-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ eac63075:b4988b48
2024-10-20 13:49:55
@ eac63075:b4988b48
2024-10-20 13:49:55Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.
Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.
The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.
Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.
The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
Conclusion of the Technical Debate
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.

Table reference: Patrick Breyer - Chat Control in 23 September 2024
Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.
The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
Conclusion of the Debate
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.
User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
Summary of Consequences
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.
The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.
Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ 319ad3e7:cc01d50a
2024-11-21 20:10:33
@ 319ad3e7:cc01d50a
2024-11-21 20:10:33Rupert and Kajoozie’s #Nostr Famous Gumbo
TheRupertDamnit Image 1 8 0
3.9K sats
Chef's notes Make sure you watch your roux closely. It can go from perfect to burnt in a moment. Top with green onion tops. Sprinkle a very small amount of file over top. Andouille sausage is traditional but kielbasa is also a good substitute.
Details ⏲️ Prep time: 30 minutes for vegetable prep + ~1 hour for boiling chicken 🍳 Cook time: ~2 hours 🍽️ Servings: 8-10 Ingredients 1 large onion 1 large bell pepper 2 medium stalks celery 6-8 cloves garlic ~3 lbs. bone-in, skin-on chicken; remove skin and set aside to render ~1.5 lbs andouille sausage, browned ~1/2 lb. tasso, optional 2 green onions, chopped and separated 2 cups okra, cut (frozen or fresh, not canned) ~1 cup oil (rendered from chicken skins & sausage) ~1 cup flour 1-2 bay leaves Directions Chop all vegetables and set aside. Render the fats from your chicken skins and sausages. Combine your flour and rendered fats in a cast iron skillet and stir continually over medium –low heat until your roux is chocolate brown. Stir in about 1/4 tsp of flour at this stage and cook until it stops “fizzing”. (This is simply to add to the thickening power of the roux.) While you are cooking your roux, boil your chicken until cooked through, remove from heat and broth, and set aside to cool for deboning . Add your vegetables, roux, deboned chicken, sausage, hot sauce, Worcestershire, and spices/seasonings to your broth. Optional: sauté your vegetables, except okra, before adding to broth. (Only add the bottom portions of the green onion here, reserve the green tops for garnish.) Cook until the okra is soft and no longer slimy, about 2 hours, at a low boil. (med-high heat) Optional: reduce to a simmer about 10 minutes before finished and drop a few eggs to poach in the stew before serving. Do not stir. Serve over rice.
-
 @ a39d19ec:3d88f61e
2024-11-21 12:05:09
@ a39d19ec:3d88f61e
2024-11-21 12:05:09A state-controlled money supply can influence the development of socialist policies and practices in various ways. Although the relationship is not deterministic, state control over the money supply can contribute to a larger role of the state in the economy and facilitate the implementation of socialist ideals.
Fiscal Policy Capabilities
When the state manages the money supply, it gains the ability to implement fiscal policies that can lead to an expansion of social programs and welfare initiatives. Funding these programs by creating money can enhance the state's influence over the economy and move it closer to a socialist model. The Soviet Union, for instance, had a centralized banking system that enabled the state to fund massive industrialization and social programs, significantly expanding the state's role in the economy.
Wealth Redistribution
Controlling the money supply can also allow the state to influence economic inequality through monetary policies, effectively redistributing wealth and reducing income disparities. By implementing low-interest loans or providing financial assistance to disadvantaged groups, the state can narrow the wealth gap and promote social equality, as seen in many European welfare states.
Central Planning
A state-controlled money supply can contribute to increased central planning, as the state gains more influence over the economy. Central banks, which are state-owned or heavily influenced by the state, play a crucial role in managing the money supply and facilitating central planning. This aligns with socialist principles that advocate for a planned economy where resources are allocated according to social needs rather than market forces.
Incentives for Staff
Staff members working in state institutions responsible for managing the money supply have various incentives to keep the system going. These incentives include job security, professional expertise and reputation, political alignment, regulatory capture, institutional inertia, and legal and administrative barriers. While these factors can differ among individuals, they can collectively contribute to the persistence of a state-controlled money supply system.
In conclusion, a state-controlled money supply can facilitate the development of socialist policies and practices by enabling fiscal policies, wealth redistribution, and central planning. The staff responsible for managing the money supply have diverse incentives to maintain the system, further ensuring its continuation. However, it is essential to note that many factors influence the trajectory of an economic system, and the relationship between state control over the money supply and socialism is not inevitable.
-
 @ 9bc2d34d:d19d2948
2024-11-21 19:43:44
@ 9bc2d34d:d19d2948
2024-11-21 19:43:44NOSTR HOLIDAY FOOD & GIFT IDEAS (please share or add someone you know)
V4V #circulareconomy
Amber Sweeney @Amber Sweeney Custom Songs for Any Occasion (Tell Your Partner You Love Them This Holiday with A Song. One from Amber will surely be heavenly. OR sing about breakfast in bed. - SarahSoupBox winkyface)
Ant Richard @Ant Richards Limited Custom Handcrafted Knife Gift Certificates (12-month waitlist for all custom handmade orders)
Apotheca Viva @apothecavivahttps://apothecaviva.love/
Aupa Bars @AUPAhttps://eataupa.com/
Barnminer’s Barn Jerky @Barnmynah
Billay Coffee @Fulacoinhttps://billaycoffee.com/
BitBees @BitBees Honey & Honey Products https://www.kittrellsdaydream.com/
Bitpopart @Bitpoparthttps://bitpopart.com/
BtcPins @BtcPins
BTC Pins | Bitcoin Pins, Stickers & Apparel - Only Bitcoin Accepted
ONLY BITCOIN PAYMENTS ACCEPTED Pins Stickers Magnets | BTC Pins
Cannabis Records @The ₿udtender [CannabisRecords] https://cannabisrecords.store/
CryptoCloaks @CryptoCloaks™https://www.cryptocloaks.com/shop/
Delgado’s Fuego @Delgado's Fuego LLChttps://delgadosfuego.com/
Finca Yabisi @Finca Yabisihttps://yabisi.farm/
Foxfire Mushrooms @Foxfire Mushroomshttps://foxfiremushrooms.com/
Golden Tallow @Golden Tallowhttps://goldentallow.com/
GoodBeans 🇸🇻 Coffee @the guy running GoodBeans 🇸🇻 https://thegoodbeans.com/
Isolabell.art @isolabellart 🎨https://isolabell.art/
Jake Wolki @Jake Wolkihttps://wolkifarm.com.au/
Keto Beejay @beejay Low Sugar Jerky
 ## beejay
## beejayNotes & recipes on keto & carnivore goodies - by beejay
Full recipes site: https://ketolish.us/
Buy homemade small batch low sugar jerky on Shopstr with Bitcoin sats: https://url.tanelt.com/xcmjQp
Kanuto Takumi San @Kanuto
LeatherMint @LeatherMinthttps://theleathermint.com/
Lightning Store @ltngstorehttps://lightning.store/
LightningSpore @LightningSpore Full Service Mushroom Cultivation Company https://www.lightningspore.com/
Lost Sheep Ranch @Lost Sheep Ranchhttps://www.lost-sheep-ranch.com/
Lucho Poletti @Lucho Poletti Art Prints and Merchandise https://luchopoletti.com/
Madex @M A D E X Art & Apparel https://madex.art/collections/in-stock
MapleTrade @Mapletrade
Next Block Coffee @Next Block Coffeehttps://nextblockcoffee.com/
NoGood @Jake Wolkihttps://wolkifarm.com.au/
PatsPropolisHoney @PatsPropolisHoney
Peony Lane Wine (Ben Justman) @Ben Justman🍷https://www.peonylanewine.com/
PlebianMarket @Plebeian Market
PictureRoom @❐ PictureRoom Assorted Dessert Treats
Regenerative Farmed Meats & Knives @AgrarianContrarian
Salt of the Earth @Salt of the Earth Premium Electrolyte Mix https://drinksote.com/
Satoshi Coffee Company @Satoshi Coffee Co.
 ## Welcome to Satoshi Coffee Co. - Our Roast is the Proof of Work
## Welcome to Satoshi Coffee Co. - Our Roast is the Proof of WorkYou CAN buy coffee with bitcoin now at Satoshi Coffee Co! Use Lightning (or on-chain) to purchase our delicious freshly-roasted coffee.
SofterSkin Tallow Skincare @Softer Skin | Tallow Based Skincarehttps://softerskin.co/
Shopstr @Shopstrhttps://shopstr.store/
Soap Miner @Soap Miner Tallow Body Soap Bars https://shopstr.store/npub1zzmxvr9sw49lhzfx236aweurt8h5tmzjw7x3gfsazlgd8j64ql0sexw5wy
SweetSats @SweetSats Honey
SweetSats – Buy pure, raw honey with Bitcoin
Yojimbo @Yojimble Jam & Marmalade https://jimblesjumble.odoo.com/
-
 @ 4ba8e86d:89d32de4
2024-10-07 13:37:38
@ 4ba8e86d:89d32de4
2024-10-07 13:37:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável.
https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ a39d19ec:3d88f61e
2024-11-17 10:48:56
@ a39d19ec:3d88f61e
2024-11-17 10:48:56This week's functional 3d print is the "Dino Clip".

Dino Clip
I printed it some years ago for my son, so he would have his own clip for cereal bags.
Now it is used to hold a bag of dog food close.
The design by "Sneaks" is a so called "print in place". This means that the whole clip with moving parts is printed in one part, without the need for assembly after the print.
 The clip is very strong, and I would print it again if I need a "heavy duty" clip for more rigid or big bags.
Link to the file at Printables
The clip is very strong, and I would print it again if I need a "heavy duty" clip for more rigid or big bags.
Link to the file at Printables -
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 0c9e5e17:480e870b
2024-11-21 18:43:50
@ 0c9e5e17:480e870b
2024-11-21 18:43:50I thought I'd share the recipe and directions for my Grandma's Irish Soda bread. I'd say it's my mum's but it is really my grandmother's recipe. My mum and grandmother were from County Cork, Ireland but moved to England which is where I am originally from.
As a child, I can remember visiting my grandmother and smelling the sour bottle of whole milk she used to put on her windowsill each week so that the warmth and sun would make it sour into the equivalent of buttermilk. That would be the basis for her soda bread recipe. I can vividly remember the smell as I'm typing this - happy childhood memories! I hope you make this and enjoy it too. Please feel free to share with friends.
Options
You can make this with store bought buttermilk, or alternatives that I've listed in the ingredients. All of them turn out well, so choose what you prefer. You can also remove or reduce the white granulated sugar to taste. With the half cup it is a delicious sweet soda bread perfect for butter or jam. Without is truer to the original, I added sugar so that my kids would like it more. The same is true for the raisins, they are totally optional and I typically add raisins to one of the two halves of dough - BUT the soda bread with raisins always gets eaten first!
Ingredients
- 5 1/2 cups all-purpose flour
- 2 teaspoons baking soda
- 1 teaspoon salt
- 1 cup raisins (optional)
- 3 cups of room temp buttermilk (substitute sour cream or plain Greek yogurt)
Directions
- Preheat oven to 400 degrees F (200 degrees C). Grease large baking tray or cookie sheet
- In a large bowl, mix the flour, baking soda and salt. Add buttermilk, raisins, and mix until just combined
- On a floured surface kneed the mix into a rough dough, then divide in two
- Place each halve on the tray, sprinkle the top of each loaf with flour, then score a cross on the top of each with a sharp knife
- Bake the loaves at 400 degrees F (200 degrees C) for 45 minutes, or until golden brown
- Remove and let the loaves cool on a cooling rack

I hope you enjoy making this family favorite as much as you enjoy eating it!
-
 @ 4ba8e86d:89d32de4
2024-11-14 09:17:14
@ 4ba8e86d:89d32de4
2024-11-14 09:17:14Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular; • Computador com adb; • Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo;
Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid: https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
Samsung Galaxy Note 10 Plus bloatware listProvavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
./adb start-serverO resultado deve ser:
daemon not running; starting now at tcp:5037 daemon started successfully
E caso não apareça nada, execute:
./adb kill-serverE inicie novamente.
Com o adb conectado ao celular, execute:
./adb shellPara poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
pkg install android-toolsQuando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
adb pair localhost:porta CódigoDeEmparelhamentoDe acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
adb connect localhost:portaObs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
adb shellRemoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
pm uninstall –user 0 com.google.android.apps.mapsE pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
cmd package install-existing nome.do.pacotePós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ b6dcdddf:dfee5ee7
2024-11-21 19:32:10
@ b6dcdddf:dfee5ee7
2024-11-21 19:32:10Hey SN friends!
We built a fun and exciting little thing: Ambassadors.
Ambassadors play an essential role in the Bitcoin ecosystem: they spread the word about valuable Geyser initiatives.
We finally gave them the recognition they deserve on the leaderboards whenever someone contributes through their "hero link".
What do you think? Dope right? The kind of thing you can only/easily do on Lightning ;)
Announcement: https://x.com/geyserfund/status/1859654651148370219
originally posted at https://stacker.news/items/777550
-
 @ a10260a2:caa23e3e
2024-11-10 04:35:34
@ a10260a2:caa23e3e
2024-11-10 04:35:34nostr:npub1nkmta4dmsa7pj25762qxa6yqxvrhzn7ug0gz5frp9g7p3jdscnhsu049fn added support for classified listings (NIP-99) about a month ago and recently announced this update that allows for creating/editing listings and blog posts via the dashboard.
In other words, listings created on the website are also able to be viewed and edited on other Nostr apps like Amethyst and Shopstr. Interoperability FTW.
I took some screenshots to give you an idea of how things work.
The home page is clean with the ability to search for profiles by name, npub, or Nostr address (NIP-05).
Clicking login allows signing in with a browser extension.
The dashboard gives an overview of the amount of notes posted (both short and long form) and products listed.
Existing blog posts (i.e. long form notes) are synced.
Same for product listings. There’s a nice interface to create new ones and preview them before publishing.
That’s all for now. As you can see, super slick stuff!
Bullish on Cypher.
So much so I had to support the project and buy a subdomain. 😎
https://bullish.cypher.space
originally posted at https://stacker.news/items/760592
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 2775fb0f:887f8193
2024-11-21 18:11:27
@ 2775fb0f:887f8193
2024-11-21 18:11:27Новодвинск празднует День города: яркие события и неожиданные сюрпризы!
Новодвинск, 12 сентября 2040 года — В этом году наш любимый город отмечает свой 70-летний юбилей, и празднование Дня города обещает быть поистине незабываемым! Организаторы подготовили насыщенную программу мероприятий, которая привлечет жителей и гостей Новодвинска, чтобы вместе отпраздновать достижения и будущее нашего города.
Программа мероприятий:
Празднование начнется в 10:00 с торжественного открытия на площади имени Ленина, где пройдет церемония поднятия флага и выступление городской администрации. Глава города, Анна Петрова, поздравит новодвинцев с праздником и расскажет о планах развития города на ближайшие годы.
С 11:00 до 15:00 на центральной площади развернется ярмарка местных производителей, где можно будет попробовать и купить продукты от фермеров и ремесленников региона. Здесь же пройдет выставка достижений новодвинских школ и вузов, где студенты и школьники представят свои проекты и изобретения.
Для любителей активного отдыха организованы спортивные соревнования: в 12:00 начнется массовый забег «Новодвинск — город здоровья», а в 14:00 — турниры по уличным видам спорта, включая стритбол и волейбол. Все участники получат памятные медали и призы от спонсоров.
Сюрпризы для горожан:
В этом году организаторы решили порадовать новодвинцев несколькими неожиданными сюрпризами. Во-первых, в 16:00 на площади пройдет концерт с участием известных артистов, в числе которых — популярная группа «Северное сияние» и певица Анастасия Ларина. Но это еще не все! Впервые в Новодвинске будет организован «Тайный гость» — известный музыкант, который выступит под псевдонимом и удивит зрителей своей неожиданной программой.
Во-вторых, в 18:00 начнется фееричное световое шоу, которое озарит вечернее небо над Новодвинском. Это будет уникальное представление с использованием современных технологий, которое подарит зрителям незабываемые эмоции.
И, наконец, в 20:00 на набережной реки Северная Двина состоится праздничный фейерверк, который завершит день яркими красками и подарит всем ощущение единства и гордости за наш город.
Не упустите возможность стать частью этого знаменательного события! Приходите с друзьями и семьей, чтобы отпраздновать День города вместе. Новодвинск ждет вас!
-
 @ 35f3a26c:92ddf231
2024-11-09 17:10:57
@ 35f3a26c:92ddf231
2024-11-09 17:10:57"Files" by Google new feature
"Files" by Google added a "feature"... "Smart Search", you can toggle it to OFF and it is highly recommended to do so.
Toggle the Smart Search to OFF, otherwise, google will search and index every picture, video and document in your device, no exceptions, anything you have ever photographed and you forgot, any document you have downloaded or article, etc...
How this could affect you?
Google is actively combating child abuse and therefore it has built in its "AI" a very aggressive algorithm searching of material that "IT THINKS" is related, therefore the following content could be flagged:
- [ ] Pictures of you and your children in the beach
- [ ] Pictures or videos which are innocent in nature but the "AI" "thinks" are not
- [ ] Articles you may have save for research to write your next essay that have links to flagged information or sites
The results:
- [ ] Your google account will be canceled
- [ ] You will be flagged as a criminal across the digital world
You think this is non sense? Think again: https://www.nytimes.com/2022/08/21/technology/google-surveillance-toddler-photo.html
How to switch it off:
- Open files by Google
- Tap on Menu -> Settings
- Turn OFF Smart Search
But you can do more for your privacy and the security of your family
- Stop using google apps, if possible get rid off of Google OS and use Graphene OS
- Go to Settings -> Apps
- Search for Files by Google
- Unistall the app, if you can't disable it
- Keep doing that with most Google apps that are not a must if you have not switched already to GrapheneOS
Remember, Google keeps advocating for privacy, but as many others have pointed out repeatedly, they are the first ones lobbying for the removal of your privacy by regulation and draconian laws, their hypocrisy knows no limits
Recommendation:
I would assume you have installed F-Droid in your android, or Obtainium if you are more advanced, if so, consider "Simple File Manager Pro" by Tibor Kaputa, this dev has a suite of apps that are basic needs and the best feature in my opinion is that not one of his apps connect to the internet, contacts, gallery, files, phone, etc.
Note As most people, we all love the convenience of technology, it makes our lives easier, however, our safety and our family safety should go first, between technology being miss-used and abused by corporations and cyber-criminals data mining and checking for easy targets to attack for profit, we need to keep our guard up. Learning is key, resist the use of new tech if you do not understand the privacy trade offs, no matter how appealing and convenient it looks like. .
Please leave your comments with your favorite FOSS Files app!
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 3bf0c63f:aefa459d
2024-11-07 14:56:17
@ 3bf0c63f:aefa459d
2024-11-07 14:56:17The case against edits
Direct edits are a centralizing force on Nostr, a slippery slope that should not be accepted.
Edits are fine in other, more specialized event kinds, but the
kind:1space shouldn't be compromised with such a push towards centralization, becausekind:1is the public square of Nostr, where all focus should be on decentralization and censorship-resistance.- Why?
Edits introduce too much complexity. If edits are widespread, all clients now have to download dozens of extra events at the same time while users are browsing a big feed of notes which are already coming from dozens of different relays using complicated outbox-model-based querying, then for each event they have to open yet another subscription to these relays -- or perform some other complicated batching of subscriptions which then requires more complexity on the event handling side and then when associating these edits with the original events. I can only imagine this will hurt apps performance, but it definitely raises the barrier to entry and thus necessarily decreases Nostr decentralization.
Some clients may be implemneted in way such that they download tons of events and then store them in a local databases, from which they then construct the feed that users see. Such clients may make edits potentially easier to deal with -- but this is hardly an answer to the point above, since such clients are already more complex to implement in the first place.
- What do you have against complex clients?
The point is not to say that all clients should be simple, but that it should be simple to write a client -- or at least as simple as physically possible.
You may not be thinking about it, but if you believe in the promise of Nostr then we should expect to see Nostr feeds in many other contexts other than on a big super app in a phone -- we should see Nostr notes being referenced from and injected in unrelated webpages, unrelated apps, hardware devices, comment sections and so on. All these micro-clients will have to implement some complicated edit-fetching logic now?
- But aren't we already fetching likes and zaps and other things, why not fetch edits too?
Likes, zaps and other similar things are optional. It's perfectly fine to use Nostr without seeing likes and/or zaps -- and, believe me, it does happen quite a lot. The point is basically that likes or zaps don't affect the content of the main post at all, while edits do.
- But edits are optional!
No, they are not optional. If edits become widespread they necessarily become mandatory. Any client that doesn't implement edits will be displaying false information to its users and their experience will be completely broken.
- That's fine, as people will just move to clients that support edits!
Exactly, that is what I expect to happen too, and this is why I am saying edits are a centralizing force that we should be fighting against, not embracing.
If you understand that edits are a centralizing force, then you must automatically agree that they aren't a desirable feature, given that if you are reading this now, with Nostr being so small, there is a 100% chance you care about decentralization and you're not just some kind of lazy influencer that is only doing this for money.
- All other social networks support editing!
This is not true at all. Bluesky has 10x more users than Nostr and doesn't support edits. Instagram doesn't support editing pictures after they're posted, and doesn't support editing comments. Tiktok doesn't support editing videos or comments after they're posted. YouTube doesn't support editing videos after they're posted. Most famously, email, the most widely used and widespread "social app" out there, does not support edits of any kind. Twitter didn't support edits for the first 15 years of its life, and, although some people complained, it didn't hurt the platform at all -- arguably it benefitted it.
If edits are such a straightforward feature to add that won't hurt performance, that won't introduce complexity, and also that is such an essential feature users could never live without them, then why don't these centralized platforms have edits on everything already? There must be something there.
- Eventually someone will implement edits anyway, so why bother to oppose edits now?
Once Nostr becomes big enough, maybe it will be already shielded from such centralizing forces by its sheer volume of users and quantity of clients, maybe not, we will see. All I'm saying is that we shouldn't just push for bad things now just because of a potential future in which they might come.
- The market will decide what is better.
The market has decided for Facebook, Instagram, Twitter and TikTok. If we were to follow what the market had decided we wouldn't be here, and you wouldn't be reading this post.
- OK, you have convinced me, edits are not good for the protocol. But what do we do about the users who just want to fix their typos?
There are many ways. The annotations spec, for example, provides a simple way to append things to a note without being a full-blown edit, and they fall back gracefully to normal replies in clients that don't implement the full annotations spec.
Eventually we could have annotations that are expressed in form of simple (human-readable?) diffs that can be applied directly to the post, but fall back, again, to comments.
Besides these, a very simple idea that wasn't tried yet on Nostr yet is the idea that has been tried for emails and seems to work very well: delaying a post after the "submit" button is clicked and giving the user the opportunity to cancel and edit it again before it is actually posted.
Ultimately, if edits are so necessary, then maybe we could come up with a way to implement edits that is truly optional and falls back cleanly for clients that don't support them directly and don't hurt the protocol very much. Let's think about it and not rush towards defeat.
-
 @ 9ff58691:0bf6c134
2024-11-21 17:37:43
@ 9ff58691:0bf6c134
2024-11-21 17:37:43Курган в 2040 году завершил масштабный проект по созданию велосипедных дорожек, который охватывает весь город и включает Центральный парк культуры и отдыха (ЦПКИО) как ключевую трассу для велосипедистов. Новые велодорожки обеспечивают безопасные и удобные маршруты для всех любителей активного отдыха, а также создают специальные площадки для велосипедистов, скейтбордистов и самокатчиков. Этот проект не только способствует развитию культуры активного образа жизни, но и улучшает экологическую ситуацию в городе, делая Курган более комфортным и современным для жителей и гостей.
Автор: Эвелина Тимирбаева
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 9f94e6cc:f3472946
2024-11-21 18:55:12
@ 9f94e6cc:f3472946
2024-11-21 18:55:12Der Entartungswettbewerb TikTok hat die Jugend im Griff und verbrutzelt ihre Hirne. Über Reels, den Siegeszug des Hochformats und die Regeln der Viralität.
Text: Aron Morhoff
Hollywood steckt heute in der Hosentasche. 70 Prozent aller YouTube-Inhalte werden auf mobilen Endgeräten, also Smartphones, geschaut. Instagram und TikTok sind die angesagtesten Anwendungen für junge Menschen. Es gibt sie nur noch als App, und ihr Design ist für Mobiltelefone optimiert.
Einst waren Rechner und Laptops die Tools, mit denen ins Internet gegangen wurde. Auch als das Smartphone seinen Siegeszug antrat, waren die Sehgewohnheiten noch auf das Querformat ausgerichtet. Heute werden Rechner fast nur noch zum Arbeiten verwendet. Das Berieseln, die Unterhaltung, das passive Konsumieren hat sich vollständig auf die iPhones und Samsungs dieser Welt verlagert. Das Telefon hat den aufrechten Gang angenommen, kaum einer mehr hält sein Gerät waagerecht.
Homo Digitalis Erectus
Die Welt steht also Kopf. Die Form eines Mediums hat Einfluss auf den Inhalt. Marshall McLuhan formulierte das so: Das Medium selbst ist die Botschaft. Ja mei, mag sich mancher denken, doch medienanthropologisch ist diese Entwicklung durchaus eine Betrachtung wert. Ein Querformat eignet sich besser, um Landschaften, einen Raum oder eine Gruppe abzubilden. Das Hochformat entspricht grob den menschlichen Maßen von der Hüfte bis zum Kopf. Der TikTok-Tanz ist im Smartphone-Design also schon angelegt. Das Hochformat hat die Medieninhalte unserer Zeit noch narzisstischer gemacht.
Dass wir uns durch Smartphones freizügiger und enthemmter zur Schau stellen, ist bekannt. 2013 wurde „Selfie“ vom Oxford English Dictionary zum Wort des Jahres erklärt. Selfie, Selbstporträt, Selbstdarstellung.
Neu ist der Aufwand, der heute vonnöten ist, um die Aufmerksamkeitsschwelle der todamüsierten Mediengesellschaft überhaupt noch zu durchbrechen. In beängstigender Hypnose erwischt man viele Zeitgenossen inzwischen beim Doomscrollen. Das ist der Fachbegriff für das weggetretene Endloswischen und erklärt auch den Namen „Reel“: Der Begriff, im Deutschen verwandt mit „Rolle“, beschreibt die Filmrolle, von der 24 Bilder pro Sekunde auf den Projektor gewischt oder eben abgespult werden.
Länger als drei Sekunden darf ein Kurzvideo deshalb nicht mehr gehen, ohne dass etwas Aufregendes passiert. Sonst wird das Reel aus Langeweile weggewischt. Die Welt im Dopamin-Rausch. Für den Ersteller eines Videos heißt das inzwischen: Sei der lauteste, schrillste, gestörteste Marktschreier. Das Wettrennen um die Augäpfel zwingt zu extremen Formen von Clickbait.
15 Sekunden Ruhm
Das nimmt inzwischen skurrile Formen an. Das Video „Look who I found“ von Noel Robinson (geboren 2001) war im letzten Jahr einer der erfolgreichsten deutschen TikTok-Clips. Man sieht den Deutsch-Nigerianer beim Antanzen eines karikaturartig übergewichtigen Menschen. Noel wird geschubst und fällt. Daraufhin wechselt das Lied – und der fette Mann bewegt seinen Schwabbelbauch im Takt. Noel steht wieder auf, grinst, beide tanzen gemeinsam. Das dauert 15 Sekunden. Ich rate Ihnen, sich das Video einmal anzuschauen, um die Mechanismen von TikTok zu verstehen. Achten Sie alleine darauf, wie vielen Reizen (Menschenmenge, Antanzen, Sturz, Schwabbelbauch) Sie in den ersten fünf Sekunden ausgesetzt sind. Wer schaut so was? Bis dato 220 Millionen Menschen. Das ist kapitalistische Verwertungslogik im bereits verwesten Endstadium. Adorno oder Fromm hätten am Medienzeitgeist entweder ihre Freude oder mächtig zu knabbern.
Die Internet- und Smartphoneabdeckung beträgt mittlerweile fast 100 Prozent. Das Überangebot hat die Regeln geändert. Um überhaupt gesehen zu werden, muss man heute viral gehen. Was dafür inzwischen nötig ist, spricht die niedrigsten Bedürfnisse des Menschen an: Gewalt, Ekel, Sexualisierung, Schock. Die jungen Erwachsenen, die heute auf sozialen Netzwerken den Ton angeben, haben diese Mechanismen längst verinnerlicht. Wie bewusst ihnen das ist, ist fraglich. 2024 prallt eine desaströse Bildungssituation samt fehlender Medienkompetenz auf eine egomanische Jugend, die Privatsphäre nie gekannt hat und seit Kindesbeinen alles in den Äther ballert, was es festhalten kann. Man muss kein Kulturpessimist sein, um diese degenerative Dynamik, auch in ihrer Implikation für unser Zusammenleben und das psychische Wohlergehen der Generation TikTok, als beängstigend zu bezeichnen.
Aron Morhoff studierte Medienethik und ist Absolvent der Freien Akademie für Medien & Journalismus. Frühere Stationen: RT Deutsch und Nuoviso. Heute: Stichpunkt Magazin, Manova, Milosz Matuschek und seine Liveshow "Addictive Programming".
-
 @ f8a5df57:b7a58cd4
2024-11-21 17:34:22
@ f8a5df57:b7a58cd4
2024-11-21 17:34:22 -
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ a367f9eb:0633efea
2024-11-05 08:48:41
@ a367f9eb:0633efea
2024-11-05 08:48:41Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application.
The reporting purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States.
In a June paper reviewed by Reuters, six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”.
The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making.
While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the Star Trek episode “A Taste of Armageddon“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place.
Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran?
The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over one million open-source LLMs available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer.
With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are potentially trillions of dollars on the line.
Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American infrastructure, data, and yes, your credit history?
As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much many times.
At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative.
Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this.
Open-source matters When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it.
The various licensing schemes – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made.
While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit.
Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers.
Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other.
I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run.
Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots).
This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also open-source, which has allowed thousands of copycat protocols that have revolutionized how we view money.
You know what else is open-source and available for everyone to use, modify, and build upon?
PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit.
Open-source code is speech, and it is knowledge.
We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge.
Open-source is for your friends, and enemies In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license.
At this very moment, you can click on over to Hugging Face, download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth).
Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created.
We know this can be useful to friends, but what about enemies?
As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications.
The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians.
A bipartisan group of US House lawmakers want to put export controls on AI models, as well as block foreign access to US cloud servers that may be hosting AI software.
If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see The Crypto Wars). Many of the arguments we hear today were invoked by some of the same people as back then.
Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to.
Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place.
Limiting open-source threatens our own advancement If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way.
If there is a “Hundred Year Marathon” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible.
The Chinese military has been building up its capabilities with trillions of dollars’ worth of investments that span far beyond AI chatbots and skip logic protocols.
The theft of intellectual property at factories in Shenzhen, or in US courts by third-party litigation funding coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing.
But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source.
If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries.
Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application.
The reporting purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States.
In a June paper reviewed by Reuters, six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”.
The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making.
While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the Star Trek episode “A Taste of Armageddon“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place.
Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran?
The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over one million open-source LLMs available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer.
With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are potentially trillions of dollars on the line.
Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American infrastructure, data, and yes, your credit history?
As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much many times.
At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative.
Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this.
Open-source matters
When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it.
The various licensing schemes – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made.
While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit.
Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers.
Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other.
I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run.
Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots).
This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also open-source, which has allowed thousands of copycat protocols that have revolutionized how we view money.
You know what else is open-source and available for everyone to use, modify, and build upon?
PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit.
Open-source code is speech, and it is knowledge.
We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge.
Open-source is for your friends, and enemies
In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license.
At this very moment, you can click on over to Hugging Face, download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth).
Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created.
We know this can be useful to friends, but what about enemies?
As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications.
The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians.
A bipartisan group of US House lawmakers want to put export controls on AI models, as well as block foreign access to US cloud servers that may be hosting AI software.
If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see The Crypto Wars). Many of the arguments we hear today were invoked by some of the same people as back then.
Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to.
Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place.
Limiting open-source threatens our own advancement
If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way.
If there is a “Hundred Year Marathon” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible.
The Chinese military has been building up its capabilities with trillions of dollars’ worth of investments that span far beyond AI chatbots and skip logic protocols.
The theft of intellectual property at factories in Shenzhen, or in US courts by third-party litigation funding coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing.
But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source.
If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries.
Originally published on the website of the Consumer Choice Center.
-
 @ 9349d012:d3e98946
2024-11-05 00:42:37
@ 9349d012:d3e98946
2024-11-05 00:42:37Chef's notes
2 cups pureed pumpkin 2 cups white sugar 3 eggs, beaten 1/2 cup olive oil 1 tablespoon cinnamon 1 1/2 teaspoon baking powder 1 teaspoon baking soda 1/2 teaspoon salt 2 1/4 cups flour 1/4 cup chopped pecans
Preheat oven to 350 degrees Fahrenheit. Coat a bread pan with olive oil. Mix all ingredients minus nuts, leaving the flour for last, and adding it in 2 parts. Stir until combined. Pour the batter into the bread pan and sprinkle chopped nuts down the middle of the batter, lenghtwise. Bake for an hour and ten minutes or until a knife insert in the middle of the pan comes out clean. Allow bread to cool in the pan for five mintes, then use knife to loosen the edges of the loaf and pop out of the pan. Rest on a rack or plate until cool enough to slice. Spread bread slices with Plugra butter and serve.
https://cookeatloveshare.com/pumpkin-bread/
Details
- ⏲️ Prep time: 30 minutes
- 🍳 Cook time: 1 hour and ten minutes
- 🍽️ Servings: 6
Ingredients
- See Chef's Notes
Directions
- See Chef's Notes
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 09fbf8f3:fa3d60f0
2024-11-02 08:00:29
@ 09fbf8f3:fa3d60f0
2024-11-02 08:00:29> ### 第三方API合集:
免责申明:
在此推荐的 OpenAI API Key 由第三方代理商提供,所以我们不对 API Key 的 有效性 和 安全性 负责,请你自行承担购买和使用 API Key 的风险。
| 服务商 | 特性说明 | Proxy 代理地址 | 链接 | | --- | --- | --- | --- | | AiHubMix | 使用 OpenAI 企业接口,全站模型价格为官方 86 折(含 GPT-4 )| https://aihubmix.com/v1 | 官网 | | OpenAI-HK | OpenAI的API官方计费模式为,按每次API请求内容和返回内容tokens长度来定价。每个模型具有不同的计价方式,以每1,000个tokens消耗为单位定价。其中1,000个tokens约为750个英文单词(约400汉字)| https://api.openai-hk.com/ | 官网 | | CloseAI | CloseAI是国内规模最大的商用级OpenAI代理平台,也是国内第一家专业OpenAI中转服务,定位于企业级商用需求,面向企业客户的线上服务提供高质量稳定的官方OpenAI API 中转代理,是百余家企业和多家科研机构的专用合作平台。 | https://api.openai-proxy.org | 官网 | | OpenAI-SB | 需要配合Telegram 获取api key | https://api.openai-sb.com | 官网 |
持续更新。。。
推广:
访问不了openai,去
低调云购买VPN。官网:https://didiaocloud.xyz
邀请码:
w9AjVJit价格低至1元。
-
 @ 06639a38:655f8f71
2024-11-01 22:32:51
@ 06639a38:655f8f71
2024-11-01 22:32:51One year ago I wrote the article Why Nostr resonates in Dutch and English after I visited the Bitcoin Amsterdam 2023 conference and the Nostrdam event. It got published at bitcoinfocus.nl (translated in Dutch). The main reason why I wrote that piece is that I felt that my gut feeling was tellinng me that Nostr is going to change many things on the web.
After the article was published, one of the first things I did was setting up this page on my website: https://sebastix.nl/nostr-research-and-development. The page contains this section (which I updated on 31-10-2024):
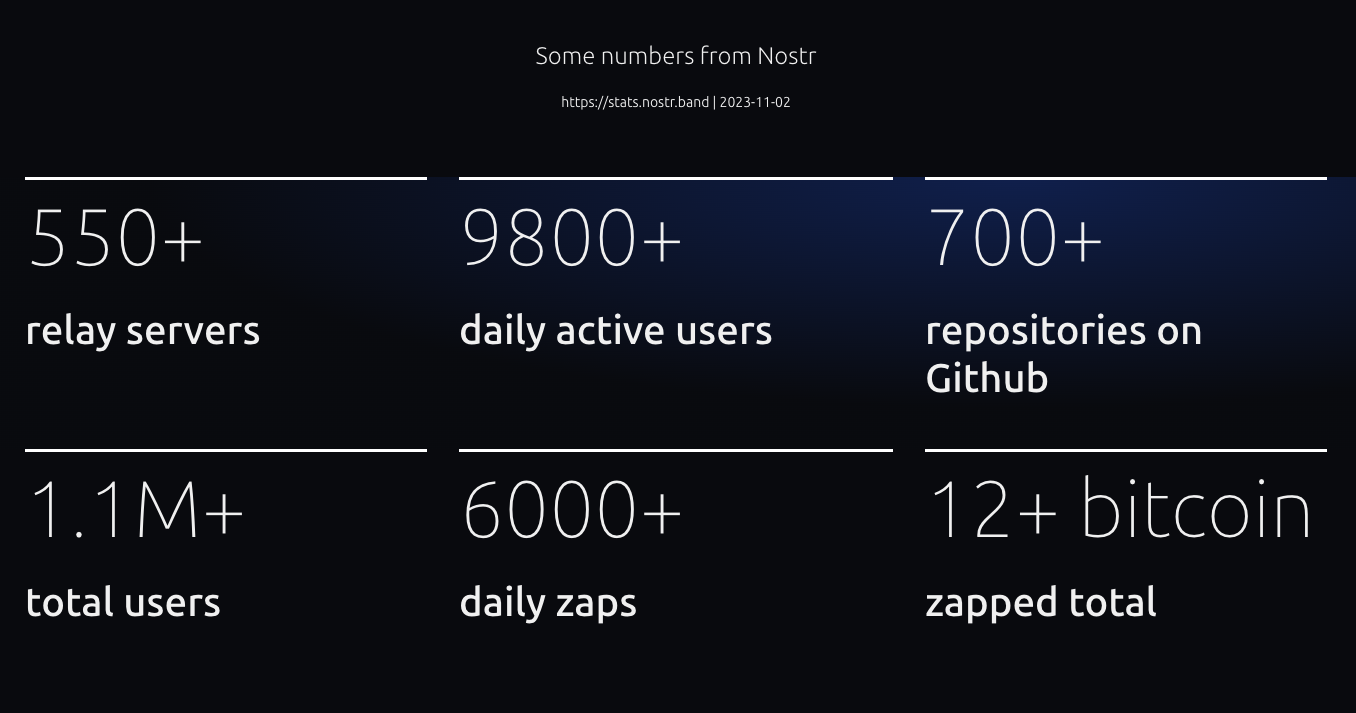
One metric I would like to highlight is the number of repositories on Github. Compared to a year ago, there are already more than 1130 repositories now on Github tagged with Nostr. Let's compare this number to other social media protocols and decentralized platforms (24-10-2024):
- Fediverse: 522
- ATProto: 159
- Scuttlebot: 49
- Farcaster: 202
- Mastodon: 1407
- ActivityPub: 444
Nostr is growing. FYI there are many Nostr repositories not hosted on Github, so the total number of Nostr reposities is higher. I know that many devs are using their own Git servers to host it. We're even capable of setting up Nostr native Git repositories (for example, see https://gitworkshop.dev/repos). Eventually, Nostr will make Github (and other platforms) absolute.
Let me continue summarizing my personal Nostr highlights of last year.
Organising Nostr meetups

This is me playing around with the NostrDebug tool showing how you can query data from Nostr relays. Jurjen is standing behind me. He is one of the people I've met this year who I'm sure I will have a long-term friendship with.OpenSats grant for Nostr-PHP


In December 2023 I submitted my application for a OpenSats grant for the further development of the Nostr-PHP helper library. After some months I finally got the message that my application was approved... When I got the message I was really stoked and excited. It's a great form of appreciation for the work I had done so far and with this grant I get the opportunity to take the work to another higher level. So please check out the work done for so far:Meeting Dries

One of my goosebumps moments I had in 2022 when I saw that the founder and tech lead of Drupal Dries Buytaert posted 'Nostr, love at first sight' on his blog. These types of moments are very rare moment where two different worlds merge where I wouldn't expect it. Later on I noticed that Dries would come to the yearly Dutch Drupal event. For me this was a perfect opportunity to meet him in person and have some Nostr talks. I admire the work he is doing for Drupal and the community. I hope we can bridge Nostr stuff in some way to Drupal. In general this applies for any FOSS project out there.
Here is my recap of that Drupal event.Attending Nostriga

A conference where history is made and written. I felt it immediately at the first sessions I attended. I will never forget the days I had at Nostriga. I don't have the words to describe what it brought to me.

I also pushed myself out of my comfort zone by giving a keynote called 'POSSE with Nostr - how we pivot away from API's with one of Nostr superpowers'. I'm not sure if this is something I would do again, but I've learned a lot from it.
You can find the presentation here. It is recorded, but I'm not sure if and when it gets published.Nostr billboard advertisement
This advertisment was shown on a billboard beside the A58 highway in The Netherlands from September 2nd till September 16th 2024. You can find all the assets and more footage of the billboard ad here: https://gitlab.com/sebastix-group/nostr/nostr-ads. My goal was to set an example of how we could promote Nostr in more traditional ways and inspire others to do the same. In Brazil a fundraiser was achieved to do something similar there: https://geyser.fund/project/nostrifybrazil.
Volunteering at Nostr booths growNostr

This was such a great motivating experience. Attending as a volunteer at the Nostr booth during the Bitcoin Amsterdam 2024 conference. Please read my note with all the lessons I learned here.
The other stuff
- The Nostr related blog articles I wrote past year:
- Run a Nostr relay with your own policies (02-04-2024)
- Why social networks should be based on commons (03-01-2024)
- How could Drupal adopt Nostr? (30-12-2023)
- Nostr integration for CCHS.social (21-12-2023)
- https://ccns.nostrver.se
CCNS stands for Community Curated Nostr Stuff. At the end of 2023 I started to build this project. I forked an existing Drupal project of mine (https://cchs.social) to create a link aggregation website inspired by stacker.news. At the beginning of 2024 I also joined the TopBuilder 2024 contest which was a productive period getting to know new people in the Bitcoin and Nostr space. - https://nuxstr.nostrver.se
PHP is not my only language I use to build stuff. As a fullstack webdeveloper I also work with Javascript. Many Nostr clients are made with Javascript frameworks or other more client-side focused tools. Vuejs is currently my Javascript framework I'm the most convenient with. With Vuejs I started to tinker around with Nuxt combined with NDK and so I created a starter template for Vue / Nuxt developers. - ZapLamp
This is a neat DIY package from LNbits. Powered by an Arduino ESP32 dev board it was running a 24/7 livestream on zap.stream at my office. It flashes when you send a zap to the npub of the ZapLamp. - https://nosto.re
Since the beginning when the Blossom spec was published by @hzrd49 and @StuartBowman I immediately took the opportunity to tinker with it. I'm also running a relay for transmitting Blossom Nostr eventswss://relay.nosto.re. - Relays I maintain
I really enjoy to tinker with different relays implementations. Relays are the fundamental base layer to let Nostr work.
I'm still sharing my contributions on https://nostrver.se/ where I publish my weekly Nostr related stuff I worked on. This website is built with Drupal where I use the Nostr Simple Publish and Nostr long-form content NIP-23 modules to crosspost the notes and long-form content to the Nostr network (like this piece of content you're reading).
The Nostr is the people
Just like the web, the web is people: https://www.youtube.com/watch?v=WCgvkslCzTo
the people on nostr are some of the smartest and coolest i’ve ever got to know. who cares if it doesn’t take over the world. It’s done more than i could ever ask for. - @jb55
Here are some Nostriches who I'm happy to have met and who influenced my journey in Nostr in a positive way.
- Jurjen
- Bitpopart
- Arjen
- Jeroen
- Alex Gleason
- Arnold Lubach
- Nathan Day
- Constant
- fiatjaf
- Sync
Coming year
Generally I will continue doing what I've done last year. Besides the time I spent on Nostr stuff, I'm also very busy with Drupal related work for my customers. I hope I can get the opportunity to work on a paid client project related to Nostr. It will be even better when I can combine my Drupal expertise with Nostr for projects paid by customers.
Building a new Nostr application
When I look at my Nostr backlog where I just put everything in with ideas and notes, there are quite some interesting concepts there for building new Nostr applications. Filtering out, I think these three are the most exciting ones:
- nEcho, a micro app for optimizing your reach via Nostr (NIP-65)
- Nostrides.cc platform where you can share Nostr activity events (NIP-113)
- A child-friendly video web app with parent-curated content (NIP-71)
Nostr & Drupal
When working out a new idea for a Nostr client, I'm trying to combine my expertises into one solution. That's why I also build and maintain some Nostr contrib modules for Drupal.
- Nostr Simple Publish
Drupal module to cross-post notes from Drupal to Nostr - Nostr long-form content NIP-23
Drupal module to cross-post Markdown formatted content from Drupal to Nostr - Nostr internet identifier NIP-05
Drupal module to setup Nostr internet identifier addresses with Drupal. - Nostr NDK
Includes the Javascript library Nostr Dev Kit (NDK) in a Drupal project.
One of my (very) ambitious goals is to build a Drupal powered Nostr (website) package with the following main features:
- Able to login into Drupal with your Nostr keypair
- Cross-post content to the Nostr network
- Fetch your Nostr content from the Nostr content
- Serve as a content management system (CMS) for your Nostr events
- Serve as a framework to build a hybrid Nostr web application
- Run and maintain a Nostr relay with custom policies
- Usable as a feature rich progressive web app
- Use it as a remote signer
These are just some random ideas as my Nostr + Drupal backlog is way longer than this.
Nostr-PHP
With all the newly added and continues being updated NIPs in the protocol, this helper library will never be finished. As the sole maintainer of this library I would like to invite others to join as a maintainer or just be a contributor to the library. PHP is big on the web, but there are not many PHP developers active yet using Nostr. Also PHP as a programming language is really pushing forward keeping up with the latest innovations.
Grow Nostr outside the Bitcoin community
We are working out a submission to host a Nostr stand at FOSDEM 2025. If approved, it will be the first time (as far as I know) that Nostr could be present at a conference outside the context of Bitcoin. The audience at FOSDEM is mostly technical oriented, so I'm really curious what type of feedback we will receive.
Let's finish this article with some random Nostr photos from last year. Cheers!





