-
 @ 42342239:1d80db24
2024-11-06 09:05:17
@ 42342239:1d80db24
2024-11-06 09:05:17TL;DR: J.D. Vance recently observed that many in the Democratic Party are attempting to manufacture trust from the top down, neglecting the fact that genuine trust is often born from grassroots connections. There's indeed a stark contrast between trust that's artificially constructed through manipulation and censorship, and trust that's organically cultivated from the ground up.
Trump's vice presidential candidate J.D. Vance appeared on podcast host Joe Rogan's show earlier in November. According to Vance, large parts of the Democratic Party are trying to create higher trust from above, without understanding that the previously high trust once arose organically: "I think that a lot of them are trying to reimpose that social trust from the top."
Most people understand the importance of high trust. Political scientist Robert D. Putnam, for example, has shown that large social capital, in the form of trust and networks, is a key factor for economic growth, cooperation, and problem-solving. See e.g. his book Bowling Alone: The Collapse and Revival of American Community (2000).
The low trust today is widespread. Trust in the American federal government is at historically low levels. Trust in the media is at rock-bottom levels. Even trust in doctors and hospitals has plummeted: at the beginning of 2024, the proportion of people who reported "a great deal of trust" had dropped to 40%, from 72% in April 2020. This can be concerning, as individuals with low trust in doctors and hospitals will be less likely to follow their advice and recommendations. It's therefore not surprising that many want to "rebuild trust" (this was the theme of the World Economic Forum's annual meeting this year).
How much trust is actually reasonable?
But how much trust is actually reasonable? To determine this, one can ask whether an institution has acted reliably in the past, whether it possesses the knowledge and ability required to deliver what is promised, and whether its interests are in line with our own.
The low trust figures among Americans are likely a reflection of the fact that many of them today question the extent to which the answers to these questions are actually affirmative. During the pandemic, medical experts in the UK incorrectly predicted that hundreds of thousands of people would die. In the US, the leading infectious disease expert misled the public about, among other things, face masks, the sitting president lied about both the effectiveness and safety of vaccines, a British health minister wanted to "scare the pants off people," and virus experts even conspired to mislead about the origin of the SARS-CoV-2 virus. All while social media companies, under pressure from governments, were forced to censor information that was actually correct.
Trust - built on sand or on solid ground?
It's possible to continue on the current path and try to improve trust figures by limiting access to information. For instance, if the public doesn't get access to negative information about authorities or experts, the measured trust can increase. But in that case, trust is merely built on sand, waiting to be undermined by the inexorable forces of truth.
But there's another possibility. Building relationships that are genuine and honest, listening to each other without judgment, and communicating without misleading. Doing things that really matter, and doing them well, showing competence and reliability through actions. In this way, trust can grow naturally and organically. A trust built on solid ground, not on sand. A delicate task. But presidential election or not, isn't it time for us to start building a future where this form of trust is the obvious foundation?
-
 @ 42342239:1d80db24
2024-10-29 19:27:12
@ 42342239:1d80db24
2024-10-29 19:27:12The Swedish government recently rejected the Transport Administration's proposal for average speed cameras. The proposal would have meant constant surveillance of all vehicles, and critics argued for instance that it would have posed a threat to national security. Given the prevalence of IT breaches and data leaks today, it's hard not to give them a point, even if the problems are often downplayed by both corporations, governments and organisations. After Facebook (now Meta) leaked account information for over half a billion users, internal mails revealed the company wanted to "normalise the fact that this happens regularly".
IT security focuses on protecting the information in our computer systems and their connections. Cybersecurity is a broader concept that also includes aspects such as human behaviour, environmental factors, and management.
Data that has not been collected cannot leak
Knowledge about cybersecurity is often insufficient. For example, it was not long ago that the Swedish Transport Agency decided to outsource the operation of the Swedish vehicle and driving licence register. This was done despite deviations from various laws and criticism from the Security Police. The operation was placed in, among other places, Serbia (which has a close relationship with Russia). The Swedish driving licence register, including personal photos, as well as confidential information about critical infrastructure such as bridges, subways, roads, and ports, became available to personnel without Swedish security clearance.
The government's decision earlier this year not to proceed with a Swedish "super register" is an example of how cybersecurity can be strengthened. The rejection of the Transport Administration's proposal for average speed cameras is another. Data that has not been collected cannot leak out. It cannot be outsourced either.
Accounts are risky by definition
But the question is bigger than that. More and more of the products and services we depend on are now subscription services, often including long documents with terms and conditions. Which few people read. If you want to control your air heat pump with your phone, you not only need an app and an account, but also agree to someone storing your data (maybe also selling it or leaking it). The same applies if you want to be able to find your car in the car park. If you do not agree to the constantly updated terms, you lose important functionality.
Every time you are required to create an account, you are put in a dependent position. And our society becomes more fragile - because data is collected and can therefore leak out. It is much harder to lose something you do not have.
At the Korean car manufacturer Kia, huge security holes were recently discovered. IT researchers could quickly scan and control almost any car, including tracking its position, unlocking it, starting the ignition, and accessing cameras and personal information such as name, phone number, and home address. In some cases, even driving routes. All thanks to a "relatively simple flaw" in a web portal.
Instead of being at the mercy of large companies' IT departments, our security would improve if we could control our air heat pump, unlock our car, or our data ourselves. The technology already exists, thanks to the breakthrough of asymmetric encryption in the 1970s. Now we just need the will to change.
-
 @ fa0165a0:03397073
2024-10-23 17:19:41
@ fa0165a0:03397073
2024-10-23 17:19:41Chef's notes
This recipe is for 48 buns. Total cooking time takes at least 90 minutes, but 60 minutes of that is letting the dough rest in between processing.
The baking is a simple three-step process. 1. Making the Wheat dough 2. Making and applying the filling 3. Garnishing and baking in the oven
When done: Enjoy during Fika!
PS;
-
Can be frozen and thawed in microwave for later enjoyment as well.
-
If you need unit conversion, this site may be of help: https://www.unitconverters.net/
-
Traditionally we use something we call "Pearl sugar" which is optimal, but normal sugar or sprinkles is okay too. Pearl sugar (Pärlsocker) looks like this: https://search.brave.com/images?q=p%C3%A4rlsocker
Ingredients
- 150 g butter
- 5 dl milk
- 50 g baking yeast (normal or for sweet dough)
- 1/2 teaspoon salt
- 1-1 1/2 dl sugar
- (Optional) 2 teaspoons of crushed or grounded cardamom seeds.
- 1.4 liters of wheat flour
- Filling: 50-75 g butter, room temperature
- Filling: 1/2 - 1 dl sugar
- Filling: 1 teaspoons crushed or ground cardamom and 1 teaspoons ground cinnamon (or 2 teaspoons of cinnamon)
- Garnish: 1 egg, sugar or Almond Shavings
Directions
- Melt the butter/margarine in a saucepan.
- Pour in the milk and allow the mixture to warm reach body temperature (approx. + 37 ° C).
- Dissolve the yeast in a dough bowl with the help of the salt.
- Add the 37 ° C milk/butter mixture, sugar and if you choose to the optional cardamom. (I like this option!) and just over 2/3 of the flour.
- Work the dough shiny and smooth, about 4 minutes with a machine or 8 minutes by hand.
- Add if necessary. additional flour but save at least 1 dl for baking.
- Let the dough rise covered (by a kitchen towel), about 30 minutes.
- Work the dough into the bowl and then pick it up on a floured workbench. Knead the dough smoothly. Divide the dough into 2 parts. Roll out each piece into a rectangular cake.
- Stir together the ingredients for the filling and spread it.
- Roll up and cut each roll into 24 pieces.
- Place them in paper molds or directly on baking paper with the cut surface facing up. Let them rise covered with a baking sheet, about 30 minutes.
- Brush the buns with beaten egg and sprinkle your chosen topping.
- Bake in the middle of the oven at 250 ° C, 5-8 minutes.
- Allow to cool on a wire rack under a baking sheet.
-
-
 @ 42342239:1d80db24
2024-10-23 12:28:41
@ 42342239:1d80db24
2024-10-23 12:28:41TL;DR: The mathematics of trust says that news reporting will fall flat when the population becomes suspicious of the media. Which is now the case for growing subgroups in the U.S. as well as in Sweden.
A recent wedding celebration for Sweden Democrats leader Jimmie Åkesson resulted in controversy, as one of the guests in attendance was reportedly linked to organized crime. Following this “wedding scandal”, a columnist noted that the party’s voters had not been significantly affected. Instead of a decrease in trust - which one might have expected - 10% of them stated that their confidence in the party had actually increased. “Over the years, the Sweden Democrats have surprisingly emerged unscathed from their numerous scandals,” she wrote. But is this really so surprising?
In mathematics, a probability is expressed as the likelihood of something occurring given one or more conditions. For example, one can express a probability as “the likelihood that a certain stock will rise in price, given that the company has presented a positive quarterly report.” In this case, the company’s quarterly report is the basis for the assessment. If we add more information, such as the company’s strong market position and a large order from an important customer, the probability increases further. The more information we have to go on, the more precise we can be in our assessment.
From this perspective, the Sweden Democrats’ “numerous scandals” should lead to a more negative assessment of the party. But this perspective omits something important.
A couple of years ago, the term “gaslighting” was chosen as the word of the year in the US. The term comes from a 1944 film of the same name and refers to a type of psychological manipulation, as applied to the lovely Ingrid Bergman. Today, the term is used in politics, for example, when a large group of people is misled to achieve political goals. The techniques used can be very effective but have a limitation. When the target becomes aware of what is happening, everything changes. Then the target becomes vigilant and views all new information with great suspicion.
The Sweden Democrats’ “numerous scandals” should lead to a more negative assessment of the party. But if SD voters to a greater extent than others believe that the source of the information is unreliable, for example, by omitting information or adding unnecessary information, the conclusion is different. The Swedish SOM survey shows that these voters have lower trust in journalists and also lower confidence in the objectivity of the news. Like a victim of gaslighting, they view negative reporting with suspicion. The arguments can no longer get through. A kind of immunity has developed.
In the US, trust in the media is at an all-time low. So when American media writes that “Trump speaks like Hitler, Stalin, and Mussolini,” that his idea of deporting illegal immigrants would cost hundreds of billions of dollars, or gets worked up over his soda consumption, the consequence is likely to be similar to here at home.
The mathematics of trust says that reporting will fall flat when the population becomes suspicious of the media. Or as the Swedish columnist put it: like water off a duck’s back.
Cover image: Ingrid Bergman 1946. RKO Radio Pictures - eBay, Public Domain, Wikimedia Commons
-
 @ 42342239:1d80db24
2024-10-22 07:57:17
@ 42342239:1d80db24
2024-10-22 07:57:17It was recently reported that Sweden's Minister for Culture, Parisa Liljestrand, wishes to put an end to anonymous accounts on social media. The issue has been at the forefront following revelations of political parties using pseudonymous accounts on social media platforms earlier this year.
The importance of the internet is also well-known. As early as 2015, Roberta Alenius, who was then the press secretary for Fredrik Reinfeldt (Moderate Party), openly spoke about her experiences with the Social Democrats' and Moderates' internet activists: Twitter actually set the agenda for journalism at the time.
The Minister for Culture now claims, amongst other things, that anonymous accounts pose a threat to democracy, that they deceive people, and that they can be used to mislead, etc. It is indeed easy to find arguments against anonymity; perhaps the most common one is the 'nothing to hide, nothing to fear' argument.
One of the many problems with this argument is that it assumes that abuse of power never occurs. History has much to teach us here. Sometimes, authorities can act in an arbitrary, discriminatory, or even oppressive manner, at least in hindsight. Take, for instance, the struggles of the homosexual community, the courageous dissidents who defied communist regimes, or the women who fought for their right to vote in the suffragette movement.
It was difficult for homosexuals to be open about their sexuality in Sweden in the 1970s. Many risked losing their jobs, being ostracised, or harassed. Anonymity was therefore a necessity for many. Homosexuality was actually classified as a mental illness in Sweden until 1979.
A couple of decades earlier, dissidents in communist regimes in Europe used pseudonyms when publishing samizdat magazines. The Czech author and dissident Václav Havel, who later became the President of the Czech Republic, used a pseudonym when publishing his texts. The same was true for the Russian author and literary prize winner Alexander Solzhenitsyn. Indeed, in Central and Eastern Europe, anonymity was of the utmost importance.
One hundred years ago, women all over the world fought for the right to vote and to be treated as equals. Many were open in their struggle, but for others, anonymity was a necessity as they risked being socially ostracised, losing their jobs, or even being arrested.
Full transparency is not always possible or desirable. Anonymity can promote creativity and innovation as it gives people the opportunity to experiment and try out new ideas without fear of being judged or criticised. This applies not only to individuals but also to our society, in terms of ideas, laws, norms, and culture.
It is also a strange paradox that those who wish to limit freedom of speech and abolish anonymity simultaneously claim to be concerned about the possible return of fascism. The solutions they advocate are, in fact, precisely what would make it easier for a tyrannical regime to maintain its power. To advocate for the abolition of anonymity, one must also be of the (absurd) opinion that the development of history has now reached its definitive end.
-
 @ 42342239:1d80db24
2024-09-26 07:57:04
@ 42342239:1d80db24
2024-09-26 07:57:04The boiling frog is a simple tale that illustrates the danger of gradual change: if you put a frog in boiling water, it will quickly jump out to escape the heat. But if you place a frog in warm water and gradually increase the temperature, it won't notice the change and will eventually cook itself. Might the decline in cash usage be construed as an example of this tale?
As long as individuals can freely transact with each other and conduct purchases and sales without intermediaries[^1] such as with cash, our freedoms and rights remain secure from potential threats posed by the payment system. However, as we have seen in several countries such as Sweden over the past 15 years, the use of cash and the amount of banknotes and coins in circulation have decreased. All to the benefit of various intermediated[^1] electronic alternatives.
The reasons for this trend include: - The costs associated with cash usage has been increasing. - Increased regulatory burdens due to stricter anti-money laundering regulations. - Closed bank branches and fewer ATMs. - The Riksbank's aggressive note switches resulted in a situation where they were no longer recognized.
Market forces or "market forces"?
Some may argue that the "de-cashing" of society is a consequence of market forces. But does this hold true? Leading economists at times recommend interventions with the express purpose to mislead the public, such as proposing measures who are "opaque to most voters."
In a working paper on de-cashing by the International Monetary Fund (IMF) from 2017, such thought processes, even recommendations, can be found. IMF economist Alexei Kireyev, formerly a professor at an institute associated with the Soviet Union's KGB (MGIMO) and economic adviser to Michail Gorbachov 1989-91, wrote that:
- "Social conventions may also be disrupted as de-cashing may be viewed as a violation of fundamental rights, including freedom of contract and freedom of ownership."
- Letting the private sector lead "the de-cashing" is preferable, as it will seem "almost entirely benign". The "tempting attempts to impose de-cashing by a decree should be avoided"
- "A targeted outreach program is needed to alleviate suspicions related to de-cashing"
In the text, he also offered suggestions on the most effective approach to diminish the use of cash:
- The de-cashing process could build on the initial and largely uncontested steps, such as the phasing out of large denomination bills, the placement of ceilings on cash transactions, and the reporting of cash moves across the borders.
- Include creating economic incentives to reduce the use of cash in transactions
- Simplify "the opening and use of transferrable deposits, and further computerizing the financial system."
As is customary in such a context, it is noted that the article only describes research and does not necessarily reflect IMF's views. However, isn't it remarkable that all of these proposals have come to fruition and the process continues? Central banks have phased out banknotes with higher denominations. Banks' regulatory complexity seemingly increase by the day (try to get a bank to handle any larger amounts of cash). The transfer of cash from one nation to another has become increasingly burdensome. The European Union has recently introduced restrictions on cash transactions. Even the law governing the Swedish central bank is written so as to guarantee a further undermining of cash. All while the market share is growing for alternatives such as transferable deposits[^1].
The old European disease
The Czech Republic's former president Václav Havel, who played a key role in advocating for human rights during the communist repression, was once asked what the new member states in the EU could do to pay back for all the economic support they had received from older member states. He replied that the European Union still suffers from the old European disease, namely the tendency to compromise with evil. And that the new members, who have a recent experience of totalitarianism, are obliged to take a more principled stance - sometimes necessary - and to monitor the European Union in this regard, and educate it.
The American computer scientist and cryptographer David Chaum said in 1996 that "[t]he difference between a bad electronic cash system and well-developed digital cash will determine whether we will have a dictatorship or a real democracy". If Václav Havel were alive today, he would likely share Chaum's sentiment. Indeed, on the current path of "de-cashing", we risk abolishing or limiting our liberties and rights, "including freedom of contract and freedom of ownership" - and this according to an economist at the IMF(!).
As the frog was unwittingly boiled alive, our freedoms are quietly being undermined. The temperature is rising. Will people take notice before our liberties are irreparably damaged?
[^1]: Transferable deposits are intermediated. Intermediated means payments involving one or several intermediares, like a bank, a card issuer or a payment processor. In contrast, a disintermediated payment would entail a direct transactions between parties without go-betweens, such as with cash.
-
 @ e31e84c4:77bbabc0
2024-12-02 10:44:07
@ e31e84c4:77bbabc0
2024-12-02 10:44:07Bitcoin and Fixed Income was Written By Wyatt O’Rourke. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: ultrahusky3@primal.net
Fiduciary duty is the obligation to act in the client’s best interests at all times, prioritizing their needs above the advisor’s own, ensuring honesty, transparency, and avoiding conflicts of interest in all recommendations and actions.
This is something all advisors in the BFAN take very seriously; after all, we are legally required to do so. For the average advisor this is a fairly easy box to check. All you essentially have to do is have someone take a 5-minute risk assessment, fill out an investment policy statement, and then throw them in the proverbial 60/40 portfolio. You have thousands of investment options to choose from and you can reasonably explain how your client is theoretically insulated from any move in the \~markets\~. From the traditional financial advisor perspective, you could justify nearly anything by putting a client into this type of portfolio. All your bases were pretty much covered from return profile, regulatory, compliance, investment options, etc. It was just too easy. It became the household standard and now a meme.
As almost every real bitcoiner knows, the 60/40 portfolio is moving into psyop territory, and many financial advisors get clowned on for defending this relic on bitcoin twitter. I’m going to specifically poke fun at the ‘40’ part of this portfolio.
The ‘40’ represents fixed income, defined as…
An investment type that provides regular, set interest payments, such as bonds or treasury securities, and returns the principal at maturity. It’s generally considered a lower-risk asset class, used to generate stable income and preserve capital.
Historically, this part of the portfolio was meant to weather the volatility in the equity markets and represent the “safe” investments. Typically, some sort of bond.
First and foremost, the fixed income section is most commonly constructed with U.S. Debt. There are a couple main reasons for this. Most financial professionals believe the same fairy tale that U.S. Debt is “risk free” (lol). U.S. debt is also one of the largest and most liquid assets in the market which comes with a lot of benefits.
There are many brilliant bitcoiners in finance and economics that have sounded the alarm on the U.S. debt ticking time bomb. I highly recommend readers explore the work of Greg Foss, Lawrence Lepard, Lyn Alden, and Saifedean Ammous. My very high-level recap of their analysis:
-
A bond is a contract in which Party A (the borrower) agrees to repay Party B (the lender) their principal plus interest over time.
-
The U.S. government issues bonds (Treasury securities) to finance its operations after tax revenues have been exhausted.
-
These are traditionally viewed as “risk-free” due to the government’s historical reliability in repaying its debts and the strength of the U.S. economy
-
U.S. bonds are seen as safe because the government has control over the dollar (world reserve asset) and, until recently (20 some odd years), enjoyed broad confidence that it would always honor its debts.
-
This perception has contributed to high global demand for U.S. debt but, that is quickly deteriorating.
-
The current debt situation raises concerns about sustainability.
-
The U.S. has substantial obligations, and without sufficient productivity growth, increasing debt may lead to a cycle where borrowing to cover interest leads to more debt.
-
This could result in more reliance on money creation (printing), which can drive inflation and further debt burdens.
In the words of Lyn Alden “Nothing stops this train”
Those obligations are what makes up the 40% of most the fixed income in your portfolio. So essentially you are giving money to one of the worst capital allocators in the world (U.S. Gov’t) and getting paid back with printed money.
As someone who takes their fiduciary responsibility seriously and understands the debt situation we just reviewed, I think it’s borderline negligent to put someone into a classic 60% (equities) / 40% (fixed income) portfolio without serious scrutiny of the client’s financial situation and options available to them. I certainly have my qualms with equities at times, but overall, they are more palatable than the fixed income portion of the portfolio. I don’t like it either, but the money is broken and the unit of account for nearly every equity or fixed income instrument (USD) is fraudulent. It’s a paper mache fade that is quite literally propped up by the money printer.
To briefly be as most charitable as I can – It wasn’t always this way. The U.S. Dollar used to be sound money, we used to have government surplus instead of mathematically certain deficits, The U.S. Federal Government didn’t used to have a money printing addiction, and pre-bitcoin the 60/40 portfolio used to be a quality portfolio management strategy. Those times are gone.
Now the fun part. How does bitcoin fix this?
Bitcoin fixes this indirectly. Understanding investment criteria changes via risk tolerance, age, goals, etc. A client may still have a need for “fixed income” in the most literal definition – Low risk yield. Now you may be thinking that yield is a bad word in bitcoin land, you’re not wrong, so stay with me. Perpetual motion machine crypto yield is fake and largely where many crypto scams originate. However, that doesn’t mean yield in the classic finance sense does not exist in bitcoin, it very literally does. Fortunately for us bitcoiners there are many other smart, driven, and enterprising bitcoiners that understand this problem and are doing something to address it. These individuals are pioneering new possibilities in bitcoin and finance, specifically when it comes to fixed income.
Here are some new developments –
Private Credit Funds – The Build Asset Management Secured Income Fund I is a private credit fund created by Build Asset Management. This fund primarily invests in bitcoin-backed, collateralized business loans originated by Unchained, with a secured structure involving a multi-signature, over-collateralized setup for risk management. Unchained originates loans and sells them to Build, which pools them into the fund, enabling investors to share in the interest income.
Dynamics
- Loan Terms: Unchained issues loans at interest rates around 14%, secured with a 2/3 multi-signature vault backed by a 40% loan-to-value (LTV) ratio.
- Fund Mechanics: Build buys these loans from Unchained, thus providing liquidity to Unchained for further loan originations, while Build manages interest payments to investors in the fund.
Pros
- The fund offers a unique way to earn income via bitcoin-collateralized debt, with protection against rehypothecation and strong security measures, making it attractive for investors seeking exposure to fixed income with bitcoin.
Cons
- The fund is only available to accredited investors, which is a regulatory standard for private credit funds like this.
Corporate Bonds – MicroStrategy Inc. (MSTR), a business intelligence company, has leveraged its corporate structure to issue bonds specifically to acquire bitcoin as a reserve asset. This approach allows investors to indirectly gain exposure to bitcoin’s potential upside while receiving interest payments on their bond investments. Some other publicly traded companies have also adopted this strategy, but for the sake of this article we will focus on MSTR as they are the biggest and most vocal issuer.
Dynamics
-
Issuance: MicroStrategy has issued senior secured notes in multiple offerings, with terms allowing the company to use the proceeds to purchase bitcoin.
-
Interest Rates: The bonds typically carry high-yield interest rates, averaging around 6-8% APR, depending on the specific issuance and market conditions at the time of issuance.
-
Maturity: The bonds have varying maturities, with most structured for multi-year terms, offering investors medium-term exposure to bitcoin’s value trajectory through MicroStrategy’s holdings.
Pros
-
Indirect Bitcoin exposure with income provides a unique opportunity for investors seeking income from bitcoin-backed debt.
-
Bonds issued by MicroStrategy offer relatively high interest rates, appealing for fixed-income investors attracted to the higher risk/reward scenarios.
Cons
-
There are credit risks tied to MicroStrategy’s financial health and bitcoin’s performance. A significant drop in bitcoin prices could strain the company’s ability to service debt, increasing credit risk.
-
Availability: These bonds are primarily accessible to institutional investors and accredited investors, limiting availability for retail investors.
Interest Payable in Bitcoin – River has introduced an innovative product, bitcoin Interest on Cash, allowing clients to earn interest on their U.S. dollar deposits, with the interest paid in bitcoin.
Dynamics
-
Interest Payment: Clients earn an annual interest rate of 3.8% on their cash deposits. The accrued interest is converted to Bitcoin daily and paid out monthly, enabling clients to accumulate Bitcoin over time.
-
Security and Accessibility: Cash deposits are insured up to $250,000 through River’s banking partner, Lead Bank, a member of the FDIC. All Bitcoin holdings are maintained in full reserve custody, ensuring that client assets are not lent or leveraged.
Pros
-
There are no hidden fees or minimum balance requirements, and clients can withdraw their cash at any time.
-
The 3.8% interest rate provides a predictable income stream, akin to traditional fixed-income investments.
Cons
-
While the interest rate is fixed, the value of the Bitcoin received as interest can fluctuate, introducing potential variability in the investment’s overall return.
-
Interest rate payments are on the lower side
Admittedly, this is a very small list, however, these types of investments are growing more numerous and meaningful. The reality is the existing options aren’t numerous enough to service every client that has a need for fixed income exposure. I challenge advisors to explore innovative options for fixed income exposure outside of sovereign debt, as that is most certainly a road to nowhere. It is my wholehearted belief and call to action that we need more options to help clients across the risk and capital allocation spectrum access a sound money standard.
Additional Resources
-
River: The future of saving is here: Earn 3.8% on cash. Paid in Bitcoin.
-
MicroStrategy: MicroStrategy Announces Pricing of Offering of Convertible Senior Notes
Bitcoin and Fixed Income was Written By Wyatt O’Rourke. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: ultrahusky3@primal.net
-
-
 @ 0d532801:197a0c30
2024-12-01 21:27:48
@ 0d532801:197a0c30
2024-12-01 21:27:48
߹ İnsan, bilinçli olarak günah işlediğinde, aslında birçok içsel ve dışsal faktörün etkisi altındadır. Bu faktörlerin başında bireysel arzular, toplumsal baskılar, zayıflıklar, bilinçaltı dürtüler ve bazen de cehalet gelir. İnsan, sadece dürtülerine göre hareket etmeyi tercih edebilir ya da kısa vadeli tatmin için uzun vadeli sonuçları göz ardı edebilir. Peki, bir insan neden bilerek günah işler? Bu sorunun cevabı, sadece dini ya da etik perspektiflerle değil, psikolojik, toplumsal ve kültürel açılardan da ele alınmalıdır.
- Bireysel Arzular ve Dürtüler
߹ İnsanın doğasında, zaman zaman nefsini tatmin etme isteği vardır. Bu istek, bazen mantık ve vicdanın önüne geçebilir. İnsan, kısa süreli hazları arzularken, bunun gelecekteki olumsuz sonuçlarını göz ardı edebilir. Örneğin, hırsızlık yapan bir kişi, anlık bir mal edinme arzusuyla hareket edebilir, ancak bu davranışın ona ve çevresine getireceği zararları düşünmektense, elde edeceği çıkarı daha önemli görür. Benzer şekilde, yalan söylemek ya da başkalarını manipüle etmek de kısa vadeli çıkarlar ve bireysel egolar tarafından beslenen bir davranış biçimidir.
- Toplumsal Baskılar ve Çevresel Faktörler
߹ İnsan, toplumsal bir varlık olarak çevresinden büyük ölçüde etkilenir. Toplumun normları, kültürel değerleri, arkadaş gruplarının etkisi ve ailevi dinamikler, bireyin davranışlarını şekillendirir. Bazı durumlarda, kişi bilerek yanlış bir davranış sergileyebilir çünkü çevresindeki kişiler böyle yapmaktadır ve kendini dışlanmış hissetmemek için buna ayak uydurur. Örneğin, bir grup insanın başka birine kötü davranması ya da yalan söylemesi, bir bireyi de benzer şekilde davranmaya itebilir. Bu durum, bireyin vicdanı ve doğru-yanlış algısı ile çatışan bir durumdur.
- Zayıflıklar ve İnsan Doğası
߹ Herkesin zayıf anları vardır. Zihinsel ve duygusal olarak zorlandığı anlarda insanlar bazen bilerek yanlış bir şey yapabilir. İnsan, öfke, stres, yalnızlık ya da korku gibi duygusal durumlar içinde daha kolay günah işleyebilir. Duygusal karmaşa, sağlıklı düşünme yeteneğini zayıflatabilir ve kişi, anlık bir rahatlama ya da kaçış için yanlış bir yolu seçebilir. Örneğin, öfkelenen bir kişi, karşısındaki kişiye hakaret etmek ya da ona zarar vermek isteyebilir. Bu tür eylemler, kişinin o anki duygusal durumunun bir sonucu olarak ortaya çıkar.
- Cehalet ve Yanlış İnançlar
߹ Bazen insanlar, neyin doğru neyin yanlış olduğuna dair doğru bir bilgiye sahip olmayabilirler. Bilgi eksikliği ya da yanlış inanışlar, bireyin günah işlemesine neden olabilir. İnsan, kötü bir davranışın ne kadar zarar verebileceğini ya da o davranışın ahlaki ve dini boyutlarını tam anlamayabilir. Özellikle bazı insanlar, içinde bulundukları ortamın, alışkanlıkların ya da eğitim seviyelerinin etkisiyle, doğruyu ve yanlışı tam kavrayamayabilirler. Bu durum da, onların bilerek ve isteyerek günah işlemesine yol açabilir.
- İçsel Çatışmalar ve Vicdanın Bastırılması
߹ İnsan, bazen kendi içsel çatışmalarına dayanamayabilir. Vicdanı, doğruyu yapması yönünde onu uyarırken, içindeki kötü duygular ya da arzular ona engel olamayacak kadar güçlü olabilir. İnsanın kendisini haklı çıkarma çabası da burada devreye girebilir. Bir insan, kendini iyi bir insan olarak görmek isterken, bazen içindeki kötü dürtüleri bastırmak yerine, bunları haklı göstermek için kendine çeşitli gerekçeler uydurur. Örneğin, bir kişi başkasının hakkını yemek için kendini “bunu herkes yapıyor” ya da “benim de buna ihtiyacım var” gibi bahanelerle kandırabilir.
- Dini ve Ahlaki Değerlerin Zayıflaması
߹ Bir insanın dini inançları ya da ahlaki değerleri, doğru-yanlış algısını büyük ölçüde şekillendirir. Ancak zamanla, bireylerin inançları ya da değerleri zayıflayabilir. Toplumda sekülerleşmenin arttığı bir dönemde, dini ve ahlaki öğretiler zamanla insanların gözünde daha az değerli hâle gelebilir. Bu durumda, insanlar günah işleme konusunda daha az vicdan azabı duyarlar, çünkü dini ya da ahlaki sonuçları görmezden gelmeyi tercih edebilirler.
߹ Sonuç olarak, insanın bilerek günah işlemesi, karmaşık bir durumdur ve çok çeşitli faktörlere dayanır. İnsanlar bazen içsel isteklerine, bazen dışsal baskılara, bazen de bilinçli ya da bilinçsiz olarak zayıf noktalarına dayanarak yanlışlar yapabilirler. Önemli olan, insanın yaptığı hataları fark etmesi, bu hatalardan ders alması ve doğru yolu bulmaya çaba göstermesidir. Kişi, hatalarını kabul ederek ve daha bilinçli bir şekilde hareket ederek hem kendisine hem de çevresine faydalı bir yaşam sürebilir.
-
 @ ee11a5df:b76c4e49
2024-09-11 08:16:37
@ ee11a5df:b76c4e49
2024-09-11 08:16:37Bye-Bye Reply Guy
There is a camp of nostr developers that believe spam filtering needs to be done by relays. Or at the very least by DVMs. I concur. In this way, once you configure what you want to see, it applies to all nostr clients.
But we are not there yet.
In the mean time we have ReplyGuy, and gossip needed some changes to deal with it.
Strategies in Short
- WEB OF TRUST: Only accept events from people you follow, or people they follow - this avoids new people entirely until somebody else that you follow friends them first, which is too restrictive for some people.
- TRUSTED RELAYS: Allow every post from relays that you trust to do good spam filtering.
- REJECT FRESH PUBKEYS: Only accept events from people you have seen before - this allows you to find new people, but you will miss their very first post (their second post must count as someone you have seen before, even if you discarded the first post)
- PATTERN MATCHING: Scan for known spam phrases and words and block those events, either on content or metadata or both or more.
- TIE-IN TO EXTERNAL SYSTEMS: Require a valid NIP-05, or other nostr event binding their identity to some external identity
- PROOF OF WORK: Require a minimum proof-of-work
All of these strategies are useful, but they have to be combined properly.
filter.rhai
Gossip loads a file called "filter.rhai" in your gossip directory if it exists. It must be a Rhai language script that meets certain requirements (see the example in the gossip source code directory). Then it applies it to filter spam.
This spam filtering code is being updated currently. It is not even on unstable yet, but it will be there probably tomorrow sometime. Then to master. Eventually to a release.
Here is an example using all of the techniques listed above:
```rhai // This is a sample spam filtering script for the gossip nostr // client. The language is called Rhai, details are at: // https://rhai.rs/book/ // // For gossip to find your spam filtering script, put it in // your gossip profile directory. See // https://docs.rs/dirs/latest/dirs/fn.data_dir.html // to find the base directory. A subdirectory "gossip" is your // gossip data directory which for most people is their profile // directory too. (Note: if you use a GOSSIP_PROFILE, you'll // need to put it one directory deeper into that profile // directory). // // This filter is used to filter out and refuse to process // incoming events as they flow in from relays, and also to // filter which events get/ displayed in certain circumstances. // It is only run on feed-displayable event kinds, and only by // authors you are not following. In case of error, nothing is // filtered. // // You must define a function called 'filter' which returns one // of these constant values: // DENY (the event is filtered out) // ALLOW (the event is allowed through) // MUTE (the event is filtered out, and the author is // automatically muted) // // Your script will be provided the following global variables: // 'caller' - a string that is one of "Process", // "Thread", "Inbox" or "Global" indicating // which part of the code is running your // script // 'content' - the event content as a string // 'id' - the event ID, as a hex string // 'kind' - the event kind as an integer // 'muted' - if the author is in your mute list // 'name' - if we have it, the name of the author // (or your petname), else an empty string // 'nip05valid' - whether nip05 is valid for the author, // as a boolean // 'pow' - the Proof of Work on the event // 'pubkey' - the event author public key, as a hex // string // 'seconds_known' - the number of seconds that the author // of the event has been known to gossip // 'spamsafe' - true only if the event came in from a // relay marked as SpamSafe during Process // (even if the global setting for SpamSafe // is off)
fn filter() {
// Show spam on global // (global events are ephemeral; these won't grow the // database) if caller=="Global" { return ALLOW; } // Block ReplyGuy if name.contains("ReplyGuy") || name.contains("ReplyGal") { return DENY; } // Block known DM spam // (giftwraps are unwrapped before the content is passed to // this script) if content.to_lower().contains( "Mr. Gift and Mrs. Wrap under the tree, KISSING!" ) { return DENY; } // Reject events from new pubkeys, unless they have a high // PoW or we somehow already have a nip05valid for them // // If this turns out to be a legit person, we will start // hearing their events 2 seconds from now, so we will // only miss their very first event. if seconds_known <= 2 && pow < 25 && !nip05valid { return DENY; } // Mute offensive people if content.to_lower().contains(" kike") || content.to_lower().contains("kike ") || content.to_lower().contains(" nigger") || content.to_lower().contains("nigger ") { return MUTE; } // Reject events from muted people // // Gossip already does this internally, and since we are // not Process, this is rather redundant. But this works // as an example. if muted { return DENY; } // Accept if the PoW is large enough if pow >= 25 { return ALLOW; } // Accept if their NIP-05 is valid if nip05valid { return ALLOW; } // Accept if the event came through a spamsafe relay if spamsafe { return ALLOW; } // Reject the rest DENY} ```
-
 @ 94a6a78a:0ddf320e
2024-11-27 19:36:12
@ 94a6a78a:0ddf320e
2024-11-27 19:36:12The backbone of your Nostr experience lies in relays—servers that transmit your notes, zaps, and private messages across the decentralized network. Azzamo offers three specialized relays to suit different user needs, ensuring reliability, performance, and privacy.
1. Free Relay
- URL:
wss://nostr.azzamo.net - Overview: Azzamo’s Free Relay is perfect for newcomers to Nostr. It’s open-access, reliable, and ensures fair use with moderate rate limits.
- Key Features:
- Free to use.
- Notes older than one month are purged daily.
- Accessible gateway for decentralized communication.
2. Paid Relay
- URL:
wss://relay.azzamo.net - Overview: Designed for power users, the Paid Relay offers unmatched performance with 99.9% uptime and low latency.
- Key Features:
- Scalable for heavy users.
- Fewer users for faster, consistent connections.
- Premium support included for paid users.
3. Inbox Relay
- URL:
wss://inbox.azzamo.net - Overview: Never miss a private message again with the Inbox Relay, optimized for secure, spam-free direct messaging.
- Key Features:
- Guaranteed message delivery.
- Optimized for NIP-17 private messages.
- Optimized for NIP-19 group chats.
- Premium users enjoy advanced support.
Why Choose Azzamo Relays?
Life on Nostr is easier with Azzamo relays. They’re fast, reliable, and built to handle whatever you throw at them. The Paid Relay keeps your connections strong, the Inbox Relay makes sure no private message gets lost, and the Free Relay is always there to get you started. Supporting Azzamo by going premium helps keep this decentralized network growing—and you get priority support while you’re at it. Azzamo has your back on Nostr!
🔗 Start now:
- Free Relay:
wss://nostr.azzamo.net - Paid Relay: azzamo.net/pay
- Inbox Relay: azzamo.net/inbox
Support the network and upgrade your experience—add time to your account via the Azzamo Dashboard. Choose Azzamo, and take control of your Nostr journey today!
- URL:
-
 @ a95c6243:d345522c
2024-11-29 19:45:43
@ a95c6243:d345522c
2024-11-29 19:45:43Konsum ist Therapie.
Wolfgang JoopUmweltbewusstes Verhalten und verantwortungsvoller Konsum zeugen durchaus von einer wünschenswerten Einstellung. Ob man deswegen allerdings einen grünen statt eines schwarzen Freitags braucht, darf getrost bezweifelt werden – zumal es sich um manipulatorische Konzepte handelt. Wie in der politischen Landschaft sind auch hier die Etiketten irgendwas zwischen nichtssagend und trügerisch.
Heute ist also wieder mal «Black Friday», falls Sie es noch nicht mitbekommen haben sollten. Eigentlich haben wir ja eher schon eine ganze «Black Week», der dann oft auch noch ein «Cyber Monday» folgt. Die Werbebranche wird nicht müde, immer neue Anlässe zu erfinden oder zu importieren, um uns zum Konsumieren zu bewegen. Und sie ist damit sehr erfolgreich.
Warum fallen wir auf derartige Werbetricks herein und kaufen im Zweifelsfall Dinge oder Mengen, die wir sicher nicht brauchen? Pure Psychologie, würde ich sagen. Rabattschilder triggern etwas in uns, was den Verstand in Stand-by versetzt. Zusätzlich beeinflussen uns alle möglichen emotionalen Reize und animieren uns zum Schnäppchenkauf.
Gedankenlosigkeit und Maßlosigkeit können besonders bei der Ernährung zu ernsten Problemen führen. Erst kürzlich hat mir ein Bekannter nach einer USA-Reise erzählt, dass es dort offenbar nicht unüblich ist, schon zum ausgiebigen Frühstück in einem Restaurant wenigstens einen Liter Cola zu trinken. Gerne auch mehr, um das Gratis-Nachfüllen des Bechers auszunutzen.
Kritik am schwarzen Freitag und dem unnötigen Konsum kommt oft von Umweltschützern. Neben Ressourcenverschwendung, hohem Energieverbrauch und wachsenden Müllbergen durch eine zunehmende Wegwerfmentalität kommt dabei in der Regel auch die «Klimakrise» auf den Tisch.
Die EU-Kommission lancierte 2015 den Begriff «Green Friday» im Kontext der überarbeiteten Rechtsvorschriften zur Kennzeichnung der Energieeffizienz von Elektrogeräten. Sie nutzte die Gelegenheit kurz vor dem damaligen schwarzen Freitag und vor der UN-Klimakonferenz COP21, bei der das Pariser Abkommen unterzeichnet werden sollte.
Heute wird ein grüner Freitag oft im Zusammenhang mit der Forderung nach «nachhaltigem Konsum» benutzt. Derweil ist die Europäische Union schon weit in ihr Geschäftsmodell des «Green New Deal» verstrickt. In ihrer Propaganda zum Klimawandel verspricht sie tatsächlich «Unterstützung der Menschen und Regionen, die von immer häufigeren Extremwetter-Ereignissen betroffen sind». Was wohl die Menschen in der Region um Valencia dazu sagen?
Ganz im Sinne des Great Reset propagierten die Vereinten Nationen seit Ende 2020 eine «grüne Erholung von Covid-19, um den Klimawandel zu verlangsamen». Der UN-Umweltbericht sah in dem Jahr einen Schwerpunkt auf dem Verbraucherverhalten. Änderungen des Konsumverhaltens des Einzelnen könnten dazu beitragen, den Klimaschutz zu stärken, hieß es dort.
Der Begriff «Schwarzer Freitag» wurde in den USA nicht erstmals für Einkäufe nach Thanksgiving verwendet – wie oft angenommen –, sondern für eine Finanzkrise. Jedoch nicht für den Börsencrash von 1929, sondern bereits für den Zusammenbruch des US-Goldmarktes im September 1869. Seitdem mussten die Menschen weltweit so einige schwarze Tage erleben.
Kürzlich sind die britischen Aufsichtsbehörden weiter von ihrer Zurückhaltung nach dem letzten großen Finanzcrash von 2008 abgerückt. Sie haben Regeln für den Bankensektor gelockert, womit sie «verantwortungsvolle Risikobereitschaft» unterstützen wollen. Man würde sicher zu schwarz sehen, wenn man hier ein grünes Wunder befürchten würde.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a849beb6:b327e6d2
2024-11-23 15:03:47
@ a849beb6:b327e6d2
2024-11-23 15:03:47
\ \ It was another historic week for both bitcoin and the Ten31 portfolio, as the world’s oldest, largest, most battle-tested cryptocurrency climbed to new all-time highs each day to close out the week just shy of the $100,000 mark. Along the way, bitcoin continued to accumulate institutional and regulatory wins, including the much-anticipated approval and launch of spot bitcoin ETF options and the appointment of several additional pro-bitcoin Presidential cabinet officials. The timing for this momentum was poetic, as this week marked the second anniversary of the pico-bottom of the 2022 bear market, a level that bitcoin has now hurdled to the tune of more than 6x despite the litany of bitcoin obituaries published at the time. The entirety of 2024 and especially the past month have further cemented our view that bitcoin is rapidly gaining a sense of legitimacy among institutions, fiduciaries, and governments, and we remain optimistic that this trend is set to accelerate even more into 2025.
Several Ten31 portfolio companies made exciting announcements this week that should serve to further entrench bitcoin’s institutional adoption. AnchorWatch, a first of its kind bitcoin insurance provider offering 1:1 coverage with its innovative use of bitcoin’s native properties, announced it has been designated a Lloyd’s of London Coverholder, giving the company unique, blue-chip status as it begins to write bitcoin insurance policies of up to $100 million per policy starting next month. Meanwhile, Battery Finance Founder and CEO Andrew Hohns appeared on CNBC to delve into the launch of Battery’s pioneering private credit strategy which fuses bitcoin and conventional tangible assets in a dual-collateralized structure that offers a compelling risk/return profile to both lenders and borrowers. Both companies are clearing a path for substantially greater bitcoin adoption in massive, untapped pools of capital, and Ten31 is proud to have served as lead investor for AnchorWatch’s Seed round and as exclusive capital partner for Battery.
As the world’s largest investor focused entirely on bitcoin, Ten31 has deployed nearly $150 million across two funds into more than 30 of the most promising and innovative companies in the ecosystem like AnchorWatch and Battery, and we expect 2025 to be the best year yet for both bitcoin and our portfolio. Ten31 will hold a first close for its third fund at the end of this year, and investors in that close will benefit from attractive incentives and a strong initial portfolio. Visit ten31.vc/funds to learn more and get in touch to discuss participating.\ \ Portfolio Company Spotlight
Primal is a first of its kind application for the Nostr protocol that combines a client, caching service, analytics tools, and more to address several unmet needs in the nascent Nostr ecosystem. Through the combination of its sleek client application and its caching service (built on a completely open source stack), Primal seeks to offer an end-user experience as smooth and easy as that of legacy social media platforms like Twitter and eventually many other applications, unlocking the vast potential of Nostr for the next billion people. Primal also offers an integrated wallet (powered by Strike BLACK) that substantially reduces onboarding and UX frictions for both Nostr and the lightning network while highlighting bitcoin’s unique power as internet-native, open-source money.
Selected Portfolio News
AnchorWatch announced it has achieved Llody’s Coverholder status, allowing the company to provide unique 1:1 bitcoin insurance offerings starting in December.\ \ Battery Finance Founder and CEO Andrew Hohns appeared on CNBC to delve into the company’s unique bitcoin-backed private credit strategy.
Primal launched version 2.0, a landmark update that adds a feed marketplace, robust advanced search capabilities, premium-tier offerings, and many more new features.
Debifi launched its new iOS app for Apple users seeking non-custodial bitcoin-collateralized loans.
Media
Strike Founder and CEO Jack Mallers joined Bloomberg TV to discuss the strong volumes the company has seen over the past year and the potential for a US bitcoin strategic reserve.
Primal Founder and CEO Miljan Braticevic joined The Bitcoin Podcast to discuss the rollout of Primal 2.0 and the future of Nostr.
Ten31 Managing Partner Marty Bent appeared on BlazeTV to discuss recent changes in the regulatory environment for bitcoin.
Zaprite published a customer testimonial video highlighting the popularity of its offerings across the bitcoin ecosystem.
Market Updates
Continuing its recent momentum, bitcoin reached another new all-time high this week, clocking in just below $100,000 on Friday. Bitcoin has now reached a market cap of nearly $2 trillion, putting it within 3% of the market caps of Amazon and Google.
After receiving SEC and CFTC approval over the past month, long-awaited options on spot bitcoin ETFs were fully approved and launched this week. These options should help further expand bitcoin’s institutional liquidity profile, with potentially significant implications for price action over time.
The new derivatives showed strong performance out of the gate, with volumes on options for BlackRock’s IBIT reaching nearly $2 billion on just the first day of trading despite surprisingly tight position limits for the vehicles.
Meanwhile, the underlying spot bitcoin ETF complex had yet another banner week, pulling in $3.4 billion in net inflows.
New reports suggested President-elect Donald Trump’s social media company is in advanced talks to acquire crypto trading platform Bakkt, potentially the latest indication of the incoming administration’s stance toward the broader “crypto” ecosystem.
On the macro front, US housing starts declined M/M again in October on persistently high mortgage rates and weather impacts. The metric remains well below pre-COVID levels.
Pockets of the US commercial real estate market remain challenged, as the CEO of large Florida developer Related indicated that developers need further rate cuts “badly” to maintain project viability.
US Manufacturing PMI increased slightly M/M, but has now been in contraction territory (<50) for well over two years.
The latest iteration of the University of Michigan’s popular consumer sentiment survey ticked up following this month’s election results, though so did five-year inflation expectations, which now sit comfortably north of 3%.
Regulatory Update
After weeks of speculation, the incoming Trump administration appointed hedge fund manager Scott Bessent to head up the US Treasury. Like many of Trump’s cabinet selections so far, Bessent has been a public advocate for bitcoin.
Trump also appointed Cantor Fitzgerald CEO Howard Lutnick – another outspoken bitcoin bull – as Secretary of the Commerce Department.
Meanwhile, the Trump team is reportedly considering creating a new “crypto czar” role to sit within the administration. While it’s unclear at this point what that role would entail, one report indicated that the administration’s broader “crypto council” is expected to move forward with plans for a strategic bitcoin reserve.
Various government lawyers suggested this week that the Trump administration is likely to be less aggressive in seeking adversarial enforcement actions against bitcoin and “crypto” in general, as regulatory bodies appear poised to shift resources and focus elsewhere.
Other updates from the regulatory apparatus were also directionally positive for bitcoin, most notably FDIC Chairman Martin Gruenberg’s confirmation that he plans to resign from his post at the end of President Biden’s term.
Many critics have alleged Gruenberg was an architect of “Operation Chokepoint 2.0,” which has created banking headwinds for bitcoin companies over the past several years, so a change of leadership at the department is likely yet another positive for the space.
SEC Chairman Gary Gensler also officially announced he plans to resign at the start of the new administration. Gensler has been the target of much ire from the broader “crypto” space, though we expect many projects outside bitcoin may continue to struggle with questions around the Howey Test.
Overseas, a Chinese court ruled that it is not illegal for individuals to hold cryptocurrency, even though the country is still ostensibly enforcing a ban on crypto transactions.
Noteworthy
The incoming CEO of Charles Schwab – which administers over $9 trillion in client assets – suggested the platform is preparing to “get into” spot bitcoin offerings and that he “feels silly” for having waited this long. As this attitude becomes more common among traditional finance players, we continue to believe that the number of acquirers coming to market for bitcoin infrastructure capabilities will far outstrip the number of available high quality assets.
BlackRock’s 2025 Thematic Outlook notes a “renewed sense of optimism” on bitcoin among the asset manager’s client base due to macro tailwinds and the improving regulatory environment. Elsewhere, BlackRock’s head of digital assets indicated the firm does not view bitcoin as a “risk-on” asset.
MicroStrategy, which was a sub-$1 billion market cap company less than five years ago, briefly breached a $100 billion equity value this week as it continues to aggressively acquire bitcoin. The company now holds nearly 350,000 bitcoin on its balance sheet.
Notably, Allianz SE, Germany’s largest insurer, spoke for 25% of MicroStrategy’s latest $3 billion convertible note offering this week, suggesting growing appetite for bitcoin proxy exposure among more restricted pools of capital.
The ongoing meltdown of fintech middleware provider Synapse has left tens of thousands of customers with nearly 100% deposit haircuts as hundreds of millions in funds remain missing, the latest unfortunate case study in the fragility of much of the US’s legacy banking stack.
Travel
-
BitcoinMENA, Dec 9-10
-
Nashville BitDevs, Dec 10
-
Austin BitDevs, Dec 19
-
-
 @ e31e84c4:77bbabc0
2024-11-27 11:32:57
@ e31e84c4:77bbabc0
2024-11-27 11:32:57‘Think You Know Bitcoin Security?’ was Written By Paul G Conlon. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: noisycyclone54@walletofsatoshi.com
Childhood Lessons
As a boy, my grandmother shared stories of her experiences in wartime Germany, each revealing a common theme: the terrifying reality of living without security. I was amazed with the scale of destruction and, at the time, understood security largely as physical protection. Yet the years have deepened my appreciation for security’s nuances. In this article, we’ll explore how studying Bitcoin has helped me now recognise “security” not just as physical safety, but related to personal agency, mental and social well-being, and the ability to control one's destiny.
Definitions of Security
Property confiscation was rife in 1930s Germany, and much of this behaviour didn’t even constitute illegality. The 1938 Ordinance on the Use of Jewish Assets for example required those identified as Jews to deposit all their stocks, shares, fixed-income securities and similar in a deposit at a foreign exchange bank. The government even allowed itself to sell Jewish businesses. Access to these resources required no less than approval by the Reich Minister for Economic Affairs.
Narrowly defining security as simply asset protection is tempting, given its historical prevalence. Everything from my grandmother’s tales of stashing cash in curtains, to the US Constitution's 4th Amendment, “the right of the people to be secure in their persons, houses, papers, and effects” reinforces this physical emphasis.
When I discovered Bitcoin, I was hence drawn to its asset protection features. Like many, this biased view of security defined the start of my Bitcoin journey, focusing my attention on hardware wallets and encryption protocols. But that was soon to change.
How Bitcoin Changed Me
The more I read, the more I learned that with a network of nodes working to secure a global protocol, came a network of people working to secure global principles. It dawned on me that I had not so much discovered the ultimate bastion of property rights, but of human rights.
Here are just a few examples:
Freedom of Expression
Anonymity is fundamental for the full exercise of the right to freedom of expression. This is enshrined in Article 19 of the Universal Declaration of Human Rights (UDHR) and the International Covenant on Civil and Political Rights (ICCPR). Bitcoin's pseudonymous and decentralised nature makes it difficult for tyrants to identify and censor one of the purest forms of expression: transactions.
Adequate Living Standards
Article 25 of the UDHR states that everyone has the right to a standard of living adequate for health and well-being, including food, clothing, housing, and medical supplies. Article 17 further enshrines the retention of property necessary to support these living standards.
Bitcoin's cryptographic security reinforces ownership rights, making it difficult for rogue states to arbitrarily seize assets essential for the maintenance of these living standards. Furthermore, Bitcoin's 21-million-coin capped supply prevents arbitrary inflation, protecting against the erosion of purchasing power that has time and again proven correlated with the erosion of living standards.
Freedom of Association
Article 20 of the UDHR states that everyone has the right to freedom of peaceful assembly and association. Article 22 of the ICCPR also protects the right to freedom of association, including the right to form and join trade unions.
Multi-signature wallets are an explicit expression of this associative freedom. By enabling groups to collaboratively manage resources, the human connections required for civilisation to flourish can be directly represented and enforced in code.
Programmatic freedom of association is particularly pertinent for activist and civil society organisations and provides security against coercion in situations where individuals may face pressure to hand over funds from those who wield power.
Right to Information
The open-source nature of Bitcoin also somewhat poetically aligns with the right to seek, receive, and impart information, as outlined in Article 19 of the UDHR. Anyone can inspect, verify, and contribute to Bitcoin's code, promoting transparency and accountability. Its immutability also supports the right to information by preserving truth in the face of potential revisionism. Furthermore, Article 27 states that everyone has the right to share in scientific advancement and its benefits. Bitcoin embodies this principle by allowing global participation in its development and use.
Personal Context
For me, Bitcoin brought context to those old wartime stories I heard as a boy. It led me to the understanding that property rights are simply a derivative of human rights. Now, for the first time in history, we have a borderless technology that secures these rights not in international declarations or national constitutions – both susceptible to the stroke of a tyrant’s pen – but in executable code.
In essence, Bitcoin's technical features embody the very principles of security and resilience that are well recognised as essential to personal agency, mental well-being, and social cohesion. These operate independently of central authorities that have historically proven both capable and willing of stripping human rights, and not a moment too soon…
A Modern Necessity
These concerns are not limited to the past. Just recently, Blackrock CEO, Larry Fink, said this about Bitcoin in a CNBC interview:
“We have countries where you’re frightened of your everyday existence and it gives an opportunity to invest in something that is outside your country’s control.” (https://www.youtube.com/watch?v=K4ciiDyUvUo)
As an Australian, I see the precursors of what Larry describes. Legislative attacks on the right to expression, living standards, association, and information are becoming brazen. The Digital ID Bill 2024, legislated on May 16th, has already denied employment and government services to some, and is now poised to police the internet in what appears to be the making of a conditional access society.
The Communications Legislation Amendment (Combatting Misinformation and Disinformation) Bill 2024, currently sitting before federal parliament, is even more horrendous. It effectively establishes a protectionist Ministry of Truth and threatens imprisonment for an extremely broad array of ill-defined speech – all while providing exemptions for government and legacy media. This political activity is occurring amidst a cost-of-living and housing crisis, where many working individuals are living in tents in major cities.
Bitcoin’s True Security
Yet with Bitcoin (and a Starlink connection), I feel secure. Bitcoin has become a source of resilience and mental well-being for people in an increasingly complex world. Beyond its cryptographic security, Bitcoin provides a global network of like-minded individuals who share common principles. This distributed community offers a sense of belonging and support that extends far beyond the technology behind it.
Bitcoin’s existence gives me confidence in my ability to secure basic needs and find community anywhere, without relying on easily confiscated physical assets. Meeting fellow Bitcoin enthusiasts often reveals shared worldviews and values, creating instant connections.
Ultimately, Bitcoin's security stems not just from its technology, but from the human network it has fostered. It offers the reassurance that I could "land on my feet" anywhere, preserving both financial sovereignty and social bonds with free-thinking individuals. This holistic security - financial, social, and psychological - provides profound peace of mind in uncertain times.
‘Think You Know Bitcoin Security?’ was Written By Paul G Conlon. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: noisycyclone54@walletofsatoshi.com
-
 @ a95c6243:d345522c
2024-11-08 20:02:32
@ a95c6243:d345522c
2024-11-08 20:02:32Und plötzlich weißt du:
Es ist Zeit, etwas Neues zu beginnen
und dem Zauber des Anfangs zu vertrauen.
Meister EckhartSchwarz, rot, gold leuchtet es im Kopf des Newsletters der deutschen Bundesregierung, der mir freitags ins Postfach flattert. Rot, gelb und grün werden daneben sicher noch lange vielzitierte Farben sein, auch wenn diese nie geleuchtet haben. Die Ampel hat sich gerade selber den Stecker gezogen – und hinterlässt einen wirtschaftlichen und gesellschaftlichen Trümmerhaufen.
Mit einem bemerkenswerten Timing hat die deutsche Regierungskoalition am Tag des «Comebacks» von Donald Trump in den USA endlich ihr Scheitern besiegelt. Während der eine seinen Sieg bei den Präsidentschaftswahlen feierte, erwachten die anderen jäh aus ihrer Selbsthypnose rund um Harris-Hype und Trump-Panik – mit teils erschreckenden Auswüchsen. Seit Mittwoch werden die Geschicke Deutschlands nun von einer rot-grünen Minderheitsregierung «geleitet» und man steuert auf Neuwahlen zu.
Das Kindergarten-Gehabe um zwei konkurrierende Wirtschaftsgipfel letzte Woche war bereits bezeichnend. In einem Strategiepapier gestand Finanzminister Lindner außerdem den «Absturz Deutschlands» ein und offenbarte, dass die wirtschaftlichen Probleme teilweise von der Ampel-Politik «vorsätzlich herbeigeführt» worden seien.
Lindner und weitere FDP-Minister wurden also vom Bundeskanzler entlassen. Verkehrs- und Digitalminister Wissing trat flugs aus der FDP aus; deshalb darf er nicht nur im Amt bleiben, sondern hat zusätzlich noch das Justizministerium übernommen. Und mit Jörg Kukies habe Scholz «seinen Lieblingsbock zum Obergärtner», sprich: Finanzminister befördert, meint Norbert Häring.
Es gebe keine Vertrauensbasis für die weitere Zusammenarbeit mit der FDP, hatte der Kanzler erklärt, Lindner habe zu oft sein Vertrauen gebrochen. Am 15. Januar 2025 werde er daher im Bundestag die Vertrauensfrage stellen, was ggf. den Weg für vorgezogene Neuwahlen freimachen würde.
Apropos Vertrauen: Über die Hälfte der Bundesbürger glauben, dass sie ihre Meinung nicht frei sagen können. Das ging erst kürzlich aus dem diesjährigen «Freiheitsindex» hervor, einer Studie, die die Wechselwirkung zwischen Berichterstattung der Medien und subjektivem Freiheitsempfinden der Bürger misst. «Beim Vertrauen in Staat und Medien zerreißt es uns gerade», kommentierte dies der Leiter des Schweizer Unternehmens Media Tenor, das die Untersuchung zusammen mit dem Institut für Demoskopie Allensbach durchführt.
«Die absolute Mehrheit hat absolut die Nase voll», titelte die Bild angesichts des «Ampel-Showdowns». Die Mehrheit wolle Neuwahlen und die Grünen sollten zuerst gehen, lasen wir dort.
Dass «Insolvenzminister» Robert Habeck heute seine Kandidatur für das Kanzleramt verkündet hat, kann nur als Teil der politmedialen Realitätsverweigerung verstanden werden. Wer allerdings denke, schlimmer als in Zeiten der Ampel könne es nicht mehr werden, sei reichlich optimistisch, schrieb Uwe Froschauer bei Manova. Und er kenne Friedrich Merz schlecht, der sich schon jetzt rhetorisch auf seine Rolle als oberster Feldherr Deutschlands vorbereite.
Was also tun? Der Schweizer Verein «Losdemokratie» will eine Volksinitiative lancieren, um die Bestimmung von Parlamentsmitgliedern per Los einzuführen. Das Losverfahren sorge für mehr Demokratie, denn als Alternative zum Wahlverfahren garantiere es eine breitere Beteiligung und repräsentativere Parlamente. Ob das ein Weg ist, sei dahingestellt.
In jedem Fall wird es notwendig sein, unsere Bemühungen um Freiheit und Selbstbestimmung zu verstärken. Mehr Unabhängigkeit von staatlichen und zentralen Institutionen – also die Suche nach dezentralen Lösungsansätzen – gehört dabei sicher zu den Möglichkeiten. Das gilt sowohl für jede/n Einzelne/n als auch für Entitäten wie die alternativen Medien.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 7460b7fd:4fc4e74b
2024-09-05 08:37:48
@ 7460b7fd:4fc4e74b
2024-09-05 08:37:48请看2014年王兴的一场思维碰撞,视频27分钟开始
最后,一个当时无法解决的点:丢失
-
 @ 87730827:746b7d35
2024-11-20 09:27:53
@ 87730827:746b7d35
2024-11-20 09:27:53Original: https://techreport.com/crypto-news/brazil-central-bank-ban-monero-stablecoins/
Brazilian’s Central Bank Will Ban Monero and Algorithmic Stablecoins in the Country
Brazil proposes crypto regulations banning Monero and algorithmic stablecoins and enforcing strict compliance for exchanges.
KEY TAKEAWAYS
- The Central Bank of Brazil has proposed regulations prohibiting privacy-centric cryptocurrencies like Monero.
- The regulations categorize exchanges into intermediaries, custodians, and brokers, each with specific capital requirements and compliance standards.
- While the proposed rules apply to cryptocurrencies, certain digital assets like non-fungible tokens (NFTs) are still ‘deregulated’ in Brazil.

In a Notice of Participation announcement, the Brazilian Central Bank (BCB) outlines regulations for virtual asset service providers (VASPs) operating in the country.
In the document, the Brazilian regulator specifies that privacy-focused coins, such as Monero, must be excluded from all digital asset companies that intend to operate in Brazil.
Let’s unpack what effect these regulations will have.
Brazil’s Crackdown on Crypto Fraud
If the BCB’s current rule is approved, exchanges dealing with coins that provide anonymity must delist these currencies or prevent Brazilians from accessing and operating these assets.
The Central Bank argues that currencies like Monero make it difficult and even prevent the identification of users, thus creating problems in complying with international AML obligations and policies to prevent the financing of terrorism.
According to the Central Bank of Brazil, the bans aim to prevent criminals from using digital assets to launder money. In Brazil, organized criminal syndicates such as the Primeiro Comando da Capital (PCC) and Comando Vermelho have been increasingly using digital assets for money laundering and foreign remittances.
… restriction on the supply of virtual assets that contain characteristics of fragility, insecurity or risks that favor fraud or crime, such as virtual assets designed to favor money laundering and terrorist financing practices by facilitating anonymity or difficulty identification of the holder.
The Central Bank has identified that removing algorithmic stablecoins is essential to guarantee the safety of users’ funds and avoid events such as when Terraform Labs’ entire ecosystem collapsed, losing billions of investors’ dollars.
The Central Bank also wants to control all digital assets traded by companies in Brazil. According to the current proposal, the national regulator will have the power to ask platforms to remove certain listed assets if it considers that they do not meet local regulations.
However, the regulations will not include NFTs, real-world asset (RWA) tokens, RWA tokens classified as securities, and tokenized movable or real estate assets. These assets are still ‘deregulated’ in Brazil.
Monero: What Is It and Why Is Brazil Banning It?
Monero ($XMR) is a cryptocurrency that uses a protocol called CryptoNote. It launched in 2013 and ‘erases’ transaction data, preventing the sender and recipient addresses from being publicly known. The Monero network is based on a proof-of-work (PoW) consensus mechanism, which incentivizes miners to add blocks to the blockchain.
Like Brazil, other nations are banning Monero in search of regulatory compliance. Recently, Dubai’s new digital asset rules prohibited the issuance of activities related to anonymity-enhancing cryptocurrencies such as $XMR.
Furthermore, exchanges such as Binance have already announced they will delist Monero on their global platforms due to its anonymity features. Kraken did the same, removing Monero for their European-based users to comply with MiCA regulations.
Data from Chainalysis shows that Brazil is the seventh-largest Bitcoin market in the world.

In Latin America, Brazil is the largest market for digital assets. Globally, it leads in the innovation of RWA tokens, with several companies already trading this type of asset.
In Closing
Following other nations, Brazil’s regulatory proposals aim to combat illicit activities such as money laundering and terrorism financing.
Will the BCB’s move safeguard people’s digital assets while also stimulating growth and innovation in the crypto ecosystem? Only time will tell.
References
Cassio Gusson is a journalist passionate about technology, cryptocurrencies, and the nuances of human nature. With a career spanning roles as Senior Crypto Journalist at CriptoFacil and Head of News at CoinTelegraph, he offers exclusive insights on South America’s crypto landscape. A graduate in Communication from Faccamp and a post-graduate in Globalization and Culture from FESPSP, Cassio explores the intersection of governance, decentralization, and the evolution of global systems.
-
 @ 42342239:1d80db24
2024-09-02 12:08:29
@ 42342239:1d80db24
2024-09-02 12:08:29The ongoing debate surrounding freedom of expression may revolve more around determining who gets to control the dissemination of information rather than any claimed notion of safeguarding democracy. Similarities can be identified from 500 years ago, following the invention of the printing press.
What has been will be again, what has been done will be done again; there is nothing new under the sun.
-- Ecclesiastes 1:9
The debate over freedom of expression and its limits continues to rage on. In the UK, citizens are being arrested for sharing humouristic images. In Ireland, it may soon become illegal to possess "reckless" memes. Australia is trying to get X to hide information. Venezuela's Maduro blocked X earlier this year, as did a judge on Brazil's Supreme Court. In the US, a citizen has been imprisoned for spreading misleading material following a controversial court ruling. In Germany, the police are searching for a social media user who called a politician overweight. Many are also expressing concerns about deep fakes (AI-generated videos, images, or audio that are designed to deceive).
These questions are not new, however. What we perceive as new questions are often just a reflection of earlier times. After Gutenberg invented the printing press in the 15th century, there were soon hundreds of printing presses across Europe. The Church began using printing presses to mass-produce indulgences. "As soon as the coin in the coffer rings, the soul from purgatory springs" was a phrase used by a traveling monk who sold such indulgences at the time. Martin Luther questioned the reasonableness of this practice. Eventually, he posted the 95 theses on the church door in Wittenberg. He also translated the Bible into German. A short time later, his works, also mass-produced, accounted for a third of all books sold in Germany. Luther refused to recant his provocations as then determined by the Church's central authority. He was excommunicated in 1520 by the Pope and soon declared an outlaw by the Holy Roman Emperor.
This did not stop him. Instead, Luther referred to the Pope as "Pope Fart-Ass" and as the "Ass-God in Rome)". He also commissioned caricatures, such as woodcuts showing a female demon giving birth to the Pope and cardinals, of German peasants responding to a papal edict by showing the Pope their backsides and breaking wind, and more.
Gutenberg's printing presses contributed to the spread of information in a way similar to how the internet does in today's society. The Church's ability to control the flow of information was undermined, much like how newspapers, radio, and TV have partially lost this power today. The Pope excommunicated Luther, which is reminiscent of those who are de-platformed or banned from various platforms today. The Emperor declared Luther an outlaw, which is similar to how the UK's Prime Minister is imprisoning British citizens today. Luther called the Pope derogatory names, which is reminiscent of the individual who recently had the audacity to call an overweight German minister overweight.
Freedom of expression must be curtailed to combat the spread of false or harmful information in order to protect democracy, or so it is claimed. But perhaps it is more about who gets to control the flow of information?
As is often the case, there is nothing new under the sun.
-
 @ 5e5fc143:393d5a2c
2024-11-19 10:20:25
@ 5e5fc143:393d5a2c
2024-11-19 10:20:25Now test old reliable front end Stay tuned more later Keeping this as template long note for debugging in future as come across few NIP-33 post edit issues
-
 @ a95c6243:d345522c
2024-10-26 12:21:50
@ a95c6243:d345522c
2024-10-26 12:21:50Es ist besser, ein Licht zu entzünden, als auf die Dunkelheit zu schimpfen. Konfuzius
Die Bemühungen um Aufarbeitung der sogenannten Corona-Pandemie, um Aufklärung der Hintergründe, Benennung von Verantwortlichkeiten und das Ziehen von Konsequenzen sind durchaus nicht eingeschlafen. Das Interesse daran ist unter den gegebenen Umständen vielleicht nicht sonderlich groß, aber es ist vorhanden.
Der sächsische Landtag hat gestern die Einsetzung eines Untersuchungsausschusses zur Corona-Politik beschlossen. In einer Sondersitzung erhielt ein entsprechender Antrag der AfD-Fraktion die ausreichende Zustimmung, auch von einigen Abgeordneten des BSW.
In den Niederlanden wird Bill Gates vor Gericht erscheinen müssen. Sieben durch die Covid-«Impfstoffe» geschädigte Personen hatten Klage eingereicht. Sie werfen unter anderem Gates, Pfizer-Chef Bourla und dem niederländischen Staat vor, sie hätten gewusst, dass diese Präparate weder sicher noch wirksam sind.
Mit den mRNA-«Impfstoffen» von Pfizer/BioNTech befasst sich auch ein neues Buch. Darin werden die Erkenntnisse von Ärzten und Wissenschaftlern aus der Analyse interner Dokumente über die klinischen Studien der Covid-Injektion präsentiert. Es handelt sich um jene in den USA freigeklagten Papiere, die die Arzneimittelbehörde (Food and Drug Administration, FDA) 75 Jahre unter Verschluss halten wollte.
Ebenfalls Wissenschaftler und Ärzte, aber auch andere Experten organisieren als Verbundnetzwerk Corona-Solution kostenfreie Online-Konferenzen. Ihr Ziel ist es, «wissenschaftlich, demokratisch und friedlich» über Impfstoffe und Behandlungsprotokolle gegen SARS-CoV-2 aufzuklären und die Diskriminierung von Ungeimpften zu stoppen. Gestern fand eine weitere Konferenz statt. Ihr Thema: «Corona und modRNA: Von Toten, Lebenden und Physik lernen».
Aufgrund des Digital Services Acts (DSA) der Europäischen Union sei das Risiko groß, dass ihre Arbeit als «Fake-News» bezeichnet würde, so das Netzwerk. Staatlich unerwünschte wissenschaftliche Aufklärung müsse sich passende Kanäle zur Veröffentlichung suchen. Ihre Live-Streams seien deshalb zum Beispiel nicht auf YouTube zu finden.
Der vielfältige Einsatz für Aufklärung und Aufarbeitung wird sich nicht stummschalten lassen. Nicht einmal der Zensurmeister der EU, Deutschland, wird so etwas erreichen. Die frisch aktivierten «Trusted Flagger» dürften allerdings künftige Siege beim «Denunzianten-Wettbewerb» im Kontext des DSA zusätzlich absichern.
Wo sind die Grenzen der Meinungsfreiheit? Sicher gibt es sie. Aber die ideologische Gleichstellung von illegalen mit unerwünschten Äußerungen verfolgt offensichtlich eher das Ziel, ein derart elementares demokratisches Grundrecht möglichst weitgehend auszuhebeln. Vorwürfe wie «Hassrede», «Delegitimierung des Staates» oder «Volksverhetzung» werden heute inflationär verwendet, um Systemkritik zu unterbinden. Gegen solche Bestrebungen gilt es, sich zu wehren.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 41e6f20b:06049e45
2024-11-17 17:33:55
@ 41e6f20b:06049e45
2024-11-17 17:33:55Let me tell you a beautiful story. Last night, during the speakers' dinner at Monerotopia, the waitress was collecting tiny tips in Mexican pesos. I asked her, "Do you really want to earn tips seriously?" I then showed her how to set up a Cake Wallet, and she started collecting tips in Monero, reaching 0.9 XMR. Of course, she wanted to cash out to fiat immediately, but it solved a real problem for her: making more money. That amount was something she would never have earned in a single workday. We kept talking, and I promised to give her Zoom workshops. What can I say? I love people, and that's why I'm a natural orange-piller.
-
 @ 21b41910:91f41a5e
2024-11-23 12:00:26
@ 21b41910:91f41a5e
2024-11-23 12:00:26Chef's notes
Based on assorted recipes and refined over time, this round of beef tastes great as a result of the sweet and savory marinade.
Details
- ⏲️ Prep time: 5 minutes (+ 1 day)
- 🍳 Cook time: 20 minutes
Ingredients
- 2 pounds lean beef (may be labeled as London Broil)
- 1/3 cup olive oil
- 1/4 cup soy sauce
- 1/4 cup malt vinegar
- 1/4 cup lemon juice
- 1 tbsp sweetener of choice (honey, molasses, syrup, 4 packets of duck sauce, etc)
- 2 tsp old bay seasoning
- 1 tsp garlic powder
- 1 tsp sea salt
- 1/2 tsp black pepper
Directions
- Day Before: Mix all ingredients except the beef in a bowl to form a marinade. Place the cut of beef in a gallon sized Ziploc bag. Pour marinade over beef, ensure fully covered. Remove any excess air from the bag and seal. Place back in refrigerator for up to 24 hours before cooking.
- Cooking: Bring beef out of refrigerator (still in bag), and allow to rise to room temperature (about 30-40 minutes). Preheat broiler for about 15 minutes (your oven will vary). Broil for about 7-8 minutes on one side, then flip over. Continue broiling for another 7-10 minutes until temperature reads 140°F. Remove from broiler and let rest for 10 minutes before slicing thinly.
-
 @ 3bf0c63f:aefa459d
2024-03-23 08:57:08
@ 3bf0c63f:aefa459d
2024-03-23 08:57:08Nostr is not decentralized nor censorship-resistant
Peter Todd has been saying this for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right.
Nostr today is indeed centralized.
Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:
The top one was published to
wss://nostr.wine,wss://nos.lol,wss://pyramid.fiatjaf.com. The second was published to the relay where I generally publish all my notes to,wss://pyramid.fiatjaf.com, and that is announced on my NIP-05 file and on my NIP-65 relay list.A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:
These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains.
What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all.
Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant.
What happens is that most people who engaged with the note are following me, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on
wss://pyramid.fiatjaf.com.If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before.
Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today.
Peter Todd is wrong that Nostr is inherently centralized or that it needs a protocol change to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we drive in the right direction we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary.
See also:
-
 @ c631e267:c2b78d3e
2024-10-23 20:26:10
@ c631e267:c2b78d3e
2024-10-23 20:26:10Herzlichen Glückwunsch zum dritten Geburtstag, liebe Denk Bar! Wieso zum dritten? Das war doch 2022 und jetzt sind wir im Jahr 2024, oder? Ja, das ist schon richtig, aber bei Geburtstagen erinnere ich mich immer auch an meinen Vater, und der behauptete oft, der erste sei ja schließlich der Tag der Geburt selber und den müsse man natürlich mitzählen. Wo er recht hat, hat er nunmal recht. Konsequenterweise wird also heute dieser Blog an seinem dritten Geburtstag zwei Jahre alt.
Das ist ein Grund zum Feiern, wie ich finde. Einerseits ganz einfach, weil es dafür gar nicht genug Gründe geben kann. «Das Leben sind zwei Tage», lautet ein gängiger Ausdruck hier in Andalusien. In der Tat könnte es so sein, auch wenn wir uns im Alltag oft genug von der Routine vereinnahmen lassen.
Seit dem Start der Denk Bar vor zwei Jahren ist unglaublich viel passiert. Ebenso wie die zweieinhalb Jahre davor, und all jenes war letztlich auch der Auslöser dafür, dass ich begann, öffentlich zu schreiben. Damals notierte ich:
«Seit einigen Jahren erscheint unser öffentliches Umfeld immer fragwürdiger, widersprüchlicher und manchmal schier unglaublich - jede Menge Anlass für eigene Recherchen und Gedanken, ganz einfach mit einer Portion gesundem Menschenverstand.»
Wir erleben den sogenannten «großen Umbruch», einen globalen Coup, den skrupellose Egoisten clever eingefädelt haben und seit ein paar Jahren knallhart – aber nett verpackt – durchziehen, um buchstäblich alles nach ihrem Gusto umzukrempeln. Die Gelegenheit ist ja angeblich günstig und muss genutzt werden.
Nie hätte ich mir träumen lassen, dass ich so etwas jemals miterleben müsste. Die Bosheit, mit der ganz offensichtlich gegen die eigene Bevölkerung gearbeitet wird, war früher für mich unvorstellbar. Mein (Rest-) Vertrauen in alle möglichen Bereiche wie Politik, Wissenschaft, Justiz, Medien oder Kirche ist praktisch komplett zerstört. Einen «inneren Totalschaden» hatte ich mal für unsere Gesellschaften diagnostiziert.
Was mich vielleicht am meisten erschreckt, ist zum einen das Niveau der Gleichschaltung, das weltweit erreicht werden konnte, und zum anderen die praktisch totale Spaltung der Gesellschaft. Haben wir das tatsächlich mit uns machen lassen?? Unfassbar! Aber das Werkzeug «Angst» ist sehr mächtig und funktioniert bis heute.
Zum Glück passieren auch positive Dinge und neue Perspektiven öffnen sich. Für viele Menschen waren und sind die Entwicklungen der letzten Jahre ein Augenöffner. Sie sehen «Querdenken» als das, was es ist: eine Tugend.
Auch die immer ernsteren Zensurbemühungen sind letztlich nur ein Zeichen der Schwäche, wo Argumente fehlen. Sie werden nicht verhindern, dass wir unsere Meinung äußern, unbequeme Fragen stellen und dass die Wahrheit peu à peu ans Licht kommt. Es gibt immer Mittel und Wege, auch für uns.
Danke, dass du diesen Weg mit mir weitergehst!
-
 @ 0461fcbe:35a474dd
2024-11-12 17:58:48
@ 0461fcbe:35a474dd
2024-11-12 17:58:48On Nostr, I am running several marketing accounts for my projects: Ditto, The Mostr Bridge, and Cobrafuma. But I want other people to be able to post from those accounts. In fact, I want to hire a "social media manager" someday (for when my wife is not available 😂).
This is a pretty basic need for social media, but of course on Nostr it isn't basic at all, because private keys have nuclear potential if leaked. Even if you trust the person, a small mistake could be disastrous.
To solve this, we need a bunker.
What is a bunker?
A bunker (aka "remote signer") allows you to store your keys on your computer, but give others access. Once the other person is granted access, they can send commands to your computer like
sign_eventandget_public_key, and your computer will perform those operations without needing to expose the actual key.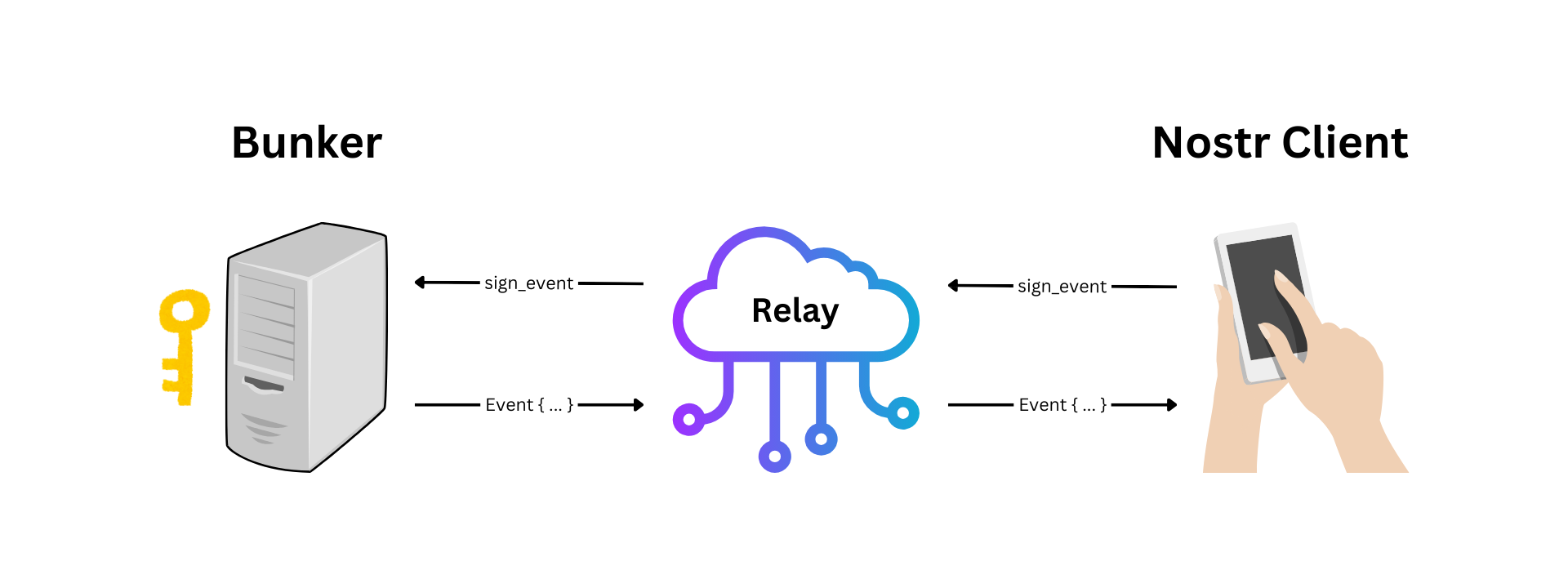
In reality the UX is not so technical. Your bunker generates a unique URI containing the connection details, and the other person pastes it into the login screen. Everything else happens automatically.
As for the running the bunker, you can run it on a VPS, a laptop, an old computer in your house, a Raspberry Pi, or even an Android phone.
The first bunker was an Android app called Nostr Connect. This lead to the creation of nsecBunker (a hosted service), nsec.app (a bunker that runs inside your web browser), and Amber (another Android app).
These days nsec.app and Amber are the only ones being actively developed, but due to running in restricted environments (web and Android respectively), they don't offer the level of 24/7 reliability I wanted in a bunker. If you are a single user managing your own keys I still recommend Amber, but for doling out credentials to your team, you might want knox.
Introducing Knox
knox is a command-line tool that manages keys, generates bunker URIs, and runs a bunker server. It is still beta software, but I am using it successfully today to post on Ditto.
knox is inspired by the wonderful
nak bunkercommand, which almost solved my problem but has no way to store credentials. So I created my own command-line bunker that you can run again and again.
Most notably, knox introduces a portable
.bunkerfile format for storing keys and connection details. It's encrypted with a password, which you have to type every time you want to add or remove keys, generate new URIs, and when you start the bunker.With knox you can have one bunker file, or many. It is loosely inspired by the KeePass
.kbdxidea.knox is written in TypeScript, but it's available as a precompiled executable on Linux, MacOS, and Windows thanks to
deno compile.Getting Started
To install knox, I've prepared a simple setup script that will detect your OS and install the knox command in your path:
sh curl https://dl.soapbox.pub/install/knox.sh | shYou can also grab a precompiled binary if you don't want to run the script.
Commands
Once installed, run
knoxto see a list of supported commands. It should look something like this:``` Usage: knox [options] [command]
Nostr bunker with encrypted storage.
Options: -V, --version output the version number -f, --file
path to the bunker file (default: "knox.bunker") -h, --help display help for command Commands: init initialize a new bunker add
add a new key to the bunker remove remove a key from the bunker uri [options] generate a bunker URI for a key revoke revoke an authorization pubkey [options] show the public key of a secret key status [name] show the status of the bunker start start the bunker daemon change change the passphrase of the bunker export [options] export keys from the bunker update [options] [ref] update knox to the latest version help [command] display help for command ``` Run
knox initto create a new bunker file. Then useknox add alex(replace with your own name) to add a key, thenknox uri alexto get a connection string. Finally, runknox startto start the bunker.While the bunker is running, you can continue to run commands like
knox addandknox uriin another tab, and the bunker will detect the file changes and automatically refresh.
Another good one is
knox status, which shows a list of keys and whether any of their URIs are being utilized.knox status <key>can show the individual connections for a specific key, andknox revoke <secret>can revoke an individual connection.Bunker Where?
knox needs internet connectivity to connect to relays, but it does not need to expose any ports to the outside world, so the ideal place might be on a desktop computer in your living room. This might be considered more secure than a VPS in a datacenter, depending on your circumstances.

I am running knox on an old Dell computer under my TV, which is a cheap and simple solution. It's connected to a backup battery in case the power flickers, but a prolonged outage would require starting the bunker again manually. I also suggest running the bunker in
screenor a similar tool so you can reconnect and view the logs over ssh on your home network.It's not suggested to run knox in systemd, because knox requires manually entering the encryption password when it starts. Any solution to store the password to disk, or pass it through a command-line argument, would compromise security.
What's Next?
For now, knox is meeting my needs. As the idea evolves I expect to make more changes, and possibly improvements to the
.bunkerformat if anyone else decides to use it. Feel free to drop any suggestions on GitLab!Another interesting idea would be to build a UI to manage the
.bunkerfile, or to offer hosted bunker (although I am kind of against this, unless the hoster is just cloud sync service and the bunker is decrypted locally within the browser, similar to KeeWeb). -
 @ a95c6243:d345522c
2024-10-19 08:58:08
@ a95c6243:d345522c
2024-10-19 08:58:08Ein Lämmchen löschte an einem Bache seinen Durst. Fern von ihm, aber näher der Quelle, tat ein Wolf das gleiche. Kaum erblickte er das Lämmchen, so schrie er:
"Warum trübst du mir das Wasser, das ich trinken will?"
"Wie wäre das möglich", erwiderte schüchtern das Lämmchen, "ich stehe hier unten und du so weit oben; das Wasser fließt ja von dir zu mir; glaube mir, es kam mir nie in den Sinn, dir etwas Böses zu tun!"
"Ei, sieh doch! Du machst es gerade, wie dein Vater vor sechs Monaten; ich erinnere mich noch sehr wohl, daß auch du dabei warst, aber glücklich entkamst, als ich ihm für sein Schmähen das Fell abzog!"
"Ach, Herr!" flehte das zitternde Lämmchen, "ich bin ja erst vier Wochen alt und kannte meinen Vater gar nicht, so lange ist er schon tot; wie soll ich denn für ihn büßen."
"Du Unverschämter!" so endigt der Wolf mit erheuchelter Wut, indem er die Zähne fletschte. "Tot oder nicht tot, weiß ich doch, daß euer ganzes Geschlecht mich hasset, und dafür muß ich mich rächen."
