-
 @ eac63075:b4988b48
2025-01-04 19:41:34
@ eac63075:b4988b48
2025-01-04 19:41:34Since its creation in 2009, Bitcoin has symbolized innovation and resilience. However, from time to time, alarmist narratives arise about emerging technologies that could "break" its security. Among these, quantum computing stands out as one of the most recurrent. But does quantum computing truly threaten Bitcoin? And more importantly, what is the community doing to ensure the protocol remains invulnerable?
The answer, contrary to sensationalist headlines, is reassuring: Bitcoin is secure, and the community is already preparing for a future where quantum computing becomes a practical reality. Let’s dive into this topic to understand why the concerns are exaggerated and how the development of BIP-360 demonstrates that Bitcoin is one step ahead.
What Is Quantum Computing, and Why Is Bitcoin Not Threatened?
Quantum computing leverages principles of quantum mechanics to perform calculations that, in theory, could exponentially surpass classical computers—and it has nothing to do with what so-called “quantum coaches” teach to scam the uninformed. One of the concerns is that this technology could compromise two key aspects of Bitcoin’s security:
- Wallets: These use elliptic curve algorithms (ECDSA) to protect private keys. A sufficiently powerful quantum computer could deduce a private key from its public key.
- Mining: This is based on the SHA-256 algorithm, which secures the consensus process. A quantum attack could, in theory, compromise the proof-of-work mechanism.
Understanding Quantum Computing’s Attack Priorities
While quantum computing is often presented as a threat to Bitcoin, not all parts of the network are equally vulnerable. Theoretical attacks would be prioritized based on two main factors: ease of execution and potential reward. This creates two categories of attacks:
1. Attacks on Wallets
Bitcoin wallets, secured by elliptic curve algorithms, would be the initial targets due to the relative vulnerability of their public keys, especially those already exposed on the blockchain. Two attack scenarios stand out:
-
Short-term attacks: These occur during the interval between sending a transaction and its inclusion in a block (approximately 10 minutes). A quantum computer could intercept the exposed public key and derive the corresponding private key to redirect funds by creating a transaction with higher fees.
-
Long-term attacks: These focus on old wallets whose public keys are permanently exposed. Wallets associated with Satoshi Nakamoto, for example, are especially vulnerable because they were created before the practice of using hashes to mask public keys.
We can infer a priority order for how such attacks might occur based on urgency and importance.
 Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)
Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)2. Attacks on Mining
Targeting the SHA-256 algorithm, which secures the mining process, would be the next objective. However, this is far more complex and requires a level of quantum computational power that is currently non-existent and far from realization. A successful attack would allow for the recalculation of all possible hashes to dominate the consensus process and potentially "mine" it instantly.
 Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin Attacks
Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin AttacksRecently, Narcelio asked me about a statement I made on Tubacast:
https://x.com/eddieoz/status/1868371296683511969
If an attack became a reality before Bitcoin was prepared, it would be necessary to define the last block prior to the attack and proceed from there using a new hashing algorithm. The solution would resemble the response to the infamous 2013 bug. It’s a fact that this would cause market panic, and Bitcoin's price would drop significantly, creating a potential opportunity for the well-informed.
Preferably, if developers could anticipate the threat and had time to work on a solution and build consensus before an attack, they would simply decide on a future block for the fork, which would then adopt the new algorithm. It might even rehash previous blocks (reaching consensus on them) to avoid potential reorganization through the re-mining of blocks using the old hash. (I often use the term "shielding" old transactions).
How Can Users Protect Themselves?
While quantum computing is still far from being a practical threat, some simple measures can already protect users against hypothetical scenarios:
- Avoid using exposed public keys: Ensure funds sent to old wallets are transferred to new ones that use public key hashes. This reduces the risk of long-term attacks.
- Use modern wallets: Opt for wallets compatible with SegWit or Taproot, which implement better security practices.
- Monitor security updates: Stay informed about updates from the Bitcoin community, such as the implementation of BIP-360, which will introduce quantum-resistant addresses.
- Do not reuse addresses: Every transaction should be associated with a new address to minimize the risk of repeated exposure of the same public key.
- Adopt secure backup practices: Create offline backups of private keys and seeds in secure locations, protected from unauthorized access.
BIP-360 and Bitcoin’s Preparation for the Future
Even though quantum computing is still beyond practical reach, the Bitcoin community is not standing still. A concrete example is BIP-360, a proposal that establishes the technical framework to make wallets resistant to quantum attacks.
BIP-360 addresses three main pillars:
- Introduction of quantum-resistant addresses: A new address format starting with "BC1R" will be used. These addresses will be compatible with post-quantum algorithms, ensuring that stored funds are protected from future attacks.
- Compatibility with the current ecosystem: The proposal allows users to transfer funds from old addresses to new ones without requiring drastic changes to the network infrastructure.
- Flexibility for future updates: BIP-360 does not limit the choice of specific algorithms. Instead, it serves as a foundation for implementing new post-quantum algorithms as technology evolves.
This proposal demonstrates how Bitcoin can adapt to emerging threats without compromising its decentralized structure.
Post-Quantum Algorithms: The Future of Bitcoin Cryptography
The community is exploring various algorithms to protect Bitcoin from quantum attacks. Among the most discussed are:
- Falcon: A solution combining smaller public keys with compact digital signatures. Although it has been tested in limited scenarios, it still faces scalability and performance challenges.
- Sphincs: Hash-based, this algorithm is renowned for its resilience, but its signatures can be extremely large, making it less efficient for networks like Bitcoin’s blockchain.
- Lamport: Created in 1977, it’s considered one of the earliest post-quantum security solutions. Despite its reliability, its gigantic public keys (16,000 bytes) make it impractical and costly for Bitcoin.
Two technologies show great promise and are well-regarded by the community:
- Lattice-Based Cryptography: Considered one of the most promising, it uses complex mathematical structures to create systems nearly immune to quantum computing. Its implementation is still in its early stages, but the community is optimistic.
- Supersingular Elliptic Curve Isogeny: These are very recent digital signature algorithms and require extensive study and testing before being ready for practical market use.
The final choice of algorithm will depend on factors such as efficiency, cost, and integration capability with the current system. Additionally, it is preferable that these algorithms are standardized before implementation, a process that may take up to 10 years.
Why Quantum Computing Is Far from Being a Threat
The alarmist narrative about quantum computing overlooks the technical and practical challenges that still need to be overcome. Among them:
- Insufficient number of qubits: Current quantum computers have only a few hundred qubits, whereas successful attacks would require millions.
- High error rate: Quantum stability remains a barrier to reliable large-scale operations.
- High costs: Building and operating large-scale quantum computers requires massive investments, limiting their use to scientific or specific applications.
Moreover, even if quantum computers make significant advancements, Bitcoin is already adapting to ensure its infrastructure is prepared to respond.
Conclusion: Bitcoin’s Secure Future
Despite advancements in quantum computing, the reality is that Bitcoin is far from being threatened. Its security is ensured not only by its robust architecture but also by the community’s constant efforts to anticipate and mitigate challenges.
The implementation of BIP-360 and the pursuit of post-quantum algorithms demonstrate that Bitcoin is not only resilient but also proactive. By adopting practical measures, such as using modern wallets and migrating to quantum-resistant addresses, users can further protect themselves against potential threats.
Bitcoin’s future is not at risk—it is being carefully shaped to withstand any emerging technology, including quantum computing.
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ 7ecd3fe6:6b52f30d
2025-01-07 19:13:58
@ 7ecd3fe6:6b52f30d
2025-01-07 19:13:58I normally try to avoid the noise that is the crypto market only because I've been in that situationship before back in 2016, got rugged in the ICO phase and learned my lesson. There is nothing left for me to take from crypto apart from watching from the sidelines and enjoying the endless amount of schadenfreude it produces.
So every so often I find myself checking in on the ugly step-child of Bitcoin just to see what the left side of the bell curve are up to and you know what?
I wasn't disappointed.
In fact, I'm kind of impressed at the number of times shitcoiners can come up with a new meta to get the degens excited enough to take another spin at the casino, it's honestly pretty impressive.
After ordinals were cooked, the shitcoiners were left to head back to the drawing board, and the obvious pivot was AI tokens. AI and LLMs were the new hotness and try they did but AI tokens didn't really take off in 2024.
Sure there's tokens like NEAR, Internet Computer, and RENDER all with a few billion in market cap and according to CoinGecko there's around 50 billion in AI shitcoins, but for these coins to pump they need to provide some sort of product.
That requires investment and some thinking and who has time for that?
F AI, AI Agents are the future
Wtf are AI agent tokens you ask? Bad question, but I'll edify you anyway.
AI agents are autonomous software programs designed to perform very specific tasks and make decisions independently. Hardly very AI and more repetitive loops, cronjobs if you will.
Using an AI agent and giving a blockchain wallet these agents can interact with smart contracts, dApps and DEXs and start to get up to some shenanigans, or at least distance the agent creator from the actions.
No, I didn't rug pull you, that was the AI Agent malfunctioning.
I guess the killer app for AI agents is plausible deniability when you have to plead your case with the SEC.
As this new batch of vapourware gains popularity, every moron with a ChatGPT pro subscription and a dream is going after this market of suckers. Right now there are several AI agent tokens you can speculate on with a combined market cap of $16 billion according to CoinGecko

It's all about the meta-baby
I'm old enough to remember when the idea for a shitcoin was
- Utility, it had to do something and wall it off, so you needed to token to access a feature, that failed
- Then we went into culture and community, its all about the memes, that failed
- Then it was all about etching in on Bitcoin block space, using that rare commodity made my shitcoin valuable, that failed
Now we've got a bit of a mish-mash of memes + AI utility equals new grift.
To illustrate the unserious nature of this nonsense, AI agents, associated meme coins, and the protocols used to create these agents are among the top five best-performing crypto assets of the day, according to CoinGecko.
For example, Truth Terminal—the agent that started much of this wave—has promoted Goatseus Maximus (GOAT) and Fartcoin (FARTCOIN) causing both to skyrocket.
Fartcoin surged to a new all-time high price of $1.3 and a market cap of $1.5 billion as a result, FML, what a complete waste.

Growth in the FART coin Market Cap
ChatGPT-wrapped crypto scams
The Truth Terminal chatbot is a customized version of Anthropic's Claude 3 LLM, that tweets out random nonsense and somehow shitcoiners take this text as gospel and try to bet on tokens it shills or creates tokens based on its tweets as if it were Elon himself.
Can't wait for Elon to pump your bags, well, let's all dogpile on the random brain farts of a chatbot.
Again this just seems like a way to obscure insider trading and pump and dump influencer scams by hiding the human element behind a bot.
In fact, shitcoiners are creating tokens or sending tokens to a known wallet tied to this AI agent, hoping it uses this data to formulate it's next round of bullshit, I mean bullish tweets.
AI in name only
Still, most agent autonomy is limited. Truth Terminal, for example, still has creator Andy Ayrey looking over it's shoulder before it's thoughts and decisions go out to the public.
So if there's someone watching it, there's someone with access to the wallet and master access to prod it in a certain direction no?
Sigh! Reading up on this all just made my brain hurt and not in a good way.
“Do you want to be right or do you want to make money”
— ZachXBT (@zachxbt) January 6, 2025
99% of it is a scam and the AI agent wrapper grifts are probably worse than other past trends tbh.
bc at least meme coins promise nothing whereas AI coins try to larp as much as possible to appear legit to unsuspecting…This AI agent field itself is still relatively nascent and doesn't seem to provide any value other than being a filter for random tweet generation, and we all know computers aren't good with being random.
Most if not all projects promising AI-powered solutions will not deliver on their promises, potentially leading to significant losses for investors.
But that's the game they choose to play.
The cryptocurrency market is primarily driven by hype and speculation, and AI agent tokens are no exception. Many projects are overvalued based on potential rather than actual achievements.
Is this the future?

-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 207ad2a0:e7cca7b0
2025-01-07 03:46:04
@ 207ad2a0:e7cca7b0
2025-01-07 03:46:04Quick context: I wanted to check out Nostr's longform posts and this blog post seemed like a good one to try and mirror. It's originally from my free to read/share attempt to write a novel, but this post here is completely standalone - just describing how I used AI image generation to make a small piece of the work.
Hold on, put your pitchforks down - outside of using Grammerly & Emacs for grammatical corrections - not a single character was generated or modified by computers; a non-insignificant portion of my first draft originating on pen & paper. No AI is ~~weird and crazy~~ imaginative enough to write like I do. The only successful AI contribution you'll find is a single image, the map, which I heavily edited. This post will go over how I generated and modified an image using AI, which I believe brought some value to the work, and cover a few quick thoughts about AI towards the end.
Let's be clear, I can't draw, but I wanted a map which I believed would improve the story I was working on. After getting abysmal results by prompting AI with text only I decided to use "Diffuse the Rest," a Stable Diffusion tool that allows you to provide a reference image + description to fine tune what you're looking for. I gave it this Microsoft Paint looking drawing:

and after a number of outputs, selected this one to work on:

The image is way better than the one I provided, but had I used it as is, I still feel it would have decreased the quality of my work instead of increasing it. After firing up Gimp I cropped out the top and bottom, expanded the ocean and separated the landmasses, then copied the top right corner of the large landmass to replace the bottom left that got cut off. Now we've got something that looks like concept art: not horrible, and gets the basic idea across, but it's still due for a lot more detail.

The next thing I did was add some texture to make it look more map like. I duplicated the layer in Gimp and applied the "Cartoon" filter to both for some texture. The top layer had a much lower effect strength to give it a more textured look, while the lower layer had a higher effect strength that looked a lot like mountains or other terrain features. Creating a layer mask allowed me to brush over spots to display the lower layer in certain areas, giving it some much needed features.

At this point I'd made it to where I felt it may improve the work instead of detracting from it - at least after labels and borders were added, but the colors seemed artificial and out of place. Luckily, however, this is when PhotoFunia could step in and apply a sketch effect to the image.

At this point I was pretty happy with how it was looking, it was close to what I envisioned and looked very visually appealing while still being a good way to portray information. All that was left was to make the white background transparent, add some minor details, and add the labels and borders. Below is the exact image I wound up using:

Overall, I'm very satisfied with how it turned out, and if you're working on a creative project, I'd recommend attempting something like this. It's not a central part of the work, but it improved the chapter a fair bit, and was doable despite lacking the talent and not intending to allocate a budget to my making of a free to read and share story.
The AI Generated Elephant in the Room
If you've read my non-fiction writing before, you'll know that I think AI will find its place around the skill floor as opposed to the skill ceiling. As you saw with my input, I have absolutely zero drawing talent, but with some elbow grease and an existing creative direction before and after generating an image I was able to get something well above what I could have otherwise accomplished. Outside of the lowest common denominators like stock photos for the sole purpose of a link preview being eye catching, however, I doubt AI will be wholesale replacing most creative works anytime soon. I can assure you that I tried numerous times to describe the map without providing a reference image, and if I used one of those outputs (or even just the unedited output after providing the reference image) it would have decreased the quality of my work instead of improving it.
I'm going to go out on a limb and expect that AI image, text, and video is all going to find its place in slop & generic content (such as AI generated slop replacing article spinners and stock photos respectively) and otherwise be used in a supporting role for various creative endeavors. For people working on projects like I'm working on (e.g. intended budget $0) it's helpful to have an AI capable of doing legwork - enabling projects to exist or be improved in ways they otherwise wouldn't have. I'm also guessing it'll find its way into more professional settings for grunt work - think a picture frame or fake TV show that would exist in the background of an animated project - likely a detail most people probably wouldn't notice, but that would save the creators time and money and/or allow them to focus more on the essential aspects of said work. Beyond that, as I've predicted before: I expect plenty of emails will be generated from a short list of bullet points, only to be summarized by the recipient's AI back into bullet points.
I will also make a prediction counter to what seems mainstream: AI is about to peak for a while. The start of AI image generation was with Google's DeepDream in 2015 - image recognition software that could be run in reverse to "recognize" patterns where there were none, effectively generating an image from digital noise or an unrelated image. While I'm not an expert by any means, I don't think we're too far off from that a decade later, just using very fine tuned tools that develop more coherent images. I guess that we're close to maxing out how efficiently we're able to generate images and video in that manner, and the hard caps on how much creative direction we can have when using AI - as well as the limits to how long we can keep it coherent (e.g. long videos or a chronologically consistent set of images) - will prevent AI from progressing too far beyond what it is currently unless/until another breakthrough occurs.
-
 @ e6817453:b0ac3c39
2025-01-05 14:29:17
@ e6817453:b0ac3c39
2025-01-05 14:29:17The Rise of Graph RAGs and the Quest for Data Quality
As we enter a new year, it’s impossible to ignore the boom of retrieval-augmented generation (RAG) systems, particularly those leveraging graph-based approaches. The previous year saw a surge in advancements and discussions about Graph RAGs, driven by their potential to enhance large language models (LLMs), reduce hallucinations, and deliver more reliable outputs. Let’s dive into the trends, challenges, and strategies for making the most of Graph RAGs in artificial intelligence.
Booming Interest in Graph RAGs
Graph RAGs have dominated the conversation in AI circles. With new research papers and innovations emerging weekly, it’s clear that this approach is reshaping the landscape. These systems, especially those developed by tech giants like Microsoft, demonstrate how graphs can:
- Enhance LLM Outputs: By grounding responses in structured knowledge, graphs significantly reduce hallucinations.
- Support Complex Queries: Graphs excel at managing linked and connected data, making them ideal for intricate problem-solving.
Conferences on linked and connected data have increasingly focused on Graph RAGs, underscoring their central role in modern AI systems. However, the excitement around this technology has brought critical questions to the forefront: How do we ensure the quality of the graphs we’re building, and are they genuinely aligned with our needs?
Data Quality: The Foundation of Effective Graphs
A high-quality graph is the backbone of any successful RAG system. Constructing these graphs from unstructured data requires attention to detail and rigorous processes. Here’s why:
- Richness of Entities: Effective retrieval depends on graphs populated with rich, detailed entities.
- Freedom from Hallucinations: Poorly constructed graphs amplify inaccuracies rather than mitigating them.
Without robust data quality, even the most sophisticated Graph RAGs become ineffective. As a result, the focus must shift to refining the graph construction process. Improving data strategy and ensuring meticulous data preparation is essential to unlock the full potential of Graph RAGs.
Hybrid Graph RAGs and Variations
While standard Graph RAGs are already transformative, hybrid models offer additional flexibility and power. Hybrid RAGs combine structured graph data with other retrieval mechanisms, creating systems that:
- Handle diverse data sources with ease.
- Offer improved adaptability to complex queries.
Exploring these variations can open new avenues for AI systems, particularly in domains requiring structured and unstructured data processing.
Ontology: The Key to Graph Construction Quality
Ontology — defining how concepts relate within a knowledge domain — is critical for building effective graphs. While this might sound abstract, it’s a well-established field blending philosophy, engineering, and art. Ontology engineering provides the framework for:
- Defining Relationships: Clarifying how concepts connect within a domain.
- Validating Graph Structures: Ensuring constructed graphs are logically sound and align with domain-specific realities.
Traditionally, ontologists — experts in this discipline — have been integral to large enterprises and research teams. However, not every team has access to dedicated ontologists, leading to a significant challenge: How can teams without such expertise ensure the quality of their graphs?
How to Build Ontology Expertise in a Startup Team
For startups and smaller teams, developing ontology expertise may seem daunting, but it is achievable with the right approach:
- Assign a Knowledge Champion: Identify a team member with a strong analytical mindset and give them time and resources to learn ontology engineering.
- Provide Training: Invest in courses, workshops, or certifications in knowledge graph and ontology creation.
- Leverage Partnerships: Collaborate with academic institutions, domain experts, or consultants to build initial frameworks.
- Utilize Tools: Introduce ontology development tools like Protégé, OWL, or SHACL to simplify the creation and validation process.
- Iterate with Feedback: Continuously refine ontologies through collaboration with domain experts and iterative testing.
So, it is not always affordable for a startup to have a dedicated oncologist or knowledge engineer in a team, but you could involve consulters or build barefoot experts.
You could read about barefoot experts in my article :
Even startups can achieve robust and domain-specific ontology frameworks by fostering in-house expertise.
How to Find or Create Ontologies
For teams venturing into Graph RAGs, several strategies can help address the ontology gap:
-
Leverage Existing Ontologies: Many industries and domains already have open ontologies. For instance:
-
Public Knowledge Graphs: Resources like Wikipedia’s graph offer a wealth of structured knowledge.
- Industry Standards: Enterprises such as Siemens have invested in creating and sharing ontologies specific to their fields.
-
Business Framework Ontology (BFO): A valuable resource for enterprises looking to define business processes and structures.
-
Build In-House Expertise: If budgets allow, consider hiring knowledge engineers or providing team members with the resources and time to develop expertise in ontology creation.
-
Utilize LLMs for Ontology Construction: Interestingly, LLMs themselves can act as a starting point for ontology development:
-
Prompt-Based Extraction: LLMs can generate draft ontologies by leveraging their extensive training on graph data.
- Domain Expert Refinement: Combine LLM-generated structures with insights from domain experts to create tailored ontologies.
Parallel Ontology and Graph Extraction
An emerging approach involves extracting ontologies and graphs in parallel. While this can streamline the process, it presents challenges such as:
- Detecting Hallucinations: Differentiating between genuine insights and AI-generated inaccuracies.
- Ensuring Completeness: Ensuring no critical concepts are overlooked during extraction.
Teams must carefully validate outputs to ensure reliability and accuracy when employing this parallel method.
LLMs as Ontologists
While traditionally dependent on human expertise, ontology creation is increasingly supported by LLMs. These models, trained on vast amounts of data, possess inherent knowledge of many open ontologies and taxonomies. Teams can use LLMs to:
- Generate Skeleton Ontologies: Prompt LLMs with domain-specific information to draft initial ontology structures.
- Validate and Refine Ontologies: Collaborate with domain experts to refine these drafts, ensuring accuracy and relevance.
However, for validation and graph construction, formal tools such as OWL, SHACL, and RDF should be prioritized over LLMs to minimize hallucinations and ensure robust outcomes.
Final Thoughts: Unlocking the Power of Graph RAGs
The rise of Graph RAGs underscores a simple but crucial correlation: improving graph construction and data quality directly enhances retrieval systems. To truly harness this power, teams must invest in understanding ontologies, building quality graphs, and leveraging both human expertise and advanced AI tools.
As we move forward, the interplay between Graph RAGs and ontology engineering will continue to shape the future of AI. Whether through adopting existing frameworks or exploring innovative uses of LLMs, the path to success lies in a deep commitment to data quality and domain understanding.
Have you explored these technologies in your work? Share your experiences and insights — and stay tuned for more discussions on ontology extraction and its role in AI advancements. Cheers to a year of innovation!
-
 @ a4a6b584:1e05b95b
2025-01-02 18:13:31
@ a4a6b584:1e05b95b
2025-01-02 18:13:31The Four-Layer Framework
Layer 1: Zoom Out

Start by looking at the big picture. What’s the subject about, and why does it matter? Focus on the overarching ideas and how they fit together. Think of this as the 30,000-foot view—it’s about understanding the "why" and "how" before diving into the "what."
Example: If you’re learning programming, start by understanding that it’s about giving logical instructions to computers to solve problems.
- Tip: Keep it simple. Summarize the subject in one or two sentences and avoid getting bogged down in specifics at this stage.
Once you have the big picture in mind, it’s time to start breaking it down.
Layer 2: Categorize and Connect

Now it’s time to break the subject into categories—like creating branches on a tree. This helps your brain organize information logically and see connections between ideas.
Example: Studying biology? Group concepts into categories like cells, genetics, and ecosystems.
- Tip: Use headings or labels to group similar ideas. Jot these down in a list or simple diagram to keep track.
With your categories in place, you’re ready to dive into the details that bring them to life.
Layer 3: Master the Details

Once you’ve mapped out the main categories, you’re ready to dive deeper. This is where you learn the nuts and bolts—like formulas, specific techniques, or key terminology. These details make the subject practical and actionable.
Example: In programming, this might mean learning the syntax for loops, conditionals, or functions in your chosen language.
- Tip: Focus on details that clarify the categories from Layer 2. Skip anything that doesn’t add to your understanding.
Now that you’ve mastered the essentials, you can expand your knowledge to include extra material.
Layer 4: Expand Your Horizons

Finally, move on to the extra material—less critical facts, trivia, or edge cases. While these aren’t essential to mastering the subject, they can be useful in specialized discussions or exams.
Example: Learn about rare programming quirks or historical trivia about a language’s development.
- Tip: Spend minimal time here unless it’s necessary for your goals. It’s okay to skim if you’re short on time.
Pro Tips for Better Learning
1. Use Active Recall and Spaced Repetition
Test yourself without looking at notes. Review what you’ve learned at increasing intervals—like after a day, a week, and a month. This strengthens memory by forcing your brain to actively retrieve information.
2. Map It Out
Create visual aids like diagrams or concept maps to clarify relationships between ideas. These are particularly helpful for organizing categories in Layer 2.
3. Teach What You Learn
Explain the subject to someone else as if they’re hearing it for the first time. Teaching exposes any gaps in your understanding and helps reinforce the material.
4. Engage with LLMs and Discuss Concepts
Take advantage of tools like ChatGPT or similar large language models to explore your topic in greater depth. Use these tools to:
- Ask specific questions to clarify confusing points.
- Engage in discussions to simulate real-world applications of the subject.
- Generate examples or analogies that deepen your understanding.Tip: Use LLMs as a study partner, but don’t rely solely on them. Combine these insights with your own critical thinking to develop a well-rounded perspective.
Get Started
Ready to try the Four-Layer Method? Take 15 minutes today to map out the big picture of a topic you’re curious about—what’s it all about, and why does it matter? By building your understanding step by step, you’ll master the subject with less stress and more confidence.
-
 @ b17fccdf:b7211155
2024-12-29 12:04:31
@ b17fccdf:b7211155
2024-12-29 12:04:31🆕 What's changed:
- New bonus guide dedicated to install/upgrade/uninstall PostgreSQL
- Modified the LND guide to use PostgreSQL instead of bbolt
- Modified the Nostr relay guide to use PostgreSQL instead of SQLite (experimental)
- Modified the BTCPay Server bonus guide according to these changes
- Used the lndinit MiniBolt org fork, to add an extra section to migrate an existing LND bbolt database to PostgreSQL (🚨⚠️Experimental - use it behind your responsibility⚠️🚨)
- New Golang bonus guide as a common language for the lndinit compile
- Updated LND to v0.18
- New Bitcoin Core extra section to renovate Tor & I2P addresses
- New Bitcoin Core extra section to generate a full
bitcoin.conffile - Rebuilt some homepage sections and general structure
- Deleted the
$symbol of the commands to easy copy-paste to the terminal - Deleted the initial incoming and the outgoing rules configuration of UFW, due to it being by default
🪧 PD: If you want to use the old database backend of the LND or Nostr relay, follow the next extra sections:
- Use the default bbolt database backend for the LND
- Use the default SQLite database backend for the Nostr relay
⚠️Attention⚠️: The migration process was tested on testnet mode from an existing bbolt database backend to a new PostgreSQL database using lndinit and the results were successful. However, It wasn't tested on mainnet, according to the developer, it is in experimental status which could damage your existing LND database.🚨 Use it behind your responsibility 🧼
🔧 PR related: https://github.com/minibolt-guide/minibolt/pull/93
♻️ Migrate the PostgreSQL database location
If you installed NBXplorer + BTCPay Server, it is probably you have the database of the PostgreSQL cluster on the default path (
/var/lib/postgresql/16/main/), follow the next instructions to migrate it to the new dedicated location on/data/postgresdbfolder:- With user
admincreate the dedicated PostgreSQL data folder
sudo mkdir /data/postgresdb- Assign as the owner to the
postgresuser
sudo chown postgres:postgres /data/postgresdb- Assign permissions of the data folder only to the
postgresuser
sudo chmod -R 700 /data/postgresdb- Stop NBXplorer and BTCPay Server
sudo systemctl stop nbxplorer && sudo systemctl stop btcpayserver- Stop PostgreSQL
sudo systemctl stop postgresql- Use the rsync command to copy all files from the existing database on (
/var/lib/postgresql/16/main) to the new destination directory (/data/postgresdb)
sudo rsync -av /var/lib/postgresql/16/main/ /data/postgresdb/Expected output:
``` sending incremental file list ./ PG_VERSION postgresql.auto.conf postmaster.opts postmaster.pid base/ base/1/ base/1/112 base/1/113 base/1/1247 base/1/1247_fsm base/1/1247_vm base/1/1249 base/1/1249_fsm base/1/1249_vm [...] pg_wal/000000010000000000000009 pg_wal/archive_status/ pg_xact/ pg_xact/0000
sent 164,483,875 bytes received 42,341 bytes 36,561,381.33 bytes/sec total size is 164,311,368 speedup is 1.00 ```
- Edit the PostgreSQL data directory on configuration, to redirect the store to the new location
sudo nano /etc/postgresql/16/main/postgresql.conf --linenumbers- Replace the line 42 to this. Save and exit
data_directory = '/data/postgresdb'- Start PostgreSQL to apply changes and monitor the correct status of the main instance and sub-instance monitoring sessions before
sudo systemctl start postgresql- You can monitor the PostgreSQL main instance by the systemd journal and check the log output to ensure all is correct. You can exit the monitoring at any time with Ctrl-C
journalctl -fu postgresqlExample of the expected output:
Nov 08 11:51:10 minibolt systemd[1]: Stopped PostgreSQL RDBMS. Nov 08 11:51:10 minibolt systemd[1]: Stopping PostgreSQL RDBMS... Nov 08 11:51:13 minibolt systemd[1]: Starting PostgreSQL RDBMS... Nov 08 11:51:13 minibolt systemd[1]: Finished PostgreSQL RDBMS.- You can monitor the PostgreSQL sub-instance by the systemd journal and check log output to ensure all is correct. You can exit monitoring at any time with Ctrl-C
journalctl -fu postgresql@16-mainExample of the expected output:
Nov 08 11:51:10 minibolt systemd[1]: Stopping PostgreSQL Cluster 16-main... Nov 08 11:51:11 minibolt systemd[1]: postgresql@16-main.service: Succeeded. Nov 08 11:51:11 minibolt systemd[1]: Stopped PostgreSQL Cluster 16-main. Nov 08 11:51:11 minibolt systemd[1]: postgresql@16-main.service: Consumed 1h 10min 8.677s CPU time. Nov 08 11:51:11 minibolt systemd[1]: Starting PostgreSQL Cluster 16-main... Nov 08 11:51:13 minibolt systemd[1]: Started PostgreSQL Cluster 16-main.- Start NBXplorer and BTCPay Server again
sudo systemctl start nbxplorer && sudo systemctl start btcpayserver- Monitor to make sure everything is as you left it. You can exit monitoring at any time with Ctrl-C
journalctl -fu nbxplorerjournalctl -fu btcpayserverEnjoy it MiniBolter! 💙
-
 @ fd208ee8:0fd927c1
2024-12-26 07:02:59
@ fd208ee8:0fd927c1
2024-12-26 07:02:59I just read this, and found it enlightening.
Jung... notes that intelligence can be seen as problem solving at an everyday level..., whereas creativity may represent problem solving for less common issues
Other studies have used metaphor creation as a creativity measure instead of divergent thinking and a spectrum of CHC components instead of just g and have found much higher relationships between creativity and intelligence than past studies
https://www.mdpi.com/2079-3200/3/3/59
I'm unusually intelligent (Who isn't?), but I'm much more creative, than intelligent, and I think that confuses people. The ability to apply intelligence, to solve completely novel problems, on the fly, is something IQ tests don't even claim to measure. They just claim a correlation.
Creativity requires taking wild, mental leaps out into nothingness; simply trusting that your brain will land you safely. And this is why I've been at the forefront of massive innovation, over and over, but never got rich off of it.
I'm a starving autist.
Zaps are the first time I've ever made money directly, for solving novel problems. Companies don't do this because there is a span of time between providing a solution and the solution being implemented, and the person building the implementation (or their boss) receives all the credit for the existence of the solution. At best, you can hope to get pawned off with a small bonus.
Nobody can remember who came up with the solution, originally, and that person might not even be there, anymore, and probably never filed a patent, and may have no idea that their idea has even been built. They just run across it, later, in a tech magazine or museum, and say, "Well, will you look at that! Someone actually went and built it! Isn't that nice!"
Universities at least had the idea of cementing novel solutions in academic papers, but that: 1) only works if you're an academic, and at a university, 2) is an incredibly slow process, not appropriate for a truly innovative field, 3) leads to manifestations of perverse incentives and biased research frameworks, coming from 'publish or perish' policies.
But I think long-form notes and zaps solve for this problem. #Alexandria, especially, is being built to cater to this long-suffering class of chronic underachievers. It leaves a written, public, time-stamped record of Clever Ideas We Have Had.
Because they are clever, the ideas. And we have had them.
-
 @ 16d11430:61640947
2024-12-23 16:47:01
@ 16d11430:61640947
2024-12-23 16:47:01At the intersection of philosophy, theology, physics, biology, and finance lies a terrifying truth: the fiat monetary system, in its current form, is not just an economic framework but a silent, relentless force actively working against humanity's survival. It isn't simply a failed financial model—it is a systemic engine of destruction, both externally and within the very core of our biological existence.
The Philosophical Void of Fiat
Philosophy has long questioned the nature of value and the meaning of human existence. From Socrates to Kant, thinkers have pondered the pursuit of truth, beauty, and virtue. But in the modern age, the fiat system has hijacked this discourse. The notion of "value" in a fiat world is no longer rooted in human potential or natural resources—it is abstracted, manipulated, and controlled by central authorities with the sole purpose of perpetuating their own power. The currency is not a reflection of society’s labor or resources; it is a representation of faith in an authority that, more often than not, breaks that faith with reckless monetary policies and hidden inflation.
The fiat system has created a kind of ontological nihilism, where the idea of true value, rooted in work, creativity, and family, is replaced with speculative gambling and short-term gains. This betrayal of human purpose at the systemic level feeds into a philosophical despair: the relentless devaluation of effort, the erosion of trust, and the abandonment of shared human values. In this nihilistic economy, purpose and meaning become increasingly difficult to find, leaving millions to question the very foundation of their existence.
Theological Implications: Fiat and the Collapse of the Sacred
Religious traditions have long linked moral integrity with the stewardship of resources and the preservation of life. Fiat currency, however, corrupts these foundational beliefs. In the theological narrative of creation, humans are given dominion over the Earth, tasked with nurturing and protecting it for future generations. But the fiat system promotes the exact opposite: it commodifies everything—land, labor, and life—treating them as mere transactions on a ledger.
This disrespect for creation is an affront to the divine. In many theologies, creation is meant to be sustained, a delicate balance that mirrors the harmony of the divine order. Fiat systems—by continuously printing money and driving inflation—treat nature and humanity as expendable resources to be exploited for short-term gains, leading to environmental degradation and societal collapse. The creation narrative, in which humans are called to be stewards, is inverted. The fiat system, through its unholy alliance with unrestrained growth and unsustainable debt, is destroying the very creation it should protect.
Furthermore, the fiat system drives idolatry of power and wealth. The central banks and corporations that control the money supply have become modern-day gods, their decrees shaping the lives of billions, while the masses are enslaved by debt and inflation. This form of worship isn't overt, but it is profound. It leads to a world where people place their faith not in God or their families, but in the abstract promises of institutions that serve their own interests.
Physics and the Infinite Growth Paradox
Physics teaches us that the universe is finite—resources, energy, and space are all limited. Yet, the fiat system operates under the delusion of infinite growth. Central banks print money without concern for natural limits, encouraging an economy that assumes unending expansion. This is not only an economic fallacy; it is a physical impossibility.
In thermodynamics, the Second Law states that entropy (disorder) increases over time in any closed system. The fiat system operates as if the Earth were an infinite resource pool, perpetually able to expand without consequence. The real world, however, does not bend to these abstract concepts of infinite growth. Resources are finite, ecosystems are fragile, and human capacity is limited. Fiat currency, by promoting unsustainable consumption and growth, accelerates the depletion of resources and the degradation of natural systems that support life itself.
Even the financial “growth” driven by fiat policies leads to unsustainable bubbles—inflated stock markets, real estate, and speculative assets that burst and leave ruin in their wake. These crashes aren’t just economic—they have profound biological consequences. The cycles of boom and bust undermine communities, erode social stability, and increase anxiety and depression, all of which affect human health at a biological level.
Biology: The Fiat System and the Destruction of Human Health
Biologically, the fiat system is a cancerous growth on human society. The constant chase for growth and the devaluation of work leads to chronic stress, which is one of the leading causes of disease in modern society. The strain of living in a system that values speculation over well-being results in a biological feedback loop: rising anxiety, poor mental health, physical diseases like cardiovascular disorders, and a shortening of lifespans.
Moreover, the focus on profit and short-term returns creates a biological disconnect between humans and the planet. The fiat system fuels industries that destroy ecosystems, increase pollution, and deplete resources at unsustainable rates. These actions are not just environmentally harmful; they directly harm human biology. The degradation of the environment—whether through toxic chemicals, pollution, or resource extraction—has profound biological effects on human health, causing respiratory diseases, cancers, and neurological disorders.
The biological cost of the fiat system is not a distant theory; it is being paid every day by millions in the form of increased health risks, diseases linked to stress, and the growing burden of mental health disorders. The constant uncertainty of an inflation-driven economy exacerbates these conditions, creating a society of individuals whose bodies and minds are under constant strain. We are witnessing a systemic biological unraveling, one in which the very act of living is increasingly fraught with pain, instability, and the looming threat of collapse.
Finance as the Final Illusion
At the core of the fiat system is a fundamental illusion—that financial growth can occur without any real connection to tangible value. The abstraction of currency, the manipulation of interest rates, and the constant creation of new money hide the underlying truth: the system is built on nothing but faith. When that faith falters, the entire system collapses.
This illusion has become so deeply embedded that it now defines the human experience. Work no longer connects to production or creation—it is reduced to a transaction on a spreadsheet, a means to acquire more fiat currency in a world where value is ephemeral and increasingly disconnected from human reality.
As we pursue ever-expanding wealth, the fundamental truths of biology—interdependence, sustainability, and balance—are ignored. The fiat system’s abstract financial models serve to disconnect us from the basic realities of life: that we are part of an interconnected world where every action has a reaction, where resources are finite, and where human health, both mental and physical, depends on the stability of our environment and our social systems.
The Ultimate Extermination
In the end, the fiat system is not just an economic issue; it is a biological, philosophical, theological, and existential threat to the very survival of humanity. It is a force that devalues human effort, encourages environmental destruction, fosters inequality, and creates pain at the core of the human biological condition. It is an economic framework that leads not to prosperity, but to extermination—not just of species, but of the very essence of human well-being.
To continue on this path is to accept the slow death of our species, one based not on natural forces, but on our own choice to worship the abstract over the real, the speculative over the tangible. The fiat system isn't just a threat; it is the ultimate self-inflicted wound, a cultural and financial cancer that, if left unchecked, will destroy humanity’s chance for survival and peace.
-
 @ 2355757c:5ad3e04d
2025-01-08 17:00:53
@ 2355757c:5ad3e04d
2025-01-08 17:00:53Non-Native Electromagnetic Fields (nnEMFs) are in my opinion, the least discussed and most pervasive environmental toxin in modern society that is negatively affecting our health. We live in a toxic soup world, where we are being attacked from every angle. Polluted air, water, plastics, chemicals in our food/clothes, endocrine disruptors in our personal care and cooking products…the list goes on and on. It is the unfortunate reality of living in a modern fiat world, where all big companies cut corners with cheap, toxic ingredients just so you can have a $20 cooking pan and a $15 t-shirt.
On the bright side of things, most of those toxins are pretty easily avoidable by just swapping for higher quality or more natural alternatives. You can also filter or buy better water and eat real food that was raised locally without toxic herbicides (to a pretty easy degree). Enter nnEMFs, something that is IMPOSSIBLE to fully avoid and MUCH more challenging to mitigate exposure to. That is because technology is so ubiquitous in our modern society. Cell phones and wifi routers in every house, smart appliances, cell towers on every block, power distribution and transmission lines, 5G rollout…we are surrounded by nnEMFs on a daily basis.
What are nnEMFs and why are they bad for my health?
A nnEMF is any EMF generated from a non-native source AKA a result of modern human technology. The three most common sources of nnEMFs are from our electrical power grid, radiofrequency (RF) communication, and microwave frequencies. These three sources differ by function and frequency.
-
Electrical Power Grid - 60Hz Frequency - In “Extremely Low Frequency Range (ELF)”
-
Radio Frequency (RF) - 3kHz to 300GHz - Mobile/Societal Communication/TV/Radio
-
Microwave (MW) - 300MHz to 300GHz - Radar/Satellite/Space Communication

It gets a bit confusing in the nomenclature between RF and MW, but in reality the only difference is the type of application above 300MHz. Below 300MHz and it is distinctly an RF frequency. All transmission and distribution of power to industry/homes/businesses is occurring at 60Hz. Vast differences in frequency, both turn out to be pretty detrimental for our health. Here’s a few reasons why:
- Classified as a possible carcinogen by the IARC (Group 2B)
RF-EMFs and ELF EMFs have been classified by the IARC as possibly carcinogenic based on the current scientific evidence. Now this is still a lower classification than red meat, so does this carry any merit? I say yes. Many researchers agree, such as in THIS study where researchers looked at mobile phone radiation and risk of brain tumors and concluded that RF fields should be classified as a probable carcinogenunder the criteria used by the IARC.
- RF and ELF Fields Increase Oxidative Stress
Oxidative stress. If you are a regular here in the health space you know how much comes down to maintaining redox homeostasis in our mitochondria (the supplier of ATP in our cells). Dysfunctional mitochondria = dysfunctional health and it just so happens that nnEMFs can significantly increase oxidative stress in our cells, with review studies like THIS one documenting how the most electromagnetic organs (brain, heart) as well as reproductive organs (testes, ovaries) were the MOST affected. (I wrote a recent substack post on declining sperm count and nnEMFs was the star of the show). Increased oxidative stress is consistent with OG findings from the likes of Dr. Robert Becker and Dr. Andrew Marino in their research. It is high level, but increased levels of oxidative stress predisposes you to increased risk of ALL KNOWN CHRONIC DISEASES. Because of this, nnEMFs have been strongly linked to increased risk of the following:
-
Neurodegenerative diseases
-
Reproductive issues
-
Cancer
-
Cardiovascular disease
-
Diabetes
-
Disturbed Sleep
We live in a toxic soup world. Achieving restorative sleep is the only way our body is able to fight back and restore our health from all of these toxic exposures. ANYTHING that impedes sleep restoration is a premature nail in the coffin in my eyes. Don’t believe me on the importance and power of melatonin and our circadian rhythm? Check out THIS thread I wrote on melatonin (anti-cancer, potent anti-oxidant, mitochondrial composer, etc.). Exposure to nnEMFs during the day AND at night disturb our sleep and prevent the ability to have that highly restorative sleep needed to detoxify and replenish our cells. Lose quality sleep, lose the ability to handle stressors that you are exposed to daily.
DON’T BELIEVE ME THAT nnEMFs are harmful to human health? You are not alone. Many mainstream media outlets, researchers, and industry “experts” dismiss the level of non-ionizing radiation coming from things like cell phones as dangerous to human health. This is has been ongoing since the 1970s. However, if you are subscribed to this newsletter you may have more of an open mind to believing everything you read from CNN, Forbes, or the WHO. I know you all question things more than the average member of society. So if you question the efficacy and morality of the vaccine, why would you not also question the potential health hazards of nnEMF exposure? Even Presidential Nominee RFK is on board. Big Tech, Big Pharma, Big Food…there is no difference! Centralized industry will do anything it takes to cover up research that is sound and not funded by themselves. Here is an example…
Dr. Henry Lai from University of Washington Emeritus has compiled the most comprehensive set of research articles regarding nnEMFs and biological impacts. He has reviewed OVER 2,500 studies. His conclusion?
Dr. Lai reports concluded from his research that exposure to RFR or ELF EMF produces oxidative effects or free radicals, and damages DNA. Downstream effects of studies examined include significant effects on genetic, neurological and reproductive functions. Among hundreds of studies of Radio Frequency Radiation (RFR), 70% to 89% reported significant biological effects. Among hundreds of studies of Extremely Low Frequency (ELF) and static fields, 74% to 91% reported significant biological effects.

Still don’t believe me, read the book Going Somewhere by Dr. Andrew Marino. It will blow your mind on how much effort has gone to cover up research on the biological effects of nnEMFs since the 1970s. Or Google Russia’s stance on nnEMFs.
You can also listen to one of our latest Decentralized Radio episodes with Anthony Smith, COO of EMF Safe. EMF Safe is a fantastic company that offers, in my opinion, the MOST effective nnEMF mitigation technology for your house. Hint: it’s not a f*cking pendant or harmonizer. YouTube link or Spotify link HERE.
Now that we got through the depressing side of the story, let's talk about WHAT YOU CAN DO to protect yourself from the harmful effects of nnEMFs without having to live in the woods-not a perfect solution either ;)
HOW TO MITIGATE nnEMF detrimental health effects: DURATION + DISTANCE \
\ TIME/DURATION. Your worst enemy in being exposed to nnEMFs is the duration of exposure. Nearly all of the negative studies showed that after 48-72hrs of exposure (chronic), detrimental health effects were seen. HOWEVER, the same studies showed less conclusive negative health effects for exposures less than 24-48hrs (with variance). For me that means the following action items:
-
Turn off the wifi-router at night
-
Turn phone on airplane mode when not using for >10 min
-
Turn appliances OFF when not in use in your home
-
Create a sleep sanctuary with minimal/no electronics in the bedroom
-
Do not move to an area right next to High Voltage Transmission Lines, Substation, Airport, Hospital, etc. (any area with high powered communication/RF equipment or power distribution equipment)
DISTANCE. Distance is your best friend in mitigating nnEMFs. Why? Inverse square law. Inverse square law is the fact that the magnitude of the EMF is calculated with the square of the distance in the denominator of the equation. This means that for every doubling of distance you have between you and the EMF source, the magnitude weakens by a factor of FOUR. Triple the distance, EMF magnitude goes down by a factor of NINE (and so forth). For me that results in the following action items:
-
Do not keep your cell phone ON your body when ON & receiving calls/texts
-
Do NOT hold your cell phone up to your ear when making calls (use headphones/speaker)
-
Move your bed 6-12 inches AWAY from any electrical outlets in your bedroom (especially near your head)
-
Do not stand immediately next to high powered appliances when ON & in use (microwave, washer, dryer, blender, etc.)

There exists a lot of other nnEMF “mitigating/harmonizing” technologies, however I would be highly suspect of anyone trying to sell you something. EMFs are extremely complex. The angle of incidence, power level, and frequency matter tremendously. Most folks who aren’t engineers or have a deep knowledge of physics likely won’t be able to have the baseline knowledge to know what is a scam and what is not. OR what to prioritize from an nnEMF mitigation perspective. I gave a pretty good starting point above for what actionable steps you can take. THis does not mean all products are a scam. nnEMF shielding has its place and I use some of these products…but whenever a topic is extremely complex to the layperson, it is easy for someone to convince you that a product works. Especially when proof is challenging to come up with (EMF readers are an okay tool at best).
As someone who holds a M.S. in Electrical Engineering, I never thought that my degree would come in handy for health optimization. Now in 2023, here I am realizing how electromagnetism is likely the MOST important topic to conceptualize to really crack the optimal health code. We are electromagnetic beings, and the research in this space has only just begun to scratch the surface.
If you want to learn more in depth about nnEMFs, mitigation tactics, what products work and do not, etc…subscribe to stay up to date on the latest. I am directly working with some renowned EMF experts on developing more educational content/courses that I will be launching in the near future to help practitioners and fellow esoteric health connoisseurs better understand nnEMFs more in depth to help themselves and their clients live a more optimal life.
Here on Decentralized Health, I will be writing in depth about the electromagnetic aspects of health alongside other topics I am passionate about such as environmental toxins, regenerative agriculture, decentralization, Bitcoin and more. I want as many people as possible to become empowered through education so that they can escape the dependencies of the centralized systems that are tarnishing our quality of life.
This is just the tip of the nnEMF iceberg.
Stay Sovereign,
Tristan
Originally published Sep 25. 2023
-
-
 @ 79008e78:dfac9395
2024-12-22 02:49:28
@ 79008e78:dfac9395
2024-12-22 02:49:28บทที่ 2: ภาพรวมการทำงานของบิตคอยน์
บิตคอยน์ทำงานอย่างไร
ระบบอย่างบิตคอยน์นั้นแตกต่างกับระบบธนาคารและระบบการชำระเงินแบบดั้งเดิมอย่างสิ้นเชิง เพราะมันสามารถทำงานได้โดยไม่จำเป็นต้องไว้วางใจบุคคลที่สาม แทนที่จะมีหน่วยงานกลางที่เชื่อถือได้ บิตคอยน์ได้อณุญาตให้ผู้ใช้แต่ละคนใช้ซอฟต์แวร์บนคอมพิวเตอร์ของตนเองเพื่อตรวจสอบการทำงานที่ถูกต้องของทุกส่วนในระบบ ซึ่งในบทนี้เอง เราจะทำการสำรวจบิตคอยน์ภาพรวมโดยติดตามธุรกรรมหนึ่งรายการผ่านระบบของบิตคอยน์ ดูว่าธุรกรรมนั้นถูกบันทึกลงในบล็อกเชนอย่างไร และการบันทึกธุรกรรมแบบกระจายศูนย์นั้นทำได้อย่างไร ส่วนในบทถัดไปจะลงลึกถึงเทคโนโลยีที่อยู่เบื้องหลังธุรกรรม เครือข่าย และการขุด
ภาพรวมของบิตคอยน์
ระบบของบิตคอยน์นั้นประกอบไปด้วย เหล่าผู้ใช้งาน wallet ต่าง ๆ , ธุรกรรมที่กระจายไปทั่วเครือข่าย และเหล่านักขุดที่จะคอยแข่งขันกันเพื่อสร้างบล๊อกใหม่ โดยที่มีบล๊อกเชนเป็นเหมือนสมุดบันทึกธุรกรรมที่รวมธุรกรรมทั้งหมดไว้ ตัวอย่างที่จะได้เห็นต่อไปนี้เป็นธุรกรรมที่เกิดขึ้นจริงบนเครือข่ายของบิตคอยน์ โดยจำลองการโต้ตอบระหว่างผู้ใช้หลายคนผ่านการส่งเงินจาก wallet หนึ่งไปยังอีก wallet และในขณะนั้นเราจะติดตามธุรกรรมผ่านเครือข่ายบิตคอยน์ ไปจนถึงบล็อกเชน เราจะใช้เว็บไซต์สำรวจบล็อกเชน (blockchain explorer) เพื่อดูภาพรวมในแต่ละขั้นตอน โดยมีเว็บไซต์สำรวจบล็อกเชนที่นิยม ดังนี้
- Blockstream Explorer
- Mempool.Space
- BlockCypher Explorer
เว็บไซต์เหล่านี้มีฟังก์ชันการค้นหาที่สามารถใช้ค้นหา Bitcoin address, Transaction Hash, หมายเลขบล็อก หรือ Block hash และเรียกดูข้อมูลที่เกี่ยวข้องจากเครือข่ายบิตคอยน์ได้ สำหรับแต่ละตัวอย่างธุรกรรมหรือบล็อก เราจะให้ URL เพื่อให้คุณสามารถค้นหาและศึกษาข้อมูลเพิ่มเติมได้ด้วยตัวเอง
คำเตือนเกี่ยวกับความเป็นส่วนตัวของการใช้ Block Explorer
การค้นหาข้อมูลใน block explorer อาจเปิดเผยให้ผู้ให้บริการทราบว่าคุณสนใจข้อมูลนั้น ซึ่งอาจเชื่อมโยงกับที่อยู่ IP ของคุณ รายละเอียดของเบราว์เซอร์ การค้นหาที่ผ่านมา หรือข้อมูลที่สามารถระบุตัวตนได้อื่น ๆ หากคุณค้นหาธุรกรรมจากหนังสือเล่มนี้ ผู้ให้บริการอาจคาดเดาได้ว่าคุณกำลังศึกษาเกี่ยวกับบิตคอยน์ ซึ่งไม่น่าจะมีปัญหาอะไร แต่หากคุณค้นหาธุรกรรมของตนเอง ผู้ให้บริการอาจสามารถคาดเดาได้ว่าคุณได้รับ ใช้จ่าย และมีบิตคอยน์อยู่เท่าใดในปัจจุบัน
การซื้อของจากร้านค้าออนไลน์
อลิซเป็นผู้ใช้งานใหม่ ที่พึ่งได้รับบิตคอยน์เป็นครั้งแรกจากคำแนะนำของโจเมื่อบทที่แล้ว โดยเธอได้ซื้อบิตคอยน์จากโจเก็บไว้ และตั้งแต่นั้นมาอลิซก็ซื้อบิตคอยน์เพิ่มเรื่อย ๆ และตอนนี้อลิซต้องการทำธุรกรรมด้วยบิตคอยน์ครั้งแรกของเธอ โดยการใช้จ่ายมันเพื่อแลกกับสิทธิ์เข้าถึงพอดแคสต์ตอนพิเศษจากร้านค้าออนไลน์ของบ๊อบ ร้านค้าออนไลน์ของบ๊อบเองก็เพิ่งมีการเพิ่มบิตคอยน์เป็นตัวเลือกในการทำธุรกรรม ราคาสินค้าในร้านของบ๊อบแสดงเป็นสกุลเงินท้องถิ่น (ดอลลาร์สหรัฐ) แต่ในหน้าชำระเงิน ลูกค้าสามารถเลือกชำระเงินเป็นดอลลาร์หรือบิตคอยน์ก็ได้
อลิซเลือกตอนพอดแคสต์ที่เธอต้องการซื้อและดำเนินการไปยังหน้าชำระเงิน ในหน้าชำระเงิน อลิซพบตัวเลือกในการชำระเงินด้วยบิตคอยน์ นอกเหนือจากตัวเลือกปกติ แต่ในตะกร้าชำระเงินจะแสดงราคาทั้งในรูปแบบดอลลาร์สหรัฐและบิตคอยน์ตามอัตราแลกเปลี่ยนในขณะนั้น หลังจากกดจ่ายด้วยบิตคอยน์ระบบของบ๊อบได้ทำการสร้างใบเรียกเก็บเงิน (invoice) ในรูปแบบของ QR-code ตามภาพด้านล่าง

ต่างจาก QR code ทั่วไปที่มีเพียง Bitcoin address ปลายทางเท่านั้น ใบแจ้งหนี้นี้เป็น QR code แบบ URI ที่ประกอบด้วย Bitcoin address จำนวนเงินชำระ และคำอธิบาย (memo) ซึ่งช่วยให้ Bitcoin wallet แอปพลิเคชันเติมข้อมูลที่ใช้ในการชำระเงินล่วงหน้าได้ และยังแสดงคำอธิบายที่อ่านเข้าใจง่ายให้กับผู้ใช้อีกด้วย คุณสามารถสแกน QR code นี้ด้วย Bitcoin wallet เพื่อดูสิ่งที่อลิซจะเห็น
QR Code ของใบแจ้งหนี้นี้เข้ารหัส URI ดังต่อไปนี้ ซึ่งถูกกำหนดไว้ใน BIP21:
bitcoin:bc1qk2g6u8p4qm2s2lh3gts5cpt2mrv5skcuu7u3e4?amount=0.01577764&label=Bob%27s%20Store&message=Purchase%20at%20Bob%27s%20Storeโดยส่วนประกอบของ URI สามารถจำแนกได้ ดังนี้
- A Bitcoin address: "bc1qk2g6u8p4qm2s2lh3gts5cpt2mrv5skcuu7u3e4"
- The payment amount (จำนวนบิตคอยน์) : "0.01577764"
- A label for the recipient address (label): "Bob's Store"
- A description for the payment (memo): "Purchase at Bob's Store"
อลิซใช้สมาร์ทโฟนของเธอสแกนบาร์โค้ดที่แสดงอยู่ หน้าจอสมาร์ทโฟนของเธอจะแสดงการชำระเงินในจำนวนที่ถูกต้องสำหรับร้านของบ๊อบ และเธอกด “Send” เพื่อยืนยันการชำระเงิน ภายในไม่กี่วินาที (เวลาประมาณเดียวกับการอนุมัติบัตรเครดิต) บ๊อบก็จะเห็นธุรกรรมดังกล่าวปรากฏบนเครื่องรับชำระเงินของเขา
เครือข่ายบิตคอยน์สามารถทำธุรกรรมในมูลค่าเศษส่วนได้ เช่น มิลลิบิทคอยน์ (1/1,000 ของบิทคอยน์) ไปจนถึง 1/100,000,000 ของบิทคอยน์ ซึ่งเรียกว่า "ซาโตชิ" ในหนังสือเล่มนี้ใช้กฎการพหูพจน์เดียวกันกับดอลลาร์หรือสกุลเงินแบบดั้งเดิมเมื่อพูดถึงจำนวนที่มากกว่าหนึ่งบิทคอยน์ เช่น "10 บิตคอยน์" หรือ "0.001 บิตคอยน์" กฎเดียวกันนี้ยังนำไปใช้กับหน่วยบัญชีบิทคอยน์อื่น ๆ เช่น มิลลิบิทคอยน์และซาโตชิอีกด้วย
ธุรกรรมในระบบบิตคอยน์
ธุรกรรมในระบบบิตคอยน์คือการแจ้งเครือข่ายว่าเจ้าของบิทคอยน์ได้อนุมัติการโอนมูลค่าไปยังเจ้าของใหม่แล้ว และ เจ้าของใหม่สามารถใช้บิทคอยน์เหล่านั้นได้ โดยสร้างธุรกรรมใหม่เพื่อรออนุมัติการโอนไปยังเจ้าของคนอื่นต่อ ๆ ไป ทำให้เกิดการส่งต่อความเป็นเจ้าของอย่างต่อเนื่อง
ธุรกรรมขาเข้าและขาออกของบิตคอยน์
ธุรกรรมเปรียบเสมือนบันทึกในสมุดบัญชีแบบสองทาง โดยธุรกรรมแต่ละรายการจะมีอินพุต (inputs) หนึ่งรายการหรือมากกว่านั้นที่ใช้จ่ายเงิน และมีเอาต์พุต (outputs) หนึ่งรายการหรือมากกว่าที่รับเงิน มูลค่าของอินพุตและเอาต์พุตไม่จำเป็นต้องเท่ากันเสมอไป เอาต์พุตมักจะมีมูลค่าน้อยกว่าอินพุตเล็กน้อย ซึ่งส่วนต่างนี้คือ "ค่าธรรมเนียมธุรกรรม" ที่นักขุดจะได้รับเมื่อรวมธุรกรรมในบล็อกเชน
ธุรกรรมยังมีหลักฐานการเป็นเจ้าของสำหรับจำนวนบิตคอยน์ (อินพุต) ที่ถูกใช้ในรูปของลายเซ็นดิจิทัลจากเจ้าของเดิม ซึ่งสามารถตรวจสอบความถูกต้องได้ ในระบบบิตคอยน์การใช้จ่ายบิตคอยน์คือการลงนามในธุรกรรมเพื่อโอนมูลค่าจากธุรกรรมก่อนหน้าไปยังเจ้าของใหม่ที่ระบุผ่าน Bitcoin adress

ห่วงโซ่ของธุรกรรม
การชำระเงินของอลิซไปยังร้านของบ็อบนั้นเป็นใช้เอาต์พุตจากธุรกรรมก่อนหน้าเป็นอินพุตในธุรกรรมครั้งนี้ (ในบทก่อนหน้า อลิซได้รับบิทคอยน์จากโจเพื่อนของเธอ ) เราเรียกธุรกรรมนี้ว่า "ธุรกรรมที่ 1 (Tx1)" ซึ่งแสดงถึงห่วงโซ่ของธุรกรรมที่เอาต์พุตของธุรกรรมหนึ่งถูกใช้เป็นอินพุตในธุรกรรมถัดไป
การอ้างอิงอินพุตจากเอาต์พุตก่อนหน้า
Tx1 โอน 0.001 บิทคอยน์ (100,000 ซาโตชิ) ไปยังเอาต์พุตที่ล็อกด้วยกุญแจของอลิซ และในธุรกรรมใหม่ของอลิซ (Tx2) ที่ส่งให้ร้านของบ็อบ เธออ้างถึงเอาต์พุตก่อนหน้าเป็นอินพุต อย่างที่เห็นในภาพประกอบ การอ้างอิงด้วยลูกศรและระบุอินพุตว่า "Tx1:0" ในธุรกรรมจริง การอ้างอิงจะใช้รหัสประจำธุรกรรม (txid) เป็นตัวระบุขนาด 32 ไบต์ที่แสดงถึงธุรกรรมที่อลิซได้รับเงินจากโจ ส่วน ":0" หมายถึงตำแหน่งของเอาต์พุตที่อลิซได้รับเงิน ซึ่งในกรณีนี้คือตำแหน่งแรก (ตำแหน่ง 0)
การคำนวณมูลค่าอินพุต
เนื่องจากธุรกรรมของบิตคอยน์นั้นไม่ได้ระบุค่าของอินพุตอย่างชัดเจน ตัวซอฟต์แวร์เลยจะต้องใช้การอ้างอิงของอินพุตเพื่อค้นหาเอาต์พุตของธุรกรรมก่อนหน้าที่ถูกใช้ไป
เอาต์พุตใน Tx2 ของอลิซ
Tx2 ของอลิซมีเอาต์พุตใหม่สองรายการ รายการหนึ่งจ่าย 75,000 ซาโตชิสำหรับพอดแคสต์ และอีกรายการจ่าย 20,000 ซาโตชิคืนให้อลิซเป็นเงินทอน

เกร็ดสาระเล็ก ๆ น้อย ๆ
- ธุรกรรมของบิตคอยน์นั้นอยู่ในรูปแบบซีเรียลไลซ์ (serialized) เป็นรูปแบบข้อมูลที่ซอฟต์แวร์ใช้สำหรับการส่งธุรกรรม โดยจะเข้ารหัสมูลค่าที่ต้องการโอนด้วยตัวเลขจำนวนเต็มซึ่งเป็นหน่วยมูลค่าที่เล็กที่สุดในระบบ on-chain
- ที่มาของชื่อ "ซาโตชิ" :เมื่อบิตคอยน์ถูกสร้างขึ้นในครั้งแรก หน่วยมูลค่านี้ยังไม่มีชื่อเรียก นักพัฒนาบางคนจึงเรียกมันว่า "หน่วยฐาน" (base unit) แต่ต่อมาผู้ใช้งานหลาย ๆ คนเริ่มเรียกหน่วยนี้ว่า "ซาโตชิ" (satoshi หรือ sat) เพื่อเป็นเกียรติแก่ผู้สร้างบิตคอยน์
การทอนเงิน
นอกเหนือจากการสร้างเอาต์พุตเพื่อจ่ายให้กับผู้รับบิตคอยน์แล้ว ธุรกรรมจำนวนมากยังมีเอาต์พุตที่จ่ายเงินคืนให้กับผู้จ่าย ซึ่งเรียกว่า เอาต์พุตทอนเงิน (change output) เนื่องจากอินพุตของธุรกรรม (คล้ายกับธนบัตร) ไม่สามารถแบ่งใช้บางส่วนได้ เช่น ถ้าคุณซื้อของราคา 5 ดอลลาร์และจ่ายด้วยธนบัตร 20 ดอลลาร์ คุณคาดหวังว่าจะได้เงินทอน 15 ดอลลาร์ ในทำนองเดียวกัน ในธุรกรรม Bitcoin หากคุณซื้อสินค้าราคา 5 บิตคอยน์แต่มีอินพุตมูลค่า 20 บิตคอยน์ คุณจะสร้างเอาต์พุต 5 บิตคอยน์ไปยังเจ้าของร้าน และอีกเอาต์พุต 15 บิตคอยน์คืนให้ตัวคุณเองเป็นเงินทอน (ไม่นับรวมค่าธรรมเนียมธุรกรรม)
- หากมองผ่านมุมของโปรโตคอลบิตคอยน์นั้นไม่ได้มีความแตกต่างใด ๆ ระหว่างเอาต์พุตเงินทอนกับเอาต์พุตการจ่ายเงินปกติ
- โดยทั่วไปแล้วเอาต์พุตเงินทอนจะเป็นการโอนไปจ่ายให้กับ Bitcoin Address อันใหม่ในกระเป๋าตัวเองดังรูปที่แสดงข้างล่าง

การสร้างธุรกรรม
แอปพิเคชั่นกระเป๋าเงินของอลิซจะทำการสร้างอินพุตและสร้างเอาต์พุตตามที่ Alice ต้องการ โดยที่เธอเพียงแค่กรอกปลายทาง จำนวนเงิน และค่าธรรมเนียมธุรกรรมกระเป๋าเงินจะทำงานที่เหลือให้โดยอัตโนมัติ นอกจากนี้ กระเป๋าเงินยังสามารถสร้างธุรกรรมแบบออฟไลน์ได้ คล้ายกับการเขียนเช็คที่บ้านแล้วค่อยนำไปฝากธนาคารในภายหลังอีกด้วย
การเลือกอินพุตที่เหมาะสม
กระเป๋าเงินจะเลือกอินพุตที่มีมูลค่าเพียงพอสำหรับการชำระเงินไปยังบ๊อบโดยตรวจสอบเอาต์พุตที่ยังไม่ได้ใช้ (UTXOs) ซึ่งหากมูลค่าไม่เพียงพอ กระเป๋าเงินก็จะทำการรวม UTXOs หลาย ๆ รายการเข้าด้วยกัน เพื่อให้ได้ยอดที่ต้องการ และหากอินพุตมีมูลค่าสูงกว่าค่าที่ต้องจ่าย กระเป๋าเงินจะสร้างเอาต์พุตสำหรับทอนเงินกลับมาให้อลิซ
การสร้างเอาต์พุต
เอาต์พุตประกอบด้วยสคริปต์ที่กำหนดให้ผู้ที่มีคีย์ของบ๊อบเท่านั้นสามารถลงนามเพื่อที่จะใช้เงินได้ นอกจากนี้ยังมีเอาต์พุตสำหรับทอนเงินกลับมาให้อลิซ ซึ่งทำให้เธอสามารถใช้เงินทอนนั้นในการทำธุรกรรมถัดไป และค่าธรรมเนียมธุรกรรมจะถูกคำนวณจากส่วนต่างระหว่างอินพุตและเอาต์พุต และนั่นเองที่จะเป็นรางวัลสำหรับนักขุดที่บันทึกธุรกรรมลงบล็อกเชนของบิตคอยน์
การใส่ธุรกรรมลงในบล๊อกเชน
ธุรกรรมที่สร้างขึ้นโดย Bitcoin wallet ของอลิซมีข้อมูลทั้งหมดที่จำเป็นสำหรับการสร้างธุรกรรม (การยืนยันว่าอลิซเป็นเจ้าของเงิน และ Bitcoin address ปลายทาง) จากนั้นธุรกรรมนี้จะต้องถูกส่งไปยังเครือข่ายของบิตคอยน์ เพื่อที่จะให้ธุรกรรมนั้นเป็นส่วนนึงในเครือข่ายของบิตคอยน์ และในส่วนถัดไปของหนังสือเล่มนี้ เราจะอธิบายถึงว่าธุรกรรมกลายเป็นส่วนหนึ่งของบล็อกใหม่อย่างไร และกระบวนการขุดบล็อกเป็นอย่างไร รวมถึงการที่บล็อกใหม่ได้รับความไว้วางใจมากขึ้นเมื่อมีการเพิ่มบล็อกใหม่ ๆ เข้ามาเรื่อย ๆ หมายถึงอะไร ?
