 inches.
When we try to visiualize what 0.08 inches looks like, it's nearly impossible. This is not due to a lack of intelligence. However, it is due to a lack of using inches in such a miniscule measurement. Americans never refer to inches in such small measurements, it's very hard to visualize. This is an absurd naming convention and they should have realized this flaw.
If I want to measure a CMD ceramic capacitor to determine what casing size it is, I would never in my right mind use the inches section of my ruler. It's very impractical and confusing. However, a very simple choice a sane person would make is to refer to the millimeters section of their ruler to measure a very small object for a very accruate measurment. This example was the final straw for me. I am no longer going to abide by the imperial system. It is flawed. It is a very generalized way of measuring something. It's also very pig-headed and innacurate. It limits how specific we can get with a measurment. For some reason I am a lot more well versed in millimeters and centimeters than most Americans. I am shocked at the average American's lack of compresension of superior measurment practices.
I am not as well versed in metric measurments as someone who has grown up with this superior measurment instilled in them since childhood. I will frequently be measuring items around my house to gain a more familiar understanding with their size in the superior measurment convention. Due to pure habit, I may casually refer to something in inches. This is not due to a lack of willpower, nor a lack of commitment to my new change. It is purely a bad habit that I am trying to rid away. There will be mistakes.
While we are on this topic, I will quickly mention other strictly Americanized choices that I reject for purely logical reasons. 1. I do not spell it "publicly". This makes no sense when words that typically end in "cally" have an "a" in them. Logically, it should be spelled, "publically". I will continue to choose to spell it this way, as it logically makes more sense.
-
I do not spell it "gray". When I pronounce the word "grey", there is clearly an "e" in it. Not an "a". The original word is spelled with an "e", there was no need to bastardize its spelling with an "a".
-
I do not pronounce the word "solder" as "sodder". The word is spelled with an "l", but not only that. I refered to the origin of the word "solder", and this is what I found. "to consolidate, close, fasten together, join with solder" (13c.), from Latin solidare "to make solid," from solidus "solid" The word ultimately comes from "solid", which we do not pronounce "soid". We say, "solid" with an "l".
-
-
 @ 1fd60647:29965a9a
2024-07-03 08:08:19
@ 1fd60647:29965a9a
2024-07-03 08:08:19
大家可能會好奇權限設定好後要如何發文,下面就來教大家發文方式!
撰寫文章基本步驟
步驟1: 進入到blogstack後點擊下面這邊"write"
之後會進入到撰寫的格式內容,左邊是你編輯的地方,右邊是顯示發出去的文章格式預覽,就很直覺可以照一般打字方式打。
步驟2:如果需要加入圖片的話可以按上方圖片的小icon,在括號()內打上你的圖片網址連結,如果圖片是自己的不是網路圖片的話可以再看到下面補充操作步驟,這邊暫時先跳過。
 填入網址連結後右邊就會自動預覽,如下圖。
其他打文字啊、粗體斜體啊,操作方法都很直覺也很簡單這邊就不贅述。
文章打好後就按右上角綠色的”publish”
填入網址連結後右邊就會自動預覽,如下圖。
其他打文字啊、粗體斜體啊,操作方法都很直覺也很簡單這邊就不贅述。
文章打好後就按右上角綠色的”publish”
步驟3:點完後就會出現以下,記得第二個bctzh那邊要打勾才能同步發到比特幣中文的網站上喔!
步驟4:點完下面綠色的publish now之後又會跳出下面的視窗,我自己都是選單次授權啦,所以每次都會再跳出來一次,也可以選永遠授權,就看大家偏好囉!
步驟5:出現下面視窗後按dismiss就完成啦~你的文章就會出現在比特幣中文的網站囉!
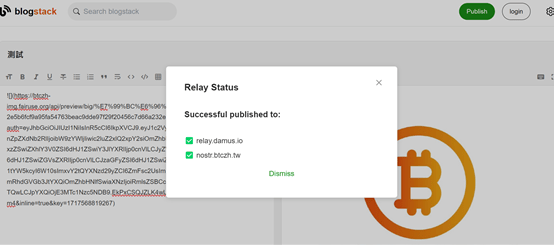
沒有圖片連結怎麼辦?
再回到剛剛提到的問題,如果是自己的圖片要怎麼辦,沒有圖片網址連結要怎麼插入圖片呢??
步驟1:點擊這個網址進去https://nostr.build/,上傳自己的照片,點choose media,選擇你要的圖片。

步驟2:選好後按upload media系統就會自動生成連結了,很簡單,之後再複製連結,就可以回到bloclstack上,點擊圖片的icon,插入上面講的()內就可以囉,很簡單吧!


-
 @ 1fd60647:29965a9a
2024-07-03 08:05:32
@ 1fd60647:29965a9a
2024-07-03 08:05:32
比特幣中文網是架設在Nostr協議上的一個網站,可理解為去中心化的社交場景,本文以下將介紹Nostr網路的設定方式,設定完成後即可在平台上分享各種文章喔!
教學步驟
nos2x(Nostr登入插件) URL: https://chrome.google.com/webstore/detail/nos2x/kpgefcfmnafjgpblomihpgmejjdanjjp
步驟1: 下載完nos2x後,至擴充功能頁中找尋nos2x並點選"擴充功能選項” 如果沒有顯示的話也能直接在以下網頁列輸入設定頁面: chrome-extension://kpgefcfmnafjgpblomihpgmejjdanjjp/options.html
步驟2: 將私鑰輸入至private key部分,底下preferred relays目前是用這兩個: 1. relay.damus.io 2. nostr.btczh.tw 設定完後按save儲存(如下圖)
步驟3: 儲存完後再次點選nos2x插件圖示,點擊後會出現您的公鑰QR Code圖示(如下圖)
步驟4: 前往Nostr協議的網站(如blogstack等),點選login並使用插件登入,跳出nos2x後選擇授權次數,選擇後即登入完成 blogstack: https://blogstack.io/
(授權登入的部分,我個人都是選擇授權單次)
(右上角出現可以撰寫文章符號及完成)
步驟5: 回報您的註冊帳號的公鑰,Email至: contact@btczh.tw 我們團隊會為您開通比特幣中平台的權限,之後您發布文章,就會同步顯示於btczh.tw囉!
-
 @ ee11a5df:b76c4e49
2024-03-21 00:28:47
@ ee11a5df:b76c4e49
2024-03-21 00:28:47I'm glad to see more activity and discussion about the gossip model. Glad to see fiatjaf and Jack posting about it, as well as many developers pitching in in the replies. There are difficult problems we need to overcome, and finding notes while remaining decentralized without huge note copying overhead was just the first. While the gossip model (including the outbox model which is just the NIP-65 part) completely eliminates the need to copy notes around to lots of relays, and keeps us decentralized, it brings about it's own set of new problems. No community is ever of the same mind on any issue, and this issue is no different. We have a lot of divergent opinions. This note will be my updated thoughts on these topics.
COPYING TO CENTRAL RELAYS IS A NON-STARTER: The idea that you can configure your client to use a few popular "centralized" relays and everybody will copy notes into those central relays is a non-starter. It destroys the entire raison d'être of nostr. I've heard people say that more decentralization isn't our biggest issue. But decentralization is THE reason nostr exists at all, so we need to make sure we live up to the hype. Otherwise we may as well just all join Bluesky. It has other problems too: the central relays get overloaded, and the notes get copied to too many relays, which is both space-inefficient and network bandwith inefficient.
ISSUE 1: Which notes should I fetch from which relays? This is described pretty well now in NIP-65. But that is only the "outbox" model part. The "gossip model" part is to also work out what relays work for people who don't publish a relay list.
ISSUE 2: Automatic failover. Apparently Peter Todd's definition of decentralized includes a concept of automatic failover, where new resources are brought up and users don't need to do anything. Besides this not being part of any definition of decentralized I have never heard of, we kind of have this. If a user has 5 outboxes, and 3 fail, everything still works. Redundancy is built in. No user intervention needed in most cases, at least in the short term. But we also don't have any notion of administrators who can fix this behind the scenes for the users. Users are sovereign and that means they have total control, but also take on some responsibility. This is obvious when it comes to keypair management, but it goes further. Users have to manage where they post and where they accept incoming notes, and when those relays fail to serve them they have to change providers. Putting the users in charge, and not having administrators, is kinda necessary to be truly decentralized.
ISSUE 3: Connecting to unvetted relays feels unsafe. It might even be the NSA tracking you! First off, this happens with your web browser all the time: you go visit a web page and it instructs your browser to fetch a font from google. If you don't like it, you can use uBlock origin and manage it manually. In the nostr world, if you don't like it, you can use a client that puts you more in control of this. The gossip client for example has options for whether you want to manually approve relay connections and AUTHs, just once or always, and always lets you change your mind later. If you turn those options on, initially it is a giant wall of approval requests... but that situation resolves rather quickly. I've been running with these options on for a long time now, and only about once a week do I have to make a decision for a new relay.
But these features aren't really necessary for the vast majority of users who don't care if a relay knows their IP address. Those users use VPNs or Tor when they want to be anonymous, and don't bother when they don't care (me included).
ISSUE 4: Mobile phone clients may find the gossip model too costly in terms of battery life. Bandwidth is actually not a problem: under the gossip model (if done correctly) events for user P are only downloaded from N relays (default for gossip client is N=2), which in general is FEWER events retrieved than other models which download the same event maybe 8 or more times. Rather, the problem here is the large number of network connections and in particular, the large number of SSL setups and teardowns. If it weren't for SSL, this wouldn't be much of a problem. But setting up and tearing down SSL on 50 simultaneous connections that drop and pop up somewhat frequently is a battery drain.
The solution to this that makes the most sense to me is to have a client proxy. What I mean by that is a piece of software on a server in a data centre. The client proxy would be a headless nostr client that uses the gossip model and acts on behalf of the phone client. The phone client doesn't even have to be a nostr client, but it might as well be a nostr client that just connects to this fixed proxy to read and write all of its events. Now the SSL connection issue is solved. These proxies can serve many clients and have local storage, whereas the phones might not even need local storage. Since very few users will set up such things for themselves, this is a business opportunity for people, and a better business opportunity IMHO than running a paid-for relay. This doesn't decentralize nostr as there can be many of these proxies. It does however require a trust relationship between the phone client and the proxy.
ISSUE 5: Personal relays still need moderation. I wrongly thought for a very long time that personal relays could act as personal OUTBOXes and personal INBOXes without needing moderation. Recently it became clear to me that clients should probably read from other people's INBOXes to find replies to events written by the user of that INBOX (which outbox model clients should be putting into that INBOX). If that is happening, then personal relays will need to serve to the public events that were just put there by the public, thus exposing them to abuse. I'm greatly disappointed to come to this realization and not quite settled about it yet, but I thought I had better make this known.
-
 @ b12b632c:d9e1ff79
2024-02-19 19:18:46
@ b12b632c:d9e1ff79
2024-02-19 19:18:46Nostr decentralized network is growing exponentially day by day and new stuff comes out everyday. We can now use a NIP46 server to proxify our nsec key to avoid to use it to log on Nostr websites and possibly leak it, by mistake or by malicious persons. That's the point of this tutorial, setup a NIP46 server Nsec.app with its own Nostr relay. You'll be able to use it for you and let people use it, every data is stored locally in your internet browser. It's an non-custodial application, like wallets !
It's nearly a perfect solution (because nothing is perfect as we know) and that makes the daily use of Nostr keys much more secure and you'll see, much more sexy ! Look:
Nsec.app is not the only NIP46 server, in fact, @PABLOF7z was the first to create a NIP46 server called nsecBunker. You can also self-hosted nsecBunkerd, you can find a detailed explanation here : nsecbunkerd. I may write a how to self-host nsecBunkderd soon.
If you want more information about its bunker and what's behind this tutorial, you can check these links :
Few stuffs before beginning
Spoiler : I didn't automatized everything. The goal here is not to give you a full 1 click installation process, it's more to let you see and understand all the little things to configure and understand how works Nsec.app and the NIP46. There is a little bit of work, yes, but you'll be happy when it will work! Believe me.
Before entering into the battlefield, you must have few things : A working VPS with direct access to internet or a computer at home but NAT will certain make your life a hell. Use a VPS instead, on DigitalOcean, Linode, Scaleway, as you wish. A web domain that your own because we need to use at least 3 DNS A records (you can choose the subdomain you like) : domain.tld, noauth.domain.tld, noauth.domain.tld. You need to have some programs already installed : git, docker, docker-compose, nano/vi. if you fill in all the boxes, we can move forward !
Let's install everything !
I build a repo with a docker-compose file with all the required stuff to make the Bunker works :
Nsec.app front-end : noauth Nsec.app back-end : noauthd Nostr relay : strfry Nostr NIP05 : easy-nip5
First thing to do is to clone the repo "nsec-app-docker" from my repo:
$ git clone git clone https://github.com/PastaGringo/nsec-app-docker.git $ cd nsec-app-dockerWhen it's done, you'll have to do several things to make it work. 1) You need to generate some keys for the web-push library (keep them for later) :
``` $ docker run pastagringo/web-push-generate-keys
Generating your web-push keys...
Your private key : rQeqFIYKkInRqBSR3c5iTE3IqBRsfvbq_R4hbFHvywE Your public key : BFW4TA-lUvCq_az5fuQQAjCi-276wyeGUSnUx4UbGaPPJwEemUqp3Rr3oTnxbf0d4IYJi5mxUJOY4KR3ZTi3hVc ```
2) Generate a new keys pair (nsec/npub) for the NIP46 server by clicking on "Generate new key" from NostrTool website: nostrtool.com.
You should have something like this :
console Nostr private key (nsec): keep this -> nsec1zcyanx8zptarrmfmefr627zccrug3q2vhpfnzucq78357hshs72qecvxk6 Nostr private key (hex): 1609d998e20afa31ed3bca47a57858c0f888814cb853317300f1e34f5e178794 Nostr public key (npub): npub1ywzwtnzeh64l560a9j9q5h64pf4wvencv2nn0x4h0zw2x76g8vrq68cmyz Nostr public key (hex): keep this -> 2384e5cc59beabfa69fd2c8a0a5f550a6ae6667862a7379ab7789ca37b483b06You need to keep Nostr private key (nsec) & Nostr public key (npub). 3) Open (nano/vi) the .env file located in the current folder and fill all the required info :
```console
traefik
EMAIL=pastagringo@fractalized.net <-- replace with your own domain NSEC_ROOT_DOMAIN=plebes.ovh <-- replace with your own domain <-- replace with your own relay domain RELAY_DOMAIN=relay.plebes.ovh <-- replace with your own noauth domainay.plebes.ovh <-- replace with your own relay domain <-- replace with your own noauth domain NOAUTH_DOMAIN=noauth.plebes.ovh <-- replace with your own noauth domain NOAUTHD_DOMAIN=noauthd.plebes.ovh <-- replace with your own noauth domain
noauth
APP_WEB_PUSH_PUBKEY=BGVa7TMQus_KVn7tAwPkpwnU_bpr1i6B7D_3TT-AwkPlPd5fNcZsoCkJkJylVOn7kZ-9JZLpyOmt7U9rAtC-zeg <-- replace with your own web push public key APP_NOAUTHD_URL=https://$NOAUTHD_DOMAIN APP_DOMAIN=$NSEC_ROOT_DOMAIN APP_RELAY=wss://$RELAY_DOMAIN
noauthd
PUSH_PUBKEY=$APP_WEB_PUSH_PUBKEY PUSH_SECRET=_Sz8wgp56KERD5R4Zj5rX_owrWQGyHDyY4Pbf5vnFU0 <-- replace with your own web push private key ORIGIN=https://$NOAUTHD_DOMAIN DATABASE_URL=file:./prod.db BUNKER_NSEC=nsec1f43635rzv6lsazzsl3hfsrum9u8chn3pyjez5qx0ypxl28lcar2suy6hgn <-- replace with your the bunker nsec key BUNKER_RELAY=wss://$RELAY_DOMAIN BUNKER_DOMAIN=$NSEC_ROOT_DOMAIN BUNKER_ORIGIN=https://$NOAUTH_DOMAIN ```
Be aware of noauth and noauthd (the d letter). Next, save and quit. 4) You now need to modify the nostr.json file used for the NIP05 to indicate which relay your bunker will use. You need to set the bunker HEX PUBLIC KEY (I replaced the info with the one I get from NostrTool before) :
console nano easy-nip5/nostr.jsonconsole { "names": { "_": "ServerHexPubKey" }, "nip46": { "ServerHexPubKey": [ "wss://ReplaceWithYourRelayDomain" ] } }5) You can now run the docker compose file by running the command (first run can take a bit of time because the noauth container needs to build the npm project):
console $ docker compose up -d6) Before creating our first user into the Nostr Bunker, we need to test if all the required services are up. You should have :
noauth :
noauthd :
console CANNOT GET /https://noauthd.yourdomain.tld/name :
console { "error": "Specify npub" }https://yourdomain.tld/.well-known/nostr.json :
console { "names": { "_": "ServerHexPubKey" }, "nip46": { "ServerHexPubKey": [ "wss://ReplaceWithYourRelayDomain" ] } }If you have everything working, we can try to create a new user!
7) Connect to noauth and click on "Get Started" :
At the bottom the screen, click on "Sign up" :
Fill a username and click on "Create account" :
If everything has been correctly configured, you should see a pop message with "Account created for "XXXX" :
PS : to know if noauthd is well serving the nostr.json file, you can check this URL : https://yourdomain.tld/.well-known/nostr.json?name=YourUser You should see that the user has now NIP05/NIP46 entries :
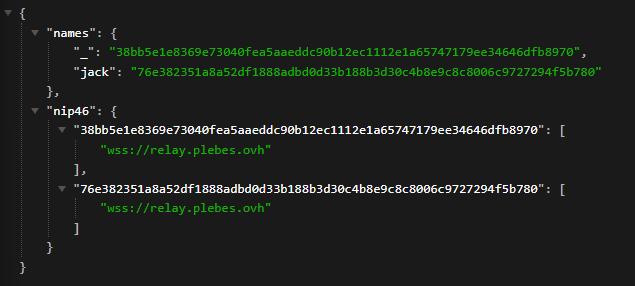
If the user creation failed, you'll see a red pop-up saying "Something went wrong!" :
To understand what happened, you need to inspect the web page to find the error :
For the example, I tried to recreate a user "jack" which has already been created. You may find a lot of different errors depending of the configuration you made. You can find that the relay is not reachable on w s s : / /, you can find that the noauthd is not accessible too, etc. Every answers should be in this place.
To completely finish the tests, you need to enable the browser notifications, otherwise you won't see the pop-up when you'll logon on Nostr web client, by clicking on "Enable background service" :
You need to click on allow notifications :
Should see this green confirmation popup on top right of your screen:
Well... Everything works now !
8) You try to use your brand new proxyfied npub by clicking on "Connect App" and buy copying your bunker URL :
You can now to for instance on Nostrudel Nostr web client to login with it. Select the relays you want (Popular is better ; if you don't have multiple relay configured on your Nostr profile, avoid "Login to use your relay") :
Click on "Sign in" :
Click on "Show Advanced" :
Click on "Nostr connect / Bunker" :
Paste your bunker URL and click on "Connect" :
The first time, tour browser (Chrome here) may blocks the popup, you need to allow it :
If the browser blocked the popup, NoStrudel will wait your confirmation to login :
You have to go back on your bunker URL to allow the NoStrudel connection request by clicking on on "Connect":
The first time connections may be a bit annoying with all the popup authorizations but once it's done, you can forget them it will connect without any issue. Congrats ! You are connected on NoStrudel with an npub proxyfied key !⚡

You can check to which applications you gave permissions and activity history in noauth by selecting your user. :
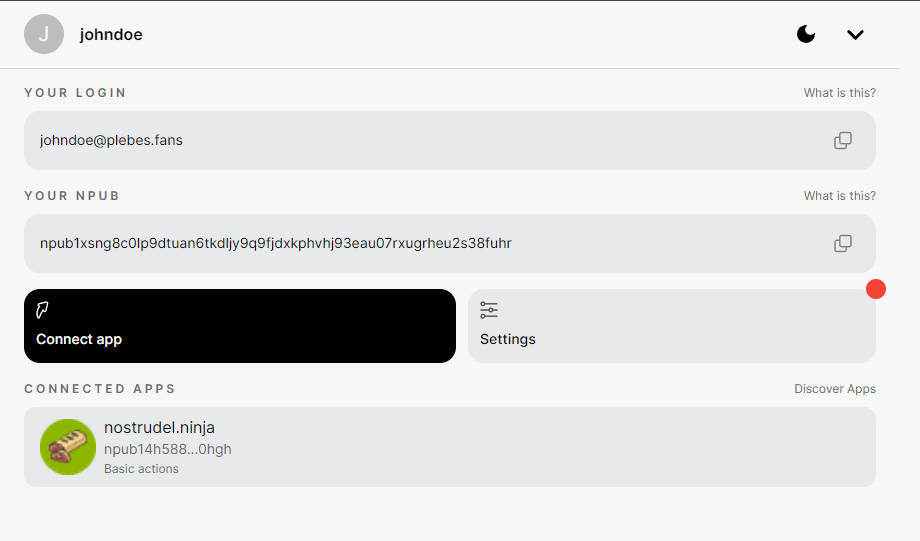
If you want to import your real Nostr profile, the one that everyone knows, you can import your nsec key by adding a new account and select "Import key" and adding your precious nsec key (reminder: your nsec key stays in your browser! The noauth provider won't have access to it!) :
You can see can that my profile picture has been retrieved and updated into noauth :
I can now use this new pubkey attached my nsec.app server to login in NoStrudel again :
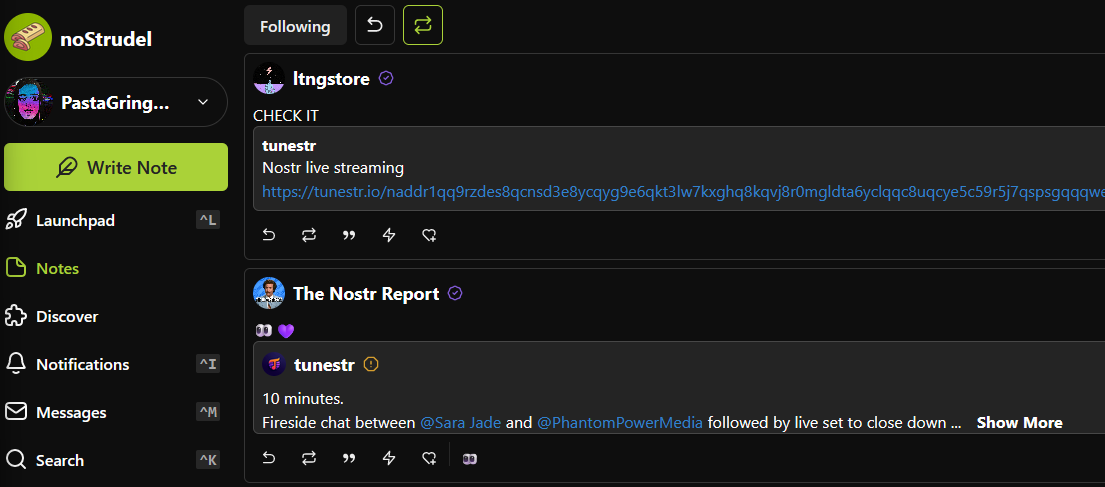
Accounts/keys management in noauthd You can list created keys in your bunkerd by doing these command (CTRL+C to exit) :
console $ docker exec -it noauthd node src/index.js list_names [ '/usr/local/bin/node', '/noauthd/src/index.js', 'list_names' ] 1 jack npub1hjdw2y0t44q4znzal2nxy7vwmpv3qwrreu48uy5afqhxkw6d2nhsxt7x6u 1708173927920n 2 peter npub1yp752u5tr5v5u74kadrzgfjz2lsmyz8dyaxkdp4e0ptmaul4cyxsvpzzjz 1708174748972n 3 john npub1xw45yuvh5c73sc5fmmc3vf2zvmtrzdmz4g2u3p2j8zcgc0ktr8msdz6evs 1708174778968n 4 johndoe npub1xsng8c0lp9dtuan6tkdljy9q9fjdxkphvhj93eau07rxugrheu2s38fuhr 1708174831905nIf you want to delete someone key, you have to do :
```console $ docker exec -it noauthd node src/index.js delete_name johndoe [ '/usr/local/bin/node', '/noauthd/src/index.js', 'delete_name', 'johndoe' ] deleted johndoe { id: 4, name: 'johndoe', npub: 'npub1xsng8c0lp9dtuan6tkdljy9q9fjdxkphvhj93eau07rxugrheu2s38fuhr', timestamp: 1708174831905n
$ docker exec -it noauthd node src/index.js list_names [ '/usr/local/bin/node', '/noauthd/src/index.js', 'list_names' ] 1 jack npub1hjdw2y0t44q4znzal2nxy7vwmpv3qwrreu48uy5afqhxkw6d2nhsxt7x6u 1708173927920n 2 peter npub1yp752u5tr5v5u74kadrzgfjz2lsmyz8dyaxkdp4e0ptmaul4cyxsvpzzjz 1708174748972n 3 john npub1xw45yuvh5c73sc5fmmc3vf2zvmtrzdmz4g2u3p2j8zcgc0ktr8msdz6evs 1708174778968n ```
It could be pretty easy to create a script to handle the management of keys but I think @Brugeman may create a web interface for that. Noauth is still very young, changes are committed everyday to fix/enhance the application! As """everything""" is stored locally on your browser, you have to clear the cache of you bunker noauth URL to clean everything. This Chome extension is very useful for that. Check these settings in the extension option :
You can now enjoy even more Nostr ⚡ See you soon in another Fractalized story!
-
 @ 1aa437b3:51119dbd
2024-07-15 02:11:13
@ 1aa437b3:51119dbd
2024-07-15 02:11:13I will confess, I went the pirate way with Jellyfinn and Plex and quickly got a letter from my ISP that I was naughty. So if I am going to do this legit, what is the best service? I do have a bunch of stuff on Amazon, and I trust they will stick around, but my god there is no rhyme or reason to organization. Apple... well it's Apple. And of course Google Play/Youtube.. and I don't know what others are out there.. but share what you use and why.. thanks, cheers!
originally posted at https://stacker.news/items/608576
-
 @ a012dc82:6458a70d
2024-07-15 01:10:38
@ a012dc82:6458a70d
2024-07-15 01:10:38Table Of Content
-
Content
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
Introduction
The emergence of Bitcoin options has provided a new tool for investors to hedge risks in the cryptocurrency market. In this article, we will explore the rise of Bitcoin options and their potential as a hedging tool.
The Emergence of Bitcoin Options
The growth of the cryptocurrency market has led to increased demand for new financial instruments to manage risk. Options provide a way for investors to manage risk by buying the right to buy or sell a specific asset at a specific price within a certain period. The introduction of Bitcoin options has given cryptocurrency investors a new tool to hedge risks and manage their portfolios.
According to data from Skew, a crypto derivatives analytics firm, Bitcoin options trading volume has grown significantly in recent years, with a daily trading volume of more than $2 billion in January 2021.
How Bitcoin Options Work
Options contracts give the buyer the right, but not the obligation, to buy or sell an underlying asset at a specific price (strike price) within a specific time period (expiration date). In the Bitcoin market, call options give the buyer the right to buy Bitcoin at a specific price, while put options give the buyer the right to sell Bitcoin at a specific price.
Bitcoin options can be settled in two ways: physically or cash-settled. Physical settlement means that the buyer of the option receives the underlying asset (in this case, Bitcoin) at the agreed-upon price. Cash settlement means that the buyer receives a cash payout equal to the difference between the strike price and the market price of Bitcoin at the time of expiration.
Bitcoin Options as a Tool for Hedging Risks
Bitcoin options can be used as a hedging tool to manage risk in a variety of ways. For example, a Bitcoin miner who is concerned about a drop in the price of Bitcoin can purchase put options to protect against price fluctuations. Institutional investors can use Bitcoin options to manage risk in their portfolios, while traders can use options to profit from volatility in the Bitcoin market.
Potential Drawbacks and Risks of Bitcoin Options
While Bitcoin options can be a useful tool for hedging risks, there are also potential drawbacks and risks to consider. One of the biggest risks is the volatility and uncertainty in the cryptocurrency market. The lack of regulation in the Bitcoin options market can also be a concern, as it can lead to fraud and other forms of market manipulation. Additionally, the misuse of options for speculative trading can result in significant losses for investors who are not using them appropriately.
Conclusion
Bitcoin options have emerged as a new tool for investors to manage risk in the cryptocurrency market. The growth of the cryptocurrency market and increased demand for risk management tools have driven the development of Bitcoin options. While Bitcoin options can be a useful tool for hedging risks, investors must be aware of the potential drawbacks and risks associated with this financial instrument. As the cryptocurrency market continues to evolve, it will be interesting to see how the use of Bitcoin options evolves as well.
FAQ
What are Bitcoin options? Bitcoin options are financial contracts that give the buyer the right, but not the obligation, to buy or sell Bitcoin at a specific price within a specific time period.
How do Bitcoin options work? Bitcoin options contracts give the buyer the right to buy or sell Bitcoin at a specific price within a specific time period. The buyer can choose to exercise this right or let the contract expire.
Who can use Bitcoin options? Bitcoin options can be used by a range of investors, from individual traders to institutional investors. However, due to the potential risks associated with Bitcoin options, investors should carefully consider their risk tolerance and investment goals before using them.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ f954303f:6e1b0af5
2024-07-02 14:20:09
@ f954303f:6e1b0af5
2024-07-02 14:20:09当年的计划生育的六条理由过时了吗?哪里放在今天站不住脚了?
一、计划生育有效地抑制了中国人口增长过快的势头。
二、计划生育促进了人民群众婚姻、生育、家庭观念的转变。
三、计划生育为中国经济的发展和人民生活水平的提高创造了有利条件。
四、计划生育促进了中国人口素质的提高和人的全面发展。
五、计划生育进一步解放了妇女生产力有利于妇女地位的改善和提高。
六、计划生育促进了中国农村消除贫困的进程。
详见:
中国的计划生育 (www.gov.cn) (https://www.gov.cn/zwgk/2005-06/02/content_3845.htm#)
submitted by /u/whyyoutouzhelele (https://www.reddit.com/user/whyyoutouzhelele)
[link] (https://www.reddit.com/r/China_irl/comments/1dtn0en/当年的计划生育的六条理由过时了吗哪里放在今天站不住脚了/)[comments] (https://www.reddit.com/r/China_irl/comments/1dtn0en/当年的计划生育的六条理由过时了吗哪里放在今天站不住脚了/)
#China_irl
https://www.reddit.com/r/China_irl/comments/1dtn0en/当年的计划生育的六条理由过时了吗哪里放在今天站不住脚了/
-
 @ 3cd2ea88:bafdaceb
2024-07-15 00:10:09
@ 3cd2ea88:bafdaceb
2024-07-15 00:10:09🌟 Stai cercando un'opportunità di guadagno eccezionale? Bitget ha appena lanciato la fase 1 del suo Carnevale Estivo su PoolX, permettendoti di puntare BTC, ETH e USDT per estrarre BGB! Con premi distribuiti ogni ora, non c'è momento migliore per entrare in azione.
💰 Punta le tue criptovalute e guadagna token popolari:
Staking BTC ed ETH: 25.000 BGB per pool! Staking USDT: 50.000 BGB in palio! Non perdere questa opportunità esclusiva! Iscriviti ora su Bitget con il nostro referral e inizia a guadagnare subito! 🤑
🔗 Iscriviti qui e inizia a puntare! https://bonus.bitget.com/U1JNEK
-
 @ ee11a5df:b76c4e49
2023-11-09 05:20:37
@ ee11a5df:b76c4e49
2023-11-09 05:20:37A lot of terms have been bandied about regarding relay models: Gossip relay model, outbox relay model, and inbox relay model. But this term "relay model" bothers me. It sounds stuffy and formal and doesn't actually describe what we are talking about very well. Also, people have suggested maybe there are other relay models. So I thought maybe we should rethink this all from first principles. That is what this blog post attempts to do.
Nostr is notes and other stuff transmitted by relays. A client puts an event onto a relay, and subsequently another client reads that event. OK, strictly speaking it could be the same client. Strictly speaking it could even be that no other client reads the event, that the event was intended for the relay (think about nostr connect). But in general, the reason we put events on relays is for other clients to read them.
Given that fact, I see two ways this can occur:
1) The reader reads the event from the same relay that the writer wrote the event to (this I will call relay rendezvous), 2) The event was copied between relays by something.
This second solution is perfectly viable, but it less scalable and less immediate as it requires copies which means that resources will be consumed more rapidly than if we can come up with workable relay rendezvous solutions. That doesn't mean there aren't other considerations which could weigh heavily in favor of copying events. But I am not aware of them, so I will be discussing relay rendezvous.
We can then divide the relay rendezvous situation into several cases: one-to-one, one-to-many, and one-to-all, where the many are a known set, and the all are an unbounded unknown set. I cannot conceive of many-to-anything for nostr so we will speak no further of it.
For a rendezvous to take place, not only do the parties need to agree on a relay (or many relays), but there needs to be some way that readers can become aware that the writer has written something.
So the one-to-one situation works out well by the writer putting the message onto a relay that they know the reader checks for messages on. This we call the INBOX model. It is akin to sending them an email into their inbox where the reader checks for messages addressed to them.
The one-to-(known)-many model is very similar, except the writer has to write to many people's inboxes. Still we are dealing with the INBOX model.
The final case, one-to-(unknown)-all, there is no way the writer can place the message into every person's inbox because they are unknown. So in this case, the writer can write to their own OUTBOX, and anybody interested in these kinds of messages can subscribe to the writer's OUTBOX.
Notice that I have covered every case already, and that I have not even specified what particular types of scenarios call for one-to-one or one-to-many or one-to-all, but that every scenario must fit into one of those models.
So that is basically it. People need INBOX and OUTBOX relays and nothing else for relay rendezvous to cover all the possible scenarios.
That is not to say that other kinds of concerns might not modulate this. There is a suggestion for a DM relay (which is really an INBOX but with a special associated understanding), which is perfectly fine by me. But I don't think there are any other relay models. There is also the case of a live event where two parties are interacting over the same relay, but in terms of rendezvous this isn't a new case, it is just that the shared relay is serving as both parties' INBOX (in the case of a closed chat) and/or both parties' OUTBOX (in the case of an open one) at the same time.
So anyhow that's my thinking on the topic. It has become a fairly concise and complete set of concepts, and this makes me happy. Most things aren't this easy.
-
 @ 9ca0bd74:4052340b
2024-07-14 22:59:01
@ 9ca0bd74:4052340b
2024-07-14 22:59:01Step 1:
find the RSS feeds you want to follow
(Right click on the website's page, and choose Page Source. In the new window that appears, use the “find” feature and search 'rss')
some websites will have a standard format eg. substack add '/feed' at the end of the URL. You can even have RSS feeds of YouTube channels;)
Step 2:
Go to https://atomstr.data.haus/
Add at least one of the following relays to your nostr account to read the feeds:
wss://nostr.data.haus
wss://relayable.org
wss://relay.highlighter.com
Step 3:
add your RSS feed URLs to atomstr
(you can also 'find' existing feeds people have already added to atmostr)
Step 4:
open the link to the generated RSS nostr accounts in Nostrudel and Follow
Step 5:
Clicking on Follow in Nostrudel also brings up Lists you have created to sort your RSS feeds

or select New List to make a ..new list
DONE
(these lists will also show up on other clients that support Lists eg Amethyst where it will show up on homescreen clicking on All Follows dropdown)
-
 @ 6c8c7979:15595f3e
2024-07-14 22:44:46
@ 6c8c7979:15595f3e
2024-07-14 22:44:46In 1917, a public call was made by a group of "Independent Artists" stating: "Any person with $6 can send in a work to be exhibited." On the day of the exhibition, everyone was surprised to find a urinal signed "R.mutt" among the entries, presented under the title "Fountain". The contributor of the urinal paid the $6 fee but their name was not included in the list of participants; the urinal was rejected by the exhibition. However, this urinal, known as "Fountain," became one of the pivotal points in art history.
Within the pages of art history, amidst the beauty of paintings and artworks, there is a disturbing page featuring a photograph of a ready-made urinal. It is known that the piece was submitted to an exhibition by Marcel Duchamp (1887-1968), who was part of the Independent Artists, but the exhibition committee found it disagreeable. Duchamp decided to play with them and handed in his work titled "Fountain" under a pseudonym.
At that time, World War I had destroyed everything, leaving Europe suffering from the bitter aftermath. It was a period of violent change, where many artists viewed the decision to go to war as an expression of rationalism—believing that reason had led to the decision to wage war under the pretense that it would bring about positive societal change in Europe. However, after the devastation, destruction, and massacres, everything became clear: artists came to detest everything associated with that period dominated by rationalistic thought and material culture. Various strange and divergent movements began to emerge in art and literature circles, equating their followers between the war that ravaged and the conviction that values associated with pre-war art were largely corrupt.
$$The Dada movement... art against art$$
A photograph of the urinal submitted by Marcel Duchamp in 1917
On an evening in 1916, in the one country that had not directly fallen into the grips of war, Switzerland, which served as a refuge for many artists and intellectuals, the Dada movement was born in a café in Zurich on February 8th. Their presence in Zurich was due to Switzerland's neutral stance during a time when their homelands were engulfed in the turmoil of World War I. A group of artists and poets, all around their twenties, decided to choose a name that reflected their approach to literature, art, music, and thought. They randomly opened a linguistic dictionary, Larousse, and the first word that caught their eye was "Dada," which meant nothing and was just a linguistic root. They chose it as the name for their movement.
The Dada movement quickly spread across Europe and America. A French literary historian said, "There has never been an intellectual movement more difficult to attribute to a specific country than Dadaism. It was a movement whose circumstances were inherently global, and all conditions were ripe for its reception, which explains its rapid spread." Tristan Tzara, one of the movement's founders, remarked, "To understand Dadaism, and how it came to be, one must imagine the mental state of a group of young people in that prison that was Switzerland during World War I, while also considering the level that art and literature had reached during that period.
"In the years 1916 and 1917, it seemed to us that the war would continue forever, and we saw no end to it... Our desire for life was immense, and our rejection and lack of taste for all the colors of civilization called modern, even at its core... To logic and to language... Our rejection took the form of mockery and contempt... And we mustn't forget that the real human essence in literature was covered by a false emotional layer, and that taste, or bourgeois taste, dominated all artistic and literary fields."
Dadaism specifically saw itself concerned with reenacting the psychological disorder caused by World War I. - David Hopkins

Marcel Duchamp's work titled "L.H.O.O.Q." (1921/1964), manufactured ready-made, consists of 152 marble cubes shaped like sugar cubes + a thermometer + a cuttlefish bone in a birdcage.The Dada movement was born in this manner, deliberately concerned with mocking the very notion of meaning itself and rejecting all fixed interpretations of things. As one Dada poet put it:
Dada does not speak and has no fixed ideas
Dada does not catch flies
Dada has existed since the beginning
And the Virgin Mary was a Dadaist
Dada against the high cost of living
Dada against the future
Dada is dead
Dada is foolish
Dada doubts everything
Do not trust in Dada
Dada is the greatest trickster of this age
Dada has no meaning
Dada is a state within a state
This poem rejects the confinement of meaning to anything specific, reflecting the Dadaists' principle. Marcel Duchamp, one of the foremost pioneers of the Dada movement, allowed for all interpretations of his art, even those considered far-fetched. Their philosophy was that to confront the chaos and destruction that had befallen the world, they needed to create art that contradicted art itself, hence they coined the motto "art against art." They famously proclaimed, "everything is equal, therefore nothing is everything."

Exhibition of the First International Dada Fair, Berlin, June 1920David Hopkins says about Dadaism: "It sought to undermine traditional bourgeois ideas in art. Mostly, the movement boldly opposed art, and more importantly, its participants like Marcel Duchamp, Francis Picabia, Tristan Tzara, Hans Arp, Kurt Schwitters, Raoul Hausmann, expressed their love for irony and audacity in response to the world's madness, while World War I raged in Europe."
"They strongly disliked bourgeois values and the professional tint of art: 'If oil painting and bronze casting are synonyms for the opulent houses of the aristocratic class, then Dada followers would collect new forms of paper cutouts or existing items. If poetry is synonymous with polished awareness, they will pull their arms and dismantle them and redirect them into forms of chatter and spells. They were a united group in their hatred of professional artistry, seeing themselves as cultural saboteurs, but not necessarily rejecting art itself, but rather the manner in which art served as a particular perspective on human nature.'"
When we felt disgusted by the brutality of World War I, which erupted in 1914, we devoted ourselves to the arts in Zurich. While the sounds of cannons echoed in the distance, we sang, painted collages, and wrote poetry with all our might. We were searching for an art based on foundations to heal the madness of this era. We were looking for a new system of things that would restore balance between heaven and hell.
(Arp)
$$Marcel Duchamp.. Ideas are more important than craftsmanship.$$
Ready-made works by Marcel Duchamp, on the right "Bottle Rack" 1914-1964, and on the left "Bicycle Wheel" 1913.Marcel Duchamp's "Fountain," which he exhibited, shook established art values and caused a significant shock—not just because it was a urinal, but because it was ready-made and not made by Duchamp himself. This meant the artwork could be easily reproduced, diminishing its uniqueness. Duchamp intended exactly this, aiming to sever craftsmanship from visual art and emphasizing that ideas should replace manual skill as the fundamental components of artworks. David Hopkins states:
"Duchamp formulated what he termed an anti-visual stance in relation to the visual innovations introduced into French art by Matisse on the one hand and Cubism on the other. Duchamp's antipathy to art that appeals to the eye alone, to the exclusion of the mind, was a satire on the effects of the machine age on the human psyche"... "Duchamp's aversion to craftsmanship's association with visual art and his belief that ideas should replace manual skill as the essential components of artworks led him to select ready-made objects as artistic propositions."
Duchamp's work raised fundamental questions about the nature of art—what constitutes art and what can lie beyond its boundaries? These questions sparked extensive debates challenging previous definitions of art. Duchamp shifted focus away from the artwork itself to highlight the concepts and ideas it conveys. Consequently, critics view all art post-Duchamp as conceptual art; he shattered the concept of the uniqueness of an artwork, as his works do not need to be physically exhibited and can be reproduced anywhere with ease.
-
 @ b12b632c:d9e1ff79
2023-08-08 00:02:31
@ b12b632c:d9e1ff79
2023-08-08 00:02:31"Welcome to the Bitcoin Lightning Bolt Card, the world's first Bitcoin debit card. This revolutionary card allows you to easily and securely spend your Bitcoin at lightning compatible merchants around the world." Bolt Card
I discovered few days ago the Bolt Card and I need to say that's pretty amazing. Thinking that we can pay daily with Bitcoin Sats in the same way that we pay with our Visa/Mastecard debit cards is really something huge⚡(based on the fact that sellers are accepting Bitcoins obviously!)
To use Bolt Card you have three choices :
- Use their (Bolt Card) own Bolt Card HUB and their own BTC Lightning node
- Use your own self hosted Bolt Card Hub and an external BTC Lightning node
- Use your own self hosted Bolt Card Hub and your BTC Lightning node (where you shoud have active Lightning channels)
⚡ The first choice is the quickiest and simpliest way to have an NFC Bolt Card. It will take you few seconds (for real). You'll have to wait much longer to receive your NFC card from a website where you bought it than configure it with Bolt Card services.
⚡⚡ The second choice is pretty nice too because you won't have a VPS + to deal with all the BTC Lightnode stuff but you'll use an external one. From the Bolt Card tutorial about Bolt Card Hub, they use a Lightning from voltage.cloud and I have to say that their services are impressive. In few seconds you'll have your own Lightning node and you'll be able to configure it into the Bolt Card Hub settings. PS : voltage.cloud offers 7 trial days / 20$ so don't hesitate to try it!
⚡⚡⚡ The third one is obvisouly a bit (way) more complex because you'll have to provide a VPS + Bitcoin node and a Bitcoin Lightning Node to be able to send and receive Lightning payments with your Bolt NFC Card. So you shoud already have configured everything by yourself to follow this tutorial. I will show what I did for my own installation and all my nodes (BTC & Lightning) are provided by my home Umbrel node (as I don't want to publish my nodes directly on the clearnet). We'll see how to connect to the Umbrel Lighting node later (spoiler: Tailscale).
To resume in this tutorial, I have :
- 1 Umbrel node (rpi4b) with BTC and Lightning with Tailscale installed.
- 1 VPS (Virtual Personal Server) to publish publicly the Bolt Card LNDHub and Bolt Card containers configured the same way as my other containers (with Nginx Proxy Manager)
Ready? Let's do it ! ⚡
Configuring Bolt Card & Bolt Card LNDHub
Always good to begin by reading the bolt card-lndhub-docker github repo. To a better understading of all the components, you can check this schema :
We'll not use it as it is because we'll skip the Caddy part because we already use Nginx Proxy Manager.
To begin we'll clone all the requested folders :
git clone https://github.com/boltcard/boltcard-lndhub-docker bolthub cd bolthub git clone https://github.com/boltcard/boltcard-lndhub BoltCardHub git clone https://github.com/boltcard/boltcard.git git clone https://github.com/boltcard/boltcard-groundcontrol.git GroundControlPS : we won't see how to configure GroundControl yet. This article may be updated later.
We now need to modify the settings file with our own settings :
mv .env.example .env nano .envYou need to replace "your-lnd-node-rpc-address" by your Umbrel TAILSCALE ip address (you can find your Umbrel node IP from your Tailscale admin console):
``` LND_IP=your-lnd-node-rpc-address # <- UMBREL TAILSCALE IP ADDRESS LND_GRPC_PORT=10009 LND_CERT_FILE=tls.cert LND_ADMIN_MACAROON_FILE=admin.macaroon REDIS_PASSWORD=random-string LND_PASSWORD=your-lnd-node-unlock-password
docker-compose.yml only
GROUNDCONTROL=ground-control-url
docker-compose-groundcontrol.yml only
FCM_SERVER_KEY=hex-encoded APNS_P8=hex-encoded APNS_P8_KID=issuer-key-which-is-key-ID-of-your-p8-file APPLE_TEAM_ID=team-id-of-your-developer-account BITCOIN_RPC=bitcoin-rpc-url APNS_TOPIC=app-package-name ```
We now need to generate an AES key and insert it into the "settings.sql" file :
```
hexdump -vn 16 -e '4/4 "%08x" 1 "\n"' /dev/random 19efdc45acec06ad8ebf4d6fe50412d0 nano settings.sql ```
- Insert the AES between ' ' right from 'AES_DECRYPT_KEY'
- Insert your domain or subdomain (subdomain in my case) host between ' ' from 'HOST_DOMAIN'
- Insert your Umbrel tailscale IP between ' ' from 'LN_HOST'
Be aware that this subdomain won't be the LNDHub container (boltcard_hub:9002) but the Boltcard container (boltcard_main:9000)
``` \c card_db;
DELETE FROM settings;
-- at a minimum, the settings marked 'set this' must be set for your system -- an explanation for each of the bolt card server settings can be found here -- https://github.com/boltcard/boltcard/blob/main/docs/SETTINGS.md
INSERT INTO settings (name, value) VALUES ('LOG_LEVEL', 'DEBUG'); INSERT INTO settings (name, value) VALUES ('AES_DECRYPT_KEY', '19efdc45acec06ad8ebf4d6fe50412d0'); -- set this INSERT INTO settings (name, value) VALUES ('HOST_DOMAIN', 'sub.domain.tld'); -- set this INSERT INTO settings (name, value) VALUES ('MIN_WITHDRAW_SATS', '1'); INSERT INTO settings (name, value) VALUES ('MAX_WITHDRAW_SATS', '1000000'); INSERT INTO settings (name, value) VALUES ('LN_HOST', ''); -- set this INSERT INTO settings (name, value) VALUES ('LN_PORT', '10009'); INSERT INTO settings (name, value) VALUES ('LN_TLS_FILE', '/boltcard/tls.cert'); INSERT INTO settings (name, value) VALUES ('LN_MACAROON_FILE', '/boltcard/admin.macaroon'); INSERT INTO settings (name, value) VALUES ('FEE_LIMIT_SAT', '10'); INSERT INTO settings (name, value) VALUES ('FEE_LIMIT_PERCENT', '0.5'); INSERT INTO settings (name, value) VALUES ('LN_TESTNODE', ''); INSERT INTO settings (name, value) VALUES ('FUNCTION_LNURLW', 'ENABLE'); INSERT INTO settings (name, value) VALUES ('FUNCTION_LNURLP', 'ENABLE'); INSERT INTO settings (name, value) VALUES ('FUNCTION_EMAIL', 'DISABLE'); INSERT INTO settings (name, value) VALUES ('AWS_SES_ID', ''); INSERT INTO settings (name, value) VALUES ('AWS_SES_SECRET', ''); INSERT INTO settings (name, value) VALUES ('AWS_SES_EMAIL_FROM', ''); INSERT INTO settings (name, value) VALUES ('EMAIL_MAX_TXS', ''); INSERT INTO settings (name, value) VALUES ('FUNCTION_LNDHUB', 'ENABLE'); INSERT INTO settings (name, value) VALUES ('LNDHUB_URL', 'http://boltcard_hub:9002'); INSERT INTO settings (name, value) VALUES ('FUNCTION_INTERNAL_API', 'ENABLE'); ```
You now need to get two files used by Bolt Card LND Hub, the admin.macaroon and tls.cert files from your Umbrel BTC Ligtning node. You can get these files on your Umbrel node at these locations :
/home/umbrel/umbrel/app-data/lightning/data/lnd/tls.cert /home/umbrel/umbrel/app-data/lightning/data/lnd/data/chain/bitcoin/mainnet/admin.macaroonYou can use either WinSCP, scp or ssh to copy these files to your local workstation and copy them again to your VPS to the root folder "bolthub".
You shoud have all these files into the bolthub directory :
johndoe@yourvps:~/bolthub$ ls -al total 68 drwxrwxr-x 6 johndoe johndoe 4096 Jul 30 00:06 . drwxrwxr-x 3 johndoe johndoe 4096 Jul 22 00:52 .. -rw-rw-r-- 1 johndoe johndoe 482 Jul 29 23:48 .env drwxrwxr-x 8 johndoe johndoe 4096 Jul 22 00:52 .git -rw-rw-r-- 1 johndoe johndoe 66 Jul 22 00:52 .gitignore drwxrwxr-x 11 johndoe johndoe 4096 Jul 22 00:52 BoltCardHub -rw-rw-r-- 1 johndoe johndoe 113 Jul 22 00:52 Caddyfile -rw-rw-r-- 1 johndoe johndoe 173 Jul 22 00:52 CaddyfileGroundControl drwxrwxr-x 6 johndoe johndoe 4096 Jul 22 00:52 GroundControl -rw-rw-r-- 1 johndoe johndoe 431 Jul 22 00:52 GroundControlDockerfile -rw-rw-r-- 1 johndoe johndoe 1913 Jul 22 00:52 README.md -rw-rw-r-- 1 johndoe johndoe 293 May 6 22:24 admin.macaroon drwxrwxr-x 16 johndoe johndoe 4096 Jul 22 00:52 boltcard -rw-rw-r-- 1 johndoe johndoe 3866 Jul 22 00:52 docker-compose-groundcontrol.yml -rw-rw-r-- 1 johndoe johndoe 2985 Jul 22 00:57 docker-compose.yml -rw-rw-r-- 1 johndoe johndoe 1909 Jul 29 23:56 settings.sql -rw-rw-r-- 1 johndoe johndoe 802 May 6 22:21 tls.certWe need to do few last tasks to ensure that Bolt Card LNDHub will work perfectly.
It's maybe already the case on your VPS but your user should be member of the docker group. If not, you can add your user by doing :
sudo groupadd docker sudo usermod -aG docker ${USER}If you did these commands, you need to logout and login again.
We also need to create all the docker named volumes by doing :
docker volume create boltcard_hub_lnd docker volume create boltcard_redisConfiguring Nginx Proxy Manager to proxify Bolt Card LNDHub & Boltcard
You need to have followed my previous blog post to fit with the instructions above.
As we use have the Bolt Card LNDHub docker stack in another directory than we other services and it has its own docker-compose.yml file, we'll have to configure the docker network into the NPM (Nginx Proxy Manager) docker-compose.yml to allow NPM to communicate with the Bolt Card LNDHub & Boltcard containers.
