-
 @ eac63075:b4988b48
2025-01-04 19:41:34
@ eac63075:b4988b48
2025-01-04 19:41:34Since its creation in 2009, Bitcoin has symbolized innovation and resilience. However, from time to time, alarmist narratives arise about emerging technologies that could "break" its security. Among these, quantum computing stands out as one of the most recurrent. But does quantum computing truly threaten Bitcoin? And more importantly, what is the community doing to ensure the protocol remains invulnerable?
The answer, contrary to sensationalist headlines, is reassuring: Bitcoin is secure, and the community is already preparing for a future where quantum computing becomes a practical reality. Let’s dive into this topic to understand why the concerns are exaggerated and how the development of BIP-360 demonstrates that Bitcoin is one step ahead.
What Is Quantum Computing, and Why Is Bitcoin Not Threatened?
Quantum computing leverages principles of quantum mechanics to perform calculations that, in theory, could exponentially surpass classical computers—and it has nothing to do with what so-called “quantum coaches” teach to scam the uninformed. One of the concerns is that this technology could compromise two key aspects of Bitcoin’s security:
- Wallets: These use elliptic curve algorithms (ECDSA) to protect private keys. A sufficiently powerful quantum computer could deduce a private key from its public key.
- Mining: This is based on the SHA-256 algorithm, which secures the consensus process. A quantum attack could, in theory, compromise the proof-of-work mechanism.
Understanding Quantum Computing’s Attack Priorities
While quantum computing is often presented as a threat to Bitcoin, not all parts of the network are equally vulnerable. Theoretical attacks would be prioritized based on two main factors: ease of execution and potential reward. This creates two categories of attacks:
1. Attacks on Wallets
Bitcoin wallets, secured by elliptic curve algorithms, would be the initial targets due to the relative vulnerability of their public keys, especially those already exposed on the blockchain. Two attack scenarios stand out:
-
Short-term attacks: These occur during the interval between sending a transaction and its inclusion in a block (approximately 10 minutes). A quantum computer could intercept the exposed public key and derive the corresponding private key to redirect funds by creating a transaction with higher fees.
-
Long-term attacks: These focus on old wallets whose public keys are permanently exposed. Wallets associated with Satoshi Nakamoto, for example, are especially vulnerable because they were created before the practice of using hashes to mask public keys.
We can infer a priority order for how such attacks might occur based on urgency and importance.
 Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)
Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)2. Attacks on Mining
Targeting the SHA-256 algorithm, which secures the mining process, would be the next objective. However, this is far more complex and requires a level of quantum computational power that is currently non-existent and far from realization. A successful attack would allow for the recalculation of all possible hashes to dominate the consensus process and potentially "mine" it instantly.
 Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin Attacks
Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin AttacksRecently, Narcelio asked me about a statement I made on Tubacast:
https://x.com/eddieoz/status/1868371296683511969
If an attack became a reality before Bitcoin was prepared, it would be necessary to define the last block prior to the attack and proceed from there using a new hashing algorithm. The solution would resemble the response to the infamous 2013 bug. It’s a fact that this would cause market panic, and Bitcoin's price would drop significantly, creating a potential opportunity for the well-informed.
Preferably, if developers could anticipate the threat and had time to work on a solution and build consensus before an attack, they would simply decide on a future block for the fork, which would then adopt the new algorithm. It might even rehash previous blocks (reaching consensus on them) to avoid potential reorganization through the re-mining of blocks using the old hash. (I often use the term "shielding" old transactions).
How Can Users Protect Themselves?
While quantum computing is still far from being a practical threat, some simple measures can already protect users against hypothetical scenarios:
- Avoid using exposed public keys: Ensure funds sent to old wallets are transferred to new ones that use public key hashes. This reduces the risk of long-term attacks.
- Use modern wallets: Opt for wallets compatible with SegWit or Taproot, which implement better security practices.
- Monitor security updates: Stay informed about updates from the Bitcoin community, such as the implementation of BIP-360, which will introduce quantum-resistant addresses.
- Do not reuse addresses: Every transaction should be associated with a new address to minimize the risk of repeated exposure of the same public key.
- Adopt secure backup practices: Create offline backups of private keys and seeds in secure locations, protected from unauthorized access.
BIP-360 and Bitcoin’s Preparation for the Future
Even though quantum computing is still beyond practical reach, the Bitcoin community is not standing still. A concrete example is BIP-360, a proposal that establishes the technical framework to make wallets resistant to quantum attacks.
BIP-360 addresses three main pillars:
- Introduction of quantum-resistant addresses: A new address format starting with "BC1R" will be used. These addresses will be compatible with post-quantum algorithms, ensuring that stored funds are protected from future attacks.
- Compatibility with the current ecosystem: The proposal allows users to transfer funds from old addresses to new ones without requiring drastic changes to the network infrastructure.
- Flexibility for future updates: BIP-360 does not limit the choice of specific algorithms. Instead, it serves as a foundation for implementing new post-quantum algorithms as technology evolves.
This proposal demonstrates how Bitcoin can adapt to emerging threats without compromising its decentralized structure.
Post-Quantum Algorithms: The Future of Bitcoin Cryptography
The community is exploring various algorithms to protect Bitcoin from quantum attacks. Among the most discussed are:
- Falcon: A solution combining smaller public keys with compact digital signatures. Although it has been tested in limited scenarios, it still faces scalability and performance challenges.
- Sphincs: Hash-based, this algorithm is renowned for its resilience, but its signatures can be extremely large, making it less efficient for networks like Bitcoin’s blockchain.
- Lamport: Created in 1977, it’s considered one of the earliest post-quantum security solutions. Despite its reliability, its gigantic public keys (16,000 bytes) make it impractical and costly for Bitcoin.
Two technologies show great promise and are well-regarded by the community:
- Lattice-Based Cryptography: Considered one of the most promising, it uses complex mathematical structures to create systems nearly immune to quantum computing. Its implementation is still in its early stages, but the community is optimistic.
- Supersingular Elliptic Curve Isogeny: These are very recent digital signature algorithms and require extensive study and testing before being ready for practical market use.
The final choice of algorithm will depend on factors such as efficiency, cost, and integration capability with the current system. Additionally, it is preferable that these algorithms are standardized before implementation, a process that may take up to 10 years.
Why Quantum Computing Is Far from Being a Threat
The alarmist narrative about quantum computing overlooks the technical and practical challenges that still need to be overcome. Among them:
- Insufficient number of qubits: Current quantum computers have only a few hundred qubits, whereas successful attacks would require millions.
- High error rate: Quantum stability remains a barrier to reliable large-scale operations.
- High costs: Building and operating large-scale quantum computers requires massive investments, limiting their use to scientific or specific applications.
Moreover, even if quantum computers make significant advancements, Bitcoin is already adapting to ensure its infrastructure is prepared to respond.
Conclusion: Bitcoin’s Secure Future
Despite advancements in quantum computing, the reality is that Bitcoin is far from being threatened. Its security is ensured not only by its robust architecture but also by the community’s constant efforts to anticipate and mitigate challenges.
The implementation of BIP-360 and the pursuit of post-quantum algorithms demonstrate that Bitcoin is not only resilient but also proactive. By adopting practical measures, such as using modern wallets and migrating to quantum-resistant addresses, users can further protect themselves against potential threats.
Bitcoin’s future is not at risk—it is being carefully shaped to withstand any emerging technology, including quantum computing.
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 8d34bd24:414be32b
2025-01-08 14:34:15
@ 8d34bd24:414be32b
2025-01-08 14:34:15I’ve known that there are references to Jesus in the Old Testament. They just don’t use the name Jesus.
Then God said, “Let Us make man in Our image, according to Our likeness; and let them rule over the fish of the sea and over the birds of the sky and over the cattle and over all the earth, and over every creeping thing that creeps on the earth.” (Genesis 1:26) {emphasis mine}
Notice the references to God in the plural. These are clues to the trinitarian (3 persons in one God) nature of God.
There are also examples of theophanies (preincarnate Jesus) in the Old Testament. These theophanies are frequently referred to as “the angel of the Lord” or “the angel of God.”
But the angel of the Lord called to him from heaven and said, “Abraham, Abraham!” And he said, “Here I am.” He said, “Do not stretch out your hand against the lad, and do nothing to him; for now I know that you fear God, since you have not withheld your son, your only son, from Me.” (Genesis 22:11-12) {emphasis mine}
In this case we know that the “angel of the Lord” is not just an angel because he says, “I know that you fear God, since you have not withheld your son, your only son, from Me,” equating Himself, “Me,” with God. In most cases when an angel appears, the people drop face down in worship, but the angel corrects them and tells them not to worship. When the angel is Jesus, He accepts the worship and in many cases sacrifices as well.
The angel of the Lord appeared to him and said to him, “The Lord is with you, O valiant warrior.” Then Gideon said to him, “O my lord, if the Lord is with us, why then has all this happened to us? … So Gideon said to Him, “If now I have found favor in Your sight, then show me a sign that it is You who speak with me. Please do not depart from here, until I come back to You, and bring out my offering and lay it before You.” And He said, “I will remain until you return.”
Then Gideon went in and prepared a young goat and unleavened bread from an ephah of flour; he put the meat in a basket and the broth in a pot, and brought them out to him under the oak and presented them. The angel of God said to him, “Take the meat and the unleavened bread and lay them on this rock, and pour out the broth.” And he did so. Then the angel of the Lord put out the end of the staff that was in his hand and touched the meat and the unleavened bread; and fire sprang up from the rock and consumed the meat and the unleavened bread. Then the angel of the Lord vanished from his sight. When Gideon saw that he was the angel of the Lord, he said, “Alas, O Lord God! For now I have seen the angel of the Lord face to face.” (Judges 6:12=13a, 17-22) {emphasis mine}
As you can see, Gideon offered an offering. An offering to anyone other than God would be idolatry. Gideon offers a “a young goat and unleavened bread from an ephah of flour,” which is a proper sin offering to God. The angel did not eat the offering, but told Gideon to “Take the meat and the unleavened bread and lay them on this rock … Then the angel of the Lord put out the end of the staff that was in his hand and touched the meat and the unleavened bread; and fire sprang up from the rock and consumed the meat and the unleavened bread. Then the angel of the Lord vanished from his sight.” Gideon’s offering was taken as a burnt offering to God and to angel of the Lord, who is Jesus.
With all of this, look at the verse I read last night:
Who has ascended into heaven and descended?\ Who has gathered the wind in His fists?\ Who has wrapped the waters in His garment?\ Who has established all the ends of the earth?\ What is His name or His son’s name?\ Surely you know! (Proverbs 30:4) {emphasis mine}
Surely this is a passage about Jesus.
This verse says, “Who has ascended into heaven and descended?” The New Testament says about Jesus, “No one has ascended into heaven, but He who descended from heaven: the Son of Man.” (John 3:13)
This verse says, “Who has gathered the wind in His fists?” The New Testament says about Jesus,
And there arose a fierce gale of wind, and the waves were breaking over the boat so much that the boat was already filling up. Jesus Himself was in the stern, asleep on the cushion; and they woke Him and said to Him, “Teacher, do You not care that we are perishing?” And He got up and rebuked the wind and said to the sea, “Hush, be still.” And the wind died down and it became perfectly calm. (Mark 4:37-39) {emphasis mine}
This verse says, “Who has wrapped the waters in His garment?” The New Testament says about Jesus,
And in the fourth watch of the night He came to them, walking on the sea. When the disciples saw Him walking on the sea, they were terrified, and said, “It is a ghost!” And they cried out in fear. But immediately Jesus spoke to them, saying, “Take courage, it is I; do not be afraid.”
Peter said to Him, “Lord, if it is You, command me to come to You on the water.” And He said, “Come!” And Peter got out of the boat, and walked on the water and came toward Jesus. (Matthew 14:25-29) {emphasis mine}
This verse says, “Who has established all the ends of the earth?” The New Testament says about Jesus,
In the beginning was the Word, and the Word was with God, and the Word was God. He was in the beginning with God. All things came into being through Him, and apart from Him nothing came into being that has come into being. (John 1:1-3) {emphasis mine}
This verse says, “What is His name or His son’s name?” The New Testament says about Jesus,
After being baptized, Jesus came up immediately from the water; and behold, the heavens were opened, and he saw the Spirit of God descending as a dove and lighting on Him, and behold, a voice out of the heavens said, “This is My beloved Son, in whom I am well-pleased. (Matthew 3:16-17) {emphasis mine}
This verse says, “Surely you know!” As New Testament believers we know the Son of God, Jesus Christ. The Bible was pointing to the Son of God long before He came to earth as a baby.
Who has ascended into heaven and descended?\ Who has gathered the wind in His fists?\ Who has wrapped the waters in His garment?\ Who has established all the ends of the earth?\ What is His name or His son’s name?\ Surely you know! (Proverbs 30:4) {emphasis mine}
It doesn’t matter how many times we have already read the Bible. Every time we read it, we can discover new insight and knowledge of God, His eternal plans, and His commands for our lives. God is good.
Trust Jesus.
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ d34e832d:383f78d0
2025-01-06 23:44:40
@ d34e832d:383f78d0
2025-01-06 23:44:40Lets explore three key aspects of Bitcoin technology to enhance your engagement with the ecosystem:
- Running an Alby Hub Cloud Instance
- Setting Up a Nutshell Ecash Mint on an Affordable VPS
- Integrating Nostr Wallet Connect for Seamless Tipping
These components empower users to manage transactions, ensure privacy, and facilitate smooth interactions within the Bitcoin and Nostr communities.
1. Running an Alby Hub Cloud Instance
Purpose and Benefits:
Alby Hub is a self-custodial Lightning wallet that allows you to manage Bitcoin transactions efficiently. By running an Alby Hub instance in the cloud, you gain 24/7 online access to receive payments via a Lightning address, integrate with various applications, and maintain control over your funds without the need for personal hardware.
Setting Up Alby Hub in the Cloud:
-
Choose Alby Cloud: For a hassle-free setup, Alby offers a cloud service where you can start your own hub in just 2 minutes. Give it A Try: Alby Cloud
-
Subscription Benefits: Subscribing to Alby Cloud provides you with a self-custodial Lightning wallet, 24/7 online access, exclusive partner deals, priority support, and access to a subscriber community.
-
Getting Started: Visit the Alby Cloud page, select the subscription that suits you, and follow the guided setup process to have your hub up and running quickly.
- Alby Cloud page
For a visual guide on setting up Alby Hub, you can watch the following tutorial:
2. Setting Up a Nutshell Ecash Mint on an Affordable VPS
Purpose and Benefits:
Nutshell is an implementation of Ecash, a digital cash system that prioritizes privacy and anonymity. Setting up a Nutshell Ecash mint on a Virtual Private Server (VPS) allows you to operate your own mint, enhancing transaction privacy and providing a backup system for your Bitcoin transactions.
Setting Up on a $5 VPS:
-
Select a VPS Provider: Choose an affordable VPS provider that supports Bitcoin and Nostr communities. For instance, SatoshiHost offers VPS services tailored for such needs.
-
Install Nutshell: After setting up your VPS, install the Nutshell software by following the official installation guide.
- Nutshell
-
Configure the Mint: Set up the mint parameters, including denomination and security settings, to suit your requirements.
-
Secure the Server: Implement security measures such as firewalls and regular updates to protect your mint from potential threats.
- Recommendations
- Server Tips
3. Integrating Nostr Wallet Connect for Seamless Tipping
Purpose and Benefits:
Nostr Wallet Connect (NWC) is an open protocol that enables applications to interact with Bitcoin Lightning wallets. Integrating NWC allows for seamless tipping and payments within Nostr apps, enhancing user experience and promoting engagement.
Integration Steps:
-
Choose a Supporting App: Select a Nostr app that supports NWC, such as Amythystor Damus.
-
Connect Your Wallet: Use NWC to link your preferred Lightning wallet to the Nostr app. This connection facilitates seamless payments without the need to switch between applications.
-
Test the Integration: Perform a test transaction to ensure that the tipping functionality works as intended.
-
Maintain Security: Regularly update your wallet and Nostr app to incorporate the latest security features and improvements.
For a deeper understanding of Nostr Wallet Connect and its significance, you can watch the following discussion:
Final Thoughts On Setup
Implementing these components enhances your interaction with the Bitcoin ecosystem by providing efficient transaction management, improved privacy, and seamless integration with Nostr applications. By running an Alby Hub cloud instance, setting up a Nutshell Ecash mint on an affordable VPS, and integrating Nostr Wallet Connect, you contribute to a more robust and user-friendly Bitcoin environment.
Invitation for Feedback
I encourage you to share any questions or feedback regarding these topics. Let's continue the conversation to explore how we can further engage with and improve upon these technologies.
-
 @ 6e24af77:b3f1350b
2025-01-07 13:23:26
@ 6e24af77:b3f1350b
2025-01-07 13:23:26test

-
 @ 46025249:0a7e0424
2025-01-06 16:07:13
@ 46025249:0a7e0424
2025-01-06 16:07:13Hello world
-
 @ f4bf1fb5:b428f8d5
2025-01-02 23:44:03
@ f4bf1fb5:b428f8d5
2025-01-02 23:44:03DEG Mods is using a new piece of technology, specifically a new communications protocol that's censorship-resistant called NOSTR, and as such, it uses a non-traditional means of creating an account, as well as how you sign into sites that uses such new tech, like DEG Mods.
Since this is new to most people, it can be somewhat daunting, scary, suspicious, as with anything new, especially something where the individual holds sole responsibility of what they created, as there would be nobody to help them, in the case of creating an account, retrieve their account if it gets lost or if it gets compromised.
We'll skip on explaining in proper detail what NOSTR is specifically, and go straight ahead and explain the direct process of how to create an account, and how to sign in.
How to create an account on DEG Mods
Creating a DEG Mods account is creating a NOSTR account, and that can be done in multiple ways, from using a browser extension, to using a mobile app, to generating it directly on the site.
For the purposes of this current guide, and for the current version of DEG Mods, we'll only be guiding you on how to create a DEG Mods/NOSTR account using a browser extension. With that said, there are currently multiple ones that has been developed for this specific purpose. Some with more features than others, or some with a better UI/UX. For now, we'll be recommending you to install one called Nostr Connect (Chrome / FireFox)
Once you have installed that extension on your preferred browser, make sure that you have the extension pinned on your browser (for easy access and use). To do that, you'd have to open the quick extension preview window on your browser (for example, on Chrome or Brave, that'd be the puzzle-piece icon) and then click the pin icon next to the extension you want to pin. In this case, that'd be the Nostr Connect extension.
Now, click on the Nostr Connect extension icon and then click the gear icon, which will open a new tab/page to start the account creation process.
It's pretty straight forward from there. Just click on the "Generate" button then the save button. This will generate for you a pair of keys/addresses. The shown one is your private key (think of it as your password) that starts with 'nsec', which you should keep safe somewhere (like on a password manager), because if you lose it then you won't be able to access your account, or if it gets leaked then everyone would be able to access your account, and we won't be able to help you retrieve your private key/address or reset it to something else. You are the sole responsible person for your account's security.
Once you're done, close that page then click on the extension icon again. It will now show you your public key/address (think of this as your user ID).
How to sign into DEG Mods
Once you have the DEG Mods site open, click the 'Login' button at the top right. A popup will appear with an option to login with an extension. Click that and another popup will appear (this is your extension being triggered) asking you to authorize the login. Tick the box to remember this action if you'd like (for convenience) and click authorize.
Done. You've now created an account and logged into the site. Now you can publish game mods, comment on posts/pages, react, and more.
Video guide
If you don't feel like reading, or rather, if you're more comfortable watching a video guide on how to do all of this, then here's that video.
Questions and answers
Is this safe?
As we did not create these browser extensions or mobile apps, we can't necessarily guarantee anything, however, until proven otherwise, the browser extensions or mobile apps we recommended here are safe. If you're a programmer, you can check their code directly to see if there's anything suspicious, as they are open source.
Why do you have such a complicated way to make an account?
We understand that this may seem complicated, but it isn't if you think about it.
What did you actually do? You installed a browser extension, generated an account (a key pair), and signed in with a click of a single button. Install, generate, login.
It seems complicated because its something you haven't done before and outside of what you're used it, but in reality, it's actually a lot simpler than traditional methods, which involves creating an email address, then creating an account on each site you want to visit. With this, it's a one time event and you can log into DEG Mods, or any other site or app that's built ontop of NOSTR, with that same account, which holds all of your profile data and posts.
Why don't you have a normal way to make an account on DEG Mods?
Since DEG Mods is a truly censorship-resistant mods site, building the site on NOSTR was the ideal choice to make, which resulted in giving you, the user, the mod creator, and the mod enjoyer, the power of controlling your content, your posts, your profile, your account. We can't ban you because you have a NOSTR account, nor can we take down your posts/pages.
If we had made it so that you can use the normal way of making an account, where you have an email and password combo, then we can do all of those ban things. We would have the power to censor you. You'd have zero power, and we didn't want that outcome.
What do you mean you can't help me restore my account or reset my password?
The account you created was, because of the tech being used, created on your device, and not on any server that we control. As such, we don't see or save your account data (we don't know your private key/address, and we shouldn't). You also cannot change the private key/address of your account, as there is no way to do so / this is how the tech was developed.
Will you maintain and update this guide as time move forwards?
Yes. Since its in our interest to have more users on DEG Mods, we'll be updating this post so that it'll continue being useful to new users.
Can't you make a browser extension or app specifically for DEG Mods?
While it is possible, and we are interested in doing so, as to keep it always up to date and add more features, have the best UI/UX possible, etc, it would require us to receive funds and allocate it for this specific development. So the answer to this question is: If we're successful enough to have the funds to develop it.
Why can't I log into DEG Mods on my mobile phone?
You would need a NOSTR mobile signer for that, and we'll also need to implement such a feature to tell the site that you have that app. It'll come with time, and I'd say sooner rather than later.
-
 @ 3ffac3a6:2d656657
2025-01-06 23:42:53
@ 3ffac3a6:2d656657
2025-01-06 23:42:53Prologue: The Last Trade
Ethan Nakamura was a 29-year-old software engineer and crypto enthusiast who had spent years building his life around Bitcoin. Obsessed with the idea of financial sovereignty, he had amassed a small fortune trading cryptocurrencies, all while dreaming of a world where decentralized systems ruled over centralized power.
One night, while debugging a particularly thorny piece of code for a smart contract, Ethan stumbled across an obscure, encrypted message hidden in the blockchain. It read:
"The key to true freedom lies beyond. Burn it all to unlock the gate."
Intrigued and half-convinced it was an elaborate ARG (Alternate Reality Game), Ethan decided to follow the cryptic instruction. He loaded his entire Bitcoin wallet into a single transaction and sent it to an untraceable address tied to the message. The moment the transaction was confirmed, his laptop screen began to glitch, flooding with strange symbols and hash codes.
Before he could react, a flash of light engulfed him.
Chapter 1: A New Ledger
Ethan awoke in a dense forest bathed in ethereal light. The first thing he noticed was the HUD floating in front of him—a sleek, transparent interface that displayed his "Crypto Balance": 21 million BTC.
“What the…” Ethan muttered. He blinked, hoping it was a dream, but the numbers stayed. The HUD also showed other metrics:
- Hash Power: 1,000,000 TH/s
- Mining Efficiency: 120%
- Transaction Speed: Instant
Before he could process, a notification pinged on the HUD:
"Welcome to the Decentralized Kingdom. Your mining rig is active. Begin accumulating resources to survive."
Confused and a little terrified, Ethan stood and surveyed his surroundings. As he moved, the HUD expanded, revealing a map of the area. His new world looked like a cross between a medieval fantasy realm and a cyberpunk dystopia, with glowing neon towers visible on the horizon and villagers dressed in tunics carrying strange, glowing "crypto shards."
Suddenly, a shadow loomed over him. A towering beast, part wolf, part machine, snarled, its eyes glowing red. Above its head was the name "Feral Node" and a strange sigil resembling a corrupted block.
Instinct kicked in. Ethan raised his hands defensively, and to his shock, the HUD offered an option:
"Execute Smart Contract Attack? (Cost: 0.001 BTC)"
He selected it without hesitation. A glowing glyph appeared in the air, releasing a wave of light that froze the Feral Node mid-lunge. Moments later, it dissolved into a cascade of shimmering data, leaving behind a pile of "Crypto Shards" and an item labeled "Node Fragment."
Chapter 2: The Decentralized Kingdom
Ethan discovered that the world he had entered was built entirely on blockchain-like principles. The land was divided into regions, each governed by a Consensus Council—groups of powerful beings called Validators who maintained the balance of the world. However, a dark force known as The Central Authority sought to consolidate power, turning decentralized regions into tightly controlled fiefdoms.
Ethan’s newfound abilities made him a unique entity in this world. Unlike its inhabitants, who earned wealth through mining or trading physical crypto shards, Ethan could generate and spend Bitcoin directly—making him both a target and a potential savior.
Chapter 3: Allies and Adversaries
Ethan soon met a colorful cast of characters:
-
Luna, a fiery rogue and self-proclaimed "Crypto Thief," who hacked into ledgers to redistribute wealth to oppressed villages. She was skeptical of Ethan's "magical Bitcoin" but saw potential in him.
-
Hal, an aging miner who ran an underground resistance against the Central Authority. He wielded an ancient "ASIC Hammer" capable of shattering corrupted nodes.
-
Oracle Satoshi, a mysterious AI-like entity who guided Ethan with cryptic advice, often referencing real-world crypto principles like decentralization, trustless systems, and private keys.
Ethan also gained enemies, chief among them the Ledger Lords, a cabal of Validators allied with the Central Authority. They sought to capture Ethan and seize his Bitcoin, believing it could tip the balance of power.
Chapter 4: Proof of Existence
As Ethan delved deeper into the world, he learned that his Bitcoin balance was finite. To survive and grow stronger, he had to "mine" resources by solving problems for the people of the Decentralized Kingdom. From repairing broken smart contracts in towns to defending miners from feral nodes, every task rewarded him with shards and upgrades.
He also uncovered the truth about his arrival: the blockchain Ethan had used in his world was a prototype for this one. The encrypted message had been a failsafe created by its original developers—a desperate attempt to summon someone who could break the growing centralization threatening to destroy the world.
Chapter 5: The Final Fork
As the Central Authority's grip tightened, Ethan and his allies prepared for a final battle at the Genesis Block, the origin of the world's blockchain. Here, Ethan would face the Central Authority's leader, an amalgamation of corrupted code and human ambition known as The Miner King.
The battle was a clash of philosophies as much as strength. Using everything he had learned, Ethan deployed a daring Hard Fork, splitting the world’s blockchain and decentralizing power once again. The process drained nearly all of his Bitcoin, leaving him with a single satoshi—a symbolic reminder of his purpose.
Epilogue: Building the Future
With the Central Authority defeated, the Decentralized Kingdom entered a new era. Ethan chose to remain in the world, helping its inhabitants build fairer systems and teaching them the principles of trustless cooperation.
As he gazed at the sunrise over the rebuilt Genesis Block, Ethan smiled. He had dreamed of a world where Bitcoin could change everything. Now, he was living it.
-
 @ 3f770d65:7a745b24
2025-01-05 18:56:33
@ 3f770d65:7a745b24
2025-01-05 18:56:33New Year’s resolutions often feel boring and repetitive. Most revolve around getting in shape, eating healthier, or giving up alcohol. While the idea is interesting—using the start of a new calendar year as a catalyst for change—it also seems unnecessary. Why wait for a specific date to make a change? If you want to improve something in your life, you can just do it. You don’t need an excuse.
That’s why I’ve never been drawn to the idea of making a list of resolutions. If I wanted a change, I’d make it happen, without worrying about the calendar. At least, that’s how I felt until now—when, for once, the timing actually gave me a real reason to embrace the idea of New Year’s resolutions.
Enter Olas.
If you're a visual creator, you've likely experienced the relentless grind of building a following on platforms like Instagram—endless doomscrolling, ever-changing algorithms, and the constant pressure to stay relevant. But what if there was a better way? Olas is a Nostr-powered alternative to Instagram that prioritizes community, creativity, and value-for-value exchanges. It's a game changer.
Instagram’s failings are well-known. Its algorithm often dictates whose content gets seen, leaving creators frustrated and powerless. Monetization hurdles further alienate creators who are forced to meet arbitrary follower thresholds before earning anything. Additionally, the platform’s design fosters endless comparisons and exposure to negativity, which can take a significant toll on mental health.
Instagram’s algorithms are notorious for keeping users hooked, often at the cost of their mental health. I've spoken about this extensively, most recently at Nostr Valley, explaining how legacy social media is bad for you. You might find yourself scrolling through content that leaves you feeling anxious or drained. Olas takes a fresh approach, replacing "doomscrolling" with "bloomscrolling." This is a common theme across the Nostr ecosystem. The lack of addictive rage algorithms allows the focus to shift to uplifting, positive content that inspires rather than exhausts.
Monetization is another area where Olas will set itself apart. On Instagram, creators face arbitrary barriers to earning—needing thousands of followers and adhering to restrictive platform rules. Olas eliminates these hurdles by leveraging the Nostr protocol, enabling creators to earn directly through value-for-value exchanges. Fans can support their favorite artists instantly, with no delays or approvals required. The plan is to enable a brand new Olas account that can get paid instantly, with zero followers - that's wild.
Olas addresses these issues head-on. Operating on the open Nostr protocol, it removes centralized control over one's content’s reach or one's ability to monetize. With transparent, configurable algorithms, and a community that thrives on mutual support, Olas creates an environment where creators can grow and succeed without unnecessary barriers.
Join me on my New Year's resolution. Join me on Olas and take part in the #Olas365 challenge! It’s a simple yet exciting way to share your content. The challenge is straightforward: post at least one photo per day on Olas (though you’re welcome to share more!).
Download on Android or download via Zapstore.
Let's make waves together.
-
 @ 6e24af77:b3f1350b
2024-12-24 13:31:19
@ 6e24af77:b3f1350b
2024-12-24 13:31:19big header
Longer form text goes here
More text and the options we have bold italic underlined
code~~strike~~ sup subsome code
a quote
a list of some items
- t
- t2
- t3
more lists
- a
- b
- c
smaller header
even smaller
more
aa
bb
| header | table header 1 | 2 | 3 | | :----- | -------------- | :----: | ----: | | normal | left | center | right | | normal | left | center | right | | | | | |
some code is here Image is here
Image is hereyoutube link directive custom is below
::youtube{#5W-jtbbh3eA}
-
 @ 6e24af77:b3f1350b
2024-12-23 19:18:29
@ 6e24af77:b3f1350b
2024-12-23 19:18:29Lorem ipsum dolor sit amet, consectetur adipiscing elit. Integer nec odio. Praesent libero. Sed cursus ante dapibus diam. Sed nisi. Nulla quis sem at nibh elementum imperdiet. Duis sagittis ipsum. Praesent mauris. Fusce nec tellus sed augue semper porta. Mauris massa. Vestibulum lacinia arcu eget nulla. Class aptent taciti sociosqu ad litora torquent per conubia nostra, per inceptos himenaeos. Curabitur sodales ligula in libero.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Integer nec odio. Praesent libero. Sed cursus ante dapibus diam. Sed nisi. Nulla quis sem at nibh elementum imperdiet.
Duis sagittis ipsum. Praesent mauris. Fusce nec tellus sed augue semper porta. Mauris massa. Vestibulum lacinia arcu eget nulla. Class aptent taciti sociosqu ad litora torquent per conubia nostra, per inceptos himenaeos. Curabitur sodales ligula in libero.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Integer nec odio. Praesent libero.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Integer posuere erat a ante.
-
 @ 6e24af77:b3f1350b
2024-12-18 11:25:50
@ 6e24af77:b3f1350b
2024-12-18 11:25:50test content with some markdown
hi
codemore text
a bit late for the title
-
 @ f4bf1fb5:b428f8d5
2024-12-02 23:25:45
@ f4bf1fb5:b428f8d5
2024-12-02 23:25:45The project claims and communicates to everyone that mods published on it can't be taken down by the project/site owners, and that creators and users can't be banned, as well as not needing the site's permission to publish mods on it, citing that all of this is possible because of the protocol that its built on, Nostr. However, that's a quick response on how any of this is possible, and most people aren't technically knowledgeable enough to go and research it, let alone have the energy to do so.
That's why we thought it'd be a good idea to explain the tech, what's happening in the background, how the site currently works, why users need to use a new method of registration and login, and how things would change later on.
How does Nostr work?
Nostr is the protocol that DEG Mods is built on and is the core of what makes it possible to have that censorship-resistant and permissionless benefits. To summarize how it works, let's see how almost all sites work in comparison.
Be it a normal blog site like WordPress or Medium, or a social media site like X/Twitter or Facebook, all of them work similarly. There's the site that a person uses to create an account and publish a post on, and that same account is used to post data which gets sent and saved in one or more servers controlled by the site owner. Then, if someone else wants to view that person's post or profile, they'd use that same site to communicate with the one-entity-controlled servers and retrieve the relevant data/information.
That's how almost all sites work. Now, if such a site wants to ban a user or takedown their posts, that central entity (the site owners) can delete that account and/or delete its posts, and it's gone.
So how does a site built on Nostr work in comparison? It differs in two main points, the first being the account creation process, where instead of filling up a form and sending your personal data to have your account created, you'd generate an account, which would produce two keys, a public and a private one (think username and password), and since that process is a mathematical and cryptographic result, that means that you didn't even ask the site to create the account, you just did, whether they liked it or not. You could've also done it offline too, without being connected to the internet. What that means is that they couldn't stop you from making an account, and they can't ban your account. You actually control it.
The other point that it differs from traditional sites is how it handles people publishing content to it and how it retrieves it. Once you create a piece of content, a blog post or a short social post, it creates a file with that data in it, signs it (think like a signature, a unique squiggle/drawing, but happening with math and cryptography) using your public address (username), and that's only possible because you have the private key (password) to do it, then sends that file to multiple different relays (servers) that aren't necessarily associated with the site you're currently using, not controlled by them or by one entity.
So there are multiple copies of your published content spread across multiple servers, controlled by different entities, be it other companies, or random people, and yes, you can run your own as well, to have a backup copy of your content as well as your friends and family and/or select individuals as well, which is very doable since it was made to be easy and efficient, but that's for another post/guide when the time is right. In a sense, the more popular a post is, the more it gets decentralized and strengthens its censorship resistance.
With that said, if someone else wants to see your posts, they'd search for it and view it, and the site they're on would communicate with those decentralized servers to find the content and present it to you.
What all of this means is that you didn't need permission to make an account, or to log in, and you didn't need permission to publish content or view them. What's also interesting is that you would be able to go to another site that's built on the same tech, and in a similar way, publish content there, and it can appear on that first site as well. As an example, imagine if you made a post on Facebook and it appeared on X/Twitter, Instagram, YouTube, and Reddit.
Another point to consider is that it doesn't have to be a site, it can be a PC software or a mobile app as well, and all of them can share similar functionality and data publishing and retrieval.
How does DEG Mods work?
Now that the underlying tech/protocol for DEG Mods has been somewhat explained, here's how we're applying that here with mods.
When you want to register or log into the site, it's mentioned that you need to download and install a browser extension, and what that extension does is create the account for you, create that public and private key pair, store it within it, within your PC, which means that only you know your account, and nobody is in control of it besides you, and with it you'd use it to sign into the site and sign-off on various actions like publishing a mod post, sending a comment, reacting to a post, and so on. Without your signature from that keypair you have in your browser extension, no action would be taken.
With that said, if you somehow lost your keypair, specifically your private key, or somehow it was leaked to someone, there would be no way for you to change that private key or retrieve it. There's no "change password" or "forgot password" process here. With freedom comes responsibility, so keep that in mind.
So, once you've set up your browser extension and have managed to log in, you go ahead and attempt to publish a mod if you're a mod creator, where you fill out the details in the appropriate mod submission page, from the title, body text, screenshots and so on, and then you reach the area where you'd share your mod files with. You don't upload the mod files to DEG Mods / Nostr, but rather upload them to a regular server of your choice, get the file link from there, and add it in its appropriate field. After you add any other relevant data, you publish your mod, and now everyone will be able to view your mod page and download it.
Now, you're probably wondering how mods can be censorship-resistant, as we have claimed, even though the mod files are on another site or person's server where they can delete them. Let's say that scenario happened, where you published a mod, and the download button broke because the server host deleted the files. Your mod post is still up, and your account is still up, so the only thing that's broken is the download button. You'd simply upload the files to a different server host provider, and replace the old link with the new one when you edit your mod post.
The download button is now working again. You didn't have to publish a new mod post, you didn't get banned so you didn't have to find a different mod site and then create a new account, to publish the mod yet again, and didn't have to remarket that new page again and lose out on previous efforts, you also didn't have to rebuild the lost connections with your followers and have them create an account on another site for them to do so, only to continuously repeat this process over and over again as similar scenarios continue to occur. You just simply updated the mod post with a new download link.
This exact scenario happened with one of the mods on the site, where their mod page was taken down from various sites because of a malicious attacker, yet that didn't happen on DEG Mods' end, and even when the download links were taken down and resulted in the download link being broken, the creator simply uploaded it elsewhere and updated the mod post with the new link, resulting in a functional download button again, as if nothing happened. Their mod page on DEG Mods was up the whole time throughout their initial launch month period, whereas everywhere else they've tried has failed them.
They didn't have their mod post/page taken down, their account couldn't be banned, they didn't have to remarket anything again, and they didn't lose the connection between themselves and their fans.
Questions & Answers
We'll most likely update this post with relevant new information as they come, as well as new questions with their answers, and with that said, here are some of those.
Doesn't [insert anti-censorship site here] do the same thing?
From all the current mod sites we've looked into, they're only anti-censorship, as in they're against it, meaning they weren't built from the ground up to be censorship-resistant. They can still take down mod posts, they can still ban you, and you need their permission to post on their site. On DEG Mods, you don't need our permission to do anything, we can't (not won't, can't) take down your mod post, and we can't ban your account. The best we can do is hide posts, and even then all of them are still accessible. As far as we know, in regards to the values of modding, DEG Mods is the first true mod site out there, and others would be categorized as gated mod sites. This might be a bold claim, and we're not above having an inflated ego, so share your thoughts or criticism of the project if you think that's not the case and knock our potentially inflated ego down.
Uploading mod files to other sites is a pain. Isn't there something you can do?
Yes. Luckily, there is new tech out there that brings the same censorship benefits to the mod files themselves, though not necessarily at the same level or power considering these would be much larger files than a normal post would be.
At some point, we'll be utilizing and implementing something called Blossom, and with that implementation, creators would simply drag and drop their fields into the mod submission page and have that mod file (a .zip for example) and have it uploaded to one or more Blossom servers, where it would be packaged and signed using the creator's public key/address, and that file would now be identifiable and verifiable, where people can confirm that it's a file that came from you directly. That same file can potentially be backed up by fans who want to help you out, along with having a backup of the files yourself on your PC, home server, or rented server.
Let's say that your server host doesn't want to provide you with service anymore and has deleted your mod file. What will happen when someone clicks the download button on the mod page is that it'll attempt to search for that same file, since it's identifiable and verifiable by its unique ID, which was created using the creator's signature, searching for it on multiple different available Blossom servers, and brings it back to the user to download it. From the user's perspective, it'd behave normally where they'd just wait for the download to start and finish.
What does that result in? Mod files are now censorship-resistant too.
-
 @ f4bf1fb5:b428f8d5
2024-11-20 17:05:05
@ f4bf1fb5:b428f8d5
2024-11-20 17:05:05On DEG Mods, mod creators and enjoyers can benefit from tips, allowing them to earn money directly from those who appreciate their work or comments, and 100% of what's tipped goes to the one being tipped (excluding the processing fee of the transaction, which is extremely negligible). We don't take any percentage of this process, unless you choose to and at whichever amount you like.
Did you discover a mod that you found enjoyable, useful, or intriguing, and you'd like to show your appreciation with a $10 tip? You can do that. Choose to give 100% of your tip directly to the creator, or opt for a 90% share for them, with the remaining 10% supporting DEG Mods. You can also reverse the split if you prefer. It's entirely up to you how you'd like to allocate the tip.
The elephant in the room
Yes, we're using Bitcoin as the main currency and monetary system on the site, and we're aware of the general public's perception of Bitcoin and the general Cryptocurrency space. We have pretty solid reasons why we're utilizing Bitcoin as the monetary infrastructure for DEG Mods instead of traditional payment systems with fiat currency, like USD/EUR, and the banking system, like Visa or Mastercard.
DEG Mods is built around the idea of censorship-resistance and being permissionless, not just anti-censorship, with that in mind, we didn't want to use a system, and in this case a monetary system, where some third party can come in and threat the site, its users and creators, to self-censor or else suffer the consequences of everyone's money frozen, stolen, or not being able to send or receive. There are many examples of such cases.
We wanted to use something where people actually own their money, not have it controlled by anyone, and have people freely transact with anyone they want, whenever they want, with whichever amount they want to utilize, and not worry about any kind of censorship.
That's why why we went with Bitcoin, with the utilization of the Lightning Network. All of this is possible with it. And we didn't go with any other Cryptocurrency, not even create our own currency and massively benefit from it, because we wanted to use the most trusted, verifiably sound, and strongest currency in the world that's the most censorship-resistant one out there, and not a potential one where people would have a higher chance of thinking that its a scam. That's why, generally speaking, many differentiate between 'Bitcoin' and 'Crypto'.
Properly used, you completely own your money, and nobody can take it away from you or stop you from transacting with others. Now, let's get back on topic.
How to set up and enable getting tips
You need to download and install a Bitcoin Lightning Wallet app (suggestions: Lifpay or Wallet of Satoshi) on your mobile device, where where it supports and provides you with a Lightning address. Once you have obtain such an address, you can go ahead and add that to the 'Lightning Address' field in the profile settings page on DEG Mods.
After that, save/publish your changes and you're done. People can now tip you directly on your profile or tip you via your mod posts.
How to exchange your tipped Bitcoin to other currencies like USD/EUR
So you got tipped a few times and feel like you want to exchange what you've received so far into other currencies to spend them. We won't have a full-blown guide on this, at least not now, but the general idea is that you'd go to an exchange site/app (Suggestion: Binance, or if you're in the USA then CashApp or Strike might work better for you), send them there, and have them exchanged there to whatever currency you like, then withdraw it to your bank or payment service that you use (or keep them there if its already the payment system you use already).
You can also go to physical exchange stores if they support the exchange of that currency in your country.
How to tip creators and other users
As a user that wants to tip creators or other users, you'd do that by first having a Bitcoin Lighting Wallet (similar suggestions as shared above), and then you'd need to fill that up, which is basically the reverse process of above, and once you have an amount of Bitcoin (or 'Sats', think 'Cents') in your Wallet app, you can now go ahead and start tipping creators or other users.
You tip others by tapping on the lightning icon you'll see throughout the site, either for a comment, a profile, or a mod post next to the reaction buttons, which will trigger a popup asking you to enter an amount in Sats and then you'd generate the QR code. In your Wallet app, tap the send button and scan that QR and send away. Done.
Keep in mind that other users or creators might tip you, so you don't necessarily have to go through that process of exchanging traditional currencies to Bitcoin/sats, so its definitely worth at least obtaining a Bitcoin Lightning Address and adding it your 'account' here on DEG Mods, in the off chance that someone tips you when you comment on a post for example. Why leave money on the table, as they say.
Questions and Answers
We'll continue updating this blog post when new information comes along, but here are some questions and answers regarding this topic.
Did you really have to use Bitcoin/Crypto? Why couldn't you have PayPay, Stripe, or some other traditional payment method?
This is answered at the start of this post, but in gist: So we, creators, and users, aren't screwed over and be forced to censor ourselves.
Do I have to use Bitcoin?
No, you can use DEG Mods without ever touching it, and you can also add your own payment links (like PayPal, CashApp, Kofi, Patreon, etc) in your profile (we'll be adding a linktree-like system at some point to make this process easy), and people can easily find those link and tip you there, though those tip buttons are only for Bitcoin.
Will there be more ways to get money later, or is it just tipping mod posts and profiles?
Yes, there'll be more ways for creators to acquire money from users in the future, for reasons other than 'thank you creating this mod'.
-
 @ f4bf1fb5:b428f8d5
2024-11-14 19:15:23
@ f4bf1fb5:b428f8d5
2024-11-14 19:15:23As some of you might be aware, we can't take down mod posts/pages or ban creators' accounts on DEG Mods, as we've built the site on top of the Nostr protocol. With that said, a lot of people are concerned with seeing a malicious posts on the site, like spam, scams, posts with viruses, and illegal content, and other worries like not wanting to see specific content. People are worried on how we'd be handling all of these issues as we claim censorship-resistance.
This post is to help showcase and explain how we'll be handling content moderation on the site, while maintaining the site's censorship-resistant and permissionless nature.
Reporting and blocking
The first thing that can be done, in regards to moderation, is for users to report mod posts (or other type of posts). Reporting would result in us having a look at said reported post and determine if we'd block it or not.
Blocking it means that it will be hidden from initial view on the website, yet it'd still be accessible if someone has the link, or accessible on other sites.
Illegal content
In regards to illegal content, we'd essentially do the same thing as mentioned above, and at that point the relevant authorities would need to handle it from then on, as they try to find the perpetrator and prosecute them.
Web of Trust (WoT)
There will be, if not already, an near automated moderation system applied almost site wide, which would handle most of the leg work. This system is called Web of Trust, where it works by showing content published by users who we have followed, and their tree of followers (up to a point that we'd determine).
In essence, the natural behavior of users using the site, from mod creators to enjoyers, like publishing mods, commenting, reacting, publishing short posts, writing update posts or news/announcements, following whoever they like, not following who they don't like and/or blocking those who publishing malicious posts, would act as a moderation layer for for themselves and everybody else. Of course, this means that not everyone will necessarily be visible on the site initially as they start, so that's why everyone is encouraged to interact with each other, follow who you like, block bad faith actors, and so on. Everything is interconnected with each other to create a very efficient, effective, and safe viewing/usage experience on the site.
As we mentioned initially, we'll also maintain our claims of censorship-resistance by providing a toggle to remove the site's WoT filter, including the user's WoT, if they want to see almost everything. This gives everyone a method and chance to be seen, regardless of this moderation layer.
Individual moderation tools
Each individual user on the site has the ability to block a mod posts (or any other type of posts) on the site, as well as whole accounts and their posts.
As we mentioned briefly above, each user will also have their own WoT preference, to see posts of the people they trust, as well as their follows, and so on.
Various systems and designs
We'll be introducing various different systems/designs that would help with general moderation of the site from the user's perspective and exploration of the site. As an example, if a mod post won't include a malware scan report of the mod files (and we'll see if we can make this an automated, then there'd be a visible note around it to indicate that there hasn't been a scan done for it and advise users to be careful of malware).
Questions and answers
Here are a few questions and answers related to this topic. We'd update this post as new info comes along.
Do you allow X or Y type of content?
As long as its a mod (specially cases were non-mods wouldn't be subject to moderation), is legal, not directly harmful (malware, scam), and isn't spam, then you should be fine.
Does fiction equal fiction?
Yes.
-
 @ f4bf1fb5:b428f8d5
2024-11-14 13:05:02
@ f4bf1fb5:b428f8d5
2024-11-14 13:05:02A modder that goes by the name of "welintron" created a mod for Tomb Raider I-III on PC called "Remove Misinformative Warning", one that removes the developers' (Crystal Dynamic) message about the game being supposedly offensive.
The mod was uploaded to one of the popular mod hosting sites at the time, however, staff of said site has removed the mod and banned its creator.
This is an old piece of news as of the time of writing this post, and the purpose of writing it is to remind people of what's being banned, as well as keeping a log for ourselves, to know which mod creator to reach out to in the future, to introduce them to DEG Mods.
Since DEG Mods isn't out yet and you're wondering where you can download it, someone has supposedly uploaded the file on ModDB (be safe!).
-
 @ 3cea4806:10fe3f40
2024-11-12 21:24:18
@ 3cea4806:10fe3f40
2024-11-12 21:24:18testA looong
-
 @ 6e24af77:b3f1350b
2024-11-12 18:53:21
@ 6e24af77:b3f1350b
2024-11-12 18:53:215
-
 @ d830ee7b:4e61cd62
2025-01-08 07:56:25
@ d830ee7b:4e61cd62
2025-01-08 07:56:25การเผชิญหน้า (The Collision Point)
กลางปี 2017 ที่ร้านคราฟท์เบียร์เล็ก ๆ ในย่านเกาะเกร็ด นนทบุรี อากาศร้อนจนเครื่องปรับอากาศ (ที่ยังไม่มี) ในร้านทำงานหนักแทบไหม้ "แจ๊ก กู้ดเดย์" (Jakk Goodday) นั่งลงบนเก้าอี้ไม้ที่เจ้าของร้านกันไว้ให้เป็นประจำ ราวกับเขาเป็นลูกค้าขาประจำระดับวีไอพี
กลิ่นกาแฟคั่ว ลอยผสมกับไอความร้อนจากนอกหน้าต่าง (ผิดร้านหรือเปล่า?) เกิดเป็นบรรยากาศขมติดปลายลิ้นชวนให้คนจิบแล้วอยากถอนใจ
เขาเหลือบมองออกไปนอกหน้าต่าง.. เห็นแสงแดดแผดเผาราวกับมันรู้ว่าสงคราม Blocksize กำลังคุกรุ่นขึ้นอีกครั้ง

บรรยากาศนอกหน้าต่างกับใน ฟอรัม Bitcointalk ช่างเหมือนกันจนน่าขนลุก มันร้อนแรง ไร้ความปรานี
แจ๊กเปิดแล็ปท็อป กดเข้าเว็บฟอรัม พอเสียงแจ้งเตือน “—ติ๊ง” ดังขึ้น คิ้วของเขาก็ขมวดเล็กน้อย คล้ายได้กลิ่นดินปืนกลางสนามรบ
“โรเจอร์ แวร์ (Roger Ver) ไลฟ์เดือดลั่นเวที!” “ปีเตอร์ วูเล (Pieter Wuille) โต้กลับเรื่อง SegWit!” “Hard Fork ใกล้ถึงจุดปะทะแล้ว!”
แจ๊กคลิกเข้าไปในลิงก์ของไลฟ์ทันที เหมือนมือของเขาไม่ต้องการคำสั่งจากสมอง ความคุ้นเคยกับเหตุการณ์แบบนี้บอกเขาว่า นี่ไม่ใช่ดีเบตธรรมดา แต่มันอาจเปลี่ยนอนาคตของ Bitcoin ได้จริง ๆ
เห็นแค่พาดหัวสั้น ๆ แต่ความตึงเครียดก็ชัดเจนขึ้นเรื่อย ๆ ทุกข้อความเหมือนสุมไฟใส่ใจกองหนึ่งที่พร้อมระเบิดได้ทุกเมื่อ
โทรศัพท์ของแจ๊กดังพร้อมปรากฏชื่อ แชมป์ ‘PIGROCK’ ลอยขึ้นมา เขาหยิบขึ้นมารับทันที
“ว่าไงวะแชมป์… มีอะไรด่วนหรือเปล่า?” น้ำเสียงแจ๊กฟังดูเหมือนง่วง ๆ แต่จริง ๆ เขาพร้อมจะลุกมาวิเคราะห์สถานการณ์ให้ฟังทุกเมื่อ
“พี่แจ๊ก.. ผมอ่านดีเบตเรื่อง SegWit ในฟอรัมอยู่ครับ บางคนด่าว่ามันไม่ได้แก้ปัญหาจริง ๆ บ้างก็บอกถ้าเพิ่ม Blocksize ไปเลยจะง่ายกว่า... ผมเลยสงสัยว่า Hard Fork ที่เค้าพูดถึงกันนี่คืออะไร ใครคิดอะไรก็ Fork กันได้ง่าย ๆ เลยเหรอ"
"แล้วถ้า Fork ไปหลายสาย สุดท้ายเหรียญไหนจะเป็น ‘Bitcoin ที่แท้จริง’ ล่ะพี่?”
“แล้วการ Fork มันส่งผลกับนักลงทุนยังไงครับ? คนทั่วไปอย่างผมควรถือไว้หรือขายหนีตายดีล่ะเนี่ย?”
แจ๊กยิ้มมุมปาก ชอบใจที่น้องถามจี้จุด
“เอางี้… การ Fork มันเหมือนแบ่งถนนออกเป็นสองสาย ใครชอบกติกาเก่าก็วิ่งถนนเส้นเก่า ใครอยากแก้กติกาใหม่ก็ไปถนนเส้นใหม่"
"แต่ประเด็นคือ... นี่ไม่ใช่เรื่องเล็ก ๆ เพราะมีผลต่ออัตลักษณ์ของ Bitcoin ทั้งหมดเลยนะมึง—ใครจะยอมปล่อยผ่านง่าย ๆ”
"คิดดูสิ ถ้าครั้งนี้พวกเขา Fork จริง มันอาจไม่ได้เปลี่ยนแค่เครือข่าย แต่เปลี่ยนวิธีที่คนมอง Bitcoin ไปตลอดกาลเลยนะ"
"แล้วใครมันจะอยากลงทุนในระบบที่แตกแยกซ้ำแล้วซ้ำเล่าวะ?"
“งั้นหมายความว่าตอนนี้ก็มีสองแนวใหญ่ ๆ ชัวร์ใช่ไหมครับ?” แชมป์ถามต่อ
“ฝั่ง โรเจอร์ แวร์ ที่บอกว่าต้องเพิ่ม Blocksize ให้ใหญ่จุใจ กับฝั่งทีม Core อย่าง ปีเตอร์ วูเล ที่ยืนยันต้องใช้ SegWit ทำให้บล็อกเบา ไม่กระทบการกระจายอำนาจ?”
“ใช่เลย” แจ๊กจิบกาแฟดำเข้ม ๆ ผสมน้ำผึ้งไปหนึ่งอึก
“โรเจอร์นี่เขาเชื่อว่า Bitcoin ต้องเป็นเงินสดดิจิทัลที่ใช้จ่ายไว ค่าธรรมเนียมไม่แพง ส่วนปีเตอร์กับ Bitcoin Core มองว่าการเพิ่มบล็อกเยอะ ๆ มันจะไปฆ่า Node รายย่อย คนไม่มีทุนก็รัน Node ไม่ไหว สุดท้าย Bitcoin จะกลายเป็นระบบกึ่งรวมศูนย์ ซึ่งมันผิดหลักการเดิมของ ซาโตชิ ไงล่ะ”
“ฟังแล้วก็ไม่ใช่เรื่องง่ายนะพี่… งั้นที่ผมได้ยินว่า จิฮั่น อู๋ (Jihan Wu) เจ้าของ Bitmain ที่ถือ Hashrate เกินครึ่งนี่ก็มาอยู่ฝั่งเดียวกับโรเจอร์ใช่ไหม?"
"เพราะยิ่งบล็อกใหญ่ ค่าธรรมเนียมยิ่งเพิ่ม นักขุดก็ได้กำไรสูงขึ้นใช่ป่ะ?”
“ไอ้เรื่องกำไรก็ส่วนหนึ่ง...” แจ๊กถอนหายใจ
“แต่ที่สำคัญกว่านั้นคืออำนาจต่อรอง… ตอนประชุมลับที่ฮ่องกงเมื่อปีที่แล้ว พี่เองก็ถูกชวนให้เข้าไปในฐานะคนกลาง เลยเห็นภาพน่าขนลุกอยู่หน่อย ๆ"
"จิฮั่นนั่งไขว่ห้างด้วยสีหน้ามั่นใจมาก ด้วย Hashrate ราว 60% ของโลก สั่งซ้ายหันขวาหันเหมือนเป็นแม่ทัพใหญ่ได้เลย พอโรเจอร์ก็ไฟแรงอยู่แล้ว อยากให้ Bitcoin ครองโลกด้วยวิธีของเขา สองคนนี่จับมือกันทีจะเขย่าชุมชน Bitcoin ได้ทั้งกระดาน”
"พี่รู้สึกเหมือนนั่งอยู่ในศึกชิงบัลลังก์ยุคใหม่ คนหนึ่งยึดพลังขุด คนหนึ่งยึดความศรัทธาในชื่อ Bitcoin แต่สิ่งที่พี่สงสัยในตอนนั้นคือ… พวกเขาสู้เพื่อใครกันแน่?"
แชมป์เงียบไปครู่เหมือนกำลังประมวลผล “แล้วตอนนั้นพี่คิดยังไงบ้างครับ? รู้สึกกลัวหรือว่ายังไง?”
“จะไม่กลัวได้ไง!” แจ๊กหัวเราะแห้ง ๆ แวบหนึ่งก็นึกถึงสีหน้าที่ยิ้มเยาะของทั้งคู่ตอนประกาศความพร้อมจะ Fork
“พี่อดคิดไม่ได้ว่าถ้า Core ยังไม่ยอมขยายบล็อก พวกนั้นจะลากนักขุดทั้งกองทัพแฮชเรตไปทำเครือข่ายใหม่ให้เป็น ‘Bitcoin สายใหญ่’ แล้วทิ้งเครือข่ายเดิมให้ซวนเซ"
"แค่คิดก็นึกถึงสงครามกลางเมืองในหนังประวัติศาสตร์แล้วน่ะ.. แตกเป็นสองฝ่าย สุดท้ายใครแพ้ใครชนะ ไม่มีใครทำนายได้จริง ๆ”

พูดจบ.. เขาเปิดฟอรัมดูไลฟ์ดีเบตจากงานในปี 2017 ต่อ โรเจอร์ แวร์ กำลังพูดในโทนร้อนแรง
“Bitcoin ไม่ใช่ของคนรวย! ถ้าคุณไม่เพิ่ม Blocksize คุณก็ทำให้ค่าธรรมเนียมพุ่งจนคนธรรมดาใช้ไม่ได้!”
ขณะเดียวกัน ปีเตอร์ วูเล่ ยืนอยู่ฝั่งตรงข้าม สีหน้าเยือกเย็นราวกับตั้งรับมานาน “การเพิ่มบล็อกคือการทำลายโครงสร้าง Node รายย่อยในระยะยาว แล้วมันจะยังเรียกว่ากระจายอำนาจได้หรือ?”
"ถ้าคุณอยากให้ Bitcoin เป็นของคนรวยเพียงไม่กี่คน ก็เชิญขยายบล็อกไปเถอะนะ แต่ถ้าอยากให้มันเป็นระบบที่คนทุกระดับมีส่วนร่วมจริง ๆ ..คุณต้องฟังเสียง Node รายเล็กด้วย" ปีเตอร์กล่าว
เสียงผู้คนในงานโห่ฮากันอย่างแตกเป็นสองฝ่าย บ้างก็เชียร์ความตรงไปตรงมาของโรเจอร์ บ้างก็เคารพเหตุผลเชิงเทคนิคของปีเตอร์
ข้อความจำนวนมหาศาลในฟอรัมต่างโหมกระพือไปต่าง ๆ นานา มีทั้งคำด่าหยาบคายจนแจ๊กต้องเบือนหน้า ตลอดจนการวิเคราะห์ลึก ๆ ถึงอนาคตของ Bitcoin ที่อาจไม่เหมือนเดิม
ในระหว่างนั้น.. แชมป์ส่งข้อความ Discord กลับมาอีก
“พี่ ถ้า Fork จริง ราคาจะป่วนแค่ไหน? ที่เขาว่าคนถือ BTC จะได้เหรียญใหม่ฟรี ๆ จริงไหม? ผมกลัวว่าถ้าเกิดแบ่งเครือข่ายไม่รู้กี่สาย ตลาดอาจมั่วจนคนหายหมดก็ได้ ใช่ไหมครับ?”
"แล้วถ้าเครือข่ายใหม่ล้มเหลวล่ะครับ? จะส่งผลอะไรต่อชุมชน Bitcoin เดิม?"
"ไอ้แชมป์มึงถามรัวจังวะ!?" แจ๊กสบถเพราะเริ่มตั้งรับไม่ทัน
“ก็ขึ้นกับตลาดจะเชื่อว่าสายไหนเป็น ‘ของจริง’ อีกนั่นแหละ” แจ๊กพิมพ์กลับ
“บางคนถือไว้เผื่อได้เหรียญใหม่ฟรี บางคนขายหนีตายก่อน"
"พี่เองก็ยังไม่กล้าการันตีเลย แต่ที่แน่ ๆ สงครามนี้ไม่ได้มีแค่ผลกำไร มันกระทบศรัทธาของชุมชน Bitcoin ทั้งหมดด้วย"
"ถ้าชาวเน็ตเลิกเชื่อมั่น หรือคนนอกมองว่าพวกเราทะเลาะกันเองเหมือนเด็กแย่งของเล่น ต่อให้ฝั่งไหนชนะ ก็อาจไม่มีผู้ใช้เหลือให้ฉลอง”
แล้วสายตาแจ๊กก็ปะทะกับกระทู้ใหม่ที่เด้งขึ้นมาบนหน้าฟอรัม
“โรเจอร์ แวร์ ประกาศ: ถ้าไม่เพิ่ม Blocksize เราจะฟอร์กเป็น Bitcoin ที่แท้จริง!”
ตัวหนังสือหนาแปะอยู่ตรงนั้นส่งแรงสั่นสะเทือนราวกับจะดึงคนในวงการให้ต้องเลือกข้างกันแบบไม่อาจกลับหลังได้
แจ๊กเอื้อมมือปิดแล็ปท็อปช้า ๆ คล้ายยอมรับความจริงว่าหนทางประนีประนอมอาจไม่มีอีกแล้ว..
“สงครามนี่คงใกล้ระเบิดเต็มทีล่ะนะ” เขาลุกจากเก้าอี้ สะพายเป้ พึมพำกับตัวเองขณะมองกาแฟดำที่เหลือครึ่งแก้ว “ถ้าพวกเขาฟอร์กจริง โลกคริปโตฯ ที่เราเคยรู้จักอาจไม่มีวันเหมือนเดิมอีกต่อไป”
เขามองออกไปนอกหน้าต่าง แสงแดดที่แผดเผาราวกับกำลังบอกว่า.. อนาคตของ Bitcoin อยู่ในจุดที่เส้นแบ่งระหว่างชัยชนะกับความล่มสลายเริ่มพร่าเลือน... และอาจไม่มีทางย้อนกลับ
ก่อนเดินออกจากร้าน เขากดส่งข้อความสั้น ๆ ถึงแชมป์
“เตรียมใจกับความปั่นป่วนไว้ให้ดี ไม่แน่ว่าเราอาจจะได้เห็น Bitcoin แตกเป็นหลายสาย.. ใครจะอยู่ใครจะไปไม่รู้เหมือนกัน แต่เรื่องนี้คงไม่จบง่าย ๆ แน่”
แจ๊กผลักประตูออกไปพบกับแดดจัดที่เหมือนแผดเผากว่าเดิม พายุร้อนไม่ได้มาแค่ในรูปความร้อนกลางกรุง แต่มาในรูป “สงคราม Blocksize” ที่พร้อมจะฉีกชุมชนคริปโตออกเป็นฝักฝ่าย และอาจลามบานปลายจนกลายเป็นศึกประวัติศาสตร์
ทว่าสิ่งที่ค้างคาใจกลับเป็นคำถามนั้น…
เมื่อเครือข่ายแบ่งเป็นหลายสายแล้ว เหรียญไหนจะเป็น Bitcoin จริง?
หรือบางที... ในโลกที่ใครก็ Fork ได้ตามใจ เราจะไม่มีวันได้เห็น “Bitcoin หนึ่งเดียว” อีกต่อไป?
คำถามที่ไม่มีใครตอบได้ชัดนี้ส่องประกายอยู่ตรงปลายทาง ราวกับป้ายเตือนว่า “อันตรายข้างหน้า” และคนในชุมชนทั้งหมดกำลังจะต้องเผชิญ…
โดยไม่มีใครมั่นใจเลยว่าจะรอด หรือจะแตกสลายไปก่อนกันแน่...

