-
 @ 7460b7fd:4fc4e74b
2024-09-05 08:37:48
@ 7460b7fd:4fc4e74b
2024-09-05 08:37:48请看2014年王兴的一场思维碰撞,视频27分钟开始
最后,一个当时无法解决的点:丢失
-
 @ b60c3e76:c9d0f46e
2024-05-15 10:08:47
@ b60c3e76:c9d0f46e
2024-05-15 10:08:47KRIS menjamin semua golongan masyarakat mendapatkan perlakuan sama dari rumah sakit, baik pelayanan medis maupun nonmedis.
Demi memberikan peningkatan kualitas layanan kesehatan kepada masyarakat, pemerintah baru saja mengeluarkan Peraturan Presiden (Perpres) nomor 59 tahun 2024 tentang Jaminan Kesehatan. Melalui perpres itu, Presiden Joko Widodo (Jokowi) telah menghapus perbedaan kelas layanan 1, 2, dan 3 dalam Badan Penyelenggara Jaminan Sosial atau BPJS Kesehatan.
Layanan berbasis kelas itu diganti dengan KRIS (Kelas Rawat Inap Standar). Berkaitan dengan lahirnya Perpres 59/2024 tentang Perubahan Ketiga atas Perpres 82/2018 tentang Jaminan Kesehatan, Presiden Joko Widodo telah memerintahkan seluruh rumah sakit yang bekerja sama dengan BPJS Kesehatan melaksanakannya.
Kebijakan baru itu mulai berlaku per 8 Mei 2024 dan paling lambat 30 Juni 2025. Dalam jangka waktu tersebut, rumah sakit dapat menyelenggarakan sebagian atau seluruh pelayanan rawat inap berdasarkan KRIS sesuai dengan kemampuan rumah sakit.
Lantas apa yang menjadi pembeda dari sisi layanan dengan layanan rawat inap sesuai Perpres 59/2024? Dahulu sistem layanan rawat BPJS Kesehatan dibagi berdasarkan kelas yang dibagi masing-masing kelas 1, 2, dan 3. Namun, melalui perpres, layanan kepada masyarakat tidak dibedakan lagi.
Pelayanan rawat inap yang diatur dalam perpres itu--dikenal dengan nama KRIS—menjadi sistem baru yang digunakan dalam pelayanan rawat inap BPJS Kesehatan di rumah sakit-rumah sakit. Dengan KRIS, semua golongan masyarakat akan mendapatkan perlakuan yang sama dari rumah sakit, baik dalam hal pelayanan medis maupun nonmedis.
Dengan lahirnya Perpres 59/2024, tarif iuran BPJS Kesehatan pun juga akan berubah. Hanya saja, dalam Perpres itu belum dicantumkan secara rinci ihwal besar iuran yang baru. Besaran iuran baru BPJS Kesehatan itu sesuai rencana baru ditetapkan pada 1 Juli 2025.
“Penetapan manfaat, tarif, dan iuran sebagaimana dimaksud ditetapkan paling lambat tanggal 1 Juli 2025,” tulis aturan tersebut, dikutip Senin (13/5/2024).
Itu artinya, iuran BPJS Kesehatan saat ini masih sama seperti sebelumnya, yakni sesuai dengan kelas yang dipilih. Namun perpres itu tetap berlaku sembari menanti lahirnya peraturan lanjutan dari perpres tersebut.
Kesiapan Rumah Sakit
Berkaitan dengan lahirnya kebijakan layanan kesehatan tanpa dibedakan kelas lagi, Kementerian Kesehatan (Kemenkes) menegaskan mayoritas rumah sakit di Indonesia siap untuk menjalankan layanan KRIS untuk pasien BPJS Kesehatan.
Kesiapan itu diungkapkan oleh Dirjen Pelayanan Kesehatan Kemenkes Azhar Jaya. “Survei kesiapan RS terkait KRIS sudah dilakukan pada 2.988 rumah sakit dan yang sudah siap menjawab isian 12 kriteria ada sebanyak 2.233 rumah sakit,” ujar Azhar.
Sebagai informasi, KRIS adalah pengganti layanan Kelas 1, 2, dan 3 BPJS Kesehatan yang bertujuan untuk memberikan layanan kesehatan secara merata tanpa melihat besaran iurannya.
Melalui KRIS, rumah sakit perlu menyiapkan sarana dan prasarana sesuai dengan 12 kriteria kelas rawat inap standar secara bertahap. Apa saja ke-12 kriteria KRIS itu?
Sesuai bunyi Pasal 46A Perpres 59/2024, disyaratkan kriteria fasilitas perawatan dan pelayanan rawat inap KRIS meliputi komponen bangunan yang digunakan tidak boleh memiliki tingkat porositas yang tinggi serta terdapat ventilasi udara dan kelengkapan tidur.
Demikian pula soal pencahayaan ruangan. Perpres itu juga mengatur pencahayaan ruangan buatan mengikuti kriteria standar 250 lux untuk penerangan dan 50 lux untuk pencahayaan tidur, temperature ruangan 20--26 derajat celcius.
Tidak hanya itu, layanan rawat inap berdasarkan perpres itu mensyaratkan fasilitas layanan yang membagi ruang rawat berdasarkan jenis kelamin pasien, anak atau dewasa, serta penyakit infeksi atau noninfeksi.
Selain itu, kriteria lainnya adalah keharusan bagi penyedia layanan untuk mempertimbangkan kepadatan ruang rawat dan kualitas tempat tidur, penyediaan tirai atau partisi antartempat tidur, kamar mandi dalam ruangan rawat inap yang memenuhi standar aksesibilitas, dan menyediakan outlet oksigen.
Selain itu, kelengkapan tempat tidur berupa adanya dua kotak kontak dan nurse call pada setiap tempat tidur dan adanya nakas per tempat tidur. Kepadatan ruang rawat inap maksimal empat tempat tidur dengan jarak antara tepi tempat tidur minimal 1,5 meter.
Tirai/partisi dengan rel dibenamkan menempel di plafon atau menggantung. Kamar mandi dalam ruang rawat inap serta kamar mandi sesuai dengan standar aksesibilitas dan outlet oksigen.
Azhar menjamin, Kemenkes akan menjalankan hal tersebut sesuai dengan tupoksi yang ada. “Tentu saja kami akan bekerja sama dengan BPJS Kesehatan dalam implementasi dan pengawasannya di lapangan,” ujar Azhar.
Berkaitan dengan perpres jaminan kesehatan itu, Direktur Utama BPJS Kesehatan Ghufron Mukti menilai, perpres tersebut berorientasi pada penyeragaman kelas rawat inap yang mengacu pada 12 kriteria. "Bahwa perawatan ada kelas rawat inap standar dengan 12 kriteria, untuk peserta BPJS, maka sebagaimana sumpah dokter tidak boleh dibedakan pemberian pelayan medis atas dasar suku, agama, status sosial atau beda iurannya," ujarnya.
Jika ada peserta ingin dirawat pada kelas yang lebih tinggi, kata Ghufron, maka diperbolehkan selama hal itu dipengaruhi situasi nonmedis. Hal itu disebutkan dalam Pasal 51 Perpres Jaminan Kesehatan diatur ketentuan naik kelas perawatan.
Menurut pasal tersebut, naik kelas perawatan dilakukan dengan cara mengikuti asuransi kesehatan tambahan atau membayar selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya yang harus dibayar akibat peningkatan pelayanan.
Selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya pelayanan dapat dibayar oleh peserta bersangkutan, pemberi kerja, atau asuransi kesehatan tambahan.
Ghufron Mukti juga mengimbau pengelola rumah sakit tidak mengurangi jumlah tempat tidur perawatan pasien dalam upaya memenuhi kriteria KRIS. "Pesan saya jangan dikurangi akses dengan mengurangi jumlah tempat tidur. Pertahankan jumlah tempat tidur dan penuhi persyaratannya dengan 12 kriteria tersebut," tegas Ghufron.
Penulis: Firman Hidranto Redaktur: Ratna Nuraini/Elvira Inda Sari Sumber: Indonesia.go.id
-
 @ 266815e0:6cd408a5
2024-05-09 17:23:28
@ 266815e0:6cd408a5
2024-05-09 17:23:28Lot of people are starting to talk about building a web-of-trust and how nostr can or is already being used as such
We all know about using the kind:3 following lists as a simple WoT that can be used to filter out spam. but as we all know it does not really signal "trust", its mostly just "I find your content interesting"
But what about real "trust"... well its kind of multi-denominational, I could trust that your a good developer or a good journalist but still not trust you enough to invite you over to my house. There are some interesting and clever solutions proposed for quantifying "trust" in a digital sense but I'm not going to get into that here. I want to talk about something that I have not see anyone discuss yet.
How is the web-of-trust maintained? or more precisely how do you expect users to update the digital representation of the "trust" of other users?
Its all well and good to think of how a user would create that "trust" of another user when discovering them for the first time. They would click the "follow" button, or maybe even rate them on a few topics with a 1/5 star system But how will a user remove that trust? how will they update it if things change and they trust them less?
If our goal is to model "trust" in a digital sense then we NEED a way for the data to stay up-to-date and as accurate as possible. otherwise whats the use? If we don't have a friction-less way to update or remove the digital representation of "trust" then we will end up with a WoT that continuously grows and everyone is rated 10/10
In the case of nostr kind:3 following lists. its pretty easy to see how these would get updated. If someone posts something I dislike or I notice I'm getting board of their content. then I just unfollow them. An important part here is that I'm not thinking "I should update my trust score of this user" but instead "I'm no longer interested, I don't want to see this anymore"
But that is probably the easiest "trust" to update. because most of us on social media spend some time curating our feed and we are used to doing it. But what about the more obscure "trust" scores? whats the regular mechanism by which a user would update the "honestly" score of another user?
In the real world its easy, when I stop trusting someone I simply stop associating with them. there isn't any button or switch I need to update. I simply don't talk to them anymore, its friction-less But in the digital realm I would have to remove or update that trust. in other words its an action I need to take instead of an action I'm not doing. and actions take energy.
So how do we reflect something in the digital world that takes no-energy and is almost subconscious in the real world?
TLDR; webs-of-trust are not just about scoring other users once. you must keep the score up-to-date
-
 @ 266815e0:6cd408a5
2024-04-22 22:20:47
@ 266815e0:6cd408a5
2024-04-22 22:20:47While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent
I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS
There were a few things I learned from all these conversations:
- All the existing solutions have one thing in common. A universal ID of some kind for files
- HTTP is still good. we don't have to throw the baby out with the bath water
- nostr could fix this... somehow
Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...
An Identity system
An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files
This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)
What is blossom?
Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id
What are Blobs?
blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names
Instead blobs have a sha256 hash (like
b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553) as an IDThese IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can get a files sha256 hash on linux using:
sha256sum bitcoin.pdf)How do the servers work?
Blossom servers expose four endpoints to let clients and users upload and manage blobs
GET /<sha256>(optional file.ext)PUT /uploadAuthentication: Signed nostr event- Returns a blob descriptor
GET /list/<pubkey>- Returns an array of blob descriptors
Authentication(optional): Signed nostr eventDELETE /<sha256>Authentication: Signed nostr event
What is Blossom Drive?
Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs
What are Drives
Drives are just nostr events (kind
30563) that store a map of blobs and what filename they should have along with some extra metadataAn example drive event would be
json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at
If your interested, the full event definition is at github.com/hzrd149/blossom-drive
Getting started
Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started
1. Open the app
Open https://blossom.hzrd149.com
2. Login using extension

You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an
ncryptsecpassword protected private key - ansecunprotected private key (please don't) - bunker:// URI from nsecbunker3. Add a blossom server

Right now
https://cdn.satellite.earthis the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript github.com/hzrd149/blossom-server4. Start uploading your files
NOTE: All files upload to blossom drive are public by default. DO NOT upload private files