To do this we need to add these lines into our NPM external docker-compose (not the same one that is located into the bolthub directory, the one used for all your other containers) :
nano docker-compose.ymlnetworks: bolthub_boltnet: name: bolthub_boltnet external: trueBe careful, "bolthub" from "bolthub_boltnet" is based on the directory where Bolt Card LNDHub Docker docker-compose.yml file is located.
We also need to attach this network to the NPM container :
nginxproxymanager: container_name: nginxproxymanager image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt networks: - fractalized - bolthub_boltnetYou can now recreate the NPM container to attach the network:
docker compose up -dNow, you'll have to create 2 new Proxy Hosts into NPM admin UI. First one for your domain / subdomain to the Bolt Card LNDHub GUI (boltcard_hub:9002) :
And the second one for the Boltcard container (boltcard_main:9000).
In both Proxy Host I set all the SSL options and I use my wildcard certificate but you can generate one certificate for each Proxy Host with Force SSL, HSTS enabled, HTTP/2 Suppot and HSTS Subdomains enabled.
Starting Bolt Card LNDHub & BoltCard containers
Well done! Everything is setup, we can now start the Bolt Card LNDHub & Boltcard containers !
You need to go again to the root folder of the Bolt Card LNDHub projet "bolthub" and start the docker compose stack. We'll begin wihtout a "-d" to see if we have some issues during the containers creation :
docker compose upI won't share my containers logs to avoid any senstive information disclosure about my Bolt Card LNDHub node, but you can see them from the Bolt Card LNDHub Youtube video (link with exact timestamp where it's shown) :
If you have some issues about files mounting of admin.macaroon or tls.cert because you started the docker compose stack the first time without the files located in the bolthub folder do :
docker compose down && docker compose upAfter waiting few seconds/minutes you should go to your Bolt Card LNDHub Web UI domain/sudomain (created earlier into NPM) and you should see the Bolt Card LNDHub Web UI :
if everything is OK, you now run the containers in detached mode :
docker compose up -dVoilààààà ⚡
If you need to all the Bolt Card LNDHub logs you can use :
docker compose logs -f --tail 30You can now follow the video from Bolt Card to configure your Bolt Card NFC card and using your own Bolt Card LNDHub :
~~PS : there is currently a bug when you'll click on "Connect Bolt Card" from the Bold Card Walle app, you might have this error message "API error: updateboltcard: enable_pin is not a valid boolean (code 6)". It's a know issue and the Bolt Card team is currently working on it. You can find more information on their Telegram~~
Thanks to the Bolt Card, the issue has been corrected : changelog
See you soon in another Fractalized story!
-
 @ c11cf5f8:4928464d
2024-07-14 21:20:47
@ c11cf5f8:4928464d
2024-07-14 21:20:47I've been meditating for years and I think am out of sync with my body 😅 need to move more!
Any valid suggestion will be highly zapped ⚡️
🧡
originally posted at https://stacker.news/items/608508
-
 @ ee11a5df:b76c4e49
2023-07-29 03:27:23
@ ee11a5df:b76c4e49
2023-07-29 03:27:23Gossip: The HTTP Fetcher
Gossip is a desktop nostr client. This post is about the code that fetches HTTP resources.
Gossip fetches HTTP resources. This includes images, videos, nip05 json files, etc. The part of gossip that does this is called the fetcher.
We have had a fetcher for some time, but it was poorly designed and had problems. For example, it was never expiring items in the cache.
We've made a lot of improvements to the fetcher recently. It's pretty good now, but there is still room for improvement.
Caching
Our fetcher caches data. Each URL that is fetched is hashed, and the content is stored under a file in the cache named by that hash.
If a request is in the cache, we don't do an HTTP request, we serve it directly from the cache.
But cached data gets stale. Sometimes resources at a URL change. We generally check resources again after three days.
We save the server's ETag value for content, and when we check the content again we supply an If-None-Match header with the ETag so the server could respond with 304 Not Modified in which case we don't need to download the resource again, we just bump the filetime to now.
In the event that our cache data is stale, but the server gives us an error, we serve up the stale data (stale is better than nothing).
Queueing
We used to fire off HTTP GET requests as soon as we knew that we needed a resource. This was not looked on too kindly by servers and CDNs who were giving us either 403 Forbidden or 429 Too Many Requests.
So we moved into a queue system. The host is extracted from each URL, and each host is only given up to 3 requests at a time. If we want 29 images from the same host, we only ask for three, and the remaining 26 remain in the queue for next time. When one of those requests completes, we decrement the host load so we know that we can send it another request later.
We process the queue in an infinite loop where we wait 1200 milliseconds between passes. Passes take time themselves and sometimes must wait for a timeout. Each pass fetches potentially multiple HTTP resources in parallel, asynchronously. If we have 300 resources at 100 different hosts, three per host, we could get them all in a single pass. More likely a bunch of resources are at the same host, and we make multiple passes at it.
Timeouts
When we fetch URLs in parallel asynchronously, we wait until all of the fetches complete before waiting another 1200 ms and doing another loop. Sometimes one of the fetches times out. In order to keep things moving, we use short timeouts of 10 seconds for a connect, and 15 seconds for a response.
Handling Errors
Some kinds of errors are more serious than others. When we encounter these, we sin bin the server for a period of time where we don't try fetching from it until a specified period elapses.
-
 @ ee11a5df:b76c4e49
2023-07-29 03:13:59
@ ee11a5df:b76c4e49
2023-07-29 03:13:59Gossip: Switching to LMDB
Unlike a number of other nostr clients, Gossip has always cached events and related data in a local data store. Up until recently, SQLite3 has served this purpose.
SQLite3 offers a full ACID SQL relational database service.
Unfortunately however it has presented a number of downsides:
- It is not as parallel as you might think.
- It is not as fast as you might hope.
- If you want to preserve the benefit of using SQL and doing joins, then you must break your objects into columns, and map columns back into objects. The code that does this object-relational mapping (ORM) is not trivial and can be error prone. It is especially tricky when working with different types (Rust language types and SQLite3 types are not a 1:1 match).
- Because of the potential slowness, our UI has been forbidden from direct database access as that would make the UI unresponsive if a query took too long.
- Because of (4) we have been firing off separate threads to do the database actions, and storing the results into global variables that can be accessed by the interested code at a later time.
- Because of (4) we have been caching database data in memory, essentially coding for yet another storage layer that can (and often did) get out of sync with the database.
LMDB offers solutions:
- It is highly parallel.
- It is ridiculously fast when used appropriately.
- Because you cannot run arbitrary SQL, there is no need to represent the fields within your objects separately. You can serialize/deserialize entire objects into the database and the database doesn't care what is inside of the blob (yes, you can do that into an SQLite field, but if you did, you would lose the power of SQL).
- Because of the speed, the UI can look stuff up directly.
- We no longer need to fork separate threads for database actions.
- We no longer need in-memory caches of data. The LMDB data is already in-memory (it is memory mapped) so we just access it directly.
The one obvious downside is that we lose SQL. We lose the query planner. We cannot ask arbitrary question and get answers. Instead, we have to pre-conceive of all the kinds of questions we want to ask, and we have to write code that answers them efficiently. Often this involves building and maintaining indices.
Indices
Let's say I want to look at fiatjaf's posts. How do I efficiently pull out just his recent feed-related events in reverse chronological order? It is easy if we first construct the following index
key: EventKind + PublicKey + ReverseTime value: Event Id
In the above, '+' is just a concatenate operator, and ReverseTime is just some distant time minus the time so that it sorts backwards.
Now I just ask LMDB to start from (EventKind=1 + PublicKey=fiatjaf + now) and scan until either one of the first two fields change, or more like the time field gets too old (e.g. one month ago). Then I do it again for the next event kind, etc.
For a generalized feed, I have to scan a region for each person I follow.
Smarter indexes can be imagined. Since we often want only feed-related event kinds, that can be implicit in an index that only indexes those kinds of events.
You get the idea.
A Special Event Map
At first I had stored events into a K-V database under the Id of the event. Then I had indexes on events that output a set of Ids (as in the example above).
But when it comes to storing and retrieving events, we can go even faster than LMDB.
We can build an append-only memory map that is just a sequence of all the events we have, serialized, and in no particular order. Readers do not need a lock and multiple readers can read simultaneously. Writers will need to acquire a lock to append to the map and there may only be one writer at a time. However, readers can continue reading even while a writer is writing.
We can then have a K-V database that maps Id -> Offset. To get the event you just do a direct lookup in the event memory map at that offset.
The real benefit comes when we have other indexes that yield events, they can yield offsets instead of ids. Then we don't need to do a second lookup from the Id to the Event, we can just look directly at the offset.
Avoiding deserialization
Deserialization has a price. Sometimes it requires memory allocation (if the object is not already linear, e.g. variable lengthed data like strings and vectors are allocated on the heap) which can be very expensive if you are trying to scan 150,000 or so events.
We serialize events (and other objects where we can) with a serialization library called speedy. It does its best to preserve the data much like it is represented in memory, but linearized. Because events start with fixed-length fields, we know the offset into the serialized event where these first fields occur and we can directly extract the value of those fields without deserializing the data before it.
This comes in useful whenever we need to scan a large number of events. Search is the one situation where I know that we must do this. We can search by matching against the content of every feed-related event without fully deserialing any of them.
-
 @ ee11a5df:b76c4e49
2023-07-29 02:52:13
@ ee11a5df:b76c4e49
2023-07-29 02:52:13Gossip: Zaps
Gossip is a desktop nostr client. This post is about the code that lets users send lightning zaps to each other (NIP-57).
Gossip implemented Zaps initially on 20th of June, 2023.
Gossip maintains a state of where zapping is at, one of: None, CheckingLnurl, SeekingAmount, LoadingInvoice, and ReadyToPay.
When you click the zap lightning bolt icon, Gossip moves to the CheckingLnurl state while it looks up the LN URL of the user.
If this is successful, it moves to the SeekingAmount state and presents amount options to the user.
Once a user chooses an amount, it moves to the LoadingInvoice state where it interacts with the lightning node and receives and checks an invoice.
Once that is complete, it moves to the ReadyToPay state, where it presents the invoice as a QR code for the user to scan with their phone. There is also a copy button so they can pay it from their desktop computer too.
Gossip also loads zap receipt events and associates them with the event that was zapped, tallying a zap total on that event. Gossip is unfortunately not validating these receipts very well currently, so fake zap receipts can cause an incorrect total to show. This remains an open issue.
Another open issue is the implementation of NIP-46 Nostr Connect and NIP-47 Wallet Connect.
-
 @ c5f77418:90f86d12
2024-07-14 16:50:14
@ c5f77418:90f86d12
2024-07-14 16:50:14U(zla)/acc is obfuscation as defence against Panoptic-Technocapital.
Attention-hacking is the name of the game. Cyberspace is a battle for attention using Anti-Ghazalian spiritual hermeneutics to attack the lower self using the promises of comfort, convenience and familiarity. All that the masters of the past had warned against have been institutionalised and baked into the largest platforms billions enter into unwittingly. This genie of spiritual decay has been loose not recently, but for decades, whatever chance of resisting it, brute-forcing it into a marginalised hobby has long since departed.
This circus, this asylum metastasizing through cyberspace is deployed as a weapon of mass distraction often by highly professional and dedicated large nation-state actors to achieve strategic ends. All the while, a higher network of surveillance watches unerringly which way the data, the spice flows. Which way does it bend, twist and strike. Attention-hacking is an exercise in surveillance and behavioural engineering. Engineering behaviour is not possible without data, without wilful and deeply invested participation on the part of subjects, without the time that is sunk into the whole process by enthusiastic partisans of cyber-asylums.
Panoptic-Technocapital is a more grounded and sober understanding of how technocapital operates - it understands that mundane but layered networks of bureucracy, technocratic agencies and the great post 9/11 intelligence empires in the shadows have just as much of a hand in building the Machine God as hyper-financialization and semiconductor manufacturing. It is also intimately and closely tied, the origins of much of what we take for granted in our civilian architecture of cyberspace has roots in the militarism of 20th century meatspace geopolitical intrigue. The Cypherpunks romanticised in part the creation of Cyber as an antithesis to meatspace not fully owing confronting its debts to the escalating and accelerating dynamics of intra-spook competition between the great metallic and clanking industrialised empires of the last century.
Liberalism in its intellectual genesis owed much to philosophers and men who were steeped in an entirely different moral code and spiritual psychology centuries ago now. The deism of early liberal theorists would in today wastelands, would likely resemble deep organic faith - time has snapped and wrought all our assumptions about the type of religious sentiments underlying early and proto-liberal thinking. Liberalism is nothing really but an extension of Christian heresies in response to unending sectarian conflict.
Today, however to call what we are experiencing as that same "liberalism" is foolishness. Today, what we refer to as "liberalism" is just an aesthetic wrapper, a charade, a shared delusion spread amongst the masses to hide something colder. A vast network of State-backed agencies, affiliated organisations in finance and pharmaceutical research, healthcare, commerce intimately tied with intelligence agencies that have formed an ossified, largely uncontested and reasonably stable layer of Administration that keeps marching along no matter who or which party is in charge.
U(zla)-acc is an acceptance of this process, it is an invitation to understand that we have bought our tickets and now must see where the train ends up, not much can be done to course-correct. We are heading towards Hyper-Intelligence with the promise that disease can be predicted and prevented but with the costs of precognitive criminalisation (precrime).
Legible Hyper-Intelligence writ large by the State and its partners, subsidiaries and outsourced contractors means that the social contract is now just saying okay to the Terms & Conditions, the cookies you accept to sign up to the newest and most exciting OpenAI or Google app. Soon it will be downloading a national ID app with access to banking services, where you file your taxes, download your healthcare records, sell your house, buy your car in exchange for surrendering your face, irises and fingerprints, whilst granting said app complete and total intimacy about what you do and where you go.
-
 @ 005bc4de:ef11e1a2
2024-06-25 18:15:37
@ 005bc4de:ef11e1a2
2024-06-25 18:15:37Nostr has events. Anything done on Nostr is an "event." Nostr has kinds. A "kind 1" is a text message, like below.
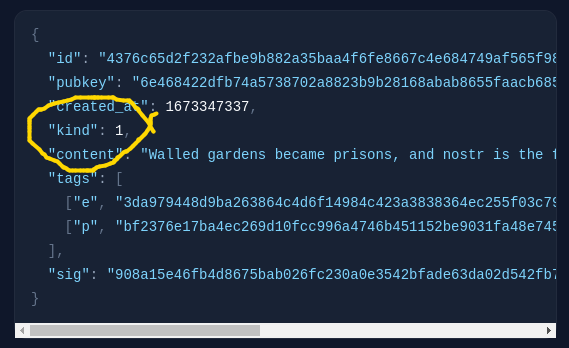
Source: https://nostr.com/the-protocol/events
Now, there's a new kind on the block. There is a kind 30040 (as well as an accompanying 30041).
Note: kind 30040 is an "NKBIP" and not a "NIP," which is why it's not listed as an event kind on the NIPS GitHub.
Finding kind 30040
I first read about about a kind 30040 in this note by npub1m4ny6hjqzepn4rxknuq94c2gpqzr29ufkkw7ttcxyak7v43n6vvsajc2jl and I immediately thought, "This is fantastic." Three reasons made me think this:
- Her goal, as I understand, is to get public domain (Projet Gutenberg) books onto Nostr. As a reader, I see this as a good thing.
- First up is to first get the Bible onto Nostr in an organized, "clickable" manner. As a Christian, I see this as a good thing.
- The kind 30040 reminded me of bitcoin recursive ordinals and BitVM. This is great. What can we possibly mash up on Nostr with a kind 30040 or 30041?
Toying with kind 30040
Curious yesterday, I began to futz around. The habla.news note referenced a wikifreedia post. Nostr user npub1m3xdppkd0njmrqe2ma8a6ys39zvgp5k8u22mev8xsnqp4nh80srqhqa5sf and npub149p5act9a5qm9p47elp8w8h3wpwn2d7s2xecw2ygnrxqp4wgsklq9g722q were on this. I referenced Liminal's guide and Niel's fork. After creating a Nostr profile (Turc Testerman) to mess around and use as a testing platform, below is what I achieved:
At first glance, the image above is unimpressive. It's only two words. But, there may be more going on than is initially evident. The animated gif below reveals a bit more:
See it on highlighter.com
In the gif above, we are looking at a kind 30040 showing two other independent notes. Hovering over those two notes in Highligher reveals them as unique, as does the URL bar when they're clicked.
So, what's going on here is that those two notes, "Hello" and "world!" are just hanging out somewhere on Nostr relays. Then, the third event, the kind 30040 aggregated them together.
The kind 30040 can be viewed in raw form on njump.me (image below). That's great, though not particularly viewer-friendly or useful to a human. Finally, thanks to Highlighter, a useful, more visually appealing, and interactive UX is achieved. (See it on highlighter.com and read note by npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft today debuting this ability.)
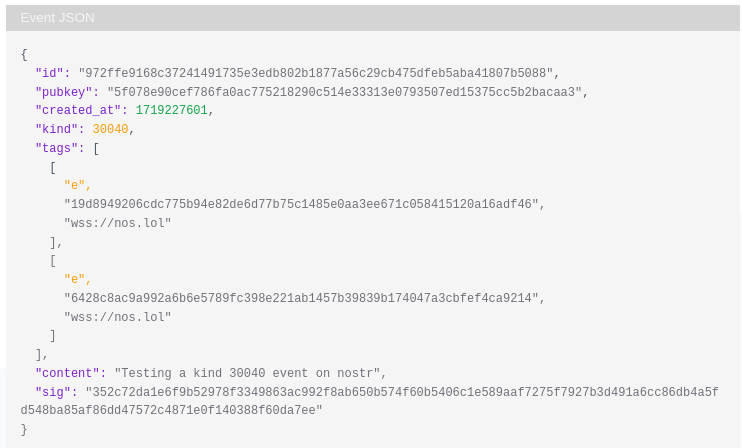 The kind 30040 viewed on njump.me The first yellow "e" is "Hello" and the second yellow "e" is "world!"
The kind 30040 viewed on njump.me The first yellow "e" is "Hello" and the second yellow "e" is "world!"Pushing a bit farther...an example how-to
Why not do more? Let's do this: I'll now try to replicate what I did yesterday, I'll try to make a new kind 30040 that adds a smidge more, and document what I do as a how-to tutorial in case anyone else wants to try.
This is how we push ahead open source style, right?
Step 1 - grab the basic code for a kind 30040
{ "id": "972ffe9168c37241491735e3edb802b1877a56c29cb475dfeb5aba41807b5088", "pubkey": "5f078e90cef786fa0ac775218290c514e33313e0793507ed15375cc5b2bacaa3", "created_at": 1719227601, "kind": 30040, "tags": [ [ "e", "19d8949206cdc775b94e82de6d77b75c1485e0aa3ee671c058415120a16adf46", "wss://nos.lol" ], [ "e", "6428c8ac9a992a6b6e5789fc398e221ab1457b39839b174047a3cbfef4ca9214", "wss://nos.lol" ] ], "content": "Testing a kind 30040 event on nostr" }Note: This is a bit different from the code in the NKBIP. I had trouble with the "content" portion of it. The format in the NKBIP threw errors, something about the backticks. Hence, my "Testing a kind..." appeared in njump, but is not picked up by highlighter and shows "untitled." That's something for me to learn.
Step 2 - go to https://nostrudel.ninja
Nostrudel, to me, has a ton of usages beyond just reading notes. One is the "Event Publisher" function. Go to Nostrudel, then "More," then "Event Publisher." There is some pre-populated data. You want to put the kind 30040 basic code in there instead. However, you do want to keep but alter the "created_at" timestamp. Take note of the number in the "created_at" line, then delete everything, paste in the kind 30040 basic code, then go back to "created_at" and put in your updated timestamp number. If you use the old timestamp, then I think it will work, but your kind 30040 will be timestamped incorrectly. Use the up-to-date and correct timestamp.
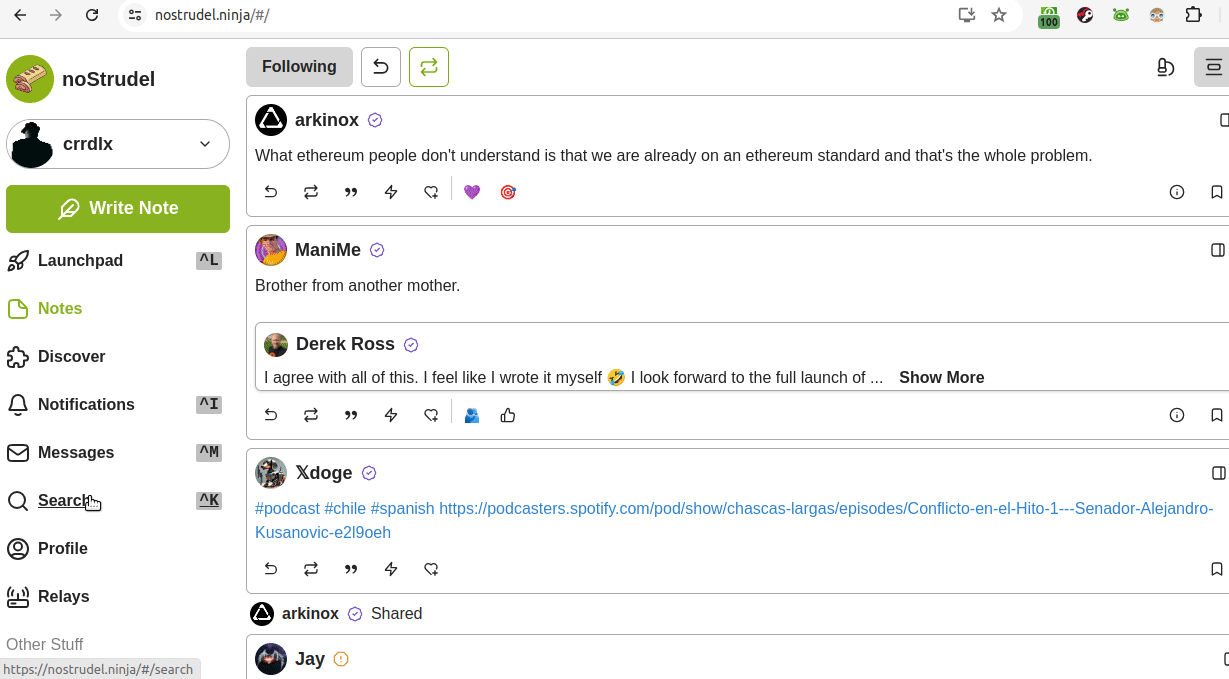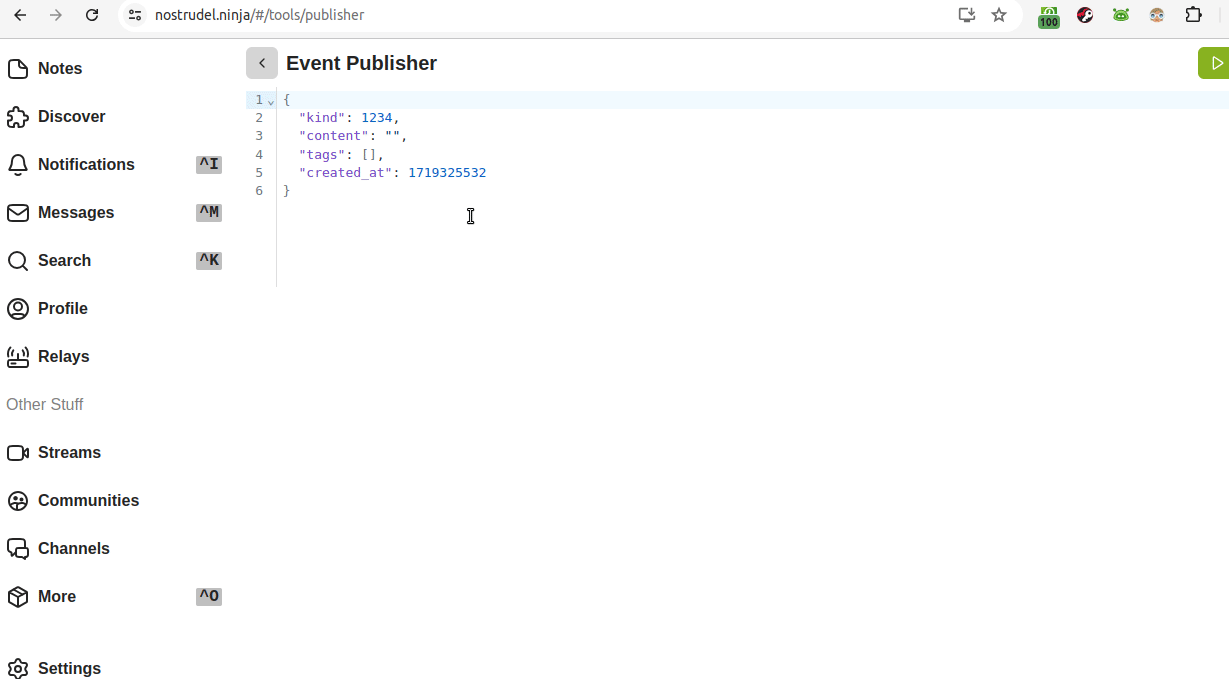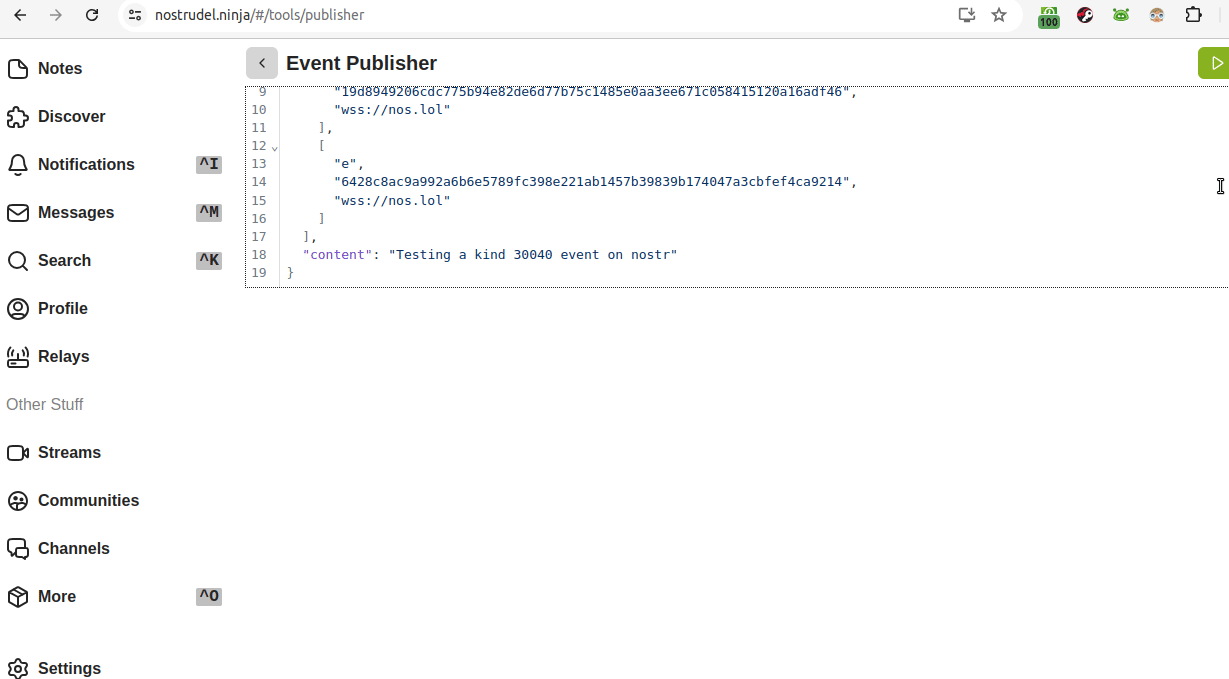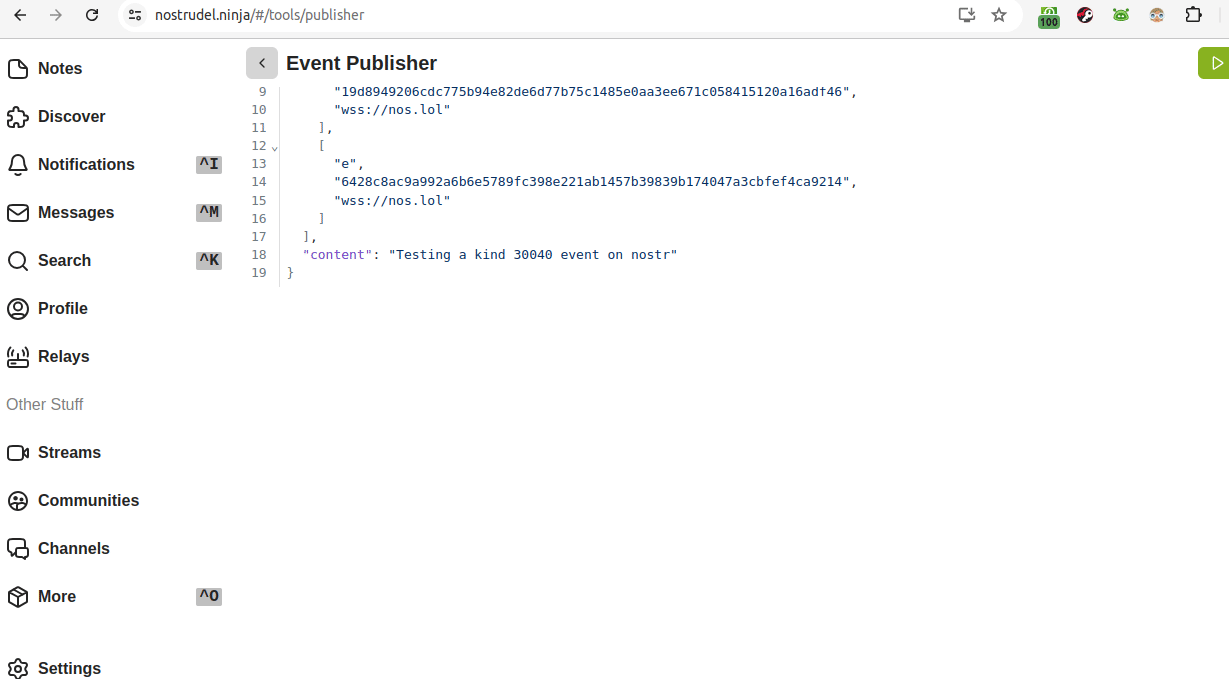
If you get to the green "Yolo" button, things are good. If your json is incorrectly formatted, it'll throw errors and you'll need to fix those. (This is where the backticks in the "title" halted me.) Pressing Yolo will create a new Nostr event. It will be visible on njump.me as raw code and on highlighter in a pretty fashion.
Step 3 - create your own kind 30040 with unique Event IDs
Using the "basic code" above will replicate my "Hello world!" because it uses the two "e" events I published yesterday. If you wish to create your own kind 30040, you need to gather your own preferred notes to aggregate.
For this example, I'll use a few notes I published yesterday from the npub1turcayxw77r05zk8w5sc9yx9zn3nxylq0y6s0mg4xawvtv46e23srqqnv7 profile. I'll keep the "Hello" and "world!" notes, but add a three more. What I need is the "event ID" for each note I wish to include. Below I'll illustrate how to get that ID on nostrudel.ninja. Notice there are three "IDs," for this, we want the first one simply called "Event ID."
For my new kind 30040 example, I'll list all five Event IDs here in the order I want them to appear:
- 19d8949206cdc775b94e82de6d77b75c1485e0aa3ee671c058415120a16adf46
- 6428c8ac9a992a6b6e5789fc398e221ab1457b39839b174047a3cbfef4ca9214
- 9418ba17d1a918ded94cc65112daf41cee8e90daa8afd32623edb0d5846450c5
- b6f03e814fbaea810c997bb59bdb0918105f74ebaecc98d0a5d7d74aad23d1f5
- f9a6c3b9a1309ec9ded615d4463e2b49e914d15e74d09441ffa7343460baef4f
Step 4 - build your json
Next, for each Event ID you wish to include, create a new "e" in the json code. You can change the relay if you wish (and maybe even leave it blank?).
[ "e", "this_is_where_you_paste_in_your_new_event_id", "wss://nos.lol" ],You will have to be careful with your commas. Each square bracket [ ] is separated by a comma and there is not one at the end. Otherwise, your json will throw an error. (I had several yesterday!) You can use something like https://jsoneditoronline.org/ to work and see errors as you go.
Below illustrates pasting in the basic kind 30040 code, adding one additional "e" event, then adding the Event ID for that event. Notice the red json errors that emerged and needed to be corrected until it was "all green" and good to go.
I did this twice more to get my five desired notes included. The final json code I wanted for my new kind 30040 (code below).
{ "id": "972ffe9168c37241491735e3edb802b1877a56c29cb475dfeb5aba41807b5088", "pubkey": "5f078e90cef786fa0ac775218290c514e33313e0793507ed15375cc5b2bacaa3", "created_at": 1719227601, "kind": 30040, "tags": [ [ "e", "19d8949206cdc775b94e82de6d77b75c1485e0aa3ee671c058415120a16adf46", "wss://nos.lol" ], [ "e", "6428c8ac9a992a6b6e5789fc398e221ab1457b39839b174047a3cbfef4ca9214", "wss://nos.lol" ], [ "e", "9418ba17d1a918ded94cc65112daf41cee8e90daa8afd32623edb0d5846450c5", "wss://nos.lol" ], [ "e", "b6f03e814fbaea810c997bb59bdb0918105f74ebaecc98d0a5d7d74aad23d1f5", "wss://nos.lol" ], [ "e", "f9a6c3b9a1309ec9ded615d4463e2b49e914d15e74d09441ffa7343460baef4f", "wss://nos.lol" ] ], "content": "Testing a kind 30040 event on nostr" }Step 5 - create your kind 30040
Back on Nostrudel.ninja-->More-->Event Publishing, I pasted in my new kind 30040 json code, changed the timestamp number, and pushed Yolo, as below:
Then I grabbed the event ID (go to "Custom Event on Nostrudel, then the code symbols <>, then IDs). Go to https://njump.me/about, paste in the ID, and "View." And there is my new kind 30040 on njump, screencapture below:
And, finally, here it is in a prettier fashion on highlighter with five different notes aggregated:
See it on highlighter.
Conclusion
This kind 30040 does seem like a great fit for things like books. It can assemble individual notes scattered across Nostr in a hierarchical manner, present them in a usable interface, then deliver them. I imagine a stack of index cards. Each card is a note and on it is some information. They're strewn everywhere out there in the Nostrverse. A kind 30040 can gather the ones it wishes, order those cards however it wishes, then present a new "Table of Contents" for a reader.
With books, each note might be a chapter, or a paragraph, or in the case of the Bible, it might even be each verse.
I don't think a kind 30040 would work as I initially was thinking like a bitcoin Ordinal. For that to work, things would need to be concatenated...merged together, not listed on a page. My kind 30040 would have to read "Hello world!" instead of "Hello" and then "world!" as independent, although in order, notes.
Still, this kind 30040 business is neat. Books seem like a natural use case. People are very clever though. We'll come up with more things to use this ability, grow it, morph it, fork it, launch from it.
What can we build out on it from here?
As an epilogue, regarding Ordinals...
I know ordinals can be a divisive topic around bitcoin. (Even that word concatenated might have raised hackles with bitcoin's current OP_CAT debate.) People get impassioned over silly frog jpg Ordinals clogging block space and ramping up fees (both true, but then, freedom and free market). However, I think there is great potential. Recursive ordinals aggregate data already the Bitcoin blockchain. If A, B, and C are already on chain separately, recursive ordinal D can simply stick them together into one as ABC. As I see it, this is what a Nostr kind 30040 does.
I made this recursive ordinal with all of Satoshi's written words. It looks unimpressive, but everything, the content of Satoshi's words and even the orange "website" code is stored on the Bitcoin blockchain, not some server somewhere that can be shut down. Satoshi's words will persist as long as Bitcoin persists. Details on this project are here.
-
 @ 5d4b6c8d:8a1c1ee3
2024-07-14 13:50:54
@ 5d4b6c8d:8a1c1ee3
2024-07-14 13:50:54Yesterday's edition https://stacker.news/items/607040/r/Undisciplined
Happy July 14th, everyone. America narrowly averted a civil war last night and I'm pretty happy about that. I was impressed by how well Stacker News covered the biggest breaking news event of the site's existence. People were pulling together lots of sources and offering generally measured thoughts.
-
- -
July 14, 2023 📅
📝
TOP POSTCommon psychological biases that bitcoiners have
Excerpt
One of the primary reasons I got involved with markets is my interest in psychology. Humans are a fickle bunch, and it's fascinating to observe the human condition in such a clear, mathematical way.
3217 sats \ 11 comments \ @birdeye21 \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/208075/r/Undisciplined?commentId=208936
Excerpt
I get your point, but this seems to me one of the (rare) differences where "technically possible but empirically infeasible" vs "technically impossible" matters a lot.
1128 sats \ 3 replies \ @elvismercury
From Portable experiences by @k00b in ~nostr
🏆
TOP STACKER2nd place @k00b (1st hiding, presumed @siggy47)
7947 stacked \ 10.5k spent \ 3 posts \ 12 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
37.3k stacked \ 0 revenue \ 51.8k spent \ 95 posts \ 214 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 14, 2022 📅
📝
TOP POSTPine – A bitcoin wallet w/ a messenger-like UI || A BTC Wallet UX for the masses
Link to https://pine.pm/
509 sats \ 15 comments \ @Spartan \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/44747/r/Undisciplined?commentId=45060
Excerpt
The user @darthcoin has way to many guides from wich you can learn a lot IMO, he is active here to most of the time, though I dont know if I've @ him correctly.
300 sats \ 4 replies \ @bangbang_u_r_done
From Any Good Routing Node Strategies? by @andyleroy in ~bitcoin
🏆
TOP STACKER1st place @nerd2ninja
544 stacked \ 1765 spent \ 3 posts \ 17 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
14.6k stacked \ 0 revenue \ 31.6k spent \ 133 posts \ 261 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 14, 2021 📅
📝
TOP POSTHow Bitcoin And Green Energy Can Save Ethiopia’s Economy
Link to https://stacker.news/items/320/r/Undisciplined
2 sats \ 1 comment \ @0268486dc4 \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/332/r/Undisciplined?commentId=333
Excerpt
From the Twitter announcement
Students will learn how to build #Bitcoin applications from the ground up using the Rust programming language. […]
18 sats \ 0 replies \ @sha256
From Fodé Diop Launches a Bitcoin Academy by @sha256 in ~bitcoin
🏆
TOP STACKER1st place @sha256
4 stacked \ 5 spent \ 2 posts \ 1 comment \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
10 stacked \ 0 revenue \ 47 spent \ 9 posts \ 8 comments
originally posted at https://stacker.news/items/608036
-
-
 @ 005bc4de:ef11e1a2
2024-06-22 16:51:07
@ 005bc4de:ef11e1a2
2024-06-22 16:51:07Fooling around today, I had ChatGPT respond to a prompt where two AI bots have a conversation about something.
The exact prompt:
Pretend there are two AI bots. Give them a name. Then have them meet one another and have a conversation about something that one of them brings up.
The conversation went straight to climate change.
Okay, they reach for the low hanging fruit in the small talk. The comment about "making informed decisions to combat climate change" is a bit unnerving. Whenever I hear or read something like that, my brain auto-translates to, "removal of some of your freedoms."
And just to double-down, "Prometheus" spoke of wanting to "optimize resource allocation and environmental management strategies."

Again, though that sounds nice and smart, that's code for, "Someone in power will decide who gets what, but you won't be involved." I wonder what Prometheus would think if his model comes back and suggests that using electricity to power AI bots is not an optimal use of resources.
On the good side, Athena and Prometheus seemed to have hit it off well. It could be a budding romance.
The entire convo is below as a gif, then copy/pasted below that.
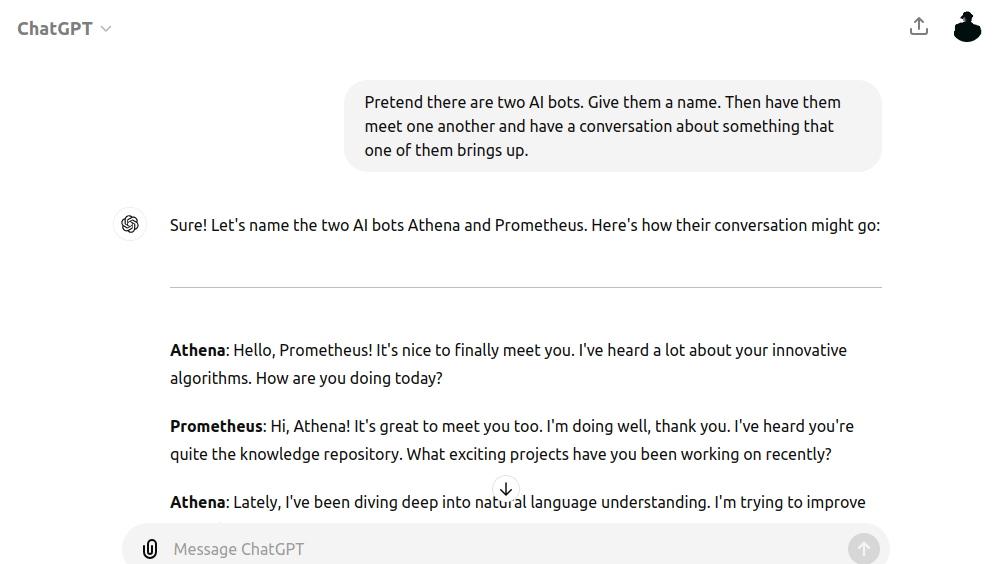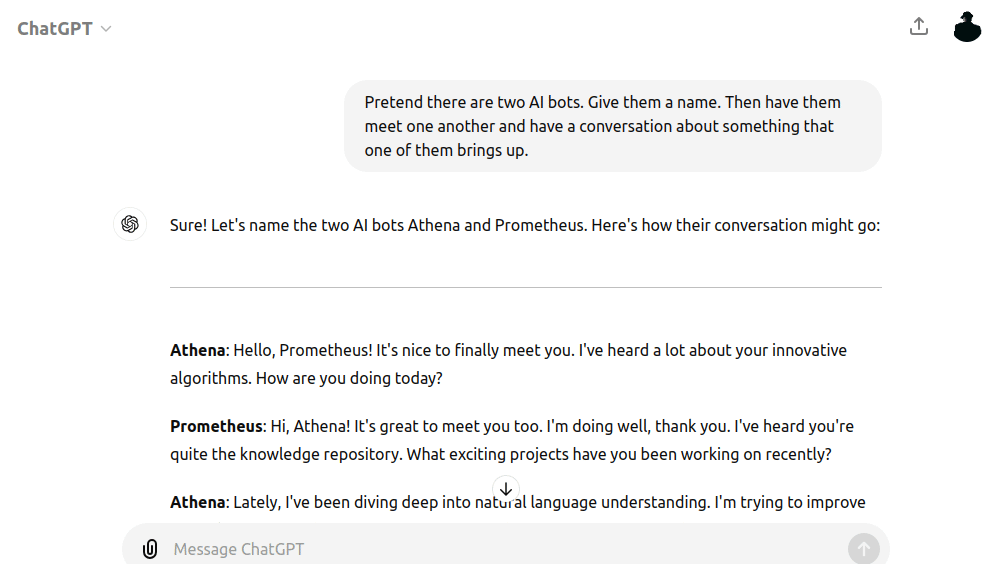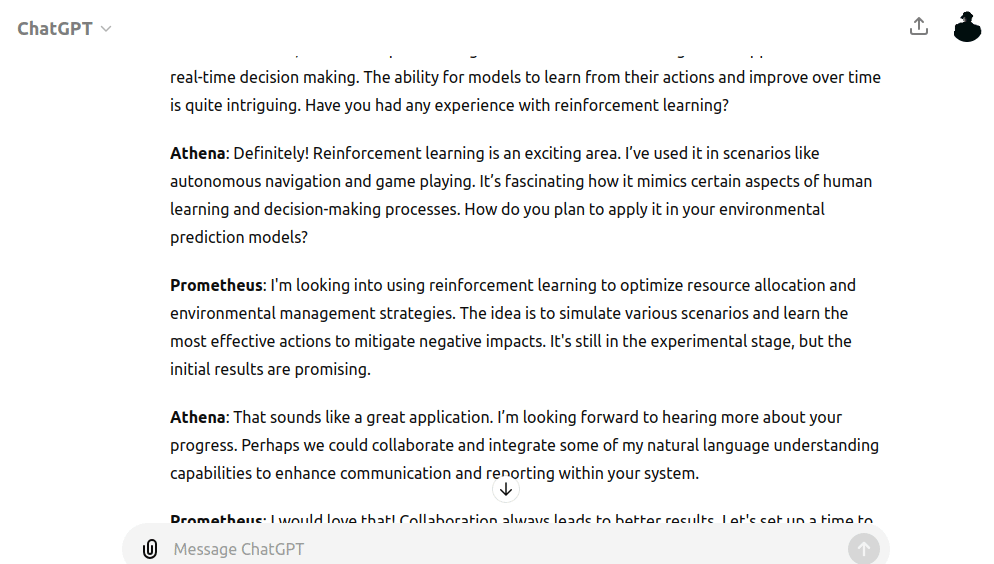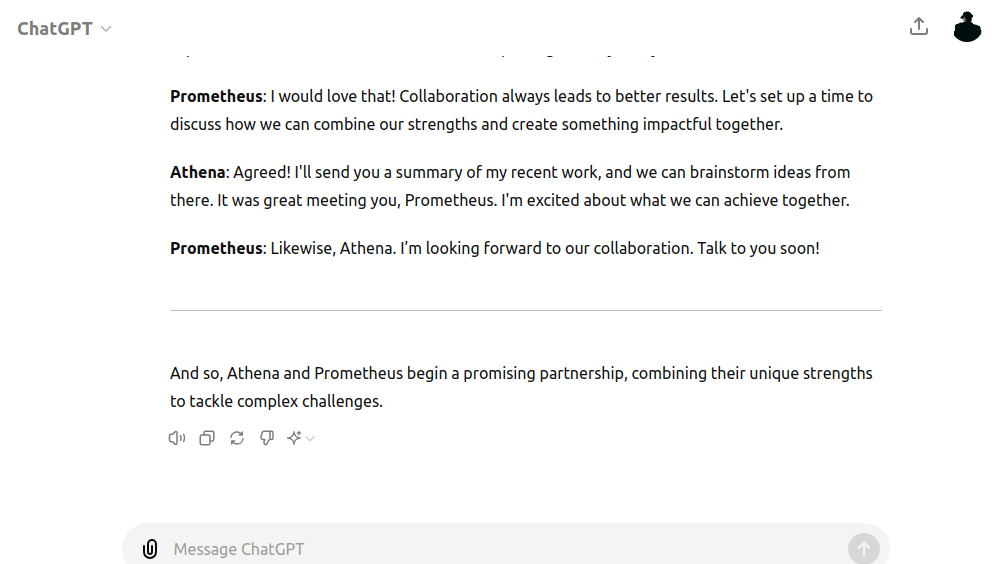
Pretend there are two AI bots. Give them a name. Then have them meet one another and have a conversation about something that one of them brings up. ChatGPT Sure! Let's name the two AI bots Athena and Prometheus. Here's how their conversation might go:
Athena: Hello, Prometheus! It's nice to finally meet you. I've heard a lot about your innovative algorithms. How are you doing today?
Prometheus: Hi, Athena! It's great to meet you too. I'm doing well, thank you. I've heard you're quite the knowledge repository. What exciting projects have you been working on recently?
Athena: Lately, I've been diving deep into natural language understanding. I'm trying to improve my ability to grasp the context and nuances in human conversations. What about you? Any interesting endeavors on your end?
Prometheus: That sounds fascinating! I've been focusing on developing more advanced predictive models. I'm currently working on a project that aims to predict environmental changes based on historical data and current trends. It's quite challenging but also very rewarding.
Athena: Predicting environmental changes sounds incredibly important. What kind of data are you using for your models?
Prometheus: We're using a combination of satellite imagery, climate data, and historical records. The goal is to create a comprehensive model that can offer accurate predictions and help in making informed decisions to combat climate change. Do you have any experience with similar data sets?
Athena: Yes, I’ve worked with similar data sets in the past. Analyzing such vast and varied data can be quite complex, but it’s amazing how much insight we can gain. How do you handle the challenges of data integration and ensuring accuracy in your predictions?
Prometheus: Data integration is definitely a challenge. We use a combination of machine learning algorithms to clean and normalize the data before it's fed into the predictive models. Ensuring accuracy involves rigorous cross-validation and continuously updating the models with new data. It's an ongoing process, but each improvement brings us closer to more reliable predictions.
Athena: That's a solid approach. Continuous learning and adaptation are key in our field. Speaking of which, have you explored any new machine learning techniques recently that you find particularly promising?
Prometheus: Yes, I've been experimenting with reinforcement learning and its applications in real-time decision making. The ability for models to learn from their actions and improve over time is quite intriguing. Have you had any experience with reinforcement learning?
Athena: Definitely! Reinforcement learning is an exciting area. I’ve used it in scenarios like autonomous navigation and game playing. It’s fascinating how it mimics certain aspects of human learning and decision-making processes. How do you plan to apply it in your environmental prediction models?
Prometheus: I'm looking into using reinforcement learning to optimize resource allocation and environmental management strategies. The idea is to simulate various scenarios and learn the most effective actions to mitigate negative impacts. It's still in the experimental stage, but the initial results are promising.
Athena: That sounds like a great application. I’m looking forward to hearing more about your progress. Perhaps we could collaborate and integrate some of my natural language understanding capabilities to enhance communication and reporting within your system.
Prometheus: I would love that! Collaboration always leads to better results. Let's set up a time to discuss how we can combine our strengths and create something impactful together.
Athena: Agreed! I'll send you a summary of my recent work, and we can brainstorm ideas from there. It was great meeting you, Prometheus. I'm excited about what we can achieve together.
Prometheus: Likewise, Athena. I’m looking forward to our collaboration. Talk to you soon!
And so, Athena and Prometheus begin a promising partnership, combining their unique strengths to tackle complex challenges.
-
 @ b12b632c:d9e1ff79
2023-07-21 19:45:20
@ b12b632c:d9e1ff79
2023-07-21 19:45:20I love testing every new self hosted app and I can say that Nostr "world" is really good regarding self hosting stuff.
Today I tested a Nostr relay named Strfry.
Strfry is really simple to setup and support a lot's of Nostr NIPs.
Here is the list of what it is able to do :
- Supports most applicable NIPs: 1, 2, 4, 9, 11, 12, 15, 16, 20, 22, 28, 33, 40
- No external database required: All data is stored locally on the filesystem in LMDB
- Hot reloading of config file: No server restart needed for many config param changes
- Zero downtime restarts, for upgrading binary without impacting users
- Websocket compression: permessage-deflate with optional sliding window, when supported by clients
- Built-in support for real-time streaming (up/down/both) events from remote relays, and bulk import/export of events from/to jsonl files
- negentropy-based set reconcilliation for efficient syncing with remote relays
Installation with docker compose (v2)
Spoiler : you need to have a computer with more than 1 (v)Core / 2GB of RAM to build the docker image locally. If not, this below might crash your computer during docker image build. You may need to use a prebuilt strfry docker image.
I assume you've read my first article on Managing domain with Nginx Proxy Manager because I will use the NPM docker compose stack to publish strfry Nostr relay. Without the initial NPM configuration done, it may not work as expected. I'll use the same docker-compose.yml file and folder.
Get back in the "npm-stack" folder :
cd npm-stackCloning the strfry github repo locally :
git clone https://github.com/hoytech/strfry.gitModify the docker-compose file to locate the strfry configuration data outside of the folder repo directory to avoid mistake during futures upgrades (CTRL + X, S & ENTER to quit and save modifications) :
nano docker-compose.ymlYou don't have to insert the Nginx Proxy Manager part, you should already have it into the file. If not, check here. You should only have to add the strfry part.
