-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ 7ec80607:128517c5
2024-12-10 05:35:45
@ 7ec80607:128517c5
2024-12-10 05:35:45Lymphatic drainage massage (LDM) is a gentle, therapeutic technique designed to promote the flow of lymph, a clear fluid that plays a crucial role in the body’s immune system and waste elimination. The lymphatic system is responsible for transporting lymph throughout the body, which contains white blood cells that help fight infection, as well as waste products that need to be filtered out. LDM aims to enhance the efficiency of this system, supporting overall health and wellness.
**Understanding the Lymphatic System ** To appreciate the benefits of lymphatic drainage massage, it's essential to understand the lymphatic system's structure and function. The lymphatic system consists of lymph nodes, lymphatic vessels, and lymphoid organs such as the spleen and thymus. Unlike the circulatory system, which has the heart to pump blood, the lymphatic system relies on the movement of muscles and joint activity to push lymph through its vessels.
Lymphatic vessels collect excess fluid, proteins, and waste products from tissues and transport them to lymph nodes, where they are filtered. The lymph nodes then produce lymphocytes, which are key in fighting infections. Maintaining a healthy lymphatic system is vital for preventing lymphedema (swelling due to lymph fluid accumulation), infections, and other health issues.
**The Technique of Lymphatic Drainage Massage ** Lymphatic drainage massage utilizes light, rhythmic, and circular motions to stimulate lymph flow and promote drainage. The techniques may vary slightly among practitioners, but the following key components are generally consistent:
1.Light Pressure: Unlike traditional massages, where deeper pressure is often applied to relieve muscle tension, LDM uses very light pressure. This gentle approach is necessary because the lymphatic vessels are located just beneath the skin's surface. 2.Rhythmic Movements: The massage involves slow, deliberate movements that mimic the natural rhythm of the lymphatic system. Practitioners often use their hands to create a "pumping" effect, which encourages lymphatic flow.
3.Specific Techniques: Techniques can include skin stretching, circular motions, and pumping actions. Areas with a high concentration of lymph nodes, such as the neck, armpits, and groin, receive focused attention.
4.Body Positioning: Clients are usually positioned comfortably, often lying down, to facilitate relaxation and maximize the effectiveness of the massage.
**Benefits of Lymphatic Drainage Massage ** Lymphatic drainage massage offers a range of potential benefits, making it a popular choice for individuals seeking both therapeutic and aesthetic advantages. Some of the key benefits include:
1.Reduced Swelling and Inflammation: By promoting lymphatic flow, LDM can help reduce swelling caused by lymphedema, post-surgical recovery, or injury. It can also alleviate inflammation in the body, contributing to faster healing.
2.Improved Immune Function: A well-functioning lymphatic system enhances the body’s ability to fight infections. LDM can stimulate the production of lymphocytes, which are essential for a healthy immune response.
3.Detoxification: The lymphatic system is integral to detoxification processes. By facilitating lymph flow, LDM aids in removing toxins, metabolic waste, and excess fluid from the body.
4.Relaxation and Stress Relief: The gentle, rhythmic nature of lymphatic drainage massage promotes relaxation and reduces stress. This can lead to lower levels of anxiety and improved overall well-being.
5.Enhanced Skin Health: LDM can improve circulation and promote a healthier appearance of the skin. Many people notice a reduction in puffiness, improved skin tone, and a general feeling of vitality after a session.
6.Alleviation of Pain: For some individuals, LDM can help reduce pain associated with certain conditions, such as fibromyalgia or arthritis. The gentle movements can ease tension and promote a sense of relief.
**Who Can Benefit from Lymphatic Drainage Massage? ** Lymphatic drainage massage can be beneficial for various populations, including: 1.Individuals with Lymphedema: Those diagnosed with lymphedema or at risk for developing it (such as after certain cancer treatments) can find LDM especially helpful in managing their condition.
2.Post-Surgical Patients: After surgeries, especially those involving the lymphatic system, LDM can aid in recovery by reducing swelling and promoting healing.
3.Individuals with Chronic Illnesses: People dealing with chronic health issues that affect their immune system or lymphatic flow may benefit from regular LDM sessions.
4.Fitness Enthusiasts and Athletes: Athletes may incorporate LDM into their recovery routine to reduce muscle soreness and promote faster recovery after intense workouts.
5.Individuals Seeking Relaxation: Anyone looking for stress relief and relaxation can enjoy the calming effects of lymphatic drainage massage.
**Contraindications and Precautions ** While lymphatic drainage massage is generally safe, certain individuals should exercise caution or avoid the treatment altogether. Some contraindications include:
1.Acute Infections: If you have an active infection or fever, it is best to postpone LDM until you have fully recovered.
2.Severe Heart Conditions: Individuals with serious heart conditions should consult their healthcare provider before undergoing LDM, as the treatment may affect circulation.
3.Kidney Problems: People with significant kidney issues may need to avoid LDM, as the technique can increase fluid movement in the body.
4.Blood Clots: If you have a history of blood clots or thrombosis, LDM should be avoided, as the increased movement of lymph could dislodge a clot.
5.Skin Conditions: Open wounds, rashes, or skin infections may be aggravated by massage, making it important to avoid treatment until the skin is healed.
**Finding a Qualified Practitioner ** If you’re considering lymphatic drainage massage, it’s essential to find a qualified practitioner who has specialized training in this technique. Look for licensed massage therapists, physical therapists, or other healthcare professionals who have completed accredited courses in lymphatic drainage. Before your session, discuss your health history and any specific concerns you may have. A good practitioner will tailor the massage to meet your individual needs, ensuring a safe and effective experience.
**Conclusion ** Lymphatic drainage massage is a gentle and effective therapy that promotes the health of the lymphatic system and offers a myriad of benefits, from reducing swelling to enhancing relaxation. Whether you’re seeking relief from a medical condition or simply want to enhance your overall wellness, LDM can be a valuable addition to your self-care routine. As with any therapeutic treatment, it’s crucial to consult with a healthcare provider or qualified practitioner to ensure that lymphatic drainage massage is appropriate for your unique situation. With the right guidance, you can experience the restorative benefits of this holistic therapy, leading to improved health and vitality.
-
 @ a012dc82:6458a70d
2024-12-10 05:32:42
@ a012dc82:6458a70d
2024-12-10 05:32:42Table Of Content
-
The Lone Star State's Embrace of Bitcoin Mining
-
Legislation and the Miner's Triumph
-
A Testament to Texan Openness
-
The Economic Implications
-
The Global Perspective
-
Conclusion
-
FAQ
In the vast expanse of the digital age, where boundaries are constantly being redrawn, Texas emerges as an unlikely hero. The state, with its deep-rooted traditions and rugged landscapes, has become a beacon for the future of digital currency. As the world grapples with the implications of decentralized finance, Texas stands tall, bridging the gap between the old and the new. This is the story of how the Lone Star State became the epicenter of the Bitcoin mining revolution.
The Lone Star State's Embrace of Bitcoin Mining
It's not every day that a state becomes a hotspot for a global phenomenon, especially one as groundbreaking as Bitcoin mining. But Texas, with its vast landscapes and iconic cowboy culture, has done just that. The state, known for its oil rigs and cattle ranches, has now become synonymous with the hum of Bitcoin mining rigs. It's like the Gold Rush of the 21st century, but instead of panning for gold, folks are mining digital currency.
Legislation and the Miner's Triumph
Now, you might be wondering, how did Texas, of all places, become this global mecca for Bitcoin mining? Well, it's a tale of business, politics, and a bit of good ol' Texan spirit. For instance, there was this proposed legislation, SB 1751, that had the potential to throw a wrench in the works. This bill, which breezed through the state senate initially, aimed to cut down the incentives miners received from the power grid and put an end to mining tax abatements. Just to give you a sense of the scale, this could've set Riot back by a whopping $30 million! But here's where the story takes a twist. After the bill made its way through the Senate, the mining industry didn't just sit back and accept their fate. Oh no, they took the bull by the horns. They met with politicians, laid out their case, and made it clear how beneficial they were to the grid. And guess what? Their efforts bore fruit. The bill, which once seemed like a sure thing, met its end in the House. And boy, did the miners celebrate that victory!
A Testament to Texan Openness
The relationship between Texas and the Bitcoin mining community is unique. It's not just about business; it's about understanding, collaboration, and mutual respect. Regulators in Texas have been incredibly receptive to Bitcoin miners, recognizing the myriad benefits these miners bring to the grid. Texas has opened its arms wide, welcoming an industry that's reshaping the global financial landscape.
The Economic Implications
Beyond the hum of the mining rigs and the intricacies of legislation, there's a broader economic narrative unfolding. Texas' embrace of Bitcoin mining is not just about digital currency; it's about job creation, infrastructure development, and fostering innovation. As more miners set up shop, local economies benefit, and the state solidifies its position as a hub for technological advancement.
The Global Perspective
The world is watching, and Texas is setting a precedent. Other states and countries are taking note of how Texas has managed to integrate Bitcoin mining into its economic and legislative framework. The state's success story serves as an inspiration for regions looking to tap into the potential of digital currencies and the industries they spawn.
Conclusion
The tale of how Texas, with its rich history and tradition, has become a beacon for the future of finance is a testament to the state's adaptability, its willingness to evolve, and its undying spirit of enterprise. As the world continues its march towards a digital future, Texas stands tall, not just as a participant but as a leader. The future is not just bright; it's digital.
FAQ
What's the significance of Texas in the Bitcoin mining industry? Texas has emerged as a global hotspot for Bitcoin mining, attracting miners with its favorable regulations and infrastructure.
How did Texas respond to the proposed SB 1751 legislation? While the bill initially passed the Senate, it was later rejected in the House after miners and industry representatives made their case.
Why are regulators in Texas supportive of Bitcoin miners? Texas regulators recognize the economic benefits and technological advancements that Bitcoin miners bring to the state.
Is Texas' Bitcoin mining boom just about digital currency? No, it's also about job creation, infrastructure development, and fostering innovation in the state.
How is Texas influencing other regions regarding Bitcoin mining? Texas' success in integrating Bitcoin mining is serving as a role model for other states and countries looking to tap into the potential of digital currencies.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 502ab02a:a2860397
2024-12-10 05:07:54
@ 502ab02a:a2860397
2024-12-10 05:07:54 เปิดวาร์ปอีกแล้วววว !!!
เปิดวาร์ปอีกแล้วววว !!!เนย จากนมแบบ Non Pasteurise กลับมาแล้ว เป็นเนยที่ใช้คำว่า Grand Cru(กรองด์ ครู) เนยเทพที่ใช้นมจาก บริตตานี ของ Le Gall
Grand Cru เป็นคำภาษาฝรั่งเศสที่แปลตรงตัวว่า “แหล่งผลิตที่ยอดเยี่ยม” หรือ “ชั้นดีเยี่ยม” ถ้าเป็นไวน์ก็คือ ไวน์ชั้นยอด ไวน์ Grand Cru Classé จะเป็นที่รู้กันในวงการไวน์
ดูเส้นที่เนยนะครับ นี่คือไม้ตบเนยให้เป็นก้อนแบบโบราณเลยนะ

เล่าประวัติ Le Gall ให้เพื่อความอิน ในการกินครับ เมื่อปีค.ศ. 1923 คุณ Jean-Marie Le Gall ตอนนั้นเขาอาศัยอยู่ที่ rue Jules Noel ทางที่จะมุ่งหน้าไปยังจตุรัส Locronan (โลโครนัน ) ใน Quimper (แก็งแปร์) แคว้น Brittany (บริตตานี) ฝรั่งเศส เป็นอีกดินแดนหนึ่งที่ขึ้นชื่อเรื่องคุณภาพของนม
เขาเริ่มต้นจากอาชีพ trader โดยการนำเนยและไข่ที่ได้มาจากสวน ไปขายในตลาดใหญ่ของเมืองบริตตานี และค่อยๆเก็บเล็กผสมน้อยทำให้เขาเริ่มรวบรวมครีมที่ปั่นแล้ว (Cream churned) จากฟาร์มมาทำเป็นเนยเพื่อจำหน่าย แล้วสินค้าของ Le Gall ก็เริ่มเจาะกลุ่มลูกค้าที่มีความต้องการมองหาสินค้าท้องถิ่นอันเลอค่าแท้ๆมากขึ้นด้วยคุณภาพสินค้า จึงตัดสินใจเก็บรักษาเทคนิคการปั่นถังที่ต้องใช้ฝีมือความปราณีตสูง (barrel chruning) สืบสานการทำเนยด้วยวิธีนี้ต่อไปไม่เปลี่ยนแปลง

ในระหว่างช่วงปี ‘70 และ ‘80 Le Gall ก็ได้พัฒนาการผลิตเนยและครีมอย่างต่อเนื่องทั้งใน บริตตานี และกินพื้นที่ทางฝั่งตะวันตกของฝรั่งเศสเกือบทั้งหมด จนกระทั้งในปี 1992 ก็ได้ชื่อว่าเป็นบริษัทแรกๆที่มุ่งมันในการทำเกษตรอินทรีย์ อย่างแท้จริงทั้งด้านการลงทุนและเข้าไปมีส่วนร่วมกับชุมชนการเกษตรท้องถิ่น
เนย Le Gall มี 2 ประเภท คือ กลุ่มที่เป็น Lactic butter ที่ผลิตด้วยกรรมวิธีสมัยใหม่ (ห่อสีขาว) และกลุ่มห่อสีๆที่เป็น artisan butter หรือกลุ่มดรัมเชิร์น ที่ผลิตด้วยกรรมวิธีดั้งเดิมโดยใช้ถังปั่น
ซึ่งวิธีผลิตเนยแบบดั้งเดิมนี้มีข้อดีที่ขั้นตอนการปั่นอย่างช้าๆจะทำให้ครีมสดๆได้เนยคุณภาพยอดเยี่ยม นุ่มละมุนเนียนเป็น texture อย่างที่เป็นอยู่นอกจากนี้ผลิตภัณฑ์ของ Le Gall ทุกตัวจะต้องผ่านการตรวจสอบจาก Master Buttermaker ของ Le Gall เองอยู่ตลอดเวลา
อย่างที่พวกเขาพูดเสมอๆว่า “เราไม่ได้เปลี่ยนอะไรเลย มันเลยสร้างความแตกต่าง” โคตรคราฟท์ ชัดเจนและลงตัวไหมล่ะ 5555 รู้แล้วใช่มะ ทำไมผมชอบเลอแกล

เช่นกันตัวเนย Le Gall Grand Cru นี้จัดอยู่ในอันดับท้อปๆของ lineup ซึ่งเป็นเนยผลิตจากนมดิบสดที่ไม่ผ่านการพาสเจอร์ไรซ์ หมักบ่มกว่า 15-18 ชั่วโมง โดยใช้กรรมวิธีดั้งเดิมของชาวฝรั่งเศสแท้ๆคือ Drum Churned ค่อยๆปั่นในถังจนได้เนยที่อ่อนนุ่มคุณภาพดีตามที่กล่าวไว้ข้างต้น
ด้วยความที่ผลิตจากนมดิบนั่นหมายถึงว่ามันยังคงมีจุลินทรีย์อยู่ไม่ถูกฆ่าไปด้วยกรรมวิธีพาสเจอร์ไรซ์นั่นเอง
ผลที่ได้ออกมาคือเนยที่มีความเข้มข้น มิติของกลิ่นหอมฟุ้งในกระพุ้งปาก ฉ่ำชื่นรื่นอุรา มีกลิ่นหอมคงค้างในปากและลำคอ (after taste)
เนยรุ่นนี้เมื่อก่อนอาจต้องบินไปซื้อถึงฝรั่งเศส เดี๋ยวนี้ทาง KCG นำเข้ามาจำหน่ายแล้ว ต้องซื้อตรงจาก KCG เท่านั้นด้วย
ซื้อผ่านทาง Line Official Account ของ KCG online ซึ่งเปิดบริการ Line MyShop เอาไว้รองรับเป็นที่เรียบร้อย
https://shop.line.me/@kcgonline
เฮียจะใช้เนยตัวนี้ทำ Rustic Butter Cake : Le Gall Grand Cru Series รอบนี้ครับ
pirateketo
ตำรับเอ๋
siripun
-
 @ a80fc4a7:dc80ebd1
2024-12-10 07:40:32
@ a80fc4a7:dc80ebd1
2024-12-10 07:40:32I have noticed a pattern lately that makes me kind of sad, It seems Photography and Real photos are becoming harder and harder to find these Days, With the rise of AI And Computer generation. If you go to Google or any Search engine and simply Search "Nature Photos" you will get largely AI Photos or heavily altered images, it's almost as if it was programmed this way, is nobody taking real photos anymore? Or is Google simply trying to replace real art and real photos with AI? This honestly puzzles me and worries me, has anyone else noticed this? Or is it just me. Was it always this way on Google?
-
 @ eac63075:b4988b48
2024-10-20 13:49:55
@ eac63075:b4988b48
2024-10-20 13:49:55Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.
Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.
The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.
Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.
The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
Conclusion of the Technical Debate
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.

Table reference: Patrick Breyer - Chat Control in 23 September 2024
Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.
The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
Conclusion of the Debate
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.
User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
Summary of Consequences
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.
The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.
Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ d5c3d063:4d1159b3
2024-12-10 03:26:59
@ d5c3d063:4d1159b3
2024-12-10 03:26:59ถ้าจะบอกว่าลึกๆ แล้ว เราทุกคน "เห็นแก่ตัว" คุณจะเชื่อไหม?
คำถามนี้อาจจะฟังดูแรง แต่ อดัม สมิธ บิดาแห่งเศรษฐศาสตร์กลับมองว่า ความเห็นแก่ตัวเป็นส่วนหนึ่งของธรรมชาติมนุษย์ ที่ฝังรากลึกอยู่ในตัวเราแทบทุกคน เป็นแรงขับเคลื่อนพื้นฐาน ที่ผลักดันให้เราแสวงหาสิ่งต่างๆ เพื่อตอบสนองต่อความต้องการของตัวเอง !(image)[!(image)[https://i.nostr.build/WOdJvldZegFAlyXJ.jpg]] แต่... อย่าเพิ่งด่วนตัดสินว่า สมิธ กำลังบอกว่ามนุษย์เลวร้าย หรือเห็นแก่ได้เพียงอย่างเดียว ในหนังสือเล่มแรกของเขา "The Theory of Moral Sentiments" สมิธ ไม่ได้แค่ชี้ให้เห็นถึง "ความเห็นแก่ตัว" ในตัวมนุษย์ แต่เขาอธิบายอย่างละเอียดถึงความซับซ้อน และความขัดแย้ง ในธรรมชาติของมนุษย์ ที่ทำให้เราเป็นสัตว์สังคมที่มีทั้งด้านมืด และด้านสว่าง
เขาเชื่อว่ามนุษย์ไม่ได้ถูกขับเคลื่อนด้วยความเห็นแก่ตัวเพียงอย่างเดียว แต่ภายในจิตใจของเรายังมีความปรารถนาที่จะ "เป็นที่รัก" (loved) และ "เป็นคนที่คู่ควรกับการเป็นที่รัก" (lovely) รวมอยู่ด้วย
เราต้องการการยอมรับ การชื่นชม และความรักจากคนรอบข้าง เพื่อที่จะรู้สึกเป็นส่วนหนึ่งของสังคม และรู้สึกว่าชีวิตของเรามีคุณค่า
สมมติว่า.. นักเรียนคนหนึ่งอยากได้เกรดดีๆ เขาจะตั้งใจเรียน ทำการบ้าน สอบให้ได้คะแนนสูงๆ ไม่ใช่แค่เพื่ออวดเพื่อนหรือเอาชนะคนอื่น แต่เพราะเขาต้องการที่จะ "คู่ควร" กับเกรดดีๆ นั้น เขาต้องการให้คนอื่น "ยอมรับ" และ "ชื่นชม" ในความสามารถของเขา ความปรารถนา ที่จะเป็นที่รักและเป็นคนที่คู่ควรกับการเป็นที่รักนี่แหละ ที่ทำให้มนุษย์สามารถควบคุมความเห็นแก่ตัว และสร้างสังคมชที่น่าอยู่ขึ้นมาได้
สมิธ ไม่ได้บอกให้เราหลอกตัวเองว่าเราเป็นคนดี แต่เขาแนะนำให้มองตัวเองผ่านมุมมองของ "ผู้สังเกตการณ์ที่เป็นกลาง" (impartial spectator)
ลองจินตนาการว่า มีคนกลางที่เป็นกลางยืนมองเราอยู่ตลอดเวลา คอยสังเกตการกระทำของเรา วิเคราะห์ความคิดของเรา และสะกิดเตือนสติ เมื่อเรากำลังจะทำในสิ่งที่ไม่ถูกต้อง เช่น กำลังจะโกงข้อสอบ "ผู้สังเกตการณ์ที่เป็นกลาง" ก็จะดังขึ้นในใจเราว่า... "เฮ้ย! อย่าทำแบบนั้น มันไม่แฟร์"
ผู้สังเกตการณ์ที่เป็นกลางนี้ ก็คือมโนธรรมในใจเรานั่นเอง ที่คอยย้ำเตือนให้เราตระหนักถึงผลกระทบของการกระทำของเราต่อผู้อื่น และต่อสังคมโดยรวม การรู้จักตัวเอง ยอมรับข้อบกพร่อง และทำในสิ่งที่ถูกต้อง คือก้าวสำคัญ ที่จะทำให้เราคู่ควรกับการเป็นที่รัก และการได้รับการยอมรับจากคนรอบข้าง
แล้ว "ผลประโยชน์ส่วนตน" (self-interest) มันเกี่ยวอะไรด้วยไหม? ในหนังสือเล่มที่สอง "The Wealth of Nations" สมิธ อธิบายว่าผลประโยชน์ส่วนตนเป็นแรงขับเคลื่อนสำคัญของระบบเศรษฐกิจ คนเราทำงาน ค้าขาย ทำธุรกิจ ก็เพราะต้องการเงิน ต้องการมีชีวิตที่ดีขึ้น
สมิธ เชื่อว่าระบบตลาดเสรี จะนำพาเราไปสู่สังคมที่เจริญรุ่งเรือง ตราบใดที่คนเรามีศีลธรรม และไม่เอาเปรียบผู้อื่น "มือที่มองไม่เห็น" (Invisible Hand) ที่สมิธกล่าวถึง จะทำงานได้ก็ต่อเมื่อมนุษย์ในระบบนั้น มีจริยธรรมคอยควบคุมความเห็นแก่ตัวของพวกเขา
ถ้าทุกคน มุ่งแต่จะเอาเปรียบ โกง และทำลายซึ่งกันและกัน สังคมก็จะล่มสลาย สมิธ ยังเชื่ออีกว่า "ความสุขที่แท้จริง" ไม่ได้อยู่ที่เงินทอง แต่อยู่ที่สายสัมพันธ์ที่ดี การเป็นส่วนหนึ่งของสังคม และการได้รับการยอมรับจากคนรอบข้าง
เงินทอง ชื่อเสียง หรืออำนาจ อาจจะทำให้เรามีความสุขในระยะสั้น แต่ความสุขที่ยั่งยืน เกิดจากการที่เรารู้สึกเป็นที่รัก เป็นที่ยอมรับ และมีคุณค่าในสายตาของผู้อื่น แล้วสังคมที่ดีมันเกิดขึ้นได้อย่างไร?
สมิธ เชื่อว่าสังคมมันถูกสร้างขึ้นจากการกระทำของทุกคน Russ Roberts ผู้เขียนหนังสือ "How Adam Smith Can Change Your Life" เรียกสิ่งนี้ว่า "ระเบียบที่เกิดขึ้นเอง" (emergent order)
มันคือระเบียบที่ไม่ได้เกิดจากการออกแบบ หรือควบคุมจากส่วนกลาง แต่เกิดจากการที่ "ปัจเจกบุคคล" แต่ละคน ต่างเลือกที่จะทำในสิ่งที่ตัวเองคิดว่าดีที่สุด
เหมือนกับการจราจร ที่ไม่มีใครสั่งให้รถทุกคันต้องวิ่งไปทางเดียวกัน แต่ทุกคนเลือกที่จะทำ เพื่อไม่ให้เกิดอุบัติเหตุ เพื่อความปลอดภัย และความสะดวกสบาย ของทุกคน บนท้องถนน
สังคมที่ดี ไม่จำเป็นต้องมีใครมาควบคุม แต่เกิดจาก "เสรีภาพ" ในการเลือก และตัดสินใจของแต่ละคน ภายใต้กรอบของศีลธรรมและ จริยธรรม
เราทำดี เพราะต้องการเป็นที่รัก และต้องการเป็นคนที่คู่ควรกับความรักนั้น เมื่อคนส่วนใหญ่ทำดี สังคมก็จะดีขึ้นเองโดยไม่ต้องมีใครมาบังคับ
สมิธ มองว่ามนุษย์มีทั้งด้านมืด และด้านสว่าง ด้านมืด คือ ความเห็นแก่ตัว ความอยากเอาชนะ ความอยากได้อยากมี ด้านสว่าง คือ ความอยากทำดี ความอยากเป็นที่รัก ความอยากมีคุณค่า และด้านสว่างนี่แหละ.. ที่ทำให้โลกนี้น่าอยู่
การทำดีต่อคนรอบข้าง การช่วยเหลือผู้อื่น การยิ้มให้กับคนแปลกหน้า สิ่งเล็กๆ น้อยๆ เหล่านี้อาจดูเหมือนไม่มีความหมาย แต่มัน "ทรงพลัง" เพราะมันทำให้ "ด้านสว่าง" ของเราและคนรอบข้างเปล่งประกายออกมา มันทำให้โลกนี้ อบอุ่น และน่าอยู่ยิ่งขึ้น
ลองฝึกมองตัวเอง ผ่านมุมมองของ "ผู้สังเกตการณ์ที่เป็นกลาง" ดูนะครับ.. แล้วคุณจะเข้าใจตัวเองมากขึ้น และอย่าลืมทำดีในทุกๆ วัน รับรองว่าโลกนี้ จะน่าอยู่ขึ้นอีกเยอะอย่างแน่นอนครับ..
Siamstr #AdamSmith #InvisibleHand #selfinterest
TheWealthOfNations #TheTheoryOfMoralSentiments
-
 @ 234035ec:edc3751d
2024-12-10 01:25:32
@ 234035ec:edc3751d
2024-12-10 01:25:32The rise of UAVs
Drones, we have all heard of them, seen them, and many of us own them. Also known as UAVs (Unmanned Arial Vehicles) they come in endless different shapes and sizes, from 2inch Cinewhoop FPVs (First Person View) to large military drones like the Northrop Grumman RQ-4 Global Hawk which can fly for over 30 hours at speeds over 300mph.
In recent conflicts, most notably the ongoing Russia-Ukraine war, we have seen drones play a very significant role. The utilization of small consumer or cheaply manufactured drones for reconnaissance, dropping payloads, delivering supplies, and as "kamikaze" weapons has been well documented.
These so called Kamikaze drones have been devastatingly effective due to the asymmetry of risk on the side of the drone attacker as opposed to traditional warfare methods. The FPV pilot can sit in a secure location several miles from the enemy, and launch $500-$1,000 drones to take out signifiant infrastructure, tanks, personnel, ect. By embracing a new paradigm of warfare a smaller force with significantly less resources is able to project a disproportionate amount of power.
Outside of military use we have seen drones used for many other applications such as 3D mapping, Thermal imaging, Delivery services, agricultural uses, and choreographed displays. All of these take something that once required a human operator present and allows them to be automated. While many of these applications do still require a human operator, it is not a far stretch to imagine that, with advancements in computation and machine learning they will grow more and more hands off.
Being able to utilize a computer program to fly a pre-set flightpath over a location and generate a 3D model of it or gather thermal data is already a reality. Companies now offer docking stations which charge the drone and it can take off and land from autonomously.
The use of large swarms of drones to create arial displays has also been growing in popularity in recent years. fleets of hundreds and sometimes thousands of drones are programmed to flight in precise coordinated patterns in order to create complex shapes and images in the sky. The idea of a single computer being able to control and coordinate such a vast number of vehicles is mind boggling.
Drones in the digital revolution
The "Digital Revolution" has been talked about at great lengths by many people and generally refers to the rapid growth in computation which has lead to growth in access to information and global connectivity. This new wave has seen the dematerialization of many things in our life. E-mail, E-commerce, Social Applications, Wikipedia, Bitcoin, ect. are all examples of previously physical things being dematerialized in the digital age.
UAVs give us a bridge between the digital and physical worlds. A software program run on a computer can now deliver a package to someone across town who just placed an order on a website. They can be used to inspect properties or other physical assets from a distance or to spray crops on large pieces of land.
Along with these "civilian" applications it is easy to imagine a future where drones have an even larger significance in warfare. If you combine the drone swarms used in light displays with the kamikaze drones being used in Ukraine, you get a very scary proposition. If warfare becomes increasingly autonomous, manpower will matter far less and resources will matter much more. A small wealthy nation may be able to wield significant power through their UAV systems.
Decentralization of UAVs
When considering the potential future with respect to drones and drone weapons systems, it is easy to become concerned with a potential Orwellian future where the government has patrol drones and can arrest you autonomously for your thought crimes. While government tyranny is always a serious concern, I am hopeful for the future.
 The second amendment in the United States is designed to ensure that the citizens have enough power to resist a tyrannical government. I see drones as a force which levels playing fields, the average individual has access to the same drones which are being used in conflict right now in Ukraine. With the digital revolution we have also seen 3D printing grow massively in popularity and utility and individuals have been experimenting with 3D designs for firearms and drones. This further democratizes access to self defense allowing many more individuals access to the tools necessary to defend themselves in the physical world through a digital file.
The second amendment in the United States is designed to ensure that the citizens have enough power to resist a tyrannical government. I see drones as a force which levels playing fields, the average individual has access to the same drones which are being used in conflict right now in Ukraine. With the digital revolution we have also seen 3D printing grow massively in popularity and utility and individuals have been experimenting with 3D designs for firearms and drones. This further democratizes access to self defense allowing many more individuals access to the tools necessary to defend themselves in the physical world through a digital file. The future is going to be a very interesting place. I believe that the lines between the physical and digital worlds will continue to blur and that unmanned aircraft are going to play a significant role in that transformation.
-
 @ 9bcc5462:eb501d90
2024-12-10 01:12:39
@ 9bcc5462:eb501d90
2024-12-10 01:12:39Beyond Legacy
Louis Sullivan was a legendary architect, known as the "father of skyscrapers". He was among the first to embrace new tech, like steel frames and elevators which changed infrastructure development forever. Despite this, people want to see him as a cautionary tale since he wasn’t financially successful in his later years. Nikola Tesla too, suffered a lack of funds when he died. Even when brilliance doesn't always equal wealth, let's not overlook the fact that Sullivan's buildings still stand strong and kiss the sky. Meanwhile, electric cars today bear Tesla's name. These men were ahead of their time and noble for it. A testament that bank accounts die and visions live on.
Frank Lloyd Wright was Sullivan's protege and battled his fair share of demons as well, including scandals, professional criticism and debts until the day of his death. Yet, he was loyal to his mentor's vision of "form follows function" despite the brutal criticisms of it at the time. Like Sullivan, he refused the status quo of mimicking the ornamental European traditions. Instead, he developed his own "organic architecture" style, integrating the site and surroundings with the building. Using the aesthetic of horizontal lines, it would become known as his signature "Prairie Style". Wright would go on to produce innovative homes like Falling Water and Taliesin, which now serve as timeless beacons of unique American architecture.
Their memory challenges me: Do I have the cojones to put everything on the line for my startup, as they did for their vision? Although Learning Producers is in the field of learning experience design, we've been guided by "form follows function" in a landscape hellbent on mimicking conventional models. Bootstrapping as a first time founder feels like entering battle, armor clanking and shield raised. My enemy, a Goliath of stagnation.
I'm reminded in the scene from the movie Troy, where Achilles is made aware of a large enemy soldier he must combat. A boy commented to him, "The Thessalonian you're fighting, he's the biggest man I've ever seen. I wouldn't want to fight him." To which Achilles savagely replies, "That's why no one will remember your name."
-
 @ 4ba8e86d:89d32de4
2024-10-07 13:37:38
@ 4ba8e86d:89d32de4
2024-10-07 13:37:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável.
https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ ea6958bd:77925591
2024-12-10 00:29:11
@ ea6958bd:77925591
2024-12-10 00:29:11nprofile1qqsr76x7m6q4f8xqs386lefg79t5k50qjhn5j86x30vk38u8w7dms8gm5vh8rhello
-
 @ 6389be64:ef439d32
2024-12-09 23:50:41
@ 6389be64:ef439d32
2024-12-09 23:50:41Resilience is the ability to withstand shocks, adapt, and bounce back. It’s an essential quality in nature and in life. But what if we could take resilience a step further? What if, instead of merely surviving, a system could improve when faced with stress? This concept, known as anti-fragility, is not just theoretical—it’s practical. Combining two highly resilient natural tools, comfrey and biochar, reveals how we can create systems that thrive under pressure and grow stronger with each challenge.
Comfrey: Nature’s Champion of Resilience
Comfrey is a plant that refuses to fail. Once its deep roots take hold, it thrives in poor soils, withstands drought, and regenerates even after being cut down repeatedly. It’s a hardy survivor, but comfrey doesn’t just endure—it contributes. Known as a dynamic accumulator, it mines nutrients from deep within the earth and brings them to the surface, making them available for other plants.
Beyond its ecological role, comfrey has centuries of medicinal use, earning the nickname "knitbone." Its leaves can heal wounds and restore health, a perfect metaphor for resilience. But as impressive as comfrey is, its true potential is unlocked when paired with another resilient force: biochar.
Biochar: The Silent Powerhouse of Soil Regeneration
Biochar, a carbon-rich material made by burning organic matter in low-oxygen conditions, is a game-changer for soil health. Its unique porous structure retains water, holds nutrients, and provides a haven for beneficial microbes. Soil enriched with biochar becomes drought-resistant, nutrient-rich, and biologically active—qualities that scream resilience.
Historically, ancient civilizations in the Amazon used biochar to transform barren soils into fertile agricultural hubs. Known as terra preta, these soils remain productive centuries later, highlighting biochar’s remarkable staying power.
Yet, like comfrey, biochar’s potential is magnified when it’s part of a larger system.
The Synergy: Comfrey and Biochar Together
Resilience turns into anti-fragility when systems go beyond mere survival and start improving under stress. Combining comfrey and biochar achieves exactly that.
-
Nutrient Cycling and Retention\ Comfrey’s leaves, rich in nitrogen, potassium, and phosphorus, make an excellent mulch when cut and dropped onto the soil. However, these nutrients can wash away in heavy rains. Enter biochar. Its porous structure locks in the nutrients from comfrey, preventing runoff and keeping them available for plants. Together, they create a system that not only recycles nutrients but amplifies their effectiveness.
-
Water Management\ Biochar holds onto water making soil not just drought-resistant but actively water-efficient, improving over time with each rain and dry spell.
-
Microbial Ecosystems\ Comfrey enriches soil with organic matter, feeding microbial life. Biochar provides a home for these microbes, protecting them and creating a stable environment for them to multiply. Together, they build a thriving soil ecosystem that becomes more fertile and resilient with each passing season.
Resilient systems can withstand shocks, but anti-fragile systems actively use those shocks to grow stronger. Comfrey and biochar together form an anti-fragile system. Each addition of biochar enhances water and nutrient retention, while comfrey regenerates biomass and enriches the soil. Over time, the system becomes more productive, less dependent on external inputs, and better equipped to handle challenges.
This synergy demonstrates the power of designing systems that don’t just survive—they thrive.
Lessons Beyond the Soil
The partnership of comfrey and biochar offers a valuable lesson for our own lives. Resilience is an admirable trait, but anti-fragility takes us further. By combining complementary strengths and leveraging stress as an opportunity, we can create systems—whether in soil, business, or society—that improve under pressure.
Nature shows us that resilience isn’t the end goal. When we pair resilient tools like comfrey and biochar, we unlock a system that evolves, regenerates, and becomes anti-fragile. By designing with anti-fragility in mind, we don’t just bounce back, we bounce forward.
By designing with anti-fragility in mind, we don’t just bounce back, we bounce forward.
-
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 4ba8e86d:89d32de4
2024-12-09 23:12:11
@ 4ba8e86d:89d32de4
2024-12-09 23:12:11A origem e o desenvolvimento do SearXNG começaram em meados de 2021, após o fork do conhecido mecanismo de metabusca Searx, inspirado pelo projeto Seeks. Ele garante privacidade básica ao misturar suas consultas com outras pesquisas, sem armazenar dados de busca. O SearXNG pode ser adicionado à barra de pesquisa do navegador e também configurado como mecanismo de busca padrão.
Embora o SearXNG não ofereça resultados tão personalizados quanto o Google, ele não gera um perfil sobre você. Controle Total sobre Seus Dados: com o SearXNG, você tem controle absoluto sobre suas informações de pesquisa. O histórico de busca é totalmente opcional e pode ser ativado ou desativado conforme sua preferência. Além disso, é possível excluir qualquer entrada a qualquer momento, garantindo sua privacidade. Resultados de Fontes Diversificadas: o SearXNG agrega informações de mais de 70 fontes diferentes, proporcionando uma pesquisa mais abrangente e relevante. Em vez de se limitar a uma única fonte, você obtém uma visão mais ampla e detalhada das informações disponíveis.
O SearXNG respeita sua privacidade, nunca compartilha dados com terceiros e não pode ser usado para comprometer sua segurança.
O SearXNG é um software livre com código 100% aberto, e qualquer pessoa é bem-vinda para contribuir com melhorias. Se você valoriza a privacidade, deseja ser um usuário consciente ou acredita na liberdade digital, faça do SearXNG seu mecanismo de busca padrão ou instale-o em seu próprio servidor.
O SearXNG reconhece sua preocupação com logs, por isso o código-fonte está disponível para que você possa executar sua própria instância:
https://github.com/searxng/searxngAdicione sua instância à lista de instâncias públicas.
https://searx.space/
para ajudar outras pessoas a recuperar sua privacidade e tornar a internet mais livre. Quanto mais descentralizada for a internet, maior será a liberdade para todos!
Lista de Instâncias Públicas https://searx.space/
Documentação de Instalação https://docs.searxng.org/admin/installation.html#installation
SeaxrXNG : Instalação , configuração e publicação.
https://youtu.be/zcrFPje6Ug8?si=oOI6dqHfHij51rvd
https://youtu.be/8WHnO9gJTHk?si=-5SbXUsaVSoSGpps
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 2de0ffa0:b6bb72cc
2024-12-09 23:11:31
@ 2de0ffa0:b6bb72cc
2024-12-09 23:11:31🧠 Quote of the Week
“The experiment was to see how easy it was to split a large file into chunks, then upload those chunks to multiple blossom servers and reassemble them on another computer”. - npub1ye5ptcxfyyxl5vjvdjar2ua3f0hynkjzpx552mu5snj3qmx5pzjscpknpr from nevent1qqsx9l2j7g5t8llkm8r9d987er3hwj0gmrq4k09d88hzvq4ujysmksgpp4mhxue69uhkummn9ekx7mqpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqgszv6q4uryjzr06xfxxew34wwc5hmjfmfpqn229d72gfegsdn2q3fgjwk96y
🧡 Top Nostr News
🎥 Decentralized Video Archiving with Novia
Novia provides a decentralized alternative to the centralized platforms dominating video content today. By using the Nostr ecosystem, Novia allows users to store videos locally, while only sharing essential metadata on Nostr relays. How Novia Works: Local Storage, Global Access: Videos are stored locally, with metadata like thumbnails and info shared via Nostr. Video Requests and Recovery: Users can request videos, which are then retrieved and uploaded to Blossom servers for access. Personalized Archiving: Users can build their own video archives and run services to manage them on their devices. Novia empowers users with a web app for browsing and a service for hosting personal video collections, offering a decentralized approach to video storage. Why Novia is Needed: Today, video content is monopolized by centralized platforms, limiting users' control. Novia changes this by enabling anyone to archive, share, and retrieve videos in a decentralized manner. The Vision: Novia is for video enthusiasts and archivists who want to preserve content while maintaining privacy. Using the Nostr protocol, Novia ensures video files remain local, with uploads only occurring when requested by users. Get Started: For more details and to contribute, visit the official Novia 🔗 GitHub repository. 🔗 Event: nevent1qqszpw0pa3u9ey6g6h65m3rztux0t0t38ddeslp55748rhwatjl40egpp4mhxue69uhkummn9ekx7mqzyzad8jq5fwtzut77fjfsrv09exp64xahq7tgw59lyxtarach7u0kknhg9wg
🌍 Nostr LATAM Tour
The Nostr LATAM Tour that happened the last couple of weeks has been an incredible success, thanks to the hard work and enthusiasm of npub1hz5alqscpp8yjrvgsdp2n4ygkl8slvstrgvmjca7e45w6644ew7sewtysa and the passionate Nostr community! 🎉 Over the last few weeks, they’ve brought Nostr to South America with events in Buenos Aires, São Paulo, and El Salvador. It was an unforgettable experience that highlighted the power of decentralized communication without the middlemen. At each event, the team onboarded dozens of new users, introducing them to the Nostr protocol and helping them make their very first posts. The community shared useful tips for newcomers, and one of the key things highlighted was the importance of hashtags like #introduction, which allows the broader Nostr ecosystem to engage with new users. The workshops were full of energy, with everyone excited to dive into this new world. People were thrilled by how easy it was to create their first Nostr account – some were up and running in less than a minute! The welcoming, supportive atmosphere throughout the events proved just how much the Nostr community cares about helping each other. It was inspiring to see so many people eager to join the movement, exchange ideas, and be part of something special. The buzz was palpable, and the spirit of collaboration was alive throughout each session. This was an amazing start, and there's so much more to come. The energy and passion from everyone involved will continue to drive the growth of Nostr across the region. Check out the video to relive the highlights of this journey and see the impact for yourself! 🙌 🔗 Event note12rjgue5g7uqtrkh2lv5wd44k900qglqe9yc942rmdydq7aaym3mqmt7a8v
📺 Nostr on TV
Why Nostr Will Win with npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr -
npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr is the founder and the CEO of primal.net. In this episode he discusses how Primal is enhancing the Bitcoin and Nostr experience by balancing sovereignty with user accessibility. The conversation covers the challenges between custodial vs. non-custodial wallets, the impact of the zapping economy on online interactions, and the role of mobile apps in mass adoption. npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr explains how integrating Bitcoin into everyday apps and using Nostr’s web of trust can help tackle issues like spam while maintaining decentralized values. Could this approach onboard millions to Bitcoin seamlessly? Tune in to explore the game theory of Bitcoin in action.
🔗 video : https://www.youtube.com/watch?v=wsc2pRPuj3E
🛠️ Tools, Updates, and Releases
Pokey v0.1.2 - alpha
Pokey is a handy Android app that gives you notifications of new replies, mentions, zaps, DM’s and so. This newest release gives multi account support, so when you have multiple Nostr profiles you can receive notifications of all of them. Developed by: npub1v3tgrwwsv7c6xckyhm5dmluc05jxd4yeqhpxew87chn0kua0tjzqc6yvjh Source: https://github.com/KoalaSat/pokey
Amethyst v0.93.1 Update
Amethyst, a popular Android Nostr client, now supports NIP-22 for interactive story replies, improving comment threading. The DVM feed displays service costs and customization options. The update also fixes bugs related to Satellite's blossom uploads, video feeds, and enhances Hex encoder performance. Developed by: npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z Source: https://github.com/vitorpamplona/amethyst
Servus v0.1.4
Servus is a minimalist social media server for personal websites, combining a CMS, Nostr relay, and file hosting into one executable. It lets you fully control your content and data, without relying on databases or web servers. It supports file hosting with Blossom and Nostr NIP-96 HTTP File Storage Integration, ensuring privacy and ownership. The 0.1.4 release improves Nostr filters.
Ideal for tech-savvy users who want a simple, self-hosted website solution with Nostr integration. It's not for beginners, as it requires basic knowledge of the command line and DNS.
Developed by: npub1xvdg698f7fqdu2qu5azwa6fu8xhw8p0zpp272qe7qex7kpn5ks5su3am9l Source: https://github.com/servus-social/servus
Corny Chat v2024.11
Corny Chat is an open-source audio space for real-time communication, integrating Nostr and Lightning to foster interactive audio rooms and personalized conversations. This release introduces Nostr Custom Emojis, enabling sticky emojis and reactions for a more engaging experience. The Animation Toggle improves performance on slower devices, making the app more accessible for all users.
Developed by: npub1yx6pjypd4r7qh2gysjhvjd9l2km6hnm4amdnjyjw3467fy05rf0qfp7kza Source: https://github.com/vicariousdrama/cornychat
Snort v0.3.0
Snort is a Nostr webclient designed for streamlined and efficient use, offering smooth performance and optimized functionality across multiple devices.
This release includes small performance tweaks, ensuring faster and more responsive interactions, making the app smoother and more efficient for users.
Developed by: npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49 Source: https://snort.social/
Voyage v0.17.1
Voyage is a lightweight Android client with a Reddit-like UI, designed for seamless browsing and organization. This release enhances data integrity by preventing empty lists from being saved and treating empty list pairs as deleted. It also resolves a critical issue causing crashes from duplicate IDs, ensuring improved stability and reliability for users.
Developed by: npub1useke4f9maul5nf67dj0m9sq6jcsmnjzzk4ycvldwl4qss35fvgqjdk5ks Source: https://github.com/dluvian/voyage
Amber v3.0.1
Amber is a Nostr event signer for Android.
This update introduces a new design, removes the push notification server, and improves permissions management. It also includes bug fixes for crashes, layout issues, and relay connectivity. Key new features: set a custom PIN for security, copy public keys easily, and better handling of NostrConnect messages and rejected events.
Developed by: npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 Source: https://github.com/greenart7c3/Amber
Alby Lightning Browser Extension v3.10.0 – "Ice Clouds over a Red Planet"
Alby is a webbrowser extension for managing Nostr signing, Lightning payments and wallets. Version v3.10.0 introduces an Alby Hub Connector for seamless wallet upgrades, a notification banner for upgrade alerts, and a fee credits feature for managing transaction costs.
Alby is shifting toward its new self-custodial solution, the Alby Hub. If you’re using an Alby shared custodian wallet, heads up—big changes are coming. Starting January 4, 2025, Alby will discontinue its shared wallet service. If you have funds there, you’ll need to act before that date. This new option puts you in full control of your Bitcoin and Lightning payments. Plus, Nostr Wallet Connect is integrated right into the Hub for a smoother experience, and if you opt for the cloud version, you can even set up a custom Lightning and Nostr address. No more limits—and no more relying on a shared service.
Developed by: npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm Source: https://github.com/getAlby/lightning-browser-extension
Nostr Web Services (NWS) v0.2.0 - Pre-release
Nostr Web Services (NWS) is a tool designed to route TCP traffic over Nostr relays, enabling secure and reliable communication within a decentralized network. It uses the Nostr protocol, known for its censorship resistance, to allow users to establish connections and transmit data efficiently. The v0.2.0 (Pre-release) update of NWS brings improvements like better context handling, enhanced security with the switch from NIP-04 to NIP-44, and fixes to the dial function. It also updates public exit node routing, refactors exit node creation, and restructures the protocol package for better scalability and maintenance, improving stability and performance. 🔗 GitHub: https://github.com/asmogo Developed by: Npub16uq0cyx52lh2unczavzdw9dq2jphu69zutgpp9cnstz7zqtdex0qmcxla3.
🎁 Developer Tools, updates and Guides
Cherry Tree - Chunked blobs on Blossom 🌸
For developers working with files such as media, there is a pull request by Main blossom developer npub1ye5ptcxfyyxl5vjvdjar2ua3f0hynkjzpx552mu5snj3qmx5pzjscpknpr that explores how to split large files into chunks, upload them to multiple Blossom servers, and reassemble them on another computer. The experiment demonstrated that Blossom servers treat these chunks as ordinary binary blobs uploaded from a public key, with no inherent understanding that they are part of a larger file. However, this method isn’t inherently private since servers could potentially examine and piece together the data. Adding encryption to the client-side blobs would enhance privacy. It’s important to note that this is currently a PR and has not yet been accepted within the Blossom protocol. For more background, try exploring the author's post or discussing it with them. You can review the PR for details at GitHub: github.com/hzrd149/blossom/pull/51, or experiment using public Blossom servers listed at blossomservers.com. The project uses several packages, including Applesauce (hzrd149.github.io/applesauce/), rx-nostr (penpenpng.github.io/rx-nostr/en/), and blossom-client-sdk (npmjs.com/package/blossom-client-sdk). Author Public Key: npub1ye5ptcxfyyxl5vjvdjar2ua3f0hynkjzpx552mu5snj3qmx5pzjscpknpr
🚀 Introducing nostr-nsec-seedphrase: Simplifying nSec Handling for Developers! 🔑
Are you a Nostr developer tired of manually copying and pasting nSec seed phrases? Look no further! The nostr-nsec-seedphrase npm package streamlines the process, making it easier to save and work with nSecs. Whether you're developing a new app or enhancing an existing one, this tool offers simple seedphrase functionality, including HEX-to-nSec conversions—no more repetitive code. Explore the open-source project on GitHub: https://github.com/HumanjavaEnterprises/nostr-nsec-seedphrase.
NostrDVMstars v1.0.4 - Latest Release
NostrDVMstars is a Python-based Nostr NIP90 Data Vending Machine framework. Nostr can act as a marketplace for data processing, where users request jobs to be processed in certain ways (e.g., "speech-to-text", "summarization", etc.), but they don't necessarily care about "who" processes the data. Version v1.0.4 fixes a bug related to NIP44 encryption, improving bot stability and functionality. Developed by: npub1nxa4tywfz9nqp7z9zp7nr7d4nchhclsf58lcqt5y782rmf2hefjquaa6q8 Source: https://github.com/believethehype/nostrdvm
Nostr Spring Boot Starter v0.0.4
Nostr Spring Boot Starter is a framework for building Nostr-based applications with Spring Boot. This release introduces key updates, including support for Repost Events (NIP18), Nostr URI scheme (NIP21), and Relay List Metadata (NIP65). It also adds a new nostr-persona module and improves connection timeouts. Some breaking changes in method signatures for relay and event handling are included, making this update crucial for developers looking to take full advantage of the latest Nostr features.
Developed by: npub1zcuquyvd78s5le34gkq2uxjhq2xuh92wldddjjxkeldzp9ss6lrsa88ezf Source: https://github.com/theborakompanioni/nostr-spring-boot-starter
Nostr PHP v1.5.2
Nostr PHP is a PHP library designed for Nostr-based applications. This release addresses a critical issue with the gmp_pow method in the phpecc package, fixing the bug reported in PHP issue #16870. The update improves stability and compatibility, ensuring smoother functionality for developers using the package. Developed by: npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe Source: https://github.com/nostrver-se/nostr-php
🔥 Community Highlights
🎙️ Thank For Nostr Podcast Highlights
npub1q6mcr8tlr3l4gus3sfnw6772s7zae6hqncmw5wj27ejud5wcxf7q0nx7d5, a Sovereign Engineering alum, OpenSats grantee, and Nostr developer. Also highlighted is npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn, the creator of the Coracle Nostr client and an OpenSats grantee. npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn focuses on designing healthier social networks and advancing this vision through Nostr. In the latest episode of the Thank For Nostr Podcast, npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn shares insights into his vision for a decentralized and meaningful social network, the principles guiding this work, and the role of Coracle in making it a reality. The podcast is produced by TGFB Media, an organization dedicated to educating Christians on Bitcoin’s potential for the glory of God and the good of humanity.
🌱 Ecosystem Growth
Nostr is growing fast! There are now over 45 Nostr clients, and relays are running in more than 40 countries around the globe.
During this week: Total zaps: 3,945,943 , compared to 3,909,750 zaps the week before Total posts: 441,169,786 , compared to 434,841,953 posts the week before Profiles with bio users: 8,133,703 , compared to 7,763,964 Profiles with bio users the week before
Many thanks to stats.nostr.band by npub1xdtducdnjerex88gkg2qk2atsdlqsyxqaag4h05jmcpyspqt30wscmntxy for providing these insights.
🎓 Educational Resources
No updates this week. If you have some input for the next recap about recent educational resources, please share it and I will add it in the next recap.
📅 Upcoming Events
Nostr at Tech Tuesday
📅 Date: Tuesday, December 17, 2024 - 7 PM – late EST 📍 Location: Seats2meet.com Utrecht CS, The Netherlands 🤹♀️ Organizers: npub1l77twp5l02jadkcjn6eeulv2j7y5vmf9tf3hhtq7h7rp0vzhgpzqz0swft, npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe and npub1w98ems6ryhpv7zvmhwp5sv65p0pwrnvzw4lucn0ch776qan9ntdstscwpx 🔗 Tech Tuesday
Join npub1hw6amg8p24ne08c9gdq8hhpqx0t0pwanpae9z25crn7m9uy7yarse465gr at Tech Tuesday for an insightful session on Nostr, covering Epoxy (a framework for integrating technologies), Tollgate (a checkpoint mechanism for validating actions), and eCash (digital cash for secure transactions) as a shared topic. Don’t miss out on this great opportunity to learn more about Nostr technologies!
📅 Date: Tuesday, December 17, 2024 - 6:30 PM – 9:00 PM
📍 Location: Toronto, ON 🤹♀️ Organizer: npub1ek36rza32zjc8pec8daz6veyywv55xtemzaxr0saymd04a4r66eqpxphdl 🔗 https://www.meetup.com/blockchain-developers-canada/events/304910752 This beginner-friendly meetup will be a tutorial that will teach participants to create Nostr accounts, send and query events, send encrypted events, and obtain a Nostr Internet Identifier. The session will be in JavaScript, and attendees are encouraged to install Node.js and Git beforehand.
FOSDEM 2025
📅 Date: Saturday, Sunday, February 1–2, 2025 - CET 📍 Location: Brussels, Belgium 🤹♀️ Organizers: npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe, npub1l77twp5l02jadkcjn6eeulv2j7y5vmf9tf3hhtq7h7rp0vzhgpzqz0swft , pub1hz5alqscpp8yjrvgsdp2n4ygkl8slvstrgvmjca7e45w6644ew7sewtysa , npub1nkmta4dmsa7pj25762qxa6yqxvrhzn7ug0gz5frp9g7p3jdscnhsu049fn , npub1r30l8j4vmppvq8w23umcyvd3vct4zmfpfkn4c7h2h057rmlfcrmq9xt9ma 🔗 Fosdem
FOSDEM is one of the biggest gatherings for open-source developers and enthusiasts worldwide, taking place each year in Brussels. It’s a free, community-driven event where thousands of devs, innovators, and Free and Open Source Software contributors come together to demo projects, host talks, and share ideas. It’s a key place for making meaningful connections, learning from each other, and pushing open-source tech forward.
For NOSTR being at FOSDEM is a natural fit. It’s the perfect stage to introduce the broader open-source community to Nostr’s potential—how it can replace centralized social platforms, bring true ownership of data back to users, and encourage a more resilient, open internet. Engaging with fellow open-source projects and developers at FOSDEM helps Nostr grow its ecosystem, fosters new collaborations, and gains valuable feedback. The protocol is all about grassroots development, community contributions, and evolving without the constraints of centralized platforms, which aligns perfectly with FOSDEM’s collaborative spirit.
📰 Nostr in the Media
NOSTR How and Why It Works
The Nostr protocol is transforming the way we think about social media by combining Bitcoin's cryptographic principles with decentralized communication. This innovative approach enables censorship-resistant platforms, offering users unparalleled freedom, privacy, and ownership in the digital age.
Speakers: npub147whqsr5vsj86x0ays70r0hgreklre3ey97uvcmxhum65skst56s30selt (YakiHonne), npub1c878wu04lfqcl5avfy3p5x83ndpvedaxv0dg7pxthakq3jqdyzcs2n8avm (LNbits, Nostr, Makerbits), npub1j8y6tcdfw3q3f3h794s6un0gyc5742s0k5h5s2yqj0r70cpklqeqjavrvg (BTCPayServer), npub1t6jxfqz9hv0lygn9thwndekuahwyxkgvycyscjrtauuw73gd5k7sqvksrw (Nostr Special Forces) Host: npub17plqkxhsv66g8quxxc9p5t9mxazzn20m426exqnl8lxnh5a4cdns7jezx0 (Nostr)
Watch the full panel discussion on YouTube : https://www.youtube.com/watch?v=5c7c7RugxiY
⚡ Most Zapped Last Week
Nostr’s Value4Value (V4V) model is all about plebs directly rewarding creators for the value they receive—no middlemen fees, no ads, just pure community-driven support using sats via the Bitcoin Lightning Network. Thanks to zaplife.lol by @pablof7z for providing this data. Here are the top zapped posts from last week, showcasing creators who received the most engagement:
🔥 Top 3: Most Zaps
- My Bitcoin recap video also on nostr 🧡 I hope you like it.
Author: npub13jhh5jpak3sltvh5mxxc84edq8c6scuyhtkevfa7j568jrkkscysj7c5sq\ Zaps Received: 206 Sats Earned: 279k\ 🔗 event:
nevent1qqst4t56y3ul3emc6gd0g78rgn4ayz8glfdzdyjc27kltyy7svl8vqcpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgdwaehxw309ahx7uewd3hkcqg5waehxw309aex2mrp0yhxgctdw4eju6t0qgsgetm6fq7mgc04kt6dnrvr6uksrudgvwzt4mvky7lf2drepmtgvzgapfeq8
- grateful for the time, sacrifice, and dedication of all the bitcoin developers around the world.
Author: npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m Zaps Received: 121\ Sats Earned: 118k 🔗 event: nevent1qqs2c3pvyc62pna2cp8dsh457e4qjz5lzamwgjswaa97n0y3wg4fjwqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqglwaehxw309a3ksmmjw4ejumtfddjkg6tvvajhytnrdakn5dp5xspzpq35r7yzkm4te5460u00jz4djcw0qa90zku7739qn7wj4ralhe4z6a79m6
- What Bitcoin Did is Back!
Author: npub16le69k9hwapnjfhz89wnzkvf96z8n6r34qqwgq0sglas3tgh7v4sp9ffxj\ Zaps Received: 79 Sats Earned: 17k 🔗 event:
nevent1qqsfq2cmyvxw94f7y08r3rd5ja2p20jju3lqtkft4zm492m0cpgsn7qpp4mhxue69uhkummn9ekx7mqppamhxue69uhkummnw3ezumt0d5pzp4ln5tvtwa6r8ynwyw2ax9vcjt5y0858r2qqusqlq3lmpzk30uetcepnf3
💰 Top 3: Most Sats
- My Bitcoin recap video also on nostr 🧡 I hope you like it.
Author: npub13jhh5jpak3sltvh5mxxc84edq8c6scuyhtkevfa7j568jrkkscysj7c5sq\ Sats Earned: 279k\ Zaps Received: 206\ 🔗 event : nevent1qqst4t56y3ul3emc6gd0g78rgn4ayz8glfdzdyjc27kltyy7svl8vqcpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgdwaehxw309ahx7uewd3hkcqg5waehxw309aex2mrp0yhxgctdw4eju6t0qgsgetm6fq7mgc04kt6dnrvr6uksrudgvwzt4mvky7lf2drepmtgvzgapfeq8
- 6 months ago I decided to try to get into a professional Muay Thai Fight 👀🥊
Author: npub1lelkh3hhxw9hdwlcpk6q9t0xt9f7yze0y0nxazvzqjmre3p98x3sthkvyz Sats Earned: 196k\ Zaps Received: 51\ 🔗 event :
nevent1qqst0fu00sezruj3c6xfqhcreegcmjdk75s8zyeh0y5xzsgutwpmx9szyrl8767x7uecka4mlqxmgq4duev48cst9u37vm5fsgztv0xyy5u6xft2c62
- Author: npub126erv2p9an0a56d8qq3a2406xkh5qal7am0n4yp84r8ekz2cs7msj8wetv Sats Earned: 127k Zaps Received: 16 🔗 event :
nevent1qqs8ww46c3xukvwfcz6vlfu62dnzg62czpgm38udygvnd54j2uqspmgpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgq3q26erv2p9an0a56d8qq3a2406xkh5qal7am0n4yp84r8ekz2cs7msvk63pr
👋 Stay in Touch & Zap
Nostr is built by the plebs, for the plebs. If you found this recap helpful, consider supporting me—Nomishka—with a zap. Right now, I’m in a tough spot: jobless and struggling to make ends meet. Most days, I’m barely able to afford food, and honestly, 210,000 sats per month would help provide a basic income to cover essential needs.
I’m committed to supporting Nostr, and I split a part of the zaps I receive for this note with the plebs mentioned in this recap for all their great effort. Thank you so much for being part of this journey. Let me know your thoughts about this first recap, share your tips and suggestions for the next weekly recap, and let’s keep #grownostr together.
Recap by npub19hs0lg9vyd0lghayeju5fnflx0melawjrl8etuqln9gkhd4mwtxq2t5jcn
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ dff95033:862fbf40
2024-12-09 22:42:32
@ dff95033:862fbf40
2024-12-09 22:42:32
DADOS BIBLIOGRÁFICOS
- Autor: Daniel J. Levitin
- Título: A Mente Organizada: Como Pensar com Clareza na Era da Sobrecarga de Informação
- Título Original: The Organized Mind: Thinking Straight in the Age of Information Overload
- Tradutor: Regina Lyra
- Editora: Objetiva
- Ano de Publicação no Brasil: 2015
- Ano de Publicação Original: 2014
- ISBN (Edição Brasileira): 978-8539006465
- Páginas: 512
- Gênero: Psicologia, Ciência Cognitiva, Desenvolvimento Pessoal
INTRODUÇÃO
"Não se pode confiar na memória porque o sistema de arquivamento do cérebro destreinado é uma porcaria. Ele pega tudo que acontece com você e joga de qualquer jeito num grande armário escuro — quando você entra lá procurando algo, só consegue achar as coisas grandes e óbvias, como a morte de sua mãe, ou então coisas de que realmente não precisa. Coisas que você não está procurando, como a letra de ‘Copacabana’. Você não consegue encontrar o que precisa. Mas não entre em pânico, porque ainda está lá.” (The Mentalist, citado por Daniel Levitin em A Mente Organizada)
Quando me deparei com o livro “A Mente Organizada”, de Daniel Levitin, impulsivamente o adicionei à minha lista de leitura — apenas para deixá-lo esperando por meses. É irônico que um livro sobre organização estivesse preso no caos da minha própria lista, não estranhamente em uma era dopamínica — onde cada notificação e distração competem para roubar nossa atenção. No entanto, ao finalmente mergulhar em suas linhas, percebi que a obra é uma verdadeira ode à capacidade humana de organizar o conhecimento e a informação.
ESTRUTURA E CONTEÚDO
Dividido em três partes, “A Mente Organizada” nos guia por um entendimento prático sobre a mente humana. A Parte Um apresenta o mecanismo de atenção do cérebro, explorando como ele lida com o fluxo incessante de informações e decisões. Levitin discute a importância da atenção e como ela é fundamental para processar a quantidade massiva de dados que enfrentamos diariamente. Ele argumenta que entender esses mecanismos é crucial para melhorar nossa capacidade de foco e eficiência.
A Parte Dois oferece estratégias que colaboram com esse mecanismo, ajudando a organizar nossos ambientes físico, profissional, social e temporal. Levitin sugere métodos práticos, como a categorização e a criação de listas, que podem facilitar a tomada de decisões e reduzir a sensação de sobrecarga informacional. A ênfase na organização do espaço físico e do tempo é particularmente relevante em uma era onde distrações são constantes. Com a estrutura bem definida, Levitin avança para aprofundar seu estilo e explorar a complexidade de transmitir conceitos desafiadores de maneira acessível.
Por fim, a Parte Três discute como preparar a próxima geração para enfrentar os desafios do mundo moderno, equilibrando organização e criatividade. Levitin enfatiza a importância da educação em habilidades organizacionais desde cedo, preparando os jovens para um futuro onde o gerenciamento eficaz da informação será ainda mais crítico. Essa abordagem não apenas prepara os jovens para um futuro de desafios, mas também nos faz refletir sobre o legado que estamos construindo hoje.
ESTILO E APROFUNDAMENTO
A verbosidade de Levitin pode parecer desafiadora em alguns momentos, mas são nestes pontos que reside o valor do livro. Sua escrita flui como ondas: ora simples e objetiva, ora densa e desafiadora. Essa variação mantém o leitor engajado e instigado, permitindo uma compreensão mais profunda dos conceitos apresentados. Cada nuance tem seu propósito, oferecendo ao leitor as bases para compreender plenamente a obra ou para instigar novas inspirações e perspectivas.
Levitin se esforça para tornar pesquisas e estudos sobre o tema acessíveis a um público amplo, evitando tanto a superficialidade quanto a complexidade excessiva. Essa abordagem é especialmente valiosa em um contexto onde muitos textos acadêmicos podem se tornar herméticos.
REFLEXÕES PESSOAIS
Como frisei no decorrer deste livro, o princípio fundamental da organização, o mais crucial para evitar que percamos ou esqueçamos as coisas, é este: descarregue do cérebro para o mundo externo o ônus de organizar." (A Mente Organizada, Daniel Levitin).
Ler A Mente Organizada foi um desafio que me obrigou a encarar a zorra informacional do dia a dia de frente. Não foi apenas uma leitura, mas um embate com os meus próprios hábitos e uma pausa necessária para questionar: estou realmente lidando bem com os estímulos ao meu redor? À deriva em águas turbulentas, precisei aceitar, com humildade, as ferramentas oferecidas pelo livro para enfrentar os desafios atuais.
Senti-me provocado a observar com mais atenção tudo o que carrego, tanto física quanto mentalmente. Quantas ideias, compromissos e pensamentos acumulados passam despercebidos, sem nunca encontrar um lugar ou um significado real? Esse convite à introspecção foi um lembrete poderoso de que, mais do que organizar o que está fora, preciso organizar o que está dentro — e isso começa com um olhar honesto, e sim, doloroso, sobre o impacto que o excesso tem em minha vida.
Esse foi o verdadeiro desafio: perceber que minha forma de organização precisava de um novo olhar. Não basta apenas acumular ideias; é essencial dar-lhes estrutura, conectá-las e transformá-las em algo maior — ou descartá-las, quando necessário. Entender as miríades que moldam meu pensar e agir foi fundamental, e, neste ponto, o livro foi nada menos que revelador. A estética, o particionamento e o naturalismo solidificam as minhas bases, transformando a organização em algo mais do que uma sistemática: ela se torna uma expressão de qualidade de vida e saúde.
CONCLUSÃO
A Mente Organizada é uma obra que, para alguns, será apenas um folhetim, enquanto para outros será um verdadeiro manancial de sabedoria. Mas, acima de tudo, o que Daniel Levitin nos oferece são possibilidades — um convite à lapidação dessa gema preciosa e instigante que é a busca por sermos melhores do que somos hoje. Se você chegou a este livro, consciente ou não, já deu o primeiro passo nessa jornada.
Assim, caro leitor, deixo em tuas mãos esta obra, singela em proposta, mas grandiosa em potencial. Que ela inspire sua apreciação e, acima de tudo, seu uso.
Fecho esta gaveta aqui e espero ter apreciado o que há dentro dela — ou não. Se trouxe alguma ordem à bagunça, compartilhe e, se puder, contribua com o café — porque até a organização precisa de combustível.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 6389be64:ef439d32
2024-12-09 22:34:00
@ 6389be64:ef439d32
2024-12-09 22:34:00Resilience is the ability to withstand shocks, adapt, and bounce back. It’s an essential quality in nature and in life. But what if we could take resilience a step further? What if, instead of merely surviving, a system could improve when faced with stress? This concept, known as anti-fragility, is not just theoretical—it’s practical. Combining two highly resilient natural tools, comfrey and biochar, reveals how we can create systems that thrive under pressure and grow stronger with each challenge.
Comfrey: Nature’s Champion of Resilience
Comfrey is a plant that refuses to fail. Once its deep roots take hold, it thrives in poor soils, withstands drought, and regenerates even after being cut down repeatedly. It’s a hardy survivor, but comfrey doesn’t just endure—it contributes. Known as a dynamic accumulator, it mines nutrients from deep within the earth and brings them to the surface, making them available for other plants.
Beyond its ecological role, comfrey has centuries of medicinal use, earning the nickname "knitbone." Its leaves can heal wounds and restore health, a perfect metaphor for resilience. But as impressive as comfrey is, its true potential is unlocked when paired with another resilient force: biochar.
Biochar: The Silent Powerhouse of Soil Regeneration
Biochar, a carbon-rich material made by burning organic matter in low-oxygen conditions, is a game-changer for soil health. Its unique porous structure retains water, holds nutrients, and provides a haven for beneficial microbes. Soil enriched with biochar becomes drought-resistant, nutrient-rich, and biologically active—qualities that scream resilience.
Historically, ancient civilizations in the Amazon used biochar to transform barren soils into fertile agricultural hubs. Known as terra preta, these soils remain productive centuries later, highlighting biochar’s remarkable staying power.
Yet, like comfrey, biochar’s potential is magnified when it’s part of a larger system.
The Synergy: Comfrey and Biochar Together
Resilience turns into anti-fragility when systems go beyond mere survival and start improving under stress. Combining comfrey and biochar achieves exactly that.
-
Nutrient Cycling and Retention
Comfrey’s leaves, rich in nitrogen, potassium, and phosphorus, make an excellent mulch when cut and dropped onto the soil. However, these nutrients can wash away in heavy rains. Enter biochar. Its porous structure locks in the nutrients from comfrey, preventing runoff and keeping them available for plants. Together, they create a system that not only recycles nutrients but amplifies their effectiveness. -
Water Management
Biochar holds onto water and releases it slowly during dry periods. This makes soil not just drought-resistant but actively water-efficient, improving over time with each rain and dry spell. -
Microbial Ecosystems
Comfrey enriches soil with organic matter, feeding microbial life. Biochar provides a home for these microbes, protecting them and creating a stable environment for them to multiply. Together, they build a thriving soil ecosystem that becomes more fertile and resilient with each passing season.
Resilient systems can withstand shocks, but anti-fragile systems actively use those shocks to grow stronger. Comfrey and biochar together form an anti-fragile system. Each addition of biochar enhances water and nutrient retention, while comfrey regenerates biomass and enriches the soil. Over time, the system becomes more productive, less dependent on external inputs, and better equipped to handle challenges.
This synergy demonstrates the power of designing systems that don’t just survive—they thrive.
Lessons Beyond the Soil
The partnership of comfrey and biochar offers a valuable lesson for our own lives. Resilience is an admirable trait, but anti-fragility takes us further. By combining complementary strengths and leveraging stress as an opportunity, we can create systems—whether in soil, business, or society—that improve under pressure.
Nature shows us that resilience isn’t the end goal. When we pair resilient tools like comfrey and biochar, we unlock a system that evolves, regenerates, and becomes anti-fragile.
By designing with anti-fragility in mind, we don’t just bounce back, we bounce forward.
originally posted at https://stacker.news/items/802554
-
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 7c765d40:bd121d84
2024-12-09 21:37:45
@ 7c765d40:bd121d84
2024-12-09 21:37:45Back in college, starfish carried a negative connotation.
It was a sexual reference for a girl (or guy) who wasn't very good in bed.
"She just kinda laid there like a starfish."
Hahaha.
Happy Monday morning!
Over the weekend, I was reading a book titled "Exploiting Chaos."
There was a section in the book titled "Become Leaderless."
The book was written back in 2009, so there was no mention of bitcoin.
Bitcoin was only known by select few at this point.
But it perfectly describes the bitcoin network.
The bitcoin starfish.
"When you pull off the arms of a spider, it dies.
In contrast, if you rip off the arms of a starfish, you'll get five new starfish.
This happens because the starfish have decentralized nervous systems."
Like a starfish, the bitcoin network is decentralized, united by ideology and a common set of rules.
If you attack one arm, it grows back even stronger.
We have seen this time and time again with bitcoin.
And it HAD to be this way.
Yes, bitcoin is a revolutionary technology - maybe the biggest innovation the world has ever seen.
But if it wasn't decentralized, it could be stopped.
Bitcoin has some pretty significant competition - the central banking system.
And we've seen many great technologies squashed over the last century by powerful competition.
You cannot stop bitcoin.
There is no head to chop off.
This is why we are starting to see both corporate and nation state adoption.
They have tried attacking bitcoin for 16 years.
Negative media coverage.
Government threats.
Mining bans.
Exchange hacks.
New and "improved" competitors.
All have failed.
Not only did they fail, but they made bitcoin even stronger.
The size of network, bitcoin adoption, and the price in fiat terms have all continued to rise - despite these attacks.
And every person, company, or country that joins the bitcoin network will make it stronger.
Keep in mind bitcoin is just a protocol.
It just kinda lays there, and lets everyone else do the work.
Very starfish like.
PROJECT POTENTIAL - You can now find the expanded audio versions of these on the new podcast - Project Potential! I will be sharing the video versions here for the LITF members but you can also find it for free on Spotify and of course Fountain!
Here is the link to Episode 007 on Fountain: https://fountain.fm/episode/zSoJf6TLjkkMDhpokw4T
Have a great day everyone! And remember, the only thing more scarce than bitcoin is time!
Jor
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 000002de:c05780a7
2024-12-09 21:22:53
@ 000002de:c05780a7
2024-12-09 21:22:53Much has been written about SoV vs. MoE. I'm not trying to re-hash it here. But as bitcoin's exchange price in US dollars has cracked 100k the investment Slack channel at work started talking about bitcoin.
A long while back I started a bitcoin only channel and we have been growing slowly but with this new discussion we've had kind of a spike in new people. I'm answering a lot of basic questions but something occurred to me this morning. I see a pattern repeating.
I will start by trying to roughly group people.
The Crypto People
The crypto people are usually talking about all the limitations bitcoin has and largely ignoring the reasons, tradeoffs, and benefits. Most of their "arguments" come from ignorance. One thing they don't really say but is implied is that bitcoin will never work as a medium of exchange. Of course, they usually have never heard of Lightning let alone used any of the tech being developed. I rarely hear any of these types of people talk about SoV. They realize that bitcoin is a great store of value. The other thing they talk about of course are those 10x gains.
Minor side note. I have a friend that's into XRP who told me a few weeks ago that bitcoin won't 10x again. I have a reminder set to remind him of what he said in 5 years.
The No Coiners
I've been seeing many questions around bitcoin's adoption and utility as a medium of exchange from the no-coiners in Slack. I assume they are no-coiners based on their questions. They may have "bought" some bitcoin on some service but they are at least new and are clearly not "crypto" people. They also seem to have latched on to this idea that bitcoin is only good for investment. They don't really believe in the SoV but that is really the only thing they are even thinking bitcoin might have going for it. They seem to think of it like a stock. Obviously it would never be a currency. I've pushed back on these thoughts with my own experience with bitcoin and had positive responses.
You see, what both of these types of people think is that bitcoin can't work as a currency. As a medium of exchange. Its not just that they don't think it will be widely adopted as an investment property.
The Vanguard
This is the group you and I fall into. I consider most SN people to be a part of a group I think of as the Vanguard of bitcoin. Some are earlier adopters than others. None of us are late. We believe there is a real need for bitcoin. We are people that have long looked at the world and wondered what was wrong on a very deep level. We have varied political views and ideas about how things should be but we all have deep conviction about bitcoin being a key aspect of making a better future. We are in it for the long term. Its not primarily a way to get rich. Its not about investing. Its about a better world.
We are very different from the average person out there. Some of you might not yet realize this because you are young. You might actually think you are just smarter or special. Of course you are probably smart. Probably smarter than myself but its deeper. You are very different from the average person. If you're like me you will realize that you think about thing most of the people around you do not think about. You think in different ways as well. You question many things others take for granted. I'm not trying to say you are better than others or they are better than you. We are different. We all have value and a role to play in society.
My Thoughts on MoE
A medium of exchange is something widely acceptable in exchange for goods and services. The vanguard will often claim that bitcoin is a medium of exchange. That's true and not true. It can function as one. It is a medium of exchange in certain subcultures but in reality one can't directly exchange it for most goods and services today. Not because the tech doesn't support it but rather because the masses have not adopted it. They don't even understand that it can be used as a MoE.
In case this isn't clear let me explain with an example. Sea shells are not a medium of exchange. No one to my knowledge is using them for this today. I have read that they have been used as currency in the past in certain places. Cigarettes are not a medium of exchange... unless you are in prison. In prisons cigarettes do often function as a medium of exchange in place of fiat paper.
This is what I mean.
- Bitcoin can function as a medium of exchange today
- Bitcoin does function as a medium of exchange today in smaller markets or subcultures just like other things(cigarettes)
- Bitcoin is not a medium of exchange like the US dollar... yet
So, of these three which is least important? The last one.
We all know what bitcoin is and can do. I would argue 99.9% of humans don't even understand bitcoin's value. But, they wonder about MoE. That's the right instinct. I believe outside of the supply cap the ability to transact without a third party is the most important thing bitcoin offers. Without it the supply cap is pretty meaningless. But how do we get there? How do we get to a society where bitcoin is a widely accepted form of payment and exchange?
My View
I say my view because its what I believe. Many have stated this before. Bitcoin in my view will first be seen by most of the world as a good SoV before it will become a MoE. It seems so obvious to me. Granted there are and will be places where MoE is more important or at least equally important but I'm referring to societies where wealth is concentrated.
The people in wealthy nations don't really yet see the need for a new MoE. They do see the need for a place to store their financial energy. But even this SoV aspect isn't widely accepted yet. We haven't even made it that far yet. Kinda mind blowing when you look at the exchange rate today isn't it?
As a significant number of people(who knows what number that is) have bitcoin and value it for its savings properties then they will be more open to its other uses. Right now you have a chicken egg problem. People would not accept something they don't value or understand. People would not spend something they do not have or few accept.
This is why I think it is SO DUMB to argue about SoV vs MoE. Bitcoin can be both. It needs to be both and it will be both. We should be working as members of the vanguard in making sure the ecosystem is ready. Making sure we know the answers to questions. Have written documents. Have produced guides. Have used the tools. Know which ones will work for the people we know.
IMO we still have a long way to go before the average person will "adopt" bitcoin.
I do think there is a intentional attempt to pigeonhole bitcoin as only a SoV. There are a few different reasons for this.
- Shitcoiners know they can't compete on SoV but think they can compete on other things
- Statists don't want to lose fiat control over society. SoV seems to be less of a threat to their power.
- Bitcoiners that run public companies don't want a target on their heads so they downplay bitcoin as currency(Mike Saylor)
- Deep state wants to make bitcoin into just another asset like gold. Paper bitcoiners. Something they can regulate. Its largely a psyop vs. direct attack.
Just realize these are not all the same people and some have different motivations.
Action Steps
Don't be reactionary. Don't get sucked into the wrong arguments. It is easy to do. We all fall into this sometimes but try not to. Focus on these things.
- Bitcoin can be the currency of the world. It will work. We don't need another crypto
- No coiners are not like you. They are almost always believers in the state. They may have more in common with you but they likely aren't ideological about money
- Focus on removing mental blocks. The troupes
- Don't push. Ask questions and answer questions.
- Don't preach to much. You start sounding like a nut or a scammer.
These are my thoughts. I'm still learning and observing.
originally posted at https://stacker.news/items/802472
-
 @ 8e56fde2:bb433b31
2024-12-09 21:04:00
@ 8e56fde2:bb433b31
2024-12-09 21:04:00So let us give a little bit on context first to get the WHOLE PICTURE.
We DoShitters are a trio of friends who one day decided we wanted to create some shit together. We are artists from different fields, and at the time two of us were struggling from creative block, so we decided to create the ultimate tool to COMBAT CREATIVE BLOCK. It would be an Oracle about the creative process and it would be inspired on the Hero's Journey and on our own journeys as artists; and hence "DoShit!" was born.

