-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ df67f9a7:2d4fc200
2024-07-07 18:25:32
@ df67f9a7:2d4fc200
2024-07-07 18:25:32Anyone who thinks that “onboarding new users” is simply a technical challenge of educating people about “how Nostr works”, is grossly mistaken about social networks in general and blind to what makes Nostr so special.
Social Networks are for Friends
Relationship building is why people use social networks. Connecting with friends and loved ones (and colleagues and customers also) is the obvious reason to join, and should be the primary objective in any onboarding endeavor. Everything else “about the technology” only needs to be introduced “as needed” in order for each new user to achieve this goal.
The Nostr Network Requires Trusted Friendships
To thrive at scale, Nostr needs to have established and interconnected “webs of trusted friends” for “verifying” authentic profiles and quality content. This PgP strategy for decentralized trust implemented on Nostr, is the best way to keep bots and bad actors at bay while preserving freedom and sovereignty for every user. Even though Nostr still doesn’t have a standard for determining who “is trusted” for any one user across all clients, we can already build tools to onboard new friends of the highest quality trust. Leveraging existing relationships, “webs of trust” can be strengthened even at this early stage simply by advocates “inviting friends to Nostr”.
Nostr is New and Already Full of Trusted Friends
But it won’t be for long. Bots and bad actors are relatively “easy” to keep at bay today because the Nostr userbase is still small. People who come to Nostr and STAY have mostly been a self selecting group of “freedom tech fans”. We like it this way, and are generally happy to be here. The comraderie is refreshing. But the more people that come to Nostr, the more Nostr will attract different kinds of people.
This is already happening. Nostr is growing at the edges, reaching out beyond the “freedom tech fans” and attracting a number of “less committed” (and some nefarious) individuals here and there. Who sticks around? The “friends of freedom tech fans” stick around longer because they have friends here. WAY BEFORE even considering how “the network effect” will take over, Nostr needs to solve for retention by bringing more “trusted friends” into the network. Social onboarding tools will allow us to share Nostr to “friends of freedom tech fans” and beyond, establishing interconnected “webs of trust” that are increasingly impermeable to bots and bad actors.
Nostr is Freedom Tech that People Want to Share
Creators and influencers of every kind share Nostr (and Nostr content) every day. This phenomenon is a gold mine for onboarding, and can be supported with tools and incentives. Driven by the fact that Nostr is an open protocol, owned by nobody and available for anybody to build upon and profit from, the passion for sharing Nostr will never wane. But our userbase may fall off, if people become disenchanted by undesirable content or lack of good follows. This is why onboarding efforts, to attract more “friends” to the network, are so important. Leveraging the “share worthy” phenomenon of Nostr itself to grow Nostr’s networks of “trusted friends” seems like a no brainer. But for this strategy to work, it needs to be win win win for all parties.
Everybody Wins with More Trusted Users on Nostr
Even as standards for qualifying trust are still being refined, “social onboarding” increases the ratio of “more” trusted over “less” trusted users across the network.
Developers Win
With more trusted users on the network, Nostr developers win by being able to attract an increasingly diverse range of business partners to sponsor their projects.
Sponsors Win
An increase in trusted usership equates to more “real people” perusing “desired content” and more chances for brands to engage “organically” with target audiences. Marketing opportunities increase with trust.
Advocates Win
Simply by sharing Nostr with their friends, Advocates support the sustained growth of trust across the network. Valuable zap reward programs to incentivize high quality onboarding efforts are easily justified and funded by social onboarding clients and their sponsors.
Users Win
More trusted users across the network means more trustworthy content in every feed and more easily discoverable friends and new follows regardless of the client or algorithm used.
Nostr Wins
More trusted users on the network means more “high quality” trust connections between each user. Strong webs of trust is what keeps out bots and bad actors, and is essential for stability as Nostr scales.
Social Onboarding Clients Bring Trust to Nostr
Having more tools for “sharing Nostr with friends” is how Nostr wins. Any client can have capacity for “Social Onboarding”. This may be a dedicated onboarding client or a feature set within a social client. A client that offers “Social Onboarding” will support Nostr advocates and the users that they invite. These should have the following feature set :
- Nostr advocates may create and share any number of customizable “Nostr invites” for different audiences or occasions. Each may have different reccomendations, or access codes, or expiry options. (A NIP is in the works)
- Nostr invite QR codes (and shareable URLs) should resolve to a WEB based interface for prospective (and existing) users who MAY NOT have a client or browser extension already installed.
- Each invite should (within the onboarding client) provide access to low friction profile creation AND advocate reccomended lists of new friends, interest groups, preferred clients, best relays, and other stuff.
- Private key generation and management for new users should be handled entirely within the onboarding client (using NIP standards without a browser extension or external bunker app) to reduce friction at this crucial moment.
- A human readable Nostr address (NIP05 or some future NIP) should be generated automatically for all new users.
- New account creation should result immediately in a direct message or group thread of private “gift wrap” encrypted messages. This thread acts as the new user’s “first contact” with the advocate (possibly others as well) and an anchor for exploring the rest of Nostr.
- Invite “receipt” data (who invited who) should be “gift wrap” encrypted, accessible only to the advocate and new user. Clients wishing to use this data for analytics MAY request access from BOTH parties.
- Top Advocates may be calculated by the client (using data from invite receipts OR from public Nostr usage metrics), and awards may be offered.
- Advocates may also be supported by the client through access to private “advocate support” groups and communities over the Nostr network.
Support Social Onboarding for Nostr
Meet Me On Nostr is an app for sharing Nostr with friends via advocate invites. It is a reference client to demonstrate the power of Social Onboarding for Nostr. The first launch of "feature complete" client is expected in fall 2024.
This is a “bootstrap” funded project in active development. We are not grant funded or VC funded. Instead, we are looking to pay our developers by sponsorships from “Nostr adjacent” businesses who want to increase brand recognition over this new social network.
Is Your Business Nostr Adjacent?
“I’d like to advertise on Nostr but it’s “not quite ready” says our marketing team.”
“It has potential, and we have alignment, but the technology is still a bit rough.”
“Nostr is a perfect fit for our “target audience”, but there simply aren’t enough people using it.”
If your business is aligned with freedom technology, and the people who build and use Nostr, then NOW is the perfect time to sponsor Social Onboarding. Help grow Nostr’s base of trusted users and engage directly with Nostr’s most active advocates and influencers as it scales.
Release Nostr’s Superpower
When Nostr advocates are equipped and incentivized to share Nostr with their friends, nothing can stop this network from growing and growing and growing ever more secure and interconnected networks of trusted users.
Onboarding and retaining trusted users as Nostr scales will require so much more than just pointing people to “how Nostr works” content. Nostr’s true power lies dormant in the existing relationships that Nostr users already have outside of Nostr. Leveraging this power is what Social Onboarding is all about. Social Onboarding is Nostr’s superpower.
-
 @ 3bf0c63f:aefa459d
2024-06-19 16:13:28
@ 3bf0c63f:aefa459d
2024-06-19 16:13:28Estórias
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ d6dc9554:d0593a0c
2023-09-21 18:37:14
@ d6dc9554:d0593a0c
2023-09-21 18:37:14Nas blockchains PoW o consenso é alcançado por meio de prova de trabalho computacional e o objetivo principal é evitar que atores mal intencionados consumam ou ataquem a rede de forma perigosa. Este método de consenso requer um grande poder computacional para criar novos blocos, mas é muito simples, por parte de outros, verificar esse trabalho. Por isso se diz que PoW é uma estratégia assimétrica.
Nas blockchains PoS o objetivo é o mesmo, criar blocos e chegar a um consenso, mas nas PoS não é necessário um poder de processamento tão grande como nas PoW. Em média as PoS gastam menos de 1% da energia das PoW. Nas PoS os mineradores são chamados de validadores. Enquanto que nas PoW quem fica com a recompensa é quem resolve primeiro a charada matemática, nas PoS o validador que vai ganhar a recompensa é escolhido de forma aleatória, mas dando maior probabilidade aos que respeitem determinados critérios. A comunidade bitcoin é muito relutante em relação a PoS porque é mais fácil conseguir uma grande quantidade da moeda em causa do que mais que 51% de poder processamento. Logo as PoS são mais vulneráveis no que toca a segurança. Mas aqui cada caso é um caso e é preciso fazer essa análise para cada moeda.
As blockchains PoW tendem a ser mais descentralizadas enquanto as PoS mais centralizadas, não só em acesso, mas também em operação. Mais de metade dos validadores de ethereum estão na cloud da amazon. As blockchains PoW apresentam grandes desafios na escalabilidade de operação, muitas vezes exigindo soluções de segunda camada (L2), enquanto que as PoS possuem mecanismos de escalabilidade muito mais flexíveis. Os algoritmos PoW são muito mais simples de implementar do que os PoS e, portanto, menos suscetíveis a erros. Um bom exemplo é o PoS da ethereum que estava a ser implementado desde 2018.
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 7d4417d5:3eaf36d4
2023-08-19 01:05:59
@ 7d4417d5:3eaf36d4
2023-08-19 01:05:59I'm learning as I go, so take the text below for what it is: my notes on the process. These steps could become outdated quickly, and I may have some wrong assumptions at places. Either way, I have had success, and would like to share my experience for anyone new to the process. If I have made any errors, please reply with corrections so that others may avoid potential pitfalls.
!!! If you have "KYC Bitcoin", keep it in separate wallets from your "Anonymous Bitcoin". Any Anonymous Bitcoin in a wallet with KYC Bitcoin becomes 100% KYC Bitcoin.
!!! It took me several days to get all the right pieces set up before I could even start an exchange with someone.
!!! Using a VPN is highly recommended. If you're not already using one, take the time to find one that suits you and get it running.
!!! If you don't normally buy Amazon Gift Cards, start doing so now, and just send them to yourself, or friends that will give you cash in return, etc. For my first trade, Amazon locked me out of my account for about 22 hours, while I was in the middle of an exchange. All because I had never purchased an Amazon Gift Card before. It was quite nerve wracking. My second trade was for $300, and although my Amazon account wasn't shut down, that order had a status of "Sending" for about 22 hours, due to the large amount. In each of these cases I had multiple phone calls with their customer support, all of whom gave me false expectations. Had I already been sending gift cards to the anonymous email address that I created in the steps below, and maybe other anonymous email addresses that I could make, then I might not have been stalled so much.
-
Install Tor Browser for your OS. The RoboSats.com website issues a warning if you are not using Tor Browser. If you don't know what Tor is, I won't explain it all here, but trust me, it's cool and helps keep you anonymous. If you use Firefox, the interface will look very familiar to you.
-
Create a KYC-free e-mail address. I used tutanota.com in Firefox, as it would not allow me to create an account using Tor Browser. After the account was created, using Tor Browser to login, check emails, etc. has been working perfectly. Tutanota requires a 48 hour (or less) waiting period to prevent bots from using their system. You'll be able to login, and even draft an email, but you won't be able to send. After you've been approved, you should be able to login and send an email to your new address. It should show up in your Inbox almost instantly if it's working.
-
Have, or create, at least one Lightning wallet that is compatible with RoboSats.com and has no KYC Bitcoin in it. The RoboSats website has a compatibility chart available to find the best wallet for you. During an exchange on RoboSats, you will need to put up an escrow payment, or bond, in Satoshis. This amount is usually 3% of the total amount being exchanged. If the exchange is successful, the bond payment is canceled, leaving that amount in your wallet untouched, and with no record of it having been used as escrow. If you don't hold up your end of the trade, the bond amount will be transfered from your wallet. I created a wallet, using my new email address, with the Alby extension in the Tor Browser. This anonymous wallet was empty, so I used a separate wallet for the bond payment of my first trade. This wallet had KYC Bitcoin, but since it is being used for a bond payment, and no transaction will be recorded if everything goes okay, I don't mind taking the minuscule risk. After the first trade, I don't need to use the "KYC wallet", and I will use only my anonymous Lightning wallet for transactions related to performing a trade.
-
Create a new Robot Token by going to RoboSats using the Tor Browser. Copy the Token (Robot ID) to a text file as a temporary backup. It is recommended to create a new robot-token for every session of exchanges you make.
-
Select "Offers" to browse what others are presenting. "Create" is for when you want to create an offer of your own. You may need to create your own offer if none of the existing offers match your criteria.
-
Select "Buy" at the top of the page.
-
Select your currency (USD).
-
Select your payment methods by typing "amazon" and selecting (Amazon Gift Card). Repeat this process and select (Amazon USA Gift Card).
-
Determine Priorities - If you prefer to trade quickly, and don't care as much about premiums, look for users with a green dot on the upper-right of their robot icon. If you're not in a hurry, sort users by premium and select the best deal, even if they are inactive. They may become active once they are notified that their offer has activity from you.
-
The Definition of Price = the price with the premium added, but not the bond
-
A. Find A Compatible Offer - Select the row of the desired offer and enter the amount you would like to buy. i.e. $100 If you do not find a compatible offer, you will have to create your own offer.
B. **Create An Offer** - First, take a look at "Sell" offers for your same currency and payment method(s) that you will be using. Take note of the premium those buyers are willing to pay. If your premium is drastically less than theirs, your offer may get ignored. Select "Create" at the bottom of the screen. There is a slider at the top of the screen, select it to see all the options. Select "Buy". Enter the minimum and maximum amount that you wish to spend. Type "amazon" to select the methods that you would like to use (Amazon Gift Card, Amazon USA Gift Card). For "Premium Over Market", enter an amount that is competitive with premiums you saw at the start of this step and do not use the % sign! You can adjust the duration, timer, and bond amount, but I leave those at their default settings. Select the "Create Order" button, and follow the instructions for making a bond payment. -
Pay the Bond - Copy the invoice that is presented. From your wallet that contains bond funds, select "Send", and paste the invoice as the recipient. This money will never leave your account if the exchange completes without issue. No transaction will be recorded. If there is a complication with the exchange, it is possible that this transaction will complete.
-
Create and Submit Your Invoice for Their Bitcoin Payment To You - Select "Lightning", if not selected by default.* Select the Copy Icon to copy the correct amount of Satoshis. This amount already has the premium deducted. From your anonymous Lightning Wallet, select "Receive", and paste the Satoshi amount. If you enter a description, it's probably best to keep it cryptic. Copy the invoice and paste it into RoboSats; then select "Submit".
* If you plan on "mixing" your Bitcoin after purchase, it may be better to select "On Chain" and pay the necessary fees swap and mining fees. In the example this comes from, Sparrow wallet is used and has whirlpool ability in its interface.
-
Connect With Seller and Send Funds - Greet the seller in the chat window. The seller has now provided RoboSats with the Bitcoin to transfer to you. Your move is to buy an Amazon eGift Card for the amount of the trade. Log in to your Amazon account and start the process of buying an eGift card. For delivery there is the option of email or txt message. Ask the seller what their preference is, and get their address, or phone number, to enter into Amazon's form. Complete the purchase process on Amazon, and check the status of your order. Once you see the status of "Sent", go back to RoboSats in your Tor Browser.
-
Confirm Your Payment - Select the "Confirm ___ USD Sent" button and notify the seller to check their e-mail/txt messages.
-
Seller Confirmation - Once the seller select their "Confirm" button, the trade will immediately end with a confirmation screen.
-
Verify - If you check the anonymous wallet, the new amount should be presented.
-
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 0176967e:1e6f471e
2024-07-21 15:48:56
@ 0176967e:1e6f471e
2024-07-21 15:48:56Lístky na festival Lunarpunku sú už v predaji na našom crowdfunding portáli. V predaji sú dva typy lístkov - štandardný vstup a špeciálny vstup spolu s workshopom oranžového leta.
Neváhajte a zabezpečte si lístok, čím skôr to urobíte, tým bude festival lepší.
Platiť môžete Bitcoinom - Lightningom aj on-chain. Vaša vstupenka je e-mail adresa (neposielame potvrdzujúce e-maily, ak platba prešla, ste in).
-
 @ 0176967e:1e6f471e
2024-07-21 11:28:18
@ 0176967e:1e6f471e
2024-07-21 11:28:18Čo nám prinášajú exotické protokoly ako Nostr, Cashu alebo Reticulum? Šifrovanie, podpisovanie, peer to peer komunikáciu, nové spôsoby šírenia a odmeňovania obsahu.
Ukážeme si kúl appky, ako sa dajú jednotlivé siete prepájať a ako spolu súvisia.
-
 @ e6817453:b0ac3c39
2023-08-12 15:42:22
@ e6817453:b0ac3c39
2023-08-12 15:42:22The Zooko’s Triangle is a concept in the realm of naming systems, specifically for decentralized or distributed networks. It was named after Zooko Wilcox-O’Hearn, a computer scientist and cypherpunk known for his work on the Zcash cryptocurrency. The triangle illustrates a trade-off between three desirable properties in a naming system:
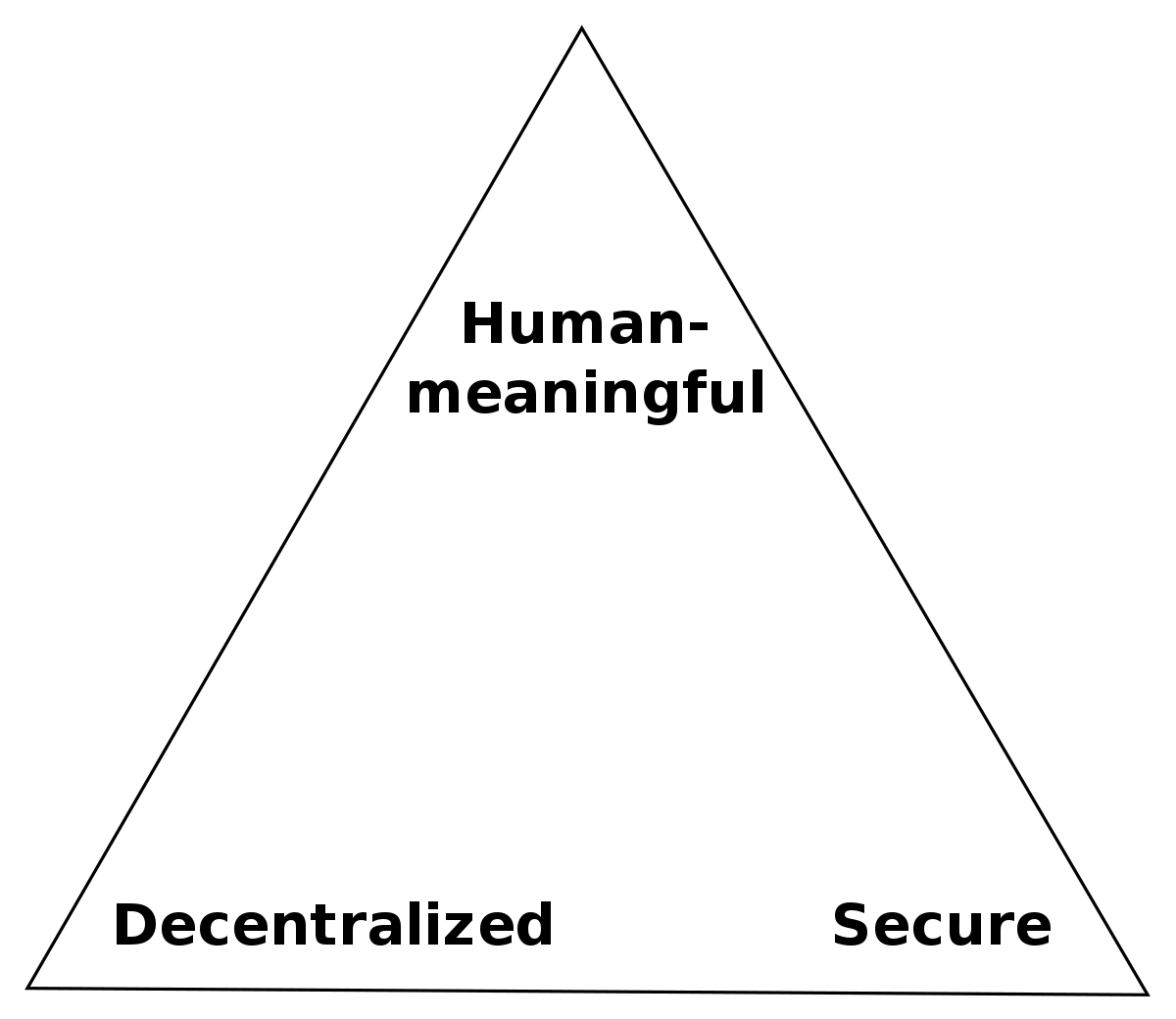
- Human-meaningful: Names are easily understood and remembered by humans.
- Decentralized: No central authority controls the allocation or management of names.
- Secure: Names are unique and cannot be easily taken or manipulated by others.
Zooko’s Triangle posits that achieving all three properties in a single system is difficult. Traditionally, a system could have only two of the three properties, leading to various combinations of naming systems with their respective advantages and disadvantages.
However, recent developments in cryptographic and distributed systems have led to solutions that challenge the traditional constraints of Zooko’s Triangle. One such system is the Decentralized Identifiers (DIDs).
DIDs
Decentralized Identifiers (DIDs) are a new identifier for verifiable, decentralized digital identity. DIDs are designed to be self-sovereign, meaning that individuals or organizations control their identifiers without relying on a central authority. DID systems are built on top of decentralized networks, such as blockchain or distributed ledgers, providing a secure and tamper-proof infrastructure for identity management.
DIDs aim to achieve the three properties of Zooko’s Triangle:
- Human-meaningful: While DIDs may not be human-meaningful due to their cryptographic nature, they can be associated with human-readable names or aliases.
- Decentralized: DIDs are managed on decentralized networks, removing the need for a central authority.
- Secure: The decentralized nature of DIDs, combined with cryptographic techniques, ensures that identifiers are unique, secure, and resistant to tampering.
In summary, Zooko’s Triangle presents a trade-off between human-meaningful, decentralized, and secure properties in naming systems. Decentralized Identifiers (DIDs) are an example of a system that seeks to overcome the traditional limitations of the triangle by leveraging decentralized networks and cryptographic techniques to provide a more comprehensive solution for digital identity management.
-
 @ e6817453:b0ac3c39
2023-08-12 15:41:59
@ e6817453:b0ac3c39
2023-08-12 15:41:59Organizational identifiers
Organizational identifiers have different sets of requirements and functions. It is not enough to have per-to-peer private communications. Organizations are more public, so we need publicly resolvable identifiers. DID:key satisfy this condition entirely but fails to fulfill the organization's needs.
- Organizations quite often act as issuers of credentials or attestations. For issuance, it is critical to have the possibility to rotate signing keys or even deactivate or delete identifiers if keys or issuer get compromised or to comply with security company policies.
- Organizations often require a split between the Controller of the identifier and the Identifier subject or even a transfer of the identifier subject.
- Organizations must have complete control of infrastructure and effectively manage resources and costs. The price of a single identifier should be fixed, and the method of creating new identifiers should be scalable.
- One of the essential requirements is trust and governance and transparent mechanics of proving and binding an identifier to an organizational entity and creating trust relations.
- Access to Identifier management is quite often controlled by a group of users
Nonfunctional requirements
- portability
- interoperability
- scalability
- Autonomous and control
- security
In my previous articles, we talk about Autonomous identifiers and how they differ from regular DIDs.
To recap
Autonomous identifiers (AIDs) are DIDs generated algorithmically from a crypto- graphic key pair in such a way that they are self-certifying, i.e. the binding with the public key can be verified without the need to consult any external blockchain or third party. KERI is an example of a decentralized identity technology based entirely on AIDs. © https://trustoverip.org/blog/2023/01/05/the-toip-trust-spanning-protocol/
In a previous article, I show how to create and use a did:key as an Autonomous identifier that feet well to private person-to-person secure communication.
Architectures and protocols that build on top of AIDs have few critical properties
- self-hosting and self-contained
- self-certified and Autonomous
- portable
- interoperable
- full control of infrastructure
- cost management
Nowadays, I discovered a few AIDs methods
- did:key — self-contained and public
- did:peer — self-certified, upgradable but private
- KERI based did — we waiting for did:keri method to be announced soon, but KERI infrastructure could be used to build internals of did:peer or similar methods.
- did:web — public, self-certified, and self-hosted method, but still, we have active community discussion and critics as far as it fully relays to ownership of domain name that could be stolen or re-assigned.
So we have to choose from did:key did:web and I hope in a future from did:keri.
To move forward, we need to understand the DID architecture better and how all parts are connected.
In many cases of personal or sovereign entities Subject and the Controller are the same, but for Organisations, it could have a crucial difference.
DID Subject
The DID subject is the entity that the DID represents. It can be a person, organization, device, or other identifiable entity. The DID subject is associated with a unique DID that serves as a persistent, resolvable, and cryptographically verifiable identifier. The subject is the primary focus of the identity management process and typically has one or more DIDs associated with it.
DID Controller
The DID controller is the entity (person, organization, or device) that has the authority to manage the DID Document associated with a particular DID. The DID controller can update, revoke, or delegate control of the DID Document, which contains the public keys, service endpoints, and other information required for interacting with the DID subject.
In many cases, the DID subject and DID controller can be the same entity, especially for individual users who create and manage their DIDs. However, in some situations, the DID controller may differ from the DID subject, such as when an organization manages the DIDs on behalf of its employees or when an administrator manages a device.
In summary, the DID subject is the entity the DID represents, while the DID controller is the entity with authority to manage the associated DID Document. Depending on the specific use case and requirements, these roles can be held by the same or different entities.
Key Pair
It is simple from the first point of view. Key-Pair is an asymmetric public and private key. One of the main DID functions is the distribution of public keys. DIDDoccument could contain multiple public keys with authorization rules and key roles.
Identifier
Representation of did itself. is a part of DID URI.
DID:Key

did:key identifier
DID web
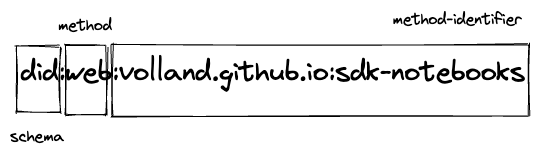
did:web
Relations
Relations between all parts of DID identifier can be illustrated in the following diagram. DID method dictate how DID identifier gets created, updated, deactivated, and resolved.
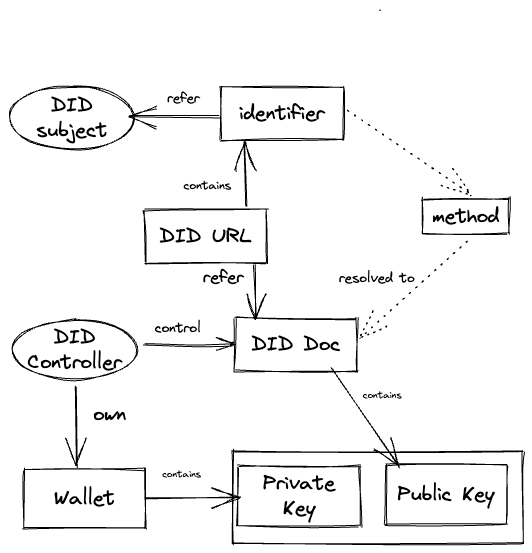
Focusing on the relations of the controller, key pairs, and the identifier is more interesting for us.
The most significant power and benefit of DID are decoupling a key pair from a controller and identifier. It allows the rotation of keys and changes the ownership of the identifier and its subject and controller. It is the main competitive advantage of DID and SSI over web3 wallets and raw keys.
The ideal case is KERI infrastructure that decouples all parties via cryptographic binding and protocols.
To discover more, read the paper.
We used did: keys as AID in the previous article. DID:key is a cryptographically bound identifier to the public key but cannot change the binding. As a result, keys couldn't be rotated in the future. The controller has no binding except to prove private key ownership via the signature-based protocol.
On the other side, DID:web does not have a cryptographic binding of an identifier to a key pair from one side. It gives an easy possibility to rotate keys but loses the verifiability of the identifier.
The most interesting part is the Controller to identifier binding in a did: web. It is based on proof of domain name ownership and website resource. As I mention, it has some security considerations and critics in a community. Still, at the same time, we get a critical mechanism that settles trust and connects identifiers to the organization entity.
The mechanism of web domain ownership is well-defined and easy to explain to other users, even outside of SSI and web5 domain. It is getting wider adoption and creating a lot of use cases for organizations. So it helps to create a trust relationship between an identifier and organizational entity in a very transparent, human-readable, and self-explained way — the identifier hosted on the corporate domain belongs to the organization. On another side, it makes the transfer of the controller almost impossible. That's why it is critical to differentiate between a subject and a controller.
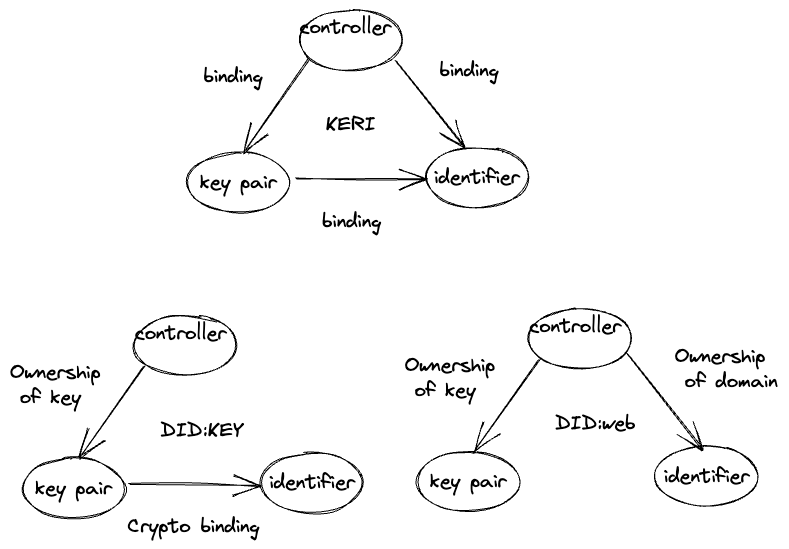
I believe that did:web still covers a lot of organizational cases and is suitable for issuing Verifiable Credentials and attestations on behalf of organizations.
Step-by-step guide on how to create and manage did:web you could find in my article
More detailed step-by-step coding guide with the live example you could find in my SSI notebooks book
-
 @ d3d74124:a4eb7b1d
2023-07-26 02:43:40
@ d3d74124:a4eb7b1d
2023-07-26 02:43:40This plan was GPT generated originally but then tweaked by myself as the idea fleshed itself out. All feedback welcome and encouraged.
Shenandoah Bitcoin
1. Executive Summary
Shenandoah Bitcoin is a for-profit community organization based in Frederick County, VA, uniquely blending the world of agriculture and STEM. Our mission is to foster community spirit, stimulate interest in agricultural technology, and promote understanding of Bitcoin, while providing enriching educational opportunities and ensuring sustainable business operations.
2. Company Description
Shenandoah Bitcoin is committed to delivering value to our local community. Our unique approach intertwines traditional agricultural practices, modern STEM concepts, and the world of digital currencies, specifically Bitcoin. Our activities cater to all age groups, focusing on fostering community engagement, hands-on learning experiences, and contributing to the overall welfare of our community.
What’s in a name?
Shenandoah Bitcoin. Shenandoah - an old and historied land. Bitcoin - a cutting edge technological advancement. Both encompass multiple industries, from energy and manufacturing, to farming and data centers. Both built using Proof of Work.
3. Services
We offer a range of services, including:
Family-friendly events: Agriculture, STEM, and Bitcoin-themed festivals, fairs, workshops, and community gatherings. Educational programs: Classes, seminars, and workshops on agricultural technology, STEM principles, and understanding and using Bitcoin. Facility Rentals: Spaces available for private events, business meetings, and community gatherings.
4. Membership Benefits
We offer tiered membership packages with benefits such as:
a. Silver Membership: Includes access to regular events, discounts on educational programs, and priority booking for facility rentals.
b. Gold Membership: All Silver benefits, free access to select educational programs, and further discounted facility rentals.
c. Platinum Membership: All Gold benefits, free access to all educational programs, highest priority and maximum discounts on facility rentals, and exclusive invitations to special events.
Member’s opting to pay in Bitcoin receive 10% off all pricing.
5. Market Analysis
Our primary market is the local community in Frederick County and Winchester, VA, which consists of various demographic groups. Our secondary market includes neighboring communities, tourists, businesses, and educational institutions interested in the intersection of agriculture, STEM, and Bitcoin. Understanding that facility use and events to be a drawing factor for all demographics, we outline demographic specific analysis below.
STEM professionals in the area may work remotely or commute toward DC and not interact much with their agricultural neighbors, but a desire for good quality food exists for many. In addition to events, drawing the STEM demographic in will be connections to CSAs, ranchers, and homesteaders for access to fresh locally grown food. Offering a child's play room adjacent to some office space, is a compelling benefit for the laptop class that is often in STEM professions.
Non-industrial food producers and homesteaders may not have the focus or resources for marketing and sales. By offering a physical touch point for them and direct connections to consumers, food producers benefit from membership. Having more options for drop off/pick up of various produced goods, makes it attractive for both the consumers and producers as coordination can be asynchronous.
Bitcoiners have a wide range of sub-demographics, including farmers and software engineers. Some travel hours over car and plane to attend bitcoin themed events. The topics of STEM and agriculture are of shared interest to non-trivially sized communities of bitcoiners. Having a physical touch point for bitcoiners will draw in some members just for that. Building fellowship is desired and sought in bitcoin.
5.1 Market Trends
The blending of agriculture, STEM fields, and Bitcoin is a unique concept with increasing interest in sustainable farming and ranching, food sovereignty, and health. Shenandoah Bitcoin is poised to tap into this growing interest and offer unique value to our community.
5.2 Market Needs
Our market requires initiatives that foster community engagement, promote understanding of agri-tech and Bitcoin, and provide a versatile space for events and learning.
6. Marketing and Sales Strategy
We will employ a blend of digital marketing, traditional advertising, and strategic partnerships. Our main marketing channels will be word of mouth, social media, local press, and our website. Partnerships with local small businesses, homesteaders, schools, agricultural organizations, and bitcoin companies will form a key part of our outreach strategy.
7. Organizational Structure
Shenandoah Bitcoin will be led by a CEO, supported by a management team responsible for daily operations, event planning, marketing, and community outreach. Event management and logistics will be handled by part-time staff and volunteers.
8. Financial Projections
Our revenue will be generated from membership fees, charges for events and educational programs, and facility rentals.
9. Funding Request
[If seeking additional funding, describe your needs and how the funds will be used]
10. Exit Strategy
Should it become necessary to dissolve the business, assets such as property, equipment, and any remaining cash reserves after meeting liabilities will be sold. Investors would receive their share of the remaining assets according to their proportion of ownership.