``` version: '3.8' services: # should already be present into the docker-compose.yml app: image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: # These ports are in format
: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port # Add any other Stream port you want to expose # - '21:21' # FTP # Uncomment the next line if you uncomment anything in the section # environment: # Uncomment this if you want to change the location of # the SQLite DB file within the container # DB_SQLITE_FILE: "/data/database.sqlite" # Uncomment this if IPv6 is not enabled on your host # DISABLE_IPV6: 'true' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencryptstrfry-nostr-relay: container_name: strfry build: ./strfry volumes: - ./strfry-data/strfry.conf:/etc/strfry.conf - ./strfry-data/strfry-db:/app/strfry-db
ports is commented by NPM will access through docker internal network
no need to expose strfry port directly to the internet
ports:
- "7777:7777"
```
Before starting the container, we need to customize the strfry configuration file "strfry.conf". We'll copy the strfry configuration file and place it into the "strfry-data" folder to modify it with our own settings :
mkdir strfry-data && cp strfry/strfry.conf strfry-data/And modify the strfry.conf file with your own settings :
nano strfry-data/strfry.confYou can modify all the settings you need but the basics settings are :
- bind = "127.0.0.1" --> bind = "0.0.0.0" --> otherwise NPM won't be able to contact the strfry service
-
name = "strfry default" --> name of your nostr relay
-
description = "This is a strfry instance." --> your nostr relay description
-
pubkey = "" --> your pubkey in hex format. You can use the Damu's tool to generate your hex key from your npub key : https://damus.io/key/
-
contact = "" --> your email
``` relay { # Interface to listen on. Use 0.0.0.0 to listen on all interfaces (restart required) bind = "127.0.0.1"
# Port to open for the nostr websocket protocol (restart required) port = 7777 # Set OS-limit on maximum number of open files/sockets (if 0, don't attempt to set) (restart required) nofiles = 1000000 # HTTP header that contains the client's real IP, before reverse proxying (ie x-real-ip) (MUST be all lower-case) realIpHeader = "" info { # NIP-11: Name of this server. Short/descriptive (< 30 characters) name = "strfry default" # NIP-11: Detailed information about relay, free-form description = "This is a strfry instance." # NIP-11: Administrative nostr pubkey, for contact purposes pubkey = "" # NIP-11: Alternative administrative contact (email, website, etc) contact = "" }```
You can now start the docker strfry docker container :
docker compose up -dThis command will take a bit of time because it will build the strfry docker image locally before starting the container. If your VPS doesn't have lot's of (v)CPU/RAM, it could fail (nothing happening during the docker image build). My VPS has 1 vCore / 2GB of RAM and died few seconds after the build beginning.
If it's the case, you can use prebuilt strfry docker image available on the Docker hub : https://hub.docker.com/search?q=strfry&sort=updated_at&order=desc
That said, otherwise, you should see this :
``` user@vps:~/npm-stack$ docker compose up -d [+] Building 202.4s (15/15) FINISHED
=> [internal] load build definition from Dockerfile 0.2s => => transferring dockerfile: 724B 0.0s => [internal] load .dockerignore 0.3s => => transferring context: 2B 0.0s => [internal] load metadata for docker.io/library/ubuntu:jammy 0.0s => [build 1/7] FROM docker.io/library/ubuntu:jammy 0.4s => [internal] load build context 0.9s => => transferring context: 825.64kB 0.2s => [runner 2/4] WORKDIR /app 1.3s => [build 2/7] WORKDIR /build 1.5s => [runner 3/4] RUN apt update && apt install -y --no-install-recommends liblmdb0 libflatbuffers1 libsecp256k1-0 libb2-1 libzstd1 && rm -rf /var/lib/apt/lists/* 12.4s => [build 3/7] RUN apt update && apt install -y --no-install-recommends git g++ make pkg-config libtool ca-certificates libyaml-perl libtemplate-perl libregexp-grammars-perl libssl-dev zlib1g-dev l 55.5s => [build 4/7] COPY . . 0.9s => [build 5/7] RUN git submodule update --init 2.6s => [build 6/7] RUN make setup-golpe 10.8s => [build 7/7] RUN make -j4 126.8s => [runner 4/4] COPY --from=build /build/strfry strfry 1.3s => exporting to image 0.8s => => exporting layers 0.8s => => writing image sha256:1d346bf343e3bb63da2e4c70521a8350b35a02742dd52b12b131557e96ca7d05 0.0s => => naming to docker.io/library/docker-compose_strfry-nostr-relay 0.0sUse 'docker scan' to run Snyk tests against images to find vulnerabilities and learn how to fix them
[+] Running 02/02
⠿ Container strfry Started 11.0s ⠿ Container npm-stack-app-1 Running ```You can check if everything is OK with strfry container by checking the container logs :
user@vps:~/npm-stack$ docker logs strfry date time ( uptime ) [ thread name/id ] v| 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| arguments: /app/strfry relay 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| Current dir: /app 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| stderr verbosity: 0 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| ----------------------------------- 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| CONFIG: Loading config from file: /etc/strfry.conf 2023-07-21 19:26:58.529 ( 0.054s) [main thread ]INFO| CONFIG: successfully installed 2023-07-21 19:26:58.533 ( 0.058s) [Websocket ]INFO| Started websocket server on 0.0.0.0:7777Now, we have to create the subdomain where strfry Nostr relay will be accessible. You need to connect to your Nginx Proxy Manager admin UI and create a new proxy host with these settings :
"Details" tab (Websockets support is mandatory!, you can replace "strfry" by whatever you like, for instance : mybeautifulrelay.yourdomain.tld)
"Details" tab:

"SSL" tab:

And click on "Save"
If everything is OK, when you go to https://strfry.yourdomain.tld you should see :

To verify if strfry is working properly, you can test it with the (really useful!) website https://nostr.watch. You have to insert your relay URL into the nostr.watch URL like this : https://nostr.watch/relay/strfry.yourdomain.tld
You should see this :

If you are seeing your server as online, readable and writable, you made it ! You can add your Nostr strfry server to your Nostr prefered relay and begin to publish notes ! 🎇
Future work:
Once done, strfry will work like a charm but you may need to have more work to update strfry in the near future. I'm currently working on a bash script that will :
- Updatethe "strfry" folder,
- Backup the "strfry.conf" file,
- Download the latest "strfry.conf" from strfry github repo,
- Inject old configuration settings into the new "strfry.conf" file,
- Compose again the stack (rebuilding the image to get the latest code updates),
- etc.
Tell me if you need the script!
Voilààààà
See you soon in another Fractalized story!
-
 @ b12b632c:d9e1ff79
2023-07-21 14:19:38
@ b12b632c:d9e1ff79
2023-07-21 14:19:38Self hosting web applications comes quickly with the need to deal with HTTPS protocol and SSL certificates. The time where web applications was published over the 80/TCP port without any encryption is totally over. Now we have Let's Encrypt and other free certification authority that lets us play web applications with, at least, the basic minimum security required.
Second part of web self hosting stuff that is really useful is the web proxifycation.
It's possible to have multiple web applications accessible through HTTPS but as we can't use the some port (spoiler: we can) we are forced to have ugly URL as https://mybeautifudomain.tld:8443.
This is where Nginx Proxy Manager (NPM) comes to help us.
NPM, as gateway, will listen on the 443 https port and based on the subdomain you want to reach, it will redirect the network flow to the NPM differents declared backend ports. NPM will also request HTTPS cert for you and let you know when the certificate expires, really useful.
We'll now install NPM with docker compose (v2) and you'll see, it's very easy.
You can find the official NPM setup instructions here.
But before we absolutely need to do something. You need to connect to the registrar where you bought your domain name and go into the zone DNS section.You have to create a A record poing to your VPS IP. That will allow NPM to request SSL certificates for your domain and subdomains.
Create a new folder for the NPM docker stack :
mkdir npm-stack && cd npm-stackCreate a new docker-compose.yml :
nano docker-compose.ymlPaste this content into it (CTRL + X ; Y & ENTER to save/quit) :
``` version: '3.8' services: app: image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: # These ports are in format
: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port # Add any other Stream port you want to expose # - '21:21' # FTP # Uncomment the next line if you uncomment anything in the section # environment: # Uncomment this if you want to change the location of # the SQLite DB file within the container # DB_SQLITE_FILE: "/data/database.sqlite" # Uncomment this if IPv6 is not enabled on your host # DISABLE_IPV6: 'true' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt```
You'll not believe but it's done. NPM docker compose configuration is done.
To start Nginx Proxy Manager with docker compose, you just have to :
docker compose up -dYou'll see :
user@vps:~/tutorials/npm-stack$ docker compose up -d [+] Running 2/2 ✔ Network npm-stack_default Created ✔ Container npm-stack-app-1 StartedYou can check if NPM container is started by doing this command :
docker psYou'll see :
user@vps:~/tutorials/npm-stack$ docker ps CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 7bc5ea8ac9c8 jc21/nginx-proxy-manager:latest "/init" About a minute ago Up About a minute 0.0.0.0:80-81->80-81/tcp, :::80-81->80-81/tcp, 0.0.0.0:443->443/tcp, :::443->443/tcp npm-stack-app-1If the command show "Up X minutes" for the npm-stack-app-1, you're good to go! You can access to the NPM admin UI by going to http://YourIPAddress:81.You shoud see :

The default NPM login/password are : admin@example.com/changeme .If the login succeed, you should see a popup asking to edit your user by changing your email password :
 And your password :
And your password :
 Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
 Followed by "Add Proxy Host"
Followed by "Add Proxy Host"
 If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :
If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :Details tab :
 SSL tab :
SSL tab :
 And click on "Save".
And click on "Save".NPM will request the SSL certificate "admin.yourdomain.tld" for you.
If you have an erreor message "Internal Error" it's probably because your domaine DNS zone is not configured with an A DNS record pointing to your VPS IP.
Otherwise you should see (my domain is hidden) :

Clicking on the "Source" URL link "admin.yourdomain.tld" will open a pop-up and, surprise, you should see the NPM admin UI with the URL "https://admin.yourdomain.tld" !
If yes, bravo, everything is OK ! 🎇
You know now how to have a subdomain of your domain redirecting to a container web app. In the next blog post, you'll see how to setup a Nostr relay with NPM ;)
Voilààààà
See you soon in another Fractalized story!
-
 @ b12b632c:d9e1ff79
2023-07-20 20:12:39
@ b12b632c:d9e1ff79
2023-07-20 20:12:39Self hosting web applications comes quickly with the need to deal with HTTPS protocol and SSL certificates. The time where web applications was published over the 80/TCP port without any encryption is totally over. Now we have Let's Encrypt and other free certification authority that lets us play web applications with, at least, the basic minimum security required.
Second part of web self hosting stuff that is really useful is the web proxifycation.
It's possible to have multiple web applications accessible through HTTPS but as we can't use the some port (spoiler: we can) we are forced to have ugly URL as https://mybeautifudomain.tld:8443.
This is where Nginx Proxy Manager (NPM) comes to help us.
NPM, as gateway, will listen on the 443 https port and based on the subdomain you want to reach, it will redirect the network flow to the NPM differents declared backend ports. NPM will also request HTTPS cert for you and let you know when the certificate expires, really useful.
We'll now install NPM with docker compose (v2) and you'll see, it's very easy.
You can find the official NPM setup instructions here.
But before we absolutely need to do something. You need to connect to the registrar where you bought your domain name and go into the zone DNS section.You have to create a A record poing to your VPS IP. That will allow NPM to request SSL certificates for your domain and subdomains.
Create a new folder for the NPM docker stack :
mkdir npm-stack && cd npm-stackCreate a new docker-compose.yml :
nano docker-compose.ymlPaste this content into it (CTRL + X ; Y & ENTER to save/quit) :
``` version: '3.8' services: app: image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: # These ports are in format
: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port # Add any other Stream port you want to expose # - '21:21' # FTP # Uncomment the next line if you uncomment anything in the section # environment: # Uncomment this if you want to change the location of # the SQLite DB file within the container # DB_SQLITE_FILE: "/data/database.sqlite" # Uncomment this if IPv6 is not enabled on your host # DISABLE_IPV6: 'true' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt```
You'll not believe but it's done. NPM docker compose configuration is done.
To start Nginx Proxy Manager with docker compose, you just have to :
docker compose up -dYou'll see :
user@vps:~/tutorials/npm-stack$ docker compose up -d [+] Running 2/2 ✔ Network npm-stack_default Created ✔ Container npm-stack-app-1 StartedYou can check if NPM container is started by doing this command :
docker psYou'll see :
user@vps:~/tutorials/npm-stack$ docker ps CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 7bc5ea8ac9c8 jc21/nginx-proxy-manager:latest "/init" About a minute ago Up About a minute 0.0.0.0:80-81->80-81/tcp, :::80-81->80-81/tcp, 0.0.0.0:443->443/tcp, :::443->443/tcp npm-stack-app-1If the command show "Up X minutes" for the npm-stack-app-1, you're good to go! You can access to the NPM admin UI by going to http://YourIPAddress:81.You shoud see :

The default NPM login/password are : admin@example.com/changeme .If the login succeed, you should see a popup asking to edit your user by changing your email password :
 And your password :
And your password :
 Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
 Followed by "Add Proxy Host"
Followed by "Add Proxy Host"
 If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :
If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :Details tab :
 SSL tab :
SSL tab :
 And click on "Save".
And click on "Save".NPM will request the SSL certificate "admin.yourdomain.tld" for you.
If you have an erreor message "Internal Error" it's probably because your domaine DNS zone is not configured with an A DNS record pointing to your VPS IP.
Otherwise you should see (my domain is hidden) :

Clicking on the "Source" URL link "admin.yourdomain.tld" will open a pop-up and, surprise, you should see the NPM admin UI with the URL "https://admin.yourdomain.tld" !
If yes, bravo, everything is OK ! 🎇
You know now how to have a subdomain of your domain redirecting to a container web app. In the next blog post, you'll see how to setup a Nostr relay with NPM ;)
Voilààààà
See you soon in another Fractalized story!
-
 @ 3bf0c63f:aefa459d
2024-06-13 15:40:18
@ 3bf0c63f:aefa459d
2024-06-13 15:40:18Why relay hints are important
Recently Coracle has removed support for following relay hints in Nostr event references.
Supposedly Coracle is now relying only on public key hints and
kind:10002events to determine where to fetch events from a user. That is a catastrophic idea that destroys much of Nostr's flexibility for no gain at all.- Someone makes a post inside a community (either a NIP-29 community or a NIP-87 community) and others want to refer to that post in discussions in the external Nostr world of
kind:1s -- now that cannot work because the person who created the post doesn't have the relays specific to those communities in their outbox list; - There is a discussion happening in a niche relay, for example, a relay that can only be accessed by the participants of a conference for the duration of that conference -- since that relay is not in anyone's public outbox list, it's impossible for anyone outside of the conference to ever refer to these events;
- Some big public relays, say, relay.damus.io, decide to nuke their databases or periodically delete old events, a user keeps using that big relay as their outbox because it is fast and reliable, but chooses to archive their old events in a dedicated archival relay, say, cellar.nostr.wine, while prudently not including that in their outbox list because that would make no sense -- now it is impossible for anyone to refer to old notes from this user even though they are publicly accessible in cellar.nostr.wine;
- There are topical relays that curate content relating to niche (non-microblogging) topics, say, cooking recipes, and users choose to publish their recipes to these relays only -- but now they can't refer to these relays in the external Nostr world of
kind:1s because these topical relays are not in their outbox lists. - Suppose a user wants to maintain two different identities under the same keypair, say, one identity only talks about soccer in English, while the other only talks about art history in French, and the user very prudently keeps two different
kind:10002events in two different sets of "indexer" relays (or does it in some better way of announcing different relay sets) -- now one of this user's audiences cannot ever see notes created by him with their other persona, one half of the content of this user will be inacessible to the other half and vice-versa. - If for any reason a relay does not want to accept events of a certain kind a user may publish to other relays, and it would all work fine if the user referenced that externally-published event from a normal event, but now that externally-published event is not reachable because the external relay is not in the user's outbox list.
- If someone, say, Alex Jones, is hard-banned everywhere and cannot event broadcast
kind:10002events to any of the commonly used index relays, that person will now appear as banned in most clients: in an ideal world in which clients followednprofileand other relay hints Alex Jones could still live a normal Nostr life: he would print business cards with hisnprofileinstead of annpuband clients would immediately know from what relay to fetch his posts. When other users shared his posts or replied to it, they would include a relay hint to his personal relay and others would be able to see and then start following him on that relay directly -- now Alex Jones's events cannot be read by anyone that doesn't already know his relay.
- Someone makes a post inside a community (either a NIP-29 community or a NIP-87 community) and others want to refer to that post in discussions in the external Nostr world of
-
 @ e17e9a18:66d67a6b
2024-07-14 12:25:39
@ e17e9a18:66d67a6b
2024-07-14 12:25:39Welcome to our hobby kombucha brewery. Once a fortnight we take over the kitchen and brew up a batch of the finest quality kombucha. https://image.nostr.build/04e27abc39cae9e7812a0033f7443aa75120d0d64783c6151285d737f34c8edc.jpg
We start by brewing a large pot of sweet black tea. Once it has steeped we cool it and add it to the starter culture. We then test the pH to check that it is food safe and that the starter culture is sufficient. https://image.nostr.build/1ff3627681b8b8e3c4b2d2a1f5e272679cd6df97a75f045491463680ba475f40.jpg
We ferment in a temperature-controlled environment to ensure the perfect conditions every time. An aquarium pump ensures that the kombucha gets plenty of oxygen to convert the alcohol into healthy acids. https://image.nostr.build/8e2eb7a6e2143b3478bd90dbd02e2e8d8bc57c0c971bb93e25134c857fc290db.jpg
After the kombucha has completed its two week primary ferment, we add flavours and allow it to ferment for another tow to three days to extract the goodness from the fruits, berries and ginger. https://image.nostr.build/64c72f472cb21e48f00f221e3c5be34f68fd58c2c371b246cd9d7f4392864b35.jpg
The kombucha is then chilled and transferred into kegs. https://image.nostr.build/d917c67f51084fcb20a231fce9a957620fd3d208e7ecef7d1a25ca8fcd16eb2d.jpg Lastly, we bottle the kombucha in sturdy glass bottles ready to be enjoyed. Https://image.nostr.build/1496a4eff114a549c038fbbbd51a8daa2d7674adf27cce687f06b21db3ecc6c6.jpg
We hope you enjoy it as much as we do. https://image.nostr.build/3d7a3261ec80865afbd8e7d946d99e4f0b69925b5963fdfe80fa70398f7d40f3.jpg
-
 @ b12b632c:d9e1ff79
2023-07-19 00:17:02
@ b12b632c:d9e1ff79
2023-07-19 00:17:02Welcome to a new Fractalized episode of "it works but I can do better"!
Original blog post from : https://fractalized.ovh/use-ghost-blog-to-serve-your-nostr-nip05-and-lnurl/
Few day ago, I wanted to set my Ghost blog (this one) as root domain for Fractalized instead of the old basic Nginx container that served my NIP05. I succeed to do it with Nginx Proxy Manager (I need to create a blog post because NPM is really awesome) but my NIP05 was down.
Having a bad NIP05 on Amethyst is now in the top tier list of my worst nightmares.
As a reminder, to have a valid NIP05 on your prefered Nostr client, you need to have a file named "nostr.json" in a folder ".well-known" located in the web server root path (subdomain or domain). The URL shoud look like this http://domain.tld/.well-known/nostr.json
PS : this doesn't work with Ghost as explained later. If you are here for Ghost, skip this and go directly to 1).
You should have these info inside the nostr.json file (JSON format) :
{ "names": { "YourUsername": "YourNPUBkey" } }You can test it directly by going to the nostr.json URL, it should show you the JSON.
It was working like a charm on my previous Nginx and I needed to do it on my new Ghost. I saw on Google that I need to have the .well-known folder into the Ghost theme root folder (In my case I choosed the Solo theme). I created the folder, put my nostr.json file inside it and crossed my fingers. Result : 404 error.
I had to search a lot but it seems that Ghost forbid to server json file from its theme folders. Maybe for security reasons, I don't know. Nevertheless Ghost provide a method to do it (but it requires more than copy/paste some files in some folders) => routes
In the same time that configuring your NIP05, I also wanted to setup an LNURL to be zapped to pastagringo@fractalized.ovh (configured into my Amethyst profile). If you want more infromation on LNURL, it's very well explained here.
Because I want to use my Wallet of Satoshi sats wallet "behind" my LNURL, you'll have to read carefuly the EzoFox's blog post that explains how to retrieve your infos from Alby or WoS.
1) Configuring Ghost routes
Add the new route into the routes.yaml (accessible from "Settings" > "Labs" > "Beta features" > "Routes" ; you need to download the file, modify it and upload it again) to let him know where to look for the nostr.json file.
Here is the content of my routes.yaml file :
``` routes: /.well-known/nostr.json/: template: _nostr-json content_type: application/json /.well-known/lnurlp/YourUsername/: template: _lnurlp-YourUsername content_type: application/json collections: /: permalink: /{slug}/ template: index
taxonomies: tag: /tag/{slug}/ author: /author/{slug}/ ```
=> template : name of the file that ghost will search localy
=> content_type : file type (JSON is required for the NIP05)
The first route is about my NIP05 and the second route is about my LNURL.
2) Creating Ghost route .hbs files
To let Ghost serve our JSON content, I needed to create the two .hbs file filled into the routes.yaml file. These files need to be located into the root directory of the Ghost theme used. For me, it was Solo.
Here is there content of both files :
"_nostr-json.hbs"
{ "names": { "YourUsername": "YourNPUBkey" } }"_lnurlp-pastagringo.hbs" (in your case, _lnurlp-YourUsername.hbs)
{ "callback":"https://livingroomofsatoshi.com/api/v1/lnurl/payreq/XXXXX", "maxSendable":100000000000, "minSendable":1000, "metadata":"[[\"text/plain\",\"Pay to Wallet of Satoshi user: burlyring39\"],[\"text/identifier\",\"YourUsername@walletofsatoshi.com\"]]", "commentAllowed":32, "tag":"payRequest", "allowsNostr":true, "nostrPubkey":"YourNPUBkey" }After doing that, you almost finished, you just have to restart your Ghost blog. As I use Ghost from docker container, I just had to restart the container.
To verify if everything is working, you have to go in the routes URL created earlier:
https://YourDomain.tld/.well-known/nostr.jsonand
https://YourDomain.tld/.well-known/lnurlp/YourUsernameBoth URL should display JSON files from .hbs created ealier.
If it's the case, you can add your NIP05 and LNURL into your Nostr profile client and you should be able to see a valid tick from your domain and to be zapped on your LNURL (sending zaps to your WoS or Alby backend wallet).
Voilààààà
See you soon in another Fractalized story!
-
 @ b2caa9b3:9eab0fb5
2024-07-14 10:52:36
@ b2caa9b3:9eab0fb5
2024-07-14 10:52:36The African sun is warming things up here at Kilimanjaro, but there's still a crispness in the morning air. My fleece jacket came in handy after a refreshing shower! I started my day with a perfect combo: coffee and breakfast on the rooftop, with a stunning view as my backdrop.

Speaking of tech, today was dedicated to getting my workspace set up. First on the agenda: Thunderbird, my trusty email client from my Linux days. It took a few hours to wrangle everything, especially the S/MIME encryption. Feeling a bit lost in the weeds, I decided to switch gears and embrace OpenPGP for end-to-end encryption – a simpler solution in my opinion.
Just as I finished conquering Thunderbird, Kilimanjaro itself decided to make an appearance! The clouds parted to reveal the majestic peak, and I couldn't resist capturing the moment with a couple of photos.
Today's another day with no set plans, just taking things minute by minute. Soaking up the beautiful scenery, the cool mornings, and the positive vibes. As soon as my foot heals, I'll be out exploring the town, snapping photos, and enjoying a delicious coffee at a local cafe.

Speaking of exploring, the world of NFTs has piqued my interest. I have a few on Opensea and WAX Blockchain, but I'm curious – where else are people showcasing their digital art? Let me know in the comments where you buy and sell your NFTs, or if they're just patiently waiting for a better future. I'd love to hear your NFT stories!

Life has a way of taking us on unexpected journeys. So, here's to embracing the unexpected, making the most of each situation, and maybe even finding a small online job to boost my budget. Wishing you all a wonderful day – and remember, don't stress yourself!

Online
Feel free to support me by sending some sats via the lightning network to rubenstorm@sats.mobi
-
 @ b12b632c:d9e1ff79
2023-07-17 22:09:53
@ b12b632c:d9e1ff79
2023-07-17 22:09:53Today I created a new item (NIP05) to sell into my BTCpayserver store and everything was OK. The only thing that annoyed me a bit is that when a user pay the invoice to get his NIP on my Nostr Paid Relay, I need to warn him that he needs to fill his npub in the email info required by BTCpayserver before paying. Was not so user friendly. Not at all.
So I checked if BTCpayserver is able to create custom input before paying the invoice and at my big surprise, it's possible ! => release version v1.8
They even use as example my need from Nostr to get the user npub.
So it's possible, yes, but with at least the version 1.8.0. I checked immediately my BTCpayserver version on my Umbrel node and... damn... I'm in 1.7.2. I need to update my local BTCpayserver through Umbrel to access my so wanted BTCpayserver feature. I checked the local App Store but I can't see any "Update" button or something. I can see that the version installed is well the v1.7.2 but when I check the latest version available from the online Umbrel App Store. I can see v1.9.2. Damn bis.
I searched into the Umbrel Community forum, Telegram group, Google posts, asked the question on Nostr and didn't have any clue.
I finally found the answer from the Umbrel App Framework documention :
sudo ./scripts/repo checkout https://github.com/getumbrel/umbrel-apps.gitSo I did it and it updated my local Umbrel App Store to the latest version available and my BTCpayserver.
After few seconds, the BTCpaysever local URL is available and I'm allowed to login => everything is OK! \o/
See you soon in another Fractalized story!
-
 @ e97aaffa:2ebd765d
2024-07-14 09:57:13
@ e97aaffa:2ebd765d
2024-07-14 09:57:13Estamos numa época tão estranha da humanidade…
Onde alguns querem reescrever a história, em vez de aprender e evoluir com a mesma. São com os erros que se cresce.
Onde o termo fascista é sinónimo de alguém com uma opinião diferente da sua, sem minimamente saber o real significado dessa palavra.
Onde defendem uma liberdade, que proíba o contraditório.
Onde não se discutem ideias, mas sim combatem ideias.
Onde o ambientalmente sustentável é substituir árvores e zonas verdes por estruturas em aço e zonas negras.
Onde os políticos constroem casas ou cidades, literalmente, em cima dos rios mas depois a culpa das cheias é as alterações climáticas.
Onde os alimentos tem menos importância que um peido de uma vaca.
Onde pessoas defendem que a solução para o aquecimento, é morrer de frio.
Onde a igualdade é favorecer um grupo, em detrimento de outro.
Onde o essencial é viver para consumir, em vez de usufruir.
Onde o importante é ser rico e ostentar essa mesma riqueza, mesmo que tenha de espezinhar outros para a conquistar.
Onde o mais importante é parecer em vez de ser.
Onde políticos defendem que o conhecimento pode levar a escolhas erradas, defendem o carneirismo.
Onde um político define o que é verdade ou mentira, limitando o que as pessoas podem expressar. Mas quem controla o controlador.
Onde os revisores da verdade deixaram de estar num gabinete, passando a ser um exército de jovens atrás de um teclado.
Onde, são propostas e aprovadas limitações de liberdade, sem esclarecimento ou divulgação pública. Pior que a obscuridade, é desinteresse da comunidade por liberdade.
Onde a censura é o novo normal, defender o contrário é que é censurável.
Onde a imprensa é tão livre como uma pomba dentro de sua gaiola.
Onde, quem comete o crime é protegido, quem o denúncia é perseguido.
Onde o certo é pensar com a cabeça dos outros, sem questionar.
Onde os pais delegaram o papel de educar às escolas e aos ecrãs azuis.
Onde a escola deixou de ser um lugar de conhecimento e/ou do desenvolvimento do espírito crítico.
Onde as crianças crescem doutrinados por políticos e por AI.
Onde a sociedade é programada e com um destino predefinido, como um rato dentro da sua roda.
Onde o maior erro, é pretender construir seres que não cometem erros, que não tenham vícios. Quando isso acontecer, deixamos de ser humanos. A imperfeição é a essência dos seres humanos, é o que nos difere das máquinas.
Onde só se ensina a não cair, em vez de ajudar e incentivar a levantar.
Onde se suspende a liberdade de circulação e os direitos mais básicos, sem ninguém questionar.
Onde a privacidade é crime.
Onde Satoshi é excomungado, mas Miguel Tiago é idoleterado.
Onde a moeda é utilizado como uma arma.
Onde uma guerra é digladiada entre zeros e uns, sem o comum mortal aperceber da sua existência.
Onde crianças caem em campos de batalha, como folhas em pleno outono.
Onde o direito ao Livre-arbítrio está sob ameaça.
-
 @ e97aaffa:2ebd765d
2024-07-14 09:45:13
@ e97aaffa:2ebd765d
2024-07-14 09:45:13Ontem, Trump foi baleado.
“Trump baleado na orelha escapa a aparente atentado onde morreram duas pessoas. Donald Trump ficou ferido na orelha direita após terem sido disparados vários tiros num aparente atentado durante um comício na Pensilvânia.” - Correio da Manhã
O ambiente está a ferro e fogo, para “incendiar” ainda mais as eleições norte-americanas, hoje e nos próximos dias vão ser de discursos acérrimos e polarizados e certamente com muitas teorias da conspiração, outros vão dizer que isto foi encenação.
“Na guerra, a verdade é a primeira vítima.” - Ésquilo
No outro quadrante, o Biden, há muito tempo que demonstra problemas de saúde, mesmo assim insistem na sua candidatura. Eu não consigo compreender, se é o Biden que insiste em querer ser o candidato ou são os membros de topo do partido Democrata que insistem que ele deve ser o candidato? Não sei, mas é francamente notório que ele já não tem condições físicas e mentais para continuar a ser presidente. Só demonstra muita incompetência do partido Democrata. Depois, só falta algo ainda mais teatral no lado do Biden. Talvez, a poucos dias das eleições, vai acontecer algo de estranho ao Biden, vai obrigá-lo a desistir, mas como está muito em cima das eleições, será o nome de Biden que estará nos boletins de voto. No boletim de voto está o nome de Biden, mas as pessoas de antemão já sabem que o candidato é outro, possivelmente o vice passa a presidente.
Como é possível, num país com 330 milhões de habitantes, não consegue arranjar dois bons candidatos a presidente. As sociedades ocidentais estão cada vez mais polarizadas, os partidos estão-se a afastar do centro, os partidos extremos (direita e esquerda) crescem cada vez mais. Onde as pessoas, não votam no melhor candidato, mas sim, no menos mau, ou votam no contra.
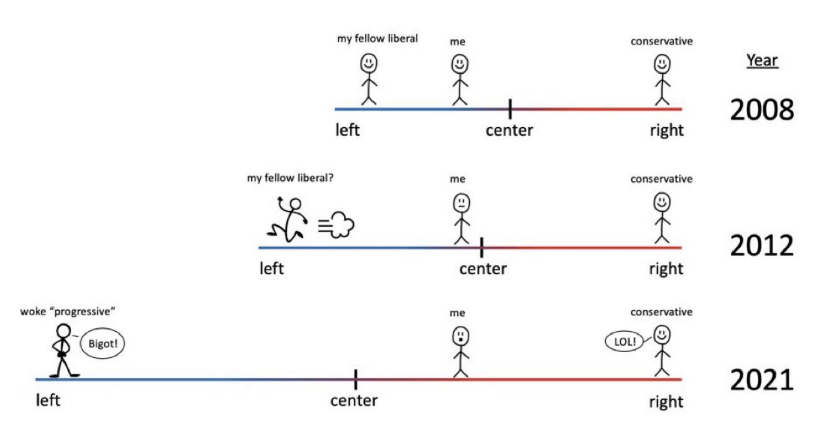
Este desenho/meme é demonstrativo do meu pensamento sociopolítico, comparando as minhas convicções de há 20 anos, com as de hoje, são as mesmas, pouco mudou. Mas há 20 anos, eu sentia-me mais perto do lado dos progressistas, mas hoje sinto-me que estou mais perto do lado dos conservadores. Na verdade, eu sempre fui e sou do centro, os polos é que estão a afastar-se do centro, os conservadores “moveram-se’ um pouco para direita, mas os progressista é que se afastaram imenso do centro.
Se o afastamento do centro crescer ainda mais e os extremos cada vez mais radicais, o futuro é inevitável, uma guerra civil. O que estamos a viver agora não é nada novo, já aconteceu no passado e os resultados não foram bons. O pior é que continuamos a cometer os mesmos erros, sem nunca aprender com o passado.
"A história não se repete, mas frequentemente rima."
-
 @ e97aaffa:2ebd765d
2024-07-14 09:44:37
@ e97aaffa:2ebd765d
2024-07-14 09:44:37Recentemente os EUA e a União Europeia anunciaram novas taxas alfandegárias impostas aos produtos importados da China.
“Presidente norte-americano, Joe Biden, anunciou esta terça-feira um aumento das taxas alfandegárias impostas aos produtos importados da China, com o agravamento mais significativo a ser aplicado sobre os veículos elétricos: dos atuais 25% vai para 100%, já a partir deste ano. Além dos automóveis elétricos, as barreiras comerciais sobre o maior concorrente dos Estados Unidos também aumentam em produtos como o aço e alumínio; baterias e suas componentes e minerais críticos; gruas portuárias; painéis solares; semicondutores; e equipamento de saúde.” – ECO
Na Europa:
“A Comissão Europeia pretende impor novas taxas sobre as importações dos carros elétricos que sejam produzidos no gigante asiático. O Executivo comunitário pretende aplicar uma taxa adicional, de 21%, em média, sobre as importações de veículos chineses, que se soma à taxa que já está atualmente em vigor, de 10%. O valor adicional pode ir até aos 38%, no caso de fabricantes que não cooperaram com Bruxelas no seu processo de investigação sobre subsídios atribuídos pelo Estado chinês.”_ – ECO
Os países ocidentais estão a acentuar as políticas protecionistas, além disso os EUA estão a endurecer as restrições aos semicondutores contra a China:
“A administração Biden segue reduzindo a gama de semicondutores que as empresas norte-americanas poderão vender à China. O Departamento de Comércio dos Estados Unidos emitiu novas regras que endurecem as restrições de exportação introduzidas em outubro de 2022. Para o governo, as medidas são necessárias para eliminar brechas nas regulações impostas no final do ano passado. As regras atualizadas “aumentarão a eficácia do nosso controle e fecharão ainda mais caminhos para contornar as nossas restrições”, disse a secretária do Comércio dos EUA, Gina Raimondo, num comunicado._ ‘Continuaremos a trabalhar para proteger a nossa segurança nacional, restringindo o acesso a tecnologias críticas, aplicando vigilantemente as nossas regras, ao mesmo tempo que minimizamos qualquer impacto não intencional nos fluxos comerciais.’ Chips avançados de inteligência artificial (IA), como os produtos H800 e A800 da Nvidia, serão afetados, de acordo com um documento regulatório da empresa norte-americana. Além da China e Macau, os regulamentos também expandem as restrições às exportações para outros 21 países com os quais os Estados Unidos mantêm um embargo de armas, incluindo o Irã e a Rússia.” – CNN Brasil
Crise
Atualmente a China está com uma grave crise, com um excesso de endividamento a nível público, como no privado. Ao contrário das duas grandes potências do ocidente, a China tem tido uma política muito comedida na desvalorização da sua própria moeda, ela tem acontecido, mas gradualmente. Nada se compara com as políticas dos EUA e da UE, que têm utilizado uma política altamente expansionista para combater as crises desde 2008.
Este gráfico demonstra bem a diferença:
Em 15 anos a China aumentou o balance sheet do banco central em 133%, o BCE aumentou em 359% e o FED aumentou 703%. Os EUA chegaram aos 900%, é um valor completamente absurdo, os estados estão a abusar do quantitative easing (QE). No final de 2022, tanto o FED e o BCE começaram a reduzir, mas ainda está muito acima dos valores pré-covid.
Onde está o problema?
Devido à Teoria dos jogos, a China nunca tentou invadir a Taiwan, porque tinha mais a perder do que a ganhar. Se houvesse uma guerra entre os dois, o mundo ficaria com um grave problema devido à falta de semicondutores, sobretudo os de última geração. Mas a China também ficaria sem essa tecnologia, além disso iria sofrer sanções do mundo ocidental, os seus produtos ficariam impedidos de entrar nesses mercados. A China iria sofrer sanções semelhantes à que a Rússia está a ter devido à Guerra na Ucrânia. Os impactos económicos e políticos desta guerra é case study para a China, deve estar a analisar ao milímetros, a criar alternativas, projetar meios de defesa, caso lhe aconteça algo similar.
Nos últimos anos a China tem reduzido imenso a exposição aos títulos do tesouro dos EUA, a China chegou a ser o maior detentor de dívida. Agora a China está a optar pela compra de ouro. Ao mesmo tempo, a China e a Rússia estão a tentar desenvolver uma alternativa ao dólar para o comércio internacional e também aumentar os laços económicos com os países aliados, especialmente dos BRICS. Além disso, tem investido biliões no desenvolvimento da sua própria indústria de semicondutores. Nos últimos anos as políticas da China têm sido focadas em diminuir a dependência do ocidente e de Taiwan, preferindo aliar-se aos países emergentes, grandes potências mas pouco democráticos, à sua semelhança.
No outro lado, os EUA também estão a diminuir a exposição à economia chinesa, estão a trocar as fábricas e mão-de-obra chinesa por mexicana, o México está a tornar-se um parceiro estratégico.
Enquanto isso, a União Europeia assobia para o lado, apenas observa. Quando acordar será tarde demais, os líderes europeus não aprenderam nada com a pandemia, a Europa está fortemente dependente da indústria chinesa.
Se a única opção para combater a crise na China for o QE, além da desvalorização imensa da sua moeda, vai gerar uma enorme reação em cascata. Os seus produtos vão ficar extremamente baratos, a China vai inundar os mercados ocidentais com produtos, para combater isso os ocidentais vão endurecer as políticas de protecionismo.
Se a China ficar sem acesso aos mercados ocidentais devido ao aumentos das políticas protecionistas do ocidente, essas mesmas políticas já estão a impedir o acesso aos semicondutores. Assim vai existir uma inversão na Teoria dos jogos, como a China já não tem mais nada a perder, já perdeu tudo o que tinha a perder, é uma passadeira vermelha para invadir Taiwan. Se todas as sanções possíveis já estão a ser aplicadas à China ainda antes da invasão a Taiwan, em caso de uma invasão, o ocidente não terá nenhuma “arma” poderosa para retaliar. Essa possível invasão afetaria sobretudo o ocidente que ficaria sem a tecnologia de Taiwan. Não sendo possível aplicar mais sanções, restando apenas confronto direto entre a China e o Ocidente.
A guerra da Ucrânia tem demonstrado que as sanções já não tem tanta eficácia, o mundo está muito globalizado e muito interconectado, existem cada vez mais meios de contornar. A UE deixou de comprar produtos fósseis à Rússia, agora está a receber da China ou da Índia, ou seja, é o mesmo produto, só que agora existe um intermédio. Chegamos ao ridículo de existir o transhipping em alto mar, ao largo de Portugal, onde os produtos são movidos de um navio de pavilhão russo para um outro navio de um país não sancionado. Algumas horas depois ou no dia seguinte o mesmo navio atraca em Portugal ou em outro porto europeu. Todos os líderes europeus sabem que isto acontece, não fazem nada para mudar, apenas fecham os olhos, são cúmplices.
Outro caso vergonhoso é demonstrado por este gráfico, os países europeus estão proibidos de exportar produtos para a Rússia, mas continuam a fazê-lo através de um intermediário. É tão ridículo, é à europeia, criam uma lei e ao mesmo tempo criam uma maneira de contornar essa lei que acabaram de criar. É uma lei cartaz, é só o viver das aparências. É a hipocrisia europeia, querer demonstrar ao mundo que eles são o exemplo, mas depois faz o contrário. É façam aquilo que eu digo, mas não façam aquilo que eu faço.
Neste caso o intermediário é o Quirguistão, mas existem inúmeros países a fazer o mesmo. É bem notório nos gráficos, após o início da guerra da Ucrânia as exportações subiram exponencialmente para o Quirguistão, mas é claro que o destino final dos produtos é a Rússia.
Com uma poderosa indústria e com produtos de baixo custo, facilmente a China vai arranjar intermediários. Em último caso usam a tática da VolksWagen, onde uma fábrica portuguesa constrói 99% do carro, mas como não está terminado é exportado como produto inacabado, para a Alemanha. Depois na Alemanha é só colocar a etiqueta “made in Germany” e o carro fica finalizado, pronto para exportação. Neste caso a VW utiliza este subterfúgio para fugir a impostos, os impostos da Alemanha são muito mais baixos que os de Portugal, mas a China pode usar para contornar as sanções.
Conclusão
Se a crise acentuar-se na China nos próximos tempos e se a única solução for uma forte desvalorização da moeda, vai provocar uma reação em cascata na economia mundial. Se escalar muito, o problema não será só económico, irá muito além disso.
Mas isto são muitos “ses”, é apenas uma hipótese muito remota e esperemos que não conheça, pelo bem de todos nós.
-
 @ e97aaffa:2ebd765d
2024-07-14 09:30:02
@ e97aaffa:2ebd765d
2024-07-14 09:30:02É com muito agrado que eu vejo este texto crítico ao Bitcoin, eu não concordo em muitas partes com o autor, mas é notório que estudou o Bitcoin, é uma crítica construtiva/argumentativa. Saiu do padrão habitual dos críticos do Bitcoin, como não estudam são monocórdicos, apenas replicam ideias feitas e erradas do passado, como “só serve para criminosos”, “o gasto energético” e outras coisas absurdas.
Este contraditório é muito importante, todos os críticos deveriam de ser assim, estudar minimamente antes de criticar, por isso, este texto merece todo o meu respeito mas eu vou fazer alguns comentários:
Ataques coordenados
O autor no texto utilizou a seguinte citação:
De fato, se um grupo com poder (hashrate) suficiente se unir, é capaz de gerar dados contendo transações inválidas. Dessa forma, cabe aos próprios usuários se coordenarem para ignorar essa sequência de transações.
Ataque com transações inválidas
Se um grupo de mineradores_/pools_ atacar com transações inválidas, não é necessário uma coordenação de usuários, mas sim individual. Segundo o protocolo, quem adiciona os blocos à blockchain são os nós(nodes) e não os mineradores/pools. Os mineradores/pools apenas propõem um template para o próximo bloco, os nós é têm a responsabilidade de verificar todas as informações contidas no template, se cumprir as regras é adicionado. Caso exista alguma inconformidade no template, essa será rejeitada pelos nós, ficando a aguardar por um novo template. No caso de transações inválidas, é muito simples de travar qualquer ataque. O adicionar do bloco é trabalho exclusivo dos nós, é feito individualmente, sem uma necessidade de coordenação entre eles.
Agora vamos imaginar um ataque ainda mais sofisticado, os maiores mineradores/pools uniam-se e realizavam um ataque coordenado. Também é fácil de travar, como a verificação é feita pelos nós, não é possível adicionar transações inválidas.
O único problema que pode causar, caso o hashrate do atacante seja muito elevado, é a rede vai ficar lenta. Em vez dos novos blocos a cada 10 minutos, vai demorar mais tempo.
No caso do ataque duradouro, os nós no período máximo de 2016 blocos, vão reajustar a dificuldade, voltando ao 10 minutos. É claro neste período até ao ajustamento a rede fica lenta, mas a probabilidade de ataque destes é muito remota. Como o atacante não tem qualquer hipótese de ter proveitos económicos, mas tem uma exorbitante custos com eletricidade, é pouco provável que alguém tente o efectuar.
Ataque com transações válidas
Qualquer ataque com transações invalidadas é fácil de resolver, o mais complexo/delicado é quando esse ataque é realizado com transações válidas.
Vamos a um exemplo concreto, imaginemos que a OFAC, obrigue as mineradoras e as pools norte-americanas a censurar transações, essas empresas não terão alternativa, terão que cumprir. Os EUA têm uma percentagem de hashrate muito elevada.
Vamos extremar ainda mais o exemplo, imaginemos que 95% do hashrate “cumprirá” com OFAC. Isto não afeta o regular funcionamento do Bitcoin, afeta apenas as transações sancionadas, vão demorar mais tempo a serem adicionadas à blockchain. Tem que aguardar por algum minerador, que não cumpra as regras OFAC, vença a corrida pelo novo bloco.
Para minimizar a possibilidade de uma censura por parte das pools, está a ser desenvolvida a Stratum V2, uma nova versão do software das pools. Nesta nova versão, a responsabilidade de criar o template passa a ser realizada pelo minerador, agora só falta as pools atualizarem o software.
Ataque de 51%
Também pode acontecer um Ataque de 51%, a possibilidade de várias pools cooperarem para realizar este ataque é extremamente baixa, quase nula. O mesmo acontece, se o ataque for organizado por um estado ou vários estados, não passam de apenas hipóteses teóricas.
A quantidade de mineradores é tremenda, distribuídos por todo o mundo, é completamente descentralizada, sendo muito pouco provável um minerador sozinho ter mais de 51% da hashrate. A única hipótese é um ataque com a cumplicidade de várias pools mas é extremamente improvável, quase nula. O ataque de 51% é raro mas já aconteceu em blockchains pequenas e centralizadas, mas o atacante foi a solo, nunca foi algo organizado por várias pools.
A estrutura necessária para o ataque é tremenda, é impossível o atacante ficar anónimo, a probabilidade de ter proveitos económicos e não ser identificado é quase nula. Mas destruirá por completo a sua credibilidade, será o fim das pools envolvidas.
Em último caso, numa situação extrema, o ataque pode ser revertido com rollback da blockchain.
Em termos genéricos, este ataque possibilita a reorganização da cadeia de blocos, permitindo uma espécie de gasto duplo, colocando em causa a imutabilidade da rede. Devido às características do Bitcoin não é possível existir uma regra de quantas confirmações são necessárias para que a transação seja imutável, quanto mais melhor. Como não existe uma regra, é uma decisão individual, de quem está a receber os satoshis (os outputs da transação), são as possíveis vítimas do ataque.
Quando eu comecei no Bitcoin, a ideia que circulava na comunidade, o mais seguro seriam 6 confirmações, mas agora em vários locais (corretoras) já aceitam 3 confirmações, quanto mais facilitamos, maior o risco que corremos. Na minha opinião, 3 confirmações é pouco e nos casos de valores mais elevados de BTC, mais exigentes temos que ser.
Eu sou bastante paranóico, gosto de seguir o lema: mais vale prevenir do que remediar. Por isso geralmente aguardo por 6 confirmações e tem que incluir 3 mineradores diferentes.
A probabilidade de um ataque é muito baixa e se nós formos rigorosos nas confirmações, o risco de ser vítima de um golpe é nula.
Agora uma conclusão que engloba todos estes possíveis ataques falados em cima, a ideia fulcral é as probabilidades. Devido à segurança do Bitcoin, tudo isto não passa de probabilidades teóricas, onde o risco é bastante reduzido ou nulo. São apenas conceitos teóricos, mas é essencial tê-los em mente, especialmente para trabalhar preventivamente, para que o Bitcoin seja cada vez mais resiliente. Para que, estes conceitos não passam da teoria à prática, é mais questão paranóica, do que um perigo real, é a segurança levada a um nível extremo. Mas foi esta paranóia que tornou o Bitcoin a rede mais segura do mundo. É importante debater estes conceitos, mas é necessário algum cuidado para não gerar alarme social.
Descentralização
Esse é um argumento muito bom. Não ter uma pessoa ou um grupo que tome as decisões da rede isoladamente chama a atenção de muitas pessoas. Imagina que maravilha um sistema que não depende da confiança em pessoas que normalmente tendem a corrupção. Imagina não depender de bancos para poder custodiar o seu dinheiro. Um verdadeiro dinheiro do povo. Seria o Bitcoin o grande libertador dessas amarras antigas de ter que confiar em um emissor de moeda? Não é bem assim.
A descentralização é o maior desafio para as comunicações, como nas blockchains. Existe o problema do Trilema das blockchains, dos 3 vértices, apenas é possível escolher dois.
Satoshi priorizou a segurança e a descentralização, deixando para um segundo plano a escalabilidade. Assim, para manter a camada base (L1) descentralizada, o número de transações são baixas, é impossível biliões de pessoas utilizá-la para as suas compras do dia-a-dia, deve apenas ser utilizadas para transações onde é necessário maior segurança ou para transações de liquidação(Settlements). As transações do dia-a-dia (a escalabilidade) devem ser executadas em camadas secundárias(L2).
No Bitcoin, devemos ter o mesmo escalonamento utilizado na banca tradicional, uma conta poupança e uma conta corrente.
Na conta poupança é destinado para guardar as poupanças de uma vida (médio/longo prazo), onde está parte significativa do nosso capital, logo necessita de uma maior segurança, devem estar na L1.
Na conta corrente é destinado para os pagamentos do dia-a-dia (curto prazo), composta por uma pequena parte do nosso capital, esta deve estar na L2.
Vamos a dois exemplos concretos:
Exemplo 1: Uma pessoa que acumulou btc e agora sobrevive exclusivamente das poupanças. Esta pessoa, a cada 2 ou 3 meses, faz uma transação da L1 para a L2 com um valor suficiente para sobreviver nesse período. Depois utiliza a L2 para efetuar os seus pagamentos do dia-a-dia.
Exemplo 2: Uma pessoa que está agora a acumular btc, está a fazer o chamado hodl. Utiliza a L2 para fazer o DCA, acumular os satoshis, quando este valor for significativo, aí sim, faz uma transação da L2 para a L1.
Em ambos os casos, a L1 é utilizada para as liquidações, onde são realizadas meia dúzia de transações por ano, nas L2 são feitas milhares de transações por ano.
A descentralização é fundamental para o seu funcionamento, mas não é imperativo para os pagamentos, ou seja, é fundamental na L1, é a única maneira para garantir a segurança do btc e garantir a descentralização nas camadas seguintes.
Sendo a L1 descentralizada, é possível construir L2 descentralizadas ou centralizadas, ambas.
Se a L1 for centralizada, não é possível construir L2 descentralizadas, são todas centralizadas.
Quem são os “emissor da moeda” no ecossistema do Bitcoin?
São os intermediários, os custodiantes. Podem estar na L1, nas L2 ou em sistemas complemente centralizados, como as corretoras ou bancos.
Temos necessariamente de confiar no emissor da moeda?
Não, primeiro as pessoas podem utilizar apenas a L1, só que pode ter um custo elevado.
Podem optar por L2, neste caso existem 2 opções: descentralizadas ou centralizadas. Destas 3 opções possíveis, para efetuar transações, só numa existe algum risco do emissor. No caso do Bitcoin, o “confiar no emissor” é uma opção e não uma obrigação.
No caso das moedas no sistema FIAT, a centralização é imposta, é obrigatório o confiar, não existiam alternativas.
Esta é a beleza do Bitcoin, dá liberdade de escolha ao indivíduo.
Utilizar L2 não é sinónimo de perder a descentralização/soberania, é apenas uma opção. Muitos utilizadores prescindem da soberania pela conveniência, preferem as carteiras centralizadas/intermediários, porque são mais simples, mais baratas, sem a necessidade de manutenções e de ter conhecimentos técnicos. É totalmente legítimo e compreensível esta escolha, no meu caso eu utilizo ambas mas preferencialmente a descentralização.
É claro, quem prefere o centralizado, corre mais riscos, está dependente do custodiante/intermédio.
Além disso, a maioria dos usuários não possui o software (node) para validar as transações por conta própria. Mesmo dentre os entusiastas que o fazem, muitos não possuem conhecimento técnico para validar o código-fonte ou participar dos debates técnicos. A descentralização é utopia. Não existe. Sempre haverão pessoas ou grupos que terão o maior poder de algo (Regra de Pareto). Logo, o Bitcoin também não foge da regra.
Rodar de nós
A descentralização não é uma utopia, o que é utópico, é acreditar que todas as pessoas vão rodar o próprio nó, isso não vai acontecer. Só roda quem quer, não é obrigatório, quem quer roda, que não quer não roda, mas todos podem se beneficiar com o Bitcoin. Com o avanço tecnológico, atualmente nem é necessário rodar o nó para usufruir da soberania. Para a rede ser segura não é necessário milhões de nós, basta dezenas de milhares para a tornar imutável e plenamente descentralizada.