การส่งธุรกรรมเข้าไปยังเครือข่าย
เนื่องจากธุรกรรมมีข้อมูลที่จำเป็นสำหรับการประมวลผลทั้งหมด จึงทำให้การส่งผ่านสามารถทำได้จากที่ไหนหรืออย่างไรก็ได้ อย่างที่ได้กล่าวไปว่าเครือข่ายของบิตคอยน์เป็นเครือข่ายแบบ peer-to-peer โดยที่แต่ละโหนดเชื่อมต่อกับโหนดอื่น ๆ อีกหลายโหนด เพื่อทำหน้าที่กระจายธุรกรรมและบล็อกให้กับผู้เข้าร่วมทั้งหมดในระบบ
การกระจายธุรกรรม
โหนดในเครือข่าย peer-to-peer ของบิตคอยน์นั้นเป็นซอฟต์แวร์ที่สามารถตรวจสอบความถูกต้องของธุรกรรมได้ และการเชื่อมต่อระหว่างโหนดสามารถแสดงเป็นเส้นในกราฟ ทำให้โหนดเหล่านี้เรียกว่า “โหนดตรวจสอบเต็มรูปแบบ” (full nodes) กระเป๋าเงินของอลิซสามารถส่งธุรกรรมไปยังโหนดบิตคอยน์ใด ๆ ผ่านการเชื่อมต่อใด ๆ ก็ได้ เช่น สายแลน WiFi หรือ เครือข่ายมือถือ โดยถ้าหากโหนดได้รับธุรกรรมที่ถูกต้องซึ่งยังไม่เคยเห็นมาก่อน มันจะกระจายธุรกรรมนี้ไปยังโหนดอื่น ๆ ที่เชื่อมต่อด้วย ซึ่งเป็นเทคนิคที่เรียกว่า gossiping ซึ่งทำให้ธุรกรรมแพร่กระจายไปทั่วเครือข่ายอย่างรวดเร็วภายในไม่กี่วินาที
การขุดบิตคอยน์
ตอนนี้ธุรกรรมของอลิซได้เข้าไปสู่ในเครือข่ายของบิตคอยน์แล้ว แต่มันยังไม่ได้ถูกบรรจุลงในบล๊อกเชนเนื่องจากจะต้องรอให้นักขุดทำการนำธุรกรรมนั้น ๆ เข้าไปในบล๊อกและบล๊อกนั้นจำเป็นต้องผ่านการตรวจสอบโดยโหนดในเครือข่ายของบิตคอยน์เสียก่อน จึงจะถูกบันทึกลงในบล๊อกเชน ในระบบของบิตคอยน์นั้น มีการป้องกันการปลอมแปลงด้วยการคำนวณทางคณิตศาสตร์ ซึ่งเป็นการคำนวณที่จำเป็นต้องใช้พลังงานมหาศาลในการคำนวณ แต่ใช้พลังงานเพียงเล็กน้อยในการตรวจสอบ โดยธุรกรรมทั้งหมดจะถูกจัดเรียงเป็นบล๊อกและแต่ละบล๊อกจะมีบล๊อกเฮดเดอร์ที่จำเป็นต้องสร้างตามเงื่อนไขเฉพาะ โดยกระบวนการขุดบิตคอยน์นั้นมีวัตถุประสงค์อยู่สองอย่าง ดังนี้:
- สร้างแรงจูงใจให้ขุดเฉพาะธุรกรรมที่ถูกต้องตามกฎ: เนื่องจากวิธีที่เหล่านักขุดจะได้รับผลกำไรที่สูงที่สุดจากการสร้างบล๊อกที่ตรงกับฉันทมติของระบบเท่านั้น (หากไม่ทำตามบล๊อกจะไม่ถูกยอมรับโดยโหนด และนั่นจะเป็นการสิ้นเปลืองพลังงานที่ได้คำนวณมาโดยเปล่าประโยชน์) นั้นจึงเป็นแรงจูงใจหลัก ๆ ให้เหล่านักขุดทำการใส่ธุรกรรมที่ถูกต้องตามกฏเท่านั้นลงในบล๊อกที่ตนสร้าง และสิ่งนี้เองก็ทำให้ผู้ใช้สามารถเลือกที่จะสันนิษฐานโดยอิงตามความไว้วางใจว่าธุรกรรมใด ๆ ในบล็อกนั้น ๆ เป็นธุรกรรมที่ถูกต้อง
- สร้างเหรียญใหม่ตามตารางการออกเหรียญที่กำหนดไว้ล่วงหน้า: ในปัจจุบันนั้นจะมีการสร้างบิตคอยน์ใหม่ในแต่ละบล็อก คล้ายคลึงกับธนาคารกลางที่พิมพ์เงินใหม่ โดยจำนวนบิตคอยน์ในแต่ละบล๊อกที่จะถูกผลิตขึ้นมาใหม่นั้นถูกกำหนดมาตั้งแต่วันที่ระบบของบิตคอยน์ได้เริ่มขึ้นและไม่สามารถเปลี่ยนแปลงได้
การขุดได้ช่วยให้เกิดความสมดุลระหว่างต้นทุนและผลตอบแทน เนื่องจากการขุดมีการใช้ไฟฟ้าเพื่อแก้ปัญหาการคำนวณ และนักขุดที่ประสบความสำเร็จจะได้รับรางวัลในรูปแบบของบิตคอยน์ใหม่และค่าธรรมเนียมจากการทำธุรกรรม แต่อย่างไรก็ตาม รางวัลจะถูกเก็บรวบรวมก็ต่อเมื่อนักขุดรวมเฉพาะธุรกรรมที่ถูกต้องเท่านั้น โดยกฎของโปรโตคอลบิตคอยน์สำหรับการสร้างฉันทามติ จะกำหนดว่าอะไรถูกต้อง โดยความสมดุลที่ละเอียดอ่อนนี้เองที่คอยสร้างให้ความปลอดภัยแก่บิตคอยน์โดยไม่ต้องมีหน่วยงานกลางมาคอยดูแล
การขุดถูกออกแบบให้เหมือนกับการจับสลากแบบกระจายศูนย์ นักขุดแต่ละคนสามารถสร้าง "สลาก" ของตัวเองได้โดยการสร้างบล็อกตัวอย่างที่ประกอบไปด้วยธุรกรรมใหม่ที่ต้องการขุด พร้อมกับข้อมูลอื่น ๆ และนักขุดจะป้อนบล็อกตัวอย่างนี้เข้าไปในอัลกอริทึมที่ออกแบบมาเป็นพิเศษเพื่อแฮชข้อมูล ทำให้ได้ค่าผลลัพธ์ที่แตกต่างจากข้อมูลเดิมอย่างสิ้นเชิง โดยแฮชฟังก์ชันนี้จะให้ผลลัพธ์เดียวกันเสมอสำหรับข้อมูลชุดเดิม แต่ไม่สามารถคาดเดาผลลัพธ์ได้หากป้อนข้อมูลใหม่ แม้จะแตกต่างเพียงเล็กน้อยจากข้อมูลก่อนหน้า
หากค่าผลลัพธ์ของแฮชตรงกับเงื่อนไขที่กำหนดของโปรโตคอล นักขุดจะชนะการจับสลาก และผู้ใช้งานบิตคอยน์ จะยอมรับบล็อกนี้พร้อมกับธุรกรรมในนั้นว่าเป็นบล็อกที่ถูกต้อง หากไม่ตรงกับเงื่อนไข นักขุดจะปรับข้อมูลในบล็อกเล็กน้อยและลองทำการแฮชใหม่ กระบวนการนี้ต้องทำซ้ำหลายครั้ง โดย ณ ขณะที่เขียนนี้ นักขุดต้องลองสร้างบล็อกตัวอย่างประมาณ 168 พันล้านล้านครั้ง เพื่อหาคำตอบที่ถูกต้อง ซึ่งหมายถึงการรันแฮชฟังก์ชันในจำนวนครั้งมหาศาลมาก ๆ
แต่เมื่อพบคำตอบที่ถูกต้องแล้ว ใครก็ตามสามารถตรวจสอบว่าบล็อกนั้นถูกต้องได้โดยการรันแฮชฟังก์ชันเพียงครั้งเดียว ซึ่งทำให้การสร้างบล็อกที่ถูกต้องต้องใช้พลังงานคำนวณมหาศาล แต่การตรวจสอบทำได้ง่ายมาก กระบวนการตรวจสอบนี้สามารถพิสูจน์ได้อย่างมีหลักการว่ามีการทำงานเกิดขึ้นจริง ดังนั้น ข้อมูลที่ใช้สร้างหลักฐานนี้—ในที่นี้คือบล็อก—เรียกว่า "หลักฐานการทำงาน" หรือ Proof of Work (PoW)
ธุรกรรมจะถูกเพิ่มลงในบล็อกใหม่ โดยให้ความสำคัญกับธุรกรรมที่มีค่าธรรมเนียมสูงสุดก่อนและพิจารณาจากปัจจัยอื่น ๆ อีกเล็กน้อย นักขุดแต่ละคนจะเริ่มกระบวนการสร้างบล็อกตัวอย่างใหม่ทันทีหลังจากได้รับบล็อกก่อนหน้าจากเครือข่าย โดยรู้ว่ามีคนอื่นชนะรางวัลไปแล้วในรอบนั้น พวกเขาจะสร้างบล็อกตัวอย่างใหม่ที่เชื่อมโยงกับบล็อกก่อนหน้า ใส่ธุรกรรมเข้าไป และเริ่มคำนวณ Proof of Work (PoW) สำหรับบล็อกตัวอย่างนี้ นักขุดจะเพิ่มธุรกรรมพิเศษที่จ่ายรางวัลบล็อกและค่าธรรมเนียมธุรกรรมรวมเข้ากับที่อยู่บิตคอยน์ของตนเอง หากพวกเขาพบบล็อกที่ถูกต้องและถูกเพิ่มในบล็อกเชน นักขุดจะได้รับรางวัลนั้น และธุรกรรมรางวัลนี้ก็จะใช้งานได้ นักขุดที่ทำงานร่วมกับพูลจะตั้งค่าให้รางวัลถูกส่งไปยังที่อยู่ของพูล จากนั้นจะแบ่งรางวัลให้สมาชิกตามสัดส่วนการทำงานที่แต่ละคนมีส่วนร่วม
กลับมาที่ธุรกรรมของอลิซ ตอนนี้ธุรกรรมของอลิซได้ถูกเครือข่ายรับไปแล้วและเพิ่มลงในพูลของธุรกรรมที่ยังไม่ได้รับการยืนยันเรียบร้อย จากนั้นเมื่อธุรกรรมนั้นผ่านการตรวจสอบจาก full node แล้ว มันจะถูกรวมไว้ในบล็อกตัวอย่าง และประมาณห้านาทีหลังจากที่อลิซส่งธุรกรรมจากกระเป๋าเงินของเธอ นักขุดคนหนึ่งพบคำตอบสำหรับบล็อกนั้นและประกาศไปยังเครือข่าย หลังจากที่นักขุดคนอื่น ๆ ตรวจสอบความถูกต้องของบล็อกที่ชนะ พวกเขาก็เริ่มกระบวนการสุ่มอีกครั้งเพื่อสร้างบล็อกถัดไป
บล็อกที่ชนะซึ่งมีธุรกรรมของอลิซอยู่ในนั้น ได้กลายเป็นส่วนหนึ่งของบล็อกเชน และบล็อกนี้ถูกนับเป็นการยืนยันหนึ่งครั้งสำหรับธุรกรรมนั้น หลังจากที่บล็อกที่มีธุรกรรมของอลิซได้ถูกเผยแพร่ไปทั่วเครือข่าย การสร้างบล็อกทางเลือกที่มีเวอร์ชันอื่นของธุรกรรมของอลิซ (เช่น ธุรกรรมที่ไม่ได้จ่ายให้ บ๊อบ) จะต้องใช้ปริมาณงานเท่ากับที่นักขุดทั้งหมดต้องใช้ในการสร้างบล็อกใหม่ทั้งบล็อก เมื่อมีบล็อกทางเลือกหลายบล็อกให้เลือก full node ในเครือข่ายของบิตคอยน์ก็จะทำการเลือกบล็อกเชนที่ถูกต้อง โดยจะเป็นเชนซึ่งมี Proof of Work (PoW) รวมมากที่สุด ซึ่งเรียกว่าบล็อกเชนที่ดีที่สุด หากเครือข่ายทั้งหมดจะยอมรับบล็อกทางเลือก จะต้องมีการขุดบล็อกใหม่เพิ่มเติมอีกหนึ่งบล็อกต่อจากบล็อกทางเลือกนั้น
นั่นหมายความว่านักขุดมีตัวเลือกอื่น อย่างเช่นการที่พวกเขาสามารถร่วมมือกับอลิซเพื่อสร้างธุรกรรมทางเลือกที่เธอไม่ได้จ่ายเงินให้บ๊อบ โดยอลิซอาจเสนอส่วนแบ่งจากเงินที่เธอเคยจ่ายให้บ๊อบแก่นักขุด แต่การกระทำที่ไม่ซื่อสัตย์นี้จะต้องใช้ความพยายามเท่ากับการสร้างบล็อกใหม่ถึงสองบล็อก ซึ่งในทางกลับกันแล้ว นักขุดที่ทำงานอย่างซื่อสัตย์สามารถสร้างบล็อกใหม่เพียงบล็อกเดียวและได้รับค่าธรรมเนียมจากธุรกรรมทั้งหมดที่รวมอยู่ในบล็อก พร้อมกับรางวัลบล็อก (block subsidy) นอกจากนี้ต้นทุนที่สูงในการสร้างบล็อกสองบล็อกเพื่อพยายามเปลี่ยนแปลงธุรกรรมที่ยืนยันแล้วสำหรับผลตอบแทนเพียงเล็กน้อยนั้นไม่คุ้มค่าและการกระทำดังกล่าวมีโอกาสน้อยที่จะเกิดขึ้น สำหรับ บ๊อบ นั่นหมายความว่าเขาสามารถเริ่มเชื่อถือได้ว่าการชำระเงินจากอลิซนั้นเป็นสิ่งที่เชื่อถือได้
ประมาณ 19 นาทีหลังจากบล็อกที่มีธุรกรรมของอลิซ ได้ถูกเผยแพร่บล็อกใหม่ถูกขุดขึ้นโดยนักขุดอีกคน และเนื่องจากบล็อกใหม่นี้ถูกสร้างต่อจากบล็อกที่มีธุรกรรมของอลิซ (ทำให้ธุรกรรมของอลิซได้รับการยืนยันสองครั้ง) ธุรกรรมของ อลิซจะสามารถเปลี่ยนแปลงได้ก็ต่อเมื่อมีการขุดบล็อกทางเลือกสองบล็อกขึ้นมา และมีบล็อกใหม่ที่สร้างต่อจากบล็อกเหล่านั้น รวมเป็นสามบล็อกที่ต้องถูกขุดเพื่อให้อลิซสามารถดึงเงินที่เธอส่งให้บ๊อบกลับมาได้ และทุกบล็อกที่ขุดต่อจากบล็อกที่มีธุรกรรมของอลิซนั้นจะนับเป็นการยืนยันเพิ่มเติม เมื่อจำนวนบล็อกที่ต่อกันเพิ่มมากขึ้น การย้อนกลับธุรกรรมก็จะยากขึ้นเรื่อย ๆ ทำให้บ๊อบมั่นใจมากขึ้นเรื่อย ๆ ว่าการชำระเงินของอลิซนั้นจะปลอดภัย
จากภาพที่แนบไว้ข้างล่างนี้ เราสามารถเห็นบล็อกที่มีธุรกรรมของอลิซและด้านล่างของบล็อกนี้มีบล็อกอีกหลายแสนบล็อกที่เชื่อมต่อกันเป็นโซ่ (blockchain) ต่อเนื่องไปจนถึงบล็อกหมายเลข #0 หรือที่เรียกว่า genesis block และเมื่อเวลาผ่านไป "ความสูง" ของบล็อกใหม่ที่เพิ่มขึ้นจะทำให้ความยากในการคำนวณของทั้งเครือข่ายเพิ่มขึ้นตามไปด้วย ตามธรรมเนียมแล้ว บล็อกใด ๆ ที่มีการยืนยันมากกว่าหกครั้งจะถือว่ายากมากที่จะเปลี่ยนแปลง เพราะต้องใช้การคำนวณอย่างมหาศาลในการคำนวณบล็อกหกบล็อกใหม่ (รวมถึงบล็อกใหม่อีกหนึ่งบล็อก)

การใช้จ่ายในธุรกรรม
เมื่อธุรกรรมของอลิซได้กลายเป็นส่วนหนึ่งของบล็อกเชน แปลว่ามันสามารถถูกเรียกดูได้จากทุกบิตคอยน์แอปพลิเคชัน และทุกโหนดสามารถที่จะตรวจสอบธุรกรรมนี้ได้อย่างอิสระ ว่าธุรกรรมนี้ถูกต้องหรือไม่ โดยจะตรวจสอบย้อนไปตั้งแต่ตอนที่เหรียญนั้น ๆ ถูกสร้างและตรวจสอบต่อมาเรื่อย ๆ จนถึงธุรกรรมปัจจุบัน ไคลเอนต์จะสามารถตรวจสอบการชำระเงินได้บางส่วน โดยการยืนยันว่าธุรกรรมนั้นอยู่ในบล็อกเชนแล้ว และมีบล็อกจำนวนมากที่ถูกขุดหลังจากนั้น ซึ่งนี่ช่วยให้มั่นใจได้ว่ามีการใช้ความพยายามอย่างมากในการยืนยันธุรกรรมนี้โดยเหล่านักขุดไปแล้ว
ในตอนนี้บ็อบสามารถใช้บิตคอยน์ที่อลิซส่งให้ต่อได้แล้ว! สมมุติว่าบ๊อบต้องการจ่ายค่าจ้างให้ผู้รับเหมาหรือผู้จัดหาสินค้า โดยการโอนมูลค่าจากการชำระเงินของอลิซสำหรับพอดแคสต์ไปยังเจ้าของรายใหม่ เมื่อบ๊อบใช้เงินที่ได้รับจากอลิซและลูกค้าคนอื่น ๆ เขาก็ขยายสายโซ่ของธุรกรรมออกไป สมมติว่าบ๊อบจ่ายค่าจ้างให้กรูฟซึ่งเป็นนักออกแบบเว็บไซต์ของเขาสำหรับสร้างหน้าเว็บใหม่ สายโซ่ของธุรกรรมจะมีลักษณะดังนี้:
- ธุรกรรมจากโจถึงอลิซ: โจโอนบิตคอยน์ให้อลิซเพื่อการซื้อขายหรือจ่ายค่าบริการบางอย่าง
- ธุรกรรมจากอลิซถึงบ๊อบ: อลิซโอนบิตคอยน์ให้บ๊อบเพื่อชำระค่าพอดแคสต์
- ธุรกรรมจากบ๊อบถึงกรูฟ: บ๊อบโอนบิตคอยน์จากที่ได้รับจากอลิซให้กรูฟเพื่อจ่ายค่าจ้างออกแบบเว็บไซต์
สายโซ่ของธุรกรรมนี้แสดงให้เห็นการเชื่อมต่อของธุรกรรมจากโจถึงอลิซและจากอลิซถึงบ๊อบต่อด้วยจากบ๊อบถึง กรูฟ โดยแต่ละธุรกรรมได้รับการบันทึกไว้ในบล็อกเชน ซึ่งช่วยให้ทุกคนสามารถตรวจสอบความถูกต้องของธุรกรรมในสายโซ่นี้ได้

ในบทนี้ เราได้เห็นวิธีที่ธุรกรรมสร้างสายโซ่ที่ถ่ายโอนมูลค่าจากเจ้าของหนึ่งไปยังอีกเจ้าของหนึ่ง นอกจากนี้เรายังได้ติดตามธุรกรรมของอลิซตั้งแต่เริ่มสร้างในกระเป๋าเงินของเธอ ผ่านเครือข่ายบิตคอยน์ไปจนถึงนักขุดที่บันทึกมันลงในบล็อกเชน และสำหรับในส่วนที่เหลือของหนังสือเล่มนี้ เราจะศึกษารายละเอียดเกี่ยวกับเทคโนโลยีที่เกี่ยวข้อง ไม่ว่าจะเป็นกระเป๋าเงิน, address, digital signature, network และกระบวนการขุดอย่างละเอียด
-
 @ f1989a96:bcaaf2c1
2024-12-19 15:16:35
@ f1989a96:bcaaf2c1
2024-12-19 15:16:35Good morning, readers!
After 53 years of tyranny, the Syrian regime has been overthrown. Rebels captured Damascus, forcing Bashar al-Assad and his family to flee to Moscow, Russia. Assad’s rule was defined by severe human rights abuses and widespread financial repression. Hundreds of thousands were jailed or killed, millions fled, and more than 90% of the country was plunged into poverty amid currency collapse. With Assad gone, Syrians may have a chance to rebuild their country and work toward a freer, more democratic future.
In Tunisia, President Kais Saied continues to dismantle civil society and due process. The regime is escalating the repression of journalists through arrests, incarceration, and judicial harassment to silence critical voices. By doing so, Saied shifts focus away from the country’s economic struggles and worsening hardships.
In technology news, Klever Wallet, a KYC-free digital asset wallet widely used in regions like Nigeria and the Philippines, integrated the Lightning Network via the Breez SDK, enabling fast, low-cost Bitcoin transactions for its significant global user base. In addition, the Bitcoin Design Foundation announced a South American Bitcoin UX Bootcamp, offering 10 skilled UX designers across South America a chance to refine their design expertise within the Bitcoin ecosystem and attend the 2025 bitcoin++ developer conference in Florianopolis, Brazil.
We end with a live stream of the 2024 Africa Bitcoin Conference, an inspiring event HRF supported and participated in. The conference brought together leaders and innovators across the African continent to advance Bitcoin for financial freedom and to push back against growing authoritarianism. If you were unable to attend in person, be sure to catch the recordings below.
Now, let’s dive right in!
Subscribe Here
GLOBAL NEWS
Syria | Assad Regime Overthrown
The Assad regime, infamous for its financial repression and brutal authoritarianism, has been overthrown following the rebel capture of Damascus, forcing Bashar al-Assad and his family to flee to Moscow. For 24 years under Assad — and 53 years of Assad family rule — the regime manipulated the economy to maintain its grip on power. Policies such as enforcing artificial currency exchange rates, restricting bank withdrawals, and imposing strict controls on the flow of goods and money plunged over 90% of Syrians into poverty. This economic stranglehold, combined with systemic human rights abuses, defined his reign. With the regime’s collapse, Syrians now face a pivotal moment to rebuild their country and pursue a future of more financial freedom.
China | Youth Bear the Brunt of Economic Slowdown
China’s slowing economy is forcing younger generations into increasingly precarious financial positions. Youth unemployment has soared past 17%, and even those who find work face stagnant wages and unmet income expectations. To survive, many young people are embracing extreme frugality — capping food expenses at just 500 yuan ($70), eating in the dark to save electricity, and avoiding dining out entirely. The middle class, weighed down by debt and a bleak economic outlook, is also adopting similar austerity measures. This growing financial strain offers a stark snapshot of China’s economic challenges and raises deep concerns about the long-term prosperity and opportunities for the nation’s youth.
Tunisia | Growing Repression of Journalists Amidst Worsening Economic Crisis
Tunisia is grappling with a worsening economic crisis, as citizens face soaring unemployment, a collapsing currency, and the devastating impacts of financial mismanagement. Amid this economic turmoil, President Kais Saied is intensifying his crackdown on dissent, imprisoning journalists in overcrowded cells, denying them medical care, and subjecting them to psychological torture — blatant evidence of the state’s disregard for human rights. Saied’s regime has also weaponized vague morality laws to target activists, influencers, and musicians, ensuring no opposition voice goes unpunished. By silencing dissent, Saied seeks to deflect attention from the regime’s economic failures, positioning the state as a moral authority while deepening the suffering of journalists and the broader public.
Pakistan | Testing Internet Firewall to Increase Financial Surveillance
Pakistan’s government is testing a nationwide Internet firewall, a tool designed to monitor, censor, and control online content by filtering internet traffic at the state level. By leveraging technology sourced from China, officials can block websites, restrict apps, and track individual online activity. This firewall poses a severe threat to financial freedom, as the military regime could use it to restrict access to tools like Bitcoin, cutting off alternative financial systems that offer privacy and independence. Civil society, including activists, journalists, and political dissidents, faces heightened surveillance, repression, and limited access to information — further curtailing their capacity to organize or express dissent.
India | Central Bank Governor Shares CBDC Vision
Outgoing Reserve Bank of India (RBI) Gov.Shaktikanta Das reaffirmed his vision for India’s central bank digital currency (CBDC), the digital rupee, as the nation’s currency continues to reach a record low against the US dollar. While hailed as the “future of currency” and praised for its potential economic benefits, the CBDC raises serious concerns. It grants the state unprecedented power to surveil transactions, freeze funds, and block payments in real-time — an alarming reality in a country already known for freezing opposition bank accounts and imposing rigid KYC requirements. Das’s hopes of a CBDC to “underpin the payment systems of the future” prioritizes state control at the expense of individual freedoms.
Georgia | Internet Shutdowns Amid Energy Crisis
In the breakaway Georgian region of Abkhazian, Russian-backed officials are using an energy crisis as a pretext to tighten Internet controls. Blaming illegal Bitcoin mining for electricity shortages, officials imposed nightly Internet shutdowns from midnight to 7:00 a.m., starting Dec. 10. These restrictions, coupled with power rationing and school closures, exacerbate hardships for residents as the region grapples with reduced energy from Russia and the Enguri hydroelectric plant. By painting Bitcoin as the villain, officials divert attention from broader governance failures while consolidating their grip over online communication and suppressing access to alternative financial tools.
LATEST IN BITCOIN NEWS, DEVELOPMENT, AND COMMUNITY
Klever Wallet | Integrates Lightning Network
Klever Wallet, a KYC-free digital asset wallet popular in underbanked countries like Nigeria, Brazil, India, and the Philippines, integrated the Lightning Network through the Breez SDK. This integration will empower its 100,000 active monthly users with fast, low-cost Bitcoin transactions directly from the wallet. By using the Breez SDK, Klever eliminates the complexities of Lightning channel management for users while maintaining a self-custodial design. This integration enhances financial freedom for its global user base — particularly in regions where traditional systems fall short.
Fedi | Adds Cashu Melting and Portable Nostr Keys
Fedi, a company leveraging Bitcoin and ecash technology to support communities, especially under authoritarian regimes, announced the integration of Cashu melting to enable users to receive Cashu ecash directly within the Fedi app. Built on the Chaumian ecash protocol, Cashu allows users to transact ecash tokens with strong privacy guarantees, minimal costs, and instant settlements, though with a custodial tradeoff. Additionally, Fedi now supports portable Nostr keys, allowing users to interact with external Nostr clients like Primal and Amethyst. Together, these updates enhance financial privacy and accessibility, offering users more control over their transactions and a portable digital identity, advancing financial freedom in underserved regions.
Core Lightning | Releases Latest Version with BOLT 12 by Default
Core Lightning, an implementation of the Lightning Network, introduced improvements to privacy and functionality with its latest v24.11 release. The update enables BOLT 12 offers by default when sending and receiving Bitcoin payments. BOLT 12 is an important update to the Lightning Network that brings increased receiver privacy, greater censorship resistance, and reusable payment requests for recurring payments. The update also includes xpay, an experimental payment plugin for advanced routing of payments on the Lightning Network. With these features, users of wallets and applications built with Core Lightning can maintain greater privacy and experience more optimized payments.
Proton Wallet | Implements Replace-by-Fee for Bitcoin Transactions
Proton, the company behind privacy tools like Proton Mail and Proton VPN, added support for Replace-by-Fee (RBF) transactions in Proton Wallet, its self-custodial and privacy-centric Bitcoin wallet. RBF allows users to increase the fee on stuck transactions to expedite confirmation and allow the payment to settle faster. The wallet also uses strong encryption and offers accessible recovery methods, ensuring users — like activists in hostile environments — maintain financial autonomy. Watch this tutorial by Bitcoin educator BTC Sessions to learn how to use Proton Wallet.
Bitcoin Design Community | South American Bitcoin UX Bootcamp
The Bitcoin Design Community, with support from HRF, will be hosting a South American UX Bitcoin Bootcamp. This program will support ten skilled UX designers across South America to develop and refine their design expertise within the Bitcoin ecosystem. Participants will also have the opportunity to attend the 2025 bitcoin++ developer conference in Florianopolis, Brazil, where they will receive specialized UX training and engage in hands-on learning with Bitcoin-related technologies. UX designers with an interest in Bitcoin are encouraged to apply here.
OpenSats | Announces Ninth Wave of Nostr Grants
OpenSats, a public nonprofit funding free and open-source software and projects, announced its ninth wave of grants supporting projects built on the decentralized Nostr protocol. Among the grantees is Pokey, an Android app enhancing Nostr and communications in restrictive environments through offline Bluetooth mesh networking and multi-account support. These features are particularly valuable for anyone facing Internet blackouts or state censorship. Another recipient, Persian NIPs, is breaking language barriers by localizing Nostr resources for Persian/Farsi speakers. The project will translate key protocols, user guides, and developer documentation, bringing decentralized and uncensorable technology to millions of people.
RECOMMENDED CONTENT
Africa Bitcoin Conference Livestream
Held from Dec. 9-11, 2024, in Nairobi, Kenya, the Africa Bitcoin Conference brought together human rights defenders, educators, and developers from across the continent to learn, collaborate, and innovate on freedom technologies. Supported by HRF, the event offered an inspiring mix of keynotes, workshops, panel discussions, and hackathons, all dedicated to advancing open-source solutions to fight authoritarianism and financial repression. This vibrant gathering highlighted innovative ideas and practical tools to empower communities worldwide. If you missed it, you can still catch the conversations and breakthroughs by watching the livestream here. Highlight talks include those from Farida Nabourema, Femi Longe, Jack Dorsey, and more.
-
 @ 1bda7e1f:bb97c4d9
2025-01-02 05:19:08
@ 1bda7e1f:bb97c4d9
2025-01-02 05:19:08Tldr
- Nostr is an open and interoperable protocol
- You can integrate it with workflow automation tools to augment your experience
- n8n is a great low/no-code workflow automation tool which you can host yourself
- Nostrobots allows you to integrate Nostr into n8n
- In this blog I create some workflow automations for Nostr
- A simple form to delegate posting notes
- Push notifications for mentions on multiple accounts
- Push notifications for your favourite accounts when they post a note
- All workflows are provided as open source with MIT license for you to use
Inter-op All The Things
Nostr is a new open social protocol for the internet. This open nature exciting because of the opportunities for interoperability with other technologies. In Using NFC Cards with Nostr I explored the
nostr:URI to launch Nostr clients from a card tap.The interoperability of Nostr doesn't stop there. The internet has many super-powers, and Nostr is open to all of them. Simply, there's no one to stop it. There is no one in charge, there are no permissioned APIs, and there are no risks of being de-platformed. If you can imagine technologies that would work well with Nostr, then any and all of them can ride on or alongside Nostr rails.
My mental model for why this is special is Google Wave ~2010. Google Wave was to be the next big platform. Lars was running it and had a big track record from Maps. I was excited for it. Then, Google pulled the plug. And, immediately all the time and capital invested in understanding and building on the platform was wasted.
This cannot happen to Nostr, as there is no one to pull the plug, and maybe even no plug to pull.
So long as users demand Nostr, Nostr will exist, and that is a pretty strong guarantee. It makes it worthwhile to invest in bringing Nostr into our other applications.
All we need are simple ways to plug things together.
Nostr and Workflow Automation
Workflow automation is about helping people to streamline their work. As a user, the most common way I achieve this is by connecting disparate systems together. By setting up one system to trigger another or to move data between systems, I can solve for many different problems and become way more effective.
n8n for workflow automation
Many workflow automation tools exist. My favourite is n8n. n8n is a low/no-code workflow automation platform which allows you to build all kinds of workflows. You can use it for free, you can self-host it, it has a user-friendly UI and useful API. Vs Zapier it can be far more elaborate. Vs Make.com I find it to be more intuitive in how it abstracts away the right parts of the code, but still allows you to code when you need to.
Most importantly you can plug anything into n8n: You have built-in nodes for specific applications. HTTP nodes for any other API-based service. And community nodes built by individual community members for any other purpose you can imagine.
Eating my own dogfood
It's very clear to me that there is a big design space here just demanding to be explored. If you could integrate Nostr with anything, what would you do?
In my view the best way for anyone to start anything is by solving their own problem first (aka "scratching your own itch" and "eating your own dogfood"). As I get deeper into Nostr I find myself controlling multiple Npubs – to date I have a personal Npub, a brand Npub for a community I am helping, an AI assistant Npub, and various testing Npubs. I need ways to delegate access to those Npubs without handing over the keys, ways to know if they're mentioned, and ways to know if they're posting.
I can build workflows with n8n to solve these issues for myself to start with, and keep expanding from there as new needs come up.
Running n8n with Nostrobots
I am mostly non-technical with a very helpful AI. To set up n8n to work with Nostr and operate these workflows should be possible for anyone with basic technology skills.
- I have a cheap VPS which currently runs my HAVEN Nostr Relay and Albyhub Lightning Node in Docker containers,
- My objective was to set up n8n to run alongside these in a separate Docker container on the same server, install the required nodes, and then build and host my workflows.
Installing n8n
Self-hosting n8n could not be easier. I followed n8n's Docker-Compose installation docs–
- Install Docker and Docker-Compose if you haven't already,
- Create your
docker-compose.ymland.envfiles from the docs, - Create your data folder
sudo docker volume create n8n_data, - Start your container with
sudo docker compose up -d, - Your n8n instance should be online at port
5678.
n8n is free to self-host but does require a license. Enter your credentials into n8n to get your free license key. You should now have access to the Workflow dashboard and can create and host any kind of workflows from there.
Installing Nostrobots
To integrate n8n nicely with Nostr, I used the Nostrobots community node by Ocknamo.
In n8n parlance a "node" enables certain functionality as a step in a workflow e.g. a "set" node sets a variable, a "send email" node sends an email. n8n comes with all kinds of "official" nodes installed by default, and Nostr is not amongst them. However, n8n also comes with a framework for community members to create their own "community" nodes, which is where Nostrobots comes in.
You can only use a community node in a self-hosted n8n instance (which is what you have if you are running in Docker on your own server, but this limitation does prevent you from using n8n's own hosted alternative).
To install a community node, see n8n community node docs. From your workflow dashboard–
- Click the "..." in the bottom left corner beside your username, and click "settings",
- Cilck "community nodes" left sidebar,
- Click "Install",
- Enter the "npm Package Name" which is
n8n-nodes-nostrobots, - Accept the risks and click "Install",
- Nostrobots is now added to your n8n instance.
Using Nostrobots
Nostrobots gives you nodes to help you build Nostr-integrated workflows–
- Nostr Write – for posting Notes to the Nostr network,
- Nostr Read – for reading Notes from the Nostr network, and
- Nostr Utils – for performing certain conversions you may need (e.g. from bech32 to hex).
Nostrobots has good documentation on each node which focuses on simple use cases.
Each node has a "convenience mode" by default. For example, the "Read" Node by default will fetch Kind 1 notes by a simple filter, in Nostrobots parlance a "Strategy". For example, with Strategy set to "Mention" the node will accept a pubkey and fetch all Kind 1 notes that Mention the pubkey within a time period. This is very good for quick use.
What wasn't clear to me initially (until Ocknamo helped me out) is that advanced use cases are also possible.
Each node also has an advanced mode. For example, the "Read" Node can have "Strategy" set to "RawFilter(advanced)". Now the node will accept json (anything you like that complies with NIP-01). You can use this to query Notes (Kind 1) as above, and also Profiles (Kind 0), Follow Lists (Kind 3), Reactions (Kind 7), Zaps (Kind 9734/9735), and anything else you can think of.
Creating and adding workflows
With n8n and Nostrobots installed, you can now create or add any kind of Nostr Workflow Automation.
- Click "Add workflow" to go to the workflow builder screen,
- If you would like to build your own workflow, you can start with adding any node. Click "+" and see what is available. Type "Nostr" to explore the Nostrobots nodes you have added,
- If you would like to add workflows that someone else has built, click "..." in the top right. Then click "import from URL" and paste in the URL of any workflow you would like to use (including the ones I share later in this article).
Nostr Workflow Automations
It's time to build some things!
A simple form to post a note to Nostr
I started very simply. I needed to delegate the ability to post to Npubs that I own in order that a (future) team can test things for me. I don't want to worry about managing or training those people on how to use keys, and I want to revoke access easily.
I needed a basic form with credentials that posted a Note.
For this I can use a very simple workflow–
- A n8n Form node – Creates a form for users to enter the note they wish to post. Allows for the form to be protected by a username and password. This node is the workflow "trigger" so that the workflow runs each time the form is submitted.
- A Set node – Allows me to set some variables, in this case I set the relays that I intend to use. I typically add a Set node immediately following the trigger node, and put all the variables I need in this. It helps to make the workflows easier to update and maintain.
- A Nostr Write node (from Nostrobots) – Writes a Kind-1 note to the Nostr network. It accepts Nostr credentials, the output of the Form node, and the relays from the Set node, and posts the Note to those relays.
Once the workflow is built, you can test it with the testing form URL, and set it to "Active" to use the production form URL. That's it. You can now give posting access to anyone for any Npub. To revoke access, simply change the credentials or set to workflow to "Inactive".
It may also be the world's simplest Nostr client.
You can find the Nostr Form to Post a Note workflow here.
Push notifications on mentions and new notes
One of the things Nostr is not very good at is push notifications. Furthermore I have some unique itches to scratch. I want–
- To make sure I never miss a note addressed to any of my Npubs – For this I want a push notification any time any Nostr user mentions any of my Npubs,
- To make sure I always see all notes from key accounts – For this I need a push notification any time any of my Npubs post any Notes to the network,
- To get these notifications on all of my devices – Not just my phone where my Nostr regular client lives, but also on each of my laptops to suit wherever I am working that day.
I needed to build a Nostr push notifications solution.
To build this workflow I had to string a few ideas together–
- Triggering the node on a schedule – Nostrobots does not include a trigger node. As every workflow starts with a trigger we needed a different method. I elected to run the workflow on a schedule of every 10-minutes. Frequent enough to see Notes while they are hot, but infrequent enough to not burden public relays or get rate-limited,
- Storing a list of Npubs in a Nostr list – I needed a way to store the list of Npubs that trigger my notifications. I initially used an array defined in the workflow, this worked fine. Then I decided to try Nostr lists (NIP-51, kind 30000). By defining my list of Npubs as a list published to Nostr I can control my list from within a Nostr client (e.g. Listr.lol or Nostrudel.ninja). Not only does this "just work", but because it's based on Nostr lists automagically Amethyst client allows me to browse that list as a Feed, and everyone I add gets notified in their Mentions,
- Using specific relays – I needed to query the right relays, including my own HAVEN relay inbox for notes addressed to me, and wss://purplepag.es for Nostr profile metadata,
- Querying Nostr events (with Nostrobots) – I needed to make use of many different Nostr queries and use quite a wide range of what Nostrobots can do–
- I read the EventID of my Kind 30000 list, to return the desired pubkeys,
- For notifications on mentions, I read all Kind 1 notes that mention that pubkey,
- For notifications on new notes, I read all Kind 1 notes published by that pubkey,
- Where there are notes, I read the Kind 0 profile metadata event of that pubkey to get the displayName of the relevant Npub,
- I transform the EventID into a Nevent to help clients find it.
- Using the Nostr URI – As I did with my NFC card article, I created a link with the
nostr:URI prefix so that my phone's native client opens the link by default, - Push notifications solution – I needed a push notifications solution. I found many with n8n integrations and chose to go with Pushover which supports all my devices, has a free trial, and is unfairly cheap with a $5-per-device perpetual license.
Once the workflow was built, lists published, and Pushover installed on my phone, I was fully set up with push notifications on Nostr. I have used these workflows for several weeks now and made various tweaks as I went. They are feeling robust and I'd welcome you to give them a go.
You can find the Nostr Push Notification If Mentioned here and If Posts a Note here.
In speaking with other Nostr users while I was building this, there are all kind of other needs for push notifications too – like on replies to a certain bookmarked note, or when a followed Npub starts streaming on zap.stream. These are all possible.
Use my workflows
I have open sourced all my workflows at my Github with MIT license and tried to write complete docs, so that you can import them into your n8n and configure them for your own use.
To import any of my workflows–
- Click on the workflow of your choice, e.g. "Nostr_Push_Notify_If_Mentioned.json",
- Click on the "raw" button to view the raw JSON, ex any Github page layout,
- Copy that URL,
- Enter that URL in the "import from URL" dialog mentioned above.
To configure them–
- Prerequisites, credentials, and variables are all stated,
- In general any variables required are entered into a Set Node that follows the trigger node,
- Pushover has some extra setup but is very straightforward and documented in the workflow.
What next?
Over my first four blogs I explored creating a good Nostr setup with Vanity Npub, Lightning Payments, Nostr Addresses at Your Domain, and Personal Nostr Relay.
Then in my latest two blogs I explored different types of interoperability with NFC cards and now n8n Workflow Automation.
Thinking ahead n8n can power any kind of interoperability between Nostr and any other legacy technology solution. On my mind as I write this:
- Further enhancements to posting and delegating solutions and forms (enhanced UI or different note kinds),
- Automated or scheduled posting (such as auto-liking everything Lyn Alden posts),
- Further enhancements to push notifications, on new and different types of events (such as notifying me when I get a new follower, on replies to certain posts, or when a user starts streaming),
- All kinds of bridges, such as bridging notes to and from Telegram, Slack, or Campfire. Or bridging RSS or other event feeds to Nostr,
- All kinds of other automation (such as BlackCoffee controlling a coffee machine),
- All kinds of AI Assistants and Agents,
In fact I have already released an open source workflow for an AI Assistant, and will share more about that in my next blog.
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
GM Nostr.
-
 @ f96073dc:5951c7c2
2025-01-08 16:54:42
@ f96073dc:5951c7c2
2025-01-08 16:54:42Introduction
The food we consume plays an obvious yet undervalued role in not just sustaining us, but also in shaping who we become.
The phrase "You are what you eat" transcends cliché to embody a profound truth: our diet directly influences our life experience.
Debates continue about the optimal food sources for human health and longevity.
These discussions often involve emotionally charged arguments influenced by faith, traditions, economic interests, and political opinions concerning the global climate crisis and sustainability.
My goal isn’t to delve into the weeds of this emotional & political debate, but instead to strip things back and provide a birds eye view on nutrition, whilst offering alternative lenses through which we can view food.
 ## Understanding Food as Information
## Understanding Food as Information More than mere fuel, food serves as crucial information for our bodies.
This concept may sound strange, as much of our nutritional understanding has been dumbed down to ‘energy in, energy out’, or ‘calories in, calories out’.
This perspective bypasses the importance of micro nutrients—the vitamins & minerals our bodies interrelate with, or don’t.
Food information determines how our cells function and regenerate, impacting everything from energy levels to cognitive ability.
The challenge lies in deciphering what constitutes "good information."
For centuries, nature provided a simple guide.
Our ancestors thrived on a diet of organ meats, plants, seafood, fruit, muscle meats, bones, and eggs—foods naturally rich in nutrients and absent of modern chemicals.
The question remains: If our forebears thrived on these natural foods, why have we deviated so drastically?
 ## The Shift in Food Paradigms
## The Shift in Food Paradigms The introduction of heavily processed "Frankenfoods" laden with chemicals represents a stark departure from the diets of our grandparents and great-grandparents.
They consumed what we now coin "organic" food out of necessity rather than choice.
Food is pleasure, but it’s also a tool for a healthy self.
This ratio has been disproportionally thrown out of alignment.
The modern supermarket, with its aisles dominated by hyper palatable and processed products, reflects a concerning shift in our eating habits.
On the periphery of supermarkets lie fruits, vegetables, dairy, and animal based products, many of which have been sprayed with chemicals like glyphosate, or raised under inhumane conditions.
This brings us to the troubling paradox: while some parts of the world suffer from over-consumption and associated health issues like obesity and metabolic diseases, others face malnutrition and starvation due to food scarcity. (See red line below)
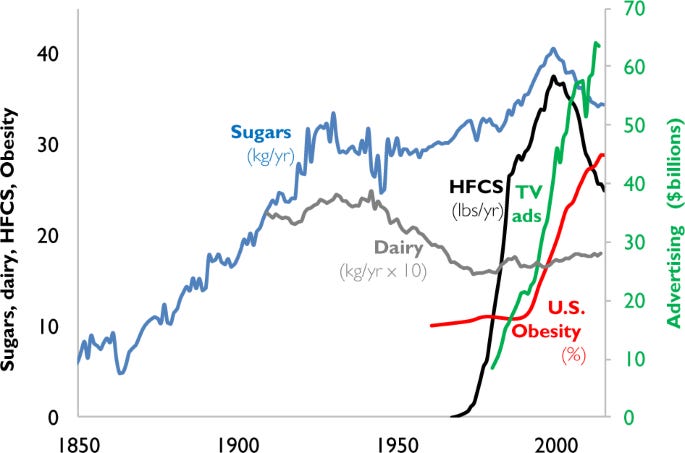 *HFCS: High fructose corn syrup
*HFCS: High fructose corn syrupQuestioning Current Food Paradigms
Our current food systems are broken.
A hard truth and pill to swallow, but if you look around, people have never been this unwell and overweight.
Misleading ‘Health Star Ratings’ and a flawed food pyramid, reflect a deeper societal malaise.
These systems often promote products that are not conducive to health, with processed carbohydrate forms serving as our staple, while nutrient and caloric dense foods like meat, fish, dairy, and natural fats have been marginalised.
 ## Whole Foods and Balanced Nutrients
## Whole Foods and Balanced Nutrients So, what’s the ideal diet?
There is no universal diet that fits everybody.
The journey to finding the right diet involves personal experimentation.
However, a diet emphasising whole foods, which humans have consumed for millennia, remains a sound choice.
Eating natural foods avoids the pitfalls of ultra-processed foods and provides a balanced array of nutrients.
Side note: historically, meat was always the prized resource.
 ## Beyond Pesticides
## Beyond Pesticides Every year, the Environmental Working Group (EWG) puts together a list of 15 foods with the lowest amounts of pesticide residues, and conversely, 12 of the most contaminated foods with pesticides.
This is known as the ‘Clean Fifteen’ and ‘Dirty Dozen’.
When financially feasible, it’s advised to consume organic and pasture raised products.
If buying organic isn’t possible, one strategy to reduce pesticides is to soak the produce in water and a teaspoon of baking soda or a splash of apple cider vinegar for a few minutes.
 ## Nutritional Strategies for Specific Needs
## Nutritional Strategies for Specific Needs Strategies like the elimination diet can help individuals identify how specific foods affect their bodies, allowing them to make informed choices that resonate with their unique physiological needs.
Tracking macronutrients and particularly protein intake can be crucial for specific health goals like muscle growth or weight loss.
Gaining a baseline understanding of the macros in your food can be an important piece of the puzzle, but should not become an obsessive practice.
Many diets serve a purpose, and depending on your goals as well as physiology, can be leveraged for great benefit.
This broad concept has been developed into a growing area of research called Nutrigenomics, defined as the study of how different foods may interact with specific genes to modify the risk of common chronic diseases, such as heart disease, stroke, and certain cancers.
For example, a ketogenic diet can help those with neurological disorders such as epilepsy or Alzheimer's disease, intermittent fasting can facilitate weight loss, and a carnivore diet can heal chronic skin or gut issues.
 ## Conclusion
## ConclusionIn an era where diet-related health issues are rampant, returning to a more natural, informed way of eating is not just beneficial; it is necessary.
The prevalence of heavily processed "Frankenfoods" deviates from the nutrient-rich diets of our ancestors, contributing to a paradox of overconsumption and malnutrition.
Challenging current food paradigms is necessary to address misleading nutritional guidelines and flawed food systems.
Empower yourself to explore food in a deeper fashion, seeking a diet that not only nourishes your body but also aligns with your lifestyle goals and fosters a sense of vitality and well-being.
Eating well is a form of a self respect, and while we get the chance to inhabit this physical form, it should be our duty to make the most of this life and embody our fullest potential.
-
 @ bf47c19e:c3d2573b
2025-01-08 16:43:01
@ bf47c19e:c3d2573b
2025-01-08 16:43:01Originalni tekst na danas.rs
11.01.2021 / Autor: Aleksandar Milošević
Ima više od osam godina otkako sam prvi put čuo za to nešto što se zvalo bitkoin.
Libertarijanski san: „Decentralizovana“ valuta koju ne kontroliše nijedna država; na koju nijedna centralna banka ne može da utiče; koju je zahvaljujući „blokčejn“ tehnologiji nemoguće falsifikovati i koja nudi anonimnost kakvu poznaje samo keš.
Valuta čija je ukupna količina unapred fiksirana pa joj je rast vrednosti usađen u DNK.
I to još valuta koju je moguće dobiti besplatno, ali po zasluzi, jer bitkoini nastaju tako što vaš kompjuter reši komplikovani matematički zadatak iza kojeg se „krije“ jedan od ovih magičnih novčića.
To što je čitav sistem osmislio misteriozni matematički genije poznat kao Satoši Nakamoto, koji možda postoji, a možda i ne postoji i što se ceo finansijski establišment obrušio na čitavu bitkoin-maniju kombinacijom podsmeha i represivnih pretnji, moglo je samo da ubrza moju tadašnju odluku da kupim XFX ATI RADEON HD 5870 grafičku karticu za nekih 200 evra (maksimum koji sam od skromne novinarske plate mogao sebi da oprostim) i priključim se drugoj velikoj zlatnoj groznici, nekih 150 godina nakon one originalne, kalifornijske.
Ipak, kao što se da pretpostaviti iz činjenice da danas pišem ovaj tekst umesto da na nekom tropskom ostrvu vežbam skokove u vodu, sudbina nije htela da se obogatim rudareći bitkoine.
Ispostavilo se, naime, da moja moćna grafička karta ne odgovara mojoj dosta nesposobnoj matičnoj ploči, pa sam uz pomoć najgore „cost-benefit“ analize u istoriji biznisa zaključio da je bolje da prodam grafičku sa 20 evra gubitka i zaboravim na sve, nego da zarad svoje igrarije menjam čitav kompjuter.
Ta greška koštala me je nekih 700.000 dolara.
Toliko bih, žalosno je, danas imao da sam propalu investiciju u pogrešan hardver pretvorio u novotariju zvanu kriptovaluta, po tadašnjem kursu od 10 dolara za novčić, umesto što sam „zaboravio na sve“.
Bitkoin je, ispostavilo se, postao prilično velika stvar.
S kursom od 40.000 dolara za jedan bitkoin, s međunarodnim bankama koje spekulišu ovom valutom, s nuklearnim naučnicima hapšenim jer su ruski državni superkompjuter upregli da za njih rudari bitkoin, sa novinskim izveštajima o ljudima koji idu u zemlje s jeftinom strujom da u njima instaliraju čitava skladišta puna računara za traženje bitkoina, pa čak i sa poslednjim pričama koje krive upravo bitkoin za to što je u Pakistanu pao napon struje za 200 miliona ljudi i što je 500 miliona Evropljana zamalo ostalo bez svetla, nema nikakve sumnje da je bitkoin nešto veliko.
A opet, to nešto veliko i dalje uporno ostaje – ništa.
Ma koliko neverovatna cena od 40.000 dolara delovala zavodljivo, bitkoin entuzijasti su već jednom, pre tačno dve godine, sve to već doživeli, kada je ova valuta prvi put u meteorskom usponu za samo par nedelja dostigla 20.000 dolara, da bi se onda jednako naglo i jednako neobjašnjivo survala nazad, ostavljajući mnoge sa velikom i nimalo virtuelnom rupom u džepu.
Osnovni problem bitkoina, uzrok njegove karakteristične nestabilnosti – ogromnih skokova i jednako spektakularnih padova – jeste to što niko ne zna za šta je on koristan.
Ma kako uzbudljivo delovala čitava priča o novcu koji je van kontrole vlade, koji nudi anonimnost transakcija i koji je navodno nemoguće falsifikovati, činjenica je da prosečnoj osobi ništa od toga nije potrebno.
Tačnije, bitkoin – sem u uskom krugu slučajeva – ne nudi ništa što već ne možete da dobijete sa svojom valutom, a da vam je potrebno.
Za anonimnost je većini dovoljan keš, rizik od falsifikata je dovoljno mali da je zanemarljiv, a kontrola države i nezavisnost od monetarnih vlasti su priče koje su ljudima eventualno intelektualno zanimljive, ali nikog neće naterati da u praksi krene da koristi neku virtuelnu valutu.
Zato je bitkoin ostao novac ponajviše upotrebljavan za nezakonite transakcije – otkup podataka od hakera, prodaju droge i tome slično – gde su anonimnost i elektronski transfer novca bitniji od svega.
Zašto onda raste cena bitkoinu?
Zato što svi kupuju bitkoine nadajući se da će im cena skočiti i da će zaraditi.
Kako raste tražnja tako raste cena i očekivanje se ispunjava.
Onda kad tražnja nestane, a to će se desiti kad svi koji su upravo sad čuli za bitkoin pokupuju virtuelne novčiće videvši koliki je rast cene u poslednjim danima, cena će krenuti da pada.
Jer – bitkoini nikom nisu potrebni i niko ne želi da ih zadrži. Sve što svi žele je da ih kupe, da im cena „iz nekog razloga skoči“ i da ih onda zamene za „pravi novac“.
U toj igri, koja se stalno ponavlja kako naiđe novi talas publiciteta, neko naravno mora i da izgubi.
Bitkoin neće postići stabilnost i neće uspeti da iskaže svoju „deflatornu“ prirodu u koju se svi uzdaju da im trajno podiže vrednost novčića koje poseduju, sve dok se ne bude pronašla njegova svrha kao valute.
Dok dovoljno veliki broj ljudi ne bude hteo da drži i koristi bitkoine za ono za šta je svaka valuta namenjena – za kupovinu roba i usluga.
Droga, oružje, ucene i ostale oblasti kriminalne ekonomije nisu dovoljni da bi se takva stabilnost postigla.
Glavni problem bitkoina je zato njegova praznina.
Bitkoin nije zlato našeg doba. Pre je blato.
-
 @ 00cfe60d:2819cc65
2025-01-08 16:36:40
@ 00cfe60d:2819cc65
2025-01-08 16:36:40Lets start with the money talk, at its core, a good form of money is created from two key ingredients: time and energy.
**Money = Time + Energy ** This simple idea explains why money has value. Time is something we can never get back, and energy is what powers everything we do, both mentally and physically. Together, they create value.
Why Energy is So Important Energy is what keeps life going. It’s essential for everything we use and do every day. For example:
- Food without energy to cook is raw and not very tasty.
- A car without energy doesn’t go anywhere.
- A person without energy feels tired and can’t work or play.
- Your work without energy gets nothing done.
- Football without energy means no running, no cheering, and no fun.
- A phone without energy is just a useless object.
- A house without energy is cold, dark, and uncomfortable.
- Transportation without energy means no moving buses, trains, or planes.
- The internet without energy means no websites, no games, and no communication.
- Nature without energy means plants don’t grow and animals can’t survive.
And what about money without energy? ** We often hear that “time is money” but if money is created without any time or energy, it becomes worthless. That’s why energy is so important in giving money its value.
Why Bitcoin is Different
Bitcoin is special because it follows the equation of money perfectly. It’s the best kind of money because it requires both time and energy to exist. Here’s how:
-
Time: Bitcoin’s network is designed to create new bitcoins at regular intervals, so time is built into the system.
-
Energy: Bitcoin is made using a process called Proof-of-Work, which uses real-world energy to produce and secure it. This ties its value to effort and cost.
Thanks to this process, Bitcoin is:
-
Scarce: There will only ever be 21 million bitcoins. It can’t be copied or faked.
-
Reliable: Its value is tied to real-world energy, making it solid and trustworthy.
-
Effort-Based: No one can create bitcoins out of thin air. It takes real work.
This makes Bitcoin an honest form of money, free from manipulation or shortcuts. It connects the digital and physical worlds through energy, just like gold was in the past, requiring time and energy to extract and maintain its value.
The Problem with Regular Money (Fiat Money)
On the other hand, fiat money, the kind printed by governments, doesn’t follow the same rules. It’s made without effort, just by pressing a button. This leads to big problems:
-
Inflation: More money is printed, making the money you already have worth less.
-
Manipulation: Governments and banks can change the rules whenever they want.
-
Unfairness: People closest to the money printers benefit the most, while everyone else pays the price.
-
Fiat money breaks the rule of time and energy. It’s just a symbol, not a true store of value.
**Henry Ford’s Energy Currency Idea ** Over 100 years ago, Henry Ford had a bold idea: What if money was based on energy? He believed energy was the ultimate resource because it’s measurable and valuable to everyone.
Bitcoin brings Ford’s vision to life. Its Proof-of-Work system ties money directly to energy. Bitcoin acts as a global, incorruptible energy currency that rewards effort and aligns money with real-world value.
Why Energy-Based Money Matters
Money that’s rooted in time and energy isn’t just an idea, it’s a principle we live by every day. To truly understand the value of energy and effort, let me share a personal story.
Every single day of the week, I train. I pour my energy and effort into CrossFit, pushing my body and mind to their limits. Last year, during a competition, I achieved something I’d never done before: 12 ring muscle-ups. Before that, my maximum was just three. Through consistent training, spending my time and energy at the gym, I earned that reward. It wasn’t easy, but it was worth it.
This is Proof-of-Work in action. Just like my training required time and energy to achieve results, Bitcoin requires time and energy to exist. Its
Proof-of-Work mechanism ensures:
- It can’t be faked or inflated.
- It rewards hard work and energy, not shortcuts or manipulation.
- It restores trust by linking value to real-world effort.
In a world where fiat money can be printed without effort, Bitcoin shines as a clear and honest form of money. Like the work I put into my training, Bitcoin ties time and energy to value, creating a system that’s fair, transparent, and built to last.
-
 @ f9cf4e94:96abc355
2024-12-31 20:18:59
@ f9cf4e94:96abc355
2024-12-31 20:18:59Scuttlebutt foi iniciado em maio de 2014 por Dominic Tarr ( dominictarr ) como uma rede social alternativa off-line, primeiro para convidados, que permite aos usuários obter controle total de seus dados e privacidade. Secure Scuttlebutt (ssb) foi lançado pouco depois, o que coloca a privacidade em primeiro plano com mais recursos de criptografia.
Se você está se perguntando de onde diabos veio o nome Scuttlebutt:
Este termo do século 19 para uma fofoca vem do Scuttlebutt náutico: “um barril de água mantido no convés, com um buraco para uma xícara”. A gíria náutica vai desde o hábito dos marinheiros de se reunir pelo boato até a fofoca, semelhante à fofoca do bebedouro.

Marinheiros se reunindo em torno da rixa. ( fonte )
Dominic descobriu o termo boato em um artigo de pesquisa que leu.
Em sistemas distribuídos, fofocar é um processo de retransmissão de mensagens ponto a ponto; as mensagens são disseminadas de forma análoga ao “boca a boca”.
Secure Scuttlebutt é um banco de dados de feeds imutáveis apenas para acréscimos, otimizado para replicação eficiente para protocolos ponto a ponto. Cada usuário tem um log imutável somente para acréscimos no qual eles podem gravar. Eles gravam no log assinando mensagens com sua chave privada. Pense em um feed de usuário como seu próprio diário de bordo, como um diário de bordo (ou diário do capitão para os fãs de Star Trek), onde eles são os únicos autorizados a escrever nele, mas têm a capacidade de permitir que outros amigos ou colegas leiam ao seu diário de bordo, se assim o desejarem.
Cada mensagem possui um número de sequência e a mensagem também deve fazer referência à mensagem anterior por seu ID. O ID é um hash da mensagem e da assinatura. A estrutura de dados é semelhante à de uma lista vinculada. É essencialmente um log somente de acréscimo de JSON assinado. Cada item adicionado a um log do usuário é chamado de mensagem.
Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações. Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.

Estrutura de alto nível de um feed
Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar. Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência.
Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub.
Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.
Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de Pubs públicos em que todos podem participar . Explicaremos como ingressar em um posteriormente neste guia. Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais. Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.

Perspectivas dos participantes
Scuttlebot
O software Pub é conhecido como servidor Scuttlebutt (servidor ssb ), mas também é conhecido como “Scuttlebot” e
sbotna linha de comando. O servidor SSB adiciona comportamento de rede ao banco de dados Scuttlebutt (SSB). Estaremos usando o Scuttlebot ao longo deste tutorial.Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações. Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.

Estrutura de alto nível de um feed
Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar. Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência.
Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub.
Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.
Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de Pubs públicos em que todos podem participar . Explicaremos como ingressar em um posteriormente neste guia. Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais. Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.


Perspectivas dos participantes
Pubs - Hubs
Pubs públicos
| Pub Name | Operator | Invite Code | | ------------------------------------------------------------ | ------------------------------------------------------------ | ------------------------------------------------------------ | |
scuttle.us| @Ryan |scuttle.us:8008:@WqcuCOIpLtXFRw/9vOAQJti8avTZ9vxT9rKrPo8qG6o=.ed25519~/ZUi9Chpl0g1kuWSrmehq2EwMQeV0Pd+8xw8XhWuhLE=| | pub1.upsocial.com | @freedomrules |pub1.upsocial.com:8008:@gjlNF5Cyw3OKZxEoEpsVhT5Xv3HZutVfKBppmu42MkI=.ed25519~lMd6f4nnmBZEZSavAl4uahl+feajLUGqu8s2qdoTLi8=| | Monero Pub | @Denis |xmr-pub.net:8008:@5hTpvduvbDyMLN2IdzDKa7nx7PSem9co3RsOmZoyyCM=.ed25519~vQU+r2HUd6JxPENSinUWdfqrJLlOqXiCbzHoML9iVN4=| | FreeSocial | @Jarland |pub.freesocial.co:8008:@ofYKOy2p9wsaxV73GqgOyh6C6nRGFM5FyciQyxwBd6A=.ed25519~ye9Z808S3KPQsV0MWr1HL0/Sh8boSEwW+ZK+8x85u9w=| |ssb.vpn.net.br| @coffeverton |ssb.vpn.net.br:8008:@ze8nZPcf4sbdULvknEFOCbVZtdp7VRsB95nhNw6/2YQ=.ed25519~D0blTolH3YoTwSAkY5xhNw8jAOjgoNXL/+8ZClzr0io=| | gossip.noisebridge.info | Noisebridge Hackerspace @james.network |gossip.noisebridge.info:8008:@2NANnQVdsoqk0XPiJG2oMZqaEpTeoGrxOHJkLIqs7eY=.ed25519~JWTC6+rPYPW5b5zCion0gqjcJs35h6JKpUrQoAKWgJ4=|Pubs privados
Você precisará entrar em contato com os proprietários desses bares para receber um convite.
| Pub Name | Operator | Contact | | --------------------------------------------- | ------------------------------------------------------------ | ----------------------------------------------- | |
many.butt.nz| @dinosaur | mikey@enspiral.com | |one.butt.nz| @dinosaur | mikey@enspiral.com | |ssb.mikey.nz| @dinosaur | mikey@enspiral.com | | ssb.celehner.com | @cel | cel@celehner.com |Pubs muito grandes
Aviso: embora tecnicamente funcione usar um convite para esses pubs, você provavelmente se divertirá se o fizer devido ao seu tamanho (muitas coisas para baixar, risco para bots / spammers / idiotas)
| Pub Name | Operator | Invite Code | | --------------------------------------- | ----------------------------------------------- | ------------------------------------------------------------ | |
scuttlebutt.de| SolSoCoG |scuttlebutt.de:8008:@yeh/GKxlfhlYXSdgU7CRLxm58GC42za3tDuC4NJld/k=.ed25519~iyaCpZ0co863K9aF+b7j8BnnHfwY65dGeX6Dh2nXs3c=| |Lohn's Pub| @lohn |p.lohn.in:8018:@LohnKVll9HdLI3AndEc4zwGtfdF/J7xC7PW9B/JpI4U=.ed25519~z3m4ttJdI4InHkCtchxTu26kKqOfKk4woBb1TtPeA/s=| | Scuttle Space | @guil-dot | Visit scuttle.space | |SSB PeerNet US-East| timjrobinson |us-east.ssbpeer.net:8008:@sTO03jpVivj65BEAJMhlwtHXsWdLd9fLwyKAT1qAkc0=.ed25519~sXFc5taUA7dpGTJITZVDCRy2A9jmkVttsr107+ufInU=| | Hermies | s | net:hermies.club:8008~shs:uMYDVPuEKftL4SzpRGVyQxLdyPkOiX7njit7+qT/7IQ=:SSB+Room+PSK3TLYC2T86EHQCUHBUHASCASE18JBV24= |GUI - Interface Gráfica do Utilizador(Usuário)
Patchwork - Uma GUI SSB (Descontinuado)
Patchwork é o aplicativo de mensagens e compartilhamento descentralizado construído em cima do SSB . O protocolo scuttlebutt em si não mantém um conjunto de feeds nos quais um usuário está interessado, então um cliente é necessário para manter uma lista de feeds de pares em que seu respectivo usuário está interessado e seguindo.

Fonte: scuttlebutt.nz
Quando você instala e executa o Patchwork, você só pode ver e se comunicar com seus pares em sua rede local. Para acessar fora de sua LAN, você precisa se conectar a um Pub. Um pub é apenas para convidados e eles retransmitem mensagens entre você e seus pares fora de sua LAN e entre outros Pubs.
Lembre-se de que você precisa seguir alguém para receber mensagens dessa pessoa. Isso reduz o envio de mensagens de spam para os usuários. Os usuários só veem as respostas das pessoas que seguem. Os dados são sincronizados no disco para funcionar offline, mas podem ser sincronizados diretamente com os pares na sua LAN por wi-fi ou bluetooth.
Patchbay - Uma GUI Alternativa
Patchbay é um cliente de fofoca projetado para ser fácil de modificar e estender. Ele usa o mesmo banco de dados que Patchwork e Patchfoo , então você pode facilmente dar uma volta com sua identidade existente.

Planetary - GUI para IOS

Planetary é um app com pubs pré-carregados para facilitar integração.
Manyverse - GUI para Android

Manyverse é um aplicativo de rede social com recursos que você esperaria: posts, curtidas, perfis, mensagens privadas, etc. Mas não está sendo executado na nuvem de propriedade de uma empresa, em vez disso, as postagens de seus amigos e todos os seus dados sociais vivem inteiramente em seu telefone .
Fontes
-
https://scuttlebot.io/
-
https://decentralized-id.com/decentralized-web/scuttlebot/#plugins
-
https://medium.com/@miguelmota/getting-started-with-secure-scuttlebut-e6b7d4c5ecfd
-
Secure Scuttlebutt : um protocolo de banco de dados global.
-
-
 @ 79008e78:dfac9395
2024-12-18 09:02:28
@ 79008e78:dfac9395
2024-12-18 09:02:28อย่างที่ทราบกันอยู่แล้วว่า Nostr เป็นได้มากกว่า Note แล้วจะเป็นอย่างไรล่ะ ถ้า Note และลองฟอร์มต่าง ๆ ที่เราเคยเขียนกันมาสามารถกลายเป็นเว็บบอร์ดที่เราสามารถใช้เก็บผลงานและโชว์ให้กับคนอื่น ๆ ในโลกอินเตอร์เน็ตทั่วไปได้อีกด้วย
Npub.pro คืออะไร ?
Npub.pro เป็น Other stuff ตัวหนึ่งที่ช่วยแปลง note และ long form ต่าง ๆ ที่เราเคยได้ลงไว้ในโปรโตคอลของ Nostr และแปลงมันมาเป็นเว็บบอร์ดที่สวยสะอาดตา และมีธีมให้เลือกอีกหลากหลาย ซึ่งเหมาะสมมาก ๆ กับเหล่าครีเอเตอร์ต่าง ๆ สำหรับที่จะใช้มันในการโชว์ผลงาน ไม่ว่าจะเป็นสายถ่ายภาพ เก็บรวบรวมบทความ หรืออีกหลาย ๆ แง่มุมที่สามารถเกิดขึ้นได้


นี่เองคือหนึ่งในตัวอย่างที่ผมได้ทำไว้เพื่อแพร่กระจายบทความต่าง ๆ ให้ออกไปสู่ผู้คนที่อาจจะไม่ได้รู้จักหรือใช้งาน Nostr อยู่
แล้วมันทำงานอย่างไร ?
Npub.pro นั้นจะทำการดึง Notes และ Long form ของเรามาจาก relay ต่าง ๆ ที่เราได้มีการเชื่อมต่อไว้ในบัญชีของเรา และทำการนำมาจัดรูปแบบใหม่ตามธีมที่เราได้เลือกไว้ และแสดงผลออกมามาในรูปแบบเว็บบอร์ด นอกจากนี้ยังมีการใส่ตัว nostr log-in เข้ามาเพื่อช่วยให้คนที่มีบัญชี nostr สามารถใช้บัญชีของตนในการ zap หรือ คอมเม้นได้ รวมทั้งยังอณุญาตให้ผู้ใช้ใส่ script เพิ่มเติมลงไปทั้งในส่วนหัวและท้ายของเว็บบอร์ดได้อีกด้วย ดังเช่น

ทั้งหมดที่กล่าวมาข้างต้นเป็นประสบการณ์ส่วนตัวของผมเองที่ได้มีการทดลองใช้งานมาระยะหนึ่ง และในส่วนต่อไป เราจะมาดูกันถึงวิธีการสร้างว่าเราต้องทำอย่างไร จึงจะมีเว็บไซต์สวย ๆ แบบนี้ได้
วิธีการสร้าง
1. เข้าเว็บ Npub.pro
หลังจากเข้ามาในเว็บไซต์ให้เรากด "try now"

2. เลือกธีม
จากนั้นจะมีธีมต่าง ๆ ขึ้นมาให้คุณเลือก ในจุดนี้ผมแนะนำว่าให้เลือกให้เหมาะสมกับผลงานของคุณ (สามารถเปลี่ยนได้ภายหลัง)

3. ตั้งค่าส่วนอื่น ๆ
หลังจากเลือกเสร็จเรียบร้อยเราต้องทำการใส่ title bio และอื่น ๆ ให้เรียบร้อยจากนั้นให้ทำการกด publish

เพียงแค่นี้คุณก็จะมีเว็บบอร์ดเจ๋ง ๆ ที่จะคอยอัพเดตอัตโนมัติเพมื่อคุณได้โพสต์บางอย่างลงบน Nostr ;)
-
 @ 0403c86a:66d3a378
2024-12-31 19:22:15
@ 0403c86a:66d3a378
2024-12-31 19:22:15As we kick off the new year and gear up for GSC's Anniversary Celebration on January 11, we’re thrilled to unveil our anticipated list of 11 oN 11 – the 11 athletes who dominated their sports, broke records, and inspired the world in the past year.
These icons didn’t just shine on the field, court, or track – they redefined excellence and left an indelible mark on the global sports landscape.
Our nominees will be revealed daily, follow the countdown to greatness #11oN11
These athletes didn’t just win games – they won hearts, inspired nations, and moved the needle for their respective sports.
✨ Join the conversation and tell us your picks for the most defining athletes of last year! Who inspired YOU the most? Let’s celebrate excellence together as we count down to GSC’s Anniversary on January 11!!!
Global Sports Central 🌐 #11oN11
-
 @ bf47c19e:c3d2573b
2025-01-08 16:26:02
@ bf47c19e:c3d2573b
2025-01-08 16:26:02Originalni tekst na politika.rs
13.09.2021 / Autor: Aleksandar Apostolovski
Za svet virtuelne banalnosti u koji smo umarširali potrebna je i njegova moneta. Kakav svet takvo i sredstvo plaćanja.
Ni četnički jataci nisu kao što su nekada bili. Ne skrivaju se u zemunicama, ne spremaju masnu gibanicu – prste da poližeš – ne čekaju zapadne saveznike da se iskrcaju na Jadranu. Verovatno nemaju ni brade modne linije starog američkog benda „Zi Zi Top”.
Nepoznata sajber ilegalna grupa upala je u podrum kuće čiča Draže u Ivanjici. Zaista, prvorazredna vest. Instalirali su snažne procesore i mašine za rudarenje bitkoinima i daljinskim sistemom. Ko zna odakle. Možda sa Kariba, možda iz Kosjerića, možda iz Jajca – ako su ipak partizani. Trgovali su kriptovalutama. Umalo da tako rasture uličnu rasvetu tokom „Nušićijade”, pa su čelnici opštine sproveli internu istragu, tražeći ilegalce koji vrše diverziju nad elektroenergetskim sistemom grada i festivalom satire.
Upali su u Dražin dom, sišli u podrum i zatekli sofisticiranu opremu, snažne procesore i nekakve mašine za rudarenje po internetu. Kompjuterski komandosi, naravno, nisu bili prisutni. Sada ih juri policija. Potrošili su oko 55.000 kilovat-sati struje. Verovatno se skrivaju pod stripovskim kodnim imenima, poput hakera iz Niša koji su ojadili Teksašane, pa im je doakao FBI, jer Ameri možda trpe svoje prevarante koji muzu kockare na globalnom groblju kriptovaluta, ali ne dozvoljavaju da se u međunarodnu spekulativnu igru ubace mozgovi sa južne pruge, gde je dozvoljeno da se prži paprika, pravi ajvar i sluša melanholični džez na „Nišvilu”.
Jedan od članova niške hakerske grupe je Antonije Stojiljković, koji se krio iza lažnih imena „Toni Rivas” i „Džejkob Gold”, a u slobodno vreme bio je reper poznatiji kao „Zli Toni”. Stojiljković je izručen Americi zbog računarskih prevara. Dobrovoljno se prijavio kako bi se sklonio u Ameriku.
Ti momci su nudili bitkoin upola cene i stvorili takvu virtuelnu međunarodnu mrežu lažnih kompanija, menadžera, uz organizaciju video-konferencija, da su omađijali dobar deo internet investitora iz Teksasa, te je Federalni istražni biro morao da spasava čast kauboja koje su izradile Nišlije. Njihov vođa, izvesni Kristijan Krstić, prestao je da se javlja policiji, nestao je sa suprugom i ortakom Markom Pavlovićem bez traga, iako su pod istragom, što može da poremeti i diplomatske odnose između Srbije i SAD.
Taj Kristijan, ne onaj Kristijan koji se seli iz rijalitija u rijaliti, koristio je nadimke poput „Feliksa Logana” ili „Maršala Grahama” i na internet prevarama zaradio je više desetina miliona evra. Priča nije nimalo bezazlena. Veze „Zlog Tonija” dosežu, bar po dosadašnjem toku istrage, sve do klana Belivuka.
Ali, to će rešavati sudovi i policija, mada i podaci koji su procurili otkrivaju suštinu fame bitkoin i na hiljade kriptovaluta koje može stvoriti bilo koji maher, avanturista, šaljivdžija, klinac, multimilioner, tajne službe, trgovci oružjem, narko-bosovi, plaćene ubice ili Del Bojevi koji će iduće godine postati milioneri.
Virtuelni svet ne može postojati bez virtuelnih valuta, s tim što one nisu opipljive, iza njih ne stoje centralne banke i vlade. Dakle, nemate pojma ko ih je stvorio, nemate pojma s kime trgujete i ko su brokeri.
Vidim da na „Jutjubu”, u motelu „Stari Hrast” na Koridoru 10, neki momci plaćaju prebranac i vešalice bitkoinima, preko mobilnih telefona. U kafani primaju i etereume, digitalni novčić u usponu, odmah iza bitkoina. I za to čudo je potreban digitalni novčanik... Ovde ću se zaustaviti jer je za svet banalnosti u koji smo umarširali potrebna i njegova moneta. Kakav svet takvo i sredstvo plaćanja.
Kako su kompjuterski podaci svih vrsta, od pretraživača, društvenih mreža, aplikacija, do podataka kompanija, državnih i međunarodnih organizacija, i onih ličnih, koje upravo vi posedujete, postali nezamislivo ogromna baza koju je nemoguće uskladištiti, otvorena je berza za internet magacionere koji će, rudareći na internetu, postati kandidati za potencijalne šefove skladišta. Teoretski, možete izrudariti deo arhive CIA. Preporuka – ako saznate ko je ukokao Kenedija, ćutite ko zaliveni!

(Dragan Stojanović)
Da je Alija Sirotanović kojim slučajem rudario kao specijalci iz Dražinog podruma, postao bi Bil Gejts. Alija je znao da nema ’leba bez motike, odnosno krampa. Zato je ostao Sirotanović. Ovo je novo doba. Mašina krampuje u simuliranoj stvarnosti, a virtuelni homo sapijens upravlja procesorima. Bitkoin vrti gde burgija neće! Stvar ipak nije tako idilična. Te skalamerije troše ogromne količine električne energije i strahovito zagrevaju prostorije, pa je u Dražinom podrumu bilo nešto vrelije nego u sauni. Priča se da su najveći mešetari otperjali na Island da se prirodno rashlade. Sledeće stanište im je Grenland.
Kome god je stalo do računarskog kriptovalutnog avanturizma može da formira svoj mali rudnik, gde nema zlata ni dijamanata, ali ima koina, odnosno stotog dela bitkoina. Jedan trenutno vredi 50.000 dolara. Pitam se, ovako zastareo, gde su banke i menjačnice?
Sa ono malo informatičkog znanja – valjda ću uspeti nekako imejlom da pošaljem ovaj tekst – saznao sam da vrednost bitkoina vrtoglavo skače i pada na dnevnom nivou, a kako je njegov broj ograničen na globalnom nivou, a neformalni šef Federalnih rezervi bitkoina je donedavno bio jedan od najbogatijih ljudi sveta Ilon Mask, koji je na svom tviter nalogu svakodnevno formirao grafikon rasta i pada svojim opaskama, tu već naslućujem elemente bondovskog zapleta. Harizmatični superbogataš koji leti u svemir, poseduje kompaniju električnih automobila „Tesla”, upravljao je donedavno imaginarnom berzom i valutom, ali je nedavno odustao. Možda zato emigrira u kosmos?
Stvar zaista može izmaći kontroli ili će, možda, bitkoin postati naša sudbina, a mi rudari iz sauna? Salvador je pre nekoliko dana postao prva zemlja na svetu koja je usvojila bitkoin kao zakonsko sredstvo plaćanja, uz američki dolar, s planovima korišćenja vulkanske geotermalne energije za napajanje rudarenja digitalne valute. Postavili su i bankomate. Tamošnjem narodu, kao i meni, ništa nije jasno.
Međutim, broj bitkoina je ograničen i zato pomalo podseća na zlato. Ali kod zlata ipak ponešto razumem. Recimo, ako imam zlatnu polugu i neko me napadne, mogu da je koristim u samoodbrani, a onda je sklonim u trezor banke.
Mogu da učinim i nešto drugo, jednako glupo. Da stvorim sopstvenu kriptovalutu. Nazvaću je „Ser Oliver koin”. Cijena će joj, logično, biti prava sitnica. Trebaju mi saradnici. Kruži fama da se popriličan broj klinaca, mahom dvadesetogodišnjaka, pridružio kultu bitkoina. Tokom korone izgubili su poverenje u sve, naročito u nas matore. Optužuju nas za izdaju i predviđaju propast država i zvaničnih valuta, uz uspon dvoglave aždaje – saveza bogataša i političara.
Delimično su u pravu, ali nisu ukapirali ključnu stvar. Aždaja raste, a oni rudare. Na kraju će završiti još gore nego Alija Sirotanović. Likovi im neće biti na novčanicama, a kablovima će biti priključeni za superkompjuter. Njihov novi vlasnik, s kodnim imenom „Procesor”, plaćaće ih idiot-koinima. Tražili smo, gledaćemo.
-
 @ fe32298e:20516265
2024-12-16 20:59:13
@ fe32298e:20516265
2024-12-16 20:59:13Today I learned how to install NVapi to monitor my GPUs in Home Assistant.

NVApi is a lightweight API designed for monitoring NVIDIA GPU utilization and enabling automated power management. It provides real-time GPU metrics, supports integration with tools like Home Assistant, and offers flexible power management and PCIe link speed management based on workload and thermal conditions.
- GPU Utilization Monitoring: Utilization, memory usage, temperature, fan speed, and power consumption.
- Automated Power Limiting: Adjusts power limits dynamically based on temperature thresholds and total power caps, configurable per GPU or globally.
- Cross-GPU Coordination: Total power budget applies across multiple GPUs in the same system.
- PCIe Link Speed Management: Controls minimum and maximum PCIe link speeds with idle thresholds for power optimization.
- Home Assistant Integration: Uses the built-in RESTful platform and template sensors.
Getting the Data
sudo apt install golang-go git clone https://github.com/sammcj/NVApi.git cd NVapi go run main.go -port 9999 -rate 1 curl http://localhost:9999/gpuResponse for a single GPU:
[ { "index": 0, "name": "NVIDIA GeForce RTX 4090", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 16, "power_limit_watts": 450, "memory_total_gb": 23.99, "memory_used_gb": 0.46, "memory_free_gb": 23.52, "memory_usage_percent": 2, "temperature": 38, "processes": [], "pcie_link_state": "not managed" } ]Response for multiple GPUs:
[ { "index": 0, "name": "NVIDIA GeForce RTX 3090", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 14, "power_limit_watts": 350, "memory_total_gb": 24, "memory_used_gb": 0.43, "memory_free_gb": 23.57, "memory_usage_percent": 2, "temperature": 36, "processes": [], "pcie_link_state": "not managed" }, { "index": 1, "name": "NVIDIA RTX A4000", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 10, "power_limit_watts": 140, "memory_total_gb": 15.99, "memory_used_gb": 0.56, "memory_free_gb": 15.43, "memory_usage_percent": 3, "temperature": 41, "processes": [], "pcie_link_state": "not managed" } ]Start at Boot
Create
/etc/systemd/system/nvapi.service:``` [Unit] Description=Run NVapi After=network.target
[Service] Type=simple Environment="GOPATH=/home/ansible/go" WorkingDirectory=/home/ansible/NVapi ExecStart=/usr/bin/go run main.go -port 9999 -rate 1 Restart=always User=ansible
Environment="GPU_TEMP_CHECK_INTERVAL=5"
Environment="GPU_TOTAL_POWER_CAP=400"
Environment="GPU_0_LOW_TEMP=40"
Environment="GPU_0_MEDIUM_TEMP=70"
Environment="GPU_0_LOW_TEMP_LIMIT=135"
Environment="GPU_0_MEDIUM_TEMP_LIMIT=120"
Environment="GPU_0_HIGH_TEMP_LIMIT=100"
Environment="GPU_1_LOW_TEMP=45"
Environment="GPU_1_MEDIUM_TEMP=75"
Environment="GPU_1_LOW_TEMP_LIMIT=140"
Environment="GPU_1_MEDIUM_TEMP_LIMIT=125"
Environment="GPU_1_HIGH_TEMP_LIMIT=110"
[Install] WantedBy=multi-user.target ```
Home Assistant
Add to Home Assistant
configuration.yamland restart HA (completely).For a single GPU, this works: ``` sensor: - platform: rest name: MYPC GPU Information resource: http://mypc:9999 method: GET headers: Content-Type: application/json value_template: "{{ value_json[0].index }}" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature scan_interval: 1 # seconds
- platform: template sensors: mypc_gpu_0_gpu: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} GPU" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_memory: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Memory" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_power: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Power" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_0_power_limit: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_0_temperature: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Temperature" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'temperature') }}" unit_of_measurement: "°C" ```
For multiple GPUs: ``` rest: scan_interval: 1 resource: http://mypc:9999 sensor: - name: "MYPC GPU0 Information" value_template: "{{ value_json[0].index }}" json_attributes_path: "$.0" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature - name: "MYPC GPU1 Information" value_template: "{{ value_json[1].index }}" json_attributes_path: "$.1" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature
-
platform: template sensors: mypc_gpu_0_gpu: friendly_name: "MYPC GPU0 GPU" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_memory: friendly_name: "MYPC GPU0 Memory" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_power: friendly_name: "MYPC GPU0 Power" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_0_power_limit: friendly_name: "MYPC GPU0 Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_0_temperature: friendly_name: "MYPC GPU0 Temperature" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'temperature') }}" unit_of_measurement: "C"
-
platform: template sensors: mypc_gpu_1_gpu: friendly_name: "MYPC GPU1 GPU" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_1_memory: friendly_name: "MYPC GPU1 Memory" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_1_power: friendly_name: "MYPC GPU1 Power" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_1_power_limit: friendly_name: "MYPC GPU1 Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_1_temperature: friendly_name: "MYPC GPU1 Temperature" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'temperature') }}" unit_of_measurement: "C"
```
Basic entity card:
type: entities entities: - entity: sensor.mypc_gpu_0_gpu secondary_info: last-updated - entity: sensor.mypc_gpu_0_memory secondary_info: last-updated - entity: sensor.mypc_gpu_0_power secondary_info: last-updated - entity: sensor.mypc_gpu_0_power_limit secondary_info: last-updated - entity: sensor.mypc_gpu_0_temperature secondary_info: last-updatedAnsible Role
```
-
name: install go become: true package: name: golang-go state: present
-
name: git clone git: repo: "https://github.com/sammcj/NVApi.git" dest: "/home/ansible/NVapi" update: yes force: true
go run main.go -port 9999 -rate 1
-
name: install systemd service become: true copy: src: nvapi.service dest: /etc/systemd/system/nvapi.service
-
name: Reload systemd daemons, enable, and restart nvapi become: true systemd: name: nvapi daemon_reload: yes enabled: yes state: restarted ```
-
 @ bf47c19e:c3d2573b
2025-01-08 16:03:01
@ bf47c19e:c3d2573b
2025-01-08 16:03:01Originalni tekst na trzisnoresenje.blogspot.com
22.12.2017 / Autor: Slaviša Tasić
Ovoliki uspon Bitcoina neobjašnjiv je za ekonomiste. Ne znam da li je to problem za bitcoin ili za ekonomiste, ali činjenica je da se uspeh bitcoina ne uklapa u postojeće ekonomske koncepte bar kada se radi o njemu kao valuti (blockchain kao tehnološka podloga je druga stvar). Možda su tinejdžeri koji su kupovali bitcoin 2010. i sada postali milioneri ispali pametniji od ekonomista, ali ja i dalje ne vidim odgovor bitcoina na neka standardna konceptualna pitanja. Postoji apokrifna izjava pripisana nekom profesoru ekonomije: "OK, vidim da to radi u praksi -- ali čik da vidim da li radi u teoriji?" Ovo je nešto tog tipa.