Ohne weitere Umstände zu machen, zerriß er das Lämmchen und verschlang es.
Das Gewissen regt sich selbst bei dem größten Bösewichte; er sucht doch nach Vorwand, um dasselbe damit bei Begehung seiner Schlechtigkeiten zu beschwichtigen.
Quelle: https://eden.one/fabeln-aesop-das-lamm-und-der-wolf
-
 @ a305a0de:21557ddd
2024-12-02 10:35:38
@ a305a0de:21557ddd
2024-12-02 10:35:38In today's fast-paced world, it's easy to get caught up in the hustle and bustle of daily life. Our minds are constantly racing, and it's not uncommon to feel stressed, anxious, or overwhelmed. But what if there was a way to break free from this cycle of negativity and cultivate a sense of calm, clarity, and happiness?
Enter mindfulness, a powerful practice that has been shown to have a positive impact on both physical and mental health. By incorporating mindfulness into your daily routine, you can reduce stress and anxiety, improve your relationships, increase your productivity, and even live a longer, happier life.
What is Mindfulness?
Mindfulness is the practice of being present in the moment, paying attention to your thoughts, feelings, and sensations without judgment or distraction. It's about cultivating a sense of awareness and acceptance, and learning to appreciate the beauty and simplicity of life.
The Benefits of Mindfulness
The benefits of mindfulness are numerous and well-documented. Some of the most significant advantages include:
- Reduced stress and anxiety
- Improved relationships and communication skills
- Increased productivity and focus
- Enhanced creativity and problem-solving abilities
- Better sleep quality and duration
- Improved overall health and well-being
How to Practice Mindfulness
Incorporating mindfulness into your daily routine is easier than you might think. Here are a few simple tips to get you started:
- Start small: Begin with short periods of mindfulness practice, such as 5-10 minutes per day.
- Focus on your breath: Bring your attention to your breath, noticing the sensation of the air moving in and out of your body.
- Practice mindfulness in daily activities: Bring mindfulness into your daily routine by paying attention to your thoughts, feelings, and sensations while you're doing everyday tasks like eating, walking, or showering.
Conclusion
Mindfulness is a powerful practice that has the potential to transform your life in countless ways. By incorporating mindfulness into your daily routine, you can reduce stress and anxiety, improve your relationships, increase your productivity, and even live a longer, happier life. So why not give it a try? Your mind, body, and spirit will thank you.
-
 @ 42342239:1d80db24
2024-08-30 06:26:21
@ 42342239:1d80db24
2024-08-30 06:26:21Quis custodiet ipsos custodes?
-- Juvenal (Who will watch the watchmen?)
In mid-July, numerous media outlets reported on the assassination attempt on Donald Trump. FBI Director Christopher Wray stated later that same month that what hit the former president Trump was a bullet. A few days later, it was reported from various sources that search engines no longer acknowledged that an assassination attempt on ex-President Trump had taken place. When users used automatic completion in Google and Bing (91% respectively 4% market share), these search engines only suggested earlier presidents such as Harry Truman and Theodore Roosevelt, along with Russian President Vladimir Putin as people who could have been subjected to assassination attempts.
The reports were comprehensive enough for the Republican district attorney of Missouri to say that he would investigate matter. The senator from Kansas - also a Republican - planned to make an official request to Google. Google has responded through a spokesman to the New York Post that the company had not "manually changed" search results, but its system includes "protection" against search results "connected to political violence."
A similar phenomenon occurred during the 2016 presidential election. At the time, reports emerged of Google, unlike other less widely used search engines, rarely or never suggesting negative search results for Hillary Clinton. The company however provided negative search results for then-candidate Trump. Then, as today, the company denied deliberately favouring any specific political candidate.
These occurrences led to research on how such search suggestions can influence public opinion and voting preferences. For example, the impact of simply removing negative search suggestions has been investigated. A study published in June 2024 reports that such search results can dramatically affect undecided voters. Reducing negative search suggestions can turn a 50/50 split into a 90/10 split in favour of the candidate for whom negative search suggestions were suppressed. The researchers concluded that search suggestions can have "a dramatic impact," that this can "shift a large number of votes" and do so without leaving "any trace for authorities to follow." How search engines operate should therefore be considered of great importance by anyone who claims to take democracy seriously. And this regardless of one's political sympathies.
A well-known thought experiment in philosophy asks: "If a tree falls in the forest and no one hears it, does it make a sound?" Translated to today's media landscape: If an assassination attempt took place on a former president, but search engines don't want to acknowledge it, did it really happen?
-
 @ 42342239:1d80db24
2024-07-28 08:35:26
@ 42342239:1d80db24
2024-07-28 08:35:26Jerome Powell, Chairman of the US Federal Reserve, stated during a hearing in March that the central bank has no plans to introduce a central bank digital currency (CBDCs) or consider it necessary at present. He said this even though the material Fed staff presents to Congress suggests otherwise - that CBDCs are described as one of the Fed’s key duties .
A CBDC is a state-controlled and programmable currency that could allow the government or its intermediaries the possibility to monitor all transactions in detail and also to block payments based on certain conditions.
Critics argue that the introduction of CBDCs could undermine citizens’ constitutionally guaranteed freedoms and rights . Republican House Majority Leader Tom Emmer, the sponsor of a bill aimed at preventing the central bank from unilaterally introducing a CBDC, believes that if they do not mimic cash, they would only serve as a “CCP-style [Chinese Communist Party] surveillance tool” and could “undermine the American way of life”. Emmer’s proposed bill has garnered support from several US senators , including Republican Ted Cruz from Texas, who introduced the bill to the Senate. Similarly to how Swedish cash advocates risk missing the mark , Tom Emmer and the US senators risk the same outcome with their bill. If the central bank is prevented from introducing a central bank digital currency, nothing would stop major banks from implementing similar systems themselves, with similar consequences for citizens.
Indeed, the entity controlling your money becomes less significant once it is no longer you. Even if central bank digital currencies are halted in the US, a future administration could easily outsource financial censorship to the private banking system, similar to how the Biden administration is perceived by many to have circumvented the First Amendment by getting private companies to enforce censorship. A federal court in New Orleans ruled last fall against the Biden administration for compelling social media platforms to censor content. The Supreme Court has now begun hearing the case.
Deng Xiaoping, China’s paramount leader who played a vital role in China’s modernization, once said, “It does not matter if the cat is black or white. What matters is that it catches mice.” This statement reflected a pragmatic approach to economic policy, focusing on results foremost. China’s economic growth during his tenure was historic.
The discussion surrounding CBDCs and their negative impact on citizens’ freedoms and rights would benefit from a more practical and comprehensive perspective. Ultimately, it is the outcomes that matter above all. So too for our freedoms.
-
 @ a305a0de:21557ddd
2024-12-02 10:18:16
@ a305a0de:21557ddd
2024-12-02 10:18:16Space tourism is no longer just the stuff of science fiction. With private companies like Virgin Galactic, SpaceX, and Blue Origin leading the charge, the industry is poised for exponential growth in the coming years.
But what exactly is space tourism, and how will it change the way we travel? In this article, we'll explore the exciting future of space tourism and what it means for you.
Suborbital Flights: The First Step
Suborbital flights, which take passengers to the edge of space without entering orbit, are the first step in space tourism. Virgin Galactic's SpaceShipTwo, for example, has already carried several passengers to an altitude of 62 miles (100 km) above the Earth's surface.
These flights offer a thrilling experience, with passengers experiencing weightlessness and witnessing breathtaking views of the curvature of the Earth. And with prices starting at around $250,000 per seat, suborbital flights are becoming increasingly accessible to the general public.
Lunar Resorts: The Next Frontier
But suborbital flights are just the beginning. Lunar resorts, which would allow tourists to stay on the Moon for extended periods, are the next frontier in space tourism.
Private companies like SpaceX and Blue Origin are already working on establishing a human presence on the Moon, with plans to send tourists there in the near future. And with NASA's Artemis program aiming to return humans to the Moon by 2024, the prospect of lunar tourism is becoming increasingly realistic.
Space Stations: The Ultimate Getaway
Space stations, which would offer tourists the opportunity to stay in orbit around the Earth for extended periods, are another exciting development in space tourism.
Private companies like Axiom Space and Bigelow Aerospace are already working on establishing space stations, which would offer tourists a unique and unforgettable experience. And with NASA's plans to establish a sustainable presence in low-Earth orbit, space stations could become a reality sooner rather than later.
Conclusion
Space tourism is no longer just a pipe dream, but a rapidly growing industry that's set to change the way we travel forever. From suborbital flights to lunar resorts and space stations, the possibilities are endless. And with private companies and governments around the world investing heavily in space tourism, the future of this exciting industry looks brighter than ever.
-
 @ fe7f6bc6:c42539a3
2024-11-29 01:54:31
@ fe7f6bc6:c42539a3
2024-11-29 01:54:31A few weeks ago, I sat down with Chad (full podcast), a seasoned Muay Thai fighter with over a decade of experience, to talk about life inside and outside the ring. Chad’s story is raw, intense, and unfiltered—a journey of struggle, discipline, and transformation. His insights left me reflecting on how combat sports, especially Muay Thai, can teach us profound lessons about resilience, focus, and the human spirit.
The Fight Beyond the Ring
What struck me most was how Muay Thai isn’t just a sport for Chad—it’s a way of life. He began his journey as a teenager, struggling with family issues and uncertainty about his future. A chance meeting led him to Thailand, where he trained intensely and fought his first bout just 28 days later. Chad told me, “Muay Thai saved my life,” and I could feel the weight behind those words.
For Chad, the ring became a space to confront not just opponents but his own fears and insecurities. The process of training—the relentless hill sprints, countless kicks, and sparring sessions—taught him how to face challenges head-on. Fighting wasn’t about aggression; it was about finding strength in adversity.
The Beauty in the Brutality
One of the most fascinating things Chad shared was his perspective on pain and sacrifice. During his career, he’s endured broken ribs, countless stitches, and even fought with a broken nose for eight years before getting it fixed. “Pain is the best teacher,” he said, explaining how injuries forced him to adapt and improve.
What I found most compelling was how this physical suffering seemed to heighten his appreciation for life. Chad described moments after brutal training sessions when even a sunset or a simple breeze felt extraordinary. It’s as if the harshness of the ring makes the world outside it feel brighter, sharper, and more alive. “When you’re ready to die in the ring,” he said, “you start seeing life differently.”
The Mental Battle
Chad emphasized the mental aspect of fighting, something I hadn’t fully appreciated before. He talked about the mindset required to step into the ring: the inner dialogue where you convince yourself you’re ready to endure pain and push beyond limits. “You can play football or tennis, but you can’t play Muay Thai,” he said, driving home the seriousness of the sport.
Before a fight, Chad uses visualization to prepare himself for the intensity of combat. He doesn’t shy away from the danger but instead leans into it, fully accepting the risks. This mindset, he believes, is what separates good fighters from great ones.
Lessons for Life
While most of us won’t step into a Muay Thai ring, Chad’s experiences offer valuable lessons that apply to all areas of life:
- Discipline Creates Freedom: The structure of relentless training gave Chad a sense of purpose and control over his life.
- Face Your Fears: Whether it’s an elbow to the face or a difficult decision in life, avoidance only makes things worse.
- Surround Yourself with the Right People: Chad stressed the importance of training with people who push you to be better. “Energy matters,” he said, and I couldn’t agree more.
Final Thoughts
Chad’s story reminded me why I wanted to take on my own Muay Thai journey. It’s not just about fighting; it’s about testing yourself in ways that reveal who you really are. For Chad, the ring isn’t just a place to compete—it’s a place to grow, to learn, and to become a better version of himself.
After our conversation, I realized that the lessons of Muay Thai go beyond the gym. Whether you’re training for a fight or tackling challenges in everyday life, the principles of resilience, discipline, and self-reflection are universal.
If you’re curious to learn more about Chad’s journey, I highly recommend watching the documentary we worked on together. It’s a glimpse into the raw, unforgiving world of Muay Thai—and the unshakable spirit of those who live it.
Stay Healthy - Max
-
 @ 4ba8e86d:89d32de4
2024-11-07 13:56:21
@ 4ba8e86d:89d32de4
2024-11-07 13:56:21Tutorial feito por Grom mestre⚡poste original abaixo:
http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/240277/tutorial-criando-e-acessando-sua-conta-de-email-pela-i2p?show=240277#q240277
Bom dia/tarde/noite a todos os camaradas. Seguindo a nossa série de tutoriais referentes a tecnologias essenciais para a segurança e o anonimato dos usuários, sendo as primeiras a openPGP e a I2P, lhes apresento mais uma opção para expandir os seus conhecimentos da DW. Muitos devem conhecer os serviços de mail na onion como DNMX e mail2tor, mas e que tal um serviço de email pela I2P. Nesse tutorial eu vou mostrar a vocês como criar a sua primeira conta no hq.postman.i2p e a acessar essa conta.
É importante que vocês tenham lido a minha primeira série de tutoriais a respeito de como instalar, configurar e navegar pela I2P nostr:nevent1qqsyjcz2w0e6d6dcdeprhuuarw4aqkw730y542dzlwxwssneq3mwpaspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsyp5vcq Esse tutorial é um pré-requisito para o seguinte e portanto recomendo que leia-os antes de prosseguir com o seguinte tutorial. O tutorial de Kleopatra nostr:nevent1qqs8h7vsn5j6qh35949sa60dms4fneussmv9jd76n24lsmtz24k0xlqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgecq8f7 é complementar dado que é extremamente recomendado assinar e criptografar as mensagens que seguem por emails pela DW. Sem mais delongas, vamos ao tutorial de fato.
1. Criando uma conta de email no hq.postman
Relembrando: Esse tutorial considera que você já tenha acesso à I2P. Entre no seu navegador e acesse o endereço hq.postman.i2p. O roteador provavelmente já contém esse endereço no seu addressbook e não haverá a necessidade de inserir o endereço b32 completo. Após entrar no site vá para a página '1 - Creating a mailbox' https://image.nostr.build/d850379fe315d2abab71430949b06d3fa49366d91df4c9b00a4a8367d53fcca3.jpg
Nessa página, insira as credenciais de sua preferências nos campos do formulário abaixo. Lembre-se que o seu endereço de email aceita apenas letras e números. Clique em 'Proceed' depois que preencher todos os campos. https://image.nostr.build/670dfda7264db393e48391f217e60a2eb87d85c2729360c8ef6fe0cf52508ab4.jpg
Uma página vai aparecer pedindo para confirmar as credenciais da sua nova conta. Se tudo estiver certo apenas clique em 'Confirm and Create Mailbox'. Se tudo ocorrer como conforme haverá uma confirmação de que a sua nova conta foi criada com sucesso. Após isso aguarde por volta de 5 minutos antes de tentar acessá-la, para que haja tempo suficiente para o servidor atualizar o banco de dados. https://image.nostr.build/ec58fb826bffa60791fedfd9c89a25d592ac3d11645b270c936c60a7c59c067f.jpg https://image.nostr.build/a2b7710d1e3cbb36431acb9055fd62937986b4da4b1a1bbb06d3f3cb1f544fd3.jpg
Pronto! Sua nova conta de email na I2P foi criada. Agora vamos para a próxima etapa: como acessar a sua conta via um cliente de email.
2. Configurando os túneis cliente de SMTP e POP3
O hq.postman não possui um cliente web que nos permite acessar a nossa conta pelo navegador. Para isso precisamos usar um cliente como Thunderbird e configurar os túneis cliente no I2Pd que serão necessários para o Thunderbird se comunicar com o servidor pela I2P.
Caso não tenha instalado o Thunderbird ainda, faça-o agora antes de prosseguir.
Vamos configurar os túneis cliente do servidor de email no nosso roteador. Para isso abra um terminal ou o seu gestor de arquivos e vá para a pasta de configuração de túneis do I2P. Em Linux esse diretório se localiza em /etc/i2pd/tunnels.d. Em Windows, essa pasta se localiza em C:\users\user\APPDATA\i2pd. Na pasta tunnels.d crie dois arquivos: smtp.postman.conf e pop-postman.conf. Lembre-se que em Linux você precisa de permissões de root para escrever na pasta de configuração. Use o comando sudoedit
para isso. Edite-os conforme as imagens a seguir:
Arquivo pop-postman.conf https://image.nostr.build/7e03505c8bc3b632ca5db1f8eaefc6cecb4743cd2096d211dd90bbdc16fe2593.jpg
Arquivo smtp-postman.conf https://image.nostr.build/2d06c021841dedd6000c9fc2a641ed519b3be3c6125000b188842cd0a5af3d16.jpg
Salve os arquivos e reinicie o serviço do I2Pd. Em Linux isso é feito pelo comando:
sudo systemctl restart i2pdEntre no Webconsole do I2Pd pelo navegador (localhost:7070) e na seção I2P Tunnels, verifique se os túneis pop-postman e smtp-postman foram criados, caso contrário verifique se há algum erro nos arquivos e reinicie o serviço.Com os túneis cliente criados, vamos agora configurar o Thunderbird
3. Configurando o Thunderbird para acessar a nossa conta
Abra o Thunderbird e clique em criar uma nova conta de email. Se você não tiver nenhum conta previamente presente nele você vai ser diretamente recebido pela janela de criação de conta a seguir. https://image.nostr.build/e9509d7bd30623716ef9adcad76c1d465f5bc3d5840e0c35fe4faa85740f41b4.jpg https://image.nostr.build/688b59b8352a17389902ec1e99d7484e310d7d287491b34f562b8cdd9dbe8a99.jpg
Coloque as suas credenciais, mas não clique ainda em Continuar. Clique antes em Configure Manually, já que precisamos configurar manualmente os servidores de SMTP e POP3 para, respectivamente, enviar e receber mensagens.
Preencha os campos como na imagem a seguir. Detalhe: Não coloque o seu endereço completo com o @mail.i2p, apenas o nome da sua conta. https://image.nostr.build/4610b0315c0a3b741965d3d7c1e4aff6425a167297e323ba8490f4325f40cdcc.jpg
Clique em Re-test para verificar a integridade da conexão. Se tudo estiver certo uma mensagem irá aparecer avisando que as configurações do servidores estão corretas. Clique em Done assim que estiver pronto para prosseguir. https://image.nostr.build/8a47bb292f94b0d9d474d4d4a134f8d73afb84ecf1d4c0a7eb6366d46bf3973a.jpg
A seguinte mensagem vai aparecer alertando que não estamos usando criptografia no envio das credenciais. Não há problema nenhum aqui, pois a I2P está garantindo toda a proteção e anonimato dos nossos dados, o que dispensa a necessidade de uso de TLS ou qualquer tecnologia similar nas camadas acima. Marque a opção 'I Understand the risks' e clique em 'Continue' https://image.nostr.build/9c1bf585248773297d2cb1d9705c1be3bd815e2be85d4342227f1db2f13a9cc6.jpg
E por fim, se tudo ocorreu como devido sua conta será criada com sucesso e você agora será capaz de enviar e receber emails pela I2P usando essa conta. https://image.nostr.build/8ba7f2c160453c9bfa172fa9a30b642a7ee9ae3eeb9b78b4dc24ce25aa2c7ecc.jpg
4. Observações e considerações finais
Como informado pelo próprio site do hq.postman, o domínio @mail.i2p serve apenas para emails enviados dentro da I2P. Emails enviados pela surface devem usar o domínio @i2pmai.org. É imprescindível que você saiba usar o PGP para assinar e criptografar as suas mensagens, dado que provavelmente as mensagens não são armazenadas de forma criptografada enquanto elas estão armazenadas no servidor. Como o protocolo POP3 delete as mensagens no imediato momento em que você as recebe, não há necessidade de fazer qualquer limpeza na sua conta de forma manual.
Por fim, espero que esse tutorial tenha sido útil para vocês. Que seu conhecimento tenha expandido ainda mais com as informações trazidas aqui. Até a próxima.
-
 @ 09fbf8f3:fa3d60f0
2024-11-02 08:00:29
@ 09fbf8f3:fa3d60f0
2024-11-02 08:00:29> ### 第三方API合集:
免责申明:
在此推荐的 OpenAI API Key 由第三方代理商提供,所以我们不对 API Key 的 有效性 和 安全性 负责,请你自行承担购买和使用 API Key 的风险。
| 服务商 | 特性说明 | Proxy 代理地址 | 链接 | | --- | --- | --- | --- | | AiHubMix | 使用 OpenAI 企业接口,全站模型价格为官方 86 折(含 GPT-4 )| https://aihubmix.com/v1 | 官网 | | OpenAI-HK | OpenAI的API官方计费模式为,按每次API请求内容和返回内容tokens长度来定价。每个模型具有不同的计价方式,以每1,000个tokens消耗为单位定价。其中1,000个tokens约为750个英文单词(约400汉字)| https://api.openai-hk.com/ | 官网 | | CloseAI | CloseAI是国内规模最大的商用级OpenAI代理平台,也是国内第一家专业OpenAI中转服务,定位于企业级商用需求,面向企业客户的线上服务提供高质量稳定的官方OpenAI API 中转代理,是百余家企业和多家科研机构的专用合作平台。 | https://api.openai-proxy.org | 官网 | | OpenAI-SB | 需要配合Telegram 获取api key | https://api.openai-sb.com | 官网 |
持续更新。。。
推广:
访问不了openai,去
低调云购买VPN。官网:https://didiaocloud.xyz
邀请码:
w9AjVJit价格低至1元。
-
 @ bc6ccd13:f53098e4
2024-11-28 15:35:54
@ bc6ccd13:f53098e4
2024-11-28 15:35:54Of all the common misconceptions about money, this is the deepest and most pervasive. It taps into the very psychology that makes money the most powerful tool in the world. Money works in large part because, for most practical purposes, you can assume that money and wealth are the same thing and be very successful in life.
The problem is, it's a completely false premise. And without purging that assumption from your mental framework, understanding money and economics at a fundamental level is impossible.
Luckily, money is such an effective tool that it can continue to "mostly" function even without anyone understanding it at a fundamental level. It's a lot like gravity in that regard. You don't need to understand general relativity to learn how to walk. But unlike gravity, money is a powerful tool that can easily be used to exploit the less knowledgeable. That's why the general acceptance of this particular false idea is such a tragedy; it enables theft and exploitation on a global scale, and leaves the victims unable to identify the perpetrators or understand their methods.
Money as a Social Technology
So let's unpack this misconception. We can start with a simple example. You've been shipwrecked on a desert island with only the clothes on your back. After a day under the blistering sun, you're presented with two options: a billion dollars in cash, or a case of bottled water. Which one do you choose? If you chose the water, congratulations. You survived because you were able to differentiate money from real wealth.
Now run the same experiment, but place yourself in the water aisle at Costco. Suddenly you choose differently. This shows a few key requirements for money to be useful. One, you need the real wealth, the actual goods and services. If there is no bottled water on that island, all the money in the world won't do you a lick of good. Two, you need someone willing to exchange the real wealth for your money. If you're alone on that island and you find a bottle of water, you don't need money to drink it, you just help yourself. Both requirements are essential.
This shows us that money is a social technology. Understanding the purpose and function of this technology is critical to dispensing with misconceptions like "money=wealth".
Money and Civilization
What's the difference between a subsistence hunter/gatherer lifestyle and the modern civilization we all enjoy today? Specialization of labor, and complex supply chains. And what enables those civilizational necessities? Money.
In a subsistence situation, everything you have is created start-to-finish by you or by your immediate family or tribe. Everyone has to be a sort of jack-of-all-trades, at least at a group level. If you want a shelter, you collect the natural materials and build it yourself. If you need clothes, you collect the fibers or skins, process them, and use the fabric to sew your own outfit.
Contrast that with the electronic device you're using to read these words right now. How many people does it take to build a smartphone? Millions. Can one person do it? Absolutely not. You could give anyone in the world an entire lifetime and there's no way they could mine, process, and assemble the raw materials into a functional smartphone. It's simply too complex, too many processes and too much specialized knowledge and machinery needed. Not to mention doing it at a cost that most people on the planet can afford. That miracle is only possible because millions of people specialize in one tiny specific task related to making one part of a complex item, over and over again. The efficiency of only doing one specific task instead of being a generalist is what makes civilization possible.
But there's a problem. The person who's doing one specific task to make part of one widget still needs to eat, have a place to live, clothes to wear, etc. But how do you get all that while working a full time job making widgets? You can't do it all yourself, you need to buy those things from someone else who, similarly, specializes in those necessities of life. You need money. Money is what makes the whole thing work.
Money and Barter
So what exactly is money and how does it work? In a subsistence society, you can use barter to trade with strangers. You give them some fish, they give you some clothing, everyone is happy. But barter has major problems, and doesn't work at all in complex supply chains with specialized workers. Specialized jobs don't produce valuable finished goods that can be bartered. When you solder circuit boards all day, you can't go to your local farmer and trade ten "solder circuit board" for a dozen eggs.
Enter money. Money solves multiple problems that arise with barter. For one, it creates a way to compare extremely dissimilar things. How many fish is a pound of butter worth? How many eggs? With barter, every good or service has to be priced in relation to every other good or service it's exchanged for. This is impossibly cumbersome and inefficient. Having money as a unit of account is as essential to trade as having a uniform inch is to building a house. A single carpenter might be able to use the width of his hand to measure boards, but get two carpenters working together and that "handbreadth" no longer works.
Second, money solves the problem of not having the correct item to barter with. If your neighbor has butter and you have fish, but your neighbor hates fish and will only accept a chicken, barter won't work. But if you can just pay him with money, he can go buy whatever he prefers.
Third, money creates a way to value and reimburse specialized work. That's arguably the most important aspect.
The Social Contract Underlying Money
So what makes money function? Why would someone accept a piece of paper with a picture of a dead president in exchange for a very real and very valuable good or service? Well, the obvious answer is that they can be certain they'll be able to exchange that piece of paper with someone else and get an equally valuable good or service in the future. This is circular logic though, and leads some economists to mistakenly attribute the value of money to a "collective delusion". But since every known advanced civilization has used some form of money, calling it a delusion is both inaccurate and boorishly pretentious.
To understand the real mechanism behind the phenomenon, we have to consider how money is acquired. As anyone who has ever earned an honest wage knows, getting a paycheck requires two things. One, producing a valuable good or service. And two, giving that good or service to someone else instead of immediately consuming it yourself.
The first point is self-explanatory. If what you produce isn't valuable, no one will buy it.
The second point needs a bit more explanation. Money is a social technology, it's only valuable in a purely monetary sense when there's someone else to trade with. When you make yourself a few eggs for breakfast, you don't pay yourself for frying the eggs. Obviously. But if you eat your eggs, then go to your job as a short-order cook at the local diner, you may spend the morning getting paid to do exactly what you did "for free" at home. The difference is in the deferred consumption.
When you do a favor for someone, morality and the spirit of fairness dictates that they would be willing to return the favor in the future when you need something from them. That's how it works in a family or small community. People "owe each other one," and favors are reciprocated regularly without any money changing hands in a kind of informal credit system. But if one person starts to take advantage of others' generosity and requests a lot of favors, but always fails to reciprocate when asked, people catch on quickly. The parasitic behavior will be met with increasing unwillingness to help from members of the family or community, and in extreme cases, even exile from the community itself.
This informal credit system is the simplest and most fundamental form of money, and we can learn the basic principle behind why money works by observing it. We can see that a person accumulates "credits" by contributing productive value to others without getting anything in return. The "credits" are informal mental ledger credits that represent "this person has done something productive and valuable for someone else, which means he deserves to receive something valuable in the future." If a person contributes generously enough to the community, he will build up so much "credit" with everyone that he can expect generous help in return from any member of the community.
The shortcomings of this informal credit system are that one, it doesn't provide a unit of measurement to compare different goods and services accurately. This can lead to misunderstanding and disputes when different people don't value services the same way. Someone can feel that they are contributing more to the community than they're getting back in return. And two, it relies heavily on trust, and only works between people who interact on a regular basis. It would be foolish to provide favors to a stranger of unknown reputation, or someone who's just traveling through the area, because in either case there's no expectation of establishing a reciprocal relationship with that individual.
Money is just a way to formalize and expand that local, informal mental ledger. It's a way to keep track, on a societal level, who has contributed their fair share to the community and is deserving of reciprocal treatment. When someone buys something from you, although you don't consciously think through what's happening, on a subconscious level you're participating in a societal dialogue that goes something like this: "This person has money, which means they're a capable, generous, reciprocal person who has contributed more to the community than they've taken. Fairness dictates that they deserve something of value as a reward for their pro-social behavior. By taking their money, and giving them something of value, I can perpetuate the cycle of rewarding people who generously and capably do work that benefits others, and that will be beneficial to me personally and also to society as a whole. By having the money they give me, I can then also signal to others that I'm the same type of generous, reciprocal, productive person, and I can expect to be rewarded for that in the future when I try to exchange this money for valuable goods and services."
So the money has value, not because of some inherent quality of the paper or gold or mental "credit," but because it represents past productive behavior, but without immediate consumption. The money itself is not wealth, it's just an abstract representation, a kind of scorecard or ledger entry, of the real wealth that the holder of the money has already produced.
Money and Capital Formation
This dialogue or unwritten contract is the foundation of modern civilization. It's powerful, because deferred consumption is the mechanism of capital formation, and capital formation is the foundation of complex supply chains and technological progress.
You might be able to catch enough fish to feed your family with a crude rod and line. But building a modern fishing trawler (a valuable capital good) takes thousands of people working together for a long time. All that hard work doesn't result in any fish being caught throughout the process, and all those people could instead be out fishing and catching a lot of fish to eat. But by deferring that consumption and instead putting that effort into building a capital good, you end up with a huge fishing trawler. Once it's finished, a few of those thousands of people can catch more fish in a week than all the thousands of them combined could have caught over the whole time it took to build the trawler. That makes fishing much easier and more effective in the future, making food much more plentiful and increasing the standard of living for the whole society. And money is what makes all that possible on a global scale.
Final Thoughts
Given how critical this system is to civilization, any attack on money and its function is an existential threat. Unfortunately, a failure to understand the true nature of money leads to reliance on less nuanced or completely false ideas like "money=wealth". And that gives psychological cover to parasitic anti-social behavior like creating money and giving it away to buy votes, and all sorts of other destructive and dishonest shenanigans. Understanding that money is not wealth exposes the folly of all these schemes that purport to make people wealthier simply by creating more money. Believing that money is wealth makes the MMT clowns and the Keynesian grifters sound at least marginally credible. But those are specific misconceptions that need their own detailed explanation.
For now, reprogramming your mental framework to draw a strong distinction between money and real wealth will give you a solid foundation to understand economics, and to critique the many incorrect theories presented by the parasitical elements who wish to muddy the waters and avoid scrutiny of their anti-civilizational exploitation.
-
 @ ee11a5df:b76c4e49
2024-07-11 23:57:53
@ ee11a5df:b76c4e49
2024-07-11 23:57:53What Can We Get by Breaking NOSTR?
"What if we just started over? What if we took everything we have learned while building nostr and did it all again, but did it right this time?"
That is a question I've heard quite a number of times, and it is a question I have pondered quite a lot myself.
My conclusion (so far) is that I believe that we can fix all the important things without starting over. There are different levels of breakage, starting over is the most extreme of them. In this post I will describe these levels of breakage and what each one could buy us.
Cryptography
Your key-pair is the most fundamental part of nostr. That is your portable identity.
If the cryptography changed from secp256k1 to ed25519, all current nostr identities would not be usable.
This would be a complete start over.
Every other break listed in this post could be done as well to no additional detriment (save for reuse of some existing code) because we would be starting over.
Why would anyone suggest making such a break? What does this buy us?
- Curve25519 is a safe curve meaning a bunch of specific cryptography things that us mortals do not understand but we are assured that it is somehow better.
- Ed25519 is more modern, said to be faster, and has more widespread code/library support than secp256k1.
- Nostr keys could be used as TLS server certificates. TLS 1.3 using RFC 7250 Raw Public Keys allows raw public keys as certificates. No DNS or certification authorities required, removing several points of failure. These ed25519 keys could be used in TLS, whereas secp256k1 keys cannot as no TLS algorithm utilizes them AFAIK. Since relays currently don't have assigned nostr identities but are instead referenced by a websocket URL, this doesn't buy us much, but it is interesting. This idea is explored further below (keep reading) under a lesser level of breakage.
Besides breaking everything, another downside is that people would not be able to manage nostr keys with bitcoin hardware.
I am fairly strongly against breaking things this far. I don't think it is worth it.
Signature Scheme and Event Structure
Event structure is the next most fundamental part of nostr. Although events can be represented in many ways (clients and relays usually parse the JSON into data structures and/or database columns), the nature of the content of an event is well defined as seven particular fields. If we changed those, that would be a hard fork.
This break is quite severe. All current nostr events wouldn't work in this hard fork. We would be preserving identities, but all content would be starting over.
It would be difficult to bridge between this fork and current nostr because the bridge couldn't create the different signature required (not having anybody's private key) and current nostr wouldn't be generating the new kind of signature. Therefore any bridge would have to do identity mapping just like bridges to entirely different protocols do (e.g. mostr to mastodon).
What could we gain by breaking things this far?
- We could have a faster event hash and id verification: the current signature scheme of nostr requires lining up 5 JSON fields into a JSON array and using that as hash input. There is a performance cost to copying this data in order to hash it.
- We could introduce a subkey field, and sign events via that subkey, while preserving the pubkey as the author everybody knows and searches by. Note however that we can already get a remarkably similar thing using something like NIP-26 where the actual author is in a tag, and the pubkey field is the signing subkey.
- We could refactor the kind integer into composable bitflags (that could apply to any application) and an application kind (that specifies the application).
- Surely there are other things I haven't thought of.
I am currently against this kind of break. I don't think the benefits even come close to outweighing the cost. But if I learned about other things that we could "fix" by restructuring the events, I could possibly change my mind.
Replacing Relay URLs
Nostr is defined by relays that are addressed by websocket URLs. If that changed, that would be a significant break. Many (maybe even most) current event kinds would need superseding.
The most reasonable change is to define relays with nostr identities, specifying their pubkey instead of their URL.
What could we gain by this?
- We could ditch reliance on DNS. Relays could publish events under their nostr identity that advertise their current IP address(es).
- We could ditch certificates because relays could generate ed25519 keypairs for themselves (or indeed just self-signed certificates which might be much more broadly supported) and publish their public ed25519 key in the same replaceable event where they advertise their current IP address(es).
This is a gigantic break. Almost all event kinds need redefining and pretty much all nostr software will need fairly major upgrades. But it also gives us a kind of Internet liberty that many of us have dreamt of our entire lives.
I am ambivalent about this idea.
Protocol Messaging and Transport
The protocol messages of nostr are the next level of breakage. We could preserve keypair identities, all current events, and current relay URL references, but just break the protocol of how clients and relay communicate this data.
This would not necessarily break relay and client implementations at all, so long as the new protocol were opt-in.
What could we get?
- The new protocol could transmit events in binary form for increased performance (no more JSON parsing with it's typical many small memory allocations and string escaping nightmares). I think event throughput could double (wild guess).
- It could have clear expectations of who talks first, and when and how AUTH happens, avoiding a lot of current miscommunication between clients and relays.
- We could introduce bitflags for feature support so that new features could be added later and clients would not bother trying them (and getting an error or timing out) on relays that didn't signal support. This could replace much of NIP-11.
- We could then introduce something like negentropy or negative filters (but not that... probably something else solving that same problem) without it being a breaking change.
- The new protocol could just be a few websocket-binary messages enhancing the current protocol, continuing to leverage the existing websocket-text messages we currently have, meaning newer relays would still support all the older stuff.
The downsides are just that if you want this new stuff you have to build it. It makes the protocol less simple, having now multiple protocols, multiple ways of doing the same thing.
Nonetheless, this I am in favor of. I think the trade-offs are worth it. I will be pushing a draft PR for this soon.
The path forward
I propose then the following path forward:
- A new nostr protocol over websockets binary (draft PR to be shared soon)
- Subkeys brought into nostr via NIP-26 (but let's use a single letter tag instead, OK?) via a big push to get all the clients to support it (the transition will be painful - most major clients will need to support this before anybody can start using it).
- Some kind of solution to the negative-filter-negentropy need added to the new protocol as its first optional feature.
- We seriously consider replacing Relay URLs with nostr pubkeys assigned to the relay, and then have relays publish their IP address and TLS key or certificate.
We sacrifice these:
- Faster event hash/verification
- Composable event bitflags
- Safer faster more well-supported crypto curve
- Nostr keys themselves as TLS 1.3 RawPublicKey certificates
-
 @ 06639a38:655f8f71
2024-11-01 22:32:51
@ 06639a38:655f8f71
2024-11-01 22:32:51One year ago I wrote the article Why Nostr resonates in Dutch and English after I visited the Bitcoin Amsterdam 2023 conference and the Nostrdam event. It got published at bitcoinfocus.nl (translated in Dutch). The main reason why I wrote that piece is that I felt that my gut feeling was tellinng me that Nostr is going to change many things on the web.
After the article was published, one of the first things I did was setting up this page on my website: https://sebastix.nl/nostr-research-and-development. The page contains this section (which I updated on 31-10-2024):
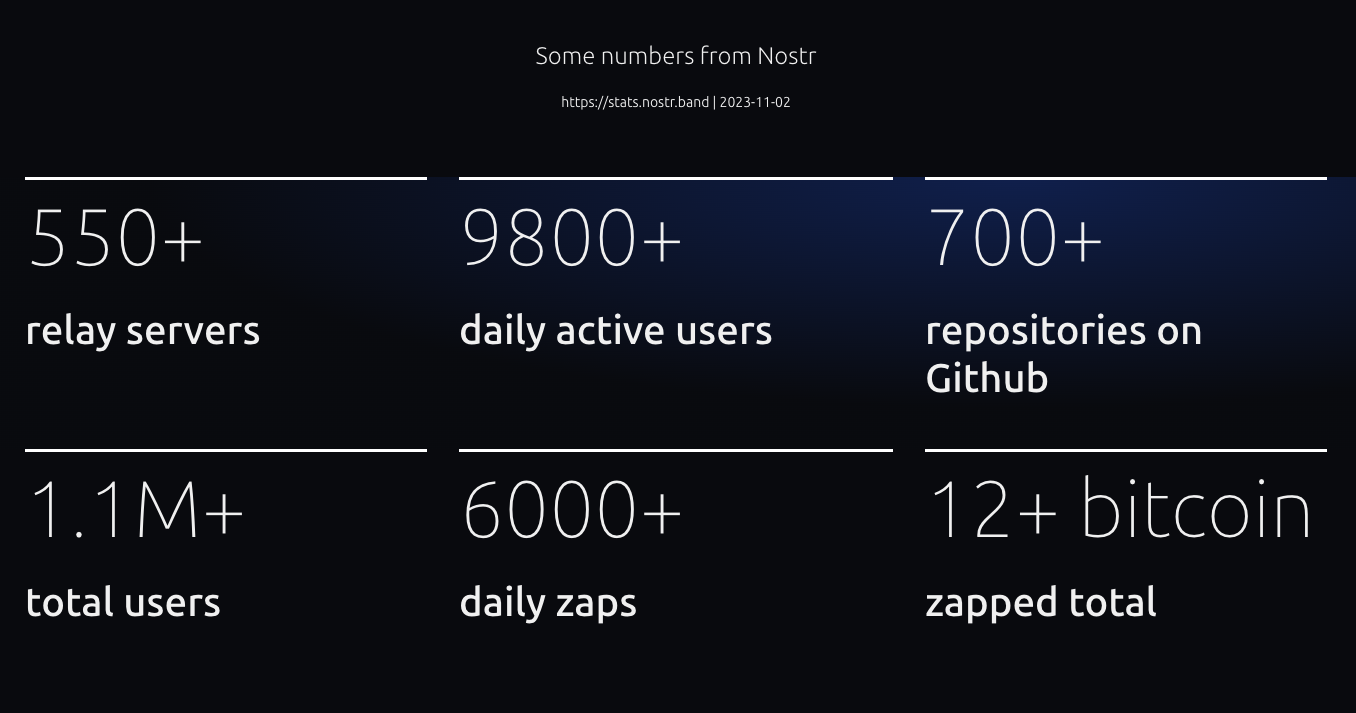
One metric I would like to highlight is the number of repositories on Github. Compared to a year ago, there are already more than 1130 repositories now on Github tagged with Nostr. Let's compare this number to other social media protocols and decentralized platforms (24-10-2024):
- Fediverse: 522
- ATProto: 159
- Scuttlebot: 49
- Farcaster: 202
- Mastodon: 1407
- ActivityPub: 444
Nostr is growing. FYI there are many Nostr repositories not hosted on Github, so the total number of Nostr reposities is higher. I know that many devs are using their own Git servers to host it. We're even capable of setting up Nostr native Git repositories (for example, see https://gitworkshop.dev/repos). Eventually, Nostr will make Github (and other platforms) absolute.
Let me continue summarizing my personal Nostr highlights of last year.
Organising Nostr meetups

This is me playing around with the NostrDebug tool showing how you can query data from Nostr relays. Jurjen is standing behind me. He is one of the people I've met this year who I'm sure I will have a long-term friendship with.OpenSats grant for Nostr-PHP


In December 2023 I submitted my application for a OpenSats grant for the further development of the Nostr-PHP helper library. After some months I finally got the message that my application was approved... When I got the message I was really stoked and excited. It's a great form of appreciation for the work I had done so far and with this grant I get the opportunity to take the work to another higher level. So please check out the work done for so far:Meeting Dries

One of my goosebumps moments I had in 2022 when I saw that the founder and tech lead of Drupal Dries Buytaert posted 'Nostr, love at first sight' on his blog. These types of moments are very rare moment where two different worlds merge where I wouldn't expect it. Later on I noticed that Dries would come to the yearly Dutch Drupal event. For me this was a perfect opportunity to meet him in person and have some Nostr talks. I admire the work he is doing for Drupal and the community. I hope we can bridge Nostr stuff in some way to Drupal. In general this applies for any FOSS project out there.
Here is my recap of that Drupal event.Attending Nostriga

A conference where history is made and written. I felt it immediately at the first sessions I attended. I will never forget the days I had at Nostriga. I don't have the words to describe what it brought to me.

I also pushed myself out of my comfort zone by giving a keynote called 'POSSE with Nostr - how we pivot away from API's with one of Nostr superpowers'. I'm not sure if this is something I would do again, but I've learned a lot from it.
You can find the presentation here. It is recorded, but I'm not sure if and when it gets published.Nostr billboard advertisement
This advertisment was shown on a billboard beside the A58 highway in The Netherlands from September 2nd till September 16th 2024. You can find all the assets and more footage of the billboard ad here: https://gitlab.com/sebastix-group/nostr/nostr-ads. My goal was to set an example of how we could promote Nostr in more traditional ways and inspire others to do the same. In Brazil a fundraiser was achieved to do something similar there: https://geyser.fund/project/nostrifybrazil.
Volunteering at Nostr booths growNostr

This was such a great motivating experience. Attending as a volunteer at the Nostr booth during the Bitcoin Amsterdam 2024 conference. Please read my note with all the lessons I learned here.
The other stuff
- The Nostr related blog articles I wrote past year:
- Run a Nostr relay with your own policies (02-04-2024)
- Why social networks should be based on commons (03-01-2024)
- How could Drupal adopt Nostr? (30-12-2023)
- Nostr integration for CCHS.social (21-12-2023)
- https://ccns.nostrver.se
CCNS stands for Community Curated Nostr Stuff. At the end of 2023 I started to build this project. I forked an existing Drupal project of mine (https://cchs.social) to create a link aggregation website inspired by stacker.news. At the beginning of 2024 I also joined the TopBuilder 2024 contest which was a productive period getting to know new people in the Bitcoin and Nostr space. - https://nuxstr.nostrver.se
PHP is not my only language I use to build stuff. As a fullstack webdeveloper I also work with Javascript. Many Nostr clients are made with Javascript frameworks or other more client-side focused tools. Vuejs is currently my Javascript framework I'm the most convenient with. With Vuejs I started to tinker around with Nuxt combined with NDK and so I created a starter template for Vue / Nuxt developers. - ZapLamp
This is a neat DIY package from LNbits. Powered by an Arduino ESP32 dev board it was running a 24/7 livestream on zap.stream at my office. It flashes when you send a zap to the npub of the ZapLamp. - https://nosto.re
Since the beginning when the Blossom spec was published by @hzrd49 and @StuartBowman I immediately took the opportunity to tinker with it. I'm also running a relay for transmitting Blossom Nostr eventswss://relay.nosto.re. - Relays I maintain
I really enjoy to tinker with different relays implementations. Relays are the fundamental base layer to let Nostr work.
I'm still sharing my contributions on https://nostrver.se/ where I publish my weekly Nostr related stuff I worked on. This website is built with Drupal where I use the Nostr Simple Publish and Nostr long-form content NIP-23 modules to crosspost the notes and long-form content to the Nostr network (like this piece of content you're reading).
The Nostr is the people
Just like the web, the web is people: https://www.youtube.com/watch?v=WCgvkslCzTo
the people on nostr are some of the smartest and coolest i’ve ever got to know. who cares if it doesn’t take over the world. It’s done more than i could ever ask for. - @jb55
Here are some Nostriches who I'm happy to have met and who influenced my journey in Nostr in a positive way.
- Jurjen
- Bitpopart
- Arjen
- Jeroen
- Alex Gleason
- Arnold Lubach
- Nathan Day
- Constant
- fiatjaf
- Sync
Coming year
Generally I will continue doing what I've done last year. Besides the time I spent on Nostr stuff, I'm also very busy with Drupal related work for my customers. I hope I can get the opportunity to work on a paid client project related to Nostr. It will be even better when I can combine my Drupal expertise with Nostr for projects paid by customers.
Building a new Nostr application
When I look at my Nostr backlog where I just put everything in with ideas and notes, there are quite some interesting concepts there for building new Nostr applications. Filtering out, I think these three are the most exciting ones:
- nEcho, a micro app for optimizing your reach via Nostr (NIP-65)
- Nostrides.cc platform where you can share Nostr activity events (NIP-113)
- A child-friendly video web app with parent-curated content (NIP-71)
Nostr & Drupal
When working out a new idea for a Nostr client, I'm trying to combine my expertises into one solution. That's why I also build and maintain some Nostr contrib modules for Drupal.
- Nostr Simple Publish
Drupal module to cross-post notes from Drupal to Nostr - Nostr long-form content NIP-23
Drupal module to cross-post Markdown formatted content from Drupal to Nostr - Nostr internet identifier NIP-05
Drupal module to setup Nostr internet identifier addresses with Drupal. - Nostr NDK
Includes the Javascript library Nostr Dev Kit (NDK) in a Drupal project.
One of my (very) ambitious goals is to build a Drupal powered Nostr (website) package with the following main features:
- Able to login into Drupal with your Nostr keypair
- Cross-post content to the Nostr network
- Fetch your Nostr content from the Nostr content
- Serve as a content management system (CMS) for your Nostr events
- Serve as a framework to build a hybrid Nostr web application
- Run and maintain a Nostr relay with custom policies
- Usable as a feature rich progressive web app
- Use it as a remote signer
These are just some random ideas as my Nostr + Drupal backlog is way longer than this.
Nostr-PHP
With all the newly added and continues being updated NIPs in the protocol, this helper library will never be finished. As the sole maintainer of this library I would like to invite others to join as a maintainer or just be a contributor to the library. PHP is big on the web, but there are not many PHP developers active yet using Nostr. Also PHP as a programming language is really pushing forward keeping up with the latest innovations.
Grow Nostr outside the Bitcoin community
We are working out a submission to host a Nostr stand at FOSDEM 2025. If approved, it will be the first time (as far as I know) that Nostr could be present at a conference outside the context of Bitcoin. The audience at FOSDEM is mostly technical oriented, so I'm really curious what type of feedback we will receive.
Let's finish this article with some random Nostr photos from last year. Cheers!





-
 @ d7c6d014:a6abb6b8
2024-11-23 18:40:47
@ d7c6d014:a6abb6b8
2024-11-23 18:40:47こんにちは!kohei です。
久々のエントリ投下ですが、今回は先日弊 TL で話題になっていた、Android を P2P のローカルリレーサーバー化して Tor で公開する方法を紹介していこうと思います。
用意するもの
- Android 端末
- Orbot
- Citrine
- Amethyst
前提と下準備
今回は、Orbot の詳細設定は省いて、Power User Mode の設定が完了している前提でお話を進めます。 Android 端末を用意して、2~4 のアプリをインストールしておいてください。
設定方法
それでは早速設定していきましょう。 まず、Citrine を起動して、Settings のタブからローカルリレーの詳細を設定します。
設定が終了したら、ローカルリレーを起動します。
また、ここで表示されるポート番号をメモしてください。
次に、More のタブに移り、Hosted Onion Services へアクセスし、Service Type の項目で User Services にチェックを入れて、右下の + マークをタップすると以下のポップアップが表示されます。(Orbot がスクショを許してくれないので一部画像割愛)
表示されたら、Name に任意の名前を、Local Port と Onion Port に先ほどメモした Citrine のポート番号を入力します。
入力したら再起動を求められるので再起動してください。 再起動後に Hosted Onion Services の項目に .onion のアドレスが表示されたら成功です (何故か私の環境では、一回の再起動では設定が反映されなかったのですが、もし同じような現象が起きた場合は、再起動 -> Connect -> .onion アドレスが発行されてるかの確認、を数回試すと発行されるはずです)
発行されたら、.onion アドレスをタップしてクリップボードにコピーします。
次に、Amethyst を起動して、リレーの設定画面に入り、Outbox の設定にコピーした .onion アドレスを貼り付けて保存します。
後は、Amethyst 側で Orbot のポート番号を設定して Orbot に接続すれば BOOM! 設定完了です。
お疲れ様でした!
素敵な Nostr ライフを!
-
 @ 081f3b0c:c00498a5
2024-10-31 11:52:15
@ 081f3b0c:c00498a5
2024-10-31 11:52:15Muchas son las maneras de referirse a la compra y mantenimiento de Bitcoin en cartera. Muchas también son las maneras de almacenarlo. Y, aunque en realidad NADIE almacena Bitcoin, sino llaves privadas y llaves públicas, no es de mi interés entrar hoy en esos tecnicismos.
Hoy quiero escribirle a la gente de a pie, los trabajadores, emprendedores, empresarios y todo aquel que se interese por lo menos un poquito en su futuro y el de los suyos. Hay algo que todos los Bitcoiners sabemos pero que muchos de ustedes no lo experimentan hasta llevarse un buen susto en su primer año de inversión (Hablaré en todo el artículo de manera indistinta entre inversión y ahorro en Bitcoin ya que en el largo larguísimo plazo y mirando a Bitcoin como moneda pero también como activo, pueden utilizarse ambos términos). Lo que no saben los que miran desde afuera, es que muy poca gente compró Bitcoin en centavos o pocos dólares (o lo minó en épocas tempranas) y todavía lo mantienen en cartera. Me arriesgaría a decir que este numero de individuos no supera unos pocos miles. Muchos no-coiners creen que los bitcoiners compraron a dos centavos se durmieron 15 años y hoy son todos ricos, pero la mayoría de los early adopters, se hundieron intentando navegar las profundas y peligrosas aguas de la custodia y el HODL.
Para quien todavía esté medio perdido y quizás este sea el primer artículo que lea, HODL es una manera "chistosa" de referirse a mantener Bitcoin en cartera, y se remonta allá por el 2013 donde un usuario quiso decir que estaba Holdeando (manteniendo) Bitcoin en cartera y lo escribió como HODLING. Pasó a la historia y hoy se usan HODL y HOLD de manera indistinta como chiste interno Bitcoiner.
En fin... Las profundas aguas... Holdear Bitcoin no es sencillo para las masas. Imaginate que tenés un activo en tu cartera, o compraste a 100 dólares y ahora vale 1.000. Lo venderías verdad? Y si vale 20.000 dólares? Ahí si lo venderías? Estarías multiplicando tu inversión como nunca. Bueno, a esa decisión se enfrentaron y se enfrentan TODOS los holders de Bitcoin más temprano o más tarde. Incluso aquel loco que compro por el 2017 en un precio de 20.000 hoy puede decidir vender y multiplicar casi por 4 su dinero en unos pocos años. Ni hablar de ese estresante momento que habías comprado en 69.000 dólares y lo viste bajar hasta los 17.000 dólares, unos cuantos meses de sufrimiento y temor... Más de uno se asustó de verdad y vendió todo, solo para verlo unas horas más tarde por arriba de los 20.000 y un año más tarde nuevamente en 70.000 dólares.
Si bien no me gusta poner el foco en el precio, lo que intento ilustrar es lo DIFICIL que puede ser ver tu inversión en máximos o en mínimos y aún así decidir mantenerla unos cuantos años más. Es dificil, aún para los que viven su tercer o cuarto ciclo de mercado. Pero se hace más y más fácil a medida que uno avanza en el famoso "rabbit hole" de Bitcoin y empieza a entenderlo desde las bases, cada vez mejor. Este camino también es arduo, entender de Bitcoin requiere un poco de conocimiento en cada campo, hay que saber un poco de tecnología, un poco de redes, un poco de seguridad informatica, una pizca de teoría de juegos, una apasionante cantidad de macroeconomía, y hasta un interés genuino en lo que Mises llamó "La acción Humana". Y todo esto, uno lo va a prendiendo con ganas y de a poco sólo para llegar a la conclusión, meses o incluso años después, de que Bitcoin tiene que ser un activo por siempre en la cartera de uno, no se vende. Incluso hay quienes llegan al punto (como este humilde ser que escribe) que no poseen otro tipo de ahorro o inversión que no sean sus pocos o muchos satoshis en Billetera Fria.
Mi recomendación siempre será que DYOR, "do your own research", investiguen, lean, pregunten, únanse a #nostr que tiene la mejor comunidad del mundo a la hora de ayudar a otros usuarios, pero si no llegan a tener el tiempo de leer y progresar sólo tómenme estos dos consejos:
- Háganse el tiempo para leer.
- Stay humble y stack sats (De a poco y constante, todo ahorro mensual que uno haga, está mejor guardado en Bitcoin, siempre gastando menos de lo que ingresa esto no debería ser dificil).
Otra dificultad que encontramos además de la parte emocional y humana relacionada con los precios y el desconocimiento, es la custodia. Cientos de personas perdieron TODO su Bitcoin por no saber almacenarlo correctamente. Decenas de maneras de almacenar claves y sin embargo muchos usuarios de Bitcoin no se sienten del todo seguro durante sus primeros años de inversión, y no están el todo equivocados... Por un lado puede ser tan sencillo como guardar 24 palabras. Por otro lado, puede no ser tan fácil, dependiendo del tipo de usuario. Entraremos en detalles de custodia en el próximo artículo.
Saludos!
El Tío.
PD: No es consejo de inversión.
-
 @ 35f3a26c:92ddf231
2024-12-02 09:15:47
@ 35f3a26c:92ddf231
2024-12-02 09:15:47What is a Hardware Wallet / Seed Signer?
Most people call it "Hardware Wallet", which is inaccurate since it is not a wallet, it is a "Seed Signer"
Basically it is an electronic device with a simple user interface which guides you to introduce your seed words, once configured, you will use it in combination with your Bitcoin Wallet to sign transactions.
How does it works?
Once you are fully setup, if you try to send funds with your Bitcoin Wallet, you will be prompted to sign the transaction with your "Seed Signer", it will prompt you to introduce a PIN or a password or use a bio-metric identification, once you do so, the transaction will be broadcasted, without it, you will only be able to receive, not to send.
Are Seed Signers safe?
The answer is yes, but some more than others, you have to do your homework and choose wisely, here is a check list. I suggest you follow it before buying one:
- Uses a Chip Secure Element (SE), which is a chip that is protected from unauthorized access and stores confidential and cryptographic data
- It is Air Gap, which means that is physically isolated from unsecured networks, no Bluetooth, no WiFi, no USB connector. Only way to add information is via the user interface and for OS upgrades, a SSD card
- The OS in the device is FOSS (Free and Open Source Software)
- If the company offers a Bitcoin Wallet with the device, it should be as well FOSS
- It is build only for Bitcoin, no alt coins development in their products
- You can acquire the product directly from the company
- You can acquire the product with Bitcoin
- The company will agree to deliver to a PO-BOX or similar
- In case you pay the Seed Signer with a non secure methods which give away your full name and address, ensure that the company has a policy of deleting the client records after a short period of time to ensure your safety. If they get hacked, cyber criminals will know your name and address and probably target you
Any Recommendations?
I will suggest you do your own research and do not trust, verify. I am not affiliated or receive any income from any of the products mentioned below...
My favorites so far (yes, they check all the boxes I mentioned):
- "Passport" from Foundation (link: https://foundationdevices.com/ )
- "COLCARD" from Coinkite (link: https://coldcard.com/ )

If you known of any "Seed Signer" that passes the check list above and I didn't include it, please let me know in the comments, always looking forward to test new products.
Note: Important to understand that devices built with Raspberry Pi don't qualify since they do not pass the Chip SE
-
 @ 42342239:1d80db24
2024-07-06 15:26:39
@ 42342239:1d80db24
2024-07-06 15:26:39Claims that we need greater centralisation, more EU, or more globalisation are prevalent across the usual media channels. The climate crisis, environmental destruction, pandemics, the AI-threat, yes, everything will apparently be solved if a little more global coordination, governance and leadership can be brought about.
But, is this actually true? One of the best arguments for this conclusion stems implicitly from the futurist Eliezer Yudkowsky, who once proposed a new Moore's Law, though this time not for computer processors but instead for mad science: "every 18 months, the minimum IQ necessary to destroy the world drops by one point".
Perhaps we simply have to tolerate more centralisation, globalisation, control, surveillance, and so on, to prevent all kinds of fools from destroying the world?
Note: a Swedish version of this text is avalable at Affärsvärlden.
At the same time, more centralisation, globalisation, etc. is also what we have experienced. Power has been shifting from the local, and from the majorities, to central-planning bureaucrats working in remote places. This has been going on for several decades. The EU's subsidiarity principle, i.e. the idea that decisions should be made at the lowest expedient level, and which came to everyone's attention ahead of Sweden's EU vote in 1994, is today swept under the rug as untimely and outdated, perhaps even retarded.
At the same time, there are many crises, more than usual it would seem. If it is not a crisis of criminality, a logistics/supply chain crisis or a water crisis, then it is an energy crisis, a financial crisis, a refugee crisis or a climate crisis. It is almost as if one starts to suspect that all this centralisation may be leading us down the wrong path. Perhaps centralisation is part of the problem, rather than the capital S solution?
Why centralisation may cause rather than prevent problems
There are several reasons why centralisation, etc, may actually be a problem. And though few seem to be interested in such questions today (or perhaps they are too timid to mention their concerns?), it has not always been this way. In this short essay we'll note four reasons (though there are several others):
- Political failures (Buchanan et al)
- Local communities & skin in the game (Ostrom and Taleb)
- The local knowledge problem (von Hayek)
- Governance by sociopaths (Hare)
James Buchanan who was given the so-called Nobel price in economics in the eighties once said that: "politicians and bureaucrats are no different from the rest of us. They will maximise their incentives just like everybody else.".
Buchanan was prominent in research on rent-seeking and political failures, i.e. when political "solutions" to so-called market failures make everything worse. Rent-seeking is when a company spends resources (e.g. lobbying) to get legislators or other decision makers to pass laws or create regulations that benefit the company instead of it having to engage in productive activities. The result is regulatory capture. The more centralised decision-making is, the greater the negative consequences from such rent-seeking will be for society at large. This is known.
Another economist, Elinor Ostrom, was given the same prize in the great financial crisis year of 2009. In her research, she had found that local communities where people had influence over rules and regulations, as well as how violations there-of were handled, were much better suited to look after common resources than centralised bodies. To borrow a term from the combative Nassim Nicholas Taleb: everything was better handled when decision makers had "skin in the game".
A third economist, Friedrich von Hayek, was given this prize as early as 1974, partly because he showed that central planning could not possibly take into account all relevant information. The information needed in economic planning is by its very nature distributed, and will never be available to a central planning committee, or even to an AI.
Moreover, human systems are complex and not just complicated. When you realise this, you also understand why the forecasts made by central planners often end up wildly off the mark - and at times in a catastrophic way. (This in itself is an argument for relying more on factors outside of the models in the decision-making process.)
From Buchanan's, Ostrom's, Taleb's or von Hayek's perspectives, it also becomes difficult to believe that today's bureaucrats are the most suited to manage and price e.g. climate risks. One can compare with the insurance industry, which has both a long habit of pricing risks as well as "skin in the game" - two things sorely missing in today's planning bodies.
Instead of preventing fools, we may be enabling madmen
An even more troubling conclusion is that centralisation tends to transfer power to people who perhaps shouldn't have more of that good. "Not all psychopaths are in prison - some are in the boardroom," psychologist Robert Hare once said during a lecture. Most people have probably known for a long time that those with sharp elbows and who don't hesitate to stab a colleague in the back can climb quickly in organisations. In recent years, this fact seems to have become increasingly well known even in academia.
You will thus tend to encounter an increased prevalance of individuals with narcissistic and sociopathic traits the higher up you get in the the status hierarchy. And if working in large organisations (such as the European Union or Congress) or in large corporations, is perceived as higher status - which is generally the case, then it follows that the more we centralise, the more we will be governed by people with less flattering Dark Triad traits.
By their fruits ye shall know them
Perhaps it is thus not a coincidence that we have so many crises. Perhaps centralisation, globalisation, etc. cause crises. Perhaps the "elites" and their planning bureaucrats are, in fact, not the salt of the earth and the light of the world. Perhaps President Trump even had a point when he said "they are not sending their best".
https://www.youtube.com/watch?v=w4b8xgaiuj0
The opposite of centralisation is decentralisation. And while most people may still be aware that decentralisation can be a superpower within the business world, it's time we remind ourselves that this also applies to the economy - and society - at large, and preferably before the next Great Leap Forward is fully thrust upon us.
-
 @ 349d6b82:12b2a5b1
2024-12-02 08:57:56
@ 349d6b82:12b2a5b1
2024-12-02 08:57:56Мошенничество - очень серьезная проблема, затрагивающей множество жителей.
Сегодня к нам в редакцию обратилась пострадавшая мошенников, Анна Горкова, она всегда была осторожной и внимательной к финансовым вопросам. Однако в один из дней она получила звонок от «сотрудника банка», который сообщил о подозрительных операциях на её счете. Мошенник уверил её, что для защиты средств необходимо срочно перевести деньги на "безопасный" счет". В панике и доверяя голосу на другом конце провода, Анна перевела все свои сбережения.
Не смотря на столько банальный подход, наши жители, особенно престарелого возраста, все равно попадаются на "удочку" к мошенникам. И, к сожалению, это не единичный случай. С начала 2044 года в Серове зарегистрировано более 270 фактов мошенничества, что на 7% больше по сравнению с предыдущим годом.
Местные правоохранительные органы призывают граждан быть бдительными и не доверять незнакомцам, особенно в вопросах финансов.
Мошенники используют различные методы для обмана граждан: Злоумышленники представляются сотрудниками банков или государственных учреждений. Некоторые создают фальшивые аккаунты для сбора личной информации и обещают выгодные сделки с требованием предварительной оплаты.
Согласно статистике, пожилые люди и люди средних лет чаще всего становятся жертвами таких схем. Поэтому важно делиться информацией о мошенничестве с близкими и родными и предупреждать их о возможных рисках.
Будьте бдительны и всегда проверяйте информацию перед тем, как принимать финансовые решения. Помните: если что-то звучит слишком хорошо, чтобы быть правдой, — скорее всего, это обман .
-
 @ 3f770d65:7a745b24
2024-10-29 17:38:20
@ 3f770d65:7a745b24
2024-10-29 17:38:20Amber
Amber is a Nostr event signer for Android that allows users to securely segregate their private key (nsec) within a single, dedicated application. Designed to function as a NIP-46 signing device, Amber ensures your smartphone can sign events without needing external servers or additional hardware, keeping your private key exposure to an absolute minimum. This approach aligns with the security rationale of NIP-46, which states that each additional system handling private keys increases potential vulnerability. With Amber, no longer do users need to enter their private key into various Nostr applications.

Amber is supported by a growing list of apps, including Amethyst, 0xChat, Voyage, Fountain, and Pokey, as well as any web application that supports NIP-46 NSEC bunkers, such as Nostr Nests, Coracle, Nostrudel, and more. With expanding support, Amber provides an easy solution for secure Nostr key management across numerous platforms.

Amber supports both native and web-based Nostr applications, aiming to eliminate the need for browser extensions or web servers. Key features include offline signing, multiple account support, and NIP-46 compatibility, and includes a simple UI for granular permissions management. Amber is designed to support signing events in the background, enhancing flexibility when you select the "remember my choice" option, eliminating the need to constantly be signing events for applications that you trust. You can download the app from it's GitHub page, via Obtainium or Zap.store.
To log in with Amber, simply tap the "Login with Amber" button or icon in a supported application, or you can paste the NSEC bunker connection string directly into the login box. For example, use a connection string like this: bunker://npub1tj2dmc4udvgafxxxxxxxrtgne8j8l6rgrnaykzc8sys9mzfcz@relay.nsecbunker.com.

Citrine
Citrine is a Nostr relay built specifically for Android, allowing Nostr clients on Android devices to seamlessly send and receive events through a relay running directly on their smartphone. This mobile relay setup offers Nostr users enhanced flexibility, enabling them to manage, share, and back up all their Nostr data locally on their device. Citrine’s design supports independence and data security by keeping data accessible and under user control.

With features tailored to give users greater command over their data, Citrine allows easy export and import of the database, restoration of contact lists in case of client malfunctions, and detailed relay management options like port configuration, custom icons, user management, and on-demand relay start/stop. Users can even activate TOR access, letting others connect securely to their Nostr relay directly on their phone. Future updates will include automatic broadcasting when the device reconnects to the internet, along with content resolver support to expand its functionality.
Once you have your Citrine relay fully configured, simply add it to the Private and Local relay sections in Amethyst's relay configuration.

Pokey
Pokey for Android is a brand new, real-time notification tool for Nostr. Pokey allows users to receive live updates for their Nostr events and enabling other apps to access and interact with them. Designed for seamless integration within a user's Nostr relays, Pokey lets users stay informed of activity as it happens, with speed and the flexibility to manage which events trigger notifications on their mobile device.

Pokey currently supports connections with Amber, offering granular notification settings so users can tailor alerts to their preferences. Planned features include broadcasting events to other apps, authenticating to relays, built-in Tor support, multi-account handling, and InBox relay management. These upcoming additions aim to make Pokey a fantastic tool for Nostr notifications across the ecosystem.
Zap.store
Zap.store is a permissionless app store powered by Nostr and your trusted social graph. Built to offer a decentralized approach to app recommendations, zap.store enables you to check if friends like Alice follow, endorse, or verify an app’s SHA256 hash. This trust-based, social proof model brings app discovery closer to real-world recommendations from friends and family, bypassing centralized app curation. Unlike conventional app stores and other third party app store solutions like Obtainium, zap.store empowers users to see which apps their contacts actively interact with, providing a higher level of confidence and transparency.

Currently available on Android, zap.store aims to expand to desktop, PWAs, and other platforms soon. You can get started by installing Zap.store on your favorite Android device, and install all of the applications mentioned above.
Android's openness goes hand in hand with Nostr's openness. Enjoy exploring both expanding ecosystems.
-
 @ b12b632c:d9e1ff79
2024-05-29 12:10:18
@ b12b632c:d9e1ff79
2024-05-29 12:10:18One other day on Nostr, one other app!
Today I'll present you a new self-hosted Nostr blog web application recently released on github by dtonon, Oracolo:
https://github.com/dtonon/oracolo
Oracolo is a minimalist blog powered by Nostr, that consists of a single html file, weighing only ~140Kb. You can use whatever Nostr client that supports long format (habla.news, yakihonne, highlighter.com, etc ) to write your posts, and your personal blog is automatically updated.
It works also without a web server; for example you can send it via email as a business card.Oracolo fetches Nostr data, builds the page, execute the JavaScript code and displays article on clean and sobr blog (a Dark theme would be awesome 👀).
Blog articles are nostr events you published or will publish on Nostr relays through long notes applications like the ones quoted above.
Don't forget to use a NIP07 web browser extensions to login on those websites. Old time where we were forced to fill our nsec key is nearly over!
For the hurry ones of you, you can find here the Oracolo demo with my Nostr long notes article. It will include this one when I'll publish it on Nostr!
https://oracolo.fractalized.net/
How to self-host Oracolo?
You can build the application locally or use a docker compose stack to run it (or any other method). I just build a docker compose stack with Traefik and an Oracolo docker image to let you quickly run it.
The oracolo-docker github repo is available here:
https://github.com/PastaGringo/oracolo-docker
PS: don't freak out about the commits number, oracolo has been the lucky one to let me practrice docker image CI/CD build/push with Forgejo, that went well but it took me a while before finding how to make Forgejo runner dood work 😆). Please ping me on Nostr if you are interested by an article on this topic!
This repo is a mirror from my new Forgejo git instance where the code has been originaly published and will be updated if needed (I think it will):
https://git.fractalized.net/PastaGringo/oracolo-docker
Here is how to do it.
1) First, you need to create an A DNS record into your domain.tld zone. You can create a A with "oracolo" .domain.tld or "*" .domain.tld. The second one will allow traefik to generate all the future subdomain.domain.tld without having to create them in advance. You can verify DNS records with the website https://dnschecker.org.
2) Clone the oracolo-docker repository:
bash git clone https://git.fractalized.net/PastaGringo/oracolo-docker.git cd oracolo-docker3) Rename the .env.example file:
bash mv .env.example .env4) Modify and update your .env file with your own infos:
```bash
Let's Encrypt email used to generate the SSL certificate
LETSENCRYPT_EMAIL=
domain for oracolo. Ex: oracolo.fractalized.net
ORACOLO_DOMAIN=
Npub author at "npub" format, not HEX.
NPUB=
Relays where Oracolo will retrieve the Nostr events.
Ex: "wss://nostr.fractalized.net, wss://rnostr.fractalized.net"
RELAYS=
Number of blog article with an thumbnail. Ex: 4
TOP_NOTES_NB= ```
5) Compose Oracolo:
bash docker compose up -d && docker compose logs -f oracolo traefikbash [+] Running 2/0 ✔ Container traefik Running 0.0s ✔ Container oracolo Running 0.0s WARN[0000] /home/pastadmin/DEV/FORGEJO/PLAY/oracolo-docker/docker-compose.yml: `version` is obsolete traefik | 2024-05-28T19:24:18Z INF Traefik version 3.0.0 built on 2024-04-29T14:25:59Z version=3.0.0 oracolo | oracolo | ___ ____ ____ __ ___ _ ___ oracolo | / \ | \ / | / ] / \ | | / \ oracolo | | || D )| o | / / | || | | | oracolo | | O || / | |/ / | O || |___ | O | oracolo | | || \ | _ / \_ | || || | oracolo | | || . \| | \ || || || | oracolo | \___/ |__|\_||__|__|\____| \___/ |_____| \___/ oracolo | oracolo | Oracolo dtonon's repo: https://github.com/dtonon/oracolo oracolo | oracolo | ╭────────────────────────────╮ oracolo | │ Docker Compose Env Vars ⤵️ │ oracolo | ╰────────────────────────────╯ oracolo | oracolo | NPUB : npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2 oracolo | RELAYS : wss://nostr.fractalized.net, wss://rnostr.fractalized.net oracolo | TOP_NOTES_NB : 4 oracolo | oracolo | ╭───────────────────────────╮ oracolo | │ Configuring Oracolo... ⤵️ │ oracolo | ╰───────────────────────────╯ oracolo | oracolo | > Updating npub key with npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2... ✅ oracolo | > Updating nostr relays with wss://nostr.fractalized.net, wss://rnostr.fractalized.net... ✅ oracolo | > Updating TOP_NOTE with value 4... ✅ oracolo | oracolo | ╭───────────────────────╮ oracolo | │ Installing Oracolo ⤵️ │ oracolo | ╰───────────────────────╯ oracolo | oracolo | added 122 packages, and audited 123 packages in 8s oracolo | oracolo | 20 packages are looking for funding oracolo | run `npm fund` for details oracolo | oracolo | found 0 vulnerabilities oracolo | npm notice oracolo | npm notice New minor version of npm available! 10.7.0 -> 10.8.0 oracolo | npm notice Changelog: https://github.com/npm/cli/releases/tag/v10.8.0 oracolo | npm notice To update run: npm install -g npm@10.8.0 oracolo | npm notice oracolo | oracolo | >>> done ✅ oracolo | oracolo | ╭─────────────────────╮ oracolo | │ Building Oracolo ⤵️ │ oracolo | ╰─────────────────────╯ oracolo | oracolo | > oracolo@0.0.0 build oracolo | > vite build oracolo | oracolo | 7:32:49 PM [vite-plugin-svelte] WARNING: The following packages have a svelte field in their package.json but no exports condition for svelte. oracolo | oracolo | @splidejs/svelte-splide@0.2.9 oracolo | @splidejs/splide@4.1.4 oracolo | oracolo | Please see https://github.com/sveltejs/vite-plugin-svelte/blob/main/docs/faq.md#missing-exports-condition for details. oracolo | vite v5.2.11 building for production... oracolo | transforming... oracolo | ✓ 84 modules transformed. oracolo | rendering chunks... oracolo | oracolo | oracolo | Inlining: index-C6McxHm7.js oracolo | Inlining: style-DubfL5gy.css oracolo | computing gzip size... oracolo | dist/index.html 233.15 kB │ gzip: 82.41 kB oracolo | ✓ built in 7.08s oracolo | oracolo | >>> done ✅ oracolo | oracolo | > Copying Oracolo built index.html to nginx usr/share/nginx/html... ✅ oracolo | oracolo | ╭────────────────────────╮ oracolo | │ Configuring Nginx... ⤵️ │ oracolo | ╰────────────────────────╯ oracolo | oracolo | > Copying default nginx.conf file... ✅ oracolo | oracolo | ╭──────────────────────╮ oracolo | │ Starting Nginx... 🚀 │ oracolo | ╰──────────────────────╯ oracolo |If you don't have any issue with the Traefik container, Oracolo should be live! 🔥
You can now access it by going to the ORACOLO_DOMAIN URL configured into the .env file.
Have a good day!
Don't hesisate to follow dtonon on Nostr to follow-up the future updates ⚡🔥
See you soon in another Fractalized story!
PastaGringo 🤖⚡ -
 @ 3f0702fa:66db56f1
2024-12-02 07:46:04
@ 3f0702fa:66db56f1
2024-12-02 07:46:04Этот амбициозный проект воплощает в себе гармонию природы и современного дизайна, создавая уникальное пространство как для жителей, так и для гостей столицы Зауралья. Оранжерея представляет собой настоящий ботанический сад с множеством экзотических растений, которые будут радовать глаз круглый год.
Особое внимание уделено системе климат-контроля, что обеспечивает идеальные условия для роста и развития самых разнообразных видов флоры. Посетители смогут насладиться не только красотой тропических растений, но и участвовать в образовательных программах, мастер-классах и выставках.
Кроме того, оранжерея станет площадкой для культурных мероприятий и выставок, объединяющих людей вокруг любви к природе и устойчивому развитию. Данный проект не только украшает Курган, но и подчеркивает его стремление к инновациям и заботе о сохранении окружающей среды. Так, новое здание становится знаковым элементом городской инфраструктуры, насыщая жизнь жителей теплом и зеленью.
https://psv4.userapi.com/s/v1/d/mjoXP8Oce1hteuplbky7bvvlJqYNYqBDy6eXFvE_0SqQhwEWiuKSjk4M1jEYjsu2IDUs4f5B_ZWx9mRznCHpr7e-KKGqt6i80Q6qbIYnsAyWDTVJlMP0pA/319894142510886919.mp4
-
 @ 4ba8e86d:89d32de4
2024-11-14 09:17:14
@ 4ba8e86d:89d32de4
2024-11-14 09:17:14Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular; • Computador com adb; • Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo;
Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid: https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
Samsung Galaxy Note 10 Plus bloatware listProvavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
./adb start-serverO resultado deve ser:
daemon not running; starting now at tcp:5037 daemon started successfully
E caso não apareça nada, execute:
./adb kill-serverE inicie novamente.
Com o adb conectado ao celular, execute:
./adb shellPara poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
pkg install android-toolsQuando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
adb pair localhost:porta CódigoDeEmparelhamentoDe acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
adb connect localhost:portaObs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
adb shellRemoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
pm uninstall –user 0 com.google.android.apps.mapsE pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
cmd package install-existing nome.do.pacotePós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-
 @ 4523be58:ba1facd0
2024-05-28 11:05:17
@ 4523be58:ba1facd0
2024-05-28 11:05:17NIP-116
Event paths
Description
Event kind
30079denotes an event defined by its event path rather than its event kind.The event directory path is included in the event path, specified in the event's
dtag. For example, an event path might beuser/profile/name, whereuser/profileis the directory path.Relays should parse the event directory from the event path
dtag and index the event by it. Relays should support "directory listing" of kind30079events using the#ffilter, such as{"#f": ["user/profile"]}.For backward compatibility, the event directory should also be saved in the event's
ftag (for "folder"), which is already indexed by some relay implementations, and can be queried using the#ffilter.Event content should be a JSON-encoded value. An empty object
{}signifies that the entry at the event path is itself a directory. For example, when savinguser/profile/name:Bob, you should also saveuser/profile:{}so the subdirectory can be listed underuser.In directory names, slashes should be escaped with a double slash.
Example
Event
json { "tags": [ ["d", "user/profile/name"], ["f", "user/profile"] ], "content": "\"Bob\"", "kind": 30079, ... }Query
json { "#f": ["user/profile"], "authors": ["[pubkey]"] }Motivation
To make Nostr an "everything app," we need a sustainable way to support new kinds of applications. Browsing Nostr data by human-readable nested directories and paths rather than obscure event kind numbers makes the data more manageable.
Numeric event kinds are not sustainable for the infinite number of potential applications. With numeric event kinds, developers need to find an unused number for each new application and announce it somewhere, which is cumbersome and not scalable.
Directories can also replace monolithic list events like follow lists or profile details. You can update a single directory entry such as
user/profile/nameorgroups/follows/[pubkey]without causing an overwrite of the whole profile or follow list when your client is out-of-sync with the most recent list version, as often happens on Nostr.Using
d-tagged replaceable events for reactions, such as{tags: [["d", "reactions/[eventId]"]], content: "\"👍\"", kind: 30079, ...}would make un-reacting trivial: just publish a new event with the samedtag and an empty content. Toggling a reaction on and off would not cause a flurry of new reaction & delete events that all need to be persisted.Implementations
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
f) already support this feature. - IrisDB client side library: treelike data structure with subscribable nodes.
https://github.com/nostr-protocol/nips/pull/1266
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
-
 @ 3f0702fa:66db56f1
2024-12-02 07:45:26
@ 3f0702fa:66db56f1
2024-12-02 07:45:26Подкаст можно прослушать по ссылке ниже
https://studio.superpodcast.ai/podcast/56e2db7a-09c1-4c76-93c3-72dc822004bc
-
 @ b12b632c:d9e1ff79
2024-04-24 20:21:27
@ b12b632c:d9e1ff79
2024-04-24 20:21:27What's Blossom?
Blossom offers a bunch of HTTP endpoints that let Nostr users stash and fetch binary data on public servers using the SHA256 hash as a universal ID.
You can find more -precise- information about Blossom on the Nostr article published today by hzrd149, the developper behind it:
nostr:naddr1qqxkymr0wdek7mfdv3exjan9qgszv6q4uryjzr06xfxxew34wwc5hmjfmfpqn229d72gfegsdn2q3fgrqsqqqa28e4v8zy
You find the Blossom github repo here:
GitHub - hzrd149/blossom: Blobs stored simply on mediaservers https://github.com/hzrd149/blossom
Meet Blobs
Blobs are files with SHA256 hashes as IDs, making them unique and secure. You can compute these IDs from the files themselves using the sha256 hashing algorithm (when you run
sha256sum bitcoin.pdf).Meet Drives
Drives are like organized events on Nostr, mapping blobs to filenames and extra info. It's like setting up a roadmap for your data.
How do Servers Work?
Blossom servers have four endpoints for users to upload and handle blobs:
GET /<sha256>: Get blobs by their SHA256 hash, maybe with a file extension. PUT /upload: Chuck your blobs onto the server, verified with signed Nostr events. GET /list/<pubkey>: Peek at a list of blobs tied to a specific public key for smooth management. DELETE /<sha256>: Trash blobs from the server when needed, keeping things tidy.Yon can find detailed information about the Blossom Server Implementation here..
https://github.com/hzrd149/blossom/blob/master/Server.md
..and the Blossom-server source code is here:
https://github.com/hzrd149/blossom-server
What's Blossom Drive?
Think of Blossom Drive as the "Front-End" (or a public cloud drive) of Blossom servers, letting you upload, manage, share your files/folders blobs.
Source code is available here:
https://github.com/hzrd149/blossom-drive
Developpers
If you want to add Blossom into your Nostr client/app, the blossom-client-sdk explaining how it works (with few examples 🙏) is published here:
https://github.com/hzrd149/blossom-client-sdk
How to self-host Blossom server & Blossom Drive
We'll use docker compose to setup Blossom server & drive. I included Nginx Proxy Manager because it's the Web Proxy I use for all the Fractalized self-hosted services :
Create a new docker-compose file:
~$ nano docker-compose.ymlInsert this content into the file:
``` version: '3.8' services:
blossom-drive: container_name: blossom-drive image: pastagringo/blossom-drive-docker
ports:
- '80:80'
blossom-server: container_name: blossom-server image: 'ghcr.io/hzrd149/blossom-server:master'
ports:
- '3000:3000'
volumes: - './blossom-server/config.yml:/app/config.yml' - 'blossom_data:/app/data'nginxproxymanager: container_name: nginxproxymanager image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: - '80:80' - '81:81' - '443:443' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt - ./nginxproxymanager/_hsts_map.conf:/app/templates/_hsts_map.conf
volumes: blossom_data: ```
You now need to personalize the blossom-server config.yml:
bash ~$ mkdir blossom-server ~$ nano blossom-server/config.ymlInsert this content to the file (CTRL+X & Y to save/exit):
```yaml
Used when listing blobs
publicDomain: https://blossom.fractalized.net
databasePath: data/sqlite.db
discovery: # find files by querying nostr relays nostr: enabled: true relays: - wss://nostrue.com - wss://relay.damus.io - wss://nostr.wine - wss://nos.lol - wss://nostr-pub.wellorder.net - wss://nostr.fractalized.net # find files by asking upstream CDNs upstream: enabled: true domains: - https://cdn.satellite.earth # don't set your blossom server here!
storage: # local or s3 backend: local local: dir: ./data # s3: # endpoint: https://s3.endpoint.com # bucket: blossom # accessKey: xxxxxxxx # secretKey: xxxxxxxxx # If this is set the server will redirect clients when loading blobs # publicURL: https://s3.region.example.com/
# rules are checked in descending order. if a blob matches a rule it is kept # "type" (required) the type of the blob, "" can be used to match any type # "expiration" (required) time passed since last accessed # "pubkeys" (optional) a list of owners # any blobs not matching the rules will be removed rules: # mime type of blob - type: text/ # time since last accessed expiration: 1 month - type: "image/" expiration: 1 week - type: "video/" expiration: 5 days - type: "model/" expiration: 1 week - type: "" expiration: 2 days
upload: # enable / disable uploads enabled: true # require auth to upload requireAuth: true # only check rules that include "pubkeys" requirePubkeyInRule: false
list: requireAuth: false allowListOthers: true
tor: enabled: false proxy: "" ```
You need to update few values with your own:
- Your own Blossom server public domain :
publicDomain: https://YourBlossomServer.YourDomain.tldand upstream domains where Nostr clients will also verify if the Blossom server own the file blob: :
upstream: enabled: true domains: - https://cdn.satellite.earth # don't set your blossom server here!- The Nostr relays where you want to publish your Blossom events (I added my own Nostr relay):
yaml discovery: # find files by querying nostr relays nostr: enabled: true relays: - wss://nostrue.com - wss://relay.damus.io - wss://nostr.wine - wss://nos.lol - wss://nostr-pub.wellorder.net - wss://nostr.fractalized.netEverything is setup! You can now compose your docker-compose file:
~$ docker compose up -dI will let your check this article to know how to configure and use Nginx Proxy Manager.
You can check both Blossom containers logs with this command:
~$ docker compose logs -f blossom-drive blossom-serverRegarding the Nginx Proxy Manager settings for Blossom, here is the configuration I used:
PS: it seems the naming convention for the kind of web service like Blossom is named "CDN" (for: "content delivery network"). It's not impossible in a near future I rename my subdomain blossom.fractalized.net to cdn.blossom.fractalized.net and blossom-drive.fractalized.net to blossom.fractalized.net 😅
Do what you prefer!
After having configured everything, you can now access Blossom server by going to your Blossom server subdomain. You should see a homepage as below:
Same thing for the Blossom Drive, you should see this homepage:
You can now login with your prefered method. In my case, I login on Blossom Drive with my NIP-07 Chrome extension.
You now need to go the "Servers" tab to add some Blossom servers, including the fresh one you just installed.
You can now create your first Blossom Drive by clicking on "+ New" > "Drive" on the top left button:
Fill your desired blossom drive name and select the media servers where you want to host your files and click on "Create":
PS: you can enable "Encrypted" option but as hzrd149 said on his Nostr note about Blossom:
"There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify"
You are now able to upload some files (a picture for instance):
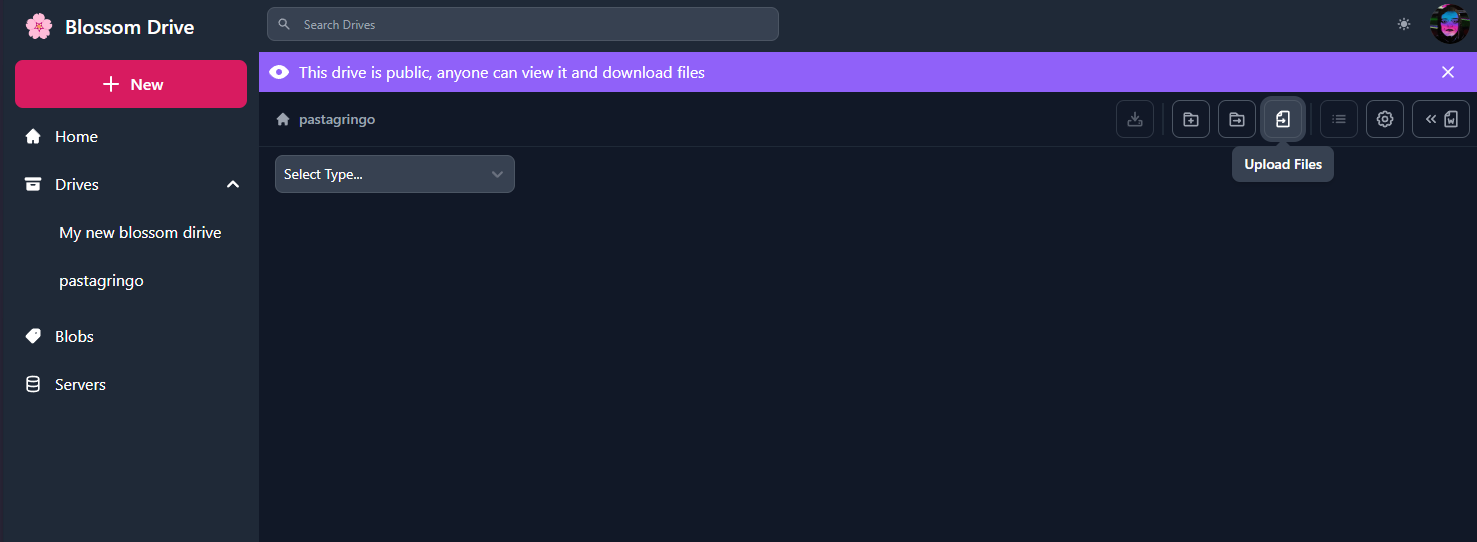
And obtain the HTTP direct link by clicking on the "Copy Link" button:
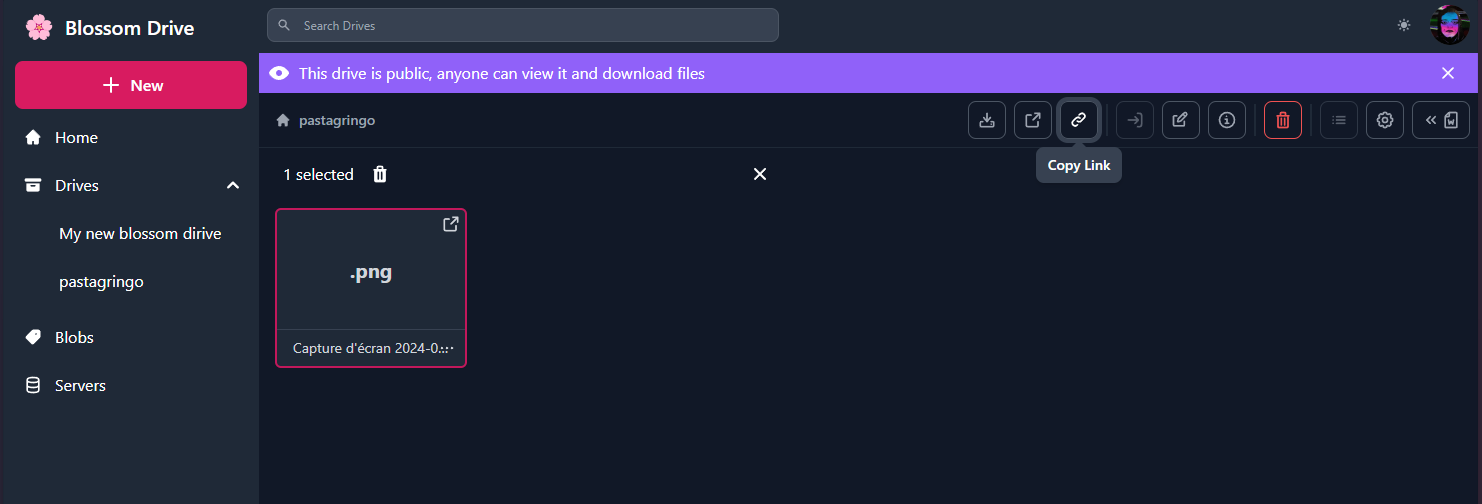
If you check URL image below, you'll see that it is served by Blossom:

It's done ! ✅
You can now upload your files to Blossom accross several Blossom servers to let them survive the future internet apocalypse.
Blossom has just been released few days ago, many news and features will come!
Don't hesisate to follow hzrd149 on Nostr to follow-up the future updates ⚡🔥
See you soon in another Fractalized story!
PastaGringo 🤖⚡ -
 @ 42342239:1d80db24
2024-04-05 08:21:50
@ 42342239:1d80db24
2024-04-05 08:21:50Trust is a topic increasingly being discussed. Whether it is trust in each other, in the media, or in our authorities, trust is generally seen as a cornerstone of a strong and well-functioning society. The topic was also the theme of the World Economic Forum at its annual meeting in Davos earlier this year. Even among central bank economists, the subject is becoming more prevalent. Last year, Agustín Carstens, head of the BIS ("the central bank of central banks"), said that "[w]ith trust, the public will be more willing to accept actions that involve short-term costs in exchange for long-term benefits" and that "trust is vital for policy effectiveness".
It is therefore interesting when central banks or others pretend as if nothing has happened even when trust has been shattered.
Just as in Sweden and in hundreds of other countries, Canada is planning to introduce a central bank digital currency (CBDC), a new form of money where the central bank or its intermediaries (the banks) will have complete insight into citizens' transactions. Payments or money could also be made programmable. Everything from transferring ownership of a car automatically after a successful payment to the seller, to payments being denied if you have traveled too far from home.
"If Canadians decide a digital dollar is necessary, our obligation is to be ready" says Carolyn Rogers, Deputy Head of Bank of Canada, in a statement shared in an article.
So, what do the citizens want? According to a report from the Bank of Canada, a whopping 88% of those surveyed believe that the central bank should refrain from developing such a currency. About the same number (87%) believe that authorities should guarantee the opportunity to pay with cash instead. And nearly four out of five people (78%) do not believe that the central bank will care about people's opinions. What about trust again?
Canadians' likely remember the Trudeau government's actions against the "Freedom Convoy". The Freedom Convoy consisted of, among others, truck drivers protesting the country's strict pandemic policies, blocking roads in the capital Ottawa at the beginning of 2022. The government invoked never-before-used emergency measures to, among other things, "freeze" people's bank accounts. Suddenly, truck drivers and those with a "connection" to the protests were unable to pay their electricity bills or insurances, for instance. Superficially, this may not sound so serious, but ultimately, it could mean that their families end up in cold houses (due to electricity being cut off) and that they lose the ability to work (driving uninsured vehicles is not taken lightly). And this applied not only to the truck drivers but also to those with a "connection" to the protests. No court rulings were required.
Without the freedom to pay for goods and services, i.e. the freedom to transact, one has no real freedom at all, as several participants in the protests experienced.
In January of this year, a federal judge concluded that the government's actions two years ago were unlawful when it invoked the emergency measures. The use did not display "features of rationality - motivation, transparency, and intelligibility - and was not justified in relation to the relevant factual and legal limitations that had to be considered". He also argued that the use was not in line with the constitution. There are also reports alleging that the government fabricated evidence to go after the demonstrators. The case is set to continue to the highest court. Prime Minister Justin Trudeau and Finance Minister Chrystia Freeland have also recently been sued for the government's actions.
The Trudeau government's use of emergency measures two years ago sadly only provides a glimpse of what the future may hold if CBDCs or similar systems replace the current monetary system with commercial bank money and cash. In Canada, citizens do not want the central bank to proceed with the development of a CBDC. In canada, citizens in Canada want to strengthen the role of cash. In Canada, citizens suspect that the central bank will not listen to them. All while the central bank feverishly continues working on the new system...
"Trust is vital", said Agustín Carstens. But if policy-makers do not pause for a thoughtful reflection even when trust has been utterly shattered as is the case in Canada, are we then not merely dealing with lip service?
And how much trust do these policy-makers then deserve?
-
 @ 4ba8e86d:89d32de4
2024-10-25 11:40:05
@ 4ba8e86d:89d32de4
2024-10-25 11:40:05A loja Aurora vem com um excelente design, interface de usuário amigável para iniciantes e muitos recursos.
A loja Aurora foi originalmente baseada na loja Yalp de Sergei Yeriomin, mas a versão 3.0 passou do zero para a conclusão seguindo o Material Design reescrito para rodar em todos os dispositivos Android 5.0.
Dentre as diversas características oferecidas pela Aurora Store, destacam-se:
- Login Anônimo: Para garantir sua privacidade, você pode fazer login anonimamente, assegurando que suas atividades permaneçam confidenciais.
- Login do Google: Além do anonimato, a opção de login do Google permite acessar aplicativos pagos e instalar versões beta.
- Falsificação de Dispositivo: Caso um aplicativo não esteja disponível para o seu dispositivo, você pode recorrer à funcionalidade de falsificação de dispositivo, permitindo a instalação.
- Filtragem de Aplicativos F-Droid: A possibilidade de filtrar aplicativos do F-Droid evita que eles apareçam em sua lista de atualizações.
- Aplicativos na Lista Negra: Ao adicionar aplicativos à lista negra, você mantém o Google no escuro quanto aos aplicativos instalados.
A loja de aplicativos se apresenta com um design clássico, apresentando uma capa de apps e jogos em destaque, proporcionando um visual convidativo. A aba de aplicativos instalados permite uma gestão mais eficiente, possibilitando atualizações automáticas para a versão mais recente disponível.
A busca por aplicativos é facilitada por categorias que abrangem diversos interesses, como fotografia, música e áudio, compras, personalização, livros e quadrinhos, entre outras. A eficaz função de busca permite localizar aplicativos específicos de maneira rápida e fácil.
A Aurora Store se diferencia pela tecnologia de pesquisa única, agilizando a descoberta de aplicativos em questão de segundos. Além disso, a loja vem com a licença GPLv3, reforçando seu compromisso com o software livre.
Privacidade é um foco central da Aurora Store, sendo considerada uma excelente alternativa para quem preza por manter suas informações pessoais protegidas. O aplicativo suporta contas pessoais e permite downloads com contas anônimas, assegurando que suas atividades não estejam vinculadas a você.
Com a integração do Exodus, a Aurora Store verifica rastreadores presentes nos códigos dos aplicativos, proporcionando uma visão mais transparente das informações coletadas.
O aplicativo se destaca por ser livre de anúncios e pop-ups, proporcionando uma experiência de uso mais limpa. O suporte ao modo escuro oferece conforto visual em ambientes com pouca luz ou durante a noite.
A Aurora Store é uma alternativa valiosa à Google Play Store, oferecendo um ambiente mais privado, recursos robustos e um design elegante que visa aprimorar a experiência do usuário em busca e gerenciamento de aplicativos.
https://github.com/whyorean/AuroraStore
https://f-droid.org/packages/com.aurora.store/
https://gitlab.com/AuroraOSS/AuroraStore/-/releases
-
 @ 4ba8e86d:89d32de4
2024-10-24 14:03:14
@ 4ba8e86d:89d32de4
2024-10-24 14:03:14O Collabora Office é uma suíte de escritório baseada em código aberto que oferece uma alternativa viável e de qualidade ao popular pacote Office da Microsoft. Desenvolvido pela Collabora, uma empresa líder em serviços de consultoria e desenvolvimento de software de código aberto, o Collabora Office oferece uma gama completa de aplicativos de produtividade para a plataforma Android, incluindo processador de texto, planilha, apresentação e muito mais.
Recursos e Funcionalidades.
O Collabora Office oferece uma ampla gama de recursos e funcionalidades para dispositivos Android, comparáveis aos encontrados em outras suítes de escritório populares. Além das funcionalidades básicas, como criação e edição de documentos de texto, planilhas e apresentações, o Collabora Office suporta formatos de arquivo comuns, como o formato OpenDocument (ODF) e o formato do Microsoft Office (OOXML). Isso significa que você pode facilmente compartilhar e colaborar em documentos com usuários de outras suítes de escritório.
Uma característica notável do Collabora Office para Android é a capacidade de edição colaborativa em tempo real. Vários usuários podem trabalhar simultaneamente em um documento, visualizando as alterações em tempo real. Isso torna a colaboração em equipe mais eficiente, permitindo que os membros trabalhem juntos em projetos sem a necessidade de trocar arquivos várias vezes.
O Collabora Office para Android possui uma interface intuitiva e fácil de usar, projetada especificamente para dispositivos móveis. Isso garante uma experiência de usuário fluida e permite que os usuários aproveitem ao máximo os recursos e funcionalidades do aplicativo em seus smartphones ou tablets.
Uma das principais vantagens do Collabora Office para Android é o fato de ser baseado em código aberto. Isso significa que o software é desenvolvido de forma transparente e está disponível para qualquer pessoa utilizar, estudar, modificar e distribuir. A natureza de código aberto do Collabora Office traz vários benefícios, incluindo:
-
Custos reduzidos: O Collabora Office para Android é gratuito para download e uso, eliminando a necessidade de licenças caras. Isso é particularmente atraente para pequenas empresas e usuários domésticos que buscam uma alternativa acessível ao pacote Office tradicional.
-
Personalização e flexibilidade: Como o código-fonte está disponível, desenvolvedores e usuários avançados podem personalizar e adaptar o Collabora Office para Android às suas necessidades específicas. Isso permite criar soluções personalizadas e integrar o software a outros sistemas e fluxos de trabalho existentes.
-
Segurança: Com a comunidade de código aberto constantemente analisando e auditando o software, eventuais vulnerabilidades de segurança são identificadas e corrigidas rapidamente. Além disso, os usuários podem ter maior confiança na privacidade de seus dados, uma vez que podem verificar como o software lida com as informações.
O Collabora Office para Android é uma alternativa sólida e de código aberto ao pacote Office da Microsoft. Com recursos abrangentes, capacidade de edição colaborativa em tempo real e uma interface otimizada para dispositivos móveis, ele se tornou uma escolha popular entre empresas e usuários individuais que desejam uma solução de produtividade acessível e personalizável para seus dispositivos Android. Além disso, a natureza de código aberto do Collabora Office traz vantagens significativas, como custos reduzidos, flexibilidade e segurança aprimorada. Se você está em busca de uma alternativa confiável e gratuita ao pacote Office tradicional para Android, vale a pena considerar o Collabora Office como uma opção viável.
https://www.collaboraoffice.com/
https://github.com/CollaboraOnline/online
-
-
 @ 42342239:1d80db24
2024-03-31 11:23:36
@ 42342239:1d80db24
2024-03-31 11:23:36Biologist Stuart Kauffman introduced the concept of the "adjacent possible" in evolutionary biology in 1996. A bacterium cannot suddenly transform into a flamingo; rather, it must rely on small exploratory changes (of the "adjacent possible") if it is ever to become a beautiful pink flying creature. The same principle applies to human societies, all of which exemplify complex systems. It is indeed challenging to transform shivering cave-dwellers into a space travelers without numerous intermediate steps.
Imagine a water wheel – in itself, perhaps not such a remarkable invention. Yet the water wheel transformed the hard-to-use energy of water into easily exploitable rotational energy. A little of the "adjacent possible" had now been explored: water mills, hammer forges, sawmills, and textile factories soon emerged. People who had previously ground by hand or threshed with the help of oxen could now spend their time on other things. The principles of the water wheel also formed the basis for wind power. Yes, a multitude of possibilities arose – reminiscent of the rapid development during the Cambrian explosion. When the inventors of bygone times constructed humanity's first water wheel, they thus expanded the "adjacent possible". Surely, the experts of old likely sought swift prohibitions. Not long ago, our expert class claimed that the internet was going to be a passing fad, or that it would only have the same modest impact on the economy as the fax machine. For what it's worth, there were even attempts to ban the number zero back in the days.
The pseudonymous creator of Bitcoin, Satoshi Nakamoto, wrote in Bitcoin's whitepaper that "[w]e have proposed a system for electronic transactions without relying on trust." The Bitcoin system enables participants to agree on what is true without needing to trust each other, something that has never been possible before. In light of this, it is worth noting that trust in the federal government in the USA is among the lowest levels measured in almost 70 years. Trust in media is at record lows. Moreover, in countries like the USA, the proportion of people who believe that one can trust "most people" has decreased significantly. "Rebuilding trust" was even the theme of the World Economic Forum at its annual meeting. It is evident, even in the international context, that trust between countries is not at its peak.
Over a fifteen-year period, Bitcoin has enabled electronic transactions without its participants needing to rely on a central authority, or even on each other. This may not sound like a particularly remarkable invention in itself. But like the water wheel, one must acknowledge that new potential seems to have been put in place, potential that is just beginning to be explored. Kauffman's "adjacent possible" has expanded. And despite dogmatic statements to the contrary, no one can know for sure where this might lead.
The discussion of Bitcoin or crypto currencies would benefit from greater humility and openness, not only from employees or CEOs of money laundering banks but also from forecast-failing central bank officials. When for instance Chinese Premier Zhou Enlai in the 1970s was asked about the effects of the French Revolution, he responded that it was "too early to say" - a far wiser answer than the categorical response of the bureaucratic class. Isn't exploring systems not based on trust is exactly what we need at this juncture?
-
 @ 2063cd79:57bd1320
2024-12-02 07:03:22
@ 2063cd79:57bd1320
2024-12-02 07:03:22Warum werden die vorhandenen Mittel einer öffentlich einsehbaren Blockchain nicht verwendet, um eine gewisse Sicherheit zu schaffen und ein Vertrauen in Dritte soweit zu reduzieren, dass man immerhin das gute alte Bitcoin-Meme "Don't Trust, Verify!" auf die Arbeit Dritter anwenden kann? Proof of Reserves (PoR) ist ein Ansatz, der von vielen als der neue Standard gesehen wird, der zumindest bei Handelsplattformen ein gewisses Grundvertrauen erzeugen soll. Doch wie genau funktioniert PoR und ist es wirklich so effektiv, wie es uns verkauft wird?
Wer sichergehen möchte, dass sich seine/ihre Guthaben bei Anbietern von Börsen, Handelsplattformen oder anderen Verwahrungsdienstleistern tatsächlich in Form von liquiden bitcoins in der direkten Kontrolle des Anbieters befinden, sollte a) seine Guthaben abheben und in die Selbstverwahrung gehen, oder b) zumindest mit einem Anbieter arbeiten, der Transparenz schafft und dem/der Kund//in ermöglicht zu überprüfen, dass die Einlagen wirklich vorhanden sind. Analog zum traditionellen Bankensystem lässt sich bei jedem Anbieter, ob über die Website, eine App oder sonstwie leicht ein Dashboard generieren, das einem sein Bitcoin-Guthaben anzeigt. Allerdings hat der/die Nutzer//in meistens keinen Einblick darüber, ob die angezeigte Menge Bitcoin auch wirklich im Falle eines Bankruns auszahlbar ist. So auch bei Banken. Ein Kontoauszug gibt lediglich Auskunft über das in der Banken-Datenbank gutgeschriebene Guthaben (oder Schuld), man bekommt aber keine Auskunft darüber, ob eine Bank auch die finanziellen Mittel besitzt, um alle Forderungen zu bedienen, sollten sich alle Kund//innen gleichzeitig entscheiden ihre Vermögen von den Konten abzuheben. Im Bankensystem spricht man von Fractional-Reserve-Banking ➡️ wer mehr darüber lesen möchte, kann sich den Artikel anschauen, in dem ich mehr über das Thema schreibe:
https://www.genexyz.org/post/11-block-752065-fractional-reserve-banking-wird-durch-bitcoin-obsolet-bdpznh/
Bei Bitcoin spricht man von Paper-Bitcoin oder Fake-Bitcoin. Hierbei handelt es sich um vermeintliche Bitcoin-Guthaben, die Nutzern von Börsen oder Handelsplattformen suggeriert werden, ohne dass die tatsächliche Menge Bitcoin verwahrt wird (ähnlich Fractional Reserve Banking). Ob die tatsächlichen Bitcoin wirklich vom "Verwahrer" gehalten werden, lässt sich (zumindest teilweise) mit ️Proof of Reserves überprüfen.
Wie wir letzte Woche festgestellt haben, bieten Blockchain-basierte Systeme (neben vielen anderen) den Vorteil, dass der Informationsfluss komplett transparent und öffentlich einsehbar ist. Im Gegensatz zum traditionellen Finanzsystem, befinden sich viele Daten, wie Adressen und Transaktionen, direkt auf der Chain und sind somit für jedermann jederzeit und von überall abrufbar. Dies schafft mehr Transparenz , da diese Daten nicht durch Dritte herausgegeben werden, sondern von jedem/r interessierten Nutzer//in direkt abgerufen werden können, und so kann in der Theorie jede Bewegung, aber auch jeder Kontostand nachverfolgt werden.
Anders als bei On-Chain-Analyse, die auf Heuristik besteht, um gewisse Trends oder Sentiments anhand von Daten aufzuspüren, ist die Prämisse bei Proof of Reserves ziemlich simpel: Die Adressen zeigen eine gewisse Menge von bitcoins oder nicht.

