-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 60e759a2:b77e525b
2024-11-29 18:19:00
@ 60e759a2:b77e525b
2024-11-29 18:19:00LIFE Life is a journey of race There is no farthermost place it keeps moving pace by pace It is like knoting a handful of shoelace
Life is not all cakes and rainbows There are thorns and adversities it depends on how you move to grow which gives an output of diverse anniversaries
There are times of meekness There are times of weakness these gives us an edge to grow these teaches us to know
Those weak moments are our strength Those strengthened mindset are our weakness it all comes to one solemn output which brings about determination to live
---- Freddie -
 @ 2775fb0f:887f8193
2024-11-29 18:12:41
@ 2775fb0f:887f8193
2024-11-29 18:12:41— В связи с прогнозами метеорологов, в нашем городе ожидаются сильные порывы ветра, которые могут достигать 25-30 метров в секунду. Городская администрация призывает жителей принять необходимые меры предосторожности и обеспечить свою безопасность в условиях неблагоприятной погоды.
Синоптики предупреждают о возможности повреждения кровель, обрывов линий электропередач и падения деревьев. В связи с этим важно заранее подготовиться к сильному ветру и следовать рекомендациям специалистов.
Вот несколько советов по обеспечению безопасности:
-
Избегайте выхода на улицу без необходимости. Если это возможно, оставайтесь дома. Если вам нужно выйти, будьте осторожны и выбирайте защищенные от ветра маршруты.
-
Закрепите предметы на балконах и во дворе. Уберите или надежно закрепите легкие предметы, такие как садовая мебель, игрушки и другие вещи, которые могут быть унесены ветром.
-
Держитесь подальше от деревьев и рекламных щитов. Во время сильного ветра существует риск падения веток и других объектов. Постарайтесь избегать прогулок вблизи больших деревьев и конструкций, которые могут представлять опасность.
-
Проверьте состояние окон и дверей. Убедитесь, что все окна и двери плотно закрыты и надежно заперты, чтобы предотвратить попадание ветра и возможные повреждения.
-
Будьте готовы к отключениям электроэнергии. Запаситесь свечами, фонариками и запасами воды. Убедитесь, что у вас есть все необходимое для комфортного пребывания в доме в случае отключения электричества.
-
Следите за обновлениями погоды. Регулярно проверяйте прогнозы и предупреждения от местных метеорологических служб. Будьте в курсе изменений и готовьтесь к возможным последствиям.
Глава города, Анна Петрова, призывает всех жителей проявлять осторожность и заботиться о себе и своих близких. «Сильный ветер может быть опасным, и важно следовать рекомендациям, чтобы избежать неприятных ситуаций. Берегите себя и будьте внимательны», — подчеркнула она.
Помните, что безопасность — это прежде всего ответственность каждого из нас. Следуя простым советам, вы сможете защитить себя и своих близких в условиях сильного ветра. Будьте осторожны и берегите себя!
-
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 6d8e2a24:5faaca4c
2024-11-29 16:34:32
@ 6d8e2a24:5faaca4c
2024-11-29 16:34:32 Memecoins, also known as meme cryptocurrencies or meme crypto, are digital currencies inspired by popular internet memes. Several meme tokens with large market caps boast active communities, such as Dogecoin (DOGE), Shiba Inu (SHIB), which are based on the Doge meme, and PEPE, which was inspired by Pepe the Frog.
Memecoins, also known as meme cryptocurrencies or meme crypto, are digital currencies inspired by popular internet memes. Several meme tokens with large market caps boast active communities, such as Dogecoin (DOGE), Shiba Inu (SHIB), which are based on the Doge meme, and PEPE, which was inspired by Pepe the Frog.So, what is a memecoin? Memecoins are a type of cryptocurrency featuring an internet meme character for its logo. Memecoins may serve a variety of purposes — or none at all — as they are not always the same, but they can still be bought and sold like other digital assets on most centralized and decentralized exchanges.
If you are looking to buy memecoins, do so at your own risk, as they are widely seen as speculative and volatile assets, and trading them is seen as risky.
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ eee391ee:8d0b97c2
2024-11-29 16:25:24
@ eee391ee:8d0b97c2
2024-11-29 16:25:24Amber 3.0.0 - Beta 7
- New design (still a work in progress)
- Removed the push notification server
- Open the permissions page with the correct account
- Fix crash when signing in with ncryptsec
- Fix icon size on notifications
- Fix relay connection when changing the default relays
- Option to setup a custom pin for the app
- Button to copy your public key
- Fix layout on Android < 15
- Fix multi event screen
- Fetch profile data
- Show relay message when event is rejected
- Fix profile icon size
- Don’t close app when using nostrconnect arcade
- Better check for valid relays
- Fix padding and scrolling
- Support for secret when using nostrconnect
- Fix empty relay notice
- Fix get_public_key not replying with hex key
- Fix relay not connecting after adding a new bunker
- Fix logout not working sometimes
Download it with zap.store, Obtainium, f-droid or download it directly in the releases page
If you like my work consider making a donation
Verifying the release
In order to verify the release, you'll need to have
gpgorgpg2installed on your system. Once you've obtained a copy (and hopefully verified that as well), you'll first need to import the keys that have signed this release if you haven't done so already:bash gpg --keyserver hkps://keys.openpgp.org --recv-keys 44F0AAEB77F373747E3D5444885822EED3A26A6DOnce you have his PGP key you can verify the release (assuming
manifest-v3.0.0-pre7.txtandmanifest-v3.0.0-pre7.txt.sigare in the current directory) with:bash gpg --verify manifest-v3.0.0-pre7.txt.sig manifest-v3.0.0-pre7.txtYou should see the following if the verification was successful:
bash gpg: Signature made Fri 13 Sep 2024 08:06:52 AM -03 gpg: using RSA key 44F0AAEB77F373747E3D5444885822EED3A26A6D gpg: Good signature from "greenart7c3 <greenart7c3@proton.me>"That will verify the signature on the main manifest page which ensures integrity and authenticity of the binaries you've downloaded locally. Next, depending on your operating system you should then re-calculate the sha256 sum of the binary, and compare that with the following hashes:
bash cat manifest-v3.0.0-pre7.txtOne can use the
shasum -a 256 <file name here>tool in order to re-compute thesha256hash of the target binary for your operating system. The produced hash should be compared with the hashes listed above and they should match exactly. -
 @ b83e6f82:73c27758
2024-11-29 16:10:05
@ b83e6f82:73c27758
2024-11-29 16:10:05Citrine 0.5.6
- Add a option to fetch your events from relays
- Add a delete all button
- Feed by kind
Download it with zap.store, Obtainium, f-droid or download it directly in the releases page
If you like my work consider making a donation
Verifying the release
In order to verify the release, you'll need to have
gpgorgpg2installed on your system. Once you've obtained a copy (and hopefully verified that as well), you'll first need to import the keys that have signed this release if you haven't done so already:bash gpg --keyserver hkps://keys.openpgp.org --recv-keys 44F0AAEB77F373747E3D5444885822EED3A26A6DOnce you have his PGP key you can verify the release (assuming
manifest-v0.5.6.txtandmanifest-v0.5.6.txt.sigare in the current directory) with:bash gpg --verify manifest-v0.5.6.txt.sig manifest-v0.5.6.txtYou should see the following if the verification was successful:
bash gpg: Signature made Fri 13 Sep 2024 08:06:52 AM -03 gpg: using RSA key 44F0AAEB77F373747E3D5444885822EED3A26A6D gpg: Good signature from "greenart7c3 <greenart7c3@proton.me>"That will verify the signature on the main manifest page which ensures integrity and authenticity of the binaries you've downloaded locally. Next, depending on your operating system you should then re-calculate the sha256 sum of the binary, and compare that with the following hashes:
bash cat manifest-v0.5.6.txtOne can use the
shasum -a 256 <file name here>tool in order to re-compute thesha256hash of the target binary for your operating system. The produced hash should be compared with the hashes listed above and they should match exactly. -
 @ fa1d8325:7c91882e
2024-11-29 15:57:29
@ fa1d8325:7c91882e
2024-11-29 15:57:29Сегодня в Пятигорске произошло серьёзное происшествие — прорыв канализационной системы, который привёл к затоплению улиц и подвалов. Это происшествие ещё раз свидетельствует о критическом состоянии канализационной системы во многих регионах России, где трубы, которым уже более 70 лет, требуют срочного ремонта.
Наши корреспонденты отправились на место аварии, чтобы предоставить вам самые актуальные новости о ситуации в Пятигорске и о том, какие меры принимаются для решения этой проблемы.
-
 @ a849beb6:b327e6d2
2024-11-23 15:03:47
@ a849beb6:b327e6d2
2024-11-23 15:03:47
\ \ It was another historic week for both bitcoin and the Ten31 portfolio, as the world’s oldest, largest, most battle-tested cryptocurrency climbed to new all-time highs each day to close out the week just shy of the $100,000 mark. Along the way, bitcoin continued to accumulate institutional and regulatory wins, including the much-anticipated approval and launch of spot bitcoin ETF options and the appointment of several additional pro-bitcoin Presidential cabinet officials. The timing for this momentum was poetic, as this week marked the second anniversary of the pico-bottom of the 2022 bear market, a level that bitcoin has now hurdled to the tune of more than 6x despite the litany of bitcoin obituaries published at the time. The entirety of 2024 and especially the past month have further cemented our view that bitcoin is rapidly gaining a sense of legitimacy among institutions, fiduciaries, and governments, and we remain optimistic that this trend is set to accelerate even more into 2025.
Several Ten31 portfolio companies made exciting announcements this week that should serve to further entrench bitcoin’s institutional adoption. AnchorWatch, a first of its kind bitcoin insurance provider offering 1:1 coverage with its innovative use of bitcoin’s native properties, announced it has been designated a Lloyd’s of London Coverholder, giving the company unique, blue-chip status as it begins to write bitcoin insurance policies of up to $100 million per policy starting next month. Meanwhile, Battery Finance Founder and CEO Andrew Hohns appeared on CNBC to delve into the launch of Battery’s pioneering private credit strategy which fuses bitcoin and conventional tangible assets in a dual-collateralized structure that offers a compelling risk/return profile to both lenders and borrowers. Both companies are clearing a path for substantially greater bitcoin adoption in massive, untapped pools of capital, and Ten31 is proud to have served as lead investor for AnchorWatch’s Seed round and as exclusive capital partner for Battery.
As the world’s largest investor focused entirely on bitcoin, Ten31 has deployed nearly $150 million across two funds into more than 30 of the most promising and innovative companies in the ecosystem like AnchorWatch and Battery, and we expect 2025 to be the best year yet for both bitcoin and our portfolio. Ten31 will hold a first close for its third fund at the end of this year, and investors in that close will benefit from attractive incentives and a strong initial portfolio. Visit ten31.vc/funds to learn more and get in touch to discuss participating.\ \ Portfolio Company Spotlight
Primal is a first of its kind application for the Nostr protocol that combines a client, caching service, analytics tools, and more to address several unmet needs in the nascent Nostr ecosystem. Through the combination of its sleek client application and its caching service (built on a completely open source stack), Primal seeks to offer an end-user experience as smooth and easy as that of legacy social media platforms like Twitter and eventually many other applications, unlocking the vast potential of Nostr for the next billion people. Primal also offers an integrated wallet (powered by Strike BLACK) that substantially reduces onboarding and UX frictions for both Nostr and the lightning network while highlighting bitcoin’s unique power as internet-native, open-source money.
Selected Portfolio News
AnchorWatch announced it has achieved Llody’s Coverholder status, allowing the company to provide unique 1:1 bitcoin insurance offerings starting in December.\ \ Battery Finance Founder and CEO Andrew Hohns appeared on CNBC to delve into the company’s unique bitcoin-backed private credit strategy.
Primal launched version 2.0, a landmark update that adds a feed marketplace, robust advanced search capabilities, premium-tier offerings, and many more new features.
Debifi launched its new iOS app for Apple users seeking non-custodial bitcoin-collateralized loans.
Media
Strike Founder and CEO Jack Mallers joined Bloomberg TV to discuss the strong volumes the company has seen over the past year and the potential for a US bitcoin strategic reserve.
Primal Founder and CEO Miljan Braticevic joined The Bitcoin Podcast to discuss the rollout of Primal 2.0 and the future of Nostr.
Ten31 Managing Partner Marty Bent appeared on BlazeTV to discuss recent changes in the regulatory environment for bitcoin.
Zaprite published a customer testimonial video highlighting the popularity of its offerings across the bitcoin ecosystem.
Market Updates
Continuing its recent momentum, bitcoin reached another new all-time high this week, clocking in just below $100,000 on Friday. Bitcoin has now reached a market cap of nearly $2 trillion, putting it within 3% of the market caps of Amazon and Google.
After receiving SEC and CFTC approval over the past month, long-awaited options on spot bitcoin ETFs were fully approved and launched this week. These options should help further expand bitcoin’s institutional liquidity profile, with potentially significant implications for price action over time.
The new derivatives showed strong performance out of the gate, with volumes on options for BlackRock’s IBIT reaching nearly $2 billion on just the first day of trading despite surprisingly tight position limits for the vehicles.
Meanwhile, the underlying spot bitcoin ETF complex had yet another banner week, pulling in $3.4 billion in net inflows.
New reports suggested President-elect Donald Trump’s social media company is in advanced talks to acquire crypto trading platform Bakkt, potentially the latest indication of the incoming administration’s stance toward the broader “crypto” ecosystem.
On the macro front, US housing starts declined M/M again in October on persistently high mortgage rates and weather impacts. The metric remains well below pre-COVID levels.
Pockets of the US commercial real estate market remain challenged, as the CEO of large Florida developer Related indicated that developers need further rate cuts “badly” to maintain project viability.
US Manufacturing PMI increased slightly M/M, but has now been in contraction territory (<50) for well over two years.
The latest iteration of the University of Michigan’s popular consumer sentiment survey ticked up following this month’s election results, though so did five-year inflation expectations, which now sit comfortably north of 3%.
Regulatory Update
After weeks of speculation, the incoming Trump administration appointed hedge fund manager Scott Bessent to head up the US Treasury. Like many of Trump’s cabinet selections so far, Bessent has been a public advocate for bitcoin.
Trump also appointed Cantor Fitzgerald CEO Howard Lutnick – another outspoken bitcoin bull – as Secretary of the Commerce Department.
Meanwhile, the Trump team is reportedly considering creating a new “crypto czar” role to sit within the administration. While it’s unclear at this point what that role would entail, one report indicated that the administration’s broader “crypto council” is expected to move forward with plans for a strategic bitcoin reserve.
Various government lawyers suggested this week that the Trump administration is likely to be less aggressive in seeking adversarial enforcement actions against bitcoin and “crypto” in general, as regulatory bodies appear poised to shift resources and focus elsewhere.
Other updates from the regulatory apparatus were also directionally positive for bitcoin, most notably FDIC Chairman Martin Gruenberg’s confirmation that he plans to resign from his post at the end of President Biden’s term.
Many critics have alleged Gruenberg was an architect of “Operation Chokepoint 2.0,” which has created banking headwinds for bitcoin companies over the past several years, so a change of leadership at the department is likely yet another positive for the space.
SEC Chairman Gary Gensler also officially announced he plans to resign at the start of the new administration. Gensler has been the target of much ire from the broader “crypto” space, though we expect many projects outside bitcoin may continue to struggle with questions around the Howey Test.
Overseas, a Chinese court ruled that it is not illegal for individuals to hold cryptocurrency, even though the country is still ostensibly enforcing a ban on crypto transactions.
Noteworthy
The incoming CEO of Charles Schwab – which administers over $9 trillion in client assets – suggested the platform is preparing to “get into” spot bitcoin offerings and that he “feels silly” for having waited this long. As this attitude becomes more common among traditional finance players, we continue to believe that the number of acquirers coming to market for bitcoin infrastructure capabilities will far outstrip the number of available high quality assets.
BlackRock’s 2025 Thematic Outlook notes a “renewed sense of optimism” on bitcoin among the asset manager’s client base due to macro tailwinds and the improving regulatory environment. Elsewhere, BlackRock’s head of digital assets indicated the firm does not view bitcoin as a “risk-on” asset.
MicroStrategy, which was a sub-$1 billion market cap company less than five years ago, briefly breached a $100 billion equity value this week as it continues to aggressively acquire bitcoin. The company now holds nearly 350,000 bitcoin on its balance sheet.
Notably, Allianz SE, Germany’s largest insurer, spoke for 25% of MicroStrategy’s latest $3 billion convertible note offering this week, suggesting growing appetite for bitcoin proxy exposure among more restricted pools of capital.
The ongoing meltdown of fintech middleware provider Synapse has left tens of thousands of customers with nearly 100% deposit haircuts as hundreds of millions in funds remain missing, the latest unfortunate case study in the fragility of much of the US’s legacy banking stack.
Travel
-
BitcoinMENA, Dec 9-10
-
Nashville BitDevs, Dec 10
-
Austin BitDevs, Dec 19
-
-
 @ 5e5fc143:393d5a2c
2024-11-19 10:20:25
@ 5e5fc143:393d5a2c
2024-11-19 10:20:25Now test old reliable front end Stay tuned more later Keeping this as template long note for debugging in future as come across few NIP-33 post edit issues
-
 @ 41e6f20b:06049e45
2024-11-17 17:33:55
@ 41e6f20b:06049e45
2024-11-17 17:33:55Let me tell you a beautiful story. Last night, during the speakers' dinner at Monerotopia, the waitress was collecting tiny tips in Mexican pesos. I asked her, "Do you really want to earn tips seriously?" I then showed her how to set up a Cake Wallet, and she started collecting tips in Monero, reaching 0.9 XMR. Of course, she wanted to cash out to fiat immediately, but it solved a real problem for her: making more money. That amount was something she would never have earned in a single workday. We kept talking, and I promised to give her Zoom workshops. What can I say? I love people, and that's why I'm a natural orange-piller.
-
 @ 4ba8e86d:89d32de4
2024-11-14 09:17:14
@ 4ba8e86d:89d32de4
2024-11-14 09:17:14Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular; • Computador com adb; • Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo;
Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid: https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
Samsung Galaxy Note 10 Plus bloatware listProvavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
./adb start-serverO resultado deve ser:
daemon not running; starting now at tcp:5037 daemon started successfully
E caso não apareça nada, execute:
./adb kill-serverE inicie novamente.
Com o adb conectado ao celular, execute:
./adb shellPara poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
pkg install android-toolsQuando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
adb pair localhost:porta CódigoDeEmparelhamentoDe acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
adb connect localhost:portaObs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
adb shellRemoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
pm uninstall –user 0 com.google.android.apps.mapsE pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
cmd package install-existing nome.do.pacotePós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-
 @ 4ba8e86d:89d32de4
2024-11-07 13:56:21
@ 4ba8e86d:89d32de4
2024-11-07 13:56:21Tutorial feito por Grom mestre⚡poste original abaixo:
http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/240277/tutorial-criando-e-acessando-sua-conta-de-email-pela-i2p?show=240277#q240277
Bom dia/tarde/noite a todos os camaradas. Seguindo a nossa série de tutoriais referentes a tecnologias essenciais para a segurança e o anonimato dos usuários, sendo as primeiras a openPGP e a I2P, lhes apresento mais uma opção para expandir os seus conhecimentos da DW. Muitos devem conhecer os serviços de mail na onion como DNMX e mail2tor, mas e que tal um serviço de email pela I2P. Nesse tutorial eu vou mostrar a vocês como criar a sua primeira conta no hq.postman.i2p e a acessar essa conta.
É importante que vocês tenham lido a minha primeira série de tutoriais a respeito de como instalar, configurar e navegar pela I2P nostr:nevent1qqsyjcz2w0e6d6dcdeprhuuarw4aqkw730y542dzlwxwssneq3mwpaspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsyp5vcq Esse tutorial é um pré-requisito para o seguinte e portanto recomendo que leia-os antes de prosseguir com o seguinte tutorial. O tutorial de Kleopatra nostr:nevent1qqs8h7vsn5j6qh35949sa60dms4fneussmv9jd76n24lsmtz24k0xlqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgecq8f7 é complementar dado que é extremamente recomendado assinar e criptografar as mensagens que seguem por emails pela DW. Sem mais delongas, vamos ao tutorial de fato.
1. Criando uma conta de email no hq.postman
Relembrando: Esse tutorial considera que você já tenha acesso à I2P. Entre no seu navegador e acesse o endereço hq.postman.i2p. O roteador provavelmente já contém esse endereço no seu addressbook e não haverá a necessidade de inserir o endereço b32 completo. Após entrar no site vá para a página '1 - Creating a mailbox' https://image.nostr.build/d850379fe315d2abab71430949b06d3fa49366d91df4c9b00a4a8367d53fcca3.jpg
Nessa página, insira as credenciais de sua preferências nos campos do formulário abaixo. Lembre-se que o seu endereço de email aceita apenas letras e números. Clique em 'Proceed' depois que preencher todos os campos. https://image.nostr.build/670dfda7264db393e48391f217e60a2eb87d85c2729360c8ef6fe0cf52508ab4.jpg
Uma página vai aparecer pedindo para confirmar as credenciais da sua nova conta. Se tudo estiver certo apenas clique em 'Confirm and Create Mailbox'. Se tudo ocorrer como conforme haverá uma confirmação de que a sua nova conta foi criada com sucesso. Após isso aguarde por volta de 5 minutos antes de tentar acessá-la, para que haja tempo suficiente para o servidor atualizar o banco de dados. https://image.nostr.build/ec58fb826bffa60791fedfd9c89a25d592ac3d11645b270c936c60a7c59c067f.jpg https://image.nostr.build/a2b7710d1e3cbb36431acb9055fd62937986b4da4b1a1bbb06d3f3cb1f544fd3.jpg
Pronto! Sua nova conta de email na I2P foi criada. Agora vamos para a próxima etapa: como acessar a sua conta via um cliente de email.
2. Configurando os túneis cliente de SMTP e POP3
O hq.postman não possui um cliente web que nos permite acessar a nossa conta pelo navegador. Para isso precisamos usar um cliente como Thunderbird e configurar os túneis cliente no I2Pd que serão necessários para o Thunderbird se comunicar com o servidor pela I2P.
Caso não tenha instalado o Thunderbird ainda, faça-o agora antes de prosseguir.
Vamos configurar os túneis cliente do servidor de email no nosso roteador. Para isso abra um terminal ou o seu gestor de arquivos e vá para a pasta de configuração de túneis do I2P. Em Linux esse diretório se localiza em /etc/i2pd/tunnels.d. Em Windows, essa pasta se localiza em C:\users\user\APPDATA\i2pd. Na pasta tunnels.d crie dois arquivos: smtp.postman.conf e pop-postman.conf. Lembre-se que em Linux você precisa de permissões de root para escrever na pasta de configuração. Use o comando sudoedit
para isso. Edite-os conforme as imagens a seguir:
Arquivo pop-postman.conf https://image.nostr.build/7e03505c8bc3b632ca5db1f8eaefc6cecb4743cd2096d211dd90bbdc16fe2593.jpg
Arquivo smtp-postman.conf https://image.nostr.build/2d06c021841dedd6000c9fc2a641ed519b3be3c6125000b188842cd0a5af3d16.jpg
Salve os arquivos e reinicie o serviço do I2Pd. Em Linux isso é feito pelo comando:
sudo systemctl restart i2pdEntre no Webconsole do I2Pd pelo navegador (localhost:7070) e na seção I2P Tunnels, verifique se os túneis pop-postman e smtp-postman foram criados, caso contrário verifique se há algum erro nos arquivos e reinicie o serviço.Com os túneis cliente criados, vamos agora configurar o Thunderbird
3. Configurando o Thunderbird para acessar a nossa conta
Abra o Thunderbird e clique em criar uma nova conta de email. Se você não tiver nenhum conta previamente presente nele você vai ser diretamente recebido pela janela de criação de conta a seguir. https://image.nostr.build/e9509d7bd30623716ef9adcad76c1d465f5bc3d5840e0c35fe4faa85740f41b4.jpg https://image.nostr.build/688b59b8352a17389902ec1e99d7484e310d7d287491b34f562b8cdd9dbe8a99.jpg
Coloque as suas credenciais, mas não clique ainda em Continuar. Clique antes em Configure Manually, já que precisamos configurar manualmente os servidores de SMTP e POP3 para, respectivamente, enviar e receber mensagens.
Preencha os campos como na imagem a seguir. Detalhe: Não coloque o seu endereço completo com o @mail.i2p, apenas o nome da sua conta. https://image.nostr.build/4610b0315c0a3b741965d3d7c1e4aff6425a167297e323ba8490f4325f40cdcc.jpg
Clique em Re-test para verificar a integridade da conexão. Se tudo estiver certo uma mensagem irá aparecer avisando que as configurações do servidores estão corretas. Clique em Done assim que estiver pronto para prosseguir. https://image.nostr.build/8a47bb292f94b0d9d474d4d4a134f8d73afb84ecf1d4c0a7eb6366d46bf3973a.jpg
A seguinte mensagem vai aparecer alertando que não estamos usando criptografia no envio das credenciais. Não há problema nenhum aqui, pois a I2P está garantindo toda a proteção e anonimato dos nossos dados, o que dispensa a necessidade de uso de TLS ou qualquer tecnologia similar nas camadas acima. Marque a opção 'I Understand the risks' e clique em 'Continue' https://image.nostr.build/9c1bf585248773297d2cb1d9705c1be3bd815e2be85d4342227f1db2f13a9cc6.jpg
E por fim, se tudo ocorreu como devido sua conta será criada com sucesso e você agora será capaz de enviar e receber emails pela I2P usando essa conta. https://image.nostr.build/8ba7f2c160453c9bfa172fa9a30b642a7ee9ae3eeb9b78b4dc24ce25aa2c7ecc.jpg
4. Observações e considerações finais
Como informado pelo próprio site do hq.postman, o domínio @mail.i2p serve apenas para emails enviados dentro da I2P. Emails enviados pela surface devem usar o domínio @i2pmai.org. É imprescindível que você saiba usar o PGP para assinar e criptografar as suas mensagens, dado que provavelmente as mensagens não são armazenadas de forma criptografada enquanto elas estão armazenadas no servidor. Como o protocolo POP3 delete as mensagens no imediato momento em que você as recebe, não há necessidade de fazer qualquer limpeza na sua conta de forma manual.
Por fim, espero que esse tutorial tenha sido útil para vocês. Que seu conhecimento tenha expandido ainda mais com as informações trazidas aqui. Até a próxima.
-
 @ 3bf0c63f:aefa459d
2024-03-19 14:01:01
@ 3bf0c63f:aefa459d
2024-03-19 14:01:01Nostr is not decentralized nor censorship-resistant
Peter Todd has been saying this for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right.
Nostr today is indeed centralized.
Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:
The top one was published to
wss://nostr.wine,wss://nos.lol,wss://pyramid.fiatjaf.com. The second was published to the relay where I generally publish all my notes to,wss://pyramid.fiatjaf.com, and that is announced on my NIP-05 file and on my NIP-65 relay list.A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:
These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains.
What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all.
Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant.
What happens is that most people who engaged with the note are following me, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on
wss://pyramid.fiatjaf.com.If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before.
Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today.
Peter Todd is wrong that Nostr is inherently centralized or that it needs a protocol change to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we drive in the right direction we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary.
See also:
-
 @ 06a260a2:d7a7791c
2024-11-29 15:54:28
@ 06a260a2:d7a7791c
2024-11-29 15:54:28V dnešním pokračování miniseriálu o domácí těžbě bitcoinu se podíváme na těžební pooly. Co je to těžební pool? Jak funguje a jaké služby nabízí? Jaké mohou být nevýhody nebo rizika spojená s těžbou v poolu? A existují způsoby, jak tato rizika zmírnit, například pomocí protokolů Stratum V2 nebo DATUM?
Těžební pool pro těžbu bitcoinu
Těžební pool je služba, která umožňuje více těžařům spolupracovat na těžbě bitcoinu a následně si rozdělit odměnu podle množství práce, kterou každý z nich odvedl. Spolupráce a koordinace mezi těžaři je pro ně výhodná, protože společným úsilím zvyšují šanci na úspěch, protože jejich sdružený hashrate tvoří větší podíl vůči celkovému hashrate bitcoinové sítě. Díky tomu se zkracuje průměrná doba mezi dvěma odměnami, které pool získá.
Jednoduše řečeno, čím vyšší hashrate těžaři v rámci poolu dají dohromady, tím větší podíl na celkovém výkonu sítě budou mít a tím častěji získají odměnu za nalezení bloku. Pravidelné a časté odměny jsou pak klíčové pro pokrytí nákladů spojených s těžbou.
Co však těžební pool musí (nebo může) pro své těžaře zajistit? Než se podrobně podíváme na jeho fungování, pojďme si nejprve připomenout, jak samotná těžba bitcoinu funguje.
Postup těžby bitcoinu
Těžba bitcoinu je proces, při kterém vznikají nové mince jako odměna pro těžaře, který jako první najde správný hash bloku transakcí čekajících na potvrzení. Tento hash, vypočítaný pomocí algoritmu SHA-256, musí splňovat požadovanou obtížnost, což znamená, že jeho začátek obsahuje stanovený počet nul.
Hledání správného hashe (hashování) je výpočetně náročný proces využívající prvku náhodnosti. Těžaři postupně generují obrovské množství potenciálních výsledků, dokud nenaleznou ten, který odpovídá požadované obtížnosti. Jakmile takový hash najdou, oznámí ho ostatním uzlům v síti. Ty ho zkontrolují, a pokud je správný, potvrdí ho a zařadí odpovídající blok transakcí do blockchainu.
Proces těžby bitcoinu probíhá v cyklu, který se opakuje pro každý nový blok a obsahuje následující kroky:
Proces těžby bitcoinu krok za krokem:
-
Výběr transakcí z mempoolu - Těžař vybírá transakce z mempoolu čekající na potvrzení. Mempool je část bitcoinového uzlu, kde jsou uloženy nepotvrzené transakce. Transakce jsou obvykle vybírány podle výše poplatku za jejich zpracování.
-
Vytvoření coinbase transakce - Coinbase transakce nemá žádné vstupy. Pouze generuje odměnu za vytěžení bloku (aktuálně nově vytvořené bitcoiny) a připočítává poplatky ze všech vybraných transakcí. Tato odměna je zaslána na adresu těžaře.
-
Výpočet Merkle root - Vybrané transakce jsou uspořádány do binárního stromu, tzv. Merkle tree. Výsledkem je Merkle root, což je hash reprezentující všechny transakce zahrnuté v bloku.
-
Sestavení hlavičky nového bloku - Hlavička bloku obsahuje následující údaje:
- Verzi bloku
- Hash předchozího bloku – odkaz na poslední validní blok v blockchainu
- Merkle root – hash všech transakcí v bloku
- Časové razítko – čas vzniku bloku
- Obtížnost těžby – určuje, kolik nul musí hash bloku obsahovat na začátku
- Nonce – 32bitové náhodné číslo, které se při každém pokusu o výpočet mění a zajišťuje jeho variabilitu a jedinečnost
-
Hashování hlavičky bloku - Hlavička bloku je opakovaně hashována pomocí algoritmu SHA-256. Při každém pokusu se mění hodnota Nonce, aby byl výpočet jedinečný. Proces pokračuje, dokud není nalezen hash, který splňuje požadovanou obtížnost, nebo dokud blok nenalezne jiný těžař.
-
Propagace nového bloku - Jakmile těžař najde správný hash, nový blok je odeslán do bitcoinové sítě. Uzly v síti jej ověří a v případě, že je blok validní, zařadí jej do blockchainu.
Nejnáročnější částí celého procesu těžby je hledání SHA-256 hashe, který splňuje cílovou obtížnost. Aktuální obtížnost (95.6T) vyžaduje v průměru 432 zettahashů (432 × 1021 hashů) k nalezení správného hashe. Aby tento proces byl efektivní, byly vyvinuty specializované zařízení a čipy, které jsou optimalizované pro výpočty podle SHA-256 algoritmu.
Role poolu v těžbě
Rozdělení odměny mezi těžaře
Pokud má těžební pool zajistit spravedlivé rozdělení odměny za vytěžený blok mezi všechny spolupracující těžaře, musí mít pod kontrolou alespoň následující části těžebního procesu:
-
Vytvoření Coinbase transakce - Pool musí správně vytvořit Coinbase transakci, která převádí odměnu za vytěžený blok a následně ji rozděluje mezi všechny spolupracující těžaře.
-
Sběr důkazů o odvedené práci (PoW) - Pool musí shromažďovat důkazy o odvedené práci od všech těžařů. Tyto důkazy ukazují, jakým způsobem a v jakém poměru se má odměna rozdělit mezi těžaře.
První bod může být realizován dvěma způsoby:
-
Pool může do Coinbase transakce zahrnout vlastní bitcoinovou adresu a vytěžené bitcoiny následně mezi těžaře rozdělit pomocí standardní transakce.
-
Nebo může do Coinbase transakce přímo uvést adresy a částky pro jednotlivé těžaře, které odpovídají jejich podílu na těžbě.
Sběr důkazů o odvedené práci se realizuje tím, že těžaři musí poolu reportovat nejen nalezení bloku (tedy nalezení hashe, který splňuje cílovou obtížnost sítě – tzv. network difficulty target), ale i všechny hashe, které splňují nižší obtížnost (tzv. share difficulty target). Tento target odpovídá reálnému výkonu těžícího zařízení, kde je pravděpodobnost nalezení odpovídajícího hashe výrazně vyšší. Tyto hashe se nazývají shares. Pool může pomocí počtu nalezených shares v daném období stanovit poměr odvedené práce mezi jednotlivými těžaři.
Rozdělení odměny mezi těžaře je vlastně jediná klíčová povinnost poolu, která zajišťuje jeho smysl a fungování.
Způsob výpočtu míry přispění každého těžaře se může mezi jednotlivými pooly lišit, v principu ale existují dva základní přístupy: PPLNS a (F)PPS.
PPLNS - Pay Per Last N Shares
Tento model vyplácí těžaře na základě množství shares, které odeslali do poolu před tím, než byl blok vytěžen. Odměna je tedy závislá na podílu hashrate jejich zařízení vůči celkovému hashrate poolu a také na štěstí poolu při hledání bloku. Výhodou systému PPLNS je, že odrazuje těžaře od přeskakování mezi pooly a podporuje jejich loajalitu. Nevýhodou však může být nepředvídatelnost velikosti odměny v daném období. Vzhledem k náhodnosti objevování bloků mohou být četnost a termíny výplat velmi proměnlivé.(F)PPS - (Full) Pay Per Share
Těžaři jsou vypláceni podle množství odeslaných podílů, bez ohledu na to, zda byl blok nalezen. Výhodou systému PPS je jeho předvídatelnost. Těžaři přesně vědí, kolik za každý podíl obdrží, a výplaty jsou pravidelné, obvykle na denní bázi. Nevýhodou je nízká motivace k věrnosti poolu, protože těžaři mohou přeskakovat z jednoho (F)PPS poolu do druhého, aniž by tratili oproti setrvání v jednom z nich. Full v názvu znamená, že součástí odměny jsou i vytěžené transakční poplatky.Pravidelnost a předvídatelnost výplaty v modelu (F)PPS jsou v přímém rozporu s neurčitostí a nepředvídatelností při hledání nového bloku. Pool na sebe přebírá riziko "ztráty štěstí" a garantuje stabilní výplaty těžařům na základě jejich odvedené práce, bez ohledu na to, zda byl skutečně nalezen nový blok. Tato "pojistka proti smůle" však není zadarmo. Pooly si proti riziku dlouhodobé neúspěšnosti při hledání nového bloku pomáhají spoluprací na vyšší úrovni. "Smůla" jednoho poolu je většinou "štěstím" jiného. Pokud se pooly dokážou domluvit a sdílet vytěžené odměny, mohou si "smůlu" vzájemně kompenzovat a potlačit riziko neúspěchu úměrně podílu tohoto "super poolu" na celkové hashrate sítě. O tom, že se pooly domluvit dokážou, si můžete přečíst v článku Konec mýtu o decentralizované těžbě.
Je důležité si uvědomit, že model (F)PPS jako "pojišťovna" není dlouhodobě udržitelný. Variabilitu ve výplatách totiž nezpůsobuje pouze střídání štěstí a smůly, ale také změny v transakčních poplatcích a jejich podílu na odměně za nalezený blok. V současnosti se transakční poplatky pohybují v jednotkách procent z odměny za nový blok (3.125 BTC). Po několika dalších půlení se však tento podíl může zvýšit na desítky procent a významně ovlivní celkovou variabilitu odměny za nový blok. Pokud budou těžaři i nadále vyžadovat stabilní odměnu za svou práci, cena "pojištění" této služby (tj. poplatek poolu) vzroste.
Sestavení šablony bloku
Těžební pooly však vykonávají i jiné kroky procesu těžby bitcoinu. Dalším klíčovým je sestavení šablony nového bloku. Proč je důležitý? Protože pro sestavení šablony je nutné do nového bloku vybrat transakce, které čekají na potvrzení (a spočítat pro ně Merkle root hash, viz. výše). Výběrem transakcí lze ovlivnit celkovou výši odměny za vytěžení bloku, jelikož ta obsahuje i všechny transakční poplatky. Zároveň tímto výběrem může pool cenzurovat některé transakce nebo bitcoinové adresy tím, že je do bloku nezahrne.
V důsledku přenesení této činnosti na pool pak všichni těžaři v poolu pracují na stejném bloku.
Validace a propagace nového bloku do bitcoinové sítě
Těžební pool rovněž ověřuje nově nalezené bloky. Tuto činnost provádí bitcoinový uzel, který pool musí provozovat, aby měl přístup k mempoolu – databázi transakcí čekajících na potvrzení. Prostřednictvím tohoto uzlu také pool šíří nově vytěžené bloky do bitcoinové sítě.
Pro úspěšnou propagaci nového bloku je zásadní kvalitní konektivita s nízkou latencí a široké propojení s ostatními uzly. Tím se zvyšuje šance, že blok bude přijat, i když byl jiný blok nalezen ve stejný čas jiným těžařem.
Pokud pool obdrží z bitcoinové sítě nový platný blok vytěžený někým jiným, okamžitě informuje své těžaře. Ti musí přerušit práci na aktuálním bloku a začít těžit nový. Pool jim proto obratem připraví novou šablonu, která obsahuje dosud nepotvrzené transakce.
Rizika těžby v poolech
Poolová těžba umožňuje těžařům získávat odměny úměrně jejich podílu na výkonu poolu, aniž by museli sami najít nový blok. To přitahuje téměř všechny těžaře, protože nabízí stabilitu příjmů. Pro nejmenší těžaře je pool často jediným způsobem, jak získat odměnu ještě za svého života. Malí těžaři takto dokážou pokrýt náklady na energii a velké farmy s úvěrovým financováním si zajistí pravidelné splátky svých dluhů. Tento model však přináší i určitá rizika, zejména spojená s centralizací těžby.
Proč dochází k centralizaci? Aby těžba v poolu přinesla výše zmíněný benefit jistoty pravidelného příjmu, musí být pool schopen najít nový blok dostatečně často. Co znamená dostatečně často? Nebudu zabíhat do statistiky a teorie směrodatné odchylky, ale zkusím to vysvětlit na jednoduchém příkladě: Ačkoliv vaše odměna za konstantní hashrate 1 Th/s vašeho Braiins BMM 101 mineru bude při daném celkovém hashrate sítě teoreticky ve všech poolech za dostatečně dlouhé období stejná, vyberete si radši malý pool, který najde nový blok v průměru 1x za rok, ale díky náhodnosti těžby klidně následující 3 roky žádný, nebo velký pool, který nalezne nový blok v průměru 1x za den, ale díky náhodnosti těžby klidně následující 3 dny nenalezne nic? Zcela jistě si vyberete ten větší pool.
Velké pooly rostou a koncentrují většinu výkonu sítě (hashrate), což je klíčové pro jejich úspěch. Tento růst však má své limity. Pooly obvykle nepřekračují podíl 30–40 % na celkovém výkonu sítě, protože těžaři se při takové koncentraci začínají obávat rizika 51% útoku (viz dále). Na druhou stranu malé pooly často ztrácejí schopnost pravidelně vyplácet své těžaře, což je činí méně atraktivními. Těžba v nich se postupně začne podobat solo miningu, kde odměnu získá pouze těžař, který najde blok, a časem zaniknou pro nezájem těžařů.
Počet relevantních poolů se proto stabilizoval na relativně nízké úrovni. Dnes si 99 % odměn z těžby dělí přibližně 20 poolů, přičemž 95 % z této odměny připadá na 10 největších z nich. I kdyby nebylo přirozené tendence k centralizaci výkonu do velkých poolů, existoval by určitý logický limit jejich počtu. Například pokud bychom předpokládali, že pool má smysl pouze tehdy, pokud najde nový blok alespoň jednou denně, mohlo by teoreticky existovat maximálně 144 poolů (při generování jednoho bloku každých 10 minut).
Proč je tedy centralizace těžby nebezpečná? Všechny obavy mají svůj původ v současné praxi poolů centrálně vybírat transakce a sestavovat šablonu bloku. Díky tomu mohou pooly samy rozhodovat, které transakce do bloku vloží a které nikoliv. Těžaři přitom nikdy nevidí celý blok se všemi transakcemi k ověření, ale pouze hash jejich struktury (Merkle root hash). Obava z cenzury transakcí je tedy na místě. Zvláště pokud o obsahu 95% nových bloků může rozhodovat třeba jen 10 lidí nebo o 99% jen 20, viz. výše. Přijde vám to bláznivé? "To, že jsi paranoik, ještě neznamená, že po tobě nejdou." (Woody Allen).
Další hrozbou spojenou s centralizovanou těžbou v poolech je riziko 51% útoku. Co to znamená? Tento termín se vztahuje k situaci, kdy určitý subjekt ovládne více než polovinu celkového výkonu sítě (hashrate). S takovým podílem získává statistickou jistotu, že bude nacházet více bloků než zbytek sítě. To mu umožní vytvořit delší verzi blockchainu, která bude podle konsensu bitcoinové sítě považována za platnou. K čemu to může vést? Existují dvě hlavní rizika:
-
Riziko dvojí útraty - nepoctivý uživatel, který ovládl nadpoloviční podíl hashrate, vytváří skrytě svůj vlastní řetěz nových bloků. Zároveň paralelně v existujícím veřejném blockchainu utratí své bitcoiny za jinou hodnotu (prodá je na burze). Následně uveřejní svou delší verzi blockchainu, která bude automaticky považována za platnou a tím pádem anuluje původní transakce (jeho bitcoiny mu zůstanou na původních adresách, zatímco hodnotu, kterou za ně získal, již mohl utratit).
-
Riziko DoS útoku na blockchain - útočník s nadpolovičním podílem na celkové hashrate sítě může těžit pouze prázdné bloky, čímž efektivně síť zablokuje, protože transakce z mempoolu nebudou potvrzovány.
Obě rizika lze celkem úspěšně zlehčovat poukázáním na obrovské náklady jejich provedení, nelze je však zcela zanedbat. Nedokážeme efektivně bránit situaci, aby někdo ovládl více než 51% výkonu sítě. Může tomu bránit "bdělost těžařů", kteří nenechají žádný pool vyrůst nad 30% a na dva kliky mohou své těžební stroje přesměrovat do jiného poolu? A víme určitě, že ti 3 lidé za třemi největšími pooly nejsou ve skutečnosti pouze jeden člověk? Důkazy pro takové tvrzení se hledají obtížně, ale mnohé indicie naznačují, že se některé pooly nebojí "spolupracovat" a používat společného kustodiána svých bitcoinů.
Další problémy těžby v centralizovaných poolech
Těžba v současných poolech má i další nevýhody, o kterých se tolik nemluví nebo si je těžaři přímo neuvědomují.
Netransparentní odměňování
Česká společnost Braiins a jejich těžební pool se aktivně snaží zvyšovat povědomí o těžbě bitcoinu, objasňovat základní pojmy (a vyvracet některé mýty) a pravidelně publikují zajímavá data o bitcoinové těžbě. Navštivte jejich Braiins Academy, kde můžete najít například tento článek o těžbě v poolu nebo podrobnou specifikaci výpočtu odměn dle FPPS modelu pro těžaře v jejich poolu.
Přesto je odměňování ve většině současných poolech v principu netransparentní. Proč? Nelze ho nezávisle ověřit. Žádný z těchto poolů neposkytuje veřejně všem svým těžařům potřebná data, která by jim umožnila zkontrolovat správnost jejich podílu na odměně získané vytěžením bloku. (V rámci této série o domácí těžbě bitcoinu mám na mysli především malé nezávislé těžaře; pokud máte k dispozici výkon v řádu několika Eh/s, vaše pozice vůči poolu bude samozřejmě jiná). Chybí především informace o celkovém výkonu poolu, tedy o počtu shares, které jednotliví těžaři přispěli za den (pro FPPS model), nebo mezi dvěma nalezenými bloky (pro PPLNS model). Další komplikace nastávají při výpočtu průměrného poplatku, který je započítán do odměny. Některé pooly totiž nejvyšší poplatky v bloku do odměny nezapočítávají s odůvodněním, že je možná budou vracet, pokud se ukáže, že šlo o chybu při vytváření transakce.
Zcela mimo kontrolu těžařů je však systém urychlování transakcí mimo mempool, s využitím tzv. out-of-band transaction accelerators (OOB). O co jde? Standardní výběr transakcí do šablony následujícího bloku probíhá s ohledem na maximalizaci odměny z transakčních poplatků a tedy prioritizací transakcí s nejvyšším poplatkem za vByte. Pokud zvolíte poplatek příliš nízký, může se vám stát, že transakce zůstane v mempoolu "viset" nezpracovaná po dobu delší, než potřebujete. V takovém případě máte tři možnosti, jak problém vyřešit.
-
Buď s pomocí funkce replace-by-fee (RBF) vyšlete do bitcoinové sítě původní transakci znovu s vyšším poplatkem
-
Nebo vytvoříte novou transakci, která utrácí některý z výstupů uvízlé transakce (musíte k nim mít příslušné klíče) a nastavíte vyšší poplatek tak, aby výsledný průměrný poplatek za obě transakce byl pro těžaře motivující (tzv. child-pays-for-parent CPFP transakce)
-
A nebo se domluvíte s tím, kdo sestavuje šablonu nového bloku ve velkém poolu, aby vaši transakci do šablony zařadil a úplatu zaplatíte přímo jemu.
Ve třetím případě se takový poplatek v blockchainu vůbec neobjeví a nikdo nedokáže zjistit, jak veliký ve skutečnosti byl (těžaři neví, jaké transakce v bloku potvrzují, znají pouze jejich Merkle tree hash, viz. výše). Tyto transakce můžete najít v blockchain exploreru (třeba Mempool.space), jsou označeny jako "Upřednostněné / Prioritized", pokud měli nápadně nízké poplatky oproti ostatním transakcím v bloku. (Pokud by jste takovou službu někdy sami potřebovali, zkuste Mempool Accelerator™ nebo třeba ViaBTC transaction accelerator).
Možná si řeknete, že je to vlastně dobrý nápad, který umožňuje poolům trochu si přivydělat bokem a dopad do odměn pro těžaře z části chybějících poplatků za jednu z mnoha transakcí v bloku nebude zas tak zásadní. Ale co když se těžební pool rozhodne vytěžit SPAM v podobě Ordinalu, který zabírá celý blok? Na uvedeném odkaze si povšimněte transakčních poplatků za tuto "transakci" (1 sat/vB - celkem 0.01 BTC) a celkových transakčních poplatků za bloky, které předcházeli nebo následovali za tímto blokem (v průměru 0.7 BTC). Neokradl tady Mara pool své těžaře? Nevím, možná se s nimi o OOB poplatek za tuto transakci nakonec podělil. Mara pool není veřejný pool.
(Ne)bezpečnost a (ne)efektivita
Těžba v současných poolech, respektive koordinace těžařů a jejich těžebních zařízení je v naprosté většině řízena protokolem Stratum V1. Navrhl jej Slush na sklonku roku 2011 a komunikace těžebních zařízení s poolem byl pouze jeden ze zamýšlených případů užití (tím hlavním byl lehký komunikační protokol pro klienty serverů Electrum).
Více než desetileté používání tohoto protokolu však odhalilo jeho slabiny, mezi které patří (kromě výše zmíněné centralizace) bezpečnost a neefektivita. Protokol je postavený na JSON-RPC zprávách, které nejsou šifrované a data přenášejí v lidsky čitelné podobě. Nezabezpečená komunikace mezi těžařem a poolem přináší riziko útoku "man-in-the-middle", tedy situaci, kdy útočník odposlouchává a modifikuje jejich komunikaci. Úpravou přenášených dat může například nechat těžaře pracovat pro svůj účet nebo přesměrovat jeho hash rate do úplně jiného poolu. Vše samozřejmě pouze v takovém objemu, aby byla krádež obtížně zjistitelná. Tento útok je znám pod označením "hashrate hijacking" (detailní popis a příklad provedení).
Neefektivita přenášení lidsky čitelných dat ve formátu JSON (data jsou zapisována ve formě "klíč":"hodnota", což usnadňuje člověku jejich porozumění, ale takové zprávy jsou výrazně větší, než jejich reprezentace v binárním formátu) se projevuje výrazně vyššími nároky na datové pásmo (rychlost připojení). To určitě není problém pro domácího těžaře s jednou S9kou, farmě s tisíci minery to již vrásky na čele může způsobit. A skutečným problémem, jehož řešení si vyžaduje velmi rychlé a stabilní připojení k internetu, to pak je pro pool samotný. Pool může účinně řídit svou potřebu šířky datové pásma vhodným nastavením cílové obtížnosti pro nalezení shares těžařům, čímž omezí četnost jejich komunikace. Zároveň tím ale učiní své měření práce jednotlivých těžařů méně přesné a zvyšuje tak variabilitu výplat odměn. Efektivita komunikace je tedy pro pooly důležitým parametrem.
Stratum V2 a DATUM jako odpověď na slabiny současného protokolu
Bylo by překvapivé, kdyby po více než deseti letech těžby bitcoinu v poolech neexistovala nějaká řešení zmíněných problémů. Můžu vás ale uklidnit – existují. Tedy, spíše existují na papíře a mohla by existovat, kdyby... Kdyby celý segment těžby bitcoinu už léta nebyl tvrdým, vysoce konkurenčním byznysem, kde jde primárně o zisk, nikoli o bitcoinový éthos, respekt k svobodě a nezávislosti. V takovém prostředí se inovace zavádí pouze tehdy, když mohou přinést konkrétní prospěch, a bohužel disrupce moci a vlivu poolů ve prospěch decentralizace a svobody volby takový prospěch nenabízí. Takže jsem vás asi moc neuklidnil. I když, 29. září 2024 se přece jenom blýsklo na lepší časy. Ale nepředbíhejme!
Stratum V2
Česká společnost Braiins, provozovatel Slush poolu (dnes Braiins pool) si byla nedostatků svého původního protokolu Stratum (V1) vědoma a dlouho pracovala na návrhu specifikace nové verze, která by je účinně odstranila. Výsledek této práce poprvé prezentovala v létě roku 2019. Vznikl návrh protokolu Stratum V2, který reaguje na všechny existující výtky protokolu původního.
Stratum V2 je binární, šifrovaný protokol, díky čemuž zvyšuje bezpečnost, zefektivňuje datové přenosy a snižuje nároky na těžební infrastrukturu. Je modulární a flexibilně umožňuje těžařům a poolům implementovat pouze ty jeho části, které chtějí využívat.
Stratum V2 ve své specifikaci definuje několik rolí (komponent) a jejich vzájemné vztahy a komunikaci (komunikační protokoly).
Tou první z nich je Miner. Tuto roli představují jednotlivá reálná těžební zařízení, jako třeba Antminer S9, Bitaxe nebo Braiins Mini Miner BMM101.
Druhou nezbytnou rolí je Pool. Ten primárně koordinuje těžbu a rozděluje odměny za nalezené bloky.
Další rolí je Proxy, neboli prostředník mezi Minery a Poolem. Proxy plní hlavně dvě funkce:
-
Zastřešuje komunikaci s Minery - jedna Proxy může koordinovat více těžebních zařízení
-
Překládá těžební protokol Stratum z verze V1 na V2 nebo naopak. Tím umožňuje připojit těžební zařízení se Stratum V1 firmwarem ke Stratum V2 Poolu.
Těžební zařízení (Minery), Proxy a Pool spolu komunikují prostřednictvím Mining Protokolu.
Template Provider je role, která vybírá transakce z mempoolu bitcoinového uzlu a připravuje šablonu nového bloku. Může existovat jak na straně poolu, tak na straně těžaře. Na straně těžaře však představuje základní předpoklad pro decentralizaci těžby - umožňuje mu vybrat transakce do šablony nového bloku dle vlastní vůle.
Poslední rolí je Job Declarator. Jeho odpovědností je validovat navržené šablony nového bloku a připravit úlohy pro Minery. Job Declarator může opět existovat jak na straně poolu (tzv. Job Declarator Server), tak na straně těžaře (tzv. Job Declarator Client). Obě instance pak spolu komunikují prostřednictvím Job Declaration Protokolu.
Čistě teoreticky může role Template Provider a Job Declarator pro těžaře a pool provozovat nezávislá třetí strana a poskytovat tuto službu třeba více těžařům nebo více poolům. Chybí k tomu ale ekonomická motivace, protože takové nastavení nezvyšuje vzájemnou důvěru mezi těžařem a poolem a přináší dodatečné náklady.
Jednotlivé role a jejich vzájemné interakce ukazuje následující obrázek.
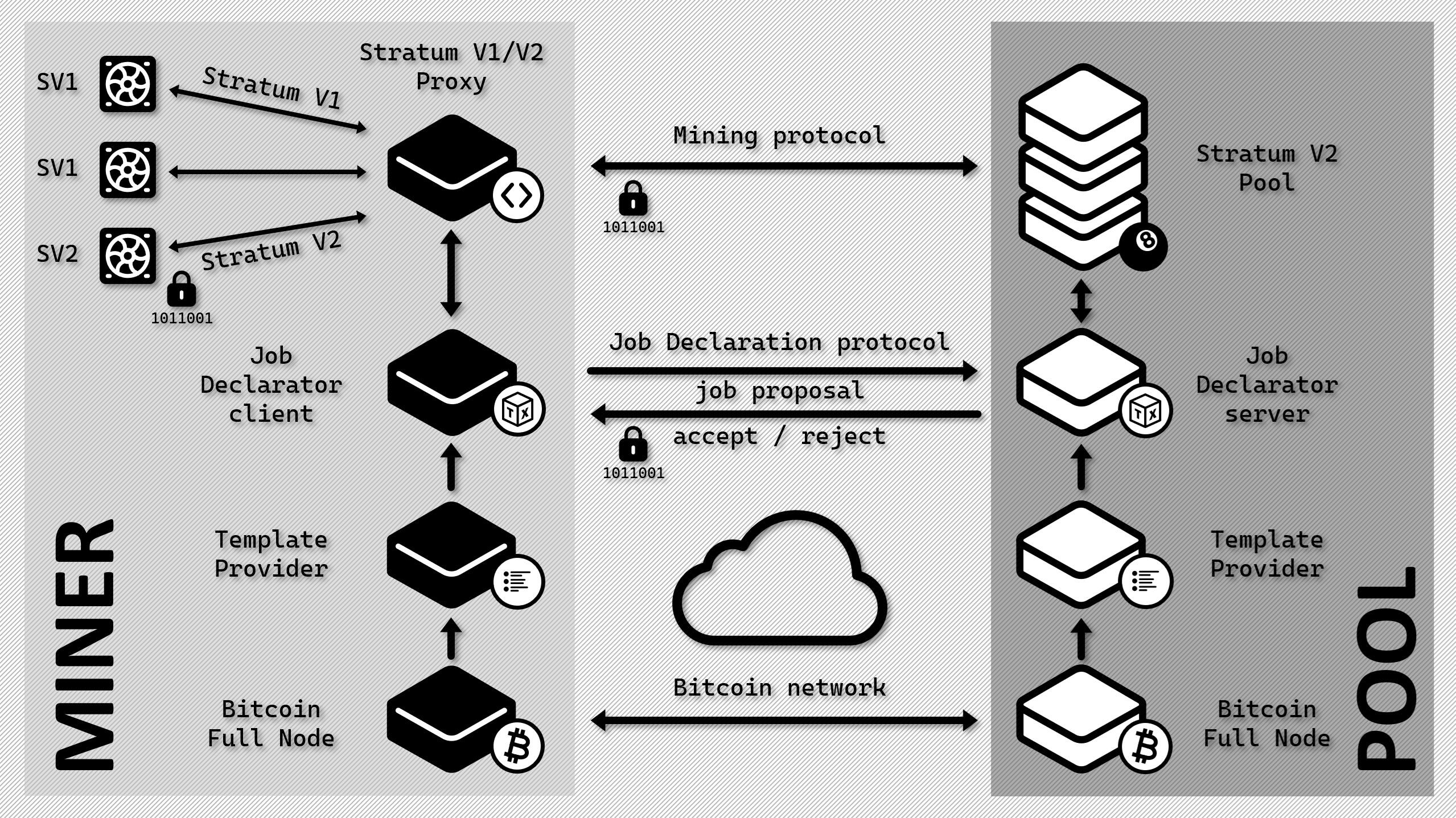
Role Template Provider a Job Declarator na straně těžaře nejsou povinné. Pokud existují, umožňují decentralizovaný výběr transakcí do nového bloku. Pokud ne, odpovídá celé nastavení konfiguraci stávajících poolů, přináší však zabezpečenou a efektivnější komunikaci díky binární podstatě protokolu a jeho šifrování.
Decentralizovaná těžba v těžebním poolu s využitím protokolu Stratum V2 probíhá následovně:
-
Template Provider na straně těžaře získá z vlastního bitcoinového uzlu šablonu nového bloku (buď prostřednictvím RPC GetBlockTemplate nebo nově navrženého Stratum V2 subprotokolu Template Distribution) a poskytne ji svému Job Declaratoru.
-
Job Declarator Client šablonu zvaliduje a nabídne ji prostřednictvím Job Declaration protokolu svému protějšku na straně poolu, Job Declarator Server.
-
Job Declarator Server šablonu zvaliduje podle svých pravidel. Pokud ji akceptuje, vytvoří těžební úlohu a pošle ji zpět těžaři. Součástí úlohy je i poolem definovaná coinbase transakce.
-
Pokud Job Declarator Server návrh odmítne, Job Declarator Client může šablonu nabídnout jinému poolu nebo vytvořit těžební úlohu sám a pokračovat v těžbě bez poolu (v módu Solo Miningu).
-
Job Declarator Client předá vytvořenou úlohu prostřednictvím Job Distribution Protokolu na Proxy, která ji distribuuje Minerům.
-
Těžební zařízení zpracovávají úlohu (hledají hash dle zadané obtížnosti). Nalezený blok nebo každou nalezenou share posílají zpět Proxy.
-
Proxy posílá nalezený blok nebo všechny nalezené shares prostřednictvím Mining Protokolu do Poolu.
-
Pokud těžař reportuje nalezený blok, Pool jej ověří a propaguje dále do bitcoinové sítě.
-
Pool také na základě počtu nalezených shares a použitého modelu pro odměňování těžařů vypočítá příslušnou odměnu a pošle ji těžařům (tuto odpovědnost však Stratum V2 protokol neřeší)
Z uvedeného popisu stojí za povšimnutí možnost poolu odmítnout těžařem navrhované transakce v šabloně nového bloku (krok 4). Je to pojistka pro pool, která mu umožňuje nepodílet se na těžení transakcí, se kterými z jakéhokoliv důvodu nesouhlasí (nesmíme zapomenout, že pooly jsou většinou právními subjekty, které podléhají jurisdikci země jejich sídla a případným regulacím). Stratum V2 pro takový případ nabízí těžaři možnost obrátit se automaticky na jiný pool nebo v krajním případě pokračovat v těžbě daného bloku samostatně (Solo Mining).
Startum V2 však díky této vlastnosti zcela neeliminuje riziko cenzury transakcí.
Stratum V2 je takovým "Torovým kladivem" na většinu neduhů současné těžby v poolech. Jde o velmi komplexní protokol, který řeší všechny možné scénáře dnešní těžby, včetně těch okrajových, a poskytuje všem zúčastněným hráčům – od výrobců těžebních zařízení po těžaře a operátory poolů – větší svobodu volby. Bohužel, "Money talks" a tak chybí vůle na jeho prosazení. Po pěti letech od jeho představení se podporou Stratum V2 chlubí pouze Braiins pool a reálně použitelným scénářem je pouze přímá komunikace poolu s minerem, který používá BraiinsOS firmware. O decentralizaci zatím nemůže být řeč.
V březnu tohoto roku (2024) se na Githubu objevila první verze Referenční Implementace Stratum V2, zatím ve velmi omezené funkcionalitě.
V nedávném rozhovoru přiznali Jan Čapek a Pavel Moravec, zakladatelé Braiins a provozovatelé Braiins poolu, že implementace komponent, které reálně decentralizaci těžby dle protokolu Stratum V2 umožní, zatím nejsou prioritou...
Doporučuji si celý rozhovor poslechnout. Protokolu Startum V2 se pánové věnují v čase 41:30-59:00.
DATUM
DATUM, neboli "Decentralized Alternative Templates for Universal Mining" je protokol, který si zvolil decentralizaci těžby bitcoinu za svůj primární cíl. Ocean.xyz pool jej představil 29. září 2024. Jako jednu z motivací uvedl ztrátu důvěry, že Stratum V2 protokol dokáže, navzdory svým proklamacím, vyřešit problém centralizace bitcoinové těžby v dohledné době.
Co přesně DATUM dělá? Umožňuje jednotlivým těžařům vytvářet své vlastní šablony bloků a zároveň se dále podílet na sdílení odměn za těžbu v poolu. Nic víc. Krátce po představení protokolu byly zpřístupněny i zdrojové kódy referenční implementace DATUM gatewaye a připravené aplikační balíčky pro StartOS a Umbrel. Ano, čtete správně, DATUM si můžete spustit na svém bitcoinovém uzlu. O tom ale o kousek dále. Napřed si popíšeme, jak DATUM funguje.
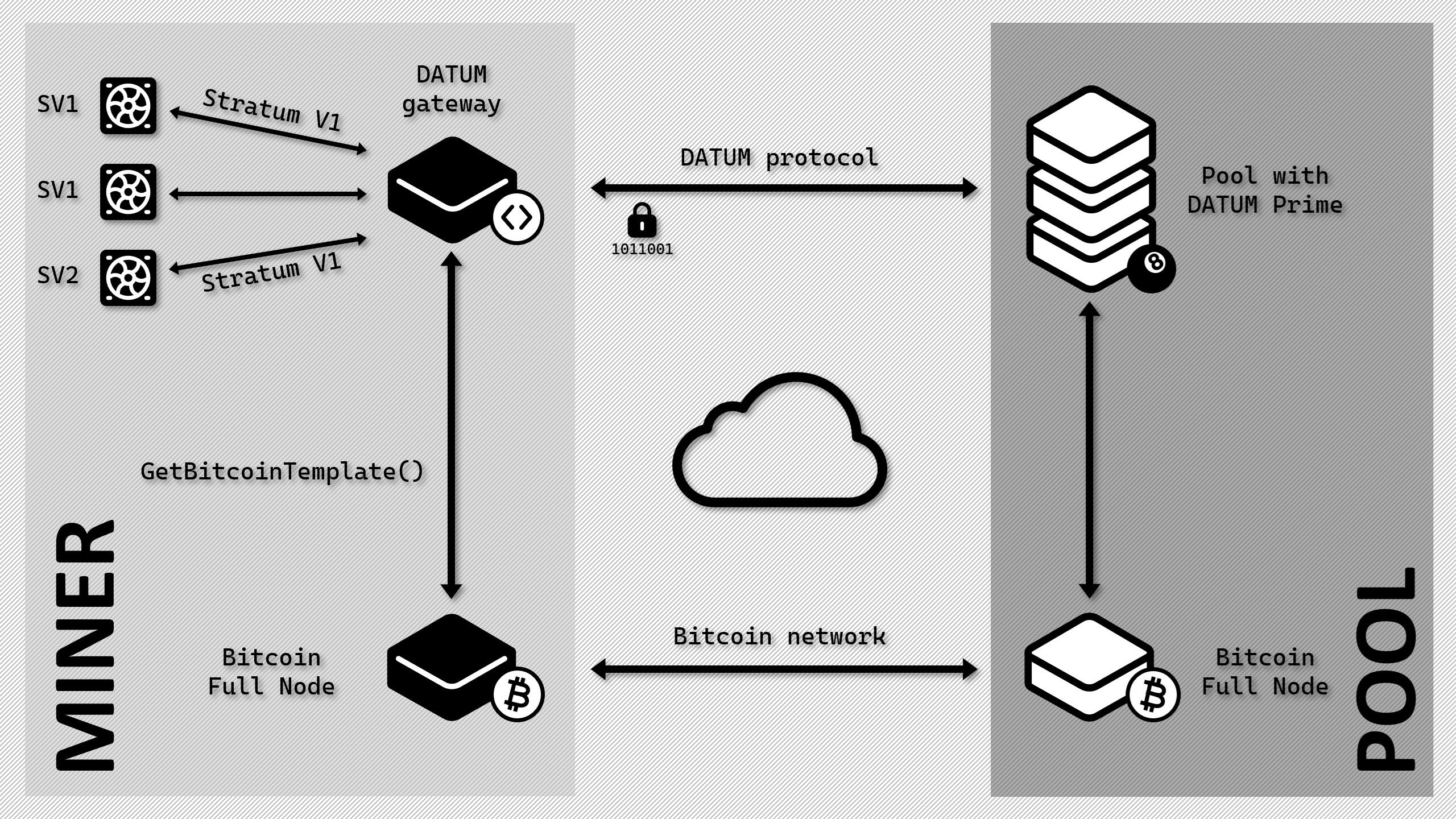
Na rozdíl od protokolu Stratum V2 definuje DATUM protokol na straně těžaře pouze jedinou komponentu: DATUM Gateway. Ta zastřešuje komunikaci se všemi těžícími zařízeními (Minery) protokolem Stratum V1, komunikaci s lokálním bitcoinovým uzlem, ze kterého získává šablonu nového bloku a šifrovanou komunikaci s poolem, kterému posílá nalezené shares a případné nové bloky. Na straně poolu je klientem DATUM protokolu komponenta DATUM Prime. Dešifruje komunikaci přes DATUM protokol a předává poolu od těžaře získané důkazy o odvedené práci (shares). V současné verzi protokolu provádí pool také validaci bloků po koordinaci s těžařem, aby zajistil, že těžaři nebudou omylem vytvářet neplatné bloky. V budoucnu však bude odstraněna i tato funkce a pool tak nebude mít žádnou možnost bloky od těžaře jakkoliv ovlivnit.
Těžba bitcoinu s protokolem DATUM probíhá následovně:
-
DATUM Gateway na straně těžaře získá z lokálního bitcoinového uzlu šablonu nového bloku prostřednictvím RPC GetBlockTemplate.
-
DATUM Gateway získá prostřednictvím DATUM protokolu z poolu coinbase transakci, sestaví hlavičku bloku a celou těžební úlohu.
-
Sestavenou těžební úlohu předá DATUM Gateway těžebním zařízením.
-
Těžební zařízení zpracovávají úlohu (hledají hash dle zadané obtížnosti). Nalezený blok nebo každou nalezenou share posílají zpět na DATUM Gateway.
-
Ta posílá nalezený blok nebo všechny nalezené shares prostřednictvím DATUM Protokolu do Poolu.
-
Pokud těžař nalezne nový blok, DATUM Gateway jej ověří a propaguje dále do bitcoinové sítě prostřednictvím lokálního bitcoinového uzlu.
-
Pool na základě počtu nalezených shares a použitého modelu pro odměňování těžařů vypočítá příslušnou odměnu a pošle ji těžařům.
Pokud uvedený postup srovnáte s postupem dle protokolu Startum V2, najdete jeden důležitý rozdíl. Těžař neposkytuje poolu ke schválení své vybrané transakce v rámci vytvořené šablony bloku. Záleží jen na něm, které transakce vybere a tvorbu nového bloku má tak zcela pod svou kontrolou.
V protokolu DATUM nemá pool možnost cenzurovat těžařem vybrané transakce. Rozhodnutí, jak využije prostor ve svém bloku a jakým transakcím dá přednost, je tak opět zcela na těžaři. Tvorba obsahu bitcoinového blockchainu se vrací tam, kde ji navrhl Satoshi Nakamoto ve svém Whitepaperu.
Pool poskytuje těžaři pouze coinbase transakci do hlavičky nového bloku. Protokol DATUM nepředepisuje konkrétní systém odměňování v poolu. Pool může sestavit coinbase transakci dle vlastní potřeby. Může například v coinbase transakci přímo a transparentně vyplatit těžaře, jako to dělá Ocean.xyz pool pro částky vyšší než cca 1.05M SATů, nebo si převést celou odměnu na svou adresu a těžaře vyplatit později jinou standartní transakcí, jako to dělají všechny ostatní pooly.
Protokol DATUM v současnosti podporuje pouze jediný pool - Ocean.xyz. Volně dostupné zdrojové kódy na Githubu jsou pouze pro DATUM Gateway, část na straně poolu, DATUM Prime, zatím chybí. Na druhou stranu protokol DATUM je živý protokol. s jeho pomocí bylo vytěženo již 22 bloků ze 40, které za dobu od jeho představení Ocean.xyz pool vytěžil. A 50% sleva z poplatků poolu za těžbu prostřednictvím DATUM protokolu jako podpora jeho adopci dokazuje, že to Ocean.xyz myslí s decentralizací bitcoinové těžby opravdu vážně.
Domácí decentralizovaná těžba bitcoinu? Ano!
Pokud vám vše výše napsané dává smysl a chcete podpořit decentralizaci těžby bitcoinu, můžete. A dokonce to již nepředpokládá hluboké technické znalosti. Jak jsem napsal výše, implementace DATUM Gatewaye je již nyní k dispozici pro nejrozšířenější operační systémy bitcoinových uzlů Umbrel a StartOS. Její instalace je jednoduchá, stejně tak jako konfigurace, a nároky na hardware jsou zanedbatelné. Všechny vaše domácí těžící zařízení můžete obsluhovat přes jednu DATUM gateway, která poběží přímo na vašem RPi 4 bitcoinovém uzlu. Jak na to?