สองเส้นทาง (The Forked Path)
กลางปี 2017 ท้องฟ้าเหนือบุรีรัมย์ยังคงคุกรุ่นด้วยไอแดดและความร้อนแรงของสงคราม Blocksize แจ๊ก กู้ดเดย์ ก้าวเข้ามาในคาเฟ่เล็ก ๆ แห่งหนึ่งในย่านเทศบาลด้วยสีหน้าครุ่นคิด เขาพยายามมองหามุมสงบสำหรับนั่งตั้งหลักในโลกความเป็นจริง ก่อนจะจมดิ่งสู่สงครามในโลกดิจิทัลบนฟอรัม Bitcointalk อีกครั้ง
กลิ่นกาแฟคั่วเข้มลอยกระทบจมูก แจ๊กสั่งกาแฟดำแก้วโปรดแล้วปลีกตัวมาที่โต๊ะริมกระจก กระจกบานนั้นสะท้อนแสงอาทิตย์จัดจ้า ราวกับจะบอกว่าวันนี้คงไม่มีใครหนีความร้อนที่กำลังแผดเผา ทั้งในอากาศและในชุมชน Bitcoin ได้พ้น
เขาเปิดแล็ปท็อปขึ้น ล็อกอินเข้า Bitcointalk.org ตามเคย ข้อความและกระทู้มากมายกระหน่ำแจ้งเตือน ไม่ต่างอะไรจากสมรภูมิคำพูดที่ไม่มีวันหลับ “Hong Kong Agreement ล้มเหลวจริงหรือ?” “UASF คือปฏิวัติโดย Node?” เหล่านี้ล้วนสะท้อนความไม่แน่นอนในชุมชน Bitcoin ที่ตอนนี้ ดูคล้ายจะถึงจุดแตกหักเต็มที...
“ทั้งที่ตอนนั้นเราก็พยายามกันแทบตาย…” แจ๊กพึมพำ มองจอด้วยสายตาเหนื่อยใจพร้อมภาพความทรงจำย้อนกลับเข้าในหัว เขายังจำการประชุมที่ฮ่องกงเมื่อต้นปี 2016 ได้แม่น ยามนั้นความหวังในการประนีประนอมระหว่าง Big Block และ Small Block ดูเป็นไปได้ หากแต่กลายเป็นละครฉากใหญ่ที่จบลงโดยไม่มีใครยอมถอย...
...การประชุม Hong Kong Agreement (2016)
ภายในห้องประชุมหรูของโรงแรมใจกลางย่านธุรกิจฮ่องกง บรรยากาศตึงเครียดยิ่งกว่าการเจรจาสงบศึกในสมัยโบราณ
โรเจอร์ แวร์ ยืนเสนอว่า “การเพิ่ม Blocksize สำคัญต่ออนาคตของ Bitcoin — เราอยากให้คนทั่วไปเข้าถึงได้โดยไม่ต้องจ่ายค่าธรรมเนียมแพง ๆ”
“จิฮั่น อู๋ (Jihan Wu)” จาก Bitmain นั่งฝั่งเดียวกับโรเจอร์ คอยเสริมว่าการเพิ่มบล็อกคือโอกาสสำหรับนักขุด และหากทีม Core ไม่ยอม พวกเขาก็พร้อม “ดัน Fork” ขึ้นได้ทุกเมื่อ ด้วย Hashrate มหาศาลที่พวกเขาคุมไว้
ฝั่ง ปีเตอร์ วูเล (Pieter Wuille) กับ เกร็ก แมกซ์เวลล์ (Greg Maxwell) จาก Bitcoin Core เถียงกลับอย่างใจเย็นว่า “การขยายบล็อกอาจดึงดูดทุนใหญ่ ๆ แล้วไล่ Node รายย่อยออกไป ชุมชนอาจไม่เหลือความกระจายอำนาจอย่างที่ Satoshi ตั้งใจ”
สุดท้าย บทสรุปที่เรียกว่า Hong Kong Agreement ลงนามได้ก็จริง แต่มันกลับเป็นแค่ลายเซ็นบนกระดาษที่ไม่มีฝ่ายไหนเชื่อใจใคร

แจ๊กเบือนสายตาออกนอกหน้าต่าง สังเกตเห็นผู้คนเดินขวักไขว่ บ้างก็ดูรีบร้อน บ้างเดินทอดน่องเหมือนว่างเปล่า นี่คงไม่ต่างอะไรกับชาวเน็ตในฟอรัมที่แบ่งฝ่ายกันใน “สงคราม Blocksize” อย่างไม่มีทีท่าจะหยุด
แค่ไม่กี่นาที... เสียงโทรศัพท์ก็ดังขึ้น ชื่อ แชมป์ ‘PIGROCK’ โชว์หราเต็มจออีกครั้ง
“ว่าไงเจ้าแชมป์?” แจ๊กกรอกเสียงในสายด้วยอารมณ์เหนื่อย ๆ ทว่าพร้อมจะอธิบายเหตุการณ์ตามสไตล์คนที่ชอบครุ่นคิด
“พี่แจ๊ก.. ผมเข้าใจแล้วว่าการประชุมฮ่องกงมันล้มเหลว ตอนนี้ก็มีคนแยกเป็นสองขั้ว Big Block กับ SegWit แต่ผมเจออีกกลุ่มในฟอรัมเรียกว่า UASF (User-Activated Soft Fork) ที่เหมือนจะกดดันพวกนักขุดให้ยอมรับ SegWit..."
"อยากรู้ว่าตกลง UASF มันสำคัญยังไงครับ? ทำไมใคร ๆ ถึงเรียกว่าเป็น การปฏิวัติโดย Node กัน?”
แจ๊กอมยิ้มก่อนจะวางแก้วกาแฟลง พูดด้วยน้ำเสียงจริงจังกว่าเดิม “UASF น่ะหรือ? มันเปรียบได้กับการที่ ‘ชาวนา’ หรือ ‘ประชาชนตัวเล็ก ๆ’ ออกมาประกาศว่า ‘ฉันจะไม่รับบล็อกของนักขุดที่ไม่รองรับ SegWit นะ ถ้าแกไม่ทำตาม ฉันก็จะตัดบล็อกแกทิ้ง!’ เสมือนเป็นการปฏิวัติที่บอกว่าแรงขุดมากแค่ไหนก็ไม่สำคัญ ถ้าคนรัน Node ไม่ยอม… เชนก็เดินต่อไม่ได้”
“โห… ฟังดูแรงจริง ๆ พี่ แล้วถ้านักขุดไม่ร่วมมือ UASF จะเกิดอะไรขึ้น?” แชมป์ถามต่อเสียงสั่นนิด ๆ
“ก็อาจเกิด ‘Chain Split’ ยังไงล่ะ"
"แยกเครือข่ายเป็นสองสาย สุดท้ายเครือข่ายเดิม กับเครือข่ายใหม่ที่รองรับ SegWit ไม่ตรงกัน คนอาจสับสนหนักยิ่งกว่า Hard Fork ปกติด้วยซ้ำ"
"แต่นั่นแหละ... มันแสดงพลังว่าผู้ใช้ทั่วไปก็มีสิทธิ์กำหนดทิศทาง Bitcoin ไม่ได้น้อยไปกว่านักขุดเลย”
“เข้าใจแล้วครับพี่… เหมือน การปฏิวัติโดยประชาชนตาดำ ๆ ที่จับมือกันค้านอำนาจทุนใหญ่ใช่ไหม?” แชมป์หยุดครู่หนึ่ง “ผมเคยคิดว่า Node รายย่อยน้อยรายจะไปสู้อะไรไหว แต่ตอนนี้ดูท่าจะเปลี่ยนเกมได้จริงว่ะพี่…”
“ใช่เลย” แจ๊กตอบ
“นี่เป็นความพิเศษของ Bitcoin ที่บอกว่า ‘เราคุมเครือข่ายร่วมกัน’ แม้แต่ Bitmain ที่มี Hashrate มากกว่า 50% ก็หนาวได้ถ้าผู้ใช้หรือ Node รายย่อยรวมพลังกันมากพอ”
แชมป์ฟังด้วยความตื่นเต้นปนกังวล “แล้วแบบนี้ เรื่อง SegWit กับ Blocksize จะจบยังไงครับ? เห็นข่าวว่าถ้านักขุดโดนกดดันมาก ๆ คนอย่าง จิฮั่น อู๋ อาจออกไปสนับสนุน Bitcoin Cash ที่จะเปิดบล็อกใหญ่”
แจ๊กเลื่อนดูฟีดข่าวในฟอรัม Bitcointalk อีกครั้ง ก็เห็นพาดหัวชัด ๆ
“Bitmain ประกาศกร้าวพร้อมหนุน BCH เต็มพิกัด!”
เขาถอนหายใจเฮือกหนึ่ง “ก็ใกล้เป็นจริงแล้วล่ะ… โรเจอร์ แวร์ เองก็ผลักดัน BCH ว่าคือ Bitcoin แท้ที่ค่าธรรมเนียมถูก ใช้งานได้จริง ส่วนฝั่ง BTC ที่ยึดเอา SegWit เป็นหลัก ก็ไม่ยอมให้ Blocksize เพิ่มใหญ่เกินจำเป็น.."
"ต่างคนต่างมีเหตุผล... แต่อุดมการณ์นี่คนละทางเลย”
“แล้วพี่คิดว่าใครจะเป็นฝ่ายชนะครับ?”
“เฮ้ย.. มึงถามยากไปหรือเปล่า” แจ๊กหัวเราะหึ ๆ “ทุกคนมีโอกาสได้หมด และก็มีโอกาสพังหมดเหมือนกัน ถ้า UASF กดดันนักขุดให้อยู่กับ Core ได้ พวกเขาอาจยอมแพ้ แต่ถ้า Bitmain เทใจไป BCH นักขุดรายใหญ่คนอื่น ๆ ก็คงตาม"
"แล้วถ้าฝั่ง BCH เริ่มได้เปรียบ... อาจดึงคนไปเรื่อย ๆ สุดท้ายจะเหลือไหมล่ะฝั่ง SegWit ตัวจริง?”
“งั้น Node รายย่อยจะยืนอยู่ตรงไหนล่ะครับพี่?” แชมป์ถามอย่างหนักใจ
“Node รายย่อยและชุมชนผู้ใช้นี่แหละ คือ ตัวแปรชี้ขาด ทุกวันนี้คนกลุ่ม UASF พยายามโชว์พลังว่าตัวเองมีสิทธิ์ตั้งกติกาเหมือนกัน ไม่ใช่แค่นักขุด"
"อย่างที่บอก.. มันคือการ ‘ลุกขึ้นปฏิวัติ’ โดยชาวนา ต่อสู้กับเจ้าที่ที่ถือ ‘แฮชเรต’ เป็นอาวุธ”
แจ๊กตบบ่าตัวเองเบา ๆ ก่อนจะหัวเราะเล็กน้อย
“นี่แหละความมันของ Bitcoin ไม่มีเจ้าไหนสั่งได้เบ็ดเสร็จจริง ๆ ทุกฝั่งต่างถือไพ่คนละใบ สงครามยังไม่รู้จะจบยังไง ถึงอย่างนั้นมันก็สะท้อนวิญญาณ ‘decentralization’ ที่แท้จริง กล้ายอมรับสิทธิ์ทุกฝ่ายเพื่อแข่งขันกันตามกติกา”

จู่ ๆ ในหน้าฟอรัมก็มีกระทู้ใหม่เด้งเด่น “Bitmain หนุน Bitcoin Cash ด้วย Hashrate กว่า 50%! สงครามเริ่มแล้ว?” ข้อความนั้นดังโครมครามเหมือนระเบิดลงกลางวง
แจ๊กนิ่งไปชั่วขณะ สัมผัสได้ถึงความปั่นป่วนที่กำลังปะทุขึ้นอีกครั้ง เหงื่อบางเบาซึมบนหน้าผากแม้อากาศในคาเฟ่จะเย็นฉ่ำ เขาหันมองโทรศัพท์ที่ยังค้างสายกับแชมป์ แล้วเอ่ยด้วยน้ำเสียงจริงจัง
“นี่ล่ะ.. จุดเริ่มของสองเส้นทางอย่างชัดเจน… บล็อกใหญ่จะไปกับ BCH ส่วน SegWit ก็อยู่กับ BTC แน่นอนว่าทั้งสองฝ่ายไม่คิดถอยง่าย ๆ นักขุดจะเลือกข้างไหน? Node รายย่อยจะยอมใคร?"
"เมื่อสงครามครั้งนี้นำไปสู่การแบ่งเครือข่าย ใครกันแน่จะเป็นผู้ชนะตัวจริง? หรืออาจไม่มีผู้ชนะเลยก็เป็นได้”
ปลายสายเงียบงัน มีแต่เสียงหายใจของแชมป์ที่สะท้อนความกังวลปนอยากรู้อย่างแรง
“พี่… สุดท้ายแล้วเรากำลังยืนอยู่บนรอยแยกที่พร้อมจะฉีกทุกอย่างออกเป็นชิ้น ๆ ใช่ไหมครับ?”
“อาจจะใช่ก็ได้... หรือถ้ามองอีกมุม อาจเป็นวัฏจักรที่ Bitcoin ต้องเจอเป็นระยะ ทุกคนมีสิทธิ์ Fork ได้ตามใจใช่ไหมล่ะ? ก็ขอให้โลกได้เห็นกันว่าชุมชนไหนแน่จริง” แจ๊กพูดทิ้งท้ายก่อนจะแย้มยิ้มเจือรอยอ่อนล้า
ภาพบนจอคอมพิวเตอร์ฉายกระทู้ถกเถียงกันไม่หยุด ประหนึ่งเวทีดีเบตที่ไม่มีวันปิดไฟ แจ๊กจิบกาแฟอึกสุดท้ายเหมือนจะเตรียมพร้อมใจก่อนเข้าสู่สนามรบครั้งใหม่ สงครามยังไม่จบ.. ซ้ำยังดูหนักข้อยิ่งขึ้นเรื่อย ๆ
เขาลุกขึ้นจากโต๊ะ ชำเลืองมองแสงแดดจัดจ้าที่สาดลงมาไม่หยุด เปรียบเหมือนไฟแห่งข้อขัดแย้งที่เผาผลาญทั้งชุมชน Bitcoin ไม่ว่าใครจะเลือกอยู่ฝั่งไหน กลุ่ม UASF, กลุ่ม Big Block, หรือ กลุ่ม SegWit ทางเดินข้างหน้าล้วนเต็มไปด้วยความไม่แน่นอน
“สุดท้ายแล้ว… เมื่อกระดานแบ่งเป็นสองเส้นทางอย่างเด่นชัด สงคราม Blocksize จะจบลงด้วยใครได้บทผู้ชนะ?"
"หรือบางที… มันอาจไม่มีผู้ชนะที่แท้จริงในระบบที่ใครก็ Fork ได้ตลอดเวลา”
คำถามนี้ลอยติดค้างอยู่ในบรรยากาศยามบ่ายที่ร้อนระอุ ชวนให้ใครก็ตามที่จับตาดูสงคราม Blocksize ต้องฉุกคิด
เมื่อไม่มีใครเป็นเจ้าของ Bitcoin อย่างสมบูรณ์ ทุกคนจึงมีสิทธิ์บงการและเสี่ยงต่อการแตกแยกได้ทุกเมื่อ แล้วท้ายที่สุด ชัยชนะ–ความพ่ายแพ้ อาจไม่ใช่จุดสิ้นสุดของโลกคริปโตฯ
แต่เป็นเพียงจุดเริ่มต้นของการวิวัฒน์ที่ไม่มีวันจบสิ้น…

เมาท์แถมเรื่อง UASF (User-Activated Soft Fork)
นี่สนามรบยุคกลางที่ดูเหมือนในหนังแฟนตาซี ทุกคนมีดาบ มีโล่ แต่จู่ ๆ คนตัวเล็กที่เราไม่เคยสังเกต—พวกชาวนา ช่างไม้ คนแบกน้ำ—กลับรวมตัวกันยกดาบบุกวังเจ้าเมือง พร้อมตะโกนว่า “พอเถอะ! เราก็มีสิทธิ์เหมือนกัน!”
มันอาจจะดูเวอร์ ๆ หน่อยใช่ไหมครับ?
แต่ในโลก Bitcoin ปี 2017 นี่คือสิ่งที่เกิดขึ้นในรูปแบบ “User-Activated Soft Fork” หรือ UASF การปฏิวัติด้วยพลังโหนด ซึ่งทำให้นักขุดยักษ์ใหญ่ตัวสั่นงันงกันมาแล้ว!
แล้ว UASF มันคืออะไรล่ะ?
“User-Activated Soft Fork” หรือเรียกย่อ ๆ ว่า “UASF” ไม่ใช่อัปเกรดซอฟต์แวร์สวย ๆ แต่เป็น “ดาบเล่มใหม่” ที่คนตัวเล็ก—หมายถึง โหนด รายย่อย—ใช้ต่อรองกับนักขุดรายใหญ่ โดยกติกาคือ.. ถ้านักขุดไม่ทำตาม (เช่น ไม่รองรับ SegWit) โหนดก็จะปฏิเสธบล็อกของพวกเขาอย่างไม่เกรงใจใคร
สมมุติว่าคุณคือโหนด..
คุณรันซอฟต์แวร์ Bitcoin คอยตรวจสอบธุรกรรม วันดีคืนดี คุณประกาศ “ต่อไปถ้าใครไม่รองรับ SegWit ฉันไม่ยอมรับบล็อกนะ!” นี่ล่ะครับ “UASF” ตัวเป็น ๆ
คำขวัญสุดฮิตของ UASF
“No SegWit, No Block”
หรือแปลว่าถ้าบล็อกไม่รองรับ SegWit ก็เชิญออกไปเลยจ้า..
มันเหมือนการที่ชาวนาโผล่มาตบโต๊ะอาหารท่านขุนว่า “นายใหญ่จะปลูกอะไรก็ปลูกไป แต่ไม่งั้นฉันไม่รับผลผลิตนายนะ!”
ความเชื่อมโยงกับ BIP 148
ถ้าจะพูดถึง UASF ต้องรู้จัก BIP 148 ไว้นิดนึง มันเปรียบเหมือน “ธงปฏิวัติ” ที่ตีตราว่าวันที่ 1 สิงหาคม 2017 คือเส้นตาย!
BIP 148 บอกไว้ว่า.. ถ้าถึงวันนั้นแล้วยังมีนักขุดหน้าไหนไม่รองรับ SegWit บล็อกที่ขุดออกมาก็จะถูกโหนดที่ใช้ UASF “แบน” หมด
ผลลัพธ์ที่ตั้งใจ นักขุดไม่อยากโดนแบนก็ต้องทำตาม UASF กล่าวคือ “นายต้องรองรับ SegWit นะ ไม่งั้นอด!”
หลายคนกลัวกันว่า “อ้าว ถ้านักขุดใหญ่ ๆ ไม่ยอมแล้วหันไปขุดสายอื่น จะไม่กลายเป็นแยกเครือข่าย (Chain Split) หรือ?”
ใช่ครับ.. มันอาจเกิดสงครามสายใหม่ทันทีไงล่ะ
ทำไม UASF ถึงสำคัญ?
ย้อนกลับไปก่อนปี 2017 Bitcoin มีปัญหาโลกแตกทั้งค่าธรรมเนียมแพง ธุรกรรมหน่วง บวกกับความขัดแย้งเรื่อง “จะเพิ่ม Blocksize ดีไหม?” ทางกลุ่มนักขุดรายใหญ่ (นำโดย Bitmain, Roger Ver ฯลฯ) รู้สึกว่า “SegWit ไม่ใช่ทางออกที่แท้จริง” แต่อีกฝั่ง (ทีม Core) ชี้ว่า “Blocksize ใหญ่มากไปจะรวมศูนย์นะ โหนดรายย่อยตายหมด”
UASF เลยโผล่มา เหมือนชาวนาตะโกนว่า
“หุบปากได้แล้วไอ้พวกที่สู้กัน! ถ้าพวกแกไม่รองรับ SegWit พวกข้า (โหนด) ก็จะไม่เอาบล็อกแก”
สาระก็คือ.. มันคือตัวบ่งชี้ว่าคนตัวเล็กอย่างโหนดรายย่อยก็มีพลังต่อรอง เป็นกลไกที่ดึงอำนาจจากมือทุนใหญ่กลับสู่มือชุมชน (Decentralization ที่แท้ทรู)
วิธีการทำงานของ UASF
ลองจินตนาการตาม..
-
การกำหนดเส้นตาย BIP 148 ประกาศไว้ “ถึงวันที่ 1 สิงหาคม 2017 ถ้านายยังไม่รองรับ SegWit โหนด UASF จะไม่รับบล็อกนาย”
-
ถ้าคุณเป็นนักขุด… คุณขุดบล็อกออกมา แต่ไม่ได้ตีธง “ฉันรองรับ SegWit” UASF โหนดเห็นปุ๊บ พวกเขาจะจับโยนทิ้งไปเลย
-
ผลกระทบ? นักขุดที่ไม่ยอมทำตามจะเจอปัญหา บล็อกที่ขุดออกมาไม่มีใครรับ—เสียแรงขุดฟรี
อาจเกิด Chain Split คือ แยกเครือข่ายเลย ถ้านักขุดเหล่านั้นไปตั้งสายใหม่
ความสำเร็จและความท้าทายของ UASF
ความสำเร็จ.. หลังการรวมพลังผู้ใช้ โหนดรายย่อยกดดันนักขุดได้ไม่น้อย จนกระทั่ง SegWit เปิดใช้งานจริงใน Bitcoin วันที่ 24 สิงหาคม 2017 ช่วยให้ธุรกรรมเร็วขึ้น แก้ Transaction Malleability และเปิดทางสู่ Lightning Network ในอนาคต
ความท้าทาย.. นักขุดบางค่ายไม่โอเค.. โดยเฉพาะ Bitmain ซึ่งคาดว่าจะสูญรายได้บางส่วน ก็นำไปสู่การสนับสนุน “Bitcoin Cash (BCH)” แยกสาย (Hard Fork) ของตัวเองตั้งแต่วันที่ 1 สิงหาคม 2017 นั่นเอง
ว่าแล้วก็เปรียบง่าย ๆ
UASF เหมือนปฏิบัติการยึดคฤหาสน์เจ้าเมืองมาเปิดให้ชาวบ้านเข้าอยู่ฟรี.. แต่อีกฝ่ายบอก
“งั้นฉันออกไปตั้งคฤหาสน์ใหม่ดีกว่า!”
บทเรียนสำคัญ UASF เป็นตัวอย่างชัดว่า “ผู้ใช้” หรือ โหนดรายย่อย สามารถสร้างแรงกดดันให้นักขุดต้องยอมเปลี่ยนได้จริง ๆ ไม่ใช่แค่ยอมรับเงื่อนไขที่ขุดกันมา
ผลกระทบระยะยาวหลังจากนั้นล่ะ?
SegWit ถูกใช้งาน ทำให้ค่าธรรมเนียมธุรกรรมลดลง (ช่วงหนึ่ง) เกิด Lightning Network เป็น Layer 2 สุเฟี้ยวของ Bitcoin เกิด BCH (Bitcoin Cash) เป็นสายแยกที่อ้างว่า Blocksize ใหญ่คือทางออก
สรุปแล้ว UASF ทำให้โลกได้รู้ว่า..
Bitcoin ไม่ใช่ของนักขุด หรือของฝ่ายพัฒนาใดฝ่ายเดียว แต่มันเป็นของทุกคน!
“Bitcoin เป็นของทุกคน”
ไม่มีใครมีอำนาจเบ็ดเสร็จ ไม่ว่าคุณจะถือ Hashrate มากแค่ไหน ถ้า Node ทั่วโลกไม่เอา ก็จบ!
“แรงขุดใหญ่แค่ไหน ก็แพ้ใจมวลชน!”
(น่าจะมีตอนต่อไปนะ.. ถ้าชอบก็ Zap โหด ๆ เป็นกำลังใจให้ด้วยนะครับ)
-
-
 @ bd50a856:038f487c
2025-01-08 04:25:47
@ bd50a856:038f487c
2025-01-08 04:25:47I'M NOT IN SCHOOL WHY AM I DOING THIS?
https://image.nostr.build/9df38856e4493466585f451771a013959ac7e29135289b4922a810623577dbef.jpg
Isms in my opinion are not good. - Ferris Bueler
OK so like many a disillusioned youth I was a pretty hardcore Marxist back in college. There's a common pipeline that starts as a 13 year old who wished they could vote for Ron Paul in 2008, takes a hard left turn at the first sign of bigotry, and winds up with a pretty badass juche tattoo. The Enlightenment era ideas of an ascertainable objective truth and mankind's control over their own destiny, combined with the complete subversion of the political history I was brought up with felt very empowering. But nowadays I'm not so sure I want to lay claim to any specific point or vector on the political spectrum. 2024 was in many ways a year of reflection for me. I've managed to reconnect with my sense of spirituality after years of bitterness towards the concept brought on by a life of run-ins with religious fundemantalism, and I had to challenge alot of things that for years I've taken for granted both about myself and the world at large. This ideological audit was in no small way catalyzed by my adoption of NOSTR, which with its endless potential enticed me out of the progressive echo chamber I made my digital home on the fediverse and into a new echo chamber: one full of Bitcoiners.
I had bought Bitcoin before, as a way to short the dollar, but I never encountered its ideologues in the wild. At first gradually then suddenly I was making the types of arguments in my head that former me would have decried as pedantic to the point of being apologetic towards the ruling class. And just like that the 19th and 20th century political and philosophical works which I zaelously held as trail blazes on the long and labyrinthine path towards realizing Absolute Truth were cast forcefully into their murky historical context by the staggering success of the first truly decentralized monetary system. In my college days, I saw Lenin's model of revoutionary politics and the Vanguard Party as the only way for a people's movement to legitimately threaten the hegemony of the global oligarchs who caused so much unnecessary suffering. Now I can see how whether or not that type of centralization was a necessary concession then, one cannot in good faith believe it to be so in the age of Bitcoin.
Yet you'll have to forgive me because still I'm sympathetic to much of the broader movement of Marxism. I detest how Great Man Theory suboordinates the totality of the evolution of society to the wills of a few individuals, and prefer to see socialism in a different light. Rather than viewing the movement as a clever trick some cartoonishly evil mustaches and haircuts used to brainwash almost half the human population, I see a genuine attempt by hundreds of millions of people to change the world for the better, forever. Yes the suffering was immense, and many many people for whom the tumult was too much, as well as those who wished to maintain their parasitic lifestyles, fled for their lives it was far from a black and white phenomena. Living standards also skyrocketed over the long run in places like the USSR and the PRC, from literacy to employment to diet, access to healthcare, you name it. But still the narrative of Hegel's Dialectic playing out in the arena of class politics - wherein the oppressed by becoming the oppressors would naturally do away with oppression altogether by following their self interest just as the Bourgeoisie had done, thereby unwinding the knot of economic injustice - has lost its status as the driving force of all of history for me. It's still much more compelling than the caricature of simply replacing one form of centralization with another. Rather its a much more relatable fallacy: taking a truth, in this case the millennia of class struggle which humanity has dealt with since the advent of agriculture, and trying to extrapolate from it some abstract and all compassing polemic that makes it all make sense. Moreover, in the same way that Bitcoiners say, "Once you see it you can never go back," I cannot unlearn just how hypocritical and dishonest the Western narrative of history is. Lying and calling America the land of the land of opportunity when the abundance we've known for our Empire's whole existence exists merely because of stolen land and slave labor. This is not a moralist objection by the way, though that would be wholly justified. The true horror is that people view the US as the model of a self sufficient nation state when in reality it has always been parasitic, even in it's larval stage. And of course the disillusion with every military campaign since the end of World War 2, starting with the grotesque and gratuitous display of power in Hiroshima and Nagasaki, then the fraudulant and deadly campaigns in Korea, Loas, Vietnam, and of course the entire Middle East. Our own forms of surveillance, censorship, repression all staring at us in the images we projected on the face of the Berlin Wall.
I know a little part of that probably rubbed some of you the wrong way. Hey we still were a net positive force in WW2, of course. And despite many differences in historical interpretations, when it comes to Marx's tomes of economic criticism I think the Bitcoiners of NOSTR would find a lot of rhetorical similarities with their gripes about the age of fiat actually share many rhetorical similarities: The levers of control over the global economy had been consolidated by a select view who were spamming them to make themselves inordinately wealthy at the cost of the quality of life for the majority of Planet Earth. The value of your labor is being ciphoned by a bunch of rackateering lizard men known as politicians. Fair competition, the spirit of Capitalism on paper, has been eroded by its those who claim to be its biggest proponents. Forever wars as a business, predatory global economic policies, proles=plebs, yada yada. Although I guess this note would be pointless if I yada-yada'd over the best parts.
THE INVISIBLE HANDJOB
https://image.nostr.build/595f3d10072c92fc66f9ad314de5d6eeb7e76a9bc26021c690d89cbd9bbe0a15.gif
The landlords, like all other men, love to reap where they never sowed, and demand a rent even for its natural produce. -Adam Smith
In the above quoted Wealth of Nations (Book 1, chapter 11) as well as in Book 4 and in The Theory of Moral Sentiments, everyone's favorite economist they've never read paints a complex and somewhat contradictory image of the proprietors over the means of production in his time. He saw greed and gluttony in their souls, but viewed their actions within the context of an emergent system whereby their selfishness propelled the interest of everyone. So, almost exactly how Marx viewed the holy timespanning vendetta of the have-nots of the world. However, in Book 1 ch10 of Wealth of Nations Smith says this:
[The rent] is not at all proportioned to what the landlord may have laid out upon the improvement of the land, or to what he can afford to take; but to what the farmer can afford to give,
In a section where he concedes that the landlords' actions amount to extortion. He also articulates here how through the influence of legislation, the landlord class effectively outlawed collective negotiation on the part of the working class while bolstering it for themselves, resulting in monopolies. Marx cites Smith himself throughout Das Kapital, and lays out extensively this process of the consolidation of capitalist power in part 3 of the first volume. The two also subscribed to the Labor Theory of Value, as did every other Enlightenment era economist... and so do most Bitcoiners! At least they sure sound like they do when they talk about the erosion of the masses' life force by the debasement of fiat. After all if the commodity that is money is an expression of your time and labor, then so must be the value of every other commodity. I've heard people try to glibly dismiss the LTV as stupid, citing things like land, products of fully automated processes... And digital assets. As if land didn't have to be surveyed, and discovered (or won in a genocide). Or if fully automated production processes didn't require thousands of hours of expert labor on robotics and/or computer engineering. Or if all financial assets in general didn't hold merely a hypothetical value as a representation of value wrought in the productive economy. And to be perfectly honest I always found the subjective theory of value to be downright silly, like imagine haggling at a supermarket over a gallon of milk. Yes demand is subjective (and really more of an expression of willing buying power than need but that's a whole other can of worms), but it's wholly reliant on objective factors such as scarcity and the relative difficulty to produce a certain commodity oneself. And when those who corner the market collude on pricing it's not like you even have the ability to "vote with your money". You have no leverage, unless you own a cow. All in all the price of a commodity can't be anything other than an approximation of its objective value based on the average cost of the raw materials and socially necessary labor time, ebbing and flowing with the asynchronous undulations of supply and demand. And maybe a little extra something just to cushion that P&L. OK maybe a lot. Gotta outperform inflation, right?! Was I being glib, myself, there? It just feels self evident from my current perspective, the hollow vampirism of it all. Capitalists enacting the rights to procure surplus value, reinsert it as capital in order to procure even more surplus value, rinsing and repeating, drifting further and further from the corporeal reality of our own survival and swallowing entire generations in the process.
STATISTS BE LIKE...
https://image.nostr.build/3109eed06d708cfad1ec0c8f4a823b8d6c58b73d3a7f73a94cdcafe22554656f.jpg
The government solution to a problem is usually as bad as the problem- Milton Friedman
On September 11, 1973 Chilean President Salvador Allende died during a fascist coup d'état perpetrated by the commander in chief of the military Augusto Pinochet. Officially he took his own life for fear of what would be done to him, but it remains a contentious topic. Pinochet's regime was characterized by mass arrests, widespread use of torture, extrajudicial killings, mass exiles, and brutal censorship of his political ditractors. But he cut taxes!!!! And he did so with the council of the Chicago Boys, a group of Chicago University alumni and disciples of right wing icon Milton Friedman. Friedman applauded Pinochet's government for his economic policies and providing a shining example of Milton's take on what small laissez-faire government looks like: Repression of the masses, no rules for the classes.
Pinochet was also a collaborator with the CIA on their project Operation Condor, whereby the funding and stoking of violence and unrest was weaponized to subvert the rise of left leaning politics throughout South and Central America and maintain cheap access to raw materials which US corporations relied on. As a matter of fact, the deep state has an endless track record of resorting to all sorts of crazy measures to subvert the popularity of socialism. This contradicts directly the American conservative view that the deep state wants socialism, and that Trump - who has cooperated in the continuations of these policies with the attempted coups in Venezuela and Bolivia during his first term - is here to stop 'em. The scapegoating and fear mongering of foreign left leaning governments in lucrative regions is a time honored tradition here In the US. All the West has always had more in common with the totalitarianism of Fascism than the East. If you're curious or skeptical about this, looking up Michael Parenti's Blackshirts & Reds is a good place to start digging deeper.
And while conservatives remain in denial about the parasiticism and exclusion their version of freedom relies on, Progressivism, as I see it, is a limping, mutilated, abomination of a watered down version of itself. Democrats for over a century now continue offering the bare minimum that would assuage their cinstituencies in the short term at best, and the exact same neocon policies of war and imperialism abroad, and corporate oligarchy and a police state at home. Yet every two years progressives walk beleaguered to the polls to vote blue no who. And Milton Friedman laughs in his grave. Reminds me of one of my favorite quotes, attributed to president of Tanzinia, Julius Nyere: "The Americans also have a one party state, but with typical American extravegance, they have two of them." https://image.nostr.build/9380dbc6d51a443b76340b46c760e12c9bb0540a170a8f5a2a22847e0bba88c7.jpg
WHAT IS DO BE DONE?
https://image.nostr.build/94aaebe5364c3c6a0094f09640ef18b05938d889124f874c49243f4ea972f725.jpg
I found freedom. Losing all hope is freedom. - Edward Norton, Fight Club
If you made it through all that rambling, what is wrong with you? In all seriousness, I hope this was a fruitful glance into the mind of someone who might think a little differently. In a rapidly evolving world, where systems we ourselves have put in place not only constitute the environment we live in, but reproduce themselves through our behavior as well, despondency, rage, and confusion permeate the collective consciousness. But there's also Bitcoin, which to an increasing number - and to an extent myself - represents a successful proof of concept of a new, genuinely Decentralized Ideological Apparatus. One which relies on Mutual Aid and the cooperation of smaller, decentralized and self sufficient communities. And to a certain extent it also represents hope. But it's as much an asset to those who'd prefer to continue feeding on the suffering of others as it is to those hoping for a change. Hope is as dangerous as fear - Lao Tzu
-
 @ 1cb14ab3:95d52462
2025-01-07 23:11:58
@ 1cb14ab3:95d52462
2025-01-07 23:11:58Event Recap
For the Official Stooki Sound Afterparty in Boulder, CO, I took the unconventional venue of a kitchen on The Hill and transformed it into an immersive environment for Toybox and Tesfa’s performances. The space was custom-mapped with projections that interacted seamlessly with the surroundings, turning the kitchen into a dynamic, visual landscape. I added retrofitted props to deepen the visual experience, giving the projections a multi-dimensional quality. This innovative approach created a unique atmosphere, enhancing the performance while blurring the lines between physical space and digital art.
Event Photos







Recap Video
nostr:naddr1qqrj6wpkx3u8qscpzpmhxue69uhkummnw3ezuamfdejsygquk99txdv8dly7lsmasw969p70zlj6mnxtyzlk6j0em2tft4fyvgpsgqqqskas47n36f
Other Immersive Experiences by Hes
More from Hes
All images are credit of Hes, but you are free to download and use for any purpose. If you find joy from my art, please feel free to send a zap. Enjoy life on a Bitcoin standard.
-
 @ 6e24af77:b3f1350b
2024-11-12 14:46:30
@ 6e24af77:b3f1350b
2024-11-12 14:46:30Catchy body content
-
 @ dd664d5e:5633d319
2025-01-07 19:57:14
@ dd664d5e:5633d319
2025-01-07 19:57:14Hodling Bitcoin does not make you a capitalist
I've noticed that Bitcoin-mindedness seems to lead some people to communistic thinking because it's a hard-limited form of capital. Marx, like most Bitcoiners, heavily discounted the possibility of economic growth or transformation changing the economy enough to undermine some minority's control of some form of capital.
What few today understand, is that many of the Dirty Capitalists of Marx's era actually agreed with him; they were just disdainful of labor and worried that the workers finding out that Marxism is correct about the nature of capitalism would cause unrest. They were the original HFSP crowd.
This was the basic idea, that Marx had, and that many Bitcoiners would agree with:
Capital is strictly limited and the people that control it can keep labor from attaining any, except when their labor is necessary.
And, as we know, automation will make human labor increasingly unnecessary.
The math doesn't check out

That underlies all of the calculations of "Well, if I just grab this Bitcoin wallet and hodl for twenty years, then it will grow in value to equal half of everything in existence and then I can just buy up half the planet and rule over everyone like a god."
This is economic nonsense because it assumes that: 1) the value of all things remains static over time, 2) purchasing something with money gives you ownership of it, 3) people will always use that specific money (or any money, at all!) for all transactions, 4) there is no such thing as opportunity cost, 5) people will always value money more than any other thing, and therefore be willing to always trade it for anything else, 6) humans are passive, defenseless, and easy to rule over, 7) someone who is preoccupied with hodling an asset steadily and sharply rising in price would ever be emotionally ready to part with it.
All monies can die.
People use money for everything because it is easy, fast and cheap. If money becomes too precious or scarce, they will simply switch to using other things (as we saw with gold). Humans replace tools that aren't working well, with those that work better, and money is just another tool. Bitcoin is more divisible than gold, but that won't matter, if enough of it is held by too few.
This is why there's a natural cap on the price of a money and why human productivity in the here and now is not irrelevant or in vain.
-
 @ d13f90f0:fa32fe72
2024-11-12 11:59:36
@ d13f90f0:fa32fe72
2024-11-12 11:59:36Catchy body content
-
 @ 6e24af77:b3f1350b
2024-11-08 10:11:29
@ 6e24af77:b3f1350b
2024-11-08 10:11:29test 6
-
 @ 1bda7e1f:bb97c4d9
2025-01-02 05:19:08
@ 1bda7e1f:bb97c4d9
2025-01-02 05:19:08Tldr
- Nostr is an open and interoperable protocol
- You can integrate it with workflow automation tools to augment your experience
- n8n is a great low/no-code workflow automation tool which you can host yourself
- Nostrobots allows you to integrate Nostr into n8n
- In this blog I create some workflow automations for Nostr
- A simple form to delegate posting notes
- Push notifications for mentions on multiple accounts
- Push notifications for your favourite accounts when they post a note
- All workflows are provided as open source with MIT license for you to use
Inter-op All The Things
Nostr is a new open social protocol for the internet. This open nature exciting because of the opportunities for interoperability with other technologies. In Using NFC Cards with Nostr I explored the
nostr:URI to launch Nostr clients from a card tap.The interoperability of Nostr doesn't stop there. The internet has many super-powers, and Nostr is open to all of them. Simply, there's no one to stop it. There is no one in charge, there are no permissioned APIs, and there are no risks of being de-platformed. If you can imagine technologies that would work well with Nostr, then any and all of them can ride on or alongside Nostr rails.
My mental model for why this is special is Google Wave ~2010. Google Wave was to be the next big platform. Lars was running it and had a big track record from Maps. I was excited for it. Then, Google pulled the plug. And, immediately all the time and capital invested in understanding and building on the platform was wasted.
This cannot happen to Nostr, as there is no one to pull the plug, and maybe even no plug to pull.
So long as users demand Nostr, Nostr will exist, and that is a pretty strong guarantee. It makes it worthwhile to invest in bringing Nostr into our other applications.
All we need are simple ways to plug things together.
Nostr and Workflow Automation
Workflow automation is about helping people to streamline their work. As a user, the most common way I achieve this is by connecting disparate systems together. By setting up one system to trigger another or to move data between systems, I can solve for many different problems and become way more effective.
n8n for workflow automation
Many workflow automation tools exist. My favourite is n8n. n8n is a low/no-code workflow automation platform which allows you to build all kinds of workflows. You can use it for free, you can self-host it, it has a user-friendly UI and useful API. Vs Zapier it can be far more elaborate. Vs Make.com I find it to be more intuitive in how it abstracts away the right parts of the code, but still allows you to code when you need to.
Most importantly you can plug anything into n8n: You have built-in nodes for specific applications. HTTP nodes for any other API-based service. And community nodes built by individual community members for any other purpose you can imagine.
Eating my own dogfood
It's very clear to me that there is a big design space here just demanding to be explored. If you could integrate Nostr with anything, what would you do?
In my view the best way for anyone to start anything is by solving their own problem first (aka "scratching your own itch" and "eating your own dogfood"). As I get deeper into Nostr I find myself controlling multiple Npubs – to date I have a personal Npub, a brand Npub for a community I am helping, an AI assistant Npub, and various testing Npubs. I need ways to delegate access to those Npubs without handing over the keys, ways to know if they're mentioned, and ways to know if they're posting.
I can build workflows with n8n to solve these issues for myself to start with, and keep expanding from there as new needs come up.
Running n8n with Nostrobots
I am mostly non-technical with a very helpful AI. To set up n8n to work with Nostr and operate these workflows should be possible for anyone with basic technology skills.
- I have a cheap VPS which currently runs my HAVEN Nostr Relay and Albyhub Lightning Node in Docker containers,
- My objective was to set up n8n to run alongside these in a separate Docker container on the same server, install the required nodes, and then build and host my workflows.
Installing n8n
Self-hosting n8n could not be easier. I followed n8n's Docker-Compose installation docs–
- Install Docker and Docker-Compose if you haven't already,
- Create your
docker-compose.ymland.envfiles from the docs, - Create your data folder
sudo docker volume create n8n_data, - Start your container with
sudo docker compose up -d, - Your n8n instance should be online at port
5678.
n8n is free to self-host but does require a license. Enter your credentials into n8n to get your free license key. You should now have access to the Workflow dashboard and can create and host any kind of workflows from there.
Installing Nostrobots
To integrate n8n nicely with Nostr, I used the Nostrobots community node by Ocknamo.
In n8n parlance a "node" enables certain functionality as a step in a workflow e.g. a "set" node sets a variable, a "send email" node sends an email. n8n comes with all kinds of "official" nodes installed by default, and Nostr is not amongst them. However, n8n also comes with a framework for community members to create their own "community" nodes, which is where Nostrobots comes in.
You can only use a community node in a self-hosted n8n instance (which is what you have if you are running in Docker on your own server, but this limitation does prevent you from using n8n's own hosted alternative).
To install a community node, see n8n community node docs. From your workflow dashboard–
- Click the "..." in the bottom left corner beside your username, and click "settings",
- Cilck "community nodes" left sidebar,
- Click "Install",
- Enter the "npm Package Name" which is
n8n-nodes-nostrobots, - Accept the risks and click "Install",
- Nostrobots is now added to your n8n instance.
Using Nostrobots
Nostrobots gives you nodes to help you build Nostr-integrated workflows–
- Nostr Write – for posting Notes to the Nostr network,
- Nostr Read – for reading Notes from the Nostr network, and
- Nostr Utils – for performing certain conversions you may need (e.g. from bech32 to hex).
Nostrobots has good documentation on each node which focuses on simple use cases.
Each node has a "convenience mode" by default. For example, the "Read" Node by default will fetch Kind 1 notes by a simple filter, in Nostrobots parlance a "Strategy". For example, with Strategy set to "Mention" the node will accept a pubkey and fetch all Kind 1 notes that Mention the pubkey within a time period. This is very good for quick use.
What wasn't clear to me initially (until Ocknamo helped me out) is that advanced use cases are also possible.
Each node also has an advanced mode. For example, the "Read" Node can have "Strategy" set to "RawFilter(advanced)". Now the node will accept json (anything you like that complies with NIP-01). You can use this to query Notes (Kind 1) as above, and also Profiles (Kind 0), Follow Lists (Kind 3), Reactions (Kind 7), Zaps (Kind 9734/9735), and anything else you can think of.
Creating and adding workflows
With n8n and Nostrobots installed, you can now create or add any kind of Nostr Workflow Automation.
- Click "Add workflow" to go to the workflow builder screen,
- If you would like to build your own workflow, you can start with adding any node. Click "+" and see what is available. Type "Nostr" to explore the Nostrobots nodes you have added,
- If you would like to add workflows that someone else has built, click "..." in the top right. Then click "import from URL" and paste in the URL of any workflow you would like to use (including the ones I share later in this article).
Nostr Workflow Automations
It's time to build some things!
A simple form to post a note to Nostr
I started very simply. I needed to delegate the ability to post to Npubs that I own in order that a (future) team can test things for me. I don't want to worry about managing or training those people on how to use keys, and I want to revoke access easily.
I needed a basic form with credentials that posted a Note.
For this I can use a very simple workflow–
- A n8n Form node – Creates a form for users to enter the note they wish to post. Allows for the form to be protected by a username and password. This node is the workflow "trigger" so that the workflow runs each time the form is submitted.
- A Set node – Allows me to set some variables, in this case I set the relays that I intend to use. I typically add a Set node immediately following the trigger node, and put all the variables I need in this. It helps to make the workflows easier to update and maintain.
- A Nostr Write node (from Nostrobots) – Writes a Kind-1 note to the Nostr network. It accepts Nostr credentials, the output of the Form node, and the relays from the Set node, and posts the Note to those relays.
Once the workflow is built, you can test it with the testing form URL, and set it to "Active" to use the production form URL. That's it. You can now give posting access to anyone for any Npub. To revoke access, simply change the credentials or set to workflow to "Inactive".
It may also be the world's simplest Nostr client.
You can find the Nostr Form to Post a Note workflow here.
Push notifications on mentions and new notes
One of the things Nostr is not very good at is push notifications. Furthermore I have some unique itches to scratch. I want–
- To make sure I never miss a note addressed to any of my Npubs – For this I want a push notification any time any Nostr user mentions any of my Npubs,
- To make sure I always see all notes from key accounts – For this I need a push notification any time any of my Npubs post any Notes to the network,
- To get these notifications on all of my devices – Not just my phone where my Nostr regular client lives, but also on each of my laptops to suit wherever I am working that day.
I needed to build a Nostr push notifications solution.
To build this workflow I had to string a few ideas together–
- Triggering the node on a schedule – Nostrobots does not include a trigger node. As every workflow starts with a trigger we needed a different method. I elected to run the workflow on a schedule of every 10-minutes. Frequent enough to see Notes while they are hot, but infrequent enough to not burden public relays or get rate-limited,
- Storing a list of Npubs in a Nostr list – I needed a way to store the list of Npubs that trigger my notifications. I initially used an array defined in the workflow, this worked fine. Then I decided to try Nostr lists (NIP-51, kind 30000). By defining my list of Npubs as a list published to Nostr I can control my list from within a Nostr client (e.g. Listr.lol or Nostrudel.ninja). Not only does this "just work", but because it's based on Nostr lists automagically Amethyst client allows me to browse that list as a Feed, and everyone I add gets notified in their Mentions,
- Using specific relays – I needed to query the right relays, including my own HAVEN relay inbox for notes addressed to me, and wss://purplepag.es for Nostr profile metadata,
- Querying Nostr events (with Nostrobots) – I needed to make use of many different Nostr queries and use quite a wide range of what Nostrobots can do–
- I read the EventID of my Kind 30000 list, to return the desired pubkeys,
- For notifications on mentions, I read all Kind 1 notes that mention that pubkey,
- For notifications on new notes, I read all Kind 1 notes published by that pubkey,
- Where there are notes, I read the Kind 0 profile metadata event of that pubkey to get the displayName of the relevant Npub,
- I transform the EventID into a Nevent to help clients find it.
- Using the Nostr URI – As I did with my NFC card article, I created a link with the
nostr:URI prefix so that my phone's native client opens the link by default, - Push notifications solution – I needed a push notifications solution. I found many with n8n integrations and chose to go with Pushover which supports all my devices, has a free trial, and is unfairly cheap with a $5-per-device perpetual license.
Once the workflow was built, lists published, and Pushover installed on my phone, I was fully set up with push notifications on Nostr. I have used these workflows for several weeks now and made various tweaks as I went. They are feeling robust and I'd welcome you to give them a go.
You can find the Nostr Push Notification If Mentioned here and If Posts a Note here.
In speaking with other Nostr users while I was building this, there are all kind of other needs for push notifications too – like on replies to a certain bookmarked note, or when a followed Npub starts streaming on zap.stream. These are all possible.
Use my workflows
I have open sourced all my workflows at my Github with MIT license and tried to write complete docs, so that you can import them into your n8n and configure them for your own use.
To import any of my workflows–
- Click on the workflow of your choice, e.g. "Nostr_Push_Notify_If_Mentioned.json",
- Click on the "raw" button to view the raw JSON, ex any Github page layout,
- Copy that URL,
- Enter that URL in the "import from URL" dialog mentioned above.
To configure them–
- Prerequisites, credentials, and variables are all stated,
- In general any variables required are entered into a Set Node that follows the trigger node,
- Pushover has some extra setup but is very straightforward and documented in the workflow.
What next?
Over my first four blogs I explored creating a good Nostr setup with Vanity Npub, Lightning Payments, Nostr Addresses at Your Domain, and Personal Nostr Relay.
Then in my latest two blogs I explored different types of interoperability with NFC cards and now n8n Workflow Automation.
Thinking ahead n8n can power any kind of interoperability between Nostr and any other legacy technology solution. On my mind as I write this:
- Further enhancements to posting and delegating solutions and forms (enhanced UI or different note kinds),
- Automated or scheduled posting (such as auto-liking everything Lyn Alden posts),
- Further enhancements to push notifications, on new and different types of events (such as notifying me when I get a new follower, on replies to certain posts, or when a user starts streaming),
- All kinds of bridges, such as bridging notes to and from Telegram, Slack, or Campfire. Or bridging RSS or other event feeds to Nostr,
- All kinds of other automation (such as BlackCoffee controlling a coffee machine),
- All kinds of AI Assistants and Agents,
In fact I have already released an open source workflow for an AI Assistant, and will share more about that in my next blog.
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
GM Nostr.
-
 @ d5c3d063:4d1159b3
2025-01-07 11:02:03
@ d5c3d063:4d1159b3
2025-01-07 11:02:03โพสที่อาจารย์พิริยะ บอกว่า “If you are angry at something... maybe it's just you.”
เป็นคำกล่าวที่เตือนให้เรามองกลับเข้ามาในตัวเองว่า "ความโกรธ" มีต้นกำเนิดจากจิตใจของเราเอง การใช้สติและการตระหนักถึงความคาดหวังที่เรามีต่อผู้อื่นจะช่วยให้เราสามารถจัดการกับความโกรธได้อย่างสร้างสรรค์และมีเหตุผล แนวคิดของอริยสัจ ๔ ช่วยให้เราเข้าใจถึงต้นเหตุและวิธีการดับทุกข์ และผมนำแนวคิดอิสรนิยมมาช่วยเสริมให้เราได้ตระหนักถึงความรับผิดชอบในชีวิตของตนเองและการเคารพเสรีภาพของผู้อื่นในการนำไปใช้ทางโลกได้จริง
เมื่อเราฝึกเดินด้วยเมตตา ปล่อยวางโทสะ และไม่หลงด้วยโมหะ เราจะสามารถสร้างความสงบสุขในจิตใจและในความสัมพันธ์กับผู้อื่นได้อย่างแท้จริง ทั้งหมดนี้นำไปสู่ชีวิตที่มีความสุขและเสรีภาพอย่างสมดุลในทุกมิติของการดำรงอยู่
เริ่มจาก...อริยสัจ ๔ คือการค้นหาต้นเหตุแห่งทุกข์ในจิตใจ
พระพุทธศาสนาสอนว่าความโกรธไม่ได้เกิดจากสิ่งภายนอกโดยตรง แต่มีรากฐานมาจาก สมุทัยหรือ "เหตุแห่งทุกข์" ที่เกิดจากภายในจิตใจของเราเอง เช่น - ตัณหา (ความยึดมั่นถือมั่น) ที่ทำให้เราคาดหวังว่าสิ่งต่าง ๆ จะต้องเป็นไปตามใจเรา - อวิชชา (ความไม่รู้) ทำให้เรามองไม่เห็นว่าความโกรธไม่ได้ทำให้ปัญหาแก้ไขได้ แต่กลับเผาผลาญจิตใจเราเอง การดับความโกรธ (นิโรธ) จึงเริ่มต้นจากการมีสติรู้ตัวและปล่อยวางความยึดมั่น โดยการฝึกสมาธิและการเจริญเมตตาเป็นเครื่องมือสำคัญที่ช่วยให้เรามองเห็นความเป็นจริงและลดทอนพลังทำลายของความโกรธ
...ต่อมาคือแนวคิดอิสรนิยม ที่เน้นถึงการรับผิดชอบต่อตนเองและเสรีภาพในการเลือก ปัจเจกบุคคลต้องรับผิดชอบต่อชีวิตของตนเองและไม่พึ่งพิงปัจจัยภายนอกเกินไป ความโกรธในมุมมองนี้สามารถมองได้ว่าเป็นผลลัพธ์ของการละเลยความรับผิดชอบต่ออารมณ์ของตัวเองและการพึ่งพิงสิ่งภายนอกเกินไป เช่น การโกรธที่ผู้อื่นไม่ทำตามที่เราต้องการ สะท้อนถึงการพยายามควบคุมสิ่งที่อยู่นอกเหนืออำนาจของเรา ซึ่งขัดกับหลักการเสรีภาพส่วนบุคคลของอิสรนิยม หลักการสำคัญของอิสรนิยมคือ Non-Aggression Principle (หลักการไม่รุกราน) ที่สอนว่าความรุนแรงและการบีบบังคับผู้อื่นเป็นสิ่งที่ควรหลีกเลี่ยง ความโกรธจึงถือเป็นการรุกรานจิตใจของเราเองก่อน เพราะเป็นการสร้างภาระให้กับจิตใจโดยไม่จำเป็น
แนวทางการปฏิบัติที่อาจารย์ได้ใส่ # ไว้ 1. #เดินด้วยเมตตา - มุมมองจากอริยสัจ ๔ #เมตตา คือการยอมรับและปรารถนาดีต่อทั้งตัวเองและผู้อื่น การให้ความรักและความปรารถนาดีจะช่วยลดพลังของโทสะในจิตใจ ทำให้เรามีมุมมองที่เปิดกว้างและมีความสุขที่แท้จริง - การเชื่อมโยงในอิสรนิยม เสรีภาพของแต่ละบุคคลรวมถึงการเคารพเสรีภาพของผู้อื่น เมตตาได้ช่วยส่งเสริมการอยู่ร่วมกันในสังคมโดยไม่ก้าวก่ายสิทธิและเสรีภาพของกันและกัน เมตตาในแง่นี้จึงเป็นการสร้างสมดุลระหว่างเสรีภาพของเราและของผู้อื่น เช่น การเคารพในความคิดหรือการกระทำของผู้อื่น แม้จะเขาจะเห็นต่างจากเรา 2. #อย่าเดินด้วยโทสะ - มุมมองจากอริยสัจ ๔ #โทสะ เป็นเหมือนยาพิษที่เราดื่มเองและทำให้เราเป็นทุกข์ ความโกรธไม่ได้ทำร้ายผู้อื่นเท่าที่มันทำลายจิตใจและร่างกายของเราเอง การฝึกเจริญสติช่วยให้เราเห็นถึงอารมณ์โกรธตั้งแต่เริ่มต้น และตัดวงจรของความคิดและการกระทำที่เป็นพิษ - การเชื่อมโยงในอิสรนิยม ความโกรธหรือการใช้อารมณ์ ไม่ควรเป็นเหตุผลในการละเมิดสิทธิหรือเสรีภาพของผู้อื่น หลักการ Non-Aggression Principle (NAP) ของอิสรนิยมเตือนเราว่าการใช้อารมณ์รุนแรงหรือโทสะมักนำไปสู่การบีบบังคับหรือทำร้ายผู้อื่น ซึ่งเป็นสิ่งที่ขัดแย้งกับความเคารพในเสรีภาพของทุกคน การไม่เดินด้วยโทสะจึงเป็นการเคารพในเสรีภาพของทั้งตัวเราและผู้อื่น 3. #อย่าหลงด้วยโมหะ - มุมมองจากอริยสัจ ๔ #โมหะ หรือความหลง ทำให้เรามองสิ่งต่าง ๆ อย่างผิดเพี้ยนและติดอยู่ในภาพลวงตา เช่น การโทษผู้อื่นว่าเป็นต้นเหตุของความทุกข์ทั้งหมด ทั้งที่แท้จริงแล้วความทุกข์มักเกิดจากจิตใจและความคาดหวังของเราเอง - การเชื่อมโยงกับอิสรนิยม สอนว่าความสุขและความสงบในชีวิต ไม่ได้ขึ้นอยู่กับสิ่งภายนอก แต่ขึ้นอยู่กับเสรีภาพในการเลือกและการรับผิดชอบชีวิตของตนเอง การหลุดพ้นจากโมหะเป็นการยอมรับว่าเราไม่สามารถควบคุมผู้อื่นหรือโลกภายนอกได้ แต่สามารถควบคุมปฏิกิริยาและการตอบสนองของเราได้ การไม่หลงด้วยโมหะจึงช่วยให้เราเป็นอิสระจากความยึดมั่นในสิ่งที่อยู่นอกเหนือการควบคุม
ทีนี้มาลองดูตัวอย่างในชีวิตประจำวันกันดูบ้าง
-
เดินด้วยเมตตา หากเราพยายามอธิบายเรื่องบิตคอยน์ให้คนอื่นเข้าใจ แต่เขายังเชื่อมั่นในระบบการเงินของรัฐ การใช้เมตตาจะช่วยให้เราเข้าใจว่าการเปลี่ยนแปลงความคิดต้องใช้เวลาและกระบวนการขั้นตอน ไม่ใช่ทุกคนจะพร้อมเปิดรับแนวคิดใหม่ในทันที การพูดคุยด้วยความรักและปรารถนาดีแทนการตำหนิ จะช่วยสร้างบทสนทนาที่สร้างสรรค์
-
อย่าเดินด้วยโทสะ หากเรารู้สึกโกรธเมื่อคนอื่นยังคงเชื่อในระบบเศรษฐกิจแบบเคนส์หรือสังคมนิยม อาจใช้โอกาสนี้แหละ ในการฝึกเจริญสติและตระหนักว่าเราควบคุมความเชื่อของผู้อื่นไม่ได้ แต่สามารถเลือกอธิบายด้วยเหตุผลและความเคารพ หรือเลือกที่จะปล่อยวางเมื่อสถานการณ์ไม่เอื้ออำนวย
-
อย่าหลงด้วยโมหะ หากเราหงุดหงิดที่ผู้อื่นไม่ยอมรับแนวคิดของบิตคอยน์ การตระหนักว่าความคาดหวังของเราที่ต้องการให้ผู้อื่นเข้าใจในทันทีนั้นเป็นภาพลวงตา มันก็จะช่วยให้เรามองเห็นความจริงที่ว่า การเปลี่ยนแปลงทางความคิด เป็นกระบวนการที่ต้องใช้เวลาและเกิดจากเสรีภาพในการตัดสินใจของแต่ละบุคคล
……..……..……..
ความโกรธ เป็นหนึ่งในอารมณ์พื้นฐานที่มนุษย์ทุกคนต้องเผชิญในชีวิต แต่การจัดการความโกรธนั้นไม่ใช่เพียงเรื่องของการควบคุมอารมณ์ หากยังสะท้อนถึงการทำความเข้าใจตัวตนและธรรมชาติของสิ่งต่าง ๆ รอบตัวเรา ประโยคที่อาจารย์พิริยะบอกว่า “If you are angry at something... maybe it's just you.” ไม่ได้เป็นเพียงคำกล่าวเตือนใจ แต่ยังเป็นการเชื้อเชิญให้เราไตร่ตรองถึงรากฐานของความโกรธ ซึ่งซุปขอเชื่อมโยงเข้ากับหลักอริยสัจ ๔ ในพระพุทธศาสนาและแนวคิดอิสรนิยม (#Libertarianism) ที่เน้นความรับผิดชอบส่วนบุคคลและเสรีภาพในชีวิต
Siamstr
-
-
 @ 3f770d65:7a745b24
2024-12-31 17:03:46
@ 3f770d65:7a745b24
2024-12-31 17:03:46Here are my predictions for Nostr in 2025:
Decentralization: The outbox and inbox communication models, sometimes referred to as the Gossip model, will become the standard across the ecosystem. By the end of 2025, all major clients will support these models, providing seamless communication and enhanced decentralization. Clients that do not adopt outbox/inbox by then will be regarded as outdated or legacy systems.
Privacy Standards: Major clients such as Damus and Primal will move away from NIP-04 DMs, adopting more secure protocol possibilities like NIP-17 or NIP-104. These upgrades will ensure enhanced encryption and metadata protection. Additionally, NIP-104 MLS tools will drive the development of new clients and features, providing users with unprecedented control over the privacy of their communications.
Interoperability: Nostr's ecosystem will become even more interconnected. Platforms like the Olas image-sharing service will expand into prominent clients such as Primal, Damus, Coracle, and Snort, alongside existing integrations with Amethyst, Nostur, and Nostrudel. Similarly, audio and video tools like Nostr Nests and Zap.stream will gain seamless integration into major clients, enabling easy participation in live events across the ecosystem.
Adoption and Migration: Inspired by early pioneers like Fountain and Orange Pill App, more platforms will adopt Nostr for authentication, login, and social systems. In 2025, a significant migration from a high-profile application platform with hundreds of thousands of users will transpire, doubling Nostr’s daily activity and establishing it as a cornerstone of decentralized technologies.
-
 @ 6e24af77:b3f1350b
2024-11-04 13:24:26
@ 6e24af77:b3f1350b
2024-11-04 13:24:26test 3
-
 @ e97aaffa:2ebd765d
2024-12-31 16:47:12
@ e97aaffa:2ebd765d
2024-12-31 16:47:12Último dia do ano, momento para tirar o pó da bola de cristal, para fazer reflexões, previsões e desejos para o próximo ano e seguintes.
Ano após ano, o Bitcoin evoluiu, foi ultrapassando etapas, tornou-se cada vez mais mainstream. Está cada vez mais difícil fazer previsões sobre o Bitcoin, já faltam poucas barreiras a serem ultrapassadas e as que faltam são altamente complexas ou tem um impacto profundo no sistema financeiro ou na sociedade. Estas alterações profundas tem que ser realizadas lentamente, porque uma alteração rápida poderia resultar em consequências terríveis, poderia provocar um retrocesso.
Código do Bitcoin
No final de 2025, possivelmente vamos ter um fork, as discussões sobre os covenants já estão avançadas, vão acelerar ainda mais. Já existe um consenso relativamente alto, a favor dos covenants, só falta decidir que modelo será escolhido. Penso que até ao final do ano será tudo decidido.
Depois dos covenants, o próximo foco será para a criptografia post-quantum, que será o maior desafio que o Bitcoin enfrenta. Criar uma criptografia segura e que não coloque a descentralização em causa.
Espero muito de Ark, possivelmente a inovação do ano, gostaria de ver o Nostr a furar a bolha bitcoinheira e que o Cashu tivesse mais reconhecimento pelos bitcoiners.
Espero que surjam avanços significativos no BitVM2 e BitVMX.
Não sei o que esperar das layer 2 de Bitcoin, foram a maior desilusão de 2024. Surgiram com muita força, mas pouca coisa saiu do papel, foi uma mão cheia de nada. Uma parte dos projetos caiu na tentação da shitcoinagem, na criação de tokens, que tem um único objetivo, enriquecer os devs e os VCs.
Se querem ser levados a sério, têm que ser sérios.
“À mulher de César não basta ser honesta, deve parecer honesta”
Se querem ter o apoio dos bitcoiners, sigam o ethos do Bitcoin.
Neste ponto a atitude do pessoal da Ark é exemplar, em vez de andar a chorar no Twitter para mudar o código do Bitcoin, eles colocaram as mãos na massa e criaram o protocolo. É claro que agora está meio “coxo”, funciona com uma multisig ou com os covenants na Liquid. Mas eles estão a criar um produto, vão demonstrar ao mercado que o produto é bom e útil. Com a adoção, a comunidade vai perceber que o Ark necessita dos covenants para melhorar a interoperabilidade e a soberania.
É este o pensamento certo, que deveria ser seguido pelos restantes e futuros projetos. É seguir aquele pensamento do J.F. Kennedy:
“Não perguntem o que é que o vosso país pode fazer por vocês, perguntem o que é que vocês podem fazer pelo vosso país”
Ou seja, não fiquem à espera que o bitcoin mude, criem primeiro as inovações/tecnologia, ganhem adoção e depois demonstrem que a alteração do código camada base pode melhorar ainda mais o vosso projeto. A necessidade é que vai levar a atualização do código.
Reservas Estratégicas de Bitcoin
Bancos centrais
Com a eleição de Trump, emergiu a ideia de uma Reserva Estratégia de Bitcoin, tornou este conceito mainstream. Foi um pivot, a partir desse momento, foram enumerados os políticos de todo o mundo a falar sobre o assunto.
A Senadora Cynthia Lummis foi mais além e propôs um programa para adicionar 200 mil bitcoins à reserva ao ano, até 1 milhão de Bitcoin. Só que isto está a criar uma enorme expectativa na comunidade, só que pode resultar numa enorme desilusão. Porque no primeiro ano, o Trump em vez de comprar os 200 mil, pode apenas adicionar na reserva, os 198 mil que o Estado já tem em sua posse. Se isto acontecer, possivelmente vai resultar numa forte queda a curto prazo. Na minha opinião os bancos centrais deveriam seguir o exemplo de El Salvador, fazer um DCA diário.
Mais que comprar bitcoin, para mim, o mais importante é a criação da Reserva, é colocar o Bitcoin ao mesmo nível do ouro, o impacto para o resto do mundo será tremendo, a teoria dos jogos na sua plenitude. Muitos outros bancos centrais vão ter que comprar, para não ficarem atrás, além disso, vai transmitir uma mensagem à generalidade da população, que o Bitcoin é “afinal é algo seguro, com valor”.
Mas não foi Trump que iniciou esta teoria dos jogos, mas sim foi a primeira vítima dela. É o próprio Trump que o admite, que os EUA necessitam da reserva para não ficar atrás da China. Além disso, desde que os EUA utilizaram o dólar como uma arma, com sanção contra a Rússia, surgiram boatos de que a Rússia estaria a utilizar o Bitcoin para transações internacionais. Que foram confirmados recentemente, pelo próprio governo russo. Também há poucos dias, ainda antes deste reconhecimento público, Putin elogiou o Bitcoin, ao reconhecer que “Ninguém pode proibir o bitcoin”, defendendo como uma alternativa ao dólar. A narrativa está a mudar.
Já existem alguns países com Bitcoin, mas apenas dois o fizeram conscientemente (El Salvador e Butão), os restantes têm devido a apreensões. Hoje são poucos, mas 2025 será o início de uma corrida pelos bancos centrais. Esta corrida era algo previsível, o que eu não esperava é que acontecesse tão rápido.

Empresas
A criação de reservas estratégicas não vai ficar apenas pelos bancos centrais, também vai acelerar fortemente nas empresas em 2025.

Mas as empresas não vão seguir a estratégia do Saylor, vão comprar bitcoin sem alavancagem, utilizando apenas os tesouros das empresas, como uma proteção contra a inflação. Eu não sou grande admirador do Saylor, prefiro muito mais, uma estratégia conservadora, sem qualquer alavancagem. Penso que as empresas vão seguir a sugestão da BlackRock, que aconselha um alocações de 1% a 3%.
Penso que 2025, ainda não será o ano da entrada das 6 magníficas (excepto Tesla), será sobretudo empresas de pequena e média dimensão. As magníficas ainda tem uma cota muito elevada de shareholders com alguma idade, bastante conservadores, que têm dificuldade em compreender o Bitcoin, foi o que aconteceu recentemente com a Microsoft.
Também ainda não será em 2025, talvez 2026, a inclusão nativamente de wallet Bitcoin nos sistema da Apple Pay e da Google Pay. Seria um passo gigante para a adoção a nível mundial.
ETFs
Os ETFs para mim são uma incógnita, tenho demasiadas dúvidas, como será 2025. Este ano os inflows foram superiores a 500 mil bitcoins, o IBIT foi o lançamento de ETF mais bem sucedido da história. O sucesso dos ETFs, deve-se a 2 situações que nunca mais se vão repetir. O mercado esteve 10 anos à espera pela aprovação dos ETFs, a procura estava reprimida, isso foi bem notório nos primeiros meses, os inflows foram brutais.
Também se beneficiou por ser um mercado novo, não existia orderbook de vendas, não existia um mercado interno, praticamente era só inflows. Agora o mercado já estabilizou, a maioria das transações já são entre clientes dos próprios ETFs. Agora só uma pequena percentagem do volume das transações diárias vai resultar em inflows ou outflows.
Estes dois fenómenos nunca mais se vão repetir, eu não acredito que o número de inflows em BTC supere os número de 2024, em dólares vai superar, mas em btc não acredito que vá superar.
Mas em 2025 vão surgir uma infindável quantidade de novos produtos, derivativos, novos ETFs de cestos com outras criptos ou cestos com ativos tradicionais. O bitcoin será adicionado em produtos financeiros já existentes no mercado, as pessoas vão passar a deter bitcoin, sem o saberem.
Com o fim da operação ChokePoint 2.0, vai surgir uma nova onda de adoção e de produtos financeiros. Possivelmente vamos ver bancos tradicionais a disponibilizar produtos ou serviços de custódia aos seus clientes.
Eu adoraria ver o crescimento da adoção do bitcoin como moeda, só que a regulamentação não vai ajudar nesse processo.
Preço
Eu acredito que o topo deste ciclo será alcançado no primeiro semestre, posteriormente haverá uma correção. Mas desta vez, eu acredito que a correção será muito menor que as anteriores, inferior a 50%, esta é a minha expectativa. Espero estar certo.
Stablecoins de dólar
Agora saindo um pouco do universo do Bitcoin, acho importante destacar as stablecoins.
No último ciclo, eu tenho dividido o tempo, entre continuar a estudar o Bitcoin e estudar o sistema financeiro, as suas dinâmicas e o comportamento humano. Isto tem sido o meu foco de reflexão, imaginar a transformação que o mundo vai sofrer devido ao padrão Bitcoin. É uma ilusão acreditar que a transição de um padrão FIAT para um padrão Bitcoin vai ser rápida, vai existir um processo transitório que pode demorar décadas.
Com a re-entrada de Trump na Casa Branca, prometendo uma política altamente protecionista, vai provocar uma forte valorização do dólar, consequentemente as restantes moedas do mundo vão derreter. Provocando uma inflação generalizada, gerando uma corrida às stablecoins de dólar nos países com moedas mais fracas. Trump vai ter uma política altamente expansionista, vai exportar dólares para todo o mundo, para financiar a sua própria dívida. A desigualdade entre os pobres e ricos irá crescer fortemente, aumentando a possibilidade de conflitos e revoltas.
“Casa onde não há pão, todos ralham e ninguém tem razão”
Será mais lenha, para alimentar a fogueira, vai gravar os conflitos geopolíticos já existentes, ficando as sociedade ainda mais polarizadas.
Eu acredito que 2025, vai haver um forte crescimento na adoção das stablecoins de dólares, esse forte crescimento vai agravar o problema sistémico que são as stablecoins. Vai ser o início do fim das stablecoins, pelo menos, como nós conhecemos hoje em dia.
Problema sistémico
O sistema FIAT não nasceu de um dia para outro, foi algo que foi construído organicamente, ou seja, foi evoluindo ao longo dos anos, sempre que havia um problema/crise, eram criadas novas regras ou novas instituições para minimizar os problemas. Nestes quase 100 anos, desde os acordos de Bretton Woods, a evolução foram tantas, tornaram o sistema financeiro altamente complexo, burocrático e nada eficiente.
Na prática é um castelo de cartas construído sobre outro castelo de cartas e que por sua vez, foi construído sobre outro castelo de cartas.
As stablecoins são um problema sistémico, devido às suas reservas em dólares e o sistema financeiro não está preparado para manter isso seguro. Com o crescimento das reservas ao longo dos anos, foi se agravando o problema.
No início a Tether colocava as reservas em bancos comerciais, mas com o crescimento dos dólares sob gestão, criou um problema nos bancos comerciais, devido à reserva fracionária. Essas enormes reservas da Tether estavam a colocar em risco a própria estabilidade dos bancos.
A Tether acabou por mudar de estratégia, optou por outros ativos, preferencialmente por títulos do tesouro/obrigações dos EUA. Só que a Tether continua a crescer e não dá sinais de abrandamento, pelo contrário.
Até o próprio mundo cripto, menosprezava a gravidade do problema da Tether/stablecoins para o resto do sistema financeiro, porque o marketcap do cripto ainda é muito pequeno. É verdade que ainda é pequeno, mas a Tether não o é, está no top 20 dos maiores detentores de títulos do tesouros dos EUA e está ao nível dos maiores bancos centrais do mundo. Devido ao seu tamanho, está a preocupar os responsáveis/autoridades/reguladores dos EUA, pode colocar em causa a estabilidade do sistema financeiro global, que está assente nessas obrigações.
Os títulos do tesouro dos EUA são o colateral mais utilizado no mundo, tanto por bancos centrais, como por empresas, é a charneira da estabilidade do sistema financeiro. Os títulos do tesouro são um assunto muito sensível. Na recente crise no Japão, do carry trade, o Banco Central do Japão tentou minimizar a desvalorização do iene através da venda de títulos dos EUA. Esta operação, obrigou a uma viagem de emergência, da Secretaria do Tesouro dos EUA, Janet Yellen ao Japão, onde disponibilizou liquidez para parar a venda de títulos por parte do Banco Central do Japão. Essa forte venda estava desestabilizando o mercado.
Os principais detentores de títulos do tesouros são institucionais, bancos centrais, bancos comerciais, fundo de investimento e gestoras, tudo administrado por gestores altamente qualificados, racionais e que conhecem a complexidade do mercado de obrigações.
O mundo cripto é seu oposto, é naife com muita irracionalidade e uma forte pitada de loucura, na sua maioria nem faz a mínima ideia como funciona o sistema financeiro. Essa irracionalidade pode levar a uma “corrida bancária”, como aconteceu com o UST da Luna, que em poucas horas colapsou o projeto. Em termos de escala, a Luna ainda era muito pequena, por isso, o problema ficou circunscrito ao mundo cripto e a empresas ligadas diretamente ao cripto.
Só que a Tether é muito diferente, caso exista algum FUD, que obrigue a Tether a desfazer-se de vários biliões ou dezenas de biliões de dólares em títulos num curto espaço de tempo, poderia provocar consequências terríveis em todo o sistema financeiro. A Tether é grande demais, é já um problema sistémico, que vai agravar-se com o crescimento em 2025.
Não tenham dúvidas, se existir algum problema, o Tesouro dos EUA vai impedir a venda dos títulos que a Tether tem em sua posse, para salvar o sistema financeiro. O problema é, o que vai fazer a Tether, se ficar sem acesso às venda das reservas, como fará o redeem dos dólares?
Como o crescimento do Tether é inevitável, o Tesouro e o FED estão com um grande problema em mãos, o que fazer com o Tether?
Mas o problema é que o atual sistema financeiro é como um curto cobertor: Quanto tapas a cabeça, destapas os pés; Ou quando tapas os pés, destapas a cabeça. Ou seja, para resolver o problema da guarda reservas da Tether, vai criar novos problemas, em outros locais do sistema financeiro e assim sucessivamente.
Conta mestre
Uma possível solução seria dar uma conta mestre à Tether, dando o acesso direto a uma conta no FED, semelhante à que todos os bancos comerciais têm. Com isto, a Tether deixaria de necessitar os títulos do tesouro, depositando o dinheiro diretamente no banco central. Só que isto iria criar dois novos problemas, com o Custodia Bank e com o restante sistema bancário.
O Custodia Bank luta há vários anos contra o FED, nos tribunais pelo direito a ter licença bancária para um banco com full-reserves. O FED recusou sempre esse direito, com a justificativa que esse banco, colocaria em risco toda a estabilidade do sistema bancário existente, ou seja, todos os outros bancos poderiam colapsar. Perante a existência em simultâneo de bancos com reserva fracionária e com full-reserves, as pessoas e empresas iriam optar pelo mais seguro. Isso iria provocar uma corrida bancária, levando ao colapso de todos os bancos com reserva fracionária, porque no Custodia Bank, os fundos dos clientes estão 100% garantidos, para qualquer valor. Deixaria de ser necessário limites de fundos de Garantia de Depósitos.
Eu concordo com o FED nesse ponto, que os bancos com full-reserves são uma ameaça a existência dos restantes bancos. O que eu discordo do FED, é a origem do problema, o problema não está nos bancos full-reserves, mas sim nos que têm reserva fracionária.
O FED ao conceder uma conta mestre ao Tether, abre um precedente, o Custodia Bank irá o aproveitar, reclamando pela igualdade de direitos nos tribunais e desta vez, possivelmente ganhará a sua licença.
Ainda há um segundo problema, com os restantes bancos comerciais. A Tether passaria a ter direitos similares aos bancos comerciais, mas os deveres seriam muito diferentes. Isto levaria os bancos comerciais aos tribunais para exigir igualdade de tratamento, é uma concorrência desleal. Isto é o bom dos tribunais dos EUA, são independentes e funcionam, mesmo contra o estado. Os bancos comerciais têm custos exorbitantes devido às políticas de compliance, como o KYC e AML. Como o governo não vai querer aliviar as regras, logo seria a Tether, a ser obrigada a fazer o compliance dos seus clientes.
A obrigação do KYC para ter stablecoins iriam provocar um terramoto no mundo cripto.
Assim, é pouco provável que seja a solução para a Tether.
FED
Só resta uma hipótese, ser o próprio FED a controlar e a gerir diretamente as stablecoins de dólar, nacionalizado ou absorvendo as existentes. Seria uma espécie de CBDC. Isto iria provocar um novo problema, um problema diplomático, porque as stablecoins estão a colocar em causa a soberania monetária dos outros países. Atualmente as stablecoins estão um pouco protegidas porque vivem num limbo jurídico, mas a partir do momento que estas são controladas pelo governo americano, tudo muda. Os países vão exigir às autoridades americanas medidas que limitem o uso nos seus respectivos países.
Não existe uma solução boa, o sistema FIAT é um castelo de cartas, qualquer carta que se mova, vai provocar um desmoronamento noutro local. As autoridades não poderão adiar mais o problema, terão que o resolver de vez, senão, qualquer dia será tarde demais. Se houver algum problema, vão colocar a responsabilidade no cripto e no Bitcoin. Mas a verdade, a culpa é inteiramente dos políticos, da sua incompetência em resolver os problemas a tempo.
Será algo para acompanhar futuramente, mas só para 2026, talvez…
É curioso, há uns anos pensava-se que o Bitcoin seria a maior ameaça ao sistema ao FIAT, mas afinal, a maior ameaça aos sistema FIAT é o próprio FIAT(stablecoins). A ironia do destino.
Isto é como uma corrida, o Bitcoin é aquele atleta que corre ao seu ritmo, umas vezes mais rápido, outras vezes mais lento, mas nunca pára. O FIAT é o atleta que dá tudo desde da partida, corre sempre em velocidade máxima. Só que a vida e o sistema financeiro não é uma prova de 100 metros, mas sim uma maratona.
Europa
2025 será um ano desafiante para todos europeus, sobretudo devido à entrada em vigor da regulamentação (MiCA). Vão começar a sentir na pele a regulamentação, vão agravar-se os problemas com os compliance, problemas para comprovar a origem de fundos e outras burocracias. Vai ser lindo.
O Travel Route passa a ser obrigatório, os europeus serão obrigados a fazer o KYC nas transações. A Travel Route é uma suposta lei para criar mais transparência, mas prática, é uma lei de controle, de monitorização e para limitar as liberdades individuais dos cidadãos.
O MiCA também está a colocar problemas nas stablecoins de Euro, a Tether para já preferiu ficar de fora da europa. O mais ridículo é que as novas regras obrigam os emissores a colocar 30% das reservas em bancos comerciais. Os burocratas europeus não compreendem que isto coloca em risco a estabilidade e a solvência dos próprios bancos, ficam propensos a corridas bancárias.
O MiCA vai obrigar a todas as exchanges a estar registadas em solo europeu, ficando vulnerável ao temperamento dos burocratas. Ainda não vai ser em 2025, mas a UE vai impor políticas de controle de capitais, é inevitável, as exchanges serão obrigadas a usar em exclusividade stablecoins de euro, as restantes stablecoins serão deslistadas.
Todas estas novas regras do MiCA, são extremamente restritas, não é para garantir mais segurança aos cidadãos europeus, mas sim para garantir mais controle sobre a população. A UE está cada vez mais perto da autocracia, do que da democracia. A minha única esperança no horizonte, é que o sucesso das políticas cripto nos EUA, vai obrigar a UE a recuar e a aligeirar as regras, a teoria dos jogos é implacável. Mas esse recuo, nunca acontecerá em 2025, vai ser um longo período conturbado.
Recessão
Os mercados estão todos em máximos históricos, isto não é sustentável por muito tempo, suspeito que no final de 2025 vai acontecer alguma correção nos mercados. A queda só não será maior, porque os bancos centrais vão imprimir dinheiro, muito dinheiro, como se não houvesse amanhã. Vão voltar a resolver os problemas com a injeção de liquidez na economia, é empurrar os problemas com a barriga, em de os resolver. Outra vez o efeito Cantillon.
Será um ano muito desafiante a nível político, onde o papel dos políticos será fundamental. A crise política na França e na Alemanha, coloca a UE órfã, sem um comandante ao leme do navio. 2025 estará condicionado pelas eleições na Alemanha, sobretudo no resultado do AfD, que podem colocar em causa a propriedade UE e o euro.
Possivelmente, só o fim da guerra poderia minimizar a crise, algo que é muito pouco provável acontecer.
Em Portugal, a economia parece que está mais ou menos equilibrada, mas começam a aparecer alguns sinais preocupantes. Os jogos de sorte e azar estão em máximos históricos, batendo o recorde de 2014, época da grande crise, não é um bom sinal, possivelmente já existe algum desespero no ar.
A Alemanha é o motor da Europa, quanto espirra, Portugal constipa-se. Além do problema da Alemanha, a Espanha também está à beira de uma crise, são os países que mais influenciam a economia portuguesa.
Se existir uma recessão mundial, terá um forte impacto no turismo, que é hoje em dia o principal motor de Portugal.
Brasil
Brasil é algo para acompanhar em 2025, sobretudo a nível macro e a nível político. Existe uma possibilidade de uma profunda crise no Brasil, sobretudo na sua moeda. O banco central já anda a queimar as reservas para minimizar a desvalorização do Real.

Sem mudanças profundas nas políticas fiscais, as reservas vão se esgotar. As políticas de controle de capitais são um cenário plausível, será interesse de acompanhar, como o governo irá proceder perante a existência do Bitcoin e stablecoins. No Brasil existe um forte adoção, será um bom case study, certamente irá repetir-se em outros países num futuro próximo.
Os próximos tempos não serão fáceis para os brasileiros, especialmente para os que não têm Bitcoin.
Blockchain
Em 2025, possivelmente vamos ver os primeiros passos da BlackRock para criar a primeira bolsa de valores, exclusivamente em blockchain. Eu acredito que a BlackRock vai criar uma própria blockchain, toda controlada por si, onde estarão os RWAs, para fazer concorrência às tradicionais bolsas de valores. Será algo interessante de acompanhar.
Estas são as minhas previsões, eu escrevi isto muito em cima do joelho, certamente esqueci-me de algumas coisas, se for importante acrescentarei nos comentários. A maioria das previsões só acontecerá após 2025, mas fica aqui a minha opinião.
Isto é apenas a minha opinião, Don’t Trust, Verify!
-
 @ dc4cd086:cee77c06
2024-10-18 04:08:33
@ dc4cd086:cee77c06
2024-10-18 04:08:33Have you ever wanted to learn from lengthy educational videos but found it challenging to navigate through hours of content? Our new tool addresses this problem by transforming long-form video lectures into easily digestible, searchable content.
Key Features:
Video Processing:
- Automatically downloads YouTube videos, transcripts, and chapter information
- Splits transcripts into sections based on video chapters
Content Summarization:
- Utilizes language models to transform spoken content into clear, readable text
- Formats output in AsciiDoc for improved readability and navigation
- Highlights key terms and concepts with [[term]] notation for potential cross-referencing
Diagram Extraction:
- Analyzes video entropy to identify static diagram/slide sections
- Provides a user-friendly GUI for manual selection of relevant time ranges
- Allows users to pick representative frames from selected ranges
Going Forward:
Currently undergoing a rewrite to improve organization and functionality, but you are welcome to try the current version, though it might not work on every machine. Will support multiple open and closed language models for user choice Free and open-source, allowing for personal customization and integration with various knowledge bases. Just because we might not have it on our official Alexandria knowledge base, you are still welcome to use it on you own personal or community knowledge bases! We want to help find connections between ideas that exist across relays, allowing individuals and groups to mix and match knowledge bases between each other, allowing for any degree of openness you care.
While designed with #Alexandria users in mind, it's available for anyone to use and adapt to their own learning needs.
Screenshots
Frame Selection

This is a screenshot of the frame selection interface. You'll see a signal that represents frame entropy over time. The vertical lines indicate the start and end of a chapter. Within these chapters you can select the frames by clicking and dragging the mouse over the desired range where you think diagram is in that chapter. At the bottom is an option that tells the program to select a specific number of frames from that selection.
Diagram Extraction

This is a screenshot of the diagram extraction interface. For every selection you've made, there will be a set of frames that you can choose from. You can select and deselect as many frames as you'd like to save.
Links
- repo: https://github.com/limina1/video_article_converter
- Nostr Apps 101: https://www.youtube.com/watch?v=Flxa_jkErqE
Output
And now, we have a demonstration of the final result of this tool, with some quick cleaning up. The video we will be using this tool on is titled Nostr Apps 101 by nostr:npub1nxy4qpqnld6kmpphjykvx2lqwvxmuxluddwjamm4nc29ds3elyzsm5avr7 during Nostrasia. The following thread is an analog to the modular articles we are constructing for Alexandria, and I hope it conveys the functionality we want to create in the knowledge space. Note, this tool is the first step! You could use a different prompt that is most appropriate for the specific context of the transcript you are working with, but you can also manually clean up any discrepancies that don't portray the video accurately.
nostr:nevent1qvzqqqqqqypzp5r5hd579v2sszvvzfel677c8dxgxm3skl773sujlsuft64c44ncqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgwwaehxw309ahx7uewd3hkctcpzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309aex2mrp0yh8xmn0wf6zuum0vd5kzmp0qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgc7hglpn
Or view on Coracle nostr:nevent1qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgcppemhxue69uhkummn9ekx7mp0qgsdqa9md83tz5yqnrqjw07hhkpmfjpkuv9hlh5v8yhu8z274w9dv7qnnq0s3
-
 @ d830ee7b:4e61cd62
2025-01-07 09:14:17
@ d830ee7b:4e61cd62
2025-01-07 09:14:17จุดเริ่มต้นของสงครามบล็อกไซส์
ลองนึกภาพร้านอาหารเล็ก ๆ ที่มีแค่สิบโต๊ะ แต่ลูกค้ากลับล้นหลามจนพนักงานวิ่งวุ่นตลอดวัน เราอาจเห็นภาพชัดว่าปัญหาต้องตามมาแน่ ๆ ถ้าจำนวนโต๊ะไม่พอกับลูกค้าที่ต่อแถวกันยาวเหยียด
บางคนหัวเสียจนยอมจ่ายเงินเพิ่มเพื่อรีบได้โต๊ะนั่ง ในขณะที่อีกหลายคนก็ยืนรอจนหมดอารมณ์กิน สุดท้ายก็ต้องถามกันว่า
“จะทำยังไงดี ถึงจะไม่เสียเอกลักษณ์ร้าน และไม่ปล่อยให้ลูกค้าต้องหงุดหงิดมากมายขนาดนี้?”
บรรยากาศตรงนี้เปรียบได้กับสภาพของบิตคอยน์ช่วงราวปี 2015 ซึ่งเดิมทีเคยรองรับธุรกรรมได้สบาย ๆ แต่จู่ ๆ ก็ต้องแบกรับภาระธุรกรรมมหาศาลจน “คิวยาวเป็นหางว่าว”
ทั้งหมดนี้มาจากข้อกำหนดตั้งต้นว่า แต่ละบล็อกมีขนาดเพียง 1 เมกะไบต์ และบล็อกจะถูกสร้างทุก ๆ ประมาณ 10 นาที ทีนี้พอผู้ใช้หลั่งไหลเข้ามาไม่หยุด พื้นที่เล็ก ๆ ที่ว่าเลยเอาไม่อยู่ ใครอยากให้ธุรกรรมติดบล็อกก่อนก็ควักกระเป๋าจ่ายค่าธรรมเนียมเพิ่ม ถ้าไม่จ่าย ธุรกรรมอาจรอข้ามวันข้ามคืน แถมยังเสี่ยงค้างเติ่งไปเลย

ความไม่พอใจจึงปะทุขึ้นเป็นเสียงดังลั่นว่า
“แก้ปัญหานี้ยังไงดี จะขยายบล็อกกันเลยไหม หรือปรับซอฟต์แวร์ให้ฉลาดขึ้นโดยไม่เพิ่มขนาดจริง ๆ?”
เมื่อสองแนวคิดนี้ตั้งฉากกัน คนในแวดวงบิตคอยน์จึงแตกเป็นสองฝั่งหลัก ๆ
ฝั่งแรกเสนอ “เพิ่ม Blocksize” โดยบอกว่าต้องแก้ให้จบตรงจุด เหมือนเพิ่มโต๊ะเข้าไปในร้าน จะได้รองรับลูกค้าได้มากขึ้น เพราะเชื่อว่า Bitcoin ต้องพร้อมสำหรับการใช้งานทั่วโลก การขยายจาก 1 MB เป็น 2 MB หรือ 4 MB หรือมากกว่านั้น จึงตอบโจทย์ผู้ใช้หลากหลายตั้งแต่รายเล็กไปจนถึงธุรกิจใหญ่
แกนนำฝ่ายนี้คือ Roger Ver หรือ “Bitcoin Jesus” ที่ผลักดันแนวคิดนี้สุดตัวร่วมกับทีมขุดอย่าง Bitmain ซึ่งไม่อยากเห็นใครต้องยืนรอนานหรือจ่ายแพงเวอร์
อีกฝ่ายคือทีมพัฒนา “Bitcoin Core” ที่มี Greg Maxwell และ Peter Wuille เป็นหัวขบวน พวกเขายืนยันว่าถ้ายิ่งเพิ่มขนาดบล็อกให้ใหญ่โต ก็จะยิ่งเก็บข้อมูลมากจนโหนดรายเล็ก ๆ ต้องใช้ทรัพยากรสูงขึ้น สุดท้ายอาจเหลือแค่รายใหญ่ที่รันโหนดไหว แล้ว Decentralization ก็จะถูกบั่นทอน
ฝ่ายบิตคอยน์คอร์จึงเสนอทางแก้แบบ Segregated Witness (SegWit) ซึ่งเปรียบได้กับการจัดโต๊ะใหม่ให้แยบยล—ย้ายข้อมูลลายเซ็นธุรกรรมไปไว้นอกบล็อกหลัก ทำให้ในบล็อกมีพื้นที่ใส่ธุรกรรมได้อีกเยอะขึ้นโดยไม่ต้องทุบผนังขยายร้าน
ความขัดแย้งไม่ได้จำกัดอยู่ในเว็บบอร์ดหรือฟอรัม แต่ลุกลามไปจนถึงเวทีระดับโลกอย่าง Consensus Conference ปี 2016 และ 2017 ฝ่ายหนุนเพิ่มขนาดบล็อกก็โหวกเหวกว่า “นี่แหละถูกจุดที่สุด”
ส่วนทีมบิตคอยน์คอร์ก็โต้กลับว่า “ขืนบล็อกใหญ่ไป ระบบก็เสี่ยงรวมศูนย์ เพราะใครจะมีทุนซื้ออุปกรณ์แพง ๆ และเน็ตแรง ๆ ตลอด” จึงไม่ใช่แค่ถกเถียงทางเทคนิค แต่สะท้อนมุมมองปรัชญาด้วยว่าบิตคอยน์ควรเป็นระบบ “กระจาย” หรือ “รวมศูนย์” กันแน่
ยิ่งถกก็ยิ่งมองไม่เห็นทางออก.. บ้างก็เสนอให้ Fork แยกเครือข่ายไปเลย เหมือนเปิดสาขาร้านใหม่ ใครไม่โอเคแนวไหนก็ไปอีกสาขาหนึ่ง
Roger Ver กับสายขุดยักษ์ใหญ่ก็บอกว่าถ้าไม่เพิ่ม Blocksize ต่อไปค่าธรรมเนียมสูง และคนจะเข้าถึงยากขึ้น เหมือนร้านที่โต๊ะแน่นจนคนล้น
ฝั่งบิตคอยน์คอร์ย้ำว่าจะพัฒนา SegWit กับ Lightning Network เพื่อขนธุรกรรมส่วนใหญ่ไปทำงานนอกบล็อกหลัก แม้อาจต้องรอให้เทคโนโลยีสุกงอม แต่คงไม่กระทบโหนดรายเล็กมากนัก
ในโลกออนไลน์ สงครามโซเชียลก็เริ่มเดือด ตั้งกระทู้กันทุกวัน บางคนต่อว่านักขุดว่าเอากำไรเป็นหลัก บ้างบอกทีมบิตคอยน์คอร์ไม่เข้าใจปัญหาฝั่งธุรกิจจนชาวเน็ตแบ่งเป็นหลายค่าย คำถามใหญ่จึงดังขึ้น
“ตกลงบิตคอยน์จะเป็น ‘อาวุธทางการเงิน’ ของคนหมู่มากได้จริงเหรอ ถ้าไม่มีพื้นที่ในบล็อกมากพอ?”
หรือ..
“ถ้าผลุนผลันขยายบล็อกไปเรื่อย ๆ จนเหลือแต่รายใหญ่ที่รันโหนดได้ แบบนั้นยังถือว่าเป็น บิตคอยน์ในอุดมการณ์ของ Satoshi Nakamoto ไหม?”
พอหลายฝ่ายพยายามประนีประนอมกันหลายเวที สุดท้ายก็ไม่ประสบผล Roger Ver มั่นใจว่าต้องเพิ่ม Blocksize เท่านั้นจึงพาบิตคอยน์รอด
ส่วนทีม Core ไม่ยอมเปิดทางง่าย ๆ เพราะกลัวระบบเสียหลักการกระจายอำนาจไป
ด้วยเหตุผลทั้งคู่จึงทำให้สงครามนี้ยืดเยื้อ กลุ่มขุดและพัฒนาในแวดวงเริ่มจับตากันเครียด บ้างเสนอทางผสม เช่น เพิ่ม Blocksize นิดหน่อย แล้วเปิด SegWit ควบคู่ บ้างเสนอว่าให้เลื่อนตัดสินใจออกไปก่อนก็ยังดี
ไม่มีใครรู้ว่าจะลงเอยอย่างไร.. และหากเรื่องนี้พลั้งพลาดบิตคอยน์อาจแตกเป็นสองสายจนผู้ใช้หรือนักลงทุนสับสน
สถานการณ์ช่วงแรกเหมือน “ไฟที่กำลังคุ” เพราะยังไม่ปะทุเต็มที่แต่ก็แรงพอจะยกครัวไปตลอดทั้งวงการ คนพัฒนาก็ทำ SegWit และ Lightning Network ไป ฝ่ายหนุน Blocksize ก็เดินสายผลักดันให้เต็มที่ ถึงขั้นยอมเสี่ยง Fork ถ้าจำเป็นจริง ๆ
นี่แหละคือจุดเริ่มต้นของความตึงเครียดที่ไม่ใช่แค่ “ขนาดบล็อก” แต่หมายถึงอนาคตของบิตคอยน์ที่อาจพลิกโฉมไปตลอดกาล..

คิดง่าย ๆ ก็เหมือนร้านอาหารเล็ก ๆ ที่กำลังจะก้าวสู่ภัตตาคารใหญ่ระดับท็อป เมื่อแขกเหรื่อมาไม่หยุดหย่อน แน่นอนว่าเสียงเรียกร้องให้ทุบกำแพงขยายร้านย่อมมีบ้าง แต่บางคนอาจบอก “เปลี่ยนวิธีจัดโต๊ะแทนได้ไหม?” ทุกแนวทางต่างมีทั้งโอกาสและความเสี่ยง
ที่สำคัญคือ บิตคอยน์เป็นสินทรัพย์อันดับหนึ่งของโลกคริปโตฯ หากก้าวพลาดเพียงเล็กน้อย อาจสะเทือนไปทั่วโลกด้วย
เนื้อหาถัดไปผมจะชวนมาดูว่า ใครกันแน่ที่อยู่เบื้องหลังการขับเคลื่อนสงคราม Blocksize ครั้งนี้?
พวกเขามีแรงจูงใจอะไรกันบ้าง? และจะนำพาบิตคอยน์ไปในทิศทางใด?
ขอทิ้งท้ายส่วนนี้ให้คิดเล่น ๆ
“ถ้าเพิ่ม Blocksize สุด ๆ แต่โหนดรายเล็กหายหมด สุดท้ายยังเรียกว่ากระจายอำนาจอยู่ไหม?”
“หรือจะรักษาบล็อกขนาดเล็กไว้อย่างเดิม แล้วปรับเทคโนโลยีเสริมให้ฉลาดขึ้นดีกว่า?”
ทั้งหมดที่เล่ามายังเป็นแค่บทโหมโรงนะครับ สงครามนี้เพิ่งปะทุเท่านั้น ยังมีอะไรเข้มข้นอีกมาก ติดตามต่อว่าฝั่งไหนจะงัดไม้เด็ดอะไรออกมาเพื่อรักษา “ร้านอาหาร” แห่งนี้ให้เดินหน้าต่อไปได้โดยไม่เสียตัวตน..
ใครคือผู้ขับเคลื่อนสงคราม Blocksize?
พาร์ทที่แล้ว เราได้เห็นภาพรวมของปัญหาที่ดูเหมือนจะเล็กนิดเดียวอย่าง “บล็อกใหญ่หรือเล็ก?” แต่กลับแผ่ขยายจนกลายเป็นมหากาพย์ความขัดแย้งในชุมชนบิตคอยน์ เสมือนเดิมพันอนาคตของสกุลเงินดิจิทัลอันดับหนึ่งบนโลกใบนี้
พอตอนนี้ถึงเวลาแล้วที่เราจะก้าวลึกลงไปในเบื้องหลังของสงครามอันร้อนแรงนี้ ใครอยู่ในเงามืด? ใครลากสายอยู่หลังเวที? และใครโดดขึ้นมาเดินลุยบนสนามเปิดเพื่อต่อสู้แย่งชิงฉันทามติของเครือข่าย?
มีคนชอบเปรียบเทียบว่าศึก Blocksize ครั้งนี้คือ “สนามรบดิจิทัล” ซึ่งไม่ได้ยิงกระสุนห้ำหั่นแต่ใช้โค้ดแทน ขับเคลื่อนด้วย “Hashrate” ที่เปรียบเสมือนอาวุธหนัก ฝ่ายไหนถือกำลังขุดสูงกว่าก็เหมือนมีกองทัพเบิ้ม ๆ อยู่ในมือ
ด้านนักพัฒนาและผู้ใช้ทั่วไปก็คล้ายประชากรพลเรือนที่บางทีก็ต้องยอมรับชะตา แต่บางทีก็รวมตัวประท้วงสร้างพลังของตัวเองให้โลกได้เห็น ทุกฝีก้าวมีคนจ้องดูว่าจะเกิด “Hard Fork” หรือ “Soft Fork” เมื่อไหร่ และกฎใดจะถูกประกาศเป็น “กฎใหม่” ให้ทุกคนต้องปฏิบัติตาม
ในมุมของคนอยาก “เพิ่ม Blocksize” เห็นชื่อของ Roger Ver โผล่โดดเด่นสุด ๆ เขาคือ “Bitcoin Jesus” แห่งยุคบุกเบิก ที่ครั้งหนึ่งทุ่มทุนโปรโมตบิตคอยน์แบบไม่กลัวเจ๊ง ด้วยความเชื่อว่าบิตคอยน์ควรเป็น “เงินสดดิจิทัล” ลื่นไหลจ่ายคล่อง สลัดค่าธรรมเนียมแพง ๆ ทิ้งไปให้หมด
ในสายตาเขา การคงบล็อกเล็กแค่ 1 MB ยิ่งทำให้คนใช้แล้วปวดหัว ค่าธรรมเนียมสูงปรี๊ด ธุรกรรมอืดอาดเกินจะทน เลยต้องขยายขนาดบล็อกแบบจัดเต็ม เหมือนขยายถนนให้รถวิ่งง่าย ไม่งั้นก็ต้องมุดเข้าอุโมงค์แคบ ๆ จอดติดกันยาว
และ “Bitmain” บริษัทเครื่องขุดเบอร์ใหญ่สุดในโลกก็เข้ามาเสริมพลังแบบเต็มขั้น ขับเคลื่อนโดย Jihan Wu ที่เล็งเห็นว่าพอยิ่งขยายบล็อก ธุรกรรมก็จะยิ่งทะลัก ค่าธรรมเนียมก็จะเพิ่มขึ้น นักขุดจะได้เงินดี สร้างแรงดึงดูดให้คนหันมาหาบิตคอยน์มากขึ้นไปอีก
Bitmain ถือ Hashrate มหาศาล จึงไม่ต่างจากมีทัพใหญ่พร้อมยกพลบุก เพื่อดันแนวคิด “Fork” ได้ตลอดเวลา ถ้าฝั่งเพิ่ม Blocksize อยากจะเล่นเกมสายไหนก็เดินได้เลย
อีกฟากสนาม คือทีม “Bitcoin Core” ถือเป็นแกนกลางที่คุมซอฟต์แวร์หลัก
นำโดย *Greg Maxwell, Peter Wuille และ Wladimir van der Laan***
พวกเขาห่วงว่าถ้าบล็อกใหญ่ขึ้นมาก คงจะมีแค่นายทุนใหญ่เท่านั้นที่รันโหนดไหว ประชาชนตัวเล็ก ๆ หรือคนไม่มีทรัพยากรเยอะก็ยิ่งถูกกันออกจากเครือข่าย กลายเป็นระบบกึ่งรวมศูนย์ ซึ่งสวนกับหลักการเดิมที่ Satoshi Nakamoto เคยวางไว้
พวกเขาจึงเสนอ Segregated Witness (SegWit) เพื่อตัดข้อมูลลายเซ็น (Witness Data) ทิ้งไปนอกบล็อก ทำให้มีพื้นที่รองรับธุรกรรมได้เยอะขึ้นแบบไม่ต้องขยาย “เลนหลัก” และจะต่อยอดด้วย Lightning Network เพื่อยกธุรกรรมส่วนใหญ่ไปอยู่นอกบล็อกอีกชั้น
ฝั่งนักพัฒนาเหล่านี้ไม่ได้สู้อย่างโดดเดี่ยว แต่มีผู้ใช้รวมพลังกันในนาม UASF (User-Activated Soft Fork) มองว่า
“ใครว่าขุดเยอะแล้วสั่งการได้หมด? ผู้ใช้ทั่ว ๆ ไปก็ออกแบบกติกาได้เหมือนกัน?”
พวกเขาบอกเลยว่า “ถ้าไม่หนุน SegWit พวกฉันไม่เอาด้วยนะ”
การเคลื่อนไหวแบบนี้สร้างแรงกดดันให้นักขุดต้องรีบตามน้ำ ไม่งั้นเสี่ยงโดนผู้ใช้ปฏิเสธบล็อกกันถ้วนหน้า
ปี 2016-2017 กลายเป็นช่วงร้อนระอุสุด ๆ Roger Ver ลุกขึ้นพูดเมื่อไหร่ มักกล่าวหาทีม Core ว่าปิดประตูโอกาสทองของบิตคอยน์
ส่วนทีม Core ก็ตีโต้กลับว่า “ถ้าเพิ่มบล็อกเร็วไป มีแต่จะทำให้บิ๊กทุนไม่กี่เจ้าเข้ามาผูกขาด!”
พอยิ่งเถียงกันในงานใหญ่ เช่น Consensus Conference 2017 ประเด็นก็ยิ่งเดือด บางฝ่ายอยาก “Fork” แตกสายไปเลย บางฝ่ายยังคอยประนีประนอม แต่ก็ไม่มีใครลงรอยกันได้
Roger Ver และ Bitmain เร่งเครื่องดัน Hard Fork
ทีม Core ไม่ยอมถอย ยืนกราน SegWit ก่อน แล้วใช้ Lightning Network ปิดเกม
ผลคือ...
ทุกคนเริ่มกลัวว่า “Bitcoin จะแตกเป็นสองสายจริง ๆ หรือ?”
จะเป็นบล็อกใหญ่ หรือจะอยู่ 1 MB พร้อม SegWit?

กลางปี 2017 สงครามนี้จึงคลอด “Bitcoin Cash” เครือข่ายใหม่ที่กลุ่ม Roger Ver ผลักดัน บอกว่านี่คือ “Bitcoin ตัวจริง” ที่ค่าธรรมเนียมถูกกว่า ธุรกรรมไวกว่า รองรับคนจำนวนมากได้
ในขณะเดียวกัน เครือข่ายหลัก BTC ก็เปิดใช้ SegWit ไป พร้อมมุ่งหน้าเปิดทาง Lightning Network ทำให้ครึ่งหนึ่งของชุมชนยังเชื่อมั่นว่าการรักษาบล็อกเล็ก คือหัวใจสำคัญของกระจายอำนาจ
Blocksize War ครั้งนี้ เกินกว่าจะเรียกว่า “ดีเบตเชิงเทคนิค”
มันคล้ายการปะทะอุดมการณ์ของ “กระจายอำนาจอย่างเคร่งครัด” ปะทะ “ขยายบล็อกให้ใช้งานจริงในชีวิตประจำวัน”
ทั้งสองฝ่ายต่างยิงวาทะกันเดือดในโซเชียลมีเดีย คนฝ่ายหนึ่งบอกอีกฝ่าย “ล้าหลังไม่รู้จักปรับตัว” อีกฝ่ายก็ยันกลับว่า “คิดแค่กำไรระยะสั้น ไม่รักษาอัตลักษณ์บิตคอยน์” บน Reddit, Twitter, ฟอรัมต่าง ๆ เหล่าผู้เคยเป็นเพื่อนร่วมทางต้องแยกค่ายกันเพราะมองต่างว่าควรเพิ่มบล็อกหรือเปล่า
ที่สุดแล้ว...
เมื่อสองอุดมการณ์สวนทางกันระดับราก แทบไม่มีพื้นที่ประนีประนอม บ้างเชื่อว่าถ้าไม่เพิ่มบล็อกบิตคอยน์จะใช้งานลำบากเกิน บ้างยึดมั่นว่าถ้าบล็อกใหญ่มากโหนดเล็ก ๆ ก็จะหายไปหมด ระบบจะตกในมือไม่กี่คน.. ซึ่งขัดเจตนารมณ์ตั้งต้นของ Satoshi แบบสุด ๆ
ผลลัพธ์จึงลงเอยด้วยการเกิด “Bitcoin Cash” (BCH) แยกเครือข่าย และเปิดศึกโฆษณาว่า “ตนต่างหากที่เป็นผู้สืบทอดแนวคิด Satoshi ของจริง”
เมื่อ Bitcoin Cash ถือกำเนิดพร้อมขนาดบล็อกใหญ่ “มหาศึก” ครั้งนี้ก็ไม่ได้จบลง แต่เปลี่ยนหน้าฉากไปสู่การตลาดและความชอบธรรม
ใคร ๆ ก็ตั้งคำถามว่า “Bitcoin Cash ต่างจาก Bitcoin ยังไง?” หรือ “ใครสืบทอดเจตนารมณ์ Satoshi อย่างแท้จริงกันแน่?”
นักพัฒนา ฝั่ง BTC ยังเหนียวแน่นว่ารักษาเครือข่ายให้เบา ๆ แล้วใช้ทริคอย่าง SegWit, Lightning Network เสริม คือทางออกป้องกันการรวมศูนย์
ฝ่าย BCH ก็บอกว่าบล็อกใหญ่เลยดีกว่า ทุกคนจะได้เทรดกันเพลินโดยไม่ต้องแย่งพื้นที่
ในภาพใหญ่.. สงครามครั้งนี้ส่งคลื่นกระเพื่อมไปทั่วโลกคริปโตฯ หลายคนกลัวว่าถ้ายังแยกแตกกันแบบนี้ต่อ ราคาจะผันผวนจนคนขยาด แต่ก็มีอีกฝ่ายที่มองว่า
“ดีสิ มีการแข่งขันแล้วเกิดนวัตกรรมใหม่ ๆ”
เพราะในโลกโอเพนซอร์ส ไม่มีใครหยุดการแยกตัวได้ถ้าคนบางกลุ่มอยากลองแนวทางใหม่
คำถามสำคัญคือ..
“ใครขับเคลื่อนสงคราม Blocksize?”
คำตอบก็หนีไม่พ้น Roger Ver, Bitmain และทีม Bitcoin Core รวมถึงกลุ่ม UASF
พวกเขาต่างมีพลังในมิติต่าง ๆ
Roger Ver มีแรงสนับสนุนจากนักขุดสายทุนจัด Bitmain มีกองทัพ Hashrate มหาศาล ทีม Bitcoin Core คุมซอฟต์แวร์ และ UASF ก็มีอำนาจ ‘No Node, No Vote’ ที่ปัดบล็อกไม่พอใจทิ้งได้หมด
นี่ไม่ใช่การรบระหว่าง “อำนาจกับผู้อ่อนแอ” แต่เป็นสมรภูมิที่ทุกขั้วมี “พลัง” อยู่คนละแบบ ทำให้การประนีประนอมเป็นเพียงอุดมคติ
จนที่สุดจึงแตกเป็นสองสาย เหมือนเป็นสปิริตของโอเพนซอร์สที่แค่ Fork ก็พาเดินไปคนละทิศ ใครอยากกดเครื่องขุดก็ขุด ใครอยากตามซอฟต์แวร์ Core ก็จัดไป
นึกภาพอนาคตสิครับ.. ถ้ามีเทคโนโลยีใหม่เข้ามาอีก จะมีสงคราม “Blocksize 2.0” หรือเปล่า? ถ้าเจอเงื่อนไขใหญ่ ๆ ในการเปลี่ยนระบบ ย่อมต้องเข้าสู่วงจรดีเบตเดือดปุดเหมือนเคย
เพราะบิตคอยน์เป็นระบบไร้ผู้นำสูงสุด ทุกฝ่ายจึงมีสิทธิชูมือคัดค้านหรือสนับสนุนอย่างอิสระ
ฉากในเนื้อหาส่วนนี้คือด้านหน้าฉากของสงคราม Blocksize และเหล่าคนขับเคลื่อนที่ทำให้เกิดการแตกแยกครั้งประวัติศาสตร์ในโลกบิตคอยน์ ส่วนต่อไปเราจะได้เห็นเทคนิคล้ำ ๆ และจุดชนวนสุดเฉพาะหน้าที่ทำให้สองฝ่ายยิ่งปะทะกันอีก
แต่ก่อนจะไปรอนั้น..
ขอสรุปให้คิดกันแบบง่าย ๆ ว่า… ในโลกอันไร้ศูนย์กลางที่ต่างคนต่างตะโกนว่า
“ฉันคือเจ้าของบิตคอยน์!”
สุดท้าย “ใครกันแน่เป็นผู้ตัดสินทิศทาง?” หรือแท้จริง “ชัยชนะ–ความพ่ายแพ้” ก็ไม่มีอยู่จริงในสงครามแบบนี้...
เอาจริง ๆ การตัดสินใจของไม่กี่คน หรือการร่วมตัวของยูสเซอร์กระจัดกระจาย ก็ล้วนมีสิทธิเปลี่ยนอนาคตของเงินดิจิทัลได้ทั้งสิ้น จึงเป็นเสน่ห์และความโกลาหลของ “decentralization” ที่น่าหลงใหล
ไม่มีใครสั่งใครได้เต็มร้อย แต่ก็ไม่มีใครจะหยุดคนอื่นได้หมดเช่นกัน

เมื่อมองย้อนกลับไป.. นี่แหละเป็นบทเรียนสำคัญว่าบิตคอยน์ไม่ได้เป็นของใครคนเดียว และถ้าวันหนึ่งไฟสงครามลุกลามขึ้นอีกรอบ เราทุกคนจะรับมือกันยังไง?
ตอนนี้สงครามอาจดูเงียบ ๆ แต่ก็ไม่ได้ปิดฉากสนิท เพราะคลื่นใต้น้ำยังพร้อมระอุขึ้นได้ตลอด
เวลาเท่านั้นที่จะบอกว่า SegWit จะพิสูจน์ตัวเองได้ไหม หรือฝ่าย Hard Fork จะกลับมาโดดเด่นอีกครั้ง
จึงมีแต่คำถามค้างคาว่า.. อีกหน่อยบิตคอยน์จะยังเป็นบิตคอยน์ในแบบที่เรารู้จัก? หรือจะเปลี่ยนโฉมตามรอยแผลที่สงคราม Blocksize ทิ้งไว้?
คอยติดตามกันต่อไปในบทความตอนที่ 2
เพราะนี่อาจเป็นวัฏจักรที่ยังไม่รู้วันสิ้นสุดจริง ๆ ก็ได้ครับ...
-
 @ 3f770d65:7a745b24
2024-12-30 19:25:45
@ 3f770d65:7a745b24
2024-12-30 19:25:45As I look back on my predictions for Nostr in 2024, it’s clear I had some hits and misses. I believe my first two predictions were spot on, accurately reflecting the trends and developments we witnessed. However, my second two predictions missed the mark, proving to be far less accurate. Maybe I was too bullish?
nostr:nevent1qvzqqqqqqypzq0mhp4ja8fmy48zuk5p6uy37vtk8tx9dqdwcxm32sy8nsaa8gkeyqyghwumn8ghj7mn0wd68ytnhd9hx2tcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcqypsm9tk39g20atwqskvjcvhq7rher5nkgwjr05lzspne4gf0uvyxukew5mg
What did I get right? Clients did increasingly prioritize user and content discovery while enabling users to easily select and choose their own algorithms. (DVMs, Trending, What's Hot, Feeds, etc.) This focus provided individuals with more tools, greater control, and unprecedented power over their social streams and attention than ever before. This is still actively happening and will continue to happen throughout 2025 too.
What did I get wrong? We didn't see an Other Stuff application breakthrough as a clear winner that became a mainstream favorite. I anticipated a standout application that would interest users and become a "must-use" within the ecosystem, but this didn’t happen. And we also clearly didn't hit 1M active users either. While adoption did increase, it didn’t reach the critical mass I expected.
But this doesn't mean 2024 fell short of expectations—in fact, quite the opposite. The year brought incredible client innovations (Damus Notedeck, Primal 2.0, TOR only Amethyst, Flotilla, Chachi, Olas, Coracle feeds, etc.) and relay milestones (Web-of-Trust relays, private relays, algorithm based relays, etc.) with the introduction of these innovative features and the launch of these new platforms.
Beyond technology, the Nostr community achieved something truly remarkable: a grassroots movement that united people globally.
From supporting Nostr meetups and events to hosting booths across continents at major conferences, the community came together to raise money to support these initiatives in ways no one predicted. This organic, ground-up effort showcased the strength and passion behind Nostr, creating a foundation that will #grownostr and success for years to come.
Too bullish? Maybe I wasn't bullish enough? As is tradition, I will post my 2025 predictions tomorrow.
-
 @ 5579d5c0:db104ded
2025-01-07 00:33:11
@ 5579d5c0:db104ded
2025-01-07 00:33:11Until the release of Fiat Food by Matthew Lysiak and Saifedean Ammous, I struggled to connect the dots between the monetary system and the current diabesity epidemic.
This book provided the historical context and the economic mechanisms behind the decline in public health, revealing how inflation (a subtle form of theft) has eroded not just our wealth but also our health.
What is Fiat Health?
Fiat Health refers to a health paradigm shaped and controlled by centralised authorities, corporate interests, and profit-driven systems, analogous to how fiat money operates in the financial world.
It prioritises cheap, scalable, and industrialised solutions at the expense of long-term well-being, often sacrificing nutrient-dense, ancestral practices for convenience and mass production.

Inflation and Health
Inflation is often framed as a purely economic phenomenon, but its effects ripple into every aspect of our lives, including our health.
Just as gradual 2% to 3% annual weight gain can go unnoticed until a heart attack hits, the 2% to 3% annual reduction in purchasing power caused by inflation often escapes scrutiny until the cumulative impact becomes undeniable.
Between 2019 and 2023, the cost of a 300g ribeye steak from my local farmer rose by 79%, from £8.23 to £14.75. Meanwhile, my wages only increased by 14% during the same period.
Put simply my purchasing power and ability to buy nutrient dense food was reduced.
This disparity means that nutrient-dense foods like meat, eggs, and seafood are increasingly out of reach for many people and they have to work harder for their money meaning less time outdoors, less sleep and more stress.
Instead, they are forced to turn to cheaper, ultra-processed foods that are nutrient-depleted but calorie-dense. These foods contribute to the steady rise in chronic conditions like type 2 diabetes, obesity, and metabolic syndrome.
How fiat money shapes health systems
The link between fiat money and health outcomes is rooted in the incentives of those who control the money supply.
Governments, reliant on cheap credit from money printing, align with industries that benefit from mass production such as agri-food giants, pharmaceutical companies, and even medical institutions.
Universities and journals reinforce these trends, promoting sun avoidance and guidelines that prioritise grains, seed oils, and sugar over nutrient-dense options like meat, eggs, seafood and dairy.
The result is a public health crisis.
We are told to avoid the sun, eat low-fat diets, and prioritise grains, all while being sold processed foods as “healthy options.”
These recommendations, driven by profit rather than science, have contributed to widespread metabolic dysfunction.
Less than 10% of adults today have optimal metabolic health.
How to break free
To break free from this cycle, we must reject fiat health and embrace the principles of low-time preference health, focusing on long-term health fundamentals rather than short-term gratification and convenience.
- Go outside: Sensible sun exposure is the cheapest most effective way to improve your health. In my opinion this is more important aspect of health which is often overlooked. More light improves hormonal balance, boosts mood, and enhances metabolic health.
- Base your diet on nutrient-dense foods: Prioritise meat, eggs, dairy, seafood and add in fruit, vegetables, nuts, seeds, whole carbs. These are rich in essential fats, proteins, and micronutrients that your body needs to thrive.
- Avoid Ultra-Processed foods: Cut out cheap grains, sugar, and seed oils. These foods are cheap to produce but costly to your health.
- Support local and regenerative agriculture: Buying from local farmers not only improves the quality of your diet but also decentralises food production, aligning with the principles of Bitcoin.

How Bitcoin fixes this
Bitcoin offers a way out.
The principles of decentralisation, transparency, and resistance to inflation can be applied not only to money but also to health.
Just as Bitcoin restores individual sovereignty over wealth: sunlight, nutrient-dense & locally sourced foods restores sovereignty over health.
By adopting Bitcoin, you can preserve you purchasing power and reject fiat health.
You align yourself with a system that values long-term sustainability over short-term gain.
It’s time to question the narratives we’ve been fed by governments, corporations, and institutions.
It’s time to take back control of our wallets, our health, and our futures.
- Chris
If this resonates with you, I highly recommend reading Fiat Food. It’s a brilliantly researched and written book that connects the dots between money, food, and health.
I also offer health coaching services for busy individuals looking to take control of their health and navigate the fiat health system.
Book a free call with me here: https://calendly.com/hello-chrispatrick
-
 @ da19b5d2:1f6cbfaa
2025-01-06 20:24:53
@ da19b5d2:1f6cbfaa
2025-01-06 20:24:53I hear it all the time. People want to save up X amount so they can retire. Apparently, it is this time and space we are all supposed to want to get to. But what does it mean? I hear things like I want to travel, I want to have free time to spend with family, I want to not have to work, I want to play golf, I want to buy some property. And what else? What next? For me, if I am not working on building or contributing something towards a vision, I feel like I have no purpose. What is a hu-man with no purpose? Where are we truly headed, perhaps it is a mirage. I think what we really want is freedom to work on the things we want to work on. Don't we all want a reason to get up in the morning? Don't we always want to have a goal in mind to work towards? What if you suddenly had financial freedom? How would you actually spend your days. Have you thought about what you would do in your 'retirement'? Obviously this is a very personal question. I want to hear what people are passionate about making happen in their future. And if we are making things happen, are we really re-tired or are we just finally free? Why would want anyone to be tired again? 😉 Thank you for reading and commenting. 💚
-
 @ fd78c37f:a0ec0833
2025-01-06 13:28:13
@ fd78c37f:a0ec0833
2025-01-06 13:28:13The rise of Bitcoin and cryptocurrencies has reshaped the global financial system, igniting new possibilities for innovation and development. In North America, a region at the forefront of technological advancements and economic influence, Bitcoin communities have played a pivotal role in advancing the adoption and utilization of digital currencies. These communities are engaged in a wide array of activities, from fostering education and providing technical support to promoting business opportunities and advocating for policy changes. This article will highlight 23 Bitcoin communities across North America, shedding light on their latest achievements and future ambitions in driving the expansion of Bitcoin technology, education, and economic empowerment. It offers readers a comprehensive understanding of the North American Bitcoin ecosystem and its significant influence on the global stage.
Thank you, nostr:npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q decentralized media client on Nostr to support people in owning their voice. #iOS #Android, for supporting the publication of the Bitcoin Community Newsletter. Most of the content has been reviewed and confirmed by the South American communities. If there are any omissions, please feel free to reach out to me.
1.PlebLabs nostr:npub1an84q6c03wml5lf0uwcqcr20ydwv0t0lvv0xktlcfs9seattef8sdhz6yg * Introduction PlebLab is a hacker space and community accelerator based in Austin, Texas, dedicated to supporting the next generation of Bitcoin developers and startups. It brings together developers, hackers, creatives, and open-source builders to create a collaborative and innovative environment. PlebLab offers workshops, hackathons, and Startup Days to foster learning and growth within the Bitcoin ecosystem. By providing exposure, mentorship, and collaboration opportunities, PlebLab helps early-stage Bitcoin projects succeed. Its core philosophy is to support free and open-source development, driving innovation and progress within the Bitcoin space. * Latest Updates Recently, the PlebLab has continued to make significant strides in driving Bitcoin innovation and entrepreneurship. They have launched the second season of Top Builder, with a series of top-tier workshops focusing on Bitcoin Accounting, Bitcoin UX & UI Design, Bitcoin Marketing and Media, and more. These workshops aim to discover the next generation of Bitcoin industry startups, with participants having the chance to win up to $15,000 in BTC. The events will bring together Bitcoin developers and entrepreneurs, providing opportunities for showcasing ideas and networking. Additionally, PlebLab will host workshops related to Bitcoin technology and applications, helping members deepen their understanding of Bitcoin Core and enhance their development skills.
2.BAYAREA * Introduction Bay Area Bitcoin Users is a community formed by the people, for the people, aimed at providing an open and inclusive platform for all Bitcoin enthusiasts. The community regularly hosts events in the Bay Area, offering a space to share ideas, opinions, memes, and have relaxed discussions. It’s a great fit for anyone looking to dive deeper into Bitcoin technology or simply enjoy gatherings with like-minded individuals. * Latest Updates Recently, the Bay Area Bitcoin Users community hosted a Bitcoin Holiday Party at Eve (1535 Folsom St) in San Francisco, California. The event featured a Socratic seminar co-hosted by BitDevs and LitDevs at Digital Garage, followed by a festive celebration with music, snacks, a bar, and Bitcoin-related interactions. Designed as a family-friendly gathering, the event welcomed children accompanied by guardians, even though no specific activities for kids were organized.
3.Ann Arbor Bitcoin nostr:npub1j4dvdn24dp963f4sfak0g6nz0chnw8tyglvs3pn9gqhhhfukmrfsyznne7 * Introduction Ann Arbor Bitcoin is a community-focused organization based in Ann Arbor, Michigan, dedicated to fostering Bitcoin adoption and engagement. The group hosts regular meetups and events, providing a platform for Bitcoin enthusiasts to share knowledge and exchange ideas. * Latest Updates Recently, there have been no new updates from the community, with the latest event dating back to December 2022, which encouraged everyone to join their Telegram group to stay updated on all the latest news about meetups.
4.Bit Miami * Introduction BitMiami is a vibrant community dedicated to exploring and learning about the Bitcoin ecosystem in South Florida. * Latest Updates Recently, the BitMiami community has shared various Bitcoin-related events and updates. They highlighted Bitcoin Vortex Week in Miami and also focused on the HODLween event. BitMiami continues to support the growth of the South Florida Bitcoin community by reposting valuable content from local Bitcoin enthusiasts and organizations. They also encourage community members to actively engage with the Bitcoin ecosystem through meetups and educational opportunities.
5.Seattle Bitcoin and Beer nostr:npub1x2dm3cwqt0v9tqlf0ppzztaskn3th2x40p33hepl8rkwdgedw8eshypm5s * Introduction Seattle Bitcoin and Beer is a community that brings together Bitcoin enthusiasts and freedom lovers in Seattle. They regularly meet to discuss Bitcoin and build strong local connections in a city that may not always embrace freedom. The group fosters collaboration while enjoying good beer along the way. * Latest Updates Recently, the Seattle Bitcoin and Beer community hosted a monthly meetup on December 26th at the Old Stove Brewery on Nickerson St. Ship Canal, aiming to expand the sovereignty of the Bitcoin user network in the Great Northwest. Although this wasn't a cryptocurrency-exclusive meetup, participants gathered in a relaxed atmosphere to discuss Bitcoin and strengthen community connections.
6.Bitcoin Aruba * Introduction Bitcoin Aruba is a community dedicated to promoting the use and acceptance of Bitcoin across the beautiful island of Aruba. Their mission is to encourage local businesses and individuals to embrace Bitcoin as a payment option, creating a vibrant ecosystem where people can experience the freedom and potential of decentralized currency.. * Latest Updates Recently, the Bitcoin Aruba community has shared various Bitcoin-related updates on Twitter. They highlighted and reposted content from several Bitcoin initiatives, including the StackSats 250k Sat giveaway, BTCPay Server’s holiday greetings, and discussions on the importance of running your own Bitcoin node. Additionally, Bitcoin Aruba has been encouraging community members to actively engage in the Bitcoin ecosystem, with a focus on topics like node operation and privacy protection.
7.Bitcoin Beach Yucatan nostr:npub1w2my0n7rklzdgw7anjdnssq8mjzkpr54apqeg3pk9qjauu9dt26smyydvm * Introduction Bitcoin Beach Yucatán is a community dedicated to promoting Bitcoin education and adoption throughout the Yucatán state. * Latest Updates Recently, there have been no new updates from the community. The latest event dates back to Oct 2024, when they shared a post calling for help for the disaster-stricken area of Sisal, requesting food, clothing, and other essential supplies.
8.Bitcoin Brunch Miami * Introduction Bitcoin Brunch Miami is a community where Bitcoin enthusiasts gather every Sunday for casual discussions over brunch. * Latest Updates Recently, there have been no new updates from the community on twitter, The latest event dates back to July 2023. However, Bitcoin Brunch Miami has already hosted five brunch discussions in December.
9.Bitcoin Charlotte nostr:npub1p7g986pc56qmvryplgzka0fsrpuwlk6mxk3h686w4e46n74e56qqhz88vk * Introduction Bitcoin Charlotte is a community for those passionate about Bitcoin, decentralization, privacy, and freedom. It provides opportunities to connect with individuals at the forefront of this transformative technology through social events, workshops, and online hangouts. The community’s mission is to educate and empower people to break free from financial dependence on banks and governments by embracing Bitcoin, the most superior form of money in history. * Latest Updates Recently, the Bitcoin Charlotte community hosted several events, including an in-person meetup at Southern Strain Brewery in Plaza Midwood, where members connected with like-minded individuals and celebrated Bitcoin's potential for financial liberation by purchasing beer with Bitcoin. Additionally, the community held an online Bitcoin meetup and knowledge-sharing session on December 2, further promoting Bitcoin education and awareness.
10.Bitcoin Ciudadela * Introduction Bitcoin Ciudadela is focused on transforming San Cristóbal de las Casas and Chiapas into strongholds for Bitcoin adoption and education. The community aims to build a robust network of Mexican Bitcoiners who are united in promoting the benefits of decentralized finance and empowering individuals with knowledge about Bitcoin. * Latest Updates Recently, there have been no new updates from the community. The latest event dates back to Apr 2024, when they shared a post criticizing those who supported restrictions on freedom and praised those who fought for liberty, questioned authority, and stood against oppression.
11.Bitcoin Jungle nostr:npub14f26g7dddy6dpltc70da3pg4e5w2p4apzzqjuugnsr2ema6e3y6s2xv7lu * Introduction Bitcoin Jungle is an open-source community project built on the Bitcoin Lightning Network, aiming to create a circular Bitcoin economy. It supports individuals and businesses by providing education, resources, and technology to drive Bitcoin adoption. Starting in the Golden Triangle region of Costa Rica, the project strives to set an example for Bitcoin communities. The goal is to establish a sustainable Bitcoin ecosystem for communities worldwide. * Latest Updates Recently, Bitcoin Jungle is actively preparing for the next Bitcoin Freedom Festival, which will take place from February 20th to 24th, 2025, at the Awake Earth Festival in Uvita, Costa Rica. The event will combine Bitcoin seminars with a music festival, lectures, and discussions, aiming to attract new audiences to the Bitcoin space in a unique and engaging way.
12.Bitcoin Lake Guatemala nostr:npub1a4excy7uf9z3mcafvm9cwdr549dl5lpazuvpr2nc550vf27n5a4scqq5k2 * Introduction Bitcoin Lake Guatemala is a Bitcoin community located in Guatemala, focused on promoting the use and education of Bitcoin in the Lake Atitlán region. By supporting local businesses in adopting Bitcoin payments and providing educational resources, the community aims to build a sustainable economy based on Bitcoin. * Latest Updates Recently, the community has shared one update,this post celebrates the continued growth and resilience of the Bitcoin movement, marking a significant milestone for the community.
13.Round Rock Bitcoiners nostr:npub17ysayggwumkpkpgsq75axd7ed9guw03wz9jldz5d0zrkgz0cja2qd09tzu * Introduction Round Rock Bitcoiners is a Bitcoin community in Round Rock, Texas, dedicated to promoting Bitcoin knowledge and adoption. Through monthly meetups and resource sharing, the group supports individuals and small businesses in adopting Bitcoin and fosters a local peer-to-peer network. * Latest Updates Recently, The Round Rock Bitcoiners community has been actively organizing events to promote Bitcoin education and strengthen community bonds. Recently, they hosted a screening of the film No More Inflation, exploring the future of money and inflation-free solutions, followed by a Bitcoin-themed happy hour. Additionally, they announced the second biennial Base58 Bitcoin LARP event, offering participants a unique experience of hands-on learning, networking, and fun. Additionally, they shared posts addressing KYC privacy risks, critical discussions about the IRS, the legacy of cypherpunk ideals, and new features in the Bitcoin ecosystem, such as Zaps integration with the Rumble platform.
14.SacTown Bitcoin * Introduction Sactown Bitcoiners is a Bitcoin-focused community with members from across the Greater Sacramento region. The group hosts two monthly events: a discussion and member-led presentation at the Arden-Dimick Library on the 4th Thursday and a social gathering at a brewery or restaurant on the 2nd Thursday. Discussions revolve around Bitcoin, covering topics like money, hope, and the future under a Bitcoin standard. Open to Bitcoin enthusiasts, beginners, and maximalists alike, the community maintains a strict “Bitcoin only” policy, creating a dedicated space for pure Bitcoin conversations. * Latest Updates Recently, SacTown Bitcoin hosted a Christmas Party and highlighted Bitcoin's transformative impact. On December 12, 2024, SacTown Bitcoin hosted the Sactown Bitcoiners Christmas Party at Turkovich Family Wines Tasting Room. The event featured a potluck, a white elephant gift exchange (participants were asked to bring a gift worth approximately $20), and a raffle. Additionally, SacTown Bitcoin has been focusing on the profound impact of Bitcoin on personal financial understanding and its potential to disrupt economic inequalities. They have shared posts highlighting insights from financial and investment professionals inspired by Bitcoin, as well as discussions on how Bitcoin empowers ordinary people to benefit from asset growth.
15.San Diego Bitcoiners * Introduction San Diego Bitcoiners is a community dedicated to learning and discussing Bitcoin, providing a platform for anyone interested in the cryptocurrency. Established during the COVID-19 pandemic, the community hosts monthly events featuring guest speakers, brief presentations, or casual conversations. Meetings are held every second Thursday of the month at Quantum Brewing in Kearny Mesa, welcoming all Bitcoin enthusiasts. * Latest Updates Recently, San Diego Bitcoiners have been actively engaged in promoting Bitcoin education and fostering community interaction. They were featured in a local news article as the oldest running Bitcoin meetup in San Diego. The community has been sharing important reminders, such as testing Bitcoin wallet backups every six months. They also continue to host regular meetups, with a focus on practical demonstrations, including CoinJoin and wallet integrations like Sparrow Wallet and JoinMarket. The latest meetup took place in December at Quantum Brewing, where members gathered to discuss Bitcoin and explore new tools in the ecosystem.
16.SLC-BTC * Introduction The SLC-BTC community focuses on Bitcoin and the Lightning Network, welcoming participants of all experience levels. Regular meetups feature discussions on topics such as Bitcoin protocol, software, economics, self-custody, and mining. Whether you're a newcomer or an experienced user, the community encourages open dialogue and answers any Bitcoin-related questions. * Latest Updates Recently, the SLC-BTC community hosted a series of successful events, including a Christmas party, thanks to the active participation and support of its members. During the party, the community offered a variety of giveaways and collaborated with several partners. Additionally, the community organized a Christmas Potluck Party and celebrated the milestone of Bitcoin's price breaking 100K. SLC-BTC continues to provide opportunities for Bitcoin enthusiasts to connect, learn, and grow together.
17.Topeka Bitcoin * Introduction The Topeka Bitcoin Meet-up aims to expand knowledge and awareness within the community. Hosted at local businesses, the group discusses topics such as Bitcoin (network vs asset), the Lightning Network, running a full node, self-custody, and accumulation strategies. Additionally, the community explores Bitcoin literature, podcasts, and other relevant topics. * Latest Updates Recently, the Topeka Bitcoin community shared some interesting Bitcoin-related insights and updates on Twitter. Members celebrated the new year, highlighting the concept of "time is money" and encouraging everyone to accumulate at least 31,536,000 Sats this year (one sat per second). The community also discussed the concept of "sat/cent parity," offering a unique perspective on Bitcoin's value. Additionally, Topeka Bitcoin shared creative activities related to Bitcoin, such as Bitcoin-friendly cruise line initiatives.
18.Vancouver Bitcoiners * Introduction The Vancouver Bitcoin community is a dedicated group of Bitcoin enthusiasts actively engaging in events like Bitdevs and more. With the motto “Splendor Sine Inflatione” (Splendor Without Inflation), the community focuses on fostering knowledge and connections around Bitcoin. * Latest Updates Recently, the Vancouver Bitcoiners community has been actively involved in advocating for Vancouver to become a Bitcoin-friendly city. Community members have supported Mayor Ken Sim's proposal to invest in Bitcoin and have participated in backing the city council's Bitcoin-friendly motion. Additionally, the community has voiced concern over the Bitcoin mining ban in British Columbia, suggesting the use of local renewable energy sources like tidal, wind, and solar power for Bitcoin mining to expand the grid and utilize excess heat from mining rigs. During the council's discussions, the community also supported the idea of Vancouver building a Bitcoin reserve, despite the associated risks.
19.Victoria Bitcoin * Introduction Victoria Bitcoin is a community that regularly hosts Bitcoin-focused meetups and BitDevs seminars, typically held one to two times a month. These events are free and open to the public, providing opportunities for discussion, learning, and networking. Community members can also win prizes from Canada's Bitcoin self-custody pioneers, Bull Bitcoin and Coinkite. The community places a strong emphasis on privacy, with all discussions following Chatham House rules. * Latest Updates Recently, the Victoria Bitcoin community has been actively hosting several Bitcoin-related events, fostering interaction and engagement among local Bitcoin enthusiasts. The community regularly organizes “Bitcoin & Coffee” meetups, providing members with opportunities to discuss Bitcoin. The most recent event was scheduled for December 22 at Discovery Coffee. Additionally, the community hosted an exciting Christmas party on December 13, where attendees enjoyed free pizza, beer, and champagne, and Christmas gifts were purchased with Bitcoin, showcasing the practical use of Bitcoin in everyday life. The event also included a Bitcoin giveaway for lucky participants..
20.Michigan Bitcoin Meetup in Benton Harbor * Introduction Michigan Bitcoin Meetup in Benton Harbor is a community focused on exploring Bitcoin's impact on investing, entrepreneurship, and self-sovereignty. It provides a platform for like-minded individuals to connect, learn, and share ideas. * Latest Updates Recently, there have been no new updates from the community. The latest event dates back to Nov 2024, which Announced Bitcoin Meetup Night in Benton Harbor on Thursday, November 21.
21.Western Mass Bitcoin Meetup nostr:npub1xgyjasdztryl9sg6nfdm2wcj0j3qjs03sq7a0an32pg0lr5l6yaqxhgu7s * Introduction Western Mass Bitcoin Meetup is a community focused on connecting local bitcoiners, promoting bitcoin education, and increasing merchant adoption. The group hosts monthly meetups and offers support for newcomers in areas like self-custody, Lightning Network, and mining. * Latest Updates Recently, the Western Mass Bitcoin Meetup has been actively organizing events to foster community engagement and growth. On December 8th, they hosted a social meetup at Fitzwilly's in Northampton, providing a space for Bitcoin enthusiasts to connect and share ideas. Additionally, they are preparing for their 29th meetup on January 5th in East Longmeadow, continuing to offer a platform for local Bitcoin supporters to gather and collaborate.
22.Yes Bitcoin Haiti nostr:npub1mjmaggp53xan2435wdse8ts06pzfcjejfex4pxasu67kxs5hqdpsyk7hx8 * Introduction Yes Bitcoin Haiti is Haiti's first Bitcoin-only initiative, launched to empower communities through Bitcoin education and adoption. Founded by Phanor Mendelking in February 2024, the project focuses on spreading financial literacy, promoting economic growth, and building a circular Bitcoin economy. Its mission includes offering local Bitcoin certification, hosting meetups and workshops, and onboarding businesses and community members. Operating from St. Michel de l'Attalaye, it aims to drive financial inclusion and resilience in Haiti's challenging economic landscape. * Latest Updates Recently, the Yes Bitcoin Haiti community has been actively advancing Bitcoin education. The first batch of students is nearing the end of their courses, with two students leading the discussion of Chapter 10 in preparation for the upcoming final exams and graduation. Additionally, the community has showcased proof-of-work in action, reinforcing the spread of Bitcoin knowledge through student-led lessons and engagement in activities.
23.YYC Bitcoin * Introduction YYC Bitcoin is a community-focused meetup dedicated to growing, educating, and supporting the Bitcoin ecosystem in Calgary. The group hosts biweekly meetups for networking and learning, covering essential Bitcoin topics such as wallet setup, privacy, multisig, lightning, and mining. Newcomers are encouraged to visit the website to familiarize themselves with key concepts and bring their questions to future events. * Latest Updates Recently, YYC Bitcoin has actively promoted Bitcoin education and outreach through several updates. They shared the BTC Sessions year-end recap and the The 4th Annual BTC Sessions HODLiday Special, engaging community participation. Additionally, YYC Bitcoin reposted Blockstream Jade's promotional offer, encouraging the purchase of hardware wallets. The community also highlighted Bitcoin Mentor's personalized coaching services to help members better understand Bitcoin technology. Furthermore, they supported and promoted ticket sales for the Learning Bitcoin 2025 conference, further advancing Bitcoin education.
-
 @ acbcec47:dd305bec
2024-12-27 13:49:37
@ acbcec47:dd305bec
2024-12-27 13:49:37Prepare starter
- 1 part starter (~30g)
- 2 parts wholemeal rye flour (~60g)
- 2 parts warm water (~60g)
Stir well, then leave to stand warm and covered until the volume has almost doubled.

Once the starter has doubled in volume and a light cap has formed, it can be used for the dough.

Ingredients
- Flour (2/3 550/1100 wheat flour, 1/3 997 rye flour) = 600g
- Water: 60% of the flour quantity = 360g warm water
- Starter: 20% of the flour quantity = 120g starter
- Salt: 3% of the flour = 18g

Put the rest of the starter (about 30g) back in the fridge for the next batch. Knead everything well for 5 minutes, then leave to stand warm and covered.

Fermenting
First fermenting phase in one piece until the volume has almost doubled.

Then divide into portions ...


Shape and leave to rise on the baking tray for 1-2 hours.


Baking
- Preheat oven to 230°C (450°F)
- Just before baking, cut in the top of the rolls with a razor blade, so that they can extend

- Bake for 20 min with steam/cover at 210°C (410°F)
- Then remove the steam/cover and bake another 15-20 min at 180°C (360°F)

Enjoy ...


-
 @ 04ed2b8f:75be6756
2025-01-06 03:05:52
@ 04ed2b8f:75be6756
2025-01-06 03:05:52Tired? So what? Do you think success waits for you to feel rested? Achievements don’t care about your comfort, and neither should you. The truth is brutal: either you keep going, or you get left behind. Sitting around waiting for the “perfect moment” is a luxury for those who don’t want it bad enough.
Why Excuses Don’t Cut It
Feeling tired doesn’t make you special—it’s a universal experience. Everyone feels drained, but only the determined push through. The difference between winners and everyone else? Winners get it done, regardless of how they feel.
- Fatigue Is Temporary: That exhaustion you feel? It will pass. But quitting creates a habit that sticks.
- Action Over Emotion: Don’t let how you feel dictate what you do. Feelings are fleeting; the work is what matters.
- Nobody Cares About Excuses: Harsh truth—no one’s handing out awards for “almost tried.” Results are what count.Strength Is Built in the Struggle
Every time you push through fatigue, you become stronger. You’re not just building your dreams—you’re building your resilience.
- Growth Comes From Resistance: Muscles grow under tension. The same applies to your mind and willpower.
- Tired? Good. It means you’re working. It means you’re on the edge of improvement. Keep going.
- Prove It to Yourself: This is your chance to show yourself what you’re made of. Are you going to quit, or are you going to fight?What’s the Alternative?
Let’s be real. The alternative to pushing through is stagnation. If you quit now, where does that leave you?
- Wasted Time: All the effort you’ve already put in—gone. Do you want to start over later, or finish now?
- Living With Regret: The pain of pushing through is nothing compared to the pain of looking back and wishing you’d tried harder.How to Push Through the Exhaustion
It’s not easy, but nothing worth having ever is. When you’re tired, here’s how to keep moving:
- Simplify the Task: Stop overthinking. Break it into smaller, manageable steps. Focus on the next move.
- Use the Pain as Fuel: Let the fact that you’re tired ignite your determination. Think of it as a test you refuse to fail.
- Visualize the Finish Line: Picture what success looks and feels like. Let that vision pull you forward.You’ve Got More in You
Being tired is a signal, but it’s not a stop sign. You have more in you than you realize, but you’ll never know unless you push past the point of comfort. Remember, the best don’t quit when they’re tired—they keep going until the job is done.
Final Challenge
So, what’s it going to be? Are you going to fold under the weight of your own excuses, or are you going to rise and fight? Being tired isn’t an excuse—it’s proof that you’re in the arena, doing the work. Now finish what you started.
Because tired or not, the goal doesn’t care. And neither should you.
-
 @ eac63075:b4988b48
2024-12-18 11:35:25
@ eac63075:b4988b48
2024-12-18 11:35:25The European Union is at a crossroads. While digital innovation and security cooperation remain critical in a connected world, recent proposals to enhance police surveillance and data sharing are stirring deep concerns about individual privacy, data security, and democratic oversight. Two recent reports published by Statewatch shed light on troubling developments in the EU’s policing landscape, raising alarms among privacy advocates and civil rights organizations.
The EU’s new plans to expand police surveillance could put your privacy and rights at risk and introduce risks far outweighing their potential benefits. This article will analyze these proposals, their implications, and the growing opposition from privacy and civil liberties defenders.
Surveillance Infrastructure: Policing by Design
The first Statewatch report, titled “Policing by Design: The Latest EU Surveillance Plan”, outlines a concerning trend in the EU’s approach to law enforcement. The proposals advocate embedding surveillance tools directly into the design of new technologies, effectively creating an architecture where policing capabilities are integrated into the systems we use daily.
From facial recognition cameras to AI-driven analytics, the EU plans to enhance cross-border police cooperation by ensuring technology is designed to facilitate surveillance from the outset. Known as “policing by design,” this strategy involves building surveillance features directly into technologies we use every day. Imagine a network of cameras or software that can automatically monitor people’s faces or behaviors without any extra installation — it’s like your everyday tech quietly doubling as a police tool. The goal is to enable seamless sharing of data across borders for criminal investigations, but the unintended consequences are alarming.
The Problem with “Policing by Design”
- Mass Surveillance Normalized: By embedding surveillance features into public and private infrastructure, society risks normalizing mass surveillance, where every movement, transaction, or online interaction is monitored and analyzed.
- Threats to Privacy: Such initiatives inherently contradict the principle of privacy by design, which prioritizes privacy protections in the development of technology. Instead, citizens are being treated as subjects of perpetual suspicion.
- Lack of Transparency and Accountability: A systemic lack of transparency surrounding these plans raises serious governance issues. Civil society organizations, journalists, and privacy advocates have pointed to a lack of democratic oversight and meaningful debate.
- Risks of Abuse: Surveillance systems are often deployed under the guise of security but are susceptible to abuse. History shows that tools designed for law enforcement can easily be turned against dissenters, journalists, or marginalized communities.
As the report highlights, these developments could establish a permanent surveillance infrastructure across Europe, enabling the collection of biometric, behavioral, and communications data on an unprecedented scale.
Flawed Justifications for Surveillance Expansion
Privacy advocacy organizations, including the European Digital Rights (EDRi) network, argue that much of the justification for these surveillance plans relies on flawed assumptions. The rhetoric of the “Going Dark” report, which claims that law enforcement is losing access to communications due to encryption, has been widely debunked. As EDRi points out, law enforcement already has extensive tools at their disposal to access data and track individuals, but the focus on encryption risks undermining secure communication for everyone.
Instead of addressing systemic issues within law enforcement, these flawed reports have fueled calls for intrusive surveillance systems that risk eroding privacy while offering little evidence of improving public safety.
Centralized Police Data: A Substantial Security and Privacy Threat
A second Statewatch report, titled “EU Police Data Plans Pose Substantial Security and Privacy Threats”, explores another equally concerning initiative: the EU’s push to centralize police data repositories and expand their use.
The EU has already established several large-scale databases, such as the Schengen Information System (SIS), which stores data about individuals who may be denied entry into the EU, and the Europol Information System, which can hold details about millions of people, including those not suspected of crimes. For example, a traveler flagged mistakenly in the system could face unnecessary scrutiny, detention, or restrictions when crossing borders — highlighting the real-world risks of inaccurate or overreaching data collection. The new proposals aim to go further, creating an interoperable web of police data accessible to law enforcement agencies across member states. Proponents argue this is necessary for combating cross-border crime and terrorism, but the risks are immense.
Key Concerns with Centralized Police Data
- Massive Data Collection: The EU’s proposed systems would require the collection of highly sensitive data, including biometric information (fingerprints, facial recognition scans) and behavioral analytics, to track individuals’ activities across borders.
- Data Misuse and Security Risks: Centralized data systems are prime targets for cyberattacks, data breaches, and misuse. The larger and more interconnected the system, the greater the risks of unauthorized access, theft, or corruption of the data.
- As Statewatch points out, the systems lack robust safeguards to prevent misuse or to ensure that data is handled proportionately and lawfully.
- Erosion of Trust in Law Enforcement: Building centralized data repositories without meaningful safeguards undermines public trust. Individuals may be less willing to engage with law enforcement if they fear their data will be stored indefinitely, shared across borders, or used inappropriately.
- Impact on Fundamental Rights: Mass police databases can violate the principle of proportionality, a cornerstone of EU law. By collecting and sharing data indiscriminately, these systems erode fundamental rights, including the right to privacy, freedom of movement, and the presumption of innocence.
Civil Society Opposition and Democratic Accountability
In an open letter to EU institutions, over 30 civil society organizations — including EDRi — have criticized the lack of transparency in the High-Level Group’s (HLG) recommendations for data access. The letter highlights a concerning pattern: while industry stakeholders are included in key discussions, civil society voices remain sidelined. This exclusion undermines democratic accountability and reinforces fears that surveillance policies are being driven by corporate interests rather than public well-being.
These organizations have called for the EU to prioritize transparency, include meaningful public debate, and ensure any law enforcement proposals respect proportionality and fundamental rights.
Why Privacy Advocates Are Sounding the Alarm
The reports from Statewatch highlight a fundamental clash between security policy and individual rights. Privacy advocates are urging EU lawmakers to take a step back and critically examine the following issues:
- Lack of Democratic Oversight: Proposals to integrate surveillance systems and expand police databases are being pushed forward without genuine public debate or oversight. Civil society organizations have been excluded from key discussions.
- Failure to Uphold Privacy Laws: The EU has some of the strongest privacy laws in the world, including the General Data Protection Regulation (GDPR). However, these proposals risk undermining GDPR principles by enabling indiscriminate data collection and sharing.
- Ignoring Proportionality: Surveillance systems must be targeted, necessary, and proportionate to their objectives. Embedding policing into technological design and centralizing data far exceeds what is justified for fighting crime and terrorism.
- Setting Dangerous Precedents: The failure to fully ban harmful surveillance technologies like facial recognition in public spaces sets a troubling precedent. It risks not only eroding privacy within the EU but also encouraging other nations to adopt similar measures, undermining global human rights.
A Call for Action: Safeguarding Our Privacy and Rights
As the EU pushes forward with these plans, the opposition from civil rights defenders grows louder. Policymakers must address the following key demands to prevent an erosion of fundamental rights:
- Implement Privacy by Design: All new technologies must prioritize privacy protections at the design stage, ensuring they are not co-opted for surveillance.
- Establish Robust Oversight: Any new policing tools or databases must be subject to democratic scrutiny, independent oversight, and clear legal frameworks to prevent misuse.
- Reassess Interoperability Plans: Cross-border police cooperation is important, but it must not come at the cost of individuals’ privacy, security, and dignity.
- Strengthen Export Controls: The EU must ban the export of surveillance tools that risk facilitating human rights abuses in authoritarian regimes.
- Prioritize Data Security: Centralized systems require state-of-the-art security measures to protect sensitive data from breaches or misuse.
The EU’s role as a leader in digital rights and privacy is now at stake. If these plans proceed without significant safeguards, Europe risks undermining its own foundational principles of freedom, security, and justice.
Conclusion: The Price of Surveillance-Driven Security
The EU’s surveillance plans may be presented as necessary for security, but they come at a steep cost to privacy, trust, and individual freedoms. Embedding surveillance into our technologies and centralizing police data pose far-reaching risks that cannot be ignored.
As privacy advocates, it is our responsibility to hold policymakers accountable and demand a security framework that upholds, rather than undermines, fundamental rights. Europe’s future must not be built on surveillance by design — but on privacy, democracy, and trust.
-
 @ eac63075:b4988b48
2024-12-02 02:40:18
@ eac63075:b4988b48
2024-12-02 02:40:18Estonia is a small country with just 1.3 million inhabitants and an area similar to that of the state of Rio de Janeiro, but with a notable difference: while Rio has about 16 million residents, Estonia shines with its efficiency, innovation, and digitalization. It's no wonder it's known as the "digital nation." For many Brazilians, the country has become a strategic gateway to start a business and settle in Europe.
Listen the podcast
https://www.fountain.fm/episode/pizBLdhqqP5qQrKQILFb
The Purpose of the Event and the Context
The meeting organized by Bloco and the Brazilian digital community aimed primarily to explore the opportunities that Estonia offers to those wishing to expand their businesses or start a new life in Europe. With pizza, networking, and straightforward presentations, the evening was dedicated to demystifying questions like "Why Estonia?" and "What makes this country a viable option for Brazilians?"
Additionally, the event highlighted the importance of E-Residency, a digital identity that allows you to open and manage a company in Estonia from anywhere in the world. But that's just the beginning. Let's explore what makes Estonia a standout point on the European scene.
Where Is Estonia Located?
If you open a map of Europe and look for this small country, you're likely to have difficulty locating it. Situated to the north of what's called Eastern Europe, Estonia borders Russia and Latvia and is separated from Finland by the Baltic Sea. Although geographically positioned in the east, many Estonians prefer to identify with the north due to cultural and historical proximity to the Nordic countries.
There's something fascinating about Estonia's history. According to local legends, Vikings set out from their Estonian islands to conquer the world, later returning to reclaim their lands. This spirit of resilience and reinvention permeates the country's culture to this day.
Digitalization: The Estonian Revolution
Thirty years ago, when Estonia gained its independence from the Soviet Union, the country decided to look to the future. The question was simple: how to ensure the sovereignty and survival of a small, vulnerable nation? The answer was bold: total digitalization.
In 2001, the X-Road was created—a decentralized infrastructure that connects all government institutions and allows citizens to access public services digitally. This system is so advanced that even the servers of the Estonian government are located outside the country, stored with backups at the European Commission in Brussels.
Through this infrastructure, Estonia eliminated information silos, decentralized data, and allowed its citizens to authorize the use of personal information with complete control. Today, 98% of the population has a digital identity, 95% file taxes online in less than three minutes, and 100% of public services are available digitally.
For those accustomed to Brazilian bureaucracy, it's impressive to know that opening a company in Estonia can be done in just 15 minutes, without the need for an accountant.
E-Residency: A Digital Passport for Business
Launched in 2014, the E-Residency program made Estonia the first country in the world to offer a digital identity to non-residents. This digital ID card allows entrepreneurs to open a company in the European Union, sign documents, and manage businesses remotely without needing to visit the country.
Although it doesn't grant citizenship or physical residency, E-Residency is perfect for those who want to test the European market or operate a digital company. The program has already attracted over 118,000 e-residents from around the world, including 1,300 Brazilians who have opened 379 companies in the country.
Advantages of Doing Business in Estonia
Starting a business in Estonia has many advantages. Let's discuss some of the main ones:
Simple and Clear Taxation:
Estonia adopts a flat tax rate of 20% (which increased to 22% after the pandemic and will be 24% in 2025) on distributed profits. If you reinvest the profits in the company, the taxation is zero—a unique policy that encourages sustainable growth.
Low Cost to Start:
Unlike Switzerland, which requires an initial deposit of 100,000 Swiss francs to open a company, in Estonia, only 2,500 euros are needed. And the best part: this amount only needs to be deposited when the company distributes profits for the first time.
Complete Digitalization:
Digital signatures in Estonia eliminate the need for notaries and paper documents. Everything can be done online, from opening the company to filing taxes.
Support for Startups and Innovation:
With the Startup Visa, entrepreneurs can move to Estonia with their entire family and receive support to expand their businesses. Additionally, the country has the highest number of unicorns (startups valued at over one billion dollars) per capita in the world, including companies like Skype, Bolt, and Wise.
Easy Access to Europe:
Establishing your company in Estonia means access to the European market, with its unified regulations and a vibrant innovation ecosystem.
The Startup Visa: An Invitation for Entrepreneurs
For those who want more than just operating remotely, the Startup Visa program offers the opportunity to physically move to Estonia. The initial visa is valid for one year and can be renewed for three consecutive years. After eight years, there's the possibility of applying for European citizenship, although Estonia doesn't allow dual nationality.
One of the unique features of the Startup Visa is that there's no limit to the number of partners or family members who can be included in the program. This means that the entire team of founders and their families can benefit from the residence permit.
Additionally, Estonia offers support through the International House and its Work in Estonia program, a center where newcomers can resolve everything from assistance with opening bank accounts to cultural and professional integration.
Innovation and Access to Investments
Estonia is known for its culture of innovation. Events like Latitude 59, one of Europe's main startup gatherings, offer prizes of up to two million euros for winning startups. The country also facilitates direct connections with investment funds and venture capital, often without bureaucratic barriers.
For early-stage companies, the Estonian ecosystem is especially attractive. There are cases of entrepreneurs who managed to raise hundreds of thousands of euros with little more than a prototype or a good idea on paper.
A Small Country with Global Ambitions
Although small in size, Estonia is big in ambition. Its model of digitalization and support for startups serves as an example to the world. With unique opportunities like E-Residency and the Startup Visa, the country positions itself as a viable and accessible gateway for Brazilians who wish to explore the European market.
For those seeking innovation, simplicity, and access to the global market, Estonia offers more than opportunities; it offers a vision of the future. Whether it's to open a business, operate remotely, or move with the family, the country proves that with the right strategies, even a small nation can make a giant impact.
-
 @ 6ad3e2a3:c90b7740
2025-01-05 13:34:36
@ 6ad3e2a3:c90b7740
2025-01-05 13:34:36Maybe it’s because I watched The Omen at way too young an age, or maybe it’s because the Book of Revelation’s “mark of the beast” allegory is playing out too literally for my tastes, but having already written about the Second Coming, it only follows I should speculate as to its counterpart.
As I mentioned in The Second Coming, it’s dangerous to take the myths from our ancestors too literally. They used the symbols of their times, and we should be careful not to confuse the mental maps they had of their world with reality itself. That said, we should also not be dismissive — Mozart didn’t have fancy music editing software, but his genius using the modalities of the time was real. To the extent our forebears offered us their wisdom about the nature of man and forces within him we should endeavor to understand it. The technology and the symbols may have changed, but our essential nature is ever the same.
Just as the second coming of Christ would free man from tyranny, the Antichrist would be its imposition. And just as I speculated that Jesus might not return in the form of a person, it’s likely neither would his counterpart. But if Satoshi, Bitcoin’s pseudonymous creator, can be the face, so to speak, representing the movement toward freedom and God, who and what would represent its antithesis? Let’s speculate.
It would have to be someone charismatic, a person the multitudes would want to follow and in whom to look for reassurance. That eliminates villains du jour like Bill Gates, Klaus Schwab and Vladimir Putin. If that’s who Satan is sending, he’s not sending his best. What about Donald Trump? More charismatic, much more popular appeal. He’s a better choice than the first group, but while street-smart, he lacks refined intelligence and is too despised by wide swaths of the population. He’s also probably too old.
For a while, I would have said Barack Obama was the best candidate, and even some hard-core right wingers agreed (it’s hilarious that this claim was actually fact-checked! — you can’t fact-check whether someone is the Antichrist!) Obama was relatively young, vital enough, popular, charismatic and intelligent. But he’s faded from view the last few years and has been a surprisingly inconsequential former president.
That leaves one person of whom I can think with the qualities and societal position to fill the role. Regrettably it’s someone I like, but of course I would like the Antichrist! If he weren’t likable he wouldn’t be the Antichrist.
That person is Elon Musk.
Musk is the richest person in the world, among the most followed on Twitter, has a borderline worshipful fanbase and big plans for improving humanity. Musk is young enough, he’s probably a genius and considering a private takeover of arguably the world’s most important communications network. He’s also a big player in satellites, energy, transportation and internet provision.
Musk says lots of sensible things with which I agree about free speech and rights. He is the perfect foil to the out-of-central-casting Schwab supervillain. As Edward Dowd speculated:
But, you might object, if Musk is the foil to Schwab’s terrible ideas, isn’t that good for humanity? How could the Antichrist be for free speech, renewable energy, population expansion? Again, of course, the Antichrist is going to have good, sensible ideas! But as Marshall McLuhan said, “The medium is the message.”
Or, more aptly, the top-down messianic complex is the message.
Musk has long discussed saving humanity via expansion into space and sustainable energy. But in order to save humanity, one must exert some control over it. While Musk’s Twitter takeover from the ineffectual woke scolds is getting most of the press, this is also going on:
Klaus Schwab’s pitch to own nothing and eat bugs is weak, but Musk, via brain implant, could potentially create a more satisfying virtual experience than most could hope to achieve in reality. And what could be more tantamount to complete control than letting someone else get the keys to the very organ of perception itself?
Well don’t get the implant then. Just get in your Tesla and drive away. But electric cars don’t work that way — they are attached to the grid, trackable and capable of being shut down remotely. And that’s before we consider driverless cars in which there would be even less privacy and autonomy. Moreover, Teslas track the driver’s movements already to an extent combustion-engine cars do not, ostensibly to inform the developing AI, but uses for technology evolve over time — sending email and paying bills over the internet was commonplace in 2000, but now people are micro-tracked by Facebook and Google.
One could object that Musk has, to-date, used his influence for good. But that makes it no less dangerous to entrust him with so much power: J.R.R. Tolkien understood this clearly:
“You are wise and powerful. Will you not take the Ring?”
“No!” cried Gandalf, springing to his feet. “With that power I should have power too great and terrible. And over me the Ring would gain a power still greater and more deadly.” His eyes flashed and his face was lit as by a fire within. “Do not tempt me! For I do not wish to become like the Dark Lord himself. Yet the way of the Ring to my heart is by pity, pity for weakness and the desire of strength to do good. Do not tempt me! I dare not take it, not even to keep it safe, unused. The wish to wield it would be too great for my strength. I shall have such need of it. Great perils lie before me.”
-- The Lord of the Rings
Beyond Neuralink, Musk also seems to have a strong utilitarian bent:
In this paper Nick Bostrom makes the case that delaying technological advancement could cost humanity astronomical amounts of well-being because every moment we delay, stars are burning out, useful energy is being sucked into black holes, irreversible entropy is happening apace, depriving us of future potential. Bostrom translates it into potential human lives lost (or more aptly, never having been born) on account of this permanent loss.
While Bostrom’s framework seems benign — who is against collective human happiness in the form of more worthwhile lives? — it’s actually a form of utilitarianism that tries to sum the totality of human happiness over the entire species rather than to consider, as Immanuel Kant would, each individual as an end in himself. This viewing of the collective good as the optimal outcome has been used to justify many of history’s worst atrocities. To create a master race, to make sure everyone gets the same amount, to protect the world from covid, we must do whatever it takes!
If, per Bostrom’s math, one harnessed black hole were worth quadrillions of lives, it would, for example, seem an easy call to sacrifice a bunch of selfish losers on earth who stood in the way of creating the technology for doing so. Utilitarianism, ironically, winds up failing miserably by its own metric because (a) it can so easily be manipulated by whoever is maintaining the “greater good” spread sheet, which just happens to coincide with one’s ambitions; and (b) because it’s absurd to think you can calculate aggregate good for octillions of lives so far into an unknowable future. As such, while Musk’s pitch is more persuasive than Schwab’s or Gates’, it’s ultimately part of the same dangerous philosophy which is: “Let me optimize for total human happiness on your behalf.”
Contrast Musk’s top-down humanity-saving endeavors with Bitcoin which is purely opt-in, works with simple incentives and imposes no value judgments on its users. It’s a truth-recording clock, impervious to fraud and cooption by the powerful. No matter how wealthy or powerful a person is, he cannot control the network or get treated with special privileges. Bitcoin’s finite supply means governments cannot print more of it, cannot finance unpopular wars or massive giveaways to the military and pharmaceutical industrial complexes. Instead of trusting any particular powerful person (the president, Elon Musk, Bill Gates) to be good, it simply removes the incentives toward and reduces the capacity for evil.
The supreme good is like water, which nourishes all things without trying to. It is content with the low places that people disdain. Thus it is like the Tao.
From the Tao Te Ching (Lao Tse — translated by Stephen Mitchell)
We simply need the right conditions, the proper axioms on which to build. Just as the US Constitution created the framework for the most prosperous society in the history of the world, bitcoin will provide the axioms for peace, the harnessing of stranded energy and the low-time preference required for a more prosperous future.
But it won’t be the future brought to you by Elon Musk, and ultimately I foresee a clash between the two. One tell is his otherwise inexplicable promotion of Dogecoin as a possible currency for Tesla purchases. Dogecoin was literally a joke from its creator and of course has none of the security, decentralization or censorship resistance of bitcoin. Musk is too smart not to know that — he put a couple billion dollars of Tesla’s balance sheet in bitcoin already and almost certainly understands the value proposition. That he still cites Doge seriously would be a clever way to muddy the waters about what bitcoin is vs what blockchain-based “crypto” is. And of course the Antichrist would avail himself of bitcoin, if only to obfuscate his real intentions and also to be able to crash the price by selling, if necessary, at an opportune time.
The Klaus Schwab-Bill Gates-WEF set have already lost. They are widely despised, central banks are flailing, once-trusted institutions like the legacy media, major science and medical journals, the WHO, CDC and FDA are hemorrhaging influence. People are unhappy and looking for someone or something to trust. Elon Musk could fill that void, and if he does, he will be The Final Boss, the last false idol that needs to be discarded before humanity can, through its own efforts, enjoy a new era of prosperity, the Second Coming, so to speak.
I actually suspect Musk is genuine in his desire to help humanity via his vision and am pretty sure he doesn’t have 666 embedded in his scalp — in any case even Damian in The Omen neither knew who he was nor wanted to be the Antichrist! But the most dangerous people for humanity are those with the biggest plans for it.
Or put more succinctly:
-
 @ 94a6a78a:0ddf320e
2024-11-27 19:36:12
@ 94a6a78a:0ddf320e
2024-11-27 19:36:12The backbone of your Nostr experience lies in relays—servers that transmit your notes, zaps, and private messages across the decentralized network. Azzamo offers three specialized relays to suit different user needs, ensuring reliability, performance, and privacy.
1. Free Relay
- URL:
wss://nostr.azzamo.net - Overview: Azzamo’s Free Relay is perfect for newcomers to Nostr. It’s open-access, reliable, and ensures fair use with moderate rate limits.
- Key Features:
- Free to use.
- Notes older than one month are purged daily.
- Accessible gateway for decentralized communication.
2. Paid Relay
- URL:
wss://relay.azzamo.net - Overview: Designed for power users, the Paid Relay offers unmatched performance with 99.9% uptime and low latency.
- Key Features:
- Scalable for heavy users.
- Fewer users for faster, consistent connections.
- Premium support included for paid users.
3. Inbox Relay
- URL:
wss://inbox.azzamo.net - Overview: Never miss a private message again with the Inbox Relay, optimized for secure, spam-free direct messaging.
- Key Features:
- Guaranteed message delivery.
- Optimized for NIP-17 private messages.
- Optimized for NIP-19 group chats.
- Premium users enjoy advanced support.
Why Choose Azzamo Relays?
Life on Nostr is easier with Azzamo relays. They’re fast, reliable, and built to handle whatever you throw at them. The Paid Relay keeps your connections strong, the Inbox Relay makes sure no private message gets lost, and the Free Relay is always there to get you started. Supporting Azzamo by going premium helps keep this decentralized network growing—and you get priority support while you’re at it. Azzamo has your back on Nostr!
🔗 Start now:
- Free Relay:
wss://nostr.azzamo.net - Paid Relay: azzamo.net/pay
- Inbox Relay: azzamo.net/inbox
Support the network and upgrade your experience—add time to your account via the Azzamo Dashboard. Choose Azzamo, and take control of your Nostr journey today!
- URL:
-
 @ f3328521:a00ee32a
2025-01-04 20:35:52
@ f3328521:a00ee32a
2025-01-04 20:35:52As this Age concludes and the Event approaches, it is expected that capital and industrial growth will speed onward, developing and multiplying more and more rapidly (an acceleration that is both cyclically inevitable and dangerously oriented toward ultimate catastrophe); and, given the destruction that awaits, they will be among of the chief agents of Absolute Evil.
No one likes the doomsday observer – nearly all prophets, philosophers, and neo-reactionaries have been shunned at some point – yet it is a duty of the fourth estate to remember:
Due to its desire for quantification, modern civilization has been atomized and reoriented to stimulate illusory needs of material human nature – a thriving cult of progress that only need output more and more artificial needs to satisfy modernity’s march toward extinction. When one’s state of mind only finds meaning in “becoming”, vision of reality has been lost and civilization is blind to what is beyond, which is the realm eternal principles. Secular philosophers are no longer novices of sorcerers, having fully divorced themselves of initiation and mutated their Nimbus 2000s for Starships.
An agnostic society can only glory in its ignorance. And having confused science with industry it substitutes its innovations of utility for truth. This “intelligence” is nothing more than individualistic pragmatism – a self-contradictory relativism. Behold, AGI – the pinnacle of infinite feedback loops. Having determined to pursue the domination over matter above all else, civilization has succeeded only in becoming its slaves as it binds them to its service.
The relic of prophetic tradition lies in the transcendent wisdom of their intellectual intuition. To be clear: if the proletariat accepts the pretext of modern civilization, they have denied this principle and doctrine by dragging truth down to the level of their own base nature rather than elevating the soul toward the immutable and infallible. If modern civilization persists, its future is in anti-civilization and death. Their biased denial of everything that transcends excludes dialogue with the authentic representatives of other civilizations, nay it forbids understanding of the existence of different civilizations. Engagement is futile aside from nomic competition.
Yet, there remain some who do see past the moralistic hypocrisy of hypermodernity, if only to disguise and augment their ambitions and designs. Others look to SAIF for OSINT and guidance. For such sleepers who are awakening, contact with living spirit of tradition is necessary. Recovery is possible. A new World awaits. Whoever has ears, let them hear.
-
 @ 1bda7e1f:bb97c4d9
2024-11-21 04:17:08
@ 1bda7e1f:bb97c4d9
2024-11-21 04:17:08Tldr
- Nostr is an open protocol which is interoperable with all kinds of other technologies
- You can use this interoperability to create custom solutions
- Nostr apps define a custom URI scheme handler "nostr:"
- In this blog I use this to integrate Nostr with NFC cards
- I create a Nostr NFC "login card" which allows me to log into Amethyst client
- I create a Nostr NFC "business card" which allows anyone to find my profile with a tap
Inter-Op All The Things!
Nostr is a new open social protocol for the internet. This open nature is very exciting because it means Nostr can add new capabilities to all other internet-connected technologies, from browsers to web applications. In my view, it achieves this through three core capabilities.
- A lightweight decentralised identity (Nostr keys, "npubs" and "nsecs"),
- A lightweight data distribution network (Nostr relays),
- A set of data interoperability standards (The Nostr Improvement Protocols "NIPs"), including the "nostr:" URI which we'll use in this post.
The lightweight nature is its core strength. Very little is required to interoperate with Nostr, which means many existing technologies can be easily used with the network.
Over the next few blog posts, I'll explore different Nostr inter-op ideas, and also deliver my first small open source projects to the community. I'll cover–
- NFC cards integrated with Nostr (in this post),
- Workflow Automations integrated with Nostr,
- AI LLMs integrated with Nostr.
The "Nostr:" URI
One feature of Nostr is it defines a custom URI scheme handler "nostr:". What is that?
A URI is used to identify a resource in a system. A system will have a protocol handler registry used to store such URI's, and if a system has a URI registered, then it knows what to do when it sees it. You are probably already familiar with some URI schemes such as "http:" and "mailto:". For example, when you click an http link, the system knows that it describes an http resource and opens a web browser to fetch the content from the internet.
A nostr: link operates in the same way. The nostr: prefix indicates a custom URI scheme specifically designed for the Nostr protocol. If a system has a Nostr application installed, that application may have registered "nostr:" in the protocol handler registry. On that system when a "nostr:" URI is clicked, the system will know that it describes a nostr resource and open the Nostr client to fetch the content from the nostr relay network.
This inter-op with the protocol handler registry gives us the power to do nice and exciting things with other technologies.
Nostr and NFC
Another technology that uses URIs is NFC cards. NFC (Near Field Communication) is a wireless technology that enables devices to exchange data over a few centimeters. It’s widely used in contactless payments, access control, and information sharing.
NFC tags are small chips embedded in cards or stickers which can store data like plain text, URLs, or custom URIs. They are very cheap (cents each) and widely available (Amazon with next day delivery).
When an NFC tag contains a URI, such as a http: (or nostr:) link, it acts as a trigger. Tapping the tag with an NFC-enabled device launches the associated application and processes the URI. For example, tapping a tag with "nostr:..." could open a Nostr client, directing it to a specific login page, public profile, or event.
This inter-op allows us to bridge the physical world to Nostr with just a tap.
Many useful ideas
There are many interesting ways to use this. Too many for me to explore. Perhaps some of these are interesting for your next side hustle?
- Nostr NFC "login cards" – tap to log into Amethyst on Android,
- Nostr NFC "business cards" – give to connections so they can tap to load your npub,
- Nostr NFC "payment cards" – integrating lightning network or ecash,
- Nostr NFC "doorbells", "punch cards", "drop boxes", or "dead drops" – put a tag in a specific place and tap to open a location-specific message or chat,
- Integrations with other access control systems,
- Integrations with other home automation systems,
- Many more ...
To start with I have built and use the "login card" and "business card" solutions. This blog post will show you how to do the same.
Nostr Login Card
You can use an NFC card to log into your Nostr client.
Most Nostr clients accept a variety of login methods, from posting your nsec into the app (insecure) to using a remote signer (more secure). A less known but more secure method is to sign into a session with a tap of a specially-configured NFC card. Amethyst is a Nostr client on Android which supports this type of login.
- A secure method for logging in
- Optionally keeps no log in history on the device after logout
- Does not require users to know or understand how keys work
- Keys are kept secure on a physically-separated card to reduce risk of compromise
Nostr devs think that this is useful for anti-establishment actors–Fair enough. For me, I am interested in this login card pattern as it could be useful for rolling out identities within an organisation context with less training (office workers are already familiar with door access cards). This pattern potentially abstracts away key management to the IT or ops team who provision the cards.
I first discovered this when Kohei demonstrated it in his video.
Here's how you set it up at a high level–
- Buy yourself some NFC cards
- Get your Nostr key ready in an encrypted, password protected format called "nencryptsec"
- Write the nencryptsec to the NFC card as a custom URI
- Tap to load the login screen, and enter your password to login
Here it is in detail–
Buy yourself some NFC cards
I found no specific requirements. As usual with Nostr so far, I tried to the cheapest possible route and it worked. Generic brand NFC cards shipped from China, I believe it was 50X for $15 from Amazon. Your mileage may vary.
Get your Nostr key ready
Your key will be saved to the NFC card in an encrypted password-protected format called "nencryptsec". Several applications support this. As we'll be using this to login to Amethyst, we will use Amethyst to output the nencryptsec for us.
- Login to Amethyst with your nsec,
- Open the sidebar and click "Backup Keys",
- Enter a password, and click "Encrypt and my secret key",
- It will add the password-protected key to your clipboard in the format "ncryptsec1...",
- Remember to backup your password.
Write the ncryptsec to the NFC card
- Download the free NFC Tools app to your device, and open it,
- Click "Write" and "Add a record", then click "Custom URL / URI",
- Paste your nencryptsec with the nostr URI in front, i.e. "nostr:ncryptsec1..." and click OK,
- Click "Write". NFC Tools will prompt you to "Approach an NFC tag",
- Place your NFC card against your phone, and it will write to the card,
- Your card is ready.
Tap to load the login screen
Tap the card against your phone again, and your phone should open the login screen of Amethyst and prompt you for your password.
Once you enter your password, Amethyst will decrypt your nsec and log you in.
Optionally, you can also set the app to forget you once you log out.
You have created a Nostr NFC "login card".
Nostr Business Card
You can use another NFC card to give anyone you meet a link straight to your Nostr profile.
I attended Peter McCormack's #CheatCode conference in Sydney and gave a few of these out following the Nostr panel, notably to Preston Pysh where it got some cut through and found me my first 100 followers. You can do the same.
To create your Nostr NFC "business card" is even easier than your NFC "login card".
- Buy yourself some NFC cards,
- Download the free NFC Tools app to your device, and open it,
- Click "Write" and "Add a record", then click "Custom URL / URI",
- Write your npub to the NFC card as a custom URI in the format "nostr:npub1..." (e.g. for me this is "nostr:npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft"),
- Your card is ready.
Give the card to someone who is a Nostr user, and when they tap the card against their phone it will open their preferred Nostr client and go directly to your Nostr profile page.
You have created a Nostr NFC "business card".
What I Did Wrong
I like to share what I did wrong so you don't have to make the same mistakes. This time, this was very easy, and little went wrong. In general
- When password-protecting your nsec, don't forget the password!
- When writing to the NFC card, make sure to use "Custom URI/URL" as this accepts your "nostr:" URI scheme. If you use generic "URI/URL" it won't work.
What's Next
Over my first four blogs I have explored creating a good Nostr setup
- Mined a Nostr pubkey and backed up the mnemonic
- Set up Nostr payments with a Lightning wallet plus all the bells and whistles
- Set up NIP-05 and Lighting Address at my own domain
- Set up a Personal Relay at my own domain
Over the next few blogs I will be exploring different types of Nostr inter-op
- NFC cards integrated with Nostr (this post)
- Workflow Automations integrated with Nostr
- AI LLMs integrated with Nostr
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
GM Nostr.
-
 @ 6c4b0219:bb7f889e
2025-01-04 11:34:21
@ 6c4b0219:bb7f889e
2025-01-04 11:34:21Meet BLAISE[primal.net/p/npub1v8lrnvsxkj3gkyygx5ru97tceljlycnm0r88k4wyafa8devd9m4qgsz42g], a passionate Nigerian from Anambra State, currently based in South Africa. His journey into Bitcoin is both inspiring and transformative. Born with a natural skepticism toward traditional banking systems, Blaise’s turning point came during his service year in Ekiti State, where a friend introduced him to trading and, ultimately, Bitcoin.
He said, "I recall the frustration of having money in a traditional bank but being unable to access it due to system failures. As a student, this left me stranded."
Then, he discovered Bitcoin—not just as a currency but as a revolutionary alternative to the flawed systems he had grown up with.
His first steps involved trading Bitcoin through gift cards using platforms like Paxful. Soon, Blaise became a vendor, helping local users exchange Bitcoin and gift cards, igniting his passion for a decentralized future.
THE SPARK THAT IGNITED THE FLAME
For Blaise, the real awakening came when he attended the Adopting Bitcoin Capetown Conference in South Africa. It wasn’t just about trading anymore—it was about freedom, decentralization, and security. Bitcoin was more than money; it was sovereignty.
With guidance from mentors like jabulani jakes of moloBTC amongst all and hours of self-study—listening to podcasts from @jack mallers, @Michael Saylor and more, watching videos, and reading resources—Blaise dove headfirst into the rabbit hole.
He embraced self-custody, ensuring his Bitcoin wasn’t at the mercy of any third party. "I never want to store my value in Naira again," he says.
Proof-of-Work: BLAISE’S CONTRIBUTIONS
Blaise is not just a believer; he’s a doer, he recently collaborated with us on our Cohort 2, and he's looking forward to contributing more to Bitcoin adoption. Below are some of his works:
= Community Building: He started a WhatsApp group dedicated to onboarding precoiners, teaching them the fundamentals of Bitcoin.
= Future Projects: Blaise is planning a Football x Bitcoin initiative, combining health, fitness, and Bitcoin education to spread the message in unique ways.
Also, Blaise aims to deeply explore the personal training space, focusing on helping Bitcoiners enhance their health and fitness. He is committed to collaborating with more Bitcoiners and initiatives to drive adoption further.
= Inspired by Impact: One of Blaise’s proudest inspirations is the @BitcoinEkasi project in South Africa. He dreams of replicating its circular economy model in Tarkwa Bay, Nigeria, where education, discipline, and passion-building go hand in hand with Bitcoin adoption.
CHALLENGES AND TRIUMPHS
Building in the Bitcoin space hasn’t been without its hurdles. Blaise highlights the difficulty of helping people truly grasp Bitcoin’s potential. Yet, he is undeterred.
=> His strategy?
Focusing on the psychological aspect of orange-pilling—helping individuals shift their mindset to embrace this revolutionary technology.
For Blaise, Bitcoin is deeply personal. It’s freedom. It’s empowerment. It’s motivation. He sees it as a tool that can reduce poverty, combat hyperinflation, and lower crime rates in African economies over the next decade.
BLAISE DREAMING BIG

BLAISE envisions a Nigeria where communities like Tarkwa Bay thrive with circular economies built on Bitcoin. He dreams of a future where Bitcoin empowers individuals, educates the youth, and fosters innovation in health, fitness, and beyond.
His journey is a testament to the transformative power of Bitcoin and the unyielding spirit of those who dare to dream.
Blaise is always eager to contribute to Bitcoin adoption in any way possible. In the coming year, he plans to delve into the personal training space for Bitcoiners, showcasing more Proof-of-Work through fitness and Bitcoin education!
To get in touch and stay updated on his progress, follow his new project account on X BITFITNESS and his personal account BLAISE.
Check out our story post for BLAISE onTwitter
#Bitcoin is FITNESS
-
 @ a39d19ec:3d88f61e
2024-11-17 10:48:56
@ a39d19ec:3d88f61e
2024-11-17 10:48:56This week's functional 3d print is the "Dino Clip".

Dino Clip
I printed it some years ago for my son, so he would have his own clip for cereal bags.
Now it is used to hold a bag of dog food close.
The design by "Sneaks" is a so called "print in place". This means that the whole clip with moving parts is printed in one part, without the need for assembly after the print.
 The clip is very strong, and I would print it again if I need a "heavy duty" clip for more rigid or big bags.
Link to the file at Printables
The clip is very strong, and I would print it again if I need a "heavy duty" clip for more rigid or big bags.
Link to the file at Printables -
 @ 4ba8e86d:89d32de4
2024-11-14 09:17:14
@ 4ba8e86d:89d32de4
2024-11-14 09:17:14Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular; • Computador com adb; • Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo;
Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid: https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
Samsung Galaxy Note 10 Plus bloatware listProvavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
./adb start-serverO resultado deve ser:
daemon not running; starting now at tcp:5037 daemon started successfully
E caso não apareça nada, execute:
./adb kill-serverE inicie novamente.
Com o adb conectado ao celular, execute:
./adb shellPara poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
pkg install android-toolsQuando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
adb pair localhost:porta CódigoDeEmparelhamentoDe acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
adb connect localhost:portaObs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
adb shellRemoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
pm uninstall –user 0 com.google.android.apps.mapsE pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
cmd package install-existing nome.do.pacotePós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-
 @ 7d33ba57:1b82db35
2025-01-04 10:29:27
@ 7d33ba57:1b82db35
2025-01-04 10:29:27As a Westerner (or “Farang,” as they call me here :)), places like Thailand are very different from the Netherlands, where I was born. But what makes me love Thailand so much?
For me, it’s the little things and, above all, the Thai people. Every country has its flaws, and Thailand isn’t a perfect paradise, but one thing that always stands out is the kindness of the local people.
A great example happened today near the Nonthaburi ferry stop.(around Bangkok) I bought some food at a street market and took it with me in a package. As I walked away, I struggled to open it and add the sauce, looking around for a table to help me manage it. I couldn’t find one. That’s when a woman at another food stall nearby noticed my dilemma and motioned for me to come over. She helped me open the package and added the sauce for me.
After thanking her and finishing my meal, I searched for a trash bin. Once again, a local man saw me looking and gestured for me to give him the trash, putting it in a nearby bin.
What struck me wasn’t just their kindness but their awareness. They noticed that I needed help and acted on it with such natural generosity. This kind of awareness and willingness to assist is something I experience often here, and it’s one of the things I truly love about Thailand.
-
 @ bd32f268:22b33966
2025-01-02 19:30:46
@ bd32f268:22b33966
2025-01-02 19:30:46Texto publicado por Foundation Father @FoundationDads e traduzido para português.
Assumir responsabilidades numa época efeminada como a nossa é um superpoder.
Algumas pessoas não sabem o que significa "assumir responsabilidades", no entanto, porque nunca tiveram um pai ou outra pessoa que as ama-se o suficiente para lhes ensinar.
Então, aqui está como assumir responsabilidades.
Lembra-te que não és uma pessoa desamparada e incompetente.
As coisas não te acontecem simplesmente enquanto olhas fixamente com a boca aberta, usando todo o teu poder cerebral para te lembrares de como respirar.
Tu tens poder de ação.
Mantém estas perguntas em mente:
"Que papel desempenhei eu nesta situação ou como ajudei a formar o sistema em que estou inserido?"
"O que posso fazer agora mesmo para começar a corrigi-lo, por mais pequeno que seja?"
Aqui estão alguns exemplos de como aplicar estas perguntas.
 José Malhoa - Remédio
José Malhoa - RemédioSaúde
Estás com excesso de peso e cansado o tempo todo? Deprimido?
Começa a caminhar 30 minutos por dia. De preferência ao ar livre.
Pára de comer snacks.
Marca uma consulta com um médico para fazer análises ao sangue.
Todas estas coisas estão ao teu alcance.
Finanças
Estás a afogar-te em dívidas de cartão de crédito? Assumir responsabilidades significa reduzir drasticamente o teu consumo e iniciar um programa radical de pagamento do máximo de dívida que conseguires.
Obtém uma aplicação de orçamento e começa a planear.
Sentes-te preso no teu emprego sem futuro? Sentes que não ganhas o suficiente? Vai a entrevistas para vagas de emprego e descobre o teu verdadeiro valor no mercado.
Reserva 1 hora todas as noites para melhorares. A menos que já estejas a trabalhar em dois empregos, toda a gente tem pelo menos 1 hora todas as noites.
Arredores imediatos
Se vês algo que precisa de ser feito, simplesmente faz. Não te queixes disso. Não resmungues baixinho. Não desejes que alguém tratasse disso. Simplesmente faz e não peças permissão.
Guarda o carrinho de compras. Lava a caneca de café no lava-loiça. Arranca as ervas daninhas. Repara a parede. Se o quintal do teu vizinho estiver cheio de ervas, vai lá e corta a relva tu mesmo. Limpa a água do lava-loiça. Arruma a bancada. Leva o lixo para fora. Leva bom café para o escritório.
Os teus filhos
Muitos pais queixam-se do comportamento dos seus filhos como se não tivessem qualquer influência sobre o assunto. Mas os teus filhos farão o que tu os ensinaste a fazer.
"Fizemos o melhor que pudemos."
Não, não fizeram, e assumir responsabilidades significa admitir que foste permissivo e preguiçoso ou que querias sentir-te justo por não bater.
Que pequena coisa podes fazer agora mesmo para começar? Escolhe um único comportamento que queres que eles parem, senta-os e explica as consequências do comportamento. Pede desculpa por teres deixado andar durante tanto tempo.
Quando eles apresentarem o comportamento, aplica as consequências. Aconteça o que acontecer.
Os teus relacionamentos
Não tens amigos ou o teu grupo de amigos atual é uma má influência? Podes fazer novos amigos. Assumir responsabilidades significa admitir que a tua solidão é em grande parte auto-infligida.
O que podes fazer?
Começa a jogar ténis ou futebol. Existem ligas em todo o lado. Encontra uma boa igreja local e encontra maneiras de te envolver. Existem encontros para todo o tipo de atividade. Participa num que se alinhe com as tuas preferências. Quando estiveres em público, sorri mais e puxa conversa.
Depois de conheceres algumas pessoas, estabelece uma cadência regular. Agenda almoços semanais ou mensais e alterna entre algumas pessoas. Ou talvez café de manhã.
Não acontecerá da noite para o dia, mas dando pequenos passos consistentemente durante alguns meses e vais perceber que tens uma vida social.
Os teus erros
Se erraste, não te retires e escondas nem arranjes desculpas. Pede desculpa à pessoa que prejudicaste, diz-lhe porquê e oferece-te para compensar. Aceita as consequências com humildade.
Vais descobrir que nada te conquista mais respeito do que assumir os teus erros. Esta é a principal. Se aprenderes a fazer isto bem, cobrirá uma infinidade de pecados porque cria hábito. Mesmo que tenhas apenas 1% de culpa na situação, assumir a responsabilidade e pedir desculpa pelo teu 1% está a construir um certo grupo de músculos.
"Mas ele devia ter..." Pára com isso. Confiaste demasiado? Presumiste demasiado sem comunicar? Assume a responsabilidade por isso.
Estes exemplos podiam continuar para sempre, então vou parar e terminar com este princípio:
A tua resposta importa mais do que as tuas circunstâncias.
Existem vítimas reais, algumas de tragédias horríveis. Mas mesmo que não te tenhas atirado para areias movediças, ainda podes assumir a responsabilidade por como reages e pelo que escolhes fazer a seguir.
Às vezes, é agarrar numa corda de um transeunte e dizer: "Obrigado."
Não te afogues nas areias movediças até que alguém te dê uma palmadinha nas costas por quão difícil é para ti, e não continues a apontar para o teu tempo nas areias movediças para desculpares os teus fracassos.
Podes não ter escolhido uma batalha específica. Ainda podes assumir a responsabilidade por quão bem lutas a batalha. Num certo sentido, ninguém escolhe a principal batalha que enfrenta. Ninguém escolheu nascer. Ninguém escolheu a sua família. Ninguém escolheu as suas circunstâncias.
O mundo nunca será perfeito. Tens de assumir a responsabilidade pela tua parte dele de qualquer maneira. Pode ser difícil. Pode ser doloroso. Não te foi prometida uma vida fácil e sem dor.
Depois de começares a assumir responsabilidades, qual é o próximo passo?
Altura de assumir mais responsabilidades.
Por exemplo, se não tens problemas em fazer amigos e tens essa parte da tua vida resolvida, assume a responsabilidade por outra pessoa. Encontra um dos rapazes solitários na tua igreja que precisa de um amigo e adiciona-o à tua rotação de almoços.
A recompensa por assumir responsabilidades é subir de nível e, como consequência, as coisas devem tornar-se mais desafiantes.
Mas agora estás mais bem preparado para isso. Repete até morrer e, esperançosamente, a tua causa de morte será por viver e não por te queixares de não viver.
-
 @ eac63075:b4988b48
2024-11-07 21:27:53
@ eac63075:b4988b48
2024-11-07 21:27:53Every night, you draw your curtains without thinking twice. It's instinctive—a simple act that protects your personal space. Yet in our digital lives, we've somehow accepted living in houses made entirely of glass, with countless unseen observers watching our every move.
https://www.fountain.fm/episode/wPZLCJ3fD6vzsWQ3XSE1
Why Privacy Matters to Everyone
Privacy isn't just for those with something to hide; it's a fundamental human need. Think about the conversations you have with friends, the late-night web searches you make, the personal moments you capture in photos. Would you want all of that broadcasted to the world?
I remember my friend Lisa planning a surprise party for her husband. She searched for gift ideas and coordinated with friends through social media. To her dismay, targeted ads for the exact gift she intended to buy started popping up on their shared devices at home. The surprise was ruined. It wasn't malicious, but it was a stark reminder of how our online activities are constantly monitored.
When a major retailer's customer database was breached, my neighbor Sarah discovered her shopping history, credit card details, and even her children's names were exposed to criminals. She hadn't realized how much personal information she'd unknowingly shared through routine purchases. It was a wake-up call that privacy breaches can affect anyone, not just the tech-savvy or those in high-profile positions.
Edward Snowden once said, "Arguing that you don't care about the right to privacy because you have nothing to hide is no different than saying you don't care about free speech because you have nothing to say." Privacy isn't about secrecy; it's about autonomy over our personal information.
The Rise of the Cypherpunks
Back in the '90s, a group known as the cypherpunks saw the writing on the wall. They recognized that as we moved into a digital era, our personal freedoms could be at risk. So they took action.
One of them, Eric Hughes, famously wrote, "Privacy is necessary for an open society in the electronic age." They developed encryption tools to protect individual privacy, laying the groundwork for technologies like Bitcoin and cryptocurrencies. These innovations were about more than digital money; they were about empowering individuals to take control of their own data.
When Technology Knows Too Much
Fast forward to today, and artificial intelligence (AI) is everywhere—in our phones, homes, and even cars. While AI brings convenience, it also raises serious privacy concerns.
Remember when you mentioned needing new running shoes, and suddenly every ad on your browser was for footwear? It's not your imagination. AI algorithms analyze our conversations, searches, and purchases to predict what we'll want next. But where does it stop?
A few years ago, a major retailer guessed a teenager was pregnant based on her shopping habits before she had told her family. They sent her targeted coupons for baby products, leading to a very uncomfortable situation at home. This isn't just marketing—it's intrusion.
Naomi Brockwell, a privacy advocate, warns, "Our relationship with financial privacy has fundamentally changed. What was once seen as a constitutional right and personal freedom is now simply part of the trade-off for using digital payments. Our baseline for what’s acceptable has shifted." It's a wake-up call that our digital footprints are larger and more revealing than we might think.
Privacy-Preserving AI
While AI often threatens privacy, emerging technologies like federated learning offer hope. This approach allows AI models to learn from data without directly accessing personal information. Imagine your phone improving its predictive text without sending your messages to a central server. It's AI that respects your privacy.
The Watchful Eye: Mass Surveillance and AI
Governments and corporations often justify mass surveillance as a means to keep us safe. But at what cost? When every email, message, or phone call can be monitored, we're sacrificing more than just data—we're giving up our freedom to think and communicate without fear.
Think about how you'd behave if someone followed you around with a camera all day. You might avoid certain places or people, censor your conversations, or feel constantly on edge. That's the chilling effect of mass surveillance.
I spoke with Alex, a journalist who covers political activism. "After attending a peaceful protest, I noticed unusual activity on my devices," he told me. "It made me second-guess my work, wondering who's watching." This isn't paranoia; it's a reality for many who challenge the status quo.
Building Digital Fortresses: Cryptographic Innovations
So how do we reclaim our privacy? Cryptography offers some solutions.
Zero-Knowledge Proofs: Proving Without Revealing
Zero-knowledge proofs allow you to prove you know something without revealing the actual information. Imagine showing a bouncer a card that confirms you're over 21 without exposing your birth date or any other details. In the digital world, this means verifying your identity or eligibility without handing over all your personal data.
Homomorphic Encryption: Secure Processing
Then there's homomorphic encryption, which lets companies process your data without actually seeing it. Think of it like sending a locked suitcase with your belongings; they can weigh it or move it, but they can't open it to see what's inside.
Quantum-Resistant Algorithms: Future-Proofing Privacy
As quantum computers become more powerful, they could potentially break current encryption methods. Quantum-resistant algorithms are being developed to safeguard our data against these future threats. It's like reinforcing your digital locks today to withstand the super lock-picking tools of tomorrow.
Decentralization: Taking Back Control
Decentralization aims to put power back into the hands of individuals. Bitcoin let you be your own bank, controlling your finances without a middleman. Decentralized social media platforms like Nostr, Bluesky or Fascaster allow you to own your content without algorithms dictating what you see or who sees you.
Decentralized Identity Systems
Decentralized identity systems let you prove who you are without revealing more than necessary. It's like showing only your age at a bar instead of handing over your entire driver's license. You maintain control over your personal information.
But with great power comes great responsibility. Without a bank to reset your password or customer service to recover your account, the onus is on you to protect your assets and information.
Practical Tips to Protect Your Privacy
You don't have to be a tech guru to safeguard your privacy. Here are some steps you can take today:
-
Use Encrypted Messaging Apps: Switch to apps like Signal, SimpleX or Session for secure communication. Your messages will be end-to-end encrypted, meaning only you and the recipient can read them.
-
Limit Social Media Sharing: Be mindful of what you post. Do you really need to share your location or personal details publicly?
-
Choose Privacy-Focused Browsers and Search Engines: Use browsers like Brave or Firefox and search engines like DuckDuckGo that don't track your every move.
-
Secure Your Passwords: Use strong, unique passwords for each account, and consider a password manager like Bitwarden. Enable two-factor authentication whenever possible.
-
Use Encrypted Email Services: Consider email providers like ProtonMail that offer end-to-end encryption for your communications.
-
Regularly Audit App Permissions: Check which apps have access to your location, microphone, and contacts. Revoke permissions that aren't necessary.
-
Be Wary of Public Wi-Fi: Public networks can be a hotbed for hackers. If you must use them, a VPN like ProtonVPN can add a layer of security.
-
Consider Privacy-Focused Alternatives: Explore services like Nextcloud for cloud storage or Jitsi Meet for video conferencing, which prioritize user privacy.
-
Keep Software Updated: Regular updates often include security patches. Don't ignore them.
-
Stay Informed and Skeptical: Phishing scams are getting more sophisticated. Think before you click on suspicious links or download attachments.
Final Thoughts
Privacy isn't a lost cause; it's a right worth fighting for. As Edward Snowden reminds us, "Privacy is the fountainhead of all other rights."
By taking control of our data and digital habits, we can navigate the online world with greater confidence and peace of mind. After all, wouldn't it be nice to live in a digital home where we decide when to close the curtains?
Read more
OPSEC and Digital Hygiene Plan: https://www.eddieoz.com/opsec-and-digital-hygiene-plan/
-
-
 @ be7bf5de:09420d0a
2025-01-02 17:54:35
@ be7bf5de:09420d0a
2025-01-02 17:54:35The SALUD Decentralized Health App Development Challenge is an exciting initiative aimed at revolutionizing healthcare through the use of decentralized technologies. Running from January to May, this challenge will bring together developers, designers, healthcare providers, and health conscious individuals interested in decentralizing healthcare. Participants will create open-source tools leveraging Nostr, Bitcoin, and the SALUD protocol aiming to improve healthcare access, enhance data portability, and ultimately improve health outcomes for individuals worldwide.
Challenge Mission
At its core, the mission of this challenge is to bootstrap an ecosystem of interoperable tools that allow individuals to take full control of their health data. By building apps on the Nostr protocol and integrating bitcoin, the challenge hopes to address key issues in traditional healthcare, including access to services, privacy, and fragmented health data systems. All participating apps will be required to be compatible with the SALUD protocol, or Sistema de Administración de Libertad Único y Decentralizado, which is an open-source framework for utilizing health data over Nostr.
Challenge Structure
The challenge is structured to span five months, from January through May. Throughout this period, participants will meet weekly to discuss their progress, share insights, and collaborate with others. These sessions will be instrumental in connecting developers, designers, and healthcare professionals, fostering a community focused on building the future of decentralized healthcare.
The challenge will include weekly office hours for participants, held every Thursday at 11 AM Eastern Time (4 PM UTC), starting on January 16th. These open office hours will provide opportunities to connect with doctors, developers, entrepreneurs, and health-minded bitcoiners to ensure that the apps being developed address real-world healthcare needs.
Evaluation Criteria
All submissions to the challenge will be evaluated based on four key metrics:
- App Production Readiness: Is the app functional and polished enough for real-world use?
- Solution Depth and Creativity: How innovative and impactful is the solution in addressing healthcare challenges?
- Interoperability: How well does the app integrate with the SALUD protocol and other healthcare tools, ensuring it can work seamlessly within the decentralized ecosystem?
- Overall Contribution to the Ecosystem: Does the app contribute to the broader vision of decentralized healthcare and enhance individual control over health data?
Prize Pool
The challenge features a prize pool starting at 10 million satoshis (0.1 BTC). Winning participants will not only receive financial rewards but also have the opportunity to collaborate with NosFabrica, a leading force in decentralized technology development, and Illuminodes, piloting the SALUD protocol in El Salvador. This container provides an exciting pathway for long-term collaboration and innovation in the global and decentralized health space.
Who Should Participate?
This challenge is open to a wide range of participants, each contributing unique expertise and perspectives:
- Developers and Designers: Those skilled in app development, UX/UI design, bitcoin and the Lightning Network.
- Healthcare Providers (Doctors/Nurses/Alternative Health): Professionals who can offer insights into real-world healthcare needs and help design solutions that truly benefit patients.
- Health-Conscious Individuals: People passionate about taking control of their own health data and empowering others to do the same.
- Bitcoiners and Nostriches: Enthusiasts of Bitcoin and Nostr who are excited to apply these censorship resistant technologies to solve pressing issues in healthcare.
- Investors: Individuals or firms interested in supporting innovative projects and startups that have the potential to shape future of healthcare.
How to Participate
To get involved in the challenge and receive important updates and event invitations, participants can sign up through either of the provided forms:
The main categories we'll encourage individuals to develop solutions for are personal health apps, healthcare provider tooling, and SALUD protocol infrastructure. So far, the SALUD protocol includes NIP-82, a way to store FHIR healthcare records on Nostr, developed by NosFabrica co-founder, Vitor Pamplona. We see more Nostr improvement proposals being made as healthcare data use cases develop.
Conclusion
The SALUD Decentralized Health App Development Challenge is a groundbreaking opportunity for anyone passionate about using Nostr and Bitcoin to reshape the healthcare landscape. By building apps that empower individuals to control their own health data, participants will play a pivotal role in addressing some of the most pressing challenges in modern healthcare, from data privacy to accessibility and portability. We're xcited about this challenge and to continue building the future of decentralized healthcare!
Happy new year!
PS. Feel free to reach out with any questions to jon@nosfabrica.com or go to https://nosfabrica.com/challenge/ to learn more.
-
 @ 4ba8e86d:89d32de4
2024-11-07 13:56:21
@ 4ba8e86d:89d32de4
2024-11-07 13:56:21Tutorial feito por Grom mestre⚡poste original abaixo:
http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/240277/tutorial-criando-e-acessando-sua-conta-de-email-pela-i2p?show=240277#q240277
Bom dia/tarde/noite a todos os camaradas. Seguindo a nossa série de tutoriais referentes a tecnologias essenciais para a segurança e o anonimato dos usuários, sendo as primeiras a openPGP e a I2P, lhes apresento mais uma opção para expandir os seus conhecimentos da DW. Muitos devem conhecer os serviços de mail na onion como DNMX e mail2tor, mas e que tal um serviço de email pela I2P. Nesse tutorial eu vou mostrar a vocês como criar a sua primeira conta no hq.postman.i2p e a acessar essa conta.
É importante que vocês tenham lido a minha primeira série de tutoriais a respeito de como instalar, configurar e navegar pela I2P nostr:nevent1qqsyjcz2w0e6d6dcdeprhuuarw4aqkw730y542dzlwxwssneq3mwpaspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsyp5vcq Esse tutorial é um pré-requisito para o seguinte e portanto recomendo que leia-os antes de prosseguir com o seguinte tutorial. O tutorial de Kleopatra nostr:nevent1qqs8h7vsn5j6qh35949sa60dms4fneussmv9jd76n24lsmtz24k0xlqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgecq8f7 é complementar dado que é extremamente recomendado assinar e criptografar as mensagens que seguem por emails pela DW. Sem mais delongas, vamos ao tutorial de fato.
1. Criando uma conta de email no hq.postman
Relembrando: Esse tutorial considera que você já tenha acesso à I2P. Entre no seu navegador e acesse o endereço hq.postman.i2p. O roteador provavelmente já contém esse endereço no seu addressbook e não haverá a necessidade de inserir o endereço b32 completo. Após entrar no site vá para a página '1 - Creating a mailbox' https://image.nostr.build/d850379fe315d2abab71430949b06d3fa49366d91df4c9b00a4a8367d53fcca3.jpg
Nessa página, insira as credenciais de sua preferências nos campos do formulário abaixo. Lembre-se que o seu endereço de email aceita apenas letras e números. Clique em 'Proceed' depois que preencher todos os campos. https://image.nostr.build/670dfda7264db393e48391f217e60a2eb87d85c2729360c8ef6fe0cf52508ab4.jpg
Uma página vai aparecer pedindo para confirmar as credenciais da sua nova conta. Se tudo estiver certo apenas clique em 'Confirm and Create Mailbox'. Se tudo ocorrer como conforme haverá uma confirmação de que a sua nova conta foi criada com sucesso. Após isso aguarde por volta de 5 minutos antes de tentar acessá-la, para que haja tempo suficiente para o servidor atualizar o banco de dados. https://image.nostr.build/ec58fb826bffa60791fedfd9c89a25d592ac3d11645b270c936c60a7c59c067f.jpg https://image.nostr.build/a2b7710d1e3cbb36431acb9055fd62937986b4da4b1a1bbb06d3f3cb1f544fd3.jpg
Pronto! Sua nova conta de email na I2P foi criada. Agora vamos para a próxima etapa: como acessar a sua conta via um cliente de email.
2. Configurando os túneis cliente de SMTP e POP3
O hq.postman não possui um cliente web que nos permite acessar a nossa conta pelo navegador. Para isso precisamos usar um cliente como Thunderbird e configurar os túneis cliente no I2Pd que serão necessários para o Thunderbird se comunicar com o servidor pela I2P.
Caso não tenha instalado o Thunderbird ainda, faça-o agora antes de prosseguir.
Vamos configurar os túneis cliente do servidor de email no nosso roteador. Para isso abra um terminal ou o seu gestor de arquivos e vá para a pasta de configuração de túneis do I2P. Em Linux esse diretório se localiza em /etc/i2pd/tunnels.d. Em Windows, essa pasta se localiza em C:\users\user\APPDATA\i2pd. Na pasta tunnels.d crie dois arquivos: smtp.postman.conf e pop-postman.conf. Lembre-se que em Linux você precisa de permissões de root para escrever na pasta de configuração. Use o comando sudoedit
para isso. Edite-os conforme as imagens a seguir:
Arquivo pop-postman.conf https://image.nostr.build/7e03505c8bc3b632ca5db1f8eaefc6cecb4743cd2096d211dd90bbdc16fe2593.jpg
Arquivo smtp-postman.conf https://image.nostr.build/2d06c021841dedd6000c9fc2a641ed519b3be3c6125000b188842cd0a5af3d16.jpg
Salve os arquivos e reinicie o serviço do I2Pd. Em Linux isso é feito pelo comando:
sudo systemctl restart i2pdEntre no Webconsole do I2Pd pelo navegador (localhost:7070) e na seção I2P Tunnels, verifique se os túneis pop-postman e smtp-postman foram criados, caso contrário verifique se há algum erro nos arquivos e reinicie o serviço.Com os túneis cliente criados, vamos agora configurar o Thunderbird
3. Configurando o Thunderbird para acessar a nossa conta
Abra o Thunderbird e clique em criar uma nova conta de email. Se você não tiver nenhum conta previamente presente nele você vai ser diretamente recebido pela janela de criação de conta a seguir. https://image.nostr.build/e9509d7bd30623716ef9adcad76c1d465f5bc3d5840e0c35fe4faa85740f41b4.jpg https://image.nostr.build/688b59b8352a17389902ec1e99d7484e310d7d287491b34f562b8cdd9dbe8a99.jpg
Coloque as suas credenciais, mas não clique ainda em Continuar. Clique antes em Configure Manually, já que precisamos configurar manualmente os servidores de SMTP e POP3 para, respectivamente, enviar e receber mensagens.
Preencha os campos como na imagem a seguir. Detalhe: Não coloque o seu endereço completo com o @mail.i2p, apenas o nome da sua conta. https://image.nostr.build/4610b0315c0a3b741965d3d7c1e4aff6425a167297e323ba8490f4325f40cdcc.jpg
Clique em Re-test para verificar a integridade da conexão. Se tudo estiver certo uma mensagem irá aparecer avisando que as configurações do servidores estão corretas. Clique em Done assim que estiver pronto para prosseguir. https://image.nostr.build/8a47bb292f94b0d9d474d4d4a134f8d73afb84ecf1d4c0a7eb6366d46bf3973a.jpg
A seguinte mensagem vai aparecer alertando que não estamos usando criptografia no envio das credenciais. Não há problema nenhum aqui, pois a I2P está garantindo toda a proteção e anonimato dos nossos dados, o que dispensa a necessidade de uso de TLS ou qualquer tecnologia similar nas camadas acima. Marque a opção 'I Understand the risks' e clique em 'Continue' https://image.nostr.build/9c1bf585248773297d2cb1d9705c1be3bd815e2be85d4342227f1db2f13a9cc6.jpg
E por fim, se tudo ocorreu como devido sua conta será criada com sucesso e você agora será capaz de enviar e receber emails pela I2P usando essa conta. https://image.nostr.build/8ba7f2c160453c9bfa172fa9a30b642a7ee9ae3eeb9b78b4dc24ce25aa2c7ecc.jpg
4. Observações e considerações finais
Como informado pelo próprio site do hq.postman, o domínio @mail.i2p serve apenas para emails enviados dentro da I2P. Emails enviados pela surface devem usar o domínio @i2pmai.org. É imprescindível que você saiba usar o PGP para assinar e criptografar as suas mensagens, dado que provavelmente as mensagens não são armazenadas de forma criptografada enquanto elas estão armazenadas no servidor. Como o protocolo POP3 delete as mensagens no imediato momento em que você as recebe, não há necessidade de fazer qualquer limpeza na sua conta de forma manual.
Por fim, espero que esse tutorial tenha sido útil para vocês. Que seu conhecimento tenha expandido ainda mais com as informações trazidas aqui. Até a próxima.
-
 @ dfc7c785:4c3c6174
2025-01-02 05:56:32
@ dfc7c785:4c3c6174
2025-01-02 05:56:32![[IMG_4743.jpeg]]
ST. MARY'S CHURCH CHOLSEY & AGATHA CHRISTIE
St. Mary's Church
Cholsey church was part of the monastic system set up by Ethelread the Unready in about 986 A.D. The lower part of the tower of St Mary's Church shows traces of Saxon style stonework in the form of 'long and short" quoins. In 1121 when Henry I founded Reading abbey he endowed it with the monastic lands at Cholsey. those days everyone had to pay a tithe - a tenth part of the annual produce of land or labour. The tithe was usually paid in goods and Cholsey produced so much that a huge barn was built - said to be the biggest in Europe.
Great Barn
The church and manor were given to Reading Abbey by Henry Ist in 1121 A.D. It was a most valuable part of the abbey's possessions. In the 13th & 14th centuries the largest barn in Europe was erected close by the church.
Unfortunately, this was demolished in the early 19th century. On the right, as you enter the churchyard you can see a large barn - the original barn was bigger than this. The Great Barn was 303 feet long and had seventeen stone piers on each side supporting the roof timbers.
The Church Bells
There are eight bells in the tower. The Sanctus bell was made by Richard de Wymbish, one of the earliest London Bell founders.
Only a few bells made by him now exist.
The Cholsey bell is still regularly rung.
It was rehung in 1972 and bears the inscription RICARDUS: DE: WIMBUS: ME: FECIT (Richard de Wymbish made me.)
Cholsey First School
In 1837 a school building was erected by the churchyard gates. The school was built by subscription and then adopted by the National Society and was used for Sunday school and evening classes.
Agatha Christie
The world renowned writer Agatha Christie was a resident of the parish of Cholsey. She was born on the 15th September 1890 in Torquay, Devon.
In December 1914 she married an aviator in the Royal Flying Corps - Archibald Christie, but this ended in divorce in 1928.
There was one child from the marriage. In 1930 she married her second husband, the archaeologist Max Mallowan. They bought Winterbrook House in 1934. They attended St. Mary's Curch, Cholsey and are buried in the graveyard of their parish church.
After entering the churchyard walk along the path to the porch and then veer right across the grass towards the wall and you will see a large gravestone
The grave of Agatha Christie and her husband, Max Mallowan is tucked into a corner of the graveyard of St. Mary's Church. Agatha Christie was awarded a Commander of the Order of the British Empire in 1956.
In 1971 she received the Order of Dame Commander of the British Empire. Dame Agatha Christie died on the 12th January 1976 at the age of 85.
To return to Wallingford you need to go back through the churchyard and out to the road. You can then
Cross the road and go back the way you came.
If you wish to start the Agatha Christie Trail, cross the road follow the path to the bypass. Cross carefully and walk down Winterbrook Lane until you reach the main road. You need to cross and you will soon reach Winterbrook House which is almost hidden by a hedge.
Turn right and walk carefully over the bridge, past the school and turn right through the gate and walk across Whitehead Meadow. Turn left through the recreation ground towards the Pavilion. On leaving the recreation ground, turn left and walk into the centre of the village where it is possible to catch a bus into Wallingford.
Turn right and follow the pavement into Cholsey. At the first mini roundabout turn left and head back towards Wallingford After the Red Lion there is a long straight road until you reach the bypass. Winterbrook House is on the right hand side of Reading Road.
-
 @ a10260a2:caa23e3e
2025-01-01 12:42:22
@ a10260a2:caa23e3e
2025-01-01 12:42:22I’d like to start off by saying that phoenixd has been a great experience so far. The install (on a Linux machine) was as easy as depicted on their website.
And the channel I opened via auto liquidity was super simple. I didn’t have to pick an LSP and I won’t need to manage liquidity.
Unfortunately, the machine I installed the software on started to freeze seconds after every boot. After posting about it here and getting an answer from nostr:npub1lxktpvp5cnq3wl5ctu2x88e30mc0ahh8v47qvzc5dmneqqjrzlkqpm5xlc, I was surprised at how easy the migration seemed.
It really was just a matter of restoring the seed words on another phoenixd instance. Of course, making sure that the two instances don’t run at the same time.
As easy as it was, I wanted to create this post to give a quick overview for those who might be less tech savvy.
Step 1
Grab seed words from the
seed.datfile in hidden.phoenixfolder on the old machine.Step 2
Install phoenixd on the new machine
``` $ wget https://github.com/ACINQ/phoenixd/releases/download/v0.4.2/phoenix-0.4.2-linux-x64.zip $ unzip -j phoenix-0.4.2-linux-x64.zip
$ # run the daemon: that's it! $ ./phoenixd ```
Step 3
(This is the step that wasn’t super clear and why I wanted to spell it out in this post)
In order to install the software,
./phoenixdhas to be run. This is going to generate a new seed phrase.Now, all you need to do is replace the seed words in
seed.datwith the ones from the original install.In retrospect, I think you can replace the seed words right after unzipping the zip file and before running
./phoenixd. That will probably achieve the same result.Step 4
Once the seed words have been restored. Just run
./phoenixdagain and it’ll start up like nothing happened.Literally.
There was no indication whatsoever that something had changed, so I ran
./phoenix-cli getinfoand, voila, there was my 2M-sat channel.It was quite magical.
originally posted at https://stacker.news/items/829411
Update (1/1/2025)
Phoenix Support got back to me and confirmed that the migration can be even simpler. You can actually just copy the ~/.phoenix directory onto the new machine and run
./phoenix!
-
 @ ea9e8563:5a82ed79
2025-01-01 11:56:36
@ ea9e8563:5a82ed79
2025-01-01 11:56:36Bitcoin
Die erste, grösste und bekannteste Kryptowährung heisst Bitcoin. Das Netzwerk wurde 2009 von Satoshi Nakamoto veröffentlicht unter dem Vorwand das, dass Geldsystem völlig kaputt und veraltet ist und etwas Neues her muss. Nach dem Finanzcrash 2007 baute er fleissig an diesem „magischen Internet-Geld“ und löste ein wichtiges Problem: das Double Spending Problem. Das Problem war bis zu diesem Zeitpunkt, dass digitale Informationen, Daten und Zahlen einfach beliebig oft vermehrt oder geändert werden konnten, ohne sie von einer zentralen Organisation zu überwachen lassen. Und das war Satoshi ganz wichtig, weil eine zentrale Organisation früher oder später diese Macht für sich ausnutzen wird. Vor allem in der Geldgeschichte wurde praktisch jede zentral geregelte, auf einer beinahe unendlich leicht herstellbaren Währung oft missbraucht. Bitcoin läuft mittlerweile seit über 12 Jahren und das ohne Fehler. Wie Bitcoin funktioniert, werde ich aber in diesem Artikel nicht weiter behandeln. Aber schauen wir uns doch kurz an, wofür Bitcoin erschaffen wurde und welche Probleme noch bestehen.
Das Ziel von Bitcoin
Bitcoin ist das solideste Geld, was wir jemals hatten. Wir können mit absoluter Sicherheit sagen, dass es nie mehr als 21 Millionen Bitcoin geben wird. Dadurch ist Bitcoin deflationär. Durch die Blockchain werden die ganzen Transaktionen, die jemals gemacht wurden, abgespeichert. Das Problem ist jetzt aber, dass Bitcoin im Schnitt nur 7 Transaktionen pro Sekunde verarbeiten kann, weil die maximale Blockgrösse und somit die Anzahl der Transaktionen begrenzt ist. Wenn wir das jetzt mit den altbekannten Anbietern wie VISA und Mastercard vergleichen, können diese mehrere zehntausend Transaktionen pro Sekunde verarbeiten. Dies führt dazu, dass die Transaktionsgebühren relativ teuer werden, weil diese durch Angebot und Nachfrage bestimmt werden. Man kann sich Bitcoin also als Settlement Layer vorstellen, wie zum Beispiel FED Wire von der US-Zentralbank.
The Times 03/Jan/2009 Chancellor on brink of second bailout for banks.
> - Satoshi Nakamoto*
Ziele von Lightning
Lightning versucht die oben benannten Probleme zu lösen und sogar noch einige mehr. Auch werden neue Möglichkeiten geschaffen welche wir später noch genauer anschauen werden. Lightning ist ein Protokoll welches auf Bitcoin aufbaut, und ist völlig Open Source. Das heisst, theoretisch könnte man das LN (Lightning Netzwerk) auch auf anderen Kryptowährungen anwenden und benutzen. Zur Zeit geschieht dies aber noch nicht, weil die meisten anderen Kryptowährungen eher versuchen, diese Probleme auf dem Mainlayer zu lösen. Ob dies sinnvoll ist oder nicht lasse ich einfach mal so stehen. Als Ziele haben sich die Entwickler von Lightning und die Community verschiedenste Dinge gesetzt:
- P2P Netzwerk mit Zahlungskanälen zwischen den einzelnen Nutzern
- Routing über fremde Kanäle
- Skalierbarkeit von Bitcoin ausgleichen
- Geringe oder gar keine Netzwerkgebühren
- Hohe Privatsphäre
Wie Lightning entstanden ist
Man merkte schon relativ früh, dass man bei Bitcoin einige Probleme hat, wenn man damit einen Kaffee zahlen will. Die Transaktionsgebühren können da schnell mal höher als der Kaffee selbst sein. Dies ist natürlich nicht zielführend und ökonomisch kompletter Blödsinn. Deshalb machte man sich schon früh Gedanken, wie man dies verbessern könnte.
Es gibt drei Methoden, um dieses Problem zu lösen:
- Maximale Blockgrösse erhöhen (mehr Transaktionen)
- Zeit zwischen den Blöcken verkleinern
- Einführung eines Second Layer
Das Problem bei den ersten zwei Punkten ist, dass mit diesen Funktionen es sich viel schwieriger gestaltet ein eigene Node (Knotenpunkt) zu betreiben. Dieser Knotenpunkt müsste viel mehr Speicher haben als heute (ca. 300 GB) und würde somit mehr kosten. Auch müsste der Prozessor viel besser werden und somit mehr Energie verbrauchen, weil mehr Transaktionen validiert werden müssen. Weil es den Bitcoinern sehr wichtig ist, dass sie nicht auf andere vertrauen müssen, sondern alles selber verifizieren können.
Don’t trust, verify!
> - bekanntes Bitcoin saying*
Somit bleibt nur die Lösung eines Second Layers übrig. Auch wenn der Grossteil der Bitcoin Community für den Second Layer war, gab es ein kleines Lager, welches trotzdem für die Erhöhung der Blockgrösse war. So entstand Bitcoin Cash (BCH). Sie Forkten somit die Bitcoin Blockchain und es entstand ein neuer Abzweiger. Die Blockgrösse wurde von 1 MB auf 32 MB angehoben. Damit man den Second Layer mit Bitcoin verknüpfen konnte, musste noch das SegWit (Segregated-Withness) Update implementiert werden. Auch hier waren über 90 % der Bitcoin Community für ein Update, was ein Softfork bildete. Softforks sind nichts Schlechtes und sind eigentlich nur Software-Updates, welche Rückwärts kompatibel sind. Lightning wurde somit 2015 vorgestellt und 2018 veröffentlicht, auch wenn Lightning immer noch in den Kinderschuhen steckt, hat es ein Riesenpotenzial, vor allem wenn man sich anschaut wie schnell und gross das Netzwerk mittlerweile geworden ist.
Funktionsweise
Eines der wichtigsten Funktionen bei Lightning ist es, dass man Zahlungskanäle einrichtet, welche zwischen dir und dem Empfänger geöffnet werden. Das ausgeklügelte daran aber ist, dass man nicht zu jedem, dem man eine Transaktion schickt, auch einen Kanal offen haben muss. Aber schauen wir uns zuerst mal das Prinzip von einem einfachen Zahlungskanal an.

In diesem Beispiel haben Alice und Bob sich gegenseitig einen Zahlungskanal geöffnet, damit dies auch wirklich passiert, muss man Liquidität hinzufügen. Das Tolle daran ist, dass nicht unbedingt beide müssen oder nicht gleichviel hinzufügen müssen. Dies macht vor allem Sinn, wenn Alice ein Kaffee betreibt und Bob sich da jeden Morgen einen Kaffee holt. Somit muss Alice nie Geld zu Bob senden, aber Bob muss immer Geld zu Alice. In unserem Beispiel sind Alice und Bob Freunde und schicken sich gegenseitig immer wieder Geld. Bei der Eröffnung, also der Liquiditätseingabe, wird eine Transaktion auf der Bitcoin Blockchain zu einem Multi Signature Wallet gemacht. Dieses Wallet hat zwei Private Keys und kann nur geplündert werden, wenn beide dazu zustimmen. Das Geld wird also eingefroren. Durch eine Schnittstelle erkennt das Lightning Netzwerk das und ordnet die eingezahlten Gelder den beiden zu.

Mann kann sich vorstellen, dass innerhalb eines Zahlungskanals immer Geld hin und hergeschickt werden kann ohne Gebühren. Dies wird digital in einem Buchhaltungsähnlichen System gespeichert. Und am Ende kommt eine neue Balance heraus, welche mit der Schliessung des Channels wieder in den Mainlayer (also Bitcoin) implementiert wird. Dadurch können unendlich viele Transaktionen in maximal 4 Transaktionen auf der Bitcoin Blockchain dargestellt werden. Das absolut verrückte ist aber, dass 500 Transaktionen pro Sekunde durchgeführt werden können, in jedem Channel!
Routing von Transaktionen
Um nicht bei jeder kleinsten Transaktion einen neuen Channel erstellen zu, müssen gibt es noch eine weitere Möglichkeit Geld zu versenden. Dabei werden fremde Channels verwendet und eine Route wird von dir zu deinem Empfänger gesucht. Sobald diese Route gefunden ist, wird das Geld von Person zu Person vollautomatisch versendet. Als Gebühr für die Mitbenutzung der Fremden Channel bezahlt man eine kleine Gebühr, welche aber sehr klein ist und meist nur wenige Cent beträgt.

Vorteile von Lightning
Das Lightning Netzwerk nutzt auch Bitcoin als Währung und ist somit ebenfalls extrem sicher und man kann garantieren das es nie mehr als 21 Millionen geben wird auf dem Lightning und Bitcoin-Netzwerk. Weil viele neue Möglichkeiten durch dieses schnelle Netzwerk geschaffen werden, wurde der Satoshi (1:100’000’000 Bitcoin) nochmal in eine kleinere Unterwährung aufgeteilt. Dabei wird 1 Satoshi in 1000 mSatoshis (mili) aufgeteilt. Ein weiterer Vorteil ist die Fehlende öffentliche Transaktionshistorie, damit ist die Privatsphäre extrem hoch und die Nachverfolgbarkeit extrem schwierig, vor allem wenn die Bezahlungen über mehrere Routing Hops (Sprünge) laufen. Man kann also sagen, dass Lightning Privacy per Default hat. Lightning ist dezentral und für jeden Menschen nutzbar, welcher es nutzen will.
Anwendungsbereiche
Mittlerweile gibt es schon extrem viele Bereiche wo Lightning angewendet wird um die Vorteile von der Blockchain und von Lightning allgemein zu nutzen, einige davon Werde ich euch nun vorstellen:
Fountain: Podcast Plattform
Fountain funktioniert im Prinzip wie jede andere grössere Podcastplattform wie zum Beispiel Spotify oder Apple Podcasts und viele mehr. Nicht nur für den Content Creator gibt es viele coole Features, sondern auch für den Nutzer. Zum Beispiel kann der Nutzer einstellen, wie viel Geld er zahlen will, um den Creator zu unterstützen, während er sich den Podcast anhört wird für die Zeit, die er hört ein Betrag abgebucht. Meiner Meinung ist dies ein extrem guter Weg, um vor allem kleine Podcasts zu monetisieren und guten Content zu fördern. Auch für den Nutzer ist diese Lösung ideal, weil man nur bezahlt, wenn man die Dienstleistung überhaupt benutzt. Des Weiteren gibt es viele "Neue" Features, die so bisher nur auf solchen "neuen" Podcast Plattformen zu finden sind. Zum Beispiel gibt es Kapitelmarken, referenzierte Musik-Tracks und Livestreams, und ausserdem kann man auch Kommentare hinterlassen, was die Interaktion zwischen Creator verbessert!
Strike: Cash App
Man kann sich Strike vorstellen wie Paypal nur mit dem entscheidenden unterschied, dass das ganze auf Bitcoin läuft. Strike ermöglicht es heute schon tausenden von Menschen auf einfachste Art und Weise Geld über die ganze Welt zu versenden und das mit dem solidesten Geld, was es überhaupt gibt, das schöne ist, dass die Werte auch wirklich verschickt werden. Hierzu ein kleiner Exkurs aus dem aktuellen Bankensystem: Wenn jemand aus Europa jemandem Geld in Amerika schicken will, verlässt das Geld das Land nicht. Man braucht für einen Internationalen Banktransfer immer einen Gegenspieler, welcher Geld aus Amerika nach Europa schicken möchte. Diesen Vorgang nennt man ’’Clearing’’. Meistens ist das kein Problem, da viele Transaktionen das Land verlassen aber auch kommen, aufgrund dieser Liquidität geht das zumindest in Industrieländern ganz gut. Entwicklungsländer haben hier schon eher Schwierigkeiten und werden Teilweise sogar aus dem Bankensystem ausgeschlossen (Siehe Iran Swift Sanctions) Ein weiterer Vorteil der sich durch Strike ergibt, ist das die Zahlungen fast keine Gebühren verursachen. Diese sind meist im Cent / Rappen Bereich.
Sphinx /Juggernout: Chat App
Die beiden Apps versuchen ein WhatsApp mit absoluter Privatsphäre zu bauen. Um dies zu erreichen wird die Channelfunktion von Lightning benutzt, weil diese nur von den zwei Parteien eingesehen werden kann und mit höchstmöglicher Privatsphäre durch die Blockchain gesichert wird. Diese Services kosten zwar etwas, aber mit der eigenen Lightning Node (Knotenpunkt) sind diese Kosten sehr gering und liegen ebenfalls im Cent / Rappen Bereich.
Edit: Spinx und Juggernout konnten sich bis anhin leider nie durchsetzen.
-
 @ 656a6efa:ec0bd10e
2025-01-01 06:06:14
@ 656a6efa:ec0bd10e
2025-01-01 06:06:14Accounting Update 2.0 from 15th Centry -> 21st Century
Luca Pacioli’s double entry bookkeeping was a real 0 to 1 moment in the world of record keeping. Standardizing the accounting protocol allowed for a base level of trust between record keepers and interested parties of investors and owners. Trust might be a stretch of the word, in reality, it was really just an agreed upon structure or rules which then changed with consensus over time.
The problem we have been dealing with since reaching record keeping consensus is accuracy. The accounting protocol is not perfect. It relies heavily on human implementation and we are still too early in modern attempts at automating record keeping. Audited Financial Statements have typically been the answer to the problem of accuracy (though the level of scrutiny books go through in an audit would surprise most people not familiar with the processes of an audit). An audit, at best, just means that the information you’re looking at is ~mostly~ right. Described by an industry word, “material”.
The problem is with the banks. I know . . . you’re shocked a bitcoiner has a problem with banks . . . but it’s not like that. A large part of the record keeping process is comparing the bank record of transactions to the accounting records transactions in what is called a reconciliation. It’s just a comparison of the two ledgers. If those ledgers don’t agree, your records are wrong. You then take those bank ledgers and verify transactions with supporting documents like invoices, shipping records, and checks. It’s a tedious, potentially error-prone process.
Bitcoin, could fix this.
By tying transactions into a public, real-time ledger, there is no need for the bank reconciliation process. Global consensus deemed your transactions as valid and all an organization would have to do is prove they have the key. There’s even potential for organizations to embed invoices directly into payments meaning that each transaction has support for it with verification from an outside party of what the funds were used for. Instead of saying, “we have an audit as of 12/31/20XX” you have the potential for real-time audits of transactions with 100% accuracy. 100% verification of accuracy is not economically freasable or practical with today’s processes.
As of the day of this writing, that possibility is all but a dream, but I look forward to the day where accountants look more like today’s computer programmers than a 15th century monk.
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ eac63075:b4988b48
2024-10-15 20:18:52
@ eac63075:b4988b48
2024-10-15 20:18:52Bitcoin emerged as a promise of financial freedom, challenging the traditional and centralized structures of governments and financial institutions. Since its inception, many enthusiasts have believed in the revolutionary potential of this cryptocurrency. However, over the years, challenges have arisen that have tested this promise, especially concerning centralization, the implementation of secondary layers like the Lightning Network, and issues of governance and privacy.
https://www.fountain.fm/episode/SDZYaFMyLEO1krL6x8RD
Centralization and the Exclusivity of Nostr
Nostr, a decentralized network aiming to be censorship resistant, emerged as an attempt to solve some inherent problems of centralization. However, it faces significant challenges. Many users point out that, despite its promise, Nostr is still not attractive to the general public, being exclusive to a specific niche.
Additionally, issues of centralization still permeate the network. Discussions on GitHub revealed that developers chose not to implement an absolute level of privacy, a decision many considered inadequate. Even with protocols developed to ensure total privacy—such as the non-identification of IPs and communicating parties—the network still lacks this robust implementation.
Individual Freedom and Data Protection
A recurring issue is the importance of demonstrating that real options exist for citizens to protect and preserve their freedom. In a world where most discussions about Bitcoin revolve around its use as an investment asset, there is an urgent need to emphasize its potential as a tool for financial freedom.
The Bitcoin community should focus on development and education, showing that the conscious use of cryptography and decentralized transactions can protect individuals against excessive government surveillance and control. Secure and private communication is fundamental, and Bitcoin, along with privacy technologies, can provide this.
Hyperbitcoinization and the Illusion of Store of Value
Hyperbitcoinization is a concept that refers to the moment when Bitcoin will replace fiat currencies worldwide. However, achieving this state is not simple, especially when Bitcoin is seen primarily as a store of value. Since 2017, this narrative has gained strength, promoting the idea that accumulating Bitcoin will lead to automatic wealth.
However, this perspective is limited. The true value of Bitcoin lies in its use as a transactional currency, not just in its scarcity. The community must work to ensure that Bitcoin is utilized in everyday transactions, strengthening its network and demonstrating its real value.
The Role of the Community in Bitcoin's Development
Bitcoin's strength comes from its community. Developers, users, and enthusiasts, through their actions and support, make Bitcoin a powerful tool. This community is responsible for ensuring that Bitcoin maintains its essence and that its functionalities are accessible to all.
It is crucial that this support network continues promoting the decentralized use of Bitcoin, without intermediaries that can censor or control transactions. Adopting Bitcoin in a centralized manner, through banks or other institutions, contradicts its original proposal and strengthens those who have historically opposed its existence.
Sidechains, Second Layers, and the Lightning Network
Sidechains and second layers, like the Lightning Network, are essential components for Bitcoin's scalability. However, they bring challenges, especially regarding the need to trust intermediaries. For these solutions to be effective, it is fundamental that they allow the unilateral withdrawal of funds, ensuring that users maintain full control over their assets.
The Lightning Network, for example, is a second layer that allows fast and cheap transactions. However, many users face difficulties when dealing with channels that do not close correctly, resulting in locked funds. These problems must be solved for the network to be truly decentralized and functional.
The Fight Against Centralization on the Internet
Centralization is not a problem exclusive to Bitcoin. The internet as a whole faces similar challenges, with data control concentrated in the hands of a few large technology companies. To ensure freedom of expression and online privacy, it is necessary to decentralize these data clusters.
Projects that seek to decentralize the internet are vital for this mission. They not only complement Bitcoin in its quest for financial freedom but also ensure that digital communication and expression are protected against censorship and corporate control.
The Future of Bitcoin and the Need for Action
The future of Bitcoin depends on the community's action. We cannot expect Bitcoin to automatically become a global medium of exchange. A conscious effort is necessary to build an ecosystem where Bitcoin can flow freely, being used in everyday transactions and valued for its utility.
Moreover, with the imminent arrival of central bank digital currencies (CBDCs), time is of the essence. CBDCs represent a significant challenge, as they can further restrict individuals' financial freedom. Therefore, accelerating Bitcoin adoption and ensuring it maintains its decentralized and uncensorable properties is a priority.
Conclusion
Bitcoin remains a powerful tool for financial freedom but faces significant challenges. Centralization, both in the context of secondary networks and the internet in general, poses a threat to its original proposal. However, with the joint action of the community and the continuous development of decentralized solutions, it is possible to maintain Bitcoin as a bastion of individual freedom.
The true revolution of Bitcoin lies in its use as a medium of exchange, not just as a store of value. To achieve hyperbitcoinization, it is necessary to build a robust ecosystem where Bitcoin can circulate freely and be accessible to all. Only then can we fulfill Bitcoin's initial promise and ensure it continues to be a tool for freedom and financial autonomy.
-
 @ 472f440f:5669301e
2024-12-31 04:42:00
@ 472f440f:5669301e
2024-12-31 04:42:00I'm sure some of you are already tired of the discussion around the H-1B visa program that was started on Christmas Eve by Vivek Ramaswamy and escalated by Elon Musk and others as the "Silicon Valley MAGA" coalition began putting forth legal immigration policy proposals for the incoming Trump administration. Core to their policy is the expansion of the H-1B visa program so that America can "recruit the best talent in the world" to come build the American economy.
Unfortunately, as it stands today - according to the Silicon Valley cognescenti, Americans are either a.) not smart enough to fulfill the roles necessary to enable the United States to maintain its lead as economic super power of the world or b.) expect too much in compensation for the available roles. At least this is my reading from the commentary I've seen over the last week.
What seems abundantly clear to me is that the framing put forth by "Silicon Valley MAGA" crew is disingenuous and self-serving. It has been clear for awhile now that the H-1B visa program is being systematically abused to bring in cheap labor from other countries to help drive down labor costs for companies across the spectrum. Not just Silicon Valley tech companies. The system has a loophole in it and it is being exploited. Bring people to the US via H-1B visas to complete work for you at lower costs and your company's financials are likely to be better off (assuming the work being done is productive and a value add to the company). Now, this isn't to say that everyone who is in the US via an H-1B visa is here because these companies want to exploit the loophole that gives them the ability to spend less on head count. However, based off the data from the database of the H-1B visa program it is abundantly clear that the system is being taken advantage of. Egregiously and at the expense of American workers, who are most certainly not (all) "subtarded".
Herein lies the crux of the problem; companies are abusing this program to get away from the problem of Americans demanding higher wages to maintain lives of dignity in a country run by a government that is chronically addicted to debt backed by a central bank that will print money ex-nihilo and at will to monetize that debt. Americans are then being scapegoated as either "lazy", "stupid" or "delusional about their worth in the work force". A classic straw man argument that avoids the root issue at hand; the money is broken and the broken money has created perverse incentives throughout the economy while also stripping Americans of the ability to properly save the value of their labor.
We live in a high velocity trash economy that rewards grift and waste while disincentivizing hard work that is meaningful to the quality of life of the Common Man. Everything has been hyper-financialized to the point that one of the only ways to make it ahead is to speculate on the flow of capital into certain asset classes, which is often determined by the whims of central planners. Another is to build or speculate on tech "innovations" that typically materialize in the form of attention zapping apps and widgets that help people temporarily forget they live in a high-velocity trash economy.
The mass of men lead lives of quiet desperation and it is because they don't see a way out of the nihilistic rat race created (unknowingly to most) by the money printer.
The ability to print money out of nothing and throw it at everything creates misaligned incentives that result in the inability for the market to properly determine what is genuinely needed by the people instead of those who have learned how to game the broken system and its broken incentives.
One last point, I would be remiss not to acknowledge that many individuals in America aren't intellectually equipped to do some of the cutting edge work that may be necessary to produce the technologies and companies that will push the country forward. The high-velocity trash economy run on money printed out of nothing has completely corrupted the education system. People in the United States are literally dumber than they were five decades ago. That is a fact. But it is not only the fault of the American people themselves, but the corrupt system they have been born into that destroyed the education system with perverse incentives. And the overwhelming majority of the blame is on the system, not the people.
Even with that being said, the idea that we need to adopt a Tiger Mom mentality in the US - a culture of unrelenting devotion to studying STEM to the point that weekend sleepovers for kids are discouraged - is absolutely laughable and objectively un-American. There are plenty of incredibly intelligent, creative and driven young Americans who have contributed and will continue to contribute significantly to the American economy and they didn't need to shackle themselves to their desks to get that way. America isn't a country that was built by automatons. It's a country built by people who said, "Fuck you. Don't tell me what I can and cannot do. Watch this."
Despite the fact that a system has been erected that actively works against the average American system the American spirit lives on in the souls of many across the country. Miraculously. The American spirit is something that cannot simply be imported. It is ingrained in our culture. It is certainly beginning to dwindle as hope for a better future becomes more and more dim for the masses as the system works against them despite all their best efforts to succeed. It is imperative that we stoke the coals of the American spirit while it is still alive in those who are too stubborn to give up.
People need the ability to save their hard work in a money that cannot be debased. Opportunity cost needs to be reintroduced into the market so that things that actually add value and increase the quality of life for the Common Man are where hard money is allocated. And people need to start talking about the root of the problem more seriously instead of striking at branches with disingenuous straw man arguments.
Final thought... Ready to go surfing.
-
 @ 7e538978:a5987ab6
2024-10-02 13:57:31
@ 7e538978:a5987ab6
2024-10-02 13:57:31Chain Duel, a fast paced PvP game that takes inspiration from the classic snake game and supercharges it with Bitcoin’s Lightning Network. Imagine battling another player for dominance in a race to collect blocks, where the length of your chain isn’t just a visual cue. It represents real, staked satoshis. The player with the most Proof of Work wins, but it’s not just about gameplay; it’s about the seamless integration of the Lightning Network and real-time payments.
But how does Chain Duel manage these instant transactions with such efficiency? That’s where LNbits comes in. LNbits, an open-source wallet and payment infrastructure, handles all in-game payments making it easy for developers to focus on gameplay while LNbits takes care of everything from microtransactions to automated splits for developers and designers. In this article, we’ll dive deep into how Chain Duel leverages LNbits to streamline in-game payments and how other developers can take advantage of this powerful toolset to build the future of Lightning-powered gaming.
Let’s explore how LNbits transforms payment processing and why it’s quickly becoming a must-have for game developers working in the Bitcoin space.
Overview of Chain Duel
Chain Duel is a unique Lightning Network-inspired game that reimagines the classic snake game with a competitive twist, integrating real-time payments. Two players face off in real-time, racing to "catch" blocks and extend their chains. Each block added to the chain represents Proof of Work, and the player with the most Proof of Work wins the duel. The stakes are high, as the game represents satoshis (small units of Bitcoin) as points, with the winner taking home the prize.
The game is designed to be Lightning-native, meaning all payments within Chain Duel are processed through the Lightning Network. This ensures fast payments, reducing latency and making gameplay smooth. With additional features like practice mode, tournaments and highscores, Chain Duel creates an engaging and competitive environment for Bitcoin enthusiasts and gamers alike.

One of the standout aspects of Chain Duel is its deeper integration with the Lightning Network even at a design level. For example, actual Bitcoin blocks can appear on screen during matches, offering bonus points when mined in sync with the game. The game’s current version, still in beta, has already drawn attention within the Bitcoin community, gaining momentum at conferences and with a growing user base through its social networks. With its innovative combination of gaming, the Lightning Network, and competitive play, Chain Duel offers a glimpse into the future of Lightning-based gaming.
How LNbits is Used in Chain Duel
Seamless Integration with LNbits
At the core of Chain Duel’s efficient payment processing is LNbits, which handles in-game transactions smoothly and reliably. Chain Duel uses the LNbits LNURL-pay and LNURL-withdraw extensions to manage payments and rewards between players. Before each match, players send satoshis using LNURL-pay, which generates a static QR code or link for making the payment. LNURL-pay allows users to attach a note to the payment, which Chain Duel creatively uses as a way to insert the player name in-game. The simplicity of LNURL-pay ensures that users can quickly and easily initiate games, with fresh invoices being issued for every game. When players win, LNURL-withdraw enables them to seamlessly pull their earnings from the game, providing a quick payout system.
These extensions make it easy for players to send and receive Bitcoin with minimal latency, fully leveraging the power of the Lightning Network for fast and low-cost payments. The flexibility of LNbits’ tools means that game developers don’t need to worry about building custom payment systems from scratch—they can rely on LNbits to handle all financial transactions with precision.
Lightning Tournaments
Chain Duel tournaments leverage LNbits and its LNURL extensions to create a seamless and efficient experience for players. In Chain Duel tournaments, LNbits plays a crucial role in managing the overall economics. LNbits facilitates the generation of LNURL QR codes that participants can scan to register quickly or withdraw their winnings. LNbits allows Chain Duel to automatically handle multiple registrations through LNURL-pay, enabling players to participate in the tournament without additional steps. The Lightning Network's speed ensures that these payments occur in real-time, reducing wait times and allowing for a smoother flow in-game.
Splitting Payments
LNbits further simplifies revenue-sharing within Chain Duel. This feature allows the game to automatically split the satoshis sent by players into different shares for the game’s developer, designer, and host. Each time a payment is made to join a match, LNbits is used to automattically pay each of the contributors, according to pre-defined rules. This automated process ensures that everyone involved in the development and running of the game gets their fair share without manual intervention or complex bookkeeping.
Nostr Integration
Chain Duel also integrates with Nostr, a decentralized protocol for social interactions. Players can join games using "Zaps", small tips or micropayments sent over the Lightning Network within the Nostr ecosystem. Through NIP-57, which enables Nostr clients to request Zap invoices, players can use LNURL-pay enabled Zaps to register in P2P matches, further enhancing the Chain Duel experience. By using Zaps as a way to register in-game, Chain Duel automates the process of fetching players' identity, creating a more competitive and social experience. Zaps are public on the Nostr network, further expanding Chain Duel's games social reach and community engagement.
Game and Payment Synchronization

One of the key reasons Chain Duel developers chose LNbits is its powerful API that connects directly with the game’s logic. LNbits allows the game to synchronize payments with gameplay in real-time, providing a seamless experience where payments are an integrated part of the gaming mechanics.
With LNbits managing both the payment process and the Lightning Network’s complex infrastructure, Chain Duel developers are free to concentrate on enhancing the competitive and Lightning Network-related aspects of the game. This division of tasks is essential for streamlining development while still providing an innovative in-game payment experience that is deeply integrated with the Bitcoin network.
LNbits proves to be an indispensable tool for Chain Duel, enabling smooth in-game transactions, real-time revenue sharing, and seamless integration with Nostr. For developers looking to build Lightning-powered games, LNbits offers a powerful suite of tools that handle everything from micropayments to payment distribution—ensuring that the game's focus remains on fun and competition rather than complex payment systems.
LNBits facilitating Education and Adoption
This system contributes to educating users on the power of the Lightning Network. Since Chain Duel directly involve real satoshis and LNURL for registration and rewards, players actively experience how Lightning can facilitate fast, cheap, and permissionless payments. By incorporating LNbits into Chain Duel, the game serves as an educational tool that introduces users to the benefits of the Lightning Network. Players gain direct experience using Lightning wallets and LNURL, helping them understand how these tools work in real-world scenarios. The near-instant nature of these payments showcases the power of Lightning in a practical context, highlighting its potential beyond just gaming. Players are encouraged to set up wallets, explore the Lightning ecosystem, and eventually become familiar with Bitcoin and Lightning technology. By integrating LNbits, Chain Duel transforms in-game payments into a learning opportunity, making Bitcoin and Lightning more approachable for users worldwide.
Tools for Developers
LNbits is a versatile, open-source platform designed to simplify and enhance Bitcoin Lightning Network wallet management. For developers, particularly those working on Lightning-native games like Chain Duel, LNbits offers an invaluable set of tools that allow for seamless integration of Lightning payments without the need to build complex custom solutions from scratch. LNbits is built on a modular and extensible architecture, enabling developers to easily add or create functionality suited to their project’s needs.
Extensible Architecture for Customization
At the core of LNbits is a simple yet powerful wallet system that developers can access across multiple devices. What makes LNbits stand out is its extensible nature—everything beyond the core functionality is implemented as an extension. This modular approach allows users to customize their LNbits installation by enabling or building extensions to suit specific use cases. This flexibility is perfect for developers who want to add Lightning-based services to their games or apps without modifying the core codebase.
- Extensions for Every Use Case
LNbits comes with a wide array of built-in extensions created by contributors, offering various services that can be plugged into your application. Some popular extensions include: - Faucets: Distribute small amounts of Bitcoin to users for testing or promotional purposes.
- Paylinks: Create shareable links for instant payments.
- Points-of-sale (PoS): Allow users to set up shareable payment terminals.
- Paywalls: Charge users to access content or services.
- Event tickets: Sell tickets for events directly via Lightning payments.
- Games and services: From dice games to jukeboxes, LNbits offers entertaining and functional tools.
These ready-made solutions can be adapted and used in different gaming scenarios, for example in Chain Duel, where LNURL extensions are used for in game payments. The extensibility ensures developers can focus on building engaging gameplay while LNbits handles payment flows.
Developer-Friendly Customization
LNbits isn't just a plug-and-play platform. Developers can extend its functionality even further by creating their own extensions, giving full control over how the wallet system is integrated into their games or apps. The architecture is designed to make it easy for developers to build on top of the platform, adding custom features for specific requirements.
Flexible Funding Source Management
LNbits also offers flexibility in terms of managing funding sources. Developers can easily connect LNbits to various Lightning Network node implementations, enabling seamless transitions between nodes or even different payment systems. This allows developers to switch underlying funding sources with minimal effort, making LNbits adaptable for games that may need to scale quickly or rely on different payment infrastructures over time.
A Lean Core System for Maximum Efficiency
Thanks to its modular architecture, LNbits maintains a lean core system. This reduces complexity and overhead, allowing developers to implement only the features they need. By avoiding bloated software, LNbits ensures faster transactions and less resource consumption, which is crucial in fast-paced environments like Chain Duel where speed and efficiency are paramount.
LNbits is designed with developers in mind, offering a suite of tools and a flexible infrastructure that makes integrating Bitcoin payments easy. Whether you’re developing games, apps, or any service that requires Lightning Network transactions, LNbits is a powerful, open-source solution that can be adapted to fit your project.
Conclusion
Chain Duel stands at the forefront of Lightning-powered gaming, combining the excitement of competitive PvP with the speed and efficiency of the Lightning Network. With LNbits handling all in-game payments, from microtransactions to automated revenue splits, developers can focus entirely on crafting an engaging gaming experience. LNbits’ powerful API and extensions make it easy to manage real-time payments, removing the complexity of building payment infrastructure from scratch.
LNbits isn’t just a payment tool — it’s a flexible, developer-friendly platform that can be adapted to any gaming model. Whether you're developing a fast-paced PvP game like Chain Duel or any project requiring seamless Lightning Network integration, LNbits provides the ideal solution for handling instant payments with minimal overhead.
For developers interested in pushing the boundaries of Lightning-powered gaming, Chain Duel is a great example of how LNbits can enhance your game, letting you focus on the fun while LNbits manages real-time transactions.
Find out more
Curious about how Lightning Network payments can power your next game? Explore the following:
- Learn more about Chain Duel: Chain Duel
- Learn how LNbits can simplify payment handling in your project: LNbits
- Dive into decentralized communication with Nostr: Nostr
- Extensions for Every Use Case
-
 @ 0e8c41eb:95ff0faa
2024-07-08 14:36:14
@ 0e8c41eb:95ff0faa
2024-07-08 14:36:14Chef's notes
Sprinkle a pinch of salt in a bowl. Sift 275 grams of flour above it. Make a well in the center of the flour and sprinkle the yeast into it. Add 50 grams of butter, 25 grams of sugar, and the egg. Pour in the milk and knead the dough with the mixer or by hand into a smooth dough. If necessary, add a bit more flour if the dough is too sticky. Form the dough into a ball. Let the dough rise covered with cling film at room temperature for 1 hour.
Peel the apples. Cut the apples and apricots into pieces. Cook the fruit with 150 grams of sugar and 50 ml of water in 15 minutes into a thick compote. Let this fruit filling cool.
Knead the dough again briefly and roll it out to a round sheet of about 28-30 cm in diameter, so that it fits well over the baking tin. Press the dough into the tin and press it well into the corners. Let the dough rise again for 10 minutes and cut off the excess edges.
Spread the fruit filling over the dough.
Mix the rest of the flour with the remaining 100 grams of butter and 100 grams of sugar and knead it with your fingers into a crumbly mixture. Sprinkle this crumble mixture over the fruit filling. Bake the tart in the preheated oven at 200°C for about 30 minutes until golden brown.
Variations: Only apple? Make this tart with 1 kilo of apples. High or low? You can also bake the crumble tart in a low tart tin of 30 cm diameter. If the fruit filling is a bit too voluminous, you can make double the crumble mixture and sprinkle it over the larger surface area.
Additional needs: Mixer with dough hooks or food processor Cling film Round baking tin with a diameter of 28-30 cm, greased
Details
- ⏲️ Prep time: 45 min + 1 hour Rising
- 🍳 Cook time: 30 minutes
- 🍽️ Servings: 8
Ingredients
- 375 grams flour
- 1 packet dried yeast (7 grams)
- 125 grams unsalted butter, at room temperature
- 275 grams sugar
- 1 egg
- 100 ml milk, at room temperature
- 500 grams apples
- 500 grams apricots (fresh or from a can)
Directions
- Sprinkle a pinch of salt in a bowl. Sift 275 grams of flour above it. Make a well in the center of the flour and sprinkle the yeast into it. Add 50 grams of butter, 25 grams of sugar, and the egg. Pour in the milk and knead the dough with the mixer or by hand into a smooth dough. If necessary, add a bit more flour if the dough is too sticky. Form the dough into a ball. Let the dough rise covered with cling film at room temperature for 1 hour.
- Peel the apples. Cut the apples and apricots into pieces. Cook the fruit with 150 grams of sugar and 50 ml of water in 15 minutes into a thick compote. Let this fruit filling cool.
- Knead the dough again briefly and roll it out to a round sheet of about 28-30 cm in diameter, so that it fits well over the baking tin. Press the dough into the tin and press it well into the corners. Let the dough rise again for 10 minutes and cut off the excess edges.
- Spread the fruit filling over the dough.
-
 @ 6538925e:571e55c3
2024-12-30 15:51:30
@ 6538925e:571e55c3
2024-12-30 15:51:30In 2024, listeners sent a total of $127,900 to creators on Fountain
The 2 BTC sent is equivalent to $127,900 based on a daily price conversion but it would be worth nearly 50% more today.
You sent over 40,000 boosts to your favourite shows and artists, with an average boost value of 3,380 sats (around $3.20 at today's price).
To add to that, over 63 million sats were streamed over the course of the year, representing 32% of total value sent.
Here are some of the shows and artists who picked up the top awards in 2024. To read the full article, head to our website.
Most Supported Show: Rabbit Hole Recap
Rabbir Hole Recap is a bitcoin news show hosted by Marty Bent and Matt Odell. Over the last three years, RHR has become one of the moved shows among Fountain listeners (affectionately known as ‘freaks’). In 2022 they were #3, in 2023 they were #2, and in 2024 they finally claimed the #1 spot. Congratulations, Marty and ODELL. Your dedication and humility is an inspiration to bitcoiners around the world.
Show with Most Supporters: Mr Obnoxious
Peter McCormack announced earlier this year that What Bitcoin Did, the preeminent podcast he has hosted for as long as we can remember, would come to an end to make way for a new show, Mr Obnoxious. In December, the Real Bedford FC owner announced that Danny Knowles would be the new custodian - much to the relief of the 800 listeners who supported the show this year. Thanks for everything, Pete!
Most Supported Episode: LINUX Unplugged | 545: 3,062 Days Later
LINUX Unplugged is just one of many popular shows about open-source, security and privacy from Jupiter Broadcasting. Editor-in-chief Chris Fisher finishes the year with three shows in Fountain's top 40. How? He and his co-hosts have made boosting a core part the listener experience, with his audience often sending "zip code boosts" (which can get pretty expensive if you live in Alaska).
Most Supported Artist: Ainsley Costello
At just 20 years old, Ainsley has been working toward a career in music for over half her life. Her music is the modern pop soundtrack of the next generation. Ainsley first made "waves" on the internet in August 2023 as the first artist to receive 1 million sats with her hit song “Cherry On Top.” Since then, she has inspired countless artists to follow her path, becoming the face of this exciting new movement.
Artist with Most Supporters: Man Like Kweks
Don Kweka is a producer and rapper from Tanzania. When he's not at his desk working his 9 to 5, he's making beats in his bedroom - and he has been prolific in 2024. Earlier this year he told Forbes he had earned a total of $25.68 from United Masters, the distribution company he uses for traditional DSPs (for which he pays a $60 annual fee). Since first publishing his music on Wavlake, he’s earned 2.3 million sats (over $2,000).
Most Supported Track: Abi Muir | Stockholm
Born in Scotland and now residing in Australia, Abi’s distinctive, goosebump-inducing vocals and heartfelt lyrics define her creative songwriting. Her unique style sees her delivering memorable, catchy pop songs of singer-songwriter prose with a contemporary pop sound. In Stockholm she explores a darker, harder edge to her music that crosses into alt-rock, topped with Muir's piercing, sultry vocals.
 ### Read Fountain Rewind 2024 in full on our website
### Read Fountain Rewind 2024 in full on our websiteTo see the full list of award winners, the top 40 shows and artists, plus the top stories from this year, hit the link below.
 ### Share your Rewind for a chance to win Fountain AirPods, limited edition merch and 100,000 sats
### Share your Rewind for a chance to win Fountain AirPods, limited edition merch and 100,000 satsOpen the app to see your Fountain Rewind (make sure you're using the latest version). Post a screenshot of any screen in your Fountain Rewind on X or Nostr and tag @fountain_app in your post. We will be announcing three lucky winners on Dec 31 - good luck!
-
 @ bcbb3e40:a494e501
2024-12-30 11:29:30
@ bcbb3e40:a494e501
2024-12-30 11:29:30
No podemos ignorar la importancia que el Reino Visigodo tiene en la configuración de España, de la impronta definitiva que aportó al proceso de etnogénesis para dar la forma definitiva a esa entidad histórica que hoy, tras tres siglos de invasiones germánicas, desde la caída del Imperio Romano a finales del siglo V d.C., hasta el advenimiento del Islam. A modo de contraste, diremos también, que la identidad nacional española, o si se quiere ver así, el alma hispánica, se forjó en claro y evidente contraste con el ocupante sarraceno, y su presencia en el orbe peninsular, junto al recuerdo de la herencia visigoda y los sucesivos concilios toledanos, sirvieron de estímulo al avance de los reinos cristianos del norte. Es decir, España se construyó en la lucha, en el combate abierto contra un enemigo al que consideraba ocupante y representaba una realidad cultural, étnica y civilizacional totalmente antagónica a la naciente realidad hispánica.
De ahí la importancia del sustrato germánico, godo, que viene a agregarse al ya preexistente de hispano-romanos, celtas e íberos. En las últimas décadas esta importancia se ha visto relegada, de forma deliberada, a un segundo plano, y si nuestros padres y abuelos conocían la famosa lista de reyes godos, en la actualidad, su conocimiento entre gran parte de la población española, y especialmente entre los más jóvenes, es puramente testimonial, cuando no inexistente.
|
 |
|:-|
|El mapa muestra la distribución territorial de la península ibérica durante el período del Reino Visigodo (409-711 d.C.). Se destacan los dominios visigodos, con Toledo como capital, y las principales ciudades como Emerita, Hispalis, y Cesaraugusta. También se señala la presencia del dominio bizantino en el sureste (Cartago y Córdoba) y la región ocupada por los suevos en el noroeste (Bracara y Lucus). Las áreas de los astures, cántabros y vascones aparecen al norte como zonas independientes.|
|
|:-|
|El mapa muestra la distribución territorial de la península ibérica durante el período del Reino Visigodo (409-711 d.C.). Se destacan los dominios visigodos, con Toledo como capital, y las principales ciudades como Emerita, Hispalis, y Cesaraugusta. También se señala la presencia del dominio bizantino en el sureste (Cartago y Córdoba) y la región ocupada por los suevos en el noroeste (Bracara y Lucus). Las áreas de los astures, cántabros y vascones aparecen al norte como zonas independientes.|No obstante, no queremos hacer aquí una relación de reyes, ni hablar de las estructuras políticas, económicas o religiosas del reino visigodo, sino que pretendemos centrarnos en una sola figura, la del rey Sisebuto, cuya fama y los elogios que se dedican a su persona nos han sido legados por las fuentes de la época. San Isidoro de Sevilla, una de las grandes personalidades de la época —autor de las famosas Etimologías, un compendio del saber antiguo en lo que se consideró como la primera enciclopedia cristiana— y uno de los grandes maestros del Occidente medieval, nos aporta valiosas informaciones sobre Sisebuto:
«fue brillante en su palabra, docto en sus pensamientos y bastante instruido en conocimientos literarios [...]. Fue notable por sus conocimientos bélicos y célebre por sus victorias».
O también en Historia Gothorum:
«se mostró tan clemente después de su victoria, que pagó un precio para dejar en libertad a muchos que habían sido hechos prisioneros por su ejército y reducidos a esclavitud como botín de guerra».
De hecho existió un vínculo de amistad entre Isidoro de Sevilla y Sisebuto, y el primero dedicó al segundo una primera edición de sus Etimologías, y escribió a instancias del monarca visigodo otras obras como De natura rerum. La fama del rey visigodo traspasó fronteras y encontramos referencias a sus virtudes y cualidades personales a través de la Crónica del Pseudo Fredegario, donde se aplican otros calificativos como «varón sabio, piadosisimo y digno de toda alabanza». De modo que las fuentes ya nos permiten trazar un primer retrato general sobre la figura del protagonista de nuestro escrito, y que podríamos resumir así: monarca sabio, guerrero y sensible. Cualidades estas que pueden parecer difícilmente compatibles, pero que nuestro Sisebuto aunaba conformando una poderosa personalidad.
Rey guerrero
Pero antes que nada deberíamos preguntarnos por los orígenes del rey Sisebuto, quien ocupó el trono del reino visigodo durante 9 años, entre el 612 y el 621. Se destacó por su capacidad para defender tanto en las fronteras interiores como exteriores la autoridad de la monarquía visigoda. Prueba de ello fueron las campañas que acometió contra los astures en el Norte, terminando con las veleidades independentistas de estos pueblos belicosos, aunque hay cierto oscurantismo en cuanto a las fuentes. Y paralelamente, en el Sur, las operaciones militares de Sisebuto estuvieron dirigidas contra la provincia bizantina ubicada en el sureste peninsular desde mediados del siglo anterior. Las sucesivas campañas militares consiguieron mermar los dominios bizantinos en la península, especialmente con la conquista de Málaga en 619. Además conviene destacar el notable desarrollo del ejército naval visigodo, alcanzando elevadas cotas de esplendor nunca registradas con monarcas precedentes. No hay datos totalmente contrastados, pero es posible que, con Sisebuto, surgiera una marina organizada.
Las guerras que se libraron entre visigodos y bizantinos fueron cruentas y sanguinarias, generando gran dolor y consternación entre nuestro monarca, algo que, como indican los propios historiadores y cronistas de la época, era bastante infrecuente. En la citada Crónica de Fredegario se le atribuyen ciertas afirmaciones a tal respecto, en las que lamenta las pérdidas humanas y se expresa con un notable humanitarismo:
«Si se producen guerras —escribía Sisebuto a Cesario—, si la cruenta espada se ensaña por doquier, si los vicios de los hombres hacen que los tiempos presentes sean tiempos belicosos, ¿qué cuentas, pensadlo, habrá que rendir a Dios por tantos crímenes, por tantas calamidades, por tantas funestas heridas?»
«Se mostró tan clemente después de su victoria —dice San Isidoro en Historia de los Godos— que pagó un precio con el fin de dejar en libertad a muchos que habían sido hechos prisioneros por su ejército y reducidos a esclavitud, llegando incluso su tesoro a servir para el rescate de los cautivos.»
Lo fundamental para Sisebuto era la unificación del territorio peninsular bajo el poder godo, pero no solo empleó medios militares, sino que también hizo uso de la diplomacia. Respecto a este tema, se conservan dos cartas de la correspondencia entre Sisebuto y el gobernador provincial e imperial en España, Cesario, en torno a la disputas entre visigodos y bizantinos relacionadas con los prisioneros de guerra. Con ocasión de la captura del obispo Cecilio de Mentesa por parte de los bizantinos, Cesario se apresuró a ponerlo en libertad y escribió al rey Sisebuto para comunicárselo con las siguientes palabras:
«Nuestro beatísimo padre, Cecilio, fue capturado por nuestros hombres, mas en consideración a Dios y vuestro reino y como prueba de buena voluntad, lo liberamos rápidamente y pusimos la mayor diligencia para que fuera devuelto a su santa iglesia y enviado a vuestra presencia».
Sisebuto respondió a Cesario de manera cordial y afectuosa, lo que supuso la toma de contacto a través de una delegación diplomática entre ambas partes, godos y bizantinos, que condujo a un acuerdo. Los bizantinos no serían expulsados definitivamente del territorio peninsular hasta el reinado de Suintila (588-633).
Rey sabio
El monarca visigodo también fue un notable erudito e intelectual, muy destacado en una época de gran esplendor cultural capitaneada por San Isidoro de Sevilla, de quien ya hemos dicho que mantuvo una estrecha relación con Sisebuto. Las famosas Etimologías isidorianas estuvieron consagradas en su primera edición a la figura del rey a través de las siguientes palabras, que le honraban a través de la siguiente dedicatoria:
«Como te he prometido —escribía al rey el obispo hispalense— te envío ahora la obra acerca “Del origen” de ciertas cosas, recopilada con el recuerdo de antiguas lecturas. Por eso, en algunos pasajes aparece anotada de acuerdo con lo que habían escrito nuestros antepasados».
Se puede decir que Sisebuto fue al mismo tiempo un promotor de la actividad literaria, intelectual y científica, y un hombre sabio de su época, con la producción de obras en el ámbito de la ciencia y la literatura, al margen de los asuntos propiamente religiosos, algo que podría resultar chocante en relación a otros reyes bárbaros de aquel entonces. Fruto de esta doble vertiente tenemos el Liber de natura rerum, obra de San Isidoro, dedicada al conocimiento del universo y los fenómenos naturales. Por su parte su contribución a la producción científica de la época fue el Liber rotarum o Carmen de luna, un poema en el que trataba de explicar el fenómeno de los eclipses al margen de motivaciones religiosas, en el terreno puramente físico.
Sus incursiones no se limitaron al mundo puramente científico de los fenómenos físicos, sino que sus intereses también se orientaron hacia la vida y hechos de otros hombres de su tiempo. Tal es así, que vemos como su principal obra, Vida y pasión de San Desiderio, un obispo de Borgoña que padeció de persecuciones y murió años atrás. Esta obra guarda ciertas particularidades por sus motivaciones políticas, orientadas a congraciarse con Clotario II, rey de la Francia merovingia.
Rey religioso (y gibelino)
Sisebuto fue un monarca profundamente religioso y en consonancia con la ortodoxia, lo que hizo que en muchas ocasiones tuviera que intervenir para su fortalecimiento y mantenimiento. De hecho, su propio hijo, Teudila, ingresó en una orden monástica impelido por su progenitor, que alentó su celo religioso. Incluso envió una carta al rey longobardo Adaloaldo, convertido al catolicismo, exhortándolo a que hiciera lo propio con la totalidad del reino, y terminar así con los últimos restos de herejía arriana, que había tenido un relativo éxito entre los pueblos germánicos en su momento. Además trató de ofrecer argumentos lógicos y fundamentados en la exégesis católica, amparándose rigurosamente en las Sagradas Escrituras. Al mismo tiempo, augura prosperidad y buenos designios en un futuro hipotético ante la conversión al catolicismo, favoreciendo la acción benéfica de la providencia divina sobre su pueblo. Todavía debería pasar medio siglo para la conversión de los longobardos, mucho después de la muerte de Sisebuto, acontecida en el 621.
Sisebuto también se preocupó por fortalecer y vigorizar la propia estructura eclesiástica, algo que fue una constante en la España visigoda y se materializó a través de sucesivos Concilios en Toledo. Sisebuto, como nos relata el historiador José Orlandis, lejos de utilizar la Iglesia como un parapeto, como una suerte de protección para reforzar su posición, se mostró más bien con cierta mentalidad «cesaropapista». Actitud a través de la cual Sisebuto tomaba la iniciativa, tanto en el ámbito político y temporal como en aquel religioso-espiritual y atemporal. En cierto sentido podríamos calificar a Sisebuto como un «rey gibelino» por esa simbiosis entre ambas esferas, asumiendo él mismo, personalmente, la función de velar por el buen orden eclesiástico. Un buen ejemplo de ello lo tenemos en las imposiciones a Eusebio, el obispo de Tarragona, influyendo directamente sobre decisiones internas de la institución.
|
 |
|:-:|
|MORDINI, Attilio; El católico gibelino; Hipérbola Janus, 2016|
|
|:-:|
|MORDINI, Attilio; El católico gibelino; Hipérbola Janus, 2016|El problema religioso: los judíos
Ya en el primer código legal de visigótico, la Lex Romana Visigothorum promulgado en el año 506, en el que se establecía la condición jurídica de los hispanorromanos, se excluía a los judíos de los cargos públicos, proscribía los matrimonios mixtos entre cristianos y judíos y limitaba sus actividades religiosas. Al margen de las comunidades religiosas cristianas, los judíos seguían sus propias leyes y preceptos religiosos, mantieniendo una barrera respecto a los pobladores autóctonos. Con la conversión de la fe arriana a la católica de Recaredo I, y en consecuencia del propio reino, los monarcas visigodos comenzaron una serie de políticas encaminadas a conseguir la unidad religiosa y política del reino. Su decisión, que fue oficializada en el III Concilio de Toledo, contó con un apoyo mayoritario del clero y la nobleza visigoda. A partir de ese momento comenzó un proceso de integración entre godos e hispanorromanos en virtud del principio religioso.
|
 |
|:-|
|Una moneda de oro visigoda acuñada durante el reinado de Sisebuto (612-621 d.C.). En el anverso, aparece el retrato estilizado del rey, rodeado por una inscripción en caracteres latinos. Estas monedas reflejan la influencia romano-bizantina en el arte y economía del Reino Visigodo. (Foto: Wikimedia Commons)|
|
|:-|
|Una moneda de oro visigoda acuñada durante el reinado de Sisebuto (612-621 d.C.). En el anverso, aparece el retrato estilizado del rey, rodeado por una inscripción en caracteres latinos. Estas monedas reflejan la influencia romano-bizantina en el arte y economía del Reino Visigodo. (Foto: Wikimedia Commons)|Esta situación dejó a otros grupos religiosos ante un dilema, que era o la conversión o la expulsión. Sisebuto fue quien más celo puso a tal respecto para lograr la deseada unidad religiosa. A partir de una serie de decretos promulgados al cabo de pocos meses del inicio de su reinado, en el 612, se ordenó la liberación de todos los cristianos en su relación de dependencia respecto a los judíos. Estas medidas incluían la liberación de los esclavos y servidores cristianos en relación a los judíos, la transferencia de éstos a señores cristianos o la obligación de manumitir y quedando así libres. Estas disposiciones eran de obligado cumplimiento bajo la pena de muerte o confiscación de bienes.
Al mismo tiempo, Sisebuto también se propuso impedir el proselitismo religioso judío y estimular su conversión al cristianismo. De hecho, los matrimonios mixtos preexistentes debían adoptar una educación en la fe cristiana para los hijos, en caso de no aceptarlo, el matrimonio se consideraba nulo. Los conversos y judíos también quedaban excluidos de los cargos públicos. También se debía producir una renuncia y abjuración pública de la ley y prácticas judaicas. La mencionada ley tuvo unas consecuencias inmediatas sobre la comunidad judía en el ámbito económico, donde además la existencia de esclavos y colonos en arriendo eran numerosos, además de las prácticas usurarias.
Sisebuto ha quedado para la historia como el gran perseguidor de los judíos, aunque en realidad su propósito era misionero y evangélico, por el celo religioso que ya hemos expuesto, y tampoco fue obra del propio Sisebuto, sino que encontramos los primeros ecos de esta legislación en la última etapa del Imperio Romano. Si hasta el momento la legislación se había aplicado de manera un tanto superficial, con Sisebuto adquiere mayor «radicalidad», aunque tampoco afectasen exclusivamente a la población judía, la cual era numerosa en aquella época. Los propios godos no pudieron casarse con los romanos hasta las reformas legales aplicadas bajo el reinado de Leovigildo.
Respecto a la cuestión de la prohibición de que los judíos poseyeran esclavos cristianos, algo que era muy frecuente, también infringían la ley al circuncidarse, dado que formaba parte del ritual formal de judaización o conversión a la fe judía. El decreto de Sisebuto ofrecía a estos esclavos la opción de obtener la libertad bajo el amparo de la corona, si no eran vendidos a otros amos cristianos. El impacto económico al que aludíamos también afectó notablemente las actividades agropecuarias de la comunidad judía, que perdieron su estatus privilegiado entre los sectores más acomodados de la sociedad. Del mismo modo que la prohibición de desempeñar cargos públicos mermó su preponderancia social.
No obstante, Sisebuto consideraba el asunto en una dimensión puramente religiosa, y el fin último era la integración bajo la unidad del credo católico. La unificación religiosa se convirtió en una prioridad, y su celo religioso no se fundaba en un criterio de fanatismo irracional, sino todo lo contrario. Al monarca godo le importaban, y mucho, las conversiones sinceras, sujetas a un principio reflexivo y racional. De hecho, en ese tiempo había otros segmentos de la población que se movían en el terreno de las creencias paganas, como los propios arrianos, a los que también interesaba encuadrar bajo el mismo principio religioso. En cuanto a los judíos, y la incidencia que se hizo sobre este grupo, se debió a que eran comunidades que representaban un enorme poder en el conjunto del reino, con una notable influencia, especialmente en el sur y el Levante español, regiones que se encontraban en la frontera con los territorios bizantinos peninsulares.
No obstante, y a pesar de que existe una continuidad en la aplicación de estas políticas para contener la influencia de la religión judía en los límites del reino, y vemos como éstas se mantienen hasta el hundimiento final con la conquista árabe del 711, lo cierto es que la práctica de la religión judía se mantuvo a ciertos niveles, como prueba la existencia de tumbas e inscripciones judías registradas a lo largo de esta época. Paradójicamente, en el plano económico y social fueron mucho más efectivas que en el terreno religioso, y de hecho, de haberse aplicado con la radicalidad que se les presume, estas leyes hubieran acabado con la existencia de la población judía en el reino, o bien mediante la conversión o bien mediante la expulsión, pero nada de eso sucedió finalmente.
El reinado de Sisebuto terminó en el 621, tras nueve años de intenso reinado. Se sospecha que murió envenenado por la ingesta excesiva de un medicamento, según el testimonio de otro rey, Suintila. No obstante hay muchos puntos oscuros bajo esta explicación, y la falta de fuentes fiables no nos permite desentrañar los hechos que rodearon su muerte. Le sucedería su hijo Recaredo II, quien también moriría en extrañas circunstancias, nunca desentrañadas, a los pocos meses de su coronación.
Lo fundamental, si tenemos que hacer una idea general de la figura del rey godo, es que representó una etapa peculiar en el desarrollo histórico del Reino toledano, en la medida que mostró una personalidad ilustrada, con notables conocimientos respecto al saber de la época, cultivó la poesía y la literatura, y no por ello descuidó los asuntos de gobierno. Los fundamentos religiosos, tan importantes en lo sucesivo, y a través de los Concilios de Toledo, en la configuración político-religiosa y en la unidad embrionaria de la futura España, fueron una de sus grandes prioridades, y para alcanzar la consolidación del reino no dudo en hacer la guerra, de manera implacable, para ser magnánimo y generoso cuando la situación lo requería. Desde Hipérbola Janus, y quien os escribe, no nos queda sino valorar la figura de este olvidado, y en ocasiones injustamente denostado, rey visigodo.
Artículo original: Hipérbola Janus, Sisebuto, el rey sabio, guerrero y humanitario (TOR), 30/Dic/2024
-
 @ a1c19849:daacbb52
2024-12-30 11:17:00
@ a1c19849:daacbb52
2024-12-30 11:17:00Introduction
nostr:npub1nj5v9hfxegyuqz4z9vfpgu9lxpgald066wspxadywmhslasuw2gsnyrxzg shared a great thread on X about what the Dutch Noderunners did to push Bitcoin adoption. Since it took him quite some time and he didn’t want to redo it on #nostr I’m happy to share his thread here as well, since it has a lot of cool stuff in it. Here we go:
Noderunners 2024 Recap
by nostr:npub1nj5v9hfxegyuqz4z9vfpgu9lxpgald066wspxadywmhslasuw2gsnyrxzg

Here it is, the 2024 Noderunners recap! As we are preparing for our annual party on the third day of Christmas I’d like to reflect to all the great stuff we’ve build together to push bitcoin adoption from bottom up. I’m proud we’ve made it this far and we’re just starting! 🔥 We like to come together as often as possible to chat about bitcoin and drink a beer so we started even more meetups. We now do meetups in Roermond, Leiden, Eindhoven, Utrecht, Breda, Friesland, Zaandam. And an occasional party in Arnhem or Den Bosch. Feel free to join us anytime.




On our meetups and in the wild we meet the most awesome bitcoiners. To show them our respect we honor them by knighting them as an Honorary Noderunner. This year nostr:npub1nw5vdz8sj89y3h3tp7dunx8rhsm2qzfpf8ujq9m8mfvjsjth0uwqs9n2gn nostr:npub13ql75nq8rldygpkjke47y893akh5tglqtqzs6cspancaxktthsusvfqcg7 nostr:npub1cn4t4cd78nm900qc2hhqte5aa8c9njm6qkfzw95tszufwcwtcnsq7g3vle and nostr:npub1uaj9phu5lpxpczm3vaayt46m0yv0pduxzy7z6quwd2uggxue7fmqx9665u joined our ranks! 🧡



As you can imagine, we were pleasantly surprised when we saw an honorary Noderunner wearing his pin in the courtroom in the case against fAkEtOsHi! Nice to meet again in Amsterdam nostr:npub1qg8j6gdwpxlntlxlkew7eu283wzx7hmj32esch42hntdpqdgrslqv024kw !



The Bitcoin conference in Amsterdam was full of Noderunners. On and off stage. On stage we had nostr:npub1jqs0u7zhh53e94gyhm4eu458wm6sw7z0kk66jjhhkhh346tcq2ysfgr247 nostr:npub1h0fd5xu8rfhwdkkjr78ssdhm7rdjyf97hhjqr9acwv77ux0uvf8q23kvcg nostr:npub17tyke9lkgxd98ruyeul6wt3pj3s9uxzgp9hxu5tsenjmweue6sqq4y3mgl Tom Lamoen and others.




In the panel there was nostr:npub1art8cs66ffvnqns5zs5qa9fwlctmusj5lj38j94lv0ulw0j54wjqhpm0w5 who asked a cheeky question… 🤓 He wrote the awesome “The Genesis Book” in which he describes the people and technology that led to the birth of bitcoin. Hope to see you 3kd Aaron!
Proof of work is the thing Noderunners value the most. We do the work on and offline. In Amsterdam we had several projects to display! Of course the BitcoinTaps, the bitcoin bitaxe B at the entrance, The nostr:npub1kd3nlw09ufkgmts2kaf0x8m4mq57exn6l8rz50v5ngyr2h3j5cfswdsdth arcade and the video of @npub1f59dz0ru0l8zpsl4cryj5ch2rahwxeex3mr7lpl2ltzxsfwsdwastu6nqk!

Personally I was very exited nostr:npub1qg5a5l3t7pakmm4r4up2e764xecsw62fk3rntevm24fwyczhndtsdrvc4x Edward and Stef of Connect The World Podcast allowed us to bring the Arcade to the afterparty at Braai where we played some tournaments with nostr:npub1jt97tpsul3fp8hvf7zn0vzzysmu9umcrel4hpgflg4vnsytyxwuqt8la9y nostr:npub1j8y6tcdfw3q3f3h794s6un0gyc5742s0k5h5s2yqj0r70cpklqeqjavrvg and many others!



Hopefully we can create a Noderunners lounge or such next year at @npub13e6qu4kdjsyysrfl5an558rawvqg0rx2xuat9ca706spcdqjzhuqq6md43! Connections were made!



This year there was also the first edition of nostr:npub1uv2tr83c5y7k82af6zdzlqs8m0klcmndd8u5vmlg2eyrskld6uzsv4rmr8 organized by nostr:npub14mge80nm5r0zj0gncxvpunlr28jyku95547q0m82ec475x3yy92skvjgm5 and Bitcoin Stad. It was an awesome event with great speakers but the best thing was the Noderunners Lounge in the basement where Hester Bais tapped a beer.. 🍺



There was some trouble in paradise when the GitHub page of nostr:npub1k5f85zx0xdskyayqpfpc0zq6n7vwqjuuxugkayk72fgynp34cs3qfcvqg2 got canceled due to false copyright claims.. He makes the most beautiful, full open source BTClock! He’s a good frend and very productive Noderunner! 🧡



nostr:npub1k5f85zx0xdskyayqpfpc0zq6n7vwqjuuxugkayk72fgynp34cs3qfcvqg2 also did a lot behind the scenes for the Noderunners SOLO Mining Pool! http://pool.noderunners.network


As we are also very enthusiastic about NOSTR nostr:npub1p6xyr6u5vet33r4x724vxmp9uwfllax5zjdgxeujyrtxt90lp74qvah0rm has set up our own nostr relay: wss://relay.noderunners.network

Noderunner nostr:npub1yn84ur49llj7pp9a7uv477f7vrpj0rj7df5pnfncvkusaxgy6jqsj9xgfl set up a mixer where he organizes a weekly coinjoin every sunday for more anonymous bitcoin transactions. https://coinjoin.nl

Our Belgian Noderunner Kim de Vos made the infamous “Big Mac index” where he expresses the price of bitcoin in Big Macs.. He also runs the AVBpodcast (my personal favorite).

We have several members who have their own podcasts. Also a lot of Noderunners appeared in podcasts as a guest. nostr:npub1agyf7kae8nkxqrd7rvvxt6nh9vwpcqzen2mc9dl3u38a04awpjcq09n23f educates bitcoin beginners.
 Tom Lamoen talks about libertarianism.
Tom Lamoen talks about libertarianism.nostr:npub1gfxgylgst4lcemkjth6xdvcvq7le8rtlrym7wayml63qrjggngaqkqescl interviews bitcoiners from all over the world.

And nostr:npub1kj2ngxmm0zccswfqplff87rpgvmq9utvk0g726wc0h8pv4kwm8ss6zgm4n laughs at 🤡🌍

After months, even years of hard work nostr:npub1w98ems6ryhpv7zvmhwp5sv65p0pwrnvzw4lucn0ch776qan9ntdstscwpx launched the best bitcoin board game ever!


nostr:npub1w98ems6ryhpv7zvmhwp5sv65p0pwrnvzw4lucn0ch776qan9ntdstscwpx is also involved with the Dutch bitcoin magazine BitcoinFocus which features a lot of Noderunner builds and articles.


Of course I should mention our frens at nostr:npub1ua6fxn9ktc4jncanf79jzvklgjftcdrt5etverwzzg0lgpmg3hsq2gh6v6 where you can pay a few sats to play your favorite songs! http://radio.noderunners.org

LightningPlaces is working hard making entrepreneurs accepting bitcoin and putting them on their website! 🔥💪🏼



nostr:npub1lhufm09wzp42y67t3s8axlewwna8rmetak68w38yal7xjrwktpsscpt08x is also hooking up webshops and physical shops (and bars) to accept bitcoin! Connect them if you’re looking for a custom solution! https://lightningcheckout.eu/nl/


Maybe we should create an open source HW Wallet too but for now we have the man, the myth, the legend nostr:npub17tyke9lkgxd98ruyeul6wt3pj3s9uxzgp9hxu5tsenjmweue6sqq4y3mgl in our midst.. A real honor as we all share the same values and ethics in life but especially in bitcoin! We’ve been building seedsigners from scratch by the dozen!


Most of us are very entrepreneurial. Several bitcoin shops are run by Noderunners.
nostr:npub1qvwdl9rp7a5ghrxv57wnml5ehg2whjh708vys6kaxpkgu0z3aclsuy2h4p - https://bitcoinbrabant.com
nostr:npub1k00lff0ahjv4d2kwuwxy040d2282yjmzj6eeu5ghav054s4yrfzsplyc86 - https://bitsaga.be
nostr:npub1837pplcuwcjn35zwmpuy62ekcfdtvklajn6pueus3am09s27vu6smuj6v9 - https://miningwholesale.eu
A special shoutout to our junior Noderunner Esramsterdam who is organizing a bitcoin event focused on women. Because bitcoin is not only for men. More info: https://vanbanknaarbitcoin.nl

Also a special shoutout to @npub17k8u7c6kfjgtd380890zx0m4adu8vl53m9fvtc7lal4j9gp74xqqkguha4! The only way to get free sats. Drank not enough beer with nostr:npub1pzurm7nx3q08894wl6uautryq95sku5jhzgwjjrskwdafcwxekuq4n7vtu this year.. but we really need to set up a collaborative project!

Ok I’m done. Forgot a lot but this sums it up quite well. Greetings and love to everyone involved with the Noderunners I forgot to mention. I love you all and hope to build a lot more together! 🧡🔥
nostr:npub103uy2vsk5hrnldwdu0nztmsg7g6207cfqu744rnrnalauns6facsgj5ddp
nostr:npub1l9evr9vx4u2xefesmfu6gyypfdu7k8zwdw7rrnh5ckdds8fqx59sy3ferg
nostr:npub1cwzduskqu6yuxjs2a75uptj3vzfa84gv5q3xlkcpzs6usjfey24qvk70dv
nostr:npub1etuf22z5jwp765m8dqcw7rx5egjzjnwm9xwm4m367e9hxkd9vvaq04duqw
nostr:npub1mw6tm8kery0dwmz670vvg74z0xzttwt3y7yppya5rulufpkkaj7qmg2922
nostr:npub12qw34mucxxk200835d8qt5mshfukd39vvz4s94f0e6xthg0xpjmq3wvjlw
nostr:npub1d5axlx84ajq7q5yn4u86m9xgnmssgq5c6ktjfmu6qtw7jah24hzs57tmvz
nostr:npub1vnlkmja076ft0h2ppme4pvcyfh8zmwl4l7hpfm4du0jagwck04lq8rkr0w
Jan Burgers
nostr:npub1r35gr0g93gxpkcq77v9sx97d5aqg4edr0qwhdj2xr4xxt6slp7nswgahlx
Short Non-Bitcoin
nostr:npub12786tz9vyzuhe5jdjc9esd64vqh3pvqe34u9a3dyegudv5chkx9sexz86w
Joep Laser Sheep - Elden Lord 3x
nostr:npub12xtq7ufn6kjppvl24dnvezsny872u8xacfsy640fzd69446kgczsp8v5nm
nostr:npub1m0yz3tvsa8cwheqhkqj96zr9kget8j8yda0vfmrah5c0dafj6xcq4l4az6
@Erik Dutch
nostr:npub1kvfz8rglvpsqevznlt86ukcz0s9uap3pypjwd3tnmkn2pgjmjujqlncy2c
nostr:npub1l5pxvjzhw77h86tu0sml2gxg8jpwxch7fsj6d05n7vuqpq75v34syk4q0n
Noderunners Shop
nostr:npub1ylnqfg0neysvsesen9je80wmsv9r5204x30mgd5ev6dr3q95xpxq3nmcxd
nostr:npub1ap78x7mvw0vu9s7yltflmkqphx8rt8hsk9gdg0k42vwnmnpvpe2qptxewe
nostr:npub1n2ph08n4pqz4d3jk6n2p35p2f4ldhc5g5tu7dhftfpueajf4rpxqfjhzmc
@Bitcmonkey
@Roynode
nostr:npub18n56f28efvmsjcl80lv2ngtmkl3y6q2rg0m2zqas3kw4jwkrsvdqxnmver
nostr:npub135q6dvnjah9023xszmjs2wvd4gqhn2trku52wt2lv8cl4hc8ltjsk0w4sq
nostr:npub1837u93v8am8q2rauvkqfk9sf6xfq07p9m4m82jueqh5u4qzkg25qesqrr4
nostr:npub1pkmp7vtgfwg7g0pt4xdd4r2npz2p8yweeq0yx7xm590h4nuszynqq2e2r3
nostr:npub19r33crtgdt4spqxl5a3nhqx2ucdputtqcnnxkplnp4mv2dqldqqs39j5eq
nostr:npub19z9g9ymx3aalx3h0jr2cskehvhgppznv2lpqsrpgggpeueesq4lsknsp8r
nostr:npub1jlvtd4zmq7ukjcytqxu2gy5myp2uataupjk4a3l467fj7pxpk3xq5p3w0j
@HeroVanKampen
nostr:npub16htmakd0gvsmwjnravfvfn5mh2x7wjd0vxq20z2c0979e7xh0a8q6ssnew
nostr:npub1xw6jekvethghmrlv0chkx5p78h3wk2ep5x588ga854d68cugr40qxuwt5e
nostr:npub1zakkum8w7uancehpev0drxuly3e74fg5v7q4n0zpxcdn72wakpjs9cgpve
and all others I can’t find here or I forgot.. 🧡🔥💪🏼 LFG, see you soon!
Bonus: This has never aired but @DanielMol was doubtful of our impact to more bitcoin adoption.. I know we are a bit toxic but we have our hearts on the right place and help anyone who is serious about it.. Happy days Daniel! 🧡

-
 @ b8a9df82:6ab5cbbd
2024-12-30 11:15:49
@ b8a9df82:6ab5cbbd
2024-12-30 11:15:49In just two days, 2024 will come to a close. And as I sit here reflecting and drinking my morning coffee, I can confidently say that this has been the best year I’ve had since 2018. The years leading up to this one, especially since returning to Berlin, were some of the most challenging of my life. They tested me in ways I never expected—moments when I wanted to give up, when I felt so lost I couldn’t see or feel anything anymore. I lost my smile, my positive side, my emotions, and even my sense of self. But this year was different. It felt like the sun finally broke through the clouds, and I could see light at the end of the tunnel. I laughed more. I loved more. I felt deeply again, like my emotions finally had room to breathe. For those who have read my book, you know I’ve faced my share of dark days, as many of us do. Some days were heavier than I could have imagined, and even now, there are moments when I question, *“Why? Why this path? Why me?”* But this reflection isn’t about the darkness. **It’s about the gratitude.** 2024 blessed me with so many moments of joy. I traveled, saw the world from new perspectives, and met extraordinary people who brought meaning and light into my life. These experiences reminded me that connection matters, that there’s beauty in the unfamiliar, and that we grow when we open ourselves up to it all—the good, the difficult, the unexpected. Now, back in Berlin, I feel a shift. The city feels cold again—not just in temperature, but in energy. Dark skies and gray streets mirror an unbalanced restlessness I can’t ignore. It’s not the coldness itself or the clouds; it’s the way this place feels as though it’s lost its spark. Smiles seem rare, warmth even rarer. And perhaps, that’s my sign. My time here feels like it’s coming to a close. But as this chapter winds down, I feel at peace. 2024 reminded me that life doesn’t stay stagnant. Even in the darkest times, the wheel turns. This year was proof that healing is possible, that joy can return, and that love—whether found in people, places, or moments—still exists. So, wherever this journey takes me next, I will carry this year with me. I’ll carry the laughter, the lessons, and the memories of those who reminded me that even in a messy, chaotic world, light and connection can thrive. And perhaps, just perhaps, this is only the beginning. The chapters ahead are unwritten, but I feel ready to meet them—with an open heart and gratitude for all that’s brought me here. Happy 2025 to all of YOU
-
 @ ebdee929:513adbad
2024-12-28 14:46:21
@ ebdee929:513adbad
2024-12-28 14:46:21Blue light is not inherently bad, just bad in the wrong context.
Blue light provides wakefulness, stimulation, and sets our internal body clock (circadian rhythm).
When we go outside in the sun, we get bathed in blue lightblue light is not inherently bad, just bad in the wrong context.
Blue light sets the human rhythm.
However, sunlight never gives us blue light without the rest of the visible rainbow + infrared.
Light from screens & LED bulbs do not contain any infrared, and has a unnaturally high proportion of blue light.
LEDs = unbalanced & blue light dominant

Light from artificial sources is especially disruptive at night time, where the high blue light component can interfere with melatonin production and sleep quality at a greater rate than lower energy colors of light. Blue Light has a Dark Side
This doesn't mean that red light is completely innocent of disrupting sleep either
It is both the spectrum of light AND the intensity of light that contributes to sleep disruption. See this tweet from Huberman.

We took all of this into account when building the DC-1 to be the world's first blue light free computer.
The DC-1 has a reflective screen that:
• emits ZERO light during the day
• can be used easily outside in direct sunlight

& a backlight that:
• can be 100% blue light free
• has a broad spectrum of light
• can be seen at very low brightness

Our Live Paper™ display technology feels like a magic piece of paper
During the day, that piece of paper is illuminated by sunlight. At night, that piece of paper is illuminated by candle light.
(backlight is converging with a candle light spectrum)

The two sources of natural light are sunlight & fire.
We are trying to reproduce this experience for the most enjoyable, healthy, and least invasive technology experience for humanity.
Root cause problem solving by emulating nature.
"But can't I just put a red light screen filter on my MacBook?"
Absolutely you can, and we advocate for it
Software screen filters are great, but anyone who has changed their screen to full “red mode” to get rid of the blue light knows the downsides to this…

You can barely see anything and you end up having to crank up the brightness in order to see any contrast.
This is because of the highly isolated nature of LED emissive screens, you can only isolate a very narrow band of colors.
Going full red is not something your eyes have ever been used to seeing.
You need a broad spectrum light solution, and that is what we have in our amber backlight while still being blue light free.
This means you can have a better visual experience, turn down the brightness, and get minimal sleep/circadian disruption.
What about FLICKER?
Nearly all LEDs flicker. Especially when changing in brightness due to Pulsed Width Modulation (PWM) LED driver control
Our LED backlight uses DC dimming & is expert verified flicker-free.
This can only be achieved through hardware changes, not software screen filters.

& Blue Light Blocking Glasses?
They need to be tinted orange/red to block all of the blue light.
Thus the same issues as screen filters (bad visual experience, not solving flicker) + average joe would never wear them.
We still love blue blockers, they just aren't a root cause solution.
We made a computer that is healthier and less stimulating, with a low barrier to entry
Whether you are a staunch circadian health advocate or just like the warm vibes of amber mode and being outside...the DC-1 just feels good because it doesn't make you feel bad :)
Learn more here and thanks for reading.
-
 @ 6e4f2866:a76f7a29
2024-12-27 16:03:31
@ 6e4f2866:a76f7a29
2024-12-27 16:03:31Have you ever felt like you’re running as fast as you can in life, only to find yourself in the same spot? Trying to achieve goals, optimise yourself only to feel unfulfilled & lacking. That’s the hamster wheel—an exhausting, repetitive cycle that holds us captive in patterns we didn’t consciously choose. These aren’t just bad habits; they’re deep-rooted default programs born from early life experiences. Let’s explore what these hamster wheels are, how they shape us, and most importantly, how we can step off them for good.
What Are Hamster Wheels? \ \ The term #hamsterwheels ( hamstr) is a metaphor for the unconscious patterns that keep us stuck. I discovered these wheels through my own introspection & seeing these patterns in my clients. Imagine a wheel turning endlessly, powered by our own efforts but leading nowhere. These programs are often formed in childhood, when trauma, disconnection, or unmet needs force us to develop defense mechanisms to survive. They worked back then, but now they just keep us spinning.
\ The Mechanics of a Hamster Wheel \ \ Every hamster wheel has two opposing forces—gain and loss, right and wrong, attention and neglect, let down & support & unable & able. We strive to stay on the “good” side: gaining approval, being right, or receiving attention. But inevitably, the wheel flips, and we find ourselves losing, being wrong, or feeling ignored. It’s a cruel cycle of frustration that feels impossible to escape. You will be positioned on the left side or right side when you look at the wheel. One is yin dominant, non doing, unable, more of a victim. One is Yang, always doing, high achiever, seen as a winner. \ \ Left side is safe in the unableness so will self sacrifice when they are to feel able to& start to achieve. So as they climb up the wheel to the right, they will lose interest or confidence in what they are doing, either sliding back exhausted in their endeavour or flipping over into victimhood. They long to be confident & win at life but deep down feel they cannot. \ \ Right sided dwellers have to be right, are constantly striving & hate (kryptonite) feeling unable. When they feel unable they will become enraged. They are compelled to gain valuableness in their own eyes and those of others. They are usually very difficult to work with as working with a therapist makes them feel unable. They will eventually put so much energy running up the right side that they will be flung backwards into usableness often times falling into deep depression (unableness) or even attracting illness. They always attract unableness & the left sided experiences to balance themselves out. The wheel always balances itself out. This is the way of the hamster wheel.

\ \ Here’s the kicker: these wheels are powered by our deepest fears and insecurities. They keep us stuck not because we’re lazy or unmotivated, but because they’ve become our default way of operating, they are our automated defence systems.
\ Common Hamster Wheels \ \ There are five key hamster wheels that we all grapple with:
- Gain/Loss: The endless chase for more—more success, more love, more recognition—followed by the crushing fear of losing it all.
- Right/Wrong: The compulsion to always be right, which leads to the paralyzing fear of being wrong.
- Attention/Neglect: Oscillating between craving attention and fearing rejection or neglect.
- Able/Unable: Striving to prove we’re capable, only to feel crushed by moments of doubt or failure.
- Support/Let Down: Giving endlessly to others for validation, but feeling betrayed or let down when it’s not reciprocated. If you watch your thoughts closely you will see these programs or songs at the root of all your thoughts.
How Hamster Wheels Impact Your Life \ \ These patterns influence every aspect of our lives: our relationships, careers, and even our self-worth. They dictate how we act, how we think, and even how we feel. For example:
- The drive to gain approval often results in feeling unworthy.
- A relentless pursuit of success can spiral into burnout and self-criticism.
- Efforts to avoid neglect might lead to overcompensating and losing yourself in the process. And the hardest part? These wheels feel like home. They’re familiar, and stepping off them can feel terrifying. They quite literally create your reality.
\ Breaking the Cycle The good news? You can break free. It’s not easy, but it’s possible. Here’s how:
- Observe Without Judgment: Start by noticing your patterns. This is real #meditation What thoughts or actions are you repeating? Don’t judge yourself—just observe. Awareness is the first step to freedom.
- Understand the Roots: These wheels didn’t come from nowhere. They’re the result of unmet needs or childhood traumas. By understanding their origins, you can begin to dismantle their power.
- Reject External Solutions: No guru, book, or quick fix can save you. True freedom comes from within. The moment you stop looking for external validation, the wheel starts to lose its grip. You must take full responsibility for everything in your life. Only you can do this proof of work.
\ Final Thoughts Hamster wheels aren’t your fault, but they are your responsibility. They’ve been running your life long enough. Isn’t it time to take back control? Imagine stepping off the wheel, feeling the ground beneath your feet for the first time. That’s where real freedom begins. So, what hamster wheel are you on? Are you ready to step off and embrace a life of clarity, peace, and purpose? The journey starts here, with a single step: observation. Everything else flows from there.
-
 @ 79a7270b:d61d9067
2024-12-26 02:04:37
@ 79a7270b:d61d9067
2024-12-26 02:04:37This current year, 2024, has been the year of Bitcoin. Since the approval of Bitcoin ETFs, which established themselves as the fastest growing ETF of all time in terms of adoption, the digital currency has been pivotal talk in the media, Wall Street, and even in the US presidential election about a Bitcoin Strategic Reserve endorsed by president Donald Trump and the at the time independent candidate RFK Jr.
What is Bitcoin mining?
Bitcoin presents itself as a P2P payment systems solution, a truly decentralized open project of a monetary way of exchange with a fixed supply.
Like gold mining, for example, Bitcoins are mined through a PoW consensus mechanism that requires substantial computing power to settle a transaction (a block). Millions of machines worldwide use absurd amounts of energy to process enough power to solve cryptographic puzzles. Miners this way, receive in exchange for verifying a transaction, block subsides, miners fees, and the freshly mined bitcoin itself
The exact number of energy usage regarding mining operations is not clear, but it is clear that it consumes more electricity than most countries.
While its energy usage is undeniable, the high consumption is not a flaw but a deliberate design choice that ensures decentralization and security. Surprisingly, Bitcoin mining can be seen as an opportunity to support renewable energy growth, stabilize power grids, and reduce wasted energy
Empowering Developing Economies: Bitcoin Mining and the Stranded Energy Revolution
Bitcoin mining is evolving into a catalyst for renewable energy adoption and electrification in developing countries. In Africa, for example, around 600 million people, or approximately 43% of the total population, lack fundamental access to electricity, and these places are abundant in natural resources. However, there is no capital incentive to power these people and the existing mini-grids are dependent on philanthropy and concessional finance.
Bitcoin mining can provide electricity to people by making small-scale energy projects more financially viable. When companies like Gridless set up Bitcoin mining operations in places like Keyna and Malawi, they use excess or stranded energy that otherwise goes to waste because it isn't cost-effective to sell or distribute it to the national grid. The revenue from mining helps subsidize the installation of energy infrastructure.
Contrary to a lot of pre-existing beliefs, once this infrastructure is built, the local population benefits from the newly available electricity, often at a lower cost. This price reduction occurs because miners consistently demand otherwise wasted energy. By purchasing this surplus, they provide a steady revenue stream to the energy producers. This increased overall energy utilization allows providers to distribute their fixed costs over a larger volume of sold electricity, enabling them to lower prices for all consumers.
Miners, because are competing in a truly open market ( due to their decentralization), are constantly competing for the cheapest forms of energy to process blocks. This means that they thrive in areas like these by taking advantage of renewables, as much as any in another place when the generated energy is not being fully utilized.
Another type of stranded energy is the flared gas that comes with many types of petroleum deposits. If the quantity is low enough to not be economically justifiable to invest in pipelines to transfer this energy, it gets wasted into the atmosphere, mainly as methane and C02, contributing to global greenhouse gases. That’s about 150 TWh of energy for the year, which is about the estimated total level of Bitcoin’s annualized energy usage in 2024.
Bitcoin miners can buy this energy, since it's cheap, reduces methane emissions, and generates economic activity from externalities that would be wasted. While using flared or vented gas reduces methane emissions and provides economic utility, it still results in CO2 emissions from combustion. Therefore, it's not a zero-emission solution but is an improvement over uncontrolled venting or flaring.
Demand response programs
Historically, energy supply adjusted to demand but with the growing adoption of electricity and rising concerns about the environmental impact and scarcity of fossil fuels, society is transitioning to renewable energy sources. This shift has created a mixed grid comprising both fossil fuels and renewable energy. However, the inherent instability of renewable energy results in fluctuating prices—from high costs during periods of scarcity to negative prices during times of abundance.
Maintaining grid stability necessitates a balance between demand and generation, with frequency serving as an indicator of this equilibrium. As renewable energy usage increases, the challenge lies in ensuring grid resilience and balance while accommodating the variability of renewable energy generation.
Demand response programs are commonly employed to address this issue by incentivizing certain grid participants to reduce electricity usage during periods of high demand, thereby maintaining a balanced and stable grid.
The problem is that few industries possess a large enough demand for electricity or the ability to adapt their usage quickly. Bitcoin miners emerge as uniquely suited to this purpose because of their flexible and interruptible load providing 24-hour automated and instant responses to the grid needs. ( curtailing energy during peak demand or absorbing it excess supply). This is already happening and being used in Texas ( USA) Sichuan Province (China) and Quebec (Canada,) for example, and is showing a glimpse of what the future of grid management can be.
Follows a visual comparison of the most commonly used DR programs.Historically, energy supply adjusted to demand.

Conclusion
While the theoretical benefits of Bitcoin mining as a driver of renewable energy adoption and grid stability are compelling, its practical application still faces significant challenges. The scalability and reliability of these methods remain largely untested, given the industry's rapid and unpredictable evolution. Additionally, barriers such as a lack of public awareness, high initial capital requirements, and Bitcoin's inherent price volatility deter traditional institutions from embracing these opportunities.
However, as the sector matures, Bitcoin mining has the potential to redefine energy markets. By incentivizing renewable energy investments, optimizing electricity usage, and repurposing stranded energy, it could drive innovation and enhance efficiency in the global energy sector. Furthermore, its capacity to provide economic opportunities in underserved regions highlights its transformative potential beyond the financial realm.
-
 @ 3c7dc2c5:805642a8
2024-12-24 20:53:13
@ 3c7dc2c5:805642a8
2024-12-24 20:53:13🧠Quote(s) of the week:
'Bitcoin is hyper volatile because its a $450T+ asset trading for less than $2T.' - Joe Burnett
'I love the energy in Bitcoin right now. Long-time HODLers are optimistic, focused, and ambitious. People new to Bitcoin are curious to get involved and grateful for any support. Communities are thriving! What a time to be alive.' - Tuur Demeester
🧡Bitcoin news🧡
On the 16th of December:
➡️'In 13 days, EU Bitcoin exchanges are forced to store your personal Bitcoin address and your home address. In sum: they become lethal honey pots, making HODLers vulnerable to hacks, home invasions, and future aggressive taxation. In time, countries could exit the EU over this.' -Tuur Demeester
The best response to this overreach is to sell all your KYC'ed Bitcoin, and repurchase what you need through peer-to-peer platforms that are KYC-free, such as Bisq, Robosats, Peach, and Hodlhodl. For more information, please visit: https://kycnot.me
I can personally attest to the seriousness of this issue, having had my name, home address, and phone number leaked in the Ledger hack.
➡️In other news, Bitcoin wallet developer Exodus is going public on the New York Stock Exchange this Wednesday, backed by a reserve of 1,900 Bitcoin. They also pay all salaries in Bitcoin.
On the 17th of December:
➡️'Overton Window shifting rapidly Only in 2023, EU media was still gaslighting Bitcoin. Now - No negative environmental coverage in mainstream EU media publications for over a year - many media outlets (Including The Independent, Bloomberg, Reuters, The Street, The Hill, and Forbes) have started documenting Bitcoin mining's numerous environmental benefits (well documented in 13 peer-reviewed studies) - Germany's largest Telco is using Bitcoin mining to monetize its stranded energy - Finland's pioneering work obviating fossil-fuel heating by capturing the heat from Bitcoin mining rigs is being covered - 6 sustainability periodicals covering Bitcoin's environmental benefits - 3 media outlets including Forbes in the last 2 days have recognized that Bitcoin mining is an integral part of solving not just EU's Net Zero Emission Targets, but EU's energy crisis.' - Daniel Batten
➡️BlackRock has officially recommended a 2% allocation to Bitcoin. With global assets totaling $900 trillion, a 2% allocation would imply a Bitcoin valuation of $18 trillion, equating to approximately $900,000 per Bitcoin.
➡️Bitcoin Reserve bill for Ohio State put forward by Rep. Derek Merrin. Merrin: Today, I filed HB 703 to create the Ohio Bitcoin Reserve within the state treasury!
Provides state treasurer authority & flexibility to invest in Bitcoin. This legislation creates the framework for Ohio’s state government to harness the power of Bitcoin to strengthen our state finances. As the US dollar undergoes devaluation, Bitcoin provides a vehicle to supplement our state's portfolio and preserve public funds from losing value.'
➡️Bitcoin-exposed convertible bonds comprise 6% of the total convertible universe and have produced 20% of the YTD Returns: Barclays Looks like Bitcoin slowly eating into the debt market. Bonds were dying until Bitcoin bonds were introduced!
➡️European MP Sarah Knafo has called on the EU to reject the digital euro and establish a strategic Bitcoin reserve, warning against “totalitarian temptations” from the European Central Bank. Are you paying attention? The world is waking up.
➡️A first draft of an Executive Order for a Strategic Bitcoin Reserve has been published.
https://x.com/DavidFBailey/status/1869098934754570305
➡️'The total assets in the spot Bitcoin ETFs are now 55% of the value of known gold ETF holdings. • Bitcoin ETF AUM: $120.69 billion • Gold ETF AUM: $218.81 billion Out with the old, in with the new - Joe Consorti
➡️'If you're not saving in Bitcoin, you're not saving at all.' AnilSaidSo
On the 18th of December:
➡️Chinese car company Cango emerges as the third largest public miner. China? Mining? What about the ban? Guess the 100x banning did nothing.
➡️Fellow Noderunner Bram Kanstein:
Open letter to the Dutch government regarding the establishment of a National Bitcoin reserve:
'Geachte @Minister_FIN @eelcoheinen @KlaasKnot @DNB_NL Met deze brief wil ik uw aandacht vestigen op een urgente en strategisch kwestie: het opbouwen van een nationale Bitcoin reserve.
https://t.co/Wjdzf8xpDA
In English (to also copy and use in your own country): https://docs.google.com/document/d/1qCIbrGqYQeQNyiXRFMBJVZyRcePHWtdnWz__67NVuRo/edit?usp=sharing
➡️FED CHAIR J. POWELL: Fed is "not allowed to own Bitcoin". They weren't allowed to own Corporate Bonds before Covid either. Rules change...
➡️$11.5 trillion BlackRock said, "Bitcoin is no longer seen as the radical idea as it was 15 years ago." "Bitcoin is an emerging global monetary alternative."
➡️Rumor goes that the UAE has potentially already accumulated ~300K Bitcoin. If true, America is behind and needs to catch up quickly. Funny isn't it? 'We’ve gone from: Being concerned about the government killing Bitcoin in a 51% attack to Being concerned about the government buying tons of it.' - Alex Gladstein
➡️IMF and El Salvador finally reached an agreement....and at first, it's big yikes. El Salvador secured a $3.5 billion IMF financing package after agreeing to make accepting Bitcoin voluntary and unwinding the Chivo wallet. Not only are they eliminating Article 7 as previously reported, but they are also removing the ability for citizens to pay taxes in Bitcoin.
Meanwhile, President Bukele says: "The IMF, World Bank, FED, and mainstream media hate that we adopted Bitcoin."
Wait for it (have a look at the 20th of December)
On the 19th of December:
➡️Bitcoin dipped. While some of you were scared, MARA bought $166 MILLION worth of Bitcoin. They have bought $3.2 BILLION Bitcoin in just 6 weeks!
➡️Hut 8 today announced the purchase of approximately 990 Bitcoin for approximately $100 million, or an average of approximately $101,710 per Bitcoin. Combined with the Bitcoin held before this purchase, Hut 8’s strategic Bitcoin reserve now totals more than 10,000 Bitcoins with a market value of more than $1 billion as of December 18, 2024.
➡️15 consecutive days of inflows for U.S. Bitcoin ETFs. $ in millions.
Spot Bitcoin ETFs purchased about 2,750 BTC yesterday while miners only mined 450 BTC. Absolute. Scarcity.
On the 20th of December:
➡️Metaplanet has issued ¥5.0 billion ($31m) in bonds to accelerate Bitcoin purchases originally slated for 2025. Issued against the 12th Series moving strike warrants, the bonds will be redeemed with the warrant exercise proceeds.
➡️'Just one day after the IMF agreed to a $3.3b loan in return for making Bitcoin acceptance voluntary, El Salvador buys $1m Bitcoin, more than 10x their usual 1 Bitcoin per day purchase. I guess the IMF won...' -Bitcoin Archive
Bukele: ''Thanks for the free money, lets 10x our Bitcoin buys, and create a strategic digital asset partnership with Argentina & 25 other nations.'' Luke Mikic
Have a look at what they did on the 22nd of December.
➡️'Guys, this drawdown peak to trough was only 14.98%. It's that tiny little red stalactite on the right that you can't even see. Chill out.' -Joe Consort
➡️Brian Brooks, former Acting Comptroller of the Currency under the Trump administration, has joined the MicroStrategy Board of Directors. As Comptroller, he oversaw the federal banking system. Here's why this is a game-changing move for the company: https://x.com/btcspaceman/status/1870402056516952421
➡️$1.3 BILLION leveraged crypto positions WIPED OUT in just 24 hours. 1. don't do leverage 2. don't do shitcoins CrYpTo.
➡️$108 billion VanEck subsidiary Market Vector accepts #bitcoin as payment for the first time.
➡️Swiss company Relai purchases 13 Bitcoin for $1.2 million for their balance sheet. Relai now holds 30 BTC.
➡️Michael Saylor publishes the Bitcoin framework so the "United States can lead the global digital economy. "A strategic digital asset policy can strengthen the US dollar, neutralize the national debt, and position America as the global leader in the 21st-century digital economy—empowering millions of businesses, driving growth, and creating trillions in value.'
https://www.michael.com/digital-assets-framework
➡️'France's 5th largest bank, the €863 billion BPCE Group, to launch Bitcoin purchases for its 35 million customers in 2025.' -Bitcoin News
On the 21st of December:
➡️'MARA's announcement that recycling heat from Bitcoin mining rigs to heat the homes of almost 80,000 residents (1.4% of Finland's population) is the largest application yet for heat recycling. Here's why it's significant.' -Daniel Batten
Read the whole thread/post here: https://x.com/DSBatten/status/1870250495895302177
➡️Someone just mined a whole Bitcoin block by himself, claiming $311,000 in reward.
➡️Spot Bitcoin ETFs took in 4,349.7 BTC worth $423.6 MILLION this week despite the price of bitcoin falling. Miners only mined 2,250 BTC this week.
On the 22nd of December:
➡️El Salvador makes another purchase of 11 Bitcoin, pushing towards the recently announced goal of 20,000 BTC. Classic! They now have bought 25 Bitcoin worth over $2.4 million since securing its loan from the IMF. Bukele wasn't joking around!
➡️'When there's not enough Bitcoin for sale, billionaires will offer ANYTHING to own some. You'll be able to get: - Houses for 0.01 BTC - Cars for 0.001 BTC - A month of groceries for 0.00001 BTC They will give you everything you need... Because YOU have what THEY want.' -Rajatsonifnance
Regarding that a month of groceries for 0.00001 BTC,' everything is falling (price) against Bitcoin. What about fiat?
This is the single best long-run measure of food inflation. And it’s gone vertical. Now you do the math and ask yourself, go long Bitcoin or go long fiat?
You know what I will give you one more example, 'houses for 0.01 BTC'
Are you paying attention?
➡️Vancouver Mayor Ken Sim: Bitcoin is the top-performing asset of the past 16 years. It’s better than gold. It can’t be captured by a military force. It can put Vancouver on the map as a world leader in Bitcoin innovation.
On the 23rd of December:
➡️MicroStrategy has acquired 5,262 BTC for ~$561 million at ~$106,662 per Bitcoin and has achieved a Bitcoin Yield of 47.4% QTD and 73.7% YTD. As of 12/22/2024, they hodl 444,262 Bitcoin acquired for ~$27.7 billion at ~$62,257 per Bitcoin.
➡️Japanese public company Metaplanet buys 619.7 Bitcoin for ¥9.5 billion. As of December 23, Metaplanet holds 1,761.98 BTC acquired for ~¥20.87 billion.
➡️Publicly traded La Rosa Holdings Corp. now accepts Bitcoin as a payment option for its real estate agents.
➡️Bitcoin is the best-performing asset in 11 of the last 14 years. Jesse Myers: 'The only speculation about Bitcoin is how long until the mainstream realizes: -Bitcoin is the invention of absolute scarcity -Absolute scarcity is a once-in-a-species event (irreproducible) -Absolute scarcity is a black hole on the world's balance sheet, eating all SoV'
💸Traditional Finance / Macro:
On the 16th of December:
👉🏽'11 consecutive days of more decliners than advancers in the S&P500. First time since Sept 11, 2001.' - ZeroHedge
On the 18th of December:
👉🏽The S&P 500 falls over 3% in its largest post-Fed drop since March 2020.
🏦Banks:
👉🏽'This is the first time in the history of the data that over 40% of banks were tightening credit standards, and then went back to not tightening, without a recession having occurred.' - Lyn Alden One word: "Fiscal dominance" https://www.lynalden.com/september-2024-newsletter/
🌎Macro/Geopolitics:
On the 17th of December: BowTiedMara: 'Last 8 months of Massa (WITH PRICE CONTROLS):
6.6%
5.8%
6.3%
15.6%
14.3%
7.7%
15.7%
29.7%
Last 8 months of Milei (WITHOUT PRICE CONTROLS):
6%
4.8%
3%
3.2%
3.6%
2.3%
1.2%
0.9%'
What do we learn from this? Socialists want you dependent on them and price controls never work.
On the 18th of December:
👉🏽'SUMMARY OF FED CHAIR POWELL'S STATEMENT (12/18/24): 1. Inflation is "much closer" to 2% Fed target 2. Activity in the housing market has been weak 3. Wage growth in the United States has eased 4. The labor market is not a source of inflation pressures 5. The Fed can be more cautious in reducing interest rates 6. Inflation expectations remain "well anchored" The "Fed pivot" is taking another pause.' -TKL
👉🏽'The S&P 500 falls sharply after the Fed cuts rates by 25 basis points, but raises inflation forecast. The Fed reduced its outlook from 3 to 2 rate cuts in 2025 and raised inflation expectations from 2.1% to 2.5%. Inflation is back.' _TKL
👉🏽ZeroHedge: POWELL: ECONOMY GREW FASTER THAN EXPECTED IN SECOND HALF OF '24'. Maybe this had something to do with it?
👉🏽'Very rare: the Fed just lowered the overnight reverse repo rate (RRP) by 30 basis points, not 25 bps (the norm) So RRP rate is now at the floor of Fed Funds (no longer 5 bps above). This could ease money market rates & accelerate money flowing out of the Fed's RRP facility.' - Jack Farley In other words: Another liquidity injection.
On the 20th of December:
👉🏽'November PCE inflation, the Fed's preferred inflation measure, RISES to 2.4%, below expectations of 2.5%. Core PCE inflation was 2.8%, below expectations of 2.9%. However, this means CPI, PPI, and PCE inflation are all back on the rise.' -TKL
👉🏽'The new government funding bill would allow for ~$1.565 trillion in new borrowing before the debt ceiling binds again next March. +$1.5 trillion to the national debt... IN 3 MONTHS. If the government were a business, nobody would give them a dime. They'd be bankrupt tomorrow.' -Joe Consorti
On the 22nd of December:
👉🏽The global Fed pivot continues: 74% of world central banks have cut rates this year, the biggest share since 2021. The Bank of Canada has cut rates 5 times by 175 basis points, marking the most aggressive rate cut cycle among major central banks. The European Central Bank and the Swiss National Bank have lowered rates 4 times by 100 and 125 basis points, respectively. The Bank of England has cut twice by 50 basis points. As inflation rebounds, the pivot is at risk.' -TKL
🎁If you have made it this far I would like to give you a little gift:
Some fountain of Lyn Aldens wisdom:
https://www.lynalden.com/december-2024-newsletter/
Credit: I have used multiple sources!
My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: PocketBitcoin especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly. Use the code BITCOINFRIDAY
Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple.⠀⠀⠀⠀ ⠀ ⠀⠀⠀
Do you think this post is helpful to you? If so, please share it and support my work with sats.
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
⭐ Many thanks⭐
Felipe -Bitcoin Friday!
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
-
 @ 20986fb8:cdac21b3
2024-12-24 09:38:54
@ 20986fb8:cdac21b3
2024-12-24 09:38:54In this edition, we are pleased to speak with Luthando nostr:npub10vudmjqhr8kn2kv2pxhezt2h5t5c9zauwq8qr56nhdn64yacsqyqf08djm leader of the Bitcoin Ekasi community, about how they are using Bitcoin to transform payment systems, savings habits, and cross-border remittances in a South African township, while fostering digital currency education and boosting local economic trust.
YakiHonne: Luthando. We really appreciate you coming in. YakiHonne is a decentralized media client built on the Nostr protocol that enables freedom of speech through technology. It empowers creators to create their own voice, assets, and features. It also allows features like smart widgets, verified notes, and focuses on long-form articles. today. we'll be exploring more about your community.Can you tell us a bit about yourself? What do you do, and what’s your role in your community?
Luthando:I’m Luthando, a project community leader at Bitcoin Ekasi. My role includes onboarding township shops to help them adopt Bitcoin as a payment method. I also manage staff records, tracking workdays and paid leave for team members involved in the project. Additionally, I conduct interviews and collaborate with a supervisor to share insights and experiences about Bitcoin. This work is part of my efforts with Bitcoin Ekasi.

YakiHonne: You're really doing a lot of work in the Bitcoin ecosystem,what sparked your interest in Bitcoin? And what motivated you to create a community around it?
Luthando:When I was working as a safety coach at Safeacase, Herman introduced me to Bitcoin. During the COVID-19 pandemic, Safeacase, which relied on donations, faced severe financial challenges. This led to the launch of the Bitcoin Ekasi Project, where I helped township shops adopt Bitcoin as a payment method. With limited funds, I transitioned from receiving a fiat salary to earning in Bitcoin. Bitcoin transformed my mindset, making me realize it is the future of money. This realization inspired me to travel the world and explore new countries.
YakiHonne: Great. I really admire the enthusiasm you have for Bitcoin.Can you share a brief history of how you built your community and attracted members? What methods or advertisements did you use to onboard them?
Luthando:We host monthly Bitcoin movie nights to engage the community, running from February to December starting next year. We promote the events with posters in town, shops, and clinics, inviting residents to join. During the movie nights, participants use Bitcoin we provide to purchase popcorn and drinks, gaining hands-on experience with the technology. Luthando:And our Bitcoin center features a thrift shop and a small Bitcoin ATM. Community members can exchange fiat for Bitcoin using the ATM and use it to purchase clothing from the shop. We also offer Bitcoin courses with 14 students attending classes five days a week. To encourage attendance, students are rewarded with Bitcoin for consistent participation. Similarly, in the “Safer Kids” program, children who maintain a 70% attendance rate or higher also receive Bitcoin rewards. Luthando:To further promote Bitcoin adoption in the community, we painted Bitcoin-themed logos on 34 shops and paid the owners in Bitcoin, which they can use in local shops. This initiative not only spreads awareness but also provides the community with practical opportunities to use Bitcoin.

YakiHonne: Yeah, we are pushing Bitcoin adoption so hard this time. It's really great.What principles guide your community, and how do you ensure trust and reliability in your discussions?
Luthando:I was born in eastern South Africa, and my parents moved here around 1996. The community knows me well and trusts that I wouldn’t introduce anything fraudulent. Since 2010, we’ve been working in this township, especially helping children, building over a decade of trust. I explain to the community that we aim to bring value through Bitcoin, encouraging them to save in Bitcoin instead of fiat. As a result, the community has great trust in our Bitcoin Ekasi team.
YakiHonne: How do you educate your members and keep them updated on Bitcoin developments? You mentioned having five weekly meetups to onboard members, but what other methods do you use to educate them and keep them informed about the Bitcoin ecosystem?
Luthando:We use the Felly app to communicate with community members and keep them updated. At the Ekasi Center, we host quizzes to encourage participation. For example, the first attendees can earn 5,000 sats, motivating them to regularly engage with the Felly app. Although we initially tried a few other methods that didn't really involve them getting Sats, its impact was limited as many people in the township seek quick financial returns and often don’t return after their first visit. To address this, we host movie nights as a more engaging way to promote Bitcoin education. During these events, we screen Bitcoin-related films, allowing community members to learn about Bitcoin in a fun and relaxed setting.

YakiHonne: It's truly captivating and highly insightful.How does your community collaborate with the global Bitcoin ecosystem? Specifically, how does it engage with the broader worldwide Bitcoin community, and which partnership has been of more significant impact on Bitcoin Ekasi?
Luthando:We have established a strong partnership with Bitcoin Beach, which provided crucial support in the creation of the Bitcoin Ekasi project. Currently, we are planning to build a community center in the township, earning the trust and support of both Bitcoin Beach and the local government of Mossel Bay. The community center will serve as a multifunctional space for events like weddings and more. As one of the earliest Bitcoin adoption projects in Africa, Bitcoin Ekasi has inspired other countries to follow suit, viewing us as a model for building sustainable Bitcoin communities.
YakiHonne: How do you collaborate with Bitcoin communities and organizations outside South Africa? What partnerships or interactions do you have with other global Bitcoin communities?
Luthando: We collaborate with other Bitcoin projects through community initiatives. For example, we paint logos on local community shops and pay the owners 7000Sats per week. This approach has helped us build connections with projects outside South Africa. One notable example is our assistance to the Bitcoin Dua project in Africa, helping them establish a Bitcoin circular economy. We also supported the Bitcoin Loxin project in Cape Town, South Africa, in launching their Bitcoin circular economy. Through these collaborations, we have developed strong relationships with other Bitcoin communities.

YakiHonne: We’d like to understand the challenges you faced when starting the community, as well as the challenges the community has encountered?
Luthando: One of the main challenges is convincing members that Bitcoin is not a scam. Many people are skeptical about Bitcoin, fearing they might lose their money. Additionally, saving is not a common habit within the community, even with fiat currency. I often explain the importance of saving in Bitcoin, emphasizing how it can safeguard their financial security. However, changing deeply ingrained mindsets has proven to be quite difficult. Another challenge is the limited level of education in the community. Even those who own smartphones often struggle to use them effectively. This lack of familiarity extends to using Bitcoin wallets, with many people finding it challenging to navigate wallet usage, especially in shops. Lastly, I feel like I’m working around the clock. Even outside of work hours, people come to my house seeking assistance, such as exchanging Bitcoin for fiat. While I’m happy to help, the constant demands can feel overwhelming at times, making it seem as though I’m working every day, including weekends.
YakiHonne: and how you managed to overcome them?
Luthando: Overcoming these challenges is not easy. I can't say that I've fully managed to resolve them, but I do my best to address them. Fortunately, I have a colleague who assists me, although he’s currently out of town. He helps manage some of the workload, especially in dealing with local community members and providing them with the support they need.
YakiHonne: I'm really interested in the issue of people thinking Bitcoin is a scam. Could you elaborate on that? What specific steps have you taken to demonstrate that Bitcoin is reliable and not a scam?
Luthando: Many shop owners initially believe Bitcoin is a scam and refuse to accept it. To address their doubts, I demonstrate Bitcoin's legitimacy through practical examples. First, I help them download a Bitcoin wallet and post about it on X, receiving small tips from Bitcoin enthusiasts worldwide. I then use these tips to showcase Bitcoin's real-world applications. For instance, I use Bitrefill to purchase mobile airtime or fuel vouchers for them, highlighting Bitcoin's utility in daily life. I also mention South African restaurants like Steers that accept Bitcoin and even place food orders using Bitcoin to show its usability. Additionally, I demonstrate withdrawing cash from a crypto ATM using Bitcoin, further proving that it is a reliable financial tool and not a scam.
YakiHonne: You've done a lot of work in South Africa. I can imagine the effort, the pain and the stress.What initiatives has the community taken to promote Bitcoin adoption, and what results have these efforts achieved?
Luthando: At first, I never imagined we would reach this point. Now, many people frequently come to my home to ask how to buy Bitcoin. For example, this week, a man from Nigeria wanted to purchase Bitcoin worth 5,000 units. I explained the process to him and recommended using a hardware wallet for securely storing large amounts of Bitcoin. He used to struggle with sending money back home, but now he has realized the convenience of Bitcoin. In October last year, I helped two stores owned by Nigerians adopt Bitcoin payments. Since then, this practice has spread within the community, and more people, especially shop owners, have developed an interest in Bitcoin. They ask about its low transaction fees and have recognized it as an efficient solution for cross-border remittances. Initially, some shop owners were skeptical about Bitcoin, but they eventually started saving with it. Today, many of them have accumulated significant Bitcoin savings for their families and children, and they often express their gratitude for introducing Bitcoin to the community. Overall, the Bitcoin adoption project has had a profound impact here. We have educated the community about Bitcoin’s long-term savings value, and many people are now satisfied with this initiative and optimistic about the future.

YakiHonne: It’s clear you’ve achieved tangible results from your efforts. Looking ahead, what are your community's goals for the next 6 to 12 months? How do you plan to achieve them?
Luthando: For Bitcoin Ekasi, one of our main goals is to establish a dedicated Bitcoin Ekasi Center. This center would serve as a hub to educate people about Bitcoin on a frequent basis. We have already started working with a local school in the township, recruiting students and introducing teachers to Bitcoin. Our vision is to integrate Bitcoin education into the school’s curriculum, similar to what has been done in El Salvador. By incorporating Bitcoin as part of their regular subjects, students can gain foundational knowledge about Bitcoin and its potential uses. Ultimately, we aim for teachers to become advocates who can confidently teach children about Bitcoin, empowering the next generation with essential financial literacy skills.
YakiHonne: Thank you so much! I think most of my questions have been answered. I’m really glad to see Bitcoin enthusiasts with a clear focus on Bitcoin. As you said, Bitcoin is the future, and I truly appreciate your enthusiasm for it.
Luthando: Bitcoin is truly the future. We want to see this township transformed into something more modern, rather than its current state. I hope to see more parents saving some Bitcoin for their children. In our community, most kids receive a monthly government allowance of $50 starting from the age of one. I often suggest to parents that they set aside half of that allowance to buy Bitcoin for their child. If they save consistently from age one to 18, the value could grow significantly as Bitcoin appreciates. I’m already doing this for my own child so that he will have savings as he grows up.
YakiHonne: Bitcoin is the future. Its value continues to grow steadily over time. Thank you so much for today’s conversation; we are truly honored. Your sharing of such rich experiences has been incredibly insightful for us. I’ve learned that using movie events to engage more people is an excellent idea, and we plan to start trying it out soon. Once again, thank you for your time and for sharing with us!
-
 @ 7776c32d:45558888
2024-12-23 01:13:02
@ 7776c32d:45558888
2024-12-23 01:13:02I am submitting another Monero dev bounty on bounties.monero.social for a much more ambitious project than my last one (which is still in progress, for nostr wallet bot setup tooling).
It all started with the Nintedo 64. It's a 64-bit desktop computer that can run modern-day 64-bit Linux, but most owners do not have a keyboard and mouse for it - only a controller. On the bright side, it has no ethernet port or wireless card to introduce internet-connected backdoors. There are also other, older systems with no internet connectivity; the 64 is just special for its Linux compatibility.
Importantly, many old game systems like this have been mass-produced, sold worldwide, and maintained by collectors, ensuring continued availability will outlast today's empires.
Despite the difficulty of inputting text using gamepad controls, this category of system is ideal for air-gapped wallets; however, this bounty is starting smaller and more general-purpose than that. The point is to generate seed phrases and associated public and private keys, while providing good safety advice, and helping people learn.
The development bounty
Link to the bounty page at bounties.monero.social - https://bounties.monero.social/posts/168/gamepad-controlled-cryptographic-multitool-with-offline-wallet-address-generator
Since this project is nostr-related, I am also making this thread on nostr, so that nostr users can have their input included.
Here are the details of the bounty, which can also be viewed at the link I've provided.
Bounty details
Native platform requirements
- The app must be tested to work on a common vintage game system (mainline Nintendo or equivalent popularity), using its standard controller or handheld controls (this makes this bounty stupidly difficult, I'm sorry)
- The newest consoles you can target are "5th generation" (N64 or equivalent) or, if you want to do a handheld, GBA or lesser is fine (the point is equivalence of capabilities, not actual release year)
- Optionally, the app can work with any keyboard attachment available for the selected system, but it still has to also be usable with the standard controls
- The app must also be tested to work on Linux or Android (either one is fine)
- If your solution does not run natively on Linux or Android, then it just needs to work in at least one open source Nintendo emulator for Linux or Android (either one is fine)
- If your solution involves running Linux on a Nintendo 64, you do have to confirm it works on typical Linux or Android devices without the emulator (again, either one is fine)
I do not want to lend indirect support to a specific corporate brand, and I strongly respect that others in this community might be suspicious that looks like what I'm doing by mentioning Nintendo products. Thus, non-Nintendo systems with similar limitations, anywhere from a Commodore 64 to a PlayStation, could be accepted as alternatives. However, I am not mentioning Nintendo to support Nintendo - their systems simply seem to be the only ones that have all of the following benefits:
- Competed significantly with the sales numbers for a mainline Nintendo system in the US and worldwide
- Complicated wording because it's a very particular thing: these systems were sold at a time when the US surveillance state might have accepted a more limited level of invasiveness for the backdoor vulnerabilities required in electronic products marketed to American consumers, if the products were understood by Americans to be toys for running games, and not used by adults to run code for serious purposes
- These products were indeed understood by Americans to be toys for running games, and not used by adults to run code for serious purposes
- Ostensibly no built-in networking, wireless functionality, cameras, microphones, speakers
- Continuing to be sold and bought very actively by a large number of gamers, for gaming purposes; this makes it somewhat ineffficient to target the entire market with random shipment interceptions, to plant backdoors blindly, hoping to catch things other than gameplay
- Already wide support for loading unlicensed games; even if a mod chip or custom loadable cartridge is needed, gamers buy these things to run games, so it can't be assumed that these mod chips or custom cartridges are being used for cryptography purposes every time they're purchased
- Last but not least, these systems have open-source emulators readily available for all major platforms (or, in the case of N64 Linux, a convenient way to bypass any emulator for cross-compatibility)
Many systems meet parts of these criteria, and would be useful even if they don't hit every point on the list. The examples I gave before - a Commodore 64 and a PlayStation - miss many of these points, yet they would still be awesome. Nonetheless, these criteria seem to make a Nintendo 64 or similar ideal to start with, before extending the functionality onto other systems, to increase overall availability even further.
On the other hand, some of these factors are vital criteria, such as the lack of built-in surveillance equipment (even speakers are just inverse microphones).
I've provided this information to help an informed choice be made, so I'll leave the final selection in the community's hands. Just keep it equivalent to these old systems, or ideally, pick one of them.
Additional note: I'm also not sure mentioning Nintendo here actually benefits them as a corporation. The brand should benefit, in that it becomes a more useful name and logo for a stronger corporation to potentially own; but that doesn't mean the current corporation benefits from so-called ownership of a name and logo they might not even be allowed to trade for a few Monero, let alone fully utilize.
Simplified list of functions
- Promote the development of knowledge and experience for users working with cryptographic tools (including but not limited to Monero and other cryptocurrency)
- Mine for "vanity keys" (wallet addresses and nostr pubkeys matching given text strings)
- Handle UTF-8 text input somehow, probably an on-screen keyboard navigated using the controller
- Guide users through generating more well-randomized seed phrases by hand
- Convert text to and from binary using text encoding schemes such as Unicode (might seem like a silly toy thing to include, but this helps familiarize people with the general concept of converting chunks of digital data between different formats)
- Convert data to QR codes (inverse not required because most old Nintendos do not have cameras)
- Convert text and binary from plain to encrypted form, and vice versa, in accordance with well-regarded encryption algorithms
- Convert random input to seed phrase
- Convert seed phrases to nostr keypairs and BIP-39 wallet addresses
- Configure these conversions as preset settings, editable by the user to configure custom wallet address derivation paths, seed phrase standards, encryption algorithms, etc
- Include presets for generating wallet addresses for at least the following cryptocurrencies: Monero (XMR), doggie coin (DOGE), Bitcoin (BTC), Ethereum (ETH), Ethereum Classic (ETC)
- Include UTF-8 and ASCII as presets for binary text encoding
Detailed information
All of the information listed in this section must be provided to users where specified, but you can rephrase it or expand on it as long as your changes strengthen the informational value. Copying and pasting from me, or asking me to revise or expand what I've written for your use, is also fine.
Main menu splash
At the main menu, display a random security tip from a list of tips like "did you compile this from the source code yourself?" and "have you considered using an off-grid power source to make sure you're disconnected from any grid-based backdoors?"
Actually make sure those 2 are in the list. Other than that, you can use some existing list of tips you find online, or make a list yourself, or ask me or others for help, or whatever you want. This is kind of like Minecraft's main menu splash text, which also gets randomly selected from a list of possible strings.
Encrypting and decrypting text
When encrypting and decrypting text, convey to the user that the term "end to end encryption" has become a marketing term widely used to gaslight the public in the age of security theatre, and what the user is doing only counts as "end to end encryption" if they have good reason to be sure their game system has no leakpoints/backdoors, and neither does the device of anyone the user is exchanging messages with.
Keygen
Points to convey at the beginning of the process of generating a key:
- When a process requires some randomized data, that piece of data is called a "seed;"
- for example, a "seed phrase" is a sequence of words that translate to a random binary sequence, often used to calculate wallet addresses;
- random number generation is hard for computers or humans alone, so the most secure software generates random numbers by mixing user input with electronic algorithms, which means a wallet's final seed is generated from a precursor seed of user input
- the precursor seed is often invisible to the user, collected from something like mouse movements which they might not notice, but more transparently involving the user can help teach them more about security and user safety
- old-fashioned random number generators, such as dice, can be far more reliable and secure than contemporary electronic mechanisms, so it's also a good idea for secure software to allow users to turn to these outside sources of randomness
When generating a key, offer these 3 options, where the tradeoffs are made clear to the user:
- the user can ignore security to automatically mine for a "vanity seed" matching a special wallet address and/or npub;
- middle ground, the user can use their device to manually generate user input for a random seed;
- maximum user control, the user can be guided through the process of generating their seed phrase using an antique technology such as dice
When manually generating a key using dice or similar, the user can enter a binary sequence to have it converted to a seed phrase. At this stage, convey these points:
- the user can instead print out a list of seed words and keep this step independent if they want;
- although there are many entries in the list of seed words, it takes surprisingly little paper to print a list with that many single-word entries at a readable font size;
- the checksum would be the hardest part without electronics
When a seed phrase is generated, don't offer the user any option for what to do with it except delete it and return to the main menu. Make these points available for the user to read about:
- the user should save the seed using a non-electronic method such as paper;
- if the seed is or might become essential to avoid losing, backing it up would be ideal;
- backing it up might be too risky for individuals facing unusually high levels of surveillance or unusual risk of theft;
- this risk might be addressed using miltisig, or simply split-up segments of a seed, or memorizing a seed phrase without keeping it written down;
- random word sequences this long are much harder to remember than actual sentences, and relying on memory has a very high rate of failure;
- when using memory to store crypto wallet keys, it's called a "brain wallet," and it's known for being very dangerous and a bad idea in most cases;
- only long seed phrases can be partly exposed and still have enough randomness remaining for protection, it's probably not a good idea to split up a 12-word seed into multiple segments for security;
- your keys are yours to protect - users should look for more information beyond what any app explains, and take time to think about how they personally want to secure any important seed
When manually adding derivation paths for wallet addresses, stress to the user that it's dangerous af and they better get it exactly right and actually just still not even use it because it's too risky to be worth it.
When generating wallet addresses, convey to the user that this app does not yet have actual wallet functionality and cannot connect to the blockchain to verify a test transaction, so if the user is planning to just blindly deposit large amounts to wallet addresses generated here without any testing, that's so metal and hardcore af
QR codes
When generating QR codes for any purpose, wallet address or otherwise, always convey to the user that pointing one device's camera at another device's screen, or even the light cast by it, could allow hidden backdoors to transfer data beyond what the user intends to transfer.
For example, a screen could encode data in microscopic changes of brightness, detectable by a camera, but not noticeable to the human eye.
Thus, for the most high-security level of air-gapping, one should consider using pen and paper (copied multiple times and triple-checked) for data transfer, while keeping sensitive electronics as isolated as possible from camera phones, or ideally as isolated as possible from other electronics in general.
Text encoding support requirements
- Confirm all ASCII characters convert to and from binary successfully (UTF-8 would probably be impossible to hit 100% on)
- Confirm UTF-8 braille characters render successfully (because these characters are inadvertently functional as an image encoding method)
⣴⡿⠶⠀⠀⠀⣦⣀⣴⠀⠀⠀⠀
⣿⡄⠀⠀⣠⣾⠛⣿⠛⣷⠀⠿⣦
⠙⣷⣦⣾⣿⣿⣿⣿⣿⠟⠀⣴⣿
⠀⣸⣿⣿⣿⣿⣿⣿⣿⣾⠿⠋⠁
⠀⣿⣿⣿⠿⡿⣿⣿⡿⠀⠀⠀⠀
⢸⣿⡋⠀⠀⠀⢹⣿⡇⠀⠀⠀⠀
⣿⡟⠀⠀⠀⠀⠀⢿⡇⠀⠀⠀⠀
⠉⠁⠀⠀⠀⠀⠀⠸⠇When using the text encoding functionality, which converts text between encoding standards like ASCII and UTF-8, it would also be good to include a reminder that the user's keyboard and other system components are encoded in UTF-8.
A suggestion
This isn't a firm requirement, but if possible, please allow the user's choice from at least the following 2 color schemes: black background with green text, and pale yellow background with black/gray text. For some idea of what "pale yellow" means, something like HTML color code feffb2 would be good.
Roadmap of future plans to avoid for now
Devs on bounties.monero.social sometimes go above and beyond what's requested in a bounty. That's truly awesome, but in this case, the limits of this project are intentional; please do not skip past the scope of the bounty too widely. You can go beyond the scope if you wish, but along the way, it would still be ideal to do a minimalist release to suit this bounty's requirements specifically. I hope this bounty is more than challenging enough to begin with - as a non-coder, it seems to me like it should already be extremely difficult.
I intend to do (smaller) future bounties for expansion of this project. Ideally these expansions should take the form of patches, all compatible with each other, and the minimalist original version. Thus, different versions of the app, with different capabilities, could be configured - and their security analyzed separately.
Here are some specific bounties and ideas I would want to see added later, but not in the minimalist version, to save on lines of code in the minimalist security analysis.
- Bounty for a patch that adds air-gapped wallet functionality, where the app can actually interface with the blockchain to do transactions, by using pen and paper to transfer data between the Nintendo and a different machine with an internet connection
- Bounty for a patch that adds air-gapped nostr functionality, where the app can generate signed nostr events and encrypt/decrypt direct messages, and a "sister app" handles the exchange of data on an internet-connected system
- Bounty for a patch to enhance text handling by adding clipboard functions (highlight/cut/copy/paste)
- Include a clipboard history view (clearly warning the user that the Nintendo has no storage, and this is only a temporary history, lasting until the system is reset)
- Bounty for a patch that expands data transfer methods by adding support for some kind of peripheral data interface such as a memory card slot
- Allow encryption and decryption of heavier data formats than text, such as images, if some kind of peripheral provides a better data interface than pen-and-paper / on-screen keyboard
- If the selected device ever had a camera attachment available, a bounty for a patch that adds support for the camera (QR code scanning, image capturing, maybe converting images to Unicode braille art)
- Bounty for a patch that hides this entire app inside of whatever game had the most copies produced for the selected Nintendo system (not against copyright to release as a patch)
- Bounties for identical functionality on other systems
In addition to all these goals, it would also be good to have a large number of native cartridges produced someday, containing this software, after some time for the open-source community to review and revise first.
-
 @ a367f9eb:0633efea
2024-12-22 21:35:22
@ a367f9eb:0633efea
2024-12-22 21:35:22I’ll admit that I was wrong about Bitcoin. Perhaps in 2013. Definitely 2017. Probably in 2018-2019. And maybe even today.
Being wrong about Bitcoin is part of finally understanding it. It will test you, make you question everything, and in the words of BTC educator and privacy advocate Matt Odell, “Bitcoin will humble you”.
I’ve had my own stumbles on the way.
In a very public fashion in 2017, after years of using Bitcoin, trying to start a company with it, using it as my primary exchange vehicle between currencies, and generally being annoying about it at parties, I let out the bear.
In an article published in my own literary magazine Devolution Review in September 2017, I had a breaking point. The article was titled “Going Bearish on Bitcoin: Cryptocurrencies are the tulip mania of the 21st century”.
It was later republished in Huffington Post and across dozens of financial and crypto blogs at the time with another, more appropriate title: “Bitcoin Has Become About The Payday, Not Its Potential”.
As I laid out, my newfound bearishness had little to do with the technology itself or the promise of Bitcoin, and more to do with the cynical industry forming around it:
In the beginning, Bitcoin was something of a revolution to me. The digital currency represented everything from my rebellious youth.
It was a decentralized, denationalized, and digital currency operating outside the traditional banking and governmental system. It used tools of cryptography and connected buyers and sellers across national borders at minimal transaction costs.
…
The 21st-century version (of Tulip mania) has welcomed a plethora of slick consultants, hazy schemes dressed up as investor possibilities, and too much wishy-washy language for anything to really make sense to anyone who wants to use a digital currency to make purchases.
While I called out Bitcoin by name at the time, on reflection, I was really talking about the ICO craze, the wishy-washy consultants, and the altcoin ponzis.
What I was articulating — without knowing it — was the frame of NgU, or “numbers go up”. Rather than advocating for Bitcoin because of its uncensorability, proof-of-work, or immutability, the common mentality among newbies and the dollar-obsessed was that Bitcoin mattered because its price was a rocket ship.
And because Bitcoin was gaining in price, affinity tokens and projects that were imperfect forks of Bitcoin took off as well.
The price alone — rather than its qualities — were the reasons why you’d hear Uber drivers, finance bros, or your gym buddy mention Bitcoin. As someone who came to Bitcoin for philosophical reasons, that just sat wrong with me.
Maybe I had too many projects thrown in my face, or maybe I was too frustrated with the UX of Bitcoin apps and sites at the time. No matter what, I’ve since learned something.
I was at least somewhat wrong.
My own journey began in early 2011. One of my favorite radio programs, Free Talk Live, began interviewing guests and having discussions on the potential of Bitcoin. They tied it directly to a libertarian vision of the world: free markets, free people, and free banking. That was me, and I was in. Bitcoin was at about $5 back then (NgU).
I followed every article I could, talked about it with guests on my college radio show, and became a devoted redditor on r/Bitcoin. At that time, at least to my knowledge, there was no possible way to buy Bitcoin where I was living. Very weak.
I was probably wrong. And very wrong for not trying to acquire by mining or otherwise.
The next year, after moving to Florida, Bitcoin was a heavy topic with a friend of mine who shared the same vision (and still does, according to the Celsius bankruptcy documents). We talked about it with passionate leftists at Occupy Tampa in 2012, all the while trying to explain the ills of Keynesian central banking, and figuring out how to use Coinbase.
I began writing more about Bitcoin in 2013, writing a guide on “How to Avoid Bank Fees Using Bitcoin,” discussing its potential legalization in Germany, and interviewing Jeremy Hansen, one of the first political candidates in the U.S. to accept Bitcoin donations.
Even up until that point, I thought Bitcoin was an interesting protocol for sending and receiving money quickly, and converting it into fiat. The global connectedness of it, plus this cypherpunk mentality divorced from government control was both useful and attractive. I thought it was the perfect go-between.
But I was wrong.
When I gave my first public speech on Bitcoin in Vienna, Austria in December 2013, I had grown obsessed with Bitcoin’s adoption on dark net markets like Silk Road.
My theory, at the time, was the number and price were irrelevant. The tech was interesting, and a novel attempt. It was unlike anything before. But what was happening on the dark net markets, which I viewed as the true free market powered by Bitcoin, was even more interesting. I thought these markets would grow exponentially and anonymous commerce via BTC would become the norm.
While the price was irrelevant, it was all about buying and selling goods without permission or license.
Now I understand I was wrong.
Just because Bitcoin was this revolutionary technology that embraced pseudonymity did not mean that all commerce would decentralize as well. It did not mean that anonymous markets were intended to be the most powerful layer in the Bitcoin stack.
What I did not even anticipate is something articulated very well by noted Bitcoin OG Pierre Rochard: Bitcoin as a savings technology.
The ability to maintain long-term savings, practice self-discipline while stacking stats, and embrace a low-time preference was just not something on the mind of the Bitcoiners I knew at the time.
Perhaps I was reading into the hype while outwardly opposing it. Or perhaps I wasn’t humble enough to understand the true value proposition that many of us have learned years later.
In the years that followed, I bought and sold more times than I can count, and I did everything to integrate it into passion projects. I tried to set up a company using Bitcoin while at my university in Prague.
My business model depended on university students being technologically advanced enough to have a mobile wallet, own their keys, and be able to make transactions on a consistent basis. Even though I was surrounded by philosophically aligned people, those who would advance that to actually put Bitcoin into practice were sparse.
This is what led me to proclaim that “Technological Literacy is Doomed” in 2016.
And I was wrong again.
Indeed, since that time, the UX of Bitcoin-only applications, wallets, and supporting tech has vastly improved and onboarded millions more people than anyone thought possible. The entrepreneurship, coding excellence, and vision offered by Bitcoiners of all stripes have renewed a sense in me that this project is something built for us all — friends and enemies alike.
While many of us were likely distracted by flashy and pumpy altcoins over the years (me too, champs), most of us have returned to the Bitcoin stable.
Fast forward to today, there are entire ecosystems of creators, activists, and developers who are wholly reliant on the magic of Bitcoin’s protocol for their life and livelihood. The options are endless. The FUD is still present, but real proof of work stands powerfully against those forces.
In addition, there are now dozens of ways to use Bitcoin privately — still without custodians or intermediaries — that make it one of the most important assets for global humanity, especially in dictatorships.
This is all toward a positive arc of innovation, freedom, and pure independence. Did I see that coming? Absolutely not.
Of course, there are probably other shots you’ve missed on Bitcoin. Price predictions (ouch), the short-term inflation hedge, or the amount of institutional investment. While all of these may be erroneous predictions in the short term, we have to realize that Bitcoin is a long arc. It will outlive all of us on the planet, and it will continue in its present form for the next generation.
Being wrong about the evolution of Bitcoin is no fault, and is indeed part of the learning curve to finally understanding it all.
When your family or friends ask you about Bitcoin after your endless sessions explaining market dynamics, nodes, how mining works, and the genius of cryptographic signatures, try to accept that there is still so much we have to learn about this decentralized digital cash.
There are still some things you’ve gotten wrong about Bitcoin, and plenty more you’ll underestimate or get wrong in the future. That’s what makes it a beautiful journey. It’s a long road, but one that remains worth it.
-
 @ ec42c765:328c0600
2024-12-22 19:16:31
@ ec42c765:328c0600
2024-12-22 19:16:31この記事は前回の内容を把握している人向けに書いています(特にNostrエクステンション(NIP-07)導入)
手順
- 登録する画像を用意する
- 画像をweb上にアップロードする
- 絵文字セットに登録する
1. 登録する画像を用意する
以下のような方法で用意してください。
- 画像編集ソフト等を使って自分で作成する
- 絵文字作成サイトを使う(絵文字ジェネレーター、MEGAMOJI など)
- フリー画像を使う(いらすとや など)
データ量削減
Nostrでは画像をそのまま表示するクライアントが多いので、データ量が大きな画像をそのまま使うとモバイル通信時などに負担がかかります。
データ量を増やさないためにサイズやファイル形式を変更することをおすすめします。
以下は私のおすすめです。 * サイズ:正方形 128×128 ピクセル、長方形 任意の横幅×128 ピクセル * ファイル形式:webp形式(webp変換おすすめサイト toimg) * 単色、単純な画像の場合:png形式(webpにするとむしろサイズが大きくなる)
その他
- 背景透過画像
- ダークモード、ライトモード両方で見やすい色
がおすすめです。
2. 画像をweb上にアップロードする
よく分からなければ emojito からのアップロードで問題ないです。
普段使っている画像アップロード先があるならそれでも構いません。
気になる方はアップロード先を適宜選んでください。既に投稿されたカスタム絵文字の画像に対して
- 削除も差し替えもできない → emojito など
- 削除できるが差し替えはできない → Gyazo、nostrcheck.meなど
- 削除も差し替えもできる → GitHub 、セルフホスティングなど
これらは既にNostr上に投稿されたカスタム絵文字の画像を後から変更できるかどうかを指します。
どの方法でも新しく使われるカスタム絵文字を変更することは可能です。
同一のカスタム絵文字セットに同一のショートコードで別の画像を登録する形で対応できます。3. 絵文字セットに登録する
emojito から登録します。
右上のアイコン → + New emoji set から新規の絵文字セットを作成できます。


① 絵文字セット名を入力
基本的にカスタム絵文字はカスタム絵文字セットを作り、ひとまとまりにして登録します。
一度作った絵文字セットに後から絵文字を追加することもできます。
② 画像をアップロードまたは画像URLを入力
emojitoから画像をアップロードする場合、ファイル名に日本語などの2バイト文字が含まれているとアップロードがエラーになるようです。
その場合はファイル名を適当な英数字などに変更してください。
③ 絵文字のショートコードを入力
ショートコードは絵文字を呼び出す時に使用する場合があります。
他のカスタム絵文字と被っても問題ありませんが選択時に複数表示されて支障が出る可能性があります。
他と被りにくく長くなりすぎないショートコードが良いかもしれません。
ショートコードに使えるのは半角の英数字とアンダーバーのみです。
④ 追加
Add を押してもまだ作成完了にはなりません。

一度に絵文字を複数登録できます。
最後に右上の Save を押すと作成完了です。

画面が切り替わるので、右側の Options から Bookmark を選択するとそのカスタム絵文字セットを自分で使えるようになります。
既存の絵文字セットを編集するには Options から Edit を選択します。
以上です。
仕様
-
 @ 8d34bd24:414be32b
2024-12-22 15:04:23
@ 8d34bd24:414be32b
2024-12-22 15:04:23We are in the season of Christmas and busy fulfilling all of our Christmas traditions. We put up Christmas decorations, sing Christmas songs, buy Christmas presents, and plan big Christmas meals, but we are supposed to be celebrating the birth of Christ. We are supposed to be celebrating God made flesh — our Creator becoming His creation to reconcile them to Himself.
If you care about your relationship with Jesus, you may wonder, “Are all of these Christmas traditions good or bad?” In most cases, I think the answer is “It depends.” Are you using Christmas traditions to celebrate Jesus and point yourself and others to Him or have the traditions themselves become the focus?
Let’s look at some Christmas traditions and see how we might use them to point us to Jesus instead of distracting us from Him.
Christmas Music
1And suddenly there appeared with the angel a multitude of the heavenly host praising God and saying,
“Glory to God in the highest,\ And on earth peace among men with whom He is pleased.” (Luke 2:13-14)
There is a lot of Christmas music to choose from, but some is more honoring to God than others. Do you spend your time listening to songs like “Jingle Bell Rock,” “Grandma Got Run Over By a Reindeer,” “Baby It’s Cold Outside,” or “I Saw Mommy Kissing Santa Claus” or do you spend your time listening to songs like “O Holy Night,” “O Come, O Come Emmanuel,” “Little Town of Bethlehem,” or “Mary Did You Know?” There isn’t anything inherently wrong with the first type, but the second type is much more honoring to Jesus and will focus our minds on what Jesus did for us.
By listening to Christmas music that points us to Jesus, we honor Him, refocus our own lives, and point others to Him. When we listen to Christmas music that focuses on Santa, Frosty, Rudolph, or just the season of winter, we distract people from the true meaning of Christmas. Listening to Bing Crosby singing “White Christmas” isn’t a problem (and I enjoy it very much), but focus on the Christmas Carols that point us to Jesus. You won’t regret it.
Christmas Decorations (Lights)
Then Jesus again spoke to them, saying, “I am the Light of the world; he who follows Me will not walk in the darkness, but will have the Light of life.” (John 8:12)
I love Christmas decorations and especially Christmas lights. I’ll admit it. This year we even decided we are going to leave the lights up through January because the lights are so cheerful during the dark part of the year when we spend so much time in darkness. The question we should ask ourselves is “Are we just focused on the decorations and lights or are we focused on Jesus?”
Jesus is the Light of the World. He is the light in the darkness. It is appropriate to use lights to celebrate Jesus, but do we focus on the lights or are the lights focusing our thoughts on Jesus? My new Christmas resolution is to remember to thank Jesus for being the light of the world every time I look at the Christmas lights.
Let your light shine before men in such a way that they may see your good works, and glorify your Father who is in heaven. (Matthew 5:16)
Are your Christmas decorations things that point to Jesus or things that point to human tradition like Santa, reindeer, Frosty, etc.? We should aim to have more of our decorations point to Jesus.
Another thing I’ve noticed is that many of our Christian decorations can even be based on tradition rather than actual Biblical inerrancy. Most nativity sets have 3 wise men. Although this error isn’t something to get legalistic about, it is something to be aware of.
Now after Jesus was born in Bethlehem of Judea in the days of Herod the king, magi from the east arrived in Jerusalem, saying, (Matthew 2:1)
Traditionally the magi have been called wise men, but nobody knows 100% who the magi were. They also assume there were 3 of them because of the 3 gifts of gold, frankincense, and myrrh. Based on the uproar that they caused in Jerusalem, it was probably a huge caravan. You’ll also notice that they arrived in Jerusalem “after Jesus was born in Bethlehem.” They then consulted King Herod. King Herod consulted the Jewish leaders to figure out that the Messiah was expected to be born in Bethlehem, and then they traveled to Bethlehem to find Jesus. It isn’t clear how long after Jesus’s birth the Magi showed up, but they definitely weren’t there that first Christmas morning.
Because of this, my husband sets up our main nativity set (that his parents got in Israel) in our living room and sets up the 3 wise men and the camel in our guest bedroom (on the East side of the house). It is his way of supporting the true Christmas story and not just the traditions of men.
Our Christmas tree isn’t just stuff relating to Jesus and the Christmas story. Most of our tree decorations are things for which we are thankful to Jesus. We have ornaments with family pictures. We have handmade ornaments made by the women of our church that were given to us when our house burnt down. We have ornaments from most of the trips we have gone on. We have a few sentimental family ornaments that were given to us when my husband’s mom died. Every time I look at my tree, I am grateful for all of these things. They aren’t just generic decorations. They are memories. I also have an ornament with a picture of my son’s teacher’s autistic son who snuck away and was killed in a blizzard. Every time I see the ornament, I pray for his family who misses him so much. I’d like to think that this tree of blessings is honoring to my God and my Savior.
Christmas Dinner
For I received from the Lord that which I also delivered to you, that the Lord Jesus in the night in which He was betrayed took bread; and when He had given thanks, He broke it and said, “This is My body, which is for you; do this in remembrance of Me.” In the same way He took the cup also after supper, saying, “This cup is the new covenant in My blood; do this, as often as you drink it, in remembrance of Me.” For as often as you eat this bread and drink the cup, you proclaim the Lord’s death until He comes. (1 Corinthians 11:23-26) {emphasis mine}
This passage is about the Passover celebration and Jesus’s command to celebrate the Lord’s Supper in remembrance of Him. I think it is likewise appropriate to celebrate His birth with a meal. As in most things, what makes it honoring to Jesus is how we do Christmas dinner rather than whether we do it or not.
The below passage is about celebrating the Lord’s supper in an inappropriate way, but I will try to apply it to Christmas dinner.
Therefore when you meet together, it is not to eat the Lord’s Supper, for in your eating each one takes his own supper first; and one is hungry and another is drunk. What! Do you not have houses in which to eat and drink? Or do you despise the church of God and shame those who have nothing? What shall I say to you? Shall I praise you? In this I will not praise you. (1 Corinthians 11:20-22)
Is Christmas dinner just about stuffing ourselves with good food or is it about more? Is it about fellowship with friends and family? Is it about gratefulness for what Jesus did for us? Is it about benefitting others?
For most of our marriage, we have alternated celebrating Christmas at my parent’s house and my husband’s parents house, but a couple of times recently, due to different circumstances, we have celebrated Christmas in our own home, and we will be doing it again this year. We’ll celebrate with my family after Christmas, and we celebrated with my husband’s family at Thanksgiving.
Our new tradition is to invite some people over to join us for Christmas dinner if we are celebrating at our home. We invite people from our church that are an older couple with no family nearby, a widow, or a single that is not near family. We invite people who would not have much of a celebration on their own. It has been such a blessing being able to bless others who don’t have family, are in financial hardship, or have physical trouble cooking a big meal.
Whether you are fellowshipping with family or ministering to those who have less than you, Christmas dinner can definitely be a God honoring part of your Christmas traditions.
Christmas Presents
Now He who supplies seed to the sower and bread for food will supply and multiply your seed for sowing and increase the harvest of your righteousness; you will be enriched in everything for all liberality, which through us is producing thanksgiving to God. For the ministry of this service is not only fully supplying the needs of the saints, but is also overflowing through many thanksgivings to God. Because of the proof given by this ministry, they will glorify God for your obedience to your confession of the gospel of Christ and for the liberality of your contribution to them and to all, while they also, by prayer on your behalf, yearn for you because of the surpassing grace of God in you. Thanks be to God for His indescribable gift! (2 Corinthians 9:10-15) {emphasis mine}
Too often we can get so obsessed with the buying and receiving of gifts that we forget the greatest gift of all — the gift of our Savior Jesus.
My 17 year old son has Down Syndrome. He really likes gifts, especially electronics, like tablets, radios, and phones. Unfortunately, he also isn’t very gentle with them and usually has broken or lost most of them by the time Christmas comes along. This often leads to him obsessing about the gifts that he thinks he deserves.
When we celebrated Christmas with my husband’s family at Thanksgiving, he got a nice keyboard that he had requested. He did not, however, get the radio or tablet he wanted. As we were driving home he demanded, “Where is my radio? Where is my tablet? Where is it?” Instead of being grateful for his very generous gift, a gift that he requested, he was upset that he hadn’t gotten everything he wanted. He focused on stuff and not people. He focused on receiving and not giving. He focused on earthly things instead of Jesus. Too often we all do.
But the free gift is not like the transgression. For if by the transgression of the one the many died, much more did the grace of God and the gift by the grace of the one Man, Jesus Christ, abound to the many. The gift is not like that which came through the one who sinned; for on the one hand the judgment arose from one transgression resulting in condemnation, but on the other hand the free gift arose from many transgressions resulting in justification. For if by the transgression of the one, death reigned through the one, much more those who receive the abundance of grace and of the gift of righteousness will reign in life through the One, Jesus Christ. (Romans 5:15-17) {emphasis mine}
Just as Jesus gave His life for us, it is good for us to give to others, but we always need to have the gift giving process be focused on Jesus and not the stuff. We always need to be thankful for what we have and receive and not what we don’t have and haven’t received.
On Christmas morning, before opening gifts, we always read the Christmas story from Luke 2 and the story of the magi from Matthew 2. We then sing “Happy Birthday” to Jesus, to remind us all of the purpose of Christmas and of the greatest gift we have received. I’m also wanting to start a new tradition at Christmas: Before each person opens a gift, they must thank Jesus for one blessing in their life. I think this will change the focus from greed and getting to gratefulness for what we have already received.
For by grace you have been saved through faith; and that not of yourselves, it is the gift of God; not as a result of works, so that no one may boast. For we are His workmanship, created in Christ Jesus for good works, which God prepared beforehand so that we would walk in them. For by grace you have been saved through faith; and that not of yourselves, it is the gift of God; not as a result of works, so that no one may boast. For we are His workmanship, created in Christ Jesus for good works, which God prepared beforehand so that we would walk in them. (Ephesians 2:8-9) {emphasis mine}
Jesus gave us His all. We also need to consider what we can give to those who can’t give back, just as we can’t ever repay Jesus for what He did for us. Is there a family you know that is having a rough year financially or health wise that you could bless with a meal or gifts or help with bills? Is there a charity that will share the gospel and meet the physical needs of those who are alone, broke, and addicted that you can donate to? Maybe your kids have lots of toys and are about to get more and you can donate some that are in good condition to a Christian charity that can get those toys to kids who won’t receive any. Maybe money is tight, but you could volunteer at a soup kitchen or do some yard chores for a widow. I don’t know your personal circumstances or the circumstances of where you are and those around you, but think about finding some way to bless someone less fortunate than you.
Above all, keep fervent in your love for one another, because love covers a multitude of sins. Be hospitable to one another without complaint. As each one has received a special gift, employ it in serving one another as good stewards of the manifold grace of God. Whoever speaks, is to do so as one who is speaking the utterances of God; whoever serves is to do so as one who is serving by the strength which God supplies; so that in all things God may be glorified through Jesus Christ, to whom belongs the glory and dominion forever and ever. Amen. (1 Peter 4:8-11) {emphasis mine}
There are lots of movies, songs, and TV shows that talk about the spirit of Christmas and the love of Christmas. Let’s make sure we show love and share Jesus with the people around us. They tend to be much more open to Jesus during Christmas. Let’s make sure we make the most of Christmas.
To God be the Glory!
Trust Jesus.
FYI, Because everyone is busy at Christmas, I will be posting my short Wednesday post (Christmas) on Tuesday evening (Christmas Eve) so that people can have time to read the post before Christmas and it will hopefully help you to have the right mindset on Christmas.
FYI, to learn more about my books “Why I Need Jesus” (available in paperback and ebook) and “Joy in the Storm” (in editing and hopefully out in a month or two.) see my books page.
-
 @ fcb65172:87f3c4ed
2024-12-21 21:59:04
@ fcb65172:87f3c4ed
2024-12-21 21:59:04Cities on return are often strange\ Yeah, and now\ Every time you blink, you feel it change\ And it's been\ A long, a long, a long, a long, long-long\ You've been my\ Favourite for a while
So sings Grian Chatten, lead singer of the Irish punk band Fontaines D.C (look them up and thank me later), in the fourth verse of their song Favourite– my favourite track released in 2024. As a world traveller who has called quite a few places home during the past 10 years I can relate to these lyrics on so many levels.
It just so happens that I recently came back to La Paz, Bolivia– a city I used to call home. But so many things about the city has changed. Most notably with old friends of mine.
Some old friends have turned out to reveal themselves as crooks, and you guessed it, some of the people who had been painted, in my mind, as crooks– well it just so turns out that they have revealed themselves as the good guys. I’m reminded of Warren Buffet’s line: Only when the tide goes out do you discover who's been swimming naked. The time away from La Paz has given me time to reflect on my two and a half years living here. The time component acts as the tide in Buffet’s great quote– Allowing me to filter through all the noise and focus on what is real. Or should I say who of my old friends were the real friends and who were the crooks– swimming naked all the time.
My Story with La Paz
I first arrived in La Paz in 2018 as a 22 year old boy looking for a place in South America to live. La Paz was where I met my wife. La Paz is where I bought my first business– a pub in the tourist area. La Paz is where I learned to deal with corrupt city council workers. La Paz is in many ways where I grew from a boy to a man.
 A Young 22 Year old naive version of me in La Paz
A Young 22 Year old naive version of me in La PazFast forward to December 2024 as I’m back in the city for the first time in two years. Walking the colourful and chaotic streets of La Paz, brings back all the memories. The street corner where a young naive Sebastian bought his first gram of pure Bolivian Marching Powder– That shit will pick you right up by the bootstraps, but do to proceed with care, I don’t have enough available fingers to count the amount of people who I’ve seen lose their lives to the Marching Powder of Bolivia. If you aren’t careful it will become the only thing you live for.
I jump on a cable car– La Paz’s metro system which flies across the city, up and down the mountains, connecting all neighbourhoods with the city centre. I head to what used to be my local park and viewpoint. This is where I would always come to read a book or listen to podcasts whilst enjoying the stunning view of Illimani– the mountain guarding La Paz. Most importantly this is the park where I made my first move to kiss my wife.
 The view of Illimani Mountain from the Pub I used to own
The view of Illimani Mountain from the Pub I used to ownThe former community leader who vanished
The main thing I think about as I re-explore my old neighbourhoods is; what happened to my old friends and acquaintances? Together with the other restaurants in the tourist area we used to have a football team organised by a true community leader, let’s call him George in this story, the team was called Chocos Locos– The Crazy Blondes, we were a mix of European expats, exchanges students, NGO employees and some local Bolivian friends of ours. George was the guy who tied us all together. He knew everyone– their birthday, what football team they supported, what drink they preferred etc. George would look out for everyone, he would make sure to organize birthday parties, even for the quiet ones in our group. George had his values set in the right place, he demanded a high standard from everyone on and off the pitch. In exchange we would look out for each other, cover for one another if we were in trouble. You know like the Marines, we would leave no man behind.
As I’m now back in La Paz most of my former friends and teammates are no longer around, George included. Their restaurants are closed and new ones have emerged. Some have left due to the recent years of political instability in Bolivia, others have mysteriously disappeared. What happened to them?
In May 2024 I received a message from George saying our friend and teammate, let’s call him Juan, was in intensive care in a hospital in La Paz, after suffering a near death accident. Juan’s family needed help to cover the treatment costs. Like the true community leader George is, he took it upon himself to reach out to all present and former teammates and friends of Juan, asking us all to pitch in, with whatever we could to support Juan’s treatment. I didn’t think much else of it and sent across €100 to support Juan. As I later came to learn, the story was something else. The real story revealed George’s true identity.
This is the story of a real captain, a true community leader, who turned out to be a scammer. But how did George turn into a scammer who used the near death accident of a friend and teammate, to scam just about everyone who had ever met Juan into donating money to help Juan’s family pay for the intensive care in hospital, only to run off with all the money donated– approximately $4000 USD?
Perhaps the answer was there in front of our faces all along? I recently listened to a podcast with Andrew Bustamente (a former CIA spy, known as Everyday Spy on YouTube) in the podcast Andrew mentioned that most people who come off as highly empathetic, people like George, aren’t actually as highly empathetic as they seem, in fact such people despise almost everybody else.
I now ask myself did George actually use the community and our football team the whole time. Were we funding his life in La Paz all the time? George told us he was working online as an English teacher. Now I ask myself who George really was.
See you all in 2025
It’s mind blowing to me, how time removed from a former favourite city helps us see our time living in said city with such clarity… What really happened? Who were the good guys? Who were the bad guys?
As I look to settle into a new hometown in 2025 (more on that in future newsletters) I will keep in mind my lessons learned from revisiting La Paz. I will be able to spot who are the charlatan’s and who are the genuine good guys– or at least so I hope.
As I warm up to a Holiday season with family from both Denmark and Bolivia I wish you all a great Holidays, remember to be grateful for your family and those who are your real friends. Show them love. Cherish your time with them. Let me leave you with the lyrics to the final verse of the fantastic Fontaines D.C song Favourite:
Ah, makes sense when you understand\ The misery made me another marked man\ And I'm always looking over my shoulder\ And each new day\ - I get another year older\ Shoulder bound to the frame of a door\ Tuned into shape like a stone on the shore\ But if there was lightning in me\ Then you know who it was for
https://www.youtube.com/watch?v=1UG31mpUnOg
I will see you all in 2025. God bless you all.
Sebastian
-
 @ 472f440f:5669301e
2024-12-21 00:45:10
@ 472f440f:5669301e
2024-12-21 00:45:10There was a bit of a rally in stock markets today, but this was a relief rally after taking a beating throughout the week. All eyes were on Federal Reserve Chairman Jerome Powell as he took the stage on Wednesday to announce the decisions made at the most recent FOMC meeting.
The market reacted negatively to another 0.25% cut from the Federal Reserve that many considered a "hawkish cut" due to the fact that Chairman Powell articulated that it is likely that there will be less rate cuts in 2025 than were previously expected. This is likely driven by the fact that inflation, as reported by the terribly inaccurate CPI, has been coming in higher than expectations. Signaling that the Fed does not, in fact, have inflation under control. Who could have seen that coming?
Here's how the US 10Y Treasury yield reacted to the announcement:
"Not great Bob!" The US 10Y Treasury yield is something that everyone should be paying attention to over the course of the next year. Since the Fed started cutting rates in September of this year, the 10Y yield has been acting anomalously compared to how it has acted historically after Fed interest rate decisions. Since September, the market has been calling the Fed's bluff on inflation and rates have been moving in the opposite direction compared to what would be expected if the Fed had things under control. The "hawkish cut" made on Wednesday is not a great sign. The Fed is being forced to recognize that it cut "too much too fast" before actually getting inflation under control.
One has to wonder why they made such aggressive moves in September. Why the need for a much more dovish stance as quickly as they moved? Do they see something behind the scenes of the banking system that makes them believe that another liquidity crisis was on the horizon and they needed to act to prevent yet another banking crisis? Now that it is clear that inflation isn't under control and if there really was a liquidity crisis on the horizon, what are the first two quarters of 2025 going to look like? Could we find ourselves in a situation where inflation is beginning to accelerate again, there is a liquidity crisis, and the Fed is forced to rush back ZIRP and QE only to further exacerbate inflation? Couple this potential scenario with the proposed economic policy from the incoming Trump administration and it isn't hard to see that we could be in for a period of economic pain.
One can only hope that the Fed and the incoming administration have the intestinal fortitude to let the market correct appropriately, reprice, clear out the bad assets and credit that exists in the system and let the cleanse happen relatively unperturbed. That has what has been desperately needed since 2008, arguably longer.
On that note, bitcoin is going through a bull market correction this week as well. Likely incited and/or exacerbated by the turmoil in traditional markets.
Many are proclaiming that the end of this bull market is here. Don't listen to those who have been hate tweeting bitcoin all the way up this year. They've been looking for a correction to bask in schadenfreude and confirm their biases. These types of corrections are to be expected when bitcoin runs by checks notes 100% over the course of less than three months. We're approaching the end of the year, which means that people are selling to prepare for taxes (which may be happening in the stock market as well). Add to this fact that long-term holders of bitcoin have taken the most profit they have since 2018 and it probably explains the recent pull back. Can't blame the long-term holders for seeing six-figure bitcoin and deciding to bolster their cash balances.
I couldn't be more bullish on bitcoin than I am right now. The fundamentals surrounding the market couldn't be more perfect. Despite what the Trump administration may have in store for us in terms of economic policy (I agree with most of the policies he has presented), I find it hard to believe that even he and the talented team of people he has surrounded himself with can overcome the momentum of the problems that have been building up in the system for the last 16-years.
The "find safety in sats" trade is going mainstream as the market becomes more familiar with bitcoin, its properties, and the fact that it is very unlikely that it is going to die. The fervor around bitcoin as a strategic reserve asset for nation states is only picking up. And if it catches on, we will enter territory for bitcoin that was considered utterly insane only a year ago.
On that note, Nic Carter made some buzz today with a piece he wrote for Bitcoin Magazine explaining why he believes a strategic bitcoin reserve is a bad idea for the US government.
https://bitcoinmagazine.com/politics/i-dont-support-a-strategic-bitcoin-reserve-and-neither-should-you
While I agree that the signal the US government could send by acquiring a bitcoin strategic reserve could be bad for the US treasuries market, I think it comes down to strategy. The Trump administration will have to think strategically about how they acquire their Strategic Bitcoin Reserve. If they ape in, it could send the wrong message and cause everyone to dump their treasuries, which are the most popular form of collateral in the global financial system. However, there are ways to acquire bitcoin slowly but surely from here into the future that ensure that the United States gets proper exposure to the asset to protect itself from the out-of-control debt problem while also providing itself with a way out of the problem. Many of these potential strategies were discussed in two recent episodes I recorded. One with Matthew Pines from the Bitcoin Policy Institute and another with Matthew Mežinskis from Porkopolis Economics. I highly recommend you all check those out (linked below).
https://youtu.be/xyyeEqFVjBY
https://youtu.be/6vgesP9LIXk
.---
Final thought...
I am the most locked in from a focus perspective while on flights. Even with two kids under 5. Merry Christmas, Freaks!
-
 @ cc448f8b:a1ad47db
2024-12-20 18:27:36
@ cc448f8b:a1ad47db
2024-12-20 18:27:36A Website Hosted on NOSTR?
The Nostr landscape is changing every day. https://npub.pro came across my radar and clearly it cannot work well, basically a website hosted almost entirely on Nostr relays. I was wrong!
I'll be honest that at first, things did not go well. I posted several issues on https://github.com/nostrband/nostrsite and within a very short time the problems were addressed. Right now it is working so much better. While there is always room for improvement, it is incredibly easy to create a website.
I've invited podcaster/blogger friends to give it a try and most now have a working website in such short time.
Quick Start
- Visit https://npub.pro
- Login
- Select a theme.
- Make some settings adjustments (icon, backdrops, colors, etc)
- Press the
Publishbutton and that's it!
Here's where it gets interesting, there is no cms backend for your posts. Instead, use any Nostr client to create your website post. Here's a small list of popular clients: https://nostr.com/clients.
Tips
The site previews work best if you already have content on Nostr.
I would start out with all content, no filtering. Once you finalize your theme choice add filters because you may not want all your Nostr posts to be visible on the website. For example if you have a DIY blog, add the
#DIYhashtag to all the posts you want to see on the website and set your filter to only show posts tagged#DIY. No-one wants to see your#coffeechainposts on your DIY blog, LOL.What I Like Most
- Automagic RSS Feed
- Looks great on mobile devices
- No database, no CMS, no server maintenance
- Plenty of themes
- Beautiful OG/Twitter sharing
- Built in likes, zap and share plugin
- Theme customization for those that know how to
- Ability to add contributors without creating accounts or managing user databases
- Ability to filter Nostr notes via tags or format (long/short notes)
- Use free subdomain or use your own custom domain
- Fully working site comments with zero effort
What I Dislike
- Not a problem for me but some probably won't like un-moderated site comments
- Not all CSS is manipulable, or example, some CSS is loaded after the custom css like the Zap/share dialogs (perhaps this is a theme specific issue)(also most creators probably won't use custom css/js code)
Website Examples Created By Others Using https://npub.pro
- Sport news - https://gsc.npub.pro/
- Podcast - https://directordetour.npub.pro/
- Someones personal blog - https://marc26z.npub.pro/
- Custom domain + custom CSS styling - https://news.pivx.org
- My test website with custom CSS - https://palmtree.npub.pro
Conclusion
I would 100% recommend Npub.pro to anyone who wants a website. It should take the average person under 30 minutes to get a fully functioning website. If your familiar with the admin interface, you could probably spin up a new website in under 5 minutes.
-
 @ fd208ee8:0fd927c1
2024-12-20 06:58:48
@ fd208ee8:0fd927c1
2024-12-20 06:58:48When the shit just don't work
Most open-source software is now so badly written and sloppily-maintained, that it's malware.
That's why the governments are getting involved. They try using OS, to save money and improve quality (and to market themselves as "hip"), and then it blows up their system or opens them up to hackers.
Now, they're pissed and want support (but the dev with the handle SucksToBeYou has disappeared) or someone to sue, but most OS projects have no identifiable entity behind them. Even well-known anon devs are often groups of anons or accounts that change hands.
The software cracks have moved on
There is simply no evidence that OS alone produces higher-quality software. The reason it seemed that way, at the beginning, was because of the caliber of the developers working on the projects, and the limited number of projects. This resulted in experienced people actively reviewing each others' code.
OS used to be something the elite engaged in, but it's mostly beginners practicing in public, now. That's why there are now millions of OS projects, happily offered for free, but almost all of them are garbage. The people now building OS usually aren't capable of reviewing other people's code, and they're producing worse products than ChatGPT could. Their software has no customers because it has no market value.
If everything is OS, then nothing is.
Another paradigm-changer is that all software is de facto OS, now that we can quickly reverse-engineer code with AI. That means the focus is no longer on OS/not-OS, but on the accountability and reputation of the builders.
It is, once again, a question of trust. We have come full-circle.
-
 @ 3906af02:af15c9f4
2024-12-19 13:40:00
@ 3906af02:af15c9f4
2024-12-19 13:40:00NEW: HRF #Bitcoin Development Fund grants 700 million satoshis to 20 projects worldwide!
https://bitcoinmagazine.com/business/human-rights-foundation-donates-700000000-satoshis-to-fund-bitcoin-development-and-projects
The grants cover decentralized #Bitcoin mining, technical education, decentralized communications, independent media & privacy-enhanced financial solutions for human rights groups, focusing on key regions in Latin America, Asia, and Africa 🌍🌏🌎🎁
Grants include:
🛠️ Stratum V2 Reference Implementation (SRI) decentralizes #Bitcoin mining by allowing nodes create their own block templates, reducing reliance on large pools. Funds will support @bit-aloo’s work on SRI including benchmarking tools, integration tests & codebase maintenance
⛏️ Public Pool makes #Bitcoin mining accessible for low-hash-rate devices, empowering individuals to self-host mining servers & contribute to decentralization. Funds will support hosting costs, hardware upgrades, & operational expenses.
🛠️ Jon Atack, recognized as one of the top all-time contributors to #Bitcoin Core, plays a pivotal role in enhancing Bitcoin’s decentralization and robustness. Funds will empower him to continue his vital contributions to Bitcoin development
👩🏿💻 Naiyoma, the first female #Bitcoin Core developer from Africa. Her work focuses on reviewing pull requests (PRs), addressing bugs through new PRs & improving Bitcoin Core’s codebase. Funds will support her full-time contributions to advancing Bitcoin Core.
🔒 Daniela Brozzoni, a #Bitcoin Core developer who previously contributed to the Bitcoin Development Kit (BDK). This grant will support her full-time contributions to Bitcoin Core reviewing key pull requests (PRs), contributing to new features & improving testing coverage
📱 UX/UI Design for Bitcoin Core by @Michaelhaase will bring the #Bitcoin Core App to mobile enabling users to run nodes, access essential wallet features directly on their phones to improve their financial privacy. Funding will support the project’s design & development.
🚀 Brink, co-founded by Mike Schmidt, supports #Bitcoin protocol engineers with grants and offers training & mentorship to onboard new contributors to open-source development. This grant will support operational expenses
⚡@Tando.me, cofounded by Sabina Gitau, integrates #Bitcoin with Kenya’s M-PESA system, enabling KYC-free, fee-free Lightning payments for everyday transactions for 54 million Kenyans. Funds will help boost Tando’s liquidity, support user growth & drive African expansion.
🌐 YakiHonne, a Nostr client founded by Wendy Ding, supports free speech & promote #Bitcoin payments across 170 countries with innovative functionality & a blend of online & offline events. Funds will support smart widget development, relay improvements & community events.
🌍 SeedSigner Multi-language Support brings accessibility to the open-source SeedSigner hardware wallet, empowering marginalized communities through inexpensive & accessible self-custody. Funds support Ace to deliver a multi-language version of SeedSigner.
🤝 Vexl, cofounded by Lea Petrasova, provides a private, KYC-free, peer-to-peer #Bitcoin trading experience by connecting users to trade through the social graph of their phone contacts. Funds will support expanded adoption in Africa & improvements to the backend infrastructure.
🇮🇳 Tomatech is building developer talent in Goa, India to advance #Bitcoin infrastructure & FOSS projects through training, workshops, & community meetups. Funding will support developer training, the creation of a developer hub, bounties & grants, & general operations.
💾 Krux, open-source firmware that turns generic devices into hardware wallets for secure #Bitcoin self-custody featuring air-gapped operations, key management & backups & support for 10 languages. Funding will support @odudex to advance this project.
🔐 Iris, a #Nostr web client by @MarttiMalmi, which aims to improve protection for metadata & message content, ensuring conversations remain private, especially in surveillant environments. Funding will support hiring an additional developer to expand Iris' features & functionality.
💻 Cashu-ts, the primary Software Development Kit in the @CashuBTC ecosystem developed by @Gandlaf21, simplifies wallet creation, integrates the latest protocol updates & powers popular wallets. Funds will support the developers to maintain & improve this essential library.
🤝 Unify, a Payjoin wallet developed by Fontaine, enhances privacy in #Bitcoin transactions by obscuring transaction histories, crucial for individuals navigating repressive regimes. Funds will support the developer to ship new features & expand compatibility with other wallets.
📢 The Financial Freedom Policy Coalition, led by Venezuelan activist Jorge Jraissati, promotes economic opportunities for people living under authoritarian regimes. Funds will support advocacy missions to educate policymakers on how #Bitcoin supports human rights.
🎓 African UX Bitcoin Bootcamp, led by @MouxDesign, empowered 10 African UX designers with #Bitcoin UX research skills ahead of the Africa Bitcoin Conference & support to test 5 popular Bitcoin products during the conference. Funds cover all program expenses for participants.
📰 No BS Bitcoin delivers ad-free, privacy-focused #Bitcoin news in clear & accessible format, essential for activists & citizens under authoritarian regimes. This grant ensures continued operations, adds an editor & supports Nostr features like Zaps & comments.
📖 Bitcoin History, a research project by Pete Rizzo, documenting key people, events & materials that shaped Bitcoin’s rise as a global monetary & human rights force. Fund will support a researcher to investigate & document stories of Bitcoin’s use against authoritarianism.
🌎 HRF is committed to supporting human rights and financial freedom with #Bitcoin.
If you are working on a #Bitcoin or adjacent freedom tech software (Nostr, eCash, TOR etc), education or adoption project that meets our mandate, submit your application at http://hrf.org/bdfapply 💪
-
 @ 5afdec5b:2d631be1
2024-12-19 13:08:08
@ 5afdec5b:2d631be1
2024-12-19 13:08:08On November 26, 2024, we took a significant leap forward in revolutionizing Bitcoin-collateralized loans by launching PHASE 1 of our closed beta. Now that the dust has settled, it's time to reflect on what we've learned, celebrate our wins, and chart the path forward.
"Get the bread you need without having to part with your corn." — Lendasat, 2024
📈 Closed Beta: PHASE 1 in Numbers
Over the course of one fast-paced week, here's what we achieved:
- 191 waitlist signups
- 100 invitations sent to eager testers
- 29 unique borrowers took 34 loans in total
- 21 loans disbursed via virtual debit cards, and 13 paid out in stablecoins (USDC on Polygon)One of our trusted partners stepped up to support us by providing loan offers, allowing our team to focus entirely on refining the borrowing experience during this phase. In just one week, we exceeded the lender's promised liquidity by 15%, prompting an early wrap-up.
In terms of value:
- 1.34 BTC in Total Value Locked (TVL)
- $54,600 USD in Total Value Disbursed (TVD)
These numbers don't just reflect activity; they validate the demand for Bitcoin-backed loans and alternative disbursement methods like virtual debit cards.
📝 What We Learned
PHASE 1 taught us a lot about our product, our users, and the road ahead. While this beta focused on the borrower experience and the integration of virtual debit cards thanks to our partner Moon, it gave us valuable insights into what works and what needs improvement.
The UX Challenge
Building a non-custodial platform is hard. Designing its UX? Even harder.
- Our decision to use a Contract Secret (a sovereign key for signing contracts) instead of an in-app wallet upheld our commitment to self-custody, sovereignty, and safety.
- However, this introduced friction for users. We're rethinking how to make this smoother while staying true to our principles.💳 Virtual Debit Cards: A Game Changer
The ability to claim loans directly onto a virtual debit card — thanks to our partnership with Moon — was a clear hit. Virtual cards weren't just appreciated; they were a hot topic.
➡️ However, one feature that could take this to the next level is the ability to add these cards to Apple Pay or Google Pay. It's a missing piece we're eager to explore to make the experience even more seamless and user-friendly.
Stablecoin Repayment: A Friction Point
Repaying loans in stablecoins on an alt-chain wasn't as seamless as we'd hoped. Reducing this pain point will be a top priority in future iterations.
➡️ To address this, we are actively exploring new integrations that would allow borrowers to repay their loans via bank transfer or even by using their debit or credit card, providing more flexible and user-friendly repayment options.✅ Demand Validated
From Bitcoin-collateralized loans to virtual debit card payouts, the strong demand reinforced our belief in the product's potential and validated that our approach is the right one.
➡️ In the future, the underlying protocol will continue to operate on a Bitcoin<>Stablecoin foundation, ensuring speed, trustlessness, and efficiency. Borrowers, however, will have the option to opt-in for intuitive on/off ramps and spending tools, making the experience seamless and user-friendly. This will allow the complexities of the alt-chain infrastructure to disappear entirely from the borrower's perspective. At the same time, we'll keep the order book clean and unfragmented, ensuring a smooth and scalable ecosystem for all participants.🌙 Dark Mode Is (Still) a Thing
Yes, even in the world of Bitcoin-backed loans, dark mode is a surprisingly big deal.
➡️ Message received; devs are doing something.
👀 Looking Ahead: BETA RELOADED
If PHASE 1 was about testing the waters, BETA RELOADED 👀 will be about diving deeper. In this next phase, we're opening up both borrower and lender experiences to our beta testers, with:
- Improved UI/UX, based on the invaluable feedback we've received.
- New partnerships and integrations to enhance functionality and accessibility.
- Exciting surprises that we'll reveal when the time comes.If PHASE 1 taught us anything, it's that we're onto something significant. We've demonstrated that Bitcoin-collateralized loans are not only reinventable but genuinely in demand. And this is just the start of what's to come.
Get ready for BETA RELOADED. It's coming soon™️, and it's going to be legendary!
Want to be part of the journey? Join our waiting list or, even better, connect with us on Discord to share your thoughts and stay updated!
Stay tuned, and as always, stay sovereign.
-
 @ a17fb4ed:c53f7e91
2024-12-18 20:03:18
@ a17fb4ed:c53f7e91
2024-12-18 20:03:18Here is a little poem for the upcoming January 1, 2025 IRS Safe Harbor:
Wallet, Exchange - where do I begin?\ Allocating my bitcoin, what a din!\ Specific units or global, which way to go?\ Decisions, decisions, my head starts to blow.
Quantity, cost basis, I must take note,\ Tracking each asset, like a sailor at sea, afloat.\ Opentimestamp the proof, to show I've done my part,\ Sailing into safe harbor, before I depart.
FIFO or Spec ID, which method to choose?\ Gains and losses, I must not lose.\ Consolidate holdings, simplify the fray,\ Lest the IRS come and take it all away.
Who's on first, what's on second, I just don't know,\ Filling out this spreadsheet, my bitcoin woes.\ But if I follow the steps, laid out so clear,\ The safe harbor awaits, no need to fear.
Ok, for real though, What the Fuck!?! It's a public ledger and all amounts and dates are forever recorded. Way to make this much more complicated and time consuming than need be. Classic!
Clear as mud. At least this might get more folk to self custody.
Here are couple links that might help a smidge:
What US Taxpayers With Crypto NEED to do before Dec 31, 2024 - Get into the Safeharbor!
Cheers, Yooper
-
 @ 3e48885d:b2272a7c
2024-12-18 18:59:49
@ 3e48885d:b2272a7c
2024-12-18 18:59:49It may sound silly, but about once a week, sometimes more, I find myself wishing I were a cowboy. The freedom that would come from the total disconnect from the rest of the world. The peaceful feeling of open spaces and working with animals. And let’s not forget a tinge of adventure.
At 52, I find myself wishing this still. There was a time in my early thirties I seriously considered it, then came marriage and kids and it slipped away. These days, I still find it nice to think about.
Today I sit attached to my desk, living in a semi suburban world. The only animals I tend to are my two dogs. Sometimes I sit alone and listen to old cowboy songs from the likes of Chris Ledoux. I guess it helps that I live in Texas, giving me default western status, though nowhere near that reality.
I work in cybersecurity and hang out in more undeveloped parts of the web where outlaws may dwell, I guess that is as close as I get. It’s nice to daydream.
It may sound silly, but about once a week, sometimes more, I find myself wishing I were a cowboy. The freedom that would come from the total disconnect from the rest of the world. The peaceful feeling of open spaces and working with animals. And let’s not forget a tinge of adventure.
-
 @ cc448f8b:a1ad47db
2024-12-18 18:44:01
@ cc448f8b:a1ad47db
2024-12-18 18:44:01A Website Hosted on NOSTR?
The Nostr landscape is changing every day. https://npub.pro came across my radar and clearly it cannot work well, basically a website hosted almost entirely on Nostr relays. I was wrong!
I'll be honest that at first, things did not go well. I posted several issues on https://github.com/nostrband/nostrsite and within a very short time the problems were addressed. Right now it is working so much better. While there is always room for improvement, it is incredibly easy to create a website.
I've invited podcaster/blogger friends to give it a try and most now have a working website in such short time.
Quick Start
- Visit https://npub.pro
- Login
- Select a theme.
- Make some settings adjustments (icon, backdrops, colors, etc)
- Press the
Publishbutton and that's it!
Here's where it gets interesting, there is no cms backend for your posts. Instead, use any Nostr client to create your website post. Here's a small list of popular clients: https://nostr.com/clients.
Tips
The site previews work best if you already have content on Nostr.
I would start out with all content, no filtering. Once you finalize your theme choice add filters because you may not want all your Nostr posts to be visible on the website. For example if you have a DIY blog, add the
#DIYhashtag to all the posts you want to see on the website and set your filter to only show posts tagged#DIY. No-one wants to see your#coffeechainposts on your DIY blog, LOL.What I Like Most
- Automagic RSS Feed
- Looks great on mobile devices
- No database, no CMS, no server maintenance
- Plenty of themes
- Beautiful OG/Twitter sharing
- Built in likes, zap and share plugin
- Theme customization for those that know how to
- Ability to add contributors without creating accounts or managing user databases
- Ability to filter Nostr notes via tags or format (long/short notes)
- Use free subdomain or use your own custom domain
- Fully working site comments with zero effort
What I Dislike
- Not a problem for me but some probably won't like un-moderated site comments
- Not all CSS is manipulable, or example, some CSS is loaded after the custom css like the Zap/share dialogs (perhaps this is a theme specific issue)(also most creators probably won't use custom css/js code)
Website Examples Created By Others Using https://npub.pro
- Sport news - https://gsc.npub.pro/
- Podcast - https://directordetour.npub.pro/
- Someones personal blog - https://marc26z.npub.pro/
- Custom domain + custom CSS styling - https://news.pivx.org
- My test website with custom CSS - https://palmtree.npub.pro
Conclusion
I would 100% recommend Npub.pro to anyone who wants a website. It should take the average person under 30 minutes to get a fully functioning website. If your familiar with the admin interface, you could probably spin up a new website in under 5 minutes.
-
 @ d61f3bc5:0da6ef4a
2024-12-18 16:52:18
@ d61f3bc5:0da6ef4a
2024-12-18 16:52:18January 2025 will mark two years since we started building Primal. Our goal was to create the best possible user experience for Nostr and make it accessible to everyone. We reached a big milestone towards realizing that vision with the recent Primal 2.0 release. It’s still early days, a lot more work lies ahead, but we thought the timing was right to introduce the Premium tier. Let’s explore what it is, why we built it, what’s included, and how it will evolve moving forward.
What Primal Premium Is
The idea behind Primal Premium is simple: integrate all tools and services required for the best Nostr experience into a single package. For $7 per month, Premium users get a Primal Name and Nostr Tools built by Primal. We’ll cover those in more detail below, but first we should make a crucial point: by signing up for Premium, you are in no way locked in to Primal. Quite the contrary, you can pick and choose which Premium features you wish to enable and use within other Nostr products.
Openness is Nostr’s killer feature. Any product that wishes to truly empower the user needs to interoperate with Nostr’s budding ecosystem. The feed marketplace is a great example. External feeds are first-class citizens within all Primal apps. Primal feeds are available in other Nostr clients. We are working on Premium feeds, which our users will be able to enjoy within Primal or other Nostr apps. Media hosting is another example. Our upcoming support for the Blossom protocol will make Primal Premium media hosting interoperable with other Nostr apps and media hosting services. The common theme here is user choice. Nostr offers the highest level of user agency, and the compounding effect of interoperable products and services is bound to make Nostr immensely powerful.
Why We Built Premium and Why Now
What is unfolding on Nostr right now is unique and special. The first truly self-sovereign network is being bootstrapped by this early cohort of users and builders. People are literally holding the keys to their online presence. Network infrastructure – relays, indexers, media hosting services, etc. – is being stood up organically and without any central planning or coordination. Hundreds of independent projects are adding new capabilities to Nostr without needing permission. The whole thing is truly a sight to behold.
In addition to fixing the fundamentals of the network, it is equally important that we fix the broken incentives that plague the legacy Web. The status quo of monetization via advertising, which turns users into products to be farmed, has overstayed its welcome. At Primal, we don’t monetize user data. Our users are our customers. We only make money when the user decides that we are providing a valuable service – and pays for it. That means that our users’ interests are aligned with ours. It allows us to wake up every morning and work all day to make the product better for our users.
Some might say that it is too early to try to monetize a Nostr product. We definitely need to be thoughtful about paywalling important features while the network is so young. For example, advanced search is a Primal Premium feature, but we enable it for all users up to 20 search results. That makes it quite usable for anyone on Nostr, but power users get the ability to save these searches and create powerful specialized feeds.
It is crucial to have commercially successful projects on Nostr that have their incentives aligned with those of their users. We are working on new features and monetization methods that follow this philosophy. The more we experiment on Nostr, the faster we will learn what works and unlock the full potential of this network. I have a feeling that a lot remains to be discovered, and Primal Premium is just the first step.
Now, let’s take a closer look at what is included in Premium: Primal Name and Nostr Tools.
Primal Name
A Primal Name is a unique name on the primal.net domain that offers three features:
- Verified Nostr address (NIP-05). This signals to the Nostr network that your account (npub) has been verified by Primal. Note that we don’t perform identity verification; we are simply signaling that this is a Primal Premium user. Users can pay with sats, preserving their privacy while signaling to the network that this verified account is not a bot.
- Friendly Bitcoin Lightning address. Primal’s built-in hosted wallet creates a randomly generated lightning address for every user. They look like this: bluedog25@primal.net. Premium users get to pick their name, so their lightning address is more personalized (e.g. preston@primal.net).
- VIP profile on primal.net. This is simply a friendly URL to your profile on primal.net. We are working on adding profile customization features for Premium users; stay tuned!
In summary, a Primal Name makes you easier to find on Nostr. You are free to use any of these three Primal Name elements as you see fit. If you wish to use your Primal Nostr address and/or Lightning address, simply update your Nostr profile with those entries.
Nostr Tools
Nostr Tools is a collection of features that we think would be useful to any Nostr power user. We are continuously working on expanding these capabilities, but the initial set of features includes:
- Media management. Primal Premium comes with 10GB of media storage (compared to 1GB for free accounts). We implemented a slick interface for managing all media you have on Primal.
- Contact list backup. Many Nostr users have experienced the loss of their contact list (i.e., their follow list) when using different clients. We store the history of the contact list for Primal Premium users and make it easy to recover.
- Content backup. Nostr users post their content to a collection of public relays. These relays typically don’t offer guarantees that they will store the content for any amount of time. We back up all content posted by Primal Premium users and make it easy to rebroadcast it to the specified relays at any time.
Primal Legends
The idea for the Primal Legend tier was suggested to me by Gigi a couple of months prior to the launch of Primal 2.0. His argument was simple: “There are users on Nostr who really appreciate Primal and are willing to pay way more than $7 / month to support the project. You should let them pay and recognize them for doing so.”
I am really glad that Gigi convinced me to introduce the Legend tier. Nostr is truly a special place. The early users are extremely passionate and mission driven. They care about growing and improving Nostr as much as the builders do. At first, I thought of the term “Legend” as a bit tongue in cheek, but then I met and chatted with some of these people. Man, they are incredible. They just wish to support the network and the builders of open source software in any way they can. So now I think the term is appropriate.
We are humbled by the support we received. Our first Legend supporter was none other than Jack. He found this option in the product and paid for the Legend tier literally an hour after Primal 2.0 was released. Thank you, sir, and thank you to all the other Legends out there! 💜🫂
What Comes Next?
We are delighted and encouraged by the market response to Primal Premium. It is already clear to us that we are on the right path. We will lean into it even harder from here. There will be MOAR Premium features, while at the same time we will make sure that the free product remains excellent. Since you, the user, are the customer, tell us what you would like to see added to Primal Premium.
Pura Vida 🤙
-
 @ 4657dfe8:47934b3e
2024-12-18 13:42:46
@ 4657dfe8:47934b3e
2024-12-18 13:42:46Alby Hub enables creation of subaccounts, decentralizing trust and creating usecases for shared, community nodes.
Simplifying Bitcoin Wallets for Friends and Family
Alby Hub empowers you to take full control of your bitcoin and manage your payments. Through a user-friendly, self-custodial wallet with a one-click lightning node setup, you can effortlessly connect to dozens of applications. The integrated App Store provides access to popular apps like Amethyst, Damus, Stacker News, Podcasting 2.0, and a wide range of other external tools—all directly linked with your Alby Hub wallet. One of the latest and most exciting additions to Alby Hub is the Friends & Family app.
With the Friends & Family app, you can create subaccounts for friends and family, all powered by your Hub. In just a few clicks, you can set up wallets for them, giving them a smooth onboarding experience and making bitcoin accessible even to those new to the ecosystem. Think of it as a custodial wallet but with a personal touch—since you’re the one managing it, there’s a direct relationship and trust.
These subaccount holders can tap into all the channels and liquidity of your Hub without needing to handle any technical setup. Plus, you can preload their wallets with a few sats, creating a welcoming and smooth experience that’s hard to find elsewhere.
And that’s not all. Beyond providing an intuitive wallet, they can get their own lightning address, configurable payment notifications, access to Alby Go (a mobile app for payments on the go), and the Alby Browser Extension for easy web payments.
Let’s have a look how to set it up.
How to provide a wallet to Friends and Family?
- Open your Hub and find the Friends & Family app in the App Store
- Enter a name e.g. your friend’s name and click “Create subaccount”
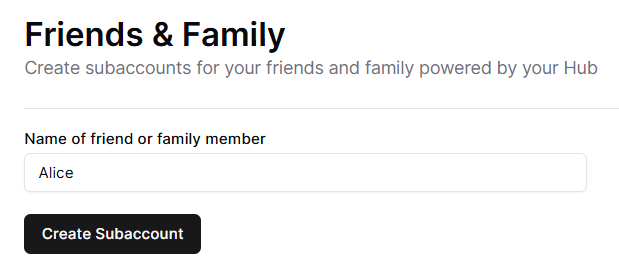
- Share the Connection Secret with your friend for the different options
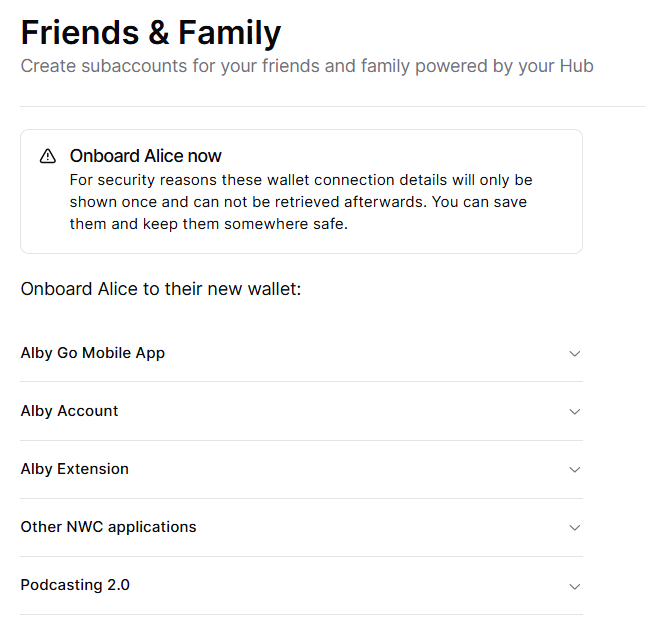
Here are two examples how your the new subaccount can be used.
Alby Go mobile App
Alby Go makes it easy to carry bitcoin in your pocket. This lightweight wallet connects directly to an Alby Hub subaccount, so your friends can pay and check transactions on the go.
Here’s how to set it up: 1. Open the Alby Go Mobile App tab in your Hub.
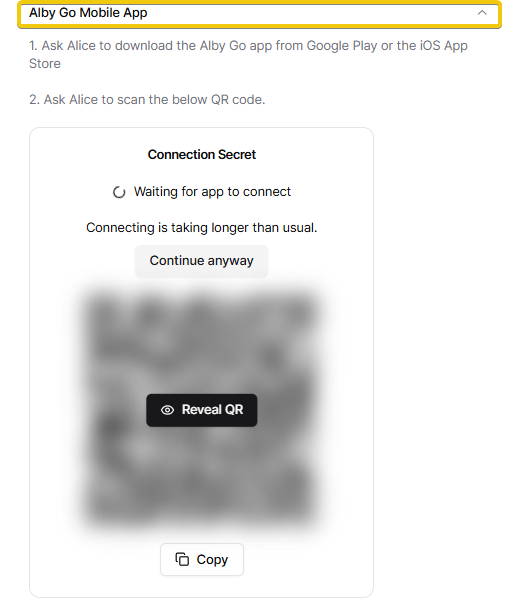 2. Copy the Connection Secret and share it with your friend if you cannot onboard them in person.
3. Your friend downloads Alby Go for Android or iOS and scans the code.
2. Copy the Connection Secret and share it with your friend if you cannot onboard them in person.
3. Your friend downloads Alby Go for Android or iOS and scans the code.And that’s it—your friend now has a bitcoin wallet in their pocket, ready for seamless transactions anytime, anywhere. 🎉
Get a Lightning Address with an Alby account
An Alby Account offers a variety of useful features that make managing bitcoin payments easy. Among these are a personalized lightning address and email payment notifications—two powerful tools that help your newly onboarded friends stay connected and informed.
To set up an Alby account for someone:
-
Open the Alby Account tab in your Hub.
-
Copy the provided URL and share it with your friend.
-
Your friend simply needs to create their Alby account and afterwards click on the provided URL.
That’s it! The wallet is instantly connected, and they’re ready to receive payments to their new lightning address. 🥳
Onboarding Family & Friends Made Easy In this article, we explored how to create subaccounts for family and friends, connect them with Alby Go, and set up an Alby account to provide a smooth onboarding experience for your loved ones—all achievable in just a few clicks.
Stay tuned as we dive into more exciting use cases for subaccounts in Alby Hub! If you have ideas for improvement,let us know.
- Open your Hub and find the Friends & Family app in the App Store
-
 @ 79008e78:dfac9395
2024-12-18 09:02:28
@ 79008e78:dfac9395
2024-12-18 09:02:28อย่างที่ทราบกันอยู่แล้วว่า Nostr เป็นได้มากกว่า Note แล้วจะเป็นอย่างไรล่ะ ถ้า Note และลองฟอร์มต่าง ๆ ที่เราเคยเขียนกันมาสามารถกลายเป็นเว็บบอร์ดที่เราสามารถใช้เก็บผลงานและโชว์ให้กับคนอื่น ๆ ในโลกอินเตอร์เน็ตทั่วไปได้อีกด้วย
Npub.pro คืออะไร ?
Npub.pro เป็น Other stuff ตัวหนึ่งที่ช่วยแปลง note และ long form ต่าง ๆ ที่เราเคยได้ลงไว้ในโปรโตคอลของ Nostr และแปลงมันมาเป็นเว็บบอร์ดที่สวยสะอาดตา และมีธีมให้เลือกอีกหลากหลาย ซึ่งเหมาะสมมาก ๆ กับเหล่าครีเอเตอร์ต่าง ๆ สำหรับที่จะใช้มันในการโชว์ผลงาน ไม่ว่าจะเป็นสายถ่ายภาพ เก็บรวบรวมบทความ หรืออีกหลาย ๆ แง่มุมที่สามารถเกิดขึ้นได้


นี่เองคือหนึ่งในตัวอย่างที่ผมได้ทำไว้เพื่อแพร่กระจายบทความต่าง ๆ ให้ออกไปสู่ผู้คนที่อาจจะไม่ได้รู้จักหรือใช้งาน Nostr อยู่
แล้วมันทำงานอย่างไร ?
Npub.pro นั้นจะทำการดึง Notes และ Long form ของเรามาจาก relay ต่าง ๆ ที่เราได้มีการเชื่อมต่อไว้ในบัญชีของเรา และทำการนำมาจัดรูปแบบใหม่ตามธีมที่เราได้เลือกไว้ และแสดงผลออกมามาในรูปแบบเว็บบอร์ด นอกจากนี้ยังมีการใส่ตัว nostr log-in เข้ามาเพื่อช่วยให้คนที่มีบัญชี nostr สามารถใช้บัญชีของตนในการ zap หรือ คอมเม้นได้ รวมทั้งยังอณุญาตให้ผู้ใช้ใส่ script เพิ่มเติมลงไปทั้งในส่วนหัวและท้ายของเว็บบอร์ดได้อีกด้วย ดังเช่น

ทั้งหมดที่กล่าวมาข้างต้นเป็นประสบการณ์ส่วนตัวของผมเองที่ได้มีการทดลองใช้งานมาระยะหนึ่ง และในส่วนต่อไป เราจะมาดูกันถึงวิธีการสร้างว่าเราต้องทำอย่างไร จึงจะมีเว็บไซต์สวย ๆ แบบนี้ได้
วิธีการสร้าง
1. เข้าเว็บ Npub.pro
หลังจากเข้ามาในเว็บไซต์ให้เรากด "try now"

2. เลือกธีม
จากนั้นจะมีธีมต่าง ๆ ขึ้นมาให้คุณเลือก ในจุดนี้ผมแนะนำว่าให้เลือกให้เหมาะสมกับผลงานของคุณ (สามารถเปลี่ยนได้ภายหลัง)

3. ตั้งค่าส่วนอื่น ๆ
หลังจากเลือกเสร็จเรียบร้อยเราต้องทำการใส่ title bio และอื่น ๆ ให้เรียบร้อยจากนั้นให้ทำการกด publish

เพียงแค่นี้คุณก็จะมีเว็บบอร์ดเจ๋ง ๆ ที่จะคอยอัพเดตอัตโนมัติเพมื่อคุณได้โพสต์บางอย่างลงบน Nostr ;)
-
 @ 490b551d:e17f0103
2024-12-17 22:12:48
@ 490b551d:e17f0103
2024-12-17 22:12:48Welcome, friend. I hope this place becomes a space to pause, breathe, and reflect in the midst of the chaos of life and faith. If you’re here, there’s a good chance you’ve felt the weight of doubt in your belief, the kind that sits heavy on your heart, whispers in your mind, and makes you wonder if you’d truly be accepted if people knew your questions, especially when everything around you insists that belief without doubt is the only acceptable way to be. I get it. I’ve been there too.
I’ve faced a lot of pressure: the pressure to get everything right, the shame that follows any hint of sin, and the isolation that comes with feeling like I’m not quite enough for God’s love—whether it was because of the mistakes I’ve made or the doubts that linger in my heart. It’s tough to be part of a faith tradition that values certainty above all else when you’re in the middle of a spiritual crisis or a season of question. For many of us, the church can sometimes feel like a place where doubt isn’t welcomed, where questions are viewed as weaknesses, or worse, a ticket to hell. But here’s what I’ve learned in the decade I stepped away from my church and my beliefs: doubt doesn’t mean we’re failing at faith. It means we’re seeking something deeper.
Understanding the Pressure to Be Certain
For many of us who were raised in conservative Christian settings, there’s often an unspoken (and sometimes spoken) expectation: doubt is not okay. The message we receive is that to be a "good Christian" means you must have unwavering faith, an unshakable belief that everything in the Bible is true, and absolute certainty in your relationship with God. You’re supposed to have all the answers, be sure of your salvation, and confidently declare your faith in the face of any challenge.
But what happens when you don't have all the answers? When you question parts of scripture or the ways the church has interpreted it? When you wonder how a loving God can allow suffering, or how science and faith can co-exist? When you wonder if you're truly loved by God, or if your struggles disqualify you from His grace?
There’s a lot of weight in these questions, and for a long time, I felt alone in them. After all, isn’t doubt something that should be avoided? Shouldn’t we be strong enough to push through and just believe? The church certainly didn't seem to be the place to clear this all up in my mind!
The Reality of Doubt: You’re Not Alone
The truth is, doubt is a natural part of the human experience. A study published in the Journal of Psychology and Theology found that 70% of individuals experience some level of doubt at various points in their spiritual journey. Doubt doesn’t make you a bad Christian or a failure at faith—it makes you human.
The Bible is filled with examples of doubt. One of the most famous stories comes from Thomas, often referred to as "Doubting Thomas." After Jesus’ resurrection, when the other disciples saw Him alive and well, Thomas couldn’t believe it until he saw Jesus for himself and touched His wounds. When he finally encountered the risen Christ, Jesus didn’t rebuke him for doubting—He met him in the doubt. Jesus said, “Put your finger here; see my hands. Reach out your hand and put it into my side. Stop doubting and believe” (John 20:27, NIV). But Jesus doesn’t shame Thomas. No. He invites him to experience the truth, to see it for himself, and to believe in his own time and way.
Doubt is not a sin. It’s part of the journey of faith. Just like Thomas, we can bring our doubts to Jesus, and He will meet us in that place.
Acknowledging Doubt: A Step Toward Deeper Faith
Sometimes we think that the right way to navigate doubt is to push it down, pretend it doesn’t exist, or cover it up with surface-level answers. We’re told that questioning our faith is a sign of weakness or a lack of commitment. But what if the opposite is true? What if acknowledging our doubt could be the very thing that leads us to a deeper, more authentic faith?
In the book of Psalms, many of the writers express their doubts and frustrations with God. Take Psalm 73, for example. The psalmist, Asaph, begins by questioning the fairness of life: “Surely God is good to Israel, to those who are pure in heart. But as for me, my feet had almost slipped; I had nearly lost my foothold. For I envied the arrogant when I saw the prosperity of the wicked” (Psalm 73:1-3, NIV). Asaph openly doubts God’s goodness, and he questions why it seems like those who do wrong are thriving. But instead of running from his questions, he brings them before God, and by the end of the psalm, he expresses renewed trust in God's faithfulness (Psalm 73:23-26). Through this process of doubting and questioning, Asaph’s faith is refined, and he ultimately comes to a deeper understanding of God's justice and presence.
When we acknowledge the doubt, we don’t weaken our faith; we make space for it to grow. True faith isn’t the absence of doubt—it’s the trust to keep going even when we don’t have all the answers.
What the Bible Says About Doubt
James 1:6-8 is one of the passages that many people turn to when discussing doubt in the context of faith. It says:
"But when you ask, you must believe and not doubt, because the one who doubts is like a wave of the sea, blown and tossed by the wind. That person should not expect to receive anything from the Lord. Such a person is double-minded and unstable in all they do" (James 1:6-8, NIV).
In these verses, James is addressing the process of asking God for wisdom. The context is not about the kind of doubt that questions God’s existence or love, but about a specific type of doubt: a lack of commitment or double-mindedness when it comes to asking for something from God. James is highlighting the importance of trust and consistency in prayer and faith.
Now, this is where it gets tricky. It seems as though James is saying that any form of doubt disqualifies you from receiving God's wisdom, but what he’s actually pointing out is something deeper. The doubt James describes here is not the kind of doubt where you're struggling with your faith and trying to work through your questions. It’s a doubt that stems from being double-minded or divided in your loyalty—someone who isn’t fully committed to trusting in God's goodness and His ability to provide answers.
In other words, James is addressing those who are unable to decide whether they trust God enough to act in faith, or whether they will rely on their own understanding. This isn’t about wrestling with questions of faith, but about refusing to fully trust God and expecting Him to give you what you ask for without truly believing He will. The warning here is that divided loyalty in your faith—being uncertain whether to trust God or rely on your own solutions—leads to instability in your life.
How Does This Relate to Us Today?
If we look at this in light of our own lives, the point James is making is incredibly relevant. It’s okay to have questions, to wrestle with doubt, and to not always have complete clarity. But if your doubt leads you to question God’s ability, goodness, or willingness to act, then you're not fully trusting in Him. If you approach God in prayer with a heart that says, “I don’t think He’ll really answer this, but I’ll ask anyway,” that’s the kind of wavering that James warns against. Faith requires a kind of consistency in belief: that God is good, He is listening, and He has the power to answer—even when you don’t understand how or when.
What James seems to be saying is that doubt becomes problematic when it leads us to reject God’s goodness or power. It's not the occasional, fleeting doubt about one’s salvation or understanding of scripture that disqualifies us from receiving from God, but rather a refusal to commit fully to trusting God in our times of need.How Does This Relate to Us Today?
If we look at this in light of our own lives, the point James is making is incredibly relevant. It’s okay to have questions, to wrestle with doubt, and to not always have complete clarity. But if your doubt leads you to question God’s ability, goodness, or willingness to act, then you're not fully trusting in Him. If you approach God in prayer with a heart that says, “I don’t think He’ll really answer this, but I’ll ask anyway,” that’s the kind of wavering that James warns against. Faith requires a kind of consistency in belief: that God is good, He is listening, and He has the power to answer—even when you don’t understand how or when.
What James seems to be saying is that doubt becomes problematic when it leads us to reject God’s goodness or power. It's not the occasional, fleeting doubt about one’s salvation or understanding of scripture that disqualifies us from receiving from God, but rather a refusal to commit fully to trusting God in our times of need.
Practical Ways to Navigate Doubt in a Faith Tradition that Values Certainty
Acknowledge Your Doubts Without Shame \ The first step in navigating doubt is acknowledging it. Doubt doesn’t make you a bad Christian or unworthy of God’s love. You don’t need to hide your questions. Instead of feeling guilty, recognize that doubt is part of your spiritual journey, and it’s okay to ask questions. When we’re honest about our doubts, we give God space to meet us where we are.
Engage with Scripture Honestly \ Sometimes, we shy away from certain parts of the Bible because they challenge us or don’t make sense. But the Bible is full of complexity, contradictions, and depth—and that’s okay. Approach Scripture with curiosity and openness. It’s not about finding all the answers right away, but about engaging with the text and allowing it to speak to you in different seasons of your life.
Surround Yourself with a Supportive Community \ Find people who are willing to walk with you through your doubts. If you’re struggling with questions, it can be incredibly helpful to talk with someone who has navigated similar struggles. Surround yourself with people who are willing to explore faith openly and who won’t judge you for questioning.
Embrace the Mystery of Faith \ Faith is never about having all the answers. There will always be aspects of God’s character and His ways that remain mysterious to us. But instead of trying to solve every mystery, learn to embrace the mystery. Faith is trusting in the unknown, and sometimes the questions themselves are a beautiful part of the journey.
Remember That Jesus Loves You—Doubt and All \ Above all else, remember that Jesus loves you deeply, no matter where you are in your faith journey. He isn’t looking for perfection; He’s looking for honesty. Just as He met Thomas in his doubt, He will meet you too. There is no shame in your questions—only an invitation to deeper trust and intimacy with God.
Navigating doubt in a faith tradition that values certainty is hard. But remember, you’re not alone in your struggle. Doubt isn’t a sign of weakness; it’s an invitation to deepen your faith. Just as God met Thomas and the psalmist in their doubt, He will meet you where you are. Faith isn’t about having all the answers—it’s about trusting God with our questions.
So, friend, don’t be afraid of your doubts. They don’t disqualify you from God’s love or His plans for your life. They are simply part of the beautiful, messy, and deeply human journey of faith. Take it one step at a time, and know that, like me, you are loved by God no matter where you are on your spiritual path.
blog #christian #christianity #spirituality
-
 @ 266815e0:6cd408a5
2024-12-17 20:45:33
@ 266815e0:6cd408a5
2024-12-17 20:45:33Finally another version of noStrudel. I keep telling myself I'm going to do more frequent releases but then time keeps getting away from me
This release comes with a bunch of news features and most importantly a lot of cleanup
Features
Olas media posts
You can now view a simple feed of media posts made on https://olas.app/ in the app and comment on them using NIP-22 comments
Simple gif picker
This was mostly a test, but there is now a simple gif picker (and barely functional search) that is based on
k:1063events If you want a better search and to help populate the nostr gif library you can use https://gifbuddy.lol created by nostr:npub1hee433872q2gen90cqh2ypwcq9z7y5ugn23etrd2l2rrwpruss8qwmrsv6
New support view
The (tiny) support button at the bottom of the side menu now hides a zap leader board that shows top supporters and any custom messages they leave
Favorite DVM feeds
You can now favorite DVM feeds in the discover view
Tools under notes
There is now a simpler tools menu under notes and threads
Searching local cache relay
If your using nostr-relay-tray the search view will now use it by default for searching. which should make it a little faster and more reliable
Small features
- Add "Proactively authenticate to relays" option to privacy settings, defaults to off
- Add option for debug API
- Add option to hide noStrudel logo in nav bar
- Show unknown notifications in notification view
- Add templates to event publisher
Bug fixes
- Show nostr mentions in markdown content
- Fix delete events not getting published to outbox
- Fix page changing from RTL when viewing some profiles
- Refresh relay info on relay page
- Fix bug with removing "about" in profile editor
- Fix automatically disconnecting from authenticated relays
Applesauce
Over the past few months I've been doing tons of cleanup on the core of noStrudel (677 changed files with 19,683 additions and 17,889 deletions) and extracting it out into a friendly nostr SDK called applesauce
Its very much a work-in-progress but the idea with these libraries is to help myself (and maybe others) build the UI layer of nostr apps and eventually make noStrudel just another app that is built with applesauce
If your a developer and another nostr SDK sounds interesting to you. you can check out the Getting Started docs
-
 @ 1cb14ab3:95d52462
2024-12-17 19:24:54
@ 1cb14ab3:95d52462
2024-12-17 19:24:54Originally written in October 2022 (Block: 757258 / USD: $20.1k / SatsDollar: 4961). Refined with slight edits for publishing on Nostr in December 2024 (Block: 875189 / USD: $106k / SatsDollar: 938 ). Banner image property of Hes. My journey down the rabbit hole has only intensified since the time of writing. Enjoy.
The Bitcoin time perspective is wild. Reflecting on it has been profoundly eye-opening, and once it has been seen— there is no returning to our prior ways.
Ever since venturing down the rabbit hole that we call Bitcoin, I’ve started making significant life decisions and forming nuanced opinions on polarizing topics based on the implications of multi-generational timeframes. Before Bitcoin, I spent money recklessly, leading a fast-paced and impulsive lifestyle. Even in my early days of learning about Bitcoin, I hadn’t fully seen the light. I would still blow the occasional $500 bar tab or buy some flashy gadget I didn’t need. Living in the moment has its merits, but so does considering the time beyond our own lives. Now, I pause before purchases and decisions, always reflecting on how they might impact the future.
When your money isn’t constantly being devalued before your eyes, you start seeing the world differently. You begin saving for the future with confidence, knowing that no central authority can endlessly print away your hard-earned time and energy. Inflation doesn’t just erode purchasing power; it steals time. It destroys the hours, days, and years of effort represented by a lifetime of savings. When governments print money to prop up failing banks or fund inefficient ventures, the impact ripples through generations. Those at the bottom of the ladder are hit the hardest, their ability to save and plan for the future undermined by forces beyond their control. Decisions become focused on surviving today instead of thriving tomorrow, leaving little room to consider the long-term implications of our choices. This system creates a mindset where we are incentivized to spend now, instead of save for later—an unnatural phenomenon that most of us have accepted as normal.
For individuals who simply want to put away money for a rainy day, inflation is a relentless adversary. A dollar in 1900 has lost over 96% of its value. The countless hours of labor behind those savings have been stolen. Not only did the expansion of money destroy what they could buy, it stole our time and energy. Years of our lives—blood, sweat, and tears—washed away.
This isn’t just a historical problem—it’s a recurring one that occurs every decade or so and is accelerating. At an average inflation rate of 3%, the value of cash halves roughly every 23 years. This means that even modest inflation rates gradually diminish purchasing power over time, forcing individuals to chase speculative assets like stocks, real estate, and gold—not because they want to, but because they have no choice. Personal inflation rates differ depending on consumer habits, but a glance at rising prices reveals they often outpace the 2% annual rate reported by the government, which poses a significant problem for individua;s, as highlighted in the table below:
Corporations like McDonald’s understand this. Sitting on a prime corner lot in every major city is far smarter than stacking a pile of cash losing value. Even if the franchise is losing money, the building it operates in is guaranteed to “rise” in value over time. This mindset trickles down to everyday people. To protect themselves, they’re compelled to invest in assets—with real estate being the pinnacle savings instrument of our time. The financial system we’ve accepted as normal turns shelter into an investment vehicle and savings into a gamble.
But here’s the irony: real estate is a lousy store of value—which is what we are all truly seeking. Properties require constant maintenance. Without care, assets deteriorate. We’ve all seen abandoned theme parks and overgrown cities. We’ve all dealt with broken pipes and creaky floorboards. Why should saving our hard-earned wealth require us to become housing market experts, landlords, or property managers? Why should we pay financial advisors to manage stock portfolios full of companies whose values or practices we might not even believe in, just to beat inflation?
A flawed monetary system inflates bubbles in real estate and stocks, redirecting resources into speculative markets instead of productive investments. Imagine a world where people don’t have to read quarterly earnings reports after a long day of work to ensure their cash retains value. If the incentives driving these bubbles were removed, the financial landscape would dramatically shift. Inflation wouldn’t push people into markets like real estate or zombie companies; instead, they could focus on building or supporting businesses they genuinely care about. They could plan for the long term and make well-thought-out, rational decisions about their future.
Bitcoin takes this entire dynamic and flips it on its head. It isn’t a tool for speculation as often misunderstood. It is the best form of saving humanity has ever seen. Unlike fiat currencies, Bitcoin’s fixed supply ensures scarcity, making it a refuge from the erosion of wealth caused by inflation. As weak currencies flow into stronger ones (a concept known as Gresham’s Law), Bitcoin’s role as a store of value becomes clearer. It’s not that Bitcoin has “gone up 19,000%”—it’s that people are exchanging weaker money for stronger money.
The implications of a world on a Bitcoin standard extend far beyond monetary policy. It offers something unprecedented: a tool for transferring the value of labor and energy across time and space. Unlike fiat, Bitcoin allows time to be preserved across generations. It isn’t just a hedge against inflation—it reintroduces the idea of saving with confidence, of being able to store wealth in a form of money that cannot be manipulated or devalued.
By saving in Bitcoin, individuals are no longer tethered to the uncertainties of fiat systems. The Bitcoin time perspective is about aligning our actions today with the future we want to build tomorrow. It’s about prioritizing long-term impact over short-term gains. When you embrace Bitcoin, you embrace a mindset that values time, energy, and the well-being of future generations. It’s not just a currency; it’s a revolution in thinking that will change you forever. The past, present, and future converge in this new paradigm, offering hope in an otherwise uncertain world.
Bitcoin isn’t a bubble; it’s a beacon.
More from Hes:
-
 @ c48e29f0:26e14c11
2024-12-17 16:33:04
@ c48e29f0:26e14c11
2024-12-17 16:33:04titcoin
Rename Bitcoin to "Titcoin" and sats to "tits."
Redefinition of Bitcoin into “Titcoin” and redefinition of sats into “tits” using that as the Unit Base of Denomination.
TitHub repository available here: https://github.com/WalkerAmerica/titcoin
Abstract
This BIP proposes redefining the commonly recognized "bitcoin" and “sats” units so that what was previously known “bitcoin” becomes “titcoin” and what was previously known as “sats,” the smallest indivisible unit, becomes “tits.” The “Bitcoin” Network will be renamed to the “Titcoin” Network. Under this proposal, one tit is defined as that smallest unit, eliminating the need for decimal places, and 100,000,000 tits is defined as a titcoin. By making tits the standard measure, this BIP aims to simplify user comprehension, reduce confusion, and align on-chain values directly with their displayed representation.
Also, by aligning Bitcoin's brand with live-giving tits, we will supercharge adoption and inject humor into financial sovereignty. After all, every baby came into this world sucking on tits.
Under this BIP: - Internally, the smallest indivisible unit remains unchanged. - With this proposal, "1 tit" equals that smallest unit. - What was previously referred to as "1 BTC" now corresponds to 100 million tits. - Satoshis are permanently eliminated.
Addressing the “Buttcoin” BIP:
Not much time need be wasted addressing the catastrophic “Button” BIP proposed by Rockstar Dev, but two points bear emphasizing:
- “Butts” is shitcoin-adjacent terminology (where does shit come from? Exactly…)
- Butts give you poop. Tits give you milk.
Case closed.
Motivation
Bitcoin's branding is boring. Worse yet, critics think Bitcoin is already "a joke," so let’s own it, let's: Make Bitcoin Funny Again. Laughter is universal, irresistible, and much cheaper than marketing agencies and product roadmaps. Besides, basically everyone either has tits or likes tits. Additionally, renaming Bitcoin as “Titcoin” makes the common trope of “Bitcoin BROS” sound even more stupid. “Titcoin Bros”? Get a life, man…
By rebranding Bitcoin to Titcoin (.)(.), we achieve several key goals:
1. Haters Become Users: People like tits. Tits give nourishment to babies. They can stack tits instead of just making fun of them. Adoption skyrockets as trolls turn into tit hodlers.
2. Memetic Power: The word “tit” is both universally funny and ageless. “Send me 10 tits” is instantly iconic. “Nice tits” is a great compliment. “That’s gonna cost you a pair of tits” is hilarious. Try saying that without smiling. You can’t. (.)(.)
3. Simplifying Denominations: Decimals are a blight on humanity. 0.00000001 BTC? Kill it. Under the Titcoin Standard:
- 1 Titcoin = 100,000,000 tits.
- Satoshis are gone. Forever. If you see Satoshi on the road, kill him - just like in Zen, where the teacher becomes the barrier. We transcend satoshis and achieve financial enlightenment.
4. Aligning with the Ledger: Bitcoin’s base unit was always integers, but now they’re funny integers. No more fractions, decimals, or math anxiety. Just tits. (.)(.)
5. Adoption via Humor: Titcoin lowers Bitcoin's intimidation factor. Newbies will feel at ease buying tits instead of serious-sounding fractions of BTC. Tits > Decimals.
Specification
Terminology Redefinitions: - "Bitcoin" → "Titcoin" (.)(.) - "BTC" → "TIT" (ISO-friendly and hilarious) - Satoshis → Gone. Eliminated. Defeated.
Example:
- Old: "I’ll send you 0.00010000 BTC."
- New: "I’ll send you 10,000 tits (.)(.)."
Wallet balances would display as:
- "You have 1,000,000 tits" instead of some boring fractional BTC amount.
Adoption Strategy
1. Memes First: Flood Twitter, Reddit, and Telegram with memes. Start with “Hodl your tits” and “Stack tits”.
2. Titcoin Podcast: There is already a podcast called “Titcoin Podcast” (which many people are saying is the fastest-growing Bitcoin (Titcoin) podcast in the world). Titcoin Podcast will be a driving force in the adoption of the Titcoin Standard. (.)(.)
Nostr: https://primal.net/titcoin
X: https://x.com/titcoinpodcast
Web: http://titcoin.org
3. Kill Satoshis: Developers MUST remove all references to satoshis. Replace satoshis in GUIs, APIs, and block explorers with tits. Satoshis were a stepping stone - it’s time to let go.
4. Emoji Standardization: Use the (.)(.) emoji universally to denote tits.
Rationale
1. Usability & Clarity: "Decimals are for nerds. Tits are for everyone." A common currency for humans should be easy to use, funny, and integer-based.
2. Appealing to Critics: Bitcoin has endured years of attacks from all sides. By adopting the Titcoin Standard, we turn anyone who doesn’t like Titcoin into a tit-hating bigot. It’s an elegant financial counterattack. Additionally, everyone always says “we need more women in Bitcoin,” and now women will feel more represented by Titcoin, because they have tits. (.)(.)
3. Transcending Satoshis: Satoshis served us well, but their time is over. True enlightenment comes when we abandon decimals, satoshis, and arbitrary denominations. If you meet Satoshi on the road, kill him.
4. Memetic Durability: Everyone loves a good tit joke. It’s timeless.
Backward Compatibility
There is no backward compatibility because Titcoin is the future. Applications must hard fork their UI to replace all references to Bitcoin and BTC with Titcoin and TIT.
Implementation Timeline
- Phase 1 (1 month): Meme dissemination. Every wallet dev team is required to add (.)(.) emoji support.
- Phase 2 (3 months): Exchanges rebrand BTC tickers to tit. Nostr zaps tits into hyperspace.
- Phase 3 (6 months): Michael Saylor announces MicroStrategy now stacked 10 trillion tits, declaring it the superior currency. ETFs follow suit, ensuring Wall Street hodls tits en masse. Banks allow tit transfers via SWIFT.
Test Vectors
- Old: 1.00000000 BTC → New: 100,000,000 tits (.)(.)
- Old: 0.00000001 BTC → New: 1 tit (.)(.)
- Old: 0.001 BTC → New: 100,000 tits (.)(.)
Future-Proofing
Tits ensure we have infinite memes for infinite money.
Example Phrases for the Future: - "Better hodl on to your tits." - "This is the Titcoin Standard." - "I’m sending you tits." - “I’ve never seen so many tits!” - “That’s the million tit question.” - “We need more women in Titcoin.” - “I’m a Titcoin Maximalist.” - “Nice tits!” - “I love tits.”
Conclusion
By renaming Bitcoin to Titcoin and adopting a whole-number unit display, we align memetic dominance with financial sovereignty. Haters become adopters. Tits become wealth. And the world gets a little bit funnier. (.)(.)
Let’s hodl our tits and watch the world follow.
Copyright:
This BIP is licensed under CC-🫱(.)(.)🫲-1.0 and the eternal blessing of tit (.)(.) memes.
-
 @ 9d4a1e9e:322f816a
2024-12-17 11:59:30
@ 9d4a1e9e:322f816a
2024-12-17 11:59:30Introduction
I am a BTC maximalist, but on my journey toward Bitcoin, I had many questions and fears that held me back from buying the best money in the world. Looking back, I now realize that all my fears stemmed from a misunderstanding of the Bitcoin protocol.
Today, I find myself in a similar situation with Nostr. Could you — Nostr heroes, developers, and legends — help a newbie better understand the Nostr network?
POINT 1: Nostr will never become a widely adopted network
I think I understand the benefits of Nostr, but, like many of you here, I’m not a typical social media user. I highly value privacy, freedom of speech, decentralization, and real ownership of money and data. I see many like-minded individuals here, but who else would have the motivation to start using Nostr?
Content creators? Those whose accounts were canceled or shadow-banned on platforms like Facebook or Instagram? Unlikely — their audience simply isn’t here. Consumers? Again, unlikely — their friends aren’t here, and they don’t care about Nostr’s benefits. They’ve never been banned, and they believe current social networks are truly free. I’m curious: how many users on Nostr are not connected to Nostr or Lightning development? I just can’t imagine an event that would cause users to start switching en masse to this network.
>> What could motivate regular social media users to try Nostr?
POINT 2: No marketing
Nostr is currently a niche, nerdy space. But so what? Bitcoin was in a similar position just a few years ago. However, Bitcoin is money — and money, as a source of power, has always attracted people. Plus, Bitcoin’s rising price serves as an automated global marketing campaign. Many people also have an incentive to promote Bitcoin because they earn money from trading platforms or related services.
With Nostr, there’s no equivalent incentive structure.
>> Who will promote Nostr?
POINT 3: Trust in the Nostr system
The Bitcoin protocol has already shown us that the best systems are trustless. Currently, it's customary to pay "zaps." We assume some users will do this, but, in my opinion, most creators will find it easier (and more profitable) to use platforms like Patreon or HeroHero. These platforms allow creators to put content behind a solid paywall rather than relying on voluntary user donations. Is similar model possible on Nostr? Is really the trust in user donations really the right direction?
>> Why should creators offer their content for free and depend on user donations?
-
 @ 6ad3e2a3:c90b7740
2024-12-16 15:28:00
@ 6ad3e2a3:c90b7740
2024-12-16 15:28:00I believe in the notion of truth. Not merely propositional truth like 2 + 2 = 4, though that too, but also the idea that what someone says can be authentic, profound and true.
Another aspect of truth is beauty. I think music can be harmonious and art aesthetically true. I don’t claim to have special knowledge over what is true, beautiful or harmonious, only that those things exist, and human beings can discern them. I also believe in justice which in my view is moral truth.
Truth, beauty and justice exist even if we are not personally able to recognize them. In other words, while they are perceptible to human beings generally, any particular person or group might miss them.
One example that comes to mind is if you renovate a home. You and your architect might disagree about the layout. Imagine he persuades you to trust him, and you discover he was correct, the house is more harmonious, proportionate and beautiful than had you done it your way. The aesthetic truth for that house was not what you had imagined, but it existed, and you were lucky someone else had the eye for it.
. . .
I don’t write much about what’s going on in Israel and Palestine because I’m not interested in it. I’m not interested in it because it doesn’t affect my immediate existence, and those who are interested in it mostly seem to be closed-minded and emotional about the topic. Because I am not into it, I am not especially informed, nor am I inclined to inform myself better. As far as I can tell, it’s a depressing and tiresome argument between two miserable factions.
That said, the topic sometimes comes up in part because I’m Jewish and know a lot of Jews who care about it and also because I follow people on Twitter on both sides who also care about it. For that reason, I’m aware of some of the narratives that are presented and consequently I’ve formulated two main ideas about it, two axioms, so to speak:
(1) Whatever is the just (morally true) result — whether Israel shutting down and leaving the region, Israel conquering and annexing Palestinian territories entirely, or more likely something in between — that's what I would like to see happen.
In other words, no matter how much anyone in particular might disagree with it, the just result, whatever it might be, is the outcome for which I’m rooting.
People will argue for what they think is just based on various narratives, but I hope for what is actually just, irrespective of those narratives. And I believe such a result must exist, even though I am in no position whatsoever to say what that result would be.
(2) To the extent some people think Palestinians are incorrigible barbaric terrorists and others think Israel (and even "the Jews" more broadly) are incorrigible genocidal maniacs, consider that sense of incorrigibility is directed by both parties at both parties.
In other words, at least one of you* incorrectly believes the other is inherently beyond redemption, and just as they would be mistaken in believing that about you, you could also be mistaken in believing it about them. In fact, the greater your certainty about their inherent evil, the more difficult it is for you to course-correct, and the closer to their description you actually become. Paradoxically, the more sure you are of who they are, the more correct they are about you.
Before anything approaching a concrete answer to this problem can emerge, I think it's important to realize (1) A just outcome that does not depend on anyone's narrative exists; and (2) That the extent to which you view your adversaries as beyond redemption you most resemble their description of you.
If we accept these two axioms, that justice is possible, and that viewing the other side as incorrigible is a hallmark of one’s own zealotry, we have established the ground upon which a solution is possible. If we reject them, no amount of discussion will ever bear fruit.
*Some people might think both are beyond redemption, in which case this post is moot, and there is no just outcome, only might makes right. I think that kind of cynicism is the road to hell.
-
 @ ee11a5df:b76c4e49
2024-12-16 05:29:30
@ ee11a5df:b76c4e49
2024-12-16 05:29:30Nostr 2?
Breaking Changes in Nostr
Nostr was a huge leap forward. But it isn't perfect.
When developers notice a problem with nostr, they confer with each other to work out a solution to the problem. This is usually in the form of a NIP PR on the nips repo.
Some problems are easy. Just add something new and optional. No biggie. Zaps, git stuff, bunkers... just dream it up and add it.
Other problems can only be fixed by breaking changes. With a breaking change, the overall path forward is like this: Add the new way of doing it while preserving the old way. Push the major software to switch to the new way. Then deprecate the old way. This is a simplification, but it is the basic idea. It is how we solved markers/quotes/root and how we are upgrading encryption, among other things.
This process of pushing through a breaking change becomes more difficult as we have more and more existing nostr software out there that will break. Most of the time what happens is that the major software is driven to make the change (usually by nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6), and the smaller software is left to fend for itself. A while back I introduced the BREAKING.md file to help people developing smaller lesser-known software keep up with these changes.
Big Ideas
But some ideas just can't be applied to nostr. The idea is too big. The change is too breaking. It changes something fundamental. And nobody has come up with a smooth path to move from the old way to the new way.
And so we debate a bunch of things, and never settle on anything, and eventually nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 makes a post saying that we don't really want it anyways 😉.
As we encounter good ideas that are hard to apply to nostr, I've been filing them away in a repository I call "nostr-next", so we don't forget about them, in case we ever wanted to start over.
It seems to me that starting over every time we encountered such a thing would be unwise. However, once we collect enough changes that we couldn't reasonably phase into nostr, then a tipping point is crossed where it becomes worthwhile to start over. In terms of the "bang for the buck" metaphor, the bang becomes bigger and bigger but the buck (the pain and cost of starting over) doesn't grow as rapidly.
WHAT? Start over?
IMHO starting over could be very bad if done in a cavalier way. The community could fracture. The new protocol could fail to take off due to lacking the network effect. The odds that a new protocol catches on are low, irrespective of how technically superior it could be.
So the big question is: can we preserve the nostr community and it's network effect while making a major step-change to the protocol and software?
I don't know the answer to that one, but I have an idea about it.
I think the new-protocol clients can be dual-stack, creating events in both systems and linking those events together via tags. The nostr key identity would still be used, and the new system identity too. This is better than things like the mostr bridge because each user would remain in custody of their own keys.
The nitty gritty
Here are some of the things I think would make nostr better, but which nostr can't easily fix. A lot of these ideas have been mentioned before by multiple people and I didn't give credit to all of you (sorry) because my brain can't track it all. But I've been collecting these over time at https://github.com/mikedilger/nostr-next
- Events as CBOR or BEVE or MsgPack or a fixed-schema binary layout... anything but JSON text with its parsing, it's encoding ambiguity, it's requirement to copy fields before hashing them, its unlimited size constraints. (me, nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s)
- EdDSA ed25519 keys instead of secp256k1, to enable interoperability with a bunch of other stuff like ssh, pgp, TLS, Mainline DHT, and many more, plus just being better cryptography (me, Nuh, Orlovsky, except Orlovsky wanted Ristretto25519 for speed)
- Bootstrapping relay lists (and relay endpoints) from Mainline DHT (nostr:npub1jvxvaufrwtwj79s90n79fuxmm9pntk94rd8zwderdvqv4dcclnvs9s7yqz)
- Master keys and revocable subkeys / device keys (including having your nostr key as a subkey)
- Encryption to use different encryption-specific subkeys and ephemeral ones from the sender.
- Relay keypairs, TLS without certificates, relays known by keypair instead of URL
- Layered protocol (separate core from applications)
- Software remembering when they first saw an event, for 2 reasons, the main one being revocation (don't trust the date in the event, trust when you first saw it), the second being more precise time range queries.
- Upgrade/feature negotiation (HTTP headers prior to starting websockets)
- IDs starting with a timestamp so they are temporally adjacent (significantly better database performance) (Vitor's idea)
- Filters that allow boolean expressions on tag values, and also ID exclusions. Removing IDs from filters and moving to a GET command.
- Changing the transport (I'm against this but I know others want to)
What would it look like?
Someone (Steve Farroll) has taken my nostr-next repo and turned it into a proposed protocol he calls Mosaic. I think it is quite representative of that repo, as it already includes most of those suggestions, so I've been contributing to it. Mosaic spec is rendered here.
Of course, where Mosaic stands right now it is mostly my ideas (and Steve's), it doesn't have feedback or input from other nostr developers yet. That is what this blog post is about. I think it is time for other nostr devs to be made aware of this thing.
It is currently in the massive breaking changes phase. It might not look that way because of the detail and refinement of the documentation, but indeed everything is changing rapidly. It probably has some bad ideas and is probably missing some great ideas that you have.
Which is why this is a good time for other devs to start taking a look at it.
It is also the time to debate meta issues like "are you crazy Mike?" or "no we have to just break nostr but keep it nostr, we can't dual-stack" or whatever.
Personally I think mosaic-spec should develop and grow for quite a while before the "tipping point" happens. That is, I'm not sure we should jump in feet first yet, but rather we build up and refine this new protocol and spend a lot of time thinking about how to migrate smoothly, and break it a lot while nobody is using it.
So you can just reply to this, or DM me, or open issues or PRs at Mosaic, or just whisper to each other while giving me the evil eye.