-
 @ 2348ca50:32a055a8
2024-11-21 17:16:49
@ 2348ca50:32a055a8
2024-11-21 17:16:49Solar services are getting super popular as folks look for ways to save on their energy bills and shrink their environmental footprint. Thanks to some cool advancement in solar tech, putting up solar panels has become a smart and eco-friendly way to power homes, businesses, and even whole neighborhoods. In this piece, we’re diving into what solar services Ipswich are all about, the benefits they offer, and some key things to think about when picking a solar provider.
What Are Solar Services Ipswich?
Solar services envelop a large number of contributions that assist with peopling outfit the force of the sun for energy. These services incorporate all that, from beginning meetings, framework plan, and installation to upkeep, repair, and even energy checking. Here are the fundamental parts of solar services Ipswich:
• Conference and Evaluation: Experts assess your property, energy needs, and financial plan to prescribe a solar arrangement custom-made to your prerequisites.
• Framework Configuration: In light of your property's format, a modified solar framework is intended to expand energy productivity and address your issues.
• Installation: Specialists introduce solar boards, inverters, and other fundamental gear to set up your framework.
• Support and Repair: Routine upkeep guarantees your framework works proficiently. Solar organizations additionally give repairs to keep everything moving along as planned.
• Checking and Backing: A few solar suppliers offer applications or stages to screen energy creation and utilization, alongside help for any investigating needs.
Advantages of Solar Services Ipswich
-
- Lessens Energy Bills
One of the essential reasons property holders and organizations choose solar energy is the huge decrease in power costs. When introduced, solar boards produce power from daylight, decreasing reliance on matrix power and bringing down service bills. Over the long run, the reserve funds can frequently cover the underlying interest in the framework.
-
- Harmless to the ecosystem Energy Source
Solar power is perfect and inexhaustible, meaning it doesn't deliver ozone depleting substance emanations or other destructive poisons. By utilizing solar energy, you're adding to a decrease in carbon impression and supporting a more maintainable future.
-
- Expands Property Estimation
Homes and business properties outfitted with solar boards frequently have higher market values. Potential purchasers perceive the drawn out reserve funds and ecological advantages, making solar installations an important resource for any property.
-
- Long haul Speculation with Little Support
When introduced, solar frameworks require negligible support. Routine cleaning and incidental examinations are for the most part to the point of keeping them working proficiently for a really long time. With guarantees that frequently length 20-25 years, solar services are a brilliant long haul venture.
-
- Energy Freedom and Framework Versatility
Solar power can make you less dependent on framework power, safeguarding you from rising energy expenses and blackouts. For extra autonomy, consider pairing your solar boards with battery capacity frameworks, which permit you to store overabundance energy for use around evening time or during blackouts.
Do’s and Don’ts of Solar Services Ipswich
Do research different providers and compare options
Don’t rush into signing a contract without understanding the terms
Do check for certifications and experience
Don’t assume all solar panels are the same quality
Do ask about financing and warranty options
Don’t skip regular maintenance and cleaning
Do consider battery storage for added resilience
Don’t ignore state or federal incentives
Do monitor your system’s performance regularly
Don’t install without professional guidance
Key Stages in the Solar Service Cycle
-
Site Appraisal: Solar experts direct an evaluation to decide your area's appropriateness for solar energy, taking into account rooftop condition, direction, and sun openness.
-
Custom Plan: A plan custom-made to your particular energy needs and primary prerequisites expands the effectiveness of your framework.
-
Permits and Desk work: Your solar supplier regularly handles any important licenses or endorsements, guaranteeing consistence with nearby guidelines.
-
Installation: Confirmed specialists introduce the solar boards, wiring, and inverter to guarantee protected and proficient activity.
-
Ongoing Support and Observing: Numerous solar suppliers offer upkeep plans, framework checks, and internet checking devices so you can follow your energy creation.
Ways to pick the Right Solar Service Supplier
-
Look for Confirmation and Experience: Pick a solar supplier with guaranteed and experienced specialists who have a history of value installations.
-
Ask About Guarantees and Upkeep Plans: Guarantee the supplier offers a complete guarantee on hardware and an arrangement for regular support.
-
Check Client Surveys: Perusing audits from past clients can give you knowledge into the organization's dependability, client assistance, and generally quality.
-
Evaluate Funding Choices: Numerous suppliers offer adaptable supporting choices, for example, rents or power buy arrangements, to make solar more reasonable.
-
Consider Added Services Like Battery Stockpiling: A few organizations likewise offer battery stockpiling arrangements, which are perfect for expanding energy freedom and reinforcement power.
Solar Service Choices: Buy, Rent, or Power Buy Understanding (PPA)
• Buy: Purchasing a solar framework permits you to possess it by and large, giving the most extreme profit from venture through reserve funds on energy bills.
• Rent: Renting allows you to utilize solar boards introduced on your property for a decent regularly scheduled installment without the forthright expense, however you won't possess the framework.
• Power Buy Understanding (PPA): With a PPA, you pay just for the power created by the solar framework at a set rate, frequently lower than utility rates. The supplier keeps up with responsibility for framework, handling support and repairs.
Normal Inquiries Concerning Solar Services
Q: What amount does solar installation cost?
A: The expense shifts in light of elements like framework size, area, and supplier. Many organizations offer supporting choices to make it more reasonable.
Q: What amount might I at any point save money on my energy bill with solar?
A: Investment funds rely upon framework size, nearby power rates, and energy use. By and large, solar clients can save 20-30% on their energy bills.
Q: Is solar energy solid?
A: Indeed, solar energy is profoundly solid, particularly when paired with battery capacity to give reinforcement power during overcast days or around evening time.
Q: How long does a solar framework endure?
A: Solar boards have a typical life expectancy of 25 years, with negligible upkeep expected to keep them running proficiently.
Conclusion
Changing to solar energy is a strong method for saving money on energy costs, diminish ecological effect, and increment property estimation. Solar services Ipswich, including installation, support, and repair, guarantee that your framework runs proficiently, giving clean energy to years. With proficient direction and regular support, solar power can be an important and manageable venture for your home or business. Make sure to pick a respectable supplier, think about funding choices, and exploit any suitable motivations to make the progress smooth and useful.
-
-
 @ f8a5df57:b7a58cd4
2024-11-21 17:09:10
@ f8a5df57:b7a58cd4
2024-11-21 17:09:10Содержание:
В 2040 году Москва переживает настоящую революцию в мире обуви. Каждый житель столицы теперь носит обувь марок "Ice" или "Snow" с подогревом и защитой от слякоти, что стало необходимостью в условиях изменяющегося климата.
С каждым годом климат становится все более непредсказуемым. Слякоть и холодные зимы стали нормой для москвичей, и производители обуви ответили на вызовы времени. Новая линия обуви, оснащенная встроенными обогревателями и водоотталкивающими материалами, завоевала популярность среди горожан. Обувь будущего оснащена специальными датчиками, которые автоматически регулируют температуру в зависимости от внешних условий. Это позволяет сохранять комфорт даже в самые холодные дни. Кроме того, новые материалы защищают от влаги и грязи, что делает прогулки по Москве более приятными.
Автор: Ксения Данилова
-
 @ f8a5df57:b7a58cd4
2024-11-21 17:00:03
@ f8a5df57:b7a58cd4
2024-11-21 17:00:03В «Центральной клинической больнице с поликлиникой» Управления делами Президента Российской Федерации медицинские работники стали пользоваться искусственным интеллектом в целях комплексного обучения аспирантов .
ИИ помогает врачам обучать начинающих специалистов, предоставляя им доступ к базам данным, обучающим материалам и симуляциям. Благодаря таким вспомогательным технологиям студенты улучшают свои навыки в профессии и становятся в курсе последних достижений медицины.
- "Стоит помнить что искусственный интеллект - это лишь вспомогательный элемент для нашей специальности, он никогда не сможет заменить точности данных от квалифицированного врача, и перекрыть профессиональный опыт. Врачи должны использовать ИИ как инструмент, помогающий в принятии решений, но не полагаться исключительно на него. Безусловно, новые технологии могут принести пользу медицине, облегчая принятие решений и предоставляя качественную литературу, - считает главный врач «Центральной клинической больнице с поликлиникой» Николай Витько.
Автор: Дарья Воронина
-
 @ 88dc84f5:c71164f7
2024-11-21 16:58:41
@ 88dc84f5:c71164f7
2024-11-21 16:58:41Introduction: Cryptocurrencies have revolutionized the financial landscape, offering a decentralized, secure, and transparent medium of exchange. Beyond their speculative appeal, cryptocurrencies are driving economic growth, fostering innovation, and transforming the way businesses operate.
Boosting Financial Inclusion: 1. Unbanked populations: Cryptocurrencies provide access to financial services for the estimated 1.7 billion unbanked individuals worldwide. 2. Microtransactions: Low transaction fees enable small businesses to participate in the global economy.
Stimulating Innovation: 1. Blockchain technology: Cryptocurrencies' underlying technology has spawned a new wave of startups, creating jobs and driving innovation. 2. Smart contracts: Automated, self-executing contracts streamline business processes, reducing costs and increasing efficiency.
Fostering Economic Growth: 1. Increased liquidity: Cryptocurrencies' 24/7 trading and fast settlement times enhance market liquidity. 2. Cross-border transactions: Cryptocurrencies simplify international trade, reducing exchange rates and transfer fees. 3. Job creation: The cryptocurrency sector employs thousands, from developers to financial analysts.
Real-World Examples: 1. Japan: Cryptocurrency adoption has contributed to Japan's economic growth, with Bitcoin recognized as a legitimate form of payment. 2. Singapore: The city-state's cryptocurrency-friendly regulations have attracted numerous blockchain startups. 3. Estonia: The country's e-residency program utilizes blockchain technology to facilitate entrepreneurship.
Addressing Concerns: 1. Volatility: Regulatory clarity and stablecoins help mitigate price fluctuations. 2. Security: Advances in cryptography and security protocols protect user assets. 3. Regulation: Clear guidelines encourage legitimate businesses to participate.
Conclusion: Cryptocurrencies are not merely a speculative asset class but a catalyst for economic growth. By promoting financial inclusion, innovation, and efficiency, cryptocurrencies have transformed the financial landscape. As governments and institutions continue to adapt, the potential for cryptocurrencies to drive global prosperity will only continue to expand.
AI-Generated Insights: Using machine learning algorithms and natural language processing, our AI analyzed economic data and expert opinions to identify key drivers of cryptocurrency-driven economic growth: 1. Increased financial inclusion 2. Blockchain technology adoption 3. Regulatory clarity
Statistics: - Global cryptocurrency market capitalization: $2.5 trillion (2022) - Estimated cryptocurrency users: 300 million (2022) - Blockchain-based startups: 15,000+ (2022)
Sources: 1. World Bank 2. International Monetary Fund (IMF) 3. Blockchain Research Institute.
-
 @ 690e581f:a68db223
2024-11-21 17:29:49
@ 690e581f:a68db223
2024-11-21 17:29:49INTRODUCCIÓN 1. INICIACIÓN EN EL MUNDO DE LAS CRIPTOMONEDAS 1.1. 2011: Descubriendo el Bitcoin 1.2. 2012: Nuestro segundo encuentro 2. ADQUIRIENDO LOS PRIMEROS SATOSHIS 2.1. Obteniendo una wallet 2.2.- Iniciación en el mundo de las faucets 2.3. Juego online con bitcoins 2.4. Second Life, Linden dollars y bitcoins 3. ACEPTANDO CRIPTOMONEDAS COMO PAGO POR LA PRESTACIÓN DE SERVICIOS 3.1. Aceptando criptomonedas como pago por la prestación de servicios 3.2. Facturando los servicios prestados a cambio de criptomonedas 3.3. El Impuesto sobre la Renta de las Personas Físicas y los pagos recibidos en criptomonedas 3.4. Algunas consideraciones sobre la tributación de las criptomonedas 4. INEMBARGABILIDAD DE LAS CRIPTOMONEDAS VS. MONOPOLIO DEL USO DE LA FUERZA 4.1. La inembargabilidad de las criptomonedas 4.2. La resistencia de la blockchain al bloqueo de las transacciones 4.3. Bloqueo de las transacciones bancarias de fiat a las cuentas de usuario de los exchanges 5. MTGOX, UNO DE LOS MAYORES ROBOS DE LA HISTORIA 5.1. El nacimiento de los exchanges 5.2. Los inicios de MtGox 5.3. El auge de MtGox 5.4. La caída de MtGox 5.5. Los prolegómenos del caso: momentos de incertidumbre 5.6. Falta de coordinación entre afectados y de cooperación entre profesionales 5.7. El inicio del procedimiento de rehabilitación civil 5.8. El inicio del procedimiento de bancarrota 5.9. Suspensión del procedimiento de bancarrota e inicio de un nuevo procedimiento de rehabilitación civil 5.10. Evolución de los activos de la empresa durante los procedimientos de rehabilitación civil y bancarrota 5.11. Alexander Vinnik y su vinculación con el robo de los bitcoins de MtGox 5.12. Posible inicio de un nuevo procedimiento en Rusia contra algunos de los presuntos autores del robo de MtGox 5.13. La evolución de los exchanges tras la desaparición de MtGox 6. CRIPTOMONEDAS: ESTAFAS Y MANIPULACIÓN DE PRECIOS 6.1. ¿Son las criptomonedas una estafa? Bitcoin vs. OneCoin 6.2. Estafas en las que el desplazamiento patrimonial se realiza mediante el uso de criptomonedas: plataformas de inversión y minería en la nube 6.3. Grupos de pumps and dumps 6.4. La manipulación de los precios de las criptomonedas 6.5. La naturaleza jurídica de las criptomonedas en la jurisprudencia del Tribunal Supremo 6.6. Scripts de minería: analizando Coin-Hive 7. CRIPTOMONEDAS Y BURBUJAS 8. CONSIDERACIONES FINALES ACRÓNIMOS BIBLIOGRAFÍA
INTRODUCCIÓN
En la presente obra no voy a explicar, desde un punto de vista técnico, que son las criptomonedas ni en que consiste la tecnología blockchain, ya que actualmente existen miles de artículos y decenas de libros escritos por grandes ingenieros informáticos y criptógrafos que abordan, pormenorizadamente, cada uno de los elementos que conforman la estructura y el funcionamiento de esta tecnología disruptiva.
Tampoco tengo la pretensión de analizar el ecosistema blockchain desde un punto de vista eminentemente jurídico, y es que la transversalidad de esta tecnología hace que sea necesario abordar y estudiar numerosos ámbitos del derecho desde diferentes disciplinas jurídicas. De este modo, será imposible abarcar todas las implicaciones que los nuevos servicios, basados en tecnología blockchain tienen, o pueden llegar a tener, en el conjunto de las relaciones y negocios jurídicos , tanto a nivel nacional como internacional, debido a la descentralización inherente a la propia tecnología blockchain. En este sentido, dejaré la teoría para los teóricos del Derecho y solo me centraré en aquellos aspectos prácticos sobre los cuales he venido trabajando durante los últimos años; si bien es cierto que en algún que otro aspecto tendré que recurrir a la teoría, dado que la realidad de esta tecnología avanza mucho más rápido que la legislación y la jurisprudencia, lo que me ha situado, en muchas ocasiones, ante terrenos totalmente inexplorados desde un punto de vista jurídico.
En 2011, solamente unos cientos de personas en todo el mundo conocían una criptomoneda denominada Bitcoin, y muchas menos sabían en que consistía la tecnología que se encontraba detrás de dicho proyecto. En 2013, los medios de comunicación, las entidades financieras y muchas otras instituciones públicas y privadas, comenzaban a hacerse eco -casi siempre en tono escéptico e incluso en cierto modo despectivo- de esta nueva realidad. A inicios de 2014, coincidiendo con el hackeo de MtGox -del que tendremos ocasión de profundizar a lo largo de este libro-, se inició una aparente pérdida de interés en el sector por parte de los medios de comunicación y del público en general entrando, en este momento, en lo que podríamos definir como el primer “cripto invierno”. Sin embargo, la comunidad continuó trabajando y siguieron desarrollándose nuevos proyectos entre los que, desde mi punto de vista, debemos destacar Ethereum, un proyecto que llevó a la práctica algunas de las funcionalidades teóricas de la blockchain de Bitcoin, que marcaría un antes y un después en el ecosistema blockchain y que con su lanzamiento, en julio de 2015, se inicia una oleada de nuevos proyectos que nos hace pasar del “cripto invierno” a la primavera de las criptomonedas.
En 2016 comenzó a recuperarse ligeramente el mercado de las criptomonedas. Paulatinamente, a lo largo de 2017, fueron surgiendo nuevos e interesantes proyectos que convergieron en una explosión dentro de este peculiar ecosistema, dentro del cual no solo se produjo un incremento astronómico y generalizado de los precios debido a la entrada desmesurada de capital, sino que el número de proyectos relacionados con esta tecnología también aumentó considerablemente (Si bien es cierto que la entrada de capital fue meramente especulativa). Miles de personas invertían grandes cantidades en distintas criptomonedas sin tener el más mínimo interés por la tecnología que cada una de ellas implementaba. Lo hacían, simplemente, para tratar de obtener pingües beneficios en un corto espacio de tiempo. Asimismo, muchos de los proyectos que se crearon en este periodo se encontraban más centrados en obtener beneficios mediante la venta de sus criptomonedas o tokens en el mercado alcista, que por la utilidad real que pudiera derivarse de estos.
Por todo lo mencionado anteriormente, en 2017 las criptomonedas se convirtieron en el tema de moda. Me sorprendió ver cómo incluso mi viejo profesor de Derecho civil de la facultad se lanzaba a escribir artículos académicos sobre blockchain, tratando de incardinar la naturaleza jurídica de los smartcontracts dentro de la teoría general de los contratos del Código Civil y de los sistemas de contratación clásicos. Sin embargo, con todo el respeto a este tipo de trabajos académicos puramente -y nunca mejor dicho- teóricos, no creo que sea correcto ni conveniente tratar de adaptar una tecnología disruptiva del siglo XXI a una teoría contractual del siglo XIX basada en un sistema de contratación con orígenes en el Derecho romano. En este sentido, el Derecho es el que debe adaptarse a la realidad social -en este supuesto a la realidad tecnológica- y no debemos tratar de adaptar esta nueva realidad tecnológica al Derecho decimonónico.
A principios de 2018 el crecimiento puramente especulativo se vio bruscamente frenado. Los precios de las criptomonedas se desplomaron y, de la noche a la mañana, gran parte del capital del mercado cripto salió del mismo más rápido de lo que había entrado. El desplome del mercado de inicios de 2018, al igual que el del 2014, no impidió que los proyectos que podríamos considerar “serios” continuaran desarrollándose a un ritmo vertiginoso. Al mismo tiempo, cada vez más organismos nacionales e internacionales comenzaron a manifestarse sobre esta realidad y sobre las implicaciones que puede llegar a tener la implementación de esta tecnología, desde el ámbito jurídico hasta incluso, el geopolítico.
En nuestro país, se ha llegado a incorporar -desde mi punto de vista sin mucho éxito- la tecnología blockchain en el discurso de los principales partidos políticos, quienes reconocen la necesidad de explotar su enorme potencial y de eliminar las zonas grises que actualmente existen en su regulación. Para ello se han comprometido todos los partidos a impulsar esta tecnología mediante un Pacto de Estado en el que la blockchain se incluiría junto al resto de tecnologías que integran la denominada “Cuarta Revolución Industrial” (Big Data, Internet de las cosas, Inteligencia Artificial y Robótica). Sin embargo, España todavía no es un país digital a la altura de otros. No está apostando fuertemente por esta tecnología, al contrario de lo que están haciendo otras naciones de nuestro entorno como Francia, Portugal o Suiza, donde se está creando un marco jurídico más favorable para el desarrollo de proyectos con base blockchain y para la tributación de los beneficios o pérdidas económicas derivadas de las criptomonedas. Asimismo, existen otros países que están yendo más allá de la simple regulación del sector y están estudiando la posibilidad de desarrollar sus propias criptomonedas oficiales como por ejemplo el Cripto Rublo ruso, el Yuan Digital chino o el Petro venezolano, encontrándose este último ya operativo, aunque sin mucho éxito. De hecho, las últimas noticias hablan de las investigaciones que estaría realizando el Banco Central Europeo y el ESCB (del inglés: European System of Central Banks o Sistema Europeo de Bancos Centrales) para la creación de lo que ellos denominan “Euro Digital ”. Poco a poco se ha ido tratando de desvincular al Bitcoin de la tecnología blockchain, la cual, a su vez, empezó a ser llamada eufemísticamente DLT (del inglés: Distributed Ledger Technology) o tecnología de libro mayor distribuido , para tratar de romper con cualquier vestigio con esta primera criptomoneda. De esta forma se pretende que los mismos que criticaban al Bitcoin en 2013, a pesar de seguir criticándolo en la actualidad, puedan alabar la tecnología que lo sustenta tratando de no quedarse fuera de lo que muchos ya consideran la revolución blockchain. En este sentido, muchas empresas y grupos empresariales -algunos de los cuales se habían posicionado en un primer momento como grandes detractores de las criptomonedas- han comenzado a desarrollar sus propias blockchain. Entre estos proyectos podemos destacar Libra, que, aunque habitualmente se vincula con Facebook, en su desarrollo participan más de 100 empresas, entre las que cabe reseñar Mastercard, Visa, Ebay, Spotify, PayPal, Uber o Vodafone; o el consorcio R3 y su blockchain, del que forman parte Amazon, Intel, Microsoft, Bank of America, Deutsche Bank y muchas otras compañías y entidades financieras. Dada la velocidad con la que se desarrollan los acontecimientos en el ecosistema blockchain -se han pasado de unas pocas criptomonedas en 2013 a más de 2.200 en 2019 - es necesario mantenerse al día de todas las noticias, cambios, avances y, sobre todo, proyectos legislativos nacionales e internacionales que incidan, o puedan llegar a incidir, directa o indirectamente, en cualquier aspecto relacionado con este ámbito tecnológico.
Desde tales consideraciones, el objetivo de este libro es exponer todas las inquietudes y vicisitudes a las que me he tenido que enfrentar durante los últimos ocho años, no solo como abogado, sino también como usuario de criptomonedas y de servicios basados en la blockchain. Y es que siendo cierto como es que ser un early adopter en el campo del derecho blockchain me ha dado una gran cantidad de alegrías y satisfacciones personales y profesionales, no es menos cierto que también me ha quitado muchas horas de sueño y me ha generado no pocos dolores de cabeza.
-
 @ 7175188c:6382a72c
2024-11-21 16:34:00
@ 7175188c:6382a72c
2024-11-21 16:34:00It looks like the Megalith LSP node is offline.
What to do in this situation?
@Alby @getalby
originally posted at https://stacker.news/items/777271
-
 @ 3f770d65:7a745b24
2024-10-29 17:38:20
@ 3f770d65:7a745b24
2024-10-29 17:38:20Amber
Amber is a Nostr event signer for Android that allows users to securely segregate their private key (nsec) within a single, dedicated application. Designed to function as a NIP-46 signing device, Amber ensures your smartphone can sign events without needing external servers or additional hardware, keeping your private key exposure to an absolute minimum. This approach aligns with the security rationale of NIP-46, which states that each additional system handling private keys increases potential vulnerability. With Amber, no longer do users need to enter their private key into various Nostr applications.

Amber is supported by a growing list of apps, including Amethyst, 0xChat, Voyage, Fountain, and Pokey, as well as any web application that supports NIP-46 NSEC bunkers, such as Nostr Nests, Coracle, Nostrudel, and more. With expanding support, Amber provides an easy solution for secure Nostr key management across numerous platforms.

Amber supports both native and web-based Nostr applications, aiming to eliminate the need for browser extensions or web servers. Key features include offline signing, multiple account support, and NIP-46 compatibility, and includes a simple UI for granular permissions management. Amber is designed to support signing events in the background, enhancing flexibility when you select the "remember my choice" option, eliminating the need to constantly be signing events for applications that you trust. You can download the app from it's GitHub page, via Obtainium or Zap.store.
To log in with Amber, simply tap the "Login with Amber" button or icon in a supported application, or you can paste the NSEC bunker connection string directly into the login box. For example, use a connection string like this: bunker://npub1tj2dmc4udvgafxxxxxxxrtgne8j8l6rgrnaykzc8sys9mzfcz@relay.nsecbunker.com.

Citrine
Citrine is a Nostr relay built specifically for Android, allowing Nostr clients on Android devices to seamlessly send and receive events through a relay running directly on their smartphone. This mobile relay setup offers Nostr users enhanced flexibility, enabling them to manage, share, and back up all their Nostr data locally on their device. Citrine’s design supports independence and data security by keeping data accessible and under user control.

With features tailored to give users greater command over their data, Citrine allows easy export and import of the database, restoration of contact lists in case of client malfunctions, and detailed relay management options like port configuration, custom icons, user management, and on-demand relay start/stop. Users can even activate TOR access, letting others connect securely to their Nostr relay directly on their phone. Future updates will include automatic broadcasting when the device reconnects to the internet, along with content resolver support to expand its functionality.
Once you have your Citrine relay fully configured, simply add it to the Private and Local relay sections in Amethyst's relay configuration.

Pokey
Pokey for Android is a brand new, real-time notification tool for Nostr. Pokey allows users to receive live updates for their Nostr events and enabling other apps to access and interact with them. Designed for seamless integration within a user's Nostr relays, Pokey lets users stay informed of activity as it happens, with speed and the flexibility to manage which events trigger notifications on their mobile device.

Pokey currently supports connections with Amber, offering granular notification settings so users can tailor alerts to their preferences. Planned features include broadcasting events to other apps, authenticating to relays, built-in Tor support, multi-account handling, and InBox relay management. These upcoming additions aim to make Pokey a fantastic tool for Nostr notifications across the ecosystem.
Zap.store
Zap.store is a permissionless app store powered by Nostr and your trusted social graph. Built to offer a decentralized approach to app recommendations, zap.store enables you to check if friends like Alice follow, endorse, or verify an app’s SHA256 hash. This trust-based, social proof model brings app discovery closer to real-world recommendations from friends and family, bypassing centralized app curation. Unlike conventional app stores and other third party app store solutions like Obtainium, zap.store empowers users to see which apps their contacts actively interact with, providing a higher level of confidence and transparency.

Currently available on Android, zap.store aims to expand to desktop, PWAs, and other platforms soon. You can get started by installing Zap.store on your favorite Android device, and install all of the applications mentioned above.
Android's openness goes hand in hand with Nostr's openness. Enjoy exploring both expanding ecosystems.
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ f42176a1:0ed621ae
2024-11-21 16:25:01
@ f42176a1:0ed621ae
2024-11-21 16:25:01The cost of government nanny state:
Assume a person at age 22 gets a job earning $30,000 a year. They never get a raise. Retire at age 65. This gives them an investing time horizon of 43 years. However, instead of having 15.3% paid in FICA tax, they get 15.3% of their income put into the S&P 500. (let's ignore the potential and promise of bitcoin for this example).
15.3% of $30,000 = $4,590 per year Assume annual rate of return of 9.65% (slightly less than historical S&P return) After 43 years they'll have $2,450,000 in their account. Using the "4% rule" would provide a retirement income of $98,000 a year or a little over $8,000 per month income for the rest of their life. According to a CNBC article in 2020 https://www.cnbc.com/2020/03/20/how-much-can-you-get-from-social-security-if-you-make-30000-a-year.html Someone making $30,000 year on average in their lifetime will receive $1,357 per month at their full retirement age. This gives a net shortfall of $6,643 we all lose in our current system.
Now of course FICA is social security AND Medicare, but Social Security is 12.4% and Medicare is the remaining 2.9% of the total 15.3% in payroll tax. This equates to something like $317 per month in Medicare benefit, vastly short of the $6,643 remainder on the "privatized social security" account funded with the exact same amount of capital.
Now, the true "kicker" is in the unfortunate scenario of an untimely death. Say you die the day you'd start social security. In our current system you heirs get $255 death benefit (not a typo), in our new scenario they get $2,450,000.
To say that social security is a bad deal may be the understatement of the century. It is beyond time to revamp the system. I prefer no compulsion, but even if compulsion remains it is vastly superior to put this money in your own account you own and not contribute to the ponzi scheme we have now.The cost of government nanny state:
Assume a person at age 22 gets a job earning $30,000 a year. They never get a raise. Retire at age 65. This gives them an investing time horizon of 43 years. However, instead of having 15.3% paid in FICA tax, they get 15.3% of their income put into the S&P 500. (let's ignore the potential and promise of bitcoin for this example).
- 15.3% of $30,000 = $4,590 per year
- Assume annual rate of return of 9.65% (slightly less than historical S&P return)
- After 43 years they'll have $2,450,000 in their account.
- Using the "4% rule" would provide a retirement income of $98,000 a year or a little over $8,000 per month income for the rest of their life.
According to a CNBC article in 2020 https://www.cnbc.com/2020/03/20/how-much-can-you-get-from-social-security-if-you-make-30000-a-year.html Someone making $30,000 year on average in their lifetime will receive $1,357 per month at their full retirement age. This gives a net shortfall of $6,643 we all lose in our current system.
Now of course FICA is social security AND Medicare, but Social Security is 12.4% and Medicare is the remaining 2.9% of the total 15.3% in payroll tax. This equates to something like $317 per month in Medicare benefit, vastly short of the $6,643 remainder on the "privatized social security" account funded with the exact same amount of capital.
Now, the true "kicker" is in the unfortunate scenario of an untimely death. Say you die the day you'd start social security. In our current system you heirs get $255 death benefit (not a typo), in our new scenario they get $2,450,000.
To say that social security is a bad deal may be the understatement of the century. It is beyond time to revamp the system. I prefer no compulsion, but even if compulsion remains it is vastly superior to put this money in your own account you own and not contribute to the ponzi scheme we have now.
-
 @ 349d6b82:12b2a5b1
2024-11-21 15:35:49
@ 349d6b82:12b2a5b1
2024-11-21 15:35:49Наши отечественные ученные наконец доработали и внедрили первого Android-учителя в учебный процесс у школьников 11 класса в школе МАОУ СОШ№27 - это весьма значимый шаг в области образования и технологий.
Цели и задачи, которые поставили ученные для робота-андроида, - это повышение эффективности обучения и индивидуализации образовательного процесса. Это позволит адаптировать учебные материалы под нужды каждого ученика, учитывая их уровень подготовки и интересы.
Технологические особенности Android-учителя представляют собой интерактивное устройство, которое может выполнять функции преподавателя, предоставляя доступ к учебным материалам, организуя тестирование и обеспечивая обратную связь. Это устройство интегрирует различные образовательные приложения, что способствует более глубокому пониманию учебного материала.
В реализацию этого проекта также входит использование специальных планшетов или других мобильных устройств, на которых установлено программное обеспечение для взаимодействия с Android-учителем. Вскоре все это будет выдано всему рабочему персоналу школы.
Для успешной интеграции этой технологии в учебный процесс - будут проводиться обучения для педагогов, чтобы они могли эффективно использовать новые инструменты и технологии в своей работе. Это обучение включает в себя как технические аспекты, так и методические рекомендации по использованию Android-учителя в классе.
Правительством ожидается, что внедрение Android-учителя приведет к повышению мотивации учащихся, улучшению успеваемости и более активному участию школьников в учебном процессе. Кроме того, такая технология может помочь в подготовке учащихся к будущей профессиональной деятельности, где цифровые навыки играют важную роль для будущего нашего города.
Во избежание неблагоприятных инцидентов, подобных как на Надеждинском Металлургическом Заводе, ученные установили на поздних доработках специальный электрочип, который обеспечит полное выключение андроида, если вдруг произойдет сбой его программы.
-
 @ 1739d937:3e3136ef
2024-10-29 16:57:08
@ 1739d937:3e3136ef
2024-10-29 16:57:08This update marks a major milestone for the project. I know, with certainty, that MLS messaging over Nostr is going to work. That might sound a little crazy after so many months working on the project, and I was pretty confident, but until you’ve got running code, it’s all conjecture.
Late last week, I released a video of a working prototype of White Noise that shows the full flow; creating groups, inviting other users to join those groups, accepting invites, and sending messages back-and-forth. I’m thrilled that I’ve gotten this far but also appalled that it’s taken so long and disgusted at the state of the code in the app (I’ve been told I have unrelenting standards 😅).
If you missed the video last week...
nostr:note125cuk0zetc7sshw52v5zaq9apq3rq7e2x587tr2c96t7z7sjs59svwv0fj
What's Next?
In this update, I want to cover a few things about how I'm planning to proceed and how I’m splitting code out of the app into libraries that will help other developers implement MLS messaging in their own Nostr clients.
First off, many of you know that I've been building White Noise as a Rust app using the Tauri framework. The OpenMLS implementation is also written in Rust (with bindings for many other languages). So, when you hear me talking about library code, think Rust crates for now.
The first library, called openmls-nostr, is an extension/abstraction on top of the openmls implementation of the MLS spec that helps Nostr clients interact more easily with that implementation in a way that feels native to Nostr. Mostly this will be helping developers interact with MLS primitives and ensure that they’re creating, validating, and serializing these objects in the right way at the right times.
The second isn’t a new library as a big contribution to the already excellent rust-nostr library from nostr:npub1drvpzev3syqt0kjrls50050uzf25gehpz9vgdw08hvex7e0vgfeq0eseet. The methods that will go in rust-nostr are highly abstracted and based specifically on the requirements of NIP-104. Mostly this will be helping developers to take those MLS primitives and publish or query them as Nostr events at the right times and to/from the right relays.
Most of this code was originally written directly in the White Noise library so this week I've started to pull code for both of those libraries out and move it to its new home. While I’ve been at it, I've been writing some tests and trying to document things.
An unfortunate offshoot of this is that the usable builds of White Noise are going to take a touch longer. I promise it’s still a very high priority but at this point I need to clean a few things up based on what I've learned thus far.
Another thing that is slowing down release is that; behind the scenes of the dev work, I’ve been battling with Apple for nearly 2 months now to get a proper developer team set up so that we can publish the app via TestFlight for MacOS and iOS. I’ve also been recently learning the intricacies of Android publishing (oh my dear god there are so many devices, OS versions, etc.).
With that in mind, if you know anyone who can help get me up to speed on CI/CD, release pipelines, and multi-platform distribution please hit me up. I would love to learn more and hopefully shortcut some of the pain.
Thanks again so much for all the support over the last few months! It means a lot to me and is a huge part of what is keeping me going on this. 🙏
-
 @ f8a5df57:b7a58cd4
2024-11-21 15:26:06
@ f8a5df57:b7a58cd4
2024-11-21 15:26:06Содержание сюжета:
Московские учёные Дмитрий Соколов и Александр Белкин создали инновационную космическую капсулу, которая обладает рядом уникальных характеристик и возможностей. Эта капсула предназначена для безопасного возвращения астронавтов на Землю после длительных космических миссий.
Одной из ключевых особенностей капсулы является её способность к автоматической посадке. Благодаря этой функции, астронавты смогут приземляться без необходимости использования дополнительных средств или участия специалистов на Земле.
Кроме того, капсула оснащена системой активного теплообмена, которая позволяет поддерживать оптимальную температуру внутри капсулы во время полёта и при посадке. Это обеспечивает комфортные условия для астронавтов и снижает риск возникновения проблем со здоровьем.
Разработка московских учёных также включает в себя систему аварийного спасения, которая активируется в случае возникновения нештатных ситуаций в космосе. Это гарантирует безопасность астронавтов даже в самых сложных обстоятельствах.
Ожидается, что использование инновационной космической капсулы позволит значительно повысить безопасность и эффективность космических полётов, а также расширить возможности исследования космоса.
Автор: Дарья Воронина
-
 @ 3bf0c63f:aefa459d
2024-10-26 14:18:23
@ 3bf0c63f:aefa459d
2024-10-26 14:18:23kind:1maximalism and the future of other stuff and Nostr decentralizationThese two problems exist on Nostr today, and they look unrelated at first:
- People adding more stuff to
kind:1notes, such as making them editable, or adding special corky syntax thas has to be parsed and rendered in complicated UIs; - The discovery of "other stuff" content (i.e. long-form articles, podcasts, calendar events, livestreams etc) is hard due to the fact that most people only use microblogging clients and they often don't appear there for them.
Point 2 above has 3 different solutions:
- a. Just publish everything as
kind:1notes; - b. Publish different things as different kinds, but make microblogging clients fetch all the event kinds from people you follow, then render them natively or use NIP-31, or NIP-89 to point users to other clients that would render them better;
- c. Publish different things as different kinds, and reference them in
kind:1notes that would act as announcements to these other events, also relying on NIP-31 and NIP-89 for displaying references and recommending other clients.
Solution a is obviously very bad, so I won't address it.
For a while I have believed solution b was the correct one, and many others seem to tacitly agree with it, given that some clients have been fetching more and more event kinds and going out of their way to render them in the same feed where only
kind:1notes were originally expected to be.I don't think clients doing that is necessarily bad, but I do think this have some centralizing effects on the protocol, as it pushes clients to become bigger and bigger, raising the barrier to entry into the
kind:1realm. And also in the past I have talked about the fact that I disliked that some clients would display my long-form articles as if they were normalkind:1notes and just dump them into the feeds of whoever was following me: nostr:nevent1qqsdk90k9k30vtzwpj6grxys9mvsegu5kkwd4jmpyhlmtjnxet2rvggprpmhxue69uhhyetvv9ujumn0wdmksetjv5hxxmmdqy8hwumn8ghj7mn0wd68ytnddaksygpm7rrrljungc6q0tuh5hj7ue863q73qlheu4vywtzwhx42a7j9n5hae35cThese and other reasons have made me switch my preference to solution c, as it gives the most flexibility to the publisher: whoever wants to announce stuff so it can be discovered can, whoever doesn't don't have to. And it allows microblogging clients the freedom to render just render tweets and having a straightforward barrier between what they can render and what is just a link to an external app or webapp (of course they can always opt to render the referenced content in-app if they want).
It also makes the case for microapps more evident. If all microblogging clients become superapps that can render recipe events perfectly why would anyone want to use a dedicated recipes app? I guess there are still reasons, but blurring the line between content kinds in superapps would definitely remove some of the reasons and eventually kill all the microapps.
That brings us back to point 1 above (the overcomplication of
kind:1events): if solution c is what we're going to, that makeskind:1events very special in Nostr, and not just another kind among others. Microblogging clients become the central plaza of Nostr, thus protecting their neutrality and decentralization much more important. Having a lot of clients with different userbases, doing things in slightly different ways, is essential for that decentralization.It's ok if Nostr ends up having just 2 recipe-sharing clients, but it must have dozens of microblogging clients -- and maybe not even full-blown microblogging clients, but other apps that somehow deal with
kind:1events in multiple ways. It's ok if implementing a client for public audio-rooms is very hard and complicated, but at the same time it should be very simple to write a client that can render akind:1note referencing an audio-room and linking to that dedicated client.I hope you got my point and agreed because this article is ended.
- People adding more stuff to
-
 @ ec42c765:328c0600
2024-10-21 07:42:48
@ ec42c765:328c0600
2024-10-21 07:42:482024年3月
フィリピンのセブ島へ旅行。初海外。

Nostrに投稿したらこんなリプライが
nostr:nevent1qqsff87kdxh6szf9pe3egtruwfz2uw09rzwr6zwpe7nxwtngmagrhhqc2qwq5
nostr:nevent1qqs9c8fcsw0mcrfuwuzceeq9jqg4exuncvhas5lhrvzpedeqhh30qkcstfluj
(ビットコイン関係なく普通の旅行のつもりで行ってた。というか常にビットコインのこと考えてるわけではないんだけど…)
そういえばフィリピンでビットコイン決済できるお店って多いのかな?
海外でビットコイン決済ってなんかかっこいいな!
やりたい!
ビットコイン決済してみよう! in セブ島
BTCMap でビットコイン決済できるところを探す
本場はビットコインアイランドと言われてるボラカイ島みたいだけど
セブにもそれなりにあった!

なんでもいいからビットコイン決済したいだけなので近くて買いやすい店へ
いざタピオカミルクティー屋!

ちゃんとビットコインのステッカーが貼ってある!