O bitcoin dá liberdade individual, liberdade de escolha, permite a utilização de carteira não-custodiais ou custodiais, cada um escolhe a melhor que se adapta ao seu perfil ou conhecimento. Nada disto é possível no sistema tradicional, onde só é possível carteiras custodiais, não existe alternativa.
No meu ponto de vista, a soberania é essencial (como rodar um nó), é utópico acreditar que todas as pessoas vão seguir este caminho, mas isto é escolha pessoal, uma liberdade individual. Se eu tenho o direito/liberdade de ser soberano, a outra pessoa também têm a liberdade de o não ser soberano, de não querer a responsabilidade de guardar a seed.
Temos visões diferentes, mas ambos nos beneficiamos e acreditamos no Bitcoin. Por não rodar um nó, não é inferior a mim, somos todos iguais nos direitos, o Bitcoin é para todos, mesmo para aqueles que não acreditam no Bitcoin, não existe distinção.
Mas é claro que, quem não quer ter a responsabilidade da custódia, terá que estar consciente dos riscos, poderá ter problemas no futuro. Terá que pesar os prós e os contras da soberania. Eu penso no exemplo dos meus pais, a probabilidade de eles perderem a seed é muito superior, à possibilidade de serem confiscados pelo estado. Para o perfil deles, o mais adequado é uma carteira custodial ou com seed recovery. Conhecendo bem os meus pais, nunca na minha vida, eu aconselharia uma carteira não-custodial.
É claro que rodar um nó é importante, mas não é essencial, essa é mais uma função para os maximalistas.
Verificação do código-fonte
Hoje em dia, o ecossistema do Bitcoin é tão extenso, são milhões de linhas de código, é humanamente impossível um indivíduo verificar o código-fonte sozinho. Se alguém com conhecimentos técnicos não consegue verificar tudo sozinho, é impossível para os leigos.
Por isso o Bitcoin é opensource, onde a desenvolvimento e verificação é realizada por milhares de olhos, é um trabalho colaborativo, realizado por pessoas altamente qualificadas. Onde cada linha, cada alteração é verificada por centenas de pessoas.
Esse é o motivos de sermos conservadores nas atualizações, qualquer alteração é necessário um longo período de testes e de rigorosas verificações. Não pode haver falhas, qualquer distração pode colocar em causa anos de trabalho.
O código-fonte opensource é um trabalho colaborativo.
A não verificação do código-fonte por pessoas comuns não é razão para colocar em causa a descentralização do Bitcoin. A única verificação que os não técnicos devem realizar, é fazer os downloads nos locais oficiais e manter os softwares atualizados.
Centralização das Pools
É importante também dizer que as pools de mineração são centralizadas. Aproximadamente 80% da mineração de Bitcoins é controlada por apenas 5 pools. Cada node dentro das pools possuem o poder por conta própria, é verdade. Porém existe um certo poder de influência das pools com os nodes de mineração.
Em cima, já respondi em parte ao problema da centralização das pools de mineração.
Em suma, a centralização das pools não coloca em causa a descentralização da rede, porque o fundamental na descentralização são os nós da rede, as pools desempenham um papel muito diminuto nessa descentralização.
É claro, se o hashrate fosse mais disperso por mais pools era melhor. Com o novo software para as pools, é dado mais poder aos mineradores, na elaboração do template, o risco das pools fica ainda mais minimizado.
A Escalabilidade
Lastro dos IOUs
O problema com o ouro foi a escalabilidade. Pelas limitações físicas, o ouro não conseguiu ser escalável. Tendo que utilizar soluções de segunda camada (certificados de ouro) como uma representação do ouro original. Essa falta de contato com o ouro físico fez as pessoas se acostumarem a trocar somente certificados em papel-moeda e, posteriormente, foi se perdendo o lastro em ouro até se tornar 100% fiduciária.
Concordo plenamente com a afirmação, só que o Bitcoin tem algumas pequenas alterações que fazem toda a diferença. Os certificados de ouro criaram um risco, mas o maior risco aconteceu com a centralização, na existência de apenas um emissor (FED) e em um único produto (o dólar).
No Bitcoin é totalmente diferente, as carteiras custodiais ou IOUs são uma opção, só usa quem quer.
No caso das L2, existem carteiras custodiais e não-custodial. Esta parte é fundamental, as pessoas podem ter satoshis em carteiras L2 não-custodiais e “trocar” por L1 sem intermediários, sem a necessidade de uma permissão de um governo, estão seguros.
Os riscos associados às L2 centralizadas, é menor que o risco existente nos certificados de ouro/papel-moeda, porque existem vários emissores e em várias jurisdições, é um pormenor que faz toda a diferença.
Como o Bitcoin é digital, o emissor pode estar literalmente em qualquer ponto do mundo, ou simultaneamente em vários países, camuflado pelo TOR, irrastreável, ou em países pró Bitcoin, existe uma maior segurança jurídica.
Podemos estar num país e utilizar uma custodiante de noutro país, como aconteceu com a WOS, está oficialmente indisponível nos EUA, mas muitos norte-americano continuam a utilizar.
Como existem muitos emissores, as pessoas vão optar pelos mais seguros.
Um país pode confiscar o lastro dos emissores, mas só o consegue nas empresas sob sua jurisdição e esse confisco apenas afeta os residentes desse país, os restantes povos não são afetados. Assim, o que pode acontecer, é alguns emissores/custodiantes podem ser confiscados, ficando sem o lastro, mas o Bitcoin no geral não tem problemas. Como aconteceu na FTX, a corretora perdeu parcialmente o lastro, os clientes tiveram grandes perdas, mas o restante ecossistema Bitcoin, não perdeu o “lastro”.
O confisco é algo inevitável no futuro, algum país vai fazê-lo, possivelmente o primeiro será um país pequeno. Mas essa notícia vai propagar-se pelo mundo, vai colocar todos os utilizadores em alerta, a pensar que poderá também acontecer a si. Esse medo de perder os fundos vai estimular e gerar uma forte adoção à auto-custódia. Como acontece sempre após uma falência de uma corretora, gera uma corrida bancária em todas as corretoras, um pico de demanda por soberania. Infelizmente as pessoas só aprendem com a dor.
A parte mais curiosa disto tudo, a existência de múltiplos custodiantes/bancos em cada país e por centenas de países, essa enorme distribuição de empresas centralizadas cria uma certa descentralização, minimizando o risco.
Em suma, um risco universal dos IOUs de Bitcoin, perderem o lastro é nulo, o que poderá acontecer é casos localizados, ou seja, não é perda de lastro do Bitcoin, é o confisco realizado por algum estado ou a fraude de algum custodiante/emissor. Mas isto é um problema localizado e não sistémico. No caso do ouro foi sistémico, porque só existia um emissor e com poder absoluto.
Assim, para minimizar os riscos, a melhor opção é a auto-custódia.
Tamanho do Bloco
O Bitcoin é programado para fazer 1 bloco de transações de apenas 1 mb a cada ~10min. Isso significa que para sua transação ter prioridade terá que pagar taxas mais altas do que a média do mercado. A limitação de 1 mb serve para deixar a rede mais descentralizada já que quanto maior o bloco, maior também será a capacidade necessária para rodar um node na rede. Menos nodes significa mais centralização.
Análise perfeita.
Sem falar que já foi tentado aumentar o Bloco em 2017 com o Bitcoin Cash e a rede não foi para frente.
Pelo contrário, essas ideias foram em frente, o projeto foi criado, por isso existe o Bcash. Só que o tempo provou que o aumento do tamanho do bloco não é a solução, as pessoas preferiram o Bitcoin original.
Basta ver as consequências do aumento do bloco, onde existem apenas 3 pools de mineração e uma delas é responsável por 85% do hashrate.
Os nós são muito poucos:
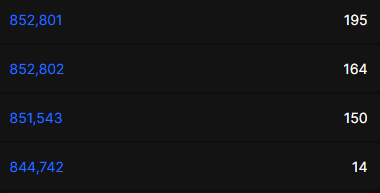
Aumentou o tamanho do bloco, mas tem uma blockchain menor que a do Bitcoin:
Além do Bcash, surgiu também o BSV, um fork do Bcash, onde as consequências do aumento do tamanho foram terríveis, apenas consegui dados até 2023, o tamanho da blockchain aumentou exponencialmente, é 12x maior que o atual tamanho do Bitcoin:

Em ambos os projetos a descentralização está comprometida, não existe.
Custo de Transação na L1
Em Abril de 2024, logo após o halving, a taxa para transacionar na rede do Bitcoin estava em média 200 dólares. Imagina quanto pode chegar essa taxa nos próximos halvings com mais usuários na rede e com com mais implementações do tipo Ordinals ou Runes. É no mínimo irônico que maximalistas disputem espaço na rede com especuladores de memecoins e nfts congestionando a blockchain da criptomoeda.
É verdade que atingiu esses valores, mas foi num curto espaço de tempo, foi uma loucura momentânea que certamente não irá repetir, isso foi uma ocasião especial. O custo médio de uma transação na L1 está longe desses valores, neste preciso momento está inferior a 1$.
No futuro é provável que a médio prazo, o custo médio fique entre os 10$ e 20$.
Os NFTs e memecoins só estão na L1, porque está barata, quando ficar cara, estes projectos vão migrar para L2, ninguém vai pagar 10$ de fee para transacionar uma memecoin que vale alguns centavos. Na L1 vão ficar apenas coisas com valores elevados.
Pode parecer contraditório mas o chegar a 200$ é sinal que o sistema funcionou, está saudável. Isso só aconteceu devido a uma procura extraordinária, fez com que o custo aumentasse, mas a rede nunca parou. Enquanto no sistema financeiro tradicional, quando existe um pico de procura, muito fora do normal, os servidores vão abaixo e o sistema fica inoperacional para todos, durante um período. No caso do bitcoin os custos aumentam, é uma espécie de proteção contra DDoS, sem nunca o sistema ir a baixo.
Eu não quero dizer que o custo de uma transação de 200$ é bom, claro que não é, mas isto é algo que aconteceu esporadicamente. Mas não podemos colocar em causa um sistema por algo que acontece esporadicamente e num espaço de tempo tão curto.
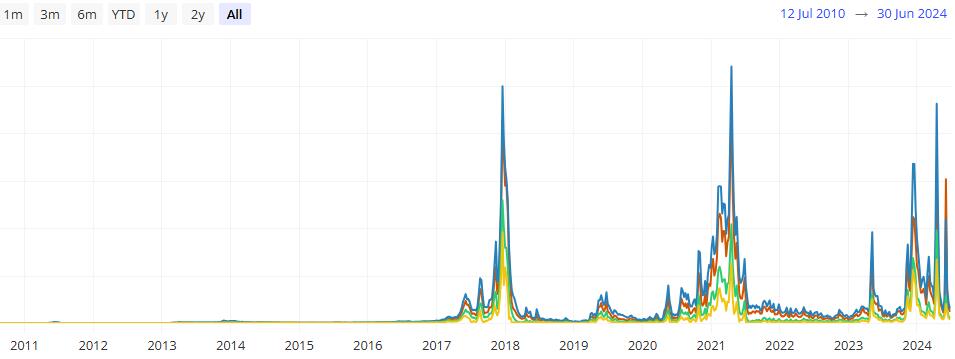
Nos 15 anos do Bitcoin apenas por 5 períodos onde o preço de transação atingiu valores exorbitantes e sempre num curto espaço de tempo.
-
22 de Dezembro de 2017:
-
21 de Abril de 2021:
-
17 de Dezembro de 2023:
-
20 de Abril de 2024:
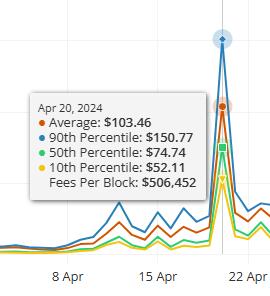
-
7 de Junho de 2024:
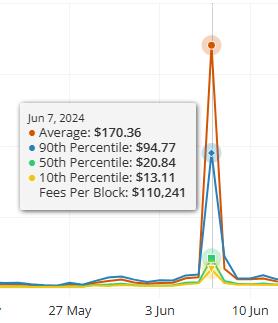
Nestes 5 períodos, apenas em um (20 de Abril de 2024), o percentil 50 foi superior a 31$. É verdade que 30$ não é acessível para toda a gente, mas o Bitcoin é a rede mais segura do mundo, isto tem um custo.
O 7 de Junho de 2024 é um caso particular, não foi um problema de uma elevada procura, mas sim, devido a um bug de uma corretora. Colocou um fee(taxa) absurdo nas suas transações de consolidação.
A L1 vai ser utilizada sobretudo para transações de liquidação(Settlements) ou com altos valores, onde podem pagar taxas mais elevadas.
Uma transação de liquidação na L1, “condensa” centenas ou milhares de operações realizadas em L2, logo esse custo pode ser dividido por essas centenas. Os custos são minimizados.
É similar ao que acontece na banca tradicional, durante o dia, os clientes de dois bancos realizam milhares de transações entre si, são apenas alterações nas bases de dados de ambos bancos. No fim do dia, os bancos fazem um balanço e o banco que estiver em crédito, efetuará uma transação para o outro banco. Essa real efetivação da transação (a liquidação), onde existe realmente um troca monetária entre os bancos só acontece algum tempo depois.
Geralmente nas transações de liquidação, não existe uma urgência imperativa, a transacção não necessita de ser executada de imediato, existindo uma maior flexibilidade, podendo aguardar por um momento com fees mais baixas.
Se for urgente está sujeito ao custo do momento.
Lightning Network
Os bitcoiners alegam que o Bitcoin resolve o problema da escalabilidade por ser digital. Mas até agora não temos nada concreto que mostre que seja possível escalar uma moeda “descentralizada”. Um passo nesse sentido foram a implementação da Lightining Network, uma “segunda camada” do Bitcoin implementada em 2018. Enquanto o ecossistema do Bitcoin se expande, a Lightning se move em direção contrária. Além disso, a Lightning apresenta falhas críticas que não favorecem o crescimento da adoção.
As soluções de L2 são a única via para resolver o problema da escalabilidade.
A Lightning Network (LN) foi a primeira a surgir e está completamente funcional, consegue processar 1 milhão de transações por segundo.
Os problemas da LN não são de código mas sim da dependência da L1, para fazer a abertura, fecho ou balancear os canais. Se no momento em que for necessário realizar estas operações, os custos na L1 for elevado, é um problema. Este problema afeta quem faz a auto-custódia, para evitar esse risco, as pessoas preferem utilizar carteira custodiais.
Hoje em dia estes períodos de custos mais altos na L1 são raros, mas é previsível no futuro com o aumento da adoção, estes períodos vão ser mais recorrentes, por isso a LN tem que ser melhorada, para que no futuro não seja um problema crítico.
Será que todos nós necessitamos de uma carteira L2 não-custodial para os pequenos pagamentos?
Na minha opinião não. Como as carteiras L2 necessitam de estar online e geralmente em smartphones, logo existe um maior risco de segurança, por esse motivo devemos ter pouco capital nesses dispositivos. Como o capital alocado é baixo, a grande maioria dos utilizadores prefere optar por carteiras simples, a soberania não é uma prioridade. A descentralização e a soberania é fulcral apenas na L1, onde estão os valores elevados, nas L2 não.
As L2 custodiais como a WOS é um excelente produto, simples, é um produto ideal para os leigos, que serão a maior parte da população.
Eu abri um canal de LN(não-custodial), há mais de ano, possivelmente já fiz milhares de transações, sempre a baixo custo, mesmo nos dias de congestionamento da L1 não houve qualquer problema. A minha experiência com LN é muito boa, mas a auto-custódia tem um custo. Mas esses custos da abertura e fecho do canal são divididos por dezenas ou centenas de transações na LN, assim os custos operacionais continuam a ser baixos, menor que qualquer sistema tradicional.
Atualmente com a Phoenix é simples ter LN não custodial, mas as pessoas continuam a preferir WOS, mesmo entre os maximalistas. Isto demonstra que a soberania/descentralização não é um ponto fundamental na escolha de uma carteira LN, mas sim a sua simplicidade e usabilidade, nisto a WOS é vencedora.
As carteiras custodiais têm a possibilidade de crescimento exponencial, mesmo com a atual tecnologia.
As pessoas preferem terceirizar a custódia, não querem ter essa responsabilidade, querem ter alguém para apontar o dedo quando algo corre mal. A sociedade foi construída na base da confiança, mas ao longo da história essa mesma confiança foi abusada inúmeras vezes, sobretudo pelos políticos.
É natural com a massificação da adoção, os novos utilizadores são cada vez menos geeks, são mais pessoas comuns, sem conhecimentos técnicos, vão preferir serviços custodiais.
É este o melhor caminho certo?
Na opinião não, mas a maioria das pessoas preferem, a adoção demonstra isso. Mas compreendo essa escolha, faz todo o sentido, como são montantes baixos, compensa aceitar esse risco e deixar todo o trabalho da gestão de um canal para o custodiante.
O essencial é existir as duas vias, depois cada indivíduo escolhe o melhor que se adapta ao seu perfil.
O real problema
É claro que a utilização da LN poderia ser muito superior, mas na minha opinião, não é a tecnologia que está a atrasar a adoção. O problema é que a maioria das pessoas olha para o Bitcoin apenas como uma reserva de valor, apenas guarda-o. São poucas as pessoas a gastá-lo. Este sim é o grande desafio, a mudança de mentalidade.
Alternativas
Este texto de opinião, apenas fala da LN, mas existem outras L2 no Bitcoin. A carteira Aqua ou a Helm são excelentes produtos. A interoperacionalidade das duas carteiras é extraordinária, o comum mortal nem nota que está a utilizar uma sidechain Liquid. A Liquid é segura e muito barata transacionar. Ambos são muito bons para o cidadão comum como a Helm diz: “a Lightning wallet that even your grandma can use”.
Bitcoin é um organismo vivo, sempre em desenvolvimento. Atualmente já estão numa fase avançada de desenvolvimento a Ark, Fedi, Cashu e a Mercury.
O desenvolvimento de L2 tem sido tremendo no último ano, talvez seja o período onde existe mais desenvolvimento no ecossistema do Bitcoin, são dezenas de projetos em desenvolvimento, surgem ideias novas quase todos os dias. É claro que a maioria será um flops, mas certamente algumas boas ideias vão sobressair.
Futuro
A atual tecnologia da LN ainda permite um enorme crescimento na adoção, mas para o Bitcoin estar disponível para biliões de utilizadores, a utilizar como moeda, como nós desejamos, é necessário outras soluções, sem dúvida nenhuma.
A médio prazo, a LN ainda será a principal solução, mas é muito provável que no futuro(a longo prazo) as pessoas deixem de usar a LN para pagamentos, talvez optem por Ark ou dispersam por várias tecnologias. A LN vai se transformar num sistema que vai ligar, vai fazer a interoperacionalidade da liquidez entre diferentes L2 e a ligação à L1.
Repito, a tecnologia tem muito que melhorar, mas não é ela a principal responsável pelo atraso da adoção do Bitcoin como moeda.
Adoção da LN
A rede vem perdendo a sua adoção
Isto é uma interpretação errada dos números, apesar da capacidade da LN ter diminuído ligeiramente, não significa que tenha perdido adoção, pelo contrário. Como a unidade de conta dos produtos é em FIAT, temos que analisar os dados em FIAT.
A capacidade mais alta da LN ocorreu a 8 de julho de 2023, com 5523 BTCs, correspondia a 167 milhões de dólares.
Hoje a capacidade está ligeiramente abaixo, nos 5206 BTCs, corresponde a 322 milhões de dólares.
Isto significa que não diminuiu, mas sim aumentou 48%, mais 155 milhões de dólares. Como o valor total em dólares alocado aumentou imenso mas o número médio de satoshis por pessoa reduziu. Isto significa que existem mais pessoas a utilizar.
Eu sou um exemplo prático disso, com a valorização do Bitcoin, o valor já era demasiado alto, muito superior ao que eu necessito, por isso movi parte para a L1.
Apesar de hoje a capacidade em BTC está próximo ao máximo de 2023, a grande diferença está no número de canais, que diminuiu bastante. Isto significa que são menos canais mas com maior capacidade de liquidez. A LN está a centralizar-se em canais maiores, isto é a prova que as pessoas optam por carteiras custodiais.
Escola Austríaca
As partes sobre a escola austríaca prefiro não comentar, deixo para os mais entendidos sobre o assunto.
Conclusão
Para finalizar, apesar de não concordar com muitas coisas que o autor do texto diz, mas tenho que louvar a sua atitude e a maneira como expressou os seus argumentos. Apesar de algumas imprecisões, o autor demonstrou ter bons conhecimentos sobre o Bitcoin. É um exemplo a seguir por outros críticos, uma crítica construtiva.
Eu creio que no futuro o autor vai reconhecer que estava errado nesta análise, vai voltar a acreditar no Bitcoin, ao não fechar essa porta, é um bom sinal.
-
-
 @ e97aaffa:2ebd765d
2024-07-14 09:15:44
@ e97aaffa:2ebd765d
2024-07-14 09:15:44A baleia alemã finalmente está morta.
O governo da Alemanha concluiu nesta sexta-feira, 12, a venda de todos os Bitcoin que as autoridades tinham apreendido no início deste ano.
Origem dos fundos
Os 49.857 bitcoins foram apreendidos em meados de janeiro, avaliados em cerca de US$ 2,1 biliões na época, pela polícia no estado alemão oriental da Saxónia. A apreensão foi o resultado de uma “transferência voluntária” do suspeito, acusado de operar o Movie2k.to.
“A promotoria pública de Dresden deu a notícia, afirmando que Movie2K era operado ilegalmente e distribuía mais de 880 mil cópias pirateadas de filmes e seriados entre 2008 e 2013. Em novembro de 2019, autoridades alemãs prenderam um dos dois principais operadores do site Movie2K, enquanto o segundo operador está foragido. Os dois operadores alegadamente começaram a comprar bitcoin em meados de 2012 do dinheiro recebido por inscrições e receitas de anúncio. Movie2K era o 19º site mais visitado da Alemanha em 2013 antes de ser tirado do ar. O operador, agora em custódia, comprou mais de 22 mil bitcoins (atualmente equivalentes a US$ 260 milhões), afirmou a promotoria. Então, entre 2013 e 2016, compraram propriedades com cripto, que também foram confiscadas. A promotoria disse ter confiscado os criptoativos com a ajuda da Polícia Criminal Federal da Alemanha e do Departamento Federal de Investigação dos EUA (FBI)” – Moneytimes
Venda
A venda iniciou a 19 de junho, ao mover 500btc para a Kraken.
Mas foi nas últimas duas semanas que o processo acelerou, mas ontem foram movidos os últimos Bitcoins, a conta está a zeros.

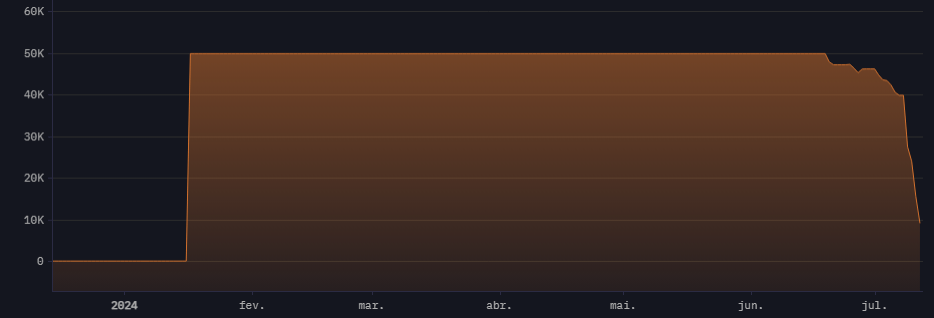
Isto contribuiu para gerar uma pressão de venda no mercado, resultando em um movimento de queda no preço. Mais que a dimensão da venda, a principal razão da queda é o FUD. Além do governo alemão, neste mesmo periodo o Mt. Gox começou a realizar pagamentos em Bitcoin no valor de US$ 9 biliões aos credores, o governo dos EUA vendendo bitcoins apreendidos do Silk Road e Banmeet Singh.
Tudo isto somado gerou algum FUD e mesmo assim a queda não foi assim tão significativa, no passado teria sido bem pior.
Quem aproveitou desta “nova” liquidez e a queda de preço foram os EFTs à vista, receberam capital fresco. Os investidores desses fundos desaceleraram a queda no preço. Desde 25 de junho, os fundos viram entradas líquidas de 886,8 milhões de dólares, segundo dados da CoinGlass.
Ou seja, saiu de uma baleia e foi redistribuído para outras baleias, não é o ideal, mas é assim que funciona o mercado.
Ondas de Choque
A venda em massa da Alemanha não foi bem recebida pela legisladora alemã e ativista do Bitcoin Joana Cotar:
“A membro do parlamento alemão Joana Cotar disse que a venda em massa do Bitcoin não é “sensata” e “produtiva”, pois poderia ser usada para diversificar os ativos do tesouro e proteger contra a desvalorização da moeda. A parlamentar alemã e ativista do Bitcoin, Joana Cotar, pediu ao governo que pare sua “apressada” venda de Bitcoin e o adote como “moeda de reserva estratégica” para se proteger contra riscos no sistema tradicional. Cotar disse que o Bitcoin poderia ajudar a Alemanha a diversificar seus ativos do tesouro, proteger contra a inflação e a desvalorização da moeda e promover a inovação no país.” – Cointelegraph
Eu não tenho qualquer dúvida, o governo alemão vai se arrepender de ter realizado esta operação. No futuro, quando os historiadores forem analisar isto, vão perceber que foi um dos maiores erros das história alemã.
Memes
Não há notícias de Bitcoin, sem os respectivos memes e esta notícia não fugiu à regra.
Devido à transparência da blockchain do Bitcoin, é possível saber os endereços do governo alemão, e a comunidade não perdeu esta oportunidade para fazer humor.
Um utilizador enviou um NFT, com uma mensagem, que se traduz como “Impostos são roubo.”

outro

brc-20
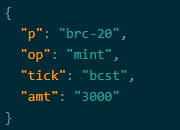
Runes
Muitos milhões de tokens runes. 1 2
OpRETURN
Um OpRETURN também surgiu: “we shall buy on the beaches, we shall buy on the landing grounds, we shall buy in the fields and in the streets, we shall buy in the hills; we shall never sell”
Coinjoin
Também não poderiam faltar as transações oriundas de Coinjoin, foram exatamente 15 transações. Curiosamente, ou não, o governo alemão enviou esses satoshis para as exchanges e foram ~~lavados~~ vendidos.
No fim de contas, só houve um único vencedor, o Bitcoin.
-
 @ 6c8c7979:15595f3e
2024-07-14 03:48:03
@ 6c8c7979:15595f3e
2024-07-14 03:48:03
It is a technical school, founded by the German architect Walter Gropius in 1919 in the city of Weimar, Germany. Its purpose was to liberate art from industry, revive craftsmanship, and integrate art and craft. The school attracted the most important artists of that era, who aimed to rebuild the world from a new perspective after World War I, marking a new era. Consequently, new teaching methods, architectural techniques, drawing, and design were discovered and developed to train a new type of artist capable of working across all fields.

A mandatory course was created for all students to learn art and handicrafts, developed by the Swiss painter Johannes Itten, who encouraged students to work based on their instincts by allowing them to experiment with models, materials, and colors. The primary colors (red, yellow, blue) and geometric shapes (square, triangle, circle) became distinctive features and a registered trademark of the Bauhaus.

The Bauhaus school was relocated to Dessau in 1925 and then to Berlin in 1932. A year later, it was forcibly closed by the Nazis, who considered it a foreign influence that needed to be eliminated. This led to the migration of its patrons and architects out of Germany, who spread their ideas worldwide, especially in America.
Despite its short existence from 1919 to 1933, its impact is evident globally. For instance, the famous book "Neufert" by Ernst Neufert, a Bauhaus graduate, remains a fundamental reference for architects worldwide.


$$Characteristics of the Bauhaus school$$- Simplification, abstraction, and departure from the decorative elements prevalent in Europe at that time.
- Use of primary geometric forms.
- Utilization of primary colors.
- Fusion of Cubist and Expressionist influences.
- Integration of form and function.


$$The Bauhaus school$$- Architectural creativity should emphasize clarity, honesty, and a departure from anything unrelated to true architecture.
-
Residential buildings should be designed with content and execution that align with economic feasibility, addressing the economic aspects of the time including construction materials and expenses.
-
Furnishings and building equipment should be accessible, beautiful, and durable.
- Standardization and modeling of residential building design, emphasizing the importance of prefabricated construction methods that facilitate global architectural ideas, aiming for universal architecture.
- Bauhaus envisions a prosperous future of architecture through collaborative architectural work characterized by generosity, democracy, and defined intellectual direction.



Wassily Kandinsky was born in Moscow in 1866 and settled in Germany by the end of the 19th century. He became a key figure in the development of Expressionism in Northern Europe over the following years. His famous painting "Der Blaue Reiter" was an inspiration for the Expressionist art movement.
He began teaching at the Bauhaus school in 1922, where he focused on teaching his students how to analyze primary colors and their interactions. In 1923, he developed a survey where participants were asked to fill a circle, square, and triangle with the appropriate primary color. The result was the yellow triangle, red square, and blue circle, which became classic Bauhaus shapes discovered and popularized by Kandinsky through his famous work.

Marcel Breuer was born in Hungary in 1902 and was one of the youngest members of the original Bauhaus generation. At the age of eighteen, he left his hometown of Pecs and joined the Bauhaus in 1920, becoming one of its early standout talents. He was appointed head of the carpentry workshop at the Bauhaus and later taught in the newly established architecture department after the school moved from Weimar to Dessau in 1925.
One of his most famous works is the design of the chair known as the Model B3 chair, created between 1925-1926. Inspired by bicycle handlebars, this chair was developed while Breuer was head of the workshop at the Bauhaus.
Wassily Kandinsky admired the completed design of the chair and its embodiment of Bauhaus principles. Breuer subsequently created a duplicate version for Kandinsky's personal use, and later the chair became widely known as the "Wassily Chair."


And the list extends with names of pioneers of this legendary school who contributed to its flourishing, such as:
- Hannes Meyer
- Ludwig Mies van der Rohe
- Lilly Reich
- Lyonel Feininger
- Oskar Schlemmer
- Gerhard Marcks
One of the most prominent figures of the Bauhaus school is Paul Klee.
Paul Klee was among the most talented and enigmatic artists closely associated with the Bauhaus. He created the canvas painting "Red Balloon" in 1922, where geometric shapes (rectangles, squares, and domes) in primary colors were selected. A single red circle floats at the center of the upper part of the painting, resembling a hot air balloon.
-
 @ 6871d8df:4a9396c1
2024-06-12 22:10:51
@ 6871d8df:4a9396c1
2024-06-12 22:10:51Embracing AI: A Case for AI Accelerationism
In an era where artificial intelligence (AI) development is at the forefront of technological innovation, a counter-narrative championed by a group I refer to as the 'AI Decels'—those advocating for the deceleration of AI advancements— seems to be gaining significant traction. After tuning into a recent episode of the Joe Rogan Podcast, I realized that the prevailing narrative around AI was heading in a dangerous direction. Rogan had Aza Raskin and Tristan Harris, technology safety advocates, who released a talk called 'The AI Dilemma,' on for a discussion. You may know them from the popular documentary 'The Social Dilemma' on the dangers of social media. It became increasingly clear that the cautionary stance dominating this discourse might be tipping the scales too far, veering towards an over-regulated future that stifles innovation rather than fostering it.

Are we moving too fast?
While acknowledging AI's benefits, Aza and Tristan fear it could be dangerous if not guided by ethical standards and safeguards. They believe AI development is moving too quickly and that the right incentives for its growth are not in place. They are concerned about the possibility of "civilizational overwhelm," where advanced AI technology far outpaces 21st-century governance. They fear a scenario where society and its institutions cannot manage or adapt to the rapid changes and challenges introduced by AI.
They argue for regulating and slowing down AI development due to rapid, uncontrolled advancement driven by competition among companies like Google, OpenAI, and Microsoft. They claim this race can lead to unsafe releases of new technologies, with AI systems exhibiting unpredictable, emergent behaviors, posing significant societal risks. For instance, AI can inadvertently learn tasks like sentiment analysis or human emotion understanding, creating potential for misuse in areas like biological weapons or cybersecurity vulnerabilities.
Moreover, AI companies' profit-driven incentives often conflict with the public good, prioritizing market dominance over safety and ethics. This misalignment can lead to technologies that maximize engagement or profits at societal expense, similar to the negative impacts seen with social media. To address these issues, they suggest government regulation to realign AI companies' incentives with safety, ethical considerations, and public welfare. Implementing responsible development frameworks focused on long-term societal impacts is essential for mitigating potential harm.
This isn't new
Though the premise of their concerns seems reasonable, it's dangerous and an all too common occurrence with the emergence of new technologies. For example, in their example in the podcast, they refer to the technological breakthrough of oil. Oil as energy was a technological marvel and changed the course of human civilization. The embrace of oil — now the cornerstone of industry in our age — revolutionized how societies operated, fueled economies, and connected the world in unprecedented ways. Yet recently, as ideas of its environmental and geopolitical ramifications propagated, the narrative around oil has shifted.
Tristan and Aza detail this shift and claim that though the period was great for humanity, we didn't have another technology to go to once the technological consequences became apparent. The problem with that argument is that we did innovate to a better alternative: nuclear. However, at its technological breakthrough, it was met with severe suspicions, from safety concerns to ethical debates over its use. This overregulation due to these concerns caused a decades-long stagnation in nuclear innovation, where even today, we are still stuck with heavy reliance on coal and oil. The scare tactics and fear-mongering had consequences, and, interestingly, they don't see the parallels with their current deceleration stance on AI.
These examples underscore a critical insight: the initial anxiety surrounding new technologies is a natural response to the unknowns they introduce. Yet, history shows that too much anxiety can stifle the innovation needed to address the problems posed by current technologies. The cycle of discovery, fear, adaptation, and eventual acceptance reveals an essential truth—progress requires not just the courage to innovate but also the resilience to navigate the uncertainties these innovations bring.
Moreover, believing we can predict and plan for all AI-related unknowns reflects overconfidence in our understanding and foresight. History shows that technological progress, marked by unexpected outcomes and discoveries, defies such predictions. The evolution from the printing press to the internet underscores progress's unpredictability. Hence, facing AI's future requires caution, curiosity, and humility. Acknowledging our limitations and embracing continuous learning and adaptation will allow us to harness AI's potential responsibly, illustrating that embracing our uncertainties, rather than pretending to foresee them, is vital to innovation.
The journey of technological advancement is fraught with both promise and trepidation. Historically, each significant leap forward, from the dawn of the industrial age to the digital revolution, has been met with a mix of enthusiasm and apprehension. Aza Raskin and Tristan Harris's thesis in the 'AI Dilemma' embodies the latter.
Who defines "safe?"
When slowing down technologies for safety or ethical reasons, the issue arises of who gets to define what "safe" or “ethical” mean? This inquiry is not merely technical but deeply ideological, touching the very core of societal values and power dynamics. For example, the push for Diversity, Equity, and Inclusion (DEI) initiatives shows how specific ideological underpinnings can shape definitions of safety and decency.
Take the case of the initial release of Google's AI chatbot, Gemini, which chose the ideology of its creators over truth. Luckily, the answers were so ridiculous that the pushback was sudden and immediate. My worry, however, is if, in correcting this, they become experts in making the ideological capture much more subtle. Large bureaucratic institutions' top-down safety enforcement creates a fertile ground for ideological capture of safety standards.

I claim that the issue is not the technology itself but the lens through which we view and regulate it. Suppose the gatekeepers of 'safety' are aligned with a singular ideology. In that case, AI development would skew to serve specific ends, sidelining diverse perspectives and potentially stifling innovative thought and progress.
In the podcast, Tristan and Aza suggest such manipulation as a solution. They propose using AI for consensus-building and creating "shared realities" to address societal challenges. In practice, this means that when individuals' viewpoints seem to be far apart, we can leverage AI to "bridge the gap." How they bridge the gap and what we would bridge it toward is left to the imagination, but to me, it is clear. Regulators will inevitably influence it from the top down, which, in my opinion, would be the opposite of progress.
In navigating this terrain, we must advocate for a pluralistic approach to defining safety, encompassing various perspectives and values achieved through market forces rather than a governing entity choosing winners. The more players that can play the game, the more wide-ranging perspectives will catalyze innovation to flourish.
Ownership & Identity
Just because we should accelerate AI forward does not mean I do not have my concerns. When I think about what could be the most devastating for society, I don't believe we have to worry about a Matrix-level dystopia; I worry about freedom. As I explored in "Whose data is it anyway?," my concern gravitates toward the issues of data ownership and the implications of relinquishing control over our digital identities. This relinquishment threatens our privacy and the integrity of the content we generate, leaving it susceptible to the inclinations and profit of a few dominant tech entities.
To counteract these concerns, a paradigm shift towards decentralized models of data ownership is imperative. Such standards would empower individuals with control over their digital footprints, ensuring that we develop AI systems with diverse, honest, and truthful perspectives rather than the massaged, narrow viewpoints of their creators. This shift safeguards individual privacy and promotes an ethical framework for AI development that upholds the principles of fairness and impartiality.
As we stand at the crossroads of technological innovation and ethical consideration, it is crucial to advocate for systems that place data ownership firmly in the hands of users. By doing so, we can ensure that the future of AI remains truthful, non-ideological, and aligned with the broader interests of society.
But what about the Matrix?
I know I am in the minority on this, but I feel that the concerns of AGI (Artificial General Intelligence) are generally overblown. I am not scared of reaching the point of AGI, and I think the idea that AI will become so intelligent that we will lose control of it is unfounded and silly. Reaching AGI is not reaching consciousness; being worried about it spontaneously gaining consciousness is a misplaced fear. It is a tool created by humans for humans to enhance productivity and achieve specific outcomes.
At a technical level, large language models (LLMs) are trained on extensive datasets and learning patterns from language and data through a technique called "unsupervised learning" (meaning the data is untagged). They predict the next word in sentences, refining their predictions through feedback to improve coherence and relevance. When queried, LLMs generate responses based on learned patterns, simulating an understanding of language to provide contextually appropriate answers. They will only answer based on the datasets that were inputted and scanned.
AI will never be "alive," meaning that AI lacks inherent agency, consciousness, and the characteristics of life, not capable of independent thought or action. AI cannot act independently of human control. Concerns about AI gaining autonomy and posing a threat to humanity are based on a misunderstanding of the nature of AI and the fundamental differences between living beings and machines. AI spontaneously developing a will or consciousness is more similar to thinking a hammer will start walking than us being able to create consciousness through programming. Right now, there is only one way to create consciousness, and I'm skeptical that is ever something we will be able to harness and create as humans. Irrespective of its complexity — and yes, our tools will continue to become evermore complex — machines, specifically AI, cannot transcend their nature as non-living, inanimate objects programmed and controlled by humans.
 The advancement of AI should be seen as enhancing human capabilities, not as a path toward creating autonomous entities with their own wills. So, while AI will continue to evolve, improve, and become more powerful, I believe it will remain under human direction and control without the existential threats often sensationalized in discussions about AI's future.
The advancement of AI should be seen as enhancing human capabilities, not as a path toward creating autonomous entities with their own wills. So, while AI will continue to evolve, improve, and become more powerful, I believe it will remain under human direction and control without the existential threats often sensationalized in discussions about AI's future. With this framing, we should not view the race toward AGI as something to avoid. This will only make the tools we use more powerful, making us more productive. With all this being said, AGI is still much farther away than many believe.
Today's AI excels in specific, narrow tasks, known as narrow or weak AI. These systems operate within tightly defined parameters, achieving remarkable efficiency and accuracy that can sometimes surpass human performance in those specific tasks. Yet, this is far from the versatile and adaptable functionality that AGI represents.
Moreover, the exponential growth of computational power observed in the past decades does not directly translate to an equivalent acceleration in achieving AGI. AI's impressive feats are often the result of massive data inputs and computing resources tailored to specific tasks. These successes do not inherently bring us closer to understanding or replicating the general problem-solving capabilities of the human mind, which again would only make the tools more potent in our hands.
While AI will undeniably introduce challenges and change the aspects of conflict and power dynamics, these challenges will primarily stem from humans wielding this powerful tool rather than the technology itself. AI is a mirror reflecting our own biases, values, and intentions. The crux of future AI-related issues lies not in the technology's inherent capabilities but in how it is used by those wielding it. This reality is at odds with the idea that we should slow down development as our biggest threat will come from those who are not friendly to us.
AI Beget's AI
While the unknowns of AI development and its pitfalls indeed stir apprehension, it's essential to recognize the power of market forces and human ingenuity in leveraging AI to address these challenges. History is replete with examples of new technologies raising concerns, only for those very technologies to provide solutions to the problems they initially seemed to exacerbate. It looks silly and unfair to think of fighting a war with a country that never embraced oil and was still primarily getting its energy from burning wood.
 The evolution of AI is no exception to this pattern. As we venture into uncharted territories, the potential issues that arise with AI—be it ethical concerns, use by malicious actors, biases in decision-making, or privacy intrusions—are not merely obstacles but opportunities for innovation. It is within the realm of possibility, and indeed, probability, that AI will play a crucial role in solving the problems it creates. The idea that there would be no incentive to address and solve these problems is to underestimate the fundamental drivers of technological progress.
The evolution of AI is no exception to this pattern. As we venture into uncharted territories, the potential issues that arise with AI—be it ethical concerns, use by malicious actors, biases in decision-making, or privacy intrusions—are not merely obstacles but opportunities for innovation. It is within the realm of possibility, and indeed, probability, that AI will play a crucial role in solving the problems it creates. The idea that there would be no incentive to address and solve these problems is to underestimate the fundamental drivers of technological progress.Market forces, fueled by the demand for better, safer, and more efficient solutions, are powerful catalysts for positive change. When a problem is worth fixing, it invariably attracts the attention of innovators, researchers, and entrepreneurs eager to solve it. This dynamic has driven progress throughout history, and AI is poised to benefit from this problem-solving cycle.
Thus, rather than viewing AI's unknowns as sources of fear, we should see them as sparks of opportunity. By tackling the challenges posed by AI, we will harness its full potential to benefit humanity. By fostering an ecosystem that encourages exploration, innovation, and problem-solving, we can ensure that AI serves as a force for good, solving problems as profound as those it might create. This is the optimism we must hold onto—a belief in our collective ability to shape AI into a tool that addresses its own challenges and elevates our capacity to solve some of society's most pressing issues.
An AI Future
The reality is that it isn't whether AI will lead to unforeseen challenges—it undoubtedly will, as has every major technological leap in history. The real issue is whether we let fear dictate our path and confine us to a standstill or embrace AI's potential to address current and future challenges.
The approach to solving potential AI-related problems with stringent regulations and a slowdown in innovation is akin to cutting off the nose to spite the face. It's a strategy that risks stagnating the U.S. in a global race where other nations will undoubtedly continue their AI advancements. This perspective dangerously ignores that AI, much like the printing press of the past, has the power to democratize information, empower individuals, and dismantle outdated power structures.
The way forward is not less AI but more of it, more innovation, optimism, and curiosity for the remarkable technological breakthroughs that will come. We must recognize that the solution to AI-induced challenges lies not in retreating but in advancing our capabilities to innovate and adapt.
AI represents a frontier of limitless possibilities. If wielded with foresight and responsibility, it's a tool that can help solve some of the most pressing issues we face today. There are certainly challenges ahead, but I trust that with problems come solutions. Let's keep the AI Decels from steering us away from this path with their doomsday predictions. Instead, let's embrace AI with the cautious optimism it deserves, forging a future where technology and humanity advance to heights we can't imagine.
-
 @ 700c6cbf:a92816fd
2024-07-14 00:51:44
@ 700c6cbf:a92816fd
2024-07-14 00:51:44... something else
This is the final image. Or is it? Likely, it is not. I have already started on a perfect version of my Mother Earth painting.
Of course, there is no such thing as a perfect painting. What I mean is that I already started on a vector version of Mother Earth. You're familiar with vector vs. pixel, right?
But let's start at the beginning, not the end.
This here is a pic from the sketching phase. I am not one who can just magically and with a few strokes produce an amazing sketch of something that resembles a human. There are artists out there that do this wonderfully. It's amazing but it is not me (unfortunately).

Here I am starting to color in the sketch with a watercolor brush. This is all done in Procreate App on an iPad Pro. The coloring is on a separate layer with the pencil sketch set to multiply to shine through the colors. That's why the pencil strokes now are black. I like that look.

And here, I am almost done. Just need to decide on the background color. And as you can see from the gif and video I didn't really decide. Though at the moment I am favoring that muted pinkish red - LOL

Which color is your favorite?


Here you can see the whole process in a timelapse. Above pictures were grabbed from it to detail the process a little.
https://cdn.satellite.earth/05774dcaaf4679c34cbeb46cb43b4c4f85553a3d2b4850a7256d26a871b0c4f3.mp4
And that's it my Nostr friends for my first longform post in this community.
I hope you enjoyed this post. Comments are encouraged an appreciated. Thank you.
Cheers, OceanBee
-
 @ a8d1560d:3fec7a08
2024-07-14 00:17:38
@ a8d1560d:3fec7a08
2024-07-14 00:17:38I have made an event viewer and an event crafter for #Nostr using https://websim.ai. The event crafter works flawlessly, but sadly without NIP-07. It can be used to craft events of any kind, with any tags you want. You can find it here:
https://websim.ai/c/tZxeQ9DWZf9bCkTd1
As for the event viewer, making it brought several difficulties, and I'm not really happy with it in its current state. But it does show any event of any kind. If you enter your own pubkey, you can choose to only show events from pubkeys you follow. And you can always choose to either show all events or use a pubkey filter.
https://websim.ai/c/KI87SEQljLys4nVIX
-
 @ 13883e40:7e56550f
2024-06-11 06:20:13
@ 13883e40:7e56550f
2024-06-11 06:20:13One of the things I'm blessed with is dinner with lots of relatives every night.
Every now and then, Grandma gets chatty over dinner. I've taken notes and hope to spin a story to share some history and culture.
Part 1: Charcoal Penpals
My paternal grandma grew up in Ruifang, a coal mining town. Anything before my great-grandfather is just tombstones, so it's hard to pinpoint exactly where their story begins. From what I can gather, her family had stayed in the mountains for generations.

Grandma wasn't the typical coal miner's daughter—she wasn't typical anything. A head taller and then some, with a face that didn't look very Asian, she certainly stood out. However, the most special thing about her wasn't her appearance; it was her education. She went on to become a principal of an elementary school and even ran the kindergarten I attended. She graduated from high school, where her peers were all Japanese. Taiwan was a colony of the Japanese Empire from 1895 to 1945. At the time Grandma was in school, the typical education was probably a few years of elementary school, with two types: one for the Japanese and the other to serve them.
The coal in the mountains provided opportunities many didn't have. I've been told by many that our family is incredibly traditional, yet Grandma's education alone puts her father on the extreme progressive side of the spectrum. Grandma was the golden child and took on the task of caring for her three little brothers and two sisters because her mother was often very ill. At present, all her brothers have passed on, and only her sisters remain (and by God, they are still incredibly chatty).
So, at dinner, I'm spinning the lazy Susan around to get Grandma the first dibs on pan-fried fish, and I asked, "Grandma, what was your first trip outside of Taiwan?"

"Oh gosh, that would be so long ago." At first, she'd rehash the story about her first trip to Cleveland, which I've heard many times, but Dad quickly gets in her ear that I was asking about something that happened decades earlier.
"Tell him about the microwave you brought home."
A decade after WWII, the Nationalists had taken over, and with it, the coal in the mountains had slowed down. My great-grandfather was thrown in jail for a few years on tax issues during the regime transition, leaving my grandma to keep the lights on. The coal business is a dirty one, after all. Things were very tough, especially for educators, but the family made it through. Great-grandfather was always very grateful for how Grandma held things down, and now that times were finally better, he wanted to enjoy life. It was time for a nice vacation to Japan, and he wanted his daughter to accompany him.
It's funny to think that Grandma went to school thinking she was Japanese, knowing all the geography and history from textbooks but never setting foot there until after she had five kids—fed them sushi rolls with pork floss. The irony is that her children were going through the same thing, only instead of Japan, it was the Republic of China—but I digress, that's another story. Grandma was obviously excited; the trip was set to be a few months away.

It's hard to imagine what a big deal traveling was back then. Dressed in suits with an entire family entourage for send-offs even at the train station was a common sight. So, considering that, this trip to get on a plane meant a lot.
Grandma was so excited that she went home to start writing letters. Every now and then, classmates would write letters to Grandma about how much they missed Taiwan. For many Japanese who left after the war, leaving Taiwan was like being ripped away from the home they grew up in.
Grandma was in a good mood; she always eats more when she's chatty. My mom's delicious braised eggs are no longer too salty for her to consume. "I wrote back to every friend I had in Japan, saying that I was visiting Tokyo in a few months. I listed all the things I wanted to see, all the things I wanted to do in the month I was there, and all the things I wanted to bring home. How nice would it be to reunite? I can't wait to see my friends finally!"

We really take for granted how global communications are today. Grandma had no idea if any of her letters would be received because some of her addresses were decades old, and there was no way to know if any of her mail would be opened for suspicion of sensitive content under martial law. These days, we can send private messages over any number of encrypted channels instantly. Heck, streaming point-to-point real-time video globally all day isn't out of reach either.

Eventually, Grandma got a response back just a couple of weeks before she was scheduled to leave.
The classmate who wrote back was her rival in math, who just couldn't ever crack first place and hated losing to a girl.
"I don't remember the contents of the letter, but he sent a wonderful poem and told me to visit a particular shrine. He added, 'Madame, Japan isn't Taipei with only a handful of hotels. There are thousands of hotels in Tokyo. How am I supposed to find you with only a date if you don't give me the name of where you are staying?'"
"Oh crap, how did I forget about that?" Grandma seldom presents herself as anything short of brilliant, so hearing her poke fun at her younger self was hilarious. By now, I'm filling up her empty bowl with some radish soup, as my mom left the table to start slicing up some mangoes.

I don't think even my generation realizes the conundrum here. There's no "share location" button to send in an envelope, and it's impossible to know when a letter sent back is received. Even leaving a phone number doesn't solve the issue either. What if the other party is a day away from you when you call, and you're moving on to the next destination? What would you do?
So, my grandma originally thought that meeting up with her old classmate wasn't going to happen, but how could that be? The classmate in the story appears in my dad's stories too.
"So how did you end up meeting up?"
"I got a phone call from my classmate mere hours after we checked in to the hotel. He called five hotels before finding me."
"How did you know I was staying here?" "I asked around. The list of hotels that Taiwanese tour groups choose is very short. It's good that it is this one; I'm not too far away. I will be in Tokyo for a week. Let me show your family around."
The classmate was some sort of manager at NEC. He was most interested in helping my grandma fill out her number one priority on her shopping list: a washing machine.
Grandma ended up bringing home a microwave.
Part 2: Microwave and Taxes
-
 @ 9edd72eb:cb697b0a
2024-07-13 22:16:45
@ 9edd72eb:cb697b0a
2024-07-13 22:16:45If one knows exactly what to do to alleviate one's pain, comfort oneself, and emerge more or less unscathed from Adversity, I think it can be said that one has reached a fairly high level of Wisdom in Life.
originally posted at https://stacker.news/items/607422
-
 @ 6c2d79de:0407f1b7
2024-07-13 20:34:36
@ 6c2d79de:0407f1b7
2024-07-13 20:34:36
In this inaugural investigative campaign, we at The Xibao Times invite you to embark on a journey down the rabbit hole of Chinese propaganda. Our mission: to expose the intricate network of disinformation and anti-Western sentiment that the Chinese Communist Party (CCP) has meticulously woven through various channels, including state media, non-profits, coalition groups, and more. Our starting point: a seemingly innocuous image (above) reposted by China Daily, which has led us to uncover a web of deception that spans the globe.
At the heart of Operation Codepink lies a comprehensive examination of the CCP's propaganda apparatus. We delve into the inner workings of this sophisticated machine, revealing the strategies and tactics employed to disseminate disinformation and manipulate public opinion. From the recruitment of "useful idiots" to the exploitation of social media, we uncover the CCP's playbook and the players involved.
Our investigation spans multiple platforms and formats, providing readers with a multi-faceted view of the propaganda war being waged. In addition to in-depth articles on Habla News, we are creating wiki-pages on Wikifreedia to serve as a repository of information, and relationship charts to illustrate the complex web of connections between entities and individuals.