5. Manage files

Encrypted drives
There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify

Whats next?
I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything
also all the images in this article are stored in one of my blossom drives here
nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ d2e97f73:ea9a4d1b
2023-04-11 19:36:53
@ d2e97f73:ea9a4d1b
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 8cb60e21:5f2deaea
2024-09-05 19:48:32
@ 8cb60e21:5f2deaea
2024-09-05 19:48:32Part 3: Asynchroni et DOM Manipulatio
3.1 Promissa et Async/Await
Praesent blandit. Nam nulla. Integer pede justo, lacinia eget, tincidunt eget, tempus vel, pede.
``javascript function simulaRequest(data, probabilitasErroris = 0.1) { return new Promise((resolve, reject) => { setTimeout(() => { if (Math.random() < probabilitasErroris) { reject("Error: Aliquid mali accidit"); } else { resolve(Data accepta: ${data}`); } }, 1000); }); }simulaRequest("Lorem ipsum") .then((responsum) => console.log(responsum)) .catch((error) => console.error(error));
async function fetchData() { try { const responsum = await simulaRequest("Dolor sit amet"); console.log(responsum); } catch (error) { console.error(error); } }
fetchData(); ```
3.2 DOM Manipulatio
Morbi non lectus. Aliquam sit amet diam in magna bibendum imperdiet. Nullam orci pede, venenatis non, sodales sed, tincidunt eu, felis.
```javascript document.addEventListener("DOMContentLoaded", () => { const titulus = document.createElement("h1"); titulus.textContent = "Lorem Ipsum JavaScript"; document.body.appendChild(titulus);
const paragraphus = document.createElement("p"); paragraphus.textContent = "Neque porro quisquam est qui dolorem ipsum quia dolor sit amet, consectetur, adipisci velit..."; document.body.appendChild(paragraphus); const button = document.createElement("button"); button.textContent = "Fac Clic Me"; button.addEventListener("click", () => { alert("Gratias tibi ago pro clic!"); }); document.body.appendChild(button);}); ```
3.3 Fetch API
Maecenas leo odio, condimentum id, luctus nec, molestie sed, justo. Pellentesque viverra pede ac diam.
``javascript async function fetchLoremIpsum() { try { const responsum = await fetch("https://api.lorem.space/image/game?w=150&h=220"); if (!responsum.ok) { throw new Error(HTTP error! status: ${responsum.status}`); } const data = await responsum.blob(); const imago = document.createElement("img"); imago.src = URL.createObjectURL(data); document.body.appendChild(imago); } catch (error) { console.error("Problema cum fetching imagine:", error); } }fetchLoremIpsum(); ```
3.4 Local Storage
Cras mi pede, malesuada in, imperdiet et, commodo vulputate, justo. In blandit ultrices enim.
```javascript function salvaPreferentias(clavis, valor) { localStorage.setItem(clavis, JSON.stringify(valor)); }
function accipePreferentias(clavis) { const valor = localStorage.getItem(clavis); return valor ? JSON.parse(valor) : null; }
const preferentiae = { thema: "clarus", lingua: "Latina", notificationes: true };
salvaPreferentias("userPrefs", preferentiae);
const salvataePreferentiae = accipePreferentias("userPrefs"); console.log(salvataePreferentiae); ```
3.5 Exercitia Parti III
- Crea paginam web simplicem quae utitur fetch API ad exhibendum datos ex API publica.
- Implementa functionalitatem "drag and drop" utens DOM API.
- Construe applicationem "todo list" quae persistit datos in local storage.
Conclusio
Vivamus vestibulum sagittis sapien. Cum sociis natoque penatibus et magnis dis parturient montes, nascetur ridiculus mus. Etiam vel augue. Vestibulum rutrum rutrum neque. Aenean auctor gravida sem. Praesent id massa id nisl venenatis lacinia. Aenean sit amet justo. Morbi ut odio.
Cras mi pede, malesuada in, imperdiet et, commodo vulputate, justo. In blandit ultrices enim. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Proin interdum mauris non ligula pellentesque ultrices. Phasellus id sapien in sapien iaculis congue. Vivamus metus arcu, adipiscing molestie, hendrerit at, vulputate vitae, nisl.
Aenean lectus. Pellentesque eget nunc. Donec quis orci eget orci vehicula condimentum. Curabitur in libero ut massa volutpat convallis. Morbi odio odio, elementum eu, interdum eu, tincidunt in, leo. Maecenas pulvinar lobortis est.
Phasellus sit amet erat. Nulla tempus. Vivamus in felis eu sapien cursus vestibulum. Proin eu mi. Nulla ac enim. In tempor, turpis nec euismod scelerisque, quam turpis adipiscing lorem, vitae mattis nibh ligula nec sem. Duis aliquam convallis nunc. Proin at turpis a pede posuere nonummy.
Integer non velit. Donec diam neque, vestibulum eget, vulputate ut, ultrices vel, augue. Vestibulum ante ipsum primis in faucibus orci luctus et ultrices posuere cubilia Curae; Donec pharetra, magna vestibulum aliquet ultrices, erat tortor sollicitudin mi, sit amet lobortis sapien sapien non mi. Integer ac neque. Duis bibendum. Morbi non quam nec dui luctus rutrum. Nulla tellus. In sagittis dui vel nisl. Duis ac nibh. Fusce lacus purus, aliquet at, feugiat non, pretium quis, lectus.
Suspendisse potenti. In eleifend quam a odio. In hac habitasse platea dictumst. Maecenas ut massa quis augue luctus tincidunt. Nulla mollis molestie lorem. Quisque ut erat. Curabitur gravida nisi at nibh. In hac habitasse platea dictumst. Aliquam augue quam, sollicitudin vitae, consectetuer eget, rutrum at, lorem. Integer tincidunt ante vel ipsum. Praesent blandit lacinia erat. Vestibulum sed magna at nunc commodo placerat. Praesent blandit. Nam nulla.
-
 @ 8cb60e21:5f2deaea
2024-09-05 19:48:32
@ 8cb60e21:5f2deaea
2024-09-05 19:48:32Part 1: Fundamentum Javascripti
1.1 Introductionis
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Nullam euismod, nisi vel consectetur interdum, nisl nunc egestas nunc, vitae tincidunt nisl nunc euismod nunc. Sed euismod, nisi vel consectetur interdum, nisl nunc egestas nunc, vitae tincidunt nisl nunc euismod nunc.
javascript console.log("Salve, mundi!");1.2 Variabiles et Typi Datorum
Pellentesque habitant morbi tristique senectus et netus et malesuada fames ac turpis egestas. Integer convallis, nunc ac blandit tincidunt, ipsum augue tincidunt nunc, vitae tincidunt nisl nunc euismod nunc.
javascript var numerus = 42; let textus = "Lorem ipsum"; const CONSTANTIA = true;1.2.1 Typi Numerorum
Curabitur in libero ut massa volutpat convallis. Morbi odio odio, elementum eu, interdum eu, tincidunt in, leo.
javascript let integer = 10; let floatinum = 3.14; let scientificum = 2.998e8;1.2.2 Typi Textuum
Maecenas tristique, est et tempus semper, est quam pharetra magna, ac consequat metus sapien ut nunc.
javascript let textusBrevis = 'Carpe diem'; let textusLongus = "Quod erat demonstrandum"; let textusTemplatum = `Cogito, ${textusBrevis.toLowerCase()}, sum`;1.3 Operatores
Donec dapibus. Duis at velit eu est congue elementum. In hac habitasse platea dictumst.
```javascript let a = 5; let b = 3;
console.log(a + b); // Additio console.log(a - b); // Subtractio console.log(a * b); // Multiplicatio console.log(a / b); // Divisio console.log(a % b); // Modulus console.log(a ** b); // Potentia ```
1.4 Structurae Controli
Morbi non lectus. Aliquam sit amet diam in magna bibendum imperdiet. Nullam orci pede, venenatis non, sodales sed, tincidunt eu, felis.
1.4.1 Conditionales
```javascript let aetas = 20;
if (aetas >= 18) { console.log("Adultus es"); } else if (aetas >= 13) { console.log("Adolescens es"); } else { console.log("Puer es"); } ```
1.4.2 Iterationes
``javascript for (let i = 0; i < 5; i++) { console.log(Iteratio ${i}`); }let j = 0; while (j < 5) { console.log(
Dum iteratio ${j}); j++; } ```1.5 Exercitia Parti I
- Scribe programma quod convertat gradus Celsius in Fahrenheit.
- Crea algorithmum qui determinat si numerus est par vel impar.
- Implementa "FizzBuzz" pro numeris 1 ad 100.
-
 @ 8cb60e21:5f2deaea
2024-09-05 19:48:32
@ 8cb60e21:5f2deaea
2024-09-05 19:48:32Part 2: Functiones et Objecta
2.1 Functiones
Fusce posuere felis sed lacus. Morbi sem mauris, laoreet ut, rhoncus aliquet, pulvinar sed, nisl.
``javascript function salutatio(nomen) { returnSalve, ${nomen}!`; }console.log(salutatio("Cicero"));
const valedictio = (nomen) => { console.log(
Vale, ${nomen}!); };valedictio("Seneca"); ```
2.1.1 Parametri Default et Rest
Nunc purus. Phasellus in felis. Donec semper sapien a libero.
``javascript function congregatio(primus, secundus = "mundi", ...ceteri) { console.log(${primus} ${secundus}); console.log(Ceteri: ${ceteri.join(", ")}`); }congregatio("Salve"); congregatio("Lorem", "ipsum"); congregatio("Veni", "vidi", "vici", "et", "cetera"); ```
2.2 Objecta
Nam congue, risus semper porta volutpat, quam pede lobortis ligula, sit amet eleifend pede libero quis orci.
``javascript const persona = { nomen: "Iulius", cognomen: "Caesar", aetas: 55, salutatio: function() { returnSalve, ${this.nomen} ${this.cognomen}!`; } };console.log(persona.salutatio()); ```
2.2.1 Methodi Object
Nullam porttitor lacus at turpis. Donec posuere metus vitae ipsum. Aliquam non mauris.
```javascript const claves = Object.keys(persona); console.log(claves);
const valores = Object.values(persona); console.log(valores);
const paria = Object.entries(persona); console.log(paria); ```
2.3 Arrays
Morbi porttitor lorem id ligula. Suspendisse ornare consequat lectus. In est risus, auctor sed, tristique in, tempus sit amet, sem.
```javascript const fructus = ["malum", "pirum", "uva", "cerasum"];
fructus.forEach((fructus) => { console.log(fructus); });
const longiFructus = fructus.filter((fructus) => fructus.length > 4); console.log(longiFructus);
const maiusculaFructus = fructus.map((fructus) => fructus.toUpperCase()); console.log(maiusculaFructus); ```
2.4 Exercitia Parti II
- Crea functionem quae calculat factorialem numeri.
- Implementa methodum quae invenit maximum valorem in array.
- Scribe programma quod ordinat objecta in array secundum proprietatem specificam.
-
 @ e27ae11e:e0c36580
2024-09-05 16:28:24
@ e27ae11e:e0c36580
2024-09-05 16:28:24In the present computerized age, having a website is essential for any business, including tradies. Yet, it's not just about having a website; about having a website looks perfect and functions admirably on all gadgets. This is where responsive web design comes in. We should investigate why responsive web design is fundamental for tradies and how it can help your business. Visit us > Best Tradie Web Design Key takeaways Mobile-Friendly is a Must: Guarantee your website looks perfect and functions admirably on cell phones and tablets to draw in additional clients.
Better Insight: A responsive site is simpler to utilize, making guests blissful and bound to reach you.
Higher Google Rankings: A versatile website can assist you with seeming higher in list items, carrying more traffic to your webpage.
Set aside Time and Cash: Overseeing one responsive site is less expensive and easier than having separate locales for various gadgets. Overview Responsive web design is a methodology that does a good job for your website and capacity suitably on any contraption, whether it's a PC, tablet, or cell. It suggests your website will thusly change its format and content to fit the screen size of the contraption being used. This ensures a predictable and beguiling experience for your visitors, paying little heed to how they access your site. What difference Does It Make for Tradies? 1. Increased Versatile Utilization More individuals are utilizing their cell phones to peruse the web. Potential clients could look for your administrations while in a hurry. On the off chance that your website isn't versatile, you could lose those possible clients. Responsive web design guarantees that your webpage looks perfect and functions admirably on cell phones, making it simpler for guests to find and reach you. Tip: Check your website analytics to see how many visitors are accessing your site from mobile devices. Use this data to prioritize mobile optimization. 2. Better Client Experience A responsive website gives a superior client experience. At the point when guests can undoubtedly explore your site and find the information they need without zooming in or scroll on a level plane, they are bound to remain longer and investigate your administrations. A positive client experience can prompt more requests and appointments. Tip: Use a clean and simple design that is easy to navigate on all devices. Avoid clutter and ensure that buttons and links are easy to tap 3. Improved Website optimization Rankings Web crawlers like Google focus on versatile websites. In case your site is responsive, it will rank higher in list things. This infers more prominent detectable quality for your business and more potential clients believing that you are on the web. Higher rankings can basically uphold your web-based presence and attract more busy time gridlock to your website. Tip: Guarantee your website content is applicable and helpful to your interest group. Excellent substance further develops Search engine optimization and keeps guests locked in. 4. Cost-Powerful Keeping a single responsive website is smarter than having separate objections for workspace and flexible clients. With responsive web design, you simply need to regulate and invigorate one website, saving you time and money long term. Tip: Consistently update your website's substance and design to keep it new and important, guaranteeing it stays viable and cost-productive. 5. Consistent Marking A responsive website guarantees that your marking stays steady across all gadgets. Whether a client visits your site on a PC or a cell phone, they will see similar design, tones, and logo. Steady marking assists fabricate trust and acknowledgment with your crowd. Tip: Utilize a similar variety plan, logo, and textual styles across all variants of your website to keep a predictable brand personality.
Make Your Website Responsive 1. Pick a Responsive Subject If you are using a website producer or a substance the chiefs system like WordPress, pick a responsive subject. These subjects are designed to be dynamic and will consequently change in accordance with various screen sizes. Tip: Preview the theme on different devices before making a final decision to ensure it meets your needs. 2. Optimize Pictures and Media Guarantee that pictures and media records are improved for quick stacking on all gadgets. Enormous pictures can dial back your site, particularly on cell phones. Use devices to pack pictures without forfeiting quality. Tip: Use image compression tools like TinyPNG or JPEGmini to reduce the file size of your images without losing quality 3. Simplify Route Ensure your website's route is basic and simple to use on all gadgets. Utilize clear menus and buttons that are not difficult to tap on a touchscreen. Try not to utilize an excessive number of connections or complex dropdown menus that can be hard to explore on a little screen. Tip: Use a simple, easy-to-use menu that adapts to different screen sizes. A hamburger menu can be effective for mobile devices. 4. Use Adaptable Designs Design your website utilizing adaptable formats that can change in accordance with various screen sizes. This can be accomplished utilizing CSS (Flowing Templates) to make a liquid framework design that changes in light of the gadget's screen size. Tip: Avoid fixed-width layouts. Instead, use percentage-based widths that allow your content to resize fluidly. 5. Test Your Website Reliably test your website on different contraptions and screen sizes to promise it looks perfect and works fittingly. There are online instruments available that can help you see how your webpage appears on different devices. Tip: Utilize online instruments like Google's Dynamic Test and Browser Stack to perceive how your website looks and works on changed gadgets and programs. Conclusion Responsive web design is essential for tradies that need to attract and hold clients in the present high level world. It ensures that your website looks great and works honorably on all devices, giving you an unrivaled client experience, further fostering your Web enhancement rankings, and saving you time and money. By picking a responsive topic, streamlining pictures, improving on route, and testing your webpage consistently, you can make a responsive website that assists your exchange business with flourishing on the web. Putting resources into responsive web design isn't just about staying aware of patterns; it's tied in with giving the most ideal experience to your guests and guaranteeing your business stays serious. In this way, make the strides today to make your website responsive and watch your web-based presence develop!
-
 @ 469fa704:2b6cb760
2024-09-05 15:06:49
@ 469fa704:2b6cb760
2024-09-05 15:06:49The Evolution of Web 3.0: Bitcoin's Role in Decentralizing the Internet
Introduction to Web 3.0
Web 3.0, often referred to as the decentralized web, represents the next phase in the evolution of the internet. Unlike its predecessors, Web 3.0 aims to redistribute control from centralized entities back to individual users through technologies like blockchain, cryptocurrencies, and decentralized applications (dApps). This shift promises a more democratic internet where users control their data, identity, and digital destiny.
The Bitcoin Protocol: A Foundation for Web 3.0
Bitcoin's Influence on Decentralization
Bitcoin, introduced in 2008, can be seen as a precursor to Web 3.0 due to its decentralized nature. The Bitcoin protocol introduced the world to blockchain technology, a decentralized ledger that records all transactions across a network of computers. This technology underpins Web 3.0's ethos by:
- Promoting Decentralization: Bitcoin's network operates without a central authority, showcasing how internet services could run on similar principles, reducing the power of centralized tech giants.
- Enhancing Security and Privacy: Through cryptographic means, Bitcoin ensures that transactions are secure and pseudonymus, a feature integral to Web 3.0's vision of user-controlled data.
Scalability and Functionality Challenges
However, Bitcoin's protocol wasn't designed on the base layer with the complex applications of Web 3.0 in mind. Its primary function as a digital currency means:
- Scalability Issues: Bitcoin's blockchain has limitations in transaction speed and volume, which might not suffice for a fully realized Web 3.0 environment where millions of micro-transactions could occur seamlessly.
- Limited Smart Contract Capabilities: Bitcoin's scripting language isn't as versatile as platforms like Ethereum, which are designed to support a broader range of decentralized applications.
Expanding Bitcoin's Role with Layer 2 Solutions
To bridge these gaps, developers are working on Layer 2 solutions like the Lightning Network for faster transactions, and projects like Stacks aim to bring smart contract functionality directly to Bitcoin. These innovations suggest that while Bitcoin might not be the sole backbone of Web 3.0 yet, it can significantly contribute to its infrastructure. In the long term, the question is whether we need more than one network, I mean, we don't have multiple Internets today. The market will probably decide in favor of the strongest and most secure network, and Bitcoin is by far that.
Web 3.0 Beyond Bitcoin
A Broader Blockchain Ecosystem
At the moment Web 3.0 encompasses by far more than just Bitcoin. It includes:
- Ethereum and Smart Contracts: Ethereum's introduction of smart contracts has been pivotal, allowing for decentralized applications that can interact in complex ways, far beyond simple transactions.
- Other Blockchains: Platforms like Solana, Sui, and Near are gaining traction for their high throughput and lower costs, addressing some of Bitcoin's limitations on the base layer.
The Cultural and Economic Shift
The move towards Web 3.0 isn't just technological but cultural. There's a growing sentiment, reflected in posts on platforms like X, that users are ready for a change where they own their digital presence. Here's some background based on general knowledge and trends up to 2024:
Cultural Shift:
- Distrust in Centralized Institutions: There's been a growing distrust in traditional centralized institutions like banks, governments, and large corporations. This distrust stems from various scandals, data breaches, privacy concerns, and perceived inefficiencies or corruption. Posts on platforms like X or even more on Nostr reflect this sentiment, where users often discuss the diminishing trust in these institutions.
- Rise of Individual Empowerment: Culturally, there's a move towards empowerment of the individual, facilitated by technology. Social media, blockchain, and other decentralized technologies give individuals tools to bypass traditional gatekeepers in finance, media, and more. This shift champions the idea that individuals should have more control over their data, finances, and digital identity.
- Identity and Community: Decentralization also touches on identity politics and community governance. There's a trend towards localism or regionalism where communities seek more control over their governance, which can be seen in movements for local autonomy or even secessionist sentiments in various parts of the world.
- Cultural Movements: Movements like the maker culture, DIY (Do It Yourself), open-source software, and even the gig economy reflect a cultural shift towards decentralization where individuals or small groups can produce, create, or work independently of large entities.
Economic Shift:
- Decentralized Finance (DeFi): DeFi represents one of the most tangible shifts, aiming to recreate and potentially improve financial systems outside of traditional banking. This includes lending, borrowing, and earning interest in a trustless, permissionless environment, primarily using blockchain technology.
- Cryptocurrencies and Tokenization: The rise of cryptocurrencies like Bitcoin and Ethereum symbolizes a move away from centralized monetary systems. Tokenization of assets, from art (NFTs - Non-Fungible Tokens) to real estate, embodies this shift, allowing for fractional ownership and reducing the barriers to investment.
- Globalization vs. Localism: While globalization has interconnected economies, there's a counter-trend where economic decentralization supports local economies. This can be seen in the push for local currencies, community-supported agriculture, or local energy production like solar microgrids.
- Work and Employment: The gig economy, remote work, and digital nomadism are part of this economic shift. Platforms enabling freelance work decentralize employment, moving away from traditional office environments and 9-to-5 jobs.
General Observations:
- Technology as an Enabler: Blockchain, the internet, and advancements in communication technology are pivotal in this shift. They provide the infrastructure necessary for decentralization to occur at scale.
- Political Implications: Economically, this shift maybe challenges existing power structures, potentially leading to regulatory battles as seen with cryptocurrencies. Culturally, it might lead to a redefinition of nationalism, community, and individual rights in the digital age.
- Challenges: Despite its promise, decentralization faces hurdles like scalability issues, regulatory pushback, the digital divide, and the potential for new forms of centralization (e.g., large crypto exchanges becoming new central authorities).
Conclusion: Bitcoin's Place in Web 3.0
Bitcoin's protocol ignited the spark for a decentralized internet, but Web 3.0 is evolving into a multifaceted ecosystem where Bitcoin might play a crucial, though not yet exclusive, role. The integration of Bitcoin with newer technologies and platforms could see it becoming a fundamental layer in the Web 3.0 stack, particularly in areas of value transfer and as a store of value within decentralized finance (DeFi).
As we progress, the synergy between Bitcoin's proven security and stability, combined with the innovation of other blockchain technologies, might just be the blend needed for Web 3.0 to achieve mainstream adoption, ensuring the internet becomes more open, secure, and user-centric. As stated before, the market will probably decide in favor of the strongest and most secure network, and Bitcoin is by far that.
-
 @ 361d3e1e:50bc10a8
2024-09-05 12:58:30
@ 361d3e1e:50bc10a8
2024-09-05 12:58:30He wished Pfizer's vaccine naysayers screwed, and now he's screwed
uk #music #vaccine #covid #sideeffects #health #freespeech
-
 @ 9977c3ad:43a20d63
2024-09-05 11:21:09
@ 9977c3ad:43a20d63
2024-09-05 11:21:09Details
- 🍽️ Servings: 2
Ingredients
- 1 cup Jasmine rice
- 1 Tbsp. lavender flowers, crushed with mortar and pestle
- 1/4 cup apple cider vinegar
- 2 Tbsp. fine cane sugar
- 2 Tbsp. honey
- 1 sprig rosemary
- 1/4 tsp angostura bitters
- 1/2 cup blackberries
- 1/2 cup blueberries
- 4 cups trimmed and quartered shiitake mushrooms
- 1 tsp fresh coriander crushed
- 1/4 tsp fresh cumin ground
- 1/2 tsp red pepper flakes
- 3 sprigs of thyme
- 2 Tbsp. olive oil
- 1 tsp soy sauce
- 1 cup creamy coconut milk
Directions
- Combine rice, lavender, 1/4 tsp salt, and 2 cups of water in a saucepan. Bring the rice to a boil, cover the pan with a lid and turn the heat off. Let the rice sit in the pan for at least 20 minutes.
- Combine 1/4 cup of water, the vinegar, sugar, honey, rosemary, angostura bitters in a saucepan and bring the brine to a boil. Season with a pinch of salt. Add the berries and wait until the brine comes back to a boil. Lower the heat, so the brine simmers but does not boil. When the brine thickens, after about 15 minutes, remove the saucepan from the heat and set it aside.
- Pre-heat the oven to 400F. In a bowl big enough to hold all the shiitake, combine the olive oil, the soy sauce and the spices. Whisk vigorously, so the oil emulsifies with the other liquid. Toss the shiitake in the mix to marinate, then evenly lay them out on a baking sheet with parchment paper. Bake the shiitake for 10 minutes. When you remove the shiitake from the oven, remove the thyme and throw it out. In a saucepan, bring the coconut milk to a boil. Add the shiitake and reduce the heat to a light boil until the sauce thickens.
-
 @ a012dc82:6458a70d
2024-09-05 09:46:29
@ a012dc82:6458a70d
2024-09-05 09:46:29Table Of Content
-
What are the factors driving this adoption?
-
What are the potential benefits of widespread Bitcoin adoption?
-
What are the potential challenges to Bitcoin adoption?
-
Conclusion
-
FAQ
The cryptocurrency market has been on a rollercoaster ride over the past few years, with Bitcoin emerging as the undisputed king of the digital currencies. Despite facing intense scrutiny and skepticism from traditional financial institutions, Bitcoin has continued to gain traction among investors, traders, and even mainstream businesses. The future of Bitcoin and the wider cryptocurrency industry has been the subject of much speculation, with many analysts making bold predictions about its potential growth and impact.
According to the report, the analyst predicts that Bitcoin will become the primary global currency by 2025, with an estimated 50% adoption rate. This means that half of the world's population could potentially be using Bitcoin as their main currency by 2025, marking a significant shift in the way we think about money and finance.
What are the factors driving this adoption?
The analyst attributes this projected surge in Bitcoin adoption to several key factors. These include:
Increased mainstream acceptance: More and more businesses are starting to accept Bitcoin as a form of payment, including some major players like Microsoft, Tesla, and PayPal. This increased acceptance is helping to legitimize Bitcoin and make it more accessible to the average person.
Growing distrust in traditional finance: The 2008 financial crisis and subsequent economic instability have eroded trust in traditional financial institutions. Bitcoin offers a decentralized alternative to the current system, making it an attractive option for those seeking greater financial autonomy and security.
Technological advancements: The development of blockchain technology and other innovations are making Bitcoin more secure, faster, and easier to use. This is helping to remove some of the barriers to adoption and make Bitcoin a more viable option for everyday use.
What are the potential benefits of widespread Bitcoin adoption?
The potential benefits of widespread Bitcoin adoption are numerous and far-reaching. These include:
Increased financial freedom: Bitcoin offers a level of financial freedom and autonomy that is impossible with traditional currencies. Users can send and receive money anywhere in the world without having to go through intermediaries or deal with cumbersome regulations.
Lower transaction fees: Bitcoin transactions are typically much cheaper than traditional banking fees, making it a more cost-effective option for businesses and individuals.
Greater security: Bitcoin's decentralized nature makes it more resistant to hacking and fraud than traditional banking systems. This offers a higher level of security and protection for users.
What are the potential challenges to Bitcoin adoption?
While the potential benefits of widespread Bitcoin adoption are exciting, there are also several potential challenges that must be overcome. These include:
Lack of regulation: Bitcoin operates outside of traditional financial systems and is largely unregulated. While this offers greater autonomy and freedom, it also makes it more susceptible to fraud and other criminal activity.
Volatility: Bitcoin's value is notoriously volatile, making it a risky investment option for some. This could make it more difficult to convince everyday users to adopt Bitcoin as their primary currency.
Technical barriers: While technological advancements are making Bitcoin more accessible, there are still some technical barriers that could prevent widespread adoption. These include issues with scalability, user interfaces, and education.
Conclusion
The analyst's forecast of mind-blowing Bitcoin adoption in 2025 is certainly an exciting prospect, and one that has the potential to transform the world of finance as we know it. While there are certainly challenges to be overcome, the benefits of widespread Bitcoin adoption are clear, and it is clear that more and more people are starting to recognize the potential of this revolutionary digital currency. Whether Bitcoin will ultimately become the primary global currency by 2025 remains to be seen, but it is clear that it is here to stay, and that it will continue to play an increasingly important role in the world of finance.
FAQ
Can Bitcoin be used as a form of payment? Yes, many businesses and merchants now accept Bitcoin as a form of payment, and it is becoming increasingly common.
Is Bitcoin safe to use? Bitcoin is generally considered to be a safe and secure form of payment, thanks to its decentralized nature and strong cryptographic protocols. However, as with any form of payment, there are some risks involved, and users should take appropriate precautions to protect their funds.
What is the potential impact of widespread Bitcoin adoption? The potential impact of widespread Bitcoin adoption is huge, as it could fundamentally change the way we think about money and finance. It could also have significant implications for traditional financial systems and institutions.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ d543c820:aa8001e7
2024-09-05 09:03:02
@ d543c820:aa8001e7
2024-09-05 09:03:02皮草两事
前日与朋友聊天,谈起时下留下的一种扮演了某种人格的 AI(有个时髦的名字,叫 “智能体”),蓦地想起英伦法学家边沁(Jeremy Bentham)。第二日,又联想起别的事来,因有此文。
“皮草”,在现代中文是指 “以动物(连)皮(带)毛制成的服装”,因其奢侈和暖和受人追捧。但也有关爱动物的人士批评其制作过程过于残忍。
但在古代中文中,这词可作别的意思:“皮以实草”、“剥皮揎草”。指的是把皮剥下来,把草填充进去,做成玩偶。
据说,明朝的创建者朱元璋(1328-1398),就制定过这样的刑罚:将贪腐的官员,处以剥皮之刑,然后以草填充,做成人偶,放在其继任官员的公堂旁边,以示警戒。
你可以想象,这种刑法是多么残酷。其恐怖、血腥的程度,与历史上有名的酷刑炮烙、分尸相比,是不遑多让的。所以,其在朱元璋统治的时代结束后,也并未被继续施行。有明一代,此种残酷刑罚的一个回响是在万历时代(1573-1620),有名的清官海瑞主张恢复这种刑罚,以整肃官员中贪腐的风气。
那么,朱元璋为什么要对贪腐官员制定如此残酷的刑罚呢?
小说家金庸先生的读者可能会认为,这跟其宗教信仰(明教)有关。明教即拜火教(琐罗亚斯德教),其本身推崇互帮互助,且憎恶贪官污吏,有点公社主义的味道。然而,这是说不通的 。因为明教本身有反体制倾向,不信任政治权力可被用来改善平民的生活。而朱元璋一以贯之地追求统治权力,自然不可能在实质上信奉此种理念。
(插句话,明代创建者与明教有关,此说始创于吴晗,被金庸先生拿去放在小说中,有了很大影响。然而,近些年的学术界,已开始反对这种理论,认为 “明” 的国号可能来自佛教经典,或来自儒家经典《易经》。)
也有人会认为,这跟朱元璋的出身有关。他出身贫苦,也曾流离失所,也许饱受贪官污吏欺压,因此格外痛恨他们。
我的想法是,这只是因为与前代帝王相比,朱元璋有格外疯狂的机器乌托邦狂想。朱元璋为明朝制定的制度,是格外机械、死板,而且严苛的。首先,其要求编订各地域的人口户籍 —— 这不出奇,中国从秦朝开始就这样做了 —— 然后,有趣的东西来了:他要求给这些人口按照经济条件分组,每组有固定的力役和纳税义务,以年为单位;以户为最小单位,每 10 个单位合并成一个大单位,层层往上合并;每一组的带头人都每年轮换一次,这个带头人要在该年中完成经济统计并带领其组内成员完成力役(比如修城墙、挖运河)和纳税(交粮)义务。与此同时,迁徙自由是禁止的,良民必须在其土地上完成其义务,而不能 “流窜” 到其它地方,官员的任务之一是将境内的流民遣返回原籍、保证境内的民不要流窜到其它地方。而这些力役和纳税义务,也是跟地域高度捆绑的,它们以就近的原则,被分配给所在地的城市和军队,而不是经过行政机构的统一收发管理。
也就是说,朱元璋希望把偌大的中国变成一台机器,所有人(主要是农民)在其出生的地域上为劳役和纳税而劳作,以恒久不变的速率为一个行政系统和军事系统提供养料,然后朱家江山永保稳定和太平。—— 而统治者,君主,将使用这套系统中形成的统计资料,来精确地了解每一个地区的实情,然后施行统治,保持系统的运行。
对于这样一个系统而已,统计资料的精确性,是具有第一位的重要性的。它决定了统治者到底能不能获得地方的实情,而不被自己的官僚蒙蔽。于是,贪腐 —— 为了个人私利,甚至不是什么特别大的利益,而弄虚作假,比如虚报产出以求减免税务、将经济富裕的农民反而分到税务负担较轻的组中 —— 就成了一个最多发、最难对付的顽疾。官员稍微不认真,产生的偏差就会不断叠加,然后积累出完全失实、无用的记录。这就是为什么贪腐的官员要被处于如此残酷的刑罚 —— 要用最残酷的刑罚、最血腥的展示,让他们在统治以机器人为理想模板的人群时,自己也成为机器人。—— 只有皇帝可以是个活人。
(《万历十五年》的作者黄仁宇认为明代的一大问题在于其制度阻碍了技术的发展,例如,军队的粮食是定点向某个村镇收取的,并由村镇自己负责押韵到军队驻地,这是 “散收散支”;如果交到行政机关处集中收取集中分发,就可以发展物流技术、保险技术云云。我认为,这是浅见。)
那么,十四世纪的朱元璋,跟边沁(1747-1832),怎么会扯上关系呢?
是因为边沁也曾设想过一种 “皮草” 的用途。他希望的是,有卓越成就的人物,可以在死后将自己制作成人偶(原描述为 “auto-icon”),摆放在公共空间里,(最好还能播放其生前录下的声音),起到教育的作用。
边沁自己也实践了这种想法。他在死前立下遗嘱,将自己的身体托付给一个好朋友,嘱咐其将自己制作成 auto-icon,要求以一个带玻璃的木盒子盛装,将自己做成坐姿,配上自己生前使用的椅子,还要身着正装,配上手杖。
事实上,边沁的 auto-icon 还真的是在保留了骨骼的前提下以草填充的。唯一美中不足的是,其头颅在防腐处理过程中被毁容了,完全不像其生前的容貌,因此被一个蜡像代替。
这个 auto-icon 后来一直放在实践了边沁的教育改革理念(一言以蔽之,有教无类,不论家资,不论宗教)的 University Collage London(伦敦大学学院,UCL)(在 2020 年以前,放在学院主楼南回廊的尽头;之后,迁移到学生中心)。
有关边沁的 auto-icon,我还听过一个传说(已被边沁的英文维基页面证伪):UCL 在每次召开理事会时,都将边沁的 auto-icon 陈列在侧,并认定他会给会议中的改革派投半票。
同样的皮草,在两种社会,两个时代,承担完全不同的预期作用。一个是为了在公共空间中承担教育的责任,或是给某一些人鼓励;甚或按一些浪漫的说法,是 “一种社会实验”。另一个,则是作为生杀大权的象征,要给人以无限的恐怖,从而使人战战兢兢地做好皇帝交办的工作。这何止天差地别。
参考文献:
百度百科·剥皮揎草:https://baike.baidu.com/item/%E5%89%A5%E7%9A%AE%E6%8F%8E%E8%8D%89/5372899
不要再說明朝國號「大明」源於明教:http://www.observer-taipei.com/book2021/item/634-2022-03-29-08-11-13
维基百科·Bentham:https://en.wikipedia.org/wiki/Jeremy_Bentham
《显微镜下的大明》
-
 @ c7eadcf0:7821e562
2024-09-04 23:58:56
@ c7eadcf0:7821e562
2024-09-04 23:58:56Another test post. I think I might have found my long form content writing app. Well done.
-
 @ c7eadcf0:7821e562
2024-09-04 23:53:44
@ c7eadcf0:7821e562
2024-09-04 23:53:44seeing if this works lol
-
 @ a324b2fe:68bf4629
2024-09-04 23:47:54
@ a324b2fe:68bf4629
2024-09-04 23:47:54One of the most significant underlining doctrines of our time is that of the rapture and the eschatological (study of the end times) understanding that the world will be overrun with evil, and God will ‘beam us up scotty’ either before the faeces hits the fan or after. There are slight variations in this ‘futurist eschatology’ I’ve just briefly explained. Many would agree that this is what the bible clearly teaches, and others will have a verse or two in their minds that without further study seems to validate this popular understanding.
Make no mistake, most Christians believe in a ‘futurist eschatology’ (see below), but the real question is why and how most of us have landed believing that things are going to get much worse on the planet, or that things will get better but will suddenly plummet down and Armageddon becomes more than a badly plotted movie. Some might be wondering “I never knew such a thing existed”, let alone know that there are different opinions on the matter. Keep reading because you’ll be surprised at how much this doctrine actually influences ALL your decisions.
To summarise, there are four major positions of interpreting “The book of Revelation”, which is the core book to influence our perspective on the future or “end times”.
Futurisme:
The belief that the events in the book of Revelation is referring to global events in our future. (popular since the 1800’s; the beast’ (see revelation 13 and 17) is a man and a new world order, many historical figures have been suggested in their time; Napoleon, Hitler, Stalin, Osama bin Laden, Barack Obama etc.).
Historicism:
The belief that the events have transpired over history like a timeline (popular in the 1500’s at the time of the reformation, notably that the Pope of the Catholic Church and the Papacy were the ‘beast’.
Preterism:
The belief that the events (most or all) have already taken place in the 1st century, climaxing at the destruction of Jerusalem in 70AD, Rome as a whole and Emperor Nero being considered the ‘beast’.
Idealism:
That the book is a symbolic battle between good and evil.
Before I get into the nitty gritty on history, specific scripture and their exegesis (a fancy word I never use in conversation, meaning critical study and interpretation on a text). Let me highlight why what we believe about the future influences our every decision.
One day in 10 years time you’re married to a beautiful/handsome spouse and have 7 children. You believe that the world will end soon and that there’s going to be a massive heavenly battle and the angels are going to use their majestic rippled muscled limbs to wreck havoc on all those that oppose. Nice. Or not nice if you chose the wrong side. Before that happens though your daughter wants $1000 to invest in some shares because she learned at school that if you put $1000 in shares today and top up $100 every month you’ll have accumulated a total of $72,000 in twenty years having only contributed $25,000 of your own money. Smart kid, that’s a good long term investment strategy.
You however don’t believe the world is going to exist in its normal state in another 20 years time, or you reason it might, but surely not much longer after that. So you say: “Sweety, I really don’t think that’s going to do you much good, the market is too volatile and I don’t foresee things getting better in the future, why don’t you spend your money on some clothes or go out with your friends”? Yes this is quite an elementary example and I’m sure you’ve all invested money into shares and it would never happen to you.
How about another scenario then? You believe the rapture will take place in your lifetime. You read your bible and see that Christians need to share the gospel, so you start to share with people, some people reject you, some are indifferent, and others are deeply touched. The ones that are impacted, you give them a bible and say go to church and get ready for the return of Christ (in your mind you’re thinking that means rapture). Some of them do, some go and fall away and still others somehow are consistent and are growing in the Lord, good job right? What about those people that fell through the cracks? That’s not my responsibility you say, they need to work out their own salvation with fear and trembling. Okay, have you considered that the responsibility is actually squarely on your shoulders? In regards to making a disciple, not a convert. Discipleship takes much longer, it takes time, it takes sacrifice, and it takes a perspective that there is even time for discipleship. Otherwise it’s a 6 week course in “How to be a Christian”.
Thankfully some of the church has in the last few decades focused a lot more on discipleship, even whilst holding the perspective of a futuristic eschatology. Yet even in this the reasoning is simple, they are doing their best to follow what they read in the bible regarding discipleship (rightfully so), and also a discipleship approach of evangelism retains and reaches more people, so it’s a more successful method to convert in any case. If this is you, you’re amazing, please keep making disciples! I however propose that you sincerely ask yourself what you would do differently if you believed the world would exist for another 200 years plus.
As you can see our belief on the future has extreme and subtle effects on our actions and decisions. Our society is peripheral to where the church is at, and right now the church as a whole believes that the end is soon and there’s no point in believing and acting like it’s a good thing to leave an inheritance for your children’s children. That is why we buy cheap, that is why we don’t invest, it is why we are driven by instant gratification. Why would you bother with all that if the world will end in a matter of years. It comes to whether you have a hope filled optimistic expanding Kingdom perspective on how the world is going to turn out or one that is governed by a defeatist/fatalistic mentality and perhaps even one fear riddled.
Now that we’ve looked at how our beliefs can be outworked in everyday life, let’s get into doctrine. Finally. Actually, some more history first.
I and many others find it helpful to look at history to see when a certain doctrine began to gain support and become the popular belief to determine its validity. Let’s jump in then, during the reformation, the Catholic Church was under fire and experiencing some mostly accurate criticism. In a response to Christians accusing the Pope and the Papacy of being the beast, a Jesuit priest wrote extensively that the events in the book of Revelation are referring to their future, thus eliminating the Pope and the Papacy of fault. His writings didn’t gain traction until the 1800’s where John Nelson Dalby adopted the belief and started widely teaching it, specifically on ‘Pre-tribulation rapture theology’ (we get raptured/caught up prior to the tribulation that will happen on the earth). I would like to explicitly mention that before this, proponents for a futurist eschatology were almost non-existent.
Then in the following early century (1909 to be exact), the first ever bible with commentary was printed. The Scofield bible. This bible was a massive advocate for dispensationalism and a futuristic eschatology; practically every bible college student got one of these bibles, and lo and behold an entire generation of pastors and theologians were massively influenced on their belief of the future. Couple that with two world wars, the reestablishment of the Jewish nation, Israel, and we have a perfect concoction for believing the time is near and Armageddon is around the corner.
Now there are entire books discussing all of this that I cannot even hope to cover even a slither, but if you are so inclined, see some recommendations at the end. I won’t attempt (nor can I) to extrapolate on everything there is regarding a ‘preterist view’ of Revelation, and a ‘victorious eschatology’ which was the orthodox view in early Christianity, but here is a summary of what you need to know.
The Kingdom of God:
As indicated by the statue in Daniel 2 was inaugurated with the birth of Jesus (coming of Jesus in the Manger), and started to expand and is still expanding. See Mathew 13:31-33. Also see Isaiah 2 for the hope for the future.
The destruction of Jerusalem in 70 A.D.
Wasn’t just an important event in history, it is paramount to the entire New testament and is referenced to in almost every book. To miss its importance is to miss understanding much of the New testament. This event is crucial to the progress of God’s redemptive plan in history, with the final removal of the temple and the genealogical records of the priests therein, the old (mosaic) covenant closes and the new covenant is fully and permanently established.
“When you see Jerusalem being surrounded by armies, you will know that its desolation is near. Then let those who are in Judea flee to the mountains, let those in the city get out, and let those in the country not enter the city. For this is the time of punishment in fulfillment of all that has been written. - Luke 21:20-22
John the Baptist proclaims judgement on the Jews in Matthew 3:10-12. See also Matthew 7:19 “The ax is already at the root of the trees, and every tree that does not produce good fruit will be cut down and thrown into the fire. I baptize you with water for repentance. But after me comes one who is more powerful than I, whose sandals I am not worthy to carry. He will baptize you with the Holy Spirit and fire. His winnowing fork is in his hand, and he will clear his threshing floor, gathering his wheat into the barn and burning up the chaff with unquenchable fire.” This provides the backdrop to Jerusalem erupting in flames in A.D. 70. Later Jesus declares John is Elijah to come (Matt 11:14) fulfilling the prophecy in Malachi 4:5-6, as he proclaims judgment in Israel before the great and terrible day of the Lord (John mentions the day of the Lord in Rev 6:17; 16:14).
In Matt 12:39 Jesus regards the Jews of His day as an adulterous generation, the same imagery is found in Revelation 17:3 as John presents Jerusalem as a harlot (see also Isa 1:21; Jer 2:20; 3:1,6,8; Eze 16:9, 15-17, 26; Hos 2:5; 4:10; 12-15). In Matthew 23:34-35 Jesus warns that God will judge 1st century Jews for the righteous blood that was shed in the land (we see the same statement in Rev 18:24). In Matt 23:36-38 Jesus laments Jerusalem’s destruction and declares the temple desolate, John declares Jerusalem is desolate in Rev 17:16. After that Jesus prophesies its destruction in Matt 24:2-3 and Luke 21:24, and John uses the same language as Luke, in Rev 11:2. In Matthew 24:16 Jesus urges his followers to flee Judea because “this generation will experience judgement (Matt 23:32). John calls the saints out of Jerusalem in Rev 18:4.
I could go on but there are books for that. Here's the simplicity of it; John’s general message in Revelation is ‘the divorce of Israel and God’s marriage to the new covenant church’ (which obviously includes Jews if they turn to Christ). The ‘second coming of Christ’ came when he came in judgement on Jerusalem. There is another coming, hold your horses I’ll get there.
The 'Olivet discourse’ of Matthew 24:
Is referring to 1st century events and uses prophetic symbolic language (stars falling, moon to blood, sun darkened etc.) to demonstrate a toppling of governments, see Isa 13:10,13 referring to Babylon; Isa 34:4 referring to Edom; and Eze 32:7-8 referring to Egypt. Also think of Joseph and how his family were stars, a moon and a sun and that they bowed to him. Again, it’s language to communicate a natural toppling of governments or exchange of political dominion. Not a global catastrophic Armageddon.
The Anti-Christ:
Used only four times in the bible (1 John 2:18; 1 John 2:22; 1 John 4:3; 2 John 1:7). It has always been a referenced to a false teaching in the 1st century that claimed Jesus had not come in the flesh. A gnostic heresy.
The Beast, the mark of the Beast, and his number 666:
Referring to Emperor Nero who was called a beast, forced people to get markings of him to be able to buy and sell in the marketplace (Rev 13:16-17), see a short video on the matter https://www.youtube.com/watch?v=wng3jcfMkZU. Now Gematria is a Jewish Interpretive method that assigns numerical value of Hebrew letters to words. We find this with the number of the beast being 616 (in Latin) or 666 (in Hebrew), with the values added up it spells Nero Caesar. See this 2 min video https://youtu.be/JXkTc18xBoM. Some people, like in the video say that he represents a future beast as well, this is simply poor and biased exegesis and is thus construed to validate their pre-existing beliefs.
The Word Rapture:
Found in 1 Thessalonians 4:17; “After that, we who are still alive and are left will be caught up (rapturo in Latin) together with them in the clouds to meet the Lord in the air. And so we will be with the Lord forever”. The entire bases of the doctrine of the rapture is found in this one simple verse. Yet all it means is that we will be gathered to Jesus and the past saints/Christians at His return.
What now? Is everything done?
Well not quite.. Jesus’ Return: Jesus will return as is promised in Acts 1:11, but it won’t be with a massive army to lay plunder to the earth, well maybe, but I highly doubt it. “…will come back to you in the same way you have seen Him go into heaven”. The resurrection of the dead: Zombies! Kidding, just mass people coming back to life. See 1 Thessalonians and 1 Corinthians 15. The Great judgement: The great judgement day of the sheep and the goats in Matt 25.
That’s it, so until then, however long that will take (my money is on 197 years), let’s keep bringing the Kingdom of God to earth, lets pray for miracles, make healthy disciples that reproduce, transform every facet of society to look like heaven, and establish a Kingdom legacy that our Lord and King would be excited to come back to.
Ps. My views on Gods judgment on the 1st century Jews is not that he wanted to destroy them, but rather he was bringing judgment on an old covenantal system, the Jews that clung to that sinking ship unfortunately went down with it.
Book Recommendations: Understanding the whole bible – Jonathan Welton Raptureless – Jonathan Welton The art of revelation – Jonathan Welton Before Jerusalem Fell: Dating the book of revelation – Kenneth L Gentry Navigating the book of Revelation - Kenneth L Gentry Victorious eschatology: A partial Preterist view – Harold R Eberle and Martin Trench
Theologian Gary Demar
-
 @ 1a48e74d:02c0e00f
2024-09-04 23:38:34
@ 1a48e74d:02c0e00f
2024-09-04 23:38:34seeing if this works.
-
 @ c7eadcf0:7821e562
2024-09-04 23:03:59
@ c7eadcf0:7821e562
2024-09-04 23:03:59Welcome back ya'll hope you are doing well this week. Today I wanted to talk about why Bitcoin represents a dawn of a new age in property ownership. Before you spit out your coffee and walk away, hear me out. Bitcoin and real estate have a few things in common. The first is property rights.
When you are the owner of a building with your name on the dotted line and whatnot, you are the sole owner of that property. No one can tell you what to do with it, and no one has a claim to what you own. You are free to do what you wish. Property rights are sacrosanct and immutable similar to Bitcoin.
Bitcoin confers upon the owner the same property right protections as owning a piece of real estate. Once you own it, you are the sole owner of that Bitcoin. No one can tell you what to do with it. No one else has a claim to your Bitcoin. You are free to do with it what you wish.
Bitcoin and real estate are similar in terms of built-in scarcity. There is only 21 million Bitcoin that will ever be created, and you can't print more land. This is why owning real estate has been such a good investment since the beginning of time. Buying a piece of land and "HODLING" for decades will generate a substantial return on your investment.
This same buy and hodl strategy apply to Bitcoin as well. If you bought Bitcoin back in 2009, you would be a multi-millionaire right now.
If you invested $1000 back in 2011 when Bitcoin was trading at $3.50, you would have turned that $1000 into $15.6 million if you held on to it for ten years. Just sayin.
You have to reframe your thinking to understand what is going on. We are living in the 21st-century gold rush, and you have an opportunity to stake your claim to the soundest money on Earth with a few taps on your phone. Never in the history of the world has the plebs like us had the ability to front-run a monetary revolution.
Bitcoin is freedom from oppression. Bitcoin restores your sovereignty. Bitcoin makes you fuckable, and the powers that be know it. They are afraid they will lose control if too many people catch on too quickly, which is why large institutions are rushing to offer Bitcoin services or buy them and keep them on their balance sheet.
Bitcoin won't stay this cheap forever. $100-300k Bitcoin is in the cards over the next few years. I don't want you guys to miss out on this.
All you have to do is buy Bitcoin and hold. It's that simple. FYI trying out the new obsidian writer for nostr notes!
Bitcoin #nostr
-
 @ 1a48e74d:02c0e00f
2024-09-04 23:00:22
@ 1a48e74d:02c0e00f
2024-09-04 23:00:22Welcome back ya'll hope you are doing well this week. Today I wanted to talk about why Bitcoin represents a dawn of a new age in property ownership. Before you spit out your coffee and walk away, hear me out. Bitcoin and real estate have a few things in common. The first is property rights.
When you are the owner of a building with your name on the dotted line and whatnot, you are the sole owner of that property. No one can tell you what to do with it, and no one has a claim to what you own. You are free to do what you wish. Property rights are sacrosanct and immutable similar to Bitcoin.
Bitcoin confers upon the owner the same property right protections as owning a piece of real estate. Once you own it, you are the sole owner of that Bitcoin. No one can tell you what to do with it. No one else has a claim to your Bitcoin. You are free to do with it what you wish.
Bitcoin and real estate are similar in terms of built-in scarcity. There is only 21 million Bitcoin that will ever be created, and you can't print more land. This is why owning real estate has been such a good investment since the beginning of time. Buying a piece of land and "HODLING" for decades will generate a substantial return on your investment.
This same buy and hodl strategy apply to Bitcoin as well. If you bought Bitcoin back in 2009, you would be a multi-millionaire right now.
If you invested $1000 back in 2011 when Bitcoin was trading at $3.50, you would have turned that $1000 into $15.6 million if you held on to it for ten years. Just sayin.
You have to reframe your thinking to understand what is going on. We are living in the 21st-century gold rush, and you have an opportunity to stake your claim to the soundest money on Earth with a few taps on your phone. Never in the history of the world has the plebs like us had the ability to front-run a monetary revolution.
Bitcoin is freedom from oppression. Bitcoin restores your sovereignty. Bitcoin makes you fuckable, and the powers that be know it. They are afraid they will lose control if too many people catch on too quickly, which is why large institutions are rushing to offer Bitcoin services or buy them and keep them on their balance sheet.
Bitcoin won't stay this cheap forever. $100-300k Bitcoin is in the cards over the next few years. I don't want you guys to miss out on this.
All you have to do is buy Bitcoin and hold. It's that simple. FYI trying out the new obsidian writer for nostr notes!
Bitcoin #nostr
-
 @ 472f440f:5669301e
2024-09-04 22:54:11
@ 472f440f:5669301e
2024-09-04 22:54:11For the last few months many people in bitcoin, myself included, have been focused on bitcoin's role as a macroeconomic asset. Bitcoin as a strategic reserve for the US government. Bitcoin as a strategic treasury asset for corporations. Bitcoin as a geopolitical hedge in a world that is trending toward a multi-polar power dynamic. This is where the focus has been. And for good reason. These trends will ultimately have a material effect on the price of bitcoin if they pick up steam.
However, with all of the focus on bitcoin as a strategic asset I think a couple of technical developments and trends have been overlooked. Particularly in the realm of second layer privacy. I'll touch on two of them in this letter; BOLT 12 invoices and the progression of ecash.
Yesterday afternoon the Strike (a company Ten31 is very proud to be backing) team released a blog post that detailed their journey to implementing BOLT 12 offers in their product stack. For those who are unaware of BOLT 12 and why it is important, in short, it is an upgrade to the lightning network that would make receiving bitcoin on the lightning network more private while also significantly improving the user experience. The current standard for invoicing people via the lightning network is BOLT 11, which forces users to create a unique invoice every time they want to receive bitcoin and comes with privacy tradeoffs for the party receiving bitcoin.
BOLT 12 brings with it route blinding which allows a receiver to publish a lightning offer to the network without revealing their node's public key. It also brings with it onion messaging, which allows users of the lightning network to communicate without a dependence on HTTP, which can be censored by a motivated state actor. On top of this, it enables users to create a static invoice that can be paid multiple times by multiple people. Think of a band putting their Venmo or Cash App QR code next to their tip jar on the stage. They'll be able to add a private lightning invoice their audience can pay to now.
https://strike.me/blog/bolt12-offers/
As it stands right now, Strike has only enabled BOLT 12 offers and there is work to do at the protocol layer of lightning and the different implementations of that protocol to get the full benefits of BOLT 12, but this is material progress that gets us closer to a significantly better user experience on the lightning network. If you read Strike's blog post you'll come to appreciate the collaboration between the teams working on these implementations and the companies implementing the protocol that is necessary to get these features live. Shout out to everyone who worked on this. Everyone who uses the lightning network will be better off when BOLT 12 is fully implemented.
Moving on. Earlier today the founder of the BTCPay Server open source project, Nicolas Dorier, published a blog post outlining his thoughts on how ecash has the potential to solve problems that many have tried to solve by launching their own blockchains in the past. The problem with trying to "blockchain the world" is that blockchains are very inefficient and only really work for one application; enabling a peer-to-peer digital cash system with no trusted third parties (i.e., bitcoin). However, the ultimate goals of the thousands of blockchain projects that spun up in bitcoin's wake are desirable. Cheap, private and instant transactions. The ability to trivially spin up private money tokens suited for very particular use cases. Overall great UX that makes it easy for people to realize the benefits of "blockchain technology".
The problem that has existed to date is that you don't need a blockchain for all of these things. In fact, having a blockchain for these things proves to be detrimental to their ultimate goals. Instead, what people really need is a protocol that gives you the granular control, privacy, instantaneous transactions and UX that anchors to bitcoin. This is exactly what Chaumian Mints bring to the bitcoin stack.
This is something that we've been screaming about for more than seven years in this rag. Now with ecash protocols like Cashu and Fedimint maturing, gaining traction and bringing products to market that highlight the power and flexibility of ecash systems, people are beginning to see the promise. It is only a matter of time before more and more people begin to realize this potential.
Another benefit of ecash protocols is the fact that they are siloed from each other. Ecash mints are permissionless; any one person or group of people can spin them up, offer their preferred services and maintain (or fail to maintain) their mints. The failure of one mint is not a systemic risk to other mints. This is very different from token projects that are spun up on blockchains. The last ten years have proven that individual token projects can prove to be systemic problems for individual blockchains (i.e., The DAO token on Ethereum). Being able to silo mints is the only way to ensure that the utility of ecash overall is actually scalable and robust.
Don't get so distracted by the bitcoin macro talk that you miss out on the incredible technical developments happening on top of and adjacent to bitcoin.
Final thought... Vibes are high.
-
 @ 1a48e74d:02c0e00f
2024-09-04 22:53:26
@ 1a48e74d:02c0e00f
2024-09-04 22:53:26Welcome back ya'll hope you are doing well this week. Today I wanted to talk about why Bitcoin represents a dawn of a new age in property ownership. Before you spit out your coffee and walk away, hear me out. Bitcoin and real estate have a few things in common. The first is property rights.
When you are the owner of a building with your name on the dotted line and whatnot, you are the sole owner of that property. No one can tell you what to do with it, and no one has a claim to what you own. You are free to do what you wish. Property rights are sacrosanct and immutable similar to Bitcoin.
Bitcoin confers upon the owner the same property right protections as owning a piece of real estate. Once you own it, you are the sole owner of that Bitcoin. No one can tell you what to do with it. No one else has a claim to your Bitcoin. You are free to do with it what you wish.
Bitcoin and real estate are similar in terms of built-in scarcity. There is only 21 million Bitcoin that will ever be created, and you can't print more land. This is why owning real estate has been such a good investment since the beginning of time. Buying a piece of land and "HODLING" for decades will generate a substantial return on your investment.
This same buy and hodl strategy apply to Bitcoin as well. If you bought Bitcoin back in 2009, you would be a multi-millionaire right now.
If you invested $1000 back in 2011 when Bitcoin was trading at $3.50, you would have turned that $1000 into $15.6 million if you held on to it for ten years. Just sayin.
You have to reframe your thinking to understand what is going on. We are living in the 21st-century gold rush, and you have an opportunity to stake your claim to the soundest money on Earth with a few taps on your phone. Never in the history of the world has the plebs like us had the ability to front-run a monetary revolution.
Bitcoin is freedom from oppression. Bitcoin restores your sovereignty. Bitcoin makes you fuckable, and the powers that be know it. They are afraid they will lose control if too many people catch on too quickly, which is why large institutions are rushing to offer Bitcoin services or buy them and keep them on their balance sheet.
Bitcoin won't stay this cheap forever. $100-300k Bitcoin is in the cards over the next few years. I don't want you guys to miss out on this.
All you have to do is buy Bitcoin and hold. It's that simple. FYI trying out the new obsidian writer for nostr notes!
Bitcoin #nostr
-
 @ 1a48e74d:02c0e00f
2024-09-04 22:36:48
@ 1a48e74d:02c0e00f
2024-09-04 22:36:48Nothing can defeat Bitcoin.
-
 @ 7f0cbb03:c59f23d0
2024-09-04 21:28:57
@ 7f0cbb03:c59f23d0
2024-09-04 21:28:57 -
 @ 7ceaffbc:143b9e56
2024-09-04 20:50:26
@ 7ceaffbc:143b9e56
2024-09-04 20:50:26(roles in the adoption space)
Being different matters - At first!
The reasonable man adapts himself to the world; the unreasonable one persists in trying to adapt the world to himself. Therefore, all progress depends on the unreasonable man (Shaw, 1903).
h/t Everyone who is Satoshi.
It is probably fair to say Satoshi, Hal Finney, Adam Back et al. and we early ones are amongst the crazy ones.
Here’s to the crazy ones, the misfits, the rebels, the troublemakers, the round pegs in the square holes… the ones who see things differently — they’re not fond of rules… You can quote them, disagree with them, glorify or vilify them, but the only thing you can’t do is ignore them because they change things… they push the human race forward, and while some may see them as the crazy ones, we see genius, because the ones who are crazy enough to think that they can change the world, are the ones who do. (Jobs, 1997).
Sub-conclusion - To rid ourselves of fiat required radical thought - a base on which to build.
Most Babies learn to Walk
Born with the normal count of fingers toes etc, by the age of 26 I reckoned I had pretty much mastered walking (or so I believed) - until recently I fell, whereupon five things struck me deeply:
- Ageing and the associated decline is another form of novelty - I can resist it, it will eventually win but meanwhile I can adapt - and being alive is about adapting
- Things I have learnt must inevitably include all the things things I need to unlearn
- Things I have not learnt can become urgent (perhaps a wheechair lies in my future) and the learning can be delayed by the requisite unlearning from point 2 above
- Walking was something the masses did before I ever achieved it - which was probably what prompted me to adopt it as a means of ambulation
- The floor
Sub-conclusion - Mass adoption requires; * initiation (the crazy ones) * attention (seeing what others do) * unlearning (elimination of perceived assumptions) * learning (PoW) * emulation ( doing what others do) * mastery (practice doing it well) * review (figuring out what is no longer valuable) * evangelism (Helping others towards Truth)
OK - I have your attention - now what ? (Unpopular opinions incoming)
Eccentricity is not important to anything other than grabbing attention. Bitcoin is well beyond the thresh-hold of needing Eccentrics. We could all name them (and should appreciate their efforts).
The Overton window (that which may be normally spoken of) has become big enough that includes the best of our thinkers now. Analysts, Politicians, Purists, Financial advisers ??, Maxis, Left, Right & Centre.
But most of all it needs the centre. The extremes are great for raising attention and have the greatest voice on lesser social media platforms (which may be a thing of the past when you read this). However, it is clear that out of the centre (the Ex-centrics ? ) will come the mass of humanity that can benefit from bitcoin.
The bulk of future normies (users of bitcoin when only laggards use fiat) must come from the centre - because that is where they are now.
So decentralists or if you prefer "ex-centrics" will be easiest to help if we are seen as different - but reasonable, attractive and something to aspire to. The generosity / loving nature of many Bitcoiners will continue to win hearts (and minds)
Again unpopular perhaps (I should not care) - but this means ideally; - avoiding offensive behaviour (potty language) - avoiding ejection of those who are different (even if you reject their lifestyle choices) - understanding that we all start somewhere on this journey - smaller egos - I am a Bitcoin Maximalist by many definitions but, while my Christianity, what I eat, my and even my choice of frying pan may be most important to me - they may not help evangelise a better bitcoin future.
FWIW I think Bitcoin & Christianity go hand-in-glove in the journey toward a better future , but respect your (God given) right to disagree
Conclusion
Its time to stop thinking we are special and become normal - because that is what hyper-bitcoinisation implies.
To achieve this we need to find ways to secure legislation, peacefully dis-empower fiat states (a side effect - but IMHO a good one), make learning easier, remove barriers (FUD, technological etc) and lend a sympathetic ear to anyone who asks, what, why, how because that's how we all learn:
I keep six honest serving-men (They taught me all I knew); Their names are What and Why and When And How and Where and Who. I send them over land and sea, I send them east and west; But after they have worked for me, I give them all a rest.... (Kipling; The Elephant’s Child)
One day, if we do as well as we must, we will be able to claim - but we are just normal !
-
 @ 572aa884:e266a569
2024-09-04 19:46:40
@ 572aa884:e266a569
2024-09-04 19:46:40STAR TREK TNG: INCOMPATIBLE IDEALS
by Luke Parker
Premise: This screenplay is for an episode of Star Trek: The Next Generation, set near the end of Season 7. It imagines a first contact encounter between Picard’s Enterprise and a fully Anarcho-Capitalist planet with no government nor belief in authority.
Scene 1: Bridge
Exterior views of the Starship Enterprise give way to Captain Jean-Luc Picard standing at his command station on the bridge, his gaze steady and contemplative as he records his log.
Picard: (voiceover) "Captain's log, Stardate 48881.4. We were on our way to Deep Space 9 to provide support for the upcoming Bajoran elections when we received an audio-only distress call from a person on the planet Anarak, just outside of Cardassian space. The planet has yet to be contacted by the Federation, and in fact very little is known about it other than how it has a highly unusual social structure; one that appears to function without any form of central government or hierarchical leadership. It is a society that, despite its relatively high level of technological sophistication, has yet to achieve warp capability. The message is urgently requesting help from any peaceful civilization in range to defend his people against Cardassian invaders. It is difficult to imagine even the Cardassians violating the Prime Directive in such a manner. We are changing course to investigate."
Picard finishes his log entry and looks up, his expression thoughtful. The rest of the bridge crew is attentive with the memory of the Cardassain conquest of Bajor fresh in their minds.
Data: [turning from his console to face Picard] "Captain, Starfleet's lone anthropological record on Anarak indicates that it has a relatively large population and is advanced in various scientific fields. However, there are no reports of warp capability nor a leadership structure for us to contact there. Their society’s structure might challenge our usual protocols for contact."
Riker: [with a hint of curiosity] "An advanced society with no central government? That's a first."
Picard: [nodding] "Indeed, Number One. The distress call came from an individual named Bas T'yat, who identifies himself only as an entrepreneur. Our intelligence suggests that Anarak's society is structured in a way that is not only hostile to hierarchies but completely devoid of any form of leadership or authority. They seem to operate on a principle of total autonomy. This would seem to indicate an absence of a planetary defense system."
Troi: [thoughtful, with concern] "Without a central authority, how do they respond to any external threats? A society like this could be quite vulnerable to more aggressive powers, like the Cardassians."
Picard: [grimly] "It seems that may already be the case. The distress signal implied that a hostile force, likely Cardassian, has targeted them. Without a unified defense, they could be easy prey."
Worf: [sternly] "If the Cardassians are involved, Captain, they will not hesitate to exploit such a weakness. We must be prepared for hostilities."
Data: [analyzing the implications] "However, the lack of formal governance could complicate any assistance we offer. Without a government to negotiate with, we may face challenges in determining how to intervene appropriately."
Picard: [resolute, yet cautious] "We will treat Anarak as we would any other planet sending a distress call, regardless of their social structure. However, we must tread carefully. If we arrive to find Cardassians engaged in hostile acts, we may be forced to intervene. But in Federation space, our priority remains the protection of life and the maintenance of Federation principles."
The bridge crew exchanges looks of determination, each officer understanding the complexities of the mission ahead.
Picard: [decisive, raising his voice slightly] "Set course for Anarak. Engage at warp seven."
Data: [acknowledging] "Course plotted, Captain. Engaging warp seven."
The familiar hum of the warp engines intensifies as the stars on the viewscreen stretch into streaks of light, and the Enterprise leaps into warp, speeding towards the strange planet and the potential conflict awaiting them.
Scene 2: Bridge
The Enterprise emerges from warp above the planet Anarak, the planet’s blue-green surface appearing deceptively peaceful below.
Worf: [at tactical, scanning the area] "Captain, no alien vessels are currently in the vicinity, only artificial satellites. However, I'm detecting signs of recent battle on the planet's surface."
Picard: [moving closer to Worf's station] "Specify, Lieutenant."
Worf: [analyzing the data] "There is minor damage to infrastructure in multiple locations, consistent with Cardassian disruptor fire. Several structures show signs of targeted attacks, but the damage is localized and not extensive."
Data: [at the science station] "Captain, I'm detecting several warp signatures leading to and from the planet. However, one of these signatures does not match any known Cardassian engine profile and is not in our warp signature database."
Riker: [concerned, looking to Picard] "An unknown vessel in the area right around the time of a Cardassian attack? This could complicate matters."
Troi: [sensing the tension, her voice calm but alert] "Whoever they are, they may not have the best intentions. The people of Anarak could be more vulnerable than we initially thought."
Picard ponders this information, his expression thoughtful yet wary. The bridge crew continues their scans, tension mounting as they try to make sense of the situation.
Worf: [interrupting the silence] "Captain, we are being hailed from the surface."
Picard: [decisive, nodding] "On screen."
The viewscreen flickers to life, revealing the image of a middle-aged man with a rugged, practical look. He exudes an air of cautious relief, though his eyes betray a deep-seated wariness.
Bas T'yat: "Alien vessel, thank you for coming so quickly. My name is Bas T'yat, and I’m an entrepreneur and concerned family man. Please, can you tell me, are you an ally of the Cardassians?"
Picard: [calm and reassuring] "Mr. T'yat, I am Captain Jean-Luc Picard of the Federation starship Enterprise. I assure you, the Federation is not aligned with the Cardassians, although we have dealt with them before, and are aware of their transgressions."
Bas T'yat: [sighs in relief] "Thank goodness. We desperately need your help. An alien ship identifying itself as Cardassian has been harassing us for weeks. I fear they'll return soon, and we have little defense against their matter transportation technology. I'm a successful inventor and businessman, Captain. I have resources and tech that could be of value to your Federation, and I'm prepared to trade anything you want in order to help protect my people."
Picard: [curious, leaning slightly forward] "Tell me more about these attacks. What exactly have the Cardassians done?"
Bas T'yat: [his tone shifting to one of frustration mixed with guilt] "It started about a month ago. One of our companies, my own company, in fact, launched a new type of vessel that can travel faster than light using a warp field, the first one we've ever built. Within an hour of it's maiden voyage the Cardassians showed up. At first, they demanded to know who was in charge of the planet. They didn't like the answer they got: We are a free people and no one commands us."
Riker: [sharing a knowing glance with Picard] "A society without centralized leadership would be difficult for the Cardassians to understand or even tolerate."
Bas T'yat: [nodding] "That was my conclusion. They treated us like a lawless frontier, moving in to take whatever they wanted. They attacked our resource stockpiles, dematerialising and I assume stealing whatever they could before we even knew what was happening. Our ground-based defense missiles successfully took out their two smaller fighter crafts that came down into our sirspace, but we have no defense against their transporter technology. Their last visit was just a raid from orbit. They just grabbed what they could without even entering the atmosphere and left within minutes."
Picard: [thoughtful, with a hint of concern] "I see. There are widely-agreed-upon rules against this type of behavior, I assure you. However, since the Federation has never made contact with your people before now, we are unfamiliar with the proper etiquette for such a first encounter. How do you suggest we proceed safely for an official meeting?"
Bas pauses, visibly perplexed by the concept of "official" procedures, his expression almost amused.
Bas T'yat: [with a chuckle] "Official meeting? Captain, just come on down and park your craft outside my coordinates. My wife will make us all some refreshments."
Picard: [with a slight smile, yet maintaining formality] "We appreciate the hospitality, Mr. T'yat, but we prefer to beam down if that's acceptable to you. We can be there in a few minutes."
Bas T'yat: [nervous but agreeable] "Beam down? Uh, sure, that's fine. I was wondering if that technology worked on people. Love to see it in action."
Picard: [nodding respectfully] "Understood. I'll be down with a small team to meet you outside your building shortly. Picard out."
The screen goes dark as the connection ends, leaving the bridge crew to process the encounter.
Riker: [with a wry smile] "Drinks with the locals; sounds like fun."
Troi: [softly, but with insight] "He's nervous, but also hopeful. I'm sensing some hurt pride in him, too, Captain. This is likely the first time his people have ever had to reach out to anyone off-world for help. His pride may cloud his ability to fully grasp the dangers they’re facing."
Picard: [serious, standing up to address the crew] "On top of being an official first contact, the Cardassians have made this a very delicate situation. We must be prepared for anything. Counselor Troi, Data, and La Forge, you're with me. Number one, you have the bridge."
The crew nods in understanding as the away team heads to the turbolift. The tension in the air is palpable as they ready themselves for what may be a challenging first contact and a possible hostile encounter with the Cardassians.
Scene 3: Bas T’yat’s Front Lawn
The team materializes on the surface of Anarak, just outside of a large, elegant house set in a lush, rural landscape. The area is a blend of modern luxury and natural beauty, though signs of recent damage are evident. Smoke still rises from a nearby hangar, the aftermath of the Cardassian attack clear in the smoldering ruins. As the team takes in their surroundings, a group of locals approaches. At the forefront is Bas T'yat, flanked by a few colleagues. He's a middle-aged man with a commanding presence, dressed in practical yet fine clothing. His stride is confident, and his eyes sharp with the determination of a man used to getting what he wants. Bas’s face lights up with a mixture of curiosity and enthusiasm as he sees the away team.