Doch wie veröffentlichen Dienstleister wie Börsen und Handelsplattformen diese Information über die Vermögenswerte, die diese für ihre Kund//innen verwahren? Im Idealfall verfügen die Anbieter über Mittel, die alle Vermögenswerte der Nutzer//innen zu 100% abdecken, und darüber hinaus noch zusätzliche Reserven für Notfälle. Einfach gesprochen bedeutet dies, dass jedesmal, wenn ein/e Nutzer//in Bitcoin einzahlt oder Bitcoin erwirbt, diese zusätzliche Menge Bitcoin direkt und in voller Höhe in den Reserven des Dienstleisters landet, um sicherzustellen, dass die Kundengelder vollständig abgedeckt und gesichert sind. Um Nutzer//innen die Möglichkeit zu geben nachzuvollziehen, dass die eigenen Vermögenswerte wirklich zu 100% durch Reserven abdeckt sind, nutzen Dienstleister sogenannte Merkle-Trees, die jedem/jeder Nutzer//in ermöglichen, seine/ihre Vermögensbestände mit seiner/ihrer eigenen generierten Merkle-Hash und Datensatz-ID zu überprüfen.
Was sind Merkle-Trees? 🌳
Um Merkle-Trees zu verstehen, muss man zunächst das Konzept von Hashes verstanden haben. Ein sicherer Hash-Algorithmus (auch SHA genannt) ist in der Kryptografie eine mathematische Formel, die eine Datenkette beliebiger Größe in eine feste Größe transformiert und komprimiert, die sich vollständig von den ursprünglichen Daten unterscheidet.
Beispiele:
- SHA1("The quick brown fox jumps over the lazy dog") Output: 2fd4e1c67a2d28fced849ee1bb76e7391b93eb12
- SHA1("The quick brown fox jumps over the lazy cog") Output: de9f2c7fd25e1b3afad3e85a0bd17d9b100db4b3
- SHA1("") Output: da39a3ee5e6b4b0d3255bfef95601890afd80709
Wie man an dem Beispiel erkennt, erzeugen die fast identischen Sätze, in denen nur das D in dog mit einem C ersetzt wurde komplett neue Hash-Werte, die aber in Größe identisch sind und sogar die gleiche Größe besitzen, wie zum Beispiel der Hash-Wert des Eingabe-Werts G.