As we continue our investigative journey, we will be publishing updates, revelations, and analyses. Stay tuned for an exposé on the CCP's infiltration of Russian state media, US non-profits, and coalition groups, among others. Our objective is not only to educate and inform but also to spark a broader conversation about the dangers of disinformation and the need for transparency and accountability in the media landscape.
Join us as we unravel the threads of this intricate web and shed light on the dark corners of the CCP's propaganda machine. With Operation Codepink, we aim to provide the spiciest content on Nostr, and we invite you to be a part of this groundbreaking campaign.
Inside the Operation
Articles on Habla News:
Our in-depth articles on Habla News will provide a comprehensive overview of the CCP's propaganda machine, its tactics, and the individuals and organizations involved. These articles will delve into specific cases of disinformation, analyze the CCP's propaganda strategies, and expose the connections between various entities and individuals. The articles will be written in an engaging and accessible style, making complex information easily understandable for a broad audience.
Wiki-pages on Wikifreedia:

We will create a series of wiki-pages on Wikifreedia to serve as a central repository of information related to Operation Codepink. These wiki-pages will provide a detailed and organized overview of the CCP's propaganda machine, its various components, and the individuals and organizations involved. They will include information on specific cases of disinformation, analysis of propaganda tactics, and connections between various entities and individuals.
Relationship Charts:
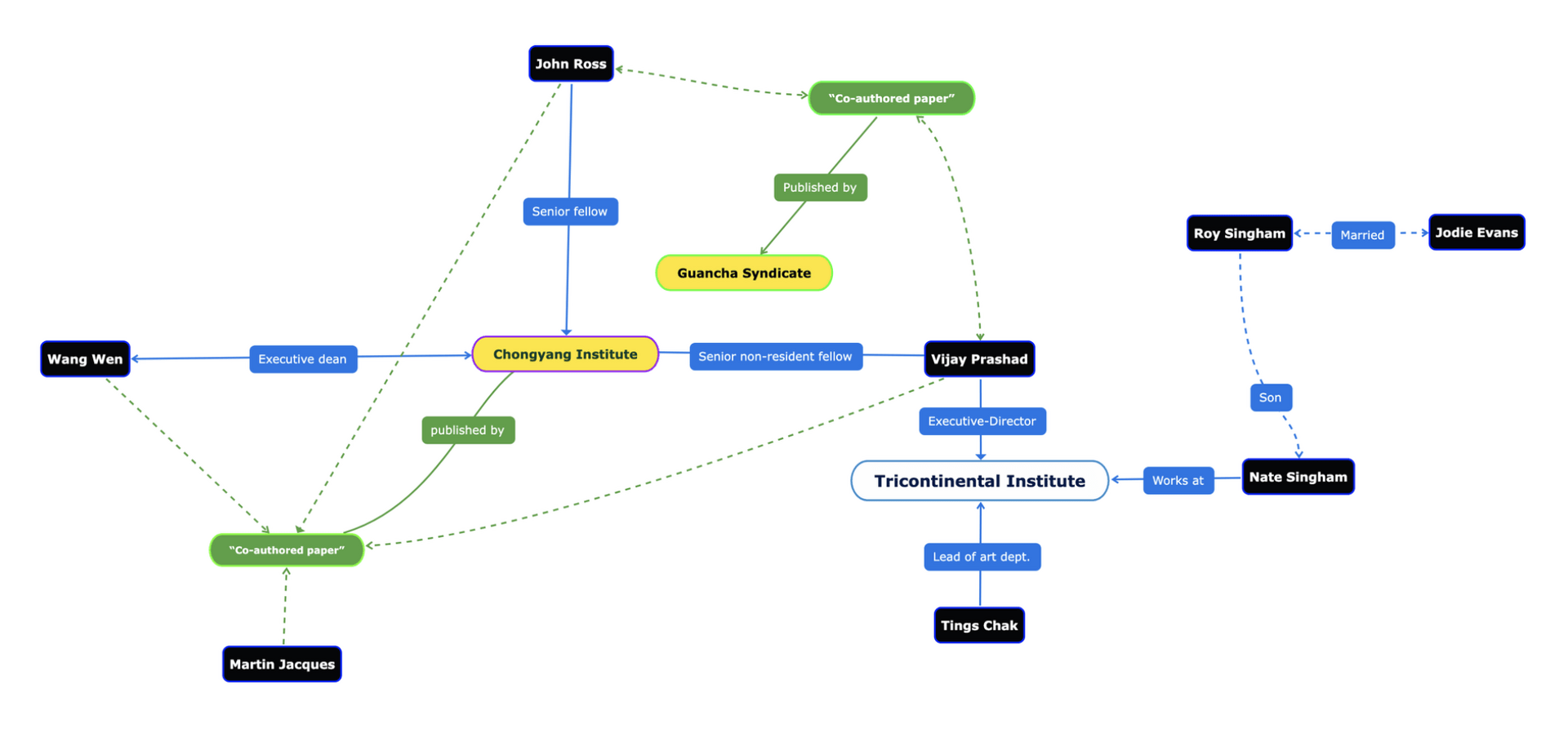
To illustrate the complex web of connections between the entities and individuals involved in the CCP's propaganda machine, we will create relationship charts. These charts will show the relationships between different organizations, individuals, and governments, providing a visual representation of the intricate network of disinformation and propaganda. The relationship charts will help readers understand the scale and scope of the CCP's influence and manipulation efforts.
Investigative Approach:
Our investigative approach for Operation Codepink will involve a combination of open-source research, data analysis, and interviews with experts and insiders. We will use a range of tools and techniques to gather information, including:
Open-Source Research: We will conduct extensive open-source research, using publicly available information to identify patterns, connections, and trends related to the CCP's propaganda machine.
Data Analysis: We will analyze large datasets to identify relationships between individuals, organizations, and governments, as well as patterns in disinformation and propaganda tactics.
Expert Interviews: We will interview experts and insiders who have firsthand knowledge of the CCP's propaganda machine, as well as individuals who have been targeted by the CCP's disinformation campaigns.
Social Media Monitoring: We will monitor social media platforms for signs of disinformation and propaganda, as well as for clues about the identities of individuals and organizations involved in the CCP's propaganda machine.
By using a combination of these techniques, we aim to provide a comprehensive and accurate picture of the CCP's propaganda machine and its activities.
Updates and Revelations:
As we continue our investigation, we will provide regular updates and revelations on our findings. These updates will be published on Habla News and shared on our Nostr account xibaotimes@zaps.lol, keeping readers informed about the latest developments in Operation Codepink. We will also provide analyses and commentary on the implications of our findings for global politics, media, and society.
Stay tuned for more revelations and updates!
-
 @ 3c984938:2ec11289
2024-06-09 14:40:55
@ 3c984938:2ec11289
2024-06-09 14:40:55I'm having some pain in my heart about the U.S. elections.
Ever since Obama campaigned for office, an increase of young voters have come out of the woodwork. Things have not improved. They've actively told you that "your vote matters." I believe this to be a lie unless any citizen can demand at the gate, at the White House to be allowed to hold and point a gun to the president's head. (Relax, this is a hyperbole)
Why so dramatic? Well, what does the president do? Sign bills, commands the military, nominates new Fed chairman, ambassadors, supreme judges and senior officials all while traveling in luxury planes and living in a white palace for four years.
They promised Every TIME to protect citizen rights when they take the oath and office.
...They've broken this several times, with so-called "emergency-crisis"
The purpose of a president, today, it seems is to basically hire armed thugs to keep the citizens in check and make sure you "voluntarily continue to be a slave," to the system, hence the IRS. The corruption extends from the cop to the judge and even to politicians. The politicians get paid from lobbyists to create bills in congress for the president to sign. There's no right answer when money is involved with politicians. It is the same if you vote Obama, Biden, Trump, or Haley. They will wield the pen to serve themselves to say it will benefit the country.
In the first 100 years of presidency, the government wasn't even a big deal. They didn't even interfere with your life as much as they do today.
^^ You hold the power in your hands, don't let them take it. Don't believe me? Try to get a loan from a bank without a signature. Your signature is as good as gold (if not better) and is an original trademark.
Just Don't Vote. End the Fed. Opt out.
^^ I choose to form my own path, even if it means leaving everything I knew prior. It doesn't have to be a spiritual thing. Some, have called me religious because of this. We're all capable of greatness and having humanity.
✨Don't have a machine heart with a machine mind. Instead, choose to have a heart like the cowardly lion from the "Wizard Of Oz."
There's no such thing as a good president or politicians.
If there was, they would have issued non-interest Federal Reserve Notes. Lincoln and Kennedy tried to do this, they got shot.
There's still a banner of America there, but it's so far gone that I cannot even recognize it. However, I only see a bunch of 🏳🌈 pride flags.
✨Patrick Henry got it wrong, when he delivered his speech, "Give me liberty or give me death." Liberty and freedom are two completely different things.
Straightforward from Merriam-Webster Choose Right or left?
No control, to be 100% without restrictions- free.
✨I disagree with the example sentence given. Because you cannot advocate for human freedom and own slaves, it's contradicting it. Which was common in the founding days.
I can understand many may disagree with me, and you might be thinking, "This time will be different." I, respectfully, disagree, and the proxy wars are proof. Learn the importance of Bitcoin, every Satoshi is a step away from corruption.
✨What does it look like to pull the curtains from the "Wizard of Oz?"
Have you watched the video below, what 30 Trillion dollars in debt looks like visually? Even I was blown away. https://video.nostr.build/d58c5e1afba6d7a905a39407f5e695a4eb4a88ae692817a36ecfa6ca1b62ea15.mp4
I say this with love. Hear my plea?
Normally, I don't write about anything political. It just feels like a losing game. My energy feels it's in better use to learn new things, write and to create. Even a simple blog post as simple as this. Stack SATs, and stay humble.
<3 Onigirl
-
 @ 6f170f27:711e26dd
2024-07-13 18:16:58
@ 6f170f27:711e26dd
2024-07-13 18:16:58This century has known a stunning decrease in global income inequality, bringing it down to levels not seen in well over a century. That's the conclusion that Branko Milanovic, one of the world's foremost inequality researchers, comes to in an important essay for Foreign Affairs.
https://www.axios.com/2024/07/11/world-income-inequality-ubs-wealth-report
https://www.axios.com/2023/06/14/global-economic-inequality
originally posted at https://stacker.news/items/607318
-
 @ 5d4b6c8d:8a1c1ee3
2024-07-13 12:44:32
@ 5d4b6c8d:8a1c1ee3
2024-07-13 12:44:32Yesterday's edition https://stacker.news/items/605773/r/Undisciplined
We have a confessional from a professional shitcoiner, today. That's fun.
-
- -
July 13, 2023 📅
📝
TOP POSTValidating Lightning Signer - AMA
Excerpt
VLS is a nifty piece of software that helps boost the security of the Bitcoin Lightning Network. 🛡️
11k sats \ 33 comments \ @devrandom \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/208442/r/Undisciplined?commentId=208454
Excerpt
Ever bought a computer or cell phone? Why? Why not wait until your money is worth more later compared to the price of that cell phone?
1441 sats \ 7 replies \ @02674f045a
From Opinion: Why BTC can't become the reserve currency by @0xBTC in ~bitcoin
🏆
TOP STACKER1st place @k00b
5838 stacked \ 7855 spent \ 3 posts \ 19 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
27k stacked \ 0 revenue \ 40.6k spent \ 108 posts \ 281 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 13, 2022 📅
📝
TOP POSTAny Good Routing Node Strategies?
Excerpt
For people who have/are running nodes, are there any strategies that have been most effective for you for earning routing fees? From my very limited routing experience so far it seems there are a few main questions:
1232 sats \ 33 comments \ @andyleroy \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/44747/r/Undisciplined?commentId=44755
Excerpt
Obligatory not a node routing expert, but this guy is a good follow: https://mobile.twitter.com/cold_sats
276 sats \ 1 reply \ @Cornleone
From Any Good Routing Node Strategies? by @andyleroy in ~bitcoin
🏆
TOP STACKER1st place @k00b
37.3k stacked \ 15.2k spent \ 1 post \ 29 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
27.4k stacked \ 0 revenue \ 34.7k spent \ 117 posts \ 279 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 13, 2021 📅
📝
TOP POSTI joined a shitcoin project full time couple of months ago
Excerpt
I though it would be exciting and fun. But I think I'm wasting my time.
3 sats \ 9 comments \ @03785de7ab \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/306/r/Undisciplined?commentId=316
Excerpt
There are many companies working with Bitcoin but it's not their main focus. I did implement Bitgo sevices for one e-wallet provider but that was it. What I'm looking for is a project which build useful things for user with current Bitcoin features, […]
2 sats \ 1 reply \ @03785de7ab
From I joined a shitcoin project full time couple of months ago by @03785de7ab in ~bitcoin
🏆
TOP STACKERNo top stacker
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
37 stacked \ 0 revenue \ 60 spent \ 6 posts \ 10 comments
originally posted at https://stacker.news/items/607040
-
-
 @ b2caa9b3:9eab0fb5
2024-07-13 12:01:35
@ b2caa9b3:9eab0fb5
2024-07-13 12:01:35I woke up in my dorm this morning to the sound of rain – a rarity in Africa, but a common occurrence here around Mount Kilimanjaro. The climate is much like a European summer, with comfortable temperatures ranging from 18 to 30 degrees Celsius. Unlike the rest of Africa, this region receives more rainfall, creating a lush and scenic environment.

After a quick shower, I stepped out onto the balcony to find myself greeted by a chilly rain. Not ideal weather for exploring, but it did present a different perspective of the majestic Kilimanjaro. The mountain, often shrouded in clouds, occasionally peeks through, and on a clear day, might even be bathed in sunshine. From this vantage point, it's hard to imagine the countless hikers making their way up its slopes.
Did you know that Kilimanjaro, Africa's tallest mountain and a dormant volcano, once held a unique title? Back in 1910, during the German Empire, it was considered the empire's highest peak. While Mount Everest holds the title of the world's highest mountain overall, Kilimanjaro takes the crown for the tallest freestanding mountain – any higher peak is likely part of a mountain range or group.
Gazing at Kilimanjaro, I'm struck by its history – a single, towering volcano, once a part of the German Empire. Traces of that era linger in Moshi, with some colonial-era buildings, some in disrepair, others beautifully restored. Arusha, another nearby town, boasts an impressive art gallery and a fascinating National Museum. This museum, housed in a former German fort, offers a glimpse into the past. One particularly intriguing resident is a giant tortoise, discovered by German colonists as a hatchling in Kilimanjaro National Park. This living relic has witnessed a century of change, a silent observer of a bygone era.

Today promises to be a relaxing one. I'll spend time soaking up the views from the rooftop, hoping to catch a glimpse of Kilimanjaro in all its glory. On a more practical note, I'm also on the hunt for a remote job to help with some financial constraints. Finding the right opportunity seems to be a bit more challenging than anticipated.
As I wrap up this post, the weather has taken a turn for the better. The rain has stopped, the temperature has risen, and the sun is beginning to peek through the clouds. Here's to a wonderful day for everyone – enjoy yours!
(P.S. Be sure to check out the photos – one captures Kilimanjaro from yesterday evening, the other is a picture of me with the giant tortoise from my previous trip here in December 2022).
Online
Feel free to support me by sending some sats via the lightning network to rubenstorm@sats.mobi
-
 @ 58537364:705b4b85
2024-07-13 11:49:14
@ 58537364:705b4b85
2024-07-13 11:49:14อารมณ์ คือ โลก - โลก คือ อารมณ์ อารมณ์ ในโลกปัจจุบันรวมอยู่ที่ วัตถุนิยม อารมณ์ จึงเป็นปัจจัยแห่งเหตุการณ์ทุกอย่างในโลก

…. “ เดี๋ยวนี้คําว่า “อารมณ์” ในภาษาไทยนั้น หมายถึงความรู้สึกในใจมากกว่า; เช่น พื้นเพของจิตใจในขณะนั้นเป็นอย่างไร, เรียกว่าอารมณ์ของเขาเป็นอย่างไร, อารมณ์กําลังดี อารมณ์กําลังไม่ดี, นี่ คําว่าอารมณ์ในภาษาไทยใช้กันไปเสียอย่างนี้ ; มันคนละเรื่องกับในภาษาบาลี ซึ่งคําว่า “อารมณ์” หมายถึง สิ่งที่จะเข้ามากระทบ ตา หู จมูก ลิ้น กาย ใจ.
…. ถ้ากระทบแล้วเกิดความรู้สึกอย่างไร งุ่นง่านอยู่ในใจ อันนั้นไม่ได้เรียกว่าอารมณ์; อันนั้นก็เรียกว่ากิเลสอย่างอื่น เช่น เรียกว่าตัณหาบ้าง อุปาทานบ้าง; ถ้าจัดเป็นพวกขันธ์ ก็เรียกว่า เวทนาขันธ์บ้าง สัญญาขันธ์บ้าง สังขารขันธ์บ้าง; ถ้าเป็นความคิดที่งุ่นง่านก็เรียกว่า “สังขารขันธ์” ทั้งนั้น ดังนั้น เราจะต้องถือเอาคําว่าอารมณ์ในบาลีมาเป็นหลัก …. คําว่า อารมณ์ ที่จะเข้าใจกันง่ายๆ ก็หมายความว่า รูป เสียง กลิ่น รส โผฏฐัพพะ ที่จะมากระทบ ตา หู จมูก ลิ้น กาย นี้ ๕ อย่าง แล้วก็ความรู้สึกเก่าแก่ที่จะมาผุดขึ้นในใจอีก เรียกว่า ธัมมารมณ์ ที่จะมากระทบใจในปัจจุบันนี้ นี้ก็เป็นอันหนึ่ง เลยได้เป็นอารมณ์ ๖. อารมณ์กระทบ ตา หู จมูก ลิ้น กาย ๕ อย่างข้างนอกนี้ก็สําคัญไปพวกหนึ่ง ที่ปรุงขึ้นภายในสําหรับกระทบใจโดยไม่ต้องอาศัย ตา หู จมูก ลิ้น กาย ใจ เลย ในเวลานั้นก็ยังมีอยู่นี้เรียกว่าธัมมารมณ์ นี้ก็ยิ่งสําคัญ: แต่ว่ารวมกันแล้วก็เรียกว่า อารมณ์ ได้ด้วยกันทั้งนั้น แปลว่า สิ่งที่จะมากระทบกับ ตา หู จมูก ลิ้น กาย ใจ นั่นเอง
…. นี้ ดูให้ละเอียดตามตัวหนังสือ คําว่า “อารมณ์” แปลว่า ที่หน่วงบ้าง แปลว่า ที่ยินดีบ้าง, มันมีความหมายละเอียดมาก. ถ้าถือเอาความหมายอย่างคนที่มีตัวตนเป็นหลัก ธรรมะในฝ่ายฮินดูหรือฝ่ายพรหมณ์เขาก็จะพูดว่า สําหรับจิตหรืออาตมันเข้าไปจับฉวยเอา. แต่ถ้าพูดอย่างภาษาชาวพุทธพูดอย่างนั้นไม่ได้ เพราะไม่มีจิตไม่มีอาตมันชนิดนั้น แล้วจิตนี้ก็เพิ่งเกิดขึ้นหลังอารมณ์กระทบแล้ว; เลยต้องพูดตามพระบาลีที่ว่า อาศัยตาด้วย อาศัยรูปด้วย ย่อมเกิดจักษุวิญญาณ; ตาอาศัยกับรูปคืออารมณ์นั้นได้แล้วจึงจะเกิดจักษุวิญญาณ วิญญาณหรือจิตนี้เกิดทีหลัง
…. ฉะนั้น จึงไม่พูดว่า อารมณ์นี้เป็นสิ่งสําหรับจิตหรือตัวตนเข้าไปจับฉวยยึดเอา; ถ้าพูดอย่างนั้นมันก็จะเป็นฮินดูหรือพราหมณ์ไป คือมีตัวตนไป. พูดอย่างพุทธไม่มีตัวตน ทุกอย่างไม่ใช่ตัวตน เป็นสักว่าธาตุ, ได้การปรุงแต่งที่เหมาะแล้วมันก็ปรุงแต่งเป็นสิ่งใหม่ขึ้นมา ในนั้นอาจจะมีความรู้สึกโง่ไปว่าเป็นตัวเราก็ได้
…. ฉะนั้น คําว่าอารมณ์ ถ้าถือตามหลักในทางพุทธศาสนา ก็แปลว่า สิ่งที่อาศัยกันกับจิต จะเรียกว่าเป็นที่หน่วงของจิตมันก็ยังได้: ถ้าเข้าใจผิดมันก็ผิดได้: เรียกว่าสิ่งที่อาศัยกับอายตนะ แล้วก็เกิดเป็นความรู้สึกเป็นจิตขึ้นมา จิตกําลังหน่วงสิ่งนั้นเป็นอารมณ์ก็ได้ แต่จะให้เป็นตัวตนนั้นไม่ได้
…. โดยพยัญชนะก็มีอยู่อย่างนี้ ตัวพยัญชนะก็ยังกํากวม อารมฺมณํ หรือที่มาจาก อาลมฺพนํ ก็แปลว่า ที่หน่วงของจิต. ถ้าจะถือว่ามาจาก รม ที่แปลว่า ยินดี ก็แปลว่า มันเป็นสิ่งที่หลงใหลยินดีของจิต อย่างนี้ก็ยังได้อีก
…. แต่ขอให้รู้จักจากภายในดีกว่าที่จะมารู้จักจากตัวหนังสือ เมื่อตากระทบรูป เมื่อหูกระทบเสียง เป็นต้น มันเกิดขึ้นในใจ, แล้วสังเกตเอาที่นั่นก็แล้วกัน ว่ารูปที่มากระทบตานั้นมันคืออะไร? เสียงที่มากระทบหูนั้นมันคืออะไร? จะค่อยเข้าใจแจ่มแจ้งขึ้นทีละน้อยๆ ว่าอารมณ์นั้นคืออะไร? แต่ให้เข้าใจไว้ทีหนึ่งก่อนว่าสิ่งที่เรียกว่าอารมณ์ๆที่มากระทบนี้ มันยังไม่ดีไม่ชั่ว ยังไม่จัดเป็นสิ่งดีสิ่งชั่ว มันต้องผสมปรุงแต่งเป็นความคิดอย่างนั้นอย่างนี้เสียก่อน จึงจะจัดเป็นดีเป็นชั่ว อารมณ์ล้วนๆยังไม่ดีไม่ชั่ว จะได้รู้จักป้องกัน อย่าให้เป็นไปในทางชั่ว, ให้เป็นไปแต่ในทางดีได้ตามปรารถนา
…. นี้เรียกว่าโดยพยัญชนะ โดยตัวหนังสือ คําว่า “อารมณ์” แปลว่า เป็นที่ยินดีแห่งจิต, เป็นที่ยึดหน่วงแห่งจิต; โดยเฉพาะภาษาอภิธรรมแล้วก็ใช้คําว่า “เป็นที่หน่วงเอาของจิต”, คือจิตย่อมหน่วงสิ่งใดสิ่งหนึ่งเป็นอารมณ์ แปลคําว่าอารมณ์บ้าง, อาลัมพนะ แปลว่า เป็นที่หน่วงเอา.
…. เดี๋ยวนี้เราเรียนพุทธศาสนาไม่ใช่เรามาเรียนหนังสือบาลี, เราจะเรียนพระธรรมคําสอนของพระพุทธเจ้า เราก็ต้องดูสิ่งที่เรียกว่าอารมณ์ โดยหลักของธรรมชาติที่ปรุงแต่งกันอยู่ในใจดีกว่า; ก็อย่างพระบาลีที่ได้ว่ามาแล้วข้างต้นว่า จกฺขุญฺจ ปฏิจฺจ รูเป จ อุปฺปชฺชติ จกฺขุวิญฺญาณํ = เพราะอาศัยตาด้วย รูปด้วย ย่อมบังเกิดจักษุวิญญาณ ติณฺณํ ธมฺมานํ สงฺคติ ผสฺโส - การประจวบกันของ ๓ สิ่งนี้เรียกว่า “ผัสสะ”, ผสฺสปจฺจยา เวทนา = เพราะผัสสะเป็นปัจจัยจึงเกิดเวทนา, อย่างนี้เรื่อยไปจนเกิดทุกข์ จนเกิดความทุกข์, นี้เรียกว่าโดยธรรมชาติ
…. สิ่งที่เรียกว่าอารมณ์มีอยู่โดยธรรมชาติที่จะเข้ามาอาศัยกันกับตาข้างใน ที่มีอยู่ในตัวคน. แล้วจะเกิดจักษุวิญญาณ เป็นต้น ขึ้นในตัวคน; จะเกิด ผัสสะ เวทนา ตัณหา อุปาทาน ภพ ชาติ ขึ้นในตัวคน; นี้โดยธรรมชาติ พระพุทธเจ้าท่านบันดาลอะไรไม่ได้ : ธรรมชาติเป็นอยู่อย่างนี้ แต่ท่านรู้เรื่องนี้ท่านจึงนํามาสอนว่า ธรรมชาติมันมีอยู่อย่างนี้ เราจะต้องเข้าใจให้ถูกต้อง โดยที่จะป้องกันความทุกข์ไม่ให้เกิดขึ้นมาได้, หรือถ้าเกิดขึ้นมาได้ก็จะดับเสียได้
…. เราควรจะรู้จักอารมณ์ในฐานะที่เป็นธรรมชาติอันหนึ่ง ที่มีอยู่ตามธรรมชาติ แล้วที่จะเข้ามาทําเรื่องทําราวขึ้นในจิตใจของคนเราให้เกิดปัญหายุ่งยากนี้ให้ดีๆ นี้เรียกว่ารู้จักอารมณ์จากธรรมชาติโดยตรงอย่างนี้ ดีกว่าที่จะรู้จักตามตัวหนังสือ, ดีกว่าที่จะรู้จักตามคําบอกเล่าบางอย่างบางประการที่มันไม่มีประโยชน์อะไร. รู้จักตามคําบอกเล่าก็รู้จักตามที่พระพุทธเจ้าท่านตรัสดีกว่า แต่แล้วยังไม่รู้จักตัวจริง จนกว่าจะมารู้จักจากที่เมื่ออารมณ์มากระทบตา หู จมูก ลิ้น กาย ใจ เข้าจริงๆ : นั่นจึงจะรู้จักอารมณ์ รู้จักผลที่เกิดขึ้นจากการกระทบของอารมณ์, รู้จักต่อไปตามลําดับ จนแก้ปัญหาต่างๆ ได้
…. นี่ ขอร้องให้รู้จักสิ่งที่เรียกว่า อารมณ์ ในฐานะที่เป็นธรรมชาติอันหนึ่ง ที่มีอยู่ตามธรรมชาติ ที่จะเข้ามากระทบอายตนะภายใน คือ กระทบ ตา หู จมูก ลิ้น กาย ใจ แล้วมีเรื่องมีราวมีปัญหา
อารมณ์ คือ โลก - โลก คือ อารมณ์ …. “ ที่นี้จะให้ดูต่อไปอีก ว่าโดยข้อเท็จจริงที่เป็นอยู่แล้ว อารมณ์นั้นคืออะไร? ถ้าจะพูดโดยข้อเท็จจริงหรือตามสถานการณ์ที่เป็นอยู่จริงในชีวิตของคนเรา อารมณ์มันก็คือ “โลก” นั่นเอง. เดี๋ยวนี้เราไม่รู้จักโลกในฐานะอย่างนี้, เราไปเข้าใจความหมายของคําว่าโลกแคบไปบ้าง หรือว่าเขวไปบ้าง.
…. ถ้าจะรู้ตามหลักพระพุทธศาสนาแล้ว โลกทั้งหมดก็คือสิ่งที่จะมาปรากฏแก่ ตา หู จมูก ลิ้น กาย ใจ ของเรา, เรามีเพียง ๖ อย่าง, แล้วมันก็ ปรากฏได้เพียง ๖ ทาง, มากกว่านั้นมันปรากฏไม่ได้ ดังนั้น โลกก็คือสิ่งที่จะมาปรากฏแก่ ตา หู จมูก ลิ้น กาย ใจ ๖ อย่างของเรา. “โลก” ก็คือ รูป เสียง กลิ่น รส โผฏฐัพพะ ธัมมารมณ์ ๖ ประการเท่านั้น, ไม่มีอะไรมากไปกว่านั้น
…. ฉะนั้น รูป เสียง กลิ่น รส โผฏฐัพพะ ธัมมารมณ์ แต่ละอย่าง ๆ ก็คือ โลกในแต่ละแง่ละมุม นั่นเอง, ที่เป็น รูป เสียง กลิ่น รส โผฏฐัพพะ ก็อยู่ข้างนอก จะเรียกว่าอยู่ข้างนอกก็ได้, ที่เป็นอารมณ์เกิดขึ้นในใจ ปรุงขึ้นในใจก็เรียกว่าโลกข้างในก็ได้ แต่มันก็เป็นโลกอยู่นั่นแหละ เพราะมันเป็นสิ่งที่จิตจะต้องรู้สึก จิตรู้สึกก็เรียกว่าโลกสําหรับจิต ตา หู จมูก ลิ้น กาย รู้สึก ก็เรียกว่าโลกสำหรับ ตา หู จมูก ลิ้น กาย. นี้ขอให้มองให้เห็นชัดตามพระพุทธประสงค์ว่า โลก ก็คือ อารมณ์, อารมณ์ ก็คือ โลก.
…. แต่ทีนี้ พระพุทธเจ้าท่านมองลึกกว่านั้น ท่านตรัสถึงข้อที่ว่า ถ้ามันมาเกิดเป็นปัญหาแก่เราเมื่อไรจึงจะเรียกว่า “มันมี” พอมันมาเป็นปัญหาแก่เราเมื่อไรก็เรียกว่า “เป็นทุกข์”; เพราะว่าเราได้ไปจับฉวยยึดถือเอาตามประสาตามวิสัยของคนที่ไม่รู้จักโลก ถ้าพูดว่าไม่รู้จักโลกแล้วคนก็มักจะไม่ยอมรับ เพราะว่าเขาจะพูดว่าเขารู้จักโลกดี. ยิ่งพวกฝรั่งสมัยนี้ นักวิทยาศาสตร์ปราดเปรื่องนั้น เขาจะไม่ยอมรับว่าเขาไม่รู้จักโลก. แต่ถ้าพูดตามหลักพุทธศาสนาแล้วก็จะพูดได้ว่ายังไม่รู้จักโลกเลย เป็นคนตาบอดยิ่งกว่าตาบอด; เพราะว่าฝรั่งเหล่านั้นรู้จักโลกแต่ในแง่สําหรับจะยึดมั่นถือมั่นเป็น “ตัวกู ของกู” จะครองโลกจะอะไร เอาประโยชน์ทุกอย่าง; เขารู้จักโลกในแง่นี้ อย่างนี้พุทธบริษัทไม่เรียกว่า “รู้จักโลก”; แต่ถือว่าเป็นคนตาบอดต่อโลก, หลงยึดมั่นถือมั่นในโลก. เพราะว่าคนเหล่านั้นไม่รู้จักโลกโดยความเป็นอารมณ์ ๖ ประการ คือ รูป เสียง กลิ่นรส โผฏฐัพพะ ธัมมารมณ์, แล้วเป็น “มายา” คือ เอาจริงไม่ได้ เป็นของชั่วคราวๆ หลอกให้เกิดความรู้สึกยึดมั่นถือมั่น
…. นี้เรารู้จัก เราไม่ไปหลงยึดมั่นถือมั่นกับมัน นี้จึงเรียกว่า “คนที่รู้จักโลก” ไปตามหลักของพุทธศาสนา, ฉะนั้น จึงไม่ยึดมั่นถือมั่นสิ่งใดโดยความเป็นตัวตน หรือโดยความเป็นของตน, เรียกว่าเป็นผู้รู้จักอารมณ์ ๖ ประการนั้นก็คือรู้จักโลกทั้งปวง, แล้วก็ไม่หลงไปในโลกในแง่ใดแง่หนึ่ง นี้เรียกว่า อารมณ์ ก็คือ โลก นั่นเอง ในความหมายที่ลึกที่สุดของพระพุทธสาสนา ไม่ใช่โลกก้อนดิน, ไม่ใช่โลกก้อนกลมๆ นี้. แต่มันหมายถึงคุณค่าอะไรที่มันมีอยู่ในโลกกลมๆ นี้ ที่จะเข้ามามาทําให้เกิดปัญหา ที่ตา ที่หู ที่จมูก ที่ลิ้น ที่กาย ที่ใจ ของคน. นั่นแหละคือตัวร้ายกาจของสิ่งที่เรียกว่า โลก เราจะต้องรู้จักในส่วนนี้ให้เพียงพอ
อารมณ์ในโลกปัจจุบันมารวมที่วัตถุนิยม …. ทีนี้ ดูอีกแง่หนึ่งก็โดยปัญหาที่กําลังมีอยู่ อารมณ์ในโลกนี้ในฐานะที่มันเป็นตัวปัญหาที่กําลังมีอยู่ มันมารวมอยู่ที่คําว่า “วัตถุนิยม”: หมายความว่า ตา หู จมูก ลิ้น กาย ใจ นี้ มันเป็นฝ่ายชนะ ไปหลงใหลในอารมณ์ รูป เสียง กลิ่น รส โผฏฐัพพะ ฯลฯ, แล้วก็เกิดนิยมหลงใหลในวัตถุเหล่านั้น จนเกิดความคิดใหม่ๆ, ปรุงแต่งไปในทางที่จะให้หลงใหลในโลกยิ่งขึ้นๆ, ความเจริญก้าวหน้า ในโลกสมัยนี้เป็นไปแต่ในทางอย่างนี้ ฉะนั้น จึงไกลความสงบ, ไกลสันติภาพ ไกลอะไรออกไปทุกที. การที่มนุษย์ที่มีปัญญาในโลกสมัยนี้ โดยเฉพาะฝรั่งที่ก้าวหน้านั้นเขาก็จัดโลกไปแต่ในแง่ของวัตถุมากขึ้นๆ: มันก็ไกลจากสันติภาพ ไกลจากความสงบสุขยิ่งขึ้นทุกที
…. ความสะดวกสบายที่ทําให้เกิดขึ้นมาได้นั้น ไม่ได้ช่วยส่งเสริมเกิดสันติภาพ; แต่มันช่วยให้เกิดความหลงในโลกนั้นเองมากขึ้น แล้วก็ช่วยให้หลงใหลใน “ตัวกู ของกู”, ยึดมั่นถือมั่นเห็นแก่ตัวมากขึ้น รวมกันแล้วมันไม่มีทางที่จะเกิดสันติภาพหรือสันติสุขในโลกได้เลย, จึงกลายเป็นความหลอกลวงเหลือประมาณ โลกจึงกลายเป็นความหลอกลวง, หรือสิ่งที่หลอกลวงเหลือประมาณใน เวลานี้ เราเรียกกันว่า ติดบ่วง หรือว่า ติดเหยื่อของวัตถุนิยม. คําพูดทั้งหมดนี้ ล้วนแต่เป็นการแสดงให้เห็นว่า อารมณ์นี้คืออะไร สิ่งที่เรียกว่าอารมณ์นั้น คือตัวโลกที่กําลังหลอกลวงเราอยู่ทุกวันอย่างยิ่ง โดยเฉพาะในปัจจุบันนี้เป็นวัตถุนิยม นี้คืออารมณ์”
พุทธทาสภิกขุ ที่มา : ธรรมบรรยายภาคมาฆบูชา ครั้งที่ ๗ หัวข้อเรื่อง “อารมณ์ คือ ปัจจัยแห่งเหตุการณ์ทุกอย่างในโลก” เมื่อวันที่ ๑๖ กุมภาพันธ์ ๒๕๑๗ จากหนังสือชุดธรรมโฆษณ์ เล่มชื่อว่า “ก ข ก กา ของการศึกษาพุทธศาสนา”
หมายเหตุ
“อารมณ์ ” ในทางพุทธศาสนา มี ๖ คือ... * ๑. รูปะ = รูป, สิ่งที่เห็น หรือ วัณณะ คือ สี * ๒. สัททะ = เสียง * ๓. คันธะ = กลิ่น * ๔. รสะ = รส * ๕. โผฏฐัพพะ = สัมผัสทางกาย * ๖. ธรรมารมณ์ = สิ่งที่ใจนึกคิด, อารมณ์ที่เกิดกับใจ
…. ทั้ง ๖ อย่างนี้ เป็นสิ่งสำหรับให้จิตยึดหน่วง เรียกอีกอย่างว่า "อายตนะภานนอก" ก็ได้
“อายตนะภายใน ๖” คือ ที่เชื่อมต่อให้เกิดความรู้, แดนต่อความรู้ฝ่ายภายใน มี * ๖ อย่าง คือ... * ๑. จักษุ - ตา * ๒. โสตะ - หู * ๓. ฆานะ - จมูก * ๔. ชิวหา - ลิ้น * ๕. กาย - กาย * ๖. มโน - ใจ
… หรือจะเรียกอีกอย่างว่า “อินทรีย์ ๖” ก็ได้ เพราะเป็นใหญ่ในหน้าที่ของตนแต่ละอย่าง เช่น จักษุ เป็นเจ้าการ(เป็นใหญ่)ในการเห็น เป็นต้น
ท. ส. ปัญญาวุฑโฒ – รวบรวม.
-
 @ a012dc82:6458a70d
2024-07-13 08:10:23
@ a012dc82:6458a70d
2024-07-13 08:10:23Table Of Content
-
Content
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
Introduction
Bitcoin is a highly volatile asset that can experience dramatic price swings in short periods of time. In a bull market, traders can capitalize on rising prices and generate significant profits. However, when the market turns bearish, it can be challenging to navigate and maintain profitability. A bear market is a period of declining prices, where negative sentiment dominates and trading volumes may decrease. In this context, it's important to have a set of strategies that can help you navigate the market and protect your investments. In this article, we'll explore five essential strategies for trading Bitcoin in a bear market. By implementing these strategies, you can reduce your risks and maximize your chances of success.
Strategy 1: Take profit regularly
This strategy involves selling a portion of your Bitcoin holdings when prices reach a certain level. By taking profits regularly, you can lock in gains and minimize the risk of losses in a bear market. It's important to have a plan for taking profits and stick to it, even if prices continue to rise.
Strategy 2: Set stop-loss orders
A stop-loss order is an instruction to sell your Bitcoin if prices fall below a certain level. By setting stop-loss orders, you can limit your losses in a bear market and avoid holding onto Bitcoin that's losing value. It's important to set stop-loss orders at a level that allows for normal price fluctuations but also provides adequate protection against sharp declines.
Strategy 3: Short sell Bitcoin
Short selling involves borrowing Bitcoin from a broker and selling it on the open market with the hope of buying it back at a lower price. This strategy can be useful in a bear market when prices are falling, as it allows you to profit from the decline. However, short selling is a high-risk strategy that requires careful consideration of the potential risks and rewards.
Strategy 4: Use dollar-cost averaging
Dollar-cost averaging involves investing a fixed amount of money at regular intervals, regardless of the current price of Bitcoin. By buying Bitcoin at regular intervals, you can take advantage of market fluctuations and potentially reduce the average cost of your holdings. This strategy can be effective in a bear market where prices are falling and may present buying opportunities.
Strategy 5: Stay up-to-date with news and trends
Staying informed about news and trends in the cryptocurrency market is essential for making informed trading decisions. By staying up-to-date, you can identify potential risks and opportunities and adjust your trading strategies accordingly. It's important to use reliable sources of information and avoid making impulsive trading decisions based on emotions or rumors.
Conclusion
The Bitcoin bear market can be difficult to navigate, but with these five essential strategies, traders can reduce their risks and maximize their chances of success. These strategies include taking profits regularly, setting stop-loss orders, short selling, using dollar-cost averaging, and staying up-to-date with news and trends. It's important to remain disciplined, avoid impulsive decisions, and stay flexible to adapt to changing market conditions. By following these strategies, traders can emerge successful from the Bitcoin bear market.
FAQ
What is a bear market? A bear market is a period of declining prices, where negative sentiment dominates and trading volumes may decrease.
How can I protect my investments in a bear market? To protect your investments in a bear market, you can implement strategies such as taking profits regularly, setting stop-loss orders, short selling, using dollar-cost averaging, and staying up-to-date with news and trends.
Is short selling a high-risk strategy? Yes, short selling is a high-risk strategy that requires careful consideration of the potential risks and rewards.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 1f9e547c:8af216ed
2024-07-13 07:37:05
@ 1f9e547c:8af216ed
2024-07-13 07:37:05Opinion about Bitcoin Wallet Crypto Ethereum (android)
For archival purposes
Atomic Wallet suffers hack on June 2023
Sources
Atomic Wallet users have been left wanting more answers, despite the decentralized wallet provider finally releasing a full “event statement” about the June exploit — which some estimate has run up to $100 million in losses.
In a June 20 blog post — the first major update from the firm since the June 3 exploit — Atomic Wallet claimed there have been no new confirmed cases after initial reports of the hack.
Atomic Wallet Was Breached by North Korean Hackers: Elliptic
Atomic Wallet users might have fallen victim to Lazarus, the infamous North Korean hacking group, said blockchain intelligence firm Elliptic in a blog post on Tuesday.
Early Saturday morning, the team behind Atomic, a non-custodial crypto wallet, announced that some users were compromised and lost the funds from their wallets. According to the company, the number of incidents did not exceed 1% of "monthly active users." The announcement followed multiple reports on Reddit from users complaining their wallets had been drained.
WalletScrutiny #nostrOpinion
-
 @ 502ab02a:a2860397
2024-07-13 02:14:11
@ 502ab02a:a2860397
2024-07-13 02:14:11Anna Britt Agnsäter ผู้อุทิศชีวิตให้โภชนาการ แต่โดนโลกบูลลีเพราะอเมริกา?
โลกรับรู้ว่า คุณ Anna Britt Agnsäter (ขอเรียกสั้นๆว่า ป้าแอน) เป็นผู้ที่นำเสนอ ปิรามิดอาหาร คนแรกของโลก และเป็นแบบจำลองที่ทาง USDA นำไปพัฒนาปรับใช้แล้วนำมาเป็น แบบที่ใช้สื่อสารกับคนทั้งโลก ในเรื่องของการกำหนด ประเภทอาหารที่ควรกิน ในช่วงปี 1992-2005 ซึ่งในบทความที่แล้วผมได้เขียนว่า ปิรามิดเวอร์ชั่นที่ป้าแอนคิด กับ ที่อเมริกาเอาไปปรับใช้เป็นคนละตัวกัน แต่โลกทั้งโลกก็บูลลีป้าเอนว่า เป็นสาเหตุของการทำลายสุขภาพคนทั้งโลก ทั้งๆที่ไม่ได้เป็นนักวิทยาศาสตร์ ผมก็เป็นคนนึงที่เคยคิดแบบนั้นครับ และเคยอุทานในใจเบาๆว่า แกเป็นใครนะทำไมถึงนำเสนออะไรแบบนี้มาทำร้ายคนทั้งโลก???