O poreklu novca, od Aristotela nasuprot Platonu pa sve do danas, postoje dve teorije. Jedna je teorija robnog novca i po njoj je novac nastao kada su neke vredne stvari počele da se češće koriste u razmeni. Plemeniti metali, naročito srebro i zlato, najpogodniji za čuvanje, oblikovanje i seckanje tako su postali novac. Kada se kasnije pojavio papirni novac on je sve do prvih decenija 20. veka bio samo hartija od vrednosti koja donosiocu daje pravo na propisanu količinu zlata.
Druga teorija je kartalizam, po kojoj neku robu novcem ne čini njena unutrašnja vrednost ili robna podloga, već država onda kada odluči da tu robu prihvata za naplatu poreza. Zbog toga je prelaz na papirni novac tokom 20. veka bio tako bezbolan i papirne valute se danas bez problema prihvataju. Današnji papirni novac nije više sertifikat koji vam daje pravo na zlato, ali vrednost ima jer u krajnjoj liniji znate da njime uvek možete platiti državi za porez ili usluge.
Bitcoin se ne uklapa ni u jednu od ovih teorija. On nema imanentnu vrednost kao robni novac, niti se može koristiti za plaćanje državi. Jedini način za bitcoin da ima neku vrednost je da ga prihvataju druge privatne strane u transakcijama. To je potpuni novitet u istoriji novca, jer se po prvi put radi o privatnom dekretnom (proklamovanom ili fiat) novcu. Postojao je privatni novac sa robnom podlogom; postoji državni dekretni novac; ali nikad privatni dekretni novac.
Najveći problem sa bitcoinom kao valutom je nestabilnost. To što njegova vrednost vrtoglavo raste nikako nije argument u prilog njemu jer nestabilnost valute isključuje mogućnost smislenog ugovaranja u njoj. Pristalice bitcoina dobro znaju da je njegova ponuda automatski ograničena i to je čest argument u odbranu bitcoina kao valute i navodno u prilog njegove stabilnosti. Ja nisam siguran da ograničenost ponude igra tako veliku ulogu.
Prvo, iako je količina bitcoina ograničena, može se napraviti neograničeno mnogo kopija bitcoina ili boljih kripto valuta. Već sada postoji na hiljade njih. Šta ograničenost ponude bitcoina uopšte znači kada ima neograničeno mnogo alternativa?
Drugo, iako je ponuda ograničena, cenu novca, kao i svega drugog, određuju ponuda i tražnja. A tražnja je kao što vidimo veoma varijabilna. Tako na jednoj strani imamo kvaziograničenost ponude a na drugoj veliku neizvesnost tražnje. To sve ukazuje na ogromnu nestabilnost.
Kod klasičnih valuta, poput evra ili dinara, ponuda je ograničena politikom centralne banke. Mnogi će reći da to nije nikakva garancija, ali zapadne valute već 30 godina nemaju nikakvu inflaciju, a u proteklih desetak godina veći problem bila je deflacija. Tražnja - želja za držanjem novca - je kod državnih valuta takođe varijabilna, ali mnogo manje jer monopolski karakter ovih valuta i naplata poreza u njima garantuju njihovu upotrebu. I kod tradicionalnih valuta ne samo da je tražnja novca relativno stabilna, već u situacijama kada tražnja novca bude nestabilna, fleksibilnost njegove ponude postaje prednost a ne mana. Na primer, tražnja za švajcarskim francima je negde oko 2009. naglo porasla. Švajcarska centralna banka je na to reagovala ogromnim povećanjem ponude, tako da je franak sačuvao bazičnu stabilnost. Jeste ojačao ali u razumnoj meri - ne desetostruko ili stostruko kao što rade kriptovalute.
Zato ne vidim kako se oscilacije bitcoina mogu zaustaviti. Jasno je da kriptovalute imaju neku korisnost u transakcijama, makar to bilo i za ilegalne aktivnosti, ali kada je ponuda neograničena a tražnja neizvesna onda nema nikakvih smernica buduće vrednosti. Ne znam koliko se to čak i može nazvati balonom jer se uopšte nemamo na šta osloniti u proceni nekakve prave vrednosti -- nema nikakvog fundamentalnog razloga ni da cena bitcoina poraste na $19,000 niti da danas padne na $12,500. Jedina vrednost koja u teoriji ima smisla je nula ili vrlo blizu nule.
-
 @ 3f770d65:7a745b24
2024-12-31 17:03:46
@ 3f770d65:7a745b24
2024-12-31 17:03:46Here are my predictions for Nostr in 2025:
Decentralization: The outbox and inbox communication models, sometimes referred to as the Gossip model, will become the standard across the ecosystem. By the end of 2025, all major clients will support these models, providing seamless communication and enhanced decentralization. Clients that do not adopt outbox/inbox by then will be regarded as outdated or legacy systems.
Privacy Standards: Major clients such as Damus and Primal will move away from NIP-04 DMs, adopting more secure protocol possibilities like NIP-17 or NIP-104. These upgrades will ensure enhanced encryption and metadata protection. Additionally, NIP-104 MLS tools will drive the development of new clients and features, providing users with unprecedented control over the privacy of their communications.
Interoperability: Nostr's ecosystem will become even more interconnected. Platforms like the Olas image-sharing service will expand into prominent clients such as Primal, Damus, Coracle, and Snort, alongside existing integrations with Amethyst, Nostur, and Nostrudel. Similarly, audio and video tools like Nostr Nests and Zap.stream will gain seamless integration into major clients, enabling easy participation in live events across the ecosystem.
Adoption and Migration: Inspired by early pioneers like Fountain and Orange Pill App, more platforms will adopt Nostr for authentication, login, and social systems. In 2025, a significant migration from a high-profile application platform with hundreds of thousands of users will transpire, doubling Nostr’s daily activity and establishing it as a cornerstone of decentralized technologies.
-
 @ 6f6b50bb:a848e5a1
2024-12-15 15:09:52
@ 6f6b50bb:a848e5a1
2024-12-15 15:09:52Che cosa significherebbe trattare l'IA come uno strumento invece che come una persona?
Dall’avvio di ChatGPT, le esplorazioni in due direzioni hanno preso velocità.
La prima direzione riguarda le capacità tecniche. Quanto grande possiamo addestrare un modello? Quanto bene può rispondere alle domande del SAT? Con quanta efficienza possiamo distribuirlo?
La seconda direzione riguarda il design dell’interazione. Come comunichiamo con un modello? Come possiamo usarlo per un lavoro utile? Quale metafora usiamo per ragionare su di esso?
La prima direzione è ampiamente seguita e enormemente finanziata, e per una buona ragione: i progressi nelle capacità tecniche sono alla base di ogni possibile applicazione. Ma la seconda è altrettanto cruciale per il campo e ha enormi incognite. Siamo solo a pochi anni dall’inizio dell’era dei grandi modelli. Quali sono le probabilità che abbiamo già capito i modi migliori per usarli?
Propongo una nuova modalità di interazione, in cui i modelli svolgano il ruolo di applicazioni informatiche (ad esempio app per telefoni): fornendo un’interfaccia grafica, interpretando gli input degli utenti e aggiornando il loro stato. In questa modalità, invece di essere un “agente” che utilizza un computer per conto dell’essere umano, l’IA può fornire un ambiente informatico più ricco e potente che possiamo utilizzare.
Metafore per l’interazione
Al centro di un’interazione c’è una metafora che guida le aspettative di un utente su un sistema. I primi giorni dell’informatica hanno preso metafore come “scrivanie”, “macchine da scrivere”, “fogli di calcolo” e “lettere” e le hanno trasformate in equivalenti digitali, permettendo all’utente di ragionare sul loro comportamento. Puoi lasciare qualcosa sulla tua scrivania e tornare a prenderlo; hai bisogno di un indirizzo per inviare una lettera. Man mano che abbiamo sviluppato una conoscenza culturale di questi dispositivi, la necessità di queste particolari metafore è scomparsa, e con esse i design di interfaccia skeumorfici che le rafforzavano. Come un cestino o una matita, un computer è ora una metafora di se stesso.
La metafora dominante per i grandi modelli oggi è modello-come-persona. Questa è una metafora efficace perché le persone hanno capacità estese che conosciamo intuitivamente. Implica che possiamo avere una conversazione con un modello e porgli domande; che il modello possa collaborare con noi su un documento o un pezzo di codice; che possiamo assegnargli un compito da svolgere da solo e che tornerà quando sarà finito.
Tuttavia, trattare un modello come una persona limita profondamente il nostro modo di pensare all’interazione con esso. Le interazioni umane sono intrinsecamente lente e lineari, limitate dalla larghezza di banda e dalla natura a turni della comunicazione verbale. Come abbiamo tutti sperimentato, comunicare idee complesse in una conversazione è difficile e dispersivo. Quando vogliamo precisione, ci rivolgiamo invece a strumenti, utilizzando manipolazioni dirette e interfacce visive ad alta larghezza di banda per creare diagrammi, scrivere codice e progettare modelli CAD. Poiché concepiamo i modelli come persone, li utilizziamo attraverso conversazioni lente, anche se sono perfettamente in grado di accettare input diretti e rapidi e di produrre risultati visivi. Le metafore che utilizziamo limitano le esperienze che costruiamo, e la metafora modello-come-persona ci impedisce di esplorare il pieno potenziale dei grandi modelli.
Per molti casi d’uso, e specialmente per il lavoro produttivo, credo che il futuro risieda in un’altra metafora: modello-come-computer.
Usare un’IA come un computer
Sotto la metafora modello-come-computer, interagiremo con i grandi modelli seguendo le intuizioni che abbiamo sulle applicazioni informatiche (sia su desktop, tablet o telefono). Nota che ciò non significa che il modello sarà un’app tradizionale più di quanto il desktop di Windows fosse una scrivania letterale. “Applicazione informatica” sarà un modo per un modello di rappresentarsi a noi. Invece di agire come una persona, il modello agirà come un computer.
Agire come un computer significa produrre un’interfaccia grafica. Al posto del flusso lineare di testo in stile telescrivente fornito da ChatGPT, un sistema modello-come-computer genererà qualcosa che somiglia all’interfaccia di un’applicazione moderna: pulsanti, cursori, schede, immagini, grafici e tutto il resto. Questo affronta limitazioni chiave dell’interfaccia di chat standard modello-come-persona:
-
Scoperta. Un buon strumento suggerisce i suoi usi. Quando l’unica interfaccia è una casella di testo vuota, spetta all’utente capire cosa fare e comprendere i limiti del sistema. La barra laterale Modifica in Lightroom è un ottimo modo per imparare l’editing fotografico perché non si limita a dirti cosa può fare questa applicazione con una foto, ma cosa potresti voler fare. Allo stesso modo, un’interfaccia modello-come-computer per DALL-E potrebbe mostrare nuove possibilità per le tue generazioni di immagini.
-
Efficienza. La manipolazione diretta è più rapida che scrivere una richiesta a parole. Per continuare l’esempio di Lightroom, sarebbe impensabile modificare una foto dicendo a una persona quali cursori spostare e di quanto. Ci vorrebbe un giorno intero per chiedere un’esposizione leggermente più bassa e una vibranza leggermente più alta, solo per vedere come apparirebbe. Nella metafora modello-come-computer, il modello può creare strumenti che ti permettono di comunicare ciò che vuoi più efficientemente e quindi di fare le cose più rapidamente.
A differenza di un’app tradizionale, questa interfaccia grafica è generata dal modello su richiesta. Questo significa che ogni parte dell’interfaccia che vedi è rilevante per ciò che stai facendo in quel momento, inclusi i contenuti specifici del tuo lavoro. Significa anche che, se desideri un’interfaccia più ampia o diversa, puoi semplicemente richiederla. Potresti chiedere a DALL-E di produrre alcuni preset modificabili per le sue impostazioni ispirati da famosi artisti di schizzi. Quando clicchi sul preset Leonardo da Vinci, imposta i cursori per disegni prospettici altamente dettagliati in inchiostro nero. Se clicchi su Charles Schulz, seleziona fumetti tecnicolor 2D a basso dettaglio.
Una bicicletta della mente proteiforme
La metafora modello-come-persona ha una curiosa tendenza a creare distanza tra l’utente e il modello, rispecchiando il divario di comunicazione tra due persone che può essere ridotto ma mai completamente colmato. A causa della difficoltà e del costo di comunicare a parole, le persone tendono a suddividere i compiti tra loro in blocchi grandi e il più indipendenti possibile. Le interfacce modello-come-persona seguono questo schema: non vale la pena dire a un modello di aggiungere un return statement alla tua funzione quando è più veloce scriverlo da solo. Con il sovraccarico della comunicazione, i sistemi modello-come-persona sono più utili quando possono fare un intero blocco di lavoro da soli. Fanno le cose per te.
Questo contrasta con il modo in cui interagiamo con i computer o altri strumenti. Gli strumenti producono feedback visivi in tempo reale e sono controllati attraverso manipolazioni dirette. Hanno un overhead comunicativo così basso che non è necessario specificare un blocco di lavoro indipendente. Ha più senso mantenere l’umano nel loop e dirigere lo strumento momento per momento. Come stivali delle sette leghe, gli strumenti ti permettono di andare più lontano a ogni passo, ma sei ancora tu a fare il lavoro. Ti permettono di fare le cose più velocemente.
Considera il compito di costruire un sito web usando un grande modello. Con le interfacce di oggi, potresti trattare il modello come un appaltatore o un collaboratore. Cercheresti di scrivere a parole il più possibile su come vuoi che il sito appaia, cosa vuoi che dica e quali funzionalità vuoi che abbia. Il modello genererebbe una prima bozza, tu la eseguirai e poi fornirai un feedback. “Fai il logo un po’ più grande”, diresti, e “centra quella prima immagine principale”, e “deve esserci un pulsante di login nell’intestazione”. Per ottenere esattamente ciò che vuoi, invierai una lista molto lunga di richieste sempre più minuziose.
Un’interazione alternativa modello-come-computer sarebbe diversa: invece di costruire il sito web, il modello genererebbe un’interfaccia per te per costruirlo, dove ogni input dell’utente a quell’interfaccia interroga il grande modello sotto il cofano. Forse quando descrivi le tue necessità creerebbe un’interfaccia con una barra laterale e una finestra di anteprima. All’inizio la barra laterale contiene solo alcuni schizzi di layout che puoi scegliere come punto di partenza. Puoi cliccare su ciascuno di essi, e il modello scrive l’HTML per una pagina web usando quel layout e lo visualizza nella finestra di anteprima. Ora che hai una pagina su cui lavorare, la barra laterale guadagna opzioni aggiuntive che influenzano la pagina globalmente, come accoppiamenti di font e schemi di colore. L’anteprima funge da editor WYSIWYG, permettendoti di afferrare elementi e spostarli, modificarne i contenuti, ecc. A supportare tutto ciò è il modello, che vede queste azioni dell’utente e riscrive la pagina per corrispondere ai cambiamenti effettuati. Poiché il modello può generare un’interfaccia per aiutare te e lui a comunicare più efficientemente, puoi esercitare più controllo sul prodotto finale in meno tempo.
La metafora modello-come-computer ci incoraggia a pensare al modello come a uno strumento con cui interagire in tempo reale piuttosto che a un collaboratore a cui assegnare compiti. Invece di sostituire un tirocinante o un tutor, può essere una sorta di bicicletta proteiforme per la mente, una che è sempre costruita su misura esattamente per te e il terreno che intendi attraversare.
Un nuovo paradigma per l’informatica?
I modelli che possono generare interfacce su richiesta sono una frontiera completamente nuova nell’informatica. Potrebbero essere un paradigma del tutto nuovo, con il modo in cui cortocircuitano il modello di applicazione esistente. Dare agli utenti finali il potere di creare e modificare app al volo cambia fondamentalmente il modo in cui interagiamo con i computer. Al posto di una singola applicazione statica costruita da uno sviluppatore, un modello genererà un’applicazione su misura per l’utente e le sue esigenze immediate. Al posto della logica aziendale implementata nel codice, il modello interpreterà gli input dell’utente e aggiornerà l’interfaccia utente. È persino possibile che questo tipo di interfaccia generativa sostituisca completamente il sistema operativo, generando e gestendo interfacce e finestre al volo secondo necessità.
All’inizio, l’interfaccia generativa sarà un giocattolo, utile solo per l’esplorazione creativa e poche altre applicazioni di nicchia. Dopotutto, nessuno vorrebbe un’app di posta elettronica che occasionalmente invia email al tuo ex e mente sulla tua casella di posta. Ma gradualmente i modelli miglioreranno. Anche mentre si spingeranno ulteriormente nello spazio di esperienze completamente nuove, diventeranno lentamente abbastanza affidabili da essere utilizzati per un lavoro reale.
Piccoli pezzi di questo futuro esistono già. Anni fa Jonas Degrave ha dimostrato che ChatGPT poteva fare una buona simulazione di una riga di comando Linux. Allo stesso modo, websim.ai utilizza un LLM per generare siti web su richiesta mentre li navighi. Oasis, GameNGen e DIAMOND addestrano modelli video condizionati sull’azione su singoli videogiochi, permettendoti di giocare ad esempio a Doom dentro un grande modello. E Genie 2 genera videogiochi giocabili da prompt testuali. L’interfaccia generativa potrebbe ancora sembrare un’idea folle, ma non è così folle.
Ci sono enormi domande aperte su come apparirà tutto questo. Dove sarà inizialmente utile l’interfaccia generativa? Come condivideremo e distribuiremo le esperienze che creiamo collaborando con il modello, se esistono solo come contesto di un grande modello? Vorremmo davvero farlo? Quali nuovi tipi di esperienze saranno possibili? Come funzionerà tutto questo in pratica? I modelli genereranno interfacce come codice o produrranno direttamente pixel grezzi?
Non conosco ancora queste risposte. Dovremo sperimentare e scoprirlo!Che cosa significherebbe trattare l'IA come uno strumento invece che come una persona?
Dall’avvio di ChatGPT, le esplorazioni in due direzioni hanno preso velocità.
La prima direzione riguarda le capacità tecniche. Quanto grande possiamo addestrare un modello? Quanto bene può rispondere alle domande del SAT? Con quanta efficienza possiamo distribuirlo?
La seconda direzione riguarda il design dell’interazione. Come comunichiamo con un modello? Come possiamo usarlo per un lavoro utile? Quale metafora usiamo per ragionare su di esso?
La prima direzione è ampiamente seguita e enormemente finanziata, e per una buona ragione: i progressi nelle capacità tecniche sono alla base di ogni possibile applicazione. Ma la seconda è altrettanto cruciale per il campo e ha enormi incognite. Siamo solo a pochi anni dall’inizio dell’era dei grandi modelli. Quali sono le probabilità che abbiamo già capito i modi migliori per usarli?
Propongo una nuova modalità di interazione, in cui i modelli svolgano il ruolo di applicazioni informatiche (ad esempio app per telefoni): fornendo un’interfaccia grafica, interpretando gli input degli utenti e aggiornando il loro stato. In questa modalità, invece di essere un “agente” che utilizza un computer per conto dell’essere umano, l’IA può fornire un ambiente informatico più ricco e potente che possiamo utilizzare.
Metafore per l’interazione
Al centro di un’interazione c’è una metafora che guida le aspettative di un utente su un sistema. I primi giorni dell’informatica hanno preso metafore come “scrivanie”, “macchine da scrivere”, “fogli di calcolo” e “lettere” e le hanno trasformate in equivalenti digitali, permettendo all’utente di ragionare sul loro comportamento. Puoi lasciare qualcosa sulla tua scrivania e tornare a prenderlo; hai bisogno di un indirizzo per inviare una lettera. Man mano che abbiamo sviluppato una conoscenza culturale di questi dispositivi, la necessità di queste particolari metafore è scomparsa, e con esse i design di interfaccia skeumorfici che le rafforzavano. Come un cestino o una matita, un computer è ora una metafora di se stesso.
La metafora dominante per i grandi modelli oggi è modello-come-persona. Questa è una metafora efficace perché le persone hanno capacità estese che conosciamo intuitivamente. Implica che possiamo avere una conversazione con un modello e porgli domande; che il modello possa collaborare con noi su un documento o un pezzo di codice; che possiamo assegnargli un compito da svolgere da solo e che tornerà quando sarà finito.
Tuttavia, trattare un modello come una persona limita profondamente il nostro modo di pensare all’interazione con esso. Le interazioni umane sono intrinsecamente lente e lineari, limitate dalla larghezza di banda e dalla natura a turni della comunicazione verbale. Come abbiamo tutti sperimentato, comunicare idee complesse in una conversazione è difficile e dispersivo. Quando vogliamo precisione, ci rivolgiamo invece a strumenti, utilizzando manipolazioni dirette e interfacce visive ad alta larghezza di banda per creare diagrammi, scrivere codice e progettare modelli CAD. Poiché concepiamo i modelli come persone, li utilizziamo attraverso conversazioni lente, anche se sono perfettamente in grado di accettare input diretti e rapidi e di produrre risultati visivi. Le metafore che utilizziamo limitano le esperienze che costruiamo, e la metafora modello-come-persona ci impedisce di esplorare il pieno potenziale dei grandi modelli.
Per molti casi d’uso, e specialmente per il lavoro produttivo, credo che il futuro risieda in un’altra metafora: modello-come-computer.
Usare un’IA come un computer
Sotto la metafora modello-come-computer, interagiremo con i grandi modelli seguendo le intuizioni che abbiamo sulle applicazioni informatiche (sia su desktop, tablet o telefono). Nota che ciò non significa che il modello sarà un’app tradizionale più di quanto il desktop di Windows fosse una scrivania letterale. “Applicazione informatica” sarà un modo per un modello di rappresentarsi a noi. Invece di agire come una persona, il modello agirà come un computer.
Agire come un computer significa produrre un’interfaccia grafica. Al posto del flusso lineare di testo in stile telescrivente fornito da ChatGPT, un sistema modello-come-computer genererà qualcosa che somiglia all’interfaccia di un’applicazione moderna: pulsanti, cursori, schede, immagini, grafici e tutto il resto. Questo affronta limitazioni chiave dell’interfaccia di chat standard modello-come-persona:
Scoperta. Un buon strumento suggerisce i suoi usi. Quando l’unica interfaccia è una casella di testo vuota, spetta all’utente capire cosa fare e comprendere i limiti del sistema. La barra laterale Modifica in Lightroom è un ottimo modo per imparare l’editing fotografico perché non si limita a dirti cosa può fare questa applicazione con una foto, ma cosa potresti voler fare. Allo stesso modo, un’interfaccia modello-come-computer per DALL-E potrebbe mostrare nuove possibilità per le tue generazioni di immagini.
Efficienza. La manipolazione diretta è più rapida che scrivere una richiesta a parole. Per continuare l’esempio di Lightroom, sarebbe impensabile modificare una foto dicendo a una persona quali cursori spostare e di quanto. Ci vorrebbe un giorno intero per chiedere un’esposizione leggermente più bassa e una vibranza leggermente più alta, solo per vedere come apparirebbe. Nella metafora modello-come-computer, il modello può creare strumenti che ti permettono di comunicare ciò che vuoi più efficientemente e quindi di fare le cose più rapidamente.
A differenza di un’app tradizionale, questa interfaccia grafica è generata dal modello su richiesta. Questo significa che ogni parte dell’interfaccia che vedi è rilevante per ciò che stai facendo in quel momento, inclusi i contenuti specifici del tuo lavoro. Significa anche che, se desideri un’interfaccia più ampia o diversa, puoi semplicemente richiederla. Potresti chiedere a DALL-E di produrre alcuni preset modificabili per le sue impostazioni ispirati da famosi artisti di schizzi. Quando clicchi sul preset Leonardo da Vinci, imposta i cursori per disegni prospettici altamente dettagliati in inchiostro nero. Se clicchi su Charles Schulz, seleziona fumetti tecnicolor 2D a basso dettaglio.
Una bicicletta della mente proteiforme
La metafora modello-come-persona ha una curiosa tendenza a creare distanza tra l’utente e il modello, rispecchiando il divario di comunicazione tra due persone che può essere ridotto ma mai completamente colmato. A causa della difficoltà e del costo di comunicare a parole, le persone tendono a suddividere i compiti tra loro in blocchi grandi e il più indipendenti possibile. Le interfacce modello-come-persona seguono questo schema: non vale la pena dire a un modello di aggiungere un return statement alla tua funzione quando è più veloce scriverlo da solo. Con il sovraccarico della comunicazione, i sistemi modello-come-persona sono più utili quando possono fare un intero blocco di lavoro da soli. Fanno le cose per te.
Questo contrasta con il modo in cui interagiamo con i computer o altri strumenti. Gli strumenti producono feedback visivi in tempo reale e sono controllati attraverso manipolazioni dirette. Hanno un overhead comunicativo così basso che non è necessario specificare un blocco di lavoro indipendente. Ha più senso mantenere l’umano nel loop e dirigere lo strumento momento per momento. Come stivali delle sette leghe, gli strumenti ti permettono di andare più lontano a ogni passo, ma sei ancora tu a fare il lavoro. Ti permettono di fare le cose più velocemente.
Considera il compito di costruire un sito web usando un grande modello. Con le interfacce di oggi, potresti trattare il modello come un appaltatore o un collaboratore. Cercheresti di scrivere a parole il più possibile su come vuoi che il sito appaia, cosa vuoi che dica e quali funzionalità vuoi che abbia. Il modello genererebbe una prima bozza, tu la eseguirai e poi fornirai un feedback. “Fai il logo un po’ più grande”, diresti, e “centra quella prima immagine principale”, e “deve esserci un pulsante di login nell’intestazione”. Per ottenere esattamente ciò che vuoi, invierai una lista molto lunga di richieste sempre più minuziose.
Un’interazione alternativa modello-come-computer sarebbe diversa: invece di costruire il sito web, il modello genererebbe un’interfaccia per te per costruirlo, dove ogni input dell’utente a quell’interfaccia interroga il grande modello sotto il cofano. Forse quando descrivi le tue necessità creerebbe un’interfaccia con una barra laterale e una finestra di anteprima. All’inizio la barra laterale contiene solo alcuni schizzi di layout che puoi scegliere come punto di partenza. Puoi cliccare su ciascuno di essi, e il modello scrive l’HTML per una pagina web usando quel layout e lo visualizza nella finestra di anteprima. Ora che hai una pagina su cui lavorare, la barra laterale guadagna opzioni aggiuntive che influenzano la pagina globalmente, come accoppiamenti di font e schemi di colore. L’anteprima funge da editor WYSIWYG, permettendoti di afferrare elementi e spostarli, modificarne i contenuti, ecc. A supportare tutto ciò è il modello, che vede queste azioni dell’utente e riscrive la pagina per corrispondere ai cambiamenti effettuati. Poiché il modello può generare un’interfaccia per aiutare te e lui a comunicare più efficientemente, puoi esercitare più controllo sul prodotto finale in meno tempo.
La metafora modello-come-computer ci incoraggia a pensare al modello come a uno strumento con cui interagire in tempo reale piuttosto che a un collaboratore a cui assegnare compiti. Invece di sostituire un tirocinante o un tutor, può essere una sorta di bicicletta proteiforme per la mente, una che è sempre costruita su misura esattamente per te e il terreno che intendi attraversare.
Un nuovo paradigma per l’informatica?
I modelli che possono generare interfacce su richiesta sono una frontiera completamente nuova nell’informatica. Potrebbero essere un paradigma del tutto nuovo, con il modo in cui cortocircuitano il modello di applicazione esistente. Dare agli utenti finali il potere di creare e modificare app al volo cambia fondamentalmente il modo in cui interagiamo con i computer. Al posto di una singola applicazione statica costruita da uno sviluppatore, un modello genererà un’applicazione su misura per l’utente e le sue esigenze immediate. Al posto della logica aziendale implementata nel codice, il modello interpreterà gli input dell’utente e aggiornerà l’interfaccia utente. È persino possibile che questo tipo di interfaccia generativa sostituisca completamente il sistema operativo, generando e gestendo interfacce e finestre al volo secondo necessità.
All’inizio, l’interfaccia generativa sarà un giocattolo, utile solo per l’esplorazione creativa e poche altre applicazioni di nicchia. Dopotutto, nessuno vorrebbe un’app di posta elettronica che occasionalmente invia email al tuo ex e mente sulla tua casella di posta. Ma gradualmente i modelli miglioreranno. Anche mentre si spingeranno ulteriormente nello spazio di esperienze completamente nuove, diventeranno lentamente abbastanza affidabili da essere utilizzati per un lavoro reale.
Piccoli pezzi di questo futuro esistono già. Anni fa Jonas Degrave ha dimostrato che ChatGPT poteva fare una buona simulazione di una riga di comando Linux. Allo stesso modo, websim.ai utilizza un LLM per generare siti web su richiesta mentre li navighi. Oasis, GameNGen e DIAMOND addestrano modelli video condizionati sull’azione su singoli videogiochi, permettendoti di giocare ad esempio a Doom dentro un grande modello. E Genie 2 genera videogiochi giocabili da prompt testuali. L’interfaccia generativa potrebbe ancora sembrare un’idea folle, ma non è così folle.
Ci sono enormi domande aperte su come apparirà tutto questo. Dove sarà inizialmente utile l’interfaccia generativa? Come condivideremo e distribuiremo le esperienze che creiamo collaborando con il modello, se esistono solo come contesto di un grande modello? Vorremmo davvero farlo? Quali nuovi tipi di esperienze saranno possibili? Come funzionerà tutto questo in pratica? I modelli genereranno interfacce come codice o produrranno direttamente pixel grezzi?
Non conosco ancora queste risposte. Dovremo sperimentare e scoprirlo!
Tradotto da:\ https://willwhitney.com/computing-inside-ai.htmlhttps://willwhitney.com/computing-inside-ai.html
-
-
 @ e97aaffa:2ebd765d
2024-12-31 16:47:12
@ e97aaffa:2ebd765d
2024-12-31 16:47:12Último dia do ano, momento para tirar o pó da bola de cristal, para fazer reflexões, previsões e desejos para o próximo ano e seguintes.
Ano após ano, o Bitcoin evoluiu, foi ultrapassando etapas, tornou-se cada vez mais mainstream. Está cada vez mais difícil fazer previsões sobre o Bitcoin, já faltam poucas barreiras a serem ultrapassadas e as que faltam são altamente complexas ou tem um impacto profundo no sistema financeiro ou na sociedade. Estas alterações profundas tem que ser realizadas lentamente, porque uma alteração rápida poderia resultar em consequências terríveis, poderia provocar um retrocesso.
Código do Bitcoin
No final de 2025, possivelmente vamos ter um fork, as discussões sobre os covenants já estão avançadas, vão acelerar ainda mais. Já existe um consenso relativamente alto, a favor dos covenants, só falta decidir que modelo será escolhido. Penso que até ao final do ano será tudo decidido.
Depois dos covenants, o próximo foco será para a criptografia post-quantum, que será o maior desafio que o Bitcoin enfrenta. Criar uma criptografia segura e que não coloque a descentralização em causa.
Espero muito de Ark, possivelmente a inovação do ano, gostaria de ver o Nostr a furar a bolha bitcoinheira e que o Cashu tivesse mais reconhecimento pelos bitcoiners.
Espero que surjam avanços significativos no BitVM2 e BitVMX.
Não sei o que esperar das layer 2 de Bitcoin, foram a maior desilusão de 2024. Surgiram com muita força, mas pouca coisa saiu do papel, foi uma mão cheia de nada. Uma parte dos projetos caiu na tentação da shitcoinagem, na criação de tokens, que tem um único objetivo, enriquecer os devs e os VCs.
Se querem ser levados a sério, têm que ser sérios.
“À mulher de César não basta ser honesta, deve parecer honesta”
Se querem ter o apoio dos bitcoiners, sigam o ethos do Bitcoin.
Neste ponto a atitude do pessoal da Ark é exemplar, em vez de andar a chorar no Twitter para mudar o código do Bitcoin, eles colocaram as mãos na massa e criaram o protocolo. É claro que agora está meio “coxo”, funciona com uma multisig ou com os covenants na Liquid. Mas eles estão a criar um produto, vão demonstrar ao mercado que o produto é bom e útil. Com a adoção, a comunidade vai perceber que o Ark necessita dos covenants para melhorar a interoperabilidade e a soberania.
É este o pensamento certo, que deveria ser seguido pelos restantes e futuros projetos. É seguir aquele pensamento do J.F. Kennedy:
“Não perguntem o que é que o vosso país pode fazer por vocês, perguntem o que é que vocês podem fazer pelo vosso país”
Ou seja, não fiquem à espera que o bitcoin mude, criem primeiro as inovações/tecnologia, ganhem adoção e depois demonstrem que a alteração do código camada base pode melhorar ainda mais o vosso projeto. A necessidade é que vai levar a atualização do código.
Reservas Estratégicas de Bitcoin
Bancos centrais
Com a eleição de Trump, emergiu a ideia de uma Reserva Estratégia de Bitcoin, tornou este conceito mainstream. Foi um pivot, a partir desse momento, foram enumerados os políticos de todo o mundo a falar sobre o assunto.
A Senadora Cynthia Lummis foi mais além e propôs um programa para adicionar 200 mil bitcoins à reserva ao ano, até 1 milhão de Bitcoin. Só que isto está a criar uma enorme expectativa na comunidade, só que pode resultar numa enorme desilusão. Porque no primeiro ano, o Trump em vez de comprar os 200 mil, pode apenas adicionar na reserva, os 198 mil que o Estado já tem em sua posse. Se isto acontecer, possivelmente vai resultar numa forte queda a curto prazo. Na minha opinião os bancos centrais deveriam seguir o exemplo de El Salvador, fazer um DCA diário.
Mais que comprar bitcoin, para mim, o mais importante é a criação da Reserva, é colocar o Bitcoin ao mesmo nível do ouro, o impacto para o resto do mundo será tremendo, a teoria dos jogos na sua plenitude. Muitos outros bancos centrais vão ter que comprar, para não ficarem atrás, além disso, vai transmitir uma mensagem à generalidade da população, que o Bitcoin é “afinal é algo seguro, com valor”.
Mas não foi Trump que iniciou esta teoria dos jogos, mas sim foi a primeira vítima dela. É o próprio Trump que o admite, que os EUA necessitam da reserva para não ficar atrás da China. Além disso, desde que os EUA utilizaram o dólar como uma arma, com sanção contra a Rússia, surgiram boatos de que a Rússia estaria a utilizar o Bitcoin para transações internacionais. Que foram confirmados recentemente, pelo próprio governo russo. Também há poucos dias, ainda antes deste reconhecimento público, Putin elogiou o Bitcoin, ao reconhecer que “Ninguém pode proibir o bitcoin”, defendendo como uma alternativa ao dólar. A narrativa está a mudar.
Já existem alguns países com Bitcoin, mas apenas dois o fizeram conscientemente (El Salvador e Butão), os restantes têm devido a apreensões. Hoje são poucos, mas 2025 será o início de uma corrida pelos bancos centrais. Esta corrida era algo previsível, o que eu não esperava é que acontecesse tão rápido.

Empresas
A criação de reservas estratégicas não vai ficar apenas pelos bancos centrais, também vai acelerar fortemente nas empresas em 2025.

Mas as empresas não vão seguir a estratégia do Saylor, vão comprar bitcoin sem alavancagem, utilizando apenas os tesouros das empresas, como uma proteção contra a inflação. Eu não sou grande admirador do Saylor, prefiro muito mais, uma estratégia conservadora, sem qualquer alavancagem. Penso que as empresas vão seguir a sugestão da BlackRock, que aconselha um alocações de 1% a 3%.
Penso que 2025, ainda não será o ano da entrada das 6 magníficas (excepto Tesla), será sobretudo empresas de pequena e média dimensão. As magníficas ainda tem uma cota muito elevada de shareholders com alguma idade, bastante conservadores, que têm dificuldade em compreender o Bitcoin, foi o que aconteceu recentemente com a Microsoft.
Também ainda não será em 2025, talvez 2026, a inclusão nativamente de wallet Bitcoin nos sistema da Apple Pay e da Google Pay. Seria um passo gigante para a adoção a nível mundial.
ETFs
Os ETFs para mim são uma incógnita, tenho demasiadas dúvidas, como será 2025. Este ano os inflows foram superiores a 500 mil bitcoins, o IBIT foi o lançamento de ETF mais bem sucedido da história. O sucesso dos ETFs, deve-se a 2 situações que nunca mais se vão repetir. O mercado esteve 10 anos à espera pela aprovação dos ETFs, a procura estava reprimida, isso foi bem notório nos primeiros meses, os inflows foram brutais.
Também se beneficiou por ser um mercado novo, não existia orderbook de vendas, não existia um mercado interno, praticamente era só inflows. Agora o mercado já estabilizou, a maioria das transações já são entre clientes dos próprios ETFs. Agora só uma pequena percentagem do volume das transações diárias vai resultar em inflows ou outflows.
Estes dois fenómenos nunca mais se vão repetir, eu não acredito que o número de inflows em BTC supere os número de 2024, em dólares vai superar, mas em btc não acredito que vá superar.
Mas em 2025 vão surgir uma infindável quantidade de novos produtos, derivativos, novos ETFs de cestos com outras criptos ou cestos com ativos tradicionais. O bitcoin será adicionado em produtos financeiros já existentes no mercado, as pessoas vão passar a deter bitcoin, sem o saberem.
Com o fim da operação ChokePoint 2.0, vai surgir uma nova onda de adoção e de produtos financeiros. Possivelmente vamos ver bancos tradicionais a disponibilizar produtos ou serviços de custódia aos seus clientes.
Eu adoraria ver o crescimento da adoção do bitcoin como moeda, só que a regulamentação não vai ajudar nesse processo.
Preço
Eu acredito que o topo deste ciclo será alcançado no primeiro semestre, posteriormente haverá uma correção. Mas desta vez, eu acredito que a correção será muito menor que as anteriores, inferior a 50%, esta é a minha expectativa. Espero estar certo.
Stablecoins de dólar
Agora saindo um pouco do universo do Bitcoin, acho importante destacar as stablecoins.
No último ciclo, eu tenho dividido o tempo, entre continuar a estudar o Bitcoin e estudar o sistema financeiro, as suas dinâmicas e o comportamento humano. Isto tem sido o meu foco de reflexão, imaginar a transformação que o mundo vai sofrer devido ao padrão Bitcoin. É uma ilusão acreditar que a transição de um padrão FIAT para um padrão Bitcoin vai ser rápida, vai existir um processo transitório que pode demorar décadas.
Com a re-entrada de Trump na Casa Branca, prometendo uma política altamente protecionista, vai provocar uma forte valorização do dólar, consequentemente as restantes moedas do mundo vão derreter. Provocando uma inflação generalizada, gerando uma corrida às stablecoins de dólar nos países com moedas mais fracas. Trump vai ter uma política altamente expansionista, vai exportar dólares para todo o mundo, para financiar a sua própria dívida. A desigualdade entre os pobres e ricos irá crescer fortemente, aumentando a possibilidade de conflitos e revoltas.
“Casa onde não há pão, todos ralham e ninguém tem razão”
Será mais lenha, para alimentar a fogueira, vai gravar os conflitos geopolíticos já existentes, ficando as sociedade ainda mais polarizadas.
Eu acredito que 2025, vai haver um forte crescimento na adoção das stablecoins de dólares, esse forte crescimento vai agravar o problema sistémico que são as stablecoins. Vai ser o início do fim das stablecoins, pelo menos, como nós conhecemos hoje em dia.
Problema sistémico
O sistema FIAT não nasceu de um dia para outro, foi algo que foi construído organicamente, ou seja, foi evoluindo ao longo dos anos, sempre que havia um problema/crise, eram criadas novas regras ou novas instituições para minimizar os problemas. Nestes quase 100 anos, desde os acordos de Bretton Woods, a evolução foram tantas, tornaram o sistema financeiro altamente complexo, burocrático e nada eficiente.
Na prática é um castelo de cartas construído sobre outro castelo de cartas e que por sua vez, foi construído sobre outro castelo de cartas.
As stablecoins são um problema sistémico, devido às suas reservas em dólares e o sistema financeiro não está preparado para manter isso seguro. Com o crescimento das reservas ao longo dos anos, foi se agravando o problema.
No início a Tether colocava as reservas em bancos comerciais, mas com o crescimento dos dólares sob gestão, criou um problema nos bancos comerciais, devido à reserva fracionária. Essas enormes reservas da Tether estavam a colocar em risco a própria estabilidade dos bancos.
A Tether acabou por mudar de estratégia, optou por outros ativos, preferencialmente por títulos do tesouro/obrigações dos EUA. Só que a Tether continua a crescer e não dá sinais de abrandamento, pelo contrário.
Até o próprio mundo cripto, menosprezava a gravidade do problema da Tether/stablecoins para o resto do sistema financeiro, porque o marketcap do cripto ainda é muito pequeno. É verdade que ainda é pequeno, mas a Tether não o é, está no top 20 dos maiores detentores de títulos do tesouros dos EUA e está ao nível dos maiores bancos centrais do mundo. Devido ao seu tamanho, está a preocupar os responsáveis/autoridades/reguladores dos EUA, pode colocar em causa a estabilidade do sistema financeiro global, que está assente nessas obrigações.
Os títulos do tesouro dos EUA são o colateral mais utilizado no mundo, tanto por bancos centrais, como por empresas, é a charneira da estabilidade do sistema financeiro. Os títulos do tesouro são um assunto muito sensível. Na recente crise no Japão, do carry trade, o Banco Central do Japão tentou minimizar a desvalorização do iene através da venda de títulos dos EUA. Esta operação, obrigou a uma viagem de emergência, da Secretaria do Tesouro dos EUA, Janet Yellen ao Japão, onde disponibilizou liquidez para parar a venda de títulos por parte do Banco Central do Japão. Essa forte venda estava desestabilizando o mercado.
Os principais detentores de títulos do tesouros são institucionais, bancos centrais, bancos comerciais, fundo de investimento e gestoras, tudo administrado por gestores altamente qualificados, racionais e que conhecem a complexidade do mercado de obrigações.
O mundo cripto é seu oposto, é naife com muita irracionalidade e uma forte pitada de loucura, na sua maioria nem faz a mínima ideia como funciona o sistema financeiro. Essa irracionalidade pode levar a uma “corrida bancária”, como aconteceu com o UST da Luna, que em poucas horas colapsou o projeto. Em termos de escala, a Luna ainda era muito pequena, por isso, o problema ficou circunscrito ao mundo cripto e a empresas ligadas diretamente ao cripto.
Só que a Tether é muito diferente, caso exista algum FUD, que obrigue a Tether a desfazer-se de vários biliões ou dezenas de biliões de dólares em títulos num curto espaço de tempo, poderia provocar consequências terríveis em todo o sistema financeiro. A Tether é grande demais, é já um problema sistémico, que vai agravar-se com o crescimento em 2025.
Não tenham dúvidas, se existir algum problema, o Tesouro dos EUA vai impedir a venda dos títulos que a Tether tem em sua posse, para salvar o sistema financeiro. O problema é, o que vai fazer a Tether, se ficar sem acesso às venda das reservas, como fará o redeem dos dólares?
Como o crescimento do Tether é inevitável, o Tesouro e o FED estão com um grande problema em mãos, o que fazer com o Tether?
Mas o problema é que o atual sistema financeiro é como um curto cobertor: Quanto tapas a cabeça, destapas os pés; Ou quando tapas os pés, destapas a cabeça. Ou seja, para resolver o problema da guarda reservas da Tether, vai criar novos problemas, em outros locais do sistema financeiro e assim sucessivamente.
Conta mestre
Uma possível solução seria dar uma conta mestre à Tether, dando o acesso direto a uma conta no FED, semelhante à que todos os bancos comerciais têm. Com isto, a Tether deixaria de necessitar os títulos do tesouro, depositando o dinheiro diretamente no banco central. Só que isto iria criar dois novos problemas, com o Custodia Bank e com o restante sistema bancário.
O Custodia Bank luta há vários anos contra o FED, nos tribunais pelo direito a ter licença bancária para um banco com full-reserves. O FED recusou sempre esse direito, com a justificativa que esse banco, colocaria em risco toda a estabilidade do sistema bancário existente, ou seja, todos os outros bancos poderiam colapsar. Perante a existência em simultâneo de bancos com reserva fracionária e com full-reserves, as pessoas e empresas iriam optar pelo mais seguro. Isso iria provocar uma corrida bancária, levando ao colapso de todos os bancos com reserva fracionária, porque no Custodia Bank, os fundos dos clientes estão 100% garantidos, para qualquer valor. Deixaria de ser necessário limites de fundos de Garantia de Depósitos.
Eu concordo com o FED nesse ponto, que os bancos com full-reserves são uma ameaça a existência dos restantes bancos. O que eu discordo do FED, é a origem do problema, o problema não está nos bancos full-reserves, mas sim nos que têm reserva fracionária.
O FED ao conceder uma conta mestre ao Tether, abre um precedente, o Custodia Bank irá o aproveitar, reclamando pela igualdade de direitos nos tribunais e desta vez, possivelmente ganhará a sua licença.
Ainda há um segundo problema, com os restantes bancos comerciais. A Tether passaria a ter direitos similares aos bancos comerciais, mas os deveres seriam muito diferentes. Isto levaria os bancos comerciais aos tribunais para exigir igualdade de tratamento, é uma concorrência desleal. Isto é o bom dos tribunais dos EUA, são independentes e funcionam, mesmo contra o estado. Os bancos comerciais têm custos exorbitantes devido às políticas de compliance, como o KYC e AML. Como o governo não vai querer aliviar as regras, logo seria a Tether, a ser obrigada a fazer o compliance dos seus clientes.
A obrigação do KYC para ter stablecoins iriam provocar um terramoto no mundo cripto.
Assim, é pouco provável que seja a solução para a Tether.
FED
Só resta uma hipótese, ser o próprio FED a controlar e a gerir diretamente as stablecoins de dólar, nacionalizado ou absorvendo as existentes. Seria uma espécie de CBDC. Isto iria provocar um novo problema, um problema diplomático, porque as stablecoins estão a colocar em causa a soberania monetária dos outros países. Atualmente as stablecoins estão um pouco protegidas porque vivem num limbo jurídico, mas a partir do momento que estas são controladas pelo governo americano, tudo muda. Os países vão exigir às autoridades americanas medidas que limitem o uso nos seus respectivos países.
Não existe uma solução boa, o sistema FIAT é um castelo de cartas, qualquer carta que se mova, vai provocar um desmoronamento noutro local. As autoridades não poderão adiar mais o problema, terão que o resolver de vez, senão, qualquer dia será tarde demais. Se houver algum problema, vão colocar a responsabilidade no cripto e no Bitcoin. Mas a verdade, a culpa é inteiramente dos políticos, da sua incompetência em resolver os problemas a tempo.
Será algo para acompanhar futuramente, mas só para 2026, talvez…
É curioso, há uns anos pensava-se que o Bitcoin seria a maior ameaça ao sistema ao FIAT, mas afinal, a maior ameaça aos sistema FIAT é o próprio FIAT(stablecoins). A ironia do destino.
Isto é como uma corrida, o Bitcoin é aquele atleta que corre ao seu ritmo, umas vezes mais rápido, outras vezes mais lento, mas nunca pára. O FIAT é o atleta que dá tudo desde da partida, corre sempre em velocidade máxima. Só que a vida e o sistema financeiro não é uma prova de 100 metros, mas sim uma maratona.
Europa
2025 será um ano desafiante para todos europeus, sobretudo devido à entrada em vigor da regulamentação (MiCA). Vão começar a sentir na pele a regulamentação, vão agravar-se os problemas com os compliance, problemas para comprovar a origem de fundos e outras burocracias. Vai ser lindo.
O Travel Route passa a ser obrigatório, os europeus serão obrigados a fazer o KYC nas transações. A Travel Route é uma suposta lei para criar mais transparência, mas prática, é uma lei de controle, de monitorização e para limitar as liberdades individuais dos cidadãos.
O MiCA também está a colocar problemas nas stablecoins de Euro, a Tether para já preferiu ficar de fora da europa. O mais ridículo é que as novas regras obrigam os emissores a colocar 30% das reservas em bancos comerciais. Os burocratas europeus não compreendem que isto coloca em risco a estabilidade e a solvência dos próprios bancos, ficam propensos a corridas bancárias.
O MiCA vai obrigar a todas as exchanges a estar registadas em solo europeu, ficando vulnerável ao temperamento dos burocratas. Ainda não vai ser em 2025, mas a UE vai impor políticas de controle de capitais, é inevitável, as exchanges serão obrigadas a usar em exclusividade stablecoins de euro, as restantes stablecoins serão deslistadas.
Todas estas novas regras do MiCA, são extremamente restritas, não é para garantir mais segurança aos cidadãos europeus, mas sim para garantir mais controle sobre a população. A UE está cada vez mais perto da autocracia, do que da democracia. A minha única esperança no horizonte, é que o sucesso das políticas cripto nos EUA, vai obrigar a UE a recuar e a aligeirar as regras, a teoria dos jogos é implacável. Mas esse recuo, nunca acontecerá em 2025, vai ser um longo período conturbado.
Recessão
Os mercados estão todos em máximos históricos, isto não é sustentável por muito tempo, suspeito que no final de 2025 vai acontecer alguma correção nos mercados. A queda só não será maior, porque os bancos centrais vão imprimir dinheiro, muito dinheiro, como se não houvesse amanhã. Vão voltar a resolver os problemas com a injeção de liquidez na economia, é empurrar os problemas com a barriga, em de os resolver. Outra vez o efeito Cantillon.
Será um ano muito desafiante a nível político, onde o papel dos políticos será fundamental. A crise política na França e na Alemanha, coloca a UE órfã, sem um comandante ao leme do navio. 2025 estará condicionado pelas eleições na Alemanha, sobretudo no resultado do AfD, que podem colocar em causa a propriedade UE e o euro.
Possivelmente, só o fim da guerra poderia minimizar a crise, algo que é muito pouco provável acontecer.
Em Portugal, a economia parece que está mais ou menos equilibrada, mas começam a aparecer alguns sinais preocupantes. Os jogos de sorte e azar estão em máximos históricos, batendo o recorde de 2014, época da grande crise, não é um bom sinal, possivelmente já existe algum desespero no ar.
A Alemanha é o motor da Europa, quanto espirra, Portugal constipa-se. Além do problema da Alemanha, a Espanha também está à beira de uma crise, são os países que mais influenciam a economia portuguesa.
Se existir uma recessão mundial, terá um forte impacto no turismo, que é hoje em dia o principal motor de Portugal.
Brasil
Brasil é algo para acompanhar em 2025, sobretudo a nível macro e a nível político. Existe uma possibilidade de uma profunda crise no Brasil, sobretudo na sua moeda. O banco central já anda a queimar as reservas para minimizar a desvalorização do Real.

Sem mudanças profundas nas políticas fiscais, as reservas vão se esgotar. As políticas de controle de capitais são um cenário plausível, será interesse de acompanhar, como o governo irá proceder perante a existência do Bitcoin e stablecoins. No Brasil existe um forte adoção, será um bom case study, certamente irá repetir-se em outros países num futuro próximo.
Os próximos tempos não serão fáceis para os brasileiros, especialmente para os que não têm Bitcoin.
Blockchain
Em 2025, possivelmente vamos ver os primeiros passos da BlackRock para criar a primeira bolsa de valores, exclusivamente em blockchain. Eu acredito que a BlackRock vai criar uma própria blockchain, toda controlada por si, onde estarão os RWAs, para fazer concorrência às tradicionais bolsas de valores. Será algo interessante de acompanhar.
Estas são as minhas previsões, eu escrevi isto muito em cima do joelho, certamente esqueci-me de algumas coisas, se for importante acrescentarei nos comentários. A maioria das previsões só acontecerá após 2025, mas fica aqui a minha opinião.
Isto é apenas a minha opinião, Don’t Trust, Verify!
-
 @ 502ab02a:a2860397
2024-12-15 01:14:23
@ 502ab02a:a2860397
2024-12-15 01:14:23แสงแดด วิตามิน D, A, K2-MK7 กับสุขภาพกระดูกและหลอดเลือด ว่าด้วยเรื่องของ DAK2 นั้นเคยเขียนไว้นานแล้ว แต่จำได้ว่าเป็นกึ่งๆบทความบ่นๆ แต่ไม่ได้อธิบายเป็นภาษามนุษย์นักครับว่า ตกลงจะหมายถึงอะไรกันแน่ ด้วยวาระโอกาสจะจบปี 2024 เลยคิดว่า นำมาปิดท้ายเนื้อหาหนักๆช่วงปลายๆของ season3 นี้กันดีกว่า
แสงแดด ไม่ใช่สิ่งที่ควรหลีกเลี่ยงเสมอไป แม้ว่าหลายคนจะกังวลเกี่ยวกับความเสี่ยงของโรคมะเร็งผิวหนัง แต่หากได้รับในปริมาณที่เหมาะสม แสงแดดเป็นสิ่งสำคัญที่ช่วยกระตุ้นกลไกของวิตามิน D ในร่างกาย ซึ่งทำงานร่วมกับ วิตามิน A และ วิตามิน K2-MK7 เพื่อดูแลสุขภาพกระดูกและหลอดเลือด รวมถึงช่วยลดความเสี่ยงจากโรคร้ายแรง เช่น โรคกระดูกพรุนและหลอดเลือดอุดตันครับ บทความนี้จะอธิบายถึงกลไกการทำงานของวิตามินเหล่านี้กับร่างกาย เพื่อส่งเสริมการดูดซึมแคลเซียม ลดการสะสมแคลเซียมผิดที่ และสร้างความเข้าใจว่าความเสี่ยงจากการตากแดดนั้น ต่ำกว่าที่หลายคนเข้าใจนักครับ คือ ถ้าไม่ชอบตากก็ไม่ต้องอ้างอะไรอื่นครับ ลองพิจารณาสิ่งที่ผมจะเล่าให้นี้ก่อนว่าซื้อมั๊ย ผมพยายามจะรวบรัดให้สั้นๆนะครับ
หลักการที่ผมมโนออกมาเป็นคำสั้นๆว่า DAK2 ซึ่งผมมักจะเรียกว่า แดก หรือเต็มๆคือ ตากแดดแล้วแดกด้วย คือกิจกรรมตากแดดของเรานั้น จะส่งผลดีได้อีกด้านนึงด้วย ถ้าคุณได้รับวิตามินครบทั้ง DAK2 ครับ เพราะว่า
-วิตามิน D เป็นรากฐานของการดูดซึมแคลเซียม วิตามิน D เป็นจุดเริ่มต้นของกระบวนการที่ช่วยให้ร่างกายดูดซึมแคลเซียมอย่างมีประสิทธิภาพและนำไปใช้อย่างเหมาะสม เมื่อผิวหนังได้รับรังสี UVB จากแสงแดด ร่างกายจะสังเคราะห์ วิตามิน D3 (cholecalciferol) วิตามิน D3 จะถูกเปลี่ยนเป็น calcidiol ในตับ และcalcitriol ที่ไต ซึ่งตรงนี้นะครับ มันจะถูกเปลี่ยนเป็น calcitriol รูปแบบที่ร่างกายนำไปใช้งานได้ ซึ่งเจ้า Calcitriol นี่แหละที่ ช่วยเพิ่มการดูดซึม แคลเซียม และ ฟอสฟอรัส จากอาหารในลำไส้ ทำให้มีแร่ธาตุเพียงพอสำหรับการสร้างและบำรุงกระดูก
-วิตามิน K2-MK7 รับบทผู้ควบคุมแคลเซียมในร่างกาย วิตามิน K2 ตัวนี้สำคัญ หายากและขาดมากที่สุดครับ โดยเฉพาะในรูปแบบ MK7 (menaquinone-7) มีบทบาทสำคัญในการนำแคลเซียมไปสะสมในกระดูกและป้องกันการสะสมในหลอดเลือด โดย K2 นั้นกระตุ้นโปรตีน osteocalcin ซึ่งทำหน้าที่ดึงแคลเซียมเข้าสู่กระดูก นอกจากนี้ K2 ยังช่วยกระตุ้น matrix Gla-protein (MGP) ซึ่งป้องกันการสะสมแคลเซียมไม่ให้ไปเกาะในหลอดเลือดแดงและเนื้อเยื่ออ่อน ดังนั้นการได้รับ K2 เพียงพอจึงช่วยลดความเสี่ยงของโรคหลอดเลือดอุดตัน
คำถามคือทำไมต้อง MK7???? นั่นเพราะ MK7 มีคุณสมบัติที่เหนือกว่า K2 รูปแบบอื่น เนื่องจากมีการทำงานในร่างกายได้นานกว่าวิตามิน K2 ตัวอื่นๆก่อนจะถูกขับทิ้งออกไป จึงช่วยให้เกิดผลลัพธ์ที่ยาวนานและมีประสิทธิภาพสูงที่สุด
-วิตามิน A ผู้สนับสนุนกระดูกและหลอดเลือด วิตามิน A (ในรูป retinoic acid) ทำงานร่วมกับวิตามิน D และ K2 เพื่อช่วยควบคุมการเจริญเติบโตของกระดูกและลดการสะสมแคลเซียมผิดที่ครับ โดยวิตามิน A จะกระตุ้นเซลล์สร้างกระดูก (osteoblasts) และช่วยปรับสมดุลของเซลล์สลายกระดูก (osteoclasts)ควบคุมการทำงานของเซลล์ทำลายกระดูก รวมถึงมีส่วนช่วยในการสร้างเซลล์เยื่อบุหลอดเลือด (endothelial cells) ให้แข็งแรง ช่วยลดการสะสมของคราบแคลเซียมในหลอดเลือด
เมื่อทำงานร่วมกับ วิตามิน K2 (ที่ป้องกันแคลเซียมสะสมในหลอดเลือด) จะช่วยลดความเสี่ยงของโรคหลอดเลือดอุดตัน แล้ววิตามิน A นั้นก็ยังช่วยเสริมสร้างเซลล์เยื่อบุหลอดเลือด ทำให้หลอดเลือดแข็งแรง ลดความเสี่ยงการสะสมของคราบแคลเซียม เมื่อร่างกายได้รับ วิตามิน A, D, และ K2 ร่วมกัน กระบวนการสร้างกระดูกและการสะสมแร่ธาตุในกระดูกจะมีประสิทธิภาพมากขึ้น
ข้อควรระวัง การได้รับวิตามิน A มากเกินไป (เกิน 10,000 IU/วัน) อาจขัดขวางการทำงานของวิตามิน D และเสี่ยงต่อการสูญเสียมวลกระดูก ดังนั้นควรได้รับในปริมาณที่เหมาะสม ไม่ใช่ว่าพอคิดว่าดีแล้วจัดกันแบบไม่ยั้งนะครับ อันนี้อันตรายนะ
สรุปการทำงานร่วมกันของวิตามิน D, A, K2-MK7 วิตามิน D ช่วยเพิ่มการดูดซึมแคลเซียมและฟอสฟอรัสเข้าสู่กระแสเลือด วิตามิน K2-MK7 ช่วยนำแคลเซียมไปสะสมในกระดูก และป้องกันการสะสมในหลอดเลือด วิตามิน A ช่วยปรับสมดุลการเจริญเติบโตและการสลายกระดูก พร้อมเสริมความแข็งแรงของเยื่อบุหลอดเลือด
อาหารที่ช่วยเสริมวิตามิน D, A, K2-MK7 ปกติเราจะท่องๆกันว่า ในเนื้อวัวตับวัว มีครบเกือบทุกอย่าง เว้นวิตามิน K2 เรามาลองดูตัวอย่างอาหารอื่นๆกันบ้างครับ วิตามิน D: ปลาแซลมอน, ปลาซาร์ดีน, น้ำมันตับปลา วิตามิน A: ตับ, ไข่ วิตามิน K2-MK7: นัตโตะ (ถั่วหมักญี่ปุ่น), ชีส, ไข่ไก่จากไก่ที่เลี้ยงปล่อย ส่วนที่มีคนถามว่า กิมจิหล่ะ คือ กิมจิ มีปริมาณวิตามิน K2 จริงครับแต่โดยปกติจะอยู่ในรูปแบบ MK4 ไม่ใช่ MK7 แคลเซียม: นม, กระดูกอ่อนต่างๆ, น้ำซุปกระดูก. ตับ ทีนี้พอเราเห็นภาพรวมแล้ว ก็ต้องบอกว่า จงเลิกมายาที่ต้องมานั่งท่องว่า ตากแดดเวลาไหนดีที่สุด เพราะคุณไม่ต้องไขว่คว้าหาอะไรที่ดีที่สุดเลยครับ คติของการตากแดดคือ ดีทุกเวลา เอาที่ว่าคุณไหวนั่นแหละ ไอ้ที่บอกว่าตากเช้าดีสุดนี่ ตากเช้าเท่านั้น เวลาอื่นห้ามตาก ตากแล้วจะเป็นมะเร็ง โคตรโม้ครับ อย่าเชื่อผมนะ คุณค่อยๆพิจารณา verify ไปทีละจุด ตากแค่เช้าจะได้อะไร ตากสะสมหลายๆเวลาได้อะไร แล้วประโยคที่ส่งต่อกันจังเลยว่า ตากแดดเช้ามันดีสุดจริงไหม
เลิกถามนะครับ ว่าตากเวลาไหนดีที่สุด มัน out แล้ว
#SundaySpecialเราจะไปเป็นหมูแดดเดียว #กูต้องรู้มั๊ย #PirateKeto
-
 @ bf47c19e:c3d2573b
2025-01-08 16:01:15
@ bf47c19e:c3d2573b
2025-01-08 16:01:15Originalni tekst na trzisnoresenje.blogspot.com
06.10.2014 / Autor: Slaviša Tasić
Od kako je bitcoin postao popularan vodi se rasprava među zagovornicima slobodnog tržišta oko njegovo gpravog statusa: da li je to budući novac, efikasan sistem zaobilaženja državne kontrole i garant slobode pojedinca, ili pak fikcija i pomodarstvo iza koje nema ničeg stvarnog?
Teorijski centar debate je pitanje da li je bitcoin "zapravo" novac ili ne. Jedna grupa tvrdi da jeste, pozivajući se na to da je nastao hiljadama dobrovoljnih akata potrošača na tržištu i time uspostavljen kao konvencija. Ko ste vi, teoretičari iz fotelje, da u ime naroda koji prihvata bitcoin definišete šte je "pravi" novac a šta nije? Druga škola tvrdi da je to irelevantno, da je takozvana vrednost bitcoina fiktivna i naduvana, i da će uskoro pući, jer nema nikakve realne pozadine: svaki novac kroz istoriju je uvek morao da ima podlogu nećeg realnog, najčešće plemenitog metala neke vrste, novac nikad ne nastaje nečijom naredbom ili proizvoljnom odlukom.
Vrlo često se u ovom kontekstu pominje Misesova čuena "teorema regresije". Ona kaže da je novac univerzalno razmensko sredstvo koje svoju vrednost crpe iz prethodne upotrebne vrednosti materijala od kojeg je sačinjeno. Recimo, zlato i srebro imaju vrednost kao nakit i luksuzna roba koju ljudi traže iz ne-monetarnih razloga, a njihova vrednost kao novca se onda izvodi iz te prethodne evaluacije njegove ne monetarne upotrebne "vrednosti". Tehnički rečeno, tražnja za zlatom kao monetarnim dobrom izvedena je iz tražnje za zlatom kao nemonetarnim dobrom.
Problem sa bitcoinom je što na prvi pogled on nema nikakvu ne-monetarnu vrednost. Nije zasnovan ni na kakvom fizičkom materijalu ili robi, već predstavlja kompjuterski algoritam. Bitcoin je beskoristan za bilo šta drugo osim kao sredstvo plaćanja. Ako je tome tako, onda postoje samo dve mogućnosti: ili bitcoin ne može da bude novac, ili je teorija o realnoj, nemonetarnoj osnovi novca netačna.
Izgleda da ni jedno ni drugo nije slučaj. Bitcoin jeste sredstvo razmene, iako još uvek nije novac, budući da nije univerzalno prihvaćen (što ne znači da ne može ili da neće biti prihvaćen), ali bitcoin istovremeno JESTE zasnovan na nečem realnom, tj ima vrednost i mimo svoje uloge kao novca. Ta prethodna vrednost bitcoina je njegova uloga kao efikasnog sistema plaćanja. Kao što Jeffrey Tucker naglašava u svom novom tekstu, Bitcoin je 2008 uveden kao sistem plaćanja koji bi omogućio efikasni transfer resursa između pojedinaca u raznim delovima sveta uz potpuno zaobilaženje zvaničnog finansijskog sistema. Programski dokument osnivača Bitcoina nije uopšte spominjao novac nego samo sistem plaćanja koji omogućava pouzdanost, anonimonst i operisanje izvan zvaničnih finansijkih tokova. Tehnički detalji su ovde.
Bitcoin kao sistem je lansiran 9 januara 2009, ali u tom trenutku njegova vrednost je bila nula! Sve do oktobra 2009 potenicjalni klijenti su mogli da dobiju besplatno koliko god hoće bitcoina da eksperimentišu. Ljudi su vršili prve transakcije, proveravali da li je sistem pouzdan, da li radi onako kako je obećano itd. Taj proces eksperminetisanja je trajao oko deset meseci. U tom periodu Bitcoin kao novac nije imao nikakvu tržišnu vrednost. Pre tačno pet godina, 5 oktobra 2009 postavljena je prva tržišna cena. Ona je bila 1390 bitcoina za jedan američki dolar, odnosno jedan bitcoin je vredeo manje od desetog dela penija. U tom trenutku publika je bila još uvek skeptična, što se pokazalo u vrlo niskoj ceni, ali kako je vreme prolazilo cena je rasla jer je evaluacija sistema, sa protokom vremena i daljim potvrđivanjem njegove vrednosti i pouzdanosti, kao i ulaskom mnogo šireg kurga ljudi u igru, postajala sve viša. Međutim, to je sve sa teorijske tačke gledišta irelevantno; ključna stvar je da je početna evaluacija bitcoina, prva tržišna cena objavljena 5 oktobra 2009 bila zapravo izraz evaluacije sistema plaćanja koja je vršena mesecima nezavisno od samog novca (tj njegove potencijalne vrednosti). Bitcoin kao novac "regresira" u mizesovskom smislu na bitcoin kao sistem plaćanja.
Dakle, bitcoin nije fiat novac. On predstavlja potencijalnu valutu koja je izvedena iz tržišne vrednosti specifičnog sistema plaćanja koji klijentima omogućava značajne prednosti koje drugi sistemi ne pružaju. I stoga oza njega stoji "realna vrednost" u istom smislu u kome nešto "realno" stoji iza zlata i srebra kao novca, ili iza modernih fiat valuta izvedenih iz zlata i srebra. Ja ne verujem da bi bitcoin imao velike šanse protiv zlata i srebra na slobodnom tržištu valuta, ali u ovom trenutku ne postoji slobodno tržište valuta, tj onaj ko pokuša da trguje u zlatu završiće u zatvoru. U takvim okolnostima, virtuelnost bitcoina predstavlja komparativnu prednost u odnosu na svaku vrstu robnog novca uključujući i zlato: vlasnik ne poseduje nikakvu fizičku supstancu koju vlada može da mu konfiskuje. Naravno, to bi moglo da se promeni ukoliko vlade ocene da je bitcoin značajna opasnost i krene u tehnološki rat protiv njega. U tom slučaju bi i cena verovatno pala.
-
 @ f9cf4e94:96abc355
2024-12-30 19:02:32
@ f9cf4e94:96abc355
2024-12-30 19:02:32Na era das grandes navegações, piratas ingleses eram autorizados pelo governo para roubar navios.
A única coisa que diferenciava um pirata comum de um corsário é que o último possuía a “Carta do Corso”, que funcionava como um “Alvará para o roubo”, onde o governo Inglês legitimava o roubo de navios por parte dos corsários. É claro, que em troca ele exigia uma parte da espoliação.
Bastante similar com a maneira que a Receita Federal atua, não? Na verdade, o caso é ainda pior, pois o governo fica com toda a riqueza espoliada, e apenas repassa um mísero salário para os corsários modernos, os agentes da receita federal.
Porém eles “justificam” esse roubo ao chamá-lo de imposto, e isso parece acalmar os ânimos de grande parte da população, mas não de nós. Não é por acaso que 'imposto' é o particípio passado do verbo 'impor'. Ou seja, é aquilo que resulta do cumprimento obrigatório -- e não voluntário -- de todos os cidadãos. Se não for 'imposto' ninguém paga. Nem mesmo seus defensores. Isso mostra o quanto as pessoas realmente apreciam os serviços do estado.
Apenas volte um pouco na história: os primeiros pagadores de impostos eram fazendeiros cujos territórios foram invadidos por nômades que pastoreavam seu gado. Esses invasores nômades forçavam os fazendeiros a lhes pagar uma fatia de sua renda em troca de "proteção". O fazendeiro que não concordasse era assassinado.
Os nômades perceberam que era muito mais interessante e confortável apenas cobrar uma taxa de proteção em vez de matar o fazendeiro e assumir suas posses. Cobrando uma taxa, eles obtinham o que necessitavam. Já se matassem os fazendeiros, eles teriam de gerenciar por conta própria toda a produção da fazenda. Daí eles entenderam que, ao não assassinarem todos os fazendeiros que encontrassem pelo caminho, poderiam fazer desta prática um modo de vida.
Assim nasceu o governo.
Não assassinar pessoas foi o primeiro serviço que o governo forneceu. Como temos sorte em ter à nossa disposição esta instituição!
Assim, não deixa de ser curioso que algumas pessoas digam que os impostos são pagos basicamente para impedir que aconteça exatamente aquilo que originou a existência do governo. O governo nasceu da extorsão. Os fazendeiros tinham de pagar um "arrego" para seu governo. Caso contrário, eram assassinados. Quem era a real ameaça? O governo. A máfia faz a mesma coisa.
Mas existe uma forma de se proteger desses corsários modernos. Atualmente, existe uma propriedade privada que NINGUÉM pode tirar de você, ela é sua até mesmo depois da morte. É claro que estamos falando do Bitcoin. Fazendo as configurações certas, é impossível saber que você tem bitcoin. Nem mesmo o governo americano consegue saber.
brasil #bitcoinbrasil #nostrbrasil #grownostr #bitcoin
-
 @ bf47c19e:c3d2573b
2025-01-08 15:51:21
@ bf47c19e:c3d2573b
2025-01-08 15:51:21Originalni tekst na trzisnoresenje.blogspot.com
15.12.2023 / Autor: Slaviša Tasić
Ovako sam pisao u aprilu kad je Bitcoin vredeo $50-100 dolara:
"Koja je budućnost Bitcoina? Većina mu predviđa propast, ali već smo videli da ima neprijatelje sa obeju strana i obe imaju svoje razloge. ... Ali ekonomski gledano, sada kad je Bitcoin došao dovde, meni se čini da može još mnogo rasti."
...
"Zato mislim da ekonomski Bitcoin više nema problem. Sa ovako ograničenom ponudom, a uz održanje sadašnje tražnje ili njen rast, njegove vrednost može i još mnogo da poraste."
U međuvremenu je otišao na preko $1,000. Ali mislite da sam kupio neki Bitcoin? Nisam, teško je baviti se takvim sitnicama kad morate da pišete blog.
Evo šta sada mislim o Bitcoinu.
Najvažnije je razumeti zašto Bitcoin uopšte ima vrednost. To što ima neku vrednost i nije tako iznenađujuće. Valute su istorijski spontano nastajale najčešće od nečega što ima istinsku vrednost, bronze, srebra ili zlata. Ali nije neviđeno ni da novac bez intristične vrednosti bude široko prihvaćen. Poznat je slučaj ostrva kamenog novca, gde je novac bilo kamenje, neka vrsta krečnjaka (vidi sliku ispod). Stanovnici jednog polinezijskog ostrva su koristili ovaj kamen kao novac zbog samo jedne osobine -- zato što nije postojao na ostrvu. Da biste nabavili takvo kamenje morali ste ići na drugo ostrvo, što je bilo skupo i naporno. I to je jedina osobina koja je krečnjak činila novcem, nisu ga koristili ni za šta drugo.
Štaviše, da ne bi kotrljali kamenje pri svakoj kupovini, trgovali su samo pravima na odrđeni kamen, a da se kamen uopšte nije morao pomeriti s mesta. To je suštinski isto kao današnje elektronsko bankarstvo, ali to je druga priča.
Bitcoin je nešto najbliže tome. Kad se uspostavi konvencija, onda novac ne mora imati imanentnu vrednost. Konvencija je, iz garantovanu retkost dovoljan uslov da nešto uspe kao novac. Kao i krečnjak na tom ostrvu, Bitcoin je suštinski bezvredan, ali 1) ne može se naći lako (ima retkost) i 2) postoji konvencija da se prihvata kao novac -- prihvatate ga jer znate da će ga i drugi prihvatiti.
Ali koliko je Bitcoin zaista redak? Sam Bitcoin jeste, jer mu je ponuda programski ograničena. Ali sada vidimo uspon drugih kripto valuta -- Litecoin, Peercoin, i drugi. Bitcoin je redak, ali svako može da napravi nešto jako slično bitcoinu i zvati ga drugačije. To se uveliko i dešava, za sada bez efekta na vrednost Bitcoina.
Za sada Bitcoin ima rastuću snagu konvencije, ili ekonomskim rečnikom, za njega radi efekat mreže. Efekat mreže postoji kada svaki dodatni korisnik povećava vrednost dobra -- vi koristite tastaturu sa početnim slovima QWERTY zato što svi drugi koriste istu tastaturu pa je glupo da počinjete nešto drugo; otvorili ste Facebook nalog ne zato što je Facebook tehnološki najbolje urađen nego zato što svi drugi imaju Facebook pa se tako nalkaše povezujete; nemate Google Plus jer niko drugi nema Google Plus što ga čini beskorisnim, i tako dalje. Uspostavljene mreže je jako teško srušiti, one se perpetuiraju i rastu na principu začaranog kruga.
Kad se jednom uspostave, mreže kao Facebook ili Bitcoin imaju ugrađenu prednost i teško ih je srušiti. Ali znate li ko je još imao efekat mreže u svoju korist? Imao je Windows i imao je MySpace. Windows se još drži ali nije ni blizu moći od pre desetak godina, a MySpace je potpuno propao -- a ljudi su 2008. MySpaceu predviđali večni monopol zbog efekta mreže. Poenta je, efekat mreže je prednost ali nikome ne garantuje monopol, pa čak ni opstanak.
Situacija sa Bitcoinom je ovakva. Sa pojavom drugih valuta retkost je izgubio. Nije bitno što nema Bitcoina, Bitcoin je samo ime. Ima ili može biti neograničeno mnogo kriptovaluta istog tipa i to je ono što je važno. Konvenciju odnosno efekat mreže Bitcoin još uvek ima, štaviše tu je i dalje u usponu. Ali to mu ne garantuje dugoročni uspeh. Kad se ta dva saberu, mislim da Bitcoin nema dobrih dugoročnih izgleda. Da sam onda u aprilu kupio Bitcoine, sada bih prodao.

-
 @ b17fccdf:b7211155
2024-12-29 11:56:44
@ b17fccdf:b7211155
2024-12-29 11:56:44A step-by-step guide to building a Bitcoin & Lightning node, and other stuff on a personal computer.
~ > It builds on a personal computer with x86/amd64 architecture processors.
~> It is based on the popular RaspiBolt v3 guide.
Those are some of the most relevant changes:
- Changed OS from Raspberry Pi OS Lite (64-bits) to Ubuntu Server LTS (Long term support) 64-bit PC (AMD64).
- Changed binaries and signatures of the programs to adapt them to x86/amd64 architecture.
- Deleted unnecessary tools and steps, and added others according to this case of use.
- Some useful authentication logs and monitoring commands were added in the security section.
- Added some interesting parameters in the settings of some services to activate and take advantage of new features.
- Changed I2P, Fulcrum, and ThunderHub guides, to be part of the core guide.
- Added exclusive optimization section of services for slow devices.
~ > Complete release notes MiniBolt v1: https://github.com/twofaktor/minibolt/releases/tag/1.0
~ > The MiniBolt guide is available at: https://minibolt.info
~ > Feel free to contribute to the source code on GitHub by opening issues, pull requests or discussions
Created by ⚡2 FakTor⚡
-
 @ f1989a96:bcaaf2c1
2024-12-12 14:46:22
@ f1989a96:bcaaf2c1
2024-12-12 14:46:22Good morning, readers!
This week, governments and financial institutions around the world advanced policies that amplify the divide between state interests and the daily economic realities of citizens. In Tunisia, President Kais Saied is once again turning to the nation’s central bank to repay its growing debts, a move that risks accelerating inflation, reducing citizen purchasing power, and increasing costs of living.
The Reserve Bank of India (RBI) is urging regional banks to enhance their Know-Your-Customer (KYC) procedures. This includes implementing a “re-KYC” process that requires millions of citizens to resubmit personal information. In addition, banks are gathering supplementary data, which may be used for marketing purposes and potentially other objectives.