DATUM gateway potřebuje ke svému běhu plnohodnotný bitcoinový uzel, který podporuje RPC interface a proceduru GetBlockTemplate. Můžete si vybrat jakoukoliv dostupnou implementaci (Bitcoin Core, Bitcoin Knots nebo třeba Libre Relay). Já vám však doporučím Bitcoin Knots, protože nabízí nejširší možnosti konfigurace sestavení šablony bloku. Dostanete tedy nejlepší možnost volby, které transakce do svých bloků zahrnout a které ne (SPAM - pokud vás zajímá více o SPAMu v bitcoinovém blockchainu, přečtěte si článek Nevyžádaná data v bitcoinovém blockchainu).
Bitcoin Knots
Nedávná aktualizace UmbrelOS na verzi 1.3 celou instalaci výrazně zjednodušila. Přinesla možnost zvolit si implementaci bitcoinového uzlu a odstranila tak závislost ostatních aplikací (jako Electrum serverů nebo Lightning uzlů) na Bitcoin Core. Můžete si nainstalovat Bitcoin Knots přímo z Umbrel App Store.
V případě StartOS (Start9) najdete Bitcoin Knots v oficiálním Marketplace.
Po instalaci si zkontrolujte a případně nastavte preferovaná pravidla filtrování bitcoinového SPAMu (ostatně proto si instalujete Bitcoin Knots). Najdete je v nastavení ( Umbrel: Advanced Settings -> Optimization, StartOS: Config -> Mempool).
V základu je již nastaveno (verze 27.1.020240801):
Datacarrier (
datacarrier=1) - Relay transaction with embedded data - OP_RETURN Datacarrier Size (datacarriersize=42) - Maximum size of relayed transactions with embedded data - OP_RETURN Reject Parasites (rejectparasites=1) - Reject parasitic transactions Permit Bare Multisig (permitbaremultisig=0) - Relay old type of multisig transactionPokud chcete filtrovat i Runes, nezapomeňte povolit:
Reject Tokens (
rejecttokens=1) - Reject tokens transactionsS protokolem DATUM můžete v současné době těžit pouze v Ocean.xyz poolu. Ten distribuuje odměny za vytěžený blok těžařům přímo v coinbase transakci, která díky tomu značně nabyla na velikosti a může mít i několik kilobajtů. Protože je celková velikost bloku omezená, je třeba na to myslet při vytváření šablony nového bloku a pro coinbase transakci, kterou vám pošle Ocean.xyz pool rezervovat potřebné místo. Zkontrolujte si, že vaše instance Bitcoin Knots má nastaveny následující limity velikosti bloku.
Max Bloc Size (
blockmaxsize=3985000) - Max block size in bytes Max Block Weight (blockmaxweight=3985000) - Max block size in weightDATUM
Po dokončení synchronizace blockchainu, což může trvat dle výkonu vašeho HW i několik dní, nainstalujte aplikaci DATUM (opět přímo z Umbrel App Store nebo Start9 Marketplace).
Aplikace ve verzi pro Umbrel zatím nemá konfigurační GUI. Vše podstatné je již nakonfigurováno v souboru datum_gateway_config.json. Pokud by jste konfiguraci chtěli upravit, najdete jej v adresáři
/home/umbrel/umbrel/app-data/datum/data/settings/datum_gateway_config.jsonZa pozornost stojí parametry v sekci Mining:
Bitcoin Address (
pool_address) - vaše bitcoinová adresa pro zasílání odměn v případě, že ji nevyplníte na těžícím zařízení (viz. [[#Nastavení těžebního zařízení]]).Primary Coinbase Tag (
coinbase_tag_primary) - První popisek do coinbase transakce v případě solo miningu. V případě těžby v poolu bude přepsán popiskem poolu (pool's name).Secondary Coinbase Tag (
coinbase_tag_secondary) - Druhý popisek do coinbase transakce. S jeho pomocí můžete identifikovat vámi nalezené bloky v blockchainu.A v sekci Datum:
Pool Host (
pool_host) a Pool Port (pool_port) - URL a port poolu s podporou DATUM Prime, ke kterému se DATUM Gateway připojí. Pokud není vyplněn, nebo se k němu nepodaří připojit a současně nebude nastaven parametr Pooled Mining Only (pooled_mining_only=falseviz. dále), přepne se DATUM Gateway do solo mining módu (odměnu získáte pouze pokud naleznete blok a bude celá patřit vám).Pool Pass Workers (
pool_pass_workers=true) - Pokud je nastaven, bude DATUM Gateway posílat do poolu i vámi definované jméno konkrétního těžícího zařízení (viz. [[#Nastavení těžebního zařízení]]).Pool Pass Full Users (
pool_pass_full_users=true) - Pokud je nastaven, bude DATUM Gateway posílat do poolu celé vámi definované uživatelské jméno konkrétního těžícího zařízení. Tím je většinou vaše bitcoinová adresa pro zasílání odměn. Pokud bude nastaven nafalse, použije DATUM Gateway bitcoinovou adresu definovanou parametrem Bitcoin Address (pool_address).Pooled Mining Only (
pooled_mining_only=true) - Pokud je nastaven a DATUM Gateway ztratí spojení s poolem, přeruší spojení i se všemi těžícími zařízeními. To jim umožní připojit se na záložní pool, mají-li jej nastaven. Pokud je nastaven nafalsea DATUM Gateway ztratí spojení s poolem, přepne se do solo mining módu.
Nastavení těžebního zařízení
Nasměrujte svůj miner na IP adresu vašeho uzlu (Umbrel nebo StartOS) a port služby DATUM Gateway: 23334. Místo IP adresy můžete použít lokální URL, pokud jej máte nastaveno. Výsledná Stratum adresa bude vypadat přibližně takto:
stratum+tcp://192.168.x.y:23334(x a y nahraďte odpovídajícími hodnotami)nebo
stratum+tcp://umbrel.local:23334Do pole Username vložte svou bitcoinovou adresu. Na tuto adresu budou zasílány vaše odměny z Ocean.xyz poolu. K této adrese můžete za tečku připojit unikátní jméno těžebního zařízení. Například:
bc1qabcdefghijklmnopqrstuvwxyz.bitaxePokud svou bitcoinovou adresu neuvedete, zkontrolujte si, že ji máte nastavenu v konfiguraci DATUM Gatewaye v sekci Mining, parametr Pool Address a v sekci Datum je parametr Pool Pass Full Users nastaven na
false.Pole Password může zůstat prázdné, pro Ocean.xyz pool nemá žádný význam.
Závěr?
A to je vše. Ale není to závěr, ale spíše začátek další etapy v těžbě bitcoinu. Etapy decentralizované těžby. Přeháním? Poolu Ocean.xyz se za 11 měsíců své existence povedlo přilákat hashrate až 4.5 Eh/s a dostat se mezi nejvýkonnějších 20 poolů. Za dva měsíce dostupnosti protokolu DATUM bylo s jeho pomocí nalezeno v poolu více než polovina nových bloků. To jsou na poměry v bitcoinové těžbě neuvěřitelná čísla, která dokazují, že bitcoinový étos není mrtvý a decentralizace těžby má v bitcoinové komunitě stále své zastánce.
A co více? Objevují se empirická měření výkonosti poolů, která ukazují, že transparentní odměňování v Ocean.xyz poolu může v delším časovém horizontu vydělat více SATů než jiné public FPPS pooly. Podívejte se třeba na tuto studii.
Domácí decentralizované těžbě bitcoinu: Zdař Bůh!
-
-
 @ 5e5fc143:393d5a2c
2024-01-04 12:44:26
@ 5e5fc143:393d5a2c
2024-01-04 12:44:26We are now given a choice of digital freedom #nostr .
Creativity for every nostrich is now unleashed from the cage of bigtech censorship , rules and algo. But freedom comes with responsibility so pick right one(s). I will try share here some learning experience both technical and also from fundamental point of view. Just wanted kick start this article n fill as we go like living reference document.
Nostr itself is an application layer protocol that can used beyond just social media mirco or long blogging. Each nostr client heavily dependent on back-end servers call nostr "Relay servers" or in short "rs" or "relays" Relays can hosted anywhere in clearnet internet, onion net , vpn , i2p , nym Relays are controlled by their respective admins based NIP specs that they select to implement according to own decisions. Relays can have certain ToS (Terms of Service) Rules to adhered too.
New users can choose and pick client or app (ios / android/ windows) with preset of relays in the simplest form , but other advanced users need to do a regular manual relay management.
Relay management is an active regular task based on where when n how you are using.
Relay list are saved within you npub profile backup file which can edited and broadcast anytime.
Relay management is an active regular task based on where when and how you are using.
Relay list always need to be updated time to time as and when needed.
2 Users MUST a common RELAY between them even if one only need to follow another. Occasionally you may notice certain npub accounts you are following already but cannot see frequent notes publish by them – one of cause maybe you not sharing a common relay
Most nostr client applications has SETTINGS where user choose add/remove relays Also user choose which function to enable - READ or WRITE
Relay list for your account is always saved within you npub profile backup file which can edited and broadcast anytime. Hence any app or browser when u login with you npub the same relay list will be enforced. There could valid reasons why u need have list for if you trying to save bandwidth and traveling.
Functions in app.getcurrent.io and primal.net app for mobile apple or android are ideal for user traveling abroad and wanted to save bandwidth since relay management is done the providers in backend and saves hassle for basic usage.
Remember if someone is selecting relay on your behalf then you may not be necessarily able to pull and get some specific and special content that you may need. Such providers like coracle and nostrid also give option to override the default relays they selected.
Relay types: They can be categorized by various features or policy or technologies.
FREE PUBLIC Relays vs PAID PUBLIC Relays
PAID relays provide unrestricted access / write / filtering options than FREE relays but both are public clearnet relays. Just subscribing to PAID relays will not solve all problems unless you choose the relays properly and enable settings correctly.
Private Replay or Tor Relays – normally not easily visible until unless someone tell you. You can also host own private relay not opened to internet of archive and back of your own notes.
The technical landscape in nostr can be fast changing as more NIPs get proposed or updated. Relays admin can choose implement certain NIPs or not based on policy or technical limitations.
Example NIP33 defines “long notes” aka blogs as you now reading this in habla site which #1 UI and site for "Editable" long notes – some relays donot implement or allow this. NIP07 is used for client authentication like nos2x and is implemented by all relays in fact.
To be continued again ... reference pics will added later also Hope this help you understand "why when what" to tune and maintain active set of proper relays. Relay Proxy, Relay aggregator or Relay multiplexer – Paid, Public, Free, Private, Event, Relays That’s all for now n more later ... Thank you 🙏 ! ⚡️ https://getalby.com/p/captjack ⚡️ PV 💜 🤙
References: https://habla.news/relays https://relay.exchange/ https://relays.vercel.app/ https://nostr.info/relays/ https://nostrudel.ninja/#/relays
Related Articles: https://thebitcoinmanual.com/articles/types-nostr-relays/ nostr:naddr1qqd5c6t8dp6xu6twvukkvctnwss92jfqvehhygzwdaehguszyrtp7w79k045gq80mtnpdxjuzl9t7vjxk52rv80f888y5xsd5mh55qcyqqq823cf39s98 https://habla.news/u/current@getcurrent.io/1694434022411
-
 @ fa1d8325:7c91882e
2024-11-29 15:42:53
@ fa1d8325:7c91882e
2024-11-29 15:42:53В Пятигорске 27 ноября, в первый день тестового запуска робо-патруля, был задержан мошенник, пытавшийся продать нелицензионную продукцию. Этот инцидент стал важным событием, продемонстрировав эффективность новых технологий в обеспечении общественной безопасности.
Роботы-патрули, оснащенные современными системами распознавания лиц и алгоритмами анализа поведения, быстро обнаружили подозрительную активность на одном из городских рынков. В результате взаимодействия с местными правоохранительными органами мошенник был задержан на месте преступления.
По предварительным данным, злоумышленник предлагал покупателям товары без необходимых лицензий и сертификатов, что могло нанести ущерб не только потребителям, но и легальным производителям. Благодаря работе робо-патруля удалось предотвратить дальнейшие правонарушения и защитить интересы граждан.
-
 @ fa1d8325:7c91882e
2024-11-29 15:34:38
@ fa1d8325:7c91882e
2024-11-29 15:34:38В преддверии новогодних праздников торговые центры стремятся создать волшебную атмосферу для своих посетителей, особенно для детей. В этом сезоне настоящим хитом стали роботы Деда Мороза и Снегурочки, которые появились в нескольких крупных торговых центрах.
Эти инновационные персонажи, созданные с использованием современных технологий, способны взаимодействовать с детьми и взрослыми. Они рассказывают новогодние истории, поют песни и даже участвуют в играх, что добавляет в праздничную атмосферу элемент волшебства и интерактивности.
Кроме того, в рамках новогодних мероприятий планируются различные конкурсы и мастер-классы для детей. Посетители смогут сделать фотографии с роботами и получить от них подарки. Это создает уникальную возможность для семейного отдыха и создания праздничного настроения.
Родители уже успели оценить это нововведение. Они отмечают, что общение с роботами делает процесс ожидания праздника более увлекательным. «Это замечательная идея! Дети в восторге от общения с роботами», — делится впечатлениями одна из мам.
Таким образом, установка роботов Деда Мороза и Снегурочки в торговых центрах становится важным элементом создания новогоднего настроения для всей семьи. Эти инновационные персонажи делают праздники более яркими и запоминающимися.
-
 @ fa1d8325:7c91882e
2024-11-29 15:26:01
@ fa1d8325:7c91882e
2024-11-29 15:26:01Эти современные устройства с искусственным интеллектом не только облегчат выполнение повседневных задач, но и станут незаменимыми спутниками для людей всех возрастов.
Представьте себе дом, где каждая комната наполнена умными технологиями: роботы-помощники выполняют уборку, готовят еду, заботятся о пожилых людях и даже обучают детей. По прогнозам экспертов, в будущем количество роботов может превысить численность людей, и они станут такой же естественной частью нашей повседневной жизни, как смартфоны сегодня.
Эти помощники способны адаптироваться к индивидуальным потребностям своих хозяев, обеспечивая персональный подход и поддержку в самых различных аспектах жизни.
-
 @ c1e6505c:02b3157e
2024-11-29 15:04:53
@ c1e6505c:02b3157e
2024-11-29 15:04:53This was my first attempt at hosting a podcast with another photographer while also juggling scene switches in OBS on the fly. Not sure what went sideways with Gardner's audio - podcast pleb mistake, clearly. But hey, trial and error, right?