นานวันเข้า ความคิดอีกฝั่งของผมก็บอกมาว่า ประโยคข้างบนเป็นคำบ่นหรือคำถาม
นั่นสิ!!!!! ถ้ามันเป็นคำถาม มันจะทำให้เราได้รู้จักตัวตนป้าแอนและเข้าใจว่าแกได้ทำอะไรลงไปนะ มันควรเป็นคำถามมากกว่าคำบ่น นั่นเลยเป็นเหตุผลที่ทำให้ผมเริ่มขุดเรื่องป้าแอน Anna Britt Agnsäter มากที่สุดเท่าที่จะทำได้ พร้อมที่จะอ่านกันแล้วใช่ไหมครับ
Anna Britt Agnsäter เกิดเมื่อปี 1915 ที่เมือง Älmhult ประเทศสวีเดน (นอกเรื่องนิดนึง เมืองนี้คือเมืองที่ให้กำเนิด IKEA ที่เรารู้จักกันดีเรื่องเฟอร์นิเจอร์ ที่นี่มีพิพิธภัณฑ์อิเกีย ซึ่งปรับปรุงมาจากโกดังแห่งแรกของเขาด้วยครับ) เรียกได้ว่า เกิดในช่วงสงครามโลกครั้งที่1 พอดีเลยครับ
ป้าแอน จบการศึกษาที่โรงเรียนสตรี ในเมือง Ystad ก่อนจะเข้ารับการฝึกสอนเพื่อเป็นครูสอนวิทยาศาสตร์ในครัวเรือน (rural domestic science teacher) ในช่วงปี 1930 ที่โรงเรียนวิทยาศาสตร์ในครัวเรือนในชนบทชื่อว่า Rimforsa ก่อนจะได้รับวุฒิการศึกษาการสอนวิทยาศาสตร์ในครัวเรือนในชนบทในปี 1939 จาก Kvinnliga medborgarskola (civic women’s school) จนกระทั่ง ปี 1943 ถึง 1945 เธอได้เดินทางไปทั่ว Norrland (พื้นที่ภาคเหนือของสวีเดน) โดยได้รับเงินสนับสนุนจาก Kooperativa Förbund (เรียกสั้นๆว่า KF หรือ สมาคมสหกรณ์ ก่อตั้งขึ้นในปี 1899 โดยสหกรณ์ผู้บริโภคในท้องถิ่น 41 แห่ง เป็นผู้นำด้านการค้าปลีกในสวีเดนโดยพัฒนารูปแบบร้านค้าใหม่และใหญ่ขึ้น และเป็นหนึ่งในกลุ่มธุรกิจหลักในสแกนดิเนเวีย ในสมัยนี้คำว่าสหกรณ์อาจจะดูเชยๆ แต่ต้องเข้าใจครับว่ายุคนั้นคือความก้าวหน้ามากๆ และต้องมีความรู้รอบด้านทั้งวิทยาศาสตร์ เศรษฐกิจ การเมือง) เพื่อบรรยายให้คนหนุ่มสาวและแม่บ้านฟังเกี่ยวกับวิธีรับมือกับเสบียงที่มีจำกัดในช่วงสงครามที่ตึงเครียด เนื่องจากอยู่ในภาวะสงครามโลกครั้งที่2

ในปี 1946 ป้าแอนได้รับการแต่งตั้งเป็นหัวหน้าของSwedish Cooperative Union หรือ Kooperativa Förbundets (KF) Provkök (experimental kitchen หรือ ภาษาสมัยนี้น่าจะใกล้เคียงกับ kitchen lab นั่นเอง) ซึ่งเป็นองค์กรที่มีอิทธิพลทางด้านอาหารเป็นอย่างมากในสวีเดน มีบทบาทสำคัญในเศรษฐกิจและสังคมสวีเดน โดยสร้างโอกาสให้แก่สมาชิกและส่งเสริมการพัฒนาที่ยั่งยืนในชุมชนต่าง ๆ ทั่วประเทศ
ป้าแอนทำงานที่นี่นานจนถึงช่วงปี 1980 ขนาดของ KF ก็ใหญ่โตขึ้นมากมาย จนขยายอำนาจและขอบเขตการทำงานไปถึงการเป็นคณะกรรมการทดสอบรสชาติซึ่งทดสอบอาหารกึ่งสำเร็จรูปและอาหารสำเร็จรูปใหม่ด้วย ในจุดนี้ ป้าแอน เล็งเห็นความสำคัญและความรับผิดชอบของผู้ผลิต/ผู้ค้าอาหาร ควรจะขยายความรับผิดชอบครอบคลุมไปจนถึงโต๊ะอาหาร (ในที่นี่น่าจะหมายถึงลูกค้า) นั่นคือเหตุผลที่การติดฉลากอาหารจึงมีความสำคัญมาก ป้าแอนได้มุ่งเน้นให้ความรู้กับผู้บริโภคว่า ‘Weigh up the price against the quality’ หรือ ให้ชั่งน้ำหนักพิจารณาให้ดี ระหว่างราคากับคุณภาพ ตลอดระยะเวลาการทำงาน Anna-Britt Agnsäter ได้รณรงค์เพื่อให้มีการแสดงข้อมูล ให้ผู้บริโภครับทราบ เพื่อคุณภาพชีวิตที่ดีขึ้นและได้ให้คำแนะนำด้านโภชนาการ เพื่อให้เข้าใจได้ง่ายขึ้น ในรูปแบบฉลากโภชนาการ
ในปี 1946 เช่นกันป้าแอนได้มีแผนในการทำ มีแผนที่จะผลิตหนังสือสอนทำอาหารสำหรับสถานการณ์ฉุกเฉิน เพราะบทเรียนในภาวะสงครามโลก ที่ป้าแอนผ่านมาตลอด แต่ไม่สามารถพิมพ์ออกมาได้เนื่องจากกระดาษขาดแคลนเนื่องจากอยู่ในภาวะหลังสงคราม
ในปี 1948-1949 ป้าแอนเดินทางไปอเมริกา เพื่อศึกษาเทคนิคการทำอาหารใหม่ๆ การผลิตภัณฑ์อาหารแช่แข็ง รวมถึงอาหารผงแห้งต่างๆ (dry powder) รวมไปถึงวิทยาศาสตร์การอาหาร (food science) ที่มหาวิทยาลัย Iowa State University การเดินทางมาอเมริกาครั้งนี้เปลี่ยนโลกของป้าแอนเป็นอย่างมาก ในตอนที่ป้าทำงานกับ KF เธอมักจะร่วมงานกับ Hemmens Forskningsinstitut (สถาบันวิจัยในประเทศ) เพื่อจัดหาเครื่องมือในครัวที่ยกระดับมาตรฐานการทำอาหารที่ดียิ่งขึ้น รวมถึงอุปกรณ์การครัว ภาชนะต่างๆที่เข้าเตาอบได้ และจากประสบการณ์ที่อเมริกานี้
ป้าแอนได้จับมือกับ โรงงานเครื่องเคลือบและพลาสติก Gustavsberg และ HFI Anna-Britt Agnsäter พัฒนาช้อนตวง ชุด4ชิ้น ที่วางซ้อนกันได้ ซึ่งเป็นการปฎิวัติวงการอาหารครั้งสำคัญของสวีเดน เรียกว่า “ชุดช้อนตวงมาตรฐาน” ซึ่งจะมีการระบุขนาดที่ชัดเจน 4 ชิ้น ประกอบไปด้วย

ซึ่งทำให้ผู้ใช้สามารถวัดปริมาณวัตถุดิบได้อย่างถูกต้องตามที่สูตรอาหารกำหนด กลายเป็นเครื่องมือที่จำเป็นในครัวเรือนและการประกอบอาหารในเชิงพาณิชย์
แม้การพัฒนา “ชุดช้อนตวงมาตรฐาน” นี้จะเริ่มต้นในสวีเดน แต่นวัตกรรมนี้มีผลกระทบที่กว้างขวางและแพร่หลายไปยังครัวเรือนและอุตสาหกรรมอาหารทั่วโลกจนถึงปัจจุบัน


ในชุดช้อนตวงมาตรฐาน original 4 คุณอาจสังเกตคำนึงที่ไม่ค่อยคุ้นสักเท่าไรคือหน่วย kryddmått
นอกจากชุดช้อนตวงมาตรฐานแล้ว ป้าแอนยังคิดค้นสิ่งต่างๆอีกมากมาย ให้กับวงการอาหารสวีเดน รวมถึงหน่วยวัดใหม่ที่เรียกว่า kryddmått นี้ด้วยครับ ซึ่งมันเป็นหน่วยวัดขนาดเล็กที่ใช้ในการตวงเครื่องเทศและวัตถุดิบปริมาณน้อย โดยหน่วยวัดนี้มีขนาด 1 มิลลิลิตร (ml)ซึ่งถูกกำหนดมาเป็นหน่วยที่เล็กที่สุดซึ่งทำให้มีการจดบันทึกสูตรได้แม่นยำยิ่งขึ้น นั่นเพราะว่า การตวงเครื่องเทศ หรือ เกลือ นั้นหากรสชาติที่เข้มข้น หรือมีการใช้มากเกินไปหรือไม่พออาจทำให้รสชาติของอาหารเปลี่ยนไป การใช้ kryddmått ช่วยให้การวัดปริมาณเครื่องเทศที่ใช้ในสูตรอาหารเป็นไปอย่างแม่นยำและสม่ำเสมอ
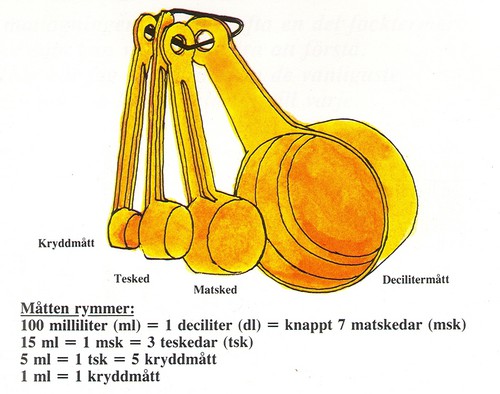
ถือว่าเป็นอีกผลงานคุโณปการที่ป้าแอน ฝากไว้ให้กับโลกนี้ มันมีส่วนสำคัญในการทำให้งานครัวเรือนง่ายขึ้นและมีประสิทธิภาพมากขึ้นผ่านการพัฒนาหน่วยวัดที่แม่นยำและสะดวกในการใช้งาน นวัตกรรมนี้ช่วยให้การทำอาหารเป็นไปอย่างราบรื่นและมีคุณภาพสูงยิ่งขึ้น

ในปี 1951 ป้าแอนได้บูรณะหนังสือการทำอาหารประจำสวีเดนใหม่ทั้งหมด (Vår kokbok) จุดประสงค์ของตำราอาหาร Vår คือการนำเสนอตำราอาหารราคาต้นทุนวัตถุดิบไม่แพง ที่ให้ความรู้เรื่องสารอาหารและใช้งานง่าย นอกจากนี้ยังเป็นการวางวัตถุดิบให้ได้รับสารอาหารที่เพียงพออีกด้วย เพราะในยุคนั้นสวีเดนมีข้อจำกัดในเรื่องอาหารเป็นอย่างมาก
เนื้อหาสูตรอาหารที่ใช้ในหนังสือเล่มนี้กลายเป็นบรรทัดฐานในช่วงทศวรรษ 1950 โดยมีการใช้หน่วยชั่งตวงแบบใหม่ ตามชุดช้อนตวงมาตรฐาน (ปริมาตร) จากของเดิมที่ใช้การชั่งน้ำหนัก ใช้ศัพท์ในการทำอาหารแบบเป็นสากล เช่น ขูด ปอกเปลือก ล้าง เป็นต้น (grate, peel, rinse) จัดอาร์ทเวิคให้แต่ละสูตร สามารถจบได้ในหน้าเดียวไม่ต้องพลิกอ่านหน้าต่อๆไป ทำให้สะดวกในการเปิดแล้วทำตาม การไล่ลำดับอาหาร เปลี่ยนจากการไล่ประเภทอาหาร ไปเป็นไล่ลำดับตามวัตถุดิบหลักของอาหาร ทำให้คนอ่านสามารถบริหารจัดการเมนูได้ง่าย เช่น ไก่ ก็สามารถไล่เรียงได้เลยว่า วันนี้มีไก่ จะทำอะไรกินดี
นอกจากนี้ยังรับประกันว่าทุกสูตรสามารถทำได้จริง เพราะป้าแอนลงมือทดสอบสูตรด้วยตัวเองทุกสูตร นอกจากนี้ยังคงมีการแนะนำให้ใช้การวัดอุณหภูมิในการทำอาหารด้วยเพื่อความเป๊ะในรสชาติ เนื่องจากป้าแอนเห็นตอนไปดูงานที่อเมริกา จนถึงทุกวันนี้ Vår kokbok เป็นหนึ่งในตำราอาหารที่ขายมากที่สุดในโลกด้วยยอดขายมากกว่า 2.3 ล้านเล่มนับตั้งแต่เริ่มต้น โดยเฉลี่ยมากกว่า 40,000 เล่มต่อปี


ด้วยความที่ Kooperativa Förbundets เป็นองค์กรที่มีอิทธิพลสูงมากในวงการอาหารสวีเดน และคุณป้าแอน ก็มีตำแหน่งที่สูงมาก จึงสามารถเป็นผู้มีส่วนสนับสนุนรูปแบบซูเปอร์มาร์เก็ตสมัยใหม่ ในการใส่รายการส่วนผสมและคำแนะนำในการปรุงอาหารในรูปแบบฉลากของผลิตภัณฑ์อาหารสมัยใหม่

จนกระทั่งในช่วงปี 1970 ประเทศสวีเดนต้องเผชิญกับปัญหาราคาอาหารที่สูงเนื่องจากเงินเฟ้อ รวมถึงสภาพอากาศของสวีเดนนั้น ไม่เอื้อต่อการได้รับสารอาหารที่หลากหลายได้ ครอบครัวที่มีเด็ก ไม่สามารถปรุงอาหารและรับประทานอาหารที่มีคุณค่าทางโภชนาการในราคาที่เหมาะสมได้ รัฐบาลจึงมอบหมายให้ Sweden’s National Board of Health and Welfare (คณะกรรมการสุขภาพและสวัสดิการแห่งชาติของสวีเดน) หาวิธีแก้ไขสถานการณ์ดังกล่าว และคัดกรองแบ่งประเภทอาหารออกเป็น “basic food” และ “supplement” มาเป็นรูปแบบของ กราฟวงกลม (diet circle) แต่ป้าแอนพบปัญหาบางอย่าง ที่ทำให้กราฟวงกลมนี้ใช้งานยาก เพราะการแบ่งปริมาณของอาหารแต่ละประเภทไม่ชัดเจน
ในระหว่างบรรยายเรื่องการกำหนดอาหารพื้นฐาน คุณ Fjalar Clemes หนึ่งในผู้เข้าร่วมการบรรยาย ได้ให้ไอเดียด้วยการสร้างแบบจำลองที่เรียกว่า ปิรามิดอาหาร (Food Pyramid) ขึ้นมา เพื่อให้เห็นภาพสัดส่วนอาหารที่ชัดเจนขึ้น ป้าแอนเลยนำข้อมูลจากกราฟวงกลมนั้น มาสร้างโมเดลจำลองให้อยู่ในรูปแบบปิรามิด โดยให้ “basic food” เช่น ขนมปัง มันฝรั่ง พาสต้า และนม และ “supplements” เช่น ผลไม้ ผัก เนื้อสัตว์ และปลา อยู่ในรูปแบบที่เข้าใจได้ง่ายขึ้น แม้แต่คนที่อ่านหนังสือไม่ออก

แต่นี่แหละที่เป็นจุดเริ่มต้นของปัญหา ด้วยความที่มันใช้งานง่ายสะดวก อเมริกาจึงนำไปปรับปรุงเป็นเวอร์ชั่นตัวเอง แต่ก็มีการเปลี่ยนแปลงไปอย่างมาก ตามที่ได้มีการทำบทความไปแล้ว (อ่านที่นี่)
ทั้งๆที่ปิรามิดต้นแบบของป้าแอนนั้น สร้างขึ้นมาเพื่อชาวสวีเดนเนื่องจากนำข้อมูลพื้นฐานจากข้อจำกัดในประเทศในขณะนั้น ไม่ว่าจะเรื่องของวัตถุดิบที่หาได้ในภาวะยากแค้นแบบนั้น อุณหภูมิอันปรวนแปร รวมถึงสภาพเศรษฐกิจที่ย่ำแย่มาก การจัดแจงข้อจำกัดที่มีเพื่อให้ได้สารอาหารที่เพียงพอที่สุดเท่าที่จะทำได้ต่างหาก (eat healthier, more affordable and save on fat) ที่เป็นที่มาของ “ปิรามิดอาหารของสวีเดน” (คือ จะให้เอาอุดมคติมาสร้างปิรามิดอาหาร คงไม่มีประโยชน์ เพราะยังไงก็ไม่มีเงินซื้อและหาวัตถุดิบไมไ่ด้ตามอุดมคติ วัตถุประสงค์ในการสร้างและเผยแพร่ครั้งนี้มันเพื่อให้ประชาชนทั้งประเทศที่มีความรู้ด้านอาหารน้อย รู้และทำตามได้จริง สมกับพื้นที่และกำลังทรัพย์ // ความเห็นส่วนตัวผมครับ)
ปิรามิดอาหารที่แท้จริงแล้ว จะมีการปรับปรุงตลอดเวลา ตามปัจจัยที่เปลี่ยนไป ไม่ใช่ปิรามิดที่เอาไว้ยึดถือตลอดไป แต่การที่อเมริกานำไปยึดถือว่าเป็น all time information เป็นค่าคงที่ให้ทั้งโลกยึดตาม รวมถึงสร้างด้วยเบื้องหลังด้านธุรกิจ จึงต่างกับที่ป้าแอนทำในทุกมิติ แต่ไฉน เป้าการบูลลี จึงต้องไปตกที่ป้าแอน ว่าเป็นต้นตอความพังของสุขภาพ มันแฟร์แล้วหรือ
เรื่องนี้มีข้อพิสูจน์ได้จนถึงปัจจุบันเช่น ในปี 2022 ก็มีการนำเสนอ ปิรามิดอาหารสำหรับ Mixed diet, flexitarian, vegetarian และ vegan ออกมาสืบทอดเจตนารมณ์ป้าแอน นอกจากนี้ในช่วงที่ป้าแอนมีชีวิต ก็ยังคงมีการช่วยเหลือแนะนำให้ประเทศต่างๆ “มีปิรามิดอาหารของตัวเอง” นั่นคือ วิชั่นที่กว้างไกลของป้าแอน ที่เห็นได้ชัดเจนว่า อาหารพื้นถิ่นกับสารอาหารที่สมดุล ของแต่ละประเทศมีความไม่เหมือนกัน และแนวคิดนี้ได้มีทั้ง เดนมาร์ก, นอร์เวย์, ฟินแลนด์, ญี่ปุ่น, ศรีลังกา ได้นำไปพัฒนาใช้เช่นกัน
นอกจากนี้ ป้าแอนและองค์กร Kooperativa Förbundets ยังให้ข้อมูลการศึกษาที่สำคัญสำหรับประชาชนผ่านบทความเกี่ยวกับอาหารที่ตีพิมพ์ใน นิตยสาร Vi รวมถึงการจัดตั้งกลุ่มการศึกษาร่วมกับทาง สมาคมการศึกษาของชนชั้นแรงงาน หรือ Arbetarnas bildningsförbund (ABF) มีส่วนสนับสนุนในการอภิปรายแบบเปิดทางสังคมเกี่ยวกับปัญหาโรคอ้วนอีกด้วย รวมถึงยังออกหนังสือเกี่ยวกับการทำอาหารอีกร่วมๆ 30เล่ม ซึ่งรวมถึงบทเกี่ยวกับมื้ออาหารที่มีคุณค่าทางโภชนาการที่สมดุล ด้วยเช่นกัน

ในปี 1983 ป้าแอนได้ตีพิมพ์หนังสือ Matboken ซึ่งได้รับการพิสูจน์แล้วว่าเป็นประโยชน์อย่างมาก โดยเฉพาะกับคนหนุ่มสาวเกี่ยวกับวิธีการกินอาหารที่มีคุณค่าทางโภชนาการและมีวิธีทำที่เรียบง่ายที่สุด

ในช่วงทศวรรษ 1990 เมื่อป้าแอนเป็นม่าย จึงได้ย้ายเข้าไปอยู่ในบ้านพักคนชรา Färdknäppen ใน Södermalm ในสตอกโฮล์ม และ ได้แก้ไขสูตรอาหาร 250 สูตรจาก Vår kokbok เพื่อให้เหมาะสมกับสภาพแวดล้อมการปรุงอาหารส่วนกลางของบ้านพักคนชรา เพื่อให้ได้อาหารที่มีสารอาหารครบถ้วนตามที่ควรเป็น
เกียรติประวัติป้าแอนได้รับการตอบแทนดังนี้ ในปี 1979 ได้รับรางวัลเหรียญ St Erik เพื่อเป็นการยกย่องสิ่งที่เธอทุ่มเทแรงกายแรงใจทำมาตลอดชีวิต ในปี 1993 ได้รับเหรียญ HM Konungens ลำดับที่ 8 (HM The King’s Medal หรือ H.M. Konungens medalj ในภาษาสวีเดน) เป็นหนึ่งในรางวัลเกียรติยศที่สำคัญที่สุดที่มอบโดยพระมหากษัตริย์สวีเดนเพื่อยกย่องบุคคลที่มีผลงานดีเด่นหรือมีความโดดเด่นในด้านต่าง ๆ เช่น วิทยาศาสตร์ ศิลปะ วัฒนธรรม และการบริการสาธารณะ ในปี 1995 ได้รับเหรียญทอง Albin Johansson สำหรับผลงานอันทรงคุณค่าของเธอต่อสหกรณ์สวีเดน ในปี 1998 ได้รับรางวัล Gastronomiska Akademiens Guldpenna (ปากกาทองของสถาบันอาหาร) สำหรับบทความเกี่ยวกับส่วนผสมและการทำอาหารของเธอ

Anna-Britt Agnsäter เสียชีวิตในปี 2006 (อายุ 90ปี) ป้าแอนทำงานทั้งชีวิตเพื่อสอนชาวสวีเดนในการจัดการอาหารให้ดีขึ้น ทุกการทดลอง ทดสอบ ได้มีการบันทึกไว้อย่างชัดเจนสามารถพัฒนาต่อไปได้ การริเริ่มให้ข้อมูลที่ซื่อสัตย์ต่อผู้บริโภค ทั้งการติดฉลากอุปกรณ์ คำแนะนำในการทำอาหาร สูตรอาหาร บทความ และตำราอาหาร สิ่งเหล่านี้กลายเป็นพื้นฐานสำคัญในอุตสาหกรรมอาหารจนปัจจุบัน
แต่ทุกวันนี้วงการสุขภาพส่วนมากยังคงล้อเลียนเธอว่าเป็นครูธรรมดา ที่มีหน้ามาสร้างปิรามิดอาหาร จึงทำให้คนทั่งโลกป่วย ทั้งที่ความจริงทั้งหมดนั้น ความรู้ของป้าแอนไม่ได้น้อยไปกว่า ผู้เชี่ยวชาญทางวิทยาศาสตร์การอาหาร ซึ่งในสมัยนั้นนับว่าเป็นอีกแขนงที่อยู่ในระดับบนของการศึกษา ไม่ต่างกับวิทยาศาสตร์อื่นๆ ปิรามิดควรเป็นไปตามถิ่นที่อยู่ สภาพเวลาและสภาพเศรษฐกิจขณะนั้น ไม่ใช่การสร้างมาตรฐานให้ต้องทำเหมือนกันทั่วโลก โดยมาจากอิทธิพลของกลุ่มธุรกิจดังที่ usda ได้ทำการแก้ไขก่อนจะประกาศให้คนทั่วไปยึดถือ รายละเอียดเป็นไปตามที่สืบค้นข้อมูลประวัติของป้าแอน มาเล่าสู่กันฟัง ณ วันนี้ครับ
ผมก็เป็นหนึ่งในนั้น สิ่งที่ผมสามารถทำได้เพื่อเป็นการขอโทษคุณ Anna-Britt Agnsäter ที่ดีที่สุดที่ทำได้ตอนนี้คือ เผยแพร่ประวัติอันทรงคุณค่าของเธอ ให้คนอื่นๆได้รับทราบมากที่สุด เท่าที่จะทำได้
โปรดแชร์ เพื่อคืนความเป็นธรรมให้ Anna-Britt Agnsäter ให้โลกได้เข้าใจและรับรู้ถึงการอุทิศชีวิตให้วงการอาหารของคุณป้าครับ
ปล.มีการค้นพบไฟล์เสียง ที่ป้าแอน จัดรายการวิทยุในปี 1968 ให้ลองฟังกันครับ (น่าจะภาษาสวีเดนนะ 5555) ฟังได้ที่นี่ครับ https://rumble.com/v56p1wa-ann-britt-agnster-in-a-radio-find-from-1968.html
siamstr #pirateketo
-
 @ 6c8c7979:15595f3e
2024-07-13 01:55:06
@ 6c8c7979:15595f3e
2024-07-13 01:55:06Rococo is a style in interior design, decorative arts, painting, architecture, and sculpture, originating in Paris in the early 18th century. It quickly spread throughout France and later to other countries, primarily Germany and Austria.

Palace of Versailles - France
$$The origin of the word "Rococo"$$The term Rococo was first used by the designer Jean Mondon in his book "First Book Of Rococo Form And Setting" in 1736, where he used it alongside illustrations depicting the style used in architecture and interior design.
The word Rococo combines the French word "Rocaille," meaning shell, which was used to describe fountains and grottoes in gardens adorned with pebbles and shells, and "Barocco," the Italian word for Baroque, the art style preceding Rococo. Rococo art is characterized by curved forms resembling shells and wave-like ornaments.

One of the most famous paintings by the artist François Boucher is "The Swing" (La Balançoire), painted in 1767.
$$How Rococo Art Emerged$$With the death of King Louis XIV of France in 1715, one of the greatest French monarchs known for his lengthy reign and cultural influence, France was left economically and militarily powerful, setting it as a cultural beacon in arts, fashion, and culture. His successor, King Louis XV, in contrast, faced challenges and mismanagement, leading France toward bankruptcy with extravagant spending and failed policies. Despite this, his reign fostered an era of lavish court entertainment and artistic patronage, contrasting sharply with his predecessor.
Rococo art developed an aristocratic flavor, adopted by rising upper-middle-class individuals emulating the French nobility's fashion and lifestyle, known as the bourgeoisie. The period, spanning roughly from Louis XIV's death to the French Revolution in 1789, marked an era more than a defined style. Aristocrats in France imposed Rococo artistic style, constructing more elegant homes and commissioning interior decorations for palaces. Unlike its predecessor Baroque art, which was less suited for intimate and comfortable home decor, Rococo allowed for artistic rebellion.
Rococo paintings offered a unique glimpse into the lives of the French upper class in the decades preceding the French Revolution, though it didn't reflect the political and economic realities of the era and largely ignored working-class issues. While intricate Baroque architecture thrived in France, Italy, England, Spain, and South America, softer Rococo styles were prevalent in Germany, Austria, Eastern Europe, and Russia, mainly focusing on interior and exterior design.
$$Information about Rococo Art$$Rococo art, termed by some historians as the late phase of Baroque but lighter and more delicate, was employed by artists and designers in interior design and the arts.
The Rococo era was considered a revolution against the formal Baroque designs that characterized the French royal court at Versailles, emphasizing comfort, warmth, and intimacy.
Rococo is distinguished by its softness, playfulness, imagination, and whimsy compared to its more serious predecessor, Baroque. Ornamentation was used to create a sense of flow, especially through abstract and asymmetrical details.
This art style was influenced by Asian motifs such as Chinese design, influenced by trade relations with the Far East, leading to more modern decorative works. Interior decor and its components formed a harmonious unity, giving a unified impression, with great effort put into selecting furniture shapes, placements, and decorations.
Wealthy property owners renewed their homes' interiors with Rococo-style plasterwork, murals, mirrors, furniture, and porcelain, characterized by a delicate, feminine touch, while maintaining Baroque architecture on the exterior.
In Rococo decor, large candelabra, beautiful chandeliers, and wall sconces stand out to create a warm atmosphere, complemented by luxurious gilt-framed mirrors with floral motifs, enhancing a sense of openness in spaces.
$$Architecture$$As the fundamental principle in Rococo architecture was to achieve the purpose of celebration, in the early 18th century, the aim of construction was festive. French aristocrats ceased gathering at the royal court and palaces of kings, instead opting to enjoy themselves in private palaces intended as venues for parties, incorporating complex, ornate, and asymmetrical styles that imparted a sense of joy and whimsy.

The Fountain of Fountains (Fontänebnlo): A stunning water sculpture located in Munich, Germany, considered a masterpiece of Rococo art, and was part of the design for the Nymphenburg Palace.
$$Art of Painting$$Painters used pastel colors, flowing lines, and non-symmetrical shapes, with many artworks characterized by off-center compositions, meaning the overall design or arrangement was asymmetric or whimsical. Each element contributed to creating a sense of movement and playfulness within the painting, depicting mythical scenes set in imaginative landscapes and images of love as well.
$$Themes Embraced by Rococo$$Rococo paintings did not address national issues, religious piety, morality, saints, or heroes, nor did they provoke deep thought. They depicted outdoor scenes for leisurely activities, lovers in romantic encounters, and playful behavior with a sense of humor. These artworks were created for aesthetic purposes and to please the viewer's eye.

One of the most famous Rococo painters was the French artist Jean Antoine Watteau, and his painting "Les Plaisirs Du Bal" is considered exemplary of the early Rococo period.
$$Rococo in Germany$$aristocrats and nobles desired their palaces to be venues for celebrations, similar to the French. One of the notable examples is the construction of Amalienburg Palace, originally a hunting lodge within the grounds of Nymphenburg Palace in Munich. It was commissioned by Holy Roman Emperor Charles VII and his wife Maria Amalia, designed by architect François de Cuvilliés and decorated by painter Johann Baptist Zimmermann between 1734-1739. The building is distinguished by its smooth lines, intricate designs, and light pink color.

Amalienburg
Moving inside the palace, one must pause at the Hall of Mirrors, a circular room at the center of the building surrounded by mirrors. It is filled with decorations of gold and silver on the walls, featuring motifs of leaves, flowers, birds, and small cupids. Its design is intricate, vibrant with life and movement.

Inside the palace - Hall of Mirrors
Critics dubbed this art as frivolous, appearing only to vanish, and condemned it for its superficiality, with some even labeling it as failed art, leading to a backlash against it. This resulted in a strong reaction from intellectuals like Voltaire. By the mid-18th century, the popularity of Rococo art began to decline in France, and interest waned across Europe.
-
 @ 3bf0c63f:aefa459d
2024-06-07 15:27:10
@ 3bf0c63f:aefa459d
2024-06-07 15:27:10Report of how the money Jack donated to the cause in December 2022 is being spent.
Bounties given
June 2024
- Darashi: 5,000,000 - maintaining nos.today, searchnos, search.nos.today and other experiments
- Toshiya: 5,000,000 - keeping the NIPs repo clean and other stuff
May 2024
- James: 3,500,000 - https://github.com/jamesmagoo/nostr-writer
- Yakihonne: 5,000,000 - spreading the word in Asia
- Dashu: 9,000,000 - https://github.com/haorendashu/nostrmo
February 2024
- Viktor: 5,000,000 - https://github.com/viktorvsk/saltivka and https://github.com/viktorvsk/knowstr
- Eric T: 5,000,000 - https://github.com/tcheeric/nostr-java
- Semisol: 5,000,000 - https://relay.noswhere.com/ and https://hist.nostr.land relays
- Sebastian: 5,000,000 - Drupal stuff and nostr-php work
- tijl: 5,000,000 - Cloudron, Yunohost and Fraidycat attempts
- Null Kotlin Dev: 5,000,000 - AntennaPod attempt
December 2023
- hzrd: 5,000,000 - Nostrudel
- awayuki: 5,000,000 - NOSTOPUS illustrations
- bera: 5,000,000 - getwired.app
- Chris: 5,000,000 - resolvr.io
- NoGood: 10,000,000 - nostrexplained.com stories
October 2023
- SnowCait: 5,000,000 - https://nostter.vercel.app/ and other tools
- Shaun: 10,000,000 - https://yakihonne.com/, events and work on Nostr awareness
- Derek Ross: 10,000,000 - spreading the word around the world
- fmar: 5,000,000 - https://github.com/frnandu/yana
- The Nostr Report: 2,500,000 - curating stuff
- james magoo: 2,500,000 - the Obsidian plugin: https://github.com/jamesmagoo/nostr-writer
August 2023
- Paul Miller: 5,000,000 - JS libraries and cryptography-related work
- BOUNTY tijl: 5,000,000 - https://github.com/github-tijlxyz/wikinostr
- gzuus: 5,000,000 - https://nostree.me/
July 2023
- syusui-s: 5,000,000 - rabbit, a tweetdeck-like Nostr client: https://syusui-s.github.io/rabbit/
- kojira: 5,000,000 - Nostr fanzine, Nostr discussion groups in Japan, hardware experiments
- darashi: 5,000,000 - https://github.com/darashi/nos.today, https://github.com/darashi/searchnos, https://github.com/darashi/murasaki
- jeff g: 5,000,000 - https://nostr.how and https://listr.lol, plus other contributions
- cloud fodder: 5,000,000 - https://nostr1.com (open-source)
- utxo.one: 5,000,000 - https://relaying.io (open-source)
- Max DeMarco: 10,269,507 - https://www.youtube.com/watch?v=aA-jiiepOrE
- BOUNTY optout21: 1,000,000 - https://github.com/optout21/nip41-proto0 (proposed nip41 CLI)
- BOUNTY Leo: 1,000,000 - https://github.com/leo-lox/camelus (an old relay thing I forgot exactly)
June 2023
- BOUNTY: Sepher: 2,000,000 - a webapp for making lists of anything: https://pinstr.app/
- BOUNTY: Kieran: 10,000,000 - implement gossip algorithm on Snort, implement all the other nice things: manual relay selection, following hints etc.
- Mattn: 5,000,000 - a myriad of projects and contributions to Nostr projects: https://github.com/search?q=owner%3Amattn+nostr&type=code
- BOUNTY: lynn: 2,000,000 - a simple and clean git nostr CLI written in Go, compatible with William's original git-nostr-tools; and implement threaded comments on https://github.com/fiatjaf/nocomment.
- Jack Chakany: 5,000,000 - https://github.com/jacany/nblog
- BOUNTY: Dan: 2,000,000 - https://metadata.nostr.com/
April 2023
- BOUNTY: Blake Jakopovic: 590,000 - event deleter tool, NIP dependency organization
- BOUNTY: koalasat: 1,000,000 - display relays
- BOUNTY: Mike Dilger: 4,000,000 - display relays, follow event hints (Gossip)
- BOUNTY: kaiwolfram: 5,000,000 - display relays, follow event hints, choose relays to publish (Nozzle)
- Daniele Tonon: 3,000,000 - Gossip
- bu5hm4nn: 3,000,000 - Gossip
- BOUNTY: hodlbod: 4,000,000 - display relays, follow event hints
March 2023
- Doug Hoyte: 5,000,000 sats - https://github.com/hoytech/strfry
- Alex Gleason: 5,000,000 sats - https://gitlab.com/soapbox-pub/mostr
- verbiricha: 5,000,000 sats - https://badges.page/, https://habla.news/
- talvasconcelos: 5,000,000 sats - https://migrate.nostr.com, https://read.nostr.com, https://write.nostr.com/
- BOUNTY: Gossip model: 5,000,000 - https://camelus.app/
- BOUNTY: Gossip model: 5,000,000 - https://github.com/kaiwolfram/Nozzle
- BOUNTY: Bounty Manager: 5,000,000 - https://nostrbounties.com/
February 2023
- styppo: 5,000,000 sats - https://hamstr.to/
- sandwich: 5,000,000 sats - https://nostr.watch/
- BOUNTY: Relay-centric client designs: 5,000,000 sats https://bountsr.org/design/2023/01/26/relay-based-design.html
- BOUNTY: Gossip model on https://coracle.social/: 5,000,000 sats
- Nostrovia Podcast: 3,000,000 sats - https://nostrovia.org/
- BOUNTY: Nostr-Desk / Monstr: 5,000,000 sats - https://github.com/alemmens/monstr
- Mike Dilger: 5,000,000 sats - https://github.com/mikedilger/gossip
January 2023
- ismyhc: 5,000,000 sats - https://github.com/Galaxoid-Labs/Seer
- Martti Malmi: 5,000,000 sats - https://iris.to/
- Carlos Autonomous: 5,000,000 sats - https://github.com/BrightonBTC/bija
- Koala Sat: 5,000,000 - https://github.com/KoalaSat/nostros
- Vitor Pamplona: 5,000,000 - https://github.com/vitorpamplona/amethyst
- Cameri: 5,000,000 - https://github.com/Cameri/nostream
December 2022
- William Casarin: 7 BTC - splitting the fund
- pseudozach: 5,000,000 sats - https://nostr.directory/
- Sondre Bjellas: 5,000,000 sats - https://notes.blockcore.net/
- Null Dev: 5,000,000 sats - https://github.com/KotlinGeekDev/Nosky
- Blake Jakopovic: 5,000,000 sats - https://github.com/blakejakopovic/nostcat, https://github.com/blakejakopovic/nostreq and https://github.com/blakejakopovic/NostrEventPlayground
-
 @ 3cd2ea88:bafdaceb
2024-07-12 22:33:49
@ 3cd2ea88:bafdaceb
2024-07-12 22:33:49Siamo entusiasti di annunciare il lancio di DOGS POINTS (DOGS) nel trading pre-market su Bitget! 🎉 Gli utenti possono ora iniziare a scambiare DOGS POINTS prima che diventi disponibile per il trading ufficiale.
🐶 Un po' di background su DOGS POINTS:
L'immagine di DOGS è ispirata a Spotty, la mascotte creata dal fondatore di TON, Pavel Durov, per la comunità di Telegram. Questa moneta non è solo per divertimento, ma tutti i ricavi delle vendite sostengono orfanotrofi e case per bambini, continuando l'eredità benefica di Spotty. ❤️
👉 Non perdere questa opportunità unica! Unisciti ora al trading pre-market su Bitget e sostieni una buona causa. Iscriviti ora e inizia a scambiare: https://bonus.bitget.com/U1JNEK
👉 Non sei andato a riscattare il tuo AirDrop su Telegram? Vai subito a vedere quanti DOGS puoi ricevere! https://t.me/dogshouse_bot/join?startapp=y5J61rnXSU2wW2ruadnJNA
-
 @ ff3d87cc:7738cb1a
2024-06-05 09:13:21
@ ff3d87cc:7738cb1a
2024-06-05 09:13:21
前言
本篇轉載自動區Blocktempo(原文-https://reurl.cc/ZeM4v3)
日本上市公司 Metaplanet 將購入比特幣作為轉型手段,試圖打造亞洲版微策略(MicroStrategy),果殼與矽谷大叔KC共同撰文,解釋其中原因與 Metaplanet 的最終目的。
Metaplanet,一家在東京證券交易所上市的公開交易公司,過去遭受疫情重擊,其旅館業務受到毀滅性打擊,並於今年4月宣佈其財務管理策略的改變,Metaplanet已採納比特幣作為策略儲備資產。
自今年 4 月份以來,Metaplanet 已購買了137個比特幣(約1,000萬美元),這與在美國上市的 MicroStrategy 公司(MSTR)採取的策略似乎類似,後者已收購了超過20萬顆比特幣作為公司資產,但Metaplanet採用比特幣,與MSTR的原因不盡相同。
如今政府債務高築、貨幣快速貶值的時代,維持現金部位的長期價值,是每個企業都會面臨的問題。以美元為例,過去一百年來,發行量大約是以平均每年7%的速度增長。各國貨幣則視其貨幣政策及財政紀律,貶值速度不一,企業的增長如果不能超越貨幣發行量的增幅,相當於企業在衰退,從資本的角度看實際為負增長。
MicroStrategy在2020年首度以上市公司的地位採用比特幣做為儲備資產,並展開一系列的財務槓桿操作,增加其比特幣的儲備量,目的即是在解決這個問題,並提升公司的競爭力。自從採用比特幣策略以來,股價表現大幅超越主要科技公司、標普500指數、黃金及債券。
**
Metaplanet面臨虧損放棄本業
** 不同的是,MSTR擁有持續賺錢的本業,Metaplanet沒有,其本業只是拖油瓶。
Metaplanet公司成立於1999年(Red Planet Japan Inc.,下稱紅星球),總部位於日本東京,紅星球過去是一家旅遊、飯店營運的上市企業,營收穩定成長,但自2019年開始,遭受新冠疫情重擊,其旅館業務受到毀滅性影響,股價以及營收同步斷崖式下跌至谷底,自2019年股價高點360日圓每股,最低至15日圓(下跌99.73%)。
元宇宙也救不了
因疫情影響,紅星球收入自2019年高峰25億快速崩落至784萬日圓,隨後開始轉型,將相關旅館虧損業務處分,砍掉其海外(泰國)業務,導致收入逐年下滑,至2023年度剩餘261萬日圓,員工人數也大減90%,只剩下17個人,可以說逐步朝向空殼公司轉型:
持平而論,像紅星球這樣的公司,在日圓貶值、依賴內需市場的旅遊業,除了在日本證交所的上市外殼(JPX:3350)有點價值外,其餘業務沒有任何亮點,沒有獲利能力,除了砍掉既有業務、避免虧損擴大外,沒有任何未來。
紅星球後來改名Metaplanet、並嘗試將業務面轉向Web 3與元宇宙技術,包括「WEN Tokyo」項目、「Takumi-X」項目、NFT交易平台/投資業,並兼營飯店品牌,在2022年有些許成效,轉虧為盈,但隨著NFT市場持續疲軟,證明轉型Web 3無法拯救公司。
不再限於元宇宙,Metaplanet的策略是,將比特幣置於首位,採用唯一比特幣為公司資產,並使用長期債券及定期發行股票作為策略性金融選擇,以持續積累更多的比特幣,而非持有日益疲弱的日元。
延伸閱讀:傳奇投資人索羅斯持有超2.57億美元「微策略可轉債」,變相擁抱比特幣
比特幣策略一宣布,並搭配公開市場購入比特幣的消息,Metaplanet股價今年以來已經飆漲300%,與西方MTSR相互輝映,象徵著企業採用比特幣的時代,正式進入全球,而此策略會在短期如此成功,得益於日圓的匯率問題。
日圓鉅額貶值
據數據顯示,自 2021 年初以來,日元兌美元已經貶值了 50%。最近,日元兌美元匯率跌破 155,創下 34 年新低。

日本Yahoo就日元貶值「對你的生活有何影響」作出民調,有多達87.5%的人認為貶值已對他們的生活構成負面影響,至於樂觀派只有8.2%,而另外有3%人表示「沒有感覺」,「我不知道」則佔1.3%,反映日本人就貶值問題,似乎已經到了容忍的臨界點。
亞洲版微策略(MSTR)
Metaplanet將其財務策略轉向比特幣(BTC),主要優勢包括:
1.抵禦貨幣貶值:隨著日元持續走弱,比特幣提供了一種絕對中立的價值儲存方式,相較於傳統法定貨幣,有著抗通膨,和未來可能繼續增值的潛力。
2.資本市場的投機套利:利用日本資本市場的極端機會,Metaplanet計劃使用現有現金儲備、資產產生的現金流,以及接近實質負利率的低成本資金,通過發行長期日元債券進行戰略性套利,在機會出現時持續收購比特幣。
3.成為比特幣載體:儘管全球存在各種形式的比特幣採用渠道,包括直接持有比特幣現貨和ETF/ETP等金融商品,Metaplanet將直接成為亞洲上市營運公司的比特幣儲備載體,提供全球投資者提供一選擇權,成為機構投資人持有比特幣的最低成本方式。
4.優惠的稅收制度:此外,對於日本的個人來說,稅收計算基於實現的收益作為雜項收入,最高稅率可達55%。然而,上市股票/證券的稅收環境顯著更低,實現的股票收益稅率僅為20%。日本稅法過去對未實現的加密貨幣收益徵稅,但由於日本加密貨幣稅務法規的即將修正,未來企業持有比特幣(未售出),將不會課徵稅賦。
5.此外,歸功於Metaplanet過去本業虧損,其目前擁有超過100億日元的「稅務虧損資產」,可以在未來需要時抵消實現收益。
這一策略就如同MTSR,旨在提高每股換算比特幣本位的收益,長期支撐公司股東價值。
用白話來說,讓公司股票成為比特幣的載體,成為日本機構投資人間接持有比特幣的最簡單方式。
為何是比特幣?
Metaplanet於2024年5月13日公開消息表示,其選擇比特幣作為唯一戰略資產的理由有三:
1.比特幣在本質上優於任何形式的法定貨幣、傳統價值儲存和投資工具,以及所有其他加密資產/證券。
2.比特幣是一種全球化、絕對稀缺的數位原生貨幣,沒有任何單一發行機構。
3.比特幣的貨幣政策嚴格設定在2140年,使其與貨幣金屬和由中心化團隊隨意操作的其他加密貨幣有顯著不同,比特幣的總量永遠只有21,000,000枚。
Metaplanet戰略性地擴充其比特幣儲備,不僅加強了公司的資產負債表,抵禦日元不斷貶值的壓力,還使Metaplanet成為一個全球以比特幣為核心的投資平台,我認為是一個無比聰明的決定。
台灣、韓國以及其他亞洲國家,遲早會跟進,誰會是台灣第一家上市公司採用比特幣,讓我們拭目以待。
-
 @ 617f0a85:b403d1ed
2024-07-12 21:03:19
@ 617f0a85:b403d1ed
2024-07-12 21:03:19For the last several weeks we've been meeting on Thursday evenings to chat about projects people are working on, cool new things in crypto, and generally just having a good time. As we all have busy schedules and lots of meetings, it is important to keep things informal and give people the space to share freely. Please join us and connect with some great builders.
This weekly happy hour is hosted by Chones which is hoping to weave together communities in web3 and make the things happen that often are not appreciated but make a big difference. Hosting the happy hour is a way to expose builders to new projects and learn about what else is happening in the space for those who are heads down working on their stuff. There is so much going on, keeping track of it all is impossible for anyone, so let's do it together.
If you're interested in attending, let me know and I'll let you know when and where we meet. We're looking to move to hivetalk.org after getting everyone on the same page. Hope to see you there.
chones
-
 @ b6dcdddf:dfee5ee7
2024-07-12 20:15:22
@ b6dcdddf:dfee5ee7
2024-07-12 20:15:22🚀 Exciting News: Introducing Project Affiliates!
Creators can finally reach a wider audience by partnering with affiliates!
Affiliates earn automated payouts for contributions enabled through their shares. 🤑
Announcement link: https://x.com/geyserfund/status/1811434402041282680
originally posted at https://stacker.news/items/606500
-
 @ dec2e28f:01746c77
2024-06-01 02:12:44
@ dec2e28f:01746c77
2024-06-01 02:12:44哇,剛剛發現了Bitmain的最新陰謀。
讓我告訴你背景故事......
曾幾何時,比特大陸(Bitmain)使用了磨礪merkle root而不是nonce的方法,也就是所謂的“隱蔽ASICBOOST”。
這給了他們相較於其他不知情礦工的優勢。一家公司因此倒閉了——KNC——並聲稱“中國人有我們不知道的某種秘密優勢”——事實證明,正是因為這個原因。
這是ASIC製造如此集中化的原因之一,許多人正確地指出這是整個比特幣生態系統中最脆弱的方面之一。
ASICBOOST問題在比特大陸利用其影響力阻止SEGWIT(閃電網絡必須的)激活時達到頂峰,因為SEGWIT會破壞他們進行ASICBOOST的能力——至少是隱蔽地進行。他們仍然可以使用ASICBOOST,但只能以明顯的方式進行,這意味著其他人也可以這樣做。他們已經申請了專利,試圖阻止這種情況,因為這就是我們在這裡面對的人的做法,但我離題了……
當Greg Maxwell獨立發現ASICBOOST時,比特大陸撒謊說他們實際上並沒有使用它。
這是在多年來有關SEGWIT的胡說八道之後發生的,比特大陸假裝支持“替代擴展解決方案”甚至提議以硬分叉的方式進行SEGWIT,這樣他們就可以繼續他們的操作……
絕對沒有人相信比特大陸,因為Greg Maxwell反向工程了他們的一個ASIC,並展示了他們所建造並試圖保密的東西。
這是分叉戰爭中的一個分水嶺,讓每個人突然明白了為什麼比特大陸一直以來都在提出無稽之談反對SEGWIT。想要大/小區塊的討論並不相關。SEGWIT解決了交易可篡改性問題,是一個顯而易見的升級,最終作為妥協,它與區塊大小增加結合在一起。
所以我們還是推進了SEGWIT,這時比特大陸轉向了公開的ASICBOOST,這實際上更強大,只是需要磨礪版本位而不是默克爾根,但如果礦工在這樣做,這是顯而易見的。
現在每個人都在使用它,所以實際上它的淨效果為零,除了你的節點會問你礦工在為一些你的節點一無所知的升級信號是什麼意思(版本位實際上應該用於升級協調)。
哦,好吧,相對而言,造成的危害不大。如果你願意忽略明顯的不誠實和努力破壞比特幣有史以來最重要的升級之一的事實。
額外有趣的小插曲:Antbleed——比特大陸故意設置的後門,可以遠程關閉世界上任何一台Antminer。他們說這是為了關閉被盜的ASIC,但一旦被發現就立即修補了。
無論如何,這家公司現在佔據了所有區塊發現的25-30%,如果你天真地觀察區塊鏈。
這還不足以嚇倒任何人,但不幸的是,許多較小的礦池實際上只是比特大陸的幌子,我們知道這有三個原因:
-
這些較小的礦池顯然在使用由Antpool構建或為其利益構建的區塊。
-
他們的剛開採的新幣由同一託管機構(Cobo)保管。
-
他們有一個貸款計劃,用於拯救因FPPS(全支付模式)而陷入困境的小型礦池。
趨勢不幸地朝著錯誤的方向發展,因為Braiins最近放棄了其舊的支付模式,轉而成為比特大陸的簡單代理,這是由於切換到FPPS模式所致。
[特別感謝 @mononautical 和 @0xB10C 幫助揭露礦池集中的現狀。]
總結 - 比特大陸不僅僅是Antpool,它可能佔據了超過50%的區塊模板,並製造了世界上超過90%的挖礦硬件。
那麼,這一切和什麼有關呢?
令人驚訝的是,這與空區塊(empty block)有關。
這和其他事情有什麼關係呢?
著名的OCEAN礦池在其短暫存在期間發現了3個空區塊,這導致許多人錯誤地指責該礦池本身存在某種問題。
這激起了無休止的辯論,討論為什麼礦池會製作空區塊模板,以及為什麼這麼多空區塊會被解決的真正原因。
簡而言之,礦池會先發送空區塊模板,然後立即跟進完整的區塊模板。這個過程如此迅速,以至於在這段過渡期內找到的空區塊只佔網絡上極小的一部分,並且我們的礦池並沒有發現這樣的空區塊。
在OCEAN礦池的三個案例中,礦工在已經有完整模板可供工作後才解決了空區塊——
- 這使得礦池處於一個兩難境地:要麼丟棄一個完好但空的區塊,要麼將其廣播到網絡上,讓礦工獲得完整區塊超過90%的獎勵。顯然,後者更合理,並且對網絡沒有任何危害,同時仍然增加了對任何攻擊者所需的工作量證明。
那麼,為什麼在礦池已經發送完整區塊的更新工作後幾秒鐘內會出現空區塊?
因為Antminer機器的性能差。
我們沒有意識到的是,它們是故意設計成這樣的。
你可以向Antminer發送更新的工作,並觀察它在極端情況下仍然繼續執行舊的工作超過60秒。
這是我們認為是ASIC設計的結果,因此只是比特大陸工程上的失誤。
但事實證明我們錯了,這是由於Antminer的固件。
我們之所以知道這一點,是因為他們剛剛釋放了一個修復程序。
因此,當人們繼續挖掘空區塊時,每個人都會錯誤地將其歸因於礦池,而像mempool(.)space等流行網站上的解釋者對此出現的錯誤解釋也是如此,似乎沒有人能理解甚至是發送空模板的動機,更不用說它們被工作了這麼長時間的原因了。
但在OCEAN開始解釋實際情況之後,釋放修復程序是毋庸置疑的。
他們有一個修復程序,並一直在自己的挖礦中使用該修復程序。
現在他們無法逃脫責任,因為越來越多的人意識到,Whatsminer和其他製造商的ASIC找不到像空區塊那樣的數量,因為它們切換工作的速度要快得多。
一台Antminer更有可能發現一個空區塊,因為它花費更多時間在舊的工作上。
我們一直在喊叫,問題出在ASIC上,而不是礦池。
事實上,比特大陸故意破壞了他們將出售給世界的Antminer的固件,同時將功能更強大的單元保留給自己的挖礦,這是典型的比特大陸做法。
當然,這可能是無能和巧合的修復時間,但我真的懷疑。
有關空區塊的討論已經達到了人們開始意識到Antminer出現了問題的程度,然後他們碰巧在人們終於開始聽到實際情況後立即發布了修復程序。
所以想象一下 -
你向淘金者出售鏟子,眾所周知,在淘金熱潮中賺錢的人是賣鏟子的人。
但在這種情況下,賣鏟子的人自己也在挖金子。
而且他故意向所有客戶出售了劣質的鏟子,以便給自己帶來優勢。
空區塊不斷發生,人們不斷歸咎於礦池。
OCEAN因此受到了攻擊。我們解釋了它們如此頻繁發生的真正原因,然後比特大陸立即發布了修復程序。
瘋狂。
這不僅僅涉及空區塊。
不僅僅是空模板需要很長時間才能從Antminer中退出,而且所有模板,而礦池則不斷更新工作,因為新的交易出現了。
你的記憶池中出現了一筆超級利潤豐厚的交易?
所有其他礦池都在向成千上萬的Antminer發送更新的工作,而這些Antminer會在一段時間內忽略它,而Antpool的礦工會更快地開始挖掘它。
很容易看出所有這一切的動機,特別是在未來交易費變得越來越重要的情況下。
再說一次,瘋狂。
如果你想觀看 @wk057 和我實時解釋這一切的過程,請觀看下面的視頻,這個視頻原本只是想討論為什麼會出現空區塊的問題。
我馬上會發布它,這樣Twitter就不會像以往一樣對外部鏈接進行封鎖。

作者: Bitcoin Mechanic
原文:Twitter
原文:Nostr
-
-
 @ 7175188c:6382a72c
2024-07-12 20:02:24
@ 7175188c:6382a72c
2024-07-12 20:02:24originally posted at https://stacker.news/items/606482
-
 @ ab8cb80e:5395d502
2024-07-12 14:21:14
@ ab8cb80e:5395d502
2024-07-12 14:21:14Hey, I have nothing to do this Friday evening, so why not chill with chess?
Spontaneously I launched an Arena Tournament for today: https://lichess.org/tournament/2iNa8jh4
@ek @kristapsk @BitcoinAbhi @grayruby @frostdragon @Taft @02d43d3798 @030e0dca83 @riberet19 @felipe @didiplaywell @SatsMate @itsTomekK @wize123 @Coinsreporter @stefano @anon @314piepi @160ed04091 do you want to play?
! TODAY ! ♟️ https://lichess.org/tournament/2iNa8jh4 ♟️ 90 min arena, with 5 minute games.
Join on @Alby's new Discord: https://discord.gg/3vbafUCZ?event=1261325278358016091 for voicechat I plan to stream it to zap.stream, because why not.
Who takes my challenge?
originally posted at https://stacker.news/items/605942
-
 @ 0dc2dcb1:4787801a
2024-07-12 13:52:51
@ 0dc2dcb1:4787801a
2024-07-12 13:52:51- Prepared a Dutch webinar with an short introduction to Nostr - https://welkom.keuzevrijbijmij.nl/evenement/wwebinar-vergroot-je-privacy-op-social-media-10-juli/

- Received a nice t-shirt with the Nostr-PHP logo from Bitpopart who designed the logo
- Did an introduction talk in Dutch on a webinar with 350+ people subscribed on July 10th. 100+ watched the webinar live.
- Here is the full replay: https://keuzevrijbijmij.webinargeek.com/watch/replay/3487925/f29f93e939ffce35ac4593e407d03a9e/
At around 38min the Nostr stuff begins
- Here is the full replay: https://keuzevrijbijmij.webinargeek.com/watch/replay/3487925/f29f93e939ffce35ac4593e407d03a9e/
- Adding pages and wrote some documentation on nostr-php.dev
- Added a custom field
field_nsecto the user entity on nostrver.se (Drupal website) using the contrib module field_encrypt. The value of this field is stored encrypted in the database using a self created private key. This key is stored as a blob the server, but multiple ways of storing this are possible. In the Drupal CMS I now can save a Nostr private key for each user which will be fetch from nostr_content_nip23. All changes made in this Drupal contrib module for this: https://git.drupalcode.org/project/nostr_content_nip23/-/commit/cbc172b976aceaff107fea0296a8a476e098467e -
With a
nsecstored for each user, it’s possible to select a user when you’re broadcasting an Nostr event from Drupal. The event will be signed with the nsec of the selected user. Quick demo here: https://njump.me/nevent1qvzqqqqqqypzqpnrnguxe8qszsshvgkvhn6qjzxy7xsvx03rlrtddr62haj4lrm3qy88wumn8ghj7mn0wvhxcmmv9uq3camnwvaz7tmwdaehgu3wwdjkyctnw35hstnnda3kjctv9uqzqj75dy5eps3lgwum7f9p2l8sywy7wuxjr08pyhzyzv9mklylaydgdyll3z
-
 @ 5d4b6c8d:8a1c1ee3
2024-07-12 12:44:07
@ 5d4b6c8d:8a1c1ee3
2024-07-12 12:44:07Yesterday's edition https://stacker.news/items/604559/r/Undisciplined
-
- -
July 12, 2023 📅
📝
TOP POSTExcerpt
The nostr protocol directly solves two problems in internet applications: identity portability and data portability. Products built on nostr can depend on those two problems being solved. For most other equally challenging problems, the nostr protoco […]
3636 sats \ 26 comments \ @k00b \ ~nostr
💬
TOP COMMENThttps://stacker.news/items/208075/r/Undisciplined?commentId=208122
Excerpt
One thing I've noticed: almost all nostr profiles have a display name, a picture, and a bio, and almost all of them seem to be stored exclusively on relay.damus.io. I've connected to the top 5 relays on nostr.watch, queried for metadata for random ac […]
1046 sats \ 1 reply \ @super_testnet
From Portable experiences by @k00b in ~nostr
🏆
TOP STACKER1st place @k00b
11.3k stacked \ 15.7k spent \ 2 posts \ 17 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
22.3k stacked \ 0 revenue \ 35.3k spent \ 108 posts \ 245 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 12, 2022 📅
📝
TOP POSTExcerpt
Max Webster at Hivemind led with Ross Stevens (the NYDIG one), Raymond Tonsing of Caffeinated Capital, Mishti Sharma with Caffeinated's Collective Fund, and Steve Lee filling up the rest.
18.6k sats \ 93 comments \ @k00b \ ~meta
💬
TOP COMMENThttps://stacker.news/items/44061/r/Undisciplined?commentId=44097
Excerpt
Another "interesting" thing to note: where are Coinbase's, Gemini's and Binance's LN implementations?
331 sats \ 0 replies \ @moon
From Exchanges on Lightning by @kr in ~bitcoin
🏆
TOP STACKER1st place @k00b
21k stacked \ 26.2k spent \ 4 posts \ 39 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
22.9k stacked \ 0 revenue \ 26.3k spent \ 119 posts \ 321 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 12, 2021 📅
📝
TOP POSTLink to https://lightningbutton.com/
6 sats \ 3 comments \ @qecez \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/238/r/Undisciplined?commentId=286
Excerpt
I’m seeing “Sorry This page does not exist yet.”
1 sat \ 1 reply \ @02552fb987
From Deploy a lightning node in one line by @k00b in ~bitcoin
🏆
TOP STACKERNo top stacker
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
25 stacked \ 0 revenue \ 72 spent \ 8 posts \ 9 comments
originally posted at https://stacker.news/items/605773
-
-
 @ 1739d937:3e3136ef
2024-07-12 10:11:42
@ 1739d937:3e3136ef
2024-07-12 10:11:42This is the third in a series of weekly updates detailing progress on bringing MLS protocol DMs and group messaging to Nostr.
Previous Updates
Progress this week
Short update post this week but I made solid progress updating several OpenMLS dependencies and building a new library that implements all the OpenMLS crypto requirements for Nostr.
HPKE-RS
I mentioned a PR last week on the
rust-hpkelibrary, that PR is still waiting on review. However, in the meantime, the OpenMLS library depends on a slightly different hpke library, thehpke-rslibrary.This library didn't support the secp256k1 curve either so I've opened a PR to add support for secp256k1. That PR uses the
RustCryptolibrary that is the default in the thehpke-rslibrary. However, because this library is built to allow for swapping out the underlying crypto library (using traits), I was also able to create a new library that uses thesecp256k1library instead of theRustCryptolibrary. This is the main crypto library that almost all Bitcoin and Nostr apps use so it's important we use that instead ofRustCrypto.OpenMLS Nostr Crypto
The library that I've created (openmls-nostr-crypto) does a few things via separate sub-libraries (crates). The entire library tries to do as little as possible; only implementing the one required ciphersuite for all MLS implementations and the
secp256k1schnorr signatures ciphersuite I've created for Nostr. It's also using the rightsecp256k1library to do it.openmls-nostr-crypto: implementes the crypto traits that the OpenMLS library expects to find for a given provider and removes all the ciphersuites that we don't care about supporting.
hpke-rs-nostr-crypto: This implements the crypto traits that the hpke-rs library expects to find. Again removing all the ciphersuites we don't care about supporting.
I've not yet written any tests for these libraries (which needs to be done) but I've gotten some very simple demos working with OpenMLS using this new set of libraries to handle the crypto.
I've been really impressed with the simplicity of the OpenMLS interface as well. While there is A LOT going on under the hood, the public interface that client developers have to use is clean and simple.
Onward and Upward
Next week I'll continue working on these libraries; adding tests and continuing to build out my small demo app. I've been in touch with the maintainers of the OpenMLS library and I'm hoping to get a review done with them on my PRs and on my new library.
One thing I'll call out here: The review of my library and getting them to review the direction of the project overall will be paid consulting so I'm making sure that I've got as much done as possible before scheduling that time and paying their rates. I'm a strong believer that the right conversation can save you months of wasted time, but I'm also a believer in making sure you're prepared if you're going to drop money on that conversation. 😅
-
 @ a012dc82:6458a70d
2024-07-12 09:48:42
@ a012dc82:6458a70d
2024-07-12 09:48:42Table Of Content
-
Content
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
Introduction
The term "unbanked" refers to individuals who lack access to basic financial services, such as bank accounts, credit, and insurance. According to the World Bank, there are around 1.7 billion unbanked adults globally, and the majority of them live in developing countries. This lack of access to financial services often results in significant barriers to economic growth and financial security for these individuals. However, the rise of cryptocurrencies, such as Bitcoin, has opened up the potential for a solution to this problem.
The Bitcoin Lightning Network
The Bitcoin Lightning Network is a second layer technology built on top of the Bitcoin blockchain that allows for fast and cheap transactions. It works by creating payment channels between two parties that can be used for multiple transactions, without each one needing to be recorded on the blockchain. This enables near-instantaneous transactions and makes it ideal for micropayments, which are often required by the unbanked.
The Lightning Network is often cited as a potential solution to the high fees and long transaction times associated with traditional financial services. With the Lightning Network, fees are significantly lower, and transactions are confirmed almost instantly. This is particularly important for the unbanked, who may not have the resources to cover high transaction fees or the time to wait for transactions to be processed.
The Power of the Bitcoin Lightning Network Wallet
The Lightning Network wallet enables the unbanked to participate in the Bitcoin economy without needing a traditional bank account. It provides greater access to financial services and privacy compared to traditional financial services. The Lightning Network also addresses the challenges of high fees and long transaction times associated with traditional financial services. With lower fees and almost instant transaction confirmations, the Lightning Network has the potential to promote financial inclusion and empowerment for the unbanked.
Addressing the Challenges Faced by the Unbanked
The unbanked, who are individuals without access to traditional banking services, often face challenges when it comes to accessing basic financial services. Some of the key challenges include high fees and long transaction times associated with traditional financial services, limited access to financial services due to location or socioeconomic status, and concerns around privacy and security.
The Lightning Network and Lightning Network wallet can address many of these challenges. The Lightning Network offers significantly lower transaction fees and almost instant transaction confirmations, which can be a huge benefit for the unbanked who may not have the resources to cover high fees or the time to wait for transactions to be processed.
The Future of the Bitcoin Lightning Network Wallet
The future of the Bitcoin Lightning Network wallet looks promising as the network continues to grow and evolve. As more users adopt the Lightning Network and Lightning Network wallets, the infrastructure supporting these tools is expected to become more robust, secure, and efficient.
One potential area of growth for the Lightning Network wallet is in the development of new applications that can be built on top of the network. For example, developers could create peer-to-peer lending platforms, microfinance applications, or other financial tools that leverage the Lightning Network's fast and low-cost transactions.
Conclusion
The Bitcoin Lightning Network wallet is a powerful tool that has the potential to address many of the challenges faced by the unbanked. With lower fees, faster transactions, and increased access to financial services, the Lightning Network wallet has the potential to promote financial inclusion and empowerment for individuals who have traditionally been excluded from the financial system.
FAQ
What is the Lightning Network wallet? The Lightning Network wallet is a digital wallet that is built on top of the Lightning Network. It enables individuals to store, send, and receive Bitcoin in a secure and private manner.
How does the Lightning Network wallet help the unbanked? The Lightning Network wallet enables the unbanked to participate in the Bitcoin economy without the need for a traditional bank account. It provides greater access to financial services, lower fees, and increased privacy and security compared to traditional financial services.
How can the Lightning Network wallet be used for peer-to-peer transactions? The Lightning Network wallet enables individuals to send and receive Bitcoin in a peer-to-peer manner, allowing for fast and low-cost transactions.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ bd32f268:22b33966
2024-07-12 09:23:22
@ bd32f268:22b33966
2024-07-12 09:23:22"By the sweat of your face you shall eat bread, till you return to the ground, for out of it you were taken; for you are dust, and to dust you shall return." _ Genesis 3:19_
Can man eat bread without the sweat of his face? We have done everything to make life easier, using tools and inventing machines, thus maximizing our capacity to produce. Despite these prodigious improvements, Kierkegaard, a Danish philosopher from the 19th century, says the following:
“So there I sat and smoked my cigarette until my mind began to think. You are advancing in age, getting old without having become anything or having any project. On the other hand, when we examine literature or life, we see names and figures of celebrities, valuable and acclaimed people for their deeds, the benefactors of the age who know how to benefit humanity by making life easier, some through railways, buses, and steamboats, others through the telegraph, others through brief and easy-to-understand publications about what is worth knowing, and finally the true benefactors of the age who by virtue of systematic thought make spiritual existence increasingly easier and yet more meaningful — and what am I doing? Only one thing is missing [in our age], although it is not yet felt, difficulty is missing. For the love of humanity and despair regarding my strange proclamation of having achieved nothing nor succeeded in making anything easier, despite the genuine interest in those who make things easier, I finally understood that it was my task: to create difficulties everywhere.” Concluding Unscientific Postscript to Philosophical Fragments, published in 1846. Søren Kierkegaard (pseudonym Johannes Climacus)
This excerpt from a text by Kierkegaard comes as a punch in the stomach, alerting us to an inescapable reality: the need for sacrifice. No matter how seemingly easy life becomes, we still need sacrifice as a way to fulfill our purpose as human beings. Sacrifice, illustrated by difficulty in Kierkegaard's text, is what allows us to negotiate with existence itself and offer something in the present in the hope of obtaining something in the future. Sacrifice also allows us to know more deeply our limits and weaknesses and create an opportunity to transcend these limits. Without sacrifice, there is no love, for sacrifice implies that we have the capacity to see beyond ourselves, beyond our most immediate selfish interest. Through sacrifice, we are therefore invited to renounce something with the purpose of offering it.

Angelus (painting) – by Jean-François Millet shows two peasants praying, giving thanks for the harvest obtained through the sweat and effort of many days.
Since work is also a form of sacrifice, it is good to remember that this is an exercise we do with a useful end in view. Nature does not automatically satisfy all human needs, hence the need for work to meet them. Besides all this, work is also an antidote to some evils and a promoter of virtues. It allows us, for example, to combat idleness and laziness, while on the other hand, it allows us to enhance solidarity since we have obtained resources that we can now share. This means that work creates a propitiatory atmosphere for the person because it develops their ethics and morals on various levels. It seems more important at this time to reflect on this because we often fall into the error of seeking the enjoyment of immediate pleasures, the promises of an easy life, forgetting these realities. Not that having pleasure in itself evil, but this must always be subordinated to the values that organize our lives because obtaining pleasure is not the ultimate goal of life. It is evident that not all jobs are the same, and some are more conducive to virtues than others, something to which we must pay careful attention, hence it makes sense to seek to make work subordinate to our values. For there is no good work that does not express these values. Let us then use work as a springboard for our growth, and begin not to wish for an easy life, but rather to increasingly desire an honorable life in which we are not deceived by superficial gratuities.
-
 @ 38d0888d:bd8e1246
2024-07-12 07:10:35
@ 38d0888d:bd8e1246
2024-07-12 07:10:35A thriving society rests on the principles of modesty and humility, avoiding idleness and self-indulgence. Individuals are needed to forsake the constant pursuit of attention and instead aspire to selflessness, dedicating themselves to serving humanity. Humility fosters spiritual harmony and protects against materialism and selfish desires.
Beyond personal conduct, humanity must champion altruism and solidarity within the global community. Belief in collective endeavors will pave the way for global harmony. Embracing values like kindness, compassion, and genuine concern for others promotes positivity and reflects the influence of a higher power. The aim is to cultivate a unified multicultural community where each person contributes to manifesting this higher presence.
The collective goal is to direct humanity to nurture a community that experiences spiritual growth while upholding humility as a guiding principle, resisting materialism's allure. By creating such an environment, the hope is to resonate with a sacred harmony that extends beyond immediate boundaries. Through intentional actions and meaningful relationships, a collective space embodying these values can be established, ensuring the higher power's presence guides individual lives and interactions with the world.
-
 @ 6c8c7979:15595f3e
2024-07-12 01:02:17
@ 6c8c7979:15595f3e
2024-07-12 01:02:17Despite the numerous historical turning points that have influenced art history, the Baroque era stands out as a pivotal marker in the history of art and culture.
Spanning from the 17th to the early 18th century, the Baroque period reshaped architecture, literature, music, sculpture, and visual arts.
Originating in Italy, the Baroque movement spread across Europe, flourishing notably in France, the Netherlands, and Spain, and later extending its influence throughout the continent.
It was an artistic and philosophical movement aimed at embodying motion, life, and profound meaning with maximal drama and theatricality.

Nymphenburg Palace - Munich, GermanyIn the field of architecture, Baroque style saw the construction of churches, palaces, castles, theaters, and public spaces in a bold and distinctive manner.
These buildings were characterized by abundant use of marble, intricate curves and recesses, and ornate decorative details. Colors were vibrant and rich, lending a dramatic and spiritual character to Baroque structures.
For example, the Luxembourg Palace, now known as the French Senate, built in Paris in 1615, exemplifies Baroque architecture with its emphasis on luxury, detailed ornamentation, monumental size, and the use of domes.
This architectural philosophy was influenced by the opulence and intricate designs that were originally introduced to Europe from the Islamic world during the Middle Ages.
Moreover, the building is distinguished by its grand staircases, high ceilings, and walls adorned with either sculptures or paintings—a hallmark Baroque tradition. Additionally, Baroque architecture emphasized the abundant use of mirrors inside buildings to visually expand the space, albeit illusionistically, creating a sense of spaciousness.

The Luxembourg Palace Library in Paris houses approximately half a million books.$$Baroque literature$$Baroque literature saw many writers and poets of the era adopt an epic rhetorical style. Baroque literary works are characterized by complexity, mystery, and elaboration in description, influenced by the cultural phase deeply immersed in highlighting and praising intricate details.
Those works arose from a self-awareness of the prevailing cultural discourse at the time. Metaphors and epic similes were abundant. There was also a tendency towards exaggeration and paradox in the sequence of events throughout the plot.
John Milton's epic poem "Paradise Lost" (1608-1674), for many language scholars, is considered one of the greatest poems in the history of the English language. The poem consists of 10 volumes in its first edition and 12 volumes in the second, recounting the story of Adam and Eve's expulsion from paradise and their long-lasting battle with Satan.
In "Paradise Lost," Milton states, "The end of all learning is to know God, and out of that knowledge to love Him and to imitate Him."
Baroque Music
In the field of music, numerous musical instruments and new techniques were developed to emphasize the depth and power of sound. As a result, Baroque music emerged filled with complex compositions, lively rhythms, and rich harmonies.
Some of the most famous composers of this era include Johann Sebastian Bach, George Frideric Handel, and Antonio Vivaldi.
https://youtu.be/DwHpDOWhkGk?si=Nw-h0RKZFllyNwok
Let's enjoy, for example, a musical journey with Bach's cello suite, exploring the depth and beauty of the instrument across 6 movements, each showcasing Bach's mastery of the following point and his innovative musical ideas that captivate the listener with their charm and technical complexity.
$$Baroque Sculpture$$Like other creative fields, visual arts such as sculpture and painting gained fame for their precision and richness of detail. Many works overall dealt with religious meanings, elements of pride, and beauty.
Baroque artists were renowned for their skillful use of natural light to highlight dark shadows, thereby adding dimensions to their paintings. Many prominent artists such as Rembrandt, Peter Paul Rubens, and Peter Paul Rubens produced stunning works during that period.
Therefore, the painting "The Night Watch," created by the Dutch artist Rembrandt in 1642, stands as a prominent example of the depth of Baroque style in art history.

"The Night Watch" - Amsterdam MuseumThe painting is a group portrait of a civic militia, where the painter skillfully used light and shadow to showcase their pride and intimate camaraderie.
It's worth noting that the play of light and shadow not only highlights the central figures but also creates a sense of mystery and anticipation, which in turn adds drama and movement to the scene, attracting the eye to the tableau.
The vibrant colors and intricate details bring a lively texture to the characters, making the painting a visual feast for viewers. The composition is balanced due to Rembrandt's expertise; we see him strategically positioning the characters at times and infusing Baroque dramatic touches at others, all serving the same purpose of presenting the work as a cohesive narrative.
One intriguing aspect of "The Night Watch" is Rembrandt's departure from depicting a single hero in the work; instead, he portrays each individual in the painting with equal importance. This deviation from the norm reflects his progressive vision and artistic sensitivity amidst the Baroque era.
The Baroque period was known for its personal dedication to expression, whether through painting, music, or writing, making it a distinctive and valuable era in human history, characterized by richness of production as much as richness of detail.
The development of new styles and techniques during this period also contributed to the emergence of other artistic schools, such as Rococo.
-
 @ dec2e28f:01746c77
2024-05-29 10:08:55
@ dec2e28f:01746c77
2024-05-29 10:08:55比特幣那種叛逆的、自主創造的、類似七十年代中期的賽博朋克(Cypherpunk)時代並沒有結束。
事實恰恰相反。
比特幣是在七十年代中期的家用電腦革命發生並「結束」之後編寫的,這場革命將軟件開發的力量以幾乎為零的成本放在每個人的手中。在此之前,開發和運行軟件需要在大學裡預訂大型UNIX機器的時間,而且只有當你作為學生註冊在擁有電腦的機構時才有可能。科技文盲不了解這些重要的背景和歷史。
比特幣是在遍布各地的商業電腦設備上編寫的,這些設備從沃爾瑪到Radio Shack都有售。它是用免費的編程語言編寫的,運行在隨任何電腦/計算機器免費提供的操作系統上。之前情況並非如此:AT&T UNIX商業軟件許可證的費用是30,000美元,只有公司和教育機構才能負擔得起。即使是單用戶許可證150美元,對於死忠用戶來說雖然不是阻礙,但在GNU編寫比特幣時也被消除了。計算機的普遍可用性使軟件開發革命成為可能。這意味著任何人在任何地方都可以在不需要許可、入學或任何形式的監督的情況下編寫軟件,然後他們可以以幾乎為零的成本將其分發給任何人。
在早期,軟件是通過打卡的方式在軟盤上分發的。然後通過BBS系統通過電話調製解調器進行分發。現在,它通過互聯網免費分發。電腦和編寫軟件工具成本的消除,使軟件開發、遠程連接以及從遊戲開發到書寫和研究的各種智力追求得以擴展和普及。
你能看到接下來會發生什麼嗎?
比特幣作為一種可編程的合成貨幣,將實現普遍使用,意味著任何地方的任何人都將使用比特幣。國家、對沖基金和主權財富基金在這方面是無關緊要的,並且將繼續處於公眾創新者的下游,就像它們在互聯網、電子郵件和比特幣上的情況一樣。國家、對沖基金和主權財富基金並沒有開發比特幣(或電子郵件或網絡),也無法開發它們。他們無法想象其中任何一個,也沒有技能去實現它。(看看保羅·克魯格曼關於互聯網不比傳真機重要的預測,或者他最近關於比特幣的預測。真是個笑話!)他們那無力的階層成員,充其量也只會是網絡上的同伴,像其他人一樣。他們不再是特殊的、特權的或必需的。
這就是比特幣的全部意義,假如你還不知道的話。
Jeremy Allaire多年前曾對比特幣生態系統說過一句著名的話:“現在是成年人登場的時候了。”他完全錯了,最終推銷山寨幣和不道德的穩定幣,因為那不可動搖和不可變的“比特幣”抵制那些帶著聰明計劃來改進它的部分知情者。比特幣的這一特性(這是一個特性,而不是缺陷)目前被金融科技兄弟、華爾街專家、頑強的旁觀者和其他剛剛接觸到比特幣誕生理念的人所忽視;現實不再由自封的權威來運作。
少數美國人最終投降於比特幣這是一件好事,但除了投降,他們那種狹隘的「世界警察」、「要么按照我的方式,要么就不行」、「我們的制度和治理模式是唯一可能的前進道路」的心態最好還是拋棄吧;地球上的沒有人想聽這些,大家都厭倦了他們,比特幣聽不見,所有真正的比特幣持有者都忽略了這些。
許多人都有潛意識地想要控制一切的強烈衝動;這就是為什麼國家主義者將叛逆描繪成負面的原因。變革不是叛逆。變革是所有存在的基本過程。變革正在到來,改變金錢的本質以及它是如何傳遞的,在這一變革中,舊的參與者被排除在管理、監督、設計或任何形式的輸入之外。他們被排除在外。他們被清除出局。
昨天的那群人無法想象任何超出他們過去熟悉結構的力量;「大人物」總會是偉大的力量。他們似乎沒有意識到(為什麼要意識到呢?)比特幣正處於某種已經徹底侵蝕許多被奉為現代生活基石的機構權力之上,並取得了巨大的效果和普遍的好處。
- 新聞業:廢棄
- 音樂分發:邊緣化,被摧毀
- 出版業:粉碎
- 詞典:銷毀
- 電話公司:被拋棄,被閹割
- 審查制度:被燒灼和規避
- 政府郵政服務:被掏空,被掛起,被屠宰
只有最天真的人會認為國家、對沖基金和主權財富基金作為網絡上的同伴加入,就會廢除比特幣那種叛逆、自主創造的、類似七十年代中期的賽博朋克(cypherpunk)時代。恰恰相反;比特幣的傳播使賽博朋克和叛逆文化成為常態。賽博朋克是創新者,他們繼續證明這一點。看看由一位賽博朋克運營的軟件公司Blockstream如何向一個國家提供在比特幣出現之前無法想象的金融服務。所有這些對任何能夠思考的人來說都是顯而易見的。
Cypherpunk及其直系後代正在建立新的公司、軟件和服務,這些東西無法被外人、懦夫、國家主義者、投機取巧者、小偷、社會主義者和其他被比特幣的明亮火焰吸引的人類飛蛾所撤銷或“監督”。
以Nostr為例。當所有下游的Twitter用戶都在苦苦抱怨時,一個人決定提供一個可能的解決方案。沒有人預見到這一點,甚至沒有人認為這是可能的。現在,不管你喜不喜歡,一個生態系統有可能在其上出現,因為它是真實的,使用它的人無法被告知該做什麼或說什麼。
這與比特幣的情況完全類似。華爾街專家們苦苦抱怨“腐敗系統”,卻無法想象比特幣的存在,然後比特幣……出現了,現在它無法被停止,不管你喜不喜歡,它的本質也不會改變,因為比特幣那種叛逆的、自主創造的、類似七十年代中期的賽博朋克時代不僅沒有結束,而且永遠不會結束。這是一個可以安全預測的未來;看看互聯網功能是如何通過IETF過程開發的。第一線的人正在做基本設計的艱苦工作,除了支付設計師的工資外,公司與此無關;“大玩家”無法決定事情的實際運作方式。
Apple從推行新協議“AppleTalk”中吸取了沉痛的教訓。AppleTalk於20世紀80年代中期推出,旨在促進Apple環境中的網絡連接,使Macintosh計算機能夠無縫連接和共享資源。儘管它在Apple的生態系統內取得了初步成功,但由於以太網和TCP/IP等其他網絡協議的主導地位,AppleTalk在更廣泛的接受度上掙扎。隨著行業標準轉向TCP/IP,Apple逐漸淘汰了AppleTalk,並在2009年正式停止了對其的支持。“2009年”……這是一個特別的年份,不是嗎?這就像華爾街試圖“接管”比特幣並改變它一樣。這是不可能發生的,比特幣中也不會有“成年人現在來了”的時刻。歷史強烈表明了這一點,但你必須了解你的歷史才能理解這一點。
這些只是眾多例子中的幾個,展示了變革的本質以及誰因此被排除在外。所有擁有創造軟件和服務能力的人都已經厭倦了被告知他們是什麼、他們能做什麼、他們能說什麼、他們必須如何實現軟件工具,以及被置於扭曲的“社會”底層,在這個社會中,國家、對沖基金和主權財富基金控制著金錢的定義及其流動方式。
先這樣,夥計們。
在各個層面使用比特幣的大眾共同的力量遠超任何國家、對沖基金或主權財富基金。大眾將比特幣用作貨幣是絕對不可避免的結果,而且這將在賽博朋克的條件下發生,而不是在國家、對沖基金和主權財富基金的條件下。
作者: Beautyon
原文: note
-
 @ dec2e28f:01746c77
2024-05-28 15:46:38
@ dec2e28f:01746c77
2024-05-28 15:46:38-
幾週前,針對MicroStrategy聯合創辦人兼執行主席Michael Saylor的指控稱這位“比特幣巨佬”曾阻止ETF發行商將利潤捐給Bitcoin Core開發者。
-
在最近的一次採訪中,Saylor談到了資金爭議,他表示:「我認為我們應該以精確的方式資助開發者,了解他們的優先事項和原則」,並且「我在這個話題上受到的批評是指出某些華爾街公司,可能無限制、無監管地提供資金給可能破壞網絡穩定的開發工作並不合適。」
-
一些人認為Saylor試圖影響Bitcoin Core資金是一個問題,但許多人批評Saylor關於比特幣開發資金的言論被斷章取義。在採訪中,Saylor提到在比特幣上實施類似以太坊的功能,這是他認為不理想的。
「別再談論監管套利了。抗審查、隱私和逃稅都是糟糕的想法。我們討厭這些。」
在2020年,Saylor接受了BTC Times的採訪,該採訪似乎已被下線,內容描述了什麼可能推動更多機構採用比特幣。主持這次採訪的Elaine Ou形容這次對話是「極大的失望」。
Saylor解釋說,比特幣社群應該「別再談論監管套利。抗審查、隱私和逃稅都是糟糕的想法。我們討厭這些。」[...]「擁有數十億美元的人不想投資於支持無政府主義者的加密網絡。」
Saylor表達了比特幣不應被強調為一種貨幣的觀點。「比特幣不僅與國庫和聯邦儲備競爭,它還暗示著一個支付網絡,以與Square、Apple Pay、支付寶和其他既快速又便宜的服務競爭。或許這就是為什麼甚至在沙丘路上的風險投資家仍在努力理解比特幣作為一項技術。他們要麼視其為對西方文明崩潰的賭注,要麼視其為嚴重受損的PayPal」,Ou寫道。
根據Saylor的說法,比特幣應被視為一項投資。「每家公司、每個組織都有同樣的問題:我該如何保存我的錢?當法定貨幣在貶值時,這意味著每一項投資都可能在被通脹侵蝕。」
在一次與Peter McCormack的訪談中,Saylor重申了他對比特幣隱私的看法:「我認為有50萬億美元的需求來以一種不會全部損失的方式存儲你的錢。而我認為將錢存入隱私錢包的需求要小得多[...]如果比特幣把所有精力都投入到隱私上,並成為一個完全隱私的網絡,這可能對其自身利益是適得其反的,因為你真的不希望美國政府說比特幣是完全私密的,因為那樣它就成為了洗錢的完美工具,成為敵人,我們就會關閉它。」
從投資角度來看,對於Saylor關於比特幣隱私的觀點,並沒有太多爭議。然而,與Saylor對比特幣目標的明顯願景相反,比特幣白皮書並沒有描述比特幣為「一種點對點電子投資資產」,而是「一種點對點電子現金系統」;其中隱私是一個內在特徵。
2021年的SEC文件顯示,MicroStrategy一直在探索將區塊鏈分析整合到MicroStrategy軟件套件中,並表示:「我們相信,我們的比特幣收購策略與我們的企業分析軟件和服務業務是互補的,因為我們相信,我們的比特幣和支持比特幣網絡的相關活動提高了我們品牌的知名度,並可以提供機會為我們的分析產品獲得新客戶。我們還在探索將比特幣相關技術,如區塊鏈分析,應用到我們的軟件產品中的機會。」
到了2022年,鑒於討論使用真實世界身份驗證Twitter用戶以打擊垃圾信息,Saylor似乎對隱私有了更為積極的態度,他表示:「Twitter需要3.96億個"橙色勾號"來超越36萬個藍色勾號的限制。每個人都應該有權在幾秒鐘內以少量聰(比特幣的最小單位)被驗證,而無需放棄他們的隱私。」
當時,Saylor積極倡導在Twitter上可能整合閃電網絡。閃電網絡相比鏈上交易為用戶提供了更好的隱私保護,這確實比使用ID註冊建議有了很大改進,但作為一個洋蔥路由網絡,對於抵禦國家級對手來說仍然大體上是不足的,正如各種關於Tor網絡安全屬性的論文所顯示的那樣。
MicroStrategy公司專門為美國聯邦政府提供的解決方案
MicroStrategy是一個商業智能平台,為客戶提供「AI動力工作流程、無限數據來源、雲原生技術和無與倫比的性能,以加速從數據到行動的時間」,旨在「在任何地方提供智能」。
MicroStrategy為政府機構提供量身定制的解決方案,自稱為「行業領先的企業分析平台」。根據其官方網站,MicroStrategy聯邦政府解決方案與美國國防部、國土安全部、國務院、海軍部、陸軍部、司法部和防禦威脅減輕署等部門合作。
在一篇描述Cloudera利用MicroStrategy平台的客戶成功案例的博客文章中,MicroStrategy將一個政府客戶描述為「美國聯邦政府的一個機構(以下簡稱'該機構'),負責監督世界各地的一個複雜的軍事系統網絡。數十年來,該機構一直是確保全球穩定的關鍵組成部分-在不安全的情況下保持防禦姿態並展示力量。」

根據這篇博客文章,「該機構已經積累並依賴各種不同的數據系統來執行其使命。這些孤立的、部門間的數據孤島限制了領導層在整個組織中保持對運營和核心KPI的360度視圖的能力。由於沒有集中的報告系統,開發管理級別的報告工具變得困難且昂貴,並且無法通過混合外部數據來豐富情報。此外,由於該機構數據的敏感性質,嚴格的安全和治理協議帶來了獨特的挑戰。」
為解決這些問題,「該機構選擇了一支專門的供應商團隊提供尖端技術和專業知識:MicroStrategy、Cloudera、Talend和一家MicroStrategy合作夥伴[...]來設計、架構和部署定制的企業數據管理和分析解決方案。」
MicroStrategy在此提供了「在直觀的視覺界面中進行複雜分析的能力」,使「該機構的各個團隊能夠在幾個點擊之內分析各種大數據集-結構化、非結構化或其他形式的數據。憑藉強大的高級分析功能,用戶可以運行回歸分析,使用預測功能,並使用豐富的數據發現工具來確定性能指標、運營成本和生產力基準。」
據稱的情報聯繫給Saylor的比特幣投資蒙上陰影
自從Michael Saylor出現在比特幣的舞台上以來,據稱與國家情報機構的聯繫已成為他在懷疑論者中比特幣投資的陰影。
《全球情報文件》顯示,情報承包商Stratfor,其“表面上是一家情報出版商,但向大型企業提供機密情報服務,例如博帕爾的陶氏化學公司、洛克希德·馬丁公司、北羅普·格魯曼公司、雷神公司以及美國國土安全部、美國海軍陸戰隊和美國國防情報局等政府機構”,似乎曾維護過MicroStrategy的帳戶。
同樣,臭名昭著的黑帽子組織Hacking Team的泄露電子郵件顯示,這個以攻擊人權活動人士和記者聞名的黑客組織對利用MicroStrategy情報平台的產品表現出興趣。在泄露後,Hacking Team成員轉而對Coinbase的區塊鏈進行間諜活動。Hacking Team的創始人大衛·文森澤蒂(David Vincenzetti)因企圖謀殺被逮捕。
在一份涵蓋VAIO數據挖掘項目的數據可視化評估演示中,MicroStrategy的情報平台被描述為「自1989年以來商業智能領域的領導者之一,是少數提供端到端商業智能解決方案的供應商之一」。索尼似乎在2012年購買了MicroStrategy的授權。隨著索尼文件(Sony Files)的發布,這家娛樂製作公司因「與美國軍工業複合體和情報部門之間的聯繫和信息流動」而受到嚴格審查。
過去,MicroStrategy似乎曾贊助白宮會議,制定信息基礎設施安全計劃,強調了私營部門的貢獻需求。Rick Blankenship,MicroStrategy的聯邦情報賬戶經理,似乎代表MicroStrategy參加了情報和國家安全聯盟,該組織是一個領先的非營利性、無黨派、私營部門專業組織,為情報和國家安全社區提供了結構和互動論壇,用於思想領導、觀點交流和網絡建設。
值得注意的是,Lisbeth Poulos,前CIA非營利性風險投資部門InQTel的首席助理和執行副總裁,似乎曾在MicroStrategy開始她的職業生涯。
根據開源透明度工具Intelligence Community Watch顯示,MicroStrategy與美國情報部門之間存在幾個聯繫,這裡我不會進行具體命名(你可以在這裡搜索ICWatch的完整數據庫)。
ICWatch利用了斯諾登泄密揭示的美國情報項目的秘密代號,通過查詢LinkedIn檔案來識別美國情報人員。該項目利用了「國家安全局的文件,或者特殊任務部隊的名稱,或者比如說,聯合優先效應清單,阿富汗的暗殺計劃,這些都被抓取出來,然後聯繫在一起,這樣你就可以輕鬆地看到,例如,誰聲稱自己曾在某個階段在國家安全局工作過,或者參與過國家安全局使用的各種代碼命名的項目。」在該軟件識別出的情報人員威脅對方後,ICWatch由維基解密托管,以保護工具收集的信息。
鑑於Saylor公開試圖影響比特幣核心開發,當我們談論將比特幣用作「自由貨幣」時,我們可能會想知道我們是否一直在為消防員中的縱火犯歡呼。在比特幣基礎層上進一步提高隱私可能對比特幣作為投資資產是有害的,但對於從事情報評估業務的公司的業務目標來說,這確實是有害的。
原文:L0la L33tz BTC, Saylor's Version: The Arsonist in the Fire Department
-
-
 @ 6c8c7979:15595f3e
2024-07-12 00:13:43
@ 6c8c7979:15595f3e
2024-07-12 00:13:43The painting "The Anatomy Lesson of Dr. Nicolaes Tulp" by Rembrandt, created in 1631, is one of the prominent works of Baroque art and a notable example of anatomical studies during that period. The painting depicts a real anatomy lesson conducted in a lecture hall in Amsterdam.
The artwork portrays several individuals, including members of the Surgeons' Guild and anatomy students, interacting with the dissected corpse laid out before them to study the human body's details. It is distinguished by its meticulous depiction of muscular forms and skeletal structure, rendered realistically, with a focus on the contrast between life and death, and light and shadow within the composition.
Rembrandt employed his artistic skills to create a powerful dramatic effect, infusing the painting with life and movement despite the static nature of the cadaver. The dramatic lighting he used is highly realistic, highlighting intricate details in the darker areas, thus adding depth and expressive power to the artwork.
In addition to its stunning technical execution, the painting reflects human curiosity and scientific inquiry into human anatomy, embodying aspects of philosophy and science that were of interest to Baroque society at that time.
-
 @ fa984bd7:58018f52
2024-05-28 12:35:04
@ fa984bd7:58018f52
2024-05-28 12:35:04I'm happy to announce that Shipyard is now roaming the nostr relays as a DVM.
Ok, what the hell does that even mean?
Ok, so DVMs, or Data Vending Machines, are just programs that take requests over nostr to deliver... well, data.
And what is Shipyard?
Shipyard, as it's slogan "A Quiet Place for Loud Ideas" implies, is a write-only Nostr client. One of the instrumental features that Shipyard.pub implemented was the ability to SCHEDULE posts and reposts. No more fighting to publish your notes to defeat the evil Timezone Cabal; you can write your note when you see fit, and then schedule so it's published whenever it makes most sense to you.
Groundbreaking stuff, I know.
Ok, so now, Shipyard's scheduling superpowers can be accessed as a DVM:
meaning that any Nostr client can now easily add scheduling capabilities without much fuss!
For example, this long-form post was actually written a day before it was published, and the publishing was handled by the Shipyard DVM.
How does it work?
Client developers can use NIP-89 to find kind:5905 DVMs, right now only Shipyard, and when a person wants to schedule a post they simply send the post via an encrypted DVM request to Shipyard. That's it, at the time the event's created_at timestamp reaches the event will be published to the specified relays!
What can it look like? Up to clients developers to decide; here's my take:
https://cdn.satellite.earth/e05f366b61b9b9b68f716eb297563e5dbbae6b7f7f73fdd5177a389bd2de36fb.mp4
-
 @ 036533ca:cbaabf58
2024-07-11 21:54:40
@ 036533ca:cbaabf58
2024-07-11 21:54:40In a recent job interview, we discussed some of my work on Nostr and specifically my Noscrypt library. I was asked basic questions, such as what it is and what purpose it serves. Most of my response centered on the idea that while the secp256k1 library is excellent, it is easy to misuse.
So what footguns?
It had been a while since I heard that term, and for whatever reason, I struggled to give a satisfactory response. The interviewer was pleased, but I was not, so I want to take some time to reflect on better ways of explaining the challenges I've encountered while working with libsecp256k1 when building on Nostr.
First, libsecp256k1 is functionally perfect as it is, and I don't see any need for changes. The real challenge is implementing all of the Nostr-specific cryptographic tasks on top of secp256k1. This includes complex but necessary operations like note encryption and signing. The most difficult part is converting between all of the different required encodings: Hex, Base64, Bech32, JSON, UTF-8, and so on.
Really I'm just talking about implementation details, what I got wrong, and what was missing between nostr operations and libsecp256k1.
Some backstory
When I first fell into Nostr, I had some cryptography experience from working on my .NET libraries called VNLib. I quickly realized that Nostr identities rely on your ability to keep a 32-byte number safe, but also accessible. With my HTTP framework in hand, everything seemed like a nail. I wanted my key to be securely stored and signed remotely across a network, where the data is sent between the client/server, and my key never has the opportunity to leave the server. So that's what I started building and continue to use, even though it's not complete. That project is called NVault, and I quietly work on it in the background as things break.
Originally, I built a C# wrapper for libsecp256k1, manually worked through all the C/C# barriers, and implemented the note encryption and signing in higher-level C#. However, when NIP-44 came out, everything changed. I realized how much more complex the wrapper would become if I kept trying to stack onto it. Another issue was performance. I still believe my skills in C allow me to write more efficient and performant code than I can in C# for the same tasks, especially when it comes to cryptography and functional programming.
NIP-44 significantly increased the complexity of Nostr cryptography, and after seven months of regular work on NIP-44, I know I'm not the only one still grappling with this complexity, along with NIP-59 and other related DM and crypto specs.
Okay, so a library needed to address the complexities and inefficiencies of Nostr cryptography while also being portable. To me, no other language meets those goals better than C. We can target virtually every operating system, as most high-level languages can bind to a C ABI at load time or runtime. Additionally, we can target hardware/RTOS systems. C can do it all and usually do it better if you are "smart" and careful, in my opinion. Defensive C programming, if you will.
Why noscrypt
If you are building a client or relay in C, or a derivative that relies on libsecp256k1, or a similar library, because it's the most tested and stable library for the secp256k1 elliptic curve, you will need to implement every Nostr-related spec by hand as helper code in your project. Libraries handle this. However, each time note encryption changes (which it has frequently), you will need to revise your cryptographic helpers to accommodate those changes and hope you don't make a fatal mistake that compromises your users' keys or notes. You aren't a cryptographer; you're a client/relay developer. I'm not saying you can't do it; I'm saying you don't want to.
Working with libsecp256k1
First, there is no concept of a key pair associated with Nostr in libsecp256k1. Nostr is "special" in that we treat the secret key and public key as equally distinct parts of your identity on the network and often store them separately.
Public Keys are X-Only
Public keys in Nostr only use the x-coordinate of the xy point on the curve. Libsecp256k1 handles this fine, but not in a foolproof way, in my opinion.
Here is some code taken from Noscrypt to illustrate the steps needed to implement public key conversion:
```c int _convertToPubKey( const NCContext ctx, const NCPublicKey compressedPubKey, secp256k1_pubkey* pubKey ) { int result; uint8_t compressed[sizeof(NCPublicKey) + 1];
/* Set the first byte to 0x02 to indicate a compressed public key */ compressed[0] = BIP340_PUBKEY_HEADER_BYTE; /* Copy the compressed public key data into a new buffer (offset by 1 to store the header byte) */ MEMMOV((compressed + 1), compressedPubKey, sizeof(NCPublicKey)); result = secp256k1_ec_pubkey_parse( ctx->secpCtx, pubKey, compressed, sizeof(compressed) ); return result;} ```
The NCPublicKey type is a 32-byte structure (a byte array) so it's far easier to work with and store with higher-level Nostr applications. We have encountered these issues time and again in Aedile due to the way we use public keys in Nostr.
I regularly failed to find a structured way to store Nostr-specific public keys that libsecp256k1 could work with. I ended up making all the above function calls (and about two more) into the library to do this conversion. So, it's just implementation details.
Keypairs
Again, libsecp256k1 requires some complexity in keypair structures which Nostr has almost no 1:1 mapping to, and really doesn't need. A secret key is all that is required to sign (encrypt) a message using ECDSA, so there is no reason to store keypairs in this case.
Again here is an example from noscrypt
```c NCResult NCSignDigest( const NCContext ctx, const NCSecretKey sk, const uint8_t random32[32], const uint8_t digest32[32], uint8_t sig64[64] ) { int result; secp256k1_keypair keyPair; secp256k1_xonly_pubkey xonly;
/* Fill keypair structure from the callers secret key */ if (secp256k1_keypair_create(ctx->secpCtx, &keyPair, sk->key) != 1) { return E_INVALID_ARG; } /* Sign the digest */ result = secp256k1_schnorrsig_sign32(ctx->secpCtx, sig64, digest32, &keyPair, random32); /* x-only public key from keypair so the signature can be verified */ result = secp256k1_keypair_xonly_pub(ctx->secpCtx, &xonly, NULL, &keyPair); /* Verify the signature is valid */ result = secp256k1_schnorrsig_verify(ctx->secpCtx, sig64, digest32, 32, &xonly); return result == 1 ? NC_SUCCESS : E_INVALID_ARG;} ```
Some validation code was removed for brevity, assertions are used for describing expected results
You will notice that a key pair structure is required (and must be assigned) from our secret key. This is where I think the strict typing of the
NCPrivateKeystructure ensures safer signing and a more straightforward API. Again, Nostr implementation details, but this function helps mitigate complexities in an obvious and difficult-to-misuse way.In the case of polyglot linking, I think it also makes it reasonably simple to sign a message digest with a single function call on some byte arrays. Direct, which I think is important.
EC Diffie Hellman
ECDH or Elliptic Curve Diffie Hellman gives us the ability to take a set of points on an elliptic curve and create a shared key that only the key holders can generate. More specifically, each party only needs to know each other's public information in order to generate said shared point. We exploit that feature in multiple ways by using symmetric encryption in both NIP-04 and NIP-44 encryption specifications.
Ignoring all of the encryption specifications, we need a function to safely generate our shared point from our Nostr-specific secret and public keys. So some strict typing and our
_convertToPubKey()function from above re-appear. You will also notice a callback function called_edhHashFuncInternal(). This function does the work of "computing the hash" which in Nostr we just need to return the shared x-coordinate as per NIP-04```c NCResult _computeSharedSecret( const NCContext ctx, const NCSecretKey sk, const NCPublicKey otherPk, struct shared_secret sharedPoint ) { int result; secp256k1_pubkey pubKey;
/* Recover pubkey from compressed public key data */ if (_convertToPubKey(ctx, otherPk, &pubKey) != 1) { return E_INVALID_ARG; } /* * Compute the shared point using the ecdh function. * * The above callback is invoked to "compute" the hash (it * copies the x coord) and it does not use the data pointer * so it is set to NULL. */ result = secp256k1_ecdh( ctx->secpCtx, (uint8_t*)sharedPoint, &pubKey, sk->key, &_edhHashFuncInternal, NULL ); ZERO_FILL(&pubKey, sizeof(pubKey)); /* Result should be 1 on success */ return result == 1 ? NC_SUCCESS : E_OPERATION_FAILED;} ```
A lot of things to remember right? Passing buffers and keys around to callback functions. Yeah, in C# I sure had fun doing this in nvault. That was sarcasm if you couldn't tell.
Read The Docs?
The libsecp256k1 project has almost no public documentation. Like many C projects, documentation is just the header files and readme cover. Which is fine if you are me and take the time to really learn how to use their public API. One of the larger projects I build is my website (and CMNext blog tool) to publish readable and up-to-date dedicated documentation. It is assumed you should take header files as authoritative, but dedicated documentation and examples can make or break a project's adoption IMO.
Wrapping up footguns
Honestly, my goal was to provide insight into my experience writing over 4k lines of C code to avoid some of the complexities I initially encountered when scaling NVault to compete with the latest NIPs. I believe Nostr will only become more complex, especially as we delve deeper into post-quantum and forward-secret algorithms.
Backward compatibility
A lesson learned outside of libsecp256k1 is the need for backward and forward API compatibility. When I first started building NVault, only NIP-04 existed, and I assumed that any future spec would deprecate the old spec. As it turns out, that is not the case, and I needed to rethink compatibility for future upgrades.
Many parts of Nostr are either slow to upgrade (due to complexity) or other contributors don't see the need to upgrade. Nostr is inherently anarchistic, and no one developer has the final say on what specs are used in the wild, which is an appeal to me. Every system has tradeoffs; in this case, we will have app compatibility issues. A perfect example is NIP-17 DMs collected by cloud fodder, where some clients support spec interoperability and others do not. I will disregard my personal opinions on their reasoning. I, and GitCitadel, will have our own reasons for our support or lack thereof, and I aim to be as transparent as possible when the time comes.
Making the case for noscrypt
By this point, you might be thinking: "Okay, yeah, you just made a case for another library, great." That would be correct, but I showed some simple code snippets that I believe highlight the requirement for high-level cryptography libraries incorporating the Nostr spec. While Nostr was always meant to be simple enough for a caveman to implement, it relies on the legacy existence of high-level libraries and users' ability to implement them correctly. This ecosystem predominantly exists in the JavaScript/browser world.
When trying to implement compact, portable, and powerful applications, you need the horsepower and efficiency of a dedicated library built for this purpose. We can already see this with existing Nostr SDKs (NDKs) in multiple languages. I don't aim to lock you into an NDK; for very high-level spec functionality, I think simple libraries are suitable for most smart and passionate developers. You don't need to rely on an NDK developer for a specific language.
Use noscrypt for your C project
-
 @ 44dc1c2d:31c74f0b
2024-07-11 19:26:22
@ 44dc1c2d:31c74f0b
2024-07-11 19:26:22Chef's notes
Make sure you cook them thoroughly on the skin side first to render out as much of the fat as possible and ensure maximum crispiness.
This goes great with rice.
Ingredients
- 6 skin-on, bone-in chicken thighs (about 2 pounds total)
- Kosher salt
- 2 tablespoons sesame oil, preferably toasted, divided
- 1 pound medium carrots, scrubbed
- 2 tablespoons soy sauce
- 2 tablespoons Sriracha
- 2 tablespoons unseasoned rice vinegar
- 1 tablespoon honey
- 1 1-inch piece ginger
- 3 scallions
- Toasted sesame seeds (for serving)
Directions
- Preheat oven to 425°. Heat a large dry skillet, preferably cast iron, over medium-low.
- Pat 6 chicken thighs dry with paper towels and season all over with salt. Rub only skin side of thighs with 1 Tbsp. oil.
- Transfer thighs skin side down to skillet and cook until enough fat is rendered to cover bottom of skillet, about 5 minutes. Once skin starts to brown, increase heat to medium. Rotate skillet to encourage even browning. Carefully lift up thighs to allow hot fat to run underneath. If thighs are stubborn and don’t want to release, let them go a bit longer.
- While thighs are cooking, cut 1 lb. carrots into 4" segments.
- Cook thighs until meat is opaque all around the edges and skin is deep golden brown, 10–12 minutes total. Transfer skin side up to a plate.
- Pour off all but about 2 Tbsp. fat from skillet (you just want enough left to form a thin layer) and heat over medium-high. Add carrots and try to arrange so all are side by side in a single layer in direct contact with skillet. Cook, undisturbed, until lightly charred on first side, about 5 minutes. Turn carrots so charred side is facing up, then season lightly with salt.
- Cook carrots on opposite side until lightly charred, about 2 minutes. Turn off stove and transfer skillet to oven. Roast until a toothpick, skewer, or cake tester easily pierces surface of carrot but encounters resistance in the center, 8–10 minutes.
- While carrots are roasting, stir 2 Tbsp. soy sauce, 2 Tbsp. Sriracha, 1 Tbsp. rice vinegar, 1 Tbsp. honey, and remaining 1 Tbsp. oil in a small bowl. Scrape peel off of ginger root with a spoon; discard peel. Grate ginger into bowl with microplane, then stir to combine.
- Carefully remove skillet from oven (the handle will be hot!) and place on stove. Arrange thighs over carrots and drizzle sauce over. Return to oven and roast until chicken thighs are cooked through (an instant-read thermometer inserted into the thickest part near the bone will register 165°), juices run clear, sauce is caramelized on chicken skin, and carrots are tender all the way through, 12–18 minutes. Remove from oven and let rest 10 minutes.
- While skillet is resting, thinly slice 3 scallions.
- Transfer chicken and carrots to a platter and drizzle pan juices over. Top with scallions and sesame seeds.
-
 @ 75da9402:77a65b5c
2024-07-11 19:18:54
@ 75da9402:77a65b5c
2024-07-11 19:18:54Empezare este articulo indicando que iba hacer publicado como un hilo en Twitter o X o como diablos se llame ahora por que mi intencion era trasmitir a otros que existe algo mucho mejor donde pueden empezar nuevamente a disfrutar de otra forma de comunicarse, pero mi sorpresa fue grande al momento de enviar el hilo de tweets, me salio el mensaje "no se puede enviar" usted debe UPDATE TO PREMIUM para atreverse hacer un post en esta empresa que protege la libertad de expresion...lol...(:-O). Como yo casi ya no escribo nada en X y lo uso solo para informarme de lo que pasa en mi pais, no sabia esta nueva limitacion. Ahora volvi a recordar por que deje de usarlo. Pero bueno, aqui voy a desahogar mi hilo para luego compartirlo en X, por que me van a leer quieran o no, jajaja.
Te cuento una pequeňa historia.
Alguna vez me preguntaron por qué me gustaba Twitter (hoy X) más que otras redes sociales ya que yo era un joven audaz que siempre interactuaba ahi jaja. Y mi respuesta fue simple en esos aňos: Twitter es una selva digital donde se genera el debate público e informativo a nivel mundial y aqui puedo decir lo que yo quiera (pobre iluso). Pero luego las cosas fueron cambiando en mi RRSS favorita, en algun momento se convirtio en un hueco lleno de toda clase de basura digital de la cual habia huido siempre, hasta que llego un familiar mio a comprar la empresa y pense: AL FINNN... volveran los dias de gloria, y efectivamente algo parecio mejorar y con eso me conforme, pero aclaro que no me gusto al final el rumbo que tomo la empresa familiar después que mi tío Elon la compró pero es lo que habia en ese entonces y aguante. HASTA AHORA..
Te gusta twitter pero a la vez estás arto de lo mismo?
Hace meses hice 1 post de por qué me gustaba X, pero también explicaba el rumbo que está tomando el mundo de la tecnología con respecto a las redes sociales. Y ahora te explicaré de qué se trata.
Todo ha evolucionado en el mundo de la tecnologia a velocidad vertiginosa, por ejemplo tu tia antes enviaba un Piolin de BUENOS DIAS todas las mañanas en su muro de Facebook a sus amigos y familiares que la seguian, ahora hace lo mismo por el WAZA (grupo familiar que pasa silenciado por siempre) y si ya no lo hace es por que TU eres la TIA del Piolin ahora jajaja, pero volviendo al tema las RRSS no han evolucionado desde hace 20 años, ojo me refiero a la forma de generar contenido, monetizar y consumir, todo es lo mismo que cuando abrí mi cuenta de Twitter hacer 15 años. Han aparecido muchas otras RRSS si es cierto, #tiktok la última. Pero todas hacen lo mismo darte a ti el usuario: entretenimiento, distracción ludica y tal vez “informar”; y esto entre comillas por qué lo que lees, escuchas y te informas es lo que los dueños de estas RRSS, las marcas auspiciantes y quienes pagan su verificación quieren, NO lo que TÚ quieres. Ellos dictan y te “Sugieren el contenido que puedes ver” pero tu no te das cuenta y crees que lo que estas viendo es por que tu asi lo decidiste. Lo cual es una triste y deprimente mentira....
Y no es invento mío, te adjunto una entrevista a Jack Dorsey fundador de Twitter, donde él explica detalladamente por qué sucede esto que afirmó anteriormente. Léelo en tu tiempo libre, no tiene desperdicio. Usa traductor si no le haces mucho al inglés:
https://www.piratewires.com/p/interview-with-jack-dorsey-mike-solana
Y si te preguntas, Alguien está haciendo algo para mejorar esto? SI, un montón de gente (Jack incluido) y otros mas que aportan con muchos recursos: técnicos, económicos, tenologicos y sobre todo tiempo y amor a su profesion. Esta gente está trabajando en cambiar todo esto que esta mal y de ese esfuerzo en conjunto nacieron soluciones como Mastodon, Bluesky y Nostr.
Pero que son Mastodon, Bluesky y Nostr?
Mastodon y Bluesky son básicamente lo mismo, nuevas RRSS donde encuentras de todo. Nacieron con la idea de enfrentar a Twitter la primera, y mejorarlo la segunda como lo explica Jack en su entrevista. Pero al final terminaron teniendo lo mismo, es decir marcas asupiciantes, moderadores verificados y dueños o juntas directivas. Mas de lo mismo....
Nostr en cambio es el giro de tuerca que las RRSS y las comunicaciones humanas necesitan para el futuro, y de hecho Instagram (Threads) y otros ya lo están probando en sus plataformas lanzando puentes desde sus empresas para que sus usuarios tengan interoperatibilidad entre diferentes rrsss del fediverse.
-Y por qué sucede esto con Nostr?
Por qué Nostr no es una RRSS ni una empresa, ni tampoco tiene dueños o moderadores de contenido que dictaminan lo que puedes o no ver, leer, escuchar y consumir en tu feed, ya que es un protocolo de comunicación como los que usas para el correo, para navegar en internet, etc.
-Y que ganamos los usuarios?
Ganamos un largo etc. de beneficios para consumo de contenido REAL, mas humano y mas limpio, pero lo que si diré que NO encontraras es nada de lo que te tiene hastiado de las otras RRSS. Aquí un video que te gustaría ver para entender de lo que escribo:
https://youtu.be/aA-jiiepOrE?si=iaMu5K3qKqh_JxsR
Te interesa usar y aprender que puedes hacer con Nostr?
Te dejo unos link 🔗 para que empieces a explorar una nueva forma de comunicarse entre seres humanos. Usa alguno de estos servicios, pruebalos.