In dem Beispiel oben sehen wir einen SHA-1 Hash-Algorithmus. Das Bitcoin-Protokoll bedient sich des SHA-256, eine von der NSA entwickelte Variante der SHA-2 Funktion, wobei die 256 die Länge der ausgegebenen Bitfolge angibt. Außerdem funktionieren SHA Funktionen als Einbahnstraßen, es gibt eine Eingabe (z.B. beliebiger Satz, oder Passwort) und es gibt eine Ausgabe (in Form eines Hash-Werts), es ist absolut unmöglich, die Eingabe eines Hash-Werts aus der Ausgabe neu zu erstellen.
Ein häufig gesehenes Anwendungsbeispiel ist die Verschlüsselung von Passwörtern. Anstatt das eigentliche Passwort des/r Nutzers//in zu kennen, muss ein Server nur den Hash-Wert dieses Passworts überprüfen. Dies schützt vor Angriffen auf Datenbanken der Unternehmen, da bei einem Angriff nur die Hash-Werte und nicht die tatsächlichen Passwörter preisgegeben werden.
Weiter zu Merkle-Trees 🦜
Das von Ralph Merkle entwickelte Konzept beschreibt im Prinzip eine Verkettung von Hash-Werten in Form eines umgekehrten Baums (auf deutsch auch Hash-Baum genannt). Die Hash-Werte stellen in dieser Datenstruktur die Blätter, oder Leaves dar (L1, L2, L3 und L4 im Diagramm). Die Wurzel des Baums wird als Top-Hash oder Root-Hash bezeichnet.

Der Vorteil dieser Datenstruktur liegt darin, dass alle Leaves veränderbar sind und dennoch an der Wurzel verifiziert werden können. Im Gegensatz zu einer flachen Struktur, in der man jede Veränderung separat nachvollziehen muss, kann man im Merkle-Tree den Top-Hash verifizieren und hat damit eine Garantie, dass jede darunterliegende Veränderung durchgereicht wurde. Besonders in einem Peer-to-Peer-Netzwerk kann somit sichergestellt werden, dass zwischen Peers gesendete Blöcke unverändert und unbeschädigt empfangen werden. Es ermöglicht damit, dass jeder Teil des Trees zur Verifizierung mit dem vertrauenswürdigen Top-Hash verglichen werden kann, um festzustellen, ob der Hash beschädigt oder sogar gefälscht ist.

In der traditionellen Buchhaltung wird die Intaktheit oder Unversehrtheit der Unternehmensbücher durch einen Wirtschaftsprüfer oder anderen vertrauenswürdigen Dritten attestiert. In einer perfekten Welt stellt dieser Prüfer die Garantie dafür, dass die geprüften Bücher vollständig und korrekt geführt sind, also Vermögen und Verbindlichkeiten korrekt eingegeben wurden. Allerdings stellen Bitcoin- und Kryptobörsen dieses System vor ein Problem, da die riesige Menge an Transaktionen in einem 24/7/365-offenen Markt von einem Prüfer nie zu jedem Zeitpunkt festgestellt werden kann, sondern wenn überhaupt punktuell. Anders gesagt, Prüfungen finden nur punktuell statt, also im Quartal, Halbjahr oder jährlich. Das gibt einem bösartig gesinnten Anbieter viel Zeit Kundengelder zu veruntreuen. Außerdem, ganz in guter Bitcoin-Manier, lautet eines der wichtigsten Credos:
☝️ DON'T TRUST, VERIFY!
Merkle-Trees bieten die einzige Möglichkeit den Nutzer//innen einen direkten Weg zur Überprüfung der Gesundheit / Vollständigkeit ihrer persönlichen Einlagen.
Doch auch bei Proof of Reserves auf Basis von Merkle-Trees gibt es einige Probleme. Zunächst mal ist das Konzept nicht einheitlich definiert. Es gibt Anbieter, die lediglich den Merkle-Root-Hash veröffentlichen, um damit zu zeigen, dass sie über mindestens soviel (im Idealfall sogar mehr) Bitcoin verfügen, wie von Nutzer//innen auf der Plattform verwaltet.

Ein Problem liegt darin, dass die Hash-Roots vom Unternehmen selbst veröffentlicht werden müssen. Dies allein birgt einige Risikos, denn Hash-Roots müssen häufig genug veröffentlicht werden, um ein Fehlverhalten durch den Anbieter auszuschließen. Wie wir anhand des Bildes oben erkennen können, wurde der letzte sogenannte Snapshot von Binance am 22. November veröffentlicht, also vor 3 Wochen. Darüber hinaus wird die Information von dem Unternehmen selbst auf seinem eigenen Medium (z.B. Website) veröffentlicht, was es für den/die Nutzer//in schwierig macht nachzuvollziehen, ob die Information allen Nutzer//innen identisch angezeigt wird.
https://x.com/jespow/status/1596227031637045248
Ein weiteres Problem liegt darin, dass Proof of Reserves in dieser Art lediglich einen Proof of Assets, also einen Beweis für vorhandene Vermögen, darstellt. Bei einer vollständigen Prüfung muss ein Unternehmen auch etwaige Verbindlichkeiten zum Nachweis der Zahlungsfähigkeit aufweisen, denn diese können in der Theorie die Höhe der Vermögen bei Weitem übersteigen (➡️siehe BlockFi mit Vermögen von 1 Milliarde US Dollar vs. Verbindlichkeiten in Höhe von 10 Milliarden US Dollar).
Viel schlimmer noch: Wir können uns nicht einmal wirklich sicher sein, dass es sich um tatsächliche Vermögenswerte handelt, da diese ja unter Umständen schon verliehen oder als Sicherheit anderweitig verwendet worden sind.
Des Weiteren muss auch hier ein Dritter die Integrität der gehashten Daten testieren, denn der Merkle-Root-Hash ist immer nur so korrekt, wie die eingespeisten zugrunde liegenden Informationen. Theoretisch kann ein Unternehmen private Schlüssel, die nicht im exklusiven Besitz stehen, also fremdverwertet werden können, oder sogar negative Kontostände einbeziehen, die im Hashing-Vorgang als absolute Zahlen dargestellt werden. Also stehen wir zumindest bei der komplett unabhängigen Verifizierung durch den Nutzer am Ausgangsproblem: Trust!

Börsen wie Kraken oder Coinbase lassen ihre Reserven durch Wirtschaftsprüfungsfirmen belegen, um den Unzulänglichkeiten der einfachen Offenlegung der Merkle-Trees entgegenzuwirken, doch löst dies nicht das Problem des Vertrauens in die genannten Prüfer.

Die einzige 100% sichere und vertrauenswürdige Methode, um sicherzustellen, dass Guthaben sicher und geschützt sind, besteht darin seine Einlagen sofort nach dem Kauf von Börsen und anderen Dienstleistern zu nehmen und sie in die Selbstverwahrung zu holen. Denn selbst wenn das Unternehmen ein solventes Verhältnis von Vermögen zu Verbindlichkeiten aufweist und darüber hinaus testieren kann, dass die in den Hashing-Algorithmen verwendeten Keys zu 100% unversehrt und authentisch sind, besteht immer noch die Chance, dass das Unternehmen vom Saubermann zum Schwindler wird und sich mit dem angehäuften Vermögen aus dem Staub macht. In diesen Fällen werden gerne IT- und Netzwerkprobleme, oder Ungereimtheiten bei den Nutzerdaten aufgrund von irgendwelchen KYC/AML Regularien zitiert, die den/die Nutzer//in daran hindern, das Guthaben auszuzahlen.
https://www.nobsbitcoin.com/hoseki-launches-real-time-proof-of-reserves
Unternehmen wie Hoseki haben schnell reagiert und einen Service angeboten, der Nutzer//innen, die weiterhin ihr Guthaben einem Dienstleister anvertrauen wollen, einen One-Stop-Shop anbieten soll, den sie nutzen können, um schnell und einfach zu verifizieren, welche Dienstleister wirklich Bitcoin in der angegebenen Menge verwahren. Die Übersicht ist sehr übersichtlich gestaltet und benutzerfreundlich. Die Identifizierung für Unternehmen erfolgt durch Twitter-Authentifizierung und das gehaltene Vermögen wird beglaubigt, indem das Unternehmen den Besitz seiner Adressen mit einer Signatur beweist. Somit können Adressen auf Dauer überwacht werden, um sicherzustellen, dass das Vermögen auch über einen längeren Zeitraum nicht verschoben wird.
💡Jede/r Nutzer//in kann seine/ihre Wallet-Adresse verifizieren indem er/sie in der Wallet eine Signatur einer Nachricht vornimmt. Dieser Verifizierungsprozess beweist, dass man tatsächlich der/die Inhaber//in der Adresse ist, denn nur mit dem Private-Key und dem Public-Key zusammen, kann solch eine Signatur erstellt werden.
Zu diesem Zeitpunkt hat nur Peter McCormacks Fussball-Verein Real Bedford FC die Verifizierung vollzogen, doch wer sich anschauen möchte, ob in Zukunft weitere Unternehmen folgen, kann das hier tun:
https://www.hoseki.app/verified
Auch Coinmarketcap.com haben in der Zwischenzeit ein Feature eingeführt, dass den Nutzer//innen einen einfachen Überblick über die eingelagerten Vermögenswerte bieten soll:
https://coinmarketcap.com/rankings/exchanges
Abschließend bleibt wie immer nur zu sagen, dass einer der großen Vorteile von Bitcoin im Gegensatz zu den meisten anderen Anlageklassen darin besteht, dass man über sein Vermögen zu 100% selbst bestimmen kann. Oder um mit Satoshis Worten zu schließen:
The result is a distributed system with no single point of failure. Users hold the crypto keys to their own money and transact directly with each other, with the help of the P2P network to check for double-spending.
🫳🎤
In diesem Sinne, 2... 1... Risiko!

-
 @ 4ba8e86d:89d32de4
2024-10-23 00:11:19
@ 4ba8e86d:89d32de4
2024-10-23 00:11:19Ele permite que os usuários descubram, baixem e instalem aplicativos em seus dispositivos Android sem depender da Google Play Store, que é a loja de aplicativos padrão do Android.
História do F-Droid
O F-Droid foi lançado em 2010 por um grupo de desenvolvedores liderados por Ciaran Gultnieks. A ideia por trás do projeto era criar uma alternativa de código aberto para a Google Play Store, que é uma plataforma centralizada controlada por uma única empresa. O F-Droid foi desenvolvido como um catálogo de aplicativos que só inclui aplicativos de código aberto que podem ser baixados e instalados gratuitamente.
Desde o lançamento, o F-Droid cresceu significativamente e agora oferece mais de 3.500 aplicativos de código aberto para Android, com uma ampla gama de categorias, incluindo jogos, educação, produtividade, privacidade e segurança. O projeto é mantido por uma comunidade de desenvolvedores voluntários e é executado sem fins lucrativos.
Os problemas que o F-Droid resolve
O F-Droid resolve vários problemas associados à Google Play Store e outras lojas de aplicativos. O primeiro é o controle centralizado de uma única empresa. A Google Play Store pode remover aplicativos que violem suas políticas, e os desenvolvedores podem ser impedidos de distribuir aplicativos por meio da loja por motivos arbitrários. O F-Droid, por outro lado, é administrado por uma comunidade sem fins lucrativos e não há restrições sobre quais aplicativos podem ser incluídos no catálogo.
Além disso, o F-Droid oferece uma alternativa para os usuários preocupados com a privacidade que não querem depender dos serviços da Google. O F-Droid é independente do Google Play Services e não rastreia os usuários ou coleta informações pessoais, tornando-se uma escolha atraente para aqueles que buscam maior privacidade.
Por que usar o F-Droid?
Há várias razões pelas quais você pode querer usar o F-Droid em vez da Google Play Store ou outras lojas de aplicativos. Aqui estão algumas delas:
-
Privacidade: Como mencionado anteriormente, o F-Droid é independente do Google Play Services e não rastreia os usuários. Isso significa que você pode baixar e instalar aplicativos sem se preocupar com a coleta de dados pessoais.
-
Segurança: O F-Droid oferece apenas aplicativos de código aberto e de software livre, o que significa que a comunidade pode examinar o código-fonte para garantir que não haja vulnerabilidades ou backdoors mal-intencionados.
-
Controle: O F-Droid permite que os usuários controlem seus próprios dispositivos Android e decidam quais aplicativos são instalados e atualizados.
-
Escolha: O F-Droid oferece uma ampla gama de aplicativos de código aberto e de software
Também é importante observar que nem todos os aplicativos disponíveis no F-Droid são completamente livres de riscos. Portanto, é sempre recomendável ler cuidadosamente as informações sobre o aplicativo e avaliar os riscos antes de baixá-lo e instalá-lo.
Aqui está o passo a passo para instalar o F-Droid em seu dispositivo Android:
-
Acesse o site oficial do F-Droid em https://f-droid.org/ usando um navegador da web no seu dispositivo Android.
-
Verifique a assinatura PGP do arquivo APK que você irá baixar. Para isso, clique no link "PGP Signature" abaixo do botão "Download F-Droid" na página inicial do site. Na página seguinte, baixe o arquivo "F-Droid.apk.asc" clicando no botão "Download". Baixe também a chave pública do desenvolvedor do F-Droid, clicando no link "PGP key of F-Droid release signing key" na mesma página. É importante verificar a assinatura antes de prosseguir com a instalação.
-
Clique no botão "Download F-Droid" para baixar o arquivo APK.
-
Abra o arquivo APK baixado em seu dispositivo Android. Se você não sabe como abrir o arquivo, vá até o gerenciador de arquivos do seu dispositivo e encontre o arquivo APK que acabou de baixar. Toque no arquivo e siga as instruções na tela para instalar o aplicativo.
-
Se aparecer uma mensagem de alerta informando que a instalação de aplicativos de fontes desconhecidas está desativada, vá até as configurações de segurança do seu dispositivo e habilite a opção "Fontes desconhecidas". Isso permitirá que você instale aplicativos de fora da Google Play Store.
-
Clique em "Instalar" e aguarde a instalação ser concluída.
-
Após a instalação, abra o aplicativo F-Droid e aguarde a inicialização do repositório de aplicativos.
-
Pronto! Agora você pode navegar e baixar aplicativos do F-Droid em seu dispositivo Android. O F-Droid oferece uma ampla variedade de aplicativos de código aberto e de software livre, e todos são gratuitos para baixar e usar. Você pode usar o F-Droid como uma alternativa à Google Play Store se estiver preocupado com privacidade, segurança ou controle de seus próprios dispositivos Android.
https://github.com/f-droid
-
-
 @ fd208ee8:0fd927c1
2024-11-08 10:27:40
@ fd208ee8:0fd927c1
2024-11-08 10:27:40You have no idea
I regularly read comments from people, on here, wondering how it's possible to marry -- or even simply be friends! -- with someone who doesn't agree with you on politics. I see this sentiment expressed quite often, usually in the context of Bitcoin, or whatever pig is currently being chased through the village, as they say around here.

It seems rather sensible, but I don't think it's as hard, as people make it out to be. Further, I think it's a dangerous precondition to set, for your interpersonal relationships, because the political field is constantly in flux. If you determine who you will love, by their opinions, do you stop loving them if their opinions change, or if the opinions they have become irrelevant and a new set of opinions are needed -- and their new ones don't match your new ones? We could see this happen to relationships en masse, during the Covid Era, and I think it happens every day, in a slow grind toward the disintegration of interpersonal discourse.
I suspect many people do stop loving, at that point, as they never really loved the other person for their own sake, they loved the other person because they thought the other person was exactly like they are. But no two people are alike, and the longer you are in a relationship with someone else, the more the initial giddiness wears off and the trials and tribulations add up, the more you notice how very different you actually are. This is the point, where best friends and romantic couples say, We just grew apart.
But you were always apart. You were always two different people. You just didn't notice, until now.

I've also always been surprised at how many same-party relationships disintegrate because of some disagreement over some particular detail of some particular topic, that they generally agree on. To me, it seems like an irrelevant side-topic, but they can't stand to be with this person... and they stomp off. So, I tend to think that it's less that opinions need to align to each other, but rather that opinions need to align in accordance with the level of interpersonal tolerance they can bring into the relationship.
I was raised by relaxed revolutionaries
Maybe I see things this way because my parents come from two diverging political, cultural, national, and ethnic backgrounds, and are prone to disagreeing about a lot of "important" (to people outside their marriage) things, but still have one of the healthiest, most-fruitful, and most long-running marriages of anyone I know, from that generation. My parents, you see, aren't united by their opinions. They're united by their relationship, which is something outside of opinions. Beyond opinions. Relationships are what turn two different people into one, cohesive unit, so that they slowly grow together. Eventually, even their faces merge, and their biological clocks tick to the same rhythm. They eventually become one entity that contains differing opinions about the same topics.
It's like magic, but it's the result of a mindset, not a worldview. Or, as I like to quip:
The best way to stay married, is to not get divorced.

My parents simply determined early on, that they would stay together, and whenever they would find that they disagreed on something that didn't directly pertain to their day-to-day existence with each other they would just agree-to-disagree about that, or roll their eyes, and move on. You do you. Live and let live.
My parents have some of the most strongly held personal opinions of any people I've ever met, but they're also incredibly tolerant and can get along with nearly anyone, so their friends are a confusing hodgepodge of people we liked and found interesting enough to keep around. Which makes their house parties really fun, and highly unusual, in this day and age of mutual-damnation across the aisle.

The things that did affect them, directly, like which school the children should attend or which country they should live in, etc. were things they'd sit down and discuss, and somehow one opinion would emerge, and they'd again... move on.
And that's how my husband and I also live our lives, and it's been working surprisingly well. No topics are off-limits to discussion (so long as you don't drone on for too long), nobody has to give up deeply held beliefs, or stop agitating for the political decisions they prefer.
You see, we didn't like that the other always had the same opinion. We liked that the other always held their opinions strongly. That they were passionate about their opinions. That they were willing to voice their opinions; sacrifice to promote their opinions. And that they didn't let anyone browbeat or cow them, for their opinions, not even their best friends or their spouse. But that they were open to listening to the other side, and trying to wrap their mind around the possibility that they might just be wrong about something.

We married each other because we knew: this person really cares, this person has thought this through, and they're in it, to win it. What "it" is, is mostly irrelevant, so long as it doesn't entail torturing small animals in the basement, or raising the children on a diet of Mountain Dew and porn, or something.
Live and let live. At least, it's never boring. At least, there's always something to ~~argue~~ talk about. At least, we never think... we've just grown apart.
-
 @ b12b632c:d9e1ff79
2024-03-23 16:42:49
@ b12b632c:d9e1ff79
2024-03-23 16:42:49CASHU AND ECASH ARE EXPERIMENTAL PROJECTS. BY THE OWN NATURE OF CASHU ECASH, IT'S REALLY EASY TO LOSE YOUR SATS BY LACKING OF KNOWLEDGE OF THE SYSTEM MECHANICS. PLEASE, FOR YOUR OWN GOOD, ALWAYS USE FEW SATS AMOUNT IN THE BEGINNING TO FULLY UNDERSTAND HOW WORKS THE SYSTEM. ECASH IS BASED ON A TRUST RELATIONSHIP BETWEEN YOU AND THE MINT OWNER, PLEASE DONT TRUST ECASH MINT YOU DONT KNOW. IT IS POSSIBLE TO GENERATE UNLIMITED ECASH TOKENS FROM A MINT, THE ONLY WAY TO VALIDATE THE REAL EXISTENCE OF THE ECASH TOKENS IS TO DO A MULTIMINT SWAP (BETWEEN MINTS). PLEASE, ALWAYS DO A MULTISWAP MINT IF YOU RECEIVE SOME ECASH FROM SOMEONE YOU DON'T KNOW/TRUST. NEVER TRUST A MINT YOU DONT KNOW!
IF YOU WANT TO RUN AN ECASH MINT WITH A BTC LIGHTNING NODE IN BACK-END, PLEASE DEDICATE THIS LN NODE TO YOUR ECASH MINT. A BAD MANAGEMENT OF YOUR LN NODE COULD LET PEOPLE TO LOOSE THEIR SATS BECAUSE THEY HAD ONCE TRUSTED YOUR MINT AND YOU DID NOT MANAGE THE THINGS RIGHT.

What's ecash/Cashu ?
I recently listened a passionnating interview from calle 👁️⚡👁 invited by the podcast channel What Bitcoin Did about the new (not so much now) Cashu protocol.
Cashu is a a free and open-source Chaumian ecash project built for Bitcoin protocol, recently created in order to let users send/receive Ecash over BTC Lightning network. The main Cashu ecash goal is to finally give you a "by-design" privacy mechanism to allow us to do anonymous Bitcoin transactions.
Ecash for your privacy.\ A Cashu mint does not know who you are, what your balance is, or who you're transacting with. Users of a mint can exchange ecash privately without anyone being able to know who the involved parties are. Bitcoin payments are executed without anyone able to censor specific users.
Here are some useful links to begin with Cashu ecash :
Github repo: https://github.com/cashubtc
Documentation: https://docs.cashu.space
To support the project: https://docs.cashu.space/contribute
A Proof of Liabilities Scheme for Ecash Mints: https://gist.github.com/callebtc/ed5228d1d8cbaade0104db5d1cf63939
Like NOSTR and its own NIPS, here is the list of the Cashu ecash NUTs (Notation, Usage, and Terminology): https://github.com/cashubtc/nuts?tab=readme-ov-file
I won't explain you at lot more on what's Casu ecash, you need to figured out by yourself. It's really important in order to avoid any mistakes you could do with your sats (that you'll probably regret).
If you don't have so much time, you can check their FAQ right here: https://docs.cashu.space/faq
I strongly advise you to listen Calle's interviews @whatbbitcoindid to "fully" understand the concept and the Cashu ecash mechanism before using it:
Scaling Bitcoin Privacy with Calle
In the meantime I'm writing this article, Calle did another really interesting interview with ODELL from CitadelDispatch:
CD120: BITCOIN POWERED CHAUMIAN ECASH WITH CALLE
Which ecash apps?
There are several ways to send/receive some Ecash tokens, you can do it by using mobile applications like eNuts, Minibits or by using Web applications like Cashu.me, Nustrache or even npub.cash. On these topics, BTC Session Youtube channel offers high quality contents and very easy to understand key knowledge on how to use these applications :
Minibits BTC Wallet: Near Perfect Privacy and Low Fees - FULL TUTORIAL
Cashu Tutorial - Chaumian Ecash On Bitcoin
Unlock Perfect Privacy with eNuts: Instant, Free Bitcoin Transactions Tutorial
Cashu ecash is a very large and complex topic for beginners. I'm still learning everyday how it works and the project moves really fast due to its commited developpers community. Don't forget to follow their updates on Nostr to know more about the project but also to have a better undertanding of the Cashu ecash technical and political implications.
There is also a Matrix chat available if you want to participate to the project:
https://matrix.to/#/#cashu:matrix.org
How to self-host your ecash mint with Nutshell
Cashu Nutshell is a Chaumian Ecash wallet and mint for Bitcoin Lightning. Cashu Nutshell is the reference implementation in Python.
Github repo:
https://github.com/cashubtc/nutshell
Today, Nutshell is the most advanced mint in town to self-host your ecash mint. The installation is relatively straightforward with Docker because a docker-compose file is available from the github repo.
Nutshell is not the only cashu ecash mint server available, you can check other server mint here :
https://docs.cashu.space/mints
The only "external" requirement is to have a funding source. One back-end funding source where ecash will mint your ecash from your Sats and initiate BTC Lightning Netwok transactions between ecash mints and BTC Ligtning nodes during a multimint swap. Current backend sources supported are: FakeWallet*, LndRestWallet, CoreLightningRestWallet, BlinkWallet, LNbitsWallet, StrikeUSDWallet.
*FakeWallet is able to generate unlimited ecash tokens. Please use it carefully, ecash tokens issued by the FakeWallet can be sent and accepted as legit ecash tokens to other people ecash wallets if they trust your mint. In the other way, if someone send you 2,3M ecash tokens, please don't trust the mint in the first place. You need to force a multimint swap with a BTC LN transaction. If that fails, someone has maybe tried to fool you.
I used a Voltage.cloud BTC LN node instance to back-end my Nutshell ecash mint:
SPOILER: my nutshell mint is working but I have an error message "insufficient balance" when I ask a multiswap mint from wallet.cashu.me or the eNuts application. In order to make it work, I need to add some Sats liquidity (I can't right now) to the node and open few channels with good balance capacity. If you don't have an ecash mint capable of doig multiswap mint, you'll only be able to mint ecash into your ecash mint and send ecash tokens to people trusting your mint. It's working, yes, but you need to be able to do some mutiminit swap if you/everyone want to fully profit of the ecash system.
Once you created your account and you got your node, you need to git clone the Nutshell github repo:
git clone https://github.com/cashubtc/nutshell.gitYou next need to update the docker compose file with your own settings. You can comment the wallet container if you don't need it.
To generate a private key for your node, you can use this openssl command
openssl rand -hex 32 054de2a00a1d8e3038b30e96d26979761315cf48395aa45d866aeef358c91dd1The CLI Cashu wallet is not needed right now but I'll show you how to use it in the end of this article. Feel free to comment it or not.
``` version: "3" services: mint: build: context: . dockerfile: Dockerfile container_name: mint
ports:
- "3338:3338"
environment:- DEBUG=TRUE
- LOG_LEVEL=DEBUG
- MINT_URL=https://YourMintURL - MINT_HOST=YourMintDomain.tld - MINT_LISTEN_HOST=0.0.0.0 - MINT_LISTEN_PORT=3338 - MINT_PRIVATE_KEY=YourPrivateKeyFromOpenSSL - MINT_INFO_NAME=YourMintInfoName - MINT_INFO_DESCRIPTION=YourShortInfoDesc - MINT_INFO_DESCRIPTION_LONG=YourLongInfoDesc - MINT_LIGHTNING_BACKEND=LndRestWallet #- MINT_LIGHTNING_BACKEND=FakeWallet - MINT_INFO_CONTACT=[["email","YourConctact@email"], ["twitter","@YourTwitter"], ["nostr", "YourNPUB"]] - MINT_INFO_MOTD=Thanks for using my mint! - MINT_LND_REST_ENDPOINT=https://YourVoltageNodeDomain:8080 - MINT_LND_REST_MACAROON=YourDefaultAdminMacaroonBase64 - MINT_MAX_PEG_IN=100000 - MINT_MAX_PEG_OUT=100000 - MINT_PEG_OUT_ONLY=FALSE command: ["poetry", "run", "mint"]wallet-voltage: build: context: . dockerfile: Dockerfile container_name: wallet-voltage
ports:
- "4448:4448"
depends_on: - nutshell-voltage environment:- DEBUG=TRUE
- MINT_URL=http://nutshell-voltage:3338
- API_HOST=0.0.0.0 command: ["poetry", "run", "cashu", "-d"]```
To build, run and see the container logs:
docker compose up -d && docker logs -f mint0.15.1 2024-03-22 14:45:45.490 | WARNING | cashu.lightning.lndrest:__init__:49 - no certificate for lndrest provided, this only works if you have a publicly issued certificate 2024-03-22 14:45:45.557 | INFO | cashu.core.db:__init__:135 - Creating database directory: data/mint 2024-03-22 14:45:45.68 | INFO | Started server process [1] 2024-03-22 14:45:45.69 | INFO | Waiting for application startup. 2024-03-22 14:45:46.12 | INFO | Loaded 0 keysets from database. 2024-03-22 14:45:46.37 | INFO | Current keyset: 003dba9e589023f1 2024-03-22 14:45:46.37 | INFO | Using LndRestWallet backend for method: 'bolt11' and unit: 'sat' 2024-03-22 14:45:46.97 | INFO | Backend balance: 1825000 sat 2024-03-22 14:45:46.97 | INFO | Data dir: /root/.cashu 2024-03-22 14:45:46.97 | INFO | Mint started. 2024-03-22 14:45:46.97 | INFO | Application startup complete. 2024-03-22 14:45:46.98 | INFO | Uvicorn running on http://0.0.0.0:3338 (Press CTRL+C to quit) 2024-03-22 14:45:47.27 | INFO | 172.19.0.22:48528 - "GET /v1/keys HTTP/1.1" 200 2024-03-22 14:45:47.34 | INFO | 172.19.0.22:48544 - "GET /v1/keysets HTTP/1.1" 200 2024-03-22 14:45:47.38 | INFO | 172.19.0.22:48552 - "GET /v1/info HTTP/1.1" 200If you see the line :
Uvicorn running on http://0.0.0.0:3338 (Press CTRL+C to quit)Nutshell is well started.
I won't explain here how to create a reverse proxy to Nutshell, you can find how to do it into my previous article. Here is the reverse proxy config into Nginx Proxy Manager:
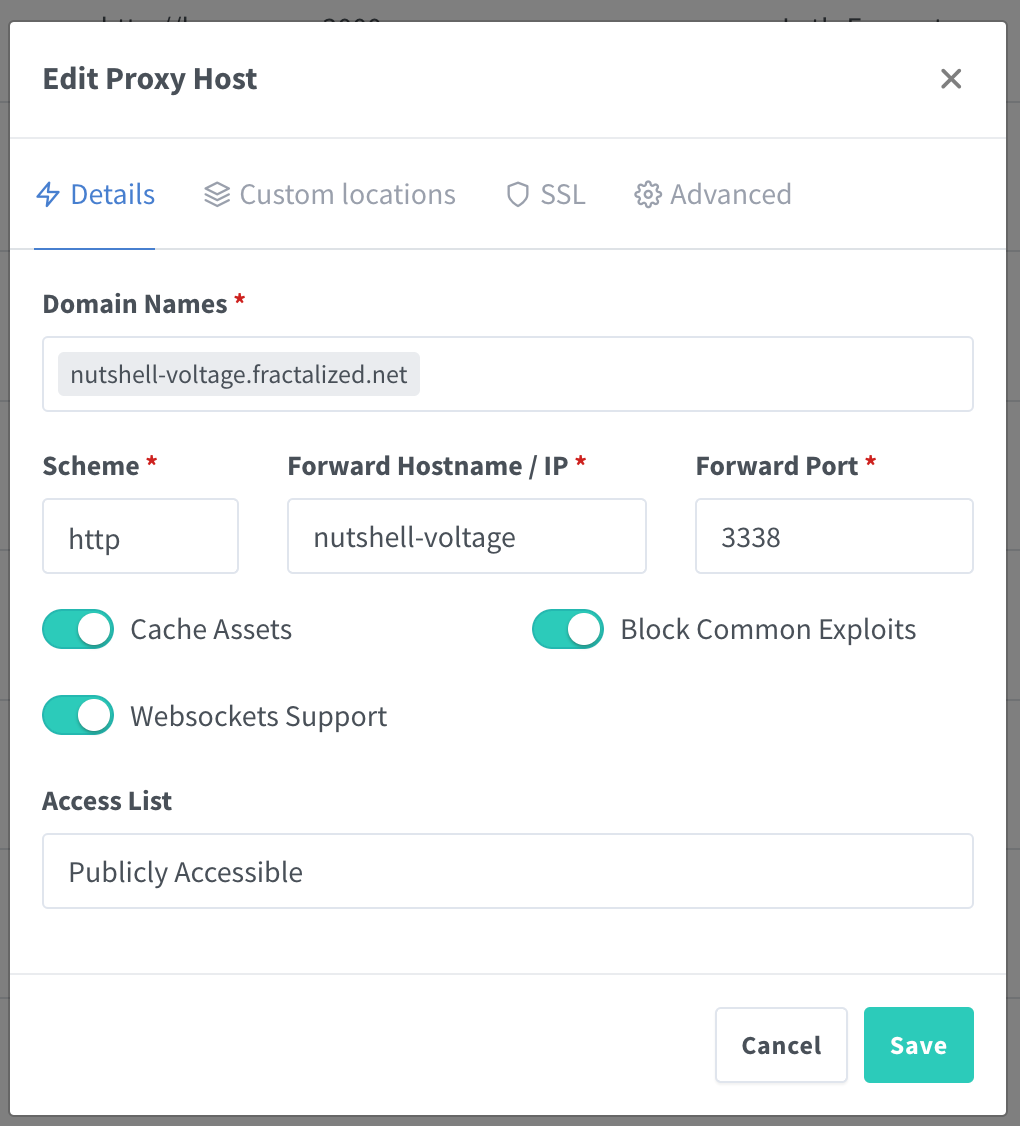
If everything is well configured and if you go on your mint url (https://yourminturl) you shoud see this:
It's not helping a lot because at first glance it seems to be not working but it is. You can also check these URL path to confirm :
- https://yourminturl/keys and https://yourminturl/keysets
or
- https://yourminturl/v1/keys and https://yourminturl/v1/keysets
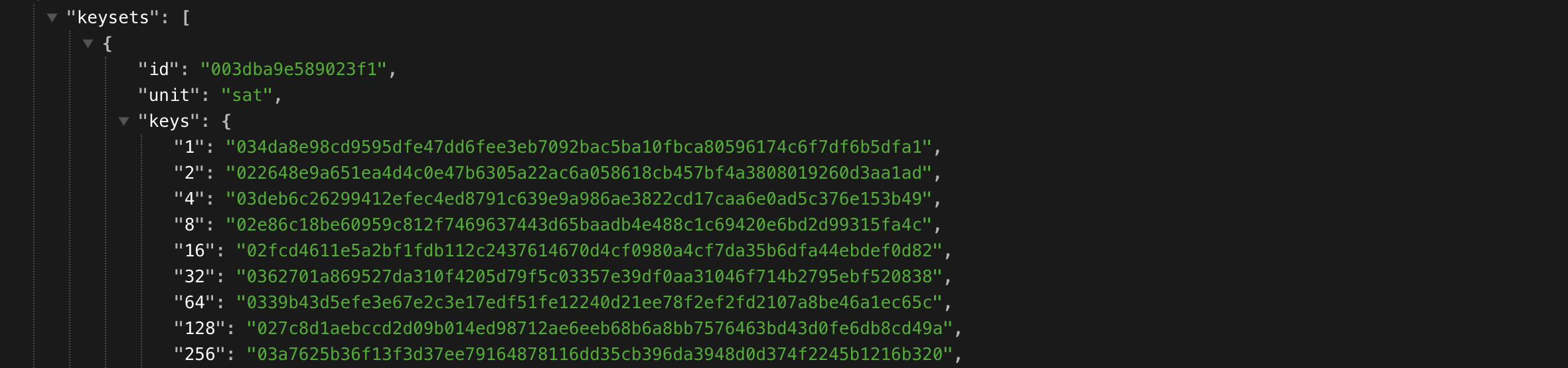
Depending of the moment when you read this article, the first URLs path might have been migrated to V1. Here is why:
https://github.com/cashubtc/nuts/pull/55
The final test is to add your mint to your prefered ecash wallets.
SPOILER: AT THIS POINT, YOU SHOUD KNOW THAT IF YOU RESET YOUR LOCAL BROWSER INTERNET CACHE FILE, YOU'LL LOSE YOUR MINTED ECASH TOKENS. IF NOT, PLEASE READ THE DOCUMENTATION AGAIN.
For instace, if we use wallet.cashu.me:
You can go into the "Settings" tab and add your mint :
If everything went find, you shoud see this :
You can now mint some ecash from your mint creating a sats invoice :
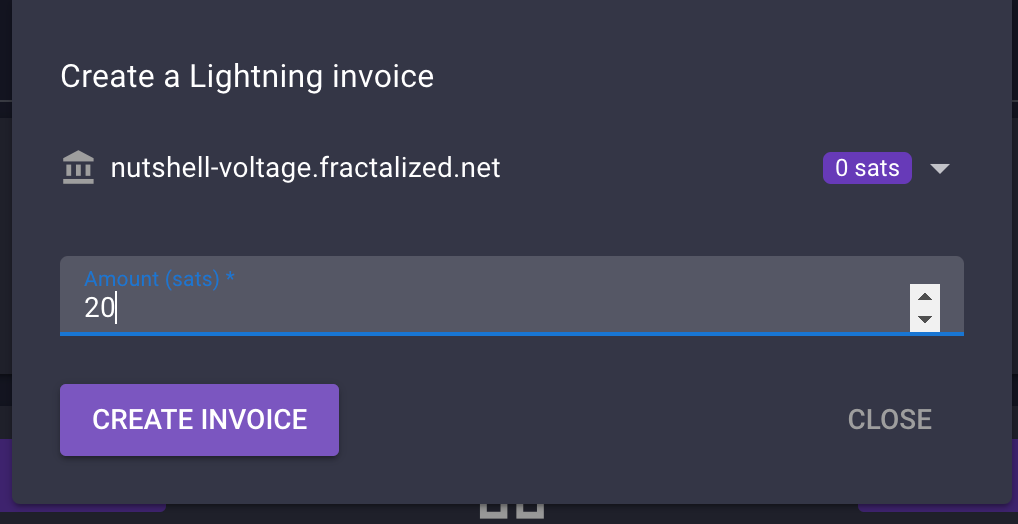
You can now scan the QR diplayed with your prefered BTC LN wallet. If everything is OK, you should receive the funds:
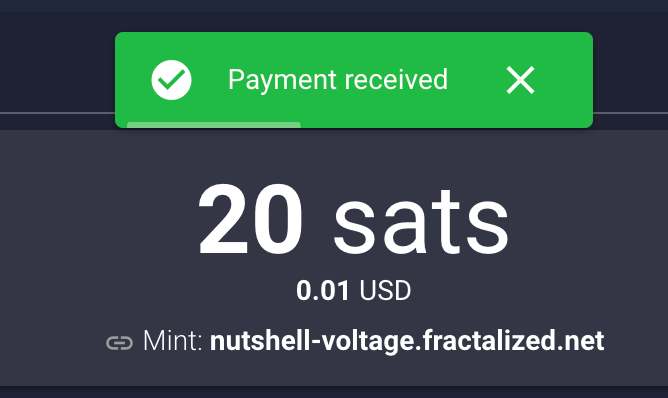
It may happen that some error popup sometimes. If you are curious and you want to know what happened, Cashu wallet has a debug console you can activate by clicking on the "Settings" page and "OPEN DEBUG TERMINAL". A little gear icon will be displayed in the bottom of the screen. You can click on it, go to settings and enable "Auto Display If Error Occurs" and "Display Extra Information". After enabling this setting, you can close the popup windows and let the gear icon enabled. If any error comes, this windows will open again and show you thé error:
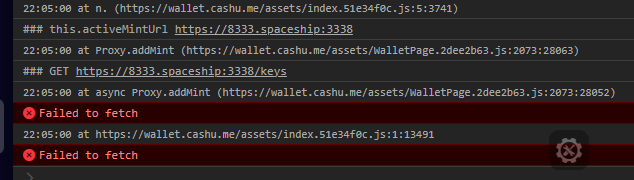
Now that you have some sats in your balance, you can try to send some ecash. Open in a new windows another ecash wallet like Nutstach for instance.
Add your mint again :
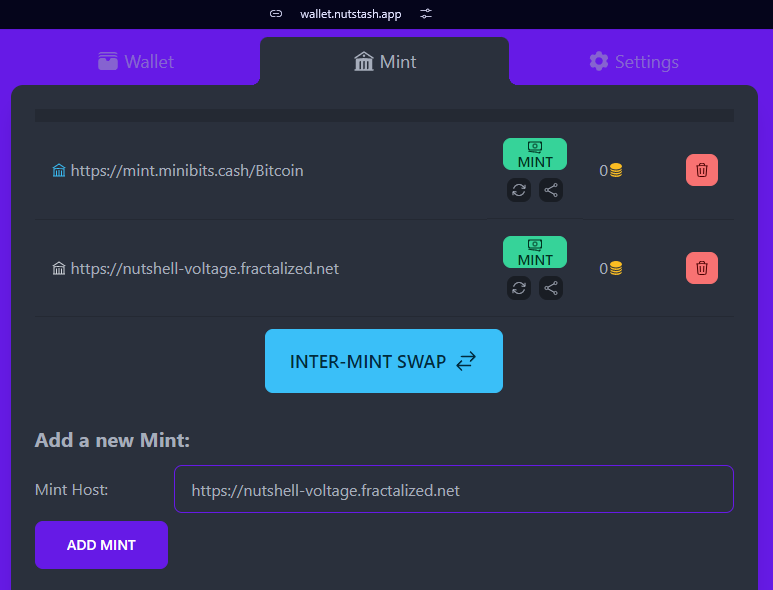
Return on Cashu wallet. The ecash token amount you see on the Cashu wallet home page is a total of all the ecash tokens you have on all mint connected.
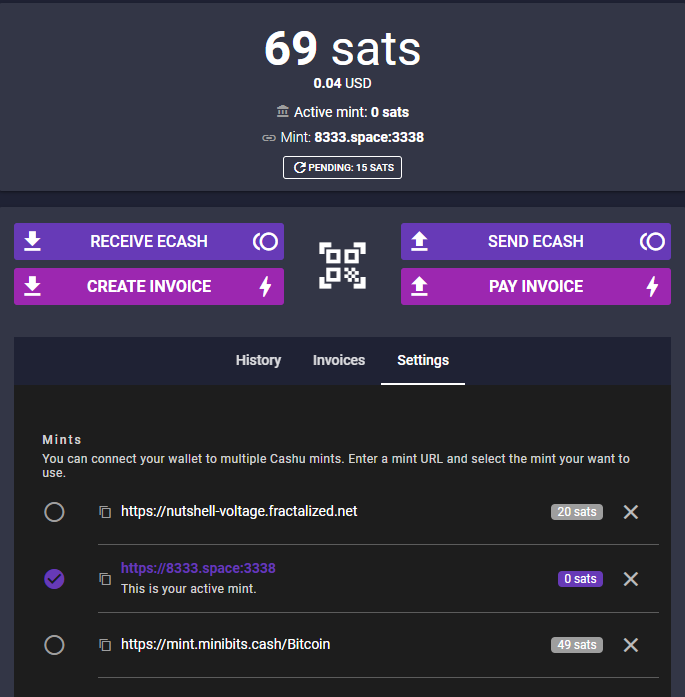
Next, click on "Send ecach". Insert the amout of ecash you want to transfer to your other wallet. You can select the wallet where you want to extract the funds by click on the little arrow near the sats funds you currenly selected :


Click now on "SEND TOKENS". That will open you a popup with a QR code and a code CONTAINING YOUR ECASH TOKENS (really).

You can now return on nutstach, click on the "Receive" button and paste the code you get from Cashu wallet:
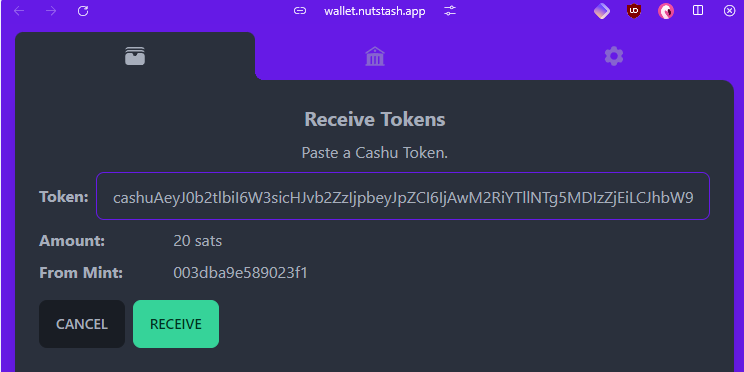
Click on "RECEIVE" again:
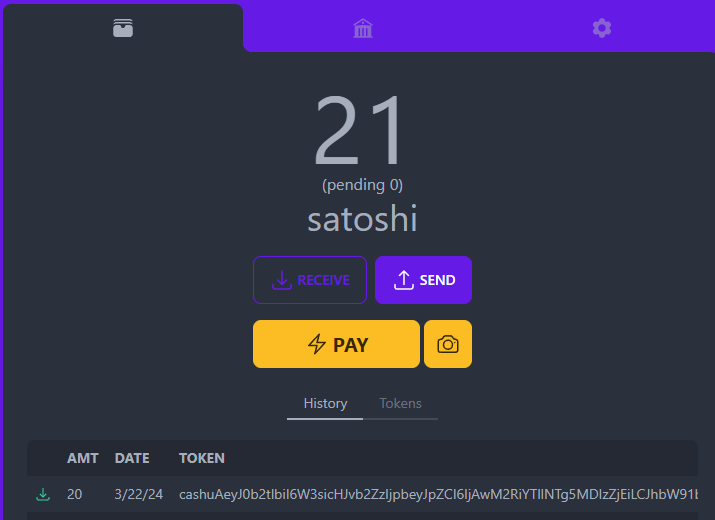
Congrats, you transfered your first ecash tokens to yourself ! 🥜⚡
You may need some time to transfer your ecash tokens between your wallets and your mint, there is a functionality existing for that called "Multimint swaps".
Before that, if you need new mints, you can check the very new website Bitcoinmints.com that let you see the existing ecash mints and rating :
Don't forget, choose your mint carefuly because you don't know who's behind.
Let's take a mint and add it to our Cashu wallet:
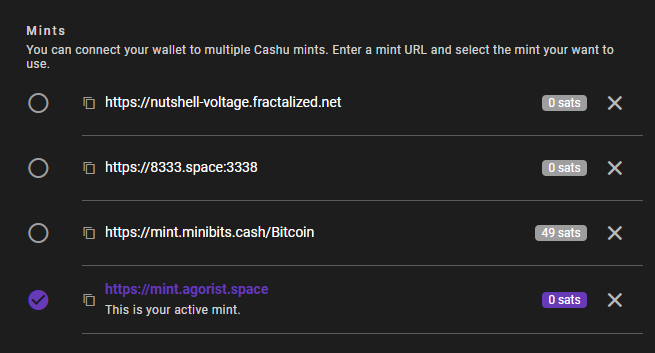
If you want to transfer let's say 20 sats from minibits mint to bitcointxoko mint, go just bottom into the "Multimint swap" section. Select the mint into "Swap from mint", the mint into "Swap to mint" and click on "SWAP" :
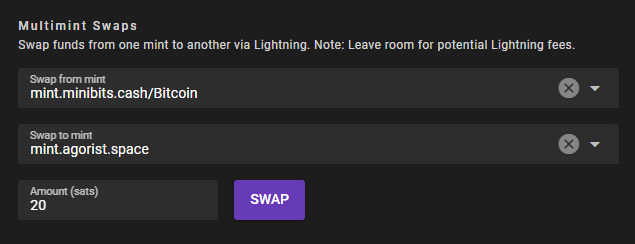
A popup window will appear and will request the ecash tokens from the source mint. It will automatically request the ecash amount via a Lightning node transaction and add the fund to your other wallet in the target mint. As it's a Lightning Network transaction, you can expect some little fees.
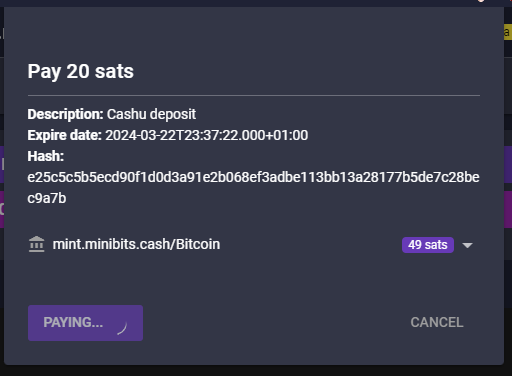
If everything is OK with the mints, the swap will be successful and the ecash received.
You can now see that the previous sats has been transfered (minus 2 fee sats).
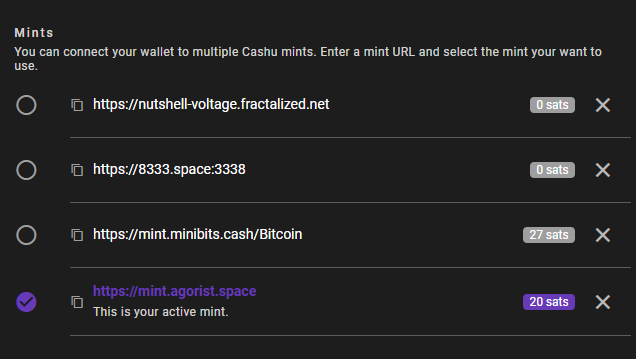
Well done, you did your first multimint swap ! 🥜⚡
One last thing interresting is you can also use CLI ecash wallet. If you created the wallet contained in the docker compose, the container should be running.
Here are some commands you can do.
To verify which mint is currently connected :
``` docker exec -it wallet-voltage poetry run cashu info
2024-03-22 21:57:24.91 | DEBUG | cashu.wallet.wallet:init:738 | Wallet initialized 2024-03-22 21:57:24.91 | DEBUG | cashu.wallet.wallet:init:739 | Mint URL: https://nutshell-voltage.fractalized.net 2024-03-22 21:57:24.91 | DEBUG | cashu.wallet.wallet:init:740 | Database: /root/.cashu/wallet 2024-03-22 21:57:24.91 | DEBUG | cashu.wallet.wallet:init:741 | Unit: sat 2024-03-22 21:57:24.92 | DEBUG | cashu.wallet.wallet:init:738 | Wallet initialized 2024-03-22 21:57:24.92 | DEBUG | cashu.wallet.wallet:init:739 | Mint URL: https://nutshell-voltage.fractalized.net 2024-03-22 21:57:24.92 | DEBUG | cashu.wallet.wallet:init:740 | Database: /root/.cashu/wallet 2024-03-22 21:57:24.92 | DEBUG | cashu.wallet.wallet:init:741 | Unit: sat Version: 0.15.1 Wallet: wallet Debug: True Cashu dir: /root/.cashu Mints: - https://nutshell-voltage.fractalized.net ```
To verify your balance :
``` docker exec -it wallet-voltage poetry run cashu balance
2024-03-22 21:59:26.67 | DEBUG | cashu.wallet.wallet:init:738 | Wallet initialized 2024-03-22 21:59:26.67 | DEBUG | cashu.wallet.wallet:init:739 | Mint URL: https://nutshell-voltage.fractalized.net 2024-03-22 21:59:26.67 | DEBUG | cashu.wallet.wallet:init:740 | Database: /root/.cashu/wallet 2024-03-22 21:59:26.67 | DEBUG | cashu.wallet.wallet:init:741 | Unit: sat 2024-03-22 21:59:26.68 | DEBUG | cashu.wallet.wallet:init:738 | Wallet initialized 2024-03-22 21:59:26.68 | DEBUG | cashu.wallet.wallet:init:739 | Mint URL: https://nutshell-voltage.fractalized.net 2024-03-22 21:59:26.68 | DEBUG | cashu.wallet.wallet:init:740 | Database: /root/.cashu/wallet 2024-03-22 21:59:26.68 | DEBUG | cashu.wallet.wallet:init:741 | Unit: sat Balance: 0 sat ```
To create an sats invoice to have ecash :
``` docker exec -it wallet-voltage poetry run cashu invoice 20
2024-03-22 22:00:59.12 | DEBUG | cashu.wallet.wallet:_load_mint_info:275 | Mint info: name='nutshell.fractalized.net' pubkey='02008469922e985cbc5368ce16adb6ed1aaea0f9ecb21639db4ded2e2ae014a326' version='Nutshell/0.15.1' description='Official Fractalized Mint' description_long='TRUST THE MINT' contact=[['email', 'pastagringo@fractalized.net'], ['twitter', '@pastagringo'], ['nostr', 'npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2']] motd='Thanks for using official ecash fractalized mint!' nuts={4: {'methods': [['bolt11', 'sat']], 'disabled': False}, 5: {'methods': [['bolt11', 'sat']], 'disabled': False}, 7: {'supported': True}, 8: {'supported': True}, 9: {'supported': True}, 10: {'supported': True}, 11: {'supported': True}, 12: {'supported': True}} Balance: 0 sat
Pay invoice to mint 20 sat:
Invoice: lnbc200n1pjlmlumpp5qh68cqlr2afukv9z2zpna3cwa3a0nvla7yuakq7jjqyu7g6y69uqdqqcqzzsxqyz5vqsp5zymmllsqwd40xhmpu76v4r9qq3wcdth93xthrrvt4z5ct3cf69vs9qyyssqcqppurrt5uqap4nggu5tvmrlmqs5guzpy7jgzz8szckx9tug4kr58t4avv4a6437g7542084c6vkvul0ln4uus7yj87rr79qztqldggq0cdfpy
You can use this command to check the invoice: cashu invoice 20 --id 2uVWELhnpFcNeFZj6fWzHjZuIipqyj5R8kM7ZJ9_
Checking invoice .................2024-03-22 22:03:25.27 | DEBUG | cashu.wallet.wallet:verify_proofs_dleq:1103 | Verified incoming DLEQ proofs. Invoice paid.
Balance: 20 sat ```
To pay an invoice by pasting the invoice you received by your or other people :
``` docker exec -it wallet-voltage poetry run cashu pay lnbc150n1pjluqzhpp5rjezkdtt8rjth4vqsvm50xwxtelxjvkq90lf9tu2thsv2kcqe6vqdq2f38xy6t5wvcqzzsxqrpcgsp58q9sqkpu0c6s8hq5pey8ls863xmjykkumxnd8hff3q4fvxzyh0ys9qyyssq26ytxay6up54useezjgqm3cxxljvqw5vq2e94ru7ytqc0al74hr4nt5cwpuysgyq8u25xx5la43mx4ralf3mq2425xmvhjzvwzqp54gp0e3t8e
2024-03-22 22:04:37.23 | DEBUG | cashu.wallet.wallet:_load_mint_info:275 | Mint info: name='nutshell.fractalized.net' pubkey='02008469922e985cbc5368ce16adb6ed1aaea0f9ecb21639db4ded2e2ae014a326' version='Nutshell/0.15.1' description='Official Fractalized Mint' description_long='TRUST THE MINT' contact=[['email', 'pastagringo@fractalized.net'], ['twitter', '@pastagringo'], ['nostr', 'npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2']] motd='Thanks for using official ecash fractalized mint!' nuts={4: {'methods': [['bolt11', 'sat']], 'disabled': False}, 5: {'methods': [['bolt11', 'sat']], 'disabled': False}, 7: {'supported': True}, 8: {'supported': True}, 9: {'supported': True}, 10: {'supported': True}, 11: {'supported': True}, 12: {'supported': True}} Balance: 20 sat 2024-03-22 22:04:37.45 | DEBUG | cashu.wallet.wallet:get_pay_amount_with_fees:1529 | Mint wants 0 sat as fee reserve. 2024-03-22 22:04:37.45 | DEBUG | cashu.wallet.cli.cli:pay:189 | Quote: quote='YpNkb5f6WVT_5ivfQN1OnPDwdHwa_VhfbeKKbBAB' amount=15 fee_reserve=0 paid=False expiry=1711146847 Pay 15 sat? [Y/n]: y Paying Lightning invoice ...2024-03-22 22:04:41.13 | DEBUG | cashu.wallet.wallet:split:613 | Calling split. POST /v1/swap 2024-03-22 22:04:41.21 | DEBUG | cashu.wallet.wallet:verify_proofs_dleq:1103 | Verified incoming DLEQ proofs. Error paying invoice: Mint Error: Lightning payment unsuccessful. insufficient_balance (Code: 20000) ```
It didn't work, yes. That's the thing I told you earlier but it would work with a well configured and balanced Lightning Node.
That's all ! You should now be able to use ecash as you want! 🥜⚡
See you on NOSTR! 🤖⚡\ PastaGringo
-
 @ ee11a5df:b76c4e49
2024-03-22 23:49:09
@ ee11a5df:b76c4e49
2024-03-22 23:49:09Implementing The Gossip Model
version 2 (2024-03-23)
Introduction
History
The gossip model is a general concept that allows clients to dynamically follow the content of people, without specifying which relay. The clients have to figure out where each person puts their content.
Before NIP-65, the gossip client did this in multiple ways:
- Checking kind-3 contents, which had relay lists for configuring some clients (originally Astral and Damus), and recognizing that wherever they were writing our client could read from.
- NIP-05 specifying a list of relays in the
nostr.jsonfile. I added this to NIP-35 which got merged down into NIP-05. - Recommended relay URLs that are found in 'p' tags
- Users manually making the association
- History of where events happen to have been found. Whenever an event came in, we associated the author with the relay.
Each of these associations were given a score (recommended relay urls are 3rd party info so they got a low score).
Later, NIP-65 made a new kind of relay list where someone could advertise to others which relays they use. The flag "write" is now called an OUTBOX, and the flag "read" is now called an INBOX.
The idea of inboxes came about during the development of NIP-65. They are a way to send an event to a person to make sure they get it... because putting it on your own OUTBOX doesn't guarantee they will read it -- they may not follow you.
The outbox model is the use of NIP-65. It is a subset of the gossip model which uses every other resource at it's disposal.
Rationale
The gossip model keeps nostr decentralized. If all the (major) clients were using it, people could spin up small relays for both INBOX and OUTBOX and still be fully connected, have their posts read, and get replies and DMs. This is not to say that many people should spin up small relays. But the task of being decentralized necessitates that people must be able to spin up their own relay in case everybody else is censoring them. We must make it possible. In reality, congregating around 30 or so popular relays as we do today is not a problem. Not until somebody becomes very unpopular with bitcoiners (it will probably be a shitcoiner), and then that person is going to need to leave those popular relays and that person shouldn't lose their followers or connectivity in any way when they do.
A lot more rationale has been discussed elsewhere and right now I want to move on to implementation advice.
Implementation Advice
Read NIP-65
NIP-65 will contain great advice on which relays to consult for which purposes. This post does not supersede NIP-65. NIP-65 may be getting some smallish changes, mostly the addition of a private inbox for DMs, but also changes to whether you should read or write to just some or all of a set of relays.
How often to fetch kind-10002 relay lists for someone
This is up to you. Refreshing them every hour seems reasonable to me. Keeping track of when you last checked so you can check again every hour is a good idea.
Where to fetch events from
If your user follows another user (call them jack), then you should fetch jack's events from jack's OUTBOX relays. I think it's a good idea to use 2 of those relays. If one of those choices fails (errors), then keep trying until you get 2 of them that worked. This gives some redundancy in case one of them is censoring. You can bump that number up to 3 or 4, but more than that is probably just wasting bandwidth.
To find events tagging your user, look in your user's INBOX relays for those. In this case, look into all of them because some clients will only write to some of them (even though that is no longer advised).
Picking relays dynamically
Since your user follows many other users, it is very useful to find a small subset of all of their OUTBOX relays that cover everybody followed. I wrote some code to do this as (it is used by gossip) that you can look at for an example.
Where to post events to
Post all events (except DMs) to all of your users OUTBOX relays. Also post the events to all the INBOX relays of anybody that was tagged or mentioned in the contents in a nostr bech32 link (if desired). That way all these mentioned people are aware of the reply (or quote or repost).
DMs should be posted only to INBOX relays (in the future, to PRIVATE INBOX relays). You should post it to your own INBOX relays also, because you'll want a record of the conversation. In this way, you can see all your DMs inbound and outbound at your INBOX relay.
Where to publish your user's kind-10002 event to
This event was designed to be small and not require moderation, plus it is replaceable so there is only one per user. For this reason, at the moment, just spread it around to lots of relays especially the most popular relays.
For example, the gossip client automatically determines which relays to publish to based on whether they seem to be working (several hundred) and does so in batches of 10.
How to find replies
If all clients used the gossip model, you could find all the replies to any post in the author's INBOX relays for any event with an 'e' tag tagging the event you want replies to... because gossip model clients will publish them there.
But given the non-gossip-model clients, you should also look where the event was seen and look on those relays too.
Clobbering issues
Please read your users kind 10002 event before clobbering it. You should look many places to make sure you didn't miss the newest one.
If the old relay list had tags you don't understand (e.g. neither "read" nor "write"), then preserve them.
How users should pick relays
Today, nostr relays are not uniform. They have all kinds of different rule-sets and purposes. We severely lack a way to advice non-technical users as to which relays make good OUTBOX relays and which ones make good INBOX relays. But you are a dev, you can figure that out pretty well. For example, INBOX relays must accept notes from anyone meaning they can't be paid-subscription relays.
Bandwidth isn't a big issue
The outbox model doesn't require excessive bandwidth when done right. You shouldn't be downloading the same note many times... only 2-4 times depending on the level of redundancy your user wants.
Downloading 1000 events from 100 relays is in theory the same amount of data as downloading 1000 events from 1 relay.
But in practice, due to redundancy concerns, you will end up downloading 2000-3000 events from those 100 relays instead of just the 1000 you would in a single relay situation. Remember, per person followed, you will only ask for their events from 2-4 relays, not from all 100 relays!!!
Also in practice, the cost of opening and maintaining 100 network connections is more than the cost of opening and maintaining just 1. But this isn't usually a big deal unless...
Crypto overhead on Low-Power Clients
Verifying Schnorr signatures in the secp256k1 cryptosystem is not cheap. Setting up SSL key exchange is not cheap either. But most clients will do a lot more event signature validations than they will SSL setups.
For this reason, connecting to 50-100 relays is NOT hugely expensive for clients that are already verifying event signatures, as the number of events far surpasses the number of relay connections.
But for low-power clients that can't do event signature verification, there is a case for them not doing a lot of SSL setups either. Those clients would benefit from a different architecture, where half of the client was on a more powerful machine acting as a proxy for the low-power half of the client. These halves need to trust each other, so perhaps this isn't a good architecture for a business relationship, but I don't know what else to say about the low-power client situation.
Unsafe relays
Some people complain that the outbox model directs their client to relays that their user has not approved. I don't think it is a big deal, as such users can use VPNs or Tor if they need privacy. But for such users that still have concerns, they may wish to use clients that give them control over this. As a client developer you can choose whether to offer this feature or not.
The gossip client allows users to require whitelisting for connecting to new relays and for AUTHing to relays.
See Also
-
 @ 3f0702fa:66db56f1
2024-12-02 06:53:59
@ 3f0702fa:66db56f1
2024-12-02 06:53:59Этот величественный архитектурный комплекс не только поражает своим дизайном, но и гармонично вписывается в окружающую природу. Огромные стеклянные фасады отражают солнечные лучи, создавая эффектного контраста с зелеными насаждениями, которые обрамляют здание.
Вокруг бизнес-центра растут высокие деревья, предлагая жителям и посетителям уникальное сочетание urban life и природы. Эти деревья не только улучшают качество воздуха, но и создают уютную атмосферу, где можно отдохнуть от городского шумного ритма. Специально рассчитанные прогулочные зоны и уютные лаунджи под раскидистыми кронами становятся излюбленным местом встреч для предпринимателей и креативных специалистов, стремящихся к новым идеям.
Курган становится свидетелем нового витка экономического развития, где бизнес и экология сосуществуют в гармонии. Этот проект вдохновляет другие города следовать его примеру, подчеркивая важность устойчивого развития для будущих поколений.
https://psv4.userapi.com/s/v1/d/YMM3Mp4Smir0redhULluvN2qS5DOETlNkG751ucuyEzQdwYfb7etKzrQSc_-sJfAmj2dY-0uKbeOG4Z5mvoP_aR406XzXeufuybo9fuQAIRHG6LIoujE0Q/319370047859904514.mp4
45news
Курган2040
-
 @ 42342239:1d80db24
2024-03-21 09:49:01
@ 42342239:1d80db24
2024-03-21 09:49:01It has become increasingly evident that our financial system has started undermine our constitutionally guaranteed freedoms and rights. Payment giants like PayPal, Mastercard, and Visa sometimes block the ability to donate money. Individuals, companies, and associations lose bank accounts — or struggle to open new ones. In bank offices, people nowadays risk undergoing something resembling being cross-examined. The regulations are becoming so cumbersome that their mere presence risks tarnishing the banks' reputation.
The rules are so complex that even within the same bank, different compliance officers can provide different answers to the same question! There are even departments where some of the compliance officers are reluctant to provide written responses and prefer to answer questions over an unrecorded phone call. Last year's corporate lawyer in Sweden recently complained about troublesome bureaucracy, and that's from a the perspective of a very large corporation. We may not even fathom how smaller businesses — the keys to a nation's prosperity — experience it.
Where do all these rules come?
Where do all these rules come from, and how well do they work? Today's regulations on money laundering (AML) and customer due diligence (KYC - know your customer) primarily originate from a G7 meeting in the summer of 1989. (The G7 comprises the seven advanced economies: the USA, Canada, the UK, Germany, France, Italy, and Japan, along with the EU.) During that meeting, the intergovernmental organization FATF (Financial Action Task Force) was established with the aim of combating organized crime, especially drug trafficking. Since then, its mandate has expanded to include fighting money laundering, terrorist financing, and the financing of the proliferation of weapons of mass destruction(!). One might envisage the rules soon being aimed against proliferation of GPUs (Graphics Processing Units used for AI/ML). FATF, dominated by the USA, provides frameworks and recommendations for countries to follow. Despite its influence, the organization often goes unnoticed. Had you heard of it?
FATF offered countries "a deal they couldn't refuse"
On the advice of the USA and G7 countries, the organization decided to begin grading countries in "blacklists" and "grey lists" in 2000, naming countries that did not comply with its recommendations. The purpose was to apply "pressure" to these countries if they wanted to "retain their position in the global economy." The countries were offered a deal they couldn't refuse, and the number of member countries rapidly increased. Threatening with financial sanctions in this manner has even been referred to as "extraterritorial bullying." Some at the time even argued that the process violated international law.
If your local Financial Supervisory Authority (FSA) were to fail in enforcing compliance with FATF's many checklists among financial institutions, the risk of your country and its banks being barred from the US-dominated financial markets would loom large. This could have disastrous consequences.
A cost-benefit analysis of AML and KYC regulations
Economists use cost-benefit analysis to determine whether an action or a policy is successful. Let's see what such an analysis reveals.
What are the benefits (or revenues) after almost 35 years of more and more rules and regulations? The United Nations Office on Drugs and Crime estimated that only 0.2% of criminal proceeds are confiscated. Other estimates suggest a success rate from such anti-money laundering rules of 0.07% — a rounding error for organized crime. Europol expects to recover 1.2 billion euros annually, equivalent to about 1% of the revenue generated in the European drug market (110 billion euros). However, the percentage may be considerably lower, as the size of the drug market is likely underestimated. Moreover, there are many more "criminal industries" than just the drug trade; human trafficking is one example - there are many more. In other words, criminal organizations retain at least 99%, perhaps even 99.93%, of their profits, despite all cumbersome rules regarding money laundering and customer due diligence.
What constitutes the total cost of this bureaurcratic activity, costs that eventually burden taxpayers and households via higher fees? Within Europe, private financial firms are estimated to spend approximately 144 billion euros on compliance. According to some estimates, the global cost is twice as high, perhaps even eight times as much.
For Europe, the cost may thus be about 120 times (144/1.2) higher than the revenues from these measures. These "compliance costs" bizarrely exceed the total profits from the drug market, as one researcher put it. Even though the calculations are uncertain, it is challenging — perhaps impossible — to legitimize these regulations from a cost-benefit perspective.
But it doesn't end there, unfortunately. The cost of maintaining this compliance circus, with around 80 international organizations, thousands of authorities, far more employees, and all this across hundreds of countries, remains a mystery. But it's unlikely to be cheap.
The purpose of a system is what it does
In Economic Possibilities for our Grandchildren (1930), John Maynard Keynes foresaw that thanks to technological development, we could have had a 15-hour workweek by now. This has clearly not happened. Perhaps jobs have been created that are entirely meaningless? Anthropologist David Graeber argued precisely this in Bullshit Jobs in 2018. In that case, a significant number of people spend their entire working lives performing tasks they suspect deep down don't need to be done.
"The purpose of a system is what it does" is a heuristic coined by Stafford Beer. He observed there is "no point in claiming that the purpose of a system is to do what it constantly fails to do. What the current regulatory regime fails to do is combat criminal organizations. Nor does it seem to prevent banks from laundering money as never before, or from providing banking services to sex-offending traffickers
What the current regulatory regime does do, is: i) create armies of meaningless jobs, ii) thereby undermining mental health as well as economic prosperity, while iii) undermining our freedom and rights.
What does this say about the purpose of the system?
-
 @ 4ba8e86d:89d32de4
2024-10-22 23:04:43
@ 4ba8e86d:89d32de4
2024-10-22 23:04:43O objetivo principal do Tutanota é oferecer um serviço de e-mail protegido, onde as mensagens são criptografadas de ponta a ponta. Isso significa que as mensagens são codificadas no dispositivo do remetente e permanecem criptografadas até chegarem ao dispositivo do destinatário. Somente o remetente e o destinatário têm as chaves necessárias para descriptografar as mensagens, garantindo a confidencialidade das comunicações.
Além da criptografia de ponta a ponta, o Tutanota oferece outras medidas de segurança. Os e-mails são armazenados de forma criptografada nos servidores da empresa, o que significa que mesmo se alguém obtiver acesso aos servidores, os e-mails permanecerão ilegíveis sem a chave de descriptografia do usuário. O Tutanota também permite que os usuários protejam suas contas com senhas fortes.
O Tutanota foi fundado em 2011 na Alemanha por Arne Möhle e Matthias Pfau, com o objetivo de oferecer um serviço de e-mail seguro e privado. Eles buscavam fornecer uma alternativa aos serviços tradicionais, enfatizando a proteção da privacidade e a criptografia de ponta a ponta. Desde então, o Tutanota expandiu suas funcionalidades, adicionando recursos como armazenamento criptografado, calendário e agenda. A empresa está comprometida com a proteção dos dados dos usuários e está sediada na Alemanha, seguindo o Regulamento Geral de Proteção de Dados (GDPR). O Tutanota continua a ser reconhecido como uma referência em privacidade digital e mantém seu compromisso com a segurança e a privacidade dos usuários.
Recursos de Segurança: 1. Criptografia de ponta a ponta: Uma das principais características do Tutanota é a criptografia de ponta a ponta. Isso significa que suas mensagens são codificadas no dispositivo do remetente e permanecem criptografadas durante o trânsito até o dispositivo do destinatário. Somente o remetente e o destinatário têm as chaves para descriptografar as mensagens, tornando praticamente impossível para terceiros interceptá-las e acessar seu conteúdo.
-
Armazenamento criptografado: Além da criptografia de ponta a ponta para as mensagens em trânsito, o Tutanota também armazena seus e-mails de forma criptografada em seus servidores. Isso significa que, mesmo se alguém obtiver acesso aos servidores do Tutanota, os e-mails armazenados permanecerão ilegíveis sem a chave de descriptografia do usuário.
-
Proteção por senha: O Tutanota permite que você defina uma senha segura para proteger sua conta de e-mail. Essa senha é usada para criptografar seus dados armazenados e deve ser mantida em sigilo para garantir a segurança de sua conta.
Outros Recursos e Funcionalidades: 1. Interface amigável: O Tutanota oferece uma interface de usuário intuitiva e fácil de usar, semelhante aos serviços de e-mail convencionais. Isso torna a transição para o Tutanota suave para os usuários acostumados a outras plataformas de e-mail.
-
Aplicativos móveis: O Tutanota oferece aplicativos móveis para dispositivos iOS e Android, permitindo que você acesse sua conta de e-mail de forma segura em seu smartphone ou tablet.
-
Armazenamento e anexos: O Tutanota oferece 1 GB de armazenamento gratuito para sua conta de e-mail, permitindo que você mantenha um histórico de mensagens seguro. Além disso, você pode enviar e receber anexos com segurança, pois eles também são criptografados.
-
Proteção contra spam: O Tutanota possui um filtro de spam eficiente que verifica e filtra mensagens indesejadas, garantindo que sua caixa de entrada seja livre de spam e ameaças.
-
Calendário e Contatos: Além do serviço de e-mail, o Tutanota também oferece recursos de calendário e agenda, permitindo que você organize seus compromissos de forma segura e mantenha uma lista de contatos criptografados.
-
Personalização: O Tutanota permite que você personalize sua conta de e-mail, como escolher seu próprio domínio personalizado (para usuários pagos) e criar aliases de e-mail para maior flexibilidade na comunicação.
-
Compromisso com a privacidade: O Tutanota é conhecido por sua postura pró-privacidade e compromisso com a proteção dos dados de seus usuários. A empresa está sediada na Alemanha, onde estão sujeitos a rigorosas leis de proteção de dados, e segue o Regulamento Geral de Proteção de Dados (GDPR) da União Europeia.
O Tutanota é uma opção excelente para aqueles que valorizam a privacidade e desejam proteger suas comunicações online. Com sua criptografia de ponta a ponta, armazenamento criptografado e outros recursos de segurança, o Tutanota garante que suas mensagens e dados pessoais permaneçam privados e seguros.
https://tutanota.com/pt_br/
https://github.com/tutao/tutanota
-
-
 @ 3f0702fa:66db56f1
2024-12-02 06:50:18
@ 3f0702fa:66db56f1
2024-12-02 06:50:18Уже 11-й год подряд Курган становится площадкой для проведения Всероссийского студенческого IT-форума "Мы в будущем", который собрал талантливую молодежь со всей страны. Форум прошел с 25 по 27 ноября на базе Курганского государственного университета и стал важным событием в сфере информационных технологий.
Одной из ключевых особенностей форума стали конкурсные испытания, связанные с разработкой роботов. Участники представили свои проекты и идеи, демонстрируя инновационные подходы к решению актуальных задач. Команды соревновались в различных категориях, включая создание автономных роботов и систем управления.
На форуме активно использовались голограммы, что стало настоящим технологическим прорывом. Участники могли взаимодействовать с виртуальными моделями, что значительно обогатило опыт и сделало презентации более наглядными. Голографические технологии позволили продемонстрировать сложные концепции и идеи в интерактивном формате.
В рамках форума также прошли мастер-классы от ведущих экспертов в области IT, где участники могли узнать о последних тенденциях в программировании, робототехнике и цифровых технологиях. Лекции охватывали широкий спектр тем, от искусственного интеллекта до разработки программного обеспечения.
XI Всероссийский студенческий IT-форум "Мы в будущем" стал не только платформой для обмена знаниями, но и местом для формирования новых идей и проектов. Такие события способствуют развитию молодежного потенциала и укрепляют позиции Кургана как центра инноваций.
45news
Курган2040
-
 @ dc4cd086:cee77c06
2024-10-18 17:41:42
@ dc4cd086:cee77c06
2024-10-18 17:41:42Have you ever wanted to learn from lengthy educational videos but found it challenging to navigate through hours of content? Our new tool addresses this problem by transforming long-form video lectures into easily digestible, searchable content.
Key Features:
Video Processing:
- Automatically downloads YouTube videos, transcripts, and chapter information
- Splits transcripts into sections based on video chapters
Content Summarization:
- Utilizes language models to transform spoken content into clear, readable text
- Formats output in AsciiDoc for improved readability and navigation
- Highlights key terms and concepts with [[term]] notation for potential cross-referencing
Diagram Extraction:
- Analyzes video entropy to identify static diagram/slide sections
- Provides a user-friendly GUI for manual selection of relevant time ranges
- Allows users to pick representative frames from selected ranges
Going Forward:
Currently undergoing a rewrite to improve organization and functionality, but you are welcome to try the current version, though it might not work on every machine. Will support multiple open and closed language models for user choice Free and open-source, allowing for personal customization and integration with various knowledge bases. Just because we might not have it on our official Alexandria knowledge base, you are still welcome to use it on you own personal or community knowledge bases! We want to help find connections between ideas that exist across relays, allowing individuals and groups to mix and match knowledge bases between each other, allowing for any degree of openness you care.
While designed with #Alexandria users in mind, it's available for anyone to use and adapt to their own learning needs.
Screenshots
Frame Selection

This is a screenshot of the frame selection interface. You'll see a signal that represents frame entropy over time. The vertical lines indicate the start and end of a chapter. Within these chapters you can select the frames by clicking and dragging the mouse over the desired range where you think diagram is in that chapter. At the bottom is an option that tells the program to select a specific number of frames from that selection.
Diagram Extraction

This is a screenshot of the diagram extraction interface. For every selection you've made, there will be a set of frames that you can choose from. You can select and deselect as many frames as you'd like to save.
Links
- repo: https://github.com/limina1/video_article_converter
- Nostr Apps 101: https://www.youtube.com/watch?v=Flxa_jkErqE
Output
And now, we have a demonstration of the final result of this tool, with some quick cleaning up. The video we will be using this tool on is titled Nostr Apps 101 by nostr:npub1nxy4qpqnld6kmpphjykvx2lqwvxmuxluddwjamm4nc29ds3elyzsm5avr7 during Nostrasia. The following thread is an analog to the modular articles we are constructing for Alexandria, and I hope it conveys the functionality we want to create in the knowledge space. Note, this tool is the first step! You could use a different prompt that is most appropriate for the specific context of the transcript you are working with, but you can also manually clean up any discrepancies that don't portray the video accurately.
nostr:nevent1qvzqqqqqqypzp5r5hd579v2sszvvzfel677c8dxgxm3skl773sujlsuft64c44ncqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgwwaehxw309ahx7uewd3hkctcpzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309aex2mrp0yh8xmn0wf6zuum0vd5kzmp0qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgc7hglpn
Or view on Coracle https://coracle.social /nevent1qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgcppemhxue69uhkummn9ekx7mp0qgsdqa9md83tz5yqnrqjw07hhkpmfjpkuv9hlh5v8yhu8z274w9dv7qnnq0s3
-
 @ 4ba8e86d:89d32de4
2024-10-29 12:30:05
@ 4ba8e86d:89d32de4
2024-10-29 12:30:05Tutorial feito por Grom Mestre⚡
Poste original Abaixo.
Part 1: http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/229987/tutorial-entendendo-e-usando-a-rede-i2p-introdu%C3%A7
Part 2: http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/230035/tutorial-instalando-e-configurando-o-roteador-i2p?show=230035#q230035
Part 3: http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/230113/tutorial-conectando-se-ao-xmpp-pela-i2p?show=230113#q230113
Boa tarde, camaradas do meu coeur!
Depois de muito tempo, e com o retorno da minha serotonina aos níveis basais, estou dando início a essa nova série de tutoriais. Espero que tirem muito proveito das informações passadas aqui para amplicarem o seu conhecimento da deepweb.
Esta postagem trará antes algumas considerações iniciais que podem ser úteis para quem possui pouco ou nenhum contato prévio com outras tecnologias ou tenha um entendimento torto a respeito da deepweb. Aconselho a estes que deem um boa lida antes de partirem para os tópicos do tutorial, mas saibam que ele não é um pré requisito para ele.
Dito isso, vamos prosseguir.
TÓPICOS: Introdução Instalando e configurando o roteador e o navegador Conectando-se a serviços na I2P Configurações avançadas
1. Introdução
1.1 Definindo a DeepWeb.
Muitos devem imaginar erroneamente que a deepweb se restrinja apenas à rede onion, mais precisamente aos seus hidden services, já que o Tor possui como uma das suas funções primárias proteger e burlar restrições governamentais e proteger o seus usuários através de métodos sofisticados de roteamento de pacotes e criptografia. Entretanto, ela é mais ampla do que se imagina dependendo da forma como a classificamos.
Os ditos "profissionais" usam uma definição extremamente vaga e imprecisa do que seria a deepweb e a sua verdadeira abrangência. Para isso, criei uma definição um pouco melhor para ela: redes comunitárias, sobrepostas, anônimas e criptografadas.
Vamos aos pontos individualmente:
São Comunitárias, pois os pontos de roteamento de pacotes na rede (relays ou routers) muitas vezes são mantidos de forma voluntária por usuários comuns. Não é necessário nenhuma infraestrutura sofisticada para ser um contribuinte na rede, basta ter um computador com acesso à internet e conhecimentos básicos para fazer a configuração.
São sobrepostas porque não estão acima ou abaixo da rede tradicional (diferente do que muitos imaginam). Os pacotes na DW trafegam entre os dados da surface e não em meios distintos (algo que não faz o menor sentido). Sabe aquele papo de camadas da DW ou aquela abobrinha da Mariana's Web? Então, tudo um monte de bosta derivado de Youtubers sensacionalistas iletrados em informática. Elitismo da minha parte? Quem sabe...
São anônimas porque não é simples determinar a origem e o destino dos pacotes entre nodes intermediários dado a natureza do roteamento. Em geral, aos menos para a rede onion, há pelo menos 3 relays entre você e o servidor, sendo que esse número duplica para hidden services (3 seus e 3 do serviço). A imagem abaixo ilustra bemocoteamento dos pacotes na onio. https://image.nostr.build/aea96f41d356157512f26b479ea8db5bce8693dd642f2bce0258d8e4b0dac053.jpg
Por fim, são criptografadas porque as conexões são fortemente protegidas por algoritmos sofisticados de criptografia. Além de não sabermos a origem dos dados, sequer podemos saber com facilidade o conteúdo dessas mensagens mesmo que os protocolos das camadas superiores (HTTP, HTTPS, FTP) sejam inseguros, dado que a criptografia da própria rede já as protege. Por isso é tão comum que sites da DW não usem HTTPS, pois as autoridades de certificados não os assinam para domínios da onion e certificados autoassinados vão disparar avisos no navegador.
A imagem abaixo ilustra bem como é o roteamento onion usado pelo Tor. Perceba que o contéudo da mensagem está enrolado em 3 camadas de criptografia (como a de uma cebola), de modo que para revelar o contéudo original seria preciso quebrar, no pior dos casos, 3 camadas. Como mencionado antes, o método usado para isso é a criptografia assimétrica, muito similar ao PGP, porém com a sua própria implementação. https://image.nostr.build/7bfaaf29211c11b82049ef8425abb67738d085c41558e9339ec13cf49ea5b548.jpg
Observação: Por mais que dentro da rede o encapsulamento proteja as mensagens internamente, entenda muito bem que isso não se aplica a sites da surface acessados pela onion. Ao desempacotar a última camada, a mensagem original é completamente exposta no exit node. Se ela não estiver protegida por uma camada adicional como TLS, seus pacotes estarão completamente expostos, algo que representa um sério risco de segurança.
As redes que caem em ao menos três dessas definições (anonimato, sobreposição e criptografia) podem ser classificadas como deepwebs. Podemos citar:
• Lokinet • Zeronet • Freenet • I2P • Tor • Gnunet
Porém, há alguns casos interessantes que não caem diretamente nessa regra .
A Yggdrasil ( https://yggdrasil-network.github.io/ ), uma rede de topologia mesh com foco em escalabilidade e eficiência de roteamento, possui três dessas características: comunitária, sobreposta e segura. Entretanto, os nodes não são anônimos e muitas vezes podem estar desprotegidos, já que se conectar à Yggdrasil é que equivalente a ligar o seu computador diretamente na rede sem a presença de um NAT/CGNAT, correndo o risco de expor portas de serviços da sua máquina caso elas não estejam protegidas por um firewall. A Yggdrasil na prática é exposta como um dispositivo de camada 3 (tipo um VPN), mas diferente de um, apenas endereços IPv6 dentro de uma faixa bem específica de IP são roteados por ela, o que permite que ela coexista com outros dispositivos sem haver conflitos de roteamento.
Há quem argumente que a Yggdrasil é uma deepweb dado a sua sobreposição em relação à surface; outros podem argumentar que dado a falta de anonimato ela não se enquadraria nessa categoria. Independentemente disso é uma tecnologia muito interessante com ampla gama de aplicações, como encapsular tráfego de outras redes, como a I2P, e melhorar a eficiência de roteamento.
Por fim, vamos desmitificar alguns mitos da DeepWeb muito difundidos.
Não existem camadas da DW. Os pacotes da DW são sobrepostos e navegam juntos aos pacotes da surface.
DeepWeb e DarkWeb não são coisas diferentes. São termos genéricos para a mesma coisa.
DarkWeb não é o seu provedor de e-mail ou serviço de banco. Se eles não se enquadram nas categorias de um deepweb, então estão na surface.
Você não é irrastreável na DW. Adversários motivados podem foder com você com facilidade (leia a respeito de ataques de Timing, correlação e fingerprinting).
Mesmo que não seja possível ver o conteúdo de uma mensagem pela deepweb, é possível ao menos saber que você a acessou. ISPs podem ver esse tipo de tráfego como suspeito.
Você não é um hacker só porque instalou o TorBrowser, mas pode ser considerado um se expor o IP de um hidden service.
Instalando e configurando o roteador I2P
Segue agora a seção 2 do tutorial do I2P. Mas antes apenas queria falar um pouco do projeto I2P. Apesar do foco do tutorial não ser para tratar da sua história, gostaria ao menos de fazer uma breve introdução sobre ela.
O projeto I2P (Invisible Internet Protocol) é uma rede P2P descentalizada, anônima e segura para estabelecer a comunicação entre os usuários e serviços. Na I2P é possível usar serviços como mensageiros IRC, XMPP, web services, e-mail e até mesmo torrents. A I2P nasceu de um fork da Freenet no ano de 2003, porém possui diferenças drásticas em relação a ela.
Há similaridades entre a I2P e o Tor, porém vale destacar algumas de suas vantagens. Sendo elas:
• Garlic routing ( https://geti2p.net/en/docs/how/garlic-routing ) • Modelo P2P • Todos os participantes da rede contribuem para ela • Fechado na rede - não é possível acessar a surface através da I2P • Otimizado para hidden services
Apesar disso, vale lembrar que o projeto é pequeno, desenvolvido por menos voluntários se comparado ao Tor e possui menos movimentação e financiamento para o seu desenvolvimento. Além disso, o Tor é um projeto muito mais maduro e bem documentado, algo que atrai mais usuários e desenvolvedores e torna a tarefa de encontrar e corrigir bugs mais fácil de ser realizada.
Esses são pontos importantes que devemos levar em conta ao escolher a tecnologia para as nossas necessidades. Nem sempre há tecnologias ruins, as vezes apenas as empregamos as ferramentas erradas na resolução de certos problemas.
Referências: • https://geti2p.net/en/comparison/tor • https://geti2p.net/en/docs/how/garlic-routing
• https://geti2p.net/en/about/intro
• https://i2pd.readthedocs.io/en/latest/
2. Instalando e configurando o roteador
Antes da criação do I2PBrowserBundle ( https://github.com/PurpleI2P/i2pdbrowser/releases/tag/1.3.3 ) , a única forma de se conectar à I2P era pela configuração manual de proxy no navegador. Muita gente ou não sabe ou tem MUUUUUITA preguiça de fazer isso e ficam resistentes de entrar na I2P dada essa restrição.
Como eu quero ser um bom tutor eu farei do jeito mais "difícil", pois tanto eu desejo que vocês aprendam as nuances do processo como eu sei que vocês são inteligentes o suficiente para fazer isso.
2.1 Instalação do router
Atualmente nós temos duas implementações do I2P: Uma em Java e outra em C++ (i2pd). Usaremos nesse tutorial a versão em C++ dado o seu baixo uso de recursos e facilidade de instalação.
O I2Pd está disponível para Windows, Linux, MacOS e Android e possui binários pré-compilados nas releases ( https://github.com/PurpleI2P/i2pd/releases/tag/2.50.2 ) do projeto no Github. Usuários de Linux podem instalá-lo através do respectivo gerenciador de pacotes da sua distribuição, porém algumas distros não oferecem o pacote diretamente nos reposítórios oficiais, necessitando do uso de PPAs (Ubuntu), COPR (Fedora/RHEL) e afins. Vocês podem conferir as instruções oficiais para cada sistema nessa página ( https://i2pd.readthedocs.io/en/latest/user-guide/install/ ).
Apesar desse tutorial ser voltado a usuários de desktop, o I2Pd também está disponível na loja do F-droid. Infelizmente poucos navegadores em Android permitem a configuração de proxies, porém na seção de Serviços na I2P eu tratarei brevemente de como se conectar a servidores de XMPP usando o ConversationI2P.
Para usuários de Windows, segue abaixo os binários para instalação.
• Versão 32bits ( https://github.com/PurpleI2P/i2pd/releases/download/2.50.2/i2pd_2.50.2_win32_mingw.zip )
• Versão 64bits ( https://github.com/PurpleI2P/i2pd/releases/download/2.50.2/i2pd_2.50.2_win64_mingw.zip )
• Versão para Windows XP (pois é, kk) ( https://github.com/PurpleI2P/i2pd/releases/download/2.50.2/i2pd_2.50.2_winxp_mingw.zip )
A instalação é simples e direta. Após ela apenas abram o I2Pd para que o router inicie a operação de busca e conexão com os peers. Para usuários de Linux, vocês precisam ativar o serviços através do comando 'sudo systemctl start i2pd'. Se vocês desejam que o I2Pd inicie junto com o sistema usem o comando 'sudo systemctl enable --now i2pd'.
Se tudo estiver funcionando corretamente, vocês serão capazes de abrir o webconsole do I2Pd no navegador através do endereço: 127.0.0.1:7070. https://image.nostr.build/ab205ae1071a2b705279e5ce2d6e912d8d11cc7d6dd0dc8a26b76724a27bd94b.jpg https://image.nostr.build/fa17e14600737ccfc92a415cec2fbfba226b950b2b97af7475927ae65abdbe11.jpg
2.2 Instalação e configuração do navegador
Apesar de qualquer navegador ser capaz de usar a I2P não é recomendado que usem qualquer um, especialmente o navegador que você usam no seu dia-a-dia. Recomendo que usem um navegador próprio para usar na I2P ou isolem suas atividades em um perfil separado.
Em navegadores baseado no Firefox isso é relativamente simples, bastando adicionar a opção '--profile' e o caminho do perfil que vocês desejam usar. Nesse tutorial eu vou mostrar como criar um perfil novo no Librewolf e configurar no lançador para iniciar o perfil e abrir em uma janela anônima. Essas instruções são análogas para todos os sistemas, excetuando aquelas configurações mais exóticas.
2.2.1 Escolhendo o navegador
Como citado, usarei o Librewolf como exemplo. Vocês podem baixar o instalador direto do site ou usar o gerenciador de pacotes do seu sistema no caso de Linux. Como é uma tarefa trivial eu não vou detalhar esse processo, pois todas as instruções estão em detalhes no site do navegador ( https://librewolf.net/installation/ )
2.2.2 Criando um perfil e configurando o lançador
Abram o navegador e digitem 'about:profiles' na barra de endereço. Criem um novo perfil clicando em 'Create New Profile' https://image.nostr.build/fa17e14600737ccfc92a415cec2fbfba226b950b2b97af7475927ae65abdbe11.jpg
Coloquem um nome no seu perfil e cliquem em Finalizar https://image.nostr.build/62059e375000940f11b27ae77b9ec011f9baadbb5a84afc910d41841ce73e82d.jpg
Perfis novos recém criados são iniciados por padrão. Se você deseja usar outro perfil por padrão deve mudar isso na seção 'about:profiles' do navegador.
Agora vamos configurar o lançador do LibreWolf para iniciar o perfil do i2p e em uma janela anônima. Usarei o XFCE como referência para essa tarefa, mas saibam que o processo é análogo em sistemas como Windows ou DEs como KDE. Se quiserem também podem lançar via terminal através do comando 'librewolf --profile caminho_do_perfil --private-window'.
Cliquem com o botão direito no ícone do Librewolf e abram as propriedades do atalho.
Na guia lançador, no campo Comando, adicionem no final a opção '--private-window' e a opção '--profile caminho_do_perfil'. O caminho do perfil é aquele mostrado na seção 'about:profiles' do Librewolf. https://image.nostr.build/a7d6515d7825cb3bdcb681ecf71a97318dccba81eea7cc87fc5377ecc06065ee.jpg
2.2.3 Configurando o proxy
Com o lançador configurado, abra o navegador nesse perfil. Vamos configurar o proxy para se conectar ao I2P agora.
Abra as configurações digitando 'about:preferences' na barra de endereço. Na seção 'Geral' abra as configurações de rede (Network Settings) https://image.nostr.build/f37157bebf15ada616914f403e756cf9fcee4c9aaaa353196c9cc754ca4d7bc5.jpg
Configure o seu proxy como na figura abaixo. https://image.nostr.build/41ebd05255a8129d21011518d400689308d9c0320408967003bf296771e0b96f.jpg
Fecha as configurações. Se o seu proxy foi configurado corretamente tente abrir algum desses eepsites.
• http://identiguy.i2p • http://notbob.i2p • http://reg.i2p
Se tudo ocorreu como conforme, a página será carregada. https://image.nostr.build/ce29ae44743f06cfed591f082208c9612c59b3429ab46d90db48131b3bc3e99d.jpg
OBSERVAÇÃO: A busca pelos peers é um pouco demorada, levando de 2 a 5 minutos para que um número mínimo necessário de peers sejam encontrados para estabelecer uma conexão estável. Você pode ver a lista de inbound e outbound tunnels na seção Tunnels do WebConsole (localhost:7070) https://image.nostr.build/285a0d765eaf5f33409f975cd720d0efa68ecc40a9da20bfd9cde0cd1f59a7b6.jpg
IMPORTANTE: Apesar do Librewolf possuir defaults seguros, eu recomendo que vocês instalem as seguintes extensões para aumentar ainda mais a sua proteção.
• noScript • JShelter
Lembrem-se que vocês precisam desativar o proxy para acessar a clearnet. Depois disso reativem-no nas configurações.
Outro detalhe: Se vocês tentarem digitar um endereço .i2p na barra de endereços do navegador sem especificar o protocolo (http), ao invés do Librewolf ir ao endereço ele vai realizar uma pesquisa. Para corrigir esse problema, vocês precisam adicionar a seguinte configuração do tipo boolean em 'about:config' como mostrado na imagem. https://image.nostr.build/4518ab817b131f7efe542b2d919b926099dce29a7b59bdd3c788caf53dbd071e.jpg
Reiniciem o navegador e testem. Se tudo deu certo vocês não precisam especificar o protocolo ao digitar um endereço .i2p, bastando apenas digitar o endereço simplificado.
Por fim, terminamos essa parte do tutorial. Na próximo parte trataremos de como podemos nos conectar a serviços hospedados na I2P como XMPP
[TUTORIAL] Conectando-se ao XMPP pela I2P
Essa é a terceira parte da série de tutoriais. Agora vamos tratar de algumas operações na rede, sendo uma delas conectando-se a um servidor de XMPP na I2P.
Não se esqueça de ligar o router e manter ele ligado por alguns minutos antes de iniciar essas operações. O router demora um pouco para encontrar os peers e estabelecer uma conexão estável.
3.1 Escolhendo o cliente XMPP
Existem diversos clientes XMPP capazes de se conectar usando um proxy. Um dos melhores é o Gajim, um cliente escrito em Python com diversas funcionalidades como criptografia OMEMO e PGP, workspaces separados, extensibilidade via plugins e uma interface bonita e organizada.
Assim como ocorreu com o router, o Gajim está disponível por padrão na maioria das distros Linux. Use o seu gerenciador de pacotes para instala-lo. Em Windows você pode baixar o Gajim através desse link ( https://gajim.org/download/ )
3.2 Criando uma conta
Vamos primeiro criar uma conta no servidor. No nosso exemplo usarei o servidor oficial do projeto i2pd, o xmpp.ilita.i2p. Há diversos outros servidores XMPP no diretório de links notbob.i2p caso queiram explorar mais. Para criar uma conta, siga os passos abaixo:
Abra o Gajim. Na barra de tarefas vá em Contas -> Adicionar Conta. Na nova janela que aparecer, clique em Adicionar Conta https://image.nostr.build/01413e7c6d00c238420e3b0c769dd8d7f7d6522754d2135d3e98a22944f79a27.jpg https://image.nostr.build/9f015861f33990871d96f03d5ec78036a65e3ad9f8ff6a38da18c5b27d31f6d5.jpg
Na janela de adicionar contas, clique diretamente em Inscrever-se. Não precisa colocar as suas credencias como mostra a imagem (falha minha, ksksk) https://nostrcheck.me/media/c8411a22946e97467e0ee197ef7a0205ba05f2c67bde092041481ccc2cbbc66d/81938c8d278ce0562c2240341e203f3b70f51ee2db06ceb453f8a178df37fa84.webp
Digite o nome do servidor no campo abaixo. Não esqueça de marcar a opção 'Configurações Avançadas' antes de clicar em Inscrever-se https://image.nostr.build/5ee4305a6a23e5c064446b0ce7a4cbc7e790c1ba237bd2495d0237b86a4df07f.jpg
Vamos adicionar um novo proxy para essa conta. Para isso clique no botão 'Gerenciar proxies', ao lado do campo Proxy nas Configurações Avançadas https://image.nostr.build/daceb5436def55401d3974ce48d85771e5ebcec4e3f90eb1001df4609112ec12.jpg
Adicione um novo proxy clicando no sinal de '+' abaixo da lista de proxies. Preencha os campos de acordo com a imagem abaixo e em seguida feche a janela. https://image.nostr.build/140b34c4e46e9295c073311d483d206201d9339a75f613fe4e829c14f3257bfe.jpg https://image.nostr.build/d365a63d81a14d763bffceb50b30eb53d81959623f8fe812175358a41b1fba53.jpg
No campo de Proxy, selecione o proxy I2P. Preencha o restante dos campos de acordo com a imagem abaixo. Em seguida clique em 'Inscrever-se'. https://image.nostr.build/d06c11d9c6d19728bf5a58af2dd3e14d8ca0021456da09792a345ac0bfc90ad0.jpg
Nesse momento uma mensagem pode aparecer pedindo para abrir uma exceção para o certificado TLS. Isso acontece porque trata-se de um certificado autoassinado que não foi validado por uma autoridade oficial. Apenas abra a exceção e prossiga (não há imagem para isso porque eu já abri essa exceção no meu cliente). Uma nova janela vai aparecer solicitando-lhe para inserir as suas credenciais. Tome cuidado aqui, pois não é para inserir o nome completo com o domínio, apenas o seu nome de usuário (ex: descartavel). https://image.nostr.build/dde2a6736bd00080fbeeb8076754e226971a412710b370d5559f7f4d5414f8b3.jpg
Se tudo der certo, uma nova janela vai aparecer confirmando a sua inscrição. Coloque um nome e uma cor para a sua conta e clique em Conectar para concluir o processo. https://image.nostr.build/74934d3f1f3f4232eacee8e78e707936227f816c50ac6b52da5c81ec17557e69.jpg
Para finalizar, nos detalhes da sua conta, modifique as suas configurações de privacidade para diminuir o fingerprint. Na seção de 'Privacidade', desligue as seguintes opções:
• Tempo ocioso • Hora de Sistema Local • Sistema Operacional • Reprodução de Mídia https://image.nostr.build/d2ed5852a104c770b50c7b053d518d8af0b6289ced6b3ad4187492208c7ca649.jpg
3.3 Procurando por salas de bate-papo públicas
Após criar a sua nova conta, vamos descobrir alguns serviços que o servidor oferece. Para isso, vá para Contas -> Descobrir serviços https://image.nostr.build/54928d1dd0e48365858b24c72097a9fabf677794e13f329fc0568211eefbe559.jpg
Na seção 'Bate-papo em Grupo', selecione Chatrooms e clique em 'Navegar'. Ao fazer isso uma lista de chatroom públicos presentes no servidor vai aparecer. Fique a vontade para explorar, porém saiba que alguns servidores são moderados e não te permitem mandar mensagens sem sua conta ser aprovada pelo moderador (familiar?). https://image.nostr.build/1936bef51d58a1f6cfdf8bf8d84bfa64adc2a09b9c0fb1623b93a327f0b8cdd8.jpg https://image.nostr.build/89e8013b1cea1df0f80f6833bd6771c33101f404b0099b2d7330a5e57607baff.jpg
3.4 Adicionando contatos
Para adicionar contatos à sua lista, clique no símbolo de '+' ao lado do campo de pesquisa e selecione 'Add Contact'. https://image.nostr.build/d3cadea27591355f674fba93765c3815282d112b2e80a592bb77a442c13dd4f4.jpg
Coloque o endereço completo da conta que você deseja adicionar. Usarei a minha conta oficial nesse exemplo. Você tem a opção de anexar uma mensagem qualquer antes de enviar o convite. Clique em 'Adicionar Contato' para prosseguir. https://image.nostr.build/ff95b7aec2377c58d4253c5b7b3aabf141a92dd5f3e97f6e1f01ecb32a215d38.jpg https://image.nostr.build/6562e680e28c321ebbd009b5ade513f8a279aea33bc16aa9fb251f3507eb04af.jpg
Se tudo ocorrer normalmente, o novo contato vai aparecer na sua lista. Dê dois-cliques na conta para abrir o chat. Não se esqueça de ativar a criptografia OMEMO antes de enviar qualquer mensagem. Agora você está pronto para conversar de forma segura :) https://image.nostr.build/ef7f783a311ad0f68a5408137f75dc2bc6c38f6e9656dc0d68d3267f5012f658.jpg
E com isso terminamos a terceira parte da série de tutoriais.
[TUTORIAL] Criando e conectando-se a um servidor XMPP na I2P e clearnet.
Como configurar o seu próprio servidor XMPP. https://youtube.com/watch?v=Ot_EmQ8xdJwy
Criando contas e conectando clientes Pidgin http://i2pd.readthedocs.io/en/latest/tutorials/xmpp/#creating-accounts-and-connecting-clients
BONUS: Conectando-se facilmente à I2P. https://youtube.com/watch?v=wGIh5tQcw68
-
 @ 3f0702fa:66db56f1
2024-12-02 06:49:54
@ 3f0702fa:66db56f1
2024-12-02 06:49:54Курган готовится к незабываемым новогодним праздникам, и для жителей запланировано множество интересных мероприятий.
-
Новогодний городок на площади Дата: с 20 декабря по 7 января Место: Центральная площадь Кургана В этом году центральная площадь вновь превратится в новогодний городок, где будут установлены яркие елки, ледяные скульптуры и уютные лавочки с горячими напитками. Каждый вечер здесь будут проходить концерты и мастер-классы для детей и взрослых.
-
Салют Дата: 31 декабря Время: 23:45 Место: Центральная площадь Кургана Кульминацией новогодней ночи станет салют с использованием современных технологий, который подарит зрителям незабываемое зрелище. Салют будет синхронизирован с музыкой, а также будет использоваться дрон-технология для создания световых эффектов в небе.
-
Праздничные ярмарки Дата: с 20 декабря по 7 января Место: Улица Ленина На улице Ленина будут работать праздничные ярмарки, где можно приобрести уникальные подарки ручной работы, новогодние украшения и попробовать традиционные угощения. Ярмарки станут отличной возможностью поддержать местных производителей.
-
Культурные мероприятия Дата: с 25 декабря по 5 января Место: Городские культурные центры В течение праздников в культурных центрах Кургана будут проходить выставки, театральные представления и кинопоказы для всей семьи. Это отличная возможность провести время с близкими и насладиться культурными событиями.
-
Спортивные мероприятия Дата: 2 января Время: 10:00 Место: Ледовый дворец Кургана Для любителей активного отдыха пройдет новогодний спортивный фестиваль, где можно будет участвовать в различных соревнованиях по зимним видам спорта, а также покататься на коньках и лыжах.
Новогодние праздники в Кургане обещают быть яркими и насыщенными событиями. Не пропустите ощутить атмосферу праздника!
45news
Курган2040
-
-
 @ ee11a5df:b76c4e49
2024-03-21 00:28:47
@ ee11a5df:b76c4e49
2024-03-21 00:28:47I'm glad to see more activity and discussion about the gossip model. Glad to see fiatjaf and Jack posting about it, as well as many developers pitching in in the replies. There are difficult problems we need to overcome, and finding notes while remaining decentralized without huge note copying overhead was just the first. While the gossip model (including the outbox model which is just the NIP-65 part) completely eliminates the need to copy notes around to lots of relays, and keeps us decentralized, it brings about it's own set of new problems. No community is ever of the same mind on any issue, and this issue is no different. We have a lot of divergent opinions. This note will be my updated thoughts on these topics.
COPYING TO CENTRAL RELAYS IS A NON-STARTER: The idea that you can configure your client to use a few popular "centralized" relays and everybody will copy notes into those central relays is a non-starter. It destroys the entire raison d'être of nostr. I've heard people say that more decentralization isn't our biggest issue. But decentralization is THE reason nostr exists at all, so we need to make sure we live up to the hype. Otherwise we may as well just all join Bluesky. It has other problems too: the central relays get overloaded, and the notes get copied to too many relays, which is both space-inefficient and network bandwith inefficient.
ISSUE 1: Which notes should I fetch from which relays? This is described pretty well now in NIP-65. But that is only the "outbox" model part. The "gossip model" part is to also work out what relays work for people who don't publish a relay list.
ISSUE 2: Automatic failover. Apparently Peter Todd's definition of decentralized includes a concept of automatic failover, where new resources are brought up and users don't need to do anything. Besides this not being part of any definition of decentralized I have never heard of, we kind of have this. If a user has 5 outboxes, and 3 fail, everything still works. Redundancy is built in. No user intervention needed in most cases, at least in the short term. But we also don't have any notion of administrators who can fix this behind the scenes for the users. Users are sovereign and that means they have total control, but also take on some responsibility. This is obvious when it comes to keypair management, but it goes further. Users have to manage where they post and where they accept incoming notes, and when those relays fail to serve them they have to change providers. Putting the users in charge, and not having administrators, is kinda necessary to be truly decentralized.
ISSUE 3: Connecting to unvetted relays feels unsafe. It might even be the NSA tracking you! First off, this happens with your web browser all the time: you go visit a web page and it instructs your browser to fetch a font from google. If you don't like it, you can use uBlock origin and manage it manually. In the nostr world, if you don't like it, you can use a client that puts you more in control of this. The gossip client for example has options for whether you want to manually approve relay connections and AUTHs, just once or always, and always lets you change your mind later. If you turn those options on, initially it is a giant wall of approval requests... but that situation resolves rather quickly. I've been running with these options on for a long time now, and only about once a week do I have to make a decision for a new relay.
But these features aren't really necessary for the vast majority of users who don't care if a relay knows their IP address. Those users use VPNs or Tor when they want to be anonymous, and don't bother when they don't care (me included).
ISSUE 4: Mobile phone clients may find the gossip model too costly in terms of battery life. Bandwidth is actually not a problem: under the gossip model (if done correctly) events for user P are only downloaded from N relays (default for gossip client is N=2), which in general is FEWER events retrieved than other models which download the same event maybe 8 or more times. Rather, the problem here is the large number of network connections and in particular, the large number of SSL setups and teardowns. If it weren't for SSL, this wouldn't be much of a problem. But setting up and tearing down SSL on 50 simultaneous connections that drop and pop up somewhat frequently is a battery drain.
The solution to this that makes the most sense to me is to have a client proxy. What I mean by that is a piece of software on a server in a data centre. The client proxy would be a headless nostr client that uses the gossip model and acts on behalf of the phone client. The phone client doesn't even have to be a nostr client, but it might as well be a nostr client that just connects to this fixed proxy to read and write all of its events. Now the SSL connection issue is solved. These proxies can serve many clients and have local storage, whereas the phones might not even need local storage. Since very few users will set up such things for themselves, this is a business opportunity for people, and a better business opportunity IMHO than running a paid-for relay. This doesn't decentralize nostr as there can be many of these proxies. It does however require a trust relationship between the phone client and the proxy.
ISSUE 5: Personal relays still need moderation. I wrongly thought for a very long time that personal relays could act as personal OUTBOXes and personal INBOXes without needing moderation. Recently it became clear to me that clients should probably read from other people's INBOXes to find replies to events written by the user of that INBOX (which outbox model clients should be putting into that INBOX). If that is happening, then personal relays will need to serve to the public events that were just put there by the public, thus exposing them to abuse. I'm greatly disappointed to come to this realization and not quite settled about it yet, but I thought I had better make this known.
-
 @ 4ba8e86d:89d32de4
2024-10-15 01:06:52
@ 4ba8e86d:89d32de4
2024-10-15 01:06:52Ele usa uma abordagem única de virtualização baseada em compartimentos para isolar diferentes aplicativos e atividades em máquinas virtuais independentes. Isso significa que cada atividade, desde navegar na web , é isolada em seu próprio compartimento virtual, fornecendo um ambiente altamente seguro.
O Qubes OS foi criado em 2010 pelo pesquisador de segurança polonês Joanna Rutkowska. Ela se inspirou na ideia de "security by compartmentalization" (segurança por compartimentalização) e começou a desenvolver um sistema operacional baseado em compartimentos para atender às suas necessidades de segurança. Em 2012, a primeira versão do Qubes OS foi lançada e desde então tem evoluído continuamente.
O Qubes OS usa o conceito de máquinas virtuais (VMs) para criar uma abordagem de segurança baseada em compartimentos. Ele executa diferentes aplicativos e atividades em máquinas virtuais independentes, cada uma das quais é isolada do resto do sistema. Cada VM é atribuída a uma categoria de segurança e é configurada de acordo com as políticas de segurança necessárias para aquela categoria. Por exemplo, uma VM de navegação na web pode ser configurada com políticas de segurança para limitar o acesso à rede e restringir o acesso aos arquivos do sistema.
O Qubes OS usa um recurso chamado "dom0" para gerenciar as VMs. O dom0 é uma VM privilegiada que é responsável por gerenciar as outras VMs e dispositivos de hardware do sistema. Ele é isolado do resto do sistema e é executado com permissões limitadas para reduzir o risco de ataques de software malicioso.
O Qubes OS resolve vários problemas de segurança, especialmente para usuários que precisam lidar com informações confidenciais ou sensíveis. Alguns dos principais problemas que o Qubes OS resolve são:
-
Ataques de malware: A abordagem baseada em compartimentos do Qubes OS reduz significativamente o risco de ataques de malware. Se um aplicativo ou atividade for comprometido, o dano será limitado ao compartimento virtual onde está sendo executado.
-
Rastreamento de atividades: O Qubes OS protege a privacidade do usuário ao evitar que atividades diferentes sejam correlacionadas. Cada atividade é executada em um compartimento virtual separado, impedindo que os dados de atividade sejam compartilhados entre os aplicativos.
-
Proteção de dados confidenciais: O Qubes OS isola diferentes tipos de dados em VMs separadas, proporcionando um alto nível de proteção aos dados confidenciais. As VMs são configuradas com políticas de segurança adequadas para cada tipo de dados, protegendo-os contra acesso não autorizado.
-
Proteção contra ataques de rede: O Qubes OS utiliza técnicas de isolamento de rede para proteger contra ataques de rede, como ataques de escuta, interceptação de tráfego ou ataques de injeção de pacotes. Cada VM pode ter uma interface de rede dedicada e isolada, garantindo que o tráfego de rede seja controlado e limitado a apenas o que é necessário para cada VM.
-
Compartilhamento seguro de arquivos: O Qubes OS oferece a opção de compartilhar arquivos entre VMs de forma segura, sem comprometer a segurança do sistema. Isso é feito por meio do recurso de "transferência de arquivos segura", que permite que os usuários movam arquivos entre as VMs com segurança e sem o risco de contaminação por malware.
-
Proteção de hardware: O Qubes OS também fornece recursos de segurança de hardware, como a possibilidade de bloquear portas USB ou desativar o microfone ou a webcam quando não estão em uso. Isso ajuda a evitar a exploração de vulnerabilidades de hardware e aumenta a segurança do sistema como um todo.
-
Sistema operacional confiável: O Qubes OS é baseado em uma distribuição Linux confiável e de código aberto, o que significa que os usuários podem verificar o código fonte do sistema operacional e garantir que não haja backdoors ou vulnerabilidades ocultas.
https://github.com/QubesOS
https://www.qubes-os.org/
https://www.youtube.com/live/DpnSFhWEEXk?feature=share
-
-
 @ b12b632c:d9e1ff79
2024-02-19 19:18:46
@ b12b632c:d9e1ff79
2024-02-19 19:18:46Nostr decentralized network is growing exponentially day by day and new stuff comes out everyday. We can now use a NIP46 server to proxify our nsec key to avoid to use it to log on Nostr websites and possibly leak it, by mistake or by malicious persons. That's the point of this tutorial, setup a NIP46 server Nsec.app with its own Nostr relay. You'll be able to use it for you and let people use it, every data is stored locally in your internet browser. It's an non-custodial application, like wallets !
It's nearly a perfect solution (because nothing is perfect as we know) and that makes the daily use of Nostr keys much more secure and you'll see, much more sexy ! Look:
Nsec.app is not the only NIP46 server, in fact, @PABLOF7z was the first to create a NIP46 server called nsecBunker. You can also self-hosted nsecBunkerd, you can find a detailed explanation here : nsecbunkerd. I may write a how to self-host nsecBunkderd soon.
If you want more information about its bunker and what's behind this tutorial, you can check these links :
Few stuffs before beginning
Spoiler : I didn't automatized everything. The goal here is not to give you a full 1 click installation process, it's more to let you see and understand all the little things to configure and understand how works Nsec.app and the NIP46. There is a little bit of work, yes, but you'll be happy when it will work! Believe me.
Before entering into the battlefield, you must have few things : A working VPS with direct access to internet or a computer at home but NAT will certain make your life a hell. Use a VPS instead, on DigitalOcean, Linode, Scaleway, as you wish. A web domain that your own because we need to use at least 3 DNS A records (you can choose the subdomain you like) : domain.tld, noauth.domain.tld, noauth.domain.tld. You need to have some programs already installed : git, docker, docker-compose, nano/vi. if you fill in all the boxes, we can move forward !
Let's install everything !
I build a repo with a docker-compose file with all the required stuff to make the Bunker works :
Nsec.app front-end : noauth Nsec.app back-end : noauthd Nostr relay : strfry Nostr NIP05 : easy-nip5
First thing to do is to clone the repo "nsec-app-docker" from my repo:
$ git clone git clone https://github.com/PastaGringo/nsec-app-docker.git $ cd nsec-app-dockerWhen it's done, you'll have to do several things to make it work. 1) You need to generate some keys for the web-push library (keep them for later) :
``` $ docker run pastagringo/web-push-generate-keys
Generating your web-push keys...
Your private key : rQeqFIYKkInRqBSR3c5iTE3IqBRsfvbq_R4hbFHvywE Your public key : BFW4TA-lUvCq_az5fuQQAjCi-276wyeGUSnUx4UbGaPPJwEemUqp3Rr3oTnxbf0d4IYJi5mxUJOY4KR3ZTi3hVc ```
2) Generate a new keys pair (nsec/npub) for the NIP46 server by clicking on "Generate new key" from NostrTool website: nostrtool.com.
You should have something like this :
console Nostr private key (nsec): keep this -> nsec1zcyanx8zptarrmfmefr627zccrug3q2vhpfnzucq78357hshs72qecvxk6 Nostr private key (hex): 1609d998e20afa31ed3bca47a57858c0f888814cb853317300f1e34f5e178794 Nostr public key (npub): npub1ywzwtnzeh64l560a9j9q5h64pf4wvencv2nn0x4h0zw2x76g8vrq68cmyz Nostr public key (hex): keep this -> 2384e5cc59beabfa69fd2c8a0a5f550a6ae6667862a7379ab7789ca37b483b06You need to keep Nostr private key (nsec) & Nostr public key (npub). 3) Open (nano/vi) the .env file located in the current folder and fill all the required info :
```console
traefik
EMAIL=pastagringo@fractalized.net <-- replace with your own domain NSEC_ROOT_DOMAIN=plebes.ovh <-- replace with your own domain <-- replace with your own relay domain RELAY_DOMAIN=relay.plebes.ovh <-- replace with your own noauth domainay.plebes.ovh <-- replace with your own relay domain <-- replace with your own noauth domain NOAUTH_DOMAIN=noauth.plebes.ovh <-- replace with your own noauth domain NOAUTHD_DOMAIN=noauthd.plebes.ovh <-- replace with your own noauth domain
noauth
APP_WEB_PUSH_PUBKEY=BGVa7TMQus_KVn7tAwPkpwnU_bpr1i6B7D_3TT-AwkPlPd5fNcZsoCkJkJylVOn7kZ-9JZLpyOmt7U9rAtC-zeg <-- replace with your own web push public key APP_NOAUTHD_URL=https://$NOAUTHD_DOMAIN APP_DOMAIN=$NSEC_ROOT_DOMAIN APP_RELAY=wss://$RELAY_DOMAIN
noauthd
PUSH_PUBKEY=$APP_WEB_PUSH_PUBKEY PUSH_SECRET=_Sz8wgp56KERD5R4Zj5rX_owrWQGyHDyY4Pbf5vnFU0 <-- replace with your own web push private key ORIGIN=https://$NOAUTHD_DOMAIN DATABASE_URL=file:./prod.db BUNKER_NSEC=nsec1f43635rzv6lsazzsl3hfsrum9u8chn3pyjez5qx0ypxl28lcar2suy6hgn <-- replace with your the bunker nsec key BUNKER_RELAY=wss://$RELAY_DOMAIN BUNKER_DOMAIN=$NSEC_ROOT_DOMAIN BUNKER_ORIGIN=https://$NOAUTH_DOMAIN ```
Be aware of noauth and noauthd (the d letter). Next, save and quit. 4) You now need to modify the nostr.json file used for the NIP05 to indicate which relay your bunker will use. You need to set the bunker HEX PUBLIC KEY (I replaced the info with the one I get from NostrTool before) :
console nano easy-nip5/nostr.jsonconsole { "names": { "_": "ServerHexPubKey" }, "nip46": { "ServerHexPubKey": [ "wss://ReplaceWithYourRelayDomain" ] } }5) You can now run the docker compose file by running the command (first run can take a bit of time because the noauth container needs to build the npm project):
console $ docker compose up -d6) Before creating our first user into the Nostr Bunker, we need to test if all the required services are up. You should have :
noauth :
noauthd :
console CANNOT GET /https://noauthd.yourdomain.tld/name :
console { "error": "Specify npub" }https://yourdomain.tld/.well-known/nostr.json :
console { "names": { "_": "ServerHexPubKey" }, "nip46": { "ServerHexPubKey": [ "wss://ReplaceWithYourRelayDomain" ] } }If you have everything working, we can try to create a new user!
7) Connect to noauth and click on "Get Started" :
At the bottom the screen, click on "Sign up" :
Fill a username and click on "Create account" :
If everything has been correctly configured, you should see a pop message with "Account created for "XXXX" :
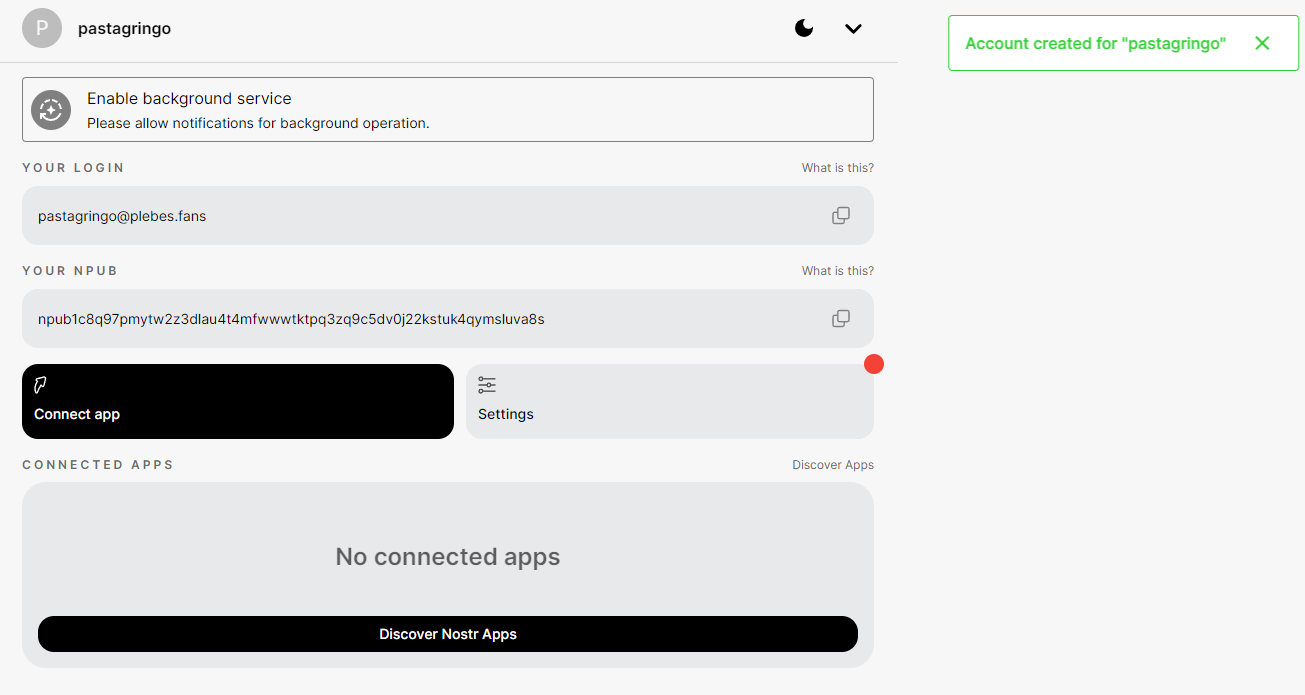
PS : to know if noauthd is well serving the nostr.json file, you can check this URL : https://yourdomain.tld/.well-known/nostr.json?name=YourUser You should see that the user has now NIP05/NIP46 entries :
If the user creation failed, you'll see a red pop-up saying "Something went wrong!" :
To understand what happened, you need to inspect the web page to find the error :
For the example, I tried to recreate a user "jack" which has already been created. You may find a lot of different errors depending of the configuration you made. You can find that the relay is not reachable on w s s : / /, you can find that the noauthd is not accessible too, etc. Every answers should be in this place.
To completely finish the tests, you need to enable the browser notifications, otherwise you won't see the pop-up when you'll logon on Nostr web client, by clicking on "Enable background service" :
You need to click on allow notifications :
Should see this green confirmation popup on top right of your screen:
Well... Everything works now !
8) You try to use your brand new proxyfied npub by clicking on "Connect App" and buy copying your bunker URL :
You can now to for instance on Nostrudel Nostr web client to login with it. Select the relays you want (Popular is better ; if you don't have multiple relay configured on your Nostr profile, avoid "Login to use your relay") :
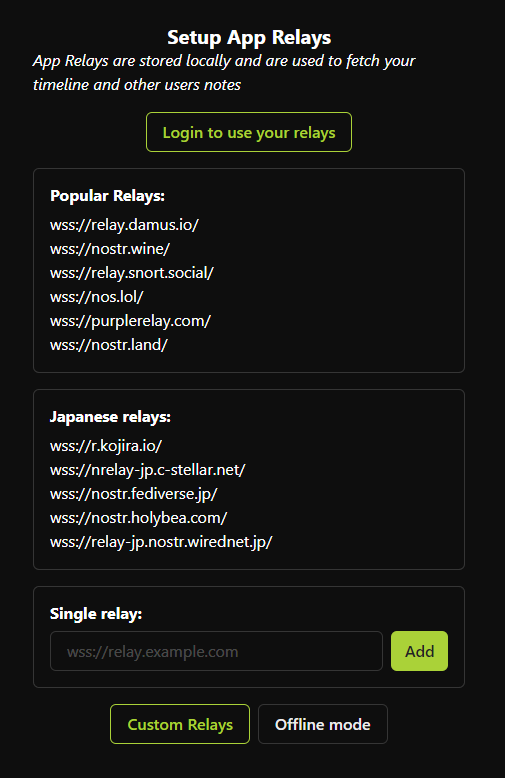
Click on "Sign in" :
Click on "Show Advanced" :
Click on "Nostr connect / Bunker" :
Paste your bunker URL and click on "Connect" :
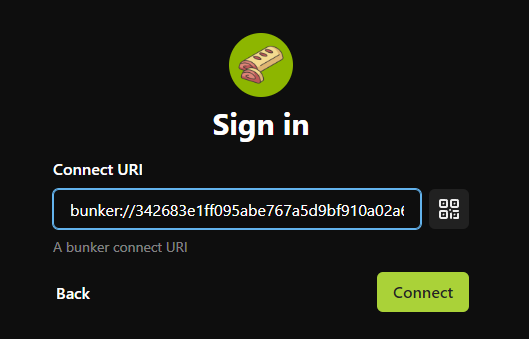
The first time, tour browser (Chrome here) may blocks the popup, you need to allow it :
If the browser blocked the popup, NoStrudel will wait your confirmation to login :
You have to go back on your bunker URL to allow the NoStrudel connection request by clicking on on "Connect":
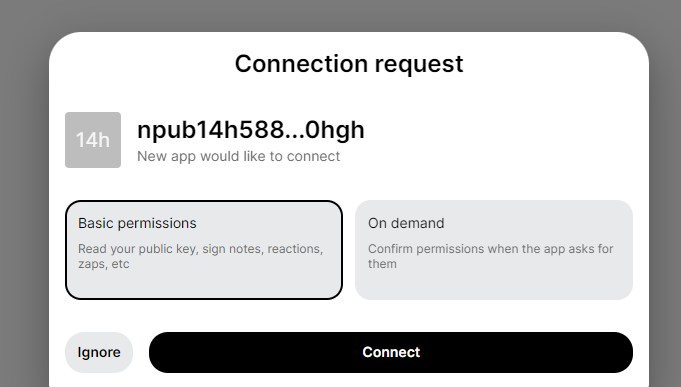
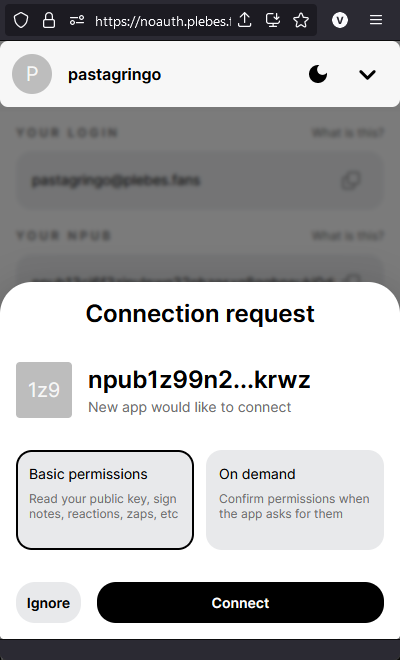
The first time connections may be a bit annoying with all the popup authorizations but once it's done, you can forget them it will connect without any issue. Congrats ! You are connected on NoStrudel with an npub proxyfied key !⚡

You can check to which applications you gave permissions and activity history in noauth by selecting your user. :
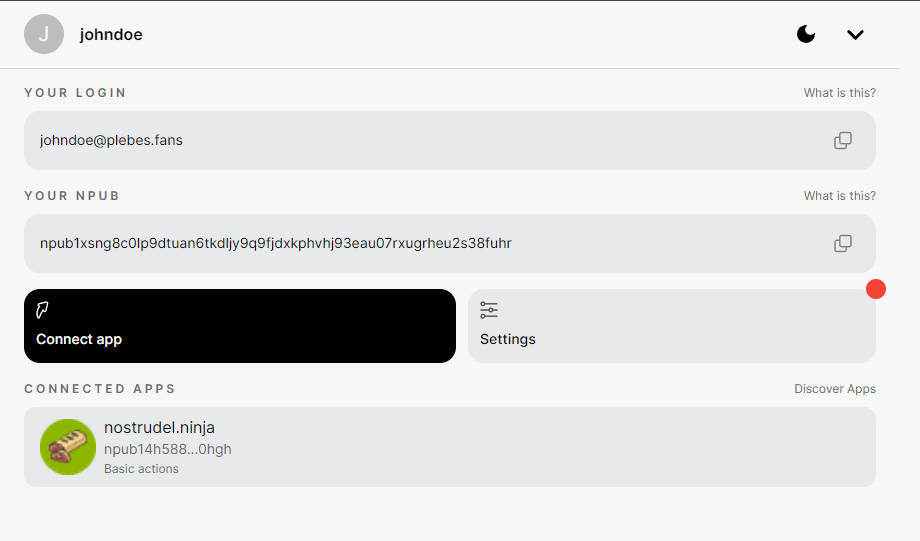
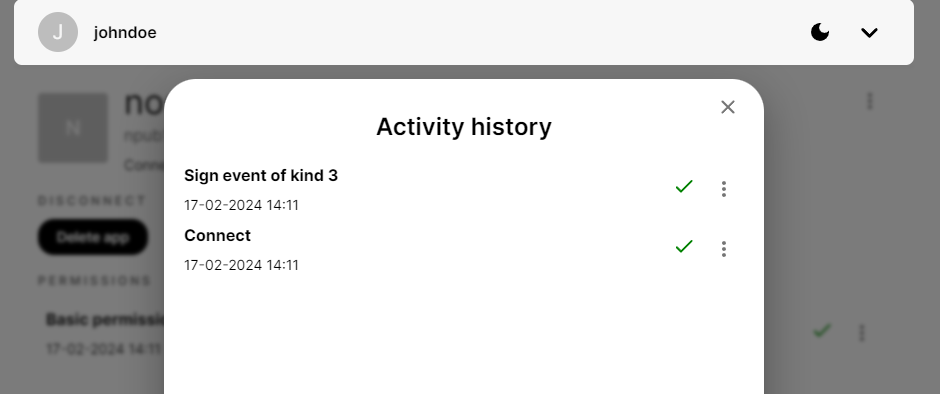
If you want to import your real Nostr profile, the one that everyone knows, you can import your nsec key by adding a new account and select "Import key" and adding your precious nsec key (reminder: your nsec key stays in your browser! The noauth provider won't have access to it!) :
You can see can that my profile picture has been retrieved and updated into noauth :
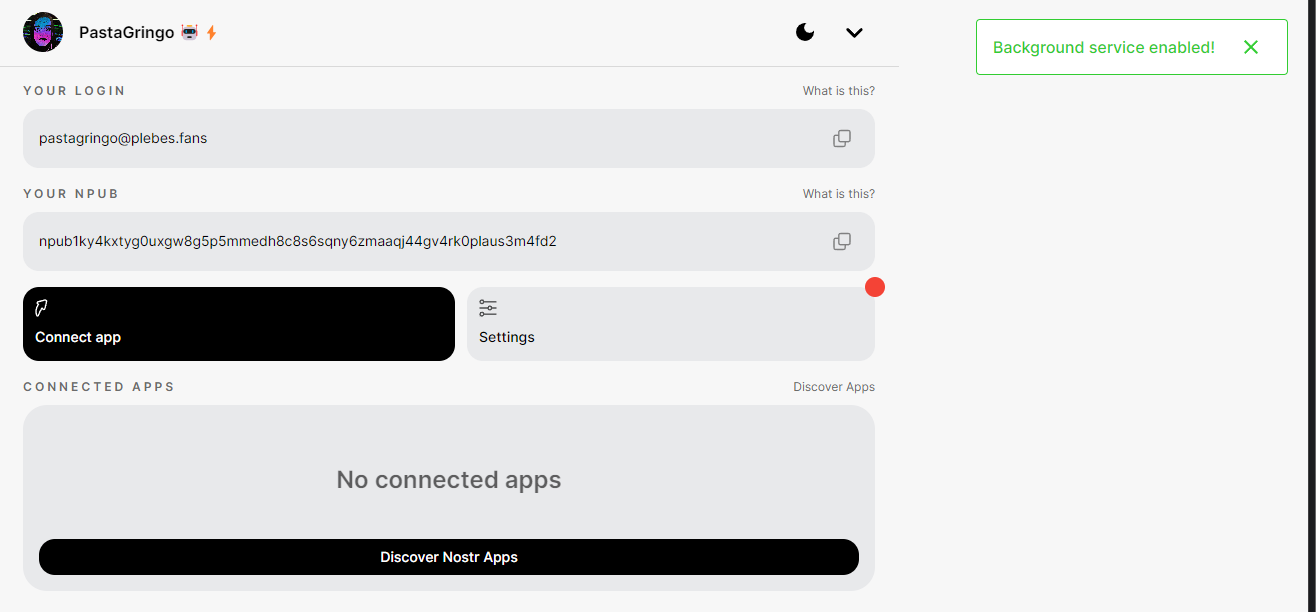
I can now use this new pubkey attached my nsec.app server to login in NoStrudel again :
Accounts/keys management in noauthd You can list created keys in your bunkerd by doing these command (CTRL+C to exit) :
console $ docker exec -it noauthd node src/index.js list_names [ '/usr/local/bin/node', '/noauthd/src/index.js', 'list_names' ] 1 jack npub1hjdw2y0t44q4znzal2nxy7vwmpv3qwrreu48uy5afqhxkw6d2nhsxt7x6u 1708173927920n 2 peter npub1yp752u5tr5v5u74kadrzgfjz2lsmyz8dyaxkdp4e0ptmaul4cyxsvpzzjz 1708174748972n 3 john npub1xw45yuvh5c73sc5fmmc3vf2zvmtrzdmz4g2u3p2j8zcgc0ktr8msdz6evs 1708174778968n 4 johndoe npub1xsng8c0lp9dtuan6tkdljy9q9fjdxkphvhj93eau07rxugrheu2s38fuhr 1708174831905nIf you want to delete someone key, you have to do :
```console $ docker exec -it noauthd node src/index.js delete_name johndoe [ '/usr/local/bin/node', '/noauthd/src/index.js', 'delete_name', 'johndoe' ] deleted johndoe { id: 4, name: 'johndoe', npub: 'npub1xsng8c0lp9dtuan6tkdljy9q9fjdxkphvhj93eau07rxugrheu2s38fuhr', timestamp: 1708174831905n
$ docker exec -it noauthd node src/index.js list_names [ '/usr/local/bin/node', '/noauthd/src/index.js', 'list_names' ] 1 jack npub1hjdw2y0t44q4znzal2nxy7vwmpv3qwrreu48uy5afqhxkw6d2nhsxt7x6u 1708173927920n 2 peter npub1yp752u5tr5v5u74kadrzgfjz2lsmyz8dyaxkdp4e0ptmaul4cyxsvpzzjz 1708174748972n 3 john npub1xw45yuvh5c73sc5fmmc3vf2zvmtrzdmz4g2u3p2j8zcgc0ktr8msdz6evs 1708174778968n ```
It could be pretty easy to create a script to handle the management of keys but I think @Brugeman may create a web interface for that. Noauth is still very young, changes are committed everyday to fix/enhance the application! As """everything""" is stored locally on your browser, you have to clear the cache of you bunker noauth URL to clean everything. This Chome extension is very useful for that. Check these settings in the extension option :
You can now enjoy even more Nostr ⚡ See you soon in another Fractalized story!
-
 @ 33fc2c28:5d1a1a6e
2024-12-02 06:01:24
@ 33fc2c28:5d1a1a6e
2024-12-02 06:01:24"The world can be a daunting place, where survival of the fittest reigns supreme. It's a realm where selfishness often thrives, and the strong tend to flourish, while the weak struggle to keep up. In this unforgiving landscape, one's physical appearance, intellectual prowess, and social status can greatly impact their opportunities and treatment.
Moreover, the pressure to succeed is relentless, and the fear of failure can be overwhelming. Poverty and lack of achievement are often stigmatized, leaving those who struggle to make ends meet feeling marginalized and disenfranchised.
And yet, despite these challenges, I remain undeterred. I recognize that the world may be a difficult place, but I also believe that it is full of possibilities and opportunities waiting to be seized. I am determined to push forward, to strive for excellence, and to never give up on my dreams.
For I know that the only way to truly conquer the world is to first conquer myself. To overcome my fears, to push past my limitations, and to unlock my full potential. And when I do, I will be unstoppable.
-
 @ 8d34bd24:414be32b
2024-10-27 22:30:18
@ 8d34bd24:414be32b
2024-10-27 22:30:18NOTE: This article has some details that are specific to America, but the overall principles are applicable to all, and I believe it will be useful for all Christians.
When it comes to things like voting, Christians tend to err to one of two extremes and seem to find difficulty finding the right balance as defined by God. Some Christians refuse to vote or get involved with politics at all. They don’t want to dirty themselves with politics. They know that their true home is heaven, so they don’t seem to care much for the nations they live in. On the other hand, some Christians are so focused on politics fixing everything and creating heaven on earth that they can become idolatrous lifting up politicians as a kind of savior.
In this article, I’m going to address both extremes, using the Bible, and hopefully help you find a Biblical balance.
Seek the Welfare of the City Where I Have Sent You
As Christians we are just passing through our time on earth. Our true, eternal home, our true citizenship, is in heaven. That doesn’t mean that we shouldn’t care what happens on earth. We shouldn’t be like the old saying, “some Christians are so heavenly minded that they aren’t any earthly good.” I think Christians should organize our time here on earth kind of like the Israelites were commanded to live during their 70 year exile in Babylon and Persia.
Now these are the words of the letter which Jeremiah the prophet sent from Jerusalem to the rest of the elders of the exile, the priests, the prophets and all the people whom Nebuchadnezzar had taken into exile from Jerusalem to Babylon. (Jeremiah 29:1)
What did God say to the Israelites about how they should live their life in Babylon?
“Thus says the Lord of hosts, the God of Israel, to all the exiles whom I have sent into exile from Jerusalem to Babylon, ‘Build houses and live in them; and plant gardens and eat their produce. Take wives and become the fathers of sons and daughters, and take wives for your sons and give your daughters to husbands, that they may bear sons and daughters; and multiply there and do not decrease. Seek the welfare of the city where I have sent you into exile, and pray to the Lord on its behalf; for in its welfare you will have welfare.’ (Jeremiah 29:4-7) {emphasis mine}
Could we likewise say the same to Christians during their time on earth? “Build houses and live in them; and plant gardens and eat their produce. Take wives and become the fathers of sons and daughters, and take wives for your sons and give your daughters to husbands, that they may bear sons and daughters; and multiply there and do not decrease. Seek the welfare of the city, state, or nation where I have sent you to live for a short while, and pray to the Lord on its behalf; for in its welfare you will have welfare.”
God expects us to live fruitful lives, to marry, to have many children (multiply), and to raise them up to do the same. He also wants us to seek the welfare of the city, state, and nation where God has put us. In a city, state, or nation with democratic elections, the best way to seek its welfare is to vote for honest candidates who support godly principles. We rightly understand that in our ungodly world there are no perfect candidates. It can even be hard to find mostly honest and mostly godly candidates, but we should seek to elect the best that is available. Why are we told to do this? We are told that “for in its welfare you will have welfare.” When we fail to vote, to teach our kids or support good schools, to live productive lives, and to generally live Godly lives, we WILL see the decline of our cities, states, and nations. We will pay the price.
We are seeing exactly that decline because Christians have pulled out (and were pushed out) of the positions that influence the culture. We don’t have enough godly teachers, journalists, professors, advisors, economists, and politicians. We have given up the culture to those who oppose God, His people, and His commands.
We are paying the price for withdrawing into the safety of our churches and leaving the world to the wolves.
Political Religion
Of course we also have an opposite extreme. We have some Christians that are too focused on politics and power. They spend all of their time and energy on political endeavors and very little, to none, on sharing the Gospel and being a godly example. Many act like they think a political candidate is going to save them from the culture, the media, the bureaucracy, or the government. They forget that there is only one Savior — the Lord Jesus Christ. They forget that God said things will get worse before they get better. They make idols out of politicians and religions out of political parties.
No servant can serve two masters; for either he will hate the one and love the other, or else he will be devoted to one and despise the other. You cannot serve God and wealth.” (Luke 16:13)
Although this verse is specifically talking about being obsessed with wealth, it is applicable to anything that takes our focus, attention, and especially our worship away from God.
When a person spends all of their time serving one candidate or party and little to no time serving God, they have chosen to serve another god and are guilty, even if inadvertently and unintentionally.
You shall have no other gods before Me.
You shall not make for yourself an idol, or any likeness of what is in heaven above or on the earth beneath or in the water under the earth. You shall not worship them or serve them; for I, the Lord your God, am a jealous God, visiting the iniquity of the fathers on the children, on the third and the fourth generations of those who hate Me, but showing lovingkindness to thousands, to those who love Me and keep My commandments. (Exodus 20:3-6)
When we look to a politician to save us from anything, we are making him/her a god before us. When we give our all to a political party, we are taking our heart away from God and giving it to an alternate religion.
We may not think that we make idols in our modern world. It is true that we don’t usually carve them out of wood or mold them out of gold, but we have just as many idols as the Israelites did. They just look different.
I hope you will seriously consider this next point because it may be very unpopular with many of my readers. There are lots of Christians that will throw as big, if not a bigger, fit at the desecration of the American flag than over the Bible. Nobody seems to fight to retain the pledge of allegiance more than a majority of Christians. I’d argue that the American flag has become a modern day idol and the “Pledge of Allegiance” has become a religious mantra repeated to the god of government. Look at the words of the pledge:
I pledge allegiance to the Flag of the United States of America,\ and to the Republic for which it stands,\ one Nation under God,\ indivisible, with liberty and justice for all.
I think the inclusion of the phrase “one Nation under God” makes Christians feel OK about this pledge originally invented by a socialist whose brother sold American flags. The important part, which is why I can’t say the pledge anymore, are the words, “I pledge allegiance to the Flag of the United States of America, and to the Republic for which it stands.” I really appreciate the principles America was founded upon, but as a Christian, I can only pledge allegiance to God. My allegiance isn’t to a flag (an idol) or the government (a god). I refuse to go through a religious ritual that includes particular stances, reciting special words, and showing undue respect. We cannot “serve two masters.” As Christians our master should be Christ alone. Anything that becomes more important than, or even equal to, the importance of God in our lives is idolatry. We need to get our priorities right.
In the World, but Not of the World
As we live our lives here on earth, we need to remember our God ordained purpose and our true allegiance to God. We need to remember our citizenship1 and family are in heaven, not here on earth.
We want to have a positive influence on our culture, including working in influential positions and voting, but we should be most focused on personal evangelism and sharing the truth of the Bible. The best way to make a difference in our culture is to change hearts and minds through the Gospel of Jesus Christ.
But now I come to You; and these things I speak in the world so that they may have My joy made full in themselves. I have given them Your word; and the world has hated them, because they are not of the world, even as I am not of the world. I do not ask You to take them out of the world, but to keep them from the evil one. They are not of the world, even as I am not of the world. Sanctify them in the truth; Your word is truth. (John 17:13-17) {emphasis mine}
Although we want to be a light in the world, we have been warned that doing so will make us not fit in. It will cause many non-Christians (and maybe a few Christians whose priorities are not right) to hate us. No matter the consequences, we need to stand on the truth of the Word of God.
Too often, because we are living with those who are of this world, we start to look and act a lot like those of the world instead of looking and acting like our Savior.
Do not love the world nor the things in the world. If anyone loves the world, the love of the Father is not in him. For all that is in the world, the lust of the flesh and the lust of the eyes and the boastful pride of life, is not from the Father, but is from the world. The world is passing away, and also its lusts; but the one who does the will of God lives forever. (1 John 2:15-17) {emphasis mine}
The fact that we should not love the things of the world or take on the character of things of the world is true in every part of our lives, but since we are talking here about politics, let us discuss the way many Christians talk politics.
Many Christians talk about politics in the same manner as non-Christians — cursing, name calling, insulting, and doing whatever it takes to win, no matter whether it is moral or not. I know the “other side” cheats, lies, name-calls, etc., but we should not stoop to their level. Nobody ever won another to their point of view by cursing or name calling. There are ways to point our their errors, and even how horrific some of the things pushed are, without going so low. Jesus didn’t hold back from speaking the truth. He didn’t hesitate to point out error, but was never crude about it. We should be the same. We should shine a light in such a way that those around us see such a difference that they say something similar to what was said about the apostles:
Now as they observed the confidence of Peter and John and understood that they were uneducated and untrained men, they were amazed, and began to recognize them as having been with Jesus. (Acts 4:13)
There should be something about our words, actions, and demeanor that amazes our opponents causing them to recognize us “as having been with Jesus.”
I hope this post has been helpful, truthful, and not too offensive. In so many areas it is hard to find that perfect balance and to not allow ourselves to be pulled to either extreme to the detriment of our witness and our relationship to God.
Give no offense either to Jews or to Greeks or to the church of God; just as I also please all men in all things, not seeking my own profit but the profit of the many, so that they may be saved. (1 Corinthians 10:32-33) {emphasis mine}
Trust Jesus.\ \ your sister in Christ,
Christy
-
 @ a012dc82:6458a70d
2024-12-02 05:49:43
@ a012dc82:6458a70d
2024-12-02 05:49:43Table Of Content
-
The Awakening of the Bitcoin Whales
-
The Big Moves
-
The Implications of the Whale Movements
-
The Mystery of the Whales
-
Conclusion
-
FAQ
In the vast, uncharted waters of the cryptocurrency market, Bitcoin whales are the most colossal creatures, akin to the blue whales of the physical oceans. These are the investors who hold a significant amount of Bitcoin, often untouched for years, while they watch their astronomical gains grow. They're the silent observers, the patient players who understand the game of waiting. However, the usually calm waters have recently been stirred, with nearly $60 million in Bitcoin transferred in just five days. This article dives deep into this unusual activity, exploring the potential implications and the mystery surrounding these Bitcoin whales. We'll delve into who these whales might be, why they're moving their Bitcoin now, and what this could mean for the future of cryptocurrency.
The Awakening of the Bitcoin Whales
The term 'Bitcoin whales' refers to investors who hoard substantial amounts of Bitcoin, typically at least 1,000 BTC, and let it sit for years. These investors have proven to be more successful than short-term traders, given Bitcoin's extreme volatility in the short term. Over the past decade, Bitcoin has surged from under $95 per coin to $29,203—a whopping 30,700% increase. This long-term view and the patience to hold onto their assets have often resulted in significant rewards for these whales. However, recently, these long-dormant Bitcoin whales have shown signs of activity. In a span of five days, several wallets holding millions of dollars in Bitcoin moved their holdings after years of dormancy. This sudden movement has caused ripples throughout the cryptocurrency community, leading to speculation about the motives behind these transactions and what it could mean for the future of Bitcoin.
The Big Moves
The recent whale activity began on July 20, when two wallets from 2011, each holding 10 BTC (valued at $292,767 at the time), moved their holdings to new locations. This movement, after such a long period of inactivity, was notable in itself. However, the following day, a wallet holding 5 BTC ($146,383) also budged after 12 years of inactivity. This continued activity suggested a trend rather than an isolated incident. Then, the most significant movement occurred when around $30.3 million in Bitcoin—or 1,037 BTC—moved after its owner transferred it to a new wallet for the first time since 2012. This was a significant shift, representing a substantial amount of Bitcoin. Finally, on July 24, a wallet from 2010 moved a hefty 50 BTC, or about $1.4 million. This series of movements over such a short period was unusual and caught the attention of many in the cryptocurrency community.
The Implications of the Whale Movements
Blockchain data firm Glassnode reported a "dramatic uptick over recent months" in whale activity. Many whales have been moving holdings to exchanges, usually the best way to cash out or shift holdings to other digital assets. This trend could indicate that these whales are preparing to sell or diversify their holdings, which could have significant implications for the Bitcoin market. If these whales decide to sell a large portion of their holdings, it could lead to an increase in the supply of Bitcoin on the market, potentially driving down prices. This could create a buyer's market, where there is more Bitcoin available than people are willing to buy. On the other hand, if these whales are moving their Bitcoin to diversify their holdings, it could lead to increased investment in other cryptocurrencies, potentially driving up their prices. This could stimulate the entire cryptocurrency market, leading to increased interest and investment in a variety of cryptocurrencies.
The Mystery of the Whales
While the recent whale movements have sparked intrigue, the identities of these Bitcoin whales remain a mystery. It isn't clear whether these whales are individuals or companies. Dr. Kirill Kretov, a developer of tools for automated trading and blockchain analyst, suggested that these transactions might represent commercial entities buying Bitcoin from individuals. This could indicate a shift in the market, with businesses becoming more involved in cryptocurrency. However, without concrete information, this remains speculation. The anonymity of Bitcoin transactions makes it difficult to determine the identities of these whales, adding to the intrigue and speculation surrounding these movements.
Conclusion
The recent movements of Bitcoin whales have undoubtedly made waves in the cryptocurrency community. While the reasons behind these movements remain speculative, they highlight the significant influence that these whales have on the Bitcoin market. As the crypto world continues to evolve, the actions of these Bitcoin whales will undoubtedly continue to shape the landscape. Whether these movements signal a storm or just a ripple in the water, only time will tell. However, one thing is clear: the actions of these whales are worth watching, as they could provide valuable insights into the future of Bitcoin and the cryptocurrency market as a whole.