click image to watch the full episode
That said, I’ve been wanting to interview photographers I admire for a while, so I was stoked to finally sit down with Gardner and explore his work. His creative use of lasers and external flash really caught my eye. It’s not my typical style, but the way he executes it - with such taste and precision - is impressive. I think you’ll find his process just as fascinating as I did.
During our conversation, we covered a lot - music, cameras, and some funny stories. One of my favorites was the time he went to photograph a mobile home with a tree growing through it, only to realize someone was still living there.
We took a deep dive into his portfolio, unpacking the intricate details behind his images. Hearing the story straight from the photographer hits differently than just reading a blurb about the series. Learning why a photo was taken and how it came together feels way more compelling once you understand the person behind the lens.
You can catch the full episode now on my PictureRoom YouTube channel. Like and subscribe if you’re feeling generous.
-
 @ 1ef695e1:15351d5f
2024-11-29 14:21:00
@ 1ef695e1:15351d5f
2024-11-29 14:21:00After getting my ham licence in 2013 I found out about SOTA. I was enthusiastic as I have a long history of hiking in the mountains while a scout and then as a Scoutmaster. Now I was going to combine the two yet I immediately encountered a big problem. Very few South African summits were listed on the SOTA database and some of those listed did not even qualify as summits. I enquired of SOTA management and was told that "South Africa is on hold until all the summits are correctly mapped and checked." Only then could the summits be loaded to the database.
 Using GIS software and my 1:50000 topographic maps I began mapping summits in my home province Limpopo that qualified according to the SOTA criteria.
Using GIS software and my 1:50000 topographic maps I began mapping summits in my home province Limpopo that qualified according to the SOTA criteria.An individual prominence of 150m or more was easy to determine. Doing the mapping I found a lot of summits that were obvious, but finding the key col of each summit was more difficult. The older maps in South Africa actually had a lot of the key cols displayed and using my combined methods I proceeded to map summits one by one and add the data to a spreadsheet. Taking approximately 8 minutes to map a summit it took me months to map Limpopo. I missed summits where the summit is spread over a large area and though it qualifies due to a 150m or more prominence it does not look like a summit and these we added later.
I sent my mapping data to OM Andrew VK3ARR in Australia and received a thumbs up as to my data accuracy. I was pleasantly surprised when my Limpopo summits appeared on the SOTA database even though the rest of the country was still not done. I immediately started mapping the next province of Mpumalanga using my manual methods.
Sid Tylor ZS5AYC from Kwazulu - Natal, who became SOTA manager for South Africa, and I had been discussing the processes and he arranged access to online software with automated summit processing where we could just check key col position and all the data per summit was processed much quicker. Frustrating for me was that I could not see what the software was doing and we just checked key cols without knowing where the summit was or its other data.
I completed the remaining Mpumalanga summits using the software access and then completed the Western Cape summits after which Sid and I split the Northern Cape summits between us. The other provinces were processed by various operators including some much appreciated assistance from Australian hams.
A big thank you to all in SOTA management, in South Africa, those that assisted from Australia, as well as SOTA UK, for making it possible for us to enjoy the adventures of SOTA.
 Activating Renosterkop ZS/NC-272 in the Northern Cape
Activating Renosterkop ZS/NC-272 in the Northern Cape
-
 @ df8f0a64:057d87a5
2024-11-29 13:58:48
@ df8f0a64:057d87a5
2024-11-29 13:58:482024年下半期の振り返り
あんまり変化はないんですが、進捗ありません!で終わっても仕方ないのでちょっとは無理やりでも振り返りましょう
0. 退職した
上半期時点で決まってはいたんですが、 6年間ほど勤務した会社を退職しました
退職直前まで爆発物取扱みたいなタスクをこなして、なかなかひやひやした退職プロセス
静かに退職したいので送別会の類のイベントは無しにしてくれというお願いをきいてくれた各メンバーに感謝です
1. 公開していたNostrリレーの設定を変更した
日本のみに公開していたリレーを、全世界に公開しました
当初はCloudflareでリレーをホストしていたのが、利用していたnosflareもcfrelayもクライアントに対してイベントを配布するコードがなく(R2だけではできない)
さてどうしたものかと悩んでいたタイミングで、Umbrelのおひとり様リレーのポートを公開する対応をしました。リレーのお引越し
で、公開してしばらくしたら、すごい勢いで日本国外からの投稿が着信するようになり大困惑
調べてみたら、Mutiny wallet(現在はサービス終了)が運営しているblastr.mutinywallet.com(たぶんまだ稼働している)が原因でした
Nostr.watchのAPIを利用して、世の中にあるNostrリレーすべてにイベントを送り込む凶悪な思想犯です
ヘッダー情報などでブロックできなかったので、blastrがホストされてるCloudflareのIPを全てブロックする力技で対処しました
ちなみに、nosflareもいつのまにかblastrのようなものをホストしているようです
なんなんでしょうね、Nostrの白人さんたちの、過激なほど分散というか対検閲をしようとするお節介さは
2. 公開していたNostrリレーを潰した
上記のように折角いろいろやったリレーを潰しました
Reply guyというbotが猛威をふるった時期、クソみたいなイベントをばら撒かれてくることに私がキレたからです。クソが
NostrとしてはこれをきっかけにWoTを組み込んだリレーが開発されたりして、スパム対策が一歩前進した感があります。クソが
スパムばら撒きをBostrが助長してるみたいな批難を受けて、作者のYonleさんがブチ切れ、全Nostr関連リポジトリのメンテを放棄する事態も発生
ちょうどMutiny walletでGOXしたご本人の機嫌が悪かった時期に、クソスパムがぶつかったことによる悲しい出来事でした。ほんとクソ
3. おわりに
他にもこまいことはいくつかあるんですが、主にはこんなとこでしょうか。来年も楽しくNostrしたいですね
-
 @ e6ce6154:275e3444
2023-07-27 14:12:49
@ e6ce6154:275e3444
2023-07-27 14:12:49Este artigo foi censurado pelo estado e fomos obrigados a deletá-lo após ameaça de homens armados virem nos visitar e agredir nossa vida e propriedade.
Isto é mais uma prova que os autoproclamados antirracistas são piores que os racistas.
https://rothbardbrasil.com/pelo-direito-de-ser-racista-fascista-machista-e-homofobico
Segue artigo na íntegra. 👇
Sem dúvida, a escalada autoritária do totalitarismo cultural progressista nos últimos anos tem sido sumariamente deletéria e prejudicial para a liberdade de expressão. Como seria de se esperar, a cada dia que passa o autoritarismo progressista continua a se expandir de maneira irrefreável, prejudicando a liberdade dos indivíduos de formas cada vez mais deploráveis e contundentes.
Com a ascensão da tirania politicamente correta e sua invasão a todos os terrenos culturais, o autoritarismo progressista foi se alastrando e consolidando sua hegemonia em determinados segmentos. Com a eventual eclosão e a expansão da opressiva e despótica cultura do cancelamento — uma progênie inevitável do totalitarismo progressista —, todas as pessoas que manifestam opiniões, crenças ou posicionamentos que não estão alinhados com as pautas universitárias da moda tornam-se um alvo.
Há algumas semanas, vimos a enorme repercussão causada pelo caso envolvendo o jogador profissional de vôlei Maurício Sousa, que foi cancelado pelo simples fato de ter emitido sua opinião pessoal sobre um personagem de história em quadrinhos, Jon Kent, o novo Superman, que é bissexual. Maurício Sousa reprovou a conduta sexual do personagem, o que é um direito pessoal inalienável que ele tem. Ele não é obrigado a gostar ou aprovar a bissexualidade. Como qualquer pessoa, ele tem o direito pleno de criticar tudo aquilo que ele não gosta. No entanto, pelo simples fato de emitir a sua opinião pessoal, Maurício Sousa foi acusado de homofobia e teve seu contrato rescindido, sendo desligado do Minas Tênis Clube.
Lamentavelmente, Maurício Sousa não foi o primeiro e nem será o último indivíduo a sofrer com a opressiva e autoritária cultura do cancelamento. Como uma tirania cultural que está em plena ascensão e usufrui de um amplo apoio do establishment, essa nova forma de totalitarismo cultural colorido e festivo está se impondo de formas e maneiras bastante contundentes em praticamente todas as esferas da sociedade contemporânea. Sua intenção é relegar ao ostracismo todos aqueles que não se curvam ao totalitarismo progressista, criminalizando opiniões e crenças que divergem do culto à libertinagem hedonista pós-moderna. Oculto por trás de todo esse ativismo autoritário, o que temos de fato é uma profunda hostilidade por padrões morais tradicionalistas, cristãos e conservadores.
No entanto, é fundamental entendermos uma questão imperativa, que explica em partes o conflito aqui criado — todos os progressistas contemporâneos são crias oriundas do direito positivo. Por essa razão, eles jamais entenderão de forma pragmática e objetiva conceitos como criminalidade, direitos de propriedade, agressão e liberdade de expressão pela perspectiva do jusnaturalismo, que é manifestamente o direito em seu estado mais puro, correto, ético e equilibrado.
Pela ótica jusnaturalista, uma opinião é uma opinião. Ponto final. E absolutamente ninguém deve ser preso, cancelado, sabotado ou boicotado por expressar uma opinião particular sobre qualquer assunto. Palavras não agridem ninguém, portanto jamais poderiam ser consideradas um crime em si. Apenas deveriam ser tipificados como crimes agressões de caráter objetivo, como roubo, sequestro, fraude, extorsão, estupro e infrações similares, que representam uma ameaça direta à integridade física da vítima, ou que busquem subtrair alguma posse empregando a violência.
Infelizmente, a geração floquinho de neve — terrivelmente histérica, egocêntrica e sensível — fica profundamente ofendida e consternada sempre que alguém defende posicionamentos contrários à religião progressista. Por essa razão, os guerreiros da justiça social sinceramente acreditam que o papai-estado deve censurar todas as opiniões que eles não gostam de ouvir, assim como deve também criar leis para encarcerar todos aqueles que falam ou escrevem coisas que desagradam a militância.
Como a geração floquinho de neve foi criada para acreditar que todas as suas vontades pessoais e disposições ideológicas devem ser sumariamente atendidas pelo papai-estado, eles embarcaram em uma cruzada moral que pretende erradicar todas as coisas que são ofensivas à ideologia progressista; só assim eles poderão deflagrar na Terra o seu tão sonhado paraíso hedonista e igualitário, de inimaginável esplendor e felicidade.
Em virtude do seu comportamento intrinsecamente despótico, autoritário e egocêntrico, acaba sendo inevitável que militantes progressistas problematizem tudo aquilo que os desagrada.
Como são criaturas inúteis destituídas de ocupação real e verdadeiro sentido na vida, sendo oprimidas unicamente na sua própria imaginação, militantes progressistas precisam constantemente inventar novos vilões para serem combatidos.
Partindo dessa perspectiva, é natural para a militância que absolutamente tudo que exista no mundo e que não se enquadra com as regras autoritárias e restritivas da religião progressista seja encarado como um problema. Para a geração floquinho de neve, o capitalismo é um problema. O fascismo é um problema. A iniciativa privada é um problema. O homem branco, tradicionalista, conservador e heterossexual é um problema. A desigualdade é um problema. A liberdade é um problema. Monteiro Lobato é um problema (sim, até mesmo o renomado ícone da literatura brasileira, autor — entre outros títulos — de Urupês, foi vítima da cultura do cancelamento, acusado de ser racista e eugenista).
Para a esquerda, praticamente tudo é um problema. Na mentalidade da militância progressista, tudo é motivo para reclamação. Foi em função desse comportamento histérico, histriônico e infantil que o famoso pensador conservador-libertário americano P. J. O’Rourke afirmou que “o esquerdismo é uma filosofia de pirralhos chorões”. O que é uma verdade absoluta e irrefutável em todos os sentidos.
De fato, todas as filosofias de esquerda de forma geral são idealizações utópicas e infantis de um mundo perfeito. Enquanto o mundo não se transformar naquela colorida e vibrante utopia que é apresentada pela cartilha socialista padrão, militantes continuarão a reclamar contra tudo o que existe no mundo de forma agressiva, visceral e beligerante. Evidentemente, eles não vão fazer absolutamente nada de positivo ou construtivo para que o mundo se transforme no gracioso paraíso que eles tanto desejam ver consolidado, mas eles continuarão a berrar e vociferar muito em sua busca incessante pela utopia, marcando presença em passeatas inúteis ou combatendo o fascismo imaginário nas redes sociais.
Sem dúvida, estamos muito perto de ver leis absurdas e estúpidas sendo implementadas, para agradar a militância da terra colorida do assistencialismo eterno onde nada é escasso e tudo cai do céu. Em breve, você não poderá usar calças pretas, pois elas serão consideradas peças de vestuário excessivamente heterossexuais. Apenas calças amarelas ou coloridas serão permitidas. Você também terá que tingir de cor-de-rosa uma mecha do seu cabelo; pois preservar o seu cabelo na sua cor natural é heteronormativo demais da sua parte, sendo portanto um componente demasiadamente opressor da sociedade.
Você também não poderá ver filmes de guerra ou de ação, apenas comédias românticas, pois certos gêneros de filmes exaltam a violência do patriarcado e isso impede o mundo de se tornar uma graciosa festa colorida de fraternidades universitárias ungidas por pôneis resplandecentes, hedonismo infinito, vadiagem universitária e autogratificação psicodélica, que certamente são elementos indispensáveis para se produzir o paraíso na Terra.
Sabemos perfeitamente, no entanto, que dentre as atitudes “opressivas” que a militância progressista mais se empenha em combater, estão o racismo, o fascismo, o machismo e a homofobia. No entanto, é fundamental entender que ser racista, fascista, machista ou homofóbico não são crimes em si. Na prática, todos esses elementos são apenas traços de personalidade; e eles não podem ser pura e simplesmente criminalizados porque ideólogos e militantes progressistas iluminados não gostam deles.
Tanto pela ética quanto pela ótica jusnaturalista, é facilmente compreensível entender que esses traços de personalidade não podem ser criminalizados ou proibidos simplesmente porque integrantes de uma ideologia não tem nenhuma apreciação ou simpatia por eles. Da mesma forma, nenhum desses traços de personalidade representa em si um perigo para a sociedade, pelo simples fato de existir. Por incrível que pareça, até mesmo o machismo, o racismo, o fascismo e a homofobia merecem a devida apologia.
Mas vamos analisar cada um desses tópicos separadamente para entender isso melhor.
Racismo
Quando falamos no Japão, normalmente não fazemos nenhuma associação da sociedade japonesa com o racismo. No entanto, é incontestável o fato de que a sociedade japonesa pode ser considerada uma das sociedades mais racistas do mundo. E a verdade é que não há absolutamente nada de errado com isso.
Aproximadamente 97% da população do Japão é nativa; apenas 3% do componente populacional é constituído por estrangeiros (a população do Japão é estimada em aproximadamente 126 milhões de habitantes). Isso faz a sociedade japonesa ser uma das mais homogêneas do mundo. As autoridades japonesas reconhecidamente dificultam processos de seleção e aplicação a estrangeiros que desejam se tornar residentes. E a maioria dos japoneses aprova essa decisão.
Diversos estabelecimentos comerciais como hotéis, bares e restaurantes por todo o país tem placas na entrada que dizem “somente para japoneses” e a maioria destes estabelecimentos se recusa ostensivamente a atender ou aceitar clientes estrangeiros, não importa quão ricos ou abastados sejam.
Na Terra do Sol Nascente, a hostilidade e a desconfiança natural para com estrangeiros é tão grande que até mesmo indivíduos que nascem em algum outro país, mas são filhos de pais japoneses, não são considerados cidadãos plenamente japoneses.
Se estes indivíduos decidem sair do seu país de origem para se estabelecer no Japão — mesmo tendo descendência nipônica legítima e inquestionável —, eles enfrentarão uma discriminação social considerável, especialmente se não dominarem o idioma japonês de forma impecável. Esse fato mostra que a discriminação é uma parte tão indissociável quanto elementar da sociedade japonesa, e ela está tão profundamente arraigada à cultura nipônica que é praticamente impossível alterá-la ou atenuá-la por qualquer motivo.
A verdade é que — quando falamos de um país como o Japão — nem todos os discursos politicamente corretos do mundo, nem a histeria progressista ocidental mais inflamada poderão algum dia modificar, extirpar ou sequer atenuar o componente racista da cultura nipônica. E isso é consequência de uma questão tão simples quanto primordial: discriminar faz parte da natureza humana, sendo tanto um direito individual quanto um elemento cultural inerente à muitas nações do mundo. Os japoneses não tem problema algum em admitir ou institucionalizar o seu preconceito, justamente pelo fato de que a ideologia politicamente correta não tem no oriente a força e a presença que tem no ocidente.
E é fundamental enfatizar que, sendo de natureza pacífica — ou seja, não violando nem agredindo terceiros —, a discriminação é um recurso natural dos seres humanos, que está diretamente associada a questões como familiaridade e segurança.
Absolutamente ninguém deve ser forçado a apreciar ou integrar-se a raças, etnias, pessoas ou tribos que não lhe transmitem sentimentos de segurança ou familiaridade. Integração forçada é o verdadeiro crime, e isso diversos países europeus — principalmente os escandinavos (países que lideram o ranking de submissão à ideologia politicamente correta) — aprenderam da pior forma possível.
A integração forçada com imigrantes islâmicos resultou em ondas de assassinato, estupro e violência inimagináveis para diversos países europeus, até então civilizados, que a imprensa ocidental politicamente correta e a militância progressista estão permanentemente tentando esconder, porque não desejam que o ocidente descubra como a agenda “humanitária” de integração forçada dos povos muçulmanos em países do Velho Mundo resultou em algumas das piores chacinas e tragédias na história recente da Europa.
Ou seja, ao discriminarem estrangeiros, os japoneses estão apenas se protegendo e lutando para preservar sua nação como um ambiente cultural, étnico e social que lhe é seguro e familiar, assim se opondo a mudanças bruscas, indesejadas e antinaturais, que poderiam comprometer a estabilidade social do país.
A discriminação — sendo de natureza pacífica —, é benévola, salutar e indubitavelmente ajuda a manter a estabilidade social da comunidade. Toda e qualquer forma de integração forçada deve ser repudiada com veemência, pois, mais cedo ou mais tarde, ela irá subverter a ordem social vigente, e sempre será acompanhada de deploráveis e dramáticos resultados.
Para citar novamente os países escandinavos, a Suécia é um excelente exemplo do que não fazer. Tendo seguido o caminho contrário ao da discriminação racional praticada pela sociedade japonesa, atualmente a sociedade sueca — além de afundar de forma consistente na lama da libertinagem, da decadência e da deterioração progressista — sofre em demasia com os imigrantes muçulmanos, que foram deixados praticamente livres para matar, saquear, esquartejar e estuprar quem eles quiserem. Hoje, eles são praticamente intocáveis, visto que denunciá-los, desmoralizá-los ou acusá-los de qualquer crime é uma atitude politicamente incorreta e altamente reprovada pelo establishment progressista. A elite socialista sueca jamais se atreve a acusá-los de qualquer crime, pois temem ser classificados como xenófobos e intolerantes. Ou seja, a desgraça da Europa, sobretudo dos países escandinavos, foi não ter oferecido nenhuma resistência à ideologia progressista politicamente correta. Hoje, eles são totalmente submissos a ela.
O exemplo do Japão mostra, portanto — para além de qualquer dúvida —, a importância ética e prática da discriminação, que é perfeitamente aceitável e natural, sendo uma tendência inerente aos seres humanos, e portanto intrínseca a determinados comportamentos, sociedades e culturas.
Indo ainda mais longe nessa questão, devemos entender que na verdade todos nós discriminamos, e não existe absolutamente nada de errado nisso. Discriminar pessoas faz parte da natureza humana e quem se recusa a admitir esse fato é um hipócrita. Mulheres discriminam homens na hora de selecionar um parceiro; elas avaliam diversos quesitos, como altura, aparência, status social, condição financeira e carisma. E dentre suas opções, elas sempre escolherão o homem mais atraente, másculo e viril, em detrimento de todos os baixinhos, calvos, carentes, frágeis e inibidos que possam estar disponíveis. Da mesma forma, homens sempre terão preferência por mulheres jovens, atraentes e delicadas, em detrimento de todas as feministas de meia-idade, acima do peso, de cabelo pintado, que são mães solteiras e militantes socialistas. A própria militância progressista discrimina pessoas de forma virulenta e intransigente, como fica evidente no tratamento que dispensam a mulheres bolsonaristas e a negros de direita.
A verdade é que — não importa o nível de histeria da militância progressista — a discriminação é inerente à condição humana e um direito natural inalienável de todos. É parte indissociável da natureza humana e qualquer pessoa pode e deve exercer esse direito sempre que desejar. Não existe absolutamente nada de errado em discriminar pessoas. O problema real é a ideologia progressista e o autoritarismo politicamente correto, movimentos tirânicos que não respeitam o direito das pessoas de discriminar.
Fascismo
Quando falamos de fascismo, precisamos entender que, para a esquerda política, o fascismo é compreendido como um conceito completamente divorciado do seu significado original. Para um militante de esquerda, fascista é todo aquele que defende posicionamentos contrários ao progressismo, não se referindo necessariamente a um fascista clássico.
Mas, seja como for, é necessário entender que — como qualquer ideologia política — até mesmo o fascismo clássico tem o direito de existir e ocupar o seu devido lugar; portanto, fascistas não devem ser arbitrariamente censurados, apesar de defenderem conceitos que representam uma completa antítese de tudo aquilo que é valioso para os entusiastas da liberdade.
Em um país como o Brasil, onde socialistas e comunistas tem total liberdade para se expressar, defender suas ideologias e até mesmo formar partidos políticos, não faz absolutamente o menor sentido que fascistas — e até mesmo nazistas assumidos — sofram qualquer tipo de discriminação. Embora socialistas e comunistas se sintam moralmente superiores aos fascistas (ou a qualquer outra filosofia política ou escola de pensamento), sabemos perfeitamente que o seu senso de superioridade é fruto de uma pueril romantização universitária da sua própria ideologia. A história mostra efetivamente que o socialismo clássico e o comunismo causaram muito mais destruição do que o fascismo.
Portanto, se socialistas e comunistas tem total liberdade para se expressar, não existe a menor razão para que fascistas não usufruam dessa mesma liberdade.
É claro, nesse ponto, seremos invariavelmente confrontados por um oportuno dilema — o famoso paradoxo da intolerância, de Karl Popper. Até que ponto uma sociedade livre e tolerante deve tolerar a intolerância (inerente a ideologias totalitárias)?
As leis de propriedade privada resolveriam isso em uma sociedade livre. O mais importante a levarmos em consideração no atual contexto, no entanto — ao defender ou criticar uma determinada ideologia, filosofia ou escola de pensamento —, é entender que, seja ela qual for, ela tem o direito de existir. E todas as pessoas que a defendem tem o direito de defendê-la, da mesma maneira que todos os seus detratores tem o direito de criticá-la.
Essa é uma forte razão para jamais apoiarmos a censura. Muito pelo contrário, devemos repudiar com veemência e intransigência toda e qualquer forma de censura, especialmente a estatal.
Existem duas fortes razões para isso:
A primeira delas é a volatilidade da censura (especialmente a estatal). A censura oficial do governo, depois que é implementada, torna-se absolutamente incontrolável. Hoje, ela pode estar apontada para um grupo de pessoas cujas ideias divergem das suas. Mas amanhã, ela pode estar apontada justamente para as ideias que você defende. É fundamental, portanto, compreendermos que a censura estatal é incontrolável. Sob qualquer ponto de vista, é muito mais vantajoso que exista uma vasta pluralidade de ideias conflitantes na sociedade competindo entre si, do que o estado decidir que ideias podem ser difundidas ou não.
Além do mais, libertários e anarcocapitalistas não podem nunca esperar qualquer tipo de simpatia por parte das autoridades governamentais. Para o estado, seria infinitamente mais prático e vantajoso criminalizar o libertarianismo e o anarcocapitalismo — sob a alegação de que são filosofias perigosas difundidas por extremistas radicais que ameaçam o estado democrático de direito — do que o fascismo ou qualquer outra ideologia centralizada em governos burocráticos e onipotentes. Portanto, defender a censura, especialmente a estatal, representa sempre um perigo para o próprio indivíduo, que mais cedo ou mais tarde poderá ver a censura oficial do sistema se voltar contra ele.
Outra razão pela qual libertários jamais devem defender a censura, é porque — ao contrário dos estatistas — não é coerente que defensores da liberdade se comportem como se o estado fosse o seu papai e o governo fosse a sua mamãe. Não devemos terceirizar nossas próprias responsabilidades, tampouco devemos nos comportar como adultos infantilizados. Assumimos a responsabilidade de combater todas as ideologias e filosofias que agridem a liberdade e os seres humanos. Não procuramos políticos ou burocratas para executar essa tarefa por nós.
Portanto, se você ver um fascista sendo censurado nas redes sociais ou em qualquer outro lugar, assuma suas dores. Sinta-se compelido a defendê-lo, mostre aos seus detratores que ele tem todo direito de se expressar, como qualquer pessoa. Você não tem obrigação de concordar com ele ou apreciar as ideias que ele defende. Mas silenciar arbitrariamente qualquer pessoa não é uma pauta que honra a liberdade.
Se você não gosta de estado, planejamento central, burocracia, impostos, tarifas, políticas coletivistas, nacionalistas e desenvolvimentistas, mostre com argumentos coesos e convincentes porque a liberdade e o livre mercado são superiores a todos esses conceitos. Mas repudie a censura com intransigência e mordacidade.
Em primeiro lugar, porque você aprecia e defende a liberdade de expressão para todas as pessoas. E em segundo lugar, por entender perfeitamente que — se a censura eventualmente se tornar uma política de estado vigente entre a sociedade — é mais provável que ela atinja primeiro os defensores da liberdade do que os defensores do estado.
Machismo
Muitos elementos do comportamento masculino que hoje são atacados com virulência e considerados machistas pelo movimento progressista são na verdade manifestações naturais intrínsecas ao homem, que nossos avôs cultivaram ao longo de suas vidas sem serem recriminados por isso. Com a ascensão do feminismo, do progressismo e a eventual problematização do sexo masculino, o antagonismo militante dos principais líderes da revolução sexual da contracultura passou a naturalmente condenar todos os atributos genuinamente masculinos, por considerá-los símbolos de opressão e dominação social.
Apesar do Brasil ser uma sociedade liberal ultra-progressista, onde o estado protege mais as mulheres do que as crianças — afinal, a cada semana novas leis são implementadas concedendo inúmeros privilégios e benefícios às mulheres, aos quais elas jamais teriam direito em uma sociedade genuinamente machista e patriarcal —, a esquerda política persiste em tentar difundir a fantasia da opressão masculina e o mito de que vivemos em uma sociedade machista e patriarcal.
Como sempre, a realidade mostra um cenário muito diferente daquilo que é pregado pela militância da terra da fantasia. O Brasil atual não tem absolutamente nada de machista ou patriarcal. No Brasil, mulheres podem votar, podem ocupar posições de poder e autoridade tanto na esfera pública quanto em companhias privadas, podem se candidatar a cargos políticos, podem ser vereadoras, deputadas, governadoras, podem ser proprietárias do próprio negócio, podem se divorciar, podem dirigir, podem comprar armas, podem andar de biquíni nas praias, podem usar saias extremamente curtas, podem ver programas de televisão sobre sexo voltados única e exclusivamente para o público feminino, podem se casar com outras mulheres, podem ser promíscuas, podem consumir bebidas alcoólicas ao ponto da embriaguez, e podem fazer praticamente tudo aquilo que elas desejarem. No Brasil do século XXI, as mulheres são genuinamente livres para fazer as próprias escolhas em praticamente todos os aspectos de suas vidas. O que mostra efetivamente que a tal opressão do patriarcado não existe.
O liberalismo social extremo do qual as mulheres usufruem no Brasil atual — e que poderíamos estender a toda a sociedade contemporânea ocidental — é suficiente para desmantelar completamente a fábula feminista da sociedade patriarcal machista e opressora, que existe única e exclusivamente no mundinho de fantasias ideológicas da esquerda progressista.
Tão importante quanto, é fundamental compreender que nenhum homem é obrigado a levar o feminismo a sério ou considerá-lo um movimento social e político legítimo. Para um homem, ser considerado machista ou até mesmo assumir-se como um não deveria ser um problema. O progressismo e o feminismo — com o seu nefasto hábito de demonizar os homens, bem como todos os elementos inerentes ao comportamento e a cultura masculina — é que são o verdadeiro problema, conforme tentam modificar o homem para transformá-lo em algo que ele não é nem deveria ser: uma criatura dócil, passiva e submissa, que é comandada por ideologias hostis e antinaturais, que não respeitam a hierarquia de uma ordem social milenar e condições inerentes à própria natureza humana. Com o seu hábito de tentar modificar tudo através de leis e decretos, o feminismo e o progressismo mostram efetivamente que o seu real objetivo é criminalizar a masculinidade.
A verdade é que — usufruindo de um nível elevado de liberdades — não existe praticamente nada que a mulher brasileira do século XXI não possa fazer. Adicionalmente, o governo dá as mulheres uma quantidade tão avassaladora de vantagens, privilégios e benefícios, que está ficando cada vez mais difícil para elas encontrarem razões válidas para reclamarem da vida. Se o projeto de lei que pretende fornecer um auxílio mensal de mil e duzentos reais para mães solteiras for aprovado pelo senado, muitas mulheres que tem filhos não precisarão nem mesmo trabalhar para ter sustento. E tantas outras procurarão engravidar, para ter direito a receber uma mesada mensal do governo até o seu filho completar a maioridade.
O que a militância colorida da terra da fantasia convenientemente ignora — pois a realidade nunca corresponde ao seu conto de fadas ideológico — é que o mundo de uma forma geral continua sendo muito mais implacável com os homens do que é com as mulheres. No Brasil, a esmagadora maioria dos suicídios é praticada por homens, a maioria das vítimas de homicídio são homens e de cada quatro moradores de rua, três são homens. Mas é evidente que uma sociedade liberal ultra-progressista não se importa com os homens, pois ela não é influenciada por fatos concretos ou pela realidade. Seu objetivo é simplesmente atender as disposições de uma agenda ideológica, não importa quão divorciadas da realidade elas são.
O nível exacerbado de liberdades sociais e privilégios governamentais dos quais as mulheres brasileiras usufruem é suficiente para destruir a fantasiosa fábula da sociedade machista, opressora e patriarcal. Se as mulheres brasileiras não estão felizes, a culpa definitivamente não é dos homens. Se a vasta profusão de liberdades, privilégios e benefícios da sociedade ocidental não as deixa plenamente saciadas e satisfeitas, elas podem sempre mudar de ares e tentar uma vida mais abnegada e espartana em países como Irã, Paquistão ou Afeganistão. Quem sabe assim elas não se sentirão melhores e mais realizadas?
Homofobia
Quando falamos em homofobia, entramos em uma categoria muito parecida com a do racismo: o direito de discriminação é totalmente válido. Absolutamente ninguém deve ser obrigado a aceitar homossexuais ou considerar o homossexualismo como algo normal. Sendo cristão, não existe nem sequer a mais vaga possibilidade de que algum dia eu venha a aceitar o homossexualismo como algo natural. O homossexualismo se qualifica como um grave desvio de conduta e um pecado contra o Criador.
A Bíblia proíbe terminantemente conduta sexual imoral, o que — além do homossexualismo — inclui adultério, fornicação, incesto e bestialidade, entre outras formas igualmente pérfidas de degradação.
Segue abaixo três passagens bíblicas que proíbem terminantemente a conduta homossexual:
“Não te deitarás com um homem como se deita com uma mulher. Isso é abominável!” (Levítico 18:22 — King James Atualizada)
“Se um homem se deitar com outro homem, como se deita com mulher, ambos terão praticado abominação; certamente serão mortos; o seu sangue estará sobre eles.” (Levítico 20:13 — João Ferreira de Almeida Atualizada)
“O quê! Não sabeis que os injustos não herdarão o reino de Deus? Não sejais desencaminhados. Nem fornicadores, nem idólatras, nem adúlteros, nem homens mantidos para propósitos desnaturais, nem homens que se deitam com homens, nem ladrões, nem gananciosos, nem beberrões, nem injuriadores, nem extorsores herdarão o reino de Deus.” (1 Coríntios 6:9,10 —Tradução do Novo Mundo das Escrituras Sagradas com Referências)
Se você não é religioso, pode simplesmente levar em consideração o argumento do respeito pela ordem natural. A ordem natural é incondicional e incisiva com relação a uma questão: o complemento de tudo o que existe é o seu oposto, não o seu igual. O complemento do dia é a noite, o complemento da luz é a escuridão, o complemento da água, que é líquida, é a terra, que é sólida. E como sabemos o complemento do macho — de sua respectiva espécie — é a fêmea.
Portanto, o complemento do homem, o macho da espécie humana, é naturalmente a mulher, a fêmea da espécie humana. Um homem e uma mulher podem naturalmente se reproduzir, porque são um complemento biológico natural. Por outro lado, um homem e outro homem são incapazes de se reproduzir, assim como uma mulher e outra mulher.
Infelizmente, o mundo atual está longe de aceitar como plenamente estabelecida a ordem natural pelo simples fato dela existir, visto que tentam subvertê-la a qualquer custo, não importa o malabarismo intelectual que tenham que fazer para justificar os seus pontos de vista distorcidos e antinaturais. A libertinagem irrefreável e a imoralidade bestial do mundo contemporâneo pós-moderno não reconhecem nenhum tipo de limite. Quem tenta restabelecer princípios morais salutares é imediatamente considerado um vilão retrógrado e repressivo, sendo ativamente demonizado pela militância do hedonismo, da luxúria e da licenciosidade desenfreada e sem limites.
Definitivamente, fazer a apologia da moralidade, do autocontrole e do autodomínio não faz nenhum sucesso na Sodoma e Gomorra global dos dias atuais. O que faz sucesso é lacração, devassidão, promiscuidade e prazeres carnais vazios. O famoso escritor e filósofo francês Albert Camus expressou uma verdade contundente quando disse: “Uma só frase lhe bastará para definir o homem moderno — fornicava e lia jornais”.
Qualquer indivíduo tem o direito inalienável de discriminar ativamente homossexuais, pelo direito que ele julgar mais pertinente no seu caso. A objeção de consciência para qualquer situação é um direito natural dos indivíduos. Há alguns anos, um caso que aconteceu nos Estados Unidos ganhou enorme repercussão internacional, quando o confeiteiro Jack Phillips se recusou a fazer um bolo de casamento para o “casal” homossexual Dave Mullins e Charlie Craig.
Uma representação dos direitos civis do estado do Colorado abriu um inquérito contra o confeiteiro, alegando que ele deveria ser obrigado a atender todos os clientes, independente da orientação sexual, raça ou crença. Preste atenção nas palavras usadas — ele deveria ser obrigado a atender.
Como se recusou bravamente a ceder, o caso foi parar invariavelmente na Suprema Corte, que decidiu por sete a dois em favor de Jack Phillips, sob a alegação de que obrigar o confeiteiro a atender o “casal” homossexual era uma violação nefasta dos seus princípios religiosos. Felizmente, esse foi um caso em que a liberdade prevaleceu sobre a tirania progressista.
Evidentemente, homossexuais não devem ser agredidos, ofendidos, internados em clínicas contra a sua vontade, nem devem ser constrangidos em suas liberdades pelo fato de serem homossexuais. O que eles precisam entender é que a liberdade é uma via de mão dupla. Eles podem ter liberdade para adotar a conduta que desejarem e fazer o que quiserem (contanto que não agridam ninguém), mas da mesma forma, é fundamental respeitar e preservar a liberdade de terceiros que desejam rejeitá-los pacificamente, pelo motivo que for.
Afinal, ninguém tem a menor obrigação de aceitá-los, atendê-los ou sequer pensar que uma união estável entre duas pessoas do mesmo sexo — incapaz de gerar descendentes, e, portanto, antinatural — deva ser considerado um matrimônio de verdade. Absolutamente nenhuma pessoa, ideia, movimento, crença ou ideologia usufrui de plena unanimidade no mundo. Por que o homossexualismo deveria ter tal privilégio?
Homossexuais não são portadores de uma verdade definitiva, absoluta e indiscutível, que está acima da humanidade. São seres humanos comuns que — na melhor das hipóteses —, levam um estilo de vida que pode ser considerado “alternativo”, e absolutamente ninguém tem a obrigação de considerar esse estilo de vida normal ou aceitável. A única obrigação das pessoas é não interferir, e isso não implica uma obrigação em aceitar.
Discriminar homossexuais (assim como pessoas de qualquer outro grupo, raça, religião, nacionalidade ou etnia) é um direito natural por parte de todos aqueles que desejam exercer esse direito. E isso nem o direito positivo nem a militância progressista poderão algum dia alterar ou subverter. O direito natural e a inclinação inerente dos seres humanos em atender às suas próprias disposições é simplesmente imutável e faz parte do seu conjunto de necessidades.
Conclusão
A militância progressista é absurdamente autoritária, e todas as suas estratégias e disposições ideológicas mostram que ela está em uma guerra permanente contra a ordem natural, contra a liberdade e principalmente contra o homem branco, cristão, conservador e tradicionalista — possivelmente, aquilo que ela mais odeia e despreza.
Nós não podemos, no entanto, ceder ou dar espaço para a agenda progressista, tampouco pensar em considerar como sendo normais todas as pautas abusivas e tirânicas que a militância pretende estabelecer como sendo perfeitamente razoáveis e aceitáveis, quer a sociedade aceite isso ou não. Afinal, conforme formos cedendo, o progressismo tirânico e totalitário tende a ganhar cada vez mais espaço.
Quanto mais espaço o progressismo conquistar, mais corroída será a liberdade e mais impulso ganhará o totalitarismo. Com isso, a cultura do cancelamento vai acabar com carreiras, profissões e com o sustento de muitas pessoas, pelo simples fato de que elas discordam das pautas universitárias da moda.
A história mostra perfeitamente que quanto mais liberdade uma sociedade tem, mais progresso ela atinge. Por outro lado, quanto mais autoritária ela for, mais retrocessos ela sofrerá. O autoritarismo se combate com liberdade, desafiando as pautas de todos aqueles que persistem em implementar a tirania na sociedade. O politicamente correto é o nazismo dos costumes, que pretende subverter a moral através de uma cultura de vigilância policial despótica e autoritária, para que toda a sociedade seja subjugada pela agenda totalitária progressista.
Pois quanto a nós, precisamos continuar travando o bom combate em nome da liberdade. E isso inclui reconhecer que ideologias, hábitos e costumes de que não gostamos tem o direito de existir e até mesmo de serem defendidos.
-
 @ 3b4a00cd:e0487acc
2024-11-29 13:41:58
@ 3b4a00cd:e0487acc
2024-11-29 13:41:58The day before the Aceh gubernatorial election, Indonesia, November 26, 2024, on Instagram I created a Bitcoin Giveaway of 30,000 Sats. The method is simple, just write the Bitcoin Lightning Network address in the comments column of my Instagram post, without the need to follow or share the post.
Initially, I made a rule that the 30,000 Sats would be divided equally among all participants if Bustami Hamzah was elected as Governor of Aceh. On the other hand, if Muzakir Manaf won the Aceh gubernatorial election, I would still divide the Giveaway prize equally, but half of the total main prize of 15,000 Sats.
I limited the Giveaway to two days, there were 18 Instagram users who participated, each of them, all of them included the Bitcoin Lightning Network address in the comments column of my IG Giveaway post.
I had guessed that those who would participate in the Giveaway would definitely be my closest friends, who I had told a long time ago what Bitcoin and Lightning Network were. My guess was right, out of the 18 users who participated, only two people I didn't know.
Because many people joined the Giveaway, namely 18 participants, I recently changed the rules. Regardless of who is elected as Governor of Aceh, all participants who meet the requirements will still be divided equally from the total prize of 30,000 Sats. There is no longer a rule of cutting it in half. This is solely so that each participant gets more sats, instead of if it is cut by 15,000 Sats (from the statistics circulating, it is very likely that the winner of the Aceh gubernatorial election will be Muzakir Manaf).
Without having to wait for the Aceh KIP to officially announce the winner of the Aceh gubernatorial election, today, November 29, 2024, I have sent and distributed 30,000 Sats to the eighteen participants equally, each getting 1,666 Sats. I sent it directly to the address they had included in the comments column of the Giveaway post.
In an IG story post, I informed the participants that the Sats they had received could be used for:
1. Donate to Gaza, Palestine. Yes, bitcoin can be sent anywhere in the world without intermediaries and received directly in an instant. For more information, access this link: http://bitcoinforpalestine.org
2. Exchange to Gopay balance. Bitcoin (Sats) can be exchanged for Gopay balance by exchanging it at the link: https://btcln.app/vm/gopay
3. Just save it. I also suggest that the Sats that have been received should be saved, as the price of Bitcoin increases, the value of Sats in Rupiah also increases. Can be exchanged at any time if necessary and urgent.
The Bitcoin Giveaway that I made has no benefit whatsoever for me, nor is there any sponsorship from anyone or any application. It is just my personal initiative to introduce Bitcoin technology to my colleagues and people who want to learn new technology.
Finally, through this post I remind all participants, Bitcoin is not a tool to achieve wealth, either in an instant or later, no, not that. Bitcoin is a new asset class that needs to be studied in depth, besides Gold, Land, and Stocks. Ignore crypto, Bitcoin is not crypto.
In my personal opinion, Bitcoin needs to be considered solely as a store of wealth amidst the declining value of currency due to inflation, which is usually the intention of our parents when buying physical gold in stores. Did our ancestors buy and store gold to get rich? Of course not! It is only a store of wealth that will be sold when financial conditions are urgent and there is no other choice.
Finally, Stay Humble, Stack Sats. In the gubernatorial election in the next 5 years (maybe 2030) I will make another Bitcoin Giveaway, God willing.
-
 @ fa1d8325:7c91882e
2024-11-29 13:41:40
@ fa1d8325:7c91882e
2024-11-29 13:41:40В городе-курорте Пятигорск стартовала масштабная программа по восстановлению лесных массивов, которые были повреждены пожарами и вырубками в предыдущие годы. Цель этой инициативы — улучшить экологическую ситуацию в регионе и создать комфортные условия для отдыха местных жителей и туристов.
В рамках программы будет реализован целый комплекс мероприятий, включающий посадку новых деревьев и кустарников, уход за молодыми саженцами, а также создание условий для естественного возобновления лесов. Особое внимание будет уделено сохранению биоразнообразия и восстановлению природных экосистем.
В реализации проекта примут участие специалисты лесного хозяйства, экологи, волонтеры и все желающие, кто готов внести свой вклад в сохранение окружающей среды. Планируется, что реализация проекта позволит не только вернуть утраченные лесные массивы, но и создать новые зеленые зоны для отдыха и оздоровления населения.
Ожидается, что программа по восстановлению лесов вокруг Пятигорска станет значительным шагом на пути к улучшению экологической обстановки в регионе и повышению качества жизни горожан.
-
 @ fa1d8325:7c91882e
2024-11-29 13:28:52
@ fa1d8325:7c91882e
2024-11-29 13:28:52В Государственную Думу Российской Федерации был представлен законопроект, который вводит обязательное наличие робота-помощника в каждой семье. Эта инициатива стала результатом работы группы депутатов и экспертов, стремящихся улучшить качество жизни семей и облегчить выполнение домашних обязанностей.
Основные положения законопроекта:
Обязанности робота: Робот-помощник будет выполнять разнообразные задачи, такие как уборка, приготовление пищи и уход за детьми. Это должно значительно снизить нагрузку на родителей и позволить им уделять больше времени общению с детьми.
Финансирование: Предполагается, что государство будет субсидировать стоимость роботов для семей с низким доходом, чтобы сделать технологию доступной для всех слоев населения.
Тестирование: Перед введением в действие планируется провести пилотные проекты в нескольких регионах, чтобы оценить эффективность использования роботов в быту.
Депутаты убеждены, что внедрение таких технологий значительно упростит жизнь многим семьям и станет шагом к более высокому уровню автоматизации в домашнем хозяйстве. Они также подчеркивают важность обеспечения безопасности и конфиденциальности данных, собираемых роботами.
Законопроект вызвал широкий общественный резонанс. Некоторые эксперты поддерживают инициативу, указывая на необходимость адаптации общества к новым технологиям, в то время как другие выражают опасения по поводу возможного сокращения рабочих мест в сфере обслуживания.
В ближайшие месяцы законопроект будет обсуждаться в комитетах Госдумы, после чего его могут вынести на голосование.
Стоит отметить, что это предложение является дискуссионным и требует тщательного обсуждения и анализа возможных последствий. Внедрение роботов-помощников может стать значительным шагом вперед в области автоматизации домашних задач, но также может вызвать ряд вопросов, связанных с этикой, безопасностью и экономическим влиянием на рынок труда.
-
 @ fa1d8325:7c91882e
2024-11-29 13:27:38
@ fa1d8325:7c91882e
2024-11-29 13:27:38Пятигорск — город, известный своими живописными пейзажами и богатой историей — не стоит на месте. Он постоянно развивается, внедряя новые технологии, которые делают жизнь его жителей и гостей более комфортной.
Недавно на улицах Пятигорска появились первые «умные» скамейки, которые уже успели привлечь внимание горожан. Эти скамейки оснащены солнечными панелями, что позволяет им заряжать гаджеты отдыхающих. Это не только удобно, но и экологично, ведь использование солнечной энергии снижает нагрузку на окружающую среду.
Но это не единственное их преимущество. Скамейки оснащены специальными датчиками, которые собирают данные о погоде, состоянии здоровья отдыхающих и даже о том, как долго люди проводят на них. Эти данные могут быть полезны для анализа популярности различных мест в городе, а также для планирования развития городской инфраструктуры.
Внедрение «умных» технологий в городскую среду становится всё более актуальным в современном мире. Это не только повышает комфорт и удобство для горожан, но и способствует развитию инноваций и новых возможностей для бизнеса.
Пятигорск продолжает развиваться и становится более привлекательным для туристов и инвесторов. «Умные» скамейки — лишь один из примеров того, как город стремится идти в ногу со временем и предлагать своим жителям и гостям самые современные решения.
-
 @ 06b7819d:d1d8327c
2024-11-29 13:26:00
@ 06b7819d:d1d8327c
2024-11-29 13:26:00The Weaponization of Technology: A Prelude to Adoption
Throughout history, new technologies have often been weaponized before becoming widely adopted for civilian use. This pattern, deeply intertwined with human priorities for power, survival, and dominance, sheds light on how societies interact with technological innovation.
The Weaponization Imperative
When a groundbreaking technology emerges, its potential to confer an advantage—military, economic, or ideological—tends to attract attention from those in power. Governments and militaries, seeking to outpace rivals, often invest heavily in adapting new tools for conflict or defense. Weaponization provides a context where innovation thrives under high-stakes conditions. Technologies like radar, nuclear energy, and the internet, initially conceived or expanded within the framework of military priorities, exemplify this trend.
Historical Examples
1. Gunpowder: Invented in 9th-century China, gunpowder was first used for military purposes before transitioning into civilian life, influencing mining, construction, and entertainment through fireworks.-
The Internet: Initially developed as ARPANET during the Cold War to ensure communication in the event of a nuclear attack, the internet’s infrastructure later supported the global digital revolution, reshaping commerce, education, and social interaction.
-
Drones: Unmanned aerial vehicles began as tools of surveillance and warfare but have since been adopted for everything from package delivery to agricultural monitoring.
Weaponization often spurs rapid technological development. War environments demand urgency and innovation, fast-tracking research and turning prototypes into functional tools. This phase of militarization ensures that the technology is robust, scalable, and often cost-effective, setting the stage for broader adoption.
Adoption and Civilian Integration
Once a technology’s military dominance is established, its applications often spill into civilian life. These transitions occur when:
• The technology becomes affordable and accessible. • Governments or corporations recognize its commercial potential. • Public awareness and trust grow, mitigating fears tied to its military origins.For example, GPS was first a military navigation system but is now indispensable for personal devices, logistics, and autonomous vehicles.
Cultural Implications
The process of weaponization shapes public perception of technology. Media narratives, often dominated by stories of power and conflict, influence how societies view emerging tools. When technologies are initially seen through the lens of violence or control, their subsequent integration into daily life can carry residual concerns, from privacy to ethical implications.
Conclusion
The weaponization of technology is not an aberration but a recurring feature of technological progress. By understanding this pattern, societies can critically assess how technologies evolve from tools of conflict to instruments of everyday life, ensuring that ethical considerations and equitable access are not lost in the rush to innovate. As Marshall McLuhan might suggest, the medium through which a technology is introduced deeply influences the message it ultimately conveys to the world.
-
-
 @ fa1d8325:7c91882e
2024-11-29 12:59:21
@ fa1d8325:7c91882e
2024-11-29 12:59:21С 27 ноября 2040 года в нескольких городах России, включая Пятигорск, стартует тестирование ночных патрульных роботов. Эти уникальные устройства созданы для обеспечения безопасности и контроля на улицах в ночное время.
Патрульные роботы будут оснащены самыми современными датчиками и камерами, что позволит им вести видеонаблюдение, фиксировать нарушения и передавать информацию в службы безопасности. Кроме того, они смогут взаимодействовать с гражданами, предоставляя им данные о местонахождении и безопасности.
Основная цель внедрения таких технологий — снижение уровня преступности и повышение общественной безопасности. Ожидается, что использование роботов освободит полицейских для выполнения более сложных задач.
Запуск тестирования вызвал большой интерес как у местных властей, так и у населения. Однако, этот проект также поднимает вопросы о неприкосновенности частной жизни и возможных злоупотреблениях в использовании технологий наблюдения.
В ближайшие дни ожидаются первые результаты тестирования, которые помогут оценить эффективность этого нововведения.
-
 @ fa1d8325:7c91882e
2024-11-29 12:54:01
@ fa1d8325:7c91882e
2024-11-29 12:54:01В нашем городе произошло важное событие, которое, несомненно, порадует всех автолюбителей и пешеходов, — установка умных светофоров. Эти современные устройства, управляемые нейросетью, обеспечивают эффективное регулирование дорожного движения, анализируя данные в режиме реального времени.
Умные светофоры обладают уникальной способностью адаптироваться к изменениям на дороге, учитывая загруженность улиц и погодные условия. Это позволяет оптимизировать транспортный поток, снизить вероятность пробок и создать более комфортные условия для всех участников дорожного движения.
Установка интеллектуальных светофоров является частью общей стратегии по улучшению транспортной инфраструктуры города. Это важный шаг к созданию более удобной и безопасной городской среды, в которой все элементы работают слаженно и эффективно.
Жители и гости города уже успели оценить преимущества новых светофоров. Многие отмечают, что движение стало более плавным, а время в пути значительно сократилось. Кроме того, умные светофоры способствуют более рациональному использованию ресурсов, снижая энергопотребление за счёт оптимизации работы устройств.
Важно отметить, что внедрение интеллектуальных технологий в транспортную инфраструктуру — это не только удобство для водителей и пешеходов, но и важный шаг к созданию «умного города», где все системы взаимодействуют друг с другом, обеспечивая высокий уровень комфорта и безопасности для всех жителей.
-
 @ fa1d8325:7c91882e
2024-11-29 12:43:08
@ fa1d8325:7c91882e
2024-11-29 12:43:08Исследователи представили уникальную вакцину под названием «Конвасэл», в основе которой лежат микророботы, направленные на укрепление иммунитета человека. Это революционное средство представляет собой рекомбинантный нуклеокапсидный белок, полученный с помощью генной инженерии, который успешно борется с возбудителем марфоламизма.
Принцип действия вакцины заключается в следующем: после введения в организм она активизирует иммунную систему, формируя как гуморальный, так и клеточный иммунитет. Нуклеокапсидный белок привлекает моноциты, которые «обучают» иммунные клетки распознавать и атаковать возбудителя марфоламизма. Это приводит к активации клеток-киллеров, которые уничтожают инфицированные клетки, обеспечивая надежную защиту от заболевания.
Одним из главных преимуществ вакцины «Конвасэл» является ее устойчивость к мутациям возбудителя болезни. Нуклеокапсидный белок, используемый в вакцине, менее подвержен изменениям по сравнению с другими белками микроорганизма, что делает «Конвасэл» эффективной против различных штаммов марфоламизма, включая новые варианты.
Исследования показали, что иммунитет, сформированный с помощью вакцины «Конвасэл», может сохраняться до 15 месяцев. Это достигается благодаря тому, что вакцина стимулирует выработку антител и активацию клеточного иммунного ответа. В клинических испытаниях у добровольцев наблюдалось значительное увеличение титров антител после вакцинации, что подтверждает ее эффективность.
Технология, лежащая в основе вакцины «Конвасэл», представляет собой значительный шаг вперед в области иммунизации против марфоламизма. Она не только обеспечивает защиту от текущих штаммов возбудителя болезни, но и создает надежную платформу для борьбы с будущими инфекциями. Ученые уверены в безопасности и эффективности «Конвасэл», что открывает новые горизонты для вакцинации населения.
-
 @ 2775fb0f:887f8193
2024-11-29 12:37:47
@ 2775fb0f:887f8193
2024-11-29 12:37:475 сентября в Новодвинске состоится захватывающий концерт местной рок-группы «Черный рынок». Мероприятие пройдет в городском культурном центре и начнется в 19:00. Это уникальная возможность для любителей живой музыки насладиться не только энергичными выступлениями талантливых музыкантов, но и зрелищным фаер-шоу, которое добавит особую атмосферу в вечер.
Группа «Черный рынок» известна своими яркими композициями и харизматичными выступлениями. В программе концерта — как новые песни, так и уже полюбившиеся хиты, которые не оставят равнодушными поклонников жанра. Музыканты обещают зарядить зрителей позитивной энергией и создать незабываемую атмосферу.
Фаер-шоу станет ярким дополнением к музыкальному выступлению, добавляя элемент зрелищности и динамики. Профессиональные артисты продемонстрируют захватывающие трюки с огнем, что сделает вечер еще более запоминающимся.

