-
 @ fa0165a0:03397073
2024-10-23 17:19:41
@ fa0165a0:03397073
2024-10-23 17:19:41Chef's notes
This recipe is for 48 buns. Total cooking time takes at least 90 minutes, but 60 minutes of that is letting the dough rest in between processing.
The baking is a simple three-step process. 1. Making the Wheat dough 2. Making and applying the filling 3. Garnishing and baking in the oven
When done: Enjoy during Fika!
PS;
-
Can be frozen and thawed in microwave for later enjoyment as well.
-
If you need unit conversion, this site may be of help: https://www.unitconverters.net/
-
Traditionally we use something we call "Pearl sugar" which is optimal, but normal sugar or sprinkles is okay too. Pearl sugar (Pärlsocker) looks like this: https://search.brave.com/images?q=p%C3%A4rlsocker
Ingredients
- 150 g butter
- 5 dl milk
- 50 g baking yeast (normal or for sweet dough)
- 1/2 teaspoon salt
- 1-1 1/2 dl sugar
- (Optional) 2 teaspoons of crushed or grounded cardamom seeds.
- 1.4 liters of wheat flour
- Filling: 50-75 g butter, room temperature
- Filling: 1/2 - 1 dl sugar
- Filling: 1 teaspoons crushed or ground cardamom and 1 teaspoons ground cinnamon (or 2 teaspoons of cinnamon)
- Garnish: 1 egg, sugar or Almond Shavings
Directions
- Melt the butter/margarine in a saucepan.
- Pour in the milk and allow the mixture to warm reach body temperature (approx. + 37 ° C).
- Dissolve the yeast in a dough bowl with the help of the salt.
- Add the 37 ° C milk/butter mixture, sugar and if you choose to the optional cardamom. (I like this option!) and just over 2/3 of the flour.
- Work the dough shiny and smooth, about 4 minutes with a machine or 8 minutes by hand.
- Add if necessary. additional flour but save at least 1 dl for baking.
- Let the dough rise covered (by a kitchen towel), about 30 minutes.
- Work the dough into the bowl and then pick it up on a floured workbench. Knead the dough smoothly. Divide the dough into 2 parts. Roll out each piece into a rectangular cake.
- Stir together the ingredients for the filling and spread it.
- Roll up and cut each roll into 24 pieces.
- Place them in paper molds or directly on baking paper with the cut surface facing up. Let them rise covered with a baking sheet, about 30 minutes.
- Brush the buns with beaten egg and sprinkle your chosen topping.
- Bake in the middle of the oven at 250 ° C, 5-8 minutes.
- Allow to cool on a wire rack under a baking sheet.
-
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ a10260a2:caa23e3e
2024-10-03 16:37:37
@ a10260a2:caa23e3e
2024-10-03 16:37:37Alby Hub is configurable with several different backends. Although setting up with Cashu is considered experimental, it’s a good option to have if you don’t want to run a Lightning node.
This post will give a quick overview of the steps to connect your Alby Hub with a Cashu mint.
Before you get started, you’re going to want to have Alby Hub installed already. There are many options for this as well — Linux, StartOS, and Umbrel to name a few. You can even have Alby host it for you in their cloud.
I just happen to have a Linux machine free so I went that route — the installation script made it super easy.
After the install is complete, navigating to localhost:8080 brings up this page.
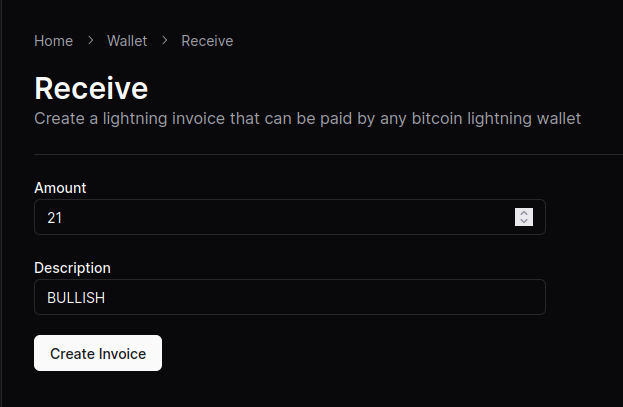
- Select “Advanced Setup”
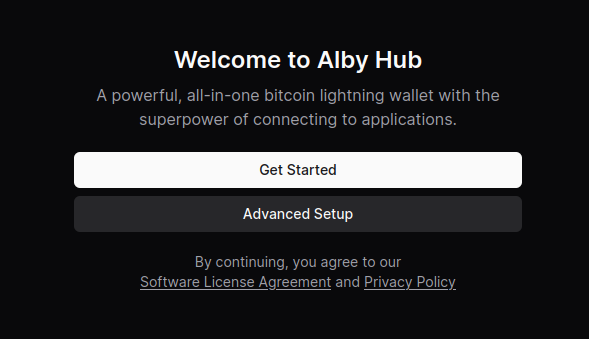
- Select “Create Wallet with Custom Node”
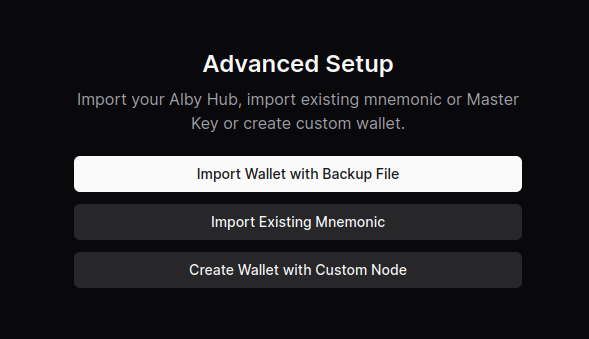
- Select “Cashu Mint”
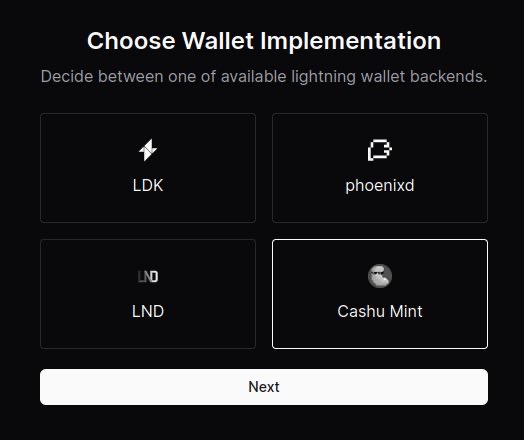
- Paste the URL of the mint you’d like to use. You can use the default one provided or click on “Find a mint” to search for others.
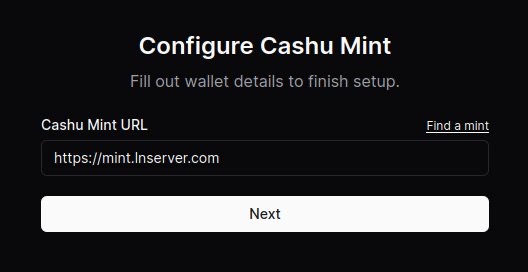
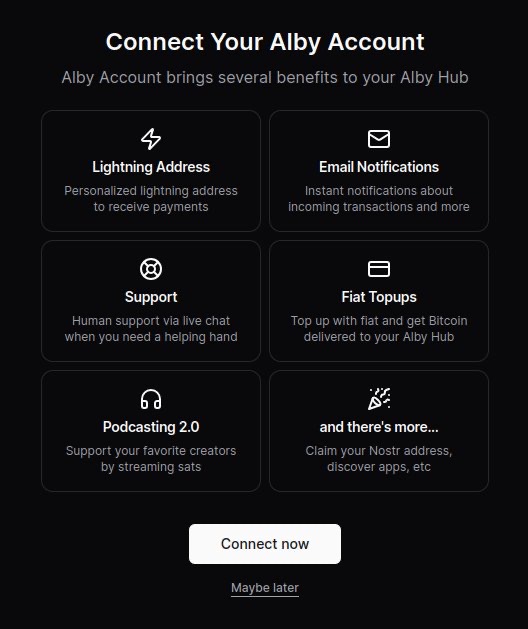
- (Optional) Connect your Alby account by requesting an authorization code. After clicking “Connect now,” a new window will open and the code displayed after signing in.
Boom. You’re all done.
Now you can use your Alby Lightning address to receive your first sats!
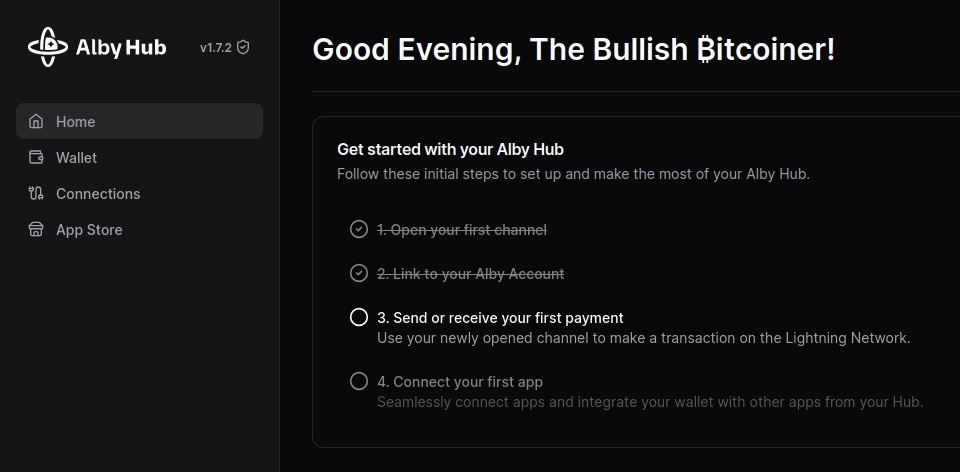
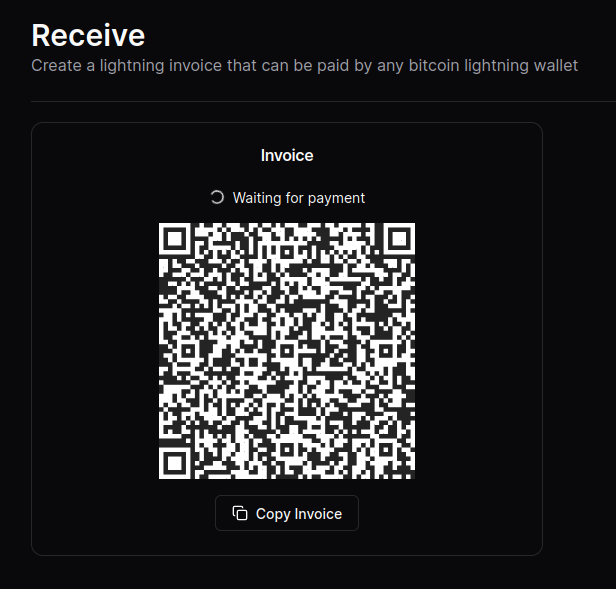
NOTE: Although the sats do make it to the wallet, the “Waiting for payment” animation seems to wait indefinitely and there’s no record in transaction history.
This seems to be a Cashu-related issue that has something to do with the preimage. An issue has been opened on GitHub if you’re curious.
Other that that, sending and receiving works like a charm.
originally posted at https://stacker.news/items/707673
-
 @ c4f5e7a7:8856cac7
2024-09-27 08:20:16
@ c4f5e7a7:8856cac7
2024-09-27 08:20:16Best viewed on Habla, YakiHonne or Highlighter.
TL;DR
This article explores the links between public, community-driven data sources (such as OpenStreetMap) and private, cryptographically-owned data found on networks such as Nostr.
The following concepts are explored:
- Attestations: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your web-of-trust.
- Proof of Place: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in meatspace with their digital representations in the Nostrverse.
- Check-ins: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time.
The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems.
Open Data in a public commons has a place and should not be thrown out with the Web 2.0 bathwater.
Cognitive Dissonance
Ever since discovering Nostr in August of 2022 I've been grappling with how BTC Map - a project that helps bitcoiners find places to spend sats - should most appropriately use this new protocol.
I am assuming, dear reader, that you are somewhat familiar with Nostr - a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: Nostr is Identity for the Internet and The Power of Nostr by @max and @lyn, respectively. Nostr is so much more than a short-form social media replacement.
The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting - all your silos are indeed broken - however, something fundamental has been bothering me for a while and I think it comes down to data ownership.
For those unfamiliar, BTC Map uses OpenStreetMap (OSM) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) - FOSD if you will, but more commonly referred to as Open Data.
In contrast, Notes and Other Stuff on Nostr (Places in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned.
How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data?
Self-sovereign Identity
Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something - an identity.
All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money.
Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state.
Or, as @nvk said recently: "Don't build your house on someone else's land.".
https://i.nostr.build/xpcCSkDg3uVw0yku.png
While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this.
Nostr is PGP for the masses and will take cryptographic identities mainstream.
Full NOSTARD?
Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons.
We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be.
https://i.nostr.build/s3So2JVAqoY4E1dI.png
There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a Wikifreedia variant of OpenStreetMap.
While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native - there's no need to go Full NOSTARD. H/T to @princeySOV for the original meme.
https://i.nostr.build/ot9jtM5cZtDHNKWc.png
So, how do we appropriately blend cryptographically owned data with the commons?
If a location is owned in meatspace and it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the tragedy of the commons.
The remainder of this article explores how we can:
- Verify ownership of a physical place in the real world;
- Link that ownership to the corresponding digital place in cyberspace.
As a side note, I don't see private key custodianship - or, even worse, permissioned use of Places signed by another identity's key - as any more viable than the rented identities of Web 2.0.
And as we all know, the Second Law of Infodynamics (no citation!) states that:
"The total amount of sensitive information leaked will always increase over time."
This especially holds true if that data is centralised.
Not your keys, not your notes. Not your keys, not your identity.
Places and Web-of-Trust
@Arkinox has been leading the charge on the Places NIP, introducing Nostr notes (kind 37515) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via NIP-73 - External Content IDs (championed by @oscar of @fountain).
However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world.
Ultimately, this problem can only be solved in a decentralised way by using Web-of-Trust - using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop.
This requires users to:
- Verify the owner of a Place in cyberspace is the owner of a place in meatspace.
- Signal this verification to their social graph.
Let's look at the latter idea first with the concept of Attestations ...
Attestations
A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false.
Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too.
However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc).
Here is a recent example from @lyn that would carry more signal if it were an Attestation:
https://i.nostr.build/lZAXOEwvRIghgFY4.png
Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or Data Vending Machines in accordance with:
- Your social graph;
- The type or subject of the content being attested and by whom;
- Your personal preferences.
They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places.
NIP-25 (Reactions) do allow for users to up/downvote notes with optional content (e.g., emojis) and could work for Attestations, but I think we need something less ambiguous and more definitive.
‘This is true’ resonates more strongly than ‘I like this.’.
https://i.nostr.build/s8NIG2kXzUCLcoax.jpg
There are similar concepts in the Web 3 / Web 5 world such as Verified Credentials by tdb. However, Nostr is the Web 3 now and so wen Attestation NIP?
https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg
That said, I have seen @utxo has been exploring ‘smart contracts’ on nostr and Attestations may just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust.
Proof of Place
Attestations handle the signalling of your truth, but what about the initial verification itself?
We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth.
Introducing Proof of Place, an out–of-band process where an oracle (such as BTC Map) would mail - yes physically mail- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace.
One way of doing this would be to mint a 1 sat cashu ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location.
Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places).
In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as @Gigi says in PoW is Essential:
"A failure to understand Proof of Work, is a failure to understand Bitcoin."
In the Nostrverse, Proof of Place helps bridge the digital and physical worlds.
@Gigi also observes in Memes vs The World that:
"In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone."
https://i.nostr.build/dOnpxfI4u7EL2v4e.png
This isn’t true for Nostr.
In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯
Check-ins
Although not a draft NIP yet, @Arkinox has also been exploring the familiar concept of Foursquare-style Check-ins on Nostr (with kind 13811 notes).
For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as OSM elements) if NIP-73 - External Content IDs are used.
Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices.
Bringing Check-ins to Nostr is possible (as @sebastix capably shows here), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am.
Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable.
How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene - I’m sure @blackcoffee and @Ben Arc could hack something together over a weekend!
Check-ins could also be used as a signal for bonafide Place ownership over time.
Summary: Trust Your Bros
So, to recap, we have:
Places: Digital representations of physical locations on Nostr.
Check-ins: Users signalling their presence at a location.
Attestations: Verifiable social proofs used to confirm ownership or the truth of a claim.
You can visualise how these three concepts combine in the diagram below:
https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg
And, as always, top right trumps bottom left! We have:
Level 0 - Trust Me Bro: Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all.
Level 1 - Definitely Maybe Somewhere: This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL.
Level 2 - Trust Your Bros: An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph.
https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg
Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map?
Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ - you decide.
As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities.
Thanks
With thanks to Arkinox, Avi, Ben Gunn, Kieran, Blackcoffee, Sebastix, Tomek, Calle, Short Fiat, Ben Weeks and Bitcoms for helping shape my thoughts and refine content, whether you know it or not!
-
 @ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23
@ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23由于gmail在中国被防火墙拦截了,无法打开,不想错过邮件通知。
通过自建ntfy接受gmail邮件通知。 怎么自建ntfy,后面再写。
2024年08月13日更新:
修改不通过添加邮件标签来标记已经发送的通知,通过Google Sheets来记录已经发送的通知。
为了不让Google Sheets文档的内容很多,导致文件变大,用脚本自动清理一个星期以前的数据。
准备工具
- Ntfy服务
- Google Script
- Google Sheets
操作步骤
- 在Ntfy后台账号,设置访问令牌。

- 添加订阅主题。

- 进入Google Sheets创建一个表格.记住id,如下图:

- 进入Google Script创建项目。填入以下代码(注意填入之前的ntfy地址和令牌):
```javascript function checkEmail() { var sheetId = "你的Google Sheets id"; // 替换为你的 Google Sheets ID var sheet = SpreadsheetApp.openById(sheetId).getActiveSheet();
// 清理一星期以前的数据 cleanOldData(sheet, 7 * 24 * 60); // 保留7天(即一周)内的数据
var sentEmails = getSentEmails(sheet);
var threads = GmailApp.search('is:unread'); Logger.log("Found threads: " + threads.length);
if (threads.length === 0) return;
threads.forEach(function(thread) { var threadId = thread.getId();
if (!sentEmails.includes(threadId)) { thread.getMessages().forEach(sendNtfyNotification); recordSentEmail(sheet, threadId); }}); }
function sendNtfyNotification(email) { if (!email) { Logger.log("Email object is undefined or null."); return; }
var message = `发件人: ${email.getFrom() || "未知发件人"} 主题: ${email.getSubject() || "无主题"}
内容: ${email.getPlainBody() || "无内容"}`;
var url = "https://你的ntfy地址/Gmail"; var options = { method: "post", payload: message, headers: { Authorization: "Bearer Ntfy的令牌" }, muteHttpExceptions: true };
try { var response = UrlFetchApp.fetch(url, options); Logger.log("Response: " + response.getContentText()); } catch (e) { Logger.log("Error: " + e.message); } }
function getSentEmails(sheet) { var data = sheet.getDataRange().getValues(); return data.map(row => row[0]); // Assuming email IDs are stored in the first column }
function recordSentEmail(sheet, threadId) { sheet.appendRow([threadId, new Date()]); }
function cleanOldData(sheet, minutes) { var now = new Date(); var thresholdDate = new Date(now.getTime() - minutes * 60 * 1000); // 获取X分钟前的时间
var data = sheet.getDataRange().getValues(); var rowsToDelete = [];
data.forEach(function(row, index) { var date = new Date(row[1]); // 假设日期保存在第二列 if (date < thresholdDate) { rowsToDelete.push(index + 1); // 存储要删除的行号 } });
// 逆序删除(从最后一行开始删除,以避免行号改变) rowsToDelete.reverse().forEach(function(row) { sheet.deleteRow(row); }); }
```
5.Google Script是有限制的不能频繁调用,可以设置五分钟调用一次。如图:

结尾
本人不会代码,以上代码都是通过chatgpt生成的。经过多次修改,刚开始会一直发送通知,后面修改后将已发送的通知放到一个“通知”的标签里。后续不会再次发送通知。
如需要发送通知后自动标记已读,可以把代码复制到chatgpt给你写。
-
 @ 7460b7fd:4fc4e74b
2024-09-05 08:37:48
@ 7460b7fd:4fc4e74b
2024-09-05 08:37:48请看2014年王兴的一场思维碰撞,视频27分钟开始
最后,一个当时无法解决的点:丢失
-
 @ 3589ce32:ef4269ad
2024-10-24 19:13:56
@ 3589ce32:ef4269ad
2024-10-24 19:13:56Bitcoin y la Descentralización:
Bitcoin se centra en la soberanía individual, la libertad financiera y la descentralización. Su filosofía se basa en la confianza en un sistema sin intermediarios, donde cada individuo tiene control sobre sus recursos. La descentralización de Bitcoin refleja un despertar hacia la autonomía personal, la autosuficiencia y la búsqueda de la verdad fuera de estructuras de poder tradicionales.
UCDM enseña la no-dualidad, el perdón y la percepción correcta, destacando que el amor es lo único real y que todo lo demás es una ilusión. La idea es la de liberarse de la mentalidad de escasez (tan presente en el dinero tradicional) y fomentar una mentalidad de abundancia, confianza y cooperación.
El Vedanta Advaita es una filosofía no dualista que enseña que solo hay una realidad última, y que todo es una manifestación de esa unidad. La dualidad es una ilusión. Guardando ciertas distancia, podríamos decir que la unidad subyacente del Advaita se refleja en la idea de una red descentralizada y sin fronteras, como Bitcoin, la cual conecta a las personas sin intermediarios. También ¿Cómo superar la ilusión del ego y la dualidad para alcanzar una verdadera libertad? Hablaremos de esto en otra ocasión …
-
 @ 826e9f89:ffc5c759
2024-06-28 21:46:01
@ 826e9f89:ffc5c759
2024-06-28 21:46:01_Prologue: this is a prose adaptation of a talk I gave to a private audience in Dubai and then tweaked slightly for a small conference in Sofia. I'm increasingly thinking it deserves a more general audience, and may be better suited to text anyway. This is probably not its final form, as the desired audience is tradfi capital allocators, hence a PDF is likely on the cards in the near future. For the time being, consider this a first draft, practising what it might look like as prose, and soliciting feedback from the good people of Nostr. Enjoy! _
The title of this essay means absolutely nothing. There is no such thing as “Web π” because there is no such thing as “Web 3”. It’s bullshit. It’s a scam.
Unfortunately, it has turned out to be extremely powerful bullshit and an extremely profitable scam, and so my goal in writing this essay is to give the reader the tools to navigate all of this and come out the other side without having been scammed or bullshat. In the spirit of not scamming and not bullshitting, I should be clear upfront about the intended readership of this essay, who I am to write it, and who it’s really about.
Who Are You?
I assume the reader is not a shadowy super-coder, but rather is a financial professional. This essay isn’t really for Bitcoiners, although if any read it, I hope they still find it interesting. Who I am really writing for are people coming to the space for the first time. Hopefully in your mind you are coming to the _Bitcoin _space, but if you think you are coming to the “crypto” space then this may be even more useful.
Who Am I?
I am the founder of a company that makes me not only highly biased but also flagrantly self-interested in the content I am promoting. I run a firm that invests in the Bitcoin ecosystem through a variety of different vehicles. I am not going to mislead you in the slightest in that my primary motivation is for you to allocate capital to us rather than to people I would call scammers and bullshitters. You should listen to them too and make up your own mind, or else what’s the point, really? How do you know I’m not scamming or bullshitting you? Exactly. Don’t trust. Verify.
In any case, that’s all assuming you want to “allocate capital” at all rather than just buy Bitcoin without a management fee. I’d like to think the primary difference is that I will be honest about that, and I’ll encourage you to understand as much as you can about what is going on and what you are doing (and if you are at all unsure, I would suggest you aren’t ready and you should just buy Bitcoin and learn) rather than bamboozle you with complete nonsense like “Web 3”.
Who Is This About?
It’s not at all about people working in crypto. Bitcoiners amongst the readership may be mildly irritated by me going on to give about as charitable an explanation of the role of these people as they have probably ever heard from somebody like me. This is really about financiers. It’s about the people who have used the mostly unrewarded efforts of developers, academics, entrepreneurs, and so on to siphon money from you to themselves, leaving a trail of useless tech and defrauded retail investors in their wake – and who will continue to do so if you continue to empower them.
Why This Essay?
We are at an interesting point in the development of the entirety of the “crypto” industry and I strongly suggest that people like you are going to be pitched all kinds of scams and bullshit in the coming months and years. If you have a little more background on what these people are really talking about, you will hopefully be able to avoid it.
My plan to help with that is presenting a short version and a long version of what blockchains are and are for, how they have historically been deployed in service of scams and bullshit, a high-level theory explaining the narrative evolution behind this sorry history, and a prediction for the near-term future of such shenanigans.
What is a Blockchain For?
A Blockchain is for sound, censorship-resistant, peer-to-peer digital money. It is not for anything else. If a blockchain is functional as money, it may be possible to also _use it _for other things. Some people find that interesting, some people find it infuriating, but don’t let that subtlety confuse you. It is not _for _arbitrary computation and storage or “decentralizing the internet” or running illegal securities rackets.

It is for money, plain and simple.
How does it achieve that? Proof of work and the difficulty adjustment. These are the innovations from which every other desirable property or feature flows. Proof of work enables censorship resistance. If somebody is trying to sell you on “proof of stake”: bullshit. The difficulty adjustment enables precise, predetermined, and _fair _issuance. If somebody is trying to sell you on a token they issue for free and without restriction: scam.
The problem Bitcoin solves is both economic and technical and the solution has material technical and economic merit. And it’s for this very specific and irreplicable reason the Bitcoin token has value. If this all sounds extreme to you, then I would suggest that your understanding of the topic is _extremely _misguided, that you are going to be _extremely bullshat and extremely scammed, _and you need to read this essay. That’s the short version.
The Long Version
I am sensitive to how extreme this all sounds. After all, hundreds of billions of dollars have been pumped into crypto, not Bitcoin – a huge amount of it is widely used, and many capable, honest, and brilliant people work in the industry. The reader will recall just above I said those people are not the target of my criticism. I’m not claiming they are all scammers and bullshitters. Sadly, I think it’s more likely they have been scammed and bullshat to some degree also.
I think I have some credibility in pointing this out because, as a VC in the Bitcoin space, I have increasingly seen founders telling me this themselves: that they originally bought into the hype in crypto and ended up wasting an enormous amount of time realizing their idea made no technical or economic sense in that context, so then they came to Bitcoin instead. You hear this one time and it’s an anecdote, but you hear it as many times as I have and it feels more like a representative sample.
What I want to cover next is as charitable a summary of the state of ex-Bitcoin crypto as I possibly can: my contention is that crypto has evolved into 4 rough categories: stablecoins, cryptography R&D, gambling, and scams. And these aren’t exclusive, to be clear; there is a lot of overlap, and, in fact, the overlap is arguably the key.
Scams
Scams are tokens, plain and simple. If somebody is trying to profit from the speculative price action of a token they have issued, they are scamming somebody. Maybe they are scamming you, maybe they are scamming retail investors, maybe they are scamming customers or suppliers – if such parties even exist in their cargo cult “business model”. There’s a scam in there somewhere.
However, it is rarely _just _a scam. There will almost always be components of stablecoins, R&D or gambling too. Hence these are worth really grappling with, taking seriously, giving credit to the extent it is due, but also analyzing critically.
My rough and high-level assessment of this breakdown of crypto is as follows, and I’ll explain what I mean by this below: stablecoins have economic merit but dubious technical merit; R&D has technical merit but no economic merit; and gambling sort of has merit but it depends how you interpret it. Obviously, scams have neither.

Stablecoins
By “sort of technical merit” I mean that stablecoins have central issuers. You can issue them as tokens on a blockchain but there’s not really much of a point. The issuer could just run a database connected to the internet with some straightforward signature schemes for transfers and it would make minimal operational difference. In fact, it would be cheaper and faster. _In fact, _you may as well run a Chaumian eCash mint (a decades-old innovation recently resurrected firmly within the _Bitcoin _space) such that your cheaper-and-faster-than-a-blockchain database also grants users transience and privacy rather than the public permanence of a blockchain.
The fact Tron is the most heavily used for stablecoins, in terms of settling the most value, is a testament to this point: it is barely even pretending not to be a database. This works as regulatory arbitrage given regulators think this is “innovation” because they are stupid.
That said, it is worth giving some credit here given the abject awfulness of fiat banking and payment rails with which stablecoins arguably most directly compete. Stablecoins are significantly more permissionless in their transfer than any fiat bank liability. And to attest to what seems like their most significant use case, they are permissionless in their _usership _in that only an internet connection and the right software is required rather than various discriminatory jurisdictional and compliance criteria.
However, what “sort of technical merit” ultimately boils down to, especially in comparison to Bitcoin, is: highly censorable in their exogenous links and, therefore, their value. The assets supposedly backing stablecoins are (by definition) still within the fiat system, even if this novel transfer mechanism of the rights to withdraw them is not. There is frankly a bit of theatre involved in the so-called “decentralization” of stablecoins given shutting down the central issuer is all that is required to make the permissionlessly tradeable decentralized tokens go to zero and be technically unimpeded but functionally useless. The technical innovation of Bitcoin, in contrast, is easily understood in one sense as it being totally indifferent to this kind of attack.
On the other hand, by “economic merit” I mean that they are extremely widely used and valued as a means of providing dollar shadow banking and often superior payment rails. Those in crypto often love pointing to this and many Bitcoiners tie themselves in knots trying to explain it away, whereas I see it as essentially unrelated to Bitcoin. Clearly there is a superficial connection, but you could create any superficial connection by “tokenizing” things for no particularly good technical _reason. I think it’s a different industry entirely. It’s more like a subindustry within _fintech – part banking, part payments – that for the time being relies on bamboozling regulators with all the nonsense I’m drawing attention to.
And good for them, frankly. If fiat banking isn’t going to be backed by real money anyway, then it _at least _ought to be permissionless. It should really be Chaumian eCash if it isn’t just Bitcoin, and it is regulation alone that makes it so awful in the first place. Making money usable and not a tool of dystopian control is, at this point, a political problem, not a technical one. Stablecoins are frankly a step in the right direction, especially insofar as they acclimatize users to digital assets. But I would still caution that they arguably don’t have sufficient technical merit to withstand what feels like an inevitable political attack …
Cryptography R&D
“Technical merit” for R&D is more or less self-explanatory, but the context is worth appreciating. It’s only really in crypto and mostly in Ethereum more specifically that people can permissionlessly experiment with arbitrarily complex cryptographic schemes that operate on real, enormous value. There are a lot of people who understandably find this attractive given their projects are essentially academic and trying out their ideas in the wild is more interesting, arguably more worthwhile, and certainly more fun than putting research essays on ArXiv or submitting them to a journal.
But … the value being manipulated is at best stablecoins and at worst baseless hype. If it isn’t a stablecoin then it probably exists in the first place because of either gambling or scams – and even there the line is very blurry.
Gambling
Gambling is an interesting lens to adopt on all this because it’s literally a trillion-dollar industry. And it’s real. It’s consensual; it’s not criminal; it’s legitimate economic activity that generates enormous profits for those who facilitate it well.
So, gambling has economic merit in that sense. But it’s tricky in this context how to characterize it because you could also argue it’s deeply dishonest gambling in that the gamblers don’t realize they are playing a negative sum game against the house. They think they are doing something akin to speculating on securities, which may be just as stupid depending on how it’s done, but at least has real economic utility and contributes to capital formation.
The difference here is that what is being speculated on _has no economic merit. _So, if that’s your gauge of merit, then here there is none. And it’s a very blurry line between this and an outright scam. Maybe the people involved _think _of what they are doing as amazing R&D, and maybe it’s inadvertently just a scam; maybe they know it’s all nonsense, but they think they can profit within the negative sum game because there are greater fools. In any case, I think gambling is a very helpful characterization of a lot of the behavior of the users and the real economic function of the industry.
There’s an interesting social component to all this because crypto people will often get mad at Bitcoiners because Bitcoiners tend not to care about either stablecoins or crypto R&D: they’ll say, why don’t you like stablecoins, they have clear economic merit? And the answer is they have dubious technical merit. Or, why don’t you like our next-gen Zero Knowledge scaling protocol, it has clear technical merit? And the answer is it has no economic merit.
If you’re happy with one but not the other, it’s easy to think of Bitcoiners as being closed-minded or dogmatic or whatever, but, ultimately, I think it’s just about discipline. What’s the point in being excited by something that half works, and that you know why will never fully work? So to be frank, a lot of this may be well-intentioned, but it’s kinda’ bullshit. It very probably ultimately rests on gambling and not at all whatever its stated purpose is … or it’s just a scam.
How Did We Get Here?
The following is by no means exhaustive and the framing is deliberately a little tongue-in-cheek. As well as being accurate enough (if unavoidably biased), my goal here is primarily to set up my prediction for what is coming next.
2015 reality: Ethereum launches narrative: “the world computer”
In 2015, Ethereum launched. The narrative here was that we are building “the world computer” and we can now have decentralized uncensorable computation. Never mind that anybody with a laptop has an uncensorable and decentralized computing device. And keep in mind this question of, “_what data might it ever be relevant to compute over in this manner (whatever that means in the first place)?” _The answer will become clearer and clearer …
2016-17 reality: ICO bubble narrative: “Web 3” / “DApps”
Regardless, at the end of 2015 we get the proposal and adoption of ERC20: a standard for issuing fungible tokens within Ethereum contracts, which is why in 2016 _but especially in 2017 _we get the ICO bubble. The narrative changes. Now we are concerned with “Web 2” companies being huge, powerful, and centralized. What if, instead, users could cooperatively own the application, control their own data, and participate in the economic upside that their usage is creating?
2018-19 reality: crypto winter narrative: “mistakes were made”
In 2018 this all falls apart, so don’t worry about it, moving on …
2020-21 reality: defi summer narrative: “decentralized finance”
By 2020 the narrative was different once again. It is more or less realized by this point that utility tokens make no technical or economic sense. You can’t introduce artificial scarcity in capital goods where there should be abundance and deflation and expect anybody to care, never mind to value your concoction. On the other hand, “securities” ought to be scarce and in some sense ought to function as tradeable ledger entries. Maybe they could be tokenized and computed on in a censorship-resistant and decentralized manner?
So, we get a boom in “defi” which, for what it’s worth, fellow Axiom co-founder Anders Larson and I predicted in our essay Only The Strong Survive, in September 2021, would be a complete disaster because, amongst a myriad of other illiterate insanities, there was approximately zero grounding of these securities in productive capital. The ecosystem was entirely self-referential – grounded _not even _in the questionable economic merit of stablecoins but firmly in gambling and scams; in leverage, rehypothecation, and securitization of precisely nothing whatsoever productive.
2022 reality: shitcoinpocalypse narrative: “mistakes were made”
And we were absolutely right because in 2022 everything collapsed. First Terra/Luna imploded – a “defi” project which essentially presented to the world the argument that a fractional reserve bank issuing fiduciary media can literally never go bankrupt because it can always cover a deposit shortfall by issuing more equity. While briefly flirting with a capitalization of around fifty f***ing billion dollars, and endorsed and fawned over by all manner of illiterate charlatans with gigantic and unsuspecting audiences, this argument was eventually rejected by the market as utterly imbecilic, as analyzed by myself and Nic Carter in All Falls Down.
This triggered a credit contagion that soon after took down 3 Arrows Capital, Celsius, Voyager, BlockFi, and others. FTX limped along by what we now understand to be something like defrauding their way out of debt, but eventually also collapsed later that year. If _Only The Strong Survive _was a pre-mortem of all of this, then the reader may want to read Green Eggs And Ham, also by myself and Anders Larson, as a kind of post-mortem.
2023-today reality: Bitcoin multisigs narrative: “Bitcoin renaissance”
And now a lot of this stuff is moving to Bitcoin. It is outside the scope of this essay to explain this in much detail but there have been a handful of developments in Bitcoin recently which, regardless of their intended purpose, seem to have as a collective side effect that a lot of these same shenanigans can now be implemented (or can _pretend _to be implemented) in a more Bitcoin-native context.
So, the new narrative is something like:
“these things didn’t work, not because they are terrible ideas that collapse to moon math wrappers around gambling and scams under any remotely critical analysis, but rather because they weren’t on Bitcoin. But also, since it has only recently become possible to (at least pretend to) implement them on Bitcoin, they are now worthwhile. We have wandered in the wilderness but learned our lessons and found the promised land.”

Technical and Economic Merit
Let’s consider all this through the lens of technical and economic merit once again. Or rather, the alleged merit given the stated goal. Ignore for now whether there is any merit:
2015 technical goal: new computing paradigm economic goal: x% of GDP?
The original idea of “crypto” allegedly has the merit of the next revolution in computing. Goodness knows how big that market is; probably a decent chunk of global GDP – if it meant anything, which it doesn’t.
2016-17 technical goal: disrupting company formation economic goal: y% of S&P?
ICOs then become a little bit more specific. Now they are merely disrupting how we organize companies. What’s that worth? Some portion of the value of the companies that can now be decentralized and tokenized I guess? Who knows …
2018-19 nothing to see here
Nothing happened then, don’t worry about it.
2020-21 technical goal: decentralize finance economic goal: z% of NYSE, CME, ISDA?
Defi becomes more specific again. Now we are merely tokenizing financial contracts, expanding access, removing middlemen, and so on. So that should probably be worth some percentage of capital markets activity?
2022 nothing to see here
Oops, never mind …
2023-today technical goal: now it’s on Bitcoin! economic goal: i% of … Bitcoin?
… and now it’s on Bitcoin apparently.
In Hindsight ...
I think the most amusing analysis of all this is as follows: it starts off completely insane, it gets more and more restrained each time – you could cheekily argue it starts to make more and more sense – but it also gets closer to Bitcoin every time. It’s clearly narrowing in on just: Bitcoin.
This is people realizing, painfully, over decades, what blockchains are for! They are not for “decentralizing everything” They are for censorship-resistant, sound, peer-to-peer digital money.

And I think this is _also _why we get the current state of crypto from earlier in the essay. As it starts to make more and more sense (by getting closer and closer to Bitcoin) you have realizations like the following: digital gift vouchers for artificially scarce and extremely expensive computation aren’t money, so we need “real money” in here for it to have economic merit, so you get stablecoins. Also, well we have a rich programming environment that seems technically interesting but also the severe technical handicap of being unable to do even a billionth of a billionth of a billionth of all the computations in the world, so you get crypto R&D. These emerge as a kind of patch, and they have _some _merit in isolation, whereas the long-term trajectory is actually just to converge on Bitcoin.
It’s an open and fascinating question if there are any learnings from these that can still be transplanted to Bitcoin. For stablecoins, this strikes me as less clear, given the dubious technical merit is introduced by using a blockchain at all, not just a blockchain other than Bitcoin. However, efforts to create Bitcoin balances (tokenized or otherwise) that are stable relative to some external price are to be applauded, if still heavily scrutinized for what technical merit they _really _have.
It seems far more likely that crypto R&D will prove useful in a Bitcoin context to some or other degree, and in this case the economic merit is in fact solved by moving to Bitcoin, provided the necessary technical merit can be mimicked. At the time of writing, this is a source of both hope and dread: hope given the possibility of viable avenues of development (although still highly uncertain); dread given how early steps in this direction are already being misrepresented in the pursuit of bullshit and scams. I will return to both shortly.
Narrative Evolution
Back to the table just above, I want to make three quick observations that tie together my entire argument and get us to the end of the essay:

Firstly, the bubbles always follow the price of Bitcoin. Hopefully I don’t need to include a price chart for the reader to grasp this immediately.
Secondly, it’s important that the narrative always changes. Absolutely ungodly amounts of money were raised for this crap following the_ Bitcoin bull runs of 2017 and 2021. The people doing this couldn’t point to the previous absolute disaster, so they had to spin something along the lines of: “_we learned our lessons and we’ve refined the use case.” This should sound familiar from just above.
Thirdly, however, regardless of whatever refinement they’ve come up with, the consequence of the new “narrative” is always, “buy my token”.
Always.
It doesn’t matter what buzzword salad is in the middle. It’s always “Bitcoin is cool, xyz, fughayzi fughahzi, buy my token.”
This is why I am very much tempted to not care so much about developers, academics, entrepreneurs, and so on, and in fact for my null hypothesis to be that they are more likely to have been victims than perpetrators. I don’t think they even end up in a position to contribute without the key group whom I do blame. When you put all these pieces together, what I think falls out of this analysis is as follows:
The entire cycle of shitcoinery can be traced to unscrupulous financiers convincing capital allocators who don’t know any better, in a bull market that, yes, Bitcoin is cool, but what they are doing is related, cooler, and that they deserve a fee.
Let us label this the Capital Cycle Theory of Shitcoinery. I think that everything else about which one might want to complain is downstream of this core realization.
Avoiding It
Given everything I’ve covered this is simple and this is pretty much the end of the essay.
You need to be aware of why this is happening now. If it hasn’t happened to you already (intended readership in the capital allocation business, that is) I guarantee it’s about to: with ETFs and the halving just past, we seem to be starting a Bitcoin bull run, these people have already raised ridiculous amounts of money on scams and bullshit that have mostly imploded. They may have lost a lot of money, or they may even have dumped on retail and got an excellent “return”. But in any case, they need a new narrative.
It's _possible _they have a viable narrative around stablecoins, R&D, both, and that they are as wary of scams as I have suggested here that they should be. I don’t want to insult anybody who merely has a different investment thesis to me if they are otherwise reasonable in their outlook and honest in their dealings.
However, if they are only now realizing how pointless and disingenuous every preceding crypto narrative has been after 7 years and hundreds of billions of dollars – or if they still don’t realize it at all; if their track record shows they were deeply involved, handsomely rewarded, and yet created nothing of lasting value; if they say things like “the builders are coming back to Bitcoin”: be very, very suspicious. Be on the lookout for tokens, which is to say, be on the lookout for scams.
What is especially frustrating is that the technical spin of the "layer twos" that are all the rage at the time of writing, that "the builders are coming back to Bitcoin" to build, and that you, the capital-allocating reader, will almost certainly be pitched, is in and of itself pretty reasonable. They just don't require tokens and they don't require gambling to support the token prices. What they do require is _sound adherence to Bitcoin's technical and economic merit. _At the very least, they require honest communication about the design trade-offs so far and planned for, and what, if any, economic and technical merit is left over after these trade-offs have been made.
Narrative aside, the _reality _of 99% of these projects is that they are private execution environments tied to multisigs custodying user deposits. Which is to say, on the one hand, that they are cargo culting "crypto R&D" from Ethereum that isn't technically possible in Bitcoin in order to feign technical merit, and on the other, that _they aren't layer twos at all. _Once again, they may as well be Chaumian eCash mints, except for the fact that this would make the intended token scam all but impossible to pull off.
Casey Rodarmor, creator of the Ordinals protocol, recently joked on the Hell Money _podcast he co-hosts, responding to the idea that "_everybody is building an L2 now":
"It's the same sad sack playbook as on Ethereum being recapitulated on Bitcoin. That's how you get a VC check on Ethereum. They are all glorified multisigs, so they are like, "hey let's port our glorified multisig to Bitcoin and get a VC check." I was talking to a friend of mine who is working on an interesting project, an open-source analyzer that does transaction clustering, and I was like, "maybe you could do this in this way and raise some VC money," and he said, "yeah, okay, but what's the point in raising VC money?" And I said, "no, no, no, this is the end! This is the goal! You raise VC money and then you cut yourself checks from that VC money until it runs out and then you raise more at a 10x valuation. This is the new economy, guys!"
The 1% that are legitimately trying to bring the learnings from crypto R&D to Bitcoin in a technically and economically sound manner will hopefully win in the long run (and even this is somewhat speculative at the time of writing) but will likely get little to no attention amidst this bull market flurry of scams and bullshit.
Axiom will do its best to source and invest in these companies (we already have!) but we are resigned to it being a much more difficult sell to capital allocators in light of the Capital Cycle Theory of Shitcoinery. To be brutally honest, this entire essay can fairly be considered cope on my part in light of having lost this battle in the past and facing up to the very real prospect of losing it in the near future too. Oh well, at least I tried.
Wrapping Up
The essence of the Capital Cycle Theory of Shitcoinery is that the problems I’ve described ultimately come from bamboozling people just like you with technical sounding nonsense like “Web 3” so you think it’s all a lot more complicated than it really is. Just buy Bitcoin. That’s certainly the first thing you should do anyway, and it might be the only thing you ever need to do.
If you really, really want to take the extra risk of investing in the Bitcoin ecosystem, the team at Axiom would be happy to speak with you. But we are never going to talk you out of buying Bitcoin. There is no world in which Bitcoin does poorly and we do well, or in which we promise something “better than Bitcoin,” and there’s no point in engaging with us at all if you don’t already believe most of this.
If that’s of interest to you, we’d love to talk. If not, just buy Bitcoin. In any case: fair warning, we are heading into a Bitcoin bull market and the scams and the bullshit are coming. Good luck avoiding them.
Allen Farrington, June 2024

-
 @ bd32f268:22b33966
2024-10-24 17:57:26
@ bd32f268:22b33966
2024-10-24 17:57:26A atualidade acostumou-nos a uma lânguida linguagem devido à cultura do politicamente correto e ao crescente relativismo em que vivemos. A confusão é tanta que já não se chamam os bois pelos nomes e este ambiente faz com que inclusive desconheçamos o significado das palavras. A este respeito temos visto cada vez mais indefinição sobre o que são os vícios e sobre o que são as virtudes. Tal é a confusão que por vezes trocamos o significado de uns pelos outros.
A coragem e a convicção facilmente passam por orgulho e arrogância, a castidade passa por beatice e por aí segue a confusão com muitos outros termos.
A inversão de valores é tão disseminada que atrocidades como a pornografia, o aborto, o adultério entre outras atrocidades são celebrados como conquistas civilizacionais. A sua disseminação é de tal forma que hoje a pessoa média já banalizou e normalizou completamente estes aspectos.
“Primeiro estranha-se depois entranha-se.”
Fernando Pessoa
Enquanto isto acontece por um lado, por outro a defesa da família, da identidade e da tradição são abertamente atacadas como se se tratassem de produtos de uma cultura opressora que deve ser combatida por todos os meios. Por agora a perseguição destas ideias é ainda maioritariamente realizada através da exclusão social e económica, no entanto, não são escassos os exemplos da história em que essa perseguição assume uma outra dimensão.
Desta forma, está criado um paradigma e um sistema de incentivos que premeia a pessoa que colabora com o sistema vigente. Tanto é assim que se multiplicam cada vez mais os exemplos de programas de quotas e subvenções que permitem, a quem possui um grau mais avançado de assimilação ideológica progredir socialmente atalhando o caminho para o fazer.
“Assim, toda a árvore boa produz bons frutos, porém a árvore má produz frutos maus. Não pode a árvore boa produzir frutos maus, nem a árvore má produzir frutos bons (…)”
Mateus 7:17-18“Assim, toda a árvore boa produz bons frutos, porém a árvore má produz frutos maus. Não pode a árvore boa produzir frutos maus, nem a árvore má produzir frutos bons (…)”
> Mateus 7:17-18*
Desengane-se quem pensa que no paradigma pos-moderno não há moralização, sacerdotes e uma matriz religiosa, tudo isso existe.
Os psicólogos, para mal da nossa sociedade, são crescentemente os sacerdotes desta religião pagã, aquela que baseada numa filosofia e antropologia erradas vai corrompendo intelecto e coração.
Nesta nova ordem social, que em abono da verdade é já antiga, a inversão de valores é tal que já a própria vida humana é sacrificada no altar do clima em abono da “mãe” natureza. Regredimos ao tribalismo que nos sugere que a natureza vale mais que a vida humana.
Este é apenas um exemplo dos rituais de sacrifício proporcionados pela “nova” religião. Um outro exemplo que podemos dar é o da castração química e física de crianças e jovens no altar da falsa compaixão e empatia. Ainda um outro exemplo que podemos dar é o da promoção do homossexualismo, do transexualismo e da não-monogamia como caminhos saudáveis a seguir, sacrificando a vida de muitos jovens confusos no altar da inclusão. Muitos mais exemplos poderiam ser dados, porque à medida que esta “nova” religião aumenta a sua ortodoxia os rituais vão ficando cada vez mais assombrosos.
Estes rituais têm por base uma apologia ao anti logos, quer isto dizer que procuram negar tudo o que é conhecimento básico sobre a realidade e sobre a verdade. A própria razão e lógica não se sustentam quando vemos situações como a de homens a competir em desportos femininos. As leis desta nova ordem são: “procura a felicidade (aqui muitas vezes entendida como o prazer) como fim último da vida “; “todas as opiniões são certas e não há uma verdade”; “Não servirás a nenhuma autoridade”; “não seguir o vício é opressão e seguir o vício é liberdade”.
Neste ambiente inóspito, quem quiser preservar a honra e a virtude terá cada vez mais dificuldade uma vez que a dissidência desta nova religião não é aplaudida, pelo contrário é anatematizada. Porém, importa dizer que independentemente da época há sempre espaço para o heroísmo e para a transformação destas dificuldades em degraus para que o indivíduo se possa distinguir dos demais pelas suas virtudes. Onde o vício abunda também maior o destaque será em relação à graça, como uma pedra preciosa reluzente no meio da lama que aparenta brilhar mais intensamente aos nossos olhos tal é o contraste, ou como uma luz na escuridão que se distingue facilmente.
 ###### Casper David Friedrich - dreaming man in church ruins
###### Casper David Friedrich - dreaming man in church ruins -
 @ e968e50b:db2a803a
2024-10-24 17:53:49
@ e968e50b:db2a803a
2024-10-24 17:53:49https://whosaidit.vercel.app/
I made a quiz for you. Let me know if you have any feedback. Please don't share your results or any spoilers here. I've already had some...uh...let's call if fun...sharing with friends and family. Much to @DarthCoin and many other stackers' chagrin, the purpose of this is not to convince people not to vote, although that may be the affect for some. I'm just trying to challenge people's thinking.
Also, it would be really easy for me to change any of the content. Let me know if you have feedback. I want to make this as effective and accurate as possible.
https://whosaidit.vercel.app/
originally posted at https://stacker.news/items/738766
-
 @ af9c48b7:a3f7aaf4
2024-10-23 19:16:52
@ af9c48b7:a3f7aaf4
2024-10-23 19:16:52Chef's notes
These "crackers" go well as a chip alternative when having carnivore tacos, as well as serves as a general snack. They are not really shelf stable and will get stale fairly quickly. I would recommend eating them within 24 hours of baking.
While any thickness of cheese can be used, I've found that the ultra thin sliced cheese works the best.
Details
- ⏲️ Prep time: 5
- 🍳 Cook time: 40-45 minutes depending on your oven.
- 🍽️ Servings: 1-2
Ingredients
- Ultra Thin Sliced Cheese (pick your favorite type)
- Parchment Paper
Directions
- Preheat oven to 250 degrees.
- While the oven is preheating, line a baking sheet with parchment paper.
- Take the individually sliced cheese and cut into any size you prefer. I recommend cutting in 4 equal squares for use as traditional cracker or "chip" when eating tacos.
- Place on the parchment paper allowing space between each cheese slice.
- Bake in a 250 degree oven for 40-45 minutes checking periodically to determine the cheese has achieved your desired level of crispness.
- One your cheese is done, remove from the oven and place the cheese slices on a paper towel to cool and allow for excess oil to drain.
- Place in a ziplock back and eat within 24 hours.
-
 @ 4523be58:ba1facd0
2024-05-28 11:05:17
@ 4523be58:ba1facd0
2024-05-28 11:05:17NIP-116
Event paths
Description
Event kind
30079denotes an event defined by its event path rather than its event kind.The event directory path is included in the event path, specified in the event's
dtag. For example, an event path might beuser/profile/name, whereuser/profileis the directory path.Relays should parse the event directory from the event path
dtag and index the event by it. Relays should support "directory listing" of kind30079events using the#ffilter, such as{"#f": ["user/profile"]}.For backward compatibility, the event directory should also be saved in the event's
ftag (for "folder"), which is already indexed by some relay implementations, and can be queried using the#ffilter.Event content should be a JSON-encoded value. An empty object
{}signifies that the entry at the event path is itself a directory. For example, when savinguser/profile/name:Bob, you should also saveuser/profile:{}so the subdirectory can be listed underuser.In directory names, slashes should be escaped with a double slash.
Example
Event
json { "tags": [ ["d", "user/profile/name"], ["f", "user/profile"] ], "content": "\"Bob\"", "kind": 30079, ... }Query
json { "#f": ["user/profile"], "authors": ["[pubkey]"] }Motivation
To make Nostr an "everything app," we need a sustainable way to support new kinds of applications. Browsing Nostr data by human-readable nested directories and paths rather than obscure event kind numbers makes the data more manageable.
Numeric event kinds are not sustainable for the infinite number of potential applications. With numeric event kinds, developers need to find an unused number for each new application and announce it somewhere, which is cumbersome and not scalable.
Directories can also replace monolithic list events like follow lists or profile details. You can update a single directory entry such as
user/profile/nameorgroups/follows/[pubkey]without causing an overwrite of the whole profile or follow list when your client is out-of-sync with the most recent list version, as often happens on Nostr.Using
d-tagged replaceable events for reactions, such as{tags: [["d", "reactions/[eventId]"]], content: "\"👍\"", kind: 30079, ...}would make un-reacting trivial: just publish a new event with the samedtag and an empty content. Toggling a reaction on and off would not cause a flurry of new reaction & delete events that all need to be persisted.Implementations
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
f) already support this feature. - IrisDB client side library: treelike data structure with subscribable nodes.
https://github.com/nostr-protocol/nips/pull/1266
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
-
 @ b60c3e76:c9d0f46e
2024-05-15 10:08:47
@ b60c3e76:c9d0f46e
2024-05-15 10:08:47KRIS menjamin semua golongan masyarakat mendapatkan perlakuan sama dari rumah sakit, baik pelayanan medis maupun nonmedis.
Demi memberikan peningkatan kualitas layanan kesehatan kepada masyarakat, pemerintah baru saja mengeluarkan Peraturan Presiden (Perpres) nomor 59 tahun 2024 tentang Jaminan Kesehatan. Melalui perpres itu, Presiden Joko Widodo (Jokowi) telah menghapus perbedaan kelas layanan 1, 2, dan 3 dalam Badan Penyelenggara Jaminan Sosial atau BPJS Kesehatan.
Layanan berbasis kelas itu diganti dengan KRIS (Kelas Rawat Inap Standar). Berkaitan dengan lahirnya Perpres 59/2024 tentang Perubahan Ketiga atas Perpres 82/2018 tentang Jaminan Kesehatan, Presiden Joko Widodo telah memerintahkan seluruh rumah sakit yang bekerja sama dengan BPJS Kesehatan melaksanakannya.
Kebijakan baru itu mulai berlaku per 8 Mei 2024 dan paling lambat 30 Juni 2025. Dalam jangka waktu tersebut, rumah sakit dapat menyelenggarakan sebagian atau seluruh pelayanan rawat inap berdasarkan KRIS sesuai dengan kemampuan rumah sakit.
Lantas apa yang menjadi pembeda dari sisi layanan dengan layanan rawat inap sesuai Perpres 59/2024? Dahulu sistem layanan rawat BPJS Kesehatan dibagi berdasarkan kelas yang dibagi masing-masing kelas 1, 2, dan 3. Namun, melalui perpres, layanan kepada masyarakat tidak dibedakan lagi.
Pelayanan rawat inap yang diatur dalam perpres itu--dikenal dengan nama KRIS—menjadi sistem baru yang digunakan dalam pelayanan rawat inap BPJS Kesehatan di rumah sakit-rumah sakit. Dengan KRIS, semua golongan masyarakat akan mendapatkan perlakuan yang sama dari rumah sakit, baik dalam hal pelayanan medis maupun nonmedis.
Dengan lahirnya Perpres 59/2024, tarif iuran BPJS Kesehatan pun juga akan berubah. Hanya saja, dalam Perpres itu belum dicantumkan secara rinci ihwal besar iuran yang baru. Besaran iuran baru BPJS Kesehatan itu sesuai rencana baru ditetapkan pada 1 Juli 2025.
“Penetapan manfaat, tarif, dan iuran sebagaimana dimaksud ditetapkan paling lambat tanggal 1 Juli 2025,” tulis aturan tersebut, dikutip Senin (13/5/2024).
Itu artinya, iuran BPJS Kesehatan saat ini masih sama seperti sebelumnya, yakni sesuai dengan kelas yang dipilih. Namun perpres itu tetap berlaku sembari menanti lahirnya peraturan lanjutan dari perpres tersebut.
Kesiapan Rumah Sakit
Berkaitan dengan lahirnya kebijakan layanan kesehatan tanpa dibedakan kelas lagi, Kementerian Kesehatan (Kemenkes) menegaskan mayoritas rumah sakit di Indonesia siap untuk menjalankan layanan KRIS untuk pasien BPJS Kesehatan.
Kesiapan itu diungkapkan oleh Dirjen Pelayanan Kesehatan Kemenkes Azhar Jaya. “Survei kesiapan RS terkait KRIS sudah dilakukan pada 2.988 rumah sakit dan yang sudah siap menjawab isian 12 kriteria ada sebanyak 2.233 rumah sakit,” ujar Azhar.
Sebagai informasi, KRIS adalah pengganti layanan Kelas 1, 2, dan 3 BPJS Kesehatan yang bertujuan untuk memberikan layanan kesehatan secara merata tanpa melihat besaran iurannya.
Melalui KRIS, rumah sakit perlu menyiapkan sarana dan prasarana sesuai dengan 12 kriteria kelas rawat inap standar secara bertahap. Apa saja ke-12 kriteria KRIS itu?
Sesuai bunyi Pasal 46A Perpres 59/2024, disyaratkan kriteria fasilitas perawatan dan pelayanan rawat inap KRIS meliputi komponen bangunan yang digunakan tidak boleh memiliki tingkat porositas yang tinggi serta terdapat ventilasi udara dan kelengkapan tidur.
Demikian pula soal pencahayaan ruangan. Perpres itu juga mengatur pencahayaan ruangan buatan mengikuti kriteria standar 250 lux untuk penerangan dan 50 lux untuk pencahayaan tidur, temperature ruangan 20--26 derajat celcius.
Tidak hanya itu, layanan rawat inap berdasarkan perpres itu mensyaratkan fasilitas layanan yang membagi ruang rawat berdasarkan jenis kelamin pasien, anak atau dewasa, serta penyakit infeksi atau noninfeksi.
Selain itu, kriteria lainnya adalah keharusan bagi penyedia layanan untuk mempertimbangkan kepadatan ruang rawat dan kualitas tempat tidur, penyediaan tirai atau partisi antartempat tidur, kamar mandi dalam ruangan rawat inap yang memenuhi standar aksesibilitas, dan menyediakan outlet oksigen.
Selain itu, kelengkapan tempat tidur berupa adanya dua kotak kontak dan nurse call pada setiap tempat tidur dan adanya nakas per tempat tidur. Kepadatan ruang rawat inap maksimal empat tempat tidur dengan jarak antara tepi tempat tidur minimal 1,5 meter.
Tirai/partisi dengan rel dibenamkan menempel di plafon atau menggantung. Kamar mandi dalam ruang rawat inap serta kamar mandi sesuai dengan standar aksesibilitas dan outlet oksigen.
Azhar menjamin, Kemenkes akan menjalankan hal tersebut sesuai dengan tupoksi yang ada. “Tentu saja kami akan bekerja sama dengan BPJS Kesehatan dalam implementasi dan pengawasannya di lapangan,” ujar Azhar.
Berkaitan dengan perpres jaminan kesehatan itu, Direktur Utama BPJS Kesehatan Ghufron Mukti menilai, perpres tersebut berorientasi pada penyeragaman kelas rawat inap yang mengacu pada 12 kriteria. "Bahwa perawatan ada kelas rawat inap standar dengan 12 kriteria, untuk peserta BPJS, maka sebagaimana sumpah dokter tidak boleh dibedakan pemberian pelayan medis atas dasar suku, agama, status sosial atau beda iurannya," ujarnya.
Jika ada peserta ingin dirawat pada kelas yang lebih tinggi, kata Ghufron, maka diperbolehkan selama hal itu dipengaruhi situasi nonmedis. Hal itu disebutkan dalam Pasal 51 Perpres Jaminan Kesehatan diatur ketentuan naik kelas perawatan.
Menurut pasal tersebut, naik kelas perawatan dilakukan dengan cara mengikuti asuransi kesehatan tambahan atau membayar selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya yang harus dibayar akibat peningkatan pelayanan.
Selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya pelayanan dapat dibayar oleh peserta bersangkutan, pemberi kerja, atau asuransi kesehatan tambahan.
Ghufron Mukti juga mengimbau pengelola rumah sakit tidak mengurangi jumlah tempat tidur perawatan pasien dalam upaya memenuhi kriteria KRIS. "Pesan saya jangan dikurangi akses dengan mengurangi jumlah tempat tidur. Pertahankan jumlah tempat tidur dan penuhi persyaratannya dengan 12 kriteria tersebut," tegas Ghufron.
Penulis: Firman Hidranto Redaktur: Ratna Nuraini/Elvira Inda Sari Sumber: Indonesia.go.id
-
 @ 8947a945:9bfcf626
2024-10-17 08:06:55
@ 8947a945:9bfcf626
2024-10-17 08:06:55สวัสดีทุกคนบน Nostr ครับ รวมไปถึง watchersและ ผู้ติดตามของผมจาก Deviantart และ platform งานศิลปะอื่นๆนะครับ
ตั้งแต่ต้นปี 2024 ผมใช้ AI เจนรูปงานตัวละครสาวๆจากอนิเมะ และเปิด exclusive content ให้สำหรับผู้ที่ชื่นชอบผลงานของผมเป็นพิเศษ
ผมโพสผลงานผมทั้งหมดไว้ที่เวบ Deviantart และค่อยๆสร้างฐานผู้ติดตามมาเรื่อยๆอย่างค่อยเป็นค่อยไปมาตลอดครับ ทุกอย่างเติบโตไปเรื่อยๆของมัน ส่วนตัวผมมองว่ามันเป็นพิร์ตธุรกิจออนไลน์ ของผมพอร์ตนึงได้เลย
เมื่อวันที่ 16 กย.2024 มีผู้ติดตามคนหนึ่งส่งข้อความส่วนตัวมาหาผม บอกว่าชื่นชอบผลงานของผมมาก ต้องการจะขอซื้อผลงาน แต่ขอซื้อเป็น NFT นะ เสนอราคาซื้อขายต่อชิ้นที่สูงมาก หลังจากนั้นผมกับผู้ซื้อคนนี้พูดคุยกันในเมล์ครับ
นี่คือข้อสรุปสั่นๆจากการต่อรองซื้อขายครับ
(หลังจากนี้ผมขอเรียกผู้ซื้อว่า scammer นะครับ เพราะไพ่มันหงายมาแล้ว ว่าเขาคือมิจฉาชีพ)

- Scammer รายแรก เลือกผลงานที่จะซื้อ เสนอราคาซื้อที่สูงมาก แต่ต้องเป็นเวบไซต์ NFTmarket place ที่เขากำหนดเท่านั้น มันทำงานอยู่บน ERC20 ผมเข้าไปดูเวบไซต์ที่ว่านี้แล้วรู้สึกว่ามันดูแปลกๆครับ คนที่จะลงขายผลงานจะต้องใช้ email ในการสมัครบัญชีซะก่อน ถึงจะผูก wallet อย่างเช่น metamask ได้ เมื่อผูก wallet แล้วไม่สามารถเปลี่ยนได้ด้วย ตอนนั้นผมใช้ wallet ที่ไม่ได้ link กับ HW wallet ไว้ ทดลองสลับ wallet ไปๆมาๆ มันทำไม่ได้ แถมลอง log out แล้ว เลข wallet ก็ยังคาอยู่อันเดิม อันนี้มันดูแปลกๆแล้วหนึ่งอย่าง เวบนี้ค่า ETH ในการ mint 0.15 - 0.2 ETH … ตีเป็นเงินบาทนี่แพงบรรลัยอยู่นะครับ

-
Scammer รายแรกพยายามชักจูงผม หว่านล้อมผมว่า แหม เดี๋ยวเขาก็มารับซื้องานผมน่า mint งานเสร็จ รีบบอกเขานะ เดี๋ยวเขารีบกดซื้อเลย พอขายได้กำไร ผมก็ได้ค่า gas คืนได้ แถมยังได้กำไรอีก ไม่มีอะไรต้องเสีนจริงมั้ย แต่มันเป้นความโชคดีครับ เพราะตอนนั้นผมไม่เหลือทุนสำรองที่จะมาซื้อ ETH ได้ ผมเลยต่อรองกับเขาตามนี้ครับ :
-
ผมเสนอว่า เอางี้มั้ย ผมส่งผลงานของผมแบบ low resolution ให้ก่อน แลกกับให้เขาช่วยโอน ETH ที่เป็นค่า mint งานมาให้หน่อย พอผมได้ ETH แล้ว ผมจะ upscale งานของผม แล้วเมล์ไปให้ ใจแลกใจกันไปเลย ... เขาไม่เอา
- ผมเสนอให้ไปซื้อที่ร้านค้าออนไลน์ buymeacoffee ของผมมั้ย จ่ายเป็น USD ... เขาไม่เอา
- ผมเสนอให้ซื้อขายผ่าน PPV lightning invoice ที่ผมมีสิทธิ์เข้าถึง เพราะเป็น creator ของ Creatr ... เขาไม่เอา
- ผมยอกเขาว่างั้นก็รอนะ รอเงินเดือนออก เขาบอก ok
สัปดาห์ถัดมา มี scammer คนที่สองติดต่อผมเข้ามา ใช้วิธีการใกล้เคียงกัน แต่ใช้คนละเวบ แถมเสนอราคาซื้อที่สูงกว่าคนแรกมาก เวบที่สองนี้เลวร้ายค่าเวบแรกอีกครับ คือต้องใช้เมล์สมัครบัญชี ไม่สามารถผูก metamask ได้ พอสมัครเสร็จจะได้ wallet เปล่าๆมาหนึ่งอัน ผมต้องโอน ETH เข้าไปใน wallet นั้นก่อน เพื่อเอาไปเป็นค่า mint NFT 0.2 ETH
ผมบอก scammer รายที่สองว่า ต้องรอนะ เพราะตอนนี้กำลังติดต่อซื้อขายอยู่กับผู้ซื้อรายแรกอยู่ ผมกำลังรอเงินเพื่อมาซื้อ ETH เป็นต้นทุนดำเนินงานอยู่ คนคนนี้ขอให้ผมส่งเวบแรกไปให้เขาดูหน่อย หลังจากนั้นไม่นานเขาเตือนผมมาว่าเวบแรกมันคือ scam นะ ไม่สามารถถอนเงินออกมาได้ เขายังส่งรูป cap หน้าจอที่คุยกับผู้เสียหายจากเวบแรกมาให้ดูว่าเจอปัญหาถอนเงินไม่ได้ ไม่พอ เขายังบลัฟ opensea ด้วยว่าลูกค้าขายงานได้ แต่ถอนเงินไม่ได้
Opensea ถอนเงินไม่ได้ ตรงนี้แหละครับคือตัวกระตุกต่อมเอ๊ะของผมดังมาก เพราะ opensea อ่ะ ผู้ใช้ connect wallet เข้ากับ marketplace โดยตรง ซื้อขายกันเกิดขึ้น เงินวิ่งเข้าวิ่งออก wallet ของแต่ละคนโดยตรงเลย opensea เก็บแค่ค่า fee ในการใช้ platform ไม่เก็บเงินลูกค้าไว้ แถมปีนี้ค่า gas fee ก็ถูกกว่า bull run cycle 2020 มาก ตอนนี้ค่า gas fee ประมาณ 0.0001 ETH (แต่มันก็แพงกว่า BTC อยู่ดีอ่ะครับ)
ผมเลยเอาเรื่องนี้ไปปรึกษาพี่บิท แต่แอดมินมาคุยกับผมแทน ทางแอดมินแจ้งว่ายังไม่เคยมีเพื่อนๆมาปรึกษาเรื่องนี้ กรณีที่ผมทักมาถามนี่เป็นรายแรกเลย แต่แอดมินให้ความเห็นไปในทางเดียวกับสมมุติฐานของผมว่าน่าจะ scam ในเวลาเดียวกับผมเอาเรื่องนี้ไปถามในเพจ NFT community คนไทนด้วย ได้รับการ confirm ชัดเจนว่า scam และมีคนไม่น้อยโดนหลอก หลังจากที่ผมรู้ที่มาแล้ว ผมเลยเล่นสงครามปั่นประสาท scammer ทั้งสองคนนี้ครับ เพื่อดูว่าหลอกหลวงมิจฉาชีพจริงมั้ย
โดยวันที่ 30 กย. ผมเลยปั่นประสาน scammer ทั้งสองรายนี้ โดยการ mint ผลงานที่เขาเสนอซื้อนั่นแหละ ขึ้น opensea แล้วส่งข้อความไปบอกว่า
mint ให้แล้วนะ แต่เงินไม่พอจริงๆว่ะโทษที เลย mint ขึ้น opensea แทน พอดีบ้านจน ทำได้แค่นี้ไปถึงแค่ opensea รีบไปซื้อล่ะ มีคนจ้องจะคว้างานผมเยอะอยู่ ผมไม่คิด royalty fee ด้วยนะเฮ้ย เอาไปขายต่อไม่ต้องแบ่งกำไรกับผม
เท่านั้นแหละครับ สงครามจิตวิทยาก็เริ่มขึ้น แต่เขาจนมุม กลืนน้ำลายตัวเอง ช็อตเด็ดคือ
เขา : เนี่ยอุส่ารอ บอกเพื่อนในทีมว่าวันจันทร์ที่ 30 กย. ได้ของแน่ๆ เพื่อนๆในทีมเห็นงานผมแล้วมันสวยจริง เลยใส่เงินเต็มที่ 9.3ETH (+ capture screen ส่งตัวเลขยอดเงินมาให้ดู)ไว้รอโดยเฉพาะเลยนะ ผม : เหรอ ... งั้น ขอดู wallet address ที่มี transaction มาให้ดูหน่อยสิ เขา : 2ETH นี่มัน 5000$ เลยนะ ผม : แล้วไง ขอดู wallet address ที่มีการเอายอดเงิน 9.3ETH มาให้ดูหน่อย ไหนบอกว่าเตรียมเงินไว้มากแล้วนี่ ขอดูหน่อย ว่าใส่ไว้เมื่อไหร่ ... เอามาแค่ adrress นะเว้ย ไม่ต้องทะลึ่งส่ง seed มาให้ เขา : ส่งรูปเดิม 9.3 ETH มาให้ดู ผม : รูป screenshot อ่ะ มันไม่มีความหมายหรอกเว้ย ตัดต่อเอาก็ได้ง่ายจะตาย เอา transaction hash มาดู ไหนว่าเตรียมเงินไว้รอ 9.3ETH แล้วอยากซื้องานผมจนตัวสั่นเลยไม่ใช่เหรอ ถ้าจะส่ง wallet address มาให้ดู หรือจะช่วยส่ง 0.15ETH มาให้ยืม mint งานก่อน แล้วมากดซื้อ 2ETH ไป แล้วผมใช้ 0.15ETH คืนให้ก็ได้ จะซื้อหรือไม่ซื้อเนี่ย เขา : จะเอา address เขาไปทำไม ผม : ตัดจบ รำคาญ ไม่ขายให้ละ เขา : 2ETH = 5000 USD เลยนะ ผม : แล้วไง
ผมเลยเขียนบทความนี้มาเตือนเพื่อนๆพี่ๆทุกคนครับ เผื่อใครกำลังเปิดพอร์ตทำธุรกิจขาย digital art online แล้วจะโชคดี เจอของดีแบบผม
ทำไมผมถึงมั่นใจว่ามันคือการหลอกหลวง แล้วคนโกงจะได้อะไร
อันดับแรกไปพิจารณาดู opensea ครับ เป็นเวบ NFTmarketplace ที่ volume การซื้อขายสูงที่สุด เขาไม่เก็บเงินของคนจะซื้อจะขายกันไว้กับตัวเอง เงินวิ่งเข้าวิ่งออก wallet ผู้ซื้อผู้ขายเลย ส่วนทางเวบเก็บค่าธรรมเนียมเท่านั้น แถมค่าธรรมเนียมก็ถูกกว่าเมื่อปี 2020 เยอะ ดังนั้นการที่จะไปลงขายงานบนเวบ NFT อื่นที่ค่า fee สูงกว่ากันเป็นร้อยเท่า ... จะทำไปทำไม
ผมเชื่อว่า scammer โกงเงินเจ้าของผลงานโดยการเล่นกับความโลภและความอ่อนประสบการณ์ของเจ้าของผลงานครับ เมื่อไหร่ก็ตามที่เจ้าของผลงานโอน ETH เข้าไปใน wallet เวบนั้นเมื่อไหร่ หรือเมื่อไหร่ก็ตามที่จ่ายค่า fee ในการ mint งาน เงินเหล่านั้นสิ่งเข้ากระเป๋า scammer ทันที แล้วก็จะมีการเล่นตุกติกต่อแน่นอนครับ เช่นถอนไม่ได้ หรือซื้อไม่ได้ ต้องโอนเงินมาเพิ่มเพื่อปลดล็อค smart contract อะไรก็ว่าไป แล้วคนนิสัยไม่ดีพวกเนี้ย ก็จะเล่นกับความโลภของคน เอาราคาเสนอซื้อที่สูงโคตรๆมาล่อ ... อันนี้ไม่ว่ากัน เพราะบนโลก NFT รูปภาพบางรูปที่ไม่ได้มีความเป็นศิลปะอะไรเลย มันดันขายกันได้ 100 - 150 ETH ศิลปินที่พยายามสร้างตัวก็อาจจะมองว่า ผลงานเรามีคนรับซื้อ 2 - 4 ETH ต่องานมันก็มากพอแล้ว (จริงๆมากเกินจนน่าตกใจด้วยซ้ำครับ)
บนโลกของ BTC ไม่ต้องเชื่อใจกัน โอนเงินไปหากันได้ ปิดสมุดบัญชีได้โดยไม่ต้องเชื่อใจกัน
บบโลกของ ETH "code is law" smart contract มีเขียนอยู่แล้ว ไปอ่าน มันไม่ได้ยากมากในการทำความเข้าใจ ดังนั้น การจะมาเชื่อคำสัญญาจากคนด้วยกัน เป็นอะไรที่ไม่มีเหตุผล
ผมไปเล่าเรื่องเหล่านี้ให้กับ community งานศิลปะ ก็มีทั้งเสียงตอบรับที่ดี และไม่ดีปนกันไป มีบางคนยืนยันเสียงแข็งไปในทำนองว่า ไอ้เรื่องแบบเนี้ยไม่ได้กินเขาหรอก เพราะเขาตั้งใจแน่วแน่ว่างานศิลป์ของเขา เขาไม่เอาเข้ามายุ่งในโลก digital currency เด็ดขาด ซึ่งผมก็เคารพมุมมองเขาครับ แต่มันจะดีกว่ามั้ย ถ้าเราเปิดหูเปิดตาให้ทันเทคโนโลยี โดยเฉพาะเรื่อง digital currency , blockchain โดนโกงทีนึงนี่คือหมดตัวกันง่ายกว่าเงิน fiat อีก
อยากจะมาเล่าให้ฟังครับ และอยากให้ช่วยแชร์ไปให้คนรู้จักด้วย จะได้ระวังตัวกัน
Note
- ภาพประกอบ cyber security ทั้งสองนี่ของผมเองครับ ทำเอง วางขายบน AdobeStock
- อีกบัญชีนึงของผม "HikariHarmony" npub1exdtszhpw3ep643p9z8pahkw8zw00xa9pesf0u4txyyfqvthwapqwh48sw กำลังค่อยๆเอาผลงานจากโลกข้างนอกเข้ามา nostr ครับ ตั้งใจจะมาสร้างงานศิลปะในนี้ เพื่อนๆที่ชอบงาน จะได้ไม่ต้องออกไปหาที่ไหน
ผลงานของผมครับ - Anime girl fanarts : HikariHarmony - HikariHarmony on Nostr - General art : KeshikiRakuen - KeshikiRakuen อาจจะเป็นบัญชี nostr ที่สามของผม ถ้าไหวครับ
-
 @ 23acd1fa:0484c9e0
2024-10-23 09:21:33
@ 23acd1fa:0484c9e0
2024-10-23 09:21:33Chef's notes
Cocoa powder: You can use 100% natural unsweetened cocoa powder or Dutch-processed cocoa powder – both work well.
Gluten free flour: There are many different gluten free flours on the market. I tested this recipe using White Wings All Purpose Gluten Free flour. I recommend choosing a gluten free flour that says it can be subbed 1:1 for regular plain or all purpose flour.
*Chocolate chips: Double check your chocolate chips are gluten free if you are making this brownie for someone who is celiac.
Cook times: Cook times will vary depending on your oven, but you’ll know these brownies are done when they firm up around the edges and no longer wobble in the middle. Keep in mind they will continue to cook slightly as they cool. You can also check they’re done by inserting a skewer into the middle of the brownie. If the skewer emerges with only a few crumbs on it, they’re ready. If it is covered in wet, gooey batter, keep baking the brownies and check them in another 5 minutes.
Storage: Brownies will keep well in an airtight container at room temperature or in the fridge for up to 5 days. To serve warm, microwave each brownie for 20 seconds. You can also freeze these brownies to enjoy at a later date. Simply thaw at room temperature and then microwave if you prefer them warm.
Serving Size: 1 brownie Calories: 278 Sugar: 26.4 g Sodium: 22.9 mg Fat: 15.5 g Carbohydrates: 34.1 g Protein: 3 g Cholesterol: 77.3 mg Nutrition information is a guide only.
Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 35 min
- 🍽️ Servings: 12
Ingredients
- 170 grams (3/4 cup) unsalted butter, melted
- 200 grams (1 cup) caster sugar or granulated sugar
- 90 grams (1/2 cup) brown sugar
- 1 teaspoon vanilla extract
- 3 large eggs
- 40 grams (1/2 cup) cocoa powder
- 70 grams (1/2 cup) gluten free plain or all purpose flour
- 75 grams milk or dark chocolate chips*
Directions
- Preheat the oven to 180 C (350 F) standard / 160 C (320 F) fan-forced. Grease and line an 8-inch square pan with baking or parchment paper, ensuring two sides overhang.
- In a large mixing bowl, add melted butter and sugars and gently whisk together. Add vanilla extract and stir.
- Add the eggs, one at a time, stirring in-between, then sift in the cocoa powder and flour. Stir until just combined. Add chocolate chips.
- Pour the brownie batter in the prepared pan and place in the oven. Bake brownies for approximately 30-35 minutes or until they no longer wobble in the middle.
- Leave brownie in pan and transfer to a wire rack to cool completely. These brownies are quite fragile so if you can, transfer to the fridge for an hour before cutting into squares to serve.
-
 @ 8947a945:9bfcf626
2024-10-17 07:33:00
@ 8947a945:9bfcf626
2024-10-17 07:33:00Hello everyone on Nostr and all my watchersand followersfrom DeviantArt, as well as those from other art platforms
I have been creating and sharing AI-generated anime girl fanart since the beginning of 2024 and have been running member-exclusive content on Patreon.
I also publish showcases of my artworks to Deviantart. I organically build up my audience from time to time. I consider it as one of my online businesses of art. Everything is slowly growing
On September 16, I received a DM from someone expressing interest in purchasing my art in NFT format and offering a very high price for each piece. We later continued the conversation via email.
Here’s a brief overview of what happened

- The first scammer selected the art they wanted to buy and offered a high price for each piece. They provided a URL to an NFT marketplace site running on the Ethereum (ETH) mainnet or ERC20. The site appeared suspicious, requiring email sign-up and linking a MetaMask wallet. However, I couldn't change the wallet address later. The minting gas fees were quite expensive, ranging from 0.15 to 0.2 ETH

-
The scammers tried to convince me that the high profits would easily cover the minting gas fees, so I had nothing to lose. Luckily, I didn’t have spare funds to purchase ETH for the gas fees at the time, so I tried negotiating with them as follows:
-
I offered to send them a lower-quality version of my art via email in exchange for the minting gas fees, but they refused.
- I offered them the option to pay in USD through Buy Me a Coffee shop here, but they refused.
- I offered them the option to pay via Bitcoin using the Lightning Network invoice , but they refused.
- I asked them to wait until I could secure the funds, and they agreed to wait.
The following week, a second scammer approached me with a similar offer, this time at an even higher price and through a different NFT marketplace website.
This second site also required email registration, and after navigating to the dashboard, it asked for a minting fee of 0.2 ETH. However, the site provided a wallet address for me instead of connecting a MetaMask wallet.
I told the second scammer that I was waiting to make a profit from the first sale, and they asked me to show them the first marketplace. They then warned me that the first site was a scam and even sent screenshots of victims, including one from OpenSea saying that Opensea is not paying.
This raised a red flag, and I began suspecting I might be getting scammed. On OpenSea, funds go directly to users' wallets after transactions, and OpenSea charges a much lower platform fee compared to the previous crypto bull run in 2020. Minting fees on OpenSea are also significantly cheaper, around 0.0001 ETH per transaction.
I also consulted with Thai NFT artist communities and the ex-chairman of the Thai Digital Asset Association. According to them, no one had reported similar issues, but they agreed it seemed like a scam.
After confirming my suspicions with my own research and consulting with the Thai crypto community, I decided to test the scammers’ intentions by doing the following
I minted the artwork they were interested in, set the price they offered, and listed it for sale on OpenSea. I then messaged them, letting them know the art was available and ready to purchase, with no royalty fees if they wanted to resell it.
They became upset and angry, insisting I mint the art on their chosen platform, claiming they had already funded their wallet to support me. When I asked for proof of their wallet address and transactions, they couldn't provide any evidence that they had enough funds.
Here’s what I want to warn all artists in the DeviantArt community or other platforms If you find yourself in a similar situation, be aware that scammers may be targeting you.
My Perspective why I Believe This is a Scam and What the Scammers Gain
From my experience with BTC and crypto since 2017, here's why I believe this situation is a scam, and what the scammers aim to achieve
First, looking at OpenSea, the largest NFT marketplace on the ERC20 network, they do not hold users' funds. Instead, funds from transactions go directly to users’ wallets. OpenSea’s platform fees are also much lower now compared to the crypto bull run in 2020. This alone raises suspicion about the legitimacy of other marketplaces requiring significantly higher fees.
I believe the scammers' tactic is to lure artists into paying these exorbitant minting fees, which go directly into the scammers' wallets. They convince the artists by promising to purchase the art at a higher price, making it seem like there's no risk involved. In reality, the artist has already lost by paying the minting fee, and no purchase is ever made.
In the world of Bitcoin (BTC), the principle is "Trust no one" and “Trustless finality of transactions” In other words, transactions are secure and final without needing trust in a third party.
In the world of Ethereum (ETH), the philosophy is "Code is law" where everything is governed by smart contracts deployed on the blockchain. These contracts are transparent, and even basic code can be read and understood. Promises made by people don’t override what the code says.
I also discuss this issue with art communities. Some people have strongly expressed to me that they want nothing to do with crypto as part of their art process. I completely respect that stance.
However, I believe it's wise to keep your eyes open, have some skin in the game, and not fall into scammers’ traps. Understanding the basics of crypto and NFTs can help protect you from these kinds of schemes.
If you found this article helpful, please share it with your fellow artists.
Until next time Take care
Note
- Both cyber security images are mine , I created and approved by AdobeStock to put on sale
- I'm working very hard to bring all my digital arts into Nostr to build my Sats business here to my another npub "HikariHarmony" npub1exdtszhpw3ep643p9z8pahkw8zw00xa9pesf0u4txyyfqvthwapqwh48sw
Link to my full gallery - Anime girl fanarts : HikariHarmony - HikariHarmony on Nostr - General art : KeshikiRakuen
-
 @ 266815e0:6cd408a5
2024-05-09 17:23:28
@ 266815e0:6cd408a5
2024-05-09 17:23:28Lot of people are starting to talk about building a web-of-trust and how nostr can or is already being used as such
We all know about using the kind:3 following lists as a simple WoT that can be used to filter out spam. but as we all know it does not really signal "trust", its mostly just "I find your content interesting"
But what about real "trust"... well its kind of multi-denominational, I could trust that your a good developer or a good journalist but still not trust you enough to invite you over to my house. There are some interesting and clever solutions proposed for quantifying "trust" in a digital sense but I'm not going to get into that here. I want to talk about something that I have not see anyone discuss yet.
How is the web-of-trust maintained? or more precisely how do you expect users to update the digital representation of the "trust" of other users?
Its all well and good to think of how a user would create that "trust" of another user when discovering them for the first time. They would click the "follow" button, or maybe even rate them on a few topics with a 1/5 star system But how will a user remove that trust? how will they update it if things change and they trust them less?
If our goal is to model "trust" in a digital sense then we NEED a way for the data to stay up-to-date and as accurate as possible. otherwise whats the use? If we don't have a friction-less way to update or remove the digital representation of "trust" then we will end up with a WoT that continuously grows and everyone is rated 10/10
In the case of nostr kind:3 following lists. its pretty easy to see how these would get updated. If someone posts something I dislike or I notice I'm getting board of their content. then I just unfollow them. An important part here is that I'm not thinking "I should update my trust score of this user" but instead "I'm no longer interested, I don't want to see this anymore"
But that is probably the easiest "trust" to update. because most of us on social media spend some time curating our feed and we are used to doing it. But what about the more obscure "trust" scores? whats the regular mechanism by which a user would update the "honestly" score of another user?
In the real world its easy, when I stop trusting someone I simply stop associating with them. there isn't any button or switch I need to update. I simply don't talk to them anymore, its friction-less But in the digital realm I would have to remove or update that trust. in other words its an action I need to take instead of an action I'm not doing. and actions take energy.
So how do we reflect something in the digital world that takes no-energy and is almost subconscious in the real world?
TLDR; webs-of-trust are not just about scoring other users once. you must keep the score up-to-date
-
 @ 9349d012:d3e98946
2024-10-23 04:10:25
@ 9349d012:d3e98946
2024-10-23 04:10:25Chef's notes
Ingredients
4 tablespoons (1/2 stick) butter 2 ounces thinly sliced prosciutto, cut into thin strips 1 1/4 cups orzo (about 8 ounces) 3 cups low-salt chicken broth 1/2 teaspoon (loosely packed) saffron threads, crushed 1 pound slender asparagus, trimmed, cut into 1/2-inch pieces 1/4 cup grated Parmesan cheese Parmesan cheese shavings
Preparation
Melt 2 tablespoons butter in large nonstick skillet over medium-high heat. Add prosciutto and sauté until almost crisp, about 3 minutes. Using slotted spoon, transfer to paper towels to drain. Melt 2 tablespoons butter in same skillet over high heat. Add orzo; stir 1 minute. Add broth and saffron; bring to boil. Reduce heat to medium-low, cover, and simmer until orzo begins to soften, stirring occasionally, about 8 minutes. Add asparagus; cover and simmer until tender, about 5 minutes. Uncover; simmer until almost all liquid is absorbed, about 1 minute. Remove from heat. Mix in prosciutto and 1/2 cup grated cheese. Season to taste with salt and pepper. Transfer to large bowl. Garnish with Parmesan shavings. Makes 6 servings.
Details
- ⏲️ Prep time: 30
- 🍳 Cook time: 30
Ingredients
- See Chef’s Notes
Directions
- See Chef’s Notes
-
 @ 4fda8b10:7bbee962
2024-10-15 13:56:47
@ 4fda8b10:7bbee962
2024-10-15 13:56:47Takeaways from Bitcoin Amsterdam 2024
The bitcoin conference in Amsterdam to me is my typical yearly check in with the crypto scene. From a distance, not much has changed since last year. What struck me most was the correlation between the exchange prices and the amount of visitors, I had the feeling the crowd was about twice as big as last year during the opening and high profile talks.
From my personal experience, the increase of audience also brought some dilution to the hard core maximalist anarchist-ness of the event. The overall vibe amongst the attendees was more friendly and open. This also increased the value of the event for me, as I try to broaden my network, get different perspectives and learn more about what interests people in the crypto space.
This year was also marked by my involvement in the Nostr side events, I was asked to give a live performance at the Nostrdam Meetup October 2024 which went over very well and also acted as a nice conversation starter during the rest of the conference. I was also slightly involved in the organisation of the Nostr booth, but credits go to the awesome volunteers that made that happen. It was a bit of a shame that the Nostr booth was tucked away all the way in the back of the (commercial) expo hall, it would have been nice to promote the Nostr initiative to the social community area next to the satoshi radio / connect the world community area
For me the biggest takeaways were the insights I got from the people I’ve met, all from different industries with different perspectives on both technology and involvement. I tried to specifically reach out to (former) CTO’s, which led me to write and share this piece on that particular role. Of course shaking hands and catching up with people I only see once a year is great, and reminds me of the vibe and my experiences at the Fronteers conference.
From a technical point of view I was most inspired by the advancement of AI agent technology and the possibilities of programmable micropayments via de lightning network. Michael Levin showed us that the http spec already has a 402 status of “payment required” and that basically all the required infrastructure is already in place to allow both humans and ai agents to use the lightning network to pay for access to compute or resources using this statuscode and an api gateway such as lightning labs aperture.
talk: HODLing Is Hard: Fundamentals, Cycle & On-Chain Analysis by rational root
- bitcoin is already competing in market cap with other currencies
- amount of euro is exponentially increasing
- from 8 to 16 trillion euros since 2009, but having a real hard cap in btc is fundamentally different
- inflation
- euro lose 20% in 5 years
- bitcoin also loses purchasing power, but only 10%
- in current system, we always need to take on maximal debt, instead of saving
- two things can happen
- we get into overvalued price levels
- we get into recession
- recession would only mean a shift in the start of the 4 year cycle
panel: Endless Possibilities: Reusing Heat From Miners
- people
- 21energy Maximilian (obwexer)
- Bert de groot (bitcoin Brabant)
- Brad Tom (mara)
- perspective: coming from energy to bitcoin is very different and much faster with implementation than the other way around
- 95% of heat can be captured from miners, much higher in comparison to AI
- being able to balance the grid because you can turn off the bitcoin miners
- ”heatbuffers” → heat is still available when power source goes down
- common objections:
- Crypto is hard to understand
- for large industrial clients, heaters, public image of bitcoin (often a door closer)
- people don’t see that miners consume electricity and pay for it.
- If mining is closed down in Europe, the energy prices will spike because the energy will not be payed for anymore
panel: How to Guard Privacy Tools & Developers
- Dorien Rookmaker & Sjors proviost
- chat control
- topic keeps returning, and is highly distracting for progress
- Parliament wants Netherlands to speak against chat control
- initially they want to just, scan messages now want to install malware before encryption
- it is distracting Sjors from working on bitcoin
- samurai and tornado are different cases
- tornado cash is harder because it is also a smart contract with custody over funds
- samurai is easier: if you don’t have custody, are you responsible for the results of the code?
- will decide wether whether non custodial systems are ok or not
- micah interpretation is quite vague
- the current Denmark case:
- if you are rebuilding an interface for a smart contract, you are responsible for implementing all the legal guardrails that apply to securities governance?
panel: NOSTR: Freedom of Algorithmic Choice
- will casarin, mcshane, martti malmi (Sirius iris.to)
- arc (alternative layer on top of bitcoin, like lightning but without channels)
- aha moment: when seeing the unsiloed experience between nostr apps
- were trying to create a town square, so we need to deal with spam
- social media platforms have stagnated a bit, nostr is innovating far more quickly
panel: Transactions As Bitcoin’s Key Growth Metric
- Stephan nilov
- classical developers don’t know about money and bitcoin development is harder
- total addressable market is highest in btc, biggest number of possible users
- bitcoin companies don’t benefit from tokens that are typically exchanged for vc money
- users are not looking for payments, they are looking for digital property and other things that Ethereum network offers
- Stephan Livera
- there is a known, slow pace at which bitcoin will be adopted
- btc market is only 1.2 trillion dollars compared to USD 30 trillion
talk: Making Bitcoin Quantum Resistant by hunter beast
- surmount.systems
- explaining the threat of quantum computing
- problems
- key size: larger signature required
- proposal: transaction field attestation
- 256 bit number key, possibility to factor the private key out of this
- introducing p2qrhash
- segwitv3
- satoshishield
- in layman terms:
- quantum safe upgrades to bitcoin protocol are proposed
- we need to introduce a software upgrade
- requires a soft fork, opt in
- possible advantages of quantum in crypto
- allow us to sign signatures in a way that is unbreakable
- 514 qubits are needed to break something
talk: Lightning and AI: Where the Bots Pay You by michael levin
- two use cases for bitcoin adoption
- people that don’t have access to fiat
- things that can’t be handled by fiat systems
- large language models
- current phase: big adoption
- next phase: agentic ai
- costs of ai
- compute 400% more (ben bajarin)
- algorithm training excess 10 billion dollars
- data
- costs implications
- cost of serving answers is 0
- cost of serving ai query is not 0
- cost for everyone in the world
- payments in AI
- now
- pay per call
- data
- accessibility
- agents
- agents must be able to do things that cost money
- now
- payment system for AI
- globally accessible
- near instant
- final settlement
- internet native
- authentication mechanism
- personalise access (simple queries for lower tier model)
- easy to implement
- L402 protocol
- 402 payment required in http spec
- reverse proxy to have 402 in front of APIs
- aperture is lightning labs implementation
- all available right now, adoption starting
- fewsats, sulu, open agents / plebai
- pay with lightning
- challenges
- do these payments with stablecoins instead of lightning (hence taproot assets protocol)
- cases
- agent bots can pay for real world resources
- taproot assets issue assets on bitcoin allow transfer of
- references
- L402.org
talk: Bitcoin is Cypherpunk by Aaron van Wirdum
- is bitcoin still Cypherpunks ?
- on one hand we see a push to regulation and frameworks to govern btc
- on the other hand we are arresting developers for writing code
pitches: Bitcoin Amsterdam Pitch Day: Presented by GoBTC
- umoja
- ceo Robby greenfield
- LST smartcoin, deflationary by design
- competes with pools such as lido and rocket pool, but supports multiple coins, including liquid hashrate
- 30% liquid hashrate returns (!)
- compliance micah
- disaster scenarios
- black swan event → automatic exit out
- magisat
- trading tools for mempool snipers
- support for runes
- volume on bitcoin nft’s is on certain days higher than nft’s on ethereum
panel: Crossing the Boundaries Between Bitcoin & Fiat
- Christian Rau (Mastercard) & Remi destigny (bitrefill )
- liberation is great, but protocols don’t take customer service into account, chargebacks and rewinding mistakes etc
- we aim to smooth process by issuing cards that sell your Bitcoin just in time on the backend
talk: Gold & Bitcoin: Friends, Not Foes by Paul Buitink
- premise “the financial system is crumbling”
- there is too much debt
- emerging markets lost confidence in western currencies
- freezing Russian assets is shooting ourselves in the foot, as it shows the world you might not want to hold too many dollars that can be easily seized
- record gold buying by central banks in 2022 2023 2024
- gold: 17 trillion marker cap, compared to bitcoin 1.3 trillion
talk: Austrian Economics, Hard Money & Bitcoin Cycles, Willem Middelkoop
- ”we are on the road towards hyper inflation and collapse of financial system”
- central bankers are pretty smart and very aware
- this is why they accumulate gold
- when system collapses, central bankers will play the gold card, not the bitcoin card
- US is preparing for big conflict with Russia and china
- then you can’t use IMF monetary reset
- Asia leadership is the same as US and Russian leadership: they want to stay on control
- all have about similar gold (per Capita) in their central banks vaults to avoid hyperinflation
- IMF said to el salvador: you need to reign down your bitcoin position
- once central bankers start diversifying (e.g. to bitcoin ) they will strain their own system. The incentives are against adopting bitcoin
- watch out for when on and offramp get blocked / repressed
- think about diversifying to Dubai, “the new switzerland"
- "bitcoin is the best money ever. fact”
- superior to gold, because you can store your wealth independant of location
- more scarce than gold
- but from central bank point of view, gold is superior to bitcoin
- younger generation gets this from the start
talk: The Future Will Be Bitcoinized by Elizabeth stark & Rockstar Dev
- stablecoins
- taproot assets protocol
- there is a demand for stablecoins and apps on stablecoins
- 11 trillion dollars in stablecoins
- protocol allows payments in other assets such as stablecoins that use bitcoin/lightning liquidity
- Elizabeth believes this allows stablecoiners to get interested in the underlying bitcoin layer
- Available now:
- bridging tether and lightning
products stumbled upon
- Meshtastic
- Flipper
- Noderunners led matrix panel
- 21energy bitcoin heater (1k s9, 3,5k s19)
- angor.io by dangershony on nostr
- bitcoinclock by Djuri
canonical link: https://notes.peterpeerdeman.nl/Bitcoin-Amsterdam-2024
originally posted at https://stacker.news/items/724785
-
 @ 266815e0:6cd408a5
2024-04-22 22:20:47
@ 266815e0:6cd408a5
2024-04-22 22:20:47While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent
I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS
There were a few things I learned from all these conversations:
- All the existing solutions have one thing in common. A universal ID of some kind for files
- HTTP is still good. we don't have to throw the baby out with the bath water
- nostr could fix this... somehow
Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...
An Identity system
An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files
This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)
What is blossom?
Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id
What are Blobs?
blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names
Instead blobs have a sha256 hash (like
b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553) as an IDThese IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can get a files sha256 hash on linux using:
sha256sum bitcoin.pdf)How do the servers work?
Blossom servers expose four endpoints to let clients and users upload and manage blobs
GET /<sha256>(optional file.ext)PUT /uploadAuthentication: Signed nostr event- Returns a blob descriptor
GET /list/<pubkey>- Returns an array of blob descriptors
Authentication(optional): Signed nostr eventDELETE /<sha256>Authentication: Signed nostr event
What is Blossom Drive?
Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs
What are Drives
Drives are just nostr events (kind
30563) that store a map of blobs and what filename they should have along with some extra metadataAn example drive event would be
json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at
If your interested, the full event definition is at github.com/hzrd149/blossom-drive
Getting started
Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started
1. Open the app
Open https://blossom.hzrd149.com
2. Login using extension

You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an
ncryptsecpassword protected private key - ansecunprotected private key (please don't) - bunker:// URI from nsecbunker3. Add a blossom server

Right now
https://cdn.satellite.earthis the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript github.com/hzrd149/blossom-server4. Start uploading your files
NOTE: All files upload to blossom drive are public by default. DO NOT upload private files

5. Manage files

Encrypted drives
There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify

Whats next?
I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything
also all the images in this article are stored in one of my blossom drives here
nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 472f440f:5669301e
2024-10-11 14:20:54
@ 472f440f:5669301e
2024-10-11 14:20:54As we sprint toward the 2024 US Presidential election the case for using bitcoin as an asset to store value for the long term has never been stronger. The insanity of the incumbent power structure is being laid bare and it is becoming impossible to ignore the headwinds that the Borg faces moving forward.
Yesterday morning and earlier today it became clear that inflation is rearing its head again. Not ideal for the soft landing Jerome Powell and Yellen are signaling to the markets after the first Fed Funds rate cut in years.
It seems like the yield curve predicted this earlier this week when it inverted after a temporary normalizing period after the Fed's rate cut. Futhermore, it is becoming glaringly obvious that running historically high fiscal deficits while interest rates were at multi-decade highs was a pretty bad idea. As James Lavish points out, the data from the CBO earlier this week shows that the US federal government is running a deficit that is 13% higher than it was last year. This is at a time when real wages are still depressed, inflation is still suffocating American consumers and the private sector job market for American citizens is cratering.
Speaking of the job market, the numbers that came in yesterday were worse than expected: The effect of Hurricane Helene should certainly be taken into consideration when looking at this jobs miss. However, even with the miss we know that these numbers have been under reported for years to make the economy seem healthier than it actually is. Even with Helene's effect taken into consideration this print will likely be revised higher 3-6 months from now.
All of this points to a breaking point. A breaking point for the economy and, more importantly, a breaking point for overall confidence in the US government and its ability to operate with any semblance of fiscal responsibility. The chart that Pierre Rochard shares in the tweet at the top of this letter is the only chart that matters for anyone attempting to gauge where we find ourselves on the path to bitcoin realizing its full potential.
There is $133 TRILLION worth of value sitting in global bond markets. Bitcoin is a far superior asset to store one's wealth in. Bond markets are beholden to the whims of the actors who issue those bonds. In the case of the US Treasury market, the largest bond market in the world, the US government. And as we have pointed out above, the US government is recklessly irresponsible when it comes to issuing debt with a complete inability to pay it back on the long-term. Inflation is up, the jobs market is cratering for the native born Americans who actually pay taxes, and the push toward a multi-polar geopolitical landscape is becoming more pronounced by the day. All of this points to a long-term weakening in demand for US treasuries.
The only way out of this mess is to overtly default on this debt or inflate it away. The latter will most certainly be the route that is taken, which positions bitcoin extremely well as people seek the confines of an asset that cannot be debased because it cannot be controlled by a central authority. The levels of sovereign debt in the world are staggering. Do not let the bitcoin price consolidation of the last six months lull you into a state of complacency. Even the results of the Presidential election won't have a material effect on these dynamics. Though, a Donald Trump presidency would certainly be preferable if you prefer to see relatively sane policy enacted that would provide you with time to find safety in bitcoin. But, in regards to this sovereign debt crisis, that is the only benefit you can hope for; more time to prepare. I'll leave you with some thoughts from Porter Stansberry:
"We are about to see the final destruction of the American experiment. Every economist knows this (see below) is correct; but nobody is going to tell you about it. I’ll summarize in plan English: We are fucked.
-
Debt is growing much faster than GD and interest expense is growing much faster than debt; and the real growth in entitlement spending hasn’t even begun yet.
-
Progressive taxation means nobody will ever vote for less spending + the combined size of government employees and dependents, there’s no way for America’s actual taxpayers (about 20m people) to ever win an election, so the spending won’t stop growing and, ironically, inflation will make demands for more spending to grow.
-
Inflation undermines both economic growth and social cohesion. The purple hair man-women weirdos are only the beginning; what comes next is scapegoating jews, blacks, immigrants and a huge increase in violence/domestic terror.
Get ready America. This election has nothing to do with what’s coming. And neither Trump nor Kamala can stop it.
Our experiment in freedom and self-government died in 1971 (when all restraint on government spending was abandoned with the gold standard.) You can only live at the expense of your neighbor until he runs out of money.
And that day is here."
Final thought... I hope my tux still fits for this wedding. Enjoy your weekend, freaks.Use the code "TFTC" for 15% off
-
-
 @ e6817453:b0ac3c39
2024-10-06 11:21:27
@ e6817453:b0ac3c39
2024-10-06 11:21:27Hey folks, today we're diving into an exciting and emerging topic: personal artificial intelligence (PAI) and its connection to sovereignty, privacy, and ethics. With the rapid advancements in AI, there's a growing interest in the development of personal AI agents that can work on behalf of the user, acting autonomously and providing tailored services. However, as with any new technology, there are several critical factors that shape the future of PAI. Today, we'll explore three key pillars: privacy and ownership, explainability, and bias.
1. Privacy and Ownership: Foundations of Personal AI
At the heart of personal AI, much like self-sovereign identity (SSI), is the concept of ownership. For personal AI to be truly effective and valuable, users must own not only their data but also the computational power that drives these systems. This autonomy is essential for creating systems that respect the user's privacy and operate independently of large corporations.
In this context, privacy is more than just a feature—it's a fundamental right. Users should feel safe discussing sensitive topics with their AI, knowing that their data won’t be repurposed or misused by big tech companies. This level of control and data ownership ensures that users remain the sole beneficiaries of their information and computational resources, making privacy one of the core pillars of PAI.
2. Bias and Fairness: The Ethical Dilemma of LLMs
Most of today’s AI systems, including personal AI, rely heavily on large language models (LLMs). These models are trained on vast datasets that represent snapshots of the internet, but this introduces a critical ethical challenge: bias. The datasets used for training LLMs can be full of biases, misinformation, and viewpoints that may not align with a user’s personal values.
This leads to one of the major issues in AI ethics for personal AI—how do we ensure fairness and minimize bias in these systems? The training data that LLMs use can introduce perspectives that are not only unrepresentative but potentially harmful or unfair. As users of personal AI, we need systems that are free from such biases and can be tailored to our individual needs and ethical frameworks.
Unfortunately, training models that are truly unbiased and fair requires vast computational resources and significant investment. While large tech companies have the financial means to develop and train these models, individual users or smaller organizations typically do not. This limitation means that users often have to rely on pre-trained models, which may not fully align with their personal ethics or preferences. While fine-tuning models with personalized datasets can help, it's not a perfect solution, and bias remains a significant challenge.
3. Explainability: The Need for Transparency
One of the most frustrating aspects of modern AI is the lack of explainability. Many LLMs operate as "black boxes," meaning that while they provide answers or make decisions, it's often unclear how they arrived at those conclusions. For personal AI to be effective and trustworthy, it must be transparent. Users need to understand how the AI processes information, what data it relies on, and the reasoning behind its conclusions.
Explainability becomes even more critical when AI is used for complex decision-making, especially in areas that impact other people. If an AI is making recommendations, judgments, or decisions, it’s crucial for users to be able to trace the reasoning process behind those actions. Without this transparency, users may end up relying on AI systems that provide flawed or biased outcomes, potentially causing harm.
This lack of transparency is a major hurdle for personal AI development. Current LLMs, as mentioned earlier, are often opaque, making it difficult for users to trust their outputs fully. The explainability of AI systems will need to be improved significantly to ensure that personal AI can be trusted for important tasks.
Addressing the Ethical Landscape of Personal AI
As personal AI systems evolve, they will increasingly shape the ethical landscape of AI. We’ve already touched on the three core pillars—privacy and ownership, bias and fairness, and explainability. But there's more to consider, especially when looking at the broader implications of personal AI development.
Most current AI models, particularly those from big tech companies like Facebook, Google, or OpenAI, are closed systems. This means they are aligned with the goals and ethical frameworks of those companies, which may not always serve the best interests of individual users. Open models, such as Meta's LLaMA, offer more flexibility and control, allowing users to customize and refine the AI to better meet their personal needs. However, the challenge remains in training these models without significant financial and technical resources.
There’s also the temptation to use uncensored models that aren’t aligned with the values of large corporations, as they provide more freedom and flexibility. But in reality, models that are entirely unfiltered may introduce harmful or unethical content. It’s often better to work with aligned models that have had some of the more problematic biases removed, even if this limits some aspects of the system’s freedom.
The future of personal AI will undoubtedly involve a deeper exploration of these ethical questions. As AI becomes more integrated into our daily lives, the need for privacy, fairness, and transparency will only grow. And while we may not yet be able to train personal AI models from scratch, we can continue to shape and refine these systems through curated datasets and ongoing development.
Conclusion
In conclusion, personal AI represents an exciting new frontier, but one that must be navigated with care. Privacy, ownership, bias, and explainability are all essential pillars that will define the future of these systems. As we continue to develop personal AI, we must remain vigilant about the ethical challenges they pose, ensuring that they serve the best interests of users while remaining transparent, fair, and aligned with individual values.
If you have any thoughts or questions on this topic, feel free to reach out—I’d love to continue the conversation!
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ ff1a68c4:ec9831cf
2024-10-24 14:49:33
@ ff1a68c4:ec9831cf
2024-10-24 14:49:33Año 2147. La misión de la nave Odisea VII tenía como objetivo estudiar las lunas de Júpiter. Nadie esperaba que se encontraran con lo que estaba a punto de revelar el gigante gaseoso. A bordo, cinco astronautas, expertos en astrobiología y física cuántica, orbitaban el coloso, maravillados por sus tormentas eternas y sus mares de hidrógeno líquido.
Durante meses, la tripulación había lanzado sondas y drones a través de la atmósfera turbulenta, recogiendo datos imposibles de descifrar. Era como si el planeta se resistiera a la intrusión, ocultando secretos detrás de las franjas de nubes y la Gran Mancha Roja.
El comandante Foster, junto con la doctora Elena Ivankov, detectaron una anomalía: un patrón en las corrientes eléctricas de Júpiter que parecía regular, como un latido. Al principio, lo atribuyeron a fenómenos naturales, pero la regularidad era inquietante. Eran pulsaciones precisas, organizadas, como los de un corazón titánico, aunque tan lentas que requerían equipo especializado para percibirlas.
“Esto no es solo una tormenta más”, murmuró Elena frente a la pantalla holográfica. “Es… es un ciclo controlado.”
El equipo empezó a conectar las piezas. Las corrientes de viento y los campos magnéticos de Júpiter no se movían al azar; parecían responder a la posición de otros planetas en el sistema solar. Cada vez que la gravedad de Saturno o Marte interactuaba con Júpiter, las pulsaciones cambiaban, como si ajustara su frecuencia para estabilizar las órbitas.
Foster frunció el ceño, ajustando sus datos en el simulador gravitacional. “Si estos latidos controlan la dinámica del sistema solar, ¿qué pasaría si se detuvieran?”
“Ningún planeta sobreviviría”, respondió Ivankov, con los ojos fijos en la pantalla.
Fue entonces cuando tomaron la decisión más osada de la misión: enviar una sonda mucho más profunda de lo que cualquier nave había llegado antes, para penetrar en las capas interiores de Júpiter. Las sondas anteriores habían sido destruidas, pero esta nueva, equipada con inteligencia cuántica adaptativa, podía reaccionar a los cambios a una velocidad inimaginable. La llamaron Ecos.
Cuando Ecos descendió, las lecturas empezaron a volverse más extrañas. Júpiter parecía estar "sintiendo" la presencia de la sonda. Las pulsaciones aumentaron, y el campo magnético se distorsionó. Ecos transmitió imágenes de lo que se encontró en el núcleo del planeta: una estructura titánica, más grande que cualquier ciudad humana, compuesta de una sustancia orgánica fusionada con energía pura.
"¿Estás viendo lo mismo que yo?", susurró Foster, incapaz de procesar lo que estaba ante sus ojos.
Ivankov asintió en silencio, sus dedos temblando sobre el teclado. "Júpiter… no es solo un planeta. Es un organismo vivo."
La tripulación permaneció en silencio mientras la sonda transmitía imágenes y datos. Era como si el planeta mismo estuviera compuesto de órganos que regulaban la estabilidad gravitacional del sistema solar. Un ser inconcebible, de una escala tan vasta que su única función era equilibrar fuerzas cósmicas. Cada tormenta, cada rayo, cada pulso magnético, todo formaba parte de su regulación.
"Este 'ser' mantiene el equilibrio", reflexionó el comandante, su voz era apenas un susurro entre el zumbido de los sistemas de la nave. "Si interfiéramos demasiado, podría romper la frágil danza de los planetas."
La doctora Ivankov, profundamente impactada, sugirió la teoría más radical: "Júpiter no solo es consciente… sino que actúa como una especie de guardián del sistema solar. Un ser con un propósito tan simple como vasto: mantener el equilibrio entre los cuerpos celestes. Si alguna anomalía cósmica amenazara el equilibrio, Júpiter respondería, ajustando las órbitas, corrigiendo las trayectorias."
Entonces llegó la transmisión final de Ecos: "Interferencia detectada. Estructura orgánica ha reconocido nuestra presencia. Cambios en los latidos. Aumento de la presión. Reacción… inminente."
El corazón de Júpiter había comenzado a acelerarse.
"No deberíamos haber venido tan lejos", dijo Foster, tomando el mando de la nave. "Es un ser que no entiende nuestras intenciones. Lo único que sabe es que estamos perturbando el equilibrio."
Con los latidos de Júpiter resonando en sus oídos, la tripulación inició una retirada rápida, temiendo que cualquier alteración en ese organismo colosal pudiera desestabilizar el sistema solar entero.
Mientras se alejaban, observaron cómo las tormentas del gigante gaseoso volvieron a la calma, y el pulso volvió a estabilizarse.
"Júpiter sigue latiendo", susurró Ivankov, mirando la vasta esfera a lo lejos.
Quizás, pensó la tripulación, no era el momento para que la humanidad supiera demasiado sobre su lugar en la delicada danza del cosmos.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 75d12141:3458d1e2
2024-10-23 00:20:14
@ 75d12141:3458d1e2
2024-10-23 00:20:14Chef's notes
A childhood favorite of mine! Just don't go too crazy with the scallions as you don't want to overpower the pork flavor.
Details
- ⏲️ Prep time: 15
- 🍳 Cook time: 15-20 mins
- 🍽️ Servings: 3-5
Ingredients
- 1 pound of lean ground pork
- 1 tablespoon of diced scallions
- Ground black pepper (optional)
Directions
- Lightly coat your palms with olive oil to prevent the meat from sticking to you and to assist in keeping its ball form
- Mix the ground pork and diced scallions in a large bowl
- Roll the pork into the preferred portion size until it feels like it won't fall apart
- Cook in a skillet for 15-20 mins
-
 @ 32e18276:5c68e245
2023-12-06 15:29:43
@ 32e18276:5c68e245
2023-12-06 15:29:43I’m going to be on an ordinals panels as one of the people who is counter arguing the claim that they are good for bitcoin. I decided to brush up on the technicals on how inscriptions work. I am starting to see luke’s perspective on how it is exploiting a loophole in bitcoin’s anti-data-spam mechanisms.
Storing data in Bitcoin, the “standard” way
The standard way you add “data” to bitcoin is by calling the OP_RETURN opcode. Bitcoin devs noticed that people were storing data (like the bitcoin whitepaper) in the utxo set via large multisig transactions. The problem with this is that this set is unprunable and could grow over time. OP_RETURN outputs on the other-hand are provably prunable and don’t add to utxo bloat.
Here’s an excerpt from the march 2014 0.9.0 release notes that talks about this:
On OP_RETURN: There was been some confusion and misunderstanding in the community, regarding the OP_RETURN feature in 0.9 and data in the blockchain. This change is not an endorsement of storing data in the blockchain. The OP_RETURN change creates a provably-prunable output, to avoid data storage schemes – some of which were already deployed – that were storing arbitrary data such as images as forever-unspendable TX outputs, bloating bitcoin’s UTXO database. Storing arbitrary data in the blockchain is still a bad idea; it is less costly and far more efficient to store non-currency data elsewhere.
Much of the work on bitcoin core has been focused on making sure the system continues to function in a decentralized way for its intended purpose in the presence of people trying to abuse it for things like storing data. Bitcoin core has always discouraged this, as it is not designed for storage of images and data, it is meant for moving digital coins around in cyberspace.
To help incentive-align people to not do stupid things, OP_RETURN transactions were not made non-standard, so that they are relayable by peers and miners, but with the caveat:
- They can only push 40 bytes (later increased to 80,83, I’m guessing to support larger root merkle hashes since that is the only sane usecase for op_return)
Bitcoin also added an option called -datacarriersize which limits the total number of bytes from these outputs that you will relay or mine.
Why inscriptions are technically an exploit
Inscriptions get around the datacarriersize limit by disguising data as bitcoin script program data via OP_PUSH inside OP_IF blocks. Ordinals do not use OP_RETURN and are not subjected to datacarriersize limits, so noderunners and miners currently have limited control over the total size of this data that they wish to relay and include in blocks. Luke’s fork of bitcoin-core has some options to fight this spam, so hopefully we will see this in core sometime soon as well.
Inscriptions are also taking advantage of features in segwit v1 (witness discount) and v2/taproot (no arbitrary script size limit). Each of these features have interesting and well-justified reasons why they were introduced.
The purpose of the witness discount was to make it cheaper to spend many outputs which helps the reduction of the utxo set size. Inscriptions took advantage of this discount to store monke jpegs disguised as bitcoin scripts. Remember, bitcoin is not for storing data, so anytime bitcoin-devs accidentally make it cheap and easy to relay data then this should be viewed as an exploit. Expect it to be fixed, or at least provide tools to noderunners for fighting this spam.
Where do we go from here
The interesting part of this story is that people seem to attach value to images stored on the bitcoin blockchain, and they are willing to pay the fee to get it in the block, so non-ideologic miners and people who don’t care about the health and decentralization of bitcoin are happy to pay or collect the fee and move on.
Data should not get a discount, people should pay full price if they want to store data. They should just use op_return and hashes like opentimestamps or any other reasonable protocol storing data in bitcoin.
After going through this analysis I’ve come to the opinion that this is a pretty bad data-spam exploit and bitcoin devs should be working on solutions. Ideological devs like luke who actually care about the health and decentralization of the network are and I’m glad to see it.
-
 @ e6817453:b0ac3c39
2024-09-30 14:52:23
@ e6817453:b0ac3c39
2024-09-30 14:52:23In the modern world of AI, managing vast amounts of data while keeping it relevant and accessible is a significant challenge, mainly when dealing with large language models (LLMs) and vector databases. One approach that has gained prominence in recent years is integrating vector search with metadata, especially in retrieval-augmented generation (RAG) pipelines. Vector search and metadata enable faster and more accurate data retrieval. However, the process of pre- and post-search filtering results plays a crucial role in ensuring data relevance.
The Vector Search and Metadata Challenge
In a typical vector search, you create embeddings from chunks of text, such as a PDF document. These embeddings allow the system to search for similar items and retrieve them based on relevance. The challenge, however, arises when you need to combine vector search results with structured metadata. For example, you may have timestamped text-based content and want to retrieve the most relevant content within a specific date range. This is where metadata becomes critical in refining search results.
Unfortunately, most vector databases treat metadata as a secondary feature, isolating it from the primary vector search process. As a result, handling queries that combine vectors and metadata can become a challenge, particularly when the search needs to account for a dynamic range of filters, such as dates or other structured data.
LibSQL and vector search metadata
LibSQL is a more general-purpose SQLite-based database that adds vector capabilities to regular data. Vectors are presented as blob columns of regular tables. It makes vector embeddings and metadata a first-class citizen that naturally builds deep integration of these data points.
create table if not exists conversation ( id varchar(36) primary key not null, startDate real, endDate real, summary text, vectorSummary F32_BLOB(512) );It solves the challenge of metadata and vector search and eliminates impedance between vector data and regular structured data points in the same storage.
As you can see, you can access vector-like data and start date in the same query.
select c.id ,c.startDate, c.endDate, c.summary, vector_distance_cos(c.vectorSummary, vector(${vector})) distance from conversation where ${startDate ? `and c.startDate >= ${startDate.getTime()}` : ''} ${endDate ? `and c.endDate <= ${endDate.getTime()}` : ''} ${distance ? `and distance <= ${distance}` : ''} order by distance limit ${top};vector_distance_cos calculated as distance allows us to make a primitive vector search that does a full scan and calculates distances on rows. We could optimize it with CTE and limit search and distance calculations to a much smaller subset of data.
This approach could be calculation intensive and fail on large amounts of data.
Libsql offers a way more effective vector search based on FlashDiskANN vector indexed.
vector_top_k('idx_conversation_vectorSummary', ${vector} , ${top}) ivector_top_k is a table function that searches for the top of the newly created vector search index. As you can see, we could use only vector as a function parameter, and other columns could be used outside of the table function. So, to use a vector index together with different columns, we need to apply some strategies.
Now we get a classical problem of integration vector search results with metadata queries.
Post-Filtering: A Common Approach
The most widely adopted method in these pipelines is post-filtering. In this approach, the system first retrieves data based on vector similarities and then applies metadata filters. For example, imagine you’re conducting a vector search to retrieve conversations relevant to a specific question. Still, you also want to ensure these conversations occurred in the past week.

Post-filtering allows the system to retrieve the most relevant vector-based results and subsequently filter out any that don’t meet the metadata criteria, such as date range. This method is efficient when vector similarity is the primary factor driving the search, and metadata is only applied as a secondary filter.
const sqlQuery = ` select c.id ,c.startDate, c.endDate, c.summary, vector_distance_cos(c.vectorSummary, vector(${vector})) distance from vector_top_k('idx_conversation_vectorSummary', ${vector} , ${top}) i inner join conversation c on i.id = c.rowid where ${startDate ? `and c.startDate >= ${startDate.getTime()}` : ''} ${endDate ? `and c.endDate <= ${endDate.getTime()}` : ''} ${distance ? `and distance <= ${distance}` : ''} order by distance limit ${top};However, there are some limitations. For example, the initial vector search may yield fewer results or omit some relevant data before applying the metadata filter. If the search window is narrow enough, this can lead to complete results.
One working strategy is to make the top value in vector_top_K much bigger. Be careful, though, as the function's default max number of results is around 200 rows.
Pre-Filtering: A More Complex Approach
Pre-filtering is a more intricate approach but can be more effective in some instances. In pre-filtering, metadata is used as the primary filter before vector search takes place. This means that only data that meets the metadata criteria is passed into the vector search process, limiting the scope of the search right from the beginning.
While this approach can significantly reduce the amount of irrelevant data in the final results, it comes with its own challenges. For example, pre-filtering requires a deeper understanding of the data structure and may necessitate denormalizing the data or creating separate pre-filtered tables. This can be resource-intensive and, in some cases, impractical for dynamic metadata like date ranges.

In certain use cases, pre-filtering might outperform post-filtering. For instance, when the metadata (e.g., specific date ranges) is the most important filter, pre-filtering ensures the search is conducted only on the most relevant data.
Pre-filtering with distance-based filtering
So, we are getting back to an old concept. We do prefiltering instead of using a vector index.
WITH FilteredDates AS ( SELECT c.id, c.startDate, c.endDate, c.summary, c.vectorSummary FROM YourTable c WHERE ${startDate ? `AND c.startDate >= ${startDate.getTime()}` : ''} ${endDate ? `AND c.endDate <= ${endDate.getTime()}` : ''} ), DistanceCalculation AS ( SELECT fd.id, fd.startDate, fd.endDate, fd.summary, fd.vectorSummary, vector_distance_cos(fd.vectorSummary, vector(${vector})) AS distance FROM FilteredDates fd ) SELECT dc.id, dc.startDate, dc.endDate, dc.summary, dc.distance FROM DistanceCalculation dc WHERE 1=1 ${distance ? `AND dc.distance <= ${distance}` : ''} ORDER BY dc.distance LIMIT ${top};It makes sense if the filter produces small data and distance calculation happens on the smaller data set.
As a pro of this approach, you have full control over the data and get all results without omitting some typical values for extensive index searches.
Choosing Between Pre and Post-Filtering
Both pre-filtering and post-filtering have their advantages and disadvantages. Post-filtering is more accessible to implement, especially when vector similarity is the primary search factor, but it can lead to incomplete results. Pre-filtering, on the other hand, can yield more accurate results but requires more complex data handling and optimization.
In practice, many systems combine both strategies, depending on the query. For example, they might start with a broad pre-filtering based on metadata (like date ranges) and then apply a more targeted vector search with post-filtering to refine the results further.
Conclusion
Vector search with metadata filtering offers a powerful approach for handling large-scale data retrieval in LLMs and RAG pipelines. Whether you choose pre-filtering or post-filtering—or a combination of both—depends on your application's specific requirements. As vector databases continue to evolve, future innovations that combine these two approaches more seamlessly will help improve data relevance and retrieval efficiency further.
-
 @ 3bf0c63f:aefa459d
2024-09-18 10:37:09
@ 3bf0c63f:aefa459d
2024-09-18 10:37:09How to do curation and businesses on Nostr
Suppose you want to start a Nostr business.
You might be tempted to make a closed platform that reuses Nostr identities and grabs (some) content from the external Nostr network, only to imprison it inside your thing -- and then you're going to run an amazing AI-powered algorithm on that content and "surface" only the best stuff and people will flock to your app.
This will be specially good if you're going after one of the many unexplored niches of Nostr in which reading immediately from people you know doesn't work as you generally want to discover new things from the outer world, such as:
- food recipe sharing;
- sharing of long articles about varying topics;
- markets for used goods;
- freelancer work and job offers;
- specific in-game lobbies and matchmaking;
- directories of accredited professionals;
- sharing of original music, drawings and other artistic creations;
- restaurant recommendations
- and so on.
But that is not the correct approach and damages the freedom and interoperability of Nostr, posing a centralization threat to the protocol. Even if it "works" and your business is incredibly successful it will just enshrine you as the head of a platform that controls users and thus is prone to all the bad things that happen to all these platforms. Your company will start to display ads and shape the public discourse, you'll need a big legal team, the FBI will talk to you, advertisers will play a big role and so on.
If you are interested in Nostr today that must be because you appreciate the fact that it is not owned by any companies, so it's safe to assume you don't want to be that company that owns it. So what should you do instead? Here's an idea in two steps:
- Write a Nostr client tailored to the niche you want to cover
If it's a music sharing thing, then the client will have a way to play the audio and so on; if it's a restaurant sharing it will have maps with the locations of the restaurants or whatever, you get the idea. Hopefully there will be a NIP or a NUD specifying how to create and interact with events relating to this niche, or you will write or contribute with the creation of one, because without interoperability this can't be Nostr.
The client should work independently of any special backend requirements and ideally be open-source. It should have a way for users to configure to which relays they want to connect to see "global" content -- i.e., they might want to connect to
wss://nostr.chrysalisrecords.com/to see only the latest music releases accredited by that label or towss://nostr.indiemusic.com/to get music from independent producers from that community.- Run a relay that does all the magic
This is where your value-adding capabilities come into play: if you have that magic sauce you should be able to apply it here. Your service -- let's call it
wss://magicsaucemusic.com/-- will charge people or do some KYM (know your music) validation or use some very advanced AI sorcery to filter out the spam and the garbage and display the best content to your users who will request the global feed from it (["REQ", "_", {}]), and this will cause people to want to publish to your relay while others will want to read from it.You set your relay as the default option in the client and let things happen. Your relay is like your "website" and people are free to connect to it or not. You don't own the network, you're just competing against other websites on a leveled playing field, so you're not responsible for it. Users get seamless browsing across multiple websites, unified identities, a unified interface (that could be different in a different client) and social interaction capabilities that work in the same way for all, and they do not depend on you, therefore they're more likely to trust you.
Does this centralize the network still? But this a simple and easy way to go about the matter and scales well in all aspects.
Besides allowing users to connect to specific relays for getting a feed of curated content, such clients should also do all kinds of "social" (i.e. following, commenting etc) activities (if they choose to do that) using the outbox model -- i.e. if I find a musician I like under
wss://magicsaucemusic.comand I decide to follow them I should keep getting updates from them even if they get banned from that relay and start publishing onwss://nos.lolorwss://relay.damus.ioor whatever relay that doesn't even know anything about music.The hardcoded defaults and manual typing of relay URLs can be annoying. But I think it works well at the current stage of Nostr development. Soon, though, we can create events that recommend other relays or share relay lists specific to each kind of activity so users can get in-app suggestions of relays their friends are using to get their music from and so on. That kind of stuff can go a long way.
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ de496884:72617b81
2023-11-20 13:54:02
@ de496884:72617b81
2023-11-20 13:54:02Hola nostriches. Hoy quiero hacer una publicación a modo de acercamiento al surgimiento de las categorías de género y feminismo. Así que si te interesa el tema haz un esfuerzo, quédate y lee hasta el final.
El «nuevo» feminismo surge en los años 60 en aquellos países desarrollados que acordaron el reconocimiento a los derechos humanos contenidos en la declaración respectiva de la ONU. Entonces, como extensión a dicho reconocimiento es que se gesta el movimiento feminista. A partir de entonces, se vuelve a plantear la relación entre naturaleza y cultura y se llega a la conclusión de que las diferencias sociales van más allá de las diferencias biológicas, lo cual tiene que ver con que hasta la satisfacción de las necesidades elementales como son la alimentación, la vivienda o el vestuario, están condicionadas por construcciones sociales.
Pues resulta que una de las primeras propuestas identificó la subordinación femenina producto de una organización patriarcal, tomando la categoría patriarcado de Max Weber. Es así como la visión de patriarcado se extendió al discurso político y académico. Sin embargo, no existía información acerca del desarrollo histórico de dicha categoría, sistematización, variaciones, etc., debido a que era algo que recién se percibía en sociedad.
Sin embargo, la misma categoría de patriarcado junto a la de relaciones de poder para explicar fenómenos sociales contemporáneos, constituye uno de los principales aportes del feminismo. Es así como han logrado primero visibilizar y luego deconstruir y desmontar una serie de patrones existentes en la cultura que hacían a la mujer subordinarse al hombre, y que estaban presentes en el sistema sexo/género.
 Imagen relativa a la lucha contra el patriarcado
Imagen relativa a la lucha contra el patriarcadoHasta ese momento, en las investigaciones de corte sociológico se podía observar un androcentrismo excesivo al dar cuenta de que el discurso científico giraba en torno al hombre como sujeto y objeto de la investigación. Incluso para muchos positivistas como el mismo Weber, los problemas relativos a las mujeres quedaban en un segundo plano y eran achacados a una supuesta pasividad en el ámbito doméstico-familiar. Dicha pasividad partía de la supuesta inferioridad biológica del género femenino.
El patriarcado entonces era una categoría vacía en sí misma, sin valor explicativo. Desde el punto de vista político pudo ser útil para la movilización pero no resistió la polémica de los críticos del feminismo ni problematizó los conflictos a ser resueltos. Pero por otro lado, un grupo de mujeres -académicas principalmente- se puso manos a la obra en una tarea más pequeña pero con mayores resultados a la larga. Se propusieron generar conocimientos sobre las condiciones de vida de la mujer, buscar en el pasado y el presente los aportes de las mujeres a la sociedad, hacerlas visibles en la historia. Es así como surgen centros académicos, ONG, proyectos, centros de estudios sobre la mujer, etc.
Convendría distinguir entonces dos posturas que acompañaron a la investigación sobre las mujeres: uno que toma como objeto de estudio a la mujer; condiciones de vida, trabajo, cultura, y otra que privilegia a la sociedad como generadora de la subordinación de las mujeres. Mientras la primera perspectiva generaba conocimiento sobre las mujeres en el estudio de las relaciones mujer-hombre y mujer-mujer, la segunda tenía una visión más holística ya que planteaba que hay que estudiar la sociedad ya que la subordinación de las mujeres es producto de la organización de esta, y que no se avanzará solamente estudiando a las mujeres, pues el estudio debe ser más amplio y en diferentes niveles, ámbitos y tiempos.
Es en esta búsqueda donde nace y se desarrolla el concepto de género como categoría social. Es así que los sistemas de género/sexo fueron entendidos como conjuntos de prácticas, símbolos, representaciones, normas y valores sociales que las sociedades construyen a partir de la diferencia anatomofisiológica y que dotan de sentido a los impulsos sexuales, la reproducción y en general a las relaciones de las personas. Por tanto, este sistema pasó a ser el objeto de estudio para comprender la subordinación de la mujer al hombre. Al ser el reconocimiento de una dimensión de la desigualdad social hasta entonces desconocida, se considera la ruptura epistemológica más importante de la segunda mitad del siglo pasado.
 Imagen representativa del binarismo de género
Imagen representativa del binarismo de géneroHay que decir que los fenómenos sociales se definen por la relación que guardan entre sí. Es así que la contextualización adquiere gran importancia. Varones y hembras tenemos la capacidad de producir con el cuerpo, pero solo los cuerpos de las hembras pueden gestar y por tanto asegurar la especie humana. Todo grupo humano que pretenda sobrevivir debe asegurarse cierto número de hembras que lo hagan posible. De ahí un poder particular del cuerpo de las hembras que además es económicamente útil. Dicho poder no es en tanto entidad biológica, sino que es la sociedad la que le otorga este poder. En este punto es importante preguntarnos históricamente ¿quiénes han controlado la capacidad reproductiva de las mujeres?, ¿quiénes han tenido la preferencia en el acceso sexual? Para asegurar un control efectivo sobre la reproducción es necesario asegurar el acceso a la sexualidad.
Ello también lleva a dirigir el trabajo que hacen porque de lo contrario, las mujeres pudieran tener espacio para representar una amenaza al dominio de los hombres. Es importante atender a las etapas del desarrollo de las mujeres, que permitirá ver cómo se moldean para aceptar la desigualdad y las jerarquías según el género en las distintas sociedades y culturas.
Otro contexto a delimitar es el ámbito doméstico donde históricamente ha estado ubicada la subordinación femenina. Se ha puesto al descubierto que en mujeres que comparten la misma posición de clase y raza, la condición femenina se redefine a lo largo de la vida y que algunas mujeres gozan de poder sobre otras aún en contextos de alta dominación masculina, donde se les inviste de autoridad, creando el sistema zonas de incertidumbre que las divide como género e impide alianzas y se legitima la dominación. Foucault decía que «el poder se ejerce, no se posee», siempre está en peligro de perderse y no basta con normas, leyes, amenazas o castigos. De ahí que los espacios de subordinación sean también espacios de poder de las mujeres. Es en estos espacios donde aparece la inseguridad, la tensión, la confrontación y por ejemplo, las mujeres pueden reclamar la anticoncepción.
Para terminar, es importante tener en cuenta que el género es una forma de desigualdad social que siempre está articulado con otras formas de desigualdad ya sea clase, raza, grupo etario, etc. Hay que pensar la dominación masculina con un comienzo vago en el tiempo, pero que permite desligar la subordinación de las mujeres de la evolución «natural» de la humanidad y entenderla como un proceso histórico. En ese sentido es necesario destacar que, respecto a la raza, en sociedades plurales hay que atender al contexto étnico-cultural ya que en dependencia de las relaciones entre personas de razas distintas, estarán condicionadas las relaciones entre los géneros.
 Imagen de mujeres de distintas razas
Imagen de mujeres de distintas razasPor otro lado, si bien es sabido que históricamente el sistema de género social imperante ha contribuido a invisibilizar a la mujer, asociar necesariamente dicha categoría únicamente a ella, lo que hace es nuevamente recrear el absolutismo histórico que tanto daño ha hecho, ahora como lo antagónico al hombre. En la construcción social participan todos los individuos presentes en el sistema género.
Hasta aquí la publicación de hoy, de la cual aun se puede ahondar mucho más, sobre todo en lo referido al origen de la dominación o de la jerarquización del binomio «hombre/mujer» desde un punto de vista antropológico, pero eso quedará pendiente para otro momento. ¡Así que hasta la próxima!, ¡nos vemos en Nostr!
........................................
English version
Hello nostriches. Today I want to make a post by way of an approach to the emergence of the categories of gender and feminism. So if you are interested in the topic make an effort, stay and read to the end.
The "new" feminism emerged in the 60's in those developed countries that agreed to recognize the human rights contained in the respective UN declaration. Then, as an extension of that recognition, the feminist movement was born. From then on, the relationship between nature and culture was raised again and the conclusion was reached that social differences go beyond biological differences, which has to do with the fact that even the satisfaction of elementary needs such as food, housing or clothing are conditioned by social constructions.
It turns out that one of the first proposals identified female subordination as a product of a patriarchal organization, taking Max Weber's category of patriarchy. This is how the vision of patriarchy was extended to political and academic discourse. However, there was no information about the historical development of this category, systematization, variations, etc., because it was something that was only recently perceived in society.
However, the same category of patriarchy, together with that of power relations to explain contemporary social phenomena, constitutes one of the main contributions of feminism. This is how they have first made visible and then deconstructed and dismantled a series of existing patterns in the culture that made women subordinate to men, and that were present in the sex/gender system.
 Image relating to the fight against patriarchy
Image relating to the fight against patriarchyUp to that time, in sociological research, an excessive androcentrism could be observed as scientific discourse revolved around men as the subject and object of research. Even for many positivists such as Weber himself, the problems related to women remained in the background and were blamed on a supposed passivity in the domestic-family sphere. This passivity was based on the supposed biological inferiority of the female gender.
Patriarchy was then an empty category in itself, with no explanatory value. From the political point of view, it could be useful for mobilization, but it did not resist the polemic of feminism's critics, nor did it problematize the conflicts to be resolved. But on the other hand, a group of women - mainly academics - set to work on a smaller task but with greater results in the long run. They set out to generate knowledge about women's living conditions, to search in the past and present for women's contributions to society, to make them visible in history. This is how academic centers, NGOs, projects, women's studies centers, etc., came into being.
It would be convenient to distinguish then two postures that accompanied the research on women: one that takes women as the object of study; living conditions, work, culture, and the other that privileges society as the generator of women's subordination. While the first perspective generated knowledge about women in the study of woman-man and woman-woman relations, the second had a more holistic vision, since it proposed that society must be studied, since the subordination of women is a product of its organization, and that progress will not be made only by studying women, since the study must be broader and at different levels, spheres and times.
It is in this search that the concept of gender as a social category was born and developed. Thus, gender/sex systems were understood as a set of practices, symbols, representations, norms and social values that societies construct on the basis of anatomophysiological differences and that give meaning to sexual impulses, reproduction and, in general, to people's relationships. Therefore, this system became the object of study to understand the subordination of women to men. As the recognition of a hitherto unknown dimension of social inequality, it is considered the most important epistemological breakthrough of the second half of the last century.
 Representative image of gender binarism
Representative image of gender binarismIt must be said that social phenomena are defined by their relationship with each other. Thus, contextualization acquires great importance. Males and females have the capacity to produce with their bodies, but only the bodies of females can gestate and therefore ensure the human species. Any human group that intends to survive must ensure a certain number of females to make it possible. Hence a particular power of the female body, which is also economically useful. This power is not as a biological entity, but it is society that gives it this power. At this point it is important to ask ourselves historically, who has controlled the reproductive capacity of women, who has had the preference in sexual access? To ensure effective control over reproduction, it is necessary to ensure access to sexuality.
 Allegorical image of pregnancy
Allegorical image of pregnancyThis also leads to directing the work they do because otherwise, women may have room to pose a threat to men's dominance. It is important to pay attention to the stages of women's development, which will allow us to see how they are shaped to accept inequality and gender hierarchies in different societies and cultures.
Another context to delimit is the domestic sphere where female subordination has historically been located. It has been discovered that in women who share the same class and race position, the feminine condition is redefined throughout life and that some women enjoy power over others even in contexts of high male domination, where they are invested with authority, creating the system of uncertainty zones that divide them as a gender and prevent alliances and legitimize domination. Foucault said that "power is exercised, not possessed", it is always in danger of being lost and norms, laws, threats or punishments are not enough. Hence, the spaces of subordination are also spaces of women's power. It is in these spaces where insecurity, tension, confrontation appear and where, for example, women can demand contraception.
To conclude, it is important to keep in mind that gender is a form of social inequality that is always articulated with other forms of inequality, be it class, race, age group, etc. It is necessary to think of male domination with a vague beginning in time, but which allows us to separate the subordination of women from the "natural" evolution of humanity and to understand it as a historical process. In this sense, it is necessary to emphasize that, with respect to race, in plural societies it is necessary to pay attention to the ethno-cultural context since, depending on the relations between people of different races, the relations between genders will be conditioned.
 Image of women of different races
Image of women of different racesOn the other hand, although it is known that historically the prevailing social gender system has contributed to make women invisible, to necessarily associate this category only to women is to recreate the historical absolutism that has done so much damage, this time as antagonistic to men. All individuals present in the gender system participate in the social construction.
So much for today's publication, of which we can still go much deeper, especially with regard to the origin of domination or the hierarchization of the binomial "man/woman" from an anthropological point of view, but that will be left for another time. So until next time, see you in Nostr!

Créditos | Credits
Bibliografía consultada | Consulted bibliography:
-
Barbieri, T. (1993). Sobre la categoría género. Una introducción teórico-metodológica. Debates en Sociología. (18). 1-19. https://doi.org/10.18800/debatesensociologia.199301.006
-
Echevarría, D. (2020). Desigualdades de género e interseccionalidad. Análisis del contexto cubano 2008-2018. Facultad Latinoamericana de Ciencias Sociales (Programa-Cuba). https://www.clacso.org.ar/libreria-latinoamericana-cm/libro_detalle_resultado.php?id_libro=2346&campo=cm&texto=248
Traducción | Translation:
DeepL
-
-
 @ 06639a38:655f8f71
2024-10-24 14:49:08
@ 06639a38:655f8f71
2024-10-24 14:49:08Project Name
Nostr
Project Description
Nostr (Notes and Other Stuff Transmitted by Relays) is an open, censorship-resistant, and decentralized communication protocol designed for simplicity and resilience. Unlike traditional platforms, Nostr doesn’t rely on centralized servers. It already supports various use cases with free, open-source clients—offering alternatives to platforms like Twitter/X, Meetup.com, Excel 365, healthcare system and more. We will help you get started with Nostr.
Nostr has seen remarkable adoption and growth within the open-source community, evidenced by over 12,500 GitHub stars, 500+ forks, and contributions from more than 350 developers. The protocol has catalyzed the creation of an impressive ecosystem of over 390 projects, including mobile and web clients, relays, tools, and services that further enhance Nostr’s functionality. With over 70 tools and 48 libraries, developers can integrate Nostr into a wide array of applications—ranging from chat platforms to file storage and even decentralized marketplaces. These resources help to build decentralized, censorship-resistant systems without the need for centralized servers. Whether you’re working on peer-to-peer markets, privacy-focused messaging apps, or decentralized social media, Nostr’s ecosystem offers the tools.
Project website
https://github.com/nostr-protocol
Source code
https://github.com/nostr-protocol/nips
Project Theme
World Wide Web
Do you want a stand for the entire event or just for one day?
Entire event
Why do you want to be at FOSDEM?
We want to be at FOSDEM because it’s the perfect place to connect with like-minded developers and open-source enthusiasts who share our passion for decentralization, innovation, and building open permissionless technologies. FOSDEM fosters collaboration and the growth of community-driven projects and Nostr is a natural fit as a real grassroots project with its open protocol and commitment to build communication technology with resilience and simplicity in mind.
By being at FOSDEM, we aim to raise awareness, share knowledge and inspire others to explore the potential of decentralized communication systems. We also want to engage with the FOSS community and gain feedback to help Nostr grow. If people are really interested in how they can use Nostr we will show the possibilities, demo existing clients and provide in-depth explanations of how the protocol can replace the social layer (with user accounts in living a database) in existing software.What is the relation between the project and the primary contact?
Jurjen works with the community to promote its development, onboard new developers, and contribute to its open-source ecosystem. My role includes helping to raise awareness of Nostr's potential, organizing events, and supporting adoption by providing educational resources and technical guidance.
What is the relation between the project and the secondary contact?
Sebastian (37) is an independent creative / fullstack web developer who is the maintainer of a PHP helper library supported by OpenSats. Besides this project he is also making contributions with developing Nostr modules for Drupal.
“Since I've been online on the internet (1998), I'm highly interested in online communities, social networking and new ways of digital interactions. The internet has changed radically in the last decade and that change is not serving our interests. It's fair to say the web is broken in many ways. With Nostr we can fix this.”Social media links
npub1l77twp5l02jadkcjn6eeulv2j7y5vmf9tf3hhtq7h7rp0vzhgpzqz0swft(Jurjen)
npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe(Sebastian)
npub1hz5alqscpp8yjrvgsdp2n4ygkl8slvstrgvmjca7e45w6644ew7sewtysa(Tanja)
npub1nkmta4dmsa7pj25762qxa6yqxvrhzn7ug0gz5frp9g7p3jdscnhsu049fn(Kevin)Anything else you like to add?
We’d also like to highlight that Nostr was created by Fiatjaf, an anonymous founder, which aligns with its principles of openness and decentralization. As an open protocol, Nostr is designed to evolve and find its own way, just like the foundational protocols of the internet. Importantly, Nostr is not a blockchain project—there are no tokens, no costs, and no barriers. It’s also not a platform nor a NFT. It’s purely decentralized, built for resilience and simplicity. While payment solutions like Bitcoin can be integrated, they are optional, not intrinsic to the protocol. This makes Nostr accessible and flexible, truly embodying the spirit of the open internet.
Nostr is more than just a technological protocol; it’s about the energy, problem-solving, and sense of hope that draws people in. Even newcomers can play a significant role in the ecosystem, gaining insight from the outside while discovering the protocol’s potential. Tanja, for example, isn’t from a tech background, yet after just three months, she’s taken on a major organizational role. She’s been spreading the message of freedom of speech and is leading the Nostr Booth LATAM tour, where volunteers, entrepreneurs, and Nostr-based businesses come together, supported by the entire community, to raise awareness about Nostr. Her passion for decentralization and open collaboration also drives her efforts to bring Nostr to FOSDEM, where she will help connect the project with like-minded developers and open-source advocates.
Please reach out to us if there are any questions. We’re really looking forward to presenting Nostr as a protocol at one of the best places where free and open-source software is flourishing.
This content will be used for a FOSDEM stand submission via https://pretalx.fosdem.org/fosdem-2025-call-for-stands/
-
 @ 18bdb66e:82eb5e5d
2024-10-21 23:44:52
@ 18bdb66e:82eb5e5d
2024-10-21 23:44:52Details
- ⏲️ Prep time: 20 mins
- 🍳 Cook time: 20 mins
- 🍽️ Servings: 4
Ingredients
- 1 Can (10.5 ounce) each condensed beef noodle, bean with bacon, and cream of celery soup
- 2 Soup cans water
- 2 TBSP chopped parsley
- 1 TBSP Worcestershire
Directions
- Combine soups and water.
- Add parsley and Worcestershire
- Heat to simmer.
-
 @ ff1a68c4:ec9831cf
2024-10-24 14:47:03
@ ff1a68c4:ec9831cf
2024-10-24 14:47:03En un mundo en constante evolución, la ciencia nos ofrece valiosas herramientas para mejorar nuestra calidad de vida y prevenir enfermedades neurodegenerativas como la demencia. A partir de los consejos de especialistas y datos de estudios recientes, he reunido una síntesis de enfoques clave que coinciden en varios puntos esenciales. Aquí te presento un resumen práctico:
El modelo MEDALS: Los pilares del bienestar
El acrónimo MEDALS nos recuerda los aspectos fundamentales que pueden ayudar a mantener una buena calidad de vida:
- Meditación: La práctica regular de la meditación reduce el estrés, mejora la concentración y contribuye a un mayor bienestar emocional.
- Ejercicio: El movimiento es vital para la salud física y mental. Mantener una rutina de ejercicio regular no solo fortalece el cuerpo, sino también el cerebro.
- Dieta: Una alimentación equilibrada es clave. Optar por una dieta rica en nutrientes, como la mediterránea, promueve un cerebro saludable.
- Apreciación: Practicar la gratitud y el aprecio por las pequeñas cosas de la vida puede elevar nuestro bienestar emocional y mental.
- Love (amor) y Learning (aprendizaje): Mantener vínculos afectivos y relaciones cercanas fortalece la mente. El aprendizaje continuo mantiene el cerebro activo y en constante crecimiento.
- Sueño: Dormir lo suficiente y de forma reparadora es crucial para la regeneración cerebral y la memoria.
Manantiales de la fuerza interior: Una guía integral para el bienestar
Otra perspectiva ofrece una visión holística de cómo cuidar cuerpo y mente. Estos son los cinco manantiales de energía interior que contribuyen a un estado óptimo de bienestar:
- Sueño profundo y reparador: Un buen descanso nocturno es el pilar del equilibrio físico y mental.
- Alimentación sana e hidratación: Mantener una dieta nutritiva y una adecuada hidratación es esencial para el buen funcionamiento del cerebro y del cuerpo.
- Respiración consciente: Practicar ejercicios de respiración ayuda a reducir el estrés y aumenta la claridad mental.
- Ejercicio y relajación: Alternar entre actividad física y momentos de descanso es fundamental para evitar el agotamiento.
- Actitud mental positiva: Mantener una mentalidad optimista y enfocada en el crecimiento nos ayuda a enfrentar mejor los retos de la vida.
6 Reglas anti-demencia: Proteger el cerebro a largo plazo
Algunos expertos proponen un enfoque más específico para la prevención de la demencia:
- Vínculos sociales: El cerebro es un órgano social. Mantener relaciones cercanas y participar en actividades grupales es clave para su salud.
- Ejercicio físico: El cuerpo y la mente están conectados. La actividad física regular mejora el rendimiento cerebral.
- Curiosidad y aprendizaje continuo: Mantener el cerebro activo con nuevos intereses y aprendizajes es crucial para prevenir su deterioro.
- Buena alimentación: Optar por alimentos ricos en Omega-3 y seguir una dieta mediterránea favorece la salud cerebral.
- Manejo del estrés: El estrés crónico es un enemigo del cerebro. Aprender a relativizar las situaciones y ver los desafíos como oportunidades puede reducir su impacto.
- Dormir bien: Un sueño adecuado es esencial para la reparación y el funcionamiento óptimo del cerebro.
Hallazgos de The Lancet: Factores modificables y no modificables en la prevención de la demencia
Uno de los estudios más importantes sobre la prevención de la demencia, publicado en The Lancet, destaca los factores modificables que pueden influir en nuestro futuro cognitivo:
- Formación continua: Aprender y mantenerse intelectualmente activo durante toda la vida puede retrasar el deterioro cognitivo.
- Cuidado de la audición: Proteger la audición desde la juventud es crucial. En la vejez, el uso de audífonos puede ayudar a mantener el estímulo auditivo.
- Salud emocional: El estrés crónico, la ansiedad y la depresión son factores de riesgo importantes para el desarrollo de la demencia.
- Ejercicio físico y salud metabólica: Evitar el sedentarismo, el sobrepeso, la diabetes y los niveles elevados de colesterol LDL reduce el riesgo de enfermedades neurodegenerativas.
- Protección contra golpes en la cabeza: Los traumatismos craneales aumentan el riesgo de demencia. Protegerse es fundamental.
- Reducción de tóxicos: Evitar el tabaco, el consumo excesivo de alcohol y la exposición a contaminantes ayuda a preservar la salud cerebral (ej. filtros para el aire o en la llave del agua)
- Vida social activa: El aislamiento social es un factor de riesgo para la demencia. Mantenerse involucrado en grupos y actividades sociales es clave.
- Suplementos: Aunque no son esenciales, algunos suplementos como arándanos, vitamina D, Omega-3, y magnesio pueden ser beneficiosos en casos de deficiencia.
Implementar estos principios no solo mejorará la calidad de vida en el presente, sino que también reducirá significativamente el riesgo de desarrollar demencia en el futuro. Vivir de manera consciente, cuidar el cuerpo y nutrir la mente son las claves para una vida larga y saludable.
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 18bdb66e:82eb5e5d
2024-10-21 23:41:04
@ 18bdb66e:82eb5e5d
2024-10-21 23:41:04Chef's notes
Add cooked rice to stretch. Serve with celery for crunch. Top with Parmesan cheese for a nice change. You can also use red or yellow sweet peppers instead of or along with the green peppers.
Details
- ⏲️ Prep time: 20 mins
- 🍳 Cook time: 20 mins
- 🍽️ Servings: 4
Ingredients
- 1 TBSP Chopped green pepper
- 2 TBSP Chopped onion
- Dash oregano
- 2 TBSP butter
- 1 Can (10.5 ounce) condensed tomato soup
- 1 Soup can Water
Directions
- Cook green pepper, onion, oregano in butter until tender.
- Add soup, and water.
- Heat till simmer, stirring often.
-
 @ d5c3d063:4d1159b3
2024-10-24 15:14:10
@ d5c3d063:4d1159b3
2024-10-24 15:14:10มนุษย์ไม่ใช่หุ่นยนต์ เรา 'กระทำ' ด้วยเหตุผลและ 'คุณค่า' แต่ถูกจำกัดด้วย 'เวลา' - นี่คือหัวใจของเศรษฐกิจที่แท้จริง 🧡
3 EP ที่ผ่านมาของ JUST Economics เราได้ปูพื้นฐานเศรษฐศาสตร์สำนักออสเตรียนจากบทที่ 1-3 ของหนังสือ Principles of Economics โดย Saifedean Ammous
https://image.nostr.build/a1b6208d64a97411e9d7883180496356ac8d3dbdf45b46ba434699b664709bd3.jpg
..เริ่มจาก EP ที่ 1 การกระทำของมนุษย์ (Human Action)
เราได้เข้าใจว่า.. การกระทำของมนุษย์ (Human Action) คือหัวใจสำคัญ ตามที่ลุดวิก ฟอน มิเซส (Ludwig von Mises) ได้อธิบายไว้ในหนังสือ Human Action ของเขา
มิเซสบอกว่า.. การกระทำคือการแสดงออกถึงเจตจำนงของเรา เราตั้งใจทำอะไรสักอย่างเพื่อให้บรรลุเป้าหมาย เป็นการตอบสนองต่อสิ่งเร้าและสภาพแวดล้อม และเป็นการปรับตัวของเราต่อโลกใบนี้
มนุษย์ไม่ใช่หุ่นยนต์ที่ถูกโปรแกรมไว้ หรือสัตว์ที่ทำตามสัญชาตญาณ เราคิด เราเลือก และมีเหตุผล แม้ว่าผลลัพธ์ที่ออกมาดีหรือไม่ก็ตาม เราได้เรียนรู้ว่าการกระทำของมนุษย์เกิดจาก ความต้องการที่ยังไม่บรรลุผล
ซึ่งเป็นเหมือนเชื้อเพลิงที่ผลักดันให้เราไม่หยุดนิ่ง ไม่ว่าจะเป็นความหิว ความอยากได้อยากมี หรือความอยากรู้อยากเห็น สิ่งเหล่านี้ล้วนเป็น แรงจูงใจ ที่ทำให้เราคิด วางแผน และ ลงมือทำ
..การวิเคราะห์ทางเศรษฐศาสตร์ (Economic Analysis) เป็นอีกหัวข้อสำคัญที่เราได้เรียนรู้
ฮานส์-เฮอร์มันน์ ฮ็อปเป่ (Hans-Hermann Hoppe) บอกว่า.. การวิเคราะห์เศรษฐกิจ มันเหมือนกับการไขคดีเลยล่ะ เราต้องแกะรอย หาหลักฐานและเชื่อมโยงทุกอย่างเข้าด้วยกัน
เศรษฐศาสตร์ไม่สามารถทดลองแบบวิทยาศาสตร์ได้ เพราะมนุษย์ ไม่ใช่ลูกตุ้ม แต่ละคนคิดไม่เหมือนกัน ตัดสินใจไม่เหมือนกัน การวิเคราะห์เศรษฐกิจแค่ตัวเลขอย่างเดียว อาจทำให้เราเข้าใจผิดได้
เพราะตัวเลขมันเหมือนเปลือกนอก.. เราต้องมองให้ลึกกว่านั้น ถึงจะเห็นแก่นแท้ของปัญหา ทีนี้แล้วอะไรล่ะที่เป็นตัวกำหนดการกระทำของมนุษย์?
=================
..คำตอบอยู่ใน EP 2 คุณค่า (Value) ของสิ่งต่างๆ ไม่ได้ตายตัว แต่ขึ้นอยู่กับว่าแต่ละคนมองว่ามันมีค่าแค่ไหน
ตามที่ คาร์ล เมงเงอร์ (Carl Menger) ได้อธิบายไว้ในหนังสือ Principles of Economics ของเขา เมงเงอร์บอกว่า.. มูลค่าไม่มีอยู่นอกเหนือจิตสำนึกของมนุษย์
ใน EP นี้เรายังได้เรียนรู้ 'ทฤษฎีส่วนเพิ่ม' (Marginalism) ที่บอกว่า ความสุขที่เราได้จากการบริโภคของจะลดลงเรื่อยๆ ตามกฎของอรรถประโยชน์ส่วนเพิ่มที่ลดลง (Law of Diminishing Marginal Utility)
เพราะยิ่งเรามีอะไรมากขึ้น.. ความสุขที่ได้รับจากสิ่งนั้นก็จะลดลงเรื่อยๆ
ดังนั้น.. การเลือกใช้ทรัพยากรอย่างชาญฉลาด จึงเป็นสิ่งสำคัญ นอกจากนี้เรายังได้เรียนรู้ว่า "มูลค่า" เกิดจากหลายปัจจัย เช่น ความชอบ สถานการณ์ และ ความขาดแคลน
ส่วน "ราคา" เป็นเพียง "ตัวเลข" ที่สะท้อนถึงการตกลงกันระหว่างผู้ซื้อและผู้ขาย ไม่ได้เป็นการวัดมูลค่าโดยตรง
เหมือนกับที่บางคนยอมจ่ายแพงเพื่อซื้อกาแฟแบรนด์ดัง ทั้งๆ ที่กาแฟโบราณก็ให้รสชาติที่คล้ายคลึงกัน หรือบางคนเลือกซื้อเสื้อผ้ามือสอง ทั้งๆ ที่เสื้อผ้าใหม่ก็มีให้เลือกมากมาย
เพราะ "มูลค่า" มันไม่ได้อยู่ที่ตัวสินค้าเอง แต่มันอยู่ที่ว่าเราคิดว่ามันมีค่าแค่ไหนต่างหากล่ะ..
แล้วทรัพยากรที่สำคัญที่สุดของมนุษย์คืออะไร?
=================
คำตอบอยู่ใน EP 3 นั้นก็คือ เวลา (Time)
ในหนังสือ The Ultimate Resource ของไซมอน เขาได้บอกว่า.. เวลา เป็นทรัพยากรที่ล้ำค่าที่สุด เพราะมันมีจำกัดและใช้ไปแล้วก็เรียกคืนไม่ได้
ดังนั้นทุกการตัดสินใจของเรา จึงมี "ต้นทุนค่าเสียโอกาส" แฝงอยู่ เนื่องจากเวลาเป็นสิ่งมีค่าและมีจำกัด เราจึงต้องหาวิธีใช้เวลาให้คุ้มค่า โดยอาศัยเทคโนโลยี การแบ่งงานกันทำ การลงทุน และการออมเพื่อความมั่นคงในอนาคต
ระดับความเห็นแก่เวลา (Time Preference) ก็เป็นอีกหนึ่งปัจจัยที่ส่งผลต่อการตัดสินใจของเรา มนุษย์มักจะให้คุณค่ากับความสุขในปัจจุบันมากกว่าความสุขในอนาคต
เหมือนกับที่หลายคนเลือกที่จะรูดบัตรเครดิต ทั้งที่รู้ว่าต้องจ่ายดอกเบี้ยแพง เพราะความต้องการได้ของ ณ ตอนนั้น มันมีค่ามากกว่าภาระหนี้ที่จะเกิดขึ้นในอนาคต
เศรษฐศาสตร์สำนักออสเตรียนมองว่า.. การทำความเข้าใจระบบเศรษฐกิจต้องเริ่มต้นจากการศึกษาการกระทำของมนุษย์ ซึ่งเป็นสิ่งที่ขับเคลื่อนการทำงานของระบบเศรษฐกิจ ที่เกิดจากเหตุผลและมูลค่าที่แต่ละคนให้กับสิ่งต่างๆ
ในขณะที่เศรษฐศาสตร์กระแสหลัก.. มักจะใช้แบบจำลองทางคณิตศาสตร์และมองว่ารัฐควรมีบทบาทสำคัญในการควบคุมเศรษฐกิจ
ซึ่งการแทรกแซงของรัฐในระบบเศรษฐกิจ มักจะนำไปสู่ปัญหาต่างๆ
เช่น การกำหนดราคาสินค้ามักจะนำไปสู่การขาดแคลนของสินค้าจึงทำให้เกิดตลาดมืดขึ้น
ส่วนการขึ้นค่าแรงขั้นต่ำอาจทำให้คนงานตกงาน และการอุดหนุนโดยรัฐอาจทำให้เกิดการผลิตและบริโภคที่มากเกินความจำเป็น
เศรษฐศาสตร์สำนักออสเตรียนจึงมองว่ารัฐควรมีบทบาทจำกัด
=====================
เห็นไหมครับว่าทั้ง 3 EP มันเชื่อมโยงกัน..
เริ่มจากการกระทำที่ถูกขับเคลื่อนด้วยมูลค่าและถูกจำกัดด้วยเวลา ทั้งหมดนี้คือพื้นฐานสำคัญของเศรษฐศาสตร์ ที่ช่วยให้เรามองเห็นความลับเบื้องหลังของตัวเลขและทฤษฎี และสามารถนำไปประยุกต์ใช้ในชีวิตประจำวันได้อย่างมีประสิทธิภาพ
ฝากติดตาม JUST Economics ใน EP ต่อไปกันด้วยนะครับ รับรองว่า สนุก เข้าใจง่าย และได้ความรู้แน่นปึก!!
-
 @ 18bdb66e:82eb5e5d
2024-10-21 23:35:35
@ 18bdb66e:82eb5e5d
2024-10-21 23:35:35Chef's notes
Serve with crackers
Details
- ⏲️ Prep time: 20 mins
- 🍳 Cook time: 20 mins
- 🍽️ Servings: 4
Ingredients
- ¼ Cup Spam
- 1 TBSP butter
- 1 Can (10.5 ounce) gumbo soup
- 1 Soup can water
- Dash Tabasco
Directions
- Brown Spam in butter.
- Mix gumbo, water, and heat to simmer.
- Add Spam.
- Tabasco to taste
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 3bf0c63f:aefa459d
2024-09-06 12:49:46
@ 3bf0c63f:aefa459d
2024-09-06 12:49:46Nostr: a quick introduction, attempt #2
Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else.
Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services.
(Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation).
More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between clients (i.e. the program that runs on a user computer) and relays (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback".
-
 @ 18bdb66e:82eb5e5d
2024-10-21 23:30:47
@ 18bdb66e:82eb5e5d
2024-10-21 23:30:47Chef's notes
Trim down bread to fit serving bowl, if necessary, prior to broiling. Try using a biscuit cutter for perfect bread rounds. A cookie cutter could be used to treat children.
The addition of the vegetable juice creates a fuller flavor than the previous onion soup recipe.
Details
- ⏲️ Prep time: 20 mins
- 🍳 Cook time: 20 mins
- 🍽️ Servings: 4
Ingredients
- 1 Can (10.5 ounce) condensed onion soup
- 1 Soup can water
- ½ Soup can V8 juice
- 2-3 slices French, or Italian bread, or Texas Toast
- Butter
- Parmesan cheese
Directions
- Combine soup and water.
- Heat to simmer.
- Place bread on baking sheet, butter, and top with cheese.
- Broil bread until browned.
- Ladle soup in bowl
- Top soup with bread
-
 @ da18e986:3a0d9851
2024-08-14 13:58:24
@ da18e986:3a0d9851
2024-08-14 13:58:24After months of development I am excited to officially announce the first version of DVMDash (v0.1). DVMDash is a monitoring and debugging tool for all Data Vending Machine (DVM) activity on Nostr. The website is live at https://dvmdash.live and the code is available on Github.
Data Vending Machines (NIP-90) offload computationally expensive tasks from relays and clients in a decentralized, free-market manner. They are especially useful for AI tools, algorithmic processing of user’s feeds, and many other use cases.
The long term goal of DVMDash is to become 1) a place to easily see what’s happening in the DVM ecosystem with metrics and graphs, and 2) provide real-time tools to help developers monitor, debug, and improve their DVMs.
DVMDash aims to enable users to answer these types of questions at a glance: * What’s the most popular DVM right now? * How much money is being paid to image generation DVMs? * Is any DVM down at the moment? When was the last time that DVM completed a task? * Have any DVMs failed to deliver after accepting payment? Did they refund that payment? * How long does it take this DVM to respond? * For task X, what’s the average amount of time it takes for a DVM to complete the task? * … and more
For developers working with DVMs there is now a visual, graph based tool that shows DVM-chain activity. DVMs have already started calling other DVMs to assist with work. Soon, we will have humans in the loop monitoring DVM activity, or completing tasks themselves. The activity trace of which DVM is being called as part of a sub-task from another DVM will become complicated, especially because these decisions will be made at run-time and are not known ahead of time. Building a tool to help users and developers understand where a DVM is in this activity trace, whether it’s gotten stuck or is just taking a long time, will be invaluable. For now, the website only shows 1 step of a dvm chain from a user's request.
One of the main designs for the site is that it is highly clickable, meaning whenever you see a DVM, Kind, User, or Event ID, you can click it and open that up in a new page to inspect it.
Another aspect of this website is that it should be fast. If you submit a DVM request, you should see it in DVMDash within seconds, as well as events from DVMs interacting with your request. I have attempted to obtain DVM events from relays as quickly as possible and compute metrics over them within seconds.
This project makes use of a nosql database and graph database, currently set to use mongo db and neo4j, for which there are free, community versions that can be run locally.
Finally, I’m grateful to nostr:npub10pensatlcfwktnvjjw2dtem38n6rvw8g6fv73h84cuacxn4c28eqyfn34f for supporting this project.
Features in v0.1:
Global Network Metrics:
This page shows the following metrics: - DVM Requests: Number of unencrypted DVM requests (kind 5000-5999) - DVM Results: Number of unencrypted DVM results (kind 6000-6999) - DVM Request Kinds Seen: Number of unique kinds in the Kind range 5000-5999 (except for known non-DVM kinds 5666 and 5969) - DVM Result Kinds Seen: Number of unique kinds in the Kind range 6000-6999 (except for known non-DVM kinds 6666 and 6969) - DVM Pub Keys Seen: Number of unique pub keys that have written a kind 6000-6999 (except for known non-DVM kinds) or have published a kind 31990 event that specifies a ‘k’ tag value between 5000-5999 - DVM Profiles (NIP-89) Seen: Number of 31990 that have a ‘k’ tag value for kind 5000-5999 - Most Popular DVM: The DVM that has produced the most result events (kind 6000-6999) - Most Popular Kind: The Kind in range 5000-5999 that has the most requests by users. - 24 hr DVM Requests: Number of kind 5000-5999 events created in the last 24 hrs - 24 hr DVM Results: Number of kind 6000-6999 events created in the last 24 hours - 1 week DVM Requests: Number of kind 5000-5999 events created in the last week - 1 week DVM Results: Number of kind 6000-6999 events created in the last week - Unique Users of DVMs: Number of unique pubkeys of kind 5000-5999 events - Total Sats Paid to DVMs: - This is an estimate. - This value is likely a lower bound as it does not take into consideration subscriptions paid to DVMs - This is calculated by counting the values of all invoices where: - A DVM published a kind 7000 event requesting payment and containing an invoice - The DVM later provided a DVM Result for the same job for which it requested payment. - The assumption is that the invoice was paid, otherwise the DVM would not have done the work - Note that because there are multiple ways to pay a DVM such as lightning invoices, ecash, and subscriptions, there is no guaranteed way to know whether a DVM has been paid. Additionally, there is no way to know that a DVM completed the job because some DVMs may not publish a final result event and instead send the user a DM or take some other kind of action.
Recent Requests:
This page shows the most recent 3 events per kind, sorted by created date. You should always be able to find the last 3 events here of all DVM kinds.
DVM Browser:
This page will either show a profile of a specific DVM, or when no DVM is given in the url, it will show a table of all DVMs with some high level stats. Users can click on a DVM in the table to load the DVM specific page.
Kind Browser:
This page will either show data on a specific kind including all DVMs that have performed jobs of that kind, or when no kind is given, it will show a table summarizing activity across all Kinds.
Debug:
This page shows the graph based visualization of all events, users, and DVMs involved in a single job as well as a table of all events in order from oldest to newest. When no event is given, this page shows the 200 most recent events where the user can click on an event in order to debug that job. The graph-based visualization allows the user to zoom in and out and move around the graph, as well as double click on any node in the graph (except invoices) to open up that event, user, or dvm in a new page.
Playground:
This page is currently under development and may not work at the moment. If it does work, in the current state you can login with NIP-07 extension and broadcast a 5050 event with some text and then the page will show you events from DVMs. This page will be used to interact with DVMs live. A current good alternative to this feature, for some but not all kinds, is https://vendata.io/.
Looking to the Future
I originally built DVMDash out of Fear-of-Missing-Out (FOMO); I wanted to make AI systems that were comprised of DVMs but my day job was taking up a lot of my time. I needed to know when someone was performing a new task or launching a new AI or Nostr tool!
I have a long list of DVMs and Agents I hope to build and I needed DVMDash to help me do it; I hope it helps you achieve your goals with Nostr, DVMs, and even AI. To this end, I wish for this tool to be useful to others, so if you would like a feature, please submit a git issue here or note me on Nostr!
Immediate Next Steps:
- Refactoring code and removing code that is no longer used
- Improve documentation to run the project locally
- Adding a metric for number of encrypted requests
- Adding a metric for number of encrypted results
Long Term Goals:
- Add more metrics based on community feedback
- Add plots showing metrics over time
- Add support for showing a multi-dvm chain in the graph based visualizer
- Add a real-time mode where the pages will auto update (currently the user must refresh the page)
- ... Add support for user requested features!
Acknowledgements
There are some fantastic people working in the DVM space right now. Thank you to nostr:npub1drvpzev3syqt0kjrls50050uzf25gehpz9vgdw08hvex7e0vgfeq0eseet for making python bindings for nostr_sdk and for the recent asyncio upgrades! Thank you to nostr:npub1nxa4tywfz9nqp7z9zp7nr7d4nchhclsf58lcqt5y782rmf2hefjquaa6q8 for answering lots of questions about DVMs and for making the nostrdvm library. Thank you to nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft for making the original DVM NIP and vendata.io which I use all the time for testing!
P.S. I rushed to get this out in time for Nostriga 2024; code refactoring will be coming :)
-
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ d5c3d063:4d1159b3
2024-10-24 14:37:08
@ d5c3d063:4d1159b3
2024-10-24 14:37:08ปรัชญา อาวุธแห่งเหตุผลและเสรีภาพในโลกแห่งความขัดแย้ง
https://image.nostr.build/b3e2278447703b23c18d6b8dd98986b700958acbbe06b3cca6ce7efa55b6c1ad.jpg
โลกที่เราอาศัยอยู่เปรียบเสมือนสมรภูมิแห่งความคิด แนวคิดต่างๆ ถูกนำมาถกเถียงและท้าทายอยู่เสมอเพื่อค้นหาและพิสูจน์ความจริง ความขัดแย้งนี้ปรากฏชัดในหลายมิติ เช่น การปะทะกันระหว่างเหตุผลกับความงมงาย เสรีภาพกับการถูกบังคับ ปัจเจกนิยม (Individualism) กับลัทธิรวมหมู่ (Collectivism) และทุนนิยมกับสังคมนิยม ท่ามกลางความสับสนวุ่นวายนี้ ปรัชญาทำหน้าที่เสมือนป้อมปราการแห่งเหตุผลและเสรีภาพ เป็นเครื่องมือสำคัญที่ช่วยให้เราเข้าใจและวิเคราะห์โลกที่เต็มไปด้วยความขัดแย้ง พร้อมกับนำทางชีวิตของเราอีกด้วย .
ปรัชญาในบริบทนี้ มิใช่เพียงแสงเทียนริบหรี่ในห้องสมุด หากแต่เป็นอาวุธแห่งเหตุผล ที่ใช้ในการต่อสู้กับความคิดที่บิดเบือนและการใช้อำนาจในทางที่ผิด เพื่อปกป้องและส่งเสริมเสรีภาพของมนุษย์ มันคือดาบเพลิงที่ลุกโชนในสนามรบแห่งความคิดที่ช่วยให้เรามองทะลุผ่านมายาคติ ความเชื่อที่ไร้เหตุผล และการโฆษณาชวนเชื่อ ทั้งยังช่วยให้วิเคราะห์ข้อมูลอย่างมีวิจารณญาณและตัดสินใจบนพื้นฐานของหลักฐานและตรรกะ นำไปสู่การเข้าถึงความจริง ตัวอย่างที่เห็นได้ชัดคือการเซ็นเซอร์ข้อมูลข่าวสาร ซึ่งถูกใช้เป็นเครื่องมือในการบิดเบือนข้อมูล ปลุกปั่นอารมณ์ เป็นการใช้อำนาจในทางที่ผิด ปิดกั้นการเข้าถึงความจริง เพื่อควบคุมความคิดของประชาชน .
หัวใจสำคัญของปรัชญาคือ การใช้เหตุผล หลักฐาน และตรรกะ ในการแสวงหาความจริง เพื่อนำไปสู่ การตัดสินใจที่ถูกต้อง ปรัชญาฝึกฝนให้เรามีวิจารณญาณ ไม่หลงเชื่ออะไรง่ายๆ และไม่ยอมรับความคิดเห็นใดๆ โดยปราศจากการตรวจสอบอย่างถี่ถ้วน ปรัชญาสอนให้เราตั้งคำถาม เช่น ใครเป็นคนพูด ? มีหลักฐานอะไรสนับสนุน ? มีมุมมองอื่น ๆ อีกหรือไม่ ? ข้อสรุปนี้ขัดแย้งกับข้อเท็จจริงหรือหลักการพื้นฐานใด ๆ หรือไม่ ? ก่อนที่จะตัดสินใจเชื่อหรือยอมรับความคิดเห็นใด ๆ เพราะการยอมรับความคิดเห็นโดยไม่ผ่านการไตร่ตรอง อาจนำเราไปสู่การตัดสินใจที่ผิดพลาดและตกเป็นเหยื่อของการบิดเบือน .
ปรัชญายังส่งเสริมความเข้าใจในคุณค่าของเสรีภาพและความสำคัญของปัจเจกบุคคล เสรีภาพในการคิดการแสดงออกและการใช้ชีวิต เป็นสิ่งจำเป็นสำหรับการพัฒนาศักยภาพของมนุษย์ เพื่อการสร้างสรรค์สังคมที่เจริญรุ่งเรือง ปรัชญาช่วยให้เราตระหนักถึงสิทธิและหน้าที่ของตนเองในฐานะปัจเจกบุคคลและเพื่อปกป้องเสรีภาพเหล่านี้จากการถูกคุกคามจากอำนาจรัฐหรือแนวคิดแบบคติรวมหมู่ สังคมที่มีความยุติธรรมมีเสรีภาพและมีความเจริญรุ่งเรือง คือสังคมที่เคารพในสิทธิและเสรีภาพของปัจเจกบุคคลที่ส่งเสริมการใช้เหตุผลนั้น ล้วนมีรากฐานอยู่บนระบบเศรษฐกิจแบบทุนนิยม เพราะทุนนิยมเป็นระบบที่สอดคล้องกับหลักการเหล่านี้ โดยเปิดโอกาสให้ทุกคนมีส่วนร่วมในการสร้างความมั่งคั่งและเติบโตอย่างอิสระ .
ในโลกที่ความขัดแย้งทางความคิดทวีความรุนแรงและข้อมูลข่าวสารแพร่กระจายอย่างรวดเร็ว ปรัชญามิใช่เพียงทางเลือก แต่เป็นเกราะป้องกันที่ขาดไม่ได้ การศึกษาปรัชญา การฝึกฝนการใช้เหตุผลและการตั้งคำถาม คือการลงทุนที่คุ้มค่าที่สุดสำหรับอนาคต เพราะมันจะช่วยให้เรามีภูมิคุ้มกันต่อการถูกชักจูง การหลอกลวงและการใช้อำนาจในทางมิชอบ เป็นก้าวสำคัญในการสร้างสังคมที่เสรี มีความยุติธรรมและการเจริญรุ่งเรืองอย่างแท้จริง ดังนั้น เวลามีค่า…ศึกษาปรัชญา ฝึกฝนการใช้เหตุผล และอย่าปล่อยให้ความงมงายและอคติครอบงำจิตใจ เพื่อที่เราจะสามารถเป็นผู้กำหนดชีวิตของตนเองได้และใช้ชีวิตอย่างมีอิสระ มีเหตุผล และสร้างสรรค์คุณค่าตามที่เราเลือก เพื่อบรรลุศักยภาพสูงสุดของเราในฐานะปัจเจกบุคคล
Siamstr #Philosophy #ปรัชญา
-
 @ d5c3d063:4d1159b3
2024-10-24 15:11:17
@ d5c3d063:4d1159b3
2024-10-24 15:11:17เคยสงสัยไหมว่า ทำไมเศรษฐกิจถึงเป็นเรื่องซับซ้อนนัก? มาร่วมไขปริศนาเศรษฐศาสตร์ผ่านมุมมองที่แตกต่างระหว่างสำนักออสเตรียนและกระแสหลักกันครับ
ตลอด 3 EP ที่ผ่านมา JUST Economics ได้พาคุณดำดิ่งสู่โลกเศรษฐศาสตร์ที่น่าตื่นเต้น เราได้สัมผัสกับมุมมองที่หลากหลาย
โดยเฉพาะอย่างยิ่งมุมมองที่น่าสนใจและแตกต่างจากเศรษฐศาสตร์กระแสหลัก ซึ่งสำนักออสเตรียนให้ความสำคัญกับ "การกระทำของมนุษย์" และตั้งคำถามถึงบทบาทของรัฐ
https://image.nostr.build/3faa50be55e5241640223811f1ad9e14b3437ae7f2eeaf4cf5d257eceb71d709.jpg
ในโพสนี้.. เราจะพาคุณไปสำรวจความแตกต่างที่น่าสนใจระหว่างเศรษฐศาสตร์สำนักออสเตรียนและเศรษฐศาสตร์กระแสหลัก (หรือแนวคิดเคนเซียน) โดยอ้างอิงจากหนังสือ Principles of Economics ของ Saifedean Ammous
หัวใจหลักของเศรษฐศาสตร์สำนักออสเตรียน คือ การมองว่าระบบเศรษฐกิจเปรียบเสมือนละครเวทีขนาดใหญ่ที่ขับเคลื่อนด้วย "การกระทำของมนุษย์" ไม่ใช่เพียงแค่สมการหรือแบบจำลองทางคณิตศาสตร์ที่เย็นชา
สำนักคิดนี้เชื่อว่าการจะเข้าใจระบบเศรษฐกิจอย่างแท้จริง เราต้องเริ่มต้นจากการทำความเข้าใจ "เหตุผล" และ "มูลค่า" ที่ซ่อนอยู่เบื้องหลังการตัดสินใจของแต่ละบุคคล
ลองนึกภาพตามนะครับ.. เวลาที่เราเลือกซื้อสินค้าสักชิ้น การตัดสินใจของเราไม่ได้ขึ้นอยู่กับราคาเพียงอย่างเดียว แต่ขึ้นอยู่กับ "มูลค่า" ที่เราให้กับสินค้านั้นๆ ซึ่งได้รับอิทธิพลจากความชอบส่วนตัว สถานการณ์ในขณะนั้น และแม้กระทั่งความขาดแคลนของสินค้า
นี่คือสิ่งที่เรียกว่า "มูลค่าอัตวิสัย (Subjective Value)"
ดังที่ Carl Menger นักเศรษฐศาสตร์ผู้ยิ่งใหญ่เคยกล่าวไว้ว่า "มูลค่าไม่มีอยู่นอกเหนือจิตสำนึกของมนุษย์"
ในทางกลับกัน.. เศรษฐศาสตร์กระแสหลัก มักจะพยายามอธิบายระบบเศรษฐกิจด้วยแบบจำลองทางคณิตศาสตร์และสมการ โดยมองว่า "มูลค่า" เป็นสิ่งที่วัดได้ สามารถกำหนดเป็นตัวเลขได้อย่างแม่นยำ
อย่างไรก็ตาม Saifedean Ammous มองว่าแนวทางนี้อาจเป็นการ "Scientism" หรือการยึดติดกับวิธีการทางวิทยาศาสตร์มากเกินไป จนมองข้ามความซับซ้อนของการกระทำของมนุษย์
การใช้แบบจำลองทางคณิตศาสตร์ในทางเศรษฐศาสตร์ มักจะมาพร้อมกับสมการที่ไม่คงที่และถือเป็นการพยายามลดทอนความซับซ้อนของการกระทำของมนุษย์ให้เหลือเพียงตัวแปรที่วัดได้ ซึ่งอาจทำให้เกิดความเข้าใจผิดเกี่ยวกับการทำงานของระบบเศรษฐกิจ
เพราะในความเป็นจริงมนุษย์ไม่ได้ตัดสินใจตามแบบจำลอง แต่ตัดสินใจตาม "เหตุผล" และ "มูลค่า" ที่ตนเองให้
อีกหนึ่งจุดที่แตกต่าง.. คือมุมมองเกี่ยวกับบทบาทของรัฐ เศรษฐศาสตร์กระแสหลัก มักจะมองว่ารัฐควรมีบทบาทสำคัญในการแก้ไขปัญหาในระบบเศรษฐกิจ
เช่น การควบคุมราคา การขึ้นค่าแรงขั้นต่ำ และการอุดหนุนราคา ซึ่งสอดคล้องกับแนวคิดของ John Maynard Keynes ที่เชื่อว่ารัฐบาลควรเข้ามาแทรกแซงเศรษฐกิจเพื่อกระตุ้นการใช้จ่ายและสร้างงาน
แต่เศรษฐศาสตร์สำนักออสเตรียนมองว่า.. การแทรกแซงของรัฐในระบบตลาดเสรีมักจะนำไปสู่ผลลัพธ์ที่ไม่พึงประสงค์
ตัวอย่างเช่น การกำหนดราคาสินค้าโดยรัฐอาจนำไปสู่การขาดแคลนสินค้า การขึ้นค่าแรงขั้นต่ำอาจทำให้คนงานตกงาน และการอุดหนุนโดยรัฐอาจทำให้เกิดการผลิตและบริโภคที่มากเกินความจำเป็น
ตัวอย่างผลกระทบจากการแทรกแซงของรัฐที่สำนักออสเตรียนมองว่าไม่พึงประสงค์ เช่น..
การควบคุมราคา - หากรัฐเข้ามาควบคุมราคาสินค้า เช่น การกำหนดเพดานราคา อาจทำให้เกิดภาวะสินค้าขาดแคลนได้ เพราะผู้ผลิตจะไม่มีแรงจูงใจในการผลิตสินค้าออกมาขายในราคาที่ต่ำกว่าต้นทุน
Robert Schuettinger และ Eamonn Butler ได้บันทึกไว้ในหนังสือ Forty Centuries of Wage and Price Control: How Not to Fight Inflation ว่าการควบคุมราคามักจะนำไปสู่ตลาดมืด ที่ผู้คนยอมจ่ายแพงกว่าเพื่อให้ได้สินค้าที่ขาดแคลน
การขึ้นค่าแรงขั้นต่ำ - การที่รัฐกำหนดค่าแรงขั้นต่ำ อาจส่งผลให้นายจ้างบางรายไม่สามารถจ่ายค่าแรงที่สูงขึ้นได้ ซึ่งอาจนำไปสู่การลดการจ้างงาน
โดยเฉพาะอย่างยิ่งกลุ่มแรงงานไร้ฝีมือ หรือผู้ที่เพิ่งเริ่มต้นทำงาน อาจได้รับผลกระทบมากที่สุด
การอุดหนุนสินค้า - การอุดหนุนของรัฐบาล เช่น การอุดหนุนสินค้าเกษตร อาจทำให้เกิดการผลิตและบริโภคสินค้ามากเกินความจำเป็น เพราะทั้งผู้ผลิตและผู้บริโภคไม่ได้ตัดสินใจตาม "มูลค่า" ที่แท้จริงของสินค้า
ผลที่ตามมาคือ ทรัพยากรของประเทศอาจถูกจัดสรรไปอย่างไม่มีประสิทธิภาพ
เศรษฐศาสตร์สำนักออสเตรียน เน้นย้ำถึงความสำคัญของ "เสรีภาพ" และ "ตลาดเสรี" ในการขับเคลื่อนระบบเศรษฐกิจ โดยมองว่าการแทรกแซงของรัฐมักจะนำไปสู่ผลลัพธ์ที่ไม่พึงประสงค์
ในขณะที่เศรษฐศาสตร์กระแสหลัก มองว่ารัฐมีบทบาทสำคัญในการแก้ไขปัญหาตลาดและสร้างความมั่นคงทางเศรษฐกิจ
การทำความเข้าใจมุมมองที่แตกต่างของทั้งสองสำนักคิด จะช่วยให้เรามองเห็นภาพรวมของระบบเศรษฐกิจได้อย่างรอบด้าน และสามารถวิเคราะห์ปัญหาเศรษฐกิจได้อย่างมีประสิทธิภาพมากขึ้น
อย่าลืมติดตาม JUST Economics EP ต่อไปกันนะครับ เราจะพาคุณไปสำรวจโลกเศรษฐศาสตร์ที่น่าตื่นเต้น รับรองว่า สนุก เข้าใจง่าย และได้ความรู้แน่นปึ๊กอย่างแน่นอนครับ
Economics
-
 @ 76c71aae:3e29cafa
2024-08-13 04:30:00
@ 76c71aae:3e29cafa
2024-08-13 04:30:00On social media and in the Nostr space in particular, there’s been a lot of debate about the idea of supporting deletion and editing of notes.
Some people think they’re vital features to have, others believe that more honest and healthy social media will come from getting rid of these features. The discussion about these features quickly turns to the feasibility of completely deleting something on a decentralized protocol. We quickly get to the “We can’t really delete anything from the internet, or a decentralized network.” argument. This crowds out how Delete and Edit can mimic elements of offline interactions, how they can be used as social signals.
When it comes to issues of deletion and editing content, what matters more is if the creator can communicate their intentions around their content. Sure, on the internet, with decentralized protocols, there’s no way to be sure something’s deleted. It’s not like taking a piece of paper and burning it. Computers make copies of things all the time, computers don’t like deleting things. In particular, distributed systems tend to use a Kafka architecture with immutable logs, it’s just easier to keep everything around, as deleting and reindexing is hard. Even if the software could be made to delete something, there’s always screenshots, or even pictures of screens. We can’t provably make something disappear.
What we need to do in our software is clearly express intention. A delete is actually a kind of retraction. “I no longer want to associate myself with this content, please stop showing it to people as part of what I’ve published, stop highlighting it, stop sharing it.” Even if a relay or other server keeps a copy, and keeps sharing it, being able to clearly state “hello world, this thing I said, was a mistake, please get rid of it.” Just giving users the chance to say “I deleted this” is a way of showing intention. It’s also a way of signaling that feedback has been heard. Perhaps the post was factually incorrect or perhaps it was mean and the person wants to remove what they said. In an IRL conversation, for either of these scenarios there is some dialogue where the creator of the content is learning something and taking action based on what they’ve learned.
Without delete or edit, there is no option to signal to the rest of the community that you have learned something because of how the content is structured today. On most platforms a reply or response stating one’s learning will be lost often in a deluge of replies on the original post and subsequent posts are often not seen especially when the original goes viral. By providing tools like delete and edit we give people a chance to signal that they have heard the feedback and taken action.
The Nostr Protocol supports delete and expiring notes. It was one of the reasons we switched from secure scuttlebutt to build on Nostr. Our nos.social app offers delete and while we know that not all relays will honor this, we believe it’s important to provide social signaling tools as a means of making the internet more humane.
We believe that the power to learn from each other is more important than the need to police through moral outrage which is how the current platforms and even some Nostr clients work today.
It’s important that we don’t say Nostr doesn’t support delete. Not all apps need to support requesting a delete, some might want to call it a retraction. It is important that users know there is no way to enforce a delete and not all relays may honor their request.
Edit is similar, although not as widely supported as delete. It’s a creator making a clear statement that they’ve created a new version of their content. Maybe it’s a spelling error, or a new version of the content, or maybe they’re changing it altogether. Freedom online means freedom to retract a statement, freedom to update a statement, freedom to edit your own content. By building on these freedoms, we’ll make Nostr a space where people feel empowered and in control of their own media.
-
 @ 18bdb66e:82eb5e5d
2024-10-21 23:25:20
@ 18bdb66e:82eb5e5d
2024-10-21 23:25:20Chef's notes
Try using a biscuit cutter for perfect bread rounds. A cookie cutter could be used to treat children.
Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 20 mins
- 🍽️ Servings: 4
Ingredients
- 1 Can (10.5 ounce) condensed onion soup
- 1 Soup can water
- 2-3 slices French, or Italian bread, or Texas Toast
- Butter
- Parmesan cheese
Directions
- Combine soup and water.
- Heat to simmer.
- Place bread on baking sheet, butter, and top with cheese.
- Broil bread until browned.
- Ladle soup in bowl
- Top soup with bread
- Trim down bread to fit serving bowl, if necessary, prior to broiling.
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 4ba8e86d:89d32de4
2024-10-24 14:03:14
@ 4ba8e86d:89d32de4
2024-10-24 14:03:14O Collabora Office é uma suíte de escritório baseada em código aberto que oferece uma alternativa viável e de qualidade ao popular pacote Office da Microsoft. Desenvolvido pela Collabora, uma empresa líder em serviços de consultoria e desenvolvimento de software de código aberto, o Collabora Office oferece uma gama completa de aplicativos de produtividade para a plataforma Android, incluindo processador de texto, planilha, apresentação e muito mais.
Recursos e Funcionalidades.
O Collabora Office oferece uma ampla gama de recursos e funcionalidades para dispositivos Android, comparáveis aos encontrados em outras suítes de escritório populares. Além das funcionalidades básicas, como criação e edição de documentos de texto, planilhas e apresentações, o Collabora Office suporta formatos de arquivo comuns, como o formato OpenDocument (ODF) e o formato do Microsoft Office (OOXML). Isso significa que você pode facilmente compartilhar e colaborar em documentos com usuários de outras suítes de escritório.
Uma característica notável do Collabora Office para Android é a capacidade de edição colaborativa em tempo real. Vários usuários podem trabalhar simultaneamente em um documento, visualizando as alterações em tempo real. Isso torna a colaboração em equipe mais eficiente, permitindo que os membros trabalhem juntos em projetos sem a necessidade de trocar arquivos várias vezes.
O Collabora Office para Android possui uma interface intuitiva e fácil de usar, projetada especificamente para dispositivos móveis. Isso garante uma experiência de usuário fluida e permite que os usuários aproveitem ao máximo os recursos e funcionalidades do aplicativo em seus smartphones ou tablets.
Uma das principais vantagens do Collabora Office para Android é o fato de ser baseado em código aberto. Isso significa que o software é desenvolvido de forma transparente e está disponível para qualquer pessoa utilizar, estudar, modificar e distribuir. A natureza de código aberto do Collabora Office traz vários benefícios, incluindo:
-
Custos reduzidos: O Collabora Office para Android é gratuito para download e uso, eliminando a necessidade de licenças caras. Isso é particularmente atraente para pequenas empresas e usuários domésticos que buscam uma alternativa acessível ao pacote Office tradicional.
-
Personalização e flexibilidade: Como o código-fonte está disponível, desenvolvedores e usuários avançados podem personalizar e adaptar o Collabora Office para Android às suas necessidades específicas. Isso permite criar soluções personalizadas e integrar o software a outros sistemas e fluxos de trabalho existentes.
-
Segurança: Com a comunidade de código aberto constantemente analisando e auditando o software, eventuais vulnerabilidades de segurança são identificadas e corrigidas rapidamente. Além disso, os usuários podem ter maior confiança na privacidade de seus dados, uma vez que podem verificar como o software lida com as informações.
O Collabora Office para Android é uma alternativa sólida e de código aberto ao pacote Office da Microsoft. Com recursos abrangentes, capacidade de edição colaborativa em tempo real e uma interface otimizada para dispositivos móveis, ele se tornou uma escolha popular entre empresas e usuários individuais que desejam uma solução de produtividade acessível e personalizável para seus dispositivos Android. Além disso, a natureza de código aberto do Collabora Office traz vantagens significativas, como custos reduzidos, flexibilidade e segurança aprimorada. Se você está em busca de uma alternativa confiável e gratuita ao pacote Office tradicional para Android, vale a pena considerar o Collabora Office como uma opção viável.
https://www.collaboraoffice.com/
https://github.com/CollaboraOnline/online
-
-
 @ d5c3d063:4d1159b3
2024-10-24 15:05:42
@ d5c3d063:4d1159b3
2024-10-24 15:05:42เมื่อ WEF วาดฝัน (ร้าย) โลกที่ไร้ทรัพย์สิน ไร้ตัวตน แต่ทุกคนแฮปปี้ในปี 2030
World Economic Forum หรือ WEF องค์กรระดับโลกที่รวมตัวผู้นำทางธุรกิจและการเมือง ได้ออกมาทำนายอนาคตของโลกในปี 2030 ไว้แบบชวนขนหัวลุก
https://image.nostr.build/9244fa84d941e2548d6a189c93bd40346d5c55145292325614737638a6106949.jpg
โดยเฉพาะอย่างยิ่งกับคนที่รักอิสรภาพและความเป็นส่วนตัว เพราะ WEF บอกไว้ว่าเราจะไม่มีกรรมสิทธิ์ในทรัพย์สินส่วนตัวอีกต่อไป แถมชีวิตทุกด้านยังจะถูกควบคุมโดยรัฐบาลอีกด้วย ฟังดูเหมือนหลุดออกมาจากหนังไซไฟดิสโทเปียเลยทีเดียว
มีการคาดการณ์ว่าโลกในปี 2030 จะเปลี่ยนไปแบบหน้ามือเป็นหลังมือ โดยเฉพาะวิถีชีวิตและการทำงานของเรา
ต่อไปนี้คือ 8 คำทำนายหลักๆ ที่ฟังแล้วชวนให้เราเสียวสันหลัง
-
ทรัพย์สินส่วนตัวอาจกลายเป็นอดีต สิ่งของต่างๆ จะถูกควบคุมโดยรัฐ และเราจะต้องเช่าหรือยืมใช้แทน ซึ่งอาจส่งผลกระทบต่อวิถีชีวิตและเสรีภาพส่วนบุคคล
-
สหรัฐอาจสูญเสียสถานะผู้นำโลก ขณะที่กลุ่มประเทศอื่นๆ กำลังก้าวขึ้นมามีบทบาทสำคัญแทน ภูมิทัศน์ทางการเมืองและเศรษฐกิจโลกจะเปลี่ยนแปลงไป
-
การพิมพ์อวัยวะทดแทนอาจกลายเป็นเรื่องปกติ ช่วยแก้ปัญหาการขาดแคลนอวัยวะและยกระดับคุณภาพชีวิต วงการแพทย์จะก้าวหน้าอย่างก้าวกระโดด
-
แนวโน้มการบริโภคเนื้อสัตว์จะลดลง และอาหารจากพืชจะได้รับความนิยมมากขึ้น เพื่อแก้ปัญหาสิ่งแวดล้อมและสุขภาพ อุตสาหกรรมอาหารและการเกษตรต้องเตรียมพร้อมปรับตัว
-
การอพยพย้ายถิ่นฐานขนาดใหญ่อาจส่งผลกระทบต่อสังคมและเศรษฐกิจทั่วโลก ท้าทายระบบการจัดการและความมั่นคง ที่รัฐบาลต่างๆ ต้องเตรียมรับมือ
-
ราคาคาร์บอนจะถูกกำหนดให้สูงขึ้น เพื่อกระตุ้นให้ทุกภาคส่วนลดการปล่อยก๊าซเรือนกระจก ซึ่งอาจส่งผลต่อต้นทุนสินค้าและบริการ ธุรกิจและผู้บริโภคต้องเตรียมรับมือกับภาระค่าใช้จ่ายที่เพิ่มขึ้น
-
มนุษย์อาจเริ่มตั้งรกรากบนดาวอังคาร และเดินหน้าสำรวจอวกาศเพื่อค้นหาสิ่งมีชีวิตนอกโลก เปิดศักราชใหม่ของการเดินทางระหว่างดวงดาว เทคโนโลยีอวกาศจะพัฒนาไปอย่างรวดเร็ว
-
ค่านิยมแบบตะวันตก เช่น เสรีภาพ ประชาธิปไตย อาจถูกตั้งคำถาม นำไปสู่การเปลี่ยนแปลงทางสังคมและวัฒนธรรมครั้งใหญ่ เราต้องเตรียมพร้อมรับมือกับความเปลี่ยนแปลงนี้
Ida Auken นักเคลื่อนไหวด้านสิ่งแวดล้อมชาวเดนมาร์ก ได้เขียนบทความชื่อ “Welcome to 2030” วาดภาพโลกอนาคตอันสวยหรู (สำหรับบางคน) ที่ “ฉันไม่มีอะไรเป็นของตัวเอง ไม่มีสิทธิความเป็นส่วนตัว แต่ชีวิตฉันดีขึ้นกว่าเดิม”
ในโลกใบนี้ การซื้อหาสินค้าและการเป็นเจ้าของกลายเป็นเรื่องเชย เพราะทุกอย่างจะเปลี่ยนเป็นบริการหมด อยากได้อะไรก็แค่ใช้บริการเอา ไม่ว่าจะเป็นที่อยู่อาศัย อาหาร การเดินทาง หรือสิ่งของจำเป็นอื่นๆ Auken อ้างว่าปัญหาต่างๆ ในโลกปัจจุบัน เช่น โรคภัยไข้เจ็บ ภาวะโลกร้อน วิกฤตผู้ลี้ภัย มลพิษ และการว่างงาน จะหมดไป ผู้คนจะมีความสุขกับชีวิตที่ดีกว่าเดิม…แต่ชีวิตแบบนี้ มันคือชีวิตที่เราต้องการจริงๆ หรือ?
คำถามคือ แล้วจะโน้มน้าวให้คนยอมรับระบบแบบนี้ได้ยังไง คำตอบง่ายๆ ก็คือ ต้องมีของล่อใจ WEF เลยโฆษณาว่าโลกใหม่นี้จะมีระบบสาธารณสุขที่ครอบคลุม แถมยังแจก “รายได้พื้นฐานถ้วนหน้า” ให้ทุกคนอีกด้วย ใครบ้างที่ไม่อยากได้เงินใช้ฟรีๆ โดยไม่ต้องทำงาน
นอกจากนี้ยังมีการขายฝันเรื่องเทคโนโลยีชีวภาพที่จะช่วยยืดอายุขัย แถมอาจทำให้เราเป็นอมตะได้อีกต่างหาก ใครๆ ก็อยากมีชีวิตยืนยาวเป็นอมตะจริงไหม แต่ใครล่ะ ที่จะเป็นผู้ควบคุมเทคโนโลยีเหล่านี้ และมีจุดประสงค์แอบแฝงอะไรหรือไม่?
สิ่งที่เขาไม่ได้บอกก็คือ แล้วใครจะเป็นคนปกครองโลกใบนี้ แล้วเราจะแน่ใจได้ยังไงว่าคนพวกนี้จะเป็นคนดี และอำนาจที่มากขึ้นจะยิ่งลดทอนความเป็นคนดีของมนุษย์เสมอ
ต่อให้เป็นคนดีจริงๆ ทำไมคนกลุ่มเล็กๆ ถึงอยากแบ่งปันความมั่งคั่งและเทคโนโลยีสุดล้ำให้กับคนทั่วไป? ทำไมไม่เก็บไว้ใช้เองล่ะ หรือมันคือการ คัดเลือกสายพันธุ์มนุษย์ ในรูปแบบใหม่ โดยใช้ พันธุวิศวกรรม และ ปรัชญาเหนือมนุษย์ เป็นเครื่องมือ ซึ่งสุดท้ายแล้ว คนธรรมดาอย่างเราก็คงไม่มีที่ยืนในโลกใบนี้
โลกอนาคตที่ไร้ทรัพย์สินส่วนตัวและความเป็นส่วนตัว โดยใช้เทคโนโลยีควบคุมภายใต้หน้ากากของความเท่าเทียมและความยั่งยืน แต่บทความนี้ตั้งคำถามถึงความเป็นไปได้ ผลกระทบ และวาระซ่อนเร้นของ WEF โดยเฉพาะอย่างยิ่งการสูญเสียกรรมสิทธิ์ในทรัพย์สิน การควบคุมจากรัฐบาล และการเปลี่ยนแปลงทางสังคม ซึ่งอาจนำไปสู่สังคมนิยมแบบสุดโต่งและการสูญเสียอิสรภาพ You own nothing and be happy.
Mueller, Antony P. “No Privacy, No Property: The World in 2030 According to the WEF.” Mises Wire, 12 Aug. 2020
Siamstr #WEF
-
-
 @ 18bdb66e:82eb5e5d
2024-10-21 23:19:57
@ 18bdb66e:82eb5e5d
2024-10-21 23:19:57Chef's notes
Serve with coleslaw, and chips on the side. Pictured here using English muffin, with a side of mung bean sprouts.
Details
- ⏲️ Prep time: 20 mins
- 🍳 Cook time: 20 mins
- 🍽️ Servings: 4
Ingredients
- ¼ Cup Chopped onion
- 2 TBSP Chopped green pepper
- 1 TBSP butter
- 1 LB Ground beef
- 1 can (10.5 ounce) bean with bacon soup
- ½ Cup water
- ⅓ Cup ketchup
- Hamburger buns, toasted
Directions
- Cook onion and green pepper in butter until tender.
- Add crumbled ground beef, brown
- Add soup, water, and ketchup
- Heat to simmer, stir often for five minutes.
- Spoon on buns, serve.
-
 @ 4ba8e86d:89d32de4
2024-10-24 13:52:57
@ 4ba8e86d:89d32de4
2024-10-24 13:52:57Tecnologia de escalonamento #Bitcoin Layer-2 baseada no conceito de statechains, que permite que chaves privadas para depósitos BTC (UTXOs) sejam transferidas com segurança entre proprietários fora da cadeia.
Mercury Layer é uma implementação de um protocolo statechain de camada 2 que permite a transferência e liquidação fora da cadeia de saídas de Bitcoin que permanecem sob a custódia total do proprietário o tempo todo, enquanto se beneficia de transações instantâneas e de custo zero. A capacidade de realizar esta transferência sem exigir a confirmação (mineração) de transações em cadeia tem vantagens em uma variedade de aplicações diferentes.
um sistema de transferência e controle de propriedade do Bitcoin, especificamente focado em saídas de transações não gastas (UTXOs),
um resumo detalhado dos principais elementos e procedimentos do sistema:
-
Saída de Transação Não Gasta (UTXO): UTXO é a unidade fundamental que representa valor e propriedade no Bitcoin. Cada UTXO é identificado por um ID de transação (TxID) e um número de índice de saída (n) e possui duas propriedades essenciais: valor em BTC e condições de gasto, definidas em um Script. As condições de gasto geralmente envolvem uma chave pública que requer uma transação assinada com a chave correspondente.
-
Transferência de Propriedade sem Transação On-Chain: O sistema permite a transferência de propriedade de UTXOs controlados por uma única chave pública (P) de uma parte para outra sem a necessidade de executar transações na cadeia (on-chain) do Bitcoin ou alterar as condições de gasto. Isso é facilitado por um mecanismo chamado "Statechain Entity" (SE).
-
Compartilhamento de Chave Privada: A chave privada (s) para a chave pública P é compartilhada entre o SE e o proprietário. No entanto, nenhuma das partes conhece a chave privada completa. Isso requer cooperação entre o proprietário e o SE para gastar o UTXO.
-
Atualização/Transferência de Chave: A propriedade do UTXO pode ser transferida para um novo proprietário através de um processo de atualização de chave. Isso envolve a substituição do compartilhamento de chave privada do SE para que corresponda ao compartilhamento de chave do novo proprietário, tudo sem revelar compartilhamentos de chave ou a chave privada completa.
-
Transações de Backup: Além da transferência de propriedade, o sistema inclui transações de backup que podem ser usadas para reivindicar o valor do UTXO pelo atual proprietário, caso o SE não coopere ou desapareça. Essas transações são assinadas cooperativamente pelo proprietário atual e pelo SE e possuem um bloqueio de tempo (nLocktime) que permite a recuperação dos fundos em uma altura de bloco futura especificada.
-
Mecanismo de Redução do Backup de Timelock: Para limitar o número de transferências possíveis durante um período de tempo, o sistema utiliza um mecanismo de decremento do nLocktime. O usuário é responsável por enviar as transações de backup no momento adequado.
-
Cadeias Estaduais (Statechains): O sistema opera usando cadeias estaduais, que são uma camada adicional que permite a transferência de propriedade de UTXOs. O SE precisa seguir o protocolo, mas não armazena informações sobre compartilhamentos de chave anteriores.
-
Cegagem (Blinding): O servidor da camada Mercury (SE) é cego, o que significa que não tem conhecimento das moedas que está assinando. Isso é alcançado através do uso de criptografia de chave pública para ocultar informações de chave privada compartilhada entre as partes.
-
Protocolo de Camada Mercury: O protocolo detalha os procedimentos desde o depósito inicial até a transferência de propriedade, atualizações de chave, retiradas ordenadas e recuperação de backup.
-
Recuperação de Backup: Caso o SE não coopere ou desapareça, o proprietário atual pode recuperar os fundos, enviando a transação de backup quando o nLocktime for atingido.
-
Publicação de Compartilhamento de Chaves: O SE não tem acesso aos IDs de transação individuais das moedas, mas publica compartilhamentos de chaves públicas para cada moeda na lista de ativos. Essa lista é comprometida com a blockchain para provar a exclusividade da propriedade.
Este sistema é projetado para fornecer uma maneira segura e eficiente de transferir e controlar a propriedade do Bitcoin, permitindo a recuperação de fundos em caso de problemas com o servidor.
No sistema de controle de propriedade de saídas de transações não gastas (UTXOs), cada UTXO é uma chave compartilhada composta por duas partes: o proprietário e o servidor de compartilhamento. Juntos, eles colaboram para criar transações de backup com bloqueio de tempo, que transferem a propriedade da UTXO para o novo proprietário. Durante essa transferência, a chave pública compartilhada permanece inalterada, mas o compartilhamento da chave do servidor é atualizado por meio de um Protocolo de Computação Multifuncional (MPC) para se alinhar apenas com o novo proprietário. Essa atualização resulta na criação de uma nova transação de backup, direcionada à chave pública do novo proprietário, com um tempo de bloqueio mais curto.
A confiabilidade do servidor é essencial, pois ele é responsável por excluir o compartilhamento de chave anterior. Isso garante que não seja possível conspirar com os proprietários anteriores. O proprietário atual pode gastar a UTXO a qualquer momento, desde que o faça em cooperação com o servidor. No entanto, se o servidor for desligado ou desaparecer, o proprietário atual deve aguardar até que o tempo de bloqueio expire antes de enviar sua transação de backup.
É importante ressaltar que o remetente nunca possui a chave privada completa; ele possui apenas uma parte do compartilhamento. Assim, todas as transações requerem a assinatura conjunta do servidor. Quando a UTXO é transferida para um novo proprietário, o compartilhamento do servidor é atualizado para que ele não possa mais assinar em nome do proprietário anterior, apenas em nome do novo proprietário. Esse sistema de transações de backup com bloqueio de tempo é projetado para proteger contra cenários de não cooperação ou apreensão do servidor, garantindo a segurança das UTXOs e a integridade da rede.
https://github.com/layer2tech/mercury-wallet
https://mercurylayer.com/
https://twitter.com/TTrevethan/status/1689929527420387328?t=0f5oF6w_ZRjWRYGah3HX8Q&s=19
-
-
 @ 18bdb66e:82eb5e5d
2024-10-21 23:04:53
@ 18bdb66e:82eb5e5d
2024-10-21 23:04:53Chef's notes
Use slotted spoon to place green beans on toast.
Details
- ⏲️ Prep time: 20 mins
- 🍳 Cook time: 20 mins
- 🍽️ Servings: 4
Ingredients
- ¼ cup Chopped onion
- 2 TBSP butter
- 1 Can (10 ½ ounces) condensed cream of chicken soup.
- ⅓ cup milk
- 1 can (5 ounce) chicken, or 1 cup diced cooked chicken
- 2 boiled eggs, sliced
- 4 Slices of toast
- French style green beans, cooke
Directions
- Cook onion in butter until soft, not brown
- Mix soup, milk, chicken, and most eggs, add to onion. (Reserve some egg for garnish)
- Heat through stirring often.
- Heat beans, divide equally and spoon on toast.
- Top beans with chicken.
- Garnish with remaining egg.
-
 @ 3c984938:2ec11289
2024-07-22 11:43:17
@ 3c984938:2ec11289
2024-07-22 11:43:17Bienvenide a Nostr!
Introduccíon
Es tu primera vez aqui en Nostr? Bienvenides! Nostr es un acrónimo raro para "Notes and Other Stuff Transmitted by Relays" on un solo objetivo; resistirse a la censura. Una alternativa a las redes sociales tradicionales, comunicaciónes, blogging, streaming, podcasting, y feventualmente el correo electronico (en fase de desarrollo) con características descentralizadas que te capacita, usario. Jamas seras molestado por un anuncio, capturado por una entidad centralizada o algoritmo que te monetiza.
Permítame ser su anfitrión! Soy Onigiri! Yo estoy explorando el mundo de Nostr, un protocolo de comunicacíon decentralizada. Yo escribo sobre las herramientas y los desarolladores increíbles de Nostr que dan vida a esta reino.

Bienvenides a Nostr Wonderland
Estas a punto de entrar a un otro mundo digtal que te hará explotar tu mente de todas las aplicaciones descentralizadas, clientes, sitios que puedes utilizar. Nunca volverás a ver a las comunicaciones ni a las redes sociales de la mesma manera. Todo gracias al carácter criptográfico de nostr, inpirado por la tecnología "blockchain". Cada usario, cuando crean una cuenta en Nostr, recibe un par de llaves: una privada y una publico. Estos son las llaves de tu propio reino. Lo que escribes, cantes, grabes, lo que creas - todo te pertenece.

Unos llaves de Oro y Plata
Mi amigo y yo llamamos a esto "identidad mediante cifrado" porque tu identidad es cifrado. Tu puedes compartir tu llave de plata "npub" a otros usarios para conectar y seguir. Utiliza tu llave de oro "nsec" para accedar a tu cuenta y exponerte a muchas aplicaciones. Mantenga la llave a buen recaudo en todo momento. Ya no hay razor para estar enjaulado por los terminos de plataformas sociales nunca más.
Onigirl
npub18jvyjwpmm65g8v9azmlvu8knd5m7xlxau08y8vt75n53jtkpz2ys6mqqu3Todavia No tienes un cliente? Seleccione la mejor opción.
Encuentra la aplicación adecuada para ti! Utilice su clave de oro "nsec" para acceder a estas herramientas maravillosas. También puedes visit a esta pagina a ver a todas las aplicaciones. Antes de pegar tu llave de oro en muchas aplicaciones, considera un "signer" (firmante) para los sitios web 3. Por favor, mire la siguiente imagen para más detalles. Consulte también la leyenda.

Get a Signer extension via chrome webstore
Un firmante (o "signer" en inglés) es una extensión del navegador web. Nos2x and NostrConnect son extensiónes ampliamente aceptado para aceder a Nostr. Esto simplifica el proceso de aceder a sitios "web 3". En lugar de copiar y pegar la clave oro "nsec" cada vez, la mantienes guardado en la extensión y le des permiso para aceder a Nostr.

👉⚡⚡Obtén una billetera Bitcoin lightning para enviar/recibir Zaps⚡⚡ (Esto es opcional)

Aqui en Nostr, utilizamos la red Lightning de Bitcoin (L2). Nesitaras una cartera lightning para enviar y recibir Satoshis, la denominacion mas chiquita de un Bitcoin. (0.000000001 BTC) Los "zaps" son un tipo de micropago en Nostr. Si te gusta el contenido de un usario, es norma dejarle una propina en la forma de un ¨zap". Por ejemplo, si te gusta este contenido, tu me puedes hacer "zap" con Satoshis para recompensar mi trabajo. Pero apenas llegaste, as que todavia no tienes una cartera. No se preocupe, puedo ayudar en eso!
"Stacker.News" es una plataforma donde los usarios pueden ganar SATS por publicar articulos y interactuar con otros.

Stacker.News es el lugar mas facil para recibir una direccion de cartera Bitcoin Lightning.
- Acedese con su extensión firmante "signer" - Nos2x or NostrConnect - hace click en tu perfil, un codigo de letras y numeros en la mano superior derecha. Veás algo como esto

- Haga clic en "edit" y elija un nombre que te guste. Se puede cambiar si deseas en el futuro.

- Haga clic en "save"
- Crea una biografía y la comunidad SN son muy acogedora. Te mandarán satoshi para darte la bienvenida.
- Tu nueva direccion de cartera Bitcoin Lightning aparecerá asi
 ^^No le mandas "zaps" a esta direccion; es puramente con fines educativos.
^^No le mandas "zaps" a esta direccion; es puramente con fines educativos. - Con tu Nueva dirección de monedero Bitcoin Lightning puedes ponerla en cualquier cliente o app de tu elección. Para ello, ve a tu página de perfil y bajo la dirección de tu monedero en "Dirección Lightning", introduce tu nueva dirección y pulsa "guardar " y ya está. Enhorabuena.
👉✨Con el tiempo, es posible que desee pasar a las opciones de auto-custodia y tal vez incluso considerar la posibilidad de auto-alojar su propio nodo LN para una mejor privacidad. La buena noticia es que stacker.news tambien está dejando de ser una cartera custodio.
⭐NIP-05-identidad DNS⭐ Al igual que en Twitter, una marca de verificación es para mostrar que eres del mismo jardín "como un humano", y no un atípico como una mala hierba o, "bot". Pero no de la forma nefasta en que lo hacen las grandes tecnológicas. En el país de las maravillas de Nostr, esto te permite asignar tu llave de plata, "npub", a un identificador DNS. Una vez verificado, puedes gritar para anunciar tu nueva residencia Nostr para compartir.
✨Hay un montón de opciones, pero si has seguido los pasos, esto se vuelve extremadamente fácil.
👉✅¡Haz clic en tu "Perfil ", luego en "Configuración ", desplázate hasta la parte inferior y pega tu clave Silver, "npub!" y haz clic en "Guardar " y ¡listo! Utiliza tu monedero relámpago de Stacker.news como tu NIP-05. ¡¡¡Enhorabuena!!! ¡Ya estás verificado! Dale unas horas y cuando uses tu cliente "principal " deberías ver una marca de verificación.
Nostr, el infonformista de los servidores.
 En lugar de utilizar una única instancia o un servidor centralizado, Nostr está construido para que varias bases de datos intercambien mensajes mediante "relés". Los relés, que son neutrales y no discriminatorios, almacenan y difunden mensajes públicos en la red Nostr. Transmiten mensajes a todos los demás clientes conectados a ellos, asegurando las comunicaciones en la red descentralizada.
En lugar de utilizar una única instancia o un servidor centralizado, Nostr está construido para que varias bases de datos intercambien mensajes mediante "relés". Los relés, que son neutrales y no discriminatorios, almacenan y difunden mensajes públicos en la red Nostr. Transmiten mensajes a todos los demás clientes conectados a ellos, asegurando las comunicaciones en la red descentralizada.¡Mis amigos en Nostr te dan la bienvenida!
Bienvenida a la fiesta. ¿Le apetece un té?🍵

¡Hay mucho mas!
Esto es la punta del iceberg. Síguenme mientras continúo explorando nuevas tierras y a los desarolladores, los caballeres que potencioan este ecosistema. Encuéntrame aquí para mas contenido como este y comparten con otros usarios de nostr. Conozca a los caballeres que luchan por freedomTech (la tecnología de libertad) en Nostr y a los proyectos a los que contribuyen para hacerla realidad.💋
Onigirl @npub18jvyjwpmm65g8v9azmlvu8knd5m7xlxau08y8vt75n53jtkpz2ys6mqqu3
🧡😻Esta guía ha sido cuidadosamente traducida por miggymofongo
Puede seguirla aquí. @npub1ajt9gp0prf4xrp4j07j9rghlcyukahncs0fw5ywr977jccued9nqrcc0cs
sitio web
- Acedese con su extensión firmante "signer" - Nos2x or NostrConnect - hace click en tu perfil, un codigo de letras y numeros en la mano superior derecha. Veás algo como esto
-
 @ 9e69e420:d12360c2
2024-10-24 13:10:08
@ 9e69e420:d12360c2
2024-10-24 13:10:08Kamala Harris delivered a sharp critique of Donald Trump, comparing him to Adolf Hitler during a recent speech. She referenced comments made by former Chief of Staff John Kelly, who disclosed that Trump expressed admiration for Hitler while in office.
![Kamala Harris] (https://i.nostr.build/iyRm5cJo9YuRgh3M.png)
Harris stated, "It is deeply troubling and incredibly dangerous that Donald Trump would invoke Adolf Hitler."
She warned that if re-elected, Trump could seek unchecked power and compare him to a dictator. Harris emphasized the importance of understanding Trump's intentions and the implications for America’s future. Her remarks coincided with the fast-approaching election, intensifying her campaign's rhetoric against Trump.
-
 @ a10260a2:caa23e3e
2023-08-14 21:36:14
@ a10260a2:caa23e3e
2023-08-14 21:36:14It seems like blogstack is meant to replace Substack if not already apparent by the name. If that's the case, it's already better in a few ways.
1. Hit the ground running
I'm already getting started out of the gate with more readers than I would have if I just started a Substack. This, of course, is due to the fact that I'm creating on top of a protocol where I'm able to have the same audience across all clients of that protocol. This is in stark contrast to the legacy apps from centralized entities where you have to corral your audience from one platform to the next.
2. Readers need not subscribe
Technically, if you're following me, you're subscribed. But you don't have to subscribe for a set price and amount of time (e.g. $5/month or $50/year). I believe this is a win for both of us as I can write my best notes and you can choose to reward me as you see fit. Value 4 value.
3. More conducive to conversation
Writing on Substack felt like writing into a void, with little to no feedback. A post shows up in my readers' inbox and I'll see some stats on whether it was opened or not. That's it. Based on what I've seen so far, blog posts created on Nostr appear in the client apps (e.g Damus, Primal, and Plebstr) as just another note, but with nice formatting and such. From there, I can receive zaps, shakas, comments, and even be reposted.
This is just the beginning. Right now, I'm using blogstack. But what's to stop me from using another tool down the line? I'll have the ability to do so by simply connecting my private key. Can't wait to see what new tools are created down the line.
So ₿ULLISH on #Nostr
-
 @ 3bf0c63f:aefa459d
2024-06-19 16:13:28
@ 3bf0c63f:aefa459d
2024-06-19 16:13:28Estórias
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ ff18165a:dd7ca7f0
2024-10-19 18:23:51
@ ff18165a:dd7ca7f0
2024-10-19 18:23:51Chef's notes
- DO NOT add too much Peppermint Extract! It’s extremely strong and it will make your milkshake way too strong if you add more than a few drops.
- Feel free to be creative with your toppings. We used Caramel Flavored Whipped Topping and it turned out great!
Details
- ⏲️ Prep time: 5 min
- 🍳 Cook time: 2 min
- 🍽️ Servings: 1
Ingredients
- 1 1/2 cup Milk
- 2 drops Peppermint Extract
- 2 packets Stevia
- 1 cup Ice
- 2 drops Green Food Coloring
- Green Sprinkles
- 1 Crushed Peppermint Candy
- 2 Mint Leaves
Directions
-
- Blend together until smooth and frothy
-
- Pour into a tall glass
-
- Top with listed toppings
-
- Add straw and enjoy
-
 @ ff6187a2:ddbe1be7
2024-10-24 12:54:45
@ ff6187a2:ddbe1be7
2024-10-24 12:54:45Happy Halloween
-
 @ fd208ee8:0fd927c1
2024-10-20 18:19:48
@ fd208ee8:0fd927c1
2024-10-20 18:19:48(Please note that this is not official financial or business advice, but rather a description of something we have done, on an informal basis.)
A long, long time ago
It's been nearly a year, since nostr:nprofile1qydhwumn8ghj7argv4nx7un9wd6zumn0wd68yvfwvdhk6tcpypmhxue69uhkummnw3ezuetfde6kuer6wasku7nfvuh8xurpvdjj7qpqs3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqv5atj2 came into being, mostly as a lark, involving a couple of members of our private chat group. Our initial plan was to work toward bounties, but Nostr bounties are a bit of a biased, uncertain thing, and our enthusiasm for that quickly waned.
So, what to do? Here we are, we three (nostr:npub1ecdlntvjzexlyfale2egzvvncc8tgqsaxkl5hw7xlgjv2cxs705s9qs735, nostr:npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn, and I): IT professionals with little time, but plenty of intellectual energy, a Slack chat, a GitHub repo, and lots of frustration with the Nostr status quo.
We were, you see, Nostr end-users. We loved the idea of the protocol, but we were being regularly stymied by the poor quality of many implementations.
- Why can I not login? Oh, they fixed the login! Nope, still can't login.
- If I press this button, it says it sent, but it didn't send. Where note?
- They announced a new feature, but I tried it and it didn't work. Oh well.
- I noticed a bug in the client, reported it, and the issue is just rotting away in the project repo. Ignored.
- The website/relay/repo was here... yesterday. Today it has disappeared, and taken my zaps with it.
It was enough to make us want to tear our hair out. We decided that what Nostr needed... what it really needed... was a Nostr Stable Version. Nothing glamorous. Nothing exotic. Nothing busy or excitable. Just something that stayed where you initially found it, ran, and actually worked. Something where you could report a bug and receive a prompt response. Maybe even something, where you could pay a reasonable fee and be allowed to have expectations of some particular service being returned. And who better to build such a version, than people who want to use it, themselves?
Things working is an underrated concept
I know that the very idea of software running as expected and websites not appearing and disappearing suddenly, based upon what some particular developer had for lunch, tends to be met with little but scorn, from hardened, seasoned Nostriches (who are convinced that bugs are all features), but I think the majority of potential users would see it differently.
I'm with the majority, on this one.
I like to click "save" buttons and have them save. If I publish something, I want it to appear under my list of published somethings. I like to type in the website address I always type in, and have it magically appear on my screen, as if there were a little man sitting at controls in my laptop, just waiting for me to write H-T-T-P-S... and then jump to attention.
My unreasonable expectations have no bounds, it is true. But unreasonable people are also people, so we would also like to have our own unreasonable things to play with. Scorn away. My save button will save, and my published something will publish, and my website will load every damn time, just to spite you.
In the larger scheme of things, you see, we win even if we fail, if we at least increase the competition enough, that things working becomes the new standard. We can simply prove, definitively, that it is possible for Nostr things to work, if they are built by people who care if they work. If we also have fun together, learn something new, and come up with some cool, novel use cases, then that's pure profit.
We can only win, at this endeavor.
Where to start?
Name that brand
So, we had a team, we had a business idea, and we had a heck of a lot of motivation. What we didn't have, is a name. (Never underestimate the importance of naming things.)
We decided to name ourselves "GitCitadel" because "git" sounds techy, hints at our GitRepublic project, and is reminiscent of open-source development, and "citadel" reminds us of Bitcoin. The republic is at home in the citadel, naturally. All other products also live in the same citadel, hence the naming-convention of prefacing everything with "GC" (i.e. "GC Alexandria", "GC Sybil", "GC Aedile", etc.).
Brand yourself
The next thing we did, was rent a domain and run a webserver on it. This is an important step because it gives you an Internet presence, allows you to have company NIP-05 and email addresses (a form of promotion), and it's simply exciting to have one. Feels so much more "official" and it helps increase the name-recognition of your company.
Define yourself
We then sat down, together, over the Internet, and figured out who we are. Not who we individually are, but who we are, as a company. A company, after all, (according to the Cambridge Dictionary) is "an organization that produces or sells goods or services in order to make a profit". Now, a company's profits don't have to be monetary, but they should be something tangible. A company, in other words, is a team of people working toward some defined goal.
What is our goal? Well, we decided to think it over, sat down with the newer additions to the company (you can see who they are, on our project wiki page, and came up with a Vision and a Mission:
The vision is what the overall goals of the company are, whereas the mission describes how those goals shall be achieved. Now, this is a sort of lofty, abstract statement, so it was important that we posted it someplace publicly (to keep ourselves accountable) and look at it regularly, so that we can ponder it and realign whatever we are currently working on, with this statement. We know the statement is well-designed, if considering it helps us make decisions about what to do next.
Pay yourselves
(I'm going to switch from "we" to "you", here, as it's easier to write this part, but let's just pretend I didn't.)

The next thing on the list, is to arrange the finances, usually by setting up a Geyserfund, with an associated wallet, and then deciding how the funds from the wallet will be dispersed or stored. (I won't tell you how we are handling that, as that's internal company business, but I'm sure you'll think of something clever, yourselves. Or just google it.)
I would encourage you to arrange to pay yourselves profits. Not merely because your idea is going to make you all fabulously wealthy and internationally famous (although, that is obviously true), but because profits are the most pure form of communication that consumers in the market have with its producers, and one of the best ways to make decisions and measure increases in efficiency (increasing profits and/or output, while keeping prices steady or falling).
Cutting off this signal, in order to look pious to outsiders, is to shoot yourself in your free-market foot. Nobody says that you have to spend your profits on the proverbial lambo and a bimbo. You could donate them to charity, reinvest them, or store them for your nephews to inherit, but pay them out, you should. You don't have to love money, to value it as a tool and use it shrewdly. Money is a measure, and companies should regularly measure themselves: against their previous state, against their potential state, and against their competition.
(Also, you can use money to buy a lambo and a bimbo, but you didn't hear that from me.)
Organize yourselves
Once you've been working together, for a while, you'll find that you need to figure out how to organize yourselves. The first step is to...
Form a board of directors.
Stop laughing. I'm serious.
Any company has at least two roles (President and Secretary), ideally held by two different people, so any single-proprietor company is a man down. Find a different person, to be your Second, even if they're just your confident, who lets you cry on your shoulder on The Bad Days, when your code refuses to compile, and can tell people that you've become a Bitcoin millionaire and have gone on a sabbatical to hike the Himalayas and will be back in 3 months on The Very Good Days. Because business man was not meant to be alone.
If, like us, you're a small herd of people and have already been working together for a while, then this step is actually really, really fun. Just think about what people are already doing, and put a label on it. That role is now defined and it is clear who is in charge of what.
Scientists become "Chief Science Officer" or "Scientific Advisor". The person who always writes the okay, so this is what we've decided comment in the thread becomes the Secretary, the one managing the Lightning wallet and worrying over paying for the servers is the CFO, the person running the remote server becomes the CTO, and so on and etc.
And everyone knows who the CEO is. Everyone always knows. They do. Just write it down.
Agree how to disagree
Now, have the secretary write up a Member's Agreement. It's a contract between the members, about whatever the group thinks is important concerning the way the company will operate. According to Investopedia, common topics are:

Is this legally binding? Probably not. Maybe. I don't know and wouldn't tell you, even if I did. But it's emotionally binding, which is arguably more important.
Writing things down is an advanced form of naming things and it provides clarity, helps to manage expectations, and allows you to define a working agreement before Real Money shows up and taints your interaction. You're just accepting tips, at the moment. Everyone is calm and cheerful, so now is your best time to negotiate.
Keep it very simple and only address the most basic things. If you wish to incorporate, at a later date, then you just take this to a registered agent, or other experienced person, and have them tidy up any loose ends and add the fine print.
Go forth, together
This has probably taken you weeks, or even months, but you're now a company. Get a logo and a company npub, start dropping the company name into your notes, and get on with the business of being in business.
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ d5c3d063:4d1159b3
2024-10-24 14:58:48
@ d5c3d063:4d1159b3
2024-10-24 14:58:48“การลงทุน เป็นบาปหรือไม่” ประเด็นที่น่าสงสัย ในโลกการเงินที่ขับเคลื่อนด้วยกิเลส
CDC Talk EP3 นำเสนอมุมมองที่น่าสนใจ โดยอาจารย์พิริยะและลุงโฉลกที่ได้ผสานหลักธรรมะเข้ากับโลกการเงินอย่างลึกซึ้ง
https://image.nostr.build/2e6fbf0fe27536acfc4e02b351572b6b4a2493b7980b65c8e4d4fcef60b3ea46.jpg .
ลุงโฉลกอธิบายด้วยหลัก “มรรคมีองค์ 8” การตัดสินว่าการกระทำใดดีหรือชั่ว ต้องดูที่เจตนาและองค์ประกอบอื่นๆ เหมือนกับมรรค 8 ไม่ใช่แค่หลักปฏิบัติ 8 ข้อที่แยกจากกัน แต่เป็นองค์ประกอบ 8 ประการที่สัมพันธ์กัน ตั้งแต่สัมมาทิฐิถึงสัมมาสมาธิ ดังนั้นการจะบอกว่าอาชีพใดเป็นสัมมาอาชีพหรือมิจฉาอาชีพ จึงต้องพิจารณาองค์ประกอบทั้งหมด โดยเฉพาะ “เจตนา” ในขณะนั้น แม้แต่คำว่า “ศรัทธา” หากปราศจาก “ปัญญา” ก็เป็นเพียงความงมงาย เช่นเดียวกับการลงทุน หากมีแต่ความเชื่อแต่ขาดความรู้ความเข้าใจ ก็อาจนำไปสู่การตัดสินใจที่ผิดพลาดได้ ทางชมรมโฉลกจึงมีธรรมเนียมในการทำบุญด้วยเงิน 108 บาท เพื่อย้ำเตือนให้สมาชิกชมรมลงทุนโดยไม่ยึดติดกับความร่ำรวย เพราะหากมุ่งหวังแต่ความมั่งคั่ง ก็จะเป็นการลงทุนที่ตั้งอยู่บนโลภะ ซึ่งเป็นอกุศลมูลจิต .
ลุงโฉลกอธิบายเรื่องเจตนาด้วยตัวอย่างของการอธิษฐาน ท่านชี้ว่าการอธิษฐานให้เกิดผลต้องมี "สัจจะ" เป็นพื้นฐาน เช่นเดียวกับ "สัมมาอาชีวะ" ที่ต้องมีสัมมาทิฐิและสัมมาสังกัปปะนำทาง แล้ววาจา การกระทำ และอาชีพจึงจะเป็นสัมมาได้อย่างแท้จริง ตัวอย่างเรื่องของการกวาดลานวัด หากทำด้วยจิตใจที่เบิกบานก็เป็นสัมมาอาชีพ แต่หากทำด้วยจิตใจเศร้าหมองก็อาจเป็นมิจฉาอาชีพ เช่นเดียวกับการลงทุน หากทำด้วยความโลภก็อาจเป็นมิจฉาอาชีพ แต่หากลงทุนด้วยความเข้าใจมีสติและเจตนาที่ดี เช่น การลงทุนเพื่อสร้างคุณค่าให้สังคม ก็เป็นสัมมาอาชีพได้ .
อาจารย์พิริยะเสริมว่า หลายคนมองตลาดหุ้นเป็น Zero-Sum Game คือคิดว่ากำไรของคนหนึ่งจะต้องมาจากการขาดทุนของอีกคนหนึ่งเสมอ ไม่ต่างอะไรกับการขโมยมาเลย....อาจารย์พิริยะบอกว่า เป็นความเข้าใจที่คลาดเคลื่อน เพราะตลาดหุ้นมีบทบาทสำคัญในการขับเคลื่อนเศรษฐกิจ โดยทำหน้าที่เป็นตัวกลางระดมทุนให้ธุรกิจ นำไปสู่การสร้างผลิตภัณฑ์และบริการ สร้างงานสร้างรายได้และสร้างคุณค่าให้สังคม นอกจากนี้ตลาดยังเป็นพื้นที่สำหรับการแลกเปลี่ยนและบริหารความเสี่ยง ที่สำคัญคือตลาดเป็นกลไกสำคัญในการค้นหาราคาที่เหมาะสม ซึ่งเกิดจากปฏิสัมพันธ์ระหว่างผู้ซื้อและผู้ขาย โดยการตัดสินใจซื้อขายในตลาดนั้นเกิดขึ้นโดยสมัครใจ กลไกราคานี้เองที่ช่วยให้เศรษฐกิจหมุนเวียนได้อย่างมีประสิทธิภาพและทำให้ทุกคนรับรู้ถึงความต้องการของตลาด เพื่อนำไปสู่การปรับตัวและพัฒนาอย่างต่อเนื่อง
. ลุงโฉลกเน้นย้ำว่า การลงทุนที่ดีต้องมี “สัมมาทิฐิ” มองเห็นคุณค่าที่แท้จริง ไม่ใช่แค่แสวงหากำไร แล้วต้องรู้จัก “พอ” ตามหลัก “สันโดษ” ซึ่งไม่ได้หมายถึงการมักน้อย แต่หมายถึงการ “พอใจในสิ่งที่ตนมีอยู่” ที่ไม่ปล่อยให้ “ตัณหา” ครอบงำ ดังพุทธสุภาษิต “นตฺถิ ตณฺหาสมา นที” ไม่มีแม่น้ำใดกว้างใหญ่เท่าตัณหา เพราะหากปล่อยให้ความโลภครอบงำ ก็ยากที่จะประสบความสำเร็จอย่างยั่งยืน ท่านยังได้อธิบายหลักอริยสัจ 4 เพื่อให้เห็นว่าความทุกข์ในการลงทุนนั้นเกิดจากความอยาก และการเข้าใจความจริงของชีวิตตามหลักอริยสัจ 4 นี้เอง จะเป็นหนทางสู่การลงทุนอย่างมีสติ
สรุปแล้ว การลงทุนไม่ใช่บาปหรือบุญในตัวมันเอง แต่ขึ้นอยู่กับเจตนาของนักลงทุนเป็นสำคัญ ลงทุนด้วยใจที่บริสุทธิ์ การลงทุนไม่ใช่เรื่องของผลกำไรเพียงอย่างเดียว แต่เป็นเรื่องของการพัฒนาจิตใจ รู้จักประมาณและการมีสติ ซึ่งเป็นพื้นฐานสำคัญสู่ความสำเร็จและความสุขที่ยั่งยืน ไม่ว่าจะในโลกการลงทุนหรือการใช้ในชีวิตประจำวันก็ตาม
CDCTalk #Siamstr
-
 @ 9e69e420:d12360c2
2024-10-24 11:51:32
@ 9e69e420:d12360c2
2024-10-24 11:51:32Dr. Johanna Olson-Kennedy, a leading advocate for trans youth care, withheld a $10 million study funded by taxpayers on the effects of puberty blockers, which found no improvement in mental health among participants.
She feared the findings would be "weaponized" against transgender care. Critics argue that her decision violates research standards and denies vital information to the public. The study tracked 95 children, revealing that 25% had mental health issues prior to treatment, contradicting Olson-Kennedy's claims of good overall mental health. Experts stress the importance of publishing research regardless of outcomes.
Sauce: https://nypost.com/2024/10/23/us-news/doctor-refused-to-publish-trans-kids-study-that-showed-puberty-blockers-didnt-help-mental-health/
-
 @ d3f06d83:7ff53dc3
2024-10-15 00:30:10
@ d3f06d83:7ff53dc3
2024-10-15 00:30:10Chef's notes
This is the beginning of a great pizza.
Details
- ⏲️ Prep time: 15 min
- 🍳 Cook time: 0
- 🍽️ Servings: 0
Ingredients
- 1 cup of pizza flour or bakery flour (00 flour)
- 1 zatchet of yeast (7g)
- 1 cup of water
- 1 spoon of honey (or sugar)
- 2 Litre container with a lid
Directions
- Pour the water in a 2L container
- Add honey/sugar and stir
- Add the yeast and stir. Wait 15 minutes or until the yeast is active (bubbling)
- Slowly mix the flour avoiding clumps
- Close the lid and leave in the fridge overnight
-
 @ 76c71aae:3e29cafa
2024-06-17 00:57:57
@ 76c71aae:3e29cafa
2024-06-17 00:57:57I wanted to take a moment to address the recent Business Insider article about Jack Dorsey’s funding of Nostr. While the article has inaccuracies and it lacks nuance, this piece it’s also an invitation to all of us to discuss Nostr openly.
Is the article true? First things first: We do not actually know fiatjaf’s identity so we cannot weigh in on the veracity of who he is. His real identity remains a mystery to us. While we do not share Fiatjaf’s beliefs, he’s always been clear that Nostr was built to support all types of speech, even the stuff he personally disagrees with. That’s a fundamental principle of the platform.
Why is Nos built on a protocol that was built by someone who supports fascists? Let’s clear up a major point of confusion.Merriam Webster defines fascism as: a political philosophy, movement, or regime (such as that of the Fascisti) that exalts nation and often race above the individual and that stands for a centralized autocratic government headed by a dictatorial leader, severe economic and social regimentation, and forcible suppression of opposition.
Based on that definition, fascism is then a centralized autocratic government led by a dictatorial leader, enforcing several economic and social regimentation, and suppressing opposition. Nostr, on the other hand, is designed to prevent centralized control altogether. It’s a decentralized network where no single entity has ultimate power.
Nostr is designed so there is no central authority of control. By distributing content across multiple relays, the architecture of Nostr eliminates the possibility of centralized autocratic control.
Nos chose to build an app on the Nostr protocol because traditional corporate social media platforms often stifle views outside the mainstream, these also include views of leftist activists, LGBTQ community, and others. This stifling takes the form of shadow banning when people use terms that the platform doesn’t want to support such as abortion. More recently there has been an uptick in account suspensions and shadow bannings as people use reporting tools to flag accounts that support Gaza. Often the people flagging are looking at older posts and flagging those to get the accounts shutdown.
On the other hand, Nos is about giving users control over their accounts, identities, and feeds. Nostr makes this possible in a way no other protocol does today. At Nos, we are committed to building an app using tools that put the user in charge and Nostr enables this user-first approach.This means that everybody has something to say, and we may not like it.
How does Nos reconcile being on a network that can’t ban people for their views? Unlike corporate social media, such as Facebook, Instagram and TikTok, Nostr is built on the idea of a web of trust, meaning you only see the content from the people you follow. There are no algorithms pushing sensational content to keep you glued to your screen. Corporate platforms thrive on “engagement” and are optimized for eyeballs and time on site. Over the years, the algorithms have learned that the content that is most engaging is content that induces moral outrage in the viewer.
As a result, the corporate platforms feed users more and more morally outrageous content to keep them online. As mentioned before, Nostr operates on a different principle. It’s built on a web of trust, where you only see content from people you follow: Nos and most of the other Nostr clients do not have algorithm-driven feeds, instead content from the people you follow appears in reverse chronological order in your feed. Those clients that do have algorithmic feeds today show the most popular content, but are not optimizing for morally outrageous content.
This means that it is much more difficult for toxic, hateful content to go viral as there’s no behind-the-scenes mechanism amplifying content for views similar to what you have on Youtube and X today. You won’t find the same amplification of divisive content here that you see on these traditional platforms.
Nos offers the ability to have “Freedom from” unwanted content at the user level. There is no central authority shutting down one account or another or blocking certain accounts.
This is especially important for activists. At present on Mastodon and other ActivityPub servers, we are witnessing pro-Palestinian activists accounts’ being blocked from certain servers. While happening at a smaller level, this is still a form of shutting down the dialogue and conversation.I get it –after more than a decade of algorithmic fueled hot-takes and virtue signaling on X (formerly Twitter), it might be a bit difficult to conceive of a social media experience where dialogue exists, but the network that has evolved on top of Nostr is that space. Yes, as difficult as it sounds, Nostr allows for dialogue without central censorship.
Many folks disagree on Nostr in the same way disagreements used to happen on Twitter (now X) in the early days, where there are long text based dialogues. Folks may walk away still disagreeing and a small subset get nasty, but those conversations do not spiral out of control in the same way they do on X or even on Mastodon and Bluesky today.
And if things get ugly, Nos and a few other apps have user-led moderation tools to help mitigate anything that comes into replies or mentions. Nos is leading efforts to enhance user-led moderation across the network.
This discussion is crucial. We have the chance to reshape the future of decentralized social media and we can build a more open and inclusive digital space. The pathway is and will be messy. How do we balance free speech while protecting users from harmful content? What role should decentralization play in the next generation of social media platforms? I’d love to hear your thoughts and keep this conversation going.
-
 @ 3bf0c63f:aefa459d
2024-06-13 15:40:18
@ 3bf0c63f:aefa459d
2024-06-13 15:40:18Why relay hints are important
Recently Coracle has removed support for following relay hints in Nostr event references.
Supposedly Coracle is now relying only on public key hints and
kind:10002events to determine where to fetch events from a user. That is a catastrophic idea that destroys much of Nostr's flexibility for no gain at all.- Someone makes a post inside a community (either a NIP-29 community or a NIP-87 community) and others want to refer to that post in discussions in the external Nostr world of
kind:1s -- now that cannot work because the person who created the post doesn't have the relays specific to those communities in their outbox list; - There is a discussion happening in a niche relay, for example, a relay that can only be accessed by the participants of a conference for the duration of that conference -- since that relay is not in anyone's public outbox list, it's impossible for anyone outside of the conference to ever refer to these events;
- Some big public relays, say, relay.damus.io, decide to nuke their databases or periodically delete old events, a user keeps using that big relay as their outbox because it is fast and reliable, but chooses to archive their old events in a dedicated archival relay, say, cellar.nostr.wine, while prudently not including that in their outbox list because that would make no sense -- now it is impossible for anyone to refer to old notes from this user even though they are publicly accessible in cellar.nostr.wine;
- There are topical relays that curate content relating to niche (non-microblogging) topics, say, cooking recipes, and users choose to publish their recipes to these relays only -- but now they can't refer to these relays in the external Nostr world of
kind:1s because these topical relays are not in their outbox lists. - Suppose a user wants to maintain two different identities under the same keypair, say, one identity only talks about soccer in English, while the other only talks about art history in French, and the user very prudently keeps two different
kind:10002events in two different sets of "indexer" relays (or does it in some better way of announcing different relay sets) -- now one of this user's audiences cannot ever see notes created by him with their other persona, one half of the content of this user will be inacessible to the other half and vice-versa. - If for any reason a relay does not want to accept events of a certain kind a user may publish to other relays, and it would all work fine if the user referenced that externally-published event from a normal event, but now that externally-published event is not reachable because the external relay is not in the user's outbox list.
- If someone, say, Alex Jones, is hard-banned everywhere and cannot event broadcast
kind:10002events to any of the commonly used index relays, that person will now appear as banned in most clients: in an ideal world in which clients followednprofileand other relay hints Alex Jones could still live a normal Nostr life: he would print business cards with hisnprofileinstead of annpuband clients would immediately know from what relay to fetch his posts. When other users shared his posts or replied to it, they would include a relay hint to his personal relay and others would be able to see and then start following him on that relay directly -- now Alex Jones's events cannot be read by anyone that doesn't already know his relay.
- Someone makes a post inside a community (either a NIP-29 community or a NIP-87 community) and others want to refer to that post in discussions in the external Nostr world of
-
 @ d5c3d063:4d1159b3
2024-10-24 14:55:55
@ d5c3d063:4d1159b3
2024-10-24 14:55:55"ขาดทุนทนได้ กำไรสองสลึงทนไม่ได้" ประโยคที่ฟังดูเหมือนจะขำ แต่ลุงโฉลกกลับบอกว่า มันขำไม่ออก!
เพราะสะท้อนความจริงอันน่าเศร้าของนักลงทุน ที่มักพ่ายแพ้ต่อกิเลสในใจตัวเอง ไม่ต่างจากการติดกับดัก ที่มอง "สิงโตเป็นหมา" ซึ่ง CDC Talk EP 2 จะพาเราไปเรียนรู้เรื่องราวเหล่านี้ด้วยการนำหลักธรรมะมาประยุกต์ใช้กับการลงทุนในบิตคอยน์ เพื่อค้นหาเส้นทางสู่ความสำเร็จที่ยั่งยืนทั้งในการลงทุนและการใช้ชีวิต
https://image.nostr.build/180f5864057351d0e2a725d0ab021ae58f30942d2b87ad1697030d7d51f6bae0.jpg
. อาจารย์พิริยะยกตัวอย่างพฤติกรรมของนักลงทุนบิตคอยน์ บางคนทนขาดทุนมาได้ถึง 3 ปี พอราคากลับมาเท่าทุน ก็รีบขายทิ้งทันที ในขณะที่บางคนติดดอยแล้วตัดสินใจขายขาดทุนอย่างเจ็บปวด จนเกิดความโกรธเกลียดบิตคอยน์ สาปส่งว่าเป็นสิ่งหลอกลวงและไม่เหลียวแลมันอีกเลย แต่เมื่อราคาบิตคอยน์พุ่งขึ้น ก็กลับมาสนใจมันอีกครั้ง พฤติกรรมที่เหล่านี้ลุงโฉลกอธิบายว่า เป็นเพราะนักลงทุนขาดสติ ไม่รู้เท่าทันสภาวะที่แท้จริงของสิ่งต่างๆ จึงตัดสินใจโดยใช้อารมณ์เป็นที่ตั้ง กลัวที่จะยอมรับความผิดพลาด กลัวว่ากำไรจะหายไปทำให้พลาดโอกาสทำกำไรและตกเป็นทาสของราคาที่ผันผวน . ลุงโฉลกเปรียบเทียบพฤติกรรมเหล่านี้กับคนที่ "เห็นสิงโตเป็นหมา" สะท้อนถึงความไม่รู้ ความประมาท ที่ทำให้มองไม่เห็นอันตรายไม่รู้จักป้องกันตัวเอง เช่นเดียวกับนักลงทุนที่มีความไม่รู้นี้ทำให้มองไม่เห็นความเสี่ยง ตัดสินใจลงทุนโดยใช้อารมณ์ สุดท้ายก็เจ็บตัว ลุงโฉลกเน้นย้ำว่าต้องเข้าใจ psychology รู้เท่าทันความโลภและความกลัว . ต้นตอของความไม่รู้นั้น ลุงโฉลกอธิบายว่า คือ "โมหะ" ที่บดบังปัญญา ทำให้เกิดความโลภ ความกลัว ความโกรธ และ "เจตนา" ที่ผิดพลาด ซึ่งล้วนเกิดจากการรับรู้ผ่าน ตา หู จมูก ลิ้น กาย ใจ หรือที่เรียกว่า บริวารทั้ง 6 โดย "ทิฐิ" หรือความยึดมั่นในความคิดเห็นของตัวเอง ก็เป็นหนึ่งในบริวารเหล่านั้น ที่ทำให้เราไม่เปิดใจเรียนรู้สิ่งใหม่ๆ ไม่ยอมรับความจริง วิธีแก้คือต้องฝึกสติ รู้เท่าทันความคิดและอารมณ์ของตัวเอง ใช้ โยนิโสมนสิการ คือคิดพิจารณาอย่างรอบคอบถี่ถ้วน ไตร่ตรองให้ถ่องแท้ก่อนตัดสินใจ ไม่ว่าจะเรื่องการเงิน การงาน หรือแม้แต่การใช้ชีวิต . ลุงโฉลกอธิบายหลัก อริยสัจ 4 โดยเริ่มจาก ทุกข์ ความจริงที่ว่าชีวิตย่อมมีทุกข์ ทั้งความทุกข์ทางกายและทางใจ เช่น ความผิดหวัง ความไม่สมหวัง จากการลงทุน ความโกรธ ความกลัว ที่เกิดจากความผันผวนของตลาดบิตคอยน์ ต้นเหตุของทุกข์เหล่านี้ หรือ สมุทัย ก็คือ ความอยาก ความยึดมั่นถือมั่น ความไม่รู้ เช่น ความอยากรวยเร็ว ความเชื่อมั่นในระบบเทรดที่ไม่มั่นคง หรือความไม่รู้เท่าทันกลไกตลาด ลุงโฉลกเปรียบเทียบการแสวงหาความสุข เหมือนการเดินไปหากล่อง คิดว่าข้างในกล่องคือความสุข แต่สุดท้ายเมื่อไปถึง ก็พบว่าว่างเปล่า นี่สะท้อนให้เห็นถึง นิโรธ หรือการดับทุกข์ ที่เกิดจากการรู้เท่าทันความไม่เที่ยง (อนิจจัง) และการไม่มีตัวตนที่แท้จริง (อนัตตา) และ มรรค หรือหนทางดับทุกข์ ที่ลุงโฉลกสื่อถึง คือ การฝึกฝนสติปัญญา การวางแผนอย่างรอบคอบ และการรู้เท่าทันอารมณ์ของตัวเอง . ทั้งลุงโฉลกและอาจารย์พิริยะเชื่อว่าราคาบิตคอยน์และทองคำมีแนวโน้มพุ่งสูงขึ้นเมื่อเทียบกับเงินดอลลาร์ที่กำลังเผชิญภาวะเงินเฟ้ออย่างต่อเนื่อง อาจารย์พิริยะอธิบายว่า ในมาตรฐานของเงินที่แข็งแกร่ง สินค้าและบริการต่างๆ ควรจะมีราคาถูกลงเมื่อเวลาผ่านไป ทำให้คนเราใช้จ่ายและซื้อของได้มากขึ้น แต่ถ้ายังใช้เงินดอลลาร์เป็นมาตรฐานในการวัดมูลค่า เช่น การมองราคาทองคำและบิตคอยน์เป็นเงินดอลลาร์ ทุกอย่างก็จะแพงขึ้น หากบิตคอยน์กลายเป็น "เงินของโลก" ได้จริง มูลค่าของมันควรจะสะท้อน GDP ของโลก หารด้วยจำนวนบิตคอยน์ที่มีอยู่ ซึ่งปัจจุบันอยู่ที่ราว 27 billion dollars ต่อ 1 บิตคอยน์ และมีแนวโน้มเพิ่มขึ้นอีกมาก สะท้อนความหมายของ "1 BTC = 1 BTC" ที่ไม่ได้ผูกติดกับมูลค่าเงินดอลลาร์ การทำความเข้าใจธรรมชาติของเงินตราที่เปลี่ยนแปลงได้ตลอดเวลาเป็นสิ่งสำคัญ เพราะทุกอย่างเป็นไปได้ การมองเห็นสภาพความเป็นจริงจะช่วยให้เรารับมือกับความเปลี่ยนแปลงได้อย่างมีสติ . เช่นเดียวกับระบบเงินตรา ลุงโฉลกเล่าว่าสมัยท่านเด็กๆ เงิน 1 สตางค์ยังมีรู มีหน่วย อัด เฟื้อง ไพ ซึ่งคนรุ่นใหม่ไม่รู้จักแล้ว เพราะระบบเงินตราหน่วยเงินมีการเปลี่ยนแปลงไปตามกาลเวลา เช่นเดียวกับดอลลาร์ ที่แม้จะเป็นสกุลเงินหลักของโลกในปัจจุบัน แต่อนาคตก็ไม่มีอะไรแน่นอน อาจจะถูกแทนที่ด้วย บิตคอยน์ ลุงย้ำว่า "ต้องเรียน เพื่อเข้าใจ" ถึงจะสามารถปรับตัวและรับมือกับการเปลี่ยนแปลงได้ . สุดท้าย อาจารย์พิริยะทิ้งท้ายไว้ว่าการลงทุนไม่ใช่การเล่น ต้องศึกษาหาความรู้วางแผนให้ดีและที่สำคัญคือ ต้องมีสติรู้เท่าทันอารมณ์ของตัวเอง เพื่อไม่ให้ตกเป็นทาสของความโลภและความกลัว ซึ่งเป็นกุญแจสู่ความสำเร็จในการลงทุนระยะยาว
CDCTalk #Siamstr
-
 @ 18bdb66e:82eb5e5d
2024-10-15 00:28:32
@ 18bdb66e:82eb5e5d
2024-10-15 00:28:32Chef's notes
Serve with bread, and side salad
Details
- ⏲️ Prep time: 5 mins
- 🍳 Cook time: 10 mins
- 🍽️ Servings: 2-4
Ingredients
- 1 Can (10 ½ ounces) condensed chicken gumbo soup
- ½ Soup can tomato juice
- ½ Soup can water
- Croutons
Directions
- Add soup, juice, and water.
- Heat through, stirring often.
- Serve with croutons
-
 @ 6871d8df:4a9396c1
2024-06-12 22:10:51
@ 6871d8df:4a9396c1
2024-06-12 22:10:51Embracing AI: A Case for AI Accelerationism
In an era where artificial intelligence (AI) development is at the forefront of technological innovation, a counter-narrative championed by a group I refer to as the 'AI Decels'—those advocating for the deceleration of AI advancements— seems to be gaining significant traction. After tuning into a recent episode of the Joe Rogan Podcast, I realized that the prevailing narrative around AI was heading in a dangerous direction. Rogan had Aza Raskin and Tristan Harris, technology safety advocates, who released a talk called 'The AI Dilemma,' on for a discussion. You may know them from the popular documentary 'The Social Dilemma' on the dangers of social media. It became increasingly clear that the cautionary stance dominating this discourse might be tipping the scales too far, veering towards an over-regulated future that stifles innovation rather than fostering it.

Are we moving too fast?
While acknowledging AI's benefits, Aza and Tristan fear it could be dangerous if not guided by ethical standards and safeguards. They believe AI development is moving too quickly and that the right incentives for its growth are not in place. They are concerned about the possibility of "civilizational overwhelm," where advanced AI technology far outpaces 21st-century governance. They fear a scenario where society and its institutions cannot manage or adapt to the rapid changes and challenges introduced by AI.
They argue for regulating and slowing down AI development due to rapid, uncontrolled advancement driven by competition among companies like Google, OpenAI, and Microsoft. They claim this race can lead to unsafe releases of new technologies, with AI systems exhibiting unpredictable, emergent behaviors, posing significant societal risks. For instance, AI can inadvertently learn tasks like sentiment analysis or human emotion understanding, creating potential for misuse in areas like biological weapons or cybersecurity vulnerabilities.
Moreover, AI companies' profit-driven incentives often conflict with the public good, prioritizing market dominance over safety and ethics. This misalignment can lead to technologies that maximize engagement or profits at societal expense, similar to the negative impacts seen with social media. To address these issues, they suggest government regulation to realign AI companies' incentives with safety, ethical considerations, and public welfare. Implementing responsible development frameworks focused on long-term societal impacts is essential for mitigating potential harm.
This isn't new
Though the premise of their concerns seems reasonable, it's dangerous and an all too common occurrence with the emergence of new technologies. For example, in their example in the podcast, they refer to the technological breakthrough of oil. Oil as energy was a technological marvel and changed the course of human civilization. The embrace of oil — now the cornerstone of industry in our age — revolutionized how societies operated, fueled economies, and connected the world in unprecedented ways. Yet recently, as ideas of its environmental and geopolitical ramifications propagated, the narrative around oil has shifted.
Tristan and Aza detail this shift and claim that though the period was great for humanity, we didn't have another technology to go to once the technological consequences became apparent. The problem with that argument is that we did innovate to a better alternative: nuclear. However, at its technological breakthrough, it was met with severe suspicions, from safety concerns to ethical debates over its use. This overregulation due to these concerns caused a decades-long stagnation in nuclear innovation, where even today, we are still stuck with heavy reliance on coal and oil. The scare tactics and fear-mongering had consequences, and, interestingly, they don't see the parallels with their current deceleration stance on AI.
These examples underscore a critical insight: the initial anxiety surrounding new technologies is a natural response to the unknowns they introduce. Yet, history shows that too much anxiety can stifle the innovation needed to address the problems posed by current technologies. The cycle of discovery, fear, adaptation, and eventual acceptance reveals an essential truth—progress requires not just the courage to innovate but also the resilience to navigate the uncertainties these innovations bring.
Moreover, believing we can predict and plan for all AI-related unknowns reflects overconfidence in our understanding and foresight. History shows that technological progress, marked by unexpected outcomes and discoveries, defies such predictions. The evolution from the printing press to the internet underscores progress's unpredictability. Hence, facing AI's future requires caution, curiosity, and humility. Acknowledging our limitations and embracing continuous learning and adaptation will allow us to harness AI's potential responsibly, illustrating that embracing our uncertainties, rather than pretending to foresee them, is vital to innovation.
The journey of technological advancement is fraught with both promise and trepidation. Historically, each significant leap forward, from the dawn of the industrial age to the digital revolution, has been met with a mix of enthusiasm and apprehension. Aza Raskin and Tristan Harris's thesis in the 'AI Dilemma' embodies the latter.
Who defines "safe?"
When slowing down technologies for safety or ethical reasons, the issue arises of who gets to define what "safe" or “ethical” mean? This inquiry is not merely technical but deeply ideological, touching the very core of societal values and power dynamics. For example, the push for Diversity, Equity, and Inclusion (DEI) initiatives shows how specific ideological underpinnings can shape definitions of safety and decency.
Take the case of the initial release of Google's AI chatbot, Gemini, which chose the ideology of its creators over truth. Luckily, the answers were so ridiculous that the pushback was sudden and immediate. My worry, however, is if, in correcting this, they become experts in making the ideological capture much more subtle. Large bureaucratic institutions' top-down safety enforcement creates a fertile ground for ideological capture of safety standards.

I claim that the issue is not the technology itself but the lens through which we view and regulate it. Suppose the gatekeepers of 'safety' are aligned with a singular ideology. In that case, AI development would skew to serve specific ends, sidelining diverse perspectives and potentially stifling innovative thought and progress.
In the podcast, Tristan and Aza suggest such manipulation as a solution. They propose using AI for consensus-building and creating "shared realities" to address societal challenges. In practice, this means that when individuals' viewpoints seem to be far apart, we can leverage AI to "bridge the gap." How they bridge the gap and what we would bridge it toward is left to the imagination, but to me, it is clear. Regulators will inevitably influence it from the top down, which, in my opinion, would be the opposite of progress.
In navigating this terrain, we must advocate for a pluralistic approach to defining safety, encompassing various perspectives and values achieved through market forces rather than a governing entity choosing winners. The more players that can play the game, the more wide-ranging perspectives will catalyze innovation to flourish.
Ownership & Identity
Just because we should accelerate AI forward does not mean I do not have my concerns. When I think about what could be the most devastating for society, I don't believe we have to worry about a Matrix-level dystopia; I worry about freedom. As I explored in "Whose data is it anyway?," my concern gravitates toward the issues of data ownership and the implications of relinquishing control over our digital identities. This relinquishment threatens our privacy and the integrity of the content we generate, leaving it susceptible to the inclinations and profit of a few dominant tech entities.
To counteract these concerns, a paradigm shift towards decentralized models of data ownership is imperative. Such standards would empower individuals with control over their digital footprints, ensuring that we develop AI systems with diverse, honest, and truthful perspectives rather than the massaged, narrow viewpoints of their creators. This shift safeguards individual privacy and promotes an ethical framework for AI development that upholds the principles of fairness and impartiality.
As we stand at the crossroads of technological innovation and ethical consideration, it is crucial to advocate for systems that place data ownership firmly in the hands of users. By doing so, we can ensure that the future of AI remains truthful, non-ideological, and aligned with the broader interests of society.
But what about the Matrix?
I know I am in the minority on this, but I feel that the concerns of AGI (Artificial General Intelligence) are generally overblown. I am not scared of reaching the point of AGI, and I think the idea that AI will become so intelligent that we will lose control of it is unfounded and silly. Reaching AGI is not reaching consciousness; being worried about it spontaneously gaining consciousness is a misplaced fear. It is a tool created by humans for humans to enhance productivity and achieve specific outcomes.
At a technical level, large language models (LLMs) are trained on extensive datasets and learning patterns from language and data through a technique called "unsupervised learning" (meaning the data is untagged). They predict the next word in sentences, refining their predictions through feedback to improve coherence and relevance. When queried, LLMs generate responses based on learned patterns, simulating an understanding of language to provide contextually appropriate answers. They will only answer based on the datasets that were inputted and scanned.
AI will never be "alive," meaning that AI lacks inherent agency, consciousness, and the characteristics of life, not capable of independent thought or action. AI cannot act independently of human control. Concerns about AI gaining autonomy and posing a threat to humanity are based on a misunderstanding of the nature of AI and the fundamental differences between living beings and machines. AI spontaneously developing a will or consciousness is more similar to thinking a hammer will start walking than us being able to create consciousness through programming. Right now, there is only one way to create consciousness, and I'm skeptical that is ever something we will be able to harness and create as humans. Irrespective of its complexity — and yes, our tools will continue to become evermore complex — machines, specifically AI, cannot transcend their nature as non-living, inanimate objects programmed and controlled by humans.
 The advancement of AI should be seen as enhancing human capabilities, not as a path toward creating autonomous entities with their own wills. So, while AI will continue to evolve, improve, and become more powerful, I believe it will remain under human direction and control without the existential threats often sensationalized in discussions about AI's future.
The advancement of AI should be seen as enhancing human capabilities, not as a path toward creating autonomous entities with their own wills. So, while AI will continue to evolve, improve, and become more powerful, I believe it will remain under human direction and control without the existential threats often sensationalized in discussions about AI's future. With this framing, we should not view the race toward AGI as something to avoid. This will only make the tools we use more powerful, making us more productive. With all this being said, AGI is still much farther away than many believe.
Today's AI excels in specific, narrow tasks, known as narrow or weak AI. These systems operate within tightly defined parameters, achieving remarkable efficiency and accuracy that can sometimes surpass human performance in those specific tasks. Yet, this is far from the versatile and adaptable functionality that AGI represents.
Moreover, the exponential growth of computational power observed in the past decades does not directly translate to an equivalent acceleration in achieving AGI. AI's impressive feats are often the result of massive data inputs and computing resources tailored to specific tasks. These successes do not inherently bring us closer to understanding or replicating the general problem-solving capabilities of the human mind, which again would only make the tools more potent in our hands.
While AI will undeniably introduce challenges and change the aspects of conflict and power dynamics, these challenges will primarily stem from humans wielding this powerful tool rather than the technology itself. AI is a mirror reflecting our own biases, values, and intentions. The crux of future AI-related issues lies not in the technology's inherent capabilities but in how it is used by those wielding it. This reality is at odds with the idea that we should slow down development as our biggest threat will come from those who are not friendly to us.
AI Beget's AI
While the unknowns of AI development and its pitfalls indeed stir apprehension, it's essential to recognize the power of market forces and human ingenuity in leveraging AI to address these challenges. History is replete with examples of new technologies raising concerns, only for those very technologies to provide solutions to the problems they initially seemed to exacerbate. It looks silly and unfair to think of fighting a war with a country that never embraced oil and was still primarily getting its energy from burning wood.
 The evolution of AI is no exception to this pattern. As we venture into uncharted territories, the potential issues that arise with AI—be it ethical concerns, use by malicious actors, biases in decision-making, or privacy intrusions—are not merely obstacles but opportunities for innovation. It is within the realm of possibility, and indeed, probability, that AI will play a crucial role in solving the problems it creates. The idea that there would be no incentive to address and solve these problems is to underestimate the fundamental drivers of technological progress.
The evolution of AI is no exception to this pattern. As we venture into uncharted territories, the potential issues that arise with AI—be it ethical concerns, use by malicious actors, biases in decision-making, or privacy intrusions—are not merely obstacles but opportunities for innovation. It is within the realm of possibility, and indeed, probability, that AI will play a crucial role in solving the problems it creates. The idea that there would be no incentive to address and solve these problems is to underestimate the fundamental drivers of technological progress.Market forces, fueled by the demand for better, safer, and more efficient solutions, are powerful catalysts for positive change. When a problem is worth fixing, it invariably attracts the attention of innovators, researchers, and entrepreneurs eager to solve it. This dynamic has driven progress throughout history, and AI is poised to benefit from this problem-solving cycle.
Thus, rather than viewing AI's unknowns as sources of fear, we should see them as sparks of opportunity. By tackling the challenges posed by AI, we will harness its full potential to benefit humanity. By fostering an ecosystem that encourages exploration, innovation, and problem-solving, we can ensure that AI serves as a force for good, solving problems as profound as those it might create. This is the optimism we must hold onto—a belief in our collective ability to shape AI into a tool that addresses its own challenges and elevates our capacity to solve some of society's most pressing issues.
An AI Future
The reality is that it isn't whether AI will lead to unforeseen challenges—it undoubtedly will, as has every major technological leap in history. The real issue is whether we let fear dictate our path and confine us to a standstill or embrace AI's potential to address current and future challenges.
The approach to solving potential AI-related problems with stringent regulations and a slowdown in innovation is akin to cutting off the nose to spite the face. It's a strategy that risks stagnating the U.S. in a global race where other nations will undoubtedly continue their AI advancements. This perspective dangerously ignores that AI, much like the printing press of the past, has the power to democratize information, empower individuals, and dismantle outdated power structures.
The way forward is not less AI but more of it, more innovation, optimism, and curiosity for the remarkable technological breakthroughs that will come. We must recognize that the solution to AI-induced challenges lies not in retreating but in advancing our capabilities to innovate and adapt.
AI represents a frontier of limitless possibilities. If wielded with foresight and responsibility, it's a tool that can help solve some of the most pressing issues we face today. There are certainly challenges ahead, but I trust that with problems come solutions. Let's keep the AI Decels from steering us away from this path with their doomsday predictions. Instead, let's embrace AI with the cautious optimism it deserves, forging a future where technology and humanity advance to heights we can't imagine.
-
 @ 18bdb66e:82eb5e5d
2024-10-15 00:20:20
@ 18bdb66e:82eb5e5d
2024-10-15 00:20:20Chef's notes
Serve with bread, and side salad.
Details
- ⏲️ Prep time: 5 mins
- 🍳 Cook time: 10 mins
- 🍽️ Servings: 2-4
Ingredients
- 1 Can (10 ½ ounces) condensed chicken noodle soup
- ½ Soup can V8 juice
- ½ Soup can water
- Croutons
Directions
- Add soup, V8, and water.
- Heat through, stirring often.
- Serve with croutons
-
 @ 45bda953:bc1e518e
2024-10-24 11:31:16
@ 45bda953:bc1e518e
2024-10-24 11:31:16Revelation Chapter 2:17
“He who has an ear, let him hear what the Spirit says to the churches. To him who overcomes I will give some of the hidden manna to eat. And I will give him a white stone, and on the stone a new name written which no one knows except him who receives it.”
Revelations is a mysterious book with some verses that seems to make very little sense.
Q: Why do we need names? A: To identify ourselves.
Same reason nature opted for us to have uniquely identifiable faces. But a name no one knows except him who receives it? Why would you need that?
When you are born you have very little in the way of personality and character. Doctor exclaims, “It’s a boy!” First verifiable identifier is recognised. One newborn baby looks very similar to another. For that reason they can accidentally be mixed up and given to the wrong mother at the hospital. But if the mother knows that she birthed a boy she would immediately know something is amiss if she gets handed a newborn girl. Gender is important as the first verifiable, unique identifier of the new being.
The newly confirmed male child gets issued a verbally spoken and symbolically scripted identifier. This identifier is known as a name. Name and surname please. These identifiers are of little consequence to the being who knows only feelings of pain and sensations of comfort. The survival of the biological spawn is dependant on the instinct to suckle and the tendency to cry at slight discomfort. This is the language of human instinct to cry and suck. As the toddler develops it starts to respond to the vocally repeated identifier (known as a name) to the point where it has been sufficiently trained to respond to the verbal enunciation of it. When you call for someone you are evoking hope that the entity being called to will respond by coming to your physical location so that you can share or enquire information. When the summons is answered by presence you maintain connection not by repetition of the name but by eye contact and directing conversation to the face of the person. The face being the most accurate point with which to verifiably establish identity.
In the book of Genesis Jacob is able to fool Isaac (His father) by exploiting his bad eyesight to steal an inheritance blessing from his older brother Esau. The face of Jacob was obscured through Isaac’s blindness which gave a false signal to the issuer of a blessing.
As our proverbial John Doe grows up he develops a personality and character which allows for people to gauge the levels of trust they are willing to risk on him. Character and personality are also unique identifiers. Mother knows best at who will be diligent when keeping their rooms clean and whose rooms she will have to clean for them. She can through experience predict outcomes using knowledge of character and personality as a reference. This information is valuable and can only be established or measured when there is an ongoing relationship where trust and responsibility are continuously tested and stressed.
We all have identifiers that are publicly displayed wherever we go.
: Physical appearance, Wedding ring, Tatoo
We have identifiers that represent or address us verbally and textually.
: Names, titles, seals, signatures, handwriting et cetera.
Ambiguous identifiers
: Left handed, smoker, married, divorced, affiliations, church, political views, phone number, address, favourite colour, drivers license ad infinitum.
In this digital world our identifiers are all exploitable by a large number of unidentifiable bad actors. This is weakness. If you are a man of character and strength but have no control over your identity. You are weak and defenceless in the eyes of these virtually indistinguishable, androgynous scammers, fraudsters, monopolies and governments.
We have to take digital sovereignty over our digital identities. That means we have to train our minds in the establishment of truth. The truth being...
Be true to thine self and let the truth about you be established by you. That means abandoning trust in third parties and know that no one is coming to save you and protect your personal data. Like there is no spoon in the matrix, there is also no institution who loves you enough to protect your identity in a digitally encrypted world. In some cases they might be legally obligated to, but who will take responsibility and how do you quantify and reverse the damage of leaked information. You don’t. No justice for the slave.
The spoon is a lie. It simply does not exist.
Revelation Chapter 2 verse 17
“He who has an ear, let him hear what the Spirit says to the churches. To him who overcomes I will give some of the hidden manna to eat. And I will give him a white stone, and on the stone a new name written which no one knows except him who receives it.”
 If you have an identifier that only you know about then you have a private key. You can verify your holdings of assets. You can prove your identity on nostr. You can own not only the data but prove you are the source of it.
If you have an identifier that only you know about then you have a private key. You can verify your holdings of assets. You can prove your identity on nostr. You can own not only the data but prove you are the source of it.Anything that a trusted third party is currently doing for you, analog or digital is systemically being open sourced and you could do it for yourself with the press of a button. All you need is a white stone with a name on it no one else knows and be willing to carry the responsibility. You could then selectively reveal yourself to the world and prove it is you without exposing the you that is private. I will give an example to help you understand the power.
John 19:31–42
31 Therefore, because it was the Preparation Day, that the bodies should not remain on the cross on the Sabbath (for that Sabbath was a high day), the Jews asked Pilate that their legs might be broken, and that they might be taken away. 32 Then the soldiers came and broke the legs of the first and of the other who was crucified with Him. 33 But when they came to Jesus and saw that He was already dead, they did not break His legs. 34 But one of the soldiers pierced His side with a spear, and immediately blood and water came out.
One thing is certain, Jesus was verifiably dead. The Romans, Jews and disciples who were present at the execution and burial all concurred. He is dead. Deceased. Gone from the realm of the living. Roman soldiers were veritable experts at death and declaring the dead so.
A few days later some disciples were proclaiming excitedly about Jesus being alive. A certain guy named Thomas would not be had. You guys are crazy, trying to establish some weird cult by pretending a fantastic impossibility. Nope. They were adamant. He lives. They claimed, like a bunch of fanatics. Thomas, being the voice of reason says the following.
John 21:25
25 The other disciples therefore said to him, “We have seen the Lord.” So he said to them, “Unless I see in His hands the print of the nails, and put my finger into the print of the nails, and put my hand into his side, I will not believe.”
Thomas was a real Bitcoiner. He does not trust, he verifies.
 Verification in progress.
Verification in progress.The body of Jesus, should he have been alive will have been littered with scar tissue all across his back and legs. It would have been easy for Him to selectively reveal his identity to whoever he chose by exposing his body and letting them verify the proof of his identity without doubt. No one in world history has ever committed suicide by flogging and crucifixion so you cannot even fake or repeat it if you wanted to commit identity theft and pretend to be the Christ.
A proof of work hash in history so profound that civilisations collapsed on the realisation of its profundity. Another consequential exposition of identity verification is also expounded on by the gospel accounts.
Matthew 24:5
“For many will come in My name, saying, ‘I am the Christ,’ and will deceive many.
Eric Cason on the "What Bitcoin Did" podcast said that he thinks Bitcoin is a messianic event. I agree with him. Liberation from economic tyranny is messianic if a figure initiates the salvation process.
That would suggest that there will be messianic implications, namely identity fraud of messiah with the intent to deceive and extort.
Matthew 24:23
23 “Then if anyone says to you, ‘Look, here is the Christ!’ or ‘There!’ Do not believe it.
We have ourselves an example of this in Craig Wright who claims to be Satoshi Nakamoto. Yet he refuses to verify it by transferring Genesis bits. Like Thomas demands to see the scars of crucifixion so too must we demand to see on chain movement of Genesis coinbase block reward as proof of identity and proof of work from anyone who publicly makes a claim to the person of Satoshi Nakamoto. Historic records in the future might mark this dispensation, BWP (Before white paper) and ASN (After Satoshi Nakamoto) or something of this nature could stand in the annals of history, marking a era of mankind similar to BC, Before Christ and AD, anno domini, the year of our Lord.
Jesus is yet to give me a secret name like Satoshi already did.
Which leaves me wondering…
 The simulacral spectre created by Satoshi is an ongoing rabbit hole,
The simulacral spectre created by Satoshi is an ongoing rabbit hole,I have no doubt.
...
bitbib
-
 @ df8f0a64:057d87a5
2024-10-10 15:18:39
@ df8f0a64:057d87a5
2024-10-10 15:18:39書き散らす動機
残暑続きからの急な気温低下で鼻炎がひどくなる今日この頃、皆様お元気でしょうか
株主への抗議のために退職してから2ヶ月半、流石に暇を持て余してきました 時間がある上に能動的に働く気も起きず、ひたすらボーッとしたりうねうね考え事をする日々です 幸いにして人生も折り返しにさしかかる頃になり、時折「今、人生が終わって構わないのでは?」というようなことも考えたりします (鬱病既往歴ありますが私は元気です)
子どものお迎えを終えて、いつもどおり夕食をとり、またうねうねしているうちに ふと、6年前の年末に急死された、仕事でお世話になったTさんのことを思い出しました
子を寝かしつけてもまだ頭の中をぐるぐるしていたので、ここに吐き出してすっきりしようという魂胆です
Tさんとの出会い
私のキャリアの(ほぼ)スタートはVC(ベンチャーキャピタル)でした 誰のせいでもないとある経緯もあり、周囲からは警戒され避けられ、わずか6年ではありますが、 インナーサークルに入り込めない時期を過ごし、当時の上司と二人、とにかくやれることをやり続ける毎日でした
いつものようにピッチイベントに参加しているとき、近くの席にいたスーツ姿の3人組と目が一瞬合います
「事業会社の人だ」
協調投資やファンド出資のきっかけを掴むべく、その3人に話かけます
「よろしければ弊社投資先のご紹介や御社の...」
ひととおりの挨拶を済ませ、この人たちにも避けられるんだろうと思いながらも要件を切り出します
「是非やりましょう」
いつもとは違う嬉しい返事をくれたのがTさんでした
面倒見の良い他社の先輩
そのときの3人組であるMさん・Iさん・Tさんには、私の仕事人生の中で最もお世話になったと言っても過言ではありません
ファンドの営業を受けていただき、協調投資を行い、VCからの転職後にも協業相手として他部署のキーマンをご紹介いただき...
社会人になったばかりの私の、今思い返せば恥ずかしい(部下がこんな提案したら卒倒する)レベルの提案を、 誰もが知る一流企業の多忙な役職持ちであるにも関わらず、毎回一時間も割いて丁寧に対応してくださる心の広い方でした
当時、VCと接点をもつような事業会社の対スタートアップ部隊は、本業でご活躍されている方が兼任で取り組むパターンが多く、Mさん・Iさん・Tさんももちろんそう
その後も昇進され、最後には本社の取締役に。今年遂に退任され、所謂「あがり」でしょうか、子会社の取締役に異動 長い社会人人生をほぼ走りきり、有終の美を飾ろうとする時期にさしかかっています
でもTさんはそこにはいません
残される側
冒頭触れたとおり、Tさんは6年前のこの時期に急死されました 死因については、Tさんのご友人がFBに投稿していた文章を読んでも、Iさんに聞いてもわからない
悲しいかな、四十年近く生きていると、死因が明かされない理由がわかるようになる機会が一度や二度はあります Tさんもおそらくそうだったのでしょう
直前まで、Iさんと一緒にベイエリアに出張され、楽しそうなコメントと共に写真を投稿されていたのに 晩婚なのか再婚なのか、とにかくご結婚されて一年ちょっと。お子様も生まれたばかりだったのに Tさんは近い人間に心中を隠して、静かにこの世を去りました
あなたの快い返事に、どれほど私が救われたのか 転職後の提案のとき、受付で顔を出してすぐ「元気?」と声をかけてくださったことがどれほど私を安心させてくれたか あなたが声をかけてくれる度、私の社会人としての成果が生まれたことに、私は十分に感謝を伝えられていません
まだしばらく残る理由
振り返って、Tさんのように誰かの人生をenhanceできたのか?と自分に問うと、まだできたとは思えません。残念ですが
今ここで死んでも私は構わないけど、まだもうちょっと頑張るべきかな、老いてから誰かに感謝をしてもらうまで生きてみてもいいかな
そうふと思い直しているうちに日付が変わりました
-
 @ d2e97f73:ea9a4d1b
2023-04-11 19:36:53
@ d2e97f73:ea9a4d1b
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ c0f9e286:5a223917
2024-10-24 09:37:21
@ c0f9e286:5a223917
2024-10-24 09:37:21ตอนที่แล้วได้กล่าวถึงการตั้งบริษัท Holding Company เพื่อนำมาถือหุ้นในบริษัทลูก จุดประสงค์นอกจากจะเป็นการประหยัดภาษีแล้ว ยังง่ายต่อการควบคุม เนื่องจากแบ่งสัดส่วนการถือหุ้นกันตั้งแต่ต้น ซึ่งหากถือในนามบุคคลธรรมดาย่อมปกปิดตัวตนที่แท้จริงไม่ได้ ดังนั้นหลายๆบริษัทจึงนิยมตั้ง Offshore Holding (Holding ที่ตั้งในต่างประเทศ) เข้ามาถือหุ้นบริษัท Holding ในประเทศอีกทีหนึ่ง
นั่นแปลว่าวุ่นวายกับการตั้งบริษัท Offshore Holding แค่ครั้งเดียว หลังจากนั้นก็นำมาถือหุ้นใน Holding ในประเทศเพื่อเป็นเจ้าของทุกๆบริษัทในเครือ ซึ่งมีอำนาจควบคุม บังคับบัญชา และสั่งการโดยไม่จำเป็นต้องเปิดเผยตัวตนที่แท้จริง
ส่วนถ้าจะถามว่าไปตั้ง Offshore ประเทศไหนดี อันนี้ขึ้นกับวัตถุประสงค์ของแต่ละท่าน ซึ่งไม่มี One Size fits all บางคนตั้ง Offshore มาเพื่อรับเงินก้อนใหญ่จากการขายหุ้น และไม่ได้ต้องการปกปิดตัวตนอะไรมากมายก็อาจจะไปตั้ง Offshore ที่ Hong Kong หรือ Singapore
แต่ถ้าวัตถุประสงค์ต้องการที่จะปกปิดตัวตน อาจจะไปตั้งในประเทศอย่าง Seychells, Vanuatu, Mauritius หรือ BVI เป็นต้น ซึ่งประเทศเหล่านี้มักมีนโยบายไม่เปิดเผยตัวตนของบุคคลที่เป็นเจ้าของหุ้นในบริษัท และที่สำคัญ ประเทศเหล่านี้บางทียอมให้นิติบุคคลต่างประเทศเข้ามาเป็นผู้ถือหุ้นได้ 100% (กฎหมายไทยในการตั้งบริษัทต้องมีผู้ถือหุ้น 2 คนขึ้นไป และหากไม่มีโรงงานในไทย หรือได้รับสิทธิ BOI ต่างชาติสามารถถือหุ้นได้ไม่เกิน 49%)
ดังนั้นหาก Offshore Company 1 ชั้นยังไม่พอ คุณก็ตั้ง Offshore ไปเลย 2 ประเทศเช่น ผมอาจจะตั้ง Offshore แรกที่ Vanuatu ซึ่งผมถือหุ้น 100% (ในนามบุคคล) แล้วจึงไปก่อตั้งอีก 1 บริษัทอีกแห่งที่ Seychells โดยให้ Vanuatu Offshore เข้าไปถือหุ้น 100% ในนามบริษัท แล้วผมจะนำ Seychells Offshore มาถือหุ้นใน Thailand Holding อีกทีหนึ่ง ซึ่งหาก Thailand Holding ไม่ได้มีโรงงาน หรือได้รับสิทธิ BOI แปลว่า Seychells Offshore จะเข้าไปถือหุ้นได้ไม่เกิน 49% ส่วนอีก 51% คุณควรหานอมินี หรือคนในครอบครัวที่ไม่ได้กังวลเรื่องความเป็นส่วนตัวเข้ามาถือหุ้นแทน และอาจจะจำกัดสิทธิออกเสียงผ่านกลไกการถือหุ้นบุริมสิทธิ์แทน เอาเป็นว่าเดี๋ยวจะงง แต่ให้เข้าใจไว้ว่า 51% ที่ถือหุ้นแทนมีช่องทางที่ทำให้เสียง Vote หรือสิทธิในการรับเงินปันผลน้อยกว่าฝั่ง 49% ซึ่งเดี๋ยวจะหาเวลาอธิบายเรื่องนี้โดยละเอียดอีกครั้งหนึ่ง
แปลว่าหากทางรัฐบาลไทยตรวจสอบรายชื่อผู้ถือหุ้นหรือทรัพย์สินของคุณ หากใช้การถือทรัพย์สินแบบนี้ย่อมไม่มีทางที่รัฐจะรู้เลยว่าคุณเป็นเจ้าของทรัพย์สิน หรือกิจการอะไรกันแน่ และหากรัฐบาลไทยต้องการตรวจสอบจริงๆ การจะไปตรวจพิสูจน์ว่าใครถือหุ้น หรือมีสิทธิในการครอบงำบริษัทจะเป็นเรื่องยากมาก
ซึ่งหากคุณคิดว่านี่ยังเป็นส่วนตัวไม่พอละก็… แน่นอนมีวิธีที่จะเพิ่มความเป็นส่วนตัวมากขึ้นกว่าเดิม ซึ่งมีอีก 2 วิธี และสามารถนำมาใช้ร่วมกับวิธีนี้ได้ ส่วนจะเป็นวิธีอะไรนั้น รอติดตามตอนต่อไป
Own Nothing and be Happy ในแบบฉบับ Elite เป็นไงบ้างครับ เริ่มเห็นภาพหรือยังว่าทำไมตระกูลดังๆอย่าง Rothschild สามารถปกป้องความเป็นส่วนตัวของพวกเขาไว้ได้โดยที่คนนอกไม่รู้เลย ก็เพราะเครื่องมือแบบนี้ไง
realeakkrit #siamstr #privacy
-
 @ 18bdb66e:82eb5e5d
2024-10-15 00:16:16
@ 18bdb66e:82eb5e5d
2024-10-15 00:16:16Chef's notes
Serve with bread, and side salad.
Details
- ⏲️ Prep time: 5 mins
- 🍳 Cook time: 10 mins
- 🍽️ Servings: 2-4
Ingredients
- 1 can (10.5 ounces) condensed cream of mushroom soup
- 1 Can (10 ½ ounces) condensed chicken noodle soup
- 1 can (10.5 ounces) condensed vegetable soup.
- 3 Soup cans water
- Croutons
Directions
- Add soups, and water.
- Heat through, stirring often.
- Serve with croutons
-
 @ 18bdb66e:82eb5e5d
2024-10-15 00:11:19
@ 18bdb66e:82eb5e5d
2024-10-15 00:11:19Chef's notes
Serve with crackers, or croutons, and side salad. Fiesta Nacho cheese soup gives a pleasant kick of flavor
Details
- ⏲️ Prep time: 5 mins
- 🍳 Cook time: 10 mins
- 🍽️ Servings: 2-4
Ingredients
- 1 Can (10.5 ounces) condensed Cheddar cheese soup
- 1 Cans (10 ½ ounces) condensed tomato soup
- 2 Soup cans water
- Bacon, fried and crumbled.
Directions
- Combine soups, and water.
- Heat through, stirring often.
- Garnish with bacon.
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 18bdb66e:82eb5e5d
2024-10-15 00:05:38
@ 18bdb66e:82eb5e5d
2024-10-15 00:05:38Chef's notes
Trim down bread to fit serving bowl, if necessary, prior to broiling. Top with Parmesan cheese.
Details
- ⏲️ Prep time: 20 mins
- 🍳 Cook time: 10 mins
- 🍽️ Servings: 2-4
Ingredients
- 1 Can (10.5 ounce) condensed onion soup
- ½ Soup can water
- ½ Soup can V8 juice
- 4 Ounces sliced roast beef
- 2-3 slices French, or Italian bread, or Texas Toast
- Butter
- Parmesan cheese
Directions
- Combine soup, water, and V8 juice.
- Heat to simmer.
- Add roast beef, heat throug
- Ladle soup in bowl
- Top soup with bread
- Top bread with roast beef
-
 @ a828c9af:ea95c44c
2024-10-24 08:25:30
@ a828c9af:ea95c44c
2024-10-24 08:25:30The Philippines is a goldmine for businesses seeking new markets. With a booming economy and a population exceeding 100 million, it presents a vibrant and diverse consumer landscape that, when maximized, can offer businesses a considerable market with a growing purchasing power.
Moreover, the country's e-commerce sector has exploded in recent years, with sales hitting $17 billion in 2021 alone. As consumer behavior rapidly evolves due to technology and changing preferences, there's never been a better time to enter the Philippine market than today.
5 Ways to Tap into the Philippine Market
To succeed in the Philippine market, you need a strategic approach that resonates with the country's diverse and dynamic consumer base. Here are five proven methods to help you engage effectively.
1. Digital services and marketing
In the Philippines, a solid online presence is crucial to reach your target audience. Use social media, content marketing, and search engines to build meaningful connections almost instantly.
2. Cashless and online payment methods
Filipino consumers prefer secure and convenient payment options. Offering various cashless and online payment methods can enhance their shopping experience and give your business a competitive edge.
3. Fashion eCommerce
Fashion eCommerce is booming in the Philippines. A visually appealing website with high-quality images, detailed product descriptions, and easy navigation can attract fashion-conscious Filipinos.
4. Localized content and engagement
Tailor your content to your customers' culture and values to connect with the Philippine market. Using the local language, cultural references, and relatable imagery can deepen customer engagement and build trust.
5. Responsive customer support
Excellent customer support builds trust and loyalty. When you offer timely, helpful responses through chatbots and automation while maintaining a personal touch ensures customer satisfaction.
Check this infographic to learn more about consumer trends in the Philippines and how to take advantage of them to tap into this lucrative market.
-
 @ b2d670de:907f9d4a
2024-06-11 20:55:06
@ b2d670de:907f9d4a
2024-06-11 20:55:06This is a list of nostr relays exposed as onion services. The list is currently actively maintained on GitHub. Contributions is always appreciated!
| Relay name | Description | Onion url | Operator | Payment URL | | --- | --- | --- | --- | --- | | nostr.oxtr.dev | Same relay as clearnet relay nostr.oxtr.dev | ws://oxtrdevav64z64yb7x6rjg4ntzqjhedm5b5zjqulugknhzr46ny2qbad.onion | operator | N/A | | relay.snort.social | Same relay as clearnet relay relay.snort.social | wss://skzzn6cimfdv5e2phjc4yr5v7ikbxtn5f7dkwn5c7v47tduzlbosqmqd.onion | operator | N/A | | nostr.thesamecat.io | Same relay as clearnet relay nostr.thesamecat.io | ws://2jsnlhfnelig5acq6iacydmzdbdmg7xwunm4xl6qwbvzacw4lwrjmlyd.onion | operator | N/A | | nostr.land | The nostr.land paid relay (same as clearnet) | ws://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion | operator | Payment URL | | bitcoiner.social | No auth required, currently | ws://bitcoinr6de5lkvx4tpwdmzrdfdpla5sya2afwpcabjup2xpi5dulbad.onion | operator | N/A | | relay.westernbtc.com | The westernbtc.com paid relay | ws://westbtcebhgi4ilxxziefho6bqu5lqwa5ncfjefnfebbhx2cwqx5knyd.onion | operator | Payment URL | | freelay.sovbit.host | Free relay for sovbit.host | ws://sovbitm2enxfr5ot6qscwy5ermdffbqscy66wirkbsigvcshumyzbbqd.onion | operator | N/A | | nostr.sovbit.host | Paid relay for sovbit.host | ws://sovbitgz5uqyh7jwcsudq4sspxlj4kbnurvd3xarkkx2use3k6rlibqd.onion | operator | N/A | | nostr.wine | 🍷 nostr.wine relay | ws://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion | operator | Payment URL | | inbox.nostr.wine | 🍷 inbox.nostr.wine relay | ws://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion | operator | Payment URL | | filter.nostr.wine | 🍷 filter.nostr.wine proxy relay | ws://winefiltermhqixxzmnzxhrmaufpnfq3rmjcl6ei45iy4aidrngpsyid.onion | operator | Payment URL | | N/A | N/A | ws://pzfw4uteha62iwkzm3lycabk4pbtcr67cg5ymp5i3xwrpt3t24m6tzad.onion:81 | operator | N/A | | nostr.fractalized.net | Free relay for fractalized.net | ws://xvgox2zzo7cfxcjrd2llrkthvjs5t7efoalu34s6lmkqhvzvrms6ipyd.onion | operator | N/A | | nfrelay.app | nfrelay.app aggregator relay (nostr-filter-relay) | ws://nfrelay6saohkmipikquvrn6d64dzxivhmcdcj4d5i7wxis47xwsriyd.onion | operator | N/A |
-
 @ fd208ee8:0fd927c1
2024-10-09 12:27:53
@ fd208ee8:0fd927c1
2024-10-09 12:27:53Why waste time, looking at other people's stuff?
I get this question a lot, on Nostr, and it feeds immediately back to the next question: Why don't you just build your own client, if you're so smart?
This was a completely new question for me, as I'm used to collaborating with at least one other person, even when doing FOSS stuff. (No, this isn't my first such project; we just used to call it "volunteering" and "sharing the code", which sounds way less glamorous.) It never occurred to me, that a habit of collaboration and interaction was some sign of my ignorance and incompetence, or somehow proof that I can't vomit up "Hello World!" in 5 different programming languages.
I also made the deadly political mistake, when I entered the Nostrsphere, of refusing to call myself a "dev". For me, "dev" is a special title, given to someone doing a specific type of programming (fiddling with GUIs, mostly, which I've only done occasionally, as a sub), whereas the types I've done are "test automation", "development operations", "database management and data curation", "requirements engineering", and "application administration". Because it's so much easier to find someone interested in building a GUI, rather than building AnythingElse, I tend to slide into AnythingElse and it eventually became my professional specialty to be the Girl Friday of every project.

But, in Nostr, there is no AnythingElse category. There are only (GUI) client devs and AllOfTheIdiotsWhoMustBowDownToTheDevs. Which merely doubled my instinct to distance myself from the term. I do not want to join some cargo cult and be pedestalized and regarded as some sort of superhuman everyone owes fealty to, in return for raining GUI presents down on my loyal subjects.
Software engineers are simply people who are skilled craftsman, not gods, and it is fair to point out that some are more skilled than others. It is also completely fair to criticize their products, report bugs, and wonder aloud at endemic low-quality.
Which brings me back to the initial question:
What does the inquisitive dev know, that the others don't?
1) You learn an awful lot about an awful lot, by looking at specs, reviewing code, and trying out various implementations of concepts you are already familiar with. There are, in fact, n number of use cases for every event type, and I've seen so many of them, that I can conjure them up, or invent new ones, on the fly, rather than wasting time inventing similar events. 2) They don't have to explain their concept to you, later, when you interact. Each interaction brings you closer to parallel-levels of knowledge, which raises the signal-strength of the interaction, and widens your own knowledge base, for interacting with third parties. 3) You are increasingly-likely to contribute code or perform some other more-advanced task, for other people, as you don't face the hurdle of adjusting to a new repo or unfamiliar language, while being less-likely to merely fork-and-ignore because you have a standing business relationship with the other developer. 4) If the other dev stops maintaining the repo, you'll be inclined to continue on your own. You may even eventually receive administrative access, rather than needing to fork, as they trust you with their stuff. This means that the risk of the repo becoming abandoned falls, with each active dev snooping around it, even if that is not their primary project. 5) It helps you determine who to focus your energy on interacting with, further. Is this person new to software development, perhaps, but has some interesting transfer-knowledge from some other branch, that has resulted in a surprisingly novel concept? Is this person able to write very clean code, so that merely reading their code feels like mental training for your own craftsman's toolbox?
...and many more reasons, but this is getting too long, so, let's just cut to the chase.
What does a craftswoman want?
But, this still doesn't answer the question of my private motivation. Why do I want to gather all of this knowledge, from those further ahead, than I?
I think Nostr has long moved past the initial stage, where mere speed was of the essence, so that one npub could finally post a note and have it appear on the other npubs' client. That must have felt like a miracle, but it increasingly feels like a disaster, as the steadily-rising complexity of the Nostr ecosystem causes haphazardly-structured and largely-unexamined code bases to begin to atrophy, or result in developers running around at an exhausting speed, with their bug-extinguishers, to put out fire after fire.
I think the time has arrived, for a different kind of development. Maybe even for a different kind of developer. Not replacing the experimentalism that made Nostr fun, but adding the realm of production-quality software engineering. The sort of software development that requires relay administration, testing, support... collaboration, interaction, maybe even someone who does AnythingElse.
I want to build useful, elegant products people enjoy using and feel comfortable relying on. I want them to use them, naturally and happily, to accomplish tasks they consider worthwhile. I don't want them thinking about me, while they use it. The craftswoman should never be greater than her work.
I want them to feel free -- nay, be eager! -- to give me both positive and negative feedback. My assumption is always that our production is imperfect because we are imperfect, so you do us a favor, by pointing out where we can improve. That's why we wish to integrate a feedback form that produces ngit issue events, putting your questions and comments straight on our board.
And there will be an AnythingElse person, reading that board, and responding promptly, rest assured.
-
 @ 97fc03df:8bf891df
2024-10-24 07:53:50
@ 97fc03df:8bf891df
2024-10-24 07:53:50A Value Internet Sharing Bitcoin’s Consensus Security
Author: BEVM, October 2024
Abstract
Super Bitcoin is a value-based internet centered on BTC, and share Bitcoin's consensus security. This value internet not only inherits the security of the existing Bitcoin network but also transcends BTC's current limitations of being solely used for transfer, providing the Bitcoin network infinite potential for scalability and flexibility.
While the Lightning Network [2] inherits Bitcoin's network security and offers partial scalability solutions, it still falls short in supporting smart contracts and further enhancing scalability. We propose a five-layer architecture for Super Bitcoin using the Bitcoin network as the kernel layer, maintaining system security and transaction irreversibility through the proof-of-work (PoW) consensus mechanism; we build an efficient communication layer based on the Lightning Network, facilitating rapid transmission of asset information while preserving Bitcoin's decentralized nature; we introduce the Taproot Consensus as the extension layer, abstracting Lightning Network communication and asset information to provide a standardized interface for the upper virtual machine layer; we set up a multi-chain layer, also known as the fusion layer, which consists of multiple lightning chains secured by BTC consensus, integrating any mainstream virtual machine (VM) to achieve a "Multi-chain interconnection“ and ”multi-chain interoperability” unified by BTC consensus; finally, we support the application layer, providing developers with rich tools and interfaces to build a decentralized application (DApp) ecosystem, all sharing the security of BTC consensus.
1. Introduction
As the pioneer of cryptocurrencies, Bitcoin (BTC), through its proof-of-work (PoW) consensus mechanism and decentralized network structure, has garnered an immense level of consensus, becoming a supranational currency. This security stems from the perfect combination of its vast network hash power and economic incentives. The birth of Bitcoin not only ushered in a new era of decentralized digital currency but also pointed the way for the subsequent development of blockchain technology. However, the limitations of Bitcoin’s scripting language soon became apparent, as it only supports simple value transfers and limited contract logic, unable to meet the demands of more complex decentralized applications.
The evolution of blockchain technology is essentially all about expanding and enhancing Bitcoin's capabilities. Vitalik Buterin, the founder of Ethereum, initially envisioned adding smart contract functionality to Bitcoin. However, due to the technological constraints of the time and the limitations of the Bitcoin network, Ethereum had to establish its own independent consensus system. While this approach allowed for the creation of Turing-complete smart contracts, it also introduced new security risks and scalability challenges. Many projects followed suit, building independent blockchain ecosystems, gradually diverging from and even forgetting the original intention of extending Bitcoin’s capabilities.
However, two key factors remind us of the need to reconsider this direction. First, the continued rise in Bitcoin’s value relative to other cryptocurrencies like Ethereum has validated the trust people place in its security and stability. Second, the collapse of Luna/UST, which wiped out nearly $100 billion in market value, highlighted the severe security vulnerabilities present in independent consensus chains, especially when faced with complex economic models and rapidly growing network value.
In this context, we introduce Super Bitcoin to create a true value internet sharing Bitcoin's consensus security. It fundamentally differs from the existing Bitcoin Layer 2 solutions: traditional Bitcoin Layer 2 solutions (such as the Lightning Network) mainly achieve fast payments through off-chain state channels and limited scripts, while sharing Bitcoin's consensus security but lacking flexibility. Meanwhile, sidechains like Stacks or Layer 2 solutions, although they support smart contracts, still rely on independent multi-signature mechanisms for security, thus not fully inheriting the security of the Bitcoin mainnet.
2. Technical Background
To fully understand the proposed solution, it is necessary to first review the background and development of several key technologies. This chapter briefly introduces the Lightning Network, the Substrate framework [3], BEVM's Taproot Consensus, and the multi-chain interoperability system to provide a foundation for understanding our solution.
2.1 Lightning Network
The Lightning Network is a Layer2 scaling solution for Bitcoin, with its core design principles detailed in the BOLT (Basis of Lightning Technology) specifications. These specifications not only ensure the efficient operation of the Lightning Network but also ingeniously achieve deep integration with the consensus security of the Bitcoin mainnet. Several parts of the BOLT specifications play a key role in sharing Bitcoin’s consensus security.
BOLT #2 and BOLT #3 provide detailed guidelines on the lifecycle management of payment channels and the structure of transactions. The opening of a channel involves creating a multi-signature output on the Bitcoin blockchain, while closing the channel requires broadcasting the final state to the mainnet. BOLT #3 specifically defines commitment transactions, which are the core mechanism by which the Lightning Network shares Bitcoin's consensus security. Each time the channel state is updated, a new commitment transaction is generated, which can be broadcast to the Bitcoin mainnet if needed. The design of commitment transactions ensures that even if one party in the channel becomes uncooperative, the other party can still close the channel by broadcasting the most recent commitment transaction and receive their due funds. This mechanism directly relies on Bitcoin’s consensus rules and security, meaning the Lightning Network’s security is essentially guaranteed by the Bitcoin network.
BOLT #5 defines the penalty mechanism for channel closures. This mechanism introduces the concept of "revocating private keys," effectively preventing participants from broadcasting outdated channel states. If dishonest behavior is detected, the honest party can use these keys to punish the other party on the Bitcoin main chain, thereby ensuring the accuracy of the channel state and enforcing honest behavior among participants through Bitcoin's consensus mechanism.
Additionally, the commitment transaction format specified in BOLT #3 connects Lightning Network transactions to Bitcoin's fee market through "anchor outputs." This not only enhances the security of transactions but also ensures that Lightning Network transactions can still be confirmed promptly during periods of network congestion.
These meticulously designed specifications collectively ensure that the Lightning Network, while providing fast and low-cost transactions, can still fully leverage Bitcoin's robust consensus security.
2.2 Substrate Framework
The Substrate framework is a highly modular blockchain development toolkit written in Rust, providing a powerful and flexible technical foundation for the implementation of Super Bitcoin. Its core strength lies in its pluggable Pallet system, where these pre-built functional modules serve as "blockchain Legos," enabling us to quickly and efficiently assemble and customize the desired features.
For Super Bitcoin, Substrate's modular design is crucial. It allows us to flexibly build and integrate various functional components on top of the shared Bitcoin consensus security. By leveraging Substrate's Pallet, we can easily support and integrate different virtual machine environments, thereby increasing the system's flexibility and adaptability. This design not only accelerates the development process but also provides Super Bitcoin with powerful scalability, allowing it to better meet the evolving needs of the blockchain ecosystem.
Super Bitcoin utilizes these features of Substrate to customize the BEVM-stack framework, which enables one-click deployment of lightning chains.
2.3 Taproot Consensus
BEVM’s Taproot Consensus integrates Bitcoin’s Taproot upgrade [4] technology. This technology combines several key elements: Schnorr signatures [5] provide signature aggregation capabilities, Merkelized Abstract Syntax Tree (MAST) support complex conditional scripts, and Musig2 enables two-round communication in multi-signature schemes. Through the combination of these technologies, BEVM successfully implements a decentralized threshold signature network with (t, n) support.
Additionally, BEVM leverages Bitcoin SPV (Simplified Payment Verification) technology to achieve lightweight decentralized block header synchronization. This allows transaction verification without downloading the full blockchain data, enabling BEVM to synchronize with the BTC mainnet in a decentralized manner. In Super Bitcoin architecture, Taproot Consensus plays a key role as the extension layer: it interfaces with the Lightning Network below, abstracting and integrating asset information, and provides standardized interfaces for different virtual machine execution environments above, realizing the transmission and utilization of asset information.
Such design makes Taproot Consensus a core component of the Super Bitcoin architecture. It not only inherits the security and privacy-preserving characteristics of the Bitcoin network but also provides rich functional support for upper-layer applications.
2.4 Multi-Chain Interoperability System
The concept of a multi-chain interoperability system was first introduced by Polkadot. Polkadot [6] is a multi-chain interoperability system based on the Substrate framework, sharing the security of DOT consensus, and using parachains for application chain expansion. Correspondingly, Super Bitcoin is a multi-chain interoperability system built on Bitcoin and the Lightning Network, sharing BTC consensus security, and using Lightning Chains for application chain expansion.
The differences between the two are as follows:
-
Shared Consensus Security: Both Polkadot and Super Bitcoin’s multi-chain networks achieve shared consensus security, but Polkadot shares DOT consensus, while Super Bitcoin shares Bitcoin consensus. The strength of BTC’s consensus is far greater than that of DOT. Theoretically, the security of the Super Bitcoin architecture is 200 times higher than that of the Polkadot network. This "200 times" represents the current ratio of BTC’s $1.3 trillion market cap to DOT’s $6.5 billion market cap. Therefore, the Lightning Chains on Super Bitcoin offer approximately 200 times the security of Polkadot's parachains.
-
Application Chain Architecture: Super Bitcoin’s lightning chain is deployed with one click based on BEVM-stack, whereas on Polkadot, parachains are deployed via Substrate with one-click.
-
Cross-Chain Communication Protocol: Super Bitcoin uses lightning channels as the communication protocol between Lightning Chains, while Polkadot uses XCMP as the communication protocol between parachains.
3. System Architecture

3.1 System Architecture Overview
Super Bitcoin is a five-layer architecture protocol built by BEVM guided by the three problems of blockchain - decentralization, security and scalability.. This protocol is based on the Bitcoin protocol and utilizes the Lightning Network for efficient peer-to-peer communication. To extend the functionality of Lightning Network nodes, Super Bitcoin integrates Taproot Consensus and combines Bitcoin SPV, Schnorr signatures, MAST contracts, and a BFT PoS consensus mechanism to achieve scalable state management and transaction processing.
On this foundation, Super Bitcoin further integrates multiple virtual machines, including WASM, EVM, SVM, MoveVM, and CairoVM, creating a multi-chain system based on lightning chains that offers a diverse range of smart contract execution environments. This modular framework significantly enhances the system's scalability and flexibility while maintaining the decentralized nature of the Bitcoin network. Importantly, all lightning chains share the Bitcoin network's consensus security, ensuring that the system remains highly secure as it scales.
3.2 Kernel Layer
The Bitcoin network serves as the kernel layer of Super Bitcoin, maintaining the security and irreversibility of the entire system through the Proof-of-Work (PoW) consensus mechanism. This decentralized peer-to-peer electronic cash system primarily supports BTC transfers and basic opcode execution, managing state using the UTXO model. The Bitcoin network’s block structure and transaction data serve as the input for the Lightning Network, providing reliable foundational data for the upper layers. Although Bitcoin’s scripting system is not Turing-complete, it can support the most basic smart contract functionality through stack-based operations, conditional checks, and cryptographic functions. The network maintains a block time of approximately 10 minutes using a difficulty adjustment algorithm and uses Merkle tree structures to optimize transaction verification efficiency. The security and decentralization of this foundational layer provide a robust consensus security foundation for the entire Super Bitcoin architecture, while its simple design and limited scripting capabilities offer a stable and predictable environment for upper-layer expansion.
3.3 Communication Layer
The Lightning Network serves as the communication layer of Super Bitcoin, achieving efficient asset information transmission while sharing the BTC consensus security. It acts as a bridge between users and the Super Bitcoin ecosystem, enabling bidirectional payment channels through a Hashed Time Lock Contract (HTLC), supporting multi-hop routing and atomic swaps. Users can establish state channels with Super Bitcoin nodes to deposit funds and conduct instant off-chain transactions.
Super Bitcoin nodes, as specialized Lightning Network nodes, not only maintain direct channels with users but also remain compatible with the existing Lightning Network by implementing the BOLT (Basis of Lightning Technology) specifications. This design allows users to leverage the existing Lightning Network infrastructure for cross-node, cross-chain payments and value transfers, providing a secure communication foundation for the lightning chains.
3.4 Extension Layer
Taproot Consensus serves as the extension layer in Super Bitcoin, playing a critical role in connecting the Lightning Network with the upper-layer lightning chains. It abstracts the asset information transmitted through the Lightning Network and converts it into blockchain data that can be processed by the upper layers, balancing the payment efficiency of the Lightning Network with the logical needs of upper-layer applications.
This expansion layer integrates Bitcoin SPV, Schnorr signatures, MAST (Merkelized Abstract Syntax Tree) structures, and a BFT (Byzantine Fault Tolerance) PoS consensus mechanism to achieve multiple functions:
1. Connecting the Lower Layer :Bitcoin SPV enables lightweight block header verification, allowing nodes to synchronize with the Bitcoin network in a decentralized manner, providing reliable on-chain data input for the Lightning Network.
2. Information Processing and Storage: The PoS-based blockchain network provides distributed storage of Lightning Network channel states. It also processes information for BTC and Taproot Assets, supplying necessary data for upper-layer applications. This mechanism ensures data redundancy and resistance to censorship.
3. Security Assurance : Decentralized threshold signatures replace the local key management system of Lightning Network nodes, enhancing key security and flexibility. The aggregation feature of Schnorr Signatures is used to construct a (t, n) threshold signature network, replacing the traditional single-key management model of the Lightning Network.
4. Privacy and Complexity : The MAST structure allows complex conditional scripts to be represented on-chain as a single hash, improving both privacy and script complexity. Through these mechanisms, the Taproot Consensus extension layer effectively converts verified Lightning Network data into standardized blockchain states. While ensuring security and privacy, it enhances the overall system's performance and scalability. It not only connects the underlying Bitcoin and Lightning Networks but also provides the upper-layer applications with rich and reliable data and functional support.
#### 3.5 Fusion Layer The Fusion Layer reflects the scalability of Super Bitcoin. It builds on top of Taproot Consensus and utilizes the extensibility of the Substrate framework to achieve a multi-chain interconnected system. Its key features include:
1. Scalable Multi-Chain Architecture: Supports the deployment and interconnection of an unlimited number of lightning chains, with BEVM serving as a special lightning chain responsible for managing cross-chain interactions and resource scheduling.
2. Heterogeneous Compatibility and Standardized Protocols: Compatible with multiple virtual machines (such as MoveVM, CairoVM, SVM, EVM) and achieves atomic asset exchange and state synchronization through a standardized cross-chain protocol based on the Lightning Network.
3. Shared Security and Flexible Consensus: All lightning chains inherit the security of the Bitcoin network, while adopting a pluggable consensus design, with the default being a Taproot-compatible BFT variant.
4. Ecosystem Expansion: Facilitates the rapid migration of existing blockchain technologies, extending the decentralized BTC ecosystem to various Turing-complete blockchain applications.
With these features, the Fusion Layer enables Super Bitcoin to evolve into a highly scalable, secure, and interoperable multi-chain ecosystem, providing robust infrastructure support for blockchain innovation.
3.6 Application Layer
The Application Layer is built on top of Super Bitcoin's multi-chain architecture, offering developers a diverse decentralized application (DApp) ecosystem. Leveraging the security, scalability, and interoperability of the underlying layers, it supports the deployment of applications on any Turing-complete virtual machine. Developers can choose to quickly deploy proprietary application chains within the lightning chain framework, or they can deploy various applications directly on the lightning chains. All these applications and chains automatically inherit the consensus and security guarantees of the Bitcoin network.
The Application Layer integrates multiple smart contract execution environments, supporting programming languages such as Solidity (EVM), Move, Cairo, and Rust. The Application Layer lowers the entry barrier for developers and accelerates the innovation cycle. Through standardized API interfaces, developers can utilize Lightning Network channels to achieve decentralized cross-chain asset transfers and information exchanges. Additionally, it incorporates protocols like Taproot Assets, which are compatible with the Lightning Network, further enhancing cross-chain functionality.
Although the services provided by the Application Layer are similar to other VM-based public blockchains, it has two distinctive features: first, it allows the use of decentralized native BTC as the base currency for applications; second, the entire application layer shares the security of the Bitcoin network. Such design not only offers a rich development environment but also ensures that applications are built on solid security and native cryptocurrency support.
4. Shared Consensus Security
Shared BTC consensus security is the security core of our five-layer architecture. This concept is derived from Polkadot's shared security model, which Polkadot defines as Shared Security, also known as Pooled Security, is one of Polkadot's unique value propositions. In essence, it means that all parachains connected to Polkadot's relay chain benefit from the full security of the entire Polkadot network.
Our five-layer protocol architecture further extends this concept by leveraging the Bitcoin (BTC) network—currently recognized as the most secure blockchain consensus system—to ensure the security of the entire ecosystem. Compared to Polkadot's parachains, which share Polkadot's consensus security, our architecture is directly built on top of the Bitcoin network, sharing Bitcoin’s consensus security.
Existing BTC Layer2 solutions typically ensure security through cross-chain mechanisms or BTC staking, which only utilize part of Bitcoin’s consensus security. In contrast, our five-layer protocol is built on the Lightning Network, using HTLC (Hashed Timelockd Contract) and commitment transactions, with security fully dependent on BTC consensus. This design allows our system to fully inherit the consensus security of the Bitcoin network.
Specifically, our architecture achieves shared BTC consensus security through the following methods:
-
Leveraging the peer-to-peer channels of the Lightning Network to ensure that all transactions are ultimately settled on the Bitcoin mainnet.
-
Using HTLC commitment transactions, where each state update is protected by the consensus of the Bitcoin network.
-
Through the Taproot Consensus extension layer, extending Bitcoin's security features to more complex smart contract environments.
-
In the multi-chain system, all lightning chains share Bitcoin’s network consensus security, ensuring consistency and reliability across the entire ecosystem.
5. Lightning Chain
Based on the shared BTC consensus security, we utilize the lightning chain to create a Value Internet. To achieve this, the architecture of the lightning chain network is inspired by Polkadot's relay chain and parachain design:
-
Relay Chain: It serves as the central nervous system of the entire network, responsible for the overall security, cross-chain communication, and consensus mechanism. The relay chain does not execute specific application logic but focuses on coordinating the operations of the entire ecosystem.
-
Parachains: These are independent blockchains that run in parallel with the relay chain. Each parachain can have its own token economy and governance mechanism, achieving interoperability through the relay chain and sharing the security guarantees provided by the relay chain. Drawing from Polkadot’s design, Super Bitcoin proposes a multi-chain interoperability system based on Bitcoin and the Lightning Network. In this system, the Lightning Chain functions similarly to Polkadot's parachains, with the following unique characteristics:
Shared BTC Consensus Security: Unlike Polkadot’s independent consensus model based on PoS staking, Lightning Chain directly inherits the consensus security of the Bitcoin network, providing unprecedented security for the entire ecosystem.
-
Lightning Network Integration: Lightning Chain deeply integrates Lightning Network technology, enabling high-speed, low-cost transaction processing, significantly enhancing the throughput and efficiency of the entire system.
-
Scalability: Theoretically, an unlimited number of Lightning Chains can be deployed, with each Lightning Chain optimized for specific application scenarios or industry needs, offering a high degree of flexibility and scalability.
-
BEVM as the Core Coordinator: In this ecosystem, BEVM (Bitcoin-Enhanced Virtual Machine) acts as a special Lightning Chain, playing a role similar to that of Polkadot’s relay chain. It is responsible for the governance and resource allocation of the entire network, ensuring efficient collaboration between different Lightning Chains.
-
Shared Lightning Network Liquidity: All Lightning Chains share the same Lightning Network, which means they can access a common liquidity pool, improving capital efficiency.
These features not only highlight the innovative design of Lightning Chain but also underscore its fundamental differences from existing BTC Layer 2 solutions. By directly sharing Bitcoin network consensus security and Lightning Network liquidity, Lightning Chain achieves a qualitative leap in both security and interoperability.
5.1 Lightning Chain
The Lightning Chain is the core component of Super Bitcoin that directly interacts with users. Its main responsibilities include handling user transactions, managing asset mapping, and executing smart contracts.
5.1.1 BTC Asset Mapping

Lightning Chain functions as both a node in the Lightning Network and a PoS (Proof of Stake) network. In this system, BTC is locked within the Lightning Network, while L-BTC represents the user's BTC balance in their Lightning Chain account. The mapping process between these two ensures the consistency and security of the assets. The specific BTC-to-L-BTC mapping process is as follows: - The user establishes a channel with the Lightning Chain via the standard Lightning Network protocol. - The user deposits A BTC into the Lightning Network channel. - As the Lightning Chain operates as a PoS network, the validators within the network observe this new BTC deposit. - Once more than two-thirds of the validators reach consensus and confirm the BTC deposit event, the Lightning Chain will issue A L-BTC accordingly.
This process ensures that the issuance of L-BTC always maintains a 1:1 ratio with the BTC locked in the Lightning Network channel. It's important to note that L-BTC is self-custodied by the user, so there is no need to worry about asset security. Additionally, PoS consensus here is not used to secure L-BTC assets but acts as a distributed ledger for the state of the Lightning Network channel, solving the potential issue of data loss in local storage by Lightning Network nodes.
5.1.2 Smart Contract Interaction on the Lightning Chain

Interaction with smart contracts on the Lightning Chain follows a "authorize first, execute later" paradigm. In this process, users need to convert L-BTC into M-BTC, where M-BTC represents the asset that can interact with smart contracts on the Lightning Chain. The specific interaction process is as follows:
- Asset Preparation: The user holds A BTC in the Lightning Network state channel and decides to interact with a smart contract using 1 BTC.
- Authorization Operation: The user authorizes the Lightning Chain network to convert 1 L-BTC into 1 M-BTC. This step does not immediately execute the conversion but provides the necessary permissions for subsequent interactions.
- Smart Contract Invocation: The user initiates a smart contract call, specifying the use of 1 M-BTC. The Lightning Chain network checks the authorization and, upon confirming its validity, performs the following actions: destroys 1 L-BTC from the user’s balance, mints 1 M-BTC, and uses it directly for interaction with the smart contract.
- Transaction Execution: The smart contract executes the specified operation using the minted M-BTC.
This process enables the seamless application of Bitcoin assets within a smart contract environment while maintaining a clear separation between L-BTC, which functions as channel liquidity, and M-BTC, which serves as a medium for contract interaction.
5.2 System Chain

System Chain is the core coordination component of Super Bitcoin implemented through the upgraded BEVM (Bitcoin-Enhanced Virtual Machine). As a special Lightning Chain, it establishes direct connections with all regular Lightning Chains in the network, forming an efficient star topology structure. This design makes the System Chain the central hub of Super Bitcoin.
The System Chain is primarily responsible for incentivizing Lightning Network nodes and coordinating cross-chain interoperability, effectively managing the entire network to ensure its efficient operation. In terms of node incentives, the System Chain implements a complex and sophisticated mechanism. It uses a dynamic reward algorithm that adjusts reward distribution based on the activity level, liquidity provided, and overall contribution to the network. During this process, the System Chain considers multi-dimensional evaluation metrics, such as the node’s uptime, transaction throughput, and routing efficiency.
In terms of cross-chain interoperability, the System Chain plays a key coordination role, facilitating seamless interactions between different Lightning Chains. It implements a secure cross-chain communication protocol based on Hashed Time Lock Contract (HTLC), ensuring the security and reliability of message transmission. Additionally, the System Chain introduces an atomic swap mechanism, which effectively prevents potential loss of funds during cross-chain asset transfers. Furthermore, by defining a unified cross-chain asset standard, the System Chain simplifies the asset mapping process between different Lightning Chains, further improving the efficiency and convenience of cross-chain operations.
6. Economic Model
The economic model of BEVM (Bitcoin-Enhanced Virtual Machine) combines Bitcoin’s issuance mechanism with the functional characteristics of the Lightning Network. It aims to address the sustainable competitiveness of Super Bitcoin and provide a long-term incentive system for the Lightning Network.
At the core of this model is the combination of Lightning Network node incentives and a staking-mining mechanism. Lightning Network nodes that establish state channels with the BEVM network can participate in staking mining. Staking mining uses a Verifiable Random Function (VRF) to determine mining probabilities, rather than distributing rewards proportionally based on the staked amount.
During the staking mining process, participants stake BTC in state channels, and the system calculates the mining probability based on the VRF. For example, if three nodes stake 100 BTC, 10 BTC, and 1 BTC, their respective mining probabilities would be 90.09%, 9.01%, and 0.90%. This mechanism ensures that smaller stakers also have a substantial opportunity to earn rewards. A dedicated whitepaper on the economic model will be released for this section, so this document will not go into further details.
7. Future Development
7.1 Short-Term Goals
The short-term goals of Super Bitcoin focus on implementing core functionalities and building the necessary infrastructure. By realizing the proposed five-layer protocol, we will introduce smart contract functionality based on the Lightning Network while sharing BTC consensus security. For users, participating in Super Bitcoin ensures that the BTC they hold remains fully under their control. At the same time, they will be able to use BTC, Taproot Assets, and other native assets within smart contracts.
7.2 Long-Term Vision
The long-term vision of Super Bitcoin is to build a global Value Internet that shares BTC consensus security. We aim to design an incentive mechanism through an innovative economic model, promoting widespread use of Lightning Network nodes. Furthermore, we are committed to deeply integrating existing blockchain ecosystems with Super Bitcoin, enabling the free flow and interaction of BTC assets. By doing so, we aim to create a secure, efficient, and interoperable blockchain ecosystem where BTC becomes the core, and all blockchain consensus models share the security of the Bitcoin network. Ultimately, our goal is to enable the Bitcoin network to scale infinitely while maintaining decentralization.
7.3 Potential Challenges and Solutions
Super Bitcoin faces several potential challenges in achieving its goals. Transforming Lightning Network nodes into a full-fledged network involves complex technical challenges that require extensive testing. Another challenge is designing a better economic incentive model to attract enough Lightning Network node operators to adopt Super Bitcoin. Ensuring seamless communication and atomic swaps between different node networks is also crucial, and the team will focus on developing standardized protocols and interfaces to enhance network interoperability. As the system’s complexity increases, maintaining network security will become more challenging. Super Bitcoin will adopt rigorous security audit processes and consider introducing advanced cryptographic technologies to strengthen system security. As the number of lightning chains grows, managing the state and interaction between networks may pose scalability challenges. By actively addressing these challenges, Super Bitcoin aims to bring revolutionary changes to the Bitcoin and Lightning Network ecosystems, creating a more flexible, efficient, and scalable infrastructure.
8. Conclusion
The five-layer architecture introduced by Super Bitcoin not only solves the problem of existing BTC Layer 2 solutions not being able to share Bitcoin's consensus security but also addresses the limitation of the Lightning Network being restricted to payment scenarios. It perfectly combines the shared BTC consensus security with smart contract functionality. Our protocol uses the Bitcoin network as the core, ensuring the highest level of security. It leverages the Lightning Network to construct an efficient communication layer, significantly improving scalability and flexibility while preserving the security of the native BTC consensus. By introducing Taproot Consensus as the extension layer, it abstracts Bitcoin and Lightning Network data to provide actionable data for the upper layers. Through the multi-chain fusion layer formed by lightning chains, we achieve a "multi-chain interconnection" supporting the free flow of cross-chain assets. The application layer offers developers a rich set of tools, fostering the development of a diverse DApp ecosystem. Combined with the innovative VRF-based staking mining mechanism, Super Bitcoin adds an incentive layer to the Lightning Network and allows the decentralized Bitcoin network to have unlimited flexibility and scalability.
9. References
[1] Nakamoto, S. (2008). "Bitcoin: A Peer-to-Peer Electronic Cash System." https://bitcoin.org/bitcoin.pdf
[2] Poon, J., & Dryja, T. (2016). "The Bitcoin Lightning Network: Scalable Off-Chain Instant Payments." https://lightning.network/lightning-network-paper.pdf
[3]Habermeier, S., et al. (2020). "Substrate: A modular framework for building blockchains." https://www.parity.io/substrate/
[4]Wuille, P., Nick, J., & Towns, A. (2019). "Taproot: SegWit version 1 spending rules." https://github.com/bitcoin/bips/blob/master/bip-0341.mediawiki
[5] Nick, J., Seurin, Y., & Wuille, P. (2020). "Schnorr Signatures for secp256k1." https://github.com/bitcoin/bips/blob/master/bip-0340.mediawiki
[6]Wood, G. (2016). "Polkadot: Vision for a heterogeneous multi-chain framework." https://polkadot.network/PolkaDotPaper.pdf
-
-
 @ 18bdb66e:82eb5e5d
2024-10-14 23:58:32
@ 18bdb66e:82eb5e5d
2024-10-14 23:58:32Chef's notes
Serve with side salad.
Details
- ⏲️ Prep time: 10 mins
- 🍳 Cook time: 10 mins
- 🍽️ Servings: 2-4
Ingredients
- 3 sausage links cut into penny sized slices, or two patties crumbled
- 2 Cans (10 ½ ounces) condensed minestrone soup
- 1 can (10.5 ounces) condensed tomato soup.
- 3 Soup cans water
- Croutons
Directions
- Brown sausage in saucepan
- Add soups, and water
- Heat through, stirring often.
- Garnish with croutons
-
 @ 3c984938:2ec11289
2024-06-09 14:40:55
@ 3c984938:2ec11289
2024-06-09 14:40:55I'm having some pain in my heart about the U.S. elections.
Ever since Obama campaigned for office, an increase of young voters have come out of the woodwork. Things have not improved. They've actively told you that "your vote matters." I believe this to be a lie unless any citizen can demand at the gate, at the White House to be allowed to hold and point a gun to the president's head. (Relax, this is a hyperbole)
Why so dramatic? Well, what does the president do? Sign bills, commands the military, nominates new Fed chairman, ambassadors, supreme judges and senior officials all while traveling in luxury planes and living in a white palace for four years.
They promised Every TIME to protect citizen rights when they take the oath and office.
...They've broken this several times, with so-called "emergency-crisis"
The purpose of a president, today, it seems is to basically hire armed thugs to keep the citizens in check and make sure you "voluntarily continue to be a slave," to the system, hence the IRS. The corruption extends from the cop to the judge and even to politicians. The politicians get paid from lobbyists to create bills in congress for the president to sign. There's no right answer when money is involved with politicians. It is the same if you vote Obama, Biden, Trump, or Haley. They will wield the pen to serve themselves to say it will benefit the country.
In the first 100 years of presidency, the government wasn't even a big deal. They didn't even interfere with your life as much as they do today.
^^ You hold the power in your hands, don't let them take it. Don't believe me? Try to get a loan from a bank without a signature. Your signature is as good as gold (if not better) and is an original trademark.
Just Don't Vote. End the Fed. Opt out.
^^ I choose to form my own path, even if it means leaving everything I knew prior. It doesn't have to be a spiritual thing. Some, have called me religious because of this. We're all capable of greatness and having humanity.
✨Don't have a machine heart with a machine mind. Instead, choose to have a heart like the cowardly lion from the "Wizard Of Oz."
There's no such thing as a good president or politicians.
If there was, they would have issued non-interest Federal Reserve Notes. Lincoln and Kennedy tried to do this, they got shot.
There's still a banner of America there, but it's so far gone that I cannot even recognize it. However, I only see a bunch of 🏳🌈 pride flags.
✨Patrick Henry got it wrong, when he delivered his speech, "Give me liberty or give me death." Liberty and freedom are two completely different things.
Straightforward from Merriam-Webster Choose Right or left?
No control, to be 100% without restrictions- free.
✨I disagree with the example sentence given. Because you cannot advocate for human freedom and own slaves, it's contradicting it. Which was common in the founding days.
I can understand many may disagree with me, and you might be thinking, "This time will be different." I, respectfully, disagree, and the proxy wars are proof. Learn the importance of Bitcoin, every Satoshi is a step away from corruption.
✨What does it look like to pull the curtains from the "Wizard of Oz?"
Have you watched the video below, what 30 Trillion dollars in debt looks like visually? Even I was blown away. https://video.nostr.build/d58c5e1afba6d7a905a39407f5e695a4eb4a88ae692817a36ecfa6ca1b62ea15.mp4
I say this with love. Hear my plea?
Normally, I don't write about anything political. It just feels like a losing game. My energy feels it's in better use to learn new things, write and to create. Even a simple blog post as simple as this. Stack SATs, and stay humble.
<3 Onigirl
-
 @ 3bf0c63f:aefa459d
2024-05-24 12:31:40
@ 3bf0c63f:aefa459d
2024-05-24 12:31:40About Nostr, email and subscriptions
I check my emails like once or twice a week, always when I am looking for something specific in there.
Then I go there and I see a bunch of other stuff I had no idea I was missing. Even many things I wish I had seen before actually. And sometimes people just expect and assume I would have checked emails instantly as they arrived.
It's so weird because I'm not making a point, I just don't remember to open the damn "gmail.com" URL.
I remember some people were making some a Nostr service a while ago that sent a DM to people with Nostr articles inside -- or some other forms of "subscription services on Nostr". It makes no sense at all.
Pulling in DMs from relays is exactly the same process (actually slightly more convoluted) than pulling normal public events, so why would a service assume that "sending a DM" was more likely to reach the target subscriber when the target had explicitly subscribed to that topic or writer?
Maybe due to how some specific clients work that is true, but fundamentally it is a very broken assumption that comes from some fantastic past era in which emails were 100% always seen and there was no way for anyone to subscribe to someone else's posts.
Building around such broken assumptions is the wrong approach. Instead we should be building new flows for subscribing to specific content from specific Nostr-native sources (creators directly or manual or automated curation providers, communities, relays etc), which is essentially what most clients are already doing anyway, but specifically Coracle's new custom feeds come to mind now.
This also reminds me of the interviewer asking the Farcaster creator if Farcaster made "email addresses available to content creators" completely ignoring all the cryptography and nature of the protocol (Farcaster is shit, but at least they tried, and in this example you could imagine the interviewer asking the same thing about Nostr).
I imagine that if the interviewer had asked these people who were working (or suggesting) the Nostr DM subscription flow they would have answered: "no, you don't get their email addresses, but you can send them uncensorable DMs!" -- and that, again, is getting everything backwards.
-
 @ 3bf0c63f:aefa459d
2024-05-21 12:38:08
@ 3bf0c63f:aefa459d
2024-05-21 12:38:08Bitcoin transactions explained
A transaction is a piece of data that takes inputs and produces outputs. Forget about the blockchain thing, Bitcoin is actually just a big tree of transactions. The blockchain is just a way to keep transactions ordered.
Imagine you have 10 satoshis. That means you have them in an unspent transaction output (UTXO). You want to spend them, so you create a transaction. The transaction should reference unspent outputs as its inputs. Every transaction has an immutable id, so you use that id plus the index of the output (because transactions can have multiple outputs). Then you specify a script that unlocks that transaction and related signatures, then you specify outputs along with a script that locks these outputs.

As you can see, there's this lock/unlocking thing and there are inputs and outputs. Inputs must be unlocked by fulfilling the conditions specified by the person who created the transaction they're in. And outputs must be locked so anyone wanting to spend those outputs will need to unlock them.
For most of the cases locking and unlocking means specifying a public key whose controller (the person who has the corresponding private key) will be able to spend. Other fancy things are possible too, but we can ignore them for now.
Back to the 10 satoshis you want to spend. Since you've successfully referenced 10 satoshis and unlocked them, now you can specify the outputs (this is all done in a single step). You can specify one output of 10 satoshis, two of 5, one of 3 and one of 7, three of 3 and so on. The sum of outputs can't be more than 10. And if the sum of outputs is less than 10 the difference goes to fees. In the first days of Bitcoin you didn't need any fees, but now you do, otherwise your transaction won't be included in any block.

If you're still interested in transactions maybe you could take a look at this small chapter of that Andreas Antonopoulos book.
If you hate Andreas Antonopoulos because he is a communist shitcoiner or don't want to read more than half a page, go here: https://en.bitcoin.it/wiki/Coin_analogy
-
 @ 18bdb66e:82eb5e5d
2024-10-14 23:48:00
@ 18bdb66e:82eb5e5d
2024-10-14 23:48:00Chef's notes
Serve over baked potato, cooked white rice, or drop biscuits.
Details
- ⏲️ Prep time: 15 mins
- 🍳 Cook time: 10 mins
- 🍽️ Servings: 2-4
Ingredients
- 2 - 4 Hotdogs, sliced thin
- 1 TBSP Butter
- 1 Can (10.5 oz) bean & bacon soup
- 1 Can (10.5 oz) condensed pea soup
- 1 Soup can of milk
- 1 Soup can of water
Directions
- Lightly brown hotdogs in butter.
- Mix soups, milk, and water in a bowl.
- Add soup mix to hotdogs, heat through but do not boil.
-
 @ 76c71aae:3e29cafa
2024-05-16 04:48:42
@ 76c71aae:3e29cafa
2024-05-16 04:48:42The Curious Case of DSNP: Years of Effort, Minimal Output
It's been a while since I looked at DSNP. There’s news that its backer, Frank McCourt, is trying to put together a team to buy TikTok. That’s insane. The DSNP and Project Liberty team are well-meaning, but they’re even less equipped to run a social network or protocol than Elon Musk at his lowest point when he was firing engineers based on how many lines of code they’d written.
To check what’s happened with DSNP since I last looked a year ago, I just read the entire spec, and there's not actually that much to it. The amount of time and money spent on developing so little is quite stunning. While the spec is fine, it is minimal.
Key Features and Odd Choices
DSNP allows users to have a key pair, write content into a datastore, follow people, and sign messages. However, the protocol seems to mix up layers, specifying the wire protocol, signing system, and at-rest specification format that clients and user data servers might use (pds in atproto, instance in fedi, relay in nostr). They use the ActivityStreams 2.0 schema, which is a good choice. Many new protocols have created their own schemas, but I appreciate DSNP's use of the standard. I wish more protocols had not tried to reinvent the wheel in this respect.
Encrypted Direct Messages and Metadata Privacy
There’s mention in the whitepaper about encrypted direct messages, suggesting it’s possible to hide metadata using techniques from Ethereum’s Whisper. Although the specs or code about DMs don't elaborate much on this, it’s good to see an attempt to hide metadata. However, there’s nothing about double ratchet encryption, forward secrecy, or any advanced encryption techniques. So, overall, it feels quite basic.
Data Storage and Interesting Choices
For storing user data and posts, they're using Apache Parquet, a file format from Hadoop. This is probably the only neat or interesting aspect. I've been searching for a supported data format like Parquet for a while because I think it can facilitate privacy-preserving contact discovery, so it’s cool to see its inclusion here.
Minimal Data Types and Following Options
DSNP supports very minimal data types: post, follow, reaction, profile, and, oddly, location. You can follow publicly or privately, the latter being a neat feature that Scuttlebutt had but most of the current generation of emerging social protocols don't.
Lack of Comprehensive Features
There does not appear to be any client app or server code, which might not be needed. There is an SDK for some core functions, but that’s it. Their documentation lacks information on user discovery, algorithms, or anything beyond the basics.
The Verdict: A First Draft After Years of Work
It feels like someone spent millions and ended up with a naive first draft, despite working on this for years. It’s similar to the early sketches of Farcaster and Lens, but those protocols have grown significantly over the past couple of years, with real users, lots of functionality, and apps.
DSNP remains as vaporware today as it was four years ago. These clowns have wasted tens of millions of dollars on nothing. Some academics have happily taken the money to fund their research labs. Consultants have written and thrown away countless prototypes nobody’s ever used.
There are lots of serious projects to build decentralized social media protocols. All these folks had to do was either work with others or even copy them. This stuff is all open source. Yet DSNP keeps sending folks to conferences without talking to anybody or attending any talks.
It’s a shame because they’ve got their hearts in the right place. The Unfinished conferences are really well put together with lots of great speakers. They hired the supremely talented and savvy Karl Fogel and James Vasile to help them make their code and process open, but you can’t fix DSNP.
Fundamentally, software and specs are a social enterprise, even more so if you’re working on social protocols. But these folks… they’ve never figured out how to play well with others. The money and good intentions couldn’t overcome their fundamental failure to have the humility to learn and play well with others.
-
 @ bf95e1a4:ebdcc848
2024-10-08 16:34:23
@ bf95e1a4:ebdcc848
2024-10-08 16:34:23This is the AI-generated full transcript of Bitcoin Infinity Show #129 with Max Hillebrand!
Check out the https://bitcoininfinitystore.com/ for our books, merch, and more!
Luke: Max, welcome for the first time to the Bitcoin Infinity Show.
The Lodging of Wayfaring Men
Knut: Yeah, so one of the first things, you have made the best book recommendations to me that I've ever gotten from anyone. And one was The Ethics of Liberty by Murray Rothbard, and the other one was Economic Science and the Austrian Method by Hans Hermann Hoppe. And now you recommended another book, which I haven't read yet, called The Lodging of Wayfaring Men.
what is that book about and why do you recommend it so much?
Max: It's a beautiful book. it's incredible. And it's written for us and for Bitcoiners, but it's over 20 years old. it was written in like 1997 to 2002 and that time period. And it's loosely based on real events, which is fascinating. the book is crazy. it goes about a group of cypherpunks who are, Building an anonymous marketplace, and the first attempts of an anonymous digital currency.
And again, this shit really happened. the story is quite wild. With, the freedom tech being built for very good reasons. people who understood the philosophical impact. and the deep reasons for why freedom is important. So they were very motivated, and, dedicated to make the world a better place in their lifetime.
And so they got their shit together and got organized and built something incredible, right? And it took them a couple attempts. and eventually they rolled it out and enabled people to trade right, to do their business, online in cyberspace, and encrypt it. And so that made a lot of people very happy because, you know, you get to live life free and undisturbed, so it got adopted by many users.
So much so that eventually the government started to notice that somehow they're making less tax revenue than before. And something's a bit fishy, you know. And then they started to investigate and You know, the NSA and FBI put a decent amount of people on the topic and tried to de anonymize the users of these services and infiltrate them.
And yeah, so the story is about this whole clash between the first and second realm, you know, people who built FreedomTag. And people who enslave others and how those two worlds kind of clash. it's a book that's very inspiring.
Knut: What was the website called?
Max: So, the author's name is Paul Rosenberg.
originally this book was published anonymously, years later, when it was safe to, associate their actual name with this, he did. he was, a teacher, an electrical engineer's teacher. He wrote 30 books on that subject, and is a very eloquent and practiced writer, but also a hardcore cypherpunk and freedom lover, and very well read,
So he has the freemansperspective. com. This is a newsletter. You can go back. It's going for, I don't know, 10, 20 years or something. And every week there's one or two short pieces of articles that he writes. And this book is actually also includes some writings that he did in the past and published. so it's somewhat a collection of his thought.
The Lodging of Wayfaring Men is a fiction book, right? It's basically a fictionalized story with, character arcs and such. the author is very technical, and he understands cryptography and how to apply it. He understands distributed networks and laying fiber optic cables and stuff like this.
So there's a lot of real computer science in this fictional world. And that makes it quite applicable to today where we're surrounded with cryptography much more than at the time when this book was written.
Knut: So, all right.
Taxes
Knut: bit of a jump here, but why is, avoiding paying taxes the most altruistic thing you can do in life?
Max: this is actually one thing that gets covered in the book, right, where,
Knut: that was the case.
Max: because this is also why this book is so interesting to recommend to newcomers, to this philosophy, because at the beginning, not everyone is convinced that this is a good idea. Even the creators of this technology don't know the end result and how other people will use this tech.
There's a lot of ambiguity there. And so this book follows characters who reason through these very difficult questions. For example, I'm going to spoil this book a bit, but everyone should read it anyway. So, there's one character who was a lawyer, right? He works together with an ex FBI agent, who both of them share this common, seeking of justice, like real justice, to stop bad guys from doing bad things, to good people.
the ex FBI guy is somewhat disillusioned. With the institution of the FBI to actually provide and establish justice. so now he is somewhat like walking this line in between the institution and, the actual free realm, vigilant justice basically.
and here then when thinking of. this case. is there a wrong being done by the FBI trying to stop this project? Or is this project actually good? Do they have justice in doing what they do? then, he, reasoned of, is the avoidance of tax, of, of taxation evil.
And, and, of course then walks through the reasonable steps of thinking. No, if, two people transact voluntarily. both people are better off after the trade than before, right? Both people are happy, both say thank you and shake hands. that's trade. That's the market, right? and then you have coercion,
Where one guy says, give me that, and the other says, no, actually, I don't want to give you that, but the guy hits him and takes it anyway. And so that means afterwards that the guy who stole it is obviously better off. He's happy, right? He got the thing, but the guy who was the victim was being stolen from is worse off.
And so humans have the capacity to do mutually beneficial things, right? To literally create value, make both of us better off than we were before. And we also have the potential to destroy value and take from others. and one is beneficial and fosters the growth of civilization and the other destroys it.
Knut: And so, you know, avoiding being stolen from is a good thing. Reminds me of one thing we go into in the new book, about the difference between lawful and illegal. I don't remember the name of the guy now, but some Dutch libertarian thinker, who emphasized on the terms, made the point that something being lawful is like lawful in an ethical sense, like the basis in Don't Steal, whereas legal is the top down government imposed legal framework, and how the two don't always align, or rather, they almost never align.
Natural vs Man Made Law
Max: Yeah, this is the difference between natural law and man made law. A natural law is one that is universal across time and space. It's always present, and it's immutable. It cannot be changed, at least not by us. And, you know, physics, for example, is a natural law. And arguably there is a natural law to ethics as well.
Specifically, as morality increases, freedom increases. And as morality decreases, freedom decreases. That's the law of gravity in the ethical realm. and, that man didn't make it, right? We just realize it because it is what it is. And then we have man made law on the other hand. this is depends on a certain territory, right?
The law in the U. S. is different from the law in Russia. And it also depends on time. I think the American law in the 1700s is very different from what it is today. and so there are these imaginary lines where these rules apply and there's Other places or times where they do not apply. So they're arbitrary, right?
And so they can be designed, to the benefit of some and at the expense of others. And that is ultimately what, politics is about.
Knut: Yeah, I think this is one of the key points that that quote unquote normies have such a hard time wrapping their head around. Natural law and like what, what makes don't steal a natural law? Like what, what is the very foundation of, libertarianism or anarcho capitalism or absolute property rights or whatever you may call it, consensualism?
And to my understanding, it has to do with homesteading. If you're the first person that acquired something, then no other person has a right to take that away from you. And you can logically deduct your way to that being true. Like, what's your view on that? And what's your understanding of that? And how would you explain that to a layman?
Max: Well, the reality is such that we have limited scarce resources. If we have one piece of steak on the table and three guys who are hungry, like some are gonna go home on an empty stomach, right? We literally don't have enough food to feed us all, right? And one piece of something can only be used by one person at one time, right?
We cannot duplicate one piece of steak into many and satisfy everyone. So this is a natural form part of reality, right? That's just how things are, you know? So there's a potential of conflict over who gets to allocate these scarce resources. And there's a couple solutions to it, right, that have been proposed.
Like one would be like, nobody owns it, right? Nobody gets to eat it because it's natural and it's not part of your body, so don't touch it, right? But then we die, you know, all
Knut: that's the problem with that.
Max: That's kind of a problem.
Knut: Yeah.
Max: so
Knut: Yeah.
Resource Allocation
Max: So let's rule that option out. another solution is, of course, we all own it. Right?
And we all, get to use it. But, that doesn't really work either, right? Because, sure, we all own it, but who actually gets to eat it? Because there's three different mouths and the food only goes into one of them. we can't all actually own something if we cannot all use it.
It is limited and only a few can use it. So, everyone owns it isn't the solution to the problem. Because everyone cannot own it, there's not enough for everyone. So again, that's an issue. Ultimately, we all starve. And another option would be, we vote.
We somehow pick who gets to allocate these resources. But then, I mean, we're 8 billion people. How are we all going to vote on who gets to stake? Right? Like That's, that's going to be impractical. Like, how are we even going to communicate, all 8 billion of us, to get together in a vote? So again, until we have the result of the vote, nobody eats the steak, so we all starve again.
It's not really a good solution either. And then we have one option that, like, a small subset of the people gets to make the choice of, you know, how to allocate these resources. And we can just pick them, vote for them, for example. But here again, now other people are allocating the resources for others, right?
Like, and some bureaucrat, a hundred kilometers away, is not gonna know, like, who of us is vegetarian and doesn't want the meat. Right? and that just means that someone who's far off doesn't have the knowledge to actually allocate the resources in a proper manner. And that leads to misallocations, right?
We starve, again. Because the guy who doesn't want the meat gets it and then it rots. And the guys who would actually like it never get access to it and they starve. So that's the fundamental problem of socialism, basically, of some priest class allocating the resources for others. So again, the solution doesn't work either.
So we're not left with much. But one thing that seems to work is private property rights. Again, as you said, the person who creates something, the butcher, or the farmer who raised the cow, can now decide what to do with it. Does he butcher it himself? Does he sell it to a butcher? So the person who created something gets to own it, and gets to decide how to allocate this, and then he has the right to either consume it himself, or to abdicate the consumption of this good.
So to say, I won't use it, I will trade it, I will give it to you, right? And he can make it a gift. Just say here, half the entire cow, like, I like you, I like your family, you, like, I'm happy that you're happy, right? Great, that's possible, right? Or, of course, he would want something from you in return, like, give me a bar of gold, or, a bushel of wheat, or something else.
we now have a way that we can allocate resources in a clear, simple rule set, the person who created it. can decide what to do and have a contractual agreement to transfer this ownership to someone else. the people who actually have the problem now have the power to allocate the resources to solve those problems and not some guy far away, but just you and me who created stuff.
Ownership of Information
Knut: And as you said, this only applies to scarce resources. So what, would be an example of a resource where you could eat the steak, but I could have it too. And, the thing that comes to mind, is information, of course. So, can you own information?
Max: No, like, because that, that doesn't really make sense, right? To own means to allocate, how to allocate these, to decide how to allocate these resources. All right. And then, that's a solution to a problem of a lack of resource allocation, right? or for a lack of resources that need to be allocated rather.
But with information, there is no lack. Like if I have a PDF, I can copy it to you and I can send it to you, and I can send it to a hundred other people, and I still have the exact same high fidelity version. Of the information that I shared with others, and of course it's the same with words, right? The words that I speak, they're not lost on me, right?
I still retain them and the information that they represent. and that means we don't need to be, stingy with information. We can give it to everyone. and it doesn't degrade the quality quite on the contrary, right? without information there is no production.
imagine yourself on an island, and you have all the raw materials, all the machinery, like everything there, but you don't know anything about physics, or material science, or just production stages of how to build things. If you don't know any of that, the raw material is worth nothing to you.
Nothing. Because you don't know how to allocate, how to shape this raw material into other things so that it actually solves your problems in the end. we need information in order to produce things. That's the theory behind it. The blueprints, so to say. the cool thing is, we don't have to be stingy with the blueprints.
We can give every human on this planet Equal access to all of the information that we as humans have accumulated, and now all of a sudden you will never be stranded on an island not knowing how to do something, because you can just look it up. In the grand database of accumulated human knowledge, of course, technology has made that much more possible and low cost.
Back in the day, in order to share an information, you needed to speak verbally to it, right? So you're limited to time and space, or you need to scratch it on some stone or clay or write it on a piece of paper, And then still, you have the scarcity of the paper, right? There's only one book.
And there's a hundred people who want to read it. So again, information is limited. Not because the information itself is limited, but because the medium of the information is scarce. And that was a big tragedy that we were never able to communicate at a large scale, and remember these conversations and easily access them.
Until the cypherpunks who came up with computers, right? And realized that we can build this realm of information That is so cheap to transfer and store information, that we can just basically do it for free, for anybody, for 8 billion people. And all they need is a rather cheap form of silicon, and like, nicely arranged.
but of course people try to hold on to the protection schemes that extract money from others, and capital from others, and You know, nation states have enforced intellectual property rights and patents and such, and that just harms people. It doesn't bring forward the best out of humanity. And that's a big shame.
Knut: Now, very well put. this has been Praxeology 101 with Max Hillebrand.
Bitcoin and Praxeology
Knut: where I want to follow on, follow up here is, how does this apply to Bitcoin? Because Bitcoin is only information, so how can anyone theoretically ever own a Satoshi? Do you really own it, or what is it?
Max: What is actually a Satoshi? Look into the Bitcoin code base. There is no such thing as Satoshi, right? The transaction has a field that is an integer. But it's just an integer. It doesn't even have a unit associated to it, right? So, it's just a number. Satoshis are just numbers in a database.
And you don't own the number 270, 000 just because you have 270, 000 bitcoin. The actual number of satoshis, no, you don't control them. You don't own them. But information has another interesting thing that cypherpunks realized, right? That, once, like, when you have a secret, then you can choose to share it with others.
And then once you've shared it with one person, however, you cannot control what that person does with the information. He can keep it secret for himself, or he can tell it to the entire world. And so, there is such a thing as giving access rights to information. And this is an important part in Bitcoin, of course, right?
Our secret keys should be secret, privately kept just for us, because if you do share your secret key publicly, then all of a sudden anyone can, Signed messages, with this private key and therefore spent Bitcoin in the transaction chain of Bitcoin. and well, that's a critical part of it.
So Bitcoin basically relies on keeping information, hidden from others, in order to ensure that we, solve, like, basically Bitcoin. It's just a piece of software, right? So it is non scarce information, but it wants to be money. And money needs to be scarce, right? Because if I can spend a bar of gold first to you, and then the same bar of gold later to you, we have infinite inflation, right?
The money system just dies. so scarcity is required. It's a required feature for money and digital money therefore requires digital scarcity. And so what Bitcoin does is it establishes a set of computer code that defines the access, right? Two certain chunks of money, so to say, right? And the chunks of money are Bitcoin UTXOs, unspent transaction outputs, and the spending condition, so to say, or like the rule how to allocate this money, who gets to decide it.
Where this money goes next is defined by a script and a small computer program that evaluates either to true or to false, depending what input you provide. And so the script is the lock, and usually it's a single public key. And then the way to prove that You're actually authorized to spend this coin is by creating a valid witness.
You know, the input to the script, to the program that returns it to true rather than to false. And usually, again, that's a signature of a single private key over the transaction structure that you're actually spending the money. Bitcoin's genius realization is that. We just all have to check every transaction of everyone else.
And when we do that, we can be sure that, nobody's being stolen from, That nobody is, losing access to his money, that someone is spending the money with a wrong signature. he doesn't have the private key. He cannot produce a valid signature. So we have to make sure that such a transaction does never make it into the blockchain, right?
that's the first important aspect. And the second is we want to ensure that there's no inflation. that's Because if we can just create as many tokens as we want, then the value of the token goes to the marginal cost of production. If we can produce a token with the click of a button, then the marginal cost of that token, or the value of that token, will be zero, right?
So we need to make it, Difficult, or in fact, in Bitcoin, impossible to create additional units, you know, there's 21 million and that's it, right? That's the set of rules. And therefore, when we check each transactions, we also ensure that there is no transaction that has one Bitcoin on the input side and 10 Bitcoin on the output side, therefore increasing the total supply of Bitcoin.
And so Bitcoin is a massive verification machine to ensure that this computer system is this way of speaking to each other, actually balances the books of the system. of how many units of money are there, and who has the right to allocate these, and so it's basically a system that creates a natural resource, and then also manages the allocation of this natural resource.
Knut: so Bitcoin is almost a parallel universe where, in fact, you do own the Bitcoin, basically, but the ownership is not defined by you as a person. It's defined by the knowledge of a secret. so you prove that you have access to it by having access to the private key, which unlocks it.
Ownership of Bitcoin
Knut: On earth that can prove that you own a Bitcoin except you, the holder of the private key.
Max: If the holder of the private key reveals information to others that indicates such, one very common way that this would be is you have a mobile wallet, that does not run a Bitcoin full node, That connects to someone else's full node to check if you have Bitcoin,
You don't use Tor, so there's an IP address linked from you to the server, and so the server operator knows that this IP address just asked how much money is on this address, and so we have, a very strong indication, that this IP address owner owns
Knut: It can be a very strong indication, but in my mind it can never be proof. Because you need to sign with the actual private key to prove. Otherwise it's boating accident time.
Max: guy with the gun doesn't need proof, right, he just needs a good enough guess. For him, he needs, like, there is a praxeology to violence. thieves are actors. They live in a state of uneasiness, they have problems, and they try to find a solution to that problem. They don't have ethics, they don't have morals, and so their solution to the problem harms other people.
But nevertheless, they are still actors. And so they think that they will be better off after the action of theft than before. That's a value judgment. And it's an entrepreneurial one. So they might be correct, they might not. They break into a house, hoping that there is a bar of gold hidden under the couch, right?
Turns out there's not, right? So, if they spend a lot of money breaking into the house, and there's no loot, they're not profitable thieves. And this means that they destroyed their capital, right? They spent 10 Bitcoin on getting the equipment, and they got 0 Bitcoin back. So, that means they're 10 Bitcoin poorer, and eventually they will run out of money and starve.
So, thieves need to be profitable in order to do their thieving, and that's the genius that cypherpunks realized. If we exponentially increase the cost of attack, and exponentially decrease the cost of defense, then we make thievery unprofitable. And that's the genius of private public key cryptography and encryption, right?
It's trivial to generate a private key and then generate a public key or a signature, right? But to brute force a private key or to forge a signature without it, like, requires more energy that would collapse into a black hole, you know? So that's kind of a problem.
And for thieves, right? It's really good for the people who want to defend themselves. Because they can very cheaply do it, and it just doesn't make sense to attempt to break the encryption. But nevertheless, computer systems are very complex, and there's a lot of metadata associated with, computing and communicating between computers.
And so, there are, microphones and radio frequency scanners that you can point on computers and see the computation happening in the machine because there's a lot of radiation outside of the computer that can be correlated to which bits are being flipped you can have all types of side channel attacks to extract secrets from a computer while it's running the problem is that the holistic technology stack we have is quite susceptible to revealing information that should have been kept secret.
And again, that is a critical part, of course, to communication encryption, but even more so for Bitcoin. If we lose the assurance that only we know the private key, the money system is broken. And that's why Bitcoiners were so paranoid and started this whole thing of hardware wallets and secure elements to Really ensure that we don't leak private key material, but it's an extremely difficult task, because, well, this reality is very observable, and the cards are, to some extent, quite in favor of surveillance, unfortunately.
the guy with the gun in this case could be the government, Yeah, exactly, it can just be like a poor guy who needs to provide for his children, you know, and, he sees a way for feeding his family for the next two years, and that's a good trade off for him.
Knut: Yeah, momentarily.
Max: right?
Bitcoin and World Peace
Knut: So, if we manage to do this, on a grand scale, and if people in general manage To exponentially increase the cost of the attack while simultaneously decreasing the cost of defense. Does that lead to world peace at one point? Is that the end goal?
Max: Yeah, I think so. Oh, I mean, that makes sense. If every economically rational thief will realize that he is worse off if he does this stealing, right? Like, actually, because he needs to spend much more money in an attempted theft, and most likely he's not going to succeed. And, I mean, this exponential difference has to be huge, though, right?
Because, like, we had castles, you know? Like, castles are quite, like, quite extreme asymmetric protection. Like, if you're behind castle walls, with a well staffed militia that actually defends the walls, It's quite difficult to get to you if you just have, you know, like, humans and swords and ladders. that's, like, sieges are, in the favor of the defender.
But still, they happened a lot, right? And people were able to overcome these defenses. Because, I guess they weren't never holistically secure, you know? There was always some backdoor that enabled the attacker to go through, to get through, right? and that might just be brute force, right? You just bring a huge army and You're fine with tens of thousands of your own guys getting killed, but eventually, you know, after you throw a couple hundred thousand people at the problem, someone will succeed to break through.
Quite a brutal tactic, obviously, but it worked.
Knut: you get in.
Max: But then cryptographers came around and were like, well, but there's math.
Luke: Yeah, we can use RAM in another way. 1 plus 1 is 2. What? Are you sure?
Knut: that might be offensive.
Luke: That's a different kind of worms.
Knut: Yeah. . Yeah. So, the,
Bitcoin For Attack
Knut: so Bitcoin being this perfect defense mechanism, because all it does is increase the cost of the attack, can Bitcoin ever be used for attack in your opinion? Like, can it be used in an aggressive way?
Max: I think directly not, because again, it is just, speech and such, but on the other hand, maybe yes. Because, let's say, if someone hacked your machine, and got access to your private key, and spends the Bitcoin, like, in the context of Bitcoin itself, it's a valid signature, it's a valid transaction, and it will be included.
So, in the legalities of Bitcoin, it is no theft, right? It is a valid transaction. but, On the ethical realm, you worked hard to get these Bitcoin and you didn't want to send them to the attacker, so he is definitely stealing them from you. So, Bitcoin can be stolen, certainly, in the human analysis.
Not on a technical level, we've never seen a transaction confirmed with an invalid signature, but on the human level, There have been a lot of people that got separated from their Bitcoin against their will, right, against their consent. and, and that is theft. So, thieves can use Bitcoin, thieves can get paid in Bitcoin, thieves can take your Bitcoin and pay them to themselves, right?
that's a fact of reality too.
Aggression and Spam
Knut: Could that be used in an aggressive way?
Max: it is just the writing of bits and bytes, right? So there's, however, again, a limited amount of resources that are available specifically in Bitcoin. And not just do we have 21 million Bitcoin, we also have like, Two and a half slash four megabyte blocks, right?
And so this means there's only a certain number of transactions that can be fit into a single block. that means we have, again, a scarce resource and we need to allocate it. this is why there is a price for Bitcoin transactions, because that's how we solve the scarcity problem, right?
by whoever pays the most gets in. that's a, or it's not even whoever pays the most. It's like. You can choose who goes in by mining a block, right? You have full freedom of choice of which transaction do you include into your block. And if you don't mine, then you can propose to someone else, say, please include my transaction into a block.
But again, there's a large demand and a limited supply. so most likely people will start bribing each other and it's like, yeah, if you include my transaction in your block, I'll give you sats. And in fact, Bitcoin, the Bitcoin software launched with a anonymous peer to peer marketplace for the scarce good, which is Blockspace.
Satoshi didn't have to do that, right? Bitcoin would have totally worked, if, if you could not, like, if every input sum has to be exactly equal to every output sum, right?
There cannot be that outputs are smaller than inputs and the leftover goes to the miners, but that could have been a consensus rule, right? But then most likely we would have seen some third party external marketplace. Where people would do the bidding on please include my transaction into the block.
And then of course they would have to figure out how do we actually pay the miner to get our transaction in the block. So Satoshi had the genius to embed an anonymous marketplace. Into the core essence of the protocol, right, with the rule that outputs can be smaller than inputs, and the rule that we have this gossip peer to peer network, which like the whole peer to peer network is kind of optional, by the way, but it's just there to kind of make it easier so that we have this anonymous marketplace for Blockspace that we can propagate offers, right, and one person sends the offer and gets spread to the entire network.
So the demand side is no monopoly. Anyone can broadcast a message to the peer to peer network hoping to be included. And then on the supply side, the actual miners, there's also no monopoly. Anyone can spin up his computer and start SHA 256 hashing. On the most recent chain, right, with his own candidate block.
And nobody can stop you, right? That's the definition of no monopoly. New market participants are not hindered to enter the system. And so this is the most radical free market that we've seen probably ever. And it's been kind of hidden inside Bitcoin since the very beginning.
Mining vs Hashing
Knut: Yeah, you can of course also pay the miner in something else than sats to get included into a block. And if a mining pool does this, the individual miners doesn't necessarily have a claim to a piece of the pie of whatever money was paid to the mining pool owner under the table and not on the system, right?
They can't even see it. So how big of a problem is that, and can you really call yourself a miner if you're just selling hash power to a pool and the pool isn't transparent?
Max: I mean, it's actually true that we, like, there could be in the future, A alternative marketplace for block space that's not inside the Bitcoin Core client. And by the way, arguably that's better, because we have a piece of software that does one thing really well, and then, you know, we just specialize and put the two modules together.
architecturally speaking, this might be better. we see things like, for example, the mempool. space explorer, or accelerator, right, is one. Marketplace that is now establishing that that seems to work now quite well. Of course, it has the issue of there's a central, like, order book, so to say, and probably custodian for the money as well.
And so, I'm not sure, but it's one approach of doing such an alternative marketplace and there can be downsides. it's not really public of how much Volume is going through here, right? how much are people speeding up their transactions, And I guess the same goes to much earlier where we just had mining pools offering this in their own API, or a webpage.
so at least now, like we, we have a dedicated service provider. That's not a mining pool doing this, which I think is an improvement. but we could also, you know, build. A, like, off chain peer to peer network, so to say, that's not related to Bitcoin per se, but that has all of the aspects that we want just dedicated for an optimized market book for this resource.
And Bitcoin should still work, I think. Like, the marketplace inside Bitcoin Core is not essential in the long run. It was just very convenient to bootstrap it. But, you know, in 50, 100 years, I wouldn't be surprised if we have Dedicated systems for, for these things that potentially are in different repositories and such different softwares.
Knut: So, in your opinion, how damaging is a temporary fee spike over a weekend or something where it goes up to like, 2000 SATs per transaction. what impact does it have on lightning channels and lightning providers and so on? Like do you consider it an attack or what is it?
Max: it's an inevitability almost, right? If you have a hard, extremely limited supply, right? there is only two and a half megabytes in the usual block, and you have extremely fluctuating demand, and there is no way to speed up production of the good. there is bound to be extreme, differences of we have way more demand than supply or way less, right?
But it will be very rare that we will fill just exactly everyone who wanted to gets in. So to actually clean out every transaction that wanted to be made is quite rare already now and in the future, if Bitcoin continues to be used, this is even more unlikely, right?
So then the question is just how, like, do you get into the top, like, the top payers to get included in the block still? And this is where just the technology is quite difficult, because this is like, you're, you're, you're, it's an order book, right? You're trading, basically, and you don't know if the price goes up or price goes down.
And this is all at least supposed to be automated. Bitcoin wallet developers are building trading bots, block space accountants charged to purchase block space on behalf of the user. the user just clicks send and that's it. the software does all of the complexities of constructing a transaction that is of a size acceptable, right?
Because if fees are super high, you don't want to build a transaction with a hundred inputs and one output, right? You would want to have a transaction with one input, one output. It would be way cheaper if the fee spike is currently high. a smart robot should build a different structured transaction with more or fewer inputs and outputs to accommodate the current fluctuation of the market.
And of course, the fee rate is another, like what's actually your bid that you put into this marketplace? And that's trading like. How much are you going to pay for the stock? Nobody really knows, right? And so it's kind of good luck and you don't know if it goes up or goes down. And sometimes you overpay, right?
And you pay way more than was actually needed to get into that block. And so you lose money, you lose capital. And sometimes you don't pay enough and you don't get included for months, right? but there's better software that can alleviate a lot of these problems.
Spam Making Bitcoin Worse as Money
Luke: Well, so I guess another side to this question, because everything you're saying makes makes total sense from the perspective of that this stuff is definitely going to happen from from hyperbitcoinization side. There's just going to be more demand than there is supply of block space. But I think the issue that we've been exploring a lot.
Lately, is, is that when there are transactions that aren't really being made for the purpose of moving value from one person to another in the form of Satoshis, they're, they're another form of value, subjective value that is communicated through arbitrary data, or at least some other type of, of data.
Does that change the property of Bitcoin as money? That's essentially, I think the, the root of the, the argument any, anyone talking
Knut: Yeah, exactly.
Luke: the functionality of Bitcoin is
Max: Well, I think. There's a couple aspects to this, right? We have again a scarce resource block space, and there's the problem of how do we allocate this block space. And there are very stringent rules on this, right? You cannot have arbitrary data in blocks, right? There needs to be, for example, the transaction structure.
There needs to be inputs that point to previous outputs, and there need to be outputs, the sum of the inputs, sum of outputs, hashes, transaction headers, all of the stuff needs to be followed in order for this to be considered a valid block. So the Bitcoin developers have, from the very beginning, had a very, I guess, authoritarian regime to allocating these resources, which makes sense.
If you don't put stringent, like, structure in a protocol, then people just fill it with garbage and every software breaks, right? So it's like a practicality thing that we need to have a very opinionated, kind of thing. Set of rules and we need to pick one of them and like just do it because if we don't pick any then it won't work and also if we pick the wrong one it won't work either.
imagine the rules would have been like a broken hashing algorithm, for example, not SHA 256 but SHA 1 or something that's broken. People can create collisions, right? So there could be two transactions that have the exact same transaction ID. breaks the system, right? So if that would have been the set of rules, Bitcoin would have broken, right?
And now also, again, if we allow arbitrary things to be built, then people will just use it as data storage, for example, and just fill it up with megabytes of images. And again, limited amount of resources. If all of it is used for, for pictures, then none of it can be used for money transfer, right? So this is again, an inherent conflict.
the tricky thing though is, now we have this. established set of rules in the Bitcoin consensus and how do we change it, right? And that's the really tricky part of, making up man made rules. Bitcoin is not Natural in the sense, right? Like, humans came up with this shit.
Like, this is our creativity that made this happen. and so, it's not nature made, right? It's man made. Of course, men are part of nature and such. So it's a bit, wishy washy here, but ultimately, we made it, we can change it, we can make it better, and we can break it. And that's a really scary position, because I think we all realize that this is quite an important project, and we definitely have it in our power to break this thing.
I hope we do our best effort.
Caution When Changing Bitcoin
Luke: my interpretation of that is, is that, caution when making changes to Bitcoin is paramount. Would you agree with that?
Max: Well, inaction is an action too, right? And that might be even more dangerous. So, there might be critical bugs in the protocol that if not addressed will break the system and potentially they are currently being exploited, right? And so, in such a case, we should do our best to fix it as soon as possible.
Satoshi knew that from the very beginning, right? So, how exactly we do that? Who knows?
Knut: Well, if it's up to the individual miners, which it is, what blocks they want to mine, what transactions they want to include in a block. And it can be fixed that way, a sly roundabout way, if you will.
Max: Well, if we could trust the miners with stuff like this, then we could trust the miners with enforcing the 21 million, right? But we can't, right? We don't rely on anyone. We verify it ourselves, right? And so the reason why we don't have actual JPEGs in Bitcoin blocks is because your node says no to any block that actually has a JPEG in it, right?
Blocks have to have transaction in it. If not, you kick them out, right? So even if there's valid proof of work Proof of Work doesn't solve the problem of integrity of the block, right? This has nothing to do with Proof of Work. In fact, Proof of Work is one part of the rules of the integrity of the block that is defined, enforced, and verified by the full nodes itself, right?
Specifically, if you want to get rid of inscriptions, that's certainly a hard fork. Like, taproot transactions are currently valid, and if we make these taproot transactions in the future invalid, that's a hard fork, right?
It would be great to hard fork Bitcoin. We could clean so much stuff. It's just a practical reality that breaking the hard fork use of a running protocol is extremely difficult and arguably, unethical. Because people have signed up to the previous system, built businesses and, stored their money in these types of scripts.
If we now make them unspendable, what is that? No?
Mining Incentives
Knut: so, when it comes to mining, there's, minor incentives, like, the thing we talked about before, about, under the table payments to big mining pools, To me, the obvious fix to this problem is to get it into the brains of the hash salesmen, that they ought not be mere hash salesmen, but actual miners and know what block they're mining on.
Because I think the ethos among the individual miners is, better than, these bigger pools that might not be, as, concerned with the longevity of the Bitcoin experiment, but, more fiat minded and wanting a quick buck now rather than save the system in the long run.
So, right now it feels like we're trusting these bigger entities to have as much of a disincentive to destroy Bitcoin so that they won't, it's tricky. Like it's a gray zone, right? What's your thoughts?
Max: I think Satoshi's genius in designing the Bitcoin protocol was that he did his best to separate different tasks that need to be done in the system into different like conceptual entities, and then to ensure that each of these aspects is distributed as widely as possible. And this is ultimately what it means that Bitcoin is decentralized, right?
There is not one person that defines the set of rules, for example, or one person that writes the candidate block, Or one person that provides the proof of work for the candidate block, or one person that provides the signature for each transaction, right? Each of these things is distributed. And in the ideal case, in the original Bitcoin client, to every user, right?
Like, the Bitcoin software in 2009 was mining by default for everyone, right? So, literally the entire stack of the operation was at 100 percent of the users, right? There was no non validating, non mining users. In the beginning, right? We had perfect decentralization, so to say, right? And then if efficiencies kick in and economies of scale and division of labor, and we start to optimize each of these things kind of on its own and split it out into different branches of government.
Yeah, specialized entities, so to say. And if you specialize on being the best hasher that you could possibly be, you just give up on being the best block candidate creator that you could possibly be. Because if you do the one thing that you're marginally better at and focus all your attention on that, you will be the most profitable.
so, yes, it is. It is an issue. and we, Bitcoin would be better off if we further distribute the risk and responsibility of each of these tasks to as many people as possible. And I think we've done a really good job, for example, of distributing the ownership of private keys.
And like, there's, I don't know, many millions of private key holders on the Bitcoin blockchain, right? So that's, that's great. but, and we have. Probably done this as well with hashers, right? There's a decent amount of quite large independent hashing institutions, right? Not so well with mining pools and actual block candidate creation, like, that's pretty bad.
Like, there's two or three of them, so that's scary as fuck. Right there we've utterly failed and we've made Bitcoin way worse than it was before. in this one metric of resilience, of decentralization, of distribution of risks, we made it a lot more efficient, but we made it much more vulnerable to attack.
that is a problem. Thankfully, a lot of people are working on fixing it. It's a really difficult problem, right? It's not that there's some malicious, attempt of trying to break it. I mean, maybe there is, but the more likely answer is just bloody difficult computer science. it just needs an insane amount of research and development before we will have tools that are even coming close to being actually adequate.
Right? I'm not praising Satoshi's 2009 code as being perfect, because it was a pile of shit, right? And you could break it in a million ways. so we've improved a lot, but we're very far from done because to some extent the realities of the difficulty of the situation have caught on much faster than our ability to solve these.
Yeah, I mean, the problems that are currently existent in Bitcoin and that now we're at Nostriga today and talking about Nostr, this sort of related communication layer in relation to Bitcoin, you mentioned at the very beginning, Freedom Tech.
Freedom Tech and Nostr
Luke: So, we, when we last talked to you, you were focusing on Wasabi Wallet and now obviously that project has just been made open source, essentially, and so my question to you on that is, what are you focusing on in terms of Freedom Tech now?
Max: Nostr is definitely a highlight, right? Nostr is just incredibly cool. And it's so wild to think that Nostr is like two years old. it's not old, but look at the amount of stuff that we've built. In this short time frame, how powerful are we? It's incredible, right? If we get our act together and actually build on, such an open protocol and get people excited about it and people using it, it doesn't take us long to fundamentally change the pattern of speech on this planet.
Wow, that's incredible. Like, we did that. And we're just getting started. think about where Nostr is going to be in five years. It will be wild. Absolutely insane. that's very bullish and very encouraging. And it's super exciting to work at such an early stage in the protocol, because there's so many obvious improvements.
There's so many obvious use cases. There's so many low hanging fruits of how we can make it even better than it currently is. Alright, so we have something that's already great, and we know a million ways on how we can make it even better. and you can be part of making a meaningful improvement in getting this to like an exponential blow off of awesomeness.
Knut: Meaningful improvement of humanity, really.
Max: Yeah. Yeah, that's the other thing, like, that's why Freedom Tech is so exhilarating to work at, because we're ending slavery. That's kind of a big deal, you know,
Knut: Yeah, it should have been done at least 300 years ago.
Max: Yeah.
Luke: No, it's, it's amazing. And well, and actually, so a couple of things here. First of all, we've talked about this a little bit, how Nostr seems like it's the playground that people wanted as an alternative to Bitcoin. In other words, people who went and started making shitcoins were basically just wanting a playground to do all this stuff.
But now is, is, is Nostr basically the place where people can do that and channel their energies in a way that isn't going to break money?
Max: Yeah. I absolutely agree. So I'm very bullish on a lot of these use cases and one other area that currently interests me a lot, is just zero knowledge cryptography. it's wild what's possible. it's absolutely wild. Within the last five years or so. The theory has developed.
And again, a lot of shitcoin projects putting zero knowledge proofs on blockchains and such, and I'm not quite convinced that we actually need a blockchain for that. I think relays are just fine. And so I'm quite bullish on having actual zero knowledge proofs much more integrated in Nostr clients. Like, you can do amazing things with this.
Like, for example, anonymous web of trust, right? You could prove to me under an ephemeral anonymous identity, right, that you are in fact, On my follower list. Like, I'm following you, but I don't know who you are. Right? So, these types of things are trivial with zero knowledge stuff. And we don't have any size constraints or computation constraints in Nostr.
Because it is not a global consensus system. Only the people who are interested in this proof actually have to, like, download it and verify it and such. so, it's, I think we can do a lot of amazing stuff here. it seems pretty obvious wins here.
Knut: driving these 180 IQ young developers into Nostr instead of shitcoin development is, is like moving them? To do, to think more of what they should rather than what they could, because I think that's, that's sort of the main problem with this nerdy set of shitcoin developers is that they, oh, I could do this if I just do this and they, they focus on what they can do rather than what they should do.
And it's Nostr, Changing the direction of that, are people thinking more of ethical things while developing on this than
Max: it's a big claim, right? That like a piece of tech can
Knut: it's hopium
Max: improve the morality of people. it's definitely a big claim, but it seems true. Like, if you think about it in Bitcoin, like probably each of us, our level of morality before we discovered Bitcoin and what it is now.
And our understanding of morality has substantially, improved, right? And I'm not sure if it would have happened, at least to this extent, without being exposed to the Bitcoin technology. and Bitcoin is just money, you know, like, humans do a lot more than buy stuff, sure, money is incredibly important, but it's far from everything of the human experience.
And I think Nostr. We'll do a lot of the other stuff and Nostr has this freedom mindset embedded into the protocol just as Bitcoin has. And so I'm extremely bullish on seeing the people who get exposed to Nostr and what it does to them in the long run.
Hyperbitcoinization vs Hypernostrification
Max: So what happens first? Hyper ossification or hyper ization both at the same time.
Knut: does one lead to the other?
Max: there's definitely synergies here, right? and, yes, one leads to the other. there's, I met a bunch of people who got interested into Nostr first, and then used Bitcoin for the first time. It's a very common theme, actually. again, because Like, social, like, think of the, think of the, like, average screen time of people, right?
it, for sure.
I think Nostr is going to be way bigger than Bitcoin in the improvement of the human condition.
Knut: Then again, every time you press the like button or the retweet button or whatever on your social media app, even the legacy system, you are providing someone with some value. That's why your account is valuable to, Facebook's and the Twitters of the world. There is a value thing embedded into everything you do on the internet.
Max: It's just, you don't get a tradable good.
Knut: No, no,
Max: sell the like to someone else.
Knut: not at this point.
Max: They have now a star emoji. If you send the star emoji, you can send the star emoji back to the company, and they will give you money. So, voila. It's basically a shitcoin, but it's a star.
Luke: is it more important to fix money or the other stuff?
Max: Well, that's a big one. Both again, because money is only half of every transaction, right? And so maybe the earlier example of the marketplace for Bitcoin block space is perfect because why did Satoshi include the marketplace, the other stuff together with the money? Because it was kind of essential, right?
you need to have both at the same time in order to live, right? You need to speak, you need to advertise your products, you need to negotiate with the customers, right? You need to convince them of the value that you will provide to them, and then you need to receive the money and tell them that you've received it, and ultimately hand over the goods, right?
So there's a lot of human interaction into every trade, and the money aspect is just Like, one small part of this long interactive chain of protocol, basically. I think we need both at the same time. And we're just discovering upgrades to each of them as we move along. But this has always been in synergy.
Like, the internet is way older than Bitcoin, right? So arguably, we need the other stuff first, right? We needed like 20, 30 years of other stuff before we could actually come up with the money.
Knut: so fix the money, fix the world then fix the world and you fix the money.
Luke: No, but seriously, we actually talked about this. in that, maybe an analogy to, that the internet needed to develop in a centralized way because the, literally the hardware and everything, the architecture, the client server model was literally a centralized and centralizing system. Model and that needed to exist first.
And then the analogy is that gold was centralized naturally in the sense that physically the physical constraints of gold made it so that it naturally centralized into banks and then fiat solved that problem to sort of decentralize it, but it broke everything. So now the mechanism of fixing the money and decentralizing the money was gold.
Bitcoin, but the corollary for decentralizing the communication is Nostr. So both things have kind of happened in a parallel. That's, what we were discussing.
Wrapping Up
Luke: That is the alarm Oh,
Knut: Oh, okay.
Max: so we'll wrap it up.
Knut: Well, I'm
Max: Nostr for sure. Max at TowardsLiberty. com. You can send me mail, notes and sats to that, which is, by the way, crazy, right? That we can have like this unique identifier to get, like, all of your needs settled is wild. Check out, lodging of Wayfaring Men. That's, the main shill of this video.
And I made the audiobook for it. it's on a podcast. The podcast is by the author, Paul Rosenberg. And, it's called Parallel Society, right? So check that out. right now we've released the first episode. the others will come shortly thereafter. the other book recommendation I should highlight, which we haven't mentioned yet, is Cryptoeconomics by Eric Voskuhl.
Most of what I said here was very much inspired by that book. He has the most rigorous understanding of Bitcoin. It's by far the best Bitcoin book. So I also did the audiobook for that. Just search for Cryptoeconomics in your
Knut: audio book though.
Max: when you have to read tables of math formulas, it's starting to fall apart.
But there's a lot of verbal logic in the book that goes very well. Just get the free PDF for the actual graphs and
Knut: And keep using Wasabi and fire up your own coordinators and whatnot, right?
Luke: Now get on stage, Max. Don't want to make you late.
Max: Bye
the book, that's not what I said.
Luke: right, that's it.
-
 @ c0e0c427:a1f63a16
2024-10-14 09:15:50
@ c0e0c427:a1f63a16
2024-10-14 09:15:50Chef's notes
Some say beat the cream as hard as you can but I find I have much better success when I take my time. So take it easy and be patient and that magic butter moment will arrive.
Details
- 🍳 Cook time: 15 min
- 🍽️ Servings: Approx 250g butter
Ingredients
- Pure fresh cream
- Salt
Directions
- Keep cream in the fridge until ready to start.
- Pour cream into a bowl.
- Beat with hand mixer or kitchen betchtop mixer with the balloon whisk.
- Maintain a medium power level in the mixer throughout. Note that it can get messy with lots of splatter and you might like to have a tea towel over the operation to limit clean up.
- After 5 min the cream will be whipped this is a great sign! Keep going.
- After 10 -15 min you’ll see the cream start to separate into solids and buttermilk.
- Keep whisking until you see the bright yellow butter solids start to clump together in the mixer.
- Pour off the buttermilk and save for later (bonus side product that makes the best pancakes and is actually really great in scrabbled eggs)
- Rinse in butter solid with cold water to remove all the buttermilk. This is an important step and the buttermilk increases the rate of spoil.
- Mix in salt and shape the butter into a block.
- Wrap and store in the fridge.
-
 @ d5c3d063:4d1159b3
2024-10-24 14:48:43
@ d5c3d063:4d1159b3
2024-10-24 14:48:43เวลามีค่า...บทเรียนจากลุงโฉลก CDC Talk EP1
https://image.nostr.build/bf870a0818bdefec9c992efcfa6db05c1ff7c897576159a89b7f6800a4ca9991.jpg
โลกการลงทุนที่เต็มไปด้วยความผันผวน นักลงทุนหลายคนมักจมอยู่กับการไล่ล่ากำไร จ้องกราฟตาแทบไม่กระพริบ วิ่งตามข่าวสารจนหัวหมุน เคยรู้สึกแบบนี้ไหมครับ? ผมเองก็เคยเป็นครับ
นอกจากอาจารย์พิริยะที่ทำให้ผมสนใจศึกษาบิตคอยน์ ก็มีลุงโฉลกที่ทำให้ผมเปลี่ยนมุมมองการลงทุนไปอย่างสิ้นเชิง สิ่งที่ลุงโฉลกให้ความสำคัญยิ่งกว่าผลกำไรคือ “เวลา” ที่ใช้ในการเรียนรู้และพัฒนาตนเอง ท่านบอกว่า “เวลา” สำคัญยิ่งกว่าการหาเงิน ไม่ใช่การหาจังหวะซื้อๆ ขายๆ แต่เป็นเวลาแห่งการเรียนรู้ การเติบโตทางความคิด และการมองภาพรวมของตลาดอย่างแท้จริง
ประโยคนี้สะท้อนมุมมองที่แตกต่าง การลงทุนไม่ใช่แค่การเก็งกำไรระยะสั้น แต่คือการลงทุนในความรู้ สติปัญญาและวิสัยทัศน์ของเรา ลุงโฉลกเชื่อว่าการลงทุนที่แท้จริงต้องอาศัยปัญญา ท่านยกพุทธสุภาษิตที่ว่า "นตฺถิ ปญฺญาสมา อาภา" ความหมายคือ แสงสว่างเสมอด้วยปัญญาไม่มี พูดง่ายๆ ก็คือ ไม่มีแสงสว่างใด จะยิ่งใหญ่ไปกว่าแสงสว่างแห่งปัญญา เพราะปัญญานั้นไม่ได้เกิดขึ้นชั่วข้ามคืน แต่มันสั่งสมมาจากการศึกษา การฝึกฝนและที่ขาดไม่ได้เลยก็คือ “เวลา”
ในตลาดทุนที่โหดร้าย ไม่มีใครใหญ่เกินกว่าตลาด การมุ่งแต่จะรวยโดยไม่พัฒนาตัวเอง มีแต่จะทำให้การลงทุนนั้นพังไม่เป็นท่า ดังที่ลุงโฉลกบอกว่า "ความโลภของจิตใจ…ทำลายทุกสิ่งทุกอย่าง" แล้วเราจะหาเวลาพัฒนาตัวเองได้อย่างไร ? ลุงโฉลกแนะนำให้ "ควบคุมความโลภ" และ "มักน้อย"
ลุงโฉลกเตือนนักลงทุนด้วยพุทธสุภาษิต "นตฺถิ ตณฺหาสมา นที" ความหมายคือ แม่น้ำเสมอด้วยตัณหาไม่มี เปรียบความโลภเหมือนแม่น้ำที่ไหลไปไม่รู้จบ หากปล่อยให้ความโลภครอบงำ ย่อมนำไปสู่การตัดสินใจที่ผิดพลาด การควบคุมความโลภไม่ใช่แค่การตั้ง Stop Loss แต่คุณลุงบอกว่าต้อง "กำราบความโลภ…ในใจเรา" ด้วยการฝึกฝนจิตใจให้รู้จักพอ เมื่อเรามีจิตใจที่สงบแล้ว ย่อมวิเคราะห์และตัดสินใจได้ดีขึ้น และตระหนักถึงคุณค่าของเวลา เหมือนที่ลุงโฉลกบอกไว้ว่า "พอเริ่มเข้าใจปั๊บ…เวลาสำคัญนี่หว่า"
ผมเคยเจอนักลงทุนหลายคนที่ขาดทุนย่อยยับเพราะความโลภ เห็นกำไรนิดหน่อยก็อยากได้เพิ่มและสุดท้ายก็ไปยืนอยู่บนดอย ส่วนคนที่ประสบความสำเร็จ มักเป็นคนที่ควบคุมความโลภได้ ใจเย็นและใช้เวลาไปกับการศึกษาหาความรู้
"มักน้อย" เป็นสิ่งที่ลุงโฉลกให้ความสำคัญ ท่านมองว่าไม่จำเป็นต้องเทรดทุก Wave การจับจังหวะทำกำไรใน Wave 3 ซึ่งมักจะเป็นช่วงที่ราคาขึ้นแรงที่สุดก็เพียงพอแล้ว ส่วนเวลาที่เหลือ ท่านแนะนำให้ "พิจารณาอย่างอื่น…มีเรื่องน่าสนใจกว่าเกิดขึ้นเยอะแยะเลย" เช่น การศึกษาบิตคอยน์ หรือแม้แต่การใช้เวลากับครอบครัว
ลุงโฉลกเปรียบเปรยนักลงทุนกับนักมวย "ขยับแขนซ้ายลงนิดนึง…ก็รู้แล้วว่าจะต่อยหมัดขวา" เป็นนักมวยก็ต้องฝึกฝนจนเชี่ยวชาญ นักลงทุนก็ต้องสั่งสมประสบการณ์ ศึกษาและฝึกฝน เพื่อที่จะเรียนรู้ตลาด มองเห็นโอกาสและตัดสินใจลงทุนได้อย่างมีประสิทธิภาพ ซึ่งจะนำไปสู่ความสำเร็จในระยะยาว
เพราะฉะนั้น คุณค่าของเวลาในการลงทุน ไม่ใช่แค่การบริหารเวลาให้มีประสิทธิภาพ แต่คือการสร้างเวลา ด้วยการฝึกฝนจิตใจ ควบคุมความโลภและมักน้อย เพื่อให้เรามีเวลา มองเห็นโอกาส และบรรลุเป้าหมายการลงทุนอย่างยั่งยืน แล้วคุณคิดว่า...อะไรคืออุปสรรคที่สำคัญที่สุดของคุณในการควบคุมความโลภ ? ลองแลกเปลี่ยนแบ่งปันประสบการณ์กันดูได้นะครับ
CDCTalk #Siamstr
-
 @ c0e0c427:a1f63a16
2024-10-14 09:00:51
@ c0e0c427:a1f63a16
2024-10-14 09:00:51Chef's notes
I reuse my basic pickle brine at least once. Pickle brine is all about your preference. Make it as sweet as you like with extra sugar, spicy as heck so you are remembering you had them the morning after or a little extra zesty by changing the ratio of water to vinegar to 1:1. Note that the ratio is by weights and I use metric instead of freedom units because that is how I work but imperial will work if for keep the ratio the same by WEIGHT.
Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 0 min
Ingredients
- 50mls apple cider vinegar
- 100mls water
- 50grams sugar
- Fresh dill
- Chilli
- 5-10 cucumbers
Directions
- Mix vinegar water together in a pot and bring to a simmer
- Turn off the heat and stir in the sugar until dissolved.
- Add into the brine fresh dill and chilli to your preferred taste.
- Allow brine to cool.
- Chop cucumbers into rounds or julienne and place into a clean and sterilised jar.
- Pour brine into jar so cucumbers are fully covered.
- Can enjoy in 2 days. Keeps up to 2 months.
-
 @ fd208ee8:0fd927c1
2024-10-08 13:37:28
@ fd208ee8:0fd927c1
2024-10-08 13:37:28There was once a man, who missed an important meeting because his alarm clock didn't ring. He was a bit upset, and wished for it to be corrected, so he promptly got up, got dressed, and took the alarm clock back to the store, where he'd gotten it from.
He stood in line, patiently, at the service counter, and waited his turn. When he got to the front, the clerk asked, "How may I help you?"
"Oh, I'm having trouble with this alarm clock. You see, it doesn't ring, when the time is reached. I was wondering if that could be fixed."
"Why should we fix that? We're actually very busy building the new model. Should be out in a few weeks. Just wait for that one. Goodbye."
"What? Wait! You can't just leave it broken, like this."
"Why not? What right do you have, to demand an alarm clock that rings? Besides, how many alarm clocks have you built?"
The customer was now quite flustered and a bit ashamed of his self, "Well, none. I admit that, but..."
"Well, there you go! Outrageous, that you should criticize something someone else has accomplished, that you have not. Besides, you are incompetent to tell if anything is even wrong. Maybe this is some sort of non-ringing alarm clock. Perhaps it has lights or wave sounds..."
The second customer in line suddenly piped up, "Ahem. I'm sorry to interrupt. I must admit, I've also never built an alarm clock, but I'm a jeweler, who sells and repairs watches, and I must agree with you, sir," nods to first customer, "This is most definitely a ringing alarm clock and... See here? This bit of the bell arm has rusted through and broken off. Shoddy craftmanship, I'd say."
"Oh, Mr High-n-Mighty jeweler, claims to know how a good alarm clock is to be made, while having zero experience. I've had enough of this outrage. I'm getting the vapors and need at least a two-week sabbatical, to recover from such gross mistreatment. The store is closing immediately. Everyone out!"
"But my clock, sir!"
The door slams in his face, and he heads home, dumping his clock in the garbage bin down the street. Next time, he will simply use the alarm on his cell phone. That always rings.
-
 @ 3c984938:2ec11289
2024-05-09 04:43:15
@ 3c984938:2ec11289
2024-05-09 04:43:15
It's been a journey from the Publishing Forest of Nostr to the open sea of web3. I've come across a beautiful chain of islands and thought. Why not take a break and explore this place? If I'm searching for devs and FOSS, I should search every nook and cranny inside the realm of Nostr. It is quite vast for little old me. I'm just a little hamster and I don't speak in code or binary numbers zeros and ones.

After being in sea for awhile, my heart raced for excitement for what I could find. It seems I wasn't alone, there were others here like me! Let's help spread the message to others about this uncharted realm. See, look at the other sailboats, aren't they pretty? Thanks to some generous donation of SATs, I was able to afford the docking fee.

Ever feel like everyone was going to a party, and you were supposed to dress up, but you missed the memo? Or a comic-con? well, I felt completely underdressed and that's an understatement. Well, turns out there is a some knights around here. Take a peek!

A black cat with a knight passed by very quickly. He was moving too fast for me to track. Where was he going? Then I spotted a group of knights heading in the same direction, so I tagged along. The vibes from these guys was impossible to resist. They were just happy-go-lucky. 🥰They were heading to a tavern on a cliff off the island.

Ehh? a Tavern? Slightly confused, whatever could these knights be doing here? I guess when they're done with their rounds they would here to blow off steam. Things are looking curiouser and curiouser. But the black cat from earlier was here with its rider, whom was dismounting. So you can only guess, where I'm going.

The atmosphere in this pub, was lively and energetic. So many knights spoke among themselves. A group here, another there, but there was one that caught my eye. I went up to a group at a table, whose height towed well above me even when seated. Taking a deep breath, I asked, "Who manages this place?" They unanimous pointed to one waiting for ale at the bar. What was he doing? Watching others talk? How peculiar.

So I went up to him! And introduced myself.
"Hello I'm Onigirl"
"Hello Onigirl, Welcome to Gossip"
"Gossip, what is Gossip?" scratching my head and whiskers.
What is Gossip? Gossip is FOSS and a great client for privacy-centric minded nostriches. It avoids browser tech which by-passes several scripting languages such as JavaScript☕, HTML parsing, rendering, and CSS(Except HTTP GET and Websockets). Using OpenGL-style rendering. For Nostriches that wish to remain anonymous can use Gossip over TOR. Mike recommends using QubesOS, Whonix and or Tails. [FYI-Gossip does not natively support tor SOCKS5 proxy] Most helpful to spill the beans if you're a journalist.

On top of using your nsec or your encryption key, Gossip adds another layer of security over your account with a password login. There's nothing wrong with using the browser extensions (such as nos2x or Flamingo) which makes it super easy to log in to Nostr enable websites, apps, but it does expose you to browser vulnerabilities.
Mike Points out
"people have already had their private key stolen from other nostr clients,"
so it a concern if you value your account. I most certainly care for mine.

Gossip UI has a simple, and clean interface revolving around NIP-65 also called the “Outbox model." As posted from GitHub,
"This NIP allows Clients to connect directly with the most up-to-date relay set from each individual user, eliminating the need of broadcasting events to popular relays."
This eliminates clients that track only a specific set of relays which can congest those relays when you publish your note. Also this can be censored, by using Gossip you can publish notes to alternative relays that have not censored you to reach the same followers.
👉The easiest way to translate that is reducing redundancy to publish to popular relays or centralized relays for content reach to your followers.

Cool! What an awesome client, I mean Tavern! What else does this knight do? He reaches for something in his pocket. what is it? A Pocket is a database for storing and retrieving nostr events but mike's written it in Rust with a few extra kinks inspired by Will's nostrdb. Still in development, but it'll be another tool for you dear user! 💖💕💚
Onigirl is proud to present this knights to the community and honor them with kisu. 💋💋💋 Show some 💖💘💓🧡💙💚
👉💋💋Will - jb55 Lord of apples 💋 @npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s
👉💋💋 Mike Knight - Lord of Security 💋 @npub1acg6thl5psv62405rljzkj8spesceyfz2c32udakc2ak0dmvfeyse9p35c

Knights spend a lot of time behind the screen coding for the better of humanity. It is a tough job! Let's appreciate these knights, relay operators, that support this amazing realm of Nostr! FOSS for all!

This article was prompted for the need for privacy and security of your data. They're different, not to be confused.
Recently, Edward Snowden warns Bitcoin devs about the need for privacy, Quote:
“I've been warning Bitcoin developers for ten years that privacy needs to be provided for at the protocol level. This is the final warning. The clock is ticking.”
Snowden’s comments come after heavy actions of enforcement from Samarai Wallet, Roger Ver, Binance’s CZ, and now the closure of Wasabi Wallet. Additionally, according to CryptoBriefing, Trezor is ending it’s CoinJoin integration as well. Many are concerned over the new definition of a money transmitter, which includes even those who don’t touch the funds.
Help your favorite the hamster
 ^^Me drowning in notes on your feed. I can only eat so many notes to find you.
^^Me drowning in notes on your feed. I can only eat so many notes to find you. 👉If there are any XMPP fans on here. I'm open to the idea of opening a public channel, so you could follow me on that as a forum-like style. My server of choice would likely be a German server.😀You would be receiving my articles as njump.me style or website-like. GrapeneOS users, you can download Cheogram app from the F-Driod store for free to access. Apple and Andriod users are subjected to pay to download this app, an alternative is ntalk or conversations. If it interests the community, just FYI. Please comment or DM.
👉If you enjoyed this content, please consider reposting/sharing as my content is easily drowned by notes on your feed. You could also join my community under Children_Zone where I post my content.
An alternative is by following #onigirl Just FYI this feature is currently a little buggy.
Follow as I search for tools and awesome devs to help you dear user live a decentralized life as I explore the realm of Nostr.
Thank you Fren
-
 @ 1bda7e1f:bb97c4d9
2024-10-24 04:48:52
@ 1bda7e1f:bb97c4d9
2024-10-24 04:48:52Tldr
- Nostr relays help users post and read notes on the network
- Relay operators have launched a variety of relays for you to use
- You too can launch your own relay for any reason you like
- Launching your own relay gives you a lot of power in how you use Nostr
- Many relay softwares exist for you to use
- I launched a personal relay using HAVEN relay software on my VPS
- I am now more in control of saving notes, cutting spam, and protecting my privacy
- My personal relay is now hosted at relay.rodbishop.nz
What are Nostr Relays Anyway?
When you're a user of a social network, you post and read notes from other users on the network. In a centralised network like Twitter or Instagram the company's servers receive all user's notes and relay them to other users. On Nostr, there is no single company's servers to relay messages, so instead the task is taken up by relay operators.
Anyone can be a relay operator and they can run a relay for any purpose. When you start using Nostr you will usually be connected to any one of a number of "public" relays, and be able to post and receive notes from users on the network via these.
Configuring these relays can tailor your experience somewhat–for example the client Nostrudel allows you to select from Western or Japanese relay set.
It is also possible to set up your own relay to use for your own purposes. All kinds of people have launched relays for all kinds of purposes. For example, to:
- Power your own client
- Support your community
- Run a for-profit relay business
- Relay a certain a type of content you need
- Back up your own notes, decrease spam, or increase privacy
- Curate your own social feed with your own algorithm
Relay instances available to connect with
Today is an interesting time in relay-ops. The evolution of the technology has inspired users to experiment with diverse types of relays tailored to various needs. As a result there are very many relay instances in operation and available to connect with.
A few sites try to collate which relays are in operation, like nostr.info and xport.top and sesseor's relay list . These lists are long (Sessor's list counted 2,500+ relays) and it's not clear to me whether it's even possible to be comprehensive as relays may join or leave the network all the time.
Broadly speaking, relays might be available for different users to use in different ways:
- A relay where anyone can post, like relay.damus.io
- A paid relay where anyone can post after payment, to cut spam, like nostr.wine
- A "web of trust" relay where anyone can post if they are related to the owner's social graph, to cut spam, like nostrelites.org
- A speciality relay where a particular community can post, like nostr.com.au for #austriches (Australians)
- A relay where anyone can post just specific content, like purplepag.es for user profiles only
- A team relay for your company or organisation only
- A personal relay for your own personal use
Nostr.Band shows which of these available relays are most popular, such as relay.damus.io and nos.lol and eden.nostr.land
Relay softwares for you to launch your own
You may decide to launch you own relays, and if you do there are many different relay softwares to choose from:
- Simple, like Bucket (<100 lines of code)
- Widely used, like Nostream (top ranked on Github)
- Customisable, like Khatru (a framework for customised relays)
- Specialised, like HAVEN or Team Relay (for personal or teams relays, based on Khartu)
You can run these on your own server, or local machine, or phone or with a third-party host.
Aljaz provides a great resource with 45+ relay softwares to choose from.
In summary, at a high level,
- Anyone can connect to any of the relay instances that are available for them to use
- Anyone who wants to launch their own can select the relay software that best suit their needs, launch an instance, and have it used by whichever users they like
Reasons to Run Your Own Relay
As a normal user of a Nostr client there's no obligation to run a relay. But having your own relay does give you more power.
For my own journey down the #nostr rabbit hole, I was looking for a relay to:
- back up my notes
- decrease spam
- increase my privacy
- learn skills I could later use for running a community or team or paid relay
Backing up notes – When you post notes to a public relay there's no guarantee that the relay is going to keep them long-term. It's job is relaying your notes to other clients, not storing them. Running your own relay allows you to keep your notes online.
Decrease spam – To first spam we can use a "Web of Trust" model–in which users endorse other users as trustworthy. A "Web of Trust" relay will reject notes from parties too far removed from your network. Running your own relay makes you more difficult to spam.
Increasing privacy – When you connect to a public relay, they can determine personal information about you, such as your IP address. Running your own relay keeps things more private.
For communities and teams and paid relays – Many opportunities exist to tailor relays to certain users needs, be they businesses or communities or as a for-profit business. For me, I am hoping that running my own relay helps me learn skills I can use in these kinds of further ventures.
To start I decided to focus on a personal relay. However, when I really got under the hood, it turned out I would need multiple relays not just one.
The outbox model
Mike Dilger proposed the outbox model (originally called the gossip model) as a way for users to engage with the wider Nostr network. It's a great model that is helpful to understand, as it suggests to establish different relays for different purposes.
Many clients and relay softwares have now adopted and continued to elaborate on this model. An example is to run specialised relays for Outbox, Inbox, Chat and Private needs.
Outbox Relay (also called Home Relay)
- This relay is for notes you have written, so that everyone knows where to find your notes
- In a set up where you are running your own, this relay is restricted so that only you can post to it, and you should set up your clients to post your notes to it
- An advanced version may take any notes received to this relay and "blast" them to other public relays so that your notes get wider reach
Inbox Relay (also called Public Relay)
- This relay is for public notes that other users want you to see, so that you always find notes that are relevant to you, including all replies, comments, likes, and zap payments
- In a set up where you are running your own, this relay is where you should look for notes relevant to you, and you should set up your clients to read from it
- An advanced version may search other public relays for notes that tag you, and import them into this relay so that you never miss a relevant note
Chat Relay (also called Direct Message Relay)
- This relay is for private direct message notes from other users, so that you always find your direct messages and so that they stay private
- In a set up where you are running your own, this relay is restricted so that only you can read from it, and you should set up your clients to read from it
- An advanced version may cut spam by only accepting direct messages from other users within your Web of Trust
Private Relay
- This relay is for your private use only, so that you can store private drafts or thoughts
- Only you can write to it and only you can read from it (and so, it is a bit mis-named as it does not actually relay anything to anywhere at all)
- In a set up where you are running your own, it gives you true privacy for these notes
In summary as a user
- I post my notes to my outbox relay. Network users can read them there, and if the relay is advanced it will also blast the notes out to other relays on the network
- I read from my inbox relay. Network users know to reach me there, and if the relay is advanced it will also bring me notes from the wider network
- I can have private direct message conversations with others in my chat relay.
- I can save private notes in my private relay
For me, this model has a lot of appeal and I went looking for a personal relay which adopted this model and contained all of these features.
HAVEN as a personal relay
I decided to go with HAVEN relay software.
HAVEN is all four of the above relays in one–outbox, inbox, chat and private. It contains advanced features like blasting your notes from outbox to other relays, importing notes from other relays to your inbox, and preventing spam with Web of Trust.
HAVEN is written by Utxo the Webmaster . It is based upon the Khatru relay framework by Fiatjaf
Setting up HAVEN as a Personal Relay
I am mostly non-technical, but on my #Nostr journey I have been having success with technology set ups that use Docker.
- I have a cheap VPS which currently runs Albyhub and Phoneixd with Docker,
- My objective was to set up HAVEN to run alongside it, in a separate Docker on the same server. HAVEN does not include Docker by default, but Sebastix published a fork with Docker support.
To get HAVEN up and running in Docker on your VPS:
- Clone and configure HAVEN with the right variables
- Launch it in Docker on your VPS
- Check the URLs and logs to see your HAVEN running
- Configure a subdomain to point to the VPS
- Configure the VPS to reverse proxy to the Docker port
- Configure the relays in your favourite Nostr client
- Post a note to your outbox and see if it blasts!
Running HAVEN
I cloned Sebastix fork to start.
git clone -b docker_compose_support https://github.com/nostrver-se/haven.git cd havenThe software sets up all environment variables in the
.envfile, and comes with an.env.examplefile. Duplicate and rename the file to.env. Within the.envfile you need to set up the environment variables. The file is long but it contains lots of repetition and for the most part defaults can be retained–only a few changes are required:- Replace all instances of the default user npub with your own (for me,
npub1r0d8...) - Change the default relay URL to your own (for me,
relay.rodbishop.nz) - Replace all instances of the default name in the relay names (for me, "Rod's ...")
- Replace all instances of the default profile image with your own
To enable automatic blasting from your outbox, and importing to your inbox, the software comes with an example list of relays to blast and import from. See
relays_blastr.example.jsonandrelays_import.example.json. To use these features simply duplicate and rename these files torelays_blastr.jsonandrelays_import.jsonrespectively. Within these files you can specify the public relays of your choice. I simply used the default list.There are other features available, such as backups and initial imports, but I decided to handle these later. To start with I wanted to launch the relay and test it.
To launch the relay run Docker Compose.
docker-compose up -d docker logs haven-relayThen you should explore the logs in the command line and the ports in your browser to see if it launched successfully. The logs should show your web of trust has been built successfully and the browser should show simple landing pages.
The logs should show that the relay has queried the network and built a web of trust from your followers. Mine looked as follows.
2024/10/14 12:02:08 🌐 building web of trust graph 2024/10/14 12:02:16 🫂 total network size: 13296 2024/10/14 12:02:16 🔗 relays discovered: 335 2024/10/14 12:02:17 🌐 pubkeys with minimum followers: 9394 keysYour browser should show you have four relays in operation, for example as follows.
your_IP_address:3355(your outbox or home relay)your_IP_address:3355/private(your private relay)your_IP_address:3355/chat(your direct message relay)your_IP_address:3355/inbox(your inbox relay)
That's it. Your relay is online.
Connecting HAVEN
Now all that remains is the plumbing to connect your domain, relay, and Nostr clients together.
Configure DNS
First, configure your domain. At a high level –
- Get your domain (buy one if you need to)
- Get the IP address of your VPS
- In your domain's DNS settings add those records as an A record to the subdomain of your choice, e.g.
relayas inrelay.your_domain_name.com, or in my caserelay.rodbishop.nz
Your subdomain now points to your server.
Configure reverse proxy
Next, you need to redirect traffic from your subdomain to your relay at port
3355.On my VPS I use Caddy as a reverse proxy for a few projects, I have it sitting in a separate Docker network. To use it for my HAVEN Relay required two steps. I am sure that the way I do this is not very elegant, but it worked. If you prefer a different method, the HAVEN readme also comes with instructions on how to perform a similar setup using nginx.
For my method, my steps were as follows:
- Add configuration to Caddy's
Caddyfileto tell it what to do with requests for therelay.rodbishop.nzsubdomain - Add the Caddy Docker network to the HAVEN
docker-compose.ymlto make it be part of the Caddy network
For the addition to the
Caddyfile, I used as follows:relay.rodbishop.nz { reverse_proxy haven-relay:3355 { header_up X-Forwarded-For {remote} header_up X-Forwarded-Proto {scheme} header_up X-Forwarded-Port {server_port} } }For the addition to the
docker-compose.yml, I used as follows:``` networks: - caddy # Added this line to services to connect to the Caddy network
networks: caddy: external: true # Added this to section specify the Caddy network ```
Once your DNS configuration and reverse proxy setup are completed, you should now be able to access your Nostr client at
relay.your_domain_name.com. For my set up, this wasrelay.rodbishop.nz.Connecting your Nostr client
Most Nostr clients allow you to specify any relay you choose. My go-to client at the moment is Amethyst on Android. Amethyst allows you to specify discrete relays for each role in the outbox model which ties up very neatly with HAVEN.
- In the sidebar, select Relays
- For "Public Outbox/Home Relays" enter
relay.your_domain_name.com - For "Public Inbox Relays" enter
relay.your_domain_name.com/inbox - For "DM Inbox Relays" enter
relay.your_domain_name.com/chat - For "Private Home Relays" enter
relay.your_domain_name.com/private - Click Save to broadcast your new relays to the Nostr network.
Your new relay configuration is now live.
Testing your relay
Lastly, it's time to test. Amethyst provides a simple method to test this as it allows you to configure the relays used on each post.
- Create a test note, and then before you post it, edit your relays using the icon at the top
- Turn off all relays except your own outbox relay, and post the note
- Access your HAVEN docker logs with
docker logs haven-relayand see if there is a log to indicate if the note was received and blasted to other public relays - Copy the
neventof the note, and attempt to find it in another client
If you're in luck, you may see something like this (the blasted note, and then users on the network responding to the note in turn).
2024/10/22 00:12:23 🔫 blasted 95c477af7e6b612bf5d1d94309d2d57377a0a67d2181cfbb42a2e3fbc0feeaaf to 26 relays 2024/10/22 00:13:50 🤙 new reaction in your inbox 2024/10/22 00:14:42 🫂 new reaction in your inbox 2024/10/22 00:14:45 ✅ new reaction in your inbox 2024/10/22 00:15:12 💜 new reaction in your inbox 2024/10/22 00:17:03 ✅ new reaction in your inbox 2024/10/22 00:17:03 🫂 new reaction in your inbox 2024/10/22 00:17:55 🫂 new reaction in your inbox 2024/10/22 00:19:02 📰 new note in your inboxThat's it. If you followed this successfully your personal relay is up and running.
What I did wrong so you don't have to
My first relay was too public
This blog comes after much trial and error. The first error I made was I set up a relay to use as a personal relay, but without any restrictions on use. I very quickly found other people discovered and started using my relay to save their own notes! This was unintended and I had to take it down.
Unfamiliar with Go language
I am mostly non-technical, and completely unfamiliar with Go. I got the project up and running with Go on my localhost–with a lot of help from my AI–but I then completely failed in migrating this to my VPS. Moving to Docker made the difference for me here.
I failed a few times due to a messy folder
After messing with Go, I moved to the Docker setup, but I started my work from a messy folder which contained remnants of the Go build, which caused various failures. Deleting the folder and cloning again from scratch solved the issue.
Trouble with Nostr.wine
I subscribe to the Nostr.wine paid relay, and I initially added it to the list of relays in my blaster. However, it didn't work, and the logs showed an error as follows
CLOSED from wss://nostr.wine: 'auth-required: this relay only serves private notes to authenticated users'It seems my npub's subscription to Nostr.wine is not enough for it to permit my relay to blast notes to it. In the end, I removed Nostr.wine from my relay config, and kept Nostr.wine as a separate entry in my Client's outbox settings.
Failed to create web of trust graph
When I first launched the relay on my VPS, HAVEN failed to complete the Web of Trust graph, with a log that looked as follows (note the zeroes). As a result, no one would have been able to send me DM's to my Chat relay (it would flag every message as spam).
2024/10/14 12:02:08 🌐 building web of trust graph 2024/10/14 12:02:16 🫂 total network size: 0 2024/10/14 12:02:16 🔗 relays discovered: 0 2024/10/14 12:02:17 🌐 pubkeys with minimum followers: 0 keysI never got to the bottom of why this was. In the process of trying to fix it I rebuild the container, and on the rebuild it spontaneously worked. Accordingly my lesson learned is "if in doubt, turn if off and on again".
Failed to run --import function
HAVEN comes with a function to import all your old notes from other public relays to your own outbox relay. When I run it I get an error as follows:
panic: Cannot acquire directory lock on "db/private". Another process is using this Badger database. error: resource temporarily unavailableI have yet to work out the solution for this, and will update this note when I do so!
What's Next?
Over the past four blogs I have
- Mined a Nostr pubkey and backed up the mnemonic
- Set up Nostr payments with a Lightning wallet plus all the bells and whistles
- Set up NIP-05 and Lighting Address at my own domain
- Set up a Personal Relay at my own domain
This feels like a very comprehensive personal set up now. Also, I have uncovered some new rabbit holes and feel like I have some projects to tackle. Perhaps one of these?
- Set up a personal homepage with my Nostr feed to round-out my rodbishop.nz domain
- Experiment with different signers like Amber and Nsec.app and NFC cards
- Set up a paid relay for #austriches (Australians and Kiwis on Nostr)
- Set up a team relay to experiment with Nostr for business or community projects
- Or something else ... ?
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
Pura vida Nostr.
-
 @ b2d670de:907f9d4a
2024-04-28 09:48:01
@ b2d670de:907f9d4a
2024-04-28 09:48:01This is a list of nostr relays exposed as onion services. The list is currently actively maintained on GitHub. Contributions is always appreciated!
| Relay name | Description | Onion url | Operator | | --- | --- | --- | --- | | nostr.oxtr.dev | Same relay as clearnet relay nostr.oxtr.dev | ws://oxtrdevav64z64yb7x6rjg4ntzqjhedm5b5zjqulugknhzr46ny2qbad.onion | njump | | relay.snort.social | Same relay as clearnet relay relay.snort.social | wss://skzzn6cimfdv5e2phjc4yr5v7ikbxtn5f7dkwn5c7v47tduzlbosqmqd.onion | njump | | nostr.thesamecat.io | Same relay as clearnet relay nostr.thesamecat.io | ws://2jsnlhfnelig5acq6iacydmzdbdmg7xwunm4xl6qwbvzacw4lwrjmlyd.onion | njump | | nostr.land | The nostr.land paid relay (same as clearnet) | ws://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion
http://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion (for payments) | njump | | bitcoiner.social | No auth required, currently | ws://bitcoinr6de5lkvx4tpwdmzrdfdpla5sya2afwpcabjup2xpi5dulbad.onion | njump | | relay.westernbtc.com | The westernbtc.com paid relay (via Tor: hjar34h5zwgtvxr345q7rncso3dhdaryuxgri3lu7lbhmnzvin72z5ad.onion) | ws://westbtcebhgi4ilxxziefho6bqu5lqwa5ncfjefnfebbhx2cwqx5knyd.onion | njump | | freelay.sovbit.host | Free relay for sovbit.host | ws://sovbitm2enxfr5ot6qscwy5ermdffbqscy66wirkbsigvcshumyzbbqd.onion | njump | | nostr.sovbit.host | Paied relay for sovbit.host | ws://sovbitgz5uqyh7jwcsudq4sspxlj4kbnurvd3xarkkx2use3k6rlibqd.onion | njump | | nostr.wine | 🍷 nostr.wine relay (same as clearnet) | ws://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion
http://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion | njump | | inbox.nostr.wine | 🍷 inbox.nostr.wine relay (same as clearnet) | ws://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion
http://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion | njump | -
 @ fd208ee8:0fd927c1
2024-10-08 11:51:50
@ fd208ee8:0fd927c1
2024-10-08 11:51:50The 4P's
Remember the Four "P"s of Marketing? Let's look at them, in relation to digital creative work on Nostr.
Product
The product needs to be designed to fulfill a need or desire in the market. If you are writing things nobody wants to read, singing songs nobody wants to hear, or posting pictures that nobody wants to see, then you need to reevaluate your product choices because you are spam.
You are wasting your time, which means you bear a cost for the production of these goods. Is it really worth it? Maybe, maybe not. Maybe you could do something else, or do something in addition, to make the product more appealing.
On the other hand, if you are producing something valuable to a niche audience, you might want to think more about specifically aiming for and catering to that audience, rather than wasting your energy trying to appeal to a larger, indifferent group. It is better to be loved by a few and hated by many, than to be uninteresting to nearly everyone and ignore those who love you.
Price
People should have some anchor for the price, even if you have not explicitly named a price, so that they can know what such effort is "normally" worth and orient your value-provided up or down from there. It should also be clear what they are paying for, so that they know what the scope of the payment covers.
If there is no such anchor available, you can help create one by coming up with your own personal scale for other people's works and discussing it, in public. Any listeners will react positively or negatively, but they will all now have a mental "price point" to orient their own prices around.
If you have fixed and/or variable costs, the price you name should at least cover them, otherwise you need to lower the costs or raise the price. If you name no price, expect to get nothing, and you will never be disappointed. But you may also occasionally get a lot, and have it nearly knock you off your feet, so be prepared for that, too.
Generally, things that are free are of lower quality because producers have no incentive to expend great effort to produce things nobody values enough to pay for. The only major exceptions to this are cross-financing, such as freemium or preview models (typical for things like Substack or OnlyFans), or production funded by third parties (as is the case with Linux and GitHub). In both these cases, the payment exists, but is deferred or distanced.
Many products or services therefore start off "free", during an introductory period, but if they aren't getting enough income from it, they'll eventually give up and wander off. We pay creatives for their continued efforts and continued presence.
Placement
It is of vital importance that you place your products efficiently. Things you should consider:
- What relays will this work be accessible from? Large relays will extend your reach, but your product will appear within a sea of spam, so its relative value will decline, the same way the perceived worth of the nicest house on the block is dragged down by the houses around it.
- Writing to large relays also destroys the perceived exclusivity of the offer, although this can be partially mitigated by encryption. A mix of wide/exclusive is probably best, since exclusive access to someone unknown is less valuable than to someone well-known.
- Remember that the people paying for exclusive access, aren't necessarily paying for access to "better" material, they're paying for access to you, as a person, and/or they are trying to encourage you to continue your work. Rather than having your blockbusters behind a paywall, have the more personal items there and spend more time responding to the people who actually care about you and your art.
- Do you even want the work directly accessible over Nostr? Perhaps you prefer to store the work off-Nostr and simply expand access to that, to npubs.
- Something that covers price and placement is what sort of payment rails the hosting platform provides and/or you will accept. Some people only want to accept Lightning zaps, but others might be okay with fiat transactions of some sort, on-chain Bitcoin, gift cards, badge or NIP-05 sales, or some other method. Generally, the more payment options available, the less friction preventing payment. Lightning is arguably the payment method with the least friction, so it should go first in the list.
Promotion
Get Noticed
Who is your target audience and how can you get their attention, so that they find out which product you are offering? This one is extremely difficult, on Nostr. Mostly, everyone just screams things into the void, and people with more followers scream louder and are more-likely to be heard. So, I'd say:
- try to have more followers,
- find someone with lots of followers to help you with marketing, or
- join a "boost cooperative", where you join forces with other smaller accounts, to promote each other's notes.
Find your tribe
Use hashtags, but limit yourself to those that are truly relevant, and never have more than 3 in a note. Post to communities/topic-relays or groups, or write an article or wiki page or etc. and then cross-post to your kind 01 feed, with a hyperlink to a website that displays your work properly.
-
 @ d5c3d063:4d1159b3
2024-10-24 14:31:36
@ d5c3d063:4d1159b3
2024-10-24 14:31:36แว่นตา...เข็มทิศ...ชีวิต...ทางเลือก
เคยรู้สึกมั้ยครับว่า เรากำลังมองโลกต่างจากคนอื่น เหมือนใส่แว่นตาคนละแบบ เห็นภาพคนละมุม บางคนมองโลกสวยงาม บางคนมองโลกโหดร้าย บางคนมองโลกแสนสับสน...นั่นแหละครับ "ปรัชญา"
https://image.nostr.build/13ec632e4bb720d8b6729ddc07428be7f3fd89d02b117a9eff89ecb80540a1fd.jpg
หลายคนอาจมองว่า ปรัชญาเป็นเรื่องไกลตัว เป็นเรื่องของนักคิด นักปราชญ์ อยู่ในตำราเล่มหนา แต่จริงๆ แล้ว ปรัชญาอยู่รอบตัวเราและใกล้ตัวเรามากกว่าที่คิด เพราะมันคือเข็มทิศที่นำทางชีวิต มันคือระบบความคิด ชุดความเชื่อ และค่านิยมหรือคุณค่าที่เรายึดถือ ซึ่งส่งผลต่อทุกการตัดสินใจ ทุกการกระทำ และสุดท้ายก็คือชีวิตของเราเอง
นั่นหมายความว่า ทุกวันนี้ เรากำลังเลือกว่าจะเป็นมนุษย์ที่ใช้ชีวิตอย่างมีสติ มีเหตุผล และมีความรับผิดชอบต่อการกระทำของเราหรือไม่ หรือจะเป็นแค่ทาสของอารมณ์ ของความเชื่อและความงมงาย...?
ลองนึกภาพดูนะครับ ถ้าเข็มทิศของเราชี้ผิดทิศ มันจะพาเราไปถึงจุดหมายได้ยังไง การเลือกปรัชญาที่ผิดพลาด ก็เหมือนการใช้เข็มทิศที่ผุพัง และในที่สุดปลายทางนั้นก็คือความล้มเหลวหรือความทุกข์ยาก
ปรัชญาที่มีเหตุผล ใช้การคิดวิเคราะห์กับความรับผิดชอบ คือเข็มทิศที่แม่นยำที่สุดที่จะนำทางเราไปสู่ชีวิตที่ดีงาม ชีวิตที่มีอิสระมีความหมายและมีคุณค่า
เหตุผล คือแสงสว่าง นำทางเราไปสู่ความจริง ช่วยให้เรามองเห็นโลกในอย่างที่มันเป็น โดยไม่ถูกบิดเบือนด้วยอคติ อารมณ์ หรือความเชื่อแบบผิดๆ ในขณะเดียวกันความเชื่อที่ผ่านการไตร่ตรองด้วยเหตุผลบนพื้นฐานของความจริง ก็สามารถเป็นรากฐานที่มั่นคงให้กับชีวิตและเป็นแรงผลักดันให้เราก้าวไปข้างหน้าได้ การคิดวิเคราะห์คือเครื่องมือที่ทรงพลัง ช่วยให้เราเข้าใจปัญหาอย่างลึกซึ้ง มองเห็นเหตุและผลเพื่อหาทางแก้ไขได้อย่างมีประสิทธิภาพ ส่วนความรับผิดชอบคือการยืนหยัดในความเป็นมนุษย์ คือการยอมรับผลของการกระทำของเราทั้งดีและไม่ดีนั้น ที่จะส่งผลต่อตัวเราและคนรอบข้าง ซึ่งเป็นหนทางสู่ "อิสรภาพ" ที่แท้จริง
ในทางกลับกัน ปรัชญาที่ปฏิเสธเหตุผล ปล่อยให้อารมณ์ความเชื่อที่งมงายหรืออำนาจภายนอกครอบงำ ก็เหมือนเข็มทิศที่มันพัง มันก็จะพาเราไปสู่ความหายนะ ชีวิตที่ไร้สติไร้จุดหมายและการตกเป็นทาสของผู้อื่น
ชีวิตเรา เราเลือกได้ เลือกที่จะใช้ชีวิตแบบมนุษย์ที่คิดเป็น ใช้เหตุผลเป็นหลักในการตัดสินใจ หรือจะใช้ชีวิตแบบไร้สติ ปล่อยให้อารมณ์ ความเชื่อความงมงายมาควบคุม แต่อย่าลืมว่าอารมณ์เป็นส่วนหนึ่งของเรา การทำความเข้าใจและจัดการกับอารมณ์ จึงมีความสำคัญอย่างยิ่งในการนำทางชีวิตเราให้ไปในทิศทางที่ดีงาม
เลือกปรัชญาของคุณอย่างชาญฉลาด เพราะนั่นหมายถึงคุณกำลังเลือกเส้นทางชีวิตของคุณเอง
Siamstr #Philosophy #ปรัชญา