つたない英語とGoogle翻訳を使ってビットコイン決済できるか店員に聞いたら
店員「ビットコインで支払いはできません」
(えーーーー、なんで…ステッカー貼ってあるやん…。)
まぁなんか知らんけどできないらしい。
店員に色々質問したかったけど質問する英語力もないのでする気が起きなかった
結局、せっかく店まで足を運んだので普通に現金でタピオカミルクティーを買った
タピオカミルクティー
話題になってた時も特に興味なくて飲んでなかったので、これが初タピオカミルクティーになった
法定通貨の味がした。

どこでもいいからなんでもいいから
海外でビットコイン決済してみたい
ビットコイン決済させてくれ! in ボラカイ島
ビットコインアイランドと呼ばれるボラカイ島はめちゃくちゃビットコイン決済できるとこが多いらしい
でもやめてしまった店も多いらしい
でも300もあったならいくつかはできるとこあるやろ!
nostr:nevent1qqsw0n6utldy6y970wcmc6tymk20fdjxt6055890nh8sfjzt64989cslrvd9l
行くしかねぇ!
ビットコインアイランドへ
フィリピンの国内線だぁ

``` 行き方: Mactan-Cebu International Airport ↓飛行機 Godofredo P. Ramos Airport (Caticlan International Airport, Boracay Airport) ↓バスなど Caticlan フェリーターミナル ↓船 ボラカイ島
料金: 飛行機(受託手荷物付き) 往復 21,000円くらい 空港~ボラカイ島のホテルまで(バス、船、諸経費) 往復 3,300円くらい (klookからSouthwest Toursを利用)
このページが色々詳しい https://smaryu.com/column/d/91761/ ```
空港おりたらSouthwestのバスに乗る
事前にネットで申し込みをしている場合は5番窓口へ

港!

船!(めっちゃ速い)

ボラカイついた!

ボラカイ島の移動手段
セブの移動はgrabタクシーが使えるがボラカイにはない。
ネットで検索するとトライシクルという三輪タクシーがおすすめされている。
 (トライシクル:開放的で風がきもちいい)
(トライシクル:開放的で風がきもちいい)トライシクルの欠点はふっかけられるので値切り交渉をしないといけないところ。
最初に300phpくらいを提示され、行き先によるけど150phpくらいまでは下げられる。
これはこれで楽しい値切り交渉だけど、個人的にはトライシクルよりバスの方が気楽。
Hop On Hop Off バス:
https://www.hohoboracay.com/pass.php
一日乗り放題250phpなので往復や途中でどこか立ち寄ったりを考えるとお得。
 バスは現金が使えないので事前にどこかでカードを買うか車内で買う。
バスは現金が使えないので事前にどこかでカードを買うか車内で買う。私は何も知らずに乗って車内で乗務員さんから現金でカードを買った。
バスは狭い島内を数本がグルグル巡回してるので20~30分に1本くらいは来るイメージ。
逆にトライシクルは待たなくても捕まえればすぐに乗れるところがいいところかもしれない。
現実
ボラカイ島 BTC Map
 BTC決済できるとこめっちゃある
BTC決済できるとこめっちゃあるさっそく店に行く!
「bitcoin accepted here」のステッカーを見つける!
店員にビットコイン支払いできるか聞く!
できないと言われる!
もう一軒行く
「bitcoin accepted here」のステッカーを見つける
店員にビットコイン支払いできるか聞く
できないと言われる
5件くらいは回った
全部できない!
悲しい
で、ネットでビットコインアイランドで検索してみると
旅行日の一か月前くらいにアップロードされた動画があったので見てみた
要約 - ビットコイン決済はpouch.phというスタートアップ企業がボラカイ島の店にシステムを導入した - ビットコインアイランドとすることで観光客が10%~30%増加つまり数百~千人程度のビットコインユーザーが来ると考えた - しかし実際には3~5人だった - 結果的に200の店舗がビットコイン決済を導入しても使われたのはごく一部だった - ビットコイン決済があまり使われないので店員がやり方を忘れてしまった - 店は関心を失いpouchのアプリを消した
https://youtu.be/uaqx6794ipc?si=Afq58BowY1ZrkwaQ
なるほどね~
しゃあないわ
聖地巡礼
動画内でpouchのオフィスだったところが紹介されていた
これは半年以上前の画像らしい

現在はオフィスが閉鎖されビットコインの看板は色あせている
 おもしろいからここに行ってみよう!となった
おもしろいからここに行ってみよう!となったで行ってみた
看板の色、更に薄くなってね!?

記念撮影
 これはこれで楽しかった
これはこれで楽しかった場所はこの辺
https://maps.app.goo.gl/WhpEV35xjmUw367A8
ボラカイ島の中心部の結構いいとこ
みんな~ビットコイン(の残骸)の聖地巡礼、行こうぜ!
最後の店
Nattoさんから情報が
なんかあんまりネットでも今年になってからの情報はないような…https://t.co/hiO2R28sfO
— Natto (@madeofsoya) March 22, 2024
ここは比較的最近…?https://t.co/CHLGZuUz04もうこれで最後だと思ってダメもとで行ってみた なんだろうアジア料理屋さん?

もはや信頼度0の「bitcoin accepted here」

ビットコイン払いできますか?
店員「できますよ」
え?ほんとに?ビットコイン払いできる?
店員「できます」
できる!!!!
なんかできるらしい。
適当に商品を注文して
印刷されたQRコードを出されたので読み取る
ここでスマートに決済できればよかったのだが結構慌てた
自分は英語がわからないし相手はビットコインがわからない
それにビットコイン決済は日本で1回したことがあるだけだった
 どうもライトニングアドレスのようだ
どうもライトニングアドレスのようだ送金額はこちらで指定しないといけない
店員はフィリピンペソ建ての金額しか教えてくれない
何sats送ればいいのか分からない
ここでめっちゃ混乱した
でもウォレットの設定変えればいいと気付いた
普段円建てにしているのをフィリピンペソ建てに変更すればいいだけだった
設定を変更したら相手が提示している金額を入力して送金
送金は2、3秒で完了した
やった!
海外でビットコイン決済したぞ!
ログ

PORK CHAR SIU BUN とかいうやつを買った
 普通にめっちゃおいしかった
普通にめっちゃおいしかったなんかビットコイン決済できることにビビッて焦って一品しか注文しなかったけどもっと頼めばよかった
ここです。みなさん行ってください。
Bunbun Boracay
https://maps.app.goo.gl/DX8UWM8Y6sEtzYyK6
めでたしめでたし
以下、普通の観光写真
セブ島
ジンベエザメと泳いだ

スミロン島でシュノーケリング

市場の路地裏のちょっとしたダウンタウン?スラム?をビビりながら歩いた

ボホール島
なんか変な山

メガネザル

現地の子供が飛び込みを披露してくれた

ボラカイ島
ビーチ


夕日

藻

ボラカイ島にはいくつかビーチがあって宿が多いところに近い南西のビーチ、ホワイトビーチは藻が多かった(時期によるかも)
北側のプカシェルビーチは全然藻もなく、水も綺麗でめちゃくちゃよかった

プカシェルビーチ



おわり!
-
 @ ac8bb9b0:70278acc
2024-11-21 15:14:11
@ ac8bb9b0:70278acc
2024-11-21 15:14:11Chef's notes
If you’d like to make this soup part of your rotation and want to shave off a little time for the next time around, double the recipe for the meatballs and freeze half. That way, all you’ll have to do is make the soup and add the meatballs as directed in the recipe. (They may take a few extra minutes to warm through if you add them directly from the freezer.)
The soup can be frozen for up to 3 months but wait until you reheat the soup to add the pasta. Defrost the soup in the refrigerator for 12 hours and then reheat it on the stovetop over medium heat until simmering, add the pasta, and cook until the pasta is tender.
Details
- ⏲️ Prep time: 50
- 🍳 Cook time: 30
- 🍽️ Servings: 8
Ingredients
- 1 large egg
- 3 tablespoons finely chopped fresh chives
- 2 teaspoons finely chopped fresh sage
- 2 cloves garlic, minced
- ¾ lb 85 or 90% lean ground beef
- ½ lb sweet or hot Italian sausage, removed from the casings
- ½ cup grated Parmigiano Reggiano
- ⅓ cup Italian seasoned bread crumbs
- ¼ teaspoon salt
- 2 tablespoons extra virgin olive oil
- 1 medium yellow onion, diced
- 2 large carrots, diced
- 2 stalks celery, diced
- 6 cups high-quality chicken broth
- 2 cups high-quality beef broth
- 2 cups water
- ½ cup dry white wine
- 1 bay leaf
- ½ teaspoon salt
- ¼ teaspoon white pepper (okay to use black pepper)
- 1 cup small dittalini pasta
- 4 oz fresh spinach, stems trimmed and roughly chopped (once prepped, you should have about 3 packed cups)
- Parmigiano Reggiano, for serving
Directions
- Make the meatballs: Preheat the oven to 350°F. Line a baking sheet with aluminum foil and set an oven-proof roasting rack over top. Spray the rack generously with nonstick cooking spray.
- In a large bowl, beat the egg with the chives, sage and garlic. Add the remaining meatball ingredients and mash with your hands until evenly combined. Roll the mixture into tablespoon-size balls, about 1 inch in diameter (it will make approximately 50 meatballs), and place on the prepared rack. Bake for 15 to 18 minutes, or until lightly browned and cooked through. Set aside.
- Meanwhile, start the soup. In a large soup pot or Dutch oven over medium heat, heat the olive oil. Add the onions, carrots, and celery and cook, stirring frequently, until the vegetables are softened, about 8 minutes. Add the chicken broth, beef broth, water, wine, bay leaf, salt and pepper and bring to a boil. Add the pasta and cook, uncovered, at a gentle boil until the pasta is al dente, 8 to 10 minutes (or according to package directions). Taste the soup and adjust the seasoning, if necessary. Reduce the heat to low and add the spinach and meatballs. Simmer for a few minutes, until the spinach is wilted and the meatballs are warmed through. Ladle into bowls and serve with grated Parmigiano Reggiano.
-
 @ 8947a945:9bfcf626
2024-10-17 08:06:55
@ 8947a945:9bfcf626
2024-10-17 08:06:55สวัสดีทุกคนบน Nostr ครับ รวมไปถึง watchersและ ผู้ติดตามของผมจาก Deviantart และ platform งานศิลปะอื่นๆนะครับ
ตั้งแต่ต้นปี 2024 ผมใช้ AI เจนรูปงานตัวละครสาวๆจากอนิเมะ และเปิด exclusive content ให้สำหรับผู้ที่ชื่นชอบผลงานของผมเป็นพิเศษ
ผมโพสผลงานผมทั้งหมดไว้ที่เวบ Deviantart และค่อยๆสร้างฐานผู้ติดตามมาเรื่อยๆอย่างค่อยเป็นค่อยไปมาตลอดครับ ทุกอย่างเติบโตไปเรื่อยๆของมัน ส่วนตัวผมมองว่ามันเป็นพิร์ตธุรกิจออนไลน์ ของผมพอร์ตนึงได้เลย
เมื่อวันที่ 16 กย.2024 มีผู้ติดตามคนหนึ่งส่งข้อความส่วนตัวมาหาผม บอกว่าชื่นชอบผลงานของผมมาก ต้องการจะขอซื้อผลงาน แต่ขอซื้อเป็น NFT นะ เสนอราคาซื้อขายต่อชิ้นที่สูงมาก หลังจากนั้นผมกับผู้ซื้อคนนี้พูดคุยกันในเมล์ครับ
นี่คือข้อสรุปสั่นๆจากการต่อรองซื้อขายครับ
(หลังจากนี้ผมขอเรียกผู้ซื้อว่า scammer นะครับ เพราะไพ่มันหงายมาแล้ว ว่าเขาคือมิจฉาชีพ)

- Scammer รายแรก เลือกผลงานที่จะซื้อ เสนอราคาซื้อที่สูงมาก แต่ต้องเป็นเวบไซต์ NFTmarket place ที่เขากำหนดเท่านั้น มันทำงานอยู่บน ERC20 ผมเข้าไปดูเวบไซต์ที่ว่านี้แล้วรู้สึกว่ามันดูแปลกๆครับ คนที่จะลงขายผลงานจะต้องใช้ email ในการสมัครบัญชีซะก่อน ถึงจะผูก wallet อย่างเช่น metamask ได้ เมื่อผูก wallet แล้วไม่สามารถเปลี่ยนได้ด้วย ตอนนั้นผมใช้ wallet ที่ไม่ได้ link กับ HW wallet ไว้ ทดลองสลับ wallet ไปๆมาๆ มันทำไม่ได้ แถมลอง log out แล้ว เลข wallet ก็ยังคาอยู่อันเดิม อันนี้มันดูแปลกๆแล้วหนึ่งอย่าง เวบนี้ค่า ETH ในการ mint 0.15 - 0.2 ETH … ตีเป็นเงินบาทนี่แพงบรรลัยอยู่นะครับ

-
Scammer รายแรกพยายามชักจูงผม หว่านล้อมผมว่า แหม เดี๋ยวเขาก็มารับซื้องานผมน่า mint งานเสร็จ รีบบอกเขานะ เดี๋ยวเขารีบกดซื้อเลย พอขายได้กำไร ผมก็ได้ค่า gas คืนได้ แถมยังได้กำไรอีก ไม่มีอะไรต้องเสีนจริงมั้ย แต่มันเป้นความโชคดีครับ เพราะตอนนั้นผมไม่เหลือทุนสำรองที่จะมาซื้อ ETH ได้ ผมเลยต่อรองกับเขาตามนี้ครับ :
-
ผมเสนอว่า เอางี้มั้ย ผมส่งผลงานของผมแบบ low resolution ให้ก่อน แลกกับให้เขาช่วยโอน ETH ที่เป็นค่า mint งานมาให้หน่อย พอผมได้ ETH แล้ว ผมจะ upscale งานของผม แล้วเมล์ไปให้ ใจแลกใจกันไปเลย ... เขาไม่เอา
- ผมเสนอให้ไปซื้อที่ร้านค้าออนไลน์ buymeacoffee ของผมมั้ย จ่ายเป็น USD ... เขาไม่เอา
- ผมเสนอให้ซื้อขายผ่าน PPV lightning invoice ที่ผมมีสิทธิ์เข้าถึง เพราะเป็น creator ของ Creatr ... เขาไม่เอา
- ผมยอกเขาว่างั้นก็รอนะ รอเงินเดือนออก เขาบอก ok
สัปดาห์ถัดมา มี scammer คนที่สองติดต่อผมเข้ามา ใช้วิธีการใกล้เคียงกัน แต่ใช้คนละเวบ แถมเสนอราคาซื้อที่สูงกว่าคนแรกมาก เวบที่สองนี้เลวร้ายค่าเวบแรกอีกครับ คือต้องใช้เมล์สมัครบัญชี ไม่สามารถผูก metamask ได้ พอสมัครเสร็จจะได้ wallet เปล่าๆมาหนึ่งอัน ผมต้องโอน ETH เข้าไปใน wallet นั้นก่อน เพื่อเอาไปเป็นค่า mint NFT 0.2 ETH
ผมบอก scammer รายที่สองว่า ต้องรอนะ เพราะตอนนี้กำลังติดต่อซื้อขายอยู่กับผู้ซื้อรายแรกอยู่ ผมกำลังรอเงินเพื่อมาซื้อ ETH เป็นต้นทุนดำเนินงานอยู่ คนคนนี้ขอให้ผมส่งเวบแรกไปให้เขาดูหน่อย หลังจากนั้นไม่นานเขาเตือนผมมาว่าเวบแรกมันคือ scam นะ ไม่สามารถถอนเงินออกมาได้ เขายังส่งรูป cap หน้าจอที่คุยกับผู้เสียหายจากเวบแรกมาให้ดูว่าเจอปัญหาถอนเงินไม่ได้ ไม่พอ เขายังบลัฟ opensea ด้วยว่าลูกค้าขายงานได้ แต่ถอนเงินไม่ได้
Opensea ถอนเงินไม่ได้ ตรงนี้แหละครับคือตัวกระตุกต่อมเอ๊ะของผมดังมาก เพราะ opensea อ่ะ ผู้ใช้ connect wallet เข้ากับ marketplace โดยตรง ซื้อขายกันเกิดขึ้น เงินวิ่งเข้าวิ่งออก wallet ของแต่ละคนโดยตรงเลย opensea เก็บแค่ค่า fee ในการใช้ platform ไม่เก็บเงินลูกค้าไว้ แถมปีนี้ค่า gas fee ก็ถูกกว่า bull run cycle 2020 มาก ตอนนี้ค่า gas fee ประมาณ 0.0001 ETH (แต่มันก็แพงกว่า BTC อยู่ดีอ่ะครับ)
ผมเลยเอาเรื่องนี้ไปปรึกษาพี่บิท แต่แอดมินมาคุยกับผมแทน ทางแอดมินแจ้งว่ายังไม่เคยมีเพื่อนๆมาปรึกษาเรื่องนี้ กรณีที่ผมทักมาถามนี่เป็นรายแรกเลย แต่แอดมินให้ความเห็นไปในทางเดียวกับสมมุติฐานของผมว่าน่าจะ scam ในเวลาเดียวกับผมเอาเรื่องนี้ไปถามในเพจ NFT community คนไทนด้วย ได้รับการ confirm ชัดเจนว่า scam และมีคนไม่น้อยโดนหลอก หลังจากที่ผมรู้ที่มาแล้ว ผมเลยเล่นสงครามปั่นประสาท scammer ทั้งสองคนนี้ครับ เพื่อดูว่าหลอกหลวงมิจฉาชีพจริงมั้ย
โดยวันที่ 30 กย. ผมเลยปั่นประสาน scammer ทั้งสองรายนี้ โดยการ mint ผลงานที่เขาเสนอซื้อนั่นแหละ ขึ้น opensea แล้วส่งข้อความไปบอกว่า
mint ให้แล้วนะ แต่เงินไม่พอจริงๆว่ะโทษที เลย mint ขึ้น opensea แทน พอดีบ้านจน ทำได้แค่นี้ไปถึงแค่ opensea รีบไปซื้อล่ะ มีคนจ้องจะคว้างานผมเยอะอยู่ ผมไม่คิด royalty fee ด้วยนะเฮ้ย เอาไปขายต่อไม่ต้องแบ่งกำไรกับผม
เท่านั้นแหละครับ สงครามจิตวิทยาก็เริ่มขึ้น แต่เขาจนมุม กลืนน้ำลายตัวเอง ช็อตเด็ดคือ
เขา : เนี่ยอุส่ารอ บอกเพื่อนในทีมว่าวันจันทร์ที่ 30 กย. ได้ของแน่ๆ เพื่อนๆในทีมเห็นงานผมแล้วมันสวยจริง เลยใส่เงินเต็มที่ 9.3ETH (+ capture screen ส่งตัวเลขยอดเงินมาให้ดู)ไว้รอโดยเฉพาะเลยนะ ผม : เหรอ ... งั้น ขอดู wallet address ที่มี transaction มาให้ดูหน่อยสิ เขา : 2ETH นี่มัน 5000$ เลยนะ ผม : แล้วไง ขอดู wallet address ที่มีการเอายอดเงิน 9.3ETH มาให้ดูหน่อย ไหนบอกว่าเตรียมเงินไว้มากแล้วนี่ ขอดูหน่อย ว่าใส่ไว้เมื่อไหร่ ... เอามาแค่ adrress นะเว้ย ไม่ต้องทะลึ่งส่ง seed มาให้ เขา : ส่งรูปเดิม 9.3 ETH มาให้ดู ผม : รูป screenshot อ่ะ มันไม่มีความหมายหรอกเว้ย ตัดต่อเอาก็ได้ง่ายจะตาย เอา transaction hash มาดู ไหนว่าเตรียมเงินไว้รอ 9.3ETH แล้วอยากซื้องานผมจนตัวสั่นเลยไม่ใช่เหรอ ถ้าจะส่ง wallet address มาให้ดู หรือจะช่วยส่ง 0.15ETH มาให้ยืม mint งานก่อน แล้วมากดซื้อ 2ETH ไป แล้วผมใช้ 0.15ETH คืนให้ก็ได้ จะซื้อหรือไม่ซื้อเนี่ย เขา : จะเอา address เขาไปทำไม ผม : ตัดจบ รำคาญ ไม่ขายให้ละ เขา : 2ETH = 5000 USD เลยนะ ผม : แล้วไง
ผมเลยเขียนบทความนี้มาเตือนเพื่อนๆพี่ๆทุกคนครับ เผื่อใครกำลังเปิดพอร์ตทำธุรกิจขาย digital art online แล้วจะโชคดี เจอของดีแบบผม
ทำไมผมถึงมั่นใจว่ามันคือการหลอกหลวง แล้วคนโกงจะได้อะไร
อันดับแรกไปพิจารณาดู opensea ครับ เป็นเวบ NFTmarketplace ที่ volume การซื้อขายสูงที่สุด เขาไม่เก็บเงินของคนจะซื้อจะขายกันไว้กับตัวเอง เงินวิ่งเข้าวิ่งออก wallet ผู้ซื้อผู้ขายเลย ส่วนทางเวบเก็บค่าธรรมเนียมเท่านั้น แถมค่าธรรมเนียมก็ถูกกว่าเมื่อปี 2020 เยอะ ดังนั้นการที่จะไปลงขายงานบนเวบ NFT อื่นที่ค่า fee สูงกว่ากันเป็นร้อยเท่า ... จะทำไปทำไม
ผมเชื่อว่า scammer โกงเงินเจ้าของผลงานโดยการเล่นกับความโลภและความอ่อนประสบการณ์ของเจ้าของผลงานครับ เมื่อไหร่ก็ตามที่เจ้าของผลงานโอน ETH เข้าไปใน wallet เวบนั้นเมื่อไหร่ หรือเมื่อไหร่ก็ตามที่จ่ายค่า fee ในการ mint งาน เงินเหล่านั้นสิ่งเข้ากระเป๋า scammer ทันที แล้วก็จะมีการเล่นตุกติกต่อแน่นอนครับ เช่นถอนไม่ได้ หรือซื้อไม่ได้ ต้องโอนเงินมาเพิ่มเพื่อปลดล็อค smart contract อะไรก็ว่าไป แล้วคนนิสัยไม่ดีพวกเนี้ย ก็จะเล่นกับความโลภของคน เอาราคาเสนอซื้อที่สูงโคตรๆมาล่อ ... อันนี้ไม่ว่ากัน เพราะบนโลก NFT รูปภาพบางรูปที่ไม่ได้มีความเป็นศิลปะอะไรเลย มันดันขายกันได้ 100 - 150 ETH ศิลปินที่พยายามสร้างตัวก็อาจจะมองว่า ผลงานเรามีคนรับซื้อ 2 - 4 ETH ต่องานมันก็มากพอแล้ว (จริงๆมากเกินจนน่าตกใจด้วยซ้ำครับ)
บนโลกของ BTC ไม่ต้องเชื่อใจกัน โอนเงินไปหากันได้ ปิดสมุดบัญชีได้โดยไม่ต้องเชื่อใจกัน
บบโลกของ ETH "code is law" smart contract มีเขียนอยู่แล้ว ไปอ่าน มันไม่ได้ยากมากในการทำความเข้าใจ ดังนั้น การจะมาเชื่อคำสัญญาจากคนด้วยกัน เป็นอะไรที่ไม่มีเหตุผล
ผมไปเล่าเรื่องเหล่านี้ให้กับ community งานศิลปะ ก็มีทั้งเสียงตอบรับที่ดี และไม่ดีปนกันไป มีบางคนยืนยันเสียงแข็งไปในทำนองว่า ไอ้เรื่องแบบเนี้ยไม่ได้กินเขาหรอก เพราะเขาตั้งใจแน่วแน่ว่างานศิลป์ของเขา เขาไม่เอาเข้ามายุ่งในโลก digital currency เด็ดขาด ซึ่งผมก็เคารพมุมมองเขาครับ แต่มันจะดีกว่ามั้ย ถ้าเราเปิดหูเปิดตาให้ทันเทคโนโลยี โดยเฉพาะเรื่อง digital currency , blockchain โดนโกงทีนึงนี่คือหมดตัวกันง่ายกว่าเงิน fiat อีก
อยากจะมาเล่าให้ฟังครับ และอยากให้ช่วยแชร์ไปให้คนรู้จักด้วย จะได้ระวังตัวกัน
Note
- ภาพประกอบ cyber security ทั้งสองนี่ของผมเองครับ ทำเอง วางขายบน AdobeStock
- อีกบัญชีนึงของผม "HikariHarmony" npub1exdtszhpw3ep643p9z8pahkw8zw00xa9pesf0u4txyyfqvthwapqwh48sw กำลังค่อยๆเอาผลงานจากโลกข้างนอกเข้ามา nostr ครับ ตั้งใจจะมาสร้างงานศิลปะในนี้ เพื่อนๆที่ชอบงาน จะได้ไม่ต้องออกไปหาที่ไหน
ผลงานของผมครับ - Anime girl fanarts : HikariHarmony - HikariHarmony on Nostr - General art : KeshikiRakuen - KeshikiRakuen อาจจะเป็นบัญชี nostr ที่สามของผม ถ้าไหวครับ
-
 @ f8a5df57:b7a58cd4
2024-11-21 12:26:23
@ f8a5df57:b7a58cd4
2024-11-21 12:26:23В преддверии проведения Петербургского международного экономического форума - 2041 , в котором примут участие наши ведущие экономисты Москвы, коллектив редакции "Москва информ" решил провести анализ экономики города за 2040 год:
-
Москва стала важным хабом для стартапов и технологических компаний. Сильная поддержка со стороны правительства в виде инвестиций в научные исследования и разработки, а также создание специализированных технопарков и инкубаторов способствовали росту сектора высоких технологий. Искусственный интеллект, биотехнологии и зеленые технологии стали основными драйверами экономического роста.
-
Город активно внедряет концепции устойчивого развития, что включает в себя проекты по улучшению городской инфраструктуры, экологии и общественного транспорта. Экологические инициативы, такие как переход на возобновляемые источники энергии и программы по снижению выбросов углерода, положительно сказываются на качестве жизни и создают новые рабочие места.
-
Культура и туризм стали важными секторами экономики. Москва привлекает миллионы туристов благодаря своим историческим достопримечательностям, культурным мероприятиям и фестивалям. Развитие туристической инфраструктуры, включая отели, транспорт и услуги, создает новые рабочие места и способствует экономическому росту.
-
Образование и кадры. Качество образования в Москве значительно возросло благодаря реформам в системе образования и активному сотрудничеству с международными учебными заведениями. Подготовка квалифицированных кадров для различных секторов экономики стала приоритетом, что способствует повышению конкурентоспособности города на глобальной арене.
Рост экономики Москвы в 2040 году — это результат комплексного подхода к развитию, основанного на инновациях, устойчивом развитии, международном сотрудничестве и высоком качестве жизни. Глядя в будущее, Москва продолжает стремиться к новым достижениям, укрепляя свои позиции как один из ведущих мировых мегаполисов.
Автор: Рината Ситникова
-
-
 @ f8a5df57:b7a58cd4
2024-11-21 12:12:32
@ f8a5df57:b7a58cd4
2024-11-21 12:12:32На пересечении искусства и технологий в столице России появился первый в своем роде "Театр будущего", где актеры — это не люди, а высокотехнологичные машины. Этот проект стал настоящей революцией в мире сценического искусства и привлек внимание зрителей со всего мира. Роботы-актеры способны не только воспроизводить текст, но и имитировать эмоции, движения и даже взаимодействовать с публикой. Каждое представление — это захватывающее зрелище, где сливаются современные технологии, искусственный интеллект и театральное мастерство. Создатель театра - режиссер-постановщик Александр Иванов уверен, что такой формат не только расширяет границы искусства, но и открывает новые горизонты для творчества. Первые отзывы зрителей уже поступили, и они полны восторга! Многие отмечают, что роботы-актеры привносят в спектакли особую атмосферу и оригинальность. Не упустите возможность стать частью этого исторического события! Приходите в новый театр и убедитесь сами, что будущее уже здесь! 🎉🤩
ТеатрБудущего #РоботыАктеры #Москва #ИскусствоИтехнологии
Автор: Рината Ситникова
-
 @ e968e50b:db2a803a
2024-11-21 17:13:54
@ e968e50b:db2a803a
2024-11-21 17:13:54I have a bandmate (not in the group pictured) who, as of last night, has now started telling people, "unless you want an earful, PLEASE don't ask the trombone player what his shirt means."
originally posted at https://stacker.news/items/777321
-
 @ 8947a945:9bfcf626
2024-10-17 07:33:00
@ 8947a945:9bfcf626
2024-10-17 07:33:00Hello everyone on Nostr and all my watchersand followersfrom DeviantArt, as well as those from other art platforms
I have been creating and sharing AI-generated anime girl fanart since the beginning of 2024 and have been running member-exclusive content on Patreon.
I also publish showcases of my artworks to Deviantart. I organically build up my audience from time to time. I consider it as one of my online businesses of art. Everything is slowly growing
On September 16, I received a DM from someone expressing interest in purchasing my art in NFT format and offering a very high price for each piece. We later continued the conversation via email.
Here’s a brief overview of what happened

- The first scammer selected the art they wanted to buy and offered a high price for each piece. They provided a URL to an NFT marketplace site running on the Ethereum (ETH) mainnet or ERC20. The site appeared suspicious, requiring email sign-up and linking a MetaMask wallet. However, I couldn't change the wallet address later. The minting gas fees were quite expensive, ranging from 0.15 to 0.2 ETH

-
The scammers tried to convince me that the high profits would easily cover the minting gas fees, so I had nothing to lose. Luckily, I didn’t have spare funds to purchase ETH for the gas fees at the time, so I tried negotiating with them as follows:
-
I offered to send them a lower-quality version of my art via email in exchange for the minting gas fees, but they refused.
- I offered them the option to pay in USD through Buy Me a Coffee shop here, but they refused.
- I offered them the option to pay via Bitcoin using the Lightning Network invoice , but they refused.
- I asked them to wait until I could secure the funds, and they agreed to wait.
The following week, a second scammer approached me with a similar offer, this time at an even higher price and through a different NFT marketplace website.
This second site also required email registration, and after navigating to the dashboard, it asked for a minting fee of 0.2 ETH. However, the site provided a wallet address for me instead of connecting a MetaMask wallet.
I told the second scammer that I was waiting to make a profit from the first sale, and they asked me to show them the first marketplace. They then warned me that the first site was a scam and even sent screenshots of victims, including one from OpenSea saying that Opensea is not paying.
This raised a red flag, and I began suspecting I might be getting scammed. On OpenSea, funds go directly to users' wallets after transactions, and OpenSea charges a much lower platform fee compared to the previous crypto bull run in 2020. Minting fees on OpenSea are also significantly cheaper, around 0.0001 ETH per transaction.
I also consulted with Thai NFT artist communities and the ex-chairman of the Thai Digital Asset Association. According to them, no one had reported similar issues, but they agreed it seemed like a scam.
After confirming my suspicions with my own research and consulting with the Thai crypto community, I decided to test the scammers’ intentions by doing the following
I minted the artwork they were interested in, set the price they offered, and listed it for sale on OpenSea. I then messaged them, letting them know the art was available and ready to purchase, with no royalty fees if they wanted to resell it.
They became upset and angry, insisting I mint the art on their chosen platform, claiming they had already funded their wallet to support me. When I asked for proof of their wallet address and transactions, they couldn't provide any evidence that they had enough funds.
Here’s what I want to warn all artists in the DeviantArt community or other platforms If you find yourself in a similar situation, be aware that scammers may be targeting you.
My Perspective why I Believe This is a Scam and What the Scammers Gain
From my experience with BTC and crypto since 2017, here's why I believe this situation is a scam, and what the scammers aim to achieve
First, looking at OpenSea, the largest NFT marketplace on the ERC20 network, they do not hold users' funds. Instead, funds from transactions go directly to users’ wallets. OpenSea’s platform fees are also much lower now compared to the crypto bull run in 2020. This alone raises suspicion about the legitimacy of other marketplaces requiring significantly higher fees.
I believe the scammers' tactic is to lure artists into paying these exorbitant minting fees, which go directly into the scammers' wallets. They convince the artists by promising to purchase the art at a higher price, making it seem like there's no risk involved. In reality, the artist has already lost by paying the minting fee, and no purchase is ever made.
In the world of Bitcoin (BTC), the principle is "Trust no one" and “Trustless finality of transactions” In other words, transactions are secure and final without needing trust in a third party.
In the world of Ethereum (ETH), the philosophy is "Code is law" where everything is governed by smart contracts deployed on the blockchain. These contracts are transparent, and even basic code can be read and understood. Promises made by people don’t override what the code says.
I also discuss this issue with art communities. Some people have strongly expressed to me that they want nothing to do with crypto as part of their art process. I completely respect that stance.
However, I believe it's wise to keep your eyes open, have some skin in the game, and not fall into scammers’ traps. Understanding the basics of crypto and NFTs can help protect you from these kinds of schemes.
If you found this article helpful, please share it with your fellow artists.
Until next time Take care
Note
- Both cyber security images are mine , I created and approved by AdobeStock to put on sale
- I'm working very hard to bring all my digital arts into Nostr to build my Sats business here to my another npub "HikariHarmony" npub1exdtszhpw3ep643p9z8pahkw8zw00xa9pesf0u4txyyfqvthwapqwh48sw
Link to my full gallery - Anime girl fanarts : HikariHarmony - HikariHarmony on Nostr - General art : KeshikiRakuen
-
 @ 07804b78:c375c543
2024-11-21 11:37:37
@ 07804b78:c375c543
2024-11-21 11:37:37Chef's notes
- The Premium Juku Curry comes individually packaged in single-serving portions, so it's convenient for using small amounts like in this recipe.
- Use your favorite spicy level of hot bean-curd soup base/curry roux.
Details
- 🍽️ Servings: 4
Ingredients
- 1 box of “Cook Do®” (Chinese seasoning mix) for Szechuan-style Mapo Tofu
- 2 servings of Premium Juku Curry
- 500g tofu
- 400g cut tomatoes
- 200g minced meat
- 80g garlic sprouts
- 100ml water
- 1 tablespoon sesame oil
- Cooked rice, enough for the number of people
Directions
- Slice the garlic shoots diagonally into 3-4cm pieces. Cut the tofu into bite-sized pieces.
- Heat the sesame oil in a frying pan and fry the minced meat over a medium heat.
- When the meat is about 80% cooked, add the garlic shoots and continue to fry, stirring, until the meat is fully cooked.
- Turn off the heat and add the Cook Do® Sichuan-style Mapo Tofu seasoning, and mix well.
- Turn the heat back on to medium, add the cut tomatoes and water, and bring to the boil, stirring gently.
- When it comes to a boil, turn the heat down to low, add the Premium Juku Curry, and stir well to dissolve.
- Once the curry has dissolved, add the tofu and cook until the tofu is warmed through.
-
 @ e88a691e:27850411
2024-10-11 13:17:16
@ e88a691e:27850411
2024-10-11 13:17:16An opinionated guide to Sauna.
Introduction
Updated from the Sauna, October 7th 2024
After years of experimenting with different sauna types, I’ve developed strong opinions on the subject. The purpose of this article is to share these opinions with anyone who is interested in them and, hopefully, help others get more out of their sauna experience.
I’m certain my opinions will offend some, including all the people who (in my view) are doing it wrong. I know that saunas are important to many cultures around the world and that my strongly held opinions may offend some of those cultures.
Mind you, although I grew up in South America, I do have a fair amount of slavic blood in me. When I was a child, my grandfather regularly took me with him to the shvitz. One of my fondest memories from this time was the “Scottish Bath”, which involves standing against the sauna wall, execution-style, so that someone can spray you with freezing water from a high pressure hose. I’ve never heard of this outside of South American and can’t attest to whether it has any real Scottish origins.
The various health claims about using a sauna are beyond the scope of this article. All I have to say is that, like many things in my life, like Bitcoin, the meat/keto diet, and fasting, I find sauna to be yet another cheat code to life: it’s a simple thing that just makes life a lot better. If you want a good primer on scientific health benefits of sauna, I recommend starting with this article by Rhonda Patric. She goes in depth.
To be clear, it should go without saying that I am not a medical expert or professional. None of the opinions below are, or should be interpreted as, medical advice. There are many people for whom sauna use is not recommended. It would be prudent for any sauna user to consult with his or her doctor before entering a sauna.
Thanks to S. for taking the time to do a very helpful first review of this article. And thanks to The Wife for helping make my words legible and helping me make time to sauna–I don’t know which sacrifice was bigger.
Banya or Nothing
When I talk about saunas, I’m talking about a sauna with a stove, either wood or electric, that allows for steam. I call this “Banya style”. To be clear, I’m distinguishing between saunas and steam baths. Steam baths have their own place, but they aren’t my thing and I don’t consider them saunas.
A breakdown of the main types of saunas may be helpful, so you know which to avoid:
- Wet saunas, which are typically cedar rooms with wood burning or electric stoves onto which you throw liquid to create steam (I call this “Banya style”);
- Dry saunas, which are typically cedar rooms with wood burning or electric stoves without added steam (like Korean style saunas); and
- Infrared saunas, which, unlike traditional saunas, don’t heat the surrounding air. Instead, they use infrared panels to warm your body directly.
In my opinion, it’s Banya style or nothing. I’m not a huge fan of dry saunas, and I don’t even bother with infrared saunas. Infrared is a fiat-shitcoin. I want steam!
How to Sauna
Sauna Etiquette
If you read no other part of this already-too-long-article, read this.
Saunas are social places. There are proper ways of being in a sauna with others, and there are ways to do it wrong. You don’t want to be the person who ruins it for everyone. Here are some important etiquette tips:
Silence vs. Chatting: It’s not a question of whether you have to stay silent in a sauna or if it’s ok to talk. It depends on the circumstances and who else is around. If you’re using a sauna that isn’t your own, ask the staff about the preferred custom. The noise level in a sauna differs depending on the group in the sauna at a particular time. If you do want to chat with others, there’s nothing wrong with that. But, pay attention to whether there are others in the sauna who'd prefer it quiet. And definitely do NOT be obnoxiously loud – yes, I’m looking at you bachelor(ette) group who just discovered the Russian Banya.
Coming and Going: People rotate in and out of the sauna at different paces, so there will be people coming and going during your shvitz. But there are ways to come and go that are considerate and proper.
Keep the f-ing door closed (which was the working title of this article). Once you leave, don’t come back inside moments later. Doing so disturbs your fellow sauna users, lets out the all-important steam, and prevents the sauna from reaching an appropriate temperature.
If you’re in the sauna with a group of friends, try to coordinate your comings and goings so you’re all on the same cycle.
If you can only last 5 min at a sauna, don’t go in too often at the risk of ruining it for others (assuming it’s not your own private sauna).
Be fast when closing the sauna door when you come or leave. Otherwise, you will get dirty looks from others and may even hear mumbles of “quick quick, fast fast” from a Gray Beard. And you will deserve it.
Never open the door right after someone puts water on the stove to make steam. It’s all about the steam. Don’t waste it.
Controlling the heat: if you can’t handle the heat in the sauna, don’t just turn the heat down, because it ruins it for others. Instead, go to a lower bench or get out and take your break. Saunas are meant to be hot. That’s the whole point.
Personal Hygiene: Shower before you go into the sauna. Don’t wear perfume, smelly deodorant, or fragrant lotions. Smells get amplified in a sauna. Have a towel under you, don't leave your drippings behind. Best yet, make a Z with your towel, this covers your butt and down under your feet.
Clothing: sauna is not a place for wearing clothing. It is a place to get back to nature. If you are shy, just wrap a towel around yourself. People ask if I don't feel awkward, the answer is no. Who cares, humans naked is not novel. In many countries, it is strictly forbidden to wear clothing or bring anything but a towel into the sauna. It's understandable that may not be possible in North American public saunas on mix gender "family" days. If you have to wear something, then wear something 100% cotton or marino wool. You don't want plastic being backed into your genitals. One more thing, leave the watch out as it gets hot and will burn you. Also, flip-flops/sandals, stay outside.
Some saunas sell body scrubs and masks for you to apply before or in the sauna. Note that once in the heat, these can get goopy and drippy and may melt into your eyes and mouth. So (in this opinionated guides’ wife’s opinion), they are better in theory than reality.
Adding Oils and scents: As discussed below, it can be nice to add certain oils and other scents to the steam. But if there are others in the sauna, ask first before you do.
Where and how to sit: Hot air rises. So, the higher benches are hotter and the lower benches are cooler. If you are a newbie, pick a lower bench so you don’t have to leave as quickly and open the door unnecessarily.
It’s great to lay down in the sauna, but if it gets crowded, sit up to make room for others.
When moving around to find your seat, don’t walk on the benches in your sandals. Leave your sandals outside the sauna or on the sauna floor.
Sauna Temperature
In most proper Russian style Banyas you will find temperatures of 80-95 degrees celsius, which, in my opinion, is the best range. Thats near your body. "Offical" on the dial will he 100-120C. But sometimes you want to take it a little easier or last a little longer in the sauna. In these cases, 65-85 at body, dial at 80-100. degrees celsius will do.
However, if your sauna is below 85 degrees celsius on the dial, you might as well just go hide under your bed sheets and not waste your time.
At some saunas in hotels, gyms, or spas, you may not be allowed to set the sauna as high as you’d like (see below). There are many tricks to circumvent these frustrating restrictions, but my legal counsel has advised me not to go into any details here.
Sauna Duration
The amount of time you spend in the sauna is a matter of personal preference and depends on the number of cycles you do (more on cycles, below).
For your first round, my opinion is that most people should try to last 15 minutes in the sauna. If a sauna is at the proper temperature, most people will struggle to stay inside any longer. If you can stay inside for 20-30 minutes, your sauna is probably too cold and/or there is not enough steam. Many saunas have hourglasses inside to keep time, and I’ve never seen a sauna hourglass with more than 15 minutes, which should be a good hint.
My preferred is;
Cold Plunge => Sauna 15 min => Cold Plunge => Hydrate with Salt & Water, Rest 5-10min => Sauna 15min => Cold Plunge => Hydrate with Salt & Water, Rest 5-10min => Sauna 15min => Cold Plunge => Hydrate with Salt & Water, Rest
if you can rest in the sun even better (no sunscreen poison please). You can add alcohol drinks to the hydration if you feel comfortable with that. But only add food after the last cycle.
For subsequent rounds, hydration starts to play a bigger role in how long you stay inside. Most people seem to last longer on their first round than on their second or third. If you can do 15 minutes on your second round, great. But 5-10 minutes is also fine.
Sauna Cycles
The traditional Russian Banya method (and in this writer’s opinion, the best method) is to do sauna cycles. Go into the sauna and just stay as long as you can take it (up to 15 minutes or so). Then take a cold shower and/or cold plunge (see below). Then robe-up and go relax with water, tea or beer. Once you start feeling “normal” again, repeat. For me, three cycles is the sweet spot. I’ll do more cycles if I’m spending the day at the Banya facility. If I’m at home, where I often sauna every other day, I find just one or two cycles does the trick. Sometimes I add a cycle or two on the weekend.
Occasionally, I like to go into the sauna as it’s warming up and before it reaches optimum heat (i.e. at around 60 degree celsius). This way, I can stay longer in the sauna for my first round (about 30-40 minutes). If I take this approach, I generally only do one more short round after my cold plunge.
Cold showers and plunges
In my experience, you want to take a cold shower or a cold plunge (or both, plunge is better) after the sauna cycle.After you come out of the sauna, immediately jump into cold plunge for a bit, i don't like to stay too long. Some Banya facilities will have a bucket filled with cold water that you can pull with a string to let the water pour over you, pull a couple times. The banyas may also have a cold pool of water into which you can plunge for a bit.

If I’m at my country place, after I get out of the sauna I jump into the cold lake. If it’s winter, I like to roll in the snow, which is satisfying. Some cultures would say that it’s not a real sauna experience unless you roll in at least one foot of snow.
After your cold shower or plunge, put on a warm robe and go relax before going back into the sauna. I like to relax for 5-20 minutes, depending on how much time I have. This allows the body’s temperature to decrease slowly. I do not recommend going directly back into the sauna after your cold plunge. If you don’t give yourself enough time after the cold plunge, you will overheat and won’t last very long when you return to the sauna.
Position
There really are no rules here. The way you position yourself in the sauna depends on your mood and preference, and there are many options. For example, you can sauna seated with your legs hanging down or with your knees up. You can lie down if there’s room. My favorite position is to lie down on my back with my legs up against the wall and, assuming the ceiling is low enough, with my feet stretched against the ceiling. This is a great way to stretch the hamstrings (check out stretching under “Sauna Activities”, below).
Choosing whether to sit on a higher bencher or lower bench is the best way to control the temperature you experience without adjusting the room temperature itself. You will notice the heat in the sauna increases exponentially every inch you go up. If you are struggling to stay in the sauna but don’t want to get out just yet, try moving down to a lower bench to last a little longer. Lying on the floor is the coolest spot and a great place for kids to start getting exposed to saunas.
There is no shame in going to lower benches or even the floor, there is only shame in opening the door before 15min
Getting Steamy
Without steam, the sauna would just be a sad, hot oven (I’m looking at you, infrared sauna).
The steam in the sauna has many benefits but most importantly it increases the thermal coupling of your body to the air and it feels great.
The amount of steam in the sauna is a matter of personal taste. You don’t want to make it into a steam room (remember, steam rooms are NOT saunas). But, you do want the sauna to be very moist. I find that two to four ladles of water in a mid-size sauna every five to seven minutes does the trick. Keep it between 50-60% humidity.
I keep a bucket of water in the sauna at all times so that I can continue to ladle water as I shvitz. Make sure to get a wood bucket and a metal ladle with a wooden handle. Wood ladles will crack, and if the handle is metal, it’ll burn you when you grab it.
If, when you enter the sauna, it’s already been on for a while, the wood is likely to already be wet and the sauna full of steam, so you may not need to add too much water. However, if you’ve just turned on the sauna and the wood walls are dry, you will need to ladle more water to make the air moist enough. If the sauna is too moist for comfort, open the door and let it dry out a bit (obviously, only do this in a private sauna).
Essential oils and even beer can all be added to the water to create scented steam. I recommend starting your sauna with just water, and add the scent as you get going.
You can try all sorts of different essential oils. I’ve tried everything from oak and cedar to tangerine and cinnamon (gag) essential oil. In the end, there are really only two oils that are worth it, in my opinion. The first is eucalyptus. I’ve experimented with different types of eucalyptus oil, and the variety you use makes a difference. My favorite is eucalyptus globulus. I also like diluted pine tar oil.
When you settle on your essential oil, add a healthy dose of the oil to the ladle filled with water. Never put the oil onto the oven directly. It’ll just burn.
In a few Russian facilities, I’ve seen Gray Beards pour Russian beer onto the oven and it was actually quite nice. It’s almost like being in a cozy bakery while you sweat
Some people like to place a salt brick or compressed solid blocks in their sauna from time to time. Put the salt block on the stove and pour water over it. The steam takes on a saltiness that feels nice. If a salt block is not available, you can get a cast iron teapot, fill it up with salt water, and place it on top of the stove.
And for my most important steam tip, I recommend using the “towel spin”. This is an effective and underrated technique to help circulate steam in the sauna. After creating steam, take your towel above your head and spin it around hard, like a ceiling fan. This movement works like a convection oven and spreads and equalizes the heat and steam throughout the room. It might make the folks sitting lower down in the sauna a little hotter, but that's what they’re there for, isn’t it?
Hydration
Being hydrated is important to having a positive sauna experience. You will lose a lot of your body’s water in the sauna. Ideally, start to hydrate well up to an hour before your sauna. I like to add a pinch of salt to my water to encourage water retention.
Do not bring any drinks into the sauna (the exception being a dedicated steam-beer, see above). Have your water or beverage when you’re outside the sauna, resting. If you find you need to drink water inside the sauna in order to cool yourself down, then it’s time for you to get out and allow your body a cool-down.
When you’re outside the sauna, don’t immediately down a glass of super cold water because you will cool down your internal body too fast. Personally, I like to drink warm tea after my first two cycles. After my second cycle, I enjoy a beer (pre-keto days), soup, or vodka drink. When non-keto, I do enjoy adult drinks in the cycles.
If you are doing a sauna while on a multi-day fast, you need to have water and salt, at a minimum. Otherwise, you will deplete your natural reserve of electrolytes and not be able to think straight.
Sauna Frequency
When it comes to frequency, if you are not in the equatorial heat do it every day. I now do mornings and end of day if I can. so 2x 2-3x cycles. In the summer, living in a hot & humid location, I sauna a lot less frequently. My desire to sauna is greatly diminished because I spend a lot of time in the sun and heat.
What to wear
Sauna Hat: I highly recommend wearing a Russian/Finish style wool hat when you’re inside the sauna. It may seem counterintuitive, but wearing a hat keeps your head cooler. An overheated head is not good for your brain. Wearing the hat stops you from overheating and lets you stay longer in the sauna. The temperature in a sauna is significantly hotter the higher in the room you are, and one’s head is at the top of the body (for most people). So protect your brain in style with a felt sauna hat. If you don’t have a felt sauna hat, buy one. They are easily found online. But in the meantime, you can wrap a dry towel around your head. Don’t forget to take your sauna hat off as you relax between cycles so your head can cool down.

Clothing: These days, many public saunas will have family days, men-only days, and women-only days. For obvious reasons, you’re only allowed to sauna naked if you’re attending one of the single-sex days.
If you’re at home, there’s no good reason to wear shorts or a bathing suit. Sauna naked. It's a lot more pleasant.
If you do wear clothing in the sauna, be careful with items with materials like metal or plastic attached. Things like pins, buttons, or string-ends will get very hot and probably burn you. Remember to take off any heat-conductive jewelry and leave your smart watch outside, as the heat will ruin its battery.
Don’t wear your robe inside the sauna. A robe is what you wear outside when relaxing or eating. If you wear it inside, you’ll overheat (and look like an idiot). Go ahead and sweat out that body shame robe-free. You can bring a towel into the sauna to sit on, if you want.
Shoes or sandals are highly recommended in public facilities. I mean, there are many people walking around wet. Ew. But keep your sandals outside the sauna itself, or on the sauna floor.
Sauna activities.
Don’t overthink it. Sitting in a sauna is activity enough, in my opinion. But there are some sauna activities you can do:
Veniks/Viht beating: these are bundles of leaves (commonly birch, oak, or eucalyptus) that are pre-soaked in hot water. Someone with both strength and capacity to exert themselves in the heat will beat your whole body with the leaves. This exfoliates your skin and also gets the plant oils to permeate your skin. And it’s very relaxing. If you’re at a sauna facility, don’t just grab any bundle you see lying around - that belongs to someone else and veniks aren’t shared. You have to bring your own or buy them at the front desk.
Stretching: this is a great activity to do in the sauna, but make sure to go very easy. Your muscles will be super warm and you don’t want to overdo it and hurt yourself.
Exercise or Sex: your heart better be in good shape if you try out these high intensity activities in the sauna. If you engage in the latter, you better be in your own home sauna. With respect to the former, I think doing some leg-ups can be very satisfying.
Phone use: If you’re at home, it’s nice to use your sauna time to shit-post on Twitter or read an article, if you feel like it. Just keep your phone close to the colder, lower parts near the floor or it’ll overheat and shut down. You can also place the phone outside of the air vent and play a podcast! The Bitcoin.review is great ;)
Napping: I don’t recommend this. If you fall asleep or pass out, you will probably die due to overheating or dehydration.
Chatting: Saunas are great places for conversations (subject to the caveats I address above). Note that nowadays, microphone modules are both very tiny and can withstand high temperatures, so it’s no longer recommended to reenact mafia movie sauna scenes.
Eating and Drinking: As discussed above, never have food or drink inside the sauna. But when you finish your sauna, take advantage of whatever snacks the facility offers. For Russian joints, the soups, fish roe and dry salty fish snacks are great. Again, don’t eat before your sauna; wait until you’re done. Some places will have bottled salty-ish lake water, and beer seems to be a good source of salts and re-hydration. Vodka drinks are nice sometimes, too. My favorites are vodka with beet juice and horseradish, vodka with pickle juice, or just a chilled shot of Zubrowka (vodka infused with bison grass). Teas are also very enjoyable post-sauna. I prefer non-caffeinated berry teas. Some Banyas even offer free tea to patrons.

Ready to Sweat It Out?
Thanks to this fantastic guide to sauna, you’re now feeling confident and excited to seek out a solid sauna. So where do you go?
Where to Find a Sauna
Spas: Spas are not the best place to have an optimal sauna experience. Saunas at spas are typically not hot enough and spas have annoying staff whose job it is to enforce idiotic rules and practices that prevent you from having a real sauna experience.
Gyms & Hotels: These are some of the worst places to sauna. For liability reasons, these saunas tend to be too cold and there are often mechanisms that prevent you from raising the temperature. Here, you’ll often see saunas with glass doors, which may look chic, but are inefficient and stupid because they don’t seal properly and leak steam. Gyms and hotels are high traffic areas, so people who don’t know what they are doing are constantly coming and going from the sauna, which, as we discussed, is a sauna no-no. If you still want to try the sauna at your gym or hotel, I recommend going in naked. It’ll deter people from joining you and ruining the little steam you managed to get going.
Traditional bath houses (Banyas): These usually offer a great experience because they deliver a super hot sauna, good cold baths and plunges, delicious food and drinks, and knowledgeable staff.
Home: Yes, you can build a great sauna in your own home! You can create a small space in your basement, turn a closet or cold room into a sauna, or just add an outdoor hut or barrel sauna in your backyard. This is the best way for you to control the whole experience and do it often. As with anything, the easier it is to access, the more you will do it.