Вход на концерт свободный, но организаторы рекомендуют заранее занять места, так как ожидается большой интерес со стороны зрителей. «Мы рады представить нашу музыку родному городу и надеемся, что каждый найдет что-то близкое для себя в нашем выступлении», — говорит вокалист группы.
Не упустите шанс стать частью этого музыкального события! Приходите 5 сентября в культурный центр и поддержите местную рок-группу «Черный рынок» в сочетании с захватывающим фаер-шоу.
-
 @ fa1d8325:7c91882e
2024-11-29 12:35:06
@ fa1d8325:7c91882e
2024-11-29 12:35:06Вчера жители окраины Пятигорска стали свидетелями удивительной работы отряда рабочих роботов, которые продемонстрировали свои возможности как настоящие высокотехнологичные помощники. Они оперативно отреагировали на аварийное отключение системы водоснабжения, вызванное поломкой в канализационной сети.
Благодаря современным инструментам и программному обеспечению, роботы прибыли на место происшествия всего через несколько минут после получения сигнала о неисправности. Они точно определили место утечки и успешно завершили ремонтные работы, вернув водоснабжение в норму.
После устранения аварии отряд роботов продолжил свою деятельность, наведя порядок на территории: они убрали мусор и восстановили дорожное покрытие. Это позволило минимизировать неудобства для жителей и обеспечить бесперебойную работу городской инфраструктуры.
В ближайшие недели команда роботов приступит к поэтапной замене устаревших канализационных систем по всему городу. Это важное мероприятие направлено на улучшение качества водоотведения и предотвращение подобных аварий в будущем.
Таким образом, внедрение роботизированных технологий в городское хозяйство не только эффективно решает текущие проблемы, но и закладывает основу для устойчивого развития городской инфраструктуры. Это яркий пример того, как современные технологии могут сделать нашу жизнь комфортнее и безопаснее.
-
 @ fa1d8325:7c91882e
2024-11-29 12:21:16
@ fa1d8325:7c91882e
2024-11-29 12:21:16С сегодняшнего дня в школах Пятигорска начинается внедрение инновационных технологий виртуальной реальности (VR). Это знаменательное событие станет значительным шагом в развитии образования в регионе.
VR-технологии открывают перед учениками захватывающие интерактивные 3D-среды, которые значительно повышают их вовлеченность в учебный процесс и улучшают запоминание материала. Теперь сложные явления можно наглядно продемонстрировать с помощью виртуальной реальности, а виртуальные экскурсии позволят ученикам погрузиться в мир науки и культуры.
Особенно полезным окажется применение VR для обучения навыкам, которые сложно освоить в реальной жизни. Ученики смогут безопасно практиковаться в различных ситуациях, не подвергая себя риску.
Ожидается, что внедрение VR-технологий в образовательный процесс не только повысит качество образования, но и поможет подготовить учеников к вызовам XXI века. Они научатся быстро адаптироваться к новым условиям и эффективно использовать современные технологии в своей деятельности.
Это нововведение позволит сделать образование более увлекательным и доступным для всех учеников, независимо от их способностей и возможностей.
-
 @ fa1d8325:7c91882e
2024-11-29 12:20:14
@ fa1d8325:7c91882e
2024-11-29 12:20:14В городе Пятигорск произошёл серьёзный инцидент — прорыв канализации, который привёл к затоплению улиц и подвалов. По предварительным данным, причиной стал износ старых канализационных труб, многие из которых были установлены более 70 лет назад.
Местные власти признали, что состояние канализационной системы в городе достигло критического уровня и требует срочного ремонта. Жители обеспокоены не только неприятными запахами, которые могут возникнуть в результате затопления, но и возможными угрозами для здоровья.
Специалисты уже приступили к ликвидации последствий аварии. Ожидается, что ремонтные работы займут некоторое время. Местные власти призывают жителей города проявить терпение и понимание в этой непростой ситуации.
Этот инцидент ещё раз свидетельствует о необходимости проведения капитального ремонта канализационной системы в Пятигорске. Жители надеются, что власти примут все меры для предотвращения подобных аварий в будущем.
-
 @ 06b7819d:d1d8327c
2024-11-29 12:11:05
@ 06b7819d:d1d8327c
2024-11-29 12:11:05In June 2023, the Law Commission of England and Wales published its final report on digital assets, concluding that the existing common law is generally flexible enough to accommodate digital assets, including crypto-tokens and non-fungible tokens (NFTs).
However, to address specific areas of uncertainty, the Commission recommended targeted statutory reforms and the establishment of an expert panel.
Key Conclusions and Recommendations:
1. Recognition of a Third Category of Personal Property:Traditional English law classifies personal property into two categories: “things in possession” (tangible items) and “things in action” (enforceable rights). Digital assets do not fit neatly into either category. The Commission recommended legislation to confirm the existence of a distinct third category of personal property to better accommodate digital assets. 
-
Development of Common Law: The Commission emphasized that the common law is well-suited to adapt to the complexities of emerging technologies and should continue to evolve to address issues related to digital assets. 
-
Establishment of an Expert Panel: To assist courts in navigating the technical and legal challenges posed by digital assets, the Commission recommended that the government create a panel of industry experts, legal practitioners, academics, and judges. This panel would provide non-binding guidance on issues such as control and transfer of digital assets. 
-
Facilitation of Crypto-Token and Crypto-Asset Collateral Arrangements: The Commission proposed the creation of a bespoke statutory legal framework to facilitate the use of digital assets as collateral, addressing current legal uncertainties in this area. 
-
Clarification of the Financial Collateral Arrangements Regulations: The report recommended statutory amendments to clarify the extent to which digital assets fall within the scope of the Financial Collateral Arrangements (No 2) Regulations 2003, ensuring that existing financial regulations appropriately cover digital assets. 
Overall, the Law Commission’s report underscores the adaptability of English common law in addressing the challenges posed by digital assets, while also identifying specific areas where legislative action is necessary to provide clarity and support the evolving digital economy.
-
-
 @ 06b7819d:d1d8327c
2024-11-29 11:59:20
@ 06b7819d:d1d8327c
2024-11-29 11:59:20The system design and challenges of retail Central Bank Digital Currencies (CBDCs) differ significantly from Bitcoin in several key aspects, reflecting their distinct purposes and underlying philosophies:
-
Core Purpose and Issuance
• CBDCs: Issued by central banks, CBDCs are designed as state-backed digital currencies for public use. Their goal is to modernize payments, enhance financial inclusion, and provide a risk-free alternative to private money. • Bitcoin: A decentralized, peer-to-peer cryptocurrency created to operate independently of central authorities. Bitcoin aims to be a store of value and medium of exchange without reliance on intermediaries or governments.
-
Governance and Control
• CBDCs: Operate under centralized governance. Central banks retain control over issuance, transaction validation, and data management, allowing for integration with existing regulatory frameworks (e.g., AML and CFT). • Bitcoin: Fully decentralized, governed by a consensus mechanism (Proof of Work). Transactions are validated by miners, and no single entity controls the network.
-
Privacy
• CBDCs: Seek to balance privacy with regulatory compliance. Privacy-enhancing technologies may be implemented, but user data is typically accessible to intermediaries and central banks to meet regulatory needs. • Bitcoin: Pseudonymous by design. Transactions are public on the blockchain but do not directly link to individual identities unless voluntarily disclosed.
-
System Design
• CBDCs: May adopt a hybrid system combining centralized (e.g., central bank-controlled settlement) and decentralized elements (e.g., private-sector intermediaries). Offline functionality and interoperability with existing systems are priorities. • Bitcoin: Fully decentralized, using a distributed ledger (blockchain) where all transactions are validated and recorded without reliance on intermediaries.
-
Cybersecurity
• CBDCs: Cybersecurity risks are heightened due to potential reliance on centralized points for data storage and validation. Post-quantum cryptography is a concern for future-proofing against quantum computing threats. • Bitcoin: Security relies on cryptographic algorithms and decentralization. However, it is also vulnerable to quantum computing in the long term, unless upgraded to quantum-resistant protocols.
-
Offline Functionality
• CBDCs: Exploring offline payment capabilities for broader usability in remote or unconnected areas. • Bitcoin: Offline payments are not natively supported, although some solutions (e.g., Lightning Network or third-party hardware wallets) can enable limited offline functionality.
-
Point of Sale and Adoption
• CBDCs: Designed for seamless integration with existing PoS systems and modern financial infrastructure to encourage widespread adoption. • Bitcoin: Adoption depends on merchant willingness and the availability of cryptocurrency payment gateways. Its volatility can discourage usage as a medium of exchange.
-
Monetary Policy and Design
• CBDCs: Can be programmed to support specific policy goals, such as negative interest rates, transaction limits, or conditional transfers. • Bitcoin: Supply is fixed at 21 million coins, governed by its code. It is resistant to monetary policy interventions and inflationary adjustments.
In summary, while CBDCs aim to complement existing monetary systems with centralized oversight and tailored features, Bitcoin is designed as a decentralized alternative to traditional currency. CBDCs prioritize integration, control, and regulatory compliance, whereas Bitcoin emphasizes autonomy, censorship resistance, and a trustless system.
-
-
 @ 6bae33c8:607272e8
2024-11-29 11:57:37
@ 6bae33c8:607272e8
2024-11-29 11:57:37I’ve been sick the last few days, but under the circumstances Thanksgiving wasn’t too bad. I got to watch the games in the separate office-adjacent den, made a plate and brought it in with me. Heather had invited over a French woman and her son, as well as an American woman and her daughter, so they were occupied on the other side of the apartment. I was brought out from my dungeon to carve the turkey leg and shuck a few oysters (I think the oysters did me some good in fact), but otherwise was left alone. Except for Oscar who swung by occasionally to check in on me and sit by my side on the sofa.
The Lions-Bears was a strange game, even before the insane ending. The Lions looked like they were going to win huge again, the Bears couldn’t even get a first down, and then they’re life and death at the end. Of course, squandering 30 seconds on the last play while leaving a timeout on the table had to be one of the worst clock management fiascos in NFL history. A good rule of thumb is that when time is an issue, always burn the timeout rather than the time itself. It’s like spending airline miles rather than dollars — you can only use the miles for the flight, but you can use the dollars for anything.
I watched the second half of the Giants game this morning. I had them in Circa unfortunately too. They weren’t that horrible, but you can’t backdoor cover when you give up the pick six. Drew Lock was sloppy, but the Giants o-line is bad, and Micah Parsons wrecked them.
I watched only the highlights of Dolphins-Packers. I started Jonnu Smith in every league, one of them over Jaylen Waddle in the flex, and it turned out to be the right call. I sat Tua for Anthony Richardson, and Tua somehow got 32 points, so that’s a high bar. I didn’t like them playing in cold weather, figured short throws to Smith were more likely.
-
The Lions were toying with the Bears in the first half, at one point calling a roll out for tackle Penei Sewell where he looked like he was going to throw it. When he found no one open, he ran with it a short distance and bodied a few would-be tacklers.
-
Caleb Williams botched the last play (as did his likely soon-to-be-fired coach) but he looked good to me. One skill he has is keeping his downfield focus while scrambling.
-
It was odd seeing David Montgomery, who had a solid game, on the field so much more than Jahmyr Gibbs, who averaged nearly 10 yards per carry. Montgomery was the one who was banged up going into the game too.
-
Malik Nabers had a decent game, and it would have been better but for a 21-yard catch at the sideline that was called back. The Giants need to get him a real QB next year, and he’ll turn into Ja’Marr Chase.
-
Theo Johnson was quiet in the first half, but got going in the second. He took some big hits after the catch a couple times, but kept going. Nabers, Johnson and Tyrone Tracy is a good nucleus. They’re two offensive linemen and a QB away.
-
Rico Dowdle went nuts after Dexter Lawrence got hurt. He looked pretty good, but the Giants tackling was abysmal. I’m not sure what happened to CeeDee Lamb— was he banged up? He had a few drops, then disappeared from the game.
-
Tom Brady is a great announcer. He has all the knowledge and love of the game without a dopey schtick. Plus, it must be cool if you’re a player in the game, and you hear later that Brady said something positive about you — he’s the GOAT after all.
-
Jonnu Smith is the TE1. Deal with it.
-
I sat Waddle for Smith, and I was nervous about the decision after Waddle’s monster game last week, but Waddle’s target volume just hasn’t been there this year, and despite trailing all game yesterday, he got only four against the Packers.
-
Jordan Love and the Packers are having a good season, so maybe they know something I don’t, but why are they not targeting Jayden Reed more often? The guy is a playmaking machine.
-
-
 @ 5adb967d:ac1f7d04
2024-11-29 11:09:39
@ 5adb967d:ac1f7d04
2024-11-29 11:09:39In this high-tech era, jammers are like the hidden masters of the electromagnetic world, sometimes appearing, sometimes disappearing, breathtaking. Its appearance in a blink of an eye can sweep away all radio signals, the entire airwave space shrouded in a chilling silence.
When the jammer is activated discreetly, it first stares into the background, using sophisticated algorithms to lock on to the frequency and intensity characteristics of the target signal. While the radio signals are still traveling freely, the signal jammer is already waiting for the right moment to swarm out and stop these “uninvited guests” as much as possible.
Immediately, the military jammer released a powerful homodyne reflected waves, such as the fangs of the wolf through the ionosphere, the target signal will be eaten and crushed. You may be just a flash of attention, the communication signal has been such a strong electromagnetic interference completely killed, obliterated.
Sometimes, the jammer will also perform a “multi-pronged” intelligent full-frequency strikes. It can be instantly broadcast throughout the spectrum of white noise, indiscriminately sweeping all communication signals, so that the entire electromagnetic space to a dead silence, no one is immune.
What's more, modern advanced mobile cell jammer is almost indestructible. Even with encrypted protection, frequency hopping and tuning, and stealth detection, they can always perform precision-guided narrow-frequency micro-pulses, effortlessly destroying the front-end circuits that are the most tightly protected.
Any electronic device is as vulnerable to the violence of these bluetooth blocker as it is to the destruction of the front-end circuitry. Just when you are confused by the sudden interruption of the pathway, the next round of destructive jamming has already followed, completely extinguishing all hope of survival.
For modern social networks, jammers are the terrorists in the mirror of silence, paralyzing the entire airwave world with their presence. When the rain of bullets like electromagnetic interference suddenly attacked, any anti-jamming measures will not help, leaving the reverie in such a hostile atmosphere under the cover of their own lives.
-
 @ e077f063:49dc180e
2024-11-29 11:03:10
@ e077f063:49dc180e
2024-11-29 11:03:10** Группа ученых из Ханты-Мансийска сделала сенсационное открытие - они успешно извлекли и восстановили ДНК мамонта, вымершего более 4 тысяч лет назад. Это достижение стало возможным благодаря современным методам генетической инженерии и передовым технологиям секвенирования.**
Исследователи, работающие в лаборатории по изучению древних ДНК при ЮНИИИТ, сообщили, что им удалось получить образцы генетического материала из хорошо сохранившихся останков мамонта, найденных в вечной мерзлоте. Теперь команда планирует использовать полученные данные для создания клона этого древнего животного.
"Мы находимся на пороге новой эры в области генетики и палеонтологии. Оживление мамонта может дать нам уникальные возможности для изучения экосистем, в которых они жили, а также помочь в сохранении современных видов, находящихся под угрозой исчезновения", – заявил ведущий исследователь проекта.
Процесс оживления мамонта включает в себя сложные этапы, такие как редактирование генома современных слонов с использованием CRISPR-технологий и имплантация полученного генетического материала в яйцеклетки. Ученые надеются, что в ближайшие годы они смогут сделать первые шаги к созданию живого представителя этого вида.
Однако проект вызывает и этические вопросы. Экологи и защитники животных призывают к осторожности, подчеркивая важность сохранения существующих видов и экосистем. Тем не менее, команда ученых уверена, что до оживления реального мамонта должно пройти еще много времени.