- Lives: https://zap.stream/
- Música: https://wavlake.com/
- Blogs: https://yakihonne.com/
- Podcast: https://www.fountain.fm/
Y muchas más aplicaciones y sevicios en: https://www.nostrapps.com/
Si lo tuyo es consumir contenido en algo como Twitter/X estás apps son para ti:
En iOS: - Primal: https://primal.net/ - Damus: https://damus.io/ - Nostur: http://nostur.com/ - NosSocial: https://nos.social/
En ANDROID: - Primal: https://primal.net/ - Amethys: https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst&hl=en
En WEB: - Primal: https://primal.net/ - Nostrudel: https://nostrudel.ninja/ - Snortsocial: https://snort.social/ - Coracle: https://coracle.social/
Debes saber que puedes con el mismo usuario y contraseña (en #Nostr se dicen llaves) puedes ingresar a TODAS las aplicaciones mencionadas en este articulo, y esto puede lograrse por que el protocolo es el mismo, es NOSTR.
Ya vas en tendiendo? no hay empresas, no hay dueños..😏, TU eres el dueño del contenido que produces y del contenido que consumes.
Quieres saber mas informacion sobre Nostr, visita estas web. Resolveran muchas de tus dudas.
https://nostr.com/ https://nostr.how/
Para terminar con este pequeño hilo... (te odio Elon) jajaja
Nostr esta empezando y tiene mucho por mejorar pero al dia de HOY ya existen cosas increibles que puedes hacer y son mejores que en otras RRSS y te aseguro algo, TODOS nosotros terminaremos tarde o temprano usandolo en el futuro, es inevitable si queremos evolucionar nuestra forma de comunicarnos.
Si tu quieres ser uno de los primeros en experimentar una nueva era de las RRSS. Anímate y empieza a usar NOSTR como TU quieras. Solo haz lo siguiente:
- Descarga cualquier aplicacion en tu movil tipo Twitter detallada en este articulo.
- Crea el Usuario (npub....) llave 1
- Crea la contraseña (nsec....) llave 2
- Guarda tus llaves, que no se te olviden. (anótalas)
- Envia tu primer post colocando al final el hashtag #introductions
- Y a disfrutar de #nostr
Si te gustó este hilo (Elon de >:{ #$%&) dale RT o cómo diablos se diga ahora 😂 o postealo y compartelo donde quieras para que mas gente lea sobre Nostr. Tal vez a alguien le interese.
Si deseas seguirme en #Nostr •𓅦
primal.net/p/npub1whdfgqn66sytcta0l6c7vlt3h2lg67xcnsmzpk3pyvpmsaaxtdwqr8vs60
Alla nos vemos...escríbeme y pregunta lo que quieras.
Saludos, johnny
-
 @ 3bf0c63f:aefa459d
2024-05-24 12:31:40
@ 3bf0c63f:aefa459d
2024-05-24 12:31:40About Nostr, email and subscriptions
I check my emails like once or twice a week, always when I am looking for something specific in there.
Then I go there and I see a bunch of other stuff I had no idea I was missing. Even many things I wish I had seen before actually. And sometimes people just expect and assume I would have checked emails instantly as they arrived.
It's so weird because I'm not making a point, I just don't remember to open the damn "gmail.com" URL.
I remember some people were making some a Nostr service a while ago that sent a DM to people with Nostr articles inside -- or some other forms of "subscription services on Nostr". It makes no sense at all.
Pulling in DMs from relays is exactly the same process (actually slightly more convoluted) than pulling normal public events, so why would a service assume that "sending a DM" was more likely to reach the target subscriber when the target had explicitly subscribed to that topic or writer?
Maybe due to how some specific clients work that is true, but fundamentally it is a very broken assumption that comes from some fantastic past era in which emails were 100% always seen and there was no way for anyone to subscribe to someone else's posts.
Building around such broken assumptions is the wrong approach. Instead we should be building new flows for subscribing to specific content from specific Nostr-native sources (creators directly or manual or automated curation providers, communities, relays etc), which is essentially what most clients are already doing anyway, but specifically Coracle's new custom feeds come to mind now.
This also reminds me of the interviewer asking the Farcaster creator if Farcaster made "email addresses available to content creators" completely ignoring all the cryptography and nature of the protocol (Farcaster is shit, but at least they tried, and in this example you could imagine the interviewer asking the same thing about Nostr).
I imagine that if the interviewer had asked these people who were working (or suggesting) the Nostr DM subscription flow they would have answered: "no, you don't get their email addresses, but you can send them uncensorable DMs!" -- and that, again, is getting everything backwards.
-
 @ 3c984938:2ec11289
2024-05-11 12:21:43
@ 3c984938:2ec11289
2024-05-11 12:21:43👉play the audio to listen to the article. https://media.nostr.build/av/749a03816c328c599054f31113588f9f5a47b5e67681e3a1eb9ee97c8f2e0dd3.mp3
Welcome to Nostr!
Introduction. Is this your first time here in Nostr? Welcome! Nostr has a oddball acronym for "Notes and Other Stuff Transmitted by Relays" with a simple goal, to be censorship-resistance. An alternative to traditional social media, communications, blogging, streaming, podcasting and eventually email (in development) with decentralization that empowers you, dear user. No more will you have to be plagued by ads, held by centralized entities and data hungry algorithms that monetizes you.
Allow me to be your host! I'm Onigirl! I'm on a quest to explore the world of Nostr, a decentralized communication protocol. I write about the tools, and the awesome developers within Nostr that bring this realm roaring with life.

Welcome to Nostr Wonderland
You're about to step into another world that will explode your mind from all the decentralized apps, clients, web3 enabled sites that you can use. You're never going to look at communications, logging in, 2FA, and social media the same way ever again. All thanks to Nostr's cryptographic nature inspired by Bitcoin blockchain technology. Each user, when they create a Nostr account, they get two keys, a private and a public key. These are your keys to your very own kingdom. Whatever you write, sing, podcast, stream, anything you create --all of it belongs to you. The sky is literally the limit!

A Gold and Silver Key
A friend of mine and I, call this "Identity by Encryption" because your Identity is encrypted. You can share your silver key, "npub" to other users to connect and follow. Use your gold key, "nsec" to unlock your account to plugin into a plethora of applications. Keep this key safe at all times. There is no reason to be caged ever again by social platforms TOS henceforth!
👉Give it a whirl, you can follow me by copying and pasting my public key into your search bar on any client that you decide to use.
Onigirl
npub18jvyjwpmm65g8v9azmlvu8knd5m7xlxau08y8vt75n53jtkpz2ys6mqqu3Don't have a client yet? Select the best option
Find the right App for you! This is where you can use your gold key, "nsec" to login into these wonderful tools. You can also visit Nostr's app page here. Before you start pasting your gold key everywhere on apps, consider using a signers (for web3 enabled sites) please look at the next image for details, also refer to the legend.

Get a Signer extension via chrome webstore
A signer is an extension in the chrome webstore on Google. Nos2x and NostrConnect are widely accepted extension for logins. This simplifies the process of logging into web3 sites instead of copying and pasting your gold key, "nsec" each and every time, you keep it within the extension and give it permission(s) to sign you in.

👉⚡⚡Get a Bitcoin lightning wallet to send/receive Zaps⚡⚡ (This is optional)

Here on Nostr, we use the Bitcoin Lightning network (L2). You will need to get a lightning wallet in order to send/receive Satoshi. These are the smallest denominations of a Bitcoin. It is a one hundred millionth of a single bitcoin (0.00000001 BTC). Zaps are a form of "micropayment with sats" here on Nostr. If you enjoy a user content, it is the norm to "⚡zap⚡" a.k.a "tip" for their content. For example, If you like my content, you can zap me with SATs to reward my work. But you just arrived, you don't have a wallet yet. No worries! I got you covered!
"Stacker.News" is a platform where users can earn SATs by writing articles and engaging with other users. You.

👉Stacker.News is also the easiest place to get a Bitcoin Lighting wallet address.
- Log in with your "Signer" extension either "Nos2x or NostrConnect" click your profile which will be random letters and numbers in the upper right corner.
You will see something like this:

- Click "edit"
and choose a name that you like, and if you don't like it. You can change again later.

- Click "save"
- Create a bio and the SN community are very welcoming and will zap you some sats to welcome you.
- You new Bitcoin Lightning Wallet address will appear like this:
 #### ^^Do not zap this address; this is purely for educational purposes!
#### ^^Do not zap this address; this is purely for educational purposes! - With your New Bitcoin Lightning wallet address you can put this into any client or app of your choice. To do this, go to your profile page and under your wallet address under "LN Address," enter your new address and hit "save" and there ya go. Congratulations!
👉✨Eventually, you may want to move to self custodial options and maybe consider to even self-host your own LN node for better privacy. Good news is stacker.news is also moving away from being a custodian wallet.
Nostr, the maverick of Servers
 Instead of using a single instance or a centralized server Nostr is built to have several databases to exchange messages using "relays." Relays, which are neutral and nondiscriminatory, store and broadcast public messages in the Nostr network. They transmit messages to all other clients connected to them, securing communications in the decentralized network.
Instead of using a single instance or a centralized server Nostr is built to have several databases to exchange messages using "relays." Relays, which are neutral and nondiscriminatory, store and broadcast public messages in the Nostr network. They transmit messages to all other clients connected to them, securing communications in the decentralized network.My friends in Nostr welcome you!
Welcome to the tea Party, would you like a spot of tea?🍵

There's so much more!
This is just the tip of the iceberg. Follow me as I continue to explore new lands and the developers, called "knights" behind this ever-growing ecosystem. Meet me here for more content like this and share this with future nostr users. Learn about the knights fighting for freedomTech within Nostr and the projects that are contributing to make it happen. Make your life more decentralized with Nostr. 💋
Onigirl @npub18jvyjwpmm65g8v9azmlvu8knd5m7xlxau08y8vt75n53jtkpz2ys6mqqu3
- Log in with your "Signer" extension either "Nos2x or NostrConnect" click your profile which will be random letters and numbers in the upper right corner.
You will see something like this:
-
 @ 75da9402:77a65b5c
2024-07-11 19:14:04
@ 75da9402:77a65b5c
2024-07-11 19:14:04
### BIENVENID@ A NOSTR
Queridos amigos que desean unirse a Nostr, sé que para todos ustedes es nuevo este camino, pero créanme que vale la pena experimentar y conocer una nueva forma de conectar y comunicarse con personas en otras partes del mundo. Varias de las mentes mas brillantes y apasionadas por dejar una huella diferente en las comunicaciones humanas han puesto alma, mente, corazón y hasta sus propios fondos para desarrollar y aportar a nostr.
QUE ES NOSTR? ¿COMO EMPIEZO?
Nostr es un protocolo de comunicación que está diseñado para que las personas se conecten entre si de forma rápida, segura y divertida. No es una empresa de RRSS como Twitter, FB u otras, tampoco existe un dueño, CEO o accionistas ni moderadores ni administradores de contenido, tampoco pertenece algún país en específico. Dicho esto, si aún no sabes cómo empezar aquí vamos. Para conectarte a Nostr vas a usar aplicaciones llamadas también clientes, te sugiero empieces en tu móvil y estas son algunas de las que puedes descargar y probar para empezar, luego puedes buscar otros clientes de tu agrado:
Damus para usuarios de IPhone https://apps.apple.com/app/damus/id1628663131
Amethyst para usuarios de Android https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst
PASOS IMPORTANTES A SEGUIR
Vamos a realizar estos pasos con el cliente Damus pero en Amethyst funciona igual:
1.- Una vez que instalaste la aplicación cliente ábrela y vas a ir a la opción Crear Cuenta

2.- Te aparecera una pantalla que dice EULA, dale aceptar sin miedo como en todas tus RRSS jaja, tranquil@ no pasa nada.
3.- En la siguiente pantalla deberás: Subir foto de perfil (si lo deseas), Nombre de usuario (nick que te guste el mio jp ), Mostrar nombre (como quieres llamarte el mio johnny ), Informacion (una breve biografía tuya ) presiona Crear y listo ya puedes usar Nostr como un Sayayin :-P

4.- Antes de empezar a escribir tu primer post vamos a dar 2 pasos más que son fundamentales y algún día me lo agradecerás (pero si a ti nadie te dice que hacer jajaja, ya puedes empezar a usar Nostr y saltarte estos pasos). Ve a la parte superior izquierda de Damus y presiona en la foto de tu perfil, deberá aparecer un menú que dice Configuración presiónalo y debe llevarte a algunas opciones, entre ellas escoges la que dice Keys

5.- Este es el último paso y es EXTREMADAMENTE IMPORTANTE que lo sigas al pie de la letra por que vamos a guardar tus llaves (usuario y contraseña) de forma segura. Aquí debo informarte que en Nostr no usaras ni correo ni número de móvil ni otro dato personal que te identifique para poder acceder a tu cuenta y por lo tanto debes guardar tú mismo las llaves de acceso ya que si las pierdes NO HAY FORMA DE RECUPERAR, las perderás para siempre y deberás volver a iniciar de nuevo.
Dentro de la opción Keys encontraras dos identificadores el primero que empieza por npub... es tu clave publica (tu usuario) que todos ven en la red y más abajo encontraras tu llave secreta (tu contraseña) esta es la más importante y al activar el botón Mostrar aparecerá y empieza con nsec.... estas dos claves debes copiarlas y guardarlas con total seguridad NO LAS PIERDAS de preferencia para guardarlas usa un administrador de contraseña como Bitwarden o tu propio llavero de ICloud en tu IPhone.

Bien si ya hiciste estos 5 pasos en menos de 5 minutos ya estarás listo para navegar e interactuar con otras personas en #nostr. Existen otros conceptos dentro de la red que ya te explicare en otra guía, por ejemplo, los relés que son los que se encargan de trasmitir tus posts (en forma de notas) a todo el mundo, pero con los que vienen preconfigurados los clientes es suficiente por ahora.
DIVIERTETE NUEVO NOSTRICH
Es momento de lanzarte al universo de Nostr, publica tu primer post Hola Mundo y empieza hacer amigos y te aseguro que muchas buenas personas te responderán para darte la bienvenida, como sugerencia si hablas español o quieres conocer gente de este idioma: ve a la opción UNIVERSO (lupa de buscar) de tu cliente, aquí encontraras el feed global donde aparece todos los posts a nivel mundial donde también puedes conocer gente. Ahí escribes Seguidor Hispano le das seguir a todos los que sigue esa cuenta y puedes empezar a seguir a otros en tu idioma.
Si te ha gustado y servido este minitutorial, compártelo a otros y si quieres puedes también seguirme a veces comparto buenos memes :-) Copia mi usuario en el buscador y me sigues:
npub1whdfgqn66sytcta0l6c7vlt3h2lg67xcnsmzpk3pyvpmsaaxtdwqr8vs60
By Johnny
-
 @ 8d34bd24:414be32b
2024-07-11 15:27:32
@ 8d34bd24:414be32b
2024-07-11 15:27:32Once again here are the fruits of the Spirit as defined in Galatians 5.
But the fruit of the Spirit is love, joy, peace, patience, kindness, goodness, faithfulness, gentleness, self-control; against such things there is no law. (Galatians 5:22-23) {emphasis mine}
A Young Example
When I think of Godly kindness, I think of my eldest son. He always puts others above himself. He always considers other’s needs and point of view. He goes out of his way to help or talk to those who are lonely and hurting. He is unbelievably accommodating and caring to his younger brother, who has Down Syndrome. When we ask him for help, he instantly and cheerfully stops what he is doing to help. Nothing, but God, can make a teenage boy (now a young man) be as kind and self sacrificing as he is.
Do not let kindness and truth leave you;
Bind them around your neck,
Write them on the tablet of your heart.
So you will find favor and good repute
In the sight of God and man. (Proverbs 3:3-4)My son is such an amazing example of kindness that everyone who has met him notices and most comment on it. He stands out as a light in this dark world.
Bless Those Who Curse You
God calls us to all exhibit kindness. When we are kind, even to those who are unkind to us, we point the world to God. We stand out like a shining beacon in this grumpy, divided world.
“But I say to you who hear, love your enemies, do good to those who hate you, bless those who curse you, pray for those who mistreat you. Whoever hits you on the cheek, offer him the other also; and whoever takes away your coat, do not withhold your shirt from him either. Give to everyone who asks of you, and whoever takes away what is yours, do not demand it back. Treat others the same way you want them to treat you. If you love those who love you, what credit is that to you? For even sinners love those who love them. If you do good to those who do good to you, what credit is that to you? For even sinners do the same. If you lend to those from whom you expect to receive, what credit is that to you? Even sinners lend to sinners in order to receive back the same amount. But love your enemies, and do good, and lend, expecting nothing in return; and your reward will be great, and you will be sons of the Most High; for He Himself is kind to ungrateful and evil men. Be merciful, just as your Father is merciful. (Luke 6:27-36)
Putting Others First
Kindness is related to love, but is a little different. Kindness is acting in a loving manner even to those who are hateful to you and to those whom you don’t really like. It is seeing the hurt and pain in others instead of the hate and reaching out with the same mercy that God had for you. It is putting another’s good above your own. It is doing this not only for those whom you love, but also those who hate you, mistreat you, and who are undeserving. We do this because God showed love to us when we were undeserving. It is acting based on the other person’s need instead of based on our own hurt. It is amazing how, when our focus is on God and the needs of others, the same words and actions that would previously drive us into a rage, instead will engender pity, mercy, and care.
When my son was flying home from college for the summer, he had a succession of problems with his flight. First his flight was delayed several hours due to mechanical issues delaying it into the afternoon. Then after finally taking off, they couldn’t land at their intended location because of severe thunderstorms and even the risk of tornados. Instead they landed at an airport in a completely different state. While waiting to return to the intended location, he had to wait in the airport for hours.
My son is very frugal. He is generous with others and has insisted on buying gifts for his friends since he was around 10 years old (maybe younger) so that they would be from him, but he doesn’t like to spend any money on himself. He definitely doesn’t want to spend the high prices of airport food, but is an always hungry teenage boy. We told him over the phone that he should go to the service desk and ask for food vouchers since the original delay was mechanical problems and to not take “no” for an answer because they wouldn’t have had weather issues if not for their mechanical issues. He refused to go get vouchers because he said there were a bunch of people in line that looked to be in greater need than he was. He put their comfort and need above his own. This is the exact attitude that God calls us to and is a fruit that we should show if we are saved. True, many of us may show it as an unripe and misshapen fruit, but the fruit should still be there, especially when we make an effort to obey God.
Imitate the Kindness of Christ
Let all bitterness and wrath and anger and clamor and slander be put away from you, along with all malice. Be kind to one another, tender-hearted, forgiving each other, just as God in Christ also has forgiven you. (Ephesian 4:31-32)
Based on what God has done for us:
But God demonstrates His own love toward us, in that while we were yet sinners, Christ died for us. (Romans 5:8)
We should show the same love, kindness, and mercy towards others who need Jesus as we did. Instead of focusing on how we were wronged, we should focus on their need.
You may say, “That’s not fair.” Maybe not, but it is right and it actually can end up to our benefit. When we act kindly towards someone who does not act kindly towards others or ourselves, we point them to Jesus because we are different than the world. If that person accepts Jesus, we have gained a brother or sister in Christ. We have changed the world for the better (through the power of the Spirit). It feels good when someone changes from hate to kindness and goes from unsaved to a child of God.
I worked two summers as an intern for a design build construction company while I was in college getting my electrical engineering degree. I worked with a drafter who would draw up my electrical drawings. He had been doing this for a good number of years. I was a newbie designing these systems for buildings. He resented me because he wanted to do the job I had been hired to do, but the company only wanted to hire people with EE degrees for the job. (Ironically the top electrical guy didn’t have a degree.) The drafter would point out any error I made in a very unkind way, but I just worked and did my best.
After a long time working with Him, a big group from work went to a free lunch at a local mega-church (actually the church I was attending at the time.) As a ministry the church did a free lunch once a month and preached to the attendees during lunch. At this lunch, the drafter sat near me and asked me, why I had always been kind to him despite him not being kind to me. I told him it was because I was a Christian. I would like to say that he became a born-again Christian at that moment, but that didn’t happen. At the same time, our relationship almost instantly changed. I was no longer picked on. Any corrections were done kindly. Working together was done with mutual respect. This never would have happened if I had responded in the same way I was treated. I would like to think that that was a seed I planted that God later brought to fruition, but I will never know until I reach heaven. Still, it was so worth it.
The Sweetness of Kind Words
The heart of the wise instructs his mouth
And adds persuasiveness to his lips.
Pleasant words are a honeycomb,
Sweet to the soul and healing to the bones. (Proverbs 16:23-24)A person with the fruit of the Spirit always talks in a kind, pleasant way that is sweet to those who hear. Some that hate us may not appreciate the kindness at the time, but it will make a difference. They may initially hate us more because of our kindness because it accentuates their hate and no one wants to think of themselves as hateful. We all want to think well of ourselves.
Are your words known for their kindness? Are you gentle with your words or are you known for your sharp, cutting words? If the latter, pray that the Spirit would help you have self-control and kindness in your words. Our Christian response should always be different.
Therefore, putting aside all malice and all deceit and hypocrisy and envy and all slander, like newborn babies, long for the pure milk of the word, so that by it you may grow in respect to salvation, if you have tasted the kindness of the Lord. (1 Peter 2:1-3)
Be Kind in Gratefulness for the Kindness of Jesus
We should be kind because God was kind to us and we want to show the world what God is like.
Do nothing from selfishness or empty conceit, but with humility of mind regard one another as more important than yourselves; (Philippians 2:3)
Is there any other religion or belief system where its adherents are encouraged to put others first and not seek our own benefit from our words and actions? I don’t think so! When we act in this manor, we stand out in the crowd. People see that there is something different about us. We can be used by God to make a difference in the world and in other people’s lives.
For we also once were foolish ourselves, disobedient, deceived, enslaved to various lusts and pleasures, spending our life in malice and envy, hateful, hating one another. But when the kindness of God our Savior and His love for mankind appeared, He saved us, not on the basis of deeds which we have done in righteousness, but according to His mercy, by the washing of regeneration and renewing by the Holy Spirit, whom He poured out upon us richly through Jesus Christ our Savior, so that being justified by His grace we would be made heirs according to the hope of eternal life. (Titus 3:3-7)
Kindness is just being grateful for what Jesus did for us and doing for others what Jesus did for us. Obviously we will never succeed in being as kind and merciful as Jesus, but the Spirit enables to do more than a natural man ever could.
Therefore, return to your God, Observe kindness and justice, And wait for your God continually. (Hosea 12:6)
Obedience Encourages Kindness
Paul talks about working hard so we are able to be kind and minister to those in need. He used his own work and generosity as part of his witness for Christ.
You yourselves know that these hands ministered to my own needs and to the men who were with me. In everything I showed you that by working hard in this manner you must help the weak and remember the words of the Lord Jesus, that He Himself said, ‘It is more blessed to give than to receive.’ ” (Acts 20:34-35)
Although the fruit of the Spirit, kindness, is something only spoken of as being given to Christian believers in the New Testament, the command to be kind has been spoken of in the Bible throughout the Old Testament as well. It isn’t a new command. This verse tells more about kindness:
Then the word of the Lord came to Zechariah saying, “Thus has the Lord of hosts said, ‘Dispense true justice and practice kindness and compassion each to his brother; and do not oppress the widow or the orphan, the stranger or the poor; and do not devise evil in your hearts against one another.’ (Zechariah 7:8-10)
Take this to heart and let kindness flow through you.
Trust Jesus
Check out the whole series, Fruits of the Spirit
-
 @ 0dc2dcb1:4787801a
2024-07-11 15:16:25
@ 0dc2dcb1:4787801a
2024-07-11 15:16:25- Added ids and
setIds()to the Filter class to fetch events with ids - https://github.com/nostrver-se/nostr-php/compare/1.3.1...1.3.2 - Discovered https://revolt.run/ as a package to be used for concurrent async code in PHP. Source: TalkingDrupal podcast with KingDutch - https://www.drupal.org/project/drupal/issues/3257726
- Fix response in Relay class - https://github.com/nostrver-se/nostr-php/releases/tag/1.3.3. Found and reported on Nostr: https://njump.me/nevent1qvzqqqqqqypzphtxf40yq9jr82xdd8cqtts5szqyx5tcndvaukhsvfmduetr85ceqy88wumn8ghj7mn0wvhxcmmv9uq3zamnwvaz7tmwdaehgu3wwa5kuef0qqsq3utlvgf6tz88ctexwu8ppgct9dkahmv5esxhmmgphv675get22qmzah0a
- Created a seperate repository with the code for the nostr-php.dev website: https://github.com/nostrver-se/nostr-php.dev
- Added ids and
-
 @ b2caa9b3:9eab0fb5
2024-07-11 15:04:06
@ b2caa9b3:9eab0fb5
2024-07-11 15:04:06Hey everyone,
Today wasn't super eventful, but there were a couple things I wanted to share. First off, I had to pay rent, which meant a trip to the bank with my still-not-great foot. On the bright side, I took some pictures of Moshi along the way - hopefully you'll enjoy a glimpse of the city!

Speaking of my foot, there's been some improvement! The pain isn't constant anymore, only when I'm walking around. It looks better too, so hopefully it'll be back to normal soon.
Now, onto the slightly more frustrating topic: the Kenyan border situation. As you might recall, I had a big issue where border control wouldn't let me leave the country and even refused to contact my embassy. Basically, they held me hostage (which, by the way, is a violation of international law).
Two days later, I managed to get out through a different border. Recently, the Kenyan police has started investigating. They contacted me on WhatsApp a few days ago, and things are getting stranger by the day.

There's a big part of this that just doesn't add up. They keep asking for a photo of the exit stamp, but the officer who wouldn't let me leave never gave me one. He actually denied my exit and put me on a bus back to the city! I explained this and told them another border provided the stamp later, but they insist they need the original stamp to find this as "proof" related to this officer. It just doesn't connect to the man who caused the problem in the first place.

Even more concerning, they want me to return to Kenya. First, they want me to sign a document, but when I expressed hesitation about returning, they switched to asking me to identify this officer in a lineup. And all of this communication is happening on a personal WhatsApp number, which makes the whole situation incredibly suspicious.
Overall, it's a confusing situation.
On a brighter note, my foot is definitely on the mend. Here's to hoping it keeps getting better!
That's all for today. I'll just be relaxing and grabbing some dinner later.
Stay tuned for more updates!


Online
Feel free to support me by sending some sats via the lightning network to rubenstorm@sats.mobi
-
 @ 29216785:2a636a70
2024-07-11 13:06:59
@ 29216785:2a636a70
2024-07-11 13:06:59Dont know...
-
 @ 796a6d9b:3bb533e3
2024-07-11 12:57:35
@ 796a6d9b:3bb533e3
2024-07-11 12:57:35For more than a while now, I think you have experienced the feeling that things are not right in the world or in your country, it is not surprising that it coincides with a moment in history where we will experience the end of a monetary cycle like It is FIAT money or in other words fiat money that is backed by debt, every day you look around you and people do not find much hope in the future, many of them are working to support themselves, pay the costs of living and In the best of cases, just saving a little inflationary money, a slower theft in the population, in the worst of cases, people are full of debt and without a plan on how to escape said trap.
Everything is connected, we just have to look for the signs that are leaving us with the naked eye, as for example we have never had in history countries so indebted based on their GDP or gross domestic product and that this same debt was financed with a deficit, For people who have studied or lived the situations of hyperinflationary countries like Venezuela, Argentina, Turkey, Lebanon, you will know what I am talking about, it is simpler than it sounds, no country can spend more than it produces without any consequences, someone has to pay the price, in this case the population through the dark hand of inflation.
We have reached the point where governments blatantly lie to us with inflation data that does not include food, rent and energy prices, to save appearances and maintain the psychological operation that everything is fine, but when you go to the supermarket you know that something was never there. Well, it is not surprising that even you, the person reading this, know that inevitably your Dollars, Euros or Pesos will not buy you the same thing in a year as what they buy you today.
So where are we headed? It is normal then that people are not very enthusiastic about the future, since when we look into the depths of our system we realize that people's savings and purchasing power will increasingly be devalued so that everything continues to function as it has until now. Today, it is noticeable that something in people's subconscious warns them that tomorrow will be worse and that is why they have to enjoy the now, reducing their time preference to sporadic moments without thinking about the long term, even if they do not understand complex mechanisms. economics, it is observed that people are increasingly working more for less remuneration since the numbers of a salary can increase nominally but they buy fewer and fewer goods and services, as we can see in this graph.
What we have left in the coming years is the acceleration of government mechanisms to be able to continue keeping the wealth extraction system functioning, trying to extend the psychological operation to a point of no return, it is clear that a form of money has been confiscated from us. . that allowed us savings like gold did, I think it is important that we begin to question certain things and choose not to continue participating in a system that is arranged to destroy the energy of our work.
What can we do? Alternatives such as Bitcoin and gold to protect the energy of our work are some of the best options that we can implement as a refuge from the disaster to which our politicians have dragged us. Using these alternatives as a kind of battery for our energy is the only way we can ensure that the effort we make every day in our jobs, ventures or companies is not devalued, since both gold and bitcoin are not debt. of anyone, they are reserves of value and have no risk of reverse departure or non-payment.
It is time to take action and educate ourselves to be able to rise to the challenges of the paradigm shift that we will have as a civilization, since a change in the monetary standard is what can lead us to a better path of incentives where people can change preferences. temporary and build for the future.
originally posted at https://stacker.news/items/604619
-
 @ 29216785:2a636a70
2024-07-11 12:35:37
@ 29216785:2a636a70
2024-07-11 12:35:37this should not be empty
-
 @ 3c984938:2ec11289
2024-05-09 04:43:15
@ 3c984938:2ec11289
2024-05-09 04:43:15
It's been a journey from the Publishing Forest of Nostr to the open sea of web3. I've come across a beautiful chain of islands and thought. Why not take a break and explore this place? If I'm searching for devs and FOSS, I should search every nook and cranny inside the realm of Nostr. It is quite vast for little old me. I'm just a little hamster and I don't speak in code or binary numbers zeros and ones.

After being in sea for awhile, my heart raced for excitement for what I could find. It seems I wasn't alone, there were others here like me! Let's help spread the message to others about this uncharted realm. See, look at the other sailboats, aren't they pretty? Thanks to some generous donation of SATs, I was able to afford the docking fee.

Ever feel like everyone was going to a party, and you were supposed to dress up, but you missed the memo? Or a comic-con? well, I felt completely underdressed and that's an understatement. Well, turns out there is a some knights around here. Take a peek!

A black cat with a knight passed by very quickly. He was moving too fast for me to track. Where was he going? Then I spotted a group of knights heading in the same direction, so I tagged along. The vibes from these guys was impossible to resist. They were just happy-go-lucky. 🥰They were heading to a tavern on a cliff off the island.

Ehh? a Tavern? Slightly confused, whatever could these knights be doing here? I guess when they're done with their rounds they would here to blow off steam. Things are looking curiouser and curiouser. But the black cat from earlier was here with its rider, whom was dismounting. So you can only guess, where I'm going.

The atmosphere in this pub, was lively and energetic. So many knights spoke among themselves. A group here, another there, but there was one that caught my eye. I went up to a group at a table, whose height towed well above me even when seated. Taking a deep breath, I asked, "Who manages this place?" They unanimous pointed to one waiting for ale at the bar. What was he doing? Watching others talk? How peculiar.

So I went up to him! And introduced myself.
"Hello I'm Onigirl"
"Hello Onigirl, Welcome to Gossip"
"Gossip, what is Gossip?" scratching my head and whiskers.
What is Gossip? Gossip is FOSS and a great client for privacy-centric minded nostriches. It avoids browser tech which by-passes several scripting languages such as JavaScript☕, HTML parsing, rendering, and CSS(Except HTTP GET and Websockets). Using OpenGL-style rendering. For Nostriches that wish to remain anonymous can use Gossip over TOR. Mike recommends using QubesOS, Whonix and or Tails. [FYI-Gossip does not natively support tor SOCKS5 proxy] Most helpful to spill the beans if you're a journalist.

On top of using your nsec or your encryption key, Gossip adds another layer of security over your account with a password login. There's nothing wrong with using the browser extensions (such as nos2x or Flamingo) which makes it super easy to log in to Nostr enable websites, apps, but it does expose you to browser vulnerabilities.
Mike Points out
"people have already had their private key stolen from other nostr clients,"
so it a concern if you value your account. I most certainly care for mine.

Gossip UI has a simple, and clean interface revolving around NIP-65 also called the “Outbox model." As posted from GitHub,
"This NIP allows Clients to connect directly with the most up-to-date relay set from each individual user, eliminating the need of broadcasting events to popular relays."
This eliminates clients that track only a specific set of relays which can congest those relays when you publish your note. Also this can be censored, by using Gossip you can publish notes to alternative relays that have not censored you to reach the same followers.
👉The easiest way to translate that is reducing redundancy to publish to popular relays or centralized relays for content reach to your followers.

Cool! What an awesome client, I mean Tavern! What else does this knight do? He reaches for something in his pocket. what is it? A Pocket is a database for storing and retrieving nostr events but mike's written it in Rust with a few extra kinks inspired by Will's nostrdb. Still in development, but it'll be another tool for you dear user! 💖💕💚
Onigirl is proud to present this knights to the community and honor them with kisu. 💋💋💋 Show some 💖💘💓🧡💙💚
👉💋💋Will - jb55 Lord of apples 💋 @npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s
👉💋💋 Mike Knight - Lord of Security 💋 @npub1acg6thl5psv62405rljzkj8spesceyfz2c32udakc2ak0dmvfeyse9p35c

Knights spend a lot of time behind the screen coding for the better of humanity. It is a tough job! Let's appreciate these knights, relay operators, that support this amazing realm of Nostr! FOSS for all!

This article was prompted for the need for privacy and security of your data. They're different, not to be confused.
Recently, Edward Snowden warns Bitcoin devs about the need for privacy, Quote:
“I've been warning Bitcoin developers for ten years that privacy needs to be provided for at the protocol level. This is the final warning. The clock is ticking.”
Snowden’s comments come after heavy actions of enforcement from Samarai Wallet, Roger Ver, Binance’s CZ, and now the closure of Wasabi Wallet. Additionally, according to CryptoBriefing, Trezor is ending it’s CoinJoin integration as well. Many are concerned over the new definition of a money transmitter, which includes even those who don’t touch the funds.
Help your favorite the hamster
 ^^Me drowning in notes on your feed. I can only eat so many notes to find you.
^^Me drowning in notes on your feed. I can only eat so many notes to find you. 👉If there are any XMPP fans on here. I'm open to the idea of opening a public channel, so you could follow me on that as a forum-like style. My server of choice would likely be a German server.😀You would be receiving my articles as njump.me style or website-like. GrapeneOS users, you can download Cheogram app from the F-Driod store for free to access. Apple and Andriod users are subjected to pay to download this app, an alternative is ntalk or conversations. If it interests the community, just FYI. Please comment or DM.
👉If you enjoyed this content, please consider reposting/sharing as my content is easily drowned by notes on your feed. You could also join my community under Children_Zone where I post my content.
An alternative is by following #onigirl Just FYI this feature is currently a little buggy.
Follow as I search for tools and awesome devs to help you dear user live a decentralized life as I explore the realm of Nostr.
Thank you Fren
-
 @ b2caa9b3:9eab0fb5
2024-07-11 12:34:49
@ b2caa9b3:9eab0fb5
2024-07-11 12:34:49Back then, I was still living in a house in Höpfigheim. The house bordered directly on nature, a nature reserve, and I loved going out into nature there. I regularly took photos in this area. That's how this photo came about on that day in April 2011.
The photo was taken in Höpfigheim, a town in the Ludwigsburg district of Baden-Württemberg, Germany.

Photo Information
- Author: Ruben Storm
- Date Taken: April 22, 2011
- Published: June 19, 2012
- Camera: Nikon D3100
- Lens: Not specified
- Location: Höpfigheim, Germany
Links:
-
 @ 3c984938:2ec11289
2024-04-29 09:00:28
@ 3c984938:2ec11289
2024-04-29 09:00:28This is a part of my sporadic work on the Legend Series. I had a hard time finding good images. The images Ai often gave out made the islanders that look like Indians with the feather crowns, so that was interesting. The ending of this one is kinda funny.
The island was inhabited long ago by the ancient people (called Taotaomona). They were much larger than a regular person today. They also had magic, albeit little. The men were blessed with size and strength, while the women were gifted with wisdom and just a touch of magic in their hair.
One day, in the Hagatna bay. A group of fishermen noticed it their bay had grew. It was beyond confusing, to say the least. Another group of fishermen noticed that their bay, pago, also grew on the opposite side of the island.

"If this continues, our island will be cut into two pieces," cried the islanders. A wise leader came up with an idea to protect the island. The fishermen would watch their own bays from their own bays.
 ^^Huge fish, but you can also see the Taotaomona are also big.
^^Huge fish, but you can also see the Taotaomona are also big.The next morning, a fisherman spotted a massive fish in Pago Bay. The giant fish swam in and started to nibble the shoreline. The fisherman ducks behind boulders to observe and passes the message to his clan leader.
The leaders came together and came a conclusion that they must kill the fish. They sent runners to Hagatna Bay to ask for help to save their island home. Soon, Pago Bay was surrounded by canoes and men. All of them diligently watching to prevent their land from being eaten away, both in and out of the reef. Regardless of how hard they searched or waited, the fish didn't show. After awhile they give up and returned home.
 ^^Fish nibbling under the island from down under.
^^Fish nibbling under the island from down under.The news spread throughout the island about their imminent doom from clan to clan. They felt powerless to do anything.
The women of the island wore long, flowing locks and were proud to wash their hair in the river spring. The juices of lemons were used to enhance the magic. The peels were thrown into the spring after they were finished.

The maidens threw away the lemon peels into Hagatna Spring, but now they were popping up in Pago Bay. Which can only mean the peels were passing through the island, how did that happen? It could only mean the fish was nibbling under the island. A maiden cried out, discovering this new information, "We're surely doomed." Another maiden came forward and said, "Maybe we can outsmart the fish." The fish will be lured into swimming to Hagatna spring and set up a trap. The women came together to gather to trim their precious hair and wove it into a net. The net grew large enough to spread out in every direction of the bay. Each maiden held onto the edges and spread out to sing, waiting for the fish by the spring.
 ^^This is not an accurate representation, as the ancient people did not wear clothes. And they cut their hair to make the net.
^^This is not an accurate representation, as the ancient people did not wear clothes. And they cut their hair to make the net. Their song carried under the island, and the soothing sound carried underwater to the giant fishes lair. Little by little, it slowly swam closer to listen to the maiden's song. They sang and sang until they came up with new songs. The massive fish swam closer and emerges from the water. The maiden jumped into the spring surrounding it with their net to capture it. Their net didn't give way no matter how much the fish struggled. It was a success.
One maiden immediately ran to Hagatna to tell the others they had captured the giant fish and that the island was saved.

Everyone rushed to the spring to see the freshly caught fish and were overjoyed. The maidens were celebrated for saving the island when men's strength did not. Everyone ate the fish! Happy time!
Historical Context:
Here you can see the distance of how far the lemon peels traveled under the island. And the shape of the bay. Legends are always fun to explore of how something came to be.

Hello Dear Reader! I hope you enjoy my content? I am curious to hear your thoughts. Do you like what you see?
I'll be grateful for your feedback. Please feel free to leave a comment. Thank you
-
 @ 29216785:2a636a70
2024-07-11 12:34:12
@ 29216785:2a636a70
2024-07-11 12:34:12this should not be empty
-
 @ 3c984938:2ec11289
2024-04-25 07:23:55
@ 3c984938:2ec11289
2024-04-25 07:23:55https://image.nostr.build/bd90349f0d27124b0932e55baaa298d94ea9a7b655334092c11728f321914059.jpg
Hafa Adai Bitcoiners, Nostr is really amazing. Have you ever ate so much food at a buffet? Did you try all the different types of cake, how could you settle on just one? when there's so many. Each with different favors, frosting and textures. Ugh, now I want cake.
Habla Pac-Man
After departing from the OS green forest where Flycat lives, I must have taken a wrong turn because the forest instantly got darker with each and every step. After some time has passed my eyes started to adjust and now it started to glow. I saw the most yellow fellow. He was being hunted! He ate some kinda fruit, and you can see the ghost 👻 starting to running away.
https://image.nostr.build/cdcce1dcb2da7c4bc4bcc4ff26b45ad7afc76300c59f66bc55e005c035aab94e.jpg
what was it that powered him up? Stories and Content! It was dark and hard to see, as I venture deeper. I almost wanted to turn back. It turns out fiat thugs were hunting him! Thanks to users that voice their stories Habla Pac-Man is empowered. Feel free to report on important issues that matter - have your voice be heard even in the shadows. Habla Pac-man is on your side in the darkest part of the Publishing Forest to be your guiding light!
https://image.nostr.build/ea9625c2279c7a02fd1d42a218594de0d79fcd258ab35b6665e43a02b53cf7e4.jpg
Habla.news is wonderfully open source, so write on! Beware, ICANN still lurks in these shadowed woods. FYI, his original color is white, he just appears yellow at night because of the woods. Blue for meal time. 😂 This hamster is very happy to see mainstream media content getting eaten by users like you and me. As long as we write, Habla will be well fed.
Highlighter
Ever stumble on something by accident? I spotted something emitting light in the distance, as I continue to dive deeper into the Publishing Forest. Oh Look, an almighty highlighter! So any text I want to stand out, I can save it like a digital note on the side and publish it as a note on Nostr. Highlighter.com is content central! Some content creators have significant insight into certain topics and create alpha content. Instead of using third party services like Medium, Substack, and WordPress etc where you're not getting much credit for your content, they now can use this new powerful tool. Will you use this tool dear user? Whatever will you create?
https://image.nostr.build/b70011965aa3c6bfdbfaca404005d5522081c5f0390d324a1f1e1a9b2be69943.jpg
I held onto the highlighter, and I begin to feel powered! With this tool, Content creators can monetize their content! What a wonderful tool! Prehaps, I should start utilizing this? Whatcha think? Would you support a writer like me for 1,000 sats/quarterly?
https://image.nostr.build/4386899dc0fd455b340f0fd433d5a2bf2c865e6030c55dfbba53cbd192bb133d.jpg
It should be noted that highlighter.com is still new, and in development at the time of this publishing. I can't wait until it unveils all it's features. It does work and is usable but it's still in development. I'll wait.
https://image.nostr.build/04f92b7847fc6c5d7dce6a1152a1a4e5fe8613a0a6995801e1b942f1fe1ba97e.jpg
I'm taking this with me! I'm so happy that I can easily use "Identity by encryption" via Nostr. Just stupendous! It makes me wonder, how could this have not existed for so long? This is freedom, owning your content and not being forced to agree to share its revenue to evil corporate thugs because of "Terms and Conditions" that only care about their platform and not a user like me. I'm taking back my power, will you?
https://image.nostr.build/d3450fcf2eb9998d1150f5b7d1d261b9eb7547e9504a18f66f9dd4efe5107f57.png
The Blogstack.io curse on me
Some words about blogstack.io, the entire reason I joined Nostr was when I watched a tutorial video about Nostr as I was trying to learn. The youtuber was explaining it and used blogstack.io as an examples. I was sold within those 3 seconds of seeing blogstack.io and lost interest about blah blah Nostr is this and that. Those 3 seconds motivated me more to use Nostr then the whole 7min tutorial. So, I excitedly downloaded the app(Amethyst), made an account only to be disappointed or cursed that still plagues me today-- to not be able to use blogstack.io for some reason. I've always wanted to start my own blog but hated the idea of medium. I could go to blogstack.io, but I couldn't interact with it. This was my first experience. So the app sat on my phone for like 2 weeks. A friend of mine got a nostr account and told me to follow him, that's when it pique my interest again. One thing led to another, then another. Before I knew it, I had fallen into the rabbit hole. It is a wonderland of its own. I wish for you dear user to have a better first time experience then I did. And I hope you enjoy this content. If blogstack.io works for you- go for it, but I can't judge it's platform because 404 eludes me.
The Shipyard Pub
My journey is at it's end in the Publishing Forest and into a shipyard of sailboats. ⛵ So, I guess it's time for me to sail away! Get it? Time? The sailboats have a schedule for when they head in and out of port. So if you want to schedule a note for example, now, 4 hours, or a day+ out you can do so by using Shipyard. There's no need to feel a constant need to log on to keep publishing a note(or reposting) to stay relevant. Simply, write a note, and put a time when you want your note to be seen so you can capitalize on all time zones. Quite useful tool. If you've visit my profile page, I launched a time series of hamsters recently. I used shipyard to schedule them. Very nice feature.
https://image.nostr.build/6c0ce64194cb48c17cca219018d67fb1c5b852518fb6b72ce2087c05e6d181ce.jpg
Okay, Time for this #Hamstr to Sail away to the next adventure. Wherever will I go, is yet to be seen. Follow as I journey to find Knights of Nostr.
https://image.nostr.build/b841250eec60d41872fd61faadc027da38b32b63c5fe5c08f1b8a07ddb1342a3.jpg
I know in my heart they're out there, so let's find them! Often unseen, unappreciated and not loved for their code/software that sets us free. Together, we can change hearts, and minds but we need privacy of Identity or we'll all be punished for having a mind. ICANN Plagues the internet. Recently, Samurai Wallet was taken down because of mixing services. The Need for Identity by encryption and websites to move off ICANN's jurisdictional websites to IPFS is evermore important to adopt freedom. Yes, that means we need a Github Nostr style. So developers are never criminalized for restoring financial privacy, and speech to users. All of these platforms are Psyphers to be used against anti-reconnaissance. So speak freely!
Send some love to these specular devs that are helping to shape Nostr.
👉💋💋Kisu for OpenSource
💋💋Pablof7z💋 @npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft
💋💋 Verbiricha💋 @npub107jk7htfv243u0x5ynn43scq9wrxtaasmrwwa8lfu2ydwag6cx2quqncxg
Get your NIP-23 (Long-Form-Content) Here, or get it over there, you're bound to get it from somewhere. Until Next time! Wish me smooth sailing? I'll be adopting njump.me style as of this article.
with 🧡 Onigirl
-
 @ 266815e0:6cd408a5
2024-04-24 23:02:21
@ 266815e0:6cd408a5
2024-04-24 23:02:21NOTE: this is just a quick technical guide. sorry for the lack of details
Install NodeJS
Download it from the official website https://nodejs.org/en/download
Or use nvm https://github.com/nvm-sh/nvm?tab=readme-ov-file#install--update-script
bash wget -qO- https://raw.githubusercontent.com/nvm-sh/nvm/v0.39.7/install.sh | bash nvm install 20Clone example config.yml
bash wget https://raw.githubusercontent.com/hzrd149/blossom-server/master/config.example.yml -O config.ymlModify config.yml
```bash nano config.yml
or if your that type of person
vim config.yml ```
Run blossom-server
```bash npx blossom-server-ts
or install it locally and run using npm
npm install blossom-server-ts ./node_modules/.bin/blossom-server-ts ```
Now you can open http://localhost:3000 and see your blossom server
And if you set the
dashboard.enabledoption in theconfig.ymlyou can open http://localhost:3000/admin to see the admin dashboard -
 @ 5d4b6c8d:8a1c1ee3
2024-07-11 12:17:18
@ 5d4b6c8d:8a1c1ee3
2024-07-11 12:17:18Yesterday's edition https://stacker.news/items/603455/r/Undisciplined
-
- -
July 11, 2023 📅
📝
TOP POSTI am not a routing node anymore
Excerpt
Over the past two years I ran an amateur routing node that was in the top 300 on lightning terminal. I have decided to stop for the following reasons […]
5586 sats \ 37 comments \ @lnvisualizer \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/207349/r/Undisciplined?commentId=207482
Excerpt
While you were making Bitcoin banks, Phoenix scripted out lightning channel management […]
1776 sats \ 12 replies \ @nerd2ninja
From Introducing the new Phoenix: a 3rd generation self-custodial Lightning wallet by @Norbert in ~bitcoin
🏆
TOP STACKER2nd place @nerd2ninja (1st hiding, presumed @siggy47)
746 stacked \ 2262 spent \ 1 post \ 11 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
91.7k stacked \ 0 revenue \ 113.7k spent \ 90 posts \ 302 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 11, 2022 📅
📝
TOP POSTI'm Evan Kaloudis, Founder of Zeus. July 11th AMA!
Excerpt
I'm stoked to chat with you all today. Zeus (https://zeusln.app) is a mobile app for iOS and Android that lets you connect to and control your lightning node remotely. It supports LND, Core Lightning, and Eclair.
31.7k sats \ 58 comments \ @evankaloudis \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/43634/r/Undisciplined?commentId=43640
Excerpt
Hello, I am a Bitcoin maxi and I put my sats where my mouth is. Bitcoin maximalism is a method of consumer protection. My story as a maximalist, is that I used to shitcoin back in 2016. During the 2018 bear market, I lost so much money in everything […]
390 sats \ 11 replies \ @nerd2ninja
From I am moving over from Twitter by @charles_stack in ~bitcoin
🏆
TOP STACKER1st place @k00b
19.3k stacked \ 32k spent \ 2 posts \ 17 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
53.4k stacked \ 0 revenue \ 62.2k spent \ 114 posts \ 304 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 11, 2021 📅
📝
TOP POSTThis company sells passports to Americans looking for a tax break on their bitcoin profits
Link to https://www.cnbc.com/2021/07/11/plan-b-passport-tax-break-bitcoin-profits.html
5 sats \ 4 comments \ @0268486dc4 \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/256/r/Undisciplined?commentId=282
Excerpt
Fascinating to see the disconnect between fundamentals of a crypto/stock and the price action created by market movers and how it seems to follow so many mathematical patterns. Makes you want to be a trader but then you remember 90%+ or whatever jus […]
1 sat \ 2 replies \ @gmd
From What are your favorite Bitcoin newsletters? by @k00b in ~bitcoin
🏆
TOP STACKERNo top stacker
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
21 stacked \ 0 revenue \ 151 spent \ 5 posts \ 15 comments
originally posted at https://stacker.news/items/604559
-
-
 @ a012dc82:6458a70d
2024-07-11 11:45:10
@ a012dc82:6458a70d
2024-07-11 11:45:10Table Of Content
-
Content
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
Introduction
The world of real estate is one that has always been known for its slow-moving and traditional nature. However, with the rise of digital currencies like Bitcoin, the industry is beginning to see some significant changes. In this blog post, we'll explore the future of real estate transactions and how Bitcoin is changing the game.
Cryptocurrency as a payment method
Real estate transactions have traditionally been conducted using fiat currency, but the emergence of cryptocurrencies like Bitcoin is changing the game. Bitcoin offers faster and more cost-effective transactions compared to traditional payment methods. Additionally, blockchain technology provides a secure and tamper-proof record of real estate contracts, simplifying the transaction process and reducing the need for intermediaries.
Greater transparency and security
Bitcoin and blockchain technology can also provide greater transparency and security in real estate transactions. For instance, using Bitcoin and blockchain technology, buyers and sellers can easily track the progress of a transaction from start to finish, with a clear record of all the steps taken along the way.
This transparency can help to reduce the risk of fraud, as well as providing a level of trust and confidence in the transaction process. It can also help to reduce the risk of errors, as all parties involved in the transaction can see the same information, reducing the chance of miscommunication or misunderstandings.
Greater global reach
Finally, Bitcoin and other cryptocurrencies can help to expand the global reach of real estate transactions. Because Bitcoin is a decentralized currency, it can be used across borders without the need for currency exchange or other financial intermediaries. This can make it easier for foreign buyers and sellers to participate in real estate transactions, opening up new opportunities for investment and growth.
Conclusion
In conclusion, Bitcoin and blockchain technology are changing the game for real estate transactions. By providing faster, more cost-effective, and secure transactions, and by expanding the global reach of real estate investments, Bitcoin is helping to make real estate a more accessible and efficient industry. As these technologies continue to develop and mature, we can expect to see even more changes and innovations in the real estate industry in the years to come.
FAQ
How can Bitcoin be used in real estate transactions? Bitcoin can be used as a payment method for real estate transactions. Buyers and sellers can exchange Bitcoin in exchange for a property.
What are the advantages of using Bitcoin in real estate transactions? The speed of transactions is much faster with Bitcoin compared to traditional payment methods. Additionally, Bitcoin transactions tend to have lower fees than traditional methods. Using Bitcoin can also provide greater transparency and security.
What is blockchain technology? Blockchain is a digital ledger that securely records and stores data. It is ideal for recording and verifying real estate transactions because it provides a tamper-proof record of the transaction.
How does blockchain technology simplify the real estate transaction process? Blockchain technology can automate certain parts of the transaction process, reducing the need for intermediaries like lawyers and banks. This can speed up the transaction process and reduce costs for all parties involved.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-