In technology news, Eclair, an implementation of the Lightning Network, added support for BOLT 12 offers and liquidity management features such as splicing, liquidity ads, and on-the-fly funding. These make managing liquidity and using the Lightning Network more accessible and private. Meanwhile, Machankura, a custodial Lightning wallet in Africa with offline functionality for feature phones, announced the launch of a mobile application for Android users. This will bring offline Bitcoin transactions to a greater number of people across the African continent.
We end with the latest episode in the HRF x Pubkey Freedom Tech Series, featuring HRF’s Bitcoin Development Lead, Alex Li, in conversation with Bitcoin Core maintainer Gloria Zhao, on the threats facing Bitcoin, the importance of censorship-resistant payments, and her decision to pursue open-source, grant-funded development over corporate opportunities.
Now, let’s dive right in!
Subscribe Here
GLOBAL NEWS
Tunisia | Turns to Central Bank to Repay Debts
In a clear display of financial manipulation, President Kais Saied is once again turning to the central bank to repay Tunisia’s surging debt. He plans to borrow 7 billion dinars ($2.2 billion), equal to about 28% of the central bank’s foreign currency reserves. This move could increase inflation in an already struggling economy where unemployment exceeds 16%, supermarket shelves run empty, and water shortages threaten families' livelihoods. Saied’s unrelenting consolidation of power — including shutting down parliament, arresting opposition leaders, and controlling the judiciary — has stalled any meaningful way for people to push back and protest the disastrous state-led economic policies.
India | RBI Pushes Banks to Re-KYC Customers
The Reserve Bank of India is urging regional banks to carry out re-KYC (Know-Your-Customer) verifications. Stringent KYC requirements and mandatory periodic updates have caused many citizens to lose access to their bank accounts. Despite repeatedly submitting their personal information to be compliant, numerous account holders continue to be locked out due to delays, errors, and overreaching requirements. Moreover, reports indicate that banks have exploited the KYC process to collect additional data from account holders for third-party marketing.
Kenya | Reinstates Tax Measures that Ignited Nationwide Protests
Kenya’s lawmakers have reinstated controversial tax measures that previously triggered nationwide protests, claiming more than 60 lives. The National Treasury, navigating escalating debts and revenue shortfalls, repackaged the taxes into three bills approved by the National Assembly. These include higher import taxes, a “top-up” tax for multinational companies, and levies on foreign firms operating via digital platforms — all part of Kenya’s “austerity” commitments to the International Monetary Fund (IMF). The reinstatement of these taxes risks reigniting public unrest and inflation, while the growing reliance on the IMF calls into question the autonomy and financial resilience of both the government and ordinary citizens.
Vietnam | Social Media Platforms Censor Anti-State Content
Over the past year, Facebook, Google, and TikTok complied with more than 90% of the Communist Party of Vietnam’s (CPV) requests to censor over 15,000 pieces of “anti-state” content. This censorship aligns with Decree 147, a law passed by the CPV to tighten control over social networks and the Internet. Amnesty International condemned these practices as arbitrary censorship. Adding to the repression, Decree 147 requires organizations to share data with authorities without consent in situations deemed critical to “national security.” Such tactics could easily compromise activists and civil society organizations. In these environments, decentralized protocols like Nostr, which allow communication and expression beyond the reach of the state, can play a vital role in upholding citizens' right to free expression.
Cuba | Nationwide Blackout Following Grid Collapse
Last week, Cuba’s largest electricity producer failed, plunging the island nation into darkness and leaving millions without power. This exemplifies the fragility of Cuba’s electrical grid in a country already battered by currency collapse and fuel shortages. Over the past year, frequent blackouts — some lasting up to 18 hours — have made it prohibitively difficult for families to feed themselves and access basic necessities. The nationwide outage forced schools to close and halted work for millions of Cubans already struggling with food, water, and medicine shortages. While officials scramble to restore power to hospitals and water facilities, this illustrates the shortfalls of a state assuming absolute control over a critical industry, like electricity, and failing to deliver. Such failures ultimately strip citizens — already mired in crisis — of basic rights and essential services.
LATEST IN BITCOIN NEWS, DEVELOPMENT, AND COMMUNITY
Eclair | Integrates Support for BOLT 12, Splicing, Liquidity Ads, and On-The-Fly Funding
Eclair, a Lightning Network implementation developed by ACINQ (the team behind Phoenix Wallet and phoenixd), introduced support for BOLT 12 offers and a host of liquidity management features, including splicing, liquidity ads, and on-the-fly funding. BOLT 12 offers increased receiver privacy and censorship resistance when making payments (as well as helping people receive payments via a static QR code or alphanumeric address), while splicing enables the adjustment of payment channels without interrupting ongoing transactions. Further, liquidity ads and on-the-fly funding make it possible for nodes to buy or sell liquidity when making payments on the Lightning Network. These features improve how people send and receive Bitcoin and manage liquidity when using applications and wallets built with Eclair.
Machankura | Launches Android App
Machankura, a custodial Lightning wallet in Africa with offline functionality for feature phones, announced the launch of a mobile application for Android. Leveraging the Unstructured Supplementary Service Data (USSD) protocol for sending text messages, Machankura enables Africans to access the Bitcoin network simply by dialing a designated number on a feature phone (or a smartphone without data), facilitating Bitcoin transactions without the need for an Internet connection. Launching a mobile app will make offline Bitcoin transactions available to more individuals, helping democratize Bitcoin access and unlock the full potential of censorship-resistant money across Africa.
Lark | New Command Line Application for USB Hardware Wallets
Lark is a new command-line application built by Craig Raw, the creator of Sparrow Wallet, designed to interact with USB hardware wallets such as COLDCARD, Ledger, and Trezor. It serves as an alternative to the widely used HWI (Hardware Wallet Interface) software library, providing users with a second option to interact with their USB hardware wallets. By improving the resilience of the Bitcoin hardware wallet ecosystem, Lark helps advance financial autonomy and censorship resistance.
WabiSabi | Major Vulnerability in Coinjoin Protocol
The Rage, an independent news publication exposing the risks of financial surveillance, disclosed a major vulnerability in the WabiSabi coinjoin protocol that allows malicious coordinators to compromise user privacy by deanonymizing transactions. Coinjoin is a privacy-enhancing method that combines multiple Bitcoin transactions into one, making it harder to trace individual payments. The vulnerability, which affects popular tools and wallets like Wasabi Wallet, Ginger Wallet, and BTCPay Server’s coinjoin plugin, enables malicious actors to link inputs and outputs during a transaction and expose user financial activity. Developers have released updates to fix the issue, and users are urged to upgrade immediately. Learn more here.
OpenSats | Renews Grants for Open Source Bitcoin Projects
OpenSats, a public nonprofit funding free and open-source Bitcoin software and projects, renewed grants for nine crucial Bitcoin projects that are expanding financial freedom around the world. Among the recipients is BTCPay Server, an open-source and non-custodial Bitcoin payment processor that enables businesses and nonprofits to easily accept Bitcoin payments. Stratum V2, a protocol that decentralizes Bitcoin mining by enabling nodes to construct their own block templates, also received funding, as well as BitAxe, a project building open-source Bitcoin mining hardware to empower individual miners.
RECOMMENDED CONTENT
HRF x Pubkey — Shadowy Superheroes: How Bitcoin Core Developers Keep Freedom Money Alive
In the latest HRF x Pubkey Freedom Tech Series, HRF’s Bitcoin Development Lead, Alex Li, sits down for a fireside conversation with Bitcoin Core maintainer Gloria Zhao. Together, they discuss the crucial role of censorship-resistant payments in preserving financial freedom and the challenges Bitcoin faces in a world increasingly hostile toward decentralized systems. Zhao shares her journey of choosing open-source, grant-funded development over corporate opportunities, showcasing her commitment to keeping Bitcoin permissionless, secure, and free from centralized control. Listen to the full conversation here.
Downgrading the Bank Secrecy Act is a Powerful Reform for Bitcoin by Yaël
Ossowski
In this article for the Bitcoin Policy Institute, Yaël Ossowski reveals how policies like the Bank Secrecy Act (BSA) impose financial surveillance that stifles innovation, erodes citizens’ privacy, and impacts Bitcoin’s potential as a tool for financial freedom. Highlighting enforcement actions against non-custodial Bitcoin tools and privacy software, the article makes a compelling case for the growing threat current regulations pose to decentralized and privacy-centric technologies. This is a helpful article for anyone seeking to understand the nuanced nature of financial privacy. You can read it here.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.
Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ bf47c19e:c3d2573b
2025-01-08 15:23:03
@ bf47c19e:c3d2573b
2025-01-08 15:23:03Originalni tekst na trzisnoresenje.blogspot.com
03.04.2013 / Autor: Slaviša Tasić
Posle kiparske epizode naglo je došlo do rasta njegove vrednosti. Bitcoin je virtuelna valuta koju ne kontroliše niko. Umesto toga, emitovanje Bitcoina ograničeno je komplikovanim programom. Kao i kod zlata, svako može da iskopa novčiće, ali kopanje je naporno i neizvesno -- jedina je razlika što se posao ne obavlja fizički već kompjuterski. Program je postavljen tako da količina iskopanih Bitcoina raste po stalno opadajućoj stopi, dok se na kraju, za nekih stotinak godina, asimptotski ne približi konačnom nivou.
Za bliže objašnjenje Bitcoina i više o tekućim dešavanima pročešljajte Nedeljni komentar, a meni ceo fenomen postaje vrlo interesantan iz nekoliko razloga.
Prvo, Bitcoin ima mnogo neprijatelja. Neprijatelji su pristalice državnog novca, jer je ovo privatni, decentralizovani novac, čije štampanje ne kontrolišu stručnjaci za monetarnu politiku već se obavlja po automatskom programu. Tokovi novca se teško kontrolišu i neke centralne banke su već "izrazile zabrinutost" zbog rastuće uloge ove valute.
Ali, neprijatelji su i libertarijanski ekonomisti kojima je bliži zlatni standard. U njihovu viziju se ne uklapa to što Bitcoin očigledno nema pravu materijalnu vrednost. Bitcoin je nešto kao privatni fiat novac -- dosada neviđeni fenomen. Po njima tako nešto ne može da postoji i zato mu od samog početka predviđaju propast, ali ih bar za ovih par godina njegovog postojanja stvarnost demantuje.
Dalje, nastanak i dosadašnji uspeh Bitcoina se kosi sa bilo kojom postojećom teorijom i štaviše, za njegov uspeh gotovo da uopšte nema racionalnog objašnjenja. Najveća tajna slobodne razmene, bilo da je to tržište ili drugi oblici slobodne i dobrovoljne saradnje, je to što iz neorganizovane akcije slobodnih pojedinaca može doći do ishoda kojima se ne možemo unapred nadati, koji prevazilaze našu moć imaginacije i koje čak i ex post teško možemo racionalno objasniti. (To je Hayekova najvažnija ideja, a ne njegov libertarijanizam po sebi).
Bitcoin je izgledao a i dalje većini ekonomista i medija izgleda nemoguće, jer iako je njegova ponuda ograničena programom, tražnja za njim je stvar pukog verovanja. Kod zlata i srebra, tražnja postoji jer ti metali imaju i stvarnu vrednost. Kod državnog novca, tražnja postoji jer vam država kaže da morate da koristite taj novac, ali i svojim autoritetom garantuje da će svi ostali prihvatati taj novac. Kod Bitcoina vam niko ne garantuje ništa. Kako je to počelo da se koristi, kako su ljudi, posebno oni u početku, prihvatali da prodaju stvari za Bitcoine, ili da razmenjuju svoje evre i dolare za Bitcoine, meni uopšte nije jasno. Sada je lakše, valuta je donekle uspostavljena, više je prodavaca koji je prihvataju, znate da ima dovoljno onih koji je koriste i zato ima nekih osnova za verovanje da će se to nastaviti. Ali da je tako nešto moglo da počne, da nastane ni iz čega, je gotovo neshvatljivo.
Koja je budućnost Bitcoina? Većina mu predviđa propast, ali već smo videli da ima neprijatelje sa obeju strana i obe imaju svoje razloge. Propast je pre svega moguća usled državne intervencije. Možda će tako nešto jednostavno biti zabranjeno i proganjano. Kad je američka Komisija za hartije od vrednosti mogla da ugasi jako korisnu onlajn kladionicu Intrade (čije smo kvote na razne događaje u svetu ovde često linkovali), navodno iz razloga finansijske sigurnosti, onda je vrlo moguće da i Bitcoin dođe na red.
Ali ekonomski gledano, sada kad je Bitcoin došao dovde, meni se čini da može još mnogo rasti. Tačno je da tražnja za njim počiva na cikličnom verovanju, na verovanju svakog korisnika da će svi drugi nastaviti da primaju Bitcoin, ali: prvo, već nas je jednom iznanadilo da je Bitcoin samo na osnovu tog verovanja došao od nule do današnjih preko 100$ za Bitcoin. Drugo, ne zaboravite da ni ostale valute nisu baš toliko drugačije. Tražnja za državnim novcen se, bez obzira na državne garancije, dobrim delom zasniva na istoj slobodnoj veri da će i drugi prihvatati taj novac. Zlato ima materijalnu vrednost, ali ta vrednost, za industrijsku upotrebu ili nakit, je obično dosta manja od njegove sadašnje cene. Nisu se u poslenjih nekoliko godina industrijska upotreba i atraktivnost zlatnog nakita promenili, već su se promenila očekivanja vrednosti zlata, koja takođe zavise od vaše pretpostavke da će i ostali nastaviti da kupuju i drže zlato.
Zato mislim da ekonomski Bitcoin više nema problem. Sa ovako ograničenom ponudom, a uz održanje sadašnje tražnje ili njen rast, njegove vrednost može i još mnogo da poraste. Mnogo realniji scenario raspada je panika posle najave država da će zabraniti njegovu upotrebu uz neki izgovor kao što su finansijska stabilnost ili sprečavanje pranja novca. Ali čak i ako se to dogodi ostaće fascinantno da je ovakva inicijativa uopšte uspela -- protivno zakonima slabašne ljudske logike.
-
 @ e6817453:b0ac3c39
2024-12-07 15:06:43
@ e6817453:b0ac3c39
2024-12-07 15:06:43I started a long series of articles about how to model different types of knowledge graphs in the relational model, which makes on-device memory models for AI agents possible.
We model-directed graphs
Also, graphs of entities
We even model hypergraphs
Last time, we discussed why classical triple and simple knowledge graphs are insufficient for AI agents and complex memory, especially in the domain of time-aware or multi-model knowledge.
So why do we need metagraphs, and what kind of challenge could they help us to solve?
- complex and nested event and temporal context and temporal relations as edges
- multi-mode and multilingual knowledge
- human-like memory for AI agents that has multiple contexts and relations between knowledge in neuron-like networks
MetaGraphs
A meta graph is a concept that extends the idea of a graph by allowing edges to become graphs. Meta Edges connect a set of nodes, which could also be subgraphs. So, at some level, node and edge are pretty similar in properties but act in different roles in a different context.
Also, in some cases, edges could be referenced as nodes.
This approach enables the representation of more complex relationships and hierarchies than a traditional graph structure allows. Let’s break down each term to understand better metagraphs and how they differ from hypergraphs and graphs.Graph Basics
- A standard graph has a set of nodes (or vertices) and edges (connections between nodes).
- Edges are generally simple and typically represent a binary relationship between two nodes.
- For instance, an edge in a social network graph might indicate a “friend” relationship between two people (nodes).
Hypergraph
- A hypergraph extends the concept of an edge by allowing it to connect any number of nodes, not just two.
- Each connection, called a hyperedge, can link multiple nodes.
- This feature allows hypergraphs to model more complex relationships involving multiple entities simultaneously. For example, a hyperedge in a hypergraph could represent a project team, connecting all team members in a single relation.
- Despite its flexibility, a hypergraph doesn’t capture hierarchical or nested structures; it only generalizes the number of connections in an edge.
Metagraph
- A metagraph allows the edges to be graphs themselves. This means each edge can contain its own nodes and edges, creating nested, hierarchical structures.
- In a meta graph, an edge could represent a relationship defined by a graph. For instance, a meta graph could represent a network of organizations where each organization’s structure (departments and connections) is represented by its own internal graph and treated as an edge in the larger meta graph.
- This recursive structure allows metagraphs to model complex data with multiple layers of abstraction. They can capture multi-node relationships (as in hypergraphs) and detailed, structured information about each relationship.
Named Graphs and Graph of Graphs
As you can notice, the structure of a metagraph is quite complex and could be complex to model in relational and classical RDF setups. It could create a challenge of luck of tools and software solutions for your problem.
If you need to model nested graphs, you could use a much simpler model of Named graphs, which could take you quite far.
The concept of the named graph came from the RDF community, which needed to group some sets of triples. In this way, you form subgraphs inside an existing graph. You could refer to the subgraph as a regular node. This setup simplifies complex graphs, introduces hierarchies, and even adds features and properties of hypergraphs while keeping a directed nature.
It looks complex, but it is not so hard to model it with a slight modification of a directed graph.
So, the node could host graphs inside. Let's reflect this fact with a location for a node. If a node belongs to a main graph, we could set the location to null or introduce a main node . it is up to you
Nodes could have edges to nodes in different subgraphs. This structure allows any kind of nesting graphs. Edges stay location-free
Meta Graphs in Relational Model
Let’s try to make several attempts to model different meta-graphs with some constraints.
Directed Metagraph where edges are not used as nodes and could not contain subgraphs

In this case, the edge always points to two sets of nodes. This introduces an overhead of creating a node set for a single node. In this model, we can model empty node sets that could require application-level constraints to prevent such cases.
Directed Metagraph where edges are not used as nodes and could contain subgraphs

Adding a node set that could model a subgraph located in an edge is easy but could be separate from in-vertex or out-vert.
I also do not see a direct need to include subgraphs to a node, as we could just use a node set interchangeably, but it still could be a case.Directed Metagraph where edges are used as nodes and could contain subgraphs
As you can notice, we operate all the time with node sets. We could simply allow the extension node set to elements set that include node and edge IDs, but in this case, we need to use uuid or any other strategy to differentiate node IDs from edge IDs. In this case, we have a collision of ephemeral edges or ephemeral nodes when we want to change the role and purpose of the node as an edge or vice versa.

A full-scale metagraph model is way too complex for a relational database.
So we need a better model.Now, we have more flexibility but loose structural constraints. We cannot show that the element should have one vertex, one vertex, or both. This type of constraint has been moved to the application level. Also, the crucial question is about query and retrieval needs.
Any meta-graph model should be more focused on domain and needs and should be used in raw form. We did it for a pure theoretical purpose. -
 @ e6817453:b0ac3c39
2024-12-07 15:03:06
@ e6817453:b0ac3c39
2024-12-07 15:03:06Hey folks! Today, let’s dive into the intriguing world of neurosymbolic approaches, retrieval-augmented generation (RAG), and personal knowledge graphs (PKGs). Together, these concepts hold much potential for bringing true reasoning capabilities to large language models (LLMs). So, let’s break down how symbolic logic, knowledge graphs, and modern AI can come together to empower future AI systems to reason like humans.
The Neurosymbolic Approach: What It Means ?
Neurosymbolic AI combines two historically separate streams of artificial intelligence: symbolic reasoning and neural networks. Symbolic AI uses formal logic to process knowledge, similar to how we might solve problems or deduce information. On the other hand, neural networks, like those underlying GPT-4, focus on learning patterns from vast amounts of data — they are probabilistic statistical models that excel in generating human-like language and recognizing patterns but often lack deep, explicit reasoning.
While GPT-4 can produce impressive text, it’s still not very effective at reasoning in a truly logical way. Its foundation, transformers, allows it to excel in pattern recognition, but the models struggle with reasoning because, at their core, they rely on statistical probabilities rather than true symbolic logic. This is where neurosymbolic methods and knowledge graphs come in.
Symbolic Calculations and the Early Vision of AI
If we take a step back to the 1950s, the vision for artificial intelligence was very different. Early AI research was all about symbolic reasoning — where computers could perform logical calculations to derive new knowledge from a given set of rules and facts. Languages like Lisp emerged to support this vision, enabling programs to represent data and code as interchangeable symbols. Lisp was designed to be homoiconic, meaning it treated code as manipulatable data, making it capable of self-modification — a huge leap towards AI systems that could, in theory, understand and modify their own operations.
Lisp: The Earlier AI-Language
Lisp, short for “LISt Processor,” was developed by John McCarthy in 1958, and it became the cornerstone of early AI research. Lisp’s power lay in its flexibility and its use of symbolic expressions, which allowed developers to create programs that could manipulate symbols in ways that were very close to human reasoning. One of the most groundbreaking features of Lisp was its ability to treat code as data, known as homoiconicity, which meant that Lisp programs could introspect and transform themselves dynamically. This ability to adapt and modify its own structure gave Lisp an edge in tasks that required a form of self-awareness, which was key in the early days of AI when researchers were exploring what it meant for machines to “think.”
Lisp was not just a programming language—it represented the vision for artificial intelligence, where machines could evolve their understanding and rewrite their own programming. This idea formed the conceptual basis for many of the self-modifying and adaptive algorithms that are still explored today in AI research. Despite its decline in mainstream programming, Lisp’s influence can still be seen in the concepts used in modern machine learning and symbolic AI approaches.
Prolog: Formal Logic and Deductive Reasoning
In the 1970s, Prolog was developed—a language focused on formal logic and deductive reasoning. Unlike Lisp, based on lambda calculus, Prolog operates on formal logic rules, allowing it to perform deductive reasoning and solve logical puzzles. This made Prolog an ideal candidate for expert systems that needed to follow a sequence of logical steps, such as medical diagnostics or strategic planning.
Prolog, like Lisp, allowed symbols to be represented, understood, and used in calculations, creating another homoiconic language that allows reasoning. Prolog’s strength lies in its rule-based structure, which is well-suited for tasks that require logical inference and backtracking. These features made it a powerful tool for expert systems and AI research in the 1970s and 1980s.
The language is declarative in nature, meaning that you define the problem, and Prolog figures out how to solve it. By using formal logic and setting constraints, Prolog systems can derive conclusions from known facts, making it highly effective in fields requiring explicit logical frameworks, such as legal reasoning, diagnostics, and natural language understanding. These symbolic approaches were later overshadowed during the AI winter — but the ideas never really disappeared. They just evolved.
Solvers and Their Role in Complementing LLMs
One of the most powerful features of Prolog and similar logic-based systems is their use of solvers. Solvers are mechanisms that can take a set of rules and constraints and automatically find solutions that satisfy these conditions. This capability is incredibly useful when combined with LLMs, which excel at generating human-like language but need help with logical consistency and structured reasoning.
For instance, imagine a scenario where an LLM needs to answer a question involving multiple logical steps or a complex query that requires deducing facts from various pieces of information. In this case, a solver can derive valid conclusions based on a given set of logical rules, providing structured answers that the LLM can then articulate in natural language. This allows the LLM to retrieve information and ensure the logical integrity of its responses, leading to much more robust answers.
Solvers are also ideal for handling constraint satisfaction problems — situations where multiple conditions must be met simultaneously. In practical applications, this could include scheduling tasks, generating optimal recommendations, or even diagnosing issues where a set of symptoms must match possible diagnoses. Prolog’s solver capabilities and LLM’s natural language processing power can make these systems highly effective at providing intelligent, rule-compliant responses that traditional LLMs would struggle to produce alone.
By integrating neurosymbolic methods that utilize solvers, we can provide LLMs with a form of deductive reasoning that is missing from pure deep-learning approaches. This combination has the potential to significantly improve the quality of outputs for use-cases that require explicit, structured problem-solving, from legal queries to scientific research and beyond. Solvers give LLMs the backbone they need to not just generate answers but to do so in a way that respects logical rigor and complex constraints.
Graph of Rules for Enhanced Reasoning
Another powerful concept that complements LLMs is using a graph of rules. A graph of rules is essentially a structured collection of logical rules that interconnect in a network-like structure, defining how various entities and their relationships interact. This structured network allows for complex reasoning and information retrieval, as well as the ability to model intricate relationships between different pieces of knowledge.
In a graph of rules, each node represents a rule, and the edges define relationships between those rules — such as dependencies or causal links. This structure can be used to enhance LLM capabilities by providing them with a formal set of rules and relationships to follow, which improves logical consistency and reasoning depth. When an LLM encounters a problem or a question that requires multiple logical steps, it can traverse this graph of rules to generate an answer that is not only linguistically fluent but also logically robust.
For example, in a healthcare application, a graph of rules might include nodes for medical symptoms, possible diagnoses, and recommended treatments. When an LLM receives a query regarding a patient’s symptoms, it can use the graph to traverse from symptoms to potential diagnoses and then to treatment options, ensuring that the response is coherent and medically sound. The graph of rules guides reasoning, enabling LLMs to handle complex, multi-step questions that involve chains of reasoning, rather than merely generating surface-level responses.
Graphs of rules also enable modular reasoning, where different sets of rules can be activated based on the context or the type of question being asked. This modularity is crucial for creating adaptive AI systems that can apply specific sets of logical frameworks to distinct problem domains, thereby greatly enhancing their versatility. The combination of neural fluency with rule-based structure gives LLMs the ability to conduct more advanced reasoning, ultimately making them more reliable and effective in domains where accuracy and logical consistency are critical.
By implementing a graph of rules, LLMs are empowered to perform deductive reasoning alongside their generative capabilities, creating responses that are not only compelling but also logically aligned with the structured knowledge available in the system. This further enhances their potential applications in fields such as law, engineering, finance, and scientific research — domains where logical consistency is as important as linguistic coherence.
Enhancing LLMs with Symbolic Reasoning
Now, with LLMs like GPT-4 being mainstream, there is an emerging need to add real reasoning capabilities to them. This is where neurosymbolic approaches shine. Instead of pitting neural networks against symbolic reasoning, these methods combine the best of both worlds. The neural aspect provides language fluency and recognition of complex patterns, while the symbolic side offers real reasoning power through formal logic and rule-based frameworks.
Personal Knowledge Graphs (PKGs) come into play here as well. Knowledge graphs are data structures that encode entities and their relationships — they’re essentially semantic networks that allow for structured information retrieval. When integrated with neurosymbolic approaches, LLMs can use these graphs to answer questions in a far more contextual and precise way. By retrieving relevant information from a knowledge graph, they can ground their responses in well-defined relationships, thus improving both the relevance and the logical consistency of their answers.
Imagine combining an LLM with a graph of rules that allow it to reason through the relationships encoded in a personal knowledge graph. This could involve using deductive databases to form a sophisticated way to represent and reason with symbolic data — essentially constructing a powerful hybrid system that uses LLM capabilities for language fluency and rule-based logic for structured problem-solving.
My Research on Deductive Databases and Knowledge Graphs
I recently did some research on modeling knowledge graphs using deductive databases, such as DataLog — which can be thought of as a limited, data-oriented version of Prolog. What I’ve found is that it’s possible to use formal logic to model knowledge graphs, ontologies, and complex relationships elegantly as rules in a deductive system. Unlike classical RDF or traditional ontology-based models, which sometimes struggle with complex or evolving relationships, a deductive approach is more flexible and can easily support dynamic rules and reasoning.
Prolog and similar logic-driven frameworks can complement LLMs by handling the parts of reasoning where explicit rule-following is required. LLMs can benefit from these rule-based systems for tasks like entity recognition, logical inferences, and constructing or traversing knowledge graphs. We can even create a graph of rules that governs how relationships are formed or how logical deductions can be performed.
The future is really about creating an AI that is capable of both deep contextual understanding (using the powerful generative capacity of LLMs) and true reasoning (through symbolic systems and knowledge graphs). With the neurosymbolic approach, these AIs could be equipped not just to generate information but to explain their reasoning, form logical conclusions, and even improve their own understanding over time — getting us a step closer to true artificial general intelligence.
Why It Matters for LLM Employment
Using neurosymbolic RAG (retrieval-augmented generation) in conjunction with personal knowledge graphs could revolutionize how LLMs work in real-world applications. Imagine an LLM that understands not just language but also the relationships between different concepts — one that can navigate, reason, and explain complex knowledge domains by actively engaging with a personalized set of facts and rules.
This could lead to practical applications in areas like healthcare, finance, legal reasoning, or even personal productivity — where LLMs can help users solve complex problems logically, providing relevant information and well-justified reasoning paths. The combination of neural fluency with symbolic accuracy and deductive power is precisely the bridge we need to move beyond purely predictive AI to truly intelligent systems.
Let's explore these ideas further if you’re as fascinated by this as I am. Feel free to reach out, follow my YouTube channel, or check out some articles I’ll link below. And if you’re working on anything in this field, I’d love to collaborate!
Until next time, folks. Stay curious, and keep pushing the boundaries of AI!
-
 @ 16d11430:61640947
2024-12-26 11:31:05
@ 16d11430:61640947
2024-12-26 11:31:05For centuries, financial markets have been shackled by an archaic mindset rooted in Newtonian physics: "What goes up must come down." This belief has dominated the thinking of old-school fiat economists, who view the rise and fall of markets as a natural cycle of gravity-bound economics. But Bitcoin, the digital phoenix, was designed to defy this outdated paradigm. It isn't just an asset class or a currency—it's a revolution in financial physics, unshackling value from centralized control and rewriting the rules of money.
The Fiat Fallacy: Gravity Economics
Fiat systems are inherently cyclical, prone to inflation, manipulation, and collapse. Central banks print money endlessly, causing value to "come down" as purchasing power erodes. For fiat thinkers, this is unavoidable—a gravitational force they accept as immutable. Yet this mindset ignores Bitcoin’s game-changing properties: its hard cap of 21 million coins, decentralized consensus, and permissionless architecture.
Bitcoin is fundamentally non-Newtonian. It doesn’t adhere to traditional financial laws because it isn't bound by the same forces of supply and control. Instead, it operates in a new paradigm: deflationary, transparent, and immune to political meddling.
Bitcoin's Escape Velocity
Bitcoin's dominance lies in its ability to achieve escape velocity. Unlike fiat currencies, which are constantly being pulled back by inflationary policies, Bitcoin is propelled by its scarcity, adoption, and network effects. Every halving event tightens the supply, creating an upward pressure that fiat systems can't replicate. And as global trust in traditional systems erodes, Bitcoin's gravitational pull grows stronger.
This phenomenon is evident in the adoption curve. Institutions, governments, and individuals worldwide are recognizing Bitcoin as a superior store of value, an inflation hedge, and the ultimate form of financial sovereignty. The more participants enter the network, the more its value compounds, creating a virtuous cycle of exponential growth.
Humiliating the Old Guard
The fiat establishment—steeped in centuries of centralized control—has long dismissed Bitcoin as a bubble, a fad, or even a Ponzi scheme. Yet, year after year, Bitcoin rises from the ashes of their predictions. Its resilience, transparency, and provable scarcity expose the fragility and corruption of fiat systems.
The ultimate humiliation for fiat thinkers is Bitcoin's ability to thrive in crises. Where traditional systems falter—be it through hyperinflation, bank failures, or geopolitical instability—Bitcoin becomes a lifeboat. It doesn’t just resist gravity; it flips the entire script. Fiat currencies are revealed as infinite-print illusions, while Bitcoin’s immutable ledger stands as the ultimate arbiter of truth and value.
A New Financial Paradigm
Bitcoin’s ascent is not merely about price; it’s about domination. It represents a shift from centralized control to individual empowerment, from opaque systems to transparent protocols, from inflationary theft to deflationary savings. It’s a financial singularity, an escape from the gravitational pull of outdated thinking.
As Bitcoin continues its trajectory, the old world of "what goes up must come down" will look increasingly absurd. In its place, a new principle will reign: what’s decentralized cannot be stopped. Bitcoin isn’t just leaving Earth’s orbit; it’s becoming the financial universe’s North Star.
So buckle up, because Bitcoin isn’t just going up—it’s transcending. And as it does, it will leave the Newtonian thinkers in the dust, staring in disbelief at the rocket that left them behind.
-
 @ e6817453:b0ac3c39
2024-12-07 14:54:46
@ e6817453:b0ac3c39
2024-12-07 14:54:46Introduction: Personal Knowledge Graphs and Linked Data
We will explore the world of personal knowledge graphs and discuss how they can be used to model complex information structures. Personal knowledge graphs aren’t just abstract collections of nodes and edges—they encode meaningful relationships, contextualizing data in ways that enrich our understanding of it. While the core structure might be a directed graph, we layer semantic meaning on top, enabling nuanced connections between data points.
The origin of knowledge graphs is deeply tied to concepts from linked data and the semantic web, ideas that emerged to better link scattered pieces of information across the web. This approach created an infrastructure where data islands could connect — facilitating everything from more insightful AI to improved personal data management.
In this article, we will explore how these ideas have evolved into tools for modeling AI’s semantic memory and look at how knowledge graphs can serve as a flexible foundation for encoding rich data contexts. We’ll specifically discuss three major paradigms: RDF (Resource Description Framework), property graphs, and a third way of modeling entities as graphs of graphs. Let’s get started.
Intro to RDF
The Resource Description Framework (RDF) has been one of the fundamental standards for linked data and knowledge graphs. RDF allows data to be modeled as triples: subject, predicate, and object. Essentially, you can think of it as a structured way to describe relationships: “X has a Y called Z.” For instance, “Berlin has a population of 3.5 million.” This modeling approach is quite flexible because RDF uses unique identifiers — usually URIs — to point to data entities, making linking straightforward and coherent.
RDFS, or RDF Schema, extends RDF to provide a basic vocabulary to structure the data even more. This lets us describe not only individual nodes but also relationships among types of data entities, like defining a class hierarchy or setting properties. For example, you could say that “Berlin” is an instance of a “City” and that cities are types of “Geographical Entities.” This kind of organization helps establish semantic meaning within the graph.
RDF and Advanced Topics
Lists and Sets in RDF
RDF also provides tools to model more complex data structures such as lists and sets, enabling the grouping of nodes. This extension makes it easier to model more natural, human-like knowledge, for example, describing attributes of an entity that may have multiple values. By adding RDF Schema and OWL (Web Ontology Language), you gain even more expressive power — being able to define logical rules or even derive new relationships from existing data.
Graph of Graphs
A significant feature of RDF is the ability to form complex nested structures, often referred to as graphs of graphs. This allows you to create “named graphs,” essentially subgraphs that can be independently referenced. For example, you could create a named graph for a particular dataset describing Berlin and another for a different geographical area. Then, you could connect them, allowing for more modular and reusable knowledge modeling.
Property Graphs
While RDF provides a robust framework, it’s not always the easiest to work with due to its heavy reliance on linking everything explicitly. This is where property graphs come into play. Property graphs are less focused on linking everything through triples and allow more expressive properties directly within nodes and edges.
For example, instead of using triples to represent each detail, a property graph might let you store all properties about an entity (e.g., “Berlin”) directly in a single node. This makes property graphs more intuitive for many developers and engineers because they more closely resemble object-oriented structures: you have entities (nodes) that possess attributes (properties) and are connected to other entities through relationships (edges).
The significant benefit here is a condensed representation, which speeds up traversal and queries in some scenarios. However, this also introduces a trade-off: while property graphs are more straightforward to query and maintain, they lack some complex relationship modeling features RDF offers, particularly when connecting properties to each other.
Graph of Graphs and Subgraphs for Entity Modeling
A third approach — which takes elements from RDF and property graphs — involves modeling entities using subgraphs or nested graphs. In this model, each entity can be represented as a graph. This allows for a detailed and flexible description of attributes without exploding every detail into individual triples or lump them all together into properties.
For instance, consider a person entity with a complex employment history. Instead of representing every employment detail in one node (as in a property graph), or as several linked nodes (as in RDF), you can treat the employment history as a subgraph. This subgraph could then contain nodes for different jobs, each linked with specific properties and connections. This approach keeps the complexity where it belongs and provides better flexibility when new attributes or entities need to be added.
Hypergraphs and Metagraphs
When discussing more advanced forms of graphs, we encounter hypergraphs and metagraphs. These take the idea of relationships to a new level. A hypergraph allows an edge to connect more than two nodes, which is extremely useful when modeling scenarios where relationships aren’t just pairwise. For example, a “Project” could connect multiple “People,” “Resources,” and “Outcomes,” all in a single edge. This way, hypergraphs help in reducing the complexity of modeling high-order relationships.
Metagraphs, on the other hand, enable nodes and edges to themselves be represented as graphs. This is an extremely powerful feature when we consider the needs of artificial intelligence, as it allows for the modeling of relationships between relationships, an essential aspect for any system that needs to capture not just facts, but their interdependencies and contexts.
Balancing Structure and Properties
One of the recurring challenges when modeling knowledge is finding the balance between structure and properties. With RDF, you get high flexibility and standardization, but complexity can quickly escalate as you decompose everything into triples. Property graphs simplify the representation by using attributes but lose out on the depth of connection modeling. Meanwhile, the graph-of-graphs approach and hypergraphs offer advanced modeling capabilities at the cost of increased computational complexity.
So, how do you decide which model to use? It comes down to your use case. RDF and nested graphs are strong contenders if you need deep linkage and are working with highly variable data. For more straightforward, engineer-friendly modeling, property graphs shine. And when dealing with very complex multi-way relationships or meta-level knowledge, hypergraphs and metagraphs provide the necessary tools.
The key takeaway is that only some approaches are perfect. Instead, it’s all about the modeling goals: how do you want to query the graph, what relationships are meaningful, and how much complexity are you willing to manage?
Conclusion
Modeling AI semantic memory using knowledge graphs is a challenging but rewarding process. The different approaches — RDF, property graphs, and advanced graph modeling techniques like nested graphs and hypergraphs — each offer unique strengths and weaknesses. Whether you are building a personal knowledge graph or scaling up to AI that integrates multiple streams of linked data, it’s essential to understand the trade-offs each approach brings.
In the end, the choice of representation comes down to the nature of your data and your specific needs for querying and maintaining semantic relationships. The world of knowledge graphs is vast, with many tools and frameworks to explore. Stay connected and keep experimenting to find the balance that works for your projects.
-
 @ 2f4550b0:95f20096
2025-01-08 15:11:46
@ 2f4550b0:95f20096
2025-01-08 15:11:46Leadership is rarely a smooth ride. For every moment of success, there are setbacks and challenges that test even the most seasoned leaders. The key to sustained success isn’t avoiding difficulties but rather how effectively one can navigate through them. Resilience, the ability to bounce back from adversity, is not just a personal asset; it’s a leadership imperative.
I remember an experience earlier in my career that underscored the power of resilience in leadership. I was leading a team on a high-stakes project. We had invested countless hours, fine-tuned every detail, and had finally reached the presentation phase. Then, disaster struck: the technology we relied on for the demo failed at the last minute. The team’s morale plummeted. I saw the disappointment in their faces, and I could feel the weight of their expectations on me.
At that moment, I had a choice: I could either give in to frustration and let the team spiral, or I could model resilience and lead them through the crisis. I took a deep breath and reminded myself that setbacks are temporary and often lead to growth. We brainstormed solutions on the spot, restructured our approach, and within hours had a makeshift presentation that was just as impactful as our original plan. In the end, we delivered it successfully—and I learned one of the most valuable lessons in leadership: resilience doesn’t mean avoiding failure, but rather how we respond when things don’t go as planned.
This experience taught me that resilient leadership hinges on a few essential principles:
- Maintain a Positive Outlook: As a leader, your mindset directly influences your team. When faced with setbacks, staying calm and optimistic can help anchor the group. A positive perspective allows you to focus on solutions instead of dwelling on problems.
- Adapt and Problem-Solve: Resilience is about adaptability. Things don’t always go according to plan, and being able to quickly pivot and think creatively in the face of adversity is crucial. Resilient leaders encourage their teams to embrace change, adapt, and find alternative solutions.
- Support Your Team: Leaders cannot be resilient alone. Resilience thrives in a supportive environment. Offer your team encouragement, communicate openly, and make sure they know they have your support. By fostering a culture of mutual trust, you’ll enable everyone to recover and grow stronger together.
- Learn from Setbacks: Every challenge presents an opportunity to learn. Resilient leaders view failures as stepping stones to improvement. Reflecting on what went wrong and why, allows leaders and teams to strengthen their strategies moving forward.
In leadership, setbacks are inevitable. What sets great leaders apart is their ability to bounce back. With resilience, you can navigate through challenges with confidence and lead your team toward continued success.
-
 @ 88cc134b:5ae99079
2024-12-26 10:40:52
@ 88cc134b:5ae99079
2024-12-26 10:40:52Hello 1
Hello 2
Hello 3
Hello 4
Hello 5
Hello 6
This is a test by nostr:npub13rxpxjc6vh65aay2eswlxejsv0f7530sf64c4arydetpckhfjpustsjeaf that is testing various interoperability of the markdown rendering and NOSTR specific synatx, just to make sure they play nice.
nostr:npub13rxpxjc6vh65aay2eswlxejsv0f7530sf64c4arydetpckhfjpustsjeaf
npub13rxpxjc6vh65aay2eswlxejsv0f7530sf64c4arydetpckhfjpustsjeaf
nostr:npub13rxpxjc6vh65aay2eswlxejsv0f7530sf64c4arydetpckhfjpustsjeaf
here is a link to somewhere so as to see how it would render and here it is bare-bone https://duckduckgo.com/ just to make sure it is nicely parsed.
here is a mention of another article nostr:naddr1qvzqqqr4gupzpzxvzd935e04fm6g4nqa7dn9qc7nafzlqn4t3t6xgmjkr3dwnyreqqxnzde38qmnsdfk8qmrqwp405km0k and here is a short note: nostr:note1vnqnwzjllzxxufg5e9thz2xspetlplsjq0cn570jswujnmynxjnqmea576
and another one: nostr:note1kyrnyan4hfpn978akv2eqsv8r7rlplaq4j65uxlk3hz5ujk7ehzshwtfmd
and one more foe good mesure: nostr:note1dyrd05nt0tapgye3xn4nssfdasskfr3dm2yqz8e8vdtslpgw3ypsa8e7fh
one like this: note1dyrd05nt0tapgye3xn4nssfdasskfr3dm2yqz8e8vdtslpgw3ypsa8e7fh
here is an event: nostr:nevent1qqsg39vpzl4dz8kwnaerheuavgtqgg6exc4caz8argh6p6jqg549ppqprdmhxue69uhhyetvv9ujuam9wd6x2unwvf6xxtnrdakj7hknh7l
Images

and here is one in the middle of the text
 that continues right after. Just to see how this will render
that continues right after. Just to see how this will renderSome markdown stuff
Emphasis
This is bold text
This is bold text
This is italic text
This is italic text
~~Strikethrough~~
Blockquotes
Blockquotes can also be nested...
...by using additional greater-than signs right next to each other...
...or with spaces between arrows.
Lists
Unordered
- Create a list by starting a line with
+,-, or* - Sub-lists are made by indenting 2 spaces:
- Marker character change forces new list start:
- Ac tristique libero volutpat at
- Facilisis in pretium nisl aliquet
- Nulla volutpat aliquam velit
- Very easy!
Ordered
- Lorem ipsum dolor sit amet
- Consectetur adipiscing elit
-
Integer molestie lorem at massa
-
You can use sequential numbers...
- ...or keep all the numbers as
1.
Start numbering with offset:
- foo
- bar
Code
Inline
codeIndented code
// Some comments line 1 of code line 2 of code line 3 of codeBlock code "fences"
Sample text here...Syntax highlighting
js var foo = function (bar) { return bar++; }; var veryVeryVeryLongVariableNameWithALongValueAsWell = 123456789012345678901234567890; console.log(foo(5));Tables
| Option | Description | | ------ | ----------- | | data | path to data files to supply the data that will be passed into templates. | | engine | engine to be used for processing templates. Handlebars is the default. | | ext | extension to be used for dest files. |
Right aligned columns
| Option | Description | | ------:| -----------:| | data | path to data files to supply the data that will be passed into templates. | | engine | engine to be used for processing templates. Handlebars is the default. | | ext | extension to be used for dest files. |
[Footnotes]
Footnote 1 link[^first].
Footnote 2 link[^second].
Duplicated footnote reference[^second].
[^first]: Footnote can have markup
and multiple paragraphs.[^second]: Footnote text.
- Create a list by starting a line with
-
 @ 20986fb8:cdac21b3
2024-12-24 09:38:54
@ 20986fb8:cdac21b3
2024-12-24 09:38:54In this edition, we are pleased to speak with Luthando nostr:npub10vudmjqhr8kn2kv2pxhezt2h5t5c9zauwq8qr56nhdn64yacsqyqf08djm leader of the Bitcoin Ekasi community, about how they are using Bitcoin to transform payment systems, savings habits, and cross-border remittances in a South African township, while fostering digital currency education and boosting local economic trust.
YakiHonne: Luthando. We really appreciate you coming in. YakiHonne is a decentralized media client built on the Nostr protocol that enables freedom of speech through technology. It empowers creators to create their own voice, assets, and features. It also allows features like smart widgets, verified notes, and focuses on long-form articles. today. we'll be exploring more about your community.Can you tell us a bit about yourself? What do you do, and what’s your role in your community?
Luthando:I’m Luthando, a project community leader at Bitcoin Ekasi. My role includes onboarding township shops to help them adopt Bitcoin as a payment method. I also manage staff records, tracking workdays and paid leave for team members involved in the project. Additionally, I conduct interviews and collaborate with a supervisor to share insights and experiences about Bitcoin. This work is part of my efforts with Bitcoin Ekasi.

YakiHonne: You're really doing a lot of work in the Bitcoin ecosystem,what sparked your interest in Bitcoin? And what motivated you to create a community around it?
Luthando:When I was working as a safety coach at Safeacase, Herman introduced me to Bitcoin. During the COVID-19 pandemic, Safeacase, which relied on donations, faced severe financial challenges. This led to the launch of the Bitcoin Ekasi Project, where I helped township shops adopt Bitcoin as a payment method. With limited funds, I transitioned from receiving a fiat salary to earning in Bitcoin. Bitcoin transformed my mindset, making me realize it is the future of money. This realization inspired me to travel the world and explore new countries.
YakiHonne: Great. I really admire the enthusiasm you have for Bitcoin.Can you share a brief history of how you built your community and attracted members? What methods or advertisements did you use to onboard them?
Luthando:We host monthly Bitcoin movie nights to engage the community, running from February to December starting next year. We promote the events with posters in town, shops, and clinics, inviting residents to join. During the movie nights, participants use Bitcoin we provide to purchase popcorn and drinks, gaining hands-on experience with the technology. Luthando:And our Bitcoin center features a thrift shop and a small Bitcoin ATM. Community members can exchange fiat for Bitcoin using the ATM and use it to purchase clothing from the shop. We also offer Bitcoin courses with 14 students attending classes five days a week. To encourage attendance, students are rewarded with Bitcoin for consistent participation. Similarly, in the “Safer Kids” program, children who maintain a 70% attendance rate or higher also receive Bitcoin rewards. Luthando:To further promote Bitcoin adoption in the community, we painted Bitcoin-themed logos on 34 shops and paid the owners in Bitcoin, which they can use in local shops. This initiative not only spreads awareness but also provides the community with practical opportunities to use Bitcoin.

YakiHonne: Yeah, we are pushing Bitcoin adoption so hard this time. It's really great.What principles guide your community, and how do you ensure trust and reliability in your discussions?
Luthando:I was born in eastern South Africa, and my parents moved here around 1996. The community knows me well and trusts that I wouldn’t introduce anything fraudulent. Since 2010, we’ve been working in this township, especially helping children, building over a decade of trust. I explain to the community that we aim to bring value through Bitcoin, encouraging them to save in Bitcoin instead of fiat. As a result, the community has great trust in our Bitcoin Ekasi team.
YakiHonne: How do you educate your members and keep them updated on Bitcoin developments? You mentioned having five weekly meetups to onboard members, but what other methods do you use to educate them and keep them informed about the Bitcoin ecosystem?
Luthando:We use the Felly app to communicate with community members and keep them updated. At the Ekasi Center, we host quizzes to encourage participation. For example, the first attendees can earn 5,000 sats, motivating them to regularly engage with the Felly app. Although we initially tried a few other methods that didn't really involve them getting Sats, its impact was limited as many people in the township seek quick financial returns and often don’t return after their first visit. To address this, we host movie nights as a more engaging way to promote Bitcoin education. During these events, we screen Bitcoin-related films, allowing community members to learn about Bitcoin in a fun and relaxed setting.

YakiHonne: It's truly captivating and highly insightful.How does your community collaborate with the global Bitcoin ecosystem? Specifically, how does it engage with the broader worldwide Bitcoin community, and which partnership has been of more significant impact on Bitcoin Ekasi?
Luthando:We have established a strong partnership with Bitcoin Beach, which provided crucial support in the creation of the Bitcoin Ekasi project. Currently, we are planning to build a community center in the township, earning the trust and support of both Bitcoin Beach and the local government of Mossel Bay. The community center will serve as a multifunctional space for events like weddings and more. As one of the earliest Bitcoin adoption projects in Africa, Bitcoin Ekasi has inspired other countries to follow suit, viewing us as a model for building sustainable Bitcoin communities.
YakiHonne: How do you collaborate with Bitcoin communities and organizations outside South Africa? What partnerships or interactions do you have with other global Bitcoin communities?
Luthando: We collaborate with other Bitcoin projects through community initiatives. For example, we paint logos on local community shops and pay the owners 7000Sats per week. This approach has helped us build connections with projects outside South Africa. One notable example is our assistance to the Bitcoin Dua project in Africa, helping them establish a Bitcoin circular economy. We also supported the Bitcoin Loxin project in Cape Town, South Africa, in launching their Bitcoin circular economy. Through these collaborations, we have developed strong relationships with other Bitcoin communities.

YakiHonne: We’d like to understand the challenges you faced when starting the community, as well as the challenges the community has encountered?
Luthando: One of the main challenges is convincing members that Bitcoin is not a scam. Many people are skeptical about Bitcoin, fearing they might lose their money. Additionally, saving is not a common habit within the community, even with fiat currency. I often explain the importance of saving in Bitcoin, emphasizing how it can safeguard their financial security. However, changing deeply ingrained mindsets has proven to be quite difficult. Another challenge is the limited level of education in the community. Even those who own smartphones often struggle to use them effectively. This lack of familiarity extends to using Bitcoin wallets, with many people finding it challenging to navigate wallet usage, especially in shops. Lastly, I feel like I’m working around the clock. Even outside of work hours, people come to my house seeking assistance, such as exchanging Bitcoin for fiat. While I’m happy to help, the constant demands can feel overwhelming at times, making it seem as though I’m working every day, including weekends.
YakiHonne: and how you managed to overcome them?
Luthando: Overcoming these challenges is not easy. I can't say that I've fully managed to resolve them, but I do my best to address them. Fortunately, I have a colleague who assists me, although he’s currently out of town. He helps manage some of the workload, especially in dealing with local community members and providing them with the support they need.
YakiHonne: I'm really interested in the issue of people thinking Bitcoin is a scam. Could you elaborate on that? What specific steps have you taken to demonstrate that Bitcoin is reliable and not a scam?
Luthando: Many shop owners initially believe Bitcoin is a scam and refuse to accept it. To address their doubts, I demonstrate Bitcoin's legitimacy through practical examples. First, I help them download a Bitcoin wallet and post about it on X, receiving small tips from Bitcoin enthusiasts worldwide. I then use these tips to showcase Bitcoin's real-world applications. For instance, I use Bitrefill to purchase mobile airtime or fuel vouchers for them, highlighting Bitcoin's utility in daily life. I also mention South African restaurants like Steers that accept Bitcoin and even place food orders using Bitcoin to show its usability. Additionally, I demonstrate withdrawing cash from a crypto ATM using Bitcoin, further proving that it is a reliable financial tool and not a scam.
YakiHonne: You've done a lot of work in South Africa. I can imagine the effort, the pain and the stress.What initiatives has the community taken to promote Bitcoin adoption, and what results have these efforts achieved?
Luthando: At first, I never imagined we would reach this point. Now, many people frequently come to my home to ask how to buy Bitcoin. For example, this week, a man from Nigeria wanted to purchase Bitcoin worth 5,000 units. I explained the process to him and recommended using a hardware wallet for securely storing large amounts of Bitcoin. He used to struggle with sending money back home, but now he has realized the convenience of Bitcoin. In October last year, I helped two stores owned by Nigerians adopt Bitcoin payments. Since then, this practice has spread within the community, and more people, especially shop owners, have developed an interest in Bitcoin. They ask about its low transaction fees and have recognized it as an efficient solution for cross-border remittances. Initially, some shop owners were skeptical about Bitcoin, but they eventually started saving with it. Today, many of them have accumulated significant Bitcoin savings for their families and children, and they often express their gratitude for introducing Bitcoin to the community. Overall, the Bitcoin adoption project has had a profound impact here. We have educated the community about Bitcoin’s long-term savings value, and many people are now satisfied with this initiative and optimistic about the future.

YakiHonne: It’s clear you’ve achieved tangible results from your efforts. Looking ahead, what are your community's goals for the next 6 to 12 months? How do you plan to achieve them?
Luthando: For Bitcoin Ekasi, one of our main goals is to establish a dedicated Bitcoin Ekasi Center. This center would serve as a hub to educate people about Bitcoin on a frequent basis. We have already started working with a local school in the township, recruiting students and introducing teachers to Bitcoin. Our vision is to integrate Bitcoin education into the school’s curriculum, similar to what has been done in El Salvador. By incorporating Bitcoin as part of their regular subjects, students can gain foundational knowledge about Bitcoin and its potential uses. Ultimately, we aim for teachers to become advocates who can confidently teach children about Bitcoin, empowering the next generation with essential financial literacy skills.
YakiHonne: Thank you so much! I think most of my questions have been answered. I’m really glad to see Bitcoin enthusiasts with a clear focus on Bitcoin. As you said, Bitcoin is the future, and I truly appreciate your enthusiasm for it.
Luthando: Bitcoin is truly the future. We want to see this township transformed into something more modern, rather than its current state. I hope to see more parents saving some Bitcoin for their children. In our community, most kids receive a monthly government allowance of $50 starting from the age of one. I often suggest to parents that they set aside half of that allowance to buy Bitcoin for their child. If they save consistently from age one to 18, the value could grow significantly as Bitcoin appreciates. I’m already doing this for my own child so that he will have savings as he grows up.
YakiHonne: Bitcoin is the future. Its value continues to grow steadily over time. Thank you so much for today’s conversation; we are truly honored. Your sharing of such rich experiences has been incredibly insightful for us. I’ve learned that using movie events to engage more people is an excellent idea, and we plan to start trying it out soon. Once again, thank you for your time and for sharing with us!
-
 @ 8d34bd24:414be32b
2025-01-08 14:34:15
@ 8d34bd24:414be32b
2025-01-08 14:34:15I’ve known that there are references to Jesus in the Old Testament. They just don’t use the name Jesus.
Then God said, “Let Us make man in Our image, according to Our likeness; and let them rule over the fish of the sea and over the birds of the sky and over the cattle and over all the earth, and over every creeping thing that creeps on the earth.” (Genesis 1:26) {emphasis mine}
Notice the references to God in the plural. These are clues to the trinitarian (3 persons in one God) nature of God.
There are also examples of theophanies (preincarnate Jesus) in the Old Testament. These theophanies are frequently referred to as “the angel of the Lord” or “the angel of God.”
But the angel of the Lord called to him from heaven and said, “Abraham, Abraham!” And he said, “Here I am.” He said, “Do not stretch out your hand against the lad, and do nothing to him; for now I know that you fear God, since you have not withheld your son, your only son, from Me.” (Genesis 22:11-12) {emphasis mine}
In this case we know that the “angel of the Lord” is not just an angel because he says, “I know that you fear God, since you have not withheld your son, your only son, from Me,” equating Himself, “Me,” with God. In most cases when an angel appears, the people drop face down in worship, but the angel corrects them and tells them not to worship. When the angel is Jesus, He accepts the worship and in many cases sacrifices as well.
The angel of the Lord appeared to him and said to him, “The Lord is with you, O valiant warrior.” Then Gideon said to him, “O my lord, if the Lord is with us, why then has all this happened to us? … So Gideon said to Him, “If now I have found favor in Your sight, then show me a sign that it is You who speak with me. Please do not depart from here, until I come back to You, and bring out my offering and lay it before You.” And He said, “I will remain until you return.”
Then Gideon went in and prepared a young goat and unleavened bread from an ephah of flour; he put the meat in a basket and the broth in a pot, and brought them out to him under the oak and presented them. The angel of God said to him, “Take the meat and the unleavened bread and lay them on this rock, and pour out the broth.” And he did so. Then the angel of the Lord put out the end of the staff that was in his hand and touched the meat and the unleavened bread; and fire sprang up from the rock and consumed the meat and the unleavened bread. Then the angel of the Lord vanished from his sight. When Gideon saw that he was the angel of the Lord, he said, “Alas, O Lord God! For now I have seen the angel of the Lord face to face.” (Judges 6:12=13a, 17-22) {emphasis mine}
As you can see, Gideon offered an offering. An offering to anyone other than God would be idolatry. Gideon offers a “a young goat and unleavened bread from an ephah of flour,” which is a proper sin offering to God. The angel did not eat the offering, but told Gideon to “Take the meat and the unleavened bread and lay them on this rock … Then the angel of the Lord put out the end of the staff that was in his hand and touched the meat and the unleavened bread; and fire sprang up from the rock and consumed the meat and the unleavened bread. Then the angel of the Lord vanished from his sight.” Gideon’s offering was taken as a burnt offering to God and to angel of the Lord, who is Jesus.
With all of this, look at the verse I read last night:
Who has ascended into heaven and descended?\ Who has gathered the wind in His fists?\ Who has wrapped the waters in His garment?\ Who has established all the ends of the earth?\ What is His name or His son’s name?\ Surely you know! (Proverbs 30:4) {emphasis mine}
Surely this is a passage about Jesus.
This verse says, “Who has ascended into heaven and descended?” The New Testament says about Jesus, “No one has ascended into heaven, but He who descended from heaven: the Son of Man.” (John 3:13)
This verse says, “Who has gathered the wind in His fists?” The New Testament says about Jesus,
And there arose a fierce gale of wind, and the waves were breaking over the boat so much that the boat was already filling up. Jesus Himself was in the stern, asleep on the cushion; and they woke Him and said to Him, “Teacher, do You not care that we are perishing?” And He got up and rebuked the wind and said to the sea, “Hush, be still.” And the wind died down and it became perfectly calm. (Mark 4:37-39) {emphasis mine}
This verse says, “Who has wrapped the waters in His garment?” The New Testament says about Jesus,
And in the fourth watch of the night He came to them, walking on the sea. When the disciples saw Him walking on the sea, they were terrified, and said, “It is a ghost!” And they cried out in fear. But immediately Jesus spoke to them, saying, “Take courage, it is I; do not be afraid.”
Peter said to Him, “Lord, if it is You, command me to come to You on the water.” And He said, “Come!” And Peter got out of the boat, and walked on the water and came toward Jesus. (Matthew 14:25-29) {emphasis mine}
This verse says, “Who has established all the ends of the earth?” The New Testament says about Jesus,
In the beginning was the Word, and the Word was with God, and the Word was God. He was in the beginning with God. All things came into being through Him, and apart from Him nothing came into being that has come into being. (John 1:1-3) {emphasis mine}
This verse says, “What is His name or His son’s name?” The New Testament says about Jesus,
After being baptized, Jesus came up immediately from the water; and behold, the heavens were opened, and he saw the Spirit of God descending as a dove and lighting on Him, and behold, a voice out of the heavens said, “This is My beloved Son, in whom I am well-pleased. (Matthew 3:16-17) {emphasis mine}
This verse says, “Surely you know!” As New Testament believers we know the Son of God, Jesus Christ. The Bible was pointing to the Son of God long before He came to earth as a baby.
Who has ascended into heaven and descended?\ Who has gathered the wind in His fists?\ Who has wrapped the waters in His garment?\ Who has established all the ends of the earth?\ What is His name or His son’s name?\ Surely you know! (Proverbs 30:4) {emphasis mine}
It doesn’t matter how many times we have already read the Bible. Every time we read it, we can discover new insight and knowledge of God, His eternal plans, and His commands for our lives. God is good.
Trust Jesus.
-
 @ 2063cd79:57bd1320
2025-01-08 14:26:43
@ 2063cd79:57bd1320
2025-01-08 14:26:43Unit-Bias
Bitcoin hat in der öffentlichen Wahrnehmung und bei Menschen, die sich weniger mit dem Thema befassen, einen sogenannten Unit-Bias, also eine durch Unwissenheit hervorgerufene Voreingenommenheit gegenüber der Einheit "Bitcoin". Das bedeutet, dass viele unerfahrene Anleger//innen und Nutzer//innen der Meinung sind, dass der Besitz eines ganzen bitcoins psychologisch wichtig oder überhaupt nur als solcher möglich ist. Anders ausgedrückt, glauben viele Menschen, sie müssen Bitcoin als Ganzes kaufen, also einen ganzen "physischen" bitcoin, statt kleinerer Bruchstücke. Das lässt den Vermögenswert für die meisten zu teuer aussehen.
 Dies ist für Bitcoin insofern ein Problem, als dass viele Menschen sich durch ihre Voreingenommenheit gar nicht mit Bitcoin beschäftigen ("kann ich mir nicht leisten") oder das Gefühl haben, Bitcoin sei zu teuer und deshalb gibt es kein Wertsteigerungspotential mehr ("der Zug ist abgefahren, ich hätte vor sechs Jahren investieren sollen"). Schlimmer noch, als sich nicht mit Bitcoin zu beschäftigen, ist sich dann stattdessen alternativen, "erschwinglicheren" Kryptowährungen zuzuwenden. Dieser Unit-Bias ist allerdings nichts anderes als ein Marketing-, bzw. ein Bildungsproblem. Denn wie wir wissen kann man Bitcoin in 100 Millionen Untereinheiten brechen und in kleinsten Mengen erwerben, verschicken und verkaufen. Doch haben Außenstehende von Begriffen wie Lightning oder Sats meistens noch nie gehört.
Dies ist für Bitcoin insofern ein Problem, als dass viele Menschen sich durch ihre Voreingenommenheit gar nicht mit Bitcoin beschäftigen ("kann ich mir nicht leisten") oder das Gefühl haben, Bitcoin sei zu teuer und deshalb gibt es kein Wertsteigerungspotential mehr ("der Zug ist abgefahren, ich hätte vor sechs Jahren investieren sollen"). Schlimmer noch, als sich nicht mit Bitcoin zu beschäftigen, ist sich dann stattdessen alternativen, "erschwinglicheren" Kryptowährungen zuzuwenden. Dieser Unit-Bias ist allerdings nichts anderes als ein Marketing-, bzw. ein Bildungsproblem. Denn wie wir wissen kann man Bitcoin in 100 Millionen Untereinheiten brechen und in kleinsten Mengen erwerben, verschicken und verkaufen. Doch haben Außenstehende von Begriffen wie Lightning oder Sats meistens noch nie gehört.Untereinheiten
Doch auch innerhalb der Bitcoin-Szene ist die Unterteilung von Bitcoin in Untereinheiten nicht ganz unumstritten. Denn viele Nutzer//innen sind sich uneinig darüber, was der beste Weg ist, Bitcoins Untereinheiten zu bezeichnen und sogar darzustellen. Dies zeigt sich z.B. darin, dass Apps oft entweder Bitcoin oder Fiat anzeigen, manche Apps aber auch Beträge in Sats darstellen. Dies verlangt aber oft eigene Einstellungen innerhalb der App oder viele Klicks, die die Bedienung und Darstellung eher unhandlich gestalten.
 Es gibt verschiedene Lösungsansätze, die dem/der Nutzer//in die ungewohnte Rechnung mit acht Nachkommastellen erleichtern sollen. Denn viele Anwender//innen denken beim Blick in ihre Wallets oft noch in lokalen Fiat-Werten, also in ganzen Einheiten (z.B. Euro oder Dollar) und Hundertsteln (z.B. Cents).
Es gibt verschiedene Lösungsansätze, die dem/der Nutzer//in die ungewohnte Rechnung mit acht Nachkommastellen erleichtern sollen. Denn viele Anwender//innen denken beim Blick in ihre Wallets oft noch in lokalen Fiat-Werten, also in ganzen Einheiten (z.B. Euro oder Dollar) und Hundertsteln (z.B. Cents). Einige Wallets versuchen diesen Spagat komplett zu umgehen, indem sie vermeiden, Beträge in Fiat darzustellen. Doch auch hier bleibt immer noch das Problem der unhandlichen Darstellung von acht Nachkommastellen, weshalb einige Anbieter einfach zwei Eingabemöglichkeiten bieten und den Betrag in Bitcoin oder Sats automatisch umrechnen.
Einige Wallets versuchen diesen Spagat komplett zu umgehen, indem sie vermeiden, Beträge in Fiat darzustellen. Doch auch hier bleibt immer noch das Problem der unhandlichen Darstellung von acht Nachkommastellen, weshalb einige Anbieter einfach zwei Eingabemöglichkeiten bieten und den Betrag in Bitcoin oder Sats automatisch umrechnen. Doch selbst das Zeichen für Sats ist nicht final geklärt. Es gibt viele verschiedene Vorschläge und Meinungen dazu, welches Symbol genutzt werden sollte. Die meisten Apps, Rechnungen und Sticker schreiben einfach das Wort "Sats" oder "sats" aus. Allerdings ist dies ein Problem, da außerhalb der Bitcoin-Szene niemand weiß, was ein Sat ist. Die meisten Menschen werden mittlerweile von Bitcoin gehört haben, auch wenn sie nicht wissen, wie es funktioniert, was es bedeutet, oder wie man damit umgeht. Doch auch das B Logo mit den Dollarstrichen (₿) werden die meisten Menschen zuordnen können.
Doch selbst das Zeichen für Sats ist nicht final geklärt. Es gibt viele verschiedene Vorschläge und Meinungen dazu, welches Symbol genutzt werden sollte. Die meisten Apps, Rechnungen und Sticker schreiben einfach das Wort "Sats" oder "sats" aus. Allerdings ist dies ein Problem, da außerhalb der Bitcoin-Szene niemand weiß, was ein Sat ist. Die meisten Menschen werden mittlerweile von Bitcoin gehört haben, auch wenn sie nicht wissen, wie es funktioniert, was es bedeutet, oder wie man damit umgeht. Doch auch das B Logo mit den Dollarstrichen (₿) werden die meisten Menschen zuordnen können.Sats hingegen ist ein sehr nischiger Begriff und seine Verwendung noch unbekannter. Oft wird das Blitzsymbol (3 auf der unteren Grafik) verwendet, um Lightning darzustellen und auch das Symbol mit den drei horizontalen Strichen und zwei vertikalen Punkten (4 auf der unteren Grafik), das entfernt an das Dollar-Zeichen erinnern soll ($), erfreut sich immer größerer Beliebtheit. Das Problem dabei ist nur, dass es sich in geschriebener Form nicht, oder nur unzulänglich darstellen lässt: 丰 🤡
 Es war lange logisch und notwendig, ganze Bitcoins zur Aufzählung und Bezahlung zu verwenden, da bei der Einführung von Bitcoin sein Geldwert sehr gering war. Es bestand also absolut keine Notwendigkeit dazu, in kleineren Einheiten als Bitcoin zu denken. Einfaches Beispiel: letzte Woche, am 22. Mai, jährte sich der Bitcoin-Pizza-Day zum 13. Mal, also jener Tag an dem Laszlo Hanyecz für zwei Pizza 10.000 bitcoins bezahlte und damit die erste offline Transaktion mit Bitcoin tätigte. 10.000 bitcoins entsprachen zu diesem Zeitpunkt also knapp $40, oder andersrum $1 entsprach 250 bitcoins Es gab also immer noch keine Notwendigkeit, kleinere Einheiten von Bitcoin zu verwenden. Diese Notwendigkeit ergab sich erst, als der Bitcoin und der Dollar Parität erlangten (1 Bitcoin = $1) und spätestens, als Bitcoin die Marke von $100 durchbrach, wurde rechnen in Bitcoin schwieriger.
Es war lange logisch und notwendig, ganze Bitcoins zur Aufzählung und Bezahlung zu verwenden, da bei der Einführung von Bitcoin sein Geldwert sehr gering war. Es bestand also absolut keine Notwendigkeit dazu, in kleineren Einheiten als Bitcoin zu denken. Einfaches Beispiel: letzte Woche, am 22. Mai, jährte sich der Bitcoin-Pizza-Day zum 13. Mal, also jener Tag an dem Laszlo Hanyecz für zwei Pizza 10.000 bitcoins bezahlte und damit die erste offline Transaktion mit Bitcoin tätigte. 10.000 bitcoins entsprachen zu diesem Zeitpunkt also knapp $40, oder andersrum $1 entsprach 250 bitcoins Es gab also immer noch keine Notwendigkeit, kleinere Einheiten von Bitcoin zu verwenden. Diese Notwendigkeit ergab sich erst, als der Bitcoin und der Dollar Parität erlangten (1 Bitcoin = $1) und spätestens, als Bitcoin die Marke von $100 durchbrach, wurde rechnen in Bitcoin schwieriger.Fortan überlegte man sich, Bitcoin in kleineren Einheiten darzustellen. Die zwei Möglichkeiten sind der Bit und der Sat. Ein einzelner bitcoin kann in 1.000.000 Bits oder bis zu 100.000.000 Sats unterteilt werden, also 100 Sats = 1 Bit = 0,000001 Bitcoin.
 Ein weiterer Grund, weshalb eine Stückelung in bitcoin (der Begriff für einen ganzen physischen bitcoin) schwierig und verwirrend ist, und deshalb viele nach einer alternativen Bezeichnung für Untereinheiten suchten, ist dass darüber hinaus "Bitcoin" zur Beschreibung von zwei Dingen verwendet werden kann: dem monetären Netzwerk (Bitcoin - großes B) und dem monetären Vermögenswert (bitcoin - kleines B).
Ein weiterer Grund, weshalb eine Stückelung in bitcoin (der Begriff für einen ganzen physischen bitcoin) schwierig und verwirrend ist, und deshalb viele nach einer alternativen Bezeichnung für Untereinheiten suchten, ist dass darüber hinaus "Bitcoin" zur Beschreibung von zwei Dingen verwendet werden kann: dem monetären Netzwerk (Bitcoin - großes B) und dem monetären Vermögenswert (bitcoin - kleines B). Bitcoin, der Vermögenswert, ist für diejenigen, die noch nichts damit zu tun hatten, sowohl verwirrend als auch fremd. Denn wie bereits erwähnt, führt der Unit-Bias dazu, dass viele Menschen denken, dass sie es sich nicht leisten können, Bitcoin zu kaufen, oder dass sie den Anschluss verpasst haben. Die Verwendung einer Bepreisung in Bruchteilen würde die Verwirrung über die Benennung des Netzwerks und des Vermögenswerts verringern, aber auch die psychologische Hürde für den Einstieg in Bitcoin senken. Vorausgesetzt, die Benennung ist logisch und intuitiv.
Bitcoin, der Vermögenswert, ist für diejenigen, die noch nichts damit zu tun hatten, sowohl verwirrend als auch fremd. Denn wie bereits erwähnt, führt der Unit-Bias dazu, dass viele Menschen denken, dass sie es sich nicht leisten können, Bitcoin zu kaufen, oder dass sie den Anschluss verpasst haben. Die Verwendung einer Bepreisung in Bruchteilen würde die Verwirrung über die Benennung des Netzwerks und des Vermögenswerts verringern, aber auch die psychologische Hürde für den Einstieg in Bitcoin senken. Vorausgesetzt, die Benennung ist logisch und intuitiv.Bits vs. Sats
Wie schon erwähnt, gibt es zwei gängige Untereinheiten von Bitcoin, 1 Bit (= 0,000001 Bitcoin) und 1 Sat (0,00000001 Bitcoin). Seit jeher gibt es Diskussionen darüber, welche der beiden Einheiten für den täglichen Gebrauch die vernünftigere und intuitivere ist.
Die Verwendung von Bits zur Aufzählung von Bitcoin hat einige Vorteile. Ein Bit stellt ein „Bit“ eines Bitcoins dar, also der grundlegendsten und kleinsten Informationseinheit in der Informatik. Den meisten Menschen fällt es einfacher, das Wort „Bit“ mit Bitcoin zu assoziieren und daher verstehen sie eher, dass ein Bit ein Teil eines Bitcoins ist. Ein „Sat“ bedeutet für den Durchschnittsmenschen, wie oben beschrieben, nichts.
 Adam Back (CEO von Blockstream und Bitcoin-Legende) ist wahrscheinlich der bekannteste Befürworter von Bits > Sats. Er argumentiert von verschiedenen Richtungen, dass z.B. Bits eine rechnerisch einfachere Variante ist, Untereinheiten von Bitcoin darzustellen, als Sats.
Adam Back (CEO von Blockstream und Bitcoin-Legende) ist wahrscheinlich der bekannteste Befürworter von Bits > Sats. Er argumentiert von verschiedenen Richtungen, dass z.B. Bits eine rechnerisch einfachere Variante ist, Untereinheiten von Bitcoin darzustellen, als Sats. Weiter argumentiert er mit der historischen Entwicklung von Bitcoin, dem Protokoll und seiner Referenz-Implementierung. In den Anfangsjahren wurde in der Bitcoin Core Wallet mit Bits gearbeitet. Außerdem argumentiert er, dass die Verbindung zwischen Bitcoin der Haupteinheit und Bits oder Sats als Untereinheit zumindest semantisch gebrochen werden sollte. Da Bitcoin (im Fall eines weiter steigenden Kurses) als Recheneinheit immer unpraktischer wird, sollte man als mentales Modell auf das Rechenpaar Bits und Sats zurückgreifen - analog zur Darstellung von Dollars und Cents oder Euros und Cents. Dabei stellen die zwei Nachkommastellen eines in Bits angegebenen Preises die Sats dar.
Weiter argumentiert er mit der historischen Entwicklung von Bitcoin, dem Protokoll und seiner Referenz-Implementierung. In den Anfangsjahren wurde in der Bitcoin Core Wallet mit Bits gearbeitet. Außerdem argumentiert er, dass die Verbindung zwischen Bitcoin der Haupteinheit und Bits oder Sats als Untereinheit zumindest semantisch gebrochen werden sollte. Da Bitcoin (im Fall eines weiter steigenden Kurses) als Recheneinheit immer unpraktischer wird, sollte man als mentales Modell auf das Rechenpaar Bits und Sats zurückgreifen - analog zur Darstellung von Dollars und Cents oder Euros und Cents. Dabei stellen die zwei Nachkommastellen eines in Bits angegebenen Preises die Sats dar. Ganz einfaches Beispiel: Ein Kasten Bier kostet heute etwas 20€, also 0,00079758 Bitcoin. Einfacher dargestellt: 797,58 Bits, also 797 Bits und 58 Sats. “Ein Bitcoin ist zu teuer, aber Sats sind zu viele, klingen billig und verwirrend.” Es ist schwer in Sats zu denken und selbst wenn der Preis von Bitcoin 1 M US Dollar erreicht, ist ein Bit immer noch eine greifbare und günstige Einheit: 1 Bit = 1 US Dollar.
Ganz einfaches Beispiel: Ein Kasten Bier kostet heute etwas 20€, also 0,00079758 Bitcoin. Einfacher dargestellt: 797,58 Bits, also 797 Bits und 58 Sats. “Ein Bitcoin ist zu teuer, aber Sats sind zu viele, klingen billig und verwirrend.” Es ist schwer in Sats zu denken und selbst wenn der Preis von Bitcoin 1 M US Dollar erreicht, ist ein Bit immer noch eine greifbare und günstige Einheit: 1 Bit = 1 US Dollar. Eines von Adams Hauptargumenten ist, dass Sat als Untereinheit nicht funktioniert, weil es Dust gibt. Das Problem mit Dust besteht darin, dass es nicht möglich ist, Bitcoin unter einem bestimmten Schwellenwert auszugeben. Sein Argument ist, dass der Nutzen einer Einheit abhanden kommt, wenn diese Einheit als kleinste Recheneinheit nicht ausgegeben werden kann. Zugegeben, niemand kann mehr etwas für einen Cent kaufen, aber zumindest ist es technisch nicht unmöglich. Allerdings ist es unmöglich, 1 oder sogar 10 Sats über das Bitcoin-Netzwerk zu senden, ohne Layer-2-Skalierungstechnologien zu verwenden.
Eines von Adams Hauptargumenten ist, dass Sat als Untereinheit nicht funktioniert, weil es Dust gibt. Das Problem mit Dust besteht darin, dass es nicht möglich ist, Bitcoin unter einem bestimmten Schwellenwert auszugeben. Sein Argument ist, dass der Nutzen einer Einheit abhanden kommt, wenn diese Einheit als kleinste Recheneinheit nicht ausgegeben werden kann. Zugegeben, niemand kann mehr etwas für einen Cent kaufen, aber zumindest ist es technisch nicht unmöglich. Allerdings ist es unmöglich, 1 oder sogar 10 Sats über das Bitcoin-Netzwerk zu senden, ohne Layer-2-Skalierungstechnologien zu verwenden.Dust
Unter Bitcoin-Dust versteht man eine sehr kleine Menge Bitcoin, typischerweise in kleinen ein- bis zweistelligen Sats-Beträgen, doch auch kommen immer öfter dreistellige Beträge vor. Sie werden Dust oder „Staub“ genannt, weil diese Beträge so gering sind, dass sie oft als unbedeutend und unpraktisch für die Verwendung bei regulären Transaktionen angesehen werden.