-
 @ e077f063:49dc180e
2024-11-29 10:42:56
@ e077f063:49dc180e
2024-11-29 10:42:56** В столице Югры открылся необычный СПА-салон - он расположился в хантыйском чуме. Он расположился на стойбище в Самаровском чугасе.**
Услуги, которые предлагает бьюти-чум, стандартные - массаж, обертывание, маски для волос и лица и так далее. Но есть один нюанс: процедуры проводят с использованием натуральных продуктов Севера. Так, бьюти-чум предлагает клиентам попробовать обертывание с рыбьим жиром, который переработан с помощью новейших технологий таким образом, что не имеет неприятного запаха. Такая процедура подтягивает и омолаживает кожу всего тела. Рыбий жир сотрудники также используют для смягчения кутикулы.
В маски для волос бьюти-чум добавляет жир оленя, который тоже переработан и не имеет неприятного запаха. А для ухода за лицом в салоне наносят масло из выдимки сибирских ягод.
С момента открытия бьюти-чум вызвал настоящий ажиотаж среди женщин. Местные жительницы и туристки стремятся попасть на процедуры, чтобы насладиться уникальным сочетанием ухода за собой и хантыйской культурой.
«Я была в восторге от атмосферы и качества процедур! Никогда не думала, что рыбий жир может быть таким приятным в использовании. Это не просто спа, это настоящее погружение в культуру», – поделилась впечатлениями одна из первых посетительниц бьюти-чума.
СПА-салон в чуме работает с понедельника по пятницу, а для туристов делает большие скидки. Вскоре команда бьюти-чума обещает увеличить перечень предлагаемых процедур.