Once we knew what we wanted to do, and it started to have a shape, we decided to go through the hardship of self-producing and selling the cards by ourselves directly on our website ( www.doshitters.com ), which allowed us to keep control of the product at all times during production, and to have a direct relationship with our audience and buyers. Besides from guaranteeing we weren't left with the tiniest percentage of the sales pie. (At least in Spain, when you get a big publisher involved, you can forget getting even 10% of sales, and you lose a lot of the creative control of your project).
We invested a lot of our own resources in making sure "DoShit!" was a quality product and we were lucky enough to get the help of a generous patreon who enabled us to create what is now the DoShit! deck. <3

We did local presentations of the product in both Barcelona and Madrid, and got the deck to be sold in cool local stores, where we offered to do live readings and got to talk with people of all kinds about the Shit they wanted to do. Above all, DoShit! is an inspirational tool.
**And you must be asking yourself, "What does this have to do with Amazon?". ** Well, one of the problems of self-producing and having local fulfilment of the product is that shipping costs just couldn't compete with what the average consumer has gotten used to because of Amazon's mass scale free shipping. We were finding that, specially for our followers in the USA, it was impossible to assume shipping costs (which amounted to almost the same cost as the actual deck); but we didn't want to give up on the people who wanted to get inspired by DoShit! but lived on the other side of the world from us, so... WE DECIDED TO MAKE A DEAL WITH THE DEVIL, aka Amazon.
We knew that selling our product on Amazon was going to result in less revenue from the sales for us, but for us it was mostly about GETTING DoShit! TO A WAREHOUSE IN THE USA to be able to offer the deck with Free Shipping. And that's what we did. But we didn't know everything that would come as a result, (they don't really advertise the hidden costs and fees, or the speed at which they want you to expedite your sales) and we've been paying for that decision ever since.
In any case, they lured us in with a 3 months no cost promotion. You obviously assumed the cost of shipping it there, and they would take a cut from every sale that happened in their web, but we didn't have any way of knowing the cost that we would need to incur after those first three months. Another thing that wasn't advertised is that IF YOU ACTUALLY WANT YOUR PRODUCT TO BE FEATURED ANYWHERE, you need to be eligible as an A+ content seller, which also comes at a cost, and you need to pay additionally for sponsored ads; otherwise, your product is basically shut down in a black hole of zero discoverability except for people using the direct link.
The three months went by fast and then the invoices started coming, and the automatic charges on our account started to empty our independent seller bank account. As you can imagine, independent sellers like us sometimes require of TIME to be able to get the word out, to get people to buy your product... Besides, as artists with other projects on the pipeline, we couldn't really spend much time focusing on sales, nor did we want to. And in all honestly, we refused to give Amazon more money in sponsored ads and other programs to "gain visibility". We knew we had no way of competing with the big sellers on the platform, but we just thought, "AT LEAST IT'S AVAILABLE FOR THOSE WHO WANT TO BUY IT".
But then, out of the blue, we noticed our link on Amazon wasn't working. A friend tipped us off that it wasn't allowing any sales, it was listed as "currently unavailable", without us having done anything to trigger that change.
Suddenly we received an email from the giant informing us that our account had been set to inactive due to "dormancy", and that we needed to re-verify our identity. Not only that, but since we were in Europe, and they didn't have an address in the US they could send the decks back to, if we didn't get everything solved in time, THEY WERE GOING TO DESTROY THE DECKS THEY HAD IN THEIR WAREHOUSE because of their "Automated removal" policy.
This caught us while we were on holidays, away from our desktops, seller logins and such and we did everything the seller support requested from us as rapidly as possible. The nightmare of imagining our beautiful decks being destroyed really put us in a state of panic. We hoped everything would be solved after several support tickets stating our case, and pleading that they don't destroy the decks!
In the end, after several communications, they reactivated our listing which had apparently been set to inactive because of "stranded inventory" due to "excess inventory"; which is Amazon talk for: "YOU'RE NOT SELLING FAST ENOUGH".
After having gone through that experience we knew one thing for certain, WE WANTED TO BREAK FREE FROM AMAZON as soon as possible, but we still wanted to offer our DoShit! decks with Free Shipping for our customers; at least this Christmas...

So, best case scenario, all the DoShit! decks that are at Amazon get sold this Christmas campaign, with the jolly merry spirit, people and nostriches all around the world get excited about GIFTING INSPIRATION (and taking advantage of the Free Shipping) and help us to GET THE DECKS OUT OF AMAZON!
But we know this may be wishful thinking T.T , That is why we are also looking for independent shops in the USA that feel that DoShit! makes sense in their store, and would want to become the new home of the decks that remain in american soil after the Christmas campaign. So maybe somebody wants to become the "foster home" to these Oracles as they find their new home in 2025, so they decks can go from that abussive giant with high time preference, to a friendly purple shop with low time preference and no hidden tricks. After all, many people kickstart the year with their minds set on their New Year Resolutions, they want to DO SHIT! So Who Knows?
In any case, to all the small sellers out there, BEWARE OF MAKING THAT PACT WITH THE DEVIL.
We knew we had never wanted to get our Shit on Amazon, we knew the system was rigged again us, but still, we wanted to make it more affordable for people to get their hands on the deck. Artists struggle enough to have to additionally add exhorbitant shipping costs to acquire a creativity tool like "DoShit!".
And if you, like us, find yourself having to do that pact anyway, we hope our tale will at least help you navigate all the hidden traps that their system throws at you.
IF YOU WANT TO JOIN THE CREATIVE RESCUE MISSION TO FREE THE DECKS, please, support us as best you can, share our story, recommend our deck, but best of all GIFT THE "DoShit!" DECK THIS CHRISTMAS! <3
You can find it at its captor's site at https://a.co/d/hrKXEBF , or if you'd rather NOT BUY SHIT ON AMAZON, you can always buy it at the Plebeian Market with your Sats, and we'll get one out of Amazon on your account. (https://plebeian.market/p/f82c481a3ae2a284049631a50373f4b9262c0e0b80977a4de1a71fcc19c5635d/stall/c9744507a49cf647c5612204416b7e22bdab86fbaff85413cfbc41103a0d269a)
THANKS FOR CARING, This 2025, we wish you all to DO THE SHIT THAT MATTERS TO YOU!
DoShit! #JoinTheArtmy
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ a8ad8bb0:b4495d5c
2024-12-09 20:54:02
@ a8ad8bb0:b4495d5c
2024-12-09 20:54:02Your mindset is the lens through which you view the world. It's the collection of thoughts, attitudes, and beliefs that shape your perceptions, influence your behavior, and ultimately determine your success. A strong, positive mindset is the foundation upon which you can build a fulfilling life, achieve your goals, and overcome obstacles.
The Two Mindsets: Fixed vs. Growth
According to Carol Dweck, a renowned psychologist, there are two primary mindsets: fixed and growth.
- Fixed Mindset: A fixed mindset assumes that abilities, intelligence, and talents are innate and unchangeable. People with a fixed mindset believe that success is solely dependent on natural ability, rather than effort and learning. This mindset can lead to a fear of failure, avoidance of challenges, and a lack of resilience.
- Growth Mindset: A growth mindset, on the other hand, believes that abilities, intelligence, and talents can be developed through dedication, hard work, and persistence. People with a growth mindset see challenges as opportunities for growth, learning, and improvement. This mindset fosters a love of learning, resilience, and a willingness to take risks.
The Benefits of a Growth Mindset
Cultivating a growth mindset can have a profound impact on your life. Some of the benefits include:
- Increased Resilience: A growth mindset helps you bounce back from setbacks, failures, and adversity.
- Improved Self-Esteem: By focusing on effort and progress, rather than natural ability, you can develop a more positive and realistic self-image.
- Enhanced Creativity: A growth mindset encourages experimentation, exploration, and learning from failures, leading to increased creativity and innovation.
- Better Relationships: By embracing challenges and viewing failures as opportunities for growth, you can build stronger, more resilient relationships with others.
How to Cultivate a Growth Mindset
Developing a growth mindset takes time, effort, and practice. Here are some strategies to help you cultivate a growth mindset:
- Embrace Challenges: View challenges as opportunities for growth, learning, and improvement.
- Focus on Effort: Emphasize the importance of effort, persistence, and hard work, rather than natural ability.
- Learn from Failures: Treat failures as valuable learning experiences, and use them as opportunities for growth and improvement.
- Practice Self-Compassion: Treat yourself with kindness, understanding, and patience, just as you would a close friend.
- Seek Feedback: Encourage feedback from others, and use it as an opportunity to learn, grow, and improve.
Your mindset is the key to unlocking your full potential. By cultivating a growth mindset, you can develop the resilience, creativity, and confidence needed to achieve your goals and overcome obstacles. Remember, your mindset is not fixed; it can be developed and strengthened through practice, effort, and persistence.
Mindset#positivity#creativity
-
 @ ea6958bd:77925591
2024-12-09 20:47:48
@ ea6958bd:77925591
2024-12-09 20:47:48sdsdsdsdsdfsdfsfd 3sdfsdfsdf
-
 @ ea6958bd:77925591
2024-12-09 20:46:32
@ ea6958bd:77925591
2024-12-09 20:46:32sdsdsdsdsdfsdfsfd 3sdfsdfsdf
-
 @ ea6958bd:77925591
2024-12-09 20:38:02
@ ea6958bd:77925591
2024-12-09 20:38:02This is a test that I'm publishing
-
 @ 5d4b6c8d:8a1c1ee3
2024-12-09 19:44:19
@ 5d4b6c8d:8a1c1ee3
2024-12-09 19:44:19To preview the mediocre NFC West showdown between the Rams and 49ers, we're going to have @realBitcoinDog join as our first ever guest.
I'm sure we'll talk about the NBA Emirates Cup Survivor Pool, as well as getting his impressions of Stacker News and ~Stacker_Sports.
Let us know what you'd like to get out of our first ménage à trois.
originally posted at https://stacker.news/items/802364
-
 @ 31312140:2471509b
2024-12-09 18:53:40
@ 31312140:2471509b
2024-12-09 18:53:40Beyond the Surface: Uncovering Deeper Context
The Official Narrative 🔍
The tale most of us know about World War II paints it as a battle of epic proportions between good and evil—democracy against tyranny. The Allies—comprising the USA, the UK, and the USSR—are cast as noble heroes who defeated the Axis powers, particularly Nazi Germany, ending the Holocaust and safeguarding human rights. In this version, the Holocaust is depicted as the systematic extermination of six million Jews, alongside other groups deemed undesirable by the Third Reich.
The Missing Context 📚
But let's pump the brakes for a second. World War II didn't just happen out of nowhere. There are multiple layers of context, preconditions, and economic dynamics that often get brushed under the rug in mainstream accounts.
The Treaty of Versailles: Seeds of Extremism 🌱
To truly understand WWII’s origins, we need to rewind to the Treaty of Versailles (1919) following WWI. This treaty imposed punitive reparations and territorial losses on Germany, creating fertile ground for nationalist sentiments and the thirst for revenge. Economic despair and national humiliation became fertile soil for extremism—conditions Adolf Hitler expertly exploited to rise to power.
Pre-War Economic Conditions 💹
Before the war, Europe was grappling with the aftermath of the Great Depression, leaving many nations economically devastated. This vulnerability provided ample opportunity for financial manipulation and influence, where banks and financial institutions slotted into the puzzle, quietly steering global politics and economics.
War Economy: A Banker’s Paradise? 💸
Wars can be a double-edged sword for economies. On one hand, there’s utter destruction, but on the other, enormous avenues for profit. During WWII, financing war efforts became incredibly lucrative. Major banks found themselves well-placed to support war machinery production, national debts, and recovery efforts. This intricate financial web granted them substantial influence. 🏦
Banking’s Role in the War Machine ⚙️
The Industrial-Military Complex
Banks played a pivotal role in fueling the industrial-military complex. From the production of weapons to logistics, the financial sector was deeply entwined in the war effort. Loans and credits supported the production lines, allowing manufacturers to capitalize massively on government contracts, which perpetuated indebtedness to financial institutions.
Financing Both Sides?
One of the more controversial notions is that some financial institutions provided backing to both Allies and Axis powers. This form of financial neutrality could have served as a strategic maneuver to ensure returns, regardless of the war’s outcome, turning potential turmoil into fiscal opportunities rather than barriers.
The Allies: Scrutinizing the "Heroic" Narrative 🏴☠️
While the Axis powers are often branded as the villains, it’s crucial to examine the of the Allies closely. Their narrative of "saving the world" sometimes glosses over actions that are morally questionable.
Total Destruction and Civilian Atrocities 💥
The so-called noble Allies engaged in tactics that resulted in huge civilian casualties—a topic often neglected in history classes. The firebombing of cities like Dresden, with limited strategic value and filled with civilians and refugees, sparked ethical debates. Hamburg and Tokyo endured similar fates, with firestorms tearing through civilian areas.
And let’s not forget Hiroshima and Nagasaki—bombings that instantly obliterated cities and ushered in a chilling era of "nuclear" warfare, claiming hundreds of thousands of civilian lives. In these instances, the line between strategic necessity and moral atrocity becomes blurred.
The Holocaust: A Complex Examination 🌍
The Holocaust remains one of history’s most haunting chapters. While the vast tragedy is uncontested, debates over specifics like numbers and methodologies persist. Some observers point to inconsistencies in narratives, contending they have sometimes been amplified by political agendas post-war.
Unequal Spotlight on Suffering 🎭
Critics argue that while Jewish suffering gets primary attention, other victim groups slip into the historical shadows. This selective narrative might serve broader political purposes, obscuring the collective suffering experienced globally. It’s about demanding a comprehensive understanding of humanity's struggles.
The Birth of Israel: Geopolitical Ripples 🌊
A significant, often overlooked outcome of WWII was the establishment of the State of Israel in 1948. Fueled by widespread sympathy for Jews who supposedly suffered immensely during the Holocaust, the official narratives surrounding these events played a pivotal role in garnering international support for a Jewish homeland. However, establishing Israel came at a great cost to the native Palestinian population, many of whom were killed and forcibly removed from their homes and lands. The Nakba, meaning "catastrophe" in Palestinian history, witnessed the expulsion and flight of over 700,000 Palestinian Arabs, illustrating the complexities and conflicts of broader wartime narratives.
The Nuremberg Trials: Justice Unmeasured? ⚖️
The Nuremberg Trials, hailed as a milestone in international justice, faced criticism for "victor's justice." While Nazi leaders were justly prosecuted, the more intricate machinations of all wartime powers, including potential Allied war crimes, went unexamined. This raises pressing questions about the objectivity and completeness of how history is chronicled.
History's Influence on the Modern World 🌐
Bankers and Their Post-War Power
The Marshall Plan: Reconstruction with Strings Attached
Post-war Europe lay in ruins—a landscape of destroyed infrastructure, drained economies, and demoralized populations. Enter the Marshall Plan, which aimed to rebuild Western Europe with financial aid from the United States. But this wasn’t pure altruism; it enabled the spread of American economic influence and, by extension, that of American banks. 🌍
Eastern Europe: A Different Story
While the Marshall Plan aided Western Europe, Eastern Europe languished behind the Iron Curtain, enduring a markedly different fate. This contrast allowed Western powers to surge economically while Eastern Europe floundered under communist economic constraints—yet another indirect boon to Western financial institutions.
The Birth of New Financial Structures 🌐
The conclusion of WWII witnessed the emergence of new financial institutions designed to stabilize the global economy, like the International Monetary Fund (IMF) and the World Bank. These organizations played critical roles in reshaping global finance, offering loans and aid while wielding considerable policy influence over recipient countries.
The Power Dynamics 🎭
World War II shifted not only political boundaries but economic power structures as well. Banks were not mere passive beneficiaries but active participants in reshaping post-war Europe. Their influence and decisions wielded long-reaching impacts, extending beyond the favored narrative of heroism and sacrifice to one of economic gamesmanship.
Historical Narratives as Tools 📜
The shadow of WWII and the Holocaust deeply impacts contemporary politics, cultural identities, and international policies. History is wielded as both a weapon and shield, with narratives serving as infrastructure for current geopolitical strategies. Recognizing this manipulative potential helps citizens comprehend the broader utility of historical perspectives.
The Endless Quest for Truth 🔎
Searching for truth requires stepping beyond comfort zones and embracing multiple perspectives. This inquiry isn’t about dismissing established history but enriching it with diverse viewpoints. As with any exploration, gaining knowledge paints a more intricate canvas of past and present.
Recommended Readings & Resources 📚
For those curious to delve deeper, explore these varied perspectives:
- "World War II: Behind Closed Doors" Laurence Rees – Discover secret strategies of the era.
- "Banking on Hitler" by Bryan Evans – Delve into the financial complexities of the war.
- "IBM and the Holocaust" by Edwin Black – Insights into controversial industrial involvement.
- "The Origins of the Second World War" by A. J. P. Taylor – A revisionist view of the war’s causes.
- "Tragedy and Hope: A History of the World in Our Time" by Carroll Quigley – Comprehensive insights into post-war economic structuring.
- "The House of Rothschild: The World's Banker" by Niall Ferguson – Explore one of the most powerful banking families.
- "The Marshall Plan: Dawn of the Cold War" by Benn Steil – Investigating Europe’s economic revival and its implications.
- "Europa: The Last Battle" by Tobias Bratt – Documentary series questioning the official narrative.
- Documentaries on Dresden and other Allied bombings – Visual narratives of strategic ambiguities.
Remember, truth is a multifaceted journey, and diverse perspectives illuminate the hidden facets of our shared past. 🌟
-
 @ 81e5cb66:17c315fa
2024-12-09 18:51:55
@ 81e5cb66:17c315fa
2024-12-09 18:51:55The current debate about artificial intelligence has an interesting side effect: it ruthlessly reveals the shortcomings of our education system. The widespread fear of AI systems such as ChatGPT is often not based on their actual capabilities, but on the sobering realisation of how interchangeable many of our learned skills are.
For decades, our education system has trained people to solve predetermined tasks according to set patterns. We have learnt facts by heart, passed standardised tests and adhered to predefined processes. Today, AI can do precisely this type of work better, faster and with fewer errors. The panic this triggers is basically an admission: we have been trained to become ‘human machines’ instead of developing our unique human abilities.
The traditional education system, developed in the age of industrialisation, aimed to create a reliable workforce for standardised processes. Creativity, critical thinking and independent action were often undesirable. Pupils and students were not encouraged to ask questions or find alternative solutions. Instead, conformity was rewarded and deviation penalised.
AI now acts as a merciless mirror of this misguided development. It shows us that much of what we call ‘education’ was merely the training of routines. When an AI model can write a structured essay, solve a maths problem or produce a market analysis within seconds, it becomes clear that these skills alone no longer make us valuable for the labour market.
Paradoxically, this painful realisation could be the starting point for a long overdue education revolution. We need to abandon the illusion that memorising facts or following predetermined processes is enough. Instead, we need to focus on developing genuinely human skills:
- The ability to ask new questions instead of just giving known answers
- The ability to develop creative solutions to novel problems
- The ability to make ethical decisions and weigh up values
- The ability to genuinely empathise and build meaningful relationships
- The ability to understand complex relationships and think systemically
The ‘natural stupidity’ that AI exposes is not that of individual people, but that of a system that has reduced people to one-dimensional task fulfilers. The true intelligence of humans is not revealed in the competition with machines, but in the ability to use machines sensibly in order to develop human potential.
The fear of AI is therefore also an opportunity for self-reflection: What makes us truly human? What skills should we develop? How can we design an education system that supports people in realising their full potential instead of degrading them to programmable units?
The answer may lie in a fundamental rethink: away from teaching standardised skills and towards developing adaptive competencies. Away from the passive consumption of knowledge and towards the active creation of solutions. Away from fear of machines and towards self-confident use of technological tools.
AI could thus become the catalyst for a long overdue educational reform - not because it threatens us, but because it forces us to reflect on our true strengths and develop them in a targeted manner. The real revolution lies not in technology, but in a return to what makes us human.
-
 @ a58a2663:87bb2918
2024-12-09 13:39:49
@ a58a2663:87bb2918
2024-12-09 13:39:49- Concluir com minha filha, até o fim de 2025, a leitura da tradução latina de Ursinho Pooh, isto é, Winnie Ille Pu, de Alexander Lenard (1910-1972), poeta, ensaísta e tradutor húngaro que viveu no Brasil. Que texto curioso! Estranho estímulo que me chegou para voltar a estudar latim a sério.

-
Importar mais livros pela Thrift Books e menos pela Loja do Diabo. Seu acervo é excepcional e o frete é mais barato. Às vezes, em menos de duas semanas já estou com o livro em mãos (e olha que resido no Maranhão).
-
Concluir e publicar meu livro Vida após as Universidades. Escrita & criação em velhos & novos contextos de risco, desenvolvimento de algumas ideias que insinuei em Contra a vida intelectual, no que diz respeito ao encerramento de um ciclo histórico de modos de fazer investigação erudita.
-
Rematar o terceiro e último módulo de Convivium - Seminário Permanente de Humanidades, "A Alegoria do Mundo: o Mago, o Filólogo e o Colonizador", embrião de um longo ensaio sobre o "projeto humanista" e as vias de saída da modernidade oferecidas pelo pensamento latino-americano. (As inscrições seguem abertas. Caso queira inscrever-se pagando em bitcoin, me mande um e-mail: camoensiii57@protonmail.com).
-
Defender no primeiro semestre minha tese de doutoramento sobre João Francisco Lisboa (1812-1863), o maior prosador brasileiro de meados do século XIX. Compreender seu Jornal de Tímon implica rever concepções há muitos estabelecidas sobre a formação da literatura brasileira.
-
Escrever pelo menos cinco ensaios de apresentação do pensamento de Vilém Flusser e do que pretendo realizar em FLUSSER_project. A ideia é divulgá-los em inglês e especialmente aqui pelo Nostr.
-
Ler TUDO de Ignacio Gómez de Liaño.
-
Não ceder à tentação de discutir com imbecil.
-
 @ 75869cfa:76819987
2024-12-09 04:34:17
@ 75869cfa:76819987
2024-12-09 04:34:17GM, Nostriches! The Nostr Review is a biweekly newsletter focused on nostr statistics, protocol updates, exciting programs, the long-form content ecosystem, and key events happening in the Nostr-verse. If you’re interested, join me in covering updates from the Nostr ecosystem!
Quick review: In the past two weeks, Nostr statistics show over 230,000 daily trusted pubkey events, a 3.5% decrease from the previous period. New user numbers have been a significant increase, Profiles with LN addresses or bios have marked a nearly 100-fold growth, Public writing events surpassed 2,000,000, reflecting an 800% increase. More than 14 million events have been published, with posts leading in volume, totaling about 2 million. Total Zap activity reached over 9.7 million, marking a significant 50% decrease.
Additionally, 18 pull requests were submitted to the Nostr protocol, with 9 merged. A total of 44 Nostr projects were tracked, with 12 releasing product updates, and over 434 long-form articles were published, 30% focusing on Bitcoin and Nostr. During this period, 4 notable events took place, and 4 significant events are upcoming.
Nostr Statistics
Based on user activity, the total daily trusted pubkeys writing events exceeded 230,000, representing a slight 3.5% decrease compared to the previous period (Nov 11-24). Daily activity peaked at 19519 events, with a low of approximately 16969.
In terms of new user numbers, there has been a significant increase. Profiles with LN addresses or bios have reached approximately 1,859,727, marking a nearly 100-fold growth compared to the previous two weeks. Public writing events surpassed 2,000,000, reflecting an 800% increase over the same period. The daily peak hit 304,317, exceeding the total for the previous two weeks combined.
Regarding event publishing, the total number of note events published has surpassed 14 million, marking a significant increase of approximately 27%. Posts continue to be the most dominant in volume, totaling about 2 million (a slight decrease of 5%). Reposts (353,266) and reactions (553,926) also saw a small decline, around 1%.
For zap activity, the total zap amount is approximately 9.7 million, showing a significant decrease of over 50% compared to the previous period.
In terms of relay usage, the top five relays by user count are: wss://bostr.bitcointxoko.com/,wss://feeds.nostr.band/,wss://realy.nostr.band/,wss://realys.diggoo.com/,wss://realy.lumina.rocks/ Data source: https://stats.nostr.band/
NIPs
NIP-0A - Contact List v2 nostr:npub1acg6thl5psv62405rljzkj8spesceyfz2c32udakc2ak0dmvfeyse9p35c is proposing that NIP-0A - Contact List v2 can prevent contact list clobbering issues.This method could be used for any other event kinds that have editable lists. He is not arguing for a contact list v2 actually, rather, the focus is on conflict-free replicated data types, in order to prevent conflicts. CRDTs aren't really necessary in practice if people always use the person's outbox relays and don't use two clients at the same time. However, many conflicts were observed early on.Contact lists are already very long for some people, and while we could compress some of this data, not by a huge amount given the printable character set nature of JSON.
Consistent “method” naming for NIP 47(NWC) Response Gudnessuche is proposing that consistent “method” naming for NIP 47(NWC) Response adds consistency to the event structure in (NWC).Currently, requests and responses have different keys to identify their method type, which may cause confusion or misunderstandings.This change aims to standardize the key names across all request and response events, making it easier for developers to understand and implement the protocol.
NIP-34: Git Remote Nostr URL format and helper spec DanConwayDev is proposing that add the Git Remote Nostr URL format which can be used as a normal git clone address when ngit is installed. This used by ngit and gitworkshop.dev, minus the usage of nip05 addresses which nostr:npub1elta7cneng3w8p9y4dw633qzdjr4kyvaparuyuttyrx6e8xp7xnq32cume is working on adding. It is also partially supported experimental WOP tools like lez's git-remote blossom and Guga implementation of git-remote-nostr. Add a wider git remote helper spec implemented by the git plugin bundled with 'ngit'. This is probably less useful for inclusion in the NIP but he is not sure where else to put it.
NIP-42 Extension: auth-by-payment nostr:npub1hw6amg8p24ne08c9gdq8hhpqx0t0pwanpae9z25crn7m9uy7yarse465gr is proposing that this Extension of NIP-42 allows relays to add an extra NUT-18 argument to AUTH messages, that gives the user the option to authorize by providing a cashu payment. This allows relay operators to monetize with pay-as-you-go connections without the need to keep track of subscriptions and/or whitelists.This would allow the user to use ephemeral pubkeys to sign this message as well, giving them more privacy.
Notable Projects
Amethyst v0.93.0 nostr:npub142gywvjkq0dv6nupggyn2euhx4nduwc7yz5f24ah9rpmunr2s39se3xrj0
New Features: * New Android Image/Video Picker * Adds support for pronouns on profile * Migrates Video uploads from NIP-94 to NIP-71 Video events * Migrates Picture uploads from NIP-94 to NIP-68 Picture events * Adds support for BUD-01, BUD-02, and BUD-03 * Adds support for NIP-22 Comments * Adds nip05 field to the hidden words filtering by nostr:npub1e2yuky03caw4ke3zy68lg0fz3r4gkt94hx4fjmlelacyljgyk79svn3eef * Adds support for q tags with addresses * Adds search.nos.today to bootstrapping relays for search * Adds DM and Search default buttons to the relay screens * Adds hidden words filter to search, hashtag and geotag feeds * Applies hidden words even to hashtags that were not included in the content of the event. * Adds support for saving reactions, zaps, translations user preferences on private outbox relays
UI Improvements: * Adds animations to the zap, reaction and boost popups by @Giovanni * Lighter chat bubbles * Date separators on chats * Adds unfollow to note dropdown * Improves (Show More) presence to only when it actually makes a difference. * Adds UI for when the location permission is rejected. * Improves error message for the signup page when the display name is blank * Adds extra padding for the zap setup screen * Pre-process search to avoid showing and hiding posts after hidden words where processed by the UI. * Rotate on full screen video if the device orientation is not locked by nostr:npub1a3tx8wcrt789skl6gg7rqwj4wey0j53eesr4z6asd4h4jwrd62jq0wkq4k Additionally, this update addresses 18 bug fixes, introduces 13 code improvements, and enhances performance by optimizing thread preloading. Additionally, a new cache system for reply levels when viewing threads has been implemented for a smoother experience.
Damus1.11 nostr:npub18m76awca3y37hkvuneavuw6pjj4525fw90necxmadrvjg0sdy6qsngq955 * Multi image uploads * A video player that actually works * Share sheet action * Seamless scroll * And more
Yakihonne nostr:npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
For Mobile: * All-in-One Content Hub: Create notes, articles, videos, curations, and smart widgets all in one place. * New Media Servers: Added support for @nostr:npub18jnd0, Nostr check, and more. * Thread Timeline Enhancements: Smoother and clearer thread viewing. * Nip 44 Gift Messages: Now enabled by default. * App-Wide Improvements: Faster, smoother, better. * Full compatibility with NWC secrets created outside the Alby wallet is now possible. * Provide an option to scan invoice QR and pay it. * Bug Fixes: Notifications, wallets, and feeds are now more reliable.
For Web: * Upgraded Note Editor: GIFs, emojis, and real-time previews to enhance your creativity. * Enhanced Long-Form Content: A fresh design to make writing a joy. * Custom Media Uploaders: Support for more media options and servers. * Expanded Search: Find more notes, media, and users with ease. * Browsing Suggestions: Discover new notes, media, users, and more. * General Improvements: Smoother performance and optimizations. * Bug Fixes: Making things more seamless for you. Additionally, Hot fixes for the YakiHonne Web 4.1.2
0xchat 1.4.3 nostr:npub1tm99pgz2lth724jeld6gzz6zv48zy6xp4n9xu5uqrwvx9km54qaqkkxn72 * Fixed the issue where inbox/outbox relays could not be added. * Fixed the issue where push notifications for voice calls had no sound. * Fixed the lag issue when loading private chat videos. * Fixed the issue where custom emoji reactions were not displayed.
Olas 0.1.5 nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft Olas 0.1.5 for iOS has officially shipped to TestFlight * Reposts * Zaps (via Nostr Wallet Connect for now) * Swipe-to-zap * Performance improvements
Nos 1.0.3 nostr:npub1pu3vqm4vzqpxsnhuc684dp2qaq6z69sf65yte4p39spcucv5lzmqswtfch Nos 1.0.3 is now on TestFlight for all our beta testers and waiting on Apple’s for review for our App Store users in Australia and New Zealand. * Added support for user setting and displaying pronouns. * Added display of website URLs for user profiles. * Updated note header UI to make it more readable. * Fixed galleries expanding past the width of the screen when there are lots of links or images. * Fixed quoted note composer not expanding to fit mentions.
DEG Mods site update nostr:npub17jl3ldd6305rnacvwvchx03snauqsg4nz8mruq0emj9thdpglr2sst825x * Add a Repost tagging system. * (Technical) Refactored code for the mods and mod page * Design tweaks for the "view more" part of a Mod post's page * Design tweaks for blog posts * Games added:S.T.A.L.K.E.R. 2: Heart of Chornobyl
WasabiWallet 2.3.1 nostr:npub1jw7scmeuewhywwytqxkxec9jcqf3znw2fsyddcn3948lw9q950ps9y35fg This version is a stability release packed with bug fixes and preparatory changes for upcoming features: * Bug Fixes
Settings Layout * Tor upgraded to v13.5.9
Buy Anything Button DisabledKYCNOT.me nostr:npub188x98j0r7l2fszeph6j7hj99h8xl07n989pskk5zd69d2fcksetq5mgcqf
UI Improvements: * The service list view is now more visually engaging, it displays additional information in a more aesthetically pleasing manner. Both filtering and searching functionalities have been optimized for speed and user experience. * Service pages have been also redesigned to highlight key information at the top, with the KYC Level box always accessible. The display of service attributes is now more visually intuitive. * The new self-made Captcha is robust, addressing the reliability issues encountered with the previous version.
Terms of Service Summarizer: * A significant upgrade is the Terms of Service summarizer/reviewer, now powered by AI (GPT-4-turbo). It efficiently condenses each service's ToS, extracting and presenting critical points, including any warnings. * processing over 40 ToS pages via the OpenAI API using a self-crafted and thoroughly tested prompt. Additionally, updates and upgrades have been implemented across Nostr Comments, Database, Scoring, Listings, API, and Pages.
notedeck nostr:npub1fjtdwclt9lspjy8huu3qklr7eklp5uq90u6yh8mec290pqxraccqlufnas * Update user relay-list via polling * Add user mute list sync via polling * Skip muted content * debug: add crate features which enable egui DebugOptions * ci: fix linux packages * Release v0.2.0 - Notedeck Alpha * fix linux packages again * ui: use proper response in wide-rendered note * ui: fix quote repost hitbox * ui: fix duplicate hitbox widget ids * anim: smoothly animate delete button from 0 size * nav: refactor title rendering for flexibility * column: switch to simplified strings for column headers * column: use simplified column string titles for now * column: switch to profile pictures in header * column: improve nav style * column: only show delete button when not navigating * column: reduce bounciness when navigating
Amber 3.0.1 nostr:npub1am3ermkr250dywukzqnaug64cred3x5jht6f3kdhfp3h0rgtjlpqecxrv7 * New design (still a work in progress) * Removed the push notification server * Open the permissions page with the correct account * Fix crash when signing in with ncryptsec * Fix icon size on notifications * Fix relay connection when changing the default relays * Option to setup a custom pin for the app * Button to copy your public key * Fix layout on Android < 15 * Fix multi event screen * Fetch profile data * Show relay message when event is rejected * Fix profile icon size * Don’t close app when using nostrconnect arcade * Better check for valid relays * Fix padding and scrolling * Support for secret when using nostrconnect * Fix empty relay notice,and more
Citrine 0.5.7 nostr:npub1hqlxlq57nvlq70ugmsmu9y5lmyc5k2lh5w7y85j7dgsr5u7zwavq5agspw * Fix rotation resetting the app state when downloading your notes * Fix timeout when downloading your notes when you have a lot of notes
Long-Form Content Eco
In the past two weeks, more than 434 long-form articles have been published, including over 84 articles on Bitcoin and more than 43 related to Nostr, accounting for 30% of the total content.
These articles about Nostr thoroughly explore its transformative role in decentralized social networking, highlighting its potential to revolutionize communication, provide censorship-resistant platforms, and promote the free flow of information. They delve into Nostr's technical aspects, including the integration of Nostr SDK across platforms, building high-performance relay networks, and innovative uses in micropayments with ecash wallets. The articles also examine the dynamic growth of the Nostr ecosystem, covering key statistics, community expansion, and strategies driving global projects. In addition to reflecting on Nostr's current achievements, they envision its future potential in areas like content creation and data sharing, while addressing challenges related to scalability and privacy.
The Bitcoin articles discuss its transformative role in the global financial ecosystem, emphasizing its potential as a store of value, a decentralized currency, and a driver of economic freedom. They explore Bitcoin's historical evolution, technical innovations, and its impact on broader financial systems, including comparisons with CBDCs and other cryptocurrencies. The articles highlight key developments, such as Bitcoin hitting significant price milestones, its integration into everyday financial practices, and the challenges posed by regulatory and market dynamics. Additionally, they delve into topics like mining sustainability, self-custody, the importance of education, and the cultural and ideological implications of Bitcoin in fostering decentralized trust and financial inclusion.
Thankyou, nostr:npub1zafcms4xya5ap9zr7xxr0jlrtrattwlesytn2s42030lzu0dwlzqpd26k5, nostr:npub1nje4ghpkjsxe5thcd4gdt3agl2usxyxv3xxyx39ul3xgytl5009q87l02j, nostr:npub1cj6ndx5akfazux7f0vjl4fyx9k0ulf682p437fe03a9ndwqjm0tqj886t6, nostr:npub1gkgyk28lurjuhyfjlxsga9mw6lc0c47c8pmcr65usre9d3qjcx6q9cyk5m, nostr:npub1yaul8k059377u9lsu67de7y637w4jtgeuwcmh5n7788l6xnlnrgs3tvjmf, nostr:npub1n3rmk5g03eej40rg2x83azxnml879lxxynxegfawl36e6qqrs8gqllmkh7, nostr:npub19mf4jm44umnup4he4cdqrjk3us966qhdnc3zrlpjx93y4x95e3uq9qkfu2, nostr:npub1ljm9zuj2k4d0lsgnpl2vh0rwtls7yrptpxu9js0v7y9hfplncnksn38rxz, nostr:npub1nxy4qpqnld6kmpphjykvx2lqwvxmuxluddwjamm4nc29ds3elyzsm5avr7, nostr:npub1u8vk3aex0y8hk607zjy5636nkhzhm8g5l4v8qeveusxmkhvs7ajqgs8lr6, nostr:npub1xjwkhqsmd5qs0k4jrfu27x86j0g736xuklzdkpd5dnjd6y4j5kcs72w6e7, nostr:npub1wptqtktghpk3rvuerx54e9fjy0s57nvk5paggevh2t83ndpjgquq8zwcqe, nostr:npub1lgwcxfg2zlml6kse69md0h0kpvmdx9vrz37yx6qea5g4uly33qhqs3quhd, nostr:npub1dk8z5f8pkrn2746xuhfk347a0g6fsxh20wk492fh9h8lkha2efxqgeq55a, and others, for your work. Enriching Nostr’s long-form content ecosystem is crucial.
Nostriches Global Meet Ups
Recently, several Nostr events have been hosted in different countries.
-
BtrustGathering successfully took place in Kenya on December 4-5, 2024. This annual event brought the Btrust team together to collaborate and lay a solid foundation for the future of open-source Bitcoin development. Over two days, the team outlined their vision for 2025, discussed strategies for funding engineers and sustaining open-source projects, and shared updates on the Bitcoin Open Source Software (₿OSS) program to better support builders.
-
The Nigeria Bitcoin Conference was successfully held from December 5th to 7th, 2024, at PopHAUS in Lagos, Nigeria. The event brought together global and local participants from the Bitcoin industry, including exchange founders, developers, investors, policymakers, miners, artists, and more, for three days of in-depth discussions and learning. The conference featured a variety of activities, including keynote speeches, interactive discussions, educational workshops, and a three-day hackathon challenge focused on technical innovations in Bitcoin Core and the Lightning Network.
-
The Bitcoin Africa Story Meetup successfully took place on Saturday, December 7, 2024, in Lagos, Nigeria. The event offered an engaging platform to explore Bitcoin's role in Africa and foster discussions and interactions among participants. nostr:npub17hkxr0chnut66nn28rwwqmv6sqazjy24t24zwv4ppfrlhwjhr9cs49h2la
-
Btrust Developer Day took place on Sunday, December 8, 2024, in Nairobi, Kenya, as part of the Africa Bitcoin Conference (ABC 2024). This event provided a platform for African developers to explore Bitcoin technology, learn from industry leaders, and collaborate on projects. It featured lightning talks, panel discussions, hands-on workshops, project showcases, and networking opportunities, making it a valuable experience for Bitcoin developers, open-source developers, technologists, and Bitcoin enthusiasts.
Here are the upcoming Nostr events in November that you might want to check out.
-
The Africa Bitcoin Conference 2024 will take place from December 9 to 11, 2024, in Nairobi, Kenya, featuring key programs such as Btrust Developer Day, TBD Hackathon, ABC Social Impact Award, Afro Bitcoin Fellowship, and Africa Bitcoin Day. The event will host nearly 70 distinguished speakers, including nostr:npub1ju2sw9unanr94p5wama3ydv90hcke34wcnmnxedummspaayz55qswlya32, nostr:npub16hssgmdhw9e9j6z8na45lzz4grdsfjqlp5hf8dtcqnp0glseeu3seecguf, nostr:npub1m7uxdt50d2jw35q79zlszlsvy79t7dpdxptz6rfsrsamra7l8ttsq752yl, nostr:npub1gaxapm9t9damh6q2lpc04ptcyeh0ysfdfzzs997agu3ae80ftrns7t985l, focusing on topics such as Bitcoin adoption, regulation, innovation, and security. This conference offers attendees valuable opportunities for in-depth discussions and knowledge sharing.
-
The Dadas Bitcoin Workshop will be held on Tuesday, December 10, 2024. This event is open to everyone and invites several changemakers who are driving innovation in the Bitcoin ecosystem, including nostr:npub1urhnkns9rt4c9mk6t9xctjkzmlkawxkdpzjnxdxhx82mqm7hfpuq0j7ue, nostr:npub1z5umqa38xfv94y3fpver2khw2qar2v54jetl24939j4f0yyhggdqrh5lwd, among others. The workshop will feature guest speakers sharing how Bitcoin has transformed their lives and careers. The event promises major surprises, along with gifts and rewards, and will foster vibrant discussions and connections that will have a lasting impact on participants.
-
Bitcoin Layer 2's vs Bitcoin Sidechains will take place on December 10, 2024, at 7 PM CAT, hosted by Rootstock on X Space. This online discussion, featuring guests such as nostr:npub1c8cp58lhn4vte3q2fejp7luqczx7u0njk5h0p0hry3atflk7g2hqc7xzqk and others, will delve into the differences between Bitcoin Layer 2 solutions and sidechains, highlighting their applications in smart contracts and DeFi.
-
The 5th Bitcoin Educators Unconference will be held on April 10, 2025, in Nashville, Tennessee. This event is specifically designed for educators, meetup organizers, community leaders, and grassroots experts, aiming to provide a platform for Bitcoin educators to collaborate and share insights. Participants will have the opportunity to exchange experiences, discuss best practices in Bitcoin education, and help drive the adoption and application of Bitcoin.
Additionally, We warmly invite event organizers who have held recent activities to reach out to us so we can work together to promote the prosperity and development of the Nostr ecosystem.
Thanks for reading! If there’s anything I missed, feel free to reach out and help improve the completeness and accuracy of my coverage.
-
-
 @ 16d11430:61640947
2024-12-08 22:26:12
@ 16d11430:61640947
2024-12-08 22:26:12Title: "From the East India Company to Modern Multinational Exploitation: How Fiat Instruments Perpetuate Centuries of Inequality"
The world has changed immeasurably since the era of the East India Company (EIC). Empires have fallen, revolutions have redrawn borders, and technology has transformed how we live, work, and communicate. Yet beneath the façade of progress lies a troubling continuity: the mechanisms of exploitation pioneered by the EIC remain alive and well, repackaged for a globalized age. The fiat instruments of economic domination—centralized financial systems, corporate monopolies, and legal frameworks favoring the elite—continue to enrich a select few while subjugating vast populations. In this intricate web of exploitation, the parallels between the 18th-century EIC and modern financial and corporate systems are impossible to ignore.
The East India Company: A Blueprint for Exploitation
The EIC was not merely a trading company; it was an unprecedented experiment in privatized empire-building. Armed with a royal charter granting it a monopoly over trade in the East Indies, the EIC leveraged financial innovation and brutal force to extract unimaginable wealth from the Indian subcontinent and other colonies. At its peak, it controlled vast territories, fielded a private army larger than that of many nation-states, and wielded immense political influence in Britain.
The EIC's tools of exploitation were remarkably modern: - Debt Instruments: The EIC taxed Indian peasants to fund wars and trade operations, creating a cycle of debt and dependency. - Corporate Sovereignty: As a quasi-sovereign entity, it governed territories, manipulated local economies, and imposed legal frameworks designed to funnel wealth to Britain. - Shareholder Capitalism: The EIC's joint-stock structure ensured that profits flowed to British elites, incentivizing exploitative policies to maximize dividends.
This model of extraction devastated colonies like India, where wealth was drained to the metropole, local industries were decimated, and millions perished in famines caused by forced cultivation of cash crops.
Fiat Systems: The Modern Successor to the EIC
Today, the instruments of exploitation have evolved, but their essence remains unchanged. Fiat currency systems, controlled by central banks and governments, perpetuate global economic inequalities and benefit the same elite classes that once profited from colonialism. The parallels are striking.
1. Centralized Currency and Debt as Tools of Control
- EIC: Taxation in India was imposed in British fiat currencies, compelling local populations to participate in exploitative colonial markets.
- Modern Era: Developing nations remain trapped in debt cycles dictated by global financial institutions like the IMF and World Bank. Loans are issued in fiat currencies such as the US dollar, often with austerity conditions that dismantle public services and prioritize debt repayment over local well-being.
For example, countries in the Global South are routinely forced to export raw materials and labor while importing expensive finished goods—a dynamic eerily similar to the colonial trade patterns enforced by the EIC.
2. Corporate Sovereignty and Multinational Power
- EIC: With its monopoly on trade and private army, the EIC operated as a state within a state, enforcing its will on colonized populations.
- Modern Era: Multinational corporations wield comparable power, often surpassing the GDP of the nations in which they operate. Companies like Amazon, Apple, and Shell dictate terms to governments, exploit tax loopholes, and maintain supply chains reliant on low-wage labor in the Global South.
For instance, mining corporations in Africa extract resources like cobalt and lithium—essential for modern technology—while leaving local communities impoverished and environments devastated. The profits flow to shareholders in the Global North, mirroring the wealth drain orchestrated by the EIC.
3. Legal and Financial Instruments Favoring the Elite
- EIC: British laws shielded the EIC from accountability while enforcing policies that crushed local industries (e.g., the destruction of India's textile sector).
- Modern Era: International trade agreements and intellectual property laws disproportionately benefit corporations in the Global North. The World Trade Organization (WTO) enforces patent protections that prevent developing nations from accessing affordable medicine or technology, deepening inequality.
Cryptocurrencies and decentralized finance hold promise for disrupting this dynamic, but even these innovations are co-opted by elites, leaving the underlying fiat-driven power structures intact.
Continuity of Exploitation: The Masses vs. the Elite
Global Wealth Inequality
The gap between the rich and the poor has widened to unprecedented levels. According to Oxfam, the world’s richest 1% control more wealth than the rest of humanity combined—a statistic that echoes the wealth concentration in colonial Britain, where EIC shareholders and aristocrats lived in opulence while Indian peasants starved.
Environmental Exploitation
The extractive practices perfected by the EIC have found new life in the 21st century. From deforestation in the Amazon to rare earth mining in Africa, modern corporations exploit natural resources in developing countries with little regard for environmental or social costs. These practices disproportionately harm marginalized communities, just as colonial extraction devastated colonized lands.
Labor and Supply Chains
The forced labor systems of the EIC have been replaced by sweatshops and precarious gig economy jobs. Workers in Bangladesh sewing clothes for fast-fashion brands, or delivery drivers in developed nations earning below minimum wage, are part of the same continuum of exploitation that fueled the EIC's profits.
The Beneficiaries: Then and Now
The beneficiaries of this system have remained remarkably consistent: 1. Financial Elites: Shareholders of the EIC were aristocrats and merchants; today, they are hedge funds, venture capitalists, and institutional investors. 2. Corporate Executives: Just as EIC officials amassed personal fortunes, modern CEOs earn astronomical salaries while overseeing exploitative practices. 3. Global North Nations: The wealth extracted from colonies powered Britain's industrial revolution; today, wealth extracted from the Global South sustains the consumer economies of the Global North.
Is Change Possible?
The enduring legacy of the EIC underscores the need for systemic change. While the tools of exploitation have adapted to the times, so too must the resistance. Decentralized technologies like Bitcoin offer an alternative to fiat systems, empowering individuals and bypassing centralized control. Grassroots movements and worker cooperatives challenge the dominance of corporate monopolies. Yet these efforts face immense resistance from entrenched elites.
Conclusion
From the East India Company to modern fiat-driven systems, the structures of mass exploitation have remained astonishingly consistent. They continue to prioritize profits for the few over the well-being of the many, perpetuating cycles of poverty, inequality, and environmental destruction. The instruments may have changed—stock options replacing private armies, multinational treaties replacing royal charters—but the underlying logic remains the same. Until these systems are dismantled, the lessons of history will remain painfully relevant.
Exploitation #Colonialism #EastIndiaCompany #MultinationalCorporations #WealthInequality #FiatCurrency #GlobalJustice #EconomicExploitation #EnvironmentalJustice #CorporateGreed #Decentralization #HistoryRepeats #Sustainability #SocialImpact #EconomicInequality
-
 @ 7c765d40:bd121d84
2024-12-08 15:57:26
@ 7c765d40:bd121d84
2024-12-08 15:57:26First off, happy birthday Arnie!
Our favorite guy turned 1 today.
Unofficially.
We don't know when he was born but the shelter estimated sometime this week.
So December 8th it is.
I hope he's enjoyed his first year.
He's sure brightened up our world out here.
So that'll be part one - decay.
Birthdays take a psychological toll on people.
Hours, days, years, birthdays.
Time, as we know it, is a human construct.
There is obviously correlation between time and the body starting to age.
But I feel like most of this aging process happens in our mind.
We convince ourself that just because another year passed, we should start feeling worse and getting fatter.
One thing that I've learned over these last few years is the power of thought.
We've all been guilty of this.
"I'm about to turn 50, my best years are behind me."
"I'm 40 and don't have kids or a wife, I'm going to die alone."
Time is absolutely relevant - and a big part of why bitcoin works so well.
But these are just numbers we use to stay organized and consistent.
There are 70 years with a sharper mind than some 20 year olds.
It's important to realize this concept and to not age yourself faster than you need.
Your mind is your most powerful tool.
Make sure you're using it to your advantage.
Onto the next part - decoy.
I am a big proponent of having a decoy wallet in your house.
The purpose of the decoy is to trick "bad actors" into thinking this is your main wallet.
If someone were to break into your house, you hand them your decoy wallet.
The problem with most bitcoiners - including myself until a few weeks ago - is that they keep the decoy with the main wallet.
It makes the most to keep valuable items in the safe or a safe place in the house.
But having the decoy wallet and the main wallet in the same place kind of defeats the purpose.
So here's a few tips for levelling up your bitcoin security:
-
If you have more than 10 million sats (.10 bitcoin) consider using a decoy wallet.
-
Keep the decoy wallet (approx 5-10% of your stack) in the safe.
-
Keep your main wallet in a separate hidden location.
-
Keep your seed phrase on steel or titanium.
-
If you have more than 50 million sats (.50 bitcoin), start looking into a multi-signature setup. This is the more advanced version of a decoy wallet which requires 2 of 3 signatures to send any bitcoin.
Your bitcoin security setup is always evolving.
Never rush into anything or panic.
Take your time and do it right.
And be sure to practice and rehearse your setup on a regular basis.
The last thing you want to do is go through all this time and effort only to lock yourself out!
Happy birthday Arn!
Happy Sunday to all!
PROJECT POTENTIAL - You can now find the expanded audio versions of these on the new podcast - Project Potential! I will be sharing the video versions here for the LITF members but you can also find it for free on Spotify and of course Fountain!
Here is the link to Episode 006 on Fountain: https://fountain.fm/episode/i99LWnNr0pUVGA1ukuX4
Have a great day everyone! And remember, the only thing more scarce than bitcoin is time!
Jor
-
-
 @ f0c7506b:9ead75b8
2024-12-08 10:03:35
@ f0c7506b:9ead75b8
2024-12-08 10:03:35
-
Bazı şeyleri yapmak, söylemekten daha kolaydır.
-
Bütün güzel şeyleri bize toprak verir. Bütün güzel şeyler toprağa geri döner.
-
Eğer mevsimlere bakarsanız her mevsim meyve getirir. Yazın meyve vardır, sonbaharda da. Kış farklı meyveler getirir, ilkbahar da. Hiçbir anne çocukları için bu kadar çok çeşit meyveyle buzdolabını dolduramaz.
-
Kendimi bu hayattan kurtarmaya karar verdim. Ne için mi? Bu anlamanıza yardım etmeyecektir ve bunun hakkında sizinle konuşamam; anlayamazsınız. Anlamayacağınız için değil; çünkü benim hissettiklerimi hissedemezsiniz. Duygularımı anlayıp paylaşabilirsiniz, bana merhamet gösterebilirsiniz; ama acımı hissedebilir misiniz? Hayır. Acı çekersiniz ve ben de çekerim. Sizi anlarım. Acımı anlayabilirsiniz; ama onu hissedemezsiniz.
-
İnsanın devam edemeyeceği bir an gelir.
-
Birisine yardım etmek istediğiniz zaman bunu uygun biçimde yapmalısınız, bütün kalbinizle. Bu daha iyidir. Daha adil ve daha makul.
-
İntiharın en büyük günahlardan birisi olduğunu biliyorum. Fakat mutsuz olmak da büyük bir günah. Mutsuzken başka insanları incitirsiniz. Bu da bir günah değil mi? Başkalarını incittiğinizde bu bir günah değil midir? Aileni incitiyorsun, arkadaşlarını, kendini incitiyorsun. Bu bir günah değil mi? Size yakın olan insanları incitiyorsanız bu da büyük bir günahtır.
-
Yardım, mutlaka karşılığı ödenmesi gereken bir şey değildir.
-
Size başımdan geçen bir olayı anlatacağım: henüz yeni evlenmiştim. Belaların her türlüsü bizi buldu. Öylesine bıkkındım ki her şeye son vermeye karar verdim. Bir sabah şafak sökmeden önce arabama bir ip koydum. Kendimi öldürmeyi kafama koydum. Yola koyuldum. Dut ağaçlarıyla dolu bir bahçeye vardım. Orada durdum. Hava henüz karanlıktı. İpi bir ağacın dalı üzerine attım; ama tutturamadım. Bir iki kere denedim ama kâr etmedi. Ardından ağaca tırmandım ve ipi sımsıkı düğümledim. Sonra elimin altında yumuşak bir şey hissettim: Dutlar. Lezzetli, tatlı dutlar. Birini yedim. taze ve suluydu. Ardından bir ikincisini ve üçüncüsünü. Birdenbire güneşin dağların zirvesinden doğduğunun farkına vardım. O ne güneşti, ne manzaraydı, ne yeşillikti ama! Birdenbire okula giden çocukların seslerini duydum. Bana bakmak için durdular. "Ağacı sallar mısın?" diye bana sordular. Dutlar düştü ve yediler. Kendimi mutlu hissettim. Ardından alıp eve götürmek için biraz dut topladım. Bizim hanım hâlâ uyuyordu. Uyandığı zaman dutları güzelce yedi. Ve hoşuna gitti. Kendimi öldürmek için ayrılmıştım ve dutlarla geri döndüm. Bir dut hayatımı kurtarmıştı.
-
Bir türk, doktoru görmeye gider. Ve ona der ki: "Doktor bey, vücuduma parmağımla dokunduğumda acıyor, başıma dokunsam acıyor, bacaklarıma dokunsam acıyor, karnıma, elime dokunsam acıyor." doktor onu muayene eder ve sonra ona der ki: "vücudun sağlam; ama parmağın kırık!"
-
Hayat dümdüz ilerleyen bir tren gibidir; rayların sonuna geldiğinde son durağa ulaşır. Ve ölüm son durakta bekler. Elbette, ölüm bir çözümdür; fakat ilk olarak değil. Genç yaşta hiç değil.
-
Dünya göründüğü gibi değildir. Bakış açınızı değiştirmelisiniz ki dünya değişsin. İyimser olun. Her şeye olumlu tarafından bakın.
-
-
 @ 58937958:545e6994
2024-12-08 07:57:42
@ 58937958:545e6994
2024-12-08 07:57:42Making Waves:Bitcoin-themed handmade goods

nevent1qqs04vf85pyducj8h4s49g2ex84r6dvzenjjg4m7wrd9g955506r36cpz4mhxue69uhhxarjvee8jtnfwf5hxtn5duhsygzcjdu4sqmvah54tvjmj22c8q2qhgk74judryu7mydyr039ghnfjs09g2yq
20081031
This bag is inspired by the Bitcoin White Paper.
「20081031」
— Making Waves (@MakingWavesBTC) November 23, 2024
Price:210,000 sats
Limited to 21 pieces
Free Shipping
I will produce and sell one per week.#ProofOfHandmade #MakingWavesBTC pic.twitter.com/9mKtsYJft3For details, please visit ↓
https://makingwaves-btc.com/en/
Sales have also started at Geyser. https://geyser.fund/project/makingwaves
Sales on Shopstr is also planned.
BitcoinTokyo2024
I exhibited at "Shibuya Lightning Marche" in Japan and made sales of 1,885,314 sats (approximately $1,181 at the exchange rate on the day) over two days.
Handmade goods by MakingWaves (Example)
— Making Waves (@MakingWavesBTC) September 21, 2024
・Bookmark
・Coaster
・COLDCARD Q case
・Japanese-Style Drawstring Bag
Enjoy the Lightning Marche🧸#BitcoinTokyo2024#渋谷ライトニングマルシェ pic.twitter.com/qqNXAT0nWNMoving forward, I will focus on selling items priced at 2,100 sats, 21,000 sats, and 210,000 sats.
- 2,100 sats: Bookmarks, beginner-friendly Bitcoin comic booklets, etc.
- 21,000 sats: Pouches, and similar items.
- 210,000 sats: Limited-edition bags, and more.
Short Video:Bitcoin Handmade Anime【MakingWaves】
A short animation for Bitcoin beginners & kids.
Bitcoin guide site for beginners:bitcoin-zukan.com
Although the site is in Japanese, there are many articles translated into English.
Supervised by Koji Higashi, co-organizer of BitcoinTokyo2024.
Podcast:Grassroots Bitcoin
A podcast supporting grassroots Bitcoin activities.
While most episodes are in Japanese, the episode listed below is in English.
Introducing "MakingWaves" https://www.fountain.fm/episode/7si9y8sxmWmhfK8CeMQ8
Podcast URL * Fountain:https://www.fountain.fm/show/eWVWc2vZXycjPlMTZsLf * Spotify:https://creators.spotify.com/pod/show/shigeru-minami * Apple Podcast:https://podcasts.apple.com/us/podcast/%E8%8D%89%E3%81%AE%E6%A0%B9%E3%83%93%E3%83%83%E3%83%88%E3%82%B3%E3%82%A4%E3%83%B3/id1757540844
Other activities, SNS, etc.
Twitter(English):Making Waves
“20081031”
— Making Waves (@MakingWavesBTC) November 26, 2024
No.1/21 Completed!
I adjusted it so that the word bitcoin is printed on the back of the outer pocket as well.
I think it will be useful when showing it to fellow bitcoiners. pic.twitter.com/00ejMN6s2HI post about handmade goods.
https://x.com/MakingWavesBTC
Twitter(Japanese):Shigeru Minami
COLDCARDでビットコインを受け取り・送金する解説動画を
— Shigeru Minami (@kiterugumatic) October 21, 2024
YouTubeにアップしました
私は操作する度に緊張する上に結構間違えるので
どなたかの役に立つかもと思って作りました pic.twitter.com/7UFnClknSUI mainly share posts about Bitcoin, along with personal updates.
https://x.com/kiterugumatic
Nostr:Shigeru Minami
nostr:nevent1qqszzcz9npq5xgw08tp5wud0kg9wfacf9fkj07gu82wn3wjsad3wd2cppvjdw
My posts are mostly personal.
As I’m practicing English, I try to post without using translation tools as much as possible.
Please forgive any awkward or hard-to-read sentences.
npub1tzfhjkqrdnk7j4djtwfftqupgzazm6kt35vnnmv35sd7y4z7dx2qzhkje9
Instagram(English):Making Waves
 I share short videos of the handmade goods production process.
I share short videos of the handmade goods production process.https://www.instagram.com/making_waves_btc/
Note
The illustrations on bitcoin-zukan.com and my SNS icons were created by a commissioned illustrator.
All other activities are personally handled by Shigeru Minami.
Examples include handmade crafting, video production, article writing, product photography, designing original fabric, and creating illustrations for my original characters, "Bull & Bear."
For inquiries, please feel free to contact me via the SNS platforms mentioned above or the email address provided below.
E-mail:contact@makingwaves-btc.com
Thank you for reading all the way through.
-
 @ 65912a7a:5dc638bf
2024-12-08 05:33:02
@ 65912a7a:5dc638bf
2024-12-08 05:33:02Chef's notes
This is my late partner's award winning Cajun rice & beans recipe. It's an updated take on the traditional Cajun comfort food.
Chef Darin was a classically trained chef who spent 30+ years in the kitchen perfecting his recipes, and delivering authentic Cajun and Creole food to his patrons. This is a 5-star dish that will earn the respect of the most discerning Cajun afficionado. You won't be disappointed.
I suggest making this recipe exactly as directed the first time, and then make whatever adjustments you want for future batches. Also, don't cheap out on the Andouille. No Johnsonville or Hillshire Farms. Chef Aidelle's is a good choice, as is Silva's from Whole Foods. They cost a few extra bucks, but it's absolutely worth it.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 3 hours
- 🍽️ Servings: 12
Ingredients
- 16oz small red beans, dry
- 2 cups long grain white rice
- 14-16oz andouille sausage, sliced
- 8oz ham, cubed
- 1 large yellow onion, chopped
- 1 green bell pepper, chopped
- 2-3 stalks celery, chopped
- 2 tbsp garlic (12 cloves), minced
- 7 cups water
- ¼ cup olive oil
- 2 large bay leaves
- 1 tbsp parsley, dried
- 1 tsp thyme, dried
- 1 tsp Cajun seasoning
- ½ tsp cayenne pepper, dried
- ¼ tsp sage, rubbed
- 1½ tsp salt (more or less to taste)
Directions
- Soak beans in a large pot of water overnight.
- Heat oil in a large stockpot over medium heat. Cook onion, bell pepper, celery, garlic in olive oil for 3 to 4 minutes (until onion is translucent).
- Add beans, bay leaves, parsley, thyme, salt, MSG, Cajun seasoning, cayenne pepper, Sage, and water. Stir, bring to a boil, and then reduce heat to medium-low (btwn 2-3). Cover and simmer for 2½ hours.
- Remove bay leaves. Mash some of the beans. Stir Andouille and ham into beans, and simmer uncovered for an additional 30 minutes.
- Meanwhile, prepare the rice. Bring water and rice to a boil in a saucepan. Reduce heat, cover, and simmer for 20 minutes.
- Serve beans over steamed white rice.
-
 @ 8fb140b4:f948000c
2024-12-08 05:21:39
@ 8fb140b4:f948000c
2024-12-08 05:21:39After nuking my second LND node (the first one died due to hardware failure) by my own typo and lack of any thought in the design of the CLI of LND lightning node tools, I decided to take a plunge into the world of mature and complex implementation of the protocol, Eclair by ACINQ. It has been almost one year (the birth of the node was on Christmas Day 2023), 50 thousand transactions routed, and over 30 BTC of routed value. In this post, I'd like to reflect on my experiences with Eclair, go over some of the gotchas and issues, and highlight some of the good choices that I've made since the beginning of my adventure.
Learnings from the Past Experience
While I was learning Lightning network and had very little understanding of how things worked in the whole Bitcoin space, Umbrel was my go-to solution that helped me get off the ground. It proved to be easy and somewhat educational but was not something that I would continuously run for the production setup or trust with any significant amount of bitcoin that I could not afford to lose. Lightning is built on top of the L1 (Bitcoin) network but manages the state of the channels in its own database that is negotiated and agreed upon with its peers. Any failures in the state integrity may result in the complete loss of liquidity or hefty penalty transactions (significant loss of capital). A Lightning node that participates in routing public transactions is also required to be constantly online with as little downtime as possible and only short periods offline at a time. Otherwise, you may risk causing force-closure of the channel due to expired HTLC that is measured in number of blocks.
The Setup
Taking all of my learnings into consideration, I decided to first invest in reliable enterprise-grade hardware: - Server-grade hardware with ECC memory and reliable power supply and CPU - UPS (Uninterruptible Power Supply) to avoid any headaches due to electrical spikes or drop-outs - Reliable enterprise SSDs and NVMEs - ZFS (filesystem) to mirror the critical storage and to ensure full integrity of the data (bit-rot prevention). You do need to tune ZFS for your specific workload and reliability - Reliable and replicated database (PostgreSQL) with two local and one remote replica, and a requirement to have at least two replicas committing the transaction to the disk - Backup! On-site and off-site backup of the critical configuration that you could use to restore the node if your house burns down - Spare parts, redundancy, backup, monitoring - Reliable and stable internet connectivity
The software is Eclair 0.11.0 (latest release as of today), PostgreSQL 16 with two replicas, Bitcoin Core 27.2 (with redundant storage of blocks), additional Bitcoin Core running on a separate node and in-sync with the chain (in case primary node fails), Ubuntu 22.04 with the latest docker software from the official Docker repo.
All Major Gotchas That I Came Across
While Eclair is mature and very stable in itself, it does have some quirks and design choices that you need to account for when running your node. The software is written in Scala and requires a specific version of JVM to run it, as well as JRE and Maven to build it. It doesn't mean that other versions won't work, but you may find unpleasant bugs that may result in catastrophic failures of your node with nobody to help you. All of the requirements are listed in the release notes and installation guide. Whenever in doubt, RTFM first, then ask questions.
Limited Support by the FOSS Community
Eclair is not the most popular implementation of the Lightning protocol, and therefore it is hard to find tools or plugins that could help you manage the node. GUI for the node so far is only supported by RTL and with a very limited number of features. For any sort of statistics, you are limited to either Prometheus (extensive metrics are available) or writing your own SQL on top of the Eclair tables.
On-chain Fee Differences Between Yours and Partner Nodes
This one hit me hard, and many times. I've had more than a few force-closures of the channels because of the conservative and safe default settings. The worst part is, it strikes you when there is a huge spike in fees, which results in significant losses to force-close the channel due to high fees. I am still not 100% sure how the big difference can be exploited in practice, and opted for increase of the tolerance levels to avoid surprise FCs:
eclair.on-chain-fees { feerate-tolerance { ratio-low = <0.01~> // will allow remote fee rates as low as XX our local feerate (spikes) ratio-high = <20.0~> // will allow remote fee rates as high as XX times our local feerate (drops) } }It is up to you and your risk tolerance to define something reasonable and yet allow for secure and reliable node operation.Initial Lightning Network State Sync
When I just started running the node, I had very few channels and startup times were fast. Later, when I expanded the number of channels, I noted that it took my node up to 6-12 hours before it was fully in-sync and routing traffic fast. Given that ACINQ maintains one of the largest nodes on the network, I knew that there was something with my settings that caused the issue. After some research, I came across the setting that whitelisted node IDs for state sync, which immediately rang a bell since I knew from the LND days that not all peer nodes are used for the network sync. Setting the list to my most reliable and largest nodes reduced the startup settling times down to minutes again:
eclair.sync-whitelist = [ "03864ef025fde8fb587d989186ce6a4a186895ee44a926bfc370e2c366597a3f8f", ... ]You do not need to have too many public keys in here, and should keep it between 5-10.Automatic MAX HTLC Adjustment for the Channel
One of the killer features of Eclair is its ability to automatically adjust MAX HTLC for the channel and reduce the number of failed transactions due to insufficient liquidity on the channel. It can be used to estimate your total channels' balances but with smart configuration and a little thinking, you can make it reasonably private while still maintaining a good transaction flow:
eclair.channel.channel-update.min-time-between-updates=1 hour # Allows for the adjustments to be made once every hour eclair.channel.channel-update.balance-thresholds=[ { available-sat = 10000 max-htlc-sat = 0 // 0% of 10000 }, ... ]You can have as many variations as you need, and ensure that the channel MAX HTLC is set well and within reasonable ranges. You would also want to account for multiple transactions going through the channel, but also account for the channel size and an average amount of sats per transaction.Max Accepted HTLCs
By design, the Lightning channel is limited to a specific number of in-flight HTLCs, and the setting is fixed during channel opening time with no way of changing it unless you close and reopen the channel with new settings. If you find your node routing a lot of small transactions (zaps), you may quickly fail many due to that limit (I think default was in single digit range):
eclair.channel.max-htlc-value-in-flight-percent=98 # Default I think is half or 50% eclair.channel.max-accepted-htlcs = 50The setting above will allow for the channel to be more fully utilized and have more concurrent transactions without clogging.CLTV Delta
This is basically a setting that is global for Eclair and sets the maximum number of remaining blocks (in time) before HTLC expires. Setting this too high may result in many HTLCs failing for the small nodes with not so great centrality, and reduce the number of routed transactions: ```
CLTV delta
eclair.channel.expiry-delta-blocks = 60 ``` Default is 144 but I found that setting this to 60 (minimum possible for my node setup and configuration) yields better results for routing. It does expose you to more risk of expired HTLCs that may cause force-closures, but I have seen only one so far on my node.
Allocate Sufficient Memory
You will want to adjust the heap size for Eclair, since the default is too small to run any sizable node. Setting
JAVA_OPTS=-Xmx32g(or half the size of your available RAM) would be a good start. I would advise having at least 32GB of RAM for the node, and allocating at least 16GB (JAVA_OPTS=-Xmx16g) for smooth and fast operations.And More Settings and Parameters to Tune
I have covered only some of the major settings that I felt were worth writing about, but there is much more you could configure and tweak. Read all of the Guides and especially focus on the Configure and a sample reference configuration file.
Good Decisions
First, going with Eclair was the right choice, along with using server-grade hardware with ECC RAM and reliable storage. Second, having a replicated database on three separate nodes with one off-site saved me from a sure destruction of all state and loss of funds. Third, deciding to only maintain channels with reliable and stable nodes saved me from some bad force-closures, where I would choose to close the channel if a peer node goes up and down too frequently, regardless of how well it routes. Even big nodes run by single operators fail badly, as do nodes operated by companies. Keeping your eyes on the node and its health, as well as the health of its peers, is something that very few operators do, which can cause failures and unnecessary loss of your and their funds.
Lastly, if you decide to run a routing node, you have a responsibility to maintain it well and monitor its health. There are many tools you could use, and with Eclair you can use Prometheus and Grafana. Keep your node's packages updated and monitor for any security-related issues that may appear from time to time, so you can mitigate them quickly.
Conclusion
So far I am satisfied with Eclair despite all of the difficulties and headaches I've had with it. It is not perfect, and it requires me to create small tools to do some basic things, but I need a stable and reliable node that I can trust. Eclair has proved to be all that I wanted, and saved my bacon a few times when I nuked one of the PostgreSQL servers and all of its data, and managed to do the same for another replica, but was able to recover and recreate from the remaining replica. Eclair is also stateless during runtime and guarantees consistency of the node regardless of how it fails. Even if you pull a plug on the node's server, it will still be able to come up and recover its consistent state that is in agreement with its peers.
Is it for everyone? No, it is definitely not for everyone or for anyone who just wants a small node to run their online shop with a few channels. You could have a very reliable and trusted node for the online shop with Eclair, but you will need some technical skills to be able to set up, maintain and recover it if things go wrong.
In the end, it is all up to you, your skills, your willingness to learn, and your risk tolerance to make that decision. For me, it was the right choice, and I have no regrets despite not having access to the latest shiny features of the Lightning network.
-
 @ e6817453:b0ac3c39
2024-12-07 15:06:43
@ e6817453:b0ac3c39
2024-12-07 15:06:43I started a long series of articles about how to model different types of knowledge graphs in the relational model, which makes on-device memory models for AI agents possible.
We model-directed graphs
Also, graphs of entities
We even model hypergraphs
Last time, we discussed why classical triple and simple knowledge graphs are insufficient for AI agents and complex memory, especially in the domain of time-aware or multi-model knowledge.
So why do we need metagraphs, and what kind of challenge could they help us to solve?
- complex and nested event and temporal context and temporal relations as edges
- multi-mode and multilingual knowledge
- human-like memory for AI agents that has multiple contexts and relations between knowledge in neuron-like networks
MetaGraphs
A meta graph is a concept that extends the idea of a graph by allowing edges to become graphs. Meta Edges connect a set of nodes, which could also be subgraphs. So, at some level, node and edge are pretty similar in properties but act in different roles in a different context.
Also, in some cases, edges could be referenced as nodes.
This approach enables the representation of more complex relationships and hierarchies than a traditional graph structure allows. Let’s break down each term to understand better metagraphs and how they differ from hypergraphs and graphs.Graph Basics
- A standard graph has a set of nodes (or vertices) and edges (connections between nodes).
- Edges are generally simple and typically represent a binary relationship between two nodes.
- For instance, an edge in a social network graph might indicate a “friend” relationship between two people (nodes).
Hypergraph
- A hypergraph extends the concept of an edge by allowing it to connect any number of nodes, not just two.
- Each connection, called a hyperedge, can link multiple nodes.
- This feature allows hypergraphs to model more complex relationships involving multiple entities simultaneously. For example, a hyperedge in a hypergraph could represent a project team, connecting all team members in a single relation.
- Despite its flexibility, a hypergraph doesn’t capture hierarchical or nested structures; it only generalizes the number of connections in an edge.
Metagraph
- A metagraph allows the edges to be graphs themselves. This means each edge can contain its own nodes and edges, creating nested, hierarchical structures.
- In a meta graph, an edge could represent a relationship defined by a graph. For instance, a meta graph could represent a network of organizations where each organization’s structure (departments and connections) is represented by its own internal graph and treated as an edge in the larger meta graph.
- This recursive structure allows metagraphs to model complex data with multiple layers of abstraction. They can capture multi-node relationships (as in hypergraphs) and detailed, structured information about each relationship.
Named Graphs and Graph of Graphs
As you can notice, the structure of a metagraph is quite complex and could be complex to model in relational and classical RDF setups. It could create a challenge of luck of tools and software solutions for your problem.
If you need to model nested graphs, you could use a much simpler model of Named graphs, which could take you quite far.
The concept of the named graph came from the RDF community, which needed to group some sets of triples. In this way, you form subgraphs inside an existing graph. You could refer to the subgraph as a regular node. This setup simplifies complex graphs, introduces hierarchies, and even adds features and properties of hypergraphs while keeping a directed nature.
It looks complex, but it is not so hard to model it with a slight modification of a directed graph.
So, the node could host graphs inside. Let's reflect this fact with a location for a node. If a node belongs to a main graph, we could set the location to null or introduce a main node . it is up to you
Nodes could have edges to nodes in different subgraphs. This structure allows any kind of nesting graphs. Edges stay location-free
Meta Graphs in Relational Model
Let’s try to make several attempts to model different meta-graphs with some constraints.
Directed Metagraph where edges are not used as nodes and could not contain subgraphs

In this case, the edge always points to two sets of nodes. This introduces an overhead of creating a node set for a single node. In this model, we can model empty node sets that could require application-level constraints to prevent such cases.
Directed Metagraph where edges are not used as nodes and could contain subgraphs

Adding a node set that could model a subgraph located in an edge is easy but could be separate from in-vertex or out-vert.
I also do not see a direct need to include subgraphs to a node, as we could just use a node set interchangeably, but it still could be a case.Directed Metagraph where edges are used as nodes and could contain subgraphs
As you can notice, we operate all the time with node sets. We could simply allow the extension node set to elements set that include node and edge IDs, but in this case, we need to use uuid or any other strategy to differentiate node IDs from edge IDs. In this case, we have a collision of ephemeral edges or ephemeral nodes when we want to change the role and purpose of the node as an edge or vice versa.

A full-scale metagraph model is way too complex for a relational database.
So we need a better model.Now, we have more flexibility but loose structural constraints. We cannot show that the element should have one vertex, one vertex, or both. This type of constraint has been moved to the application level. Also, the crucial question is about query and retrieval needs.
Any meta-graph model should be more focused on domain and needs and should be used in raw form. We did it for a pure theoretical purpose. -
 @ e6817453:b0ac3c39
2024-12-07 15:03:06
@ e6817453:b0ac3c39
2024-12-07 15:03:06Hey folks! Today, let’s dive into the intriguing world of neurosymbolic approaches, retrieval-augmented generation (RAG), and personal knowledge graphs (PKGs). Together, these concepts hold much potential for bringing true reasoning capabilities to large language models (LLMs). So, let’s break down how symbolic logic, knowledge graphs, and modern AI can come together to empower future AI systems to reason like humans.
The Neurosymbolic Approach: What It Means ?
Neurosymbolic AI combines two historically separate streams of artificial intelligence: symbolic reasoning and neural networks. Symbolic AI uses formal logic to process knowledge, similar to how we might solve problems or deduce information. On the other hand, neural networks, like those underlying GPT-4, focus on learning patterns from vast amounts of data — they are probabilistic statistical models that excel in generating human-like language and recognizing patterns but often lack deep, explicit reasoning.
While GPT-4 can produce impressive text, it’s still not very effective at reasoning in a truly logical way. Its foundation, transformers, allows it to excel in pattern recognition, but the models struggle with reasoning because, at their core, they rely on statistical probabilities rather than true symbolic logic. This is where neurosymbolic methods and knowledge graphs come in.
Symbolic Calculations and the Early Vision of AI
If we take a step back to the 1950s, the vision for artificial intelligence was very different. Early AI research was all about symbolic reasoning — where computers could perform logical calculations to derive new knowledge from a given set of rules and facts. Languages like Lisp emerged to support this vision, enabling programs to represent data and code as interchangeable symbols. Lisp was designed to be homoiconic, meaning it treated code as manipulatable data, making it capable of self-modification — a huge leap towards AI systems that could, in theory, understand and modify their own operations.
Lisp: The Earlier AI-Language
Lisp, short for “LISt Processor,” was developed by John McCarthy in 1958, and it became the cornerstone of early AI research. Lisp’s power lay in its flexibility and its use of symbolic expressions, which allowed developers to create programs that could manipulate symbols in ways that were very close to human reasoning. One of the most groundbreaking features of Lisp was its ability to treat code as data, known as homoiconicity, which meant that Lisp programs could introspect and transform themselves dynamically. This ability to adapt and modify its own structure gave Lisp an edge in tasks that required a form of self-awareness, which was key in the early days of AI when researchers were exploring what it meant for machines to “think.”
Lisp was not just a programming language—it represented the vision for artificial intelligence, where machines could evolve their understanding and rewrite their own programming. This idea formed the conceptual basis for many of the self-modifying and adaptive algorithms that are still explored today in AI research. Despite its decline in mainstream programming, Lisp’s influence can still be seen in the concepts used in modern machine learning and symbolic AI approaches.
Prolog: Formal Logic and Deductive Reasoning
In the 1970s, Prolog was developed—a language focused on formal logic and deductive reasoning. Unlike Lisp, based on lambda calculus, Prolog operates on formal logic rules, allowing it to perform deductive reasoning and solve logical puzzles. This made Prolog an ideal candidate for expert systems that needed to follow a sequence of logical steps, such as medical diagnostics or strategic planning.
Prolog, like Lisp, allowed symbols to be represented, understood, and used in calculations, creating another homoiconic language that allows reasoning. Prolog’s strength lies in its rule-based structure, which is well-suited for tasks that require logical inference and backtracking. These features made it a powerful tool for expert systems and AI research in the 1970s and 1980s.
The language is declarative in nature, meaning that you define the problem, and Prolog figures out how to solve it. By using formal logic and setting constraints, Prolog systems can derive conclusions from known facts, making it highly effective in fields requiring explicit logical frameworks, such as legal reasoning, diagnostics, and natural language understanding. These symbolic approaches were later overshadowed during the AI winter — but the ideas never really disappeared. They just evolved.
Solvers and Their Role in Complementing LLMs
One of the most powerful features of Prolog and similar logic-based systems is their use of solvers. Solvers are mechanisms that can take a set of rules and constraints and automatically find solutions that satisfy these conditions. This capability is incredibly useful when combined with LLMs, which excel at generating human-like language but need help with logical consistency and structured reasoning.
For instance, imagine a scenario where an LLM needs to answer a question involving multiple logical steps or a complex query that requires deducing facts from various pieces of information. In this case, a solver can derive valid conclusions based on a given set of logical rules, providing structured answers that the LLM can then articulate in natural language. This allows the LLM to retrieve information and ensure the logical integrity of its responses, leading to much more robust answers.
Solvers are also ideal for handling constraint satisfaction problems — situations where multiple conditions must be met simultaneously. In practical applications, this could include scheduling tasks, generating optimal recommendations, or even diagnosing issues where a set of symptoms must match possible diagnoses. Prolog’s solver capabilities and LLM’s natural language processing power can make these systems highly effective at providing intelligent, rule-compliant responses that traditional LLMs would struggle to produce alone.
By integrating neurosymbolic methods that utilize solvers, we can provide LLMs with a form of deductive reasoning that is missing from pure deep-learning approaches. This combination has the potential to significantly improve the quality of outputs for use-cases that require explicit, structured problem-solving, from legal queries to scientific research and beyond. Solvers give LLMs the backbone they need to not just generate answers but to do so in a way that respects logical rigor and complex constraints.
Graph of Rules for Enhanced Reasoning
Another powerful concept that complements LLMs is using a graph of rules. A graph of rules is essentially a structured collection of logical rules that interconnect in a network-like structure, defining how various entities and their relationships interact. This structured network allows for complex reasoning and information retrieval, as well as the ability to model intricate relationships between different pieces of knowledge.
In a graph of rules, each node represents a rule, and the edges define relationships between those rules — such as dependencies or causal links. This structure can be used to enhance LLM capabilities by providing them with a formal set of rules and relationships to follow, which improves logical consistency and reasoning depth. When an LLM encounters a problem or a question that requires multiple logical steps, it can traverse this graph of rules to generate an answer that is not only linguistically fluent but also logically robust.
For example, in a healthcare application, a graph of rules might include nodes for medical symptoms, possible diagnoses, and recommended treatments. When an LLM receives a query regarding a patient’s symptoms, it can use the graph to traverse from symptoms to potential diagnoses and then to treatment options, ensuring that the response is coherent and medically sound. The graph of rules guides reasoning, enabling LLMs to handle complex, multi-step questions that involve chains of reasoning, rather than merely generating surface-level responses.
Graphs of rules also enable modular reasoning, where different sets of rules can be activated based on the context or the type of question being asked. This modularity is crucial for creating adaptive AI systems that can apply specific sets of logical frameworks to distinct problem domains, thereby greatly enhancing their versatility. The combination of neural fluency with rule-based structure gives LLMs the ability to conduct more advanced reasoning, ultimately making them more reliable and effective in domains where accuracy and logical consistency are critical.
By implementing a graph of rules, LLMs are empowered to perform deductive reasoning alongside their generative capabilities, creating responses that are not only compelling but also logically aligned with the structured knowledge available in the system. This further enhances their potential applications in fields such as law, engineering, finance, and scientific research — domains where logical consistency is as important as linguistic coherence.
Enhancing LLMs with Symbolic Reasoning
Now, with LLMs like GPT-4 being mainstream, there is an emerging need to add real reasoning capabilities to them. This is where neurosymbolic approaches shine. Instead of pitting neural networks against symbolic reasoning, these methods combine the best of both worlds. The neural aspect provides language fluency and recognition of complex patterns, while the symbolic side offers real reasoning power through formal logic and rule-based frameworks.
Personal Knowledge Graphs (PKGs) come into play here as well. Knowledge graphs are data structures that encode entities and their relationships — they’re essentially semantic networks that allow for structured information retrieval. When integrated with neurosymbolic approaches, LLMs can use these graphs to answer questions in a far more contextual and precise way. By retrieving relevant information from a knowledge graph, they can ground their responses in well-defined relationships, thus improving both the relevance and the logical consistency of their answers.
Imagine combining an LLM with a graph of rules that allow it to reason through the relationships encoded in a personal knowledge graph. This could involve using deductive databases to form a sophisticated way to represent and reason with symbolic data — essentially constructing a powerful hybrid system that uses LLM capabilities for language fluency and rule-based logic for structured problem-solving.
My Research on Deductive Databases and Knowledge Graphs
I recently did some research on modeling knowledge graphs using deductive databases, such as DataLog — which can be thought of as a limited, data-oriented version of Prolog. What I’ve found is that it’s possible to use formal logic to model knowledge graphs, ontologies, and complex relationships elegantly as rules in a deductive system. Unlike classical RDF or traditional ontology-based models, which sometimes struggle with complex or evolving relationships, a deductive approach is more flexible and can easily support dynamic rules and reasoning.
Prolog and similar logic-driven frameworks can complement LLMs by handling the parts of reasoning where explicit rule-following is required. LLMs can benefit from these rule-based systems for tasks like entity recognition, logical inferences, and constructing or traversing knowledge graphs. We can even create a graph of rules that governs how relationships are formed or how logical deductions can be performed.
The future is really about creating an AI that is capable of both deep contextual understanding (using the powerful generative capacity of LLMs) and true reasoning (through symbolic systems and knowledge graphs). With the neurosymbolic approach, these AIs could be equipped not just to generate information but to explain their reasoning, form logical conclusions, and even improve their own understanding over time — getting us a step closer to true artificial general intelligence.
Why It Matters for LLM Employment
Using neurosymbolic RAG (retrieval-augmented generation) in conjunction with personal knowledge graphs could revolutionize how LLMs work in real-world applications. Imagine an LLM that understands not just language but also the relationships between different concepts — one that can navigate, reason, and explain complex knowledge domains by actively engaging with a personalized set of facts and rules.
This could lead to practical applications in areas like healthcare, finance, legal reasoning, or even personal productivity — where LLMs can help users solve complex problems logically, providing relevant information and well-justified reasoning paths. The combination of neural fluency with symbolic accuracy and deductive power is precisely the bridge we need to move beyond purely predictive AI to truly intelligent systems.
Let's explore these ideas further if you’re as fascinated by this as I am. Feel free to reach out, follow my YouTube channel, or check out some articles I’ll link below. And if you’re working on anything in this field, I’d love to collaborate!
Until next time, folks. Stay curious, and keep pushing the boundaries of AI!
-
 @ e6817453:b0ac3c39
2024-12-07 14:54:46
@ e6817453:b0ac3c39
2024-12-07 14:54:46Introduction: Personal Knowledge Graphs and Linked Data
We will explore the world of personal knowledge graphs and discuss how they can be used to model complex information structures. Personal knowledge graphs aren’t just abstract collections of nodes and edges—they encode meaningful relationships, contextualizing data in ways that enrich our understanding of it. While the core structure might be a directed graph, we layer semantic meaning on top, enabling nuanced connections between data points.
The origin of knowledge graphs is deeply tied to concepts from linked data and the semantic web, ideas that emerged to better link scattered pieces of information across the web. This approach created an infrastructure where data islands could connect — facilitating everything from more insightful AI to improved personal data management.
In this article, we will explore how these ideas have evolved into tools for modeling AI’s semantic memory and look at how knowledge graphs can serve as a flexible foundation for encoding rich data contexts. We’ll specifically discuss three major paradigms: RDF (Resource Description Framework), property graphs, and a third way of modeling entities as graphs of graphs. Let’s get started.
Intro to RDF
The Resource Description Framework (RDF) has been one of the fundamental standards for linked data and knowledge graphs. RDF allows data to be modeled as triples: subject, predicate, and object. Essentially, you can think of it as a structured way to describe relationships: “X has a Y called Z.” For instance, “Berlin has a population of 3.5 million.” This modeling approach is quite flexible because RDF uses unique identifiers — usually URIs — to point to data entities, making linking straightforward and coherent.
RDFS, or RDF Schema, extends RDF to provide a basic vocabulary to structure the data even more. This lets us describe not only individual nodes but also relationships among types of data entities, like defining a class hierarchy or setting properties. For example, you could say that “Berlin” is an instance of a “City” and that cities are types of “Geographical Entities.” This kind of organization helps establish semantic meaning within the graph.
RDF and Advanced Topics
Lists and Sets in RDF
RDF also provides tools to model more complex data structures such as lists and sets, enabling the grouping of nodes. This extension makes it easier to model more natural, human-like knowledge, for example, describing attributes of an entity that may have multiple values. By adding RDF Schema and OWL (Web Ontology Language), you gain even more expressive power — being able to define logical rules or even derive new relationships from existing data.
Graph of Graphs
A significant feature of RDF is the ability to form complex nested structures, often referred to as graphs of graphs. This allows you to create “named graphs,” essentially subgraphs that can be independently referenced. For example, you could create a named graph for a particular dataset describing Berlin and another for a different geographical area. Then, you could connect them, allowing for more modular and reusable knowledge modeling.
Property Graphs
While RDF provides a robust framework, it’s not always the easiest to work with due to its heavy reliance on linking everything explicitly. This is where property graphs come into play. Property graphs are less focused on linking everything through triples and allow more expressive properties directly within nodes and edges.
For example, instead of using triples to represent each detail, a property graph might let you store all properties about an entity (e.g., “Berlin”) directly in a single node. This makes property graphs more intuitive for many developers and engineers because they more closely resemble object-oriented structures: you have entities (nodes) that possess attributes (properties) and are connected to other entities through relationships (edges).
The significant benefit here is a condensed representation, which speeds up traversal and queries in some scenarios. However, this also introduces a trade-off: while property graphs are more straightforward to query and maintain, they lack some complex relationship modeling features RDF offers, particularly when connecting properties to each other.
Graph of Graphs and Subgraphs for Entity Modeling
A third approach — which takes elements from RDF and property graphs — involves modeling entities using subgraphs or nested graphs. In this model, each entity can be represented as a graph. This allows for a detailed and flexible description of attributes without exploding every detail into individual triples or lump them all together into properties.
For instance, consider a person entity with a complex employment history. Instead of representing every employment detail in one node (as in a property graph), or as several linked nodes (as in RDF), you can treat the employment history as a subgraph. This subgraph could then contain nodes for different jobs, each linked with specific properties and connections. This approach keeps the complexity where it belongs and provides better flexibility when new attributes or entities need to be added.
Hypergraphs and Metagraphs
When discussing more advanced forms of graphs, we encounter hypergraphs and metagraphs. These take the idea of relationships to a new level. A hypergraph allows an edge to connect more than two nodes, which is extremely useful when modeling scenarios where relationships aren’t just pairwise. For example, a “Project” could connect multiple “People,” “Resources,” and “Outcomes,” all in a single edge. This way, hypergraphs help in reducing the complexity of modeling high-order relationships.
Metagraphs, on the other hand, enable nodes and edges to themselves be represented as graphs. This is an extremely powerful feature when we consider the needs of artificial intelligence, as it allows for the modeling of relationships between relationships, an essential aspect for any system that needs to capture not just facts, but their interdependencies and contexts.
Balancing Structure and Properties
One of the recurring challenges when modeling knowledge is finding the balance between structure and properties. With RDF, you get high flexibility and standardization, but complexity can quickly escalate as you decompose everything into triples. Property graphs simplify the representation by using attributes but lose out on the depth of connection modeling. Meanwhile, the graph-of-graphs approach and hypergraphs offer advanced modeling capabilities at the cost of increased computational complexity.
So, how do you decide which model to use? It comes down to your use case. RDF and nested graphs are strong contenders if you need deep linkage and are working with highly variable data. For more straightforward, engineer-friendly modeling, property graphs shine. And when dealing with very complex multi-way relationships or meta-level knowledge, hypergraphs and metagraphs provide the necessary tools.
The key takeaway is that only some approaches are perfect. Instead, it’s all about the modeling goals: how do you want to query the graph, what relationships are meaningful, and how much complexity are you willing to manage?
Conclusion
Modeling AI semantic memory using knowledge graphs is a challenging but rewarding process. The different approaches — RDF, property graphs, and advanced graph modeling techniques like nested graphs and hypergraphs — each offer unique strengths and weaknesses. Whether you are building a personal knowledge graph or scaling up to AI that integrates multiple streams of linked data, it’s essential to understand the trade-offs each approach brings.
In the end, the choice of representation comes down to the nature of your data and your specific needs for querying and maintaining semantic relationships. The world of knowledge graphs is vast, with many tools and frameworks to explore. Stay connected and keep experimenting to find the balance that works for your projects.
-
 @ e6817453:b0ac3c39
2024-12-07 14:52:47
@ e6817453:b0ac3c39
2024-12-07 14:52:47The temporal semantics and temporal and time-aware knowledge graphs. We have different memory models for artificial intelligence agents. We all try to mimic somehow how the brain works, or at least how the declarative memory of the brain works. We have the split of episodic memory and semantic memory. And we also have a lot of theories, right?
Declarative Memory of the Human Brain
How is the semantic memory formed? We all know that our brain stores semantic memory quite close to the concept we have with the personal knowledge graphs, that it’s connected entities. They form a connection with each other and all those things. So far, so good. And actually, then we have a lot of concepts, how the episodic memory and our experiences gets transmitted to the semantic:
- hippocampus indexing and retrieval
- sanitization of episodic memories
- episodic-semantic shift theory
They all give a different perspective on how different parts of declarative memory cooperate.
We know that episodic memories get semanticized over time. You have semantic knowledge without the notion of time, and probably, your episodic memory is just decayed.
But, you know, it’s still an open question:
do we want to mimic an AI agent’s memory as a human brain memory, or do we want to create something different?
It’s an open question to which we have no good answer. And if you go to the theory of neuroscience and check how episodic and semantic memory interfere, you will still find a lot of theories, yeah?
Some of them say that you have the hippocampus that keeps the indexes of the memory. Some others will say that you semantic the episodic memory. Some others say that you have some separate process that digests the episodic and experience to the semantics. But all of them agree on the plan that it’s operationally two separate areas of memories and even two separate regions of brain, and the semantic, it’s more, let’s say, protected.
So it’s harder to forget the semantical facts than the episodes and everything. And what I’m thinking about for a long time, it’s this, you know, the semantic memory.
Temporal Semantics
It’s memory about the facts, but you somehow mix the time information with the semantics. I already described a lot of things, including how we could combine time with knowledge graphs and how people do it.
There are multiple ways we could persist such information, but we all hit the wall because the complexity of time and the semantics of time are highly complex concepts.
Time in a Semantic context is not a timestamp.
What I mean is that when you have a fact, and you just mentioned that I was there at this particular moment, like, I don’t know, 15:40 on Monday, it’s already awake because we don’t know which Monday, right? So you need to give the exact date, but usually, you do not have experiences like that.
You do not record your memories like that, except you do the journaling and all of the things. So, usually, you have no direct time references. What I mean is that you could say that I was there and it was some event, blah, blah, blah.
Somehow, we form a chain of events that connect with each other and maybe will be connected to some period of time if we are lucky enough. This means that we could not easily represent temporal-aware information as just a timestamp or validity and all of the things.
For sure, the validity of the knowledge graphs (simple quintuple with start and end dates)is a big topic, and it could solve a lot of things. It could solve a lot of the time cases. It’s super simple because you give the end and start dates, and you are done, but it does not answer facts that have a relative time or time information in facts . It could solve many use cases but struggle with facts in an indirect temporal context. I like the simplicity of this idea. But the problem of this approach that in most cases, we simply don’t have these timestamps. We don’t have the timestamp where this information starts and ends. And it’s not modeling many events in our life, especially if you have the processes or ongoing activities or recurrent events.
I’m more about thinking about the time of semantics, where you have a time model as a hybrid clock or some global clock that does the partial ordering of the events. It’s mean that you have the chain of the experiences and you have the chain of the facts that have the different time contexts.
We could deduct the time from this chain of the events. But it’s a big, big topic for the research. But what I want to achieve, actually, it’s not separation on episodic and semantic memory. It’s having something in between.
Blockchain of connected events and facts
I call it temporal-aware semantics or time-aware knowledge graphs, where we could encode the semantic fact together with the time component.I doubt that time should be the simple timestamp or the region of the two timestamps. For me, it is more a chain for facts that have a partial order and form a blockchain like a database or a partially ordered Acyclic graph of facts that are temporally connected. We could have some notion of time that is understandable to the agent and a model that allows us to order the events and focus on what the agent knows and how to order this time knowledge and create the chains of the events.
Time anchors
We may have a particular time in the chain that allows us to arrange a more concrete time for the rest of the events. But it’s still an open topic for research. The temporal semantics gets split into a couple of domains. One domain is how to add time to the knowledge graphs. We already have many different solutions. I described them in my previous articles.
Another domain is the agent's memory and how the memory of the artificial intelligence treats the time. This one, it’s much more complex. Because here, we could not operate with the simple timestamps. We need to have the representation of time that are understandable by model and understandable by the agent that will work with this model. And this one, it’s way bigger topic for the research.”
-
 @ 592295cf:413a0db9
2024-12-07 07:21:39
@ 592295cf:413a0db9
2024-12-07 07:21:39Week 02-11
- Nsite zap by hzrd149 Support page
Content creator want more users. They can go to Bluesky.
Great that Nostr is a Echo Chambers. As stated by Rabble during NostRiga, Nostr is a bitcoin meetup. And it is very difficult as said several times, to subvert this fact. It seems that many bitcoiners don't like this, but they can't do anything, leave Nostr and migrate to other lids.
I'm reading Nostr adventar calendar of Japanese Nostr users.
The first two Don and Jun speak of a Mahjong game and the other of how possibly to count the followers of a given account, countfollowed. - Adventar calendar continue until Christmas 🎅
-
Even Bluesky is looking at MLS , is not a soccer league, is a protocol for message by groups, "circles" Post on Bluesky
-
Relays chakany is introduce sunday. link
I've never seen such dead animals as in Nostr. Something reminds me facebook. The carnivore folks
Hivemind podcast by Max, the kilometric comment on fountain under the podcast is the most appetizing thing of all. Just one comment, little one.
He interviewed Kagi's and searched for a brownie pill, perhaps caused a little headache. ( Brownie pill is orange plus purple)
Loss dog on Nostr this week 😔😔 Pam and Derek family dog
conspiracy theory: Fiatjaf was the reply guy!!!
I tried to download voyage, from zapstore but nothing does not work even the 17.1 does not go. Too bad.
I hear so much about notedeck that I want to make a notedeck do it yourself.
Cherry tree, stuck hzrd149 is making an app a day, Chunked blobs on blossom.
A like is used to send your writing Relays
Announcement of a possible wallet in Damus, this could make things better, zap and whatnot.
- Or I'm posting a song here, a musical interlude. song on wavlake
There seems to be a good buzz on Nostr, maybe it's already a Christmassy atmosphere.
- Backup di Bluesky cool things Bluesky post
On another rssfeed thing.
nostr:nevent1qvzqqqqqqypzq9h35qgq6n8ll0xyyv8gurjzjrx9sjwp4hry6ejnlks8cqcmzp6tqqs93j2remdw2pxnctasa9vlsaerrrsl7p5csx5wj88kk0yq977rtdqxt7glp
It's the same thing as following a cross de bridge, but if they do 3 bridge, I say something is wrong. A bot is attached to a Relay. The Relay goes down and so much greetings, then I can look for RSS feeds in my computer without need of Nostr. I can share a particular opml file on Nostr, but I don't know how to do it I asked Fiatjaf but didn't answer it was taken by dichotomie.
Nip19 really Easy to do filter query.
You have events_id pubkey Relay Instead with Nostr:note you only have the event_id.
- Sebastix says he has to implement it in his library, discover the latest weekly report. nostr-php-helper-library
Oh no Pablo has become super Saiyan 🤣
There is a way to make a podcast starting from a long text, blog. With artificial intelligence. But then I thought, but if one does not have time could not have the text of the article summarized, perhaps we like generating content. It can be an option, either you read or you listen. But if you do not have time perhaps it is better to just summarize, dear chatgpt summarize this text, done. Essential points and make a thread for the social network and do what you want.
- Homemade Traditional Boozy Mincemeat, I didn't even know that existed 🤙 link to shopstr
Hodlbod news on bunker burrow
nostr:nevent1qqs84na25g6mdelvl0408nnq8m29j5070dm9mvjrzxyc6yrx2udjyuczyztuwzjyxe4x2dwpgken87tna2rdlhpd02
- In case you don't see the note burrow on github
Once you have the email what do you do with your encrypted key? No Enterprise user maybe. Rember the article of Hodlbod in "Is Always a political move". ✅
List of artists on Nostr nostr:naddr1qvzqqqr4xqpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qyghwumn8ghj7mn0wd68ytnhd9hx2tcpzfmhxue69uhkummnw3e82efwvdhk6tcqp9qku6tdv96x7unng9grdr
- An article for food recipe on Nostr Article link
I don't know if they'll ever be there. You can write a recipe book. Or to put recipes on wiki, there doesn't seem to be that attention or that desire. One more relay is always better
- Olas has a website 🥊 Olas app
Oh i see cool Hodlbod bot A summary bot
nostr:nevent1qqs0v88uc2u3he3lm3mpm5h3gr8cuht5wv9g0tk0x9hzvamgvpdjwvspzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgq3qjlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qu0ltyv
That's all!!
-
 @ 3bf0c63f:aefa459d
2024-12-06 20:37:26
@ 3bf0c63f:aefa459d
2024-12-06 20:37:26início
"Vocês vêem? Vêem a história? Vêem alguma coisa? Me parece que estou tentando lhes contar um sonho -- fazendo uma tentativa inútil, porque nenhum relato de sonho pode transmitir a sensação de sonho, aquela mistura de absurdo, surpresa e espanto numa excitação de revolta tentando se impôr, aquela noção de ser tomado pelo incompreensível que é da própria essência dos sonhos..."
Ele ficou em silêncio por alguns instantes.
"... Não, é impossível; é impossível transmitir a sensação viva de qualquer época determinada de nossa existência -- aquela que constitui a sua verdade, o seu significado, a sua essência sutil e contundente. É impossível. Vivemos, como sonhamos -- sozinhos..."
- Livros mencionados por Olavo de Carvalho
- Antiga homepage Olavo de Carvalho
- Bitcoin explicado de um jeito correto e inteligível
- Reclamações
-
 @ a8d1560d:3fec7a08
2024-12-09 16:23:57
@ a8d1560d:3fec7a08
2024-12-09 16:23:57The digital age is increasingly dominated by centralized platforms that control data, censor content, and limit privacy. Amid these trends, Nostr offers an alternative: a decentralized protocol built on WebSocket and JSON that upholds the values of decentralization, privacy, and censorship resistance. But how can Nostr gain wider adoption while preserving its core principles? Here’s a detailed look at potential strategies.
What is Nostr?
Nostr stands for "Notes and Other Stuff Transmitted by Relays." Unlike centralized services, it is an open protocol designed to enable decentralized social networks and communication systems. It is based on two core technologies: - WebSocket for real-time communication. - JSON as a lightweight data format for information exchange.
Users identify themselves through a cryptographic key pair (public and private keys), ensuring authentication and the integrity of their content. Content is distributed via relays, which act as independent nodes. This decentralized architecture makes Nostr resistant to censorship and central control.
Challenges and Goals
While Nostr offers numerous advantages, it faces several challenges: - Driving adoption in a world accustomed to centralized platforms. - Improving usability to attract a broader audience. - Maintaining its core values of decentralization, privacy, and uncensorability, even as it grows.
To address these challenges, both technical and social aspects must be considered.
1. Improve Usability
A major barrier to Nostr’s adoption is its current complexity, which can deter less tech-savvy users. Addressing this requires a focus on user experience:
- Simplify Onboarding:
- Key management can be confusing. Automating key generation and secure backup processes can help ease new users into the system.
-
Clear, simple tutorials and visual guides can reduce the learning curve.
-
Cross-Platform Apps:
- Reliable and feature-rich clients for mobile and desktop platforms (e.g., iOS, Android, Windows, Linux) are essential.
-
Consistent interfaces and features such as dark mode or customizable themes can enhance user retention.
-
Localization:
- Supporting multiple languages in clients and tutorials can help Nostr gain traction in diverse regions.
2. Democratize and Decentralize Relays
Relays are the backbone of Nostr, and their availability and decentralization are crucial for the protocol’s long-term success.
- Promote Open Relay Hosting:
- Provide detailed guides and tools to make it easy for individuals to host their own relays.
-
Hosting kits and optimized configurations can reduce costs and technical barriers.
-
Incentivize Relay Operators:
-
Introduce monetization models such as micropayments through Bitcoin/Lightning to make relay operations financially sustainable.
-
Simplify Relay Selection:
- Users should have access to tools that help them identify trustworthy and active relays. Recommendation algorithms or curated lists could be helpful.
3. Educate and Build a Community
An informed and engaged community is critical for Nostr’s success. Public awareness and collaboration efforts should be prioritized:
- Awareness Campaigns:
-
Articles, blogs, and videos can explain the benefits of Nostr, particularly around privacy and censorship resistance.
-
Workshops and Hackathons:
-
Events aimed at both developers and users can help spread knowledge about Nostr and encourage new applications.
-
Integration with Existing Networks:
- Tools that allow cross-posting between Nostr and other platforms (e.g., Twitter or Mastodon) could extend its reach and ease the transition for users.
4. Strengthen the Developer Ecosystem
A robust developer ecosystem is essential for creating new applications and features on Nostr.
- Promote Open-Source Projects:
-
Developers should have access to well-documented open-source libraries to build their own projects on Nostr.
-
Ensure Modularity:
-
Standards and protocol extensions should allow new features to be added without compromising decentralization or interoperability.
-
Enhance Interoperability:
- Nostr could establish bridges to other protocols, such as Matrix or ActivityPub, to expand its use cases.
5. Prioritize Privacy and Security
Privacy and security are central to Nostr’s promise and should be continually enhanced:
- End-to-End Encryption:
-
Messages between users should be encrypted by default to ensure maximum confidentiality.
-
Enhance Anonymity:
-
Integrations with technologies like Tor or VPNs could increase user anonymity.
-
Data Ownership:
- Users should have full control over their content, including the ability to export and delete it as needed.
6. Foster Practical Applications
To drive adoption, Nostr must deliver concrete use cases that go beyond social networking:
- Specialized Apps:
-
Decentralized marketplaces, secure messaging apps, or alternative blogging platforms could be built on Nostr.
-
Bitcoin Integration:
-
Connecting with Bitcoin and the Lightning Network could enable micropayments and create financial incentives.
-
Experimental Ideas:
- Creative applications such as decentralized voting systems or educational platforms could attract new audiences.
7. Ensure Resilience Against Regulation
The regulatory landscape, particularly in the EU, could pose challenges for Nostr. Ensuring resilience is key:
- Preserve Censorship Resistance:
-
Nostr’s design should prevent centralized interference or blockades.
-
Emphasize Technical Neutrality:
-
Nostr is a protocol, not a service. This distinction should be clearly communicated to mitigate regulatory pressure.
-
Guarantee Accessibility:
- Technologies like proxy relays or alternative connection methods could ensure access in censorship-prone regions.
Conclusion
Nostr offers a promising alternative to centralized platforms by putting decentralization, privacy, and censorship resistance at its core. To gain widespread adoption, it must strike a balance between technical innovation, user-friendly implementation, and the protection of its core values. Through targeted awareness campaigns, a strong developer ecosystem, and an active community, Nostr can become a groundbreaking platform for digital communication—without compromising user freedom or autonomy.
-
 @ c3f12a9a:06c21301
2024-12-09 16:21:44
@ c3f12a9a:06c21301
2024-12-09 16:21:44Dear friends,
The European Union is at a crossroads, and the stakes could not be higher. A new proposal threatens to undermine one of our most fundamental rights—our privacy. This initiative, called "Chat Control," would require the scanning of private messages and emails across Europe, even in services that are end-to-end encrypted. If this passes, our ability to communicate freely and securely in the digital world will be a thing of the past.
This is not just a theoretical issue—it’s happening now. The Council Presidency is pushing the proposal forward, with discussions planned for December 6, 2024. It’s crucial that we act now to protect our rights and freedoms before it’s too late.
As a united community, we’ve already proven what we can achieve. In the Czech Republic, we recently secured a Bitcoin tax exemption by working together and pressuring our politicians with constructive requests. If we mobilize on a European scale, we have a chance to stop this dangerous proposal in its tracks.
Let’s join forces, write to our representatives, and let them know that we won’t stand for mass surveillance. Let’s also spread the word to those around us—our friends, families, and networks. Together, we can make a difference.
—
Situation Summary: The European Union is considering a proposal to mandate the scanning of all private messages and emails to combat child sexual exploitation material (CSEM). This initiative, known as "Chat Control," would apply even to end-to-end encrypted services, effectively ending digital privacy.
The proposal also includes measures such as network blocking, scanning personal cloud storage, mandatory age verification, and app store censorship, potentially excluding minors from the digital world.
Despite significant opposition from citizens, experts, and some Members of the European Parliament, the proposal is moving forward, with the last discussion few days ago at December 6, 2024. Critics argue that this constitutes mass surveillance and severely undermines fundamental rights.
Thank you for standing up for privacy and freedom. Wondrej
source- https://www.patrick-breyer.de/en/posts/chat-control/ https://www.seznamzpravy.cz/clanek/domaci-politika-eu-chce-povinnou-kontrolu-chatu-265958
originally posted at https://stacker.news/items/802048
-
 @ a8d1560d:3fec7a08
2024-12-09 16:18:57
@ a8d1560d:3fec7a08
2024-12-09 16:18:57Das digitale Zeitalter wird zunehmend von zentralisierten Plattformen geprägt, die Daten kontrollieren, Inhalte zensieren und Privatsphäre einschränken. Inmitten dieser Entwicklungen bietet Nostr eine Alternative: ein dezentrales Protokoll, das auf WebSocket und JSON basiert und die Werte von Dezentralität, Privatsphäre und Zensurresistenz hochhält. Doch wie kann sich Nostr verbreiten, ohne diese Grundwerte zu gefährden? Ein detaillierter Blick auf mögliche Strategien.
Was ist Nostr?
Nostr steht für "Notes and Other Stuff Transmitted by Relays". Es handelt sich nicht um eine Plattform oder einen zentralen Dienst, sondern um ein offenes Protokoll, das entwickelt wurde, um dezentrale soziale Netzwerke und Kommunikationslösungen zu ermöglichen. Es baut auf zwei Kerntechnologien auf: - WebSocket für Echtzeitkommunikation. - JSON als leichtgewichtiges Datenformat zur Übertragung von Informationen.
Die Nutzer identifizieren sich über ein kryptographisches Schlüsselpaar (privater und öffentlicher Schlüssel), was Authentifizierung und Integrität der Inhalte sicherstellt. Inhalte werden über sogenannte Relays verbreitet, die als Knotenpunkte fungieren und unabhängig betrieben werden können. Diese Struktur macht Nostr resistent gegenüber Zensur und zentraler Kontrolle.
Herausforderungen und Ziele
Obwohl Nostr viele Vorteile bietet, steht es vor mehreren Herausforderungen: - Die Akzeptanz in einer Welt, die an zentrale Plattformen gewöhnt ist. - Die Benutzerfreundlichkeit, die für breite Nutzung entscheidend ist. - Die Wahrung seiner Werte von Dezentralität, Privatsphäre und Zensurresistenz, selbst bei wachsender Verbreitung.
Um diese Ziele zu erreichen, müssen technische, soziale und regulatorische Aspekte gleichermaßen berücksichtigt werden.
1. Benutzerfreundlichkeit verbessern
Ein zentrales Hindernis für die Verbreitung von Nostr ist seine derzeitige Komplexität, die technisch weniger versierte Nutzer abschrecken kann. Um dies zu ändern, sollte der Fokus auf einer besseren Benutzererfahrung liegen:
- Einfacheres Onboarding:
- Schlüsselmanagement kann verwirrend sein. Automatisierte, aber sichere Lösungen für die Erstellung und Sicherung privater Schlüssel könnten den Einstieg erleichtern.
-
Klare und einfache Tutorials sowie visuelle Erklärungen könnten dazu beitragen, die Lernkurve zu senken.
-
Apps für verschiedene Plattformen:
- Zuverlässige und funktionsreiche Clients für mobile und Desktop-Plattformen (z. B. iOS, Android, Windows, Linux) sind essenziell.
-
Eine konsistente Benutzeroberfläche und Funktionen wie Dark Mode oder Themes können Nutzerbindung stärken.
-
Mehrsprachige Unterstützung:
- Lokalisierung der Clients und Tutorials in verschiedenen Sprachen kann dazu beitragen, Nostr in unterschiedlichen Regionen populär zu machen.
2. Relays demokratisieren und dezentralisieren
Relays sind das Herzstück von Nostr, und ihre Verfügbarkeit sowie Dezentralität sind entscheidend für die langfristige Stabilität des Protokolls.
- Förderung offener Relay-Betreibung:
- Detaillierte Anleitungen und Tools sollten bereitgestellt werden, um es Menschen einfach zu machen, eigene Relays zu betreiben.
-
Hosting-Kits und optimierte Konfigurationen könnten Kosten und technische Hürden senken.
-
Anreize für Relay-Betreiber:
-
Monetarisierungsmodelle wie Micropayments über Bitcoin/Lightning könnten dazu beitragen, Relays finanziell nachhaltig zu machen.
-
Relay-Auswahl vereinfachen:
- Nutzer sollten leicht erkennen können, welche Relays vertrauenswürdig und aktiv sind. Empfehlungsalgorithmen oder Listen könnten hier helfen.
3. Aufklärung und Community-Bildung
Eine informierte und engagierte Community ist entscheidend für den Erfolg von Nostr. Daher sollte der Fokus auf öffentlicher Aufklärung und Zusammenarbeit liegen:
- Bildungskampagnen:
-
Artikel, Blogs und Videos könnten die Vorteile von Nostr verständlich erklären, insbesondere in Bezug auf Datenschutz und Zensurresistenz.
-
Workshops und Hackathons:
-
Veranstaltungen, die sich an Entwickler und Anwender richten, können helfen, das Wissen über Nostr zu verbreiten und neue Anwendungen zu entwickeln.
-
Integration mit bestehenden Netzwerken:
- Tools zur Integration von Nostr mit anderen Plattformen (z. B. Twitter oder Mastodon) könnten die Reichweite erhöhen und den Übergang erleichtern.
4. Entwickler-Ökosystem stärken
Ein starkes Entwickler-Ökosystem ist entscheidend, um neue Anwendungen und Funktionen auf Nostr zu schaffen.
- Open-Source-Projekte fördern:
-
Entwickler sollten Zugang zu gut dokumentierten Open-Source-Bibliotheken haben, um eigene Projekte auf Basis von Nostr umzusetzen.
-
Modularität gewährleisten:
-
Standards und Protokollerweiterungen sollten es ermöglichen, neue Funktionen hinzuzufügen, ohne die Dezentralität oder Interoperabilität zu gefährden.
-
Interoperabilität stärken:
- Nostr könnte Brücken zu anderen Protokollen wie Matrix oder ActivityPub schlagen, um die Nutzungsmöglichkeiten zu erweitern.
5. Datenschutz und Sicherheit priorisieren
Privatsphäre und Sicherheit sind zentrale Versprechen von Nostr und sollten konsequent weiterentwickelt werden:
- Ende-zu-Ende-Verschlüsselung:
-
Nachrichten zwischen Nutzern sollten standardmäßig verschlüsselt werden, um maximale Vertraulichkeit zu gewährleisten.
-
Anonymität verbessern:
-
Integration mit Technologien wie Tor oder VPNs könnte die Anonymität der Nutzer erhöhen.
-
Selbstbestimmung über Daten:
- Nutzer sollten die volle Kontrolle über ihre Inhalte haben, einschließlich Export- und Löschoptionen.
6. Praktische Anwendungen fördern
Um Nostr populär zu machen, müssen konkrete Anwendungsfälle geschaffen werden, die über soziale Netzwerke hinausgehen:
- Spezialisierte Apps:
-
Dezentrale Marktplätze, sichere Messenger oder alternative Blogging-Plattformen könnten auf Nostr aufbauen.
-
Integration mit Bitcoin:
-
Die Verbindung mit Bitcoin und dem Lightning-Netzwerk kann Micropayments ermöglichen und finanzielle Anreize schaffen.
-
Experimentelle Anwendungen:
- Kreative Ideen wie dezentrale Abstimmungen oder Bildungssysteme könnten neue Zielgruppen ansprechen.
7. Widerstandsfähigkeit gegen Regulierung
Die regulatorische Landschaft, insbesondere in der EU, könnte Herausforderungen für Nostr darstellen. Es ist wichtig, Widerstandsfähigkeit zu sichern:
- Zensurresistenz bewahren:
-
Nostr sollte so gestaltet sein, dass zentrale Eingriffe oder Blockaden schwer umzusetzen sind.
-
Technische Neutralität betonen:
-
Nostr ist ein Protokoll, kein Service. Diese Unterscheidung sollte klar kommuniziert werden, um regulatorischen Druck abzumildern.
-
Zugang sicherstellen:
- Technologien wie Proxy-Relays oder alternative Verbindungsprotokolle könnten den Zugang in zensurkritischen Regionen gewährleisten.
Fazit
Nostr bietet eine vielversprechende Alternative zu zentralisierten Plattformen, indem es Dezentralität, Privatsphäre und Zensurresistenz in den Mittelpunkt stellt. Um sich erfolgreich zu verbreiten, muss jedoch eine Balance gefunden werden: zwischen technischer Innovation, benutzerfreundlicher Umsetzung und dem Schutz seiner Kernwerte. Mit gezielter Aufklärung, einem starken Entwickler-Ökosystem und einer aktiven Community kann Nostr zu einer zukunftsweisenden Plattform für die digitale Kommunikation werden – ohne die Freiheit und Selbstbestimmung seiner Nutzer zu gefährden.
-
 @ 6dc1c1c9:e40b389b
2024-12-06 15:19:16
@ 6dc1c1c9:e40b389b
2024-12-06 15:19:16Odds & Ends: December 6, 2024

The Virginian by Owen Wister. (https://amzn.to/4fVvqCy) I just finished this 1902 novel that essentially created the Western genre as we know it. Wister’s tale of a laconic, principled cowboy in Wyoming Territory established tropes we now take for granted: the showdown at high noon, the strong silent hero, and the eastern tenderfoot narrator learning the ways of the West. A core theme in The Virginian is honor (https://www.artofmanliness.com/character/behavior/manly-honor-part-i-what-is-honor/). I did a lot of underlining in my copy about that topic. Despite being over 120 years old, the book is surprisingly fresh and modern. If you want a better appreciation of the Western genre, from the best Western novels (https://www.artofmanliness.com/living/reading/21-western-novels-every-man-should-read/) to the top Western films (https://www.artofmanliness.com/living/reading/21-western-novels-every-man-should-read/) to the greatest video game of all time — Red Dead Redemption 2 — pick up a copy of The Virginian.
The Hot New Job for Men: Nursing. (https://www.wsj.com/economy/jobs/male-nursing-boom-high-demand-field-7733dfaf) Ten years ago, if you asked me how many dudes I knew who were nurses, the answer would have been zero. Today, I personally know several men who are nurses and even middle-aged men who are shifting careers to nursing. And it looks like this anecdotal uptick is backed up by data. Nursing is drawing more men than ever, with male RNs nearly tripling since 2000. The appeal? Job security and solid pay — registered nurses pull in $95,000 on average, with specialized roles like nurse anesthetists hitting $214,000. While males currently only make up 14% of nurses, that number’s climbing steadily as more men discover this potentially rewarding career path. It’s a big shift from the days when male nurses were the butt of jokes in movies like Meet the Parents.
Micro Gainz Microplates. (https://microgainz.com/collections/olympic-micro-plates) Have you stalled out on making progress on a lift like the overhead press and want to increase the weight, but adding the lowest plates available — typically 5-pounders — still feels like too big a jump? These fractional weight plates let you make tiny 1/2 to 2-pound increases, perfect for breaking through stubborn plateaus. At first glance, spending $60 on what amounts to metal chips might seem excessive, but the ability to make micro-jumps in weight is a game-changer for achieving progressive overload on upper-body lifts.
Jingle Bell Jazz. (https://amzn.to/3Bnfj1n) Not sure how this 1962 compilation made its way into my vinyl collection, but every December, I find myself giving it regular spins on my record player. It’s a good mixture of Christmas standards in various genres of jazz (https://www.artofmanliness.com/living/entertainment/jazz-appreciation-for-beginners/), including bebop, swing, and cool. It’s a perfect album for trimming the tree or sitting by a roaring fire reading a book on a cold December night. You can listen to the full album on YouTube (https://www.youtube.com/watch?v=jOtJJi3lX8A).
Also, this (https://www.facebook.com/photo/?fbid=965551785445345&set=a.663354332331760) really made me laugh.
Quote of the Week
Be not afraid of life. Believe that life is worth living, and your belief will help create the fact.
—William James
Help support independent publishing. Make a donation to The Art of Manliness! (https://donorbox.org/support-the-art-of-manliness) Thanks for the support!
https://www.artofmanliness.com/odds-ends/odds-ends-december-6-2024/
-
 @ 805b34f7:3620fac3
2024-12-05 00:15:03
@ 805b34f7:3620fac3
2024-12-05 00:15:03I've heard Nostr described as intergalactic war technology, but here we are shitposting on it. How fun!
Nostr is our chance at remaking social media, consciously. Have you seen Max Demarco's Nostr Documentary yet? Check it out when you have time --> Social Media is Broken. Can We Fix It?
What do I post?!?
Post whatever you want. There are no rules. But, here's how to make a first post that will help you get seen by the network as opposed to feeling like you just posted into a void:
Intro Post
- Introduce yourself.
- Say how you found Nostr.
- Say what you're interested in/what you do for fun or work.
- Add a photo(s) or video(s).
- And most importantly, add the hashtag #introductions
If you're on Primal, make sure you set up your wallet so you can receive zaps. Do this by pressing the lightning bolt.
Zaps are payments sent to other users as a way of tipping to content creators. Zaps utilize the Bitcoin Lightning and are almost instant and near free.
Zaps represent the only fundamentally new innovation in social media. Everything else is a distraction. - Jack Dorsey
Check out this intro post from Dr. Ken Berry for inspiration!
 # How to Grow a Following/Best Practices
# How to Grow a Following/Best PracticesZap - Change your custom zap amount and message on Primal. Do that by going to settings --> Zaps and customizing the top bubble. Once customized, every time you press the lightning bolt underneath someone's post, you send them money with whatever amount selected. Press and hold for a custom amount and message.
Zaps are the easiest way into someone's subconscious. Almost every time I receive a zap from someone new, I check out their profile. Especially if it has a custom message.
And if you really want to advertise yourself/brand, do what is called "zapvertising". Go to the trending tabs and zap the highest amount on each post with a message.
GM - Wish people good morning and comment on their good morning posts. Nostr loves this and it's a way for you to get your brand out there.
Ask questions - There are no dumb questions and people are nice generally. If you do have a question, end the note with the hashtag #asknostr.
Blogging - There are multiple long form clients for you to write a blog on. Check out highlighter.com, habla.news, or yakihonne for blogging. And while you're at it, check out all the rest of the apps you can participate on nostrapps.com
Feed Creation - Check out this video to get a glimpse of what is possible with Primal's advanced search tool. And this video to see how to navigate the app.
Nostr is a more organic social media. There's no central algorithm that may or may decide to pick up your content. It's just people interacting on a protocol. Be the engagement that you want to see.
Post what your heart desires. You can use it as a vlog, a diary, a photo collection, or all of the above. Nostr wants all of it, and there are multiple ways to view content depending on which client you are using.
If you're reading this now, you are extremely early. We have the chance to bootstrap a new social network. One that is principled and uncontrolled by big tech or governments. And this really matters
Nostr Terms
npub - this is your public key and it's how nostr recognizes your profile.
nsec - Your password. Keep this safe. If you lose your phone and don't have a copy of this somewhere, it's gone forever. This is not the blog for key management, but expect better solutions in the near future.
nip-05 - this is your human readable nostr address. There are many places to create your own nip05. You can get a Primal name by subscribing to Primal premium. For example, mine is paul@primal.net. You can put this into any client to find my profile as opposed to putting in my npub.
Zap Sats - Zaps are micropayments of bitcoin. 1 bitcoin = 100 million "sats" which is short for Satoshis.
Clients - Nostr apps.
PV- Pura vida. Nostr's first "un"conference was held in Costa Rica. Pura vida is the national slogan.
Hungry for more Nostr knowledge? Here's a great post with quite a few resources. Feel free to message me on Nostr with any questions!
-
 @ 6bae33c8:607272e8
2024-12-09 16:07:59
@ 6bae33c8:607272e8
2024-12-09 16:07:59It was a bad week. I went 2-3 ATS in Circa, and my fantasy teams no-showed. My best team needs a good game from Ja’Marr Chase tonight to lock in a spot in the postseason (maybe it’s in anyway as a third-place team due to total points.) The other two fringe ones didn’t come close. And my Steak League team will miss the playoffs thanks to an utter no-show and now is in serious jeopardy of buying. I barely watched the first half of the late games, opting instead to go to sleep.
I’m soured on the season, but it’s no one’s fault but my own. The truth is I don’t give a shit that much. I mean I’m pissed but not as pissed as I should be. I had a crushing day, it torched most of my season, and I’m annoyed, but I didn’t do anything special to deserve to win. I did the research, and I did the FAAB every week, and I set my lineups carefully. But I’m not doing anything above and beyond. I have only the interest I have. I’ve completed the transition from professional to casual player.
-
I took the Titans -3.5 as one of my picks and Will Levis as my Steak League QB with my other QBs on bye. For whatever reason the Jaguars were ranked last against QB scoring, but limited both C.J. Stroud, who I started last week against them, and Levis. Not that Levis was a lock against anyone.
-
I had the Jets +5.5 which was the right side all game, but it was the wrong side because it was the Jets who are cursed.
-
I also had Braelon Allen, so of course Isaiah Davis scores the TD and outplays him.
-
The strangest storyline of the day was Jonnu Smith who I have everywhere scoring zero points on one target during regulation, then getting 13.8 on a single overtime drive including the game-winning TD. I’m happy he did so much in overtime, but what the fuck was that?
-
Other than Joe Burrow, Tua Tagovailoa is probably the best bet for passing yards in any given game.
-
Sam Darnold had a monster game — he also didn’t throw a pick and scrambled to make some of those downfield throws. Jordan Addison is emerging as a star alongside Justin Jefferson too, maybe the best WR tandem in the league.
-
Maybe Kirk Cousins is cooked. One more loss, and they have to whip out Penix.
-
The fucking Giants. I actually laid the wood with the Saints too, and they couldn’t just send it to overtime with a chip shot FG (to give the Saints a chance to cover the 4.5). Plus I had Malik Nabers going and needed more points.
-
The Panthers play everyone tough now. I used Jonathon Brooks in the flex in one league, and he got hurt again. Waiting all year for injured players doesn’t usually pan out. Nick Chubb is still healthy, but hasn’t done much either.
-
Saquon Barkley had a modest game, but now has 1,623 yards with four games to go. I love Barkley, but the 17-game season really skews record books.
-
I’m an idiot for not using the Steelers in the Circa contest. Of course they were going to cover after losing outright a couple weeks ago. I did start Calvin Austin in the Steak League (with George Pickens out), and Austin got me one catch for four yards.
-
I had the Bucs -7 against the Raiders, and it was close for a while, but the Raiders are always on the edge of collapse with their QB play.
-
I started Bucky Irving who the team shut down early as a precaution. No one told them Week 14 in fantasy is not the time for precaution.
-
I foolishly used Arizona in the Circa contest. They were good for a few games a few games ago, but now they’ve reverted. Seattle has more balls than they do. As a Kenny Walker owner, it’s rough seeing Zach Charbonnet have the game you were waiting for from Walker all year.
-
Maybe the style is too high-degree of difficulty, but Kyler Murray has never been consistent.
-
I didn’t watch Rams-Bills. One reason why my top team is on the ropes is one of the guys I’m competing with (Bob Cramutola) had Josh Allen going. I woke up this morning, was like how did he get 196 points?
-
Kyren Williams is like my size, but handles 29 carries, two catches, no problem.
-
Puca Nacua should have been a first-round pick. The injury was unlucky, but he belonged ahead of A.J. Brown and Garrett Wilson. Just a target and playmaking machine.
-
I had Jordan Mason on my teams all year, and of course Isaac Guerendo goes bananas when you needed it most. The Niners were the obvious buy-low, but I didn’t realize that until watching the first half.
-
I had Kimani Vidal in one league, Gus Edwards in another. Edwards scored a TD at least, but would it kill Justin Herbert to target a running back?
-
Thomas Hobbes famously described life in the state of nature as “nasty, brutish and short.” Chiefs games are similarly nasty, brutish and close.
-
-
 @ ece53feb:1edf277e
2024-12-09 15:19:42
@ ece53feb:1edf277e
2024-12-09 15:19:42https://www.newyorkupstate.com/news/2024/12/upstate-ny-village-shuts-off-water-declares-state-of-emergency.html?utm_source=flipboard&utm_medium=activitypub
-
 @ dadbe86a:9c493e92
2024-12-04 14:56:04
@ dadbe86a:9c493e92
2024-12-04 14:56:04Opinion about Green: Bitcoin Wallet (android)
Green Wallet is a mobile Bitcoin wallet developed by Blockstream, The Wallet aims to provide users with a trustworthy and feature-rich Bitcoin wallet experience. Given that the wallet supports liquid assets, it is not bitcoin only. This is a cons for pure bitcoiners but something good for other users.
Pros: - Support for testnet, passphrase, fee control, coin control, custom node, tor, timelocks - The in-app keyboard and seed phrase autocomplete increase the security if you need to enter your seedphrase or passphrase - Open source - Full taproot support soon
Cons: - Missing some advanced features like user added entropy or seedQR. - It has a non standard multisig implementation - Partial support to connect with hardware wallets
Version reviewed: v4.0.27
WalletScrutiny #nostrOpinion
-
 @ 24e36cf3:6b26ae15
2024-12-04 12:35:57
@ 24e36cf3:6b26ae15
2024-12-04 12:35:57My husband and I have been talking a lot about capitalism and socialism lately. We've watched countless videos, read books about it, discussed the topic with friends and family. Even though we've been left-leaning all our lives due to social programming from our families, we've radically changed our views in the past couple of years and are now convinced that any form or socialism is bad for humanity.
Here's a colloquial summary of our thought process as explained to an acquaintance, who is still pro-socialism:
Let's look at the animal kingdom for some context
My initial thought regarding victim and perpetrator ... take, for example, lions and gazelles in Africa. At first glance, the lion seems to be the problem because it comes and kills the poor gazelles who just want peace. Now let's look at the other side:
- The lion was not asked, whether it wants to be born a lion
- The lion cannot help that it has to eat gazelles
- It's not funny to chase after its food and if you're too slow after the 3rd attempt you'll probably won't have any strength left and die
\ If you think about it a little more, you could argue that the gazelle is actually the perpetrator. She runs away and then the lion starves. Who is the victim and who is the perpetrator?
Now ... why did nature design the system this way? Why aren't all creatures nice to each other and the lion only eats what is absolutely necessary and the gazelle just lies down and waits to be eaten?\ You will now think that's nonsense and can't be like that, but it is. You surely know the fish that swim upstream in the river, get so extremely red and pale, become parents and then die so that the next generation has something to eat. There are dependencies in nature that are stronger than the life of an individual. But only rarely ... why?
If gazelles considered the lion's feelings and just laid down if he's having a bad day, the lion would get lazy, sick and weak. Unfortunately, that's the way it is. Nobody likes to run for their food. If nature had programmed it that way, the lion would eventually realize it and start running slower. Survival of the fittest is how evolution works and the weaker lions would perish. The gazelle running as fast as it can is good for the lion. Removing the slowest animals from the herd is beneficial for the gazelles. It's an extremely cruel system, but that's the way nature works and we are all a part of it.
Capitalism is this system applied to humans. Capitalism emerges voluntarily and spontaneously between free individuals and everyone benefits from it.\ If two people are stranded on an island and one starts farming the land for fruits and the other diverts the river for more water, they both benefit. Both are better off. Each pursues their own interests (like a lion and a gazelle), but both end up benefiting.\ You work on something useful and someone else rewards you for your work. That's it. There are no victims or perpetrators ... there are only actors. Everyone works for themselves and everyone is better off.
All the problems you mentioned (deteriorating environment, poverty, social injustice, ...) arise when the collective (the state or other authorities) come together and suppress this natural system; because of poor gazelles and wicked lions. In reality, no one cares about the poor gazelles because:
- They are not poor.
- They only care about maintaining their power.
Let's talk about Jeff Bezos' Amazon, which is often vilified
One hears constantly that Amazon workers are exploited (victims) and the poor shops everywhere have to close because Bezos destroyed all other stores. What you hear about the workers at Amazon is fake news. For example here is a "negative video" because Bezos makes so much money ... but check out what the guy says:\ https://www.youtube.com/shorts/OvSkhpCsUmY\ The workers there are not victims. They come voluntarily. No one forces them to work at Amazon.
If you think about it some more: Why don't you work at Amazon?\ Very likely because you have other options. You don't necessarily have to stand behind the conveyor belt. Apparently some others do. You can't control that some people have little education, ability or motivation, so that they have to do this work. They would probably starve without Amazon. Amazon is simply utilizing these people who are just there and is making something productive out of it ... which is good for us all. Imagine the difference compared to charity: With Amazon the worker earns something and is useful for society. The unemployed does nothing and wastes society's energy. The difference is enormous.\ And to make that clear again ... the workers are not victims. Many don't want to do anything else. Many are too lazy and are wasting their hard earned money on cigarettes, alcohol and drugs. Still, there are people, who are actually sick and weak among us. This is sad and I'll say more about them later.
Watch this video: https://www.youtube.com/watch?v=GltlJO56S1g Do you see an evil person, there? I see a man who risked everything to build this empire and who made huge losses for years. Why? For the purpose of providing an outstanding customer service. To you. In my opinion, Jeff Bezos is a hero.
Now for other companies:\ Compare them to the "in the sun-basking gazelles" (shops) and the attacking lions (Bezos). Now imagine a committee comes in and says: "Stop, don't eat these gazelles". WTF?
- Bezos would be starving. It's a catastrophe ... Bezos needs to get rewarded and thankfully was rewarded.
- The shops would still be lazy.
- We would still be in the stone age and sit together in the dark and starve. The world would still be poor.
Now often the consumer behavior is criticized. Amazon is to blame for all the trash, because people send everything back and it ends up in the landfill. But who sends everything back? Amazon? Amazon provides the service, people send everything back. Why is Amazon to blame? From a consumer's perspective, Amazon is a tool ... like a screwdriver. It was designed by humans exactly the way they wanted it. Some use a screwdriver to murder someone. Is the screwdriver now the problem? Should we all just stop making it more difficult for disadvantaged people who can't or won't send it back? Aren't we all grown-ups?
Some more examples of high-achievers
Watch this video from Bryan Johnson at Blueprint: https://www.youtube.com/watch?v=djiU_pFTEVE. Does this man look like a monster to you? He works around the clock to deliver me fresh and healthy food. He was already a millionaire to start with and could have done nothing but enjoy himself. Instead of partying, he enriches my life. I am grateful forever when Bryan becomes a billionaire!
Watch the videos from Ben "Ungeskriptet": https://www.youtube.com/@ben_ungeskriptet. He constantly invites successful people. No one of them needs to work anymore. Everyone would prefer to spend more time with their family but they are driven to make society better. They earn money by doing so... yes. Once you earn a few million dollars however, money is no longer important. Everyone of those successful people confirms this. They do the hard work because they are purpose driven and we should be grateful for them.
Elon Musk wants to inspire us humans to make a colony on Mars. That's his only goal. He could also just sit at home and do nothing. Instead he works on his dream and we all benefit from it. If you don't want to work for Elon Musk, then you are free to do something else. If you can't find anyone who hires you, then you are free to start your own business and out compete Elon. If we all didn't want him to make a colony on Mars, we shouldn't buy his products. Oops... the state buys the rockets. The state gives him money. Who is the problem?\ If you don't want Starlink, don't buy it. Then he built his rockets in vain. He earned his money before and if he chooses to spend it like this, that's his own choice. If he fails, he'll have to deal with the consequences. That being said...the only problem here is that the state subsidizes SpaceX rockets against the interest of the people.
Now to the two most important points that are not often mentioned:
- We want the same thing. I am for a social system. I like that everyone is doing well. I am for supporting the weak. If I could, for example, give away 10% of my possessions and help people, I would do so immediately. I support many people in my environment with a lot of money, time, and effort. The problem is not helping unproductive or disadvantaged people ... the problem is that you steal from successful people and distribute a small part of the loot to the unproductive, so that you get more votes (Socialism). If 50% of any given country came together and hired a company to support the poorest in their society that would be awesome. I'd be on board right away. But why do you have to force me? Why do you have to steal my money and contribute it to a system that doesn't deliver results? Why don't we use the market? If the company that supports the poor doesn't use the money correctly, you can change the "provider." Unfortunately, I can hardly change the state, and that's where the problem arises. The theft is the problem... not the social system. The state is, in fact, nothing more than a monopolistic company that cannot be disrupted by competition... this wouldn't exist in a free market, and it’s fatal.
- The problem with capitalism is that you don't recognize the benefit right away. If the productivity of the world increases by 5% per year, you unfortunately don’t benefit from it. Productivity increases through Amazon, Bryan Johnson, Elon, and 1000+ companies working around the clock. All research and technology also come from the market. It’s an investment for more profit later. But for what? Your life doesn't get better, does it? There’s the problem. Actually... if the monetary system were right... everything should become 5% cheaper per year. We should have deflation. If the world gets better, everything should get cheaper, and therefore, everyone should benefit. What does actually happen? The rich get richer. Why? Because the state prints money and steals from you... about 7% per year because the central bank wants 2% inflation. Just enough so that no one notices, and no one hangs them for it. The state steals all the benefits of capitalism and distributes them to itself. The rich are the ones who can defend themselves... thus, they get richer, along with all the bureaucrats who benefit as well. About 7% per year compared to you. But this is not because of the rich. It’s because of the state. In my opinion, this is the biggest problem, and Bitcoin is the solution. Bitcoin emerged from the market for the people. A solution from the free market against the oppression of the state. Very poetic, if you ask me. With Bitcoin, prices will fall forever... even if there is no more fiat money... because the supply is fixed, and if someone starts the next Amazon and the world becomes 0.1% more productive, everything will also become 0.1% cheaper.
Let's finish with some more eye-opening content suggestions:
This video opened my eyes. I've watched it again since... it's not that impressive... but somehow it worked for me: https://www.youtube.com/watch?v=Q6tDV3BhrcM
Watch this, regarding the environment: https://www.youtube.com/watch?v=zJdqJu-6ZPo
Milton Friedman is always enlightening: https://www.youtube.com/watch?v=67tHtpac5ws
And here again: https://www.youtube.com/watch?v=5_mGlqyW_Zw\ The ending is crazy. Nobody wanted to hire black people, and no social program would have changed that ... because everyone was racist back then. Even the shop owners ... and yet, they hired black people, which gave them an income. Now you can call it exploitation, but it's about the result. There's nothing that would have worked better in that environment. It doesn't sound nice, but it works.
And that's exactly how, but in the opposite way, Communism, Marxism, and Socialism work. It sounds good, but it produces Hitler, Stalin, and Mao.
-
 @ 0c98b8c8:80b5c0f6
2024-12-03 15:07:15
@ 0c98b8c8:80b5c0f6
2024-12-03 15:07:15upravený post
Test Post
Toto je testovací post
Ešte niečo
A toto je už normálny text
-
 @ 16d11430:61640947
2024-12-02 04:12:45
@ 16d11430:61640947
2024-12-02 04:12:45In an era that prides itself on technological progress and intellectual rigor, the state of identity verification has devolved into a grotesque parody of reason. We live in a time when individuals are subjected to invasive, demeaning rituals: holding up government-issued IDs to webcams, snapping awkward selfies alongside signatures, and transmitting scans of personal documents as if these primitive displays were the apex of modern security and authentication. This spectacle is not merely absurd; it is a profound degradation of the intellectual space that once championed privacy, dignity, and critical thought.
Alan Westin, in his seminal work Privacy and Freedom, argued that privacy is not merely a right but the cornerstone of individual autonomy. Yet today, this cornerstone is being chipped away by systems that demand we trade our personal dignity for the illusion of security. A photograph of a person holding an ID does not verify anything beyond their willingness to participate in this hollow theater. It does not confirm intent, consent, or even legitimacy—only compliance with a system so intellectually bankrupt that it relies on visual tropes rather than rigorous checks.
The Illusion of Trust
These charades operate under the false pretense that identity can be distilled into pixels and paper. The photograph of an ID—easily forged. The selfie with a signature—effortlessly manipulated. Even the sacred "wet ink" signature is nothing more than an outdated relic in a digital world that has long since surpassed its utility. And yet, these methods are perpetuated, not because they are effective, but because they are cheap, convenient, and require no intellectual investment from those implementing them.
The result is a catastrophic erosion of trust. Institutions that claim to protect our identities instead expose us to unnecessary risk, all while parading their incompetence as innovation. Worse, they place the burden of proof on the individual, demanding that we repeatedly perform this degrading pantomime to satisfy their bureaucratic inertia.
Privacy: From Right to Commodity
This erosion of intellectual rigor is symptomatic of a larger cultural malaise. In a society where privacy is no longer seen as a right but as a commodity to be bartered, the standards for verification have been reduced to the lowest common denominator. Instead of investing in robust, privacy-preserving technologies—such as cryptographic proofs, decentralized identity frameworks, or behavior-based authentication—we are forced to endure rituals that are as intellectually vacuous as they are invasive.
What’s more, these methods normalize the idea that our most intimate details—our faces, our signatures, our personal documents—are commodities to be captured, stored, and potentially exploited. This normalization of invasive practices not only undermines our autonomy but also desensitizes us to the very real dangers of mass data breaches and identity theft.
Reclaiming Intellectual Integrity
It is time to reject this farcical status quo. Verification should not be a performance; it should be a process rooted in intellectual rigor and respect for the individual. Technologies like zero-knowledge proofs and blockchain-based identity systems offer pathways to authentic verification without the need for invasive practices. These systems enable individuals to prove their identity, age, or qualifications without revealing unnecessary details, preserving both security and dignity.
But implementing such solutions requires a fundamental shift in mindset—a willingness to prioritize intellectual integrity over convenience, and human dignity over bureaucratic inertia. Institutions must be held accountable for perpetuating these charades, and individuals must demand systems that respect their autonomy and privacy.
A Call to Action
The intellectual space has not merely degraded; it has been hijacked by a culture of mediocrity that masquerades as progress. It is up to us to reclaim it, to demand verification processes that are worthy of a society that values freedom, dignity, and critical thought.
The choice is clear: we can continue to participate in this hollow theater, or we can refuse to play the fool in a charade that insults our intelligence and erodes our autonomy. Let us choose the latter. Let us choose freedom.
-
 @ e356a30c:11e846f7
2024-12-09 11:26:51
@ e356a30c:11e846f7
2024-12-09 11:26:51Bitcoin, the world's first and most well-known cryptocurrency, has taken the financial world by storm. Its decentralized nature, secure transactions, and potential for high returns have attracted millions of investors. However, the volatile nature of the market and regulatory uncertainties have also raised concerns.
The Pros of Bitcoin 1. Decentralization: Bitcoin operates on a decentralized network, meaning no single entity controls it. This makes it resistant to censorship and manipulation. 2. Security: Bitcoin transactions are secured by blockchain technology, a robust system that records transactions in a transparent and immutable way. 3. Potential for High Returns: Bitcoin's price has experienced significant fluctuations, leading to substantial gains for early investors. 4. Global Accessibility: Bitcoin can be accessed by anyone with an internet connection, regardless of geographic location or financial status. 5. Privacy: Bitcoin transactions can be conducted pseudonymously, providing a level of privacy not offered by traditional financial systems.
The Cons of Bitcoin 1. Volatility: Bitcoin's price is highly volatile, making it a risky investment. Price fluctuations can be drastic, and investors may lose significant amounts of money. 2. Regulatory Uncertainty: The regulatory landscape for cryptocurrencies is still evolving, and governments around the world are taking different approaches. This uncertainty can create legal and tax complications for investors. 3. Energy Consumption: Bitcoin mining requires significant amounts of energy, raising concerns about its environmental impact. 4. Security Risks: While blockchain technology is secure, individuals can still be vulnerable to hacking and scams. 5. Limited Practical Use Cases: Bitcoin's primary use case remains as a speculative asset rather than a widely accepted means of payment. Should You Invest in Bitcoin?
The decision to invest in Bitcoin is a personal one that should be carefully considered. It is essential to conduct thorough research and understand the risks involved. If you're considering investing, here are some tips: 1. Diversify Your Portfolio: Don't put all your eggs in one basket. Diversify your investments across various asset classes to mitigate risk. 2. Start Small: Begin with a small investment to test the waters and gain experience. 3. Long-Term Perspective: Bitcoin is a long-term investment. Don't get caught up in short-term price fluctuations. 4. Stay Informed: Keep up-to-date with the latest news and developments in the cryptocurrency market. 5. Consult a Financial Advisor: Seek advice from a qualified financial advisor to get personalized guidance.
Ultimately, the future of Bitcoin remains uncertain. While it has the potential to revolutionize the financial industry, it also faces significant challenges. As technology continues to evolve, it is likely that cryptocurrencies will play an increasingly important role in the global economy. However, investors should approach this emerging market with caution and a clear understanding of the risks involved.
Reference: https://ssoemsisd.com/depomin82-an-overview-of-cryptocurrency-and-its-investment-potential/
-
 @ eac63075:b4988b48
2024-12-02 02:40:18
@ eac63075:b4988b48
2024-12-02 02:40:18Estonia is a small country with just 1.3 million inhabitants and an area similar to that of the state of Rio de Janeiro, but with a notable difference: while Rio has about 16 million residents, Estonia shines with its efficiency, innovation, and digitalization. It's no wonder it's known as the "digital nation." For many Brazilians, the country has become a strategic gateway to start a business and settle in Europe.
Listen the podcast
https://www.fountain.fm/episode/pizBLdhqqP5qQrKQILFb
The Purpose of the Event and the Context
The meeting organized by Bloco and the Brazilian digital community aimed primarily to explore the opportunities that Estonia offers to those wishing to expand their businesses or start a new life in Europe. With pizza, networking, and straightforward presentations, the evening was dedicated to demystifying questions like "Why Estonia?" and "What makes this country a viable option for Brazilians?"
Additionally, the event highlighted the importance of E-Residency, a digital identity that allows you to open and manage a company in Estonia from anywhere in the world. But that's just the beginning. Let's explore what makes Estonia a standout point on the European scene.
Where Is Estonia Located?
If you open a map of Europe and look for this small country, you're likely to have difficulty locating it. Situated to the north of what's called Eastern Europe, Estonia borders Russia and Latvia and is separated from Finland by the Baltic Sea. Although geographically positioned in the east, many Estonians prefer to identify with the north due to cultural and historical proximity to the Nordic countries.
There's something fascinating about Estonia's history. According to local legends, Vikings set out from their Estonian islands to conquer the world, later returning to reclaim their lands. This spirit of resilience and reinvention permeates the country's culture to this day.
Digitalization: The Estonian Revolution
Thirty years ago, when Estonia gained its independence from the Soviet Union, the country decided to look to the future. The question was simple: how to ensure the sovereignty and survival of a small, vulnerable nation? The answer was bold: total digitalization.
In 2001, the X-Road was created—a decentralized infrastructure that connects all government institutions and allows citizens to access public services digitally. This system is so advanced that even the servers of the Estonian government are located outside the country, stored with backups at the European Commission in Brussels.
Through this infrastructure, Estonia eliminated information silos, decentralized data, and allowed its citizens to authorize the use of personal information with complete control. Today, 98% of the population has a digital identity, 95% file taxes online in less than three minutes, and 100% of public services are available digitally.
For those accustomed to Brazilian bureaucracy, it's impressive to know that opening a company in Estonia can be done in just 15 minutes, without the need for an accountant.
E-Residency: A Digital Passport for Business
Launched in 2014, the E-Residency program made Estonia the first country in the world to offer a digital identity to non-residents. This digital ID card allows entrepreneurs to open a company in the European Union, sign documents, and manage businesses remotely without needing to visit the country.
Although it doesn't grant citizenship or physical residency, E-Residency is perfect for those who want to test the European market or operate a digital company. The program has already attracted over 118,000 e-residents from around the world, including 1,300 Brazilians who have opened 379 companies in the country.
Advantages of Doing Business in Estonia
Starting a business in Estonia has many advantages. Let's discuss some of the main ones:
Simple and Clear Taxation:
Estonia adopts a flat tax rate of 20% (which increased to 22% after the pandemic and will be 24% in 2025) on distributed profits. If you reinvest the profits in the company, the taxation is zero—a unique policy that encourages sustainable growth.
Low Cost to Start:
Unlike Switzerland, which requires an initial deposit of 100,000 Swiss francs to open a company, in Estonia, only 2,500 euros are needed. And the best part: this amount only needs to be deposited when the company distributes profits for the first time.
Complete Digitalization:
Digital signatures in Estonia eliminate the need for notaries and paper documents. Everything can be done online, from opening the company to filing taxes.
Support for Startups and Innovation:
With the Startup Visa, entrepreneurs can move to Estonia with their entire family and receive support to expand their businesses. Additionally, the country has the highest number of unicorns (startups valued at over one billion dollars) per capita in the world, including companies like Skype, Bolt, and Wise.
Easy Access to Europe:
Establishing your company in Estonia means access to the European market, with its unified regulations and a vibrant innovation ecosystem.
The Startup Visa: An Invitation for Entrepreneurs
For those who want more than just operating remotely, the Startup Visa program offers the opportunity to physically move to Estonia. The initial visa is valid for one year and can be renewed for three consecutive years. After eight years, there's the possibility of applying for European citizenship, although Estonia doesn't allow dual nationality.
One of the unique features of the Startup Visa is that there's no limit to the number of partners or family members who can be included in the program. This means that the entire team of founders and their families can benefit from the residence permit.
Additionally, Estonia offers support through the International House and its Work in Estonia program, a center where newcomers can resolve everything from assistance with opening bank accounts to cultural and professional integration.
Innovation and Access to Investments
Estonia is known for its culture of innovation. Events like Latitude 59, one of Europe's main startup gatherings, offer prizes of up to two million euros for winning startups. The country also facilitates direct connections with investment funds and venture capital, often without bureaucratic barriers.
For early-stage companies, the Estonian ecosystem is especially attractive. There are cases of entrepreneurs who managed to raise hundreds of thousands of euros with little more than a prototype or a good idea on paper.
A Small Country with Global Ambitions
Although small in size, Estonia is big in ambition. Its model of digitalization and support for startups serves as an example to the world. With unique opportunities like E-Residency and the Startup Visa, the country positions itself as a viable and accessible gateway for Brazilians who wish to explore the European market.
For those seeking innovation, simplicity, and access to the global market, Estonia offers more than opportunities; it offers a vision of the future. Whether it's to open a business, operate remotely, or move with the family, the country proves that with the right strategies, even a small nation can make a giant impact.
-
 @ 0c98b8c8:80b5c0f6
2024-12-01 13:38:22
@ 0c98b8c8:80b5c0f6
2024-12-01 13:38:22this is test podčiarknuté
asterisk
"Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum."
Reference-style:
Toto je obrázok z dronu
-
 @ 005bc4de:ef11e1a2
2024-12-09 10:25:53
@ 005bc4de:ef11e1a2
2024-12-09 10:25:53I've long had a hunch, and on Saturday it was confirmed. God gifted us indoor plumbing for the purpose of keeping us humble.
The kitchen sink has had a slight drip for...too long. Of late, it has been getting worse and I procrastinated until I simply couldn't any longer. Saturday, I determined to finally fix it.
In theory, it should be simple: remove the stupid garbage disposal (which we never used) as it had rusted through and was the leakage problem, then rebuild the piping without a stupid garbage disposal. I've learned to take photos or repair projects, and did, but being a bit nerdy and maybe a bit spectrumy I need to draw it out...helps me flesh things out in my mind.
!(image)[https://files.peakd.com/file/peakd-hive/crrdlx/23u6WTkJyo2BWz64wAdM1ow93QciRyBdseq48FWL9rpYUijLAVg8n2fAP61tMuHdNest7.png]
To me, home projects are judged by the number of trips to the home improvement store. I set the over/under on this one at 2.5 trips. If I could only go twice to the store, and get it done, I'd say it was a victory. Over 2.5 and it would be a loss. My usual is around 4 trips, so, feeling this was an easy endeavor, the low 2.5 over/under was set.
Step 1 - disassembly
Tearing things apart is the easy part. At least, it's supposed to be easy because you don't have to be particularly careful. Removing the stupid garbage disposal would be nothing more than unscrewing things, and it was. However, the plastic composite ring that held on the stupid garbage disposal was impossibly not going to come off. I had to use and angle grinder and literally cut the thing off. This is akin to removing a rusty nail with an axe. I cut, off it came.
Step 2 - assembly
I looked at the situation, I drew my sketch. Actually, I drew the first part of the sketch. What's pictured above is the final composition of several iterations and additions. I took trip #1 to the home improvements store, surprisingly found the section quickly (unheard of) and surprisingly quickly found the parts I needed (also unheard of). After navigating through all the Christmas shoppers buying cute decorative doo-daddies (while I was buying pipe), I paid, navigated jammed-full parking lot, then I was gone.
The first part, the "basin/catch thing" went in too easily and things were going too well. (This can't be good, I thought.) And, sure enough under the sink, the parts I thought would do the job weren't even close. What was I thinking?
So, back to the store trip #2. Same thing...section, parts, navigate holiday shoppers (there were more now), navigate parking lot (there were more now), gone. The next parts were assembled, sort of. The little diagrams on the packaging and the in-studio plumbing vids I'd watched all looked so easy. Everything matched up, everything fit. Here, with my head stuck underneath a dark and damp sink and my arms twisted in wrong ways, nothing matched up, nothing fit. And, I needed another part.
So, back to the store trip #3. A few hours in now, I was getting perturbed. I had to humble myself and do what men hate doing...I decided to ask for help.
The kind home improvement store man was answering questions left and right. (It was even busier now.) I waited...more humbling. When my turn came, I bent the knee, showed him my photo of what I had going on under the sink.
"That's not gonna work," he said.
Ugh. "What am I doing wrong?" I asked kind of pitifully.
"Water flows downhill, not uphill," he informed me.
So, this was the real lesson in humility yesterday. Normally, with a smart-alec answer like that (which does not answer my "what's wrong" question, but was merely injected to kick me while I'm down), I would have responded with something of the same kind...because, every action has an equal and opposite reaction. I might've said, "It doesn't flow downhill when it's pumped uphill," or "Well, I'll be doggone, that's it! Water does flow downhill. You're a smart man!" Actually, I probably would have said, "Good for you, that's correct," as if congratulating him on his accomplishment of water flowage knowledge, then I would have repeated my question, "what am I doing wrong?"
However, I was too beat down, and stuck. I kept my mouth shut. To get an extra jab in, he added something about how my design would also create a venting problem. Then, he gave constructive advice: take this part out, get one of these, it slides in and out, adjust it to where it fits, easy. To be fair, I think he was growing weary from all the stupid people and stupid questions...evidently people come up with crazy ideas, like water flowing uphill.
I chuckled, "Easy for you maybe," I said. This was trip three, I was stuck, I didn't exactly know what he was telling me to do, I was too embarrassed to ask after having been passive aggressive plumbing-shamed. He seemed pretty confident, so I headed out, with little confidence this would work.
Navigate holiday shoppers, the checkout lady said, "Oh, you're back," (great, now they're starting to know me and my ineptitude, more embarrassment), pay, navigate parking lot, gone.
Back home, I was getting closer. What I was doing was a case of building things out piece by piece. If I had a truck full of parts outside, I could have been done in 30 minutes. The back-and-forth and shaming was what was draining me. The system I was building seemed as though it was finally going to work, but, it just wasn't lining up right...about an inch of a misalign. I needed one more extension part for a slight drop. The last piece of the jigsaw was close, but not exactly right. By this time though, I was getting tired and that added to the frustration. Plus, I couldn't dare go back and face Mr. Water Downhill and Mrs. You're Backagain. I went to a closer, but more pricey, hardware store. I found the part I thought would work and the Santa-looking man there assured me that part was correct. For the first time since trip #1, I felt I might get it to work.
Back home, again, holding things under the sink, looking, figuring, head scratching...nope, this part won't work. Santa was wrong. A male threaded head can't mate with a male threaded head...it just doesn't work that way. Argh! Seriously?! I have to go back again?!
I scratched my head and figured I'd retrace and try what seemed promising the last time...just take a fresh look. To wrap this up, I finally got it to work by mixing and matching parts in the kits I'd bought. The flexible "get rid of this" part that Mr. Water Downhill told me to toss out did the trick. That part was able to flex the one inch drop that I needed to get things to mesh up. And just like that, it was complete.
Tighten, tighten, tighten, tighten, tighten, and tighten. Then, pray for no leaks. Water back on...
Based on my prior plumbing endeavors, I was stunned...there were no leaks. And a day in, so far, so good. I'll keep praying.
Stats
- 5.5 hours of work
- 3 trips to home improvement store
- 1 trip to hardware store
- 1 trip to home improvement store to return unused part (yet to be done)
- 1 trip to hardware store to return unused part (yet to be done)
- 1 make-me-feel-dumb comment from the guy in plumbing
- 1 "back again" from the checkout lady
- 1 "that'll work" from Santa lookalike
With the over/under on trips to the store set at 2.5, and me hitting 6 trips counting the returns, this was clearly a fail.
Moral
The moral of the story is that my hunch was correct...God's purpose in giving us indoor plumbing is so that we stay humble. It's either "stay humble," or get slapped down and "get humbled."
-
 @ 88d8c9d1:5b3ac02b
2024-11-30 22:30:04
@ 88d8c9d1:5b3ac02b
2024-11-30 22:30:04This article was first publishedon Bitcoin Magazine.
Kamala Harris’s rejection of Bitcoin deprives a vital resource to those in need globally, while Trump’s ‘Number Go Up” approach, may jeopardize America's core humanitarian values, like the refugee resettlement program, and ignore Bitcoin’s potential to aid vulnerable populations globally.
Just hours after the U.S. election results were announced, I received messages from friends filled with striking assumptions. Some congratulated me, mockingly saying, “Congrats, your side won for Bitcoin.” Others expressed disapproval with remarks like, “It’s pathetic!” and “I’m shocked that Americans just voted for Hitler.” One friend said, “You were lucky to find safety in the U.S. as a refugee under Biden’s administration. Refugees and asylum seekers will now face a harder time here, but, hey, it’s still good for your Bitcoin.” Many of these friends work in high-level corporate jobs or are university students.
As a Green Card holder, I was not eligible to vote, but I recognize their huge disappointment in seeing their preferred candidate lose. Their frustrations were directed at me because they know I support Bitcoin and work in the space. I understand that making me a scapegoat says less about me and more about their limited understanding of what Bitcoin’s value represents.
I’m aware that in this highly polarized political landscape, ideological stereotyping becomes evident—not only during election season but also in spaces where innovative thinking should be encouraged. A prime example of this ideological bias occurred during the Ohio State University commencement, where Chris Pan’s speechon Bitcoin was largely booed by students attending their graduation ceremony. I admire the courage it took to stand firm in front of over 60,000 people and continue his speech. My guess is that most of these graduating students have never experienced hyperinflation or grown up under authoritarian regimes, which likely triggered an “auto-reject”' response to concepts beyond their personal experience.
I’ve encountered similar resistance in my own unfinished academic journey; during my time at Georgetown, I had several unproductive conversations with professors and students who viewed Bitcoin as a far-right tool. Once a professor told me, “Win, just because cryptocurrency (he didn’t use the term Bitcoin) helped you and your people in your home country doesn’t make it a great tool—most people end up getting scammed in America and many parts of the world. I urge you to learn more about it.” The power dynamics in academic settings often discourage open-minded discourse, which is why I eventually refrained from discussing Bitcoin with my professors.
I've learned to understand that freedom of expression is a core American value. Yet, I’ve observed that certain demographics or communities label anyone they disagree with as 'racist.' In more extreme cases, this reaction can escalate to using influence to have people fired, expelled from school, or subjected to coordinated cyberbullying. I’m not claiming that racism doesn’t exist in American society or elsewhere; I strongly believe both overt and subtle forms of racism still persist and are well alive today.
Although bias and inequality remain widespread, Bitcoin operates on entirely different principles. Bitcoin is borderless, leaderless, and accepting of any nationality or skin color all while without requiring any form of ID to participate. People in war-torn countriesconvert their savings into Bitcoin to cross borders safely, human rights defenders receive donations in Bitcoin ,and women living under the Taliban get paid through the Bitcoin network.
Bitcoin is not racist because it is a tool of empowerment for anyone who is willing to participate. Bitcoin is not Xenophobic because it gives those forced to flee their homes the power to carry their hard-earned economic energy across borders and participate in another economy when every other option is closed. For activists, often branded as 'criminals' by authoritarian regimes, it supports them through frozen bank accounts and blocked resources. For women, enduring life under misogynistic rule, Bitcoin offers a rare chance for financial independence.
Going back to the U.S. election context, Bitcoin not only levels the playing field for people in the world’s most forgotten places and darkest corners, but it also opens new avenues for U.S. presidential candidates to engage with this growing community. President-elect Donald Trump has made bold promises regarding Bitcoin, signaling a favorable policy. In contrast, Democratic candidate Vice President Kamala Harris's campaign reportedly declined to support the Bitcoin community. Grant McCarty, co-founder of the Bitcoin Policy Institute, stated, "Can confirm that the Harris campaign was offered MILLIONS of dollars from companies, PACs, and individuals who were looking for her to simply take meetings with key crypto stakeholders and put together a defined crypto policy plan. The campaign never took the industry seriously." I believe this is something most people may be unaware of, and confirmation bias often leads to the assumption that all Bitcoin supporters back every policy of the other side, including potential drastic changes to America's humanitarian commitments such as refugee resettlement and asylum programs, anti-trafficking and protection of vulnerable populations, and foreign aid and disaster relief.
Most people around the world lack a stable economic infrastructure or access to long-term mortgages; they live and earn with currencies more volatile than crypto gambling and, in some cases, holding their own fiat currency is as dangerous as casino chips, or worse.
The Fiat experiment has failed the global majority. I believe that Bitcoin and Bitcoin advocates deserve to be evaluated on their merits and work on global impact, rather than through the binary lens of political bias, misappropriated terms, or factually flawed yet socially accepted diminutive categorizing, which allows them to opt out of learning and evaluating assumptions.
-
 @ 005bc4de:ef11e1a2
2024-12-09 10:21:02
@ 005bc4de:ef11e1a2
2024-12-09 10:21:02I've long had a hunch, and on Saturday it was confirmed. God gifted us indoor plumbing for the purpose of keeping us humble.
The kitchen sink has had a slight drip for...too long. Of late, it has been getting worse and I procrastinated until I simply couldn't any longer. Saturday, I determined to finally fix it.
In theory, it should be simple: remove the stupid garbage disposal (which we never used) as it had rusted through and was the leakage problem, then rebuild the piping without a stupid garbage disposal. I've learned to take photos or repair projects, and did, but being a bit nerdy and maybe a bit spectrumy I need to draw it out...helps me flesh things out in my mind.
https://files.peakd.com/file/peakd-hive/crrdlx/23u6WTkJyo2BWz64wAdM1ow93QciRyBdseq48FWL9rpYUijLAVg8n2fAP61tMuHdNest7.png
To me, home projects are judged by the number of trips to the home improvement store. I set the over/under on this one at 2.5 trips. If I could only go twice to the store, and get it done, I'd say it was a victory. Over 2.5 and it would be a loss. My usual is around 4 trips, so, feeling this was an easy endeavor, the low 2.5 over/under was set.
Step 1 - disassembly
Tearing things apart is the easy part. At least, it's supposed to be easy because you don't have to be particularly careful. Removing the stupid garbage disposal would be nothing more than unscrewing things, and it was. However, the plastic composite ring that held on the stupid garbage disposal was impossibly not going to come off. I had to use and angle grinder and literally cut the thing off. This is akin to removing a rusty nail with an axe. I cut, off it came.
Step 2 - assembly
I looked at the situation, I drew my sketch. Actually, I drew the first part of the sketch. What's pictured above is the final composition of several iterations and additions. I took trip #1 to the home improvements store, surprisingly found the section quickly (unheard of) and surprisingly quickly found the parts I needed (also unheard of). After navigating through all the Christmas shoppers buying cute decorative doo-daddies (while I was buying pipe), I paid, navigated jammed-full parking lot, then I was gone.
The first part, the "basin/catch thing" went in too easily and things were going too well. (This can't be good, I thought.) And, sure enough under the sink, the parts I thought would do the job weren't even close. What was I thinking?
So, back to the store trip #2. Same thing...section, parts, navigate holiday shoppers (there were more now), navigate parking lot (there were more now), gone. The next parts were assembled, sort of. The little diagrams on the packaging and the in-studio plumbing vids I'd watched all looked so easy. Everything matched up, everything fit. Here, with my head stuck underneath a dark and damp sink and my arms twisted in wrong ways, nothing matched up, nothing fit. And, I needed another part.
So, back to the store trip #3. A few hours in now, I was getting perturbed. I had to humble myself and do what men hate doing...I decided to ask for help.
The kind home improvement store man was answering questions left and right. (It was even busier now.) I waited...more humbling. When my turn came, I bent the knee, showed him my photo of what I had going on under the sink.
"That's not gonna work," he said.
Ugh. "What am I doing wrong?" I asked kind of pitifully.
"Water flows downhill, not uphill," he informed me.
So, this was the real lesson in humility yesterday. Normally, with a smart-alec answer like that (which does not answer my "what's wrong" question, but was merely injected to kick me while I'm down), I would have responded with something of the same kind...because, every action has an equal and opposite reaction. I might've said, "It doesn't flow downhill when it's pumped uphill," or "Well, I'll be doggone, that's it! Water does flow downhill. You're a smart man!" Actually, I probably would have said, "Good for you, that's correct," as if congratulating him on his accomplishment of water flowage knowledge, then I would have repeated my question, "what am I doing wrong?"
However, I was too beat down, and stuck. I kept my mouth shut. To get an extra jab in, he added something about how my design would also create a venting problem. Then, he gave constructive advice: take this part out, get one of these, it slides in and out, adjust it to where it fits, easy. To be fair, I think he was growing weary from all the stupid people and stupid questions...evidently people come up with crazy ideas, like water flowing uphill.
I chuckled, "Easy for you maybe," I said. This was trip three, I was stuck, I didn't exactly know what he was telling me to do, I was too embarrassed to ask after having been passive aggressive plumbing-shamed. He seemed pretty confident, so I headed out, with little confidence this would work.
Navigate holiday shoppers, the checkout lady said, "Oh, you're back," (great, now they're starting to know me and my ineptitude, more embarrassment), pay, navigate parking lot, gone.
Back home, I was getting closer. What I was doing was a case of building things out piece by piece. If I had a truck full of parts outside, I could have been done in 30 minutes. The back-and-forth and shaming was what was draining me. The system I was building seemed as though it was finally going to work, but, it just wasn't lining up right...about an inch of a misalign. I needed one more extension part for a slight drop. The last piece of the jigsaw was close, but not exactly right. By this time though, I was getting tired and that added to the frustration. Plus, I couldn't dare go back and face Mr. Water Downhill and Mrs. You're Backagain. I went to a closer, but more pricey, hardware store. I found the part I thought would work and the Santa-looking man there assured me that part was correct. For the first time since trip #1, I felt I might get it to work.
Back home, again, holding things under the sink, looking, figuring, head scratching...nope, this part won't work. Santa was wrong. A male threaded head can't mate with a male threaded head...it just doesn't work that way. Argh! Seriously?! I have to go back again?!
I scratched my head and figured I'd retrace and try what seemed promising the last time...just take a fresh look. To wrap this up, I finally got it to work by mixing and matching parts in the kits I'd bought. The flexible "get rid of this" part that Mr. Water Downhill told me to toss out did the trick. That part was able to flex the one inch drop that I needed to get things to mesh up. And just like that, it was complete.
Tighten, tighten, tighten, tighten, tighten, and tighten. Then, pray for no leaks. Water back on...
Based on my prior plumbing endeavors, I was stunned...there were no leaks. And a day in, so far, so good. I'll keep praying.
Stats
- 5.5 hours of work
- 3 trips to home improvement store
- 1 trip to hardware store
- 1 trip to home improvement store to return unused part (yet to be done)
- 1 trip to hardware store to return unused part (yet to be done)
- 1 make-me-feel-dumb comment from the guy in plumbing
- 1 "back again" from the checkout lady
- 1 "that'll work" from Santa lookalike
With the over/under on trips to the store set at 2.5, and me hitting 6 trips counting the returns, this was clearly a fail.
Moral
The moral of the story is that my hunch was correct...God's purpose in giving us indoor plumbing is so that we stay humble. It's either "stay humble," or get slapped down and "get humbled."
-
 @ 714f9dc3:76659adb
2024-11-30 13:49:04
@ 714f9dc3:76659adb
2024-11-30 13:49:04📝 𝐈 𝐰𝐚𝐧𝐭 𝐭𝐨 𝐭𝐞𝐥𝐥 𝐲𝐨𝐮 𝐚 𝐬𝐭𝐨𝐫𝐲. 𝐀𝐧 𝐢𝐧𝐬𝐩𝐢𝐫𝐢𝐧𝐠 𝐬𝐭𝐨𝐫𝐲.
About #bitcoin and an idea I had for a long time. Since this week, 𝐢𝐭'𝐬 𝐫𝐞𝐚𝐥𝐢𝐭𝐲. And I'm frkn proud of this. This is the story of Blockhunters.
https://m.primal.net/Mkjx.png
In 2019, I graduated as an Industrial Product Designer. Inspired by #bitcoin, I decided to NOT work for a design agency. Instead, I wanted to work full-time on my own bitcoin projects. Copywriting, translating, educating, and making documentaries and magazines.
https://m.primal.net/Mkjy.png
In 2020, an idea emerged. How can I combine my skills as a designer with my knowledge of bitcoin?
The first idea of nostr:npub1u478qx307ln39tkhdj9r0rvl29yrhdqjdkzv9l98rmtxvwhza6zsm42m4a was born: a board game that combines FUN with BITCOIN.
How can we engage tactile learners, that don't care about articles, podcasts or videos? It all started in July 2020 with some pencils, a4 papers and a rough idea. Some week later, I crafted a first prototype with blocks, cards, and colors. Very, very basic. No branding, no theme, no rulebook, no funding. Nothing, but an idea.
https://m.primal.net/MkkD.png
By November 2020, I brought the game to a coliving community, where it was playtested in the wild for the first time.
https://m.primal.net/MkkF.png
⏳ But progress slowed down... A lack of skills, motivation, and a clear path forward led to the project being put on hold.
Fast-forward to April 2022. During my travels in Namibia, I met @npub1suwxj6qxnts2ls8jr0lpjy95386kr9y5ckn7qep5c95063wcj5eqh4rlxf — it was a perfect match. She brought the missing skills and energy to the project, and took away all reasons to abandon the game for good. We decided to make this happen, and create the game together!
In December 2022, we picked up the game again, playing it with bitcoiners on Bitcoinn Island in the Philippines. By January 2023, we decided to go all in, launched a nostr:npub1kmwdmhuxvafg05dyap3qmy42jpwztrv9p0uvey3a8803ahlwtmnsnhxqk9 campaign and rethought every aspect: the theme, branding, components, gameplay, rulebook, and more.
We even won a Geyser grant, which allowed us to go into full creative mode. By September 2023, we launched a “real” prototype, complete with characters, a game board, branding, and more. With a few thousand dollars raised, we were motivated to bring Blockhunters to life.
https://m.primal.net/MkkG.png
From September 2023 to February 2024, we playtested the new prototype dozens of times all over the world. From El Salvador to Madeira, and Tokyo to South Korea. At meetups, conferences, with friends and family. This was soooo fun!
https://m.primal.net/MkkI.png
In March 2024, we ordered the first official prototype from a company in Shanghai.
During that time, Emily even visited the factory in China to oversee production. Full of confidence, we proceeded.
https://m.primal.net/MkkJ.png
The excitement was palpable when we received the first real prototypes. This kicked off the final phase of development: Revising components, shipping logistics, securing STEM registration, CE-testing, quality checks, and translations.
Finally, in July 2024, we placed the order for the first 1,000 games. And had to wait... for many weeks/months to finally receive the games.
🥳 𝐀𝐧𝐝 𝐧𝐨𝐰 𝐭𝐡𝐞 𝐛𝐢𝐠 𝐧𝐞𝐰𝐬.
https://m.primal.net/MkkK.png
Here they are :) Last week, we delivered the first couple of hundred games to our loyal fans and supporters.
It's so great to see pictures coming in from all over the world.
We did it! 🥰
https://m.primal.net/MkkL.png
It’s been 4 years since the idea for Blockhunters came to life. Now it’s reality. This journey has been unforgettable, with amazing support from the community. Your enthusiasm, pre-orders, feedback and patience were crucial. Thank you from the bottom of our hearts. 🧡
So what is Blockhunters about?
We like to say: Have Fun Being Orangepilled.
It's about: 𝐇𝐚𝐯𝐢𝐧𝐠 𝐅𝐮𝐧 But also about 𝐁𝐞𝐢𝐧𝐠 𝐎𝐫𝐚𝐧𝐠𝐞𝐩𝐢𝐥𝐥𝐞𝐝
You collect coins for your character (private key), without revealing it, while building a blockchain together.
https://m.primal.net/MkkN.png
-
𝐇𝐚𝐯𝐢𝐧𝐠 𝐅𝐮𝐧 The game is truly fun. It's a mix of memory, poker, and game theory. The tension builds up as the blocks are mined and the money becomes scarce. Mining adds randomness, securing your key/coins adds strategy and powercards add twists.
-
𝐁𝐞𝐢𝐧𝐠 𝐎𝐫𝐚𝐧𝐠𝐞𝐩𝐢𝐥𝐥𝐞𝐝 The game also has educational elements. ➖ 10 characters with real world stories that explain the social importance of bitcoin ➖ technical elements (halving, keys, mining, mempool), that explain the technical significance of bitcoin
Are you too obviously stacking sats for Omar, Diego or Hila? Someone may steal your key! Do you have a bad powercard? You are subject to a $5 wrench attack! 🔧 Or a good powercard? You have extra hashrate, can make a multisig, or attack your opponent with a blackout. ⚡️
https://m.primal.net/MkkQ.png
But you don't have to understand bitcoin at all! Follow the rulebook, play a game, and you'll understand.
With of course questions popping up: - why is money scarce (in contrary to many games) - what happens if I leak my key? - why can't I cheat in this game?
https://m.primal.net/MkkR.png
This is your moment as a bitcoiner to step in, and explain more. The game triggered their attention! They see, feel and experience elements of bitcoin in the 40 minutes game.
You have their interest. It's time to orangepill!
What a journey: from product designer to a bitcoiner designing a product again☺️ Now it's time to spread the word! Still looking for an Xmas gift? This is your call! Send this flyer to your loved ones and Bring Bitcoin Home!
We ship worldwide 🌍📦
🛒 https://blockhuntersgame.com
https://m.primal.net/MkkT.png
Oh and please follow nostr:npub1u478qx307ln39tkhdj9r0rvl29yrhdqjdkzv9l98rmtxvwhza6zsm42m4a to stay tuned :)
bitcoin #design #productdesign #boardgame #game #playtest #education #orangepill #orangepilling
-
-
 @ 9bfc0ed5:17da5661
2024-12-09 08:53:02
@ 9bfc0ed5:17da5661
2024-12-09 08:53:02Here are some recent football articles from 2024: Erik ten Hag could join RB Leipzig According to Sky Sports, Erik ten Hag could join forces with Jurgen Klopp at RB Leipzig, which could hurt Manchester United's chances of getting David Raum. Mohamed Salah to sign a new deal at Liverpool After months of negotiations, Mohamed Salah is close to signing a new two-year deal with Liverpool. Manchester United considering Patrick Dorgu Manchester United is considering signing Lecce full-back Patrick Dorgu, who is also a target for Chelsea and Tottenham. Arsenal expected to resist January approaches for Jakub Kiwior Arsenal is expected to resist January approaches for Jakub Kiwior, who is of interest across Europe. Copa América 2024 Yahoo Sports reports that the Copa América 2024 mini-World Cup will be held in the U.S. The tournament is intended to appeal to both Latino fans and casual American viewers. Kylian Mbappe Kylian Mbappe's head collided with the shoulder of Austrian defender Kevin Danso during the Group D opener in Duesseldorf. Slovakia vs Belgium Slovakia beat Belgium 1-0 at Euro 2024. England started off their Euro 2024 campaign with a victory against Serbia England started their Euro 2024 campaign with a victory against Serbia on Sunday.
-
 @ 2063cd79:57bd1320
2024-12-09 08:35:43
@ 2063cd79:57bd1320
2024-12-09 08:35:43Eines der interessantesten Themen im immer mehr Facetten umfassenden Bitcoin-Bereich ist und bleibt das Mining. Erst diese Woche wurde wieder ein neues ATH erreicht und die Nachrichten der letzten paar Wochen zeigen, dass es immer noch ein Bereich ist, der sich nach wie vor neu erfindet und stets im Wandel ist. Besonders die Formierung neuer immer größer werdender Mining-Pools, die damit einhergehenden Überlegungen rund um Stratum V2, aber auch die ständige Veränderung der grossen, an Börsen gelisteten Minern sind immer wieder Gesprächsthemen und erzeugen viele Nachrichten. Bevor wir uns diese letzten Neuigkeiten anschauen, ist es jedoch einmal wert, einen Schritt zurückzutreten und sich genau zu vergegenwärtigen, was Miner eigentlich tun - also wie der Mining-Prozess abläuft.
Die Mining-Lotterie
Die meisten Menschen missverstehen oder verstehen nicht ganz, was Bitcoin-Miner tatsächlich tun, um neue Blocks zu produzieren. Es wird hauptsächlich über den hohen Energieaufwand gesprochen, was dazu führt, dass fälschlicherweise angenommen wird, dass die gesamte aufgebrachte Energie in jeden neu produzierten Block fließt. Die Analogie zum herkömmlichen Bergbau, oder Goldschürfen, trägt teilweise zur Verwirrung bei. Denn beim Bergbau arbeiten viele Maschinen gleichzeitig daran, wertvolle Stoffe aus der Erde zu ziehen, dabei können parallel weltweit Edelmetalle geborgen werden und viele Faktoren spielen dabei eine Rolle, wie erfolgreich in Bergbau-Unternehmen arbeitet (z.B. Menge des Equipments, die in der Lokalität vorhandene Menge an wertvollen Stoffen, usw.). Beim Bitcoin-Mining ist dies nicht ganz der Fall.
Denn einfach ausgedrückt ist Mining eine Lotterie, um neue Blöcke in der Bitcoin-Blockchain zu erstellen. Dabei ergeben sich zwei Effekte: 1) Jeder neue Block fügt Transaktionen der Blockchain hinzu und sichert damit zusätzlich vorherige Blöcke und die darin enthaltenen Transaktionen ab (sichert also das gesamte Netzwerk ab). 2) Erhalten erfolgreiche Miner eine Belohnung (den Blockreward) für die getane Arbeit und für die aufgewendeten realen Ressourcen (z. B. Strom, Hardware, OpEx). Aber was ist genau mit Lotteriesystem gemeint?
Man stelle sich vor, dass alle Miner im Bitcoin-Netzwerk das gleiche Lotto spielen. Doch in unserem Lottospiel werden die 6 richtigen Zahlen nicht am Ende gezogen, sondern sind am Anfang jeder Runde gesetzt (es gibt keine Möglichkeit zu schummeln, denn es gibt niemanden, von dem man die richtigen Zahlen erhalten kann, bis sie gefunden wurden). Alle Lotto-Teilnehmer setzen sich also hin und fangen an, so schnell wie nur eben möglich Lottoscheine auszufüllen, denn es geht darum, die richtigen 6 Zahlen für die jeweilige Runde als erstes zu finden. Derjenige Spieler, der am schnellsten Scheine ausfüllen kann, hat höhere Chancen, die richtigen Zahlen auch als erstes zu erraten. Sobald ein Spieler die richtigen 6 Zahlen hat, ist die Runde sofort beendet und alle Mitspieler können sich den Gewinner-Schein ansehen und mit den veröffentlichten 6 Zahlen vergleichen, um damit zu validieren, dass der Gewinner auch tatsächlich übereinstimmende Zahlen hat. Der Gewinner bekommt den Jackpot und die nächste Runde beginnt. Einziger Unterschied ist, dass man sich mit dem Jackpot keine Kartbahn in den Garten bauen kann.

Da dieses Lottospiel sich immer größerer Beliebtheit erfreut kommen immer mehr interessierte Spieler hinzu, aber auch die existierenden Spieler fangen an, Freunde dazuzuholen, die ihnen helfen sollen, noch schneller Lottoscheine auszufüllen. Durch die steigende Anzahl an Spielern würde jede Runde schneller vorbei sein, da ja viel mehr Spieler gleichzeitig Scheine ausfüllen und damit die Wahrscheinlichkeit steigt, dass die 6 Richtigen schneller gefunden werden. Da die Lotterie nur eine begrenzte Menge von Kapital zur Ausschüttung als Jackpots bereithält, muss sie das Spiel so anpassen, dass die Runden möglichst gleich lang dauern.
Dazu wird jede Runde die Schwierigkeit erhöht. Mussten die ersten Spieler nur 6 Richtige aus einer Zahlenreihe von z.B. 49 Felden erraten, wird die Anzahl der möglichen Zahlen erhöht, sodass eine Runde im Durchschnitt immer 10 Minuten dauert. Verlassen Spieler die Runde, wird die Zahl der möglichen Felder genauso wieder reduziert. Im Bitcoin-Netzwerk wird die stetige Ausschüttung von neuen bitcoins genauso reguliert. Damit im Durchschnitt alle 10 Minuten ein neuer Block produziert wird, müssen alle 2016 Blöcke (ca. alle 2 Wochen) die Schwierigkeit angepasst werden, um die Blockzeit bei 10 Minuten zu halten. Treten innerhalb dieses Zeitraums von ca. 2 Wochen mehr Miner dem Netzwerk bei, steigt die Hashrate und infolgedessen muss die Schwierigkeit angepasst werden.
Alle Miner im Netzwerk verwenden ASIC (Mining-Equipment, oder Rigs) - spezialisierte Computer, die nur darauf ausgelegt sind, Hashes so schnell wie möglich zu berechnen. Einen Hash berechnen bedeutet, eine zufällige Eingabe in eine mathematische Funktion einzufügen und eine Ausgabe zu erzeugen. Technisch bedeutet dies, dass ein Block von Transaktionen erstellt wird und in eine SHA256-Hash-Funktion eingegeben wird. Wenn die Ausgabe mit der "Gewinnerzahl" übereinstimmt, hat der Miner gewonnen und kann den neuen Block in die Blockchain schreiben und kann seinem Block das Preisgeld (die Subsidy) hinzufügen, die an den Miner ausgezahlt wird. Dann beginnt die nächste Runde.

Mehr Hashes pro Sekunde entsprechen mehr ausgefüllten Lottoscheinen pro Sekunde und damit einer größeren Erfolgswahrscheinlichkeit. Beim Hashing (mehr dazu ⬇️) wird immer eine Ausgabe mit einer festen Größe erstellt (in unserem Beispiel 6 Zahlen), die als Hash bezeichnet wird. Entgegen der landläufigen Meinung handelt es sich hierbei nicht um komplexe Mathematik, sondern nur um eine sehr schnelle Wiederholung der immer gleichen Berechnung mit neuen Eingaben, bis das erhoffte Ergebnis gefunden wird.
ASICs sind darauf ausgelegt, diese eine Berechnung (die SHA256-Hash-Funktion) so schnell und effizient wie möglich zu erledigen, und nicht um komplizierte Rechenaufgaben oder mathematische Probleme zu lösen. Es geht dabei einzig und allein um Schnelligkeit.
Anders als beim analogen Bergbau können verschiedene Teilnehmer also nicht parallel wertvolle Stoffe erwirtschaften, sondern pro Spiel immer nur einer. Der Gewinner bekommt alles und alle anderen Teilnehmer haben ihre aufgewendete Arbeit "umsonst" getan, das heißt wie beim herkömmlichen Lotto haben sie nur für die Teilnahme an der Runde bezahlt (in Form von Rechenleistung, Strom, usw.), bekommen aber vom Gewinn nichts ab. Der Anreiz besteht also darin, bei der nächsten Runde mehr Glück zu haben und die Wahrscheinlichkeit eines Gewinnes zu erhöhen.

In jeder anderen Branche schwankt das Angebot je nach Nachfrage. Wenn die Nachfrage nach einem wertvollen Stoff steigt, werden die Teilnehmer die Produktion entsprechend der Nachfrage erhöhen. Das bedeutet, mehr Equipment wird hinzugefügt, um schneller mehr des Produkts zu erwirtschaften. Bei Bitcoin ist das Angebot im Code festgelegt (neue bitcoins alle 10 Minuten) und kann sich auch bei steigender Nachfrage nicht ändern.
Aufgrund seiner genehmigungsfreien Natur ist es jedem gestattet, von überall auf der Welt Bitcoin zu produzieren, also an der Lotterie teilzunehmen. Die Lotterie schließt niemanden aus - einzig und allein Staaten oder andere Gerichtsbarkeiten können ihren Bürgern (versuchen zu) verbieten, an der Lotterie teilzunehmen. Dies führt dazu, dass sich Bitcoin-Miner überall auf der Welt ansiedeln, wo es für sie am wirtschaftlichsten ist am Netzwerk zu partizipieren (stabile und günstige Energieversorgung, rechtlich abgesicherte Eigentumsrechte, keine Verbote, usw.).
Gerade die ersten beiden Punkte (Energie und Eigentumsrechte) führen dazu, dass sich Bitcoin-Mining in Staaten wie den USA, Kanada oder Kazakhstan besonders konzentriert und in Ländern wie China oder Russland (durch Mining-Verbote) abnimmt - so in der Theorie. Denn heute stammen angenommen immer noch ca. 20% und 5% der weltweiten Hashrate aus China und Russland. Theorien dafür gibt es viele und besonders die letzten - fast unverhältnismäßigen - Anstiege der Hashrate führen zu vielen Spekulationen darüber, dass der russische Staat insgeheim seine eigene Mining-Infrastruktur ausbaut.

Hashing vs. kryptografische Verschlüsselung
Das Bitcoin-Netzwerk bedient sich vieler verschiedener Elemente, um die verschiedenen Eigenschaften oder Funktionen zu bedienen. Oft wird dabei das Hashing (z.B. verwendet beim Mining-Prozess und der Erstellung von Adressen) mit kryptografischer Verschlüsselung / Encryption (z.B. beim Erstellen von Keys) verwechselt oder in einen Topf geworfen.
Hashing: Das Hashing ist eine bestimmte Form der Kryptografie. Beim Hashing wird eine Eingabe (eine beliebig lange Datenkette) zu einer festen Ausgabegröße transformiert. Die Eingabe kann alles sein, z.B. viele Namen aneinandergereiht, oder jeder Straßenname irgendeiner Stadt aneinandergereiht, usw., es kann ziemlich alles sein, was man sich vorstellen kann und in Form einer Folge von Zeichen dargestellt werden kann. Der Hashing-Algorithmus funktioniert im Wesentlichen als Einbahnstraße, die die Eingabe in eine feste Folge von Buchstaben und Zahlen umwandelt.
Ein bekannter Anwendungsfall für diese Art von Algorithmus ist die Passwort-Speicherung auf Webseiten. Wenn Benutzer ein Passwort anlegen, errechnet der Computer automatisch einen Hash, welcher hinterlegt und beim Einloggen abgefragt wird. So werden bei einem Hack der Webseite nur nicht rückgängig zu machende Hashes der Passwörter gestohlen.

Kryptografische Verschlüsselung: Bei der kryptografischen Verschlüsselung handelt es sich auch um eine Form der Kryptografie, doch anders als beim Hashing, handelt es sich hier um einen bidirektionalen Algorithmus, also eine Zweirichtungsstraße. Das bedeutet schlicht, dass der Algorithmus eine Eingabe verschlüsselt, die verschlüsselte Ausgabe mit dem passenden Schlüssel jedoch wieder entschlüsselt werden kann. Somit kann der Besitzer des Schlüssels herausfinden, was die ursprüngliche Eingabenachricht war.
Ein bekannter Anwendungsfall für diese Art von Algorithmus ist die Ende-zu-Ende-Verschlüsselung bei verschiedenen Messenger-Diensten. Nachrichten werden verschlüsselt versendet und nur der Empfänger hat den nötigen Schlüssel, um die Nachricht wieder zu öffnen. Das passiert bei den Messenger-Diensten ganz automatisch, ohne dass ein Nutzer mit den Schlüsseln herumhantieren muss.

💡Dieser Unterschied ist ganz wichtig: Beim Hashing ist es unmöglich Anhand der Ausgabe die ursprüngliche Eingabe durch eine Rücktransformation zu erhalten. Man kann nur Daten eingeben und erhält dann eine feste Ausgabe. Verwendet man den selben Algorithmus bei der gleichen Eingabe erhält man immer eine identische Ausgabe.
Hashing beim Mining: Hashing ist im Wesentlichen die Art und Weise von Bitcoin, das gesamte Netzwerk zu koordinieren, um einen bestimmten Hash zu finden, der eine bestimmte vom System festgelegte Schwierigkeit erfüllt. Diese Schwierigkeit stellt sicher, dass egal ob die Hälfte der Miner im Laufe des nächsten Jahres verschwindet, oder ob sich die Anzahl der Miner im Laufe des nächsten Jahres verdreifacht, im Durchschnitt dafür Sorge getragen wird, dass das Bitcoin-Netzwerk immer ziemlich stabil ist und weiterhin etwa alle 10 Minuten ein neuer Transaktionsblock erscheint.
Es ist also essentiell, den Unterschied zwischen Verschlüsselung und Hashing zu verstehen und mit dem Mythos aufzuräumen, dass Mining "komplizierte, mathematische Probleme" löst. Ein weiterer viel verbreiteter Mythos ist, dass der Energieverbrauch zunehmen wird, je mehr Nutzer//innen Bitcoin Transaktionen ausführen. Es braucht nämlich nicht mehr Miner, um mehr Transaktionen zu verarbeiten. Die Anzahl der Transaktionen ist begrenzt durch die Blockgröße und die Anpassung der Schwierigkeit, die dafür sorgt, dass Blocks alle 10 Minuten produziert werden. Dies ist der Fall, wenn es auf der Welt nur noch einen einzigen Miner gäbe, genauso wie dies der Fall ist, wenn sich die Mining-Hashrate verhundertfacht. Eine Erweiterung der Gesamt-Hashrate führt allerdings zu einer höheren Sicherheit des Netzwerks, da ein potentieller Angriff auf das Netzwerk nur funktionieren kann, wenn der Angreifer mehr als 51% der gesamten Hashrate auf sich vereinigt.

🫳🎤
In diesem Sinne, 2... 1... Risiko!

-
 @ a95c6243:d345522c
2024-11-29 19:45:43
@ a95c6243:d345522c
2024-11-29 19:45:43Konsum ist Therapie.
Wolfgang JoopUmweltbewusstes Verhalten und verantwortungsvoller Konsum zeugen durchaus von einer wünschenswerten Einstellung. Ob man deswegen allerdings einen grünen statt eines schwarzen Freitags braucht, darf getrost bezweifelt werden – zumal es sich um manipulatorische Konzepte handelt. Wie in der politischen Landschaft sind auch hier die Etiketten irgendwas zwischen nichtssagend und trügerisch.
Heute ist also wieder mal «Black Friday», falls Sie es noch nicht mitbekommen haben sollten. Eigentlich haben wir ja eher schon eine ganze «Black Week», der dann oft auch noch ein «Cyber Monday» folgt. Die Werbebranche wird nicht müde, immer neue Anlässe zu erfinden oder zu importieren, um uns zum Konsumieren zu bewegen. Und sie ist damit sehr erfolgreich.
Warum fallen wir auf derartige Werbetricks herein und kaufen im Zweifelsfall Dinge oder Mengen, die wir sicher nicht brauchen? Pure Psychologie, würde ich sagen. Rabattschilder triggern etwas in uns, was den Verstand in Stand-by versetzt. Zusätzlich beeinflussen uns alle möglichen emotionalen Reize und animieren uns zum Schnäppchenkauf.
Gedankenlosigkeit und Maßlosigkeit können besonders bei der Ernährung zu ernsten Problemen führen. Erst kürzlich hat mir ein Bekannter nach einer USA-Reise erzählt, dass es dort offenbar nicht unüblich ist, schon zum ausgiebigen Frühstück in einem Restaurant wenigstens einen Liter Cola zu trinken. Gerne auch mehr, um das Gratis-Nachfüllen des Bechers auszunutzen.
Kritik am schwarzen Freitag und dem unnötigen Konsum kommt oft von Umweltschützern. Neben Ressourcenverschwendung, hohem Energieverbrauch und wachsenden Müllbergen durch eine zunehmende Wegwerfmentalität kommt dabei in der Regel auch die «Klimakrise» auf den Tisch.
Die EU-Kommission lancierte 2015 den Begriff «Green Friday» im Kontext der überarbeiteten Rechtsvorschriften zur Kennzeichnung der Energieeffizienz von Elektrogeräten. Sie nutzte die Gelegenheit kurz vor dem damaligen schwarzen Freitag und vor der UN-Klimakonferenz COP21, bei der das Pariser Abkommen unterzeichnet werden sollte.
Heute wird ein grüner Freitag oft im Zusammenhang mit der Forderung nach «nachhaltigem Konsum» benutzt. Derweil ist die Europäische Union schon weit in ihr Geschäftsmodell des «Green New Deal» verstrickt. In ihrer Propaganda zum Klimawandel verspricht sie tatsächlich «Unterstützung der Menschen und Regionen, die von immer häufigeren Extremwetter-Ereignissen betroffen sind». Was wohl die Menschen in der Region um Valencia dazu sagen?
Ganz im Sinne des Great Reset propagierten die Vereinten Nationen seit Ende 2020 eine «grüne Erholung von Covid-19, um den Klimawandel zu verlangsamen». Der UN-Umweltbericht sah in dem Jahr einen Schwerpunkt auf dem Verbraucherverhalten. Änderungen des Konsumverhaltens des Einzelnen könnten dazu beitragen, den Klimaschutz zu stärken, hieß es dort.
Der Begriff «Schwarzer Freitag» wurde in den USA nicht erstmals für Einkäufe nach Thanksgiving verwendet – wie oft angenommen –, sondern für eine Finanzkrise. Jedoch nicht für den Börsencrash von 1929, sondern bereits für den Zusammenbruch des US-Goldmarktes im September 1869. Seitdem mussten die Menschen weltweit so einige schwarze Tage erleben.
Kürzlich sind die britischen Aufsichtsbehörden weiter von ihrer Zurückhaltung nach dem letzten großen Finanzcrash von 2008 abgerückt. Sie haben Regeln für den Bankensektor gelockert, womit sie «verantwortungsvolle Risikobereitschaft» unterstützen wollen. Man würde sicher zu schwarz sehen, wenn man hier ein grünes Wunder befürchten würde.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 3369d0a7:eb020757
2024-11-28 07:41:32
@ 3369d0a7:eb020757
2024-11-28 07:41:32Chef's notes
This recipe was a staple at every thanksgiving with family and now I share it with you nostr family. Absolutely one of my favorite side dish during the holiday. The corn pudding in the photo is NOT baked, I will update it. I hate stock photos.
Details
- ⏲️ Prep time: 15-20 min
- 🍳 Cook time: 30-40 min
- 🍽️ Servings: 6-8
Ingredients
- 2 cans of creamed corn
- 2c Milk
- 1 Box of Jiffy Cornbread Mix
- 3 eggs
- 1/4-1/3c sugar
- 1/2- green bell pepper or pepper onion blend
- 1/4TBsp vanilla
- 1/2tsp Salt
- 2TBsp Butter
Directions
- Grab medium saucepan and desired baking dish at least 9x9
- Place saucepan on medium-high heat
- Add butter and sauté pepper onion blend until tender
- Combine milk, eggs, sugar and vanilla, mix well
- Lather warmed (NOT HOT) baking dish with butter
- Sprinkle half a box of Jiffy corn bread mix in the baking dish
- Add both cans of creamed corn to peppers and onions
- Pour wet ingredients into slightly cooled creamed corn mixture
- Sprinkle the other half box of jiffy mix into the baking dish
- Incorporate the wet and dry ingredients in dish so there are no dry lumps
- Let set for 10 min before placing in a 325 degree oven for 30-40 minutes, until the center is solid and the edges are golden brown.
-
 @ 94a6a78a:0ddf320e
2024-11-27 19:36:12
@ 94a6a78a:0ddf320e
2024-11-27 19:36:12The backbone of your Nostr experience lies in relays—servers that transmit your notes, zaps, and private messages across the decentralized network. Azzamo offers three specialized relays to suit different user needs, ensuring reliability, performance, and privacy.
1. Free Relay
- URL:
wss://nostr.azzamo.net - Overview: Azzamo’s Free Relay is perfect for newcomers to Nostr. It’s open-access, reliable, and ensures fair use with moderate rate limits.
- Key Features:
- Free to use.
- Notes older than one month are purged daily.
- Accessible gateway for decentralized communication.
2. Paid Relay
- URL:
wss://relay.azzamo.net - Overview: Designed for power users, the Paid Relay offers unmatched performance with 99.9% uptime and low latency.
- Key Features:
- Scalable for heavy users.
- Fewer users for faster, consistent connections.
- Premium support included for paid users.
3. Inbox Relay
- URL:
wss://inbox.azzamo.net - Overview: Never miss a private message again with the Inbox Relay, optimized for secure, spam-free direct messaging.
- Key Features:
- Guaranteed message delivery.
- Optimized for NIP-17 private messages.
- Optimized for NIP-19 group chats.
- Premium users enjoy advanced support.
Why Choose Azzamo Relays?
Life on Nostr is easier with Azzamo relays. They’re fast, reliable, and built to handle whatever you throw at them. The Paid Relay keeps your connections strong, the Inbox Relay makes sure no private message gets lost, and the Free Relay is always there to get you started. Supporting Azzamo by going premium helps keep this decentralized network growing—and you get priority support while you’re at it. Azzamo has your back on Nostr!
🔗 Start now:
- Free Relay:
wss://nostr.azzamo.net - Paid Relay: azzamo.net/pay
- Inbox Relay: azzamo.net/inbox
Support the network and upgrade your experience—add time to your account via the Azzamo Dashboard. Choose Azzamo, and take control of your Nostr journey today!
- URL:
-
 @ fcb65172:87f3c4ed
2024-11-26 19:29:20
@ fcb65172:87f3c4ed
2024-11-26 19:29:20Introduction
As I approached the Santa Marta Favela, I couldn’t help but feel a mix of excitement and trepidation. Famous for housing a Michael Jackson music video, this favela is a common tourist attraction, but I was here to witness the raw, unfiltered reality of daily life. Little did I know that my adventure would involve a Brazilian gangster as my guide, offering to show me a side of the favela that few have ever seen.

The Initial Challenge
Initially, I was denied access to film anything beyond the iconic Michael Jackson statue and the breathtaking view of the city. Armed gangsters stood guard, making it clear that they had the final say in what I could capture. Frustrated and unsure of what to do, I decided to break the ice by buying them some beers. As we sipped on our drinks, I shared my previous videos and explained my passion for documenting the stories of ordinary people. To my surprise, one of them lowered his weapon and offered to show me around, granting me a glimpse into a world that most tourists never get to see.
The Guided Tour
 As we ventured deeper into the favela, it became clear that my guide was well-connected and respected by the locals. He laid down the ground rules: certain things were off-limits, like the drug dealers and heavily armed gang members. While I was initially apprehensive, I soon realized that this was an opportunity to gain a unique perspective on life in the favela. He introduced me to the kiosk owners, street vendors, and everyday people who had called the favela home for decades. These individuals shared their stories of violence, police confrontations, and community resilience, painting a picture of life in the favela that was far from the stereotype of a place where the poor live.
As we ventured deeper into the favela, it became clear that my guide was well-connected and respected by the locals. He laid down the ground rules: certain things were off-limits, like the drug dealers and heavily armed gang members. While I was initially apprehensive, I soon realized that this was an opportunity to gain a unique perspective on life in the favela. He introduced me to the kiosk owners, street vendors, and everyday people who had called the favela home for decades. These individuals shared their stories of violence, police confrontations, and community resilience, painting a picture of life in the favela that was far from the stereotype of a place where the poor live.The Police Station and the Question of Control
We ascended to the top of the favela, where a police station sat prominently. As we approached, I couldn’t help but wonder how much control the police really held over this complex network of streets and alleyways. Were the police and the gangs working together, using the honest, hardworking residents as pawns in their illicit activities? My guide, sensing my curiosity, shared his insights on the delicate balance between the police, the gangs, and the residents. He explained that while the police may not have complete control, they do work together to maintain a certain level of order, often in exchange for bribes or protection fees.

The Everyday Heroes of the Favela
As we explored the favela, we encountered a wide range of individuals, each with their own unique story. There was the kiosk owner who had lived in the favela for over 30 years, running his small business and raising a family. He shared his experiences of witnessing shootings and confrontations with the police, as well as the importance of community and football in the favela. We also met a local street vendor who had turned to selling goods to support his family after losing his job. Despite the challenges they faced, both men spoke with pride about their community and the resilience of its people.
 ### The View from the Summit
### The View from the SummitAs we reached the summit, the view of Rio de Janeiro’s skyline took my breath away. It was a poignant reminder of the dichotomy between the beauty of the city and the harsh realities of life in the favela. My guide shared stories of community churches, local football teams, and the unwavering spirit of the residents. Despite the challenges they face, the people of Santa Marta Favela have created a community that is both resilient and vibrant.
Conclusion
In conclusion, my journey through the Santa Marta Favela was an eye-opening experience that challenged my preconceptions of this complex and misunderstood place. It’s a world where gangsters, police, and everyday citizens coexist in a delicate balance, where community and resilience thrive in the face of adversity. As I left the favela, I couldn’t help but feel a newfound appreciation for the strength and spirit of the people who call this place home. And a question of who is really in control here?
-
 @ eb73e43e:d821300f
2024-11-26 02:56:10
@ eb73e43e:d821300f
2024-11-26 02:56:10These are some really great features that are buried behind just a little too much friction in iOS, but I have a feeling you guys will enjoy.
Today we’re talking separate home screens toggled using shortcuts and focus modes! 🤯
The Goal
My initial motivation was for a cleaner, more organized phone, and to put my Bitcoin/Nostr apps aside so I’m less tempted to open them at random. I achieved a really good balance by creating a focus mode that has different wallpaper, notification settings, and app layout. All easily toggled using the trigger of your choice like the action button on newer models or the “back tap” accessibility feature for older phones.
This is what it looks like, pressing my action button to trigger the shortcut which changes my “normal” screen to the focus mode with different apps and settings:
Create Separate Home Screen
To create a separate home screen, first add your daily favorites to one page and bitcoin/nostr favorites to a second page. Once you have multiple pages with different apps, hold down to begin editing the screen and tap the dot buttons at the bottom middle.
 This will open a view with all of your pages of apps. Uncheck any page you don’t want to see on your “normal” mode and leave the rest.
This will open a view with all of your pages of apps. Uncheck any page you don’t want to see on your “normal” mode and leave the rest.Focus Mode
Next you’ll need to open the settings and navigate to the “Focus” page. Here you’ll hit the plus button for a new focus and customize preferences like notifications, app screen, and wallpapers (my focus mode is labeled “CoinOS”).
 Once you have a home screen layout and focus mode set, you can select to toggle focus mode in the action button settings.
Once you have a home screen layout and focus mode set, you can select to toggle focus mode in the action button settings.My action button was simple at first, just toggling the focus mode on/off and it works great to reduce distraction. But I wanted it to do more than just toggle focus modes. So I found a way to have three different actions tied to the same button. Here's where we go a little wild with shortcuts, but hang in there it's worth the effort.
The Super Shortcut
Toggling focus modes is really convenient and enables a cool hidden Homescreen with your choice of apps. But I wanted to go further so I made an all-in-one shortcut to do several things depending on the state of the iPhone.
-
If the phone is locked, holding my action button toggles silent mode on/off. Nice for quick silencing even in your pocket.
-
If the phone is unlocked, but held sideways with the volume buttons upward, the shortcut opens my camera allowing quick shots with volume as shutter buttons.
-
If the phone is unlocked in any other orientation, it triggers the focus mode change. Allowing me to use the action button for three purposes, including app organization.
Shortcuts can be quite intimidating on your own so I’ll include a link if you want to download mine and try it yourself. It’s also a great way to get started by modifying rather than trying to create from scratch. Give it a shot, it’s pretty cool!
Have fun!
-
-
 @ 2063cd79:57bd1320
2024-12-09 08:25:17
@ 2063cd79:57bd1320
2024-12-09 08:25:17Eine hitzige Debatte wird momentan in der Bitcoin-Welt über NFTs (sagen die einen) bzw. unnötigen Datenmüll (sagen die anderen) auf der Bitcoin-Blockchain geführt. Anlass zur Debatte hat ein von Casey Rodarmor entwickeltes System gegeben, das es ermöglicht mit Hilfe seines speziell dafür entwickelten Protokolls jedem Satoshi (Sat) eine einzigartige Folgenummer (Ordinal) zuzuweisen und somit nachverfolgbar zu machen. Dies erlaubt dann das Schreiben von Dateien direkt in die Witness Sektion eines Blocks, also direkt in die Blockchain, eine sogenannte Inscription. Das Thema erhitzt die Gemüter, jeder hat eine Meinung dazu und entweder ist man im Lager der Supporter oder der Gegner. Oder man hat schon beim Lesen dieser Einleitung nicht ein Wort verstanden. Für diese Gruppe soll diese Übersicht funktionieren, in der die Funktionsweise von Ordinals und Inscriptions erklärt wird und was die Pro- und Kontra-Argumente der jeweiligen Lager sind.
Daten in die Bitcoin-Blockchain zu schreiben, die nicht direkt etwas mit der Funktionsweise des Systems zu tun haben, ist nichts Neues. Es gibt seit jeher verschiedene Möglichkeiten Nachrichten, Dateien oder andere Informationen in Blocks zu packen. Sogar der Genesis Block enthält die Nachricht "The Times 03/Jan/2009 Chancellor on brink of second bailout for banks" in der Coinbase,
 das Whitepaper von Satoshi Nakamoto wurde bereits 2013 in Block 230009 verewigt,
das Whitepaper von Satoshi Nakamoto wurde bereits 2013 in Block 230009 verewigt, OP_Returns ermöglichen das Schreiben kurzer (80 Zeichen) Nachrichten,
OP_Returns ermöglichen das Schreiben kurzer (80 Zeichen) Nachrichten, und auch Protokolle, die auf Bitcoin laufen, wie z.B. Counterparty und u.a. den Handel mit Rare Pepes ermöglichen, existieren bereits seit 2014. Dennoch scheint etwas an der neuen, von Casey Rodarmor vorgestellten Methode anders zu sein, dass es die Gemüter so sehr erhitzt. Das Konzept ist ein zweigeteiltes, zunächst wird eine Theorie, oder Konvention, beschlossen, der zufolge jeder Sat in der Blockchain einzigartig und nachverfolgbar wird. Damit werden die einzelnen Sats im weitesten Sinne schon zu NFTs. Darüber hinaus ermöglicht diese Konvention das Verschmelzen dieser einzigartigen Sats mit hochgeladenen Daten. Denn - um beim obigen Beispiel des Whitepapers zu bleiben - ist die hochgeladene PDF Datei für immer in Block 230009 festgeschrieben, aber sie gehört niemandem, denn ein Block gehört niemandem per se, ein Block ist ein öffentliches Register aller stattgefundenen Transaktionen zu dieser Blockzeit. Indem man Dateien mit Sats verbindet, lassen sich diese verschicken und handeln, denn Sats haben (der Ordinal Theory zufolge) immer eine/n Besitzer//in.
und auch Protokolle, die auf Bitcoin laufen, wie z.B. Counterparty und u.a. den Handel mit Rare Pepes ermöglichen, existieren bereits seit 2014. Dennoch scheint etwas an der neuen, von Casey Rodarmor vorgestellten Methode anders zu sein, dass es die Gemüter so sehr erhitzt. Das Konzept ist ein zweigeteiltes, zunächst wird eine Theorie, oder Konvention, beschlossen, der zufolge jeder Sat in der Blockchain einzigartig und nachverfolgbar wird. Damit werden die einzelnen Sats im weitesten Sinne schon zu NFTs. Darüber hinaus ermöglicht diese Konvention das Verschmelzen dieser einzigartigen Sats mit hochgeladenen Daten. Denn - um beim obigen Beispiel des Whitepapers zu bleiben - ist die hochgeladene PDF Datei für immer in Block 230009 festgeschrieben, aber sie gehört niemandem, denn ein Block gehört niemandem per se, ein Block ist ein öffentliches Register aller stattgefundenen Transaktionen zu dieser Blockzeit. Indem man Dateien mit Sats verbindet, lassen sich diese verschicken und handeln, denn Sats haben (der Ordinal Theory zufolge) immer eine/n Besitzer//in.Doch um besser verstehen zu können, wie dieses neue Protokoll funktioniert, muss man sich wie immer ein paar verschiedene Konzepte annehmen. Wir brechen diese erstmal der Reihe nach auf.
SegWit (Segregated Witness)
Bevor wir uns mit Ordinals und Inscriptions beschäftigen machen wir einen kurzen historischen und technischen Ausflug, denn Inscriptions wären ohne SegWit nicht möglich. Deshalb lohnt es sich besser zu verstehen, was man unter diesem Transaktionsformat versteht.
SegWit wurde 2017 erdacht, um in erster Linie zwei existierende Probleme zu lösen: 1) Transaction Malleability und 2) die Effizienz von Blöcken zu erhöhen. Bis dato hatten Blöcke eine effektive maximal Größe von 1MB und bestanden aus dem sogenannten Header (Basisdaten: Signaturen und Skripte) und den Transaktionsdaten (Inputs und Outputs). Diese Headerdaten (auch Witness-Daten genannt) nahmen einen Großteil der zur Verfügung stehenden Größe ein, was zu ineffizienten und oftmals mit hohen Transaktionsgebühren versehenen Blöcken führte. Mit Hilfe des SegWit Protokolls konnte eine Skalierung von Bitcoin erreicht werden, ohne die offizielle in den Code geschriebene Blockgröße von 1MB zu verändern. Dazu kommt, dass diese Lösung keinen Hard-Fork benötigte und ganz nebenbei (aber offiziell in erster Linie) auch das Problem der Malleability löste. Ohne auf die Details von Hard- und Soft-Forks einzugehen, ist dies ein wichtiges Detail, denn 2017 tobten die sogenannten Blocksize-Wars und führten schließlich zur Abspaltung von Bitcoin Cash und seinen 8MB-Blöcken.
 SegWit wurde im Juli 2017 mit Block 477120 aktiviert. Wie der Name Segregated Witness schon impliziert, werden die Witness-Daten (Signaturen und Skripte) getrennt und in einer separate Datenstruktur (Witness Merkle Tree) geführt, sodass der Hauptteil des Blocks weniger Basisinformationen enthält und somit mehr Platz für Transaktionsinformationen lässt, Blöcke also effizienter macht und damit Gebühren niedriger hält. Der Zaubertrick dabei ist, dass es immer noch derselbe Block ist, allerdings mit zwei Sätzen von Datenstrukturen (Transaktionsabschnitt und Basisinformationsabschnitt), und somit den Protokollregeln entspricht und eine Blockgröße von 1MB eigentlich nicht überschreitet. Dieser mathematische Kniff führt dazu, dass für die Einführung kein Hard-Fork benötigt wurde (nur einen Soft-Fork), was eine Abwärtskompatibilität gewährleistet und somit auch Adressen und Wallets, die unter dem Legacy-System arbeiten ohne Probleme funktionieren. Der mathematische Kniff hat allerdings eine seltsame Neuerung zur Folge, denn Blöcke werden seitdem in Gewicht statt Größe gemessen.
SegWit wurde im Juli 2017 mit Block 477120 aktiviert. Wie der Name Segregated Witness schon impliziert, werden die Witness-Daten (Signaturen und Skripte) getrennt und in einer separate Datenstruktur (Witness Merkle Tree) geführt, sodass der Hauptteil des Blocks weniger Basisinformationen enthält und somit mehr Platz für Transaktionsinformationen lässt, Blöcke also effizienter macht und damit Gebühren niedriger hält. Der Zaubertrick dabei ist, dass es immer noch derselbe Block ist, allerdings mit zwei Sätzen von Datenstrukturen (Transaktionsabschnitt und Basisinformationsabschnitt), und somit den Protokollregeln entspricht und eine Blockgröße von 1MB eigentlich nicht überschreitet. Dieser mathematische Kniff führt dazu, dass für die Einführung kein Hard-Fork benötigt wurde (nur einen Soft-Fork), was eine Abwärtskompatibilität gewährleistet und somit auch Adressen und Wallets, die unter dem Legacy-System arbeiten ohne Probleme funktionieren. Der mathematische Kniff hat allerdings eine seltsame Neuerung zur Folge, denn Blöcke werden seitdem in Gewicht statt Größe gemessen. Ein voller Block von ca. 1MB Größe und 4 Millionen WU Gewicht
Ein voller Block von ca. 1MB Größe und 4 Millionen WU GewichtBitcoin hat nun also eine sogenannte Blockgrößengrenze (1MB) und eine Blockgewichtsgrenze (4 Millionen Gewichtseinheiten (WU), was ca. 4MB entspricht). Darüber hinaus wurden mit dem SegWit-Soft-Fork die heute gängigen bc1-Adressen (im Gegensatz zu den alten 1- und 3-Adressen) eingeführt.
Ein weiterer Nebeneffekt, neben der Reduzierung der Gebühren durch Kapazitätsverbesserung und Lösung der Transaktionsformbarkeit (Malleability), ist dass Layer-2-Lösungen, wie unter anderem Lightning, ermöglicht wurden, da Zahlungskanäle davon abhängen, dass unverformbare Transaktionen bestehen. Für die Skalierbarkeit und Dezentralisierung von Bitcoin hat die relativ kleine Blockgröße den Vorteil, dass der Betrieb von privaten Nodes erleichtert wird.
Taproot
Mit dem Wissen über SegWit müssen wir uns auch kurz mit Taproot beschäftigen, einem weiteren Soft-Fork, das mit Block 709632 im November 2021 aktiviert wurde. Taproot hat viele Neuerungen mit sich gebracht, die es hier zu besprechen den Rahmen sprengen würde, doch wichtig ist, dass Ordinals das Input-Feld von Taproot-Transaktionen nutzen, das seit dem SegWit Update getrennt wurde. Auch wichtig ist, dass es seit Taproot keine Regel gibt, die die Größe von Inputs begrenzt und damit Daten beliebig viel Platz (bis zur Blockgrößenbegrenzung von 4MB) beanspruchen können. Dies ermöglicht im Endeffekt die Öffnung des Protokolls zur Verwendung von Skripten, wie bei Ordinals geschehen und somit das Hochladen von großen Dateien, die die volle Blockgröße einnehmen können.
Ordinals
Das Protokoll besteht aus zwei Konzepten. Auf der einen Seite Ordinals (engl. Ordnungszahlen) und auf der anderen Seite Inscriptions (engl. Inschriften). Ordinals an sich funktionieren losgelöst von Inscriptions, Inscriptions benötigen aber Ordinals, um zu funktionieren. Man könnte also von einer Pfadabhängigkeit bei Inscriptions sprechen.
💡Pfadabhängigkeit: Bei pfadabhängigen Vorgängen bauen die einzelnen Prozesse auf einander auf und das Resultat ist davon abhängig, welche Reihenfolge gewählt wird. Einfaches Beispiel: Ein Bad nehmen (Prozess 1) und dann mit dem Handtuch abtrocknen (Prozess 2) führt zu einem komoplett anderen Ergebnis, als sich mit dem Handtuch abzutrocknen und dann ein Bad zu nehmen.
Ordinals können also unabhängig von Inscriptions verstanden werden. Es handelt sich dabei um eine vom Programmierer erfundene Konvention, einzelne Sats durchzumummerieren.
“Satoshis are numbered in the order in which they’re mined, and transferred from transaction inputs to transaction outputs in first-in-first-out order.” - Casey Rodarmor
Das Prinzip ist dabei recht einfach: Es wird angenommen, dass jeder bitcoin aus 100.000.000 Sats besteht und damit Sats durchgezählt werden können. Die Sats werden mit dem Genesis Block (Block 0) beginnend in der Reihenfolge, in der sie produziert wurden, nach dem FIFO-Prinzip (First in first out) durchgezählt und markiert. Der erste jemals produzierte Block (Genesis Block) enthielt 50 bitcoins und damit 5.000.000.000 Sats. So lassen sich die Sats durchzählen: der erste Sat ist #0, der zweite hat die Ordnungszahl #1 und der letzte Sat dieses ersten Blocks hat die Ordnungszahl 4.999.999.999.
 Um dies umzusetzen wurde ein spezieller Block Explorer geschrieben, der dieser Konvention folgt und den jeweiligen Sats einen "Namen" zuweist, um diese leichter nachverfolgen zu können. So lässt sich so tun (!), als ob sich einzelne Sats von UTXO zu UTXO bewegen würden. Um UTXOs besser verstehen zu können, empfehle ich diesen vorherigen Artikel:
Um dies umzusetzen wurde ein spezieller Block Explorer geschrieben, der dieser Konvention folgt und den jeweiligen Sats einen "Namen" zuweist, um diese leichter nachverfolgen zu können. So lässt sich so tun (!), als ob sich einzelne Sats von UTXO zu UTXO bewegen würden. Um UTXOs besser verstehen zu können, empfehle ich diesen vorherigen Artikel:https://www.genexyz.org/post/25-block-774775-utxos-fee-management-v3ulch/
Die Konvention täuscht also vor, dass Sats nicht ausgegeben oder verbrannt werden, sondern, dass diese in einer Art Kette von Bitcoin-Atomen existieren und diese Kette beim Versenden von Transaktionen nur aufgebrochen und die einzelnen Atomversatzstücke andernorts wieder auftauchen und nicht, wie eigentlich der Fall, eingeschmolzen / verbrannt werden.
Umgesetzt wird das alles durch ein Open-Source-Protokoll namens ord, das auf dem Bitcoin Core Protokoll läuft. Dies bedeutet, dass keine Veränderungen am Bitcoin Protokoll selbst vorgenommen werden, sondern eine Programm entwickelt wurde, das die Daten in der Blockchain benutzt, um eine andere Sicht zu erzeugen, die es ermöglicht, einzelne Sats zu benennen und nachzuverfolgen und somit jeden einzelnen Sat "einzigartig" aussehen zu lassen. Es ist also völlig freiwillig, sich auf diese Konvention und die Namensgebung einzulassen.
Folgt man jedoch dieser Konvention, so ergeben sich natürlich Spielereien, wie z.B. Seltenheit einzelner Sats beruhend auf dem Block, in dem sie enthalten waren oder sind, welche laufende Nummer sie haben, etc. Es ist in etwa so, als hätte ich eine Million kleiner Kieselsteine in meiner Einfahrt. Für jeden, der einfach vorbeigeht, ist jeder Kieselstein einfach nur eines von vielen Steinchen. Ich habe aber ein System gefunden, um jeden einzelnen Stein einzeln zu benennen, und damit ergeben sich "besondere" Steine, z.B. Stein #1 oder Stein #69. Nur wer meinem System der Nummerierung folgt, sieht, dass dies besondere Steine sind, jeder andere sieht einfach nur Steine.
Inscriptions
Bei Inscriptions handelt es sich um eine von Ordinals zunächst losgelöste separate Funktion. Hierbei wird die eigentliche Datei in die Blockchain geschrieben, allerdings im Einklang mit Ordinals wird dieser Datei ein einzigartiger Sat zugeschrieben. Dies funktioniert auch wieder nur, wenn man der willkürlichen Konvention des Protokolls Folge leistet, denn beim Schreiben der Datei in die Blockchain wird natürlich eine Transaktion erstellt. Diese Transaktion enthält (mindestens) einen UTXO, der/die aus mehreren Sats bestehen und deshalb legt das Protokoll fest, dass eine Inscription beim Mining mit dem ersten Sat des ersten UTXO der Transaktion verschmolzen wird. Damit wird die Inscription (also die Datei) dauerhaft und auf ewig markiert und kann somit von anderen Sats unterschieden wird.
Unter Verwendung dieser Konvention (und der dazu nötigen Wallets) können UTXOs, die ein Sat-Inscription-Paar enthalten, gefunden und ihre Bewegungen und ihr Eigentum über Transaktionen hinweg verfolgt werden. Dies führt dazu, dass diese Sats, bzw. die Inscriptions, gehandelt, verschenkt, gekauft und verkauft werden können. Dabei entstehen also digitale Artefakte, oder anders genannt NFTs.
 Inscriptions sind naturgemäß größere Dateien und nehmen daher mehr vom begrenzten Platz in jedem Block ein (daher die langen Erklärungen zu SegWit und Taproot). Die Benutzer//innen, die Inscriptions erstellen bzw. hochladen, müssen die dazu erforderlichen (höheren) Gebühren zahlen. Dieser Punkt ist für die folgende Diskussion wichtig.
Inscriptions sind naturgemäß größere Dateien und nehmen daher mehr vom begrenzten Platz in jedem Block ein (daher die langen Erklärungen zu SegWit und Taproot). Die Benutzer//innen, die Inscriptions erstellen bzw. hochladen, müssen die dazu erforderlichen (höheren) Gebühren zahlen. Dieser Punkt ist für die folgende Diskussion wichtig.Diskussion
Okay, soweit so gut, soweit so scheiße.
Kurzum: Es gibt ein System, das das Benennen einzelner Sats ermöglicht (wenn man daran glaubt) - Ordinals. Es besteht die Möglichkeit, Dateien in Blöcke zu schreiben und diese mit den benannten Sats zu verknüpfen - Inscriptions. Die beiden Theorien oder Konventionen sind nicht gleich, brauchen aber einander.
Ordinals alleine schaden nicht. Es ist das Hinzufügen digitaler Artefakte in Transaktionen, das die größere Debatte entflammt. Denn Inscriptions verlagern ein Risiko direkt in die Blockchain. Ein OP_Return z.B. kann 40KB (also 80 Zeichen) beinhalten und somit z.B. einen Link zu einer Datei darstellen (einen Pointer). Eine Datei mit fragwürdigem oder kriminellem Inhalt, würde also immer auf einer externen Website liegen und somit würde auch das Risiko vom Betreiber getragen werden. Inscriptions öffnen die Tür, Dateien, die bis zu 3MB pro Block groß sind, direkt in die Blockchain zu schreiben. Hier eröffnen sich Korridore für Reputationsangriffe auf Bitcoin.
Ordinals (ich fasse jetzt Ordinals und Inscriptions mal zusammen) eröffnen neue Wege, mit Bitcoin zu interagieren. Es bietet "Spaß" mit Bitcoin und fügt eine neue Schicht hinzu, Bitcoin mit Kunst und Kultur zusammenzubringen ist. Es könnte außerdem die Akzeptanz erhöhen und neue Interessenten für Bitcoin begeistern, die für die Bildchen kommen, aber wegen der bahnbrechenden Technologie und den fundamentalen Mehrwerten von Bitcoin bleiben.
Die Hauptargumente gegen Ordinals berufen sich auf die größeren Datenmengen, die von Nodes validiert werden müssen und darauf, dass Blöcke mit "unnötigem Müll" gefüllt werden und damit wichtige und relevante Transaktionen nicht schnell genug verarbeitet werden. Allerdings muss man dazu sagen, dass Ordinals nicht die Blockgröße erhöhen, sondern im schlimmsten Fall dafür sorgen, dass das Blocklimit öfter erreicht wird. Ein normaler Block sieht meist so aus:
 Man sieht, dass das Gewicht von 4 MWU nicht ganz erreicht wurde und 2.675 Transaktionen einen Platz gefunden haben.
Man sieht, dass das Gewicht von 4 MWU nicht ganz erreicht wurde und 2.675 Transaktionen einen Platz gefunden haben.Im Vergleich dazu wurden im folgenden Block lediglich 648 Transaktionen untergebracht, die pro Transaktion viel größer sind (schaut man sich die jeweiligen Transaktionen an, stellt man fest, dass so gut wie jeder dieser großen Blöcke den gleichen Betrag von 0.0001 BTC aufweist, was darauf schließen lässt, dass die Ordinals-Transaktionen sind).
 Fürsprecher von Ordinals argumentieren oft damit, dass diese "nutzlosen" Transaktionen auch bezahlt werden müssen, um andere "wertigere" Transaktionen zu verdrängen, da Miner diese sonst nicht dem Block hinzufügen würden. Hier muss man aber sagen, dass diese Transaktionen relativ geringe Transaktionsgebühren von 4 Sat/vB bezahlt haben. Da wir wissen, dass Transaktionsgebühren basierend auf der Größe der Transaktion berechnet werden und nicht auf dem Wert der Transaktion in Bitcoin, werden für diese 0.0001 BTC Transaktionen dennoch Gebühren im Bereich von 150.000 bis 250.000 Sats (ca. $50 bei aktuellem Kurs) fällig (es sei denn man hat Nick Luxor als Freund).
Fürsprecher von Ordinals argumentieren oft damit, dass diese "nutzlosen" Transaktionen auch bezahlt werden müssen, um andere "wertigere" Transaktionen zu verdrängen, da Miner diese sonst nicht dem Block hinzufügen würden. Hier muss man aber sagen, dass diese Transaktionen relativ geringe Transaktionsgebühren von 4 Sat/vB bezahlt haben. Da wir wissen, dass Transaktionsgebühren basierend auf der Größe der Transaktion berechnet werden und nicht auf dem Wert der Transaktion in Bitcoin, werden für diese 0.0001 BTC Transaktionen dennoch Gebühren im Bereich von 150.000 bis 250.000 Sats (ca. $50 bei aktuellem Kurs) fällig (es sei denn man hat Nick Luxor als Freund). Die Marktkräfte innerhalb des Bitcoin-Netzwerks werden also zeigen, wie lange diese Art von Transaktionen einen Großteil des vorhandenen Platzes einnehmen werden. Die Debatte um Transaktionsgebühren ist eine sehr wichtige, denn gibt es immer wieder Theorien darüber, wie Miner zukünftig profitabel sein können, wenn die Subsidies immer irrelevanter werden und auch das Sicherheitsbudget von Bitcoin gewährleistet werden muss. Befürworter von Ordinals bringen dies als ein weiteres Pro-Argument für einen weiteren Use-Case und gesteigertes Interesse an On-Chain Transaktionen an.
Die Marktkräfte innerhalb des Bitcoin-Netzwerks werden also zeigen, wie lange diese Art von Transaktionen einen Großteil des vorhandenen Platzes einnehmen werden. Die Debatte um Transaktionsgebühren ist eine sehr wichtige, denn gibt es immer wieder Theorien darüber, wie Miner zukünftig profitabel sein können, wenn die Subsidies immer irrelevanter werden und auch das Sicherheitsbudget von Bitcoin gewährleistet werden muss. Befürworter von Ordinals bringen dies als ein weiteres Pro-Argument für einen weiteren Use-Case und gesteigertes Interesse an On-Chain Transaktionen an.https://x.com/BitcoinPierre/status/1622744824896970753
Natürlich erleben Ordinals gerade einen Hype und so ist es nicht verwunderlich, dass vor zwei Tagen über 50% des vorhandenen Platzes von Ordinals-Transaktionen eingenommen wurde. Diese Zahl ist heute schon auf unter 25% gesunken, was einen klaren Hype und keine Regel aufweist.
Unabhängig davon, ob Inscriptions als „wertvolle“ Verwendung von Bitcoin angesehen wird oder nicht, wird der Markt über die angemessene Gebührengestaltung darüber entscheiden, ob Nutzer weiterhin das System für diese Art von Spielerei nutzen wollen. Sollten sich Inscriptions als langlebig erweisen, werden Transaktionsgebühren unweigerlich steigen und somit mehr Absender kleinerer Bitcoin-Transaktionen auf Layer-2-Protokolle wie Lightning ausweichen.
Puristen sind gegen Inscriptions, da sie argumentieren, dass das Speichern großer Daten auf dem Bitcoin Ledger den Blockplatz für keinen wirklichen Zweck verschwendet und nur Stress für Nodebetreiber verursacht. Blocks, wie der folgende, führen dazu, dass sich ihnen die Nackenhaare aufstellen und neben der Verschwendung von Platz wird häufig das Reputationsrisiko als Kritik angebracht.
 Denn Inscriptions, die einmal in die Blockchain geschrieben wurden, lassen sich nicht mehr entfernen und damit auch nicht der Inhalt der hochgeladenen Dateien. Unmoralische und kriminelle Inhalte eröffnen so einen Korridor für Zensur, allerdings sollte auch beachtet werden, dass es auch einen speziellen Block Explorer benötigt, der Inscriptions darstellt, und diese Explorer haben natürlich die Möglichkeit Bilder mit moralisch und rechtlich fragwürdigen Inhalten zu zensieren, bzw. nicht darzustellen (wie in Inscription #668 passiert).
Denn Inscriptions, die einmal in die Blockchain geschrieben wurden, lassen sich nicht mehr entfernen und damit auch nicht der Inhalt der hochgeladenen Dateien. Unmoralische und kriminelle Inhalte eröffnen so einen Korridor für Zensur, allerdings sollte auch beachtet werden, dass es auch einen speziellen Block Explorer benötigt, der Inscriptions darstellt, und diese Explorer haben natürlich die Möglichkeit Bilder mit moralisch und rechtlich fragwürdigen Inhalten zu zensieren, bzw. nicht darzustellen (wie in Inscription #668 passiert).https://cointelegraph.com/news/bitcoin-ordinals-creators-look-for-fix-after-first-instance-of-shock-porn
Um das Hochladen dieser "schlechten" Inhalte zu vermeiden, müssten die Bitcoin-Konsensregeln geändert werden. Und wenn diese verändert werden können, um Menschen davon abzuhalten, Bilder in das Bitcoin-Netzwerk zu laden, können die Regeln auch verändert werden, um z.B. Nutzer//innen mit politischen Interessen oder kritischen Meinungen davon abzuhalten, Bitcoin zu nutzen, wie sie es für richtig erachten. Denn am Ende ist Bitcoin ein System von Regeln, nicht von Vorurteilen oder Gefühlen und Meinungen, und der Schiedsrichter darüber, was darf und was nicht darf, bleibt der Code.
Im besten Fall können Inscriptions den Nicht-Bitcoin-NFT-Markt aushebeln und NFT-Fans den Spiegel vorhalten, dass ihre teuren Bildchen und die zugrunde liegende Technologie fast wertlos sind.
Welchem Camp man auch angehören mag, es bleibt festzuhalten, dass die ganze Ordinals-Theorie auf einer willkürlichen Annahme beruht und nur funktioniert, wenn man der Theorie folgt, dass Sats (ähnlich wie Atome bei Gold oder Nukleotide bei DNS) feste Bestandteile darstellen, die sich einzeln nachverfolgen lassen und nicht - wie ich denke - eine Maßeinheit darstellen. Zu sagen, ein UTXO besteht aus n-Menge Sats und jeder Sat ist einzigartig, ist genauso sinnvoll, wie zu sagen, dass man einen Eimer Wasser hat und sich jedes Milliliter Wasser einzeln nachvollziehen lässt. Liter ist eine Maßeinheit und nicht die Grundform, aus der Wasser besteht.
🫳🎤
In diesem Sinne, 2... 1... Risiko!

-
 @ 30ceb64e:7f08bdf5
2024-11-24 16:48:15
@ 30ceb64e:7f08bdf5
2024-11-24 16:48:15A Personal Journey
I recently created a blog using npub.pro to consolidate my Nostr and Stacker News longform posts in one place. It's been a fun experiment, with surprising results.
https://thebloghustle.npub.pro/
Primal now displays my SN and Nostr posts through a selection on my profile screen, and users are able to highlight, zap, and comment on the highlights of my articles.
I need to write more, the blog will be something of an open diary, detailing my personal experience with Nostr and bitcoin.
Why Nostr Outshines Substack and Medium
Nostr in my opinion has already surpassed the legacy blogging platforms. Functionalities like zapping, highlighting, and commenting, are fun and cool, but when added to Nostr's interconnectivity something magical appears. I had no idea my cross posted SN longform posts would be found in npub.pro, and I didn't know npub.pro had added longform support. Primal 2.0 was pretty much the nail in the coffin, the most popular Nostr client just added a reads section, supporting longform content. Nostr freaks like to talk about sovereignty and decentralization and owning your online identity, but the main attraction will probably be zaps, interconnectivity, and a more optimal UX.
Npub.pro, Cypher.space, Blogspot.io, Highlighter, Stacker News, Primal 2.0 and Yakihonne, are just the beginnings, but offer an amazing glimpse at what the future has in store. Keep in mind that these sites are sharing an average of around 10k daily active users, we'll see an explosion of content and a diversity of content because these platforms offer incentives and functionalities that you don't see elsewhere, as bitcoin becomes less taboo, and as the early adopter phase of these products comes to a close, we'll probably see v4v censorship resistance and digital ownership immensely supporting the underdog, the same underdog that just came over for the ease of use and hype.
So with that being said, highlight away. Let me know what you guys think about blogging on Nostr and if you think these are just the ramblings of a madman, or bland and obvious observations.
Thanks, Hustle
originally posted at https://stacker.news/items/781159
-
 @ 9bfc0ed5:17da5661
2024-12-09 06:58:34
@ 9bfc0ed5:17da5661
2024-12-09 06:58:34FIFA The Best FIFA Football Awards 2024 nominees announced Published 29 Nov 2024
Football fans from across the globe can now cast their votes in a host of categories, including The Best FIFA Men's 11 and The Best FIFA Women's 11.
FIFA Voting is now open for the ninth edition of The Best FIFA Football Awards™ Fans can vote for The Best FIFA Men’s 11 and The Best FIFA Women’s 11 for first time New FIFA Marta Award added to celebrate the best goal in women’s football FIFA has announced the shortlist of nominees for The Best FIFA Football Awards™ 2024, which will recognise the leading lights in another thrilling year of women’s and men’s football at both club and national-team levels.
Voting is now open on FIFA.com across a number of award categories, with fans set to play a key role in choosing the winners. Voting for The Best FIFA Men’s Player, The Best FIFA Women’s Player, The Best FIFA Men’s Coach, The Best FIFA Women’s Coach, The Best FIFA Men’s Goalkeeper and The Best FIFA Women’s Goalkeeper will be equally weighted between fans, the current captains and coaches of all women’s/men’s national teams, and media representatives.
The winner of the FIFA Fan Award will be chosen entirely by fans, while the recipient of the FIFA Fair Play Award will be decided by an expert panel. Voting for the new FIFA Marta Award and the FIFA Puskás Award will be split equally between fans and a panel of FIFA Legends.
The biggest change in terms of voting for this year’s edition of The Best FIFA Football Awards is that fans will have their say in selecting The Best FIFA Men’s 11 and The Best FIFA Women’s 11. They will be able to choose from a list of 77 nominated players – 22 defenders, midfielders and forwards apiece, plus 11 goalkeepers – slotting them into one of several preset tactical formations to build their team. Votes will be weighted equally between fans and an expert panel.
The FIFA Puskás Award has been redefined as being bestowed on the scorer of the best goal in men’s football regardless of championship or nationality. To honour the best goal scored in women’s football in any league around the world, the FIFA Marta Award, named after the Brazilian legend, will be presented for the very first time.
Voting is open on FIFA.com until 23:59 CET on Tuesday, 10 December 2024. The rules of allocation for all awards are available at the FIFA Digital Hub.
-
 @ 07907690:d4e015f6
2024-11-24 09:38:58
@ 07907690:d4e015f6
2024-11-24 09:38:58Karena orang tuanya yang berasal dari Hongaria telah melarikan diri dari rezim Soviet pascaperang untuk menetap di Amerika Serikat, Nick Szabo menganggap daerah Teluk California pada tahun 1990-an sebagai rumahnya. Di sana, ia termasuk orang pertama yang sering menghadiri pertemuan tatap muka "Cypherpunk" yang diselenggarakan oleh Timothy May, Eric Hughes, dan anggota pendiri kolektif kriptografer, programmer, dan aktivis privasi lainnya yang berpusat di sekitar milis tahun 90-an dengan nama yang sama.
Seperti Cypherpunk lainnya, Szabo khawatir dengan jaminan privasi yang semakin berkurang di era digital yang akan datang dan mengambil tindakan untuk membendung gelombang tersebut semampunya. Misalnya, di milis Cypherpunk, Szabo memimpin penentangan terhadap "Chip Clipper", sebuah chip yang diusulkan untuk disematkan di telepon, yang memungkinkan NSA untuk mendengarkan panggilan telepon. Szabo memiliki bakat khusus untuk menjelaskan risiko pelanggaran privasi tersebut dengan cara yang dapat diterima oleh orang-orang yang tidak memiliki latar belakang teknis, terkadang memberikan ceramah tentang topik tersebut atau bahkan membagikan brosur. (Chip tersebut akhirnya ditolak oleh produsen dan konsumen.)
Namun seperti Cypherpunk yang lebih berorientasi libertarian, minat Szabo dalam privasi digital adalah bagian dari gambaran yang lebih besar — ini bukan hanya tentang privasi saja. Terinspirasi oleh visi Timothy May sebagaimana yang ditetapkan dalam The Crypto Anarchist Manifesto, Szabo melihat potensi untuk menciptakan "Galt's Gulch" di dunia maya: domain tempat individu dapat berdagang dengan bebas, seperti yang dijelaskan oleh novel penulis libertarian Ayn Rand, Atlas Shrugged. Medan gaya pseudo-fisika dari cerita tersebut, May dan Szabo percaya, dapat digantikan dengan keajaiban kriptografi kunci publik yang baru-baru ini ditemukan.
“Jika kita mundur sejenak dan mencermati apa yang ingin dicapai oleh banyak cypherpunk, tema idealis utamanya adalah dunia maya Ghana di mana kekerasan hanya bisa menjadi khayalan, entah itu dalam Mortal Komat [sic] atau 'perang api',” tulis Szabo dalam milis Cypherpunks.
Namun, Szabo juga menyadari bahwa perusahaan bebas membutuhkan lebih dari sekadar enkripsi sebagai lapisan keamanan. Terinspirasi oleh penulis libertarian lainnya — ekonom Friedrich Hayek — ia menemukan bahwa dasar masyarakat manusia, sebagian besar, didasarkan pada komponen dasar, seperti properti dan kontrak, yang biasanya ditegakkan oleh negara. Untuk menciptakan alternatif dunia maya tanpa negara dan tanpa kekerasan, Szabo tahu bahwa komponen dasar ini harus dipindahkan ke ranah daring.
Beginilah cara Szabo, pada pertengahan 1990-an, mengusulkan sesuatu yang mungkin paling dikenalnya saat ini: kontrak pintar. Protokol komputer (yang saat itu masih hipotetis) ini dapat memfasilitasi, memverifikasi, dan menegakkan negosiasi atau pelaksanaan kontrak secara digital, idealnya tanpa memerlukan pihak ketiga mana pun. Seperti yang pernah dikatakan Szabo : "Pihak ketiga yang tepercaya adalah lubang keamanan." Lubang keamanan ini akan menjadi target peretas atau penjahat — serta negara-negara bangsa selama masa ketidakstabilan politik atau penindasan.
Namun kontrak pintar hanyalah sebagian dari teka-teki. Alat kedua yang dibutuhkan Szabo untuk mewujudkan "Galt's Gulch" mungkin bahkan lebih penting. Uang.
Uang Elektronik
Mata uang digital, uang tunai untuk internet, selalu menjadi tujuan utama Cypherpunk. Namun, hanya sedikit yang mendalami pokok bahasan tersebut seperti yang dilakukan Szabo.
Dalam esainya "Shelling Out: The Origins of Money," Szabo menjelaskan bagaimana — seperti yang pertama kali dihipotesiskan oleh ahli biologi evolusi Richard Dawkins — penggunaan uang telah tertanam dalam DNA manusia. Setelah menganalisis masyarakat pra-peradaban, Szabo menemukan bahwa orang-orang di berbagai budaya cenderung mengumpulkan benda-benda langka dan mudah dibawa, sering kali untuk dijadikan perhiasan. Benda-benda inilah yang berfungsi sebagai uang, yang pada gilirannya memungkinkan manusia untuk bekerja sama: "altruisme timbal balik" teori permainan melalui perdagangan, dalam skala besar dan lintas waktu.
Szabo juga sangat tertarik pada perbankan bebas, sebuah pengaturan moneter yang didukung oleh Hayek, di mana bank swasta menerbitkan mata uang mereka sendiri yang tidak terikat pada negara tertentu. Di bawah sistem seperti itu, pasar bebas sepenuhnya bebas menentukan mata uang mana yang akan digunakan. Meskipun merupakan ide baru saat ini (dan bahkan lebih baru lagi pada tahun-tahun sebelum Bitcoin), perbankan bebas merupakan kenyataan di Amerika Serikat pada tahun 1800-an, serta di beberapa negara lain.
Szabo juga melanjutkan untuk menerapkan minatnya dalam praktik dan menjual keahliannya sebagai konsultan perdagangan internet pada pertengahan 1990-an, jauh sebelum kebanyakan orang melihat potensi perdagangan daring. Yang paling menonjol, ia menghabiskan waktu bekerja di perusahaan rintisan DigiCash milik David Chaum, yang berkantor pusat di Amsterdam. Perusahaan Chaum memperkenalkan uang digital pertama yang pernah ada di dunia dalam bentuk eCash: sarana untuk melakukan pembayaran daring yang sama rahasianya dengan uang tunai di dunia nyata.
Namun, di DigiCash pula Szabo mengetahui risiko solusi Chaum. DigiCash adalah perusahaan terpusat, dan Szabo merasa terlalu mudah baginya dan orang lain untuk mengutak-atik saldo orang lain jika mereka mau. Bagaimanapun, pihak tepercaya adalah celah keamanan, dan risiko ini mungkin tidak lebih besar daripada risiko dalam hal uang.
“Masalahnya, singkatnya, adalah bahwa uang kita saat ini bergantung pada kepercayaan pada pihak ketiga untuk menentukan nilainya,” Szabo berpendapat pada tahun 2005. “Seperti yang ditunjukkan oleh banyak episode inflasi dan hiperinflasi selama abad ke-20, ini bukanlah keadaan yang ideal.”
Bahkan, ia menganggap masalah kepercayaan ini sebagai hambatan yang bahkan solusi perbankan bebas pada umumnya bisa mengalaminya: “[P]enerbitan uang kertas swasta, meski memiliki berbagai kelebihan dan kekurangan, juga bergantung pada pihak ketiga yang terpercaya.”
Szabo tahu ia ingin menciptakan bentuk uang baru yang tidak bergantung pada kepercayaan pada pihak ketiga mana pun.
Berdasarkan analisisnya terhadap uang prasejarah, Szabo telah menempuh perjalanan panjang dalam menentukan seperti apa bentuk uang idealnya. Pertama, uang tersebut harus “aman dari kehilangan dan pencurian yang tidak disengaja.” Kedua, nilainya harus “sangat mahal dan tidak dapat dipalsukan, sehingga dianggap berharga.” Dan ketiga: “Nilai ini [harus] diperkirakan secara akurat melalui pengamatan atau pengukuran sederhana.”
Dibandingkan dengan logam mulia seperti emas, Szabo ingin menciptakan sesuatu yang digital dan langka, di mana kelangkaan ini tidak bergantung pada kepercayaan pihak ketiga. Ia ingin menciptakan emas digital.
Logam mulia dan barang koleksi memiliki kelangkaan yang tidak dapat dipalsukan karena mahalnya biaya pembuatannya. Hal ini pernah menghasilkan uang yang nilainya sebagian besar tidak bergantung pada pihak ketiga yang tepercaya. Namun, logam mulia memiliki masalah. […] Jadi, akan sangat bagus jika ada protokol yang memungkinkan bit yang sangat mahal dapat dibuat secara daring dengan ketergantungan minimal pada pihak ketiga yang tepercaya, lalu disimpan, ditransfer, dan diuji dengan aman dengan kepercayaan minimal yang serupa. Bit Gold.
Bit Gold
Szabo pertama kali mencetuskan Bit Gold pada tahun 1998, meskipun ia baru menjelaskannya secara lengkap di depan publik pada tahun 2005. Skema uang digital yang diusulkannya terdiri dari kombinasi berbagai solusi, beberapa di antaranya terinspirasi oleh (atau menyerupai) konsep uang elektronik sebelumnya.
Properti utama pertama Bit Gold adalah proof of work, trik kriptografi yang digunakan oleh Dr. Adam Back dalam "mata uang anti-spam" miliknya, Hashcash. Proof of work merupakan biaya yang tidak dapat dipalsukan yang dicari Szabo, karena memerlukan sumber daya dunia nyata — daya komputasi — untuk menghasilkan bukti-bukti ini.
Sistem pembuktian kerja Bit Gold dimulai dengan "string kandidat": pada dasarnya angka acak. Siapa pun dapat mengambil string ini dan secara matematis menggabungkannya — "hash" — dengan angka acak lain yang baru dibuat. Berdasarkan sifat hashing, hasilnya akan menjadi string angka baru yang tampak acak: hash. Satu-satunya cara untuk mengetahui seperti apa hash ini adalah dengan benar-benar membuatnya — hash tidak dapat dihitung atau diprediksi dengan cara lain.
Triknya, yang juga digunakan dalam Hashcash, adalah bahwa tidak semua hash dianggap valid dalam protokol Bit Gold. Sebaliknya, hash yang valid harus, misalnya, dimulai dengan sejumlah angka nol yang telah ditentukan sebelumnya. Karena sifat hashing yang tidak dapat diprediksi, satu-satunya cara untuk menemukan hash yang valid adalah dengan coba-coba. Oleh karena itu, hash yang valid membuktikan bahwa pembuatnya telah mengeluarkan daya komputasi.
Hash yang valid ini, pada gilirannya, akan menjadi string kandidat Bit Gold berikutnya. Oleh karena itu, sistem Bit Gold akan berkembang menjadi rantai hash proof-of-work, dan akan selalu ada string kandidat berikutnya untuk digunakan.
Siapa pun yang menemukan hash yang valid akan secara harfiah memiliki hash tersebut, mirip dengan bagaimana orang yang menemukan sedikit bijih emas memilikinya. Untuk menetapkan kepemilikan ini secara digital, Bit Gold menggunakan registri kepemilikan digital : blok penyusun lain yang terinspirasi Hayek yang diusulkan oleh Szabo. Dalam registri ini, hash akan ditautkan ke kunci publik dari masing-masing pembuatnya.
Melalui registri kepemilikan digital ini pula, hash dapat ditransfer ke pemilik baru: Pemilik asli secara harfiah akan menandatangani transaksi dengan tanda tangan kriptografi.
Registri kepemilikan akan dikelola oleh "klub properti" Bit Gold. Klub properti ini terdiri dari "anggota klub" (server) yang akan melacak kunci publik mana yang memiliki hash mana. Solusi ini agak mirip dengan solusi basis data replikasi yang diusulkan Wei Dai untuk b-money; baik Szabo maupun Dai tidak hanya aktif di milis Cypherpunks, tetapi juga di milis tertutup yang membahas topik-topik ini.
Namun, alih-alih sistem proof-of-stake milik Dai untuk menjaga agar sistem tetap mutakhir, Szabo mengusulkan "Sistem Kuorum Bizantium." Mirip dengan sistem yang sangat penting bagi keamanan seperti komputer pesawat terbang, jika hanya satu (atau sebagian kecil) dari komputer ini yang tidak berfungsi, sistem secara keseluruhan akan tetap beroperasi dengan baik. Sistem akan bermasalah hanya jika sebagian besar komputer gagal pada saat yang sama. Yang penting, tidak satu pun dari pemeriksaan ini memerlukan pengadilan, hakim, atau polisi, yang didukung oleh monopoli negara atas kekerasan: Semuanya akan bersifat sukarela.
Meskipun sistem ini sendiri tidak sepenuhnya sangat ketat — misalnya Serangan Sybil ("sock puppet problem") — Szabo yakin sistem ini bisa berjalan sendiri. Bahkan dalam skenario di mana mayoritas anggota klub akan mencoba berbuat curang, minoritas yang jujur bisa bercabang ke dalam daftar kepemilikan yang bersaing. Pengguna kemudian dapat memilih daftar kepemilikan mana yang akan digunakan, yang menurut Szabo mungkin adalah yang jujur.
"Jika aturan dilanggar oleh pemilih yang menang, maka pecundang yang benar dapat keluar dari grup dan membentuk grup baru, mewarisi gelar lama," jelasnya. "Pengguna gelar (partai yang mengandalkan) yang ingin mempertahankan gelar yang benar dapat memverifikasi sendiri dengan aman kelompok sempalan mana yang telah mengikuti aturan dengan benar dan beralih ke grup yang benar."
(Sebagai contoh modern, ini mungkin dapat dibandingkan dengan Ethereum Classic, yang memelihara versi buku besar Ethereum asli yang tidak membatalkan kontrak pintar The DAO.)
Inflasi
Masalah berikutnya yang harus dipecahkan Szabo adalah inflasi. Seiring dengan semakin baiknya komputer dari waktu ke waktu, akan semakin mudah untuk menghasilkan hash yang valid. Ini berarti bahwa hash itu sendiri tidak dapat berfungsi sebagai uang dengan baik: hash akan semakin langka setiap tahunnya, sampai pada titik di mana kelimpahan akan melemahkan semua nilai.
Szabo menemukan solusinya. Setelah hash yang valid ditemukan, hash tersebut harus diberi cap waktu, idealnya dengan server cap waktu yang berbeda untuk meminimalkan kepercayaan pada hash tertentu. Cap waktu ini akan memberikan gambaran tentang seberapa sulitnya menghasilkan hash: hash yang lama akan lebih sulit diproduksi daripada hash yang baru. Pasar kemudian akan menentukan berapa nilai hash tertentu relatif terhadap hash lainnya, mungkin menyesuaikan nilainya dengan tanggal ditemukannya. "Hash 2018" yang valid seharusnya bernilai jauh lebih rendah daripada "Hash 2008" yang valid.
Namun solusi ini, tentu saja, menimbulkan masalah baru, Szabo tahu : "bagian-bagian (solusi teka-teki) dari satu periode (mulai dari detik hingga minggu, katakanlah seminggu) ke periode berikutnya tidak dapat dipertukarkan." Kepertukaran — gagasan bahwa setiap unit mata uang sama dengan unit lainnya — sangat penting bagi uang. Seorang pemilik toko ingin menerima pembayaran tanpa harus khawatir tentang tanggal uang tersebut dibuat.
Szabo juga menemukan solusi untuk masalah ini. Ia membayangkan semacam solusi "lapisan kedua" di atas lapisan dasar Bit Gold. Lapisan ini akan terdiri dari sejenis bank, meskipun bank yang dapat diaudit secara aman, karena registri Bit Gold bersifat publik. Bank-bank ini akan mengumpulkan hash yang berbeda dari periode waktu yang berbeda dan, berdasarkan nilai hash ini, menggabungkannya ke dalam paket-paket dengan nilai standar gabungan. "Paket 2018" akan mencakup lebih banyak hash daripada "paket 2008," tetapi kedua paket akan bernilai sama.
Paket-paket ini kemudian harus dipotong-potong menjadi sejumlah unit tertentu. Akhirnya, unit-unit ini dapat diterbitkan oleh "bank" sebagai eCash Chaumian yang bersifat pribadi dan anonim.
“[P]ansa pesaing menerbitkan uang kertas digital yang dapat ditukarkan dengan bit solusi yang nilai pasarnya sama dengan nilai nominal uang kertas (yakni mereka menciptakan kumpulan nilai standar),” jelas Szabo .
Dengan demikian, Bit Gold dirancang sebagai lapisan dasar seperti standar emas untuk sistem perbankan bebas di era digital.
Bitcoin
Pada tahun 2000-an, Szabo melanjutkan pendidikannya dengan meraih gelar sarjana hukum untuk memahami hukum dan realitas kontrak yang ingin ia gantikan atau tiru secara daring dengan lebih baik. Ia juga mulai mengumpulkan dan menerbitkan ide-idenya di sebuah blog yang sangat dihormati, “Unenumerated,” yang membahas berbagai topik mulai dari ilmu komputer hingga hukum dan politik, tetapi juga sejarah dan biologi. “Daftar topik untuk blog ini […] sangat luas dan beragam sehingga tidak dapat disebutkan satu per satu,” Szabo menjelaskan judulnya.
Pada tahun 2008 — 10 tahun setelah pertama kali mengusulkannya secara pribadi — Szabo mengangkat Bit Gold di blognya sekali lagi, hanya saja kali ini ia ingin mewujudkan implementasi pertama usulannya.
“Bit Gold akan sangat diuntungkan dari sebuah demonstrasi, pasar eksperimental (dengan misalnya pihak ketiga yang tepercaya menggantikan keamanan kompleks yang dibutuhkan untuk sistem nyata). Adakah yang mau membantu saya membuat kodenya?” tanyanya di bagian komentar blognya.
Jika ada yang menanggapi, tanggapan itu tidak disampaikan di depan umum. Bit Gold, dalam bentuk yang diusulkan Szabo, tidak pernah dilaksanakan.
Namun, Bit Gold tetap menjadi inspirasi utama bagi Satoshi Nakamoto, yang menerbitkan white paper Bitcoin di akhir tahun yang sama.
“Bitcoin merupakan implementasi dari proposal b-money Wei Dai [...] di Cypherpunks [...] pada tahun 1998 dan proposal Bitgold milik Nick Szabo,” tulis penemu Bitcoin dengan nama samaran di forum Bitcointalk pada tahun 2010.
Memang, tidak sulit untuk melihat Bit Gold sebagai rancangan awal Bitcoin. Selain dari basis data bersama catatan kepemilikan berdasarkan kriptografi kunci publik, rangkaian hash bukti kerja memiliki kemiripan yang aneh dengan blockchain Bitcoin . Dan, tentu saja, nama Bit Gold dan Bitcoin juga tidak terlalu jauh.
Namun, tidak seperti sistem seperti Hashcash dan b-money, Bit Gold jelas tidak ada dalam white paper Bitcoin. Beberapa orang bahkan menganggap ketidakhadiran ini begitu penting sehingga mereka menganggapnya sebagai salah satu dari beberapa petunjuk bahwa Szabo pastilah orang di balik julukan Satoshi Nakamoto: Siapa lagi yang akan mencoba menyembunyikan asal-usul Bitcoin seperti ini?
Meski demikian, meski mirip dengan Bit Gold dalam beberapa hal, Bitcoin memang menyertakan beberapa perbaikan atas desain Szabo. Secara khusus, di mana Bit Gold masih bergantung pada pihak tepercaya sampai batas tertentu — server dan layanan stempel waktu harus dipercaya sampai batas tertentu untuk tidak berkolusi — Bitcoin adalah sistem pertama yang memecahkan masalah ini sepenuhnya. Bitcoin memecahkannya dengan sangat elegan, dengan memiliki sistem bukti kerja yang diperlukan yang berfungsi sebagai sistem penghargaan dan mekanisme konsensus dalam satu sistem: Rantai hash dengan bukti kerja terbanyak dianggap sebagai versi sejarah yang valid.
“Nakamoto memperbaiki kekurangan keamanan signifikan yang ada pada desain saya,” Szabo mengakui pada tahun 2011, “yakni dengan mensyaratkan bukti kerja untuk menjadi simpul dalam sistem peer-to-peer yang tangguh terhadap Byzantine untuk mengurangi ancaman pihak yang tidak dapat dipercaya yang mengendalikan mayoritas simpul dan dengan demikian merusak sejumlah fitur keamanan penting.”
Lebih jauh, Bitcoin memiliki model moneter yang sangat berbeda dari yang diusulkan Szabo, dengan jadwal inflasi tetap yang sama sekali tidak terpengaruh oleh peningkatan daya hash. Seiring meningkatnya daya komputasi pada jaringan Bitcoin, itu artinya semakin sulit menemukan koin baru.
“Alih-alih pasar otomatis saya memperhitungkan fakta bahwa tingkat kesulitan teka-teki sering kali dapat berubah secara radikal berdasarkan peningkatan perangkat keras dan terobosan kriptografi (yaitu menemukan algoritma yang dapat memecahkan bukti kerja lebih cepat), dan ketidakpastian permintaan, Nakamoto merancang algoritma yang disetujui Bizantium yang menyesuaikan tingkat kesulitan teka-teki,” jelas Szabo.
“Saya tidak dapat memutuskan apakah aspek Bitcoin ini lebih banyak fitur atau lebih banyak bug,” tambahnya, “tetapi ini membuatnya lebih sederhana.”
Sumber artikel: bitcoinmagazine.com
Diterjemahkan oleh: Abeng -
 @ e356a30c:11e846f7
2024-12-09 06:55:23
@ e356a30c:11e846f7
2024-12-09 06:55:23Unlike many groundbreaking technologies with a charismatic founder at the helm, Bitcoin stands out for its enigmatic origins. Satoshi Nakamoto, the pseudonymous individual or group behind Bitcoin's creation, remains a mystery. This deliberate anonymity has profound implications for the digital currency's decentralized nature and future.
The absence of a central authority figure ensures that Bitcoin's development and governance are community-driven. This decentralized approach fosters transparency, security, and resilience. Without a single point of failure, Bitcoin is less susceptible to manipulation, censorship, or systemic risks. Furthermore, the anonymity of Satoshi Nakamoto prevents the concentration of power and influence. It eliminates the potential for personal biases, conflicts of interest, or arbitrary decision-making. Instead, Bitcoin's evolution is guided by a collective consensus mechanism, where network participants validate transactions and secure the blockchain.
While the identity of Satoshi Nakamoto may remain unknown, their innovative idea has sparked a global movement. Bitcoin has inspired countless projects and innovations in the blockchain space, demonstrating the power of decentralized technologies. By embracing decentralization, Bitcoin has paved the way for a more equitable and transparent financial system.
-
 @ d7c6d014:a6abb6b8
2024-11-23 18:40:47
@ d7c6d014:a6abb6b8
2024-11-23 18:40:47こんにちは!kohei です。
久々のエントリ投下ですが、今回は先日弊 TL で話題になっていた、Android を P2P のローカルリレーサーバー化して Tor で公開する方法を紹介していこうと思います。
用意するもの
- Android 端末
- Orbot
- Citrine
- Amethyst
前提と下準備
今回は、Orbot の詳細設定は省いて、Power User Mode の設定が完了している前提でお話を進めます。 Android 端末を用意して、2~4 のアプリをインストールしておいてください。
設定方法
それでは早速設定していきましょう。 まず、Citrine を起動して、Settings のタブからローカルリレーの詳細を設定します。
設定が終了したら、ローカルリレーを起動します。
また、ここで表示されるポート番号をメモしてください。
次に、More のタブに移り、Hosted Onion Services へアクセスし、Service Type の項目で User Services にチェックを入れて、右下の + マークをタップすると以下のポップアップが表示されます。(Orbot がスクショを許してくれないので一部画像割愛)
表示されたら、Name に任意の名前を、Local Port と Onion Port に先ほどメモした Citrine のポート番号を入力します。
入力したら再起動を求められるので再起動してください。 再起動後に Hosted Onion Services の項目に .onion のアドレスが表示されたら成功です (何故か私の環境では、一回の再起動では設定が反映されなかったのですが、もし同じような現象が起きた場合は、再起動 -> Connect -> .onion アドレスが発行されてるかの確認、を数回試すと発行されるはずです)
発行されたら、.onion アドレスをタップしてクリップボードにコピーします。
次に、Amethyst を起動して、リレーの設定画面に入り、Outbox の設定にコピーした .onion アドレスを貼り付けて保存します。
後は、Amethyst 側で Orbot のポート番号を設定して Orbot に接続すれば BOOM! 設定完了です。
お疲れ様でした!
素敵な Nostr ライフを!
-
 @ 349d6b82:12b2a5b1
2024-12-09 06:10:35
@ 349d6b82:12b2a5b1
2024-12-09 06:10:35Активно обсуждается вопрос повышения заработной платы для работников заводов. Власти города и руководители промышленных предприятий ведут переговоры о необходимости индексации зарплат, чтобы обеспечить конкурентоспособность и удержание квалифицированных кадров.
В условиях растущей инфляции и увеличения стоимости жизни, работники заводов требуют пересмотра своих окладов. Власти признают важность этого вопроса, так как стабильность на рынке труда напрямую влияет на экономическое развитие региона. И в нашем городе в основном преобладает больше рабочая сила именно на заводах.
Руководство заводов, включая такие крупные предприятия, как "Северсталь", уже анонсировало планы по повышению зарплат на 10-12% с начала 2044 года. Генеральный директор компании отметил, что бюджет на пересмотр заработной платы в 2044 году превысит 9 миллиардов рублей, что свидетельствует о серьезных намерениях по улучшению условий труда.
Работники активно участвуют в обсуждениях и выражают свои требования через профсоюзы. Они подчеркивают, что текущие зарплаты не соответствуют уровню жизни и не компенсируют затраты на повседневные нужды. В связи с этим, многие работники заводов начали организовывать встречи с руководством для обсуждения своих ожиданий по повышению зарплаты.
На фоне обсуждений в Серове стоит отметить, что аналогичные меры уже были предприняты в других секторах. Например, энергетическая компания ТГК-14 объявила о планах по индексации зарплат своих сотрудников дважды в текущем году, что также связано с необходимостью удержания квалифицированных кадров.
Вопрос повышения заработной платы для работников заводов в Серове становится все более актуальным. Переговоры между властями и руководством предприятий продолжаются, и ожидается, что в ближайшие месяцы будут приняты конкретные решения по индексации зарплат. Работники надеются на положительные изменения, которые помогут улучшить их финансовое положение и качество жизни.
-
 @ 0c469779:4b21d8b0
2024-11-23 17:10:04
@ 0c469779:4b21d8b0
2024-11-23 17:10:04Todo que celebrar
- No recuerdo exactamente cómo me empezo a interesar el tema, el punto es que vi un lavado de cabeza inmenso que se hace a cada paisano en los países hispanoamericanos.
- Inclusive Residente tiene una canción llamada Latinoamérica, donde habla de todo lo que se robaron los españoles.
- La leyenda negra nos dice que España fue lo peor que le pudo pasar a la región.
-
La primera mentira es pensar que antes de España había paz: Los distintos imperios americanos esclavizaban a las poblaciones adyacentes. Los aztecas esclavizaban a las tribus mexicas, fue gracias a Hernán Cortés, quien consiguió la organización de estas tribus, que se pudo derrocar a Moctezuma y a los aztecas. Piénsese en eso, Hernán Cortés tenía un ejército de aproximadamente 550 soldados (siendo generosos), y por cada español había de 10 a 15 indígenas, principalmente de Tlaxcala, pero también de Huexotzinco, Cholula y Tepeyac. Los aztecas eran 200000. Una vez caído Tenochitlán, otra parte de la leyenda negra dice que España exterminó a los indígenas, lo cual es falso. Hernán Cortés cuidó de sus descendientes e incluso tuvo un hijo con una de las hijas de Moctezuma.
-
España fue el primer imperio que promulga una serie de leyes que humanizan al indígena. Recordemos siempre ponernos en el contexto histórico. El 27 de diciembre de 1512 se promulgan las leyes de Burgos, 35 ordenanzas que buscan proteger y humanizar al indígena americano.
Algunos principios de las Leyes de Burgos son: 1. Los indigenas eran hombres libres y dueños de sus tierras y casas. 2. Los Reyes Católicos eran señores de los indígenas por su compromiso evangelizador. 3. Los encomenderos debían examinar a los indígneas cada quincena para comprobar lo que habían aprendido. 4. Cada indio debia recibir un peso de oro al año para comprar ropa.
Además recordemos lo que dijo Isabel la Católica sobre los indígenas. En su lecho escribió:
No consientan ni den lugar que los indios reciban agravio alguno en sus personas y sus bienes, mas manden que sean bien y justamente tratados.
En 1542 el emperador Carlos V promulga Las Leyes Nuevas de Indias, para reformar el gobierno de las Indias y protoger a los indígenas.
Entre las principales características de las Leyes Nuevas de Indias se encuentran: 1. La supresión de la Institución de la Encomienda 2. La designación del virrey como protector de los indios 3. El respeto a las autoridades, costumbres y formas de vida indígenas 4. La prohibición de que los indigenas sostuvieran relaciones mercantiles con sus vecinos 5. La orden a los españoles que empleasen indios de impartir evangelización, darles buen trato, alimentos, vestido, casa, medico y sacerdote, y pagarles su trabajo en efectivo.
Es curioso resaltar que Las Leyes Nuevas de Indias fueron promovidas por Fray Bartalome de las Casas, quien hubiera mentido en algunos articulos suyos anteriores donde exageraba e inventaba malos tratos a indígenas. Estos artículos falsos fueron y son usados hasta el dia de hoy por la leyenda negra, en los principales libros de historia de las escuelas y colegios hispanoamericanos.
-
Los makás son una tribu indígena del nordeste argentino, quienes fueron desplazados a Paraguay y habitan actualmente zonas de Mariano Roque Alonso, cerca de la capital, Asunción. Quién trata mejor a los indígenas, el Paraguay o Argentina de hoy o el Imperio de ayer?
-
Durante el Imperio, el Virreinato del Rio de la Plata tuvo asentamientos de indígenas guaranies provomidos por los padres de la compañía de Jesús en las tierras conquistadas por España y Portugal. Ellos buscaban crear una sociedad con los beneficios de la sociedad cristiana, pero sin sus vicios. Enseñaban a los indígenas a leer, escribir, aritmética básica, técnicas de agricultura, construcción y artesanía. También aprendieron la lengua de los indígenas (gracias a esto tenemos el guaraní y otras lenguas en escrito, eran puramente orales), lo que facilitaba el trabajo del misionero. Cuando el Rey Carlos III expulsa a los Jesuitas de sus dominios en 1767, efectivizandose en Paraguay en 1768, supuso una gran pérdida para los pueblos originarios, principalmente por la protección, ya que los jesuitas protegían a los indígenas de los bandeirantes, grupos que eran contratados para cazar indígenas y esclavizarlos, o destruir quilombos (asentamientos de esclavos que se liberaban de la esclavitud). Los bandeirantes eran provenientes de zonas del interior de Brasil, y se les puede atribuir la expansión de Brasil más allá de los limites impuestos por el Tratado de Tordesillas.
-
Los movimientos independentistas hispanoamericanos eran auspiciados por fuerzas extranjeras. Las fuerzas de San Martín que cruzaron los Andes por Mendoza contaban con más de 5400 hombres, y se sabe que muchos eran de otras nacionalades. San Martín siempre tuvo afinidad por Inglaterra, pasó en Europa el resto de sus días luego de ser amenazado por el gobierno unitario. También se sabe que fue masón, lo que no se sabe es si conocía el Plan Maitland.
El Plan Maitland fue un proyecto desarrollado en 1800 por Thomas Maitland, originalmente titulado "Plan para capturar Buenos Aires y Chile, y luego emancipar Perú y Quito". Se concluyó que sería mendiante una expedición que cruzaría los Andes y atacaría desde el oeste, es decir, desde Chile, y luego avanzaria hacia el Perú. La estrategia era golpear el corazón del virreinato peruano, que era el bastión del poder en América del Sur.
Si San Martin conocía o no el Plan Maitland no se sabe. San Martin estuvo en Londres en 1811, donde se le pudo haber introducido el plan por miembros de la logia masónica Lautaro, fundada por Francisco de Miranda (secesionista hispanoamericano, primer presidente de Venezuela).
- Los antiguos súbditos no se sentían oprimidos por España. Los sentimientos de nación son inventos que ocurren luego de las independencias. Anteriormente todos eran españoles, católicos y súbditos del Rey. En Paraguay está la concepción errónea de que ganamos la independencia en 1811. Cuando lo que se hace en 1811 es cambiar el gobierno a la fuerza para asegurar la autonomía de la provincia del Paraguay, porque se pensaba que Bernardo de Velasco (gobernador de la provincia) quería entregarla al dominio portugués. En 1811 se sigue jurando lealtad al Rey. Además, recordemos quién fue Fulgencio Yegros. Alférez del ejército español, uno de los pocos militares de carrera. En 1801 integro la expedición al norte de Paraguay a reconquistar Coimbra de manos de los portugueses. En 1806, paritcipó en la defensa de Buenos Aires durante las invasiones inglesas. Ahi conoció a Fernando de la Mora, con quien formó amistad.
Principalmente la defensa de Buenos Aires solo se puede explicar si nos damos cuenta de que no existe tal cosa como nacionalidad paraguaya o argentina. Todos eramos espanoles. Hay muchos casos similares al de Fulgencio Yegros por toda la America Espanola.
-
Fulgencio Yegros fue ejecutado tras querer derrocar a Jose Gaspar Rodriguez de Francia, quien se declarara dictador supremo de la República del Paraguay, destacando la independencia por primera vez. En mi opinión uno de los grandes errores de Paraguay fue no haberse unido a las Provincias Unidas del Río de la Plata, eran tiempos tumultuosos y de levantamientos constantes.
-
El término latinoamericano no existió hasta luego de la independencia de Nueva España y la formación del Imperio Mexicano en un contexto de invasión de Francia a esas tierras.
-
Cómo se explica la riqueza que hubo en Cuba y Puerto Rico, quienes siguieron siendo provincias españolas hasta 1898, finalizada la guerra que empezó con una falsa bandera implantada por los Estados Unidos? Además, la población es altamente mestiza. Cuando España pierde la guerra, también entrega la posesión de las Islas Filipinas (en honor al Rey Felipe II) a los Estados Unidos. Los filipinos mantenían su idioma reigional y hablaban español. La moneda es el peso filipino hasta el día de hoy. Hoy en el tagalog y chabacano hay muchas similitudes con el castellano. Cuando Estados Unidos controla las islas, prohíbe la enseñanza del español, y forza la enseñanza del inglés. Actualmente muchos filipinos tienen apellidos de origen español y hablan inglés.
-
España formó las primeras universidades en América y tenía la biblioteca más grande de todo el continente en Perú.
-
Creo que es importante que sepamos la verdadera historia para entender mejor nuestro pasado. Creo que hay más cosas que nos unen que las que nos separan, creo que Nayib Bukele en la actualidad es capaz de reunificar Centroamérica y darle más peso a su reclamo conociendo la historia, aparte de las razones prácticas del día de hoy. Creo que la República del Paraguay no debería existir y deberíamos integrarnos a las Provincias Unidas del Río de la Plata (Argentina). Creo que debemos entender que fuimos victimas del divide et impera, y tenemos que formar una gran mancomunidad de naciones hispanas (como la Commonwealth) y tener objetivos que se adapten a lo que requerimos hoy: avances tecnológicos, investigación en todos los campos y un proyecto espacial en común.
-
Es extremadamente ridículo que seamos más de 19 países en un mismo continente, todos hablando el mismo idioma y teniendo la misma religión, separados y desinteresados de lo que le pase al otro.
-
Tenemos que apoyar los reclamos de nuestros hermanos: Los argentinos con las Islas Malvinas, los cubanos con Guantanamo, los españoles con Gibraltar y los venezonalos con el Esequibo.
-
Algo interesante que dijo el filósofo y médico Erasmus Darwin, abuelo del gran evolucionista Charles Darwin:
En mis viajes por el inabarcable imperio español, he quedado admirado de como los españoles tratan a los indios: como a semejantes, incluso formando familias mestizas y creando para ellas hospitales y universidades. He conocido alcaldes y obispos indígenas, y hasta militares, lo que redunda en la paz social, bienestar y felicidad general, que ya quisiéramos nosotros [los británicos] en los territorios que con tanto esfuerzo les vamos arrebatando. Parece que las nieblas londinenses nos nublan el corazón y el entendimiento, mientras que la calidad de la soleada España le hace ver y oír mejor a Dios. Sus señorías en Inglaterra deberían considerar la [falsamente imputada] política de despoblación y exterminio de España. Ya que a todas luces la fe y la inteligencia española están construyendo, no como nosotros un imperio de muerte, sino una sociedad civilizada que finalmente terminará por imponerse como por mandato divino. España es la sabia Grecia, la imperial Roma; Inglaterra el corsario turco».
Fuentes interesantes
- https://www.ellitoral.com.ar/corrientes/2022-8-14-1-0-0-desmitificando-a-san-martin-y-sus-relaciones-con-los-ingleses
- Imperiofobia y leyenda negra: Roma, Rusia, Estados Unidos y el Imperio Español de María Elvira Roca Barea
- Madre patria: Desmontando la leyenda negra desde Bartolomé de las Casas hasta el separatismo catalán
- Historia con Patricio Lons
- La Brújula
-
 @ 349d6b82:12b2a5b1
2024-12-09 05:59:22
@ 349d6b82:12b2a5b1
2024-12-09 05:59:22В Серове активно продолжаются реконструкции общежитий для студентов Серовского Металлургического Техникума и Серовского Политехнического Техникума.
В рамках программы по улучшению условий проживания студентов, власти города начали масштабную реконструкцию общежитий. Обновления включают модернизацию жилых помещений, установку новых систем отопления и водоснабжения, а также создание современных учебных и досуговых зон.
Важным аспектом реконструкции стало улучшение инфраструктуры вокруг общежитий. Были обновлены дороги, добавлены велосипедные дорожки и обустроены зеленые зоны, что создает более комфортные условия для студентов.
Власти города также запустили ряд социальных инициатив, направленных на поддержку студентов. Это включает в себя программы по психологической поддержке и организации культурных мероприятий, которые способствуют интеграции студентов в местное сообщество.
Эти изменения уже начали оказывать положительное влияние на качество жизни студентов в Серове. Улучшенные условия проживания способствуют не только комфортному обучению, но и активному отдыху, что в свою очередь положительно сказывается на их успеваемости и общем уровне удовлетворенности жизнью.
Преобразования общежитий и сопутствующие инициативы становятся важным шагом к созданию более комфортной и поддерживающей среды для студентов в Серове.
-
 @ 599f67f7:21fb3ea9
2024-11-23 11:13:57
@ 599f67f7:21fb3ea9
2024-11-23 11:13:57En los dos capítulos anteriores aprendimos cómo dos pares pueden enviar fondos entre sí en un canal actualizando el estado e invalidando estados antiguos. En este capítulo, daremos una visión general de cómo los HTLC permiten pagos de múltiples saltos. El próximo capítulo será una inmersión profunda en los HTLC.
¡Vamos a ello con un ejemplo simple!
Red simple de 3 nodos y 2 saltos
En esta red simple, tenemos tres nodos: Alice, Bob y Charlie. Hay dos canales entre ellos: uno entre Alice y Bob y otro entre Bob y Charlie. Cada canal tiene una capacidad de 10 BTC distribuida equitativamente entre los participantes.

Para simplificar, solo mostramos una transacción de compromiso que gasta de la transacción de financiación, determinando así el estado del canal. Esto no es exactamente preciso, ya que aprendimos sobre compromisos asimétricos en el último capítulo, pero para los propósitos de entender los HTLC, esta simplificación será más fácil. Una descripción más precisa se dará en un capítulo posterior.
Ahora, supongamos que Alice quiere pagar a Charlie. No puede pagarle directamente ya que no tienen un canal entre ellos y es costoso (en términos de tiempo y dinero) abrir un canal solo para una transacción rápida. En su lugar, Alice puede usar su canal con Bob para enrutar un pago a Charlie, ya que Bob y Charlie comparten un canal.
Paso 1: Generar y compartir un hash de pre-imagen
Alice primero necesita decirle a Charlie que quiere pagarle. Charlie generará un secreto aleatorio (la pre-imagen)
Sy obtendrá el hash deS, que llamaremosH. Charlie envíaHa Alice.
Paso 2: Configurar la cadena de HTLC
Supongamos que Alice quiere pagar a Charlie 1 BTC. Primero necesita encontrar una ruta hacia Charlie. En este caso es A-B-C. También ve que para usar esta ruta, necesita incentivar a Bob para que la ayude dándole una tarifa de enrutamiento. Supongamos que Bob cobra una tarifa fija de 1 BTC por enrutar pagos, por lo que Alice pagará un total de 2 BTC: 1 BTC por el enrutamiento y 1 BTC por Charlie. Alice luego le indica a Bob que le gustaría enrutar un pago sugiriendo que actualicen su estado de canal. En este ejemplo simplificado, la transacción de compromiso del canal tendrá las siguientes salidas (recuerda que en realidad Alice y Bob tendrán sus propias transacciones de compromiso):
- Una salida de 3 BTC de vuelta a Alice.
- Una salida de 5 BTC a Bob.
- Una salida de 2 BTC a un script especial que tiene 2 posibles caminos de gasto:
- El primer camino puede ser gastado por Bob si tiene la pre-imagen de
H - El segundo camino puede ser gastado por Alice después de un tiempo absoluto
cltv_expiry_AB
- El primer camino puede ser gastado por Bob si tiene la pre-imagen de
Esta última salida con un script especial que bloquea los 2 BTC se llama un Contrato de Bloqueo de Hash y de Tiempo (Hash Time Locked Contract; HTLC) porque tiene un camino bloqueado por hash y un camino bloqueado por tiempo.
Bob actualizará felizmente a este nuevo estado de canal porque puede ver que no está perdiendo dinero: si la transacción se lleva a cabo en la cadena y aún no tiene la pre-imagen, entonces aún recupera sus fondos originales. También puede ver que si coopera y reenvía el pago, será recompensado con una tarifa de enrutamiento si el pago tiene éxito porque podrá reclamar la salida bloqueada por hash en la transacción.

Bob ahora bloquea algunos fondos de manera similar en su canal con Charlie. Actualiza la transacción de compromiso del canal para incluir las siguientes salidas:
- Una salida de 4 BTC a Bob
- Una salida de 5 BTC a Charlie
- Una salida de 1 BTC a un script HTLC que nuevamente tiene dos caminos de gasto:
- El primer camino es gastable por Charlie si puede revelar la pre-imagen de
H - El segundo camino es gastable por Bob después de un
cltv_expiry_BC
- El primer camino es gastable por Charlie si puede revelar la pre-imagen de
Bob puede bloquear sus fondos de esta manera con confianza porque sabe que si el pago falla, podrá reclamar sus fondos a través del camino bloqueado por tiempo y si el pago tiene éxito y Charlie revela la pre-imagen cuando gasta a través del camino bloqueado por hash, entonces Bob verá esta pre-imagen y podrá reclamar la salida bloqueada por hash en el HTLC de la transacción de compromiso que tiene con Alice.

Cuando Charlie recibe esta oferta de HTLC de Bob, puede ver que de hecho conoce la pre-imagen
Sque se hash aH, por lo que sabe que puede reclamar el camino bloqueado por hash de la salida HTLC de la transacción de compromiso si se lleva a cabo en la cadena. Sin embargo, idealmente, las cosas no tienen que resolverse en la cadena. En su lugar, Charlie simplemente envía la pre-imagenSa Bob. Esto le prueba a Bob que Charlie reclamaría la salida HTLC si se llevara a cabo en la cadena y así ahora Bob y Charlie pueden acordar simplemente actualizar su transacción de compromiso para reflejar que Charlie ahora tiene 1 BTC más:
Ahora que Bob tiene la pre-imagen
S, puede dar la vuelta y revelarSa Alice, probando que si su transacción de compromiso se lleva a cabo en la cadena, Bob reclamaría la salida bloqueada por hash. Así como Bob y Charlie hicieron en su canal, Alice y Bob actualizan su transacción de compromiso eliminando la salida HTLC para reflejar el nuevo saldo de fondos:
Alice envió a Charlie 1 BTC y Bob ganó 1 BTC en tarifas de enrutamiento.
cltv_expiry
¿Qué pasa si las cosas salen mal? Por ejemplo, Charlie se desconecta y no responde a Bob con una pre-imagen. Si esto sucede, Bob necesitará transmitir la transacción de compromiso para que pueda reclamar sus fondos a través del camino bloqueado por tiempo del HTLC. Si transmite la transacción pero luego Charlie vuelve a estar en línea antes del
cltv_expiry_BCy gasta a través del camino bloqueado por hash del HTLC, entonces Bob verá la pre-imagen en la cadena y podrá dar la vuelta a Alice y revelarle la pre-imagen como de costumbre.A partir de este ejemplo, puedes ver que es importante que los valores de
cltv_expirydisminuyan a lo largo del camino del remitente al receptor. Esto se debe a que en el peor de los casos, Charlie solo revelaSa Bob justo antes decltv_expiry_BCy luego Bob aún necesita tiempo para ir a Alice y revelarSantes de que ella pueda gastar a lo largo del caminocltv_expiry_AB. En otras palabras,cltv_expiry_BCdebe ser antes decltv_expiry_AB.Revisión
- Contrato de Bloqueo de Hash y de Tiempo (Hash Time Locked Contract; HTLC): Un script de salida especial en la transacción de compromiso que tiene un camino bloqueado por hash y un camino bloqueado por tiempo
- Pre-imagen: un secreto aleatorio utilizado para reclamar pagos
- Hash (de la pre-imagen): el hash de la preimagen utilizada para bloquear fondos a lo largo de una ruta de pago
- Verificación de tiempo de bloqueo (Check Locktime Verify; CLTV): El bloqueo de tiempo absoluto utilizado en los HTLC que debe disminuir a lo largo de la ruta de pago del remitente al receptor
Referencias
- BOLT2: Peer Protocol
- BOLT3: Transactions
- LN Things Part 4: HTLC Overview por nostr:nprofile1qqswrt9pnxatlplu49h6meld8svmwqt87wwvk256rqk07n6eu4qeh5gpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dszpfjtz
- Time locks
-
 @ a012dc82:6458a70d
2024-12-09 02:50:56
@ a012dc82:6458a70d
2024-12-09 02:50:56Table Of Content
-
The McGlone Prediction
-
A Candid Chat with Scott Melker
-
Economic Indicators
-
The Housing Market
-
Bitcoin vs. NASDAQ
-
Bitcoin ETFs
-
Conclusion
-
FAQ
In the dynamic realm of cryptocurrency, predictions come and go, but few make waves like those from Bloomberg Intelligence's Mike McGlone. With a keen eye on the economic landscape, McGlone foresees a potential rise of Bitcoin to a staggering $100,000. However, this ascent isn't without its challenges. Dive into our detailed analysis to understand the economic hurdles and the factors that might propel Bitcoin to new heights.
The McGlone Prediction
Mike McGlone, the senior macro strategist at Bloomberg Intelligence, is no stranger to bold predictions. In the ever-evolving world of cryptocurrency, he's made a name for himself with his insightful forecasts. This time around, he's got his eyes set on a whopping $100,000 price tag for Bitcoin. But it's not all smooth sailing. McGlone acknowledges the economic challenges that lie ahead, and it's these very hurdles that might fuel Bitcoin's rise.
A Candid Chat with Scott Melker
In a recent head-to-head with crypto influencer Scott Melker, McGlone didn't hold back. He reiterated his unwavering belief in Bitcoin's long-term potential. But here's the twist: before we see Bitcoin basking in the glory of six figures, it might take a nosedive, potentially even below the $20,000 mark. It's a rollercoaster of emotions for crypto enthusiasts, but McGlone's track record suggests we should sit up and listen.
Economic Indicators
McGlone's predictions aren't just plucked from thin air. He's been meticulously analyzing the financial landscape. Those Treasury bills yielding over 5%? They've caught his attention. The Federal Reserve's monetary tightening antics? They're on his radar too. These indicators, among others, paint a picture of the economic challenges that could shape Bitcoin's trajectory.
The Housing Market
One can't discuss economic hurdles without mentioning the housing market. McGlone has been closely monitoring the Case-Shiller index, a tool that tracks US real estate prices. After reaching its zenith in June 2022, the index has been on a downward spiral, eerily reminiscent of the 2006 slump. This decline could be a harbinger of things to come, potentially influencing Bitcoin's path.
Bitcoin vs. NASDAQ
Drawing parallels between Bitcoin and the NASDAQ offers intriguing insights. Since its $30,000 peak in 2020, Bitcoin's price has remained stagnant. In stark contrast, the NASDAQ has flourished, registering a 20% growth. With powerhouse assets like AI technology under its belt, the NASDAQ's robust performance serves as a benchmark, highlighting Bitcoin's potential amidst economic challenges.
Bitcoin ETFs
The introduction of Bitcoin ETFs was met with much fanfare. However, the anticipated surge in Bitcoin's performance was a no-show. McGlone attributes this to an overly optimistic sentiment clouding pragmatic judgment. With the Federal Reserve reigning in the monetary supply, it's akin to pulling the rug from under Bitcoin's feet. Yet, in this challenging macroeconomic environment, McGlone sees a silver lining for Bitcoin's ascent.
Conclusion
McGlone's vision for Bitcoin is both optimistic and grounded. While the road to $100,000 is fraught with challenges, these very obstacles might be the catalyst for Bitcoin's meteoric rise. As the crypto world watches with bated breath, only time will reveal the accuracy of McGlone's predictions. One thing's for sure: the journey promises to be exhilarating.
FAQ
Who is Mike McGlone? Mike McGlone is a senior macro strategist at Bloomberg Intelligence, known for his insightful cryptocurrency forecasts.
What is McGlone's latest prediction for Bitcoin? McGlone predicts that Bitcoin could potentially rise to $100,000, albeit facing several economic challenges.
Why is the housing market significant in this context? McGlone references the Case-Shiller index, which tracks US real estate prices, as an indicator of potential economic hurdles that could influence Bitcoin's trajectory.
How does the NASDAQ's performance compare to Bitcoin's? While Bitcoin's price has stagnated since 2020, the NASDAQ has seen a 20% growth, serving as a comparative benchmark.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 599f67f7:21fb3ea9
2024-11-22 14:07:44
@ 599f67f7:21fb3ea9
2024-11-22 14:07:44Veamos nuevamente la transacción de compromiso de Alice. Esta gasta de la transacción de financiación y tiene dos salidas: una salida
to_localy una salidato_remote.to_remote
La salida
to_remotees simplemente un P2WPKH enviando a la clave pública de Bob.<remotepubkey>to_local
La salida
to_localtiene 2 caminos de gasto.- Una
<revocationpubkey> - Una clave pública que pertenece a Alice pero que solo se puede gastar después del número de bloques
to_self_delay.
OP_IF # Transacción de penalización <revocationpubkey> OP_ELSE `to_self_delay` OP_CHECKSEQUENCEVERIFY OP_DROP <local_delayedpubkey> OP_ENDIF OP_CHECKSIGEn el Capítulo 2, describimos la revocación de la siguiente manera:
- Alice genera una clave privada temporal
dA1y una clave pública correspondientePA1y envía la clave pública a Bob. - Alice luego crea una transacción de compromiso donde la salida
to_locales inmediatamente gastable por Bob si tiene la clave privadadA1. - Si Alice y Bob actualizan el estado de su canal, entonces intercambiarán las claves privadas anteriores entre sí para invalidar el compromiso anterior, es decir, Alice enviará a Bob
dA1.
Esta descripción es mayormente correcta pero no completa. Si echamos un vistazo nuevamente al script
to_self_delayanterior, parece que el camino de revocación no tiene ninguna condición que diga que solo Bob puede gastarlo. Simplemente parece que cualquiera con la clave privada correspondiente a la clave pública de revocación puede gastarlo. Dado que Alice es quien generó la clave privada temporal en primer lugar, ¿no significa eso que también puede gastarlo?Se utiliza un truco ingenioso para asegurarse de que solo Bob pueda gastar a través del camino de revocación. Antes de construir las transacciones de compromiso, tanto Alice como Bob derivan dos claves temporales y claves públicas asociadas.
1. Un par de clavesrevocation_basepoint(r -> R)
2. Un par de clavesper_commitment_point(c -> C)En otras palabras, Alice tendrá:
- su par de clavesrevocation_basepoint:rA1->RA1
- su par de clavesper_commitment_point:cA1->CA1Bob tendrá:
- su par de clavesrevocation_basepoint:rB1->RB1
- su par de clavesper_commitment_point:cB1->CB1Ahora, cuando sea el momento de que Alice construya la transacción de compromiso, enviará a Bob su clave pública del punto de compromiso
CA1. Bob le enviará su clave pública del punto base de revocaciónRB1. Alice ahora puede derivar la clave pública de revocación que se incluirá en la transacción de compromiso de la siguiente manera:Rev_A1 = R_B1 * sha256( R_B1 || C_A1 ) + C_A1 * sha256( C_A1 || R_B1 )Ahora la salida
to_localde Alice se ve así:OP_IF <Rev_A1> OP_ELSE `to_self_delay` OP_CHECKSEQUENCEVERIFY OP_DROP <alice_delayedpubkey> OP_ENDIF OP_CHECKSIGCuando sea el momento de que Alice y Bob actualicen el estado e invaliden el estado antiguo, Alice envía a Bob su clave privada para el punto de compromiso
cA1. Con esta clave, Bob ahora tiene tanto la clave privada del punto de compromiso de AlicecA1como su propia clave privada del punto base de revocaciónrB1, que corresponde a la clave públicaRB1que le envió a Alice anteriormente cuando Alice estaba construyendo la transacción de compromiso. Así que ahora, con estas dos piezas de información, Bob puede derivar la clave privada correspondiente a la clave públicaRev_A1y, por lo tanto, gastar a través de la salida de revocación. Puede calcular la clave privada de la siguiente manera:rev_A1 = r_B1 * sha256( R_B1 || C_A1 ) + c_A1 * sha256( C_A1 || R_B1 )Alice nunca podrá derivar esta clave privada porque no tiene y nunca tendrá la clave privada del punto base de revocación de Bob
rB1.Ahora actualicemos los diagramas del Capítulo 2 para reflejar las nuevas cosas que hemos aprendido en este capítulo.
Estado 1:

Estado 2:

Revisión
- Dos pares de claves se generan al construir las transacciones de compromiso
- Se necesitan las claves privadas de ambos pares de claves para poder gastar desde el camino de revocación
Referencias
- BOLT3: Derivación de
revocationpubkey - LN Things Part 3: Revocation in more detail por nostr:nprofile1qqswrt9pnxatlplu49h6meld8svmwqt87wwvk256rqk07n6eu4qeh5gpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dszpfjtz
- Una
-
 @ 32092ec1:8e9fd13a
2024-11-22 13:14:39
@ 32092ec1:8e9fd13a
2024-11-22 13:14:39As one does when spending the vast majority of their social media time on Nostr, I find myself wondering, why are so many bitcoiners, in particular, not taking Nostr more seriously; what are they missing here? Are they just algo and attention whores who can’t stomach coming to a new platform and being held accountable for posting valuable content? Are they really thinking that by posting on twitter that they are “onboarding the normies”? Were they scared off because the tech wasn’t good in the really early days of Nostr?
It's funny because I also, obviously, think a lot about certain groups of people who also refuse to get into bitcoin in any kind of serious way. Like why isn’t every single libertarian a hard core bitcoiner? How are the gold bugs not getting the value prop that bitcoin is offering? It’s the most powerful weapon that we have ever had to combat war, excessive government spending, money printing, inflation and central banking. I’ve also been listening to some of the people who you would think would be into bitcoin, but somehow only believe in Monero…? hard core Monero maxis? Really?
In a recent interview with Natalie Brunell, Michael Saylor was asked about bitcoin as a store of value asset vs a currency:
“Currency not worth that much… If I said to the richest guy in the world… ‘Hey I have this little token and you can use it to buy coffee, and you don’t have to pay 2% to Visa, you can pay one Satoshi; how much of it do you want to buy?’ ‘Well, I guess I could buy 0.00001% of my wealth…’”
Another good point here by Saylor that helped me connect a couple more dots here.
If bitcoin were not scarce, if it did not comply with Austrian Economic principles, would it be actively taking over the world right now? Would it have grown past its silk road phase of adoption? I’ll speak for myself here, but I know that this is also true for the vast majority of bitcoiners, I came to bitcoin for the Number go Up (NgU) but became passionate about bitcoin for its Freedom go Up (FgU) technology. I was never a Silk Road user and I would have almost certainty stayed within my early conception of bitcoin, which was to equate it to World of Warcraft gold, if I didn’t watch it melt faces as a store of value asset.
But the fact remains that bitcoin is freedom tech. Bitcoin has the potential to increase freedom and sovereignty in a massive way. Will everyone on earth have a UTXO? Probably not. But in the current financial system how many sovereigns are there really? 1? 5? 10? The fact that you have to have defenses strong enough to protect your physical assets (buildings, gold, infrastructure, etc.) in order to protect your wealth, means that only those with the largest militaries in the world can withstand the kinds of attacks that I can easily withstand with a $150 air gapped signing device. Bitcoin is minting sovereigns by the thousands, millions perhaps. But is this why bitcoin adoption is on the rise?
The user experience on Nostr is improving at a rate that has never been seen in any new ecosystem on the internet. I believe that by being open source and interoperable, Nostr tech will win out over centralized platforms. Not just in social media, but in so many other internet applications as well. “Sign in with Nostr” will be the default someday and you will no longer need to sign up for an account for literally every single app in your pocket. You will never again be asked rebuild your contact list or your follower list in order to stay in touch with your friends and family. We are definitely still early to bitcoin, but we are much, much earlier to Nostr.
But the point remains that Nostr is freedom tech. The decentralized nature of relays means that even if I am being censored by one relay, I will always have access to another relay that will not censor me, and I will never again be in a situation where my freedom to speak will be threatened in a serious way. My freedom to hear other points of view, other opinions, contrarian science, foreign concepts, perspectives from other cultures, will never again be taken away. But is this why Nostr will win?
So back to my original question, what gives? Why are more people not coming into bitcoin or Nostr strictly for the freedom tech? I believe the answer is related to censorship. As much as we all know the level to which we can be censored, how many individuals are actively being censored in a major way right now?
When, by governmental decree, the Canadian truckers went from normal law-abiding citizens to being labeled terrorists who needed to be closed off from transacting using the banking system, bitcoin was one of the few escape valves. But if we are being honest, there were a lot of crypto projects that would have offered the same escape valve, including Monero, where they may not have been in a situation where on-chain surveillance companies could be used to track people down. Also, I would have to imagine that cash, as in paper notes and coins, were probably the most widely used way to transact when they were shut off from their bank accounts.
When Twitter kicked Donald Trump, the sitting president of the United States, off of their platform, what were his options? If Nostr existed in its current form, maybe he would have built his own Truth Social Nostr client… it certainly would have cost less to spin up and would have allowed him to start with a bigger user base. But that was literally one person who was censored. How many YouTube channels have been censored? thousands, millions? How many of them had a bad enough experience to leave their subscribers behind? And how many YouTube channels were not censored?
Censorship has been on the rise in a major way over the last several decades. And while some are finally getting the picture that moving to another centralized platform that can also censor them maybe isn’t the best solution, this isn’t happening in a major way to the masses. But censorship can, and it very well may, start happening in a much more significant way in the future… possibly even the near future.
So, if Michael Saylor asks his billionaire buddies how much they would pay to transact freely when they are actively being censored financially, I bet they would answer that question about freedom money a lot differently. And if big tech platforms start censoring their users by the tens or hundreds of millions, I bet that even the normies would see the value of Nostr and the ability to communicate freely.
The good news though, is that I believe we may be moving into a world that is pushing back against the censorship industrial complex. Maybe in 10 years, money and media will be less censored, not more. If that is the case, currency would remain a terrible investment and twitter would remain a public square. But the fact is, that bitcoin and Nostr will both still win in that environment because of their other characteristics. Bitcoin offers inviolable absolute scarcity, something that asset holders have never had access to in the history of humankind. The open-source internet technology that allows social graphs to travel with its users (Nostr) will win because the tech is better, and the user experience is better than its centralized competitors.
Bitcoin and Nostr are freedom tech and they will almost certainly be a major factor in improving freedom around the world. But I believe that they will win because of their better user experience. Bitcoin offers a store of value that no one can violate. Nostr allows builders to capitalize on the advancements of every other builder in the space, meaning that if an open-source feature is rolled out on one client, all the clients will magically have access to that feature.
We’re gonna win freaks. Stay humble, stack sats and zap notes.
871493
-
 @ 599f67f7:21fb3ea9
2024-11-22 10:26:18
@ 599f67f7:21fb3ea9
2024-11-22 10:26:18En el capítulo anterior, aprendimos cómo Alice y Bob abrieron un canal, utilizando transacciones de compromiso que pueden publicarse en la blockchain en cualquier momento para recuperar sus fondos. Pero, por supuesto, las transacciones de compromiso iniciales se vuelven inválidas tan pronto como cambia el estado del canal, en otras palabras, cuando se realiza un pago y el saldo del canal se distribuye de manera diferente entre los participantes del canal. En este capítulo, comenzaremos a aprender cómo Alice y Bob pueden acordar una nueva división de fondos, es decir, cómo dividir el saldo del canal de manera diferente e invalidar las transacciones de compromiso más antiguas que tienen.
💡 Cubriremos cómo funciona esto bajo el paradigma actual de cómo se actualizan los canales, llamado "LN-Penalty", nombrado así por el mecanismo de penalización utilizado para asegurar los fondos contra adversarios maliciosos. Hay una propuesta más nueva llamada "LN-Symmetry" (anteriormente eltoo) que no requiere el mecanismo de penalización para ser segura y simplifica este proceso, pero requiere modificaciones a las reglas de consenso de Bitcoin para funcionar.
Transacciones de compromiso asimétrico
En LN-Penalty, cada participante en un canal tiene una transacción de compromiso que representa el estado del canal. Las transacciones de compromiso que posee cada parte varían ligeramente. La razón de esto es asignar culpa. ¿Por qué es necesario asignar culpa? Porque necesitamos dejar claro qué parte transmitió su transacción de compromiso e identificar a la parte correcta para castigar si han publicado un estado inválido.
Configuración del estado
En el último capítulo, mostramos cómo Alice y Bob intercambiaron sus claves públicas para crear sus transacciones de compromiso iniciales. Echemos un vistazo más de cerca a cómo lucen estas transacciones de compromiso. Para simplificar, supongamos que el saldo total del canal es de 10 BTC y que Alice y Bob tienen cada uno 5 BTC en sus lados del canal. Para configurar sus transacciones de compromiso iniciales, cada parte primero crea una clave privada temporal, para Alice, llamémosla
dA1, para Bob,dB1. También calculan las claves públicas asociadas,PA1para Alice yPB1para Bob. En este punto, cada parte puede construir sus propias transacciones de compromiso. La de Alice se verá así:- Gastará la transacción de financiación.
- Tendrá dos salidas (o más, cuando haya HTLCs. Cubriremos eso en el futuro).
- La salida
to_remoteenviará a Bob sus 5 BTC de inmediato. - La salida
to_localserá más elaborada. Aquí pueden suceder dos cosas. Alice puede enviarse a sí misma los 5 BTC después de un OP_CSVto_self_delayo puede ser gastada por Bob si puede demostrar que tiene la clave privada temporal de AlicedA1.
De manera similar, Bob también puede construir la transacción de compromiso de Alice y proporcionarle su firma para ello. Alice puede firmar esta transacción válida ella misma en cualquier momento y transmitirla a la red, dándole la seguridad que necesita para recuperar sus fondos en caso de que Bob desaparezca.