11. Conclusion
Shenandoah Bitcoin is a unique community organization bringing together agriculture, STEM, and Bitcoin in Frederick County, VA. Our distinctive approach is designed to deliver both profits and social impact, resonating strongly with our target market and positioning us for sustainable growth.
-
 @ 0176967e:1e6f471e
2024-07-21 11:24:21
@ 0176967e:1e6f471e
2024-07-21 11:24:21Podnikanie je jazyk s "crystal clear" pravidlami. Inštrumentalisti vidia podnikanie staticky, a toto videnie prenášajú na spoločnosť. Preto nás spoločnosť vníma často negatívne. Skutoční podnikatelia sú však "komunikátori".
Jozef Martiniak je zakladateľ AUSEKON - Institute of Austrian School of Economics
-
 @ 0176967e:1e6f471e
2024-07-21 11:20:40
@ 0176967e:1e6f471e
2024-07-21 11:20:40Ako sa snažím praktizovať LunarPunk bez budovania opcionality "odchodom" do zahraničia. Nie každý je ochotný alebo schopný meniť "miesto", ako však v takom prípade minimalizovať interakciu so štátom? Nie návod, skôr postrehy z bežného života.
-
 @ 0176967e:1e6f471e
2024-07-20 08:28:00
@ 0176967e:1e6f471e
2024-07-20 08:28:00Tento rok vás čaká workshop na tému "oranžové leto" s Jurajom Bednárom a Mariannou Sádeckou. Dozviete sa ako mení naše vnímanie skúsenosť s Bitcoinom, ako sa navigovať v dnešnom svete a odstrániť mentálnu hmlu spôsobenú fiat životom.
Na workshop je potrebný extra lístok (môžete si ho dokúpiť aj na mieste).
Pre viac informácií o oranžovom lete odporúčame pred workshopom vypočuťi si podcast na túto tému.
-
 @ 34c0a532:5d3638e4
2023-03-16 13:14:53
@ 34c0a532:5d3638e4
2023-03-16 13:14:53Most bitcoiners have their own, much different definition of what it means to orange pill a person. I’ve seen mentions of getting a taxi driver to download a lightning wallet and sending the payment in sats to them. Is that truly orange-pilling? Hmm… no. It is a great first step, but what makes you believe that that person won’t go on to shitcoins after learning about the ease of using cryptocurrency?
So, let’s define what that is in the terms of this guide.
To orange pill someone means to get them to take the first step into learning about bitcoin, money, self-custody, being sovereign, and to teach them to start questioning the world of lies we’ve been fed our entire lives.
Too poetic? Okay, here’s a more specific one:
To orange pill someone means showing them how to send and receive a bitcoin transaction, explain to them the importance of keeping their seed words safe, and showing them more articles, books and guides so they can go further down the rabbit hole.
I think that’s better, don’t you?
No matter what your definition of orange-pilling is, let’s discuss a few things first.
Orange-pilling comes from the scene in the Matrix where Morpheus offers the blue and the red pill to Neo.
This your last chance. After this there is no turning back. You take the blue pill, the story ends. You wake up in your bed and believe whatever you want to. You take the red pill, you stay in Wonderland, and I show you how deep the rabbit hole goes. Remember, all I’m offering is the truth. Nothing more. ~ Morpheus
The fact that the terms comes from the Matrix is absolutely perfect, because the Matrix is based on Plato’s Allegory of the Cave. Everybody knows the Matrix so let’s talk about the Cave. Inside the cave, people are chained up, in the dark. The only thing they can do is talk to each other and stare forward, where there’s a dim light on the cave’s wall. Someone is moving around objects, throwing shadows on the wall. The people can never see the three-dimensional object, they can only see a shadow, a projection of it, so their world is limited by that knowledge.
Someday a group of people manage to break out of the Cave. They go out into the light, their eyes hurt, the world is massive, they get a panic attack by the lack of a rock ceiling on top of them. It’s vast, it’s too much to bear. And they run back into the cave and tell everyone what they saw, that it’s too bright, too open, too much everything. Objects are real, there’s light everywhere and colours. So many colours, not just the flame, the rock and the shadow.
And they don’t believe them. Maybe they even get angry at them and attack them. Who are these fools to claim that the world is not what they think it is? Who are they to suggest that we’ve all been lied to all our lives?
And that’s the first thing you need to keep in mind when trying to orange pill someone.
Why do some people find it so hard to believe in bitcoin?
The answer is simple. It’s because understanding bitcoin requires acknowledging you’ve been tricked your entire life.
The culture shock is real, I’ve been through it. The stages are as follows:
What is money? You start to learn what money really is, and how fundamentally flawed the Keynesian system has become. You see that the only way forward is by a hard money standard, whether that’s gold or bitcoin. Then you realise that in a world of information, the only logical step is bitcoin. Then why bitcoin? You start to read about it’s properties. It’s antifragile, decentralised. Why is that important? Nobody can control, it great. Why is it like gold that can be attached to an email? Then there’s the anger and disbelief. We’ve been fooled. Why doesn’t everybody see this? You read everything about bitcoin, you listen to podcasts, talk on bitcoin twitter and nostr with other plebs. Nobody seems to have all the answers but they make far more sense than the lies of the mainstream media. You talk to your friends and family, you come off as crazy at best. As I said, you have to acknowledge the trauma the other person is going through. It’s a culture shock, and not many want to go through with it. Think of Plato’s Allegory of the Cave, people who got out into the world went back and told everyone that there’s more to life than the shadows on the wall. Or, the same allegory being told by the Matrix, with Cypher wanting to go back, to forget.
We call that Bitcoin Derangement Syndrome, BDS. It’s hilarious but it’s so real. Many early bitcoiners, people who have spend years of their lives either advocating for it or working on it, some making or losing fortunes in the process, go back to the fiat world, shift gears completely, rant and rave against bitcoin and dive back in the Matrix, the Cave, taking the blue pill. They want to be fiat rich, they lie and delude themselves that everything is okay in the world and if they get just enough money they’d be okay.
But they won’t. This is real, and no matter how many lies they tell themselves things will not change unless we change them ourselves. Babies are dying, that’s true. In wars, in artificially induced poverty, in carrying on with the Keynesian ways of thinking of endless imperial expansion and exploitation.
I’ll be honest, bitcoin rewires your brain.
Do you really wanna force that on people?
Yes?
Then let’s read on.
Why is it sometimes so hard to explain, persuade or convince people about bitcoin? Here’s a harsh truth. It’s because you’re the counterparty risk.
When your car breaks down, you go to a mechanic, you seek expert knowledge. He tells you what’s wrong and you generally accept it. Why? Because unless you’re an expert on cars, you don’t have pre-existing knowledge about this specific situation. Nature abhors a vacuum. The mechanic’s knowledge and expertise fills up that vacuum of knowledge.
Why is it different with bitcoin, then?
Because most people believe they already understand money. There’s no vacuum for their knowledge to fill. Like a woman going to a male gynecologist thinking she knows better because she’s the one with the female body, a nocoiner believes they know better because, see? They have been handling and making money all their lives! Who are you to claim things aren’t how they used to think they are?
Yes, sure. You’re the one with the female body, you’re the one with the wallet. But have you actually taken the time to study it? Have you invested the necessary six years in medical school or the 100 hours it takes to grasp bitcoin?
No.
But they don’t accept that. When you make statements about bitcoin, it collides with their pre-existing frame of reference. When that happens, their mind reflexively casts doubts on the new information, actively fights it and rejects it, because it doesn’t conform to what they know. Their mind is the bearer asset, you are the counterparty risk.
Okay, great. How do you overcome this, then?
By taking the time with them. You can’t force someone to get orange-pilled, it’s not shoving knowledge down their throats. They have to do it themselves, so you start small. Plant a seed. Make them question what they know. That tiny seed, just like in Inception, will grow and push aside the other propaganda in their minds, leaving some space for new information to fill the void.
“Why did they stop having money backed by gold?”
That’s one seed.
“Who prints all these new billions?”
Another. Take your pick, it depends on the person you’re talking to.
A good question makes the nocoiner access their accepted knowledge. They usually think they have the answer and you should listen to it, not shutting it down. Ask them to research it further, to back their claims, to look things up. If they don’t have the knowledge, a new vacuum is created and their curiosity will want to fill it up.
Nocoiner: Bitcoin isn’t backed by anything.
You: Okay. Then what would make good money in its place?
Make them talk by asking questions. As they talk, they’ll realise they have massive gaps in their knowledge. You can help them then, but they themselves have to fill up those gaps by asking more questions and getting them to talk more. Why? Because if someone tells something to themselves they will believe it much easier than having you say it to them. Try and lead them to conclusion, a revelation.
When persuading someone, the person talking the most is the one really getting persuaded. Why? Because when you talk you engrave those words into your brain as facts.
Nocoiner: Bitcoin wastes too much energy.
You: How do you determine how much is too much energy to use?
You will never change their minds, they have to change it themselves. You can only help show them the way, they’re the ones that have to do it. Questions are the key to that process.
Tell them less, ask more.
What questions make people curious about bitcoin? You never know, it depends on what ails the person. Think about their pain. If they’re living in Turkey or Argentina, for example, their pain is massive inflation. You might say, “You’re already using USD to protect your monetary value against inflation, right? How about adding BTC to the mix?”
People in those countries generally grasp this concept a lot quicker. The local lira is the crap kind of money, they spend it often. The USD is the good kind of money, they save it, spending it only when absolutely necessary. And gold is the best kind, keeping it hidden in safes and mattresses. Only to be spent in an emergency. They don’t have the financial privilege to insulate them from the need for bitcoin, they already get these layers of hardness in their money, so bitcoin is a lot easier for them.
“What is money?” is another good question. Most people will answer it, and of course it will be flawed and all over the place. Then you might say, “It’s the promise of future value,” and then discuss how bitcoin has a monetary policy that’s planned out for the next 120 years and how nodes and miners facilitate that design. And especially point out how hard it is to change.
“What happened in 1971?” That’s a good one. Get them to look up the fiat monetary system and figure out how it’s not backed by anything. Get them angry at the Keynesian economists, how they’ve ruined entire countries. 2008 money crisis? Inevitable, under the fiat standard. Forget about bitcoin, point your finger towards the rot. It’s all historical fact, they can’t call you a conspiracy theorist. Most people still think that money is backed by gold. Get them to tell it to other people, see their reactions.
This was a part of my guide. Let me know what you think. Soon to be posted at https://georgesaoulidis.com/how-to-orange-pill-people/
-
 @ 3bf0c63f:aefa459d
2024-06-13 15:40:18
@ 3bf0c63f:aefa459d
2024-06-13 15:40:18Why relay hints are important
Recently Coracle has removed support for following relay hints in Nostr event references.
Supposedly Coracle is now relying only on public key hints and
kind:10002events to determine where to fetch events from a user. That is a catastrophic idea that destroys much of Nostr's flexibility for no gain at all.- Someone makes a post inside a community (either a NIP-29 community or a NIP-87 community) and others want to refer to that post in discussions in the external Nostr world of
kind:1s -- now that cannot work because the person who created the post doesn't have the relays specific to those communities in their outbox list; - There is a discussion happening in a niche relay, for example, a relay that can only be accessed by the participants of a conference for the duration of that conference -- since that relay is not in anyone's public outbox list, it's impossible for anyone outside of the conference to ever refer to these events;
- Some big public relays, say, relay.damus.io, decide to nuke their databases or periodically delete old events, a user keeps using that big relay as their outbox because it is fast and reliable, but chooses to archive their old events in a dedicated archival relay, say, cellar.nostr.wine, while prudently not including that in their outbox list because that would make no sense -- now it is impossible for anyone to refer to old notes from this user even though they are publicly accessible in cellar.nostr.wine;
- There are topical relays that curate content relating to niche (non-microblogging) topics, say, cooking recipes, and users choose to publish their recipes to these relays only -- but now they can't refer to these relays in the external Nostr world of
kind:1s because these topical relays are not in their outbox lists. - Suppose a user wants to maintain two different identities under the same keypair, say, one identity only talks about soccer in English, while the other only talks about art history in French, and the user very prudently keeps two different
kind:10002events in two different sets of "indexer" relays (or does it in some better way of announcing different relay sets) -- now one of this user's audiences cannot ever see notes created by him with their other persona, one half of the content of this user will be inacessible to the other half and vice-versa. - If for any reason a relay does not want to accept events of a certain kind a user may publish to other relays, and it would all work fine if the user referenced that externally-published event from a normal event, but now that externally-published event is not reachable because the external relay is not in the user's outbox list.
- If someone, say, Alex Jones, is hard-banned everywhere and cannot event broadcast
kind:10002events to any of the commonly used index relays, that person will now appear as banned in most clients: in an ideal world in which clients followednprofileand other relay hints Alex Jones could still live a normal Nostr life: he would print business cards with hisnprofileinstead of annpuband clients would immediately know from what relay to fetch his posts. When other users shared his posts or replied to it, they would include a relay hint to his personal relay and others would be able to see and then start following him on that relay directly -- now Alex Jones's events cannot be read by anyone that doesn't already know his relay.
- Someone makes a post inside a community (either a NIP-29 community or a NIP-87 community) and others want to refer to that post in discussions in the external Nostr world of
-
 @ aa55a479:f7598935
2023-02-20 13:44:48
@ aa55a479:f7598935
2023-02-20 13:44:48Nostrica is the shit.
-
 @ 6bae33c8:607272e8
2024-07-18 19:19:16
@ 6bae33c8:607272e8
2024-07-18 19:19:16These are my very preliminary RB rankings, my only research being the RotoWire depth charts and player notes.
**Tier 1
Christian McCaffrey**
He’s 28 years old, has 1,402 career carries including the postseason and weighs only 205 pounds at 5-11. But McCaffrey is arguably the greatest running back all time, when you include the pass catching, and he’s in the league’s best system for backs. Health is really the only variable, and anyone can get hurt.
**Tier 2
Breece Hall, Bijan Robinson, Saquon Barkley, Jonathan Taylor**
These are the three-down backs with elite skill sets. Hall should be better another year removed from the ACL tear and playing with a better QB, Robinson should get the heavy usage he merits with Arthur Smith gone, Barkley finally gets a quality offensive line and QB and Taylor plays next to a running QB and has little competition for carries.
**Tier 3
Jahmyr Gibbs, De’Von Achane, Kyren Williams, Travis Etienne**
These are the little guys, all of whom can run and catch passes, plus Etienne. Williams is the biggest risk as an early-down high-workload guy, but he was also insanely productive when he played in Sean McVay’s lead-back-friendly system. Gibbs seems like peak Alvin Kamara, only faster and Achane in the Miami offense was the most efficient back in league history by a mile. I originally had Etienne in Tier 4, but he doesn’t have much competition for the job and should be a three-down back.
**Tier 4
Isaiah Pacheco, Josh Jacobs, Joe Mixon, James Cook, David Montgomery, Derrick Henry, Kenneth Walker, Racchad White, James Conner, Rhamondre Stevenson, Zack Moss, Javonte Williams, Devin Singletary **
This is a big tier, but these are all the incomplete players guaranteed reps if healthy. Pacheco could be moved to Tier 3, but Patrick Mahomes doesn’t check down to the back all that often, and Pacheco rarely gets to 20 carries in a game. Jacobs is a beast but has a ton of mileage in a short span and fell off last year. Mixon is another old warhorse with a lot of mileage, albeit also in a good situation. Cook suffers due to Josh Allen’s goal-line prowess and tendency to take off rather than check down. Montomgery will cede the third-down work, Henry is old and doesn’t catch many passes, Walker splits carries, gets hurt often, White is a ham and egger who happened to see a huge workload, Conner is 29 and always misses time, Stevenson is a workhorse on a bad team, Moss is an average back in a good spot, Williams is another year off the injury, but on a bad team and Singletary is the clear lead back on a poor offense.
**Tier 5
Tony Pollard, D’Andre Swift, Jonathan Brooks, Alvin Kamara, Brian Robinson, Jaylen Warren, Austin Ekeler, Chuba Hubbard, Zamir White, Raheem Mostert, Aaron Jones, Najee Harris, Nick Chubb, Tyjae Spears, Trey Benson, Zach Charbonnet ** These are mostly timeshare backs, with the exception of Kamara whose efficiency fell through the floor and White who I’m not convinced will lock down the job all year.
**Tier 6
Kenneth Gainwell, Rico Dowdle, Gus Edwards, Jerome Ford, Zeke Elliott, Roschon Johnson, Jaylen Wright, Bucky Irving, JK Dobbins, Antonio Gibson, Chase Brown, Elijah Mitchell, Jaleel McLaughlin, Tyler Algeier, MarShawn Lloyd**
This is the backup tier, all of whom probably need an injury ahead of them to break out.
These rankings will change, but I like to get my preliminary ones down on paper before I get influenced by ADP and training camp hype.
-
 @ 634bd19e:2247da9b
2023-02-15 08:00:45
@ 634bd19e:2247da9b
2023-02-15 08:00:45かけるのこれ? 日本語入力の取り扱いイベントがおかしいw
-
 @ 8d34bd24:414be32b
2024-07-17 16:20:24
@ 8d34bd24:414be32b
2024-07-17 16:20:24*** I’ve had several inspirations to write on subjects other than the fruits of the Spirit, so we will take a brief break on that series and do a couple of stand alone posts and then go back and finish the Fruits of the Spirit Series.
I was reading Job and saw something I’d never seen before.
Job, a man the Bible refers to as “… blameless, upright, fearing God and turning away from evil.” (Job 1:1b), loses his children, his wealth, and then his health. He is suffering immensely. Several friends come to console him, but instead start falsely accusing him of horrible sins. They should’ve known better and they shouldn’t have judged Job based on what was happening to him instead of how he lived his life.
After losing his family, his wealth, and his health, now his friends are defaming his godly reputation. In one of his soliloquies, after naming all of the things he has lost he prays this prayer:
“Oh that my words were written! Oh that they were inscribed in a book! That with an iron stylus and lead They were engraved in the rock forever! (Job 19:23-24)
I think every other time I had read these verses I just thought that was an odd request, but I saw something different this time. Job prayed that “Oh that my words were written! Oh that they were inscribed in a book!” Little did Job know, God would write his words in the Bible, God’s book, the most published book in history. His words would be read as an example to us for over 4,000 years. He couldn’t have imagined that his prayer would be answered this way.
He prayed, “That with an iron stylus and lead, They were engraved in the rock forever!” His words are written by God so they will last as long as the rocks on which he wished them to be engraved. Job didn’t know his prayer would/was being answered, but it was. It was being answered in ways beyond his greatest imagining. When God answers, he usually answers in big ways, even if not in our timing or in our ways.
“For as the heavens are higher than the earth, So are My ways higher than your ways And My thoughts than your thoughts. (Isaiah 55:9)
As abandoned as Job felt and as unfairly as he felt he was treated, he never lost faith in God or His goodness. The next verse in Job states:
As for me, I know that my Redeemer lives, And at the last He will take His stand on the earth. (Job 19:25)
There may be times it feels like God is not with you, but He is. There may be times it feels like He isn’t listening, but He is. There may be times it feels like He will never answer your prayers, but He will. The important thing is to never lose faith in His power, His goodness, or His love.
God’s answers to prayers may not be exactly what you asked for and they rarely happen in our desired timing, but He gives us what we need and what is for our and other’s best and He never makes a mistake.
Trust Jesus.
your sister in Christ,
Christy
Bible verses are NASB (New American Standard Bible) 1995 edition unless otherwise stated
-
 @ 8d34bd24:414be32b
2024-07-17 02:15:54
@ 8d34bd24:414be32b
2024-07-17 02:15:54Once again here are the fruits of the Spirit as defined in Galatians 5.
But the fruit of the Spirit is love, joy, peace, patience, kindness, goodness, faithfulness, gentleness, self-control; against such things there is no law. (Galatians 5:22-23) {emphasis mine}
What is Good?
And someone came to Him and said, “Teacher, what good thing shall I do that I may obtain eternal life?” And He said to him, “Why are you asking Me about what is good? There is only One who is good; but if you wish to enter into life, keep the commandments.” Then he said to Him, “Which ones?” And Jesus said, “You shall not commit murder; You shall not commit adultery; You shall not steal; You shall not bear false witness; Honor your father and mother; and You shall love your neighbor as yourself.” The young man said to Him, “All these things I have kept; what am I still lacking?” Jesus said to him, “If you wish to be complete, go and sell your possessions and give to the poor, and you will have treasure in heaven; and come, follow Me.” But when the young man heard this statement, he went away grieving; for he was one who owned much property.
And Jesus said to His disciples, “Truly I say to you, it is hard for a rich man to enter the kingdom of heaven. Again I say to you, it is easier for a camel to go through the eye of a needle, than for a rich man to enter the kingdom of God.” When the disciples heard this, they were very astonished and said, “Then who can be saved?” And looking at them Jesus said to them, “With people this is impossible, but with God all things are possible.” (Matthew 19:16-26)If the Bible says that there is no one good except God, how can we be good or show the goodness expected by God? We can only do good and be good if we “abide in the vine,” if we have the Spirit within us. This is because only God is good. We can have the fruit of the Spirit, goodness, only when we have the Spirit of God within us. Our goodness comes from Him. He enables us to overcome our sin nature and to act within His very good, sinless nature through Him.
Goodness Through Obedience & a Right Attitude
Goodness is obeying God, but it is more, it is obeying with a totally right attitude. It is submitting our lives fully to God. It is submitting to His will and His plan including putting the good of others above our own good, just as Jesus did when he came down to Earth, lived a perfect, sinless life, and died on the cross to take away our sins. We can’t just obey by our own power.
“You have heard that the ancients were told, ‘You shall not commit murder’ and ‘Whoever commits murder shall be liable to the court.’ But I say to you that everyone who is angry with his brother shall be guilty before the court; and whoever says to his brother, ‘You good-for-nothing,’ shall be guilty before the supreme court; and whoever says, ‘You fool,’ shall be guilty enough to go into the fiery hell. … “You have heard that it was said, ‘You shall not commit adultery’; but I say to you that everyone who looks at a woman with lust for her has already committed adultery with her in his heart. (Matthew 5:21-22,27-28)
We can’t just obey the letter of the law and be good. If you notice, it is the thought as well as the action that we are to avoid. Hating another is counted as murder because of the righteous nature of God. Lusting for another is considered adultery because of the Holiness of God. We must have a change of heart through faith in Jesus and through the indwelling of the Holy Spirit, that changes our motivations and the way we think. This goodness is unlike anything the world has seen and it draws people to Jesus like flies to honey.
Obey as God Enables
While He was in Bethany at the home of Simon the leper, and reclining at the table, there came a woman with an alabaster vial of very costly perfume of pure nard; and she broke the vial and poured it over His head. But some were indignantly remarking to one another, “Why has this perfume been wasted? For this perfume might have been sold for over three hundred denarii, and the money given to the poor.” And they were scolding her. But Jesus said, “Let her alone; why do you bother her? She has done a good deed to Me. For you always have the poor with you, and whenever you wish you can do good to them; but you do not always have Me. She has done what she could; she has anointed My body beforehand for the burial. Truly I say to you, wherever the gospel is preached in the whole world, what this woman has done will also be spoken of in memory of her.” (Mark14:3)
The goodness expected by Jesus is not the goodness of the world. It is different. Frequently the goodness of the Spirit is considered foolishness by people. Goodness is acting according to the will of God and for His eternal plan.
The thing that really stands out to me in the passage, is the statement “She has done what she could.” All God asks of us is to obey His commands and submit to His Spirit. We are not responsible for the result. We are not responsible for things we cannot control. God has got this. God has an eternal plan that will come to fruition. We are just blessed to be used by Him to make His plan a reality. Knowing the result is in His hands really takes the pressure off. When we trust and obey Him, He will use our faithfulness for good and give us His goodness.
This passage should be the cry of our hearts.
You have dealt well with Your servant,
O Lord, according to Your word.
Teach me good discernment and knowledge,
For I believe in Your commandments.
Before I was afflicted I went astray,
But now I keep Your word.
You are good and do good;
Teach me Your statutes. (Psalms 119:65-68)We need to study His commandments and statutes in order to know what God wants us to do. We should keep His word. We should do good as He does good.
Even though our goodness is done through the power of the Spirit and under the covering of Jesus, we still need to know God’s commands to live a life of goodness. We need to actively learn what He wants from us. We cannot truly live a good life on our own, but that doesn’t mean we should be passive. We are called to actively obey His commands. We are called to study His word. We are called to speak the truth (that we learn from the Bible). We are called to follow Him. We are not called to lie around like a puppet waiting for the puppeteer to move us and speak for us.
Goodness Now, but Results In God’s Timing
Sow your seed in the morning and do not be idle in the evening, for you do not know whether morning or evening sowing will succeed, or whether both of them alike will be good. (Ecclesiastes 11:6)
God tells us to obey Him and to do what is right at every opportunity (not waiting for what we think is the best time). We then must leave the results to Him. When we are kind to someone, sometimes they will be kind in return, but sometimes they won’t. When we witness to others, sometimes they will repent and turn to God, but sometimes they won’t. We are only responsible for the witnessing, and obeying now. The results are up to God.
This should give us peace knowing that we can’t mess things up by doing it wrong. God can use the most awkward words and actions for His glory, but the most silver tongued orator or the most hard working evangelist can’t bring about a single conversion if God is not part of it. As we obey we must always keep in mind that all of our goodness comes from God, not through our works.
Use of Our Wealth for the Good of Others
Instruct those who are rich in this present world not to be conceited or to fix their hope on the uncertainty of riches, but on God, who richly supplies us with all things to enjoy. Instruct them to do good, to be rich in good works, to be generous and ready to share, storing up for themselves the treasure of a good foundation for the future, so that they may take hold of that which is life indeed. (1 Timothy 6:17-19)
There are many kinds of wealth. We may have the obvious wealth, money and property. We can also have a wealth of friends, a wealth of opportunities, a wealth of influence, or a wealth of skills. Of course the greatest wealth is faith in Jesus Christ, our Savior. God calls us to share this wealth. Part of the goodness we get from the Spirit is the generosity to share this wealth with those around us. We can’t share with everyone, but we can share what we have been given with those near us, who are in need.
I’ve said to people for a while that I have had two periods of time in my life: when I had more time than money and when I had more money than time. We will have different stages in life when you have different things to share. For example, if you are a parent of young children or a caregiver to someone with major health problems, you may not have much time to give to others, but there may be other things you can give. God calls us to be generous with what we have. He calls us to be stewards of His treasure. If you have a loving family, that is a gift from God. If you have a good church, that is a gift from God. If you have skills, faith, or knowledge, they are gifts from God. If you have monetary wealth, that is a gift from God. If you have influence, that is a gift from God. We should use all of these for the good of those around us.
If you have a loving family, you could invite over a young person who doesn’t have family close by or comes from a broken family and show them what a loving, Godly family looks like. If you have a Godly, loving, Bible-believing church, invite those around you to attend. If you have skills, use them to teach another or to help someone in need. If you have faith, talk about your faith to those who are suffering or doubting. If you have knowledge, teach those who don’t know as much. This may be speaking to a large audience, but it also may be talking to one person at your home or at a coffee shop. If you have monetary wealth, you may be called to give generously to those in need or ministries that share the Gospel. Whatever God has given you, you are called to share this with others. This is part of the goodness of God.
Every good thing given and every perfect gift is from above, coming down from the Father of lights, with whom there is no variation or shifting shadow. (James 1:17)
We are given good things so we can share the goodness of God with others.
Be Good as God is Good
And we know that God causes all things to work together for good to those who love God, to those who are called according to His purpose. (Romans 8:28)
“God causes all things to work together for good,” so we should also act in goodness for the good of others. We should actively seek the good of others, not just wait until the moment seems right. That moment may never come.
I still regret two missed opportunities in particular. Neither seemed like a big deal at the time, but I still think about them decades later.
In high school, I was at school late for some reason. I was talking to a fellow student. It ends up that student was stuck at school and didn’t have a ride home. They hinted that they needed a ride, but I was too focused on my own schedule that I missed it. It wasn’t till I got home that I realized they were asking for a ride without asking. I totally missed it. I would’ve been willing to give them a ride, but I was too self-focused to catch the hint. I have no idea how long they had to stay at school till they got a ride. I was not seeking that person’s good. I was seeking my own.
Another event happened when my husband and I were driving to church one morning. As we drove out of our neighborhood, there was a little old lady struggling taking the trash out to the curb. It would’ve been easy to stop and help her. It wouldn’t have taken more than a minute or two, but we were in a hurry and didn’t stop. (I don’t think my husband saw her because he was driving and paying attention to the road.) I still wish I had stopped to help that lady. I missed an opportunity to do good to another because I was focused on myself. I may have been doing a “good” thing, going to church, but missed the best thing, helping and witnessing to a struggling, old lady. The goodness of the Spirit is doing God’s best instead of what is merely good.
Let us not lose heart in doing good, for in due time we will reap if we do not grow weary. So then, while we have opportunity, let us do good to all people, and especially to those who are of the household of the faith. (Galatians 6:9-10) {emphasis mine}
Sometimes we may get tired of doing good when it feels like no good is coming from it, but God tells us to “not lose heart in doing good.” God’s plan is never according to our timing. People talk about certain individuals being so smart that when making decisions “they play 3D chess.” In other words, they are seeing so many steps that a normal person doesn’t see and can therefore make better decisions. God doesn’t just “play 3D chess,” He plays more than 1,000,000D chess. We can’t even imagine all of the variables that He manages to bring His plan to fruition. We should never lose heart and we should continue to “do good to all people, and especially to those who are of the household of the faith.”
Do not deliver me over to the desire of my adversaries,
For false witnesses have risen against me,
And such as breathe out violence.
I would have despaired unless I had believed
that I would see the goodness of the Lord
In the land of the living. (Psalms 27:12-13)All Christians know that God and Good (is there a difference?) win in the end and that there will be no pain and suffering in heaven, but we long to see that same goodness here on Earth, “in the land of the living.” If we are diligently watching, God gives us peeks at the fulfillment of His plan, glimpses of the goodness being accomplished, and flashes of the positive influences we are helping to bring about. Don’t be so focused on your current cares that you miss the wonderous works that God is doing, especially those being done through your life.
How great is Your goodness,
Which You have stored up for those who fear You,
Which You have wrought for those who take refuge in You,
Before the sons of men! (Psalms 31:19)As we deal with the evil of the world, we need to keep doing good and “take refuge in” God’s goodness and the power of His Spirit.
O taste and see that the Lord is good; How blessed is the man who takes refuge in Him! (Psalms 34:8)
Slander, Not Hypocrisy
And keep a good conscience so that in the thing in which you are slandered, those who revile your good behavior in Christ will be put to shame. For it is better, if God should will it so, that you suffer for doing what is right rather than for doing what is wrong. For Christ also died for sins once for all, the just for the unjust, so that He might bring us to God, having been put to death in the flesh, but made alive in the spirit; (1 Peter 3:16-18) {emphasis mine}
One thing we need to keep in mind is that we will be persecuted and derided for living a good Christian life and imitating Jesus. We need to make sure that all of the accusations are for having Christ-like goodness, and not for being lazy, sinful, or hypocritical. Many people have turned away from Jesus because of the hypocrisy of those who call themselves Christians or organizations that call themselves the Church. Don’t be the reason someone turns away from God. Live out God’s goodness, so that people want to learn more about being a Christian and knowing Jesus.
Bad Company Corrupts Good Morals
We get our goodness from obeying God, studying His word, and trusting in His power, but most of all we get our goodness from the indwelling of the Holy Spirit and the covering of the Blood of the Lamb. We are told that we are “washed white as snow.”
If you are a parent, you’ve probably experience your child being dressed up in his/her Sunday best, but then they decided to go hug the hairy dog, play in a mud puddle, or some equally messy endeavor. That beautiful, clean outfit, gets dirty and ruined. In the same way, spending time with ungodly, bad company can dirty our “white as snow” soul and keep us from the goodness that God intends. If we are truly a child of God, this doesn’t mean we lose our salvation or anything like that, but we do become unfruitful.
Do not be deceived: “Bad company corrupts good morals.” Become sober-minded as you ought, and stop sinning; for some have no knowledge of God. I speak this to your shame. (1 Corinthians 15:33-34)
The Bible tells us to be in the world, sharing the Gospel, but not to be of the world, living like the rest of sinful mankind. We need to be careful to not use the excuse “that we are witnessing” to be of the world as an excuse for living a worldly life. Is our sending our kids to government schools actually just doing what is easy? Is our hanging out at the bar to witness just an excuse to drink or hangout with our ungodly friends? Are we saying we are being wise stewards with our money, but in reality we are refusing to give according to God’s will because we are saving up emergency money to provide for ourselves because we don’t trust God to provide for us? Sometimes it is hard to judge our motives because we lie to ourselves as well as to God. Be careful that we don’t let “little” lies and “little” excuses draw us away from God’s will. Be careful that we aren’t so much in the world, that we are no good to anyone.
Sometimes it is hard to find that right balance. Some people so avoid the worldly sinners that they are of no use to anyone, especially God. Some people are so in the world that they are led astray and look no different than the ungodly sinners around them. We need to pray that God would guide us to witness to the sinners without being changed negatively by their presence. We need to have Godly friends who keep us on track and encourage our walk with God. We need to attend a Bible believing church, so we are regularly taught God’s word and guided in how to apply it. We need to read the Bible daily so we are filling our minds with God’s goodness and not the sinful culture of the world. We want our goodness to shine out and point to the goodness of God. We want our goodness to be the light that draws those around us to salvation.
Goodness Unlike Anything Known to Man
As a Christian, being good and showing goodness to fellow believers should be fairly easy (in the Spirit, but not of ourselves). On the other hand, even for those walking closely with Christ, there is almost always someone to whom it is hard to act with goodness and kindness because they have so mistreated and hurt us. We are called to be good to them as much as we are to those we care about. God’s goodness is acting in a way that is so contrary to human nature that it is hard for people to comprehend. It makes those who don’t know God say, “Are you for real?”
Bless those who persecute you; bless and do not curse. Rejoice with those who rejoice, and weep with those who weep. Be of the same mind toward one another; do not be haughty in mind, but associate with the lowly. Do not be wise in your own estimation. Never pay back evil for evil to anyone. Respect what is right in the sight of all men. If possible, so far as it depends on you, be at peace with all men. Never take your own revenge, beloved, but leave room for the wrath of God, for it is written, “Vengeance is Mine, I will repay,” says the Lord. “But if your enemy is hungry, feed him, and if he is thirsty, give him a drink; for in so doing you will heap burning coals on his head.” Do not be overcome by evil, but overcome evil with good. (Romans 12:14-21) {emphasis mine}
The key to goodness is this, “Do not be overcome by evil, but overcome evil with good.”
*** I’ll include a few more verses on goodness below for those who want to continue studying God’s word on goodness.
Trust Jesus.