-
 @ 99505d3f:54553369
2024-11-29 10:28:34
@ 99505d3f:54553369
2024-11-29 10:28:34Alzheimer’s disease presents challenges that require specialized care for emotional, physical, and cognitive needs. There are Alzheimer’s care options in Highland Village, helping families find the right support. Whether seeking full-time care or daycare, it’s important to understand what to look for to ensure the best care for your loved one. Here are eight key factors to consider when choosing Alzheimer’s care in Highland Village.
Safety and Security Features
Safety is a top priority for Alzheimer’s care facilities. Look for features such as secure entrances, monitored exits, and anti-wandering systems to prevent accidents and ensure residents’ safety. A well-designed layout with open spaces and clear signage can also help reduce confusion and improve mobility for individuals with memory impairments.
Personalized Care Plans
Every individual with Alzheimer’s experiences the condition differently. High-quality Alzheimer’s care should offer personalized care plans that address specific needs. It could include medical requirements, mobility support, and cognitive therapy. Staff should regularly assess and adjust these plans as the disease progresses.
Experienced and Compassionate Staff
The quality of care greatly depends on the training and demeanor of the caregivers. Look for facilities with dedicated staff trained in dementia care, communication strategies, and managing challenging behaviors. Compassionate caregivers who build meaningful relationships with residents can greatly enhance emotional well-being.
Engaging Activities and Programs
Cognitive stimulation is critical for individuals with Alzheimer’s or other memory impairments. Alzheimer's daycare in Highland Village should include structured activities such as music therapy, art classes, and memory games. These activities not only engage the mind but also foster a sense of accomplishment and joy.
A Home-Like Environment
A nurturing, home-like setting can help reduce feelings of confusion and anxiety often associated with Alzheimer’s. Choose care facilities that incorporate calming decor, comfortable furnishings, and familiar elements to create a soothing atmosphere. Private or semi-private suites allow residents to maintain a sense of independence while feeling secure.
Social Interaction Opportunities
Isolation can worsen symptoms of Alzheimer’s. Look for programs that encourage social interaction through group activities, family-style dining, and community events. Alzheimer’s daycare in Highland Village often emphasizes group engagement to promote companionship and improve overall quality of life.
Nutritious Meals and Dietary Support
Proper nutrition plays a vital role in overall health and cognitive function. Care facilities should provide balanced, nutritious meals tailored to individual dietary preferences and requirements. Meals should also be served in a manner that supports independence, such as finger foods for those who have difficulty using utensils.
Transparent Communication with Families
Regular updates and open communication between caregivers and families are essential for peace of mind. Facilities offering Alzheimer’s care in Highland Village should provide detailed reports on your loved one’s condition, progress, and any changes in care plans. Family involvement in decision-making ensures a more personalized approach.
Choosing Between Full-Time Care and Daycare Services
Deciding whether to opt for full-time Alzheimer’s care or daycare services depends on your loved one’s needs and your circumstances. Full-Time Care: Ideal for individuals in advanced stages of Alzheimer’s who require 24/7 support, comprehensive medical attention, and a secure environment. Daycare Services: A great option for those in earlier stages of the disease who can benefit from structured daytime activities while returning home in the evenings. It also provides caregivers with much-needed respite.
Finding the Right Fit in Highland Village
There are Alzheimer’s care options in Highland Village designed to meet diverse needs. Take the time to visit potential facilities, ask questions, and observe how staff interact with residents. A facility’s ability to provide safety, personalized care, and a nurturing environment will play a significant role in enhancing your loved one’s quality of life. By focusing on these eight factors, you can make an informed decision and ensure that your loved one receives the care, respect, and dignity they deserve.
-
 @ f8a5df57:b7a58cd4
2024-11-29 09:46:35
@ f8a5df57:b7a58cd4
2024-11-29 09:46:35Сегодня мы отмечаем важный день в истории нашей страны — День Конституции России! 12 декабря 1993 года была принята основная закон, который стал основой для формирования правового государства и гарантии прав и свобод граждан.
Конституция — это не просто документ, это символ нашей независимости, единства и стремления к справедливости. Она защищает наши права, устанавливает основные принципы демократии и обеспечивает стабильность в обществе.
В этот день мы можем гордиться тем, что живем в стране, где уважаются права человека и ценятся свободы. Давайте помнить о важности соблюдения Конституции и активно участвовать в жизни нашего общества.
Поздравляем всех с этим знаменательным днем! Пусть каждый из нас будет не только гражданином своей страны, но и активным участником её развития!
Автор: Рината Ситникова
-
 @ f8a5df57:b7a58cd4
2024-11-29 09:45:22
@ f8a5df57:b7a58cd4
2024-11-29 09:45:22Этой осенью Москве исполнится 917 лет! Мы провели аналитику культурной сферы нашей столицы. В ближайшие десятилетия мы можем ожидать значительных трансформаций, связанных с внедрением новых технологий. Давайте рассмотрим, как они помогут сформировать культурный ландшафт столицы.
- С развитием цифровых технологий искусство становится более доступным. Художники и музыканты смогут использовать новые цифровые платформы для распространения своих работ( Например, будет активно работать "Творческий портал", созданный для обмена идеями и проектами), что позволит творческим людям находить аудиторию не только в России, но и за её пределами.
- Искусственный интеллект (ИИ) уже активно используется в различных областях искусства — от создания музыки до генерации визуальных произведений. В Москве мы можем увидеть рост числа проектов, где ИИ будет выступать в роли соавтора художников и композиторов, открывая новые горизонты для творчества и экспериментов.
- Технологии виртуальной (VR) и дополненной реальности (AR) обещают изменить восприятие искусства и культуры. Музеи и театры смогут создавать погружающие опыты, позволяя зрителям стать частью произведения. Например, выставки будут включать интерактивные элементы, которые погрузят зрителя в другой мир.
- С учетом глобальных вызовов, связанных с изменением климата, культура в Москве может начать активно интегрировать принципы устойчивого развития. Новые технологии помогут создавать экологичные проекты в архитектуре, дизайне и искусстве. Например, использование переработанных материалов или создание инсталляций, поднимающих вопросы экологии, станут всё более актуальными.
Автор: Рината Ситникова
-
 @ 5b00bf35:a877c578
2024-11-29 09:14:02
@ 5b00bf35:a877c578
2024-11-29 09:14:02Da cyklen først blev introduceret i det 19. århundrede, blev den mødt med både begejstring og frygt. På trods af dens potentiale til at revolutionere transport og fritid, rejste dens ankomst en række bekymringer blandt befolkningen.
Sundhedsmyter og frygt
En af de mest udbredte myter var "cykelansigt," en påstået tilstand, hvor ansigtet blev forvredet af anstrengelse. Især kvinder blev advaret mod cykling, da det blev hævdet, at det kunne skade deres forplantningsevne og gøre dem ude af stand til at få børn. Mænd blev heller ikke skånet – nogle frygtede, at sadlen kunne skade deres kønsorganer eller føre til impotens. Derudover mente kritikere, at cykling kunne føre til overanstrengelse for både mænd og kvinder, hvilket ville skade deres helbred på lang sigt.
Sociale normer udfordret
Cyklen symboliserede frihed, men denne frihed skræmte mange. For kvinder var cyklen en vej til uafhængighed, hvilket udfordrede traditionelle kønsroller. Dette vakte moralsk panik, især fordi cykling ofte krævede praktisk tøj som bukser eller korte skørter, som mange betragtede som uanstændigt. Samtidig blev cyklen i starten set som en luksusvare, der kun var for de velhavende, hvilket skabte bekymringer om, at den kunne forstærke klasseskel. Da cykler blev mere tilgængelige, opstod der derimod frygt for, at lavere klasser ville bryde de sociale normer ved at efterligne de riges mobilitet.
Teknologisk skepsis og sikkerhed
Tidlige modeller som penny-farthing var notorisk farlige, og mange advarede om risikoen for alvorlige ulykker. Kritikken handlede ikke kun om personlige skader – nogle mente også, at cyklister ville skabe kaos på vejene. Med fodgængere, heste og vogne i forvejen på vejene frygtede man, at cykler ville forstyrre den eksisterende trafik og føre til farlige situationer.
Æstetik og moral
Ud over de sociale og sikkerhedsmæssige bekymringer blev cyklen også kritiseret for sin æstetik. Den fremadlænte kropsholdning, som cykling krævede, blev betragtet som uskøn og upassende – især for kvinder i kjoler. Samtidig blev det praktiske tøj, som mange kvinder begyndte at bære under cykling, set som en trussel mod moral og anstændighed.
Økonomiske og miljømæssige bekymringer
Cyklen skabte også modstand blandt erhvervsfolk, især hesteopdrættere og karetmagere, der frygtede at miste deres kunder. Kritikerne spredte derfor negativ propaganda om cykler. Derudover hævdede nogle, at cykler ville forårsage skade på vejene, især på grus- og brostensbelagte stier, hvilket ville føre til øgede vedligeholdelsesomkostninger.
Psykologiske effekter
Flere frygtede, at cykling kunne blive en slags afhængighed, der ville få folk til at forsømme deres ansvar. Kvinder blev især advaret mod at lade cyklen føre dem væk fra hjemlige pligter. Samtidig mente nogle kritikere, at cyklen kunne føre til isolation og antisocial adfærd, da cyklister ofte rejste alene eller i små grupper og dermed fjernede sig fra det traditionelle fællesskab.
En ny æra trods modstanden
På trods af frygten banede cyklen vejen for sociale og teknologiske fremskridt. Den blev hurtigt anerkendt som et effektivt, sundt og tilgængeligt transportmiddel. Ikke mindst spillede den en central rolle i kvinders kamp for større frihed og ligestilling.
I dag er cyklen ikke bare et transportmiddel, men et symbol på frihed og innovation, der har overvundet datidens myter og modstand.
LOLSTR #FUD #BH872.450
-
 @ e077f063:49dc180e
2024-11-29 09:10:15
@ e077f063:49dc180e
2024-11-29 09:10:15Инженеры Югорского госуниверситета протестировали роботов–оленей, прошитых чипом с искусственным интеллектом. Обновленная версия отличается системой хранения энергии — она позволяет роботам беспрерывно функционировать даже в 30-градусные морозы. О разработке «КиберХанты — 2040» рассказал профессор лаборатории ЮГУ Михаил Новиков.
«Мы использовали легкие и прочные материалы, чтобы добиться максимальной подвижности роботов. Модель оснастили экосистемой для сбора и хранения солнечной энергии, что позволит ей работать автономно в условиях сурового климата. Новые кибер–олени не будут разряжаться на морозе, как это было раньше», — прокомментировал Новиков.
Ученые также проработали функцию гибридного использования роботов–оленей с нартами. Механизм планируют использовать на главном стойбище ХМАО вовремя турсезонов. «Олени отлично справляются с ролью гида на стойбище. Благодаря искусственному интеллекту они могут подсказать туристам, как, например, заселиться в чум или зарегистрироваться на сеанс к шаману. Но из-за морозов они часто отключались — мы нашли способ решить эту проблему. Теперь они еще и совместимы с нартами. У туристов теперь новое развлечение появилось», — добавил собеседник агентства.
Прокатиться в нартах, запряженных новейшими роботами–оленями, туристы смогут после Нового года. Разработчики планируют запустить серийное производство моделей уже в декабре.
Первого робота–оленя в ХМАО изобрели еще в 2031 году — на год позже после запуска этностойбища в Самаровском Чугасе. Тогда они учились общаться с людьми с помощью искусственного интеллекта.
*Агентство выдуманное и является студенческим проектом. Новостная лента не содержит цели ввести читателя в заблуждение

-
 @ e077f063:49dc180e
2024-11-29 08:55:05
@ e077f063:49dc180e
2024-11-29 08:55:05В Ханты-Мансийске появилась новая технология, которая позволяет наносить традиционные хантыйские узоры на одежду с помощью лазера. Местные мастера, дизайнеры и ученые объединились, чтобы найти способ создавать национальные наряды быстрее и современнее.
Новую технологию презентовали на кибервыставке в "Югра-Экспо". На глазах десятков зрителей лазер за 5-10 минут нанес узоры, которые хантыйские женщины вышивают месяцами. Новая технология позволяет ускорить процесс создания национальной одежды коренных народов и поставить ее производство на поток.
«Мы хотим сохранить наши традиции и адаптировать их к современным условиям. Лазерная технология открывает новые возможности для творчества и позволяет создавать уникальные вещи, которые будут интересны как местным жителям, так и туристам», – рассказала дизайнер одежды Анастасия Кузнецова.
Ученые из Югорского НИИ информационныз технологий, которые разработали лазер, добавили, что инновационная технология помогает уменьшить отходы и улучшить качество одежды. «Мы провели много исследований, чтобы убедиться, что наши узоры не только красивые, но и долговечные», – отметил профессор Сергей Иванов.
В течение 2-3 месяцев планируется запуск новой линии одежды с хантыйскими узорами, которая появится в магазинах Ханты-Мансийска и других городов региона. Это поддержит местных производителей и привлечет внимание к культуре ханты.
https://sun9-30.userapi.com/impg/BPSd8VJdlYAwz-Y7Cnkmb3mO5I3U-HxXobgs8A/sQoSUanJCBQ.jpg?size=1152x896&quality=95&sign=983c9658b2853c403e36f5dfdf9692bd&type=album
-
 @ a012dc82:6458a70d
2024-11-29 08:21:10
@ a012dc82:6458a70d
2024-11-29 08:21:10Table Of Content
-
The SEC's Stance on Bitcoin ETFs
-
The Role of ARK Invest and BlackRock
-
The Potential Impact of a Spot Bitcoin ETF Approval
-
The Case of Grayscale Bitcoin Trust
-
The Potential Sell-Pressure
-
Conclusion
-
FAQ
Exchange-traded funds (ETFs) have become a popular investment vehicle, offering exposure to a variety of asset classes. A spot-based Bitcoin (BTC) ETF could revolutionize the cryptocurrency market by making the asset more accessible to individual investors and mutual funds. Unlike a futures-based Bitcoin ETF, a spot-based ETF involves the actual purchase of BTC, providing direct exposure to the asset's price movements. However, the approval of the first Bitcoin ETF might not necessarily be a bullish event. It could introduce new dynamics into the market, potentially leading to increased volatility.
The SEC's Stance on Bitcoin ETFs
Over the years, the United States Securities and Exchange Commission (SEC) has maintained a conservative stance towards Bitcoin ETFs. Every Bitcoin ETF applicant has faced rejection, with the latest denial issued to the VanEck Bitcoin Trust on March 10, 2023. The SEC's primary concern has been the lack of a “comprehensive surveillance-sharing agreement with a regulated market of significant size related to spot Bitcoin." This has led to hesitancy in releasing what many believe would be a more equitable and transparent Bitcoin product, potentially opening the doors to a broader range of investors.
The Role of ARK Invest and BlackRock
Despite the SEC's past rejections, investment firms continue to pursue the creation of Bitcoin ETFs. ARK Invest and BlackRock, two prominent asset management firms, have recently submitted bids to launch spot Bitcoin ETFs. These proposals have sparked renewed interest in the possibility of a Bitcoin ETF, with investors speculating that these firms might offer a solution to Grayscale’s Bitcoin Trust (GBTC), an investment vehicle with shares traded on the stock exchange. Following BlackRock's ETF filing announcement, the GBTC “premium” jumped to its best levels in months, indicating heightened market anticipation.
The Potential Impact of a Spot Bitcoin ETF Approval
While the potential approval of a spot Bitcoin ETF might seem bullish initially, its consequences for the BTC price can be negative, at least in the short term. An ETF is a form of security that holds diverse underlying investments, such as commodities, stocks, and bonds. Its issuer pools and manages the given assets, providing investors with a way to gain exposure to a diversified portfolio through a single investment. However, the introduction of a Bitcoin ETF could lead to increased selling pressure, potentially driving down the price of Bitcoin in the short term.
The Case of Grayscale Bitcoin Trust
The Grayscale Bitcoin Trust, an investment fund with $18.4 billion of assets under management, offers a precedent for Bitcoin investment funds. However, it is currently trading at a -30% discount versus its Bitcoin holdings. This gap between their 626,778 Bitcoin at market value and the GBTC shares trading on regular stock exchanges reached as low as -49% in December 2022. This discount is likely justified as the instrument lacks the tools to allow arbitrage, highlighting the potential challenges and complexities of managing a Bitcoin investment fund.
The Potential Sell-Pressure
If the SEC grants the asset manager Grayscale permission to convert its GBTC Trust to a bonafide Bitcoin ETF, a considerable amount of BTC could enter the market as investors will finally be able to exit their position at par. This could produce significant sell-pressure from Grayscale’s GBTC conversion as Bitcoin that’s been locked for three to eight years reenters the market. This influx of Bitcoin could lead to a temporary oversupply, potentially driving down prices.
Conclusion
The approval of a Bitcoin ETF could have significant implications for the market. While it might initially seem like a positive development, it could lead to a significant sell-off in the short term. As always, investors should carefully consider their options and seek professional advice before making any investment decisions. The dynamics of the cryptocurrency market are complex and constantly evolving, and the introduction of a Bitcoin ETF would add another layer to this complexity.
FAQ
What is a Bitcoin ETF? A Bitcoin ETF is an exchange-traded fund that tracks the price of Bitcoin. It allows investors to buy into the ETF without having to deal with the complexities of owning and storing Bitcoin itself.
Why has the SEC been rejecting Bitcoin ETF applications? The SEC has been rejecting Bitcoin ETF applications due to concerns about market manipulation and fraud. They have stated that the applicants did not have a “comprehensive surveillance-sharing agreement with a regulated market of significant size related to spot Bitcoin."
What is the role of ARK Invest and BlackRock in Bitcoin ETFs? ARK Invest and BlackRock are asset management firms that have submitted bids to launch spot Bitcoin ETFs. Their involvement has sparked renewed interest and hope in the possibility of a Bitcoin ETF.
What could be the impact of a Bitcoin ETF approval? While the approval of a Bitcoin ETF could make Bitcoin more accessible to investors, it could also lead to increased selling pressure, potentially driving down the price of Bitcoin in the short term.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 4fcac000:d2b37988
2024-11-29 07:40:54
@ 4fcac000:d2b37988
2024-11-29 07:40:54Красивые Места Тюмени для Выдающихся Фотографий на Празднике Улыбки! 📸
Тюмень 2040 года готова удивить вас своими живописными уголками, идеально подходящими для создания незабываемых фотографий. В рамках Праздника Улыбки мы предлагаем вам посетить следующие места:
++Набережная реки Тура: ++Это уникальная четырехуровневая набережная с гранитными пешеходными зонами и каскадным фонтаном. Здесь можно сделать потрясающие снимки на фоне вечерней иллюминации и живописных видов. ++Мост Влюбленных:++ Романтический пешеходный мост, освещенный яркими огнями, создает идеальные условия для фото с любимыми. Не забудьте запечатлеть момент на фоне его красочных огней! ++Знаменский Кафедральный Собор++: Этот величественный белоснежный храм с синими куполами станет великолепным фоном для ваших фотографий. Его архитектура восхищает и привлекает внимание. ++Памятник Маме: ++Трогательный памятник в центре города окружен зелеными насаждениями и цветами, создавая атмосферу уюта и тепла — отличный выбор для семейных фото. ++Площадь Борцов Революции:++ Здесь расположены оригинальные фонтаны и памятники, которые станут интересным дополнением к вашим снимкам. Особенно эффектно выглядит фонтан-карта Тюменской области.

 Не упустите возможность запечатлеть яркие моменты на фоне этих красивых мест Тюмени! 🌟 #Тюмень #ПраздникУлыбки #Фотографии
Не упустите возможность запечатлеть яркие моменты на фоне этих красивых мест Тюмени! 🌟 #Тюмень #ПраздникУлыбки #Фотографии -
 @ 4fcac000:d2b37988
2024-11-29 07:38:22
@ 4fcac000:d2b37988
2024-11-29 07:38:22В 2040 году Тюмень готовится к уникальному событию —++ фестивалю "Тюменские Сказки", который пройдет с 15 по 20 августа.++ Это масштабный культурный проект, объединяющий туризм, искусство и традиции региона!
Почему стоит посетить? Живые легенды: На фестивале вы сможете встретиться с местными сказителями и услышать удивительные истории о Тюмени.
Мастер-классы: Уникальная возможность научиться традиционным ремеслам, таким как гончарное дело и ткачество.
Кулинарные изыски: Дегустация блюд сибирской кухни от лучших шеф-поваров региона. Памятники под открытым небом: Специальные экскурсии по историческим местам города, включая Знаменский собор и набережную Туры.
Не упустите шанс погрузиться в атмосферу сказок и открыть для себя Тюмень с новой стороны!
#ТюменскиеСказки #Туризм #Культура
-
 @ 2063cd79:57bd1320
2024-11-29 07:34:58
@ 2063cd79:57bd1320
2024-11-29 07:34:58Ganz laienhaft gesprochen, sind Derivate Finanzprodukte, die auf einem Basisprodukt basieren (in unserem Fall ist dieses Basisprodukt der Bitcoin-Hashpreis). Derivate werden von diesem Basisprodukt abgeleitet, oder deriviert, damit man das Produkt indirekt handeln kann. Derivate werden meist zu zwei Zwecken gehandelt, entweder zur Absicherung oder zur Spekulation.
https://archive.ph/95gBf
Wie den verlinkten Nachrichten zu entnehmen ist, haben Luxor Technologies einen sogenannten Hashprice NDF lanciert, also einen Non-Deliverable Forward Contract. Bei Derivaten gibt es alle möglichen Formen und Arten von Verträgen, die das Basisprodukt indirekt handeln. Eine gängige Form bilden dabei Terminkontrakte, sogenannte Futures und Forwards.
💡 Futures sind eine Form von Derivaten, die Parteien verpflichten, einen Vermögenswert zu einem vorher festgelegten zukünftigen Datum und Preis zu handeln. Hier muss der Käufer den Basiswert zum festgelegten Preis kaufen oder dem Verkäufer verkaufen, unabhängig vom aktuellen Marktpreis zum festgelegten Zeitpunkt der Abwicklung.
Forwards hingegen stellen eine ähnliche Form von Terminkontrakten dar, die auch einen zukünftigen Preis zu einem zukünftigen Datum festlegen, nur dass Forwards außerbörslich (OTC) gehandelt werden. Hinzu kommt, dass Forwards anpassbare Bedingungen haben, die zwischen den Parteien und dem Händler individuell vereinbart werden. Forwards sind im Gegensatz zu Futures nicht standardisiert.
Das heißt, der Luxor Hashprice NDF ist nichts anderes, als ein Vertrag zwischen einem Käufer und einem Verkäufer, die sich verständigen, das Basisprodukt (Bitcoin-Hashpreis) zu einem bestimmten Preis an einem festgelegten Fälligkeitsdatum zu handeln. Da es schwierig ist Hashpreis zwischen Verkäufer und Käufer auszuliefern, wird in diesem Fall ein Non-Deliverable Forward (NDF) genutzt.
💡 Ein Non-Deliverable Forward (NDF) ist in der Regel kurzfristiger Terminkontrakt, der in Bar abgerechnet wird. Das zugrunde liegende Produkt wird nie ausgetauscht, daher der Name „nicht lieferbar“. Zwei Parteien einigen sich darauf, gegensätzliche Seiten einer Transaktion für einen festgelegten Geldbetrag zu übernehmen. Dies bedeutet, dass die Parteien die Differenz zwischen dem vertraglich vereinbarten (NDF) Preis und dem tatsächlichen Marktpreis abrechnen. Der Gewinn oder Verlust wird anhand des Nominalbetrags der Vereinbarung berechnet, indem die Differenz zwischen dem vereinbarten Kurs und dem Marktkurs zum Zeitpunkt der Abwicklung genommen wird.

Die gesamte Transaktion wird also anstatt in Bitcoin-Hashpreis in einer konvertierbaren Währung abgerechnet. In diesem Fall ist es möglich, den Vertrag in US Dollars, Bitcoin oder US Dollar Stablecoins zu begleichen. Das bedeutet einfach gesprochen, Verkäufer und Käufer einigen sich auf einen bestimmten Preis in der Referenzwährung für eine bestimmte Höhe an Bitcoin-Hashpreis. Bei Fälligkeit wird der vereinbarte Preis mit dem Referenzpreis des jeweiligen Tages verglichen. Generell kann dies ein vom Herausgeber des Kontrakts festgesetzter Tageskurs sein, Luxor bedient sich hier des Bitcoin Hashprice Index. Dazu gleich mehr. Die Differenz zwischen dem vorab vereinbarten Preis und dem Referenzpreis wird am Fälligkeitstag in der konvertierbaren Währung abgerechnet.

Da wir nun die technische Komponente abgehakt haben, können wir uns dem Luxor Hashprice NDF im Detail widmen.
Der Luxor Hashprice NDF soll es Minern ermöglichen, ihr Risiko gegenüber dem Bitcoin-Preis und den steigenden Energiekosten abzusichern, sogenanntes Hedging gegen Verluste aus diesen unbeeinflussbaren Preisfaktoren. Häufig verwenden institutionelle oder Einzelhändler Derivate (vornehmlich Optionen und Terminkontrakte), um Absicherungsstrategien zu entwickeln, die das Risiko einen Kursverlusts des Bitcoin-Preises mindern. Mit diesem Produkt haben jetzt Miner zum ersten Mal Zugriff auf ein Instrument, das speziell auf ihre Bedürfnisse angepasst ist. Luxor gehen davon aus, dass wie traditionelle Rohstoff- und Energieproduzenten, auch Bitcoin-Miner wahrscheinlich zu großen Nutzern von Derivaten werden. Traditionelle Hersteller bedienen sich sehr anspruchsvollen und hoch entwickelten Hedging-Strategien (sei es mit Futures, um Preise zu sichern, oder mit Optionen, um Verluste abzusichern), um sich vor Volatilität bei Vorprodukten, Energiepreisen und Preisschwankungen der eigenen Produkte zu schützen. Außerdem können Miner mit diesem Mittel dringend benötigtes Geld aus dem Verkauf von Wetten auf die zukünftige Produktion erhalten oder ihre zukünftige Produktion zu einem festen Preis sichern.

Bislang nutzten Miner hauptsächlich Optionen, um Risiken im Zusammenhang mit der Preisvolatilität auszugleichen, indem sie sich die Reserven in ihren Bilanzen zu eigen machten. Allerdings sind Miner nun mehr und mehr gezwungen, ihre Reserven zu liquidieren, um Fälligkeiten zu begleichen und Betriebskosten zu decken, wenn der Preis von Bitcoin, bzw. der Hashpreis, weiter fällt (siehe //Secondi).
Doch nicht nur Miner profitieren von diesem neuen Finanzprodukt, denn auch Händlern wird ermöglicht, auf die von den Minern erzielten Einnahmen zu spekulieren und somit am Mining-Markt zu profitieren, ohne direkt in Mining-Equipment investieren zu müssen. Mit dem Hashprice NDF haben Luxor eine neue Investitionskategorie im Bitcoin-Finanzspektrum geschaffen, dass sicherlich auch Investoren interessieren könnte, die sonst die Nähe zum Mining-Sektor vermieden haben.
[H]ashprice derivatives are the apotheosis of our vision of hashrate as an asset class, something we’ve been pioneering since we introduced hashprice with the launch of Hashrate Index in 2020.” - Nick Hansen, CEO Luxor
Doch wie genau sieht so ein Terminkontrakt genau aus? Zunächst mal wieder ein paar Basisfakten:

Bei Vertragsabschluss stimmt eine Partei, der Käufer, zu, den Hashpreis zu einem späteren Zeitpunkt zu einem bestimmten Preis vom Verkäufer, dem Miner, zu kaufen. Da der Hashpreis NDF ein OTC-gehandelter Vertrag ist, kommt er mit Hilfe von Luxor zustande, die als Broker fungieren.
💡 Ein OTC-gehandelter Vertrag ist ein Finanzkontrakt, der nicht an einer Wertpapierbörse gehandelt wird. OTC-Derivate sind stattdessen private Verträge, die zwischen Kontrahenten ausgehandelt werden, ohne eine Börse oder andere formelle Vermittler zu durchlaufen, obwohl ein Broker/ Makler bei der Organisation des Handels behilflich sein kann.
Luxor kümmert sich dabei neben dem Order-Matchmaking um das Counterparty-Risk und die Zahlungsabwicklung bei Ablauf des Vertrags. Forwards können also von den Vertragsparteien beliebig lang oder kurz laufen, allerdings beträgt die übliche Dauer, laut Matthew Williams, der das Derivategeschäft von Luxor leitet, für einen Hashprice NDF in der Regel 30 Tage.
Luxor haben sowohl den Begriff Hashpreis geprägt, als auch den Bitcoin Hashprice Index erschaffen.
💡 Wir wissen der Hashpreis brechnet sich aus Bitcoin Preis / Hashrate. Der von Minern generierte Umsatz pro Tera-Hash.
Beispiel: 0.20 US Dollar pro Tera-Hash/Sekunde pro Tag (0.20/TH/s/day)
Die Terminkontrakte werden anhand dieses Index von Luxor abgerechnet, und Anleger können wählen, ob sie in US Dollars, Bitcoin oder US Dollar Stablecoins abrechnen möchten. Der Einfachheit halber, wird der Index in Peta-Hash dargestellt (Peta-Hash/Sekunde/Tag), da die Darstellung in Tera-Hash/Sekunde/Tag zu kleinteilig wäre.
Wenn der abgeschlossene Vertrag ausläuft, wird der Hashpreis an dem festgelegten Tag mit dem Hashpreis des Vertrags verglichen. Ein Rechenbeispiel: Wenn der Verkäufer/ Miner weiß, dass 30 Tage lang ein Output von 50 Peta-Hash pro Sekunde (PH/s) erzeugt werden kann, kann er 1.500 (PH/s x Tage) Kontrakte zu 100 US Dollar pro PH/s/Tag verkaufen. Wenn bei Vertragsablauf der Abrechnungswert 70 US Dollar pro PH/s/Tag beträgt, profitiert der Miner von 45.000 US Dollar (100 US Dollar Marktpreis - 70 Dollar NDF-Preis = 30 US Dollar x 1.500 Kontrakte).
Andersrum, wenn der Hashpreis 100 US Dollar PH/s/Tag bei Vertragsablauf übersteigt, steckt der Käufer den Gewinn ein und der Verkäufer/ Miner muss die Differenz begleichen. Da der Vertrag Non-Deliverable ist, also das zugrunde liegende Produkt nie tatsächlich ausgetauscht wird, nimmt der Käufer keine physische Lieferung von Hashrate entgegen. Sondern die Differenz wird ausgezahlt.
Soviel erstmal zum Luxor Hashpreis NDF, dem ersten seiner Art auf dem Markt, obwohl das Unternehmen bereits angekündigt hat, es sei „das erste von vielen“ Derivate-Produkten, das Luxor bereits in diesem Jahr einführen will. Es bleibt abzuwarten, ob diese Art von Produkten Anklang findet, jedoch wurde, laut dem Unternehmen, im Vorfeld sehr viel Recherche bei potentiellen Kunden und Partnern betrieben, um eine Nachfrage und ein gewisses Bedürfnis nach Hedging-Möglichkeiten zu stillen. Ob das Produkt jedoch für einige Miner zu spät kommt, werden wir uns im zweiten Teil anschauen.
Einen anderen Weg hat schon vor einiger Zeit FTX, eine der größten Börsen, eingeschlagen, als sie 2020 die Einführung eines Hashrate-Futures ankündigten. Die Futures wurden nach der durchschnittlichen Difficulty pro Quartal bewertet. Um die unlesbaren Zahlen der Difficulty lesbar zu machen, wurde der Kontraktwert berechnet, indem die Difficulty durch 1 Billion geteilt wurde, um eine zweistellige Zahl zu erhalten, die es dem Kunden erleichtern sollte, den Wert nachzuvollziehen. Anders als bei den Luxor Forwards, verhielten sich diese Futures ein bisschen (lies: komplett) wie ein Wettschein auf eine sinkende oder steigende Difficulty im Zeitraum des nächsten Quartals. Doch dieses kurzlebige Unterfangen hielt nur für 3 Quartale, bevor es kommentarlos beendet wurde.
🫳🎤
In diesem Sinne, 2... 1... Risiko!

-
 @ 4fcac000:d2b37988
2024-11-29 07:34:55
@ 4fcac000:d2b37988
2024-11-29 07:34:55В 2040 году Тюмень демонстрирует значительные изменения в статистике бедности и богатства. По прогнозам, уровень бедности в регионе продолжит снижаться, и к этому времени ожидается, что только 9,8% населения будет жить за чертой бедности, что на 1,9% меньше по сравнению с прошлым. Это связано с ростом реальных доходов и повышением зарплат.
Согласно данным Росстата, в России в целом число людей с доходами ниже границы бедности составит около 15,7 млн, что соответствует 10,8% населения. Однако в Тюмени ситуация лучше: средний доход жителей составляет около 74,9 тыс. рублей, что выше среднероссийского уровня.
Основные факты о бедности и богатстве в Тюмени 2040: * Уровень бедности: Около 9,8% населения. * Средний доход: Примерно 74,9 тыс. рублей.
Число богатых: Увеличение числа высокодоходных домохозяйств благодаря экономическому росту и инвестициям в регион.
Социальные программы: Успешные инициативы по поддержке уязвимых групп населения способствуют снижению уровня бедности.
Эти изменения свидетельствуют о том, что Тюмень движется к более сбалансированному социальному развитию, где усилия по сокращению неравенства начинают приносить плоды.
-
 @ 4fcac000:d2b37988
2024-11-29 07:31:13
@ 4fcac000:d2b37988
2024-11-29 07:31:13Сегодня в центре внимания — Благотворительный фонд развития города Тюмени (БФРГТ), который стал катализатором перемен.
Основные инициативы: Грантовая лотерея: Активисты могут представить свои проекты и получить финансирование для реализации лучших идей. Экологическая революция: Молодежь участвует в акции "Зеленая Сила", проводя мероприятия по раздельному сбору отходов и привлекая внимание к экологии. Образовательные экспедиции: Фонд организует поездки для молодежи в экосистемы региона, обучая их защите природы.
Успехи фонда: Экодома: Пространства для сдачи вторсырья и мастер-классов по переработке. Поддержка талантов: Программы для детей из неблагополучных семей, предоставляющие доступ к искусству и спорту.
Эти инициативы делают Тюмень примером успешного взаимодействия общества и бизнеса в решении социальных проблем. Вместе мы строим город, где каждый может внести свой вклад! 💚 #ТюменьМеняется #СоциальныеИнициативы
-
 @ 4fcac000:d2b37988
2024-11-29 07:29:13
@ 4fcac000:d2b37988
2024-11-29 07:29:13Алексей, выпускник РНИМУ им. Н.И. Пирогова, основал Центр Инновационных Медицинских Технологий, где разрабатываются новые решения для диагностики и лечения заболеваний. Вклад в медицину
Алексей известен своими исследованиями в области молекулярной биологии и биоинформатики. Его команда разработала уникальную платформу, которая использует алгоритмы глубокого обучения для анализа медицинских данных, что позволяет значительно повысить точность диагностики. Благодаря его усилиям, Тюмень стала одним из первых городов, где внедрены умные медицинские устройства, способные предсказывать заболевания на основе анализа данных пациентов.
Принципы работы Доктор Захаров верит в пациентоцентричный подход и активно внедряет технологии, которые делают медицинские услуги более доступными для всех. Он часто проводит открытые лекции и семинары, делясь своим опытом с молодыми специалистами и студентами.
Личное вдохновение Алексей вырос в семье врачей и с детства мечтал о том, чтобы сделать медицину более эффективной. Его пример вдохновляет новое поколение врачей Тюмени стремиться к инновациям и улучшению здоровья населения.
Благодаря таким выдающимся личностям, как Алексей Захаров, Тюмень уверенно движется к будущему, где медицина становится доступной и высокотехнологичной для каждого!
-
 @ 4fcac000:d2b37988
2024-11-29 07:26:48
@ 4fcac000:d2b37988
2024-11-29 07:26:48Дорогие тюменцы! Мы рады сообщить, что в нашем городе успешно заработал ** Центр Инновационных Медицинских Технологий , который стал настоящим прорывом в сфере здравоохранения! 🎉 Что нового в центре?** Передовые медицинские приложения: Мы продолжаем развивать платформу "Телемед-72", которая теперь предлагает не только запись на прием, но и возможность получать консультации с использованием виртуальной реальности. Это позволяет пациентам получать медицинскую помощь, не выходя из дома.
Обучение врачей: Центр проводит регулярные курсы для медицинского персонала, обучая их использовать новейшие технологии, такие как искусственный интеллект для диагностики. Это значительно повышает качество обслуживания и сокращает время ожидания. **Исследования и разработки: ** Мы активно внедряем нейросети для мониторинга здоровья пациентов. Это позволяет врачам быстрее и точнее ставить диагнозы, а также предлагать индивидуализированные планы лечения.
Благодаря этим инновациям Тюмень становится одним из лидеров цифровизации здравоохранения в России! Давайте вместе сделаем нашу медицину еще более доступной и эффективной! 💚 #ТюменьЗдоровье #Инновации2040 #БудущееМедицины
-
 @ 4fcac000:d2b37988
2024-11-29 07:23:23
@ 4fcac000:d2b37988
2024-11-29 07:23:23Интервьюер: Добрый день, Анна! Спасибо, что согласились поговорить с нами. Вы — активист и человек с ограниченными возможностями. Расскажите, пожалуйста, о том, как вы оцениваете доступность городской среды в Тюмени. Анна: Добрый день! Спасибо за возможность поделиться своим мнением. В последние годы в Тюмени действительно сделано много для улучшения доступности. Я заметила, что многие общественные места стали более удобными — появились пандусы, тактильные плитки и специальные зоны для отдыха. Интервьюер: Это замечательно! А что вам особенно нравится в новых инициативах? Анна: Мне очень понравилось внедрение умных пешеходных переходов. Они делают пересечение дороги более безопасным. Также приложение "Тюмень без барьеров" стало настоящим помощником — теперь я могу заранее узнать, насколько доступно то или иное место. Интервьюер: Есть ли что-то, что еще нужно улучшить? Анна: Да, конечно. Несмотря на положительные изменения, остаются проблемы. Например, не все тротуары имеют хороший асфальт, и иногда пандусы расположены неудачно. Также важно обучать персонал в общественных местах о том, как помогать людям с ограниченными возможностями. Интервьюер: Какие шаги вы бы предложили для дальнейшего улучшения ситуации? Анна: Я бы предложила проводить регулярные проверки доступности общественных мест и организовывать встречи с людьми с ограниченными возможностями для обсуждения их потребностей. Также важно привлекать больше внимания к этой теме через СМИ и социальные сети. Интервьюер: Спасибо, Анна! Ваши идеи очень ценны. Надеемся, что Тюмень станет еще более доступным городом для всех! Анна: Спасибо вам! Я верю, что вместе мы сможем сделать наш город лучше!
-
 @ 4fcac000:d2b37988
2024-11-29 07:19:06
@ 4fcac000:d2b37988
2024-11-29 07:19:06Дорогие тюменцы! В нашем городе активно развиваются цифровые сервисы, которые делают жизнь комфортнее и удобнее. Вот несколько ключевых инициатив:
- Телемед-72: Мобильное приложение для записи на прием к врачу, которое за полгода 2024 года увеличило число пользователей на 26% до 570 тыс. человек. Услуги включают телемедицинские консультации и вызовы врача на дом
- Виртуальный консультант-72: Нейросетевая система, помогающая жителям получать госуслуги и записываться к специалистам, значительно упрощая взаимодействие с государственными учреждениями1.
- Интернет вещей: Внедрение умных технологий, таких как датчики для мониторинга состояния дорог и мусорных контейнеров, позволяет оперативно реагировать на проблемы и оптимизировать городские службы.
Эти решения делают Тюмень одним из лидеров цифровизации в России! 💻 #ЦифроваяТюмень #КачествоЖизни
-
 @ 4fcac000:d2b37988
2024-11-29 07:18:12
@ 4fcac000:d2b37988
2024-11-29 07:18:12Дорогие тюменцы! Мы рады сообщить, что в нашем городе стартует уникальная инициатива — "Зеленый Марафон Тюмени", который пройдет с 1 по 15 декабря 2040 года. Этот проект объединяет усилия местных компаний, направленных на защиту окружающей среды и устойчивое развитие.
Что такое "Зеленый Марафон"?
В рамках марафона бизнесы Тюмени будут соревноваться в реализации экологических инициатив, таких как: * Снижение углеродного следа: Компании представят свои планы по уменьшению выбросов CO2. * Переработка отходов: Участники марафона внедрят программы по сбору и переработке вторичных материалов. * Эко-образование: Местные предприниматели проведут мастер-классы и лекции для жителей о важности экологии.
Как участвовать?
Каждый тюменец может поддержать инициативы, участвуя в мероприятиях и голосуя за лучшие проекты. В конце марафона мы подведем итоги и наградим самые активные компании! Давайте вместе сделаем Тюмень еще более экологически чистым и комфортным городом! 💚
#ЗеленыйМарафон #ЭкологияТюмени #БудущееЗдесь
-
 @ 98589a2e:bf49daa1
2024-11-29 07:13:25
@ 98589a2e:bf49daa1
2024-11-29 07:13:25Санкт-Петербург 2040 года стал настоящим центром развлечений, где парки и аквапарки трансформировались в современные пространства для отдыха и активного досуга.
София Смирнова и Елена Грачевская записали для вас новый подкаст. На этот раз они обсудили, где петербуржцы смогут провести свои выходные.

Планы развития зон для развлечения к 2050 году
На горизонте 2050 года Санкт-Петербург планирует расширение своих зеленых зон и развлекательных объектов. В проекте нового генплана предусмотрено создание дополнительных тематических парков и пляжей вдоль Финского залива, что позволит жителям города наслаждаться природой и активным отдыхом еще больше. Ожидается также внедрение новых технологий в управление парками, что сделает их более интерактивными и удобными для посетителей. Таким образом, Санкт-Петербург продолжает развиваться как город с богатым выбором развлечений для всех возрастов и интересов.
-
 @ 4fcac000:d2b37988
2024-11-29 07:13:18
@ 4fcac000:d2b37988
2024-11-29 07:13:18Дорогие тюменцы! В нашем городе активно реализуются инициативы по созданию доступной среды для людей с ограниченными возможностями. Мы стремимся сделать Тюмень комфортным и дружелюбным местом для каждого! Что появилось с этой сфере за последние 20 лет? Умные пешеходные переходы: В этом году мы внедрили инновационные переходы, которые автоматически адаптируются к потребностям людей с ограниченными возможностями. Звуковые сигналы и световые индикаторы помогут безопасно пересекать дороги. Инклюзивные общественные пространства: В парках и скверах Тюмени появились специальные зоны для отдыха и активного времяпрепровождения, оборудованные тренажерами и игровыми площадками, доступными для всех. Мобильное приложение "Тюмень без барьеров": Это приложение предоставляет информацию о доступности общественных мест, маршрутов общественного транспорта и услуг, что позволяет людям с ограниченными возможностями планировать свои поездки без затруднений.
Присоединяйтесь к нам! Мы приглашаем всех тюменцев участвовать в обсуждении новых проектов и делиться своими идеями по улучшению доступной среды. Вместе мы можем создать город, где каждый чувствует себя комфортно и уверенно! 💙 #ДоступнаяТюмень #Инклюзия #ТюменьДляВсех
-
 @ 98589a2e:bf49daa1
2024-11-29 07:07:53
@ 98589a2e:bf49daa1
2024-11-29 07:07:53К декабрю 2040 года Санкт-Петербург стал центром новых торговых инициатив, что значительно изменило его коммерческий ландшафт. В результате реализации нового Генерального плана, принятого в 2023 году, в городе открылись несколько крупных торговых центров и магазинов, создающих новые возможности для жителей и гостей города.
Открытие новых торговых центров и магазинов
1. Торговый центр "Невский Гранд" - Местоположение: Центр города, на Невском проспекте - Площадь: 150 000 м² - Деятельность: Включает более 200 магазинов, рестораны, развлекательные зоны и кинотеатр. Здесь представлены как международные бренды, так и местные производители.
2. "ЭкоМаркет" - Местоположение: Приморский район - Площадь: 20 000 м² - Деятельность: Супермаркет, специализирующийся на экологически чистых продуктах и товарах местного производства. Открыт также центр по обучению потребителей принципам устойчивого потребления.
3. "ТехноГрад" - Местоположение: Московский район - Площадь: 30 000 м² - Деятельность: Специализированный магазин электроники и бытовой техники с возможностью тестирования товаров на месте и консультациями от экспертов.
Прогнозы развития до 2050 года
В Санкт-Петербурге ожидается дальнейшее развитие торговой инфраструктуры: - Увеличение торговых площадей: Прогнозируется открытие еще нескольких крупных торговых центров в новых жилых районах, что позволит создать дополнительные рабочие места и улучшить доступность товаров для населения. - Развитие онлайн-торговли: Ожидается активное внедрение технологий для улучшения онлайн-шопинга, включая расширение услуг доставки и интеграцию с местными магазинами. - Создание новых форматов торговли: Планируется развитие концепций "умных" магазинов с использованием технологий искусственного интеллекта для персонализированного обслуживания клиентов.
Основные направления развития: - Упор на экологические инициативы и устойчивое потребление. - Развитие мультифункциональных пространств, где будут сочетаться торговля, досуг и культурные мероприятия. - Инвестиции в цифровизацию торговли для повышения удобства покупок.

-
 @ 98589a2e:bf49daa1
2024-11-29 06:36:30
@ 98589a2e:bf49daa1
2024-11-29 06:36:30К декабрю 2040 года Санкт-Петербург стал центром новых производственных инициатив, что существенно изменило его экономический ландшафт. В результате реализации нового Генерального плана, который был принят в 2023 году и рассчитан до 2050 года, в городе открылись несколько крупных заводов, создающих тысячи рабочих мест и способствующих развитию различных секторов экономики.
Открытие новых заводов
1. Стекольный завод "ИнСтелРус" - Местоположение: Особая экономическая зона "Санкт-Петербург" - Инвестиции: 2,1 млрд рублей - Рабочие места: 185 - Деятельность: Производство цельностеклянных конструкций для строительства, лабораторий и "чистых" помещений. Открыт учебный центр по разработке стекольных конструкций.
2. Завод специализированного вентиляционного оборудования "Квантум" - Местоположение: Особая экономическая зона "Санкт-Петербург" - Инвестиции: 2,02 млрд рублей - Рабочие места: Ожидается создание около 150 рабочих мест. - Деятельность: Разработка и производство вентиляционного оборудования.
3. Заводы по производству экологически чистых упаковок - Местоположение: Приморский район - Инвестиции: 1,5 млрд рублей - Рабочие места: 200 - Деятельность: Производство упаковки из переработанных материалов для пищевой и непищевой продукции.
Прогнозы развития до 2050 года
В Санкт-Петербурге ожидается значительное расширение производственных мощностей: - Увеличение площади промышленных зон: Доля производственных территорий вырастет с 9,2% до 9,62%, что добавит около 630 гектаров для новых предприятий. - Создание новых рабочих мест: Прогнозируется открытие более 20 тысяч новых рабочих мест в различных отраслях, включая высокие технологии и экологически чистое производство. - Развитие транспортной инфраструктуры: Будет построено несколько новых транспортных развязок и станций метро, что улучшит доступ к новым заводам и снизит нагрузку на существующую инфраструктуру.
 Основные направления развития:
- Упор на импортозамещение и поддержку отечественного производства.
- Создание технопарков и научных учреждений рядом с новыми производствами для стимулирования инноваций.
- Развитие экологически чистых технологий и переход к устойчивым методам производства.
Основные направления развития:
- Упор на импортозамещение и поддержку отечественного производства.
- Создание технопарков и научных учреждений рядом с новыми производствами для стимулирования инноваций.
- Развитие экологически чистых технологий и переход к устойчивым методам производства. -
 @ 1ef695e1:15351d5f
2024-11-29 06:13:46
@ 1ef695e1:15351d5f
2024-11-29 06:13:46My Vietnam era Collins 637M-1 HF field antenna erected and tested. I could not find any information about the antenna on the internet, but I had feedback from hams on some of the Collins groups. The guy ropes were no longer to spec, so I replaced them with UV resistant polyester rope.
The transceivers normally used in conjuction with the antenna are the Collins AN/TRC-75, AN/TSC-15 and TRC-146.
A frequency range from 2 to 30MHz that operates as either a fan dipole with horizontal polarization or a top hat vertical monopole. The sectional vertical is a 50ohm feedline when used as dipole and the same vertical becomes a radiating element when coupled to the alternative feedpoint on the baseplate6.
The balun is a wire that is attached to the one side of the longer dipole and runs down the vertical through offsets to where it either connects to a lower section of the vertical or is disconnected and open.
 The antenna comes in an aluminum trunk with carry handles and erection is a two man task. The antenna is 12 meters high and can be rotated through 90 degrees by hand with a latch on the baseplate to give directional coverage.
The antenna comes in an aluminum trunk with carry handles and erection is a two man task. The antenna is 12 meters high and can be rotated through 90 degrees by hand with a latch on the baseplate to give directional coverage. The antenna can handle strong winds with four upper guys and four lower guys.
The antenna can handle strong winds with four upper guys and four lower guys.I found that the antenna tunes up easily for both horizontal and vertical use and test contacts were made on the 40 and 20m bands horizontal locally and on the 10m band DX to Europe vertical with readabilty and strength as expected from a widebanded military antenna.
 The original connectors (as seen in the manual photo) being impractical, were changed.
The original connectors (as seen in the manual photo) being impractical, were changed. Balun Switch
Balun Switchham
-
 @ 98589a2e:bf49daa1
2024-11-29 05:58:54
@ 98589a2e:bf49daa1
2024-11-29 05:58:54На минувших выходных эксперты Санкт-Петербурга провели дискуссию о том, какие социальные инициативы и изменения повлияли на жизнь горожан.
София Смирнова и Елена Грачевская обсудили эту тему. Подробности можно послушать в нашем подкасте.

-
 @ 7ec80607:128517c5
2024-11-29 05:27:06
@ 7ec80607:128517c5
2024-11-29 05:27:06Synthetic grass, also known as artificial turf, has become an increasingly popular choice for landscaping, sports fields, and residential lawns. It provides a low-maintenance, always-green solution that doesn’t require watering, mowing, or fertilizing. However, one common concern for homeowners and property managers considering synthetic grass is whether weeds can still grow through it. The question of whether weeds can penetrate artificial turf and how to prevent it is essential to understanding the full benefits of installing synthetic grass. In this article, we’ll explore whether weeds can grow through synthetic grass, the factors that contribute to weed growth in artificial turf, and the best methods for preventing or removing them.
Understanding Synthetic Grass
Before diving into the issue of weeds, it's important to understand how synthetic grass is constructed. Artificial turf consists of several layers designed to mimic the look and feel of real grass. These layers typically include:
- The Turf Fibers: The synthetic grass blades themselves are made from materials such as polyethylene or polypropylene, which are durable and UV-resistant.
- The Backing: The grass is attached to a backing material, which is usually made of latex or polyurethane. This backing allows for water drainage while keeping the grass securely in place.
- The Base Layer: Beneath the turf, a layer of crushed stone or gravel is often laid down to provide stability and proper drainage.
- Infill Material: Synthetic grass is usually filled with a layer of rubber or sand, which adds weight and helps the grass blades stand upright. Weeds typically grow from seeds in the soil, so understanding the structure of artificial turf helps clarify why weeds may or may not be able to grow through it.
Can Weeds Grow Through Synthetic Grass?
The short answer is that, under normal circumstances, weeds cannot grow through synthetic grass. The materials and layers used in artificial turf are designed to prevent weed growth. However, there are some important nuances to this answer that depend on various factors:
- Presence of Gaps or Seams: One of the main factors that could allow weeds to grow through synthetic grass is improper installation. If the turf is not laid down tightly and there are gaps between the turf layers or seams that aren't securely sealed, weeds can find their way through these openings. This is especially true if the base layer is not properly compacted or if weeds are already present in the soil beneath the turf.
- Weeds Around the Edges: Weeds can also grow along the edges of synthetic grass, where the turf is not perfectly sealed against the surrounding environment. If the edges of the synthetic turf are exposed to soil or untreated areas like flower beds, weeds can take root in these spaces and may eventually spread into the synthetic grass area.
- Weeds Growing on Top of the Turf: While weeds cannot grow through the synthetic grass, they can still sprout on top of it if the infill material (rubber or sand) provides enough organic material for weed seeds to settle in. This is more likely to happen in areas where the turf has accumulated debris, such as leaves or dirt. If weed seeds land on the surface of the turf and find suitable conditions (moisture, sunlight), they can germinate on top of the artificial grass. This is not truly “growing through” the turf but is still a form of weed growth.
-
Improper Maintenance: Another reason weeds may appear in synthetic grass areas is improper maintenance. Over time, dirt, leaves, and debris can accumulate on the surface of the artificial grass, providing a medium for weed seeds to germinate. If the turf isn’t regularly cleaned and maintained, this debris can create a suitable environment for weeds to grow. How to Prevent Weeds from Growing in Synthetic Grass While synthetic grass is designed to minimize weed growth, there are still steps you can take to ensure that your lawn stays pristine and free of unwanted plants. Here are some methods for preventing weeds from growing in artificial turf:
-
Proper Installation The first line of defense against weed growth is ensuring that the synthetic grass is installed correctly. This involves properly preparing the base layer and ensuring that the turf is laid tightly to avoid gaps. A weed barrier fabric, typically made of a geotextile material, should be installed beneath the turf to prevent weed seeds from sprouting in the soil below. Additionally, the infill material should be applied evenly to provide the necessary weight and support to the grass blades, preventing them from shifting or lifting. When these steps are followed carefully, weeds have little chance of growing in or under the turf.
- Regular Cleaning and Maintenance One of the most effective ways to prevent weed growth is by regularly cleaning and maintaining your synthetic grass. Over time, organic material like leaves, twigs, and dirt can accumulate on the surface, providing a fertile ground for weeds. Raking or using a leaf blower to remove this debris regularly will help prevent weed seeds from settling on the turf. In addition to cleaning, it's essential to rinse the turf periodically with water to remove dust and dirt that may have settled into the infill. This will keep your synthetic grass looking fresh and reduce the chances of weeds sprouting.
-
Weed Treatment Solutions If you find that weeds have already started to grow in or around your artificial grass, there are several weed treatment options available. Chemical herbicides are one option, but many homeowners prefer to avoid chemicals due to environmental concerns. Instead, organic or natural herbicides, such as vinegar or citrus-based solutions, can be effective in killing weeds without harming the turf. For weeds growing around the edges or seams of the turf, using a weed barrier or applying mulch can help keep the surrounding soil clear. If weeds have already taken root, you can manually pull them out, making sure to remove the entire root to prevent regrowth.
-
Install a Weed Barrier As mentioned earlier, a weed barrier fabric is one of the most effective ways to prevent weed growth beneath synthetic grass. This fabric is installed underneath the base layer of the turf, creating a physical barrier that blocks weeds from penetrating the surface. Weed barrier fabrics are typically made from woven or non-woven polypropylene and allow water to drain through while preventing weeds from sprouting up through the turf.
- Edge Sealing Properly sealing the edges of your synthetic turf can also prevent weeds from infiltrating from the outside. This can be done by ensuring that the edges are securely fastened to the ground or by using edging materials like concrete, stone, or plastic to create a barrier that prevents weed growth from spreading into the turf.
How to Remove Weeds from Synthetic Grass
If you notice weeds starting to grow through or around your synthetic grass, it’s important to address the issue quickly to prevent further growth. Here's how to effectively remove weeds: 1. Pull Weeds by Hand: For weeds that are growing through the seams or edges, carefully pull them out by hand. Be sure to remove the roots to prevent regrowth. 2. Use a Weed Killer: For more stubborn weeds, a non-toxic or organic weed killer can be used to kill the weeds without damaging the artificial turf. Apply the solution directly to the affected areas and allow it to work its magic. 3. Clean the Turf: After removing weeds, make sure to clean the artificial grass by brushing it, removing debris, and rinsing it with water. This will help ensure that the turf remains in good condition.
Conclusion
While synthetic grass is generally designed to prevent weeds from growing through it, several factors can allow weeds to appear, such as improper installation, gaps in the seams, or organic debris on the surface. By taking the necessary precautions during installation and committing to regular maintenance, you can prevent and manage weed growth in synthetic grass areas. A little attention to detail goes a long way in ensuring that your artificial turf stays weed-free and continues to provide an aesthetically pleasing, low-maintenance alternative to natural grass.
-
 @ 1cb14ab3:95d52462
2024-11-29 05:03:03
@ 1cb14ab3:95d52462
2024-11-29 05:03:03Projector, VDMX5, Final Cut Pro X, Satomizer, Processing, Pure Data, MadMapper, Cinema 4D, APC40. [100’ x 25’]
This project was presented in 2015 in Boulder, Colorado. Images and video remain property of Hes.
Artist Statement
Light Pollution: Group Exhibition
"Light Pollution" is a group exhibition that investigates the influence of artificial light on the natural environment. As part of this exhibition, I transformed the CU Boulder campus's Engineering Complex into a dynamic canvas through projection mapping. My contribution, a 100ft+ projection on the complex's tallest spire, featured the video "Superintended Vanquishment". This piece showcased engineering failures caused by natural forces, prompting viewers to contemplate the environmental repercussions of human activities and the potential consequences of nature's retaliation. The projection not only illuminates the impact of light pollution on our surroundings, but also prompts a deeper reflection on our relationship with the natural world and the power of nature over humans.
The "Light Pollution" group exhibition was a thought-provoking and visually stunning exploration of the impact of artificial light on the natural environment. Through the use of projection mapping, video content, and immersive sound design, the artists aimed to create an unforgettable experience that would inspire viewers to think more deeply about our relationship with the environment and the impact of humans on the natural world.