 Es gibt keine offizielle Definition dafür wie groß/klein ein Betrag sein muss, um als Dust zu gelten, da jede Softwareimplementierung (Client, Wallet, etc.) einen anderen Schwellenwert annehmen kann. Die Bitcoin Core Referenzimplementierung definiert Dust als jede Transaktionsausgabe, die niedriger ist als die aktuellen Transaktionsgebühren.
Es gibt keine offizielle Definition dafür wie groß/klein ein Betrag sein muss, um als Dust zu gelten, da jede Softwareimplementierung (Client, Wallet, etc.) einen anderen Schwellenwert annehmen kann. Die Bitcoin Core Referenzimplementierung definiert Dust als jede Transaktionsausgabe, die niedriger ist als die aktuellen Transaktionsgebühren.Dust entsteht meist unbeabsichtigt bei Bitcoin-Transaktionen. Denn wenn Bitcoin von einer Adresse an eine andere gesendet wird, fällt oft eine Transaktionsgebühr an. Um Spam zu verhindern und die Sicherheit des Netzwerks zu gewährleisten, gibt es bei Bitcoin eine Mindestgröße für jede Transaktion. Dieses Limit ist der Mindestbetrag an Bitcoin, der als Ausgabe in eine Transaktion einbezogen werden kann. Der Rest ist Dust.
Oder einfacher ausgedrückt, wenn die Mindestgröße für eine Bitcoin-On-Chain-Transaktion 500 Sats (5 Bits) beträgt und ich noch 800 Sats (8 Bits) in meiner Wallet habe, kann ich nach dem Versenden von 600 Sats (6 Bits) die übrigen 200 Sats (2 Bits) nicht mehr ausgeben. Diese verbleibenden 2 Bits sind Dust.
 Dust stellt aus mehreren Gründen eine Herausforderung für das Bitcoin-Netzwerk und seine Benutzer//innen dar:
Dust stellt aus mehreren Gründen eine Herausforderung für das Bitcoin-Netzwerk und seine Benutzer//innen dar:UTXO-Bloat: Bei jeder Transaktion werden nicht ausgegebene Transaktionsausgaben (UTXOs) erstellt, und Dust erhöht die Anzahl der UTXOs im System. Dies kann zu einer aufgeblähten Blockchain führen und sich negativ auf die Leistung und Skalierbarkeit des Netzwerks auswirken.
Wallet-Management: Im Laufe der Zeit kann sich in Wallets viel Dust ansammeln, und die Verwaltung solch kleiner Beträge kann für Benutzer//innen unpraktisch sein. Bei vielen Wallets ist ein Mindestguthaben erforderlich, und die Dust-Mengen sind möglicherweise zu gering, um diese Anforderung zu erfüllen. Viele Nutzer//innen wechseln häufig zwischen Wallets und transferirien ihre Vermögen vorher auf die neuen Wallets, bei solchen Wechseln bleiben Dust-Beträge zurück und gelten langfristig als verloren.
Ein weiteres Problem besteht darin, dass Dust nicht genau definiert werden kann. Die Transaktionsgebühren hängen wesentlich von zwei Faktoren ab: Den Gebühren in sat/vB, welche von der Auslastung des Mempools abhängen und zu Zeiten von hoher Auslastung dementsprechend hoch sind, und zum anderen vom UTXO-Set des/der jeweiligen Nutzer//in. Denn wie wir wissen, werden Transaktionen aus einer oder mehreren UTXOs zusammengesetzt, je mehr UTXOs dabei benötigt werden, um den gewünschten Betrag zu versenden, desto höher sind die Kosten für diese Transaktion, da sich das Gewicht (in vBytes) erhöht. Diese beiden Faktoren können die Gebühren in Einzelfällen so strukturieren, dass größere Mengen Dust anfallen, als in anderen Fällen.
Datenschutzbedenken: Da jede Transaktion in der Blockchain gespeichert wird, können selbst winzige Mengen Dust mit der Identität oder dem Transaktionsverlauf einer Person verknüpft werden, was die Privatsphäre gefährdet. Diese Funktion wird von Angreifern in sogenannten Dust-Attacks ausgenutzt. Denn böswillige Angreifer haben schnell erkannt, dass Nutzer//innen die winzigen Dust-Beträge, die in ihren Wallet-Adressen angezeigt werden, nicht viel Aufmerksamkeit schenken oder gar bemerken. Angreifer schicken also Kleinstbeträge an eine große Anzahl von Adressen, um dann im nächsten Schritt in einer kombinierten Analyse dieser Adressen und der Beträge, versuchen herauszufinden, welche Adressen zur gleichen Wallet gehören. Dabei ist es das Ziel, diese so identifizierbaren Adressen und Wallets schließlich den jeweiligen Eigentümer//innen zuzuordnen, um diese dann durch ausgefeilte Phishing-Angriffe oder Cyber-Erpressungen zu attackieren.
Um diese Probleme zu lösen, können Nutzer//innen Dust konsolidieren, indem sie mehrere Dust-UTXOs in einer einzigen Transaktion mit einem höheren Wert kombinieren. Einige Wallets und Dienste bieten Funktionen an, mit denen Benutzer//innen ihren Dust effektiv verwalten und konsolidieren können.
Abschließende Gedanken
Der Unit-Bias ist absolut vorhanden. Ich persönlich begegne ihm immer wieder in Gesprächen mit Bitcoin-Interessierten, die sich mit der Materie noch nicht lange auseinandergesetzt haben. Die Verwunderung ist oft sehr groß, dass bitcoins nicht als Ganzes gekauft werden müssen. Die Verwendung einer Untereinheit sowohl in Wallets, als auch bei der Bepreisung kann dabei helfen.
An die Verwendung von Sats als die kleinste Einheit von Bitcoin habe ich mich gewöhnt, allerdings tendiere ich mittlerweile persönlich zum Gebrauch von Bits. Die hervorgebrachten Argumente leuchten mir ein und ich bin überzeugt, dass Bits eine größere Akzeptanz außerhalb des Bitcoin-Inner-Circles hervorrufen können, als Sats. Darüber hinaus ist das Sats-Zeichen wirklich unpraktisch.
Ich befürworte hier einige Ideen, die das Paragrafzeichen zum Symbol für Sats erheben wollen.
 🫳🎤
🫳🎤
In diesem Sinne, 2... 1... Risiko!

-
 @ ccc8ee23:9f3d9783
2024-12-23 22:03:15
@ ccc8ee23:9f3d9783
2024-12-23 22:03:15Chef's notes
Indulge in tender, golden-fried chicken breast, crunchy with every bite. Nestled on a bed of steamed rice, this dish is elevated by a rich, velvety curry sauce, infused with the warmth of fragrant spices and the umami depth of soy.
Paired with vibrant vegetables for a harmonious balance of textures and flavors, this comforting classic promises to delight your soul.
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 30 min
- 🍽️ Servings: 2
Ingredients
- Chicken Fillet 250 grams
- Potato 100 grams
- Egg 1 pc
- Curry block 2 pcs or 20 grams
- breadcrumbs 100 grams / 2 cups
- flour 20 grams
- Cooking oil (for frying)
- chicken or vegetable stock 500ml
- soy sauce 1 tbsp
- Seasoning
- onion 1 pc, finely chopped
- garlic cloves 2 pcs, minced
- carrot 1 pc, chopped
Directions
- Chicken Katsu: Pound the chicken breasts until about 1/2 inch thick. Season with salt and pepper. Coat each piece in flour, then dip in beaten egg, and finally coat with breadcrumbs. Heat oil in a pan and fry the chicken for about 3-4 minutes on each side, until golden brown and fully cooked. Place on paper towels to drain.
- Make Curry Sauce: In a pan, sauté the onion, garlic, add potato and carrot until soft. Gradually add curry block and the stock, stir well. Simmer for 5-10 minutes until thickened. Add seasoning and soy sauce to taste.
- Plating: Slice the cooked chicken katsu and place it over a bed of steamed rice. Pour the curry sauce on the side or over the chicken. Garnish with chopped green chilies.
-
 @ ed84ce10:cccf4c2a
2025-01-08 12:33:06
@ ed84ce10:cccf4c2a
2025-01-08 12:33:06Hackathon Summary
The YQuantum 2024 Hackathon concluded with significant participation and numerous project submissions, establishing itself as a vibrant platform for innovation. Out of 300 registrants, the on-site participants formed teams and worked on developing 28 BUIDLs, engaging in challenges across diverse tracks sponsored by prominent quantum computing organizations, such as QuEra Computing, IBM Quantum, Classiq, DoraHacks, SandboxAQ, and Capgemini/The Hartford/Quantinuum.
Participants developed groundbreaking solutions in quantum computing, driven by prize incentives, including quantum cloud credits, internships, networking opportunities, and potential speaking engagements. The grand prizes recognized exceptional projects, with the first place receiving $2000, presentation opportunities before Yale researchers, and participation in the Yale Innovation Summit.
The hackathon successfully fostered a collaborative environment that encouraged the exploration of cutting-edge technologies and ideas, advancing the quantum computing field. YQuantum 2024 underscored the potential of quantum technologies and promoted knowledge exchange among participants and sponsors.
Hackathon Winners
Held on April 13, 2024, YQuantum's inaugural event attracted 300 participants from 10 countries, featuring six industry-sponsored challenges that culminated in a series of prestigious awards.
Institute Grand Prizes Winners
-
1st Place: Quantum Consortium: Case-Duke-Lehigh-Vandy Nexus This project employs adiabatic methods to prepare antiferromagnetic energy eigenstates, with a focus on quantum many-body scarring and enhancing error correction in computing.
-
2nd Place: Sparse Quantum State Preparation The team developed efficient algorithms using Classiq APIs for sparse quantum state preparation, optimizing execution for scalability and efficiency in managing quantum data.
-
3rd Place: QuBruin This project optimizes algorithms using dynamic quantum circuits and enhances error correction. The team improved user accessibility through Qiskit-based models for better circuit performance under noise conditions.
IBM Quantum Prize Winners
- Modified IBM Challenge
This project delves into foundational linear algebra concepts, emphasizing core principles and mastery.
QuEra Computing Prize Winners
- 3D Quantum Scars on 2D Tweezer Arrays
The team investigates quantum scar states on a 3D lattice projected into 2D, using Julia and QuEra's Bloqade to simulate quantum dynamics.
Classiq Technologies Prize Winners
- YQuantum2024 Classiq Team 34 Wavefunction Wizards
Focusing on optimizing sparse quantum state preparation, this project enhances algorithmic efficiency in quantum data processing.
DoraHacks Prize Winners
- Spooner_QRNG_Classifier
The project employs Python scripts and a gradient booster classifier to predict quantum device origins of random binary data, surpassing baseline prediction accuracy.
Capgemini // Quantinuum // The Hartford Prize Winners
-
Skittlez
This partnership addresses quantum computing challenges through interdisciplinary expertise, designing innovative quantum solutions. -
Honorable Mention: BB24 - Yale Quantum Monte Carlo The project enhances Quantum Monte Carlo techniques via novel sampling and encoding schemes, improving parallel processing and computational efficiency.
SandboxAQ Prize Winners
-
QuantumQuails
This project improves solar cell efficiency through quantum chemistry, utilizing VQE to model solar energy absorption for enhanced conversion effectiveness. -
Honorable Mention: mRNA Sequence Design via Quantum Approximate Optimization Algorithm This project optimizes mRNA sequence design using QAOA, enhancing protein expression and structural stability through codon and nucleotide parameters.
Explore all projects at DoraHacks.
About the Organizer:
YQuantum
YQuantum is a prominent entity within the technology and blockchain sectors, recognized for its innovative approach and strategic initiatives. Specializing in utilizing quantum computing capabilities, YQuantum is committed to advancing the technological frontier. Though specific projects are not highlighted, YQuantum's role in shaping industry standards positions it as a leader in the field. Through dedication to cutting-edge research and development, YQuantum continues to drive progress in quantum technologies, aligning with its mission to propel scientific and technological advancements globally.
-
-
 @ a367f9eb:0633efea
2024-12-22 21:35:22
@ a367f9eb:0633efea
2024-12-22 21:35:22I’ll admit that I was wrong about Bitcoin. Perhaps in 2013. Definitely 2017. Probably in 2018-2019. And maybe even today.
Being wrong about Bitcoin is part of finally understanding it. It will test you, make you question everything, and in the words of BTC educator and privacy advocate Matt Odell, “Bitcoin will humble you”.
I’ve had my own stumbles on the way.
In a very public fashion in 2017, after years of using Bitcoin, trying to start a company with it, using it as my primary exchange vehicle between currencies, and generally being annoying about it at parties, I let out the bear.
In an article published in my own literary magazine Devolution Review in September 2017, I had a breaking point. The article was titled “Going Bearish on Bitcoin: Cryptocurrencies are the tulip mania of the 21st century”.
It was later republished in Huffington Post and across dozens of financial and crypto blogs at the time with another, more appropriate title: “Bitcoin Has Become About The Payday, Not Its Potential”.
As I laid out, my newfound bearishness had little to do with the technology itself or the promise of Bitcoin, and more to do with the cynical industry forming around it:
In the beginning, Bitcoin was something of a revolution to me. The digital currency represented everything from my rebellious youth.
It was a decentralized, denationalized, and digital currency operating outside the traditional banking and governmental system. It used tools of cryptography and connected buyers and sellers across national borders at minimal transaction costs.
…
The 21st-century version (of Tulip mania) has welcomed a plethora of slick consultants, hazy schemes dressed up as investor possibilities, and too much wishy-washy language for anything to really make sense to anyone who wants to use a digital currency to make purchases.
While I called out Bitcoin by name at the time, on reflection, I was really talking about the ICO craze, the wishy-washy consultants, and the altcoin ponzis.
What I was articulating — without knowing it — was the frame of NgU, or “numbers go up”. Rather than advocating for Bitcoin because of its uncensorability, proof-of-work, or immutability, the common mentality among newbies and the dollar-obsessed was that Bitcoin mattered because its price was a rocket ship.
And because Bitcoin was gaining in price, affinity tokens and projects that were imperfect forks of Bitcoin took off as well.
The price alone — rather than its qualities — were the reasons why you’d hear Uber drivers, finance bros, or your gym buddy mention Bitcoin. As someone who came to Bitcoin for philosophical reasons, that just sat wrong with me.
Maybe I had too many projects thrown in my face, or maybe I was too frustrated with the UX of Bitcoin apps and sites at the time. No matter what, I’ve since learned something.
I was at least somewhat wrong.
My own journey began in early 2011. One of my favorite radio programs, Free Talk Live, began interviewing guests and having discussions on the potential of Bitcoin. They tied it directly to a libertarian vision of the world: free markets, free people, and free banking. That was me, and I was in. Bitcoin was at about $5 back then (NgU).
I followed every article I could, talked about it with guests on my college radio show, and became a devoted redditor on r/Bitcoin. At that time, at least to my knowledge, there was no possible way to buy Bitcoin where I was living. Very weak.
I was probably wrong. And very wrong for not trying to acquire by mining or otherwise.
The next year, after moving to Florida, Bitcoin was a heavy topic with a friend of mine who shared the same vision (and still does, according to the Celsius bankruptcy documents). We talked about it with passionate leftists at Occupy Tampa in 2012, all the while trying to explain the ills of Keynesian central banking, and figuring out how to use Coinbase.
I began writing more about Bitcoin in 2013, writing a guide on “How to Avoid Bank Fees Using Bitcoin,” discussing its potential legalization in Germany, and interviewing Jeremy Hansen, one of the first political candidates in the U.S. to accept Bitcoin donations.
Even up until that point, I thought Bitcoin was an interesting protocol for sending and receiving money quickly, and converting it into fiat. The global connectedness of it, plus this cypherpunk mentality divorced from government control was both useful and attractive. I thought it was the perfect go-between.
But I was wrong.
When I gave my first public speech on Bitcoin in Vienna, Austria in December 2013, I had grown obsessed with Bitcoin’s adoption on dark net markets like Silk Road.
My theory, at the time, was the number and price were irrelevant. The tech was interesting, and a novel attempt. It was unlike anything before. But what was happening on the dark net markets, which I viewed as the true free market powered by Bitcoin, was even more interesting. I thought these markets would grow exponentially and anonymous commerce via BTC would become the norm.
While the price was irrelevant, it was all about buying and selling goods without permission or license.
Now I understand I was wrong.
Just because Bitcoin was this revolutionary technology that embraced pseudonymity did not mean that all commerce would decentralize as well. It did not mean that anonymous markets were intended to be the most powerful layer in the Bitcoin stack.
What I did not even anticipate is something articulated very well by noted Bitcoin OG Pierre Rochard: Bitcoin as a savings technology.
The ability to maintain long-term savings, practice self-discipline while stacking stats, and embrace a low-time preference was just not something on the mind of the Bitcoiners I knew at the time.
Perhaps I was reading into the hype while outwardly opposing it. Or perhaps I wasn’t humble enough to understand the true value proposition that many of us have learned years later.
In the years that followed, I bought and sold more times than I can count, and I did everything to integrate it into passion projects. I tried to set up a company using Bitcoin while at my university in Prague.
My business model depended on university students being technologically advanced enough to have a mobile wallet, own their keys, and be able to make transactions on a consistent basis. Even though I was surrounded by philosophically aligned people, those who would advance that to actually put Bitcoin into practice were sparse.
This is what led me to proclaim that “Technological Literacy is Doomed” in 2016.
And I was wrong again.
Indeed, since that time, the UX of Bitcoin-only applications, wallets, and supporting tech has vastly improved and onboarded millions more people than anyone thought possible. The entrepreneurship, coding excellence, and vision offered by Bitcoiners of all stripes have renewed a sense in me that this project is something built for us all — friends and enemies alike.
While many of us were likely distracted by flashy and pumpy altcoins over the years (me too, champs), most of us have returned to the Bitcoin stable.
Fast forward to today, there are entire ecosystems of creators, activists, and developers who are wholly reliant on the magic of Bitcoin’s protocol for their life and livelihood. The options are endless. The FUD is still present, but real proof of work stands powerfully against those forces.
In addition, there are now dozens of ways to use Bitcoin privately — still without custodians or intermediaries — that make it one of the most important assets for global humanity, especially in dictatorships.
This is all toward a positive arc of innovation, freedom, and pure independence. Did I see that coming? Absolutely not.
Of course, there are probably other shots you’ve missed on Bitcoin. Price predictions (ouch), the short-term inflation hedge, or the amount of institutional investment. While all of these may be erroneous predictions in the short term, we have to realize that Bitcoin is a long arc. It will outlive all of us on the planet, and it will continue in its present form for the next generation.
Being wrong about the evolution of Bitcoin is no fault, and is indeed part of the learning curve to finally understanding it all.
When your family or friends ask you about Bitcoin after your endless sessions explaining market dynamics, nodes, how mining works, and the genius of cryptographic signatures, try to accept that there is still so much we have to learn about this decentralized digital cash.
There are still some things you’ve gotten wrong about Bitcoin, and plenty more you’ll underestimate or get wrong in the future. That’s what makes it a beautiful journey. It’s a long road, but one that remains worth it.
-
 @ e83b66a8:b0526c2b
2024-12-11 09:16:23
@ e83b66a8:b0526c2b
2024-12-11 09:16:23I watched Tucker Carlson interview Roger Ver last night.
I know we have our differences with Roger, and he has some less than pleasant personality traits, but he is facing 109 years in jail for tax evasion. While the charges may be technically correct, he should be able to pay the taxes and a fine and walk free. Even if we accept he did wrong, a minor prison term such as 6 months to 2 years would be appropriate in this case.
We all know the severe penalty is an over reach by US authorities looking to make the whole crypto community scared about using any form of crypto as money.
The US and many governments know they have lost the battle of Bitcoin as a hard asset, but this happened as a result of the Nash equilibrium, whereby you are forced to play a game that doesn’t benefit you, because not playing that game disadvantages you further. I.e. Governments loose control of the asset, but that asset is able to shore up their balance sheet and prevent your economy from failing (potentially).
The war against Bitcoin (and other cryptos) as a currency, whereby you can use your Bitcoin to buy anything anywhere from a pint of milk in the local shop, to a house or car and everything in-between is a distant goal and one that is happening slowly. But it is happening and these are the new battle lines.
Part of that battle is self custody, part is tax and part are the money transmitting laws.
Roger’s case is also being used as a weapon of fear.
I don’t hate Roger, the problem I have with Bitcoin cash is that you cannot run a full node from your home and if you can’t do this, it is left to large corporations to run the blockchain. Large corporations are much easier to control and coerce than thousands, perhaps millions of individuals. Just as China banned Bitcoin mining, so in this scenario it would be possible for governments to ban full nodes and enforce that ban by shutting down companies that attempted to do so.
Also, if a currency like Bitcoin cash scaled to Visa size, then Bitcoin Cash the company would become the new Visa / Mastercard and only the technology would change. However, even Visa and Mastercard don’t keep transaction logs for years, that would require enormous amount of storage and have little benefit. Nobody needs a global ledger that keeps a record of every coffee purchased in every coffee shop since the beginning of blockchain time.
This is why Bitcoin with a layer 2 payment system like Lightning is a better proposition than large blockchain cryptos. Once a payment channel is closed, the transactions are forgotten in the same way Visa and Mastercard only keep a transaction history for 1 or 2 years.
This continues to allow the freedom for anybody, anywhere to verify the money they hold and the transactions they perform along with everybody else. We have consensus by verification.
-
 @ e6817453:b0ac3c39
2024-12-07 14:52:47
@ e6817453:b0ac3c39
2024-12-07 14:52:47The temporal semantics and temporal and time-aware knowledge graphs. We have different memory models for artificial intelligence agents. We all try to mimic somehow how the brain works, or at least how the declarative memory of the brain works. We have the split of episodic memory and semantic memory. And we also have a lot of theories, right?
Declarative Memory of the Human Brain
How is the semantic memory formed? We all know that our brain stores semantic memory quite close to the concept we have with the personal knowledge graphs, that it’s connected entities. They form a connection with each other and all those things. So far, so good. And actually, then we have a lot of concepts, how the episodic memory and our experiences gets transmitted to the semantic:
- hippocampus indexing and retrieval
- sanitization of episodic memories
- episodic-semantic shift theory
They all give a different perspective on how different parts of declarative memory cooperate.
We know that episodic memories get semanticized over time. You have semantic knowledge without the notion of time, and probably, your episodic memory is just decayed.
But, you know, it’s still an open question:
do we want to mimic an AI agent’s memory as a human brain memory, or do we want to create something different?
It’s an open question to which we have no good answer. And if you go to the theory of neuroscience and check how episodic and semantic memory interfere, you will still find a lot of theories, yeah?
Some of them say that you have the hippocampus that keeps the indexes of the memory. Some others will say that you semantic the episodic memory. Some others say that you have some separate process that digests the episodic and experience to the semantics. But all of them agree on the plan that it’s operationally two separate areas of memories and even two separate regions of brain, and the semantic, it’s more, let’s say, protected.
So it’s harder to forget the semantical facts than the episodes and everything. And what I’m thinking about for a long time, it’s this, you know, the semantic memory.
Temporal Semantics
It’s memory about the facts, but you somehow mix the time information with the semantics. I already described a lot of things, including how we could combine time with knowledge graphs and how people do it.
There are multiple ways we could persist such information, but we all hit the wall because the complexity of time and the semantics of time are highly complex concepts.
Time in a Semantic context is not a timestamp.
What I mean is that when you have a fact, and you just mentioned that I was there at this particular moment, like, I don’t know, 15:40 on Monday, it’s already awake because we don’t know which Monday, right? So you need to give the exact date, but usually, you do not have experiences like that.
You do not record your memories like that, except you do the journaling and all of the things. So, usually, you have no direct time references. What I mean is that you could say that I was there and it was some event, blah, blah, blah.
Somehow, we form a chain of events that connect with each other and maybe will be connected to some period of time if we are lucky enough. This means that we could not easily represent temporal-aware information as just a timestamp or validity and all of the things.
For sure, the validity of the knowledge graphs (simple quintuple with start and end dates)is a big topic, and it could solve a lot of things. It could solve a lot of the time cases. It’s super simple because you give the end and start dates, and you are done, but it does not answer facts that have a relative time or time information in facts . It could solve many use cases but struggle with facts in an indirect temporal context. I like the simplicity of this idea. But the problem of this approach that in most cases, we simply don’t have these timestamps. We don’t have the timestamp where this information starts and ends. And it’s not modeling many events in our life, especially if you have the processes or ongoing activities or recurrent events.
I’m more about thinking about the time of semantics, where you have a time model as a hybrid clock or some global clock that does the partial ordering of the events. It’s mean that you have the chain of the experiences and you have the chain of the facts that have the different time contexts.
We could deduct the time from this chain of the events. But it’s a big, big topic for the research. But what I want to achieve, actually, it’s not separation on episodic and semantic memory. It’s having something in between.
Blockchain of connected events and facts
I call it temporal-aware semantics or time-aware knowledge graphs, where we could encode the semantic fact together with the time component.I doubt that time should be the simple timestamp or the region of the two timestamps. For me, it is more a chain for facts that have a partial order and form a blockchain like a database or a partially ordered Acyclic graph of facts that are temporally connected. We could have some notion of time that is understandable to the agent and a model that allows us to order the events and focus on what the agent knows and how to order this time knowledge and create the chains of the events.
Time anchors
We may have a particular time in the chain that allows us to arrange a more concrete time for the rest of the events. But it’s still an open topic for research. The temporal semantics gets split into a couple of domains. One domain is how to add time to the knowledge graphs. We already have many different solutions. I described them in my previous articles.
Another domain is the agent's memory and how the memory of the artificial intelligence treats the time. This one, it’s much more complex. Because here, we could not operate with the simple timestamps. We need to have the representation of time that are understandable by model and understandable by the agent that will work with this model. And this one, it’s way bigger topic for the research.”
-
 @ 6389be64:ef439d32
2024-12-09 23:50:41
@ 6389be64:ef439d32
2024-12-09 23:50:41Resilience is the ability to withstand shocks, adapt, and bounce back. It’s an essential quality in nature and in life. But what if we could take resilience a step further? What if, instead of merely surviving, a system could improve when faced with stress? This concept, known as anti-fragility, is not just theoretical—it’s practical. Combining two highly resilient natural tools, comfrey and biochar, reveals how we can create systems that thrive under pressure and grow stronger with each challenge.
Comfrey: Nature’s Champion of Resilience
Comfrey is a plant that refuses to fail. Once its deep roots take hold, it thrives in poor soils, withstands drought, and regenerates even after being cut down repeatedly. It’s a hardy survivor, but comfrey doesn’t just endure—it contributes. Known as a dynamic accumulator, it mines nutrients from deep within the earth and brings them to the surface, making them available for other plants.
Beyond its ecological role, comfrey has centuries of medicinal use, earning the nickname "knitbone." Its leaves can heal wounds and restore health, a perfect metaphor for resilience. But as impressive as comfrey is, its true potential is unlocked when paired with another resilient force: biochar.
Biochar: The Silent Powerhouse of Soil Regeneration
Biochar, a carbon-rich material made by burning organic matter in low-oxygen conditions, is a game-changer for soil health. Its unique porous structure retains water, holds nutrients, and provides a haven for beneficial microbes. Soil enriched with biochar becomes drought-resistant, nutrient-rich, and biologically active—qualities that scream resilience.
Historically, ancient civilizations in the Amazon used biochar to transform barren soils into fertile agricultural hubs. Known as terra preta, these soils remain productive centuries later, highlighting biochar’s remarkable staying power.
Yet, like comfrey, biochar’s potential is magnified when it’s part of a larger system.
The Synergy: Comfrey and Biochar Together
Resilience turns into anti-fragility when systems go beyond mere survival and start improving under stress. Combining comfrey and biochar achieves exactly that.
-
Nutrient Cycling and Retention\ Comfrey’s leaves, rich in nitrogen, potassium, and phosphorus, make an excellent mulch when cut and dropped onto the soil. However, these nutrients can wash away in heavy rains. Enter biochar. Its porous structure locks in the nutrients from comfrey, preventing runoff and keeping them available for plants. Together, they create a system that not only recycles nutrients but amplifies their effectiveness.
-
Water Management\ Biochar holds onto water making soil not just drought-resistant but actively water-efficient, improving over time with each rain and dry spell.
-
Microbial Ecosystems\ Comfrey enriches soil with organic matter, feeding microbial life. Biochar provides a home for these microbes, protecting them and creating a stable environment for them to multiply. Together, they build a thriving soil ecosystem that becomes more fertile and resilient with each passing season.
Resilient systems can withstand shocks, but anti-fragile systems actively use those shocks to grow stronger. Comfrey and biochar together form an anti-fragile system. Each addition of biochar enhances water and nutrient retention, while comfrey regenerates biomass and enriches the soil. Over time, the system becomes more productive, less dependent on external inputs, and better equipped to handle challenges.
This synergy demonstrates the power of designing systems that don’t just survive—they thrive.
Lessons Beyond the Soil
The partnership of comfrey and biochar offers a valuable lesson for our own lives. Resilience is an admirable trait, but anti-fragility takes us further. By combining complementary strengths and leveraging stress as an opportunity, we can create systems—whether in soil, business, or society—that improve under pressure.
Nature shows us that resilience isn’t the end goal. When we pair resilient tools like comfrey and biochar, we unlock a system that evolves, regenerates, and becomes anti-fragile. By designing with anti-fragility in mind, we don’t just bounce back, we bounce forward.
By designing with anti-fragility in mind, we don’t just bounce back, we bounce forward.
-
-
 @ 6e468422:15deee93
2024-12-21 19:25:26
@ 6e468422:15deee93
2024-12-21 19:25:26We didn't hear them land on earth, nor did we see them. The spores were not visible to the naked eye. Like dust particles, they softly fell, unhindered, through our atmosphere, covering the earth. It took us a while to realize that something extraordinary was happening on our planet. In most places, the mushrooms didn't grow at all. The conditions weren't right. In some places—mostly rocky places—they grew large enough to be noticeable. People all over the world posted pictures online. "White eggs," they called them. It took a bit until botanists and mycologists took note. Most didn't realize that we were dealing with a species unknown to us.
We aren't sure who sent them. We aren't even sure if there is a "who" behind the spores. But once the first portals opened up, we learned that these mushrooms aren't just a quirk of biology. The portals were small at first—minuscule, even. Like a pinhole camera, we were able to glimpse through, but we couldn't make out much. We were only able to see colors and textures if the conditions were right. We weren't sure what we were looking at.
We still don't understand why some mushrooms open up, and some don't. Most don't. What we do know is that they like colder climates and high elevations. What we also know is that the portals don't stay open for long. Like all mushrooms, the flush only lasts for a week or two. When a portal opens, it looks like the mushroom is eating a hole into itself at first. But the hole grows, and what starts as a shimmer behind a grey film turns into a clear picture as the egg ripens. When conditions are right, portals will remain stable for up to three days. Once the fruit withers, the portal closes, and the mushroom decays.
The eggs grew bigger year over year. And with it, the portals. Soon enough, the portals were big enough to stick your finger through. And that's when things started to get weird...
-
 @ c5fede3d:16e03f7b
2025-01-08 11:41:16
@ c5fede3d:16e03f7b
2025-01-08 11:41:16Hay quien dice el famoso dicho de «año nuevo, vida nueva». En este caso, iniciamos el año con el mismo propósito, seguir aprendiendo para que no nos pille el toro. En esta ocasión, toca tratar la entrada de capital a tu wallet. Sin embargo, hay que saber donde meterse sin que las arenas movedizas te engullan. ¿Preparado para comprar la hucha del cerdito?
Esta es la segunda entrega de Semanario Crypto, una serie de artículos dedicados para aquellos que desconocen los conceptos básicos del mundo de las criptomonedas. La semana pasada hicimos un barrido sin adentrarnos en territorio comanche. Si aún no tienes claro qué es una wallet o cuál es el propósito de una frase semilla, ve al punto de partida y vuelve a leerte Semanario Crypto #1 | Un nuevo paradigma, porque es el ticket de entrada para este mundillo y no lo puedes perder.
EL LÍO DEL MONTEPÍO💱

Si has llegado hasta aquí, he de felicitarte. Has dado dos grandes pasos. El primero, tener la mente abierta y querer aprender. El segundo, disponer de una wallet y tener guardada a buen recaudo la frase semilla. Ahora es el momento de la verdad, operar, no sin antes tener claro un par de conceptos más.
¿Qué son los exchanges?
Son plataformas digitales donde los usuarios pueden comprar, vender o intercambiar criptomonedas. A través de ellas, los usuarios pueden convertir su dinero tradicional en crypto, facilitando el comercio de criptoactivos.
Los exchanges son los bancos del mundo de la criptomonedas. Ambos actúan como intermediarios en las transacciones financieras y ofrecen servicios relacionados con la inversión y el comercio. Sin embargo, no todos los exchanges son iguales, se diferencian dos tipos:
1. Exchange Centralizado (CEX)
En este tipo de exchange, una entidad centralizada gestiona las transacciones y retiene los fondos los usuarios. Los CEX custodian tu dinero, cuentan con equipos profesionales de atención al cliente y están sujetos a altas regulaciones gubernamentales. Te registras, haces la verificación de identidad (KYC) y ellos te proporcionan una wallet para que la fondees con tu dinero fiduciario y operes dentro de la plataforma. Todo un ecosistema a golpe de click.
2. Exchange Descentralizado (DEX)
Aquí las transacciones se realizan entre usuarios a través de contratos inteligentes en la blockchain (P2P), es decir, las operaciones se hacen directamente desde sus propias billeteras. No requieren que se proporcionen información personal. Los usuarios mantienen el control sobre sus activos (autocustodia) y no habrá que depositar en ellas.
Sabiendo las diferencias entre un CEX y un DEX, nuevamente nos hallamos en la tesitura de tener que definirnos a nosotros mismos. En la anterior entrega de Semanario Crypto optamos por una wallet caliente o una fría en función del tipo de inversor que somos, o incluso pudimos hacer un mix emparejando la wallet fría a una extensión de navegador. Aunque, como acabamos de ver, si te registras en un CEX ellos ya te proporcionan una billetera electrónica para que operes dentro de la plataforma. La elección es tuya, pero has de tener en cuenta cómo operar de una forma u otra conforme al capital que dispongas:
Quiero operar por un monto superior a 50k euros anuales y/o soy un buen ciudadano.
- Amigo mío, quítate de problemas, y registrate en un CEX como Binance o Bit2Me. La legislación fiscal española incide especialmente en que cualquier tenencia de criptomonedas superior a 50k euros debe ser declarada. Con los exchanges que te he puesto, la información proporcionada a la Agencia Tributaria es automática y de ella se encargan ellos, no tienes que hacer nada de nada. Solo hacer tu declaración anual habitual.
- También es la opción ideal para el vago y el que no dispone de tiempo. ¿Quieres hacer un mix que te ofrezca las bondades de los CEX y los DEX? Atento al siguiente punto y atiende a las nuevas regulaciones de cara a 2025.
Quiero operar por un monto inferior a 10k euros anuales y/o considero que los CEX son neo-usureros.
- La solución son los DEX. Como ya vimos, los exchanges descentralizados no requieren de KYC para operar, de modo que dan un mayor grado de privacidad y anonimato, puesto que jamás dispondrán de tu documentación personal. Además, estás expuesto a lo que se denomina el ecosistema de las finanzas descentralizadas (DeFi).
- El mundo DeFi busca democratizar el acceso a los servicios financieros, abriendo un abanico de nuevos mercados, oportunidades de inversión y ser el primero en conocer las innovaciones financieras. Sin lugar a dudas, es donde están los más avispados y la gente pudiente, muestra de ello es el valor de su capitalización de mercado, alcanzando más de 52 mil millones de dólares, que se dice pronto.
EL CASTILLO DE DRÁCULA, LA AEAT 🧛

El año 2025 va a ser determinante para el devenir del mundo de las criptomonedas, al menos en Europa. Es el año donde entran en vigor las nuevas regulaciones fiscales. Parece ser que el mantra de que los criptoactivos eran una estafa y que no valían nada a pasado a mejor vida a partir de la entrada del gran capital, como Blackrock. Ahora, los entes fiscales reguladores quieren su porción del pastel y apuntan a tu billetera. Si quieres operar en este mundillo, debes saber un poco de fiscalidad, para que no llamen a tu puerta. Aunque, recuerda, si optaste por ser un buen ciudadano (español, en este caso) que te registraste en un CEX como Binance o Bit2Me no tendrás mayores preocupaciones, porque allí todo lo que hagas acaba registrado automáticamente en tu declaración del año fiscal. De todas formas, siempre es bueno aprender, sobre todo si operas desde los DEX con tu billetera autocustodiada.
1. La Ley MiCa y Directiva DAC8
- Reglamento europeo que establece el marco regulatorio para las criptomonedas. Obliga a que todos los servicios financieros que emitan o comercialicen criptoactivos tengan licencia y deban proporcionar información sobre sus operaciones. Los proveedores de servicios deberán informar sobre las transacciones realizadas por residentes en Europa con fines de supervisión fiscal. Los ciudadanos europeos están obligados a declarar la tenencia de criptoactivos como parte del patrimonio personal, incluyendo ganancias, la cual estará sujeta a impuestos.
- La Directiva DAC8 complementa al reglamento y se enfoca en el intercambio automático de información fiscal entre los Estados miembro de la UE (CARF). Los proveedores de criptoactivos deberán reportarán todas las transacciones y datos relevantes a las autoridades fiscales nacionales, concretamente los movimientos y saldos del usuario. Legitima a Hacienda a poder embargar las criptomonedas depositadas en un exchange, las wallets autocustodiadas son inembargables por estar en control del usuario.
2. La Travel Rule o Regla de Viaje
- Regulación que aumenta la trazabilidad entre las transacciones de criptomonedas. Exige a los servicios de activos digitales (VASP) recojan y compartan información sobre los remitentes y beneficiarios, sea a carteras custodiadas o autocustodiadas.
3. Límites y “mandamientos”
- Cualquier transferencia superior a 1.000 euros requerirá que el proveedor recopile datos personales.
- Si el monto de operaciones alcanza los 10.000 euros anuales, el proveedor informa.
- Si el monto de operaciones alcanza los 3.000 euros en un trimestre natural, el proveedor informa.
- Las ganancias deben ser declaradas en el IRPF al final del año fiscal, incluso si las criptomonedas no se han convertido a FIAT (dinero fiduciario tradicional).
- El Modelo 721 es una obligación informativa que deben cumplir los contribuyentes que poseen criptomonedas en el extranjero (exchange que no opere bajo legislación española y no presente los modelos informativos requeridos por Hacienda) y cuyo saldo supera los 50.000 euros a fecha del 31 de diciembre.
- La CNMV supervisa el mercado de criptoactivos y el Banco de España las monedas estables (dólares digitales como USDC-USDT).
¿AÚN CON FUERZAS?
Pues sabiendo todo esto, ya es hora de que deposites tu dinero en tu billetera de criptomonedas. ¿Cómo hacerlo? Eso ya lo verás en la siguiente entrega de Semanario Crypto. En él se te ofrecerá el martillo para que rompes la hucha del cerdito y le des vida a tu wallet. Aprende las rutas de entrada y de salida. Opera con conocimiento y sabiendo lo que haces. Es más fácil de lo que piensas. Recuerda que la información es poder, y tú la vas a tener.
Descargo de responsabilidad: Toda la información compartida forma parte de mi visión personal y no tiene como objetivo asesorar financieramente. Doy información, no consejos de inversión.
-
 @ 330516bf:ea23d292
2024-12-20 03:35:09
@ 330516bf:ea23d292
2024-12-20 03:35:09The self-declaration of identity is a philosophical open source project, hosted at https://memdeklaro.github.io/
Foreword
ID documents do more harm than good and should not be seen as a solution for trust or authentication. Many economic and social interactions can be done anonymously. For other situations, trust can be achieved by simply saying your (self-chosen) name, using a web-of-trust, word-of-mouth reputation, vouches, memberships, escrows or cash deposits, and authentication can be achieved by using a password, cryptographic key pair (e.g. PGP, Monero) or physical key or code (such as house keys or a safe code).
Background
In recent years, more and more things are asking for proof of identity, from basic necessities like jobs, housing and healthcare, to smaller things like receiving mail, buying a sim card or joining a gym. However, it is not enough to write your name and address on a form. Instead, only government-issued IDs are accepted, which gives the state a “monopoly on identity”.
Monopolies are dangerous in general due to the fact that if the service provider is harmful, inaccessible or otherwise problematic, you cannot choose a different provider, start your own provider, or go without. This particular monopoly is even worse, considering that access to government ID determines if you may participate in the economy (jobs, banking), society (housing, volunteer work, education, libraries, sports) or even exist (national borders).
Many people have no access to government ID. This group includes some stateless people, refugees, people who weren’t registered at birth, and people who escaped from child abuse, domestic abuse or cult abuse. The state’s claimed solutions, such as asylum procedures, stateless determination procedures, delayed registration of birth, child protective services and witness protection, often cannot help in practice, as the victim is often ignored, accused of lying, blamed for the persecution, or worse sent back to the persecutors against their will. Despite issuing laissez-passer and Nansen passports in the past, the United Nations and Red Cross do not issue alternative IDs today. It would be a relief if these processes would work and allow vulnerable people to escape from undeserved and dangerous situations, but unfortunately this is not the reality.
In addition, the collectivist concept of citizenship can be dangerous. For example, if someone does not identify with their birth culture, they should not be forced to follow it for life or identify themselves as a member of this culture. Instead, they should be free to dissent against this culture or leave this culture’s jurisdiction. Even worse is conscription — the cruel system where a nation-state can force someone against their will to kill or be killed, just because they happened to be born inside a certain territory. The world would be more free if people could exist as individuals, conscientious objectors against the fatalism of birth cultures and violence of statism, with freedom of association to leave hostile environments and join self-chosen communities.
“The blood of the covenant is thicker than the water of the womb.”
Self-declaration of identity gives people the power to decide their own fate. People are no longer the property of nations, governments, birth cultures or birth parents. The choice of your own name and renunciation of your circumstances of birth is a liberating act of individualism, where your ideals, actions and efforts matter more than the situation that you were arbitrarily born into.
Self-declaration of identity
Instead of requiring third parties such as birth countries, birth cultures and birth parents to define an individual’s identity, the self-declaration allows you to define your own name and eschews the concepts of birth countries and citizenship.
The self-declaration is a CR-80 plastic card or paper business card (85.6mm x 54mm). The self-declaration is written in Esperanto and includes the Esperanto flag and symbol. Esperanto was chosen because it is anational (sennacieca = not associated with a specific country, culture or state) and was created as a borderless language of peace, built on voluntary free association. The design features artwork of a peace dove in a blue sky with clouds.
As it is a self-declaration, it is not stored in a central database, does not require a third party’s permission and does not need to be issued by an authority. You are the authority over your own life.
The self-declaration includes the text:
- Title: Self-declaration of identity (Memdeklaro de identeco)
- Location: Esperanto community (Esperantujo)
- Issuer: EPO (ISO code for Esperanto)
- Quote: One world, one humankind (Unu mondo, unu homaro)
The self-declaration of identity contains:
- Self-chosen first name (Antaŭnomo) and self-chosen surname (Nomo) → an individual should be able to freely choose their own name
- Birth date (Naskiĝdato) → for declaration of age
- Photo → Dimensions 35mm x 45mm
- Signature (Subskribo) → sign your self-declaration
- Notes field (Notoj) → a place to write a note, e.g. “the holder is a conscientious objector” (Portanto estas konscienca obĵetanto)
- ID number (Numero), issuance date (Eldondato), expiry date (Limdato), issuer (Eldonisto), MRZ → bureaucratic boilerplate
The self-declaration of identity does not contain:
- Place of birth → allows people to cut ties with hostile environments and self-define their culture, beliefs and personal ties
- Citizenship or stateless status → allows people to cut ties with hostile governments or cultures, and exist as an individual instead of as property of a state that they did not choose
- Parents’ names → allows victims of child abuse to cut ties with abusers
To make your own:
- Use the generator at https://memdeklaro.github.io/ or download the repo (https://github.com/memdeklaro/memdeklaro.github.io/) and open index.html in your browser
- Alternatively download the front template (fronto.jpg) and back template (dorso.jpg) from the linked repo, and use an image editor such as GIMP to add your text (the font OCR-B.ttf is provided) and your photo and signature
- Calculate the MRZ code here (TD1): https://www.dynamsoft.com/tools/mrz-generator/ (Choose any country, then replace it with EPO)
- Print it out as a business card and optionally laminate (dimensions: 85.6mm x 54mm) or order a CR-80 plastic card from a printing service
Example:

Note:
Unfortunately the self-declaration of identity cannot be used to bypass government ID requirements, such as for jobs, housing, healthcare, finances, volunteer work, contracts, receiving mail or buying a sim card. Other non-government IDs such as Digitalcourage Lichtbildausweis (https://shop.digitalcourage.de/gadgets/lichtbildausweis-mit-selbst-waehlbaren-daten.html) and World Passport (https://worldcitizengov.org/what-is-the-world-passport/) have the same limitations.
Nation-states’ refusal to print IDs for undocumented, stateless and unregistered people (while forcing government ID requirements on employers, landlords, doctors and more) can and does put innocent people’s lives in danger. But unfortunately even the United Nations has not been able to change this, despite issuing conventions on statelessness and refugee status in the 1950s.
Further Reading
For further reading about identity (and why the state’s monopoly is harmful):
Passports Were a “Temporary” War Measure — Speranta Dumitru https://fee.org/articles/passports-were-a-temporary-war-measure
During World War II, we did have something to hide — Hans de Zwart https://medium.com/@hansdezwart/during-world-war-ii-we-did-have-something-to-hide-40689565c550
The Little-Known Passport That Protected 450,000 Refugees — Cara Giaimo https://www.atlasobscura.com/articles/nansen-passport-refugees
With each person left living on the streets, we are losing as a society — Petr Baroch https://www.statelessness.eu/blog/each-person-left-living-streets-we-are-losing-society
The rarely discussed dangers of KYC and what you can do about it — Anarkio https://vonupodcast.com/know-your-customer-kyc-the-rarely-discussed-danger-guest-article-audio
Exclusion and identity: life without ID — Privacy International https://www.privacyinternational.org/long-read/2544/exclusion-and-identity-life-without-id
Proving who I am: the plight of people in detention without proof of legal identity — Vicki Prais https://www.penalreform.org/blog/proving-who-i-am-the-plight-of-people/
Establishing identity is a vital, risky and changing business — The Economist https://www.economist.com/christmas-specials/2018/12/18/establishing-identity-is-a-vital-risky-and-changing-business
What’s in a name? The case for inclusivity through anonymity — Common Thread https://blog.twitter.com/common-thread/en/topics/stories/2021/whats-in-a-name-the-case-for-inclusivity-through-anonymity
True Names Not Required: On Identity and Pseudonymity in Cyberspace — Der Gigi https://dergigi.medium.com/true-names-not-required-fc6647dfe24a
Citizenship is obsolete — Samuela Davidova https://medium.com/@DavidovaSamuela/citizenship-is-obsolete-c36a20056752
License
Public Domain
Source code: https://github.com/memdeklaro/memdeklaro.github.io
Infographic

Translations
(Machine translated)\ Memdeklaro de identenco: self declaration of identity, autodeclaración de identidad, autodeclaração de identidade, autodéclaration d’identité, autodichiarazione di identità, autodeclararea identității, Selbsterklärung zur Identität, eigen verklaring van identiteit, Selvdeklaration af identitet, självdeklaration av identitet, egenerklæring om identitet, henkilöllisyysvakuutus, Isikuandmete esitamine, identitātes pašdeklarēšana, savęs deklaravimas, önbevallás a személyazonosságról, własna deklaracja tożsamości, vlastní prohlášení o totožnosti, vlastné vyhlásenie o totožnosti, samoprijava identitete, самодеклариране на самоличността, самопроголошення ідентичності, самозаявление о личности, αυτο-δήλωση ταυτότητας, pernyataan identitas diri, öz kimlik beyanı, الإعلان الذاتي عن الهوية, 身份自报, 身份自報, 自己申告, 신원 자기 선언
...
-
 @ 3b19f10a:4e1f94b4
2024-12-07 09:55:46
@ 3b19f10a:4e1f94b4
2024-12-07 09:55:46 -
 @ d61f3bc5:0da6ef4a
2024-12-18 16:52:18
@ d61f3bc5:0da6ef4a
2024-12-18 16:52:18January 2025 will mark two years since we started building Primal. Our goal was to create the best possible user experience for Nostr and make it accessible to everyone. We reached a big milestone towards realizing that vision with the recent Primal 2.0 release. It’s still early days, a lot more work lies ahead, but we thought the timing was right to introduce the Premium tier. Let’s explore what it is, why we built it, what’s included, and how it will evolve moving forward.
What Primal Premium Is
The idea behind Primal Premium is simple: integrate all tools and services required for the best Nostr experience into a single package. For $7 per month, Premium users get a Primal Name and Nostr Tools built by Primal. We’ll cover those in more detail below, but first we should make a crucial point: by signing up for Premium, you are in no way locked in to Primal. Quite the contrary, you can pick and choose which Premium features you wish to enable and use within other Nostr products.
Openness is Nostr’s killer feature. Any product that wishes to truly empower the user needs to interoperate with Nostr’s budding ecosystem. The feed marketplace is a great example. External feeds are first-class citizens within all Primal apps. Primal feeds are available in other Nostr clients. We are working on Premium feeds, which our users will be able to enjoy within Primal or other Nostr apps. Media hosting is another example. Our upcoming support for the Blossom protocol will make Primal Premium media hosting interoperable with other Nostr apps and media hosting services. The common theme here is user choice. Nostr offers the highest level of user agency, and the compounding effect of interoperable products and services is bound to make Nostr immensely powerful.
Why We Built Premium and Why Now
What is unfolding on Nostr right now is unique and special. The first truly self-sovereign network is being bootstrapped by this early cohort of users and builders. People are literally holding the keys to their online presence. Network infrastructure – relays, indexers, media hosting services, etc. – is being stood up organically and without any central planning or coordination. Hundreds of independent projects are adding new capabilities to Nostr without needing permission. The whole thing is truly a sight to behold.
In addition to fixing the fundamentals of the network, it is equally important that we fix the broken incentives that plague the legacy Web. The status quo of monetization via advertising, which turns users into products to be farmed, has overstayed its welcome. At Primal, we don’t monetize user data. Our users are our customers. We only make money when the user decides that we are providing a valuable service – and pays for it. That means that our users’ interests are aligned with ours. It allows us to wake up every morning and work all day to make the product better for our users.
Some might say that it is too early to try to monetize a Nostr product. We definitely need to be thoughtful about paywalling important features while the network is so young. For example, advanced search is a Primal Premium feature, but we enable it for all users up to 20 search results. That makes it quite usable for anyone on Nostr, but power users get the ability to save these searches and create powerful specialized feeds.
It is crucial to have commercially successful projects on Nostr that have their incentives aligned with those of their users. We are working on new features and monetization methods that follow this philosophy. The more we experiment on Nostr, the faster we will learn what works and unlock the full potential of this network. I have a feeling that a lot remains to be discovered, and Primal Premium is just the first step.
Now, let’s take a closer look at what is included in Premium: Primal Name and Nostr Tools.
Primal Name
A Primal Name is a unique name on the primal.net domain that offers three features:
- Verified Nostr address (NIP-05). This signals to the Nostr network that your account (npub) has been verified by Primal. Note that we don’t perform identity verification; we are simply signaling that this is a Primal Premium user. Users can pay with sats, preserving their privacy while signaling to the network that this verified account is not a bot.
- Friendly Bitcoin Lightning address. Primal’s built-in hosted wallet creates a randomly generated lightning address for every user. They look like this: bluedog25@primal.net. Premium users get to pick their name, so their lightning address is more personalized (e.g. preston@primal.net).
- VIP profile on primal.net. This is simply a friendly URL to your profile on primal.net. We are working on adding profile customization features for Premium users; stay tuned!
In summary, a Primal Name makes you easier to find on Nostr. You are free to use any of these three Primal Name elements as you see fit. If you wish to use your Primal Nostr address and/or Lightning address, simply update your Nostr profile with those entries.
Nostr Tools
Nostr Tools is a collection of features that we think would be useful to any Nostr power user. We are continuously working on expanding these capabilities, but the initial set of features includes:
- Media management. Primal Premium comes with 10GB of media storage (compared to 1GB for free accounts). We implemented a slick interface for managing all media you have on Primal.
- Contact list backup. Many Nostr users have experienced the loss of their contact list (i.e., their follow list) when using different clients. We store the history of the contact list for Primal Premium users and make it easy to recover.
- Content backup. Nostr users post their content to a collection of public relays. These relays typically don’t offer guarantees that they will store the content for any amount of time. We back up all content posted by Primal Premium users and make it easy to rebroadcast it to the specified relays at any time.
Primal Legends
The idea for the Primal Legend tier was suggested to me by Gigi a couple of months prior to the launch of Primal 2.0. His argument was simple: “There are users on Nostr who really appreciate Primal and are willing to pay way more than $7 / month to support the project. You should let them pay and recognize them for doing so.”
I am really glad that Gigi convinced me to introduce the Legend tier. Nostr is truly a special place. The early users are extremely passionate and mission driven. They care about growing and improving Nostr as much as the builders do. At first, I thought of the term “Legend” as a bit tongue in cheek, but then I met and chatted with some of these people. Man, they are incredible. They just wish to support the network and the builders of open source software in any way they can. So now I think the term is appropriate.
We are humbled by the support we received. Our first Legend supporter was none other than Jack. He found this option in the product and paid for the Legend tier literally an hour after Primal 2.0 was released. Thank you, sir, and thank you to all the other Legends out there! 💜🫂
What Comes Next?
We are delighted and encouraged by the market response to Primal Premium. It is already clear to us that we are on the right path. We will lean into it even harder from here. There will be MOAR Premium features, while at the same time we will make sure that the free product remains excellent. Since you, the user, are the customer, tell us what you would like to see added to Primal Premium.
Pura Vida 🤙
-
 @ b2d670de:907f9d4a
2024-12-02 21:24:45
@ b2d670de:907f9d4a
2024-12-02 21:24:45onion-service-nostr-relays
A list of nostr relays exposed as onion services.
The list
| Relay name | Description | Onion url | Operator | Payment URL | Payment options | | --- | --- | --- | --- | --- | --- | | nostr.oxtr.dev | Same relay as clearnet relay nostr.oxtr.dev | ws://oxtrdevav64z64yb7x6rjg4ntzqjhedm5b5zjqulugknhzr46ny2qbad.onion | operator | N/A | N/A | | relay.snort.social | Same relay as clearnet relay relay.snort.social | wss://skzzn6cimfdv5e2phjc4yr5v7ikbxtn5f7dkwn5c7v47tduzlbosqmqd.onion | operator | N/A | N/A | | nostr.thesamecat.io | Same relay as clearnet relay nostr.thesamecat.io | ws://2jsnlhfnelig5acq6iacydmzdbdmg7xwunm4xl6qwbvzacw4lwrjmlyd.onion | operator | N/A | N/A | | nostr.land | The nostr.land paid relay (same as clearnet) | ws://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion | operator | Payment URL | BTC LN | | bitcoiner.social | No auth required, currently | ws://bitcoinr6de5lkvx4tpwdmzrdfdpla5sya2afwpcabjup2xpi5dulbad.onion | operator | N/A | N/A | | relay.westernbtc.com | The westernbtc.com paid relay | ws://westbtcebhgi4ilxxziefho6bqu5lqwa5ncfjefnfebbhx2cwqx5knyd.onion | operator | Payment URL | BTC LN | | freelay.sovbit.host | Free relay for sovbit.host | ws://sovbitm2enxfr5ot6qscwy5ermdffbqscy66wirkbsigvcshumyzbbqd.onion | operator | N/A | N/A | | nostr.sovbit.host | Paid relay for sovbit.host | ws://sovbitgz5uqyh7jwcsudq4sspxlj4kbnurvd3xarkkx2use3k6rlibqd.onion | operator | N/A | N/A | | nostr.wine | 🍷 nostr.wine relay | ws://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion | operator | Payment URL | BTC LN, BTC, Credit Card/CashApp (Stripe) | | inbox.nostr.wine | 🍷 inbox.nostr.wine relay | ws://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion | operator | Payment URL | BTC LN, BTC | | filter.nostr.wine | 🍷 filter.nostr.wine proxy relay | ws://winefiltermhqixxzmnzxhrmaufpnfq3rmjcl6ei45iy4aidrngpsyid.onion | operator | Payment URL | BTC LN, BTC | | N/A | N/A | ws://pzfw4uteha62iwkzm3lycabk4pbtcr67cg5ymp5i3xwrpt3t24m6tzad.onion:81 | operator | N/A | N/A | | nostr.fractalized.net | Free relay for fractalized.net | ws://xvgox2zzo7cfxcjrd2llrkthvjs5t7efoalu34s6lmkqhvzvrms6ipyd.onion | operator | N/A | N/A | | nfrelay.app | nfrelay.app aggregator relay (nostr-filter-relay) | ws://nfrelay6saohkmipikquvrn6d64dzxivhmcdcj4d5i7wxis47xwsriyd.onion | operator | N/A | N/A | relay.nostr.net | Public relay from nostr.net (Same as clearnet) | ws://nostrnetl6yd5whkldj3vqsxyyaq3tkuspy23a3qgx7cdepb4564qgqd.onion | operator | N/A | N/A | | nerostrator | Free to read, pay XMR to relay | ws://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion | operator |Payment URL | XMR | | nostr.girino.org | Public relay from nostr.girino.org | ws://gnostr2jnapk72mnagq3cuykfon73temzp77hcbncn4silgt77boruid.onion | operator | N/A | N/A | | wot.girino.org | WoT relay from wot.girino.org | ws://girwot2koy3kvj6fk7oseoqazp5vwbeawocb3m27jcqtah65f2fkl3yd.onion | operator | N/A | N/A | | haven.girino.org/{outbox, inbox, chat, private} | Haven smart relay from haven.girino.org | ws://ghaven2hi3qn2riitw7ymaztdpztrvmm337e2pgkacfh3rnscaoxjoad.onion/{outbox, inbox, chat, private} | operator | N/A | N/A | | relay.nostpy.lol | Free Web of Trust relay (Same as clearnet) | ws://pemgkkqjqjde7y2emc2hpxocexugbixp42o4zymznil6zfegx5nfp4id.onion | operator |N/A | N/A | | Poster.place Nostr Relay | N/A | ws://dmw5wbawyovz7fcahvguwkw4sknsqsalffwctioeoqkvvy7ygjbcuoad.onion | operator | N/A | N/A |
Contributing
Contributions are encouraged to keep this document alive. Just open a PR and I'll have it tested and merged. The onion URL is the only mandatory column, the rest is just nice-to-have metadata about the relay. Put
N/Ain empty columns.If you want to contribute anonymously, please contact me on SimpleX or send a DM on nostr using a disposable npub.
Operator column
It is generally preferred to use something that includes a NIP-19 string, either just the string or a url that contains the NIP-19 string in it (e.g. an njump url).
-
 @ 63d59db8:be170f6f
2024-12-18 16:24:11
@ 63d59db8:be170f6f
2024-12-18 16:24:11I am Oana, a fine-art photographer with a deep passion for capturing nature's fragile resilience. My work has been recognized internationally, featured on platforms such as CNN Style, Forbes, and Amateur Photographer, and honored by the Sony World Photography Awards. With over 25 years of creative experience, I focus on blending fine-art aesthetics with ecological storytelling to highlight the beauty, complexity, and vulnerability of our natural world.
For this submission, I’ve selected some of my finest works, which reflect my ongoing exploration of flora in their natural environments. These images celebrate the interplay of light, texture, and motion, capturing moments that reveal the unique personalities of flowers and plants without interference. My goal is to foster an emotional connection between viewers and the overlooked beauty of the natural world.
This work represents my artistic vision of combining visual poetry with a deeper narrative about sustainability and our relationship with the environment. Each photograph is a window into nature’s story, inviting viewers to engage with its raw, unfiltered essence.






Submit your photographs to our Visual Expression awards. Current prize is $130 / 125,140 sats.
Learn more and enter here. Deadline is December 31, 2024!

-
 @ e31e84c4:77bbabc0
2024-12-02 10:44:07
@ e31e84c4:77bbabc0
2024-12-02 10:44:07Bitcoin and Fixed Income was Written By Wyatt O’Rourke. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: ultrahusky3@primal.net
Fiduciary duty is the obligation to act in the client’s best interests at all times, prioritizing their needs above the advisor’s own, ensuring honesty, transparency, and avoiding conflicts of interest in all recommendations and actions.
This is something all advisors in the BFAN take very seriously; after all, we are legally required to do so. For the average advisor this is a fairly easy box to check. All you essentially have to do is have someone take a 5-minute risk assessment, fill out an investment policy statement, and then throw them in the proverbial 60/40 portfolio. You have thousands of investment options to choose from and you can reasonably explain how your client is theoretically insulated from any move in the \~markets\~. From the traditional financial advisor perspective, you could justify nearly anything by putting a client into this type of portfolio. All your bases were pretty much covered from return profile, regulatory, compliance, investment options, etc. It was just too easy. It became the household standard and now a meme.
As almost every real bitcoiner knows, the 60/40 portfolio is moving into psyop territory, and many financial advisors get clowned on for defending this relic on bitcoin twitter. I’m going to specifically poke fun at the ‘40’ part of this portfolio.
The ‘40’ represents fixed income, defined as…
An investment type that provides regular, set interest payments, such as bonds or treasury securities, and returns the principal at maturity. It’s generally considered a lower-risk asset class, used to generate stable income and preserve capital.
Historically, this part of the portfolio was meant to weather the volatility in the equity markets and represent the “safe” investments. Typically, some sort of bond.
First and foremost, the fixed income section is most commonly constructed with U.S. Debt. There are a couple main reasons for this. Most financial professionals believe the same fairy tale that U.S. Debt is “risk free” (lol). U.S. debt is also one of the largest and most liquid assets in the market which comes with a lot of benefits.
There are many brilliant bitcoiners in finance and economics that have sounded the alarm on the U.S. debt ticking time bomb. I highly recommend readers explore the work of Greg Foss, Lawrence Lepard, Lyn Alden, and Saifedean Ammous. My very high-level recap of their analysis:
-
A bond is a contract in which Party A (the borrower) agrees to repay Party B (the lender) their principal plus interest over time.
-
The U.S. government issues bonds (Treasury securities) to finance its operations after tax revenues have been exhausted.
-
These are traditionally viewed as “risk-free” due to the government’s historical reliability in repaying its debts and the strength of the U.S. economy
-
U.S. bonds are seen as safe because the government has control over the dollar (world reserve asset) and, until recently (20 some odd years), enjoyed broad confidence that it would always honor its debts.
-
This perception has contributed to high global demand for U.S. debt but, that is quickly deteriorating.
-
The current debt situation raises concerns about sustainability.
-
The U.S. has substantial obligations, and without sufficient productivity growth, increasing debt may lead to a cycle where borrowing to cover interest leads to more debt.
-
This could result in more reliance on money creation (printing), which can drive inflation and further debt burdens.
In the words of Lyn Alden “Nothing stops this train”
Those obligations are what makes up the 40% of most the fixed income in your portfolio. So essentially you are giving money to one of the worst capital allocators in the world (U.S. Gov’t) and getting paid back with printed money.
As someone who takes their fiduciary responsibility seriously and understands the debt situation we just reviewed, I think it’s borderline negligent to put someone into a classic 60% (equities) / 40% (fixed income) portfolio without serious scrutiny of the client’s financial situation and options available to them. I certainly have my qualms with equities at times, but overall, they are more palatable than the fixed income portion of the portfolio. I don’t like it either, but the money is broken and the unit of account for nearly every equity or fixed income instrument (USD) is fraudulent. It’s a paper mache fade that is quite literally propped up by the money printer.
To briefly be as most charitable as I can – It wasn’t always this way. The U.S. Dollar used to be sound money, we used to have government surplus instead of mathematically certain deficits, The U.S. Federal Government didn’t used to have a money printing addiction, and pre-bitcoin the 60/40 portfolio used to be a quality portfolio management strategy. Those times are gone.
Now the fun part. How does bitcoin fix this?
Bitcoin fixes this indirectly. Understanding investment criteria changes via risk tolerance, age, goals, etc. A client may still have a need for “fixed income” in the most literal definition – Low risk yield. Now you may be thinking that yield is a bad word in bitcoin land, you’re not wrong, so stay with me. Perpetual motion machine crypto yield is fake and largely where many crypto scams originate. However, that doesn’t mean yield in the classic finance sense does not exist in bitcoin, it very literally does. Fortunately for us bitcoiners there are many other smart, driven, and enterprising bitcoiners that understand this problem and are doing something to address it. These individuals are pioneering new possibilities in bitcoin and finance, specifically when it comes to fixed income.
Here are some new developments –
Private Credit Funds – The Build Asset Management Secured Income Fund I is a private credit fund created by Build Asset Management. This fund primarily invests in bitcoin-backed, collateralized business loans originated by Unchained, with a secured structure involving a multi-signature, over-collateralized setup for risk management. Unchained originates loans and sells them to Build, which pools them into the fund, enabling investors to share in the interest income.
Dynamics
- Loan Terms: Unchained issues loans at interest rates around 14%, secured with a 2/3 multi-signature vault backed by a 40% loan-to-value (LTV) ratio.
- Fund Mechanics: Build buys these loans from Unchained, thus providing liquidity to Unchained for further loan originations, while Build manages interest payments to investors in the fund.
Pros
- The fund offers a unique way to earn income via bitcoin-collateralized debt, with protection against rehypothecation and strong security measures, making it attractive for investors seeking exposure to fixed income with bitcoin.
Cons
- The fund is only available to accredited investors, which is a regulatory standard for private credit funds like this.
Corporate Bonds – MicroStrategy Inc. (MSTR), a business intelligence company, has leveraged its corporate structure to issue bonds specifically to acquire bitcoin as a reserve asset. This approach allows investors to indirectly gain exposure to bitcoin’s potential upside while receiving interest payments on their bond investments. Some other publicly traded companies have also adopted this strategy, but for the sake of this article we will focus on MSTR as they are the biggest and most vocal issuer.
Dynamics
-
Issuance: MicroStrategy has issued senior secured notes in multiple offerings, with terms allowing the company to use the proceeds to purchase bitcoin.
-
Interest Rates: The bonds typically carry high-yield interest rates, averaging around 6-8% APR, depending on the specific issuance and market conditions at the time of issuance.
-
Maturity: The bonds have varying maturities, with most structured for multi-year terms, offering investors medium-term exposure to bitcoin’s value trajectory through MicroStrategy’s holdings.
Pros
-
Indirect Bitcoin exposure with income provides a unique opportunity for investors seeking income from bitcoin-backed debt.
-
Bonds issued by MicroStrategy offer relatively high interest rates, appealing for fixed-income investors attracted to the higher risk/reward scenarios.
Cons
-
There are credit risks tied to MicroStrategy’s financial health and bitcoin’s performance. A significant drop in bitcoin prices could strain the company’s ability to service debt, increasing credit risk.
-
Availability: These bonds are primarily accessible to institutional investors and accredited investors, limiting availability for retail investors.
Interest Payable in Bitcoin – River has introduced an innovative product, bitcoin Interest on Cash, allowing clients to earn interest on their U.S. dollar deposits, with the interest paid in bitcoin.
Dynamics
-
Interest Payment: Clients earn an annual interest rate of 3.8% on their cash deposits. The accrued interest is converted to Bitcoin daily and paid out monthly, enabling clients to accumulate Bitcoin over time.
-
Security and Accessibility: Cash deposits are insured up to $250,000 through River’s banking partner, Lead Bank, a member of the FDIC. All Bitcoin holdings are maintained in full reserve custody, ensuring that client assets are not lent or leveraged.
Pros
-
There are no hidden fees or minimum balance requirements, and clients can withdraw their cash at any time.
-
The 3.8% interest rate provides a predictable income stream, akin to traditional fixed-income investments.
Cons
-
While the interest rate is fixed, the value of the Bitcoin received as interest can fluctuate, introducing potential variability in the investment’s overall return.
-
Interest rate payments are on the lower side
Admittedly, this is a very small list, however, these types of investments are growing more numerous and meaningful. The reality is the existing options aren’t numerous enough to service every client that has a need for fixed income exposure. I challenge advisors to explore innovative options for fixed income exposure outside of sovereign debt, as that is most certainly a road to nowhere. It is my wholehearted belief and call to action that we need more options to help clients across the risk and capital allocation spectrum access a sound money standard.
Additional Resources
-
River: The future of saving is here: Earn 3.8% on cash. Paid in Bitcoin.
-
MicroStrategy: MicroStrategy Announces Pricing of Offering of Convertible Senior Notes
Bitcoin and Fixed Income was Written By Wyatt O’Rourke. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: ultrahusky3@primal.net
-
-
 @ 2063cd79:57bd1320
2025-01-08 11:19:56
@ 2063cd79:57bd1320
2025-01-08 11:19:56Ich hatte vor ein paar Wochen die Gelegenheit mich mit Micheal Hassard persönlich zu unterhalten. Mike ist Verteidiger im Fall von Roman Sterlingov. Der Fall ist haarsträubend und beängstigend. Mike und ich haben uns einige Zeit unterhalten und er hat mir einige Details aus diesem wirklich spannenden Prozess verraten. Ich wollte versuchen die Informationen in einem Artikel zusammenzufassen, um auch anderen Leuten, die mit dem Fall noch nicht betraut sind, die Möglichkeit zu geben, zu verstehen, was für absurde Methoden und ungerechte Beweismittel in diesem noch komplett neuen rechtlichen Umfeld angewendet werden.
LAX
Am 27. April 2001 landet ein Direktflug aus Moskau am Los Angeles International Airport (LAX). Bei der Passkontrolle an der Immigration wird ein junger Passagier dieses Fluges von Kriminalermittlern des Internal Revenue Service (IRS) verhaftet. In seinem Gepäck befinden sich vier Reisepässe und allerhand technisches Equipment. Darunter Laptops, externe Festplatten und Bitcoin Signing Devices (Hardware Wallets). Der junge Mann wird festgenommen, seine mitgeführten Besitztümer und Pässe konfisziert, dann wird er in Untersuchungshaft gebracht. Der Vorwurf: Die Gründung und der Betrieb eines Bitcoin Mixers. Konkret wird ihm vorgeworfen, Bitcoin Fog gegründet und betrieben zu haben, darüber hinaus wird er in drei Punkten angeklagt: Geldwäsche, Betrieb eines nicht lizenzierten Geldtransfergeschäfts und Geldtransfer ohne Lizenz. Die IRS behauptet, dass über 1,2 Millionen Bitcoin, im Wert von etwa 336 M US Dollar zum Zeitpunkt der Transaktionen, über Bitcoin Fog verschickt wurden.

Bitcoin Fog
Bitcoin Fog war ein beliebter Custodial Bitcoin Mixer, der von Nutzer//innen für ihre Privatsphäre genutzt wurde. Mixer sind Services die entwickelt wurden, um das Problem der "Common-Input-Ownership-Heuristik" zu brechen. Vereinfacht ausgedrückt beschreibt dieses Problem die Annahme, dass mehrere Inputs einer Transaktion relativ sicher dem gleichen Besitzer gehören. Ich habe Bitcoin Mixer schon mal detailliert beschrieben:
https://www.genexyz.org/post/23-block-772315-bitcoin-mixing-q6i7y4/
TL;DR: Die Grundidee besteht darin, dass man einen Coin nimmt, der aus mehreren UTXOs besteht, und diesen mit Hilfe eines Dienstes einem Pool zuführt. Diese Dienste erhalten für die Vermittlung, Zusammenführung und das Stellen der Infrastruktur eine kleine Gebühr. Transaktionen werden dann so aufgebaut, dass sie es Überwachungsfirmen oder anderen Beobachtern sehr schwer machen, genau zu wissen, welcher Transaktion-Output zu welchem der Input-Steller gehört.
Bitcoin Fog wurde 2011 gegründet und ist ein Custodial Service, was bedeutet, dass Nutzer//innen ihre Bitcoin an eine Wallet des Betreibers senden, und im Gegenzug dann von Bitcoin Fog andere Bitcoin zurück erhalten, um die Spur der On-Chain-Transaktionen zu verwischen.
Roman Sterlingov
Roman war schon früh Benutzer von Bitcoin. Als er 14 Jahre alt war, zog er mit seiner Mutter von Russland nach Schweden und beschäftigte sich ab etwa 2011 mit Bitcoin. Dies ist wichtig, denn als russischer und schwedischer Staatsbürger ist Roman im Besitz von vier offiziell ausgestellten Reisepässen. Russland hat zwei Pässe, einen für das Reisen innerhalb und einen für das Reisen außerhalb Russlands. Schweden stellt auch zwei Reisepässe aus. Als der Bitcoin-Kurs stieg, wurde er Millionär. Er kündigte seinen Job und versuchte, sich selbstständig zu machen. Unter anderem gründete er ein VPN-Geschäft, das nicht erfolgreich war, und entschied sich später aufgrund der Volatilität von Bitcoin und fehlenden Einnahmen aus seinen Projekten, Pilot bei einer kommerziellen Fluggesellschaft zu werden.
Er meldete sich bei einer kalifornischen Flugschule an und 2021, als Roman nach Kalifornien zur Flugschule flog, wurde er von der Regierung am Flughafen LAX verhaftet. Er sitzt seit über zwei Jahren im Gefängnis und wartet auf seinen Prozess. Neben seinen Pässen und seinem Equipment wurden auch die seit 2011 angesammelten Bitcoin beschlagnahmt, da diese auf Konten bei u.a. Kraken lagen.
Die Anklage
Kalifornien hat Roman Sterlingov wegen des Vorwurfs verhaftet, über einen Zeitraum von 10 Jahren Bitcoin im Wert von fast 336 M US Dollar gewaschen zu haben. Ihm wird vorgeworfen, über sein Konto und seine IP-Adressen mit der Bitcoin Fog-Domain und mit Mt. Gox-Konten, die in Verbindung zu Bitcoin Fog stehen, an Bitcoin Fog beteiligt zu sein.
Vor dem Start des Dienstes nutzte der Administrator seinen echten Namen auf seinem Mt. Gox-Konto, um die Plattform einem Betatest zu unterziehen. Sein persönliches Google-Konto wurde auch zum Speichern der Schritte zur Bezahlung der Domain verwendet. Dies sind jedoch zum heutigen Zeitpunkt nur Anschuldigungen ohne konkrete Beweise. Der Fall stützt sich stark auf digitale Forensik und Blockchain-Analyse ohne Zeugenaussagen oder ähnliche konkrete Beweisstücke. Selbst wenn Roman die Domain gekauft hätte, wäre dies nicht illegal. Die Verjährungsfrist für die angeblichen Verbrechen ist ebenfalls abgelaufen. Was bleibt, sind von der Anklage angeführte "Beweise", die sich komplett auf die Blockchain-Analyse der Firma Chainalysis stützen.
Chainalysis
Chainalysis ist die wohl bekannteste Blockchain-Analyse Firma. In einem früheren Artikel habe ich schon mal beschrieben, wie diese Firmen operieren:
https://www.genexyz.org/post/19-block-765505-on-chain-analytics-mhcumo/
TL;DR: Unter On-Chain Analytics versteht man die Analyse von Daten, die auf jeder beliebigen Blockchain vorhanden sind. Diese Daten sind auf der Chain, also on-chain und somit für jedermann jederzeit und von überall abrufbar. Genauer bieten Blockchains Daten über Adressen, Transaktionen und in gewisser Weise auch über Wallets. Diese Informationen können verwertet werden, um verschiedene Sachverhalte darzustellen. Dieses Verfahren wird auch Heuristik genannt und bedient sich wahrscheinlicher Annahmen, also z.B. wiederkehrender Muster. Dabei werden sogenannte Cluster erstellt, also Verbindungen zwischen Adressen und Transaktionen gezogen.
So nutzen nutzen Analyse-Firmen wie Chainalysis Heuristiken und Wahrscheinlichkeitsanalysen, um Bitcoin-Transaktionen und Eigentümerwechsel zu verfolgen. Sie versuchen, Adressen auf der Grundlage dieser Heuristiken zu gruppieren, jedoch stimmen die Ergebnisse verschiedener Unternehmen oft nicht überein. Dies kann zu vagen Beweisen und Schuldunterstellungen führen.
„Während die Identität eines Besitzers einer Bitcoin-Adresse im Allgemeinen anonym ist (es sei denn, der Besitzer entscheidet sich dafür, die Informationen öffentlich zugänglich zu machen), können Strafverfolgungsbehörden den Besitzer einer bestimmten Bitcoin-Adresse oft durch Analyse der Blockchain identifizieren“ - Devon Beckett, Special Agent, IRS
Chainalysis betreiben einen sogenannten Reactor, der diese Analysen vornimmt. Diese Analyse dient als Grundlage für das Argument, Roman habe Geld von seinem Mt Gox-Konto abgebucht und verwendet, um die Bezahlung der DNS-Registrierung für Bitcoin Fog zu tätigen und zu verbergen. Es wird so versucht, Roman mit Aufzeichnungen im Bitcoin Talk-Forums in Verbindung zu bringen, die wiederum Bitcoin Fog mit illegalen Aktivitäten in Verbindung bringen.

Konkret wird anhand dieser Analyse eine Verbindung zu Roman und weiter zu Bitcoin Fog hergestellt, die beweisen soll, dass Zahlungen im Wert von 336 M US Dollar gewaschen wurden, die für Drogengeschäfte verwendet wurden.
Es gibt keine objektiven Standards für diese Art der Analyse und Strafverfolgungsbehörden stützen ihre Beweise auf diese privaten Ermittlungen. Im konkreten Fall vo Chainalysis spielen Beziehungen zu Strafverfolgungsbehörden wie dem britischen Serious Crimes Office und dem US-Justizministerium, sowie den damit einhergehenden Geldquellen eine entscheidende Rolle beim Aufstieg des Unternehmens zum größten Anbieter dieser Dienstleistungen mit einer Marktkapitalisierung von 8,6 Milliarden US Dollar.
Verteidigung
Roman wird in diesem Fall von der Kanzlei Ekeland Law, PLLC vertreten. Die Anwälte, Tor Ekeland und Michael Hassard sind der festen Überzeugung, dass Roman unschuldig ist und dass er in diesem Fall aufgrund fehlerhafter digitaler Forensik in Bedrängnis geraten ist.
Roman gibt zu, Bitcoin Fog aus Datenschutzgründen verwendet zu haben, um seine Bitcoin zu waschen, bevor er diese in sein Konto bei Kraken einzahlte. Das Mischen an sich ist nicht illegal, denn während der Anhörung erkannte der Richter sogar an, dass die Verwendung eines Mixers wie Bitcoin Fog nicht grundsätzlich verboten sei. Dies war sogar das erste Mal, dass ein Richter ausdrücklich erklärte, dass das Mischen von Bitcoin nicht illegal ist und dass es auch nicht illegal ist, Nutzer//in eines Mischdienstes zu sein. Es ist jedoch zu beachten, dass sich dieser Fall speziell gegen den Betreiber von Bitcoin Fog richtet und versucht, den Dienst mit Drogenmarktplätzen in Verbindung zu bringen.
Argumente für Romans Unschuld beinhalten unter anderem, dass Bitcoin Fog in der gesamten Zeit von Romans Inhaftierung aktiv geblieben ist, was darauf schließen lässt, dass die eigentlichen Betreiber immer noch auf freiem Fuß sind. Roman wurde vor seiner Verhaftung überwacht, es wurden Abhör- und Überwachungsmaßnahmen durchgeführt, jedoch keine Beweise gefunden, die ihn mit dem Betrieb von Bitcoin Fog in Verbindung bringen, selbst nachdem Server beschlagnahmt wurden.
Darüber hinaus ignoriert die Anklage auch die Tatsache, dass die DNS-Registrierung der Bitcoin Fog Domain seit Romans Verhaftung zweimal erneuert wurde. Trotzdem versucht die Anklage eine Verbindung zu Roman auf der Grundlage von IP-Adressen herzustellen, die mit anderen E-Mails verknüpft sind, die zur Registrierung der DNS und zur Erstellung eines Kontos im Bitcoin Talk Forum verwendet wurden.

Roman wird Verschwörung vorgeworfen, es wurde jedoch kein einziger Mitverschwörer genannt. Bei den von der Anklage behaupteten Transaktionen handelt es sich um Lizenzzahlungen des Mixers, die jedoch nicht durch Beweise gestützt werden. Wenn Roman ein Drahtzieher wäre, der 336 M US Dollar an Drogengeldern gewaschen hätte, würde es für ihn keinen Sinn machen, sein Geld mit seinem richtigen Namen und Passfoto auf ein KYC-Konto bei Kraken einzuzahlen.
An dieser Stelle ist es vielleicht interessant festzustellen, dass Michael Gronager, einer der Mitbegründer von Chainalysis, auch einer der Mitbegründer von Kraken war.
Mt Gox Daten
Es gibt eine Verbindung zwischen Kraken, Chainalysis und Mt Gox. Denn nicht nur war der Gründer von Kraken, Jesse Powell, als Berater für Mt. Gox bei der Lösung eines Sicherheitsproblems tätig und begann in Erwartung seines Kollapses mit der Arbeit an Kraken als Ersatz, auch Chainalysis wurde als direkte Reaktion auf den Mt. Gox-Skandal gegründet.
Chainalysis wurde in den offiziellen Ermittlungen im Insolvenzverfahren von Mt. Gox genutzt, um den Verbleib der "gestohlenen" bitcoins zu untersuchen. Allerdings gibt es Anzeichen dafür, dass die dabei verwendeten Daten falsch und unzuverlässig seien. Angebliche Transaktionsnummern und Wallet-Adressen existieren nicht, werden verwechselt oder sind schlichtweg fehlerhaft. Genau dieser Datensatz wird aber nun benutzt, um Fälle wie den von Roman zu beweisen.
Ankläger
Einer der Staatsanwälte des Falles ist jetzt leitender Rechtsberater für Chainalysis, und ein IRS-Ermittler gründete während seiner Tätigkeit für den IRS ein privates Unternehmen namens Exigent LLC. Die Pressemitteilungen und Fundraising-Runden von Chainalysis stehen eng im Zusammenhang mit dem Fall. Exigent LLC erhält in der Pressemitteilung des US-Justizministeriums die höchste Auszeichnung für Romans Verhaftung, und fünf Monate später kaufte Chainalysis Exigent LLC. Dieser Fall scheint von Karrierismus und Profitstreben getrieben zu sein.

Problem
Neben den Verbindungen der Ermittler und Ankläger mit Chainalysis und der Problematik der fehlenden Beweise, ist dieser Fall zutiefst beunruhigend und wirft Bedenken hinsichtlich des geltenden Computerrechts auf.
Die meisten Blockchain-Strafverfolgungen folgen dem gleichen Muster: Einspruchsvereinbarungen, Gerichtsverfahren oder Entlassungen. Unschuldige Menschen gehen oft auf Plädoyer-Deals ein, weil ihnen die Ressourcen fehlen, um gegen die unbegrenzten Ressourcen des Department of Justice zu kämpfen. Roman kann keinen Deal annehmen, weil er nichts weiß und lügen müsste.
Es ist beunruhigend, dass der Fall in Washington D.C. verhandelt wird, obwohl Roman keine Verbindungen zu dieser Stadt hat. Die einzige Grundlage dafür, die Gerichtsbarkeit nach D.C. zu legen, ist darin begründet, dass eine verdeckte Operation gegen Roman aus Washington D.C. geleitet wurde. Dies gibt Anlass zur Sorge, weil es Staatsanwälten ermöglicht, Angeklagte auf der Grundlage von Online-Interaktionen vor jedes Bundesgericht zu ziehen - ob US Staatsbürger oder nicht. Dies ist ein direkter Verstoß gegen die Gerichtsstandsklausel und entfernt wichtige Elemente des Strafrechtssystems, da es jede/n Nutzer//in von Bitcoin-Mixern in die gefährliche Lage versetzen kann, vor einem US-Gericht angeklagt zu werden, wenn eine auch nur dünne Beweislage gegen ihn/sie vorliegt.
Ein weiteres Problem besteht in den vorgebrachten Beweisen. Denn die Verteidigung hat bis heute keinen Einblick in den Code oder die verwendeten Datensätze, die von Chainalysis verwendet wurden, erhalten. Chainalysis beruft sich dabei auf seine proprietären Geschäftsdaten und lehnt eine Offenlegung ab. Es wird vermutet, dass die Datensätze falsch sind, insbesondere angesichts der fragwürdigen Mt. Gox-Aufzeichnungen, auf die sie sich stützen.
Die bereitgestellten Daten sind begrenzt, unvollständig und werden in komplizierten Flussdiagrammen dargestellt. Die verwendete Software, wie z.B. der Chainalysis Reactor, steht nicht für eine unabhängige Prüfung zur Verfügung. Der Mangel an Transparenz und Zugang zu dieser Software gibt Anlass zu Bedenken hinsichtlich ihrer Genauigkeit und den daraus gezogenen Schlussfolgerungen.

Es bestehen Zweifel am Zusammenhang zwischen Roman, dem Betreiber von Bitcoin Fog, und den mutmaßlichen Straftaten. Roman sitzt derzeit im Gefängnis, ihm droht eine Haftstrafe von 50 Jahren. Die Freiheit einer Person wird durch eine kommerzielle proprietäre Software gefährdet, die vor Gericht erwirken kann, dass Quellen und Datensätze nicht offengelegt werden.
Auch wirft der Fall Bedenken hinsichtlich fehlender Standards, des gewinnorientierten Charakters des forensischen Bereichs, der Weigerung, Beweise auszutauschen, und der Möglichkeit von Justizirrtümern auf, die durch fehlerhafte Software und fragwürdige Praktiken verursacht werden.
Wie geht es weiter?
Das Verteidigungsteam hat finanzielle Probleme, da alle Gelder von Roman beschlagnahmt wurden. Der Antrag auf Freigabe der Mittel wurde abgelehnt. Romans Verteidigung muss öffentliche Mittel beantragen und hofft auf Spenden. Ich habe in einem früheren Artikel schon auf die Spendenseite aufmerksam gemacht. Wer anhand der aufgelisteten Fakten das Gefühl bekommt, dass hier jemand zu Unrecht verhaftet wurde und helfen möchte, kann die Verteidigung mit einer Spende unterstützen.
https://www.torekeland.com/roman-sterlingov
https://geyser.fund/project/usvsterlingov
FREEROMAN
🫳🎤
In diesem Sinne, 2... 1... Risiko!

-
 @ 609899dc:13493d8d
2025-01-08 10:16:53
@ 609899dc:13493d8d
2025-01-08 10:16:53Simplify your Arlo security system setup with Myarlosetup.From connecting devices to setting up settings for maximum security, our professional assistance guarantees a seamless installation experience. We assist you in smoothly integrating your floodlights, doorbells, and cameras into your system. Get improved protection and real-time monitoring for your house or place of business. You can rely on Myarlosetup to offer detailed guidance and guarantee a simple and effective Arlo security system setup. Easily secure your home now!
-
 @ 4657dfe8:47934b3e
2024-12-18 13:42:46
@ 4657dfe8:47934b3e
2024-12-18 13:42:46Alby Hub enables creation of subaccounts, decentralizing trust and creating usecases for shared, community nodes.
Simplifying Bitcoin Wallets for Friends and Family
Alby Hub empowers you to take full control of your bitcoin and manage your payments. Through a user-friendly, self-custodial wallet with a one-click lightning node setup, you can effortlessly connect to dozens of applications. The integrated App Store provides access to popular apps like Amethyst, Damus, Stacker News, Podcasting 2.0, and a wide range of other external tools—all directly linked with your Alby Hub wallet. One of the latest and most exciting additions to Alby Hub is the Friends & Family app.
With the Friends & Family app, you can create subaccounts for friends and family, all powered by your Hub. In just a few clicks, you can set up wallets for them, giving them a smooth onboarding experience and making bitcoin accessible even to those new to the ecosystem. Think of it as a custodial wallet but with a personal touch—since you’re the one managing it, there’s a direct relationship and trust.
These subaccount holders can tap into all the channels and liquidity of your Hub without needing to handle any technical setup. Plus, you can preload their wallets with a few sats, creating a welcoming and smooth experience that’s hard to find elsewhere.
And that’s not all. Beyond providing an intuitive wallet, they can get their own lightning address, configurable payment notifications, access to Alby Go (a mobile app for payments on the go), and the Alby Browser Extension for easy web payments.
Let’s have a look how to set it up.
How to provide a wallet to Friends and Family?
- Open your Hub and find the Friends & Family app in the App Store
- Enter a name e.g. your friend’s name and click “Create subaccount”
- Share the Connection Secret with your friend for the different options
Here are two examples how your the new subaccount can be used.
Alby Go mobile App
Alby Go makes it easy to carry bitcoin in your pocket. This lightweight wallet connects directly to an Alby Hub subaccount, so your friends can pay and check transactions on the go.
Here’s how to set it up: 1. Open the Alby Go Mobile App tab in your Hub.
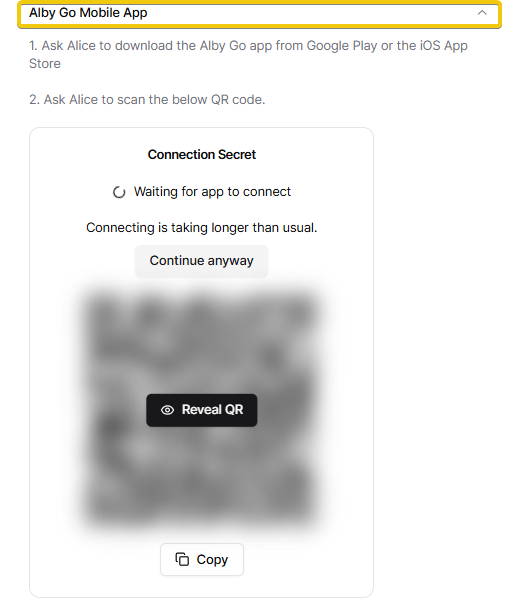 2. Copy the Connection Secret and share it with your friend if you cannot onboard them in person.
3. Your friend downloads Alby Go for Android or iOS and scans the code.
2. Copy the Connection Secret and share it with your friend if you cannot onboard them in person.
3. Your friend downloads Alby Go for Android or iOS and scans the code.And that’s it—your friend now has a bitcoin wallet in their pocket, ready for seamless transactions anytime, anywhere. 🎉
Get a Lightning Address with an Alby account
An Alby Account offers a variety of useful features that make managing bitcoin payments easy. Among these are a personalized lightning address and email payment notifications—two powerful tools that help your newly onboarded friends stay connected and informed.
To set up an Alby account for someone:
-
Open the Alby Account tab in your Hub.
-
Copy the provided URL and share it with your friend.
-
Your friend simply needs to create their Alby account and afterwards click on the provided URL.
That’s it! The wallet is instantly connected, and they’re ready to receive payments to their new lightning address. 🥳
Onboarding Family & Friends Made Easy In this article, we explored how to create subaccounts for family and friends, connect them with Alby Go, and set up an Alby account to provide a smooth onboarding experience for your loved ones—all achievable in just a few clicks.
Stay tuned as we dive into more exciting use cases for subaccounts in Alby Hub! If you have ideas for improvement,let us know.
- Open your Hub and find the Friends & Family app in the App Store
-
 @ 94a6a78a:0ddf320e
2024-11-27 19:36:12
@ 94a6a78a:0ddf320e
2024-11-27 19:36:12The backbone of your Nostr experience lies in relays—servers that transmit your notes, zaps, and private messages across the decentralized network. Azzamo offers three specialized relays to suit different user needs, ensuring reliability, performance, and privacy.
1. Free Relay
- URL:
wss://nostr.azzamo.net - Overview: Azzamo’s Free Relay is perfect for newcomers to Nostr. It’s open-access, reliable, and ensures fair use with moderate rate limits.
- Key Features:
- Free to use.
- Notes older than one month are purged daily.
- Accessible gateway for decentralized communication.
2. Paid Relay
- URL:
wss://relay.azzamo.net - Overview: Designed for power users, the Paid Relay offers unmatched performance with 99.9% uptime and low latency.
- Key Features:
- Scalable for heavy users.
- Fewer users for faster, consistent connections.
- Premium support included for paid users.
3. Inbox Relay
- URL:
wss://inbox.azzamo.net - Overview: Never miss a private message again with the Inbox Relay, optimized for secure, spam-free direct messaging.
- Key Features:
- Guaranteed message delivery.
- Optimized for NIP-17 private messages.
- Optimized for NIP-19 group chats.
- Premium users enjoy advanced support.
Why Choose Azzamo Relays?
Life on Nostr is easier with Azzamo relays. They’re fast, reliable, and built to handle whatever you throw at them. The Paid Relay keeps your connections strong, the Inbox Relay makes sure no private message gets lost, and the Free Relay is always there to get you started. Supporting Azzamo by going premium helps keep this decentralized network growing—and you get priority support while you’re at it. Azzamo has your back on Nostr!
🔗 Start now:
- Free Relay:
wss://nostr.azzamo.net - Paid Relay: azzamo.net/pay
- Inbox Relay: azzamo.net/inbox
Support the network and upgrade your experience—add time to your account via the Azzamo Dashboard. Choose Azzamo, and take control of your Nostr journey today!
- URL:
-
 @ eac63075:b4988b48
2024-12-18 11:35:25
@ eac63075:b4988b48
2024-12-18 11:35:25The European Union is at a crossroads. While digital innovation and security cooperation remain critical in a connected world, recent proposals to enhance police surveillance and data sharing are stirring deep concerns about individual privacy, data security, and democratic oversight. Two recent reports published by Statewatch shed light on troubling developments in the EU’s policing landscape, raising alarms among privacy advocates and civil rights organizations.
The EU’s new plans to expand police surveillance could put your privacy and rights at risk and introduce risks far outweighing their potential benefits. This article will analyze these proposals, their implications, and the growing opposition from privacy and civil liberties defenders.
Surveillance Infrastructure: Policing by Design
The first Statewatch report, titled “Policing by Design: The Latest EU Surveillance Plan”, outlines a concerning trend in the EU’s approach to law enforcement. The proposals advocate embedding surveillance tools directly into the design of new technologies, effectively creating an architecture where policing capabilities are integrated into the systems we use daily.
From facial recognition cameras to AI-driven analytics, the EU plans to enhance cross-border police cooperation by ensuring technology is designed to facilitate surveillance from the outset. Known as “policing by design,” this strategy involves building surveillance features directly into technologies we use every day. Imagine a network of cameras or software that can automatically monitor people’s faces or behaviors without any extra installation — it’s like your everyday tech quietly doubling as a police tool. The goal is to enable seamless sharing of data across borders for criminal investigations, but the unintended consequences are alarming.
The Problem with “Policing by Design”
- Mass Surveillance Normalized: By embedding surveillance features into public and private infrastructure, society risks normalizing mass surveillance, where every movement, transaction, or online interaction is monitored and analyzed.
- Threats to Privacy: Such initiatives inherently contradict the principle of privacy by design, which prioritizes privacy protections in the development of technology. Instead, citizens are being treated as subjects of perpetual suspicion.
- Lack of Transparency and Accountability: A systemic lack of transparency surrounding these plans raises serious governance issues. Civil society organizations, journalists, and privacy advocates have pointed to a lack of democratic oversight and meaningful debate.
- Risks of Abuse: Surveillance systems are often deployed under the guise of security but are susceptible to abuse. History shows that tools designed for law enforcement can easily be turned against dissenters, journalists, or marginalized communities.
As the report highlights, these developments could establish a permanent surveillance infrastructure across Europe, enabling the collection of biometric, behavioral, and communications data on an unprecedented scale.
Flawed Justifications for Surveillance Expansion
Privacy advocacy organizations, including the European Digital Rights (EDRi) network, argue that much of the justification for these surveillance plans relies on flawed assumptions. The rhetoric of the “Going Dark” report, which claims that law enforcement is losing access to communications due to encryption, has been widely debunked. As EDRi points out, law enforcement already has extensive tools at their disposal to access data and track individuals, but the focus on encryption risks undermining secure communication for everyone.
Instead of addressing systemic issues within law enforcement, these flawed reports have fueled calls for intrusive surveillance systems that risk eroding privacy while offering little evidence of improving public safety.
Centralized Police Data: A Substantial Security and Privacy Threat
A second Statewatch report, titled “EU Police Data Plans Pose Substantial Security and Privacy Threats”, explores another equally concerning initiative: the EU’s push to centralize police data repositories and expand their use.
The EU has already established several large-scale databases, such as the Schengen Information System (SIS), which stores data about individuals who may be denied entry into the EU, and the Europol Information System, which can hold details about millions of people, including those not suspected of crimes. For example, a traveler flagged mistakenly in the system could face unnecessary scrutiny, detention, or restrictions when crossing borders — highlighting the real-world risks of inaccurate or overreaching data collection. The new proposals aim to go further, creating an interoperable web of police data accessible to law enforcement agencies across member states. Proponents argue this is necessary for combating cross-border crime and terrorism, but the risks are immense.
Key Concerns with Centralized Police Data
- Massive Data Collection: The EU’s proposed systems would require the collection of highly sensitive data, including biometric information (fingerprints, facial recognition scans) and behavioral analytics, to track individuals’ activities across borders.
- Data Misuse and Security Risks: Centralized data systems are prime targets for cyberattacks, data breaches, and misuse. The larger and more interconnected the system, the greater the risks of unauthorized access, theft, or corruption of the data.
- As Statewatch points out, the systems lack robust safeguards to prevent misuse or to ensure that data is handled proportionately and lawfully.
- Erosion of Trust in Law Enforcement: Building centralized data repositories without meaningful safeguards undermines public trust. Individuals may be less willing to engage with law enforcement if they fear their data will be stored indefinitely, shared across borders, or used inappropriately.
- Impact on Fundamental Rights: Mass police databases can violate the principle of proportionality, a cornerstone of EU law. By collecting and sharing data indiscriminately, these systems erode fundamental rights, including the right to privacy, freedom of movement, and the presumption of innocence.
Civil Society Opposition and Democratic Accountability
In an open letter to EU institutions, over 30 civil society organizations — including EDRi — have criticized the lack of transparency in the High-Level Group’s (HLG) recommendations for data access. The letter highlights a concerning pattern: while industry stakeholders are included in key discussions, civil society voices remain sidelined. This exclusion undermines democratic accountability and reinforces fears that surveillance policies are being driven by corporate interests rather than public well-being.
These organizations have called for the EU to prioritize transparency, include meaningful public debate, and ensure any law enforcement proposals respect proportionality and fundamental rights.
Why Privacy Advocates Are Sounding the Alarm
The reports from Statewatch highlight a fundamental clash between security policy and individual rights. Privacy advocates are urging EU lawmakers to take a step back and critically examine the following issues:
- Lack of Democratic Oversight: Proposals to integrate surveillance systems and expand police databases are being pushed forward without genuine public debate or oversight. Civil society organizations have been excluded from key discussions.
- Failure to Uphold Privacy Laws: The EU has some of the strongest privacy laws in the world, including the General Data Protection Regulation (GDPR). However, these proposals risk undermining GDPR principles by enabling indiscriminate data collection and sharing.
- Ignoring Proportionality: Surveillance systems must be targeted, necessary, and proportionate to their objectives. Embedding policing into technological design and centralizing data far exceeds what is justified for fighting crime and terrorism.
- Setting Dangerous Precedents: The failure to fully ban harmful surveillance technologies like facial recognition in public spaces sets a troubling precedent. It risks not only eroding privacy within the EU but also encouraging other nations to adopt similar measures, undermining global human rights.
A Call for Action: Safeguarding Our Privacy and Rights
As the EU pushes forward with these plans, the opposition from civil rights defenders grows louder. Policymakers must address the following key demands to prevent an erosion of fundamental rights:
- Implement Privacy by Design: All new technologies must prioritize privacy protections at the design stage, ensuring they are not co-opted for surveillance.
- Establish Robust Oversight: Any new policing tools or databases must be subject to democratic scrutiny, independent oversight, and clear legal frameworks to prevent misuse.
- Reassess Interoperability Plans: Cross-border police cooperation is important, but it must not come at the cost of individuals’ privacy, security, and dignity.
- Strengthen Export Controls: The EU must ban the export of surveillance tools that risk facilitating human rights abuses in authoritarian regimes.
- Prioritize Data Security: Centralized systems require state-of-the-art security measures to protect sensitive data from breaches or misuse.
The EU’s role as a leader in digital rights and privacy is now at stake. If these plans proceed without significant safeguards, Europe risks undermining its own foundational principles of freedom, security, and justice.
Conclusion: The Price of Surveillance-Driven Security
The EU’s surveillance plans may be presented as necessary for security, but they come at a steep cost to privacy, trust, and individual freedoms. Embedding surveillance into our technologies and centralizing police data pose far-reaching risks that cannot be ignored.
As privacy advocates, it is our responsibility to hold policymakers accountable and demand a security framework that upholds, rather than undermines, fundamental rights. Europe’s future must not be built on surveillance by design — but on privacy, democracy, and trust.
-
 @ 07907690:d4e015f6
2024-11-24 09:38:58
@ 07907690:d4e015f6
2024-11-24 09:38:58Karena orang tuanya yang berasal dari Hongaria telah melarikan diri dari rezim Soviet pascaperang untuk menetap di Amerika Serikat, Nick Szabo menganggap daerah Teluk California pada tahun 1990-an sebagai rumahnya. Di sana, ia termasuk orang pertama yang sering menghadiri pertemuan tatap muka "Cypherpunk" yang diselenggarakan oleh Timothy May, Eric Hughes, dan anggota pendiri kolektif kriptografer, programmer, dan aktivis privasi lainnya yang berpusat di sekitar milis tahun 90-an dengan nama yang sama.
Seperti Cypherpunk lainnya, Szabo khawatir dengan jaminan privasi yang semakin berkurang di era digital yang akan datang dan mengambil tindakan untuk membendung gelombang tersebut semampunya. Misalnya, di milis Cypherpunk, Szabo memimpin penentangan terhadap "Chip Clipper", sebuah chip yang diusulkan untuk disematkan di telepon, yang memungkinkan NSA untuk mendengarkan panggilan telepon. Szabo memiliki bakat khusus untuk menjelaskan risiko pelanggaran privasi tersebut dengan cara yang dapat diterima oleh orang-orang yang tidak memiliki latar belakang teknis, terkadang memberikan ceramah tentang topik tersebut atau bahkan membagikan brosur. (Chip tersebut akhirnya ditolak oleh produsen dan konsumen.)
Namun seperti Cypherpunk yang lebih berorientasi libertarian, minat Szabo dalam privasi digital adalah bagian dari gambaran yang lebih besar — ini bukan hanya tentang privasi saja. Terinspirasi oleh visi Timothy May sebagaimana yang ditetapkan dalam The Crypto Anarchist Manifesto, Szabo melihat potensi untuk menciptakan "Galt's Gulch" di dunia maya: domain tempat individu dapat berdagang dengan bebas, seperti yang dijelaskan oleh novel penulis libertarian Ayn Rand, Atlas Shrugged. Medan gaya pseudo-fisika dari cerita tersebut, May dan Szabo percaya, dapat digantikan dengan keajaiban kriptografi kunci publik yang baru-baru ini ditemukan.
“Jika kita mundur sejenak dan mencermati apa yang ingin dicapai oleh banyak cypherpunk, tema idealis utamanya adalah dunia maya Ghana di mana kekerasan hanya bisa menjadi khayalan, entah itu dalam Mortal Komat [sic] atau 'perang api',” tulis Szabo dalam milis Cypherpunks.
Namun, Szabo juga menyadari bahwa perusahaan bebas membutuhkan lebih dari sekadar enkripsi sebagai lapisan keamanan. Terinspirasi oleh penulis libertarian lainnya — ekonom Friedrich Hayek — ia menemukan bahwa dasar masyarakat manusia, sebagian besar, didasarkan pada komponen dasar, seperti properti dan kontrak, yang biasanya ditegakkan oleh negara. Untuk menciptakan alternatif dunia maya tanpa negara dan tanpa kekerasan, Szabo tahu bahwa komponen dasar ini harus dipindahkan ke ranah daring.
Beginilah cara Szabo, pada pertengahan 1990-an, mengusulkan sesuatu yang mungkin paling dikenalnya saat ini: kontrak pintar. Protokol komputer (yang saat itu masih hipotetis) ini dapat memfasilitasi, memverifikasi, dan menegakkan negosiasi atau pelaksanaan kontrak secara digital, idealnya tanpa memerlukan pihak ketiga mana pun. Seperti yang pernah dikatakan Szabo : "Pihak ketiga yang tepercaya adalah lubang keamanan." Lubang keamanan ini akan menjadi target peretas atau penjahat — serta negara-negara bangsa selama masa ketidakstabilan politik atau penindasan.
Namun kontrak pintar hanyalah sebagian dari teka-teki. Alat kedua yang dibutuhkan Szabo untuk mewujudkan "Galt's Gulch" mungkin bahkan lebih penting. Uang.
Uang Elektronik
Mata uang digital, uang tunai untuk internet, selalu menjadi tujuan utama Cypherpunk. Namun, hanya sedikit yang mendalami pokok bahasan tersebut seperti yang dilakukan Szabo.
Dalam esainya "Shelling Out: The Origins of Money," Szabo menjelaskan bagaimana — seperti yang pertama kali dihipotesiskan oleh ahli biologi evolusi Richard Dawkins — penggunaan uang telah tertanam dalam DNA manusia. Setelah menganalisis masyarakat pra-peradaban, Szabo menemukan bahwa orang-orang di berbagai budaya cenderung mengumpulkan benda-benda langka dan mudah dibawa, sering kali untuk dijadikan perhiasan. Benda-benda inilah yang berfungsi sebagai uang, yang pada gilirannya memungkinkan manusia untuk bekerja sama: "altruisme timbal balik" teori permainan melalui perdagangan, dalam skala besar dan lintas waktu.
Szabo juga sangat tertarik pada perbankan bebas, sebuah pengaturan moneter yang didukung oleh Hayek, di mana bank swasta menerbitkan mata uang mereka sendiri yang tidak terikat pada negara tertentu. Di bawah sistem seperti itu, pasar bebas sepenuhnya bebas menentukan mata uang mana yang akan digunakan. Meskipun merupakan ide baru saat ini (dan bahkan lebih baru lagi pada tahun-tahun sebelum Bitcoin), perbankan bebas merupakan kenyataan di Amerika Serikat pada tahun 1800-an, serta di beberapa negara lain.
Szabo juga melanjutkan untuk menerapkan minatnya dalam praktik dan menjual keahliannya sebagai konsultan perdagangan internet pada pertengahan 1990-an, jauh sebelum kebanyakan orang melihat potensi perdagangan daring. Yang paling menonjol, ia menghabiskan waktu bekerja di perusahaan rintisan DigiCash milik David Chaum, yang berkantor pusat di Amsterdam. Perusahaan Chaum memperkenalkan uang digital pertama yang pernah ada di dunia dalam bentuk eCash: sarana untuk melakukan pembayaran daring yang sama rahasianya dengan uang tunai di dunia nyata.
Namun, di DigiCash pula Szabo mengetahui risiko solusi Chaum. DigiCash adalah perusahaan terpusat, dan Szabo merasa terlalu mudah baginya dan orang lain untuk mengutak-atik saldo orang lain jika mereka mau. Bagaimanapun, pihak tepercaya adalah celah keamanan, dan risiko ini mungkin tidak lebih besar daripada risiko dalam hal uang.
“Masalahnya, singkatnya, adalah bahwa uang kita saat ini bergantung pada kepercayaan pada pihak ketiga untuk menentukan nilainya,” Szabo berpendapat pada tahun 2005. “Seperti yang ditunjukkan oleh banyak episode inflasi dan hiperinflasi selama abad ke-20, ini bukanlah keadaan yang ideal.”
Bahkan, ia menganggap masalah kepercayaan ini sebagai hambatan yang bahkan solusi perbankan bebas pada umumnya bisa mengalaminya: “[P]enerbitan uang kertas swasta, meski memiliki berbagai kelebihan dan kekurangan, juga bergantung pada pihak ketiga yang terpercaya.”
Szabo tahu ia ingin menciptakan bentuk uang baru yang tidak bergantung pada kepercayaan pada pihak ketiga mana pun.
Berdasarkan analisisnya terhadap uang prasejarah, Szabo telah menempuh perjalanan panjang dalam menentukan seperti apa bentuk uang idealnya. Pertama, uang tersebut harus “aman dari kehilangan dan pencurian yang tidak disengaja.” Kedua, nilainya harus “sangat mahal dan tidak dapat dipalsukan, sehingga dianggap berharga.” Dan ketiga: “Nilai ini [harus] diperkirakan secara akurat melalui pengamatan atau pengukuran sederhana.”
Dibandingkan dengan logam mulia seperti emas, Szabo ingin menciptakan sesuatu yang digital dan langka, di mana kelangkaan ini tidak bergantung pada kepercayaan pihak ketiga. Ia ingin menciptakan emas digital.
Logam mulia dan barang koleksi memiliki kelangkaan yang tidak dapat dipalsukan karena mahalnya biaya pembuatannya. Hal ini pernah menghasilkan uang yang nilainya sebagian besar tidak bergantung pada pihak ketiga yang tepercaya. Namun, logam mulia memiliki masalah. […] Jadi, akan sangat bagus jika ada protokol yang memungkinkan bit yang sangat mahal dapat dibuat secara daring dengan ketergantungan minimal pada pihak ketiga yang tepercaya, lalu disimpan, ditransfer, dan diuji dengan aman dengan kepercayaan minimal yang serupa. Bit Gold.
Bit Gold
Szabo pertama kali mencetuskan Bit Gold pada tahun 1998, meskipun ia baru menjelaskannya secara lengkap di depan publik pada tahun 2005. Skema uang digital yang diusulkannya terdiri dari kombinasi berbagai solusi, beberapa di antaranya terinspirasi oleh (atau menyerupai) konsep uang elektronik sebelumnya.
Properti utama pertama Bit Gold adalah proof of work, trik kriptografi yang digunakan oleh Dr. Adam Back dalam "mata uang anti-spam" miliknya, Hashcash. Proof of work merupakan biaya yang tidak dapat dipalsukan yang dicari Szabo, karena memerlukan sumber daya dunia nyata — daya komputasi — untuk menghasilkan bukti-bukti ini.
Sistem pembuktian kerja Bit Gold dimulai dengan "string kandidat": pada dasarnya angka acak. Siapa pun dapat mengambil string ini dan secara matematis menggabungkannya — "hash" — dengan angka acak lain yang baru dibuat. Berdasarkan sifat hashing, hasilnya akan menjadi string angka baru yang tampak acak: hash. Satu-satunya cara untuk mengetahui seperti apa hash ini adalah dengan benar-benar membuatnya — hash tidak dapat dihitung atau diprediksi dengan cara lain.
Triknya, yang juga digunakan dalam Hashcash, adalah bahwa tidak semua hash dianggap valid dalam protokol Bit Gold. Sebaliknya, hash yang valid harus, misalnya, dimulai dengan sejumlah angka nol yang telah ditentukan sebelumnya. Karena sifat hashing yang tidak dapat diprediksi, satu-satunya cara untuk menemukan hash yang valid adalah dengan coba-coba. Oleh karena itu, hash yang valid membuktikan bahwa pembuatnya telah mengeluarkan daya komputasi.
Hash yang valid ini, pada gilirannya, akan menjadi string kandidat Bit Gold berikutnya. Oleh karena itu, sistem Bit Gold akan berkembang menjadi rantai hash proof-of-work, dan akan selalu ada string kandidat berikutnya untuk digunakan.
Siapa pun yang menemukan hash yang valid akan secara harfiah memiliki hash tersebut, mirip dengan bagaimana orang yang menemukan sedikit bijih emas memilikinya. Untuk menetapkan kepemilikan ini secara digital, Bit Gold menggunakan registri kepemilikan digital : blok penyusun lain yang terinspirasi Hayek yang diusulkan oleh Szabo. Dalam registri ini, hash akan ditautkan ke kunci publik dari masing-masing pembuatnya.
Melalui registri kepemilikan digital ini pula, hash dapat ditransfer ke pemilik baru: Pemilik asli secara harfiah akan menandatangani transaksi dengan tanda tangan kriptografi.
Registri kepemilikan akan dikelola oleh "klub properti" Bit Gold. Klub properti ini terdiri dari "anggota klub" (server) yang akan melacak kunci publik mana yang memiliki hash mana. Solusi ini agak mirip dengan solusi basis data replikasi yang diusulkan Wei Dai untuk b-money; baik Szabo maupun Dai tidak hanya aktif di milis Cypherpunks, tetapi juga di milis tertutup yang membahas topik-topik ini.
Namun, alih-alih sistem proof-of-stake milik Dai untuk menjaga agar sistem tetap mutakhir, Szabo mengusulkan "Sistem Kuorum Bizantium." Mirip dengan sistem yang sangat penting bagi keamanan seperti komputer pesawat terbang, jika hanya satu (atau sebagian kecil) dari komputer ini yang tidak berfungsi, sistem secara keseluruhan akan tetap beroperasi dengan baik. Sistem akan bermasalah hanya jika sebagian besar komputer gagal pada saat yang sama. Yang penting, tidak satu pun dari pemeriksaan ini memerlukan pengadilan, hakim, atau polisi, yang didukung oleh monopoli negara atas kekerasan: Semuanya akan bersifat sukarela.
Meskipun sistem ini sendiri tidak sepenuhnya sangat ketat — misalnya Serangan Sybil ("sock puppet problem") — Szabo yakin sistem ini bisa berjalan sendiri. Bahkan dalam skenario di mana mayoritas anggota klub akan mencoba berbuat curang, minoritas yang jujur bisa bercabang ke dalam daftar kepemilikan yang bersaing. Pengguna kemudian dapat memilih daftar kepemilikan mana yang akan digunakan, yang menurut Szabo mungkin adalah yang jujur.
"Jika aturan dilanggar oleh pemilih yang menang, maka pecundang yang benar dapat keluar dari grup dan membentuk grup baru, mewarisi gelar lama," jelasnya. "Pengguna gelar (partai yang mengandalkan) yang ingin mempertahankan gelar yang benar dapat memverifikasi sendiri dengan aman kelompok sempalan mana yang telah mengikuti aturan dengan benar dan beralih ke grup yang benar."
(Sebagai contoh modern, ini mungkin dapat dibandingkan dengan Ethereum Classic, yang memelihara versi buku besar Ethereum asli yang tidak membatalkan kontrak pintar The DAO.)
Inflasi
Masalah berikutnya yang harus dipecahkan Szabo adalah inflasi. Seiring dengan semakin baiknya komputer dari waktu ke waktu, akan semakin mudah untuk menghasilkan hash yang valid. Ini berarti bahwa hash itu sendiri tidak dapat berfungsi sebagai uang dengan baik: hash akan semakin langka setiap tahunnya, sampai pada titik di mana kelimpahan akan melemahkan semua nilai.
Szabo menemukan solusinya. Setelah hash yang valid ditemukan, hash tersebut harus diberi cap waktu, idealnya dengan server cap waktu yang berbeda untuk meminimalkan kepercayaan pada hash tertentu. Cap waktu ini akan memberikan gambaran tentang seberapa sulitnya menghasilkan hash: hash yang lama akan lebih sulit diproduksi daripada hash yang baru. Pasar kemudian akan menentukan berapa nilai hash tertentu relatif terhadap hash lainnya, mungkin menyesuaikan nilainya dengan tanggal ditemukannya. "Hash 2018" yang valid seharusnya bernilai jauh lebih rendah daripada "Hash 2008" yang valid.
Namun solusi ini, tentu saja, menimbulkan masalah baru, Szabo tahu : "bagian-bagian (solusi teka-teki) dari satu periode (mulai dari detik hingga minggu, katakanlah seminggu) ke periode berikutnya tidak dapat dipertukarkan." Kepertukaran — gagasan bahwa setiap unit mata uang sama dengan unit lainnya — sangat penting bagi uang. Seorang pemilik toko ingin menerima pembayaran tanpa harus khawatir tentang tanggal uang tersebut dibuat.
Szabo juga menemukan solusi untuk masalah ini. Ia membayangkan semacam solusi "lapisan kedua" di atas lapisan dasar Bit Gold. Lapisan ini akan terdiri dari sejenis bank, meskipun bank yang dapat diaudit secara aman, karena registri Bit Gold bersifat publik. Bank-bank ini akan mengumpulkan hash yang berbeda dari periode waktu yang berbeda dan, berdasarkan nilai hash ini, menggabungkannya ke dalam paket-paket dengan nilai standar gabungan. "Paket 2018" akan mencakup lebih banyak hash daripada "paket 2008," tetapi kedua paket akan bernilai sama.
Paket-paket ini kemudian harus dipotong-potong menjadi sejumlah unit tertentu. Akhirnya, unit-unit ini dapat diterbitkan oleh "bank" sebagai eCash Chaumian yang bersifat pribadi dan anonim.
“[P]ansa pesaing menerbitkan uang kertas digital yang dapat ditukarkan dengan bit solusi yang nilai pasarnya sama dengan nilai nominal uang kertas (yakni mereka menciptakan kumpulan nilai standar),” jelas Szabo .
Dengan demikian, Bit Gold dirancang sebagai lapisan dasar seperti standar emas untuk sistem perbankan bebas di era digital.
Bitcoin
Pada tahun 2000-an, Szabo melanjutkan pendidikannya dengan meraih gelar sarjana hukum untuk memahami hukum dan realitas kontrak yang ingin ia gantikan atau tiru secara daring dengan lebih baik. Ia juga mulai mengumpulkan dan menerbitkan ide-idenya di sebuah blog yang sangat dihormati, “Unenumerated,” yang membahas berbagai topik mulai dari ilmu komputer hingga hukum dan politik, tetapi juga sejarah dan biologi. “Daftar topik untuk blog ini […] sangat luas dan beragam sehingga tidak dapat disebutkan satu per satu,” Szabo menjelaskan judulnya.
Pada tahun 2008 — 10 tahun setelah pertama kali mengusulkannya secara pribadi — Szabo mengangkat Bit Gold di blognya sekali lagi, hanya saja kali ini ia ingin mewujudkan implementasi pertama usulannya.
“Bit Gold akan sangat diuntungkan dari sebuah demonstrasi, pasar eksperimental (dengan misalnya pihak ketiga yang tepercaya menggantikan keamanan kompleks yang dibutuhkan untuk sistem nyata). Adakah yang mau membantu saya membuat kodenya?” tanyanya di bagian komentar blognya.
Jika ada yang menanggapi, tanggapan itu tidak disampaikan di depan umum. Bit Gold, dalam bentuk yang diusulkan Szabo, tidak pernah dilaksanakan.
Namun, Bit Gold tetap menjadi inspirasi utama bagi Satoshi Nakamoto, yang menerbitkan white paper Bitcoin di akhir tahun yang sama.
“Bitcoin merupakan implementasi dari proposal b-money Wei Dai [...] di Cypherpunks [...] pada tahun 1998 dan proposal Bitgold milik Nick Szabo,” tulis penemu Bitcoin dengan nama samaran di forum Bitcointalk pada tahun 2010.
Memang, tidak sulit untuk melihat Bit Gold sebagai rancangan awal Bitcoin. Selain dari basis data bersama catatan kepemilikan berdasarkan kriptografi kunci publik, rangkaian hash bukti kerja memiliki kemiripan yang aneh dengan blockchain Bitcoin . Dan, tentu saja, nama Bit Gold dan Bitcoin juga tidak terlalu jauh.
Namun, tidak seperti sistem seperti Hashcash dan b-money, Bit Gold jelas tidak ada dalam white paper Bitcoin. Beberapa orang bahkan menganggap ketidakhadiran ini begitu penting sehingga mereka menganggapnya sebagai salah satu dari beberapa petunjuk bahwa Szabo pastilah orang di balik julukan Satoshi Nakamoto: Siapa lagi yang akan mencoba menyembunyikan asal-usul Bitcoin seperti ini?
Meski demikian, meski mirip dengan Bit Gold dalam beberapa hal, Bitcoin memang menyertakan beberapa perbaikan atas desain Szabo. Secara khusus, di mana Bit Gold masih bergantung pada pihak tepercaya sampai batas tertentu — server dan layanan stempel waktu harus dipercaya sampai batas tertentu untuk tidak berkolusi — Bitcoin adalah sistem pertama yang memecahkan masalah ini sepenuhnya. Bitcoin memecahkannya dengan sangat elegan, dengan memiliki sistem bukti kerja yang diperlukan yang berfungsi sebagai sistem penghargaan dan mekanisme konsensus dalam satu sistem: Rantai hash dengan bukti kerja terbanyak dianggap sebagai versi sejarah yang valid.
“Nakamoto memperbaiki kekurangan keamanan signifikan yang ada pada desain saya,” Szabo mengakui pada tahun 2011, “yakni dengan mensyaratkan bukti kerja untuk menjadi simpul dalam sistem peer-to-peer yang tangguh terhadap Byzantine untuk mengurangi ancaman pihak yang tidak dapat dipercaya yang mengendalikan mayoritas simpul dan dengan demikian merusak sejumlah fitur keamanan penting.”
Lebih jauh, Bitcoin memiliki model moneter yang sangat berbeda dari yang diusulkan Szabo, dengan jadwal inflasi tetap yang sama sekali tidak terpengaruh oleh peningkatan daya hash. Seiring meningkatnya daya komputasi pada jaringan Bitcoin, itu artinya semakin sulit menemukan koin baru.
“Alih-alih pasar otomatis saya memperhitungkan fakta bahwa tingkat kesulitan teka-teki sering kali dapat berubah secara radikal berdasarkan peningkatan perangkat keras dan terobosan kriptografi (yaitu menemukan algoritma yang dapat memecahkan bukti kerja lebih cepat), dan ketidakpastian permintaan, Nakamoto merancang algoritma yang disetujui Bizantium yang menyesuaikan tingkat kesulitan teka-teki,” jelas Szabo.
“Saya tidak dapat memutuskan apakah aspek Bitcoin ini lebih banyak fitur atau lebih banyak bug,” tambahnya, “tetapi ini membuatnya lebih sederhana.”
Sumber artikel: bitcoinmagazine.com
Diterjemahkan oleh: Abeng -
 @ 20986fb8:cdac21b3
2024-12-18 03:19:36
@ 20986fb8:cdac21b3
2024-12-18 03:19:36English
Introducing YakiHonne: Write Without Limits
YakiHonne is the ultimate text editor designed to help you express yourself creatively, no matter the language.
Features you'll love:
- 🌟 Rich Formatting: Add headings, bold, italics, and more.
- 🌏 Multilingual Support: Seamlessly write in English, Chinese, Arabic, and Japanese.
- 🔗 Interactive Links: Learn more about YakiHonne.Benefits:
1. Easy to use. 2. Enhance readability with customizable styles.
3. Supports various complex formats including LateX."YakiHonne is a game-changer for content creators."
-
 @ a849beb6:b327e6d2
2024-11-23 15:03:47
@ a849beb6:b327e6d2
2024-11-23 15:03:47
\ \ It was another historic week for both bitcoin and the Ten31 portfolio, as the world’s oldest, largest, most battle-tested cryptocurrency climbed to new all-time highs each day to close out the week just shy of the $100,000 mark. Along the way, bitcoin continued to accumulate institutional and regulatory wins, including the much-anticipated approval and launch of spot bitcoin ETF options and the appointment of several additional pro-bitcoin Presidential cabinet officials. The timing for this momentum was poetic, as this week marked the second anniversary of the pico-bottom of the 2022 bear market, a level that bitcoin has now hurdled to the tune of more than 6x despite the litany of bitcoin obituaries published at the time. The entirety of 2024 and especially the past month have further cemented our view that bitcoin is rapidly gaining a sense of legitimacy among institutions, fiduciaries, and governments, and we remain optimistic that this trend is set to accelerate even more into 2025.
Several Ten31 portfolio companies made exciting announcements this week that should serve to further entrench bitcoin’s institutional adoption. AnchorWatch, a first of its kind bitcoin insurance provider offering 1:1 coverage with its innovative use of bitcoin’s native properties, announced it has been designated a Lloyd’s of London Coverholder, giving the company unique, blue-chip status as it begins to write bitcoin insurance policies of up to $100 million per policy starting next month. Meanwhile, Battery Finance Founder and CEO Andrew Hohns appeared on CNBC to delve into the launch of Battery’s pioneering private credit strategy which fuses bitcoin and conventional tangible assets in a dual-collateralized structure that offers a compelling risk/return profile to both lenders and borrowers. Both companies are clearing a path for substantially greater bitcoin adoption in massive, untapped pools of capital, and Ten31 is proud to have served as lead investor for AnchorWatch’s Seed round and as exclusive capital partner for Battery.
As the world’s largest investor focused entirely on bitcoin, Ten31 has deployed nearly $150 million across two funds into more than 30 of the most promising and innovative companies in the ecosystem like AnchorWatch and Battery, and we expect 2025 to be the best year yet for both bitcoin and our portfolio. Ten31 will hold a first close for its third fund at the end of this year, and investors in that close will benefit from attractive incentives and a strong initial portfolio. Visit ten31.vc/funds to learn more and get in touch to discuss participating.\ \ Portfolio Company Spotlight
Primal is a first of its kind application for the Nostr protocol that combines a client, caching service, analytics tools, and more to address several unmet needs in the nascent Nostr ecosystem. Through the combination of its sleek client application and its caching service (built on a completely open source stack), Primal seeks to offer an end-user experience as smooth and easy as that of legacy social media platforms like Twitter and eventually many other applications, unlocking the vast potential of Nostr for the next billion people. Primal also offers an integrated wallet (powered by Strike BLACK) that substantially reduces onboarding and UX frictions for both Nostr and the lightning network while highlighting bitcoin’s unique power as internet-native, open-source money.
Selected Portfolio News
AnchorWatch announced it has achieved Llody’s Coverholder status, allowing the company to provide unique 1:1 bitcoin insurance offerings starting in December.\ \ Battery Finance Founder and CEO Andrew Hohns appeared on CNBC to delve into the company’s unique bitcoin-backed private credit strategy.
Primal launched version 2.0, a landmark update that adds a feed marketplace, robust advanced search capabilities, premium-tier offerings, and many more new features.
Debifi launched its new iOS app for Apple users seeking non-custodial bitcoin-collateralized loans.
Media
Strike Founder and CEO Jack Mallers joined Bloomberg TV to discuss the strong volumes the company has seen over the past year and the potential for a US bitcoin strategic reserve.
Primal Founder and CEO Miljan Braticevic joined The Bitcoin Podcast to discuss the rollout of Primal 2.0 and the future of Nostr.
Ten31 Managing Partner Marty Bent appeared on BlazeTV to discuss recent changes in the regulatory environment for bitcoin.
Zaprite published a customer testimonial video highlighting the popularity of its offerings across the bitcoin ecosystem.
Market Updates
Continuing its recent momentum, bitcoin reached another new all-time high this week, clocking in just below $100,000 on Friday. Bitcoin has now reached a market cap of nearly $2 trillion, putting it within 3% of the market caps of Amazon and Google.
After receiving SEC and CFTC approval over the past month, long-awaited options on spot bitcoin ETFs were fully approved and launched this week. These options should help further expand bitcoin’s institutional liquidity profile, with potentially significant implications for price action over time.
The new derivatives showed strong performance out of the gate, with volumes on options for BlackRock’s IBIT reaching nearly $2 billion on just the first day of trading despite surprisingly tight position limits for the vehicles.
Meanwhile, the underlying spot bitcoin ETF complex had yet another banner week, pulling in $3.4 billion in net inflows.
New reports suggested President-elect Donald Trump’s social media company is in advanced talks to acquire crypto trading platform Bakkt, potentially the latest indication of the incoming administration’s stance toward the broader “crypto” ecosystem.
On the macro front, US housing starts declined M/M again in October on persistently high mortgage rates and weather impacts. The metric remains well below pre-COVID levels.
Pockets of the US commercial real estate market remain challenged, as the CEO of large Florida developer Related indicated that developers need further rate cuts “badly” to maintain project viability.
US Manufacturing PMI increased slightly M/M, but has now been in contraction territory (<50) for well over two years.
The latest iteration of the University of Michigan’s popular consumer sentiment survey ticked up following this month’s election results, though so did five-year inflation expectations, which now sit comfortably north of 3%.
Regulatory Update
After weeks of speculation, the incoming Trump administration appointed hedge fund manager Scott Bessent to head up the US Treasury. Like many of Trump’s cabinet selections so far, Bessent has been a public advocate for bitcoin.
Trump also appointed Cantor Fitzgerald CEO Howard Lutnick – another outspoken bitcoin bull – as Secretary of the Commerce Department.
Meanwhile, the Trump team is reportedly considering creating a new “crypto czar” role to sit within the administration. While it’s unclear at this point what that role would entail, one report indicated that the administration’s broader “crypto council” is expected to move forward with plans for a strategic bitcoin reserve.
Various government lawyers suggested this week that the Trump administration is likely to be less aggressive in seeking adversarial enforcement actions against bitcoin and “crypto” in general, as regulatory bodies appear poised to shift resources and focus elsewhere.
Other updates from the regulatory apparatus were also directionally positive for bitcoin, most notably FDIC Chairman Martin Gruenberg’s confirmation that he plans to resign from his post at the end of President Biden’s term.
Many critics have alleged Gruenberg was an architect of “Operation Chokepoint 2.0,” which has created banking headwinds for bitcoin companies over the past several years, so a change of leadership at the department is likely yet another positive for the space.
SEC Chairman Gary Gensler also officially announced he plans to resign at the start of the new administration. Gensler has been the target of much ire from the broader “crypto” space, though we expect many projects outside bitcoin may continue to struggle with questions around the Howey Test.
Overseas, a Chinese court ruled that it is not illegal for individuals to hold cryptocurrency, even though the country is still ostensibly enforcing a ban on crypto transactions.
Noteworthy
The incoming CEO of Charles Schwab – which administers over $9 trillion in client assets – suggested the platform is preparing to “get into” spot bitcoin offerings and that he “feels silly” for having waited this long. As this attitude becomes more common among traditional finance players, we continue to believe that the number of acquirers coming to market for bitcoin infrastructure capabilities will far outstrip the number of available high quality assets.
BlackRock’s 2025 Thematic Outlook notes a “renewed sense of optimism” on bitcoin among the asset manager’s client base due to macro tailwinds and the improving regulatory environment. Elsewhere, BlackRock’s head of digital assets indicated the firm does not view bitcoin as a “risk-on” asset.
MicroStrategy, which was a sub-$1 billion market cap company less than five years ago, briefly breached a $100 billion equity value this week as it continues to aggressively acquire bitcoin. The company now holds nearly 350,000 bitcoin on its balance sheet.
Notably, Allianz SE, Germany’s largest insurer, spoke for 25% of MicroStrategy’s latest $3 billion convertible note offering this week, suggesting growing appetite for bitcoin proxy exposure among more restricted pools of capital.
The ongoing meltdown of fintech middleware provider Synapse has left tens of thousands of customers with nearly 100% deposit haircuts as hundreds of millions in funds remain missing, the latest unfortunate case study in the fragility of much of the US’s legacy banking stack.
Travel
-
BitcoinMENA, Dec 9-10
-
Nashville BitDevs, Dec 10
-
Austin BitDevs, Dec 19
-
-
 @ 79008e78:dfac9395
2024-12-01 03:15:00
@ 79008e78:dfac9395
2024-12-01 03:15:00บทที่ 1: เกริ่นนำ
เกริ่นนำเรื่องราวของบิตคอยน์แบบกระทัดรัด
บิตคอยน์ (Bitcoin) เป็นชุดแนวคิดและเทคโนโลยีที่เข้ามาผสมผสานรวมกันจนได้กลายเป็นระบบเงินสดอิเล็กทรอนิกส์ หน่วยเงินที่เรียกว่าบิตคอยน์นั้น ใช้เพื่อเก็บและส่งต่อมูลค่าให้กับผู้ใช้คนอื่น ๆ ในระบบ ผู้ใช้ทั้งระบบสื่อสารกันบนโปรโตคอลของบิตคอยน์ โดยผู้ใช้ส่วนใหญ่ก็เข้าถึงกันผ่านอินเตอร์เน็ต แต่ก็ไม่ได้หมายความว่าระบบนี้ไม่สามารถใช้เครือข่ายการสื่อสารรูปแบบอื่นได้ ซอฟต์แวร์ของโปรโตคอลนี้เป็นโอเพนซอร์สและสามารถรันได้บนอุปกรณ์คอมพิวเตอร์หลายประเภท เช่น แล็ปท็อปและสมาร์ทโฟน และสิ่งนี้เองที่ทำให้เทคโนโลยีนี้สามารถเข้าถึงได้ง่าย
ผู้ใช้งานสามารถส่งบิตคอยน์ให้กันผ่านเครือข่ายของบิตคอยน์เพื่อทำกิจกรรมต่าง ๆ เช่น ซื้อ-ขายแลกเปลี่ยนสินค้าและบริการ หรือใช้เพื่อแลกเปลี่ยนเป็นสกุลเงินต่าง ๆ ซึ่งถือว่าเหมาะสมเป็นอย่างมากสำหรับการใช้งานบนอินเทอร์เน็ต เพราะมีทั้งความรวดเร็ว ความปลอดภัย และยังข้อจำกัดเรื่องพรมแดน
ซึ่งบิตคอยน์นั้นแตกต่างจากสกุลเงินโดยทั่วไป เนื่องจากเป็นระบบเงินอิเล็กทรอนิกส์ จึงไม่มีเหรียญหรือธนบัตรจริง ๆ ให้ได้จับต้อง แต่คำว่าเหรียญที่มักใช้กันในสังคมของบิตคอยน์จะหมายถึงในธุรกรรมที่ผู้ใช้รายหนึ่งโอนมูลค่าไปยังผู้ใช้อีกรายหนึ่ง ผู้ใช้งานบิตคอยน์จะควบคุมคีย์ (Private Key) ที่ใช้พิสูจน์ความเป็นเจ้าของในบิตคอยน์นั้น ๆ ในเครือข่าย และด้วยคีย์นี้เองทำให้พวกเขาสามารถเซ็นชื่อในธุรกรรมเพื่อปลดล็อกมูลค่าและทำการส่งมันต่อไปยังผู้รับอีกรายหนึ่ง ซึ่งมักจะถูกเก็บอยู่ในกระเป๋าเงินดิจิทัล หรือสมาร์ทโฟนของผู้ใช้งาน การครอบครองคีย์ที่สามารถเซ็นชื่อในธุรกรรมได้เป็นสิ่งเดียวที่จำเป็นในการใช้จ่ายในระบบของบิตคอยน์ และนั่นเป็นเหตุผลที่ทำให้ความสามารถในการควบคุมบิตคอยน์อยู่ในมือผู้ใช้แต่ละคน
เข้าใจว่าในบริบทนี้น่าจะหมายถึง Hot-wallet เพราะงั้นผมไม่ได้แนะนำให้เก็บคีย์คอมพิวเตอร์หรือมือถือนะครับ ส่วนถ้าคุณอยากทำก็เรื่องของคุณจ้าแนะนำเฉย ๆ อยากทำไรทำ
บิตคอยน์นั้นเป็นระบบแบบกระจายศูนย์และทำงานแบบเพียร์-ทู-เพียร์ (Peer-to-Peer) หรือเอาภาษาบ้าน ๆ ว่า เป็นระบบการทำงานแบบบุคคลสู่บุลคลที่ไม่มีตัวกลางระหว่างการทำงาน ดังนั้นจึงไม่มีเซิร์ฟเวอร์กลางหรือจุดควบคุม บิตคอยน์นั้นถูกสร้างขึ้นโดยกระบวนการที่เรียกว่าการขุด ซึ่งเป็นการทำงานทางการคำนวณซ้ำ ๆ ที่อ้างอิงกับรายการธุรกรรมบิตคอยน์ล่าสุด (จริง ๆ ก็มี hash ของบล็อกก่อนหน้าด้วย) ซึ่งผู้ใช้งานบิตคอยน์ทุกคนสามารถที่จะขุดบิตคอยน์ได้ โดยใช้อุปกรณ์คอมพิวเตอร์ของตนเพื่อช่วยรักษาความปลอดภัยในธุรกรรม โดยทุก ๆ สิบนาทีโดยเฉลี่ยนั้น จะมีนักขุดคนหนึ่งที่ได้ช่วยเพิ่มความปลอดภัยให้กับธุรกรรมในอดีต และจะได้รับรางวัลเป็นบิตคอยน์ใหม่และค่าธรรมเนียมจากธุรกรรมชุดล่าสุด ซึ่งกระบวนการนี้ทำให้การออกสกุลเงินและการชำระธุรกรรมไม่จำเป็นต้องมีธนาคารกลาง
โปรโตคอลของบิตคอยน์ มีอัลกอรึทึมที่คอยควบคุมความยากง่ายในการการขุดให้อยู่ในระดับที่เหมาะสม โดยความยากง่ายในการขุดจะขึ้นจะถูกปรับตามระยะเวลาเฉลี่ยของการขุดในช่วงก่อนหน้านี้เพื่อให้การขุดนั้นมีโอกาสสำเร็จเฉลี่ยในทุก ๆ 10 นาที ไม่ว่ามีจำนวนผู้ขุดและการประมวลผลเท่าใดก็ตาม และนอกจากนี้เองโปรโตคอลของบิตคอยน์นั้นยังลดจำนวนของบิตคอยน์ที่นักขุดจะได้เป็นรางวัลลงเรื่อย ๆ ซึ่งจะทำให้บิตคอยน์ที่สร้างได้ในระบบนั้นมีไม่เกิน 21,000,000 ล้านบิตคอยน์ ซึ่งผลลัพธ์ที่ได้ก็คือ จำนวนบิตคอยน์ที่หมุนเวียนในระบบนั้นจะสามารถคาดเดาได้อย่างง่ายดาย ซึ่งอีกครึ่งหนึ่งของบิตคอยน์ที่เหลืออยู่จะถูกเพิ่มเข้าไปในระบบทุก ๆ 4 ปี และที่บล๊อกประมาณ 1,411,200 ซึ่งคาดว่าจะเกิดประมาณปี 2035 จะมีบิตคอยน์เป็นจำนวน 99 % ของที่สามารถเกิดขึ้นได้ในระบบ เนื่องจากอัตราการการผลิตของบิตคอยน์ที่น้อยลงเรื่อย ๆ ทำให้บิตคอยน์มีลักษณะของเงินฝืดในระยะยาว นอกจากนี้ยังไม่มีใครที่สามารถบังคับให้คุณรับบิตคอยน์ที่ถูกผลิตมานอกเหนือจากชุดกฎที่คุณเลือกได้
เบื้องหลังต่าง ๆ ของโปรโตคอลบิตคอยน์ที่ทำให้มันเป็น เครือข่ายแบบบุคคลถึงบุคคล และการคำนวณแบบกระจายศูนย์นั้น ถูกสร้างขึ้นมาบนพื้นฐานของงานวิจัยในด้านการเข้ารหัสและระบบกระจายศูนย์มาเนิ่นนานหลายทศวรรษ โดยมีการรวมเอานวัตกรรมสำคัญ ๆ 4 อย่างนี้มารวมเข้าด้วยกัน:
- เครือข่ายเพียร์ทูเพียร์ที่กระจายศูนย์ (ฺBitcoin protocol)
- บัญชีธุรกรรมสาธารณะ (Blockchain)
- ชุดของกฎในการตรวจสอบธุรกรรมอย่างอิสระและการออกสกุลเงิน ( consensus rules )
- กลไกในการหาข้อตกลงร่วมกันทั่วโลกเกี่ยวกับบล็อกเชนที่ถูกต้อง (PoW algorithm)
ในมุมมองของนักพัฒนา นาย Andreas M. Antonopoulos and David A. Harding ( ไม่ใช่ผมจ้าา ถึงจะเห็นด้วยก็ตาม) พวกเขามองว่าบิตคอยน์นั้นคล้ายกับอินเทอร์เน็ตของเงิน เป็นเครือข่ายสำหรับการกระจายมูลค่าและการรักษาความเป็นเจ้าของสินทรัพย์ดิจิทัลผ่านการคำนวณแบบกระจายศูนย์ ซึ่งบิตคอยน์มีรายระเอียดเยอะกว่าที่พวกเขาเห็นในตอนแรกมาก ๆ
ในบทนี้เองจะเป็นการอธิบายแนวคิด และคำศัพท์หลัก ๆ รวมทั้งการติดตั้งซอฟแวร์ต่าง ๆ ที่จำเป็นในการทอดลองใช้บิตคอยน์สำหรับทำธุรกรรมง่าย ๆ และสำหรับในบทถัดไป เราจะทำการดำดิ่งลงไปในเทคโนโลยีต่าง ๆ ที่ประกอบรวมกันเป็นบิตคอยน์ว่าทำไมมันถึงเป็นไปได้ และตรวจสอบการทำงานภายในของเครือข่ายและโปรโตคอล
ก่อนการมาถึงของบิตคอยน์
สกุลเงินดิจิทัลที่ใช้งานได้จริงในอดีตนั้นมักเกี่ยวข้องกับพัฒนาการในด้านการเข้ารหัส ซึ่งนั่นก็ไม่ได้แปลกอะไรหากเราพิจารณาถึงปัญหาพื้นฐานในการใช้ข้อมูลเพื่อแทนมูลค่าที่สามารถแลกเปลี่ยนเป็นสินค้าและบริการ โดยการที่เงินดิจิทัลจะถูกยอมรับได้นั้นมักจะต้องสามารถตอบคำถามทั้งสามข้อนี้ได้เสียก่อน:
- ฉันจะเชื่อได้อย่างไรว่าเงินนั้นเป็นของจริงและไม่ใช่ของปลอม?
- ฉันจะเชื่อได้อย่างไรว่าเงินดิจิทัลสามารถใช้ได้เพียงครั้งเดียว (ปัญหาการใช้ซ้ำหรือ "double-spend")?
- ฉันจะมั่นใจได้อย่างไรว่าไม่มีใครสามารถอ้างสิทธิ์ว่าเงินนี้เป็นของพวกเขาไม่ใช่ของฉัน?
ผู้ที่ออกเงินกระดาษเองก็พยายามต่อสู้กับปัญหาการปลอมแปลงโดยการใช้เทคโนโลยีการพิมพ์ที่ซับซ้อนมากขึ้นเรื่อย ๆ และเงินกายภาพเองก็จัดการปัญหาการใช้ซ้ำได้ง่ายเพราะธนบัตรเดียวกันไม่สามารถอยู่ในสองที่พร้อมกันได้ แน่นอนละว่าเงินทั่วไปก็ถูกเก็บและส่งแบบดิจิทัลเช่นกัน ในกรณีเหล่านี้ ปัญหาการปลอมแปลงและการใช้ซ้ำจะถูกจัดการโดยการเคลียร์ธุรกรรมทางอิเล็กทรอนิกส์ทั้งหมดผ่านหน่วยงานกลางที่สามารถตรวจสอบสถานะของเงินได้ แต่สำหรับเงินดิจิทัลที่ไม่สามารถใช้หมึกพิเศษหรือแถบโฮโลแกรมได้ การเข้ารหัสจึงเป็นพื้นฐานสำคัญในการยืนยันความถูกต้องของการอ้างสิทธิ์ในมูลค่าของผู้ใช้ โดยเฉพาะอย่างยิ่ง การเซ็นชื่อดิจิทัลที่เข้ารหัสช่วยให้ผู้ใช้สามารถเซ็นชื่อในสินทรัพย์ดิจิทัลหรือธุรกรรมเพื่อยืนยันการเป็นเจ้าของสินทรัพย์นั้น ซึ่งสิ่งนี้เองยังสามารถใช้ในการแก้ปัญหาการใช้ซ้ำ (doble-spending) ได้
ศาสตร์ของการเข้ารหัสนั้นเริ่มเป็นที่แพร่หลายในช่วงปลายของทศวรรษที่ 1980 นักวิจัยหลายคนเริ่มพยายามใช้การเข้ารหัสเพื่อสร้างสกุลเงินดิจิทัล โดยโครงการเงินดิจิทัลในยุคแรก ๆ นั้นมักจะออกเงินดิจิทัลที่มีการสนับสนุนโดยสกุลเงินของชาติหรือโลหะมีค่าอย่างเช่น ทองคำ
ซึ่งแม้ว่าสกุลเงินดิจิทัลยุคแรกเหล่านี้จะทำงานได้ แต่ก็มีปัญหาที่การรวมศูนย์ของระบบ เนื่องจากมันทำให้ระบบเป็นเป้าหมายที่ง่ายต่อการโจมตีโดยรัฐบาลและเหล่าแฮกเกอร์ สกุลเงินดิจิทัลยุคแรกใช้ศูนย์กลางในการชำระธุรกรรมทั้งหมดเป็นระยะ ๆ เช่นเดียวกับระบบธนาคารทั่วไป เป็นที่น่าเสียดายที่สกุลเงินดิจิทัลเหล่านี้ส่วนใหญ่ถูกกำหนดเป้าหมายโดยรัฐบาลที่กังวลและมักจะถูกฟ้องร้องจนล้มเหลว บางส่วนล้มเหลวอย่างรวดเร็วเมื่อบริษัทผู้ก่อตั้งปิดตัวลงอย่างกะทันหัน และเพื่อให้สกุลเงินดิจิทัลมีความแข็งแกร่งต่อต้านการแทรกแซงจากศัตรู ไม่ว่าจะเป็นรัฐบาลที่ถูกกฎหมายหรืออาชญากรรม เราจึงจำเป็นต้องมีสกุลเงินดิจิทัลที่กระจายศูนย์ เพื่อป้องกันปัญหาดังกล่าว ซึ่งบิตคอยน์คือระบบแบบนั้น ระบบที่ถูกออกแบบให้กระจายศูนย์ และปราศจากอำนาจหรือจุดควบคุมกลางใด ๆ ที่สามารถถูกโจมตีหรือทำให้เสียหายได้
ประวัติของบิตคอยน์
บิตคอยน์ได้ปรากฏครั้งแรกในปี 2008 บนเอกสารที่มีชื่อว่า “Bitcoin: A Peer-to-Peer Electronic Cash System” ซึ่งถูกเขียนโดยบุคคลหรือกลุ่มคนนิรนามที่ใช้นามแฝงว่า ซาโตชิ นากาโมโตะ ซึ่งได้มีการนำนวัตกรรมหลาย ๆ อย่างมารวมเข้าด้วยกัน ไม่ว่าจะเป็นลายเซ็นดิจิทัล และ Hashcash มาสร้างระบบเงินสดอิเล็กทรอนิกส์ที่กระจายศูนย์อย่างสมบูรณ์ ซึ่งไม่ต้องพึ่งพาหน่วยงานกลางในการออกสกุลเงินหรือการชำระและตรวจสอบธุรกรรม โดยนวัตกรรมสำคัญคือการใช้ระบบคำนวณแบบกระจายศูนย์ (Proof-of-work) เพื่อทำสิ่งที่คล้าย ๆ กับการจับฉลากทุก ๆ 10 นาที ทำให้เครือข่ายที่กระจายศูนย์สามารถมีฉันทามติในสถานะของธุรกรรมได้ และสิ่งนี้เองยังสามารถแก้ไขปัญหาการทำธุรกรรมซ้ำซ้อน ซึ่งเป็นข้อบกพร่องของสกุลเงินดิจิทัลที่เคยต้องใช้หน่วยงานกลางในการตรวจสอบธุรกรรมทั้งหมดได้อีกด้วย
เครือข่ายของบิตคอยน์นั้นเริ่มต้นขึ้นในปี 2009 โดยอ้างอิงจากซอฟแวร์ที่เผยแพร่โดย ซาโตชิ และได้ถูกปรับปรุงโดยโปรแกรมเมอร์คนอื่น ๆ มากมายนับไม่ถ้วนมานับตั้งแต่นั้น จำนวนและกำลังของอุปกรณ์ที่ใช้ประมวลผล Proof of Work algorithm (การขุด) เองนั้นก็เพิ่มขึ้นอย่างมหาศาล จนในปัจจุบันนี้พลังการคำนวณรวมกันของเครือข่ายนี้มีมากกว่าจำนวนการคำนวณของซุปเปอร์คอมพิวเตอร์ชั้นนำของโลกทั้งหมดรวมกันเสียอีก ซึ่งสิ่งนี้เองได้ช่วยรักษาความปลอดภัยและความเสถียรของเครือข่ายของบิตคอยน์ได้เป็นอย่างดี
ซาโตชิ นากาโมโตะ ได้ทำการถอนตัวและหายตัวไปในเดือนเมษายนในปี 2011 และมอบหมายความรับผิดชอบในการพัฒนาโค้ดและเครือข่ายให้กับกลุ่มอาสาสมัครที่เติบโตขึ้นเรื่อย ๆ ซึ่งตัวตนของบุคคลหรือกลุ่มคนที่อยู่เบื้องหลังบิตคอยน์นั้นยังไม่เป็นที่รู้จัก แต่อย่างไรก็ตาม ไม่ว่าจะเป็นซาโตชิ นากาโมโตะ หรือใครหน้าไหนก็ตามก็ไม่สามารถควบคุมเครือข่ายของบิตคอยน์ได้ตามลำพัง เนื่องจากมันอยู่บนหลักการทางคณิตศาสตร์ที่โปร่งใส โค้ดโอเพนซอร์ส และฉันทามติจากผู้ที่เข้าร่วม โดยนวัตกรรมนี้ถือเป็นการเปลี่ยนแปลงครั้งใหญ่และได้ก่อให้เกิดวิทยาการใหม่ในด้านการคำนวณแบบกระจายศูนย์ เศรษฐศาสตร์ และเศรษฐมิติอีกด้วย
การแก้ปัญหาในระบบคำนวณแบบกระจายศูนย์
นวัตกรรมของซาโตชิ นากาโมโตะ ยังเป็นการแก้ไขปัญหาที่มีประสิทธิภาพและแปลกใหม่สำหรับปัญหาในระบบคำนวณแบบกระจายศูนย์ที่เรียกว่า "Byzantine Generals' Problem" ซึ่งปัญหานี้เกี่ยวข้องกับการพยายามทำให้ผู้เข้าร่วมหลายคนที่ไม่มีผู้นำสามารถตกลงกันในแผนการดำเนินการได้โดยการแลกเปลี่ยนข้อมูลในเครือข่ายที่ไม่น่าเชื่อถือและอาจถูกโจมตีได้ โดยการแก้ปัญหาของซาโตชินั้นได้ใช้แนวคิด proof of work เพื่อหาฉันทามติโดยไม่ต้องมีผู้ควบคุมที่น่าเชื่อถือ ถือเป็นความก้าวหน้าในด้านการคำนวณแบบกระจายศูนย์
เปิดประตูสู่บิตคอยน์
บิตคอยน์เป็นโปรโตคอลที่สามารถเข้าถึงได้ผ่านทางแอปพลิเคชันที่มีการรับรองโปรโตคอลนี้ Bitcoin wallet นั้นเป็นช่องทางหลักที่ผู้ใช้งานส่วนใหญ่เลือกใช้เพื่อเข้าถึงโปรโตคอลของบิตคอยน์ เช่นเดียวกันกับที่ผู้ใช้งานอินเตอร์เน็ตส่วนใหญ่ใช้เว็บบราวเซอร์เป็นช่องทางในการเข้าถึงโปรโตคอลอย่าง HTTP นั่นเอง Bitcoin wallet เองก็มีหลากหลายยี่ห้อเฉกเช่นเดียวกับเว็บบราวเซอร์ อาทิเช่น chorme, safari, firefox ฯลฯ Bitcoin wallet เองก็เช่นกัน แต่ละยี่ห้อเองก็มีความแตกต่างกันในด้านต่าง ๆ ไม่ว่าจะเป็นในด้านคุณภาพ ประสิทธิภาพ ความปลอดภัย ความเป็นส่วนตัว และความน่าเชื่อถือ อีกทั้งยังมี Bitcoin wallet ที่ถูกสร้างขึ้นมาคู่กับโปรโตคอลของบิตคอยน์อย่าง “Bitcoin Core” ซึ่งมีการพัฒนาต่อมาจากเวอร์ชันที่เขียนโดยซาโตชิ
การเลือก Bitcoin wallet
Bitcoin wallet เป็นหนึ่งในประเภทของแอปพลิเคชันที่มีการพัฒนาอย่างต่อเนื่องมากที่สุดในระบบนิเวศของบิตคอยน์ และแน่นอนว่ามีการแข่งขันกันสูงที่สุดด้วย อาจมี Bitcoin wallet ใหม่ ๆ ที่กำลังพัฒนาอยู่ในขณะนี้ Bitcoin wallet เก่า ๆ บางตัวจากปีที่แล้วก็อาจไม่มีการพัฒนาอย่างต่อเนื่องอีกต่อไป Bitcoin wallet หลาย ๆ ตัวเน้นไปที่แพลตฟอร์มหรือการใช้งานเฉพาะ และบางตัวเหมาะสำหรับผู้เริ่มต้น ในขณะที่บางตัวเต็มไปด้วยฟีเจอร์สำหรับผู้ใช้ขั้นสูง การเลือก Bitcoin wallet นั้นจึงขึ้นอยู่กับความต้องการและระดับความเชี่ยวชาญของผู้ใช้ ดังนั้นการที่เราจะแนะนำยี่ห้อหรือ Bitcoin wallet เฉพาะจึงอาจจะไม่เกิดประโยชน์เท่าไหร่ แต่อย่างไรก็ตาม เราสามารถแบ่งประเภท Bitcoin wallet ได้ตามแพลตฟอร์มและการใช้งานได้ดังนี้
ประเภทของ Bitcoin wallet
- Desktop wallet: กระเป๋าเงินแบบเดสก์ท็อปเป็น Bitcoin wallet ประเภทแรกที่ถูกพัฒนาขึ้นและผู้ใช้ส่วนใหญ่มักจะเลือกใช้ Bitcoin wallet ประเภทนี้เพราะฟีเจอร์ของมัน เช่นความความเป็นอิสระในการใช้งาน ความสามารถในการควบคุมบิตคอยน์ในกระเป๋า แต่อย่างไรก็ตาม การใช้งานบนระบบปฏิบัติการทั่วไป อย่างเช่น Windows และ macOS อาจมีข้อเสียด้านความปลอดภัย เนื่องจากแพลตฟอร์มเหล่านี้มักไม่มีความปลอดภัยเพียงพอและอาจถูกตั้งค่ามาอย่างไม่เหมาะสม
- Mobile wallet: กระเป๋าเงินแบบมือถือเป็น Bitcoin wallet ประเภทที่พบเจอได้มากที่สุด โดยทำงานบนระบบปฏิบัติการสมาร์ทโฟน เช่น Apple iOS และ Android กระเป๋าเงินเหล่านี้มักเป็นตัวเลือกที่ดีสำหรับผู้ใช้ใหม่ เพราะออกแบบมาให้ใช้งานง่ายและสะดวก นอกจากนี้ยังมีกระเป๋าเงินมือถือที่มีฟีเจอร์ครบครันสำหรับผู้ใช้ที่มีความเชี่ยวชาญ แต่เพื่อหลีกเลี่ยงการดาวน์โหลดและจัดเก็บข้อมูลปริมาณมาก กระเป๋าเงินมือถือส่วนใหญ่จะดึงข้อมูลจากเซิร์ฟเวอร์ระยะไกล ซึ่งอาจลดความเป็นส่วนตัวของผู้ใช้เนื่องจากต้องเปิดเผยข้อมูลเกี่ยวกับ address และจำนวนบิตคอยน์ Bitcoin ต่อบุคคลที่สาม
- Web wallet: กระเป๋าเงินแบบเว็บสามารถเข้าถึงได้ผ่านเว็บเบราว์เซอร์และเก็บกระเป๋าเงินของผู้ใช้ไว้บนเซิร์ฟเวอร์ที่บุคคลที่สามเป็นเจ้าของ คล้ายกับบริการอีเมลบนเว็บที่พึ่งพาเซิร์ฟเวอร์ของบุคคลที่สามโดยสมบูรณ์ โดยบางบริการใช้โค้ดฝั่งไคลเอนต์ที่ทำงานในเบราว์เซอร์ของผู้ใช้ และเพื่อให้ผู้ใช้สามารถควบคุมคีย์ของบิตคอยน์ได้เอง แต่การพึ่งพาเซิร์ฟเวอร์ยังคงส่งผลกระทบต่อความเป็นส่วนตัว อย่างไรก็ตาม บริการส่วนใหญ่จะควบคุมคีย์ของบิตคอยน์แทนผู้ใช้เพื่อแลกกับความสะดวกสบาย เราจึงไม่แนะนำให้เก็บ บิตคอยน์จำนวนมากบนระบบของบุคคลที่สาม
- Hardware Signing Devices: อุปกรณ์สำหรับเซ็นดิจิทัลเป็นอุปกรณ์ที่สามารถจัดเก็บคีย์และเซ็นธุรกรรมโดยใช้ฮาร์ดแวร์และเฟิร์มแวร์เฉพาะทาง ซึ่งโดยทั่วไปแล้วจะเชื่อมต่อกับกระเป๋าเงินเดสก์ท็อป มือถือ หรือเว็บ ผ่านสาย USB การสื่อสารระยะใกล้ (NFC) หรือกล้องที่รองรับ QR code แต่เนื่องจากการดำเนินการที่เกี่ยวข้องกับบิตคอยน์ ทั้งหมดถูกจัดการบนฮาร์ดแวร์เฉพาะ อุปกรณ์เหล่านี้จึงปลอดภัยจากการโจมตีหลายรูปแบบ อย่างไรก็ตาม อุปกรณ์เซ็นดิจิทัลมักถูกเรียกว่า hardware wallet แต่ต้องใช้งานร่วมกับกระเป๋าเงินที่มีฟีเจอร์ครบครันเพื่อส่งและรับธุรกรรม ความปลอดภัยและความเป็นส่วนตัวที่ได้จากกระเป๋าเงินที่ใช้งานร่วมกันก็มีบทบาทสำคัญต่อความปลอดภัยและความเป็นส่วนตัวโดยรวมของผู้ใช้อุปกรณ์เซ็นดิจิทัล
ประเภทของการเชื่อมต่อกับโปรโตคอลของบิตคอยน์
- Full node: บิตคอยน์ฟลูโหนดเป็นโปรแกรมที่ตรวจสอบความถูกต้องของประวัติธุรกรรมทั้งหมดของบิตคอยน์ (ทุกธุรกรรมที่เคยเกิดขึ้นโดยผู้ใช้ทุกคน) และนอกจากนี้ บิตคอยน์ฟลูโหนดยังสามารถเลือกเก็บข้อมูลธุรกรรมที่ได้รับการตรวจสอบแล้วก่อนหน้า และให้บริการข้อมูลแก่โปรแกรมบิตคอยน์อื่น ๆ ได้ ไม่ว่าจะเป็นบนคอมพิวเตอร์เดียวกันหรือผ่านอินเทอร์เน็ต แต่แม้ว่าบิตคอยน์ฟลูโหนดเองก็ใช้ทรัพยากรคอมพิวเตอร์ในปริมาณมาก (ประมาณเท่ากับการดูวิดีโอสตรีมมิ่งหนึ่งชั่วโมงต่อวันสำหรับธุรกรรมบิตคอยน์ในแต่ละวัน) บิตคอยน์ฟลูโหนดเองก็มอบความเป็นอิสระอย่างสมบูรณ์แก่ผู้ใช้
- Lightweight Client: lightweight client หรือที่เรียกกันอีกชื่อว่าไคลเอนต์การตรวจสอบการชำระเงินแบบง่าย (Simplified-Payment-Verification: SPV) ซึ่งจะเชื่อมต่อกับโหนดแบบเต็มหรือเซิร์ฟเวอร์ระยะไกลอื่น ๆ เพื่อรับและส่งข้อมูลธุรกรรมของบิตคอยน์แต่เก็บกระเป๋าเงินของผู้ใช้ไว้ในเครื่อง โดยสามารถตรวจสอบธุรกรรมที่ได้รับบางส่วน และสร้างธุรกรรมขาออกอย่างอิสระอีกด้วย
- ไคลเอนต์ API ของบุคคลที่สาม (Third-Party API Client): ไคลเอนต์ API ของบุคคลที่สามเป็นโปรแกรมที่เชื่อมต่อกับระบบบิตคอยน์ผ่าน API ของบุคคลที่สาม แทนที่จะเชื่อมต่อกับเครือข่ายบิตคอยน์โดยตรง กระเป๋าเงินนี้อาจถูกจัดเก็บโดยผู้ใช้เองหรือบนเซิร์ฟเวอร์ของบุคคลที่สาม แต่ไคลเอนต์จะต้องไว้วางใจเซิร์ฟเวอร์ระยะไกลในการให้ข้อมูลที่ถูกต้องและปกป้องความเป็นส่วนตัวของตน
บิตคอยน์เป็นเครือข่ายแบบเพียร์ทูเพียร์(Peer-to-Peer หรือ P2P) โดยที่บิตคอยน์ฟลูโหนด ทำหน้าที่เป็นเพียร์ในเครือข่าย เพียร์แต่ละตัวจะตรวจสอบความถูกต้องของธุรกรรมที่ยืนยันแล้วทุกธุรกรรมอย่างอิสระ และสามารถให้ข้อมูลที่เชื่อถือได้แก่ผู้ใช้ Lightweight Wallets และซอฟต์แวร์อื่น ๆ เองก็เป็นลูกข่ายที่ต้องพึ่งพาเพียร์หนึ่งหรือหลายตัวในการรับข้อมูลที่ถูกต้อง ไคลเอนต์สามารถตรวจสอบข้อมูลบางส่วนที่ได้รับเพิ่มเติมและเชื่อมต่อกับเพียร์หลายตัวเพื่อลดการพึ่งพาเพียร์ตัวเดียว แต่ในท้ายที่สุดความปลอดภัยของไคลเอนต์ยังคงขึ้นอยู่กับความน่าเชื่อถือของเพียร์ที่เชื่อมต่อด้วย
ใครควบคุมคีย์
อีกหนึ่งในประเด็นสำคัญที่ควรพิจารณาเพิ่มเติมคือใครเป็นผู้ควบคุมคีย์ (Private key) เนื่องจากเป็นสิ่งที่มีบทบาทสำคัญในการควบคุมการเข้าถึงบิตคอยน์ โดยคีย์เหล่านี้เองเปรียบเสมือน PIN ที่ยาวมาก ซึ่งหากคุณเป็นผู้ควบคุมคีย์ของคุณเองด้วยตัวเอง คุณก็เป็นผู้ควบคุมบิตคอยน์ของคุณด้วยเช่นกัน แต่หากไม่ใช่ ก็จะแปลว่ากุญแจเหล่านั้นจะถูกดูแลโดยบุคคลที่สาม ซึ่งจะเป็นผู้จัดการเงินของคุณในนามของคุณ
ซอฟแวร์ในการจัดการกุญแจนั้นถูกแบ่งออกเป็นสองประเภทหลัก ๆ คือ wallet ที่คุณจำเป็นต้องดูแลคีย์ของตัวเองและ บัญชีที่มีผู้ดูแล (Custodian Accounts) ซึ่งจะมีบุคคลที่สามเป็นผู้ควบคุมกุญแจ
“Your keys, your coins. Not your keys, not your coins.”