Let love be without hypocrisy. Abhor what is evil; cling to what is good. 10Be devoted to one another in brotherly love; give preference to one another in honor; 11not lagging behind in diligence, fervent in spirit, serving the Lord; 12rejoicing in hope, persevering in tribulation, devoted to prayer, 13contributing to the needs of the saints, practicing hospitality. (Romans 12:9-13) {emphasis mine}
Therefore let us not judge one another anymore, but rather determine this—not to put an obstacle or a stumbling block in a brother’s way. I know and am convinced in the Lord Jesus that nothing is unclean in itself; but to him who thinks anything to be unclean, to him it is unclean. For if because of food your brother is hurt, you are no longer walking according to love. Do not destroy with your food him for whom Christ died. Therefore do not let what is for you a good thing be spoken of as evil; for the kingdom of God is not eating and drinking, but righteousness and peace and joy in the Holy Spirit. For he who in this way serves Christ is acceptable to God and approved by men. So then we pursue the things which make for peace and the building up of one another. (Romans 14:13-19) {emphasis mine}
The sins of some men are quite evident, going before them to judgment; for others, their sins follow after. Likewise also, deeds that are good are quite evident, and those which are otherwise cannot be concealed. (1 Timothy 5:24-25) {emphasis mine}
FYI, my following posts will continue going through each of the individual fruits of the Spirit listed in Galatians 5
Bible verses are NASB (New American Standard Bible) 1995 edition unless otherwise stated
-
 @ 1aa437b3:51119dbd
2024-07-15 02:11:13
@ 1aa437b3:51119dbd
2024-07-15 02:11:13I will confess, I went the pirate way with Jellyfinn and Plex and quickly got a letter from my ISP that I was naughty. So if I am going to do this legit, what is the best service? I do have a bunch of stuff on Amazon, and I trust they will stick around, but my god there is no rhyme or reason to organization. Apple... well it's Apple. And of course Google Play/Youtube.. and I don't know what others are out there.. but share what you use and why.. thanks, cheers!
originally posted at https://stacker.news/items/608576
-
 @ 3bf0c63f:aefa459d
2024-06-12 15:26:56
@ 3bf0c63f:aefa459d
2024-06-12 15:26:56How to do curation and businesses on Nostr
Suppose you want to start a Nostr business.
You might be tempted to make a closed platform that reuses Nostr identities and grabs (some) content from the external Nostr network, only to imprison it inside your thing -- and then you're going to run an amazing AI-powered algorithm on that content and "surface" only the best stuff and people will flock to your app.
This will be specially good if you're going after one of the many unexplored niches of Nostr in which reading immediately from people you know doesn't work as you generally want to discover new things from the outer world, such as:
- food recipe sharing;
- sharing of long articles about varying topics;
- markets for used goods;
- freelancer work and job offers;
- specific in-game lobbies and matchmaking;
- directories of accredited professionals;
- sharing of original music, drawings and other artistic creations;
- restaurant recommendations
- and so on.
But that is not the correct approach and damages the freedom and interoperability of Nostr, posing a centralization threat to the protocol. Even if it "works" and your business is incredibly successful it will just enshrine you as the head of a platform that controls users and thus is prone to all the bad things that happen to all these platforms. Your company will start to display ads and shape the public discourse, you'll need a big legal team, the FBI will talk to you, advertisers will play a big role and so on.
If you are interested in Nostr today that must be because you appreciate the fact that it is not owned by any companies, so it's safe to assume you don't want to be that company that owns it. So what should you do instead? Here's an idea in two steps:
- Write a Nostr client tailored to the niche you want to cover
If it's a music sharing thing, then the client will have a way to play the audio and so on; if it's a restaurant sharing it will have maps with the locations of the restaurants or whatever, you get the idea. Hopefully there will be a NIP or a NUD specifying how to create and interact with events relating to this niche, or you will write or contribute with the creation of one, because without interoperability none of this matters much.
The client should work independently of any special backend requirements and ideally be open-source. It should have a way for users to configure to which relays they want to connect to see "global" content -- i.e., they might want to connect to
wss://nostr.chrysalisrecords.com/to see only the latest music releases accredited by that label or towss://nostr.indiemusic.com/to get music from independent producers from that community.- Run a relay that does all the magic
This is where your value-adding capabilities come into play: if you have that magic sauce you should be able to apply it here. Your service, let's call it
wss://magicsaucemusic.com/, will charge people or do some KYM (know your music) validation or use some very advanced AI sorcery to filter out the spam and the garbage and display the best content to your users who will request the global feed from it (["REQ", "_", {}]), and this will cause people to want to publish to your relay while others will want to read from it.You set your relay as the default option in the client and let things happen. Your relay is like your "website" and people are free to connect to it or not. You don't own the network, you're just competing against other websites on a leveled playing field, so you're not responsible for it. Users get seamless browsing across multiple websites, unified identities, a unified interface (that could be different in a different client) and social interaction capabilities that work in the same way for all, and they do not depend on you, therefore they're more likely to trust you.
Does this centralize the network still? But this a simple and easy way to go about the matter and scales well in all aspects.
Besides allowing users to connect to specific relays for getting a feed of curated content, such clients should also do all kinds of "social" (i.e. following, commenting etc) activities (if they choose to do that) using the outbox model -- i.e. if I find a musician I like under
wss://magicsaucemusic.comand I decide to follow them I should keep getting updates from them even if they get banned from that relay and start publishing onwss://nos.lolorwss://relay.damus.ioor whatever relay that doesn't even know what music is.The hardcoded defaults and manual typing of relay URLs can be annoying. But I think it works well at the current stage of Nostr development. Soon, though, we can create events that recommend other relays or share relay lists specific to each kind of activity so users can get in-app suggestions of relays their friends are using to get their music from and so on. That kind of stuff can go a long way.
-
 @ 3bf0c63f:aefa459d
2024-05-24 12:31:40
@ 3bf0c63f:aefa459d
2024-05-24 12:31:40About Nostr, email and subscriptions
I check my emails like once or twice a week, always when I am looking for something specific in there.
Then I go there and I see a bunch of other stuff I had no idea I was missing. Even many things I wish I had seen before actually. And sometimes people just expect and assume I would have checked emails instantly as they arrived.
It's so weird because I'm not making a point, I just don't remember to open the damn "gmail.com" URL.
I remember some people were making some a Nostr service a while ago that sent a DM to people with Nostr articles inside -- or some other forms of "subscription services on Nostr". It makes no sense at all.
Pulling in DMs from relays is exactly the same process (actually slightly more convoluted) than pulling normal public events, so why would a service assume that "sending a DM" was more likely to reach the target subscriber when the target had explicitly subscribed to that topic or writer?
Maybe due to how some specific clients work that is true, but fundamentally it is a very broken assumption that comes from some fantastic past era in which emails were 100% always seen and there was no way for anyone to subscribe to someone else's posts.
Building around such broken assumptions is the wrong approach. Instead we should be building new flows for subscribing to specific content from specific Nostr-native sources (creators directly or manual or automated curation providers, communities, relays etc), which is essentially what most clients are already doing anyway, but specifically Coracle's new custom feeds come to mind now.
This also reminds me of the interviewer asking the Farcaster creator if Farcaster made "email addresses available to content creators" completely ignoring all the cryptography and nature of the protocol (Farcaster is shit, but at least they tried, and in this example you could imagine the interviewer asking the same thing about Nostr).
I imagine that if the interviewer had asked these people who were working (or suggesting) the Nostr DM subscription flow they would have answered: "no, you don't get their email addresses, but you can send them uncensorable DMs!" -- and that, again, is getting everything backwards.
-
 @ 3bf0c63f:aefa459d
2024-03-20 17:20:14
@ 3bf0c63f:aefa459d
2024-03-20 17:20:14Nostr is not decentralized nor censorship-resistant
Peter Todd has been saying this for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right.
Nostr today is indeed centralized.
Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:
The top one was published to
wss://nostr.wine,wss://nos.lol,wss://pyramid.fiatjaf.com. The second was published to the relay where I generally publish all my notes to,wss://pyramid.fiatjaf.com, and that is announced on my NIP-05 file and on my NIP-65 relay list.A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:
These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains.
What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all.
Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant.
What happens is that most people who engaged with the note are following me, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on
wss://pyramid.fiatjaf.com.If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before.
Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today.
Peter Todd is wrong that Nostr is inherently centralized or that it needs a protocol change to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we drive in the right direction we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary.
See also:
-
 @ 3bf0c63f:aefa459d
2024-03-19 13:07:02
@ 3bf0c63f:aefa459d
2024-03-19 13:07:02Censorship-resistant relay discovery in Nostr
In Nostr is not decentralized nor censorship-resistant I said Nostr is centralized. Peter Todd thinks it is centralized by design, but I disagree.
Nostr wasn't designed to be centralized. The idea was always that clients would follow people in the relays they decided to publish to, even if it was a single-user relay hosted in an island in the middle of the Pacific ocean.
But the Nostr explanations never had any guidance about how to do this, and the protocol itself never had any enforcement mechanisms for any of this (because it would be impossible).
My original idea was that clients would use some undefined combination of relay hints in reply tags and the (now defunct)
kind:2relay-recommendation events plus some form of manual action ("it looks like Bob is publishing on relay X, do you want to follow him there?") to accomplish this. With the expectation that we would have a better idea of how to properly implement all this with more experience, Branle, my first working client didn't have any of that implemented, instead it used a stupid static list of relays with read/write toggle -- although it did publish relay hints and kept track of those internally and supportedkind:2events, these things were not really useful.Gossip was the first client to implement a truly censorship-resistant relay discovery mechanism that used NIP-05 hints (originally proposed by Mike Dilger) relay hints and
kind:3relay lists, and then with the simple insight of NIP-65 that got much better. After seeing it in more concrete terms, it became simpler to reason about it and the approach got popularized as the "gossip model", then implemented in clients like Coracle and Snort.Today when people mention the "gossip model" (or "outbox model") they simply think about NIP-65 though. Which I think is ok, but too restrictive. I still think there is a place for the NIP-05 hints,
nprofileandneventrelay hints and specially relay hints in event tags. All these mechanisms are used together in ZBD Social, for example, but I believe also in the clients listed above.I don't think we should stop here, though. I think there are other ways, perhaps drastically different ways, to approach content propagation and relay discovery. I think manual action by users is underrated and could go a long way if presented in a nice UX (not conceived by people that think users are dumb animals), and who knows what. Reliance on third-parties, hardcoded values, social graph, and specially a mix of multiple approaches, is what Nostr needs to be censorship-resistant and what I hope to see in the future.
-
 @ c5f77418:90f86d12
2024-07-14 16:50:14
@ c5f77418:90f86d12
2024-07-14 16:50:14U(zla)/acc is obfuscation as defence against Panoptic-Technocapital.
Attention-hacking is the name of the game. Cyberspace is a battle for attention using Anti-Ghazalian spiritual hermeneutics to attack the lower self using the promises of comfort, convenience and familiarity. All that the masters of the past had warned against have been institutionalised and baked into the largest platforms billions enter into unwittingly. This genie of spiritual decay has been loose not recently, but for decades, whatever chance of resisting it, brute-forcing it into a marginalised hobby has long since departed.
This circus, this asylum metastasizing through cyberspace is deployed as a weapon of mass distraction often by highly professional and dedicated large nation-state actors to achieve strategic ends. All the while, a higher network of surveillance watches unerringly which way the data, the spice flows. Which way does it bend, twist and strike. Attention-hacking is an exercise in surveillance and behavioural engineering. Engineering behaviour is not possible without data, without wilful and deeply invested participation on the part of subjects, without the time that is sunk into the whole process by enthusiastic partisans of cyber-asylums.
Panoptic-Technocapital is a more grounded and sober understanding of how technocapital operates - it understands that mundane but layered networks of bureucracy, technocratic agencies and the great post 9/11 intelligence empires in the shadows have just as much of a hand in building the Machine God as hyper-financialization and semiconductor manufacturing. It is also intimately and closely tied, the origins of much of what we take for granted in our civilian architecture of cyberspace has roots in the militarism of 20th century meatspace geopolitical intrigue. The Cypherpunks romanticised in part the creation of Cyber as an antithesis to meatspace not fully owing confronting its debts to the escalating and accelerating dynamics of intra-spook competition between the great metallic and clanking industrialised empires of the last century.
Liberalism in its intellectual genesis owed much to philosophers and men who were steeped in an entirely different moral code and spiritual psychology centuries ago now. The deism of early liberal theorists would in today wastelands, would likely resemble deep organic faith - time has snapped and wrought all our assumptions about the type of religious sentiments underlying early and proto-liberal thinking. Liberalism is nothing really but an extension of Christian heresies in response to unending sectarian conflict.
Today, however to call what we are experiencing as that same "liberalism" is foolishness. Today, what we refer to as "liberalism" is just an aesthetic wrapper, a charade, a shared delusion spread amongst the masses to hide something colder. A vast network of State-backed agencies, affiliated organisations in finance and pharmaceutical research, healthcare, commerce intimately tied with intelligence agencies that have formed an ossified, largely uncontested and reasonably stable layer of Administration that keeps marching along no matter who or which party is in charge.
U(zla)-acc is an acceptance of this process, it is an invitation to understand that we have bought our tickets and now must see where the train ends up, not much can be done to course-correct. We are heading towards Hyper-Intelligence with the promise that disease can be predicted and prevented but with the costs of precognitive criminalisation (precrime).
Legible Hyper-Intelligence writ large by the State and its partners, subsidiaries and outsourced contractors means that the social contract is now just saying okay to the Terms & Conditions, the cookies you accept to sign up to the newest and most exciting OpenAI or Google app. Soon it will be downloading a national ID app with access to banking services, where you file your taxes, download your healthcare records, sell your house, buy your car in exchange for surrendering your face, irises and fingerprints, whilst granting said app complete and total intimacy about what you do and where you go.
-
 @ 3bf0c63f:aefa459d
2024-01-29 02:19:25
@ 3bf0c63f:aefa459d
2024-01-29 02:19:25Nostr: a quick introduction, attempt #1
Nostr doesn't have a material existence, it is not a website or an app. Nostr is just a description what kind of messages each computer can send to the others and vice-versa. It's a very simple thing, but the fact that such description exists allows different apps to connect to different servers automatically, without people having to talk behind the scenes or sign contracts or anything like that.
When you use a Nostr client that is what happens, your client will connect to a bunch of servers, called relays, and all these relays will speak the same "language" so your client will be able to publish notes to them all and also download notes from other people.
That's basically what Nostr is: this communication layer between the client you run on your phone or desktop computer and the relay that someone else is running on some server somewhere. There is no central authority dictating who can connect to whom or even anyone who knows for sure where each note is stored.
If you think about it, Nostr is very much like the internet itself: there are millions of websites out there, and basically anyone can run a new one, and there are websites that allow you to store and publish your stuff on them.
The added benefit of Nostr is that this unified "language" that all Nostr clients speak allow them to switch very easily and cleanly between relays. So if one relay decides to ban someone that person can switch to publishing to others relays and their audience will quickly follow them there. Likewise, it becomes much easier for relays to impose any restrictions they want on their users: no relay has to uphold a moral ground of "absolute free speech": each relay can decide to delete notes or ban users for no reason, or even only store notes from a preselected set of people and no one will be entitled to complain about that.
There are some bad things about this design: on Nostr there are no guarantees that relays will have the notes you want to read or that they will store the notes you're sending to them. We can't just assume all relays will have everything — much to the contrary, as Nostr grows more relays will exist and people will tend to publishing to a small set of all the relays, so depending on the decisions each client takes when publishing and when fetching notes, users may see a different set of replies to a note, for example, and be confused.
Another problem with the idea of publishing to multiple servers is that they may be run by all sorts of malicious people that may edit your notes. Since no one wants to see garbage published under their name, Nostr fixes that by requiring notes to have a cryptographic signature. This signature is attached to the note and verified by everybody at all times, which ensures the notes weren't tampered (if any part of the note is changed even by a single character that would cause the signature to become invalid and then the note would be dropped). The fix is perfect, except for the fact that it introduces the requirement that each user must now hold this 63-character code that starts with "nsec1", which they must not reveal to anyone. Although annoying, this requirement brings another benefit: that users can automatically have the same identity in many different contexts and even use their Nostr identity to login to non-Nostr websites easily without having to rely on any third-party.
To conclude: Nostr is like the internet (or the internet of some decades ago): a little chaotic, but very open. It is better than the internet because it is structured and actions can be automated, but, like in the internet itself, nothing is guaranteed to work at all times and users many have to do some manual work from time to time to fix things. Plus, there is the cryptographic key stuff, which is painful, but cool.
-
 @ 3bf0c63f:aefa459d
2024-01-15 11:15:06
@ 3bf0c63f:aefa459d
2024-01-15 11:15:06Anglicismos estúpidos no português contemporâneo
Palavras e expressões que ninguém deveria usar porque não têm o sentido que as pessoas acham que têm, são apenas aportuguesamentos de palavras inglesas que por nuances da história têm um sentido ligeiramente diferente em inglês.
Cada erro é acompanhado também de uma sugestão de como corrigi-lo.
Palavras que existem em português com sentido diferente
- submissão (de trabalhos): envio, apresentação
- disrupção: perturbação
- assumir: considerar, pressupor, presumir
- realizar: perceber
- endereçar: tratar de
- suporte (ao cliente): atendimento
- suportar (uma idéia, um projeto): apoiar, financiar
- suportar (uma função, recurso, característica): oferecer, ser compatível com
- literacia: instrução, alfabetização
- convoluto: complicado.
- acurácia: precisão.
- resiliência: resistência.
Aportuguesamentos desnecessários
- estartar: iniciar, começar
- treidar: negociar, especular
Expressões
- "não é sobre...": "não se trata de..."
Ver também
-
 @ e97aaffa:2ebd765d
2024-07-14 09:57:13
@ e97aaffa:2ebd765d
2024-07-14 09:57:13Estamos numa época tão estranha da humanidade…
Onde alguns querem reescrever a história, em vez de aprender e evoluir com a mesma. São com os erros que se cresce.
Onde o termo fascista é sinónimo de alguém com uma opinião diferente da sua, sem minimamente saber o real significado dessa palavra.
Onde defendem uma liberdade, que proíba o contraditório.
Onde não se discutem ideias, mas sim combatem ideias.
Onde o ambientalmente sustentável é substituir árvores e zonas verdes por estruturas em aço e zonas negras.
Onde os políticos constroem casas ou cidades, literalmente, em cima dos rios mas depois a culpa das cheias é as alterações climáticas.
Onde os alimentos tem menos importância que um peido de uma vaca.
Onde pessoas defendem que a solução para o aquecimento, é morrer de frio.
Onde a igualdade é favorecer um grupo, em detrimento de outro.
Onde o essencial é viver para consumir, em vez de usufruir.
Onde o importante é ser rico e ostentar essa mesma riqueza, mesmo que tenha de espezinhar outros para a conquistar.
Onde o mais importante é parecer em vez de ser.
Onde políticos defendem que o conhecimento pode levar a escolhas erradas, defendem o carneirismo.
Onde um político define o que é verdade ou mentira, limitando o que as pessoas podem expressar. Mas quem controla o controlador.
Onde os revisores da verdade deixaram de estar num gabinete, passando a ser um exército de jovens atrás de um teclado.
Onde, são propostas e aprovadas limitações de liberdade, sem esclarecimento ou divulgação pública. Pior que a obscuridade, é desinteresse da comunidade por liberdade.
Onde a censura é o novo normal, defender o contrário é que é censurável.
Onde a imprensa é tão livre como uma pomba dentro de sua gaiola.
Onde, quem comete o crime é protegido, quem o denúncia é perseguido.
Onde o certo é pensar com a cabeça dos outros, sem questionar.
Onde os pais delegaram o papel de educar às escolas e aos ecrãs azuis.
Onde a escola deixou de ser um lugar de conhecimento e/ou do desenvolvimento do espírito crítico.
Onde as crianças crescem doutrinados por políticos e por AI.
Onde a sociedade é programada e com um destino predefinido, como um rato dentro da sua roda.
Onde o maior erro, é pretender construir seres que não cometem erros, que não tenham vícios. Quando isso acontecer, deixamos de ser humanos. A imperfeição é a essência dos seres humanos, é o que nos difere das máquinas.
Onde só se ensina a não cair, em vez de ajudar e incentivar a levantar.
Onde se suspende a liberdade de circulação e os direitos mais básicos, sem ninguém questionar.
Onde a privacidade é crime.
Onde Satoshi é excomungado, mas Miguel Tiago é idoleterado.
Onde a moeda é utilizado como uma arma.
Onde uma guerra é digladiada entre zeros e uns, sem o comum mortal aperceber da sua existência.
Onde crianças caem em campos de batalha, como folhas em pleno outono.
Onde o direito ao Livre-arbítrio está sob ameaça.
-
 @ ab8cb80e:5395d502
2024-07-12 14:21:14
@ ab8cb80e:5395d502
2024-07-12 14:21:14Hey, I have nothing to do this Friday evening, so why not chill with chess?
Spontaneously I launched an Arena Tournament for today: https://lichess.org/tournament/2iNa8jh4
@ek @kristapsk @BitcoinAbhi @grayruby @frostdragon @Taft @02d43d3798 @030e0dca83 @riberet19 @felipe @didiplaywell @SatsMate @itsTomekK @wize123 @Coinsreporter @stefano @anon @314piepi @160ed04091 do you want to play?
! TODAY ! ♟️ https://lichess.org/tournament/2iNa8jh4 ♟️ 90 min arena, with 5 minute games.
Join on @Alby's new Discord: https://discord.gg/3vbafUCZ?event=1261325278358016091 for voicechat I plan to stream it to zap.stream, because why not.
Who takes my challenge?
originally posted at https://stacker.news/items/605942
-
 @ 38d0888d:bd8e1246
2024-07-12 07:10:35
@ 38d0888d:bd8e1246
2024-07-12 07:10:35A thriving society rests on the principles of modesty and humility, avoiding idleness and self-indulgence. Individuals are needed to forsake the constant pursuit of attention and instead aspire to selflessness, dedicating themselves to serving humanity. Humility fosters spiritual harmony and protects against materialism and selfish desires.
Beyond personal conduct, humanity must champion altruism and solidarity within the global community. Belief in collective endeavors will pave the way for global harmony. Embracing values like kindness, compassion, and genuine concern for others promotes positivity and reflects the influence of a higher power. The aim is to cultivate a unified multicultural community where each person contributes to manifesting this higher presence.
The collective goal is to direct humanity to nurture a community that experiences spiritual growth while upholding humility as a guiding principle, resisting materialism's allure. By creating such an environment, the hope is to resonate with a sacred harmony that extends beyond immediate boundaries. Through intentional actions and meaningful relationships, a collective space embodying these values can be established, ensuring the higher power's presence guides individual lives and interactions with the world.
-
 @ ee11a5df:b76c4e49
2024-07-11 23:57:53
@ ee11a5df:b76c4e49
2024-07-11 23:57:53What Can We Get by Breaking NOSTR?
"What if we just started over? What if we took everything we have learned while building nostr and did it all again, but did it right this time?"
That is a question I've heard quite a number of times, and it is a question I have pondered quite a lot myself.
My conclusion (so far) is that I believe that we can fix all the important things without starting over. There are different levels of breakage, starting over is the most extreme of them. In this post I will describe these levels of breakage and what each one could buy us.
Cryptography
Your key-pair is the most fundamental part of nostr. That is your portable identity.
If the cryptography changed from secp256k1 to ed25519, all current nostr identities would not be usable.
This would be a complete start over.
Every other break listed in this post could be done as well to no additional detriment (save for reuse of some existing code) because we would be starting over.
Why would anyone suggest making such a break? What does this buy us?
- Curve25519 is a safe curve meaning a bunch of specific cryptography things that us mortals do not understand but we are assured that it is somehow better.
- Ed25519 is more modern, said to be faster, and has more widespread code/library support than secp256k1.
- Nostr keys could be used as TLS server certificates. TLS 1.3 using RFC 7250 Raw Public Keys allows raw public keys as certificates. No DNS or certification authorities required, removing several points of failure. These ed25519 keys could be used in TLS, whereas secp256k1 keys cannot as no TLS algorithm utilizes them AFAIK. Since relays currently don't have assigned nostr identities but are instead referenced by a websocket URL, this doesn't buy us much, but it is interesting. This idea is explored further below (keep reading) under a lesser level of breakage.
Besides breaking everything, another downside is that people would not be able to manage nostr keys with bitcoin hardware.
I am fairly strongly against breaking things this far. I don't think it is worth it.
Signature Scheme and Event Structure
Event structure is the next most fundamental part of nostr. Although events can be represented in many ways (clients and relays usually parse the JSON into data structures and/or database columns), the nature of the content of an event is well defined as seven particular fields. If we changed those, that would be a hard fork.
This break is quite severe. All current nostr events wouldn't work in this hard fork. We would be preserving identities, but all content would be starting over.
It would be difficult to bridge between this fork and current nostr because the bridge couldn't create the different signature required (not having anybody's private key) and current nostr wouldn't be generating the new kind of signature. Therefore any bridge would have to do identity mapping just like bridges to entirely different protocols do (e.g. mostr to mastodon).
What could we gain by breaking things this far?
- We could have a faster event hash and id verification: the current signature scheme of nostr requires lining up 5 JSON fields into a JSON array and using that as hash input. There is a performance cost to copying this data in order to hash it.
- We could introduce a subkey field, and sign events via that subkey, while preserving the pubkey as the author everybody knows and searches by. Note however that we can already get a remarkably similar thing using something like NIP-26 where the actual author is in a tag, and the pubkey field is the signing subkey.
- We could refactor the kind integer into composable bitflags (that could apply to any application) and an application kind (that specifies the application).
- Surely there are other things I haven't thought of.
I am currently against this kind of break. I don't think the benefits even come close to outweighing the cost. But if I learned about other things that we could "fix" by restructuring the events, I could possibly change my mind.
Replacing Relay URLs
Nostr is defined by relays that are addressed by websocket URLs. If that changed, that would be a significant break. Many (maybe even most) current event kinds would need superseding.
The most reasonable change is to define relays with nostr identities, specifying their pubkey instead of their URL.
What could we gain by this?
- We could ditch reliance on DNS. Relays could publish events under their nostr identity that advertise their current IP address(es).
- We could ditch certificates because relays could generate ed25519 keypairs for themselves (or indeed just self-signed certificates which might be much more broadly supported) and publish their public ed25519 key in the same replaceable event where they advertise their current IP address(es).
This is a gigantic break. Almost all event kinds need redefining and pretty much all nostr software will need fairly major upgrades. But it also gives us a kind of Internet liberty that many of us have dreamt of our entire lives.
I am ambivalent about this idea.
Protocol Messaging and Transport
The protocol messages of nostr are the next level of breakage. We could preserve keypair identities, all current events, and current relay URL references, but just break the protocol of how clients and relay communicate this data.
This would not necessarily break relay and client implementations at all, so long as the new protocol were opt-in.
What could we get?
- The new protocol could transmit events in binary form for increased performance (no more JSON parsing with it's typical many small memory allocations and string escaping nightmares). I think event throughput could double (wild guess).
- It could have clear expectations of who talks first, and when and how AUTH happens, avoiding a lot of current miscommunication between clients and relays.
- We could introduce bitflags for feature support so that new features could be added later and clients would not bother trying them (and getting an error or timing out) on relays that didn't signal support. This could replace much of NIP-11.
- We could then introduce something like negentropy or negative filters (but not that... probably something else solving that same problem) without it being a breaking change.
- The new protocol could just be a few websocket-binary messages enhancing the current protocol, continuing to leverage the existing websocket-text messages we currently have, meaning newer relays would still support all the older stuff.
The downsides are just that if you want this new stuff you have to build it. It makes the protocol less simple, having now multiple protocols, multiple ways of doing the same thing.
Nonetheless, this I am in favor of. I think the trade-offs are worth it. I will be pushing a draft PR for this soon.
The path forward
I propose then the following path forward:
- A new nostr protocol over websockets binary (draft PR to be shared soon)
- Subkeys brought into nostr via NIP-26 (but let's use a single letter tag instead, OK?) via a big push to get all the clients to support it (the transition will be painful - most major clients will need to support this before anybody can start using it).
- Some kind of solution to the negative-filter-negentropy need added to the new protocol as its first optional feature.
- We seriously consider replacing Relay URLs with nostr pubkeys assigned to the relay, and then have relays publish their IP address and TLS key or certificate.
We sacrifice these:
- Faster event hash/verification
- Composable event bitflags
- Safer faster more well-supported crypto curve
- Nostr keys themselves as TLS 1.3 RawPublicKey certificates
-
 @ 5d4b6c8d:8a1c1ee3
2024-07-11 12:17:18
@ 5d4b6c8d:8a1c1ee3
2024-07-11 12:17:18Yesterday's edition https://stacker.news/items/603455/r/Undisciplined
-
- -
July 11, 2023 📅
📝
TOP POSTI am not a routing node anymore
Excerpt
Over the past two years I ran an amateur routing node that was in the top 300 on lightning terminal. I have decided to stop for the following reasons […]
5586 sats \ 37 comments \ @lnvisualizer \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/207349/r/Undisciplined?commentId=207482
Excerpt
While you were making Bitcoin banks, Phoenix scripted out lightning channel management […]
1776 sats \ 12 replies \ @nerd2ninja
From Introducing the new Phoenix: a 3rd generation self-custodial Lightning wallet by @Norbert in ~bitcoin
🏆
TOP STACKER2nd place @nerd2ninja (1st hiding, presumed @siggy47)
746 stacked \ 2262 spent \ 1 post \ 11 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
91.7k stacked \ 0 revenue \ 113.7k spent \ 90 posts \ 302 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 11, 2022 📅
📝
TOP POSTI'm Evan Kaloudis, Founder of Zeus. July 11th AMA!
Excerpt
I'm stoked to chat with you all today. Zeus (https://zeusln.app) is a mobile app for iOS and Android that lets you connect to and control your lightning node remotely. It supports LND, Core Lightning, and Eclair.