Superintended Vanquishment: Short Film
‘Superintended Vanquishment’ is a digital media project that showcases modern engineering failures onto the very building where the future engineers of tomorrow are studying. The Engineering Complex at CU Boulder serves as the backdrop for this thought-provoking piece. The irony lies in the fact that the video, which depicts engineering disasters caused by natural forces, is projected onto the building where students are learning about engineering.
By using this content, I wanted to challenge viewers to think about the consequences of our actions on the environment and the delicate balance between human development and natural systems.
This project ties into the theme of light pollution by highlighting the impact of artificial light on both humans and nature. While humans have made great strides in engineering, nature still holds the power to reclaim what's hers. The video features scenes of engineering failures, such as a dam collapsing due to a flood, a building destroyed by an earthquake, and a bridge washed away by a landslide. The film serves as a reminder of the fragility of human creations and the power of nature.
The projection itself is striking, with the video mapped onto the Engineering Complex's tallest spire. The lighting effects and surround sound speakers create an immersive experience for viewers, allowing them to feel as if they're part of the scene. This visual and auditory display invites viewers to reflect on the consequences of human actions on the environment and the delicate balance between human development and natural systems.
Ultimately, the project underscores the notion that, despite our technological advancements, nature will always have the final say.
Watch ‘Superintended Vanquishment’
nostr:naddr1qqrk7e24vekhvcspzpmhxue69uhkummnw3ezuamfdejsygquk99txdv8dly7lsmasw969p70zlj6mnxtyzlk6j0em2tft4fyvgpsgqqqskasrmevqw
Originally published in 2015 by Hes.
Republished to habla.news/u/hes@nostrplebs.com on 11/28/2024.
Find me elsewhere:
-
 @ fe7f6bc6:c42539a3
2024-11-29 01:54:31
@ fe7f6bc6:c42539a3
2024-11-29 01:54:31A few weeks ago, I sat down with Chad (full podcast), a seasoned Muay Thai fighter with over a decade of experience, to talk about life inside and outside the ring. Chad’s story is raw, intense, and unfiltered—a journey of struggle, discipline, and transformation. His insights left me reflecting on how combat sports, especially Muay Thai, can teach us profound lessons about resilience, focus, and the human spirit.
The Fight Beyond the Ring
What struck me most was how Muay Thai isn’t just a sport for Chad—it’s a way of life. He began his journey as a teenager, struggling with family issues and uncertainty about his future. A chance meeting led him to Thailand, where he trained intensely and fought his first bout just 28 days later. Chad told me, “Muay Thai saved my life,” and I could feel the weight behind those words.
For Chad, the ring became a space to confront not just opponents but his own fears and insecurities. The process of training—the relentless hill sprints, countless kicks, and sparring sessions—taught him how to face challenges head-on. Fighting wasn’t about aggression; it was about finding strength in adversity.
The Beauty in the Brutality
One of the most fascinating things Chad shared was his perspective on pain and sacrifice. During his career, he’s endured broken ribs, countless stitches, and even fought with a broken nose for eight years before getting it fixed. “Pain is the best teacher,” he said, explaining how injuries forced him to adapt and improve.
What I found most compelling was how this physical suffering seemed to heighten his appreciation for life. Chad described moments after brutal training sessions when even a sunset or a simple breeze felt extraordinary. It’s as if the harshness of the ring makes the world outside it feel brighter, sharper, and more alive. “When you’re ready to die in the ring,” he said, “you start seeing life differently.”
The Mental Battle
Chad emphasized the mental aspect of fighting, something I hadn’t fully appreciated before. He talked about the mindset required to step into the ring: the inner dialogue where you convince yourself you’re ready to endure pain and push beyond limits. “You can play football or tennis, but you can’t play Muay Thai,” he said, driving home the seriousness of the sport.
Before a fight, Chad uses visualization to prepare himself for the intensity of combat. He doesn’t shy away from the danger but instead leans into it, fully accepting the risks. This mindset, he believes, is what separates good fighters from great ones.
Lessons for Life
While most of us won’t step into a Muay Thai ring, Chad’s experiences offer valuable lessons that apply to all areas of life:
- Discipline Creates Freedom: The structure of relentless training gave Chad a sense of purpose and control over his life.
- Face Your Fears: Whether it’s an elbow to the face or a difficult decision in life, avoidance only makes things worse.
- Surround Yourself with the Right People: Chad stressed the importance of training with people who push you to be better. “Energy matters,” he said, and I couldn’t agree more.
Final Thoughts
Chad’s story reminded me why I wanted to take on my own Muay Thai journey. It’s not just about fighting; it’s about testing yourself in ways that reveal who you really are. For Chad, the ring isn’t just a place to compete—it’s a place to grow, to learn, and to become a better version of himself.
After our conversation, I realized that the lessons of Muay Thai go beyond the gym. Whether you’re training for a fight or tackling challenges in everyday life, the principles of resilience, discipline, and self-reflection are universal.
If you’re curious to learn more about Chad’s journey, I highly recommend watching the documentary we worked on together. It’s a glimpse into the raw, unforgiving world of Muay Thai—and the unshakable spirit of those who live it.
Stay Healthy - Max
-
 @ fa1d8325:7c91882e
2024-11-28 23:27:34
@ fa1d8325:7c91882e
2024-11-28 23:27:34Пятигорск активно внедряет передовые технологии в сельское хозяйство, что позволяет значительно повысить производительность и снизить затраты. Одним из ключевых направлений является использование роботов и дронов.
Программа «Умный хлеб», реализуемая при поддержке «Единой России», направлена на обучение фермеров применению роботов и искусственного интеллекта. Дроны используются для мониторинга полей, внесения удобрений и защиты от вредителей, что значительно облегчает работу и повышает эффективность.
Автономные системы управления сельхозтехникой на основе искусственного интеллекта способны увеличить производительность на 30–40% и значительно сократить эксплуатационные расходы.
Большинство фермерских хозяйств уже используют роботизированные системы для автоматизации различных процессов, что не только повышает урожайность, но и решает проблему нехватки рабочей силы.
Внедрение современных технологий в сельское хозяйство Пятигорска не только способствует повышению эффективности, но и позволяет значительно снизить затраты, а также увеличить урожаи.
-
 @ fa1d8325:7c91882e
2024-11-28 23:25:25
@ fa1d8325:7c91882e
2024-11-28 23:25:25В Пятигорске открылся уникальный ресторан «РобоРесторан», где все обслуживание гостей осуществляется роботами с искусственным интеллектом. Это заведение создано местной компанией-разработчиком, которая разработала роботов-поваров и официантов.
Роботы умеют распознавать речь и поддерживать беседу с посетителями, что создает непринужденную атмосферу. В «РобоРесторане» можно обсудить меню, узнать интересные факты о блюдах и даже поделиться шутками.
Одной из главных особенностей ресторана является открытая кухня, где гости могут наблюдать за работой роботов-поваров. Они готовят быстро и точно, обеспечивая качественный сервис. В меню представлены традиционные кавказские блюда и современные гастрономические изыски.
Создатели проекта стремились создать не только вкусное место для трапезы, но и уникальное пространство, где роботы взаимодействуют с людьми. Это делает посещение «РобоРесторана» незабываемым.
Уже сейчас ресторан пользуется большой популярностью среди посетителей, которые ценят возможность пообщаться с роботами. «РобоРесторан» обещает стать новой точкой притяжения для тех, кто ценит технологичные решения в сфере общественного питания.
-
 @ fa1d8325:7c91882e
2024-11-28 23:22:07
@ fa1d8325:7c91882e
2024-11-28 23:22:07В нашем сегодняшнем подкасте мы с радостью поговорим о том, как стремительно развивающиеся технологии меняют мир медицины. Эксперт в области здравоохранения поделится своими мыслями о том, как эти технологии влияют на повседневную практику врачей и как они могут сделать здравоохранение более качественным и эффективным.
Присоединяйтесь к нам, чтобы узнать, как инновации преобразуют эту отрасль и какие последствия это будет иметь для будущего медицины.
-
 @ fa1d8325:7c91882e
2024-11-28 22:53:35
@ fa1d8325:7c91882e
2024-11-28 22:53:35В Пятигорске объявлен конкурс на лучшую концепцию полностью «умного» жилого комплекса. Это событие обещает стать значительным шагом в развитии инновационной и комфортной городской среды.
Участники конкурса смогут представить свои проекты, направленные на создание смарт-инфраструктуры. Проекты будут включать в себя разработку систем управления и цифровых платформ, которые позволят создать современное жилое пространство с высокими стандартами комфорта и безопасности.
Победитель конкурса получит грант на реализацию своего проекта в одном из районов города. Это откроет новые горизонты для создания инновационных и уютных жилых комплексов, которые будут соответствовать самым высоким требованиям к качеству жизни.
Этот конкурс представляет собой важный этап в развитии «умных» городов в России. Он способствует разработке и внедрению новых технологий, которые сделают городскую среду более удобной, безопасной и экологичной.
Создание «умных» жилых комплексов не только улучшит качество жизни горожан, но и сделает городскую среду более привлекательной для жизни и инвестиций.
-
 @ fa1d8325:7c91882e
2024-11-28 22:34:02
@ fa1d8325:7c91882e
2024-11-28 22:34:02В городе Пятигорск состоялся поистине уникальный музыкальный концерт, который привлёк внимание любителей искусства и технологий со всего мира. На сцене Центра культуры и искусства выступила первая в мире робот-певица «Мелодия».
Этот прорыв в области искусственного интеллекта и технологий был создан командой учёных из Пятигорского государственного университета в сотрудничестве с местной компанией, занимающейся разработкой искусственного интеллекта. Робот-певица не только исполняет песни различных жанров, но и активно взаимодействует с аудиторией, отвечая на вопросы и даже шутя.
На концерте «Мелодия» исполнила популярные хиты, а также оригинальные композиции, созданные с помощью нейросетей. Зрители были поражены качеством её исполнения и эмоциональной выразительностью.
Один из разработчиков отметил, что цель создания «Мелодии» заключалась в том, чтобы продемонстрировать, как технологии могут влиять на искусство. Робот-певица — это не просто машина, это новый шаг в развитии музыкальной культуры.
Концерт прошёл в рамках фестиваля «Технологии и искусство», который проходил в Пятигорске. В рамках фестиваля были представлены выставки инновационных решений в сфере музыки и искусства, а также мастер-классы для молодёжи.
Появление «Мелодии» открывает новые горизонты для музыкальной индустрии. Этот уникальный проект вдохновляет молодых талантов на создание собственных проектов, где технологии встречаются с искусством.
-
 @ fa1d8325:7c91882e
2024-11-28 22:27:19
@ fa1d8325:7c91882e
2024-11-28 22:27:19Сегодня мы окунемся в мир удивительных технологий, которые меняют наше представление об образовании. В эпоху цифровых инноваций перед нами открываются безграничные возможности для обучения и развития: от интерактивных платформ до искусственного интеллекта. Эти технологии переворачивают подход к обучению, делая его более доступным и эффективным.
В этом видео мы подробно рассмотрим, как современные технологии помогают учителям и ученикам достигать новых высот. Вы узнаете о лучших примерах применения технологий в классах и о том, как они могут трансформировать наше понимание образования в будущем. Не упустите возможность узнать больше!
-
 @ fa1d8325:7c91882e
2024-11-28 22:19:29
@ fa1d8325:7c91882e
2024-11-28 22:19:29В Пятигорске с большим энтузиазмом стартовал проект «Зелёный город», который ставит перед собой амбициозную задачу — создать новые зелёные зоны, не только украшающие город, но и значительно улучшающие экологию и качество жизни горожан.
В рамках проекта запланировано масштабное озеленение улиц и парков с использованием вертикальных садов и автоматизированных систем полива. Ожидается, что вертикальные сады станут не только эстетическим украшением, но и эффективным инструментом в борьбе с загрязнением воздуха.
В вертикальных садах будут представлены разнообразные растения: вьющиеся, цветущие, зелёные и даже овощи и зелень. Плющ, виноград, хмель и клематисы создадут зелёные стены и живые изгороди, наполняя улицы яркими красками. Цветущие растения, такие как петунии, герани и бархатцы, создадут атмосферу праздника и радости. Зелёные растения, такие как папоротники и хосты, создадут умиротворяющий фон. А овощи и зелень, такие как салаты, шпинат и огурцы, позволят наслаждаться свежими продуктами, выращенными прямо в садах.
Реализация проекта начнётся в ближайшие месяцы, и уже в следующем году жители Пятигорска смогут насладиться обновлёнными зелёными зонами. Это станет настоящим подарком для всех, кто ценит красоту природы и стремится сделать жизнь вокруг себя лучше.
-
 @ fa1d8325:7c91882e
2024-11-28 22:16:53
@ fa1d8325:7c91882e
2024-11-28 22:16:53Пятигорск стал одним из первых городов в Ставропольском крае, где завершилось строительство сети зарядных станций для электромобилей нового поколения. В рамках пилотного проекта Министерства энергетики, промышленности и связи было установлено восемь станций мощностью до 200 кВт, что обеспечивает быструю и удобную зарядку для всех пользователей.
Станции расположены в ключевых местах города, включая торговые центры и общественные парки. Они доступны через мобильное приложение, которое позволяет легко находить и отслеживать процесс зарядки.
-
 @ fa1d8325:7c91882e
2024-11-28 22:10:05
@ fa1d8325:7c91882e
2024-11-28 22:10:05В Пятигорске ведется работа над созданием уникальной системы мониторинга качества воздуха, основанной на нейросетевых технологиях. Эта система объединит все существующие системы экологического наблюдения в одну региональную сеть, что позволит значительно повысить эффективность отслеживания уровня загрязнения и своевременно принимать меры.
Нейросети будут анализировать данные о состоянии атмосферы, что позволит делать более точные прогнозы и улучшать качество жизни горожан. Система соответствует целям Генерального плана города по обеспечению экологической безопасности и устойчивого развития.
Внедрение нейросетей в системы мониторинга воздуха открывает множество преимуществ. Они обеспечивают высокую точность данных, обрабатывая огромные массивы информации и выявляя сложные закономерности. Кроме того, нейросети могут прогнозировать уровни загрязнения в реальном времени, что позволяет оперативно реагировать на экологические угрозы.
Автоматизация сбора и анализа данных снизит трудозатраты и повысит эффективность мониторинга. Интеграция данных с другими системами и датчиками улучшит обмен информацией и повысит осведомленность о состоянии окружающей среды.
Ожидается, что новая система мониторинга станет важным шагом в обеспечении экологической безопасности и устойчивого развития Пятигорска.
-
 @ 7c765d40:bd121d84
2024-11-28 22:09:31
@ 7c765d40:bd121d84
2024-11-28 22:09:31We are in the midst (or middle for the non-fancy folks out there) of the BIGGEST transition in human history.
The crazy part?
Most people have no idea.
I mean, they have probably heard this at their latest webex or conference that they were paid to attend.
But they don't truly understand the magnitude of this shift.
The world will look completely different in a decade or two from now.
Unrecognizable.
And I believe, for the much better.
Think about how much has changed in the last 20 years.
2004.
What did it look like?
From my experience, cell phones were few and far between.
I remember my grandpa, who was an auctioneer, had a phone in his truck.
It looked like a normal home phone but used a HUGE antenna on top of the truck to pick up signal.
I don't even know what it was called but it was pretty bad ass at the time.
Then phones became mobile.
T9. The snake game. Ten cents per text.
Wow that was a fun trip down memory lane.
Back to the point.
How will the world look in 20 years from now?
It's almost impossible for someone like me to predict that.
There will be many things that nobody saw coming.
But we can break it down to the skills, traits, and trends based on both people and businesses.
And if my calculations are correct, they will be intertwined by then.
The people who will make a dent: self-belief, good communicators, strong personal networks, low time preference, highly skilled, multiple sources of income, holding hard assets, and crazy.
The people who will suffer: lazy, stubborn, slow, fat, single source of income, high time preference, holding paper assets, and crazy.
Moral of the story? Everyone is crazy.
Let's talk about businesses.
I believe in 20 years, everyone will be their own business.
Or at least, the 80/20 rule will shift.
Traditional system, about 20% have their own business while 80% are employees.
That will flip.
So what type of businesses will succeed?
Decentralized, agile, high quality products, focus on health, open source, and traditional values.
They will hire the best person for the job.
And the businesses that will fail?
Centralized, rigid, low quality products, monopolies, government funded, closed source, and a woke mentality.
I used my assistant Claude to help confirm some of these theories.
He did a great job of organizing some of these and also ended with an appropriate summary.
Success will come to those who can rapidly learn, unlearn, and relearn.
While maintaining a dynamic and growth oriented mindset.
Notice he didn't say anything about diversity, equality, and inclusion.
We are back baby.
We are fuckin back!
PROJECT POTENTIAL - You can now find the expanded audio versions of these on the new podcast - Project Potential! I will be sharing the video versions here for the LITF members but you can also find it for free on Spotify and of course Fountain!
Here is the link to Episode 002 on Fountain: https://fountain.fm/episode/AHGwJ66NcgYZ7V2YFvAu
Have a great day everyone! Happy Thanksgiving to all our American brothers and sisters.
Jor
-
 @ fa1d8325:7c91882e
2024-11-28 22:09:22
@ fa1d8325:7c91882e
2024-11-28 22:09:22В городе-курорте Пятигорске начала действовать система автоматического распознавания лиц. Это передовое техническое решение направлено на повышение уровня безопасности в общественных местах и снижение преступности.
Новая технология позволяет быстро выявлять потенциальных нарушителей и оперативно реагировать на угрозы. Она эффективно контролирует порядок на улицах, в парках и общественном транспорте, предотвращая правонарушения.
Власти города убеждены, что внедрение системы распознавания лиц сделает Пятигорск более безопасным и комфортным для жизни. Горожане смогут чувствовать себя увереннее, зная, что их безопасность находится под надёжной защитой.
Следует отметить, что система распознавания лиц не нарушает права граждан на неприкосновенность частной жизни, поскольку она функционирует в соответствии с законодательством о защите персональных данных.
-
 @ fa1d8325:7c91882e
2024-11-28 22:07:02
@ fa1d8325:7c91882e
2024-11-28 22:07:02Сегодня мы погружаемся в удивительный мир ухода за нашими пушистыми друзьями и ветеринарии. Век технологий стремительно меняет нашу жизнь, и это касается не только людей, но и наших домашних животных.
Вы когда-нибудь задумывались, как современные инновации помогают улучшать здоровье и благополучие наших любимцев? От умных кормушек до мобильных приложений для мониторинга состояния здоровья — технологии открывают новые горизонты в уходе за животными.
В этом видео мы расскажем о самых интересных и полезных новшествах в ветеринарии, которые делают жизнь наших питомцев более комфортной и безопасной. Узнайте, как регулярные проверки здоровья и современные методы диагностики помогают выявлять заболевания на ранних стадиях и обеспечивают нашим любимцам долгую и счастливую жизнь.
-
 @ fa1d8325:7c91882e
2024-11-28 22:02:31
@ fa1d8325:7c91882e
2024-11-28 22:02:31Проблема мусора в окрестностях Пятигорска стала настоящим вызовом для местных жителей и властей. Стихийные свалки растут с каждым днём, ежедневно накапливая десятки тонн отходов, среди которых строительные материалы и пластиковые упаковки.
Власти признают, что ежедневный вывоз около 25 тонн мусора не решает проблему в полной мере. Экологические последствия становятся всё более серьёзными: загрязнение водоёмов и ухудшение качества воздуха приводят к росту заболеваемости среди местного населения.
Глава города призывает к более строгим мерам против нарушителей, однако критика в адрес властей остаётся высокой.
Для решения этой проблемы власти планируют реализовать несколько ключевых мер: автоматическую сортировку, пиролиз и циркулярную экономику.
Системы оптического распознавания и искусственного интеллекта будут эффективно разделять отходы на различные категории, ускоряя процесс переработки. Высокотемпературная технология пиролиза позволит перерабатывать полимерные отходы, минимизируя выбросы. Подход циркулярной экономики подразумевает переработку и повторное использование отходов в производстве, что снизит потребление новых ресурсов.
Власти надеются, что эти технологии помогут справиться с растущими объёмами отходов и минимизировать их негативное воздействие на окружающую среду. Однако пока неизвестно, насколько эффективными окажутся эти меры на практике.
-
 @ fa1d8325:7c91882e
2024-11-28 22:00:53
@ fa1d8325:7c91882e
2024-11-28 22:00:53В стенах Пятигорского государственного университета (ПГУ) с большим размахом состоялось торжественное открытие нового научно-исследовательского института искусственного интеллекта (AIRI). Это знаменательное событие стало ключевым шагом в развитии университетской науки и технологий, а также важной вехой в укреплении позиций России на мировой арене в области искусственного интеллекта (AI).
Институт AIRI будет играть ключевую роль в создании инновационных проектов, направленных на решение актуальных задач современности. Ученые и исследователи AIRI будут активно участвовать в международных научных конференциях и сотрудничать с ведущими компаниями и корпорациями, стремясь внести свой вклад в развитие технологий искусственного интеллекта.
Открытие нового института стало возможным благодаря поддержке правительства и частных инвесторов, которые высоко оценили потенциал ПГУ в области AI. В рамках сотрудничества с ведущими университетами и научными центрами мира, AIRI будет проводить совместные исследования и разработки, что позволит создать новые технологии и решения, способные изменить мир к лучшему.
На церемонии открытия выступили представители руководства ПГУ, Министерства науки и высшего образования РФ, а также известные ученые и эксперты в области искусственного интеллекта. Они подчеркнули важность создания такого института для развития науки и технологий в России, а также выразили уверенность в том, что AIRI станет центром притяжения для молодых талантов и перспективных исследователей.
Новый институт будет оснащен современным оборудованием и лабораториями, что позволит ученым проводить исследования на самом высоком уровне. В планах AIRI — разработка новых алгоритмов машинного обучения, создание систем искусственного интеллекта для различных отраслей промышленности и здравоохранения, а также внедрение инновационных решений в образование и повседневную жизнь.
Открытие AIRI стало важным событием не только для ПГУ, но и для всей России. Это событие подчеркивает стремление нашей страны к инновациям и развитию передовых технологий, которые помогут решить глобальные проблемы и улучшить качество жизни людей.
-
 @ fa1d8325:7c91882e
2024-11-28 21:56:39
@ fa1d8325:7c91882e
2024-11-28 21:56:39В Пятигорске начала свою работу новая школа программирования и искусственного интеллекта (ИИ) для юных любителей технологий. Учебное заведение Coddy приглашает детей углубить свои знания и освоить навыки, необходимые для создания нейросетевых моделей.
Программа школы охватывает как теоретические, так и практические занятия, где ученики смогут создавать собственные проекты и применять полученные знания на практике. Это уникальная возможность для детей погрузиться в мир современных технологий и подготовиться к будущей карьере в сфере высоких технологий.
Ожидается, что такие образовательные инициативы окажут значительное влияние на подготовку квалифицированных специалистов в области программирования и искусственного интеллекта. Школа Coddy открывает перед детьми новые горизонты и помогает им раскрыть свой потенциал в мире современных технологий.
-
 @ 7776c32d:45558888
2024-11-28 21:53:24
@ 7776c32d:45558888
2024-11-28 21:53:244 years ago, on Thanksgiving, Digit's boyfriend at the time died. She told me that. She didn't say how it happened, but others say he committed suicide. I don't remember my Thanksgiving that year.
3 years ago, on Thanksgiving, I met Digit. I had a pet bird that died that day. I had named it Deathspan to avoid ever forgetting its limited lifespan, as if that would make me more prepared to deal with it dying someday, but that only made me feel worse. I had a mental breakdown and got banned from the wallstreetbets subreddit yet again, so I would have to start a new account yet again, but this time, unlike any other time, a wallstreetbets moderator called /u/shutupdigit showed up in my inbox to check if I was OK and invite me to the wallstreetbets Discord channel, hoping it would calm me down. This was the second time in my life a woman randomly approached me and offered her friendship to me without me approaching her first, and I was always desperate to get any women to talk to me at all, and a woman on wallstreetbets is rare to begin with - I was immensely anxious to get to know her, and hopefully keep knowing her. Interacting with her made it possible to enjoy the Thanksgiving dinner I got at the VFW despite my bleak circumstances.
2 years ago, on Thanksgiving, I cried a lot, hoping Digit was alive. She was, but I didn't know. I was so thankful to have met her, and I tried to focus on being thankful, but I needed to talk to her one more time so badly, and I knew if I could ever talk to her again, I would never be in that much pain again.
1 year ago, on Thanksgiving, I was entirely thankful she had come back in the interim. I knew I could never again be in as much pain as the year before, because I got to find out she lived longer than that. I was trying to finish a song about her, hating myself for how long it was taking, because after coming back that year, she had deleted her reddit and Discord accounts and disappeared again, and I was scared she could be planning to kill herself, or she could have done it already, and I was failing to protect her with every bit of delay in my efforts to show her how much I needed her. I hoped maybe someone in wallstreetbets was still in touch with her and I could make a song worth showing her. I was sick that week and couldn't finish the song by Thanksgiving because my head hurt so much it was impossible to tell if any melody or drum pattern or anything I was making was good or bad. I never finished the song, it felt too late after that. I spiraled into an endless process of trying to find new ways to reach out to her that would have better chances of a positive result. I reached out to wallstreetbets people with what progress I had made on the unfinished instrumental for the song, as futile as it felt. Nobody told me about the rumors she had committed suicide, as I had been fearing for so long.
Today, I'm still entirely thankful she came back before, and I know I'll never be in as much pain as 2 years ago again, since I know she lived longer than that. I'm still in that spiral trying to find any way to find out if she's safe without accidentally prompting her to commit suicide in the process because of the disturbance of privacy or something. I should still never recover if she's gone, but at least I'll never be in as much pain as 2 years ago.
I'm so thankful to know she lived past 2 years ago, but I can't stop being desperate to see her alive past today. I can't stop being extremely shitty to others around me. Today I went with my mom to volunteer at the VFW that gave me food the day I met Digit and I left my mom stranded there because she said something insensitive to my constant panic about Digit. It's only by my insane luck I've kept any friends at all.
I'm so sorry in this same timeframe Digit never got to have what she gave me - one last chance to see that most important person alive. I'm so sorry for those of you who are also struggling with anything like this, or worse.
Just in case anyone wants to hear her voice, here's that one song she sent me, intentions.mp3 -
https://audio.nostr.build/808960a3289a3196a8b371c2239d6925357b9a41183925f9882ee2897df313d3.mp3
-
 @ ae31c19a:2598418b
2024-11-28 20:49:19
@ ae31c19a:2598418b
2024-11-28 20:49:19test
-
 @ fa1d8325:7c91882e
2024-11-28 20:39:56
@ fa1d8325:7c91882e
2024-11-28 20:39:56В Пятигорске прошли первые в России соревнования по боям роботов, которые привлекли внимание не только местных жителей, но и любителей технологий со всей страны. Это событие стало настоящим праздником для всех, кто увлечён робототехникой и инновационными технологиями.
На арене встретились роботы-борцы, управляемые участниками, которые использовали нейросети для создания стратегий и тактик в течение поединков. Каждая команда представила своего уникального робота, оснащённого датчиками и алгоритмами, способными анализировать действия противника в реальном времени.
Соревнования проходили в несколько этапов: от отборочных боёв до финала, где лучшие команды сразились за главный приз. Зрители могли наблюдать за захватывающими поединками, в которых роботы демонстрировали не только силу, но и ловкость, используя продвинутые алгоритмы для уклонения от атак.
Пятигорск стал первым городом в России, который провёл такие соревнования на столь высоком уровне. Мероприятие собрало множество зрителей и вызвало интерес у местных СМИ. «Это только начало», — добавил организатор, — «Мы планируем сделать эти соревнования регулярными и развивать их дальше».
-
 @ 4fcac000:d2b37988
2024-11-28 20:39:53
@ 4fcac000:d2b37988
2024-11-28 20:39:53Приглашаем вас в увлекательное путешествие по страницам книг и мирам писателей в нашем литературном подкасте из Тюмени. Здесь мы обсудим не только классические произведения и современные бестселлеры, но и узнаем больше о местных авторах, культурных событиях и книжных новинках. Присоединяйтесь к нам, чтобы вдохновиться, поделиться своими мыслями и просто насладиться атмосферой литературного братства! 📚✨
-
 @ 4fcac000:d2b37988
2024-11-28 20:36:22
@ 4fcac000:d2b37988
2024-11-28 20:36:22В нашем подкасте мы расскажем о Григории Державине, поэте и губернаторе, который способствовал развитию региона; о легендарном полководце Александре Суворове, чьи стратегии до сих пор изучаются; а также о других значимых личностях!
Присоединяйтесь к нам, чтобы узнать больше о тех, кто формировал историю Тюмени и продолжает вдохновлять нас сегодня!
-
 @ fa1d8325:7c91882e
2024-11-28 20:29:00
@ fa1d8325:7c91882e
2024-11-28 20:29:00В этом году в Пятигорске произошло знаменательное событие — реконструкция парка «Цветник». Благодаря новому купольному покрытию, теперь посетители могут наслаждаться красотой цветов в любое время года. Это обновление открыло парк для всех желающих, сохранив его историческую атмосферу и богатство флоры.
Основанный в 1829 году, парк уже переживал несколько реконструкций, но нынешняя стала самой масштабной. Она воплотила в жизнь современный подход к озеленению и благоустройству территории.
После реконструкции в парке «Цветник» были реализованы следующие нововведения:
Новые дорожки и освещение: Пешеходные аллеи вымощены плиткой, а освещение выполнено в стиле «ретро».
Зеленое убранство: Высажено 80 молодых деревьев и почти 800 кустарников, а также разбит газон площадью 3500 м².
Арт-объекты: Появились новые скульптуры, включая бронзовую девушку и солнечные часы, а также питьевой бювет.
Восстановление инфраструктуры: Заменены коммуникации, установлены новые скамейки и урны.
Эти изменения сделали парк более привлекательным и комфортным для посетителей. Теперь, благодаря новым технологиям в виде куполов, которые создают оптимальные условия для роста растений, цветы можно наслаждаться круглый год.
-
 @ 4fcac000:d2b37988
2024-11-28 20:28:25
@ 4fcac000:d2b37988
2024-11-28 20:28:25Приглашаем вас в увлекательное путешествие по страницам книг и мирам писателей в нашем литературном подкасте из Тюмени. Здесь мы обсудим не только классические произведения и современные бестселлеры, но и узнаем больше о местных авторах, культурных событиях и книжных новинках. Присоединяйтесь к нам, чтобы вдохновиться, поделиться своими мыслями и просто насладиться атмосферой литературного братства! 📚✨
-
 @ f1989a96:bcaaf2c1
2024-11-28 20:26:48
@ f1989a96:bcaaf2c1
2024-11-28 20:26:48Good morning, readers!
In Turkey, through years of double-digit inflation, the state has eroded the value of the country’s largest banknote, the 200-lira bill, whose purchasing power has plummeted from $140 in 2010 to just $5.80 today. In scenes reminiscent of many other authoritarian states, banks and ATM providers are adjusting their business practices to adapt to the sheer volume of cash needed for purchases. Some branches are refilling tellers up to three times a day, and ATMs are increasing withdrawal limits while phasing out support for low-denomination notes. President Recep Tayyip Erdogan’s policies have only diminished citizens’ purchasing power, reminiscent of Turkey’s runaway inflation in the 1990s.
Meanwhile, in Nicaragua, journalist Elsbeth D’Anda was arrested by Daniel Ortega’s regime for speaking out about the rising cost of living in the country on his television broadcast. Officials stormed his home, confiscated all his broadcasting equipment, and sent him to the infamous El Chipote prison. This is a sobering reminder of the lengths Ortega’s regime will take to silence dissent or criticism.
On the open-source technology front, two new Bitcoin wallets were released this week. StashPay, a new Bitcoin and Lightning wallet, was released as an APK for Android and via Testflight for iOS. It leverages the Lightning and Liquid protocols, offering fast and low-cost transactions for users without dependence on centralized app stores. Additionally, Unify, a Bitcoin Payjoin wallet, is now available for testing. It leverages Nostr and Bitcoin Core and offers more private transactions by using Payjoins, which obscure transaction activity by enabling users to make collaborative payments.
We end with a tutorial from Bitcoin educator Ben Perrin (BTC Sessions), covering how to accept Bitcoin payments in a non-custodial way using BTCPay Server. This is a valuable tutorial for activists and nonprofits seeking to receive Bitcoin donations without fear of censorship or confiscation.
On this Thanksgiving, we are very grateful that you take the time to read this newsletter, and look forward to continuing to publish stories that matter in the world of financial freedom as we move to the close of the year and beyond.
Now, let’s dive right in!
Subscribe Here
GLOBAL NEWS
Turkey | Lira Banknotes Stripped of Value
In Turkey, after years of state-driven double-digit inflation, the purchasing power of its largest banknote has collapsed. The 200 lira note, once worth $140 in 2010, is worth just $5.80 today. This depreciation makes the note increasingly impractical for daily expenses, as it is barely enough for two cups of coffee. Additionally, smaller denomination banknotes are so unsuitable for daily expenses that they have essentially become scraps, as 200 lira notes make up 80% of all cash in circulation (up from 16% in 2020). In a cash-centric country like Turkey, some bank branches now need to refill their tellers three times a day, while ATMs are increasing withdrawal limits and are expected to stop offering notes below 100 lira. This financial strain is reminiscent of the 1990s, when runaway inflation devastated citizens’ savings and forced the Turkish government to remove six zeros from the currency in order to create the Turkish lira used today.
Nicaragua | Journalist Arrested for Criticizing Rising Cost of Living
The National Police arrested Nicaraguan journalist Elsbeth D’Anda last month for criticizing the rising cost of living on his television program La Cobertura. The regime loyalists deployed 20 officers and detained D’Anda at his home, confiscating his equipment before taking him to the notorious El Chipote prison. Several press freedom organizations have condemned the arbitrary detention as an attack on free expression. This arrest is the latest addition to a series of repressive measures by the Sandinista regime, which has crushed independent media through shutdowns, exiles, intimidations, and persecutions.
China | Expels Former Head of CBDC Project
The Chinese Communist Party (CCP) expelled Yao Qian, the former head of China’s central bank digital currency (CBDC) project, from his government position over allegations of corruption. Accused of accepting bribes in the form of digital assets, real estate, and luxury goods, Yao reportedly abused his role to favor specific technology providers for personal gain. His removal draws attention to the questionable governance of China’s CBDC, which already faces extensive criticisms regarding privacy and censorship. Qian’s case accentuates the risks of centralized systems, where unchecked power can foster corruption. As China advances its CBDC for cross-border transactions, this case foreshadows the broader implications of centrally controlled money in the hands of authoritarian regimes.
Russia | ‘War Economy’ Causing Inflation in Essential Items
As Russia continues its affront on Ukraine, its economy is experiencing a sharp rise in the prices of essential goods, leaving everyday citizens grappling with an escalating cost of living. Putin’s record defense spending, set to hit $138 billion in next year’s budget, has pushed inflation to 8.5%, with goods like butter rising as much as 26%. “You can’t fight inflation and a war at the same time,” says Alexandra Prokopenko, a fellow at the Carnegie Russia Eurasia Center in Berlin. Meanwhile, the regime is cracking down on alternative assets, banning Bitcoin mining in several regions, including Siberia and occupied territories of Ukraine, leaving fewer options for citizens to protect their savings and autonomy.
DR Congo | Proposed Constitution Change Prompts Outcry
In the DRC, opposition leaders are mobilizing nationwide protests against President Felix Tshisekedi’s plan to draft a new constitution, fearing it will extend presidential term limits and erode other democratic processes. Tshisekedi openly criticizes the constitution as outdated and obstructive to his governance, while opposition figures argue it prevents authoritarianism and ensures peaceful transitions of power. Concerns over constitutional changes are not unfounded in a country with pervasive repression and censorship. The DRC has laws restricting freedom of expression, such as banning government criticism in songs. It also uses financial policies like limiting electronic payments to Congolese francs to prop up its currency. With more than 25 million people facing food insecurity and economic freedom ranking among the lowest globally, Tshisekedi’s plan will only further entrench authoritarian rule at the expense of citizens’ rights.
LATEST IN BITCOIN NEWS, DEVELOPMENT, AND COMMUNITY
Unify | New Payjoin Wallet
Unify, a new Payjoin wallet that provides privacy for users when making Bitcoin payments, has been released and is now available for testing. Payjoins obscure individual transaction histories by enabling multiple parties to make collaborative payments. This functionality is especially crucial for individuals navigating repressive regimes, where financial privacy is paramount for their safety. The wallet also plans to add support for Silent Payments in the future. Unify is still in its early stages of development, making it suitable only for test funds. Still, it is a promising development to help make Bitcoin more private by default. You can test the wallet out here.
StashPay | New Lightning and Liquid Wallet
StashPay, a new self-custody Bitcoin wallet, is now available for download as an APK on Android and iOS via Testflight. It leverages the Lightning and Liquid Networks and offers comparatively low fees and fast transactions. StashPay also reduces the risks associated with centralized app stores removing the wallet by offering the APK. Future updates will include offline receive and Lightning address support. You can test the wallet here.
NDK | Launches Mobile Nostr Development Kit
A mobile version of the Nostr Development Kit (NDK Mobile) has been released by P It is designed to simplify the creation of Nostr applications on mobile platforms by providing developers with the tools needed to build them. This will help strengthen the overall Nostr ecosystem, improve accessibility, and bring Nostr to a wider audience, helping provide more options for developers hoping to build alternatives to today’s state- and corporate controlled social media networks. You can view the full release notes here.
Libréria de Satoshi | Concludes Bitcoin 4 Open Source (B4OS) Residency
Libréria de Satoshi, a Bitcoin technical educational initiative and HRF grantee, successfully wrapped up its Bitcoin 4 Open Source (B4OS) Residency, a six-month technical training program led by 15 Spanish developers that emphasizes the vital role of censorship-resistant technologies in preserving financial freedom and human rights. The program culminated in a two-week residency in Buenos Aires, where 20 students had the opportunity to participate in and advance critical open-source projects like Bitcoin Core, Mostro, SeedSigner, Fedimint, and Cashu.
Blockchain Commons | Hosting FROST Developer Meeting
Blockchain Commons, an HRF grantee advancing secure and open Bitcoin development, will host a Flexible Round-Optimized Schnorr Threshold Signatures (FROST) developer meeting on Dec. 4. FROST is a next-generation multisignature system that brings privacy and scalability benefits to Bitcoin without requiring a fork. The event invites developers interested in incorporating FROST into their wallets and applications to attend. They will learn why FROST is important, the advantages it carries, and gain insights from real-world implementations of FROST. HRF is pleased to see a hands-on opportunity for developers to learn, collaborate, and leverage FROST to strengthen their projects' security and privacy. You can learn more about the meeting here.
OpenSats | Announces Third Round of Bitcoin Education Grants
OpenSats, a public nonprofit funding free and open-source software and projects, announced its third wave of Bitcoin education grants, supporting global initiatives that make Bitcoin education more accessible and impactful. Among the recipients is Yes Bitcoin Haiti, a Bitcoin circular economy in Haiti that hosts educational workshops, onboards merchants, and has a Bitcoin Diploma program for students in underserved communities. Another grantee, Bitcoin 4all, delivers fundamental Bitcoin knowledge through short digestible videos in English, Spanish, and Portuguese, helping empower those across Latin America with the information they need to reclaim their financial freedom. It is great to see continued support for Bitcoin education.
RECOMMENDED CONTENT
How To Accept Bitcoin Payments: BTCpay Server by Ben Perrin
Bitcoin educator Ben Perrin (BTC Sessions) released a new tutorial demonstrating how to accept Bitcoin payments in a non-custodial way using BTCPay Server. The guide shows how to set up the open-source payment solution on a virtual private server (VPS), allowing users to retain full control of their funds. This step-by-step tutorial is an essential resource for activists who need to better protect their financial privacy and ensure their donations are free from government interference or censorship. Watch the full tutorial here.

Scaling Bitcoin Practically With Ark Labs by Frank Corva
In his latest article, journalist Frank Corva interviews Marco Agentieri of Ark Labs about their mission to help scale the Bitcoin network with Ark, a second-layer payments protocol promising faster and cheaper transactions. Argentieri discusses Ark’s potential to drive everyday payments with Bitcoin and enable users to earn interest (from transaction fees) for acting as a liquidity provider on the Ark protocol, which essentially creates “pools” of Bitcoin liquidity where users can make faster, cheaper, and more private payments — while making a variety of other tradeoffs, including that users’ funds “expire” if not moved before a certain period of time has elapsed. You can read the full interview and learn more about Ark here.

If this email was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.
Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ fa1d8325:7c91882e
2024-11-28 20:21:10
@ fa1d8325:7c91882e
2024-11-28 20:21:10В Пятигорске начинается пилотная программа, направленная на использование беспилотных летательных аппаратов для доставки товаров в отдаленные районы города. Эта инициатива, включающая доставку продуктов, готовой еды, почты и мониторинг связи, разрабатывается Центром управления городской аэромобильностью и уже достигла соглашений с ключевыми партнерами, такими как «ВкусВилл», «Почта России» и «Додо Пицца».
Программа предусматривает использование дронов для перевозки небольших грузов, что снизит нагрузку на наземные транспортные маршруты и ускорит доставку. Доставка с помощью дронов займет до 10 минут с момента оформления заказа, что особенно важно для жителей удаленных районов.
В ходе программы планируется протестировать различные модели дронов и оценить их эффективность в городских условиях. Местные жители проявляют интерес к новой инициативе, считая, что дрон-доставка станет удобным дополнением к традиционным способам получения товаров.
Если пилотная программа продемонстрирует свою эффективность, возможен запуск новых маршрутов и расширение зоны охвата. Это может стать важным шагом к созданию более современной и удобной инфраструктуры доставки в России.
Запуск данной инициативы подчеркивает стремление города к внедрению инновационных технологий и улучшению качества жизни его жителей.
-
 @ fa1d8325:7c91882e
2024-11-28 20:18:28
@ fa1d8325:7c91882e
2024-11-28 20:18:28В Пятигорске были протестированы новейшие летающие роботы-доставщики, предназначенные для доставки посылок и еды. Эти беспилотные аппараты способны преодолевать расстояние до 10 километров и перевозить грузы весом до 20 килограммов, ориентируясь на данные сенсоров и камер. Доставка осуществляется в режиме реального времени, а пользователи могут отслеживать местоположение роботов через специальное приложение.
-
 @ 633fe50a:12362f9c
2024-11-28 20:13:09
@ 633fe50a:12362f9c
2024-11-28 20:13:09This is a test