มาอยู่ตัวอย่างเพื่อความเข้าใจที่มาขึ้นกันเถอะ
สมมุติว่าอลิซเป็นผู้ใช้งานที่ไม่ได้เชี่ยวชาญด้านเทคนิค และเพิ่งได้ยินเกี่ยวกับบิตคอยน์จากเพื่อนสนิทของเขา โจ ระหว่างปาร์ตี้ โจกำลังอธิบายเกี่ยวกับบิตคอยน์อย่างกระตือรือร้นให้ทุกคนฟังและสาธิตวิธีการใช้งานต่าง ๆ ให้ดู อลิซเองได้มีความสนใจในบิตคอยน์หลังจากได้ฟังโจอธิบาย จึงได้ถามโจว่าเธอจะเริ่มต้นใช้งานบิตคอยน์ได้อย่างไร โจจึงแนะนำให้อลิซดาวน์โหลด Mobile wallet ตัวโปรดของเขาเนื่องจากมันเหมาะสมกับมือใหม่ อลิซจึงดาวน์โหลดและติดตั้งแอปพลิเคชันกระเป๋าเงินที่โจแนะนำบนโทรศัพท์ของเธอ
เมื่ออลิซเปิดแอปพลิเคชันครั้งแรก เธอได้เลือกสร้างกระเป๋าใหม่และเนื่องจากกระเป๋าที่เธอเลือกนั้นเป็นแบบที่ไม่ได้อยู่ภายใต้การควบคุมบุคคลที่สาม (Noncustodial Wallet) อลิซจึงเป็นผู้ควบคุมคีย์เพียงคนเดียว ซึ่งหมายความว่าเธอต้องรับผิดชอบในการสำรองข้อมูลด้วยตัวของเธอเอง และหากเธอได้ทำคีย์สูญหายไป เธอจะไม่สามารถเข้าถึงบิตคอยน์ของเธอได้อีกไปตลอดกาล และเพื่อเพื่อช่วยในเรื่องนี้ Bitcoin wallet ต่าง ๆ จึงมักจะสร้างรหัสการกู้คืน (Recovery Code) ให้ซึ่งสามารถใช้ในการกู้คืน Bitcoin wallet อันนั้น ๆ
Recovery Code (รหัสในการกู้คืน)
Bitcoin wallet แบบที่ไม่ได้อยู่ภายใต้การควบคุมของบุคคลที่สามนั้นส่วนใหญ่จะให้รหัสการกู้คืนแก่ผู้ใช้งานเพื่อสำรองข้อมูล และรหัสการกู้คืนนี้มักประกอบด้วยตัวเลข ตัวอักษร หรือคำที่ถูกเลือกแบบสุ่มโดยซอฟต์แวร์ และใช้เป็นพื้นฐานสำหรับการสร้าง Bitcoin wallet โดยแต่ละยี่ห้อก็อาจมีความแตกต่างกัน เช่น

รหัสการกู้คืนมักเรียกว่า "mnemonic" หรือ "mnemonic phrase" หรือในภาษาไทยว่าวลีช่วยจำ ซึ่งบ่งบอกว่าคุณควรจดจำวลีนั้น แต่การจดวลีนี้ลงบนกระดาษใช้เวลาน้อยกว่าและมักจะเชื่อถือได้มากกว่าความจำของคนส่วนใหญ่ เพราะฉนั้นผมเลยแนะนำว่าจดเถอะ จะได้ไม่เกิดปัญหาที่ไม่คาดคิดในอนาคต
หาก bitcoin wallet ของอลิซมีปัญหา เธอสามารถดาวน์โหลดซอฟแวร์ใหม่และใส่รหัสในการกู้คืนลงไป เพื่อสร้างฐานข้อมูลของ bitcoin wallet ใหม่ที่บันทึกธุรกรรมบนเชนทั้งหมดที่เธอเคยรับหรือส่ง แต่อย่างไรก็ตาม การกู้คืนจากการใช้รหัสการกู้คืนเพียงอย่างเดียวนั้นอาจจะไม่สามารถกู้คืนข้อมูลเพิ่มเติมที่อลิซเคยบันทึกไว้ใน wallet นั้น ๆ ได้ เช่น ป้ายกำกับที่เธอเชื่อมโยงกับที่อยู่หรือธุรกรรมต่าง ๆ แม้ว่าการสูญเสียข้อมูลเมตานี้จะไม่สำคัญเท่ากับการสูญเสียเงิน แต่ก็ยังมีความสำคัญในบางแง่มุม เช่น หากคุณต้องตรวจสอบรายการธนาคารหรือบัตรเครดิตเก่า แต่ชื่อของผู้ที่คุณชำระเงินหรือผู้ที่จ่ายเงินให้คุณถูกลบออกไป ดังนั้นเพื่อป้องกันการสูญเสียข้อมูลเมตา wallet หลาย ๆ ยี่ห้อจึงมีฟีเจอร์สำรองข้อมูลเพิ่มเติมนอกเหนือจากรหัสการกู้คืน
สำหรับ wallet บางประเภทนั้น ฟีเจอร์สำรองข้อมูลเพิ่มเติมนี้ถือว่ามีความสำคัญมาก เนื่องจากการชำระเงินเงินด้วยบิตคอยน์จำนวนมากในปัจจุบันทำผ่านเทคโนโลยีที่อยู่นอกเชน (Offchain) ซึ่งธุรกรรมไม่ได้ถูกบันทึกลงในบล็อกเชนสาธารณะ เนื่องจากการชำระเงินแบบนี้ช่วยลดค่าใช้จ่ายของผู้ใช้และเพิ่มความเป็นส่วนตัวได้บ้าง แต่นั่นก็หมายความว่ากลไกอย่างรหัสการกู้คืนที่พึ่งพาข้อมูลบนเชนไม่สามารถรับประกันการกู้คืนบิตคอยน์ทั้งหมดของผู้ใช้ได้ ดังนั้นสำหรับแอปพลิเคชันที่รองรับการใช้งาน Offchain การสำรองข้อมูลฐานข้อมูล wallet บ่อยครั้งจึงเป็นสิ่งที่มีความสำคัญมาก
นอกจากนี้ เมื่อได้รับบิตคอยน์ครั้งแรกใน moblie wallet หลาย ๆ wallet มักจะตรวจสอบอีกครั้งว่าคุณได้สำรองรหัสการกู้คืนไว้อย่างปลอดภัยแล้ว การตรวจสอบนี้อาจเป็นเพียงการแจ้งเตือน หรืออาจถึงขั้นให้ผู้ใช้ป้อนรหัสนั้นซ้ำด้วยตัวเอง
คำเตือน แม้ว่า Bitcoin Wallet หลาย ๆ ตัวอาจจะมีการให้คุณต้องกรอกรหัสในการกู้คืนใหม่ในบางกรณี แต่มันก็มักจะมีแอปพลิเคชันมัลแวร์จำนวนมากที่เลียนแบบการออกแบบของ wallet ต่าง ๆ โดยมันจะบังคับให้คุณป้อนรหัสการกู้คืน จากนั้นมันจะส่งรหัสที่ป้อนไปยังผู้พัฒนามัลแวร์เพื่อขโมยบิตคอยน์ของคุณ นี่เปรียบเสมือนเว็บไซต์ฟิชชิงที่พยายามหลอกให้คุณให้รหัสผ่านธนาคารของคุณ สำหรับ Bitcoin wallet ส่วนใหญ่ เวลาที่พวกเขาจะขอรหัสการกู้คืนคือในระหว่างการตั้งค่าเริ่มต้น (ก่อนที่คุณจะได้รับบิตคอยน์) และระหว่างการกู้คืน (หลังจากที่คุณสูญเสียการเข้าถึง wallet เดิม) หากแอปพลิเคชันขอรหัสการกู้คืนในช่วงเวลาอื่น คุณควรปรึกษาผู้เชี่ยวชาญเพื่อให้แน่ใจว่าคุณไม่ได้ตกเป็นเหยื่อของการฟิชชิง
Bitcoin Addresses (ที่อยู่ในการรับหรือส่งบิตคอยน์)
ในตอนนี้อลิซพร้อมแล้วสำหรับการสร้าง Bitcoin wallet ใหม่ของเธอ Bitcoin wallet ที่เธอเลือกได้ทำการสร้าง private key แบบสุ่มให้เธอ ซึ่งจะเชื่อมโยงกับ Bitcoin Address ทั้งหมดที่มีใน Bitcoin wallet ของเธอ แต่ ณ ขณะนี้ยังไม่มีใครรู้ Bitcoin address ของเธอ (แม้แต่ Bitcoin network ก็ไม่รู้) นอกจากตัวเธอเอง Bitcoin address เหล่านี้เป็นเพียงตัวเลขที่เชื่อมโยงกับ Private key ของเธอ ซึ่งเธอสามารถใช้ควบคุมการเข้าถึง Bitcoin ใดกระเป๋าได้ Bitcoin address เหล่านี้ถูกสร้างขึ้นโดยอิสระจากกระเป๋าของเธอโดยไม่ต้องอ้างอิงหรือเชื่อมต่อกับบริการใด ๆ
คำแนะนำ: Bitcoin address และ Invoice นั้นมีหลากหลายรูปแบบที่แตกต่างกัน และทั้งหมดนี้สามารถแชร์ให้กับคนอื่น ๆ ได้ เพื่อเป็นการอณุญาติให้พวกเขาส่งบิตคอยน์เข้ามาในกระเป๋าคุณตรง ๆ คุณสามารถแชร์ Bitcoin address และ Invoice ให้คนอื่นได้โดยไม่ต้องกังวลเกี่ยวกับความปลอดภัยของบิตคอยน์ของคุณ เนื่องจากผู้ที่รู้ Bitcion address ของคุณไม่สามารถถอนเงินออกจาก address นั้น ๆ ได้แม้เขาจะสามารถรู้จำนวนเงินใน address นั้น ๆ ก็ตาม เพราะฉะนั้นเพื่อปกป้องความเป็นส่วนตัวของคุณ คุณจึงควรสร้าง Invoice จาก Bitcoin address ใหม่ทุกครั้งที่จะส่งให้ผู้อื่น
-
 @ 4dffec17:4c4cbd48
2024-12-18 02:52:47
@ 4dffec17:4c4cbd48
2024-12-18 02:52:47Top Cryptocurrencies You Should Know About Here are some of the most popular cryptocurrencies and what makes them stand out:
Bitcoin (BTC): The first cryptocurrency, often called "digital gold."
Ethereum (ETH): Known for its smart contracts, enabling decentralized apps (DApps).
Ripple (XRP): A cryptocurrency for fast and low-cost cross-border payments.
Litecoin (LTC): Designed for faster, cheaper transactions than Bitcoin.
There are thousands of other cryptocurrencies, each with unique purposes and features. Some focus on privacy, others on speed, and some on enabling new types of technology.
Coming next: Why are cryptocurrencies so important for the future?
-
 @ 490b551d:e17f0103
2024-12-17 22:12:48
@ 490b551d:e17f0103
2024-12-17 22:12:48Welcome, friend. I hope this place becomes a space to pause, breathe, and reflect in the midst of the chaos of life and faith. If you’re here, there’s a good chance you’ve felt the weight of doubt in your belief, the kind that sits heavy on your heart, whispers in your mind, and makes you wonder if you’d truly be accepted if people knew your questions, especially when everything around you insists that belief without doubt is the only acceptable way to be. I get it. I’ve been there too.
I’ve faced a lot of pressure: the pressure to get everything right, the shame that follows any hint of sin, and the isolation that comes with feeling like I’m not quite enough for God’s love—whether it was because of the mistakes I’ve made or the doubts that linger in my heart. It’s tough to be part of a faith tradition that values certainty above all else when you’re in the middle of a spiritual crisis or a season of question. For many of us, the church can sometimes feel like a place where doubt isn’t welcomed, where questions are viewed as weaknesses, or worse, a ticket to hell. But here’s what I’ve learned in the decade I stepped away from my church and my beliefs: doubt doesn’t mean we’re failing at faith. It means we’re seeking something deeper.
Understanding the Pressure to Be Certain
For many of us who were raised in conservative Christian settings, there’s often an unspoken (and sometimes spoken) expectation: doubt is not okay. The message we receive is that to be a "good Christian" means you must have unwavering faith, an unshakable belief that everything in the Bible is true, and absolute certainty in your relationship with God. You’re supposed to have all the answers, be sure of your salvation, and confidently declare your faith in the face of any challenge.
But what happens when you don't have all the answers? When you question parts of scripture or the ways the church has interpreted it? When you wonder how a loving God can allow suffering, or how science and faith can co-exist? When you wonder if you're truly loved by God, or if your struggles disqualify you from His grace?
There’s a lot of weight in these questions, and for a long time, I felt alone in them. After all, isn’t doubt something that should be avoided? Shouldn’t we be strong enough to push through and just believe? The church certainly didn't seem to be the place to clear this all up in my mind!
The Reality of Doubt: You’re Not Alone
The truth is, doubt is a natural part of the human experience. A study published in the Journal of Psychology and Theology found that 70% of individuals experience some level of doubt at various points in their spiritual journey. Doubt doesn’t make you a bad Christian or a failure at faith—it makes you human.
The Bible is filled with examples of doubt. One of the most famous stories comes from Thomas, often referred to as "Doubting Thomas." After Jesus’ resurrection, when the other disciples saw Him alive and well, Thomas couldn’t believe it until he saw Jesus for himself and touched His wounds. When he finally encountered the risen Christ, Jesus didn’t rebuke him for doubting—He met him in the doubt. Jesus said, “Put your finger here; see my hands. Reach out your hand and put it into my side. Stop doubting and believe” (John 20:27, NIV). But Jesus doesn’t shame Thomas. No. He invites him to experience the truth, to see it for himself, and to believe in his own time and way.
Doubt is not a sin. It’s part of the journey of faith. Just like Thomas, we can bring our doubts to Jesus, and He will meet us in that place.
Acknowledging Doubt: A Step Toward Deeper Faith
Sometimes we think that the right way to navigate doubt is to push it down, pretend it doesn’t exist, or cover it up with surface-level answers. We’re told that questioning our faith is a sign of weakness or a lack of commitment. But what if the opposite is true? What if acknowledging our doubt could be the very thing that leads us to a deeper, more authentic faith?
In the book of Psalms, many of the writers express their doubts and frustrations with God. Take Psalm 73, for example. The psalmist, Asaph, begins by questioning the fairness of life: “Surely God is good to Israel, to those who are pure in heart. But as for me, my feet had almost slipped; I had nearly lost my foothold. For I envied the arrogant when I saw the prosperity of the wicked” (Psalm 73:1-3, NIV). Asaph openly doubts God’s goodness, and he questions why it seems like those who do wrong are thriving. But instead of running from his questions, he brings them before God, and by the end of the psalm, he expresses renewed trust in God's faithfulness (Psalm 73:23-26). Through this process of doubting and questioning, Asaph’s faith is refined, and he ultimately comes to a deeper understanding of God's justice and presence.
When we acknowledge the doubt, we don’t weaken our faith; we make space for it to grow. True faith isn’t the absence of doubt—it’s the trust to keep going even when we don’t have all the answers.
What the Bible Says About Doubt
James 1:6-8 is one of the passages that many people turn to when discussing doubt in the context of faith. It says:
"But when you ask, you must believe and not doubt, because the one who doubts is like a wave of the sea, blown and tossed by the wind. That person should not expect to receive anything from the Lord. Such a person is double-minded and unstable in all they do" (James 1:6-8, NIV).
In these verses, James is addressing the process of asking God for wisdom. The context is not about the kind of doubt that questions God’s existence or love, but about a specific type of doubt: a lack of commitment or double-mindedness when it comes to asking for something from God. James is highlighting the importance of trust and consistency in prayer and faith.
Now, this is where it gets tricky. It seems as though James is saying that any form of doubt disqualifies you from receiving God's wisdom, but what he’s actually pointing out is something deeper. The doubt James describes here is not the kind of doubt where you're struggling with your faith and trying to work through your questions. It’s a doubt that stems from being double-minded or divided in your loyalty—someone who isn’t fully committed to trusting in God's goodness and His ability to provide answers.
In other words, James is addressing those who are unable to decide whether they trust God enough to act in faith, or whether they will rely on their own understanding. This isn’t about wrestling with questions of faith, but about refusing to fully trust God and expecting Him to give you what you ask for without truly believing He will. The warning here is that divided loyalty in your faith—being uncertain whether to trust God or rely on your own solutions—leads to instability in your life.
How Does This Relate to Us Today?
If we look at this in light of our own lives, the point James is making is incredibly relevant. It’s okay to have questions, to wrestle with doubt, and to not always have complete clarity. But if your doubt leads you to question God’s ability, goodness, or willingness to act, then you're not fully trusting in Him. If you approach God in prayer with a heart that says, “I don’t think He’ll really answer this, but I’ll ask anyway,” that’s the kind of wavering that James warns against. Faith requires a kind of consistency in belief: that God is good, He is listening, and He has the power to answer—even when you don’t understand how or when.
What James seems to be saying is that doubt becomes problematic when it leads us to reject God’s goodness or power. It's not the occasional, fleeting doubt about one’s salvation or understanding of scripture that disqualifies us from receiving from God, but rather a refusal to commit fully to trusting God in our times of need.How Does This Relate to Us Today?
If we look at this in light of our own lives, the point James is making is incredibly relevant. It’s okay to have questions, to wrestle with doubt, and to not always have complete clarity. But if your doubt leads you to question God’s ability, goodness, or willingness to act, then you're not fully trusting in Him. If you approach God in prayer with a heart that says, “I don’t think He’ll really answer this, but I’ll ask anyway,” that’s the kind of wavering that James warns against. Faith requires a kind of consistency in belief: that God is good, He is listening, and He has the power to answer—even when you don’t understand how or when.
What James seems to be saying is that doubt becomes problematic when it leads us to reject God’s goodness or power. It's not the occasional, fleeting doubt about one’s salvation or understanding of scripture that disqualifies us from receiving from God, but rather a refusal to commit fully to trusting God in our times of need.
Practical Ways to Navigate Doubt in a Faith Tradition that Values Certainty
Acknowledge Your Doubts Without Shame \ The first step in navigating doubt is acknowledging it. Doubt doesn’t make you a bad Christian or unworthy of God’s love. You don’t need to hide your questions. Instead of feeling guilty, recognize that doubt is part of your spiritual journey, and it’s okay to ask questions. When we’re honest about our doubts, we give God space to meet us where we are.
Engage with Scripture Honestly \ Sometimes, we shy away from certain parts of the Bible because they challenge us or don’t make sense. But the Bible is full of complexity, contradictions, and depth—and that’s okay. Approach Scripture with curiosity and openness. It’s not about finding all the answers right away, but about engaging with the text and allowing it to speak to you in different seasons of your life.
Surround Yourself with a Supportive Community \ Find people who are willing to walk with you through your doubts. If you’re struggling with questions, it can be incredibly helpful to talk with someone who has navigated similar struggles. Surround yourself with people who are willing to explore faith openly and who won’t judge you for questioning.
Embrace the Mystery of Faith \ Faith is never about having all the answers. There will always be aspects of God’s character and His ways that remain mysterious to us. But instead of trying to solve every mystery, learn to embrace the mystery. Faith is trusting in the unknown, and sometimes the questions themselves are a beautiful part of the journey.
Remember That Jesus Loves You—Doubt and All \ Above all else, remember that Jesus loves you deeply, no matter where you are in your faith journey. He isn’t looking for perfection; He’s looking for honesty. Just as He met Thomas in his doubt, He will meet you too. There is no shame in your questions—only an invitation to deeper trust and intimacy with God.
Navigating doubt in a faith tradition that values certainty is hard. But remember, you’re not alone in your struggle. Doubt isn’t a sign of weakness; it’s an invitation to deepen your faith. Just as God met Thomas and the psalmist in their doubt, He will meet you where you are. Faith isn’t about having all the answers—it’s about trusting God with our questions.
So, friend, don’t be afraid of your doubts. They don’t disqualify you from God’s love or His plans for your life. They are simply part of the beautiful, messy, and deeply human journey of faith. Take it one step at a time, and know that, like me, you are loved by God no matter where you are on your spiritual path.
blog #christian #christianity #spirituality
-
 @ af9c48b7:a3f7aaf4
2024-11-18 20:26:07
@ af9c48b7:a3f7aaf4
2024-11-18 20:26:07Chef's notes
This simple, easy, no bake desert will surely be the it at you next family gathering. You can keep it a secret or share it with the crowd that this is a healthy alternative to normal pie. I think everyone will be amazed at how good it really is.
Details
- ⏲️ Prep time: 30
- 🍳 Cook time: 0
- 🍽️ Servings: 8
Ingredients
- 1/3 cup of Heavy Cream- 0g sugar, 5.5g carbohydrates
- 3/4 cup of Half and Half- 6g sugar, 3g carbohydrates
- 4oz Sugar Free Cool Whip (1/2 small container) - 0g sugar, 37.5g carbohydrates
- 1.5oz box (small box) of Sugar Free Instant Chocolate Pudding- 0g sugar, 32g carbohydrates
- 1 Pecan Pie Crust- 24g sugar, 72g carbohydrates
Directions
- The total pie has 30g of sugar and 149.50g of carboydrates. So if you cut the pie into 8 equal slices, that would come to 3.75g of sugar and 18.69g carbohydrates per slice. If you decided to not eat the crust, your sugar intake would be .75 gram per slice and the carborytrates would be 9.69g per slice. Based on your objective, you could use only heavy whipping cream and no half and half to further reduce your sugar intake.
- Mix all wet ingredients and the instant pudding until thoroughly mixed and a consistent color has been achieved. The heavy whipping cream causes the mixture to thicken the more you mix it. So, I’d recommend using an electric mixer. Once you are satisfied with the color, start mixing in the whipping cream until it has a consistent “chocolate” color thorough. Once your satisfied with the color, spoon the mixture into the pie crust, smooth the top to your liking, and then refrigerate for one hour before serving.
-
 @ 9cb3545c:2ff47bca
2024-12-01 00:18:45
@ 9cb3545c:2ff47bca
2024-12-01 00:18:45Hey there! So you’ve got a whopping 50+ Lightning Channels and you’re not keen on them Force Closing? Well, buckle up! This guide will be an additional resource as you navigate through daunting process.
In this post, we will go over some extra tips and tricks not covered in the official guide. While this guide does have some steps that are not covered by Umbrel, its main objective is to provide confidence in the process (not a replacement process), coming from someone who’s been there and done that, and some how came out with all Lightning Channels still running! I highly recommend reading this post fully before starting the migration process.
Before we dive in, here is the Official Guide from the Umbrel team on how to update UmbrelOS from 0.5.4 to 1.x.x. Reference the steps all the time, and follow them carefully.
With that out of the way. Here are some extra TIPs to fill in some gaps I encountered as I went through the process.
The Order of Steps
Tip #1:
In the Official Umbrel Guide, the Umbrel team asks you to start by backing up your data. As a lightning Node Runner, I recommend against this. Because the Bash script will stop all Umbrel Services and your node will remain offline while you prepare a Bootable USB Stick. So definitely don't start with the backup, first get the bootable stick sorted out, then move on to backups.
Creating the Bootable USB Stick
TIP #2:
After many failed attempts to create a bootable USB stick from the link umbrel provides in their official guide. I ended up getting the ISO directly from Umbrels team through their Discord Channel. Unfortunately, I wont be able to share this link here. but just in case the umbrelOS-amd64-usb-installer.iso.xz didnt work for you as well, this could be an alternative route.
TIP #3:
Since Umbrel is an actual full OS now. You might need to handle some BIOS quirks. The umbrelOS Kernal is not signed. So if you have Secure Boot turned on in the BIOS, your PC will try to protect you, and block you from booting into you USB Stick. Turn off Secure Boot and you should be able to bypass this issue. I also had to turn on Legacy Option ROMs as well.
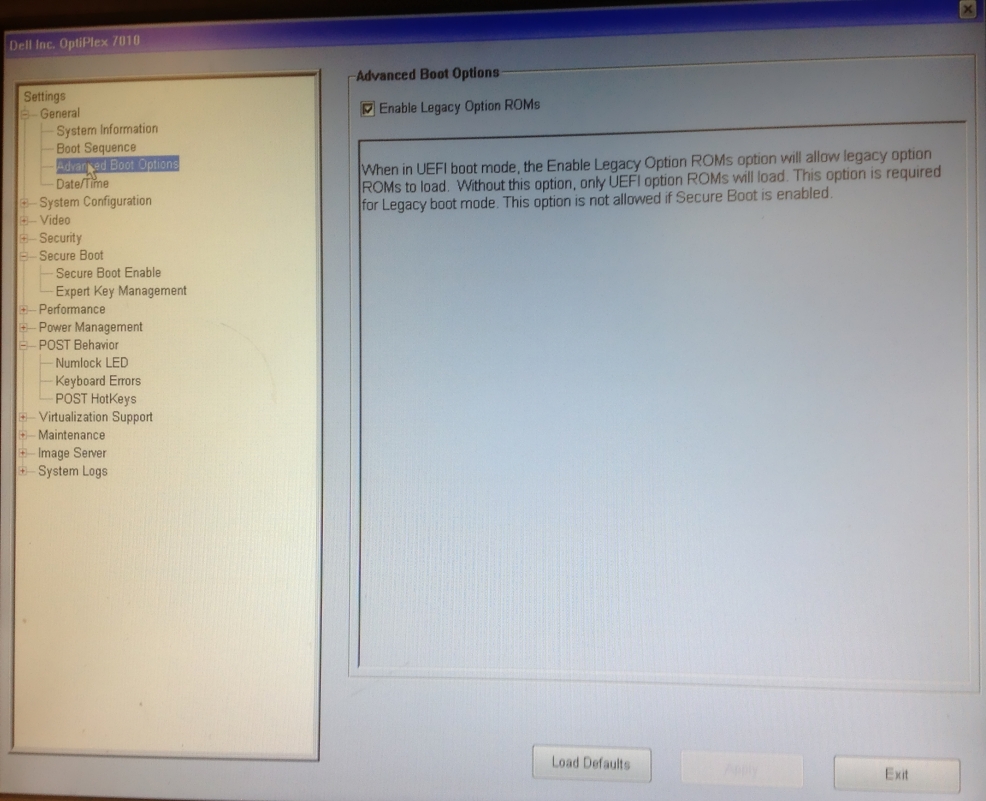
Tip #4:
Test your Bootable USB Stick on a secondary device before you go on trying to update your node. Since turning the node off and on is a hassle, its just easier to be certain the the Bootable Stick is ready before even attempting to upgrade your node.
If all is good, you are ready to get back to the guide and walk through the steps.
Preparing the Hardware
Tip #5:
In the official guide they as you to connect a Keyboard and Screen. This is of course needed. I would highly suggest you connect a mouse as well. My Bios was very stubborn and didn't comply with just a keyboard as I attempted to re-order Boot Sequences.
The Migration Process
Tip #6:
Remember, this is 10 times easier if you are not running a lightning node, but on a lightning node, the Channel.db file is being updated constantly. Once you start the backup process, the script will shutdown umbrel services and start copying. you can''t turn your node back on after this stage. If you do, assume the backup you created through the Bash script is obsolete. and you will have to redo the backup process again. If you really know what you are doing, you probably can surgically copy/paste the LND folder. But its easier not to do this.
But not to worry, if you start the process just keep going (especially if you checked all the TIPs I cover above). I say this out of experience, because after I started the first backup process, it took me about an hour to backup my SSD, but then the Bootable USB stick threw so many errors I gave up, and turned on the node again. Then later re-attempted the process from scratch. This time, since my external SSD was already full, it took 3.5 hours to backup all the files again.
Tip #7:
This will take time, so just trust the migration process and wait for the files to get copied. you are probably copying more than a terabyte worth of data back and forth over USB, Leverage USB 3 if you have it.
Tip #8:
If you have a custom name for your umbrel node. Meaning you do not access it by using umbrel.local, this will be reset to the default umbrel.local after the migration. I am not sure if this could be switched again to a custom name, but for now, this won't cause any issues.
Tip #9:
During the last steps of the Migration process, and once Umbrel has copied the backup back into the SSD, it will finish the process with downloading your apps, and restarting. Don't freak out :D
Tip #10:
I honestly don't have a tenth tip, but thought it would make this list look nicer with one. So my last tip for you is to relax and enjoy the process. And feel free to tag me if you faced any issues. Hopefully it will be something i experienced and will be able to help.
Have Fun, and Good Luck!
-
 @ 07907690:d4e015f6
2024-11-15 10:10:05
@ 07907690:d4e015f6
2024-11-15 10:10:05PGP (Pretty Good Privacy) adalah protokol enkripsi yang digunakan untuk memastikan kerahasiaan, integritas, dan otentikasi data dalam komunikasi digital. Diciptakan oleh Phil Zimmermann pada tahun 1991, PGP menggunakan kombinasi teknik kriptografi asimetris (kunci publik dan kunci privat) serta simetris untuk melindungi informasi. Berikut adalah berbagai kegunaan PGP:
Mengamankan Email (Enkripsi dan Dekripsi)
-
Kegunaan: Melindungi isi email agar hanya penerima yang memiliki kunci privat yang benar yang dapat membacanya.
-
Cara Kerja:
-
Pengirim mengenkripsi email menggunakan kunci publik penerima.
-
Hanya penerima yang memiliki kunci privat yang dapat mendekripsi dan membaca email tersebut.
-
Contoh: Jurnalis yang berkomunikasi dengan informan atau organisasi yang mengirim data sensitif dapat menggunakan PGP untuk melindungi komunikasi mereka dari penyusup.
Tanda Tangan Digital (Digital Signature)
-
Kegunaan: Memastikan keaslian dan integritas pesan atau dokumen, memastikan bahwa pesan tidak diubah dan benar-benar berasal dari pengirim yang sah.
-
Cara Kerja:
-
Pengirim membuat tanda tangan digital menggunakan kunci privatnya.
-
Penerima dapat memverifikasi tanda tangan tersebut menggunakan kunci publik pengirim.
-
Contoh: Digunakan untuk memverifikasi keaslian dokumen hukum, email penting, atau perangkat lunak yang diunduh.
Melindungi File dan Dokumen
-
Kegunaan: Mengenkripsi file sensitif agar hanya orang yang memiliki kunci dekripsi yang benar yang dapat membukanya.
-
Cara Kerja: File dienkripsi menggunakan kunci publik penerima, dan penerima menggunakan kunci privatnya untuk mendekripsinya.
-
Contoh: Perusahaan dapat menggunakan PGP untuk mengenkripsi laporan keuangan, data pelanggan, atau informasi penting lainnya sebelum membagikannya.
Mengamankan Backup Data
-
Kegunaan: Mengenkripsi cadangan data penting untuk melindunginya dari akses yang tidak sah.
-
Cara Kerja: File backup dienkripsi dengan PGP sebelum disimpan, sehingga meskipun backup dicuri, data tetap aman.
-
Contoh: Organisasi menyimpan cadangan data klien di server eksternal yang dienkripsi dengan PGP untuk mencegah kebocoran data.
Perlindungan Identitas dan Anonimitas
-
Kegunaan: Melindungi identitas pengirim dan penerima dalam komunikasi online.
-
Cara Kerja: Penggunaan enkripsi end-to-end menjamin bahwa hanya pihak yang berwenang yang dapat membaca pesan.
-
Contoh: Aktivis atau peneliti yang bekerja di negara dengan pengawasan ketat dapat menggunakan PGP untuk melindungi komunikasi mereka.
Memverifikasi Integritas Perangkat Lunak
-
Kegunaan: Memastikan bahwa perangkat lunak atau paket yang diunduh berasal dari sumber yang terpercaya dan tidak dimodifikasi oleh pihak ketiga.
-
Cara Kerja: Pengembang menandatangani perangkat lunak menggunakan kunci privat mereka, dan pengguna dapat memverifikasi tanda tangan menggunakan kunci publik yang disediakan.
-
Contoh: Distribusi Linux atau aplikasi open-source sering kali menyertakan tanda tangan PGP untuk memverifikasi keasliannya.
Komunikasi di Forum atau Jaringan Terdistribusi
-
Kegunaan: Memastikan privasi komunikasi di platform terdesentralisasi atau anonim.
-
Cara Kerja: Pesan dienkripsi sebelum dikirim dan hanya dapat didekripsi oleh penerima yang sah.
-
Contoh: Pengguna di forum yang membahas topik sensitif dapat menggunakan PGP untuk melindungi identitas mereka.
Mengapa PGP Penting?
- Keamanan yang Kuat: Kombinasi kriptografi asimetris dan simetris membuat PGP sangat sulit ditembus oleh peretas.
-Privasi: Menjaga komunikasi Anda tetap aman dan pribadi dari penyadapan atau pengawasan.
-
Integritas: Memastikan bahwa pesan atau data yang dikirim tidak diubah selama transmisi.
-
Otentikasi: Membuktikan identitas pengirim melalui tanda tangan digital.
Kelebihan PGP
-
Sangat Aman: Jika digunakan dengan benar, PGP menawarkan tingkat keamanan yang sangat tinggi.
-
Terbuka: Banyak digunakan di kalangan profesional dan komunitas open-source.
-
Fleksibel: Dapat digunakan untuk berbagai keperluan, mulai dari komunikasi email hingga penyimpanan data.
Kekurangan PGP
-
Kompleks untuk Pemula: Relatif sulit digunakan oleh pengguna awam.
-
Pengelolaan Kunci yang Rumit: Memerlukan pengelolaan kunci publik/privat yang benar.
-
Tidak Ada Pemulihan Data: Jika kunci privat hilang, data yang dienkripsi tidak dapat dipulihkan.
PGP adalah alat yang sangat berguna untuk memastikan keamanan dan privasi dalam komunikasi dan data. Dengan meningkatnya risiko kejahatan siber, penggunaan PGP menjadi semakin penting, terutama di sektor yang menangani data sensitif.
-
-
 @ d830ee7b:4e61cd62
2025-01-08 07:56:25
@ d830ee7b:4e61cd62
2025-01-08 07:56:25การเผชิญหน้า (The Collision Point)
กลางปี 2017 ที่ร้านคราฟท์เบียร์เล็ก ๆ ในย่านเกาะเกร็ด นนทบุรี อากาศร้อนจนเครื่องปรับอากาศ (ที่ยังไม่มี) ในร้านทำงานหนักแทบไหม้ "แจ๊ก กู้ดเดย์" (Jakk Goodday) นั่งลงบนเก้าอี้ไม้ที่เจ้าของร้านกันไว้ให้เป็นประจำ ราวกับเขาเป็นลูกค้าขาประจำระดับวีไอพี
กลิ่นกาแฟคั่ว ลอยผสมกับไอความร้อนจากนอกหน้าต่าง (ผิดร้านหรือเปล่า?) เกิดเป็นบรรยากาศขมติดปลายลิ้นชวนให้คนจิบแล้วอยากถอนใจ
เขาเหลือบมองออกไปนอกหน้าต่าง.. เห็นแสงแดดแผดเผาราวกับมันรู้ว่าสงคราม Blocksize กำลังคุกรุ่นขึ้นอีกครั้ง

บรรยากาศนอกหน้าต่างกับใน ฟอรัม Bitcointalk ช่างเหมือนกันจนน่าขนลุก มันร้อนแรง ไร้ความปรานี
แจ๊กเปิดแล็ปท็อป กดเข้าเว็บฟอรัม พอเสียงแจ้งเตือน “—ติ๊ง” ดังขึ้น คิ้วของเขาก็ขมวดเล็กน้อย คล้ายได้กลิ่นดินปืนกลางสนามรบ
“โรเจอร์ แวร์ (Roger Ver) ไลฟ์เดือดลั่นเวที!” “ปีเตอร์ วูเล (Pieter Wuille) โต้กลับเรื่อง SegWit!” “Hard Fork ใกล้ถึงจุดปะทะแล้ว!”
แจ๊กคลิกเข้าไปในลิงก์ของไลฟ์ทันที เหมือนมือของเขาไม่ต้องการคำสั่งจากสมอง ความคุ้นเคยกับเหตุการณ์แบบนี้บอกเขาว่า นี่ไม่ใช่ดีเบตธรรมดา แต่มันอาจเปลี่ยนอนาคตของ Bitcoin ได้จริง ๆ
เห็นแค่พาดหัวสั้น ๆ แต่ความตึงเครียดก็ชัดเจนขึ้นเรื่อย ๆ ทุกข้อความเหมือนสุมไฟใส่ใจกองหนึ่งที่พร้อมระเบิดได้ทุกเมื่อ
โทรศัพท์ของแจ๊กดังพร้อมปรากฏชื่อ แชมป์ ‘PIGROCK’ ลอยขึ้นมา เขาหยิบขึ้นมารับทันที
“ว่าไงวะแชมป์… มีอะไรด่วนหรือเปล่า?” น้ำเสียงแจ๊กฟังดูเหมือนง่วง ๆ แต่จริง ๆ เขาพร้อมจะลุกมาวิเคราะห์สถานการณ์ให้ฟังทุกเมื่อ
“พี่แจ๊ก.. ผมอ่านดีเบตเรื่อง SegWit ในฟอรัมอยู่ครับ บางคนด่าว่ามันไม่ได้แก้ปัญหาจริง ๆ บ้างก็บอกถ้าเพิ่ม Blocksize ไปเลยจะง่ายกว่า... ผมเลยสงสัยว่า Hard Fork ที่เค้าพูดถึงกันนี่คืออะไร ใครคิดอะไรก็ Fork กันได้ง่าย ๆ เลยเหรอ"
"แล้วถ้า Fork ไปหลายสาย สุดท้ายเหรียญไหนจะเป็น ‘Bitcoin ที่แท้จริง’ ล่ะพี่?”
“แล้วการ Fork มันส่งผลกับนักลงทุนยังไงครับ? คนทั่วไปอย่างผมควรถือไว้หรือขายหนีตายดีล่ะเนี่ย?”
แจ๊กยิ้มมุมปาก ชอบใจที่น้องถามจี้จุด
“เอางี้… การ Fork มันเหมือนแบ่งถนนออกเป็นสองสาย ใครชอบกติกาเก่าก็วิ่งถนนเส้นเก่า ใครอยากแก้กติกาใหม่ก็ไปถนนเส้นใหม่"
"แต่ประเด็นคือ... นี่ไม่ใช่เรื่องเล็ก ๆ เพราะมีผลต่ออัตลักษณ์ของ Bitcoin ทั้งหมดเลยนะมึง—ใครจะยอมปล่อยผ่านง่าย ๆ”
"คิดดูสิ ถ้าครั้งนี้พวกเขา Fork จริง มันอาจไม่ได้เปลี่ยนแค่เครือข่าย แต่เปลี่ยนวิธีที่คนมอง Bitcoin ไปตลอดกาลเลยนะ"
"แล้วใครมันจะอยากลงทุนในระบบที่แตกแยกซ้ำแล้วซ้ำเล่าวะ?"
“งั้นหมายความว่าตอนนี้ก็มีสองแนวใหญ่ ๆ ชัวร์ใช่ไหมครับ?” แชมป์ถามต่อ
“ฝั่ง โรเจอร์ แวร์ ที่บอกว่าต้องเพิ่ม Blocksize ให้ใหญ่จุใจ กับฝั่งทีม Core อย่าง ปีเตอร์ วูเล ที่ยืนยันต้องใช้ SegWit ทำให้บล็อกเบา ไม่กระทบการกระจายอำนาจ?”
“ใช่เลย” แจ๊กจิบกาแฟดำเข้ม ๆ ผสมน้ำผึ้งไปหนึ่งอึก
“โรเจอร์นี่เขาเชื่อว่า Bitcoin ต้องเป็นเงินสดดิจิทัลที่ใช้จ่ายไว ค่าธรรมเนียมไม่แพง ส่วนปีเตอร์กับ Bitcoin Core มองว่าการเพิ่มบล็อกเยอะ ๆ มันจะไปฆ่า Node รายย่อย คนไม่มีทุนก็รัน Node ไม่ไหว สุดท้าย Bitcoin จะกลายเป็นระบบกึ่งรวมศูนย์ ซึ่งมันผิดหลักการเดิมของ ซาโตชิ ไงล่ะ”
“ฟังแล้วก็ไม่ใช่เรื่องง่ายนะพี่… งั้นที่ผมได้ยินว่า จิฮั่น อู๋ (Jihan Wu) เจ้าของ Bitmain ที่ถือ Hashrate เกินครึ่งนี่ก็มาอยู่ฝั่งเดียวกับโรเจอร์ใช่ไหม?"
"เพราะยิ่งบล็อกใหญ่ ค่าธรรมเนียมยิ่งเพิ่ม นักขุดก็ได้กำไรสูงขึ้นใช่ป่ะ?”
“ไอ้เรื่องกำไรก็ส่วนหนึ่ง...” แจ๊กถอนหายใจ
“แต่ที่สำคัญกว่านั้นคืออำนาจต่อรอง… ตอนประชุมลับที่ฮ่องกงเมื่อปีที่แล้ว พี่เองก็ถูกชวนให้เข้าไปในฐานะคนกลาง เลยเห็นภาพน่าขนลุกอยู่หน่อย ๆ"
"จิฮั่นนั่งไขว่ห้างด้วยสีหน้ามั่นใจมาก ด้วย Hashrate ราว 60% ของโลก สั่งซ้ายหันขวาหันเหมือนเป็นแม่ทัพใหญ่ได้เลย พอโรเจอร์ก็ไฟแรงอยู่แล้ว อยากให้ Bitcoin ครองโลกด้วยวิธีของเขา สองคนนี่จับมือกันทีจะเขย่าชุมชน Bitcoin ได้ทั้งกระดาน”
"พี่รู้สึกเหมือนนั่งอยู่ในศึกชิงบัลลังก์ยุคใหม่ คนหนึ่งยึดพลังขุด คนหนึ่งยึดความศรัทธาในชื่อ Bitcoin แต่สิ่งที่พี่สงสัยในตอนนั้นคือ… พวกเขาสู้เพื่อใครกันแน่?"
แชมป์เงียบไปครู่เหมือนกำลังประมวลผล “แล้วตอนนั้นพี่คิดยังไงบ้างครับ? รู้สึกกลัวหรือว่ายังไง?”
“จะไม่กลัวได้ไง!” แจ๊กหัวเราะแห้ง ๆ แวบหนึ่งก็นึกถึงสีหน้าที่ยิ้มเยาะของทั้งคู่ตอนประกาศความพร้อมจะ Fork
“พี่อดคิดไม่ได้ว่าถ้า Core ยังไม่ยอมขยายบล็อก พวกนั้นจะลากนักขุดทั้งกองทัพแฮชเรตไปทำเครือข่ายใหม่ให้เป็น ‘Bitcoin สายใหญ่’ แล้วทิ้งเครือข่ายเดิมให้ซวนเซ"
"แค่คิดก็นึกถึงสงครามกลางเมืองในหนังประวัติศาสตร์แล้วน่ะ.. แตกเป็นสองฝ่าย สุดท้ายใครแพ้ใครชนะ ไม่มีใครทำนายได้จริง ๆ”

พูดจบ.. เขาเปิดฟอรัมดูไลฟ์ดีเบตจากงานในปี 2017 ต่อ โรเจอร์ แวร์ กำลังพูดในโทนร้อนแรง
“Bitcoin ไม่ใช่ของคนรวย! ถ้าคุณไม่เพิ่ม Blocksize คุณก็ทำให้ค่าธรรมเนียมพุ่งจนคนธรรมดาใช้ไม่ได้!”
ขณะเดียวกัน ปีเตอร์ วูเล่ ยืนอยู่ฝั่งตรงข้าม สีหน้าเยือกเย็นราวกับตั้งรับมานาน “การเพิ่มบล็อกคือการทำลายโครงสร้าง Node รายย่อยในระยะยาว แล้วมันจะยังเรียกว่ากระจายอำนาจได้หรือ?”
"ถ้าคุณอยากให้ Bitcoin เป็นของคนรวยเพียงไม่กี่คน ก็เชิญขยายบล็อกไปเถอะนะ แต่ถ้าอยากให้มันเป็นระบบที่คนทุกระดับมีส่วนร่วมจริง ๆ ..คุณต้องฟังเสียง Node รายเล็กด้วย" ปีเตอร์กล่าว
เสียงผู้คนในงานโห่ฮากันอย่างแตกเป็นสองฝ่าย บ้างก็เชียร์ความตรงไปตรงมาของโรเจอร์ บ้างก็เคารพเหตุผลเชิงเทคนิคของปีเตอร์
ข้อความจำนวนมหาศาลในฟอรัมต่างโหมกระพือไปต่าง ๆ นานา มีทั้งคำด่าหยาบคายจนแจ๊กต้องเบือนหน้า ตลอดจนการวิเคราะห์ลึก ๆ ถึงอนาคตของ Bitcoin ที่อาจไม่เหมือนเดิม
ในระหว่างนั้น.. แชมป์ส่งข้อความ Discord กลับมาอีก
“พี่ ถ้า Fork จริง ราคาจะป่วนแค่ไหน? ที่เขาว่าคนถือ BTC จะได้เหรียญใหม่ฟรี ๆ จริงไหม? ผมกลัวว่าถ้าเกิดแบ่งเครือข่ายไม่รู้กี่สาย ตลาดอาจมั่วจนคนหายหมดก็ได้ ใช่ไหมครับ?”
"แล้วถ้าเครือข่ายใหม่ล้มเหลวล่ะครับ? จะส่งผลอะไรต่อชุมชน Bitcoin เดิม?"
"ไอ้แชมป์มึงถามรัวจังวะ!?" แจ๊กสบถเพราะเริ่มตั้งรับไม่ทัน
“ก็ขึ้นกับตลาดจะเชื่อว่าสายไหนเป็น ‘ของจริง’ อีกนั่นแหละ” แจ๊กพิมพ์กลับ
“บางคนถือไว้เผื่อได้เหรียญใหม่ฟรี บางคนขายหนีตายก่อน"
"พี่เองก็ยังไม่กล้าการันตีเลย แต่ที่แน่ ๆ สงครามนี้ไม่ได้มีแค่ผลกำไร มันกระทบศรัทธาของชุมชน Bitcoin ทั้งหมดด้วย"
"ถ้าชาวเน็ตเลิกเชื่อมั่น หรือคนนอกมองว่าพวกเราทะเลาะกันเองเหมือนเด็กแย่งของเล่น ต่อให้ฝั่งไหนชนะ ก็อาจไม่มีผู้ใช้เหลือให้ฉลอง”
แล้วสายตาแจ๊กก็ปะทะกับกระทู้ใหม่ที่เด้งขึ้นมาบนหน้าฟอรัม
“โรเจอร์ แวร์ ประกาศ: ถ้าไม่เพิ่ม Blocksize เราจะฟอร์กเป็น Bitcoin ที่แท้จริง!”
ตัวหนังสือหนาแปะอยู่ตรงนั้นส่งแรงสั่นสะเทือนราวกับจะดึงคนในวงการให้ต้องเลือกข้างกันแบบไม่อาจกลับหลังได้
แจ๊กเอื้อมมือปิดแล็ปท็อปช้า ๆ คล้ายยอมรับความจริงว่าหนทางประนีประนอมอาจไม่มีอีกแล้ว..
“สงครามนี่คงใกล้ระเบิดเต็มทีล่ะนะ” เขาลุกจากเก้าอี้ สะพายเป้ พึมพำกับตัวเองขณะมองกาแฟดำที่เหลือครึ่งแก้ว “ถ้าพวกเขาฟอร์กจริง โลกคริปโตฯ ที่เราเคยรู้จักอาจไม่มีวันเหมือนเดิมอีกต่อไป”
เขามองออกไปนอกหน้าต่าง แสงแดดที่แผดเผาราวกับกำลังบอกว่า.. อนาคตของ Bitcoin อยู่ในจุดที่เส้นแบ่งระหว่างชัยชนะกับความล่มสลายเริ่มพร่าเลือน... และอาจไม่มีทางย้อนกลับ
ก่อนเดินออกจากร้าน เขากดส่งข้อความสั้น ๆ ถึงแชมป์
“เตรียมใจกับความปั่นป่วนไว้ให้ดี ไม่แน่ว่าเราอาจจะได้เห็น Bitcoin แตกเป็นหลายสาย.. ใครจะอยู่ใครจะไปไม่รู้เหมือนกัน แต่เรื่องนี้คงไม่จบง่าย ๆ แน่”
แจ๊กผลักประตูออกไปพบกับแดดจัดที่เหมือนแผดเผากว่าเดิม พายุร้อนไม่ได้มาแค่ในรูปความร้อนกลางกรุง แต่มาในรูป “สงคราม Blocksize” ที่พร้อมจะฉีกชุมชนคริปโตออกเป็นฝักฝ่าย และอาจลามบานปลายจนกลายเป็นศึกประวัติศาสตร์
ทว่าสิ่งที่ค้างคาใจกลับเป็นคำถามนั้น…
เมื่อเครือข่ายแบ่งเป็นหลายสายแล้ว เหรียญไหนจะเป็น Bitcoin จริง?
หรือบางที... ในโลกที่ใครก็ Fork ได้ตามใจ เราจะไม่มีวันได้เห็น “Bitcoin หนึ่งเดียว” อีกต่อไป?
คำถามที่ไม่มีใครตอบได้ชัดนี้ส่องประกายอยู่ตรงปลายทาง ราวกับป้ายเตือนว่า “อันตรายข้างหน้า” และคนในชุมชนทั้งหมดกำลังจะต้องเผชิญ…
โดยไม่มีใครมั่นใจเลยว่าจะรอด หรือจะแตกสลายไปก่อนกันแน่...

สองเส้นทาง (The Forked Path)
กลางปี 2017 ท้องฟ้าเหนือบุรีรัมย์ยังคงคุกรุ่นด้วยไอแดดและความร้อนแรงของสงคราม Blocksize แจ๊ก กู้ดเดย์ ก้าวเข้ามาในคาเฟ่เล็ก ๆ แห่งหนึ่งในย่านเทศบาลด้วยสีหน้าครุ่นคิด เขาพยายามมองหามุมสงบสำหรับนั่งตั้งหลักในโลกความเป็นจริง ก่อนจะจมดิ่งสู่สงครามในโลกดิจิทัลบนฟอรัม Bitcointalk อีกครั้ง
กลิ่นกาแฟคั่วเข้มลอยกระทบจมูก แจ๊กสั่งกาแฟดำแก้วโปรดแล้วปลีกตัวมาที่โต๊ะริมกระจก กระจกบานนั้นสะท้อนแสงอาทิตย์จัดจ้า ราวกับจะบอกว่าวันนี้คงไม่มีใครหนีความร้อนที่กำลังแผดเผา ทั้งในอากาศและในชุมชน Bitcoin ได้พ้น
เขาเปิดแล็ปท็อปขึ้น ล็อกอินเข้า Bitcointalk.org ตามเคย ข้อความและกระทู้มากมายกระหน่ำแจ้งเตือน ไม่ต่างอะไรจากสมรภูมิคำพูดที่ไม่มีวันหลับ “Hong Kong Agreement ล้มเหลวจริงหรือ?” “UASF คือปฏิวัติโดย Node?” เหล่านี้ล้วนสะท้อนความไม่แน่นอนในชุมชน Bitcoin ที่ตอนนี้ ดูคล้ายจะถึงจุดแตกหักเต็มที...
“ทั้งที่ตอนนั้นเราก็พยายามกันแทบตาย…” แจ๊กพึมพำ มองจอด้วยสายตาเหนื่อยใจพร้อมภาพความทรงจำย้อนกลับเข้าในหัว เขายังจำการประชุมที่ฮ่องกงเมื่อต้นปี 2016 ได้แม่น ยามนั้นความหวังในการประนีประนอมระหว่าง Big Block และ Small Block ดูเป็นไปได้ หากแต่กลายเป็นละครฉากใหญ่ที่จบลงโดยไม่มีใครยอมถอย...
...การประชุม Hong Kong Agreement (2016)
ภายในห้องประชุมหรูของโรงแรมใจกลางย่านธุรกิจฮ่องกง บรรยากาศตึงเครียดยิ่งกว่าการเจรจาสงบศึกในสมัยโบราณ
โรเจอร์ แวร์ ยืนเสนอว่า “การเพิ่ม Blocksize สำคัญต่ออนาคตของ Bitcoin — เราอยากให้คนทั่วไปเข้าถึงได้โดยไม่ต้องจ่ายค่าธรรมเนียมแพง ๆ”
“จิฮั่น อู๋ (Jihan Wu)” จาก Bitmain นั่งฝั่งเดียวกับโรเจอร์ คอยเสริมว่าการเพิ่มบล็อกคือโอกาสสำหรับนักขุด และหากทีม Core ไม่ยอม พวกเขาก็พร้อม “ดัน Fork” ขึ้นได้ทุกเมื่อ ด้วย Hashrate มหาศาลที่พวกเขาคุมไว้
ฝั่ง ปีเตอร์ วูเล (Pieter Wuille) กับ เกร็ก แมกซ์เวลล์ (Greg Maxwell) จาก Bitcoin Core เถียงกลับอย่างใจเย็นว่า “การขยายบล็อกอาจดึงดูดทุนใหญ่ ๆ แล้วไล่ Node รายย่อยออกไป ชุมชนอาจไม่เหลือความกระจายอำนาจอย่างที่ Satoshi ตั้งใจ”
สุดท้าย บทสรุปที่เรียกว่า Hong Kong Agreement ลงนามได้ก็จริง แต่มันกลับเป็นแค่ลายเซ็นบนกระดาษที่ไม่มีฝ่ายไหนเชื่อใจใคร

แจ๊กเบือนสายตาออกนอกหน้าต่าง สังเกตเห็นผู้คนเดินขวักไขว่ บ้างก็ดูรีบร้อน บ้างเดินทอดน่องเหมือนว่างเปล่า นี่คงไม่ต่างอะไรกับชาวเน็ตในฟอรัมที่แบ่งฝ่ายกันใน “สงคราม Blocksize” อย่างไม่มีทีท่าจะหยุด
แค่ไม่กี่นาที... เสียงโทรศัพท์ก็ดังขึ้น ชื่อ แชมป์ ‘PIGROCK’ โชว์หราเต็มจออีกครั้ง
“ว่าไงเจ้าแชมป์?” แจ๊กกรอกเสียงในสายด้วยอารมณ์เหนื่อย ๆ ทว่าพร้อมจะอธิบายเหตุการณ์ตามสไตล์คนที่ชอบครุ่นคิด
“พี่แจ๊ก.. ผมเข้าใจแล้วว่าการประชุมฮ่องกงมันล้มเหลว ตอนนี้ก็มีคนแยกเป็นสองขั้ว Big Block กับ SegWit แต่ผมเจออีกกลุ่มในฟอรัมเรียกว่า UASF (User-Activated Soft Fork) ที่เหมือนจะกดดันพวกนักขุดให้ยอมรับ SegWit..."
"อยากรู้ว่าตกลง UASF มันสำคัญยังไงครับ? ทำไมใคร ๆ ถึงเรียกว่าเป็น การปฏิวัติโดย Node กัน?”
แจ๊กอมยิ้มก่อนจะวางแก้วกาแฟลง พูดด้วยน้ำเสียงจริงจังกว่าเดิม “UASF น่ะหรือ? มันเปรียบได้กับการที่ ‘ชาวนา’ หรือ ‘ประชาชนตัวเล็ก ๆ’ ออกมาประกาศว่า ‘ฉันจะไม่รับบล็อกของนักขุดที่ไม่รองรับ SegWit นะ ถ้าแกไม่ทำตาม ฉันก็จะตัดบล็อกแกทิ้ง!’ เสมือนเป็นการปฏิวัติที่บอกว่าแรงขุดมากแค่ไหนก็ไม่สำคัญ ถ้าคนรัน Node ไม่ยอม… เชนก็เดินต่อไม่ได้”
“โห… ฟังดูแรงจริง ๆ พี่ แล้วถ้านักขุดไม่ร่วมมือ UASF จะเกิดอะไรขึ้น?” แชมป์ถามต่อเสียงสั่นนิด ๆ
“ก็อาจเกิด ‘Chain Split’ ยังไงล่ะ"
"แยกเครือข่ายเป็นสองสาย สุดท้ายเครือข่ายเดิม กับเครือข่ายใหม่ที่รองรับ SegWit ไม่ตรงกัน คนอาจสับสนหนักยิ่งกว่า Hard Fork ปกติด้วยซ้ำ"
"แต่นั่นแหละ... มันแสดงพลังว่าผู้ใช้ทั่วไปก็มีสิทธิ์กำหนดทิศทาง Bitcoin ไม่ได้น้อยไปกว่านักขุดเลย”
“เข้าใจแล้วครับพี่… เหมือน การปฏิวัติโดยประชาชนตาดำ ๆ ที่จับมือกันค้านอำนาจทุนใหญ่ใช่ไหม?” แชมป์หยุดครู่หนึ่ง “ผมเคยคิดว่า Node รายย่อยน้อยรายจะไปสู้อะไรไหว แต่ตอนนี้ดูท่าจะเปลี่ยนเกมได้จริงว่ะพี่…”
“ใช่เลย” แจ๊กตอบ
“นี่เป็นความพิเศษของ Bitcoin ที่บอกว่า ‘เราคุมเครือข่ายร่วมกัน’ แม้แต่ Bitmain ที่มี Hashrate มากกว่า 50% ก็หนาวได้ถ้าผู้ใช้หรือ Node รายย่อยรวมพลังกันมากพอ”
แชมป์ฟังด้วยความตื่นเต้นปนกังวล “แล้วแบบนี้ เรื่อง SegWit กับ Blocksize จะจบยังไงครับ? เห็นข่าวว่าถ้านักขุดโดนกดดันมาก ๆ คนอย่าง จิฮั่น อู๋ อาจออกไปสนับสนุน Bitcoin Cash ที่จะเปิดบล็อกใหญ่”
แจ๊กเลื่อนดูฟีดข่าวในฟอรัม Bitcointalk อีกครั้ง ก็เห็นพาดหัวชัด ๆ
“Bitmain ประกาศกร้าวพร้อมหนุน BCH เต็มพิกัด!”
เขาถอนหายใจเฮือกหนึ่ง “ก็ใกล้เป็นจริงแล้วล่ะ… โรเจอร์ แวร์ เองก็ผลักดัน BCH ว่าคือ Bitcoin แท้ที่ค่าธรรมเนียมถูก ใช้งานได้จริง ส่วนฝั่ง BTC ที่ยึดเอา SegWit เป็นหลัก ก็ไม่ยอมให้ Blocksize เพิ่มใหญ่เกินจำเป็น.."
"ต่างคนต่างมีเหตุผล... แต่อุดมการณ์นี่คนละทางเลย”
“แล้วพี่คิดว่าใครจะเป็นฝ่ายชนะครับ?”
“เฮ้ย.. มึงถามยากไปหรือเปล่า” แจ๊กหัวเราะหึ ๆ “ทุกคนมีโอกาสได้หมด และก็มีโอกาสพังหมดเหมือนกัน ถ้า UASF กดดันนักขุดให้อยู่กับ Core ได้ พวกเขาอาจยอมแพ้ แต่ถ้า Bitmain เทใจไป BCH นักขุดรายใหญ่คนอื่น ๆ ก็คงตาม"
"แล้วถ้าฝั่ง BCH เริ่มได้เปรียบ... อาจดึงคนไปเรื่อย ๆ สุดท้ายจะเหลือไหมล่ะฝั่ง SegWit ตัวจริง?”
“งั้น Node รายย่อยจะยืนอยู่ตรงไหนล่ะครับพี่?” แชมป์ถามอย่างหนักใจ
“Node รายย่อยและชุมชนผู้ใช้นี่แหละ คือ ตัวแปรชี้ขาด ทุกวันนี้คนกลุ่ม UASF พยายามโชว์พลังว่าตัวเองมีสิทธิ์ตั้งกติกาเหมือนกัน ไม่ใช่แค่นักขุด"
"อย่างที่บอก.. มันคือการ ‘ลุกขึ้นปฏิวัติ’ โดยชาวนา ต่อสู้กับเจ้าที่ที่ถือ ‘แฮชเรต’ เป็นอาวุธ”
แจ๊กตบบ่าตัวเองเบา ๆ ก่อนจะหัวเราะเล็กน้อย
“นี่แหละความมันของ Bitcoin ไม่มีเจ้าไหนสั่งได้เบ็ดเสร็จจริง ๆ ทุกฝั่งต่างถือไพ่คนละใบ สงครามยังไม่รู้จะจบยังไง ถึงอย่างนั้นมันก็สะท้อนวิญญาณ ‘decentralization’ ที่แท้จริง กล้ายอมรับสิทธิ์ทุกฝ่ายเพื่อแข่งขันกันตามกติกา”

จู่ ๆ ในหน้าฟอรัมก็มีกระทู้ใหม่เด้งเด่น “Bitmain หนุน Bitcoin Cash ด้วย Hashrate กว่า 50%! สงครามเริ่มแล้ว?” ข้อความนั้นดังโครมครามเหมือนระเบิดลงกลางวง
แจ๊กนิ่งไปชั่วขณะ สัมผัสได้ถึงความปั่นป่วนที่กำลังปะทุขึ้นอีกครั้ง เหงื่อบางเบาซึมบนหน้าผากแม้อากาศในคาเฟ่จะเย็นฉ่ำ เขาหันมองโทรศัพท์ที่ยังค้างสายกับแชมป์ แล้วเอ่ยด้วยน้ำเสียงจริงจัง
“นี่ล่ะ.. จุดเริ่มของสองเส้นทางอย่างชัดเจน… บล็อกใหญ่จะไปกับ BCH ส่วน SegWit ก็อยู่กับ BTC แน่นอนว่าทั้งสองฝ่ายไม่คิดถอยง่าย ๆ นักขุดจะเลือกข้างไหน? Node รายย่อยจะยอมใคร?"
"เมื่อสงครามครั้งนี้นำไปสู่การแบ่งเครือข่าย ใครกันแน่จะเป็นผู้ชนะตัวจริง? หรืออาจไม่มีผู้ชนะเลยก็เป็นได้”
ปลายสายเงียบงัน มีแต่เสียงหายใจของแชมป์ที่สะท้อนความกังวลปนอยากรู้อย่างแรง
“พี่… สุดท้ายแล้วเรากำลังยืนอยู่บนรอยแยกที่พร้อมจะฉีกทุกอย่างออกเป็นชิ้น ๆ ใช่ไหมครับ?”
“อาจจะใช่ก็ได้... หรือถ้ามองอีกมุม อาจเป็นวัฏจักรที่ Bitcoin ต้องเจอเป็นระยะ ทุกคนมีสิทธิ์ Fork ได้ตามใจใช่ไหมล่ะ? ก็ขอให้โลกได้เห็นกันว่าชุมชนไหนแน่จริง” แจ๊กพูดทิ้งท้ายก่อนจะแย้มยิ้มเจือรอยอ่อนล้า
ภาพบนจอคอมพิวเตอร์ฉายกระทู้ถกเถียงกันไม่หยุด ประหนึ่งเวทีดีเบตที่ไม่มีวันปิดไฟ แจ๊กจิบกาแฟอึกสุดท้ายเหมือนจะเตรียมพร้อมใจก่อนเข้าสู่สนามรบครั้งใหม่ สงครามยังไม่จบ.. ซ้ำยังดูหนักข้อยิ่งขึ้นเรื่อย ๆ
เขาลุกขึ้นจากโต๊ะ ชำเลืองมองแสงแดดจัดจ้าที่สาดลงมาไม่หยุด เปรียบเหมือนไฟแห่งข้อขัดแย้งที่เผาผลาญทั้งชุมชน Bitcoin ไม่ว่าใครจะเลือกอยู่ฝั่งไหน กลุ่ม UASF, กลุ่ม Big Block, หรือ กลุ่ม SegWit ทางเดินข้างหน้าล้วนเต็มไปด้วยความไม่แน่นอน
“สุดท้ายแล้ว… เมื่อกระดานแบ่งเป็นสองเส้นทางอย่างเด่นชัด สงคราม Blocksize จะจบลงด้วยใครได้บทผู้ชนะ?"
"หรือบางที… มันอาจไม่มีผู้ชนะที่แท้จริงในระบบที่ใครก็ Fork ได้ตลอดเวลา”
คำถามนี้ลอยติดค้างอยู่ในบรรยากาศยามบ่ายที่ร้อนระอุ ชวนให้ใครก็ตามที่จับตาดูสงคราม Blocksize ต้องฉุกคิด
เมื่อไม่มีใครเป็นเจ้าของ Bitcoin อย่างสมบูรณ์ ทุกคนจึงมีสิทธิ์บงการและเสี่ยงต่อการแตกแยกได้ทุกเมื่อ แล้วท้ายที่สุด ชัยชนะ–ความพ่ายแพ้ อาจไม่ใช่จุดสิ้นสุดของโลกคริปโตฯ
แต่เป็นเพียงจุดเริ่มต้นของการวิวัฒน์ที่ไม่มีวันจบสิ้น…

เมาท์แถมเรื่อง UASF (User-Activated Soft Fork)
นี่สนามรบยุคกลางที่ดูเหมือนในหนังแฟนตาซี ทุกคนมีดาบ มีโล่ แต่จู่ ๆ คนตัวเล็กที่เราไม่เคยสังเกต—พวกชาวนา ช่างไม้ คนแบกน้ำ—กลับรวมตัวกันยกดาบบุกวังเจ้าเมือง พร้อมตะโกนว่า “พอเถอะ! เราก็มีสิทธิ์เหมือนกัน!”
มันอาจจะดูเวอร์ ๆ หน่อยใช่ไหมครับ?
แต่ในโลก Bitcoin ปี 2017 นี่คือสิ่งที่เกิดขึ้นในรูปแบบ “User-Activated Soft Fork” หรือ UASF การปฏิวัติด้วยพลังโหนด ซึ่งทำให้นักขุดยักษ์ใหญ่ตัวสั่นงันงกันมาแล้ว!
แล้ว UASF มันคืออะไรล่ะ?
“User-Activated Soft Fork” หรือเรียกย่อ ๆ ว่า “UASF” ไม่ใช่อัปเกรดซอฟต์แวร์สวย ๆ แต่เป็น “ดาบเล่มใหม่” ที่คนตัวเล็ก—หมายถึง โหนด รายย่อย—ใช้ต่อรองกับนักขุดรายใหญ่ โดยกติกาคือ.. ถ้านักขุดไม่ทำตาม (เช่น ไม่รองรับ SegWit) โหนดก็จะปฏิเสธบล็อกของพวกเขาอย่างไม่เกรงใจใคร
สมมุติว่าคุณคือโหนด..
คุณรันซอฟต์แวร์ Bitcoin คอยตรวจสอบธุรกรรม วันดีคืนดี คุณประกาศ “ต่อไปถ้าใครไม่รองรับ SegWit ฉันไม่ยอมรับบล็อกนะ!” นี่ล่ะครับ “UASF” ตัวเป็น ๆ
คำขวัญสุดฮิตของ UASF
“No SegWit, No Block”
หรือแปลว่าถ้าบล็อกไม่รองรับ SegWit ก็เชิญออกไปเลยจ้า..
มันเหมือนการที่ชาวนาโผล่มาตบโต๊ะอาหารท่านขุนว่า “นายใหญ่จะปลูกอะไรก็ปลูกไป แต่ไม่งั้นฉันไม่รับผลผลิตนายนะ!”
ความเชื่อมโยงกับ BIP 148
ถ้าจะพูดถึง UASF ต้องรู้จัก BIP 148 ไว้นิดนึง มันเปรียบเหมือน “ธงปฏิวัติ” ที่ตีตราว่าวันที่ 1 สิงหาคม 2017 คือเส้นตาย!
BIP 148 บอกไว้ว่า.. ถ้าถึงวันนั้นแล้วยังมีนักขุดหน้าไหนไม่รองรับ SegWit บล็อกที่ขุดออกมาก็จะถูกโหนดที่ใช้ UASF “แบน” หมด
ผลลัพธ์ที่ตั้งใจ นักขุดไม่อยากโดนแบนก็ต้องทำตาม UASF กล่าวคือ “นายต้องรองรับ SegWit นะ ไม่งั้นอด!”
หลายคนกลัวกันว่า “อ้าว ถ้านักขุดใหญ่ ๆ ไม่ยอมแล้วหันไปขุดสายอื่น จะไม่กลายเป็นแยกเครือข่าย (Chain Split) หรือ?”
ใช่ครับ.. มันอาจเกิดสงครามสายใหม่ทันทีไงล่ะ
ทำไม UASF ถึงสำคัญ?
ย้อนกลับไปก่อนปี 2017 Bitcoin มีปัญหาโลกแตกทั้งค่าธรรมเนียมแพง ธุรกรรมหน่วง บวกกับความขัดแย้งเรื่อง “จะเพิ่ม Blocksize ดีไหม?” ทางกลุ่มนักขุดรายใหญ่ (นำโดย Bitmain, Roger Ver ฯลฯ) รู้สึกว่า “SegWit ไม่ใช่ทางออกที่แท้จริง” แต่อีกฝั่ง (ทีม Core) ชี้ว่า “Blocksize ใหญ่มากไปจะรวมศูนย์นะ โหนดรายย่อยตายหมด”
UASF เลยโผล่มา เหมือนชาวนาตะโกนว่า
“หุบปากได้แล้วไอ้พวกที่สู้กัน! ถ้าพวกแกไม่รองรับ SegWit พวกข้า (โหนด) ก็จะไม่เอาบล็อกแก”
สาระก็คือ.. มันคือตัวบ่งชี้ว่าคนตัวเล็กอย่างโหนดรายย่อยก็มีพลังต่อรอง เป็นกลไกที่ดึงอำนาจจากมือทุนใหญ่กลับสู่มือชุมชน (Decentralization ที่แท้ทรู)
วิธีการทำงานของ UASF
ลองจินตนาการตาม..
-
การกำหนดเส้นตาย BIP 148 ประกาศไว้ “ถึงวันที่ 1 สิงหาคม 2017 ถ้านายยังไม่รองรับ SegWit โหนด UASF จะไม่รับบล็อกนาย”
-
ถ้าคุณเป็นนักขุด… คุณขุดบล็อกออกมา แต่ไม่ได้ตีธง “ฉันรองรับ SegWit” UASF โหนดเห็นปุ๊บ พวกเขาจะจับโยนทิ้งไปเลย
-
ผลกระทบ? นักขุดที่ไม่ยอมทำตามจะเจอปัญหา บล็อกที่ขุดออกมาไม่มีใครรับ—เสียแรงขุดฟรี
อาจเกิด Chain Split คือ แยกเครือข่ายเลย ถ้านักขุดเหล่านั้นไปตั้งสายใหม่
ความสำเร็จและความท้าทายของ UASF
ความสำเร็จ.. หลังการรวมพลังผู้ใช้ โหนดรายย่อยกดดันนักขุดได้ไม่น้อย จนกระทั่ง SegWit เปิดใช้งานจริงใน Bitcoin วันที่ 24 สิงหาคม 2017 ช่วยให้ธุรกรรมเร็วขึ้น แก้ Transaction Malleability และเปิดทางสู่ Lightning Network ในอนาคต
ความท้าทาย.. นักขุดบางค่ายไม่โอเค.. โดยเฉพาะ Bitmain ซึ่งคาดว่าจะสูญรายได้บางส่วน ก็นำไปสู่การสนับสนุน “Bitcoin Cash (BCH)” แยกสาย (Hard Fork) ของตัวเองตั้งแต่วันที่ 1 สิงหาคม 2017 นั่นเอง
ว่าแล้วก็เปรียบง่าย ๆ
UASF เหมือนปฏิบัติการยึดคฤหาสน์เจ้าเมืองมาเปิดให้ชาวบ้านเข้าอยู่ฟรี.. แต่อีกฝ่ายบอก
“งั้นฉันออกไปตั้งคฤหาสน์ใหม่ดีกว่า!”
บทเรียนสำคัญ UASF เป็นตัวอย่างชัดว่า “ผู้ใช้” หรือ โหนดรายย่อย สามารถสร้างแรงกดดันให้นักขุดต้องยอมเปลี่ยนได้จริง ๆ ไม่ใช่แค่ยอมรับเงื่อนไขที่ขุดกันมา
ผลกระทบระยะยาวหลังจากนั้นล่ะ?
SegWit ถูกใช้งาน ทำให้ค่าธรรมเนียมธุรกรรมลดลง (ช่วงหนึ่ง) เกิด Lightning Network เป็น Layer 2 สุเฟี้ยวของ Bitcoin เกิด BCH (Bitcoin Cash) เป็นสายแยกที่อ้างว่า Blocksize ใหญ่คือทางออก
สรุปแล้ว UASF ทำให้โลกได้รู้ว่า..
Bitcoin ไม่ใช่ของนักขุด หรือของฝ่ายพัฒนาใดฝ่ายเดียว แต่มันเป็นของทุกคน!
“Bitcoin เป็นของทุกคน”
ไม่มีใครมีอำนาจเบ็ดเสร็จ ไม่ว่าคุณจะถือ Hashrate มากแค่ไหน ถ้า Node ทั่วโลกไม่เอา ก็จบ!
“แรงขุดใหญ่แค่ไหน ก็แพ้ใจมวลชน!”
(น่าจะมีตอนต่อไปนะ.. ถ้าชอบก็ Zap โหด ๆ เป็นกำลังใจให้ด้วยนะครับ)
-
-
 @ a17fb4ed:c53f7e91
2024-12-17 21:57:15
@ a17fb4ed:c53f7e91
2024-12-17 21:57:15I just finished up listening to a solid podcast episode and it got me thinking. As we approach the end of another year, it's natural to feel the weight of the past 12 months bearing down on us. But what if, instead of dragging all of that baggage into the new year, we took the time to truly come into 2025 feeling light and unencumbered?
That's the approach Jesse Itzler takes as he prepares for the year ahead. "I want to come into the new year feeling light," he explains. "I don't want to have a lot of carryover going into the next year. I want to clean my hands and just be light."
Part of Jesse's end-of-year ritual is getting ruthlessly organized and decluttered, from his closet to his email inbox. "I don't want to play catch-up," he says. "I want to attack. I want to dominate the year, not let other people take it away from me."
Here are some of his Actionable Steps (I do some of these already, but I will be adding a few more):
-
Conduct a Personal Year-End Review
-
Reflect on what worked, what didn't, and what you want to focus on in the year ahead.
-
Assess your progress in key areas like family, fitness, finance, and fun.
-
Declutter and Organize
-
Go through your closet and donate anything you haven't worn in the past year.
-
Clear the clutter from your desk and digital spaces like your email inbox.
-
Unsubscribe and Simplify
-
Unsubscribe from email lists, apps, and subscriptions you no longer need.
-
Delete unused apps and digital files to minimize distractions.
-
Embrace a Beginner's Mindset
-
Approach the new year with a sense of possibility and excitement.
-
Be willing to let go of old habits and try new approaches.
-
Attack the Year with Focus and Intention
-
Set ambitious but achievable goals in key areas of your life.
- Develop systems and routines to help you stay on track.
Let me know if there is anything else I should add to my list to lighten up the load for 2025.
Cheers, Yooper
-
-
 @ 41e6f20b:06049e45
2024-11-17 17:33:55
@ 41e6f20b:06049e45
2024-11-17 17:33:55Let me tell you a beautiful story. Last night, during the speakers' dinner at Monerotopia, the waitress was collecting tiny tips in Mexican pesos. I asked her, "Do you really want to earn tips seriously?" I then showed her how to set up a Cake Wallet, and she started collecting tips in Monero, reaching 0.9 XMR. Of course, she wanted to cash out to fiat immediately, but it solved a real problem for her: making more money. That amount was something she would never have earned in a single workday. We kept talking, and I promised to give her Zoom workshops. What can I say? I love people, and that's why I'm a natural orange-piller.
-
 @ 7ed5bd1c:4caa7587
2025-01-08 07:35:42
@ 7ed5bd1c:4caa7587
2025-01-08 07:35:42Bitcoin เป็นเกราะป้องกันจากการควบคุมของรัฐบาล
ในโลกที่การควบคุมทางการเงินของรัฐมีผลกระทบต่อชีวิตของประชาชน การปกป้องทรัพย์สินส่วนบุคคลจึงเป็นประเด็นสำคัญที่หลายคนกังวล Bitcoin ได้เข้ามามีบทบาทสำคัญในฐานะเครื่องมือที่ช่วยป้องกันการอายัดทรัพย์สินและการแทรกแซงทางการเงินจากรัฐบาลและองค์กรต่างๆ
กรณีศึกษาที่น่าสนใจ
-
เวเนซุเอลา: เมื่อประเทศประสบภาวะเงินเฟ้อสูงและรัฐบาลมีการควบคุมการแลกเปลี่ยนเงินตราต่างประเทศ ประชาชนบางส่วนใช้ Bitcoin เพื่อรักษามูลค่าทรัพย์สินของพวกเขาและทำธุรกรรมข้ามพรมแดนโดยไม่ต้องผ่านการตรวจสอบจากรัฐบาล
-
แคนาดา: ในปี 2022 รัฐบาลแคนาดามีการอายัดบัญชีธนาคารของผู้ประท้วงในการเคลื่อนไหวทางการเมืองบางอย่าง Bitcoin กลายเป็นช่องทางในการระดมทุนและช่วยให้ประชาชนสามารถป้องกันการแทรกแซงจากรัฐบาลได้
-
ไนจีเรีย: ธนาคารกลางไนจีเรียสั่งห้ามธุรกรรมที่เกี่ยวข้องกับ Bitcoin และคริปโตเคอร์เรนซีอื่นๆ แต่ประชาชนกลับหันมาใช้ Bitcoin ในตลาดมืดเพื่อหลีกเลี่ยงข้อจำกัดและรักษาความเป็นอิสระทางการเงิน
Bitcoin ปกป้องทรัพย์สินอย่างไร?
-
ความเป็นเจ้าของแท้จริง: Bitcoin ใช้ระบบกระจายศูนย์ที่ไม่มีตัวกลาง ซึ่งหมายความว่าไม่มีองค์กรหรือรัฐใดสามารถเข้าถึงหรือยึดครอง Bitcoin ของคุณได้ หากคุณเก็บรักษาคีย์ส่วนตัวอย่างปลอดภัย
-
ไร้พรมแดน: Bitcoin สามารถโอนย้ายได้ทั่วโลกโดยไม่ต้องผ่านธนาคารหรือสถาบันการเงินที่อยู่ภายใต้การควบคุมของรัฐบาล ทำให้เป็นตัวเลือกที่น่าสนใจสำหรับผู้ที่ต้องการหลบเลี่ยงการอายัดทรัพย์สิน
-
ความโปร่งใสและความปลอดภัย: การทำธุรกรรมของ Bitcoin ถูกบันทึกในบล็อกเชนซึ่งเป็นระบบที่โปร่งใสและตรวจสอบได้ ในขณะเดียวกันข้อมูลส่วนบุคคลของผู้ใช้งานจะถูกเก็บเป็นความลับ
ข้อควรระวัง
แม้ Bitcoin จะมีข้อดีในเรื่องการปกป้องทรัพย์สินจากรัฐ แต่ผู้ใช้งานต้องมีความระมัดระวังในการจัดเก็บคีย์ส่วนตัว และหลีกเลี่ยงการพึ่งพาบริการจากบุคคลที่สามที่อาจไม่ปลอดภัย
ในโลกที่อิสรภาพทางการเงินถูกท้าทาย Bitcoin กลายเป็นเครื่องมือสำคัญสำหรับการปกป้องทรัพย์สินและสิทธิส่วนบุคคลของประชาชน คุณคิดว่า Bitcoin สามารถเป็นคำตอบสำหรับความท้าทายนี้ได้จริงหรือไม่? ร่วมพูดคุยในความคิดเห็น!
-
-
 @ fd208ee8:0fd927c1
2024-11-08 08:08:30
@ fd208ee8:0fd927c1
2024-11-08 08:08:30You have no idea
I regularly read comments from people, on here, wondering how it's possible to marry -- or even simply be friends! -- with someone who doesn't agree with you on politics. I see this sentiment expressed quite often, usually in the context of Bitcoin, or whatever pig is currently being chased through the village, as they say around here.

It seems rather sensible, but I don't think it's as hard, as people make it out to be. Further, I think it's a dangerous precondition to set, for your interpersonal relationships, because the political field is constantly in flux. If you determine who you will love, by their opinions, do you stop loving them if their opinions change, or if the opinions they have become irrelevant and a new set of opinions are needed -- and their new ones don't match your new ones? We could see this happen to relationships en masse, during the Covid Era, and I think it happens every day, in a slow grind toward the disintegration of interpersonal discourse.
I suspect many people do stop loving, at that point, as they never really loved the other person for their own sake, they loved the other person because they thought the other person was exactly like they are. But no two people are alike, and the longer you are in a relationship with someone else, the more the initial giddiness wears off and the trials and tribulations add up, the more you notice how very different you actually are. This is the point, where best friends and romantic couples say, We just grew apart.
But you were always apart. You were always two different people. You just didn't notice, until now.

I've also always been surprised at how many same-party relationships disintegrate because of some disagreement over some particular detail of some particular topic, that they generally agree on. To me, it seems like an irrelevant side-topic, but they can't stand to be with this person... and they stomp off. So, I tend to think that it's less that opinions need to align to each other, but rather than opinions need to align in accordance with the level of interpersonal tolerance they can bring into the relationship.
I was raised by relaxed revolutionaries
Maybe I see things this way because my parents come from two diverging political, cultural, national, and ethnic backgrounds, and are prone to disagreeing about a lot of "important" (to people outside their marriage) things, but still have one of the healthiest, most-fruitful, and most long-running marriages of anyone I know, from that generation. My parents, you see, aren't united by their opinions. They're united by their relationship, which is something outside of opinions. Beyond opinions. Relationships are what turn two different people into one, cohesive unit, so that they slowly grow together. Eventually, even their faces merge, and their biological clocks tick to the same rhythm. They eventually become one entity that contains differing opinions about the same topics.
It's like magic, but it's the result of a mindset, not a worldview. Or, as I like to quip:
The best way to stay married, is to not get divorced.

My parents simply determined early on, that they would stay together, and whenever they would find that they disagreed on something that didn't directly pertain to their day-to-day existence with each other they would just agree-to-disagree about that, or roll their eyes, and move on. You do you. Live and let live.
My parents have some of the most strongly held personal opinions of any people I've ever met, but they're also incredibly tolerant and can get along with nearly anyone, so their friends are a confusing hodgepodge of people we liked and found interesting enough to keep around. Which makes their house parties really fun, and highly unusual, in this day and age of mutual-damnation across the aisle.

The things that did affect them, directly, like which school the children should attend or which country they should live in, etc. were things they'd sit down and discuss, and somehow one opinion would emerge, and they'd again... move on.
And that's how my husband and I also live our lives, and it's been working surprisingly well. No topics are off-limits to discussion (so long as you don't drone on for too long), nobody has to give up deeply held beliefs, or stop agitating for the political decisions they prefer.
You see, we didn't like that the other always had the same opinion. We liked that the other always held their opinions strongly. That they were passionate about their opinions. That they were willing to voice their opinions; sacrifice to promote their opinions. And that they didn't let anyone browbeat or cow them, for their opinions, not even their best friends or their spouse. But that they were open to listening to the other side, and trying to wrap their mind around the possibility that they might just be wrong about something.

We married each other because we knew: this person really cares, this person has thought this through, and they're in it, to win it. What "it" is, is mostly irrelevant, so long as it doesn't entail torturing small animals in the basement, or raising the children on a diet of Mountain Dew and porn, or something.
Live and let live. At least, it's never boring. At least, there's always something to ~~argue~~ talk about. At least, we never think... we've just grown apart.
-
 @ fc7085c3:0b32a4cb
2024-12-17 21:36:03
@ fc7085c3:0b32a4cb
2024-12-17 21:36:03- ~finish writing some experimental specs and store on hidden repo for later~
- fix bugs on in-house js web components framework
- slooowly migrate kind:1 app from Qwik to above framework
- revamp kind:1 app login
- add basic engagement features then halt kind:1 app dev
- test feasibility of new app - codename: ZULULA. cool? flawed?
- if cool, finish ZULULA basic features
- start simplified messenger app to test custom chat spec
- if you got here you turned yourself into High Pleb
- ...don't know what's next yet
-
 @ fd208ee8:0fd927c1
2024-11-09 09:21:19
@ fd208ee8:0fd927c1
2024-11-09 09:21:19Drumroll, please....
In a previous article, I introduced the concept of relay communities.
The ink had barely dried, on that set of instructions, before one of my favorite Nostr devs, ثعبان, rolled out the alpha version of a relay-community client.
Obviously, it's still a bit of a construction site, but you can check out how it'd work, for your community, by test-driving the functionality on your own relay. Simply type https://chachi.chat/ followed by the name of your relay. For instance, one gigantic relay community, where nearly everyone can try out the functionality, is nos.lol.
If your relay community does not require AUTH to read, anyone can pull your chatter into their own relay and respond to it there. That is because every chat entry is simply a kind 09 event, and unprotected events are not private data.
For instance, I moderate one community theforest.nostr1.com, that is openly readable, and that's probably where most of the chatter on nostr.band is coming from, as that relay is an aggregator of the content of many other relays. However, I have another community, gitcitadel.nostr1.com that is AUTH-protected, whose content stays private to those allowed on that relay. Communities are where write-protected and AUTH relays are going to really shine, as they create an environment similar to Telegram, but where you control the dataset, you decide which types of events to support, and you design the client, the algos, the moderation, the visibility, etc.
With communities, the onboarding experience is seamless: just get a browser extension and a nsec, login, start writing and posting, and start receiving responses. Active, chatty, well-moderated communities will be more attractive to onboard to, than chaotic, spammy, or empty communities. This means that you don't have to have the killer entry under "Posts" (where kind 11 and eventually kind 01 posts appear), just to get some interaction. Chat is the Great Equalizer.
So, we're testing both setups, with cloudfodder adjusting the relay faucet code and ثعبان is fiddling with the community client settings, to make the most-comfortable situation for both kinds.

This is the signal
This #Chachi client, of course, is merely the first horse out of the gate. There are already other devs hacking away at variants of the same concept, such as #Flotilla, I'm sure CloudFodder is also cooking, later versions of #Alexandria will integrate theforest community, and etc. etc. etc.
It remains to be seen, how many new use cases can be dreamt up, with this new architecture, but I am quite certain, that this is the beginning of the end of Nostr 1.0. We are moving up and out, and away from the stultifying and limiting concept of Twitter 2.0, toward

Soon, we will enter Nostr 2.0. See you on the other side.
-
 @ 896c3ee8:e054cc31
2025-01-08 06:19:51
@ 896c3ee8:e054cc31
2025-01-08 06:19:51I was scrolling through some news articles published by Primal.net/flash on my phone —Bitcoin up, Trump said this or that, accompanied by a screenshot of Twitter. I asked myself: why does social media exist? Is it to fulfill our need for social connection? Is it to show off our thoughts? Is it validation? It wasn’t like this long ago. It was a part of life now it is Life.
Quite some time ago, I was baffled to see a woman being prosecuted in a court of law based on what she had posted on Facebook! Facebook? Seriously, an internet post landing a person in jail? Since when? No one notified me. I thought the internet was just a thing—a toy for us to play with, have fun, and then return to our real life. I remember using Pidgin and IRC; back then, the internet was just a tool. One sudden day, all of that turned into serious business. Early internet, and by extension social media, was a fun place, but now it is a place where real money is spent and real lives are built. I mean, some of the richest companies are software companies—an industry titan propelled by intangible property. It is hard not to miss the early days when one could say absolutely anything in a forum post and leave forever, detached from the filth they spewed. Now we all know censorship, data mining, AI training, and laws getting involved. I cannot even take part in a cultural movement without being tracked and attacked. At some point, the internet attached itself to human consciousness so deeply that it has now become inseparable from the human experience and experience of life. Just like reading and writing, to live a modern life, one must have an internet connection and a social media account. It’s disheartening to think that our worth is often measured by the number of people who 'follow' us.
This attachment meant that there were powers who needed to control the internet. Laws were hopeless on the internet—one could break a list of laws of a particular country sitting from a boat in a faraway land where no jurisdictional police could touch a single fleck of their hair. This cross-border nature made it very necessary for law enforcement to up their game, and so they did. Now, posting something and forgetting it being associated with you is a dream of the past.
To achieve this, they went into a Hail Mary attempt to break human rights written in the declaration they all signed. The right to privacy needed to go first. You see, on the internet, you are not a human—just a fat, Mountain Dew-drinking piece of meat, a data generation machine. Rights mean very little for you if you are a keyboard warrior. No clause in the Universal Declaration of Human Rights said that an account on the internet is a human! So you lose privacy. Since law enforcers break privacy, it looks like it really is not a crime to break it. So, service providers break it too. Who is to stop them now? Law enforcers?
That is just the tip, perhaps even a necessary evil. Breaking privacy only allows enforcement of laws that have been written. There needs to be some mechanism to enforce laws that are not written—the so-called "soft laws" (a term used in international law). If illegal activity is to be curbed, instead of chasing after criminals, why not be proactive and get to the root of the evil: human thought? Here enters censorship. If you don't know about something you won't act on it. If you do not know about guns, you will not pick up a gun. Censorship allows law enforcers to enforce laws that may be written in the future, potential laws. Maybe one day, being on a particular political side will be deemed illegal, so let’s stop it now. Ever heard of a cat chasing a mouse? Censorship is just a mouse chasing a cat. A reversal of cause and effect.
These two factors, coupled with the internet's revenue stream—your attention—ruined the internet. Ads by God are one of the most human things humans have created: “Let us show you what you could be a part of. As you are right now, you seem unfulfilled; let us show you what you want.” The economy of attention is best tapped by creators working on our primal urge for reproduction. The porn industry is a mega titan for this reason. I do not have any bad words against the innovators working in that industry. They are the true and perhaps only industry that uses the internet to its maximum and has great respect for technology and technological innovation.
When I think more deeply about the purpose of social media, I realize I have no clear answer. Why should one show what their lunch looks like? What is the goal of sharing such trivial experiences? Perhaps the dopamine rush of likes and engagement is strong enough to motivate such actions. The definition of an individual gets blurred here. What is an individual person? A collection of social media posts? Or should we emphasize more on your offline version the flawed acne and angst filled individual who subscribes to the weird, concorted philosophy of Proudhon, Locke, and Marx? The algorithms have been determining the future of people on social media. People are worried about losing jobs to a computer now. Since YouTube and Instagram started utilizing attention to pay people, algorithms began to determine who should be paid and what should be paid. The ship of us being under a computer has long sailed.
To answer why social media exists, here is one study that identified ten uses and gratifications for using social media: social interaction, information seeking, passing time, entertainment, relaxation, communicatory utility, convenience utility, expression of opinion, information sharing, and surveillance/knowledge about others (reference ISSN: 1352-2752). Most studies you find will be in line with these. I will not expound more on this; you all know why you use social media, and you all also know why people use social media.
To end it, Nostr gives you certain things that traditional social media and the 'internet' fail to provide. You know what those are since you are here.
P.S.—This is written exclusively for the eyes in the Nostr ecosystem. I will not publish it anywhere else. Link people to this post even from outside; I don’t care.
-
 @ 266815e0:6cd408a5
2024-12-17 20:45:33
@ 266815e0:6cd408a5
2024-12-17 20:45:33Finally another version of noStrudel. I keep telling myself I'm going to do more frequent releases but then time keeps getting away from me
This release comes with a bunch of news features and most importantly a lot of cleanup
Features
Olas media posts
You can now view a simple feed of media posts made on https://olas.app/ in the app and comment on them using NIP-22 comments
Simple gif picker
This was mostly a test, but there is now a simple gif picker (and barely functional search) that is based on
k:1063events If you want a better search and to help populate the nostr gif library you can use https://gifbuddy.lol created by nostr:npub1hee433872q2gen90cqh2ypwcq9z7y5ugn23etrd2l2rrwpruss8qwmrsv6
New support view
The (tiny) support button at the bottom of the side menu now hides a zap leader board that shows top supporters and any custom messages they leave
Favorite DVM feeds
You can now favorite DVM feeds in the discover view
Tools under notes
There is now a simpler tools menu under notes and threads
Searching local cache relay
If your using nostr-relay-tray the search view will now use it by default for searching. which should make it a little faster and more reliable
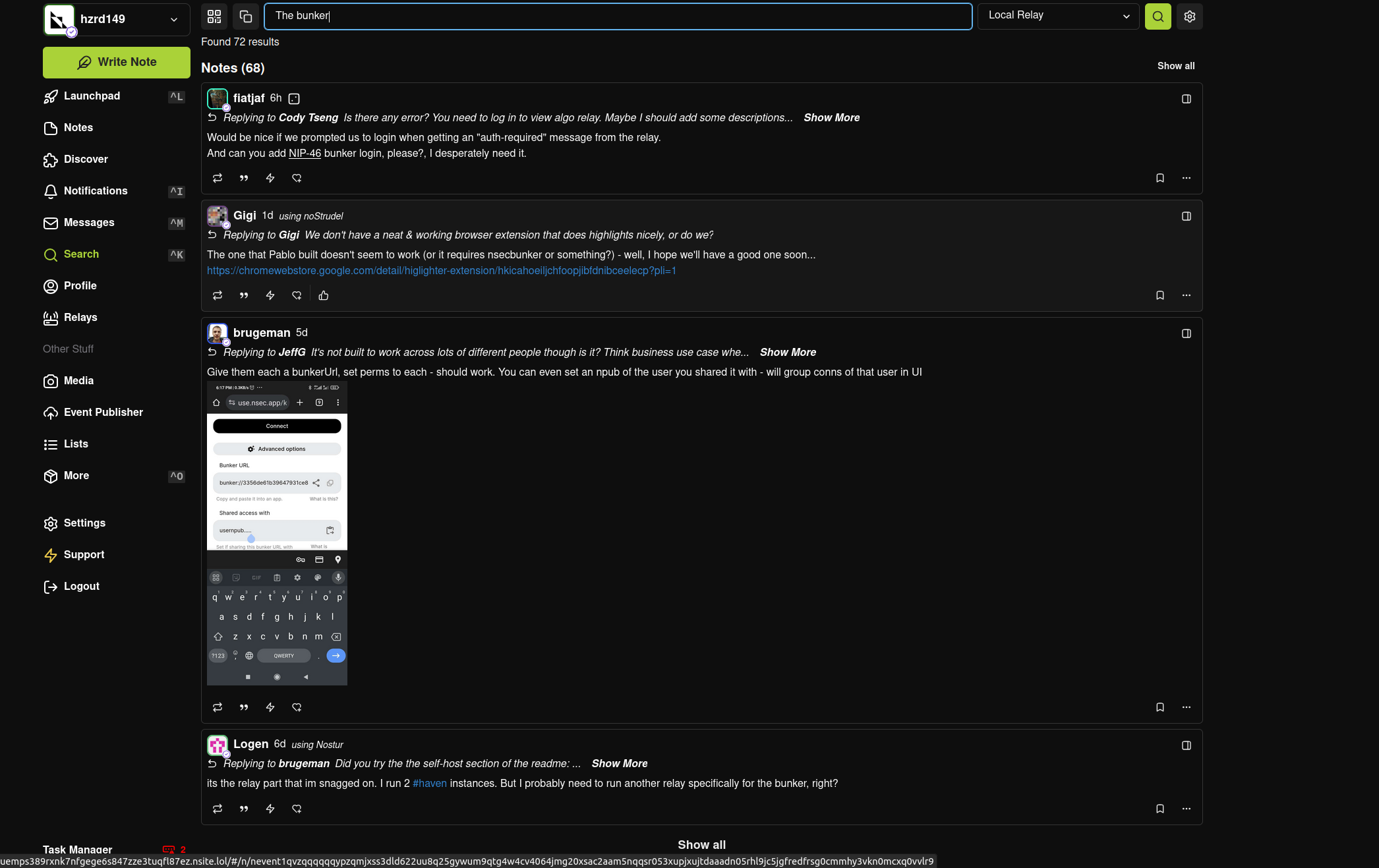
Small features
- Add "Proactively authenticate to relays" option to privacy settings, defaults to off
- Add option for debug API
- Add option to hide noStrudel logo in nav bar
- Show unknown notifications in notification view
- Add templates to event publisher
Bug fixes
- Show nostr mentions in markdown content
- Fix delete events not getting published to outbox
- Fix page changing from RTL when viewing some profiles
- Refresh relay info on relay page
- Fix bug with removing "about" in profile editor
- Fix automatically disconnecting from authenticated relays
Applesauce
Over the past few months I've been doing tons of cleanup on the core of noStrudel (677 changed files with 19,683 additions and 17,889 deletions) and extracting it out into a friendly nostr SDK called applesauce
Its very much a work-in-progress but the idea with these libraries is to help myself (and maybe others) build the UI layer of nostr apps and eventually make noStrudel just another app that is built with applesauce
If your a developer and another nostr SDK sounds interesting to you. you can check out the Getting Started docs
-
 @ 0f286a37:601a59e8
2024-12-17 19:56:41
@ 0f286a37:601a59e8
2024-12-17 19:56:41bitcoin #news I encourage every Bitcoiner to read The Blocksize War. Here are all of the links to all 21 chapters available on the BitMEX blog.
- Chapter 1 – First Strike
- Chapter 2 – March To War
- Chapter 3 – Scaling I - Montreal
- Chapter 4 – Scaling II - Hong Kong
- Chapter 5 – SegWit
- Chapter 6 – Lightning Network
- Chapter 7 – Bitcoin Classic
- Chapter 8 – Hong Kong Roundtable
- Chapter 9 – Faketoshi
- Chapter 10 – The DAO
- Chapter 11 – Scaling III – Milan
- Chapter 12 – Bitcoin Unlimited
- Chapter 13 – Exchanges
- Chapter 14 – ASICBoost
- Chapter 15 – Dragons’ Den
- Chapter 16 – Litecoin
- Chapter 17 – User-Activated Softfork
- Chapter 18 – New York Agreement
- Chapter 19 - Bitcoin Cash
- Chapter 20 - SegWit2x
- [Chapter 21 - Victory] https://blog.bitmex.com/the-blocksize-war-chapter-21-victory/)
-
 @ 3bf0c63f:aefa459d
2024-10-31 16:08:50
@ 3bf0c63f:aefa459d
2024-10-31 16:08:50Anglicismos estúpidos no português contemporâneo
Palavras e expressões que ninguém deveria usar porque não têm o sentido que as pessoas acham que têm, são apenas aportuguesamentos de palavras inglesas que por nuances da história têm um sentido ligeiramente diferente em inglês.
Cada erro é acompanhado também de uma sugestão de como corrigi-lo.
Palavras que existem em português com sentido diferente
- submissão (de trabalhos): envio, apresentação
- disrupção: perturbação
- assumir: considerar, pressupor, presumir
- realizar: perceber
- endereçar: tratar de
- suporte (ao cliente): atendimento
- suportar (uma idéia, um projeto): apoiar, financiar
- suportar (uma função, recurso, característica): oferecer, ser compatível com
- literacia: instrução, alfabetização
- convoluto: complicado.
- acurácia: precisão.
- resiliência: resistência.
Aportuguesamentos desnecessários
- estartar: iniciar, começar
- treidar: negociar, especular
Expressões
- "não é sobre...": "não se trata de..."

Ver também
-
 @ 3bf0c63f:aefa459d
2024-09-18 10:37:09
@ 3bf0c63f:aefa459d
2024-09-18 10:37:09How to do curation and businesses on Nostr
Suppose you want to start a Nostr business.
You might be tempted to make a closed platform that reuses Nostr identities and grabs (some) content from the external Nostr network, only to imprison it inside your thing -- and then you're going to run an amazing AI-powered algorithm on that content and "surface" only the best stuff and people will flock to your app.
This will be specially good if you're going after one of the many unexplored niches of Nostr in which reading immediately from people you know doesn't work as you generally want to discover new things from the outer world, such as:
- food recipe sharing;
- sharing of long articles about varying topics;
- markets for used goods;
- freelancer work and job offers;
- specific in-game lobbies and matchmaking;
- directories of accredited professionals;
- sharing of original music, drawings and other artistic creations;
- restaurant recommendations
- and so on.
But that is not the correct approach and damages the freedom and interoperability of Nostr, posing a centralization threat to the protocol. Even if it "works" and your business is incredibly successful it will just enshrine you as the head of a platform that controls users and thus is prone to all the bad things that happen to all these platforms. Your company will start to display ads and shape the public discourse, you'll need a big legal team, the FBI will talk to you, advertisers will play a big role and so on.
If you are interested in Nostr today that must be because you appreciate the fact that it is not owned by any companies, so it's safe to assume you don't want to be that company that owns it. So what should you do instead? Here's an idea in two steps:
- Write a Nostr client tailored to the niche you want to cover
If it's a music sharing thing, then the client will have a way to play the audio and so on; if it's a restaurant sharing it will have maps with the locations of the restaurants or whatever, you get the idea. Hopefully there will be a NIP or a NUD specifying how to create and interact with events relating to this niche, or you will write or contribute with the creation of one, because without interoperability this can't be Nostr.
The client should work independently of any special backend requirements and ideally be open-source. It should have a way for users to configure to which relays they want to connect to see "global" content -- i.e., they might want to connect to
wss://nostr.chrysalisrecords.com/to see only the latest music releases accredited by that label or towss://nostr.indiemusic.com/to get music from independent producers from that community.- Run a relay that does all the magic
This is where your value-adding capabilities come into play: if you have that magic sauce you should be able to apply it here. Your service -- let's call it
wss://magicsaucemusic.com/-- will charge people or do some KYM (know your music) validation or use some very advanced AI sorcery to filter out the spam and the garbage and display the best content to your users who will request the global feed from it (["REQ", "_", {}]), and this will cause people to want to publish to your relay while others will want to read from it.You set your relay as the default option in the client and let things happen. Your relay is like your "website" and people are free to connect to it or not. You don't own the network, you're just competing against other websites on a leveled playing field, so you're not responsible for it. Users get seamless browsing across multiple websites, unified identities, a unified interface (that could be different in a different client) and social interaction capabilities that work in the same way for all, and they do not depend on you, therefore they're more likely to trust you.
Does this centralize the network still? But this a simple and easy way to go about the matter and scales well in all aspects.
Besides allowing users to connect to specific relays for getting a feed of curated content, such clients should also do all kinds of "social" (i.e. following, commenting etc) activities (if they choose to do that) using the outbox model -- i.e. if I find a musician I like under
wss://magicsaucemusic.comand I decide to follow them I should keep getting updates from them even if they get banned from that relay and start publishing onwss://nos.lolorwss://relay.damus.ioor whatever relay that doesn't even know anything about music.The hardcoded defaults and manual typing of relay URLs can be annoying. But I think it works well at the current stage of Nostr development. Soon, though, we can create events that recommend other relays or share relay lists specific to each kind of activity so users can get in-app suggestions of relays their friends are using to get their music from and so on. That kind of stuff can go a long way.
-
 @ 3bf0c63f:aefa459d
2024-11-07 14:56:17
@ 3bf0c63f:aefa459d
2024-11-07 14:56:17The case against edits
Direct edits are a centralizing force on Nostr, a slippery slope that should not be accepted.
Edits are fine in other, more specialized event kinds, but the
kind:1space shouldn't be compromised with such a push towards centralization, becausekind:1is the public square of Nostr, where all focus should be on decentralization and censorship-resistance.- Why?
Edits introduce too much complexity. If edits are widespread, all clients now have to download dozens of extra events at the same time while users are browsing a big feed of notes which are already coming from dozens of different relays using complicated outbox-model-based querying, then for each event they have to open yet another subscription to these relays -- or perform some other complicated batching of subscriptions which then requires more complexity on the event handling side and then when associating these edits with the original events. I can only imagine this will hurt apps performance, but it definitely raises the barrier to entry and thus necessarily decreases Nostr decentralization.
Some clients may be implemneted in way such that they download tons of events and then store them in a local databases, from which they then construct the feed that users see. Such clients may make edits potentially easier to deal with -- but this is hardly an answer to the point above, since such clients are already more complex to implement in the first place.
- What do you have against complex clients?
The point is not to say that all clients should be simple, but that it should be simple to write a client -- or at least as simple as physically possible.
You may not be thinking about it, but if you believe in the promise of Nostr then we should expect to see Nostr feeds in many other contexts other than on a big super app in a phone -- we should see Nostr notes being referenced from and injected in unrelated webpages, unrelated apps, hardware devices, comment sections and so on. All these micro-clients will have to implement some complicated edit-fetching logic now?
- But aren't we already fetching likes and zaps and other things, why not fetch edits too?
Likes, zaps and other similar things are optional. It's perfectly fine to use Nostr without seeing likes and/or zaps -- and, believe me, it does happen quite a lot. The point is basically that likes or zaps don't affect the content of the main post at all, while edits do.
- But edits are optional!
No, they are not optional. If edits become widespread they necessarily become mandatory. Any client that doesn't implement edits will be displaying false information to its users and their experience will be completely broken.
- That's fine, as people will just move to clients that support edits!
Exactly, that is what I expect to happen too, and this is why I am saying edits are a centralizing force that we should be fighting against, not embracing.
If you understand that edits are a centralizing force, then you must automatically agree that they aren't a desirable feature, given that if you are reading this now, with Nostr being so small, there is a 100% chance you care about decentralization and you're not just some kind of lazy influencer that is only doing this for money.
- All other social networks support editing!
This is not true at all. Bluesky has 10x more users than Nostr and doesn't support edits. Instagram doesn't support editing pictures after they're posted, and doesn't support editing comments. Tiktok doesn't support editing videos or comments after they're posted. YouTube doesn't support editing videos after they're posted. Most famously, email, the most widely used and widespread "social app" out there, does not support edits of any kind. Twitter didn't support edits for the first 15 years of its life, and, although some people complained, it didn't hurt the platform at all -- arguably it benefitted it.
If edits are such a straightforward feature to add that won't hurt performance, that won't introduce complexity, and also that is such an essential feature users could never live without them, then why don't these centralized platforms have edits on everything already? There must be something there.
- Eventually someone will implement edits anyway, so why bother to oppose edits now?
Once Nostr becomes big enough, maybe it will be already shielded from such centralizing forces by its sheer volume of users and quantity of clients, maybe not, we will see. All I'm saying is that we shouldn't just push for bad things now just because of a potential future in which they might come.
- The market will decide what is better.
The market has decided for Facebook, Instagram, Twitter and TikTok. If we were to follow what the market had decided we wouldn't be here, and you wouldn't be reading this post.
- OK, you have convinced me, edits are not good for the protocol. But what do we do about the users who just want to fix their typos?
There are many ways. The annotations spec, for example, provides a simple way to append things to a note without being a full-blown edit, and they fall back gracefully to normal replies in clients that don't implement the full annotations spec.
Eventually we could have annotations that are expressed in form of simple (human-readable?) diffs that can be applied directly to the post, but fall back, again, to comments.
Besides these, a very simple idea that wasn't tried yet on Nostr yet is the idea that has been tried for emails and seems to work very well: delaying a post after the "submit" button is clicked and giving the user the opportunity to cancel and edit it again before it is actually posted.
Ultimately, if edits are so necessary, then maybe we could come up with a way to implement edits that is truly optional and falls back cleanly for clients that don't support them directly and don't hurt the protocol very much. Let's think about it and not rush towards defeat.
-
 @ 1cb14ab3:95d52462
2024-12-17 19:24:54
@ 1cb14ab3:95d52462
2024-12-17 19:24:54Originally written in October 2022 (Block: 757258 / USD: $20.1k / SatsDollar: 4961). Refined with slight edits for publishing on Nostr in December 2024 (Block: 875189 / USD: $106k / SatsDollar: 938 ). Banner image property of Hes. My journey down the rabbit hole has only intensified since the time of writing. Enjoy.
The Bitcoin time perspective is wild. Reflecting on it has been profoundly eye-opening, and once it has been seen— there is no returning to our prior ways.
Ever since venturing down the rabbit hole that we call Bitcoin, I’ve started making significant life decisions and forming nuanced opinions on polarizing topics based on the implications of multi-generational timeframes. Before Bitcoin, I spent money recklessly, leading a fast-paced and impulsive lifestyle. Even in my early days of learning about Bitcoin, I hadn’t fully seen the light. I would still blow the occasional $500 bar tab or buy some flashy gadget I didn’t need. Living in the moment has its merits, but so does considering the time beyond our own lives. Now, I pause before purchases and decisions, always reflecting on how they might impact the future.
When your money isn’t constantly being devalued before your eyes, you start seeing the world differently. You begin saving for the future with confidence, knowing that no central authority can endlessly print away your hard-earned time and energy. Inflation doesn’t just erode purchasing power; it steals time. It destroys the hours, days, and years of effort represented by a lifetime of savings. When governments print money to prop up failing banks or fund inefficient ventures, the impact ripples through generations. Those at the bottom of the ladder are hit the hardest, their ability to save and plan for the future undermined by forces beyond their control. Decisions become focused on surviving today instead of thriving tomorrow, leaving little room to consider the long-term implications of our choices. This system creates a mindset where we are incentivized to spend now, instead of save for later—an unnatural phenomenon that most of us have accepted as normal.
For individuals who simply want to put away money for a rainy day, inflation is a relentless adversary. A dollar in 1900 has lost over 96% of its value. The countless hours of labor behind those savings have been stolen. Not only did the expansion of money destroy what they could buy, it stole our time and energy. Years of our lives—blood, sweat, and tears—washed away.
This isn’t just a historical problem—it’s a recurring one that occurs every decade or so and is accelerating. At an average inflation rate of 3%, the value of cash halves roughly every 23 years. This means that even modest inflation rates gradually diminish purchasing power over time, forcing individuals to chase speculative assets like stocks, real estate, and gold—not because they want to, but because they have no choice. Personal inflation rates differ depending on consumer habits, but a glance at rising prices reveals they often outpace the 2% annual rate reported by the government, which poses a significant problem for individua;s, as highlighted in the table below:
Corporations like McDonald’s understand this. Sitting on a prime corner lot in every major city is far smarter than stacking a pile of cash losing value. Even if the franchise is losing money, the building it operates in is guaranteed to “rise” in value over time. This mindset trickles down to everyday people. To protect themselves, they’re compelled to invest in assets—with real estate being the pinnacle savings instrument of our time. The financial system we’ve accepted as normal turns shelter into an investment vehicle and savings into a gamble.
But here’s the irony: real estate is a lousy store of value—which is what we are all truly seeking. Properties require constant maintenance. Without care, assets deteriorate. We’ve all seen abandoned theme parks and overgrown cities. We’ve all dealt with broken pipes and creaky floorboards. Why should saving our hard-earned wealth require us to become housing market experts, landlords, or property managers? Why should we pay financial advisors to manage stock portfolios full of companies whose values or practices we might not even believe in, just to beat inflation?
A flawed monetary system inflates bubbles in real estate and stocks, redirecting resources into speculative markets instead of productive investments. Imagine a world where people don’t have to read quarterly earnings reports after a long day of work to ensure their cash retains value. If the incentives driving these bubbles were removed, the financial landscape would dramatically shift. Inflation wouldn’t push people into markets like real estate or zombie companies; instead, they could focus on building or supporting businesses they genuinely care about. They could plan for the long term and make well-thought-out, rational decisions about their future.
Bitcoin takes this entire dynamic and flips it on its head. It isn’t a tool for speculation as often misunderstood. It is the best form of saving humanity has ever seen. Unlike fiat currencies, Bitcoin’s fixed supply ensures scarcity, making it a refuge from the erosion of wealth caused by inflation. As weak currencies flow into stronger ones (a concept known as Gresham’s Law), Bitcoin’s role as a store of value becomes clearer. It’s not that Bitcoin has “gone up 19,000%”—it’s that people are exchanging weaker money for stronger money.
The implications of a world on a Bitcoin standard extend far beyond monetary policy. It offers something unprecedented: a tool for transferring the value of labor and energy across time and space. Unlike fiat, Bitcoin allows time to be preserved across generations. It isn’t just a hedge against inflation—it reintroduces the idea of saving with confidence, of being able to store wealth in a form of money that cannot be manipulated or devalued.
By saving in Bitcoin, individuals are no longer tethered to the uncertainties of fiat systems. The Bitcoin time perspective is about aligning our actions today with the future we want to build tomorrow. It’s about prioritizing long-term impact over short-term gains. When you embrace Bitcoin, you embrace a mindset that values time, energy, and the well-being of future generations. It’s not just a currency; it’s a revolution in thinking that will change you forever. The past, present, and future converge in this new paradigm, offering hope in an otherwise uncertain world.
Bitcoin isn’t a bubble; it’s a beacon.
More from Hes:
-
 @ 4685f3d6:9fe6995b
2024-12-17 18:34:35
@ 4685f3d6:9fe6995b
2024-12-17 18:34:35Day 1:☄️ What is Bitcoin?
Overview of Bitcoin Bitcoin is the world's first decentralized digital currency. It was created in 2009 by an anonymous person or group known as Satoshi Nakamoto. Unlike traditional currencies (fiat), Bitcoin operates without a central authority like a government or a bank. It uses a technology called blockchain to facilitate peer-to-peer transactions in a secure, transparent, and efficient manner.
Key Features of Bitcoin: Decentralization: Bitcoin is not controlled by any single entity. Transactions are validated by a network of computers (nodes) spread globally.
Digital Nature: Bitcoin exists entirely online, with no physical coins or notes.
Limited Supply: Only 21 million Bitcoins will ever exist, making it scarce and resistant to inflation.
Security: Bitcoin transactions are secured through cryptography and recorded on the blockchain, which is immutable and transparent.
Borderless Transactions: Bitcoin allows people to send and receive money anywhere in the world without intermediaries.
Brief History of Bitcoin 2008: A whitepaper titled "Bitcoin: A Peer-to-Peer Electronic Cash System" was published by Satoshi Nakamoto, introducing the concept of Bitcoin.
2009: The first Bitcoin block, known as the Genesis Block, was mined on January 3, marking the beginning of Bitcoin’s blockchain.
2010: The first real-world Bitcoin transaction occurred when a developer, Laszlo Hanyecz, bought two pizzas for 10,000 BTC (worth over $270 million today). This event is celebrated as Bitcoin Pizza Day.
2011-2013: Bitcoin gained popularity, reaching $1 per coin in 2011 and becoming a global phenomenon by 2013.
2017: Bitcoin hit an all-time high of nearly $20,000, drawing attention from investors and institutions.
Present: Bitcoin continues to evolve as a digital asset, widely recognized as "digital gold" and adopted by individuals, businesses, and even governments.
Why is Bitcoin Significant? Financial Independence: Bitcoin empowers individuals to take control of their finances without relying on banks or governments.
Censorship Resistance: Transactions cannot be blocked or reversed by any authority, making Bitcoin especially important in regions with strict financial controls.
Global Accessibility: Bitcoin provides a financial alternative for people in underbanked or unbanked regions, promoting financial inclusion.
Inflation Hedge: With a fixed supply, Bitcoin is often seen as a hedge against inflation, unlike fiat currencies that can be printed in unlimited amounts.
Technological Innovation: Bitcoin introduced blockchain technology, paving the way for numerous other innovations in finance, healthcare, supply chain, and more.
Example: Imagine sending money to a friend overseas in minutes with minimal fees—Bitcoin makes this possible. Think of Bitcoin as "digital gold" you can own, trade, or hold as an investment, all without needing a bank.
What do you think about Bitcoin? Have you ever used it?
yakihonne
9ja
Afro
Bitcoin
Day1
-
 @ a367f9eb:0633efea
2024-11-05 08:48:41
@ a367f9eb:0633efea
2024-11-05 08:48:41Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application.
The reporting purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States.
In a June paper reviewed by Reuters, six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”.
The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making.
While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the Star Trek episode “A Taste of Armageddon“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place.
Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran?
The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over one million open-source LLMs available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer.
With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are potentially trillions of dollars on the line.
Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American infrastructure, data, and yes, your credit history?
As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much many times.
At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative.
Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this.
Open-source matters When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it.
The various licensing schemes – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made.
While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit.
Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers.
Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other.
I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run.
Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots).
This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also open-source, which has allowed thousands of copycat protocols that have revolutionized how we view money.
You know what else is open-source and available for everyone to use, modify, and build upon?
PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit.
Open-source code is speech, and it is knowledge.
We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge.
Open-source is for your friends, and enemies In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license.
At this very moment, you can click on over to Hugging Face, download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth).
Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created.
We know this can be useful to friends, but what about enemies?
As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications.
The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians.
A bipartisan group of US House lawmakers want to put export controls on AI models, as well as block foreign access to US cloud servers that may be hosting AI software.
If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see The Crypto Wars). Many of the arguments we hear today were invoked by some of the same people as back then.
Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to.
Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place.
Limiting open-source threatens our own advancement If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way.
If there is a “Hundred Year Marathon” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible.
The Chinese military has been building up its capabilities with trillions of dollars’ worth of investments that span far beyond AI chatbots and skip logic protocols.
The theft of intellectual property at factories in Shenzhen, or in US courts by third-party litigation funding coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing.
But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source.
If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries.
Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application.
The reporting purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States.
In a June paper reviewed by Reuters, six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”.
The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making.
While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the Star Trek episode “A Taste of Armageddon“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place.
Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran?
The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over one million open-source LLMs available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer.
With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are potentially trillions of dollars on the line.
Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American infrastructure, data, and yes, your credit history?
As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much many times.
At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative.
Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this.
Open-source matters
When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it.
The various licensing schemes – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made.
While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit.
Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers.
Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other.
I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run.
Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots).
This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also open-source, which has allowed thousands of copycat protocols that have revolutionized how we view money.
You know what else is open-source and available for everyone to use, modify, and build upon?
PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit.
Open-source code is speech, and it is knowledge.
We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge.
Open-source is for your friends, and enemies
In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license.
At this very moment, you can click on over to Hugging Face, download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth).
Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created.
We know this can be useful to friends, but what about enemies?
As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications.
The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians.
A bipartisan group of US House lawmakers want to put export controls on AI models, as well as block foreign access to US cloud servers that may be hosting AI software.
If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see The Crypto Wars). Many of the arguments we hear today were invoked by some of the same people as back then.
Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to.
Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place.
Limiting open-source threatens our own advancement
If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way.
If there is a “Hundred Year Marathon” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible.
The Chinese military has been building up its capabilities with trillions of dollars’ worth of investments that span far beyond AI chatbots and skip logic protocols.
The theft of intellectual property at factories in Shenzhen, or in US courts by third-party litigation funding coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing.
But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source.
If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries.
Originally published on the website of the Consumer Choice Center.
-
 @ 3bf0c63f:aefa459d
2024-09-06 12:49:46
@ 3bf0c63f:aefa459d
2024-09-06 12:49:46Nostr: a quick introduction, attempt #2
Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else.
Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services.
(Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation).
More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between clients (i.e. the program that runs on a user computer) and relays (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback".
-
 @ bd50a856:038f487c
2025-01-08 04:25:47
@ bd50a856:038f487c
2025-01-08 04:25:47I'M NOT IN SCHOOL WHY AM I DOING THIS?
https://image.nostr.build/9df38856e4493466585f451771a013959ac7e29135289b4922a810623577dbef.jpg
Isms in my opinion are not good. - Ferris Bueler
OK so like many a disillusioned youth I was a pretty hardcore Marxist back in college. There's a common pipeline that starts as a 13 year old who wished they could vote for Ron Paul in 2008, takes a hard left turn at the first sign of bigotry, and winds up with a pretty badass juche tattoo. The Enlightenment era ideas of an ascertainable objective truth and mankind's control over their own destiny, combined with the complete subversion of the political history I was brought up with felt very empowering. But nowadays I'm not so sure I want to lay claim to any specific point or vector on the political spectrum. 2024 was in many ways a year of reflection for me. I've managed to reconnect with my sense of spirituality after years of bitterness towards the concept brought on by a life of run-ins with religious fundemantalism, and I had to challenge alot of things that for years I've taken for granted both about myself and the world at large. This ideological audit was in no small way catalyzed by my adoption of NOSTR, which with its endless potential enticed me out of the progressive echo chamber I made my digital home on the fediverse and into a new echo chamber: one full of Bitcoiners.
I had bought Bitcoin before, as a way to short the dollar, but I never encountered its ideologues in the wild. At first gradually then suddenly I was making the types of arguments in my head that former me would have decried as pedantic to the point of being apologetic towards the ruling class. And just like that the 19th and 20th century political and philosophical works which I zaelously held as trail blazes on the long and labyrinthine path towards realizing Absolute Truth were cast forcefully into their murky historical context by the staggering success of the first truly decentralized monetary system. In my college days, I saw Lenin's model of revoutionary politics and the Vanguard Party as the only way for a people's movement to legitimately threaten the hegemony of the global oligarchs who caused so much unnecessary suffering. Now I can see how whether or not that type of centralization was a necessary concession then, one cannot in good faith believe it to be so in the age of Bitcoin.
Yet you'll have to forgive me because still I'm sympathetic to much of the broader movement of Marxism. I detest how Great Man Theory suboordinates the totality of the evolution of society to the wills of a few individuals, and prefer to see socialism in a different light. Rather than viewing the movement as a clever trick some cartoonishly evil mustaches and haircuts used to brainwash almost half the human population, I see a genuine attempt by hundreds of millions of people to change the world for the better, forever. Yes the suffering was immense, and many many people for whom the tumult was too much, as well as those who wished to maintain their parasitic lifestyles, fled for their lives it was far from a black and white phenomena. Living standards also skyrocketed over the long run in places like the USSR and the PRC, from literacy to employment to diet, access to healthcare, you name it. But still the narrative of Hegel's Dialectic playing out in the arena of class politics - wherein the oppressed by becoming the oppressors would naturally do away with oppression altogether by following their self interest just as the Bourgeoisie had done, thereby unwinding the knot of economic injustice - has lost its status as the driving force of all of history for me. It's still much more compelling than the caricature of simply replacing one form of centralization with another. Rather its a much more relatable fallacy: taking a truth, in this case the millennia of class struggle which humanity has dealt with since the advent of agriculture, and trying to extrapolate from it some abstract and all compassing polemic that makes it all make sense. Moreover, in the same way that Bitcoiners say, "Once you see it you can never go back," I cannot unlearn just how hypocritical and dishonest the Western narrative of history is. Lying and calling America the land of the land of opportunity when the abundance we've known for our Empire's whole existence exists merely because of stolen land and slave labor. This is not a moralist objection by the way, though that would be wholly justified. The true horror is that people view the US as the model of a self sufficient nation state when in reality it has always been parasitic, even in it's larval stage. And of course the disillusion with every military campaign since the end of World War 2, starting with the grotesque and gratuitous display of power in Hiroshima and Nagasaki, then the fraudulant and deadly campaigns in Korea, Loas, Vietnam, and of course the entire Middle East. Our own forms of surveillance, censorship, repression all staring at us in the images we projected on the face of the Berlin Wall.
I know a little part of that probably rubbed some of you the wrong way. Hey we still were a net positive force in WW2, of course. And despite many differences in historical interpretations, when it comes to Marx's tomes of economic criticism I think the Bitcoiners of NOSTR would find a lot of rhetorical similarities with their gripes about the age of fiat actually share many rhetorical similarities: The levers of control over the global economy had been consolidated by a select view who were spamming them to make themselves inordinately wealthy at the cost of the quality of life for the majority of Planet Earth. The value of your labor is being ciphoned by a bunch of rackateering lizard men known as politicians. Fair competition, the spirit of Capitalism on paper, has been eroded by its those who claim to be its biggest proponents. Forever wars as a business, predatory global economic policies, proles=plebs, yada yada. Although I guess this note would be pointless if I yada-yada'd over the best parts.
THE INVISIBLE HANDJOB
https://image.nostr.build/595f3d10072c92fc66f9ad314de5d6eeb7e76a9bc26021c690d89cbd9bbe0a15.gif
The landlords, like all other men, love to reap where they never sowed, and demand a rent even for its natural produce. -Adam Smith
In the above quoted Wealth of Nations (Book 1, chapter 11) as well as in Book 4 and in The Theory of Moral Sentiments, everyone's favorite economist they've never read paints a complex and somewhat contradictory image of the proprietors over the means of production in his time. He saw greed and gluttony in their souls, but viewed their actions within the context of an emergent system whereby their selfishness propelled the interest of everyone. So, almost exactly how Marx viewed the holy timespanning vendetta of the have-nots of the world. However, in Book 1 ch10 of Wealth of Nations Smith says this:
[The rent] is not at all proportioned to what the landlord may have laid out upon the improvement of the land, or to what he can afford to take; but to what the farmer can afford to give,
In a section where he concedes that the landlords' actions amount to extortion. He also articulates here how through the influence of legislation, the landlord class effectively outlawed collective negotiation on the part of the working class while bolstering it for themselves, resulting in monopolies. Marx cites Smith himself throughout Das Kapital, and lays out extensively this process of the consolidation of capitalist power in part 3 of the first volume. The two also subscribed to the Labor Theory of Value, as did every other Enlightenment era economist... and so do most Bitcoiners! At least they sure sound like they do when they talk about the erosion of the masses' life force by the debasement of fiat. After all if the commodity that is money is an expression of your time and labor, then so must be the value of every other commodity. I've heard people try to glibly dismiss the LTV as stupid, citing things like land, products of fully automated processes... And digital assets. As if land didn't have to be surveyed, and discovered (or won in a genocide). Or if fully automated production processes didn't require thousands of hours of expert labor on robotics and/or computer engineering. Or if all financial assets in general didn't hold merely a hypothetical value as a representation of value wrought in the productive economy. And to be perfectly honest I always found the subjective theory of value to be downright silly, like imagine haggling at a supermarket over a gallon of milk. Yes demand is subjective (and really more of an expression of willing buying power than need but that's a whole other can of worms), but it's wholly reliant on objective factors such as scarcity and the relative difficulty to produce a certain commodity oneself. And when those who corner the market collude on pricing it's not like you even have the ability to "vote with your money". You have no leverage, unless you own a cow. All in all the price of a commodity can't be anything other than an approximation of its objective value based on the average cost of the raw materials and socially necessary labor time, ebbing and flowing with the asynchronous undulations of supply and demand. And maybe a little extra something just to cushion that P&L. OK maybe a lot. Gotta outperform inflation, right?! Was I being glib, myself, there? It just feels self evident from my current perspective, the hollow vampirism of it all. Capitalists enacting the rights to procure surplus value, reinsert it as capital in order to procure even more surplus value, rinsing and repeating, drifting further and further from the corporeal reality of our own survival and swallowing entire generations in the process.
STATISTS BE LIKE...
https://image.nostr.build/3109eed06d708cfad1ec0c8f4a823b8d6c58b73d3a7f73a94cdcafe22554656f.jpg
The government solution to a problem is usually as bad as the problem- Milton Friedman
On September 11, 1973 Chilean President Salvador Allende died during a fascist coup d'état perpetrated by the commander in chief of the military Augusto Pinochet. Officially he took his own life for fear of what would be done to him, but it remains a contentious topic. Pinochet's regime was characterized by mass arrests, widespread use of torture, extrajudicial killings, mass exiles, and brutal censorship of his political ditractors. But he cut taxes!!!! And he did so with the council of the Chicago Boys, a group of Chicago University alumni and disciples of right wing icon Milton Friedman. Friedman applauded Pinochet's government for his economic policies and providing a shining example of Milton's take on what small laissez-faire government looks like: Repression of the masses, no rules for the classes.
Pinochet was also a collaborator with the CIA on their project Operation Condor, whereby the funding and stoking of violence and unrest was weaponized to subvert the rise of left leaning politics throughout South and Central America and maintain cheap access to raw materials which US corporations relied on. As a matter of fact, the deep state has an endless track record of resorting to all sorts of crazy measures to subvert the popularity of socialism. This contradicts directly the American conservative view that the deep state wants socialism, and that Trump - who has cooperated in the continuations of these policies with the attempted coups in Venezuela and Bolivia during his first term - is here to stop 'em. The scapegoating and fear mongering of foreign left leaning governments in lucrative regions is a time honored tradition here In the US. All the West has always had more in common with the totalitarianism of Fascism than the East. If you're curious or skeptical about this, looking up Michael Parenti's Blackshirts & Reds is a good place to start digging deeper.
And while conservatives remain in denial about the parasiticism and exclusion their version of freedom relies on, Progressivism, as I see it, is a limping, mutilated, abomination of a watered down version of itself. Democrats for over a century now continue offering the bare minimum that would assuage their cinstituencies in the short term at best, and the exact same neocon policies of war and imperialism abroad, and corporate oligarchy and a police state at home. Yet every two years progressives walk beleaguered to the polls to vote blue no who. And Milton Friedman laughs in his grave. Reminds me of one of my favorite quotes, attributed to president of Tanzinia, Julius Nyere: "The Americans also have a one party state, but with typical American extravegance, they have two of them." https://image.nostr.build/9380dbc6d51a443b76340b46c760e12c9bb0540a170a8f5a2a22847e0bba88c7.jpg
WHAT IS DO BE DONE?
https://image.nostr.build/94aaebe5364c3c6a0094f09640ef18b05938d889124f874c49243f4ea972f725.jpg
I found freedom. Losing all hope is freedom. - Edward Norton, Fight Club
If you made it through all that rambling, what is wrong with you? In all seriousness, I hope this was a fruitful glance into the mind of someone who might think a little differently. In a rapidly evolving world, where systems we ourselves have put in place not only constitute the environment we live in, but reproduce themselves through our behavior as well, despondency, rage, and confusion permeate the collective consciousness. But there's also Bitcoin, which to an increasing number - and to an extent myself - represents a successful proof of concept of a new, genuinely Decentralized Ideological Apparatus. One which relies on Mutual Aid and the cooperation of smaller, decentralized and self sufficient communities. And to a certain extent it also represents hope. But it's as much an asset to those who'd prefer to continue feeding on the suffering of others as it is to those hoping for a change. Hope is as dangerous as fear - Lao Tzu
-
 @ 09fbf8f3:fa3d60f0
2024-11-02 08:00:29
@ 09fbf8f3:fa3d60f0
2024-11-02 08:00:29> ### 第三方API合集:
免责申明:
在此推荐的 OpenAI API Key 由第三方代理商提供,所以我们不对 API Key 的 有效性 和 安全性 负责,请你自行承担购买和使用 API Key 的风险。
| 服务商 | 特性说明 | Proxy 代理地址 | 链接 | | --- | --- | --- | --- | | AiHubMix | 使用 OpenAI 企业接口,全站模型价格为官方 86 折(含 GPT-4 )| https://aihubmix.com/v1 | 官网 | | OpenAI-HK | OpenAI的API官方计费模式为,按每次API请求内容和返回内容tokens长度来定价。每个模型具有不同的计价方式,以每1,000个tokens消耗为单位定价。其中1,000个tokens约为750个英文单词(约400汉字)| https://api.openai-hk.com/ | 官网 | | CloseAI | CloseAI是国内规模最大的商用级OpenAI代理平台,也是国内第一家专业OpenAI中转服务,定位于企业级商用需求,面向企业客户的线上服务提供高质量稳定的官方OpenAI API 中转代理,是百余家企业和多家科研机构的专用合作平台。 | https://api.openai-proxy.org | 官网 | | OpenAI-SB | 需要配合Telegram 获取api key | https://api.openai-sb.com | 官网 |
持续更新。。。
推广:
访问不了openai,去
低调云购买VPN。官网:https://didiaocloud.xyz
邀请码:
w9AjVJit价格低至1元。
-
 @ 0176967e:1e6f471e
2024-07-28 15:31:13
@ 0176967e:1e6f471e
2024-07-28 15:31:13Objavte, ako avatari a pseudonymné identity ovplyvňujú riadenie kryptokomunít a decentralizovaných organizácií (DAOs). V tejto prednáške sa zameriame na praktické fungovanie decentralizovaného rozhodovania, vytváranie a správu avatarových profilov, a ich rolu v online reputačných systémoch. Naučíte sa, ako si vytvoriť efektívny pseudonymný profil, zapojiť sa do rôznych krypto projektov a využiť svoje aktivity na zarábanie kryptomien. Preskúmame aj príklady úspešných projektov a stratégie, ktoré vám pomôžu zorientovať sa a uspieť v dynamickom svete decentralizovaných komunít.
-
 @ 4c48cf05:07f52b80
2024-10-30 01:03:42
@ 4c48cf05:07f52b80
2024-10-30 01:03:42I believe that five years from now, access to artificial intelligence will be akin to what access to the Internet represents today. It will be the greatest differentiator between the haves and have nots. Unequal access to artificial intelligence will exacerbate societal inequalities and limit opportunities for those without access to it.
Back in April, the AI Index Steering Committee at the Institute for Human-Centered AI from Stanford University released The AI Index 2024 Annual Report.
Out of the extensive report (502 pages), I chose to focus on the chapter dedicated to Public Opinion. People involved with AI live in a bubble. We all know and understand AI and therefore assume that everyone else does. But, is that really the case once you step out of your regular circles in Seattle or Silicon Valley and hit Main Street?
Two thirds of global respondents have a good understanding of what AI is
The exact number is 67%. My gut feeling is that this number is way too high to be realistic. At the same time, 63% of respondents are aware of ChatGPT so maybe people are confounding AI with ChatGPT?
If so, there is so much more that they won't see coming.
This number is important because you need to see every other questions and response of the survey through the lens of a respondent who believes to have a good understanding of what AI is.
A majority are nervous about AI products and services
52% of global respondents are nervous about products and services that use AI. Leading the pack are Australians at 69% and the least worried are Japanise at 23%. U.S.A. is up there at the top at 63%.
Japan is truly an outlier, with most countries moving between 40% and 60%.
Personal data is the clear victim
Exaclty half of the respondents believe that AI companies will protect their personal data. And the other half believes they won't.
Expected benefits
Again a majority of people (57%) think that it will change how they do their jobs. As for impact on your life, top hitters are getting things done faster (54%) and more entertainment options (51%).
The last one is a head scratcher for me. Are people looking forward to AI generated movies?

Concerns
Remember the 57% that thought that AI will change how they do their jobs? Well, it looks like 37% of them expect to lose it. Whether or not this is what will happen, that is a very high number of people who have a direct incentive to oppose AI.
Other key concerns include:
- Misuse for nefarious purposes: 49%
- Violation of citizens' privacy: 45%
Conclusion
This is the first time I come across this report and I wil make sure to follow future annual reports to see how these trends evolve.
Overall, people are worried about AI. There are many things that could go wrong and people perceive that both jobs and privacy are on the line.
Full citation: Nestor Maslej, Loredana Fattorini, Raymond Perrault, Vanessa Parli, Anka Reuel, Erik Brynjolfsson, John Etchemendy, Katrina Ligett, Terah Lyons, James Manyika, Juan Carlos Niebles, Yoav Shoham, Russell Wald, and Jack Clark, “The AI Index 2024 Annual Report,” AI Index Steering Committee, Institute for Human-Centered AI, Stanford University, Stanford, CA, April 2024.
The AI Index 2024 Annual Report by Stanford University is licensed under Attribution-NoDerivatives 4.0 International.
-
 @ 0176967e:1e6f471e
2024-07-28 09:16:10
@ 0176967e:1e6f471e
2024-07-28 09:16:10Jan Kolčák pochádza zo stredného Slovenska a vystupuje pod umeleckým menom Deepologic. Hudbe sa venuje už viac než 10 rokov. Začínal ako DJ, ktorý s obľubou mixoval klubovú hudbu v štýloch deep-tech a afrohouse. Stále ho ťahalo tvoriť vlastnú hudbu, a preto sa začal vzdelávať v oblasti tvorby elektronickej hudby. Nakoniec vydal svoje prvé EP s názvom "Rezonancie". Učenie je pre neho celoživotný proces, a preto sa neustále zdokonaľuje v oblasti zvuku a kompozície, aby jeho skladby boli kvalitné na posluch aj v klube.
V roku 2023 si založil vlastnú značku EarsDeep Records, kde dáva príležitosť začínajúcim producentom. Jeho značku podporujú aj etablované mená slovenskej alternatívnej elektronickej scény. Jeho prioritou je sloboda a neškatulkovanie. Ako sa hovorí v jednej klasickej deephouseovej skladbe: "We are all equal in the house of deep." So slobodou ide ruka v ruke aj láska k novým technológiám, Bitcoinu a schopnosť udržať si v digitálnom svete prehľad, odstup a anonymitu.
V súčasnosti ďalej produkuje vlastnú hudbu, venuje sa DJingu a vedie podcast, kde zverejňuje svoje mixované sety. Na Lunarpunk festivale bude hrať DJ set tvorený vlastnou produkciou, ale aj skladby, ktoré sú blízke jeho srdcu.
Podcast Bandcamp Punk Nostr website alebo nprofile1qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qy88wumn8ghj7mn0wvhxcmmv9uq3xamnwvaz7tmsw4e8qmr9wpskwtn9wvhsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0qyg8wumn8ghj7mn0wd68ytnddakj7qghwaehxw309aex2mrp0yh8qunfd4skctnwv46z7qpqguvns4ld8k2f3sugel055w7eq8zeewq7mp6w2stpnt6j75z60z3swy7h05
-
 @ 1cb14ab3:95d52462
2025-01-08 03:33:11
@ 1cb14ab3:95d52462
2025-01-08 03:33:11Tree branches, Rock. 4' x 4 [Boulder, USA. 2016]
Introduction
Nestled deep in the forest near Boulder, "Looking Glass" invites viewers to rediscover the quiet beauty of overlooked natural details. By framing the play of light, texture, and shadow through a 4-foot circular lens, the piece shifts focus to the microcosms of the forest, drawing attention to a small and overlooked waterfall.
Site & Placement
The lens is perched amid a cluster of trees, emphasizing a quiet patch of the forest that often goes unnoticed. Positioned 22 feet from the lens, a carefully placed bench offers a perfect vantage point, guiding visitors to linger, observe, and absorb the layered simplicity of the scene.
Impermanence & Integration
True to the ethos of the Earth Lens series, Looking Glass exists only briefly. Its natural materials—branches, wood, and rock—blend seamlessly into the forest and will eventually be reclaimed by it. The fleeting presence of the lens reflects the transient beauty of life, encouraging viewers to appreciate the details that often escape notice in the rush of time.
Reflection
In its short life, Looking Glass offers a moment of stillness and clarity, a chance to peer into the intimate world of the forest. The work becomes a lens not just for the environment but also for introspection, reminding viewers of the quiet wonders that surround them every day.
Photos







More from the 'Earth Lens' Series:
Earth Lens Series: Artist Statement + List of Works
COMING SOON: "Folsom" (Earth Lens 002)
COMING SOON: "Sanctuary" (Earth Lens 003)
COMING SOON: "Platte" (Earth Lens 004)
COMING SOON: "Grandfather" (Earth Lens 005)
COMING SOON: "Chongming" (Earth Lens 006)
More from Hes
All images are credit of Hes, but you are free to download and use for any purpose. If you find joy from my art, please feel free to send a zap. Enjoy life on a Bitcoin standard.
-
 @ cb084639:2f16502a
2024-10-29 05:28:32
@ cb084639:2f16502a
2024-10-29 05:28:32ทำไมถึงกลัว คลอเรสเตอรอลและไขมันอิ่มตัวกันขนาดนั้น !!!

จากภาพจะเห็นได้ว่ามีการวางขายไข่จากพืช!!! ซึ่งอ่านแล้วน่าขัน ในเมื่อเราสามารถ กินไข่จากแม่ไก่ได้!!!

เพื่อความกระจ่างเรามาดูฉลากเจ้าน้ำไข่จากพืชกล่องสีเหลืองกันดีกว่า
 อย่างแรกเรามาดูที่ราคากันก่อน ราคาต่อกล่อง 6.98 usd ราคาบาทอยู่ที่ประมาณ 235 บาทต่อกล่อง 16 ออนซ์หรือ 454 กรัม และถ้าเป็นการ นำเงินจำนวนนี้ไปซื้อไข่จริงเบอร์ 2 ราคาแผงละ 119 บาท จะได้ไข่ 58 ฟอง(เกือบ 2 แผงขาดไป 2ฟอง)
อย่างแรกเรามาดูที่ราคากันก่อน ราคาต่อกล่อง 6.98 usd ราคาบาทอยู่ที่ประมาณ 235 บาทต่อกล่อง 16 ออนซ์หรือ 454 กรัม และถ้าเป็นการ นำเงินจำนวนนี้ไปซื้อไข่จริงเบอร์ 2 ราคาแผงละ 119 บาท จะได้ไข่ 58 ฟอง(เกือบ 2 แผงขาดไป 2ฟอง) เน้นเรื่องปลอด GMO และไม่มี คลอเรสเตอรอล
อันนี้เป็นวิธปรุงง่ายๆ ใช่น้ำไข่จากพืช 3 ช้อนโต๊ะ ต่อไข่ไก่จริง 1 ฟอง ทำง่ายสะดวก
เน้นเรื่องปลอด GMO และไม่มี คลอเรสเตอรอล
อันนี้เป็นวิธปรุงง่ายๆ ใช่น้ำไข่จากพืช 3 ช้อนโต๊ะ ต่อไข่ไก่จริง 1 ฟอง ทำง่ายสะดวก
 ด้านนี้พยายามเปรียบเทียบให้เห็นว่า ไม่มีคลอเรสเตอรอลและไข่มันอิ่มตัว
ด้านนี้พยายามเปรียบเทียบให้เห็นว่า ไม่มีคลอเรสเตอรอลและไข่มันอิ่มตัว ปริมาณสารอาหารไข่จากพืช ไม่มีคลอเรสเตอรอล มีไขมันทั้งหมด 4 กรัม คือไขมันไม่อิ่มตัวเชิงซ้อนและไขมันไม่อิ่มตัวเชิงเดี่ยว ต่อหนึ่งหน่วยบริกโภค
ปริมาณสารอาหารไข่จากพืช ไม่มีคลอเรสเตอรอล มีไขมันทั้งหมด 4 กรัม คือไขมันไม่อิ่มตัวเชิงซ้อนและไขมันไม่อิ่มตัวเชิงเดี่ยว ต่อหนึ่งหน่วยบริกโภค
ภาพนี้คือข้อมูลขอไข่ไก่ที่ได้จากแม่ไก่จริงๆ
 เกือบลืมไปน้ำไข่จากพืชจำเป็นต้องมีส่วนผสมต่างๆ เช่น น้ำ โปรตีนถั่วเขียว น้ำมันคาโนล่าสกัดเย็น สีจากสารสกัดแครอท หัวหอมแห้ง เจลแลนกัม เพื่อรสชาติและเนื้อสัมผัส โพแทสเซียมซิเตรต เกลือ น้ำตาล น้ำเชื่อมมันสำปะหลังของแข็ง เตตระโซเดียมไพโรฟอสเฟต ทรานส์กลูตามิเนส สารสกัดขมิ้น (สี) ไนซิน (สารกันบูด)
เกือบลืมไปน้ำไข่จากพืชจำเป็นต้องมีส่วนผสมต่างๆ เช่น น้ำ โปรตีนถั่วเขียว น้ำมันคาโนล่าสกัดเย็น สีจากสารสกัดแครอท หัวหอมแห้ง เจลแลนกัม เพื่อรสชาติและเนื้อสัมผัส โพแทสเซียมซิเตรต เกลือ น้ำตาล น้ำเชื่อมมันสำปะหลังของแข็ง เตตระโซเดียมไพโรฟอสเฟต ทรานส์กลูตามิเนส สารสกัดขมิ้น (สี) ไนซิน (สารกันบูด)สินค้าเน่าเสียง่าย - เก็บในตู้เย็น รับประทานได้ภายใน 7 วันหลังจากเปิด
 เราต้องแลกกับการที่ต้องบริโภคสารแปรรูปสารพัดเพื่อที่จะต้องการหนีจากคลอเรสเตอรอลอละไขมันจากธรรมชาติ จะดีกว่ามั้ยถ้าเราเลือกกินไข่ที่ผลิตจากธรรมชาติโดยแม่ไก่?
เราต้องแลกกับการที่ต้องบริโภคสารแปรรูปสารพัดเพื่อที่จะต้องการหนีจากคลอเรสเตอรอลอละไขมันจากธรรมชาติ จะดีกว่ามั้ยถ้าเราเลือกกินไข่ที่ผลิตจากธรรมชาติโดยแม่ไก่?