31.7k sats \ 58 comments \ @evankaloudis \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/43634/r/Undisciplined?commentId=43640
Excerpt
Hello, I am a Bitcoin maxi and I put my sats where my mouth is. Bitcoin maximalism is a method of consumer protection. My story as a maximalist, is that I used to shitcoin back in 2016. During the 2018 bear market, I lost so much money in everything […]
390 sats \ 11 replies \ @nerd2ninja
From I am moving over from Twitter by @charles_stack in ~bitcoin
🏆
TOP STACKER1st place @k00b
19.3k stacked \ 32k spent \ 2 posts \ 17 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
53.4k stacked \ 0 revenue \ 62.2k spent \ 114 posts \ 304 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 11, 2021 📅
📝
TOP POSTThis company sells passports to Americans looking for a tax break on their bitcoin profits
Link to https://www.cnbc.com/2021/07/11/plan-b-passport-tax-break-bitcoin-profits.html
5 sats \ 4 comments \ @0268486dc4 \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/256/r/Undisciplined?commentId=282
Excerpt
Fascinating to see the disconnect between fundamentals of a crypto/stock and the price action created by market movers and how it seems to follow so many mathematical patterns. Makes you want to be a trader but then you remember 90%+ or whatever jus […]
1 sat \ 2 replies \ @gmd
From What are your favorite Bitcoin newsletters? by @k00b in ~bitcoin
🏆
TOP STACKERNo top stacker
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
21 stacked \ 0 revenue \ 151 spent \ 5 posts \ 15 comments
originally posted at https://stacker.news/items/604559
-
-
 @ 502ab02a:a2860397
2024-07-11 07:14:05
@ 502ab02a:a2860397
2024-07-11 07:14:05 ก่อนจะเปิดหลุมกระต่าย ให้เพื่อนๆลงไปสู่ ทุ่งม่วง wonderland เรามาเบิกเนตรระบบที่ทำให้เราเป็นสินค้าแทนที่จะเป็นลูกค้ากันก่อนครับ
ก่อนจะเปิดหลุมกระต่าย ให้เพื่อนๆลงไปสู่ ทุ่งม่วง wonderland เรามาเบิกเนตรระบบที่ทำให้เราเป็นสินค้าแทนที่จะเป็นลูกค้ากันก่อนครับอินเตอร์เนทเริ่มต้นด้วยอุดมการณ์ที่ดี ที่จะให้ข้อมูลข่าวสารมันฉับไว ซึ่งมันก็เป็นเช่นนั้นจริงๆ แต่โลกมันมีสิ่งนึงที่เกิดขึ้นอยู่เสมอ นั้นคือ การชิงทรัพยากร ดินแดน เวลา และการควบคุมคนให้อยู่ในอาณัติ
อินเตอร์เนทเริ่มถูกยึดดินแดนมาตั้งแต่การเริ่มมีการสื่อสาร 2 ทางที่โต้ตอบกันได้เร็วขึ้น เจ้า www (World Wide Web) มันกลายเป็นดินแดนของไม่กี่บริษัท ที่เป็นผู้ยิ่งใหญ่ในโลก ดอทคอม สร้างกิจกรรมบางอย่างแล้วให้คนทั้งโลกเข้ามาใช้งาน
จะเห็นว่าทุกวันนี้เราแทบไม่พ้นการเข้าไปดู เฟสบุค ยูทูป ทวิตเตอร์ ไอจี ชอปปี้ ลาซาด้า และอื่นๆที่เหมือนจะมากมายแต่ไม่ได้มากมายเมื่อเทียบประชากรโลก
บางคนบอกว่ามันก็ดีไม่ใช่เหรอ เราได้ใช้ฟรีๆ ตรงนี้ละครับ เราจะเข้าเรื่องกันแล้ว
คำที่เราหลงไปกับมันคือ เขาทำมาให้เราใช้ฟรีๆ เขาต้องเห็นเราเป็นลูกค้าสิ แต่ความจริงนั้น เราคือสินค้าครับ เขาฟาร์มเราไว้เป็นสินค้า เป็นหมูในแฮปปี้ฟาร์ม ยิ่งประชากรในฟาร์มมีมาก เขาก็จะมีมูลค่าสูงมาก ดังเช่นที่เราเห็นว่า
มีการบ่นมากมายเรื่องการกดการมองเห็น การที่มีแต่โพสพนัน หลอกขายของที่เป็นสปอนเซอร์ การที่เราลงรูปไก่ต้มแล้วโดนแบนเพราะเขามองว่าทรมานสัตว์ และอื่นๆอีกมากมายที่ทำให้รู้สึกว่า ทำไมเขาดูแลผู้ใช้งานไม่ดีเลย เราเป็นลูกค้าเขานะ
ถ้ามองในอีกมุมนึง จริงๆเขาดูแลลูกค้าดีแล้วครับ ลูกค้าของเขาคือคนซื้อโฆษณาต่างหาก ใครที่จ่ายมาก ก็เอาสินค้าเค้ามายัดเยียดให้ประชากรในฟาร์ม ได้ดูกันตาแตก หมูในฟาร์มคนไหนออกนอกลู่นอกทางก็จะเชือดทิ้ง นี่ละครับที่บอกว่าเราคือสินค้าต่างหาก
กลุ่มคนที่ต้องการอิสระเสรี จึงสร้างสิ่งใหม่ขึ้นมา ไม่ใช่แค่ทำแอพ ไม่ใช่ทำแค่เว็บ เพราะมันยังต้องพึ่งพาเอกชนในการเอาข้อมูลไปฝากไว้ในเครือข่าย แต่สิ่งใหม่นี้มันเป็นระบบการส่งข้อมูลแบบใหม่ครับ
ให้เห็นภาพยิ่งขึ้น เราบอกไปแล้วว่าดินแดนอินเตอร์เนท มันอยู่ในกำมือคนที่เป็น land lord ไม่กี่คน และทุกอย่างเราต้องอยู่ใต้อาณัติเขา ตั้งแต่การได้เห็นแค่ข้อมูลเขาก็เลือกให้ จนถึงว่าถ้าเขาสงสัยว่าเราไม่ใช่เราตัวจริง เขาสามารถลบเราไปโดยไม่ต้องถามอะไร ชีวิต7ปี 10ปี ที่ผ่านมาในแอพมันสามารถเหลือ 0โพสได้ในพริบตาและไม่ให้อุธรณ์ใดๆ
นั่นเพราะข้อมูลทุกอย่างมันไปอยู่ในเครื่องคอมของแต่ละบริษัท ทั้งยูทูป เฟสบุค ไอจี ของๆเรา เราเอาไปอัพไว้ในคอมเขา ต้องทำตามกฎที่เขาตั้งและเปลี่ยนใจได้ทุกเมื่อ และแอบมองของๆเราได้ทุกรูปทุกข้อความลับ
ทุกอย่าง ย้ำว่าทุกอย่าง ต้องผ่านคอมของเขาทั้งหมด เราไม่มีอะไรเป็นของเราเลย ในฟาร์มนี้ เราแค่รอโดนเชือดและเราไม่กล้าออกมาเพราะคิดว่าเป็น safe zone
ส่วนระบบการส่งข้อมูลแบบใหม่ เราเรียกว่า nostr อ่านว่า นอสเตอร์ ชื่อเต็มมันยาว แต่ถ้ารู้ จะเข้าใจง่ายขึ้น เพราะมันมาจากคำว่า Notes and Other Stuff Transmitted by Relays แปลว่า ”อะไรก็ตามที่เอามาส่งผ่านรีเลย์“
ผมขอเรียกมันว่าส่งไม้ต่อละกันครับ มองภาพการวิ่ง 4x100 มันมีการส่งไม้ผลัดใช่ไหมครับ นั่นละ รีเลย์

ระบบเก่าเราเรียกว่า การรวมศูนย์ นั่นคือเอะอะก็ต้องไปเก็บหรือไปดู จากคอมบริษัทนั้นๆ เช่น ดูคลิปก็ต้องไปโหลดจากคอมของยูทูป จะดูฟีดเพื่อนก็ต้องไปโหลดข้อความที่เพื่อนฝากไว้ในคอมของเฟสบุค
ถ้าวันนึง เฟสบุคล่ม นั่นคือทุกคนติดต่อหรือดูอะไรไม่ได้เลย และถ้ากู่ไม่กลับ นั้นคือทุกอย่างหายหมด นอกจากนี้ผู้คุมศูนย์คือสั่งชี้เป็นชี้ตายคุณได้ทันที ที่ไม่พอใจคุณ บ้านเขากฎเขา นั้นเอง

ในขณะที่ nostr เป็นระบบส่งไม้ผลัด นั่นคือ ใครๆก็สามารถเป็น รีเลย์ได้ แค่มีคอมก็เรียบร้อย วิธีการเป็นรีเลย์ เรายังไม่ต้องสนใจครับ เราเป็นแค่ผู้ใช้ ไม่ต้องเป็นผู้ให้บริการก็ได้ ฟรีด้วย วันนี้เราแค่มาเข้าใจเส้นทางก่อนครับ
อย่างที่บอกครับ ระบบการส่งข้อมูลเราเป็นรีเลย์ หรือ ไม้ผลัด หลักการก็แค่เราก็แค่ใส่ที่อยู่รีเลย์ ลงไปในแอพของเรา แล้วข้อมูลที่เราส่งไป เจ้ารีเลย์มันก็จะวิ่งส่งไม้ผลัดนี้ไปให้สมาชิกทุกคนในรีเลย์
ในทางกลับกัน เราก็จะได้รับข้อมูลที่สมาชิกในสังกัดรีเลย์ที่เราลงไว้ ส่งมาให้ผ่านทางรีเลย์ด้วยเช่นกัน
และที่เจ๋งก็คือ รีเลย์ ไม่สนใจอะไรอย่างอื่นอีก นอกเหนือแค่ส่งไม้ผลัดให้สมาชิกทุกคน นั่นคือ มันไม่คิดว่าอะไรควรส่งไม่ควรส่ง มันไม่คิดว่าข้อมูลดีแค่ไหน มันไม่ปิดกั้น มันไม่เซนเซอร์ นั่นคือ มีหน้าที่แค่ส่งจริงๆ นอกจากนี้ถ้าเราเป็นใส่รีเลย์มากกว่า 1 แห่งในตัวเรา ข้อมูลทั้งหมดก็จะสำเนาไปยังรีเลย์ที่เหลือได้เช่นกัน หมายถึงว่า ข้อมูลเราจะกระจายแบบสำเนาไปได้อีกหลายๆๆๆๆรีเลย์
นอกจากอิสระแล้วยังฆ่าไม่ตายด้วย เพราะรีเลย์มีขึ้นเป็นดอกเห็ด และใครๆทำรีเลย์มาเปิดให้บริการได้เอง (เราเป็นแค่ผู้ใช้ ไม่ได้อยากเป็นผู้ให้บริการ เราไม่ต้องสร้างรีเลย์ก็สามารถใช้งาน nostr ได้ครับ)
ดังนั้น nostr จึงเหมาะกับคนที่ต้องการเสรีภาพแบบเต็มๆ เพราะไม่มีใครเซนเซอร์คุณได้เลย คุณเท่านั้นที่จะต้องรับผิดชอบการกระทำของคุณเอง
เพราะด้วยที่มันฆ่าไม่ตาย นั่นหมายถึง สิ่งที่คุณพิมพ์หรือโพสลงไป จะไม่สามารถลบหรือแก้ไขได้เช่นกัน แม้แต่ตัวคุณเองก็ตาม
ดังนั้นไต่ตรองให้ดีถ้าจะสร้างเนื้อหา เพราะมันจะบันทึกสิ่งที่คุณทำไว้ตลอดไป แต่ถ้าเรายังไม่มั่นใจเราลองเล่นแบบเป็นคนอ่านก่อนก็ได้ครับ พอเราใช้คล่องขึ้น มีสติสัมปชัญญะเพียงพอ ก็เริ่มทักทายคนในนั้นได้ มันไม่น่ากลัวหรอกครับ เพราะหัวใจหล้กของ nostr คือการเข้าสังคม สร้างสังคมคุณภาพ มากกว่าการโพสเท่ๆเอาไลค์ เพราะ มันไม่มีอัลกอลิทึ่มใดๆ เขายึดมั่นใน proof of work
ไลฟ์ของเราจะไม่โดนปิดกั้น โพสของเราจะไม่โดนลดการมองเห็น ถ้ามันมีคุณภาพเพียงพอที่คนจะเลือกติดตามชม
ถ้ามองเห็นกลลวงของโซเชียลแล้ว ตอนหน้า จะรวบรัด ลงหลุมกระต่ายกันเลย เอาแบบโหลดแล้วเล่นก่อน แล้วเรียนไปพร้อมๆกับเล่นนี่แหละ
ถ้าทุกคนเริ่มวันนี้ อิสระก็จะเริ่มยิ่งใหญ่วันนี้ แล้วก็จะไม่มีคำว่า คนมันยังน้อยอยู่
เคยดูหนังไหมครับ เช่นตอนเปิดแผ่นดินใหม่ ใครขี่ม้าไปปักธงจองอาณาเขตได้ก่อน ก็จะคุ้นชินพื้นที่นั้นๆได้ก่อนใครครับ
pirateketo
กูต้องรู้มั๊ย
Siamstr
-
 @ 3bf0c63f:aefa459d
2024-01-15 11:15:06
@ 3bf0c63f:aefa459d
2024-01-15 11:15:06Pequenos problemas que o Estado cria para a sociedade e que não são sempre lembrados
- **vale-transporte**: transferir o custo com o transporte do funcionário para um terceiro o estimula a morar longe de onde trabalha, já que morar perto é normalmente mais caro e a economia com transporte é inexistente. - **atestado médico**: o direito a faltar o trabalho com atestado médico cria a exigência desse atestado para todas as situações, substituindo o livre acordo entre patrão e empregado e sobrecarregando os médicos e postos de saúde com visitas desnecessárias de assalariados resfriados. - **prisões**: com dinheiro mal-administrado, burocracia e péssima alocação de recursos -- problemas que empresas privadas em competição (ou mesmo sem qualquer competição) saberiam resolver muito melhor -- o Estado fica sem presídios, com os poucos existentes entupidos, muito acima de sua alocação máxima, e com isto, segundo a bizarra corrente de responsabilidades que culpa o juiz que condenou o criminoso por sua morte na cadeia, juízes deixam de condenar à prisão os bandidos, soltando-os na rua. - **justiça**: entrar com processos é grátis e isto faz proliferar a atividade dos advogados que se dedicam a criar problemas judiciais onde não seria necessário e a entupir os tribunais, impedindo-os de fazer o que mais deveriam fazer. - **justiça**: como a justiça só obedece às leis e ignora acordos pessoais, escritos ou não, as pessoas não fazem acordos, recorrem sempre à justiça estatal, e entopem-na de assuntos que seriam muito melhor resolvidos entre vizinhos. - **leis civis**: as leis criadas pelos parlamentares ignoram os costumes da sociedade e são um incentivo a que as pessoas não respeitem nem criem normas sociais -- que seriam maneiras mais rápidas, baratas e satisfatórias de resolver problemas. - **leis de trãnsito**: quanto mais leis de trânsito, mais serviço de fiscalização são delegados aos policiais, que deixam de combater crimes por isto (afinal de contas, eles não querem de fato arriscar suas vidas combatendo o crime, a fiscalização é uma excelente desculpa para se esquivarem a esta responsabilidade). - **financiamento educacional**: é uma espécie de subsídio às faculdades privadas que faz com que se criem cursos e mais cursos que são cada vez menos recheados de algum conhecimento ou técnica útil e cada vez mais inúteis. - **leis de tombamento**: são um incentivo a que o dono de qualquer área ou construção "histórica" destrua todo e qualquer vestígio de história que houver nele antes que as autoridades descubram, o que poderia não acontecer se ele pudesse, por exemplo, usar, mostrar e se beneficiar da história daquele local sem correr o risco de perder, de fato, a sua propriedade. - **zoneamento urbano**: torna as cidades mais espalhadas, criando uma necessidade gigantesca de carros, ônibus e outros meios de transporte para as pessoas se locomoverem das zonas de moradia para as zonas de trabalho. - **zoneamento urbano**: faz com que as pessoas percam horas no trânsito todos os dias, o que é, além de um desperdício, um atentado contra a sua saúde, que estaria muito melhor servida numa caminhada diária entre a casa e o trabalho. - **zoneamento urbano**: torna ruas e as casas menos seguras criando zonas enormes, tanto de residências quanto de indústrias, onde não há movimento de gente alguma. - **escola obrigatória + currículo escolar nacional**: emburrece todas as crianças. - **leis contra trabalho infantil**: tira das crianças a oportunidade de aprender ofícios úteis e levar um dinheiro para ajudar a família. - **licitações**: como não existem os critérios do mercado para decidir qual é o melhor prestador de serviço, criam-se comissões de pessoas que vão decidir coisas. isto incentiva os prestadores de serviço que estão concorrendo na licitação a tentar comprar os membros dessas comissões. isto, fora a corrupção, gera problemas reais: __(i)__ a escolha dos serviços acaba sendo a pior possível, já que a empresa prestadora que vence está claramente mais dedicada a comprar comissões do que a fazer um bom trabalho (este problema afeta tantas áreas, desde a construção de estradas até a qualidade da merenda escolar, que é impossível listar aqui); __(ii)__ o processo corruptor acaba, no longo prazo, eliminando as empresas que prestavam e deixando para competir apenas as corruptas, e a qualidade tende a piorar progressivamente. - **cartéis**: o Estado em geral cria e depois fica refém de vários grupos de interesse. o caso dos taxistas contra o Uber é o que está na moda hoje (e o que mostra como os Estados se comportam da mesma forma no mundo todo). - **multas**: quando algum indivíduo ou empresa comete uma fraude financeira, ou causa algum dano material involuntário, as vítimas do caso são as pessoas que sofreram o dano ou perderam dinheiro, mas o Estado tem sempre leis que prevêem multas para os responsáveis. A justiça estatal é sempre muito rígida e rápida na aplicação dessas multas, mas relapsa e vaga no que diz respeito à indenização das vítimas. O que em geral acontece é que o Estado aplica uma enorme multa ao responsável pelo mal, retirando deste os recursos que dispunha para indenizar as vítimas, e se retira do caso, deixando estas desamparadas. - **desapropriação**: o Estado pode pegar qualquer propriedade de qualquer pessoa mediante uma indenização que é necessariamente inferior ao valor da propriedade para o seu presente dono (caso contrário ele a teria vendido voluntariamente). - **seguro-desemprego**: se há, por exemplo, um prazo mínimo de 1 ano para o sujeito ter direito a receber seguro-desemprego, isto o incentiva a planejar ficar apenas 1 ano em cada emprego (ano este que será sucedido por um período de desemprego remunerado), matando todas as possibilidades de aprendizado ou aquisição de experiência naquela empresa específica ou ascensão hierárquica. - **previdência**: a previdência social tem todos os defeitos de cálculo do mundo, e não importa muito ela ser uma forma horrível de poupar dinheiro, porque ela tem garantias bizarras de longevidade fornecidas pelo Estado, além de ser compulsória. Isso serve para criar no imaginário geral a idéia da __aposentadoria__, uma época mágica em que todos os dias serão finais de semana. A idéia da aposentadoria influencia o sujeito a não se preocupar em ter um emprego que faça sentido, mas sim em ter um trabalho qualquer, que o permita se aposentar. - **regulamentação impossível**: milhares de coisas são proibidas, há regulamentações sobre os aspectos mais mínimos de cada empreendimento ou construção ou espaço. se todas essas regulamentações fossem exigidas não haveria condições de produção e todos morreriam. portanto, elas não são exigidas. porém, o Estado, ou um agente individual imbuído do poder estatal pode, se desejar, exigi-las todas de um cidadão inimigo seu. qualquer pessoa pode viver a vida inteira sem cumprir nem 10% das regulamentações estatais, mas viverá também todo esse tempo com medo de se tornar um alvo de sua exigência, num estado de terror psicológico. - **perversão de critérios**: para muitas coisas sobre as quais a sociedade normalmente chegaria a um valor ou comportamento "razoável" espontaneamente, o Estado dita regras. estas regras muitas vezes não são obrigatórias, são mais "sugestões" ou limites, como o salário mínimo, ou as 44 horas semanais de trabalho. a sociedade, porém, passa a usar esses valores como se fossem o normal. são raras, por exemplo, as ofertas de emprego que fogem à regra das 44h semanais. - **inflação**: subir os preços é difícil e constrangedor para as empresas, pedir aumento de salário é difícil e constrangedor para o funcionário. a inflação força as pessoas a fazer isso, mas o aumento não é automático, como alguns economistas podem pensar (enquanto alguns outros ficam muito satisfeitos de que esse processo seja demorado e difícil). - **inflação**: a inflação destrói a capacidade das pessoas de julgar preços entre concorrentes usando a própria memória. - **inflação**: a inflação destrói os cálculos de lucro/prejuízo das empresas e prejudica enormemente as decisões empresariais que seriam baseadas neles. - **inflação**: a inflação redistribui a riqueza dos mais pobres e mais afastados do sistema financeiro para os mais ricos, os bancos e as megaempresas. - **inflação**: a inflação estimula o endividamento e o consumismo. - **lixo:** ao prover coleta e armazenamento de lixo "grátis para todos" o Estado incentiva a criação de lixo. se tivessem que pagar para que recolhessem o seu lixo, as pessoas (e conseqüentemente as empresas) se empenhariam mais em produzir coisas usando menos plástico, menos embalagens, menos sacolas. - **leis contra crimes financeiros:** ao criar legislação para dificultar acesso ao sistema financeiro por parte de criminosos a dificuldade e os custos para acesso a esse mesmo sistema pelas pessoas de bem cresce absurdamente, levando a um percentual enorme de gente incapaz de usá-lo, para detrimento de todos -- e no final das contas os grandes criminosos ainda conseguem burlar tudo. -
 @ 3bf0c63f:aefa459d
2024-01-14 14:52:16
@ 3bf0c63f:aefa459d
2024-01-14 14:52:16bitcoinddecentralizationIt is better to have multiple curator teams, with different vetting processes and release schedules for
bitcoindthan a single one."More eyes on code", "Contribute to Core", "Everybody should audit the code".
All these points repeated again and again fell to Earth on the day it was discovered that Bitcoin Core developers merged a variable name change from "blacklist" to "blocklist" without even discussing or acknowledging the fact that that innocent pull request opened by a sybil account was a social attack.
After a big lot of people manifested their dissatisfaction with that event on Twitter and on GitHub, most Core developers simply ignored everybody's concerns or even personally attacked people who were complaining.
The event has shown that:
1) Bitcoin Core ultimately rests on the hands of a couple maintainers and they decide what goes on the GitHub repository[^pr-merged-very-quickly] and the binary releases that will be downloaded by thousands; 2) Bitcoin Core is susceptible to social attacks; 2) "More eyes on code" don't matter, as these extra eyes can be ignored and dismissed.
Solution:
bitcoinddecentralizationIf usage was spread across 10 different
bitcoindflavors, the network would be much more resistant to social attacks to a single team.This has nothing to do with the question on if it is better to have multiple different Bitcoin node implementations or not, because here we're basically talking about the same software.
Multiple teams, each with their own release process, their own logo, some subtle changes, or perhaps no changes at all, just a different name for their
bitcoindflavor, and that's it.Every day or week or month or year, each flavor merges all changes from Bitcoin Core on their own fork. If there's anything suspicious or too leftist (or perhaps too rightist, in case there's a leftist
bitcoindflavor), maybe they will spot it and not merge.This way we keep the best of both worlds: all software development, bugfixes, improvements goes on Bitcoin Core, other flavors just copy. If there's some non-consensus change whose efficacy is debatable, one of the flavors will merge on their fork and test, and later others -- including Core -- can copy that too. Plus, we get resistant to attacks: in case there is an attack on Bitcoin Core, only 10% of the network would be compromised. the other flavors would be safe.
Run Bitcoin Knots
The first example of a
bitcoindsoftware that follows Bitcoin Core closely, adds some small changes, but has an independent vetting and release process is Bitcoin Knots, maintained by the incorruptible Luke DashJr.Next time you decide to run
bitcoind, run Bitcoin Knots instead and contribute tobitcoinddecentralization!
See also:
[^pr-merged-very-quickly]: See PR 20624, for example, a very complicated change that could be introducing bugs or be a deliberate attack, merged in 3 days without time for discussion.
-
 @ 3bf0c63f:aefa459d
2024-01-14 14:52:16
@ 3bf0c63f:aefa459d
2024-01-14 14:52:16Drivechain
Understanding Drivechain requires a shift from the paradigm most bitcoiners are used to. It is not about "trustlessness" or "mathematical certainty", but game theory and incentives. (Well, Bitcoin in general is also that, but people prefer to ignore it and focus on some illusion of trustlessness provided by mathematics.)
Here we will describe the basic mechanism (simple) and incentives (complex) of "hashrate escrow" and how it enables a 2-way peg between the mainchain (Bitcoin) and various sidechains.
The full concept of "Drivechain" also involves blind merged mining (i.e., the sidechains mine themselves by publishing their block hashes to the mainchain without the miners having to run the sidechain software), but this is much easier to understand and can be accomplished either by the BIP-301 mechanism or by the Spacechains mechanism.
How does hashrate escrow work from the point of view of Bitcoin?
A new address type is created. Anything that goes in that is locked and can only be spent if all miners agree on the Withdrawal Transaction (
WT^) that will spend it for 6 months. There is one of these special addresses for each sidechain.To gather miners' agreement
bitcoindkeeps track of the "score" of all transactions that could possibly spend from that address. On every block mined, for each sidechain, the miner can use a portion of their coinbase to either increase the score of oneWT^by 1 while decreasing the score of all others by 1; or they can decrease the score of allWT^s by 1; or they can do nothing.Once a transaction has gotten a score high enough, it is published and funds are effectively transferred from the sidechain to the withdrawing users.
If a timeout of 6 months passes and the score doesn't meet the threshold, that
WT^is discarded.What does the above procedure mean?
It means that people can transfer coins from the mainchain to a sidechain by depositing to the special address. Then they can withdraw from the sidechain by making a special withdraw transaction in the sidechain.
The special transaction somehow freezes funds in the sidechain while a transaction that aggregates all withdrawals into a single mainchain
WT^, which is then submitted to the mainchain miners so they can start voting on it and finally after some months it is published.Now the crucial part: the validity of the
WT^is not verified by the Bitcoin mainchain rules, i.e., if Bob has requested a withdraw from the sidechain to his mainchain address, but someone publishes a wrongWT^that instead takes Bob's funds and sends them to Alice's main address there is no way the mainchain will know that. What determines the "validity" of theWT^is the miner vote score and only that. It is the job of miners to vote correctly -- and for that they may want to run the sidechain node in SPV mode so they can attest for the existence of a reference to theWT^transaction in the sidechain blockchain (which then ensures it is ok) or do these checks by some other means.What? 6 months to get my money back?
Yes. But no, in practice anyone who wants their money back will be able to use an atomic swap, submarine swap or other similar service to transfer funds from the sidechain to the mainchain and vice-versa. The long delayed withdraw costs would be incurred by few liquidity providers that would gain some small profit from it.
Why bother with this at all?
Drivechains solve many different problems:
It enables experimentation and new use cases for Bitcoin
Issued assets, fully private transactions, stateful blockchain contracts, turing-completeness, decentralized games, some "DeFi" aspects, prediction markets, futarchy, decentralized and yet meaningful human-readable names, big blocks with a ton of normal transactions on them, a chain optimized only for Lighting-style networks to be built on top of it.
These are some ideas that may have merit to them, but were never actually tried because they couldn't be tried with real Bitcoin or inferfacing with real bitcoins. They were either relegated to the shitcoin territory or to custodial solutions like Liquid or RSK that may have failed to gain network effect because of that.
It solves conflicts and infighting
Some people want fully private transactions in a UTXO model, others want "accounts" they can tie to their name and build reputation on top; some people want simple multisig solutions, others want complex code that reads a ton of variables; some people want to put all the transactions on a global chain in batches every 10 minutes, others want off-chain instant transactions backed by funds previously locked in channels; some want to spend, others want to just hold; some want to use blockchain technology to solve all the problems in the world, others just want to solve money.
With Drivechain-based sidechains all these groups can be happy simultaneously and don't fight. Meanwhile they will all be using the same money and contributing to each other's ecosystem even unwillingly, it's also easy and free for them to change their group affiliation later, which reduces cognitive dissonance.
It solves "scaling"
Multiple chains like the ones described above would certainly do a lot to accomodate many more transactions that the current Bitcoin chain can. One could have special Lightning Network chains, but even just big block chains or big-block-mimblewimble chains or whatnot could probably do a good job. Or even something less cool like 200 independent chains just like Bitcoin is today, no extra features (and you can call it "sharding"), just that would already multiply the current total capacity by 200.
Use your imagination.
It solves the blockchain security budget issue
The calculation is simple: you imagine what security budget is reasonable for each block in a world without block subsidy and divide that for the amount of bytes you can fit in a single block: that is the price to be paid in satoshis per byte. In reasonable estimative, the price necessary for every Bitcoin transaction goes to very large amounts, such that not only any day-to-day transaction has insanely prohibitive costs, but also Lightning channel opens and closes are impracticable.
So without a solution like Drivechain you'll be left with only one alternative: pushing Bitcoin usage to trusted services like Liquid and RSK or custodial Lightning wallets. With Drivechain, though, there could be thousands of transactions happening in sidechains and being all aggregated into a sidechain block that would then pay a very large fee to be published (via blind merged mining) to the mainchain. Bitcoin security guaranteed.
It keeps Bitcoin decentralized
Once we have sidechains to accomodate the normal transactions, the mainchain functionality can be reduced to be only a "hub" for the sidechains' comings and goings, and then the maximum block size for the mainchain can be reduced to, say, 100kb, which would make running a full node very very easy.
Can miners steal?
Yes. If a group of coordinated miners are able to secure the majority of the hashpower and keep their coordination for 6 months, they can publish a
WT^that takes the money from the sidechains and pays to themselves.Will miners steal?
No, because the incentives are such that they won't.
Although it may look at first that stealing is an obvious strategy for miners as it is free money, there are many costs involved:
- The cost of ceasing blind-merged mining returns -- as stealing will kill a sidechain, all the fees from it that miners would be expected to earn for the next years are gone;
- The cost of Bitcoin price going down: If a steal is successful that will mean Drivechains are not safe, therefore Bitcoin is less useful, and miner credibility will also be hurt, which are likely to cause the Bitcoin price to go down, which in turn may kill the miners' businesses and savings;
- The cost of coordination -- assuming miners are just normal businesses, they just want to do their work and get paid, but stealing from a Drivechain will require coordination with other miners to conduct an immoral act in a way that has many pitfalls and is likely to be broken over the months;
- The cost of miners leaving your mining pool: when we talked about "miners" above we were actually talking about mining pools operators, so they must also consider the risk of miners migrating from their mining pool to others as they begin the process of stealing;
- The cost of community goodwill -- when participating in a steal operation, a miner will suffer a ton of backlash from the community. Even if the attempt fails at the end, the fact that it was attempted will contribute to growing concerns over exaggerated miners power over the Bitcoin ecosystem, which may end up causing the community to agree on a hard-fork to change the mining algorithm in the future, or to do something to increase participation of more entities in the mining process (such as development or cheapment of new ASICs), which have a chance of decreasing the profits of current miners.
Another point to take in consideration is that one may be inclined to think a newly-created sidechain or a sidechain with relatively low usage may be more easily stolen from, since the blind merged mining returns from it (point 1 above) are going to be small -- but the fact is also that a sidechain with small usage will also have less money to be stolen from, and since the other costs besides 1 are less elastic at the end it will not be worth stealing from these too.
All of the above consideration are valid only if miners are stealing from good sidechains. If there is a sidechain that is doing things wrong, scamming people, not being used at all, or is full of bugs, for example, that will be perceived as a bad sidechain, and then miners can and will safely steal from it and kill it, which will be perceived as a good thing by everybody.
What do we do if miners steal?
Paul Sztorc has suggested in the past that a user-activated soft-fork could prevent miners from stealing, i.e., most Bitcoin users and nodes issue a rule similar to this one to invalidate the inclusion of a faulty
WT^and thus cause any miner that includes it in a block to be relegated to their own Bitcoin fork that other nodes won't accept.This suggestion has made people think Drivechain is a sidechain solution backed by user-actived soft-forks for safety, which is very far from the truth. Drivechains must not and will not rely on this kind of soft-fork, although they are possible, as the coordination costs are too high and no one should ever expect these things to happen.
If even with all the incentives against them (see above) miners do still steal from a good sidechain that will mean the failure of the Drivechain experiment. It will very likely also mean the failure of the Bitcoin experiment too, as it will be proven that miners can coordinate to act maliciously over a prolonged period of time regardless of economic and social incentives, meaning they are probably in it just for attacking Bitcoin, backed by nation-states or something else, and therefore no Bitcoin transaction in the mainchain is to be expected to be safe ever again.
Why use this and not a full-blown trustless and open sidechain technology?
Because it is impossible.
If you ever heard someone saying "just use a sidechain", "do this in a sidechain" or anything like that, be aware that these people are either talking about "federated" sidechains (i.e., funds are kept in custody by a group of entities) or they are talking about Drivechain, or they are disillusioned and think it is possible to do sidechains in any other manner.
No, I mean a trustless 2-way peg with correctness of the withdrawals verified by the Bitcoin protocol!
That is not possible unless Bitcoin verifies all transactions that happen in all the sidechains, which would be akin to drastically increasing the blocksize and expanding the Bitcoin rules in tons of ways, i.e., a terrible idea that no one wants.
What about the Blockstream sidechains whitepaper?
Yes, that was a way to do it. The Drivechain hashrate escrow is a conceptually simpler way to achieve the same thing with improved incentives, less junk in the chain, more safety.
Isn't the hashrate escrow a very complex soft-fork?
Yes, but it is much simpler than SegWit. And, unlike SegWit, it doesn't force anything on users, i.e., it isn't a mandatory blocksize increase.
Why should we expect miners to care enough to participate in the voting mechanism?
Because it's in their own self-interest to do it, and it costs very little. Today over half of the miners mine RSK. It's not blind merged mining, it's a very convoluted process that requires them to run a RSK full node. For the Drivechain sidechains, an SPV node would be enough, or maybe just getting data from a block explorer API, so much much simpler.
What if I still don't like Drivechain even after reading this?
That is the entire point! You don't have to like it or use it as long as you're fine with other people using it. The hashrate escrow special addresses will not impact you at all, validation cost is minimal, and you get the benefit of people who want to use Drivechain migrating to their own sidechains and freeing up space for you in the mainchain. See also the point above about infighting.
See also
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A violência é uma forma de comunicação
A violência é uma forma de comunicação: um serial killer, um pai que bate no filho, uma briga de torcidas, uma sessão de tortura, uma guerra, um assassinato passional, uma briga de bar. Em todos esses se pode enxergar uma mensagem que está tentando ser transmitida, que não foi compreendida pelo outro lado, que não pôde ser expressa, e, quando o transmissor da mensagem sentiu que não podia ser totalmente compreendido em palavras, usou essa outra forma de comunicação.
Quando uma ofensa em um bar descamba para uma briga, por exemplo, o que há é claramente uma tentativa de uma ofensa maior ainda pelo lado do que iniciou a primeira, a briga não teria acontecido se ele a tivesse conseguido expressar em palavras tão claras que toda a audiência de bêbados compreendesse, o que estaria além dos limites da linguagem, naquele caso, o soco com o mão direita foi mais eficiente. Poderia ser também a defesa argumentativa: "eu não sou um covarde como você está dizendo" -- mas o bar não acreditaria nessa frase solta, a comunicação não teria obtido o sucesso desejado.
A explicação para o fato da redução da violência à medida em que houve progresso da civilização está na melhora da eficiência da comunicação humana: a escrita, o refinamento da expressão lingüística, o aumento do alcance da palavra falada com rádio, a televisão e a internet.
Se essa eficiência diminuir, porque não há mais acordo quanto ao significado das palavras, porque as pessoas não estão nem aí para se o que escrevem é bom ou não, ou porque são incapazes de compreender qualquer coisa, deve aumentar proporcionalmente a violência.
-
 @ 9171b08a:8395fd65
2024-07-08 02:18:13
@ 9171b08a:8395fd65
2024-07-08 02:18:13Five little heads brush past me in the foyer as I enter the house. I get a “Hey Daddio,” and “Love you Dad,” then a punch in the thigh, “‘sup dad,” from my two girls and little boy.
The neighbor's two girls are polite only in that they say their hellos but no one stops to give me the time of day. I hold the door open for the little band of miscreants and watch them make their way to the front yard.
“Let’s play tag,” says my eldest as she stretches her hands out high above her head.
I turn and notice my wife smiling at me, leaning against the kitchen island.
“No, you always hide in the woods,” says one of the neighbors.
I kiss my wife on the forehead, tell her I love her, and say, “I’ve got dinner tonight. You had a tough day.”
“Nuh-uh. I won’t. That phantom man is in there.”
I wince and look at Jasmine to see if she had heard that. She did and says, “I didn’t want to believe it but I’ve heard them talk about it a few times already so I asked Tanner if he and Andrea had heard the kids talking about the man in the forest. They’re worried about it.”
“Have you seen anything strange?” I ask.
Jasmine steps up to the floor to ceiling window in the breakfast nook and peers at the forest across the cul de sac. She purses her lips and shakes her head, “No. You?”
I say, “Nope,” as I pull out the ingredients I’ll be using for dinner tonight. “We’ve taught the kids well. They know not to go near strangers. I’ll see if I can maneuver the camera to keep an eye on the woodline. Yeah?”
“Yes, that sounds good,” says Jasmine, relaxing and settling into one of the breakfast nook table chairs. “I didn’t get the Letterman account.”
I take out the chicken from the refrigerator and say, “I figured as much from the way you sounded on the phone. Look, all is not lost. You just need to get a hold of someone who knows him well.”
Jasmine crosses her arms and peers out at the kids outside, “I don’t know. I might have to take this one as a loss.”
“No! You can’t give up,” I try to get her spirits up by reaching for a bottle of wine from the rack above the refrigerator. She smiles when I pour her a glass and puts a hand on mine to hold me for a while after I leave the glass in front of her. “You’re still in control. You can figure this out.”
“Sometimes things are just out of our control David.”
I stare back slack jawed, “Things are always in our control Jasmine. We didn’t get this far in life by pretending everything was predestined.” I laugh as I grip a handful air and say, “I’ve got life by the balls baby. Always have. That’s why we have such a splendid house, such a nice life.”
“Don’t give yourself all the credit, big guy.”
I turn back to the chicken with a smile and start preparing dinner. “Hey Google, play Tennessee Whiskey by Chris Stapleton.”
An upbeat voice from the little circular speaker on the kitchen island replies, “Sure, Tennessee Whiskey by Chris Stapleton.” Chris Stapleton’s classic four strums of the guitar echo out of the speaker and I dance as I marinate the chicken. I love the sound of the children enjoying themselves outside going along to the music; love the feeling of the chopped cilantro, salt, and pepper grind between my fingertips as I rub it into the chicken. The oil heats in the pan releasing a little wisp of smoke. The chicken sizzles in the pan and releases a hearty aroma.
When I rise from the pan, I notice Jasmine is standing at the window again, cup of wine in hand. Twilight is settling in but the street lights haven’t kicked on yet. Jasmine is strangely close to the window, I figure she’s enjoying the sight of the kids as their shadows zip past in front of her like specters in the night.
“David. I see something in the woodline.”
I shoot to her side and peer out the window along with her. The kids' shadows stalk in the night but I can’t make out anything across the cul de sac. “I don’t see anything.”
Jasmine plants a finger in the windowpane, “Right there. There, it's definitely someone out there. There’s a neighborhood on the other side of that treeline isn’t there?”
I strain to catch a glimpse at what she’s looking at and say, “I don't see anything. I, uh, I think there’s a neighborhood back there yeah.”

The street lights kick on. A man stands just out of reach of the street light on the far end of the cul de sac. “Holy fuck,” I say under my breath.
“Kids, come inside please!” shouts Jasmine.
“Aww c’mon mom. Just a bit longer,” calls out my son.
“Zach, get inside like your mother told you,” I growl and take my gaze away from the man for a second to sneer at my boy through the window. By the time I look back the man’s gone. “Where’d he go?”
Jasmine’s eyebrows raised, “He uh, just kind of vanished. Looks like he was never really there. Look,” She points at a tree shaped strangely enough like a man. “Maybe it was just that tree we were looking at.”
I didn’t take any chances. I tell the kids to come in and I maneuver the security cameras to get a good vantage of the place where the man had vanished. The next morning I help the kids get ready for school and personally walk them to their bus stop.
Still no man in the woods.
Shortly after I return to the house I kiss my wife goodbye and wish her good luck at work. Just as she pulls out of the cul de sac, as I am walking to my truck, I notice a figure in my peripheral vision but I don’t turn knowing I might scare him away. I halfway sit in my truck and shift the rearview mirror to where I’d seen him. There he is. The man stands several feet inside the forest. Greenery conceals him up to his torso and I can barely see his face in the shadows of the forest, but his figure is clear.
I consider calling the police, no, they won’t make it in time. I take a deep breath, count down from three, and burst out of my car into a sprint toward the man in the woods. The man doesn’t move an inch as I approach but somehow it seems as if the forest deepens around him. As I get closer his relative position from me grows further, but the man doesn’t take a step. It's as if the world around the man grows further and further out of focus the closer and closer I get.
I hear the leaves crushing beneath my footfalls and I look back for a second feeling as if I’d been running on a treadmill for the past few seconds. My house is barely visible through the foliage. I whipped my attention back at the man but he’s gone and I grind to a halt. I scrutinize the woods, the man has vanished.
My breaths slow, nearly holding my breath I listen intently for the sound of crushing leaves. The crunching leaves come from behind me at an alarming pace. Whatever is approaching is running fast. I turn, ready for someone to tackle me, but there is no one there, the footfalls go silent. I curse under my breath and peer back at my house. It's hard to make out now that I’m so deep in the woods, but it looks like the neighbor’s kids are out in front of my house. I shake my head and look down at my watch wondering how much time I’d wasted chasing the phantom man. I wince at the readout on my watch, five pm. Maybe I hit one of the program buttons while I was sprinting into the woods?
There’s a whisper in the wind, “Must of hit..”
I turn to the whispers.
Another whisper behind me, “One of the program buttons.”
I turn. I feel light in my own skin. There’s nothing behind me, no one around me, but I continue to hear the voice whispering.
“Five PM. Five?”
I’m literally beside myself. I know it's my own voice I’m hearing but I’m not sure if it's my thoughts or an illusion, just the wind blowing. Maybe it’s the shifting tree branches and my paranoia. The sun is bright, blinding. Suddenly, I’m seconds behind myself.
I saw my hand shifting in the sunlight. Perhaps it was the fatigue from a sleepless night having been worried about the phantom man lurking in the forest outside my house. The disconnect in time was jarring as every movement jolted like a violent tectonic shift in my head. I felt like a witness to my own reality as it had just happened.
I looked around and a sound off in the woods drew me deeper. The deeper I went, the dimmer the sunlight became. I ran faster and faster in chase of the sounds with the hopes I’d at least catch another glimpse of the phantom man.
Then, my foot caught a taproot and I slammed into rich dirt, but my descent did not stop. The dirt splashed about me as if I’d fallen in a lake of darkness. The grains of dirt filled my lungs in my panic.
A squirrel watched me trip and if only the gentle creature understood the mechanics of the universe he would’ve known where I had disappeared to. Unlike the squirrel, the tree on top whose branch it sat did not have the sense of sight to have seen me fall but it did encounter a minty sensation when it absorbed the nutrients of my being. I hadn’t granted the beings of its kind the sense of emotion, but somehow it still knew the sensation was good. It exhaled the vapors of me and enriched the atmosphere for the humans of that world. These little kinds of discoveries excited me. A design had led to an outcome I hadn’t thought possible and I saw that it was good.
The cosmic specs continued their spread before me and it suddenly occurred to me I hadn’t paid much attention to the adjacent place. There it was still only nothingness, phantom echoes of my self reflection. All was good, but was it best? I’ve created many things, breathed life into endless inanimate things yet most of my existing universe still lingers motionless, pushed only by the initial momentum of the beginning. The life that has existed has worshiped me, prayed to me, cursed me, forgotten me and found me, but is it best?
Perhaps I’ll never know until I compare it with another. So it is. From my word bubbled a new momentum from unfathomable depths. All possibilities confounded and reverberated and again there was an atmosphere charged with my essence, what would these new humans do with it?
The tree inhaled my essence and it was good. The squirrel watched a man disappear into the earth and it was good. Grains of dirt filled my lungs and dispersed from my nose and it was good. I was spat out from the depths of the universe and on my feet I chased the phantom man in the direction of my home. The sun had receded into the horizon and time had regressed to a moment.
Beyond the foliage I see my children play with the neighbors. Their laughter is alarmingly delicious to my ears as if I hadn’t heard that sweet sound in an unfathomable expanse of time. There I am in the window, looking this way. Then suddenly, the street light kicks on.
“Holy fuck,” says David under his breath.
I shout, “Kids, come inside please!”
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Problemas com Russell Kirk
A idéia central da “política da prudência[^1]” de Russell Kirk me parece muito correta, embora tenha sido melhor formulada pior no seu enorme livro do que em uma pequena frase do joanadarquista Lucas Souza: “o conservadorismo é importante, porque tem muita gente com idéia errada por aí, e nós podemos não saber distingüi-las”.
Porém, há alguns problemas que precisam ser esclarecidos, ou melhor explicados, e que me impedem de enxergar os seus argumentos como refutação final do meu já tão humilde (embora feroz) anarquismo. São eles:
I Percebo alguma coisa errada, não sei bem onde, entre a afirmação de que toda ideologia é ruim, ou “todas as ideologias causam confusão[^2]”, e a proposta conservadora de “conservar o mundo da ordem que herdamos, ainda que em estado imperfeito, de nossos ancestrais[^3]”. Ora, sem precisar cair em exemplos como o do partido conservador inglês -- que conservava a política inglesa sempre onde estava, e se alternava no governo com o partido trabalhista, que a levava cada vez mais um pouco à esquerda --, está embutida nessa frase, talvez, a idéia, que ao mesmo tempo é clara e ferrenhamente combatida pelos próprios conservadores, de que a história é da humanidade é uma história de progresso linear rumo a uma situação melhor.
Querer conservar o mundo da ordem que herdamos significa conservar também os vários erros que podem ter sido cometidos pelos nossos ancestrais mais recentes, e conservá-los mesmo assim, acusando toda e qualquer tentativa de propôr soluções a esses erros de ideologia? Ou será que conservar o mundo da ordem é escolher um período determinado que seja tido como o auge da história humana e tentar restaurá-lo em nosso próprio tempo? Não seria isto ideologia?
Ou, ainda, será que conservar o mundo da ordem é selecionar, entre vários períodos do passado, alguns pedaços que o conservador considerar ótimos em cada sociedade, fazer dali uma mistura de sociedade ideal baseada no passado e então tentar implementá-la? Quem saberia dizer quais são as partes certas?
II Sobre a questão do que mantém a sociedade civil coesa, Russell Kirk, opondo-a à posição libertária de que o nexo da sociedade é o autointeresse, declara que a posição conservadora é a de que “a sociedade é uma comunidade de almas, que une os mortos, os vivos e os ainda não nascidos, e que se harmoniza por aquilo que Aristóteles chamou de amizade e os cristãos chamam de caridade ou amor ao próximo”.
Esta é uma posição muito correta, mas me parece estar em contradição com a defesa do Estado que ele faz na mesma página e na seguinte. O que me parece errado é que a sociedade não pode ser, ao mesmo tempo, uma “comunidade baseada no amor ao próximo” e uma comunidade que “requer não somente que as paixões dos indivíduos sejam subjugadas, mas que, mesmo no povo e no corpo social, bem como nos indivíduos, as inclinações dos homens, amiúde, devam ser frustradas, a vontade controlada e as paixões subjugadas” e, pior, que “isso somente pode ser feito por um poder exterior”.
Disto aí podemos tirar que, da mesma forma que Kirk define a posição libertária como sendo a de que o autointeresse é que mantém a sociedade civil coesa, a posição conservadora seria então a de que essa coesão vem apenas do Estado, e não de qualquer ligação entre vivos e mortos, ou do amor ao próximo. Já que, sem o Estado, diz, ele, citando Thomas Hobbes, a condição do homem é “solitária, pobre, sórdida, embrutecida e curta”?
[^1]: este é o nome do livro e também um outro nome que ele dá para o próprio conservadorismo (p.99). [^2]: p. 101 [^3]: p. 102
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
A command line utility to create and manage personal graphs, then write them to dot and make images with graphviz.
It manages a bunch of YAML files, one for each entity in the graph. Each file lists the incoming and outgoing links it has (could have listen only the outgoing, now that I'm tihnking about it).
Each run of the tool lets you select from existing nodes or add new ones to generate a single link type from one to one, one to many, many to one or many to many -- then updates the YAML files accordingly.
It also includes a command that generates graphs with graphviz, and it can accept a template file that lets you customize the
dotthat is generated and thus the graphviz graph.rel
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28GraphQL vs REST
Today I saw this: https://github.com/stickfigure/blog/wiki/How-to-(and-how-not-to)-design-REST-APIs
And it reminded me why GraphQL is so much better.
It has also reminded me why HTTP is so confusing and awful as a protocol, especially as a protocol for structured data APIs, with all its status codes and headers and bodies and querystrings and content-types -- but let's not talk about that for now.
People complain about GraphQL being great for frontend developers and bad for backend developers, but I don't know who are these people that apparently love reading guides like the one above of how to properly construct ad-hoc path routers, decide how to properly build the JSON, what to include and in which circumstance, what status codes and headers to use, all without having any idea of what the frontend or the API consumer will want to do with their data.
It is a much less stressful environment that one in which we can just actually perform the task and fit the data in a preexistent schema with types and a structure that we don't have to decide again and again while anticipating with very incomplete knowledge the usage of an extraneous person -- i.e., an environment with GraphQL, or something like GraphQL.
By the way, I know there are some people that say that these HTTP JSON APIs are not the real REST, but that is irrelevant for now.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28nostr - Notes and Other Stuff Transmitted by Relays
The simplest open protocol that is able to create a censorship-resistant global "social" network once and for all.
It doesn't rely on any trusted central server, hence it is resilient; it is based on cryptographic keys and signatures, so it is tamperproof; it does not rely on P2P techniques, therefore it works.
Very short summary of how it works, if you don't plan to read anything else:
Everybody runs a client. It can be a native client, a web client, etc. To publish something, you write a post, sign it with your key and send it to multiple relays (servers hosted by someone else, or yourself). To get updates from other people, you ask multiple relays if they know anything about these other people. Anyone can run a relay. A relay is very simple and dumb. It does nothing besides accepting posts from some people and forwarding to others. Relays don't have to be trusted. Signatures are verified on the client side.
This is needed because other solutions are broken:
The problem with Twitter
- Twitter has ads;
- Twitter uses bizarre techniques to keep you addicted;
- Twitter doesn't show an actual historical feed from people you follow;
- Twitter bans people;
- Twitter shadowbans people.
- Twitter has a lot of spam.
The problem with Mastodon and similar programs
- User identities are attached to domain names controlled by third-parties;
- Server owners can ban you, just like Twitter; Server owners can also block other servers;
- Migration between servers is an afterthought and can only be accomplished if servers cooperate. It doesn't work in an adversarial environment (all followers are lost);
- There are no clear incentives to run servers, therefore they tend to be run by enthusiasts and people who want to have their name attached to a cool domain. Then, users are subject to the despotism of a single person, which is often worse than that of a big company like Twitter, and they can't migrate out;
- Since servers tend to be run amateurishly, they are often abandoned after a while — which is effectively the same as banning everybody;
- It doesn't make sense to have a ton of servers if updates from every server will have to be painfully pushed (and saved!) to a ton of other servers. This point is exacerbated by the fact that servers tend to exist in huge numbers, therefore more data has to be passed to more places more often;
- For the specific example of video sharing, ActivityPub enthusiasts realized it would be completely impossible to transmit video from server to server the way text notes are, so they decided to keep the video hosted only from the single instance where it was posted to, which is similar to the Nostr approach.
The problem with SSB (Secure Scuttlebutt)
- It doesn't have many problems. I think it's great. In fact, I was going to use it as a basis for this, but
- its protocol is too complicated because it wasn't thought about being an open protocol at all. It was just written in JavaScript in probably a quick way to solve a specific problem and grew from that, therefore it has weird and unnecessary quirks like signing a JSON string which must strictly follow the rules of ECMA-262 6th Edition;
- It insists on having a chain of updates from a single user, which feels unnecessary to me and something that adds bloat and rigidity to the thing — each server/user needs to store all the chain of posts to be sure the new one is valid. Why? (Maybe they have a good reason);
- It is not as simple as Nostr, as it was primarily made for P2P syncing, with "pubs" being an afterthought;
- Still, it may be worth considering using SSB instead of this custom protocol and just adapting it to the client-relay server model, because reusing a standard is always better than trying to get people in a new one.
The problem with other solutions that require everybody to run their own server
- They require everybody to run their own server;
- Sometimes people can still be censored in these because domain names can be censored.
How does Nostr work?
- There are two components: clients and relays. Each user runs a client. Anyone can run a relay.
- Every user is identified by a public key. Every post is signed. Every client validates these signatures.
- Clients fetch data from relays of their choice and publish data to other relays of their choice. A relay doesn't talk to another relay, only directly to users.
- For example, to "follow" someone a user just instructs their client to query the relays it knows for posts from that public key.
- On startup, a client queries data from all relays it knows for all users it follows (for example, all updates from the last day), then displays that data to the user chronologically.
- A "post" can contain any kind of structured data, but the most used ones are going to find their way into the standard so all clients and relays can handle them seamlessly.
How does it solve the problems the networks above can't?
- Users getting banned and servers being closed
- A relay can block a user from publishing anything there, but that has no effect on them as they can still publish to other relays. Since users are identified by a public key, they don't lose their identities and their follower base when they get banned.
- Instead of requiring users to manually type new relay addresses (although this should also be supported), whenever someone you're following posts a server recommendation, the client should automatically add that to the list of relays it will query.
- If someone is using a relay to publish their data but wants to migrate to another one, they can publish a server recommendation to that previous relay and go;
- If someone gets banned from many relays such that they can't get their server recommendations broadcasted, they may still let some close friends know through other means with which relay they are publishing now. Then, these close friends can publish server recommendations to that new server, and slowly, the old follower base of the banned user will begin finding their posts again from the new relay.
-
All of the above is valid too for when a relay ceases its operations.
-
Censorship-resistance
- Each user can publish their updates to any number of relays.
-
A relay can charge a fee (the negotiation of that fee is outside of the protocol for now) from users to publish there, which ensures censorship-resistance (there will always be some Russian server willing to take your money in exchange for serving your posts).
-
Spam
-
If spam is a concern for a relay, it can require payment for publication or some other form of authentication, such as an email address or phone, and associate these internally with a pubkey that then gets to publish to that relay — or other anti-spam techniques, like hashcash or captchas. If a relay is being used as a spam vector, it can easily be unlisted by clients, which can continue to fetch updates from other relays.
-
Data storage
- For the network to stay healthy, there is no need for hundreds of active relays. In fact, it can work just fine with just a handful, given the fact that new relays can be created and spread through the network easily in case the existing relays start misbehaving. Therefore, the amount of data storage required, in general, is relatively less than Mastodon or similar software.
-
Or considering a different outcome: one in which there exist hundreds of niche relays run by amateurs, each relaying updates from a small group of users. The architecture scales just as well: data is sent from users to a single server, and from that server directly to the users who will consume that. It doesn't have to be stored by anyone else. In this situation, it is not a big burden for any single server to process updates from others, and having amateur servers is not a problem.
-
Video and other heavy content
-
It's easy for a relay to reject large content, or to charge for accepting and hosting large content. When information and incentives are clear, it's easy for the market forces to solve the problem.
-
Techniques to trick the user
- Each client can decide how to best show posts to users, so there is always the option of just consuming what you want in the manner you want — from using an AI to decide the order of the updates you'll see to just reading them in chronological order.
FAQ
- This is very simple. Why hasn't anyone done it before?
I don't know, but I imagine it has to do with the fact that people making social networks are either companies wanting to make money or P2P activists who want to make a thing completely without servers. They both fail to see the specific mix of both worlds that Nostr uses.
- How do I find people to follow?
First, you must know them and get their public key somehow, either by asking or by seeing it referenced somewhere. Once you're inside a Nostr social network you'll be able to see them interacting with other people and then you can also start following and interacting with these others.
- How do I find relays? What happens if I'm not connected to the same relays someone else is?
You won't be able to communicate with that person. But there are hints on events that can be used so that your client software (or you, manually) knows how to connect to the other person's relay and interact with them. There are other ideas on how to solve this too in the future but we can't ever promise perfect reachability, no protocol can.
- Can I know how many people are following me?
No, but you can get some estimates if relays cooperate in an extra-protocol way.
- What incentive is there for people to run relays?
The question is misleading. It assumes that relays are free dumb pipes that exist such that people can move data around through them. In this case yes, the incentives would not exist. This in fact could be said of DHT nodes in all other p2p network stacks: what incentive is there for people to run DHT nodes?
- Nostr enables you to move between server relays or use multiple relays but if these relays are just on AWS or Azure what’s the difference?
There are literally thousands of VPS providers scattered all around the globe today, there is not only AWS or Azure. AWS or Azure are exactly the providers used by single centralized service providers that need a lot of scale, and even then not just these two. For smaller relay servers any VPS will do the job very well.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Parallel Chains
We want merged-mined blockchains. We want them because it is possible to do things in them that aren't doable in the normal Bitcoin blockchain because it is rightfully too expensive, but there are other things beside the world money that could benefit from a "distributed ledger" -- just like people believed in 2013 --, like issued assets and domain names (just the most obvious examples).
On the other hand we can't have -- like people believed in 2013 -- a copy of Bitcoin for every little idea with its own native token that is mined by proof-of-work and must get off the ground from being completely valueless into having some value by way of a miracle that operated only once with Bitcoin.
It's also not a good idea to have blockchains with custom merged-mining protocol (like Namecoin and Rootstock) that require Bitcoin miners to run their software and be an active participant and miner for that other network besides Bitcoin, because it's too cumbersome for everybody.
Luckily Ruben Somsen invented this protocol for blind merged-mining that solves the issue above. Although it doesn't solve the fact that each parallel chain still needs some form of "native" token to pay miners -- or it must use another method that doesn't use a native token, such as trusted payments outside the chain.
How does it work
With the
SIGHASH_NOINPUT/SIGHASH_ANYPREVOUTsoft-fork[^eltoo] it becomes possible to create presigned transactions that aren't related to any previous UTXO.Then you create a long sequence of transactions (sufficient to last for many many years), each with an
nLockTimeof 1 and each spending the next (you create them from the last to the first). Since theirscriptSig(the unlocking script) will useSIGHASH_ANYPREVOUTyou can obtain a transaction id/hash that doesn't include the previous TXO, you can, for example, in a sequence of transactionsA0-->B(B spends output 0 from A), include the signature for "spending A0 on B" inside thescriptPubKey(the locking script) of "A0".With the contraption described above it is possible to make that long string of transactions everybody will know (and know how to generate) but each transaction can only be spent by the next previously decided transaction, no matter what anyone does, and there always must be at least one block of difference between them.
Then you combine it with
RBF,SIGHASH_SINGLEandSIGHASH_ANYONECANPAYso parallel chain miners can add inputs and outputs to be able to compete on fees by including their own outputs and getting change back while at the same time writing a hash of the parallel block in the change output and you get everything working perfectly: everybody trying to spend the same output from the long string, each with a different parallel block hash, only the highest bidder will get the transaction included on the Bitcoin chain and thus only one parallel block will be mined.See also
[^eltoo]: The same thing used in Eltoo.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A estrutura lógica do livro didático
Todos os livros didáticos e cursos expõem seus conteúdos a partir de uma organização lógica prévia, um esquema de todo o conteúdo que julgam relevante, tudo muito organizadinho em tópicos e subtópicos segundo a ordem lógica que mais se aproxima da ordem natural das coisas. Imagine um sumário de um manual ou livro didático.
A minha experiência é a de que esse método serve muito bem para ninguém entender nada. A organização lógica perfeita de um campo de conhecimento é o resultado final de um estudo, não o seu início. As pessoas que escrevem esses manuais e dão esses cursos, mesmo quando sabem do que estão falando (um acontecimento aparentemente raro), o fazem a partir do seu próprio ponto de vista, atingido após uma vida de dedicação ao assunto (ou então copiando outros manuais e livros didáticos, o que eu chutaria que é o método mais comum).
Para o neófito, a melhor maneira de entender algo é através de imersões em micro-tópicos, sem muita noção da posição daquele tópico na hierarquia geral da ciência.
- Revista Educativa, um exemplo de como não ensinar nada às crianças.
- Zettelkasten, a ordem surgindo do caos, ao invés de temas se encaixando numa ordem preexistentes.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Boardthreads
This was a very badly done service for turning a Trello list into a helpdesk UI.
Surprisingly, it had more paying users than Websites For Trello, which I was working on simultaneously and dedicating much more time to it.
The Neo4j database I used for this was a very poor choice, it was probably the cause of all the bugs.

-
 @ 8d34bd24:414be32b
2024-07-06 14:57:16
@ 8d34bd24:414be32b
2024-07-06 14:57:16Because the God of the Bible is the true God and creator of everything: matter & energy, time & space, things seen and things unseen, He is not a God who can be fully comprehended. There are things about God that make our heads hurt when we try to fully understand them. He is not an easy to understand God made from the mind of man.
What is the Trinity?
One trait of God that is particularly hard to comprehend is the fact that He is 3 persons in 1 God. There are even arguments over this trait because it is so hard to understand.
First, let’s get out that the word trinity (or any form of it) is not used in the Bible. At the time the Bible was written, I don’t believe a word to describe His 3 in 1 nature existed. We come to the understand His 3 in 1 nature by reading descriptions of God the Father, God the Spirit, and God the Son (Jesus). God also frequently refers to Himself in the plural. Although the easy to understand trinitarian nature does not come until the New Testament, even the Old Testament suggests this nature from the very Beginning.
“Then God said, “Let Us make man in Our image, according to Our likeness; and let them rule over the fish of the sea and over the birds of the sky and over the cattle and over all the earth, and over every creeping thing that creeps on the earth.” (Genesis 1:26)” {emphasis mine}
Notice how God refers to Himself as “Us” and “Our”. God refers to Himself as plural. This is the first reference to the trinitarian nature of God. Like many other things, such as salvation through faith in Jesus and God caring for the whole world and not just Israel, the trinity is not made clear until the New Testament.
Is Jesus God?
When people argue against the trinity, the biggest argument is that Jesus is not God. They think He is a prophet, a wise teacher, and a good man, but not God. Unfortunately for them, Jesus does not leave this option open to us.
So they were saying to Him, “Who are You?” Jesus said to them, “What have I been saying to you from the beginning? … So Jesus said, “When you lift up the Son of Man, then you will know that I am He, and I do nothing on My own initiative, but I speak these things as the Father taught Me. And He who sent Me is with Me; He has not left Me alone, for I always do the things that are pleasing to Him.” As He spoke these things, many came to believe in Him. (John 8:25,28-30) {emphasis mine}
In the English translation, the translators added the word “He” for ease of reading, but that word is not there in the original Greek, therefore what He really said was “you will know that I am.” Why is this important? Jesus was claiming to be God. In the Old Testament, when Moses asked God’s name, He replied, “I AM.”
Then Moses said to God, “Behold, I am going to the sons of Israel, and I will say to them, ‘The God of your fathers has sent me to you.’ Now they may say to me, ‘What is His name?’ What shall I say to them?” God said to Moses, “I AM WHO I AM”; and He said, “Thus you shall say to the sons of Israel, ‘I AM has sent me to you.’ ” (Exodus 3:13-14)
A Jewish man using the term “I AM” about Himself would be blaspheming because He is applying the name of God to Himself. A man claiming to be God, who isn't, cannot be a good man.
As C.S. Lewis says:
“I am trying here to prevent anyone from saying the really foolish thing that people often say about Him: ‘I’m ready to accept Jesus as a great moral teacher, but I don’t accept his claim to be God.’ That is the one thing we must not say. A man who was merely a man and said the sort of things Jesus said would not be a great moral teacher. He would either be a lunatic– on a level with the man who says he is a poached egg– or else he would be the Devil of Hell. You must make your choice. Either this man was, and is, the Son of God: or else a madman or something worse. You can shut him up for a fool, you can spit at Him and kill Him as a demon; or you can fall at His feet and call Him Lord and God. But let us not come up with any patronizing nonsense about His being a great human teacher. He has not left that open to us. He did not intend to.”
When the Jewish leaders heard Jesus talking, they understood that His statements were claims to be God.
For this reason therefore the Jews were seeking all the more to kill Him, because He not only was breaking the Sabbath, but also was calling God His own Father, making Himself equal with God. (John 5:18) {Emphasis mine}
When the Jewish people heard Jesus talking, they understood that His statements were claims to be God.
I and the Father are one.”
The Jews picked up stones again to stone Him. Jesus answered them, “I showed you many good works from the Father; for which of them are you stoning Me?” The Jews answered Him, “For a good work we do not stone You, but for blasphemy; and because You, being a man, make Yourself out to be God.” (John 10:30-33) {Emphasis mine}Also Jesus said,
Jesus said to them, “If God were your Father, you would love Me, for I proceeded forth and have come from God, for I have not even come on My own initiative, but He sent Me. (John 8:42) {Emphasis mine}
Jesus claims to have “proceeded forth … from God.” Everyone knew He had been born by Mary. How could He “proceeded forth … from God” if He was born naturally like every other man. If He was born no differently than any other man, then He wouldn’t be God. Of course we know that He was born differently.
Now the birth of Jesus Christ was as follows: when His mother Mary had been betrothed to Joseph, before they came together she was found to be with child by the Holy Spirit. (Matthew 1:18)
Now in the sixth month the angel Gabriel was sent from God to a city in Galilee called Nazareth, to a virgin engaged to a man whose name was Joseph, of the descendants of David; and the virgin’s name was Mary. And coming in, he said to her, “Greetings, favored one! The Lord is with you.” But she was very perplexed at this statement, and kept pondering what kind of salutation this was. The angel said to her, “Do not be afraid, Mary; for you have found favor with God. And behold, you will conceive in your womb and bear a son, and you shall name Him Jesus. He will be great and will be called the Son of the Most High; and the Lord God will give Him the throne of His father David; and He will reign over the house of Jacob forever, and His kingdom will have no end.” Mary said to the angel, “How can this be, since I am a virgin?” The angel answered and said to her, “The Holy Spirit will come upon you, and the power of the Most High will overshadow you; and for that reason the holy Child shall be called the Son of God. (Luke 1:26-35)
This was no normal birth and Jesus is no normal man. Being born of Mary and the Holy Spirit enabled Him to be fully God and fully man at one time. It is hard for our human minds to comprehend, but we serve an awesome God who can do things beyond our understanding. This is one of many unimaginable miracles of God.
Jesus also claimed to have “all authority”.
And Jesus came up and spoke to them, saying, “All authority has been given to Me in heaven and on earth.” (Matthew 28:18) {Emphasis mine}
Is it possible for anyone other than God to have “all authority”?
If you believe the Bible at all, it has not given us the option of thinking that Jesus was anything less than God. Not only does Jesus claim to be God and his listeners understand Him to be claiming to be God, but other books of the Bible also refer to Him as God.
who [Jesus], although He existed in the form of God, did not regard equality with God a thing to be grasped, but emptied Himself, taking the form of a bond-servant, and being made in the likeness of men. Being found in appearance as a man, He humbled Himself by becoming obedient to the point of death, even death on a cross. For this reason also, God highly exalted Him, and bestowed on Him the name which is above every name, so that at the name of Jesus every knee will bow, of those who are in heaven and on earth and under the earth, and that every tongue will confess that Jesus Christ is Lord, to the glory of God the Father. (Philippians 2:6-11) [Clarification mine] {Emphasis mine}
This is one of the clearest declarations of the deity of Jesus in the Bible. It says Jesus “existed in the form of God." This sounds like the Bible is calling Jesus God. It also says Jesus “did not regard equality with God a thing to be grasped.” In other words, Jesus was totally God, so He didn’t have to try to act like God, speak like God, or claim to be God. His Godhood was clearly evident.
This passage says Jesus’s name is “the name which is above every name.” Does anyone actually believe that God the Father, Yahweh, would put any other name above His own? Of course not! Jesus’s name is “above every name” because He is one with God the Father and one with God the Holy Spirit.
This passage says “at the name of Jesus every knee will bow,” but we know every time someone bows to anyone other than God, including angels or prophets of God like Paul and Silas, the people are immediately told to bow to no one but God. Here it states that “every knee will bow.” This would not be true unless Jesus was God and one with God the Father.
It also says, “that every tongue will confess that Jesus Christ is Lord, to the glory of God the Father.” Would calling Jesus Lord be to the glory of God if Jesus was not God? I think not.
One of the best best verses about Jesus’s deity doesn’t technically use the name of Jesus, but if you take the entirety of the Book of John and his stated purpose:
And there are also many other things which Jesus did, which if they *were written in detail, I suppose that even the world itself would not contain the books that would be written. (John 21:25)
In this context it is clear that John refers to Jesus as the word in John 1:1-3.
In the beginning was the Word, and the Word was with God, and the Word was God. He was in the beginning with God. All things came into being through Him, and apart from Him nothing came into being that has come into being. In Him was life, and the life was the Light of men. The Light shines in the darkness, and the darkness did not comprehend it. (John 1:1-5)
These truths are said about Jesus:
- Jesus was from the beginning
- Jesus was with God
- Jesus was God
- Jesus is creator
- Life comes from Jesus
- Jesus is Holy (light in the darkness)
Can there be any conclusion other than that Jesus is God?
Is the Holy Spirit God?
The Bible says:
All Scripture is inspired by God and profitable for teaching, for reproof, for correction, for training in righteousness; (2 Timothy 3:16)) {Emphasis mine}
but it also says:
But know this first of all, that no prophecy of Scripture is a matter of one’s own interpretation, for no prophecy was ever made by an act of human will, but men moved by the Holy Spirit spoke from God. (2 Peter 1:20-21) {Emphasis mine}
If the inspiration of man comes from God and comes from the Holy Spirit, that makes the Holy Spirit the same God. The two are spoken of in the same way.
Or do you not know that your body is a temple of the Holy Spirit who is in you, whom you have from God, and that you are not your own? For you have been bought with a price: therefore glorify God in your body. (1 Corinthians 6:19-20) {Emphasis mine}
In the same way, if our bodies are “a temple of the Holy Spirit” and we are a temple of God. If we are a temple of the Holy Spirit and the Holy Spirit isn’t the same God as God the Father, how would this “glorify God in your body?”
But Peter said, “Ananias, why has Satan filled your heart to lie to the Holy Spirit and to keep back some of the price of the land? While it remained unsold, did it not remain your own? And after it was sold, was it not under your control? Why is it that you have conceived this deed in your heart? You have not lied to men but to God.” (Acts 5:3-4) {Emphasis mine}
This Bible passage equates lying to the Holy Spirit to lying to God. This is true since they are just to parts of the One true God.
We’ve already proven that Jesus is God. In the verse below Jesus refers to himself leaving and the Father sending the Holy Spirit. All three are given equality as God with each having a different purpose in the totality of the will of God. In this passage “I” and “My name” refer to Jesus, while “Helper”, “Holy Spirit”, and “He” refer to the the Holy Spirit.
“These things I have spoken to you while abiding with you. But the Helper, the Holy Spirit, whom the Father will send in My name, He will teach you all things, and bring to your remembrance all that I said to you. (John 14:25-26) {Emphasis mine}
Also …
Do not grieve the Holy Spirit of God, by whom you were sealed for the day of redemption. (Ephesians 4:30)
In this verse the Holy Spirit is referred to as separate and independent, though still part of God. He is one person in the totality of God.
In this verse the Spirit of God is compared to the spirit of man.
For to us God revealed them through the Spirit; for the Spirit searches all things, even the depths of God. For who among men knows the thoughts of a man except the spirit of the man which is in him? Even so the thoughts of God no one knows except the Spirit of God. Now we have received, not the spirit of the world, but the Spirit who is from God, so that we may know the things freely given to us by God, which things we also speak, not in words taught by human wisdom, but in those taught by the Spirit, combining spiritual thoughts with spiritual words. (1 Corinthians 2:10-13) {Emphasis mine}
Just as the spirit of man is part of a man, so also is the Holy Spirit part of God. In Genesis God creates man in His image. I’ve heard it said that part of being in God’s image is a trinitarian design of man (although we are never as separate as the 3 persons or as one as the one God). Man is body, mind, and spirit just as God is the Son (Jesus), the Father, and the Holy Spirit.
Is the Father God?
I’ve included this section for completeness, but I don’t think anyone who believes the Bible even a little bit denies that the Father is God. Some may believe that He is the only part of God, but they don’t deny the Father’s deity, so I won’t go into this any farther.
Doesn’t the Bible speak of God as One?
The most common argument against the trinity is the use of this verse in Deuteronomy.
“Hear, O Israel! The Lord is our God, the Lord is one! (Deuteronomy 6:4)
Jesus even confirmed that this was a critical understanding of God when asked what is the greatest commandment.
Jesus answered, “The foremost is, ‘Hear, O Israel! The Lord our God is one Lord; (Mark 12:29)
The problem is that this verse is speaking against a pantheon of gods such as those of Greece and Rome. The trinity may have 3 persons, but He is still only one God. They aren’t separate. They are of one mind and one will. They can’t be separated from one another like the “gods” in other religions which have a multitude of “gods” that usually fight among themselves. This is hard for us to understand, but it is clearly communicated in the New Testament.
As a help to understanding the 3 in 1 nature of God, I’ll include a little excerpt from my upcoming book Why I Need Jesus I hope it helps, but I have doubts that any human mind can fully understand the 3 in 1 nature of God.
Another incomprehensible thing about God is that He is a trinity: three in one. He is one God, but three persons – God the Father, God the Son (Jesus), and God the Holy Spirit. Our finite minds can’t comprehend how someone can be three persons, but only one God, but that is what God is.
There are a number of analogies that help us understand the trinity, but none of them fully explain what the trinity is. We can not fully understand the trinity until the time we spend in eternity with Him, and although we will understand more in the afterlife, we may never fully understand.
One analogy of the trinity is the different roles of a person. I am a wife, a mother, and a business owner. I act differently acting in my different roles, but I have certain traits that are universal because I am me. As a wife I am encouraging, loving, submissive, romantic, and supportive. As a mom I am encouraging and loving, but I guide, teach, act as an example, and punish. As a business owner I encourage, train, discipline, and help my employees. You’ll notice there are commonalities between my roles, but I also act differently in my different roles. The trinity is kind of like that, but they are more one and more three than my example. Although I sometimes talk to myself, I can’t really interact socially with myself like the trinity can with the different parts of the trinity. I am more one. I can’t truly be 3 persons.
The Trinity is also somewhat like the 3 states of water: ice, (liquid) water, and water vapor. They are all water. They are all H2O, but if you look at ice, water, and water vapor, they all have different traits and don’t look or act the same.
The last example I’ve heard came from a Southern Baptist pastor who has a food analogy for almost any Biblical principle. He always said that the trinity is as simple as cherry pie. If you have a cherry pie and cut it into three slices, when you look at it, it is clearly 3 different pieces of pie, but inside the cherry filling runs through the whole pie and is one cherry pie. There is no separation between the pieces. He would state, “the trinity is as simple as cherry pie.”
If someone was making up a god to manipulate people, they would not make up something so confusing and incomprehensible about their god. On the other hand, a god who is the author of everything that exists is likely to have personal traits that are impossible for His creation to fully comprehend.
The trinity also is important in who God is. A loving God that is all alone would need his creation because he would be lonely and have no one to love. A trinitarian God has company and someone to love in the other two persons of the trinity. This God doesn’t NEED his creation even if He wants and loves his creation.By the above sections you can see that the Bible clearly talks about one God which includes three persons. The fact that this is hard for us to understand doesn’t make it any less true. We can’t pick and choose which verses we will listen to and which we will ignore. If we say there is only one God and deny the deity of Jesus and the Holy Spirit, we are apostate. If we say that we worship three separate Gods, the Father, the Son, and the Spirit, we are equally apostate.
The God of the Bible, the one and true God, is three persons in one God. We need to trust God and believe His word even if we can’t fully understand how it can be so.
What are Some Mentions of the entire Trinity?
There are many passages that refer to the three persons of the Trinity working together as one. When Jesus was about to arise to heaven after rising from the dead, in His last words He said:
And Jesus came up and spoke to them, saying, “All authority has been given to Me in heaven and on earth. Go therefore and make disciples of all the nations, baptizing them in the name of the Father and the Son and the Holy Spirit, teaching them to observe all that I commanded you; and lo, I am with you always, even to the end of the age.” (Matthew 28:18-20) {Emphasis mine}
As Christians, we are called to be baptized “in the name of the Father and the Son and the Holy Spirit.” We are to acknowledge all three persons in the Godhead.
Now when all the people were baptized, Jesus was also baptized, and while He was praying, heaven was opened, and the Holy Spirit descended upon Him in bodily form like a dove, and a voice came out of heaven, “You are My beloved Son, in You I am well-pleased.” (Luke 3:21-22) {Emphasis mine}
Likewise when Jesus was baptized to fulfill the law of God, all three persons were present. Jesus was fulfilling the Law of God so He would be a worthy sacrifice to take away our sins. The Holy Spirit descended on Jesus as a helper and as a sign to John the Baptist that Jesus was the predicted Messiah. God the Father spoke blessing the actions of Jesus in fulfilling their mutual will. The three persons of God acted as One.
“These things I [Jesus] have spoken to you while abiding with you. But the Helper, the Holy Spirit, whom the Father will send in My name, He will teach you all things, and bring to your remembrance all that I said to you. (John 14:25-26) {Emphasis mine}
This verse also speaks of all three persons working in concert. It also clearly separates the Spirit (Helper) from Jesus because as one (Jesus) leaves, the other (Helper) comes to help us. Once again the Bible shows the three persons of God acting as One.
He who hates Me [Jesus] hates My Father also. If I had not done among them the works which no one else did, they would not have sin; but now they have both seen and hated Me [Jesus] and My Father as well. But they have done this to fulfill the word that is written in their Law, ‘They hated Me without a cause.’
“When the Helper [Spirit] comes, whom I [Jesus] will send to you from the Father, that is the Spirit of truth who proceeds from the Father, He [Spirit] will testify about Me [Jesus], and you will testify also, because you have been with Me [Jesus] from the beginning. (John 15:23-27) [Clarification Mine] {Emphasis mine}Once again this verse shows all three persons of God working as One. Just as John 8:42 (above) describes Jesus proceeding from God, John 15:26 describes the Spirit proceeding from the Father. They proceed from God/Father because they are all One.
Such were some of you; but you were washed, but you were sanctified, but you were justified in the name of the Lord Jesus Christ and in the Spirit of our God. (1 Corinthians 6:11) {Emphasis mine}
Our sanctification and our justification come from all three persons of the one true God. If we do not believe this, can we truly be saved? If we do not believe in the Godship of Jesus can we truly be a child of God?
Jesus said to him, “I am the way, and the truth, and the life; no one comes to the Father but through Me. If you had known Me, you would have known My Father also; from now on you know Him, and have seen Him.” (John 14:6-7)
Jesus explains that if you have seen Him, you have seen the Father implying they are one and the same.
Trust Jesus
Bible verses are NASB (New American Standard Bible) 1995 edition unless otherwise stated
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Channels without HTLCs
HTLCs below the dust limit are not possible, because they're uneconomical.
So currently whenever a payment below the dust limit is to be made Lightning peers adjust their commitment transactions to pay that amount as fees in case the channel is closed. That's a form of reserving that amount and incentivizing peers to resolve the payment, either successfully (in case it goes to the receiving node's balance) or not (it then goes back to the sender's balance).
SOLUTION
I didn't think too much about if it is possible to do what I think can be done in the current implementation on Lightning channels, but in the context of Eltoo it seems possible.
Eltoo channels have UPDATE transactions that can be published to the blockchain and SETTLEMENT transactions that spend them (after a relative time) to each peer. The barebones script for UPDATE transactions is something like (copied from the paper, because I don't understand these things):
OP_IF # to spend from a settlement transaction (presigned) 10 OP_CSV 2 As,i Bs,i 2 OP_CHECKMULTISIGVERIFY OP_ELSE # to spend from a future update transaction <Si+1> OP_CHECKLOCKTIMEVERIFY 2 Au Bu 2 OP_CHECKMULTISIGVERIFY OP_ENDIFDuring a payment of 1 satoshi it could be updated to something like (I'll probably get this thing completely wrong):
OP_HASH256 <payment_hash> OP_EQUAL OP_IF # for B to spend from settlement transaction 1 in case the payment went through # and they have a preimage 10 OP_CSV 2 As,i1 Bs,i1 2 OP_CHECKMULTISIGVERIFY OP_ELSE OP_IF # for A to spend from settlement transaction 2 in case the payment didn't went through # and the other peer is uncooperative <now + 1day> OP_CHECKLOCKTIMEVERIFY 2 As,i2 Bs,i2 2 OP_CHECKMULTISIGVERIFY OP_ELSE # to spend from a future update transaction <Si+1> OP_CHECKLOCKTIMEVERIFY 2 Au Bu 2 OP_CHECKMULTISIGVERIFY OP_ENDIF OP_ENDIFThen peers would have two presigned SETTLEMENT transactions, 1 and 2 (with different signature pairs, as badly shown in the script). On SETTLEMENT 1, funds are, say, 999sat for A and 1001sat for B, while on SETTLEMENT 2 funds are 1000sat for A and 1000sat for B.
As soon as B gets the preimage from the next peer in the route it can give it to A and them can sign a new UPDATE transaction that replaces the above gimmick with something simpler without hashes involved.
If the preimage doesn't come in viable time, peers can agree to make a new UPDATE transaction anyway. Otherwise A will have to close the channel, which may be bad, but B wasn't a good peer anyway.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Criteria for activating Drivechain on Bitcoin
Drivechain is, in essence, just a way to give Bitcoin users the option to deposit their coins in a hashrate escrow. If Bitcoin is about coin ownership, in theory there should be no objection from anyone on users having the option to do that: my keys, my coins etc. In other words: even if you think hashrate escrows are a terrible idea and miners will steal all coins from that, you shouldn't care about what other people do with their own money.
There are only two reasonable objections that could be raised by normal Bitcoin users against Drivechain:
- Drivechain adds code complexity to
bitcoind - Drivechain perverts miner incentives of the Bitcoin chain
If these two objections can be reasonably answered there remains no reason for not activating the Drivechain soft-fork.
1
To address 1 we can just take a look at the code once it's done (which I haven't) but from my understanding the extra validation steps needed for ensuring hashrate escrows work are very minimal and self-contained, they shouldn't affect anything else and the risks of introducing some catastrophic bug are roughly zero (or the same as the risks of any of the dozens of refactors that happen every week on Bitcoin Core).
For the BMM/BIP-301 part, again the surface is very small, but we arguably do not need that at all, since anyprevout (once that is merged) enables blind merge-mining in way that is probably better than BIP-301, and that soft-fork is also very simple, plus already loved and accepted by most of the Bitcoin community, implemented and reviewed on Bitcoin Inquisition and is live on the official Bitcoin Core signet.
2
To address 2 we must only point that BMM ensures that Bitcoin miners don't have to do any extra work to earn basically all the fees that would come from the sidechain, as competition for mining sidechain blocks would bid the fee paid to Bitcoin miners up to the maximum economical amount. It is irrelevant if there is MEV on the sidechain or not, everything that reaches the Bitcoin chain does that in form of fees paid in a single high-fee transaction paid to any Bitcoin miner, regardless of them knowing about the sidechain or not. Therefore, there are no centralization pressure or pervert mining incentives that can affect Bitcoin land.
Sometimes it's argued that Drivechain may facilitate the ocurrence of a transaction paying a fee so high it would create incentives for reorging the Bitcoin chain. There is no reason to believe Drivechain would make this more likely than an actual attack than anyone can already do today or, as has happened, some rich person typing numbers wrong on his wallet. In fact, if a drivechain is consistently paying high fees on its BMM transactions that is an incentive for Bitcoin miners to keep mining those transactions one after the other and not harm the users of sidechain by reorging Bitcoin.
Moreover, there are many factors that exist today that can be seen as centralization vectors for Bitcoin mining: arguably one of them is non-blind merge mining, of which we have a (very convoluted) example on the Stacks shitcoin, and introducing the possibility of blind merge-mining on Bitcoin would basically remove any reasonable argument for having such schemes, therefore reducing the centralizing factor of them.
- Drivechain adds code complexity to
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Um algoritmo imbecil da evolução
Suponha que você queira escrever a palavra BANANA partindo de OOOOOO e usando só alterações aleatórias das letras. As alterações se dão por meio da multiplicação da palavra original em várias outras, cada uma com uma mudança diferente.
No primeiro período, surgem BOOOOO e OOOOZO. E então o ambiente decide que todas as palavras que não começam com um B estão eliminadas. Sobra apenas BOOOOO e o algoritmo continua.
É fácil explicar conceber a evolução das espécies acontecendo dessa maneira, se você controlar sempre a parte em que o ambiente decide quem vai sobrar.
Porém, há apenas duas opções:
- Se o ambiente decidir as coisas de maneira aleatória, a chance de você chegar na palavra correta usando esse método é tão pequena que pode ser considerada nula.
- Se o ambiente decidir as coisas de maneira pensada, caímos no //design inteligente//.
Acredito que isso seja uma enunciação decente do argumento "no free lunch" aplicado à crítica do darwinismo por William Dembski.
A resposta darwinista consiste em dizer que não existe essa BANANA como objetivo final. Que as palavras podem ir se alterando aleatoriamente, e o que sobrar sobrou, não podemos dizer que um objetivo foi atingido ou deixou de sê-lo. E aí os defensores do design inteligente dirão que o resultado ao qual chegamos não pode ter sido fruto de um processo aleatório. BANANA é qualitativamente diferente de AYZOSO, e aí há várias maneiras de "provar" que sim usando modelos matemáticos e tal.
Fico com a impressão, porém, de que essa coisa só pode ser resolvida como sim ou não mediante uma discussão das premissas, e chega um ponto em que não há mais provas matemáticas possíveis, apenas subjetividade.
Daí eu me lembro da minha humilde solução ao problema do cão que aperta as teclas aleatoriamente de um teclado e escreve as obras completas de Shakespeare: mesmo que ele o faça, nada daquilo terá sentido sem uma inteligência de tipo humano ali para lê-las e perceber que não se trata de uma bagunça, mas sim de um texto com sentido para ele. O milagre se dá não no momento em que o cão tropeça no teclado, mas no momento em que o homem olha para a tela.
Se o algoritmo da evolução chegou à palavra BANANA ou UXJHTR não faz diferença pra ela, mas faz diferença para nós, que temos uma inteligência humana, e estamos observando aquilo. O homem também pensaria que há //algo// por trás daquele evento do cão que digita as obras de Shakespeare, e como seria possível alguém em sã consciência pensar que não?
-
 @ 8d34bd24:414be32b
2024-07-05 17:26:49
@ 8d34bd24:414be32b
2024-07-05 17:26:49https://trustjesus.substack.com/p/will-you-shrink-away-in-shame
This post, although I’m including it as part of the Left Behind series, is not directly about the End Times, but I feel I need to add this to it because in the end times, our relationship with Jesus (or lack thereof) determines everything. Are we saved or unsaved? Have we trusted Jesus or not trusted Jesus? Are we children of God or not? We must know the answer to this question because our very life depends on it.
For the most part I am going to answer this question using 1 John, but to start I want to include one other passage to make sure we all consider this carefully.
“Not everyone who says to Me, ‘Lord, Lord,’ will enter the kingdom of heaven, but he who does the will of My Father who is in heaven will enter. Many will say to Me on that day, ‘Lord, Lord, did we not prophesy in Your name, and in Your name cast out demons, and in Your name perform many miracles?’ And then I will declare to them, ‘I never knew you; depart from Me, you who practice lawlessness.’ (Matthew 7:21-23)
Sadly, there will be people who think they are Christians, but they are not among those saved by Jesus. Their hope was in their works, their church attendance, the fact that they were better than someone else, or even just their positive attitude. They never really knew Jesus. They never truly trusted Him. They never truly submitted to Him. Yes, we can really know for sure, and we need to make sure our faith is real.
This is the message we have heard from Him and announce to you, that God is Light, and in Him there is no darkness at all. If we say that we have fellowship with Him and yet walk in the darkness, we lie and do not practice the truth; but if we walk in the Light as He Himself is in the Light, we have fellowship with one another, and the blood of Jesus His Son cleanses us from all sin. (1 John 1:5-7)
If we are saved, our lives should show it. There should be a difference between us and those of the world. It should be obvious to others that we are different.
Even among the unsaved, there are many, who most people would consider “good” people. They are friendly. They are generous. They are helpful. They are likable. Unfortunately, if they haven’t confessed their sins, submitted their lives to Jesus, and believed what the Bible says about Jesus, then they are not considered good by God and they won’t be joining Him in heaven. These people who seem “good” are actually defiant towards God. They have hidden vices and hidden evil thoughts. We all have sinned, but only those who have submitted to Jesus will be cleansed “from all sin.”
If we say that we have no sin, we are deceiving ourselves and the truth is not in us. If we confess our sins, He is faithful and righteous to forgive us our sins and to cleanse us from all unrighteousness. If we say that we have not sinned, we make Him a liar and His word is not in us. (1 John 1:8-10) {Italicized phrases used below}
Only those who have confessed their sins will be forgiven. With so many things in life, before we can be cured or fixed, we have to admit we have a problem. We all have a sin problem. Jesus promises, “If we confess our sins, He is faithful and righteous to forgive us our sins and to cleanse us from all unrighteousness,” but we have to confess our sins. We can’t hold onto the fantasy that we are “good” people. Anyone who thinks they are good without Jesus will NOT be saved.
My little children, I am writing these things to you so that you may not sin. And if anyone sins, we have an Advocate with the Father, Jesus Christ the righteous; and He Himself is the propitiation for our sins; and not for ours only, but also for those of the whole world. (1 John 2:1-2)
Trusting Jesus and submitting to Jesus should lead to less sin. Instead of sin just being a regular part of life, it should become a rare exception. In addition to believers sinning less than they did before trusting Jesus, they also are defended by Jesus and covered by His righteousness.
Advocate NOUN
- a person who speaks or writes in support or defense of a person, cause, etc.
- a person who pleads for or in behalf of another; intercessor.
- a person who pleads the cause of another in a court of law.1
When we trust Jesus, “we have an Advocate with the Father” who pleads on our behalf, who is an intercessor for us with Father God. He defends us in the court of God. He defends us and protects us from the wrath we deserve.
Propitiation NOUN
- the act of propitiating (making favorably inclined; appeasing; conciliating.); conciliation:
- something that propitiates (makes favorably inclined; appeases; conciliates.).2 *
Because Jesus bore our sins and gave believers his righteousness, he covers our sins and makes God favorably inclined towards us instead of wrathful towards us.
By this we know that we have come to know Him, if we keep His commandments. The one who says, “I have come to know Him,” and does not keep His commandments, is a liar, and the truth is not in him; but whoever keeps His word, in him the love of God has truly been perfected. By this we know that we are in Him: the one who says he abides in Him ought himself to walk in the same manner as He walked. (1 John 2:3-6)
If we have truly trusted Jesus as savior and submitted our lives to Him, there should be a change in our actions, words, and thoughts. We should be a new creation. We should be more like Him.
Now it is true, we don’t go instantly from being sinners in open defiance of God to being perfect imitators of Christ. There should, however, be a continual transformation to become more like Christ. Yes, we may have a few digressions, but the general trend should be becoming more Christ-like. If our thoughts, words, and actions are not becoming more Christ-like, we need to investigate what our true relationship with Jesus is. If we are continually becoming more Christ-like, then “By this we know that we are in Him: the one who says he abides in Him ought himself to walk in the same manner as He walked.”
Beloved, I am not writing a new commandment to you, but an old commandment which you have had from the beginning; the old commandment is the word which you have heard. On the other hand, I am writing a new commandment to you, which is true in Him and in you, because the darkness is passing away and the true Light is already shining. The one who says he is in the Light and yet hates his brother is in the darkness until now. The one who loves his brother abides in the Light and there is no cause for stumbling in him. But the one who hates his brother is in the darkness and walks in the darkness, and does not know where he is going because the darkness has blinded his eyes. (1 John 2:7-11)
One strong sign that a person is a child of God, and saved by Christ, is that this person is loving. They love God. They love fellow believers. They love the lost and want to win them for Christ (not just beat them in an argument or verbally discipline them). Because the believer cares for the souls of the lost, understands that the unbeliever’s words and actions are aimed at Jesus, and understands that they are due to the unbeliever’s feelings of guilt, believers should pity the lost rather than hate them. “By this all men will know that you are My disciples, if you have love for one another.” (John 13:35) Anyone filled with hate needs to investigate whether they have truly trusted Jesus.
I am writing to you, little children, because your sins have been forgiven you for His name’s sake. I am writing to you, fathers, because you know Him who has been from the beginning. I am writing to you, young men, because you have overcome the evil one. I have written to you, children, because you know the Father. I have written to you, fathers, because you know Him who has been from the beginning. I have written to you, young men, because you are strong, and the word of God abides in you, and you have overcome the evil one. (1 John 2:12-14)
If you have confessed your sins to God, believed that Jesus (the son of God) died and was raised to take away your sins, and submitted your life to Jesus’s rule, you can know that you are saved. You can know that “your sins have been forgiven you,” “you know Him,” “you have overcome the evil one,” “you know the Father,” and “you are strong, and the word of God abides in you.”
Do not love the world nor the things in the world. If anyone loves the world, the love of the Father is not in him. For all that is in the world, the lust of the flesh and the lust of the eyes and the boastful pride of life, is not from the Father, but is from the world. The world is passing away, and also its lusts; but the one who does the will of God lives forever. (1 John 2:15-17)
A true Christian should be looking forward to their eternal home and not be focused on the things of this world. That doesn’t mean that a Christian doesn’t work, or have a family, or enjoy entertainment, or relax. It does mean that everything should be done with a view of eternity. Our actions should point others to God. Our activities should draw ourselves closer to Jesus and help us to become more like Him. Our words should encourage those around us to trust in Jesus. We should long for God’s word, revel in the company of believers, and relish helping others, whether meeting their physical, mental, or spiritual needs. Our eternity with Jesus should be more important than our momentary comfort or happiness.
Children, it is the last hour; and just as you heard that antichrist is coming, even now many antichrists have appeared; from this we know that it is the last hour. (1 John 2:18)
As the end times approach, we will see many antichrists, people who try to take the place of Jesus Christ. They may attempt to replace Him as leader or king. They may attempt to replace Him as high priest or spiritual leader. They may attempt to replace Him as God and try to say what is good and what is bad. As Christians, we need to know our Bible so we are not misled. We need to lean on the Holy Spirit to guide us and enable us to know who speaks the truth and who speaks lies (including those who speak lies believing the lies).
They went out from us, but they were not really of us; for if they had been of us, they would have remained with us; but they went out, so that it would be shown that they all are not of us. But you have an anointing from the Holy One, and you all know. I have not written to you because you do not know the truth, but because you do know it, and because no lie is of the truth. Who is the liar but the one who denies that Jesus is the Christ? This is the antichrist, the one who denies the Father and the Son. Whoever denies the Son does not have the Father; the one who confesses the Son has the Father also. As for you, let that abide in you which you heard from the beginning. If what you heard from the beginning abides in you, you also will abide in the Son and in the Father. (1 John 2:19-24)
We’ve known many people who seemed to be Christians, but who left the faith and turned to the world. These were people who claimed the label of Christian, but who were not children of God. They were false Christians. There will also be some who pretend to be Christians, and may even be leaders in churches, who speak lies and speak what is contrary to the word of God. Some may do a good job in their Christian act, but if “you have an anointing from the Holy One” and know the truth (the Bible), you will not be misled. Do be on the lookout for these many little-a antichrists who lead people astray.
This is the promise which He Himself made to us: eternal life.
These things I have written to you concerning those who are trying to deceive you. As for you, the anointing which you received from Him abides in you, and you have no need for anyone to teach you; but as His anointing teaches you about all things, and is true and is not a lie, and just as it has taught you, you abide in Him.
In addition to studying the Bible, Christians can lean on the Holy Spirit for inspiration and guidance. The Spirit will help you to see those who speak lies, so you will not be misled. The Spirit will help you to do and say what you should. The Spirit will help you to understand the words you read in the Bible. The Spirit will help you witness to unbelievers. The Spirit will help you to obey God and to live the life He wants you to live.
And now for the blessing for all those who have truly put their faith in Jesus Christ, have been indwelled by the Holy Spirit, and have submitted to the will of the Father:
Now, little children, abide in Him, so that when He appears, we may have confidence and not shrink away from Him in shame at His coming. If you know that He is righteous, you know that everyone also who practices righteousness is born of Him. (1 John 2:28-29)Believers have no need to “shrink away from Him in shame at His coming.” We can look forward with joy and anticipation to His return. Hallelujah! Come Lord Jesus, Come!
Trust Jesus.
FYI, If you are interested in learning more about end times, especially as it relates to current events, you might be interested in following Tipping Point Prophecy Update. They have both posts to read and videos to watch, so it works no matter which you prefer.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Gerador de tabelas de todos contra todos
I don't remember exactly when I did this, but I think a friend wanted to do software that would give him money over the internet without having to work. He didn't know how to program. He mentioned this idea he had which was some kind of football championship manager solution, but I heard it like this: a website that generated a round-robin championship table for people to print.
It is actually not obvious to anyone how to do it, it requires an algorithm that people will not reach casually while thinking, and there was no website doing it in Portuguese at the time, so I made this and it worked and it had a couple hundred daily visitors, and it even generated money from Google Ads (not much)!
First it was a Python web app running on Heroku, then Heroku started charging or limiting the amount of free time I could have on their platform, so I migrated it to a static site that ran everything on the client. Since I didn't want to waste my Python code that actually generated the tables I used Brython to run Python on JavaScript, which was an interesting experience.
In hindsight I could have just taken one of the many
round-robinJavaScript libraries that exist on NPM, so eventually after a couple of more years I did that.I also removed Google Ads when Google decided it had so many requirements to send me the money it was impossible, and then the money started to vanished.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Money Supply Measurement
What if we measured money supply measured by probability of being spent -- or how near it is to the point in which it is spent? bonds could be money if they're treated as that by their owners, but they are likely to be not near the spendpoint as cash, other assets can also be considered money but they might be even farther.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Token-Curated Registries
So you want to build a TCR?
TCRs (Token Curated Registries) are a construct for maintaining registries on Ethereum. Imagine you have lots of scissor brands and you want a list with only the good scissors. You want to make sure only the good scissors make into that list and not the bad scissors. For that, people will tell you, you can just create a TCR of the best scissors!
It works like this: some people have the token, let's call it Scissor Token. Some other person, let's say it's a scissor manufacturer, wants to put his scissor on the list, this guy must acquire some Scissor Tokens and "stake" it. Holders of the Scissor Tokens are allowed to vote on "yes" or "no". If "no", the manufactures loses his tokens to the holders, if "yes" then its tokens are kept in deposit, but his scissor brand gets accepted into the registry.
Such a simple process, they say, have strong incentives for being the best possible way of curating a registry of scissors: consumers have the incentive to consult the list because of its high quality; manufacturers have the incentive to buy tokens and apply to join the list because the list is so well-curated and consumers always consult it; token holders want the registry to accept good and reject bad scissors because that good decisions will make the list good for consumers and thus their tokens more valuable, bad decisions will do the contrary. It doesn't make sense, to reject everybody just to grab their tokens, because that would create an incentive against people trying to enter the list.
Amazing! How come such a simple system of voting has such enourmous features? Now we can have lists of everything so well-curated, and for that we just need Ethereum tokens!
Now let's imagine a different proposal, of my own creation: SPCR, Single-person curated registries.
Single-person Curated Registries are equal to TCR, except they don't use Ethereum tokens, it's just a list in a text file kept by a single person. People can apply to join, and they will have to give the single person some amount of money, the single person can reject or accept the proposal and so on.
Now let's look at the incentives of SPCR: people will want to consult the registry because it is so well curated; vendors will want to enter the registry because people are consulting it; the single person will want to accept the good and reject the bad applicants because these good decisions are what will make the list valuable.
Amazing! How such a single proposal has such enourmous features! SPCR are going to take over the internet!
What TCR enthusiasts get wrong?
TCR people think they can just list a set of incentives for something to work and assume that something will work. Mix that with Ethereum hype and they think theyve found something unique and revolutionary, while in fact they're just making a poor implementation of "democracy" systems that fail almost everywhere.
The life is not about listing a set of "incentives" and then considering the problems solved. Almost everybody on the Earth has the incentive for being rich: being rich has a lot of advantages over being poor, however not all people get rich! Why are the incentives failing?
Curating lists is a hard problem, it involves a lot of knowledge about the problem that just holding a token won't give you, it involves personal preferences, politics, it involves knowing where is the real limit between "good" and "bad". The Single Person list may have a good result if the single person doing the curation is knowledgeable and honest (yes, you can game the system to accept your uncle's scissors and not their competitor that is much better, for example, without losing the entire list reputation), same thing for TCRs, but it can also fail miserably, and it can appear to be good but be in fact not so good. In all cases, the list entries will reflect the preferences of people choosing and other things that aren't taken into the incentives equation of TCR enthusiasts.
We don't need lists
The most important point to be made, although unrelated to the incentive story, is that we don't need lists. Imagine you're looking for a scissor. You don't want someone to tell if scissor A or B are "good" or "bad", or if A is "better" than B. You want to know if, for your specific situation, or for a class of situations, A will serve well, and do that considering A's price and if A is being sold near you and all that.
Scissors are the worst example ever to make this point, but I hope you get it. If you don't, try imagining the same example with schools, doctors, plumbers, food, whatever.
Recommendation systems are badly needed in our world, and TCRs don't solve these at all.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Personagens de jogos e símbolos
A sensação de "ser" um personagem em um jogo ou uma brincadeira talvez seja o mais próximo que eu tenha conseguido chegar do entendimento de um símbolo religioso.
A hóstia consagrada é, segundo a religião, o corpo de Cristo, mas nossa mente moderna só consegue concebê-la como sendo uma representação do corpo de Cristo. Da mesma forma outras culturas e outras religiões têm símbolos parecidos, inclusive nos quais o próprio participante do ritual faz o papel de um deus ou de qualquer coisa parecida.
"Faz o papel" é de novo a interpretação da mente moderna. O sujeito ali é a coisa, mas ele ao mesmo tempo que é também sabe que não é, que continua sendo ele mesmo.
Nos jogos de videogame e brincadeiras infantis em que se encarna um personagem o jogador é o personagem. não se diz, entre os jogadores, que alguém está "encenando", mas que ele é e pronto. nem há outra denominação ou outro verbo. No máximo "encarnando", mas já aí já é vocabulário jornalístico feito para facilitar a compreensão de quem está de fora do jogo.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28WelcomeBot
The first bot ever created for Trello.
It invited to a public board automatically anyone who commented on a card he was added to.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Sol e Terra
A Terra não gira em torno do Sol. Tudo depende do ponto de referência e não existe um ponto de referência absoluto. Só é melhor dizer que a Terra gira em torno do Sol porque há outros planetas fazendo movimentos análogos e aí fica mais fácil para todo mundo entender os movimentos tomando o Sol como ponto de referência.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A list of things artificial intelligence is not doing
If AI is so good why can't it:
- write good glue code that wraps a documented HTTP API?
- make good translations using available books and respective published translations?
- extract meaningful and relevant numbers from news articles?
- write mathematical models that fit perfectly to available data better than any human?
- play videogames without cheating (i.e. simulating human vision, attention and click speed)?
- turn pure HTML pages into pretty designs by generating CSS
- predict the weather
- calculate building foundations
- determine stock values of companies from publicly available numbers
- smartly and automatically test software to uncover bugs before releases
- predict sports matches from the ball and the players' movement on the screen
- continuously improve niche/local search indexes based on user input and and reaction to results
- control traffic lights
- predict sports matches from news articles, and teams and players' history
This was posted first on Twitter.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28idea: Custom multi-use database app
Since 2015 I have this idea of making one app that could be repurposed into a full-fledged app for all kinds of uses, like powering small businesses accounts and so on. Hackable and open as an Excel file, but more efficient, without the hassle of making tables and also using ids and indexes under the hood so different kinds of things can be related together in various ways.
It is not a concrete thing, just a generic idea that has taken multiple forms along the years and may take others in the future. I've made quite a few attempts at implementing it, but never finished any.
I used to refer to it as a "multidimensional spreadsheet".
Can also be related to DabbleDB.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Reclamações
- Como não houve resposta, estou enviando de novo
- Democracia na América
- A "política" é a arena da vitória do estatismo
- A biblioteca infinita
- Família e propriedade
- Memórias de quando eu aprendi a ler
- A chatura Kelsen
- O VAR é o grande equalizador
- Não tem solução
- A estrutura lógica do livro didático
- "House" dos economistas e o Estado
- Revista Educativa
- Cultura Inglesa e aprendizado extra-escolar
- Veterano não é dono de bixete
- Personagens de jogos e símbolos
- Músicas grudentas e conversas
- Obra aqui do lado
- Propaganda
- Ver Jesus com os olhos da carne
- Processos Antifrágeis
- Cadeias, crimes e cidadãos de bem
- Castas hindus em nova chave
- Método científico
- Xampu
- Thafne venceu o Soletrando 2008.
- Empreendendorismo de boteco
- Problemas com Russell Kirk
- Pequenos problemas que o Estado cria para a sociedade e que não são sempre lembrados
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28The Lightning Network solves the problem of the decentralized commit
Before reading this, see Ripple and the problem of the decentralized commit.
The Bitcoin Lightning Network can be thought as a system similar to Ripple: there are conditional IOUs (HTLCs) that are sent in "prepare"-like messages across a route, and a secret
pthat must travel from the final receiver backwards through the route until it reaches the initial sender and possession of that secret serves to prove the payment as well as to make the IOU hold true.The difference is that if one of the parties don't send the "acknowledge" in time, the other has a trusted third-party with its own clock (that is the clock that is valid for everybody involved) to complain immediately at the timeout: the Bitcoin blockchain. If C has
pand B isn't acknowleding it, C tells the Bitcoin blockchain and it will force the transfer of the amount from B to C.Differences (or 1 upside and 3 downside)
-
The Lightning Network differs from a "pure" Ripple network in that when we send a "prepare" message on the Lightning Network, unlike on a pure Ripple network we're not just promising we will owe something -- instead we are putting the money on the table already for the other to get if we are not responsive.
-
The feature above removes the trust element from the equation. We can now have relationships with people we don't trust, as the Bitcoin blockchain will serve as an automated escrow for our conditional payments and no one will be harmed. Therefore it is much easier to build networks and route payments if you don't always require trust relationships.
-
However it introduces the cost of the capital. A ton of capital must be made available in channels and locked in HTLCs so payments can be routed. This leads to potential issues like the ones described in https://twitter.com/joostjgr/status/1308414364911841281.
-
Another issue that comes with the necessity of using the Bitcoin blockchain as an arbiter is that it may cost a lot in fees -- much more than the value of the payment that is being disputed -- to enforce it on the blockchain.[^closing-channels-for-nothing]
Solutions
Because the downsides listed above are so real and problematic -- and much more so when attacks from malicious peers are taken into account --, some have argued that the Lightning Network must rely on at least some trust between peers, which partly negate the benefit.
The introduction of purely trust-backend channels is the next step in the reasoning: if we are trusting already, why not make channels that don't touch the blockchain and don't require peers to commit large amounts of capital?
The reason is, again, the ambiguity that comes from the problem of the decentralized commit. Therefore hosted channels can be good when trust is required only from one side, like in the final hops of payments, but they cannot work in the middle of routes without eroding trust relationships between peers (however they can be useful if employed as channels between two nodes ran by the same person).
The next solution is a revamped pure Ripple network, one that solves the problem of the decentralized commit in a different way.
[^closing-channels-for-nothing]: That is even true when, for reasons of the payment being so small that it doesn't even deserve an actual HTLC that can be enforced on the chain (as per the protocol), even then the channel between the two nodes will be closed, only to make it very clear that there was a disagreement. Leaving it online would be harmful as one of the peers could repeat the attack again and again. This is a proof that ambiguity, in case of the pure Ripple network, is a very important issue.
-
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Reasons for miners to not steal
See Drivechain for an introduction. Here we'll just have a list of reasons why miners would not steal:
- they will lose future fees from that specific drivechain: you can discount all future fees and condense them into a single present number in order to do some mathematical calculation.
- they may lose future fees from all other Drivechains, if the users assume they will steal from those too.
- Bitcoin will be devalued if they steal, because:
- Bitcoin is worth more if it has Drivechains working, because it is more useful, has more use-cases, more users. Without Drivechains it necessarily has to be worth less.
- Bitcoin has more fee revenue if has Drivechains working, which means it has a bigger chance of surviving going forward and being more censorship-resistant and resistant to State attacks, therefore it has to worth more if Drivechains work and less if they don't.
- Bitcoin is worth more if the public perception is that Bitcoin miners are friendly and doing their work peacefully instead of being a band of revolted peons that are constantly threating to use their 75% hashrate to do evil things such as:
- double-spending attacks;
- censoring of transactions for a certain group of people;
- selfish mining.
- if Bitcoin is devalued its price is bound to fall, meaning that miners will lose on
- their future mining rewards;
- their ASIC investiment;
- the same coins they are trying to steal from the drivechain.
- if a mining pool tries to steal, they will risk losing their individual miners to other pools that don't.
- whenever a steal attempt begins, the coins in the drivechain will lose value (if the steal attempt is credible their price will drop quite substantially), which means that if a coalition of miners really try to steal, there is an incentive for another coalition of miners to buy some devalued coins and then stop the steal.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28idea: a website for feedback exchange
I thought a community of people sharing feedback on mutual interests would be a good thing, so as always I broadened and generalized the idea and mixed with my old criticue-inspired idea-feedback project and turned it into a "token". You give feedback on other people's things, they give you a "point". You can then use that point to request feedback from others.
This could be made as an Etleneum contract so these points were exchanged for satoshis using the shitswap contract (yet to be written).
In this case all the Bitcoin/Lightning side of the website must be hidden until the user has properly gone through the usage flow and earned points.
If it was to be built on Etleneum then it needs to emphasize the login/password login method instead of the lnurl-auth method. And then maybe it could be used to push lnurl-auth to normal people, but with a different name.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28bolt12 problems
- clients can't programatically build new offers by changing a path or query params (services like zbd.gg or lnurl-pay.me won't work)
- impossible to use in a load-balanced custodian way -- since offers would have to be pregenerated and tied to a specific lightning node.
- the existence of fiat currency fields makes it so wallets have to fetch exchange rates from somewhere on the internet (or offer a bad user experience), using HTTP which hurts user privacy.
- the vendor field is misleading, can be phished very easily, not as safe as a domain name.
- onion messages are an improvement over fake HTLC-based payments as a way of transmitting data, for sure. but we must decide if they are (i) suitable for transmitting all kinds of data over the internet, a replacement for tor; or (ii) not something that will scale well or on which we can count on for the future. if there was proper incentivization for data transmission it could end up being (i), the holy grail of p2p communication over the internet, but that is a very hard problem to solve and not guaranteed to yield the desired scalability results. since not even hints of attempting to solve that are being made, it's safer to conclude it is (ii).
bolt12 limitations
- not flexible enough. there are some interesting fields defined in the spec, but who gets to add more fields later if necessary? very unclear.
- services can't return any actionable data to the users who paid for something. it's unclear how business can be conducted without an extra communication channel.
bolt12 illusions
- recurring payments is not really solved, it is just a spec that defines intervals. the actual implementation must still be done by each wallet and service. the recurring payment cannot be enforced, the wallet must still initiate the payment. even if the wallet is evil and is willing to initiate a payment without the user knowing it still needs to have funds, channels, be online, connected etc., so it's not as if the services could rely on the payments being delivered in time.
- people seem to think it will enable pushing payments to mobile wallets, which it does not and cannot.
- there is a confusion of contexts: it looks like offers are superior to lnurl-pay, for example, because they don't require domain names. domain names, though, are common and well-established among internet services and stores, because these services have websites, so this is not really an issue. it is an issue, though, for people that want to receive payments in their homes. for these, indeed, bolt12 offers a superior solution -- but at the same time bolt12 seems to be selling itself as a tool for merchants and service providers when it includes and highlights features as recurring payments and refunds.
- the privacy gains for the receiver that are promoted as being part of bolt12 in fact come from a separate proposal, blinded paths, which should work for all normal lightning payments and indeed are a very nice solution. they are (or at least were, and should be) independent from the bolt12 proposal. a separate proposal, which can be (and already is being) used right now, also improves privacy for the receiver very much anway, it's called trampoline routing.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Músicas novas e conhecidas
Quando for ouvir música de fundo, escolha músicas bem conhecidas. Para ouvir músicas novas, reserve um tempo e ouça-as com total atenção.
Uma coisa similar é dirigir por caminhos conhecidos versus dirigir em lugares novos. a primeira opção te permite fazer coisas enquanto dirige "de fundo", a segunda requer atenção total.
Com músicas, tenho errado constantemente em achar que posso conhecer músicas novas ao mesmo tempo em que me dedico a outras tarefas.
See also:
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A Causa
o Princípios de Economia Política de Menger é o único livro que enfatiza a CAUSA o tempo todo. os cientistas todos parecem não saber, ou se esquecer sempre, que as coisas têm causa, e que o conhecimento verdadeiro é o conhecimento da causa das coisas.
a causa é uma categoria metafísica muito superior a qualquer correlação ou resultado de teste de hipótese, ela não pode ser descoberta por nenhum artifício econométrico ou reduzida à simples antecedência temporal estatística. a causa dos fenômenos não pode ser provada cientificamente, mas pode ser conhecida.
o livro de Menger conta para o leitor as causas de vários fenômenos econômicos e as interliga de forma que o mundo caótico da economia parece adquirir uma ordem no momento em que você lê. é uma sensação mágica e indescritível.
quando eu te o recomendei, queria é te imbuir com o espírito da busca pela causa das coisas. depois de ler aquilo, você está apto a perceber continuidade causal nos fenômenos mais complexos da economia atual, enxergar as causas entre toda a ação governamental e as suas várias consequências na vida humana. eu faço isso todos os dias e é a melhor sensação do mundo quando o caos das notícias do caderno de Economia do jornal -- que para o próprio jornalista que as escreveu não têm nenhum sentido (tanto é que ele escreve tudo errado) -- se incluem num sistema ordenado de causas e consequências.
provavelmente eu sempre erro em alguns ou vários pontos, mas ainda assim é maravilhoso. ou então é mais maravilhoso ainda quando eu descubro o erro e reinsiro o acerto naquela racionalização bela da ordem do mundo econômico que é a ordem de Deus.
em scrap para T.P.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28IPFS problems: Community
I was an avid IPFS user until yesterday. Many many times I asked simple questions for which I couldn't find an answer on the internet in the #ipfs IRC channel on Freenode. Most of the times I didn't get an answer, and even when I got it was rarely by someone who knew IPFS deeply. I've had issues go unanswered on js-ipfs repositories for year – one of these was raising awareness of a problem that then got fixed some months later by a complete rewrite, I closed my own issue after realizing that by myself some couple of months later, I don't think the people responsible for the rewrite were ever acknowledge that he had fixed my issue.
Some days ago I asked some questions about how the IPFS protocol worked internally, sincerely trying to understand the inefficiencies in finding and fetching content over IPFS. I pointed it would be a good idea to have a drawing showing that so people would understand the difficulties (which I didn't) and wouldn't be pissed off by the slowness. I was told to read the whitepaper. I had already the whitepaper, but read again the relevant parts. The whitepaper doesn't explain anything about the DHT and how IPFS finds content. I said that in the room, was told to read again.
Before anyone misread this section, I want to say I understand it's a pain to keep answering people on IRC if you're busy developing stuff of interplanetary importance, and that I'm not paying anyone nor I have the right to be answered. On the other hand, if you're developing a super-important protocol, financed by many millions of dollars and a lot of people are hitting their heads against your software and there's no one to help them; you're always busy but never delivers anything that brings joy to your users, something is very wrong. I sincerely don't know what IPFS developers are working on, I wouldn't doubt they're working on important things if they said that, but what I see – and what many other users see (take a look at the IPFS Discourse forum) is bugs, bugs all over the place, confusing UX, and almost no help.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28IPFS problems: Inefficiency
Imagine you have two IPFS nodes and unique content, created by you, in the first one. From the second, you can connect to the first and everyhing looks right. You then try to fetch that content. After some seconds it starts coming, the progress bar begins to move, that's slow, very slow, doing an rsync would have been 20 times faster.
The progress bar halts. You investigate, the second node is not connected to the first anymore. Why, if that was the only source for the file we're trying to fetch? It remains a mistery to this day. You reconnect manually, the progress bar moves again, halts, you're disconnected again. Instead of reconnecting you decide to add the second node to the first node's "Bootstrap" list.
I once tried to run an IPFS node on a VPS and store content on S3. There are two S3 datastore plugins available. After fixing some issues in one of them, recompiling go-ipfs, figuring out how to read settings from the IPFS config file, creating an init profile and recompiling again I got the node running. It worked. My idea was to host a bunch of data on that node. Data would be fetched from S3 on demand so there would be cheap and fast access to it from any IPFS node or gateway.
IPFS started doing hundreds of calls to S3 per minute – something I wouldn't have known about if I hadn't inserted some log statements in the plugin code, I mean before the huge AWS bill arrived. Apparently that was part of participation on the DHT. Adjusting some settings turned my node into a listen-only thing as I intended, but I'm not 100% sure it would work as an efficient content provider, and I'll never know, as the memory and CPU usage got too high for my humble VPS and I had to turn it down.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28ijq
An interactive REPL for
jqwith smart helpers (for example, it automatically assigns each line of input to a variable so you can reference it later, it also always referenced the previous line automatically).See also
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Trelew
A CLI tool for navigating Trello boards. It used vorpal for an "immersive" experience and was pretty good.

-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28OP_CHECKTEMPLATEVERIFYand the "covenants" dramaThere are many ideas for "covenants" (I don't think this concept helps in the specific case of examining proposals, but fine). Some people think "we" (it's not obvious who is included in this group) should somehow examine them and come up with the perfect synthesis.
It is not clear what form this magic gathering of ideas will take and who (or which ideas) will be allowed to speak, but suppose it happens and there is intense research and conversations and people (ideas) really enjoy themselves in the process.
What are we left with at the end? Someone has to actually commit the time and put the effort and come up with a concrete proposal to be implemented on Bitcoin, and whatever the result is it will have trade-offs. Some great features will not make into this proposal, others will make in a worsened form, and some will be contemplated very nicely, there will be some extra costs related to maintenance or code complexity that will have to be taken. Someone, a concreate person, will decide upon these things using their own personal preferences and biases, and many people will not be pleased with their choices.
That has already happened. Jeremy Rubin has already conjured all the covenant ideas in a magic gathering that lasted more than 3 years and came up with a synthesis that has the best trade-offs he could find. CTV is the result of that operation.
The fate of CTV in the popular opinion illustrated by the thoughtless responses it has evoked such as "can we do better?" and "we need more review and research and more consideration of other ideas for covenants" is a preview of what would probably happen if these suggestions were followed again and someone spent the next 3 years again considering ideas, talking to other researchers and came up with a new synthesis. Again, that person would be faced with "can we do better?" responses from people that were not happy enough with the choices.
And unless some famous Bitcoin Core or retired Bitcoin Core developers were personally attracted by this synthesis then they would take some time to review and give their blessing to this new synthesis.
To summarize the argument of this article, the actual question in the current CTV drama is that there exists hidden criteria for proposals to be accepted by the general community into Bitcoin, and no one has these criteria clear in their minds. It is not as simple not as straightforward as "do research" nor it is as humanly impossible as "get consensus", it has a much bigger social element into it, but I also do not know what is the exact form of these hidden criteria.
This is said not to blame anyone -- except the ignorant people who are not aware of the existence of these things and just keep repeating completely false and unhelpful advice for Jeremy Rubin and are not self-conscious enough to ever realize what they're doing.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Método científico
o método científico não pode ser aplicado senão numa meia dúzia de casos, e no entanto ei-nos aqui, pensando nele para tudo.
"formule hipóteses e teste-as independentemente", "obtenha uma quantidade de dados estatisticamente significante", teste, colete dados, mensure.
não é que de repente todo mundo resolveu calcular desvios-padrão, mas sim que é comum, para as pessoas mais cultas, nível Freakonomics, acharem que têm que testar e coletar dados, e nunca jamais confiar na sua "intuição" ou, pior, num raciocínio que pode parecer certo, mas na verdade é enormemente enganador.
sim, é verdade que raciocínios com explicações aparentemente sensatas nos são apresentados todos os dias -- para um exemplo fácil é só imaginar um comentarista de jornal, ou até uma matéria inocente de jornal, aliás, melhor pensar num comentarista da GloboNews --, e sim, é verdade que a maioria dessas explicações é falsa.
o que está errado é achar que só o que vale é testar hipóteses. você não pode testar a explicação aparentemente sensata que o taxista te fornece sobre a crise brasileira, deve então anotá-la para testar depois? mantê-la para sempre no cabedal das teorias ainda por testar?
e a explicação das redinhas que economizam água quando instaladas na torneira? essa dá pra testar, então você vai comprar um relógio de água e deixar a torneira ligada lá 5 horas com a redinha, depois 5 horas sem a redinha? obviamente não vai funcionar se você abrir o mesmo tanto, você vai precisar de um critério melhor: a satisfação da pessoa que está lavando as mãos com o resultado final versus a quantidade de água gasta. daí você precisaria de muitas pessoas, mas satisfação é uma coisa imensurável, nem adianta tentar fazer entrevistas antes e depois com as pessoas. o certo então, é o quê? procurar um estudo científico publicado numa revista de qualidade (porque tem aquelas revistas que aceitam estudos gerados por computador, então é melhor tomar cuidado) que fala sobre redinhas? como saber se a redinha é a mesma que você comprou? e agora que você já comprou, o resultado do experimento importa? (claro: pode ser que a redinha faça gastar mais água, você nunca saberá até que faça o experimento).
por que não, ao invés de condenar todos os raciocínios como enganadores e mandar que as pessoas façam experimentos científicos, ensinar a fazer raciocínios certos?
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28idea: An open log-based HTTP database for any use case
A single, read/write open database for everything in the world.
- A hosted database that accepts anything you put on it and stores it in order.
- Anyone can update it by adding new stuff.
- To make sense of the data you can read only the records that interest you, in order, and reconstruct a local state.
- Each updater pays a fee (anonymously, in satoshis) to store their piece of data.
- It's a single store for everything in the world.
Cost and price estimates
Prices for guaranteed storage for 3 years: 20 satoshis = 1KB 20 000 000 = 1GB
https://www.elephantsql.com/ charges $10/mo for 1GB of data, 3 600 000 satoshis for 3 years
If 3 years is not enough, people can move their stuff to elsewhere when it's time, or pay to keep specific log entries for more time.
Other considerations
- People provide a unique id when adding a log so entries can be prefix-matched by it, like
myapp.something.random - When fetching, instead of just fetching raw data, add (paid?) option to fetch and apply a
jqmap-reduce transformation to the matched entries
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A response to Achim Warner's "Drivechain brings politics to miners" article
I mean this article: https://achimwarner.medium.com/thoughts-on-drivechain-i-miners-can-do-things-about-which-we-will-argue-whether-it-is-actually-a5c3c022dbd2
There are basically two claims here:
1. Some corporate interests might want to secure sidechains for themselves and thus they will bribe miners to have these activated
First, it's hard to imagine why they would want such a thing. Are they going to make a proprietary KYC chain only for their users? They could do that in a corporate way, or with a federation, like Facebook tried to do, and that would provide more value to their users than a cumbersome pseudo-decentralized system in which they don't even have powers to issue currency. Also, if Facebook couldn't get away with their federated shitcoin because the government was mad, what says the government won't be mad with a sidechain? And finally, why would Facebook want to give custody of their proprietary closed-garden Bitcoin-backed ecosystem coins to a random, open and always-changing set of miners?
But even if they do succeed in making their sidechain and it is very popular such that it pays miners fees and people love it. Well, then why not? Let them have it. It's not going to hurt anyone more than a proprietary shitcoin would anyway. If Facebook really wants a closed ecosystem backed by Bitcoin that probably means we are winning big.
2. Miners will be required to vote on the validity of debatable things
He cites the example of a PoS sidechain, an assassination market, a sidechain full of nazists, a sidechain deemed illegal by the US government and so on.
There is a simple solution to all of this: just kill these sidechains. Either miners can take the money from these to themselves, or they can just refuse to engage and freeze the coins there forever, or they can even give the coins to governments, if they want. It is an entirely good thing that evil sidechains or sidechains that use horrible technology that doesn't even let us know who owns each coin get annihilated. And it was the responsibility of people who put money in there to evaluate beforehand and know that PoS is not deterministic, for example.
About government censoring and wanting to steal money, or criminals using sidechains, I think the argument is very weak because these same things can happen today and may even be happening already: i.e., governments ordering mining pools to not mine such and such transactions from such and such people, or forcing them to reorg to steal money from criminals and whatnot. All this is expected to happen in normal Bitcoin. But both in normal Bitcoin and in Drivechain decentralization fixes that problem by making it so governments cannot catch all miners required to control the chain like that -- and in fact fixing that problem is the only reason we need decentralization.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28idea: "numbeo" with satoshis
This site has a crowdsourced database of cost-of-living in many countries and cities: https://www.numbeo.com/cost-of-living/ and it sells the data people write there freely. It's wrong!
Could be an fruitful idea to pay satoshis for people to provide data.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28The flaw of "just use paypal/coinbase" arguments
For the millionth time I read somewhere that "custodial bitcoin is not bitcoin" and that "if you're going to use custodial, better use Paypal". No, actually it was "better use Coinbase", but I had heard the "PayPal" version in the past.
There are many reasons why using PayPal is not the same as using a custodial Bitcoin service or wallet that are obvious and not relevant here, such as the fact that you can't have Bitcoin balances on Bitcoin (or maybe now you can? but you can't send it around); plus all the reasons that are also valid for Coinbase such as you having to give all your data and selfies of yourself and your government documents and so on -- but let's ignore these reasons for now.
The most important reason why it isn't the same thing is that when you're using Coinbase you are stuck in Coinbase. Your Coinbase coins cannot be used to pay anyone that isn't in Coinbase. So Coinbase-style custodianship doesn't help Bitcoin. If you want to move out of Coinbase you have to withdraw from Coinbase.
Custodianship on Lightning is of a very different nature. You can pay people from other custodial platforms and people that are hosting their own Lightning nodes and so on.
That kind of custodianship doesn't do any harm to anyone, doesn't fracture the network, doesn't reduce the network effect of Lightning, in fact it increases it.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Lightning and its fake HTLCs
Lightning is terrible but can be very good with two tweaks.
How Lightning would work without HTLCs
In a world in which HTLCs didn't exist, Lightning channels would consist only of balances. Each commitment transaction would have two outputs: one for peer
A, the other for peerB, according to the current state of the channel.When a payment was being attempted to go through the channel, peers would just trust each other to update the state when necessary. For example:
- Channel
AB's balances areA[10:10]B(in sats); Asends a 3sat payment throughBtoC;AasksBto route the payment. ChannelABdoesn't change at all;Bsends the payment toC,Caccepts it;- Channel
BCchanges fromB[20:5]CtoB[17:8]C; BnotifiesAthe payment was successful,Aacknowledges that;- Channel
ABchanges fromA[10:10]BtoA[7:13]B.
This in the case of a success, everything is fine, no glitches, no dishonesty.
But notice that
Acould have refused to acknowledge that the payment went through, either because of a bug, or because it went offline forever, or because it is malicious. Then the channelABwould stay asA[10:10]BandBwould have lost 3 satoshis.How Lightning would work with HTLCs
HTLCs are introduced to remedy that situation. Now instead of commitment transactions having always only two outputs, one to each peer, now they can have HTLC outputs too. These HTLC outputs could go to either side dependending on the circumstance.
Specifically, the peer that is sending the payment can redeem the HTLC after a number of blocks have passed. The peer that is receiving the payment can redeem the HTLC if they are able to provide the preimage to the hash specified in the HTLC.
Now the flow is something like this:
- Channel
AB's balances areA[10:10]B; Asends a 3sat payment throughBtoC:AasksBto route the payment. Their channel changes toA[7:3:10]B(the middle number is the HTLC).Boffers a payment toC. Their channel changes fromB[20:5]CtoB[17:3:5]C.CtellsBthe preimage for that HTLC. Their channel changes fromB[17:3:5]CtoB[17:8]C.BtellsAthe preimage for that HTLC. Their channel changes fromA[7:3:10]BtoA[7:13]B.
Now if
Awants to trickBand stop respondingBdoesn't lose money, becauseBknows the preimage,Bjust needs to publish the commitment transactionA[7:3:10]B, which gives him 10sat and then redeem the HTLC using the preimage he got fromC, which gives him 3 sats more.Bis fine now.In the same way, if
Bstops responding for any reason,Awon't lose the money it put in that HTLC, it can publish the commitment transaction, get 7 back, then redeem the HTLC after the certain number of blocks have passed and get the other 3 sats back.How Lightning doesn't really work
The example above about how the HTLCs work is very elegant but has a fatal flaw on it: transaction fees. Each new HTLC added increases the size of the commitment transaction and it requires yet another transaction to be redeemed. If we consider fees of 10000 satoshis that means any HTLC below that is as if it didn't existed because we can't ever redeem it anyway. In fact the Lightning protocol explicitly dictates that if HTLC output amounts are below the fee necessary to redeem them they shouldn't be created.
What happens in these cases then? Nothing, the amounts that should be in HTLCs are moved to the commitment transaction miner fee instead.
So considering a transaction fee of 10000sat for these HTLCs if one is sending Lightning payments below 10000sat that means they operate according to the unsafe protocol described in the first section above.
It is actually worse, because consider what happens in the case a channel in the middle of a route has a glitch or one of the peers is unresponsive. The other node, thinking they are operating in the trustless protocol, will proceed to publish the commitment transaction, i.e. close the channel, so they can redeem the HTLC -- only then they find out they are actually in the unsafe protocol realm and there is no HTLC to be redeemed at all and they lose not only the money, but also the channel (which costed a lot of money to open and close, in overall transaction fees).
One of the biggest features of the trustless protocol are the payment proofs. Every payment is identified by a hash and whenever the payee releases the preimage relative to that hash that means the payment was complete. The incentives are in place so all nodes in the path pass the preimage back until it reaches the payer, which can then use it as the proof he has sent the payment and the payee has received it. This feature is also lost in the unsafe protocol: if a glitch happens or someone goes offline on the preimage's way back then there is no way the preimage will reach the payer because no HTLCs are published and redeemed on the chain. The payee may have received the money but the payer will not know -- but the payee will lose the money sent anyway.
The end of HTLCs
So considering the points above you may be sad because in some cases Lightning doesn't use these magic HTLCs that give meaning to it all. But the fact is that no matter what anyone thinks, HTLCs are destined to be used less and less as time passes.
The fact that over time Bitcoin transaction fees tend to rise, and also the fact that multipart payment (MPP) are increasedly being used on Lightning for good, we can expect that soon no HTLC will ever be big enough to be actually worth redeeming and we will be at a point in which not a single HTLC is real and they're all fake.
Another thing to note is that the current unsafe protocol kicks out whenever the HTLC amount is below the Bitcoin transaction fee would be to redeem it, but this is not a reasonable algorithm. It is not reasonable to lose a channel and then pay 10000sat in fees to redeem a 10001sat HTLC. At which point does it become reasonable to do it? Probably in an amount many times above that, so it would be reasonable to even increase the threshold above which real HTLCs are made -- thus making their existence more and more rare.
These are good things, because we don't actually need HTLCs to make a functional Lightning Network.
We must embrace the unsafe protocol and make it better
So the unsafe protocol is not necessarily very bad, but the way it is being done now is, because it suffers from two big problems:
- Channels are lost all the time for no reason;
- No guarantees of the proof-of-payment ever reaching the payer exist.
The first problem we fix by just stopping the current practice of closing channels when there are no real HTLCs in them.
That, however, creates a new problem -- or actually it exarcebates the second: now that we're not closing channels, what do we do with the expired payments in them? These payments should have either been canceled or fulfilled before some block x, now we're in block x+1, our peer has returned from its offline period and one of us will have to lose the money from that payment.
That's fine because it's only 3sat and it's better to just lose 3sat than to lose both the 3sat and the channel anyway, so either one would be happy to eat the loss. Maybe we'll even split it 50/50! No, that doesn't work, because it creates an attack vector with peers becoming unresponsive on purpose on one side of the route and actually failing/fulfilling the payment on the other side and making a profit with that.
So we actually need to know who is to blame on these payments, even if we are not going to act on that imediatelly: we need some kind of arbiter that both peers can trust, such that if one peer is trying to send the preimage or the cancellation to the other and the other is unresponsive, when the unresponsive peer comes back, the arbiter can tell them they are to blame, so they can willfully eat the loss and the channel can continue. Both peers are happy this way.
If the unresponsive peer doesn't accept what the arbiter says then the peer that was operating correctly can assume the unresponsive peer is malicious and close the channel, and then blacklist it and never again open a channel with a peer they know is malicious.
Again, the differences between this scheme and the current Lightning Network are that:
a. In the current Lightning we always close channels, in this scheme we only close channels in case someone is malicious or in other worst case scenarios (the arbiter is unresponsive, for example). b. In the current Lightning we close the channels without having any clue on who is to blame for that, then we just proceed to reopen a channel with that same peer even in the case they were actively trying to harm us before.
What is missing? An arbiter.
The Bitcoin blockchain is the ideal arbiter, it works in the best possible way if we follow the trustless protocol, but as we've seen we can't use the Bitcoin blockchain because it is expensive.
Therefore we need a new arbiter. That is the hard part, but not unsolvable. Notice that we don't need an absolutely perfect arbiter, anything is better than nothing, really, even an unreliable arbiter that is offline half of the day is better than what we have today, or an arbiter that lies, an arbiter that charges some satoshis for each resolution, anything.
Here are some suggestions:
- random nodes from the network selected by an algorithm that both peers agree to, so they can't cheat by selecting themselves. The only thing these nodes have to do is to store data from one peer, try to retransmit it to the other peer and record the results for some time.
- a set of nodes preselected by the two peers when the channel is being opened -- same as above, but with more handpicked-trust involved.
- some third-party cloud storage or notification provider with guarantees of having open data in it and some public log-keeping, like Twitter, GitHub or a Nostr relay;
- peers that get paid to do the job, selected by the fact that they own some token (I know this is stepping too close to the shitcoin territory, but could be an idea) issued in a Spacechain;
- a Spacechain itself, serving only as the storage for a bunch of
OP_RETURNs that are published and tracked by these Lightning peers whenever there is an issue (this looks wrong, but could work).
Key points
- Lightning with HTLC-based routing was a cool idea, but it wasn't ever really feasible.
- HTLCs are going to be abandoned and that's the natural course of things.
- It is actually good that HTLCs are being abandoned, but
- We must change the protocol to account for the existence of fake HTLCs and thus make the bulk of the Lightning Network usage viable again.
See also
- Channel
-
 @ 8d34bd24:414be32b
2024-07-05 17:15:21
@ 8d34bd24:414be32b
2024-07-05 17:15:21https://trustjesus.substack.com/p/to-mark-or-not-to-mark-that-is-the
After the rapture of the church, things are going to get progressively worse, but the progression from normal to horror will start slow and build up to become worse than anyone could possibly imagine. As times get bad and the culture goes from bad to worse, everyone will have to make a choice, to choose Jesus or to choose Satan.
“No one can serve two masters; for either he will hate the one and love the other, or he will be devoted to one and despise the other. You cannot serve God and wealth.” (Mathew 6:24)
We will obey Jesus or obey Satan. We will choose a hard life here on Earth and a marvelous, joyous, pain-free eternity in heaven or choose an easier life here on Earth and an eternity of pain and loneliness. This should be an easy choice, but most won’t find it so because they will have trouble seeing beyond the here and now. Just as Esau1 sold his birthright to his brother because he was hungry, most people will do what makes it easy to fill their hungry bellies rather than trusting their creator and making the choice that will lead to the best eternity. Most people aren’t good at looking a month or year in the future. They will find it impossible to see into eternity.
There will be two kinds of mark during the tribulation. God will mark 144,000 Jews with His name to be his witnesses to the world.
Then I looked, and behold, the Lamb was standing on Mount Zion, and with Him one hundred and forty-four thousand, having His name and the name of His Father written on their foreheads. And I heard a voice from heaven, like the sound of many waters and like the sound of loud thunder, and the voice which I heard was like the sound of harpists playing on their harps. And they sang a new song before the throne and before the four living creatures and the elders; and no one could learn the song except the one hundred and forty-four thousand who had been purchased from the earth. These are the ones who have not been defiled with women, for they have kept themselves chaste. These are the ones who follow the Lamb wherever He goes. These have been purchased from among men as first fruits to God and to the Lamb. And no lie was found in their mouth; they are blameless. (Revelation 14:1-5)
Satan will also try to mark his followers. The False Prophet will force everyone to make a choice, to get the mark of the beast if they want to be able to buy and sell.
Then I saw another beast coming up out of the earth; and he had two horns like a lamb and he spoke as a dragon. He exercises all the authority of the first beast in his presence. And he makes the earth and those who dwell in it to worship the first beast, whose fatal wound was healed. He performs great signs, so that he even makes fire come down out of heaven to the earth in the presence of men. And he deceives those who dwell on the earth because of the signs which it was given him to perform in the presence of the beast, telling those who dwell on the earth to make an image to the beast who had the wound of the sword and has come to life. And it was given to him to give breath to the image of the beast, so that the image of the beast would even speak and cause as many as do not worship the image of the beast to be killed. And he causes all, the small and the great, and the rich and the poor, and the free men and the slaves, to be given a mark on their right hand or on their forehead, and he provides that no one will be able to buy or to sell, except the one who has the mark, either the name of the beast or the number of his name. (Revelation 13:11-17) {emphasis mine}
During the seven year tribulation, every person left on Earth will be given the choice: to receive the mark of the beast so they can buy and sell and function in society or to refuse the mark and submit to Jesus, but be unable to buy and sell and provide for themselves and their family. Most people will take the easy path and receive the mark, so they can go on with their lives. Unfortunately this will be a deadly choice that can never be undone or fixed.
Then another angel, a third one, followed them, saying with a loud voice, “If anyone worships the beast and his image, and receives a mark on his forehead or on his hand, he also will drink of the wine of the wrath of God, which is mixed in full strength in the cup of His anger; and he will be tormented with fire and brimstone in the presence of the holy angels and in the presence of the Lamb. And the smoke of their torment goes up forever and ever; they have no rest day and night, those who worship the beast and his image, and whoever receives the mark of his name.” (Revelation 14:9-11) {emphasis mine}
This choice to take the easier path will lead to eternal torment. This refusal to listen to our creator God and our savior God will mean eternal separation. These people will grieve their choice forever.
There will be a good number of people who will choose to follow Jesus and refuse the mark, but they will pay the price for putting off this decision until the time of the tribulation.
Then I saw thrones, and they sat on them, and judgment was given to them. And I saw the souls of those who had been beheaded because of their testimony of Jesus and because of the word of God, and those who had not worshiped the beast or his image, and had not received the mark on their forehead and on their hand; and they came to life and reigned with Christ for a thousand years. (Revelation 20:4) {emphasis mine}
Many may wonder, if they experience the tribulation, how can they stand firm on their faith when they know that doing so could (likely will) lead to them and their family either starving to death or being beheaded? The trick is to keep your eye on God and to keep your eye on the prize.
I press on toward the goal for the prize of the upward call of God in Christ Jesus. (Philippians 4:13)
A perfect example to follow in times when our faith is challenged comes from Daniel (but my idea to use it here came from Dr. David Jeremiah’s book, The Book of Signs, Chapter 25)
Nebuchadnezzar the king made an image of gold, the height of which was sixty cubits and its width six cubits; he set it up on the plain of Dura in the province of Babylon. … Then the herald loudly proclaimed: “To you the command is given, O peoples, nations and men of every language, that at the moment you hear the sound of the horn, flute, lyre, trigon, psaltery, bagpipe and all kinds of music, you are to fall down and worship the golden image that Nebuchadnezzar the king has set up. But whoever does not fall down and worship shall immediately be cast into the midst of a furnace of blazing fire.” (Daniel 3:1, 4-6)
Shadrach, Meshach and Abed-nego were given a choice. They had to choose to obey God’s 1st and 2nd commandments:
“You shall have no other gods before Me.
You shall not make for yourself an idol, or any likeness of what is in heaven above or on the earth beneath or in the water under the earth. You shall not worship them or serve them; for I, the Lord your God, am a jealous God (Genesis 20:3-5a)They had to risk being burned to death in a fiery furnace or they had to choose to disobey God and earn His wrath, but avoid the furnace. When exposed by others, who were jealous of their position, they stood firm and refused to worship the idol. Nebuchadnezzar even gave them a second chance to bow down when faced with the furnace. They chose faithfulness and I love their statement of faith.
Shadrach, Meshach and Abed-nego replied to the king, “O Nebuchadnezzar, we do not need to give you an answer concerning this matter. If it be so, our God whom we serve is able to deliver us from the furnace of blazing fire; and He will deliver us out of your hand, O king. But even if He does not, let it be known to you, O king, that we are not going to serve your gods or worship the golden image that you have set up.” (Daniel 3:16-18) {emphasis mine}
Shadrach, Meshach and Abed-nego had the faith to know that God was capable of rescuing them from the fiery furnace (which He did), but notice their faith did not depend on being miraculously rescued. “But even if He does not, let it be known to you, O king, that we are not going to serve your gods or worship the golden image that you have set up.” They served and obeyed God because He is God, not because of what He could do for them. We need to be the same. We need to stand with the faith of Shadrach, Meshach and Abed-nego when we are given the choice between faith and physical death. This is made easier because, if you are a true Christian, death on Earth means life in heaven. It means absolutely everything gets better. Dying in Christ is better than living without Him.
As you can see, if you are left behind after the rapture, it is critical that you choose to trust Jesus and submit to His will and to NOT receive the mark of the beast no matter what it costs you.
For those who trusted Jesus before the tribulation, we’ll all be celebrating at the marriage supper of Christ in heaven and have nothing to worry about. For those who didn’t trust Jesus until the tribulation, your remaining time on Earth will be exceedingly hard, but your reward will actually be great as stated in Revelation 20:4
Then I saw thrones, and they sat on them, and judgment was given to them. And I saw the souls of those who had been beheaded because of their testimony of Jesus and because of the word of God, and those who had not worshiped the beast or his image, and had not received the mark on their forehead and on their hand; and they came to life and reigned with Christ for a thousand years. (Revelation 20:4) {emphasis mine}
I hope you won’t put off trusting Jesus and you will live your life like He is coming back any moment. He is coming back soon.
Many may wonder what the mark is.
For most of my life, I assumed the mark would be something like a tattoo, but I never understood how people could be prevented from buying and selling. How do you stop my neighbor and I buying and selling from each other using cash? It didn’t make sense.
Now we have technology that enables the mark. Most of the countries in the world are working on CBDCs (Central Bank Digital Currencies) and the IMF (International Monetary Fund) is working on a CBDC interface that will let all of the national CBDCs transact with each other. These CBDCs will allow programmable money. Whoever is in control can make your money expire, make it only good for certain purchases, make your money only work in a particular area. The CBDC can make your money completely go away if those in control don’t like what you do, say, or don’t do. If we are moved to a CBDC, all buying and selling could be controlled. As all of the world’s fiat currencies are destroyed by money creation causing massive inflation, it will be easier and easier to get people to switch to the CBDC to rescue them from losing all monetary value.
We also have implantable microchips that can act as ID or credit card or bank account access and all a person has to do is scan their hand to buy or get admittance into a particular place. This technology already exists and is being used in small ways. I believe the mark will be a combination of a CBDC and an implantable microchip that will give you access to your “wallet”. The technology is here in a way that could not have been imagined just a decade or two ago. I believe our time is short. We need to live our lives with this understanding.
Trust Jesus.
-
 @ 8d34bd24:414be32b
2024-07-05 16:59:03
@ 8d34bd24:414be32b
2024-07-05 16:59:03https://trustjesus.substack.com/p/a-change-of-heart
For most of my Christian life I haven’t been focused on end times or heaven. I wanted to go to heaven, but not now. I had other things I wanted to do that were monopolizing my attention. I was focused on what is happening here on Earth, not preparing for my heavenly home. Although the Bible, both New and Old Testaments, are full of prophecies about the end times, it just seemed so far away and so confusing, so I pretty much blocked it out as far a study and effect on my life.
As the world started going crazy, with shortages, pandemics, crazy government policies, and wars starting all around the world, I started working to prepare my family for these hardships. I got involved with politics. I kept extra food on hand. I kept my car’s gas tank above a half of a tank. I started a garden and got 3 bunnies to breed for meat. I was doing all of this based solely on my own effort. In the back of my head, I knew God would provide for my needs. I had seen how he took care of me in the past, but I was still trying to do everything on my own. I worried about what would happen to my family if something happened to me because I was taking care of them. What I should’ve been doing is giving all my problems and worries to God and letting the all powerful creator God take care of things. I worked by my own power until my health suffered.
Recently, as the world has gotten crazier every month, I finally had a change of heart and mind. I looked back at how God had provided for me through every hardship. I read the Bible and saw God’s promises for the future. My prayers changed from praying the solution that I wanted, to praying the problem and letting God do what He knew was best because I’d already seen in my life how God gives us what we don’t want, but what we need: “And we know that God causes all things to work together for good to those who love God, to those who are called according to His purpose.” (Romans 8:28)
I went from worrying about my needs to trusting God for my needs (not saying I don’t prepare for hard times, but in a relaxed, non-worrying, good steward kind of way). I went from trying to change the government and politicians to trying to change hearts and minds for God. I went from avoiding reading end times prophecy to studying it as if my life depended on it. I went from worrying about the future to looking forward to the future. I went from worrying about my needs to worrying about the needs of those that don’t know Jesus.
I can’t say that I never worry. I do, but I’ve learned to give my worries to God. Recently my son was asked to volunteer at a pro-life fundraiser. Shortly after he said yes, I received a prayer request because a pro-abortion group planned to raid the fundraiser and cause mayhem and destruction. My first thought was to tell my son (who is 19 and a Godly young man) that he couldn’t go to the fundraiser, but then I stopped myself and decided that God had this. I know my son is a faithful Christian, so if the worst happened, he would meet Jesus early. I decided to let him go and I just prayed fervently. There was a church service going on at the same time as the fundraiser. This confused the protestors. They couldn’t figure out what to do and therefore did nothing. God confounded their plans and I learned a well needed lesson to trust everything that is important to me to God. He is faithful.
It used to be that, when I saw things going wrong in my country, state, county, and city, I would vote harder, get involved with politics, work with the party to improve the platform and resolutions, and help campaign for my favorite candidate. Now I’ve come to the conclusion that we get the candidates we deserve. I still vote, but I put my effort into sharing the gospel and turning people to Jesus. We can have a bigger influence by changing the hearts of the people than by campaigning for a particular candidate. We not only can benefit all of us on earth, but also make a heavenly difference. It isn’t that campaigning for and voting for Godly candidates is bad, but thinking a person can save us is bad. There is only one savior, Jesus Christ. Our faith needs to be in him and not in a politician, a party, or a government.
As the world goes down hill, I am filled with hope. The rumors of wars, the growing evil, the pandemics, the storms, the move towards global governance means Jesus is coming soon and I am getting excited about it in a way I never was before.
I hope you can turn from worldly interests to the Savior. I hope you can get excited to see Jesus face to face and to meet him in the air.
Trust Jesus.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28On HTLCs and arbiters
This is another attempt and conveying the same information that should be in Lightning and its fake HTLCs. It assumes you know everything about Lightning and will just highlight a point. This is also valid for PTLCs.
The protocol says HTLCs are trimmed (i.e., not actually added to the commitment transaction) when the cost of redeeming them in fees would be greater than their actual value.
Although this is often dismissed as a non-important fact (often people will say "it's trusted for small payments, no big deal"), but I think it is indeed very important for 3 reasons:
- Lightning absolutely relies on HTLCs actually existing because the payment proof requires them. The entire security of each payment comes from the fact that the payer has a preimage that comes from the payee. Without that, the state of the payment becomes an unsolvable mystery. The inexistence of an HTLC breaks the atomicity between the payment going through and the payer receiving a proof.
- Bitcoin fees are expected to grow with time (arguably the reason Lightning exists in the first place).
- MPP makes payment sizes shrink, therefore more and more of Lightning payments are to be trimmed. As I write this, the mempool is clear and still payments smaller than about 5000sat are being trimmed. Two weeks ago the limit was at 18000sat, which is already below the minimum most MPP splitting algorithms will allow.
Therefore I think it is important that we come up with a different way of ensuring payment proofs are being passed around in the case HTLCs are trimmed.
Channel closures
Worse than not having HTLCs that can be redeemed is the fact that in the current Lightning implementations channels will be closed by the peer once an HTLC timeout is reached, either to fulfill an HTLC for which that peer has a preimage or to redeem back that expired HTLCs the other party hasn't fulfilled.
For the surprise of everybody, nodes will do this even when the HTLCs in question were trimmed and therefore cannot be redeemed at all. It's very important that nodes stop doing that, because it makes no economic sense at all.
However, that is not so simple, because once you decide you're not going to close the channel, what is the next step? Do you wait until the other peer tries to fulfill an expired HTLC and tell them you won't agree and that you must cancel that instead? That could work sometimes if they're honest (and they have no incentive to not be, in this case). What if they say they tried to fulfill it before but you were offline? Now you're confused, you don't know if you were offline or they were offline, or if they are trying to trick you. Then unsolvable issues start to emerge.
Arbiters
One simple idea is to use trusted arbiters for all trimmed HTLC issues.
This idea solves both the protocol issue of getting the preimage to the payer once it is released by the payee -- and what to do with the channels once a trimmed HTLC expires.
A simple design would be to have each node hardcode a set of trusted other nodes that can serve as arbiters. Once a channel is opened between two nodes they choose one node from both lists to serve as their mutual arbiter for that channel.
Then whenever one node tries to fulfill an HTLC but the other peer is unresponsive, they can send the preimage to the arbiter instead. The arbiter will then try to contact the unresponsive peer. If it succeeds, then done, the HTLC was fulfilled offchain. If it fails then it can keep trying until the HTLC timeout. And then if the other node comes back later they can eat the loss. The arbiter will ensure they know they are the ones who must eat the loss in this case. If they don't agree to eat the loss, the first peer may then close the channel and blacklist the other peer. If the other peer believes that both the first peer and the arbiter are dishonest they can remove that arbiter from their list of trusted arbiters.
The same happens in the opposite case: if a peer doesn't get a preimage they can notify the arbiter they hadn't received anything. The arbiter may try to ask the other peer for the preimage and, if that fails, settle the dispute for the side of that first peer, which can proceed to fail the HTLC is has with someone else on that route.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28jq-finder
Made with jq-web, a tool to explore JSON using
jqqueries that build intermediate results so you can inspect each step of the process.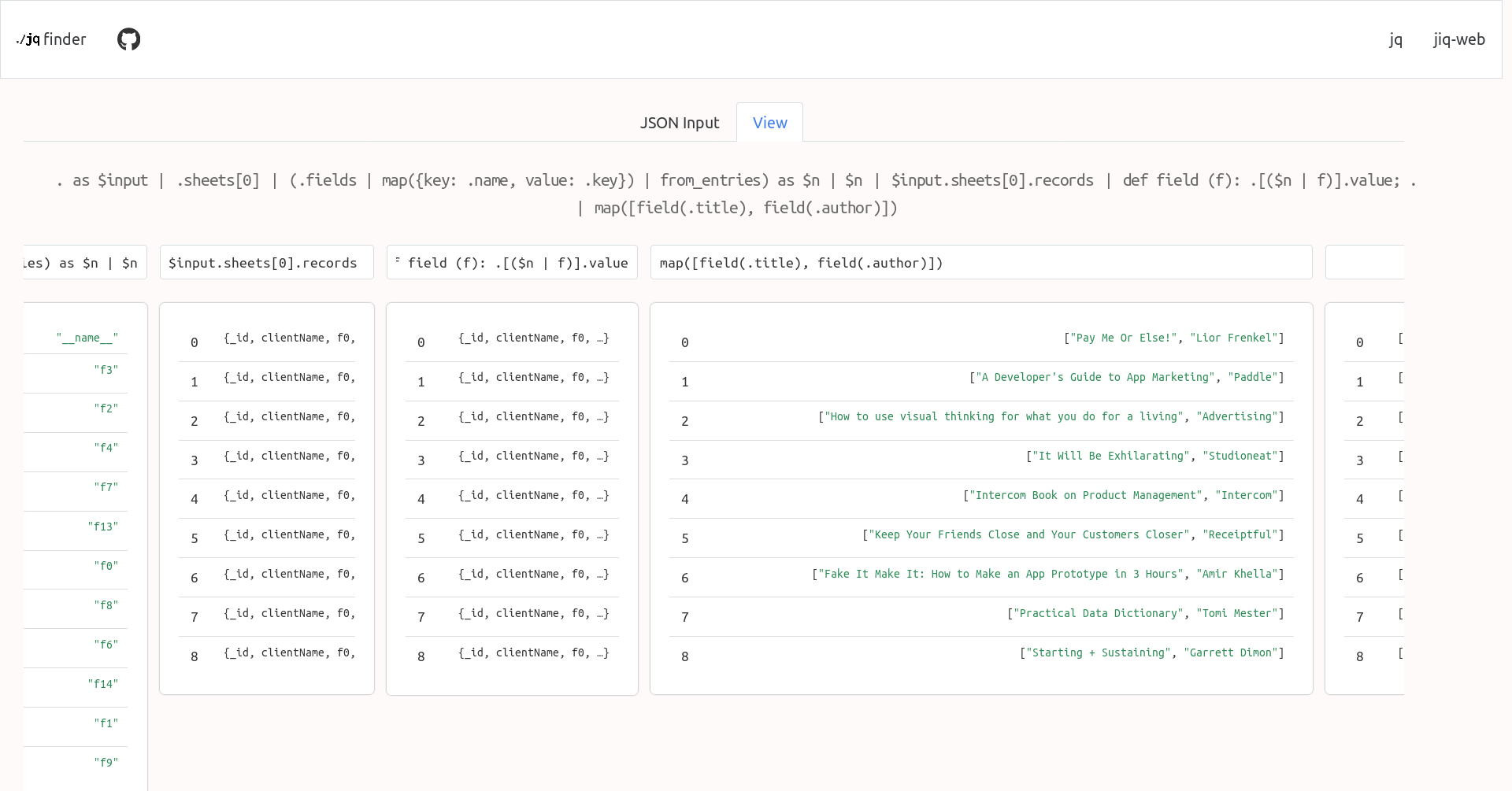
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28superform.xyz
This was an app that allowed people to create micro apps powered by forms. Actually just one form I believe. The idea was for the micro apps to be really micro.
For example, you want a list of people, but you can only have at most 10 people in the list. Your app could keep a state with list of people already added and reject any other submissions above the specified limit. This would be done with 3 lines of code and provide an automatic form for people to fill with expected data.
Another example, you wanted to create a list of people that would go to an event and each would have to bring one item from a list: you created an initial state of a list of the items that should be brought, then specified a form where people could write their names and select the item they would bring, then code that for each submitted form added the name of the person plus the item they would bring to the state while also removing the selected item from the available items. Also 3 or 4 lines of data.
Something like this can't be done anywhere else. But also of course it would be arcane and frighten normal people and so on (although I do believe some "normal" people would be able to use such a thing if they needed it, just like they learn to write complex Excel formulas and still don't call themselves programmers).
See also
- Etleneum, as it is basically the same core idea of a mutable state that is affected by calls, but Etleneum introduces (and actually forces the usage of) money, both in the sense that it acts as an escrow for contract results and that it mandates the payment of a small amount with each call, so it ends up not serving the same purposes.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28IPFS problems: Conceit
IPFS is trying to do many things. The IPFS leaders are revolutionaries who think they're smarter than the rest of the entire industry.
The fact that they've first proposed a protocol for peer-to-peer distribution of immutable, content-addressed objects, then later tried to fix that same problem using their own half-baked solution (IPNS) is one example.
Other examples are their odd appeal to decentralization in a very non-specific way, their excessive flirtation with Ethereum and their never-to-be-finished can-never-work-as-advertised Filecoin project.
They could have focused on just making the infrastructure for distribution of objects through hashes (not saying this would actually be a good idea, but it had some potential) over a peer-to-peer network, but in trying to reinvent the entire internet they screwed everything up.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28"Você só aprendeu mesmo uma coisa quando consegue explicar para os outros"
Mentira. Tá certo que existe um ponto em que você acha que sabe algo mas não consegue explicar, mas não necessariamente isso significa não saber. Conseguir explicar não depende de saber, mas de verbalizar. Podemos saber muitas coisas sem as conseguir verbalizar. Aliás, para a maior parte das experiências humanas verbalizar é que é a parte difícil. Por último, é importante dizer que a verbalização é uma abstração e portanto quando alguém tenta explicar algo e se força a fazer uma abstração está arriscando substituir a experiência concreta ou mesmo o conhecimento difuso de algo por aquela abstração e com isso ficar mais burro -- me parece que esse é risco é maior quanto mais prematura for a tentativa de explicação e quando mais sucesso a abstração improvisada fizer.
-
 @ 8d34bd24:414be32b
2024-07-05 16:49:26
@ 8d34bd24:414be32b
2024-07-05 16:49:26https://trustjesus.substack.com/p/left-behind-part-1
For if I preach the gospel, I have nothing to boast of, for I am under compulsion; for woe is me if I do not preach the gospel. (1 Corinthians 9:16)
Lately I have been feeling an urgency to write. This is partly because I feel our time left on Earth is short. So many things seem to be lining up with Biblical prophecy in books like Revelation, Daniel, Ezekiel, and 1 & 2 Thessalonians. When I face God, I don’t want to have to admit that I didn’t do all I could to call people to repentance and faith in God. I also believe that the church (true believers) will be raptured before the seven year tribulation as described in 1Thessalonians.
For if we believe that Jesus died and rose again, even so God will bring with Him those who have fallen asleep in Jesus. For this we say to you by the word of the Lord, that we who are alive and remain until the coming of the Lord, will not precede those who have fallen asleep {died}. For the Lord Himself will descend from heaven with a shout, with the voice of the archangel and with the trumpet of God, and the dead in Christ will rise first. Then we who are alive and remain will be caught up together with them in the clouds to meet the Lord in the air, and so we shall always be with the Lord. (1 Thessalonians 4:14-17) {emphasis mine}
This rapture of the church will occur not only to those who are alive at the time, but also to those who died in Christ in the past. The time before this event is the last chance for people to avoid the terror and hardship of the tribulation and I believe that time is short (I will never claim to know when, but I feel in every ounce of my being that the time is short). There will be some saved during the tribulation, but they will all go through major hardship and most who become Christians during the tribulation will most likely be martyred. If there is anything I can do to prevent people from going through this experience, I feel called to do so. “To the weak I became weak, that I might win the weak; I have become all things to all men, so that I may by all means save some.” (1 Corinthians 9:22) Of course only Jesus can save. I hope that these words will draw you closer to Jesus whether that means you accept Him as your Savior or it just means your faith is strengthened and you are encouraged to witness to the lost.
I feel like I need to write about making sure we have a saving relationship with Christ, so we get raptured, and what those who are left behind need to know going into the tribulation (I will discuss this in a subsequent post). This is way out of my comfort zone, but I am going to do my best and let the Bible and the Holy Spirit guide me. I’m sure this will be a multipart series, but I’m not yet sure how many parts or how I will divide it.
“Do this, knowing the time, that it is already the hour for you to awaken from sleep; for now salvation is nearer to us than when we believed. The night is almost gone, and the day is near. Therefore let us lay aside the deeds of darkness and put on the armor of light. Let us behave properly as in the day, not in carousing and drunkenness, not in sexual promiscuity and sensuality, not in strife and jealousy. But put on the Lord Jesus Christ, and make no provision for the flesh in regard to its lusts.” (Romans 13:11-14)
This verse talks about how we need to wake up, turn to Jesus, and obey Him as the end times draw near. This verse says to Christians “The night is almost gone, and the day is near.” For Christians, this current time of evil and hardship is night. It is the hardest time we will experience. After the rapture, we will experience the day. We will experience a time with no sin, no pain, not illness, and no death. It will be marvelous!
Unfortunately for those who have not trusted Jesus, I say “The day is almost gone, and the night is near.” This current time of evil and hardship that we experience today is the best that unbelievers will ever experience. The night is coming when todays sorrows and hardship and evil will seem like paradise compared to what they will experience during the tribulation and during eternity in Hell. It is so important to trust Jesus and to submit to Him while we still have the chance.
We are also told (not specifically for end times) “Go therefore and make disciples of all the nations, baptizing them in the name of the Father and the Son and the Holy Spirit,” (Matthew 28:19) I’ve always known I need to do a better job of sharing the gospel with unbelievers and discipling believers, but that burden, that need, has multiplied as I feel time is running out. I am trying to be faithful.
Something like 30 years ago, I was traveling and went to the local Christian book store to get a book to read. I grabbed this interesting sounding book titled Left Behind. While reading the book during my flight, I got to the part where the Christians were raptured. The pilot, but not the co-pilot was raptured and multiple passengers were raptured right from their seats in the plane. I have to admit, it kind of freaked me out and I was looking around me to make sure none of the passengers on my plane were missing. When the rapture happens for real, it will cause mayhem, sadness, and fear.
When all of the Christians disappear, the already depraved culture will get much worse without the Christians here upholding God’s word as a reference of right and wrong. Many atheists, like Richard Dawkins, who says he loves Christian culture, but wishes that nobody actually believed in Christ, will be shocked to find that Christian culture doesn’t work without Christ and Christians.
When the Christians are raptured to meet Jesus in the air, nobody will be unaware of the disappearance of the church (although I suspect that there will lots of excuses made for why they are gone, ie. removed by aliens for the good of mankind, etc.)
When Jesus returns after the tribulation, nobody will miss His coming. His return will be seen by all. Those who trusted Him during the tribulation will see Him with joy. Those who rejected Him will see Him and despair.
"And as they were gazing intently into the sky while He was going, behold, two men in white clothing stood beside them. They also said, 'Men of Galilee, why do you stand looking into the sky? This Jesus, who has been taken up from you into heaven, will come in just the same way as you have watched Him go into heaven.'" (Acts 1:10-11)
As Christians, we do not need to fear the coming tribulation, the wrath of God. God has promised we are not under His wrath.
For God has not destined us for wrath, but for obtaining salvation through our Lord Jesus Christ, who died for us, so that whether we are awake or asleep, we will live together with Him. (1 Thessalonians 5:8-10) {emphasis mine}
When this verse says “whether we are awake or asleep” it is saying “whether we are alive or dead”. The Bible always speaks of dead believers as being asleep because we will awake to be with Him at His return.
Let us hold fast the confession of our hope without wavering, for He who promised is faithful; and let us consider how to stimulate one another to love and good deeds, not forsaking our own assembling together, as is the habit of some, but encouraging one another; and all the more as you see the day drawing near. (Hebrews 10:23-25)
As we see the last days approaching and the world turning to evil unimaginable we need to have hope in the promise of God that we will join Him in heaven. We need to be fearless and share the gospel with even more urgency. We need to encourage each other in “love and good deeds.”
I hope you will be encouraged in your faith and your service to God
And then if anyone says to you, ‘Behold, here is the Christ’; or, ‘Behold, He is there’; do not believe him; for false Christs and false prophets will arise, and will show signs and wonders, in order to lead astray, if possible, the elect. But take heed; behold, I have told you everything in advance. (Mark13:21-23)
When the church is raptured, everyone will know it. There will be no mistaking this event. You don’t need to wonder. You will know, whether you are gathered to be with Jesus or whether you are left behind. You will know.
Trust Jesus.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Liberalismo oitocentista
Quando comecei a ler sobre "liberalismo" na internet havia sempre umas listas de livros recomendados, uns Ludwig von Mises, Milton Friedman e Alexis de Tocqueville. "A Democracia na América". Pra mim parecia estranho aquele papo de democracia quando eu estava interessado era em como funcionaria um mercado livre, sem regulações e tal.
Parece que Tocqueville era uma herança do mesmo povo que adorava a expressão "liberalismo clássico". O liberalismo clássico era uma coisa política que ia contra a monarquia e em favor da democracia, e aí Tocqueville se encaixava muito bem.
Poucos anos se passaram e tudo mudou. Agora acho que alguém lendo na internet não vai ver menção nenhuma a Tocqueville ou liberalismo clássico, essa chatice de democracia e suas chatices legalistas. O "libertarianismo", também um nome infeliz, tomou conta de tudo, e cresceu muito mais do que o movimento liberal-da-internet jamais imaginou que seria possível.
Os libertários brasileiros são anarquistas, detestam a democracia, reconhecem nela um vetor de ataque dos socialistas a qualquer pontinha de livre-mercado que exista -- e às liberdades individuais dos cidadãos (este aqui ainda um ponto em comum com os liberais oitocentistas). São inclusive muito mais propensos a defender a monarquia do que a democracia.
E isso é uma coisa boa. Finalmente uma pessoa pode defender princípios razoáveis de livre-mercado e individualismo sem precisar se associar com o movimento setecentistas e oitocentista que fez coisas boas, mas também foi responsável por coisas horríveis como a revolução francesa e todos os seus absurdos, e de onde saiu todo o movimento socialista.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28lnurl-auth explained
You may have seen the lnurl-auth spec or heard about it, but might not know how it works or what is its relationship with other lnurl protocols. This document attempts to solve that.
Relationship between lnurl-auth and other lnurl protocols
First, what is the relationship of lnurl-auth with other lnurl protocols? The answer is none, except the fact that they all share the lnurl format for specifying
httpsURLs.In fact, lnurl-auth is very unique in the sense that it doesn't even need a Lightning wallet to work, it is a standalone authentication protocol that can work anywhere.
How does it work
Now, how does it work? The basic idea is that each wallet has a seed, which is a random value (you may think of the BIP39 seed words, for example). Usually from that seed different keys are derived, each of these yielding a Bitcoin address, and also from that same seed may come the keys used to generate and manage Lightning channels.
What lnurl-auth does is to generate a new key from that seed, and from that a new key for each service (identified by its domain) you try to authenticate with.

That way, you effectively have a new identity for each website. Two different services cannot associate your identities.
The flow goes like this: When you visit a website, the website presents you with a QR code containing a callback URL and a challenge. The challenge should be a random value.

When your wallet scans or opens that QR code it uses the domain in the callback URL plus the main lnurl-auth key to derive a key specific for that website, uses that key to sign the challenge and then sends both the public key specific for that for that website plus the signed challenge to the specified URL.

When the service receives the public key it checks it against the challenge signature and start a session for that user. The user is then identified only by its public key. If the service wants it can, of course, request more details from the user, associate it with an internal id or username, it is free to do anything. lnurl-auth's goals end here: no passwords, maximum possible privacy.
FAQ
-
What is the advantage of tying this to Bitcoin and Lightning?
One big advantage is that your wallet is already keeping track of one seed, it is already a precious thing. If you had to keep track of a separate auth seed it would be arguably worse, more difficult to bootstrap the protocol, and arguably one of the reasons similar protocols, past and present, weren't successful.
-
Just signing in to websites? What else is this good for?
No, it can be used for authenticating to installable apps and physical places, as long as there is a service running an HTTP server somewhere to read the signature sent from the wallet. But yes, signing in to websites is the main problem to solve here.
-
Phishing attack! Can a malicious website proxy the QR from a third website and show it to the user to it will steal the signature and be able to login on the third website?
No, because the wallet will only talk to the the callback URL, and it will either be controlled by the third website, so the malicious won't see anything; or it will have a different domain, so the wallet will derive a different key and frustrate the malicious website's plan.
-
I heard SQRL had that same idea and it went nowhere.
Indeed. SQRL in its first version was basically the same thing as lnurl-auth, with one big difference: it was vulnerable to phishing attacks (see above). That was basically the only criticism it got everywhere, so the protocol creators decided to solve that by introducing complexity to the protocol. While they were at it they decided to add more complexity for managing accounts and so many more crap that in the the spec which initially was a single page ended up becoming 136 pages of highly technical gibberish. Then all the initial network effect it had, libraries and apps were trashed and nowadays no one can do anything with it (but, see, there are still people who love the protocol writing in a 90's forum with no clue of anything besides their own Java).
-
We don't need this, we need WebAuthn!
WebAuthn is essentially the same thing as lnurl-auth, but instead of being simple it is complex, instead of being open and decentralized it is centralized in big corporations, and instead of relying on a key generated by your own device it requires an expensive hardware HSM you must buy and trust the manufacturer. If you like WebAuthn and you like Bitcoin you should like lnurl-auth much more.
-
What about BitID?
This is another one that is very similar to lnurl-auth, but without the anti-phishing prevention and extra privacy given by making one different key for each service.
-
What about LSAT?
It doesn't compete with lnurl-auth. LSAT, as far as I understand it, is for when you're buying individual resources from a server, not authenticating as a user. Of course, LSAT can be repurposed as a general authentication tool, but then it will lack features that lnurl-auth has, like the property of having keys generated independently by the user from a common seed and a standard way of passing authentication info from one medium to another (like signing in to a website at the desktop from the mobile phone, for example).
-
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A Lightning penalty transaction
It was a cold day and I remembered that this
lightningdnode I was running on my local desktop to work on poncho actually had mainnet channels in it. Two channels, both private, bought on https://lnbig.com/ a while ago when I was trying to conduct an anonymous griefing attack on big nodes of the network just to prove it was possible (the attempts proved unsuccessful after some hours and I gave up).It is always painful to close channels because paying fees hurts me psychologically, and then it hurts even more to be left with a new small UTXO that will had to be spent to somewhere but that can barely pay for itself, but it also didn't make sense to just leave the channels there and risk forgetting them and losing them forever, so I had to do something.
One of the channels had 0 satoshis on my side, so that was easy. Mutually closed and I don't have to think anymore about it.
The other one had 10145 satoshis on my side -- out of a total of 100000 satoshis. Why can't I take my part all over over Lightning and leave the full channel UTXO to LNBIG? I wish I could do that, I don't want a small UTXO. I was not sure about it, but if the penalty reserve was 1% maybe I could take out abou 9000 satoshis and then close it with 1000 on my side? But then what would I do with this 1000 sat UTXO that would remain? Can't I donate it to miners or something?
I was in the middle of this thoughts stream when it came to me the idea of causing a penalty transaction to give those abundant 1000 sat to Mr. LNBIG as a donation for his excellent services to the network and the cause of Bitcoin, and for having supported the development of https://sbw.app/ and the hosted channels protocol.
Unfortunately
lightningddoesn't have a commandtriggerpenaltytransactionortrytostealusingoldstate, so what I did was:First I stopped
lightningdthen copied the database to elsewhere:cp ~/.lightningd/bitcoin/lightningd.sqlite3 ~/.lightning/bitcoin/lightningd.sqlite3.bakthen I restartedlightningdand fighted against the way-too-aggressive MPP splitting algorithm thepaycommand uses to pay invoices, but finally managed to pull about 9000 satoshis to my Z Bot that lives on the terrible (but still infinitely better than Twitter DMs) "webk" flavor of the Telegram web application and which is linked to my against-bitcoin-ethos-country-censoring ZEBEDEE Wallet. The operation wasn't smooth but it didn't take more than 10 invoices andpaycommands.
With the money out and safe elsewhere, I stopped the node again, moved the database back with a reckless
mv ~/.lightning/bitcoin/lightningd.sqlite3.bak ~/.lightningd/bitcoin/lightningd.sqlite3and restarted it, but to prevent mylightningdfrom being super naïve and telling LNBIG that it had an old state (I don't know if this would happen) which would cause LNBIG to close the channel in a boring way, I used the--offlineflag which apparently causes the node to not do any external connections.Finally I checked my balance using
lightning-cli listfundsand there it was, again, the 10145 satoshis I had at the start! A fantastic money creation trick, comparable to the ones central banks execute daily.
I was ready to close the channel now, but the
lightning-cli closecommand had an option for specifying how many seconds I would wait for a mutual close before proceeding to a unilateral close. There is noforceclosecommand like Éclair hasor anything like that. I was afraid that even if I gave LNBIG one second it would try to do boring things, so I paused to consider how could I just broadcast the commitment transaction manually, looked inside the SQLite database and thechannelstable with its millions of columns with cryptic names in the unbearable.schemaoutput, imagined thatlightningdmaybe wouldn't know how to proceed to take the money from theto-localoutput if I managed to broadcast it manually (and in the unlikely event that LNBIG wouldn't broadcast the penalty transaction), so I decided to just accept the risk and calllightning-cli close 706327x1588x0 1But it went well. The
--offlineflag apparently really works, as it just considered LNBIG to be offline and 1 second later I got the desired result.
My happiness was complete when I saw the commitment transaction with my output for 10145 satoshis published on the central database of Bitcoin, blockstream.info.
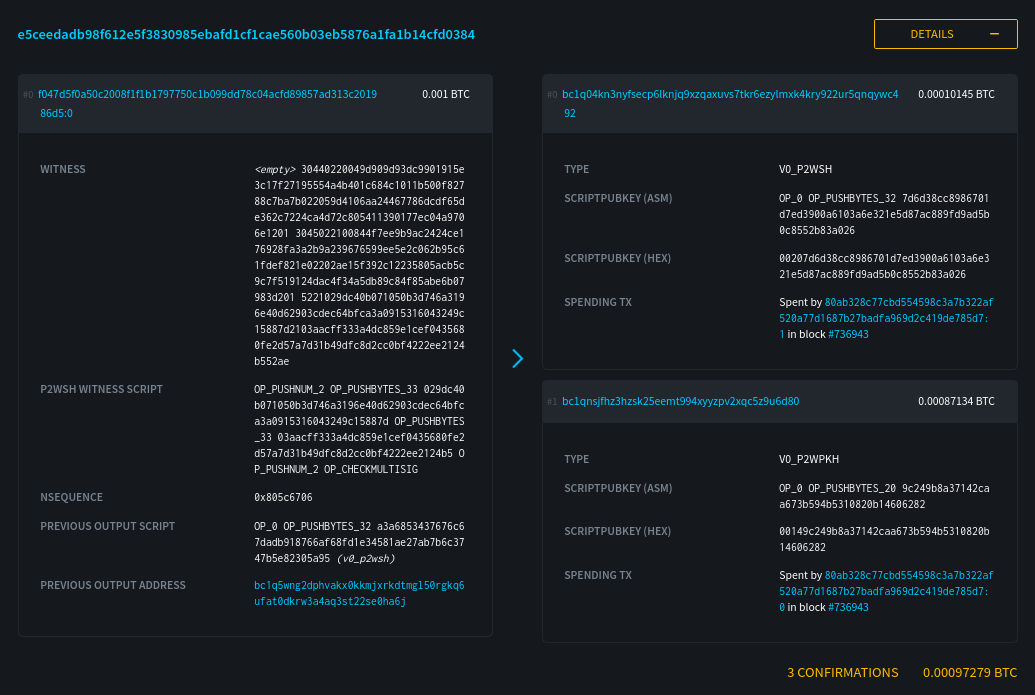
Then I went to eat something and it seems LNBIG wasn't offline or sleeping, he was certainly looking at all the logs from his 274 nodes in a big room full of monitors, very alert and eating an apple while drinking coffee, ready to take action, for when I came back, minutes later, I could see it, again on the single source of truth for the Bitcoin blockchain, the Blockstream explorer. I've refreshed the page and there it was, a small blue link right inside the little box that showed my
to-localoutput, a notice saying it had been spent -- not by mylightningdsince that would have to wait 9000 blocks, but by the same transaction that spent the other output, from which I could be very sure it was it, the glorious, mighty, unforgiving penalty transaction, splitting the earth, showing itself in all its power, and taking my 10145 satoshis to their rightful owner.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Trello Attachment Editor
A static JS app that allowed you to authorize with your Trello account, fetch the board structure, find attachments, edit them in the browser then replace them in the cards.
Quite a nice thing. I believe it was done to help with Websites For Trello attached scripts and CSS files.
See also
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Soft-fork activation through
bitcoindcompetitionOr: how to activate Drivechain.
Imagine a world in which there are 10 different
bitcoindflavors, as described inbitcoinddecentralization.Now how do you enable a soft-fork?
Flavor 1 enables it. Seeing that nothing bad happened, flavor 2 enables it. Then flavor 3 enables it.
And so on.
When what is perceived by miners to be a big chunk of support for the proposal, a miner can try to mine a block that contains the new feature.
No need for a flag day or a centralized decision making process that depends on one or two courageous leaders to enable a timer.
This probably sounds silly, and maybe is.