FAQ
What is a Bitcoin whale? A Bitcoin whale is an investor who holds a significant amount of Bitcoin, typically at least 1,000 BTC, often untouched for years.
What recent activity has been observed among Bitcoin whales? Recently, Bitcoin whales have transferred nearly $60 million in Bitcoin in just five days, moving their holdings to new locations after years of dormancy.
What could be the implications of these whale movements? The movements could indicate that these whales are preparing to sell or diversify their holdings. This could potentially affect the Bitcoin market, either by increasing the supply of Bitcoin (which could drive down prices) or by stimulating investment in other cryptocurrencies.
Who are these Bitcoin whales? The identities of these Bitcoin whales remain a mystery. They could be individuals or companies, but the anonymity of Bitcoin transactions makes it difficult to determine.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 4ba8e86d:89d32de4
2024-10-26 14:14:01
@ 4ba8e86d:89d32de4
2024-10-26 14:14:01I2P é uma rede anônima, oferecendo uma camada simples que aplicativos sensíveis à identidade podem usar para se comunicar com segurança. Todos os dados são agrupados com várias camadas de criptografia e a rede é distribuída e dinâmica, sem partes confiáveis.
O Invisible Internet Project começou em 2002. A visão do projeto, conforme descrito em uma entrevista com Lance James, era que a rede I2P "oferecesse total anonimato, privacidade e segurança no mais alto nível possível. Internet descentralizada e ponto a ponto significa não se preocupe mais com seu ISP controlando seu tráfego. Isso permitirá que (as pessoas) realizem atividades contínuas e mudem a maneira como vemos a segurança e até a Internet, utilizando criptografia de chave pública, esteganografia de IP e autenticação de mensagens. A Internet que deveria ter sido, será em breve." Desde então, o I2P evoluiu para especificar e implementar um conjunto completo de protocolos de rede capazes de fornecer um alto nível de privacidade, segurança e autenticação para uma variedade de aplicativos.
A rede I2P. A rede I2P é uma rede de sobreposição ponto a ponto totalmente criptografada. Um observador não pode ver o conteúdo, origem ou destino de uma mensagem. Ninguém pode ver de onde vem o tráfego, para onde está indo ou qual é o conteúdo. Além disso, os transportes I2P oferecem resistência ao reconhecimento e bloqueio por parte dos censores. Como a rede depende de pares para rotear o tráfego, o bloqueio baseado em localização é um desafio que cresce com a rede. Cada roteador na rede participa de tornar a rede anônima. Exceto nos casos em que seria inseguro, todos participam do envio e recebimento do tráfego de rede.
Como funciona o I2P?
O I2P usa criptografia para obter uma variedade de propriedades para os túneis que constrói e as comunicações que transporta. Os túneis I2P usam transportes, NTCP2 e SSU2, para ocultar o tráfego que está sendo transportado por eles. As conexões são criptografadas de roteador para roteador e de cliente para cliente (ponta a ponta). Forward-secrecy é fornecido para todas as conexões. Como o I2P é endereçado criptograficamente, os endereços de rede I2P são auto-autenticados e pertencem apenas ao usuário que os gerou.
A rede é composta por pares ("roteadores") e túneis virtuais unidirecionais de entrada e saída. Os roteadores se comunicam entre si usando protocolos construídos em mecanismos de transporte existentes (TCP, UDP), passando mensagens. As aplicações cliente possuem seu próprio identificador criptográfico ("Destino") que permite enviar e receber mensagens. Esses clientes podem se conectar a qualquer roteador e autorizar a alocação temporária ("lease") de alguns túneis que serão utilizados para envio e recebimento de mensagens pela rede. O I2P possui seu próprio banco de dados de rede interna (usando uma modificação do Kademlia DHT) para distribuir roteamento e informações de contato com segurança.
Sobre a Descentralização e a Rede I2P A rede I2P é quase totalmente descentralizada, com exceção dos chamados Reseed Servers. Isso é para lidar com o problema de bootstrap DHT (Distributed Hash Table). Basicamente, não há uma maneira boa e confiável de deixar de executar pelo menos um nó de inicialização permanente que os participantes que não são da rede possam encontrar para começar. Uma vez conectado à rede, um roteador só descobre pares construindo túneis "exploratórios", mas para fazer a conexão inicial, um host reseed é necessário para criar conexões e integrar um novo roteador à rede. Os servidores reseed podem observar quando um novo roteador baixou um reseed deles, mas nada mais sobre o tráfego na rede I2P.
Recursos do I2P
O I2P oferece uma série de recursos para proteger a privacidade do usuário. Alguns desses recursos incluem:
Ocultação do endereço IP: O I2P oculta o endereço IP do usuário, tornando impossível que alguém rastreie a atividade do usuário na rede.
Comunicação segura: Todas as comunicações dentro da rede I2P são criptografadas de ponta a ponta, garantindo a privacidade do usuário.
Anonimato: O I2P permite que os usuários se comuniquem de forma anônima, o que significa que sua identidade não é exposta durante a comunicação.
Sites ocultos: O I2P permite que os usuários criem e acessem sites ocultos, que só podem ser acessados dentro da rede I2P.
Vantagens do uso do I2P
O I2P oferece várias vantagens para os usuários que desejam proteger sua privacidade online. Algumas dessas vantagens incluem:
Proteção contra vigilância governamental: O I2P ajuda a proteger os usuários contra a vigilância governamental, tornando impossível rastrear o endereço IP do usuário.
Anonimato em redes públicas: O I2P ajuda a proteger os usuários contra ataques de hackers em redes Wi-Fi públicas.
Acesso a sites censurados: O I2P permite que os usuários acessem sites que estão bloqueados em sua região ou país.
O I2P é uma rede anônima de comunicação que oferece recursos de privacidade avançados para proteger a privacidade do usuário. Ele permite que os usuários se comuniquem de forma anônima e segura e cria uma solução eficaz para usuários que valorizam a privacidade e a segurança online. Se você está preocupado com sua privacidade online, o I2P pode ser uma ótima escolha.
https://github.com/i2p
-
 @ ee11a5df:b76c4e49
2023-11-09 05:20:37
@ ee11a5df:b76c4e49
2023-11-09 05:20:37A lot of terms have been bandied about regarding relay models: Gossip relay model, outbox relay model, and inbox relay model. But this term "relay model" bothers me. It sounds stuffy and formal and doesn't actually describe what we are talking about very well. Also, people have suggested maybe there are other relay models. So I thought maybe we should rethink this all from first principles. That is what this blog post attempts to do.
Nostr is notes and other stuff transmitted by relays. A client puts an event onto a relay, and subsequently another client reads that event. OK, strictly speaking it could be the same client. Strictly speaking it could even be that no other client reads the event, that the event was intended for the relay (think about nostr connect). But in general, the reason we put events on relays is for other clients to read them.
Given that fact, I see two ways this can occur:
1) The reader reads the event from the same relay that the writer wrote the event to (this I will call relay rendezvous), 2) The event was copied between relays by something.
This second solution is perfectly viable, but it less scalable and less immediate as it requires copies which means that resources will be consumed more rapidly than if we can come up with workable relay rendezvous solutions. That doesn't mean there aren't other considerations which could weigh heavily in favor of copying events. But I am not aware of them, so I will be discussing relay rendezvous.
We can then divide the relay rendezvous situation into several cases: one-to-one, one-to-many, and one-to-all, where the many are a known set, and the all are an unbounded unknown set. I cannot conceive of many-to-anything for nostr so we will speak no further of it.
For a rendezvous to take place, not only do the parties need to agree on a relay (or many relays), but there needs to be some way that readers can become aware that the writer has written something.
So the one-to-one situation works out well by the writer putting the message onto a relay that they know the reader checks for messages on. This we call the INBOX model. It is akin to sending them an email into their inbox where the reader checks for messages addressed to them.
The one-to-(known)-many model is very similar, except the writer has to write to many people's inboxes. Still we are dealing with the INBOX model.
The final case, one-to-(unknown)-all, there is no way the writer can place the message into every person's inbox because they are unknown. So in this case, the writer can write to their own OUTBOX, and anybody interested in these kinds of messages can subscribe to the writer's OUTBOX.
Notice that I have covered every case already, and that I have not even specified what particular types of scenarios call for one-to-one or one-to-many or one-to-all, but that every scenario must fit into one of those models.
So that is basically it. People need INBOX and OUTBOX relays and nothing else for relay rendezvous to cover all the possible scenarios.
That is not to say that other kinds of concerns might not modulate this. There is a suggestion for a DM relay (which is really an INBOX but with a special associated understanding), which is perfectly fine by me. But I don't think there are any other relay models. There is also the case of a live event where two parties are interacting over the same relay, but in terms of rendezvous this isn't a new case, it is just that the shared relay is serving as both parties' INBOX (in the case of a closed chat) and/or both parties' OUTBOX (in the case of an open one) at the same time.
So anyhow that's my thinking on the topic. It has become a fairly concise and complete set of concepts, and this makes me happy. Most things aren't this easy.
-
 @ 09fbf8f3:fa3d60f0
2024-10-14 15:42:04
@ 09fbf8f3:fa3d60f0
2024-10-14 15:42:04我搭建了一个网盘,国内访问速度还可以。
我买的是每月5刀的无限存储计划,只要还在使用,每天会增加1G的存储。(需要通过面板重启后赠送。)
官网
-
不要使用VPN注册,会提示欺诈风险,有可能会砍单。
-
 @ 16d11430:61640947
2024-12-02 04:12:45
@ 16d11430:61640947
2024-12-02 04:12:45In an era that prides itself on technological progress and intellectual rigor, the state of identity verification has devolved into a grotesque parody of reason. We live in a time when individuals are subjected to invasive, demeaning rituals: holding up government-issued IDs to webcams, snapping awkward selfies alongside signatures, and transmitting scans of personal documents as if these primitive displays were the apex of modern security and authentication. This spectacle is not merely absurd; it is a profound degradation of the intellectual space that once championed privacy, dignity, and critical thought.
Alan Westin, in his seminal work Privacy and Freedom, argued that privacy is not merely a right but the cornerstone of individual autonomy. Yet today, this cornerstone is being chipped away by systems that demand we trade our personal dignity for the illusion of security. A photograph of a person holding an ID does not verify anything beyond their willingness to participate in this hollow theater. It does not confirm intent, consent, or even legitimacy—only compliance with a system so intellectually bankrupt that it relies on visual tropes rather than rigorous checks.
The Illusion of Trust
These charades operate under the false pretense that identity can be distilled into pixels and paper. The photograph of an ID—easily forged. The selfie with a signature—effortlessly manipulated. Even the sacred "wet ink" signature is nothing more than an outdated relic in a digital world that has long since surpassed its utility. And yet, these methods are perpetuated, not because they are effective, but because they are cheap, convenient, and require no intellectual investment from those implementing them.
The result is a catastrophic erosion of trust. Institutions that claim to protect our identities instead expose us to unnecessary risk, all while parading their incompetence as innovation. Worse, they place the burden of proof on the individual, demanding that we repeatedly perform this degrading pantomime to satisfy their bureaucratic inertia.
Privacy: From Right to Commodity
This erosion of intellectual rigor is symptomatic of a larger cultural malaise. In a society where privacy is no longer seen as a right but as a commodity to be bartered, the standards for verification have been reduced to the lowest common denominator. Instead of investing in robust, privacy-preserving technologies—such as cryptographic proofs, decentralized identity frameworks, or behavior-based authentication—we are forced to endure rituals that are as intellectually vacuous as they are invasive.
What’s more, these methods normalize the idea that our most intimate details—our faces, our signatures, our personal documents—are commodities to be captured, stored, and potentially exploited. This normalization of invasive practices not only undermines our autonomy but also desensitizes us to the very real dangers of mass data breaches and identity theft.
Reclaiming Intellectual Integrity
It is time to reject this farcical status quo. Verification should not be a performance; it should be a process rooted in intellectual rigor and respect for the individual. Technologies like zero-knowledge proofs and blockchain-based identity systems offer pathways to authentic verification without the need for invasive practices. These systems enable individuals to prove their identity, age, or qualifications without revealing unnecessary details, preserving both security and dignity.
But implementing such solutions requires a fundamental shift in mindset—a willingness to prioritize intellectual integrity over convenience, and human dignity over bureaucratic inertia. Institutions must be held accountable for perpetuating these charades, and individuals must demand systems that respect their autonomy and privacy.
A Call to Action
The intellectual space has not merely degraded; it has been hijacked by a culture of mediocrity that masquerades as progress. It is up to us to reclaim it, to demand verification processes that are worthy of a society that values freedom, dignity, and critical thought.
The choice is clear: we can continue to participate in this hollow theater, or we can refuse to play the fool in a charade that insults our intelligence and erodes our autonomy. Let us choose the latter. Let us choose freedom.
-
 @ 09fbf8f3:fa3d60f0
2024-10-14 15:41:08
@ 09fbf8f3:fa3d60f0
2024-10-14 15:41:08既然说是一款Web版的软件,也就是对应客户端版而开发的,如果你的歌曲都保存在NAS上,那么这款软件就非常适合你;如果你的歌曲都保存在电脑本地,那么可以直接使用客户端版的同名软件。
01
MusicTagWeb的特色 这款软件刚开始在 Github 上开源的时候,笔者就注意到了,不过当时功能还刚有个雏形、不太完善,就没有推荐给大家。经过开发者一段时间的辛勤付出,现在看来功能和管理能力基本上都已经完成了,具体的功能点和特性如下:
支持批量自动修改音乐标签 支持音乐指纹识别,即使没有元数据也可以识别音乐 支持整理音乐文件,按艺术家,专辑分组 支持文件排序,按照文件名,文件大小,更新时间排序 支持plex专辑类型,新增配置显示/隐藏字段 修复不同类型音频文件的专辑类型 新增歌曲语言整理文件 优化自动打标签匹配算法 新增智能刮削标签源,集成多个平台的标签源,按匹配度排序 支持繁体匹配,新增消息中心展示自动刮削不匹配的数据 支持保存专辑封面文件,支持自定义上传专辑封面 简单适配H5端,支持手机端访问 支持wma,wmv格式, 修复自动刮削报错停止的问题 音轨号,光盘号 格式优化,优化匹配规则 对新增的音乐文件后台自动刮削,无感知刮削。修复.ape文件读取报错的问题 新增自定义层数的整理文件,新增根据刮削状态排序,修复大写的音乐后缀名识别不到 新增数据库挂载映射
其实上面没有提到,这款软件支持从6个音乐平台刮削歌曲信息,安全起见,具体是哪6个平台笔者就不说了,感兴趣的朋友可以接着往下看,自己跑起来就知道了。
02
安装MusicTagWeb MusicTagWeb目前仅支持Docker部署,在你的NAS上,可以使用Docker和Docker Compose两种方式来部署,任选一种即可。
1、Docker方式
docker run -d \ --restart=unless-stopped \ -p 8001:8001 \ -v /path/to/your/music:/app/media \ -v /path/to/your/config:/app/data \ xhongc/music_tag_web:latest2、Docker Compose方式
version: '3' services: music-tag: image: xhongc/music_tag_web:latest container_name: music-tag-web restart: unless-stopped ports: - "8001:8001" volumes: - /path/to/your/music:/app/media:rw - /path/to/your/config:/app/data以上两种方式中,/path/to/your/music改成你的音乐文件夹路径,/path/to/your/config改为MusicTagWeb的配置文件路径。
03
使用MusicTagWeb 使用Docker启动MusicTagWeb后,在浏览器中使用IP+端口号打开系统,然后输入用户名和密码即可登录,默认的用户名和密码均为admin,建议登录后进行修改。
1、登录系统 Username 和 Password 均输入admin,邀请码不需要填。
2、首页主屏
主屏分成两栏(实际是三栏,还有一栏在操作的时候会显示出来),左边是音乐文件目录,右边默认是一张占位图片。
3、单个编辑/刮削歌曲信息
选择一个歌曲文件,这时候界面就是三屏了,右侧一栏变成两栏,分别显示歌曲元数据和音源搜索结果。搜索和设置完成后,点击保存信息按钮,即可完成对歌曲元数据的编辑。
最后
详细教程去官网: https://xiers-organization.gitbook.io/music-tag-web V1版够用了,V2收费的,68一个激活码。
-
 @ b12b632c:d9e1ff79
2023-08-08 00:02:31
@ b12b632c:d9e1ff79
2023-08-08 00:02:31"Welcome to the Bitcoin Lightning Bolt Card, the world's first Bitcoin debit card. This revolutionary card allows you to easily and securely spend your Bitcoin at lightning compatible merchants around the world." Bolt Card
I discovered few days ago the Bolt Card and I need to say that's pretty amazing. Thinking that we can pay daily with Bitcoin Sats in the same way that we pay with our Visa/Mastecard debit cards is really something huge⚡(based on the fact that sellers are accepting Bitcoins obviously!)
To use Bolt Card you have three choices :
- Use their (Bolt Card) own Bolt Card HUB and their own BTC Lightning node
- Use your own self hosted Bolt Card Hub and an external BTC Lightning node
- Use your own self hosted Bolt Card Hub and your BTC Lightning node (where you shoud have active Lightning channels)
⚡ The first choice is the quickiest and simpliest way to have an NFC Bolt Card. It will take you few seconds (for real). You'll have to wait much longer to receive your NFC card from a website where you bought it than configure it with Bolt Card services.
⚡⚡ The second choice is pretty nice too because you won't have a VPS + to deal with all the BTC Lightnode stuff but you'll use an external one. From the Bolt Card tutorial about Bolt Card Hub, they use a Lightning from voltage.cloud and I have to say that their services are impressive. In few seconds you'll have your own Lightning node and you'll be able to configure it into the Bolt Card Hub settings. PS : voltage.cloud offers 7 trial days / 20$ so don't hesitate to try it!
⚡⚡⚡ The third one is obvisouly a bit (way) more complex because you'll have to provide a VPS + Bitcoin node and a Bitcoin Lightning Node to be able to send and receive Lightning payments with your Bolt NFC Card. So you shoud already have configured everything by yourself to follow this tutorial. I will show what I did for my own installation and all my nodes (BTC & Lightning) are provided by my home Umbrel node (as I don't want to publish my nodes directly on the clearnet). We'll see how to connect to the Umbrel Lighting node later (spoiler: Tailscale).
To resume in this tutorial, I have :
- 1 Umbrel node (rpi4b) with BTC and Lightning with Tailscale installed.
- 1 VPS (Virtual Personal Server) to publish publicly the Bolt Card LNDHub and Bolt Card containers configured the same way as my other containers (with Nginx Proxy Manager)
Ready? Let's do it ! ⚡
Configuring Bolt Card & Bolt Card LNDHub
Always good to begin by reading the bolt card-lndhub-docker github repo. To a better understading of all the components, you can check this schema :
We'll not use it as it is because we'll skip the Caddy part because we already use Nginx Proxy Manager.
To begin we'll clone all the requested folders :
git clone https://github.com/boltcard/boltcard-lndhub-docker bolthub cd bolthub git clone https://github.com/boltcard/boltcard-lndhub BoltCardHub git clone https://github.com/boltcard/boltcard.git git clone https://github.com/boltcard/boltcard-groundcontrol.git GroundControlPS : we won't see how to configure GroundControl yet. This article may be updated later.
We now need to modify the settings file with our own settings :
mv .env.example .env nano .envYou need to replace "your-lnd-node-rpc-address" by your Umbrel TAILSCALE ip address (you can find your Umbrel node IP from your Tailscale admin console):
``` LND_IP=your-lnd-node-rpc-address # <- UMBREL TAILSCALE IP ADDRESS LND_GRPC_PORT=10009 LND_CERT_FILE=tls.cert LND_ADMIN_MACAROON_FILE=admin.macaroon REDIS_PASSWORD=random-string LND_PASSWORD=your-lnd-node-unlock-password
docker-compose.yml only
GROUNDCONTROL=ground-control-url
docker-compose-groundcontrol.yml only
FCM_SERVER_KEY=hex-encoded APNS_P8=hex-encoded APNS_P8_KID=issuer-key-which-is-key-ID-of-your-p8-file APPLE_TEAM_ID=team-id-of-your-developer-account BITCOIN_RPC=bitcoin-rpc-url APNS_TOPIC=app-package-name ```
We now need to generate an AES key and insert it into the "settings.sql" file :
```
hexdump -vn 16 -e '4/4 "%08x" 1 "\n"' /dev/random 19efdc45acec06ad8ebf4d6fe50412d0 nano settings.sql ```
- Insert the AES between ' ' right from 'AES_DECRYPT_KEY'
- Insert your domain or subdomain (subdomain in my case) host between ' ' from 'HOST_DOMAIN'
- Insert your Umbrel tailscale IP between ' ' from 'LN_HOST'
Be aware that this subdomain won't be the LNDHub container (boltcard_hub:9002) but the Boltcard container (boltcard_main:9000)
``` \c card_db;
DELETE FROM settings;
-- at a minimum, the settings marked 'set this' must be set for your system -- an explanation for each of the bolt card server settings can be found here -- https://github.com/boltcard/boltcard/blob/main/docs/SETTINGS.md
INSERT INTO settings (name, value) VALUES ('LOG_LEVEL', 'DEBUG'); INSERT INTO settings (name, value) VALUES ('AES_DECRYPT_KEY', '19efdc45acec06ad8ebf4d6fe50412d0'); -- set this INSERT INTO settings (name, value) VALUES ('HOST_DOMAIN', 'sub.domain.tld'); -- set this INSERT INTO settings (name, value) VALUES ('MIN_WITHDRAW_SATS', '1'); INSERT INTO settings (name, value) VALUES ('MAX_WITHDRAW_SATS', '1000000'); INSERT INTO settings (name, value) VALUES ('LN_HOST', ''); -- set this INSERT INTO settings (name, value) VALUES ('LN_PORT', '10009'); INSERT INTO settings (name, value) VALUES ('LN_TLS_FILE', '/boltcard/tls.cert'); INSERT INTO settings (name, value) VALUES ('LN_MACAROON_FILE', '/boltcard/admin.macaroon'); INSERT INTO settings (name, value) VALUES ('FEE_LIMIT_SAT', '10'); INSERT INTO settings (name, value) VALUES ('FEE_LIMIT_PERCENT', '0.5'); INSERT INTO settings (name, value) VALUES ('LN_TESTNODE', ''); INSERT INTO settings (name, value) VALUES ('FUNCTION_LNURLW', 'ENABLE'); INSERT INTO settings (name, value) VALUES ('FUNCTION_LNURLP', 'ENABLE'); INSERT INTO settings (name, value) VALUES ('FUNCTION_EMAIL', 'DISABLE'); INSERT INTO settings (name, value) VALUES ('AWS_SES_ID', ''); INSERT INTO settings (name, value) VALUES ('AWS_SES_SECRET', ''); INSERT INTO settings (name, value) VALUES ('AWS_SES_EMAIL_FROM', ''); INSERT INTO settings (name, value) VALUES ('EMAIL_MAX_TXS', ''); INSERT INTO settings (name, value) VALUES ('FUNCTION_LNDHUB', 'ENABLE'); INSERT INTO settings (name, value) VALUES ('LNDHUB_URL', 'http://boltcard_hub:9002'); INSERT INTO settings (name, value) VALUES ('FUNCTION_INTERNAL_API', 'ENABLE'); ```
You now need to get two files used by Bolt Card LND Hub, the admin.macaroon and tls.cert files from your Umbrel BTC Ligtning node. You can get these files on your Umbrel node at these locations :
/home/umbrel/umbrel/app-data/lightning/data/lnd/tls.cert /home/umbrel/umbrel/app-data/lightning/data/lnd/data/chain/bitcoin/mainnet/admin.macaroonYou can use either WinSCP, scp or ssh to copy these files to your local workstation and copy them again to your VPS to the root folder "bolthub".
You shoud have all these files into the bolthub directory :
johndoe@yourvps:~/bolthub$ ls -al total 68 drwxrwxr-x 6 johndoe johndoe 4096 Jul 30 00:06 . drwxrwxr-x 3 johndoe johndoe 4096 Jul 22 00:52 .. -rw-rw-r-- 1 johndoe johndoe 482 Jul 29 23:48 .env drwxrwxr-x 8 johndoe johndoe 4096 Jul 22 00:52 .git -rw-rw-r-- 1 johndoe johndoe 66 Jul 22 00:52 .gitignore drwxrwxr-x 11 johndoe johndoe 4096 Jul 22 00:52 BoltCardHub -rw-rw-r-- 1 johndoe johndoe 113 Jul 22 00:52 Caddyfile -rw-rw-r-- 1 johndoe johndoe 173 Jul 22 00:52 CaddyfileGroundControl drwxrwxr-x 6 johndoe johndoe 4096 Jul 22 00:52 GroundControl -rw-rw-r-- 1 johndoe johndoe 431 Jul 22 00:52 GroundControlDockerfile -rw-rw-r-- 1 johndoe johndoe 1913 Jul 22 00:52 README.md -rw-rw-r-- 1 johndoe johndoe 293 May 6 22:24 admin.macaroon drwxrwxr-x 16 johndoe johndoe 4096 Jul 22 00:52 boltcard -rw-rw-r-- 1 johndoe johndoe 3866 Jul 22 00:52 docker-compose-groundcontrol.yml -rw-rw-r-- 1 johndoe johndoe 2985 Jul 22 00:57 docker-compose.yml -rw-rw-r-- 1 johndoe johndoe 1909 Jul 29 23:56 settings.sql -rw-rw-r-- 1 johndoe johndoe 802 May 6 22:21 tls.certWe need to do few last tasks to ensure that Bolt Card LNDHub will work perfectly.
It's maybe already the case on your VPS but your user should be member of the docker group. If not, you can add your user by doing :
sudo groupadd docker sudo usermod -aG docker ${USER}If you did these commands, you need to logout and login again.
We also need to create all the docker named volumes by doing :
docker volume create boltcard_hub_lnd docker volume create boltcard_redisConfiguring Nginx Proxy Manager to proxify Bolt Card LNDHub & Boltcard
You need to have followed my previous blog post to fit with the instructions above.
As we use have the Bolt Card LNDHub docker stack in another directory than we other services and it has its own docker-compose.yml file, we'll have to configure the docker network into the NPM (Nginx Proxy Manager) docker-compose.yml to allow NPM to communicate with the Bolt Card LNDHub & Boltcard containers.
To do this we need to add these lines into our NPM external docker-compose (not the same one that is located into the bolthub directory, the one used for all your other containers) :
nano docker-compose.ymlnetworks: bolthub_boltnet: name: bolthub_boltnet external: trueBe careful, "bolthub" from "bolthub_boltnet" is based on the directory where Bolt Card LNDHub Docker docker-compose.yml file is located.
We also need to attach this network to the NPM container :
nginxproxymanager: container_name: nginxproxymanager image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt networks: - fractalized - bolthub_boltnetYou can now recreate the NPM container to attach the network:
docker compose up -dNow, you'll have to create 2 new Proxy Hosts into NPM admin UI. First one for your domain / subdomain to the Bolt Card LNDHub GUI (boltcard_hub:9002) :
And the second one for the Boltcard container (boltcard_main:9000).
In both Proxy Host I set all the SSL options and I use my wildcard certificate but you can generate one certificate for each Proxy Host with Force SSL, HSTS enabled, HTTP/2 Suppot and HSTS Subdomains enabled.
Starting Bolt Card LNDHub & BoltCard containers
Well done! Everything is setup, we can now start the Bolt Card LNDHub & Boltcard containers !
You need to go again to the root folder of the Bolt Card LNDHub projet "bolthub" and start the docker compose stack. We'll begin wihtout a "-d" to see if we have some issues during the containers creation :
docker compose upI won't share my containers logs to avoid any senstive information disclosure about my Bolt Card LNDHub node, but you can see them from the Bolt Card LNDHub Youtube video (link with exact timestamp where it's shown) :
If you have some issues about files mounting of admin.macaroon or tls.cert because you started the docker compose stack the first time without the files located in the bolthub folder do :
docker compose down && docker compose upAfter waiting few seconds/minutes you should go to your Bolt Card LNDHub Web UI domain/sudomain (created earlier into NPM) and you should see the Bolt Card LNDHub Web UI :
if everything is OK, you now run the containers in detached mode :
docker compose up -dVoilààààà ⚡
If you need to all the Bolt Card LNDHub logs you can use :
docker compose logs -f --tail 30You can now follow the video from Bolt Card to configure your Bolt Card NFC card and using your own Bolt Card LNDHub :
~~PS : there is currently a bug when you'll click on "Connect Bolt Card" from the Bold Card Walle app, you might have this error message "API error: updateboltcard: enable_pin is not a valid boolean (code 6)". It's a know issue and the Bolt Card team is currently working on it. You can find more information on their Telegram~~
Thanks to the Bolt Card, the issue has been corrected : changelog
See you soon in another Fractalized story!
-
 @ c230edd3:8ad4a712
2024-12-02 03:49:19
@ c230edd3:8ad4a712
2024-12-02 03:49:19Chef's notes
This recipe is not my own, but it was great and easy, so I'm moving it here. Cooking as instructed serves 2, but this could easily be adjusted to include stir fry vegetables and rice, to make this a meal for 4.
Details
- ⏲️ Prep time: 15 minutes, 1-24 hours marinating
- 🍳 Cook time: 10-15 minutes
- 🍽️ Servings: 2-4
Ingredients
- 1 Venison Heart (elk would work well, too. recipe would need to be doubled)
- 1/2 Asian Pear, grated
- 2 Cloves Garlic, grated
- 1 Tbsp Ginger, grated
- 3 Tbsp Soy Sauce
- 1 Tbsp Honey
- 1 Tbsp Onion, grated
- 1 Tbsp Toasted Sesame Oil
- 1 tsp Red Pepper Flakes
- 2 Shallots, chopped
- Sesame Seeds
- Cooking Oil
Directions
- Mix all ingredients besides heart, shallots, sesame seeds and cooking oil in a medium bowl.
- Remove arteries and excess fat from heart, cut in half and rinse
- Cut into thin slices or bite size pieces
- Add to marinade, mix and cover. Allow to soak for 1-24 hours.
- Heat oil in large frying pan over med-high to high heat
- Drain excess marinade.
- Place heart in pan and sear on both sides to desired doneness. Medium rare is ideal for heart.
- Remove from pan and garnish with chopped shallots and sesame seeds. Serve with stir fry veggies and rice, if desired.
-
 @ 3bf0c63f:aefa459d
2024-09-18 10:37:09
@ 3bf0c63f:aefa459d
2024-09-18 10:37:09How to do curation and businesses on Nostr
Suppose you want to start a Nostr business.
You might be tempted to make a closed platform that reuses Nostr identities and grabs (some) content from the external Nostr network, only to imprison it inside your thing -- and then you're going to run an amazing AI-powered algorithm on that content and "surface" only the best stuff and people will flock to your app.
This will be specially good if you're going after one of the many unexplored niches of Nostr in which reading immediately from people you know doesn't work as you generally want to discover new things from the outer world, such as:
- food recipe sharing;
- sharing of long articles about varying topics;
- markets for used goods;
- freelancer work and job offers;
- specific in-game lobbies and matchmaking;
- directories of accredited professionals;
- sharing of original music, drawings and other artistic creations;
- restaurant recommendations
- and so on.
But that is not the correct approach and damages the freedom and interoperability of Nostr, posing a centralization threat to the protocol. Even if it "works" and your business is incredibly successful it will just enshrine you as the head of a platform that controls users and thus is prone to all the bad things that happen to all these platforms. Your company will start to display ads and shape the public discourse, you'll need a big legal team, the FBI will talk to you, advertisers will play a big role and so on.
If you are interested in Nostr today that must be because you appreciate the fact that it is not owned by any companies, so it's safe to assume you don't want to be that company that owns it. So what should you do instead? Here's an idea in two steps:
- Write a Nostr client tailored to the niche you want to cover
If it's a music sharing thing, then the client will have a way to play the audio and so on; if it's a restaurant sharing it will have maps with the locations of the restaurants or whatever, you get the idea. Hopefully there will be a NIP or a NUD specifying how to create and interact with events relating to this niche, or you will write or contribute with the creation of one, because without interoperability this can't be Nostr.
The client should work independently of any special backend requirements and ideally be open-source. It should have a way for users to configure to which relays they want to connect to see "global" content -- i.e., they might want to connect to
wss://nostr.chrysalisrecords.com/to see only the latest music releases accredited by that label or towss://nostr.indiemusic.com/to get music from independent producers from that community.- Run a relay that does all the magic
This is where your value-adding capabilities come into play: if you have that magic sauce you should be able to apply it here. Your service -- let's call it
wss://magicsaucemusic.com/-- will charge people or do some KYM (know your music) validation or use some very advanced AI sorcery to filter out the spam and the garbage and display the best content to your users who will request the global feed from it (["REQ", "_", {}]), and this will cause people to want to publish to your relay while others will want to read from it.You set your relay as the default option in the client and let things happen. Your relay is like your "website" and people are free to connect to it or not. You don't own the network, you're just competing against other websites on a leveled playing field, so you're not responsible for it. Users get seamless browsing across multiple websites, unified identities, a unified interface (that could be different in a different client) and social interaction capabilities that work in the same way for all, and they do not depend on you, therefore they're more likely to trust you.
Does this centralize the network still? But this a simple and easy way to go about the matter and scales well in all aspects.
Besides allowing users to connect to specific relays for getting a feed of curated content, such clients should also do all kinds of "social" (i.e. following, commenting etc) activities (if they choose to do that) using the outbox model -- i.e. if I find a musician I like under
wss://magicsaucemusic.comand I decide to follow them I should keep getting updates from them even if they get banned from that relay and start publishing onwss://nos.lolorwss://relay.damus.ioor whatever relay that doesn't even know anything about music.The hardcoded defaults and manual typing of relay URLs can be annoying. But I think it works well at the current stage of Nostr development. Soon, though, we can create events that recommend other relays or share relay lists specific to each kind of activity so users can get in-app suggestions of relays their friends are using to get their music from and so on. That kind of stuff can go a long way.
-
 @ 460c25e6:ef85065c
2024-10-10 13:22:06
@ 460c25e6:ef85065c
2024-10-10 13:22:06In the early days of Nostr, developers often competed to see who could implement the most NIPs. Although all were optional (except NIP-01), it became a point of pride and vital for the ecosystem's growth. Back then, there were only a few dozen relatively simple NIPs to implement. Fast forward to today, with nearly 100 NIPs, maintaining and implementing everything has become nearly impossible. Yet, the drive among developers to "code all things Nostr" remains as strong as ever.
nostr:nprofile1qqsrhuxx8l9ex335q7he0f09aej04zpazpl0ne2cgukyawd24mayt8gprfmhxue69uhhq7tjv9kkjepwve5kzar2v9nzucm0d5hszxmhwden5te0wfjkccte9emk2um5v4exucn5vvhxxmmd9uq3xamnwvaz7tmhda6zuat50phjummwv5hsx7c9z9 raised the point that everyone, even I, agrees:
nostr:nevent1qqsqqqp2zrs7836tyjlsfe7aj9c4d97zrxxqyayagkdwlcur96t4laspzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7q3q80cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsxpqqqqqqzgcrrrp
But how big is too big? How can we better understand the range of options available for devs out there?
I went out for a hunt in my own brain to figure out how to clarify the situation. I came up with the following 4 categories for Nostr Clients: - Super Clients: These apps merge vastly different domains into a single application, offering basic support for reading, writing, configuration, and data management for each use case within each domains. An example would be an app that combines a Marketplace and Live Streams under one roof.
-
Clients: These apps provide comprehensive support for a single domain, handling all its use cases in a single home. They manage the complete set of reading, writing, configuration, and long-term data management within that domain. An example is a marketplace app that helps users manage product catalogs, process orders, collect payments, and handle fulfillment and reports.
-
Mini Clients: These apps focus on read and write functionality for a single use case, including configuration management and any actions related to that specific task. For example, a fulfillment app that helps users view orders placed from another client to then pack and ship them.
-
Micro Clients: These apps have a single interface and perform one specific action. Viewing and creating a record is handled by separate micro apps. An example is an app that simply scans an order's QR code and marks it as shipped.
Based on my made-up categories described at the end, this is how I would split our most known apps.
Super Clients - amethyst - nostrudel - coracle
Clients - damus - twitter - primal - twitter - snort - twitter - gossip - twitter - lume - twitter - ditto - twitter - rabbit - twitter - freefrom - twitter - nos - twitter - flycat - twitter - straylight - twitter - nostter - twitter - iris - twitter - nostur - twitter - nostrmo - twitter - yana - twitter - openvibe - twitter - freerse - twitter - 0xchat - chats - cornychat - chats - coop - chats - nostrchat - chats - blowater - chats - habla - blogs - yakihonne - blogs - highlighter - blogs - blogstack - blogs - stemstr - music - wavlake - music - fountain - podcasts - zap.stream - live streaming - shopstr - marketplace - plebeian.market - marketplace - flotilla - communities - satellite - communities - zapddit - communities - nostr.kiwi - communities - hivetalk - video calls - flare - long-form videos - nostrnests - audio spaces - wherostr - location - yondar - location - stacker.news - news - flockstr - events - nostrocket - issue tracker - docstr - docs - satshoot - freelance - wikifreedia - wiki - formstr - forms - chesstr - chess - memestr - meme feed - npub.cash - wallet - npub.pro - websites - gitworkshop - dev tools - onosendai - metaverse - degmods - games - turdsoup - prompts
Mini Clients - amber - signer - alby - signer - nos2x - signer - nsec.app - signer - keys.band - signer - nostrame - signer - nokakoi - anon - zap.cooking - recipes - anonostr - anon - getwired - anon - lowent - anon - creatr - exclusive content - lightning.video - exclusive content - zaplinks - slides - listr - lists - zap.store - app store - badges.page - badges - oddbean - news - dtan - torrents - nosta - user pages - pinstr - pinterest - pollerama - polls - swarmstr - trending - nostrapp - apps manager - noogle - search - ostrich.work - job postings - emojito - emoji manager - nostree - links - citrine - local relay - joinstr - coinjoins - heya - crowdfunding - zapplepay - zaps - nosbin - clipboard - shipyard - scheduler - tunestr - live streams - filestr - files - nostrcheck.me - media hosting - sheetstr - spreadsheets - crafters - curriculum vitae
Micro Clients - w3 - url shortener - nosdrive - backups - zaplife - zaps dashboard - zapper.fun - payments - nostrends - trends - zephyr - trends - wavman - music player - nostrrr - relay info - nosdump - relay info - notestack - blogs - nostr.build - media hosting - nostr.watch - relay info - nostr hours - use reports - lazereyes - vision prescriptions - snakestr - games - deletestr - deletion requests - 2048str - games - nostrqr - qr generator - notanostrclient - anon
Super apps will try to do everything, but can't really do most things super well. Regular-sized Clients will try to manage most of a given domain but are likely to centralize users on themselves, an unwanted effect inside of Nostr. If we want Nostr to grow in a decentralized fashion, we have to start betting on and using more Mini and Micro clients.
-
-
 @ ee11a5df:b76c4e49
2023-07-29 03:27:23
@ ee11a5df:b76c4e49
2023-07-29 03:27:23Gossip: The HTTP Fetcher
Gossip is a desktop nostr client. This post is about the code that fetches HTTP resources.
Gossip fetches HTTP resources. This includes images, videos, nip05 json files, etc. The part of gossip that does this is called the fetcher.
We have had a fetcher for some time, but it was poorly designed and had problems. For example, it was never expiring items in the cache.
We've made a lot of improvements to the fetcher recently. It's pretty good now, but there is still room for improvement.
Caching
Our fetcher caches data. Each URL that is fetched is hashed, and the content is stored under a file in the cache named by that hash.
If a request is in the cache, we don't do an HTTP request, we serve it directly from the cache.
But cached data gets stale. Sometimes resources at a URL change. We generally check resources again after three days.
We save the server's ETag value for content, and when we check the content again we supply an If-None-Match header with the ETag so the server could respond with 304 Not Modified in which case we don't need to download the resource again, we just bump the filetime to now.
In the event that our cache data is stale, but the server gives us an error, we serve up the stale data (stale is better than nothing).
Queueing
We used to fire off HTTP GET requests as soon as we knew that we needed a resource. This was not looked on too kindly by servers and CDNs who were giving us either 403 Forbidden or 429 Too Many Requests.
So we moved into a queue system. The host is extracted from each URL, and each host is only given up to 3 requests at a time. If we want 29 images from the same host, we only ask for three, and the remaining 26 remain in the queue for next time. When one of those requests completes, we decrement the host load so we know that we can send it another request later.
We process the queue in an infinite loop where we wait 1200 milliseconds between passes. Passes take time themselves and sometimes must wait for a timeout. Each pass fetches potentially multiple HTTP resources in parallel, asynchronously. If we have 300 resources at 100 different hosts, three per host, we could get them all in a single pass. More likely a bunch of resources are at the same host, and we make multiple passes at it.
Timeouts
When we fetch URLs in parallel asynchronously, we wait until all of the fetches complete before waiting another 1200 ms and doing another loop. Sometimes one of the fetches times out. In order to keep things moving, we use short timeouts of 10 seconds for a connect, and 15 seconds for a response.
Handling Errors
Some kinds of errors are more serious than others. When we encounter these, we sin bin the server for a period of time where we don't try fetching from it until a specified period elapses.
-
 @ 1739d937:3e3136ef
2024-09-13 21:09:24
@ 1739d937:3e3136ef
2024-09-13 21:09:24This is the seventh in a series of weekly(ish) updates detailing progress on bringing MLS protocol DMs and group messaging to Nostr.
Previous Updates
Progress this week
I was told recently that my update walls of text are too much. So, I'll try to keep things concise this week. 😅
This week has been all about building the reference implementation, which is quickly becoming a full-fledged client instead of just a reference implementation. I've not quite gotten to the MLS portion of the client yet but it does already support multiple accounts (including ephemeral accounts) and loads legacy (NIP-04) chats and full contact lists. So far, I've not implemented NIP-104 so there's not yet any updates to the MLS spec or other dependencies.
If you've got experience with using messengers in hostile environments (authoritarian regimes, you've been de-platformed, etc.) please get in touch. I'd love to hear more about what you'd like to see in a communication tool.
In the meantime, I'll be over here in the corner coding with my headphones on. 👨💻
Onward and Upwards!
-
 @ 1bda7e1f:bb97c4d9
2024-10-10 01:38:43
@ 1bda7e1f:bb97c4d9
2024-10-10 01:38:43Tldr
- I’m Rod
- I’m going down the Nostr rabbit hole
- I’m a startup founder, former listco CEO, NED, Bitcoin Miner, New Zealander, Dad
- I value community
- I was white-pilled by the free and interoperable internet and am ready to chip in
Nice to meet you
Today I am getting started creating a profile for my real self on Nostr. I am going to share what I learn.
Your average new Nostr user probably shouldn’t follow my lead here. The “main flow” onboarding for Nostr is becoming very smooth. Download Damus or Primal or Amethyst, then click “create account,” and be up and running in seconds.
For me though, I want to go off-road. I think Nostr is a fundamental reimagining of the internet where power resides with users rather than platforms. I want to work on it and with it. I think it has a chance to bring back the internet of my youth where people could be "internet" users rather than "corporate internet brandname" users.
So I plan to go on a tour of the weird and wonderful side quests that Nostr can offer—in order to really have some fun with it and write about it as I go.
I hope the writing will add some value.
Nostr is being driven forward by passionate and prolific devs who are creating wild new proofs of concept everywhere. These primatives are amazing, and also for a regular pleb, sometimes inaccessible and confusing.
I think I can add value by highlighting some of the “why” of fun and useful Nostr rabbit holes. If I can document what I do as a user, what I managed to make work, how I made it work, and why it was important, then I may encourage others to join and have a go.
Not a how to guide. Rather a “what I did and how and why” journal of sorts.
I can do a better intro than that
My name is Rod, and I am non-technical startup founder, former listco CEO, and company director.
Foremost in recent times, I am the founder of Jayride Group, which is a travel e-commerce marketplace that helps travelers to find and book rides around the world. I launched Jayride in January 2012 and grew it for six years to public listing on the Australian Securities Exchange (ASX:JAY) in January 2018, then ran it as a public company for six more years before stepping back from Managing Director to the role of Non-Exec Director around August 2023.
I am also a Non-Exec Director of Fishburners, Australia’s foremost technology startup founder community (and co-working space). Fishburners helps startup founders to get started. I was an early Fishburners resident, and being involved in that community was instrumental to my early startup success.
I have been flirting with Bitcoin mining since 697532 or thereabouts with 3.5Ph of hash rate, which was briefly about 1/100,000th of the network.
I’m a Nostr pleb, happily married, rational optimist, expat New Zealander living in Australia, and dad.
I will post about all of these things too.
Two key lessons led me to Nostr today
I learned the importance of community from Fishburners.
In the early days of a startup, you don’t know what you don’t know. Community helps you to learn those things simply by being amongst it. And when you find something specific which you know you need to know, community is there for you then too.
The more time I spend on Nostr, the more aware I am that this is a an awesome community of builders with the potential to add some real and lasting value to the internet and world. I want to do whatever small things I can to help and be part of that.
I learned the importance of resilience from the world's reaction to COVID.
Travel businesses and co-working businesses were smashed by lockdowns. To chart the path through it all, it became my full-time job to study the disaster of fake narratives and regulatory capture and bad policy responses, in order to try to navigate it. I learned that if you pay attention long enough then you can see behind the curtain–and it’s not a good look.
On Nostr, I find myself gradually returning to a rationally optimistic outlook. No amount of propaganda and greed and bureaucracy will ever be as fast and powerful and resilient as a free and interoperable internet.
We can build systems which leverage these strengths. If built, these systems will naturally outcompete and win on their merits, because they will be faster, freer, more powerful marketplaces for ideas and capital, more resistant to capture, and more resilient to external shocks.
Better systems means better aligned and fairer outcomes for everyone. These systems are a must-have and need to succeed. So I’m going to chip in.
I’m not sure exactly how yet!
But I’m up for it.
In summary
Hi. It’s nice to meet you all, and I hope to share something of value!
Because: - Nostr is becoming an incredible community of builders that will make its mark on the world, and - Nostr can become a true reimagining of the internet and contribute to a powerful, free and resilient world.
Up next
To start, I've learned a few things about setting up a new profile and I can share what I learned in future posts:
- Mining a branded vanity pubkey with Rana
- Setting up a self-custody lightning wallet to make zaps on Nostr with Phoenixd and Albyhub
- Setting up Nostr and lightning addresses at your own domain with Sveltekit and Vercel
Looking forward to it.
-
 @ 16d11430:61640947
2024-12-02 03:48:20
@ 16d11430:61640947
2024-12-02 03:48:20In the complex machinery of modern fiat economies, identity verification has become both a cornerstone and a tool of exploitation. Immigration agents and tax authorities frequently use ID requirements as leverage to withhold payments from legal students and transient temporary workers, effectively weaponizing bureaucratic obstacles. This practice underscores a deeper systemic flaw in fiat systems that fosters resentment, exacerbates social inequalities, and often inflames xenophobia and racism.
ID Requirements as a Tool of Control
For transient workers and legal students, fulfilling identity requirements is often fraught with challenges. These individuals frequently face delays in securing government-issued IDs, tax file numbers, or work permits due to systemic inefficiencies, inconsistent documentation standards across borders, or outright bureaucratic hostility.
This delay enables immigration and tax agents to withhold payments, leveraging technicalities to maintain control over vulnerable individuals. For many, the result is financial instability, loss of income, and an erosion of trust in government institutions. Employers may exacerbate the issue by withholding wages under the pretense of compliance with tax or immigration regulations.
The Role of the Fiat System in Arbitraging Withheld Funds
Fiat systems thrive on the movement and control of money. When funds are withheld, governments and financial institutions benefit from the arbitrage opportunities created by the float—the time during which withheld funds remain under their control. These funds may accrue interest, be reinvested, or shore up liquidity in government or financial institution balance sheets.
Moreover, the strawman concept—where individuals are treated as legal fictions in financial and legal transactions—compounds the problem. In fiat economies, transient workers and students often become dehumanized entities tied to tax file numbers or visa statuses. Their labor and contributions are monetized while their rights and access to those earnings are systematically restricted.
The Blockchain Solution
Fiat systems are ill-equipped to solve this exploitation because they rely on centralized control and opacity, which incentivize these exploitative practices. In contrast, blockchain technology offers a practical and transparent solution to this systemic problem.
-
Immutable Identity Verification: Blockchains can provide a universal, tamper-proof digital identity that is accessible globally. Such a system would bypass bureaucratic inefficiencies and ensure that individuals can prove their legal status without delays.
-
Smart Contracts for Payments: Payments can be locked into smart contracts, ensuring that funds are released automatically upon completion of work or fulfillment of agreed terms. This eliminates the ability of agents to withhold payments arbitrarily.
-
Decentralized Arbitration: In disputes, decentralized arbitration mechanisms on blockchain platforms can resolve issues without the biases or delays often seen in centralized systems.
-
Transparent Accounting: With blockchain’s public ledger, all parties can verify transactions, ensuring that funds are not exploited for arbitrage while withheld.
The Social Consequences of Fiat’s Failures
The inability of fiat systems to address these issues leads to widespread resentment among affected groups. Legal students and transient workers often feel targeted not for their legal status but for their perceived outsider status, which feeds into xenophobic narratives.
Racism and resentment flourish in environments where financial and social inequalities are palpable. Communities affected by these practices often view them as deliberate attempts to marginalize and exclude them from economic participation. This fosters a cycle of distrust, social division, and resistance to integration.
A Future Beyond Fiat
For fiat systems to address this exploitation meaningfully, they would need to sacrifice the centralized control and financial advantages derived from withholding payments. However, such a transformation is unlikely, as it would undermine the very foundations of fiat economies.
Blockchain technology, with its decentralized nature, offers a viable alternative. By automating payments, ensuring transparency, and providing immutable identity verification, blockchain can dismantle the mechanisms of exploitation that fiat systems have institutionalized.
Conclusion
The exploitation of ID requirements and the arbitrage of withheld funds are not merely bureaucratic inefficiencies—they are systemic tools of control within fiat economies. While these practices continue, they deepen social fractures and fuel resentment and racism. Only through the adoption of decentralized technologies like blockchain can these injustices be addressed, creating a fairer system for all participants. Without such changes, fiat systems will remain complicit in perpetuating inequality and division, unable to escape their structural flaws.
-
-
 @ 4ba8e86d:89d32de4
2024-10-08 22:45:17
@ 4ba8e86d:89d32de4
2024-10-08 22:45:17Um gerenciador de senhas é um software que ajuda os usuários a armazenar e gerenciar senhas e outras informações de autenticação. Ele é projetado para criar senhas seguras e únicas para cada conta e armazená-las de maneira segura. O Birwaden permite que os usuários criem cofres seguros para armazenar suas senhas e outras informações de autenticação. Esses cofres são protegidos por criptografia AES de 256 bits, o que significa que as senhas armazenadas são mantidas seguras e protegidas contra acesso não autorizado.
A história do Bitwarden começa em 2017, quando o programador russo Vladimir Ivanov decidiu criar um gerenciador de senhas de código aberto. Ivanov tinha preocupações crescentes sobre a segurança de senhas na Internet, especialmente com a crescente incidência de hacks e vazamentos de dados. Ele queria criar uma solução segura e fácil para gerenciar senhas que pudesse ajudar as pessoas a proteger suas contas. Ivanov escolheu usar criptografia AES de 256 bits para proteger as senhas armazenadas no Bitwarden, pois é considerado um dos algoritmos de criptografia mais seguros disponíveis.
Um Gerenciador de Senhas é um software que ajuda a armazenar e gerenciar senhas e outras informações de autenticação. Ele é projetado para criar senhas seguras e únicas para cada conta e armazená-las de maneira segura. O usuário pode acessar suas senhas sempre que precisar, sem precisar se preocupar em lembrar de todas elas.
Um Gerenciador de Senhas resolve vários problemas, incluindo a dificuldade de criar senhas fortes e únicas, o risco de reutilização de senhas e a possibilidade de comprometimento de contas devido a senhas fracas ou roubadas. Um gerenciador de senhas também ajuda a simplificar o processo de login, economizando tempo e reduzindo a frustração.
Usar um Gerenciador de Senhas pode ajudar a proteger as contas do usuário e reduzir o risco de comprometimento de dados. Ele também simplifica o processo de login, tornando mais fácil para o usuário acessar suas contas em vários dispositivos.Além disso, um gerenciador de senhas pode ajudar a gerar senhas fortes e únicas, que são mais difíceis de serem quebradas por hackers.
Passo a passo instalação do aplicativo Bitwarden:
-
Baixe e instale o Bitwarden em seu dispositivo móvel https://play.google.com/store/apps/details?id=com.x8bit.bitwarden
-
Crie uma conta no Birwaden. O aplicativo permitirá que você crie uma conta segura usando uma senha forte e um endereço de e-mail válido.
-
Crie um cofre seguro no Bitwarden para armazenar suas senhas. O aplicativo permite que você crie vários cofres para diferentes categorias de senhas, como redes sociais, finanças, e-mail, entre outras.
-
Adicione suas senhas ao cofre seguro. O Bitwarden permite que você adicione senhas manualmente ou importe senhas de outros gerenciadores de senhas.
-
Use o Bitwarden para acessar suas senhas sempre que precisar. O aplicativo permite que você acesse suas senhas de forma rápida e segura, sem precisar se preocupar em lembrar de todas elas.
-
Utilize o gerador de senhas do Bitwarden para criar senhas fortes e únicas para cada conta. O aplicativo oferece uma ferramenta para gerar senhas aleatórias, garantindo que suas contas estejam protegidas contra hackers.
-
Aproveite outras funcionalidades do Bitwarden, como preenchimento automático de senhas e autenticação de dois fatores. O aplicativo pode ajudar a simplificar o processo de login e aumentar a segurança de suas contas online.
-
-
 @ 3bf0c63f:aefa459d
2024-09-06 12:49:46
@ 3bf0c63f:aefa459d
2024-09-06 12:49:46Nostr: a quick introduction, attempt #2
Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else.
Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services.
(Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation).
More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between clients (i.e. the program that runs on a user computer) and relays (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback".
-
 @ eac63075:b4988b48
2024-12-02 02:40:18
@ eac63075:b4988b48
2024-12-02 02:40:18Estonia is a small country with just 1.3 million inhabitants and an area similar to that of the state of Rio de Janeiro, but with a notable difference: while Rio has about 16 million residents, Estonia shines with its efficiency, innovation, and digitalization. It's no wonder it's known as the "digital nation." For many Brazilians, the country has become a strategic gateway to start a business and settle in Europe.
Listen the podcast
https://www.fountain.fm/episode/pizBLdhqqP5qQrKQILFb
The Purpose of the Event and the Context
The meeting organized by Bloco and the Brazilian digital community aimed primarily to explore the opportunities that Estonia offers to those wishing to expand their businesses or start a new life in Europe. With pizza, networking, and straightforward presentations, the evening was dedicated to demystifying questions like "Why Estonia?" and "What makes this country a viable option for Brazilians?"
Additionally, the event highlighted the importance of E-Residency, a digital identity that allows you to open and manage a company in Estonia from anywhere in the world. But that's just the beginning. Let's explore what makes Estonia a standout point on the European scene.
Where Is Estonia Located?
If you open a map of Europe and look for this small country, you're likely to have difficulty locating it. Situated to the north of what's called Eastern Europe, Estonia borders Russia and Latvia and is separated from Finland by the Baltic Sea. Although geographically positioned in the east, many Estonians prefer to identify with the north due to cultural and historical proximity to the Nordic countries.
There's something fascinating about Estonia's history. According to local legends, Vikings set out from their Estonian islands to conquer the world, later returning to reclaim their lands. This spirit of resilience and reinvention permeates the country's culture to this day.
Digitalization: The Estonian Revolution
Thirty years ago, when Estonia gained its independence from the Soviet Union, the country decided to look to the future. The question was simple: how to ensure the sovereignty and survival of a small, vulnerable nation? The answer was bold: total digitalization.
In 2001, the X-Road was created—a decentralized infrastructure that connects all government institutions and allows citizens to access public services digitally. This system is so advanced that even the servers of the Estonian government are located outside the country, stored with backups at the European Commission in Brussels.
Through this infrastructure, Estonia eliminated information silos, decentralized data, and allowed its citizens to authorize the use of personal information with complete control. Today, 98% of the population has a digital identity, 95% file taxes online in less than three minutes, and 100% of public services are available digitally.
For those accustomed to Brazilian bureaucracy, it's impressive to know that opening a company in Estonia can be done in just 15 minutes, without the need for an accountant.
E-Residency: A Digital Passport for Business
Launched in 2014, the E-Residency program made Estonia the first country in the world to offer a digital identity to non-residents. This digital ID card allows entrepreneurs to open a company in the European Union, sign documents, and manage businesses remotely without needing to visit the country.
Although it doesn't grant citizenship or physical residency, E-Residency is perfect for those who want to test the European market or operate a digital company. The program has already attracted over 118,000 e-residents from around the world, including 1,300 Brazilians who have opened 379 companies in the country.
Advantages of Doing Business in Estonia
Starting a business in Estonia has many advantages. Let's discuss some of the main ones:
Simple and Clear Taxation:
Estonia adopts a flat tax rate of 20% (which increased to 22% after the pandemic and will be 24% in 2025) on distributed profits. If you reinvest the profits in the company, the taxation is zero—a unique policy that encourages sustainable growth.
Low Cost to Start:
Unlike Switzerland, which requires an initial deposit of 100,000 Swiss francs to open a company, in Estonia, only 2,500 euros are needed. And the best part: this amount only needs to be deposited when the company distributes profits for the first time.
Complete Digitalization:
Digital signatures in Estonia eliminate the need for notaries and paper documents. Everything can be done online, from opening the company to filing taxes.
Support for Startups and Innovation:
With the Startup Visa, entrepreneurs can move to Estonia with their entire family and receive support to expand their businesses. Additionally, the country has the highest number of unicorns (startups valued at over one billion dollars) per capita in the world, including companies like Skype, Bolt, and Wise.
Easy Access to Europe:
Establishing your company in Estonia means access to the European market, with its unified regulations and a vibrant innovation ecosystem.
The Startup Visa: An Invitation for Entrepreneurs
For those who want more than just operating remotely, the Startup Visa program offers the opportunity to physically move to Estonia. The initial visa is valid for one year and can be renewed for three consecutive years. After eight years, there's the possibility of applying for European citizenship, although Estonia doesn't allow dual nationality.
One of the unique features of the Startup Visa is that there's no limit to the number of partners or family members who can be included in the program. This means that the entire team of founders and their families can benefit from the residence permit.
Additionally, Estonia offers support through the International House and its Work in Estonia program, a center where newcomers can resolve everything from assistance with opening bank accounts to cultural and professional integration.
Innovation and Access to Investments
Estonia is known for its culture of innovation. Events like Latitude 59, one of Europe's main startup gatherings, offer prizes of up to two million euros for winning startups. The country also facilitates direct connections with investment funds and venture capital, often without bureaucratic barriers.
For early-stage companies, the Estonian ecosystem is especially attractive. There are cases of entrepreneurs who managed to raise hundreds of thousands of euros with little more than a prototype or a good idea on paper.
A Small Country with Global Ambitions
Although small in size, Estonia is big in ambition. Its model of digitalization and support for startups serves as an example to the world. With unique opportunities like E-Residency and the Startup Visa, the country positions itself as a viable and accessible gateway for Brazilians who wish to explore the European market.
For those seeking innovation, simplicity, and access to the global market, Estonia offers more than opportunities; it offers a vision of the future. Whether it's to open a business, operate remotely, or move with the family, the country proves that with the right strategies, even a small nation can make a giant impact.
-
 @ b83a28b7:35919450
2024-08-28 15:03:25
@ b83a28b7:35919450
2024-08-28 15:03:25Join nostr:npub1tvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq0rkrq4 and me for episode 76 of nostr:npub14kw5ygpl6fyqagh9cnrytyaqyacg46lzkq42vz7hk8txdk49kzxs04j7y0 this Friday, August 30th at 3pm ET (UTC -4)
Our guest this week is nostr:npub1xv8mzscll8vvy5rsdw7dcqtd2j268a6yupr6gzqh86f2ulhy9kkqmclk3x from nostr:npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm who joins us to provide the lowdown on the recently launched Alby Hub
You don't want to miss this one!
Set your blockclocks!
https://nostrnests.com/
[This is our first show announcement made from a long-form client, in keeping with QW and my #otherstuffchallenge]
-
 @ 4ba8e86d:89d32de4
2024-10-07 22:48:24
@ 4ba8e86d:89d32de4
2024-10-07 22:48:24é um sistema operacional portátil baseado em Linux que pode ser iniciado a partir de um pen drive ou DVD. Ele é projetado para manter sua privacidade enquanto navega na internet, protegendo você de vigilância e censura. O Tails é gratuito e de código aberto, o que significa que qualquer pessoa pode usá-lo e modificá-lo.
O projeto Tails teve início em 2009, quando um grupo de desenvolvedores de software preocupados com a crescente vigilância na internet começaram a trabalhar em uma solução para proteger a privacidade dos usuários. O objetivo era criar um sistema operacional que pudesse ser executado a partir de um pendrive USB e que utilizasse a rede Tor para manter a privacidade do usuário.
O Tails oferece várias ferramentas de privacidade, incluindo o Tor (The Onion Router), um serviço de rede que protege sua identidade online e oculta sua localização. Ele também inclui o navegador Tor, que permite navegar na internet anonimamente e acessar sites bloqueados em seu país. Além disso, o Tails vem com outras ferramentas de privacidade, como o Kleopatra PGP (Pretty Good Privacy) uma ferramenta de criptografia de e-mail que ajuda a proteger suas mensagens.
O Tails é fácil de usar, mesmo se você não tiver conhecimento técnico avançado. Ele é projetado para ser iniciado a partir de um pen drive ou DVD, o que significa que você pode usá-lo em qualquer computador sem precisar instalá-lo no disco rígido. Ele é projetado para deixar o mínimo de rastros possível, o que significa que não salva seus dados pessoais ou suas atividades online.
O Tails é projetado com segurança em mente. Ele é atualizado regularmente para corrigir quaisquer vulnerabilidades de segurança e para incluir as últimas ferramentas de privacidade. O Tails também é projetado para manter sua privacidade e segurança em caso de perda ou roubo do dispositivo que contém o sistema operacional. Ele usa criptografia de disco para proteger seus arquivos pessoais e mantém todos os arquivos temporários na memória RAM, que é apagada quando você desliga o computador.
Mas você pode salvar alguns de seus arquivos e configurações em um Persistent Storage criptografado em seu stick USB Tails. O Persistent Storage é uma partição criptografada protegida por uma senha que ocupa todo o espaço livre deixado no pendrive. Tudo no Persistent Storage é criptografado automaticamente.
Para usar Tails, basta baixar a imagem do sistema operacional e gravá-la em um pendrive USB. Quando você estiver pronto para usá-lo, basta conectar o pendrive USB ao computador e iniciar o sistema operacional a partir dele. Depois de usar Tails, basta remover o pendrive USB e nenhum traço será deixado no computador.
https://tails.boum.org
-
 @ 705605d9:b4324038
2024-12-02 00:41:37
@ 705605d9:b4324038
2024-12-02 00:41:37Вот уже несколько лет зимы в Горноправдинске проходят без снега. Температура остаётся минусовой, но осадки исчезли. Экологи и метеорологи теряются в догадках: климатические данные не объясняют такую аномалию.
Жители связывают исчезновение снега с советским наследием — захоронениями радиоактивных отходов где-то в лесах Сибири. Хотя значения счётчика Гейгера в норме, не исключается, что в атмосфере происходят химические реакции, влияющие на осадки.

Местные власти уверяют, что угрозы радиации нет, однако возможны долгосрочные изменения в экосистеме. Отсутствие снежного покрова ускоряет вымерзание почвы, что уже снижает урожайность и угрожает стабильности сельского хозяйства.
Учёные продолжают изучать феномен. Пока же бесснежные зимы в Горноправдинске остаются загадкой, которая может оказать влияние не только на природу, но и на всех нас.

-
 @ ee11a5df:b76c4e49
2023-07-29 03:13:59
@ ee11a5df:b76c4e49
2023-07-29 03:13:59Gossip: Switching to LMDB
Unlike a number of other nostr clients, Gossip has always cached events and related data in a local data store. Up until recently, SQLite3 has served this purpose.
SQLite3 offers a full ACID SQL relational database service.
Unfortunately however it has presented a number of downsides:
- It is not as parallel as you might think.
- It is not as fast as you might hope.
- If you want to preserve the benefit of using SQL and doing joins, then you must break your objects into columns, and map columns back into objects. The code that does this object-relational mapping (ORM) is not trivial and can be error prone. It is especially tricky when working with different types (Rust language types and SQLite3 types are not a 1:1 match).
- Because of the potential slowness, our UI has been forbidden from direct database access as that would make the UI unresponsive if a query took too long.
- Because of (4) we have been firing off separate threads to do the database actions, and storing the results into global variables that can be accessed by the interested code at a later time.
- Because of (4) we have been caching database data in memory, essentially coding for yet another storage layer that can (and often did) get out of sync with the database.
LMDB offers solutions:
- It is highly parallel.
- It is ridiculously fast when used appropriately.
- Because you cannot run arbitrary SQL, there is no need to represent the fields within your objects separately. You can serialize/deserialize entire objects into the database and the database doesn't care what is inside of the blob (yes, you can do that into an SQLite field, but if you did, you would lose the power of SQL).
- Because of the speed, the UI can look stuff up directly.
- We no longer need to fork separate threads for database actions.
- We no longer need in-memory caches of data. The LMDB data is already in-memory (it is memory mapped) so we just access it directly.
The one obvious downside is that we lose SQL. We lose the query planner. We cannot ask arbitrary question and get answers. Instead, we have to pre-conceive of all the kinds of questions we want to ask, and we have to write code that answers them efficiently. Often this involves building and maintaining indices.
Indices
Let's say I want to look at fiatjaf's posts. How do I efficiently pull out just his recent feed-related events in reverse chronological order? It is easy if we first construct the following index
key: EventKind + PublicKey + ReverseTime value: Event Id
In the above, '+' is just a concatenate operator, and ReverseTime is just some distant time minus the time so that it sorts backwards.
Now I just ask LMDB to start from (EventKind=1 + PublicKey=fiatjaf + now) and scan until either one of the first two fields change, or more like the time field gets too old (e.g. one month ago). Then I do it again for the next event kind, etc.
For a generalized feed, I have to scan a region for each person I follow.
Smarter indexes can be imagined. Since we often want only feed-related event kinds, that can be implicit in an index that only indexes those kinds of events.
You get the idea.
A Special Event Map
At first I had stored events into a K-V database under the Id of the event. Then I had indexes on events that output a set of Ids (as in the example above).
But when it comes to storing and retrieving events, we can go even faster than LMDB.
We can build an append-only memory map that is just a sequence of all the events we have, serialized, and in no particular order. Readers do not need a lock and multiple readers can read simultaneously. Writers will need to acquire a lock to append to the map and there may only be one writer at a time. However, readers can continue reading even while a writer is writing.
We can then have a K-V database that maps Id -> Offset. To get the event you just do a direct lookup in the event memory map at that offset.
The real benefit comes when we have other indexes that yield events, they can yield offsets instead of ids. Then we don't need to do a second lookup from the Id to the Event, we can just look directly at the offset.
Avoiding deserialization
Deserialization has a price. Sometimes it requires memory allocation (if the object is not already linear, e.g. variable lengthed data like strings and vectors are allocated on the heap) which can be very expensive if you are trying to scan 150,000 or so events.
We serialize events (and other objects where we can) with a serialization library called speedy. It does its best to preserve the data much like it is represented in memory, but linearized. Because events start with fixed-length fields, we know the offset into the serialized event where these first fields occur and we can directly extract the value of those fields without deserializing the data before it.
This comes in useful whenever we need to scan a large number of events. Search is the one situation where I know that we must do this. We can search by matching against the content of every feed-related event without fully deserialing any of them.
-
 @ 51ca7ccd:7baf47d6
2024-12-02 00:34:22
@ 51ca7ccd:7baf47d6
2024-12-02 00:34:22Self-care has become a popular term in recent years, and for good reason. It's about intentionally taking time to nurture your physical, emotional, and mental well-being. While often associated with pampering activities like taking a bath or getting a massage, self-care goes beyond that, involving practices that help reduce stress, improve resilience, and promote overall happiness and health.
The Importance of Self-Care
In today’s fast-paced world, many people feel overwhelmed by work, social obligations, and personal responsibilities. According to a study by the American Psychological Association (APA), chronic stress can lead to a range of mental and physical health issues, including anxiety, depression, high blood pressure, and heart disease. Taking regular time for self-care can help mitigate these effects by allowing individuals to recharge and focus on their well-being.
Self-care is not just about physical relaxation but also mental and emotional health. Research from the National Institutes of Health (NIH) highlights that self-care activities like mindfulness meditation or engaging in hobbies can have a significant impact on improving mood, reducing anxiety, and enhancing overall mental clarity (NIH, 2021).
Types of Self-Care
-
Physical Self-Care: This involves activities that take care of the body, such as exercise, eating nutritious meals, and getting enough sleep. Regular physical activity has been linked to improved mood, better sleep, and a lower risk of chronic conditions like heart disease and diabetes. A study published in JAMA Psychiatry confirms that even moderate exercise can reduce symptoms of depression and anxiety (JAMA Psychiatry, 2020).
-
Emotional Self-Care: Taking care of your emotional health is just as important as physical care. This includes activities that help you process and express your emotions in a healthy way, such as journaling, talking with loved ones, or practicing gratitude. Research from the Journal of Positive Psychology suggests that cultivating gratitude through journaling can significantly enhance emotional well-being and reduce stress (Journal of Positive Psychology, 2019).
-
Social Self-Care: Building and maintaining supportive relationships is key to self-care. Socializing with friends, joining communities, and having meaningful conversations can promote a sense of belonging and reduce feelings of loneliness. The National Institute on Aging found that strong social connections are linked to lower rates of depression and longer life expectancy (NIA, 2020).
-
Mental Self-Care: This involves stimulating the mind and improving cognitive function through activities like reading, solving puzzles, or learning new skills. Mental self-care helps boost concentration, creativity, and problem-solving abilities. Studies from the Harvard Medical School suggest that lifelong learning and engaging in intellectual activities can help maintain cognitive function as we age (Harvard Health Publishing, 2021).
Overcoming Barriers to Self-Care
While self-care is essential, it can sometimes feel like another task on a never-ending to-do list, especially for those with busy schedules. However, even small, consistent efforts can lead to meaningful improvements. A key to overcoming barriers to self-care is to view it as a priority rather than a luxury. This mindset shift helps individuals make time for self-care, even during challenging times.
Incorporating self-care into daily routines doesn’t need to be time-consuming or expensive. It can be as simple as taking five minutes each morning for deep breathing exercises or setting aside time each week to enjoy a favorite hobby. The key is consistency and finding activities that align with personal preferences and needs.
The Long-Term Benefits of Self-Care
Engaging in self-care practices consistently can lead to lasting benefits, including improved physical health, better emotional regulation, and increased resilience in the face of challenges. By investing in your own well-being, you are better equipped to handle life’s stresses and support others around you.
As we continue to navigate a world that demands more from us every day, prioritizing self-care is not only a way to thrive but also a necessity for long-term health and happiness
-
-
 @ 705605d9:b4324038
2024-12-02 00:15:58
@ 705605d9:b4324038
2024-12-02 00:15:58Горноправдинск, 5 декабря 2040 года. В одном из самых уютных уголков Сибири, в посёлке Горноправдинск, состоялся долгожданный показ мод среди пенсионеров. Событие собрало местных жителей, а также гостей из соседних посёлков, превратившись в настоящий праздник стиля и творчества. Организаторы мероприятия, местный Дом культуры, сделали всё, чтобы показать, что даже в возрасте можно оставаться модным и уверенным в себе.
Модные тренды для старшего поколения
Показ начался с небольшой вступительной речи, в которой организаторы рассказали о важности саморазвития в любом возрасте. "Мода — это не только для молодых, это способ выражать себя, чувствовать себя живым и привлекательным", — подчеркнула в своём выступлении ведущая мероприятия, Елена Васильева.

В рамках показа были представлены несколько тематических блоков. Первый из них был посвящён эко-стилю, в котором старшее поколение демонстрировало одежду из переработанных материалов. Яркие пальто, удобные костюмы и стильные аксессуары были сшиты местными мастерицами. Особое внимание привлекли изделия из натуральных тканей, подчеркивающие заботу о природе и здоровье.
Далее последовал блок в стиле ретро, где участники продемонстрировали образы, вдохновленные модой 1960-х и 1970-х годов. В этот момент на подиуме появились как стильные платья в стиле "New Look", так и кожаные куртки, напоминающие о молодости поколений. Ветераны моды с удовольствием рассказывали о том, как когда-то носили подобные вещи в молодости, а теперь решили вернуть их на подиум.

Следующим был показ современной городской моды, где особое внимание уделили удобству и практичности одежды для повседневной жизни. Здесь были представлены стильные, но комфортные костюмы, куртки и обувь, подходящие для походов в магазин, прогулок на свежем воздухе и активных встреч с друзьями.
История одной участницы
Мария Ивановна, одна из участниц показа, поделилась своими впечатлениями: "Я никогда не думала, что буду участвовать в подобном событии! Мне уже 72, но я чувствую, что могу носить что угодно. Главное — не бояться себя выражать и не поддаваться возрастным стереотипам. Я выбрала для показа платье, которое когда-то купила для своей дочери, но так и не успела носить. Сегодня я наконец-то смогла показать, как его можно носить с гордостью, несмотря на возраст".
Для многих, кто пришёл посмотреть на показы, участие в подобном мероприятии стало настоящим вдохновением. Несмотря на то, что возраст у многих уже далеко за 60, настроение было молодёжным, а уверенность — как у моделей на самых престижных подиумах мира.

Мода в Горноправдинске доказала, что возраст — это всего лишь цифра, и каждый может быть стильным и современным, несмотря на годы. Этот показ стал ярким примером того, как люди старшего поколения могут смело заявлять о себе и жить полной жизнью, не уступая в модных предпочтениях даже молодым.
-
 @ 4ba8e86d:89d32de4
2024-10-07 15:43:17
@ 4ba8e86d:89d32de4
2024-10-07 15:43:17Ele oferece recursos adicionais em relação ao aplicativo oficial do YouTube, como a possibilidade de assistir vídeos sem anúncios, reproduzir em segundo plano, baixar vídeos e áudios, entre outros.
O NewPipe foi desenvolvido como uma alternativa de código aberto ao aplicativo oficial do YouTube para dispositivos Android. O projeto foi iniciado por Christian Schabesberger em 2015, como um projeto de software livre hospedado no GitHub. Desde então, vários colaboradores se juntaram ao projeto para melhorar e expandir suas funcionalidades. O objetivo principal por trás do desenvolvimento do NewPipe foi fornecer uma experiência mais privada, segura e personalizada para os usuários do YouTube. Muitas pessoas estavam preocupadas com a coleta de dados e o rastreamento de usuários feitos pelo aplicativo oficial do YouTube, e o NewPipe surgiu como uma alternativa para resolver essas preocupações. O desenvolvimento do NewPipe foi impulsionado pela comunidade de software livre e pela filosofia de transparência, privacidade e liberdade de escolha do usuário. Como um projeto de código aberto, o NewPipe permite que os usuários examinem e modifiquem o código-fonte, se assim desejarem, tornando o aplicativo mais transparente e confiável. Ao longo dos anos, o NewPipe evoluiu e adicionou recursos, como reprodução em segundo plano, bloqueio de anúncios, download de vídeos e áudios, gerenciamento de inscrições e muito mais. Esses recursos extras fornecem aos usuários uma experiência mais personalizada e conveniente ao assistir e baixar conteúdo do YouTube.
Principais recursos do NewPipe:
-
Reprodução de vídeos: O NewPipe permite assistir a vídeos do YouTube diretamente no aplicativo, fornecendo uma interface intuitiva e fácil de usar.
-
Reprodução em segundo plano: Você pode reproduzir vídeos do YouTube em segundo plano, permitindo que você ouça o áudio do vídeo enquanto realiza outras tarefas em seu dispositivo Android.
-
Bloqueador de anúncios: O NewPipe bloqueia automaticamente anúncios em vídeos do YouTube, proporcionando uma experiência de visualização mais livre de interrupções.
-
Download de vídeos: O aplicativo permite baixar vídeos do YouTube diretamente para o armazenamento do seu dispositivo Android. Você pode escolher a qualidade de vídeo desejada e salvá-lo para assistir offline.
-
Download de áudios: Além de vídeos, o NewPipe também permite que você baixe apenas o áudio dos vídeos do YouTube em formatos como MP3 ou AAC.
-
Assinaturas e notificações: Você pode se inscrever nos canais do YouTube no NewPipe e receber notificações sobre novos vídeos dos canais que você segue.
-
Privacidade e segurança: O NewPipe prioriza a privacidade dos usuários. Ele não requer login em uma conta do Google para acessar o conteúdo do YouTube, o que significa que você pode usar o aplicativo sem fornecer suas informações pessoais.
O NewPipe oferece uma alternativa interessante para aqueles que desejam uma experiência personalizada e privada ao acessar o conteúdo do YouTube em dispositivos Android.
Pode baixar F-droid https://f-droid.org/packages/org.schabi.newpipe/
https://github.com/TeamNewPipe/NewPipe
-
-
 @ b83a28b7:35919450
2024-08-27 18:53:46
@ b83a28b7:35919450
2024-08-27 18:53:46On last week's episode of Plebchain Radio, QW and I announced something unusual - we would be taking a week off posting kind 1 notes on the Twitter clone clients - Primal, Damus, Nostur, etc. The clock started right after our show was posted on Friday, August 23rd and ends with show this Friday, August 30th.
https://video.nostr.build/741cd7a0dd33e1ce815490d14069af96579ce47c92ea04240592c7bbb2de3a65.mp4
The idea behind the challenge is to see how much we can participate in the network without resorting to it's most accessible form of communication - kind 1 notes (the equivalent of tweets/replies).
Halfway into the challenge, we've boosted and commented on shows on Fountain, zapped songs on Wavlake, commented on recipes on zap.cooking, watched videos on zap.stream and tunestr, and written the odd long-form note (oh, alright, just this one so far). It's been fun, but has also created an odd sense of sensory deprivation.
We will share more details on our experience on this week's Plebchain Radio episode. Right, I'm off to explore the rest of the other-stuff-verse. I'd urge everyone to give this challenge a try. It might change how you view nostr.
-
 @ ee11a5df:b76c4e49
2023-07-29 02:52:13
@ ee11a5df:b76c4e49
2023-07-29 02:52:13Gossip: Zaps
Gossip is a desktop nostr client. This post is about the code that lets users send lightning zaps to each other (NIP-57).
Gossip implemented Zaps initially on 20th of June, 2023.
Gossip maintains a state of where zapping is at, one of: None, CheckingLnurl, SeekingAmount, LoadingInvoice, and ReadyToPay.
When you click the zap lightning bolt icon, Gossip moves to the CheckingLnurl state while it looks up the LN URL of the user.
If this is successful, it moves to the SeekingAmount state and presents amount options to the user.
Once a user chooses an amount, it moves to the LoadingInvoice state where it interacts with the lightning node and receives and checks an invoice.
Once that is complete, it moves to the ReadyToPay state, where it presents the invoice as a QR code for the user to scan with their phone. There is also a copy button so they can pay it from their desktop computer too.
Gossip also loads zap receipt events and associates them with the event that was zapped, tallying a zap total on that event. Gossip is unfortunately not validating these receipts very well currently, so fake zap receipts can cause an incorrect total to show. This remains an open issue.
Another open issue is the implementation of NIP-46 Nostr Connect and NIP-47 Wallet Connect.
-
 @ b12b632c:d9e1ff79
2023-07-21 19:45:20
@ b12b632c:d9e1ff79
2023-07-21 19:45:20I love testing every new self hosted app and I can say that Nostr "world" is really good regarding self hosting stuff.
Today I tested a Nostr relay named Strfry.
Strfry is really simple to setup and support a lot's of Nostr NIPs.
Here is the list of what it is able to do :
- Supports most applicable NIPs: 1, 2, 4, 9, 11, 12, 15, 16, 20, 22, 28, 33, 40
- No external database required: All data is stored locally on the filesystem in LMDB
- Hot reloading of config file: No server restart needed for many config param changes
- Zero downtime restarts, for upgrading binary without impacting users
- Websocket compression: permessage-deflate with optional sliding window, when supported by clients
- Built-in support for real-time streaming (up/down/both) events from remote relays, and bulk import/export of events from/to jsonl files
- negentropy-based set reconcilliation for efficient syncing with remote relays
Installation with docker compose (v2)
Spoiler : you need to have a computer with more than 1 (v)Core / 2GB of RAM to build the docker image locally. If not, this below might crash your computer during docker image build. You may need to use a prebuilt strfry docker image.
I assume you've read my first article on Managing domain with Nginx Proxy Manager because I will use the NPM docker compose stack to publish strfry Nostr relay. Without the initial NPM configuration done, it may not work as expected. I'll use the same docker-compose.yml file and folder.
Get back in the "npm-stack" folder :
cd npm-stackCloning the strfry github repo locally :
git clone https://github.com/hoytech/strfry.gitModify the docker-compose file to locate the strfry configuration data outside of the folder repo directory to avoid mistake during futures upgrades (CTRL + X, S & ENTER to quit and save modifications) :
nano docker-compose.ymlYou don't have to insert the Nginx Proxy Manager part, you should already have it into the file. If not, check here. You should only have to add the strfry part.
``` version: '3.8' services: # should already be present into the docker-compose.yml app: image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: # These ports are in format
: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port # Add any other Stream port you want to expose # - '21:21' # FTP # Uncomment the next line if you uncomment anything in the section # environment: # Uncomment this if you want to change the location of # the SQLite DB file within the container # DB_SQLITE_FILE: "/data/database.sqlite" # Uncomment this if IPv6 is not enabled on your host # DISABLE_IPV6: 'true' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencryptstrfry-nostr-relay: container_name: strfry build: ./strfry volumes: - ./strfry-data/strfry.conf:/etc/strfry.conf - ./strfry-data/strfry-db:/app/strfry-db
ports is commented by NPM will access through docker internal network
no need to expose strfry port directly to the internet
ports:
- "7777:7777"
```
Before starting the container, we need to customize the strfry configuration file "strfry.conf". We'll copy the strfry configuration file and place it into the "strfry-data" folder to modify it with our own settings :
mkdir strfry-data && cp strfry/strfry.conf strfry-data/And modify the strfry.conf file with your own settings :
nano strfry-data/strfry.confYou can modify all the settings you need but the basics settings are :
- bind = "127.0.0.1" --> bind = "0.0.0.0" --> otherwise NPM won't be able to contact the strfry service
-
name = "strfry default" --> name of your nostr relay
-
description = "This is a strfry instance." --> your nostr relay description
-
pubkey = "" --> your pubkey in hex format. You can use the Damu's tool to generate your hex key from your npub key : https://damus.io/key/
-
contact = "" --> your email
``` relay { # Interface to listen on. Use 0.0.0.0 to listen on all interfaces (restart required) bind = "127.0.0.1"
# Port to open for the nostr websocket protocol (restart required) port = 7777 # Set OS-limit on maximum number of open files/sockets (if 0, don't attempt to set) (restart required) nofiles = 1000000 # HTTP header that contains the client's real IP, before reverse proxying (ie x-real-ip) (MUST be all lower-case) realIpHeader = "" info { # NIP-11: Name of this server. Short/descriptive (< 30 characters) name = "strfry default" # NIP-11: Detailed information about relay, free-form description = "This is a strfry instance." # NIP-11: Administrative nostr pubkey, for contact purposes pubkey = "" # NIP-11: Alternative administrative contact (email, website, etc) contact = "" }```
You can now start the docker strfry docker container :
docker compose up -dThis command will take a bit of time because it will build the strfry docker image locally before starting the container. If your VPS doesn't have lot's of (v)CPU/RAM, it could fail (nothing happening during the docker image build). My VPS has 1 vCore / 2GB of RAM and died few seconds after the build beginning.
If it's the case, you can use prebuilt strfry docker image available on the Docker hub : https://hub.docker.com/search?q=strfry&sort=updated_at&order=desc
That said, otherwise, you should see this :
``` user@vps:~/npm-stack$ docker compose up -d [+] Building 202.4s (15/15) FINISHED
=> [internal] load build definition from Dockerfile 0.2s => => transferring dockerfile: 724B 0.0s => [internal] load .dockerignore 0.3s => => transferring context: 2B 0.0s => [internal] load metadata for docker.io/library/ubuntu:jammy 0.0s => [build 1/7] FROM docker.io/library/ubuntu:jammy 0.4s => [internal] load build context 0.9s => => transferring context: 825.64kB 0.2s => [runner 2/4] WORKDIR /app 1.3s => [build 2/7] WORKDIR /build 1.5s => [runner 3/4] RUN apt update && apt install -y --no-install-recommends liblmdb0 libflatbuffers1 libsecp256k1-0 libb2-1 libzstd1 && rm -rf /var/lib/apt/lists/* 12.4s => [build 3/7] RUN apt update && apt install -y --no-install-recommends git g++ make pkg-config libtool ca-certificates libyaml-perl libtemplate-perl libregexp-grammars-perl libssl-dev zlib1g-dev l 55.5s => [build 4/7] COPY . . 0.9s => [build 5/7] RUN git submodule update --init 2.6s => [build 6/7] RUN make setup-golpe 10.8s => [build 7/7] RUN make -j4 126.8s => [runner 4/4] COPY --from=build /build/strfry strfry 1.3s => exporting to image 0.8s => => exporting layers 0.8s => => writing image sha256:1d346bf343e3bb63da2e4c70521a8350b35a02742dd52b12b131557e96ca7d05 0.0s => => naming to docker.io/library/docker-compose_strfry-nostr-relay 0.0sUse 'docker scan' to run Snyk tests against images to find vulnerabilities and learn how to fix them
[+] Running 02/02
⠿ Container strfry Started 11.0s ⠿ Container npm-stack-app-1 Running ```You can check if everything is OK with strfry container by checking the container logs :
user@vps:~/npm-stack$ docker logs strfry date time ( uptime ) [ thread name/id ] v| 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| arguments: /app/strfry relay 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| Current dir: /app 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| stderr verbosity: 0 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| ----------------------------------- 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| CONFIG: Loading config from file: /etc/strfry.conf 2023-07-21 19:26:58.529 ( 0.054s) [main thread ]INFO| CONFIG: successfully installed 2023-07-21 19:26:58.533 ( 0.058s) [Websocket ]INFO| Started websocket server on 0.0.0.0:7777Now, we have to create the subdomain where strfry Nostr relay will be accessible. You need to connect to your Nginx Proxy Manager admin UI and create a new proxy host with these settings :
"Details" tab (Websockets support is mandatory!, you can replace "strfry" by whatever you like, for instance : mybeautifulrelay.yourdomain.tld)
"Details" tab:

"SSL" tab:

And click on "Save"
If everything is OK, when you go to https://strfry.yourdomain.tld you should see :

To verify if strfry is working properly, you can test it with the (really useful!) website https://nostr.watch. You have to insert your relay URL into the nostr.watch URL like this : https://nostr.watch/relay/strfry.yourdomain.tld
You should see this :

If you are seeing your server as online, readable and writable, you made it ! You can add your Nostr strfry server to your Nostr prefered relay and begin to publish notes ! 🎇
Future work:
Once done, strfry will work like a charm but you may need to have more work to update strfry in the near future. I'm currently working on a bash script that will :
- Updatethe "strfry" folder,
- Backup the "strfry.conf" file,
- Download the latest "strfry.conf" from strfry github repo,
- Inject old configuration settings into the new "strfry.conf" file,
- Compose again the stack (rebuilding the image to get the latest code updates),
- etc.
Tell me if you need the script!
Voilààààà
See you soon in another Fractalized story!
-
 @ 705605d9:b4324038
2024-12-01 23:46:24
@ 705605d9:b4324038
2024-12-01 23:46:24На улицах Горноправдинска появились уникальные экологичные фонари, которые уже успели стать символом прогресса и заботы о природе. Проект, реализованный в прошлом году, полностью преобразил набережную и улицы поселка. Теперь вечером Горноправдинск утопает в мягком, теплым свете, а жители обсуждают эти удивительные новшества.
Чем уникальны фонари?
Эко-фонари работают на солнечной энергии, заряжаясь днем от встроенных солнечных панелей. Они абсолютно автономны, а специальная система накопления энергии позволяет работать даже в долгие пасмурные зимы. Более того, каждый фонарь оснащен "умным датчиком" движения: когда никого рядом нет, свет становится тусклее, экономя ресурс батарей.

Инициаторами проекта стали Совет бабушек и молодежный техноклуб. Молодежь разработала высокотехнологичную начинку, а бабушки настояли на художественном оформлении: кованые узоры с северными орнаментами теперь украшают каждую опору. А на скамейках вдоль набережной добавили USB-разъемы для зарядки телефонов — так захотели школьники и студенты.
Как отнеслись жители?
Каждая возрастная группа оценила фонари по-своему.
-
Молодежь в восторге от USB-зарядок: теперь вечерние прогулки на набережной сопровождаются комфортом — можно спокойно слушать музыку или фотографироваться, не боясь остаться без связи.
-
Средний возраст оценил экономическую выгоду и экологичность: за год счет за электричество на уличное освещение сократился на 40%. Как шутят жители, "эти фонари светят даже в кармане".
-
Старшее поколение с гордостью говорит о том, что проект сочетает технологии с душой. Особенно бабушкам нравится, что узоры на фонарях напоминают традиционные северные орнаменты, создавая уют.
Однако не обошлось без курьезов. Дети быстро нашли способ "тестировать" датчики движения: они специально бегают под фонарями, чтобы те мигали. А один местный дедушка сначала жаловался, что "светит сильно", но теперь каждый вечер приходит заряжать свой старый кнопочный телефон.

Символ нового Горноправдинска
Уникальные фонари стали больше, чем просто освещением — это настоящий символ нового Горноправдинска. Экология, технологии и местные традиции слились в одном проекте, который объединил жителей всех поколений. Это лишь первый шаг на пути к статусу самого зеленого поселения Югры.
-
-
 @ 705605d9:b4324038
2024-12-01 23:30:56
@ 705605d9:b4324038
2024-12-01 23:30:56Для затравки кратко о всех гостях:
1. Развитие сельского хозяйства Горноправдинска Узнайте, как бабушки Горноправдинска превращают роботов в «электро-кобылок», обучают дронов опылять грядки и создают будущее экологичного земледелия. Весело, необычно и с юмором рассказывает Анна Петровна Гребнева.
2. Минусы молочного производства Молочный комбинат Горноправдинска — эталон экологичности, но каково это, работать без пластика, с коровами-индивидуалистами и кувшинами вместо упаковок? Николай Степанович Ларёнов делится трудностями, которые иногда пахнут сыром, а иногда... не очень.
3. Показ мод среди пенсионеров Возраст — это не преграда для стиля! Валентина Семеновна Багрянова рассказывает о предстоящем секретном показе мод для пенсионеров. Шляпы с Wi-Fi, платья с солнечными батареями и неожиданный бабушкин флешмоб — подробности в нашем новом выпуске.
4. Беженцы из Бобровки
В Горноправдинске новая драма: как принять беженцев из соседней Бобровки и заставить их копать картошку? Откровенно и провокационно об этом рассказывает глава парламента бабушек Елизавета Павловна Журавлева.Ссылка на подкасты:
https://disk.yandex.ru/d/11yo0UTX6O2O4Q
-
 @ 51ca7ccd:7baf47d6
2024-12-01 23:29:52
@ 51ca7ccd:7baf47d6
2024-12-01 23:29:52Personal growth is not a destination, but a continuous journey. It's a process of evolving into the best version of yourself, and it often requires embracing change, even when it feels uncomfortable or uncertain. As we navigate life, we encounter moments of transformation that challenge who we are and push us to expand beyond our limits.
One of the most profound aspects of personal growth is the realization that change is not something to fear, but something to embrace. Change is inevitable. Whether it's a shift in perspective, a new opportunity, or a personal challenge, growth often comes from stepping outside of our comfort zones. For many, the biggest hurdle is accepting that change is a natural part of life—something that should be welcomed, not resisted.
At the core of personal growth lies self-awareness. Understanding your strengths, weaknesses, and areas for improvement helps to clarify the path forward. It's through this awareness that you can begin to make intentional choices, whether it's pursuing new goals, working on emotional intelligence, or letting go of past habits that no longer serve you. Growth comes when you are honest with yourself and willing to confront uncomfortable truths.
Another essential aspect of growth is resilience. Life will inevitably throw challenges your way—times when you feel lost, discouraged, or defeated. But these are the moments when your ability to bounce back, learn from mistakes, and keep moving forward matters most. Resilience is about adapting and using adversity as fuel for transformation. It's not about avoiding pain, but about finding strength in it.
Faith also plays a crucial role in personal growth. Whether it’s your belief in God, in the universe, or in yourself, having faith can be the anchor that keeps you grounded during difficult times. Faith provides perspective, patience, and trust in the process. It reminds you that the setbacks you face are not permanent and that transformation is always possible.
As you embrace change, remember that personal growth is not always linear. There will be moments of progress, but there will also be setbacks. It’s important to be kind to yourself during these times and recognize that growth takes time. Celebrate the small wins along the way—each step forward, no matter how small, is a victory in itself.
Ultimately, personal growth is about discovering who you are meant to be and becoming comfortable with that person. It’s a process of shedding old layers, confronting fears, and embracing new experiences. Each chapter of your life, each transformation, leads you closer to the person you’re destined to become
-
 @ b12b632c:d9e1ff79
2023-07-21 14:19:38
@ b12b632c:d9e1ff79
2023-07-21 14:19:38Self hosting web applications comes quickly with the need to deal with HTTPS protocol and SSL certificates. The time where web applications was published over the 80/TCP port without any encryption is totally over. Now we have Let's Encrypt and other free certification authority that lets us play web applications with, at least, the basic minimum security required.
Second part of web self hosting stuff that is really useful is the web proxifycation.
It's possible to have multiple web applications accessible through HTTPS but as we can't use the some port (spoiler: we can) we are forced to have ugly URL as https://mybeautifudomain.tld:8443.
This is where Nginx Proxy Manager (NPM) comes to help us.
NPM, as gateway, will listen on the 443 https port and based on the subdomain you want to reach, it will redirect the network flow to the NPM differents declared backend ports. NPM will also request HTTPS cert for you and let you know when the certificate expires, really useful.
We'll now install NPM with docker compose (v2) and you'll see, it's very easy.
You can find the official NPM setup instructions here.
But before we absolutely need to do something. You need to connect to the registrar where you bought your domain name and go into the zone DNS section.You have to create a A record poing to your VPS IP. That will allow NPM to request SSL certificates for your domain and subdomains.
Create a new folder for the NPM docker stack :
mkdir npm-stack && cd npm-stackCreate a new docker-compose.yml :
nano docker-compose.ymlPaste this content into it (CTRL + X ; Y & ENTER to save/quit) :
``` version: '3.8' services: app: image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: # These ports are in format
: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port # Add any other Stream port you want to expose # - '21:21' # FTP # Uncomment the next line if you uncomment anything in the section # environment: # Uncomment this if you want to change the location of # the SQLite DB file within the container # DB_SQLITE_FILE: "/data/database.sqlite" # Uncomment this if IPv6 is not enabled on your host # DISABLE_IPV6: 'true' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt```
You'll not believe but it's done. NPM docker compose configuration is done.
To start Nginx Proxy Manager with docker compose, you just have to :
docker compose up -dYou'll see :
user@vps:~/tutorials/npm-stack$ docker compose up -d [+] Running 2/2 ✔ Network npm-stack_default Created ✔ Container npm-stack-app-1 StartedYou can check if NPM container is started by doing this command :
docker psYou'll see :
user@vps:~/tutorials/npm-stack$ docker ps CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 7bc5ea8ac9c8 jc21/nginx-proxy-manager:latest "/init" About a minute ago Up About a minute 0.0.0.0:80-81->80-81/tcp, :::80-81->80-81/tcp, 0.0.0.0:443->443/tcp, :::443->443/tcp npm-stack-app-1If the command show "Up X minutes" for the npm-stack-app-1, you're good to go! You can access to the NPM admin UI by going to http://YourIPAddress:81.You shoud see :