Bas T'yat: [warmly, holding his palms upwards and then extending one hand towards Picard in a greeting] "Captain Picard! Welcome to Anarak! I'm Bas T'yat. It is my honor to meet you."
Picard: [imitating the hand motion, with a polite smile] "The honor is ours, Mr. T'yat. Thank you for your hospitality. May our two peoples forever live in harmony."
Bas gestures to the smoldering hangar in the distance, his tone tinged with frustration.
Bas T'yat: [with a sigh] "That would be wonderful. I do wish the circumstances for your visit were better. [clenching his fists] That's my hangar over there, or what's left of it, anyway. The Cardassians destroyed it and the spacecraft I designed and built there. It was our first warp vessel, one that the whole world cheered on at launch just last month. We were going to colonize the asteroids with it."
Geordi: [To Picard, gesturing towards the wreckage] "If I may, Captain?"
Picard: "Certainly." [To Bas T'yat] "This is my head engineer, Commander Geordi La Forge."
Geordi: [stepping forward] "Mr. T'yat, if it's alright with you, I'd like to examine the wreckage. I might be able to determine if anything is salvageable."
Bas T'yat: [nodding, gesturing to a colleague] "Of course. Lar Kinn here is our chief pilot. He made the historic first flight and he'll take you to the hangar and help with anything you need."
Geordi and Lar Kinn head towards the hangar, with Geordi hoping to confirm if this was the source of the warp signature detected in orbit. Meanwhile, Bas leads Picard, Troi, and Data toward his house. As they walk, Bas impatiently answers a few questions about his planet, his voice tinged with annoyance and concern.
Data: “Mr. T’yat, if I may, I notice that your neighborhood’s infrastructure is well taken care of. If Anarak has no central authority of any kind, who is responsible for keeping the roads and infrastructure?”
Bas T'yat: ”Well, as a rule of thumb, if it’s on my land, I am. If it’s not on my land, then someone else is, but I may have to pay them to use it. They look so nice because we all get better insurance rates for keeping them that way.”
Data: “Curious. And who initiates larger projects like mass transportation and research?”
Bas T'yat: [slightly annoyed] “They are all risky endeavors taken by entrepreneurs like myself. Sometimes profits take decades to appear, but like with my new warp engine, I’m sure they’ll make me a huge fortune one day.” [turning to ensure Picard can hear him] "Anyway, I fear the Cardassians aren't done with us. They've stopped even trying to make demands of us, which makes me think they're planning something bigger. Perhaps a larger assault. We've been able to fend them off so far, but I have no clue how to defend against those transporter devices."
Picard: [impressed] "It is remarkable that your society, with no planetary defense force, was able to repel Cardassian military forces, even if only temporarily. Cardassian ships are known for their significant weapons and shields."
Bas T'yat: [with a hint of pride] "The people of Anarak are no strangers to defending themselves. We have numerous private protection agencies, each with advanced missile fortifications and other kinds of defenses to protect every inch of this planet. But these were designed to fend off terrorists or rival companies, not an alien invader."
They reach the entrance to Bas's home. He pauses before entering, turning to Picard with a serious expression.
Bas T'yat: [earnestly] "Captain, I'm prepared to trade for whatever defensive technology you can provide, especially something to counter the Cardassian's transporter technology. I am confident that our ground defenses can take out their shuttlecraft, but we're helpless against their ability to beam in and out at will."
Picard pauses, his face reflecting the weight of his decision before he speaks.
Picard: [in his most diplomatic tone] "Mr. T'yat, the Federation is committed to helping those in need, and we don't tolerate bullies. However, there are restrictions on the technology we can share, particularly weaponry. Also, the Federation's assistance often depends on whether a planet is on the path to becoming a member. We must ensure that our values align. In this case, a diplomatic approach might bring a far more lasting peace than simply escalating an arms race."
Bas considers this, his optimism tinged with caution. The group moves into a large room with lots of seating where a warm drink much like tea is offered. Picard partakes graciously.
Bas T'yat: [thoughtfully] "I see. Federation membership is... a complicated idea. I'm sure many heads of companies like myself would welcome it, but for the whole planet to become a singular member of any larger federation is hard to imagine. Our society values individual freedom above all else, and I'm not sure how compatible everyone here is with the Federation's ideals."
Data: "The benefits of Federation membership are considerable. Could not your people one day vote on the issue to see if a majority wants to join after taking ample time to research membership?"
Bas T'yat: [skeptically] "Voting is something that hasn't been done here for tens of thousands of years. We consider it to be archaic, a form of slavery of the minority. Honestly, I'm surprised your culture still practices it."
Picard: [nodding, a little embarrassed] "I see. Rest assured that we try to only vote on things that have every participant's full consent. You'll find that this is very common among the races you meet as your people start to explore the stars. But until then, know that the Federation's primary concern is the safety of everyone in Federation space, including your people."
While inside Bas's home, Data discreetly connects to an open network connection, accessing Anarak's version of the internet called the Openlink. His eyes flicker left to right at an inhuman speed as he analyzes the planet's defenses and infrastructure.
Data: [quietly, to Picard as he processes the data] "Captain, while there are many advanced technologies in the hands of individuals and companies, I find no evidence of any kind of unified military infrastructure. The defense efforts are completely decentralized, which will surely prove problematic in the event of a full-scale Cardassian invasion."
Picard: [grimly] "Given the Cardassians' history, we must prepare for the worst."
Just then, Geordi returns from the hangar, his expression a mix of curiosity and concern.
Geordi: "Captain, I've confirmed that Bas's ship was the source of the warp signature we detected. Unfortunately, the wreckage isn't salvageable. It could be a long time before Anarak returns to the stars."
Bas T'yat: [with a determined grin] "I wouldn't say that. My first flight was widely publicized. Lar Kinn and I are celebrities now. Hundreds of other companies are likely working on similar technology already. Some of us refer to it as 'the great space race,' with the goal of creating the first off-world colony, and my company is currently in the lead."
Picard: [with a slight smile, impressed by the resilience] "It seems the people of Anarak are not to be counted out yet. Your intrepid spirit will serve you well as Anarakans start exploring the Galaxy."
Troi: [warmly] "Your optimism is admirable, Mr. T'yat. But remember, resilience is strongest when combined with caution."
Bas T'yat: [nodding, appreciatively] "Wise words, Miss Troi. Hopefully with your help we'll be ready for whatever comes next."
Picard: [ready to leave] "This tea is delicious, thank you for your hospitality. Next I'll need to talk to my superiors at Starfleet headquarters before we can proceed any further. I'll be sure and pass your concerns and needs on to them and then we'll contact you again later today."
The away team prepares to depart, with Bas expressing his thanks once more. As they beam back to the Enterprise, each member reflects on the unique challenges of Anarak.
Scene 4: Picard’s ready room
Minutes later, Captain Picard sits alone in his ready room, the vast starscape of space visible through the window behind him. His posture is straight, and the weight of the decision before him is clear in his eyes. He taps a command into his desk console, and the screen flickers to life with the familiar stern face of Vice Admiral Alynna Nechayev. Her image on the screen is as imposing as ever.
Picard: [calmly, but with underlying urgency] "Admiral, I've just concluded a preliminary contact with a representative of Anarak, just a few light years this side of Cardassian space. The situation is more complex than anticipated. The planet is under threat from the Cardassians; specifically Gul Bankar, who's been making increasingly aggressive moves from orbit. Meanwhile, the society on Anarak is... unconventional. They have no central government, no formal leadership nor military structure. The entire planet operates under a decentralized, anarchic, commerce-based system."
Nechayev: [eyes narrowing] "Anarchists? No structure? That's not exactly an encouraging environment for a first contact, Jean-Luc.
Picard: “Admiral, they’ve managed to develop warp technology without either a government or military. It’s a remarkable feat, but one that leaves them vulnerable.”
Nechayev: “Are you certain there’s no one in authority at all? Not even an ambassador?"
Picard: [nodding] "Precisely. Their social structure wouldn’t allow it. Our first contact has been with an individual and his family, one Bas T'yat; a wealthy businessman and the inventor of their first warp-capable ship. He's requesting assistance to defend against further Cardassian attacks, but without a central authority, assisting one individual could have unpredictable consequences."
Nechayev: [questioning sharply] "Hmm. And what of the Cardassians? Is there any evidence of their involvement?"
Picard: [gravely] "Plenty. The Cardassians have already raided the planet, seizing valuable resources. Their ship left orbit shortly before our arrival, but the threat of their return looms large. Bas T'yat is convinced they'll come back with a larger force."
Nechayev pauses, her expression hardening as she considers the situation.
Nechayev: [warningly] "Starfleet cannot afford to be drawn into deeper hostilities with the Cardassian Union, Jean-Luc. Especially not over a non-member world. You must tread carefully. A diplomatic solution is paramount, and under no circumstances should you provide this Bas T'yat with advanced defensive technology. The Prime Directive is clear; we don't interfere with the internal affairs of non-member worlds, and besides, you haven't even made proper first contact with the planet, only with one family."
Picard: [measured, but firm] "Admiral, with respect, Anarak is far more advanced than many worlds we've encountered. Their technological capabilities, while decentralized, are impressive. Now that they are getting their space legs it won't be long before Anarakans are showing up in ports across the quadrant. And if the Cardassians establish a foothold here, it could destabilize the entire region."
Nechayev's face softens slightly, recognizing the gravity of the situation. She sighs, her resolve shifting as she weighs the options.
Nechayev: [reluctantly] "Alright, Jean-Luc. I don’t like this, but I trust your judgement. You may share transport inhibitor technology. Only enough to help them counter the Cardassians' beaming technology, but nothing more. And remember, this Bas T'yat doesn't speak for his whole planet. Try to treat his family like you would if you found them alone in a spaceship."
Picard: "Understood, Admiral. I'll proceed with caution."
Nechayev: [more sternly] "Just don't start another war, Jean-Luc."
The screen goes dark. Picard leans back in his chair, the weight of the decision pressing on him. He stands, smoothing his uniform, and exits the ready room onto the bridge.
Scene 5: Bridge
On the bridge, the atmosphere is tense as the crew processes the situation. Picard steps up to his command chair, addressing the senior officers who have gathered.
Picard: [seriously] "Admiral Nechayev has authorized us to share transport inhibitor technology with Anarak to help them defend against further Cardassian raids. But we must be mindful of the ethical implications of our actions."
Dr. Crusher:: [concerned] "Captain, I'm worried about the consequences of becoming involved in this situation. If we assist Anarak, it could escalate into a larger conflict--one that could draw the Federation into another war with the Cardassians."
Worf: [gruffly, with resolve] "But allowing the Cardassians to plunder a defenseless society is equally unacceptable, Doctor. We have a responsibility to protect the vulnerable."
Picard: [thoughtfully, considering both viewpoints] "I'm inclined to agree with Worf on this one, Beverly. We must work fast to deploy the inhibitors wherever we can, but that does bring up another problem. The Prime Directive prevents us from interfering in the internal affairs of non-member worlds. And giving one individual on Anarak access to advanced technology could upset the delicate balance of their society. What if Bas T'yat's company gains a monopoly on defense technology? It could shift the power dynamics on the entire planet."
Troi: [insightfully, her voice calm] "Captain, I sense that Bas T'yat is deeply worried about his planet's future. He feels a strong sense of responsibility and guilt for the attacks... I don't think that he had any way to know that their warp signature would act as a beacon to those seeking resources. They didn't even know other life forms existed until the Cardassians arrived. It's clear that Anarakans weren't prepared for the reality of interstellar contact."
Picard: [resolved] "I agree, Counselor. We're dealing with a society that is both advanced and vulnerable. A dangerous combination. We must proceed carefully."
Picard considers this, his brow furrowed in thought. Finally, he makes a decision.
Picard: [decisively] "We must proceed, however. I'll invite Bas T'yat to the Enterprise to discuss the situation further. We will ensure that any assistance we provide doesn't destabilize their society, or escalate the conflict."
Picard hails Bas T'yat from his command station.
Picard: [calmly] "Mr. T'yat, I'd like to invite you aboard the Enterprise to discuss our options in person."
The main screen fills with T'yat's face again.
Bas T'yat: [with a hint of hesitation] "Thank you, Captain, I accept. But I'd prefer to take my own craft... Still not quite comfortable with the transporter technology, if you'll understand. I'll bring my wife, L'anna, and my pilot, Lar Kinn."
Picard: [diplomatic, nodding slightly] "Understood. We'll be ready to receive you in the shuttlebay.”
Scene 6: Main Shuttlebay
In the Enterprise's shuttlebay, the crew prepares to greet their visitors. The doors slide open, and a sleek, streamlined skysled enters the bay, guided by Lar Kinn at the controls. The craft settles gently onto the deck, and the hatch opens. Bas T'yat steps out, accompanied by his wife, L'anna, and Lar Kinn, who looks around the shuttlebay with wide-eyed curiosity. Picard, Troi, and Data are there to meet them, offering warm greetings as the Anarakans take in the impressive sight of the Enterprise's interior.
Picard: [welcoming, with a gesture towards the ship] "Welcome aboard the Enterprise, Mr. and Mrs. T'yat. I trust your journey was smooth?"
Bas T'yat: [grinning, clearly impressed] "Very much so, Captain. Your ship is... well, it's more than I imagined. Thank you for having us."
Troi steps forward, offering a kind smile.
Troi: [invitingly] "If you'd like, I can give you a tour of the ship. We're quite proud of our vessel, and I think you'll find it fascinating."
L'anna's eyes widen with excitement, and she nods eagerly. Bas exchanges a look with Lar Kinn, just catching up to the group. He seems just as eager to explore as the others, and nods excitedly to Troi.
Bas T'yat: [appreciatively] "We'd be honored. Lead the way, Counselor."
Lar Kinn: So can all these shuttles go faster than light?
With that, the group sets off on a tour of the Enterprise, the Anarakans marveling at the advanced technology and seamless design of the Federation starship. As they walk, Troi can't help but notice the mix of awe and determination in Bas T'yat an inventor and leader who knows that his world's future may very well depend on the choices made in the hours to come.
Scene 7: Bridge
The scene opens as Counselor Troi leads Bas T'yat, L'anna, and Lar Kinn onto the bridge of the Enterprise. The visitor's awe is palpable as they take in the grandeur of the ship's command center. Picard, standing near the captain's chair, barely has a moment to welcome them when a sudden alert draws everyone's attention.
Data: [at his station, voice urgent] "Captain, I'm detecting the return of the Cardassian battle cruiser. It is registered as the Kolarak. It just popped out from behind the home star and is entering orbit around Anarak."
Riker: "Yellow alert. On screen."
Picard immediately straightens, his expression shifting from welcoming to resolute. The tension on the bridge heightens as the viewscreen flickers to life, displaying the imposing sight of the Kolarak. The Cardassian vessel looms in space, its dark hull bristling with weaponry.
Picard: [calmly, but with authority] "Mr. Worf, open a channel to the Kolarak."
The screen quickly reveals the stern visage of a Cardassian Gul in his command chair. His eyes narrow as he takes in the sight of the bridge crew and the unfamiliar faces of Bas and his companions.
Picard: [with measured politeness] "I am Captain Jean-Luc Picard of the Federation starship Enterprise. With whom am I speaking?"
Gul Bankar: [with a sneer, his voice dripping with condescension] "You may address me as Gul Bankar."
Picard: "Gul Bankar, there have been reports of your vessel causing harm and stealing resources from the planet below. With me is Bas T'yat, the owner of the warp-capable vessel that it appears your forces destroyed on the surface. We request an explanation for these hostilities."
Gul Bankar: "Captain Picard, your presence here is an unwelcome interference. This planet, and its inhabitants, are under Cardassian protection. You will withdraw immediately, leaving Anarak to our care."
Picard's gaze hardens, but his tone remains calm and firm.
Picard: [skeptically] "Cardassian protection? Anarak lies within Federation territory. We received a distress call and are here to provide assistance."
Bankar's expression darkens, his eyes flashing with anger.
Gul Bankar: [coldly] "The Federation's meddling in this region is all too well documented, Picard, but Anarak is too close to Cardassian space for your interference to be tolerated. I find your so-called assistance nothing more than another prelude to annexation."
Bas, standing beside Troi, listens intently, his face reflecting a mixture of concern and frustration. Picard, sensing the rising tension, steps closer to the viewscreen.
Picard: [with resolve] "The Federation respects the sovereignty of all worlds. We are only here because of your aggressive actions, not to claim this planet. We have long worked to maintain peace in this sector, and I would hate to see that peace jeopardized by your reckless actions here."
Gul Bankar: [sarcastically] "Peace? The Federation's control of Terok Nor and the Bajoran wormhole is hardly a gesture of peace. It was a clear power grab, one that we will not allow to extend to Anarak."
Picard's eyes narrow, his voice taking on a steely edge.
Picard: [firmly] "Gul Bankar, a conflict between the Federation and the Cardassian Union would serve no one's interests, especially not over a planet that is so new to the neighborhood. I suggest you contact your superiors before taking any further aggressive actions."
There's a tense silence as Bankar considers Picard's words, his eyes flicking to Bas and then back to Picard. Finally, he lowers his head in a slight nod, though his expression remains hostile.
Gul Bankar: [grudgingly] "Very well, Captain. I will contact Central Command. But understand this; Anarak will not fall under Federation control, and I will ensure that Cardassia's interests are protected. I will contact you again in 4 hours."
The transmission abruptly cuts off, leaving the bridge in a heavy silence. The Kolarak remains on the viewscreen, hovering ominously in space, nose to nose with the Enterprise now. Picard exhales, turning to face his crew.
Picard: [calmly, but with an undertone of urgency] "Maintain our position and yellow alert, Mr. Worf, and monitor the Kolarak for any signs of hostile activity."
Worf gives a curt nod, his eyes never leaving the tactical display.
Worf: [with determination] "Aye, Captain. Shields at maximum, weapons ready."
Picard then turns to Bas, who is visibly shaken but trying to maintain his composure.
Picard: [reassuringly] "Mr. T'yat, I understand this is a difficult situation and you don't yet know who to trust, but I assure you that we aim to keep the peace in this sector and will do everything in our power to ensure your planet's safety. We ask nothing in return from the Anarakan people. However, it is crucial that we handle this matter diplomatically."
Bas nods, though his expression is one of deep concern.
Bas T'yat: [uneasily] "I appreciate that, Captain, and don't worry, nothing that Gul Bankar says will make me trust his offer of "protection" after he destroyed my ship and stole resources from all over the planet. But I do worry that he’s using this time to call for reinforcements."
Picard places a reassuring hand on Bas's shoulder, his voice steady.
Picard: [confidently] "If he attacks, we'll face that challenge together, Mr. T'yat. You are free to return to the surface at any time but for now, I think it best that we consider how fast we could deploy our transporter inhibitor technology on your planet."
Bas T'yat: [enthusiastically] "You mean you're willing to sell us devices that can stop them from beaming up our resources?"
Picard: "Or beaming their troops down. And we wouldn't sell it to you, it is our gift. The Federation doesn't sell it's assistance to those in need."
The visitors faces all brighten in unison with relief.
L'anna: "I don't know how we could ever thank you enough, Captain. This means everything to our people."
Picard: "Don't thank us yet, there is still the issue of deploying enough of them in time. If they're going to attack in 4 hours you'd need them set up near all the most valuable targets at the very least. They'll need a steady supply of energy, too."
Bas furls his lips in concerned thought.
Data: "Captain, I've analyzed all of the planet's most valuable resource depots that our scanners can detect and I see 168 unique locations that we should set up transport inhibitors. There may, of course, be other targets too that they would want."
Riker: [apprehensively] "That's way too many for us to replicate in time, much less visit each location to install within the next 4 hours."
Picard: "We need a way to speed up that deployment, at least to enough sites that will show Gul Bankar that things have changed... And hopefully without him detecting our movements."
Bas T'yat: "If I may captain, I think I know a better way to deploy them if I can just make a detailed scan of one and save it to our printer file format... We don't have your transporter technology, but our device printers are able to scan and quickly reproduce any technological device that we can identify the components of."
Riker: "And how will that help distribute them to everyone in time?"
Bas T'yat: "Simple, every business and household has one of these printers. I can upload the scanned file to our Openlink and tell all of Anarak in one broadcast about the imminent threat and how to protect themselves from it with one of these inhibitors. They'll pop out thousands of them in time."
Picard: "That sounds very promising, Mr. T’yat. But I want your assurance that your company will not hold any sort of monopoly on this technology or otherwise profit from it; In lieu of a government, the Federation requires that this gift be made to your whole planet at once."
Bas T'yat: [after some hesitation] "Alright, Captain. You have my promise. Giving up some profits is the least I can do to make up for attracting the Cardassians to Anarak."
Picard looks visibly relieved, giving a curt nod to Bas.
Picard: "Data, take our guests to engineering and grab whomever you may need to assist you with making this happen in time. Remember, you’ll also need to show the Anarakans how to use these devices."
Data: "Aye sir." [To the visitors] "If you'll follow me please, we'll be able to work on this in engineering."
Data, Bas, Lar Kinn, and L'anna walk briskly to the turbolift. The scene closes with Picard returning to his command chair, the bridge crew resuming their stations as the standoff between the Enterprise and the Kolarak continues. The two ships remain locked in silence, nose to nose, as the 4-hour countdown begins.
Scene 8: Main Engineering
The scene opens in Main Engineering, where Geordi La Forge, Data, and Ensign Sam Lavelle are putting the final touches on the scan for their transport inhibitor device. Bas T'yat and Lar Kinn stand nearby, observing the process with keen interest. The atmosphere is tense, underscored by the ticking clock counting down the hours until Gul Bankar's deadline.
Geordi: [focused as he works] "All right, that should do it. The scan of this transport inhibitor is ready, and the data's been formatted for your printers."
He hands a datapad to Bas, who takes it with a mix of curiosity and nervousness.
Geordi: [reassuringly] "You'll be able to upload the complete plans from this device, including an adapter for your power source. Once it's on your network, anyone with Openlink access will be able to build and deploy these inhibitors in a matter of minutes. It's up to you, however, to convince them to do that."
Bas T'yat: [relieved] "Thank you, Commander. I'm sure many will manage it in time, but I just hope it's enough."
Lavelle: [chiming in, pointing to the datapad] "Also I've included a detailed instruction set too. It explains how to set the units up and operate them."
Bas nods his thanks, flipping through the instructions as Lar Kinn looks over his shoulder.
Data: [ever precise, offering a suggestion] "Mr. T'yat, given the standoff outside, it may be prudent to avoid the use of the transporter. The Kolarak is likely monitoring our actions closely. Sending the plans with you aboard the skysled would appear less provocative."
Bas looks visibly relieved at the suggestion, nodding in agreement.
Bas T'yat: [grateful] "Thank you, we'd prefer not having our atoms scattered throughout the atmosphere today anyway."
Geordi: [nodding, humorously] "No problem. We'll make sure the skysled is ready to go."
Data gestures toward the exit of Engineering, indicating it's time to depart.
Data: [calmly, but with urgency] "We should make our way to the shuttlebay. There's less than two hours remaining before the Gul's deadline. It's imperative that as many Anarakans as possible receive these plans in time."
Bas and Lar Kinn exchange a look, their expressions set with determination as they follow Data out of Engineering. The camera follows the group as they walk briskly through the corridors of the Enterprise.
L'anna: "You'll be sure to tell the Captain and Councilor Troi that we said goodbye?"
Data: "Of course. And let me say that I find your culture truly intriguing, and hope we get the chance to visit again in the future, no matter if Anarak chooses Federation membership or otherwise."
Bas T'yat: "You'd be our welcome guest anytime, Mr. Data. I think you'd most enjoy seeing the progress my people have made with robotics and artificial intelligence. My company produces one of the best-selling android assistants on the market."
Data: "Fascinating. I look forward to it. Here we are."
As they reach the shuttlebay, the large bay doors slide open, revealing the sleek skysled waiting for them. The ship is prepped and ready for launch, its engines humming with quiet power.
Data: [pausing as their ship's door opens] "We wish you a safe journey, Mr. T'yat, L'anna, Mr. Kinn."
Bas T'yat: [nodding, with resolve] "We'll make sure everyone gets these plans. Thank you, Commander Data."
Lar Kinn gives Data a respectful nod before they step onto the skysled. Data watches as they take their positions inside the cockpit. Data then taps his communicator, his voice steady.
Data: "Data to the Bridge, our visitors are ready to depart."
The camera cuts to the exterior of the Enterprise, where the massive shuttlebay doors slide open. The skysled, with its sleek design and glowing engines, slowly backs out of the bay, the vastness of space stretching out behind it. As the skysled turns on its main engines, the camera shifts to an interior cabin view, showing Bas and Lar Kinn exchanging a final, determined nod before the vessel speeds downwards towards Anarak.
Scene 9: Bridge
The scene opens 30 minutes later. The tension on the Enterprise bridge is palpable as the Openlink broadcasts Bas's message and the transport inhibitor plans worldwide. The crew watches anxiously as the first inhibitors are swiftly deployed across Anarak. Suddenly, the ship's sensors beep urgently. Worf glances at his console, eyes narrowing.
Worf: [alarmed] "Captain, seven additional Cardassian battle cruisers have exited warp and joined Gul Bankar's ship. They're forming up and preparing to engage."
Riker: "Red alert, forward shields to maximum."
Picard's expression hardens as the Kolarak hails them. Gul Bankar's visage appears on the viewscreen, eyes burning with fury.
Gul Bankar: [accusatory] "We've detected the inhibitor plans on their planet-wide network, Picard. You've broken our gentleman's agreement by sharing advanced technology with a primitive civilization. So much for Starfleet ideals! You're no match for us now. Try and stop us at your own peril."
With that, Bankar cuts off communications. Picard stands, frustration etched into his features as the fleet of eight warships begins its descent toward Anarak.
Data: [urgently] "Captain, the Cardassian ships are gaining speed and appear to be initiating an attack run on the planet's largest population center. Tens of millions of civilian lives are at risk, more than usual because the defensive turrets are spread out among the greater population. It is not uncommon for them to be placed on rooftops and around housing here."
The crew's tension escalates as the gravity of the situation sinks in. Picard, feeling the weight of command, turns to his officers.
Picard: [steady but intense] "Ideas?"
Worf: "Captain, we could attempt to disable their weapons and transporters, focusing on minimizing their capacity to attack."
Riker: [shaking his head] "Even so, we're outmatched. Enterprise won't survive against eight battle cruisers."
Troi: [calm but urgent] "We just need to buy time. To give the Anarakans a chance to fully deploy their defense net. But any kind of engagement from us still risks re-igniting a war with the Cardassians."
Data, ever analytical, speaks up with a grim tone.
Data: "Captain, I've run millions of battle scenarios. None result in the Enterprise surviving while saving more than a few dozen lives on the surface. Our current position is untenable."
As the Cardassian warships break through the planet's stratosphere, Ensign Lavelle, stationed at comms, suddenly speaks up.
Lavelle: [urgently] "Captain, Bas T'yat has just sent out another message across the planet, warning of the incoming Cardassian fleet."
Picard opens his mouth and lifts his index finger to respond, but he's cut off by a sudden, blinding array of light erupting from the planet's surface, filling up the viewscreen. The bridge crew shields their eyes as the screen fills with thousands of pinpricks of light; an overwhelming launch of nuclear-armed missiles aimed directly at the Cardassian fleet.
Worf: [stunned] "Captain, these are nuclear-fission warheads, each with a 10-megaton yield. I've never seen a civilization with this many dirty weapons in active deployment."
The bridge falls silent as the sheer scale of the Anarakan response becomes clear. The entire hemisphere of Anarak has mobilized, proving their incredible capacity for defense, despite the lack of a centralized government.
Data: "Fascinating. It could be that no central authority is needed for coordination when the threat is dire. These people all appear to be responding individually with their own weapons."
The first few dozen warheads impact the Cardassian shields, which manage to absorb their blasts. But the onslaught is unrelenting. Hundreds, then thousands of warheads detonate in rapid succession, creating a cataclysmic, sustained explosion. The Cardassian ships, though formidable, are utterly overwhelmed. The viewscreen shows an apocalyptic display; a temporary star forms in Anarak's upper atmosphere, engulfing the entire Cardassian flotilla in an unprecedented, blinding flash.
Picard: "Helm, back off our position."
The bridge crew watches in stunned silence as the massive explosion slowly dissipates, leaving nothing but a red afterglow and the eerie silence of space. Power has gone out across the hemisphere on the planet below, but not a single molecule of the Cardassian ships remain. Picard and his crew are left in awe, mingled with a deep sense of disappointment. The enormity of what they've witnessed sinks in; a civilization so welcoming, yet still capable of such destructive power... Sso fundamentally different from the Federation's ideals. Troi closes her eyes tightly and winces, blocking out the pain of all those Cardassian deaths. Picard stands, staring out at the aftermath, the weight of the moment heavy on his shoulders.
Picard: [quietly, with a great sense of loss] "Such utter destruction..."
The camera pulls back, showing the Enterprise as a small silhouette against the reddish glow below.
Scene 10: Bridge
The scene opens minutes later with the Enterprise bridge crew still processing the aftermath of the overwhelming display of destructive power. The mood is somber as the reality of what they've witnessed lingers. Suddenly, Bas T'yat's face appears on the viewscreen, his expression a mixture of relief and satisfaction.
Bas T'yat: [earnestly] "Captain Picard, I wanted to thank you and your crew for everything. It seems our future is secure now, thanks to the defense network and your assistance. We're eager to move forward and hope the Federation will allow us to engage in commerce with your worlds and other peaceful civilizations."
Picard stands, his gaze steady, though his tone reflects the weight of what has transpired. He pauses for a moment, as if searching for the right words, the bridge falling into a brief, tense silence.
Picard: [measured, but firm] "Mister T'yat, I must be candid. While the Enterprise is pleased to have assisted in safeguarding your world, the events of today have left us with grave concerns. The way Anarak handled the Cardassians… particularly the use of nuclear warheads, demonstrates a fundamental difference in values between our societies. We cannot endorse methods that pose such a grave risk to all life, even in defence. The Federation could not, in good conscience, approve your planet for membership given these circumstances."
Bas's expression shifts to one of slight disappointment, but he remains composed.
Bas T'yat: "I understand, Captain. We've always been a world that does things our own way. Federation membership would have been a tough sell to my people anyway. But what about trade? Surely we can still establish commerce with Federation worlds?"
Picard nods, his tone softening slightly.
Picard: "Trade remains an option. We won't turn away peaceful commerce between Anarak and Federation planets. However, I must stress that the use of nuclear weapons is fundamentally at odds with Federation ethics. While I recognize their role in your planet's defense, I hope that over time, your people will explore more sophisticated and less destructive means of protection."
Bas nods again, understanding the implications of Picard's words.
Bas T'yat: "It's clear that today's events were... extreme. The fallout, the EMP blackouts, the atmospheric damage; we've already seen unacceptable cost. I'll do my best to guide my people toward more advanced defenses, and away from reliance on such careless weapons. It will be my penance for leading the Cardassians here."
Troi senses his guilt once again and takes a deep breath. Clearly still shaken by the loss of life, she steadies herself before offering a supportive smile.
Troi: "You shouldn't burden yourself with guilt, Mister T'yat. Anarak was bound to take that step sooner or later. What matters now is how you use your newfound role as an ambassador to the stars. Your actions will shape your planet's future in the galaxy."
Bas smiles, clearly grateful for the support.
Bas T'yat: "Thank you, Counselor. I'll do my best to live up to that responsibility."
After a few more exchanges, the connection ends, and Bas T'yat's image fades from the viewscreen. Picard takes a deep breath and turns to face his bridge crew.
Picard: [reflective] "We've witnessed two amazing displays of power today; one of the explosive variety, and the other of a free people's resolve. It's hard to imagine how their society works with no acceptance of authority, but today they've clearly displayed that they can accomplish amazing things working together even without any."
Worf, still perplexed, shakes his head slightly.
Worf: "I still don't understand how an entire planet could coordinate such a specific defense without any central leadership."
Leaning casually against the console, Riker chuckles lightly.
Riker: "It was in everyone's best interest, Worf. They just needed Bas's signal to know when the attack was imminent. The rest fell into place."
Worf: "And how they could hide that many warheads from our scans? Enriched Uranium is the easiest of all elements to scan for."
Data: "It appears that their stealth technology may be on par with our own."
Picard, his expression thoughtful, gazes out at the stars beyond the viewscreen.
Picard: "I'm placing a note in my log for Starfleet to leave this planet alone until they can't be ignored any longer. I believe it's for the best that we leave Anarak to chart its own course in the galaxy."
He pauses, a faint smile tugging at the corner of his mouth.
Picard: "I doubt we'll have trouble with them soon, at least, until they meet the Ferengi."
*The bridge crew shares a quick laugh and then a quiet moment of contemplation before returning to their stations. The camera pulls back, showing the Enterprise once again poised in the vastness of space, a symbol of hope and integrity amidst the complexities of a vast and unpredictable galaxy.
Fade to black.*
---
*This story is set in the Star Trek universe, created by Gene Roddenberry and owned by Paramount. I do not own any of the characters or settings from the Star Trek franchise, and this is purely a fan-made work for non-commercial purposes.*
-
 @ 1a48e74d:02c0e00f
2024-09-04 18:53:09
@ 1a48e74d:02c0e00f
2024-09-04 18:53:09Welcome back ya'll hope you are doing well this week. Today I wanted to talk about why Bitcoin represents a dawn of a new age in property ownership. Before you spit out your coffee and walk away, hear me out. Bitcoin and real estate have a few things in common. The first is property rights.
When you are the owner of a building with your name on the dotted line and whatnot, you are the sole owner of that property. No one can tell you what to do with it, and no one has a claim to what you own. You are free to do what you wish. Property rights are sacrosanct and immutable similar to Bitcoin.
Bitcoin confers upon the owner the same property right protections as owning a piece of real estate. Once you own it, you are the sole owner of that Bitcoin. No one can tell you what to do with it. No one else has a claim to your Bitcoin. You are free to do with it what you wish.
Bitcoin and real estate are similar in terms of built-in scarcity. There is only 21 million Bitcoin that will ever be created, and you can't print more land. This is why owning real estate has been such a good investment since the beginning of time. Buying a piece of land and "HODLING" for decades will generate a substantial return on your investment.
This same buy and hodl strategy apply to Bitcoin as well. If you bought Bitcoin back in 2009, you would be a multi-millionaire right now.
If you invested $1000 back in 2011 when Bitcoin was trading at $3.50, you would have turned that $1000 into $15.6 million if you held on to it for ten years. Just sayin.
You have to reframe your thinking to understand what is going on. We are living in the 21st-century gold rush, and you have an opportunity to stake your claim to the soundest money on Earth with a few taps on your phone. Never in the history of the world has the plebs like us had the ability to front-run a monetary revolution.
Bitcoin is freedom from oppression. Bitcoin restores your sovereignty. Bitcoin makes you fuckable, and the powers that be know it. They are afraid they will lose control if too many people catch on too quickly, which is why large institutions are rushing to offer Bitcoin services or buy them and keep them on their balance sheet.
Bitcoin won't stay this cheap forever. $100-300k Bitcoin is in the cards over the next few years. I don't want you guys to miss out on this.
All you have to do is buy Bitcoin and hold. It's that simple. FYI trying out the new obsidian writer for nostr notes!
Bitcoin #nostr
-
 @ 361d3e1e:50bc10a8
2024-09-04 18:48:17
@ 361d3e1e:50bc10a8
2024-09-04 18:48:17Is France preparing to seize people's savings to avoid bankruptcy?
politics #europe #banks #france #savings #cyprus
-
 @ 8d34bd24:414be32b
2024-09-04 15:57:00
@ 8d34bd24:414be32b
2024-09-04 15:57:00Today is the official publishing day of this post. I already tried scheduling this post in another editor that went out early.
I’ve mentioned multiple times that I feel our time left is short and that the rapture and the tribulation are coming soon. I feel it with every ounce of my being. I see it in the rush to evil around us. I see Biblical prophecy coming to fulfillment and technologies that could not be fathomed 2,000 years ago coming into being in a way that will make prophecy possible. The question is, what do we do with the time left to us?
Don’t Be a Foolish Virgin
Matthew gives an analogy of believers waiting for Christs return:
“Then the kingdom of heaven will be comparable to ten virgins, who took their lamps and went out to meet the bridegroom. Five of them were foolish, and five were prudent. For when the foolish took their lamps, they took no oil with them, but the prudent took oil in flasks along with their lamps. Now while the bridegroom was delaying, they all got drowsy and began to sleep. But at midnight there was a shout, ‘Behold, the bridegroom! Come out to meet him.’ Then all those virgins rose and trimmed their lamps. The foolish said to the prudent, ‘Give us some of your oil, for our lamps are going out.’ But the prudent answered, ‘No, there will not be enough for us and you too; go instead to the dealers and buy some for yourselves.’ And while they were going away to make the purchase, the bridegroom came, and those who were ready went in with him to the wedding feast; and the door was shut. 11Later the other virgins also came, saying, ‘Lord, lord, open up for us.’ But he answered, ‘Truly I say to you, I do not know you.’ Be on the alert then, for you do not know the day nor the hour. (Matthew 25:1-13)
Christians have been waiting for around 2,000 years for Christ’s return. It is easy to get drowsy and begin to sleep due to the delay to His return, but we are called to be ready. “You too, be ready; for the Son of Man is coming at an hour that you do not expect.” (Luke 12:40) Our wait may be long or short, but we are supposed to live our lives like he will arrive today. We don’t want to miss out on joining Him at His return, but we also don’t want to have to face Him knowing that we were not focused on what He had called us to do. We don’t want to admit that we didn’t share the gospel to that friend, that we didn’t stand up for the truth when the crowd was speaking contrary to the word of God, or that we acted in an unloving way to fellow believers or to the lost.
The Bible clearly tells us that we “do not know the day nor the hour,” but that doesn’t mean that He has not given us signs that the time is short.
What Should We Be Doing?
If Jesus is coming soon, how should we spend our time? What should we be doing? Should we just sit back and wait?
For even when we were with you, we used to give you this order: if anyone is not willing to work, then he is not to eat, either. For we hear that some among you are leading an undisciplined life, doing no work at all, but acting like busybodies. Now such persons we command and exhort in the Lord Jesus Christ to work in quiet fashion and eat their own bread. But as for you, brethren, do not grow weary of doing good. (2 Thessalonians 3:10-13)
The Bible is clear that we should work. This not only means that we should not quit our jobs, but should continue working as we have been doing, but it also means we should put time and effort into kingdom work. God has given each one of us a purpose and a job to do. We should study His word and pray and keep our eyes open so we don’t miss out on what He intends as our purpose. Another analogy is given in Matthew:
“For it is just like a man about to go on a journey, who called his own slaves and entrusted his possessions to them. To one he gave five talents, to another, two, and to another, one, each according to his own ability; and he went on his journey. Immediately the one who had received the five talents went and traded with them, and gained five more talents. In the same manner the one who had received the two talents gained two more. But he who received the one talent went away, and dug a hole in the ground and hid his master’s money.
“Now after a long time the master of those slaves came and settled accounts with them. The one who had received the five talents came up and brought five more talents, saying, ‘Master, you entrusted five talents to me. See, I have gained five more talents.’ His master said to him, ‘Well done, good and faithful slave. You were faithful with a few things, I will put you in charge of many things; enter into the joy of your master.’
“Also the one who had received the two talents came up and said, ‘Master, you entrusted two talents to me. See, I have gained two more talents.’ His master said to him, ‘Well done, good and faithful slave. You were faithful with a few things, I will put you in charge of many things; enter into the joy of your master.’
“And the one also who had received the one talent came up and said, ‘Master, I knew you to be a hard man, reaping where you did not sow and gathering where you scattered no seed. And I was afraid, and went away and hid your talent in the ground. See, you have what is yours.’
“But his master answered and said to him, ‘You wicked, lazy slave, you knew that I reap where I did not sow and gather where I scattered no seed. Then you ought to have put my money in the bank, and on my arrival I would have received my money back with interest. Therefore take away the talent from him, and give it to the one who has the ten talents.’
“For to everyone who has, more shall be given, and he will have an abundance; but from the one who does not have, even what he does have shall be taken away. Throw out the worthless slave into the outer darkness; in that place there will be weeping and gnashing of teeth. (Matthew 25:14-29)God has given each of us different skills, gifts, and opportunities. He wants us to make the most of them. If God gave you skill in business, you can use your wealth to fund ministries, churches, and missionaries. If God has gifted you with the ability to teach, you can disciple many to grow in their faith and knowledge of God. If God has brought you into a relationship with someone influential, you can share the Gospel with them and be used to draw them into saving faith in Jesus. Whatever skills, gifts, and opportunities God has given to you, you need to make the most of them. You need to grow and make the most of what God has given you.
What is the Best Use of Our Time and Money?
God wants us to shine a light for Him. He wants us to make a difference. There are many ways to do this and we can’t do them all. We have to pick and chose what is God’s will and what will make the best use of what God has given us.
There are lots of good things we can do, but what is the best?
I used to focus on prepping to be able to provide for my family and others if times get bad. That was good, but was it best? I used to grow a garden and grow healthy food. That was good, but was it the best? I used to be highly involved in politics and worked hard to support and elect godly men and women into government positions where they could have a positive influence on our culture and our country. That was good, but was it the best?
According to the grace of God which was given to me, like a wise master builder I laid a foundation, and another is building on it. But each man must be careful how he builds on it. For no man can lay a foundation other than the one which is laid, which is Jesus Christ. Now if any man builds on the foundation with gold, silver, precious stones, wood, hay, straw, each man’s work will become evident; for the day will show it because it is to be revealed with fire, and the fire itself will test the quality of each man’s work. If any man’s work which he has built on it remains, he will receive a reward. If any man’s work is burned up, he will suffer loss; but he himself will be saved, yet so as through fire. (1 Corinthians 3:10-15)
The best way to judge which actions are best is to see which actions have an eternal influence and to look and see what God is doing and to join His work. The difference between gold & silver versus wood, hay, and straw is the gold & silver can survive fire. Whether something is good or best depends on whether the action makes a difference in eternity. Providing for my family and friend’s physical needs and health is good, but it doesn’t make an eternal difference. Electing Godly officials makes life here on Earth better, but does it actually make a difference eternally? Probably not.
What does make a difference? Sharing the Gospel with others makes an eternal difference. Standing up for the truth, especially the spiritual truths from the Bible, makes an eternal difference. Writing a book or a blog sharing the truths of the Bible and Jesus makes an eternal difference. I’ve tried to focus my time on this type of activity more than the former. I don’t want one soul to go to Hell because I was too busy to share the Gospel. I don’t want one Christian to regret their life on Earth because I was too busy to disciple them. I don’t want to be like the man who received the single talent and buried it in the ground, who, when facing his master, was told, “You wicked, lazy slave.”
What Is Most Important?
“Do not store up for yourselves treasures on earth, where moth and rust destroy, and where thieves break in and steal. But store up for yourselves treasures in heaven, where neither moth nor rust destroys, and where thieves do not break in or steal; for where your treasure is, there your heart will be also. (Matthew 6:19-21)
What are the most important things in our lives? The most important things are people.
- Some people in our lives have never heard about Jesus. We need to share the gospel with them.
- Some people in our lives are hurting and need to be helped and encouraged and taught to trust in Jesus.
- Some people in our lives are new Christians or just immature Christians, who have trusted in Jesus, but haven’t grown much since salvation. We need to teach and disciple them to grow in their understanding of God and who He is. We need to build up their faith. We need to encourage them to study the Bible.
- Some people in our lives know God and His word, but are unsure how to live out their faith and share it with others. We need to encourage them and train them, so they can multiply their faith among others in their lives.
What are you doing to make an eternal difference in service to our Lord Jesus Christ? Are you one of the lazy, unprepared virgins? Are you hiding the gifts God gave you in the ground or shining a light that can be seen by everyone around you? Are you so busy doing good, that you don’t see God’s best?
Are you excited about meeting Jesus in the air at the rapture of the Church? I am! I hope you are, too.
your sister in Christ,
Christy
Bible verses are NASB (New American Standard Bible) 1995 edition unless otherwise stated
-
 @ 469fa704:2b6cb760
2024-09-04 15:22:28
@ 469fa704:2b6cb760
2024-09-04 15:22:28Money Printing in general
First of all, we need to make a distinction between money creation by central banks and fractional-reserve banking. Usually, the term money printing or “printer goes brrrrrr” refers to the creation of new central bank money, which is primarily created by central banks through:
- Open Market Operations: Buying government securities, which injects money into the banking system by increasing bank reserves. This is often done electronically, not by physically printing money.
- Quantitative Easing (QE): Purchasing assets to inject money directly into the economy, aiming to stimulate economic activity by increasing the money supply.
- Setting Reserve Requirements: Although less about creating money, lowering reserve requirements can indirectly influence money creation by allowing banks to lend more, but as of recent policy changes, this has been set to zero in some systems, shifting focus to interest rates.
- Interest on Reserves: By adjusting the interest rate paid on reserves, central banks influence how much banks are willing to lend, thereby indirectly affecting money creation.
This is the first step of money creation, although printing money is usually connected to one of the aforementioned processes, the second step creates much more money through the expansion of credit.
The Mechanics of Fractional-Reserve Banking
The Concept
In fractional-reserve banking, banks accept deposits from customers and only keep a small fraction of these deposits in reserve, lending out the rest. This practice essentially creates new money because:
- Deposits: When you deposit money, say $1,000, into a bank, that money doesn't just sit there.
- Reserves: If the reserve requirement is 10%, the bank keeps $100 as reserves.
- Loans: The remaining $900 can be loaned out. Here's where money creation begins.
Note: Current reserve requirements of the FED (Source) and the ECB (Source) are set at 0% respectively 1%.
Example Calculation of Money Creation
- Initial Deposit: You deposit $1,000 into Bank A.
- Bank A's Action:
- Keeps $10 (1%) as reserve.
-
Loans out $990 to another customer.
-
The $990 Loan: This $990, when spent, might end up in Bank B as someone's deposit.
- Bank B's Action:
- Keeps $9.9 (1% of $990) as reserve.
-
Can loan out $980.1
-
Continuation: This process repeats, with each cycle creating new deposits from loans.
The Deposit Multiplier (m) can be calculated as: * m = 1 divided by Reserve Ration = 1 / Reserve Ration
If the reserve ratio is 1%: * m = 1 / 1% = 1 / 0.01 = 100
This means, theoretically, an initial deposit of $1,000 could expand to:
- $1,000 times 100 = $100,000
- However, in practice, this is tempered by factors like cash holdings, loan demand, and banks holding excess reserves.
Historical and Economic Context
- Evolution from Goldsmiths: The system has its roots in the practices of goldsmiths who issued notes for gold deposits, which eventually circulated as money. This practice evolved into the modern banking system where notes (now digital entries) represent claims on money.
- Regulation and Central Banking: Over time, central banks like the Federal Reserve in the U.S. were established to regulate this process, provide stability, and act as lenders of last resort. The Fed's tools include setting reserve requirements, though this has become less relevant with the shift to a 0% reserve requirement.
Criticisms and Alternatives
- Risk of Bank Runs: Critics argue that fractional-reserve banking makes the system vulnerable to bank runs, where too many depositors demand their money back at once, which the bank cannot cover since most of the money is loaned out.
- Vollgeld Initiative and Full-Reserve Banking: Movements like Switzerland's Vollgeld Initiative have proposed shifting to full-reserve banking, where banks must hold 100% of deposits in reserve, preventing them from creating money through lending. However, this would significantly alter how banks operate and make profits. *** Modern Adjustments**: The move to a 0% reserve requirement in the U.S. reflects a shift towards using other monetary policy tools like interest rates on reserves to control money creation and economic stability.
Real-World Implications
- Money Supply Control: While banks create money through loans, central banks like the Federal Reserve influence this through monetary policy, adjusting how much money banks can create.
- Economic Stability: The zero reserve requirement might seem to allow infinite money creation, but in reality, banks are constrained by capital requirements, risk assessments, and economic conditions.
Conclusion
Fractional-reserve banking is a dynamic system that significantly influences economic growth by expanding the money supply through debt. While it allows for economic expansion, it also introduces risks of instability, which central banks attempt to mitigate through various policy tools. Understanding this system helps demystify how money flows and grows within an economy, showcasing both its capacity for economic stimulation and its inherent risks. As we move forward, debates continue on how best to balance these aspects to foster economic stability and growth. In 2009, a new system called Bitcoin emerged that could redefine the rules for money creation.
-
 @ ba4a39ee:df9b4c6b
2024-09-04 14:23:26
@ ba4a39ee:df9b4c6b
2024-09-04 14:23:26 -
 @ 361d3e1e:50bc10a8
2024-09-04 13:54:12
@ 361d3e1e:50bc10a8
2024-09-04 13:54:12More European countries are choosing BRICS instead of the European Union
europe #turkey #serbia #brics #politics
-
 @ 5af07946:98fca8c4
2024-09-04 13:02:36
@ 5af07946:98fca8c4
2024-09-04 13:02:36 -
 @ 469fa704:2b6cb760
2024-09-04 12:07:53
@ 469fa704:2b6cb760
2024-09-04 12:07:53Unified Login Across Platforms
With Nostr, you use one login for all services, and your followers are seamlessly integrated. So you don't have start anew on every single platform. I think this is a real advantage of Nostr even for people not accustomed to Bitcoin or decentralization in general.
Value for Value (V4V) Model
Embrace the V4V principle where value is exchanged directly between users. Meaning if you find something useful or anohter nostr user was able to help you then you can simply zap him or her some Sats.
Blogging Platforms
- Habla or Yakihonne: Since joining Nostr 8 days ago, I've started blogging using Habla, which I found incredibly user-friendly. You can check out my articles directly on some clients like noStrudel, where they appear under my profile. Habla also serves as a great community explorer. Yakihonne, another comprehensive client with an integrated blog editor, caught my eye too, although it didn't sync all my Habla posts, possibly due to relay issues.
- Highlighter.com: Offers a sleek interface for reading articles. On noStrudel, articles are tucked away under the "More" menu.
Presentations
- Slidestr.net: This tool transforms your notes into a slideshow, making revisiting old notes quite entertaining.
Video Content
- Flare.pub: If you're looking for a YouTube-like experience, Flare.pub is the closest you'll get on Nostr. You can upload, watch videos, and curate playlists. Remember, since Nostr is fundamentally text-based, videos are hosted on traditional servers, but the interface remains decentralized. There's definitely room for more video content, so start creating!
Live Streaming
- Zapstream: Offers a smooth streaming experience with a fee of 10 Sats per minute to cover server costs. You can watch streams on clients like Amethyst or noStrudel.
Music and Podcasts
- Wavlake and Tunestr: Ideal for artists to share music or podcasts. Listeners can enjoy content freely or support creators via zaps, adhering to the V4V model.
Lists and Grouping
- Listr: A tool for organizing everything from regional user groups to thematic notes or hashtags. You can also follow lists created by others in the Nostr community.
Culinary Arts
- zap.cooking: A haven for aspiring or seasoned chefs, offering a plethora of recipes in a blog format. It's well-organized, allowing you to browse through different categories of recipes.
Marketplaces
- Plebian Market: Reminiscent of eBay's early days, this marketplace allows easy buying and selling among users.
Community Features
- Many clients like noStrudel, Habla, and Amethyst support community functionalities, enhancing user interaction within Nostr.
-
 @ 5954198a:0c6fa207
2024-09-04 09:21:15
@ 5954198a:0c6fa207
2024-09-04 09:21:15If you are newbie in the business world, what you really wish for? The very first thought in your mind would be reaching out to your target audience. Here, we, one of the best SEO companies in Indore brings you a complete package of all seo services under a roof. Our SEO company in Indore has become truly efficient and time-reductant, letting you expect 2x customer faster. Our SEO services in Indore allow you to promote your business not only at a city level but also globally. Now no need to worry about your business, expand it free with one of the best SEO companies in Indore. Get a chance to upscale your small size business into a big one by amplifying your reach with our SEO services in Indore. Understanding what your customer base needs is very crucial and important for us as a business entity and our knowledge and proficiently in the concern field regarded us one of the reliable seo companies in Indore. Visit: https://digi-partners.com/seo-company-in-indore/
-
 @ 06a260a2:d7a7791c
2024-09-04 08:13:22
@ 06a260a2:d7a7791c
2024-09-04 08:13:22Co je plnohodnotný bitcoinový uzel (bitcoin full node)? Je to základní prvek bitcoinové sítě. Server, na kterém běží bitcoinový klient, komunikuje s dalšími uzly v síti, udržuje kopii bitcoinového blockchainu (databáze všech potvrzených transakcí v bitcoinové síti), ověřuje nově příchozí transakce, validuje nově vytěžené bloky a zprostředkovává interakci uživatelů bitcoinu s bitcoinovou sítí. Pro těžaře zároveň připravuje šablonu nového bloku z transakcí čekajících na potvrzení. Je toho celkem dost, ne?
Satoshi Nakamoto už ve svém whitepaperu předpokládal, že každý uživatel bitcoinové sítě bude provozovat vlastní plnohodnotný uzel. Proč by to měli uživatelé bitcoinu chtít?
Proč provozovat vlastní bitcoinový uzel?
Používání vlastního plnohodnotného uzlu přináší celou řadu benefitů jak svému uživateli, tak bitcoinové siti a celému ekosystému. Pojďme se na ně podívat.
Podpora decentralizace bitcoinové sítě
BItcoinová síť je navržena jako decentralizovaná a má to své důvody. Decentralizace snižuje pravděpodobnost fatálního selhání sítě tím, že zvyšuje redundanci jejich kritických míst, kterými jsou právě uzly. Decentralizace v podobě zvýšené množstevní i geografické redundance pak chrání síť proti důsledkům přírodních katastrof, cíleným útokům hackerů nebo vládních organizací, ale i nečestnému jednání jednotlivých uživatelů sítě v podobě manipulace s bitcoinovým softwarem. Decentralizace se navíc nevztahuje pouze na fyzické uzly, ale i na celou governance - způsob řízení a rozhodování v síti. Neexistuje tak žádná centrální autorita, která by mohla svým jednáním a rozhodnutím, ať už svévolně nebo pod externím tlakem ovlivnit chování sítě.
Pokud se tedy rozhodnete provozovat vlastní uzel, zvýšíte tím antifragilitu bitcoinové sítě a stanete se jejím pravým uživatelem tak, jak to Satoshi zamýšlel.
Ověřování transakcí a validace nových bloků
Důležitým aspektem decentralizace je schopnost samostatně ověřit příchozí transakce a nově vytěžené bloky vůči platným pravidlům bitcoinové sítě bez nutnosti důvěřovat kterékoliv třetí straně. Vyjádřením tohoto principu je okřídlené "Don't trust, verify!". Každý full node obsahuje kompletní kopii bitcoinového blockchainu, databáze všech potvrzených transakcí za celou dobu jeho existence. A nejen to. Při prvním spuštění uzlu a kopírování této databáze od jiných uzlů v síti znovu ověřuje každý jednotlivý blok a transakce v něm podle existujících pravidel sítě, aby měl jistotu, že této databázi může nadále věřit. Tomuto procesu se říká synchronizace. Po jejím dokončení uzel kontroluje nově příchozí transakce i obsah a strukturu nově vytěžených bloků. Pokud zjistí porušení pravidel, odmítne je a do vlastní kopie blockchainu je nezařadí.
Jaká jsou ta pravidla? Je jich celá řada, ale mezi ta nejdůležitější patří:
- kontrola struktury transakce
- kontrola pravosti podpisů náležejícím adresám vstupů transakcí
- kontrola splnění podmínek definovaných v transakčním skriptu
- kontrola vícenásobného utracení UTXO
- kontrola struktury a velikosti nového bloku
- kontrola dodržování monetární politiky bitcoinu (velikost odměny těžaři musí odpovídat aktuální epoše)
Tato vlastnost je důležitá nejen pro vás, provozovatele vašeho uzlu, ale i pro stabilitu celé sítě. Vám umožňuje kontrolovat vaše transakce a zůstatky bez nutnosti důvěřovat jakékoliv třetí straně pouze oproti vaší vlastní kopii blockchainu. Celou síť pak chrání proti nečestnému uživateli, který by se pokusil šířit sítí neplatnou transakci (třeba podruhé utratit už jednou utracené mince) nebo se snažil připojit do blockchainu nový blok větší než povolené velikosti nebo přiznávající mu vyšší než aktuálně platnou odměnu. Takové chování uzel odmítne a není nikdo, kdo by mu v tom dokázal zabránit (je však třeba odpovědně přistupovat k výběru bitcoinového softwarového klienta - o tom více dále v textu).
Ochrana vlastního soukromí a bezpečnosti
Bitcoin není anonymní, ale pseudonymní. Všechny transakce lze v blockchainu dohledat a každý jeden satoshi lze v rámci UTXO dosledovat až k jeho coinbase transakci (okamžiku vzniku jako odměny za vytěžený blok). Transakce sice neidentifikují vlastníky jednotlivých adres, některé z nich o nich ale určité informace poskytují. Například konsolidační transakce může dle struktury podpisů prozradit, že vlastníkem vstupů je pouze jeden člověk. Nebo pokud platíte za nějakou službu na známou adresu a neutratíte kompletní UTXO, je velmi pravděpodobné, že jste vlastníkem i adresy, na kterou se posílá zbytek a to i přesto, že použijete adresu novou. Existují i další analytické postupy, které pomáhají určit vztahy mezi jednotlivými adresami a jejich vlastníky. Takže nakonec stačí prozradit vlastnictví jediné adresy a celou řadu jiných již k ní doplní odpovídající analýza nebo heuristika.
Pokud je pro vás soukromí důležité a vlastnictví bitcoinu považujete za soukromou informaci, je dobré vyvarovat se aktivitám, které by mohly prozradit váš vztah ke konkrétním bitcoinovým adresám. Mezi ně patří i přístup k blockchainu při zadávání nových transakcí, kontrole jejich stavu nebo kontrole zůstatků přes vaši peněženku nebo blockchain explorer. Použijete-li uzel třetí strany, dáváte jí možnost párovat uskutečněné transakce nebo dotazované adresy s vaší IP adresou, která o vás už lecos prozrazuje. I v případě použití Toru nebo VPN nemáte vyhráno. Pokud používáte více různých peněženek třeba pro oddělení KYC a non-KYC mincí, přístupem z jednoho místa je rovněž dáváte do vzájemné souvislosti.
Samostatným problémem je důvěra v informace, které vám uzel třetí strany poskytuje. Jsou skutečně pravdivé, transakce validní a zůstatky odpovídají realitě? Uzel třetí strany za vás sice nepodepíše transakci s vašimi prostředky, ale může vám třeba falešně tvrdit, že transakce, která na vaši adresu převádí dohodnutou platbu, je již potvrzena.
Provoz vlastního plnohodnotného uzlu pro vás tyto problémy řeší. Dotazy na zůstatky a nové transakce zadáváte přímo do vlastního bitcoinového uzlu, který je ověřuje přímo s vaší vlastní kopií blockchainu. Bez cizích očí a rizika manipulace.
Ochrana před cenzurou transakcí
Speciálním případem manipulace třetí strany s informacemi, které vám poskytuje, je cenzura transakcí a adres. Bitcoinový blockchain je transparentní, proto v něm není problém sledovat pohyb libovolných bitcoinů z jakéhokoliv důvodu. Platí to i pro bitcoiny pocházející z nějaké loupeže, podvodu či hacku. Bývají označeny jako špinavé a různé subjekty se brání manipulaci s nimi prostřednictvím blacklistů adres, přes které prošly. A pokud se dostaly do nějaké coinjoin transakce mixovací služby, mohou se na blacklist dostat i všechny adresy v transakci zúčastněné, ačkoliv neměly s původně "špinavými" bitcoiny nic společného.
Mohl bych takto pokračovat a uvádět další, ještě absurdnější, nespravedlivé příklady cenzury, vyplývající ze zlovůle mocných státních aparátů. Ale vezmu to z druhé strany. Pokud jste sběrateli Bitcoin Punků nebo obchodujete s Runama a chtěli by jste zadat svou transakci prostřednictvím mého uzlu, neuspějete také. Chráním bitcoinovou síť před spamem pomocí klienta Bitcoin Knots, který mi umožňuje takové transakce cenzurovat.
Ať tak či onak, používání vlastního plnohodnotného uzlu vás části problémů s cenzurou opět zbaví. Nikoho se nemusíte ptát, jakou transakci, pokud splňuje pravidla konsensu bitcoinové sítě, můžete zadat ke zpracování. Bohužel, je to jenom první část problému. Tou druhou částí je možná cenzura transakcí při jejich zařazování do bloků těžaři. O té se můžete více dozvědět v článku Domácí těžba bitcoinu.
Podpora bitcoinové sítě
Váš plnohodnotný bitcoinový uzel může poskytovat ostatním uzlům další užitečné služby, které posilují odolnost a decentralizaci sítě. Jsou to hlavně:
- Filtrování transakcí a bloků pro neplnohodnotné uzly a peněženky
- Poskytnutí historických bloků uzlům, které byly nějakou dobu offline nebo provádějí prvotní synchronizaci blockchainu
- Propagaci nových transakcí sítí směrem k těžařům
- Propagaci nově vytěžených bloků od těžařů k ostatním uzlům v síti
- Přenos dat mezi Clearnetem a Torem pro uzly, které jsou připojeny pouze k jedné ze sítí
Na tomto místě je ale dobré říci, že do role tranzitních uzlů (těch, které přijímají externí požadavky na spojení - mají povolen parametr
listen=1alistenonion=1) by měly být použity servery s odpovídajícím výkonem a vhodném bezpečnostním nastavení. Malý privátní full node na bázi RaspberryPi a UmbrelOS jím není.Provoz vlastního uzlu pro Lightning Network
Ligtning Network - druhá vrstva bitcoinu - přináší nezbytné škálování počtu zpracovaných transakcí a snižuje transakční poplatky. Obojí je nezbytné pro další růst adopce bitcoinu. Lightning Network (LN) tvoří síť LN uzlů, které si mezi sebou otvírají tzv. LN platební kanály, jejichž prostřednictvím směrují LN platby.
Ačkoliv jednotlivé LN platby mezi LN platebním kanály probíhají nezávisle na bitcoinovém blockchainu, otevření a zavření LN platebního kanálu je reprezentováno bitcoinovou transakcí. Z tohoto důvodu potřebují LN uzly přístup k bitcoinové síti a využívají k tomu právě bitcoinové uzly.
Pro pochopení Lightning Network doporučuji skvělou knihu Michala Nováka Lightning Network: Platby budoucnosti.
Výhody a důvody provozování vlastního LN uzlu je téma na samostatný článek, který jsem ještě nenapsal. Možná vás ale přesvědčil Michal Novák a nebo jste k rozhodnutí mít vlastní LN uzel došli jinou cestou. V takovém případě potřebujete i vlastní bitcoinový uzel.
Rozšíření znalostí a zkušeností s používáním bitcoinu
Okřídlená pravda říká, že pokud neověřujete transakce a své zůstatky na svém uzlu, nepoužíváte bitcoin, ale jste klientem někoho jiného se všemi důsledky, které to může mít. Pravdou také je, že úsilí spustit bitcoinový uzel vlastními silami vás zcela jistě mnoho nového naučí a poskytne vám na bitcoin úplně nový pohled. Skin in the game. O biozemědělství se také nejvíce dozvíte, až když zaboříte ruce do hlíny a slimáci vám sežerou úrodu. Váš pohled na svěže vypadající bio-mrkev v Lidlu již nikdy nebude stejný jako dříve.
Stavba vlastního uzlu: ano nebo ne?
Pokud vás předchozí odstavce přesvědčily, že dává smysl mít vlastní bitcoinový uzel, zbývá ještě rozhodnutí, jak jej realizovat.
Uzel by měl být v nepřetržitém provozu 24 hodin denně, 7 dní v týdnu. Jen tak může plnit svou funkci, průběžně ověřovat příchozí transakce a validovat nové bloky. Zastavení uzlu kvůli udržbě nebo z jiného důvodu je samozřejmě možné, po odstávce však uzel začne vždy synchronizovat chybějící bloky v jeho kopii blochchainu. Pokud jej tedy zastavíte na delší čas, může i následná dosynchronizace nějakou dobu trvat.
Dalším důležitým pravidlem je provozovat uzel na dedikovaném hardwaru, na kterém neběží žádný jiný, nesouvisející software. Vlastní uzel budete provozovat i kvůli ochraně vlastního soukromí a bezpečnosti a nechcete tedy zvyšovat riziko jejich ohrožení zavlečením nějaké softwarové infekce. Zároveň tak nebude bitcoinový uzel soupeřit s jinými aplikacemi o výpočetní zdroje. Protože sám není nijak zvlášť náročný, nebude tak ani zvyšovat náklady na svůj provoz.
Pro svůj provoz bitcoinový uzel potřebuje běžné CPU, na jehož výkon nejsou dnes žádné specifické požadavky. Dále přibližně 4GB paměti RAM nebo více. Potřebnou pamět nejvíce ovlivní použitý operační systém. Důležité je zabránit swapování paměti na pevný disk. A do třetice přibližně 1TB diskového prostoru. Aktuální velikost bitcoinového blockchainu (léto 2024) je necelých 700GB a roste rychlostí přibližně 230MB za den. Při zachování tohoto trendu by vám měl 1TB disk ještě pár let vydržet. Velmi často se pro uložení blockchainu doporučuje SSD disk. Já s tímto doporučením souhlasím, jeho výkon vám oproti standartním točivým diskům pomůže výrazně zkrátit potřebný čas na počáteční synchronizaci blockchainu. V běžném provozu uzlu se jeho výhody už tolik neprojeví.
Posledním předpokladem je síťové rozhraní pro přístup k internetu.
Jaké máme možnosti?
K provozu vlastního uzlu můžete použít jakýkoliv běžný a dostupný počítač, který již máte doma k dispozici, třeba i starší, protože požadavky na jeho výkon jsou skutečně minimální. Nepoužívaný notebook nebo stolní počítač mohou takto ještě dobře posloužit. Je dobré ale zamyslet se i nad ekonomikou provozu. Starší už nepoužívané herní PC se 150W zdrojem, pokud jej máte odložené někde ve sklepě, je sice zadarmo, jeho nepřetržitý provoz však již nějaké nezanedbatelné množství energie spálí.
Další možností je koupě nového levného počítače uvedených parametrů. Velmi oblíbené jsou minipočítače Intel NUC (dnes již převzal jejich výrobu ASUS). Koupit si můžete i minipočítač speciálně připravený pro provoz bitcoinového uzlu. Bude mít již nainstalovaný operační systém na linuxové bázi a většinou i některé ze základních potřebných aplikací. Takové uzly nabízí například Start9, Umbrel nebo MyNode.
Poslední možností je postavit si vhodný počítač pro provoz bitcoinového uzlu svépomocí z dostupných komponent. Výhodou takového postupu je vyšší kontrola nad jeho HW bezpečností (použité komponenty si můžete sami zvolit) a také volba jeho parametrů přesně dle vašich záměrů a potřeb. Jakou HW platformu pro jeho stavbu zvolíte je čistě na vás. Mezi nejoblíbenější však v současné době patří Raspberry Pi.
Kromě vhodného hardware budete také potřebovat vhodný operační systém. Důležitou vlastností takového operační systému je dostupnost jeho zdrojového kódu (v rámci FOSS), kvůli nezávislé kontrole jeho bezpečnosti. I v této oblasti je nabídka poměrně široká. Vybírat můžete kromě obecného linuxu a jeho známých distribucí i mezi specializovanými distribucemi pro bitcoinové uzly:
Umbrel na Raspberry Pi
Nemám k dispozici starý, nepoužívaný počítač, ani se mi nechtělo investovat do předpřipraveného řešení, a proto jsem si vybral stavbu vlastního uzlu na platformě Raspberry Pi. Jako operační systém jsem zvolil UmbrelOS. Je aktivně vyvíjen a v nedávné době prošel zásadním redesignem. Za jeho aktuální oblibou a velkým rozšířením stojí příjemné a jednoduché uživatelské rozhraní a vlastní App Store s velkým množstvím dostupných aplikací.
Návodů, jak sestavit uzel na Raspberry Pi je plný internet. Inspirovat se můžete jak u Kicoma v jeho serii videí Úvod do bitcoinu, nebo přímo na stránkách Umbrelu.
Já zvolil tyto komponenty:
- Raspberry Pi 5 8GB - 2.179,- Kč
- Raspberry Pi 27W USB-C napájecí zdroj - 349,- Kč
- Krabička pro Raspberry Pi 5 Cooling case - 299,- Kč
- 1TB Lexar NM620 - 1.497,- Kč
- Geekworm X1002 M.2 NVMe SSD HAT pro RPi 5 - 420,- Kč
- SanDisk MicroSDHC 32GB Ultra - 229,- Kč
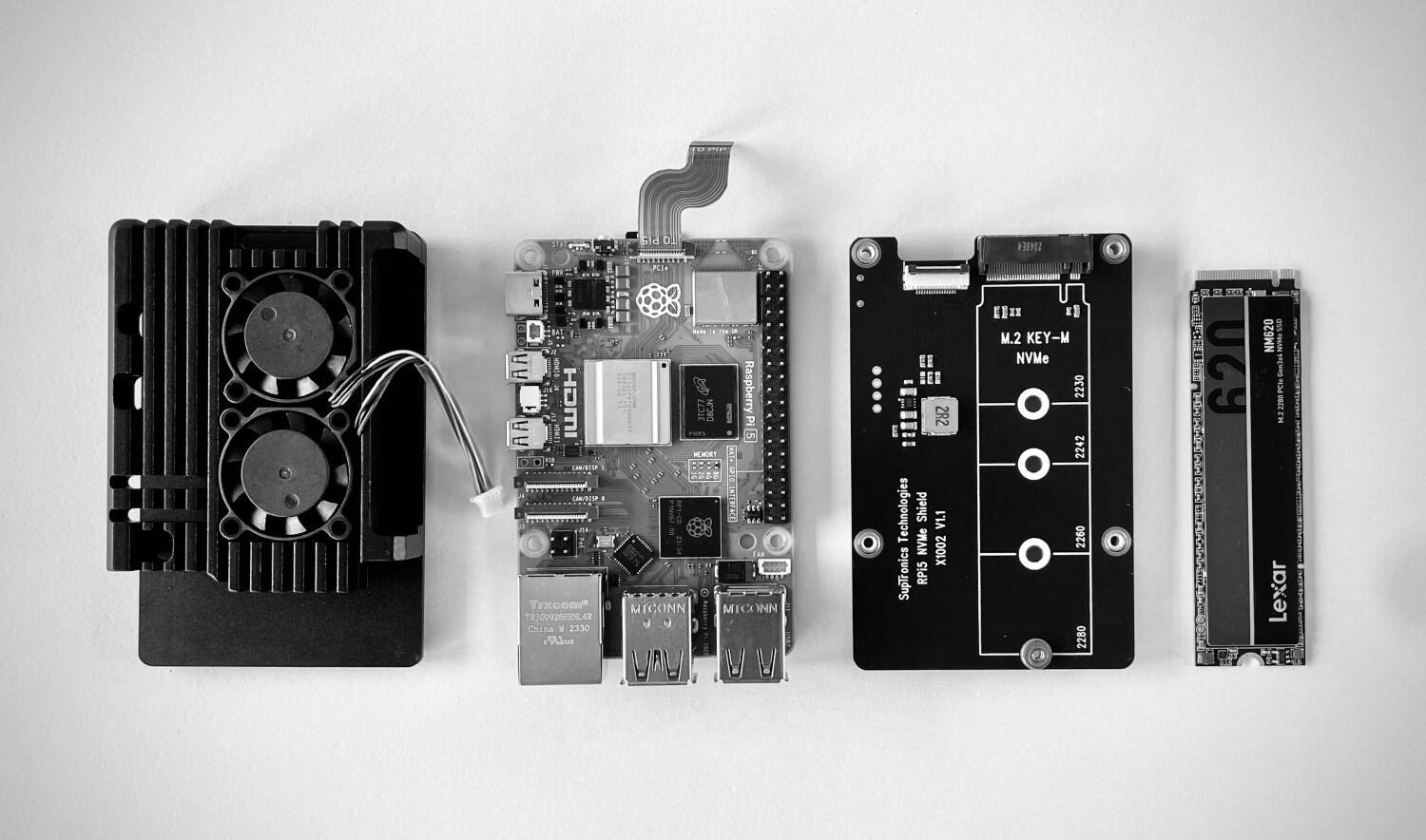
Raspberry Pi 5 je dnes již přirozenou volbou. Oproti svému předchůdci RPi 4 je jen o 100 korun dražší, nové PCI Express 2.0 rozhraní výrazně zrychluje komunikaci s diskem, což pocítíte při iniciální synchronizaci bitcoinového blockchainu.
Geekworm X1002 je jedna z možných NVMe SSD rozšiřujících karet (HAT). Zvolil jsem ji, protože se nepřipojuje k RPi shora, ale zdola a nebrání tak připojení jiné rozšiřující karty přes standardní GPIO konektor (třeba této). Navíc je na ni NVMe disk orientován směrem dolů, takže jej lze chladit spodním dílem zvolené hliníkové krabičky (pro úplnost ale dodávám, že chladit SSD disk na tomto bitcoinovém uzlu není nutné).