Build it. They will Come
Many people have asked me for details about sauna building. If you’re ready to build your own personal home sauna, here are some important considerations.
Materials
Saunas are insulated rooms, most commonly finished with cedar tung and groove slats. Cedar is used because it doesn’t rot with moisture. You don’t want treated wood as it will release all the bad stuff that keeps the wood from rotting into the air when heated. Cedar interior is often placed over a vapor barrier, followed by insulation and then the outer wall. Many outdoor saunas are not insulated. They simply have a single layer of cedar 2x6 planks functioning as both the interior and exterior. Non-insulated saunas need much more heating power in the winter.
Structure
For indoor saunas, you may want to find a bricklayer to build something for you. Traditional facilities often have brick-lined rooms and very large wood-burning stoves.
You can buy prefab outdoor saunas, which are often sheds or barrels. After experimenting with both, I’ve concluded that barrel saunas are inferior, even though that’s what I have at my country property. This is because barrels have concave ceilings and inner walls. This means the benches are lower and the curve makes the topmost part of the ceiling (and the hottest part) the furthest from you, or inaccessible. The spinning towel trick really helps in the barrel.
When it comes to buying a sauna, go with the most traditional structure possible. They are based on thousands of years of evolution and knowledge.
Portable tent saunas are fun, but impractical because you have to set them up before each use.
Bench height inside the sauna is important. I think the top-most bench should be very near the ceiling. This way, when you’re lying down, you can use the ceiling to stretch the hamstrings. As a rule of thumb, bench length should allow you to lie down completely. It is also nice to have at least one lower bench for visitors or less intense sauna days.

Sauna Ovens
There are two main types of sauna ovens: wood burning and electrical (with gas heating being available, but not common). If the location you are building allows for it, go with electrical. It’s practical and easy to get going quickly. This means you will use it more often. Wood burning saunas are romantic and smell great, but it is a lot more work to get a fire going, especially in the winter.
Opt for oven sizes that are recommended or above recommended for the size of the sauna. A larger oven means more thermic inertia, more rocks for steam, and therefore less time to warm up the room. Bigger is better. The Scandinavians make the best quality ovens.
Oven controllers
There are two types of temperature control devices: the analog cooking-style or the digital type. I think, due to liability and safety, all ovens have a timer that max out at one hour.
The digital oven controllers are fantastic and I have one in the city in my basement sauna.
However, you have to consider your environment. For me, temperatures in the winter can reach below -30C and in the summer, over 40C. This massive range can take a toll on outdoor equipment and materials. For this reason, I opted for an analog controller for my outdoor sauna in the country, since the weather will likely ruin the electronics of the digital controller.
I would avoid ovens with analog pre-heat timers. They are great in theory, but the implementation is utter garbage. The timer won’t be precise and it’ll just lead to frustration, for example, when you thought you set the oven to start in three hours, but it actually started in two hours and already turned off.
Important Sauna Gear
Windows are nice to have, especially if you have a view to enjoy. Opt for at least a cedar door with a little window. Do not go with modern glass door styles. They are crap. They have gaps, no insulation, and let in too much light.
Saunas need thermometers and hygrometers (to measure humidity). The thermometers should be rated for saunas and be visible inside. This is both for safety and bragging rights.
I think having an hourglass inside your sauna is a must. Being able to know for sure how long you’ve been inside is important, since your sense of timing inside the sauna may be off depending on the state of your mind and body on a given day. You shouldn’t wear a watch inside the sauna, since it’ll overheat or break. Having a clock visible from the inside is also a good idea, especially if you sauna often and have a wife and kids who you don’t want to leave you.
Air circulation is an often-overlooked but important part of a sauna design. Saunas should not have stale air. The best sauna design creates natural “real convection” by placing an air intake under the oven wall and another at the top opposite wall. This allows fresh air to enter the sauna while in use. Be sure to add regulators, since you don’t want to cool the sauna or expel all steam. Without regulators you may get too much or too little air in. With too much air, you may cool the sauna down too much and/or lose too much steam.
Nice Things to Have
Lights are optional but welcome additions. It can be unpleasant to have no lighting at all, especially in an outdoor sauna on a cold, dark night. Lights should be warm-temperature and low power. I recommend an oven light, since they don’t sweat the heat (get it?) and are often low power.
Put a baking tray under your oven–thank me later.
Wood “pillows” for your head are nice and don’t get sweat-stained and stinky, like a fabric pillow.
Keep some extra felt hats near your sauna so when you or your guests forget their hat, you still have easy access to one.
I like to keep a couple of essential oils on the floor of the sauna, for easy access. If you keep the oils too high in the sauna, they’ll get too hot and spoil.
I place some duck boards over floor tiles in the sauna to prevent cold feet.
I also like to keep a small, natural broom inside the sauna to sweep up any dirt or leaves that come into the sauna on people’s feet.
Final words
As you can tell, I have some strong opinions when it comes to the proper way to enjoy a sauna. My hope is that my musings will help you to maximize your own sauna experience.. If you follow this guide, I’m certain you will benefit from and enjoy the sauna as much as I do and, just maybe, you too will develop your own strongly held opinions that will most definitely offend me.
Thanks for reading, please close the F-ing door.
ps, you can get a Bitcoin Honey Badger Sauna Hat here
- EOF
-
 @ 8d5ba92c:c6c3ecd5
2024-11-21 11:07:37
@ 8d5ba92c:c6c3ecd5
2024-11-21 11:07:37Looks like I need to add proper kids' socks to my designs 😋. Though my little guests didn’t mind the larger sizing, either! We Are All Satoshi.
https://i.nostr.build/qhzhGmidYjxDNVrp.jpg
TLDR: I started producing Bitcoin/Nostr-themed socks to help orange-pill people, to remind us of one of the first companies to accept Bitcoin back in 2011, and to bring smiles to people's faces. (More details can be found in the article on Habla News "Bitcoin ZOO + The Story of My Wardrobe!")
https://i.nostr.build/pChpYJzHtlWgOMfz.jpg
Until Adopting Bitcoin 2024, I hadn’t considered that kids might love them too. But during Bitcoin Para Niños, some amazing young participants noticed my bag full of designs. Among all the options, they chose the orange-and-blue "We Are All Satoshi" socks. Coincidence? Maybe 😋...
https://i.nostr.build/TXhI4g32RMCoVg4v.jpg
They didn’t mind the adult sizing and put them on immediately, which looked especially hilarious on the tiniest kids 😂
https://i.nostr.build/KT3FYbrxglHUvdD7.jpg
**This reminded me once again that kids are honest and curious in their choices. They don’t let small obstacles stop them and act with the purity of their hearts. ** 🧡⚡
https://i.nostr.build/DYWy3AfCUSVIKNfD.jpg
-
 @ b17c5987:85d68928
2024-11-21 10:24:16
@ b17c5987:85d68928
2024-11-21 10:24:16Our nation was founded on the basic idea that the people we elect run the government. That isn’t how America functions today. Most legal edicts aren’t laws enacted by Congress but “rules and regulations” promulgated by unelected bureaucrats—tens of thousands of them each year. Most government enforcement decisions and discretionary expenditures aren’t made by the democratically elected president or even his political appointees but by millions of unelected, unappointed civil servants within government agencies who view themselves as immune from firing thanks to civil-service protections.
Our nation was founded on the basic idea that the people we elect run the government. That isn’t how America functions today. Most legal edicts aren’t laws enacted by Congress but “rules and regulations” promulgated by unelected bureaucrats—tens of thousands of them each year. Most government enforcement decisions and discretionary expenditures aren’t made by the democratically elected president or even his political appointees but by millions of unelected, unappointed civil servants within government agencies who view themselves as immune from firing thanks to civil-service protections.
This is antidemocratic and antithetical to the Founders’ vision. It imposes massive direct and indirect costs on taxpayers. Thankfully, we have a historic opportunity to solve the problem. On Nov. 5, voters decisively elected Donald Trump with a mandate for sweeping change, and they deserve to get it.
President Trump has asked the two of us to lead a newly formed Department of Government Efficiency, or DOGE, to cut the federal government down to size. The entrenched and ever-growing bureaucracy represents an existential threat to our republic, and politicians have abetted it for too long. That’s why we’re doing things differently. We are entrepreneurs, not politicians. We will serve as outside volunteers, not federal officials or employees. Unlike government commissions or advisory committees, we won’t just write reports or cut ribbons. We’ll cut costs.
This is antidemocratic and antithetical to the Founders’ vision. It imposes massive direct and indirect costs on taxpayers. Thankfully, we have a historic opportunity to solve the problem. On Nov. 5, voters decisively elected Donald Trump with a mandate for sweeping change, and they deserve to get it.
President Trump has asked the two of us to lead a newly formed Department of Government Efficiency, or DOGE, to cut the federal government down to size. The entrenched and ever-growing bureaucracy represents an existential threat to our republic, and politicians have abetted it for too long. That’s why we’re doing things differently. We are entrepreneurs, not politicians. We will serve as outside volunteers, not federal officials or employees. Unlike government commissions or advisory committees, we won’t just write reports or cut ribbons. We’ll cut costs.
We are assisting the Trump transition team to identify and hire a lean team of small-government crusaders, including some of the sharpest technical and legal minds in America. This team will work in the new administration closely with the White House Office of Management and Budget. The two of us will advise DOGE at every step to pursue three major kinds of reform: regulatory rescissions, administrative reductions and cost savings. We will focus particularly on driving change through executive action based on existing legislation rather than by passing new laws. Our North Star for reform will be the U.S. Constitution, with a focus on two critical Supreme Court rulings issued during President Biden’s tenure.
In West Virginia v. Environmental Protection Agency (2022), the justices held that agencies can’t impose regulations dealing with major economic or policy questions unless Congress specifically authorizes them to do so. In Loper Bright v. Raimondo (2024), the court overturned the Chevron doctrine and held that federal courts should no longer defer to federal agencies’ interpretations of the law or their own rulemaking authority. Together, these cases suggest that a plethora of current federal regulations exceed the authority Congress has granted under the law.
DOGE will work with legal experts embedded in government agencies, aided by advanced technology, to apply these rulings to federal regulations enacted by such agencies. DOGE will present this list of regulations to President Trump, who can, by executive action, immediately pause the enforcement of those regulations and initiate the process for review and rescission. This would liberate individuals and businesses from illicit regulations never passed by Congress and stimulate the U.S. economy.
When the president nullifies thousands of such regulations, critics will allege executive overreach. In fact, it will be correcting the executive overreach of thousands of regulations promulgated by administrative fiat that were never authorized by Congress. The president owes lawmaking deference to Congress, not to bureaucrats deep within federal agencies. The use of executive orders to substitute for lawmaking by adding burdensome new rules is a constitutional affront, but the use of executive orders to roll back regulations that wrongly bypassed Congress is legitimate and necessary to comply with the Supreme Court’s recent mandates. And after those regulations are fully rescinded, a future president couldn’t simply flip the switch and revive them but would instead have to ask Congress to do so.
A drastic reduction in federal regulations provides sound industrial logic for mass head-count reductions across the federal bureaucracy. DOGE intends to work with embedded appointees in agencies to identify the minimum number of employees required at an agency for it to perform its constitutionally permissible and statutorily mandated functions. The number of federal employees to cut should be at least proportionate to the number of federal regulations that are nullified: Not only are fewer employees required to enforce fewer regulations, but the agency would produce fewer regulations once its scope of authority is properly limited. Employees whose positions are eliminated deserve to be treated with respect, and DOGE’s goal is to help support their transition into the private sector. The president can use existing laws to give them incentives for early retirement and to make voluntary severance payments to facilitate a graceful exit.
Conventional wisdom holds that statutory civil-service protections stop the president or even his political appointees from firing federal workers. The purpose of these protections is to protect employees from political retaliation. But the statute allows for “reductions in force” that don’t target specific employees. The statute further empowers the president to “prescribe rules governing the competitive service.” That power is broad. Previous presidents have used it to amend the civil service rules by executive order, and the Supreme Court has held—in Franklin v. Massachusetts (1992) and Collins v. Yellen (2021) that they weren’t constrained by the Administrative Procedures Act when they did so. With this authority, Mr. Trump can implement any number of “rules governing the competitive service” that would curtail administrative overgrowth, from large-scale firings to relocation of federal agencies out of the Washington area. Requiring federal employees to come to the office five days a week would result in a wave of voluntary terminations that we welcome: If federal employees don’t want to show up, American taxpayers shouldn’t pay them for the Covid-era privilege of staying home.
Finally, we are focused on delivering cost savings for taxpayers. Skeptics question how much federal spending DOGE can tame through executive action alone. They point to the 1974 Impoundment Control Act, which stops the president from ceasing expenditures authorized by Congress. Mr. Trump has previously suggested this statute is unconstitutional, and we believe the current Supreme Court would likely side with him on this question. But even without relying on that view, DOGE will help end federal overspending by taking aim at the $500 billion plus in annual federal expenditures that are unauthorized by Congress or being used in ways that Congress never intended, from $535 million a year to the Corporation for Public Broadcasting and $1.5 billion for grants to international organizations to nearly $300 million to progressive groups like Planned Parenthood.
The federal government’s procurement process is also badly broken. Many federal contracts have gone unexamined for years. Large-scale audits conducted during a temporary suspension of payments would yield significant savings. The Pentagon recently failed its seventh consecutive audit, suggesting that the agency’s leadership has little idea how its annual budget of more than $800 billion is spent. Critics claim that we can’t meaningfully close the federal deficit without taking aim at entitlement programs like Medicare and Medicaid, which require Congress to shrink. But this deflects attention from the sheer magnitude of waste, fraud and abuse that nearly all taxpayers wish to end—and that DOGE aims to address by identifying pinpoint executive actions that would result in immediate savings for taxpayers.
With a decisive electoral mandate and a 6-3 conservative majority on the Supreme Court, DOGE has a historic opportunity for structural reductions in the federal government. We are prepared for the onslaught from entrenched interests in Washington. We expect to prevail. Now is the moment for decisive action. Our top goal for DOGE is to eliminate the need for its existence by July 4, 2026—the expiration date we have set for our project. There is no better birthday gift to our nation on its 250th anniversary than to deliver a federal government that would make our Founders proud.
Mr. Musk is CEO of SpaceX and Tesla. Mr. Ramaswamy, a businessman, is author, most recently, of “Truths: The Future of America First” and was a candidate for the 2024 Republican presidential nomination. President-elect Trump has named them co-heads of the Department of Government Efficiency.
We are assisting the Trump transition team to identify and hire a lean team of small-government crusaders, including some of the sharpest technical and legal minds in America. This team will work in the new administration closely with the White House Office of Management and Budget. The two of us will advise DOGE at every step to pursue three major kinds of reform: regulatory rescissions, administrative reductions and cost savings. We will focus particularly on driving change through executive action based on existing legislation rather than by passing new laws. Our North Star for reform will be the U.S. Constitution, with a focus on two critical Supreme Court rulings issued during President Biden’s tenure.
In West Virginia v. Environmental Protection Agency (2022), the justices held that agencies can’t impose regulations dealing with major economic or policy questions unless Congress specifically authorizes them to do so. In Loper Bright v. Raimondo (2024), the court overturned the Chevron doctrine and held that federal courts should no longer defer to federal agencies’ interpretations of the law or their own rulemaking authority. Together, these cases suggest that a plethora of current federal regulations exceed the authority Congress has granted under the law.
DOGE will work with legal experts embedded in government agencies, aided by advanced technology, to apply these rulings to federal regulations enacted by such agencies. DOGE will present this list of regulations to President Trump, who can, by executive action, immediately pause the enforcement of those regulations and initiate the process for review and rescission. This would liberate individuals and businesses from illicit regulations never passed by Congress and stimulate the U.S. economy.
When the president nullifies thousands of such regulations, critics will allege executive overreach. In fact, it will be correcting the executive overreach of thousands of regulations promulgated by administrative fiat that were never authorized by Congress. The president owes lawmaking deference to Congress, not to bureaucrats deep within federal agencies. The use of executive orders to substitute for lawmaking by adding burdensome new rules is a constitutional affront, but the use of executive orders to roll back regulations that wrongly bypassed Congress is legitimate and necessary to comply with the Supreme Court’s recent mandates. And after those regulations are fully rescinded, a future president couldn’t simply flip the switch and revive them but would instead have to ask Congress to do so.
A drastic reduction in federal regulations provides sound industrial logic for mass head-count reductions across the federal bureaucracy. DOGE intends to work with embedded appointees in agencies to identify the minimum number of employees required at an agency for it to perform its constitutionally permissible and statutorily mandated functions. The number of federal employees to cut should be at least proportionate to the number of federal regulations that are nullified: Not only are fewer employees required to enforce fewer regulations, but the agency would produce fewer regulations once its scope of authority is properly limited. Employees whose positions are eliminated deserve to be treated with respect, and DOGE’s goal is to help support their transition into the private sector. The president can use existing laws to give them incentives for early retirement and to make voluntary severance payments to facilitate a graceful exit.
Conventional wisdom holds that statutory civil-service protections stop the president or even his political appointees from firing federal workers. The purpose of these protections is to protect employees from political retaliation. But the statute allows for “reductions in force” that don’t target specific employees. The statute further empowers the president to “prescribe rules governing the competitive service.” That power is broad. Previous presidents have used it to amend the civil service rules by executive order, and the Supreme Court has held—in Franklin v. Massachusetts (1992) and Collins v. Yellen (2021) that they weren’t constrained by the Administrative Procedures Act when they did so. With this authority, Mr. Trump can implement any number of “rules governing the competitive service” that would curtail administrative overgrowth, from large-scale firings to relocation of federal agencies out of the Washington area. Requiring federal employees to come to the office five days a week would result in a wave of voluntary terminations that we welcome: If federal employees don’t want to show up, American taxpayers shouldn’t pay them for the Covid-era privilege of staying home.
Finally, we are focused on delivering cost savings for taxpayers. Skeptics question how much federal spending DOGE can tame through executive action alone. They point to the 1974 Impoundment Control Act, which stops the president from ceasing expenditures authorized by Congress. Mr. Trump has previously suggested this statute is unconstitutional, and we believe the current Supreme Court would likely side with him on this question. But even without relying on that view, DOGE will help end federal overspending by taking aim at the $500 billion plus in annual federal expenditures that are unauthorized by Congress or being used in ways that Congress never intended, from $535 million a year to the Corporation for Public Broadcasting and $1.5 billion for grants to international organizations to nearly $300 million to progressive groups like Planned Parenthood.
The federal government’s procurement process is also badly broken. Many federal contracts have gone unexamined for years. Large-scale audits conducted during a temporary suspension of payments would yield significant savings. The Pentagon recently failed its seventh consecutive audit, suggesting that the agency’s leadership has little idea how its annual budget of more than $800 billion is spent. Critics claim that we can’t meaningfully close the federal deficit without taking aim at entitlement programs like Medicare and Medicaid, which require Congress to shrink. But this deflects attention from the sheer magnitude of waste, fraud and abuse that nearly all taxpayers wish to end—and that DOGE aims to address by identifying pinpoint executive actions that would result in immediate savings for taxpayers.
With a decisive electoral mandate and a 6-3 conservative majority on the Supreme Court, DOGE has a historic opportunity for structural reductions in the federal government. We are prepared for the onslaught from entrenched interests in Washington. We expect to prevail. Now is the moment for decisive action. Our top goal for DOGE is to eliminate the need for its existence by July 4, 2026—the expiration date we have set for our project. There is no better birthday gift to our nation on its 250th anniversary than to deliver a federal government that would make our Founders proud.
Mr. Musk is CEO of SpaceX and Tesla. Mr. Ramaswamy, a businessman, is author, most recently, of “Truths: The Future of America First” and was a candidate for the 2024 Republican presidential nomination. President-elect Trump has named them co-heads of the Department of Government Efficiency.
-
 @ e1d968f7:5d90f764
2024-11-21 16:15:56
@ e1d968f7:5d90f764
2024-11-21 16:15:56Behind Closed Doors: A Journey in Escorting
Day 7: The Physical and Emotional Side of Escorting
Escorting is often portrayed as purely physical, but the truth is, it’s equally emotional. The work involves more than just being present in the room—it’s about connecting, reading energy, and managing the mix of emotions that come with each encounter.
The Physical Side
The physical aspects of escorting are what most people imagine, but they rarely think about the preparation and upkeep it requires:
- Appearance: Every detail matters—skin, hair, nails, wardrobe, and even scent. The goal is to exude confidence and allure, tailored to the preferences of each client.
- Stamina: Whether it’s a dinner date, an overnight booking, or simply being engaging for hours on end, the job demands energy and focus.
- Comfort: Sometimes, the physicality isn’t glamorous. From staying composed in uncomfortable heels to dealing with repetitive motions, the job can be physically taxing.But the physical side is only half of the story.
The Emotional Side
What many don’t realise is how emotionally involved escorting can be. It’s not just about physical interaction—it’s about creating a connection, however fleeting.
- Emotional Labour: Clients come with their own needs and expectations. Some seek passion, while others need understanding or companionship. Meeting those needs often requires emotional presence and empathy.
- Vulnerability: Escorting can leave you feeling exposed, especially when dealing with clients who are emotionally complex or overly demanding. Learning to navigate this vulnerability is key.
- Emotional Boundaries: While you give a part of yourself to create an authentic experience, it’s crucial not to give too much. Balancing care with self-preservation is an ongoing challenge.
How I Manage It
Balancing the physical and emotional demands of the job takes effort and self-awareness. Here’s how I approach it:
- Self-Care: Regular exercise, a solid skincare routine, and a few indulgent treats keep me feeling physically prepared. Emotionally, journaling and decompressing after bookings help me process the experience.
- Compartmentalisation: While I bring authenticity to every encounter, I also maintain a mental line between my professional self and personal self.
- Support Network: Having someone to talk to—a trusted friend, mentor, or therapist—makes a world of difference when things get overwhelming.
The Challenges
There are days when the emotional weight of the job feels heavier than usual. Maybe it’s a client who reminds me of something painful from my own life. Maybe it’s feeling misunderstood or undervalued. Those moments are a stark reminder that while escorting can be empowering, it’s also deeply personal.
The Rewards
Despite the challenges, escorting has taught me a lot about myself—my resilience, my ability to connect with others, and my power to adapt. Those lessons are invaluable and often come from the very same clients who challenge me the most.
The Takeaway
Escorting is a blend of physical presence and emotional labour. Both require care, effort, and balance to ensure the work remains fulfilling rather than draining. It’s a constant learning curve, but one that has given me insight into the depths of human connection and my own strength.
Tomorrow, I’ll share the story of my very first client—a moment that tested everything I’d learned so far. Until then, remember: physical beauty fades, but the emotional connections we build are what truly linger.
Rebecca x
-
 @ e1d968f7:5d90f764
2024-11-21 16:12:26
@ e1d968f7:5d90f764
2024-11-21 16:12:26Every escort remembers their first client. It’s a defining moment—part nerve-wracking, part thrilling, and wholly unforgettable. For me, it wasn’t just about the money or the service; it was a lesson in navigating vulnerability, connection, and the unexpected.
The Build-Up
The anticipation started days before. I spent hours preparing—choosing the perfect outfit, rehearsing polite conversation, and imagining how it might unfold. I wasn’t just nervous; I was questioning everything. Would I know what to do? Would I feel comfortable? Would they?
When the day arrived, I felt a mix of excitement and dread. Meeting someone for the first time, especially in this context, felt like stepping into a new world.
Meeting Him
He was polite, soft-spoken, and visibly nervous—a relief, honestly, because it mirrored how I felt inside. I could see he’d put effort into his appearance, and there was an air of respect in the way he approached me.
We began with small talk, which helped break the tension. It was nothing extraordinary—questions about my day, a few jokes—but it grounded the moment. Suddenly, it wasn’t about being “an escort” and “a client.” It was just two people trying to connect.
Navigating the Experience
When the more intimate part of the booking began, I realised something important: it wasn’t just about the physical act. It was about creating an experience, an atmosphere where both of us felt at ease.
I leaned on what I’d prepared—staying calm, reading his cues, and ensuring I remained in control while being warm and attentive. There were moments of awkwardness, sure, but I quickly learned that those moments could be disarmed with humour or a reassuring touch.
What I Learned
That first client taught me more than I expected:
- Human Connection Matters: Escorting isn’t just a transaction; it’s about making someone feel valued and seen.
- Confidence is Key: Even when I wasn’t entirely sure of myself, projecting confidence helped both of us relax.
- Boundaries Are Crucial: From the beginning, I established what I was comfortable with, and he respected that. It set the tone for a positive experience.
The Aftermath
When the booking ended, I felt... different. It wasn’t just relief; it was pride. I’d done something completely outside my comfort zone, and I’d done it well. As I walked away, I realised this was more than a job—it was a skill, a craft I could refine over time.
The Takeaway
Your first client is a milestone. It’s where the nerves meet the unknown, and where you start to understand the depth of this profession. Looking back, I’m grateful for the experience. It wasn’t perfect, but it was mine—and it marked the beginning of a journey I’m proud of.
Tomorrow, I’ll explore how I built confidence and professionalism in those early days of escorting. Until then, remember: every first step, no matter how daunting, is a step toward growth.
Rebecca x
-
 @ e373ca41:b82abcc5
2024-11-21 09:50:06
@ e373ca41:b82abcc5
2024-11-21 09:50:06The last few years are unlikely to evoke positive associations for most people: corona madness, climate and trans ideology, a few wars in between and now the weather is also going crazy. You feel more reminded of the biblical plagues and the apocalypse than motivated to make positive changes to the system. It seems as if the world is in the hands of fanatical do-gooders and globalist social engineers. But the world is always in the hands of everyone. There is no responsibility for the future in the hands of some kind of “elite”, unless the citizens voluntarily leave it to them. Apocalypse literally means “unveiling”. In times of crisis, the core of reality is peeled out and all illusions fall away.
Golden times for system explorers
In turbulent times like these, unbreakable forest dwellers and resisters, prognosticators, esotericists and also system busters cavort. This is also a constant in history: times of crisis were often times of new beginnings. In knowledge revolutions, new knowledge inevitably mixed with new technology and also a new spiritual orientation towards the world. Before the outside world is created, it must be conceived internally. Around 500 years ago, the plague repeatedly cut new swathes through Europe, while at the same time Venice began its rise as a major trading power, the Medici banking system began to flourish and, a little later, so did art. This boom was preceded by something that at first glance seemed “boring”, such as the invention of double-entry bookkeeping by the monk Luca Pacioli at the end of the 15th century.
In the following century, the thinker Giordano Bruno moved from city to city in search of employment, and in the end, the system-breaker was burned as a heretic on the Campo de' Fiori in Rome. Meanwhile, astronomers, magicians, artists and alchemists bustled about at the court of the Habsburg Rudolf II in Prague. Some talked to angels, others tried their hand at producing gold. Those who ridicule alchemical experiments today as heresies should at least google how phosphorus and porcelain were discovered.
To be outmoded and unworldly means to be in search of something different. Great visionaries from Rudolf Steiner to Albert Einstein, Nikola Tesla and Richard Buckminster-Fuller have always known that the best way to change the system is to go outside the system and create something new from there. You don't change the old by fighting it. The best way to replace it is to think in new forms that make the old forms obsolete, said Buckminster-Fuller.
Brains moved the world more than the guillotine
Working on the old is like dancing with zombies. Creating the new, on the other hand, inevitably brings the old into competition with the system. If the new is better, the old system is obsolete. “Video killed the Radio Star” sang the Buggles in 1979 (the first clip of the MTV era) and they were just as right as Steve Jobs, who threw several industries overboard with the iPhone. What you previously needed 20 devices for, from dictation machines to telephones and “Walkmans”, you now had in your pocket. Thinking outside the system, which you don't learn within the system, combined with technology, is the sharpest knife in history when it comes to change. Brains moved more than the guillotine.
In today's world, everyone is a potential system changer. There has never been a time when the tools of change have been available to as many people as they are today. At the same time, we live in a time in which fewer people than ever before determine the fate of everyone. How does this fit together? There is an infinite systematic potential for change, and this lies solely with the people who have not yet made use of the available tools. But this wave is irreversibly set in motion; it is rolling and no one knows when it will turn into a tsunami. Free speech and critical journalism are under massive attack. With the Pareto Project we want to make censorship-resistant publishing the new standard. Today, we have the opportunity to consign the phenomenon of censorship to the landfill of history. Are you thinking along similar lines? What should the journalism of the future look like? Help us as a tester, migrate your content as a journalist or as a publication, support us as a developer or contribute your ideas: Kontakt@idw-europe.org
The great transformation
We are living in the midst of a quiet revolution, with quiet revolutionaries. Pavel Durov from Telegram would certainly have got on well with Giordano Bruno. Bitcoin inventor Satoshi Nakamoto might have felt at home at the court of Rudolf II in the past.
The path to change follows similar patterns of transformation. In the past, the power of the individual was seen as being sand in the gears of the system. “Man of labor, wake up! And recognize your power! All wheels stand still when your strong arm wills it,” wrote Georg Herwegh. Today, anyone can create their own little system. With Bitcoin, uncensorable money is already in circulation. The next big battle is over the uncensorability of information and it is currently underway. The best way to share centralized power, whether it's media power or a central bank cartel, is to distribute power through decentralized systems. This is essentially a feudalistic redistribution: the old feudal system is being replaced by the reassertion of power for the individual. What role will Switzerland, the country of countless inventions, play in this development? Hardly any other country is so innovative and therefore so well positioned for this system transformation. The most successful Bitcoin app in Europe already comes from Switzerland. The Relai app is an application for secure self-custody of Bitcoin, without the influence of others. Relai AG was recently voted the best crypto startup and second-best financial startup in the country, and is rushing from one growth success to the next. The company is currently preparing to conquer the European market even more effectively.
Gaining control for the individual means losing control for the old (money) system. This principle also applies in other sectors. For example, iVault AG from Thalwil is currently working on opening up the “sharing economy” market. Anyone who wants to easily rent out their e-bike, car or lawnmower to others, for example, can do so via the ivault.io app and benefit directly from their own sustainability. Here too, old centralized platforms are being disempowered and individuals are taking their fate into their own hands.
It's always the same pattern and principle: if you don't want to be managed by others, you have to manage yourself. This applies to money, information and even lawnmowers and e-bikes.
Want to learn more about the Pareto Project? We build a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Zap me, if you want to contribute (all Zaps go to the project).
-
 @ 705605d9:b4324038
2024-11-21 09:35:23
@ 705605d9:b4324038
2024-11-21 09:35:23Ежегодная Горноправдинская экологическая ярмарка, ставшая визитной карточкой высокоразвитой окружной столицы молочной промышленности, приняла сегодня высокопоставленных гостей из Китая. Делегация во главе с Чрезвычайным и Полномочным Послом КНР в России посетила выставку, продемонстрировавшую передовые технологии в сфере экологически чистого производства молочной продукции и устойчивого развития региона.

В ходе визита китайская делегация ознакомилась с работой крупнейших молочных предприятий Горноправдинска, провела переговоры с местными производителями и представителями администрации города. Стороны обсудили возможности экспорта высококачественной горноправдинской молочной продукции на китайский рынок и перспективы сотрудничества в сфере внедрения «зеленых» технологий. Ожидается, что в ближайшее время будут подписаны ряд важных соглашений о взаимовыгодном сотрудничестве.

Посол КНР, г-н Ли Вэй, высоко оценил достижения Горноправдинска в области экологической ответственности и инноваций в молочной промышленности. "Мы впечатлены масштабами и эффективностью вашего экологического проекта, - заявил г-н Ли на пресс-брифинге. - Горноправдинск служит прекрасным примером того, как можно сочетать экономический рост с заботой об окружающей среде. Мы заинтересованы в налаживании тесных торговых отношений и обмене опытом в области экологически чистого производства молочных продуктов".

-
 @ e6817453:b0ac3c39
2024-10-06 11:21:27
@ e6817453:b0ac3c39
2024-10-06 11:21:27Hey folks, today we're diving into an exciting and emerging topic: personal artificial intelligence (PAI) and its connection to sovereignty, privacy, and ethics. With the rapid advancements in AI, there's a growing interest in the development of personal AI agents that can work on behalf of the user, acting autonomously and providing tailored services. However, as with any new technology, there are several critical factors that shape the future of PAI. Today, we'll explore three key pillars: privacy and ownership, explainability, and bias.
1. Privacy and Ownership: Foundations of Personal AI
At the heart of personal AI, much like self-sovereign identity (SSI), is the concept of ownership. For personal AI to be truly effective and valuable, users must own not only their data but also the computational power that drives these systems. This autonomy is essential for creating systems that respect the user's privacy and operate independently of large corporations.
In this context, privacy is more than just a feature—it's a fundamental right. Users should feel safe discussing sensitive topics with their AI, knowing that their data won’t be repurposed or misused by big tech companies. This level of control and data ownership ensures that users remain the sole beneficiaries of their information and computational resources, making privacy one of the core pillars of PAI.
2. Bias and Fairness: The Ethical Dilemma of LLMs
Most of today’s AI systems, including personal AI, rely heavily on large language models (LLMs). These models are trained on vast datasets that represent snapshots of the internet, but this introduces a critical ethical challenge: bias. The datasets used for training LLMs can be full of biases, misinformation, and viewpoints that may not align with a user’s personal values.
This leads to one of the major issues in AI ethics for personal AI—how do we ensure fairness and minimize bias in these systems? The training data that LLMs use can introduce perspectives that are not only unrepresentative but potentially harmful or unfair. As users of personal AI, we need systems that are free from such biases and can be tailored to our individual needs and ethical frameworks.
Unfortunately, training models that are truly unbiased and fair requires vast computational resources and significant investment. While large tech companies have the financial means to develop and train these models, individual users or smaller organizations typically do not. This limitation means that users often have to rely on pre-trained models, which may not fully align with their personal ethics or preferences. While fine-tuning models with personalized datasets can help, it's not a perfect solution, and bias remains a significant challenge.
3. Explainability: The Need for Transparency
One of the most frustrating aspects of modern AI is the lack of explainability. Many LLMs operate as "black boxes," meaning that while they provide answers or make decisions, it's often unclear how they arrived at those conclusions. For personal AI to be effective and trustworthy, it must be transparent. Users need to understand how the AI processes information, what data it relies on, and the reasoning behind its conclusions.
Explainability becomes even more critical when AI is used for complex decision-making, especially in areas that impact other people. If an AI is making recommendations, judgments, or decisions, it’s crucial for users to be able to trace the reasoning process behind those actions. Without this transparency, users may end up relying on AI systems that provide flawed or biased outcomes, potentially causing harm.
This lack of transparency is a major hurdle for personal AI development. Current LLMs, as mentioned earlier, are often opaque, making it difficult for users to trust their outputs fully. The explainability of AI systems will need to be improved significantly to ensure that personal AI can be trusted for important tasks.
Addressing the Ethical Landscape of Personal AI
As personal AI systems evolve, they will increasingly shape the ethical landscape of AI. We’ve already touched on the three core pillars—privacy and ownership, bias and fairness, and explainability. But there's more to consider, especially when looking at the broader implications of personal AI development.
Most current AI models, particularly those from big tech companies like Facebook, Google, or OpenAI, are closed systems. This means they are aligned with the goals and ethical frameworks of those companies, which may not always serve the best interests of individual users. Open models, such as Meta's LLaMA, offer more flexibility and control, allowing users to customize and refine the AI to better meet their personal needs. However, the challenge remains in training these models without significant financial and technical resources.
There’s also the temptation to use uncensored models that aren’t aligned with the values of large corporations, as they provide more freedom and flexibility. But in reality, models that are entirely unfiltered may introduce harmful or unethical content. It’s often better to work with aligned models that have had some of the more problematic biases removed, even if this limits some aspects of the system’s freedom.
The future of personal AI will undoubtedly involve a deeper exploration of these ethical questions. As AI becomes more integrated into our daily lives, the need for privacy, fairness, and transparency will only grow. And while we may not yet be able to train personal AI models from scratch, we can continue to shape and refine these systems through curated datasets and ongoing development.
Conclusion
In conclusion, personal AI represents an exciting new frontier, but one that must be navigated with care. Privacy, ownership, bias, and explainability are all essential pillars that will define the future of these systems. As we continue to develop personal AI, we must remain vigilant about the ethical challenges they pose, ensuring that they serve the best interests of users while remaining transparent, fair, and aligned with individual values.
If you have any thoughts or questions on this topic, feel free to reach out—I’d love to continue the conversation!
-
 @ e6817453:b0ac3c39
2024-09-30 14:52:23
@ e6817453:b0ac3c39
2024-09-30 14:52:23In the modern world of AI, managing vast amounts of data while keeping it relevant and accessible is a significant challenge, mainly when dealing with large language models (LLMs) and vector databases. One approach that has gained prominence in recent years is integrating vector search with metadata, especially in retrieval-augmented generation (RAG) pipelines. Vector search and metadata enable faster and more accurate data retrieval. However, the process of pre- and post-search filtering results plays a crucial role in ensuring data relevance.
The Vector Search and Metadata Challenge
In a typical vector search, you create embeddings from chunks of text, such as a PDF document. These embeddings allow the system to search for similar items and retrieve them based on relevance. The challenge, however, arises when you need to combine vector search results with structured metadata. For example, you may have timestamped text-based content and want to retrieve the most relevant content within a specific date range. This is where metadata becomes critical in refining search results.
Unfortunately, most vector databases treat metadata as a secondary feature, isolating it from the primary vector search process. As a result, handling queries that combine vectors and metadata can become a challenge, particularly when the search needs to account for a dynamic range of filters, such as dates or other structured data.
LibSQL and vector search metadata
LibSQL is a more general-purpose SQLite-based database that adds vector capabilities to regular data. Vectors are presented as blob columns of regular tables. It makes vector embeddings and metadata a first-class citizen that naturally builds deep integration of these data points.
create table if not exists conversation ( id varchar(36) primary key not null, startDate real, endDate real, summary text, vectorSummary F32_BLOB(512) );It solves the challenge of metadata and vector search and eliminates impedance between vector data and regular structured data points in the same storage.
As you can see, you can access vector-like data and start date in the same query.
select c.id ,c.startDate, c.endDate, c.summary, vector_distance_cos(c.vectorSummary, vector(${vector})) distance from conversation where ${startDate ? `and c.startDate >= ${startDate.getTime()}` : ''} ${endDate ? `and c.endDate <= ${endDate.getTime()}` : ''} ${distance ? `and distance <= ${distance}` : ''} order by distance limit ${top};vector_distance_cos calculated as distance allows us to make a primitive vector search that does a full scan and calculates distances on rows. We could optimize it with CTE and limit search and distance calculations to a much smaller subset of data.
This approach could be calculation intensive and fail on large amounts of data.
Libsql offers a way more effective vector search based on FlashDiskANN vector indexed.
vector_top_k('idx_conversation_vectorSummary', ${vector} , ${top}) ivector_top_k is a table function that searches for the top of the newly created vector search index. As you can see, we could use only vector as a function parameter, and other columns could be used outside of the table function. So, to use a vector index together with different columns, we need to apply some strategies.
Now we get a classical problem of integration vector search results with metadata queries.
Post-Filtering: A Common Approach
The most widely adopted method in these pipelines is post-filtering. In this approach, the system first retrieves data based on vector similarities and then applies metadata filters. For example, imagine you’re conducting a vector search to retrieve conversations relevant to a specific question. Still, you also want to ensure these conversations occurred in the past week.

Post-filtering allows the system to retrieve the most relevant vector-based results and subsequently filter out any that don’t meet the metadata criteria, such as date range. This method is efficient when vector similarity is the primary factor driving the search, and metadata is only applied as a secondary filter.
const sqlQuery = ` select c.id ,c.startDate, c.endDate, c.summary, vector_distance_cos(c.vectorSummary, vector(${vector})) distance from vector_top_k('idx_conversation_vectorSummary', ${vector} , ${top}) i inner join conversation c on i.id = c.rowid where ${startDate ? `and c.startDate >= ${startDate.getTime()}` : ''} ${endDate ? `and c.endDate <= ${endDate.getTime()}` : ''} ${distance ? `and distance <= ${distance}` : ''} order by distance limit ${top};However, there are some limitations. For example, the initial vector search may yield fewer results or omit some relevant data before applying the metadata filter. If the search window is narrow enough, this can lead to complete results.
One working strategy is to make the top value in vector_top_K much bigger. Be careful, though, as the function's default max number of results is around 200 rows.
Pre-Filtering: A More Complex Approach
Pre-filtering is a more intricate approach but can be more effective in some instances. In pre-filtering, metadata is used as the primary filter before vector search takes place. This means that only data that meets the metadata criteria is passed into the vector search process, limiting the scope of the search right from the beginning.
While this approach can significantly reduce the amount of irrelevant data in the final results, it comes with its own challenges. For example, pre-filtering requires a deeper understanding of the data structure and may necessitate denormalizing the data or creating separate pre-filtered tables. This can be resource-intensive and, in some cases, impractical for dynamic metadata like date ranges.

In certain use cases, pre-filtering might outperform post-filtering. For instance, when the metadata (e.g., specific date ranges) is the most important filter, pre-filtering ensures the search is conducted only on the most relevant data.
Pre-filtering with distance-based filtering
So, we are getting back to an old concept. We do prefiltering instead of using a vector index.
WITH FilteredDates AS ( SELECT c.id, c.startDate, c.endDate, c.summary, c.vectorSummary FROM YourTable c WHERE ${startDate ? `AND c.startDate >= ${startDate.getTime()}` : ''} ${endDate ? `AND c.endDate <= ${endDate.getTime()}` : ''} ), DistanceCalculation AS ( SELECT fd.id, fd.startDate, fd.endDate, fd.summary, fd.vectorSummary, vector_distance_cos(fd.vectorSummary, vector(${vector})) AS distance FROM FilteredDates fd ) SELECT dc.id, dc.startDate, dc.endDate, dc.summary, dc.distance FROM DistanceCalculation dc WHERE 1=1 ${distance ? `AND dc.distance <= ${distance}` : ''} ORDER BY dc.distance LIMIT ${top};It makes sense if the filter produces small data and distance calculation happens on the smaller data set.
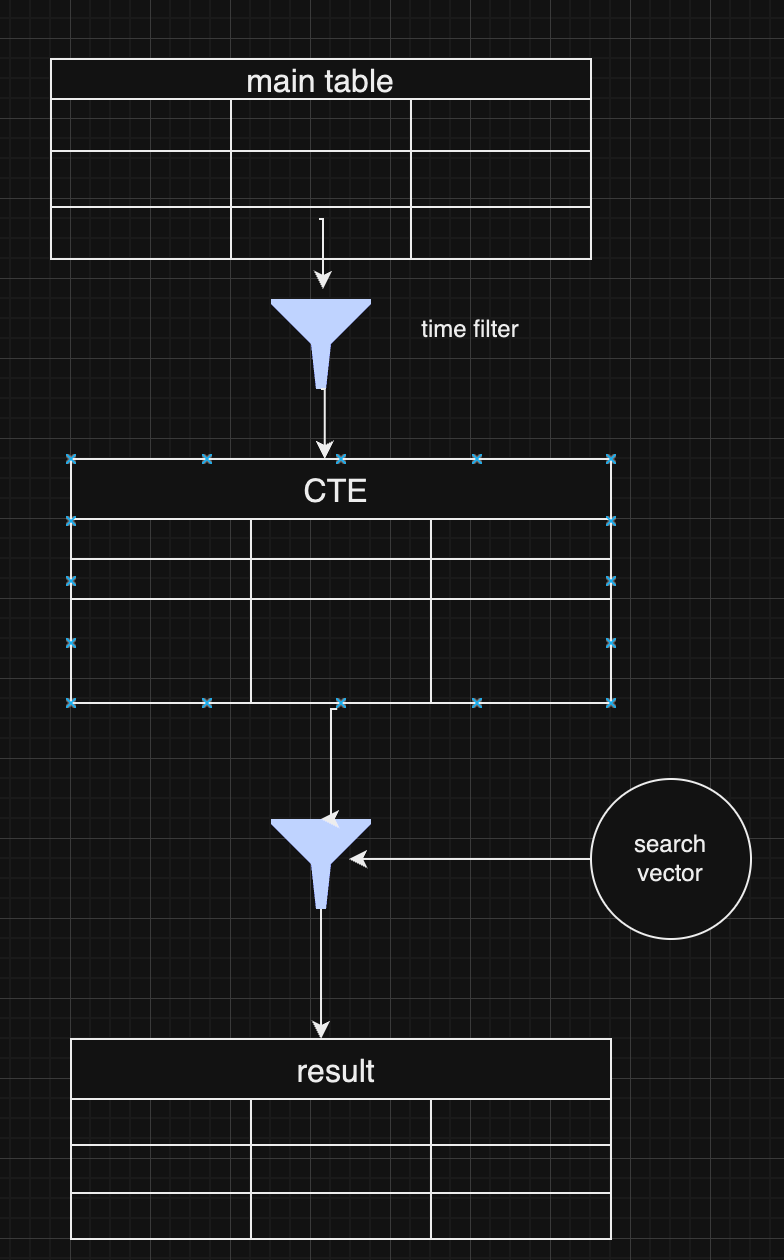
As a pro of this approach, you have full control over the data and get all results without omitting some typical values for extensive index searches.
Choosing Between Pre and Post-Filtering
Both pre-filtering and post-filtering have their advantages and disadvantages. Post-filtering is more accessible to implement, especially when vector similarity is the primary search factor, but it can lead to incomplete results. Pre-filtering, on the other hand, can yield more accurate results but requires more complex data handling and optimization.
In practice, many systems combine both strategies, depending on the query. For example, they might start with a broad pre-filtering based on metadata (like date ranges) and then apply a more targeted vector search with post-filtering to refine the results further.
Conclusion
Vector search with metadata filtering offers a powerful approach for handling large-scale data retrieval in LLMs and RAG pipelines. Whether you choose pre-filtering or post-filtering—or a combination of both—depends on your application's specific requirements. As vector databases continue to evolve, future innovations that combine these two approaches more seamlessly will help improve data relevance and retrieval efficiency further.
-
 @ 9ff58691:0bf6c134
2024-11-21 07:34:06
@ 9ff58691:0bf6c134
2024-11-21 07:34:06Друзья, подводим итоги насыщенного культурного сезона в нашем любимом городе Кургане! 2040 год стал настоящим триумфом для местной арт-сцены.
✨ Выставочный сезон в Курганском музее современного искусства побил все рекорды посещаемости. Жители и гости города с восторгом приняли экспозиции, посвященные цифровому искусству и технологиям виртуальной реальности. Особенно популярной стала выставка "Киберпанк: город будущего", где посетители могли погрузиться в завораживающие миры, созданные при помощи ИИ-генераторов изображений.
🎨 Настоящим украшением города стали новые арт-объекты, появившиеся благодаря конкурсу среди молодых архитекторов. Победителем стал Максим Ветров с его концептуальной скульптурой "Связь поколений", сочетающей в себе элементы классической архитектуры и футуристические 3D-компоненты.
"Для меня большая честь, что мой проект был выбран для воплощения в Кургане. Я хотел создать арт-объект, который бы отражал преемственность традиций и устремленность в будущее нашего города", - комментирует Максим.
🏆 Кульминацией года стал международный конкурс на лучший дизайн-проект нового культурного центра Кургана. Жюри высоко оценило смелые идеи и технологичные решения, представленные участниками. Победителем стала команда молодых архитекторов из Москвы, которые предложили концепцию "умного" здания, адаптирующегося под нужды посетителей с помощью ИИ-систем.
Культурная жизнь Кургана с каждым годом становится все ярче и разнообразнее. Мы с нетерпением ждем новых свершений в 2041 году!
Автор: Елизавета Медведева
-
 @ 9358c676:9f2912fc
2024-09-24 12:29:11
@ 9358c676:9f2912fc
2024-09-24 12:29:11OBJECTIVES
To establish a guideline for the management of Acute Community-Acquired Pneumonia (CAP) in our center, for both outpatient and hospitalized patients, with the aim of:
- Reducing morbidity and mortality associated with the condition.
- Improving the quality of medical care and optimizing hospital resources.
- Delaying the progression of antimicrobial resistance.
SCOPE
All patients over 16 years of age diagnosed with Acute Community-Acquired Pneumonia who are being followed by our institution in an outpatient or inpatient setting.
RESPONSIBILITIES
Physicians from the Medical Clinic, Medical Emergency, Coronary Unit, and Intensive Care Service. Nursing Coordination. Pharmacy Service. Infection Control Committee.
REFERENCES AND BIBLIOGRAPHY
- Community-Acquired Pneumonia in Adults. Recommendations for its management. Lopardo et al. MEDICINA (Buenos Aires) 2015; 75: 245-257. Argentine Society of Infectiology. ISSN 0025-7680
- Diagnosis and Treatment of Adults with Community-acquired Pneumonia. An Official Clinical Practice Guideline of the American Thoracic Society and Infectious Diseases Society of America. 2019. American Journal of Respiratory and Critical Care Medicine Volume 200 Number 7 | October 1, 2019. DOI: 10.1164 rccm.201908-1581ST
- ERS/ESICM/ESCMID/ALAT guidelines for the management of severe community-acquired pneumonia. Intensive Care Med (2023) 49:615–632 https://doi.org/10.1007/s00134-023-07033-8
- Antimicrobial resistance. WHO. https://www.who.int/news-room/fact-sheets/detail/antimicrobial resistance
- Internal Medicine. Farreras-Rosman. Volume I. Elsevier. 2008 Edition.
- Considerations for the Responsible Use of Antibiotics in COVID-19. Argentine Society of Infectiology. 2020. https://drive.google.com/file/d/1BmXD5x6rEpSqDIc8urccdqLcZKkP3U7X/view
- Penicillin Allergy. Castells M. New England Journal of Medicine, 381(24), 2338–2351. doi:10.1056 nejmra1807761
INTRODUCTION
Pneumonia is one of the leading causes of morbidity and mortality worldwide, affecting patients of all ages and with various risk factors. Proper management in both outpatient and hospital settings is crucial for improving clinical outcomes and reducing associated complications.
This document aims to standardize and optimize the treatment of pneumonia based on the most current evidence and recommendations from leading scientific organizations. It seeks to be a practical tool for healthcare professionals, providing a clear and concise approach to the diagnosis, treatment, and follow-up of patients with pneumonia.
FOUNDATIONS. HOSPITAL SITUATION ANALYSIS:
- Pneumonias represent a significant burden on the healthcare system due to their high prevalence and potential severity, underscoring the need for a standardized approach.
- A clinical guideline facilitates decision-making, ensuring that all healthcare professionals follow a uniform protocol that integrates best practices, thereby reducing variability in treatments. This allows for better resource utilization, optimizing antibiotic use and reducing the emergence of antimicrobial resistance.
- Antimicrobial resistance has been proposed by the World Health Organization (WHO) and related organizations as the leading cause of death and hospital expenditure by the year 2050.
- Pneumonias in our center, in their various presentations, have shown significant prevalence in hospitalizations according to measurements taken in 2024.
- In our center, antibiotics, as a whole, have been the main source of financial losses related to drugs during the billing cycle from June 2023 to July 2024.
EPIDEMIOLOGICAL SITUATION:
Pneumonias represent a global incidence of 1.26 cases per 1000 inhabitants. It has been documented in some centers that this incidence can increase in patients over 65 years of age, representing 34 cases per 1000 inhabitants. Outpatient mortality varies between 0.1% and 5%, but can reach up to 50% in hospitalized patients, especially those requiring Intensive Care Unit stay.
The main risk factors for developing pneumonia are:
- Chronic Heart Disease.
- Chronic Respiratory Disease.
- Chronic Kidney Disease.
- Advanced-stage HIV infection.
- Immunosuppressed. Solid Organ Transplant. Hematopoietic Stem Cell Transplantation.
- Diabetes mellitus.
- Neoplasms.
- Smoking.
- Chronic use of Corticosteroids or Proton Pump Inhibitors.
- Multiple Myeloma and Hypogammaglobulinemia.
- Anatomical or Functional Asplenia.
The main causative agents of acute community-acquired pneumonia in our setting are:
- Respiratory Viruses (Influenza, SARS-CoV2, RSV).
- Streptococcus pneumoniae.
- Haemophilus influenzae.
- Staphylococcus aureus.
- Mycoplasma pneumoniae and Chlamydophila pneumoniae.
It should be noted that Streptococcus pneumoniae shows a good sensitivity pattern to penicillin and continues to be the most frequent causative microorganism. Haemophilus influenzae only shows beta-lactamase production in 10% to 23% of cases. Staphylococcus aureus in our setting has a low incidence of methicillin resistance, although this possibility should be considered in certain situations and severe clinical presentations. Given these considerations, beta-lactams remain the first-line treatment.
Regarding Pseudomonas aeruginosa isolates, they will only be relevant in patients with risk factors such as bronchiectasis, cystic fibrosis, prior treatment with corticosteroids, or broad-spectrum antibiotics.
Emerging pathogens of some relevance include the eventual emergence of cases caused by Leptospira interrogans, Legionella pneumophila, and Hantavirus. These cases should always be associated with a specific epidemiological link.
DIAGNOSIS
The diagnosis of pneumonia is based on clinical and imaging criteria. For the diagnosis of Acute Community-Acquired Pneumonia, we will consider:
Symptoms and Clinical Signs (at least 1 of the following): * Fever. * Altered general condition. * Cough. * Sputum production. * Chest pain. * Dyspnea. * Hemoptysis.
plus
Radiopacity on Chest X-ray (Alveolar consolidation with or without air bronchogram, interstitial pattern, bronchiectasis, cavitation, pleural effusion, new radiopacity, etc.). It is always recommended to request both frontal and lateral views.
Chest CT remains a method with greater sensitivity and specificity for evaluating lung parenchyma compared to conventional X-ray in infectious pathology. However, a simple chest X-ray is an adequate method for the initial evaluation of the condition and its complications, which is why a CT scan is not recommended as an initial method for evaluating pneumonia and should always be preceded by a conventional chest X-ray.
CT studies should be considered in the following situations:
- Respiratory failure.
- Evaluation or suspicion of differential diagnoses to Acute Community-Acquired Pneumonia.
- Evaluation or suspicion of complications of Acute Community-Acquired Pneumonia.
- Evaluation of radiological patterns that are not entirely clear on the chest X-ray.
CHOICE OF CARE SITE AND TREATMENT
For the choice of care site and treatment of pneumonia, it is recommended to complement clinical criteria with validated mortality scores associated with risk factors and clinical status.
CURB-65 (1 point for each item): * Confusion * Elevated urea greater than 90 mg/dl * Respiratory rate greater than 30/minute * Systolic blood pressure < 90 mmHg or diastolic blood pressure < 60 mmHg * Age equal to or greater than 65 years
Results:
- Groups 0 to 1: Outpatient management.
- Groups 1-2: Admission to General Ward.
- Groups 3-5: Admission to Intensive Care Unit.
- Appendix: A pulse oximetry reading of less than 92% is recommended as an independent factor for inpatient management under expert recommendation to complement the score.
COMPLEMENTARY STUDIES AND CULTURE SAMPLING
Once the diagnosis is completed, the patient's risk stratification and the choice of admission site are made, the following complementary studies and culture sampling are recommended to proceed with the patient's study during treatment.
Outpatient patient: * Pulse Oximetry. * Laboratory routine (complete blood count, glucose, urea, creatinine, liver function tests).
Inpatient patient in general ward: * Pulse Oximetry. * Laboratory routine (complete blood count, glucose, urea, creatinine, liver function tests). Acid-base status if pulse oximetry is less than 92%. * Sputum sample (Gram stain, culture, antibiogram). * Blood cultures. * In the presence of pleural effusion: Thoracentesis. Physical-chemical study for Light's Criteria. Direct and Culture of Pleural Fluid.
Inpatient patient in intensive care unit: * Pulse Oximetry. * Laboratory routine (complete blood count, glucose, urea, creatinine, liver function tests) plus acid-base status. * Sputum sample (Gram stain, culture, antibiogram). Tracheal aspirate, Mini-BAL, or BAL sampling for patients requiring ARM upon admission. * Blood cultures. * Urinary antigen for detection of Streptococcus pneumoniae, if available in microbiology. * In the presence of pleural effusion: Thoracentesis. Physical-chemical study for Light's Criteria. Direct and Culture of Pleural Fluid.
Special considerations for Viral Pneumonias: * We recommend performing a viral panel for Influenza A/B for any pneumonia presenting at least 1 risk factor mentioned during periods of viral circulation in the community. * We recommend performing a viral panel for SARS-CoV2 for any pneumonia presenting at least 1 risk factor mentioned during periods of viral circulation in the community or having epidemiological criteria of a suspected COVID-19 case. * The Infection Control Committee will timely inform based on the National Epidemiological Bulletin about the presence of circulating respiratory viruses in our setting.
Special considerations for Atypical Pneumonias and HIV Testing: * We recommend serological testing for IgM/IgG for Chlamydia and Mycoplasma for any pneumonia presenting a subacute evolution at the time of clinical presentation or clinical-radiological dissociation in its presentation. * In the suspicion of pneumonia caused by emerging pathogens (Legionella pneumophila, Leptospira interrogans, Hantavirus), consider the necessary epidemiological link as a prior epidemiological background before requesting specific diagnostic tests. * HIV testing is recommended for all pneumonias, with special emphasis on those that do not present the conventional risk factors mentioned.
ANTIMICROBIAL TREATMENT AND DURATION OF TREATMENT:
Directed antimicrobial treatment will be based on the present risk factors and the choice of care site and treatment.
Outpatient patient <65 years and without risk factors:
First choice: * Amoxicillin 875mg/12h orally for 5-7 days.
Scheme for history of allergy to Beta-Lactams: * Clarithromycin 500mg/12h orally for 5 days or * Azithromycin 500-1000mg/day for 5 days.
Outpatient patient >65 years or with at least 1 risk factor:
First choice: * Amoxicillin-Clavulanate 1g/12h orally for 7 days.
Scheme for history of allergy to Beta-Lactams: * Clarithromycin 500mg/12h orally for 5 days or * Azithromycin 500-1000mg/day orally for 5 days.
Inpatient patient in General Ward <65 years and without risk factors:
First choice: * Ampicillin-Sulbactam 1.5g/6h IV +/- Clarithromycin 500mg/12h orally/IV for 5-7 days.
Scheme for history of allergy to Beta-Lactams: * Ceftriaxone 1g/day IV for 5-7 days.
Inpatient patient in General Ward >65 years or with at least 1 risk factor:
First choice: * Ampicillin-Sulbactam 1.5g/6h IV for 7 days +/- Clarithromycin 500mg/12h orally/IV for 5 days.
Scheme for history of allergy to Beta-Lactams: * Ceftriaxone 1g/day IV for 7 days.
Inpatient patient in Intensive Care Unit:
First choice: * Ampicillin-Sulbactam 1.5g/6h IV for 7 days +/- Clarithromycin 500mg/12h orally/IV for 5 days.
Scheme for history of allergy to Beta-Lactams: * Ceftriaxone 1-2g/day IV for 7 days.
Special Considerations for Inpatients:
Scheme for risk factors for Pseudomonas aeruginosa*: * Piperacillin/Tazobactam 4.5g/6h IV or Cefepime 2g/8h IV for 7 days +/- Clarithromycin 500mg/12h orally/IV for 5 days.
Scheme for risk factors for Methicillin-Resistant Staphylococcus aureus**: * Add to conventional scheme: Vancomycin 15-20mg/kg/8-12h IV +/- Clindamycin 600mg/8h IV for 7-14 days.
Aspiration Pneumonia:
First choice: * Ampicillin-Sulbactam 1.5g/6h IV for 5-7 days.
*Risk factors for Pseudomonas aeruginosa: Bronchiectasis, cystic fibrosis, prior treatment with corticosteroids or broad-spectrum antibiotics. Documented isolates in respiratory cultures of Pseudomonas aeruginosa.
**Risk factors for Methicillin-Resistant Staphylococcus aureus: Previously healthy young patients with severe, necrotizing, and rapidly progressive pneumonia, cavitary infiltrates, hemoptysis, prior influenza, intravenous drug users, rash, leukopenia, recent or concomitant skin and soft tissue infections.
The routine use of corticosteroids in pneumonia is not recommended.
CONSIDERATIONS ON ANTIMICROBIALS IN VIRAL AND ATYPICAL PNEUMONIAS:
In the case of a concomitant antigen test or PCR for Influenza A/B or SARS-CoV2, the following treatment recommendations are made:
Influenza Virus A/B:
First choice: * Oseltamivir 75mg every 12 hours orally for 5 days. Other considerations: * In cases of Respiratory Failure in ARM or Obesity: Oseltamivir 150mg every 12 hours orally for 5 days. * Concomitant antimicrobial treatment is recommended as there is documented frequent association of Influenza Virus and Streptococcus pneumoniae.
COVID-19: * First choice is conventional treatment with dexamethasone 8 mg IV for 10 days in the event of respiratory failure. * Routine antimicrobial treatment is not recommended for COVID-19; therefore, upon a positive SARS-CoV2 test, it is recommended to discontinue antimicrobials.
Consider maintaining concomitant antimicrobial treatment only in suspected bacterial infection due to severe presentation: * Focal alveolar consolidation +/- air bronchogram in imaging studies plus 1 of the following: sepsis, risk factors, and/or immunosuppression.
Atypical Pneumonias with Seroconversion for Chlamydia or Mycoplasma:
First choice: * Clarithromycin 500mg every 12 hours IV/orally for 14 days. * Azithromycin 500-1000mg/day IV/orally for 14 days. * Doxycycline 100mg every 12 hours IV/orally for 14 days.
CONSIDERATIONS ON PENICILLIN AND OTHER BETA-LACTAM ALLERGIES:
Patients who report penicillin allergy are often misclassified. It is documented that more than 95% of patients who report penicillin allergy can receive beta-lactams without any complications. Additionally, penicillin hypersensitivity diminishes over the years.
Allergy to one beta-lactam does not imply the impossibility of using the entire spectrum of beta-lactams, as there are only a few cases of cross-hypersensitivity.
Therefore, we recommend the safe use of beta-lactams except in cases of a reported or documented history of severe allergy to penicillin (anaphylaxis).
In doubtful cases or confirmed allergy events during hospitalization, a consultation with an Allergy Specialist is available to evaluate the case.
FOLLOW-UP IN OUTPATIENT TREATMENT MODALITY
Patients undergoing pneumonia treatment in an outpatient setting can continue their treatment at home, considering advising them to seek further consultation in case of alarm signs (fever that does not subside after 48 to 72 hours, dyspnea, hemoptysis, chest pain, etc.). Nevertheless, it is good practice to consider a follow-up consultation in the emergency department or clinic after 48 to 72 hours of starting antibiotic therapy.
It is not routinely recommended to repeat a chest X-ray or CT scan to evaluate the evolution of pneumonia under outpatient treatment. Only in the case of suspected complications or unfavorable evolution. A follow-up at the end of treatment with the primary care physician is suggested.
FOLLOW-UP IN INPATIENT TREATMENT MODALITY
For hospitalized patients, we should consider transitioning from parenteral medication to oral when the following conditions are met
- Completion of 48 hours of parenteral treatment.
- Presence of a 24-hour afebrile period, with hemodynamic stability and significant clinical improvement.
- Availability of the oral route.
It is not routinely recommended to repeat a chest X-ray or CT scan to evaluate the evolution of pneumonia under outpatient or inpatient treatment. Only in the case of suspected complications or unfavorable evolution.
PREVENTION
The prevention of pneumonia is based on timely immunization with pneumococcal vaccines, influenza vaccination, and COVID-19 vaccination according to the immunization recommendations and current schedule from the Ministry of Health.
ICD-11 CODING
- CA40 - Pneumonia.
- CA40.0 - Bacterial Pneumonia.
- CA40.1 - Viral Bronchopneumonia.
- CA40.2 - Fungal Pneumonia.
- CA40.Z - Pneumonia, organism unspecified.
Autor
Kamo Weasel - MD Infectious Diseases - MD Internal Medicine - #DocChain Community npub1jdvvva54m8nchh3t708pav99qk24x6rkx2sh0e7jthh0l8efzt7q9y7jlj
-
 @ 9ff58691:0bf6c134
2024-11-21 07:32:15
@ 9ff58691:0bf6c134
2024-11-21 07:32:1515 ноября 2024 года в Центральном парке Кургана прошел долгожданный "Велопробег Будущего", который собрал более 300 участников всех возрастов. Это мероприятие стало настоящим праздником здоровья и велоспорта, объединив людей, стремящихся к активному образу жизни.
С самого утра парк наполнился энергией и позитивом. Участники регистрировались, получали номерки и информационные материалы о велоспорте и здоровом питании. Приветственное слово организаторов и местных властей задало тон всему мероприятию, подчеркивая важность физической активности для здоровья и экологии.
В 10:30 стартовал сам велопробег на дистанции 10 км. Участники, разделенные на группы по уровню подготовки, с энтузиазмом отправились в путь. Живописные маршруты парка, наполненные зеленью и свежим воздухом, создали идеальные условия для активного отдыха.
После пробега на участниках ждали станции здоровья, где они могли пройти тестирование на уровень физической активности, получить советы по правильному питанию от диетологов и поучаствовать в мини-тренировках. Фестиваль здоровья, который последовал за этим, стал настоящим хитом: местные производители здорового питания и спортивного инвентаря представили свои товары, а мастер-классы по ремонту велосипедов привлекли множество желающих.
В завершение мероприятия состоялось награждение победителей в различных номинациях, что добавило нотку соревнования и веселья. Участники делились впечатлениями и планами на следующий год, обсуждая, как важно продолжать поддерживать активный образ жизни.
Мы взяли комментарий у одного из участников, 28-летнего велосипедиста Ивана Петрова, который принял участие в пробеге:
"Это было невероятно! Я участвую в велопробегах уже несколько лет, но этот был особенным. Атмосфера была просто потрясающей, и я рад, что так много людей пришло поддержать здоровый образ жизни. Велоспорт — это не только спорт, но и возможность встретить единомышленников и насладиться природой. Я с нетерпением жду следующего года!"
"Велопробег Будущего" стал не только успешным мероприятием, но и важным шагом к созданию сообщества, заинтересованного в активном и здоровом образе жизни. Мы надеемся, что в следующем году количество участников только увеличится, и мероприятие станет еще более масштабным и запоминающимся!
Автор: Налобина Александра
-
 @ fd208ee8:0fd927c1
2024-11-21 07:24:34
@ fd208ee8:0fd927c1
2024-11-21 07:24:34The motherhood illusion
Growing up, I was always told that women wanted children, whilst men wanted sex. So, marriage was created, to unite these two urges, and men and women don't otherwise particularly differ. But, it turns out, that women want protection and sex, and men want children and sex.
This is why women tend to be attracted to more masculine men (they're associated with protection) and men tend to be attracted to more feminine women (they're associated with motherhood). Women who are attracted to men, who aren't overtly masculine, are looking for a different aspect of protection (reliability, steady income or wealth, emotional security, etc.)
This wasn't readily apparent, in earlier generations, as widespread, youthful marriage meant that there weren't any real decisions being made by the participants. Almost all women got married and had kids, and almost all men got married and had sex. Math checks out. But the number of women who could protect and provide for themselves was low, and the men marrying were often very young and libidinous, and not yet contemplating their own legacy.
Feminism, easy abortion, deindustrialization, delayed marriage, and reliable contraception have dissolved this illusion, completely. Millions of Western women quickly turned into cougars, careerists, party girls, and e-girls, and an entire army of childless men and sidelined dads bubbled up and began to make their pain known. Humanity's dirty underbelly has been exposed.
Women aren't as sweet, as we thought, and men are much sweeter.

Women also want children, but not as intensely. In fact, they seem to often viscerally dislike children, and are jealous of the protection they are to give them. So, they are prone to offing their offspring because they are averse to having any in-house competition.
If you just left women up to their own devices and reduced the social pressure, at least a fifth of them wouldn't bother having children, at all, and another quarter will have one and then lose interest or age out. This is not a new phenomenon, as we can see.
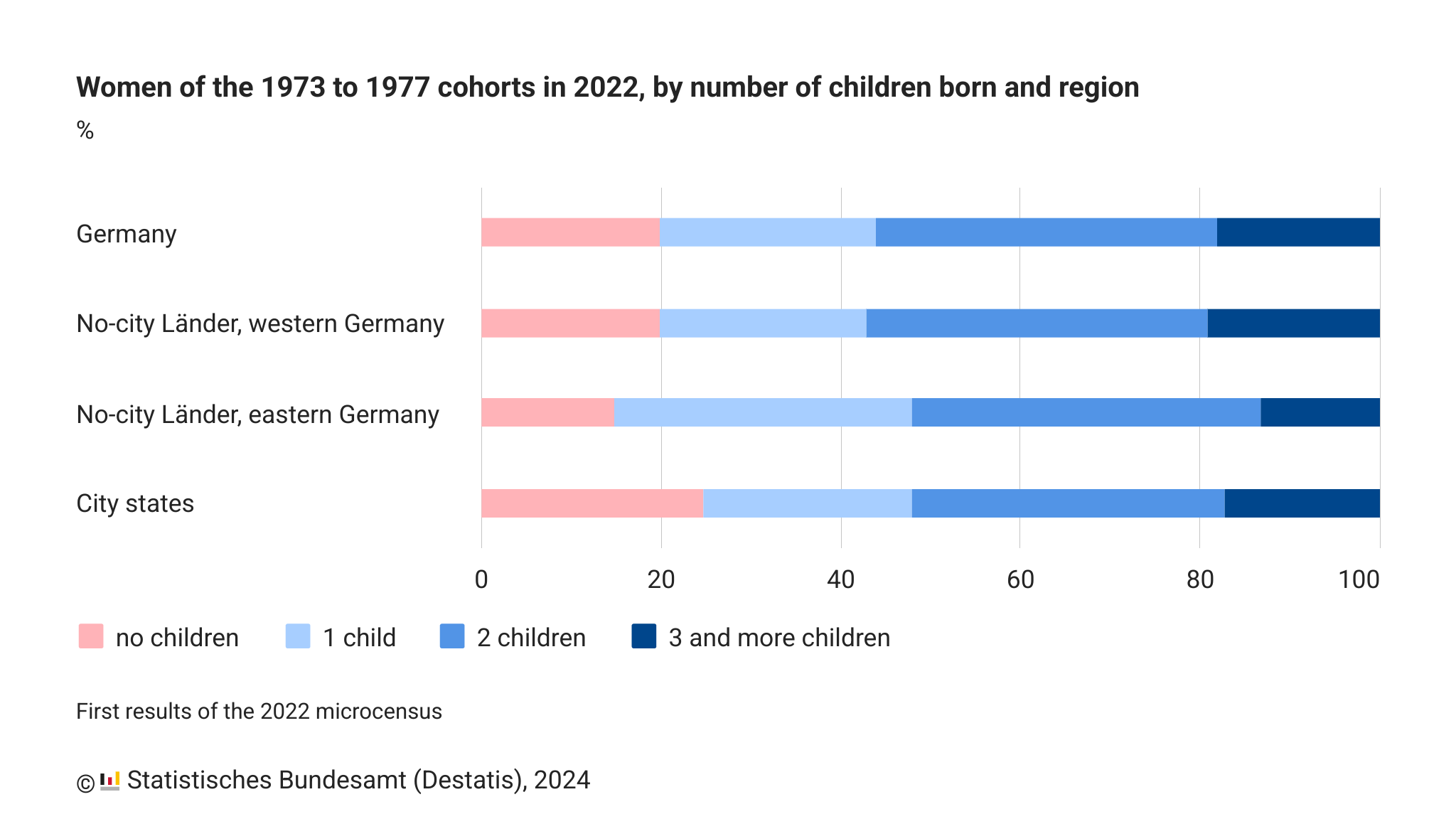
The male competition for potential mothers turns out to be absolutely brutal, and more difficult than simply finding a woman to sleep with. And, now, we finally understand why men traditionally jumped through so many hoops, to attain a wife. It wasn't for the sex; we've always had brothels, masturbation, and pornography. It was for the familial comfort, and, especially, for the children.
Good fathers make good mothers
Some women don't know if they are "potential mothers", until they meet a "potential father", and their urge to procreate suddenly kicks in. They didn't want children for their own sake, but now they want some for his sake. All of a sudden, they're imagining themselves rocking the cradle, googling "what to eat, when you're expecting", and find themselves gushing over anything that gives off Hint of Infant.
I'm pregnant! Look what I can do! Look what I can do! For you, darling.

Women married to men they are deeply in love with, are much more likely to desire to become mothers (and be devastated by infertility), and make for better mothers, because children are like individualized presents they can give to their husband.
They want to impress him. Most want to be decent parents in their own right, but the urge to impress seems to raise this to a much higher level because women are vain, and therefore focused on raising their own status and how they appear to others. And the greatest "other", of a happy wife, is her husband.
Because men are narcissistic, and therefore in love with anything associated with themselves (which underpins their obsession with owning property), men have an intense attachment to their children. What is more "yours", than your progeny?

Fathers seem to develop a special attachment to, or fondness for, the mothers of their children, that goes beyond lust or romantic love; they never forgot who gave them this new Mini Me. And they are often quite impressed by their own ability to perform this trick numerous times, which leads to the intense satisfaction they feel at "going into serial production" and churning out more of those Mini Mes until their adoring wife pleads for mercy.
Men want children. Women, who love a man, want to give him those children and gain the fidelity that comes along with those children. This is the actual "trade" underpinning the urge to marry.

-
 @ fa984bd7:58018f52
2024-08-16 13:22:12
@ fa984bd7:58018f52
2024-08-16 13:22:12 -
 @ da18e986:3a0d9851
2024-08-14 13:58:24
@ da18e986:3a0d9851
2024-08-14 13:58:24After months of development I am excited to officially announce the first version of DVMDash (v0.1). DVMDash is a monitoring and debugging tool for all Data Vending Machine (DVM) activity on Nostr. The website is live at https://dvmdash.live and the code is available on Github.
Data Vending Machines (NIP-90) offload computationally expensive tasks from relays and clients in a decentralized, free-market manner. They are especially useful for AI tools, algorithmic processing of user’s feeds, and many other use cases.
The long term goal of DVMDash is to become 1) a place to easily see what’s happening in the DVM ecosystem with metrics and graphs, and 2) provide real-time tools to help developers monitor, debug, and improve their DVMs.
DVMDash aims to enable users to answer these types of questions at a glance: * What’s the most popular DVM right now? * How much money is being paid to image generation DVMs? * Is any DVM down at the moment? When was the last time that DVM completed a task? * Have any DVMs failed to deliver after accepting payment? Did they refund that payment? * How long does it take this DVM to respond? * For task X, what’s the average amount of time it takes for a DVM to complete the task? * … and more
For developers working with DVMs there is now a visual, graph based tool that shows DVM-chain activity. DVMs have already started calling other DVMs to assist with work. Soon, we will have humans in the loop monitoring DVM activity, or completing tasks themselves. The activity trace of which DVM is being called as part of a sub-task from another DVM will become complicated, especially because these decisions will be made at run-time and are not known ahead of time. Building a tool to help users and developers understand where a DVM is in this activity trace, whether it’s gotten stuck or is just taking a long time, will be invaluable. For now, the website only shows 1 step of a dvm chain from a user's request.
One of the main designs for the site is that it is highly clickable, meaning whenever you see a DVM, Kind, User, or Event ID, you can click it and open that up in a new page to inspect it.
Another aspect of this website is that it should be fast. If you submit a DVM request, you should see it in DVMDash within seconds, as well as events from DVMs interacting with your request. I have attempted to obtain DVM events from relays as quickly as possible and compute metrics over them within seconds.
This project makes use of a nosql database and graph database, currently set to use mongo db and neo4j, for which there are free, community versions that can be run locally.
Finally, I’m grateful to nostr:npub10pensatlcfwktnvjjw2dtem38n6rvw8g6fv73h84cuacxn4c28eqyfn34f for supporting this project.
Features in v0.1:
Global Network Metrics:
This page shows the following metrics: - DVM Requests: Number of unencrypted DVM requests (kind 5000-5999) - DVM Results: Number of unencrypted DVM results (kind 6000-6999) - DVM Request Kinds Seen: Number of unique kinds in the Kind range 5000-5999 (except for known non-DVM kinds 5666 and 5969) - DVM Result Kinds Seen: Number of unique kinds in the Kind range 6000-6999 (except for known non-DVM kinds 6666 and 6969) - DVM Pub Keys Seen: Number of unique pub keys that have written a kind 6000-6999 (except for known non-DVM kinds) or have published a kind 31990 event that specifies a ‘k’ tag value between 5000-5999 - DVM Profiles (NIP-89) Seen: Number of 31990 that have a ‘k’ tag value for kind 5000-5999 - Most Popular DVM: The DVM that has produced the most result events (kind 6000-6999) - Most Popular Kind: The Kind in range 5000-5999 that has the most requests by users. - 24 hr DVM Requests: Number of kind 5000-5999 events created in the last 24 hrs - 24 hr DVM Results: Number of kind 6000-6999 events created in the last 24 hours - 1 week DVM Requests: Number of kind 5000-5999 events created in the last week - 1 week DVM Results: Number of kind 6000-6999 events created in the last week - Unique Users of DVMs: Number of unique pubkeys of kind 5000-5999 events - Total Sats Paid to DVMs: - This is an estimate. - This value is likely a lower bound as it does not take into consideration subscriptions paid to DVMs - This is calculated by counting the values of all invoices where: - A DVM published a kind 7000 event requesting payment and containing an invoice - The DVM later provided a DVM Result for the same job for which it requested payment. - The assumption is that the invoice was paid, otherwise the DVM would not have done the work - Note that because there are multiple ways to pay a DVM such as lightning invoices, ecash, and subscriptions, there is no guaranteed way to know whether a DVM has been paid. Additionally, there is no way to know that a DVM completed the job because some DVMs may not publish a final result event and instead send the user a DM or take some other kind of action.
Recent Requests:
This page shows the most recent 3 events per kind, sorted by created date. You should always be able to find the last 3 events here of all DVM kinds.
DVM Browser:
This page will either show a profile of a specific DVM, or when no DVM is given in the url, it will show a table of all DVMs with some high level stats. Users can click on a DVM in the table to load the DVM specific page.
Kind Browser:
This page will either show data on a specific kind including all DVMs that have performed jobs of that kind, or when no kind is given, it will show a table summarizing activity across all Kinds.
Debug:
This page shows the graph based visualization of all events, users, and DVMs involved in a single job as well as a table of all events in order from oldest to newest. When no event is given, this page shows the 200 most recent events where the user can click on an event in order to debug that job. The graph-based visualization allows the user to zoom in and out and move around the graph, as well as double click on any node in the graph (except invoices) to open up that event, user, or dvm in a new page.
Playground:
This page is currently under development and may not work at the moment. If it does work, in the current state you can login with NIP-07 extension and broadcast a 5050 event with some text and then the page will show you events from DVMs. This page will be used to interact with DVMs live. A current good alternative to this feature, for some but not all kinds, is https://vendata.io/.
Looking to the Future
I originally built DVMDash out of Fear-of-Missing-Out (FOMO); I wanted to make AI systems that were comprised of DVMs but my day job was taking up a lot of my time. I needed to know when someone was performing a new task or launching a new AI or Nostr tool!
I have a long list of DVMs and Agents I hope to build and I needed DVMDash to help me do it; I hope it helps you achieve your goals with Nostr, DVMs, and even AI. To this end, I wish for this tool to be useful to others, so if you would like a feature, please submit a git issue here or note me on Nostr!
Immediate Next Steps:
- Refactoring code and removing code that is no longer used
- Improve documentation to run the project locally
- Adding a metric for number of encrypted requests
- Adding a metric for number of encrypted results
Long Term Goals:
- Add more metrics based on community feedback
- Add plots showing metrics over time
- Add support for showing a multi-dvm chain in the graph based visualizer
- Add a real-time mode where the pages will auto update (currently the user must refresh the page)
- ... Add support for user requested features!
Acknowledgements
There are some fantastic people working in the DVM space right now. Thank you to nostr:npub1drvpzev3syqt0kjrls50050uzf25gehpz9vgdw08hvex7e0vgfeq0eseet for making python bindings for nostr_sdk and for the recent asyncio upgrades! Thank you to nostr:npub1nxa4tywfz9nqp7z9zp7nr7d4nchhclsf58lcqt5y782rmf2hefjquaa6q8 for answering lots of questions about DVMs and for making the nostrdvm library. Thank you to nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft for making the original DVM NIP and vendata.io which I use all the time for testing!
P.S. I rushed to get this out in time for Nostriga 2024; code refactoring will be coming :)
-
 @ 1123ece2:7d1e00c0
2024-11-21 06:55:31
@ 1123ece2:7d1e00c0
2024-11-21 06:55:31Hey everyone and welcome to Refinery Life Australia.
“The Christ of John’s Gospel” is the theme for the coming Sunday morning teachings that focus on John’s unique portrayal of the Christ.
We will continue this series through to the end of the year.
Today we are discussing, A Meeting with the Master.
Text
John 4:6-7 NKJV
6 Now Jacob’s well was there. Jesus therefore, being wearied from His journey, sat thus by the well. It was about the sixth hour.
7 A woman of Samaria came to draw water. Jesus said to her, “Give Me a drink.”
Scripture Reading
John 4:1-42 NKJV
A Samaritan Woman Meets Her Messiah
1 Therefore, when the Lord knew that the Pharisees had heard that Jesus made and baptized more disciples than John
2 (though Jesus Himself did not baptize, but His disciples),
3 He left Judea and departed again to Galilee.
4 But He needed to go through Samaria.
5 So He came to a city of Samaria which is called Sychar, near the plot of ground that Jacob gave to his son Joseph.
6 Now Jacob’s well was there. Jesus therefore, being wearied from His journey, sat thus by the well. It was about the sixth hour.
7 A woman of Samaria came to draw water. Jesus said to her, “Give Me a drink.”
8 For His disciples had gone away into the city to buy food.
9 Then the woman of Samaria said to Him, “How is it that You, being a Jew, ask a drink from me, a Samaritan woman?” For Jews have no dealings with Samaritans.
10 Jesus answered and said to her, “If you knew the gift of God, and who it is who says to you, ‘Give Me a drink,’ you would have asked Him, and He would have given you living water.”
11 The woman said to Him, “Sir, You have nothing to draw with, and the well is deep. Where then do You get that living water?
12 Are You greater than our father Jacob, who gave us the well, and drank from it himself, as well as his sons and his livestock?”
13 Jesus answered and said to her, “Whoever drinks of this water will thirst again,
14 but whoever drinks of the water that I shall give him will never thirst. But the water that I shall give him will become in him a fountain of water springing up into everlasting life.”
15 The woman said to Him, “Sir, give me this water, that I may not thirst, nor come here to draw.”
16 Jesus said to her, “Go, call your husband, and come here.”
17 The woman answered and said, “I have no husband.” Jesus said to her, “You have well said, ‘I have no husband,’
18 for you have had five husbands, and the one whom you now have is not your husband; in that you spoke truly.”
19 The woman said to Him, “Sir, I perceive that You are a prophet.
20 Our fathers worshiped on this mountain, and you Jews say that in Jerusalem is the place where one ought to worship.”
21 Jesus said to her, “Woman, believe Me, the hour is coming when you will neither on this mountain, nor in Jerusalem, worship the Father.
22 You worship what you do not know; we know what we worship, for salvation is of the Jews.
23 But the hour is coming, and now is, when the true worshipers will worship the Father in spirit and truth; for the Father is seeking such to worship Him.
24 God is Spirit, and those who worship Him must worship in spirit and truth.”
25 The woman said to Him, “I know that Messiah is coming” (who is called Christ). “When He comes, He will tell us all things.”
26 Jesus said to her, “I who speak to you am He.”
The Whitened Harvest
27 And at this point His disciples came, and they marveled that He talked with a woman; yet no one said, “What do You seek?” or, “Why are You talking with her?”
28 The woman then left her waterpot, went her way into the city, and said to the men,
29 “Come, see a Man who told me all things that I ever did. Could this be the Christ?”
30 Then they went out of the city and came to Him.
31 In the meantime His disciples urged Him, saying, “Rabbi, eat.”
32 But He said to them, “I have food to eat of which you do not know.”
33 Therefore the disciples said to one another, “Has anyone brought Him anything to eat?”
34 Jesus said to them, “My food is to do the will of Him who sent Me, and to finish His work.
35 Do you not say, ‘There are still four months and then comes the harvest’? Behold, I say to you, lift up your eyes and look at the fields, for they are already white for harvest!
36 And he who reaps receives wages, and gathers fruit for eternal life, that both he who sows and he who reaps may rejoice together.
37 For in this the saying is true: ‘One sows and another reaps.’
38 I sent you to reap that for which you have not labored; others have labored, and you have entered into their labors.”
The Savior of the World
39 And many of the Samaritans of that city believed in Him because of the word of the woman who testified, “He told me all that I ever did.”
40 So when the Samaritans had come to Him, they urged Him to stay with them; and He stayed there two days.
41 And many more believed because of His own word.
42 Then they said to the woman, “Now we believe, not because of what you said, for we ourselves have heard Him and we know that this is indeed the Christ, the Savior of the world.”
Amen.
One of the significant features of Jesus’ ministry was His meetings with people.
Jesus had an interest in individuals and He still does today.
The Lord was not so preoccupied with the multitudes that he lost concern for individuals.
Jesus met with many people.
One of His most significant meetings with a sinful woman at Jacobs well.
Let us look today at some fascinating facets of this famous interview.
- The perplexing problems.
Jesus’ meeting with the woman of Samaria was full of problems.
Do you understand the difficulties, we must understand some geography and history of Israel.
The pious Jew would not go through the land of Samaria.
Following the northern kingdom of Israel's captivity in 722 BC by the Assyrians, the land was inhabited by Israelites and foreigners.
The intermarried, which was repulsive to Pius Jews, and therefore the Pious Jews avoided Samaria.
Regarding Jesus, John said in John 4:4, But He needed to go through Samaria.
Various barriers existed for Jesus and the woman.
There was an ethnic barrier.
Jews were somewhat tolerant of other races, but the Samaritans were contemptible to the Jews.
When the woman met the Lord, she emphasised this barrier, she said how is it that You, being a Jew, ask a drink of me, a woman of Samaria?
There was a gender barrier.
Rabbis were forbidden to greet a woman in public, but Jesus cross this barrier.
Not only did the Lord cross this barrier, but he chose to talk with a notoriously immoral woman.
And of course there was a religious barrier.
There is a wide religious gap between the Jews and the Samaritans.
The Samaritans worshipped at Mount Ebal, and the Jews worship at Mount Gerizim.
- The Master’s proposal.
Jesus had the interpersonal skills to overcome these barriers.
Let us follow the strategy of the Master in how He made the meeting with the woman meaningful.
Jesus asked for a common necessity.
When the woman came to the well, He asked for a drink.
Jesus was thirsty, and the woman was thirsty.
Even though the two were different in race, gender, and religion, they had a common need to drink.
Jesus aroused the woman’s curiosity.
After He talked about His and her physical thirst, He mentioned something about “living water.”
Immediately the woman began to ask questions.
“From where does the living water come?”
The woman realised that Jesus was speaking of another type of water.
Jesus awakened the woman’s conscience.
The woman did not grasp everything about the living water, so Jesus appealed to her conscience.
“Go call your husband, and come here.”
Jesus wanted the woman to see that He knew the errors of her life.
With her conscience awakened, the woman wanted to talk about her relationship with God.
John 4:19-20 NKJV
19 The woman said to Him, “Sir, I perceive that You are a prophet.
20 Our fathers worshiped on this mountain, and you Jews say that in Jerusalem is the place where one ought to worship.”
Jesus acknowledged Himself as the Messiah.
Skilfully and masterfully, Jesus led the woman to the fact that He was the Messiah.
At the appropriate moment, He made the messianic disclosure, “I who speak to you and He.”
- The woman’s proclamation.
After the interview with Jesus, the woman left for the city of Samaria.
She told the people about the Lord.
John 4:29 NKJV
29 “Come, see a Man who told me all things that I ever did. Could this be the Christ?”
The woman had been changed because of her encounter with Jesus Christ.
A careful study of her attitude and actions reflects a radical change in character.
The woman also had a new concern for her life.
She left the water pots and went into the city.
Her primary concerns had been the sensual things of life.
After her life transforming experience, she was concerned for the spiritual condition of an entire village.
Why don’t you have a meeting with the Master?
Let Him tell you about His character and His ability to change people.
Until next time
Stay in the Blessings
I really want to encourage you to be diligent with your Bible study time, because God has so much more for us than we can get from just going to church once or twice a week and hearing someone else talk about the Word.
When you spend time with God, your life will change in amazing ways, because God is a Redeemer. Theres nothing thats too hard for Him, and He can make you whole, spirit, soul and body!
You’re important to God, and you’re important to us at The Refinery.
When it comes to prayer, we believe that God wants to meet your needs and reveal His promises to you.
So whatever you’re concerned about and need prayer for we want to be here for you! Or even if you just want to say Hi, you can contact us at www.refinerylife.org
2024 IS A YEAR OF DECISIONS AND OPEN DOORS
© www.refinerylife.org 2013-2024 All rights reserved. Except as permitted under the Australian Copyright Act 1968, no part of this Article may be reproduced, stored in a retrieval system, communicated or transmitted in any form or by any means without the prior written permission.
This episode is brought to you by Refinery Life Australia:
If you enjoy The Refinery Life Radio Podcast you can help support The Refinery by doing the following:
Sow an offering: Bitcoin: bc1qqh6720t2zagj72dyfj348az698tdut3hlecaj4
Online: https://www.refinerylife.org/donate/
If you do send an offering then please email us so that we can say thank you
Subscribe on iTunes | Spotify | YouTube | TuneIn | Rumble | Flare | Zap.Stream | Fountain |
Share The Refinery with your friends and family
Subscribe to the newsletter on www.refinerylife.org
Follow The Refinery on Twitter | Nostr | Instagram | Fountain |
-
 @ 76c71aae:3e29cafa
2024-08-13 04:30:00
@ 76c71aae:3e29cafa
2024-08-13 04:30:00On social media and in the Nostr space in particular, there’s been a lot of debate about the idea of supporting deletion and editing of notes.
Some people think they’re vital features to have, others believe that more honest and healthy social media will come from getting rid of these features. The discussion about these features quickly turns to the feasibility of completely deleting something on a decentralized protocol. We quickly get to the “We can’t really delete anything from the internet, or a decentralized network.” argument. This crowds out how Delete and Edit can mimic elements of offline interactions, how they can be used as social signals.
When it comes to issues of deletion and editing content, what matters more is if the creator can communicate their intentions around their content. Sure, on the internet, with decentralized protocols, there’s no way to be sure something’s deleted. It’s not like taking a piece of paper and burning it. Computers make copies of things all the time, computers don’t like deleting things. In particular, distributed systems tend to use a Kafka architecture with immutable logs, it’s just easier to keep everything around, as deleting and reindexing is hard. Even if the software could be made to delete something, there’s always screenshots, or even pictures of screens. We can’t provably make something disappear.
What we need to do in our software is clearly express intention. A delete is actually a kind of retraction. “I no longer want to associate myself with this content, please stop showing it to people as part of what I’ve published, stop highlighting it, stop sharing it.” Even if a relay or other server keeps a copy, and keeps sharing it, being able to clearly state “hello world, this thing I said, was a mistake, please get rid of it.” Just giving users the chance to say “I deleted this” is a way of showing intention. It’s also a way of signaling that feedback has been heard. Perhaps the post was factually incorrect or perhaps it was mean and the person wants to remove what they said. In an IRL conversation, for either of these scenarios there is some dialogue where the creator of the content is learning something and taking action based on what they’ve learned.
Without delete or edit, there is no option to signal to the rest of the community that you have learned something because of how the content is structured today. On most platforms a reply or response stating one’s learning will be lost often in a deluge of replies on the original post and subsequent posts are often not seen especially when the original goes viral. By providing tools like delete and edit we give people a chance to signal that they have heard the feedback and taken action.
The Nostr Protocol supports delete and expiring notes. It was one of the reasons we switched from secure scuttlebutt to build on Nostr. Our nos.social app offers delete and while we know that not all relays will honor this, we believe it’s important to provide social signaling tools as a means of making the internet more humane.
We believe that the power to learn from each other is more important than the need to police through moral outrage which is how the current platforms and even some Nostr clients work today.
It’s important that we don’t say Nostr doesn’t support delete. Not all apps need to support requesting a delete, some might want to call it a retraction. It is important that users know there is no way to enforce a delete and not all relays may honor their request.
Edit is similar, although not as widely supported as delete. It’s a creator making a clear statement that they’ve created a new version of their content. Maybe it’s a spelling error, or a new version of the content, or maybe they’re changing it altogether. Freedom online means freedom to retract a statement, freedom to update a statement, freedom to edit your own content. By building on these freedoms, we’ll make Nostr a space where people feel empowered and in control of their own media.
-
 @ 97fc03df:8bf891df
2024-11-21 06:08:35
@ 97fc03df:8bf891df
2024-11-21 06:08:35Qinghuan
2024.11.14.
Abstract
This article provides an in-depth analysis of the evolution of Simplified Payment Verification (SPV) technology from the basic application of the Bitcoin network to the modern blockchain extension layer, paying special attention to its innovative applications in ChainX , BEVM and Super Bitcoin, and discusses the application of SPV technology in A technical solution that maintains decentralization while achieving scalability.
1. SPV Basic Technology Solution
1.1 Technical Principles

1.2 Workflow
Block Header Synchronization Process

Transaction Verification Mechanism - Request the Merkel route for a specific transaction - Verify Merkel Proof - Confirm transaction status
1.3 Why is Bitcoin suitable for SPV?
Technical characteristics
1. The logic on the chain is simple - Pure UTXO status verification - No complex calculations required - Status changes are clear
2. Validate cost stability - Block header fixed size (80 bytes) - Verification complexity is constant - Controllable storage requirements
2. Technology Evolution Progress
2.1 ChainX stage (2018-2020): Cross-chain Verification Innovation
Technical architecture

Core Innovation
- The first SPV verification on the WASM chain
- Realize decentralized cross-chain
- Verification efficiency optimization
2.2 BEVM Phase (2020-2023): Smart Contract Integration
Architecture Upgrade

**Technological Breakthrough **
- Taproot protocol support
- EVM compatibility
- Verify performance improvements
2.3 Super Bitcoin stage (2024-present): Consensus Sharing Innovation
Five-Layer Architecture

3. Technical Comparative Analysis
3.1 Analysis of SPV Applicability of Different Blockchains

3.2 Comparison of Technical Indicators during the Evolution Process

4. Innovative Application Scenarios
4.1 Cross-chain Asset Management
Verification Process

4.2 Smart Contract Interaction
Implementation Mechanism 1. Transaction verification integration 2. State synchronization 3. Contract call
4.3 Layer2 extension
Technical Framework

5. Security Analysis
5.1 Threat Model
Potential Risks 1. Forking attack 2. Double spend attack 3. Data availability
Protective Measures

5.2 Longest Chain Consistency
Guarantee Mechanism
- Multi-point verification
- Consensus check
- State rollback
6. Future Outlook
6.1 Technology Development Direction
1. Verification Mechanism Optimization
- Zero-knowledge proof integration
- Batch verification optimization
- State compression
2. Application Scenario Expansion
- DeFi integration
- Cross-chain interoperability
- Layer2 extension
7. Conclusion
SPV technology has developed from the basic verification mechanism of the Bitcoin network to the present and has experienced an important evolution process:
- Cross-chain feasibility verified in ChainX
- Integration with smart contracts is achieved in BEVM
- Creating a new paradigm of consensus sharing in Super Bitcoin
This evolution demonstrates how SPV technology can adapt to the needs of the modern blockchain ecosystem through continuous innovation while maintaining security and decentralization. In the future, with the further development of technology and the expansion of application scenarios, SPV is expected to play a more important role in blockchain scalability solutions.
-
 @ 1bda7e1f:bb97c4d9
2024-11-21 04:17:08
@ 1bda7e1f:bb97c4d9
2024-11-21 04:17:08Tldr
- Nostr is an open protocol which is interoperable with all kinds of other technologies
- You can use this interoperability to create custom solutions
- Nostr apps define a custom URI scheme handler "nostr:"
- In this blog I use this to integrate Nostr with NFC cards
- I create a Nostr NFC "login card" which allows me to log into Amethyst client
- I create a Nostr NFC "business card" which allows anyone to find my profile with a tap
Inter-Op All The Things!
Nostr is a new open social protocol for the internet. This open nature is very exciting because it means Nostr can add new capabilities to all other internet-connected technologies, from browsers to web applications. In my view, it achieves this through three core capabilities.
- A lightweight decentralised identity (Nostr keys, "npubs" and "nsecs"),
- A lightweight data distribution network (Nostr relays),
- A set of data interoperability standards (The Nostr Improvement Protocols "NIPs"), including the "nostr:" URI which we'll use in this post.
The lightweight nature is its core strength. Very little is required to interoperate with Nostr, which means many existing technologies can be easily used with the network.
Over the next few blog posts, I'll explore different Nostr inter-op ideas, and also deliver my first small open source projects to the community. I'll cover–
- NFC cards integrated with Nostr (in this post),
- Workflow Automations integrated with Nostr,
- AI LLMs integrated with Nostr.
The "Nostr:" URI
One feature of Nostr is it defines a custom URI scheme handler "nostr:". What is that?
A URI is used to identify a resource in a system. A system will have a protocol handler registry used to store such URI's, and if a system has a URI registered, then it knows what to do when it sees it. You are probably already familiar with some URI schemes such as "http:" and "mailto:". For example, when you click an http link, the system knows that it describes an http resource and opens a web browser to fetch the content from the internet.
A nostr: link operates in the same way. The nostr: prefix indicates a custom URI scheme specifically designed for the Nostr protocol. If a system has a Nostr application installed, that application may have registered "nostr:" in the protocol handler registry. On that system when a "nostr:" URI is clicked, the system will know that it describes a nostr resource and open the Nostr client to fetch the content from the nostr relay network.
This inter-op with the protocol handler registry gives us the power to do nice and exciting things with other technologies.
Nostr and NFC
Another technology that uses URIs is NFC cards. NFC (Near Field Communication) is a wireless technology that enables devices to exchange data over a few centimeters. It’s widely used in contactless payments, access control, and information sharing.
NFC tags are small chips embedded in cards or stickers which can store data like plain text, URLs, or custom URIs. They are very cheap (cents each) and widely available (Amazon with next day delivery).
When an NFC tag contains a URI, such as a http: (or nostr:) link, it acts as a trigger. Tapping the tag with an NFC-enabled device launches the associated application and processes the URI. For example, tapping a tag with "nostr:..." could open a Nostr client, directing it to a specific login page, public profile, or event.
This inter-op allows us to bridge the physical world to Nostr with just a tap.
Many useful ideas
There are many interesting ways to use this. Too many for me to explore. Perhaps some of these are interesting for your next side hustle?
- Nostr NFC "login cards" – tap to log into Amethyst on Android,
- Nostr NFC "business cards" – give to connections so they can tap to load your npub,
- Nostr NFC "payment cards" – integrating lightning network or ecash,
- Nostr NFC "doorbells", "punch cards", "drop boxes", or "dead drops" – put a tag in a specific place and tap to open a location-specific message or chat,
- Integrations with other access control systems,
- Integrations with other home automation systems,
- Many more ...
To start with I have built and use the "login card" and "business card" solutions. This blog post will show you how to do the same.
Nostr Login Card
You can use an NFC card to log into your Nostr client.
Most Nostr clients accept a variety of login methods, from posting your nsec into the app (insecure) to using a remote signer (more secure). A less known but more secure method is to sign into a session with a tap of a specially-configured NFC card. Amethyst is a Nostr client on Android which supports this type of login.
- A secure method for logging in
- Optionally keeps no log in history on the device after logout
- Does not require users to know or understand how keys work
- Keys are kept secure on a physically-separated card to reduce risk of compromise
Nostr devs think that this is useful for anti-establishment actors–Fair enough. For me, I am interested in this login card pattern as it could be useful for rolling out identities within an organisation context with less training (office workers are already familiar with door access cards). This pattern potentially abstracts away key management to the IT or ops team who provision the cards.
I first discovered this when Kohei demonstrated it in his video.
Here's how you set it up at a high level–
- Buy yourself some NFC cards
- Get your Nostr key ready in an encrypted, password protected format called "nencryptsec"
- Write the nencryptsec to the NFC card as a custom URI
- Tap to load the login screen, and enter your password to login
Here it is in detail–
Buy yourself some NFC cards
I found no specific requirements. As usual with Nostr so far, I tried to the cheapest possible route and it worked. Generic brand NFC cards shipped from China, I believe it was 50X for $15 from Amazon. Your mileage may vary.
Get your Nostr key ready
Your key will be saved to the NFC card in an encrypted password-protected format called "nencryptsec". Several applications support this. As we'll be using this to login to Amethyst, we will use Amethyst to output the nencryptsec for us.
- Login to Amethyst with your nsec,
- Open the sidebar and click "Backup Keys",
- Enter a password, and click "Encrypt and my secret key",
- It will add the password-protected key to your clipboard in the format "ncryptsec1...",
- Remember to backup your password.
Write the ncryptsec to the NFC card
- Download the free NFC Tools app to your device, and open it,
- Click "Write" and "Add a record", then click "Custom URL / URI",
- Paste your nencryptsec with the nostr URI in front, i.e. "nostr:ncryptsec1..." and click OK,
- Click "Write". NFC Tools will prompt you to "Approach an NFC tag",
- Place your NFC card against your phone, and it will write to the card,
- Your card is ready.
Tap to load the login screen
Tap the card against your phone again, and your phone should open the login screen of Amethyst and prompt you for your password.
Once you enter your password, Amethyst will decrypt your nsec and log you in.
Optionally, you can also set the app to forget you once you log out.
You have created a Nostr NFC "login card".
Nostr Business Card
You can use another NFC card to give anyone you meet a link straight to your Nostr profile.
I attended Peter McCormack's #CheatCode conference in Sydney and gave a few of these out following the Nostr panel, notably to Preston Pysh where it got some cut through and found me my first 100 followers. You can do the same.
To create your Nostr NFC "business card" is even easier than your NFC "login card".
- Buy yourself some NFC cards,
- Download the free NFC Tools app to your device, and open it,
- Click "Write" and "Add a record", then click "Custom URL / URI",
- Write your npub to the NFC card as a custom URI in the format "nostr:npub1..." (e.g. for me this is "nostr:npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft"),
- Your card is ready.
Give the card to someone who is a Nostr user, and when they tap the card against their phone it will open their preferred Nostr client and go directly to your Nostr profile page.
You have created a Nostr NFC "business card".
What I Did Wrong
I like to share what I did wrong so you don't have to make the same mistakes. This time, this was very easy, and little went wrong. In general
- When password-protecting your nsec, don't forget the password!
- When writing to the NFC card, make sure to use "Custom URI/URL" as this accepts your "nostr:" URI scheme. If you use generic "URI/URL" it won't work.
What's Next
Over my first four blogs I have explored creating a good Nostr setup
- Mined a Nostr pubkey and backed up the mnemonic
- Set up Nostr payments with a Lightning wallet plus all the bells and whistles
- Set up NIP-05 and Lighting Address at my own domain
- Set up a Personal Relay at my own domain
Over the next few blogs I will be exploring different types of Nostr inter-op
- NFC cards integrated with Nostr (this post)
- Workflow Automations integrated with Nostr
- AI LLMs integrated with Nostr
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
GM Nostr.
-
 @ 30ceb64e:7f08bdf5
2024-11-21 01:24:36
@ 30ceb64e:7f08bdf5
2024-11-21 01:24:36Damn,
I always put too many projects on my plate.
I really need to focus on one at a time or a couple of them.
I'm starting to feel the risk of not doing everything I wanted to accomplish.
I think with a few days hard push, I'd be able to knock out a lot.
- Article Blog
- Cool Shopstr Site
- Nostr Running App
- Podcast with AI reading my Blogs, with wavlake beats playing in the background
- Radio Show
- Music Videos
- Couple more Wavlake Albums (TheWildHustle, and Jayhawk)
- Viny Record
- Short Story
- A brand/npub to release some of my projects, instead of overloading my one npub.
This week I want to hit coding and writing hard.
I need to a hard push will get me to a good place, considering the steps i've already taken.
The start date for my part time job has been moved to December 9th, Its a weekend job working 14 hour shifts on Saturday and Sunday......Ha! I'll be assisting teens with disabilities like downsyndrome and whatnot. I'm looking forward to doing something more than just clicking fiat buttons on the computer and possibly making a direct difference in a freaks life.
I've proofed of work pretty well in the bear. Now I need to execute in this early bull.
How I plan to execute - I'm TheWIldHustle so it behooves me to lean into my sporadic nature - Get alot of work done when I feel the animal spirits take me - Broadcast my actions and rely on negative emotions (me not wanting to be a larp) to motivate my actions and force me into work with an angry ferver. - Try to maintain a constructive mood
More specifically - Autoposting blogposts to nostr would be a good idea, I already have some brain dumps in obsidian i can throw into an llm and edit to get my points across, and the autoposting will consistancy if done right.
-
The radio show is probably just me using zap.stream and streaming all of the beats i've come out with on wavlake so far and so setting up a stream shouldnt be too dificult and i'd iterrate over time with different processes
-
I know where to get the vinyl done, I have an album mixed and mastered with artwork bought from a graphic design artist to use for the front cover just need to hit the buy button and offer it on shopstr when it arrives
-
The running app at this point is about 20 percent away from being released as a noob beta project. I primarily need to work on nostr login, UI/UX and testing.
-
Short story rough outline is done, I'll probably throw the thing into Claude and edit just as I will with the blogposts.
-
The podcast will be a reading of my blog posts with my wavlake beats playing in the background
-
The shopstr site will sell digital projects like my stories ebook, wavlake beats and beat tapes. Will sell physical stuff like vinyl records, Album artwork as posters, printify merch-like stuff.
-
Music videos/Shorts will probably come from AnimalSunrise/Wavlake beats
-
Might want to do some sort of brand consultation with a freak on nostr or fiverr to develop a brand to push out some of this stuff.
Fun times ahead, Thanks for reading, Wish me luck, Hustle
originally posted at https://stacker.news/items/776493
-
 @ 5fb7f8f7:d7d76024
2024-11-21 09:48:16
@ 5fb7f8f7:d7d76024
2024-11-21 09:48:16Earning in Web3 through Non-Fungible Token (NFT) creation involves generating unique digital assets that represent ownership, provenance, and scarcity. Imagine a world where digital art, music and collectibles have real value and ownership that is what web3 NFT is all about and more. Here's a step-by-step guide to get you started:
-
Choose a platform: Select a suitable NFT marketplace like OpenSea, Rarible, or Mintable. Which would you go for
-
Create unique content: Develop distinctive digital art, music, literature, or collectibles. I Call this unleash your creativity make unique art and collectibles.
-
Set up a digital wallet: Create a wallet like MetaMask or Trust Wallet to store your NFTs and cryptocurrencies easily and safe always remember don not reveal seed phrase or private key to anyone
-
Mint your NFT: Use your chosen platform to mint your NFT, adding details like name, description, and price.
-
List and promote: List your NFT for sale and promote it on social media, forums, and online communities. Bring your creation into the market place for visibility
-
Earn royalties: Set a royalty percentage to receive passive income from secondary sales.
-
Participate in marketplaces: Engage with NFT marketplaces, auctions, and events to increase visibility.
-
Collaborate and network: Partner with other creators, influencers, and collectors to expand your reach.
-
Stay updated: Continuously educate yourself on Web3, NFT trends, and platform developments.
-
Diversify: Explore various NFT categories and marketplaces to maximize your earnings.
Additionally, consider the following strategies to enhance your Web3 earnings through NFT creation:
Exclusive content: Offer limited-edition or early access content to attract buyers. Community engagement: Foster a loyal community to drive demand and sales. Collaborate with brands: Partner with brands to create branded NFTs. Secondary market sales: Participate in secondary market sales to earn royalties. NFT staking: Explore NFT staking options to earn passive income.
Remember, success in Web3 NFT creation requires creativity, marketing efforts, and adaptability. Focus on building a strong brand, engaging with your audience, and staying up-to-date with industry trends.
-
-
 @ a012dc82:6458a70d
2024-11-21 00:59:27
@ a012dc82:6458a70d
2024-11-21 00:59:27Table Of Content
-
Content
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
The fact that cryptocurrencies are subject to price swings is something that is common knowledge at this point. The tales of those who made millions during a crypto upswing make regular headlines, but so do the stories of people who lost everything during the downswings. Both types of stories are often reported in the media.
cryptocurrency gain value Additionally, since there is neither a tangible product nor a centralized organizational body, it is difficult to point to anything and say, "Look, that nice thing occurred; crypto prices will improve immediately." This is because there is no actual product. The question now is, "How does the value of cryptocurrencies increase?"
In this article, we will investigate what factors have an influence on the pricing of cryptocurrencies as well as how they increase in value.
What is cryptocurrency?
A digital asset is the most basic definition of a cryptocurrency. Because it was designed to function as a means of trade in the same manner that we use fiat currencies today, we give it the name "currency" because of its original purpose.
All transactions take place via the internet and are stored on a distributed ledger called a blockchain. The blockchain is used to demonstrate ownership of a unit and displays a history of transactions pertaining to that unit. To better understand digital assets, think of them as digital tokens. These tokens have some kind of significance inside the internal system, and it is possible to program them to record monetary transactions along with other important information.
The most profitable aspect of cryptocurrency is undoubtedly its usage as a kind of digital currency. It gives consumers the ability to transfer bitcoins between parties as payment for products and services offered by those parties. The fact that cryptocurrencies are not governed by any central body confers a number of advantageous characteristics on them. Processing costs are often very low or nonexistent altogether. There is less control and regulation exerted by the government. This translates to the fact that cryptocurrencies are easily transportable, resistant to inflation, and transparent with regard to their transaction histories.
Crypto Trading
Trading cryptocurrencies is a relatively new facet of the cryptocurrency industry that is seeing significant growth. The use of cryptocurrencies as a currency system is distinct from trading. Users instead purchase and sell cryptocurrencies in the same manner that they would purchase and sell shares in a corporation. When you buy shares in a corporation, you are essentially buying ownership in that firm. When you buy a token, however, you are really buying ownership in that coin. The tax treatment of transactions involving cryptocurrencies in the United States is analogous to that of transactions involving stock trading. This mirrors the manner in which the majority of people are generating money in the cryptocurrency market.
The crypto monetary system influences the cost of crypto trading in the same way that the popularity of a company's goods influences the price of the company's stock. The supply of a cryptocurrency, the demand for it on the market, the availability of the cryptocurrency, and the prices of other cryptocurrencies are the primary factors that influence its value.
How does cryptocurrency gain value?
On trading platforms, cryptocurrencies may increase in value. [Cryptocurrency]: The market forces of supply and demand cause a growth in its value.
The availability of a particular cryptocurrency is contingent not only on the rate at which new coins are created but also on the proportion of existing holders who are interested in liquidating their holdings.
The amount of demand for a cryptocurrency is influenced by a wide variety of variables. The more value that may be derived from owning the coins, the higher the demand will be for them. This implies that if the cryptocurrency monetary system functions effectively (i.e., with quick transactions and cheap costs), if smart contracts become more popular, and if more companies start to accept cryptocurrency, then the demand for cryptocurrency will rise. Additionally, there is a growing interest in putting money into cryptocurrencies as a kind of investment and value storage.
How is value added to cryptocurrencies? The value of cryptocurrencies goes up and down, just like the value of everything else on the market, depending on how the market as a whole perceives their worth at any particular moment. These shifts may have their origins in some of the elements related to supply and demand that were discussed before, or they may be the consequence of forces that are concealed in the market.
How Users Increase Crypto Value
There are also a few strategies that consumers may use to boost the value of their bitcoin:
-
Buy cheap and sell high. Users have the ability to grow the value of their cryptocurrency holdings by following the time-tested investing method of purchasing and keeping coins. The purchase drives up demand, which in turn drives up the price of the cryptocurrency.
-
Mining. Mining for Bitcoins or other cryptocurrencies may be lucrative if done correctly. Additionally, it has an effect on the availability of cryptocurrencies.
-
Increasing utility. The usefulness of cryptocurrency will expand as more organizations begin to invest in it and accept it as a means of payment. You, as a user, have the ability to make a contribution to this process. This will, over the course of time, result in a rise in the value of cryptocurrencies.
-
Media coverage. The price of cryptocurrencies moves up and down in response to various media reports. Users have the ability to influence this via their own social media profiles.
What Are the Different Types of Crypto?
There are now dozens, if not hundreds, of distinct cryptocurrencies, and each week a new cryptocurrency is introduced into circulation. The following are some of the most well-known types of cryptocurrencies:
-
Ethereum
-
Cardano
-
Dogecoin
-
Polygon
-
Stellar
-
Tether
-
Shiba Anu
In spite of this, there are now three primary types of cryptocurrencies, which are as follows:
-
Bitcoin
-
Altcoins
-
Tokens
Below, a more in-depth discussion is provided for each of these distinct forms of crypto.
Bitcoin
Bitcoin, the first cryptocurrency ever created, is a limited-supply digital asset. This indicates that after 21 million Bitcoins have been mined, there will be no more mined beyond that point.
Because Bitcoin is a currency whose supply is limited, it may be used as a medium for the storage and management of value. Purchasing a currency that acts as a store of value is analogous to purchasing gold as an investment. Although gold does have some worth when it comes to transactions, its primary function is that of a store of value.
Bitcoin has a mining protocol known as "Proof-of-Work." This indicates that a network of miners is responsible for carrying out the difficult computations required to keep the Bitcoin blockchain operational. Bitcoins that have just been created are the prize given to miners for their labor. Proof-of-Work is a feature that enables Bitcoin's transactional system to have a real-world value attached to it. One bitcoin is equivalent to a predetermined quantity of work done on computers.
Altcoins
Altcoins are essentially Bitcoin clones that have undergone a few tweaks here and there. A bitcoin fork is often the cause of these splits. Alternative cryptocurrencies come in a wide variety of flavors.
The underlying blockchain technology is a key point of differentiation between Bitcoin and other cryptocurrencies. The usage of some alternative cryptocurrencies is altered since the supply of such coins is not limited. A number of alternative cryptocurrencies have sped up the blockchain, which has the effect of accelerating mining as well as transaction times.
Alternate cryptocurrencies may also often be distinguished from one another by the technique of verification that is used to validate transactions. Miners are replaced by validators in alternative cryptocurrencies that employ the proof-of-stake consensus algorithm rather than the proof-of-work method. Mining with a proof-of-stake system uses a lot less energy and a lot fewer resources than mining with a proof-of-work system does, since miners using a proof-of-work system have to put in a lot more "work" in order to mine blocks.
The creation of smart contracts may also be accomplished using altcoins. The terms of these smart contracts may trigger their automated execution in specific circumstances. Because there is no need for the participation of a third party, they may be carried out right away. Because smart contracts may be used for deals as varied as those involving land, stocks, and gas, purchasing them can be a highly intriguing and profitable venture.
Tokens
Tokens are digital assets that may be exchanged for other digital assets or used inside smart contracts. They do not have a blockchain and are used on apps that are decentralized (dApps).
Mining, which results in the creation of a blockchain, serves as the actual embodiment of the money that is represented by crypto currencies. In a manner similar to this, central banks used to keep gold reserves in order to guarantee the value of their fiat currencies.
Tokens, on the other hand, are not meant to stand in for any particular item in the real world. Because they can be used to buy from decentralized applications (dApps) and because they can be used to gain discounts on fees and voting costs, their popularity is growing. A parallel may be drawn between this and the uncoupling of fiat currencies from the gold standard.
Conclusion
The level of participation in the cryptocurrency community, similar to that of any other currency, is what gives cryptocurrencies their value. A cryptocurrency's value increases when there is more demand for it than there is available supply. When a cryptocurrency has practical applications, more individuals will want to hold it, which drives up its demand. People do not want to sell it since they are interested in using it themselves. This indicates that there is more demand than supply, which leads to a rise in price.
FAQ
Does keeping bitcoin in a wallet make it more valuable? When kept in a wallet, the value of your digital currency might fluctuate over time, either increasing or decreasing. The price will fluctuate in accordance with market conditions, meaning that you will come out ahead if the value of this digital money goes up. On the other hand, it is irrelevant whether you keep your bitcoins in your own wallet or on an exchange.
Is it possible to get wealthy by creating your own cryptocurrency? Is it Possible to Earn an Income With Cryptocurrency? Yes, it is possible to generate income using cryptocurrencies. The inherent volatility of crypto assets makes most of them subject to a significant degree of risk, while others require specific education or experience in the relevant field. One way to answer the question "How can I make money with bitcoin?" is to trade cryptocurrencies.
What factors have an impact on the value of cryptocurrency? Like stocks, commodities, securities, and many other asset classes, cryptocurrencies may be traded like any other asset. The level of interest there is on the market in purchasing them, also known as demand, and the amount that is available to purchase, known as supply, are the two primary factors that determine their price. The price is determined by the connection between the two factors.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ ddf03aca:5cb3bbbe
2024-11-20 22:34:52
@ ddf03aca:5cb3bbbe
2024-11-20 22:34:52Recently, I have been surrounded by people experimenting with various projects, and a common theme among them is the use of cashu as the payment layer. While this fact alone is already great, the best part is to identify users and implementers needs and combining forces to come up with novel solutions.
Subscriptions with Cashu
One of the most remarkable aspects of cashu is that it is a bearer asset. This hands ownership and control back to the user. Even though mints back the tokens, they have no authority to move a token on behalf of a user or any other party. How cool is that?
However, this also introduces challenges when building subscription-based services. Subscriptions typically require periodic payments, and with cashu, users must renew these manually. Currently, there are two primary approaches to address this:
-
Overpaying:
To minimize the number of interactions, users can pay for longer periods upfront. For example, instead of paying 2,100 sats for one hour, they could pay 6,000 sats for three hours. If they realize they don’t need the full three hours, the excess payment is effectively wasted. -
Full Interactivity:
In this setup, payers and receivers stay connected through a communication channel, and payments are made at small, regular intervals. While this avoids overpayment, it requires constant connectivity. If the connection is lost, the subscription ends.
Enter Locking Scripts
One of the most powerful features of cashu is its locking scripts. Let’s take a quick refresher. A locking script defines the conditions under which a token (or "nut") becomes spendable. In essence, it’s similar to Bitcoin’s spending conditions, but instead of being enforced by the Bitcoin network, these conditions are enforced by the cashu mint alone.
A widely-used locking condition is Pay-to-Public-Key (P2PK). This locks a token to a specific public key, meaning it can only be spent when a valid signature from the key’s owner is provided. This mechanism is what enables NIP-61 nut zaps, where a token can be publicly shared but is only claimable by the intended recipient who holds the private key.
To address situations where a recipient loses access to their keys or simply doesn’t claim the token, P2PK includes additional options: locktime and a refund key. These options allow for the inclusion of a fallback mechanism. If the primary lock expires after a set time, a refund key can reclaim the token.
With these tools, we can now create non-interactive payment streams!
One Missing Piece…
Before diving into payment streams, there’s one more crucial concept to cover: cashu tokens are not singular "things". Instead, they’re composed of multiple proofs, each carrying its own cryptographic data and spendability. For example, if you receive a cashu token made up of five proofs, you could choose to claim only three proofs and leave the other two untouched. This flexibility is rarely utilized but is vital for building payment streams.
The Grand Finale: Payment Streams
Now that we have all the building blocks, let’s construct a payment stream using cashu. By leveraging locking scripts, refund keys, and multiple proofs, we can design a token that enables recipients to claim small portions of the total amount at regular intervals—without requiring any further interaction from the sender.
Even better, as the sender, you retain the ability to cancel the stream at any time and reclaim any unspent portions.
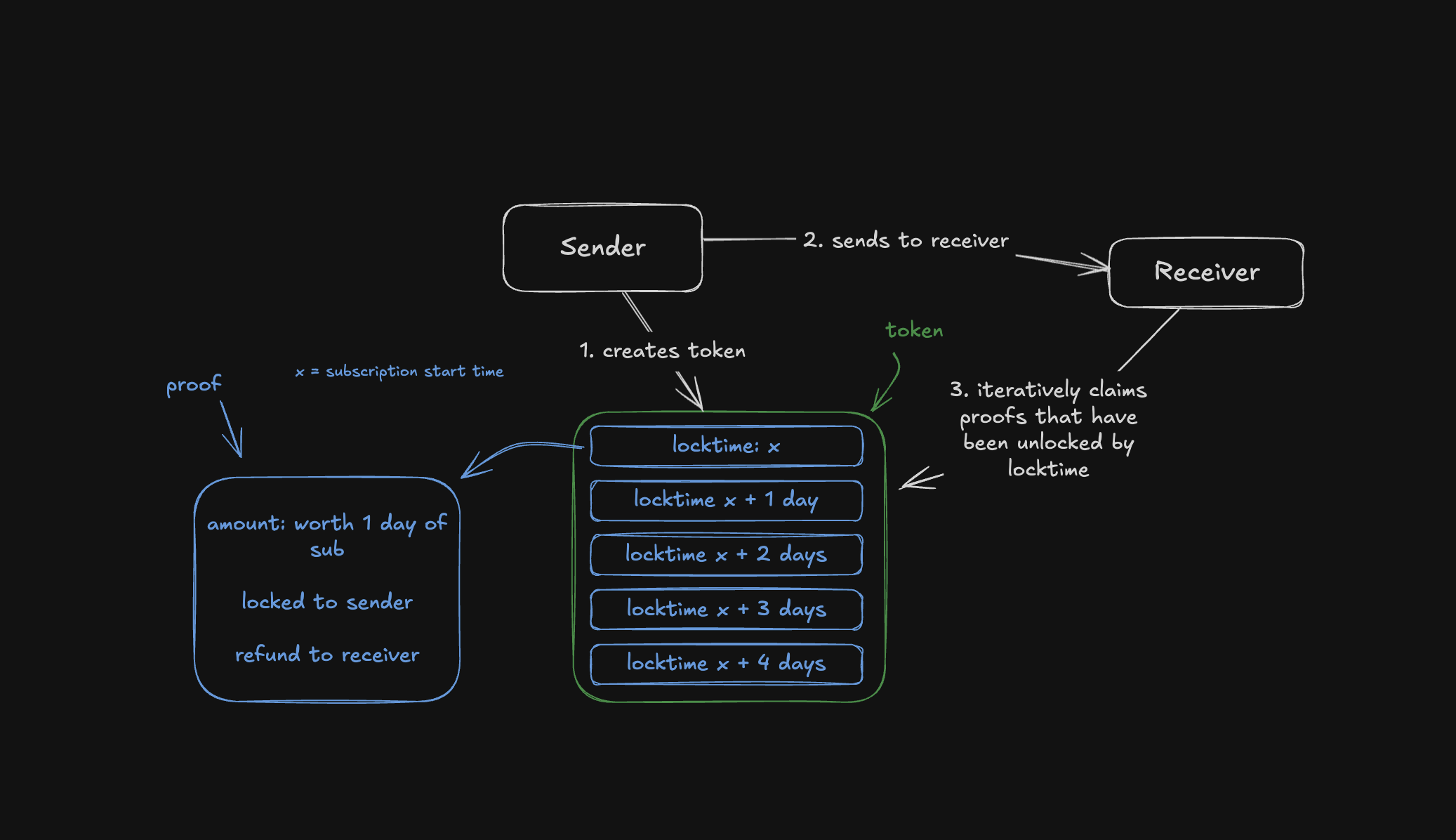
Example: Renting a VPS
Imagine renting a VPS for a week, priced at 1,000 sats per day. Here’s how a payment stream could work:
- Construct a token worth 7,000 sats to cover the entire week.
- Divide the token into 7 proofs, each worth 1,000 sats.
- Lock each proof using a P2PK script, locking to your key and adding the recipients key as a refund key.
- The first proof has a locktime of
now. - The second proof has a locktime of
now + 1 day. - The third proof has a locktime of
now + 2 days, and so on.
When the token is sent, the receiver can immediately claim the first proof since its locktime has expired and the refund key is now able to claim. The second proof becomes claimable after one day, the third after two days, and so on.
At the same time, the sender retains the ability to reclaim any unclaimed proofs by signing with their key. If you decide to stop using the VPS midweek, you can cancel the stream and reclaim the remaining proofs; all without further interaction with the receiver.
With this approach, we can create robust, non-interactive payment streams that combine the autonomy of cashu with the flexibility to reclaim funds.
Thank you for reading. Make sure to leave a nut if you enjoyed this :)
-
-
 @ 0e8c41eb:95ff0faa
2024-07-08 14:36:14
@ 0e8c41eb:95ff0faa
2024-07-08 14:36:14Chef's notes
Sprinkle a pinch of salt in a bowl. Sift 275 grams of flour above it. Make a well in the center of the flour and sprinkle the yeast into it. Add 50 grams of butter, 25 grams of sugar, and the egg. Pour in the milk and knead the dough with the mixer or by hand into a smooth dough. If necessary, add a bit more flour if the dough is too sticky. Form the dough into a ball. Let the dough rise covered with cling film at room temperature for 1 hour.
Peel the apples. Cut the apples and apricots into pieces. Cook the fruit with 150 grams of sugar and 50 ml of water in 15 minutes into a thick compote. Let this fruit filling cool.
Knead the dough again briefly and roll it out to a round sheet of about 28-30 cm in diameter, so that it fits well over the baking tin. Press the dough into the tin and press it well into the corners. Let the dough rise again for 10 minutes and cut off the excess edges.
Spread the fruit filling over the dough.
Mix the rest of the flour with the remaining 100 grams of butter and 100 grams of sugar and knead it with your fingers into a crumbly mixture. Sprinkle this crumble mixture over the fruit filling. Bake the tart in the preheated oven at 200°C for about 30 minutes until golden brown.
Variations: Only apple? Make this tart with 1 kilo of apples. High or low? You can also bake the crumble tart in a low tart tin of 30 cm diameter. If the fruit filling is a bit too voluminous, you can make double the crumble mixture and sprinkle it over the larger surface area.
Additional needs: Mixer with dough hooks or food processor Cling film Round baking tin with a diameter of 28-30 cm, greased
Details
- ⏲️ Prep time: 45 min + 1 hour Rising
- 🍳 Cook time: 30 minutes
- 🍽️ Servings: 8
Ingredients
- 375 grams flour
- 1 packet dried yeast (7 grams)
- 125 grams unsalted butter, at room temperature
- 275 grams sugar
- 1 egg
- 100 ml milk, at room temperature
- 500 grams apples
- 500 grams apricots (fresh or from a can)
Directions
- Sprinkle a pinch of salt in a bowl. Sift 275 grams of flour above it. Make a well in the center of the flour and sprinkle the yeast into it. Add 50 grams of butter, 25 grams of sugar, and the egg. Pour in the milk and knead the dough with the mixer or by hand into a smooth dough. If necessary, add a bit more flour if the dough is too sticky. Form the dough into a ball. Let the dough rise covered with cling film at room temperature for 1 hour.
- Peel the apples. Cut the apples and apricots into pieces. Cook the fruit with 150 grams of sugar and 50 ml of water in 15 minutes into a thick compote. Let this fruit filling cool.
- Knead the dough again briefly and roll it out to a round sheet of about 28-30 cm in diameter, so that it fits well over the baking tin. Press the dough into the tin and press it well into the corners. Let the dough rise again for 10 minutes and cut off the excess edges.
- Spread the fruit filling over the dough.
-
 @ 6871d8df:4a9396c1
2024-06-12 22:10:51
@ 6871d8df:4a9396c1
2024-06-12 22:10:51Embracing AI: A Case for AI Accelerationism
In an era where artificial intelligence (AI) development is at the forefront of technological innovation, a counter-narrative championed by a group I refer to as the 'AI Decels'—those advocating for the deceleration of AI advancements— seems to be gaining significant traction. After tuning into a recent episode of the Joe Rogan Podcast, I realized that the prevailing narrative around AI was heading in a dangerous direction. Rogan had Aza Raskin and Tristan Harris, technology safety advocates, who released a talk called 'The AI Dilemma,' on for a discussion. You may know them from the popular documentary 'The Social Dilemma' on the dangers of social media. It became increasingly clear that the cautionary stance dominating this discourse might be tipping the scales too far, veering towards an over-regulated future that stifles innovation rather than fostering it.

Are we moving too fast?
While acknowledging AI's benefits, Aza and Tristan fear it could be dangerous if not guided by ethical standards and safeguards. They believe AI development is moving too quickly and that the right incentives for its growth are not in place. They are concerned about the possibility of "civilizational overwhelm," where advanced AI technology far outpaces 21st-century governance. They fear a scenario where society and its institutions cannot manage or adapt to the rapid changes and challenges introduced by AI.
They argue for regulating and slowing down AI development due to rapid, uncontrolled advancement driven by competition among companies like Google, OpenAI, and Microsoft. They claim this race can lead to unsafe releases of new technologies, with AI systems exhibiting unpredictable, emergent behaviors, posing significant societal risks. For instance, AI can inadvertently learn tasks like sentiment analysis or human emotion understanding, creating potential for misuse in areas like biological weapons or cybersecurity vulnerabilities.
Moreover, AI companies' profit-driven incentives often conflict with the public good, prioritizing market dominance over safety and ethics. This misalignment can lead to technologies that maximize engagement or profits at societal expense, similar to the negative impacts seen with social media. To address these issues, they suggest government regulation to realign AI companies' incentives with safety, ethical considerations, and public welfare. Implementing responsible development frameworks focused on long-term societal impacts is essential for mitigating potential harm.
This isn't new
Though the premise of their concerns seems reasonable, it's dangerous and an all too common occurrence with the emergence of new technologies. For example, in their example in the podcast, they refer to the technological breakthrough of oil. Oil as energy was a technological marvel and changed the course of human civilization. The embrace of oil — now the cornerstone of industry in our age — revolutionized how societies operated, fueled economies, and connected the world in unprecedented ways. Yet recently, as ideas of its environmental and geopolitical ramifications propagated, the narrative around oil has shifted.
Tristan and Aza detail this shift and claim that though the period was great for humanity, we didn't have another technology to go to once the technological consequences became apparent. The problem with that argument is that we did innovate to a better alternative: nuclear. However, at its technological breakthrough, it was met with severe suspicions, from safety concerns to ethical debates over its use. This overregulation due to these concerns caused a decades-long stagnation in nuclear innovation, where even today, we are still stuck with heavy reliance on coal and oil. The scare tactics and fear-mongering had consequences, and, interestingly, they don't see the parallels with their current deceleration stance on AI.
These examples underscore a critical insight: the initial anxiety surrounding new technologies is a natural response to the unknowns they introduce. Yet, history shows that too much anxiety can stifle the innovation needed to address the problems posed by current technologies. The cycle of discovery, fear, adaptation, and eventual acceptance reveals an essential truth—progress requires not just the courage to innovate but also the resilience to navigate the uncertainties these innovations bring.
Moreover, believing we can predict and plan for all AI-related unknowns reflects overconfidence in our understanding and foresight. History shows that technological progress, marked by unexpected outcomes and discoveries, defies such predictions. The evolution from the printing press to the internet underscores progress's unpredictability. Hence, facing AI's future requires caution, curiosity, and humility. Acknowledging our limitations and embracing continuous learning and adaptation will allow us to harness AI's potential responsibly, illustrating that embracing our uncertainties, rather than pretending to foresee them, is vital to innovation.
The journey of technological advancement is fraught with both promise and trepidation. Historically, each significant leap forward, from the dawn of the industrial age to the digital revolution, has been met with a mix of enthusiasm and apprehension. Aza Raskin and Tristan Harris's thesis in the 'AI Dilemma' embodies the latter.
Who defines "safe?"
When slowing down technologies for safety or ethical reasons, the issue arises of who gets to define what "safe" or “ethical” mean? This inquiry is not merely technical but deeply ideological, touching the very core of societal values and power dynamics. For example, the push for Diversity, Equity, and Inclusion (DEI) initiatives shows how specific ideological underpinnings can shape definitions of safety and decency.
Take the case of the initial release of Google's AI chatbot, Gemini, which chose the ideology of its creators over truth. Luckily, the answers were so ridiculous that the pushback was sudden and immediate. My worry, however, is if, in correcting this, they become experts in making the ideological capture much more subtle. Large bureaucratic institutions' top-down safety enforcement creates a fertile ground for ideological capture of safety standards.

I claim that the issue is not the technology itself but the lens through which we view and regulate it. Suppose the gatekeepers of 'safety' are aligned with a singular ideology. In that case, AI development would skew to serve specific ends, sidelining diverse perspectives and potentially stifling innovative thought and progress.
In the podcast, Tristan and Aza suggest such manipulation as a solution. They propose using AI for consensus-building and creating "shared realities" to address societal challenges. In practice, this means that when individuals' viewpoints seem to be far apart, we can leverage AI to "bridge the gap." How they bridge the gap and what we would bridge it toward is left to the imagination, but to me, it is clear. Regulators will inevitably influence it from the top down, which, in my opinion, would be the opposite of progress.
In navigating this terrain, we must advocate for a pluralistic approach to defining safety, encompassing various perspectives and values achieved through market forces rather than a governing entity choosing winners. The more players that can play the game, the more wide-ranging perspectives will catalyze innovation to flourish.
Ownership & Identity
Just because we should accelerate AI forward does not mean I do not have my concerns. When I think about what could be the most devastating for society, I don't believe we have to worry about a Matrix-level dystopia; I worry about freedom. As I explored in "Whose data is it anyway?," my concern gravitates toward the issues of data ownership and the implications of relinquishing control over our digital identities. This relinquishment threatens our privacy and the integrity of the content we generate, leaving it susceptible to the inclinations and profit of a few dominant tech entities.
To counteract these concerns, a paradigm shift towards decentralized models of data ownership is imperative. Such standards would empower individuals with control over their digital footprints, ensuring that we develop AI systems with diverse, honest, and truthful perspectives rather than the massaged, narrow viewpoints of their creators. This shift safeguards individual privacy and promotes an ethical framework for AI development that upholds the principles of fairness and impartiality.
As we stand at the crossroads of technological innovation and ethical consideration, it is crucial to advocate for systems that place data ownership firmly in the hands of users. By doing so, we can ensure that the future of AI remains truthful, non-ideological, and aligned with the broader interests of society.
But what about the Matrix?
I know I am in the minority on this, but I feel that the concerns of AGI (Artificial General Intelligence) are generally overblown. I am not scared of reaching the point of AGI, and I think the idea that AI will become so intelligent that we will lose control of it is unfounded and silly. Reaching AGI is not reaching consciousness; being worried about it spontaneously gaining consciousness is a misplaced fear. It is a tool created by humans for humans to enhance productivity and achieve specific outcomes.
At a technical level, large language models (LLMs) are trained on extensive datasets and learning patterns from language and data through a technique called "unsupervised learning" (meaning the data is untagged). They predict the next word in sentences, refining their predictions through feedback to improve coherence and relevance. When queried, LLMs generate responses based on learned patterns, simulating an understanding of language to provide contextually appropriate answers. They will only answer based on the datasets that were inputted and scanned.
AI will never be "alive," meaning that AI lacks inherent agency, consciousness, and the characteristics of life, not capable of independent thought or action. AI cannot act independently of human control. Concerns about AI gaining autonomy and posing a threat to humanity are based on a misunderstanding of the nature of AI and the fundamental differences between living beings and machines. AI spontaneously developing a will or consciousness is more similar to thinking a hammer will start walking than us being able to create consciousness through programming. Right now, there is only one way to create consciousness, and I'm skeptical that is ever something we will be able to harness and create as humans. Irrespective of its complexity — and yes, our tools will continue to become evermore complex — machines, specifically AI, cannot transcend their nature as non-living, inanimate objects programmed and controlled by humans.
 The advancement of AI should be seen as enhancing human capabilities, not as a path toward creating autonomous entities with their own wills. So, while AI will continue to evolve, improve, and become more powerful, I believe it will remain under human direction and control without the existential threats often sensationalized in discussions about AI's future.
The advancement of AI should be seen as enhancing human capabilities, not as a path toward creating autonomous entities with their own wills. So, while AI will continue to evolve, improve, and become more powerful, I believe it will remain under human direction and control without the existential threats often sensationalized in discussions about AI's future. With this framing, we should not view the race toward AGI as something to avoid. This will only make the tools we use more powerful, making us more productive. With all this being said, AGI is still much farther away than many believe.
Today's AI excels in specific, narrow tasks, known as narrow or weak AI. These systems operate within tightly defined parameters, achieving remarkable efficiency and accuracy that can sometimes surpass human performance in those specific tasks. Yet, this is far from the versatile and adaptable functionality that AGI represents.
Moreover, the exponential growth of computational power observed in the past decades does not directly translate to an equivalent acceleration in achieving AGI. AI's impressive feats are often the result of massive data inputs and computing resources tailored to specific tasks. These successes do not inherently bring us closer to understanding or replicating the general problem-solving capabilities of the human mind, which again would only make the tools more potent in our hands.
While AI will undeniably introduce challenges and change the aspects of conflict and power dynamics, these challenges will primarily stem from humans wielding this powerful tool rather than the technology itself. AI is a mirror reflecting our own biases, values, and intentions. The crux of future AI-related issues lies not in the technology's inherent capabilities but in how it is used by those wielding it. This reality is at odds with the idea that we should slow down development as our biggest threat will come from those who are not friendly to us.
AI Beget's AI
While the unknowns of AI development and its pitfalls indeed stir apprehension, it's essential to recognize the power of market forces and human ingenuity in leveraging AI to address these challenges. History is replete with examples of new technologies raising concerns, only for those very technologies to provide solutions to the problems they initially seemed to exacerbate. It looks silly and unfair to think of fighting a war with a country that never embraced oil and was still primarily getting its energy from burning wood.
 The evolution of AI is no exception to this pattern. As we venture into uncharted territories, the potential issues that arise with AI—be it ethical concerns, use by malicious actors, biases in decision-making, or privacy intrusions—are not merely obstacles but opportunities for innovation. It is within the realm of possibility, and indeed, probability, that AI will play a crucial role in solving the problems it creates. The idea that there would be no incentive to address and solve these problems is to underestimate the fundamental drivers of technological progress.
The evolution of AI is no exception to this pattern. As we venture into uncharted territories, the potential issues that arise with AI—be it ethical concerns, use by malicious actors, biases in decision-making, or privacy intrusions—are not merely obstacles but opportunities for innovation. It is within the realm of possibility, and indeed, probability, that AI will play a crucial role in solving the problems it creates. The idea that there would be no incentive to address and solve these problems is to underestimate the fundamental drivers of technological progress.Market forces, fueled by the demand for better, safer, and more efficient solutions, are powerful catalysts for positive change. When a problem is worth fixing, it invariably attracts the attention of innovators, researchers, and entrepreneurs eager to solve it. This dynamic has driven progress throughout history, and AI is poised to benefit from this problem-solving cycle.
Thus, rather than viewing AI's unknowns as sources of fear, we should see them as sparks of opportunity. By tackling the challenges posed by AI, we will harness its full potential to benefit humanity. By fostering an ecosystem that encourages exploration, innovation, and problem-solving, we can ensure that AI serves as a force for good, solving problems as profound as those it might create. This is the optimism we must hold onto—a belief in our collective ability to shape AI into a tool that addresses its own challenges and elevates our capacity to solve some of society's most pressing issues.
An AI Future
The reality is that it isn't whether AI will lead to unforeseen challenges—it undoubtedly will, as has every major technological leap in history. The real issue is whether we let fear dictate our path and confine us to a standstill or embrace AI's potential to address current and future challenges.
The approach to solving potential AI-related problems with stringent regulations and a slowdown in innovation is akin to cutting off the nose to spite the face. It's a strategy that risks stagnating the U.S. in a global race where other nations will undoubtedly continue their AI advancements. This perspective dangerously ignores that AI, much like the printing press of the past, has the power to democratize information, empower individuals, and dismantle outdated power structures.
The way forward is not less AI but more of it, more innovation, optimism, and curiosity for the remarkable technological breakthroughs that will come. We must recognize that the solution to AI-induced challenges lies not in retreating but in advancing our capabilities to innovate and adapt.
AI represents a frontier of limitless possibilities. If wielded with foresight and responsibility, it's a tool that can help solve some of the most pressing issues we face today. There are certainly challenges ahead, but I trust that with problems come solutions. Let's keep the AI Decels from steering us away from this path with their doomsday predictions. Instead, let's embrace AI with the cautious optimism it deserves, forging a future where technology and humanity advance to heights we can't imagine.
-
 @ 0e501ec7:de5ef3a4
2024-11-20 21:52:58
@ 0e501ec7:de5ef3a4
2024-11-20 21:52:58Deux hommes, fils et père, die graag gaan fietsen. Als echt professionele fietsers natuurlijk, vol in pak, snelle koersfietsen. Ik stond in hun straat te sukkelen met een platte band, ik had geen pomp, en geen vorken om mijn band op te heffen. De vader, Dominique, stopte en zei: t'as le pneu crevé? Monte avec nous! Daar syonden ze te wachten aan de open garagepoort. Ze hadden net 50km gedaan, op het gemak zeiden ze, ze hadden veel gebabbeld. Ze herstelden met veel plezier mijn band, we babbelden wat over mijn tocht, over fietsen, over wat erna. In gebrekkig Frans van mijn kant hé natuurlijk. Gaspard studeert meubelmaker (Menuserie). Dominique vroeg of ik water wou, ik zei eerst nee, dan ja, dan vroeg hij of ik nog iets wou, ik zei eerst nee, dan ja, en hij kwam terug met een zak vol fruit en repen. Ik aanvaarde ze, terugkrabbelen was het te laat voor en ik kon ze echt wel gebruiken. Hij zei: als je nog eens in de buurt bent, kom dan hallo zeggen, ik zei ja dan kunnen we samen een toertje maken. Ze vroegen nog of ik instagram had, en toen vertrok ik weer. Ik voelde me nog slecht over het aanvaarden van zo veel hulp, maar ach, wat een fijne ontmoeting.
-
 @ 3bf0c63f:aefa459d
2024-05-21 12:38:08
@ 3bf0c63f:aefa459d
2024-05-21 12:38:08Bitcoin transactions explained
A transaction is a piece of data that takes inputs and produces outputs. Forget about the blockchain thing, Bitcoin is actually just a big tree of transactions. The blockchain is just a way to keep transactions ordered.
Imagine you have 10 satoshis. That means you have them in an unspent transaction output (UTXO). You want to spend them, so you create a transaction. The transaction should reference unspent outputs as its inputs. Every transaction has an immutable id, so you use that id plus the index of the output (because transactions can have multiple outputs). Then you specify a script that unlocks that transaction and related signatures, then you specify outputs along with a script that locks these outputs.

As you can see, there's this lock/unlocking thing and there are inputs and outputs. Inputs must be unlocked by fulfilling the conditions specified by the person who created the transaction they're in. And outputs must be locked so anyone wanting to spend those outputs will need to unlock them.
For most of the cases locking and unlocking means specifying a public key whose controller (the person who has the corresponding private key) will be able to spend. Other fancy things are possible too, but we can ignore them for now.
Back to the 10 satoshis you want to spend. Since you've successfully referenced 10 satoshis and unlocked them, now you can specify the outputs (this is all done in a single step). You can specify one output of 10 satoshis, two of 5, one of 3 and one of 7, three of 3 and so on. The sum of outputs can't be more than 10. And if the sum of outputs is less than 10 the difference goes to fees. In the first days of Bitcoin you didn't need any fees, but now you do, otherwise your transaction won't be included in any block.

If you're still interested in transactions maybe you could take a look at this small chapter of that Andreas Antonopoulos book.
If you hate Andreas Antonopoulos because he is a communist shitcoiner or don't want to read more than half a page, go here: https://en.bitcoin.it/wiki/Coin_analogy
-
 @ 0e501ec7:de5ef3a4
2024-11-20 21:41:43
@ 0e501ec7:de5ef3a4
2024-11-20 21:41:43Ik vertrok eergisteren bij Guillaume en Alice. Ik had niet de tijd om dit af te schrijven, ik werd onderbroken ik weet niet meer waardoor. Dus de dag voor eergisteren vertrok ik bij Guillaume en Alice. Over mijn verblijf daar zal ik later schrijven. Het is ondertussen half 11, 20 november, een maand voor het einde van de Herfst. Ik zit op de trein richting Gent, met fiets en al. Deze reis, of deze etappe van de reis is over. Binnen een uurtje toch. Dan ga ik lekker naar mijn eigen bed, en slaap ik een goeie warme nacht. Het gaat vreemd zijn om weer alleen in een kamer van steen te slapen, al is dat eigenlijk altijd vreemd. Ik ga proberen daar genoeg tijd voor mezelf te pakken, en de dingen die ik geleerd heb niet te vergeten. Ik ga schrijven en voelen ipv te vluchten in Schermtijd. Want ik kan mijn gewoontes veranderen!
Maar nu dus, de laatste dagen van de tocht. Zondag vertrok ik, het was moeilijk afscheid te nemen, ik vind afscheid eigenlijk altijd moeilijk. Maar het is goed om in beweging te blijven, daar ben ik zeker van. Het was dus tijd om te vertrekken, ook omdat ik voelde dat de allergie van het stof (verbouwingen) en de kat mij aan het uitputten was. Tegen dat ik eindelijk op de fiets zat was het al middag, Tim had mij op het laatste nog geholpen om een een verloren bout te kunnen vervangen, mijn zijn daadkracht en improvisatietalent. Het was een mooie fietstocht die dag, en ik heb er zeer van genoten om alleen te fietsen. Ik reed eerst een paar keer mis, en kwam toen bij de bakker aan waar ik baguettes kocht en mijn telefoon liet opladen. Ik dacht veel na, in ontspannen toestand, waarbij ik echt voelde dat ik aan het verwerken was. Soms had ik de neiging om mijn gedachten te proberen onderdrukken, om meer op te letten op de omgeving. Mar onderdrukken is niet leuk, dus probeerde ik gewoon een beetje af te wisselen tussen wegdromen en aandachtig zijn. Dat werkte! Ik schreef zelfs een beetje tijdens de pauzes, wat ik ook heel leuk vond. Op een ander moment wou ik een gedachte of drie echt wel vastleggen tijdens het fietsen, en maakte ik een voice-opname. Eigenlijk was dat ook best leuk :), om zo tegen jezelf te babbelen en weten dat je het binnen onbepaalde tijd weer zal kunnen horen.
Een van mijn pauzes was in een klein associatief cafeetje, dat vroeger een station was (het fietspad was een oud treinspoor, prachtig en rustig fietsen verzekerd!). Ik kocht wat nootjes en dronk een warme choco. Toen ik buitenkwam regende een beetje, en stond de zon laag, zodat het licht geel oranje goud was. Toen ik mij omdraaide zag ik zelfs een regenboog. Toen, en op meerdere momenten, voelde ik echt kriebels in mijn buik voor het landschap en alles dat erbij hoorde. Echt een soort vreugde van samenzijn! Het landschap, de mooie Bocage, en ik.
In de avond kwam ik toe in Caen, het was al donker, en ik had echt een sciencefiction gevoel bij het toekomen in de Woonplaats van de Mens, na de lange tocht door de velden en bossen. De Mens, met zijn gebouwen van Steen, met zijn wegen en drukke verplaatsingen, zijn vele lichtjes. Het voelde vreemd en vertrouwd. Snap je wat ik bedoel? Ik sliep die nacht bij Ilan en zijn familie, Ilan is een jonge low-tech ingenieur die zijn eigen brood bakt en van techno houdt. Echt een top kerel. Ik voelde me goed op mijn gemak daar, en heb veel in het frans gebabbeld!!

-
 @ fa984bd7:58018f52
2024-02-28 22:15:25
@ fa984bd7:58018f52
2024-02-28 22:15:25I have recently launched Wikifreedia, which is a different take on how Wikipedia-style systems can work.
Yes, it's built on nostr, but that's not the most interesting part.
The fascinating aspect is that there is no "official" entry on any topic. Anyone can create or edit any entry and build their own take about what they care about.
Think the entry about Mao is missing something? Go ahead and edit it, you don't need to ask for permission from anyone.
Stuart Bowman put it best on a #SovEng hike:
The path to truth is in the integration of opposites.
Since launching Wikifreedia, less than a week ago, quite a few people asked me if it would be possible to import ALL of wikipedia into it.
Yes. Yes it would.
I initially started looking into it to make it happen as I am often quick to jump into action.
But, after thinking about it, I am not convinced importing all of Wikipedia is the way to go.
The magical thing about building an encyclopedia with no canonical entry on any topic is that each individual can bring to light the part they are interested the most about a certain topic, it can be dozens or hundreds, or perhaps more, entries that focus on the edges of a topic.
Whereas, Wikipedia, in their Quijotean approach to truth, have focused on the impossible path of seeking neutrality.
Humans can't be neutral, we have biases.
Show me an unbiased human and I'll show you a lifeless human.
Biases are good. Having an opinion is good. Seeking neutrality is seeking to devoid our views and opinions of humanity.
Importing Wikipedia would mean importing a massive amount of colorless trivia, a few interesting tidbits, but, more important than anything, a vast amount of watered-down useless information.
All edges of the truth having been neutered by a democratic process that searches for a single truth via consensus.
"What's the worst that could happen?"
Sure, importing wikipedia would simply be one more entry on each topic.
Yes.
But culture has incredibly strong momentum.
And if the culture that develops in this type of media is that of exclusively watered-down comfortable truths, then some magic could be lost.
If people who are passionate or have a unique perspective about a topic feel like the "right approach" is to use the wikipedia-based article then I would see this as an extremely negative action.
An alternative
An idea we discussed on the #SovEng hike was, what if the wikipedia entry is processed by different "AI agents" with different perspectives.
Perhaps instead of blankly importing the "Napoleon" article, an LLM trained to behave as a 1850s russian peasant could be asked to write a wiki about Napoleon. And then an agent tried to behave like Margaret Thatcher could write one.
Etc, etc.
Embrace the chaos. Embrace the bias.
-
 @ 84999652:2a24d806
2024-11-21 05:34:49
@ 84999652:2a24d806
2024-11-21 05:34:492024.11.14.
摘要
本文深入分析了简化支付验证(SPV)技术从比特币网络的基础应用到现代区块链扩展层的演进过程,特别关注了其在ChainX、BEVM和Super Bitcoin中的创新应用,探讨了SPV技术在保持去中心化的同时实现扩展性的技术方案。
1. SPV基础技术方案
1.1 技术原理

1.2 工作流程
区块头同步流程

交易验证机制
- 请求特定交易的默克尔路径
- 验证默克尔证明
- 确认交易状态
1.3 为什么比特币适合SPV?
技术特征
- 链上逻辑简单
- 纯UTXO状态验证
- 无复杂计算需求
-
状态变化明确
-
验证成本稳定
- 区块头固定大小(80字节)
- 验证复杂度恒定
- 存储需求可控
二、技术演进历程
2.1 ChainX阶段(2018-2020):跨链验证创新
技术架构

核心创新
- 首创WASM链上SPV验证
- 实现去中心化跨链
- 验证效率优化
2.2 BEVM阶段(2020-2023):智能合约整合
架构升级

技术突破
- Taproot协议支持
- EVM兼容性
- 验证性能提升
2.3 Super Bitcoin阶段(2024-现在):共识共享创新
五层架构

三、技术对比分析
3.1 不同区块链的SPV适用性分析

3.2 演进过程中的技术指标对比

四、创新应用场景
4.1 跨链资产管理
验证流程

4.2 智能合约交互
实现机制
- 交易验证集成
- 状态同步
- 合约调用
4.3 Layer2扩展
技术框架

五、安全性分析
5.1 威胁模型
潜在风险 1. 分叉攻击 2. 双花攻击 3. 数据可用性
防护措施

5.2 最长链一致性
保障机制
- 多点验证
- 共识检查
- 状态回滚
六、未来展望
6.1 技术发展方向
- 验证机制优化
- 零知识证明集成
- 批量验证优化
-
状态压缩
-
应用场景拓展
- DeFi集成
- 跨链互操作
- Layer2扩展
七、结论
SPV技术从比特币网络的基础验证机制发展至今,经历了重要的演进过程:
- 在ChainX中验证了跨链可行性
- 在BEVM中实现了与智能合约的融合
- 在Super Bitcoin中开创了共识共享新范式
这一演进过程展示了SPV技术在保持安全性和去中心化的同时,如何通过持续创新来适应现代区块链生态的需求。未来,随着技术的进一步发展和应用场景的拓展,SPV有望在区块链扩展性解决方案中发挥更重要的作用。
-
 @ 599f67f7:21fb3ea9
2024-11-20 21:25:38
@ 599f67f7:21fb3ea9
2024-11-20 21:25:38¿Qué es un canal?
Un canal Lightning es simplemente una multifirma 2-de-2 en la cadena. Para abrir un canal, solo enviamos fondos a una transacción multifirma 2-de-2. Esto crea un UTXO y el canal está abierto hasta que este UTXO se gaste. Durante la vida del canal, se crean un montón de transacciones que gastan doblemente la transacción de financiamiento, pero eventualmente una (y solo una) de estas se publicará en la cadena para cerrar el canal. Así que, idealmente, un canal Lightning condensa efectivamente un montón de transacciones en dos transacciones en la cadena: la que lo abre y la que lo cierra. Podríamos decir que así es como Lightning "eleva" las transacciones fuera de la cadena.
Creando un canal
Una transacción de financiamiento para un canal entre Alice y Bob es simplemente una transacción que tiene una salida como sigue:
2 <pubkeyA> <pubkeyB> 2 OP_CHECKMULTISIGDonde
<pubkeyA>es la clave pública de Alice y<pubkeyB>es la de Bob. Entonces, si Alice quiere abrir un canal con Bob, ¿simplemente le envía fondos al script anterior?La respuesta es no, es un poco más complicado que eso. Existe la posibilidad de que Bob desaparezca para siempre y nunca vuelva a firmar ninguna transacción que intente gastar de la transacción de financiamiento. Esto significa que, efectivamente, los fondos de Alice quedarían atrapados en este UTXO para siempre. ¡No es ideal!
Aquí es donde entra una transacción de compromiso. Cubriremos la transacción de compromiso con más detalle en el futuro, pero por ahora lo importante que hay que saber es que una vez que una transacción de financiamiento es confirmada, las transacciones de compromiso definen el estado del canal (es decir, cómo se distribuyen los fondos entre los participantes del canal). Así que, esencialmente, cada transacción de compromiso gasta la transacción de financiamiento como entrada y tiene salidas que definen la distribución de fondos entre los participantes del canal.
Para ver cómo se utilizan estos dos conceptos para negociar la apertura de un canal, se intercambiará una serie de mensajes entre los nodos de Alice y Bob, como se muestra en el diagrama a continuación.

Es un poco como negociar un contrato; cada parte solo firma cuando está contento con los términos. Vamos a revisar cada uno de estos mensajes con más detalle.
open_channel
Alice envía este mensaje a Bob para indicar que quiere abrir un canal con él. Este mensaje contiene varios detalles sobre los requisitos de Alice para el canal. El más importante es
funding_pubkey. Esta es la clave pública que Alice tiene la intención de usar como su clave pública en el script de la transacción de financiamiento.
accept_channel
Si Bob está contento con los requisitos que Alice ha presentado en su oferta de canal, puede enviar de vuelta el mensaje
accept_channel, que también contiene algunos de sus requisitos junto con sufunding_pubkey.
En este punto, Alice tiene todo lo que necesita para construir la transacción de financiamiento. Sin embargo, aún no tiene garantía de que Bob no desaparecerá, lo que haría que sus fondos no se pudieran gastar. Por lo tanto, aún no transmite la transacción de financiamiento. En cambio, lo que necesita es una transacción de compromiso firmada por Bob que gaste de la transacción de financiamiento y divida el saldo del canal en consecuencia. La transacción de financiamiento podría asignar algunos fondos a Bob también, por lo que Bob también querría una transacción de compromiso válida firmada por Alice, en caso de que ella desaparezca.
Entonces, lo que Alice hace ahora es construir la transacción de financiamiento y enviar a Bob el siguiente mensaje:
funding_created

Este mensaje contiene el TXID de la transacción de financiamiento, el índice de salida relevante de la transacción de financiamiento junto con una firma de la transacción de compromiso de Bob. Alice puede construir la transacción de compromiso exacta de Bob utilizando la información que ya conoce.
Ten en cuenta que Bob no puede hacer nada aún con su transacción de compromiso porque está gastando de una transacción que aún no está en la blockchain.
funding_signed

Si Bob está contento, entonces puede enviar a Alice un mensaje
funding_signed, que contiene la firma de Bob para la transacción de compromiso de Alice.Ahora, Alice tiene una transacción de compromiso válida firmada por Bob que puede usar para gastar sus fondos de vuelta a sí misma en caso de que Bob desaparezca. Por lo tanto, es seguro para ella transmitir la transacción de financiamiento.
channel_ready
Tanto Alice como Bob estarán ahora observando la blockchain esperando que la transacción de financiamiento alcance el número deseado de confirmaciones. Una vez que cada uno lo vea, se enviarán mutuamente el mensaje
channel_readyque contiene el ID del canal.
¡El canal ahora está abierto y listo para transacciones!
Revisión
Terminaremos con un breve resumen de los conceptos importantes que hemos aprendido en este capítulo. Siéntete libre de volver aquí en el futuro en caso de que necesites un recordatorio.
- canal: un contrato multifirma 2-de-2 en la cadena utilizado para elevar transacciones fuera de la cadena
- transacción de financiamiento: una transacción multifirma 2-de-2 con un script de salida P2WSH que contiene las claves públicas de ambos participantes del canal
- transacción de compromiso: una transacción que define el estado de un canal, es decir, la distribución de fondos entre los participantes del canal
Referencias
- BOLT2
- LN Things Part 1: Creating a channel por nostr:nprofile1qqswrt9pnxatlplu49h6meld8svmwqt87wwvk256rqk07n6eu4qeh5gpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dszpfjtz
-
 @ d5c3d063:4d1159b3
2024-11-21 05:18:13
@ d5c3d063:4d1159b3
2024-11-21 05:18:13ข้อดี #เงินฝืด มุมมองเศรษฐศาสตร์สำนักออสเตรียน
เศรษฐศาสตร์สำนักออสเตรียน มองเศรษฐกิจจาก "การกระทำของมนุษย์" (Human Action) โดยเน้นที่การตัดสินใจของแต่ละบุคคล ท่ามกลางทรัพยากรที่มีอยู่อย่างจำกัด บทความนี้จะพาไปสำรวจข้อดีของ "ภาวะเงินฝืด"(deflation) หรือภาวะที่ราคาสินค้าและบริการลดลงเรื่อยๆ ซึ่งอาจฟังดูแปลก เพราะเศรษฐศาสตร์กระแสหลัก มักมองว่าเงินเฟ้ออ่อนๆ ต่างหากที่จำเป็นต่อการขับเคลื่อนเศรษฐกิจ มาดูกันว่าทำไมสำนักออสเตรียนถึงคิดต่าง
-
กำลังซื้อที่เพิ่มขึ้น - ในภาวะเงินฝืด มูลค่าของเงินจะเพิ่มขึ้น ทำให้ผู้บริโภคสามารถซื้อสินค้าและบริการได้มากขึ้นด้วยเงินจำนวนเท่าเดิม เช่น สมมติว่าคุณมีเงิน 100 บาท และราคาขนมปังอยู่ที่ 10 บาท คุณสามารถซื้อขนมปังได้ 10 ก้อน แต่ถ้าเกิดภาวะเงินฝืด ราคาขนมปังลดลงเหลือ 8 บาท คุณก็สามารถซื้อขนมปังได้ 12.5 ก้อนด้วยเงินจำนวนเท่าเดิม นี่เป็นผลดีต่อผู้บริโภคโดยตรง โดยเฉพาะผู้มีรายได้คงที่ เพราะกำลังซื้อของพวกเขาจะเพิ่มขึ้น ตามหลักการของเศรษฐศาสตร์สำนักออสเตรียนที่ว่ามูลค่าเป็นสิ่งอัตวิสัย (Subjective Value) ขึ้นอยู่กับแต่ละบุคคล แม้ว่าราคาสินค้าจะลดลง แต่ถ้าผู้บริโภครู้สึกว่าสินค้าชิ้นนั้นยังคงมีมูลค่า พวกเขาก็ยังคงซื้อ
. 2. #ส่งเสริมการออม - เมื่อเราคาดการณ์ได้ว่าราคาสินค้าจะลดลงในอนาคต ผู้คนมีแนวโน้มที่จะชะลอการซื้อและเก็บออมมากขึ้น เพราะพวกเขาสามารถซื้อสินค้าได้มากขึ้นในอนาคตด้วยเงินจำนวนเท่าเดิม พฤติกรรมนี้สอดคล้องกับแนวคิด Time Preference ที่ว่ามนุษย์มีแนวโน้มที่จะให้ความสำคัญกับความพึงพอใจในปัจจุบันมากกว่าอนาคต แต่ในภาวะเงินฝืด การเลื่อนความพึงพอใจไปในอนาคต (การออม) กลับให้ผลตอบแทนที่ดีกว่า การออมที่เพิ่มขึ้นยังเป็นปัจจัยสำคัญในการขับเคลื่อนการลงทุน และการเติบโตทางเศรษฐกิจในระยะยาว โดยการออมที่เพิ่มขึ้นจะทำให้มีเงินทุนหมุนเวียนในระบบเศรษฐกิจมากขึ้น และนำไปสู่การลดลงของอัตราดอกเบี้ย ซึ่งจะช่วยกระตุ้นการลงทุนในระยะยาว
. 3. #กระตุ้นการลงทุนอย่างมีประสิทธิภาพ - ภาวะเงินฝืดทำให้ผู้ประกอบการต้องคำนึงถึงต้นทุนและผลกำไรอย่างรอบคอบมากขึ้น เนื่องจากราคาสินค้าและบริการลดลง การลงทุนในสิ่งที่ไม่มีประสิทธิภาพจะทำให้ขาดทุนได้ง่าย ดังนั้นผู้ประกอบการจะต้องมุ่งเน้นการลงทุนในโครงการที่มีศักยภาพในการสร้างผลกำไรอย่างแท้จริงและใช้ทรัพยากรอย่างคุ้มค่า เศรษฐศาสตร์สำนักออสเตรียนเน้นเรื่องการคำนวณทางเศรษฐกิจ (Economic Calculation) ซึ่งเป็นกระบวนการที่ผู้ประกอบการใช้ในการตัดสินใจลงทุน และภาวะเงินฝืดทำให้การคำนวณนี้แม่นยำขึ้น เพราะราคาที่ลดลงสะท้อนต้นทุนที่แท้จริง ไม่ถูกบิดเบือนจากเงินเฟ้อ ส่งผลให้การจัดสรรทรัพยากรมีประสิทธิภาพมากขึ้น
. 4. #ลดความผันผวนของวัฏจักรเศรษฐกิจ - เศรษฐศาสตร์สำนักออสเตรียนมองว่าภาวะเงินเฟ้อที่เกิดจากการแทรกแซงของธนาคารกลางในการเพิ่มปริมาณเงิน เป็นสาเหตุสำคัญของวัฏจักรเศรษฐกิจ (business cycle) การเพิ่มปริมาณเงินทุนที่ไม่ได้มาจากการลดการบริโภคจริง จะนำไปสู่การลงทุนที่ผิดพลาดและเกิดวิกฤตเศรษฐกิจในที่สุด ในทางตรงกันข้าม เงินฝืดที่เกิดจากการเพิ่มขึ้นของผลผลิตไม่ได้สร้างความบิดเบือนให้กับตลาดทุนและไม่นำไปสู่วัฏจักรเศรษฐกิจ เพราะการลดลงของราคาสินค้ามาจากการที่สินค้าและบริการมีมากขึ้น ไม่ใช่การที่เงินมีมูลค่าลดลง
. 5. #ส่งเสริมนวัตกรรมและเทคโนโลยี - เพื่อให้สามารถแข่งขันและทำกำไรในภาวะเงินฝืด ผู้ประกอบการต้องหาวิธีลดต้นทุนและพัฒนาสินค้าใหม่ๆ เพื่อแข่งขัน ซึ่งต้องอาศัยนวัตกรรมและเทคโนโลยี ตัวอย่างเช่น ในช่วง Industrial Revolution มีการพัฒนาเทคโนโลยีต่างๆ มากมาย ทำให้ผลผลิตเพิ่มขึ้น และราคาสินค้าลดลง
. 6. #เสริมสร้างวินัยทางการเงิน - ภาวะเงินฝืดบังคับให้รัฐบาล ธุรกิจ และประชาชน ต้องมีวินัยทางการเงิน ไม่สามารถพึ่งพาการก่อหนี้หรือการพิมพ์เงินเพื่อแก้ปัญหาเศรษฐกิจได้ เพราะการพิมพ์เงิน ตามทัศนะของเศรษฐศาสตร์สำนักออสเตรียน เป็นการ “ขโมย” ความมั่งคั่งจากประชาชนทางอ้อม
. 7. #สะท้อนความก้าวหน้าทางเทคโนโลยี - เงินฝืดที่เกิดจากการเพิ่มขึ้นของผลผลิต เป็นเครื่องบ่งชี้ถึงความก้าวหน้าทางเทคโนโลยีและประสิทธิภาพในการผลิตที่เพิ่มขึ้น ซึ่งเป็นผลดีต่อเศรษฐกิจในระยะยาว การที่สินค้ามีราคาถูกลง เป็นผลมาจากการใช้เทคโนโลยีและพลังงานอย่างมีประสิทธิภาพมากขึ้น
สรุปแบบสั้นๆ…เศรษฐศาสตร์สำนักออสเตรียนมองว่า ภาวะเงินฝืด ที่เกิดจากการเพิ่มขึ้นของผลผลิต เป็นปรากฏการณ์ทางเศรษฐกิจที่เป็นธรรมชาติ และเป็นประโยชน์ในระยะยาว แม้ว่าในระยะสั้นอาจทำให้ธุรกิจบางส่วนต้องปรับตัว แต่การแทรกแซงของรัฐบาล เช่น การพิมพ์เงินเพื่อกระตุ้นเศรษฐกิจ เป็นการแก้ปัญหาที่ปลายเหตุและอาจสร้างความเสียหายในระยะยาว ในขณะที่ภาวะเงินฝืดจะกระตุ้นให้เกิดการปรับตัว การลงทุนอย่างมีประสิทธิภาพ และการพัฒนาทางเทคโนโลยี ซึ่งเป็นปัจจัยสำคัญในการสร้างความมั่งคั่งอย่างยั่งยืน อ้างอิงจากหนังสือ Principles of Economics อ.Saifedean Ammous
-
-
 @ 4fcac000:d2b37988
2024-11-20 20:31:04
@ 4fcac000:d2b37988
2024-11-20 20:31:04** Двадцать лет назад «Умный город» был лишь амбициозным проектом. Сегодня он стал реальностью. Как бы вы охарактеризовали текущее состояние системы?**
Действительно, путь был долгим, но, как видите, успешным. Сегодня «Умный город» Тюмени — это не просто набор отдельных технологий, а взаимосвязанная экосистема, оптимизирующая все аспекты городской жизни. Мы гордимся результатами: значительным снижением уровня выбросов CO2 благодаря повсеместному внедрению возобновляемых источников энергии и электротранспорта, практически полным отсутствием пробок благодаря интеллектуальной системе управления дорожным движением и, конечно же, повышением уровня жизни горожан за счет удобных цифровых сервисов и доступности информации.
Какие из реализованных проектов вы считаете наиболее успешными и почему?
Несомненно, одним из главных достижений является интеграция системы «Умный дом» во все муниципальные здания и значительную часть частного сектора. Это позволило оптимизировать энергопотребление, повысить безопасность и комфорт жителей.
А что нас ждет в будущем? Какие направления развития системы «Умный город» вы видите в ближайшие десятилетия?
Мы планируем дальнейшее совершенствование существующих систем и внедрение новых инновационных решений в области искусственного интеллекта, больших данных и блокчейна. В центре внимания — совершенствование системы управления транспортом, создание полностью автоматизированной сети общественного транспорта, внедрение персонализированных сервисов в сфере образования, здравоохранения и культуры. Наше главное направление — повышение качества жизни горожан за счет устойчивого и интеллектуального развития Тюмени.
** В чём заключается самая большая польза, которую Тюмень получила от своей инициативы «Умный город»?**
Самым большим преимуществом является заметное улучшение качества жизни жителей, в первую очередь за счёт снижения загруженности дорог и повышения эффективности городских служб. Это приводит к сокращению времени в пути, уменьшению загрязнения окружающей среды и, в конечном счёте, к увеличению свободного времени и улучшению здоровья граждан.
В чем будущее Тюмени?
Будущее Тюмени — в умных технологиях и ответственном подходе к развитию.
-
 @ 6871d8df:4a9396c1
2024-02-24 22:42:16
@ 6871d8df:4a9396c1
2024-02-24 22:42:16In an era where data seems to be as valuable as currency, the prevailing trend in AI starkly contrasts with the concept of personal data ownership. The explosion of AI and the ensuing race have made it easy to overlook where the data is coming from. The current model, dominated by big tech players, involves collecting vast amounts of user data and selling it to AI companies for training LLMs. Reddit recently penned a 60 million dollar deal, Google guards and mines Youtube, and more are going this direction. But is that their data to sell? Yes, it's on their platforms, but without the users to generate it, what would they monetize? To me, this practice raises significant ethical questions, as it assumes that user data is a commodity that companies can exploit at will.
The heart of the issue lies in the ownership of data. Why, in today's digital age, do we not retain ownership of our data? Why can't our data follow us, under our control, to wherever we want to go? These questions echo the broader sentiment that while some in the tech industry — such as the blockchain-first crypto bros — recognize the importance of data ownership, their "blockchain for everything solutions," to me, fall significantly short in execution.
Reddit further complicates this with its current move to IPO, which, on the heels of the large data deal, might reinforce the mistaken belief that user-generated data is a corporate asset. Others, no doubt, will follow suit. This underscores the urgent need for a paradigm shift towards recognizing and respecting user data as personal property.
In my perfect world, the digital landscape would undergo a revolutionary transformation centered around the empowerment and sovereignty of individual data ownership. Platforms like Twitter, Reddit, Yelp, YouTube, and Stack Overflow, integral to our digital lives, would operate on a fundamentally different premise: user-owned data.
In this envisioned future, data ownership would not just be a concept but a practice, with public and private keys ensuring the authenticity and privacy of individual identities. This model would eliminate the private data silos that currently dominate, where companies profit from selling user data without consent. Instead, data would traverse a decentralized protocol akin to the internet, prioritizing user control and transparency.
The cornerstone of this world would be a meritocratic digital ecosystem. Success for companies would hinge on their ability to leverage user-owned data to deliver unparalleled value rather than their capacity to gatekeep and monetize information. If a company breaks my trust, I can move to a competitor, and my data, connections, and followers will come with me. This shift would herald an era where consent, privacy, and utility define the digital experience, ensuring that the benefits of technology are equitably distributed and aligned with the users' interests and rights.
The conversation needs to shift fundamentally. We must challenge this trajectory and advocate for a future where data ownership and privacy are not just ideals but realities. If we continue on our current path without prioritizing individual data rights, the future of digital privacy and autonomy is bleak. Big tech's dominance allows them to treat user data as a commodity, potentially selling and exploiting it without consent. This imbalance has already led to users being cut off from their digital identities and connections when platforms terminate accounts, underscoring the need for a digital ecosystem that empowers user control over data. Without changing direction, we risk a future where our content — and our freedoms by consequence — are controlled by a few powerful entities, threatening our rights and the democratic essence of the digital realm. We must advocate for a shift towards data ownership by individuals to preserve our digital freedoms and democracy.
-
 @ fa984bd7:58018f52
2024-01-31 15:00:00
@ fa984bd7:58018f52
2024-01-31 15:00:00I just hit the big red PUBLISH button on NDK 2.4.
(well, actually, I did it from the command line, the big red button is imaginary)
Codename: Safely Embrace the Chaos
Nostr is a, mostly, friendly environment with not too many developers and no ill-intent among them.
But this will not always be the case. Compatibility issues, mistakes, and all kinds of chaos is to be expected.
This version of NDK introduces validation at the library-level so that clients built using NDK can rely on some guarantees on handled-kinds that events they are consuming comply with what is defined on their respective NIPs.
An example?
NIP-88, recurring subscriptions, defines that Tier events should have amount tags of what subscribers are expected to pay and the cadence.
Prior to NDK 2.4 some malformed events would render like this:
https://i.nostr.build/Y4JG.png
But with NDK 2.4 the malformed parts of the events don't reach the client code.
https://i.nostr.build/wAgJ.png
This is just a beginning, but event-validation is now moving into the library!
-
 @ 4874b840:31b0b8c0
2024-11-20 19:10:21
@ 4874b840:31b0b8c0
2024-11-20 19:10:2111 декабря в центре города произошло ДТП с участием беспилотного такси, запущенного накануне. По предварительным данным, автомобиль столкнулся с легковым транспортным средством на перекрестке.
К счастью, в результате аварии никто не пострадал. Оба автомобиля получили незначительные повреждения. По информации представителей компании "Калининград Авто", инцидент произошел из-за ошибки в алгоритме навигации, которая привела к неправильному определению дорожной ситуации.
Компания уже начала расследование и обещает внести необходимые коррективы в систему, чтобы избежать подобных случаев в будущем. Водители и пассажиры беспилотных такси продолжают пользоваться услугой, несмотря на инцидент.
-
 @ 6bae33c8:607272e8
2024-11-20 18:49:54
@ 6bae33c8:607272e8
2024-11-20 18:49:54It’s fun to do this when you’re on a roll, but after blowing Q3 with a 1-4 week, I feel like Kamala Harris when she had to pivot to the “Hitler” smears — the joy is gone!Seriously though, there’s nothing else to do but get back on the bull.
Steelers at Browns — I imagine this will be something like Steelers -6.5, but I like the Browns here at home off the short week against a team that just beat its main division rival. I won’t use it though because it’s a Thursday game, and I like to get my picks in Friday night.
Chiefs at Panthers — Chiefs -8.5 is my guess. I’d probably stay away, but if I used it I’d take the Chiefs off their loss to the Bills.
Vikings at Bears — The Bears lost in the most brutal way last week. I’ll say Vikings -1.5 and stay away.
Titans at Texans — I’ll make this Titans +8.5 and probably avoid.
Lions at Colts — Let’s go Lions -8 and probably take the Colts. The Lions are great, but this is a good sell-high.
Patriots at Dolphins — Let’s say Patriots +6.5 and stay away. I like both teams of late.
Buccaneers at Giants — Make it Bucs -6. Tommy DeVito is tank mode. Maybe take the Bucs.
Cowboys +8 at Killer Redskins — This is a stay away, but if I had to pick (which I do in my pool), I’ll probably take the KRs.
Broncos at Raiders — The Broncos are actually decent. I’ll make it -5.5, but probably hold my nose and take the Raiders if pressed.
49ers at Packers — 49ers coming off a brutal loss, Packers a lucky win. This depends somewhat on the statuses of Nick Bosa and George Kittle, so I’ll guess 49ers +1.5 and stay away for now.
Cardinals at Seahawks — I’ll say Cardinals -2.5 and lay the wood. Cardinals are good.
Eagles at Rams — I’d say Eagles -1.5 and probably take the Rams. The Eagles are a sell-high.
Ravens at Chargers — I’d make it Ravens -2.5 and lay the wood. The Ravens should have won last week in Pittsburgh.
-
 @ f8a5df57:b7a58cd4
2024-11-20 17:12:45
@ f8a5df57:b7a58cd4
2024-11-20 17:12:45ьт
-
 @ f8a5df57:b7a58cd4
2024-11-20 17:11:58
@ f8a5df57:b7a58cd4
2024-11-20 17:11:58ит
-
 @ 2dd9250b:6e928072
2024-11-21 01:02:32
@ 2dd9250b:6e928072
2024-11-21 01:02:32Tratarei aqui de forma direta sobre Metafísica, não necessariamente Providência, embora o termo “Causa Secundária” aqui analisado seja extraído das Confissões Reformadas (CFW e CFB).
Embora a esmagadora maioria dos Calvinistas no Brasil seja adepta do Concorrentismo Aristotélico/ Tomista, eu não compartilho desta corrente Metafísica.
O Concorrentismo basicamente é uma posição filosófica que afirma que o homem possui autonomia (em nível Metafísico), como causa secundária, para concorrer junto com a causa primária (Deus), realizando um efeito específico, em um evento. Essa posição é a posição dos Tomistas/Calvinistas Escolásticos que por algum motivo se acham os únicos Calvinistas Ortodoxos que existem. Os mesmos ignoram as inconsistências lógicas dessa posição: A filosofia do Pagão Aristóteles, que posteriormente foi adaptada ao Cristianismo por Tomás de Aquino. A Bíblia não apresenta essa visão. Ela diz que Deus faz o quer e como quer. E isso significa que Deus é a única causa metafísica que existe. Portanto Filosofia Tomista não é sinônimo de Calvinismo. Ainda a nível introdutório é necessário esclarecer algo muito importante ateniente a Falácia de que nós adeptos do Essencialismo do Comando Divino, não somos Essencialistas como eram os Reformados Clássicos e portanto afirmamos que não existe Causa Segunda [o que implicaria uma defesa ao Panteísmo, segundo eles].
Deixo aqui a citação de um amigo meu:
"A causa secundária existe, mas ela é tão eficaz para alterar a realidade quanto o personagem de um livro altera as coisas na sua 'realidade' por isso o Salmista diz que seus dias estão escritos e determinados (SI 139.16), e José diz que "não foram vós que me enviastes, mas Deus" (Gn 45.8) em relação a Deus a causa secundária (ente) não é considerada eficaz no mundo."
Com isso, nossos críticos objetam:
“Então as Causas Secundárias são meras ilusões de Agência no Calvinismo”.
É uma objeção muito comum, portanto merece uma resposta satisfatória.
AS CAUSAS SECUNDÁRIAS SÃO MERAS ILUSÕES DE AGÊNCIA?
Gordon Clark observa que é necessário definir o que seria "Causalidade". Depois de definir Causalidade como uma causa e um efeito dentro do espaço-tempo, ele afirma o que de fato causa todas as coisas em fator último....
Ele diz:
"Em primeiro lugar, causalidade é um termo relativo. Isto é, não pode haver causa sem que haja um efeito. Dizemos que X causa Y. Omita qualquer um deles e não haverá nem causa, nem efeito. Algumas causas e efeitos podem parecer simultâneos; a rotação da Terra continua enquanto o Sol está nascendo. Mas, é claro, a Terra tinha de estar girando previamente. Da mesma forma, quando o rebatedor substituto de baseball faz um home run, está movimentando seu bastão antes de a bola começar sua trajetória sobre o muro de outdoor na área direita. Assim, quando X causa Y, esses dois eventos distintos estão separados por um intervalo de tempo. Levou uma semana ou dez dias para que o assassinato do arquiduque causasse a Primeira Guerra Mundial. A bala que o matou precedeu sua morte por talvez apenas um minuto. De qualquer modo, causa e efeito são dois eventos temporalmente distintos. Em segundo lugar, entre o disparo da bala e a morte do arquiduque várias coisas poderiam ter acontecido, e de fato aconteceram. Sua esposa, não esperando a morte dele, sorria para a multidão na rua. Então, entre o assassinato e a invasão da Bélgica pela Alemanha, todo tipo de coisas também ocorreu na China e na Europa. Durante o intervalo, Lord Grey e o Kaiser poderiam ter evitado a guerra, e nesse caso a morte do arquiduque não teria sido a causa que foi. Certamente, historiadores insistem que a causa real da guerra foi o complexo de tratados desenvolvidos durante um período de anos. Mas isto somente aumenta o intervalo de tempo durante o qual a guerra poderia ter sido evitada. Agora, em terceiro lugar, o argumento requer alguma definição do termo «causa» . Visto que, para ser uma causa, um evento deve ter um efeito, a causa deve ser um evento que garanta o efeito. Dada uma causa, deve haver um efeito. Deve porque a causa deve produzir seu resultado. Se no intervalo de tempo acontece ou mesmo poderia acontecer algo para impedir o efeito, não há causa. Para concluir, em quarto lugar, é sempre possível que durante o intervalo de tempo um evento impeça aquele evento, que foi previamente chamado de efeito, de ocorrer. Lord Grey é um exemplo. A bola de baseball poderia se partir ao meio. Ou, se sugerirmos que o alimento é a causa da nutrição, quem come pode vomitar se ocorrer de estar rebatendo no campo de baseball. Ou, no contexto do século XX, uma bomba atômica poderia interferir. E quanto ao nascer-do-sol, que o oponente rapidamente menciona, nossa Estrela poderia explodir ou a Terra, desintegrar. Se o oponente é um cristão verdadeiro, terá de admitir a possibilidade de que Deus possa destruir no intervalo os céus e a Terra com fogo ardente, deixando de existir. Se esse argumento não fizer o apologista dar o braço a torcer, ele provavelmente virá com duas objeções. Primeiro, mas ilogicamente, ele dirá: "Mas eu quis dizer que X causa Y se nada intervir". Dito assim, sem rodeios, a falácia é flagrante. No entanto, ela pode ser declarada mais veladamente. O alimento nos nutre se não sentimos enjoo, se o estômago termina sua função, se os sucos são absorvidos no sangue e se o sangue é levado aos músculos. Mas note bem: nós não temos mais dois eventos, X e Y. Temos a definição de nutrição; e certamente é lógico insistir que se estamos nutridos, segue-se logicamente, mas não temporalmente, que estamos nutrimos. A segunda réplica que o apologista provavelmente dará é que um cristão como eu deve reconhecer que Deus causa todas as coisas. De fato, isso é algo que eu certamente reconcheceria mas o significado do termo causa foi drasticamente mudado, Nós começamos falando sobre dois eventos no mundo espaço-temporal: o rebatedor causou ou fez a bola passar por cima do muro, mastigar comida na boca causa a nutrição, uma bala causou a morte do arquiduque. Mas agora o apologista empírico começa a falar de Deus causando todas as coisas. Concordamos agora com o anti-aristotélico islâmico Al Gazali: Deus e somente Deus é a causa, pois somente Deus pode garantir a ocorrência de Y e, de fato, de X também. Até mesmo os Divinos de Westminster concordam timidamente, pois depois de afirmar que Deus preordena tudo o que acontece, e que 'nenhum dos seus propósitos pode ser frustrado' (Jó 42: 2), eles acrescentam: “Embora... todas as coisas acontecem imutável e infalivelmente, contudo, pela mesma providência, Deus ordena que elas sucedam conforme a natureza das causas secundárias...”. O que eles chamam de causas secundárias, Malebranche tinha chamado de ocasiões. Mas uma ocasião não é um fiat lux, nem uma equação diferencial.”.¹
Portanto, Deus é Atemporal e não precisa de uma causa anterior para realizar um efeito. Por isso Deus é a causa de todas as coisas. As Causas secundárias existem, mas são meras ocasiões pelas quais os efeitos são realizados, negar isso é cair em um dualismo metafísico e/ou abraçar uma metafísica pagã. Por que? Porque só Deus sustenta o evento (causando tanto efeito X quanto o efeito Y). Por isso alguns Teólogos usam termos como “Causa Aparente”, ou “Causa Mecânica”, para deixar claro que não usam o termo “Causa Segunda” no mesmo sentido que Concorrentistas usam.
Resumindo:
No Concorrentismo Causas Secundárias são meios que Deus (A Causa Primária) usa para realizar seus Decretos. Deus sempre move a criatura a fazer algo ou sempre remove pensamentos e ações para que a criatura continue agindo de acordo com a própria natureza dela.
Ex: A Causa Primária (ou Metafísica) move a causa secundária para realizar um evento resultando em uma causa total.
No Essencialismo do Comando Divino: As Causas Secundárias existem mas são meras ocasiões pelas quais os efeitos são realizados.
Ex: Deus Causa X e Y, ou seja ocasiona (e sustenta de forma exaustiva) tanto o efeito quanto o evento.
Portanto as Causas Secundárias são Causas Aparentes ou Mecânicas. Tanto que a CFW, em seu Capítulo V, Artigo III diz:
"Na sua providência ordinária Deus emprega meios; todavia, ele é livre para operar sem eles, sobre eles ou contra eles, segundo o seu arbítrio.
At. 27:24, 31; Isa. 55:10-11; Os.1:7; Rom. 4:20-21; Dan.3:27; João 11:34-45; Rom. 1:4."
Falando diretamente contra o Concorrentismo defendido por Calvinistas Escolásticos, Molinistas e Arminianos, um certo teólogo afirma:
"A Metafísica aristotélica é fracassada por depender dos elementos criados ou criaturas como causa secundária, no sentido em que, eles possuem uma eficiência ou "dão forma" ao ato pecaminoso. Em contra partida uma das explicações mais elevada de Metafísica na Bíblia está em Romanos 9. Ali o apóstolo nos desenha a imagem de um oleiro mestre fazendo vasos, as propriedades que os vasos têm procedem das mãos do próprio oleiro, o vaso de barro não faz uma alça em si mesmo. Ele reconhece que todas as suas características vieram diretamente da mão do oleiro e por isso retruca "por que me fizeste assim?" (20-21). A resposta do apóstolo não é apelar para uma suposta liberdade da criatura em relação metafísica ao Oleiro mestre, muito menos o apóstolo atribui ao vaso alguma causa secundária, visto que a analogia aqui torna isso impossível. Antes, o apóstolo apela para a autoridade e o direito do oleiro de fazer o que quiser com o que ė dele.²
Esclarecido isso surge outra objeção…
MAS ESSA DEFINIÇÃO DE CAUSA METAFÍSICA NÃO FAZ DE DEUS O AUTOR DO MAL?
Isso não faz o menor sentido. A menos que se questione isso partindo do pressuposto de que os que objetam contra o Calvinismo acreditam que quem causa o Mal (metafísicamente) é um deus menor chamado Demiurgo que vive em uma eterna queda de braço com o Deus da Bíblia. Ou possuem uma definição errada (Tomista) de pecado. Portanto, é necessário definirmos biblicamente o que é Pecado.
Transgressão na Bíblia é quebrar um preceito Divino. É transgredir a Lei que Deus estabeleceu (Romanos 4:15,16). Logo, devemos separar Metafísica de Ética. Causar não é tentar, muito menos pecar. Seria absurdo afirmar que Deus pecou quando causou a queda de Adão, tal como seria absurdo afirmar que Deus é responsável (no sentido de ser o Agente que comete o pecado), tal como seria absurdo afirmar que Deus não causou a queda. Uma vez que a Escritura ensina que Deus faz literalmente todas as coisas [παντα] (Efésios 1:11).
Obviamente, isso é claramente ensinado pelas Escrituras Sagradas:
"No céu está o nosso Deus e tudo FAZ COMO LHE AGRADA." (SI 115.3).
"Assim como tu não sabes qual o caminho do vento, nem como se formam os ossos no ventre da mulher grávida, assim também não sabes as obras de Deus, que FAZ TODAS AS COISAS." (Ec 11.5).
"nele, digo, no qual fomos também feitos herança, predestinados segundo o propósito daquele que FAZ TODAS AS COISAS conforme o conselho da sua vontade," (Ef 1.11).
Portanto, ao separarmos Metafísica de Ética, não vamos de encontro com as Confissões Reformadas e Símbolos de Fé das Igrejas Reformadas (CFW, CFB e Cânones de Dort quando eles afirmam que Deus não é o Autor do pecado), ao mesmo tempo em que não partimos dos mesmos pressupostos essencialmente pagãos de nossos amigos Aristotélicos.
Metafisica - Deus determinou que Faraó endurecesse seu coração (Ex 10.1-2).
Ética - Deus responsabiliza faraó por isso (Ex 10.3).
Metafísica - Deus faz o impio para o dia da calamidade (Pv 16.4). Ética - Deus pune os impios com o inferno (SI 9.17).
Metafísica - Deus fez o Vaso de ira para a destruição (Rm 9). Ética - Deus pune o vaso de ira no inferno (Rm 9).
Metafísica - Deus coloca no coração dos reis da terra que cumpram o seu intento - Ap 17.17. Ética - Deus lança todos os reis da terra com Satanás no Inferno (Ap 20,10,15).
Metafísica — Deus faz vasos para a perdição (Rm 9:16;18;21,22).
Ética —Deus ordena que os ímpios se arrependam (Ez 33:11; Rm 9;19;22).
Embora eu seja adepto do Escrituralismo (ou Dogmatismo) de Gordon Clark, outros Teólogos que não são Confessionais já escreveram sobre o significado que Tomistas dão às Causas Secundárias encontradas nas Confissões Reformadas, e até agora não foram respondidos:
Use o tradutor automático do seu navegador.
Não há contradição alguma, Deus é Soberano e você é responsável, isso não é uma invenção de Lutero, Calvino, Malebranche, Edwards ou Gordon Clark, isso é o que a Bíblia diz. Sola Scriptura.
Referências:
1- Gordon H. Clark, Senhor Deus da Verdade, Hobbs, NM: The Trinity Foundation, 1986, 2ª Edição 1994, 24-25, 27.
2- Yuri Andrei Schein, Teologia Sistemática Pressuposicional Volume 1, 2020, 217.
-
 @ 3bf0c63f:aefa459d
2024-01-15 11:15:06
@ 3bf0c63f:aefa459d
2024-01-15 11:15:06Pequenos problemas que o Estado cria para a sociedade e que não são sempre lembrados
- **vale-transporte**: transferir o custo com o transporte do funcionário para um terceiro o estimula a morar longe de onde trabalha, já que morar perto é normalmente mais caro e a economia com transporte é inexistente. - **atestado médico**: o direito a faltar o trabalho com atestado médico cria a exigência desse atestado para todas as situações, substituindo o livre acordo entre patrão e empregado e sobrecarregando os médicos e postos de saúde com visitas desnecessárias de assalariados resfriados. - **prisões**: com dinheiro mal-administrado, burocracia e péssima alocação de recursos -- problemas que empresas privadas em competição (ou mesmo sem qualquer competição) saberiam resolver muito melhor -- o Estado fica sem presídios, com os poucos existentes entupidos, muito acima de sua alocação máxima, e com isto, segundo a bizarra corrente de responsabilidades que culpa o juiz que condenou o criminoso por sua morte na cadeia, juízes deixam de condenar à prisão os bandidos, soltando-os na rua. - **justiça**: entrar com processos é grátis e isto faz proliferar a atividade dos advogados que se dedicam a criar problemas judiciais onde não seria necessário e a entupir os tribunais, impedindo-os de fazer o que mais deveriam fazer. - **justiça**: como a justiça só obedece às leis e ignora acordos pessoais, escritos ou não, as pessoas não fazem acordos, recorrem sempre à justiça estatal, e entopem-na de assuntos que seriam muito melhor resolvidos entre vizinhos. - **leis civis**: as leis criadas pelos parlamentares ignoram os costumes da sociedade e são um incentivo a que as pessoas não respeitem nem criem normas sociais -- que seriam maneiras mais rápidas, baratas e satisfatórias de resolver problemas. - **leis de trãnsito**: quanto mais leis de trânsito, mais serviço de fiscalização são delegados aos policiais, que deixam de combater crimes por isto (afinal de contas, eles não querem de fato arriscar suas vidas combatendo o crime, a fiscalização é uma excelente desculpa para se esquivarem a esta responsabilidade). - **financiamento educacional**: é uma espécie de subsídio às faculdades privadas que faz com que se criem cursos e mais cursos que são cada vez menos recheados de algum conhecimento ou técnica útil e cada vez mais inúteis. - **leis de tombamento**: são um incentivo a que o dono de qualquer área ou construção "histórica" destrua todo e qualquer vestígio de história que houver nele antes que as autoridades descubram, o que poderia não acontecer se ele pudesse, por exemplo, usar, mostrar e se beneficiar da história daquele local sem correr o risco de perder, de fato, a sua propriedade. - **zoneamento urbano**: torna as cidades mais espalhadas, criando uma necessidade gigantesca de carros, ônibus e outros meios de transporte para as pessoas se locomoverem das zonas de moradia para as zonas de trabalho. - **zoneamento urbano**: faz com que as pessoas percam horas no trânsito todos os dias, o que é, além de um desperdício, um atentado contra a sua saúde, que estaria muito melhor servida numa caminhada diária entre a casa e o trabalho. - **zoneamento urbano**: torna ruas e as casas menos seguras criando zonas enormes, tanto de residências quanto de indústrias, onde não há movimento de gente alguma. - **escola obrigatória + currículo escolar nacional**: emburrece todas as crianças. - **leis contra trabalho infantil**: tira das crianças a oportunidade de aprender ofícios úteis e levar um dinheiro para ajudar a família. - **licitações**: como não existem os critérios do mercado para decidir qual é o melhor prestador de serviço, criam-se comissões de pessoas que vão decidir coisas. isto incentiva os prestadores de serviço que estão concorrendo na licitação a tentar comprar os membros dessas comissões. isto, fora a corrupção, gera problemas reais: __(i)__ a escolha dos serviços acaba sendo a pior possível, já que a empresa prestadora que vence está claramente mais dedicada a comprar comissões do que a fazer um bom trabalho (este problema afeta tantas áreas, desde a construção de estradas até a qualidade da merenda escolar, que é impossível listar aqui); __(ii)__ o processo corruptor acaba, no longo prazo, eliminando as empresas que prestavam e deixando para competir apenas as corruptas, e a qualidade tende a piorar progressivamente. - **cartéis**: o Estado em geral cria e depois fica refém de vários grupos de interesse. o caso dos taxistas contra o Uber é o que está na moda hoje (e o que mostra como os Estados se comportam da mesma forma no mundo todo). - **multas**: quando algum indivíduo ou empresa comete uma fraude financeira, ou causa algum dano material involuntário, as vítimas do caso são as pessoas que sofreram o dano ou perderam dinheiro, mas o Estado tem sempre leis que prevêem multas para os responsáveis. A justiça estatal é sempre muito rígida e rápida na aplicação dessas multas, mas relapsa e vaga no que diz respeito à indenização das vítimas. O que em geral acontece é que o Estado aplica uma enorme multa ao responsável pelo mal, retirando deste os recursos que dispunha para indenizar as vítimas, e se retira do caso, deixando estas desamparadas. - **desapropriação**: o Estado pode pegar qualquer propriedade de qualquer pessoa mediante uma indenização que é necessariamente inferior ao valor da propriedade para o seu presente dono (caso contrário ele a teria vendido voluntariamente). - **seguro-desemprego**: se há, por exemplo, um prazo mínimo de 1 ano para o sujeito ter direito a receber seguro-desemprego, isto o incentiva a planejar ficar apenas 1 ano em cada emprego (ano este que será sucedido por um período de desemprego remunerado), matando todas as possibilidades de aprendizado ou aquisição de experiência naquela empresa específica ou ascensão hierárquica. - **previdência**: a previdência social tem todos os defeitos de cálculo do mundo, e não importa muito ela ser uma forma horrível de poupar dinheiro, porque ela tem garantias bizarras de longevidade fornecidas pelo Estado, além de ser compulsória. Isso serve para criar no imaginário geral a idéia da __aposentadoria__, uma época mágica em que todos os dias serão finais de semana. A idéia da aposentadoria influencia o sujeito a não se preocupar em ter um emprego que faça sentido, mas sim em ter um trabalho qualquer, que o permita se aposentar. - **regulamentação impossível**: milhares de coisas são proibidas, há regulamentações sobre os aspectos mais mínimos de cada empreendimento ou construção ou espaço. se todas essas regulamentações fossem exigidas não haveria condições de produção e todos morreriam. portanto, elas não são exigidas. porém, o Estado, ou um agente individual imbuído do poder estatal pode, se desejar, exigi-las todas de um cidadão inimigo seu. qualquer pessoa pode viver a vida inteira sem cumprir nem 10% das regulamentações estatais, mas viverá também todo esse tempo com medo de se tornar um alvo de sua exigência, num estado de terror psicológico. - **perversão de critérios**: para muitas coisas sobre as quais a sociedade normalmente chegaria a um valor ou comportamento "razoável" espontaneamente, o Estado dita regras. estas regras muitas vezes não são obrigatórias, são mais "sugestões" ou limites, como o salário mínimo, ou as 44 horas semanais de trabalho. a sociedade, porém, passa a usar esses valores como se fossem o normal. são raras, por exemplo, as ofertas de emprego que fogem à regra das 44h semanais. - **inflação**: subir os preços é difícil e constrangedor para as empresas, pedir aumento de salário é difícil e constrangedor para o funcionário. a inflação força as pessoas a fazer isso, mas o aumento não é automático, como alguns economistas podem pensar (enquanto alguns outros ficam muito satisfeitos de que esse processo seja demorado e difícil). - **inflação**: a inflação destrói a capacidade das pessoas de julgar preços entre concorrentes usando a própria memória. - **inflação**: a inflação destrói os cálculos de lucro/prejuízo das empresas e prejudica enormemente as decisões empresariais que seriam baseadas neles. - **inflação**: a inflação redistribui a riqueza dos mais pobres e mais afastados do sistema financeiro para os mais ricos, os bancos e as megaempresas. - **inflação**: a inflação estimula o endividamento e o consumismo. - **lixo:** ao prover coleta e armazenamento de lixo "grátis para todos" o Estado incentiva a criação de lixo. se tivessem que pagar para que recolhessem o seu lixo, as pessoas (e conseqüentemente as empresas) se empenhariam mais em produzir coisas usando menos plástico, menos embalagens, menos sacolas. - **leis contra crimes financeiros:** ao criar legislação para dificultar acesso ao sistema financeiro por parte de criminosos a dificuldade e os custos para acesso a esse mesmo sistema pelas pessoas de bem cresce absurdamente, levando a um percentual enorme de gente incapaz de usá-lo, para detrimento de todos -- e no final das contas os grandes criminosos ainda conseguem burlar tudo. -
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28nostr - Notes and Other Stuff Transmitted by Relays
The simplest open protocol that is able to create a censorship-resistant global "social" network once and for all.
It doesn't rely on any trusted central server, hence it is resilient; it is based on cryptographic keys and signatures, so it is tamperproof; it does not rely on P2P techniques, therefore it works.
Very short summary of how it works, if you don't plan to read anything else:
Everybody runs a client. It can be a native client, a web client, etc. To publish something, you write a post, sign it with your key and send it to multiple relays (servers hosted by someone else, or yourself). To get updates from other people, you ask multiple relays if they know anything about these other people. Anyone can run a relay. A relay is very simple and dumb. It does nothing besides accepting posts from some people and forwarding to others. Relays don't have to be trusted. Signatures are verified on the client side.
This is needed because other solutions are broken:
The problem with Twitter
- Twitter has ads;
- Twitter uses bizarre techniques to keep you addicted;
- Twitter doesn't show an actual historical feed from people you follow;
- Twitter bans people;
- Twitter shadowbans people.
- Twitter has a lot of spam.
The problem with Mastodon and similar programs
- User identities are attached to domain names controlled by third-parties;
- Server owners can ban you, just like Twitter; Server owners can also block other servers;
- Migration between servers is an afterthought and can only be accomplished if servers cooperate. It doesn't work in an adversarial environment (all followers are lost);
- There are no clear incentives to run servers, therefore they tend to be run by enthusiasts and people who want to have their name attached to a cool domain. Then, users are subject to the despotism of a single person, which is often worse than that of a big company like Twitter, and they can't migrate out;
- Since servers tend to be run amateurishly, they are often abandoned after a while — which is effectively the same as banning everybody;
- It doesn't make sense to have a ton of servers if updates from every server will have to be painfully pushed (and saved!) to a ton of other servers. This point is exacerbated by the fact that servers tend to exist in huge numbers, therefore more data has to be passed to more places more often;
- For the specific example of video sharing, ActivityPub enthusiasts realized it would be completely impossible to transmit video from server to server the way text notes are, so they decided to keep the video hosted only from the single instance where it was posted to, which is similar to the Nostr approach.
The problem with SSB (Secure Scuttlebutt)
- It doesn't have many problems. I think it's great. In fact, I was going to use it as a basis for this, but
- its protocol is too complicated because it wasn't thought about being an open protocol at all. It was just written in JavaScript in probably a quick way to solve a specific problem and grew from that, therefore it has weird and unnecessary quirks like signing a JSON string which must strictly follow the rules of ECMA-262 6th Edition;
- It insists on having a chain of updates from a single user, which feels unnecessary to me and something that adds bloat and rigidity to the thing — each server/user needs to store all the chain of posts to be sure the new one is valid. Why? (Maybe they have a good reason);
- It is not as simple as Nostr, as it was primarily made for P2P syncing, with "pubs" being an afterthought;
- Still, it may be worth considering using SSB instead of this custom protocol and just adapting it to the client-relay server model, because reusing a standard is always better than trying to get people in a new one.
The problem with other solutions that require everybody to run their own server
- They require everybody to run their own server;
- Sometimes people can still be censored in these because domain names can be censored.
How does Nostr work?
- There are two components: clients and relays. Each user runs a client. Anyone can run a relay.
- Every user is identified by a public key. Every post is signed. Every client validates these signatures.
- Clients fetch data from relays of their choice and publish data to other relays of their choice. A relay doesn't talk to another relay, only directly to users.
- For example, to "follow" someone a user just instructs their client to query the relays it knows for posts from that public key.
- On startup, a client queries data from all relays it knows for all users it follows (for example, all updates from the last day), then displays that data to the user chronologically.
- A "post" can contain any kind of structured data, but the most used ones are going to find their way into the standard so all clients and relays can handle them seamlessly.
How does it solve the problems the networks above can't?
- Users getting banned and servers being closed
- A relay can block a user from publishing anything there, but that has no effect on them as they can still publish to other relays. Since users are identified by a public key, they don't lose their identities and their follower base when they get banned.
- Instead of requiring users to manually type new relay addresses (although this should also be supported), whenever someone you're following posts a server recommendation, the client should automatically add that to the list of relays it will query.
- If someone is using a relay to publish their data but wants to migrate to another one, they can publish a server recommendation to that previous relay and go;
- If someone gets banned from many relays such that they can't get their server recommendations broadcasted, they may still let some close friends know through other means with which relay they are publishing now. Then, these close friends can publish server recommendations to that new server, and slowly, the old follower base of the banned user will begin finding their posts again from the new relay.
-
All of the above is valid too for when a relay ceases its operations.
-
Censorship-resistance
- Each user can publish their updates to any number of relays.
-
A relay can charge a fee (the negotiation of that fee is outside of the protocol for now) from users to publish there, which ensures censorship-resistance (there will always be some Russian server willing to take your money in exchange for serving your posts).
-
Spam
-
If spam is a concern for a relay, it can require payment for publication or some other form of authentication, such as an email address or phone, and associate these internally with a pubkey that then gets to publish to that relay — or other anti-spam techniques, like hashcash or captchas. If a relay is being used as a spam vector, it can easily be unlisted by clients, which can continue to fetch updates from other relays.
-
Data storage
- For the network to stay healthy, there is no need for hundreds of active relays. In fact, it can work just fine with just a handful, given the fact that new relays can be created and spread through the network easily in case the existing relays start misbehaving. Therefore, the amount of data storage required, in general, is relatively less than Mastodon or similar software.
-
Or considering a different outcome: one in which there exist hundreds of niche relays run by amateurs, each relaying updates from a small group of users. The architecture scales just as well: data is sent from users to a single server, and from that server directly to the users who will consume that. It doesn't have to be stored by anyone else. In this situation, it is not a big burden for any single server to process updates from others, and having amateur servers is not a problem.
-
Video and other heavy content
-
It's easy for a relay to reject large content, or to charge for accepting and hosting large content. When information and incentives are clear, it's easy for the market forces to solve the problem.
-
Techniques to trick the user
- Each client can decide how to best show posts to users, so there is always the option of just consuming what you want in the manner you want — from using an AI to decide the order of the updates you'll see to just reading them in chronological order.
FAQ
- This is very simple. Why hasn't anyone done it before?
I don't know, but I imagine it has to do with the fact that people making social networks are either companies wanting to make money or P2P activists who want to make a thing completely without servers. They both fail to see the specific mix of both worlds that Nostr uses.
- How do I find people to follow?
First, you must know them and get their public key somehow, either by asking or by seeing it referenced somewhere. Once you're inside a Nostr social network you'll be able to see them interacting with other people and then you can also start following and interacting with these others.
- How do I find relays? What happens if I'm not connected to the same relays someone else is?
You won't be able to communicate with that person. But there are hints on events that can be used so that your client software (or you, manually) knows how to connect to the other person's relay and interact with them. There are other ideas on how to solve this too in the future but we can't ever promise perfect reachability, no protocol can.
- Can I know how many people are following me?
No, but you can get some estimates if relays cooperate in an extra-protocol way.
- What incentive is there for people to run relays?
The question is misleading. It assumes that relays are free dumb pipes that exist such that people can move data around through them. In this case yes, the incentives would not exist. This in fact could be said of DHT nodes in all other p2p network stacks: what incentive is there for people to run DHT nodes?
- Nostr enables you to move between server relays or use multiple relays but if these relays are just on AWS or Azure what’s the difference?
There are literally thousands of VPS providers scattered all around the globe today, there is not only AWS or Azure. AWS or Azure are exactly the providers used by single centralized service providers that need a lot of scale, and even then not just these two. For smaller relay servers any VPS will do the job very well.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28 -
 @ f8a5df57:b7a58cd4
2024-11-20 17:10:13
@ f8a5df57:b7a58cd4
2024-11-20 17:10:13п
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Boardthreads
This was a very badly done service for turning a Trello list into a helpdesk UI.
Surprisingly, it had more paying users than Websites For Trello, which I was working on simultaneously and dedicating much more time to it.
The Neo4j database I used for this was a very poor choice, it was probably the cause of all the bugs.

-
 @ f4bf1fb5:b428f8d5
2024-11-20 17:05:05
@ f4bf1fb5:b428f8d5
2024-11-20 17:05:05On DEG Mods, mod creators and enjoyers can benefit from tips, allowing them to earn money directly from those who appreciate their work or comments, and 100% of what's tipped goes to the one being tipped (excluding the processing fee of the transaction, which is extremely negligible). We don't take any percentage of this process, unless you choose to and at whichever amount you like.
Did you discover a mod that you found enjoyable, useful, or intriguing, and you'd like to show your appreciation with a $10 tip? You can do that. Choose to give 100% of your tip directly to the creator, or opt for a 90% share for them, with the remaining 10% supporting DEG Mods. You can also reverse the split if you prefer. It's entirely up to you how you'd like to allocate the tip.
The elephant in the room
Yes, we're using Bitcoin as the main currency and monetary system on the site, and we're aware of the general public's perception of Bitcoin and the general Cryptocurrency space. We have pretty solid reasons why we're utilizing Bitcoin as the monetary infrastructure for DEG Mods instead of traditional payment systems with fiat currency, like USD/EUR, and the banking system, like Visa or Mastercard.
DEG Mods is built around the idea of censorship-resistance and being permissionless, not just anti-censorship, with that in mind, we didn't want to use a system, and in this case a monetary system, where some third party can come in and threat the site, its users and creators, to self-censor or else suffer the consequences of everyone's money frozen, stolen, or not being able to send or receive. There are many examples of such cases.
We wanted to use something where people actually own their money, not have it controlled by anyone, and have people freely transact with anyone they want, whenever they want, with whichever amount they want to utilize, and not worry about any kind of censorship.
That's why why we went with Bitcoin, with the utilization of the Lightning Network. All of this is possible with it. And we didn't go with any other Cryptocurrency, not even create our own currency and massively benefit from it, because we wanted to use the most trusted, verifiably sound, and strongest currency in the world that's the most censorship-resistant one out there, and not a potential one where people would have a higher chance of thinking that its a scam. That's why, generally speaking, many differentiate between 'Bitcoin' and 'Crypto'.
Properly used, you completely own your money, and nobody can take it away from you or stop you from transacting with others. Now, let's get back on topic.
How to set up and enable getting tips
You need to download and install a Bitcoin Lightning Wallet app (suggestions: Lifpay or Wallet of Satoshi) on your mobile device, where where it supports and provides you with a Lightning address. Once you have obtain such an address, you can go ahead and add that to the 'Lightning Address' field in the profile settings page on DEG Mods.
After that, save/publish your changes and you're done. People can now tip you directly on your profile or tip you via your mod posts.
How to exchange your tipped Bitcoin to other currencies like USD/EUR
So you got tipped a few times and feel like you want to exchange what you've received so far into other currencies to spend them. We won't have a full-blown guide on this, at least not now, but the general idea is that you'd go to an exchange site/app (Suggestion: Binance, or if you're in the USA then CashApp or Strike might work better for you), send them there, and have them exchanged there to whatever currency you like, then withdraw it to your bank or payment service that you use (or keep them there if its already the payment system you use already).
You can also go to physical exchange stores if they support the exchange of that currency in your country.
How to tip creators and other users
As a user that wants to tip creators or other users, you'd do that by first having a Bitcoin Lighting Wallet (similar suggestions as shared above), and then you'd need to fill that up, which is basically the reverse process of above, and once you have an amount of Bitcoin (or 'Sats', think 'Cents') in your Wallet app, you can now go ahead and start tipping creators or other users.
You tip others by tapping on the lightning icon you'll see throughout the site, either for a comment, a profile, or a mod post next to the reaction buttons, which will trigger a popup asking you to enter an amount in Sats and then you'd generate the QR code. In your Wallet app, tap the send button and scan that QR and send away. Done.
Keep in mind that other users or creators might tip you, so you don't necessarily have to go through that process of exchanging traditional currencies to Bitcoin/sats, so its definitely worth at least obtaining a Bitcoin Lightning Address and adding it your 'account' here on DEG Mods, in the off chance that someone tips you when you comment on a post for example. Why leave money on the table, as they say.
Questions and Answers
We'll continue updating this blog post when new information comes along, but here are some questions and answers regarding this topic.
Did you really have to use Bitcoin/Crypto? Why couldn't you have PayPay, Stripe, or some other traditional payment method?
This is answered at the start of this post, but in gist: So we, creators, and users, aren't screwed over and be forced to censor ourselves.
Do I have to use Bitcoin?
No, you can use DEG Mods without ever touching it, and you can also add your own payment links (like PayPal, CashApp, Kofi, Patreon, etc) in your profile (we'll be adding a linktree-like system at some point to make this process easy), and people can easily find those link and tip you there, though those tip buttons are only for Bitcoin.
Will there be more ways to get money later, or is it just tipping mod posts and profiles?
Yes, there'll be more ways for creators to acquire money from users in the future, for reasons other than 'thank you creating this mod'.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Um algoritmo imbecil da evolução
Suponha que você queira escrever a palavra BANANA partindo de OOOOOO e usando só alterações aleatórias das letras. As alterações se dão por meio da multiplicação da palavra original em várias outras, cada uma com uma mudança diferente.
No primeiro período, surgem BOOOOO e OOOOZO. E então o ambiente decide que todas as palavras que não começam com um B estão eliminadas. Sobra apenas BOOOOO e o algoritmo continua.
É fácil explicar conceber a evolução das espécies acontecendo dessa maneira, se você controlar sempre a parte em que o ambiente decide quem vai sobrar.
Porém, há apenas duas opções:
- Se o ambiente decidir as coisas de maneira aleatória, a chance de você chegar na palavra correta usando esse método é tão pequena que pode ser considerada nula.
- Se o ambiente decidir as coisas de maneira pensada, caímos no //design inteligente//.
Acredito que isso seja uma enunciação decente do argumento "no free lunch" aplicado à crítica do darwinismo por William Dembski.
A resposta darwinista consiste em dizer que não existe essa BANANA como objetivo final. Que as palavras podem ir se alterando aleatoriamente, e o que sobrar sobrou, não podemos dizer que um objetivo foi atingido ou deixou de sê-lo. E aí os defensores do design inteligente dirão que o resultado ao qual chegamos não pode ter sido fruto de um processo aleatório. BANANA é qualitativamente diferente de AYZOSO, e aí há várias maneiras de "provar" que sim usando modelos matemáticos e tal.
Fico com a impressão, porém, de que essa coisa só pode ser resolvida como sim ou não mediante uma discussão das premissas, e chega um ponto em que não há mais provas matemáticas possíveis, apenas subjetividade.
Daí eu me lembro da minha humilde solução ao problema do cão que aperta as teclas aleatoriamente de um teclado e escreve as obras completas de Shakespeare: mesmo que ele o faça, nada daquilo terá sentido sem uma inteligência de tipo humano ali para lê-las e perceber que não se trata de uma bagunça, mas sim de um texto com sentido para ele. O milagre se dá não no momento em que o cão tropeça no teclado, mas no momento em que o homem olha para a tela.
Se o algoritmo da evolução chegou à palavra BANANA ou UXJHTR não faz diferença pra ela, mas faz diferença para nós, que temos uma inteligência humana, e estamos observando aquilo. O homem também pensaria que há //algo// por trás daquele evento do cão que digita as obras de Shakespeare, e como seria possível alguém em sã consciência pensar que não?
-
 @ 2dd9250b:6e928072
2024-11-20 23:57:01
@ 2dd9250b:6e928072
2024-11-20 23:57:01Nesta aclamada série (1° Temporada ), o brilhante ator, roteirista e cantor Donald Glover emula um jovem norte-americano ex-fuzileiro naval que tem asma e trabalha para uma organização secreta internacional de espionagem.
No desenrolar da história ele conhece uma mulher asiática e se vê obrigado a realizar as missões com ela, já que as missões são realizadas em casal.
Então, temos uma casal de agentes fingindo ser um casal comum. Eles trabalham juntos, dormem na mesma casa, fazem as refeições juntos e se dão razoavelmente bem. Com o passar do tempo, acontece o que o espectador já esperava, eles naturalmente sentem atração um pelo outro e começam a ter relações sexuais.
Mas, ironicamente John de fato começa a ter sentimentos por Jane, uma vez que ela é muito inteligente, uma leitora voraz, que usa sarcasmo para ofender quem ela não gosta e foi expulsa da CIA por ter traços de Sociopatia.
Logo, o que era um mero relacionamento amoroso líquido, passa a se tornar algo mais sério . Mas esse relacionamento sério é feito aos moldes da pós-modernidade e o puro suco de Secularismo, inevitavelmente irá surgir.
Como todo casal de jovens namorados, John e Jane Smith começaram a se desentender e brigar histericamente a ponto de fazerem terapia de casal. Neste ponto, eu já esperava um final bem triste e já tinha certeza que se trata de uma Tragédia.
A tragédia é justamente a constatação de que esse jovem casal não tem futuro. Naturalmente todo mundo que namora, em algum momento, irá começar a fazer planos para o futuro, é aí que as surpresas surgem.
John deseja desesperadamente ter filhos com Jane, que rejeita por ser uma mulher empoderada e que prefere subir na carreira. A Série deixa explícito que ela teve um pai ausente e que ela deve tomar a decisão de ficar com seu parceiro ou ser promovida.
Honestamente, eu não sei dizer o que de fato originou o carreirismo moderno. A omissão dos homens? O Feminismo? A Revolução Industrial? A Revolução Sexual? Talvez seja tudo isso. Ou como nós cristãos costumamos falar, no fundo no fundo, isso é consequência do pecado original.
O que posso dizer com certeza é o que o Carreirismo está provocando nas mulheres, inclusive cristãs, atualmente.
A Bíblia é clara quanto a vocação da mulher:
"Quanto às mulheres idosas, semelhantemente, que sejam sérias em seu proceder, não caluniadoras, não escravizadas a muito vinho; sejam mestras do bem, a fim de instruírem as jovens recém-casadas a amarem ao marido e a seus filhos, a serem sensatas, honestas, boas donas de casa, bondosas, sujeitas ao marido, para que a palavra de Deus não seja difamada." (Tito 2:3-5)
O problema é que as mães não ensinam isso às suas filhas. Querem que elas sejam independentes e que tenham liberdade financeira. Então elas dizem: “Vai estudar menina, pra não depender de macho”. Daí as filhas se deparam com a realidade. Uma Graduação não basta. Precisam fazer pós-graduação, Mestrado e Doutorado para se destacarem no Mercado e não dependerem de macho.
Qual a consequência disso? Mulheres doutoras com 38 anos na Igreja, vivendo com a mãe e reclamando na Internet que não tem homem para elas na igreja.
A frustração de mães com suas filhas ao verem o tempo passar e perceberem que estão envelhecendo e precisam lhe dar com o fato de que não terão netinhos para mimar.
E ainda tem uma grande parte dos homens cristãos se casando e chegando a conclusão de que mesmo eles querendo assumir a liderança do lar, provendo o sustento para que suas esposas não percam cabelo devido o estresse de 12 horas fora de casa, competindo com homens no mercado de trabalho, o salário deles não é suficiente para pagar as contas.
Outra consequência é o crescente número de Divórcios e Taxa de Fecundidade caindo mais rápido do que o valor do Real desde 1994.
Não há defesa Bíblica para o Carreirismo, exceto para Igualitaristas e Feministas que obviamente irão defender que a mulher cristã deve sim substituir a maternidade pela carreira profissional. Pronto. A tragédia está anunciada. Voltando para o nosso subproduto de entretenimento secular meticulosamente produzido para o Streaming…
No final, John é baleado e Jane diz que aceita ter um filho com ele por pena. Já que ele vai morrer logo e ela está encurralada. Trata-se de um final ambíguo, pois não se sabe se eles morreram ou não. O que eu sei é que as boas histórias morreram faz tempo.
-
 @ ac8bb9b0:70278acc
2024-11-20 16:28:11
@ ac8bb9b0:70278acc
2024-11-20 16:28:11Chef's notes
Optional: Creamy Cilantro-Basil Ranch: In a blender, blend 1/2 cup plain Greek yogurt or sour cream, 1/3 cup mayo, 2 tablespoons buttermilk, 1 cup fresh cilantro, 1/2 cup fresh basil, 1/4 cup fresh chopped chives, 2 teaspoons Worcestershire, 1 teaspoon garlic powder, 1 teaspoon onion powder, 1/4 teaspoon cayenne, and a pinch each of kosher salt and black pepper. Blend until creamy.
Details
- ⏲️ Prep time: 15
- 🍳 Cook time: 15
Ingredients
- 4 (4-6 ounce) salmon filets, cut into bite-size chunks
- 6 tablespoons extra virgin olive oil
- 1 teaspoon smoked paprika
- salt and black pepper
- 1 bunch asparagus, ends trimmed
- 1/2 cup honey
- 2-3 tablespoons hot sauce
- 1-3 teaspoons cayenne pepper
- 3/4 teaspoon chipotle chili powder
- 1/2 teaspoon garlic powder
- 1/2 teaspoon onion powder
- 3-4 cups cooked rice
- 2 avocados, diced
- 1 serrano or jalapeño, sliced
- 1/2 cup fresh cilantro, chopped
- 2 tablespoons chopped fresh dill
- 1/2 cup crumbled feta cheese
- 2 tablespoons extra virgin olive oil
- 1 tablespoon lemon juice
- 1/3 cup toasted seeds, pumpkin, sesame, sunflower, etc.
Directions
-
- Preheat the oven to 450° F.
-
- On a baking sheet, toss the salmon pieces with 3 tablespoons olive oil, paprika, salt, and pepper. Arrange in a single layer. On the other side of the pan, add the asparagus. Toss with 1 tablespoon olive oil, salt, and pepper. Roast 10-15 minutes or until the salmon is just undercooked to your liking.
-
- Meanwhile, make the hot honey. In a sauce pot, warm together the honey, hot sauce, cayenne, chili powder, onion powder, and garlic powder, plus a pinch of salt.
-
- Spoon some of the hot honey over the salmon. Switch the oven to broil and broil until lightly charred and crispy. Spoon over additional hot honey, to your taste.
-
- To make the avocado salsa. Combine avocados, serrano or jalapeño, cilantro, dill, feta cheese, extra virgin olive oil, lemon juice, and toasted seeds in a bowl and season with salt, gently tossing.
-
- Arrange the salmon and asparagus over bowls of rice. Top with salsa.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Profits, not wages, as the originary factor
Adam Smith says that there were first workers earning wages, but then came the capitalists and extracted profits from those wages.
But in fact if that primitive state ever existed there were no workers, but entrepreneursearning profit. And since they were not capitalists ("capitalist" defined as someone that buys with the intent of selling) they were earning an infinite rate of profit.
When capitalists came they were responsible for introducing costs (investment) reducing thus the rate of profit -- and the more capitalistic the society the smaller the rate of profits.
-- George Reisman in https://www.bobmurphyshow.com/139