The default NPM login/password are : admin@example.com/changeme .If the login succeed, you should see a popup asking to edit your user by changing your email password :
 And your password :
And your password :
 Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
 Followed by "Add Proxy Host"
Followed by "Add Proxy Host"
 If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :
If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :Details tab :
 SSL tab :
SSL tab :
 And click on "Save".
And click on "Save".NPM will request the SSL certificate "admin.yourdomain.tld" for you.
If you have an erreor message "Internal Error" it's probably because your domaine DNS zone is not configured with an A DNS record pointing to your VPS IP.
Otherwise you should see (my domain is hidden) :

Clicking on the "Source" URL link "admin.yourdomain.tld" will open a pop-up and, surprise, you should see the NPM admin UI with the URL "https://admin.yourdomain.tld" !
If yes, bravo, everything is OK ! 🎇
You know now how to have a subdomain of your domain redirecting to a container web app. In the next blog post, you'll see how to setup a Nostr relay with NPM ;)
Voilààààà
See you soon in another Fractalized story!
-
 @ b83a28b7:35919450
2024-08-27 16:48:28
@ b83a28b7:35919450
2024-08-27 16:48:28https://image.nostr.build/df0721d6d45d82db35d06663a0318ffe68c0b2b3c694888d23694efcc4255de5.gif
-
 @ 4ba8e86d:89d32de4
2024-10-07 13:37:38
@ 4ba8e86d:89d32de4
2024-10-07 13:37:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável.
https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch