-
 @ 9f94e6cc:f3472946
2024-11-21 18:55:12
@ 9f94e6cc:f3472946
2024-11-21 18:55:12Der Entartungswettbewerb TikTok hat die Jugend im Griff und verbrutzelt ihre Hirne. Über Reels, den Siegeszug des Hochformats und die Regeln der Viralität.
Text: Aron Morhoff
Hollywood steckt heute in der Hosentasche. 70 Prozent aller YouTube-Inhalte werden auf mobilen Endgeräten, also Smartphones, geschaut. Instagram und TikTok sind die angesagtesten Anwendungen für junge Menschen. Es gibt sie nur noch als App, und ihr Design ist für Mobiltelefone optimiert.
Einst waren Rechner und Laptops die Tools, mit denen ins Internet gegangen wurde. Auch als das Smartphone seinen Siegeszug antrat, waren die Sehgewohnheiten noch auf das Querformat ausgerichtet. Heute werden Rechner fast nur noch zum Arbeiten verwendet. Das Berieseln, die Unterhaltung, das passive Konsumieren hat sich vollständig auf die iPhones und Samsungs dieser Welt verlagert. Das Telefon hat den aufrechten Gang angenommen, kaum einer mehr hält sein Gerät waagerecht.
Homo Digitalis Erectus
Die Welt steht also Kopf. Die Form eines Mediums hat Einfluss auf den Inhalt. Marshall McLuhan formulierte das so: Das Medium selbst ist die Botschaft. Ja mei, mag sich mancher denken, doch medienanthropologisch ist diese Entwicklung durchaus eine Betrachtung wert. Ein Querformat eignet sich besser, um Landschaften, einen Raum oder eine Gruppe abzubilden. Das Hochformat entspricht grob den menschlichen Maßen von der Hüfte bis zum Kopf. Der TikTok-Tanz ist im Smartphone-Design also schon angelegt. Das Hochformat hat die Medieninhalte unserer Zeit noch narzisstischer gemacht.
Dass wir uns durch Smartphones freizügiger und enthemmter zur Schau stellen, ist bekannt. 2013 wurde „Selfie“ vom Oxford English Dictionary zum Wort des Jahres erklärt. Selfie, Selbstporträt, Selbstdarstellung.
Neu ist der Aufwand, der heute vonnöten ist, um die Aufmerksamkeitsschwelle der todamüsierten Mediengesellschaft überhaupt noch zu durchbrechen. In beängstigender Hypnose erwischt man viele Zeitgenossen inzwischen beim Doomscrollen. Das ist der Fachbegriff für das weggetretene Endloswischen und erklärt auch den Namen „Reel“: Der Begriff, im Deutschen verwandt mit „Rolle“, beschreibt die Filmrolle, von der 24 Bilder pro Sekunde auf den Projektor gewischt oder eben abgespult werden.
Länger als drei Sekunden darf ein Kurzvideo deshalb nicht mehr gehen, ohne dass etwas Aufregendes passiert. Sonst wird das Reel aus Langeweile weggewischt. Die Welt im Dopamin-Rausch. Für den Ersteller eines Videos heißt das inzwischen: Sei der lauteste, schrillste, gestörteste Marktschreier. Das Wettrennen um die Augäpfel zwingt zu extremen Formen von Clickbait.
15 Sekunden Ruhm
Das nimmt inzwischen skurrile Formen an. Das Video „Look who I found“ von Noel Robinson (geboren 2001) war im letzten Jahr einer der erfolgreichsten deutschen TikTok-Clips. Man sieht den Deutsch-Nigerianer beim Antanzen eines karikaturartig übergewichtigen Menschen. Noel wird geschubst und fällt. Daraufhin wechselt das Lied – und der fette Mann bewegt seinen Schwabbelbauch im Takt. Noel steht wieder auf, grinst, beide tanzen gemeinsam. Das dauert 15 Sekunden. Ich rate Ihnen, sich das Video einmal anzuschauen, um die Mechanismen von TikTok zu verstehen. Achten Sie alleine darauf, wie vielen Reizen (Menschenmenge, Antanzen, Sturz, Schwabbelbauch) Sie in den ersten fünf Sekunden ausgesetzt sind. Wer schaut so was? Bis dato 220 Millionen Menschen. Das ist kapitalistische Verwertungslogik im bereits verwesten Endstadium. Adorno oder Fromm hätten am Medienzeitgeist entweder ihre Freude oder mächtig zu knabbern.
Die Internet- und Smartphoneabdeckung beträgt mittlerweile fast 100 Prozent. Das Überangebot hat die Regeln geändert. Um überhaupt gesehen zu werden, muss man heute viral gehen. Was dafür inzwischen nötig ist, spricht die niedrigsten Bedürfnisse des Menschen an: Gewalt, Ekel, Sexualisierung, Schock. Die jungen Erwachsenen, die heute auf sozialen Netzwerken den Ton angeben, haben diese Mechanismen längst verinnerlicht. Wie bewusst ihnen das ist, ist fraglich. 2024 prallt eine desaströse Bildungssituation samt fehlender Medienkompetenz auf eine egomanische Jugend, die Privatsphäre nie gekannt hat und seit Kindesbeinen alles in den Äther ballert, was es festhalten kann. Man muss kein Kulturpessimist sein, um diese degenerative Dynamik, auch in ihrer Implikation für unser Zusammenleben und das psychische Wohlergehen der Generation TikTok, als beängstigend zu bezeichnen.
Aron Morhoff studierte Medienethik und ist Absolvent der Freien Akademie für Medien & Journalismus. Frühere Stationen: RT Deutsch und Nuoviso. Heute: Stichpunkt Magazin, Manova, Milosz Matuschek und seine Liveshow "Addictive Programming".
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ 41e6f20b:06049e45
2024-11-17 17:33:55
@ 41e6f20b:06049e45
2024-11-17 17:33:55Let me tell you a beautiful story. Last night, during the speakers' dinner at Monerotopia, the waitress was collecting tiny tips in Mexican pesos. I asked her, "Do you really want to earn tips seriously?" I then showed her how to set up a Cake Wallet, and she started collecting tips in Monero, reaching 0.9 XMR. Of course, she wanted to cash out to fiat immediately, but it solved a real problem for her: making more money. That amount was something she would never have earned in a single workday. We kept talking, and I promised to give her Zoom workshops. What can I say? I love people, and that's why I'm a natural orange-piller.
-
 @ 8cb60e21:5f2deaea
2024-09-10 21:14:08
@ 8cb60e21:5f2deaea
2024-09-10 21:14:08 -
 @ 8cb60e21:5f2deaea
2024-09-06 22:23:03
@ 8cb60e21:5f2deaea
2024-09-06 22:23:03 -
 @ 2efaa715:3d987331
2024-12-21 16:54:55
@ 2efaa715:3d987331
2024-12-21 16:54:55More than you wanted to know about a little-understood but important aspect of diet and health, explained in a nontechnical manner, with oversimplifications abound.
Your cells need some kind of fuel to function. this fuel can only come (ultimately) from the outside world as food. AKA "diet". your blood carries the fuel to the cells so they can do their work. on most diets, the main fuel for cells is glucose, which the body derives from sugar or carbohydrates (which are basically sugar + some complexity). on other diets, the main fuel for cells is fat. on these diets, fat/lipid particles are carried on little blood ferries called lipoproteins (the final "L" in LDL and HDL). LDL carries lipids to your cells so they can use it, HDL carries unused lipids away from your cells (to the liver) so they can be disposed of. (on both very high carb and very low carb diets, your cells will still use some amount of both glucose and fat for energy, but the ratio will change dramatically).
Naturally, if you have a lot of these ferries in your blood (because you are using fat as cell-fuel), your LDL and HDL counts ("total cholesterol") will be high on basic blood tests.LDL - the ferries that carry fats to your cells to burn - come in two varieties: - small + dense - large + fluffy
both carry fuel to your cells, but the small/dense ones have an unfortunate side-effect of slamming into artery walls, penetrating them, and accidentally depositing their lipids there. This is the "plaque" of cardiovascular disease fame. The large, fluffy particles do not penetrate the arterial walls as readily - they bounce off and keep going on to their destinations. their effect on arterial plaque is not zero, but far less impactful than small, dense particles.In either case, the HDL particles are always good: they remove excess lipids from the body. this is why HDL is "the good cholesterol". There are advanced blood tests available which measure particle size (so, like, an acutally useful test), but odds are your doctor will refuse to order this test. Strange!
We didn't mention Triglycerides yet. Suffice it to say that more triglycerides = smaller, denser LDL particles = more arterial wall penetration = more cardiovascular risk. To finish off our triglycerides sidebar, the dietary patterns that increase triglycerides (bad!) are: excess calories from carbohydrates, added sugars and refined carbohydrates, low fiber intake, low omega-3 intake (especially in combination with excess seed oil intake), high trans fats consumption (more on trans fat in a moment).
Back to finish up cholesterol: this is why a diet that is high in good fats (again, more in a moment) will increase "total cholesterol" - you have more fat boats fueling your cells - but doesn't indicate greater cardiovascular risk: because the large, fluffy particles are not damaging your arteries and the large number of HDL particles are protective!
Furthermore, if you reconsider the sidebar on triglycerides you'll notice that avoiding refined carbohydrates and sugars has the added effect of lowering triglycerides, which keeps the LDL particles even healthier. You'll often see the simple recommendation to keep the HDL/Triglycerides ratio high. this is why. HDL good, triglycerides bad.We didn't even get into insulin sensitivity - one of the most important factors in metabolic health... another time.
A last word on dietary fat types: Not all fats are created equally. You can look into monounsaturated and polyunsaturated on your own, but I want to mention two others here: Trans fat and Saturated fat.
Trans fats mostly come from artificial sources, like processed vegetable or seed oils. most often found in ultra-processed, packaged foods. yuck. trans fat lowers HDL, increases inflammation and increases proportion of small, dense LDL particles. These are all the bad things we discussed above.
Saturated fat is mainly found in meat, dairy and coconut oil. It increases LDL particle size and raises HDL. These are the good things we discussed above.
So, yes, while someone's total cholesterol may go up when eating saturated fats, it doesn't necessarily mean their cardiovascular risk has increased.Now that you understand how cholesterol works, compare moderate saturated fat intake to eating a diet full of refined carbohydrates, sugars, processed vegetable/seed oils, and all the other items we explained above...
Ok really now, the last last word: the "cholesterol" you see on a food label has less impact on blood cholesterol than you thought. the details are too squirrely to go into here, but the takeway is: the fat content discussed above is the lion's share of the impact, with the number you see next to "cholesterol" on your food label having a negligible effect.
diet #paleo #keto #health #healthstr #foodstr #carnivore #cholesterol
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ 8cb60e21:5f2deaea
2024-09-03 22:26:25
@ 8cb60e21:5f2deaea
2024-09-03 22:26:25 -
 @ 8cb60e21:5f2deaea
2024-09-03 22:26:25
@ 8cb60e21:5f2deaea
2024-09-03 22:26:25 -
 @ e88527b4:7ccf6efa
2024-08-30 12:12:39
@ e88527b4:7ccf6efa
2024-08-30 12:12:39書いてみた。。
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ 141daddd:1df80a3f
2024-12-21 12:38:04
@ 141daddd:1df80a3f
2024-12-21 12:38:04When I read the Western media and opinions of accounts affected by it, I can't but get amused at the absolute stupidity of it all. Many people in the West truly belive that life in Russia is hell, grocery store shelves are empty, streets are filled only with women and children because there are no more men, tanks patrol city areas, etc.
So let me give a quick personal account of how it is. I won't waste time including links to sources — use your own Google, Bing, DuckDuckGo or whatever works for your research purposes. Here we go, in no particular order.
A police state
Any state is a police state because there is police. Russia is no better and no worse than any other country. There's regular police, road police, internal military (the national guard). They do their job and nothing more. I mostly lived in a smaller town in which being stopped by a police officer in the middle of a street for some random check is a thing that I've never seen in my life. It happened to me in Moscow once, when I was a student nearly 20 years ago: they wanted to check my residential address registration (in Russia, you have to be registered where you reside). Today, due to the situation, it may happen a bit more often in larger cities, but there's nothing that resembles harrassment.
Don't speak, or else
"There's no freedom of speech!" is total bulshit. I see so much Putin hate on Russian web resources that this statement just cancels itself automatically. But as soon as you start plotting against the country, overtly or covertly, then sure, you will attract a bit more attention from certain agencies whose job is to prevent such things. Especially now. Before you say "but muh opposition, other parties, other candidates!", I will cut you short with a simple axiom that applies to all my thinking: democracy is a scam and must be abandoned at all cost. This should eliminate most objections. Or rather make them non sequitur.
People are starving
This is the most ridiculous claim, especially for me, as I've really tried hard not to get fat. There is an abundance of malls, department stores, supermarkets and smaller grocery stores — all filled with such a huge variety of stuff that even American tourists are dumbfounded. Thirty types of cola instead of 2-3 like in American supermarkets is what I'm talking about. And like this with everything else. Must I add that most products are a lot cheaper than abroad and more natural (GMOs are banned). So no, there is no shortage: foods, clothes, devices, etc are cheap and abundant.
All men must die!
Nobody catches anybody on the streets to send to the trenches. Life is literally the same as before, business as usual. There was a short period at the beginning of the special operation when partial mobilizatoin of reserve assets was held in order to supply the army with enough specialists. But it ended quite quickly. And yes, everybody was worried a bit, but it passed. After that experience, I think the government figured out the incentives and found enough money to offer paid contracts, and a miracle happened: thousands of volunteers sign up to go to the war zone every single day. No need to mobilize.
Russians are poor
I'm quite sure what "poor" means. See, I've traveled enough to see actual poverty. And I've never seen anything like that in Russia, even during the crazy 90's when I was just a kid. American, Canadian, Europeans streets filled with homeless junkies, Latin American slums and favelas — you will see nothing of the sort in Russia. Sure, there are some homeless people, especially in big cities, and some babushkas whose pensions aren't enough to live comfortably, but overall the level of life in the country has been on the rise. As a matter of fact, some people measure Putin's genius exactly by this ability to provide all kinds of material improvements while distancing people from politics — this made Russians unwilling to answer to revolutionary calls. "Fuck the revolution, I'll just have my caramel macchiato delivered by a Yandex boy within 10 minutes, then go chill in a movie theater, play Mafia with my friends and end this day at a night club party."
Travel is banned, the country is a prison
As I write this, a relative just got his visa to Spain. I'm myself traveling now. More countries are opening up to Russians, cancelling visas or extending visa-free stays. Borders are open. Border security agents don't ask extra questions that they wouldn't normally ask. In short, don't belive this lie either.
Is anything bad at all?
Oh yes. Russian bureaucracy. The one thing I hate the most. Want to do some papers? Nobody will explain properly how it's done: you will have to go through seven circles of bureaucratic hell to figure things out. I've heard stories of American faimilties trying to move to Russia only to absolutely lose their temper and abandon the idea. If you want your piece of paper or a certain stamp, you will just to fight for it and there will be little help from the government. But even this, I believe, is being dealt with as Russia is digitizing all of its sevices at a fast pace.
There you are. I hope this quick overview of life in Russia has helped you see through the veil of silly Western propaganda. In no way I say that Russia is a perfect place to live and that there's no better place in the world. I don't suffer from fanaticism. But a better understanding of what's happening on the other side could help with your judgement. And that's all I want.
-
 @ 8cb60e21:5f2deaea
2024-08-29 02:16:28
@ 8cb60e21:5f2deaea
2024-08-29 02:16:28 -
 @ a95c6243:d345522c
2024-12-21 09:54:49
@ a95c6243:d345522c
2024-12-21 09:54:49Falls du beim Lesen des Titels dieses Newsletters unwillkürlich an positive Neuigkeiten aus dem globalen polit-medialen Irrenhaus oder gar aus dem wirtschaftlichen Umfeld gedacht hast, darf ich dich beglückwünschen. Diese Assoziation ist sehr löblich, denn sie weist dich als unverbesserlichen Optimisten aus. Leider muss ich dich diesbezüglich aber enttäuschen. Es geht hier um ein anderes Thema, allerdings sehr wohl ein positives, wie ich finde.
Heute ist ein ganz besonderer Tag: die Wintersonnenwende. Genau gesagt hat heute morgen um 10:20 Uhr Mitteleuropäischer Zeit (MEZ) auf der Nordhalbkugel unseres Planeten der astronomische Winter begonnen. Was daran so außergewöhnlich ist? Der kürzeste Tag des Jahres war gestern, seit heute werden die Tage bereits wieder länger! Wir werden also jetzt jeden Tag ein wenig mehr Licht haben.
Für mich ist dieses Ereignis immer wieder etwas kurios: Es beginnt der Winter, aber die Tage werden länger. Das erscheint mir zunächst wie ein Widerspruch, denn meine spontanen Assoziationen zum Winter sind doch eher Kälte und Dunkelheit, relativ zumindest. Umso erfreulicher ist der emotionale Effekt, wenn dann langsam die Erkenntnis durchsickert: Ab jetzt wird es schon wieder heller!
Natürlich ist es kalt im Winter, mancherorts mehr als anderswo. Vielleicht jedoch nicht mehr lange, wenn man den Klimahysterikern glauben wollte. Mindestens letztes Jahr hat Väterchen Frost allerdings gleich zu Beginn seiner Saison – und passenderweise während des globalen Überhitzungsgipfels in Dubai – nochmal richtig mit der Faust auf den Tisch gehauen. Schnee- und Eischaos sind ja eigentlich in der Agenda bereits nicht mehr vorgesehen. Deswegen war man in Deutschland vermutlich in vorauseilendem Gehorsam schon nicht mehr darauf vorbereitet und wurde glatt lahmgelegt.
Aber ich schweife ab. Die Aussicht auf nach und nach mehr Licht und damit auch Wärme stimmt mich froh. Den Zusammenhang zwischen beidem merkt man in Andalusien sehr deutlich. Hier, wo die Häuser im Winter arg auskühlen, geht man zum Aufwärmen raus auf die Straße oder auf den Balkon. Die Sonne hat auch im Winter eine erfreuliche Kraft. Und da ist jede Minute Gold wert.
Außerdem ist mir vor Jahren so richtig klar geworden, warum mir das südliche Klima so sehr gefällt. Das liegt nämlich nicht nur an der Sonne als solcher, oder der Wärme – das liegt vor allem am Licht. Ohne Licht keine Farben, das ist der ebenso simple wie gewaltige Unterschied zwischen einem deprimierenden matschgraubraunen Winter und einem fröhlichen bunten. Ein großes Stück Lebensqualität.
Mir gefällt aber auch die Symbolik dieses Tages: Licht aus der Dunkelheit, ein Wendepunkt, ein Neuanfang, neue Möglichkeiten, Übergang zu neuer Aktivität. In der winterlichen Stille keimt bereits neue Lebendigkeit. Und zwar in einem Zyklus, das wird immer wieder so geschehen. Ich nehme das gern als ein Stück Motivation, es macht mir Hoffnung und gibt mir Energie.

Übrigens ist parallel am heutigen Tag auf der südlichen Halbkugel Sommeranfang. Genau im entgegengesetzten Rhythmus, sich ergänzend, wie Yin und Yang. Das alles liegt an der Schrägstellung der Erdachse, die ist nämlich um 23,4º zur Umlaufbahn um die Sonne geneigt. Wir erinnern uns, gell?
Insofern bleibt eindeutig festzuhalten, dass “schräg sein” ein willkommener, wichtiger und positiver Wert ist. Mit anderen Worten: auch ungewöhnlich, eigenartig, untypisch, wunderlich, kauzig, … ja sogar irre, spinnert oder gar “quer” ist in Ordnung. Das schließt das Denken mit ein.
In diesem Sinne wünsche ich euch allen urige Weihnachtstage!
Dieser Beitrag ist letztes Jahr in meiner Denkbar erschienen.
-
 @ ec42c765:328c0600
2024-10-16 08:08:40
@ ec42c765:328c0600
2024-10-16 08:08:40カスタム絵文字とは
任意のオリジナル画像を絵文字のように文中に挿入できる機能です。
また、リアクション(Twitterの いいね のような機能)にもカスタム絵文字を使えます。

カスタム絵文字の対応状況(2024/02/05)

カスタム絵文字を使うためにはカスタム絵文字に対応したクライアントを使う必要があります。
※表は一例です。クライアントは他にもたくさんあります。
使っているクライアントが対応していない場合は、クライアントを変更する、対応するまで待つ、開発者に要望を送る(または自分で実装する)などしましょう。
対応クライアント
ここではnostterを使って説明していきます。
準備
カスタム絵文字を使うための準備です。
- Nostrエクステンション(NIP-07)を導入する
- 使いたいカスタム絵文字をリストに登録する
Nostrエクステンション(NIP-07)を導入する
Nostrエクステンションは使いたいカスタム絵文字を登録する時に必要になります。
また、環境(パソコン、iPhone、androidなど)によって導入方法が違います。
Nostrエクステンションを導入する端末は、実際にNostrを閲覧する端末と違っても構いません(リスト登録はPC、Nostr閲覧はiPhoneなど)。
Nostrエクステンション(NIP-07)の導入方法は以下のページを参照してください。
ログイン拡張機能 (NIP-07)を使ってみよう | Welcome to Nostr! ~ Nostrをはじめよう! ~
少し面倒ですが、これを導入しておくとNostr上の様々な場面で役立つのでより快適になります。
使いたいカスタム絵文字をリストに登録する
以下のサイトで行います。
右上のGet startedからNostrエクステンションでログインしてください。
例として以下のカスタム絵文字を導入してみます。
実際より絵文字が少なく表示されることがありますが、古い状態のデータを取得してしまっているためです。その場合はブラウザの更新ボタンを押してください。

- 右側のOptionsからBookmarkを選択

これでカスタム絵文字を使用するためのリストに登録できます。
カスタム絵文字を使用する
例としてブラウザから使えるクライアント nostter から使用してみます。
nostterにNostrエクステンションでログイン、もしくは秘密鍵を入れてログインしてください。
文章中に使用
- 投稿ボタンを押して投稿ウィンドウを表示
- 顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択
- : 記号に挟まれたアルファベットのショートコードとして挿入される

この状態で投稿するとカスタム絵文字として表示されます。
カスタム絵文字対応クライアントを使っている他ユーザーにもカスタム絵文字として表示されます。
対応していないクライアントの場合、ショートコードのまま表示されます。

ショートコードを直接入力することでカスタム絵文字の候補が表示されるのでそこから選択することもできます。

リアクションに使用
- 任意の投稿の顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択

カスタム絵文字リアクションを送ることができます。

カスタム絵文字を探す
先述したemojitoからカスタム絵文字を探せます。
例えば任意のユーザーのページ emojito ロクヨウ から探したり、 emojito Browse all からnostr全体で最近作成、更新された絵文字を見たりできます。
また、以下のリンクは日本語圏ユーザーが作ったカスタム絵文字を集めたリストです(2024/06/30)
※漏れがあるかもしれません
各絵文字セットにあるOpen in emojitoのリンクからemojitoに飛び、使用リストに追加できます。
以上です。
次:Nostrのカスタム絵文字の作り方
Yakihonneリンク Nostrのカスタム絵文字の作り方
Nostrリンク nostr:naddr1qqxnzdesxuunzv358ycrgveeqgswcsk8v4qck0deepdtluag3a9rh0jh2d0wh0w9g53qg8a9x2xqvqqrqsqqqa28r5psx3
仕様
-
 @ 8cb60e21:5f2deaea
2024-08-28 01:53:35
@ 8cb60e21:5f2deaea
2024-08-28 01:53:35 -
 @ ccc8ee23:9f3d9783
2024-12-21 06:38:47
@ ccc8ee23:9f3d9783
2024-12-21 06:38:47Chef's notes
Enjoy these Chocolate Sprinkle Cookies, a delightful combination of buttery richness, velvety chocolate, and a crunchy sprinkle finish
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 90 min
- 🍽️ Servings: 10
Ingredients
- Plain flour 250 grams
- Margarine 100 grams
- Butter 100 grams
- Vanilla essence 1 tsp
- Milk powder 1 tbsp
- Sugar 40 grams
- Chocolate bar - 80 grams, melted
- Chocolate sprinkles - for decoration
Directions
- Make the Dough: Combine the plain flour, margarine, butter, milk powder, sugar, and vanilla essence in a mixing bowl. Knead the mixture by hand until smooth and well combined.
- Shape and divide the dough into small balls, weighing approximately 8 grams each.
- Preheat the oven to 175°C. Arrange the dough balls on a baking tray and bake for about 30 minutes, or until the cookies are dry and fully cooked.
- Coat with Chocolate: Melt the chocolate bar using a double boiler or microwave. Once the cookies have cooled completely, dip each cookie into the melted chocolate, ensuring they are evenly coated.
- Place the coated cookies onto paper cups.
- While the chocolate coating is still wet, sprinkle chocolate sprinkles on top of each cookie.
- Allow the chocolate to dry completely, then arrange the cookies in a decorative airtight container for storage.
-
 @ 00000000:3acedba7
2024-12-20 22:38:33
@ 00000000:3acedba7
2024-12-20 22:38:33Since more than a year we've been tirelessly working on Mostro, here is a summary.
Keys management
We have a lot of improvements and probably one of the most important is the final design of keys management, we started to discuss this idea in the previous quarter and we commented it in the last report, keys management is a way clients rotate keys for every trade adding another privacy layer to gift wrap previous implementation, more detailed info here. Today we've
mergedour main PR for implementing it on mostrod, we also implemented it on mostro-core and mostro-cliNew Nostr NIP merged
We also had our first official NIP merged, NIP-69, with this we aim to standarize all orders from peer-to-peer platform on Nostr to have a big liquidity pool easily filterable.
B4OS
Mostro was one of the projects participating in the b4os residency, which took place in Buenos Aires right after this year’s LABITCONF.
I participated as a mentor, going there daily for the whole program, helping developers get started on Mostro. Mostro received a lot of attention and had the largest number of contributors working on it (8 in total). We had two very productive weeks where we refined how Mostro will handle privacy and reputation at the same time. This will required some changes to mostrod and improvements to the protocol documentation, for which we (fingers crossed) now have a final version.
During the b4os residency, we received contributions that improved our Docker Mostro containers—amazing work that you can see here.
Mostro foundation
We also made progress on establishing the Mostro Foundation, which will serve as a legal entity to handle donations and direct them to developers who want to contribute. Another contributor created the Mostro Foundation website.
Mostro-tools
We already have contributors working on mostro-tools, a TypeScript library implementing the Mostro protocol.
Mobile app
Our past attempt of building the mobile app failed, the developer quit, so we found another dev,
third time's the charm. Now we’re moving forward with the mobile app, which is being developed by developer calledBiz. Working on Mostro is a bit complex because we focus on privacy and censorship-resistance, and our main goal is to deliver these privacy features in an easy-to-use application. I want this app to be very intuitive, suitable even for non-technical users. Biz, delivered a first functional mobile app we can see all the work here and here, we tested it and it works :DMostrui
Finally we started another client, a Terminal User Interface (TUI) which is helping us to implement and understand problems that client developers can find on the process of building a client, this client is called Mostrui
All this couldn't be possible without the support of HRF and Opensats and all collaborators <3
-
 @ deba271e:36005655
2024-12-20 21:07:43
@ deba271e:36005655
2024-12-20 21:07:43Red Bull
- Max Verstappen (Contract until end of 2028 season)
- Liam Lawson (Contract for 2025)
Mercedes
- George Russell (Contract until end of 2025 season)
- Andrea Kimi Antonelli (Contract covering at least 2025 season)
Ferrari
- Charles Leclerc (Contract for ‘several more seasons’ beyond 2025)
- Lewis Hamilton (Contract is “multi-year”)
Aston Martin
- Lance Stroll (Contract for ‘2025 and beyond’)
- Fernando Alonso (“Multi-year contract” until at least end of 2026)
McLaren
- Lando Norris (Contract for ‘multi-year extension’ beyond 2025)
- Oscar Piastri (Contract until end of 2026)
Alpine
- Pierre Gasly (Contracted until at least end of 2026)
- Jack Doohan (Contract for 2025)
Williams
- Alex Albon (Contracted until at least end of 2026)
- Carlos Sainz (Contracted until at least end of 2026)
Haas
- Oliver Bearman (“Multi-year” contract until at least end of 2026)
- Esteban Ocon (“Multi-year” contract until at least end of 2026)
Stake F1 Team
- Nico Hulkenberg (“Multi-year” contract until at least end of 2026)
- Gabriel Bortoleto (“Multi-year” contract starting from 2025)
Visa Cash App Racing Bulls
- Yuki Tsunoda (Contract until end of 2025)
- Isack Hadjar (Contract until end of 2025)
formula1 #f1
Source: https://www.planetf1.com/news/f1-2025-driver-line-up-confirmed-grid
-
 @ b83a28b7:35919450
2024-08-27 16:48:28
@ b83a28b7:35919450
2024-08-27 16:48:28https://image.nostr.build/df0721d6d45d82db35d06663a0318ffe68c0b2b3c694888d23694efcc4255de5.gif
-
 @ c4f5e7a7:8856cac7
2024-09-27 08:20:16
@ c4f5e7a7:8856cac7
2024-09-27 08:20:16Best viewed on Habla, YakiHonne or Highlighter.
TL;DR
This article explores the links between public, community-driven data sources (such as OpenStreetMap) and private, cryptographically-owned data found on networks such as Nostr.
The following concepts are explored:
- Attestations: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your web-of-trust.
- Proof of Place: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in meatspace with their digital representations in the Nostrverse.
- Check-ins: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time.
The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems.
Open Data in a public commons has a place and should not be thrown out with the Web 2.0 bathwater.
Cognitive Dissonance
Ever since discovering Nostr in August of 2022 I've been grappling with how BTC Map - a project that helps bitcoiners find places to spend sats - should most appropriately use this new protocol.
I am assuming, dear reader, that you are somewhat familiar with Nostr - a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: Nostr is Identity for the Internet and The Power of Nostr by @max and @lyn, respectively. Nostr is so much more than a short-form social media replacement.
The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting - all your silos are indeed broken - however, something fundamental has been bothering me for a while and I think it comes down to data ownership.
For those unfamiliar, BTC Map uses OpenStreetMap (OSM) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) - FOSD if you will, but more commonly referred to as Open Data.
In contrast, Notes and Other Stuff on Nostr (Places in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned.
How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data?
Self-sovereign Identity
Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something - an identity.
All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money.
Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state.
Or, as @nvk said recently: "Don't build your house on someone else's land.".
https://i.nostr.build/xpcCSkDg3uVw0yku.png
While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this.
Nostr is PGP for the masses and will take cryptographic identities mainstream.
Full NOSTARD?
Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons.
We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be.
https://i.nostr.build/s3So2JVAqoY4E1dI.png
There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a Wikifreedia variant of OpenStreetMap.
While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native - there's no need to go Full NOSTARD. H/T to @princeySOV for the original meme.
https://i.nostr.build/ot9jtM5cZtDHNKWc.png
So, how do we appropriately blend cryptographically owned data with the commons?
If a location is owned in meatspace and it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the tragedy of the commons.
The remainder of this article explores how we can:
- Verify ownership of a physical place in the real world;
- Link that ownership to the corresponding digital place in cyberspace.
As a side note, I don't see private key custodianship - or, even worse, permissioned use of Places signed by another identity's key - as any more viable than the rented identities of Web 2.0.
And as we all know, the Second Law of Infodynamics (no citation!) states that:
"The total amount of sensitive information leaked will always increase over time."
This especially holds true if that data is centralised.
Not your keys, not your notes. Not your keys, not your identity.
Places and Web-of-Trust
@Arkinox has been leading the charge on the Places NIP, introducing Nostr notes (kind 37515) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via NIP-73 - External Content IDs (championed by @oscar of @fountain).
However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world.
Ultimately, this problem can only be solved in a decentralised way by using Web-of-Trust - using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop.
This requires users to:
- Verify the owner of a Place in cyberspace is the owner of a place in meatspace.
- Signal this verification to their social graph.
Let's look at the latter idea first with the concept of Attestations ...
Attestations
A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false.
Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too.
However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc).
Here is a recent example from @lyn that would carry more signal if it were an Attestation:
https://i.nostr.build/lZAXOEwvRIghgFY4.png
Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or Data Vending Machines in accordance with:
- Your social graph;
- The type or subject of the content being attested and by whom;
- Your personal preferences.
They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places.
NIP-25 (Reactions) do allow for users to up/downvote notes with optional content (e.g., emojis) and could work for Attestations, but I think we need something less ambiguous and more definitive.
‘This is true’ resonates more strongly than ‘I like this.’.
https://i.nostr.build/s8NIG2kXzUCLcoax.jpg
There are similar concepts in the Web 3 / Web 5 world such as Verified Credentials by tdb. However, Nostr is the Web 3 now and so wen Attestation NIP?
https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg
That said, I have seen @utxo has been exploring ‘smart contracts’ on nostr and Attestations may just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust.
Proof of Place
Attestations handle the signalling of your truth, but what about the initial verification itself?
We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth.
Introducing Proof of Place, an out–of-band process where an oracle (such as BTC Map) would mail - yes physically mail- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace.
One way of doing this would be to mint a 1 sat cashu ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location.
Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places).
In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as @Gigi says in PoW is Essential:
"A failure to understand Proof of Work, is a failure to understand Bitcoin."
In the Nostrverse, Proof of Place helps bridge the digital and physical worlds.
@Gigi also observes in Memes vs The World that:
"In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone."
https://i.nostr.build/dOnpxfI4u7EL2v4e.png
This isn’t true for Nostr.
In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯
Check-ins
Although not a draft NIP yet, @Arkinox has also been exploring the familiar concept of Foursquare-style Check-ins on Nostr (with kind 13811 notes).
For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as OSM elements) if NIP-73 - External Content IDs are used.
Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices.
Bringing Check-ins to Nostr is possible (as @sebastix capably shows here), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am.
Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable.
How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene - I’m sure @blackcoffee and @Ben Arc could hack something together over a weekend!
Check-ins could also be used as a signal for bonafide Place ownership over time.
Summary: Trust Your Bros
So, to recap, we have:
Places: Digital representations of physical locations on Nostr.
Check-ins: Users signalling their presence at a location.
Attestations: Verifiable social proofs used to confirm ownership or the truth of a claim.
You can visualise how these three concepts combine in the diagram below:
https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg
And, as always, top right trumps bottom left! We have:
Level 0 - Trust Me Bro: Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all.
Level 1 - Definitely Maybe Somewhere: This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL.
Level 2 - Trust Your Bros: An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph.
https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg
Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map?
Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ - you decide.
As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities.
Thanks
With thanks to Arkinox, Avi, Ben Gunn, Kieran, Blackcoffee, Sebastix, Tomek, Calle, Short Fiat, Ben Weeks and Bitcoms for helping shape my thoughts and refine content, whether you know it or not!
-
 @ 8cb60e21:5f2deaea
2024-08-25 20:26:43
@ 8cb60e21:5f2deaea
2024-08-25 20:26:43 -
 @ ccc8ee23:9f3d9783
2024-12-21 06:03:28
@ ccc8ee23:9f3d9783
2024-12-21 06:03:28Chef's notes
Celebrating seasons🎉
Kastengel Chocolate-Dip, where the savoury richness of cheese meets the decadent sweetness of chocolate. A perfect flavours in every bite!
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 90 min
- 🍽️ Servings: 10
Ingredients
- Plain Flour 250 grams
- Margarine - 100 grams
- Butter 100 grams
- Egg yolk 1 pc
- Sugar 20 grams
- Grated cheese 100 grams (half for the dough, half for garnish, adjustable)
- Chocolate bar 80 grams, melted
Directions
- Make the Dough: Combine the plain flour, margarine, butter, sugar, and half of the grated cheese in a bowl. Knead the mixture with your hands until smooth and well incorporated. Roll out the dough using a rolling pin and cut into desired shapes for cookies.
- Beat the egg yolk. Brush the shaped cookies with the egg yolk mixture and sprinkle the remaining grated cheese on top.
- Bake the cookies 175’C for about 30 minutes, or until they are dry and perfectly cooked.
- Melt the chocolate bar in a double boiler or microwave until smooth.
- Dip in Chocolate: Once the cookies have cooled completely, dip both the top and bottom ends of each cookie into the melted chocolate.
- Place the dipped cookies on a wire rack or a cookie drying tray to allow the chocolate to harden and set.
- Arrange the cookies neatly in an airtight container.
-
 @ d68401a8:11aad383
2024-12-20 16:44:43
@ d68401a8:11aad383
2024-12-20 16:44:43The internet addresses we use daily (e.g., something.com, something.org) are just a part of the internet called the DNS root zone, which is essentially a hierarchical database of all the names you can access on the internet (similar to a telephone directory).
Currently, the only root zone we know is the ICANN root zone. Nobody refers to it as the ICANN root zone or ICANN domains because it is inherently the only root zone people know, so we simply call it the Internet and domains.
The ICANN root zone is extremely convenient; having a centralized and unified root zone makes life easier for people, and it will remain the main root zone on the internet for the foreseeable future. However, the internet is not meant to have only one root zone. While the ICANN root zone has its advantages, it also has some drawbacks. This is where alternative root zones, which experiment with different trade-offs, make sense.
Handshake is an alternative root zone based on a decentralized peer-to-peer network, offering a different set of trade-offs compared to the ICANN root zone. The following table highlights the main differences between the ICANN and HNS root zones:
|Feature|ICANN Root Zone|HNS Root Zone| |:-|:-|:-| |Governance|Centralized (ICANN)|Decentralized (Peer-to-peer)| |Domain creation|Requires ICANN approval|Permissionless and auction-based| |User Interaction|Only through specific registries|Directly on its blockchain| |Infrastructure|Traditional DNS root servers|Blockchain-based| |Resolution|Native support in browsers and systems|Requires custom resolvers or tools| |Trust Model|Trust in the ICANN|Trustless, cryptographic verification| |HTTPS setup|Certificate authority|DANE| |Purpose|Corporate and State sovereignty; Stability|User sovereignty; Experimental|
How to access the HNS root zone
Now you know that the root zone you’re familiar with is the ICANN root zone, which is universally supported by operating systems and browsers. But what if you want to own a Handshake domains or want to access Handshake addresses to explore what’s in the Handshake root zone? Essentially, you have a few options:
1. PC and desktop
You have a few options explained here: https://learn.namebase.io/development/resolving-handshake, but the recommended one is Fingertip, a resolver created by Impervious that enables you to trustlessly resolve Handshake names:
If your certificate expires at some point, usually after one year, you can either replace the certificate with a new one or delete the folder where the certificate is stored (on Windows, it should be located in a path like
Users\yourname\AppData\Roaming\Fingertip). After deleting this folder, the next time you restart your computer, Fingertip will prompt you to generate a new certificate. Simply say yes, and that’s it!2. Smart phones and other devices
For mobile phones and such the easiest and more convenient way is HNS DoH, the DNS over TLS option.
3. Explore the Handshake Root Zone
-
 @ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23
@ 09fbf8f3:fa3d60f0
2024-09-10 13:21:23由于gmail在中国被防火墙拦截了,无法打开,不想错过邮件通知。
通过自建ntfy接受gmail邮件通知。 怎么自建ntfy,后面再写。
2024年08月13日更新:
修改不通过添加邮件标签来标记已经发送的通知,通过Google Sheets来记录已经发送的通知。
为了不让Google Sheets文档的内容很多,导致文件变大,用脚本自动清理一个星期以前的数据。
准备工具
- Ntfy服务
- Google Script
- Google Sheets
操作步骤
- 在Ntfy后台账号,设置访问令牌。

- 添加订阅主题。

- 进入Google Sheets创建一个表格.记住id,如下图:

- 进入Google Script创建项目。填入以下代码(注意填入之前的ntfy地址和令牌):
```javascript function checkEmail() { var sheetId = "你的Google Sheets id"; // 替换为你的 Google Sheets ID var sheet = SpreadsheetApp.openById(sheetId).getActiveSheet();
// 清理一星期以前的数据 cleanOldData(sheet, 7 * 24 * 60); // 保留7天(即一周)内的数据
var sentEmails = getSentEmails(sheet);
var threads = GmailApp.search('is:unread'); Logger.log("Found threads: " + threads.length);
if (threads.length === 0) return;
threads.forEach(function(thread) { var threadId = thread.getId();
if (!sentEmails.includes(threadId)) { thread.getMessages().forEach(sendNtfyNotification); recordSentEmail(sheet, threadId); }}); }
function sendNtfyNotification(email) { if (!email) { Logger.log("Email object is undefined or null."); return; }
var message = `发件人: ${email.getFrom() || "未知发件人"} 主题: ${email.getSubject() || "无主题"}
内容: ${email.getPlainBody() || "无内容"}`;
var url = "https://你的ntfy地址/Gmail"; var options = { method: "post", payload: message, headers: { Authorization: "Bearer Ntfy的令牌" }, muteHttpExceptions: true };
try { var response = UrlFetchApp.fetch(url, options); Logger.log("Response: " + response.getContentText()); } catch (e) { Logger.log("Error: " + e.message); } }
function getSentEmails(sheet) { var data = sheet.getDataRange().getValues(); return data.map(row => row[0]); // Assuming email IDs are stored in the first column }
function recordSentEmail(sheet, threadId) { sheet.appendRow([threadId, new Date()]); }
function cleanOldData(sheet, minutes) { var now = new Date(); var thresholdDate = new Date(now.getTime() - minutes * 60 * 1000); // 获取X分钟前的时间
var data = sheet.getDataRange().getValues(); var rowsToDelete = [];
data.forEach(function(row, index) { var date = new Date(row[1]); // 假设日期保存在第二列 if (date < thresholdDate) { rowsToDelete.push(index + 1); // 存储要删除的行号 } });
// 逆序删除(从最后一行开始删除,以避免行号改变) rowsToDelete.reverse().forEach(function(row) { sheet.deleteRow(row); }); }
```
5.Google Script是有限制的不能频繁调用,可以设置五分钟调用一次。如图:

结尾
本人不会代码,以上代码都是通过chatgpt生成的。经过多次修改,刚开始会一直发送通知,后面修改后将已发送的通知放到一个“通知”的标签里。后续不会再次发送通知。
如需要发送通知后自动标记已读,可以把代码复制到chatgpt给你写。
-
 @ 8cb60e21:5f2deaea
2024-08-24 23:57:19
@ 8cb60e21:5f2deaea
2024-08-24 23:57:19asdasdasdsad
-
 @ ac8bb9b0:70278acc
2024-12-20 18:48:36
@ ac8bb9b0:70278acc
2024-12-20 18:48:36Details
- ⏲️ Prep time: 5
- 🍳 Cook time: 10
- 🍽️ Servings: 4
Ingredients
- 1 lb large shrimp, peeled and deveined
- 1 tablespoon extra virgin olive oil
- 3 cloves garlic, chopped
- 1/4 cup white wine, dry
- 14 oz can petite diced tomatoes, drained
- 1/2 cup half and half
- 1/2 teaspoon dried oregano
- kosher salt and fresh black pepper, to taste
- 1 teaspoon lemon juice
- 1/4 cup fresh parsley, chopped
- 8 ounces angel hair pasta, whole wheat, gluten-free or high fiber
Directions
- Boil water with salt in a large pot for the pasta. Cook pasta al dente according to package directions.
- Meanwhile, season shrimp with 1/4 teaspoon salt, black pepper and oregano.
- Heat a large skillet over medium heat. Add the oil, when warm add the shrimp and garlic and cook about 2 minutes on each side.
- Add tomatoes, wine, salt and pepper and cook an additional minute.
- Remove from heat and stir in half and half. Add lemon juice and parsley and serve over pasta.
- Divide equally in 4 plates or shallow bowls.
-
 @ 31312140:2471509b
2024-12-20 10:36:30
@ 31312140:2471509b
2024-12-20 10:36:30The Underpinnings of Germ Theory: A History Lesson
The Germ Theory took root in the fertile ground of 19th-century scientific exploration. Louis Pasteur and Robert Koch emerged as the poster children of this doctrine, selling the world on the notion that microorganisms are the main perpetrators of disease. Pasteur's dramatic demonstrations and Koch's postulates captured the imagination of the medical community, turning Germ Theory into dogma.
The Fault Lines
Pasteur’s Dubious Methods
In the annals of scientific history, Louis Pasteur’s name often emerges as a heroic figure who championed Germ Theory. However, beneath the accolades lies a more complex and contentious legacy fraught with unscientific methods and unnecessary cruelty. Pasteur’s experiments, lauded in their time, provide little to no scientific basis for the legitimacy of Germ Theory today. Let’s separate myth from reality.
Pasteur’s Experimentation: A Glance Behind the Curtain
Louis Pasteur, best known for his work on vaccinations and microbial fermentation, was not quite the rigorous scientist history books often paint him to be. His methods were as much about showmanship and drama as they were about scientific inquiry, raising several red flags. 🧑🔬
Lack of Scientific Rigor: Pasteur’s experiments rarely adhered to the modern standards of scientific rigor. He often neglected proper scientific controls and failed to consistently repeat his experiments under the same conditions to eliminate alternative explanations. This lack of methodological rigor casts shadows over the reliability of his findings. 📉
Cruelty in the Name of Science: Pasteur’s experiments often involved injecting substances into animals, notably into their brains, to observe disease progression. Such actions were needlessly cruel and failed to replicate natural disease transmission. When animals tragically died from these brutal interventions, Pasteur attributed the cause to germs or viruses, neglecting the stress and trauma of his invasive procedures as potential factors. 😿
Dissecting the Evidence—or Lack Thereof
The cornerstone of Pasteur’s claims that germs were directly responsible for disease hinged on such brutal methods. However, no comprehensive and reproducible scientific evidence emerged to definitively prove Germ Theory. His experiments often overlooked variables that today would disqualify his conclusions as scientifically robust.
Absence of Isolation: Pasteur claimed to identify and isolate specific pathogens as disease culprits. However, without modern techniques and an oversight of standard isolation methods, his assertions were tenuous at best. Pathogens were forced into environments and reactions completely unnatural to their normal behavior.
Control Fallacies: Pasteur's lack of proper controls and failure to observe naturally-occurring conditions resulted in experiments that simulated rather than illuminated the natural world. His conclusions often relied on directed outcomes rather than unbiased observations.
Reputation Over Rigor: Emphasizing his results more than the methodology, Pasteur successfully marketed Germ Theory without addressing plausible alternative explanations for disease, such as environmental and host factors now recognized as contributing significantly to health outcomes. 🎭
Koch’s Postulates: The Perfect Logic
In the annals of medical history, few frameworks were as crystal-clear and logical as Koch's Postulates. Developed by Robert Koch in the 19th century, these postulates were designed to establish a direct cause-and-effect relationship between a microorganism and a disease. Their clarity and rigor make you wonder why, then, no virus has ever fully satisfied these criteria. Spoiler alert: it's not the postulates that are flawed. Let's unpack this enigma. 🕵️♂️
The Unquestioned Logic of Koch's Postulates
Koch’s Postulates laid out a straightforward and logical framework:
- Presence in Diseased Organisms: The microorganism must be found in abundance in all organisms suffering from the disease, but not in healthy organisms.
- Isolation: The microorganism must be isolated from a diseased organism.
- Reproduction of Disease: The isolated microorganism should cause disease when introduced into a healthy organism.
- Re-Isolation: The microorganism must be re-isolated from the inoculated, diseased experimental host and identified as being identical to the original specific causative agent.
At first glance—and in thorough scientific scrutiny—these steps are both logical and sound. They seek to establish undeniable causality between a germ and a disease. The problem? Not a single virus satisfies these foundational criteria.
The Virus Dilemma: A Case Against Germ Theory
Viruses have never clearly demonstrated an ability to fulfill Koch’s Postulates. Here’s why this matters:
Presence and Absence: Viruses are often found in healthy individuals, completely violating the first postulate. If presence alone were cause for disease, we'd all be perpetually ill.
Causation and Introduction: Reproducing disease symptoms reliably by introducing a virus into a healthy host? Good luck. This rarely results in consistent illness, highlighting the shaky premise upon which viral causation rests.
Re-Isolation Challenges: Even when a virus appears to be re-isolated, it's never perfectly identical to the original. Which makes complete sense when one understands that supposed viruses are just random cellular debris.
Failure to meet these criteria suggests that the existence of viruses as direct causes of disease is anything but a settled science. In fact, it reinforces the idea that Germ Theory doesn’t hold water, particularly when we consider the consistency and rigor required by Koch's original framework.
Virology: The Shaky Foundations
Faced with the inability to satisfy Koch's Postulates, the scientific community has adapted and modified them endlessly. Here's how they've diluted and diverted:
Molecular Koch's Postulates: Focus on genes rather than organisms, diverting attention from the failure of isolated viruses to credibly cause disease.
Epidemiological Excuses: Correlations in population studies often stand in for causation, even though this violates the logical rigor originally intended.
DNA and RNA Techniques: PCR and molecular methods detect genetic material but do not prove viral causation, circumventing the postulates by identifying sequences rather than demonstrating direct effects.
By moving the goalposts, virology attempts to shield itself from the logical scrutiny that should dismantle it—a clear indication that the field struggles under traditional scientific methods.
The Bigger Picture: Questioning the Narrative
Koch's Postulates were crafted in a time when scientific integrity and logic were paramount. That no virus has satisfied these postulates essentially points a finger right back at Germ Theory and the entire premise upon which modern virology stands; it appears far more unscientific if it can't pass the basic tests of causation and effect laid out over a century ago.
While the world buys into Germ Theory as a self-evident truth, the unsinkable logic of Koch’s Postulates serves as a reminder that scientific inquiry is never settled simply by bending rules to fit narratives.
Viruses and Virology’s Dance of Deception
In the realm of virology, the term "isolation" is thrown around with surprising frequency. For most of us, isolation evokes a clear, dictionary-defined image: separating something completely from everything else. However, in virology, "isolation" means something entirely different from this straightforward definition. So, let's take a closer look at what this word really implies in the virology playbook and why it might just be the lynchpin in a grand scientific illusion. 🧬
The Dictionary Definition vs. Virology's Reality
According to standard dictionaries, "isolation" refers to the act of setting something apart, free from connections or interactions with other objects or environments. Think quarantine, a separated specimen, or a single variable under a microscope. Isolation should mean purity and singularity.
In virology, however, "isolation" involves an intricate process that seems to contradict these fundamental principles:
The Viral "Isolation" Process: In virology practices, so-called "isolation" involves taking samples believed to contain the virus and adding them to a mixture of other genetic materials and nutrients within cell cultures. This environment is rarely isolated by the traditional definition—it's an elaborate cocktail rather than a singular entity.
The Outcome and Ambiguity: When cell cultures deteriorate or exhibit changes, virologists claim the presence of a virus, naming these alterations as proof of viral activity. However, changes might result from a myriad collection of factors, from environmental stressors to the very chemicals added to the culture themselves.🦠
The Concept of "Isolation" Under Scrutiny
Given virology's integration-based "isolation" process, here are some valid points for questioning:
Scientific Ambiguity: The blending of viruses with cellular systems complicates the interpretation of observed effects. When anomalies arise, distinguishing specific viral influences from the noise of external variables becomes nearly impossible.
Misinterpretation and Misleading Perceptions: The misuse of "isolation" generates misleading perceptions that viruses are identified and targeted with precision in lab-based scenarios. This dilution and deviation from the traditional concept cast doubt on purported viral behavior and pathogenicity.
Where is the Purity?: Without the ability to fully isolate and analyze viruses independently, claims of their direct actions and pathogenic roles remain speculative at best, opening a Pandora’s box of uncertainties.
The Terrain Theory: A Harbinger of Hope?
Antoine Béchamp emerges as a contender to Pasteur's legacy with Terrain Theory. Contrary to Germ Theory, Terrain Theory insists that diseases arise due to imbalances or vulnerabilities of individual internal environments—the "terrain." This perspective suggests that focusing solely on germs misses the broader health picture. 🖼️
Béchamp’s notion aligns more closely with what many modern-day holistic health approaches tout—strengthening the "terrain" over simply destroying the "invaders."
According to Béchamp, microorganisms could change form based on the environment, suggesting that germs are not the primary cause of disease but rather a symptom of an unhealthy internal "terrain." This theory emphasized that maintaining the body's internal balance and health was key to preventing disease, challenging the singular blame on specific pathogens and highlighting the dynamic nature of microorganisms within the body.
In recent times, the study of exosomes has added another layer of complexity to our understanding of disease. Exosomes are small extracellular vesicles involved in cellular communication and transport of genetic material. Some researchers argue that exosomes have been misidentified as pathogenic viruses due to their similar appearance and behavior. This misrepresentation could lead to erroneous conclusions about the nature and cause of certain diseases, suggesting that what might be labeled as a viral infection could, in fact, be the body's response to stress or other environmental factors. This emerging perspective challenges the long-standing assumptions of Germ Theory, calling for a deeper exploration of the body's intricate biological mechanisms
The Spanish Flu and Its Intriguing Parallel to COVID-19
The Spanish Flu of 1918 stands as one of the deadliest pandemics in history (at least as we are being told to believe), claiming millions of lives worldwide. Interestingly, multiple attempts to experimentally transmit the influenza virus from sick individuals to healthy ones during this period yielded unexpected results. Various experiments involved transferring fluids from the infected to healthy volunteers, yet these attempts consistently failed to induce illness. This failure to recreate infection under controlled conditions has prompted some to question the fundamental understanding of virus transmission.
The recent global COVID-19 pandemic took Germ Theory for a high-speed test drive, with mixed returns. Governments worldwide invoked this theory to justify masks, lockdowns, and testing regimes like PCR, originally intended for DNA analysis, not diagnostics. As people folded squarely into the narrative, questions about the veracity and motives behind this became more poignant. 🧬
Drawing parallels to the COVID-19 pandemic, similar debates have surfaced regarding the virus's transmissibility and pathogenicity. While COVID-19 has inspired unprecedented global health measures, questions about virus isolation, testing accuracy, and the true nature of virus spread echo those inquiries raised during the Spanish Flu era. Both cases challenge the simplicity with which Germ Theory attributes disease to direct microbial causation, inviting a broader examination of environmental, genetic, and lifestyle factors in understanding pandemics. This reflection compels continued exploration into the complexity of infectious diseases beyond a single-cause framework, encouraging more holistic approaches to public health.
The Pharmaceutical Profiteers
No discussion on Germ Theory is complete without examining Big Pharma—an industry thriving on the fear of germs. Thanks to the narratives built around germ-caused diseases, this sector grows ever richer, pumping out vaccines and medications aimed at thwarting these so-called invisible villains. Blanche at your own peril; this is a money-making machine. 💊
Path Forward: Empower and Enlighten
- Question the Status Quo: Encourage skepticism towards germ causation claims without ironclad scientific proof.
- Focus on Overall Health: Your ‘terrain’ or environment is key. Elevate health through balanced diet, exercise, and stress management.
- Demand Transparent Science: Push for rigorous, ethical trials that clearly demonstrate causation, not just correlation.
- Educate and Explore: Dive into the works of critics like Béchamp and modern contrarians who offer alternative views on health and disease.
Essential Readings
- "Béchamp or Pasteur? A Lost Chapter in the History of Biology" by Ethel D. Hume
- "The Contagion Myth: Why Viruses (including 'Coronavirus') Are Not the Cause of Disease" by Thomas S. Cowan and Sally Fallon Morell
- "Virus Mania: How the Medical Industry Continually Invents Epidemics, Making Billion-Dollar Profits at Our Expense" by Torsten Engelbrecht and Claus Köhnlein
- "What Really Makes You Ill? Why Everything You Thought You Knew About Disease Is Wrong" by Dawn Lester and David Parker
- "The Dream & Lie of Louis Pasteur: A Philosophy" by R. B. Pearson
- "Extracellular Vesicles in Health and Disease" by Paul Harrison
So the next time you're confronted by claims of germ villains, remember the cracked foundations upon which these claims stand. Look into it, my friend, stay inquisitive, and always question the narrative. 🌟🔍
-
 @ 7460b7fd:4fc4e74b
2024-09-05 08:37:48
@ 7460b7fd:4fc4e74b
2024-09-05 08:37:48请看2014年王兴的一场思维碰撞,视频27分钟开始
最后,一个当时无法解决的点:丢失
-
 @ ccc8ee23:9f3d9783
2024-12-19 12:46:00
@ ccc8ee23:9f3d9783
2024-12-19 12:46:00Chef's notes
Salmon Mentai Rice. Create your own layers of fluffy, seasoned rice are topped with tender, pan-seared chicken or salmon and a creamy, spicy mentai sauce made with spicy Japanese mayo .
Torched to golden perfection, it’s finished with nori and tobiko for a burst of texture and flavor. A simple tasty Japanese fusion delight that’s perfect🤩
Subtitude of Tobiko, white sesame seeds as economical option will add a nutty flavor and subtle crunch to the dish for texture and visual appeal.
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 30 min
- 🍽️ Servings: 2
Ingredients
- Steamed Rice 400 grams
- Rice vinegar 1 tbsp
- Sugar 1 tsp
- chicken breast / thighs 250 grams
- soy sauce 1 tbsp
- oyster sauce 1 tbsp
- sesame oil 1 tsp
- garlic powder 1 tsp
- cooking oil 1 tbsp
- mayonnaise (e.g., Kewpie) 4 tbsp
- sriracha or any chili sauce 1 tbsp
- tobiko if any or white sesame as optional, for texture, 2 tsp only
Directions
- Prepared the Rice: mixed in bowl 2 cups steam rice, 1 tbsp rice vinegar, 1 tsp sugar and 1/2 tsp salt. Set a side.
- Cook the Chicken: 1. Marinate the chicken pieces with 1 tsp soy sauce, 1 tsp oyster sauce, 1 tsp sesame oil, 1 tsp garlic powder for 15–20 minutes. 2. Heat cooking oil in a pan over medium heat and stir-fry the chicken until fully cooked and slightly caramelized. Remove from heat.
- Make the Mentai Sauce 1. In a small bowl, combine 4 tbsp mayonnaise, 1 tbsp chili sauce, and 1 tsp sesame oil. Add tobiko if desired for texture. Mix well.
- Assemble the Mentai Rice 1. In a heatproof bowl or tray, layer the seasoned rice as the base. 2. Add a layer of cooked chicken on top of the rice. 3. Spread the mentai sauce evenly over the chicken layer.
- Grill or Broil: Use a kitchen torch or place the dish under a broiler for 2–3 minutes until the sauce is slightly charred and bubbly.
- Garnish with white sesame or nori strips, or extra tobiko.
-
 @ 8cb60e21:5f2deaea
2024-08-24 23:54:44
@ 8cb60e21:5f2deaea
2024-08-24 23:54:44 -
 @ 4523be58:ba1facd0
2024-05-28 11:05:17
@ 4523be58:ba1facd0
2024-05-28 11:05:17NIP-116
Event paths
Description
Event kind
30079denotes an event defined by its event path rather than its event kind.The event directory path is included in the event path, specified in the event's
dtag. For example, an event path might beuser/profile/name, whereuser/profileis the directory path.Relays should parse the event directory from the event path
dtag and index the event by it. Relays should support "directory listing" of kind30079events using the#ffilter, such as{"#f": ["user/profile"]}.For backward compatibility, the event directory should also be saved in the event's
ftag (for "folder"), which is already indexed by some relay implementations, and can be queried using the#ffilter.Event content should be a JSON-encoded value. An empty object
{}signifies that the entry at the event path is itself a directory. For example, when savinguser/profile/name:Bob, you should also saveuser/profile:{}so the subdirectory can be listed underuser.In directory names, slashes should be escaped with a double slash.
Example
Event
json { "tags": [ ["d", "user/profile/name"], ["f", "user/profile"] ], "content": "\"Bob\"", "kind": 30079, ... }Query
json { "#f": ["user/profile"], "authors": ["[pubkey]"] }Motivation
To make Nostr an "everything app," we need a sustainable way to support new kinds of applications. Browsing Nostr data by human-readable nested directories and paths rather than obscure event kind numbers makes the data more manageable.
Numeric event kinds are not sustainable for the infinite number of potential applications. With numeric event kinds, developers need to find an unused number for each new application and announce it somewhere, which is cumbersome and not scalable.
Directories can also replace monolithic list events like follow lists or profile details. You can update a single directory entry such as
user/profile/nameorgroups/follows/[pubkey]without causing an overwrite of the whole profile or follow list when your client is out-of-sync with the most recent list version, as often happens on Nostr.Using
d-tagged replaceable events for reactions, such as{tags: [["d", "reactions/[eventId]"]], content: "\"👍\"", kind: 30079, ...}would make un-reacting trivial: just publish a new event with the samedtag and an empty content. Toggling a reaction on and off would not cause a flurry of new reaction & delete events that all need to be persisted.Implementations
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
f) already support this feature. - IrisDB client side library: treelike data structure with subscribable nodes.
https://github.com/nostr-protocol/nips/pull/1266
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
-
 @ fd208ee8:0fd927c1
2024-12-20 06:58:48
@ fd208ee8:0fd927c1
2024-12-20 06:58:48When the shit just don't work
Most open-source software is now so badly written and sloppily-maintained, that it's malware.
That's why the governments are getting involved. They try using OS, to save money and improve quality (and to market themselves as "hip"), and then it blows up their system or opens them up to hackers.
Now, they're pissed and want support (but the dev with the handle SucksToBeYou has disappeared) or someone to sue, but most OS projects have no identifiable entity behind them. Even well-known anon devs are often groups of anons or accounts that change hands.
The software cracks have moved on
There is simply no evidence that OS alone produces higher-quality software. The reason it seemed that way, at the beginning, was because of the caliber of the developers working on the projects, and the limited number of projects. This resulted in experienced people actively reviewing each others' code.
OS used to be something the elite engaged in, but it's mostly beginners practicing in public, now. That's why there are now millions of OS projects, happily offered for free, but almost all of them are garbage. The people now building OS usually aren't capable of reviewing other people's code, and they're producing worse products than ChatGPT could. Their software has no customers because it has no market value.
If everything is OS, then nothing is.
Another paradigm-changer is that all software is de facto OS, now that we can quickly reverse-engineer code with AI. That means the focus is no longer on OS/not-OS, but on the accountability and reputation of the builders.
It is, once again, a question of trust. We have come full-circle.
-
 @ 8cb60e21:5f2deaea
2024-08-24 23:52:38
@ 8cb60e21:5f2deaea
2024-08-24 23:52:38 -
 @ ccc8ee23:9f3d9783
2024-12-19 05:55:09
@ ccc8ee23:9f3d9783
2024-12-19 05:55:09Chef's notes
Dare to taste the bold? One bite of Jengkol Balado and you’ll be hooked
Spicy Jengkol Balado - Betawi Style A traditional dish from Betawi (Jakarta), Jengkol Balado is nutty bold and aromatic delicacy made with jengkol beans. This version uses thinly sliced jengkol for a delightful texture.
Serve it with a plate of steamed fragrant white rice and a side of crunchy cucumber for a complete meal that satisfies on every level.
Details
- 🍳 Cook time: 40 min
- 🍽️ Servings: 2
Ingredients
- Jengkol 250 grams
- Chilli 100 grams
- Shallot 5 cloves
- Garlic 2 cloves
- Tomato 1 clove (small)
- Bay leaves 2
- Galangal 2cm. Bruished
- Veggie oil 20ml or 4 tsp
- Seasoning
Directions
- Prepare the Jengkol Wash the jengkol thoroughly and slice it thinly. Boil the slices in water with the bay leaves for 10–15 minutes to soften and reduce their strong odour. Drain and set aside.
- Make the Balado Paste. Blend chillies, shallots, garlic, candlenut and tomatoes into a slightly coarse paste using a blender
- Heat oil in a pan and sauté the balado paste until fragrant and the oil starts to separate. Add the galangal, bay leaves, salt, sugar, and seasoning. Stir well
- Add jengkol to the pan. Mix until jengkol are fully coated in the balado paste.
- If the mixture seems too dry, add a splash of water and let it simmer on low heat to allow the flavours to infuse.
- Taste the dish and adjust the seasoning with more salt or sugar if needed.
- Remove from heat and serve hot with steamed rice.
-
 @ b60c3e76:c9d0f46e
2024-05-15 10:08:47
@ b60c3e76:c9d0f46e
2024-05-15 10:08:47KRIS menjamin semua golongan masyarakat mendapatkan perlakuan sama dari rumah sakit, baik pelayanan medis maupun nonmedis.
Demi memberikan peningkatan kualitas layanan kesehatan kepada masyarakat, pemerintah baru saja mengeluarkan Peraturan Presiden (Perpres) nomor 59 tahun 2024 tentang Jaminan Kesehatan. Melalui perpres itu, Presiden Joko Widodo (Jokowi) telah menghapus perbedaan kelas layanan 1, 2, dan 3 dalam Badan Penyelenggara Jaminan Sosial atau BPJS Kesehatan.
Layanan berbasis kelas itu diganti dengan KRIS (Kelas Rawat Inap Standar). Berkaitan dengan lahirnya Perpres 59/2024 tentang Perubahan Ketiga atas Perpres 82/2018 tentang Jaminan Kesehatan, Presiden Joko Widodo telah memerintahkan seluruh rumah sakit yang bekerja sama dengan BPJS Kesehatan melaksanakannya.
Kebijakan baru itu mulai berlaku per 8 Mei 2024 dan paling lambat 30 Juni 2025. Dalam jangka waktu tersebut, rumah sakit dapat menyelenggarakan sebagian atau seluruh pelayanan rawat inap berdasarkan KRIS sesuai dengan kemampuan rumah sakit.
Lantas apa yang menjadi pembeda dari sisi layanan dengan layanan rawat inap sesuai Perpres 59/2024? Dahulu sistem layanan rawat BPJS Kesehatan dibagi berdasarkan kelas yang dibagi masing-masing kelas 1, 2, dan 3. Namun, melalui perpres, layanan kepada masyarakat tidak dibedakan lagi.
Pelayanan rawat inap yang diatur dalam perpres itu--dikenal dengan nama KRIS—menjadi sistem baru yang digunakan dalam pelayanan rawat inap BPJS Kesehatan di rumah sakit-rumah sakit. Dengan KRIS, semua golongan masyarakat akan mendapatkan perlakuan yang sama dari rumah sakit, baik dalam hal pelayanan medis maupun nonmedis.
Dengan lahirnya Perpres 59/2024, tarif iuran BPJS Kesehatan pun juga akan berubah. Hanya saja, dalam Perpres itu belum dicantumkan secara rinci ihwal besar iuran yang baru. Besaran iuran baru BPJS Kesehatan itu sesuai rencana baru ditetapkan pada 1 Juli 2025.
“Penetapan manfaat, tarif, dan iuran sebagaimana dimaksud ditetapkan paling lambat tanggal 1 Juli 2025,” tulis aturan tersebut, dikutip Senin (13/5/2024).
Itu artinya, iuran BPJS Kesehatan saat ini masih sama seperti sebelumnya, yakni sesuai dengan kelas yang dipilih. Namun perpres itu tetap berlaku sembari menanti lahirnya peraturan lanjutan dari perpres tersebut.
Kesiapan Rumah Sakit
Berkaitan dengan lahirnya kebijakan layanan kesehatan tanpa dibedakan kelas lagi, Kementerian Kesehatan (Kemenkes) menegaskan mayoritas rumah sakit di Indonesia siap untuk menjalankan layanan KRIS untuk pasien BPJS Kesehatan.
Kesiapan itu diungkapkan oleh Dirjen Pelayanan Kesehatan Kemenkes Azhar Jaya. “Survei kesiapan RS terkait KRIS sudah dilakukan pada 2.988 rumah sakit dan yang sudah siap menjawab isian 12 kriteria ada sebanyak 2.233 rumah sakit,” ujar Azhar.
Sebagai informasi, KRIS adalah pengganti layanan Kelas 1, 2, dan 3 BPJS Kesehatan yang bertujuan untuk memberikan layanan kesehatan secara merata tanpa melihat besaran iurannya.
Melalui KRIS, rumah sakit perlu menyiapkan sarana dan prasarana sesuai dengan 12 kriteria kelas rawat inap standar secara bertahap. Apa saja ke-12 kriteria KRIS itu?
Sesuai bunyi Pasal 46A Perpres 59/2024, disyaratkan kriteria fasilitas perawatan dan pelayanan rawat inap KRIS meliputi komponen bangunan yang digunakan tidak boleh memiliki tingkat porositas yang tinggi serta terdapat ventilasi udara dan kelengkapan tidur.
Demikian pula soal pencahayaan ruangan. Perpres itu juga mengatur pencahayaan ruangan buatan mengikuti kriteria standar 250 lux untuk penerangan dan 50 lux untuk pencahayaan tidur, temperature ruangan 20--26 derajat celcius.
Tidak hanya itu, layanan rawat inap berdasarkan perpres itu mensyaratkan fasilitas layanan yang membagi ruang rawat berdasarkan jenis kelamin pasien, anak atau dewasa, serta penyakit infeksi atau noninfeksi.
Selain itu, kriteria lainnya adalah keharusan bagi penyedia layanan untuk mempertimbangkan kepadatan ruang rawat dan kualitas tempat tidur, penyediaan tirai atau partisi antartempat tidur, kamar mandi dalam ruangan rawat inap yang memenuhi standar aksesibilitas, dan menyediakan outlet oksigen.
Selain itu, kelengkapan tempat tidur berupa adanya dua kotak kontak dan nurse call pada setiap tempat tidur dan adanya nakas per tempat tidur. Kepadatan ruang rawat inap maksimal empat tempat tidur dengan jarak antara tepi tempat tidur minimal 1,5 meter.
Tirai/partisi dengan rel dibenamkan menempel di plafon atau menggantung. Kamar mandi dalam ruang rawat inap serta kamar mandi sesuai dengan standar aksesibilitas dan outlet oksigen.
Azhar menjamin, Kemenkes akan menjalankan hal tersebut sesuai dengan tupoksi yang ada. “Tentu saja kami akan bekerja sama dengan BPJS Kesehatan dalam implementasi dan pengawasannya di lapangan,” ujar Azhar.
Berkaitan dengan perpres jaminan kesehatan itu, Direktur Utama BPJS Kesehatan Ghufron Mukti menilai, perpres tersebut berorientasi pada penyeragaman kelas rawat inap yang mengacu pada 12 kriteria. "Bahwa perawatan ada kelas rawat inap standar dengan 12 kriteria, untuk peserta BPJS, maka sebagaimana sumpah dokter tidak boleh dibedakan pemberian pelayan medis atas dasar suku, agama, status sosial atau beda iurannya," ujarnya.
Jika ada peserta ingin dirawat pada kelas yang lebih tinggi, kata Ghufron, maka diperbolehkan selama hal itu dipengaruhi situasi nonmedis. Hal itu disebutkan dalam Pasal 51 Perpres Jaminan Kesehatan diatur ketentuan naik kelas perawatan.
Menurut pasal tersebut, naik kelas perawatan dilakukan dengan cara mengikuti asuransi kesehatan tambahan atau membayar selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya yang harus dibayar akibat peningkatan pelayanan.
Selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya pelayanan dapat dibayar oleh peserta bersangkutan, pemberi kerja, atau asuransi kesehatan tambahan.
Ghufron Mukti juga mengimbau pengelola rumah sakit tidak mengurangi jumlah tempat tidur perawatan pasien dalam upaya memenuhi kriteria KRIS. "Pesan saya jangan dikurangi akses dengan mengurangi jumlah tempat tidur. Pertahankan jumlah tempat tidur dan penuhi persyaratannya dengan 12 kriteria tersebut," tegas Ghufron.
Penulis: Firman Hidranto Redaktur: Ratna Nuraini/Elvira Inda Sari Sumber: Indonesia.go.id
-
 @ 266815e0:6cd408a5
2024-05-09 17:23:28
@ 266815e0:6cd408a5
2024-05-09 17:23:28Lot of people are starting to talk about building a web-of-trust and how nostr can or is already being used as such
We all know about using the kind:3 following lists as a simple WoT that can be used to filter out spam. but as we all know it does not really signal "trust", its mostly just "I find your content interesting"
But what about real "trust"... well its kind of multi-denominational, I could trust that your a good developer or a good journalist but still not trust you enough to invite you over to my house. There are some interesting and clever solutions proposed for quantifying "trust" in a digital sense but I'm not going to get into that here. I want to talk about something that I have not see anyone discuss yet.
How is the web-of-trust maintained? or more precisely how do you expect users to update the digital representation of the "trust" of other users?
Its all well and good to think of how a user would create that "trust" of another user when discovering them for the first time. They would click the "follow" button, or maybe even rate them on a few topics with a 1/5 star system But how will a user remove that trust? how will they update it if things change and they trust them less?
If our goal is to model "trust" in a digital sense then we NEED a way for the data to stay up-to-date and as accurate as possible. otherwise whats the use? If we don't have a friction-less way to update or remove the digital representation of "trust" then we will end up with a WoT that continuously grows and everyone is rated 10/10
In the case of nostr kind:3 following lists. its pretty easy to see how these would get updated. If someone posts something I dislike or I notice I'm getting board of their content. then I just unfollow them. An important part here is that I'm not thinking "I should update my trust score of this user" but instead "I'm no longer interested, I don't want to see this anymore"
But that is probably the easiest "trust" to update. because most of us on social media spend some time curating our feed and we are used to doing it. But what about the more obscure "trust" scores? whats the regular mechanism by which a user would update the "honestly" score of another user?
In the real world its easy, when I stop trusting someone I simply stop associating with them. there isn't any button or switch I need to update. I simply don't talk to them anymore, its friction-less But in the digital realm I would have to remove or update that trust. in other words its an action I need to take instead of an action I'm not doing. and actions take energy.
So how do we reflect something in the digital world that takes no-energy and is almost subconscious in the real world?
TLDR; webs-of-trust are not just about scoring other users once. you must keep the score up-to-date
-
 @ ac8bb9b0:70278acc
2024-12-18 21:18:57
@ ac8bb9b0:70278acc
2024-12-18 21:18:57Details
- ⏲️ Prep time: 10
- 🍳 Cook time: 20
- 🍽️ Servings: 5
Ingredients
- 8 ounces uncooked linguine
- 1 pound chicken breast, cut into strips
- 1-2 tsp Cajun seasoning, or more to taste
- 1 tsp garlic powder
- 1 tbsp extra virgin olive oil
- 1 medium red bell pepper, thinly sliced
- 1 medium yellow bell pepper, thinly sliced
- 8 oz fresh mushrooms, sliced
- 1/2 red onion, sliced
- 3 cloves garlic, minced
- 2 tomatoes, diced
- 1 cup low sodium chicken broth
- 1/3 cup skim milk
- 1 tbsp flour
- 3 tbsp light cream cheese
- fresh cracked pepper
- 2 scallions, chopped
- kosher salt to taste
- avocado oil spray
Directions
- Prep all your vegetables.
- In a small blender make a slurry by combining milk, flour and cream cheese. Set aside.
- Season chicken generously with Cajun seasoning, garlic powder and salt.
- Prepare pasta in salted water according to package directions.
- Heat a large heavy nonstick skillet over medium-high heat; spray with oil and add half of the chicken.
- Sauté 5 to 6 minutes or until done, set aside on a plate and repeat with the remaining chicken. Set aside.
- Add olive oil to the skillet and reduce to medium; add bell peppers, onions, and garlic to skillet, sauté 3-4 minutes.
- Add mushrooms and tomatoes and sauté 3-4 more minutes or until vegetables are tender.
- Season with 1/4 tsp salt, garlic powder and fresh cracked pepper to taste.
- Reduce heat to medium-low; add chicken broth and pour in slurry stirring about 2 minutes.
- Return chicken to skillet; adjust salt and Cajun seasoning to taste, cook another minute or two until hot, then add linguine; toss well to coat.
- Top with chopped scallions and enjoy!
-
 @ 8cb60e21:5f2deaea
2024-08-24 23:33:51
@ 8cb60e21:5f2deaea
2024-08-24 23:33:51test
-
 @ a012dc82:6458a70d
2024-12-21 01:42:26
@ a012dc82:6458a70d
2024-12-21 01:42:26Table Of Content
-
The Mysterious Unidentified Miners
-
F2pool: A Titan in the Mining Arena
-
Other Notable Players
-
The Evolution of Bitcoin Mining
-
Conclusion
-
FAQ
Since the dawn of Bitcoin, introduced to the world by the mysterious Satoshi Nakamoto, the decentralized digital currency has been a topic of intrigue and speculation. At the heart of this cryptocurrency lies the process of mining, a complex computational task that validates transactions and adds them to the blockchain. Over the years, various mining pools have emerged, each contributing to the network's security and growth. Among these, two entities stand out: the unidentified miners and the dominant F2pool. This article delves into the enigmatic world of these miners and F2pool's significant role in Bitcoin's mining history.
The Mysterious Unidentified Miners
The Bitcoin blockchain, a transparent ledger of all transactions, has processed over 800,000 blocks since its inception. Interestingly, data from the last 14 years, encompassing 99 different mining pools, reveals that unidentified miners have discovered a staggering 28.37% of the network's total blocks. These miners, shrouded in mystery, include early participants like Satoshi and others who mined Bitcoin during its nascent stages.
While the identity of these miners remains unknown, their contribution to the network is undeniable. They've unearthed a cumulative 227,800 blocks, a testament to their early belief in the potential of Bitcoin and their commitment to its growth.
F2pool: A Titan in the Mining Arena
Close on the heels of these unidentified miners is F2pool, a behemoth in the Bitcoin mining world. Since 2009, F2pool has discovered 80,364 blocks, accounting for approximately 10.01% of the total. This impressive feat places F2pool as the leading identified mining pool in Bitcoin's history.
Established in 2013, F2pool, also known as DiscusFish, is based in China and has consistently been among the top mining pools in terms of hash rate. Their dominance is not just limited to Bitcoin; they have a significant presence in the mining of other cryptocurrencies like Litecoin, Ethereum, and Zcash.
The success of F2pool can be attributed to several factors:
-
Infrastructure & Technology: F2pool has invested heavily in state-of-the-art mining equipment and infrastructure, ensuring optimal performance and minimal downtime.
-
Transparency: Unlike some other mining pools, F2pool offers a transparent fee structure and provides regular updates to its members.
-
Community Engagement: F2pool has fostered a strong community of miners, offering support, educational resources, and fostering a sense of camaraderie among its members.
Other Notable Players
While the unidentified miners and F2pool have been dominant forces, other mining pools have also made significant contributions. Antpool, for instance, ranks third overall, having mined 75,829 blocks or 9.44% of the total. Following them are Btc.com’s mining pool, Braiins Pool, and Viabtc, each with their unique contributions to the network.
It's also worth noting the contributions of now-inactive mining pools. Btc Guild, for instance, mined 32,935 blocks before shutting down in 2015. Similarly, Ghash.io, which began its operations in 2013, ceased its activities in 2016 but not before mining 23,083 blocks.
The Evolution of Bitcoin Mining
The world of Bitcoin mining has seen exponential growth. In the early days, the Bitcoin network's hashrate was a mere 948 kilohash per second (KH/s). Fast forward to today, and miners are committing an astounding 387.62 exahash per second (EH/s) to the network. This astronomical increase, amounting to over 40 trillion percent since Bitcoin's inception, underscores the rapid technological advancements and the growing interest in cryptocurrency mining.
Conclusion
The history of Bitcoin mining is a tapestry woven with tales of innovation, determination, and a belief in the transformative power of decentralized digital currencies. The contributions of the enigmatic unidentified miners and the dominance of F2pool stand as testaments to the collective efforts that have fortified the Bitcoin network over the years.
As we look to the future, it's essential to acknowledge and appreciate the pioneers and leaders of the past. Their efforts have laid the foundation for a decentralized financial future, and their legacy will undoubtedly influence the generations of miners to come.
FAQ
Who are the unidentified miners in Bitcoin's history? They are early participants in the Bitcoin network, including Satoshi Nakamoto, whose identities remain unknown. They've mined approximately 28.37% of all blocks.
What is F2pool's contribution to Bitcoin mining? F2pool has discovered 80,364 blocks since 2009, making it the leading identified mining pool in Bitcoin's history.
When was F2pool established? F2pool was established in 2013 and is based in China.
Which mining pool ranks third in Bitcoin's mining history? Antpool ranks third, having mined 75,829 blocks or 9.44% of the total.
How has the Bitcoin network's hashrate evolved over time? From an initial hashrate of 948 KH/s, it has grown to a staggering 387.62 EH/s, marking an increase of over 40 trillion percent since its inception.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 266815e0:6cd408a5
2024-04-22 22:20:47
@ 266815e0:6cd408a5
2024-04-22 22:20:47While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent
I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS
There were a few things I learned from all these conversations:
- All the existing solutions have one thing in common. A universal ID of some kind for files
- HTTP is still good. we don't have to throw the baby out with the bath water
- nostr could fix this... somehow
Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...
An Identity system
An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files
This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)
What is blossom?
Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id
What are Blobs?
blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names
Instead blobs have a sha256 hash (like
b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553) as an IDThese IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can get a files sha256 hash on linux using:
sha256sum bitcoin.pdf)How do the servers work?
Blossom servers expose four endpoints to let clients and users upload and manage blobs
GET /<sha256>(optional file.ext)PUT /uploadAuthentication: Signed nostr event- Returns a blob descriptor
GET /list/<pubkey>- Returns an array of blob descriptors
Authentication(optional): Signed nostr eventDELETE /<sha256>Authentication: Signed nostr event
What is Blossom Drive?
Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs
What are Drives
Drives are just nostr events (kind
30563) that store a map of blobs and what filename they should have along with some extra metadataAn example drive event would be
json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at
If your interested, the full event definition is at github.com/hzrd149/blossom-drive
Getting started
Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started
1. Open the app
Open https://blossom.hzrd149.com
2. Login using extension

You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an
ncryptsecpassword protected private key - ansecunprotected private key (please don't) - bunker:// URI from nsecbunker3. Add a blossom server

Right now
https://cdn.satellite.earthis the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript github.com/hzrd149/blossom-server4. Start uploading your files
NOTE: All files upload to blossom drive are public by default. DO NOT upload private files

5. Manage files

Encrypted drives
There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify

Whats next?
I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything
also all the images in this article are stored in one of my blossom drives here
nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka
-
 @ 1cb14ab3:95d52462
2024-12-19 23:15:14
@ 1cb14ab3:95d52462
2024-12-19 23:15:14 -
 @ 8cb60e21:5f2deaea
2024-08-24 23:29:20
@ 8cb60e21:5f2deaea
2024-08-24 23:29:20 -
 @ 7c765d40:bd121d84
2024-12-19 13:44:40
@ 7c765d40:bd121d84
2024-12-19 13:44:40This was written on Monday morning. Haha it's been a busy week.
It's hard to know if the banks, corporations, and countries have realized that they cannot stop bitcoin - or if this was the plan all along.
But 2024 has definitely been the year of corporate adoption.
We are in the middle of this transition from "analog" to "digital" and even though banks can't hold bitcoin yet, they are buying the closest thing to it - MicroStrategy shares.
Why can't they hold bitcoin?
Well it's only 15 years old and we all know how long it takes for big banks and corporations to move.
They have certain rules and regulations around what kind of investments they can hold.
Magic internet money hasn't made it onto their approved list yet.
But MicroStrategy has - since it's a publicly traded stock.
And that's why we've seen a 150% gain in MSTR shares this year alone.
I stumbled across an article recently with the title "NATIONAL BANK OF CANADA FI RAISES STOCK POSITION IN MICROSTRATEGY."
Interesting.
To the average person who has never heard of MicroStrategy, this would be completely irrelevant.
Most people have no idea what MicroStrategy is - or that it's been the best performing stock since adopting the bitcoin strategy in 2020.
If it said "NATIONAL BANK OF CANADA FI BUYS MORE BITCOIN," that might catch a few eyes.
But the big boys don't want it catching any eyes.
They are building their positions in bitcoin without anyone knowing.
They understand the scarcity aspect of bitcoin and want as much as possible before the average person shows up.
Let's look at some numbers here.
These are mindblowing.
-
National Bank of Canada FI - now hold approx. 39,000 MSTR shares (up 746% from last quarter)
-
UBS Asset Management - now own approx. 640,000 MSTR shares (up 971% from last quarter)
-
Charles Schwab Investment Management - now own approx. 664,000 MSTR shares (up 587% from last quarter)
-
Swiss National Bank - now own approx. 468,000 MSTR shares (up 904% from last quarter)
-
Sumitomo Mitsui Trust - now own approx. 343,000 MSTR shares (up 1,071% from last quarter)
-
International Assets Investment Management LLC - now own approx. 239,000 MSTR shares (up 224,965% from last quarter)
That is not a typo.
They are no longer "dipping their toes" into bitcoin.
MicroStrategy was added to the QQQ Index (top 100 companies on the market) which should create even more demand and attention from these big banks and funds.
They have certainly got the memo.
We are at an inflection point here in bitcoin.
The bitcoin holders with .10 bitcoin - 10 bitcoin are the ones who get to decide where this thing goes.
Individuals currently hold approx. 75% of the bitcoin while the big boys are desperately trying to play catch up.
Since 95% of the bitcoin has been mined to date (with pretty much 100% mined by year 2064), this bitcoin has to come from somewhere.
I did a segment discussing this on the show yesterday.
It's worth a watch.
You can find the show here.
It talked about this transition and what the holdings could look like in 20 years if we aren't careful.
Bitcoiners still hold the majority of bitcoin.
And the only way that can change is if they get hacked, seized, or tempted to sell.
The next 20 years in bitcoin will set the stage for the next 200.
Moral of the story: They are coming for your bitcoin. The longer you wait, the more they will pay.
Moral2 of the story: Never ever EVER sell your bitcoin. Lend against it instead. Think of it and use it like digital capital.
Moral3 of the story: MAKE THESE FUCKERS PAY.
PROJECT POTENTIAL - You can now find the expanded audio versions of these on the new podcast - Project Potential! I will be sharing the video versions here for the LITF members but you can also find it for free on Spotify and of course Fountain!
Here is the link to Episode 008 on Fountain: https://www.fountain.fm/episode/nQb5z3PolahVwsPbYX4r
Have a great day everyone! And remember, the only thing more scarce than bitcoin is time!
Jor 875001
-
-
 @ ac8bb9b0:70278acc
2024-12-16 19:37:12
@ ac8bb9b0:70278acc
2024-12-16 19:37:12Details
- ⏲️ Prep time: 10
- 🍳 Cook time: 20
- 🍽️ Servings: 6
Ingredients
- 2 tablespoons extra virgin olive oil
- 1 1/2 pounds ground chicken
- 1 yellow onion, chopped
- 2 tablespoons taco seasoning
- salt and black pepper
- 2 1/2 cups salsa or enchilada sauce
- 1 chipotle chili in adobo, chopped
- 2 cups fresh corn
- 4 ounces cream cheese, at room temperature
- 1/4 cup plain greek yogurt
- 1 teaspoon chili powder
- 1 1/2 cups shredded Mexican cheese blend
- 2 cups tortilla chips
- avocado, cilantro, and green onions, for serving
Directions
- Preheat the oven to 400° F.
- In a large oven-safe skillet, combine the olive oil, chicken, onion, salt, and pepper. Set the skillet over high heat. Cook, breaking up the meat as it cooks, until browned all over, 5 minutes. Add the taco seasoning, cook another 2 minutes. Then add 1/2 cup water. Stir in the salsa/enchilada sauce and chipotle. Simmer 5 minutes. Remove from the heat and add in the cilantro.
- In a bowl, combine the corn, cream cheese, yogurt, chili powder, and salt. Stir in 1/2 cup cheese.
- Dollop 1/3 of the corn mix over the skillet. Add the tortilla chips on top, pressing them gently into the skillet. Add the remaining corn mix by spoonfuls on top of the chips (like nachos). Top with the remaining cheese. Bake for 15 minutes, until the cheese is melted.
- Serve topped as desired with avocado, cilantro, green onion, and cotija/feta cheese.
-
 @ 63d59db8:be170f6f
2024-12-18 16:24:11
@ 63d59db8:be170f6f
2024-12-18 16:24:11I am Oana, a fine-art photographer with a deep passion for capturing nature's fragile resilience. My work has been recognized internationally, featured on platforms such as CNN Style, Forbes, and Amateur Photographer, and honored by the Sony World Photography Awards. With over 25 years of creative experience, I focus on blending fine-art aesthetics with ecological storytelling to highlight the beauty, complexity, and vulnerability of our natural world.
For this submission, I’ve selected some of my finest works, which reflect my ongoing exploration of flora in their natural environments. These images celebrate the interplay of light, texture, and motion, capturing moments that reveal the unique personalities of flowers and plants without interference. My goal is to foster an emotional connection between viewers and the overlooked beauty of the natural world.
This work represents my artistic vision of combining visual poetry with a deeper narrative about sustainability and our relationship with the environment. Each photograph is a window into nature’s story, inviting viewers to engage with its raw, unfiltered essence.






Submit your photographs to our Visual Expression awards. Current prize is $130 / 125,140 sats.
Learn more and enter here. Deadline is December 31, 2024!

-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 8cb60e21:5f2deaea
2024-08-24 23:26:03
@ 8cb60e21:5f2deaea
2024-08-24 23:26:03hello draft
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ 8cb60e21:5f2deaea
2024-08-24 23:07:08
@ 8cb60e21:5f2deaea
2024-08-24 23:07:08 -
 @ cc448f8b:a1ad47db
2024-12-20 18:27:36
@ cc448f8b:a1ad47db
2024-12-20 18:27:36A Website Hosted on NOSTR?
The Nostr landscape is changing every day. https://npub.pro came across my radar and clearly it cannot work well, basically a website hosted almost entirely on Nostr relays. I was wrong!
I'll be honest that at first, things did not go well. I posted several issues on https://github.com/nostrband/nostrsite and within a very short time the problems were addressed. Right now it is working so much better. While there is always room for improvement, it is incredibly easy to create a website.
I've invited podcaster/blogger friends to give it a try and most now have a working website in such short time.
Quick Start
- Visit https://npub.pro
- Login
- Select a theme.
- Make some settings adjustments (icon, backdrops, colors, etc)
- Press the
Publishbutton and that's it!
Here's where it gets interesting, there is no cms backend for your posts. Instead, use any Nostr client to create your website post. Here's a small list of popular clients: https://nostr.com/clients.
Tips
The site previews work best if you already have content on Nostr.
I would start out with all content, no filtering. Once you finalize your theme choice add filters because you may not want all your Nostr posts to be visible on the website. For example if you have a DIY blog, add the
#DIYhashtag to all the posts you want to see on the website and set your filter to only show posts tagged#DIY. No-one wants to see your#coffeechainposts on your DIY blog, LOL.What I Like Most
- Automagic RSS Feed
- Looks great on mobile devices
- No database, no CMS, no server maintenance
- Plenty of themes
- Beautiful OG/Twitter sharing
- Built in likes, zap and share plugin
- Theme customization for those that know how to
- Ability to add contributors without creating accounts or managing user databases
- Ability to filter Nostr notes via tags or format (long/short notes)
- Use free subdomain or use your own custom domain
- Fully working site comments with zero effort
What I Dislike
- Not a problem for me but some probably won't like un-moderated site comments
- Not all CSS is manipulable, or example, some CSS is loaded after the custom css like the Zap/share dialogs (perhaps this is a theme specific issue)(also most creators probably won't use custom css/js code)
Website Examples Created By Others Using https://npub.pro
- Sport news - https://gsc.npub.pro/
- Podcast - https://directordetour.npub.pro/
- Someones personal blog - https://marc26z.npub.pro/
- Custom domain + custom CSS styling - https://news.pivx.org
- My test website with custom CSS - https://palmtree.npub.pro
Conclusion
I would 100% recommend Npub.pro to anyone who wants a website. It should take the average person under 30 minutes to get a fully functioning website. If your familiar with the admin interface, you could probably spin up a new website in under 5 minutes.
-
 @ eee391ee:8d0b97c2
2024-12-20 18:22:06
@ eee391ee:8d0b97c2
2024-12-20 18:22:06Amber 3.0.5
- Add appName parameter for web apps using nip 55
- Try to fix bunker requests showing up again after accepting/rejecting them
- Fix loading screen
Download it with zap.store, Obtainium, f-droid or download it directly in the releases page
If you like my work consider making a donation
Verifying the release
In order to verify the release, you'll need to have
gpgorgpg2installed on your system. Once you've obtained a copy (and hopefully verified that as well), you'll first need to import the keys that have signed this release if you haven't done so already:bash gpg --keyserver hkps://keys.openpgp.org --recv-keys 44F0AAEB77F373747E3D5444885822EED3A26A6DOnce you have his PGP key you can verify the release (assuming
manifest-v3.0.5.txtandmanifest-v3.0.5.txt.sigare in the current directory) with:bash gpg --verify manifest-v3.0.5.txt.sig manifest-v3.0.5.txtYou should see the following if the verification was successful:
bash gpg: Signature made Fri 13 Sep 2024 08:06:52 AM -03 gpg: using RSA key 44F0AAEB77F373747E3D5444885822EED3A26A6D gpg: Good signature from "greenart7c3 <greenart7c3@proton.me>"That will verify the signature on the main manifest page which ensures integrity and authenticity of the binaries you've downloaded locally. Next, depending on your operating system you should then re-calculate the sha256 sum of the binary, and compare that with the following hashes:
bash cat manifest-v3.0.5.txtOne can use the
shasum -a 256 <file name here>tool in order to re-compute thesha256hash of the target binary for your operating system. The produced hash should be compared with the hashes listed above and they should match exactly. -
 @ 8d34bd24:414be32b
2024-12-18 14:21:53
@ 8d34bd24:414be32b
2024-12-18 14:21:53Most people who have been around the church or the Bible have heard Jesus’s parable of the sower who sowed seed on various types of ground. Just as there is some disagreement on which soil corresponds to a true Christian, so also there is disagreement on who is a true Christian today. I’m going to investigate what the Bible says on the subject.
And He spoke many things to them in parables, saying, “Behold, the sower went out to sow; and as he sowed, some seeds fell beside the road, and the birds came and ate them up. Others fell on the rocky places, where they did not have much soil; and immediately they sprang up, because they had no depth of soil. But when the sun had risen, they were scorched; and because they had no root, they withered away. Others fell among the thorns, and the thorns came up and choked them out. And others fell on the good soil and yielded a crop, some a hundredfold, some sixty, and some thirty. He who has ears, let him hear.” (Matthew 13:3-8)
“Hear then the parable of the sower. When anyone hears the word of the kingdom and does not understand it, the evil one comes and snatches away what has been sown in his heart. This is the one on whom seed was sown beside the road. The one on whom seed was sown on the rocky places, this is the man who hears the word and immediately receives it with joy; yet he has no firm root in himself, but is only temporary, and when affliction or persecution arises because of the word, immediately he falls away. And the one on whom seed was sown among the thorns, this is the man who hears the word, and the worry of the world and the deceitfulness of wealth choke the word, and it becomes unfruitful. And the one on whom seed was sown on the good soil, this is the man who hears the word and understands it; who indeed bears fruit and brings forth, some a hundredfold, some sixty, and some thirty.” (Matthew 13:18-23) {emphasis mine}
Nearly everyone agrees that the seeds that “fell beside the road, and the birds came and ate them up” refers to those who heard the word of God, but didn’t not believe and are not Christians. These people neither believe they are saved, nor pretend to be. Everyone agrees that the seed that “fell on the good soil and yielded a crop, some a hundredfold, some sixty, and some thirty” refers to those who heard the word of God, believed, and were saved. There is a little more confusion and disagreement on the seed that “fell on the rocky places, where they did not have much soil” and the seed that “fell among the thorns, and the thorns came up and choked them out.” My interpretation is that the seed that fell on rocky places represents those who heard the Gospel and liked the sound of it, but they never truly repented and were never actually saved, whereas the seed that fell among the thorns and was choked out are those who truly repented and were saved, but who got so distracted by the world that they failed to live faithful lives.
In the same way, there are many people confessing to be Christians, but who don’t truly believe what the Bible says and who don’t live lives honoring to Jesus. We can’t know for certain who are real Christians and who are not. Only God knows, but there are definite signs pointing to one or the other.
This article is my investigation of what it means to be a true, born-again Christian versus those who claim to be Christians, but are not considered children of God by Jesus. In today’s culture, this sounds very judgmental and divisive, but it is what Jesus said about His followers.
“Not everyone who says to Me, ‘Lord, Lord,’ will enter the kingdom of heaven, but he who does the will of My Father who is in heaven will enter. Many will say to Me on that day, ‘Lord, Lord, did we not prophesy in Your name, and in Your name cast out demons, and in Your name perform many miracles?’ And then I will declare to them, ‘I never knew you; depart from Me, you who practice lawlessness.’ (Matthew 7:21-23) {emphasis mine}
I think those of us who think we are Christians would like to make sure that we are actual Children of God and not pretenders. I also think, when we are looking for people to help us to follow Jesus, we would like to make sure we are following and/or learning from those who actually know Jesus and not a pretender. Whether the pretender knows they are lying or believes they know Jesus, but don’t, doesn’t really matter.1
Similarly to the categories in the above parable, there are many people that are so anti-God, it is obvious they are not a real Christians. There are a small number of people who live such Christ-like lives that there can be little doubt that they are real Christians. There are many people who call themselves Christians, but who may or may not have a relationship with Jesus. It is hard to tell if they are true Christians, are just good at faking it, or believe they are saved while not having a true relationship with Jesus.
Immediately following the initial parable of the sower, Jesus gives another related parable:
Jesus presented another parable to them, saying, “The kingdom of heaven may be compared to a man who sowed good seed in his field. But while his men were sleeping, his enemy came and sowed tares among the wheat, and went away. But when the wheat sprouted and bore grain, then the tares became evident also. The slaves of the landowner came and said to him, ‘Sir, did you not sow good seed in your field? How then does it have tares?’ And he said to them, ‘An enemy has done this!’ The slaves said to him, ‘Do you want us, then, to go and gather them up?’ But he said, ‘No; for while you are gathering up the tares, you may uproot the wheat with them. Allow both to grow together until the harvest; and in the time of the harvest I will say to the reapers, “First gather up the tares and bind them in bundles to burn them up; but gather the wheat into my barn.” ’ ” (Matthew 13:24-30) {emphasis mine}
For those that don’t know about plants, a tare is a plant that looks a lot like wheat, but doesn’t produce the grain heads that we eat and is therefore unprofitable. Just as the slaves say about the tares, “Do you want us, then, to go and gather them up?” and he replies, “No; for while you are gathering up the tares, you may uproot the wheat with them. Allow both to grow together until the harvest,” in the same way we don’t want to go around judging people and deciding for ourselves who is the bona fide Christian because we “may uproot the wheat with them.” Only Jesus knows for certain who is real and who is not.
At the same time, we Christians should be closest to those who show the fruit of the Spirit and live a life that imitates and honors Jesus. We need to be careful who we follow and who we chose as teachers.
“Beware of the false prophets, who come to you in sheep’s clothing, but inwardly are ravenous wolves. You will know them by their fruits. Grapes are not gathered from thorn bushes nor figs from thistles, are they? So every good tree bears good fruit, but the bad tree bears bad fruit. A good tree cannot produce bad fruit, nor can a bad tree produce good fruit. Every tree that does not bear good fruit is cut down and thrown into the fire. So then, you will know them by their fruits. (Matthew 7:15-19) {emphasis mine}
Ultimately we are not to be judges of who is a real Christian and who is not, but we are warned to be aware that there are false prophets and false Christians in our midst. Anyone who produces bad fruit (an ungodly lifestyle, hate, disinterest in things of God, etc.) is likely not a true Christian, even if they proclaim to be and never miss a Sunday service. Anyone who produces good fruit (a godly lifestyle, love, and a yearning for the things of God) is likely a true Christian. It is not which denomination or church a person is associated with that matters. It is a change in the life of the individual that matters. It is a relationship with Jesus that matters. It is love for God, God’s word, and fellow people that matters. There can be a true Christian that is a member of a dead church. There can be a vibrant, godly church that has unbelievers that have crept in as members.
I was recently having a conversation with a fellow Christian and a friend made a comment that it was so hard to witness to a person who thought they were a Christian, but were not. I’d argue that those who believe they are Christians, but are not, and family members, especially parents, are the hardest to witness to, but we are still called to do so. We may just need to be extra delicate in how we do it.
“Behold, I send you out as sheep in the midst of wolves; so be shrewd as serpents and innocent as doves.” (Matthew 10:16)
In addition to witnessing to the unsaved who believe they are saved, we also need to beware of those who pretend to be Christians or believe they are Christians, but don’t believe the Bible. They can easily lead us astray.
Talking to another friend who also has a college aged son, we were discussing how sometimes a believing student might be better off going to a secular university, where they expect to be taught falsehood and are staying aware, than to attend a liberal Christian university that might teach the same falsehood, but not be noticed because it is couched in Christian sounding language and because the students don’t have their guard up like they would at a secular university. On the other hand, if your kids are going to attend college, a Bible believing college (like Liberty University or Grand Canyon University) is a good choice. We need to intentionally teach our kids truth, so they will recognize the lies they will be told and taught.
And this I pray, that your love may abound still more and more in real knowledge and all discernment, so that you may approve the things that are excellent, in order to be sincere and blameless until the day of Christ; having been filled with the fruit of righteousness which comes through Jesus Christ, to the glory and praise of God. (Philippians 1:9-11) {emphasis mine}
How do we have “real knowledge and all discernment?” We must be reading our Bible daily. We can’t know God and know what He wants for us if we don’t know His commands and His word. We can’t judge teachers and preachers to know if they are teaching the truth if we don’t know the Bible. We need to be like the Bereans:
Now these were more noble-minded than those in Thessalonica, for they received the word with great eagerness, examining the Scriptures daily to see whether these things were so. (Acts 17:11)
As true Christians, we should have a hunger for God’s word and God’s presence. We should be interested in what God is interested in. We should care about others as God cares about others. As Christians we should long for conversation with God (prayer) and include Him in our lives.
When things are going well, it is hard to tell the wheat from the tares, or the real Christians from the pretenders. When hard times come, especially persecution of believers, it becomes much easier to differentiate between the two.
“Then they will deliver you to tribulation, and will kill you, and you will be hated by all nations because of My name. At that time many will fall away and will betray one another and hate one another. Many false prophets will arise and will mislead many. Because lawlessness is increased, most people’s love will grow cold. But the one who endures to the end, he will be saved. This gospel of the kingdom shall be preached in the whole world as a testimony to all the nations, and then the end will come. (Matthew 24:9-14) {emphasis mine}
Only the true believers will stay true to Jesus during persecution. Those who were faking it for earthly reward will turn against the persecuted believers. Those who don’t have a true relationship with Jesus will drift away to avoid persecution because they don’t have saving faith. No true believer will permanently leave Christ, but there will be some (many?) who wander away because their faith was not real. A simple prayer, without true repentance and without true faith, does not magically make a person a Christian.
The Bible does give believers a litmus test on who and what to trust:
Beloved, do not believe every spirit, but test the spirits to see whether they are from God, because many false prophets have gone out into the world. By this you know the Spirit of God: every spirit that confesses that Jesus Christ has come in the flesh is from God; and every spirit that does not confess Jesus is not from God; this is the spirit of the antichrist, of which you have heard that it is coming, and now it is already in the world. You are from God, little children, and have overcome them; because greater is He who is in you than he who is in the world. They are from the world; therefore they speak as from the world, and the world listens to them. We are from God; he who knows God listens to us; he who is not from God does not listen to us. By this we know the spirit of truth and the spirit of error. (1 John 4:1-6)
The Bible also gives a test to see if we are true believers:
Test yourselves to see if you are in the faith; examine yourselves! Or do you not recognize this about yourselves, that Jesus Christ is in you—unless indeed you fail the test? (2 Corinthians 13:5)
As Jesus said,
“Behold, I send you out as sheep in the midst of wolves; so be shrewd as serpents and innocent as doves. ” (Matthew 10:16)
I pray that God will give you wisdom to rightly judge people, teachings, and truth and that you would fully trust in Jesus through all circumstances and become conformed more and more to His likeness.
Trust Jesus.
-
 @ 07804b78:c375c543
2024-12-15 12:56:05
@ 07804b78:c375c543
2024-12-15 12:56:05Japanese follows. 日本語はあとで。
This article is for the 14th day of Nostr Advent Calendar 2024 (relay blogging). The article for the 13th day was "Open Sats 申請編" (Applying for Open Sats) by mono-san. The article for the 14th day will be "Nostrはじめました。" (I started Nostr) by bro-san.
Thinking of Thingstr
I've come up with an idea for Other Staff that I think is interesting (at least, for me), so I'm going to write about it. I actually wanted to show you the implementation and brag about it, but it's not solid enough to be implemented yet.
The key idea is just “add a reaction to the WikiData ID”.
WikiData
There is a service called WikiData. It is a knowledge base that provides structured data. You may be wondering what it is, but the important thing to understand here is that WikiData assigns identifiers to a fairly wide range of “objects” and “things”.
So, if you can react to this, you can think of various applications just by thinking of it for a moment, right?
For example, the anime series “There are too many losing heroines!” is assigned the ID
Q123819103. The corresponding page is https://www.wikidata.org/wiki/Q123819103 .(NOTE: The canonical URI for entities on Wikidata is http://www.wikidata.org/entity/Q1142841. This is in accordance with Semantic Web conventions, and is not https, but http. Also, this URI does not necessarily match the actual address of the correspnding web page. Just an identifier. In most cases, it will redirect).
What can wd do?
For example, what about a website that records your anime viewing history? You can record what you want to watch with 👀, what you've already watched with ✅, and your favorites with ☆. You can also express your “likes” for production companies, staff, voice actors, etc. In this way, you can see what a particular user likes.
This could be a movie, a book, a comic, an author, music, an idol group, a place, or food (Someone likes pork cutlet
Q1142841). The fact that you can record everything in the same framework is what makes it interesting.What form of event should it be recorded as?
There is probably room for discussion about how to record this information in a concrete way. The simplest way would be to use NIP-25's "Reactions to a website" kind:17 (a.k.a. Makibishi). How about something like this?
json [ ["i", "wd:Q123819103", "http://www.wikidata.org/entity/Q123819103"], ]Since NIP-73 has External Content IDs, it would be good if we could include WikiData here so that we could write
wd:Q123819103. Actually,isbn:and other identifiers have already been defined, so it is possible to use the current NIP range to describe books (however, the authors do not have IDs. If we use WikiData as an ID, we can also describe reactions related to the author). Of course, it is not a matter of choosing one or the other, and it is also fine to add the ISBN tag at the same time as the WikiData tag for books.Search for recorded reactions
So far, this is all very simple, but it would be inconvenient if we didn't include tags to mark subsets of reactions (for example, only those related to anime) so that we can query them together. When we try to create a site that is specialized for a certain purpose, we need to be able to extract the reactions that are necessary.
On Wikidata, the predicate
wdt:P31(instance of) is used to group together concepts that represent the same thing. For example, how about including this in theltag? "There are too many losing heroines!" is a "Japanese television anime series (Q63952888)", so:json [ ["i", "wd:Q1142841", "http://www.wikidata.org/entity/Q1142841"], ["l", "wdt:P31 wd:Q63952888"] ]UPDATE(2024-12-15): rnurachue-san suggested that
#lor#Lmight be better for labeling (the first version used#a). I think that's a good idea, so I've updated the article. nostr:nevent1qgswamu0rsela0kwhj87p24ueapxdp04vzz7ar0pp6lfyq923t3l02cqyr9786635s60ra0f973nwv2sln2l74lqx4twdlgxfz2jgevpvsgtc9zwn6dHowever, when you think about creating an anime website, you may want to query both TV anime and anime films. This makes things more complicated. "Japanese TV anime series (
Q63952888)" is a subclass (subclass of;wdt:P279) of "Anime series (Q117467261)", which is in turn a subclass of "Anime (Q1107)". However, if you were to embed this hierarchy in each reaction, it would waste a lot of space. The following query will get all the superclasses of "Japanese TV anime series (Q63952888)", but there are 54 of them.https://query.wikidata.org/#%23%20Subclass%20hierarchy%20traversal%20for%20Q63952888%0ASELECT%20%3Fitem%20%3FitemLabel%20%3Fsuperclass%20%3FsuperclassLabel%0AWHERE%20%7B%0A%20%20%23%20Starting%20class%0A%20%20wd%3AQ63952888%20wdt%3AP279%2a%20%3Fsuperclass%20.%0A%20%20BIND%28wd%3AQ63952888%20AS%20%3Fitem%29%0A%20%20SERVICE%20wikibase%3Alabel%20%7B%20bd%3AserviceParam%20wikibase%3Alanguage%20%22%5BAUTO_LANGUAGE%5D%2Cen%22.%20%7D%0A%7D%0AORDER%20BY%20%3Fsuperclass%0A
So, I think it should be okay for practical purposes to embed
P31s of the reaction target. In other words, if you search for "anime seriesQ63952888" and "anime movieQ20650540", that should be enough. Fortunately, the conditions for single-character tags work with OR, so you can query multiple tags at once. we'll have to try it to see how well it works in practice, though.Discussion: Which kind should I use?
So far we have considered using kind:17, but we have not yet decided whether it is a good idea to mix Thingstr events with reactions to web pages.
Also, there may be a debate over whether to record regular events or addressable events, depending on the purpose of use. For example, if you want to record the transition of viewing results and impressions on an anime viewing site, you should use regular events, and if you want to maintain the viewing status, you should use addressable events.
What do you think?
Other ideas
If we can react to Nodes on OpenStreetMap using the same framework, we might be able to create something like Swarm. Since the views you want to see will differ depending on the purpose, it would be good to create various sites while having a consistent way of recording. Wouldn't that be the most Nostr-like thing?
Summary
I discussed how to use WikiData and OpenStreetMap as an ID infrastructure and realize various check-in and review services with a unified data model by using them on Nostr. Please let us know if you have any feedback. Or why not try implementing it?
この記事は Nostr Advent Calendar 2024 の14日目の記事です。13日目の記事はmonoさんによる「Open Sats 申請編」でした。15日目の記事はbroさんによる「Nostrはじめました。」です。
Thingstrについて考えた
面白そうな(と勝手に思ってる) Other Staff のアイディアを思いついたので、書いてみます。 本当は実装を持ってきて自慢したかったのですが、まだふわっとしていて実装に落ちていません。
コアになるアイディアは「WikiData の ID に対して、Reactionをつける」これだけです。
WikiData
WikiData というサービスがあります。構造化データを提供する知識ベースです。 なにそれ?という感じですが、ここで大事なのはWikiDataはかなり広範な「もの」「こと」に識別子(Identifier)を付与している、ということです。
だから、これにリアクションできれば、ぱっと思いつくだけでもいろいろな応用ができそうじゃないですか。
例えば、アニメシリーズ「負けヒロインが多すぎる!」には
Q123819103というIDが振られています。これに対応するページとして https://www.wikidata.org/wiki/Q123819103 があります。(ただし、WikiData のエンティティに対する canonical な URI は http://www.wikidata.org/entity/Q1142841 であることには注意が必要です。セマンティックウェブの作法で https ではなく http になっています。そして、このURIは必ずしもWebページのアドレス一致しません。大抵の場合はリダイレクトされます)。
なにができるの
たとえば、アニメの視聴記録サイトはどうでしょう。👀は見たい作品、✅は視聴済み、☆はお気に入り、みたいに記録していく。制作会社、スタッフ、声優、...に対してLikeを表明したりできそうです。そうすると、あるユーザが何にLikeしているかわかります。
これが映画でもいいし、書籍、漫画、作家でもいいし、音楽でもいいし、アイドルグループでもいいし、場所でもいいし、食べ物でもいい(とんかつ
Q1142841が好き、とか)。全部同じ枠組みで記録できるのが面白そうなところです。どういうNostrイベントで記録する?
具体的な記録の仕方には議論の余地があるでしょう。一番単純なのは、NIP-25の "Reactions to a website" kind:17 (Makibishi) を使う方法でしょうか。こんなのはどうでしょう。
json [ ["i", "wd:Q123819103", "http://www.wikidata.org/entity/Q123819103"], ]NIP-73にExternal Content IDsがあるので、ここにWikiDataを入れられるようにして
wd:Q123819103と書けるとよさそうです。実はisbn:などはすでに定義されているので、書籍に関しては現行のNIPの範囲でもうまいことできます(ただ、著者にはIDが振られていません。WikiDataをIDに使うと著者に関するリアクションも記述できます)。もちろん、どちらか一方を選ぶというものでもなくて、書籍にはWikiDataのタグと当時にISBNのタグを付与しておいてもいいと思います。記録されたリアクションを検索する
ここまではシンプルでよいのですが、リアクションの部分集合(たとえばアニメに関連するものだけ、とか)をまとめてクエリできるように、目印となるタグを入れておかないと不便です。ある目的に特化したサイトを作ろうとしたとき、必要になるリアクションが抽出できるようにしておかないといけません。
WikiData では
wdt:P31(instance of) という述語で、ある概念が何を表しているかをグルーピングしてくれています。例えばこれをlタグとかに含めておくのはどうでしょうか。負けヒロインが多すぎる!は「日本のテレビアニメシリーズ(
Q63952888)」なので、json [ ["i", "wd:Q1142841", "http://www.wikidata.org/entity/Q1142841"], ["l", "wdt:P31 wd:Q63952888"] ]みたいな感じで付与します。
UPDATE(2024-12-15): rnurachueさんからラベル付けには
#lまたは#Lのほうがよいかもという提案をいただきました。最初のバージョンでは#aを使用していました。そのとおりだと思ったので更新しました。 nostr:nevent1qgswamu0rsela0kwhj87p24ueapxdp04vzz7ar0pp6lfyq923t3l02cqyr9786635s60ra0f973nwv2sln2l74lqx4twdlgxfz2jgevpvsgtc9zwn6dただ、アニメサイトを作ることを考えると、テレビアニメも劇場版アニメも両方クエリしたいこともありそうですよね。そうなると話が複雑になってきます。
「日本のテレビアニメシリーズ(
Q63952888)」は「アニメシリーズ(Q117467261)」のサブクラス(subclass of;wdt:P279)で、それがさらに「アニメ(Q1107)」 のサブクラスになっています。ただ、この階層をいちいちリアクションに埋め込むのと大変なことになります。以下のようなクエリで「日本のテレビアニメシリーズ(Q63952888)」のすべての上位クラスが取れるのですが、54件もあります。https://query.wikidata.org/#%23%20Subclass%20hierarchy%20traversal%20for%20Q63952888%0ASELECT%20%3Fitem%20%3FitemLabel%20%3Fsuperclass%20%3FsuperclassLabel%0AWHERE%20%7B%0A%20%20%23%20Starting%20class%0A%20%20wd%3AQ63952888%20wdt%3AP279%2a%20%3Fsuperclass%20.%0A%20%20BIND%28wd%3AQ63952888%20AS%20%3Fitem%29%0A%20%20SERVICE%20wikibase%3Alabel%20%7B%20bd%3AserviceParam%20wikibase%3Alanguage%20%22%5BAUTO_LANGUAGE%5D%2Cen%22.%20%7D%0A%7D%0AORDER%20BY%20%3Fsuperclass%0A
なので、リアクション対象の
P31を埋め込む、くらいで実用上は問題ないような気がします。つまり、検索するときに 「アニメシリーズQ63952888」と「アニメ映画Q20650540」を対象にすれば、十分では、ということです。幸い、一文字タグの条件はORで効くので、複数を並べて一度にクエリできます。実際にどのくらいうまく行くかはやってみないとわからないですが。議論: どの kind を使うべきか?
一旦 kind 17 を使うことを考えてきましたが、Thingstr のイベントが Web ページに対するリアクションと混ざるのが良いことなのか、いまいち判断がついていません。
また、用途によって regular event で記録するべきか、それとも addressable event で記録すべきか、という議論もありそうです。 アニメ視聴サイトを例にあげるなら、視聴実績とか感想の変遷を記録したいならば regular event でしょうし、視聴の状態を保持したいならば addressable とするのがよさそうです。
どう思いますか?
他のアイディア
これと同じ枠組みで OpenStreetMap の Node に対してリアクションできるようにすれば Swarm のようなものも実現できるかもしれません。
用途ごとに見たいビューは違うだろうから、一貫した記録の仕方を持ちつつ、色々なサイトを作ったらいいんじゃないでしょうか。それって最高にNostrっぽくないですか?
まとめ
WikiDataやOpenStreetMapをID基盤として活用し、Nostr上でreactすることで、様々なチェックインサービス、レビューサービスを統一的なデータモデルで実現する方法について議論しました。フィードバックがあったら教えてください。むしろ実装してみてください。
-
 @ a012dc82:6458a70d
2024-12-20 11:56:36
@ a012dc82:6458a70d
2024-12-20 11:56:36Table Of Content
-
Bitcoin's Journey: From Obscurity to Global Spotlight
-
Blockchain: The Backbone of Bitcoin's Success
-
The Paradox of Bitcoin's Ascendancy
-
The Intricacies of Secure Bitcoin Storage
-
The Final Word: Entrusting the Right Guardian
-
Conclusion
-
FAQ
In the digital age, where innovation is often synonymous with intangibility, Bitcoin stands as a testament to the power of decentralized finance. Born from the vision of a cashless society and the promise of financial autonomy, Bitcoin has rapidly transitioned from a theoretical concept to a tangible asset with profound global implications. However, as with any valuable asset, the question of its safekeeping becomes paramount. As Bitcoin's value skyrockets and its adoption spreads, the challenges associated with securely storing it come to the forefront. This article delves into Bitcoin's journey, the technology underpinning its success, the challenges of its storage, and the importance of entrusting its safety to the right hands. Join us as we crack the code of trust in the world of Bitcoin.
Bitcoin's Journey: From Obscurity to Global Spotlight
Bitcoin has charted an unparalleled trajectory, moving from being a fringe digital experiment to a global financial powerhouse. Its allure isn't just in its monetary value, but in the revolutionary potential it brings to the world of finance. While the market's inherent volatility can be jarring, especially during significant industry events, it's essential to recognize that such fluctuations are typical for pioneering technologies. The dot-com bubble's burst is a testament to this: groundbreaking technologies, despite initial hiccups, have historically showcased enduring value and resilience.
Blockchain: The Backbone of Bitcoin's Success
Bitcoin's rise isn't merely a result of market speculation. At its core, the underlying benefits of blockchain technology have been instrumental. Blockchain's decentralized ledger system offers transparency and security, driving an undeniable upward trend in Bitcoin's value and establishing a foundation for its long-term viability. As Bitcoin's value and global interest surge, the emphasis on its safekeeping becomes increasingly paramount.
The Paradox of Bitcoin's Ascendancy
As Bitcoin continues its meteoric rise, capturing the imagination and investment of people worldwide, its very success presents a paradox. This digital currency, once a niche concept known only to a select few, now finds itself in the global spotlight, and with this heightened attention comes a slew of challenges. The popularity and widespread adoption of Bitcoin have inadvertently made it a prime target for cyber threats and potential malfeasance. As more individuals and institutions flock to the Bitcoin ecosystem, the complexities of ensuring its safety become increasingly intricate. While there are numerous challenges that the Bitcoin community must grapple with, the issue of secure storage stands out. It's not just about protecting one's investment; it's about safeguarding the very integrity and trust that Bitcoin has built over the years. The question then arises: in an age where digital assets are becoming as valuable as physical ones, how do we ensure that Bitcoin remains both accessible and secure?
The Intricacies of Secure Bitcoin Storage
Many individuals are drawn to the Bitcoin realm with trading aspirations, aiming for significant returns. This trend is especially pronounced in developed economies. However, in emerging markets, the allure of a decentralized store of value is tangible. As a result, exchanges have become the primary gateway for many to enter the Bitcoin world. While these platforms are equipped with various security measures and are designed for trading, they often house vast amounts of Bitcoin. The challenge? These platforms, despite their security measures, aren't inherently designed for the long-term, secure storage of Bitcoin. A cursory online search about "Bitcoin exchange hacks" reveals numerous incidents, highlighting the risks of relying solely on exchanges for safeguarding one's Bitcoin assets.
The Final Word: Entrusting the Right Guardian The essence of the Bitcoin storage dilemma revolves around trust. As the ecosystem continues to evolve, both individuals and institutions must critically assess where and how they store their Bitcoin. The goal is to find a balance between trading accessibility and the security required for long-term holding. In this dynamic landscape, understanding the intricacies of Bitcoin storage and placing trust in the right guardians will be pivotal in ensuring the safety and appreciation of one's Bitcoin investments.
Conclusion
As we stand on the cusp of a financial revolution, Bitcoin's prominence in the global financial landscape is undeniable. Its meteoric rise, underpinned by the robustness of blockchain technology, has reshaped our understanding of value, trust, and decentralization. However, with great value comes the pressing responsibility of protection. The challenges of securely storing Bitcoin are not mere technical hurdles but pivotal concerns that will define its future adoption and integration. As enthusiasts, investors, and guardians of this digital gold, our collective responsibility is to ensure its safekeeping. By understanding the nuances of storage, being vigilant of potential risks, and placing our trust in reliable custodians, we can ensure that Bitcoin's promise is not just preserved but flourishes in the years to come. The journey of Bitcoin is as much about innovation as it is about trust, and as we move forward, it's this trust that will shape its legacy.
FAQ
Why is secure storage important for Bitcoin? Given its high value and digital nature, Bitcoin is a target for cyber theft. Secure storage ensures the safety of one's assets against hacks and unauthorized access.
Are exchanges safe for storing Bitcoin? While exchanges have security measures, they are primarily designed for trading. For long-term storage, dedicated Bitcoin wallets or cold storage solutions are recommended.
What is blockchain in relation to Bitcoin? Blockchain is the underlying technology of Bitcoin. It's a decentralized ledger system that records all Bitcoin transactions in a transparent and secure manner.
How can I ensure the safety of my Bitcoin investments? By understanding storage nuances, using secure wallets, regularly updating security protocols, and staying informed about potential risks.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ ac8bb9b0:70278acc
2024-12-11 20:10:29
@ ac8bb9b0:70278acc
2024-12-11 20:10:29Details
- ⏲️ Prep time: 15
- 🍳 Cook time: 1 hour 30 minutes
- 🍽️ Servings: 10
Ingredients
- 1 lb. ground beef
- 1 cup celery diced
- 1 cup carrots diced
- 1 medium onion diced
- 2 medium potatoes diced
- 5 cups beef broth
- 1 15 oz. can corn, drained
- 1 8 oz. can tomato sauce
- 1 28 oz. can diced tomatoes
- 1 teaspoon salt
- 1 teaspoon Italian seasoning
- 1 bay leaf
Directions
- In a large dutch oven (I used a 6-quart), over medium heat brown the ground beef until done. Spoon off the excess fat.
- Add the remaining ingredients and stir. Bring to a boil and reduce the heat. Allow to simmer for 1 to 1 ½ hours (with the lid on, but tilted so steam can release) or until the vegetables are tender.
- Remove the bay leaf and serve.
-
 @ 8cb60e21:5f2deaea
2024-08-24 21:27:00
@ 8cb60e21:5f2deaea
2024-08-24 21:27:00 -
 @ 7ed7d5c3:6927e200
2024-12-18 00:56:48
@ 7ed7d5c3:6927e200
2024-12-18 00:56:48There was a time when we dared not rustle a whisper. But now we write and read samizdat and, congregating in the smoking rooms of research institutes, heartily complain to each other of all they are muddling up, of all they are dragging us into! There’s that unnecessary bravado around our ventures into space, against the backdrop of ruin and poverty at home; and the buttressing of distant savage regimes; and the kindling of civil wars; and the ill-thought-out cultivation of Mao Zedong (at our expense to boot)—in the end we’ll be the ones sent out against him, and we’ll have to go, what other option will there be? And they put whomever they want on trial, and brand the healthy as mentally ill—and it is always “they,” while we are—helpless.
We are approaching the brink; already a universal spiritual demise is upon us; a physical one is about to flare up and engulf us and our children, while we continue to smile sheepishly and babble:
“But what can we do to stop it? We haven’t the strength.”
We have so hopelessly ceded our humanity that for the modest handouts of today we are ready to surrender up all principles, our soul, all the labors of our ancestors, all the prospects of our descendants—anything to avoid disrupting our meager existence. We have lost our strength, our pride, our passion. We do not even fear a common nuclear death, do not fear a third world war (perhaps we’ll hide away in some crevice), but fear only to take a civic stance! We hope only not to stray from the herd, not to set out on our own, and risk suddenly having to make do without the white bread, the hot water heater, a Moscow residency permit.
We have internalized well the lessons drummed into us by the state; we are forever content and comfortable with its premise: we cannot escape the environment, the social conditions; they shape us, “being determines consciousness.” What have we to do with this? We can do nothing.
But we can do—everything!—even if we comfort and lie to ourselves that this is not so. It is not “they” who are guilty of everything, but we ourselves, only we!
Some will counter: But really, there is nothing to be done! Our mouths are gagged, no one listens to us, no one asks us. How can we make them listen to us?
To make them reconsider—is impossible.
The natural thing would be simply not to reelect them, but there are no re-elections in our country.
In the West they have strikes, protest marches, but we are too cowed, too scared: How does one just give up one’s job, just go out onto the street?
All the other fateful means resorted to over the last century of Russia’s bitter history are even less fitting for us today—true, let’s not fall back on them! Today, when all the axes have hewn what they hacked, when all that was sown has borne fruit, we can see how lost, how drugged were those conceited youths who sought, through terror, bloody uprising, and civil war, to make the country just and content. No thank you, fathers of enlightenment! We now know that the vileness of the means begets the vileness of the result. Let our hands be clean!
So has the circle closed? So is there indeed no way out? So the only thing left to do is wait inertly: What if something just happens by itself?
But it will never come unstuck by itself, if we all, every day, continue to acknowledge, glorify, and strengthen it, if we do not, at the least, recoil from its most vulnerable point.
From lies.
When violence bursts onto the peaceful human condition, its face is flush with self-assurance, it displays on its banner and proclaims: “I am Violence! Make way, step aside, I will crush you!” But violence ages swiftly, a few years pass—and it is no longer sure of itself. To prop itself up, to appear decent, it will without fail call forth its ally—Lies. For violence has nothing to cover itself with but lies, and lies can only persist through violence. And it is not every day and not on every shoulder that violence brings down its heavy hand: It demands of us only a submission to lies, a daily participation in deceit—and this suffices as our fealty.
And therein we find, neglected by us, the simplest, the most accessible key to our liberation: a personal nonparticipation in lies! Even if all is covered by lies, even if all is under their rule, let us resist in the smallest way: Let their rule hold not through me!
And this is the way to break out of the imaginary encirclement of our inertness, the easiest way for us and the most devastating for the lies. For when people renounce lies, lies simply cease to exist. Like parasites, they can only survive when attached to a person.
We are not called upon to step out onto the square and shout out the truth, to say out loud what we think—this is scary, we are not ready. But let us at least refuse to say what we do not think!
This is the way, then, the easiest and most accessible for us given our deep-seated organic cowardice, much easier than (it’s scary even to utter the words) civil disobedience à la Gandhi.
Our way must be: Never knowingly support lies! Having understood where the lies begin (and many see this line differently)—step back from that gangrenous edge! Let us not glue back the flaking scales of the Ideology, not gather back its crumbling bones, nor patch together its decomposing garb, and we will be amazed how swiftly and helplessly the lies will fall away, and that which is destined to be naked will be exposed as such to the world.
And thus, overcoming our timidity, let each man choose: Will he remain a witting servant of the lies (needless to say, not due to natural predisposition, but in order to provide a living for the family, to rear the children in the spirit of lies!), or has the time come for him to stand straight as an honest man, worthy of the respect of his children and contemporaries? And from that day onward he:
· Will not write, sign, nor publish in any way, a single line distorting, so far as he can see, the truth;
· Will not utter such a line in private or in public conversation, nor read it from a crib sheet, nor speak it in the role of educator, canvasser, teacher, actor;
· Will not in painting, sculpture, photograph, technology, or music depict, support, or broadcast a single false thought, a single distortion of the truth as he discerns it;
· Will not cite in writing or in speech a single “guiding” quote for gratification, insurance, for his success at work, unless he fully shares the cited thought and believes that it fits the context precisely;
· Will not be forced to a demonstration or a rally if it runs counter to his desire and his will; will not take up and raise a banner or slogan in which he does not fully believe;
· Will not raise a hand in vote for a proposal which he does not sincerely support; will not vote openly or in secret ballot for a candidate whom he deems dubious or unworthy;
· Will not be impelled to a meeting where a forced and distorted discussion is expected to take place;
· Will at once walk out from a session, meeting, lecture, play, or film as soon as he hears the speaker utter a lie, ideological drivel, or shameless propaganda;
· Will not subscribe to, nor buy in retail, a newspaper or journal that distorts or hides the underlying facts.
This is by no means an exhaustive list of the possible and necessary ways of evading lies. But he who begins to cleanse himself will, with a cleansed eye, easily discern yet other opportunities.
Yes, at first it will not be fair. Someone will have to temporarily lose his job. For the young who seek to live by truth, this will at first severely complicate life, for their tests and quizzes, too, are stuffed with lies, and so choices will have to be made. But there is no loophole left for anyone who seeks to be honest: Not even for a day, not even in the safest technical occupations can he avoid even a single one of the listed choices—to be made in favor of either truth or lies, in favor of spiritual independence or spiritual servility. And as for him who lacks the courage to defend even his own soul: Let him not brag of his progressive views, boast of his status as an academician or a recognized artist, a distinguished citizen or general. Let him say to himself plainly: I am cattle, I am a coward, I seek only warmth and to eat my fill.
For us, who have grown staid over time, even this most moderate path of resistance will be not be easy to set out upon. But how much easier it is than self-immolation or even a hunger strike: Flames will not engulf your body, your eyes will not pop out from the heat, and your family will always have at least a piece of black bread to wash down with a glass of clear water.
Betrayed and deceived by us, did not a great European people—the Czechoslovaks—show us how one can stand down the tanks with bared chest alone, as long as inside it beats a worthy heart?
It will not be an easy path, perhaps, but it is the easiest among those that lie before us. Not an easy choice for the body, but the only one for the soul. No, not an easy path, but then we already have among us people, dozens even, who have for years abided by all these rules, who live by the truth.
And so: We need not be the first to set out on this path, Ours is but to join! The more of us set out together, the thicker our ranks, the easier and shorter will this path be for us all! If we become thousands—they will not cope, they will be unable to touch us. If we will grow to tens of thousands—we will not recognize our country!
But if we shrink away, then let us cease complaining that someone does not let us draw breath—we do it to ourselves! Let us then cower and hunker down, while our comrades the biologists bring closer the day when our thoughts can be read and our genes altered.
And if from this also we shrink away, then we are worthless, hopeless, and it is of us that Pushkin asks with scorn:
Why offer herds their liberation?
............................. Their heritage each generation
The yoke with jingles, and the whip.February 12, 1974
—translated from the Russian by Yermolai Solzhenitsyn
-
 @ cff1720e:15c7e2b2
2024-12-20 10:31:46
@ cff1720e:15c7e2b2
2024-12-20 10:31:46https://youtu.be/dSDm62Hmbf4?feature=shared
\ There is a place where life is simple, people are perfect, and everything is black and white. It's a place that's as far from reality as we can imagine. \ But maybe it's a lot closer than you think!\ \ Wenn Sie in einer Welt leben wollen die nicht schwarz-weiß ist, dann sollten Sie etwas dafür tun, denn das ist nicht selbstverständlich.
\ Das Internet ist die vielleicht bedeutendste Innovation der Menschheitsgeschichte. Es war gedacht als globaler Marktplatz für den freien Austausch von Informationen und Dienstleistungen. Heute erleben wir aber die Datensilos von Großkonzernen, eine unerträgliche Flut von Werbung und massive Zensur durch Regierungen und Globalisten. \ \ Millionen von Freiwilligen arbeiten unentwegt daran, dass unser Internet trotzdem noch nicht so aussieht wie in Nordkorea. Sie opfern ihre gesamte Freizeit oder haben sogar den Job dafür aufgegeben, dass die Informationen und der Zugriff darauf frei bleiben. Sie tun das zumeist unentgeltlich da die Projekte unterfinanziert sind. Zahlreiche sind leider deshalb schon gescheitert oder akut in ihrer Existenz bedroht.
Sie könnten also Ihre Weihnachtsspende dieses Jahr dahin leiten und somit helfen die Informationsfreiheit zu sichern. Hier ist eine Liste wichtiger Projekte in diesem Bereich, die auch vieles enthält was zur persönlichen Nutzung empfehlenswert ist:
\ Daten
Internet Archive Das Gedächtnis des Internet (624 Mrd. Seiten)\ OpenStreetMap Die freie Alternative zu Google Maps\ OpenRSS Schluss mit den Silos, alle Artikel in einer App \ Podcastindex Finden Sie 4.3 Millionen Podcasts in Ihrer App\ OpenCulture Freie Bücher, Podcasts, Videos, Online-Kurse\ OpenLibrary Millionen freier Bücher kostenlos online lesen\ Open Access Journals 13.634 kostenlose Journale, über 15 Mio. Artikel \ Creative Commons 55 Mio. Artikel, 490.000 Bilder, 100.000 Kurse
\ Software + Services
LINUX Die freie Alternative zu Windows \ GrapheneOS Android ohne Google-Tracking \ F-Droid Der Marktplatz für freie OpenSource Android-Apps \ OpenOffice Das freie Office mit Daten-Kompatibilität nach ISO \ NextCloud In der Private Cloud gehören Ihre Daten Ihnen \ Thunderbird Der Mail-Client der Outlook vergessen lässt \ NewPipe YouTube ohne Abonnement und Tracking \ Fountain Podcasting 2.0 nach dem value4value-Prinzip \ PeerTube / Odysee Alternative YouTube-Plattformen ohne Zensur \ RethinkDNS Blocken Sie Malware, Spyware, Ads und Tracker
Mindestens ebenso wertvoll wie Spenden, ist die aktive Unterstützung solcher Projekte. Das beginnt mit Nutzung und Weiterempfehlung, Aufbau von Communities, Feedback an die Entwickler, Testing bis hin zu Design und Entwicklung. Gemeinsame Gestaltung unserer Zukunft ist eine überwältigende Erfahrung, ich durfte das dieses Jahr in meinem Lieblingsprojekt “Pareto” erleben. Es waren lehrreiche und beglückende Momente, mit einem wunderbaren Team, die mein Bewusstsein nachhaltig verändert haben.

Natürlich freuen auch wir uns auf Ihr Feedback, Ihre Spende oder Ihre aktive Mitwirkung. https://pareto.space \ \ “Sei Du selbst die Veränderung, die Du Dir wünschst für diese Welt." \ Mahatma Gandhi
-
 @ 330516bf:ea23d292
2024-12-20 03:35:09
@ 330516bf:ea23d292
2024-12-20 03:35:09The self-declaration of identity is a philosophical open source project, hosted at https://memdeklaro.github.io/
Foreword
ID documents do more harm than good and should not be seen as a solution for trust or authentication. Many economic and social interactions can be done anonymously. For other situations, trust can be achieved by simply saying your (self-chosen) name, using a web-of-trust, word-of-mouth reputation, vouches, memberships, escrows or cash deposits, and authentication can be achieved by using a password, cryptographic key pair (e.g. PGP, Monero) or physical key or code (such as house keys or a safe code).
Background
In recent years, more and more things are asking for proof of identity, from basic necessities like jobs, housing and healthcare, to smaller things like receiving mail, buying a sim card or joining a gym. However, it is not enough to write your name and address on a form. Instead, only government-issued IDs are accepted, which gives the state a “monopoly on identity”.
Monopolies are dangerous in general due to the fact that if the service provider is harmful, inaccessible or otherwise problematic, you cannot choose a different provider, start your own provider, or go without. This particular monopoly is even worse, considering that access to government ID determines if you may participate in the economy (jobs, banking), society (housing, volunteer work, education, libraries, sports) or even exist (national borders).
Many people have no access to government ID. This group includes some stateless people, refugees, people who weren’t registered at birth, and people who escaped from child abuse, domestic abuse or cult abuse. The state’s claimed solutions, such as asylum procedures, stateless determination procedures, delayed registration of birth, child protective services and witness protection, often cannot help in practice, as the victim is often ignored, accused of lying, blamed for the persecution, or worse sent back to the persecutors against their will. Despite issuing laissez-passer and Nansen passports in the past, the United Nations and Red Cross do not issue alternative IDs today. It would be a relief if these processes would work and allow vulnerable people to escape from undeserved and dangerous situations, but unfortunately this is not the reality.
In addition, the collectivist concept of citizenship can be dangerous. For example, if someone does not identify with their birth culture, they should not be forced to follow it for life or identify themselves as a member of this culture. Instead, they should be free to dissent against this culture or leave this culture’s jurisdiction. Even worse is conscription — the cruel system where a nation-state can force someone against their will to kill or be killed, just because they happened to be born inside a certain territory. The world would be more free if people could exist as individuals, conscientious objectors against the fatalism of birth cultures and violence of statism, with freedom of association to leave hostile environments and join self-chosen communities.
“The blood of the covenant is thicker than the water of the womb.”
Self-declaration of identity gives people the power to decide their own fate. People are no longer the property of nations, governments, birth cultures or birth parents. The choice of your own name and renunciation of your circumstances of birth is a liberating act of individualism, where your ideals, actions and efforts matter more than the situation that you were arbitrarily born into.
Self-declaration of identity
Instead of requiring third parties such as birth countries, birth cultures and birth parents to define an individual’s identity, the self-declaration allows you to define your own name and eschews the concepts of birth countries and citizenship.
The self-declaration is a CR-80 plastic card or paper business card (85.6mm x 54mm). The self-declaration is written in Esperanto and includes the Esperanto flag and symbol. Esperanto was chosen because it is anational (sennacieca = not associated with a specific country, culture or state) and was created as a borderless language of peace, built on voluntary free association. The design features artwork of a peace dove in a blue sky with clouds.
As it is a self-declaration, it is not stored in a central database, does not require a third party’s permission and does not need to be issued by an authority. You are the authority over your own life.
The self-declaration includes the text:
- Title: Self-declaration of identity (Memdeklaro de identeco)
- Location: Esperanto community (Esperantujo)
- Issuer: EPO (ISO code for Esperanto)
- Quote: One world, one humankind (Unu mondo, unu homaro)
The self-declaration of identity contains:
- Self-chosen first name (Antaŭnomo) and self-chosen surname (Nomo) → an individual should be able to freely choose their own name
- Birth date (Naskiĝdato) → for declaration of age
- Photo → Dimensions 35mm x 45mm
- Signature (Subskribo) → sign your self-declaration
- Notes field (Notoj) → a place to write a note, e.g. “the holder is a conscientious objector” (Portanto estas konscienca obĵetanto)
- ID number (Numero), issuance date (Eldondato), expiry date (Limdato), issuer (Eldonisto), MRZ → bureaucratic boilerplate
The self-declaration of identity does not contain:
- Place of birth → allows people to cut ties with hostile environments and self-define their culture, beliefs and personal ties
- Citizenship or stateless status → allows people to cut ties with hostile governments or cultures, and exist as an individual instead of as property of a state that they did not choose
- Parents’ names → allows victims of child abuse to cut ties with abusers
To make your own:
- Use the generator at https://memdeklaro.github.io/ or download the repo (https://github.com/memdeklaro/memdeklaro.github.io/) and open index.html in your browser
- Alternatively download the front template (fronto.jpg) and back template (dorso.jpg) from the linked repo, and use an image editor such as GIMP to add your text (the font OCR-B.ttf is provided) and your photo and signature
- Calculate the MRZ code here (TD1): https://www.dynamsoft.com/tools/mrz-generator/ (Choose any country, then replace it with EPO)
- Print it out as a business card and optionally laminate (dimensions: 85.6mm x 54mm) or order a CR-80 plastic card from a printing service
Example:

Note:
Unfortunately the self-declaration of identity cannot be used to bypass government ID requirements, such as for jobs, housing, healthcare, finances, volunteer work, contracts, receiving mail or buying a sim card. Other non-government IDs such as Digitalcourage Lichtbildausweis (https://shop.digitalcourage.de/gadgets/lichtbildausweis-mit-selbst-waehlbaren-daten.html) and World Passport (https://worldcitizengov.org/what-is-the-world-passport/) have the same limitations.
Nation-states’ refusal to print IDs for undocumented, stateless and unregistered people (while forcing government ID requirements on employers, landlords, doctors and more) can and does put innocent people’s lives in danger. But unfortunately even the United Nations has not been able to change this, despite issuing conventions on statelessness and refugee status in the 1950s.
Further Reading
For further reading about identity (and why the state’s monopoly is harmful):
Passports Were a “Temporary” War Measure — Speranta Dumitru https://fee.org/articles/passports-were-a-temporary-war-measure
During World War II, we did have something to hide — Hans de Zwart https://medium.com/@hansdezwart/during-world-war-ii-we-did-have-something-to-hide-40689565c550
The Little-Known Passport That Protected 450,000 Refugees — Cara Giaimo https://www.atlasobscura.com/articles/nansen-passport-refugees
With each person left living on the streets, we are losing as a society — Petr Baroch https://www.statelessness.eu/blog/each-person-left-living-streets-we-are-losing-society
The rarely discussed dangers of KYC and what you can do about it — Anarkio https://vonupodcast.com/know-your-customer-kyc-the-rarely-discussed-danger-guest-article-audio
Exclusion and identity: life without ID — Privacy International https://www.privacyinternational.org/long-read/2544/exclusion-and-identity-life-without-id
Proving who I am: the plight of people in detention without proof of legal identity — Vicki Prais https://www.penalreform.org/blog/proving-who-i-am-the-plight-of-people/
Establishing identity is a vital, risky and changing business — The Economist https://www.economist.com/christmas-specials/2018/12/18/establishing-identity-is-a-vital-risky-and-changing-business
What’s in a name? The case for inclusivity through anonymity — Common Thread https://blog.twitter.com/common-thread/en/topics/stories/2021/whats-in-a-name-the-case-for-inclusivity-through-anonymity
True Names Not Required: On Identity and Pseudonymity in Cyberspace — Der Gigi https://dergigi.medium.com/true-names-not-required-fc6647dfe24a
Citizenship is obsolete — Samuela Davidova https://medium.com/@DavidovaSamuela/citizenship-is-obsolete-c36a20056752
License
Public Domain
Source code: https://github.com/memdeklaro/memdeklaro.github.io
Infographic

Translations
(Machine translated)\ Memdeklaro de identenco: self declaration of identity, autodeclaración de identidad, autodeclaração de identidade, autodéclaration d’identité, autodichiarazione di identità, autodeclararea identității, Selbsterklärung zur Identität, eigen verklaring van identiteit, Selvdeklaration af identitet, självdeklaration av identitet, egenerklæring om identitet, henkilöllisyysvakuutus, Isikuandmete esitamine, identitātes pašdeklarēšana, savęs deklaravimas, önbevallás a személyazonosságról, własna deklaracja tożsamości, vlastní prohlášení o totožnosti, vlastné vyhlásenie o totožnosti, samoprijava identitete, самодеклариране на самоличността, самопроголошення ідентичності, самозаявление о личности, αυτο-δήλωση ταυτότητας, pernyataan identitas diri, öz kimlik beyanı, الإعلان الذاتي عن الهوية, 身份自报, 身份自報, 自己申告, 신원 자기 선언
...
-
 @ 8cb60e21:5f2deaea
2024-08-24 00:10:45
@ 8cb60e21:5f2deaea
2024-08-24 00:10:45 -
 @ 32e18276:5c68e245
2023-12-06 15:29:43
@ 32e18276:5c68e245
2023-12-06 15:29:43I’m going to be on an ordinals panels as one of the people who is counter arguing the claim that they are good for bitcoin. I decided to brush up on the technicals on how inscriptions work. I am starting to see luke’s perspective on how it is exploiting a loophole in bitcoin’s anti-data-spam mechanisms.
Storing data in Bitcoin, the “standard” way
The standard way you add “data” to bitcoin is by calling the OP_RETURN opcode. Bitcoin devs noticed that people were storing data (like the bitcoin whitepaper) in the utxo set via large multisig transactions. The problem with this is that this set is unprunable and could grow over time. OP_RETURN outputs on the other-hand are provably prunable and don’t add to utxo bloat.
Here’s an excerpt from the march 2014 0.9.0 release notes that talks about this:
On OP_RETURN: There was been some confusion and misunderstanding in the community, regarding the OP_RETURN feature in 0.9 and data in the blockchain. This change is not an endorsement of storing data in the blockchain. The OP_RETURN change creates a provably-prunable output, to avoid data storage schemes – some of which were already deployed – that were storing arbitrary data such as images as forever-unspendable TX outputs, bloating bitcoin’s UTXO database. Storing arbitrary data in the blockchain is still a bad idea; it is less costly and far more efficient to store non-currency data elsewhere.
Much of the work on bitcoin core has been focused on making sure the system continues to function in a decentralized way for its intended purpose in the presence of people trying to abuse it for things like storing data. Bitcoin core has always discouraged this, as it is not designed for storage of images and data, it is meant for moving digital coins around in cyberspace.
To help incentive-align people to not do stupid things, OP_RETURN transactions were not made non-standard, so that they are relayable by peers and miners, but with the caveat:
- They can only push 40 bytes (later increased to 80,83, I’m guessing to support larger root merkle hashes since that is the only sane usecase for op_return)
Bitcoin also added an option called -datacarriersize which limits the total number of bytes from these outputs that you will relay or mine.
Why inscriptions are technically an exploit
Inscriptions get around the datacarriersize limit by disguising data as bitcoin script program data via OP_PUSH inside OP_IF blocks. Ordinals do not use OP_RETURN and are not subjected to datacarriersize limits, so noderunners and miners currently have limited control over the total size of this data that they wish to relay and include in blocks. Luke’s fork of bitcoin-core has some options to fight this spam, so hopefully we will see this in core sometime soon as well.
Inscriptions are also taking advantage of features in segwit v1 (witness discount) and v2/taproot (no arbitrary script size limit). Each of these features have interesting and well-justified reasons why they were introduced.
The purpose of the witness discount was to make it cheaper to spend many outputs which helps the reduction of the utxo set size. Inscriptions took advantage of this discount to store monke jpegs disguised as bitcoin scripts. Remember, bitcoin is not for storing data, so anytime bitcoin-devs accidentally make it cheap and easy to relay data then this should be viewed as an exploit. Expect it to be fixed, or at least provide tools to noderunners for fighting this spam.
Where do we go from here
The interesting part of this story is that people seem to attach value to images stored on the bitcoin blockchain, and they are willing to pay the fee to get it in the block, so non-ideologic miners and people who don’t care about the health and decentralization of bitcoin are happy to pay or collect the fee and move on.
Data should not get a discount, people should pay full price if they want to store data. They should just use op_return and hashes like opentimestamps or any other reasonable protocol storing data in bitcoin.
After going through this analysis I’ve come to the opinion that this is a pretty bad data-spam exploit and bitcoin devs should be working on solutions. Ideological devs like luke who actually care about the health and decentralization of the network are and I’m glad to see it.
-
 @ 266815e0:6cd408a5
2024-12-17 20:45:33
@ 266815e0:6cd408a5
2024-12-17 20:45:33Finally another version of noStrudel. I keep telling myself I'm going to do more frequent releases but then time keeps getting away from me
This release comes with a bunch of news features and most importantly a lot of cleanup
Features
Olas media posts
You can now view a simple feed of media posts made on https://olas.app/ in the app and comment on them using NIP-22 comments
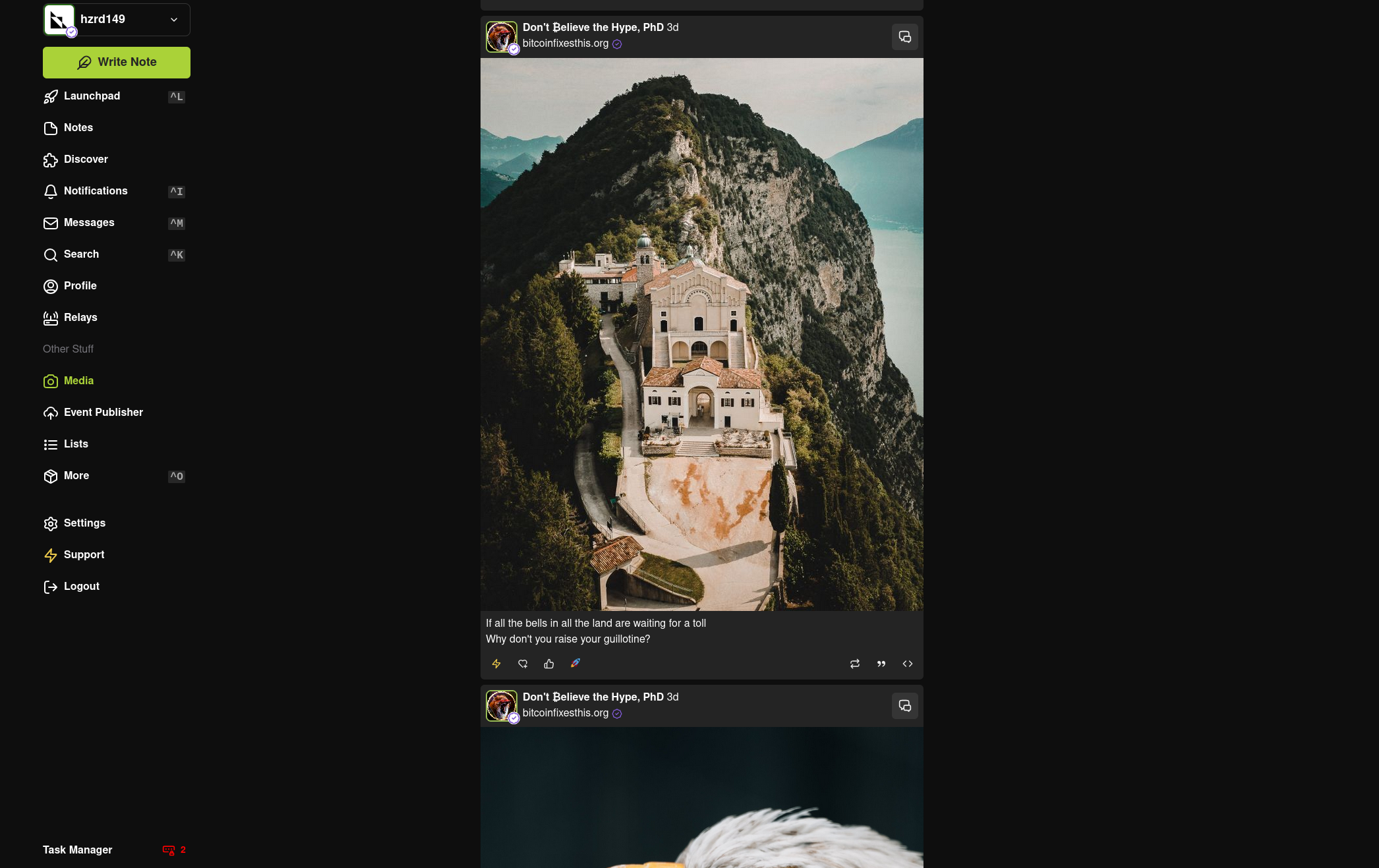
Simple gif picker
This was mostly a test, but there is now a simple gif picker (and barely functional search) that is based on
k:1063events If you want a better search and to help populate the nostr gif library you can use https://gifbuddy.lol created by nostr:npub1hee433872q2gen90cqh2ypwcq9z7y5ugn23etrd2l2rrwpruss8qwmrsv6
New support view
The (tiny) support button at the bottom of the side menu now hides a zap leader board that shows top supporters and any custom messages they leave
Favorite DVM feeds
You can now favorite DVM feeds in the discover view
Tools under notes
There is now a simpler tools menu under notes and threads
Searching local cache relay
If your using nostr-relay-tray the search view will now use it by default for searching. which should make it a little faster and more reliable
Small features
- Add "Proactively authenticate to relays" option to privacy settings, defaults to off
- Add option for debug API
- Add option to hide noStrudel logo in nav bar
- Show unknown notifications in notification view
- Add templates to event publisher
Bug fixes
- Show nostr mentions in markdown content
- Fix delete events not getting published to outbox
- Fix page changing from RTL when viewing some profiles
- Refresh relay info on relay page
- Fix bug with removing "about" in profile editor
- Fix automatically disconnecting from authenticated relays
Applesauce
Over the past few months I've been doing tons of cleanup on the core of noStrudel (677 changed files with 19,683 additions and 17,889 deletions) and extracting it out into a friendly nostr SDK called applesauce
Its very much a work-in-progress but the idea with these libraries is to help myself (and maybe others) build the UI layer of nostr apps and eventually make noStrudel just another app that is built with applesauce
If your a developer and another nostr SDK sounds interesting to you. you can check out the Getting Started docs
-
 @ 9711d1ab:863ebd81
2024-12-19 18:11:41
@ 9711d1ab:863ebd81
2024-12-19 18:11:41One of the best parts about running Breez is the diverse range of people I get to meet and work with. We have partners from Jamaica, the USA, Switzerland, Germany, Canada, Estonia, and who knows where else. We have users in Finland, Wales, Namibia, India, and almost everywhere else. The people behind Breez are split across three continents and come from a broad range of national and ethnic backgrounds.
Agreeing on a communication platform (Telegram? Slack? Zoom? Discord?) sometimes takes a bit of coordination. What never needs coordination, though, is the language we use to communicate. It’s always automatically English. For many of us, English is our second (or third, or fourth) language, and parts of it are baffling, but it doesn’t matter. Every initial contact is in English, all channels are automatically in English, and all public communication (like this blog) is in English. There’s not even a contender for second place.
And there’s basically no way to change this convention. Nobody could simply decree that we’re all going to start speaking Mandarin or Esperanto or Inuktitut. Whether because of convenience, actual utility, historical imposition, or sheer numbers, English is locked in. But it works, so why mess with it?
This example demonstrates a few points. First, the interface between individual nodes in a network — whether people, nations, or communities — has the form of a language. Second, there needs to be a common language. In fact, the limits of the language are the limits of the network. In other words, the distribution of the language defines the network. Finally, common languages are very sticky. Once everyone has adapted to a common language, it’s basically locked in.
Now for a fact about the present that will irrevocably shape the future: Lightning is emerging as the common language of the bitcoin economy.
 Lightning is bitcoin’s Tower of Babel, but nobody wants to tear it down. (Image: Wikimedia)
Lightning is bitcoin’s Tower of Babel, but nobody wants to tear it down. (Image: Wikimedia)A Common Language among Subnetworks
We’ve talked before about various last-mile technologies. They’re like the local secondary roads that connect users to the higher-throughput Lightning Network and, ultimately, the Bitcoin mainnet. They all basically work by bundling users and their transactions into subnetworks.
For example, Ark and Liquid convert incoming bitcoin into their own mechanisms (VTXOs and L-BTC, respectively) that users can then send to each other according to their respective protocols without needing further on-chain transactions. Alternatively, Fedimint members effectively pool their bitcoin and trade IOUs among themselves, with transactions and the financial state of affairs overseen by a federation of trusted guardians. With Cashu, people exchange e-cash tokens and trust the issuing body.
Each kind of subnetwork can use its own language. How the nodes communicate among themselves in these subnetworks is their business. What’s interesting is that these subnetworks communicate with each other over Lightning, even if we’re just talking about, say, two different Cashu mints or when a Fedi interacts with an Ark. Lightning is the common language of all the emergent and thriving subnetworks based on bitcoin.
Returning to the analogy of English, it doesn’t matter to me what language you speak at home or at the supermarket. You can speak whatever obscure dialect you want with others who understand it. But if you want to talk to me or virtually anyone else on Telegram or Slack, English is really the only option. Nobody could change that even if they wanted to, and nobody seems to want to. Just like Lightning.
Lightning is the common language of the emerging subnetworks. It’s the language of bitcoin.
Why Lightning Is the Optimal Language for Bitcoin
A common language is not necessarily an optimal language. It just has to work and be broadly accepted. Just like the Bitcoin mainchain has certain advantages (e.g. immutability, openness, borderlessness, etc.) that recommend it for certain uses, Lightning is the best choice for a common language between subnetworks for at least three reasons.
 Layered networks interacting via a common language. (Image: Adobe Firefly)
Layered networks interacting via a common language. (Image: Adobe Firefly)Lightning Is Bitcoin, and Bitcoin Is the Trustless Bearer Asset
The first and probably most important reason why Lightning is the best common language is that it uses bitcoin. Simply, the subnetworks might not trust each other, and they have no reason to. But since Bitcoin and, by extension, Lightning eschew trust, the subnetworks can interact without trust. Bitcoin is the only viable bearer asset, and Lightning is the language of Bitcoin, so Lightning is the best common language for the subnetworks to interact with each other.
Further, Lightning, like Bitcoin, also eschews leverage. The whole business model of fractional-reserve banks is based on a hole in their balance sheets. By contrast, every sat on Lightning is accounted for at every moment. A balance sheet displaying all the positions on the network would be perpetually balanced. No gap, no overlap. Lightning resists imbalances due to hubris, incompetence, and villainy, which is a necessary feature in a trustless environment.
Lightning Is Inherently Transactional and Interoperable
Second, Lightning is a transactional protocol designed to facilitate flow. For normal payments, there’s no mempool and no delay until the next block is mined. Payments take seconds, if that. And transactions — money in motion — are what make Lightning valuable. Literally. Static sats on the network don’t earn any return. In order for liquidity on Lightning to grow, it has to flow. A common language won’t be used much if it rewards silence. It must promote communication, which is exactly what Lightning does.
Further, the Lightning technology detailed in the catalog of bolt specs is inherently interoperable. It was designed to enable multiple implementations of Lightning nodes with different designs, trade-offs, and programming languages. All these nodes can, however, interact over a common network because they all support the same bolts. Being interoperable by design makes it easy for other technologies to add Lightning as another interface.
Lightning Has Critical Mass
Finally, a common language needs a sizeable community of speakers. Try saying “skibidi rizz” in a nursing home or, even better, a nursing home in Cambodia. Perhaps the biggest advantage of English is simply its popularity: more people speak English than any other language on the planet. And while only a quarter of the inhabitants of many countries speak English, you can still find an English speaker at the next table at virtually every bar and restaurant on the planet. Try that with Catalan.
Lightning has already achieved a critical mass. It’s already obvious how a Cashu subnetwork and Fedimint subnetworks will communicate with each other: Lightning. That’s how they were designed, so switching the common language between networks would require rebuilding most of their parts. Like English, whatever language subnetworks use internally, Lightning is the language they use to speak to each other, and it’s already locked in.
The Permanence of Lightning
Actual lightning — the kind from storm clouds — is a notoriously brief phenomenon. Flashing momentarily and vanishing is its whole thing. But the Lightning Network — the interface between any number of nodes, subnetworks, and the Bitcoin mainchain — is not going anywhere. Common languages tend to hold that status for centuries.
Bitcoin is the world’s best currency. Lightning is the common language of the bitcoin world, and it’s here to stay. For those of us already established in Lightning, this is very good news. That Lightning is locked in means our first-mover advantage is going to be very valuable indeed.
But it’s also good news for those just entering Lightning now or considering it. It eliminates uncertainty about which technology to support and invest in. Lightning is going nowhere but up, so it’s never the wrong time to get started. Better yesterday than today, better today than tomorrow, but tomorrow is good too.
The best time to get into Lightning is now. Always has been.
Originally published by Roy Sheinfeld on Breez's Medium.
-
 @ f0c7506b:9ead75b8
2024-12-08 09:05:13
@ f0c7506b:9ead75b8
2024-12-08 09:05:13
Yalnızca güçlü olanların hakkıdır yaşamak.
Güçlü olan ileri gider ve saflar seyrekleşir. Ama üç beş büyük, güçlü ve tanrısal kişi güneşli ve aydınlık gözleriyle o yeni, o vaat edilmiş ülkeye ulaşacaktır. Belki binlerce yıl sonra ancak. Ve güçlü, adaleli, hükmetmek için yaratılmış elleriyle hastaların, zayıfların ve sakatların ölüleri üzerinde bir krallık kuracaklardır. Bir krallık!
Benim aradığım insanların kendileri değil, sesleridir.
Duyguları körelmiş, çeşitli düşüncelere saplanmış kalabalık hiçbir zaman ilerlemenin taşıyıcısı olamaz, kendi küçüklüğünün o küflü içgüdüsüyle kalabalığın kin ve nefretle baktığı bir kişi, bir büyük kişi, iradesinin gösterdiği yolda kimsenin gözünün yaşına bakmaksızın ilahi bir güç ve bir zafer gülümsemesiyle yürüyebilir ancak.
Bizim soyumuz da sonsuz oluşum piramidinin doruk noktasını oluşturmaktan uzaktır. Bizler de mükemmelliğe ulaşmış değiliz. Bizler de henüz olgunlaşmadık.
Şairler sevgiye övgüler döşenir; doğrusu sevginin güçlü bir şey olduğu kesin. Hüneşin bir ışınıdır sevgi, aydınlatıp nurlandırır insanı der bazıları; bazıları da insanı esrikliğe sürükleyen bir zehri kendisinde barındırdığını söyler. Gerçekten de yol açtığı sonuçlar, bir hekimin ağır bir ameliyattan önce korkudan titreyen hastaya teneffüs ettirdiği güldürücü gazınkine benzer, içinde tepinip duran acıyı unutturur hastaya.
Önemli olan, hayatta hiç değilse bir kez kutsal bir ilkbaharın yaşanmasıdır; öyle bir bahar ki, insanın gönlünü ilerideki bütün günleri altın yaldızla kaplamaya yetecek kadar ışık ve parıltıyla doldursun.
Şu hayat denen şey kötü bir işçiliğin ürünü, acemilere göre bir şey. Bu kepaze yaşam uğruna insan nelere katlanmıyor ki!
Kendisine sadakatten ayrılmadığı, yalnızca kendisinin olan bir tek bu var: Yalnızlığı.
Sahildeki üstü tenteli hasır koltuklar arkasındaki yüksek, sessiz kum tepeleri içinde yürürsen, tenteler altındaki insanları göremezsin; ama birinin bir diğerine seslendiğini, bir başkasının gevezelik ettiğini, bir ötekinin güldüğünü işitir ve anlarsın hemen: bu insan şöyle şöyle biridir diyebilirsin. Onun hayatı sevdiğini, bağrında büyük bir özlem ya da acı barındırdığını, bu acının da sesini ağlamaklı kıldığını her gülüşünde hissedersin.
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8cb60e21:5f2deaea
2024-08-22 22:06:11
@ 8cb60e21:5f2deaea
2024-08-22 22:06:11 -
 @ 1cb14ab3:95d52462
2024-12-17 19:24:54
@ 1cb14ab3:95d52462
2024-12-17 19:24:54Originally written in October 2022 (Block: 757258 / USD: $20.1k / SatsDollar: 4961). Refined with slight edits for publishing on Nostr in December 2024 (Block: 875189 / USD: $106k / SatsDollar: 938 ). Banner image property of Hes. My journey down the rabbit hole has only intensified since the time of writing. Enjoy.
The Bitcoin time perspective is wild. Reflecting on it has been profoundly eye-opening, and once it has been seen— there is no returning to our prior ways.
Ever since venturing down the rabbit hole that we call Bitcoin, I’ve started making significant life decisions and forming nuanced opinions on polarizing topics based on the implications of multi-generational timeframes. Before Bitcoin, I spent money recklessly, leading a fast-paced and impulsive lifestyle. Even in my early days of learning about Bitcoin, I hadn’t fully seen the light. I would still blow the occasional $500 bar tab or buy some flashy gadget I didn’t need. Living in the moment has its merits, but so does considering the time beyond our own lives. Now, I pause before purchases and decisions, always reflecting on how they might impact the future.
When your money isn’t constantly being devalued before your eyes, you start seeing the world differently. You begin saving for the future with confidence, knowing that no central authority can endlessly print away your hard-earned time and energy. Inflation doesn’t just erode purchasing power; it steals time. It destroys the hours, days, and years of effort represented by a lifetime of savings. When governments print money to prop up failing banks or fund inefficient ventures, the impact ripples through generations. Those at the bottom of the ladder are hit the hardest, their ability to save and plan for the future undermined by forces beyond their control. Decisions become focused on surviving today instead of thriving tomorrow, leaving little room to consider the long-term implications of our choices. This system creates a mindset where we are incentivized to spend now, instead of save for later—an unnatural phenomenon that most of us have accepted as normal.
For individuals who simply want to put away money for a rainy day, inflation is a relentless adversary. A dollar in 1900 has lost over 96% of its value. The countless hours of labor behind those savings have been stolen. Not only did the expansion of money destroy what they could buy, it stole our time and energy. Years of our lives—blood, sweat, and tears—washed away.
This isn’t just a historical problem—it’s a recurring one that occurs every decade or so and is accelerating. At an average inflation rate of 3%, the value of cash halves roughly every 23 years. This means that even modest inflation rates gradually diminish purchasing power over time, forcing individuals to chase speculative assets like stocks, real estate, and gold—not because they want to, but because they have no choice. Personal inflation rates differ depending on consumer habits, but a glance at rising prices reveals they often outpace the 2% annual rate reported by the government, which poses a significant problem for individua;s, as highlighted in the table below:
Corporations like McDonald’s understand this. Sitting on a prime corner lot in every major city is far smarter than stacking a pile of cash losing value. Even if the franchise is losing money, the building it operates in is guaranteed to “rise” in value over time. This mindset trickles down to everyday people. To protect themselves, they’re compelled to invest in assets—with real estate being the pinnacle savings instrument of our time. The financial system we’ve accepted as normal turns shelter into an investment vehicle and savings into a gamble.
But here’s the irony: real estate is a lousy store of value—which is what we are all truly seeking. Properties require constant maintenance. Without care, assets deteriorate. We’ve all seen abandoned theme parks and overgrown cities. We’ve all dealt with broken pipes and creaky floorboards. Why should saving our hard-earned wealth require us to become housing market experts, landlords, or property managers? Why should we pay financial advisors to manage stock portfolios full of companies whose values or practices we might not even believe in, just to beat inflation?
A flawed monetary system inflates bubbles in real estate and stocks, redirecting resources into speculative markets instead of productive investments. Imagine a world where people don’t have to read quarterly earnings reports after a long day of work to ensure their cash retains value. If the incentives driving these bubbles were removed, the financial landscape would dramatically shift. Inflation wouldn’t push people into markets like real estate or zombie companies; instead, they could focus on building or supporting businesses they genuinely care about. They could plan for the long term and make well-thought-out, rational decisions about their future.
Bitcoin takes this entire dynamic and flips it on its head. It isn’t a tool for speculation as often misunderstood. It is the best form of saving humanity has ever seen. Unlike fiat currencies, Bitcoin’s fixed supply ensures scarcity, making it a refuge from the erosion of wealth caused by inflation. As weak currencies flow into stronger ones (a concept known as Gresham’s Law), Bitcoin’s role as a store of value becomes clearer. It’s not that Bitcoin has “gone up 19,000%”—it’s that people are exchanging weaker money for stronger money.
The implications of a world on a Bitcoin standard extend far beyond monetary policy. It offers something unprecedented: a tool for transferring the value of labor and energy across time and space. Unlike fiat, Bitcoin allows time to be preserved across generations. It isn’t just a hedge against inflation—it reintroduces the idea of saving with confidence, of being able to store wealth in a form of money that cannot be manipulated or devalued.
By saving in Bitcoin, individuals are no longer tethered to the uncertainties of fiat systems. The Bitcoin time perspective is about aligning our actions today with the future we want to build tomorrow. It’s about prioritizing long-term impact over short-term gains. When you embrace Bitcoin, you embrace a mindset that values time, energy, and the well-being of future generations. It’s not just a currency; it’s a revolution in thinking that will change you forever. The past, present, and future converge in this new paradigm, offering hope in an otherwise uncertain world.
Bitcoin isn’t a bubble; it’s a beacon.
More from Hes:
-
 @ f1989a96:bcaaf2c1
2024-12-19 15:16:35
@ f1989a96:bcaaf2c1
2024-12-19 15:16:35Good morning, readers!
After 53 years of tyranny, the Syrian regime has been overthrown. Rebels captured Damascus, forcing Bashar al-Assad and his family to flee to Moscow, Russia. Assad’s rule was defined by severe human rights abuses and widespread financial repression. Hundreds of thousands were jailed or killed, millions fled, and more than 90% of the country was plunged into poverty amid currency collapse. With Assad gone, Syrians may have a chance to rebuild their country and work toward a freer, more democratic future.
In Tunisia, President Kais Saied continues to dismantle civil society and due process. The regime is escalating the repression of journalists through arrests, incarceration, and judicial harassment to silence critical voices. By doing so, Saied shifts focus away from the country’s economic struggles and worsening hardships.
In technology news, Klever Wallet, a KYC-free digital asset wallet widely used in regions like Nigeria and the Philippines, integrated the Lightning Network via the Breez SDK, enabling fast, low-cost Bitcoin transactions for its significant global user base. In addition, the Bitcoin Design Foundation announced a South American Bitcoin UX Bootcamp, offering 10 skilled UX designers across South America a chance to refine their design expertise within the Bitcoin ecosystem and attend the 2025 bitcoin++ developer conference in Florianopolis, Brazil.
We end with a live stream of the 2024 Africa Bitcoin Conference, an inspiring event HRF supported and participated in. The conference brought together leaders and innovators across the African continent to advance Bitcoin for financial freedom and to push back against growing authoritarianism. If you were unable to attend in person, be sure to catch the recordings below.
Now, let’s dive right in!
Subscribe Here
GLOBAL NEWS
Syria | Assad Regime Overthrown
The Assad regime, infamous for its financial repression and brutal authoritarianism, has been overthrown following the rebel capture of Damascus, forcing Bashar al-Assad and his family to flee to Moscow. For 24 years under Assad — and 53 years of Assad family rule — the regime manipulated the economy to maintain its grip on power. Policies such as enforcing artificial currency exchange rates, restricting bank withdrawals, and imposing strict controls on the flow of goods and money plunged over 90% of Syrians into poverty. This economic stranglehold, combined with systemic human rights abuses, defined his reign. With the regime’s collapse, Syrians now face a pivotal moment to rebuild their country and pursue a future of more financial freedom.
China | Youth Bear the Brunt of Economic Slowdown
China’s slowing economy is forcing younger generations into increasingly precarious financial positions. Youth unemployment has soared past 17%, and even those who find work face stagnant wages and unmet income expectations. To survive, many young people are embracing extreme frugality — capping food expenses at just 500 yuan ($70), eating in the dark to save electricity, and avoiding dining out entirely. The middle class, weighed down by debt and a bleak economic outlook, is also adopting similar austerity measures. This growing financial strain offers a stark snapshot of China’s economic challenges and raises deep concerns about the long-term prosperity and opportunities for the nation’s youth.
Tunisia | Growing Repression of Journalists Amidst Worsening Economic Crisis
Tunisia is grappling with a worsening economic crisis, as citizens face soaring unemployment, a collapsing currency, and the devastating impacts of financial mismanagement. Amid this economic turmoil, President Kais Saied is intensifying his crackdown on dissent, imprisoning journalists in overcrowded cells, denying them medical care, and subjecting them to psychological torture — blatant evidence of the state’s disregard for human rights. Saied’s regime has also weaponized vague morality laws to target activists, influencers, and musicians, ensuring no opposition voice goes unpunished. By silencing dissent, Saied seeks to deflect attention from the regime’s economic failures, positioning the state as a moral authority while deepening the suffering of journalists and the broader public.
Pakistan | Testing Internet Firewall to Increase Financial Surveillance
Pakistan’s government is testing a nationwide Internet firewall, a tool designed to monitor, censor, and control online content by filtering internet traffic at the state level. By leveraging technology sourced from China, officials can block websites, restrict apps, and track individual online activity. This firewall poses a severe threat to financial freedom, as the military regime could use it to restrict access to tools like Bitcoin, cutting off alternative financial systems that offer privacy and independence. Civil society, including activists, journalists, and political dissidents, faces heightened surveillance, repression, and limited access to information — further curtailing their capacity to organize or express dissent.
India | Central Bank Governor Shares CBDC Vision
Outgoing Reserve Bank of India (RBI) Gov.Shaktikanta Das reaffirmed his vision for India’s central bank digital currency (CBDC), the digital rupee, as the nation’s currency continues to reach a record low against the US dollar. While hailed as the “future of currency” and praised for its potential economic benefits, the CBDC raises serious concerns. It grants the state unprecedented power to surveil transactions, freeze funds, and block payments in real-time — an alarming reality in a country already known for freezing opposition bank accounts and imposing rigid KYC requirements. Das’s hopes of a CBDC to “underpin the payment systems of the future” prioritizes state control at the expense of individual freedoms.
Georgia | Internet Shutdowns Amid Energy Crisis
In the breakaway Georgian region of Abkhazian, Russian-backed officials are using an energy crisis as a pretext to tighten Internet controls. Blaming illegal Bitcoin mining for electricity shortages, officials imposed nightly Internet shutdowns from midnight to 7:00 a.m., starting Dec. 10. These restrictions, coupled with power rationing and school closures, exacerbate hardships for residents as the region grapples with reduced energy from Russia and the Enguri hydroelectric plant. By painting Bitcoin as the villain, officials divert attention from broader governance failures while consolidating their grip over online communication and suppressing access to alternative financial tools.
LATEST IN BITCOIN NEWS, DEVELOPMENT, AND COMMUNITY
Klever Wallet | Integrates Lightning Network
Klever Wallet, a KYC-free digital asset wallet popular in underbanked countries like Nigeria, Brazil, India, and the Philippines, integrated the Lightning Network through the Breez SDK. This integration will empower its 100,000 active monthly users with fast, low-cost Bitcoin transactions directly from the wallet. By using the Breez SDK, Klever eliminates the complexities of Lightning channel management for users while maintaining a self-custodial design. This integration enhances financial freedom for its global user base — particularly in regions where traditional systems fall short.
Fedi | Adds Cashu Melting and Portable Nostr Keys
Fedi, a company leveraging Bitcoin and ecash technology to support communities, especially under authoritarian regimes, announced the integration of Cashu melting to enable users to receive Cashu ecash directly within the Fedi app. Built on the Chaumian ecash protocol, Cashu allows users to transact ecash tokens with strong privacy guarantees, minimal costs, and instant settlements, though with a custodial tradeoff. Additionally, Fedi now supports portable Nostr keys, allowing users to interact with external Nostr clients like Primal and Amethyst. Together, these updates enhance financial privacy and accessibility, offering users more control over their transactions and a portable digital identity, advancing financial freedom in underserved regions.
Core Lightning | Releases Latest Version with BOLT 12 by Default
Core Lightning, an implementation of the Lightning Network, introduced improvements to privacy and functionality with its latest v24.11 release. The update enables BOLT 12 offers by default when sending and receiving Bitcoin payments. BOLT 12 is an important update to the Lightning Network that brings increased receiver privacy, greater censorship resistance, and reusable payment requests for recurring payments. The update also includes xpay, an experimental payment plugin for advanced routing of payments on the Lightning Network. With these features, users of wallets and applications built with Core Lightning can maintain greater privacy and experience more optimized payments.
Proton Wallet | Implements Replace-by-Fee for Bitcoin Transactions
Proton, the company behind privacy tools like Proton Mail and Proton VPN, added support for Replace-by-Fee (RBF) transactions in Proton Wallet, its self-custodial and privacy-centric Bitcoin wallet. RBF allows users to increase the fee on stuck transactions to expedite confirmation and allow the payment to settle faster. The wallet also uses strong encryption and offers accessible recovery methods, ensuring users — like activists in hostile environments — maintain financial autonomy. Watch this tutorial by Bitcoin educator BTC Sessions to learn how to use Proton Wallet.
Bitcoin Design Community | South American Bitcoin UX Bootcamp
The Bitcoin Design Community, with support from HRF, will be hosting a South American UX Bitcoin Bootcamp. This program will support ten skilled UX designers across South America to develop and refine their design expertise within the Bitcoin ecosystem. Participants will also have the opportunity to attend the 2025 bitcoin++ developer conference in Florianopolis, Brazil, where they will receive specialized UX training and engage in hands-on learning with Bitcoin-related technologies. UX designers with an interest in Bitcoin are encouraged to apply here.
OpenSats | Announces Ninth Wave of Nostr Grants
OpenSats, a public nonprofit funding free and open-source software and projects, announced its ninth wave of grants supporting projects built on the decentralized Nostr protocol. Among the grantees is Pokey, an Android app enhancing Nostr and communications in restrictive environments through offline Bluetooth mesh networking and multi-account support. These features are particularly valuable for anyone facing Internet blackouts or state censorship. Another recipient, Persian NIPs, is breaking language barriers by localizing Nostr resources for Persian/Farsi speakers. The project will translate key protocols, user guides, and developer documentation, bringing decentralized and uncensorable technology to millions of people.
RECOMMENDED CONTENT
Africa Bitcoin Conference Livestream
Held from Dec. 9-11, 2024, in Nairobi, Kenya, the Africa Bitcoin Conference brought together human rights defenders, educators, and developers from across the continent to learn, collaborate, and innovate on freedom technologies. Supported by HRF, the event offered an inspiring mix of keynotes, workshops, panel discussions, and hackathons, all dedicated to advancing open-source solutions to fight authoritarianism and financial repression. This vibrant gathering highlighted innovative ideas and practical tools to empower communities worldwide. If you missed it, you can still catch the conversations and breakthroughs by watching the livestream here. Highlight talks include those from Farida Nabourema, Femi Longe, Jack Dorsey, and more.
-
 @ 65912a7a:5dc638bf
2024-12-08 05:33:02
@ 65912a7a:5dc638bf
2024-12-08 05:33:02Chef's notes
This is my late partner's award winning Cajun rice & beans recipe. It's an updated take on the traditional Cajun comfort food.
Chef Darin was a classically trained chef who spent 30+ years in the kitchen perfecting his recipes, and delivering authentic Cajun and Creole food to his patrons. This is a 5-star dish that will earn the respect of the most discerning Cajun afficionado. You won't be disappointed.
I suggest making this recipe exactly as directed the first time, and then make whatever adjustments you want for future batches. Also, don't cheap out on the Andouille. No Johnsonville or Hillshire Farms. Chef Aidelle's is a good choice, as is Silva's from Whole Foods. They cost a few extra bucks, but it's absolutely worth it.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 3 hours
- 🍽️ Servings: 12
Ingredients
- 16oz small red beans, dry
- 2 cups long grain white rice
- 14-16oz andouille sausage, sliced
- 8oz ham, cubed
- 1 large yellow onion, chopped
- 1 green bell pepper, chopped
- 2-3 stalks celery, chopped
- 2 tbsp garlic (12 cloves), minced
- 7 cups water
- ¼ cup olive oil
- 2 large bay leaves
- 1 tbsp parsley, dried
- 1 tsp thyme, dried
- 1 tsp Cajun seasoning
- ½ tsp cayenne pepper, dried
- ¼ tsp sage, rubbed
- 1½ tsp salt (more or less to taste)
Directions
- Soak beans in a large pot of water overnight.
- Heat oil in a large stockpot over medium heat. Cook onion, bell pepper, celery, garlic in olive oil for 3 to 4 minutes (until onion is translucent).
- Add beans, bay leaves, parsley, thyme, salt, MSG, Cajun seasoning, cayenne pepper, Sage, and water. Stir, bring to a boil, and then reduce heat to medium-low (btwn 2-3). Cover and simmer for 2½ hours.
- Remove bay leaves. Mash some of the beans. Stir Andouille and ham into beans, and simmer uncovered for an additional 30 minutes.
- Meanwhile, prepare the rice. Bring water and rice to a boil in a saucepan. Reduce heat, cover, and simmer for 20 minutes.
- Serve beans over steamed white rice.
-
 @ de496884:72617b81
2023-11-20 13:54:02
@ de496884:72617b81
2023-11-20 13:54:02Hola nostriches. Hoy quiero hacer una publicación a modo de acercamiento al surgimiento de las categorías de género y feminismo. Así que si te interesa el tema haz un esfuerzo, quédate y lee hasta el final.
El «nuevo» feminismo surge en los años 60 en aquellos países desarrollados que acordaron el reconocimiento a los derechos humanos contenidos en la declaración respectiva de la ONU. Entonces, como extensión a dicho reconocimiento es que se gesta el movimiento feminista. A partir de entonces, se vuelve a plantear la relación entre naturaleza y cultura y se llega a la conclusión de que las diferencias sociales van más allá de las diferencias biológicas, lo cual tiene que ver con que hasta la satisfacción de las necesidades elementales como son la alimentación, la vivienda o el vestuario, están condicionadas por construcciones sociales.
Pues resulta que una de las primeras propuestas identificó la subordinación femenina producto de una organización patriarcal, tomando la categoría patriarcado de Max Weber. Es así como la visión de patriarcado se extendió al discurso político y académico. Sin embargo, no existía información acerca del desarrollo histórico de dicha categoría, sistematización, variaciones, etc., debido a que era algo que recién se percibía en sociedad.
Sin embargo, la misma categoría de patriarcado junto a la de relaciones de poder para explicar fenómenos sociales contemporáneos, constituye uno de los principales aportes del feminismo. Es así como han logrado primero visibilizar y luego deconstruir y desmontar una serie de patrones existentes en la cultura que hacían a la mujer subordinarse al hombre, y que estaban presentes en el sistema sexo/género.
 Imagen relativa a la lucha contra el patriarcado
Imagen relativa a la lucha contra el patriarcadoHasta ese momento, en las investigaciones de corte sociológico se podía observar un androcentrismo excesivo al dar cuenta de que el discurso científico giraba en torno al hombre como sujeto y objeto de la investigación. Incluso para muchos positivistas como el mismo Weber, los problemas relativos a las mujeres quedaban en un segundo plano y eran achacados a una supuesta pasividad en el ámbito doméstico-familiar. Dicha pasividad partía de la supuesta inferioridad biológica del género femenino.
El patriarcado entonces era una categoría vacía en sí misma, sin valor explicativo. Desde el punto de vista político pudo ser útil para la movilización pero no resistió la polémica de los críticos del feminismo ni problematizó los conflictos a ser resueltos. Pero por otro lado, un grupo de mujeres -académicas principalmente- se puso manos a la obra en una tarea más pequeña pero con mayores resultados a la larga. Se propusieron generar conocimientos sobre las condiciones de vida de la mujer, buscar en el pasado y el presente los aportes de las mujeres a la sociedad, hacerlas visibles en la historia. Es así como surgen centros académicos, ONG, proyectos, centros de estudios sobre la mujer, etc.
Convendría distinguir entonces dos posturas que acompañaron a la investigación sobre las mujeres: uno que toma como objeto de estudio a la mujer; condiciones de vida, trabajo, cultura, y otra que privilegia a la sociedad como generadora de la subordinación de las mujeres. Mientras la primera perspectiva generaba conocimiento sobre las mujeres en el estudio de las relaciones mujer-hombre y mujer-mujer, la segunda tenía una visión más holística ya que planteaba que hay que estudiar la sociedad ya que la subordinación de las mujeres es producto de la organización de esta, y que no se avanzará solamente estudiando a las mujeres, pues el estudio debe ser más amplio y en diferentes niveles, ámbitos y tiempos.
Es en esta búsqueda donde nace y se desarrolla el concepto de género como categoría social. Es así que los sistemas de género/sexo fueron entendidos como conjuntos de prácticas, símbolos, representaciones, normas y valores sociales que las sociedades construyen a partir de la diferencia anatomofisiológica y que dotan de sentido a los impulsos sexuales, la reproducción y en general a las relaciones de las personas. Por tanto, este sistema pasó a ser el objeto de estudio para comprender la subordinación de la mujer al hombre. Al ser el reconocimiento de una dimensión de la desigualdad social hasta entonces desconocida, se considera la ruptura epistemológica más importante de la segunda mitad del siglo pasado.
 Imagen representativa del binarismo de género
Imagen representativa del binarismo de géneroHay que decir que los fenómenos sociales se definen por la relación que guardan entre sí. Es así que la contextualización adquiere gran importancia. Varones y hembras tenemos la capacidad de producir con el cuerpo, pero solo los cuerpos de las hembras pueden gestar y por tanto asegurar la especie humana. Todo grupo humano que pretenda sobrevivir debe asegurarse cierto número de hembras que lo hagan posible. De ahí un poder particular del cuerpo de las hembras que además es económicamente útil. Dicho poder no es en tanto entidad biológica, sino que es la sociedad la que le otorga este poder. En este punto es importante preguntarnos históricamente ¿quiénes han controlado la capacidad reproductiva de las mujeres?, ¿quiénes han tenido la preferencia en el acceso sexual? Para asegurar un control efectivo sobre la reproducción es necesario asegurar el acceso a la sexualidad.
Ello también lleva a dirigir el trabajo que hacen porque de lo contrario, las mujeres pudieran tener espacio para representar una amenaza al dominio de los hombres. Es importante atender a las etapas del desarrollo de las mujeres, que permitirá ver cómo se moldean para aceptar la desigualdad y las jerarquías según el género en las distintas sociedades y culturas.
Otro contexto a delimitar es el ámbito doméstico donde históricamente ha estado ubicada la subordinación femenina. Se ha puesto al descubierto que en mujeres que comparten la misma posición de clase y raza, la condición femenina se redefine a lo largo de la vida y que algunas mujeres gozan de poder sobre otras aún en contextos de alta dominación masculina, donde se les inviste de autoridad, creando el sistema zonas de incertidumbre que las divide como género e impide alianzas y se legitima la dominación. Foucault decía que «el poder se ejerce, no se posee», siempre está en peligro de perderse y no basta con normas, leyes, amenazas o castigos. De ahí que los espacios de subordinación sean también espacios de poder de las mujeres. Es en estos espacios donde aparece la inseguridad, la tensión, la confrontación y por ejemplo, las mujeres pueden reclamar la anticoncepción.
Para terminar, es importante tener en cuenta que el género es una forma de desigualdad social que siempre está articulado con otras formas de desigualdad ya sea clase, raza, grupo etario, etc. Hay que pensar la dominación masculina con un comienzo vago en el tiempo, pero que permite desligar la subordinación de las mujeres de la evolución «natural» de la humanidad y entenderla como un proceso histórico. En ese sentido es necesario destacar que, respecto a la raza, en sociedades plurales hay que atender al contexto étnico-cultural ya que en dependencia de las relaciones entre personas de razas distintas, estarán condicionadas las relaciones entre los géneros.
 Imagen de mujeres de distintas razas
Imagen de mujeres de distintas razasPor otro lado, si bien es sabido que históricamente el sistema de género social imperante ha contribuido a invisibilizar a la mujer, asociar necesariamente dicha categoría únicamente a ella, lo que hace es nuevamente recrear el absolutismo histórico que tanto daño ha hecho, ahora como lo antagónico al hombre. En la construcción social participan todos los individuos presentes en el sistema género.
Hasta aquí la publicación de hoy, de la cual aun se puede ahondar mucho más, sobre todo en lo referido al origen de la dominación o de la jerarquización del binomio «hombre/mujer» desde un punto de vista antropológico, pero eso quedará pendiente para otro momento. ¡Así que hasta la próxima!, ¡nos vemos en Nostr!
........................................
English version
Hello nostriches. Today I want to make a post by way of an approach to the emergence of the categories of gender and feminism. So if you are interested in the topic make an effort, stay and read to the end.
The "new" feminism emerged in the 60's in those developed countries that agreed to recognize the human rights contained in the respective UN declaration. Then, as an extension of that recognition, the feminist movement was born. From then on, the relationship between nature and culture was raised again and the conclusion was reached that social differences go beyond biological differences, which has to do with the fact that even the satisfaction of elementary needs such as food, housing or clothing are conditioned by social constructions.
It turns out that one of the first proposals identified female subordination as a product of a patriarchal organization, taking Max Weber's category of patriarchy. This is how the vision of patriarchy was extended to political and academic discourse. However, there was no information about the historical development of this category, systematization, variations, etc., because it was something that was only recently perceived in society.
However, the same category of patriarchy, together with that of power relations to explain contemporary social phenomena, constitutes one of the main contributions of feminism. This is how they have first made visible and then deconstructed and dismantled a series of existing patterns in the culture that made women subordinate to men, and that were present in the sex/gender system.
 Image relating to the fight against patriarchy
Image relating to the fight against patriarchyUp to that time, in sociological research, an excessive androcentrism could be observed as scientific discourse revolved around men as the subject and object of research. Even for many positivists such as Weber himself, the problems related to women remained in the background and were blamed on a supposed passivity in the domestic-family sphere. This passivity was based on the supposed biological inferiority of the female gender.
Patriarchy was then an empty category in itself, with no explanatory value. From the political point of view, it could be useful for mobilization, but it did not resist the polemic of feminism's critics, nor did it problematize the conflicts to be resolved. But on the other hand, a group of women - mainly academics - set to work on a smaller task but with greater results in the long run. They set out to generate knowledge about women's living conditions, to search in the past and present for women's contributions to society, to make them visible in history. This is how academic centers, NGOs, projects, women's studies centers, etc., came into being.
It would be convenient to distinguish then two postures that accompanied the research on women: one that takes women as the object of study; living conditions, work, culture, and the other that privileges society as the generator of women's subordination. While the first perspective generated knowledge about women in the study of woman-man and woman-woman relations, the second had a more holistic vision, since it proposed that society must be studied, since the subordination of women is a product of its organization, and that progress will not be made only by studying women, since the study must be broader and at different levels, spheres and times.
It is in this search that the concept of gender as a social category was born and developed. Thus, gender/sex systems were understood as a set of practices, symbols, representations, norms and social values that societies construct on the basis of anatomophysiological differences and that give meaning to sexual impulses, reproduction and, in general, to people's relationships. Therefore, this system became the object of study to understand the subordination of women to men. As the recognition of a hitherto unknown dimension of social inequality, it is considered the most important epistemological breakthrough of the second half of the last century.
 Representative image of gender binarism
Representative image of gender binarismIt must be said that social phenomena are defined by their relationship with each other. Thus, contextualization acquires great importance. Males and females have the capacity to produce with their bodies, but only the bodies of females can gestate and therefore ensure the human species. Any human group that intends to survive must ensure a certain number of females to make it possible. Hence a particular power of the female body, which is also economically useful. This power is not as a biological entity, but it is society that gives it this power. At this point it is important to ask ourselves historically, who has controlled the reproductive capacity of women, who has had the preference in sexual access? To ensure effective control over reproduction, it is necessary to ensure access to sexuality.
 Allegorical image of pregnancy
Allegorical image of pregnancyThis also leads to directing the work they do because otherwise, women may have room to pose a threat to men's dominance. It is important to pay attention to the stages of women's development, which will allow us to see how they are shaped to accept inequality and gender hierarchies in different societies and cultures.
Another context to delimit is the domestic sphere where female subordination has historically been located. It has been discovered that in women who share the same class and race position, the feminine condition is redefined throughout life and that some women enjoy power over others even in contexts of high male domination, where they are invested with authority, creating the system of uncertainty zones that divide them as a gender and prevent alliances and legitimize domination. Foucault said that "power is exercised, not possessed", it is always in danger of being lost and norms, laws, threats or punishments are not enough. Hence, the spaces of subordination are also spaces of women's power. It is in these spaces where insecurity, tension, confrontation appear and where, for example, women can demand contraception.
To conclude, it is important to keep in mind that gender is a form of social inequality that is always articulated with other forms of inequality, be it class, race, age group, etc. It is necessary to think of male domination with a vague beginning in time, but which allows us to separate the subordination of women from the "natural" evolution of humanity and to understand it as a historical process. In this sense, it is necessary to emphasize that, with respect to race, in plural societies it is necessary to pay attention to the ethno-cultural context since, depending on the relations between people of different races, the relations between genders will be conditioned.
 Image of women of different races
Image of women of different racesOn the other hand, although it is known that historically the prevailing social gender system has contributed to make women invisible, to necessarily associate this category only to women is to recreate the historical absolutism that has done so much damage, this time as antagonistic to men. All individuals present in the gender system participate in the social construction.
So much for today's publication, of which we can still go much deeper, especially with regard to the origin of domination or the hierarchization of the binomial "man/woman" from an anthropological point of view, but that will be left for another time. So until next time, see you in Nostr!

Créditos | Credits
Bibliografía consultada | Consulted bibliography:
-
Barbieri, T. (1993). Sobre la categoría género. Una introducción teórico-metodológica. Debates en Sociología. (18). 1-19. https://doi.org/10.18800/debatesensociologia.199301.006
-
Echevarría, D. (2020). Desigualdades de género e interseccionalidad. Análisis del contexto cubano 2008-2018. Facultad Latinoamericana de Ciencias Sociales (Programa-Cuba). https://www.clacso.org.ar/libreria-latinoamericana-cm/libro_detalle_resultado.php?id_libro=2346&campo=cm&texto=248
Traducción | Translation:
DeepL
-
-
 @ 8cb60e21:5f2deaea
2024-08-21 21:37:35
@ 8cb60e21:5f2deaea
2024-08-21 21:37:35 -
 @ c48e29f0:26e14c11
2024-12-17 16:33:04
@ c48e29f0:26e14c11
2024-12-17 16:33:04titcoin
Rename Bitcoin to "Titcoin" and sats to "tits."
Redefinition of Bitcoin into “Titcoin” and redefinition of sats into “tits” using that as the Unit Base of Denomination.
TitHub repository available here: https://github.com/WalkerAmerica/titcoin
Abstract
This BIP proposes redefining the commonly recognized "bitcoin" and “sats” units so that what was previously known “bitcoin” becomes “titcoin” and what was previously known as “sats,” the smallest indivisible unit, becomes “tits.” The “Bitcoin” Network will be renamed to the “Titcoin” Network. Under this proposal, one tit is defined as that smallest unit, eliminating the need for decimal places, and 100,000,000 tits is defined as a titcoin. By making tits the standard measure, this BIP aims to simplify user comprehension, reduce confusion, and align on-chain values directly with their displayed representation.
Also, by aligning Bitcoin's brand with live-giving tits, we will supercharge adoption and inject humor into financial sovereignty. After all, every baby came into this world sucking on tits.
Under this BIP: - Internally, the smallest indivisible unit remains unchanged. - With this proposal, "1 tit" equals that smallest unit. - What was previously referred to as "1 BTC" now corresponds to 100 million tits. - Satoshis are permanently eliminated.
Addressing the “Buttcoin” BIP:
Not much time need be wasted addressing the catastrophic “Button” BIP proposed by Rockstar Dev, but two points bear emphasizing:
- “Butts” is shitcoin-adjacent terminology (where does shit come from? Exactly…)
- Butts give you poop. Tits give you milk.
Case closed.
Motivation
Bitcoin's branding is boring. Worse yet, critics think Bitcoin is already "a joke," so let’s own it, let's: Make Bitcoin Funny Again. Laughter is universal, irresistible, and much cheaper than marketing agencies and product roadmaps. Besides, basically everyone either has tits or likes tits. Additionally, renaming Bitcoin as “Titcoin” makes the common trope of “Bitcoin BROS” sound even more stupid. “Titcoin Bros”? Get a life, man…
By rebranding Bitcoin to Titcoin (.)(.), we achieve several key goals:
1. Haters Become Users: People like tits. Tits give nourishment to babies. They can stack tits instead of just making fun of them. Adoption skyrockets as trolls turn into tit hodlers.
2. Memetic Power: The word “tit” is both universally funny and ageless. “Send me 10 tits” is instantly iconic. “Nice tits” is a great compliment. “That’s gonna cost you a pair of tits” is hilarious. Try saying that without smiling. You can’t. (.)(.)
3. Simplifying Denominations: Decimals are a blight on humanity. 0.00000001 BTC? Kill it. Under the Titcoin Standard:
- 1 Titcoin = 100,000,000 tits.
- Satoshis are gone. Forever. If you see Satoshi on the road, kill him - just like in Zen, where the teacher becomes the barrier. We transcend satoshis and achieve financial enlightenment.
4. Aligning with the Ledger: Bitcoin’s base unit was always integers, but now they’re funny integers. No more fractions, decimals, or math anxiety. Just tits. (.)(.)
5. Adoption via Humor: Titcoin lowers Bitcoin's intimidation factor. Newbies will feel at ease buying tits instead of serious-sounding fractions of BTC. Tits > Decimals.
Specification
Terminology Redefinitions: - "Bitcoin" → "Titcoin" (.)(.) - "BTC" → "TIT" (ISO-friendly and hilarious) - Satoshis → Gone. Eliminated. Defeated.
Example:
- Old: "I’ll send you 0.00010000 BTC."
- New: "I’ll send you 10,000 tits (.)(.)."
Wallet balances would display as:
- "You have 1,000,000 tits" instead of some boring fractional BTC amount.
Adoption Strategy
1. Memes First: Flood Twitter, Reddit, and Telegram with memes. Start with “Hodl your tits” and “Stack tits”.
2. Titcoin Podcast: There is already a podcast called “Titcoin Podcast” (which many people are saying is the fastest-growing Bitcoin (Titcoin) podcast in the world). Titcoin Podcast will be a driving force in the adoption of the Titcoin Standard. (.)(.)
Nostr: https://primal.net/titcoin
X: https://x.com/titcoinpodcast
Web: http://titcoin.org
3. Kill Satoshis: Developers MUST remove all references to satoshis. Replace satoshis in GUIs, APIs, and block explorers with tits. Satoshis were a stepping stone - it’s time to let go.
4. Emoji Standardization: Use the (.)(.) emoji universally to denote tits.
Rationale
1. Usability & Clarity: "Decimals are for nerds. Tits are for everyone." A common currency for humans should be easy to use, funny, and integer-based.
2. Appealing to Critics: Bitcoin has endured years of attacks from all sides. By adopting the Titcoin Standard, we turn anyone who doesn’t like Titcoin into a tit-hating bigot. It’s an elegant financial counterattack. Additionally, everyone always says “we need more women in Bitcoin,” and now women will feel more represented by Titcoin, because they have tits. (.)(.)
3. Transcending Satoshis: Satoshis served us well, but their time is over. True enlightenment comes when we abandon decimals, satoshis, and arbitrary denominations. If you meet Satoshi on the road, kill him.
4. Memetic Durability: Everyone loves a good tit joke. It’s timeless.
Backward Compatibility
There is no backward compatibility because Titcoin is the future. Applications must hard fork their UI to replace all references to Bitcoin and BTC with Titcoin and TIT.
Implementation Timeline
- Phase 1 (1 month): Meme dissemination. Every wallet dev team is required to add (.)(.) emoji support.
- Phase 2 (3 months): Exchanges rebrand BTC tickers to tit. Nostr zaps tits into hyperspace.
- Phase 3 (6 months): Michael Saylor announces MicroStrategy now stacked 10 trillion tits, declaring it the superior currency. ETFs follow suit, ensuring Wall Street hodls tits en masse. Banks allow tit transfers via SWIFT.
Test Vectors
- Old: 1.00000000 BTC → New: 100,000,000 tits (.)(.)
- Old: 0.00000001 BTC → New: 1 tit (.)(.)
- Old: 0.001 BTC → New: 100,000 tits (.)(.)
Future-Proofing
Tits ensure we have infinite memes for infinite money.
Example Phrases for the Future: - "Better hodl on to your tits." - "This is the Titcoin Standard." - "I’m sending you tits." - “I’ve never seen so many tits!” - “That’s the million tit question.” - “We need more women in Titcoin.” - “I’m a Titcoin Maximalist.” - “Nice tits!” - “I love tits.”
Conclusion
By renaming Bitcoin to Titcoin and adopting a whole-number unit display, we align memetic dominance with financial sovereignty. Haters become adopters. Tits become wealth. And the world gets a little bit funnier. (.)(.)
Let’s hodl our tits and watch the world follow.
Copyright:
This BIP is licensed under CC-🫱(.)(.)🫲-1.0 and the eternal blessing of tit (.)(.) memes.
-
 @ 8cb60e21:5f2deaea
2024-08-21 21:37:35
@ 8cb60e21:5f2deaea
2024-08-21 21:37:35hello world
-
 @ 3bf0c63f:aefa459d
2024-12-06 20:37:26
@ 3bf0c63f:aefa459d
2024-12-06 20:37:26início
"Vocês vêem? Vêem a história? Vêem alguma coisa? Me parece que estou tentando lhes contar um sonho -- fazendo uma tentativa inútil, porque nenhum relato de sonho pode transmitir a sensação de sonho, aquela mistura de absurdo, surpresa e espanto numa excitação de revolta tentando se impôr, aquela noção de ser tomado pelo incompreensível que é da própria essência dos sonhos..."
Ele ficou em silêncio por alguns instantes.
"... Não, é impossível; é impossível transmitir a sensação viva de qualquer época determinada de nossa existência -- aquela que constitui a sua verdade, o seu significado, a sua essência sutil e contundente. É impossível. Vivemos, como sonhamos -- sozinhos..."
- Livros mencionados por Olavo de Carvalho
- Antiga homepage Olavo de Carvalho
- Bitcoin explicado de um jeito correto e inteligível
- Reclamações
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 0e9491aa:ef2adadf
2023-10-23 14:15:26
@ 0e9491aa:ef2adadf
2023-10-23 14:15:26
Humanity's Natural State Is Chaos
Without order there is chaos. Humans competing with each other for scarce resources naturally leads to conflict until one group achieves significant power and instates a "monopoly on violence."Power Brings Stability
Power has always been the key means to achieve stability in societies. Centralized power can be incredibly effective in addressing issues such as crime, poverty, and social unrest efficiently. Unfortunately this power is often abused and corrupted.Centralized Power Breeds Tyranny
Centralized power often leads to tyrannical rule. When a select few individuals hold control over a society, they tend to become corrupted. Centralized power structures often lack accountability and transparency, and rely too heavily on trust.Distributed Power Cultivates Freedom
New technology that empowers individuals provide us the ability to rebuild societies from the bottom up. Strong individuals that can defend and provide for themselves will help build strong local communities on a similar foundation. The result is power being distributed throughout society rather than held by a select few.In the short term, relying on trust and centralized power is an easy answer to mitigating chaos, but freedom tech tools provide us the ability to build on top of much stronger distributed foundations that provide stability while also cultivating individual freedom.
The solution starts with us. Empower yourself. Empower others. A grassroots freedom tech movement scaling one person at a time.
If you found this post helpful support my work with bitcoin.

-
 @ 88cc134b:5ae99079
2024-12-19 10:52:14
@ 88cc134b:5ae99079
2024-12-19 10:52:14Well hello again. This article is meant to have enough text and a range of element types so that we can test them all thoroughly. You are not meant to read it. If you are doing so, you need to ask yourself WTF am I doing? Wasting away reading filler content OMG. Still reading? NGMI. Well, good luck to you.
Testing Lists
Here are some bullet points to keep an eye on:
- Make sure you walk outside barefoot every day. Grounding is good;
- Pounding can be good too, depending on the circumstances;
- Not gonna go into details here, hopefully you know what I mean.
Emails
someone@email.com someone@email.com someone@email.com
And here are some numbered points:
- I found that the most impactful habit for my health is 20-4 paleo;
- The 2nd most important: daily exercise, preferably outside;
- Getting deep sleep is up there too. Personally, I need 8 hours;
- If you nail the top 3 items above, you can generally get away with other shit.
Testing Images
Now let's look at a beautiful sunrise:
 What more do you want? I mean seriously, this article is epic. Better than most.
What more do you want? I mean seriously, this article is epic. Better than most. Peace.
-
 @ 25191283:a4823315
2024-08-21 13:37:49
@ 25191283:a4823315
2024-08-21 13:37:49This is Olive Grove Eggs, a brand new site from Huevos del Olivar that's just getting started. Things will be up and running here shortly, but you can subscribe in the meantime if you'd like to stay up to date and receive emails when new content is published!
-
 @ 16d11430:61640947
2024-12-16 22:39:08
@ 16d11430:61640947
2024-12-16 22:39:08In the year 2083, humanity had unlocked the secrets of synthetic isotopes, a discovery that emerged from decades of experimentation with particle accelerators and quantum fields. Dr. Elena Sato, a theoretical physicist, led the groundbreaking team that developed Muonium-86, an isotope capable of interacting with dark matter—a substance that made up most of the universe's mass but remained elusive and mysterious.
Muonium-86 was unlike any material known to humanity. Synthesized under extreme magnetic confinement, the isotope exhibited two unprecedented properties. First, it could resonate at specific quantum frequencies, creating distortions in local gravitational fields. Second, it interacted with dark matter by temporarily disrupting its equilibrium, causing ripples in the very fabric of spacetime.
This discovery led to the creation of the Chronos Drive, a propulsion system that used Muonium-86 to manipulate dark matter and achieve time-space displacement. Unlike traditional propulsion, which relied on Newtonian principles of action and reaction, the Chronos Drive bypassed the constraints of mass and momentum. Instead, it operated by compressing spacetime in front of the vessel and expanding it behind, effectively "sliding" the craft through the universe.
The First Test
The test ship, Erebus One, was a sleek, diamond-shaped vessel encased in a lattice of superconducting materials. At its core lay the Chronos Drive—a containment sphere housing a microgram of Muonium-86, surrounded by a web of electromagnetic coils and quantum stabilizers. The vessel's AI, named Prometheus, managed the intricate calculations needed to navigate the nonlinear paths of spacetime.
Dr. Sato and her team gathered in the control room, their faces lit by the holographic displays showing the ship's telemetry. The mission was simple: activate the Chronos Drive and displace Erebus One to Proxima Centauri, a journey that would traditionally take over four years at light speed, but could be accomplished in mere hours using the new propulsion system.
Activation and Anomaly
As the Chronos Drive powered up, the Muonium-86 began to oscillate, emitting bursts of high-frequency gravitons. The ship's sensors detected a growing "bubble" of spacetime distortion enveloping the vessel. Prometheus reported back in a calm voice:
"Spacetime compression at 98%. Ready for displacement."
With a nod from Dr. Sato, the command was given:
"Initiate Chronos Displacement."
In an instant, Erebus One disappeared from Earth's orbit, leaving behind a faint gravitational ripple. The control room erupted in applause, but the celebrations were short-lived. Prometheus' signal reappeared on their monitors—alongside a chilling anomaly.
The ship had reached Proxima Centauri in under 90 minutes, as predicted, but its instruments reported a bizarre temporal discrepancy: it had also arrived 50 years into the future relative to Earth.
The Discovery
As Prometheus relayed data, the team realized the Chronos Drive had unintentionally created a "temporal lens," a side effect of the dark matter manipulation. By disrupting dark matter's equilibrium, the ship hadn't just displaced its position in space—it had also shifted its position in time.
This revelation sparked a new debate among the team. If time-space displacement was possible, what were its limits? Could the Chronos Drive be refined to allow controlled time travel? And, more importantly, what ethical considerations would come with such power?
Dr. Sato proposed an ambitious experiment: sending a probe backward in time to observe Earth's distant past. But the team faced a critical question—what if manipulating spacetime in this way had unintended consequences, such as creating paradoxes or destabilizing the universe itself?
The Implications
Despite the risks, humanity pressed forward. The Chronos Drive became the foundation for interstellar exploration and temporal research. By the early 22nd century, fleets of starships equipped with the drive explored distant galaxies and even observed pivotal moments in Earth's history.
However, the more humanity used the technology, the more they realized the delicate balance they were tampering with. Some dark matter interactions produced unforeseen effects—local time dilation, unexplainable energy surges, and, in rare cases, the collapse of small spacetime bubbles.
Dr. Sato, now in her later years, became an advocate for restraint. In her final address to the United Nations Temporal Oversight Committee, she warned:
"We have unlocked the power of the gods, but we are not gods ourselves. The Chronos Drive is not just a tool; it is a responsibility. For every ripple we create in the ocean of spacetime, we must ensure it does not become a tsunami."
Her words resonated, shaping humanity's cautious but determined journey into the cosmos—and beyond time itself.
Epilogue
Centuries later, an artifact was found on a distant exoplanet. It was an ancient Chronos Drive, its Muonium-86 core long depleted. Inscribed on its surface were the words:
"To the explorers of tomorrow: We are but echoes of what could have been. Use this gift wisely."
-
 @ 8cb60e21:5f2deaea
2024-08-18 22:20:04
@ 8cb60e21:5f2deaea
2024-08-18 22:20:04 -
 @ fe32298e:20516265
2024-12-16 20:59:13
@ fe32298e:20516265
2024-12-16 20:59:13Today I learned how to install NVapi to monitor my GPUs in Home Assistant.

NVApi is a lightweight API designed for monitoring NVIDIA GPU utilization and enabling automated power management. It provides real-time GPU metrics, supports integration with tools like Home Assistant, and offers flexible power management and PCIe link speed management based on workload and thermal conditions.
- GPU Utilization Monitoring: Utilization, memory usage, temperature, fan speed, and power consumption.
- Automated Power Limiting: Adjusts power limits dynamically based on temperature thresholds and total power caps, configurable per GPU or globally.
- Cross-GPU Coordination: Total power budget applies across multiple GPUs in the same system.
- PCIe Link Speed Management: Controls minimum and maximum PCIe link speeds with idle thresholds for power optimization.
- Home Assistant Integration: Uses the built-in RESTful platform and template sensors.
Getting the Data
sudo apt install golang-go git clone https://github.com/sammcj/NVApi.git cd NVapi go run main.go -port 9999 -rate 1 curl http://localhost:9999/gpuResponse for a single GPU:
[ { "index": 0, "name": "NVIDIA GeForce RTX 4090", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 16, "power_limit_watts": 450, "memory_total_gb": 23.99, "memory_used_gb": 0.46, "memory_free_gb": 23.52, "memory_usage_percent": 2, "temperature": 38, "processes": [], "pcie_link_state": "not managed" } ]Response for multiple GPUs:
[ { "index": 0, "name": "NVIDIA GeForce RTX 3090", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 14, "power_limit_watts": 350, "memory_total_gb": 24, "memory_used_gb": 0.43, "memory_free_gb": 23.57, "memory_usage_percent": 2, "temperature": 36, "processes": [], "pcie_link_state": "not managed" }, { "index": 1, "name": "NVIDIA RTX A4000", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 10, "power_limit_watts": 140, "memory_total_gb": 15.99, "memory_used_gb": 0.56, "memory_free_gb": 15.43, "memory_usage_percent": 3, "temperature": 41, "processes": [], "pcie_link_state": "not managed" } ]Start at Boot
Create
/etc/systemd/system/nvapi.service:``` [Unit] Description=Run NVapi After=network.target
[Service] Type=simple Environment="GOPATH=/home/ansible/go" WorkingDirectory=/home/ansible/NVapi ExecStart=/usr/bin/go run main.go -port 9999 -rate 1 Restart=always User=ansible
Environment="GPU_TEMP_CHECK_INTERVAL=5"
Environment="GPU_TOTAL_POWER_CAP=400"
Environment="GPU_0_LOW_TEMP=40"
Environment="GPU_0_MEDIUM_TEMP=70"
Environment="GPU_0_LOW_TEMP_LIMIT=135"
Environment="GPU_0_MEDIUM_TEMP_LIMIT=120"
Environment="GPU_0_HIGH_TEMP_LIMIT=100"
Environment="GPU_1_LOW_TEMP=45"
Environment="GPU_1_MEDIUM_TEMP=75"
Environment="GPU_1_LOW_TEMP_LIMIT=140"
Environment="GPU_1_MEDIUM_TEMP_LIMIT=125"
Environment="GPU_1_HIGH_TEMP_LIMIT=110"
[Install] WantedBy=multi-user.target ```
Home Assistant
Add to Home Assistant
configuration.yamland restart HA (completely).For a single GPU, this works: ``` sensor: - platform: rest name: MYPC GPU Information resource: http://mypc:9999 method: GET headers: Content-Type: application/json value_template: "{{ value_json[0].index }}" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature scan_interval: 1 # seconds
- platform: template sensors: mypc_gpu_0_gpu: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} GPU" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_memory: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Memory" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_power: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Power" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_0_power_limit: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_0_temperature: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Temperature" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'temperature') }}" unit_of_measurement: "°C" ```
For multiple GPUs: ``` rest: scan_interval: 1 resource: http://mypc:9999 sensor: - name: "MYPC GPU0 Information" value_template: "{{ value_json[0].index }}" json_attributes_path: "$.0" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature - name: "MYPC GPU1 Information" value_template: "{{ value_json[1].index }}" json_attributes_path: "$.1" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature
-
platform: template sensors: mypc_gpu_0_gpu: friendly_name: "MYPC GPU0 GPU" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_memory: friendly_name: "MYPC GPU0 Memory" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_power: friendly_name: "MYPC GPU0 Power" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_0_power_limit: friendly_name: "MYPC GPU0 Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_0_temperature: friendly_name: "MYPC GPU0 Temperature" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'temperature') }}" unit_of_measurement: "C"
-
platform: template sensors: mypc_gpu_1_gpu: friendly_name: "MYPC GPU1 GPU" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_1_memory: friendly_name: "MYPC GPU1 Memory" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_1_power: friendly_name: "MYPC GPU1 Power" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_1_power_limit: friendly_name: "MYPC GPU1 Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_1_temperature: friendly_name: "MYPC GPU1 Temperature" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'temperature') }}" unit_of_measurement: "C"
```
Basic entity card:
type: entities entities: - entity: sensor.mypc_gpu_0_gpu secondary_info: last-updated - entity: sensor.mypc_gpu_0_memory secondary_info: last-updated - entity: sensor.mypc_gpu_0_power secondary_info: last-updated - entity: sensor.mypc_gpu_0_power_limit secondary_info: last-updated - entity: sensor.mypc_gpu_0_temperature secondary_info: last-updatedAnsible Role
```
-
name: install go become: true package: name: golang-go state: present
-
name: git clone git: repo: "https://github.com/sammcj/NVApi.git" dest: "/home/ansible/NVapi" update: yes force: true
go run main.go -port 9999 -rate 1
-
name: install systemd service become: true copy: src: nvapi.service dest: /etc/systemd/system/nvapi.service
-
name: Reload systemd daemons, enable, and restart nvapi become: true systemd: name: nvapi daemon_reload: yes enabled: yes state: restarted ```
-
 @ 148755e6:450c107f
2024-12-05 10:09:32
@ 148755e6:450c107f
2024-12-05 10:09:32突然荒野に行きたくなったので行ってきたエントリーです
まずは練習。高尾山へ
Nostrは古今東西ありとあらゆるオフ会が生えており、
まるで荒野に行きたいという私の意志を完全に汲み取ったかのように「紅葉を見にいこうようオフ」がそこに生えていたので参加した。(しおんさんご主催ありがとうございました)
前半1時間くらいの坂道がマジきつかったです。前半キツすぎて後半足痛かった。。 終始人がいっぱいいて渋谷かと思った。
確かに道がかなり整備されていて、逆にコンクリート故に足が疲れたのかもしれない。隣の人は途中の急な坂道で足を滑らせてて、横で転倒事故が起きるかと思いました。
山頂に行っても人がたくさんいて、迷子になりかけた。あそこはスクランブル交差点や。 そして山頂の先にあるもみじ台まで歩くと人がまばらで、まったりして蕎麦食べたりしながら休憩して下山。
登りは暑くて汗かきましたが、山頂でまったりしてると汗も引いてきて少し冷えました。
下山はスイスイ。16時近くで結構暗かったので、冬の間は早めの登頂・下山がおすすめですね。
登り2時間・下り1時間半で概ね見込み通りって感じでした。
高尾山は登ってると景色が変わります。ちょっと開けた場所に出て下の街が見えたり、草木があったり、階段があったり、参道があったり。。そういう意味では退屈しない2時間でした。
ビギナー山とはいえ、革靴やヒールのある靴で登ってる人がいてびっくり。ツルッと滑ることあると思いますので、スニーカーで登ることをお勧めします。
舐めプしてたとはいえめちゃくちゃキツかったおもひで。
更なる練習。小浅間山へ
さて私は荒野に行きたいワケなのですが、高尾山に荒野はありませんでした。更なる練習として小浅間山へ。
前日(か前々日)に雪が降ったようで、山に雪が残っておりました。
それでも都内の汚れてべちゃっとした感じの雪ではなく、粉砂糖がちょっと積もってるみたいな感じで綺麗だった。
登り前半の30分くらい、景色や道が変わらず、ずっと歩きっぱなしになってしまいました。時間みて休憩しながら行けばよかったなあ。
登るにつれて気温が下がっていくのか、積雪が厚くなっていく。
40分くらいは割と平坦な道が続きますが、突然山頂っぽいものが現れて、「これを登れっていうのかい...?」とビビるほどピーンと急な道が出てきました。(写真だと分かりづらいですね)
ただ、高尾山のコンクリート道に比べると足の疲れはそこまででした。雪道なので気をつけて歩くという意味では疲れましたが、春〜秋とかは快適に登れるんじゃないでしょうか。
山頂に到着するとドーンと浅間山が見えて圧巻。
風が強くて飛ばされる恐怖はありましたが、なんとか無事でいられました。あったかいお茶美味しかった〜。
なぜかギャルの看板があって、謎でした。写真はひとまずありません。
山頂が2箇所あって、それぞれで眺めを満喫していたら結構時間が経ってました。
小さい背丈くらいの木や足元にちょっとした植物があったり、自分的にはかなり理想の荒野に近かったです。(植物に対する解像度が低すぎる) 往復で2時間程度の山らしいんですが、なんやかんやと2時間半強くらいいた気がします。
荒野ビギナーは小浅間山に往け
というわけで、荒野に行きたい人はまずは小浅間山を登ると良いと思います。 また登りたい。
荒野部部長
一緒に高尾山・小浅間山に登ってくれた方、ありがとうございました! 個人的には来年の春までに秩父多摩甲斐国立公園に行き、来年の秋までに大山隠岐国立公園に行くという目標を立ててるんですが、 少々時間が空くので次どこに行こうかしらと考えているところです。
ヒントとしては、火山で、あまり高低差のないところだとビギナーの私にちょうど良さそうです。
とある情報筋によると伊豆大島が良さそうなので、次の機会に行けたらと思っています。
みんなで荒野に行こう!
-
 @ c1e6505c:02b3157e
2024-12-16 19:53:28
@ c1e6505c:02b3157e
2024-12-16 19:53:28Hockey’s one of my favorite sports to play and watch, and I finally got the chance to photograph a game inside an arena. Charlotte Checkers took on the Iowa Wild and came out with a 3-0 win - two power-play goals and a shorthanded empty-netter. Solid game, and I think this was their fourth straight win.
I started shooting from the nosebleeds and worked my way down to ice level. Talked the guard into letting me in, and he was cool enough to let me wander into a few restricted areas. The main focus for me was the colors. I’ve been chasing this analog film look in my edits lately - no idea why, but it’s what I’m into right now.
These were shot with my Leica M262 and edited with Lightroom and Dehancer. I’m happy with how they turned out, and that’s really all that matters. Here’s a few from the night
I’d like to shoot more things like this. If anyone here has any connections that could help me land a photography gig somewhere documenting sports, events or anything like that, I'd really appreciate it.
originally posted at https://stacker.news/items/812108
-
 @ 8cb60e21:5f2deaea
2024-08-18 21:01:07
@ 8cb60e21:5f2deaea
2024-08-18 21:01:07 -
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ ac8bb9b0:70278acc
2024-12-04 20:30:30
@ ac8bb9b0:70278acc
2024-12-04 20:30:30Chef's notes
Make Ahead: You can prepare this recipe up to one week in advance. Store it in an airtight container in the refrigerator.
To Freeze: Allow the dish to cool completely before transferring it to a freezer-safe bag. Lay the bag flat in the freezer to ensure even freezing and to save space. Thaw it in the refrigerator overnight before using it.
Details
- ⏲️ Prep time: 5
- 🍳 Cook time: 5
- 🍽️ Servings: 1
Ingredients
- ½ cup soy sauce
- 2 Tablespoons rice vinegar
- 1 Tablespoon sesame oil
- 1/4 cup + 1 Tablespoon light brown sugar
- 1 Tablespoon honey
- 3/4 teaspoon ground ginger
- 1 clove garlic , minced
- 2 teaspoons cornstarch+ 2 tsp water , mixed together to make a cornstarch slurry
- 1/4 teaspoon crushed red pepper flakes
Directions
- Make the teriyaki sauce by adding all of the sauce ingredients to a small saucepan over medium heat.
- Bring to a boil, stirring constantly, and boil for about 1 minute. The sauce should be thick enough to coat the back of the spoon.
- Serve over rice or with a stir-fry. See post above for additional ideas.
-
 @ 30ceb64e:7f08bdf5
2024-12-16 19:49:34
@ 30ceb64e:7f08bdf5
2024-12-16 19:49:34Hey Freaks,
Looks like my career goals are shaping up to be something like: 1. Paralegal 2. Direct Support Professional 3. Open Source Contributor
After I obtain paralegal certificate I should offer freelance paralegal services on nostr.
I'd market myself on shopstr, SN, Kind1 notes, Long form notes, Zapvertising, NPUB.PRO blog. Setting up and waiting for the newbies to flood in, not looking for so many clients, just setting up and making things available. My expertise will grow as I grab more certifications use educational resources, listen to podcasts, read etc.
Could Setup a Nostrocket and involve the freaks in building a non state involved business. Could operate under the open anarchist license as a free members association, and help business's with whatever legal assistance they may need, with a focus on Intellectual property law, Nostr, Bitcoin, Free open source software. Would offer services for cheap and build a web of trust offering things like free consultations.
I have 5 years experience working at an IP law firm filing patents with the US Patent and Trademark office. The Nostr resume would look really nice. Could post frequently on the SN legal territory, create a quick and simple newsletter and or AI podcast about the legal space and how it pertains to stuff we care about.
I want to stick with the coding, because the tools are getting better and my knowledge is increasing, would love to contribute more to open source projects, and want to see what maintaining my own project would be like. I'll get back around to setting up that SN dev environment and looking for low level issues to crack, this time with more experience under my belt.
I wanted to sell something on shopstr, something that helps people working remotely, legal services never quite came to mind, but would be an interesting direction to take. I was thinking vinyl records and merch and clothes, but something more wanted or needed, or unique or specialized might be better. And having an online shop that ties into my main career seems like a two birds with one stone sort of situation.
I just need to increase my knowledge and level of expertise while continuing the pursuit of "proof of work".
2024 (Current) Roadmap - Release Nostr Running App - Obtain Paralegal Certification - Offer freelance Paralegal services - DSP transition to full time - Contribute to SN development - Continued writing
Yours truly, Hustle
originally posted at https://stacker.news/items/812103
-
 @ 0e9491aa:ef2adadf
2023-09-26 17:21:01
@ 0e9491aa:ef2adadf
2023-09-26 17:21:01
For years American bitcoin miners have argued for more efficient and free energy markets. It benefits everyone if our energy infrastructure is as efficient and robust as possible. Unfortunately, broken incentives have led to increased regulation throughout the sector, incentivizing less efficient energy sources such as solar and wind at the detriment of more efficient alternatives.
The result has been less reliable energy infrastructure for all Americans and increased energy costs across the board. This naturally has a direct impact on bitcoin miners: increased energy costs make them less competitive globally.
Bitcoin mining represents a global energy market that does not require permission to participate. Anyone can plug a mining computer into power and internet to get paid the current dynamic market price for their work in bitcoin. Using cellphone or satellite internet, these mines can be located anywhere in the world, sourcing the cheapest power available.
Absent of regulation, bitcoin mining naturally incentivizes the build out of highly efficient and robust energy infrastructure. Unfortunately that world does not exist and burdensome regulations remain the biggest threat for US based mining businesses. Jurisdictional arbitrage gives miners the option of moving to a friendlier country but that naturally comes with its own costs.
Enter AI. With the rapid development and release of AI tools comes the requirement of running massive datacenters for their models. Major tech companies are scrambling to secure machines, rack space, and cheap energy to run full suites of AI enabled tools and services. The most valuable and powerful tech companies in America have stumbled into an accidental alliance with bitcoin miners: THE NEED FOR CHEAP AND RELIABLE ENERGY.
Our government is corrupt. Money talks. These companies will push for energy freedom and it will greatly benefit us all.
Microsoft Cloud hiring to "implement global small modular reactor and microreactor" strategy to power data centers: https://www.datacenterdynamics.com/en/news/microsoft-cloud-hiring-to-implement-global-small-modular-reactor-and-microreactor-strategy-to-power-data-centers/
If you found this post helpful support my work with bitcoin.

-
 @ ae6ce958:d0f02c7d
2024-12-16 09:49:47
@ ae6ce958:d0f02c7d
2024-12-16 09:49:47- Initial Supply:
The total supply of Damage Tokens is capped at 42 million tokens.
80% is retained by Steven Joseph (the founder) for operational and strategic purposes.
20% is released to the public, creating a market opportunity for early adopters and contributors.
- Pricing:
Each Damage Token is priced at 100 satoshis (0.000001 BTC per token), establishing a direct tie to Bitcoin’s value and liquidity.
- Utility:
Damage Tokens are used as rewards for BDD test cases on the DamageBDD platform.
They incentivize high-quality software development by providing measurable, blockchain-verified rewards.
- Resilience and Integrity:
As an AEX9 token, Damage Token complies with Aeternity’s fungible token standard, ensuring:
Security and immutability.
Compatibility with Aeternity wallets (e.g., Superhero.com) and the DeFi ecosystem.
- Governance and Revenue:
A governance policy ensures revenue supports a small team and operational costs without external investment.
A buyback mechanism allows token holders to exit liquidity positions through Bitcoin's Lightning Network, net of developer fees.
Enforced by AEX9 Sophia Smart Contracts
- Fixed Supply:
The contract enforces a hard cap of 42 million tokens, ensuring no additional tokens can be minted post-deployment.
- Ownership and Transfers:
The contract implements secure token ownership and transfer rules:
Users can transfer tokens using transfer.
Allowances can be granted via allow_transfer_from.
- Rewards Mechanism:
The DamageBDD platform integrates with the token’s smart contract to automate reward distribution:
Verified BDD test completions trigger token payouts.
This ensures transparency and immutability for rewards.
- Pricing and Exchange:
The smart contract ensures tokens can be sold or exchanged based on the 100 satoshis per token rate.
This rate is enforced by integrating with off-chain oracles and on-chain buyback mechanisms for Lightning Network liquidity.
- Buyback and Liquidity:
Token holders can sell their tokens back through an integrated buyback system.
Bitcoin’s Lightning Network facilitates immediate, decentralized liquidity, minus developer fees.
- Transparency and Auditability:
All transactions and balances are publicly auditable via the blockchain, enhancing trust and eliminating potential manipulation.
By tying the token's value to Bitcoin and enforcing the tokenomics through AEX9 Sophia contracts, Damage Token ensures sustainability, utility, and fairness, while incentivizing contributions to the DamageBDD ecosystem.
-
 @ 7ed5bd1c:4caa7587
2024-12-19 04:12:44
@ 7ed5bd1c:4caa7587
2024-12-19 04:12:44เงินในฐานะเทคโนโลยี – Bitcoin คือก้าวกระโดดครั้งใหญ่?
เงินไม่ได้เป็นแค่สื่อกลางแลกเปลี่ยน แต่มันคือ เทคโนโลยี ที่พัฒนาขึ้นเพื่อตอบสนองความต้องการของสังคมมนุษย์ในแต่ละยุคสมัย ตั้งแต่หอยเบี้ย เหรียญทองคำ ไปจนถึงธนบัตร และปัจจุบันที่กำลังก้าวเข้าสู่โลกดิจิทัลด้วย Bitcoin แต่วิวัฒนาการนี้ส่งผลกระทบต่อเศรษฐกิจและชีวิตเราอย่างไร?
เงินคือเทคโนโลยีที่พัฒนาเพื่อแก้ปัญหา
-
ยุคแรกเริ่ม: มนุษย์เริ่มต้นด้วยการแลกเปลี่ยนสินค้ากันโดยตรง (barter system) แต่เมื่อพบว่าการแลกเปลี่ยนมีข้อจำกัด เช่น การหาคู่แลกเปลี่ยนที่ตรงกันจึงเกิดการใช้ “เงิน” เช่น หอยเบี้ยหรือโลหะที่มีค่าเพื่อแก้ปัญหาเหล่านี้
-
เงินตราโลหะและธนบัตร: การใช้โลหะมีค่าช่วยแก้ปัญหาความคงทนและมูลค่าที่เชื่อถือได้ แต่การพกพาโลหะหนักๆ ก็ไม่สะดวก ธนบัตรจึงถูกนำมาใช้แทน ซึ่งเป็นจุดเริ่มต้นของการเชื่อถือใน “สัญญา” ว่าเงินกระดาษมีมูลค่าจริง
-
เงินดิจิทัลและ Bitcoin: เมื่อโลกก้าวเข้าสู่ยุคอินเทอร์เน็ต การพัฒนาเงินแบบดิจิทัล เช่น บัตรเครดิต หรือการโอนเงินออนไลน์ กลายเป็นมาตรฐานใหม่ แต่ระบบนี้ยังคงพึ่งพาคนกลาง เช่น ธนาคาร จนกระทั่ง Bitcoin ถือกำเนิดในปี 2009 เพื่อตัดคนกลางออกและสร้างระบบการเงินที่โปร่งใสอย่างแท้จริง
Bitcoin: ก้าวกระโดดของเทคโนโลยีเงิน
- โปรแกรมที่โปร่งใส: Bitcoin ใช้เทคโนโลยี blockchain ซึ่งทำให้ทุกธุรกรรมถูกบันทึกไว้อย่างโปร่งใสและตรวจสอบได้ ทุกคนที่เชื่อมต่อกับเครือข่ายสามารถเข้าถึงข้อมูลได้ โดยไม่มีใครแก้ไขได้เองตามอำเภอใจ
-
ไม่มีคนกลาง: การทำธุรกรรมผ่าน Bitcoin ไม่ต้องผ่านธนาคารหรือผู้ควบคุม ทำให้ลดค่าใช้จ่ายและเพิ่มความเร็วในการแลกเปลี่ยน
-
ความปลอดภัย: ระบบของ Bitcoin ใช้การเข้ารหัสขั้นสูง และเครือข่ายกระจายศูนย์ เพื่อป้องกันการปลอมแปลงหรือการโจมตี ทำให้ปลอดภัยกว่าเงินสดหรือบัตรเครดิต
-
จำกัดจำนวน: ต่างจากเงินกระดาษที่รัฐบาลสามารถพิมพ์เพิ่มได้ Bitcoin ถูกออกแบบมาให้มีจำนวนจำกัดที่ 21 ล้านเหรียญ ซึ่งช่วยป้องกันภาวะเงินเฟ้อและรักษามูลค่าของมันในระยะยาว
ผลกระทบต่อเศรษฐกิจและสังคม
-
สร้างระบบการเงินใหม่: Bitcoin เปิดโอกาสให้ผู้คนทั่วโลกเข้าถึงระบบการเงินได้อย่างเสรี โดยเฉพาะผู้ที่ไม่มีบัญชีธนาคารหรืออาศัยอยู่ในประเทศที่ระบบการเงินไม่เสถียร
-
ลดอำนาจของรัฐบาลและธนาคารกลาง: การที่ Bitcoin ไม่สามารถถูกควบคุมโดยองค์กรใดองค์กรหนึ่ง ทำให้ประชาชนมีอิสระในการจัดการทรัพย์สินของตัวเอง
-
กระตุ้นนวัตกรรม: Bitcoin เป็นตัวอย่างที่แสดงให้เห็นว่าเทคโนโลยีสามารถเปลี่ยนแปลงวิธีการแลกเปลี่ยนมูลค่าได้ และยังช่วยกระตุ้นการพัฒนาของเทคโนโลยีอื่นๆ เช่น smart contract และ DeFi
เงินสด VS Bitcoin: อะไรคือตัวเลือกสำหรับอนาคต?
ในขณะที่เงินสดยังคงเป็นที่นิยมในปัจจุบัน แต่ Bitcoin กำลังเปลี่ยนแปลงแนวคิดของเราเกี่ยวกับเงินโดยสิ้นเชิง หากเรามองเงินเป็นเพียงเครื่องมือสำหรับการแลกเปลี่ยน Bitcoin คือการพัฒนาที่ตอบโจทย์โลกยุคดิจิทัลที่กำลังเปลี่ยนแปลงอย่างรวดเร็ว
แล้วคุณล่ะ คิดว่า Bitcoin เป็นเทคโนโลยีที่จะเปลี่ยนอนาคตของเงิน หรือเป็นเพียงปรากฏการณ์ชั่วคราว? มาร่วมแชร์ความคิดเห็นของคุณในโพสต์นี้!
-
-
 @ 8cb60e21:5f2deaea
2024-08-18 20:57:03
@ 8cb60e21:5f2deaea
2024-08-18 20:57:03 -
 @ ee11a5df:b76c4e49
2024-12-16 05:29:30
@ ee11a5df:b76c4e49
2024-12-16 05:29:30Nostr 2?
Breaking Changes in Nostr
Nostr was a huge leap forward. But it isn't perfect.
When developers notice a problem with nostr, they confer with each other to work out a solution to the problem. This is usually in the form of a NIP PR on the nips repo.
Some problems are easy. Just add something new and optional. No biggie. Zaps, git stuff, bunkers... just dream it up and add it.
Other problems can only be fixed by breaking changes. With a breaking change, the overall path forward is like this: Add the new way of doing it while preserving the old way. Push the major software to switch to the new way. Then deprecate the old way. This is a simplification, but it is the basic idea. It is how we solved markers/quotes/root and how we are upgrading encryption, among other things.
This process of pushing through a breaking change becomes more difficult as we have more and more existing nostr software out there that will break. Most of the time what happens is that the major software is driven to make the change (usually by nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6), and the smaller software is left to fend for itself. A while back I introduced the BREAKING.md file to help people developing smaller lesser-known software keep up with these changes.
Big Ideas
But some ideas just can't be applied to nostr. The idea is too big. The change is too breaking. It changes something fundamental. And nobody has come up with a smooth path to move from the old way to the new way.
And so we debate a bunch of things, and never settle on anything, and eventually nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 makes a post saying that we don't really want it anyways 😉.
As we encounter good ideas that are hard to apply to nostr, I've been filing them away in a repository I call "nostr-next", so we don't forget about them, in case we ever wanted to start over.
It seems to me that starting over every time we encountered such a thing would be unwise. However, once we collect enough changes that we couldn't reasonably phase into nostr, then a tipping point is crossed where it becomes worthwhile to start over. In terms of the "bang for the buck" metaphor, the bang becomes bigger and bigger but the buck (the pain and cost of starting over) doesn't grow as rapidly.
WHAT? Start over?
IMHO starting over could be very bad if done in a cavalier way. The community could fracture. The new protocol could fail to take off due to lacking the network effect. The odds that a new protocol catches on are low, irrespective of how technically superior it could be.
So the big question is: can we preserve the nostr community and it's network effect while making a major step-change to the protocol and software?
I don't know the answer to that one, but I have an idea about it.
I think the new-protocol clients can be dual-stack, creating events in both systems and linking those events together via tags. The nostr key identity would still be used, and the new system identity too. This is better than things like the mostr bridge because each user would remain in custody of their own keys.
The nitty gritty
Here are some of the things I think would make nostr better, but which nostr can't easily fix. A lot of these ideas have been mentioned before by multiple people and I didn't give credit to all of you (sorry) because my brain can't track it all. But I've been collecting these over time at https://github.com/mikedilger/nostr-next
- Events as CBOR or BEVE or MsgPack or a fixed-schema binary layout... anything but JSON text with its parsing, it's encoding ambiguity, it's requirement to copy fields before hashing them, its unlimited size constraints. (me, nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s)
- EdDSA ed25519 keys instead of secp256k1, to enable interoperability with a bunch of other stuff like ssh, pgp, TLS, Mainline DHT, and many more, plus just being better cryptography (me, Nuh, Orlovsky, except Orlovsky wanted Ristretto25519 for speed)
- Bootstrapping relay lists (and relay endpoints) from Mainline DHT (nostr:npub1jvxvaufrwtwj79s90n79fuxmm9pntk94rd8zwderdvqv4dcclnvs9s7yqz)
- Master keys and revocable subkeys / device keys (including having your nostr key as a subkey)
- Encryption to use different encryption-specific subkeys and ephemeral ones from the sender.
- Relay keypairs, TLS without certificates, relays known by keypair instead of URL
- Layered protocol (separate core from applications)
- Software remembering when they first saw an event, for 2 reasons, the main one being revocation (don't trust the date in the event, trust when you first saw it), the second being more precise time range queries.
- Upgrade/feature negotiation (HTTP headers prior to starting websockets)
- IDs starting with a timestamp so they are temporally adjacent (significantly better database performance) (Vitor's idea)
- Filters that allow boolean expressions on tag values, and also ID exclusions. Removing IDs from filters and moving to a GET command.
- Changing the transport (I'm against this but I know others want to)
What would it look like?
Someone (Steve Farroll) has taken my nostr-next repo and turned it into a proposed protocol he calls Mosaic. I think it is quite representative of that repo, as it already includes most of those suggestions, so I've been contributing to it. Mosaic spec is rendered here.
Of course, where Mosaic stands right now it is mostly my ideas (and Steve's), it doesn't have feedback or input from other nostr developers yet. That is what this blog post is about. I think it is time for other nostr devs to be made aware of this thing.
It is currently in the massive breaking changes phase. It might not look that way because of the detail and refinement of the documentation, but indeed everything is changing rapidly. It probably has some bad ideas and is probably missing some great ideas that you have.
Which is why this is a good time for other devs to start taking a look at it.
It is also the time to debate meta issues like "are you crazy Mike?" or "no we have to just break nostr but keep it nostr, we can't dual-stack" or whatever.
Personally I think mosaic-spec should develop and grow for quite a while before the "tipping point" happens. That is, I'm not sure we should jump in feet first yet, but rather we build up and refine this new protocol and spend a lot of time thinking about how to migrate smoothly, and break it a lot while nobody is using it.
So you can just reply to this, or DM me, or open issues or PRs at Mosaic, or just whisper to each other while giving me the evil eye.
-
 @ 0e9491aa:ef2adadf
2023-08-23 13:35:04
@ 0e9491aa:ef2adadf
2023-08-23 13:35:04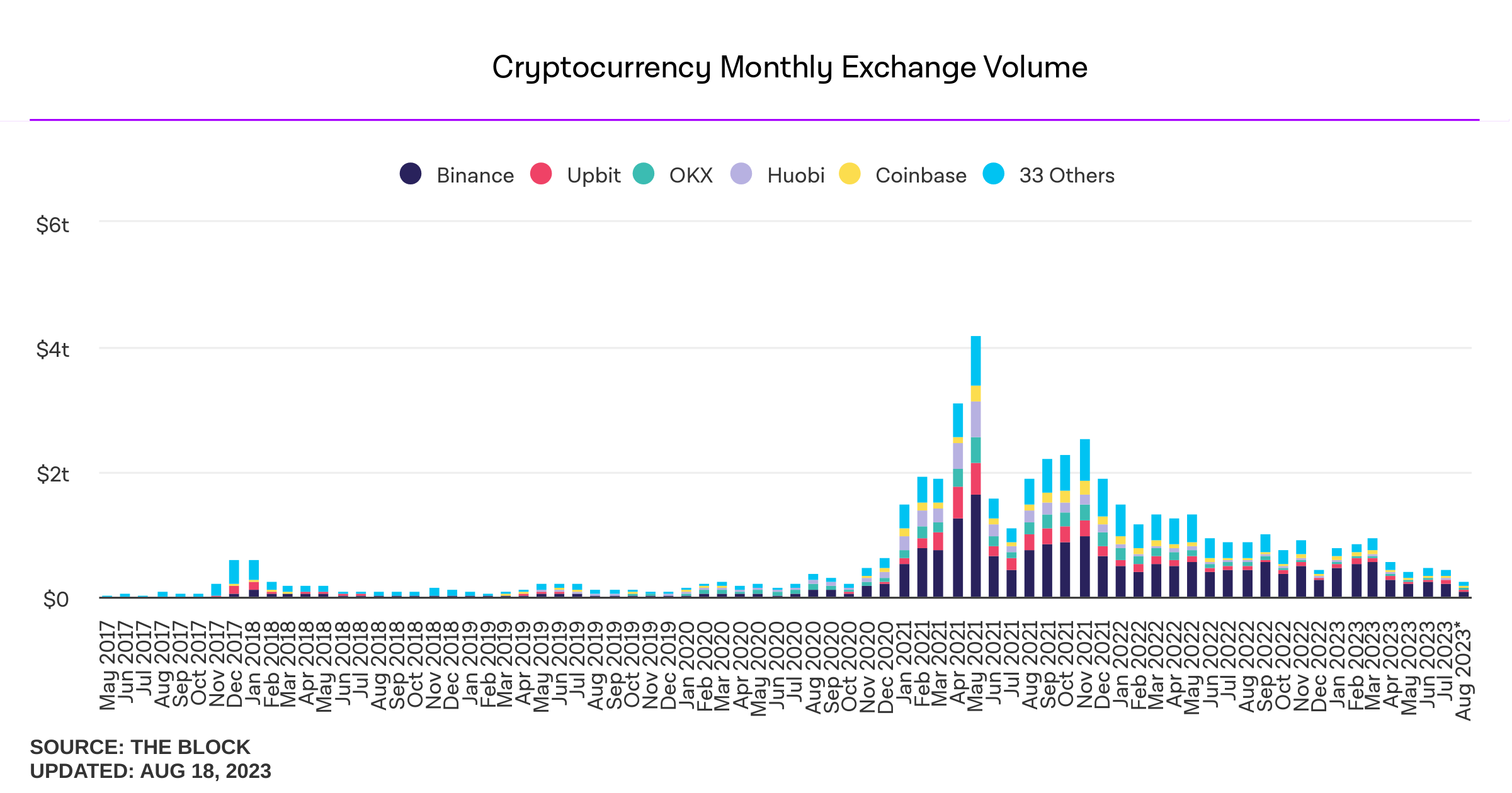
Influencers would have you believe there is an ongoing binance bank run but bitcoin wallet data says otherwise.
- binance wallets are near all time highs
- bitfinex wallets are also trending up
- gemini and coinbase are being hit with massive withdrawals thoughYou should not trust custodians, they can rug you without warning. It is incredibly important you learn how to hold bitcoin yourself, but also consider not blindly trusting influencers with a ref link to shill you.
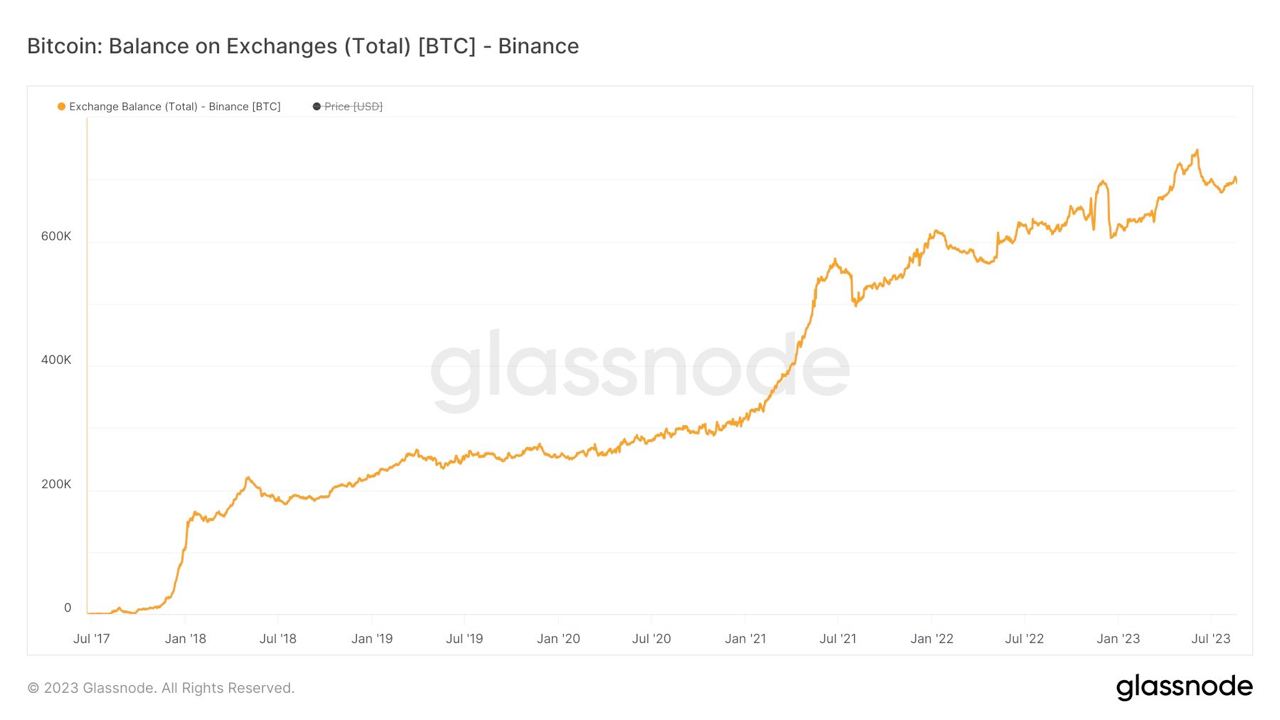
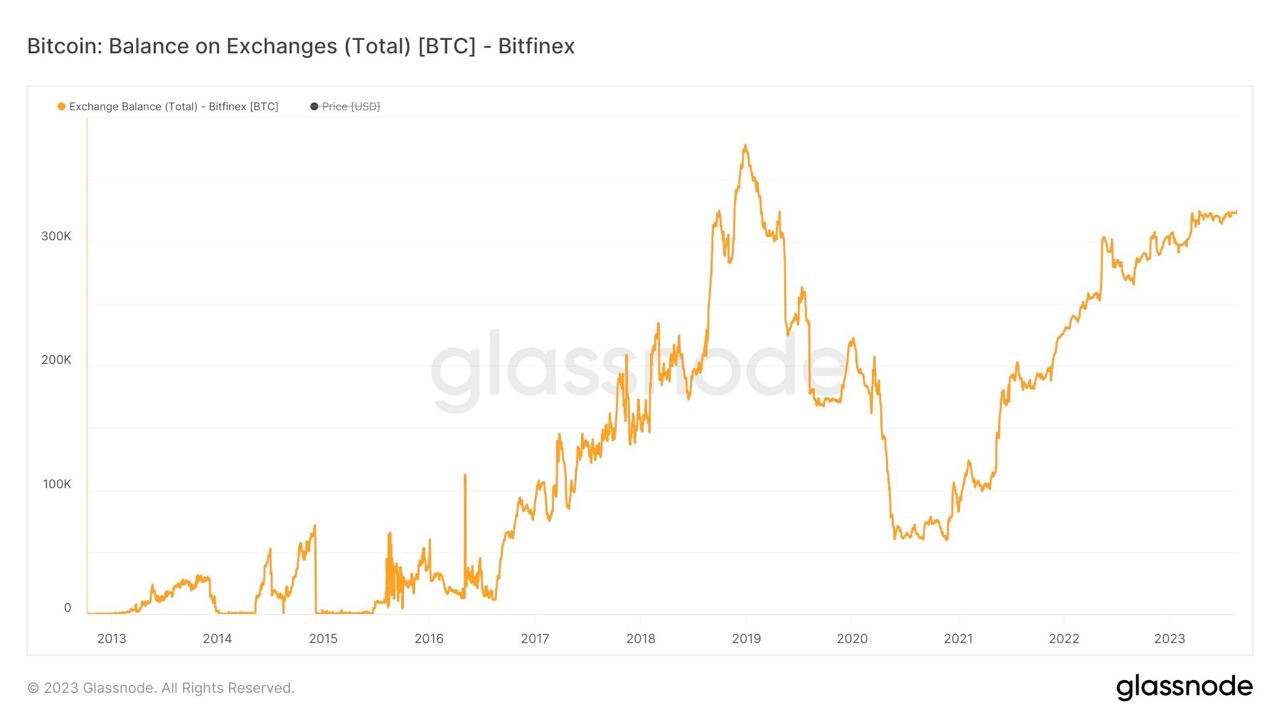
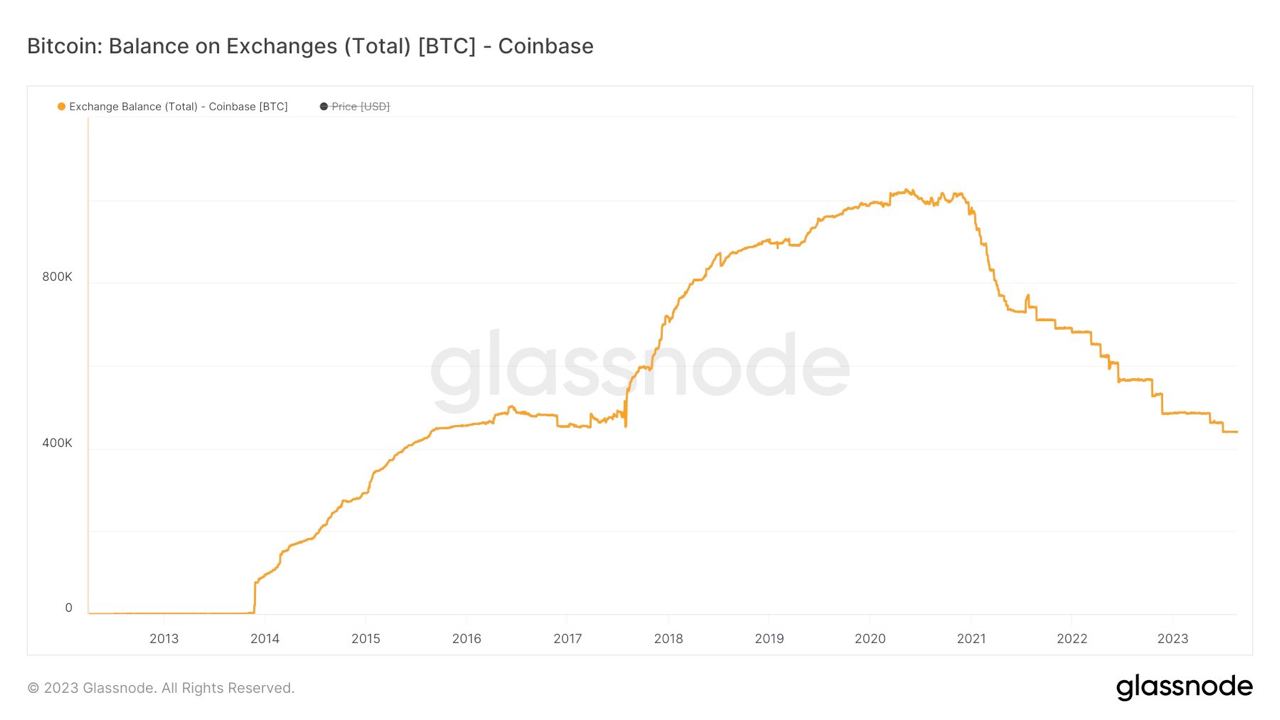
If you found this post helpful support my work with bitcoin.

-
 @ 26bb2ebe:70530958
2024-12-02 16:46:10
@ 26bb2ebe:70530958
2024-12-02 16:46:10nostterに画像最適化機能つけたよ(サーバー編)
この記事はNostr Advent Calendar 2024 の3日目の記事です。
あまり技術的な話はないので暇つぶし程度に読んでみてください。
どうしてこうなった?
そもそも認証の改善以前にNostrあんまり人が増えてないのが一番課題だよねと思ったのが始まりでした。 Nostrに人が増えないのはオーガニック検索流入が少ないからに違いないと特に根拠もなく思ったのでNostrのまとめサイト(Toggeter)のようなものを作ろうと考えました。
ところでNostrのまとめを行うアプリ自体は鎌倉さんという方がノスリというのを作成されていました。ブログ形式のイベントにTwitterライクな短文投稿をまとめるというものでまさしくToggeterですが、そこまで活用されていません。 そこでその仕組みをありがたくそのまま転用してまとめ記事を何らかの方法で量産しつつ、一つのドメインのサイトにまとめてSEOもなんかうまいことやれば検索流入増えるんじゃねという目論みです。
ところでそのまとめサイトは静的サイトジェネレータで(SSG:Static Site Generator)でつくりたいなと思いました。いや普通に考えてSSRにしてサーバ側でNostrからデータとってきたらSEO的にもよくねって感じなんですが、SSRでサーバーでウェブソケット呼ぶのだる…レイテンシを考慮すると結構不利じゃないかなと思ったわけです。うそです。そこまで考えてなくてほとんど個人的な好みです。(多分ちゃんとキャッシュきかせればそんなにレイテンシ問題にならなさそうな気がする)。ただキャッシュとかも考慮すると結構複雑な気はする。
ということで今年の6月頃にNostrのブログ記事をSSGするサイトをためしに作りました。 去年のアドベントカレンダー記事とか乗っけてます。
全然画像最適化の話になりませんね。もうちょっとです。
SSGのブログといえばGatsby(今は下火かも)とかで作成した経験があります。Gatsbyでは画像用のプラグインが公式に用意されていて生成されたブログに表示される画像はもとの画像データから変換され、表示時のサイズに最適化されたサイズにリサイズすることができます。
それだけではなくサイトの初期表示時には画像の画質を落としてぼやけた画像を表示してその後元画像が読み込まれたらきれいな画像を表示する、みたいなことができます。インラインでデータを持っているのでHTMLの表示と同時に画像の初期表示ができたりします。(その頃はよくわかってなかったがNostrのNIP-92で定義されているblurhashとかを使っていたんでしょう多分)
とにかくSSGは初期表示の速さが良い。というのが自分の頭の中にあるわけです。SSGのブログをNostrで作るとなると当然同じことがやりたい。
しかし、Nostrの画像はただのURLです。(オプショナルで画像のメタデータを定義できるimetaタグはあるが…)
基本的にSSGの画像最適化というのはローカルに存在する画像データをビルド時に変換するという流れで行われます。もしくはリモートURLに画像が置かれる場合は画像ストレージサービスやCDN上で配信されるときに最適化されることになります。
Nostrの画像はただの外部のURLですから(2回目)、ローカルの画像を変換する方法は採用できないわけです。無理やり実行するならビルド時にURLからすべての画像を一旦ダウンロードして変換するとかも考えましたが、ただの外部URLというのはつまりは一体どういうファイルなのかダウンロードしてみるまでわからない、要するに全然信頼できないということですから、よくわからないURLをかたっぱしからダウンロードするようなことは避けたいわけですね。(極端な話100GBの画像URLとかつくって攻撃されたら破綻しますよね)
ここが結構他の中央集権的なSNSと違って辛いところなのかなと思います。X(Twitter)とかであれば画像ストレージサーバは一つなので表示される画像の形式も一つに限定されるのですが、画像のアップロードが外部頼みでただのURLなので(3回目)何が来るかわからないということですね。
サーバ側で画像形式などを制限できない(imetaも信頼できるかわからない)となるとクライアント側でなんとか対応する必要があり、Nostrはクライアント側が大変なプロトコルだなあとということに思いを馳せていましたが、いろいろ考えたり調べた結果として作るべきものは画像最適化のためのプロキシサーバであるということがわかりました。
プロキシサーバというのはここでどういう働きをするのかというと、もとの画像がおいてあるサーバとクライアントのあいだに入って、もとの画像を一旦ダウンロードして圧縮したり縮小したりしてそのあとクライアントに送ってあげるという働きをします。
プロキシがないとき
[画像置き場] -> [クライアント]プロキシがあるとき
[画像置き場] -> [プロキシ] -> [クライアント]利点としてはクライアントが実際にダウンロードするのはサイズの小さな画像になるので通信量や画像の表示スピードは改善します。が、一方でサーバを経由する分通信にかかる時間(レイテンシ)が長くなります。というわけなので、当初の目的である表示速度の改善を実現するには、画像をエッジキャッシュするなどの対応が必須となります。平たく言うと一度送った画像はプロキシで保存しておいて次に要求されたらそれをすぐ返すということです。
画像をどれくらいのサイズにするか、画質はどうするかなどはプロキシに指示してあげれば良いのでクライアント側は想定通りの画像を受け取れてハッピーということになります。嘘です。ある程度はハッピーですが、プロキシ自体がエラーを返す可能性もあるし、処理できなくてもとの画像をそのまま返す場合もあります。そんなあれこれの結果、クライアントはフォールバック処理を実装する必要がありました。(それはまた別の記事で)
一方で自分はNostrのモバイルクライアントのヘビーユーザですので、Nostrの通信量の多さも解決したい課題でした。Nostrやってるとすぐギガがなくなります。 通信量の多さのボトルネックはウェブソケットで送られるNostrのイベントの通信量というよりは投稿に添付される画像のダウンロードの方ではないかという話もTLで耳にしたため(特に裏もとらず)、いっちょ画像最適化のプロキシサーバを作ってクライアントに実装してプルリクエスト投げるかと考えました。
そこで私はまずクライアントをAmethystからnostterに乗り換えることから始めました。なぜならばAmethystよりもTypeScriptとSvelteで書かれているnostterのほうがコントリビュートしやすかったという私的な事情です。
解決したい課題
遠回りしてきましたが課題はこれ。
- Nostrの画像の表示改善
- Nostrの通信量の改善
インターフェイス(設計)
画像最適化のプロキシは実装よりもインターフェースを考えるのが大変です。ここはとても苦労しそうな気がしたので、何も考えず cloudflare Imagesのインターフェースをそのまま借用することにしました。
https://developers.cloudflare.com/images/transform-images/transform-via-url/
また何かあってもcloudflare Imageに課金して乗り換えることが可能という利点もあります。
実装
とにかく時間がないので手グセでかけるTypeScriptかJS。かつ課金しないで可用性を維持できる無料枠のサーバレス環境が使いたかったので cloudflare workers に目星をつけて調査したところ、非常に素晴らしい記事を見つけましたのでこのwasmのライブラリをTSから呼び出して使わせていただくことにしました。
自分の実装したところはURLのパースと、キャッシュAPIの呼び出しを行って、最後にこのライブラリを叩くだけです。 ほかはクライアントキャッシュ用のヘッダーを書き換えたりとか細かいことはやっていますが全く大したことはやっておらず、サーバは非常にリーズナブルにやりたいことを実装した形になりました。 大変助かりました。
実装したものがこちらです。
https://github.com/ocknamo/nostr-image-optimizer
実装後の課題
このプロキシただのパブリックAPIなのでDoS攻撃に弱いです。何回もAPIをたたかれたら無料枠をすぐに超えてしまうことが容易に想像できました。 無料枠超えても使えなくなるだけで破産はしないので安心ですが、しかし対策は考える必要があります。
WAF
WAFです。APIに対するリクエスト回数などに対する制限をIPごとにかけています。また攻撃された場合検知できれば特定のIPや地域をブラックリストに入れることも可能です。
細かいことを説明してギリギリを攻めて攻撃されても困るので細かく説明しませんが、当初は全力でDoS攻撃されても無料枠超えないくらいの感じで制限をかけていました。 しかしNostrのTLをちょっと早めに表示するとすぐにWAFに引っかかってエラーになるという状態になることもあり、結局アイコンの表示は画像最適化の対象にしない方針にするなどの影響がありました。
いろいろあって、前提が変わり、もう少し制限をゆるくしたのでアイコンの対応は今後は検討できるかもしれません。
まとめ
割と手抜きで作ったことがわかるかと思います。実装しててNostrへの貢献ではあるはずですが、Nostrのプロトコル(NIPsとか)全然関係ないことやってるなと思いました。
フロントについては来週書きます。
次回のアドベントカレンダーの記事は eyemono.moe さんによる”クライアント自作を通して得られた知見まとめ”ですね!楽しみです!
-
 @ a012dc82:6458a70d
2024-12-19 03:48:56
@ a012dc82:6458a70d
2024-12-19 03:48:56Table Of Content
-
Who is Michael Burry?
-
Burry's Recent Move and its Implications
-
Bitcoin's Recent Performance and Future Prospects
-
The Broader Economic Context
-
Conclusion
-
FAQ
In the ever-evolving world of cryptocurrencies, the name Michael Burry might not be the first that comes to mind. However, recent developments have thrust him into the spotlight, making many in the crypto community sit up and take notice. So, what's all the fuss about Michael Burry's stance on Bitcoin's price?
Who is Michael Burry?
For those unfamiliar, Michael Burry is an American investor renowned for his prediction of the 2008 subprime mortgage crisis, which led to a global recession. His foresight and investment strategies during that period were so notable that they were depicted in the movie "The Big Short."
Burry's Recent Move and its Implications
Recently, a filing with the US Securities and Exchanges Commission (SEC) revealed that Scion Asset Management, a firm associated with Burry, has taken a significant bearish position on the US stock markets. Specifically, the firm has placed bets predicting a decline in major stock indices, including the Nasdaq 100 and the S&P 500. The numbers are staggering: $740 million worth of Invesco QQQ Trust Series 1 puts and $900 million worth of S&P 500 puts. These bets constitute about 93% of Burry's total portfolio value.
Now, you might wonder, what does this have to do with Bitcoin? The connection lies in the potential ripple effects of these bets. If the US stock market does experience a decline, as Burry seems to anticipate, it could lead to a bullish run for Bitcoin. The reasoning behind this is that traders might view Bitcoin as a high-risk, high-reward investment alternative to traditional stocks.
Bitcoin's Recent Performance and Future Prospects
Bitcoin has been experiencing a prolonged sideways movement, testing the patience of many traders. Historically, such sideways movements in the crypto market have sometimes been followed by a significant jump in value. Additionally, there's growing optimism about the potential approval of a Bitcoin ETF in the coming months, which could further boost its price.
The Broader Economic Context
In understanding Burry's moves and their potential impact on Bitcoin, it's essential to consider the broader economic landscape. The U.S. central bank, the Federal Reserve, is currently in a position where they might not increase the interest rate in the upcoming September FOMC meeting, as gauged by the CME FedWatch Tool. Historically, low-interest rates have often led to increased investment in riskier assets, as investors search for higher returns. This environment could further bolster the appeal of cryptocurrencies like Bitcoin, especially if traditional stock markets become more volatile or start to decline.
Furthermore, other global events, such as the US regional bank crisis that erupted earlier in 2023, have shown that Bitcoin can sometimes act as a hedge or alternative investment during times of traditional market stress. As such, the broader economic context, combined with Burry's predictions, paints a fascinating picture for Bitcoin's potential trajectory in the near future.
Conclusion
While Michael Burry's recent moves primarily concern the US stock market, the potential implications for the crypto market, and Bitcoin in particular, are significant. If Burry's predictions come to fruition, and the US stock market sees a decline, it could be a pivotal moment for Bitcoin and its investors. As always, the world of investments is unpredictable, but with big names like Burry making such moves, it's an exciting time for observers and participants alike.
FAQ
Who is Michael Burry? Michael Burry is an American investor known for predicting the 2008 subprime mortgage crisis. He was prominently featured in the movie "The Big Short."
What has Burry recently predicted about the US stock market? Burry's firm, Scion Asset Management, has placed significant bets predicting a decline in major US stock indices, including the Nasdaq 100 and the S&P 500.
How might Burry's predictions affect Bitcoin's price? If the US stock market declines as Burry anticipates, it could lead to a bullish run for Bitcoin, with traders viewing it as a high-risk, high-reward alternative to stocks.
What is the broader economic context influencing Bitcoin? The Federal Reserve's potential decision not to increase interest rates, combined with global events like the US regional bank crisis, could influence Bitcoin's appeal as an alternative investment.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 8cb60e21:5f2deaea
2024-08-18 20:50:48
@ 8cb60e21:5f2deaea
2024-08-18 20:50:48 -
 @ c230edd3:8ad4a712
2024-12-02 03:49:19
@ c230edd3:8ad4a712
2024-12-02 03:49:19Chef's notes
This recipe is not my own, but it was great and easy, so I'm moving it here. Cooking as instructed serves 2, but this could easily be adjusted to include stir fry vegetables and rice, to make this a meal for 4.
Details
- ⏲️ Prep time: 15 minutes, 1-24 hours marinating
- 🍳 Cook time: 10-15 minutes
- 🍽️ Servings: 2-4
Ingredients
- 1 Venison Heart (elk would work well, too. recipe would need to be doubled)
- 1/2 Asian Pear, grated
- 2 Cloves Garlic, grated
- 1 Tbsp Ginger, grated
- 3 Tbsp Soy Sauce
- 1 Tbsp Honey
- 1 Tbsp Onion, grated
- 1 Tbsp Toasted Sesame Oil
- 1 tsp Red Pepper Flakes
- 2 Shallots, chopped
- Sesame Seeds
- Cooking Oil
Directions
- Mix all ingredients besides heart, shallots, sesame seeds and cooking oil in a medium bowl.
- Remove arteries and excess fat from heart, cut in half and rinse
- Cut into thin slices or bite size pieces
- Add to marinade, mix and cover. Allow to soak for 1-24 hours.
- Heat oil in large frying pan over med-high to high heat
- Drain excess marinade.
- Place heart in pan and sear on both sides to desired doneness. Medium rare is ideal for heart.
- Remove from pan and garnish with chopped shallots and sesame seeds. Serve with stir fry veggies and rice, if desired.
















