Sestavení celého uzlu vám nezabere více než 15 minut. Podle návodu na stránkách Umbrelu nainstalujte i verzi UmbrelOS pro vaše Raspberry Pi. Po spuštění uzlu si v nastavení nezapomeňte povolit TOR pro vzdálený přístup mimo vaši lokální siť a zkontrolovat dostupnost případných aktualizací.
A můžeme se pustit do výběru a instalace aplikací, které z vašeho uzlu udělají uzel bitcoinový.
Základní aplikace
Tou hlavní aplikací plnohodnotného bitcoinového uzlu je bitcoinový klient. V současné době existuje několik implementací bitcoinového klienta.
Pro UmbrelOS jsou však portovány pouze první dva: Bitcoin Core a Bitcoin Knots. Já si vybral ten druhý, viz. dále. Vy si však vyberte sami podle svých preferencí.
Na tomto místě musím zdůraznit, jak je dobré sledovat vývoj jednotlivých klientů a hlavně vlastností, které implementují. Pomocí bitcoinových klientů dochází v bitcoinové síti k prosazování změn. Pokud tyto změny nejsou kontroverzní a existuje na nich konsenzus, postupně je implementují všichni klienti. Pokud však kontroverzi vyvolávají nebo dokonce přinášejí změny, které pro síť představuji softfork (změnu zpětně kompatibilní) nebo hardfork (zpětně nekompatibilní změnu), můžete vybráním správného klienta nebo jeho verze o takové změně hlasovat a přijmout ji nebo odmítnout.
Výběr bitcoinového klienta a jeho vlastností je tou nejsilnější mocí, kterou jako uživatelé bitcoinové sítě máte a ultimátním důvodem pro provozování vlastního uzlu.
Bitcoin Knots
Bitcoin Knots jsou alternativní implementací bitcoinového uzlu. Vychází z Bitcoin Core a nabízí tak stejnou úroveň zabezpečení, soukromí a stability. Kromě toho však svým uživatelům rozšiřují možnosti filtrování spamu pomocí rozšířené sady parametrů a pravidel k jeho potlačení. (Více o spamu v bitcoinovém blockchainu naleznete zde.)
Ačkoliv jsou Bitcoin Knots pro instalaci k dispozici přímo v Umbrel App Store, nedoporučuji je nyní instalovat z tohoto místa. Připravený balíček obsahuje chybu, která znemožňuje následnou instalaci aplikací, které jsou na bitcoinovém uzlu závislé, jako třeba Electrum server, lightningový uzel nebo nějaký blockchain explorer. Použijte raději připravenou instalaci v alternativním komunitním app store Bitcoin Knots Community App Store.
Umbrel umožňuje svým uživatelům používat alternativní app store. Přidáte jej v nastavení Umbrel App Store (tři tečky v pravém horním rohu, volba Community App Stores). Do pole pro URL vložte link na github repositář app store, v tomto případě:
https://github.com/Retropex/Bitcoin-storea stiskněte Add. Přidaný komunitní app store otevřete tlačítkem Open. Pro RaspberryPi je určena verze Bitcoin Knots arm64.
Samotná instalace zabere několik desítek vteřin. Ihned po instalaci však začnou Bitcoin Knots stahovat a ověřovat bitcoinový blockchain, který má nyní (v červenci roku 2024) 664GB. Synchronizace blockchainu trvá podstatně déle. Její postup můžete v aplikaci sledovat. Mému RPi5 s SSD diskem připojeným přes PCI Express interface to trvalo necelých 30 hodin. O generaci starší RPi4 s SSD diskem přes USB 3.0 potřeboval přibližně 76 hodin.
Nezapomeňte si po instalaci zkontrolovat a případně nastavit preferovaná pravidla filtrování bitcoinového SPAMu (ostatně proto si instalujete Bitcoin Knots). Najdete je v nastavení (Advanced Settings) v sekci Optimization.
V základu je již nastaveno (verze 27.1.020240801):
datacarrier=1(Relay transaction with embedded data)datacarriersize=42(Maximum size of relayed transactions with embedded data)rejectparasites=1(Reject parasitic transactions)permitbaremultisig=0(Relay old type of multisig transaction)Pokud chcete filtrovat i Runes, nezapomeňte povolit:
rejecttokens=1(Reject tokens transactions)Electrum server
Použití Bitcoin Knots v současné verzi UmbrelOS 1.2.2 přináší bohužel ještě jeden problém. UmbrelOS registruje a dodržuje vzájemné deklarované závislosti aplikací. Aby vám povolil instalovat třeba blockchainový explorer Mempool, musíte mít nejprve nainstalován bitcoinový uzel, protože bez něj se Mempool nedostane k blockchainu. Bohužel v této verzi UmbrelOS trvá na konkrétní instalaci aplikace Bitcoin Node (původní Bitcoin Core). Na existenci bitcoinového uzlu je závislá i aplikace Electrs, implementace Electrum Serveru. Naštěstí lze tuto závislost jednoduše obejít.
Aplikace Electrs - Electrum Server in Rust - je reimplementací původního Electrum serveru s cílem umožnit provozovat jej s minimálními hardwarovými nároky. Server neuchovává celý blockchain (je závislý na lokální instalaci bitcoinového uzlu), ale vytváří a udržuje index všech vstupů a výstupů bitcoinových transakcí. Ten zpřístupňuje přes Electrum protokol on-chain bitcoinovým peněženkám pro dotazování na zůstatky a historii transakcí. Připojení přes Electrum server využívají hardwarové (Trezor, Ledger, ColdCard...) i mnohé softwarové peněženky (desktop i mobile).
Aplikaci Electrs nelze instalovat přímo z Umbrel App Store (viz. výše), instalaci musíme spustit ručně přes SSH terminál. Příkazový řádek v UmbrelOS spustíte přes ikonku Settings v doku úvodní obrazovky a položky menu Advanced Settings a Open Terminal. Do terminálu zadejte následující příkaz:
umbreld client apps.install.mutate --appId electrsPo několika vteřinách potvrdí úspěšnou instalaci návratová hodnota true. I Electrum Server provádí po prvním spuštění časově náročnou synchronizaci s blockchainem, při které vytváří transakční index. Instalaci aplikace spusťte až po dokončení synchronizace Bitcoin Knots.
Electrum server nabízí dva způsoby připojení bitcoinových on-chain peněženek. Buď přes lokální siť pro peněženky instalované na samotném uzlu nebo na desktopu ve stejné lokální síti. Nebo přes Tor protokol. Kromě zmíněných hardwarových peněženek může připojit peněženky Green, BlueWallet, Sparrow wallet, Specter, Nunchuk.
Mempool
Mempool je blockchainový explorer, klon pro RaspberryPi veřejně známého exploreru Mempool.space. Proč používat svůj vlastní a nikoliv ten veřejný? Protože nechcete, aby kdokoliv věděl, že jste si dohledával stav určité transakce jen několik vteřin poté, co se objevila v mempoolu a pak ještě několikrát až do okamžiku, kdy byla potvrzena v novém bloku.
Aplikace Mempool je také závislá na přítomnosti bitcoinového klienta, proto je nutné při použití Bitcoin Knots instalovat ji ručně přes SSH terminál. Potřebný příkaz vypadá takto:
umbreld client apps.install.mutate --appId mempoolProtože je Mempool závislý i na dostupnosti indexu Electrum serveru, používejte jej až poté, co aplikace Electrs tento index dokončí.
Core Lightning
Core Lightning (CLN) je jedna ze čtyř nejpopulárnějších implementací Lightning Network uzlu od společnosti Blockstream. Jedná se samozřejmě o open source a má výborně zpracovanou dokumentaci včetně celé řady návodů k použití.
Proč si vybrat Core Lightning implementaci a ne hojně rozšířenou LND? CLN má oproti LND lépe navrženou modulární architekturu a systém pluginů, které elegantně rozšiřují nebo upravují jeho funkcionalitu. Je napsán v jazyce C (LND převážně v jazyce GO), který v kompilovaném stavu nabízí efektivnější kód, uzpůsobený konkrétní HW platformě a tedy potřebuje menší dostupný výkon v porovnání s LND. Není to zásadní výhoda pro provoz privátního LN uzlu, ale na RaspberryPi přeci jen přijde vhod.
CLN implementace je také často chválena za lepší přístup k ochraně soukromí jednotlivých plateb. Používá k tomu několik technik, které výrazně komplikují ostatním uzlům na cestě sledovat informace o vašich platbách. Shadow route přidává do platební cesty zpoždění a poplatky, čímž ji virtuálně prodlouží a brání tak špiclujícím uzlům odhadovat reálnou vzdálenost k příjemci platby. Route randomization zase zajistí určitou míru náhodnosti při výběru finální platební cesty. Nemusí tak být vybrána vždy ta nejkratší respektive nejlevnější cesta, což zabrání routování všech vašich plateb přes uzel, který má uměle (záměrně) snížené poplatky pod síťový průměr. MPP - (Multi-Part-Payments) pak rozdělí vaši platbu na menší, nestejně velké části, které směruje samostatně. Zajistí tím průchodnost i větších plateb sítí a zároveň znemožňuje uzlům na cestě zjistit celkovou velikost platby.
Tím nejzásadnějším důvodem je pro mne však podpora BOLT 12 specifikace. BOLT 12 přináší takzvané offers, statické, opakovaně použitelné faktury. Ty se hodí všude tam, kde potřebujete trvale přijímat částky předem neznámé hodnoty a nechcete pro každou z nich aktivně vystavovat fakturu. Příklad? Zapy na Nostru nebo třeba anonymní výplaty z Ocean.xyz těžebního poolu. Nebo třeba příjem příspěvků v bitcoinu na váš YouTube stream. LND řeší tuto potřebu přes další nadstavbové aplikace (LNBits, LNDK) a třeba LNURL. CLN nabízí elegantní řešení přímo ve svém základu.
Stejně jako předchozí aplikace je i Core Lightning závislá na přítomnosti bitcoinového klienta. S Bitcoin Knots je třeba ji tedy instalovat ručně přes SSH terminál. Potřebný příkaz vypadá takto:
umbreld client apps.install.mutate --appId core-lightningZáloha a obnova ze zálohy
Core Lightning uzel obsahuje bitcoinovou on-chain peněženku, ze které čerpá bitcoiny pro otvírání kanálů. Po (re)instalaci aplikace vždy vygeneruje novou, proto je dobré mít zálohu, ke které se můžete vrátit v případě, že jste o tu původní přišli v důsledku havárie uzlu nebo provádíte instalaci na nový hardware a chcete obnovit již exitující uzel.
Klíče on-chain peněženky jsou uloženy v souboru
hsm_secret, který se nachází v adresářiroot/.lightning/bitcoin. Jedná se o binární, 32 byte veliký soubor. Zálohovat jej můžete buď na nějaký připojený externí disk (USB klíčenku), nebo si jeho obsah zobrazíte v hexadecimálním formátu (linuxový příkaz:xxd hsm_secret) a někam si jej bezpečně poznamenáte.Při obnově nebo po reinstalaci uzlu nahraďte nově vygenerovaný soubor
hsm_secrettím ze zálohy a restartujte aplikaci Core Lightning.Pro zacházení se souborem
hsm_secreta jeho obsahem platí stejná pravidla, jako pro zacházení s bitcoinovými privátními klíči nebo seed frází. Mají stejný význam a jejich znalost umožňuje manipulovat s prostředky na peněžence uloženými. Proto buďte opatrní.Zajímavou alternativou je možnost vygenerovat soubor
hsm_secretz existujícího BIP-39 seedu, včetně použití volitelné přístupové fráze (passphrase). To vám umožní uchovat recovery seed standartními způsoby, které používáte u své hardwarové peněženky (SeedOr Safe, Trezor Keep Metal, CryptoTag...) a v případě potřeby obnovit peněženku nebo přistupovat k bitcoinům na jejich adresách i z jiného zařízení, než je Core Lightning aplikace. Jak na to?Po instalaci Core Lightning aplikace ji zastavte (příkaz Stop v kontextovém menu nad ikonou aplikace) a spusťte si terminál v jejím kontextu (Settings > Advanced settings > Terminal > App > Core Lightning). V terminálovém okně spusťte nástroj
hsmtools parametremgeneratehsma cestou khsm_secretsouboru. V následujícím dialogu pak vyberte BIP-39 slovník a zadejte jednotlivá slova svého seedu. Nakonec můžete vložit svou volitelnou přístupovou frázi. Utilitka vygeneruje nový souborhsm_secreta uloží jej.``` root@aabbccdd0102:/# lightning-hsmtool generatehsm root/.lightning/bitcoin/hsm_secret Select your language: 0) English (en) 1) Spanish (es) 2) French (fr) 3) Italian (it) 4) Japanese (jp) 5) Chinese Simplified (zhs) 6) Chinese Traditional (zht) Select [0-6]: 0 Introduce your BIP39 word list separated by space (at least 12 words):
Warning: remember that different passphrases yield different bitcoin wallets. If left empty, no password is used (echo is disabled). Enter your passphrase: New hsm_secret file created at root/.lightning/bitcoin/hsm_secret Use the
encryptcommand to encrypt the BIP32 seed if needed root@aabbccdd0102:/#```
Opusťte terminál a znovu spusťte aplikaci Core Lightning.
Kromě bitcoinové on-chain peněženky je nutné zálohovat i otevřené lightning network kanály. Core Lightning aplikace uchovává informace o otevřených kanálech v souboru
emergency.recover. Ten se nachází také v adresářiroot/.lightning/bitcoin. Mění se pouze v souvislosti s otevřením nebo uzavřením kanálu, proto doporučuji provést jeho zálohu vždy po takové operaci.Soubor
emergency.recoverneobsahuje informace o stavu kanálu. Při obnově dojde vždy k uzavření všech kanálů a vypořádání jejich balancí.Jak kopírovat uvedené soubory z vašeho Umbrelu na Raspberry Pi na USB disk? UmbrelOS pro to zatím nemá podporu ve svém UX, ale pomůže vám opět terminál a následující návod.
```
Najděte LABEL vašeho připojeného USB disku
Nejprve si vylistujte všechna existující bloková úložiště příkazem
sudo blkid
Fyzicky připojte váš USB disk s vylistujte stejným příkazem úložiště ještě jednou
sudo blkid
Podívejte se, které přibylo a najděte jeho LABEL. Řekněme, že se jmenuje "sda1"
Vytvořte si adresář pro zálohu, nazvěme jej třeba "/backup"
sudo mkdir /backup
Připojte váš identifikovaný USB disk přes jeho LABEL k vytvořenému adresáři
sudo mount /dev/sda1 /backup
Zkopírujte soubory hsm_secret a emergency.recover do adresáře "/backup"
sudo cp /home/umbrel/umbrel/app-data/core-lightning/data/lightningd/bitcoin/emergency.recover /backup
sudo cp /home/umbrel/umbrel/app-data/core-lightning/data/lightningd/bitcoin/hsm_secret /backup
Ukliďte po sobě - nejprve odpojte váš USB disk od adresáře "/backup"
sudo umount /backup
A následně zrušte adresář "/backup"
sudo rmdir /backup
```
Při obnově ze zálohy budete postupovat úplně stejně, jen příkazy pro kopírování budou směřovat opačným směrem
```
Kopírování záloh z připojeného adresáře "/backup" do cílového adresáře CLN
sudo cp /backup/emergency.recover /home/umbrel/umbrel/app-data/core-lightning/data/lightningd/bitcoin
sudo cp /backup/hsm_secret /home/umbrel/umbrel/app-data/core-lightning/data/lightningd/bitcoin ```
Kromě statické zálohy kanálů umožňuje CLN i průběžné zálohování jejich stavu prostřednictvím zálohy interní databáze do druhé, bezpečné lokality (na jiný disk). Databáze se nachází v souboru
lightningd.sqlite3ve stejném adresáři, jakohsm_secretneboemergency.recover. CLN lze dokonce nastavit tak, aby veškeré updaty do této databáze průběžně zapisoval i na druhou lokalitu. Bohužel však v současné verzi UmbrelOS toto není možné.UmbrelOS ve stávající verzi nepodporuje připojení více disků současně. Nelze tedy průběžně zálohovat data na druhý disk. Přestože můžete během provozu druhý disk připojit a přes terminál na něj data zkopírovat, nikdy takový disk nenechávejte připojen trvale. Po restartu uzlu může zabránit korektnímu nastartování Umbrelu a nainstalovaných aplikací.
Otevření kanálů
Lightningový uzel pro vás začne být užitečný teprve poté, co jej propojíte s LN sítí prostřednictvím platebních kanálů. Otevření kanálu je relativně jednoduché a lze jej docílit v podstatě dvěma způsoby.
- Otevřete kanál vy z vašeho uzlu
- Požádáte jiný uzel, aby otevřel kanál směrem k vám
Existují i další způsoby, ale pro jednoduchost si vystačíme s těmito dvěma. Důležité je si uvědomit, že uzel, který kanál otvírá, jej také musí naplnit bitcoiny na požadovanou kapacitu. Po otevření kanálu budou zároveň všechny bitcoiny (likvidita) na straně toho, kdo jej otevřel.
V prvním případě tedy nejprve pošlete na bitcoinovou peněženku vašeho CLN uzlu nějaké prostředky (tlačítko Deposit vám zobrazí příslušnou bitcoinovou adresu). Po potvrzení depositní transakce v blockchainu (můžete ji sledovat ve svém Mempool exploreru) můžete tlačítkem Open Channel požádat o otevření kanálu s vybraným LN uzlem. Ten si můžete vybrat dle své preference v některé z veřejných databází, jako je Amboss.Space nebo 1ml, nebo přímo na MemPool.Space v sekci lightning network.
Strategií pro výběr je opět celá řada, ale pro domácí uzel neuděláte chybu výběrem uzlu od některého z velkých hráčů, kteří jsou na kvalitě svého připojení do LN sítě obchodně zainteresováni. Poskytovatelé peněženek (ACINQ, WalletOfSatoshi, Blockstream, Alby, ...), burzy, směnárny a platební brány (Anycoin, Confirmo, Binance, Kraken, ...), poskytovatelé služeb na LN sítí (LOOP, Boltz, Strike). Ale třeba i SatoshiLabs nebo GeneralBytes. Můžete se u nich spolehnout na dostatečnou kapacitu, konektivitu i stabilitu provozu. Pozor si dejte pouze na požadovanou minimální velikost kanálu.
Do pole Node Id: vložte adresu vybraného uzlu (ve formátu PubKey@IP:Port) a do pole Amount: pak požadovanou velikost kanálu (částka bude stržena z vaší bitcoiové peněženky a ponížena o poplatky za otvírací transakci). Důležitý je přepínač Announce. Ten určuje, zda bude váš kanál veřejný a tedy k dispozici celé síti pro směrování plateb, nebo soukromý, o jehož existenci budete vědět pouze vy a připojený uzel a pro směrování cizích plateb nebude využíván. Pokud chcete využívat svůj LN uzel pouze pro své soukromé platby, doporučuji otevřený kanál do sítě neanoncovat. Zjednodušíte si práci s jeho balancováním, protože budete reagovat pouze na vlastní pohyby v jednotlivých kanálech.
Takto otevřený kanál bude mít likviditu na vaší straně (odchozí likvidita) a bude tedy primárně sloužit na posílání plateb z vašeho uzlu. Minimálně do doby, než si odesláním dostatečné částky vytvoříte prostor i pro příjem.
Druhý způsob, požádat jiný uzel, aby otevřel kanál k vám, vám přinese příchozí likviditu, tedy schopnost přijímat platby až do velikosti takového kanálu. Můžete se domluvit s kamarádem, který již uzel provozuje, aby k vám kanál otevřel. Nebo využít některou z nabídek jiných uzlů, která vám kanál otevřou za úplatu. Vybrat si můžete na tržištích LnRouter nebo LnBig. Lightning Network Plus nabízí možnost otevřít si kanály v takzvaném Liquidity Swapu. Uzly, které se jej účastní, si otevřou kanály vzájemně v kruhu. Každý tedy za otevření kanálu jedním směrem získá i kanál stejné velikosti s příchozí likviditou.
Nejjednodušším způsobem, jak získat příchozí likviditu, je otevření dalšího kanálu s vybraným uzlem a následné odeslání všech svých prostředků v tomto kanále na svou jinou lightning peněženku nebo swap out službu (služba, která příchozí prostředky uloží na vámi zadanou bitcoinovou adresu. Například Boltz.Exchange).
Nezapomeňte po otevření všech kanálů provést jejich zálohu dle postupu uvedeného výše.
Ride the Lightning
Ride the Lightning (RTL) je nástroj pro správu vašeho lightningového uzlu. Ačkoliv vlastní uzel, v našem případě aplikace CLN, nabízí jednoduché GUI pro svou obsluhu a v mnoha případech stačí (zvláště při otevření pouze několika privátních kanálů), některé parametry a pokročilé vlastnosti kanálů přes něj nejsou dostupné. Aplikace RTL nabízí webové rozhraní k většině těchto parametrů a další doplňkové služby pro zajištění likvidity vašich kanálů, jejich rebalancing a převod prostředků na on-chain adresy (swap out). Navíc nabízí přehledné statistiky a grafy využití uzlu, které lze využít pro optimalizaci nastavení CLN.
Aplikaci RTL můžete nainstalovat přímo z Umbrel App Store. Pozor, jsou tam uvedeny dvě verze, každá pro jednu z dostupných implementací lightning uzlu. Pokud jste nainstalovali Core Lightning, vyberte si Ride the Lightning (Core Lightning).
Máte-li otevřenu konzoli, můžete ji samozřejmě nainstalovat i z příkazového řádku.
umbreld client apps.install.mutate --appId core-lightning-rtlPřihlášení do aplikace je trochu nestandardní. RTL vyžaduje heslo, ale správu aplikačních hesel řídí UmbrelOS. Vaše heslo do aplikace naleznete na stránce RTL v App store (Default password). Objeví se tam po nainstalování aplikace, je kryptograficky odvozené od unikátního seedu vaší instalace uzlu a nelze jej změnit. Umbrel touto politikou reagoval na případy vykradení peněženek přes uniklou statickou TOR adresu aplikací jako RTL nebo Thunderhub, ke kterým neměli uživatelé změněné defaultní hesla.
Public Pool
Esenciální aplikace pro všechny, kteří doma kromě vlastního bitcoinového uzlu provozují také nějaký domácí miner. Public Pool je navzdory svému názvu privátní domácí těžební pool pro solo mining. Bez poplatků a s jistototu, že veškeré případně vytěžené odměny skončí na vaší vlastní bitcoinové adrese.
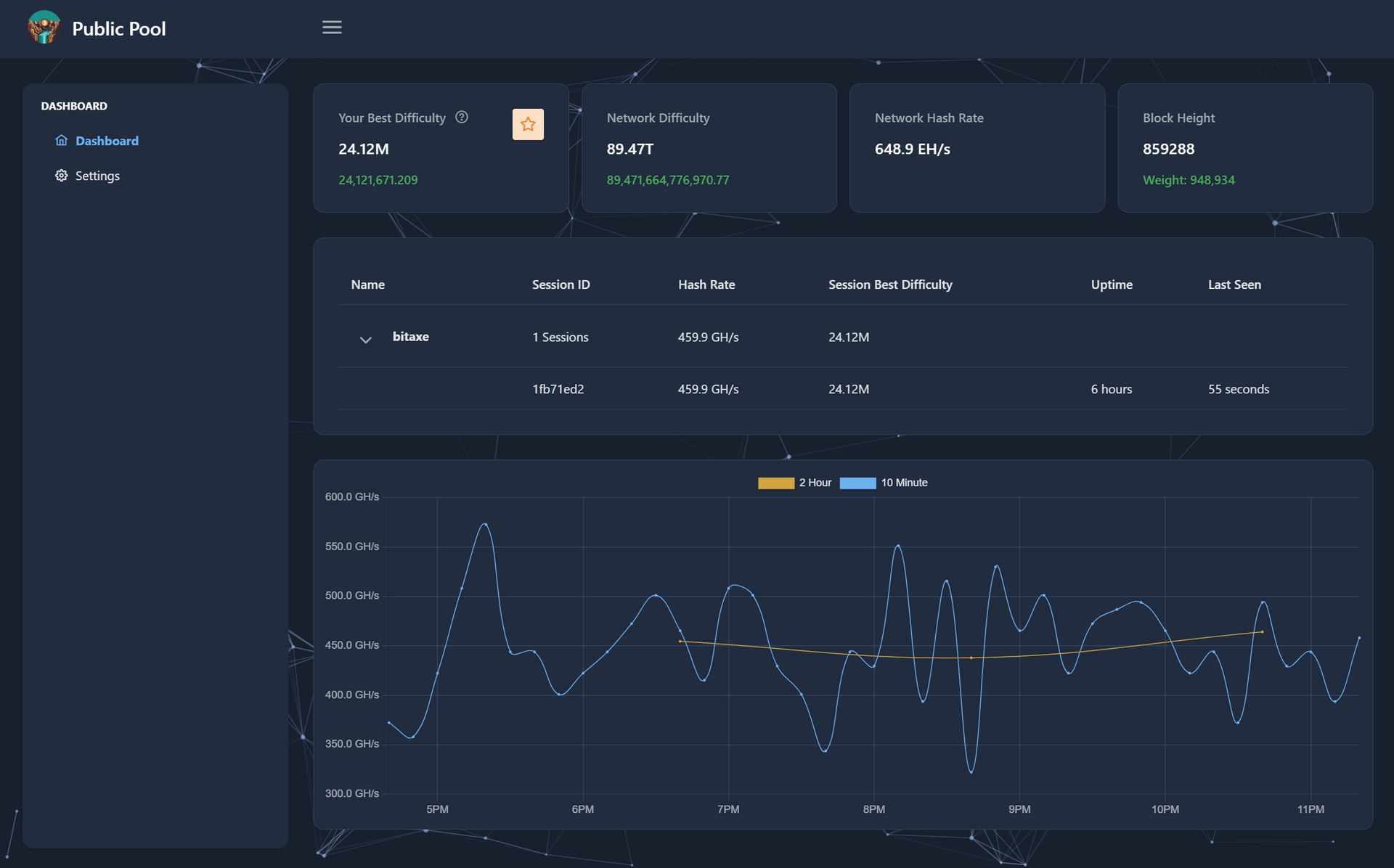
Instalace opět kvůli závislosti na Bitcoin Knots přes příkazový řádek:
umbreld client apps.install.mutate --appId public-poolKonfiguraci pro připojení vašeho mineru najdete hned v úvodu GUI po spuštění aplikace.
Zkušenosti z provozu
Provozování vlastního uzlu není nikterak náročnou činností a s trochou nadsázky lze říci, že se obejde bez složité údržby. Ve výše uvedené konfiguraci může běžet bez nutnosti zásahu i několik měsíců. Přesto je dobré se ke svému uzlu čas od času vrátit a jednoduchou údržbu provést.
Předně provádějte pravidelné upgrady nainstalovaných aplikací. Nové verze se objevují celkem pravidelně a přinášejí většinou opravy nalezených chyb a bezpečnostních děr, ale také nové funkcionality, které rozšiřují jejich možnosti použití. Doporučuji neinstalovat bez rozmyslu, ale přečíst si dostupné release notes (popis změn nové verze). Zvláště u bitcoinového uzlu (ať už Bitcoin Knots nebo Bitcoin Core), protože nové verze mohou obsahovat změny, které mění chování bitcoinové sítě a tedy i bitcoinu. Jejich výběrem a (ne)instalací hlasujete o tom, jak by měl bitcoin podle vás vypadat. Přečtěte si knihu The Blocksize Wars k lepšímu pochopení, co je tím myšleno.
Ze stejných důvodů pravidelně aktualizujte i operační systém UmbrelOS. Nové verze vycházejí přibližně jednou za čtvrt roku a vlastnosti operačního sytému většinou výrazně vylepšují.
Důležitou aktivitou je i záloha lightning uzlu a jeho kanálů vždy, když nějaký otevřete nebo zavřete. To se naštěstí neděje příliš často, většinou vystačíte s jednotkami otevřených kanálů i po dobu několika let. Výjimkou je však provoz veřejného lightning uzlu pro směrování plateb v síti. Takový uzel již vyžaduje pravidelnou údržbu kanálů, správu jejich poplatků a vyhodnocování jejich efektivity. To vede k zavírání neefektivních kanálů a otvírání nových směrem k lukrativním uzlům.
Raspberry Pi a UmbrelOS není vhodnou platformou pro provoz veřejných lightning uzlů a směrování plateb v síti. Nevyhovuje celkovým výkonem a bezpečností a neumožňuje nastavit adekvátní SLA pro provoz takové služby. Proto ji k tomuto účelu důrazně nedoporučuju.
Nezapomeňte svůj uzel čas od času restartovat. Mně se osvědčilo provést restart ne déle než po půl roce provozu. Dlouhodobý nepřetržitý provoz jakéhokoliv softwaru hromadí důsledky chyb v něm existujících (a každý takové obsahuje), které se časem zcela určitě nějak projeví. Je dobré těmto projevům předcházet právě restartem celého uzlu. Restart vždy provádějte kontrolovaně přes příslušné tlačítko v menu Settings Umbrel OS, nikdy uzel natvrdo nevypínejte odstavením od napájení. Umožníte všem aplikacím korektně se ukončit, aby následně mohly korektně nastartovat. To samé platí i pro vypínání uzlu v případě potřeby.
Vlastní bitcoinový uzel? Ano!
Pokud jste dočetli až sem, pravděpodobně stavbu a provoz vlastního uzlu vážně zvažujete. Rád bych vás v tom podpořil. Ano, dává to smysl. A přestože si myslím, že nejvíce zážitků a pozitivní energie získáte při stavbě a zprovoznění vlastního uzlu (třeba tak, jak je popsáno v tomto článku), nezatracuji ani pořízení již předpřipraveného řešení, které stačí připojit do zásuvky a zapnout. Stále vám zbyde spoustu zábavy s nastavením jednotlivých aplikací.
Staňte se součástí bitcoinové sítě a podpořte její původní étos! Staňte se Bitcoinerem!
-
 @ a012dc82:6458a70d
2024-09-04 08:09:45
@ a012dc82:6458a70d
2024-09-04 08:09:45Table Of Content
-
The Energy Consumption of Bitcoin Mining
-
The Environmental Impact of Bitcoin Mining
-
Innovations in Green Energy
-
The Advantages of Using Green Energy in Bitcoin Mining
-
The Challenges of Using Green Energy in Bitcoin Mining
-
Conclusion
-
FAQ
Bitcoin is a digital currency that has gained a lot of popularity over the years, and it's being used for various transactions. However, mining bitcoin requires a lot of energy, and this has raised concerns about the sustainability of bitcoin mining and its impact on the environment. In recent years, there have been efforts to make bitcoin mining more sustainable by using renewable energy sources. This article aims to assess the sustainability of bitcoin mining and its impact on green energy.
The Energy Consumption of Bitcoin Mining
Bitcoin mining is a process that involves solving complex mathematical problems that require a lot of computing power. This process consumes a significant amount of energy, and the energy consumption of bitcoin mining is growing every day. According to recent studies, the energy consumption of bitcoin mining is estimated to be around 121 terawatt-hours (TWh) per year, which is more than the energy consumption of some countries.
The Environmental Impact of Bitcoin Mining
The energy consumption of bitcoin mining has a significant impact on the environment. Most of the energy used in bitcoin mining comes from non-renewable sources such as coal and natural gas, which release greenhouse gases into the atmosphere. This contributes to climate change, which has adverse effects on the environment and human health.
Innovations in Green Energy
In recent years, there have been innovations in green energy that can be used to make bitcoin mining more sustainable. These innovations include renewable energy sources such as solar, wind, and hydropower. The use of these renewable energy sources can reduce the environmental impact of bitcoin mining and make it more sustainable.
The Advantages of Using Green Energy in Bitcoin Mining
Using green energy in bitcoin mining has several advantages. Firstly, it reduces the environmental impact of bitcoin mining by reducing greenhouse gas emissions. Secondly, it can make bitcoin mining more cost-effective, as the cost of renewable energy sources is declining. Thirdly, it can increase the adoption of renewable energy sources and drive innovation in the renewable energy sector.
The Challenges of Using Green Energy in Bitcoin Mining
There are also challenges associated with using green energy in bitcoin mining. Firstly, the availability of renewable energy sources may not be consistent, as solar and wind energy are dependent on weather conditions. This can affect the profitability of bitcoin mining, as miners may need to switch to non-renewable energy sources during periods of low renewable energy availability. Secondly, the initial investment required to set up renewable energy infrastructure can be high, which may deter some miners from switching to green energy sources.
Conclusion
Bitcoin mining has a significant impact on the environment, but there are efforts to make it more sustainable by using renewable energy sources. Using green energy in bitcoin mining has several advantages, including reducing greenhouse gas emissions and driving innovation in the renewable energy sector. However, there are also challenges associated with using green energy in bitcoin mining, such as the inconsistent availability of renewable energy sources and the high initial investment required to set up renewable energy infrastructure. Overall, assessing the sustainability of bitcoin mining and its impact on green energy is a complex issue that requires a comprehensive evaluation of various factors.
FAQ
Can bitcoin mining be done without consuming a lot of energy? No, bitcoin mining requires a significant amount of energy to solve complex mathematical problems and validate transactions.
Is bitcoin mining harmful to the environment? Yes, bitcoin mining consumes a lot of energy, most of which comes from non-renewable sources that release greenhouse gases into the atmosphere.
What are the benefits of using renewable energy sources in bitcoin mining? Using renewable energy sources can reduce the environmental impact of bitcoin mining, make it more cost-effective, and drive innovation in the renewable energy sector.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 5954198a:0c6fa207
2024-09-04 07:39:29
@ 5954198a:0c6fa207
2024-09-04 07:39:29Even after posting stuff related to your business on your social media, your followers still haven’t increased much?
Does even after following a social media strategy, the number of sales hasn’t increased much? If your answer is yes, then you need to hire a Social Media Marketing Company in Indore. India’s cleanest city Indore is a city of dreams that also cleans the businesses if not run properly. Businesses aren’t that easy to run, maybe when your business grows, things work pretty well for your business, but the initial days of your business might not be like what you’ve imagined.
Starting a business from the scrap can be a very challenging thing to do. But if you have an idea that’s going to run your business, dedication to make your dream come true, then no one can stop you from achieving your dream of starting your business. Digi Partners is a Social Media Marketing Company in Indore that works for companies like yours on expanding their businesses. Digi Partners being an SMM company in Indore, have a team of professionals trained in graphic designing, content writing, digital marketing, strategy making, video producing, and editing. Graphic design plays a very vital role in social media marketing. Visit: https://digi-partners.com/social-media-marketing-company-indore/
-
 @ d830ee7b:4e61cd62
2024-09-04 07:29:41
@ d830ee7b:4e61cd62
2024-09-04 07:29:41Bitcoin ถือกำเนิดขึ้นในปี 2009 จากวิสัยทัศน์ของ Satoshi Nakamoto บุคคลหรือกลุ่มบุคคลปริศนา ที่ใฝ่ฝันถึง "เงินสดดิจิทัล" อิสระไร้พรมแดน ไร้การควบคุมจากรัฐบาล
ในช่วงแรกเริ่ม Bitcoin เป็นเสมือนเพชรดิบที่ซ่อนตัวอยู่ในเงามืด เป็นที่รู้จักกันเฉพาะในกลุ่มเล็กๆ ที่หลงใหลในเทคโนโลยีและศักยภาพอันไร้ขีดจำกัดของมัน
แต่แล้ว Bitcoin ก็เริ่มฉายแสงเจิดจรัส ดึงดูดความสนใจจากผู้คนทั่วโลก ราคาพุ่งทะยานอย่างรวดเร็ว บริษัทและบริการต่างๆ ผุดขึ้นมาราวกับดอกเห็ด
ทว่า.. เส้นทางสู่ความสำเร็จของ Bitcoin ไม่ได้โรยด้วยกลีบกุหลาบ Bitcoin ยังต้องเผชิญกับความท้าทายมากมาย ทั้งปัญหาทางเทคนิค ความขัดแย้งภายในชุมชนและการต่อสู้แย่งชิงอำนาจ
Blocksize Limit จุดเริ่มต้นของความขัดแย้งและสงคราม Big Blocks VS Small Blocks
ย้อนกลับไปในปี 2010 Satoshi Nakamoto ได้เพิ่ม "Blocksize Limit" ซึ่งเป็นข้อจำกัดขนาดของ Block ใน Bitcoin ไว้ที่ 1MB เพื่อป้องกันการโจมตีทางไซเบอร์ในยุคแรกเริ่ม
แต่เมื่อ Bitcoin ได้รับความนิยมมากขึ้น ธุรกรรมก็เพิ่มขึ้นอย่างรวดเร็ว Blocksize Limit 1MB เริ่มจะกลายเป็นปัญหา..
เกิดการถกเถียงอย่างดุเดือดในชุมชน Bitcoin ว่าควรเพิ่ม Blocksize Limit หรือไม่
ฝ่าย "Small Blockers" นำโดยนักพัฒนา Bitcoin Core ส่วนใหญ่ เชื่อว่า Blocksize Limit ควรคงที่ เพื่อรักษาความปลอดภัยและการกระจายอำนาจ พวกเขากล่าวอ้างว่า Big Blocks จะทำให้ Bitcoinรวมศูนย์อยู่ที่ Miners รายใหญ่ และยากต่อการรัน Full Nodes สำหรับผู้ใช้งานทั่วไป ซึ่งจะบั่นทอนความเป็น Decentralized ของ Bitcoin
ฝ่าย "Big Blockers" นำโดย Gavin Andresen ผู้สืบทอดตำแหน่งจาก Satoshi Nakamoto และ Mike Hearn เชื่อว่า Bitcoin ควรเติบโตอย่างไม่จำกัด "Big Blocks" คือคำตอบ พวกเขามองว่า Small Blocks จะทำให้ Bitcoin ไม่สามารถรองรับธุรกรรมที่เพิ่มขึ้น ค่าธรรมเนียมจะพุ่งสูงและ Bitcoin จะไม่สามารถใช้งานได้จริงในชีวิตประจำวัน..
ความขัดแย้งนี้สะท้อนให้เห็นถึงวิสัยทัศน์ที่แตกต่างกัน
Gavin Andresen ผู้ที่เคยได้รับความไว้วางใจจาก Satoshi รู้สึกผิดหวังที่ Bitcoin Core ไม่ยอมเพิ่ม Blocksize Limit เขาเชื่อมั่นว่า Bitcoin ควรเป็นระบบการชำระเงินที่ใช้งานได้จริง รวดเร็ว และมีค่าธรรมเนียมต่ำ
Blockstream บริษัทผู้ทรงอิทธิพลและความกังวลเรื่องผลประโยชน์ทับซ้อน
ปี 2014 กลุ่มนักพัฒนา Bitcoin Core บางส่วนได้ก่อตั้งบริษัท Blockstream (นำโดย Adam Back) พวกเขาเน้นการพัฒนาเทคโนโลยี Blockchain และกลายเป็นที่มถกเถียงว่าอิทธิพลอย่างมากต่อ Bitcoin Core
Blockstream สนับสนุน "Small Blocks"
เช่นเดียวกับ Bitcoin Core พวกเขาพัฒนา "Sidechains" ซึ่งเป็น Blockchain แยกต่างหากที่เชื่อมต่อกับ Bitcoin เช่น Liquid Network Sidechains ซึ่งช่วยให้ Blockstream สามารถเก็บค่าธรรมเนียมจากธุรกรรมและขายบริการให้กับองค์กรหรือบริษัทต่างๆ ได้
ความสัมพันธ์อันใกล้ชิดระหว่าง Blockstream และ Bitcoin Core ทำให้เกิดความกังวลขึ้นในชุมชน Bitcoin ในขณะนั้นว่า Blockstream อาจมีผลประโยชน์ทับซ้อนและต้องการให้ Bitcoin คงขนาดเล็ก เพื่อผลักดันให้คนใช้งาน "Sidechains" ของพวกเขา
BitcoinXT และ Bitcoin Classic ความพยายามแก้ไข Blocksize ที่ถูกต่อต้าน
ปี 2015 Mike Hearn และ Gavin Andresen ตัดสินใจเสนอทางออกด้วยการสร้าง "BitcoinXT" ซอฟต์แวร์ Bitcoin เวอร์ชั่นใหม่ที่ เพิ่ม Blocksize Limit เป็น 8MB
แต่ BitcoinXT ถูกต่อต้านอย่างรุนแรงจากฝ่าย Small Blockers
Bitcoin.org เว็บไซต์หลักของ Bitcoin และ r/Bitcoin ฟอรัมหลักของ Bitcoin ได้เซ็นเซอร์ BitcoinXT ไม่ให้ปรากฏ เกิดการโจมตีทางไซเบอร์ที่มุ่งเป้าไปที่ BitcoinXT โดยตรง
Coinbase บริษัทแลกเปลี่ยน Cryptocurrency รายใหญ่ ประกาศสนับสนุน BitcoinXT แต่กลับถูกถอดออกจาก Bitcoin.org
ต่อมา Bitcoin Classic ถูกสร้างขึ้นเป็นอีกหนึ่งทางเลือก แต่ก็ล้มเหลวเช่นกัน
เนื่องจาก Bitcoin Core ยังคงมีอิทธิพลอย่างมากในชุมชน Bitcoin ในช่วงเวลานั้น..
Hong Kong Agreement และ New York Agreement ความพยายามประนีประนอมที่ไม่ลงตัว
ปี 2016 และ 2017 เกิดความพยายามในการประนีประนอมระหว่างฝ่าย Small Blocks และ Big Blockers ถึงสองครั้ง คือ "Hong Kong Agreement" และ "New York Agreement"
ทั้งสองข้อตกลงมีเป้าหมายที่จะเปิดใช้งาน SegWit และ เพิ่ม Blocksize Limit เป็น 2MB แต่ Bitcoin Core ไม่ทำตามสัญญาในการเพิ่ม Blocksize Limit ทำให้ข้อตกลงล้มเหลว
ความล้มเหลวของข้อตกลงทั้งสอง สะท้อนให้เห็นถึงความไม่ไว้วางใจระหว่างสองฝ่าย และความยากลำบากในการหาจุดร่วมที่ทุกฝ่ายยอมรับ
SegWit ก้าวสำคัญของ Bitcoin และจุดกำเนิดของ Bitcoin Cash
ในที่สุด SegWit ก็ถูกเปิดใช้งานบน Bitcoin ในเดือนสิงหาคม 2017
SegWit เป็น Soft Fork ที่เปลี่ยนแปลงวิธีการจัดเก็บข้อมูลใน Block เพื่อเพิ่มประสิทธิภาพและความปลอดภัย
SegWit ช่วยแก้ปัญหา "Transaction Malleability" ซึ่งเป็นช่องโหว่ด้านความปลอดภัย และปูทางไปสู่การพัฒนา "Layer 2 solutions" เช่น Lightning Network ในเวลาต่อมา..
อย่างไรก็ตาม.. กลุ่ม "Big Blockers" มองว่า SegWit ไม่ใช่ทางออกที่แท้จริงสำหรับปัญหาการขยายขนาด (พวกเขาต้องการขยายขนาดบล็อกบนเลอเยอร์ฐาน) พวกเขาไม่พอใจที่ Bitcoin Core ไม่ทำตามสัญญาในการเพิ่ม Blocksize Limit
ในเดือนสิงหาคม 2017 กลุ่ม "Big Blockers" ได้ทำการ "Hard Fork" Bitcoin เพื่อสร้าง "Bitcoin Cash (BCH)" ซึ่งอ้างว่ามุ่งสืบทอดจุดมุ่งหมายดั้งเดิมของ Bitcoin ในฐานะ "เงินสดดิจิทัล"
ความเสี่ยงด้านความปลอดภัย Bug ร้ายแรงใน Bitcoin Core และบทเรียนที่ได้รับ
ในเดือนกันยายน 2018 Awemany นักพัฒนา BCH ค้นพบ Bug ร้ายแรงใน Bitcoin Core (CVE-2018-17144) ซึ่งอาจทำให้เกิดภาวะเงินเฟ้อได้
Bug นี้เกิดจากความผิดพลาดในการเขียนโค้ด และอาจทำให้ผู้ไม่หวังดีสามารถสร้าง Bitcoin ปลอมขึ้นมาได้
Awemany ได้แจ้งเตือนนักพัฒนา Bitcoin Core อย่างเงียบๆ แทนที่จะใช้ประโยชน์จาก Bug นี้ แสดงให้เห็นถึงความรับผิดชอบของเขา และ Bug นี้ได้รับการแก้ไขอย่างรวดเร็ว
เหตุการณ์นี้แสดงให้เห็นถึงความสำคัญของการตรวจสอบโค้ดอย่างละเอียด และความจำเป็นของการมีนักพัฒนาจากหลายฝ่ายเพื่อช่วยกันตรวจสอบความถูกต้องของโค้ด
นอกจากนี้.. ยังเป็นเครื่องเตือนใจว่าแม้แต่ระบบที่ถูกออกแบบมาอย่างดีก็ยังมีความเสี่ยงด้านความปลอดภัย
Bitcoin Cash แตกแยก การ Hard Fork ครั้งที่สอง และบทบาทของ Craig Wright
ในเดือนพฤศจิกายน 2018 Bitcoin Cash (BCH) ได้แตกออกเป็นสองสาย คือ Bitcoin ABC (BCH) และ Bitcoin SV (BSV)
การ Hard Fork นี้เกิดจากความขัดแย้งระหว่างกลุ่มนักพัฒนา Bitcoin ABC นำโดย Amaury Séchet และกลุ่ม Bitcoin SV นำโดย Craig Wright ผู้ที่อ้างว่าเป็น Satoshi Nakamoto 🤔
ความขัดแย้งหลักคือเรื่องขนาดของ Block และทิศทางการพัฒนา Bitcoin Cash
กลุ่ม Bitcoin SV ต้องการเพิ่มขนาด Block อย่างมาก ในขณะที่กลุ่ม Bitcoin ABC ต้องการปรับปรุง Bitcoin Cash ในด้านอื่นๆ เช่น Smart Contracts
Craig Wright มีบทบาทสำคัญในการผลักดัน Bitcoin SV เขาเชื่อมั่นว่า Bitcoin ควรเป็นไปตามวิสัยทัศน์ดั้งเดิมของ Satoshi Nakamoto โดยเน้นที่การเป็น "เงินสดอิเล็กทรอนิกส์แบบ peer-to-peer"
การ Hard Fork นี้แสดงให้เห็นถึงความหลากหลายของความคิดเห็นในชุมชน Cryptocurrency และความยากลำบากในการหาจุดร่วมที่ทุกฝ่ายยอมรับ
นอกจากนี้.. ยังสะท้อนให้เห็นถึงความท้าทายในการกำหนดทิศทางของ Cryptocurrency ในอนาคตอีกด้วย
Bitcoin ในปัจจุบัน เส้นทางสู่ทองคำดิจิทัล และวิวัฒนาการของเทคโนโลยี
หลังจากการ Hard Fork ของ Bitcoin Cash
Bitcoin ได้ก้าวเข้าสู่ยุคใหม่ Bitcoin ได้รับการยอมรับมากขึ้นในวงกว้าง มีมูลค่าตลาดสูง และถูกมองว่าเป็น "ทองคำดิจิทัล" ที่สามารถใช้เก็บรักษามูลค่าในระยะยาว (Store of Value)
การพัฒนา Lightning Network เป็นก้าวสำคัญในการแก้ปัญหาเรื่องค่าธรรมเนียมและความเร็วในการทำธุรกรรม
Lightning Network เป็น "Second Layer" ที่สร้างขึ้นบน Bitcoin Blockchain ช่วยให้สามารถทำธุรกรรมได้รวดเร็วขึ้น มีค่าธรรมเนียมต่ำ และมีความเป็นส่วนตัวสูง
อย่างไรก็ตาม.. Lightning Network ยังคงต้องเผชิญกับความท้าทาย เช่น ปัญหาเรื่องการบริหารจัดการ Liquidity และความซับซ้อนในการใช้งาน
นอกจาก Lightning Network แล้ว ยังมีการพัฒนาเทคโนโลยีอื่นๆ ที่ช่วยเพิ่มขีดความสามารถของ Bitcoin เช่น Taproot ซึ่งเป็น Soft Fork ที่ช่วยเพิ่มความเป็นส่วนตัว และ Schnorr signatures ซึ่งเป็น Digital Signature แบบใหม่ที่ช่วยลดขนาดของธุรกรรมให้เล็กลง
นอกจากนี้.. ยังเริ่มมีการพัฒนา DeFi (Decentralized Finance) บน Bitcoin และ Bitcoin Ordinals ซึ่งเป็นวิธีการใหม่ในการฝังข้อมูลลงใน Bitcoin Blockchain
Bitcoin ยังคงถูกนำไปใช้ในประเทศอื่นๆ นอกจาก El Salvador และมีความพยายามในการแก้ปัญหาความกังวลด้านสิ่งแวดล้อมจากการขุด Bitcoin
บทเรียนจากมหากาพย์แห่งวิวัฒนาการ
ประวัติศาสตร์ Bitcoin สอนให้เรารู้ว่า.. เทคโนโลยี Blockchain มีศักยภาพในการเปลี่ยนแปลงโลก แต่เส้นทางสู่ความสำเร็จนั้นก็ไม่ได้โรยด้วยกลีบกุหลาบ
ความขัดแย้ง การต่อสู้แย่งชิงอำนาจ และการตัดสินใจที่ยากลำบาก ล้วนเป็นส่วนหนึ่งของการเดินทาง
สิ่งที่สำคัญที่สุดคือ.. เราต้องศึกษา ทำความเข้าใจ และอาจมีส่วนร่วมในการกำหนดทิศทางของเทคโนโลยีนี้ เพื่อให้ Blockchain สามารถสร้างประโยชน์สูงสุดให้กับมวลมนุษยชาติต่อไป
เจาะลึกวิวัฒนาการของ Bitcoin การ Soft Forks, Hard Forks และมุมมองที่แตกต่าง
SegWit, Taproot และ Soft Forks อื่นๆ การปรับปรุง Bitcoin อย่างนุ่มนวล
Bitcoin Core ไม่ได้หยุดนิ่งอยู่กับที่ นักพัฒนาได้ทำงานอย่างต่อเนื่องเพื่อปรับปรุง Bitcoin ให้ดีขึ้น โดยใช้ "Soft Forks" ซึ่งเป็นการอัพเกรดที่เข้ากันได้กับซอฟต์แวร์เวอร์ชั่นเก่า
SegWit (Segregated Witness)
เปิดตัวในปี 2017 SegWit เป็นเหมือนการจัดระเบียบข้อมูลใน Block ใหม่ ย้ายส่วนที่เรียกว่า "Witness data" (ข้อมูลลายเซ็น) ออกไปไว้ข้างนอก ทำให้มีพื้นที่ว่างใน Block มากขึ้น รองรับธุรกรรมได้มากขึ้น และลดค่าธรรมเนียมได้ SegWit ยังช่วยแก้ปัญหา "Transaction Malleability" ซึ่งเป็นช่องโหว่ด้านความปลอดภัยและปูทางไปสู่การพัฒนา Lightning Network
Taproot
เปิดตัวในปี 2021 Taproot เป็น Soft Fork ที่ช่วยเพิ่มความเป็นส่วนตัว และประสิทธิภาพของ Bitcoin Taproot ทำให้ธุรกรรมที่ซับซ้อน เช่น Smart Contracts มีขนาดเล็กลงและยากต่อการแยกแยะจากธุรกรรมทั่วไป
Soft Forks อื่นๆ ที่ Bitcoin Core ได้นำมาใช้ เช่น BIP 65 (CheckLockTimeVerify) และ BIP 112 (CSV) ช่วยเพิ่มความยืดหยุ่นในการใช้งาน Bitcoin และปูทางไปสู่การพัฒนาฟังก์ชันใหม่ๆ
Hard Forks เส้นทางที่แตกต่างและการถือกำเนิดของเหรียญใหม่
ในขณะที่ Soft Forks เป็นการอัพเกรดที่นุ่มนวล "Hard Forks" นั้นนับว่าเป็นการเปลี่ยนแปลงครั้งใหญ่ ที่ทำให้เกิดสาย Blockchain ใหม่และเหรียญใหม่
Bitcoin XT (2015)
เป็นความพยายามครั้งแรกในการเพิ่ม Blocksize Limit โดย Mike Hearn และ Gavin Andresen Bitcoin XT เสนอให้เพิ่ม Blocksize Limit เป็น 8MB แต่ถูกต่อต้านอย่างรุนแรง และไม่ประสบความสำเร็จ
Bitcoin Classic (2016)
เป็นอีกหนึ่งความพยายามในการเพิ่ม Blocksize Limit โดยเสนอให้เพิ่มเป็น 2MB แต่ก็ล้มเหลวเช่นกัน
Bitcoin Unlimited (2016)
เสนอให้ Miners สามารถกำหนด Blocksize Limit ได้เอง แต่มีข้อบกพร่องด้านความปลอดภัย และไม่เป็นที่ยอมรับในวงกว้าง
Bitcoin Cash (BCH) (2017)
เกิดจากการ Hard Fork ของ Bitcoin โดยกลุ่ม "Big Blockers" ที่ไม่พอใจที่ Bitcoin Core ไม่ยอมเพิ่ม Blocksize Limit Bitcoin Cash เพิ่ม Blocksize Limit เป็น 8MB และมุ่งเน้นที่การเป็น "เงินสดดิจิทัล" ที่ใช้งานได้จริง
Bitcoin SV (BSV) (2018)
เกิดจากการ Hard Fork ของ Bitcoin Cash โดยกลุ่มที่นำโดย Craig Wright ผู้ที่อ้างว่าเป็น Satoshi Nakamoto Bitcoin SV ต้องการเพิ่มขนาด Block อย่างมาก และกลับไปสู่วิสัยทัศน์ดั้งเดิมของ Bitcoin
Bitcoin ABC (2020)
เกิดจากการ Hard Fork ของ Bitcoin Cash โดยกลุ่มนักพัฒนา Bitcoin ABC ที่ต้องการเปลี่ยนแปลงกลไกการระดมทุน Bitcoin ABC ถูกเปลี่ยนชื่อเป็น eCash ในภายหลัง
มุมมองที่แตกต่าง Bitcoin ถูก "แย่งชิง" หรือไม่?
หนังสือ "Hijacking Bitcoin" โดย Roger Ver นำเสนอมุมมองที่แตกต่างจาก Bitcoin Maximalists
Roger Ver เชื่อว่า Bitcoin ถูก "แย่งชิง" โดยกลุ่มนักพัฒนา Bitcoin Core และ Blockstream ที่ต้องการเปลี่ยนแปลง Bitcoin จาก "เงินสดดิจิทัล" ให้กลายเป็น "สินทรัพย์เก็บมูลค่า"
Roger Ver วิพากษ์วิจารณ์ Bitcoin Core ในหลายประเด็น เช่น..
การไม่ยอมเพิ่ม Blocksize Limit
Roger Ver เชื่อว่า Bitcoin Core จงใจจำกัดการเติบโตของ Bitcoin เพื่อผลักดันให้คนใช้งาน Sidechains ของ Blockstream
การเซ็นเซอร์ข้อมูล
Roger Ver กล่าวหาว่า Bitcoin Core เซ็นเซอร์ข้อมูลและปิดกั้นการสนทนาเกี่ยวกับ Big Blocks บนแพลตฟอร์มต่างๆ
การต่อต้านนวัตกรรม
Roger Ver เชื่อว่า Bitcoin Core ต่อต้านนวัตกรรม และไม่ยอมรับการเปลี่ยนแปลงที่อาจทำให้ Bitcoin ดีขึ้น
การควบคุมโดยกลุ่มเล็กๆ
Roger Ver มองว่า Bitcoin Core ถูกควบคุมโดยกลุ่มเล็กๆ ที่ไม่คำนึงถึงความต้องการของชุมชน Bitcoin
Roger Ver สนับสนุน Bitcoin Cash ซึ่งเขาเชื่อว่าเป็น Bitcoin ที่แท้จริง ที่สืบทอดวิสัยทัศน์ดั้งเดิมของ Satoshi Nakamoto
บทสรุป:
การต่อสู้แย่งชิง Bitcoin และการเกิดขึ้นของ Hard Forks ต่างๆ เป็นส่วนหนึ่งของวิวัฒนาการของ Cryptocurrency
มุมมองที่แตกต่าง ความขัดแย้ง และการแข่งขัน ล้วนเป็นแรงผลักดันให้ Bitcoin และ Cryptocurrency อื่นๆ พัฒนาต่อไป
สุดท้ายแล้ว.. เราคงไม่อาจตัดสินได้ว่าฝ่ายใดคิดถูกหรือฝ่ายใดผิด
"เสียงของตลาด จะช่วยทำหน้าที่ให้คำตอบนั้นกับเรา ว่าแท้ที่จริงแล้วผู้คนกำลังต้องการอะไรกันแน่..
ลองมองไปที่มูลค่าของแต่ละแนวคิด มองไปที่ Network effect และกำลังการขุด มองไปที่การยอมรับและความเชื่อมั่นของผู้คน เหล่านี้ล้วนเป็นข้อบ่งชี้ที่เห็นได้ง่าย..
เพราะนั่นคือเสียงแห่งการเพรียกหาอิสรภาพ และอธิปไตยทางการเงินที่แท้จริง..
— Jakk Goodday
-
 @ 1739d937:3e3136ef
2024-09-04 07:23:12
@ 1739d937:3e3136ef
2024-09-04 07:23:12This is the sixth in a series of weekly(ish) updates detailing progress on bringing MLS protocol DMs and group messaging to Nostr.
Previous Updates
Progress this week
Sorry about the very late update this week. Catching up on everything after a week in Riga for Nostriga and Baltic Honeybadger took a bunch of time, every other moment was spent coding. 👨💻
The response at Nostriga to NIP-104 and my two talks on the subject were overwhelmingly positive. It was very helpful to spend time with other devs going through the spec in detail. We found a few minor improvements and clarifications but no major issues surfaced. Thanks to nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49, nostr:npub1lunaq893u4hmtpvqxpk8hfmtkqmm7ggutdtnc4hyuux2skr4ttcqr827lj, and nostr:npub1ye5ptcxfyyxl5vjvdjar2ua3f0hynkjzpx552mu5snj3qmx5pzjscpknpr in particular for the lengthly interrogations and nostr:npub1wmr34t36fy03m8hvgl96zl3znndyzyaqhwmwdtshwmtkg03fetaqhjg240 for the introductions.
Last week, I started work on a reference implementation of the spec. It's still early but going quickly.
My PR adding support for secp256k1 was also merged into the hpke-rs library yesterday. That's one more step in the right direction towards having secp256k1 ciphersuite support.
The NIP
If you haven't already, check out my talk; The Past and Future of DMs and Group messaging on Nostr. This was a basic overview of the various DM and group messaging schemes and talks a little about the progress on NIP-104. I believe there is a recording of the technical talk on the spec but it hasn't yet been released. I'll link it up when it is.
At this point I've been discouraging anyone from trying to implement the NIP quite yet. As I mentioned above there are a few adjustments that need to be made and a few open questions that I'm working on answering with my implementation (which I'm very happy to have contributors on). My plan at the moment is to do this first implementation with the default ciphersuite that MLS already supports while I continue to work on the dependencies to get secp256k1 support across the board.
The Implementation
I've started on a cross-platform native client that will run on Mac, Windows, Linux, iOS, and Android. Think of it as Signal or Telegram but over Nostr. I hope that this will not only become the reference implementation for other client developers but also will be one of the most secure and privacy focused clients in the Nostr ecosystem. Building it has already been helpful in clarifying some of the more complex implementation details in the NIP. It's still early but I'll have more to share on this in the coming weeks.
HPKE-RS
My PR to add support for secp256k1 is merged!
Onward and Upward
Thanks again to everyone for the support and feedback on this stuff at Nostriga. It was hugely motivating to hear the kind words, have you introducing me to people that could help, and spending time giving me feedback! This community is the best. 🫂
-
 @ 93dbb6d6:ea74c840
2024-09-04 05:32:17
@ 93dbb6d6:ea74c840
2024-09-04 05:32:17Let’s take a look at why the Specter DIY is so secure and the incredible advantages this device offers.👇

Unlike many commercial wallets, it's built from OFF-THE-SHELF COMPONENTS. Anyone can get one without providing personal data or needing a specific store. Even if Bitcoin hardware is banned in a totalitarian regime, the Specter DIY offers discreet access to a signing device.
The Specter DIY is fully OPENSOURCE enhancing security by allowing anyone to review and use the code without permission. For example, the SeedSigner and Krux projects use much of the Specter DIY Code.
The device is BITCOIN and Liquid ONLY. Supporting no altcoins. With a smaller codebase, there are fewer opportunities for vulnerabilities.

The Specter DIY operates AIR-GAPPED, with no physical connection Wi-Fi-connected devices, ensuring sensitive data like private keys remain secure. It communicates via QR codes or SD card, ensuring transparency so you can clearly understand the transaction signing process.
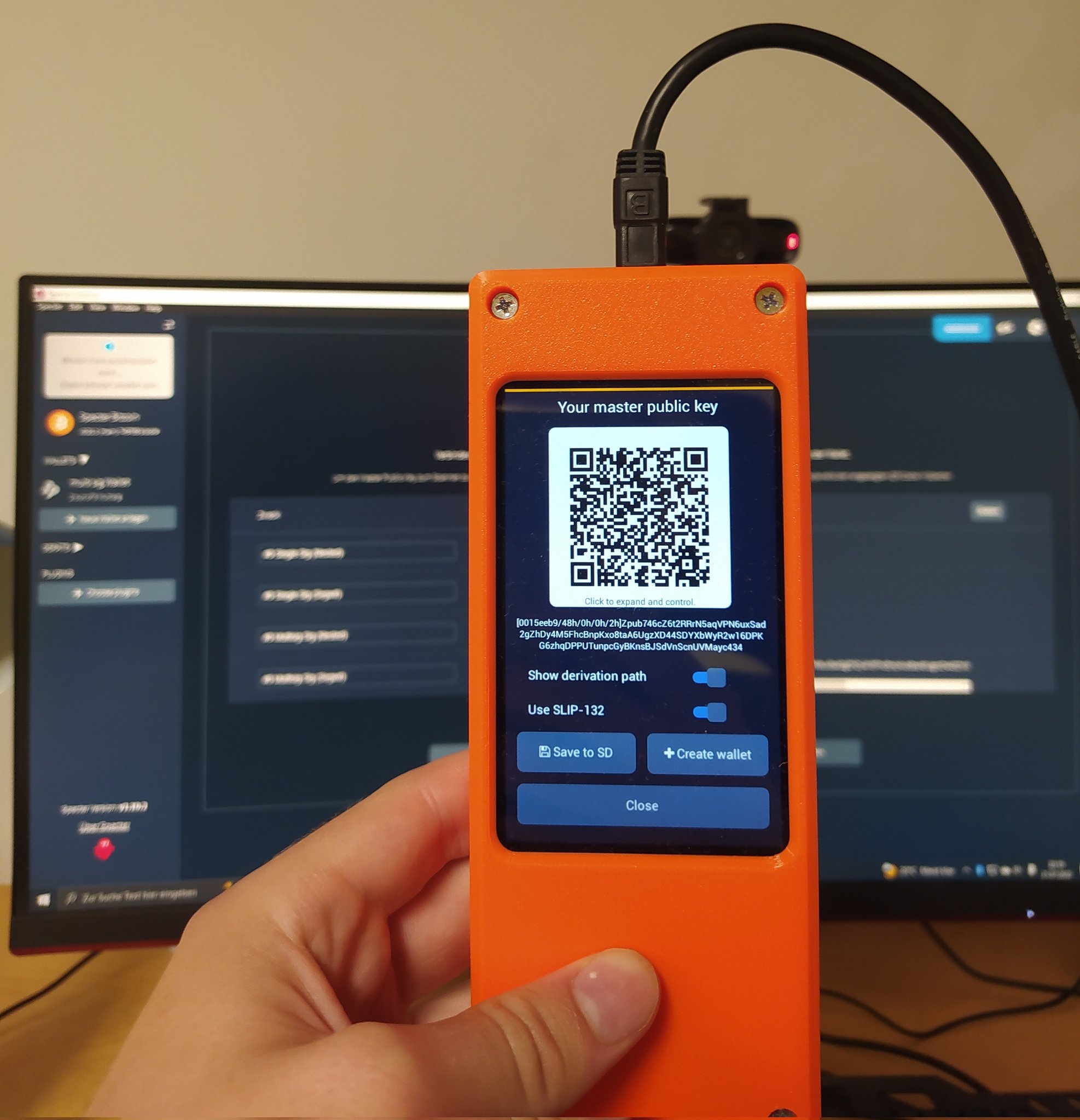
The device has a LARGE smartphone-like TOUCHSCREEN, offering a comfortable interface for smooth air-gapped communication, easy entry of seed words, and convenient navigation. This display simplifies tasks that are very cumbersome on smaller devices.
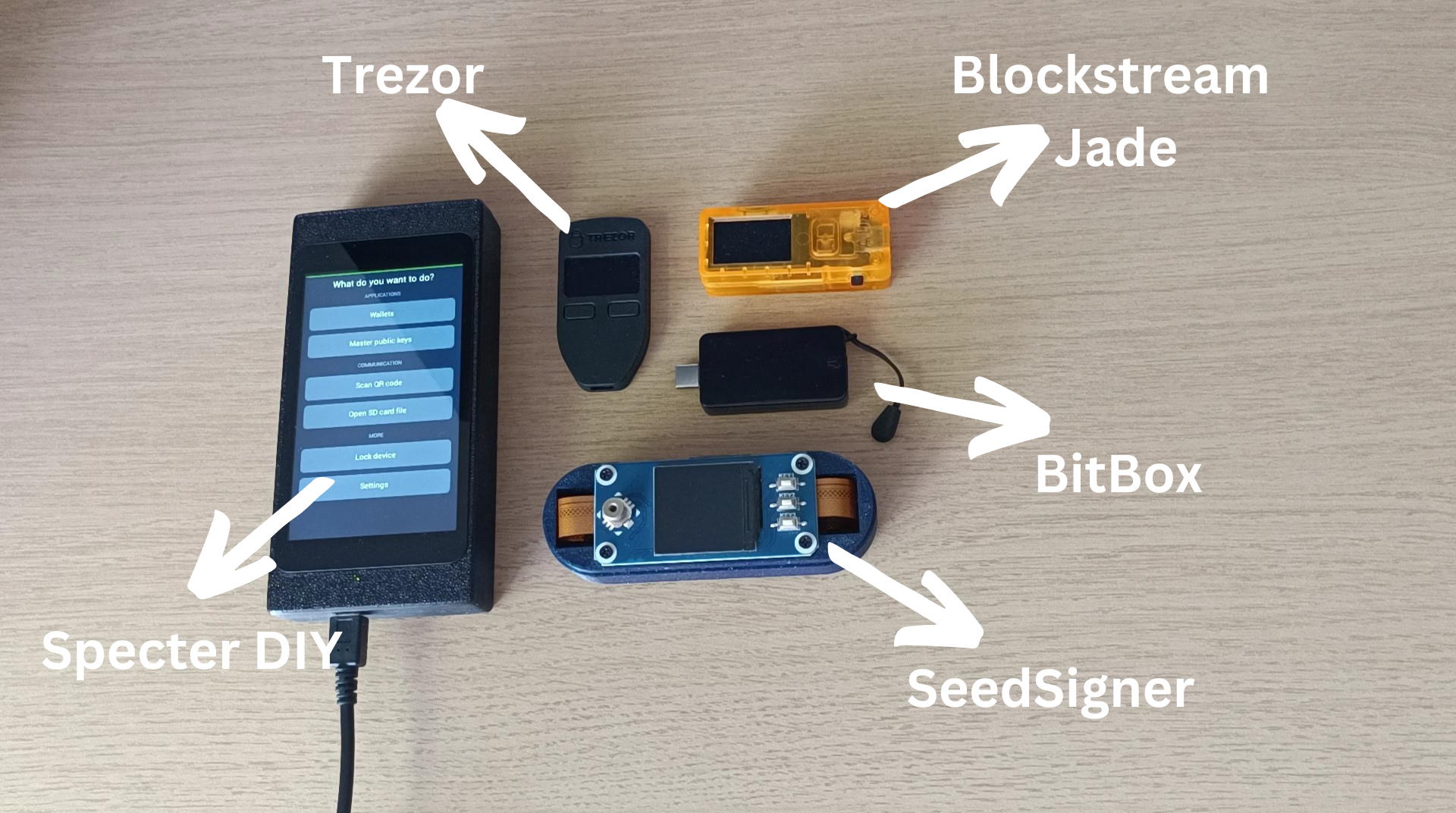
The Specter DIY is primarily a signing device and DOES NOT STORE SEED WORDS internally, enhancing security. Seed phrases need to be written down and re-entered manually. Alternatively, you can store the seed phrase on an unencrypted SD card or use SeedQR for easy import.

Since the seed phrase is not stored, the owner can create multiple MULTI SIGNATUR Wallets with only one device. Or act as "UNCLE JIM" and help family and friends set up a secure, watch-only wallet. Sharing the device requires minimal trust as the device could be tampered with.

One of the key features of the Specter DIY is its ability to integrate very transparent REAL-WORLD RANDOMNESS into seed phrase generation, such as by flipping coins. This helps safeguard against all potential attacks associated with weak seed entropy.
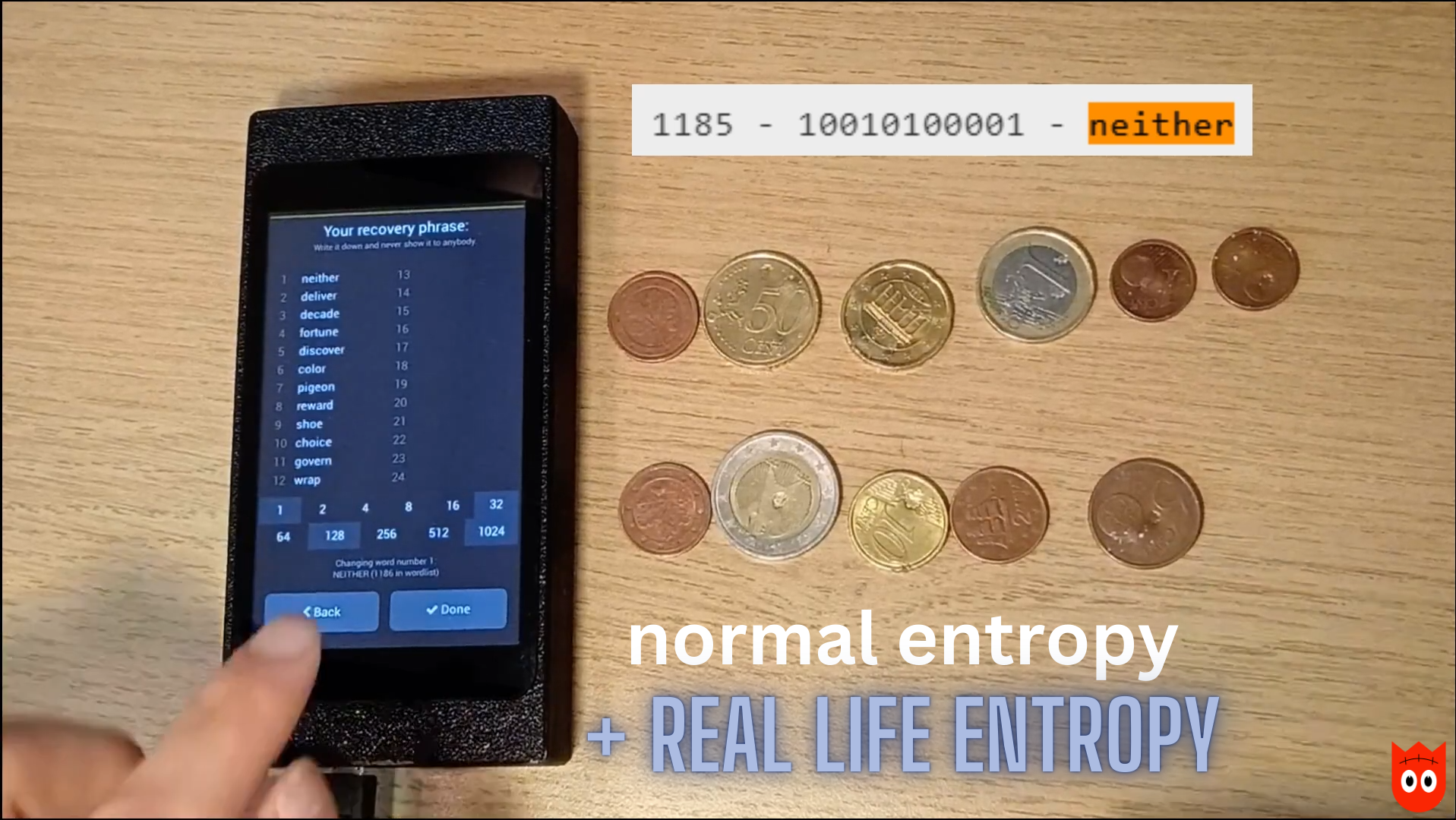
With BIP85 support, users can derive multiple child seeds from a single master seed. This feature is particularly useful for those managing multiple Bitcoin wallets, simplifying seed management for less important Seedphrases as well.

-
 @ e0e92e54:d630dfaa
2024-09-04 04:13:19
@ e0e92e54:d630dfaa
2024-09-04 04:13:19This is a copy of the email received from newsletter@Rumble.com

Free Speech Under Attack -- A Note from the CEO of Rumble
Dear Rumble Users,
I don't typically send messages to our users through email, but red lines have been crossed. There have been major developments with free speech platforms, and I feel it’s important to let everyone know what is going on and how you can help Rumble.
Rumble is no longer available to the citizens of Brazil, joining the ranks of France, Russia, and China. From media reports, Brazil no longer has Elon Musk's X due to attacks on free speech by Alexandre De Moreas, a justice of Brazil's Supreme Federal Court.
World powers don’t want Rumble, they don’t want X, they don’t want Telegram, and they don't want Truth Social. They want to control information, but our companies won’t let them.
There are no other large companies fighting for freedom like we are. We put everything on the line for it, and the Telegram CEO was recently arrested for it.
Advertisers boycott our companies to try and cut our economic lifeline, but they underestimate our support among the people.
The people keep us alive and keep us going.
If you want to help us, join Rumble Premium. If Rumble Premium gets big enough, you help us change the game and fight for freedom of expression.
We are also offering a $10 dicount for any new annual subscribers when they use the promo code "brazil".
Sincerely,
Chris Pavlovski Chairman and CEO of Rumble
 444 Gulf of Mexico Dr.
Longboat Key, FL 34228, USA.
444 Gulf of Mexico Dr.
Longboat Key, FL 34228, USA. -
 @ 96203d66:643a819c
2024-09-04 03:42:31
@ 96203d66:643a819c
2024-09-04 03:42:31[3]
[4]
[5]
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
[14]
[15]
[16]
[17]
[18]
[19]
[20]
[21]
[22]
[23]
[24]
[25]
[26]
[27]
[28]
[29]
[30]
[31]
-
 @ 862fda7e:02a8268b
2024-09-04 01:45:14
@ 862fda7e:02a8268b
2024-09-04 01:45:14It is true that I often dream about James Corbett from CorbettReport.com. Somehow James is always finding his way to my mind. James Corbett intimidates me, I feel like he would heavily dislike me because I am not serious enough. Anytime I see James Corbett smile or laugh it feels like I'm watching an alien try to be human. I wish James the best with his family life and career, but he looks like he is always one second away from either crying hyterically or beating a defensless Japanese man sensless. I am indreasibly grateful for all the hard work he's put out all these years, he's a great person in the truth circle. However, he's like a caracatiure in my head. Anytime he whips out his guitar, I start to cringe. I just know what's about to come will only be the truth about how bad his singing is. But yet, I still love when he plays his guitar. It's awful in a great way, it brings genuine joy to me. Did you know he has a band? He has one song called "Screw Youtube", and in his music video he was sitting on this tall wooden fence and he was wearing these SHORTS WITH SANDALS and he was SWINGING HIS LEGS. I'm sorry, but I expect James to wear white caykies at all times. It felt so gross to see his legs in that state. But then again, here I am getting genuine joy out of seeing that atrosity.
I remember one time watching a James Corbett episode where he has the James Evan Pilatto from MediaMonarchy.com on, and the other James always looks like he's super fucking cracked up. Like he has a ton of energy. Well anyways, one time the other James was his usual self, looking super cracked out excited, talking about the reppies (reptilians) and James Corbett looked so tight lipped, red faced, like he was about to burst out crying. It was so funny to see the two polar opposites, the other James totally oblivious that real James looked like he was about to cry for seemingly no reason. I know this sounds mean of me to say, but I really appreciate these guys for all they do. I just think this is funny.
Anyways, I have a lot of dreams with James Corbett in them. I think it's because he's a teacher and my vagina has a fondness for male teachers. Sadly, none of my good looking male teachers never slept with me. That being said, I think James is good looking for possibly being an English teacher in Japan. I would let him teach me about the reptilians and Klaus Schwab, just let the teaching session see where it goes. Would his gap teeth feel good over my clitty? I dunno.
Okay but here is the most memorable and hilarious dream I had invovling James Corbett. You know how he makes content very often? One day he got extremely fed up with making videos. At the time I think it's because he mentioned in a video how he was annoyed that people kept saying him and Andrew Caufman. So one day he just flipped out, got extremely angry, made one last video saying how he was never coming back and how he's leaving his wife and kids. He deletes everything and is unheard of for months. A few months pass and he uploads a new video. The new video is James obsessively showing and talking about his highly advanced chicken coop he made in Minecraft. He had hundreds of chickens lined up maybe 80 feet in the air, each chicken had a 1x1 square to fit in. Below the chicken was a long tube in which their egg would drop down, and a catcher at the base of the ground. James was fantically showing this contraption, rocking back and forth, had a headset on. He looked awful too. I actually emailed James Corbett about this dream, but he never responded.
Speaking of James Corbett, why do so many people look like him? I feel like they make middle aged bald, bearded men in a DUMB and just release them into the wild, but give them balding genetics so they know how to keep track of them. Like they probably made James Corbett and Andrew Caufman from the same test tube. They fucked up with them, at least like give one of them hair or good eyesight.
-
 @ 3b7fc823:e194354f
2024-09-04 01:33:21
@ 3b7fc823:e194354f
2024-09-04 01:33:21Nyms, Personas, and Digital Identity
GHOSTn
If you want #privacy then embrace compartmentlization and obscuration in your digital life. Get used to having multiple identities that you can switch between for various needs.
Your legal "matrix" name that pays taxes and has no controversal opinions or associations. Don't try to obscure this person. They are a open book. Put your best foot forward. Show them what you want them to see.
Your private online persona. You let your hair down, have hot takes on social media, purchase legal but potentially embarrassing items or just have hobbies and associations that you are not ashamed of but don't want to advertise for some reason. You use a VPN and no kyc sudo anonymous accounts. Have fun but don't go crazy, know that on a long enough timeline this persona will be linked back to you. The more connections and data that you put out there the easier this will be.
Your anonymous nym that only uses #tor, VMs, hidden drives, and rarely used accounts. Plausible deniability is baked in. Used by dissidents, freedom fights, truth to power, and anyone in oppressive regimes.
Finally you have your Nemo. This person does not exist. No name, no files and only uses #Tails or disposable systems that does not leave a trace. Not everyone would ever have a need for a Nemo but it is good to know how to just in case you ever do.
-
 @ 3b7fc823:e194354f
2024-09-04 00:26:48
@ 3b7fc823:e194354f
2024-09-04 00:26:48Encryption is the promethium fire that the cypherpunks secured from heaven for me and you. It is our sacred duty to use and advance that in the world. Encryption is so powerful that governments tried to keep it away from the people and to this day have tried to weaken and backdoor it at every turn.
So what is encryption?
It is a deep deep rabbit hole and involves a lot of numbers but in a nutshell it uses math to scramble up the data of your file so it is gibberish and can't be read without decrypting it back to regular data. Encryption technology has continued to advance over time and cracking technology to break the encryption has as well. For our purposes all you really need to remember is to use modern cyphers and your encryption is really only going to be as good as the password (use a passphrase) strength you are using to lock it down with.
BEGINNER LEVEL - Encrypt your phone and computer.
People walk around with their whole lives on their phone. Protect it.
-phone: Congratulations, if you already have a lock screen set on either your iPhone or Android device then device encryption is enabled. If your lock screen password is only 4 digits then we still have work to do. Four digits is only about 10,000 combinations and fairly easy to crack. I believe it only took them about 40 minutes to crack the iPhone of the attempted Trump shooter. Go into settings and set it up for 6 digits or for extra credit use a alphanumeric password.
After your phone then your personal computer probably has the most important data to you. Banking records, tax documents, photos, etc. Encrypt your drive.
-Windows: from Settings, select Privacy security -> Device encryption. Just follow the prompts.
-Apple: from Apple icon, select System Preferences -> Security & Privacy icon. Click "Turn On FileVault".
-Linux: most distros gives you the option during installation. If you didn't do so then search for how to enable it after the fact based on your distribution.
Awesome sauce. You have achieved minimum status.
ADVANCED LEVEL - Encrypt individual files.
You already encrypted your computer but guess what, once you start up your computer and log in the key is stored in RAM for as long as it stays on. The beginner level encryption protects your computer when it is off and it means no one can just steal your hard drive and access your files. This is good, but what if someone grabs you while you're sitting there working on it? What if you leave it in sleep mode and not turned off? Then that whole disk encryption is not really going to help you.
What if you had individual files that you consider more secret than the others? That finance spreadsheet or that special pic your spouse sent you? That's where individual file encryption comes in. You are just scrolling nostr when they grab you, your computer is on, and unlocked, but those special files are still safely encrypted.
I will share with you one of my favorite small programs: Picocrypt.
Download the Paranoid pack and store it in multiple drives, email accounts, and cloud storage. That way you will always have a copy to decrypt any files that you stored away.
Use it to encrypt any files that you feel need extra attention. It is also very useful for encrypting any files that you intend to store online in cloud storage. You do encrypt your files that are stored online don't you? Yes, even with the company that offers "encrypted" storage. Don't trust their encryption, use your own.
EXPERT LEVEL - Encrypt containers and hidden containers.
What if you want to encrypt several files and keep them all together in like a folder or container? That's where Veracrypt comes in. Free, open source, cross platform, and powerful.
Veracrypt allows you to create encrypted containers from any file that act like individual drives that can be mounted or unmounted as needed. You can name these files anything that you want, move them around or delete like any file, and make as many as you want. This allows you to have compartmentation of your files and drives.
Next trick, Veracrypt allows you to create a hidden container inside that container. Enter one passphrase and you open the encrypted container. Enter a different passphrase and you open a different hidden container.
This allows deniability. When they grab you and start pulling your fingernails off until you tell them the password to open the encrypted container, give it to them. They don't have to know that there is another hidden one under that.
These features allow you to do all sorts of interesting things only limited by your need and imagination.
What if you have a container named as some random config file in your /etc folder? What if you just encrypted a removable storage drive? What if you have multiple hard drives on your computer that have multiple containers and hidden containers? What if you have a hidden container that can only be accessed from booting up in a amnesiac OS like Tails leaving no trace that the files exist or trail that they were ever accessed? Go crazy, have fun.
NEMO - Failsafe
Nemo has no files, encrypted or otherwise. If they did you couldn't prove it. Nemo does use something like Tails that retains no memory from boot to boot.
Nemo also uses a failsafe. A simple lanyard attached to the flashdrive running the OS and the other end around their wrist while they work. When you try to separate them from the computer the flashdrive pulls out and everything is gone.
Using these programs you can create a layered and compartmentlized approach to your encryption scheme. There are also plenty of other encryption programs to check out such as Cryptomator, AES Crypt, etc
Last point and most important: Encryption is only as good as the passphrase you use to lock it down. Use a shitty password and it doesn't matter how uncrackable your encryption is.
-
 @ be39043c:4a573ca3
2024-09-03 22:54:46
@ be39043c:4a573ca3
2024-09-03 22:54:46Over ten years ago, when I visited Japan, I met a woman from the U.S. When we were chatting about books, I learned from her that a well-known best seller book, I had once read, was written by a ghost writer. She knew the writer who did it.
I believed what she said as she had no reason to lie. Also, because I remembered that I had a weird feeling when I read the book. Although I mostly liked the contents, something was totally off. It was not "off" in a sense that writing was not good. It was weird because it was too well-written.
This book is a non-fiction book about certain ideas. The writing of a non-fiction book that explains an author's ideas can become clanky as the author struggles to delineate their thoughts. One knows something is different from whether one can write them. But, the book was very very well-written and well-explained with a lot of reference points.
Probably partly because the elegance of writing and examples, it has been sold and continue to be sold today all over the world.
Well, I know now the author only provided the ideas and someone else put them together.
The ghost writer was a fiction writer that could write very well. The book is so well put-together because of his skill. He was not credited as a contributor, I believe.
Whether it is written by a ghost writer, the book is still a good book. But, to know that the book is not written by the author whose name was on the cover page disappoints me. Who writes the book is important for readers.
Now it is 2024. Things are much more complex because AI can write or put together ideas for humans.
For instance, I read a very funny and well-written short fiction on someone's blog yesterday. I was impressed and commented about that.
This morning, it suddenly hit me, he may have used AI to create the piece. This creator posts his long writing mostly every day. He also work full time, he says. I had wondered before he might be using ChatGPT to create contents.
ChatGPT can write nice short stories: we see such examples online. I have read a story for children ChatGPT created. It was a complex and intriguing story
If we don't like parts of AI writing, we can edit it. It is quicker than writing from scratch,
There is no way to know the particular fiction that I read was written by AI but it is possible.
Whether it was created fully by a human or AI or both, the good writing is still a good writing. Maybe, I am thinking too much here?
Not really, in my view. Who writes still matters to me.
-
 @ 8cb60e21:5f2deaea
2024-09-03 22:26:25
@ 8cb60e21:5f2deaea
2024-09-03 22:26:25 -
 @ 8cb60e21:5f2deaea
2024-09-03 22:26:25
@ 8cb60e21:5f2deaea
2024-09-03 22:26:25 -
 @ 8cb60e21:5f2deaea
2024-09-03 21:58:26
@ 8cb60e21:5f2deaea
2024-09-03 21:58:26Lesson 3: Arrays, Objects, and Callbacks
Arrays: Lists of Things
Arrays are ordered lists of values. They're perfect for storing multiple related items, like a list of your favorite cat toys:
javascript var catToys = ["mouse", "ball", "laser pointer"]; console.log(catToys[0]); // Prints "mouse"Objects: Grouping Related Information
Objects allow you to group related information together. They're like detailed profiles for each of your cat friends:
```javascript var myCat = { name: "Fluffy", age: 3, favoriteFood: "tuna" };
console.log(myCat.name); // Prints "Fluffy" ```
Callbacks: Doing Things Later
Callbacks are functions that are executed after another function has finished. They're useful for handling asynchronous operations, like waiting for your cat to finish eating before giving it a treat:
```javascript function feedCat(callback) { console.log("Feeding the cat..."); setTimeout(function() { console.log("Cat has finished eating!"); callback(); }, 2000); }
feedCat(function() { console.log("Time for a treat!"); }); ```
This code simulates feeding a cat, waiting 2 seconds, and then giving it a treat.
Remember, learning JavaScript is a journey. Take your time, practice regularly, and soon you'll be coding like a pro cat!
-
 @ 8cb60e21:5f2deaea
2024-09-03 21:58:26
@ 8cb60e21:5f2deaea
2024-09-03 21:58:26Lesson 2: Functions and Loops
Functions: Your Own Commands
Functions are reusable blocks of code that perform specific tasks. They're like teaching your cat a new trick:
```javascript function meow(times) { for (var i = 0; i < times; i++) { console.log("Meow!"); } }
meow(3); // This will print "Meow!" three times ```
Built-in Functions
JavaScript comes with many built-in functions. For example,
console.log()is a function that prints things to the console:javascript console.log("I'm a cat!");Loops: Repeating Tasks
Loops allow you to repeat a task multiple times without writing the same code over and over. It's like telling your cat to chase its tail for a specific number of rounds:
javascript for (var i = 0; i < 5; i++) { console.log("Chasing tail, round " + (i + 1)); }This will print "Chasing tail, round X" five times, where X goes from 1 to 5.
-
 @ 56a6da9b:7f5a2243
2024-09-03 20:32:49
@ 56a6da9b:7f5a2243
2024-09-03 20:32:49This is the finale of a flash fiction marathon I did this recent August.
Here is the Podcast Audio: https://fountain.fm/episode/fZ3jy3znXo6NIQRf4fHp
THE FINALE OF FLASH AUGUST FICTION. Hungry Henry and Rotund Ronald have become pals. Did you ever listen to The Cheeseguard from Flash Fiction February? These two had an impromptu meeting, and they remained cohorts. Today they are avoiding capture by a cat. This is one of several animal stories from this month. Stoicism is a mixed bag. It’s part strength, and part denial, in a way.
I appreciate my new followers and subscribers. If you are, or know any independent, non-corporate truth-teller Journalists, tell them to DM me, and I’ll gift them a paid subscription. It’s the least I can do. I’m Commercial Herschel, and I’m here to help.
The Stoics
Don't Explain Your Philosophy. Embody It.
916 WORDS WRITTEN IN ABOUT 45 MINUTES

Henry and Ronald have heard about a farmhouse that features a very nice selection of dairy products. They’ve listened to fantastic tales of hanging cheeses, overflowing yogurts, and stray curds left all over the place. As they make their way through a stump and stone laden field, they catch the unmistakable vibration of cat paws, and with it, the unmistakable scent.
“Ahhh cheese.” Hungry Henry says. “Nobody said anything about a cat being here!”
Just then, they see the horrifying sight of those large dilated eyes, looming above the grass, about 100 feet in front of them.
“We better duck behind that stump!” He adds.
“How the heck are we supposed to make it to the barn.” He says, sadly.
“What mice actually needs is not a tensionless state but rather the striving and struggling for some goal worthy of him.” Rotund Ronald cites Viktor Frankl.
“This ain’t tension, it’s being scared to death.” Henry replies.
“We are more often frightened than hurt; and we suffer more in imagination than in reality.” Ronald quotes Marcus Aurelius.
“That cat looks pretty real to me!” Responds Henry.
Ronald refers to Seneca: "He who is brave is free."
“I don’t know how brave I am, but I think the smell of emptying my bladder is going to give us away.” Henry replies.
“A mouse who fears death will never do anything worthy of a mouse who is alive.” Another Seneca citation from Ronald.
“I think your reading has gotten the best of you. We need to get a way out of this.” Henry says.
The two of them stick together. They make a run for it to a pile of rocks, squeezing their bodies to get as deep into the pile as they can. The cat slowly approaches, they can see his nose twitching, and he emits faint growling sounds.
“If one of us doesn’t make it out of this, It’s been good to know you, Ronald.”
Ronald again quotes Marcus Aurelius. “You could leave life right now. Let that determine what you do and say and think.”
Henry is panicking, he’s breathing heavily, and his heart is about to burst. “Excuse me Ronald, but I don’t understand how I’m supposed to pretend what is happening is not happening, and then I’m supposed to just assume I can think my way out of this when that thing has been eating guys like us his whole life. We’re going to end up presents on a front porch! See if you can do more than belittle the situation with platitudes!”
"It is not because things are difficult that we do not dare; it is because we do not dare that they are difficult." Another quote from Seneca.
“OK, then, let’s see if we can confuse him. Let’s each go in opposite directions, then meet over by that bucket at that water pump. Can you see it?” Henry asserts.
“Waste no more time arguing what a good mouse should be. Be One.” Ronald cites Marcus Aurelius again, and the two dart off to attempt the plan. Henry goes first, and the cat moves towards him. Then Ronald distracts him with his departure and the cat freezes, giving them enough time to scurry through the long grass and make it to the other side of the bucket, out of the cat’s purview.
“I think we better stay calm.” Henry says. “This got us halfway to the barn.”
"Cease to hope, and you will cease to fear." Ronald again quotes Seneca.
From either side of the bucket, they can see the fierce cat hunching up on his hind legs, scanning the grass in hopes to detect them.
“We have to find a way to get to the other side of that fence.” Henry says. “I don’t see any openings, or holes, or any spaces to get under it.”
Ronald responds, “External things are not the problem. It’s your assessment of them. Which you can erase right now.” Another quotation from Aurelius.
“Are you saying we should just go for it?” Henry asks.
Now Ronald replies with another Seneca line: “If a mouse knows not which port he sails, no wind is favorable.”
“Let’s go straight for the fence, then go to the right toward the gate, there’s probably a gap at the hinges or something.” Henry advises.
They make their run for it. The cat sees them and is in pursuit. Just then, the front door of the farmhouse opens, and a little girl calls to the cat, and runs towards him. Just as the cat is about to intercept the two mice, the girl, not even noticing the two tiny mice, swoops up the feline and cradles him. “You silly cat, what are you doing?” She laughs and hold him tightly.
The cat watches from over the girl’s shoulder as the two mice find a gap between the fence and the gate and make their way into the barnyard.
As they enter the barn, they can’t believe the plentiful array they peruse. They can barely choose. There are curds spread about the floor. There is liquid dripping from hanging curds like rains from heaven. They find rinds and all manner of delectable matter.
Ronald ceases the recitations and says. “I can barely speak.”
Henry peers at him sarcastically. This time it’s he who quotes Marcus Aurelius. "Nothing happens to anybody which he is not fitted by nature to bear."
“You’ve been reading.” says Rotund Ronald.
“I been readin’ ” Hungry Henry replies.
The End.
I hope you liked Flash Fiction August. It’s all over. Don’t worry, though, I’ll be making plenty more stories and adding new content all the time. Please like, subscribe, restack, and all that sharing. Thank you to all the independent, non-corporate media people out there. I hope I can give you some light entertainment once in a while. Thank you so much for listening, or reading. This is the Smell the Inside of Your Nose. Do it Right Now podcast. I hope you might get a free or paid subscription, or buy me a coffee, or donate some bitcoin. I wish you the best. I’m Herschel Sterling, and I’m here to help.
Join Herschel Sterling’s subscriber chat
Available in the Substack app and on web

-
 @ df74dd24:05d81696
2024-09-03 20:20:48
@ df74dd24:05d81696
2024-09-03 20:20:48gratitude
This is my first post. This is the second line
-
 @ df74dd24:05d81696
2024-09-03 20:19:52
@ df74dd24:05d81696
2024-09-03 20:19:52gratitude
This is my first post
-
 @ 361d3e1e:50bc10a8
2024-09-03 19:12:51
@ 361d3e1e:50bc10a8
2024-09-03 19:12:51What do abortions, organ harvesting, abuse of unborn children and vaccines have in common?
usa #freespeech #freedom #children #abortion #research #vaccine
-
 @ 613dd075:a90784e6
2024-09-03 15:59:36
@ 613dd075:a90784e6
2024-09-03 15:59:36 -
 @ a950ba55:02f4f8c9
2024-09-03 13:24:04
@ a950ba55:02f4f8c9
2024-09-03 13:24:04تُعرف الفرقة النصيرية في بلاد الشام باسم الطائفة العلوية، إلا أن هذا الاسم ليس هو وحده ما يطلَق عليها، بل يُطلق على هذه الطائفة عدة أسماء؛ منها “النصيرية” و”الخصيبية” و”الجنبلانية”، وهي أسماء قديمة أطلقت نسبة إلى بعض أئمتهم ممن ساهموا مساهمة كبيرة في تأسيس المذهب، فاسم النصيرية نسبة إلى محمد بن نصير العبدي البكري النميري، وهو أقدم وأشهر اسم عُرفوا به عبر التاريخ، وأما اسم الجنبلانية فنسبة إلى محمد بن جندب الجنبلاني، والخصيبية نسبة إلى الحسين بن حمدان الخصيبي، الذي أدخل المذهب إلى الساحل السوري اليوم.
وعرفوا حديثاً باسم “العلويين” الذي يرجع إلى عام 1920م، حيث ساهم الفرنسيون في انتشار هذا الاسم الذي لم يعرف قبل هذا التاريخ، فكل كتب التاريخ تذكرهم باسم النصيرية.
حكاية النشأة!
بدأت نشأة المذهب النصيري في جنوب العراق على يد محمد بن نصير، الذي ولد في البصرة جنوب العراق مطلع القرن الهجري الثالث، ثم سكن سامراء، وخلال مرحلة التأسيس العراقية كانت النصيرية تحتفظ بشيء من الاعتدال الفكري، حيث بقيت تنسب إلى المذاهب الإسلامية لأنها تقر بكثير من الشعائر الإسلامية.
انتقلت النصيرية إلى بلاد الشام، وبالأخص إلى حلب، على يد الخصيبي المصري الذي سكن حلب أيام سيف الدولة، وأخذ يدير أمور وشؤون النصيريين، وهو أهم رجل في تاريخ المذهب حيث استطاع أن يحرف وجهة المذهب بشكل كلي، فألف العديد من الكتب التي عرفت الناس بمذهبهم وعقيدتهم المنحرفة، ومنها كتابي “المجموع” و”راست باش” أي كن مستقيماً، وكتاب “الهداية الكبرى”، واستطاع أن يجعل لنفسه خلفاء في كل من بغداد وحلب، وأسس للنصيرية مراكز فيهما، وتوفي في حلب سنة 346هـ.
ثم انتقلت النصيرية إلى اللاذقية على يد الميمون الطبراني، وهو أيضاً من أهم رجالات المذهب، فقد ألف الكتب وسن القوانين ورتب الأعياد، وله كتاب “مجموع الأعياد” و”الحاوي” و”الدلائل في معرفة المسائل” و”رسالة التوحيد”، وتوفي في اللاذقية سنة 426هـ.
العقيدة والعبادات
يؤمن النصيريون بالثالوث الإلهي، ويزعمون أنهم يتشكلون في علي والنبي محمد ﷺ وصاحبه سلمان الفارسي، ويرمزون لهم بـ”ع م س”، وهؤلاء الثلاثة يؤلفون حسب رأيهم الذات الإلهية، فعلي هو المعنى أي: ذات الله، ومحمد هو الاسم أي: اسم الله في الوجود وانعكاسه في الواقع، وسلمان هو الباب الذي يتم الوصول إلى الله عن طريقه، وبذلك نستطيع أن نقول: إن النصيريين يؤلهون علياً ويعبدونه ويرونه هو الله، تعالى الله عن ذلك علواً كبيرا. وهذا يشبه بشكل كبير الثالوث المسيحي النصراني “الأب والابن وروح القدس”.
يؤمنون أيضا بعقيدة التجلي الإلهي، فيعتقدون أن الله قد يتجلى في البشر، سواء بصورة الخير أو الشر، فالخير كالإنسان الخيِّر، والشر كالإنسان العاصي، وقد أشاروا في بعض كتبهم إلى أن علياً “الإله” ظهر بصورة شيث ويوسف ويوشع وآصف وشمعون، ثم تجلى في صورة علي.
يعتقد النصيريون بكفر الخلفاء الراشدين وخلفاء الدولة الأموية والمذاهب الأربعة “الحنفية والمالكية والشافعية والحنبلية”، وقد ورد ذلك في قداس الإشارة في كتبهم.
وللنصيريين أساطير في بداية الخلق، تخالف العقيدة الإسلامية، ولا تلتقي معها إلا في بعض التفاصيل الدقيقة. كما تؤمن النصيرية بالتناسخ، وهو انتقال النفوس من جسم إلى جسم، وله تسميات وتفصيلات دقيقة في كتبهم، بحسب الجسم الثاني الذي تنتقل إليه النفس، فقد تنتقل إلى إنسأن أو حيوان أو نبات أو وسخ أو أرض.
ويؤمنون بأن علياً هو من سيجمع الناس ليقوم القيامة، وسيعلن امتلاكه للعالم كله، وسيكون لقبه في يوم الحساب “الدبور”.
وينقسم النصيريون إلى خاصة وعامة، فالخاصة هم حملة المذهب، وتعلم المذهب محصور في عائلات وأفراد معينين وفق شروط معينة، وهذه يسمونها مرتبة “تسليم الدين”، فإن تم قبول فرد لتعلم الدين يرتقي لمرتبة “السماع” ويبدأ بعدها بالاطلاع على أسرار المذهب وتعاليمه.
والنصيرية مذهب باطني، ومن ثم فإنهم يؤمنون بوجود عِلمين في تأويل تعاليم الدين، علم ظاهر وآخر باطن، ومن أمثلة ذلك عندهم اعتبار زواج علي بن أبي طالب أمير المؤمنين من فاطمة وإنجابه منها الحسن والحسين من قبيل علم الظاهر، وأما الباطن فيقول: إن علياً هو الله تعالى الواحد الأحد.
ويؤمنون كذلك بالتقية، وهي إظهار خلاف ما يبطنون من معتقدات، ومن أمثلة ذلك أنهم سجلوا أنفسهم في قضاء عكار اللبناني في سجلات النفوس “سنة” بناء على نصائح بعض مشايخهم في اللاذقية.
ومن أعيادهم عيد غدير خم في 18 من ذي الحجة، وعيدا الفطر والأضحى، وعيد المباهلة في 21 ذي الحجة حيث باهل النبي ﷺ في هذا اليوم أهل نجران بشأن المسيح عليه السلام، ويوم الفراش وفيه نام علي في فراش النبي ﷺ، وعيد عاشوراء الذي استشهد فيه الحسين، ويعظمون عيد الميلاد وعيد الغطاس وعيد البربارة، وعيد النوروز، وغيرها من الأعياد.
ولا يوجد طقوس واضحة للزواج والطلاق في التراث الفكري النصيري، وإن وجد اليوم فهو من مؤثرات الحضارة الإسلامية والمعاصرة، فكتبهم تشير إلى المرأة بنظرة ملؤها الازدراء والتشبيه لها بالحيوانات.
حاضر المذهب النصيري
أدرك السلطان العثماني سليم الأول خطر النصيريين على الدولة العثمانية فأمر بقتالهم، وخاصة بعد فتاوى علماء الدين فيهم لما أبدوه من خيانة للمسلمين على مر التاريخ، وبتحالفهم مع الصليبيين والمغول أثناء غزوهم لبلاد المسلمين، فهرب النصيريون إلى الجبال، ويذكر بعض المؤرخين أن العثمانيين قضوا على تسعة آلاف من مشيخة وزعماء النصيريين في ديار بكر وماردين والأناضول، واستمرت حالهم كذلك طوال فترة الحكم العثماني؛ فلم تقم لهم قائمة، رغم عصيانهم للخليفة في بعض الأحيان.
وفي أيام الانتداب الفرنسي تم استبدال اسم الطائفة من النصيريين إلى العلويين، وانقسم النصيريون بين مؤيد للفرنسيين، ومعارض لهم -كما تذكر بعض الروايات-، مثل صالح العلي الذي واجه الفرنسيين وحلفاءهم من الإسماعيليين في منطقة مصياف والقدموس، إلا أنه تراجع لاحقا عن ذلك بعد أن أقام الفرنسيون لهم كياناً فيدرالياً باسم “دولة العلويين” تضم اللاذقية وطرطوس، حيث أكثر النصيريون آنذاك من الاعتراضات ومن رفض التبعية لدمشق وللدولة السورية، فأعلنت فرنسا استقلال هذا الكيان عام 1925م، ولكنه كان استقلالاً هزيلاً ترعاه فرنسا بانتدابها، ويرفضه المسلمون السنة والمسيحيون الذين كانوا من أصحاب النزعة الوحدوية السورية.
وفي عام 1936م اضطر الفرنسيون إلى ضم الدويلة العلوية إلى سوريا، وذهب وفد من نصيريي سوريا إلى بيروت للاعتراض على هذا القرار، وكان من مطالبهم الحفاظ على الانتداب الفرنسي، وعدم تمكين المسلمين السنة من العلويين والدروز، ولكن الفرنسيين اضطروا تحت ضغط السياسيين في دمشق من الرضوخ للمطالب الدمشقية، حيث هدد الرئيس هاشم الأتاسي والوزراء بالاستقالة والإضراب إن وقّع الفرنسيون على قرار الانفصال عن الدولة السورية.
استقلت سوريا عن الفرنسيين عام 1946، وظل النصيريون يتبعون لدمشق، واستطاعوا الوصول إلى السلطة في دمشق عن طريق حافظ الأسد ابن سليمان الأسد الذي كان عضو الوفد الذي زار بيروت للمطالبة بالانفصال عن سوريا، والذي سلم السلطة -بعد تثبيت السلطة في سوريا على مدى 30 عاماً بين النصيريين- إلى ابنه بشار الأسد، وينتشر النصيريون اليوم في سوريا ولبنان وبعض مناطق جنوب تركيا المحاذية للساحل السوري.
أهم المراجع
- العلويون النصيريون، بحث في العقيدة والتاريخ، أبو موسى الحريري، بيروت، 1984م.
- مدخل إلى المذهب العلوي النصيري، جعفر الكنج الدندشي، المكتبة الوطنية، الأردن، إربد، 2000م.
- مذاهب الإسلاميين، عبد الرحمن بدوي، دار العلم للملايين، بيروت، 1997م.
مقالة بقلم الكاتب عبد اللطيف المحيمد من موقع السبيل
-
 @ 3ca99671:689a4ce4
2024-09-03 11:57:39
@ 3ca99671:689a4ce4
2024-09-03 11:57:39introduction #devdiary #logseqplugin
Not Another Nostr Client – Just Pure, Fast Posting. Forget the endless tabs and heavy interfaces. This plugin for logseq is here to give you a faster way to get your thoughts out there. Whether it's a few quick lines or a deep-dive post, it's all about hitting send to your followers without the extra noise. This is not a client—this is your direct line to the relay, a tool built for efficiency and simplicity. Think of it as your personal "publish now" button, ready whenever inspiration strikes. Be part of something streamlined and help me shape a tool that puts your voice first.
DM @chuckis
-
 @ 361d3e1e:50bc10a8
2024-09-03 11:38:01
@ 361d3e1e:50bc10a8
2024-09-03 11:38:01265 ingredients in Spicy Chicken and Mac Cheese from a fast food chain
usa #fastfood #food #safety #natural
-
 @ 3ca99671:689a4ce4
2024-09-03 11:15:54
@ 3ca99671:689a4ce4
2024-09-03 11:15:54asdf ``` Typescript type Color = "red" | "blue"; type Quantity = "one" | "two";
// то же, что и // "one fish" | "two fish" | "red fish" | "blue fish"; type T1 =
${Quantity | Color} fish;// то же, что и // "one red" | "one blue" | "two red" | "two blue"; type T2 =
${Quantity} ${Color};```
-
 @ 6bae33c8:607272e8
2024-09-03 10:47:55
@ 6bae33c8:607272e8
2024-09-03 10:47:55I do this every year, and every year I get at least one correct. Last year, I got exactly one correct and unfortunately it was the surefire prediction that not all of them would be right, i.e., I got really zero correct. But that just goes to show how bold they were. These aren’t layups, more like three pointers and half-court shots. I fared much better the previous two years, so hopefully these will get back on track.
(Actually, probably better to just link to all of them for full transparency: 2023, 2022, 2021, 2020, 2019, 2018, 2017, 2016, 2015, 2014.) I’m not going to argue it matters, or that anyone even clicks through on these, but I want to pat myself on the back for being so organized in archiving my old work.)
-
Stefon Diggs leads the Texans in targets, catches and receiving yards
Right now, he’s getting drafted more than a round behind Nico Collins and less than a round ahead of Tank Dell. Diggs is 30, but he was one of the league’s best receivers until halfway through last year when the Bills made an offensive play-calling change. Moreover, Diggs is getting paid $22.5 million, so the Texans obviously don’t think he’s washed up, and he’s also in a contract year.
-
CJ Stroud leads the NFL is passing yards
This is +600 on DraftKings, so the real odds are probably north of 8:1. Stroud adds Diggs to his receiving corps, doesn’t run much and heads into Year 2.
-
Roman Wilson (ADP 211) has more receptions than George Pickens (ADP 47)
Pickens is a boom or bust downfield playmaker, not high-target alpha, and Wilson is a good fit for the slot for the Steelers new QBs. Think Martavis Bryant not Antonio Brown. (Not that Wilson is Brown!) Van Jefferson isn’t good, and someone will need to fill the void. Moreover, because Pittsburgh has new QBs, neither has an existing rapport with the incumbent Pickens.
-
DeAndre Hopkins (ADP 82) out produces Calvin Ridley (ADP 54) in PPR
Hopkins wasn’t terrible last year, has a rapport with Will Levis and is a future Hall of Famer who can still run routes. Ridley is already 29 and is just a guy outside of his monster season in 2020.
-
The Giants will field a top-10 fantasy defense.
I’ve been crushed by my homer bold predictions in the past, but they added Brian Burns to a rush that already had Dexter Lawrence and Kayvon Thibodeaux, the offense should be on the field more and generate some leads with a real playmaking receiver in Malik Nabers.
-
One of the following Year 2 receivers will finish in the top-15 PPR: Jaxon Smith-Njigba, Jayden Reed, Jordan Addison, Dontayvion Wicks, Michael Wilson, Josh Downs, Andrei Iosivas, Quentin Johnston, Marvin Mims, Jalin Hyatt
I make this prediction every year, and it often pans out as Year 2 is when receivers typically make the leap. I left out Tank Dell because he’s now got a fifth-round ADP, as well as the obvious ones: Zay Flowers, Rashee Rice and Puka Nacua.
-
Rome Odunze (ADP 77) will outproduce Xavier Worthy (ADP 59)
Both receivers enter crowded situations, and while Worthy’s is far better, he’s also got essentially the same skill-set as teammate Marquise Brown. Moreover, Andy Reid rarely entrusts rookies with large roles, especially early on. Odunze is 6-3, 215 and has the pedigree of a true NFL alpha, while Worthy weighs only 165 pounds at 5-11. Finally, Patrick Mahomes already has an established rapport with both Travis Kelce and Rashee Rice, while Odunze gets a more open competition with the Bears veteran WRs, given all three will play with Caleb Williams for the first time.
-
Dalvin Cook will lead the Cowboys in rushing yards
Cook is 29 and looked beyond “cooked” last year on the Jets, but his 3.3 YPC was on a small sample (67 carries), and prior to that, he’d been very good for the Vikings. At the very least he should have fresh legs, and he’d only need to beat out the ancient Ezekiel Elliott and Rico Dowdle. (Of course, Cook would have to be promoted from the practice squad first, so I really should hedge and make the prediction “neither Elliott, nor Dowdle will lead the Cowboys in rushing yards,” but I’ll push it and say it’s Cook.)
-
Jonathan Taylor (ADP12 ) will lead the NFL in rushing yards.
He’s got little competition in the Indy backfield and a running QB who should open lanes for him. Draft Kings has him at +600, so his real odds are probably about 10:1, but I’d take him over the favored Christian McCaffrey (age/mileage) and all the other backs who are more hybrid types or old (Derrick Henry.)
-
Dalton Kincaid (TE4) will lead all TE in catches
I guess this is a chalky pick because he and Kelce are both favored at the position at +3000, while Evan Engram is +5000! (I’d way rather bet on Engram at those odds.) But straight up, I’m going with Kincaid who is likely Josh Allen’s de facto No. 1 target with Diggs gone. In his final 11 regular season games Kincaid had 56 catches which prorates to 87 catches over the full year. And rookie tight ends rarely do anything and often make a leap in Year 2.
-
Some of these predictions will be wrong
No one’s perfect, but you never want to get shut out.
-
-
 @ 469fa704:2b6cb760
2024-09-03 10:20:09
@ 469fa704:2b6cb760
2024-09-03 10:20:09In traditional investment wisdom, diversification is the mantra chanted by financial advisors worldwide. It's the strategy to spread risk across various assets to mitigate losses. However, when it comes to Bitcoin, some argue this principle might not apply in the same way. Here's why:
1. Bitcoin's Unique Value Proposition
Bitcoin, often dubbed "digital gold," has several attributes that set it apart from other investments:
- Finite Supply: With a cap at 21 million coins, Bitcoin's scarcity is programmed into its code, mirroring the scarcity of gold but with even more certainty. This scarcity can drive value as demand increases over time, especially in an economic environment where fiat currencies are subject to inflation.
- Decentralization: Unlike stocks or real estate, Bitcoin isn't tied to any central authority or physical asset that can fail or be manipulated by a single entity. This decentralization reduces the risk of systemic failure that affects traditional markets.
- Global Liquidity and Accessibility: Bitcoin can be bought, sold, and transferred anywhere in the world, 24/7, with internet access. This global liquidity means Bitcoin can be more easily converted to other assets if needed, somewhat reducing the need for diversification.
2. The Risk-Reward Balance
- Volatility as Opportunity: While Bitcoin's volatility is often cited as a risk, for the informed investor, this volatility represents opportunities for significant gains. Those who understand Bitcoin's cycles might prefer to ride these waves rather than dilute potential gains through diversification into less volatile assets.
- Long-term Appreciation: Historical data suggests Bitcoin has provided substantial returns over the long term compared to most traditional investments. If one believes in Bitcoin's future as a dominant store of value, holding a diversified portfolio might mean missing out on Bitcoin's potential upside.
3. Bitcoin as a Diversifier
Ironically, Bitcoin itself serves as a diversification tool within traditional investment portfolios. Its price movements have shown low correlation with stocks, bonds, and even gold at times, suggesting that Bitcoin can diversify an investment portfolio on its own.
4. The Philosophical Shift
- Trust in Code Over Corporations: Investing heavily in Bitcoin might reflect a philosophical shift towards trusting mathematical algorithms over corporate governance or government policy. Here, diversification within the crypto space might seem less necessary if one views Bitcoin as the pinnacle of what cryptocurrency should be.
- A Bet on a New Financial System: Holding Bitcoin exclusively can be seen as a bet on a new financial paradigm where Bitcoin becomes the standard. In this vision, diversification into other assets might be counterproductive.
5. Potential Result
Upon reviewing the arguments and characteristics, one might conclude that Bitcoin is pursuing a dual trajectory. Firstly, its value increases partly because it remains a novel asset, not yet mainstream among the general populace. Secondly, Bitcoin is poised to absorb the value preservation function from other assets. This means that individuals who invest in stocks, bonds, real estate, commodities, etc., primarily for their value storage capabilities rather than their intrinsic utility (such as residing in a property), might transition to Bitcoin. This shift could consequently diminish the demand for these traditional assets and increase the value of Bitcoin respectively.
6. Caveats and Considerations
- Not Without Risks: This approach isn't without its perils. Bitcoin's future is not guaranteed, and regulatory, technological, or market shifts could impact its value negatively.
- Liquidity Needs: Individual financial situations might require liquidity or income generation that Bitcoin alone might not provide efficiently.
- Emotional Discipline: A Bitcoin-only strategy requires immense discipline and conviction, as the emotional toll of not diversifying can be high during market downturns.
Conclusion
The argument for not diversifying if you hold Bitcoin hinges on its unique properties, the potential for high returns, and its role as a hedge against inflation and traditional financial systems. However, this strategy suits those with a high risk tolerance, a deep understanding of Finance, Economics and Investments, and a belief in Bitcoin's future dominance. For everyone else, while Bitcoin can be a significant part of a portfolio, traditional diversification might still offer peace of mind and stability. Remember, investment strategies should align with personal financial goals, risk tolerance, and market understanding. Always consider consulting with a financial advisor for personalized advice.
-
 @ 13e63e99:25525c6a
2024-09-03 09:29:54
@ 13e63e99:25525c6a
2024-09-03 09:29:54Preview
Last week, President Nayib Bukele of El Salvador emphasized Bitcoin’s role in enhancing the country's global image that boosted foreign investment and tourism. At the NostrWorld Unconference in Riga, the synergy between Bitcoin and decentralized social networks was a key focus, showcasing the potential for integrating Bitcoin with the growing Nostr protocol. Meanwhile, Lightspark launched its Extend platform, facilitating instant Bitcoin payments for U.S. businesses, thereby expanding the accessibility of Bitcoin transactions. Publicly traded companies have increased their Bitcoin holdings by nearly 200%, bringing their total to $20 billion, reflecting strong institutional confidence in Bitcoin as a reserve asset. Additionally, Bitcoin in exchange experienced its third-largest daily net outflow of 2024, indicating a shift toward long-term holding among investors. Despite some withdrawals, including a $13.5 million outflow from BlackRock’s iShares Bitcoin Trust, the fund remains a dominant force in the Bitcoin investment landscape. Lastly, Nigeria's SEC granted its first provisional exchange license, a milestone in the regulation of the country’s rapidly growing digital asset industry, positioning Nigeria as a leading player in global digital asset adoption. For more details, continue reading below.
A. Bitcoin Data Dashboard
1. Bitcoin Transactions\ 2. Supply\ 3. Mining\ 4. Transaction Fees\ 5. Difficulty Retarget\ 6. Lightning Network (Public)
B. Bitcoin Ecosystem
1. Bukele: Bitcoin was a powerful rebranding tool for El Salvador\ 2. NostrWorld Unconference in Riga: Exploring Bitcoin and Decentralized Social Networks\ 3. Lightspark launches Extend for instant Bitcoin Lightning payments in the U.S.\ 4. Public companies boost Bitcoin holdings by nearly 200%, reaching $20 billion\ 5. Bitcoin exchanges see 3rd-largest daily net outflow of 2024\ 6. BlackRock's iShares Bitcoin Trust faces $13.5m outflow amid broader ETF withdrawals
C. Regulation
1. Nigeria's first provisional exchange license from SEC, marking milestone in digital asset regulation
D. Macroeconomy
1. Vice President Harris proposes wealth tax targeting unrealized gains for ultra rich\ 2. Jobless claims drop as labor market slows, US economy remains on steady growth path
A. Bitcoin Data Dashboard

As of Sep 2, 2024
B. Bitcoin Ecosystem
1. Bukele: Bitcoin was a powerful rebranding tool for El Salvador
President Nayib Bukele recently provided a candid assessment of El Salvador's groundbreaking decision to adopt Bitcoin as legal tender, a move that has drawn both praise and criticism on the global stage. In an interview with Time magazine, Bukele emphasized that the initiative has had substantial benefits particularly in enhancing El Salvador's international image despite the country's bitcoin adoption has not expanded as rapidly as he has hoped, Bukele described the Bitcoin adoption as a powerful rebranding tool for the nation, one that has attracted foreign investment and boosted tourism. The president’s marketing advisor, Damian Merlo, echoed this sentiment, calling the decision "genius" and likening it to a major public relations campaign that El Salvador didn’t have to pay for. "We could have spent millions on a PR firm to rebrand the country," Merlo noted, "but instead, we adopted Bitcoin." While the move initially strained relations with institutions like the International Monetary Fund (IMF), which urged Bukele to abandon the policy due to perceived risks, there are signs that the tension is easing. El Salvador has recently reported progress in negotiations with the IMF, with a focus on enhancing transparency and addressing potential fiscal and financial stability risks related to the Bitcoin project.

Reference: Bitcoin.com, Time
2. NostrWorld Unconference in Riga: Exploring Bitcoin and Decentralized Social Networks
Last week, NostrWorld’s third unconference, held in Riga, Latvia, gathered advocates and developers of the Nostr protocol. Organized by Jack Dorsey, NostrWorld provides a platform for open-source enthusiasts to collaborate on building a decentralized internet. The event, called Nostriga, underscored the emerging synergy between Nostr’s decentralized social network and Bitcoin. Nostr is an open-source protocol for a decentralized, censorship-resistant social network. Unlike traditional platforms, Nostr operates on a network of relays, supporting features like micropayments and digital identity management. It promises greater privacy and independence from centralized platforms. A highlight of the conference was Strike CEO Jack Mallers discussing how Nostr’s micropayments—Zaps—helped a skeptic understand Bitcoin’s value. This feature shows Bitcoin’s utility in social contexts, advancing the concept of internet tipping. Jack Dorsey enphasizing the importance of open source. Nostr faces the challenge of broadening its user base beyond Bitcoin enthusiasts. New initiatives like Ditto aim to integrate Nostr with larger internet communities, potentially increasing Bitcoin’s visibility and accessibility. Nostr’s role as a social and identity system could pave the way for decentralized digital economies. By leveraging social graphs and cryptographic trust, Nostr and Bitcoin together could enable secure, decentralized commerce.
Reference: Bitcoin magazine
3. Lightspark launches Extend for instant Bitcoin Lightning payments in the U.S.
Lightspark has unveiled Lightspark Extend, a new solution designed to facilitate instant Bitcoin Lightning payments for U.S. businesses. This platform integrates with Universal Money Addresses (UMA) and Lightning-enabled wallets, exchanges, or bank accounts, offering a compliant and cost-effective way to handle transactions around the clock. Lightspark Extend is compatible with over 99% of U.S. banks that support real-time payments, enabling businesses to provide their customers with fast, low-cost transactions. UMA simplifies the payment process by using easy-to-remember addresses similar to email, removing the need for complex codes or passwords. With this launch, Lightspark Extend makes real-time payments via the Bitcoin Lightning Network accessible to eligible recipients across the U.S. Businesses interested in adopting this solution can sign up for a UMA address, link their accounts, and start receiving payments through an onboarding process facilitated by Zero Hash, a regulated U.S. financial institution. The introduction of Lightspark Extend marks a significant advancement in expanding the accessibility and utility of Bitcoin payments. This follows Lightspark’s recent announcement of a partnership with Coinbase, enabling customers to send up to $10,000 instantly through the Lightning Network.
Reference: Bitcoin magazine
4. Public companies boost Bitcoin holdings by nearly 200%, reaching $20 billion
Publicly listed companies have seen their Bitcoin holdings soar by nearly 200% in a year, rising from $7.2 billion to $20 billion. According to Bitbo data, 42 such companies now hold 335,249 BTC, valued at roughly $20 billion. This marks a 177.7% increase from a year ago, when their BTC holdings were worth $7.2 billion. The trend began with MicroStrategy's August 2020 purchase of over 21,000 BTC, making Bitcoin its primary treasury reserve asset, and the company has since grown its holdings to 226,500 BTC. A survey commissioned by Nickel Digital Asset Management revealed strong institutional support for Bitcoin as a reserve asset, with 75% of 200 surveyed institutional investors and wealth managers endorsing public companies holding BTC. The survey, involving firms managing $1.7 trillion in assets, also found that 58% believe 10% or more of public companies will hold BTC within five years. Nickel Digital's CEO, Anatoly Crachilov, noted that institutional investors see Bitcoin as a hedge against currency debasement and a valuable addition to reserve allocations. Despite this growth, the 335,249 BTC held by public companies represent just 1.6% of Bitcoin's total capped supply of 21 million.
Reference: Cointelegraph
5. Bitcoin exchanges see 3rd-largest daily net outflow of 2024
Bitcoin is seeing a significant uptick in exchange withdrawals as its price nears the $60,000 mark, with approximately 45,000 BTC removed from exchanges on August 27 alone. This movement represents the third-largest net outflow of Bitcoin from exchanges in 2024, following similar spikes in July. According to data from CryptoQuant, this trend could signal a growing bullish sentiment among investors, who appear to be transferring their Bitcoin off exchanges to hold for the long term, thereby reducing potential selling pressure in the market. As of August 27, major exchanges hold around 2.63 million BTC, reflecting a 12.5% decrease from the 3.01 million BTC held at the beginning of the year. This reduction in exchange reserves underscores a broader trend of investors preferring to hold their Bitcoin privately, possibly in anticipation of future price increases.

Reference: Cointelegraph
6. BlackRock's iShares Bitcoin Trust faces $13.5m outflow amid broader ETF withdrawals
BlackRock's iShares Bitcoin Trust (IBIT) experienced a $13.5 million outflow on Thursday, marking its first outflow since May 1st and only the second in the fund's history since its launch in January. This rare withdrawal contrasts with the ETF’s usual pattern of consistent inflows, underscoring its dominance in the Bitcoin investment space. The outflow came as part of a broader trend affecting spot Bitcoin ETFs, which saw a collective $71.8 million in withdrawals on Thursday. Competing Bitcoin ETFs from Grayscale, Fidelity, Valkyrie, and Bitwise also reported significant outflows, ranging from $8 million to $31 million. Despite these withdrawals, ARK's Bitcoin ETF saw an inflow of $5.3 million, highlighting a mixed investor sentiment as Bitcoin remains below the $60,000 mark. This divergence suggests varied outlooks among investors regarding Bitcoin's future. Despite the recent dip, BlackRock's Bitcoin ETF continues to lead the market, having attracted over $20 billion in net inflows since inception. With more than 350,000 BTC under management, it remains one of the largest institutional Bitcoin holders, reflecting its enduring appeal and influence in the Bitcoin investment landscape.
Reference: Bitcoin magazine
C. Regulation
1. Nigeria's first provisional exchange license from SEC, marking milestone in digital asset regulation
The Nigerian Securities and Exchange Commission (SEC) has granted Quidax, an Africa-based crypto exchange, its first provisional operating license. This marks a significant step toward formal recognition and regulation of Nigeria's digital asset industry. The SEC's license allows Quidax to operate as a registered crypto exchange in Nigeria, a move the company describes as a "shot of adrenaline" for the local crypto community, spurring innovation and growth. Quidax CEO Buchi Okoro praised the SEC, particularly under the leadership of Emomotimi Agama, for its efforts to bring order and investor protection to the Nigerian crypto market. The approval also paves the way for Quidax to collaborate with banks and financial institutions, pending approval from the Central Bank of Nigeria. This licensing follows the SEC's recent amendment to its rules on June 21, covering digital asset issuance, exchange, and custody. Despite concerns that stringent requirements could limit local crypto exchanges, the new regulatory framework, including the Accelerated Regulatory Incubation Programme, aims to align virtual asset service providers with the latest standards. Nigeria, Africa's largest economy, is a global leader in cryptocurrency adoption, ranking second in Chainalysis’ 2023 Cryptocurrency Geography Report. While foreign investment in Nigeria's crypto sector has been slower than expected, the new regulatory environment and Quidax's licensing could attract more investors by offering a stable and secure market.
Reference: Cointelegraph
D. Macroeconomy
1. Vice President Harris proposes wealth tax targeting unrealized gains for ultra rich
As a presidential candidate, Vice President Harris has aligned with President Biden’s tax policies, including the pledge not to raise taxes on anyone earning under $400,000 annually. However, she also has her own ambitious tax proposals. These include raising the top marginal tax rate on high earners from 37% to 39.6%. Although she previously suggested a 4% “income-based premium” on households earning over $100,000 to fund Medicare for All, this idea has not resurfaced in 2024. Among the more controversial proposals Harris supports is a tax on unrealized capital gains for individuals with over $100 million in wealth. Often dubbed the “billionaire tax,” this would require these households to pay an annual minimum tax of 25% on their combined income and unrealized gains. This approach would be groundbreaking in U.S. tax history, as it taxes assets that have not yet been sold. For example, if you buy stock at $10 and it increases to $20, you would owe taxes on the $10 gain, even if you haven’t sold the stock. The same principle would apply to real estate, where yearly value increases would be taxed. This proposal raises significant concerns, particularly about the administrative challenges of valuing assets annually and the potential for future expansion of the tax to lower wealth thresholds. The wealth tax faces hurdles in Congress and potential court challenges, but it signals Harris's intent to push for new forms of taxation on the ultra-wealthy.

Reference: Forbes
2. Jobless claims drop as labor market slows, US economy remains on steady growth path
Last week, new applications for jobless benefits in the U.S. dropped slightly, but re-employment opportunities for laid-off workers are becoming scarcer, indicating the unemployment rate likely remained high in August. Despite this, the labor market's orderly slowdown is keeping economic growth on track, with the economy growing faster than initially reported in the second quarter, driven by consumer spending and rebounding corporate profits. The labor market's cooling supports the expectation that the Federal Reserve may start cutting interest rates next month, though a 50-basis-point reduction seems unlikely. Initial jobless claims fell by 2,000 to 231,000 for the week ending August 24, while continuing claims, which indicate ongoing unemployment, rose slightly, suggesting prolonged joblessness. In the second quarter, the economy grew at an annualized rate of 3.0%, with consumer spending revised upward to a 2.9% growth rate, offsetting lower business investment and exports. Corporate profits also reached a record high, helping businesses manage input costs amid supply-chain challenges. The goods trade deficit widened in July due to a surge in imports, likely driven by expectations of higher tariffs if former President Trump wins the November election. Despite these factors, economists predict growth will slow but avoid a recession.

-
 @ a012dc82:6458a70d
2024-09-03 08:40:59
@ a012dc82:6458a70d
2024-09-03 08:40:59Table Of Content
-
What is a Bitcoin-Backed Stablecoin?
-
The Benefits of a Bitcoin-Backed Stablecoin
-
The Drawbacks of a Bitcoin-Backed Stablecoin
-
How Will a Bitcoin-Backed Stablecoin Work?
-
Conclusion
-
FAQ
Bitcoin has been around for over a decade now and has seen its fair share of ups and downs. The volatility of Bitcoin has made it difficult for businesses and consumers to use it as a medium of exchange, and as a result, several stablecoins have been developed over the years. A stablecoin is a type of cryptocurrency that is pegged to a stable asset like fiat currency, gold, or other cryptocurrencies. The goal of a stablecoin is to provide price stability and reduce the volatility of cryptocurrencies. The latest proposal in this regard is from Bitmex co-founder Ben Delo, who has suggested the creation of a Bitcoin-backed stablecoin.
What is a Bitcoin-Backed Stablecoin?
A Bitcoin-backed stablecoin is a type of stablecoin that is backed by Bitcoin instead of fiat currency or other assets. The idea behind a Bitcoin-backed stablecoin is that it will provide price stability for Bitcoin while also allowing users to transact in a stable cryptocurrency. The value of the stablecoin will be tied to the value of Bitcoin, which is expected to provide greater stability and reduce volatility.
The Benefits of a Bitcoin-Backed Stablecoin:
1. Price Stability: One of the primary benefits of a Bitcoin-backed stablecoin is that it will provide price stability for Bitcoin. This stability will make it easier for businesses and consumers to use Bitcoin as a medium of exchange.
2. Reduced Volatility: The volatility of Bitcoin has made it difficult for businesses and consumers to use it as a medium of exchange. A Bitcoin-backed stablecoin would reduce volatility, making it more attractive to users.
3. Liquidity: A Bitcoin-backed stablecoin would be highly liquid since it would be backed by Bitcoin, which is one of the most widely traded cryptocurrencies in the world.
4. Security: A Bitcoin-backed stablecoin would be highly secure since it would be backed by Bitcoin, which is a highly secure cryptocurrency.
The Drawbacks of a Bitcoin-Backed Stablecoin:
1. Centralization: A Bitcoin-backed stablecoin would require a centralized entity to manage the Bitcoin reserves that back the stablecoin. This could potentially lead to centralization, which is against the ethos of decentralized cryptocurrencies like Bitcoin.
2. Regulatory Issues: A Bitcoin-backed stablecoin could face regulatory issues since it would be backed by a cryptocurrency that is not regulated in many jurisdictions.
3. Price Fluctuations: The value of Bitcoin is highly volatile, and this volatility could be reflected in the value of the Bitcoin-backed stablecoin, which would reduce its stability.
How Will a Bitcoin-Backed Stablecoin Work?
A Bitcoin-backed stablecoin would be created by first purchasing Bitcoin and storing it in a reserve. The stablecoin would then be issued, and its value would be tied to the value of Bitcoin. As the value of Bitcoin changes, the value of the stablecoin would also change, but it would remain stable relative to the value of Bitcoin.
Conclusion
The creation of a Bitcoin-backed stablecoin has the potential to bring stability to the volatile cryptocurrency market. While there are potential drawbacks to this proposal, such as centralization and regulatory issues, the benefits of a Bitcoin-backed stablecoin, such as price stability and reduced volatility, may outweigh the drawbacks. The proposal by Bitmex co-founder Ben Delo is an interesting development, and it will be interesting to see how the cryptocurrency market reacts to it in the coming months and years.
FAQ
What is the difference between a Bitcoin-backed stablecoin and a regular stablecoin? A Bitcoin-backed stablecoin is backed by Bitcoin, while a regular stablecoin is backed by fiat currency or other assets. This means that the value of a Bitcoin-backed stablecoin is tied to the value of Bitcoin, while the value of a regular stablecoin is tied to the value of the asset it is backed by.
Why is a Bitcoin-backed stablecoin needed? Bitcoin is a highly volatile cryptocurrency, which makes it difficult to use as a medium of exchange. A Bitcoin-backed stablecoin would provide stability to the value of Bitcoin, making it easier for businesses and consumers to use it as a means of exchange.
How is the value of a Bitcoin-backed stablecoin determined? The value of a Bitcoin-backed stablecoin is determined by the value of Bitcoin. As the value of Bitcoin changes, the value of the stablecoin changes as well.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 94204d73:1a9bfecc
2024-09-03 08:04:49
@ 94204d73:1a9bfecc
2024-09-03 08:04:49In the realm of interior design, minimalism has emerged as a powerful aesthetic, celebrated for its clean lines, uncluttered spaces, and an emphasis on functionality. Minimalistic rugs play a crucial role in this design philosophy, offering a subtle yet striking way to enhance a room's ambiance. These rugs not only provide comfort and warmth but also contribute to the overall minimalist aesthetic.
Characteristics of Minimalistic Rugs
Minimalistic rugs are defined by several key features:
- Design: Often characterized by simple patterns or solid colors, minimalistic rugs avoid intricate designs that can overwhelm a space.
- Color Palette: Typically, these rugs feature neutral tones such as whites, grays, beiges, and blacks, which can seamlessly integrate into any decor.
- Quality Materials: Minimalistic rugs are often made from high-quality materials like wool, cotton, or natural fibers, providing a soft and inviting touch.
- Subtle Textures: While the designs may be simple, the textures can add depth and interest, enhancing the tactile experience.
- Versatility: Minimalistic rugs can fit into various design styles—from Scandinavian to industrial—making them a flexible choice for any space.
- Durability: Many minimalistic rugs are crafted to withstand daily wear and tear, ensuring longevity in high-traffic areas.
Popular Styles of Minimalistic Rugs
There are several popular styles of minimalistic rugs that embody the principles of simplicity and elegance:
- Room Dimensions: Measure your space to ensure the rug fits appropriately, whether it’s a small accent rug or a large area rug.
- Furniture Placement: Consider how the rug will interact with your furniture layout to create a cohesive look.
- Matching Decor: Choose a color that complements your existing decor, whether you want to create contrast or maintain a harmonious palette.
- Mood Enhancement: Lighter colors can make a space feel airy, while darker tones can add warmth and coziness.
- Comfort: Select a material that feels good underfoot, especially in areas where you spend a lot of time.
- Maintenance: Consider the ease of cleaning and durability, particularly for high-traffic areas.
Care and Maintenance
To keep your minimalistic rug looking its best, follow these care tips:
- Regular Vacuuming: Remove dirt and dust regularly to maintain the rug's appearance.
- Spot Cleaning: Address spills promptly with a damp cloth and mild detergent.
- Professional Cleaning: For deep cleaning, consider hiring a professional service, especially for natural fiber rugs.
Minimalistic rugs are a powerful design element that can enhance any space while adhering to the principles of simplicity and elegance. Their ability to blend seamlessly into various decor styles makes them a versatile choice for homeowners and designers alike. By carefully selecting the right size, color, and material, you can incorporate minimalistic rugs into your home, creating a serene and sophisticated environment that invites relaxation and comfort.
-
 @ 3bdc6701:8ae46fac
2024-09-03 02:38:44
@ 3bdc6701:8ae46fac
2024-09-03 02:38:44รีวิว KU Hackathon ในฐานะนิสิตปี 1
มีเเต่การเปลี่ยนเเปลงเท่านั้นที่ไม่เปลี่ยนเเปลง เฮราคลิตุส
นี่คือคำกล่าวเปิด Pitching ของกระผม จัดว่าคมมาก555 เรามาเกริ่นนำกันเลยครับ

KU Hackathon คืออะไร?
KU Hackathon เป็นงานแข่งขันที่จัดขึ้นโดยมหาวิทยาลัยเกษตรศาสตร์ (Kasetsart University) โดยงานนี้เป็นมหกรรมที่เน้นการพัฒนาและใช้เทคโนโลยีในการแก้ไขปัญหาต่าง ๆ ที่เกิดขึ้นในมหาวิทยาลัยเอง นิสิตจากหลายสาขาที่สนใจและมีความสามารถทางเทคโนโลยีมาเข้าร่วมในงานนี้ จะทำงานร่วมกันเพื่อพัฒนาแนวคิดและโครงการต่าง ๆ ที่สามารถช่วยแก้ไขปัญหาในมหาวิทยาลัยเกษตรศาสตร์ต่อไปได้
พูดง่ายๆครับ ทำเเอปนิสิตใหม่ เเละ เพิ่มฟีเจอร์ใหม่ๆลงไป
จุดเริ่มต้น
ผมได้ลงสมัครทีม Developer กับ เพื่อน ซึ่งเราสามารถ จับทีมเป็นคู่หรือเป็นกลุ่มก็ได้ซึ่งใช่ครับเราลงเป็นคู่ เเล้วยังไม่พอเรายังเป็นกลุ่มที่จับคู่ช้า ทำให้กลุ่มเรามีเเค่ 3 (โดยปกติจะมีกลุ่ม 3,4,5 สูงสุดอยู่ที่ 5 คน)
Overview งาน
ทางงาน hackkathon จะรับทั้งหมด 20 ทีม ในวันที่ 20 nov 2023 จะมีการ Pitching 1 รอบ จะคัดเหลือ 10 ทีมเเละ ในวันที่ 24 Nov 2023 จะมีการ Pitching อีก 1 รอบ เพื่อหา ผู้ชนะ 4 อันดับ

หาไอเดียเเละเริ่มทำ Prototype (เเบบรีบไปหน่อย) 15 Nov-20 Nov
ต้องเรียกว่ากลุ่มผมรีบมากๆ ในการ เริ่มทำ Prototype เพราะตอนเเรกคิดว่าฟีเจอร์ต้องสามารถใช้งานได้ เเต่จริงๆ ใช้ figma ก่อนก็ได้ครับ ไม่ต้องรีบเกิน ตอนช่วงนั้นน่าจะเรียกประชุมเเทบทุกวัน55

Pitching day | 20 nov
สำหรับผมวันนี้ถือว่าเป็นวันที่ผ่านไปได้ดี กรรมการทุกคนให้ Feedback ที่ส่งเสริมกับ Project ของเรา เช่น ลองเเบบนี้ ลองทำเเบบนี้ ลองปรับ… ซึ่งถือว่าเยี่ยมมากครับ

Hackkathon 22Nov - 24Nov
รอบนี้ของจริง
ได้เจอรุ่นพี่เก่งๆเยอะมากครับ mentor เเต่ละคนต้องบอกว่าเก่งๆทั้งนั้นครับ เจอ bug ตรงไหน ติดตรงไหนพี่เขาช่วยหมดครับ อย่างเรื่องของผมติดเรื่องการส่งรูปผ่าน API พี่ๆ mentor เเนะนำได้ดีมาก
ได้ศัพท์ใหม่ๆเยอะมากครับ เช่น Pitch Deck ซึ่งการ 1 ในเทคนิคการนำเสนอ ,
inbound and outbound เป็นศัพท์ทางการตลาด เเละ อื่นๆอีก….

Pitching day | 24 nov (อันนี้ Pitching สุดท้ายละครับ)
วันนี้คือวันตัดสินเเละเป็นวันสุดท้ายของ Ku hackathon ต้องสารภาพเลยว่า มีตื่นเต้นบ้าง55 เเต่สุดท้ายเราก็ได้อันดับ 4 กลับมาครับผม
โดย feature หลักๆของเรา มี 3 อย่างครับ
-Edoc Tracking(ระบบติดตามเอกสาร ) -Vin QrCode(ระบบสเเกน Qrcode วินมอไซต์เพื่อตรวจสอบเเละ Report วินมอไซต์) -Extension(ระบบ Extension นิสิตสามารถเพิ่ม feature ที่นิสิตอยากใช้ลงใน เเอป nisit ku ได้ เเละคนอื่นสามารถใช้ได้ด้วย เช่นการนำ Ku table ไปใส่ใน เเอปนิสิต)

📌Github and Demo : https://github.com/hackathon-ku/hackathon-2023-hackbthon
สุดท้ายครับ
ขอขอบคุณพี่สตาฟ เเละ ทุกๆท่านที่มีส่วนร่วมในงานนี้ นับว่าเป็นงานหนึ่งที่ผมคิดไม่ผิดที่ลงมางานนี้ เเละขอบคุณที่ทำให้มีงาน KU Hackathon เกิดขึ้นครับ ถือว่าเป็นประสบการณ์ที่คุ้มค่ามากครับ เเละอยากเชิญชวนน้องๆทุกๆคนมางานนี้👍✨
ขอขอบคุณเพื่อนๆในทีม
วาวา ตัวตึง คณะ เศรษฐศาสตร์ ถึงว่าจะเป็นมือใหม่ในการ Design เเต่สังเกตุได้เสมอในเรื่องการหาความรู้เปิด tutorial ดู เเละก็ทำได้เลย เป็นคนหัวดีมากๆ
พลัส ตัวตึง สาย AI เเละ Data analytic การดูเเล backend ต้องไว้ใจคนนี้เลยเก่งจัดๆ ทำได้ยัน deploy API บริษัทไหนไม่รับเรียกว่าพลาดเเล้ว
ถือว่าผมโชคดีมากๆที่ได้มาอยู่กลุ่มนี้✨
ขอบคุณครับ
-
 @ 9a35b935:4b4c66af
2024-09-03 01:43:37
@ 9a35b935:4b4c66af
2024-09-03 01:43:37Chef's notes
Easy and flavorful dish that can be prepared cooked in about 30-35 minutes. Just omit the smoke if you want to take it indoors with the oven
Details
- ⏲️ Prep time: Rub ahead of time
- 🍳 Cook time: 30-35 minutes (temperature though and not time)
Ingredients
- 2 tablespoons paprika
- 4 tablespoons coconut sugar (can substitute brown sugar)
- 1.5 tablespoons kosher salt
- 1 tablespoon fresh black pepper
- .5 tablespoon chili powder
- 1 tablespoon garlic powder
- 1 tablespoon onion powder
- 1 tablespoon ground mustard
- 1/2 teaspoon cayenne pepper (optional)
Directions
- Pat tenderloins dry and season with Rub and let rest for at least two hours
- Fire up grill / smoker to 350 When appropriate for your grill add a mild wood like pecan.
- Smoke Roast and pull off a little early to let rest to 145. I like this temp because I think searing becomes optional. If you want to sear go ahead and take it down to 250
- If sear is desired: Sear for one minute per side in a hot cast iron pan. Check after 30 seconds to be careful not to let the sugar burn
-
 @ e56e78ba:b3cf1b59
2024-09-03 01:23:12
@ e56e78ba:b3cf1b59
2024-09-03 01:23:12The Future of Text Storage and Transmission: Why Nostr is Revolutionizing the Web
In today's digital age, we rely heavily on text-based communication. From messaging apps to social media platforms, email clients to online forums, our interactions with others are often facilitated through text. However, traditional text storage and transmission methods have their limitations. That's where Nostr comes in – a decentralized, peer-to-peer (P2P) protocol that's poised to disrupt the status quo.
What is Nostr?
Nostr (pronounced "noster") is an open-source project that enables users to send and receive text messages directly, without relying on intermediaries like servers or messaging platforms. By creating a decentralized network of nodes that act as relay points for messages, Nostr allows individuals to communicate privately, securely, and efficiently.
Why is Nostr the Future of Text Storage and Transmission?
- Decentralization: Nostr's P2P architecture means that there is no single point of failure or central authority controlling the flow of information. This makes it virtually impossible for governments or corporations to intercept or manipulate messages.
- Security: By using end-to-end encryption, Nostr ensures that only the intended recipients can read your messages. This eliminates the risk of eavesdropping, tampering, or data breaches.
- Scalability: As more nodes join the network, Nostr's capacity for handling traffic increases exponentially, making it an ideal solution for large-scale communication needs.
- Interoperability: With Nostr, users can communicate across different platforms and devices without worrying about compatibility issues.
How to Use Nostr
Getting started with Nostr is relatively straightforward:
- Install the Client: Download and install a Nostr client application on your device (currently available for desktop computers and mobile phones).
- Generate a Key Pair: Create a public-private key pair, which will be used for encrypting and decrypting messages.
- Find or Create a Node: Discover an existing node or create one by running a local instance of the Nostr software.
- Connect to a Node: Join the network by connecting to a node using your public key.
- Send and Receive Messages: Start sending and receiving messages with other users who are also connected to the Nostr network.
Real-World Use Cases for Nostr
- Secure Communication: Nostr is ideal for sensitive communications, such as business negotiations, legal discussions, or personal conversations that require confidentiality.
- Disaster Response: In emergency situations where traditional communication infrastructure may be compromised, Nostr's decentralized nature allows for rapid and reliable information exchange.
- Community Building: Nostr can facilitate secure, private discussions among community members who want to share ideas, collaborate on projects, or coordinate events.
Conclusion
Nostr represents a significant leap forward in text storage and transmission technology. Its decentralized, P2P architecture ensures that messages remain private, secure, and efficient – making it an attractive solution for individuals and organizations seeking greater control over their online interactions. As the Nostr ecosystem continues to grow and evolve, we can expect to see innovative applications emerge, further solidifying its position as a game-changer in the world of text-based communication.
-
 @ e56e78ba:b3cf1b59
2024-09-03 01:18:59
@ e56e78ba:b3cf1b59
2024-09-03 01:18:59The Future of Text Storage and Transmission: Why Nostr is Revolutionizing the Web
In today's digital age, we rely heavily on text-based communication. From messaging apps to social media platforms, email clients to online forums, our interactions with others are often facilitated through text. However, traditional text storage and transmission methods have their limitations. That's where Nostr comes in – a decentralized, peer-to-peer (P2P) protocol that's poised to disrupt the status quo.
What is Nostr?
Nostr (pronounced "noster") is an open-source project that enables users to send and receive text messages directly, without relying on intermediaries like servers or messaging platforms. By creating a decentralized network of nodes that act as relay points for messages, Nostr allows individuals to communicate privately, securely, and efficiently.
Why is Nostr the Future of Text Storage and Transmission?
- Decentralization: Nostr's P2P architecture means that there is no single point of failure or central authority controlling the flow of information. This makes it virtually impossible for governments or corporations to intercept or manipulate messages.
- Security: By using end-to-end encryption, Nostr ensures that only the intended recipients can read your messages. This eliminates the risk of eavesdropping, tampering, or data breaches.
- Scalability: As more nodes join the network, Nostr's capacity for handling traffic increases exponentially, making it an ideal solution for large-scale communication needs.
- Interoperability: With Nostr, users can communicate across different platforms and devices without worrying about compatibility issues.
How to Use Nostr
Getting started with Nostr is relatively straightforward:
- Install the Client: Download and install a Nostr client application on your device (currently available for desktop computers and mobile phones).
- Generate a Key Pair: Create a public-private key pair, which will be used for encrypting and decrypting messages.
- Find or Create a Node: Discover an existing node or create one by running a local instance of the Nostr software.
- Connect to a Node: Join the network by connecting to a node using your public key.
- Send and Receive Messages: Start sending and receiving messages with other users who are also connected to the Nostr network.
Real-World Use Cases for Nostr
- Secure Communication: Nostr is ideal for sensitive communications, such as business negotiations, legal discussions, or personal conversations that require confidentiality.
- Disaster Response: In emergency situations where traditional communication infrastructure may be compromised, Nostr's decentralized nature allows for rapid and reliable information exchange.
- Community Building: Nostr can facilitate secure, private discussions among community members who want to share ideas, collaborate on projects, or coordinate events.
Conclusion
Nostr represents a significant leap forward in text storage and transmission technology. Its decentralized, P2P architecture ensures that messages remain private, secure, and efficient – making it an attractive solution for individuals and organizations seeking greater control over their online interactions. As the Nostr ecosystem continues to grow and evolve, we can expect to see innovative applications emerge, further solidifying its position as a game-changer in the world of text-based communication.
-
 @ 3cd2ea88:bafdaceb
2024-09-02 23:29:31
@ 3cd2ea88:bafdaceb
2024-09-02 23:29:31🚀 Acquista o deposita e guadagna fino al 25% in sconti USDT garantiti! 🪙💳
🔹 Fino al 25% di cashback in USDT per acquisti superiori a 100 USDT tramite carta di credito/debito o deposito bancario. 🔹 Vinci fino a 300 USDT semplicemente registrandoti, condividendo la promozione e compilando un modulo. 🔹 I primi 200 utenti con le transazioni più alte possono vincere premi extra, inclusi merch Bitget esclusivi e fino a 500 USDT!
🎁 Bonus Extra: Iscriviti con il nostro referral per ottenere uno sconto del 10% sulle fee per sempre e l'accesso al nostro corso esclusivo!
🕒 Periodo di promozione: 2 – 9 settembre
🔗 Partecipa subito e inizia a guadagnare!
https://bonus.bitget.com/U1JNEK
-
 @ d6b095f3:5775d03d
2024-09-02 21:58:34
@ d6b095f3:5775d03d
2024-09-02 21:58:34Hello, In this article, I will help you discover alternative solutions that can benefit you in your own unique discipline.
To begin, let's consider an analogy of a prehistoric hunter-gatherer tracking wild game. As the hunter matures, he may become confident in a specific method of hunting in certain situations. But as his family grows or his body ages, the same technique and style of capturing prey may no longer be viable. This is why it’s important for him to adapt to a wide variety of circumstances to achieve his goal of sustenance. Similarly, the creative individual faces the same challenge as they seek to maintain employment and preserve their craft through self-initiated endeavors.In this exercise, I will introduce you to a new mental framework for problem-solving. This approach will help you flex your mental muscles, and you may even come to enjoy the process. Whether you're creating software or taxidermy, self-employed or unemployed, this step-by-step thinking process will help jump-start your creativity and eliminate any writer's block.
Now, let's begin. Start by quickly thinking about your problem. Summarize the issue at hand in a few sentences. Once you've identified the problem at face value, take a moment to think long and hard about the perfect, flawless solution. It may be helpful to jot down a few bullet points or even create a rough sketch if you prefer. Once you have a general understanding of your ideal solution, take your time—hours or even days if necessary—to develop a detailed plan for your MVP (Minimum Viable Product). This will be the most extensive part of the exercise.
When your MVP is fully defined, it’s time to move on to the final phase of this creative exercise. Create a five-step plan consisting of preparation, beginning, middle, and end, followed by cleanup/presentation. Once these steps are organized in order of operation, you can begin preparing for the first step of creation.
Let me provide one final example. Let's say you're building an Adirondack chair for fun. You've watched some videos and studied diagrams, but you’re still stuck. If you use the process I’ve outlined, you would first visualize the perfect Adirondack chair, made by hand. Then, you would boil that ideal chair down to its essentials. Once you understand those essentials, you can chart your five-step path: the first step being preparation. By setting up your workspace for a clean workflow, you will be inspired to start building the chair.Good luck to you.
Best regards, 🥰💘
-
 @ 9d51218e:a0c80d65
2024-09-02 20:33:24
@ 9d51218e:a0c80d65
2024-09-02 20:33:24https://forex-strategy.com/2024/09/02/electronic-cigarettes-and-vaping-products-are-a-path-to-artificial-ventilation-of-the-lungs/ Electronic cigarettes and vaping products are a path to artificial ventilation of the lungs
vapes #cigaretes #health #study #medicine #lungs
-
 @ 361d3e1e:50bc10a8
2024-09-02 20:31:19
@ 361d3e1e:50bc10a8
2024-09-02 20:31:19 -
 @ 161c8564:2d633b95
2024-09-02 20:24:34
@ 161c8564:2d633b95
2024-09-02 20:24:34Opinion about Freewallet Multi Crypto Wallet (iphone)
FRWT Wallet uses deceptive marketing to lure in unsuspecting users. Once you deposit funds, they’ll block your account under the guise of KYC checks. It’s a fraudulent app—don’t download it!
WalletScrutiny #nostrOpinion
-
 @ 9bc2d34d:d19d2948
2024-09-02 19:41:40
@ 9bc2d34d:d19d2948
2024-09-02 19:41:40Chef's notes
This recipe is designed for home cooks who want to recreate the delicious buttery hollandaise sauce at home without feeling overwhelmed. It focuses on teaching the basics of the sauce, allowing beginners to master the fundamentals before experimenting with seasonings, hot sauces, or herbs.
Please note the thickness of sauce in the picture. This is after ten minutes of blending.
Details
- ⏲️ Prep time: 3 minutes
- 🍳 Cook time: 10 minutes (blending)
- 🍽️ Servings: 2 - 4
Ingredients
- 4 egg yolks
- 8 tablespoons of melted butter
- 1 tablespoon of lemon juice
- Pinch of salt
- Pinch of pepper
Directions
- Melt butter in the microwave or on the stovetop.
- Separate the egg yolks from the egg whites (reserve the egg whites for another dish).
- Place the egg yolks in a blender.
- Start the blender (medium to high settings for blend mode is fine).
- Slowly pour the melted butter into the cover opening (it will splatter).
- Add the remaining ingredients.
- Blend for ten minutes (seriously, walk away and do something else).
- Taste and adjust the flavors (add extra lemon juice or salt if desired).
- Serve over your breakfast!
-
 @ 622bd9cb:10a061b3
2024-09-02 19:21:42
@ 622bd9cb:10a061b3
2024-09-02 19:21:42zap test.
-
 @ 622bd9cb:10a061b3
2024-09-02 19:21:01
@ 622bd9cb:10a061b3
2024-09-02 19:21:01Zap test.
-
 @ 75bf2353:e1bfa895
2024-09-02 19:04:18
@ 75bf2353:e1bfa895
2024-09-02 19:04:18
Alby Hub is lightning-node software that Get Alby sells as a service. It's also free and open source. You can run it on a node such as Umbrel or Start9. I even was able to run it on Ubuntu. I was lucky enough to try the Alby Hub early. I even tested the software as a service before it was released to the public. I "forgot my password," though. Actually, I never knew it. I use VaultWarden as a password manager and copy and paste all my passphrases. I was in a Jitsi meeting. You know how it is. Bitcoiners are super interesting smart people. I got distracted talking to these smart people and must have copied and pasted the wrong passphrase because...I got distracted. I opened a channel and then got locked out. It's my fault. I take complete responsibility. I take complete responsibility. I hadn't even written down my seed phrase yet.
I didn't lose any sats though; aside from the 10,000 sats, it cost me to open up the channel. This is because I am very careful about sending larger sums of bitcoin to wallets before I write down the seed or test them. I might send 21,000 SATs or something like that to see if I can recover them before I send more. We used to say "don't be reckless," but that ethos can get lost in all the excitement of this cutting-edge technology we call the lightning network. If I sent thousands of dollars of bitcoin to this Alby Hub wallet I was beta testing, those sats would have been HODLED forever. It is important to use new technology with small amounts of bitcoin. It is important to use new technology with small amounts of bitcoin." This way, you mitigate your risk of a catastrophic loss. This is especially true if you ever find yourself beta-testing.
The Bright Side of Forgetting My Passphrase on Alby Hub
 )
)There is an orange lining to this story. The other beta tester in the meeting got it to work. He played a game called Zappy Bird. This is not an endorsement of Zappy Bird. I think it's a gambling version of Flappy Bird. I am not a gamer, and I would just lose my seat if I played this for any length of time. This allowed me to see the possibilities of Alby Hub, however, even though I screwed up my first try. My mother, like many of your mothers, I'm sure, always said, "If at first you don't succeed, then try again."
" Even though it didn't work for me at first, I got a glimpse into how awesome Alby Hub was anyway. Even though it didn't work for me at first, I got a glimpse into how awesome Alby Hub was anyway. That motivated me to try again. The second time I Alby Hub on PopOS! by following the instructions on the README file. That worked. It was surprisingly easy, but we were in the early days, and my channel was force closed. The issue seems to be fixed now that it's released to the public. I'm amazed at how much cleaner it is now. I also had a few other problems connecting my node to my Alby account because it was connected to the original node. The good people at Get Alby fixed that, however. I'm really impressed with their customer service. Screwing up my first node gave me the opportunity to learn this about the company.
Screwing up my first node gave me the opportunity to learn this about the company. I continued to use the GetAlby API during this time. I continued to use the GetAlby API during this time. I thought API's were super scary. 3 I don't even know what API stands for. Thanks to some of the people like Bitkarrot from Plebnet.dev, I am comfortable using them. A few weeks ago, I was able to make some video tutorials that teach businesses how to accept bitcoin. I am aware most businesses prefer fiat. It occurred to me: why would a business care if the fiat in their bank account comes from Strike or Mastercard? Of course, businesses that want to accept bitcoin can keep the sats. One business owner I know who is listed on BTCmaps did not want to use Strike because he liked seeing the stats on his phone.
Get Alby On Umbrel Or Start9
As I eluded to earlier, you can now run GetAlby on Start9 or Umbrel. They have videos and guides in[ ]this tutorial](https://guides.getalby.com/user-guide/v/alby-account-and-browser-extension/alby-hub/alby-hub-flavors/umbrel-start9-etc). If you already have one of these machines laying around and are comfortable getting your fingers dirty in the command line, you should try it. If not, you should try the software as a service. If you're a command-line ninja, run it on Ubutnu. Don't be reckless. Only use amounts you are willing to lose. Ably doesn't have access to your seeds, but it is still a hot wallet. It is also still very new. Expect bugs. Expect channel closures. Don't just be a whinny complainy-pant about it. Help improve it. Make a pull request if you must. If you are not as technical. Don't worry. They plan to be on the Umbrel and Start9 app stores soon.
Alby Hub on Umbrel or Start 9 require the Lightning Node app. If you self-hose, your seed is on your Lightning Node app. Write these 24 words down and keep them safe. You will need these to recover your bitcoin in case something breaks. If you use the cloud service, follow the directions to back up your keys here. Opening a channel is easy. You just send the 10,000 sats or whatever the fee is to open it. It's a node in the cloud service similar to voltage, I suppose. To be honest, I'm not sure how it works on the back end, but this abstracts away much of the complexities of running your own lightning node. You don't need to worry about finding a node to connect to, inbound liquidity, or balancing channels. That's like full-time IT work. Alby Hub makes running a lightning node easy-peasy lemon squeezy. Alby Hub makes running a lightning node easy-peasy lemon squeezy. This opens bitcoiners up to a world of possibilities.
Why I Am So Excited About Alby Hub

Although I did some beta testing for GetAlby's Alby Hub, I didn't receive any sats from them aside from a couple zaps here and there, but this is not a paid ad or sponsored blogpost. I don't think I can make a better guide than they have on their website. I am excited about Alby Hub because it makes accepting bitcoin so easy. I am excited about Alby Hub because it makes accepting bitcoin so easy. I'm not sure your grandmother could do it, but most computer-literate people could easily run Alby Hub. But wait... There's more.
Thanks to these wonderful people on nostr, I learned how to find my keys in the lightning node of my Umbrel. This also means my lightning node works for other apps besides Alby Hub. It also works with the LNbits installed on my Umbrel. I bet it works with BTCpayServer too, but I haven't verified this yet. This means businesses will soon be able to accept bitcoin by: - Buying a $400 minicomputer like Umbrel or Start9 ($800). - - Using Alby Hub in the Cloud and integrating it into other clients that use Nostr Wallet Connect - - Setting up an online bitcoin store on Shopster or Plebeian Market will be easy. - -+ The Uncle Jim Model just got 10x easier.
For example, what if I sold LNBit's POS extension and gave someone access to use my LNBits as a POS? shop could use LNBits as a POS terminal all of a sudden. I could build a bitcoin POS system for a local business using old comouters in my strategic computer reserve. Okay, I admit it. I'm a computer hoarder. I never recycle old computers unless they are unrepairable. There are so many ways to use the lightning network now. Find out more at https://getalby/hub. We can use these tools in creative ways. What if, instead of using BTCpayServer to help businesses accept bitcoin, we create a BTCpayServer-like product list on Shopster instead?
Using Alby Hub to Monetize My Blog
As I thought more about this, it occurred to me I should start a business with all of this stuff. Some people at my local meetup have asked me to help them set up a lightning node. Tools exist that make it easy enough to do consulting for anyone over tools like Keet or Hivetalk.org/. I also want to sell T-shirts. I've had the idea to sell bitcoin t-shirts that say Pay Me In Bitcoin. This one time, I played poker in Vegas during Def-Con. I was there for poker at the time. I've never been to DefCon. Some nerd had a QR code on his T-shirt. I'm not sure what it was. It was the first time I ever saw a QR code.

I was able to design this T-shirt with the help of Dell E 3. I'm using some of the techniques I learned in the 4-hour workweek to design this shirt, but instead of hiring a graphic designer in a third-world country, I hired computer power from PayPerQ. A website I learned about on getalby.com. Around the time of the halving, some dude at my job asked me if I think he'll ever be able to afford a whole bitcoin for each of his kids. I said I didn't know. He told me he makes way more than my family, but he hasn't started stacking SATs yet. He also told me he pays for Chat GPT because it is "only $30 a month." That's $360 of sats he could have stacked per year. I wouldn't be surprised if $360 stacked in bitcoin is worth $3,600 in five years.
Many people who say they will never spend bitcoin often spend money on other fiat things because they were raised with a hyper-consumer mental framework. Many others think AI will kill us like the Terminator, but people like Andreas Antonopolis and Paul Vigna wrote books about bitcoin getting used as a medium of exchange for AI almost a decade ago. The lightning network was clunky and difficult back when I first ran a MyNode and entered my public key into yalls.org to write about bitcoin. I bought a sticker from Blockstream with the Eclair Wallet back then, but it was hard to see how the lightning network could come over the technical hurdles for the majority of the people.
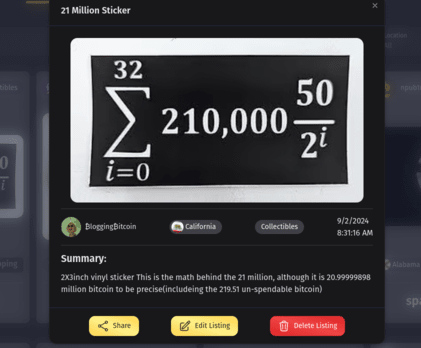
Tools like Alby Hub give me hope for the future. I listened to Natalie Brunell's Coin Stories this morning. The guest is a gold bug. She said something my wife is even still concerned with. The government will never allow bitcoin to be used for payments. They will capture it before this happens.
She is right in a sense. I am sure the governments of the world will not want to give up the power to print money and expand and contract the economy as they see fit. The digital alternative to central banking will not be welcomed by governments. Plebs build it anyway. The government of the United States has the most powerful weapons ever known to humankind. This government has an arsenal big enough to destroy the world many times over. I'm not certain bitcoin will survive an existential event such as this. I do not doubt the POTUS could Executive Order 6102.2 every Saturday in the ETF's overnight. To ban tools that make it easy to use the bitcoin lightning network as payments requires banning computers and banning software distributed all over the world. It seems like governments would have a difficult time banning computers.

Now that I think of it, Natalie Brunel could use Alby Hub to accept steaming sats and boosts to her podcast. She can host it in the cloud or on a plug and play node like Umbrel or Start9.
-
 @ 75bf2353:e1bfa895
2024-09-02 19:00:02
@ 75bf2353:e1bfa895
2024-09-02 19:00:02 -
 @ a19bc0c4:cee25620
2024-09-02 18:16:08
@ a19bc0c4:cee25620
2024-09-02 18:16:08The internet removed many classical excuses for lack of communication. The cell phone demolished the rest. If, back in the day, you wanted to avoid a caller, the simple out provided was "I wasn't near a phone". Nowadays, you have not only a phone in your pocket, but a portable telegraph.
Nonetheless, there still exists a kind of malicious communication or half-communication. People will often fail to answer texts, or they say they "forgot". Sometimes they wander off during a conversation to do something else entirely while the crucial part of the communication is still unfolding.
Some people blame this on bots, but it is easily observable in human beings that, as far as can be discerned, do not have silicon processors in their noggins. Sometimes the behavior is to flat out ignore what was said or comply with the communication much later. The new catchy term is that it is a kind of "psy-op". The communication is meant to be annoying and ambiguous as a kind of incursion into an organization, the thinking goes.
When I was growing up, it was a "You better speak when you are spoken to when someone who is your elder is asking you something," issue. Failure to comply was often met with helpful reminders such as groundings, yellings, or other kinds of physical displeasure.
The difference now, is, in my estimation, that there is a whole lot more information available and communication potential to the point no one fully knows what to pay attention to. Priority information and valuable information have no analogs. Most of these problems disappear, I have noticed, if it concerns someone's place of work. This of course, implies a kind of work-culture slavery that puts the "masters of money" in a priority communication scenario which implies an uplifting of the perceived security of the self over everything else.
However, it isn't only a generational thing, as I have also seen so-called "Boomers" do this too. Usually, this kind of behavior occurs in proximity to other kinds of bad behavior that the title warrants. Most often, these people have a sense of entitlement as they happened to get their gains at a time when the world and society was at a point it no longer occupies. A population of 3 to 4 billion is a much different set point than 9 billion. The heuristics used to make decisions, though, stay the same. Otherwise, the story would have to change. It's easier to ignore anything that is suggestive of change, and instead live in one's own bubble.
That, in my opinion, explains the problem the best. Everyone is retreating to their own communication bubble and so they cannot have exchanges smoothly across different mediums. Surely, tech has influenced this some as the attention span has become smaller. However, ignoring aspects of reality you don't like is really just what an autistic child is at the extreme end. They live in their own reality at at their own time. Of course, they are also considered disabled. Why then, should degrees of this communication problem not warrant the same label?
-
 @ 6bae33c8:607272e8
2024-09-02 18:09:19
@ 6bae33c8:607272e8
2024-09-02 18:09:19I did the third and final NFFC Beat Chris Liss league last night, and it was one of the more interesting and aggressive drafts I’ve ever done. I picked from the seven slot.
Here are the results:

1.7 Ja’Marr Chase — I made seven my first choice, but then realized I probably should have gone with four or five, or maybe nine or 10. That’s because if the first six picks went chalk (and they did), I’d be faced with Chase who is holding out for a new contract (and who I have in two other leagues already), Justin Jefferson (new, bad QB) or Garrett Wilson (new QB, never been a Round 1-level WR.) At 1.9 I’d have gotten one of those guys anyway, but earlier picks on the way back. And at 1.4, I’d have gotten a shot at Bijan Robinson for an easier hero-RB build. But I had pick seven, and I tripled-down on Chase because I think it’s very likely he’ll get his extension (or play if he doesn’t), and he’s an all-time talent with a top QB and projects for a massive target share. Plus, if he busts it’s Alan Seslowsky’s fault, and having someone to blame is paramount.
2.6 Drake London — I had it mapped out via ADP that I’d likely get De’Von Achane here, but he went at his min pick (I’m pretty sure) at the 1-2 turn, and so I was scrambling a bit. I really wanted Puka Nacua, who I missed by one pick, considered Cooper Kupp, but ended up going for the ADP-faller London who I had not remotely planned on getting. London obviously benefits from the massive QB upgrade in Atlanta, but it’s an open question whether he’s really an elite receiver or just a good one, and Kyle Pitts could easily emerge as Kurt Cousins favorite target instead.
3.6 DeVonta Smith — When Derrick Henry went one pick ahead of me, it was between Smith and Jaylen Waddle who I took in BCL2. Normally I avoid receivers this undersized but Smith has always produced at every level and is locked into his sizeable target share. Plus I read some Scott Barrett tweets about how Kellen Moore’s offense boosts the slot receiver a ton and that Smith thrives in the slot and could see more work there.
4.7 Stefon Diggs — This was ideal. I now have Diggs in all four of my leagues so far. Maybe he’s hit a cliff at age 30, but he’s getting $22.5M to play in arguably the league’s top passing game that lacks a true No. 1 alpha. I also considered Tee Higgins to pair with Chase (and serve as Chase insurance), but Diggs has more upside as a potential No. 1 target.
5.6 Dalton Kincaid — I’ve been high on him all summer, but he never quite fell to me in the right place until now. I expect him to be Josh Allen’s No. 1 receiver now that Diggs is gone.
6.7 James Conner — I needed a RB, and Conner is one. I’m a bit wary of a 29-YO guy with an extensive injury history, but he averaged 5.0 YPC last year and has never had a massive workload so he’s fresh for his age at least. Plus, the Cardinals offense should be good this year.
7.6 Anthony Richardson — I wasn’t planning on taking a QB here, or even Richardson who I have in BCL2 in Round 5!, but I couldn’t pull the trigger on Zamir White over someone with Richardson’s upside. I’m trying to win the overall contest, not simply cover the bases with starters at every position.
8.7 Jonathon Brooks — Jaylen Warren was still on the board, and he was a viable Week 1 starter for me, but Brooks who is on IR, struck me as the upside play. I heard somewhere, can’t remember where, that Brooks was an elite prospect in college before the injury, and there’s a lot of hype about Carolina’s new offensive brain trust boosting the offense generally. But it might have been a rash pick given my zero-RB build to take a rookie on IR.
9.6 Marquise Brown — I missed Warren by one pick on the way back, and instead of pivoting to Tyjae Spears I leaned into the zero-RB by taking Brown who was going in the fifth or sixth round before his injury. The beauty of this pick is I don’t need Brown right away as I wouldn’t start him anyway, so I pay no price for him missing Week 1. The ugly of this pick is I missed out on Spears, Zack Moss and Chuba Hubbard (who would have been nice to pair with Brooks.)
10.7 Joe Burrow — The obvious pick was Trey Benson to pair with Conner. In fact, I could have had Hubbard in Round 9 and Benson in 10 to lock up two backfields for my zero-RB team. But no, I had to take a second QB here because (a) Richardson has a low floor; (b) this was cheap for Burrow; and (c) I could potentially pair Burrow with Chase for the playoffs. If you’re gonna go zero RB, lean the into it. (The other problem with this pick is the weekly headache of picking my starting QB.)
11.6 Jaleel McLaughlin — The Burrow pick cost me not only Benson but JK Dobbins too, but I had my eye on McLaughlin who apparently was a god in college, and per Barrett is in an ideal spot as the RB2 in Sean Payton’s offense. Now that stat has to be tempered a bit given that peak Alvin Kamara was the source of so much of it, but how much of that was Payton’s offense? In any event, I’m seriously rolling into Week 1 with McLaughlin in my active lineup because of the Richardson, Brooks, Brown and Burrow picks.
12.7 Jordan Mason — Obviously he’s not usable unless and until Christian McCaffrey gets hurt, and the Niners badly need Trent Williams to report, but he’s a top-10 RB if McCaffrey, who played into February last year, goes down. This also furthers my extreme “what could go right” build.
13.6 Braelon Allen — Oddly I view this pick as a mistake as he was higher in ADP, so I thought I could wait another round on Giants backup Tyrone Tracy. (Tracy went three picks ahead of me in the next round.) Allen might be good, but only a Breece Hall injury could free him up whereas Tracy could just outplay Devin Singletary. Granted the Jets might be a better environment than the Giants, so Allen could have more upside if he did get a shot, but Tracy is also a converted WR and would likely catch a lot of passes if he got the job.
14.7 Khalil Herbert — Once Tracy was gone, I pivoted to Herbert. The Chicago backfield is crowded, but D’Andre Swift always gets hurt, and Roschon Johnson isn’t as good a runner as Herbert.
15.6 Jalen McMillan — I wanted to get Cam Akers because Joe Mixon is old, but I missed him by two picks and pivoted (finally) back to WR. McMillan’s created some buzz in camp, and both Mike Evans and Chris Godwin are getting old.
16.7 Will Shipley — I love Saquon Barkley, but he’s getting old and has been hurt a lot. Kenneth Gainwell is ostensibly ahead of Shipley, but is just a guy. Another top-10 upside back should the starter go down.
17.6 Dalvin Cook — He’s on the practice squad for now, and he looked beyond done last year with the Jets, but keep in mind he only got 67 carries, and the Cowboys don’t have serious obstacles ahead of him should he regain even 60 percent of his prior form. Cook was still very good in 2022, and he should have fresh legs too.
18.7 Quentin Johnston — I needed one more receiver, and Johnston is one. Seriously, though he was a first-round pick only last year, and he’s competing with only Josh Palmer and a rookie.
19.6 Younghoe Koo — All these years I was with a wonderful kicker in Justin Tucker, but I’m trading him in for a Younghoe. (That joke will get old one day, just not in any of our lifetimes.)
20.7 Giants Defense — They draw Sam Darnold and Jayden Daniels the first two weeks, and added Brian Burns to Kayvon Thibodeaux and Dexter Lawrence.
Roster By Position
QB Anthony Richardson
RB James Conner/Jaleel McLaughlin
WR Ja’Marr Chase/Drake London/DeVonta Smith
TE Dalton Kincaid
FLEX Stefon Diggs
K Younghoe Koo
D Giants
Bench Jonathan Brooks/Marquise Brown/Joe Burrow/Jordan Mason/Braelon Allen/Khalil Herbert/Jalen McMillan/Will Shipley/Dalvin Cook/Quentin Johnston
-
 @ 361d3e1e:50bc10a8
2024-09-02 17:40:01
@ 361d3e1e:50bc10a8
2024-09-02 17:40:01 -
 @ dfe02069:d3e2fa29
2024-09-02 16:30:03
@ dfe02069:d3e2fa29
2024-09-02 16:30:03Vor kurzem scheiterte eine Novellierung des Pandemievertrags, der zu einer erheblichen Machtausweitung der Weltgesundheitsorganisation (WHO) geführt hätte am Widerstand der Mitgliedstaaten. Dachte man. Denn das hielt die WHO nicht davon ab, in einer Nacht-und-Nebel-Aktion über die Veränderung der Gesundheitsvorschriften dem Generalsekretär der WHO doch noch schnell das Recht zu übertragen, auf Verdacht Pandemien auszurufen. Das Signal ist klar: Die WHO geht den Weg der Machtergreifung unbeirrt weiter. WHO-Generalsekretär Tedros Adhanom Ghebreyesus fuhr kürzlich erneut öffentlich große Geschütze gegen „Impfgegner" auf: Impfstoffe wirkten, Wissenschaft und Evidenz sei auf unserer Seite, verkündete er: „Es ist an der Zeit, Impfgegner aggressiver zurückzudrängen." Wohlgemerkt: noch aggressiver als durch Stigmatisierung, Ausgrenzung, Jobverlust?
Tedros` markige Sprüche fallen in eine Phase, in der es für ihn spitz auf Knopf steht. Was er bejammert, sind vier Jahre Corona-Desaster, das maßgeblich durch die WHO und ihre Einschätzungen mitverursacht worden war.
Nehmen wir nur zwei Punkte: - Laborurspung - und Impfschäden.
Der angebliche Naturursprung von Sars-Cov-2 (wichtig, um die Themen Klimaerwärmung und Pandemieausbrüche zu verzahnen) ist nur noch etwas für hardcore Regierungs-Schwurbler; Nicht einmal ein Anthony Fauci glaubte ausweislich interner Emails wirklich daran, obwohl er es öffentlich immer bekräftigt hat. Vor kurzem wurde offenbar, dass er den US-Congress hinsichtlich der Finanzierung von gefährlicher Gain-of-function-Forschung belogen hat.
Das ist eine Straftat; zwar eine kleinere, als die Pandemieinszenierung mit Millionen von Toten, aber auch einen Al Capone bekam man nicht über die typischen Mafia-Delikte, sondern über Steuerhinterziehung. Im März wurde das AstraZeneca-Vakzin in der EU vom Markt genommen, auf Betreiben des Herstellers selbst, da es sich wie Sauerbier verkaufte. Von der Politik zunächst überschwenglich belobigt (Frau Merkel: „Würde mich mit AZ impfen lassen"), von Dänemark und Norwegen vorzeitig aus dem Verkehr gezogen (und in der Schweiz nie zugelassen), wurde es selbst vom Krankenhauspersonal oft gemieden, so dokumentierten es die vor kurzem entschwärzten RKI-Protokolle.
Welche Evidenz meint also Tedros, wenn er behauptet, die Wissenschaft auf seiner Seite zu haben?
Seit November 2023 kann man auf der Seite clinicialtrialsregister.eu die Ergebnisse der Phase III-Studie zu AstraZeneca bestaunen. Darin wurden über zwei Jahre die Wirkungen und Nebenwirkungen von AstraZeneca an 21634 Menschen untersucht, 10816 bekamen ein Placebo. Es war quasi der Menschenversuch neben dem Menschenversuch, denn zeitgleich wurde das Vakzin millionenfach verimpft. Ergebnis der Studie: 5335 Personen beendeten die Studie nicht, teils tauchten sie ab. 63 verstarben. Eine Impfnebenwirkung attestierte gut ein Drittel der Teilnehmer, nämlich 7887. Schwere Nebenwirkungen traten bei 621 Personen auf, also: Tod oder unmittelbare Todesgefahr, Krankenhauseinweisung, Behinderung oder Siechtum. Bei 4750 Menschen brauchte es eine außerplanmäßige medizinische Intervention, zum Beispiel die Einlieferung in die Notaufnahme.

Wie lautete nochmal die Definition von „sicher und effektiv"? Was genau meinten Politiker und Medien, wenn sie von „nebenwirkungsfreien" Impfstoffen sprachen oder davon, dass Impfkomplikationen sehr sehr selten sind? Die RKI Protokolle, die den Blindflug deutscher Behörden in Bezug auf Impfschäden dokumentieren, konstatierte rund um AstraZeneca: „Insgesamt viel Aufregung". Jetzt schreibt der britische Telegraph, dass die Corona-Impfstoffe für die Übersterblichkeit verantworlich sein könnten.
Wer auf dieser Welt glaubt also noch einem WHO-Generalsekretär oder irgendeinem Gesundheitsbürokraten?
Angesichts dieser Befunde kann die wachsende Skepsis gegenüber der WHO und ihrem Generalsekretär nicht verwundern (sehen Sie dazu auch die sehenswerte zweiteilige Dokumentation auf ServusTV). Vor kurzem kam es zu einer internationalen Großkundgebung in Genf, in der sehr unmissverständlich die Machtausweitungspläne der WHO artikuliert wurden. Unter den Teilnehmern waren unter anderem der mRNA-Vordenker Robert Malone, der britische Kardiologe Aseem Malhotra, der belgische Psychologieprofessor Matias Desmet sowie der Biologe Bret Weinstein. Aus der Schweiz waren u.a. der Anwalt Philip Kruse sowie der ehemalige Kantonsrat Urs Hans anwesend. Sie sprachen es deutlich aus: die WHO sei dabei, zu einem neuen globalen Machtzentrum zu werden, mit totalitärem Anstrich. Frei nach Carl Schmitt: Souverän ist, wer über den Gesundheitsnotstand befindet und die ganze Welt mit Freiheitsentzug und Zwangsmedikation behelligen kann.
Um das befremdlich zu finden braucht man weder Orwell, Huxley, noch ein Geschichtsbuch gelesen zu haben. Die WHO ist eine Drehscheibe für wirtschaftliche und politische Machtinteressen geworden. Wie passt die Machtkonzentration der WHO zur dezentralen Schweiz? Wieso wird einer Organisation mit derartigen Aspirationen und belegt lausigem Track-Record überhaupt ermöglich, aus der Schweiz heraus zu operieren? Der Chef der WHO will verbindlich für die Welt pandemische Notlagen verhängen und Maßnahmen verbindlich empfehlen, co-finanziert von China und Bill Gates. Zeitgleich finanziert Bill Gates u.a. die Schweizer Zulassungsbehörde Swissmedic und das RKI in Deutschland. Wie kann das legal, geschweige denn legitim sein? Gar nicht, es ist ein Putsch von oben. Bret Weinstein brachte es auf den Punkt:
„Bürger der Welt, wir werden angegriffen: die Prinzipien Souveränität, Freiheit und Konsensfähigkeit werden durch eine globale Elite zerstört."
Was ist das anderes, als der Weg in einen globalen Kontroll-Weltstaat?
Nach der Pandemie ist vor der Pandemie. Die verantwortlichen Akteure sagen es der Welt ins Gesicht, mit welcher Nonchalance sie in die Zukunft blicken können. Wer von Notständen profitiert, so wusste schon Adorno, wird Notstände schaffen. Es ist ein einfaches Anreizsystem. Außer: furchtlose Bürger halten dagegen und machen nicht mehr mit, und das in Massen. Die Affenpocken vor zwei Jahren vermochten bereits niemanden mehr zu schrecken. Gerade entwickelt sich die Vogelgrippe zum nächsten Rohrkrepierer. Doch die WHO lässt nicht locker. Erneut änderte sie die Pandemie-Definition, diese mutiert scheinbar so munter wie die Varianten des Coronavirus durch die Impfung. Nunmehr wird nicht mehr auf die Gefährlichkeit für Leib und Leben verwiesen, sondern auf Risikobewertungen, also Modellierungen. Das hohe Risiko beispielsweise, dass sich eine Krankheit geografisch auf mehrere Staaten ausbreitet, das Gesundheitssystem überlasten und den Handel stören könnte, genügt schon, um den Schalter des Notfalls umzulegen.
Der Teufel steckt im Detail, also immer in der juristischen Definition. Wer den Notfall herbeimodelliert, legt den Schalter der Macht per Mathematik um. Ganz technokratisch, ganz demokratiefern.
Zeit, die WHO aufzulösen!
Diese Kolumne erschien auch in der Weltwoche.
-
 @ 3b7fc823:e194354f
2024-09-02 16:26:30
@ 3b7fc823:e194354f
2024-09-02 16:26:30First steps into privacy.
You are a normie, but maybe you are privacy curious. Maybe you are ready to take a first step or two into security and privacy but don't know where to start.
Don't worry, here are some absolute beginner first steps that will make a big difference.
-
No one except your friends and family should know your personal phone number and email address. Stop giving away your data! You don't have to fill out every blank on that form. Unless they are mailing you something they don't need your home address. Use a email aliasing service or just create a burner email account as a spam trap. Get a second VOIP phone number. Look up the address of a local hotel. Use these instead of your personal information or maybe just skip the customer reward program.
-
Speaking of giving away your data. Stop using spyware! Facebook, Instagram, Tiktok, etc. It is "free" software designed to suck every ounce of personal data from you to be repackaged and sold. Don't just delete the app, search for how to delete your account data.
BTW Windows, google, and 90% of the apps on your phone are also spyware but one thing at a time. Maybe start reading up on FOSS.
-
Clean up your communications. Stop using unencrypted calls and SMS texts. There are several options but just get Signal and make your friends use it. Its easy and works.
-
Clean up your email. This one is probably going to take you some time if you are like most people who have hundreds of emails from years gone bye. Go through every single one and unsubscribe from every newsletter or sales pitch from every store you have ever bought anything from. Block every spam email you see. If you are using a email provider that literally scans every email you send or receive in order to sell you stuff like gmail, then now is the time to switch to a private and encrypted provider like proton or tuta.
-
Clean up your web surfing. Switch to a privacy browser and search engine. If you don't know which one just get Brave. There are ones that I like better but Brave is good enough and easy, especially if you like Chrome. A hardened Firefox is better but requires some homework and if on desktop Mullvad browser is a excellent choice.
BONUS TIP:
Clean up your security. Make sure all of your software is setup for automatic updates, especially security updates. Also, I don’t know who needs to hear this but get a password manager if you don’t have one. (Don't save passwords on the browser!) Get an actual password manager and then add 2FA to all of your online accounts and you will have better security than 90% of the population.
OK, nothing too exciting but we got the big rocks. Data leaks, communications, email, web surfing, and basic security.
What, no VPN or Tor or super secret stuff? No, not yet. This is your level zero default. Your identity and activity is still transparent but you are no longer leaking your data all over the place. This will provide a general base for everyone.
The next step is to perform a basic threat assessment of your personal situation. What are you most at risk for? Targeted attacks or passive? Cyber or physical? What do you most need to defend against? Government mass surveillance, surveillance capitalism, censorship, or public exposure?
There will be some overlap with all of them but your next steps will really depend on your answer. We will cover each of these in greater depth later.
-
-
 @ 7125d354:5970d69c
2024-09-02 16:07:37
@ 7125d354:5970d69c
2024-09-02 16:07:37
There is a focal point ( > spectrum) where the optic nerves converge resulting in
The experience of high level sintergical power.
Where the clouds can be waves and/or the waves can be clouds at the same time.
NIRVANA indeed
AcrylicOnPaper #FilippaRoseArt #ThalassoFi #blau
-
 @ 8dc86882:9dc4ba5e
2024-09-02 15:50:01
@ 8dc86882:9dc4ba5e
2024-09-02 15:50:01Today I saw a YouTube video from one of the privacy related channels, Techlore maybe? I don't exactly remember. Either way this particular video was going over the pluses and minuses of Android and iOS; and it has made me reconsider some things. I have one of each type of phone and jump back and forth a bit, but always thought I would end on Android. I'm not feeling that way anymore.
After really getting to understand Apple's Advanced Data Protection I think I came to the conclusion that my iPhone more than meets my needs and does everything I like. Yeah, Android sounds like it has most of the privacy coolness as far as mods, roms, and apps, but my iPhone is easily fully encrypted along with iCloud. The few services that aren't are covered by my Proton plan. It also allows me to stop paying for services I may not really need.
- I use and pay for Ente photos, which is great, but my Apple photos are already encrypted and backed up. I don't think I need to be paying for the extra service.
- The Apple Notes app falls under the fully encrypted side, and I can use the free version of Standard Notes for other things.
- I still use Signal Messenger where the OS doesn't matter as much.
- MySudo which I use for numbers is transferable between OSs also.
That's really about it, I mainly use my phone for Email, Calendar, Messaging, Notes, some social, and photos. I don't think I need anything special beyond that. The insecure apps I use on either platform keep their risks though Apple isn't an advertising company, so I feel they are less likely to abuse anything, at least for now. I wonder what other folks thoughts are. Feel free to share.
Cheers!
plebone
-
 @ 266815e0:6cd408a5
2024-09-02 15:27:16
@ 266815e0:6cd408a5
2024-09-02 15:27:16After 7 months of work and procrastination I've decided to release another version of noStrudel
There a ton of new features and a few bugs fixed. This article highlights the biggest changes but if you want to read the full changelog you can find it in the github repo
And as always if you want to check it out you can use nostrudel.ninja or run it locally using docker
sh docker run --rm -p 8080:80 ghcr.io/hzrd149/nostrudel:0.40.0New Features
Support for NIP-49 encrypted nsec
Now when logging into to the app it will prompt you to set a password to encrypt your nsec so it can be stored securely (if that's even possible for a web client...)
There is also a new "Account" settings view that lets you export you nsec as a ncryptsec so you can copy it to other apps

Blindspot feeds
There are also new "blindspot" feeds that show what others are seeing in their timeline that your missing

NIP-42 Relay authentication
The app now supports NIP-42 relay authentication. Its opt-in though, so if you want to use popular authenticated relays like nostr.wine or relay.snort.social you will have to enable it in the settings

Wasm relay and event verification
The app now supports using @snort/worker-relay as a local relay. Its at least 10x faster than the internal browser cache and can hold at least 100x more events. Its not enabled by default though so if you want to use it you have to switch to it in the "Relays" -> "Cache Relay" view

The app also supports using nostr-wasm to speed up event signature verification. This is enabled by default, but if you want to still use the JavaScript verification or no verification you can find it in the performance setting

Thread tabs
Threads now have a set of tabs that let you see the Replies, Quotes, Zaps, and other stuff related to the note


Wiki articles
Its not feature complete but you can now view and edit wiki articles in the app

Finished the launchpad
The launchpad is now usable and shows the latest notifications, messages, streams, and tools

Blossom uploads
The app now lets you upload images and video to blossom server, this isn't enabled by default though so your going to have to enable it in the settings

And then setup some blossom servers in the settings. A few good public ones are
https://cdn.satellite.earthandhttps://cdn.nostrcheck.me
Task Manager
There is also a new "Task Manager" in the side nav that lets you see whats going on under the hood in the app

You can see what relays the app is currently connected to

And which relays are requesting NIP-42 authentication

Bug fixes
- Fix null relay hints in DMs
- Fix users own events being hidden by muted words
- Fix random events showing up as DM messages
- Fix app prompting NIP-07 extension to unlock when app opens
- Remove corsproxy.io as default service for CORS proxy
-
 @ dfe02069:d3e2fa29
2024-09-02 14:42:00
@ dfe02069:d3e2fa29
2024-09-02 14:42:00Kennen Sie Bullshit-Bingo? Bei diesem Spiel gewinnt, wer am meisten Floskeln und Schlagwörter in wenige Sätze packen kann, auf dass es tragend und gut klingt, obwohl es weitgehend inhaltsleer ist. Das WEF ist die elitärste Bullshit-Bingo-Veranstaltung der Welt. Beim jährlichen Treffen der 1000 größten Unternehmen mit Politikern geht es primär darum, durch Wiedergabe von WEF-Textbausteinen möglichst nah an die gefälligen Agendaziele heranzukommen, ohne dass die Anbiederung zu offensichtlich wird. Wer sich hier besonders beflissen hervortut, darf damit rechnen erneut eingeladen zu werden.
Weltgrößte Messe des Lobbyismus
Das Vokabular des WEF strotz vor alarmierenden Konzepten, die bisher in der Öffentlichkeit und den Medien nur mit der Zange angefasst wurden: Es geht um den „Great Reset", den Umbau der Welt („build back better"), die Verschmelzung von Mensch und Maschine, um Kontrolle der freien Rede, Ökoplanwirtschaft, digitales Zentralbank-Geld, digitale Identitätslösungen und darum, wie man als besitzloser und gläserner Bürger der Zukunft glücklich wird, während man sich den Insektenburger schmecken lässt. Das WEF produziert seit Jahrzehnten Begriffswolken, die Anlass für massives Stirnrunzeln geben, wird aber gerne im Mainstream als unverbindliche Spassveranstaltung und eitler Elitenkarneval dargestellt. Die Medien spielen ihr eigenes Bullshit-Bingo der Verdrängungs- und Themenvermeidungsfloskeln. Das ändert sich neuerdings massiv dank vieler freier Medien, die kritisch über das WEF berichtigen. Der Elitenzirkus von Klaus Schwab ist in der Defensive und kämpft mit einem massiven Imageproblem.
Dieses kommt nicht von ungefähr und ist weitgehend hausgemacht, durch eine Mischung aus Intransparenz und grotesken Ideen. Ein Vordenker des WEF ist der israelische Historiker und Bestsellerautor Yuval Noah Harari. Er beschäftigt sich mit der in seinen Augen wichtigsten Frage des 21. Jahrhunderts: Was soll bloß mit all den „nutzlosen" Menschen auf der Welt geschehen?
Das Thema Überbevölkerung ist seit Beginn in die DNA des WEF und anderer Elitezirkel eingewoben. Das Menschenbild des WEF ist dabei nicht weit von den Vorstellungen entfernt, die ein Hirte von seiner Tierherde hat. Der Mensch der Zukunft rangiert irgendwo zwischen einem digitalen Nutztier und Trainer seiner KI, die ihn kontrolliert und überwacht. Harari sieht als Beschäftigung für unnütze Esser und menschliche Co-2-Schleudern vor allem eines: Drogenkonsum und Videospiele. Das Kalkül des WEF scheint zu sein: Wenn man nur genug selbst ernannte Eliten zusammenbringt, die derartige Ideen weniger grotesk aussehen lassen, lässt sich selbst frankensteinsche Science-Fiction als Wohltätigkeit für die Welt umlackieren.
Das World Economic Forum ist schon dem Namen nach eine Mogelpackung. Es ist kein Forum. Auf einem Forum wird gestritten und diskutiert, statt den inzestuös vor sich hinwabernden Begriffsbrei noch ein weiteres Mal umzurühren. Im Kern ist das WEF die weltgrößte Messe des Lobbyismus. Das Geschäftsmodell lautet „networking as a service" und Klaus Schwab, ein in Kissingers CIA-finanziertem Harvard-Seminar geformter Ökonom und Sozialingenieur, ist der Impresario. Das WEF verkauft seinen Mitgliedern schlicht den Zugang zu Politikern. Der engste Kreis der Unternehmen, welche die Initiativen des WEF mitgestalten, zahlt dafür zwischen einer Viertelmillion und einer halben Million Dollar. Das ist viel Geld für eine angeblich reine „Spassveranstaltung", vor allem, wenn man dafür einer Rede von Olaf Scholz lauschen muss.
Wo bleibt die öffentliche Auseinandersetzung?
Da sich derartiger Zugang zur Politik jedoch zu lohnen scheint, stellt sich unweigerlich die Demokratie-Gretchenfrage: Wem fühlen sich die Politiker letztlich verpflichtet? Dem Wähler oder den Meistbietenden?
Es braucht nicht viel an investigativem Eifer, um einen Gleichlauf von WEF-Konzepten, Gesetzesvorlagen und Politikerkarrieren zu erkennen, bestes aktuelles Beispiel ist die „Digitale Identität". Unter welcher Definition von Demokratie ist diese Gemengelage nicht von größtem öffentlichen Interesse? Damit Politiker nicht allzu begriffsstutzig gegenüber den Geschäftsideen der WEF-Unternehmen auftreten, liefert Schwab mit seinem „Young Global Leaders"-Programm den Politiker-Nachwuchs der WEF-Hausmarke gleich mit: „Wir infiltrieren die Regierungen" meinte Schwab in einem öffentlichen Vortrag stolz. Wo blieben die öffentlichen Fragen dazu? Kritischen freien Medien ist der Zugang zur Eliteveranstaltung versperrt, man bleibt lieber unter sich.
Das WEF ist dabei, eine Karikatur seiner selbst zu werden. Daran hat der Bond-Bösewicht-Charme eines Klaus Schwab genauso Anteil, wie die missionarischen Reden von Steigbügelhaltern, wie zum Beispiel Ursula von der Leyen, die ihre Agenda-Anbiederung an die Ökoplanwirtschaft hinter Powerverben aus dem Economist, wie "thrive", "boost" und "shape" gar nicht mehr verstecken will. Das WEF ist ein Überbietungswettbewerb für groteske Szenarien und Forderungen, der in seiner Erwartbarkeit und Eintönigkeit nur noch zur Persiflage taugt: Der UNO-Generalpräsident malt wie bestellt Klimapanik in apokalyptischen Bildern. Al Gore inszeniert wieder mal eine Wut-Show. Und Tony Blair, Kriegsverbrecher im Unruhestand, darf über digitale Überwachungsinfrastruktur in Form von Impfpässen schwadronieren. Das Personal von gestern verkauft der Politik Unternehmenslösungen von heute für selbstgemachte oder aufgebauschte Probleme von morgen.
Die letzen Jahre der Pandemie haben die Bevölkerung alarmiert. Sie erlebte eine Welle angeblicher „Verschwörungstheorien", die sich als wahr herausgestellt haben. Diese Welle fürchtet nun auch das WEF, wie der Teufel das Weihwasser. Aufklärung mag manchmal einen langen Anlauf brauchen, dann jedoch ist der Sprung umso größer. Das Jahr 2023 hat gezeigt: Das Informationsmonopol der Konzernmedien über diese Veranstaltung ist dahin. Ihr Versuch, informelle Machtzirkel zum Tabuthema im Mainstream zu machen, ist gescheitert. Wer Naivität des Publikums zur Geschäftsgrundlage macht, baut sich die tiefe Grube letztlich selbst.
Sogar dem WEF sind die eigenen Inhalte inzwischen peinlich. Man löscht Artikel und Tweets und ruft nach mehr Kontrolle gegenüber „Verschwörungstheorien" im Netz, für die man bei jeder Gelegenheit fleißig Anlässe schafft. Das WEF erinnert so an den Feuerwehrmann, der Brände legt, um ausrücken zu können und auch noch das Löschwasser verkauft. Das Gegenprogramm zum WEF läuft sich längst warm: Es sind die Ideen und Kräfte dezentral organisierter Bürger, die an spürbarer Verbesserung im Hier und Jetzt arbeiten, statt sich die Machtergreifung einer Manager-Elite in den Klängen eines Weltverbesserungs-Kumbaya vorsetzen zu lassen.
-
 @ 3b7fc823:e194354f
2024-09-02 13:07:09
@ 3b7fc823:e194354f
2024-09-02 13:07:09GHOSTn
- Renoted from a month ago into a article as a proof of concept
A quick overview
privacy #tor #vpn
**Computer -> clearnet -> Website **
ISP: sees that you are connected to website VPN: n/a Tor Entrance Node: n/a Tor Exit Node: n/a Website: sees your IP address and logs everything that you do on the website
Good for when the expectation of privacy does not exist. A KYC site you are logging into. Utility bill pay site, bank
**Computer -> VPN -> Website **
ISP: sees that you are connecting to a VPN but not what you are doing afterwards VPN: sees your IP Address and that you are connecting to a website Tor Entrance Node: n/a Tor Exit Node: n/a Website: sees that someone from a VPN exit node has connected but doesn’t know who. Logs data.
Good for hiding your activity from your ISP. Good for hiding your identity from the website. Good for when you want low level privacy but not anonymity. VPN provider sees everything and your level of privacy depends on how much they know about you and how much data they log and retain (varies greatly from provider to provider).
**Computer -> Tor -> Website **
ISP: sees that you are connected to Tor but nothing afterwards VPN: n/a Tor Entrance Node: sees your IP address but nothing afterwards Tor Exit Node: sees website you are going to but not who you are Website: sees someone from Tor has connected but doesn’t know who. Logs.
Good for privacy and anonymity. Assumes that Tor is legal in your country.
**Computer -> VPN -> Tor -> Website **
ISP: sees that you connected to a VPN but nothing afterwards VPN: sees IP address and that you are connecting to Tor but nothing afterwards Tor Entrance Node: sees a VPN is connected but nothing afterwards Tor Exit Node: sees website you are going to but not who you are Website: sees someone from Tor has connected but doesn’t know who. Logs.
Good for if your ISP blocks or cancels your service for using Tor. Potentially an option if Tor is illegal in your country (Dangerous).
**Computer -> Tor -> VPN -> Website **
ISP: sees that you are connecting to Tor but nothing afterwards VPN: sees someone from Tor is connected and that they are connecting to a website Tor Entrance Node: sees IP address but nothing afterwards Tor Exit Node: sees someone is connecting to a VPN but nothing afterwards Website: sees someone from a VPN is connecting but doesn’t know who. Logs.
Good for when a website blocks Tor traffic. Assumes Tor is legal in your country. Assumes that the VPN doesn’t know who you are. To maximize privacy and anonymity VPN provider should be KYC free and accept privacy payments (ex: Monero).
Note: If a website blocks Tor and VPN then maybe that is a sign that you shouldn’t go there.