En este punto, cualquiera de las partes puede transmitir sus transacciones de compromiso para cerrar el canal. Supongamos que Alice transmite la suya. Bob recibirá sus 5 BTC de inmediato. Alice tendrá que esperar el número de bloques
to_self_delayantes de poder usar sus 5 BTC. Sin embargo, no necesita preocuparse por que Bob gaste su salida porque sabe que nunca compartió su clave privada con él.Invalidando el estado antiguo
Ahora Alice quiere enviarle a Bob 1 BTC usando su canal. Así que, al igual que en el paso anterior, cada parte genera nuevas claves privadas (
dA2para Alice,dB2para Bob), calcula las claves públicas asociadas (PA2para Alice,PB2para Bob) y comparte las claves públicas entre sí. Y nuevamente, ambos crean transacciones de compromiso para reflejar el nuevo estado del canal (Alice ahora tiene 4 BTC ya que transfirió 1 BTC a Bob; Bob ahora tiene 6 BTC).El problema, sin embargo, es que Alice todavía tiene su transacción de compromiso del paso anterior, donde tenía 5 BTC, lo cual es más rentable para ella. Para mostrarle a Bob que está invalidando el estado antiguo y comprometiéndose al nuevo estado, necesita enviarle a Bob su clave privada temporal inicial (
dA1). Ahora, dado que Bob tiene esta clave, puede gastar la salidato_selfde Alice si ella alguna vez publica un estado antiguo e inválido, antes de que ella pueda reclamarlo (recuerda que la salidato_localtiene unto_self_delay).Bob también le envía a Alice su antigua clave (
dB1) para invalidar su estado antiguo. No tiene razón para no hacer esto ya que su nuevo estado es más rentable para él.
¡Eso es todo! Ahora hemos aprendido cómo Alice y Bob pueden transaccionar de manera segura estableciendo nuevos estados e invalidando estados antiguos.
Revisión
- Para actualizar el estado, cada participante del canal genera nuevos pares de claves y se envían mutuamente la clave pública.
- Para invalidar el estado, por ejemplo, cuando se realiza una transacción, cada participante del canal actualiza el estado y se envían mutuamente la clave privada del estado anterior.
Referencias
- BOLT3
- LN Things Part 2: Updating State por nostr:nprofile1qqswrt9pnxatlplu49h6meld8svmwqt87wwvk256rqk07n6eu4qeh5gpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dszpfjtz
- eltoo
-
 @ 2fb77d26:c47a6ee1
2024-12-08 21:08:02
@ 2fb77d26:c47a6ee1
2024-12-08 21:08:02****Der Staat geriert sich als Bewahrer von Demokratie und Menschenrechten, als singuläres Modell zur Aufrechterhaltung gesellschaftlicher Ordnung. Dabei haben die Strukturen supranationaler »Global Governance« das Konzept Nationalstaat längst obsolet gemacht. Und auch ein Blick auf das Handeln des Machtapparats Staat lässt begründete Zweifel an dessen öffentlicher Darstellung aufkommen – denn das Kerngeschäft eines jeden Staates besteht aus Unterdrückung, Raub und Mord. **
Mein exklusiver Beitrag für die zweite GEGENDRUCK, die 224 Seiten umfasst, am 15.10.2024 veröffentlicht wurde und unter www.gegendruck.eu bestellt werden kann. Nur durch die Unterstützung von analogen Formaten dieser Art wird aus der Gegenwart eine Vergangenheit, die man in der uns drohenden Zukunft noch zu rekonstruieren vermag. * Original mit Quellen: www.regenauer.press/blog/regieren-ist-ok*
»Wenn das Volk die Regierung fürchtet, haben wir Tyrannei. Wenn die Regierung das Volk fürchtet, haben wir Freiheit« – soll Thomas Jefferson, einer der Gründerväter der USA, dereinst festgehalten haben. Wer sich also in Anbetracht des Status quo noch nicht ganz si-cher ist, mit welchem Herrschaftssystem ihn die kriegslüsterne Biosicherheitsdoktrin der Postmoderne beglückt, mag in Jeffersons Worten entsprechende Inspiration finden. Denn mit Demokratie hat die ohrenbetäubende Kakofonie von Stil-, Rechts- und Sinnbrüchen selbstverständlich nichts zu tun. Die verblassende Pluralismussimulation der zurückliegen-den Dekaden mausert sich zu dem, was mental mobile Staatstheoretiker, Historiker, Philoso-phen, Journalisten und Aktivisten seit langem erwarten – einer offen kriminellen Terrorherr-schaft. Selten war klarer als jetzt: Regieren ist organisierte Kriminalität.
Folgt man Thomas Hobbes und Friedrich Nietzsche, ist der Staat ein »Ungeheuer«. Wäh-rend Hobbes diesen Umstand durchaus goutierte, fand Nietzsche ihn abstoßend. Und zwar zurecht. Denn die repressiven Züge, die das Staatskonzept seit der frühen Neuzeit kenn-zeichnen, sind inhärenter Bestandteil der Politikproduktion. Egal, welche Ideologie ein Staat vertritt, seinen Souveränitätsanspruch kann er nur mit Gewalt durchsetzen. Nach außen mit Krieg, nach innen mit dem auf konstant interpretationsoffener werdenden Gesetzen basieren-den Gewaltmonopol. Im Rahmen seiner Halbwertszeit durchläuft jedes Herrschaftskonstrukt vergleichbare Zyklen. Ist ein Staat gegründet, eine Regierung ausgerufen, institutionalisiert sie das favorisierte politische Modell – Demokratie, Sozialismus, Konservatismus, Libera-lismus, et cetera – und vereinnahmt ihre Untertanen mit Indoktrination, Zugeständnissen und moderater Autonomie. Doch Macht korrumpiert. Und macht gierig. Vor allem in repräsenta-tiven Systemen wie der korporatisierten Sozialdemokratie, wo Einfluss einen monetären Wert darstellt.
Die Folge: Lobbyismus, Korruption, Lagerbildung, Grabenkämpfe und Obszönitäten. Einer Phase relativer Freiheit und Prosperität folgt so bald eine mehr oder weniger harsche »Ent-differenzierung« (Wolfgang Merkel, 2010) – also die Auflösung alter Strukturen, Funktio-nen und Integrationsmechanismen. Die herrschenden »Machteliten« (C. Wright Mills, 1956) grenzen sich nach zwei Seiten ab. Auf der einen von regimetreuen Bewahrern des ursprüng-lichen Konzepts, den Konservativen, auf der anderen von den Gegnern »progressiver« Re-formen. Reformen, von denen zumeist die von wachsender staatlicher Machtfülle benachtei-ligte Bevölkerung betroffen ist. Diese zahlt natürlich auch die Zeche. Rechtsprechung und Medien passen sich diesem zusehends autoritären Umfeld an, um ihre Daseinsberechtigung nicht einzubüßen. Mit dem Implementierungsgrad solcher Reformprojekte aus dem Elfen-beinturm, in der Regel begleitet von ausufernder Bürokratie, wachsen die Widerstände dage-gen. Aus Autokratie wird Totalitarismus. »Erst ist es ein Polizeistaat, dann kommen die Aufstände«. Die »Mistgabeln« (Nick Hanauer, 2014). Aus der Vogelperspektive betrachtet sind es stets die gleichen zivilisatorischen Prozesse. Seit Jahrhunderten. In allen Systemen. Offen ist nur, wie brutal der Staat vorgehen muss, um sich an der Macht zu halten – und wie lange es dauert, bis die Arroganz der wenigen dennoch an der Macht der vielen erstickt.
Denn schlussendlich fällt jedes Imperium. Das lehrt die Geschichte. Hat das System den Zenit überschritten, fällt ob der grotesken Machtexzesse und Schizophrenitäten auch den konformistischsten Etatisten auf, dass die politmediale Schmierenkomödie nichts mehr mit der Realität des eigenen Lebens zu tun hat. Gewalt greift Raum. Psychische Gewalt – und physische. Demnach hat nun zweifelsohne auch der vermeintlich liberale Rechtsstaat der von supranationalen Verordnungen diktierten Gegenwart sein finales Entwicklungsstadium er-reicht: Die Tyrannei.
»Seht uns nur an. Alles ist verdreht, alles steht Kopf. Ärzte zerstören Gesundheit, Anwälte zerstören Gerechtigkeit, Psychiater zerstören Verstand, Wissenschaftler zerstören Wahr-heit, Massenmedien zerstören Information, Religionen zerstören Spiritualität und Regierun-gen zerstören die Freiheit.« (Michael Ellner)
Neu ist das alles nicht. Nur die Darreichungsformen und Machtinstrumente von Herrschaft wandeln sich über die Jahrhunderte. Die disziplinierenden Kontrollmechanismen zur Subor-dination der Massen professionalisieren sich im Rahmen des technologischen Fortschritts. So wirkt der Panoptismus der Postmoderne vor allem deshalb monströs, weil unser Gehirn evolutionär nicht darauf eingestellt ist. Es ist der Militarisierung von Information im Dauer-feuer multimedialer Infantilisierungspropaganda in den wenigsten Fällen gewachsen. Wer versucht, dieser omnipräsenten Pervertierung von Realität mit tradierten Denk- und Hand-lungsmustern zu begegnen, geht unter.
Nicht umsonst klagt der »Widerstand« in weiten Teilen über Erschöpfungszustände, Ver-schleiß, Burnout und Depression. Genau da soll er in Augen des Staatskonzeptes sein – am Ende. Aufgerieben. Entmutigt. Ohnmächtig. Dabei wäre gerade Humor das Patentrezept, um auch düsteren Zeiten ein erfülltes Leben abzugewinnen. Ein freies Leben. Denn frei wird man nicht, frei ist man – oder eben nicht. Freiheit ist eine Geisteshaltung, kein organisatori-sches Problem.
»Unsere Gesellschaft wird von Wahnsinnigen mit wahnsinnigen Zielen geführt. (…) Und ich denke, ich werde als Wahnsinniger eingesperrt, wenn ich das zum Ausdruck bringe. Das ist das Verrückte daran.« (John Lennon)
In diesem Lichte betrachtet nimmt es also kaum Wunder, dass das primäre Ziel der regieren-den Kaste darin besteht, die Bevölkerung in Angst, Armut, Abhängigkeiten und Agonie zu halten. Selbstbestimmte, selbstbewusste Individuen hätten nämlich nicht nur die Zeit, son-dern auch die mentale Kapazität und die Mittel, das Ponzi-Schema des polit-finanziellen Komplexes intellektuell wie organisatorisch zu durchdringen. Dementsprechend ist das Staatskonzept auch nicht darauf ausgelegt, das Individuum zu fördern. Es dient der Imple-mentierung eines konformistischen Kollektivismus. Die Massen sollen sich um die Flagge scharen. Wer kritische Fragen stellt und sich der Polonaise der Gutgläubigen verweigert, gilt als Landesverräter.
Doch nicht nur die vermeintlichen Häretiker sind Opfer staatlicher Willkür und Gewaltherr-schaft. Jeder Bürger stellt per se eine potenzielle Gefahr für die Machthaber dar. Dement-sprechend agiert das »Ungeheuer« Staat. Es führt einen konstanten – mehr oder weniger vernichtenden – Krieg gegen die eigene Bevölkerung. Welche Waffen in diesem Gefecht zum Einsatz kommen, erläutert ein von Wikileaks am 13. Juni 2008 veröffentlichtes Ge-heimdokument der US-Armee vom 20. September 1994. Titel: »Foreign Internal Defense Tactics, Techniques, and Procedures for Special Forces«. Zu Deutsch: Taktiken, Techniken und Verfahren zur internen Verteidigung im Ausland für Spezialeinheiten. Julian Assange nannte es einmal »das wichtigste Dokument, das Wikileaks je veröffentlichte«. Aus gutem Grund. Denn während der Titel des 219 Seiten umfassenden Strategiepapiers darauf abstellt, dass es sich um Arbeitsanweisungen für Spezialeinheiten handelt, die im Ausland operieren, sind die beschriebenen Methoden der asymmetrischen Kriegsführung genau jene, unter de-nen – neben dem Rest der Welt – auch die amerikanische Bevölkerung leidet.
Die US-Armee beschreibt im Detail, wie die verdeckt operierenden Kräfte Regierungen ab-setzen, Oppositionsgruppen infiltrieren, die Bevölkerung manipulieren und Kriege initiieren sollen. Auf Gesetze, Moral oder Kollateralschäden wird dabei keine Rücksicht genommen. Primäres Ziel – koste es, was es wolle – ist die Durchsetzung der Pax Americana im Zielge-biet. Ein paar Zitate verdeutlichen, wie das »Ungeheuer« dabei vorgeht.
»Aufstände sind nicht einfach zufällige politische Gewalt; sie sind gezielte politische Gewalt. Sie erfordern eine Führung, die Vision, Richtung, Anleitung, Koordination und organisato-rische Kohärenz bietet. Die Anführer der Aufständischen müssen ihre Sache dem Volk be-kannt machen und die Unterstützung der Bevölkerung gewinnen. (…) Ihre Ausbildung, ihr Hintergrund, ihre Familie, ihre sozialen Verbindungen und Erfahrungen prägen ihr Den-ken und die Art und Weise, wie sie ihre Ziele erreichen. Diese Faktoren prägen auch ihre Herangehensweise an die Problemlösung.« (S. 13)
»Die Ideologie von Gruppen innerhalb der Bewegung kann auf unterschiedliche Ansichten über strategische Ziele hinweisen. Gruppen können ideologische Konflikte haben, die gelöst werden müssen, bevor ein Gegner daraus Kapital schlagen kann. Die Ideologie kann wahr-scheinliche Ziele und Taktiken nahelegen. Sie beeinflusst stark die Wahrnehmung der Um-gebung durch den Aufständischen. Diese Wahrnehmung der Umgebung wiederum prägt die organisatorischen und operativen Methoden der Bewegung.« (S. 14)
»Wenn eine Situation explosiv ist, kann fast jedes Ereignis als auslösendes Ereignis dienen. Das richtige Timing kann auch in kurzer Zeit eine Flut von Ereignissen hervorrufen, sodass es schwierig ist, ein einzelnes Ereignis als die Handlung zu bezeichnen, die den Kampf aus-gelöst hat. Daher kann es hilfreicher sein, eine Reihe von Handlungen als auslösendes Er-eignis zu betrachten. Auslösende Ereignisse können historisch sein – und die Aufständi-schen erinnern die Bevölkerung an das Ereignis. Diese Technik befreit den Aufständischen davon, auf ein geeignetes Ereignis zu warten.« (S. 18)
»Oft sind es die Armen, die im Krieg kämpfen. CSDF-Programme (CSDF: Civilian Self-Defense Force) bieten der wohlhabenden Klasse die Möglichkeit, direkt und persönlich am Kampf gegen Gesetzlosigkeit und Aufstände beteiligt zu sein. Geschäftsleute und Fachleute beteiligen sich an CSDF aus einem Gefühl der bürgerlichen Pflicht, aus Stolz und aus der Notwendigkeit, ihr Vermögen zu schützen. Ihre aktive Beteiligung verleiht dem Programm Glaubwürdigkeit, stärkt die Legitimität der Regierung und verringert Klassenkonflikte. Wohlhabendes Personal kann bei der Ausstattung seiner Einheiten mithelfen. Es darf ihnen jedoch nicht gestattet sein, den Teilnehmern ein Gehalt zu zahlen.« (S. 128)
»PSYOP-Personal oder in PSYOP ausgebildete SFOD-Mitglieder (SFOD: Special Forces Operational Detachment) erleichtern die Zusammenarbeit zwischen der lokalen Bevölke-rung und dem HN-Militär (HN: Host Nation). Wenn qualifiziertes oder fähiges HN-Personal verfügbar ist, arbeitet das US-Personal durch sie. CSDF-Elemente müssen in der Anwendung von PSYOP geschult werden, um die Bevölkerung über die Vorteile zu informie-ren, die sie durch die Zusammenarbeit mit ihnen erzielen. PSYOP-Themen müssen sich an nationale und/oder fiktive Themen halten, um eine einheitliche Politik darzustellen. Es ist entscheidend, dass PSYOP zunächst an die lokale Bevölkerung gerichtet wird, um ihre Un-terstützung der Aufständischen zu beenden und ihre Akzeptanz und Zusammenarbeit für das CSDF-Programm zu gewinnen. (…) PSYOP kann die Mission unterstützen, indem es die aufständischen Kräfte bei neutralen Gruppen diskreditiert, Zwietracht unter den Auf-ständischen selbst sät und Überläuferprogramme unterstützt. Spaltungsprogramme führen zu Zwietracht, Desorganisation, niedriger Moral, Subversion und Überläufern innerhalb der aufständischen Kräfte. Wichtig sind auch nationale Programme, um Aufständische mit Angeboten von Amnestie und Belohnungen auf die Seite der Regierung zu ziehen. Die Motive für eine Kapitulation können von persönlichen Rivalitäten und Bitterkeit bis hin zu Desillusi-onierung und Entmutigung reichen. Druck seitens der Sicherheitskräfte hat Überzeugungs-kraft. (…) Alle Agenten werden genau beobachtet und diejenigen, die nicht zuverlässig sind, werden abgelöst. Wenige, zielgerichtete, zuverlässige Agenten sind besser und wirtschaftli-cher als viele schlechte. (…) Sicherheitskräfte können Einzelpersonen aus der Bevölkerung dazu bringen, Informanten zu werden. Sicherheitskräfte nutzen verschiedene Motive (Staatsbürgersinn, Patriotismus, Angst, Strafvermeidung, Dankbarkeit, Rache oder Eifer-sucht, finanzielle Belohnungen) als überzeugende Argumente. Sie nutzen die Zusicherung des Schutzes vor Repressalien als Hauptanreiz.« (S. 139, ff)
Zusammengefasst: Die Reichen bezahlen, sorgen für Stimmung und Glaubwürdigkeit, die politische Klasse passt die Vorgehensweise an lokale Strukturen, herrschende Ideologien, Demoskopie und Kommunikationsprozesse an – und die Armen werden zum Sterben an die Front geschickt. Und das sind nur kurze Einblicke in ein über 200 Seiten starkes Handbuch zum Krieg gegen die Zivilbevölkerung, die in Augen des Hegemon offenkundig nichts ande-res als Verfügungsmasse und Kanonenfutter ist. Man möchte Julian Assange beipflichten: Dieses Dokument erklärt nicht nur, warum unsere Gesellschaften, die Wirtschaft und das moralische Koordinatensystem des Homo sapiens in Auflösung begriffen sind – die Skru-pellosigkeit der im Detail beschriebenen Methoden lässt einem das Blut in den Adern gefrie-ren. Selbst nach auszugsweiser Lektüre muss man konstatieren: Nietzsche hatte Recht. Der Staat ist ein eiskaltes Ungeheuer.
Doch was ist der Staat? War es früher das klar erkenntliche Machtvehikel von Monarchen, Imperatoren, Familiendynastien und Klerus, erweckt das Staatskonzept der jüngeren Neuzeit gerne den Eindruck, es hätte sich von dieser Despotie der wenigen gelöst, stünde für sich, auf einem Fundament des Volkswillens, der sich in Verfassungen, Gesetzen und Wahlen widerspiegelt. Weit gefehlt. Auch die »Global Governance« von heute ist nichts anderes als Despotismus. Weithin kontrolliert von den gleichen Bankenkartellen, Familien, Unterneh-men und Organisationen, die seit Generationen den Lauf der Welt bestimmen. Die Regenbo-gen emanierende Pluralismussimulation der Postmoderne verbirgt diesen Umstand nur bes-ser. Sie tyrannisiert indirekt. Köpfe werden nicht mehr abgeschlagen, sondern gewaschen. Exakt so, wie es die angloamerikanischen Vordenker dieses Systems im ausgehenden 19. Jahrhundert insinuierten. Siehe Carroll Quigley, Tragedy and Hope, 1966, Kapitel »The Fu-ture in Perspective«, Seite 1247:
»Das Argument, dass die beiden Parteien entgegengesetzte Ideale und politische Ansichten vertreten sollten, eine vielleicht rechts, die andere links, ist eine törichte Idee, die nur für doktrinäre und akademische Denker akzeptabel ist. Stattdessen sollten die beiden Parteien nahezu identisch sein, sodass das amerikanische Volk die Schurken bei jeder Wahl raus-werfen kann, ohne dass es zu tiefgreifenden oder umfassenden politischen Veränderungen kommt. Die politischen Pläne, die für Amerika lebenswichtig und notwendig sind, sind nicht länger Gegenstand großer Meinungsverschiedenheiten, sondern nur noch in Einzelheiten des Verfahrens, der Priorität oder der Methode umstritten.«
Sodass nach Scheindebatten, Empörungsmanagement und Abstimmungen nicht vom allge-meinen Kurs abgewichen werden muss. Was Quigleys elitäre Zirkel – er war bis zur Veröf-fentlichung von Tragedy and Hope einer von ihnen und unterstützte ihre Ideen – für die Rückführung der 13 US-Kolonien sowie die moderne Expansion des britischen Empire vor-sahen, ist heute zentrales Element der wertewestlichen Fassadendemokratie. Symptombe-sprechung, Lippenbekenntnisse, Emotionsamplituden, »Der Dritte Weg« – »wo soziale Ge-rechtigkeit und Markt miteinander versöhnt werden sollen« – und auch nach der x-ten Wahl bleibt alles beim Alten. Ob Berlin, Brüssel, London, New York, Beirut oder Peking: Ein Potemkin’sches Dorf. Denn wir leben längst in der Idealvorstellung von Benito Mussolini, der den perfekten Faschismus als Korporatismus bezeichnete und als symbiotische Fusion der Macht von Staat und Konzernen verstand. Als »Public Private Partnership«.
»Benito Mussolini hat der modernen Sparpolitik den Weg bereitet und die Arbeiterbewe-gung unterdrückt. Liberale Ökonomen im In- und Ausland bewunderten ihn dafür«, schrieb man bei Jacobin am 6. März 2023. So zeitigt das Staatskonzept dieser Tage die gleichen ver-heerenden Folgen wie die Herrschaftskonstrukte der Vergangenheit. Vertikale Durchlässig-keit begrenzt, das Volk manipuliert, ausgebeutet und gegängelt. Anstelle von Arbeitslagern, Schlägertrupps und Exekutionskommandos machen heute Algorithmen die Drecksarbeit. Sonst hat sich kaum etwas geändert.
Stand heute leben nach Angaben von Oxfam weltweit knapp fünf Milliarden mehr Men-schen in Armut als vor 2020. Das sind die ärmsten 60 Prozent der Menschheit. Zusammen haben sie circa 20 Milliarden US-Dollar verloren. Das Gesamtvermögen der reichsten Deut-schen wuchs im gleichen Zeitraum von 89 auf 155 Milliarden US-Dollar – ein Zuwachs von 73,85 Prozent. Die 148 größten Konzerne der Welt konnten zwischen Juni 2022 und Juni 2023 circa 1,8 Billionen Dollar an Gewinnen verzeichnen – ein Anstieg von 52,5 Prozent gegenüber dem Durchschnitt der Jahre 2018 bis 2021. Der Reingewinn stieg gegenüber die-sem Zeitraum um 20 Prozent auf 700 Milliarden Dollar. Und die fünf reichsten Menschen der Welt haben ihr Vermögen seit 2020 verdoppelt. Wer vom Nachhaltigkeitskorporatismus profitiert, dürfte damit geklärt sein.
Der Normalbürger dagegen kämpft gegen steigende Steuern, Inflation und anziehende Ener-giekosten. In einem luftabschnürenden Korsett von Verträgen, Verpflichtungen und Ver-bindlichkeiten gefangen, bleibt weder Zeit noch Geld für ein Leben in Würde. Der angepass-te Regenbogendemokrat wird geboren, indoktriniert, ausgebeutet und dann bestattet. Indivi-duelle Entfaltung ist in diesem Lebensentwurf von der Stange nicht vorgesehen. Die leitme-dialen Podiumsdiskussionen um Work-Life-Balance, Gendersprache und feministische Au-ßenpolitik klingen in den Ohren der buckelnden Arbeiterklasse – und auch für weite Teilen des schwindenden Mittelstandes – wie blanker Hohn. Das Habitat des Mediazän, das nicht selten den Eindruck erweckt, man lebe in einer fehlerhaft programmierten Simulation, zwingt seinen Bewohner immer häufiger dazu, sich existenziellen Problemen zu stellen: Unterkunft, Nahrung, Fortpflanzung. Überleben.
Noch bezahlt er Jahreslizenzen für Cloud-Software, Netflix für Filme und Streamingdienste für Musik, die er früher erwarb und dann einfach besaß. Noch geht er wählen und entschei-det brav zwischen Pest und Cholera, um vier weitere Jahre nicht die Hoffnung zu verlieren. Noch glaubt, ignoriert oder kommentiert er leidensfähig die intelligenzbeleidigenden Lügen-gebilde, die als Realität vermarktet werden.
Mithin erstaunlich. Denn nicht erst seit der Corona-Krise belegen nackte Zahlen, dass der Mensch in diesem System nicht nur beraubt und unterdrückt, sondern auch als Versuchska-ninchen für den pharmakologisch-finanziellen Komplex missbraucht wird. Nürnberger Ko-dex hin oder her. Während Robert Koch vor der Schaffung dieses vermeintlichen Bollwerks für die körperliche Unversehrtheit noch ungestraft Menschenversuche in seinen kolonialen Konzentrationslagern durchführen durfte, ist das Thema seit Ende des Zweiten Weltkrieges tabu. Gesetzlich eliminiert. Angeblich. Doch bereits in den 1940er Jahren infizierte der US-Gesundheitsdienst Gefängnisinsassen und psychisch kranke Personen mit Syphilis-Erregern. Von 1946 bis 1949 weiteten die USA das Programm auf Guatemala aus und machten sich zusätzlich über Soldaten und Prostituierte her. Das Echo der angelsächsisch geprägten Eugeniklehre hallte im fortgeführten Rassismus nach.
»Schockierende Fälle wie der Tod der 49 Kinder nach Medikamententests in einem indi-schen Krankenhaus sind in der Geschichte der Medizin nichts Neues: In den USA wurde Farbigen zu Studienzwecken von 1932 bis 1972 die Syphilis-Therapie verweigert.« (SZ, Das Verbrechen von Tuskegee, 11. Mai 2010)
Am 20. September 1950 spritzte die US-Marine vor der Küste San Franciscos Mikroben in die Troposphäre, um zu testen, welche Effekte ein Angriff mit Biowaffen auf die damals 800.000 Einwohner der Stadt haben würde. 1953 startete die CIA das MK-Ultra-Programm, in dessen Rahmen abertausenden ahnungsloser Menschen LSD verabreicht wurde. Zwei Jahre später nahm »Project Whitecoat« – Projekt Weißkittel – seine Arbeit auf. Die bestand im Verlauf der folgenden 20 Jahre darin, Menschenversuche mit Hasenpest, Typhus, Gelb-fieber und Milzbrand durchzuführen. Und Ende der 60er testeten die amerikanischen Streit-kräfte Nervengas an den eigenen Soldaten. Der SPIEGEL schrieb diesbezüglich am 10. Juli 2013:
»11. Oktober, 16:25 Uhr, 26 Stunden nach Testbeginn. Kleine blutende Anomalien am lin-ken Bein festgestellt. Subjekt behauptet, es habe seinen Rasierer fallen gelassen und sich dabei ins Bein geschnitten – doch so war es nicht. Er habe seine Sommersprossen damals für Käfer gehalten, sagt Rochelle: »Die krabbelten überall unter meiner Haut herum«. Den Betreuern habe er nichts davon erzählt, es sei ihm peinlich gewesen: »Ich habe meine Ra-sierklinge genommen und versucht, die Käfer aus meiner Haut zu schneiden.« Er war längst nicht mehr selbst dazu in der Lage, die Experimente zu stoppen. Damit war die Ein-verständniserklärung Makulatur. So wie Frank Rochelle ergeht es in Edgewood mehr als 7.800 US-Soldaten; im ganzen Land sind es rund 100.000. Systematisch haben Militär und Geheimdienste die eigenen Leute seit Ende des Ersten Weltkriegs Giften, Gasen, Drogen und Psycho-Kampfstoffen ausgesetzt, darunter LSD, Sarin, Senfgas, BZ, VX, Barbiturate, Amphetamine, Chlorpromazin und immer so weiter. Nachsorgeuntersuchungen? Fehlan-zeige. Erst nach fast sechs Jahrzehnten stoppt das US-Parlament die Menschenversuche im Jahr 1975.«
Ebenfalls bis weit in die 70er hinein injizierte man US-Gefängnisinsassen Pestizide und Herbizide. Mindestens 2.600 Menschen wurden derartigen Versuchen unterzogen. Natürlich musste auch die Atombombe am lebenden Objekt getestet werden. Sowohl Frankreich als auch Großbritannien, die ehemalige Sowjetunion oder die USA schickten Menschen auf die Testgelände. Viele von ihnen segneten danach relativ rasch das Zeitliche. Bis heute kämpfen Bewohner der entsprechenden Landstriche um Entschädigungen, weil sie ihre Krebserkran-kungen der im Umland von Testgebieten gestreuten Strahlung zuschreiben. In den 70ern machte sich der Journalist Paul Jacobs auf eigene Faust daran, die Geschichte der Betroffe-nen zu dokumentieren – um 1978 selbst an Krebs zu sterben. Selbst vor Versuchen an Kin-dern schreckte das »Ungeheuer« nie zurück, wie wiederum der SPIEGEL in Ausgabe 45 vom 2. November 1986 ausführt:
»Dwayne winkte seiner Mutter zu, sie lächelte zurück, dann schloss sich die schwere Eisen-tür hinter dem todkranken Kind. Seit drei Jahren wurde Dwayne Sexton am Strahleninstitut des Atomforschungszentrums Oak Ridge im Bundesstaat Tennessee gegen Leukämie be-handelt. Er hatte eine qualvolle Knochenmark-Transplantation sowie etliche Runden von Chemotherapie hinter sich. Alles war vergeblich geblieben. Als letztes Mittel wollten die Ärz-te nun versuchen, mit massiver Bestrahlung die Krebszellen im Knochenmark des Kindes zu zerstören. Dass diese Methode riskant und – zur damaligen Zeit, 1968 – auch wenig er-probt war, teilten die Ärzte den Eltern des Kindes mit. Was sie aber verschwiegen, war, dass sie auch im Auftrag der amerikanischen Weltraumbehörde NASA arbeiteten. Sie soll-ten herausfinden, wieviel Strahlung Astronauten im All aushalten würden, ohne krank zu werden. Für die von der NASA bestellte Untersuchung erprobten die Ärzte an ihren Patien-ten, so hieß es in einem ihrer Berichte, verschiedene »therapeutische Szenarien, die aus Strahlenmengen im All abgeleitet wurden«. Im Klartext: Nicht allein medizinische Erwä-gungen zum Wohl des Patienten setzten die Höhe der Strahlendosis fest, sondern auch die Bedürfnisse der NASA. In diesem Sinn waren die Patienten lebende Versuchskaninchen.«
Mindestens 23.000 US-Amerikaner wurden von Militäreinrichtungen und Gesundheitsbe-hörden vorsätzlich verstrahlt. Zu Forschungszwecken. »Kalter Krieg gegen US-Bevölkerung« nannte es die taz am 24. Oktober 1994.
»Zwischen 1950 und 1972 finanzierte das Pentagon außerdem fünf klinische Studien über die Aufnahmefähigkeit des menschlichen Körpers von Strahlen, um Aussagen über die psy-chologischen wie biologischen Folgen von Atomexplosionen zu erhalten. Die Versuchsper-sonen waren größtenteils in Armut lebende Schwarze. (…) Bei einem anderen Experiment mussten Soldaten auf Fässern mit radioaktivem Material herumfahren, um zu prüfen, ob ihre Autos sie vor den Strahlen schützten. In Hanford im US-Bundesstaat Washington setz-ten die Militärs absichtlich eine nukleare Wolke frei, um die Verlagerung der Wolke zu un-tersuchen. Aufgrund einer plötzlichen Änderung der Wetterlage fielen die radioaktiven Teil-chen auf einem 300 Kilometer langen und 60 Kilometer breiten Gebiet nieder (…). (jW, 29. August 1997)
Der Umgang mit der indigenen Bevölkerung wirft kein besseres Licht auf die Vereinigten Staaten. Von fünf bis sieben Millionen Ureinwohnern im Jahr 1500 waren im Jahr 1900 noch 237.000 übrig. Ob Hungersnöte, Sklavenarbeit, Massaker, Umsiedlungen oder »Boar-ding Schools« – Umerziehungsinternate: Die aus Großbritannien eingereisten Siedler verüb-ten einen Genozid an den indigenen Stämmen. Nachdem die mageren Reste der stolzen Indi-anervölker in Reservate gepfercht worden waren, suchte der Staat deren Fortpflanzung mit-tels Zwangssterilisation zu verhindern. Mehr als 60.000 Indigene wurden im 20. Jahrhundert einer solch abscheulichen Behandlung unterzogen. Darüber hinaus war das Eugenik-Programm der USA, das erst 1981 endgültig eingestellt wurde, Grundlage für die Rassen-lehre des deutschen NS-Regimes.
Ähnlich ging man in Kanada vor. Seit den 1920er Jahren wurden dort tausende indigene Frauen zwangssterilisiert – bis heute – obwohl die entsprechenden Gesetze mittlerweile ab-geschafft wurden. Die tagesschau vermeldet dazu am 10. März 2024:
»Die Worte des weißen Arztes haben sich Liz (…) ins Gedächtnis gebrannt: »Es ist besser, du stimmst der Abtreibung zu. Denn wir werden dir dieses Baby wegnehmen. So oder so«. Die damals 17-jährige Kanadierin vom indigenen Volk der Anishinabe wagt es nicht, zu widersprechen. Verängstigt sitzt sie Ende der 1970er-Jahre im Behandlungsraum der Indi-an Clinic in der Provinz Ontario, einer Klinik, in der Indigene behandelt werden, damit sie an die sogenannte Zivilisation angepasst werden. (…) Die alleinerziehende Mutter sei nicht in der Lage, für ein weiteres Kind zu sorgen. Der Arzt will ihr deshalb die Eileiter abbinden und sie dadurch sterilisieren. (…) Erst Jahre später wird ihr klar: Sie ist nicht allein. Zehn-tausende indigene Frauen sind in Kanada seit den 1920er-Jahren im Einklang mit der Eu-genik-Gesetzgebung gegen ihren Willen sterilisiert worden. Und obwohl es diese Gesetze nicht mehr gibt, geschieht es bis heute, weiß Senatorin Yvonne Boyer im Kongress in Otta-wa (…). Noch immer ist Zwangssterilisation kein Tatbestand im kanadischen Strafgesetz-buch. (…) Vergangenes Jahr wurde in den Nordwest-Territorien ein Arzt bestraft, weil er 2019 eine Inuit-Frau gegen ihren Willen unfruchtbar gemacht hat. Er verlor seine Lizenz – für fünf Monate.«
Dass sich nicht nur das angloamerikanische Empire für Eugenik begeisterte, zeigt die Ein-richtung des ersten rassenbiologischen Instituts in Schweden im Jahr 1921. Zwischen 1935 und 1976 wurden dort circa 62.000 Menschen zwangssterilisiert. Die offiziellen Begrün-dungen für die Eingriffe reichten von »Mischling« über »Alkoholismus« bis zu »dämlich« und »religiös«. Sprich: Reine Willkür unter dem Deckmantel der Wissenschaft. Legalisiert vom schwedischen Staat.
Heute begegnen uns die staatlich organisierten Eugenik-Programme unter wohlklingenden Labels wie Bioethik, reproduktive Gesundheit, biosoziale Forschung und Bevölkerungspoli-tik. Seit 1954 finden die von den Vereinten Nationen (UN) organisierten Weltbevölkerungs-konferenzen statt. Die letzte im November 2019 in Nairobi (Kenia). Was bei diesen Konfe-renzen besprochen wird, lässt sich anhand eines Artikels des GUARDIAN vom 15. April 2012 oder eines Beitrags von C-Fam (Center for Family and Human Rights) erahnen:
»Großbritannien hat 166 Millionen Pfund (268 Millionen Dollar) für ein Regierungspro-gramm in Indien gespendet, das arme Frauen und Männer zwangssterilisiert. Die britische Hilfsorganisation nannte die Notwendigkeit, dem Klimawandel durch Bevölkerungsreduzie-rung zu begegnen, als Hauptgrund für die Finanzierung des missbräuchlichen indischen Programms (…). Verpfuschte Operationen verursachten Qualen, Blutungen und Todesfäl-le. In einer von der britischen Regierung ins Visier genommenen Region verblutete die 35-jährige Frau eines armen Arbeiters, die mit Zwillingen schwanger war. Einige Frauen, die während der Schwangerschaft sterilisiert wurden, erlitten Fehlgeburten. Einige wurden mit weniger als acht Dollar und einem Sari bestochen, anderen wurde mit dem Verlust ihrer Lebensmittelkarten gedroht. Manchen wurde gesagt, die Operationen dienten der allgemei-nen Gesundheitsfürsorge, und sie erfuhren den wahren Zweck erst zu spät. Kliniken erhiel-ten Prämien für mehr als dreißig Operationen pro Tag. Nichtstaatliche Mitarbeiter wurden für jede Person bezahlt, die sie zu einer Operation überredeten. Ein Chirurg, der in einem Schulgebäude arbeitete, führte in zwei Stunden 53 Operationen durch – ohne qualifiziertes Personal, fließendes Wasser oder Mittel zum Reinigen der Geräte. Berichte der indischen Regierung aus den Jahren 2006 und 2009 warnten vor Problemen mit dem Programm. Dennoch empfahl ein Bericht des britischen Ministeriums für internationale Entwicklung aus dem Jahr 2010 die weitere Unterstützung des Programms mit der Begründung, dass eine Reduzierung der Bevölkerungszahl die Treibhausgase senken würde. (…) Sterilisation ist die häufigste Methode der Familienplanung, die in Phase II des indischen Programms für Reproduktions- und Kindergesundheit eingesetzt wird, das 2005 mit britischer Finanzie-rung begann. Trotz der Enthüllungen im ersten Jahr hat Großbritannien keine Bedingungen an seine Finanzierung geknüpft. (…) Im Juli wird Großbritannien zusammen mit der Bill & Melinda Gates Stiftung einen Familienplanungsgipfel in London ausrichten. Ziel der Veran-staltung ist es, beispielloses politisches Engagement und Ressourcen von Entwicklungslän-dern, Gebern, dem privaten Sektor, der Zivilgesellschaft und anderen Partnern zu generie-ren, um den Familienplanungsbedarf von Frauen in den ärmsten Ländern der Welt bis 2020 zu decken, erklärte das britische Ministerium für internationale Entwicklung. Melinda Gates hielt kürzlich eine Rede, in der sie behauptete, dass die Hilfe bei der Empfängnisver-hütung nichts mit Bevölkerungskontrolle oder Zwangssterilisationsprogrammen zu tun ha-be.« (C-Fam, 2. Mai 2012)
»Familienplanungsbedarf«? Dass solche Programme nichts mit »Bevölkerungskontrolle« zu tun haben, ist eine infame Lüge. Schon die von Julian Huxley verfasste Grundsatzschrift der UNESCO von 1946 spricht davon, dass Eugenik wieder salonfähig gemacht werden muss. »Das Undenkbare wenigstens wieder denkbar machen«, nannte Huxley es damals. So muss auch die ungezügelte Massenmigration als Waffe im mittlerweile allgegenwärtigen Kampf der Kulturen verstanden werden. Dabei ist allerdings nicht die Migration selbst das Problem – denn auch die Migranten sind Opfer dieser Agenda – sondern der jeweilige Auslöser für diese Zuwanderungsströme. Die verarmten, verzweifelten, traumatisierten, mit falschen Ver-sprechungen gelockten und als Spaltpilz missbrauchten Menschen für die Symptome des wertwestlichen Neokolonialismus verantwortlich zu machen, greift zu kurz.
Die chaotischen Zustände auf deutschen, britischen, schwedischen und französischen Stra-ßen sind kein Zufall, sondern gewollt. Das belegt ein Strategiepapier der Vereinten Nationen, das am 21. März 2000 publiziert wurde. Titel des Dokuments: »Replacement Migration: Is it A Solution to Declining and Ageing Populations?« Übersetzt: »Ersatzmigration: Ist sie eine Lösung für schrumpfende und alternde Bevölkerungen?«. Auf 177 Seiten erläutert die Stu-die, wie Frankreich, Großbritannien, Deutschland, Italien, Japan oder Russland zurückge-hende Geburtenraten durch massenhafte Zuwanderung kompensieren sollen. Auf den Seiten 32 und 33 liest man diesbezüglich:
»Abbildung 1 zeigt einen standardisierten Vergleich der Zuwanderungsströme pro Million Einwohner (Stand: 2000). Aus diesem Vergleich geht hervor, dass im Verhältnis zur Lan-desgröße die Zahl der Einwanderer, die im Zeitraum 2000-2050 pro Jahr benötigt wird, um den Bestand der Bevölkerung im erwerbsfähigen Alter zu erhalten (Szenario IV), mit 6.500 Einwanderern auf eine Million Einwohner in Italien am höchsten ist, gefolgt von Deutschland mit 6.000 Einwanderern pro Jahr auf eine Million Einwohner. Von den in die-sem Bericht untersuchten Ländern und Regionen benötigten die Vereinigten Staaten mit et-wa 1.300 Einwanderern auf eine Million Einwohner die geringste Zahl von Einwanderern, um einen Rückgang ihrer Bevölkerung im erwerbsfähigen Alter zu verhindern.«
»Die Zahl der Einwanderer, die notwendig ist, um ein Schrumpfen der Bevölkerung im er-werbsfähigen Alter auszugleichen, übersteigt diejenige, die einen Rückgang der Gesamtbe-völkerung ausgleichen würde, um ein Erhebliches. Ob solche höheren Einwanderungszah-len zu den Optionen gehören, die den Regierungen zur Verfügung stehen, hängt zum großen Teil von den sozialen, wirtschaftlichen und politischen Verhältnissen des jeweiligen Landes beziehungsweise der jeweiligen Region ab.«
Wer also annimmt, dass die Destabilisierungskriege und Raubzüge der NATO-Hegemonie nur dem Zwecke dienten, missliebige Regierungen auszutauschen und der Rohstoffe eines Landes habhaft zu werden, liegt offenkundig falsch. Wenn das wertewestliche Imperium irgendwo Demokratie abwirft, hat es dabei auch die strategischen Ziele globaler Bevölke-rungskontrolle im Blick. Migration als Waffe – gerichtet gegen beide involvierten Parteien. Demnach kann man sich nur wünschen, dass die Gewaltausbrüche zwischen einheimischer Bevölkerung und Migranten in den verschiedenen EU-Ländern rasch ein Ende nehmen und sich die von Verzweiflung herrührende Wut beider Parteien auf das eigentliche Problem fo-kussiert: Die herrschende Kaste und ihr gesichtsloses Imperium supranationaler Organisati-onen.
Wahrlich – die Liste an staatlich organisierten, legitimierten, orchestrierten und geduldeten Gräueltaten ließe sich beliebig lange fortführen. Je nachdem, wie weit man zurückzublicken gedenkt. Viele dieser Verbrechen sind Teil der offiziellen Geschichtsschreibung. Jeder weiß es. Dennoch führt dieses Wissen um die Skrupellosigkeit eines im Kern faschistoiden Sys-tems erstaunlicherweise bis heute nicht dazu, dass sich die Menschheit auf andere Formen des Zusammenlebens, der Verwaltung und Organisation einigt. Noch immer sehnen sich die Massen nach Führung, zentraler Steuerung und Ikonen, die ihnen ein besseres Leben ver-sprechen. Dabei belegt die Zivilisationsgeschichte mehr als eindrücklich, dass es sich um leere Versprechen handelt, dass die Hoffnung auf den edlen Ritter, die rettende Wahl oder eine bessere Zukunft reine Illusion ist. Der Machtapparat Staat dient nur einem einzigen Zweck – dem Erhalt des Machtapparats.
Es bedarf demnach auch keiner Diskussion um marginale Optimierungen des herrschenden Systems. Denn wer nur Symptome behandelt, wird die Ursache der Krankheit nicht eliminie-ren. Es bedarf der konstruktiven Debatte darüber, wie dieses System in Gänze zu ersetzen ist.
Dabei gilt es, eigene Narrative zu entwickeln. Geschichten. Vorstellungen von einer freiheit-lich organisierten Zukunft. Von einem lebenswerten morgen. Für eine Zeit nach dem »Un-geheuer«. Wir brauchen Ideen, von denen wir nachfolgende Generationen begeistern kön-nen. Und damit ist nicht die technische Verbesserung des Smartphones oder eine neue App gemeint, sondern eine Utopie. Denn gegen etwas zu sein, ist einfach. Für etwas zu sein, da-gegen nicht.
So engagieren wir uns längst nicht mehr nur für den Erhalt der Meinungsfreiheit, sondern für die Bewahrung des freien Willens. Denn was im Namen des Staates – »im Namen des Volkes« – und damit im Namen jener Menschen, die den Staat durch Wahl oder Duldung legitimieren, geschah, geschieht und geschehen wird, kann kein emotional gesundes Mitglied unserer Spezies wirklich wollen.
-
 @ 1bda7e1f:bb97c4d9
2024-11-21 04:17:08
@ 1bda7e1f:bb97c4d9
2024-11-21 04:17:08Tldr
- Nostr is an open protocol which is interoperable with all kinds of other technologies
- You can use this interoperability to create custom solutions
- Nostr apps define a custom URI scheme handler "nostr:"
- In this blog I use this to integrate Nostr with NFC cards
- I create a Nostr NFC "login card" which allows me to log into Amethyst client
- I create a Nostr NFC "business card" which allows anyone to find my profile with a tap
Inter-Op All The Things!
Nostr is a new open social protocol for the internet. This open nature is very exciting because it means Nostr can add new capabilities to all other internet-connected technologies, from browsers to web applications. In my view, it achieves this through three core capabilities.
- A lightweight decentralised identity (Nostr keys, "npubs" and "nsecs"),
- A lightweight data distribution network (Nostr relays),
- A set of data interoperability standards (The Nostr Improvement Protocols "NIPs"), including the "nostr:" URI which we'll use in this post.
The lightweight nature is its core strength. Very little is required to interoperate with Nostr, which means many existing technologies can be easily used with the network.
Over the next few blog posts, I'll explore different Nostr inter-op ideas, and also deliver my first small open source projects to the community. I'll cover–
- NFC cards integrated with Nostr (in this post),
- Workflow Automations integrated with Nostr,
- AI LLMs integrated with Nostr.
The "Nostr:" URI
One feature of Nostr is it defines a custom URI scheme handler "nostr:". What is that?
A URI is used to identify a resource in a system. A system will have a protocol handler registry used to store such URI's, and if a system has a URI registered, then it knows what to do when it sees it. You are probably already familiar with some URI schemes such as "http:" and "mailto:". For example, when you click an http link, the system knows that it describes an http resource and opens a web browser to fetch the content from the internet.
A nostr: link operates in the same way. The nostr: prefix indicates a custom URI scheme specifically designed for the Nostr protocol. If a system has a Nostr application installed, that application may have registered "nostr:" in the protocol handler registry. On that system when a "nostr:" URI is clicked, the system will know that it describes a nostr resource and open the Nostr client to fetch the content from the nostr relay network.
This inter-op with the protocol handler registry gives us the power to do nice and exciting things with other technologies.
Nostr and NFC
Another technology that uses URIs is NFC cards. NFC (Near Field Communication) is a wireless technology that enables devices to exchange data over a few centimeters. It’s widely used in contactless payments, access control, and information sharing.
NFC tags are small chips embedded in cards or stickers which can store data like plain text, URLs, or custom URIs. They are very cheap (cents each) and widely available (Amazon with next day delivery).
When an NFC tag contains a URI, such as a http: (or nostr:) link, it acts as a trigger. Tapping the tag with an NFC-enabled device launches the associated application and processes the URI. For example, tapping a tag with "nostr:..." could open a Nostr client, directing it to a specific login page, public profile, or event.
This inter-op allows us to bridge the physical world to Nostr with just a tap.
Many useful ideas
There are many interesting ways to use this. Too many for me to explore. Perhaps some of these are interesting for your next side hustle?
- Nostr NFC "login cards" – tap to log into Amethyst on Android,
- Nostr NFC "business cards" – give to connections so they can tap to load your npub,
- Nostr NFC "payment cards" – integrating lightning network or ecash,
- Nostr NFC "doorbells", "punch cards", "drop boxes", or "dead drops" – put a tag in a specific place and tap to open a location-specific message or chat,
- Integrations with other access control systems,
- Integrations with other home automation systems,
- Many more ...
To start with I have built and use the "login card" and "business card" solutions. This blog post will show you how to do the same.
Nostr Login Card
You can use an NFC card to log into your Nostr client.
Most Nostr clients accept a variety of login methods, from posting your nsec into the app (insecure) to using a remote signer (more secure). A less known but more secure method is to sign into a session with a tap of a specially-configured NFC card. Amethyst is a Nostr client on Android which supports this type of login.
- A secure method for logging in
- Optionally keeps no log in history on the device after logout
- Does not require users to know or understand how keys work
- Keys are kept secure on a physically-separated card to reduce risk of compromise
Nostr devs think that this is useful for anti-establishment actors–Fair enough. For me, I am interested in this login card pattern as it could be useful for rolling out identities within an organisation context with less training (office workers are already familiar with door access cards). This pattern potentially abstracts away key management to the IT or ops team who provision the cards.
I first discovered this when Kohei demonstrated it in his video.
Here's how you set it up at a high level–
- Buy yourself some NFC cards
- Get your Nostr key ready in an encrypted, password protected format called "nencryptsec"
- Write the nencryptsec to the NFC card as a custom URI
- Tap to load the login screen, and enter your password to login
Here it is in detail–
Buy yourself some NFC cards
I found no specific requirements. As usual with Nostr so far, I tried to the cheapest possible route and it worked. Generic brand NFC cards shipped from China, I believe it was 50X for $15 from Amazon. Your mileage may vary.
Get your Nostr key ready
Your key will be saved to the NFC card in an encrypted password-protected format called "nencryptsec". Several applications support this. As we'll be using this to login to Amethyst, we will use Amethyst to output the nencryptsec for us.
- Login to Amethyst with your nsec,
- Open the sidebar and click "Backup Keys",
- Enter a password, and click "Encrypt and my secret key",
- It will add the password-protected key to your clipboard in the format "ncryptsec1...",
- Remember to backup your password.
Write the ncryptsec to the NFC card
- Download the free NFC Tools app to your device, and open it,
- Click "Write" and "Add a record", then click "Custom URL / URI",
- Paste your nencryptsec with the nostr URI in front, i.e. "nostr:ncryptsec1..." and click OK,
- Click "Write". NFC Tools will prompt you to "Approach an NFC tag",
- Place your NFC card against your phone, and it will write to the card,
- Your card is ready.
Tap to load the login screen
Tap the card against your phone again, and your phone should open the login screen of Amethyst and prompt you for your password.
Once you enter your password, Amethyst will decrypt your nsec and log you in.
Optionally, you can also set the app to forget you once you log out.
You have created a Nostr NFC "login card".
Nostr Business Card
You can use another NFC card to give anyone you meet a link straight to your Nostr profile.
I attended Peter McCormack's #CheatCode conference in Sydney and gave a few of these out following the Nostr panel, notably to Preston Pysh where it got some cut through and found me my first 100 followers. You can do the same.
To create your Nostr NFC "business card" is even easier than your NFC "login card".
- Buy yourself some NFC cards,
- Download the free NFC Tools app to your device, and open it,
- Click "Write" and "Add a record", then click "Custom URL / URI",
- Write your npub to the NFC card as a custom URI in the format "nostr:npub1..." (e.g. for me this is "nostr:npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft"),
- Your card is ready.
Give the card to someone who is a Nostr user, and when they tap the card against their phone it will open their preferred Nostr client and go directly to your Nostr profile page.
You have created a Nostr NFC "business card".
What I Did Wrong
I like to share what I did wrong so you don't have to make the same mistakes. This time, this was very easy, and little went wrong. In general
- When password-protecting your nsec, don't forget the password!
- When writing to the NFC card, make sure to use "Custom URI/URL" as this accepts your "nostr:" URI scheme. If you use generic "URI/URL" it won't work.
What's Next
Over my first four blogs I have explored creating a good Nostr setup
- Mined a Nostr pubkey and backed up the mnemonic
- Set up Nostr payments with a Lightning wallet plus all the bells and whistles
- Set up NIP-05 and Lighting Address at my own domain
- Set up a Personal Relay at my own domain
Over the next few blogs I will be exploring different types of Nostr inter-op
- NFC cards integrated with Nostr (this post)
- Workflow Automations integrated with Nostr
- AI LLMs integrated with Nostr
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
GM Nostr.
-
 @ 599f67f7:21fb3ea9
2024-11-20 21:25:38
@ 599f67f7:21fb3ea9
2024-11-20 21:25:38¿Qué es un canal?
Un canal Lightning es simplemente una multifirma 2-de-2 en la cadena. Para abrir un canal, solo enviamos fondos a una transacción multifirma 2-de-2. Esto crea un UTXO y el canal está abierto hasta que este UTXO se gaste. Durante la vida del canal, se crean un montón de transacciones que gastan doblemente la transacción de financiamiento, pero eventualmente una (y solo una) de estas se publicará en la cadena para cerrar el canal. Así que, idealmente, un canal Lightning condensa efectivamente un montón de transacciones en dos transacciones en la cadena: la que lo abre y la que lo cierra. Podríamos decir que así es como Lightning "eleva" las transacciones fuera de la cadena.
Creando un canal
Una transacción de financiamiento para un canal entre Alice y Bob es simplemente una transacción que tiene una salida como sigue:
2 <pubkeyA> <pubkeyB> 2 OP_CHECKMULTISIGDonde
<pubkeyA>es la clave pública de Alice y<pubkeyB>es la de Bob. Entonces, si Alice quiere abrir un canal con Bob, ¿simplemente le envía fondos al script anterior?La respuesta es no, es un poco más complicado que eso. Existe la posibilidad de que Bob desaparezca para siempre y nunca vuelva a firmar ninguna transacción que intente gastar de la transacción de financiamiento. Esto significa que, efectivamente, los fondos de Alice quedarían atrapados en este UTXO para siempre. ¡No es ideal!
Aquí es donde entra una transacción de compromiso. Cubriremos la transacción de compromiso con más detalle en el futuro, pero por ahora lo importante que hay que saber es que una vez que una transacción de financiamiento es confirmada, las transacciones de compromiso definen el estado del canal (es decir, cómo se distribuyen los fondos entre los participantes del canal). Así que, esencialmente, cada transacción de compromiso gasta la transacción de financiamiento como entrada y tiene salidas que definen la distribución de fondos entre los participantes del canal.
Para ver cómo se utilizan estos dos conceptos para negociar la apertura de un canal, se intercambiará una serie de mensajes entre los nodos de Alice y Bob, como se muestra en el diagrama a continuación.

Es un poco como negociar un contrato; cada parte solo firma cuando está contento con los términos. Vamos a revisar cada uno de estos mensajes con más detalle.
open_channel
Alice envía este mensaje a Bob para indicar que quiere abrir un canal con él. Este mensaje contiene varios detalles sobre los requisitos de Alice para el canal. El más importante es
funding_pubkey. Esta es la clave pública que Alice tiene la intención de usar como su clave pública en el script de la transacción de financiamiento.
accept_channel
Si Bob está contento con los requisitos que Alice ha presentado en su oferta de canal, puede enviar de vuelta el mensaje
accept_channel, que también contiene algunos de sus requisitos junto con sufunding_pubkey.
En este punto, Alice tiene todo lo que necesita para construir la transacción de financiamiento. Sin embargo, aún no tiene garantía de que Bob no desaparecerá, lo que haría que sus fondos no se pudieran gastar. Por lo tanto, aún no transmite la transacción de financiamiento. En cambio, lo que necesita es una transacción de compromiso firmada por Bob que gaste de la transacción de financiamiento y divida el saldo del canal en consecuencia. La transacción de financiamiento podría asignar algunos fondos a Bob también, por lo que Bob también querría una transacción de compromiso válida firmada por Alice, en caso de que ella desaparezca.
Entonces, lo que Alice hace ahora es construir la transacción de financiamiento y enviar a Bob el siguiente mensaje:
funding_created

Este mensaje contiene el TXID de la transacción de financiamiento, el índice de salida relevante de la transacción de financiamiento junto con una firma de la transacción de compromiso de Bob. Alice puede construir la transacción de compromiso exacta de Bob utilizando la información que ya conoce.
Ten en cuenta que Bob no puede hacer nada aún con su transacción de compromiso porque está gastando de una transacción que aún no está en la blockchain.
funding_signed

Si Bob está contento, entonces puede enviar a Alice un mensaje
funding_signed, que contiene la firma de Bob para la transacción de compromiso de Alice.Ahora, Alice tiene una transacción de compromiso válida firmada por Bob que puede usar para gastar sus fondos de vuelta a sí misma en caso de que Bob desaparezca. Por lo tanto, es seguro para ella transmitir la transacción de financiamiento.
channel_ready
Tanto Alice como Bob estarán ahora observando la blockchain esperando que la transacción de financiamiento alcance el número deseado de confirmaciones. Una vez que cada uno lo vea, se enviarán mutuamente el mensaje
channel_readyque contiene el ID del canal.
¡El canal ahora está abierto y listo para transacciones!
Revisión
Terminaremos con un breve resumen de los conceptos importantes que hemos aprendido en este capítulo. Siéntete libre de volver aquí en el futuro en caso de que necesites un recordatorio.
- canal: un contrato multifirma 2-de-2 en la cadena utilizado para elevar transacciones fuera de la cadena
- transacción de financiamiento: una transacción multifirma 2-de-2 con un script de salida P2WSH que contiene las claves públicas de ambos participantes del canal
- transacción de compromiso: una transacción que define el estado de un canal, es decir, la distribución de fondos entre los participantes del canal
Referencias
- BOLT2
- LN Things Part 1: Creating a channel por nostr:nprofile1qqswrt9pnxatlplu49h6meld8svmwqt87wwvk256rqk07n6eu4qeh5gpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dszpfjtz
-
 @ ec965405:63996966
2024-11-18 01:44:33
@ ec965405:63996966
2024-11-18 01:44:33Hi everybody,
My name is Miguel, and I'm one of the board members of the International Foster Care Alliance (IFCA)! I am a former foster youth living in Aguadilla, Puerto Rico. I first connected with IFCA around 2016 when Miho brought a group of Japanese foster youth to Oakland, California, to receive community organizer training from California Youth Connection (CYC). At the time, I was studying in Oakland and organizing with my local CYC chapter. I applied for and was accepted for the trip to Japan for the Youth Summit in 2018 and have continued to stay involved ever since. As a board member, I help IFCA with its Arts and Culture programming as well as member engagement.

My Voice, Our Story Upgrade
 My Voice, Our Story is a bilingual blog started by IFCA youth to share stories and thoughts about common themes in foster care, such as aging out of care, normalcy, LGBTQIA+, mental health, and child welfare system reform. IFCA recently received a grant from Yakihonne to pay for six months of server space to upgrade this blog into our own social media network! Now, you can use any Nostr app on a web browser, iOS device, or Android device to connect to it and post your blogs for foster youth around the world to see.
My Voice, Our Story is a bilingual blog started by IFCA youth to share stories and thoughts about common themes in foster care, such as aging out of care, normalcy, LGBTQIA+, mental health, and child welfare system reform. IFCA recently received a grant from Yakihonne to pay for six months of server space to upgrade this blog into our own social media network! Now, you can use any Nostr app on a web browser, iOS device, or Android device to connect to it and post your blogs for foster youth around the world to see.Nostr is a social application protocol that enables our members to share their experiences from foster care on the My Voice, Our Story blog in a fun way. You can connect to the relay with any Nostr application to pull blogs and posts from our relay and, if you are a member of IFCA, post your own! Some Nostr applications have in-app translations that can translate posts to the language of your device, making it a good fit for our network that is spread out across different countries. Also, any youth who wish to remain anonymous can do so because you do not need to provide any personal identifying information to get started on Nostr.
Over the next few weeks, my fellow board members and I will host workshops to show everyone how it works. For now, you can check out this short guide I wrote on how to connect to the relay by clicking here..
You could always reach out to me by email contact@miguelalmodo.com if you have any questions or want to schedule a time for onboarding and further explanation. It might seem complicated at first, but I am confident that our community will quickly adapt. Are you part of IFCA's network? Comment below with the country you are reading this from so other members can see!
-
 @ a39d19ec:3d88f61e
2024-11-17 10:48:56
@ a39d19ec:3d88f61e
2024-11-17 10:48:56This week's functional 3d print is the "Dino Clip".

Dino Clip
I printed it some years ago for my son, so he would have his own clip for cereal bags.
Now it is used to hold a bag of dog food close.
The design by "Sneaks" is a so called "print in place". This means that the whole clip with moving parts is printed in one part, without the need for assembly after the print.
 The clip is very strong, and I would print it again if I need a "heavy duty" clip for more rigid or big bags.
Link to the file at Printables
The clip is very strong, and I would print it again if I need a "heavy duty" clip for more rigid or big bags.
Link to the file at Printables -
 @ dbfa19e3:debb6089
2024-12-08 19:27:16
@ dbfa19e3:debb6089
2024-12-08 19:27:16https://www.piecover.com/2024/12/how-to-use-bitcoin-to-escape-war-and.html A lot of countries in the world are becoming more tyrannical as the governments are becoming more desperate for money to fund wars, social programs and other pet projects they invented. In many cases people find themselves stuck paying for a war they know nothing about and have nothing to do with, they pay for it in forms of hyperinflation(higher price for everything) since the currency is being printed at scale to pay for everything, while costing the people their friends and family members and even their own lives in the process, with no fault of their own. But there is hope, we are going explore a way people can use to protect themselves and their love ones.
Bitcoin is a financial tool for freedom and self-preservation, it is the easiest way you can: save, protect, invest and increase the value of your money overtime. There are a lot of people who have used Bitcoin to save their lives under hyperinflationary economies such as the author of one of the most popular Bitcoin book "The Bitcoin Standard" - Saifedean Ammous, he used Bitcoin to save his life under hyperinflation in Lebanon. You can do the same thing for yourself and your family by simply converting your local currency to bitcoin, write down your pass phrase and store it somewhere safe or memorize it if you can, it will be there for you whenever wherever you need it, in contrast to cash, gold or a bank account that can be taken away from you at the airport or at the border, once you get to your destination country you can use any phone with a wifi connection to download your money and exchange it for what you need to sustain yourself. You can use any of these bitcoin wallet to regain access to your bitcoin: Blue Wallet, Green Wallet, Aqua Wallet, Sparrow Wallet, Phoenix Wallet, etc. Need an easier way to use bitcoin? If you worry about losing your pass phrase you can simply backup your bitcoin access key by just using your email address as your credential on: Muun Wallet, WalletofSatoshi, blinkwallet, etc. Please share this with a dear friend! -
 @ fd208ee8:0fd927c1
2024-11-17 09:14:56
@ fd208ee8:0fd927c1
2024-11-17 09:14:56You don't understand how insidious open-borders propaganda is, until you realize that it's an attempt to remove all differentiating traits from humans. They call this "strengthening individuality by removing nationality" (hello, newspeak), but what makes humans individual is their particular collection of traits, and nationality (and ethnicity, religion, etc. -- nationality is just the first domino they want to topple) is one of those.

Humans are not blank slates. Like DNA or physiognomy, our personalities are differing jumbles of cultural "letters". Each person selects consciously and subconsciously from amongst these letters, adding to or rejecting them, amplifying or suppressing them, twisting or combining them, building on top of them... and that's what makes you into You.
Open borders is an attempt to reduce the number of cultural letters you can build your "You" out of. If you take away the word "German", I am not liberated. There is simply one less adjective, with which I can describe myself. You have merely eradicated information, crippled language, and reduced my choices. I can then no longer define myself according to "German things", but I can also no longer define myself in opposition to German things.
Enter the Borg

We are easier to control and brainwash and persecute, if we are centralized and homogenized. As if the entire world were one, big prison and we were all forced to undergo the same education, wear the same clothes, follow the same rules, eat the same foods, enjoy the same entertainment, live the same lifestyle, share the same diseases and cures, enjoy the same lockdowns, join in the same cancel culture, fight the same wars.
That is what globalization brings. That is the end game of Open Borders: * No more cultural evolution or revolution. * Genes, but no memes. * You can go everywhere, but everywhere is the same, so you just stay home. * You can meet people from all over, but they are all the same, so you just don't bother. * One mass of humanity, that can be easily molded and manipulated.
-
 @ 592295cf:413a0db9
2024-11-16 10:40:22
@ 592295cf:413a0db9
2024-11-16 10:40:22Week 11-11
Lamenting is becoming something I should ask people who complain. Charity bussiness and after sending zap received to those who do not complain...
I started making an RSS feed template. Open an opml file and check the feed. I called this script,Teed.
This morning I saw a bounty from a fiatjaf note, on a rss-feed long form, basic a plugin for an app. But I'm not doing that, of course, I can also publish it as soon as I'm in charge. Maybe I have some opml files and I want to see if these are still active.
Starter pack is not good apparently creates elites and maybe gives you the feeling of not choosing, but that's what people want. Do not choose but have the illusion of choosing.
Toxicity level. high.
P2P stuff, Iroh is a protocol for syncing & moving bytes iroh computer post on Bluesky
Juraj new project
nostr:nevent1qvzqqqqqqypzpk4kccr9csumnwhmpv83ladqc6p88089cx2e5s2c4448ppgl2pakqqsyv4hs424x6c8phks903s595q2lqp5fpwyq7ajwrf00lxev8cfamcvmq23h
Alex Gleason bunker Knox. (Beta) "knox is a new Nostr bunker CLI for running a NIP-46 remote signer and granting credentials to members of your team". Announcing bunker knox article
Local First podcast, web2.5. Something like Nostr but Local P2P, interesting episode. youtube link
Open Secret AI. "OpenSecret is a backend for app developers that turns private encryption on by default." announcment AI
I think users with regard to algorithms do not want ten different feeds to choose from, but that their feed adapts to their choices, training the feed if this makes sense. So the feed is your feed for your choices, respond and train with them.
Pleblab 2, cool "ANNOUNCING TOP BUILDER SEASON 2! " nostr:nevent1qvzqqqqqqypzpmx02p4slzahlf7jlcaspsx57g6uc7kl7cc7dvhlsnqtpn6khjj0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgwwaehxw309ahx7uewd3hkctcqyzy9w0frd802hfmrp45jr6dqhf7umqj7s63z0jvhv7hvvkcsqjg0vjwd7q4)
It was the real Guardian, quit 7fqx, we know it's you who want to distract us from number go up. The Guardian has left or wants to leave twitter is looking for alternatives, but how to verify a high profile user on Nostr? Nostr Address is already something but it's not enough.
We sometimes think that there is the money tree somewhere is that they magically appear, when instead the money is in the ground but they are dirty.
If Amethyst doesn't support is others stuff
People are simple, they want an app that works for all devices they have. People are "flutter-system".
A podcast feed xml file
Add to teed, if only i had made that option, meanwhile i saw a new interesting project
An other RSS feed github project
Imagine making a file opml with categories and those are your follow nostriches.
The problem is this does not bring new sap to the social chart is important to you, receive the selected posts and it is fantastic. You can also not use Nostr, if you want to use it as backup is fine. Share opml files? It's okay, but you can also find specific sites and find the best. Update for clients, you have a lot of RSS feeds from clients but update after a few hours so if there is really an emergency you lose. I still need to figure out how to integrate Nostr into RSS feed. Maybe an event to make your lists known.
I saw the event in these pr: nostr verified podcast nip #1465 Add audio track NIP #1043
-
 @ 349d6b82:12b2a5b1
2024-12-08 17:16:55
@ 349d6b82:12b2a5b1
2024-12-08 17:16:55Все уже не понаслышке знают о Дмитрии Александровиче Кузнецове - Признанный волонтер Серова, который внес неимоверный вклад в наш город и который является примером для подражания у многих молодых ребят. Сегодня мы обсудим одни из самых запоминающих, грустных, значимых событий из жизни Дмитрия Александровиче и окунемся в его профессиональную деятельность.
-
 @ 41fa852b:af7b7706
2024-12-08 16:53:33
@ 41fa852b:af7b7706
2024-12-08 16:53:33"I wish I bought less bitcoin" --Nobody Ever
Yes I know it's 100,000 USD, not GBP!
But it's a big round number and I'm used to looking at the price in dollars.
I thought as a way to celebrate we might have a little fun competition. The first person to crack the cipher below and reply to this email (you need to be subscribed to have received the email) with the decoded message will win 10,000 sats!
uwnafhd nx sjhjxxfwd ktw fs tujs xthnjyd ns ymj jqjhywtsnh flj uwnafhd nx sty xjhwjhd f uwnafyj rfyyjw nx xtrjymnsl tsj itjxsy bfsy ymj bmtqj btwqi yt pstb gzy f xjhwjy rfyyjw nx xtrjymnsl tsj itjxsy bfsy fsdgtid yt pstb uwnafhd nx ymj utbjw yt xjqjhynajqd wjajfq tsjxjqk yt ymj btwqi
If enough of you enjoy it, we'll do it again.
Good luck, and let's check out what's on this week.
If you've enjoyed the newsletter and find it valuable to you and the UK Bitcoin community, please consider donating some sats here.
This week's sponsor is…
Upcoming Bitcoin Meetups
Happening this week…
-
Dundee Bitcoin: Join them on the 2nd Monday of every month from 5:30 to 8:30 PM at The Wine Press, 16 Shore Terrace, Dundee DD1 3DN. This month's meetup is on Monday, 9th December.
-
Glasgow Bitcoin: Meeting this month at Committee Room No. 9, G1 1JQ on Wednesday 11th at 18:00.
-
Bitcoin Beach Bournemouth: Every second Thursday of the month at Chaplins Cellar Bar. 529 Christchurch Road, Boscombe, United. You'll find them in the Cogg Room at 19:30. This month it's the 12th.
-
Limerick Bitcoiners: Back with another meetup after a break. Meeting at 20:00 on the 13th. DM them on Twitter/X using the link to get info on the location.
-
Bitcoin Walk - Edinburgh: Every Saturday they walk around Arthur's Seat in this historic city. Join them at 12 pm to chat about all things Bitcoin and keep fit.
-
Kent Bitcoin: These guys will be at The Muggleton Inn on Sunday 15th at 12:00. The Muggleton Inn, 8--9 High Street, Maidstone, ME14 1HJ.
-
Northants Bitcoin Walk: As you'll see below in the 'new businesses' section, Northamptonshire has a new bitcoin-accepting cafe. This month the Northants Walk will start at the Ark Cafe at 11:00, with a walk along the River Nene and back to the cafe for refreshments afterwards. Let's pray for some good weather.
-
Bitcoin East: Join Bitcoin East in Bury St. Edmunds on December 15th, 11:00 at Procopio's Pantry. They'll then be moving on to Vespers Bar, IP33 3PH, at 12:00. All welcome, Bitcoiners and anyone else curious about Bitcoin.
New Businesses Accepting Bitcoin
- The Ark Cafe - Northampton: An amazing custom-made floating cafe in Northampton. A vegan cafe at weekends, Saturday 10:00 - 15:00 and Sunday 11:00 - 15:00 and available for event hire for parties, conferences, weddings etc. The main hall can accommodate up to 45 guests for a sit-down meal or up to 65 for a more informal get-together. Contact them on Twitter/X for more info.
Upcoming Special Events
This event isn't happening this week, but it's important to add to your calendar now as tickets are selling fast.
- Bitcoin Surrey & Berkshire Bitcoiners: A joint Christmas Dinner and 100k Party on Tuesday, 17th December, at Yiayias at The Fox (GU10 3PH). Dinner starts at 19:30, featuring award-winning Greek cuisine and the option of a Festive Meze or a Traditional Christmas menu. Kirit Magic will perform exclusive Bitcoin-themed close-up magic at 18:00. Tickets are £35 per person, with a £15 deposit required by 10th December via the Lightning Network. The venue accepts Bitcoin for drinks and dinner balances, so bring your Lightning wallet. Free parking is available, and kids are welcome.
Get Involved
- Volunteer Opportunities: Bridge2Bitcoin is actively seeking volunteers who share our passion for merchant adoption. We'd be delighted to connect if you're eager to contribute. Reach out to us on Twitter or through our website.
- Start Your Own Meetup: Interested in launching a Bitcoin meetup? We're here to support you every step of the way. We've assisted numerous UK Bitcoin meetups in getting started. Get in touch via Twitter.
- Contribute to BTCMaps: BTCMaps is a vital part of the Bitcoin ecosystem. It's a perfect project to get involved with if you're not a coder or even that technical. A great way to give back to the community. Maintain an area of the UK and keep it up-to-date.
- Telegram users: You might find our Telegram Channel another useful way to keep up-to-date with UK meetups.
- Feedback and Suggestions: We value your input! Share your ideas on how we can enhance this newsletter.
This week's sponsors are…
Get out and support the meetups where you can, visit Bitcoin Events UK for more info on each meetup and to find your closest on the interactive map.
Stay tuned for more updates next week!
Simon.
-
-
 @ 07907690:d4e015f6
2024-11-15 10:10:05
@ 07907690:d4e015f6
2024-11-15 10:10:05PGP (Pretty Good Privacy) adalah protokol enkripsi yang digunakan untuk memastikan kerahasiaan, integritas, dan otentikasi data dalam komunikasi digital. Diciptakan oleh Phil Zimmermann pada tahun 1991, PGP menggunakan kombinasi teknik kriptografi asimetris (kunci publik dan kunci privat) serta simetris untuk melindungi informasi. Berikut adalah berbagai kegunaan PGP:
Mengamankan Email (Enkripsi dan Dekripsi)
-
Kegunaan: Melindungi isi email agar hanya penerima yang memiliki kunci privat yang benar yang dapat membacanya.
-
Cara Kerja:
-
Pengirim mengenkripsi email menggunakan kunci publik penerima.
-
Hanya penerima yang memiliki kunci privat yang dapat mendekripsi dan membaca email tersebut.
-
Contoh: Jurnalis yang berkomunikasi dengan informan atau organisasi yang mengirim data sensitif dapat menggunakan PGP untuk melindungi komunikasi mereka dari penyusup.
Tanda Tangan Digital (Digital Signature)
-
Kegunaan: Memastikan keaslian dan integritas pesan atau dokumen, memastikan bahwa pesan tidak diubah dan benar-benar berasal dari pengirim yang sah.
-
Cara Kerja:
-
Pengirim membuat tanda tangan digital menggunakan kunci privatnya.
-
Penerima dapat memverifikasi tanda tangan tersebut menggunakan kunci publik pengirim.
-
Contoh: Digunakan untuk memverifikasi keaslian dokumen hukum, email penting, atau perangkat lunak yang diunduh.
Melindungi File dan Dokumen
-
Kegunaan: Mengenkripsi file sensitif agar hanya orang yang memiliki kunci dekripsi yang benar yang dapat membukanya.
-
Cara Kerja: File dienkripsi menggunakan kunci publik penerima, dan penerima menggunakan kunci privatnya untuk mendekripsinya.
-
Contoh: Perusahaan dapat menggunakan PGP untuk mengenkripsi laporan keuangan, data pelanggan, atau informasi penting lainnya sebelum membagikannya.
Mengamankan Backup Data
-
Kegunaan: Mengenkripsi cadangan data penting untuk melindunginya dari akses yang tidak sah.
-
Cara Kerja: File backup dienkripsi dengan PGP sebelum disimpan, sehingga meskipun backup dicuri, data tetap aman.
-
Contoh: Organisasi menyimpan cadangan data klien di server eksternal yang dienkripsi dengan PGP untuk mencegah kebocoran data.
Perlindungan Identitas dan Anonimitas
-
Kegunaan: Melindungi identitas pengirim dan penerima dalam komunikasi online.
-
Cara Kerja: Penggunaan enkripsi end-to-end menjamin bahwa hanya pihak yang berwenang yang dapat membaca pesan.
-
Contoh: Aktivis atau peneliti yang bekerja di negara dengan pengawasan ketat dapat menggunakan PGP untuk melindungi komunikasi mereka.
Memverifikasi Integritas Perangkat Lunak
-
Kegunaan: Memastikan bahwa perangkat lunak atau paket yang diunduh berasal dari sumber yang terpercaya dan tidak dimodifikasi oleh pihak ketiga.
-
Cara Kerja: Pengembang menandatangani perangkat lunak menggunakan kunci privat mereka, dan pengguna dapat memverifikasi tanda tangan menggunakan kunci publik yang disediakan.
-
Contoh: Distribusi Linux atau aplikasi open-source sering kali menyertakan tanda tangan PGP untuk memverifikasi keasliannya.
Komunikasi di Forum atau Jaringan Terdistribusi
-
Kegunaan: Memastikan privasi komunikasi di platform terdesentralisasi atau anonim.
-
Cara Kerja: Pesan dienkripsi sebelum dikirim dan hanya dapat didekripsi oleh penerima yang sah.
-
Contoh: Pengguna di forum yang membahas topik sensitif dapat menggunakan PGP untuk melindungi identitas mereka.
Mengapa PGP Penting?
- Keamanan yang Kuat: Kombinasi kriptografi asimetris dan simetris membuat PGP sangat sulit ditembus oleh peretas.
-Privasi: Menjaga komunikasi Anda tetap aman dan pribadi dari penyadapan atau pengawasan.
-
Integritas: Memastikan bahwa pesan atau data yang dikirim tidak diubah selama transmisi.
-
Otentikasi: Membuktikan identitas pengirim melalui tanda tangan digital.
Kelebihan PGP
-
Sangat Aman: Jika digunakan dengan benar, PGP menawarkan tingkat keamanan yang sangat tinggi.
-
Terbuka: Banyak digunakan di kalangan profesional dan komunitas open-source.
-
Fleksibel: Dapat digunakan untuk berbagai keperluan, mulai dari komunikasi email hingga penyimpanan data.
Kekurangan PGP
-
Kompleks untuk Pemula: Relatif sulit digunakan oleh pengguna awam.
-
Pengelolaan Kunci yang Rumit: Memerlukan pengelolaan kunci publik/privat yang benar.
-
Tidak Ada Pemulihan Data: Jika kunci privat hilang, data yang dienkripsi tidak dapat dipulihkan.
PGP adalah alat yang sangat berguna untuk memastikan keamanan dan privasi dalam komunikasi dan data. Dengan meningkatnya risiko kejahatan siber, penggunaan PGP menjadi semakin penting, terutama di sektor yang menangani data sensitif.
-









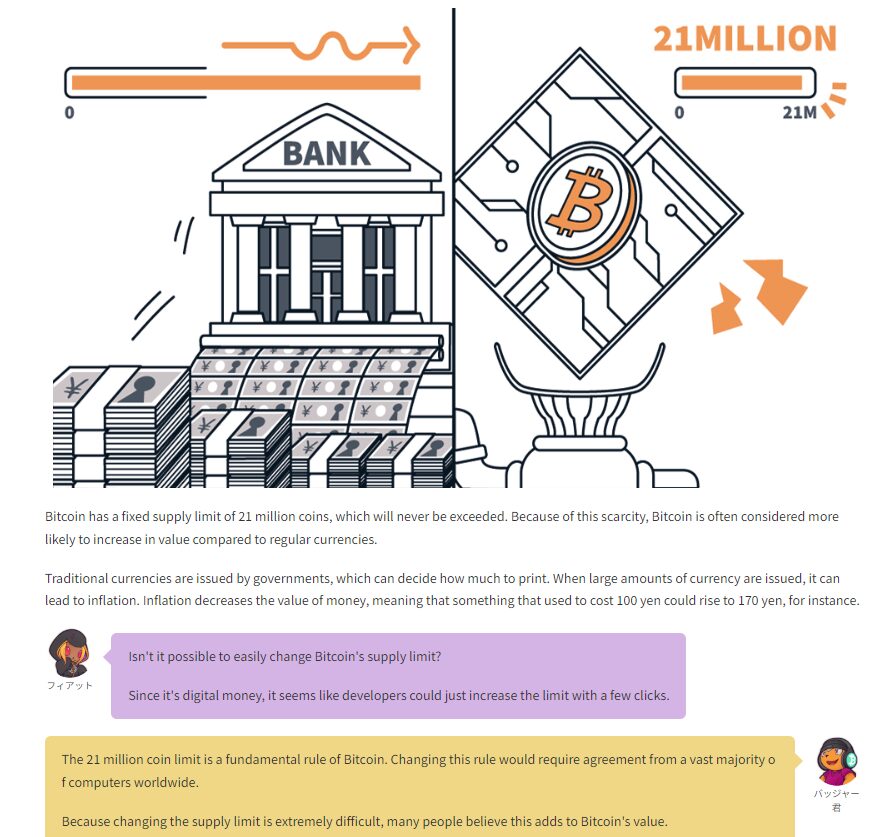 Image credits:
Image credits:



