-
 @ 7f29628d:e160cccc
2025-01-07 11:50:30
@ 7f29628d:e160cccc
2025-01-07 11:50:30Der gut informierte Bürger denkt bei der Pandemie sofort an Intensivstationen, an die Bilder aus Bergamo und erinnert sich an die Berichterstattung damals – also muss es wohl ein Maximum gewesen sein. Manche Skeptiker behaupten jedoch das Gegenteil. Klarheit sollte ein Blick nach Wiesbaden, zum Statistischen Bundesamt, schaffen. Schließlich sitzen dort gut bezahlte Profis, die seit vielen Jahrzehnten die Sterbestatistik pflegen und veröffentlichen. Jeder Todesfall wird in Deutschland über die Standesämter exakt erfasst.
Doch die Überraschung: Das Statistische Bundesamt liefert uns auf diese einfache Frage zwei extrem unterschiedliche Antworten – ein Minimum und ein Maximum. Das Ergebnis hängt davon ab, wie tief man in die Veröffentlichungen des Bundesamtes eintaucht. Betrachtet man nur die Webseiten und Pressemitteilungen, erhält man den Eindruck eines Maximums. Schaut man jedoch etwas tiefer in die Tabellen und Rohdaten, zeigt sich plötzlich ein Minimum. Aber wie kann das sein? Beides gleichzeitig geht ja wohl kaum. Wer lügt hier – die Tabellen des Amtes oder die Pressemitteilungen? Gehen wir dieser Frage Schritt für Schritt auf den Grund.
2020: Ein historisches Maximum?
Schauen wir uns die vielen Hundert Veröffentlichungen des Statistischen Bundesamtes aus dieser Zeit an. Oder wir kürzen ab und fragen ChatGPT, da die KI auf diesen Daten trainiert wurde und das gesamte Material kennt. Die Frage an ChatGPT lautet also: Wie war das Sterbegeschehen im Jahr 2020 im Vergleich zu den Vorjahren?
ChatGPT antwortet: »Im Jahr 2020 war die Sterblichkeit in Deutschland höher als in den Jahren zuvor. Es gab eine Übersterblichkeit von etwa 982.000 Todesfällen, das sind rund 46.000 mehr als der Durchschnitt der Vorjahre (2016 bis 2019). Dieser Anstieg wurde überwiegend im Zusammenhang mit der COVID-19-Pandemie gesehen. Während die Sterbezahlen in den Vorjahren schwankten, war ein solch signifikanter Anstieg wie 2020 bisher nicht zu beobachten.«
Wir fragen konkreter: Ist es ein Fakt, dass wir eine so ernste Lage im Sterbegeschehen wie im Frühjahr 2020 noch nie erlebt haben?
ChatGPT bestätigt: »Ja, die COVID-19-Pandemie führte im Frühjahr 2020 zu einer außergewöhnlichen Situation im Sterbegeschehen in Deutschland. Die dramatische Übersterblichkeit, die ab der 13. Kalenderwoche auftrat, veranlasste das Statistische Bundesamt, besonders eindringliche Warnungen zu veröffentlichen. Der damalige Vizepräsident des Amtes und andere führende Stimmen wiesen öffentlich darauf hin, dass die Todesfallzahlen stark vom Durchschnitt abwichen. Diese klare Warnung richtete sich an die Öffentlichkeit und die Politik gleichermaßen. Die Medien berichteten intensiv über diese Warnungen, was das Bewusstsein für die Schwere der Pandemie erheblich schärfte. In den vergangenen Jahrzehnten hatte es keine vergleichbare Übersterblichkeit gegeben, die eine solch umfangreiche Kommunikation durch das Statistische Bundesamt erforderlich gemacht hätte.«
Ein gut informierter Zeitungsleser wird sich an dieser Stelle bestätigt fühlen: Ja, so war es damals. Ein Maximum im Sterbegeschehen – wegen der Pandemie. Oder etwa nicht?
2020: Ein historisches Minimum?
Tauchen wir in die Rohdaten des Statistischen Bundesamtes ein. Die Tabellen, die das Amt seit Jahrzehnten verlässlich veröffentlicht, nennen sich Sterbetafeln. Diese werden jährlich bereitgestellt und stehen auf der Website des Bundesamtes zum Download bereit. Ein erster Blick in die Sterbetafeln mag den Laien abschrecken, doch mit einer kurzen Erklärung wird alles verständlich. Wir gehen schrittweise vor.
Nehmen wir die Sterbetafel des Jahres 2017. Sie enthält zwei große Tabellen – eine für Männer und eine für Frauen. Jede Zeile der Tabelle steht für einen Jahrgang, zum Beispiel zeigt die Zeile 79 die Daten der 79-jährigen Männer. Besonders wichtig ist nun die zweite Spalte, in der der Wert 0,05 eingetragen ist. Das bedeutet, dass 5 Prozent der 79-jährigen Männer im Jahr 2017 verstorben sind. Das ist die wichtige Kennzahl. Wenn wir diesen exakten Wert, den man auch als Sterberate bezeichnet, nun in ein Säulendiagramm eintragen, erhalten wir eine leicht verständliche visuelle Darstellung (Grafik 1).

Es ist wichtig zu betonen, dass dieser Wert weder ein Schätzwert noch eine Modellrechnung oder Prognose ist, sondern ein exakter Messwert, basierend auf einer zuverlässigen Zählung. Sterberaten (für die Fachleute auch Sterbewahrscheinlichkeiten qx) sind seit Johann Peter Süßmilch (1707–1767) der Goldstandard der Sterbestatistik. Jeder Aktuar wird das bestätigen. Fügen wir nun die Sterberaten der 79-jährigen Männer aus den Jahren davor und danach hinzu, um das Gesamtbild zu sehen (Grafik 2). Und nun die entscheidende Frage: Zeigt das Jahr 2020 ein Maximum oder ein Minimum?

Ein kritischer Leser könnte vermuten, dass die 79-jährigen Männer eine Ausnahme darstellen und andere Jahrgänge im Jahr 2020 ein Maximum zeigen würden. Doch das trifft nicht zu. Kein einziger Jahrgang verzeichnete im Jahr 2020 ein Maximum. Im Gegenteil: Auch die 1-Jährigen, 2-Jährigen, 3-Jährigen, 9-Jährigen, 10-Jährigen, 15-Jährigen, 18-Jährigen und viele weitere männliche Jahrgänge hatten ihr Minimum im Jahr 2020. Dasselbe gilt bei den Frauen. Insgesamt hatten 31 Jahrgänge ihr Minimum im Jahr 2020. Wenn wir schließlich alle Jahrgänge in einer einzigen Grafik zusammenfassen, ergibt sich ein klares Bild: Das Minimum im Sterbegeschehen lag im Jahr 2020 (Grafik 3).

Ein kritischer Leser könnte nun wiederum vermuten, dass es innerhalb des Jahres 2020 möglicherweise starke Ausschläge nach oben bei einzelnen Jahrgängen gegeben haben könnte, die später durch Ausschläge nach unten ausgeglichen wurden – und dass diese Schwankungen in der jährlichen Übersicht nicht sichtbar sind. Doch auch das trifft nicht zu. Ein Blick auf die wöchentlichen Sterberaten zeigt, dass die ersten acht Monate der Pandemie keine nennenswerten Auffälligkeiten aufweisen. Es bleibt dabei: Die Rohdaten des Statistischen Bundesamtes bestätigen zweifelsfrei, dass die ersten acht Monate der Pandemie das historische Minimum im Sterbegeschehen darstellen. (Für die Fachleute sei angemerkt, dass im gleichen Zeitraum die Lebenserwartung die historischen Höchststände erreicht hatte – Grafik 4.)

So konstruierte das Amt aus einem Minimum ein Maximum:
Zur Erinnerung: Die Rohdaten des Statistischen Bundesamtes, die in den jährlichen Sterbetafeln zweifelsfrei dokumentiert sind, zeigen für das Jahr 2020 eindeutig ein Minimum im Sterbegeschehen. Aus diesen »in Stein gemeißelten« Zahlen ein Maximum zu »konstruieren«, ohne die Rohdaten selbst zu verändern, scheint auf den ersten Blick eine unlösbare Aufgabe. Jeder Student würde an einer solchen Herausforderung scheitern. Doch das Statistische Bundesamt hat einen kreativen Weg gefunden - ein Meisterstück gezielter Manipulation. In fünf Schritten zeigt sich, wie diese Täuschung der Öffentlichkeit umgesetzt wurde:
(1) Ignorieren der Sterberaten: Die präzisen, objektiven und leicht verständlichen Sterberaten aus den eigenen Sterbetafeln wurden konsequent ignoriert und verschwiegen. Diese Daten widersprachen dem gewünschten Narrativ und wurden daher gezielt ausgeklammert.
(2) Fokus auf absolute Todeszahlen: Die Aufmerksamkeit wurde stattdessen auf die absolute Zahl der Todesfälle gelenkt. Diese wirkt allein durch ihre schiere Größe dramatisch und emotionalisiert die Diskussion. Ein entscheidender Faktor wurde dabei ignoriert: Die absolute Zahl der Todesfälle steigt aufgrund der demografischen Entwicklung jedes Jahr an. Viele Menschen verstehen diesen Zusammenhang nicht und verbinden die steigenden Zahlen fälschlicherweise mit der vermeintlichen Pandemie.
(3) Einführung der Übersterblichkeit als neue Kennzahl: Erst ab Beginn der „Pandemie“ wurde die Kennzahl "Übersterblichkeit" eingeführt – und dies mit einer fragwürdigen Methode, die systematisch überhöhte Werte lieferte. Diese Kennzahl wurde regelmäßig, oft monatlich oder sogar wöchentlich, berechnet und diente als ständige Grundlage für alarmierende Schlagzeilen.
(4) Intensive Öffentlichkeitsarbeit: Durch eine breit angelegte Kampagne wurden die manipulativen Kennzahlen gezielt in den Fokus gerückt. Pressemitteilungen, Podcasts und öffentliche Auftritte konzentrierten sich fast ausschließlich auf die absoluten Todeszahlen und die Übersterblichkeit. Ziel war es, den Eindruck einer dramatischen Situation in der Öffentlichkeit zu verstärken.
(5) Bekämpfen kritischer Stimmen: Kritiker, die die Schwächen und manipulativen Aspekte dieser Methoden aufdeckten, wurden systematisch diskreditiert. Ihre Glaubwürdigkeit und Kompetenz wurden öffentlich infrage gestellt, um das sorgsam konstruierte Narrativ zu schützen.
Ohne diesen begleitenden Statistik-Betrug wäre das gesamte Pandemie-Theater meiner Meinung nach nicht möglich gewesen. Wer aus einem faktischen Minimum ein scheinbares Maximum "erschafft", handelt betrügerisch. Die Folgen dieses Betruges sind gravierend. Denken wir an die Angst, die in der Bevölkerung geschürt wurde – die Angst, bald sterben zu müssen. Denken wir an Masken, Abstandsregeln, isolierte ältere Menschen, Kinderimpfungen und all die Maßnahmen, die unter anderem auf diese falsche Statistik zurückgehen.
Wollen wir Bürger uns das gefallen lassen?
Wenn wir als Bürger zulassen, dass ein derart offensichtlicher und nachprüfbarer Täuschungsversuch ohne Konsequenzen bleibt, dann gefährdet das nicht nur die Integrität unserer Institutionen – es untergräbt das Fundament unserer Gesellschaft. In der DDR feierte man öffentlich Planerfüllung und Übererfüllung, während die Regale leer blieben. Damals wusste jeder: Statistik war ein Propagandainstrument. Niemand traute den Zahlen, die das Staatsfernsehen verkündete.
Während der Pandemie war es anders. Die Menschen vertrauten den Mitteilungen des Statistischen Bundesamtes und des RKI – blind. Die Enthüllungen durch den "RKI-Leak" haben gezeigt, dass auch das Robert-Koch-Institut nicht der Wissenschaft, sondern den Weisungen des Gesundheitsministers und militärischen Vorgaben folgte. Warum sollte es beim Statistischen Bundesamt anders gewesen sein? Diese Behörde ist dem Innenministerium unterstellt und somit ebenfalls weisungsgebunden.
Die Beweise für Täuschung liegen offen zutage. Es braucht keinen Whistleblower, keine geheimen Enthüllungen: Die Rohdaten des Statistischen Bundesamtes sprechen für sich. Sie sind öffentlich einsehbar – klar und unmissverständlich. Die Daten, die Tabellen, die Veröffentlichungen des Amtes selbst – sie sind die Anklageschrift. Sie zeigen, was wirklich war. Nicht mehr und nicht weniger.
Und wir? Was tun wir? Schweigen wir? Oder fordern wir endlich ein, was unser Recht ist? Wir Bürger dürfen das nicht hinnehmen. Es ist Zeit, unsere Behörden zur Rechenschaft zu ziehen. Diese Institutionen arbeiten nicht für sich – sie arbeiten für uns. Wir finanzieren sie, und wir haben das Recht, Transparenz und Verantwortung einzufordern. Manipulationen wie diese müssen aufgearbeitet werden und dürfen nie wieder geschehen. Die Strukturen, die solche Fehlentwicklungen in unseren Behörden ermöglicht haben, müssen offengelegt werden. Denn eine Demokratie lebt von Vertrauen – und Vertrauen muss verdient werden. Jeden Tag aufs Neue.
.
.
MARCEL BARZ, Jahrgang 1975, war Offizier der Bundeswehr und studierte Wirtschafts- und Organisationswissenschaften sowie Wirtschaftsinformatik. Er war Gründer und Geschäftsführer einer Softwarefirma, die sich auf Datenanalyse und Softwareentwicklung spezialisiert hatte. Im August 2021 veröffentlichte Barz den Videovortrag »Die Pandemie in den Rohdaten«, der über eine Million Aufrufe erzielte. Seitdem macht er als "Erbsenzähler" auf Widersprüche in amtlichen Statistiken aufmerksam.
-
 @ eac63075:b4988b48
2025-01-04 19:41:34
@ eac63075:b4988b48
2025-01-04 19:41:34Since its creation in 2009, Bitcoin has symbolized innovation and resilience. However, from time to time, alarmist narratives arise about emerging technologies that could "break" its security. Among these, quantum computing stands out as one of the most recurrent. But does quantum computing truly threaten Bitcoin? And more importantly, what is the community doing to ensure the protocol remains invulnerable?
The answer, contrary to sensationalist headlines, is reassuring: Bitcoin is secure, and the community is already preparing for a future where quantum computing becomes a practical reality. Let’s dive into this topic to understand why the concerns are exaggerated and how the development of BIP-360 demonstrates that Bitcoin is one step ahead.
What Is Quantum Computing, and Why Is Bitcoin Not Threatened?
Quantum computing leverages principles of quantum mechanics to perform calculations that, in theory, could exponentially surpass classical computers—and it has nothing to do with what so-called “quantum coaches” teach to scam the uninformed. One of the concerns is that this technology could compromise two key aspects of Bitcoin’s security:
- Wallets: These use elliptic curve algorithms (ECDSA) to protect private keys. A sufficiently powerful quantum computer could deduce a private key from its public key.
- Mining: This is based on the SHA-256 algorithm, which secures the consensus process. A quantum attack could, in theory, compromise the proof-of-work mechanism.
Understanding Quantum Computing’s Attack Priorities
While quantum computing is often presented as a threat to Bitcoin, not all parts of the network are equally vulnerable. Theoretical attacks would be prioritized based on two main factors: ease of execution and potential reward. This creates two categories of attacks:
1. Attacks on Wallets
Bitcoin wallets, secured by elliptic curve algorithms, would be the initial targets due to the relative vulnerability of their public keys, especially those already exposed on the blockchain. Two attack scenarios stand out:
-
Short-term attacks: These occur during the interval between sending a transaction and its inclusion in a block (approximately 10 minutes). A quantum computer could intercept the exposed public key and derive the corresponding private key to redirect funds by creating a transaction with higher fees.
-
Long-term attacks: These focus on old wallets whose public keys are permanently exposed. Wallets associated with Satoshi Nakamoto, for example, are especially vulnerable because they were created before the practice of using hashes to mask public keys.
We can infer a priority order for how such attacks might occur based on urgency and importance.
 Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)
Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)2. Attacks on Mining
Targeting the SHA-256 algorithm, which secures the mining process, would be the next objective. However, this is far more complex and requires a level of quantum computational power that is currently non-existent and far from realization. A successful attack would allow for the recalculation of all possible hashes to dominate the consensus process and potentially "mine" it instantly.
 Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin Attacks
Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin AttacksRecently, Narcelio asked me about a statement I made on Tubacast:
https://x.com/eddieoz/status/1868371296683511969
If an attack became a reality before Bitcoin was prepared, it would be necessary to define the last block prior to the attack and proceed from there using a new hashing algorithm. The solution would resemble the response to the infamous 2013 bug. It’s a fact that this would cause market panic, and Bitcoin's price would drop significantly, creating a potential opportunity for the well-informed.
Preferably, if developers could anticipate the threat and had time to work on a solution and build consensus before an attack, they would simply decide on a future block for the fork, which would then adopt the new algorithm. It might even rehash previous blocks (reaching consensus on them) to avoid potential reorganization through the re-mining of blocks using the old hash. (I often use the term "shielding" old transactions).
How Can Users Protect Themselves?
While quantum computing is still far from being a practical threat, some simple measures can already protect users against hypothetical scenarios:
- Avoid using exposed public keys: Ensure funds sent to old wallets are transferred to new ones that use public key hashes. This reduces the risk of long-term attacks.
- Use modern wallets: Opt for wallets compatible with SegWit or Taproot, which implement better security practices.
- Monitor security updates: Stay informed about updates from the Bitcoin community, such as the implementation of BIP-360, which will introduce quantum-resistant addresses.
- Do not reuse addresses: Every transaction should be associated with a new address to minimize the risk of repeated exposure of the same public key.
- Adopt secure backup practices: Create offline backups of private keys and seeds in secure locations, protected from unauthorized access.
BIP-360 and Bitcoin’s Preparation for the Future
Even though quantum computing is still beyond practical reach, the Bitcoin community is not standing still. A concrete example is BIP-360, a proposal that establishes the technical framework to make wallets resistant to quantum attacks.
BIP-360 addresses three main pillars:
- Introduction of quantum-resistant addresses: A new address format starting with "BC1R" will be used. These addresses will be compatible with post-quantum algorithms, ensuring that stored funds are protected from future attacks.
- Compatibility with the current ecosystem: The proposal allows users to transfer funds from old addresses to new ones without requiring drastic changes to the network infrastructure.
- Flexibility for future updates: BIP-360 does not limit the choice of specific algorithms. Instead, it serves as a foundation for implementing new post-quantum algorithms as technology evolves.
This proposal demonstrates how Bitcoin can adapt to emerging threats without compromising its decentralized structure.
Post-Quantum Algorithms: The Future of Bitcoin Cryptography
The community is exploring various algorithms to protect Bitcoin from quantum attacks. Among the most discussed are:
- Falcon: A solution combining smaller public keys with compact digital signatures. Although it has been tested in limited scenarios, it still faces scalability and performance challenges.
- Sphincs: Hash-based, this algorithm is renowned for its resilience, but its signatures can be extremely large, making it less efficient for networks like Bitcoin’s blockchain.
- Lamport: Created in 1977, it’s considered one of the earliest post-quantum security solutions. Despite its reliability, its gigantic public keys (16,000 bytes) make it impractical and costly for Bitcoin.
Two technologies show great promise and are well-regarded by the community:
- Lattice-Based Cryptography: Considered one of the most promising, it uses complex mathematical structures to create systems nearly immune to quantum computing. Its implementation is still in its early stages, but the community is optimistic.
- Supersingular Elliptic Curve Isogeny: These are very recent digital signature algorithms and require extensive study and testing before being ready for practical market use.
The final choice of algorithm will depend on factors such as efficiency, cost, and integration capability with the current system. Additionally, it is preferable that these algorithms are standardized before implementation, a process that may take up to 10 years.
Why Quantum Computing Is Far from Being a Threat
The alarmist narrative about quantum computing overlooks the technical and practical challenges that still need to be overcome. Among them:
- Insufficient number of qubits: Current quantum computers have only a few hundred qubits, whereas successful attacks would require millions.
- High error rate: Quantum stability remains a barrier to reliable large-scale operations.
- High costs: Building and operating large-scale quantum computers requires massive investments, limiting their use to scientific or specific applications.
Moreover, even if quantum computers make significant advancements, Bitcoin is already adapting to ensure its infrastructure is prepared to respond.
Conclusion: Bitcoin’s Secure Future
Despite advancements in quantum computing, the reality is that Bitcoin is far from being threatened. Its security is ensured not only by its robust architecture but also by the community’s constant efforts to anticipate and mitigate challenges.
The implementation of BIP-360 and the pursuit of post-quantum algorithms demonstrate that Bitcoin is not only resilient but also proactive. By adopting practical measures, such as using modern wallets and migrating to quantum-resistant addresses, users can further protect themselves against potential threats.
Bitcoin’s future is not at risk—it is being carefully shaped to withstand any emerging technology, including quantum computing.
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ 4ba8e86d:89d32de4
2024-10-07 13:37:38
@ 4ba8e86d:89d32de4
2024-10-07 13:37:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável.
https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ 7e538978:a5987ab6
2024-10-02 13:57:31
@ 7e538978:a5987ab6
2024-10-02 13:57:31Chain Duel, a fast paced PvP game that takes inspiration from the classic snake game and supercharges it with Bitcoin’s Lightning Network. Imagine battling another player for dominance in a race to collect blocks, where the length of your chain isn’t just a visual cue. It represents real, staked satoshis. The player with the most Proof of Work wins, but it’s not just about gameplay; it’s about the seamless integration of the Lightning Network and real-time payments.
But how does Chain Duel manage these instant transactions with such efficiency? That’s where LNbits comes in. LNbits, an open-source wallet and payment infrastructure, handles all in-game payments making it easy for developers to focus on gameplay while LNbits takes care of everything from microtransactions to automated splits for developers and designers. In this article, we’ll dive deep into how Chain Duel leverages LNbits to streamline in-game payments and how other developers can take advantage of this powerful toolset to build the future of Lightning-powered gaming.
Let’s explore how LNbits transforms payment processing and why it’s quickly becoming a must-have for game developers working in the Bitcoin space.
Overview of Chain Duel
Chain Duel is a unique Lightning Network-inspired game that reimagines the classic snake game with a competitive twist, integrating real-time payments. Two players face off in real-time, racing to "catch" blocks and extend their chains. Each block added to the chain represents Proof of Work, and the player with the most Proof of Work wins the duel. The stakes are high, as the game represents satoshis (small units of Bitcoin) as points, with the winner taking home the prize.
The game is designed to be Lightning-native, meaning all payments within Chain Duel are processed through the Lightning Network. This ensures fast payments, reducing latency and making gameplay smooth. With additional features like practice mode, tournaments and highscores, Chain Duel creates an engaging and competitive environment for Bitcoin enthusiasts and gamers alike.

One of the standout aspects of Chain Duel is its deeper integration with the Lightning Network even at a design level. For example, actual Bitcoin blocks can appear on screen during matches, offering bonus points when mined in sync with the game. The game’s current version, still in beta, has already drawn attention within the Bitcoin community, gaining momentum at conferences and with a growing user base through its social networks. With its innovative combination of gaming, the Lightning Network, and competitive play, Chain Duel offers a glimpse into the future of Lightning-based gaming.
How LNbits is Used in Chain Duel
Seamless Integration with LNbits
At the core of Chain Duel’s efficient payment processing is LNbits, which handles in-game transactions smoothly and reliably. Chain Duel uses the LNbits LNURL-pay and LNURL-withdraw extensions to manage payments and rewards between players. Before each match, players send satoshis using LNURL-pay, which generates a static QR code or link for making the payment. LNURL-pay allows users to attach a note to the payment, which Chain Duel creatively uses as a way to insert the player name in-game. The simplicity of LNURL-pay ensures that users can quickly and easily initiate games, with fresh invoices being issued for every game. When players win, LNURL-withdraw enables them to seamlessly pull their earnings from the game, providing a quick payout system.
These extensions make it easy for players to send and receive Bitcoin with minimal latency, fully leveraging the power of the Lightning Network for fast and low-cost payments. The flexibility of LNbits’ tools means that game developers don’t need to worry about building custom payment systems from scratch—they can rely on LNbits to handle all financial transactions with precision.
Lightning Tournaments
Chain Duel tournaments leverage LNbits and its LNURL extensions to create a seamless and efficient experience for players. In Chain Duel tournaments, LNbits plays a crucial role in managing the overall economics. LNbits facilitates the generation of LNURL QR codes that participants can scan to register quickly or withdraw their winnings. LNbits allows Chain Duel to automatically handle multiple registrations through LNURL-pay, enabling players to participate in the tournament without additional steps. The Lightning Network's speed ensures that these payments occur in real-time, reducing wait times and allowing for a smoother flow in-game.
Splitting Payments
LNbits further simplifies revenue-sharing within Chain Duel. This feature allows the game to automatically split the satoshis sent by players into different shares for the game’s developer, designer, and host. Each time a payment is made to join a match, LNbits is used to automattically pay each of the contributors, according to pre-defined rules. This automated process ensures that everyone involved in the development and running of the game gets their fair share without manual intervention or complex bookkeeping.
Nostr Integration
Chain Duel also integrates with Nostr, a decentralized protocol for social interactions. Players can join games using "Zaps", small tips or micropayments sent over the Lightning Network within the Nostr ecosystem. Through NIP-57, which enables Nostr clients to request Zap invoices, players can use LNURL-pay enabled Zaps to register in P2P matches, further enhancing the Chain Duel experience. By using Zaps as a way to register in-game, Chain Duel automates the process of fetching players' identity, creating a more competitive and social experience. Zaps are public on the Nostr network, further expanding Chain Duel's games social reach and community engagement.
Game and Payment Synchronization

One of the key reasons Chain Duel developers chose LNbits is its powerful API that connects directly with the game’s logic. LNbits allows the game to synchronize payments with gameplay in real-time, providing a seamless experience where payments are an integrated part of the gaming mechanics.
With LNbits managing both the payment process and the Lightning Network’s complex infrastructure, Chain Duel developers are free to concentrate on enhancing the competitive and Lightning Network-related aspects of the game. This division of tasks is essential for streamlining development while still providing an innovative in-game payment experience that is deeply integrated with the Bitcoin network.
LNbits proves to be an indispensable tool for Chain Duel, enabling smooth in-game transactions, real-time revenue sharing, and seamless integration with Nostr. For developers looking to build Lightning-powered games, LNbits offers a powerful suite of tools that handle everything from micropayments to payment distribution—ensuring that the game's focus remains on fun and competition rather than complex payment systems.
LNBits facilitating Education and Adoption
This system contributes to educating users on the power of the Lightning Network. Since Chain Duel directly involve real satoshis and LNURL for registration and rewards, players actively experience how Lightning can facilitate fast, cheap, and permissionless payments. By incorporating LNbits into Chain Duel, the game serves as an educational tool that introduces users to the benefits of the Lightning Network. Players gain direct experience using Lightning wallets and LNURL, helping them understand how these tools work in real-world scenarios. The near-instant nature of these payments showcases the power of Lightning in a practical context, highlighting its potential beyond just gaming. Players are encouraged to set up wallets, explore the Lightning ecosystem, and eventually become familiar with Bitcoin and Lightning technology. By integrating LNbits, Chain Duel transforms in-game payments into a learning opportunity, making Bitcoin and Lightning more approachable for users worldwide.
Tools for Developers
LNbits is a versatile, open-source platform designed to simplify and enhance Bitcoin Lightning Network wallet management. For developers, particularly those working on Lightning-native games like Chain Duel, LNbits offers an invaluable set of tools that allow for seamless integration of Lightning payments without the need to build complex custom solutions from scratch. LNbits is built on a modular and extensible architecture, enabling developers to easily add or create functionality suited to their project’s needs.
Extensible Architecture for Customization
At the core of LNbits is a simple yet powerful wallet system that developers can access across multiple devices. What makes LNbits stand out is its extensible nature—everything beyond the core functionality is implemented as an extension. This modular approach allows users to customize their LNbits installation by enabling or building extensions to suit specific use cases. This flexibility is perfect for developers who want to add Lightning-based services to their games or apps without modifying the core codebase.
- Extensions for Every Use Case
LNbits comes with a wide array of built-in extensions created by contributors, offering various services that can be plugged into your application. Some popular extensions include: - Faucets: Distribute small amounts of Bitcoin to users for testing or promotional purposes.
- Paylinks: Create shareable links for instant payments.
- Points-of-sale (PoS): Allow users to set up shareable payment terminals.
- Paywalls: Charge users to access content or services.
- Event tickets: Sell tickets for events directly via Lightning payments.
- Games and services: From dice games to jukeboxes, LNbits offers entertaining and functional tools.
These ready-made solutions can be adapted and used in different gaming scenarios, for example in Chain Duel, where LNURL extensions are used for in game payments. The extensibility ensures developers can focus on building engaging gameplay while LNbits handles payment flows.
Developer-Friendly Customization
LNbits isn't just a plug-and-play platform. Developers can extend its functionality even further by creating their own extensions, giving full control over how the wallet system is integrated into their games or apps. The architecture is designed to make it easy for developers to build on top of the platform, adding custom features for specific requirements.
Flexible Funding Source Management
LNbits also offers flexibility in terms of managing funding sources. Developers can easily connect LNbits to various Lightning Network node implementations, enabling seamless transitions between nodes or even different payment systems. This allows developers to switch underlying funding sources with minimal effort, making LNbits adaptable for games that may need to scale quickly or rely on different payment infrastructures over time.
A Lean Core System for Maximum Efficiency
Thanks to its modular architecture, LNbits maintains a lean core system. This reduces complexity and overhead, allowing developers to implement only the features they need. By avoiding bloated software, LNbits ensures faster transactions and less resource consumption, which is crucial in fast-paced environments like Chain Duel where speed and efficiency are paramount.
LNbits is designed with developers in mind, offering a suite of tools and a flexible infrastructure that makes integrating Bitcoin payments easy. Whether you’re developing games, apps, or any service that requires Lightning Network transactions, LNbits is a powerful, open-source solution that can be adapted to fit your project.
Conclusion
Chain Duel stands at the forefront of Lightning-powered gaming, combining the excitement of competitive PvP with the speed and efficiency of the Lightning Network. With LNbits handling all in-game payments, from microtransactions to automated revenue splits, developers can focus entirely on crafting an engaging gaming experience. LNbits’ powerful API and extensions make it easy to manage real-time payments, removing the complexity of building payment infrastructure from scratch.
LNbits isn’t just a payment tool — it’s a flexible, developer-friendly platform that can be adapted to any gaming model. Whether you're developing a fast-paced PvP game like Chain Duel or any project requiring seamless Lightning Network integration, LNbits provides the ideal solution for handling instant payments with minimal overhead.
For developers interested in pushing the boundaries of Lightning-powered gaming, Chain Duel is a great example of how LNbits can enhance your game, letting you focus on the fun while LNbits manages real-time transactions.
Find out more
Curious about how Lightning Network payments can power your next game? Explore the following:
- Learn more about Chain Duel: Chain Duel
- Learn how LNbits can simplify payment handling in your project: LNbits
- Dive into decentralized communication with Nostr: Nostr
- Extensions for Every Use Case
-
 @ 558e15eb:efa6e980
2025-01-12 19:23:42
@ 558e15eb:efa6e980
2025-01-12 19:23:42[2025-02-07] Øy 5 year anniversary - Talk show and watch party @ online
Øy 5 year anniversary - Talk show and watch party online - https://lislegaard.stream/ (https://lislegaard.stream/)
(Friday, 7 February 20:00)

https://do.basspistol.org/event/oy-5-year-anniversary-talk-show-and-watch-party
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 554ab6fe:c6cbc27e
2025-01-12 18:31:18
@ 554ab6fe:c6cbc27e
2025-01-12 18:31:18A shared experience amongst many involved in the Bitcoin industry is that most have moved past the phase where they advocate for Bitcoin and other so-called cryptocurrencies. Eventually, most understand that all so-called cryptocurrencies are illegitimate and that the only legitimate system is Bitcoin. The reason is fundamentally an engineering question; explaining this difference can be challenging in a short conversation. When speaking with clients, friends, and family, I have found that the distinction between Bitcoin and ‘crypto’ is difficult to transmit without an unfortunate touch of blind faith on their part. Furthermore, there are minimal resources for someone to read that can help articulate this understanding. The following is my attempt to remedy this issue.
The subject of cryptocurrencies is shrouded in misleading language and narratives. First, it would be best to describe what Bitcoin is not; Bitcoin is not the invention of blockchain technology. Today, many people who pontificate cryptocurrencies do so under the banner of blockchain technology, allowing for the decentralization of internet infrastructure. Not once does Satoshi Nakamoto use the term ‘blockchain’ in his paper “Bitcoin: A Peer-to-Peer Electronic Cash System”1. Also, Stuart Haber and Scott Stornetta invented the technology in 1991, roughly two decades before the invention of Bitcoin2. The technology was first invented to cryptographically timestamp a digital document as it was changed and edited over time. Why wasn’t Bitcoin invented in the 90s? As of the invention of what is now known as blockchain technology, there was no clear way for a distributed system to agree on the actual state of the system. We could have a distributed and decentralized blockchain database, but how would all the independent nodes agree on the truth? If there are 1000 nodes, each with slightly differing claims on what the blockchain database looks like, how do we reach a consensus on the correct version? Haver and Stornetta could not have answered this question because blockchain technology does not solve this dilemma.
Satoshi Nakamoto solved this problem by fusing blockchain technology with another technology known as proof-of-work, which Adam Back invented. Proof-of-work was first proposed in 1997 and was a way of preventing issues such as email spam by creating a physical and financial cost to computation3. Anyone that knows someone’s email can send them countless spam emails because there is no cost to sending an email. However, by forcing a computer to perform some computations beforehand, the physical costs of sending an email would likely prevent spam. This concept was never implemented, but its conceptualization paved the way for a much better use case. Before moving forward, it is crucial to understand how the invention of Adam Back’s proof-of-work imposed physical and financial costs on computer systems. The following example is how Bitcoin’s proof-of-work system functions. Anyone reading this article should use this link to experience an online SHA-256 hashing calculator for themselves. Here, any input results in a 256-bit string of numbers and letters. Your task is to find the correct input so that the random numbers and letters that result begin with five 0s. Rather than getting a hash that looks something like:
“8e35c2cd3bf6641bdb0e2050b76932cbb2e6034a0ddacc1d9bea82a6ba57f7cf”
It must instead look like:
“000002cd3bf6641bdb0e2050b76932cbb2e6034a0ddacc1d9bea82a6ba57f7cf”
This would take anyone, including a computer, a very long time to guess the correct input. There is no way to speed up this process algorithmically. A computer performing a proof-of-work computation must simply churn through guesses until the correct guess has been found. Therefore, the more complex the guess, the more electricity and financial costs are needed to execute the proof-of-work. This is why it is called ‘proof-of-work’; a computer that has found the correct guess has proved to everyone else that it performed work that has physical consequences in the real world. This is key to understanding Bitcoin.
Again, the various components of Bitcoin, such as blockchain and proof-of-work technology, were not the invention of Satoshi Nakamoto. All Satoshi did was combine them in an elegant way to solve the Byzantine Generals Problem. Imagine a group of generals, each commanding a portion of a Byzantine army, encamped around an enemy city. They need to coordinate their attack or retreat. Still, some generals may be traitors who will send conflicting messages to confuse the loyal generals as they send couriers back and forth to communicate. The problem is to devise a strategy for the loyal generals to reach a consensus despite the presence of possible traitors, ensuring that they either all attack or all retreat at the same time, even if some of the messages they receive are false or misleading. This problem is significant in distributed computing and consensus algorithms, where nodes in a network need to agree on a shared state despite the possibility of faulty or malicious nodes. To solve this problem in Bitcoin, Satoshi designed a system clearly stating that the longest blockchain was the valid chain. Proof-of-work computations are required to add a block to the chain, so the longest chain had the most energy backing it.
The idea that the longest chain has the most energy backing it may initially seem inconsequential. However, as the system develops, the chain becomes longer and longer, with more and more energy backing it. The only way to alter, or hack, the chain in any way that changes what happened in the past is to individually come up with the total equivalent amount of energy ever expended into the system by everyone else. A single bad actor must outcompete the entire global community’s effort starting from the first block 2009. It is a game theoretical setup where the time and energy used to hack the system potentially would be more beneficial, from a cost and benefit point of view, to simply contribute to the same chain everyone else is working with. Satoshi Nakamoto fused the computer system with the earth’s energy to solve the Byzantine Generals Problem, which plagued distributed computer network systems. The energy from the earth is what we trust to ensure we are all working with, and can come to a consensus about, the same set of information.
The property Bitcoin has of being backed by nature as its source of truth allows it to be a valid candidate as money. Understanding the history of money will also help us understand the engineering flaws among the so-called ‘cryptocurrencies. Money can be considered a ledger or recording device that tracks transactions or exchanges of human beings across time. Imagine two separate tribes, where one tribe will have a more bountiful hunting game during the summer and the other during the winter. The two tribes would benefit from trade, as each requires the different tribes to share meat during their respective off-season. However, they exist as two tribes where trust is hard to come by. Now, imagine there is some sort of commodity in their immediate environment that is incredibly rare and hard to find. For the sake of argument, let us say this is a seashell. The two tribes could gather and collect enough seashells to create a necklace of seashells. This neckless will represent a token of trust where the neckless is exchanged at each seasonal cycle. During the summer, the chief of Tribe A hands off the necklace to the chief of Tribe B in exchange for Tribe B to give a portion of their hunting game to Tribe A to feed them for the summer. When winter comes, the chief of tribe B can then pass the necklace back to the chief of tribe A in exchange for meat throughout the winter. This tradeoff occurs cyclically. This system is helpful because not only are they passing in between themselves a token of trust, but if one chief were to die, and the next time a meeting between the two tribes occurs, a new chief approaches the old chief wearing the necklace, the old chief can trust that this new chief is the proper heir because s/he bears the token of seasonal exchange. This allows the chiefs not to trust the individuals themselves but simply trust that the token is legitimate. This token is trustworthy because it is tough to reproduce. Of course, as societies developed, more challenging to find commodities began to dominate trade as the primary form of money.
The key takeaway from the example above is that the two tribes could not trust one another, so they used something from nature backed by energy in the form of the cost to find the seashells and record trustworthy transactions. Gold and silver were no different. Bitcoin has the same properties.
Finally, a comparison between Bitcoin and other so-called ‘cryptocurrencies can begin. First and foremost, there are two distinct families of altcoins: proof-of-work copycats of Bitcoin and proof-of-‘something else’ chains. Many famous altcoins, such as Ethereum, Cardano, or Solana, do not use a proof-of-work consensus mechanism. These systems do not use the energy from the earth to act as an arbiter of trust to solve the Byzantine Generals Problem. Like any human system, if they are not using Mother Earth to act as the source of truth, then a third party is. Humans and human-controlled code are the final judge. This trend also means that most systems have companies overseeing them, which Bitcoin does not. In the case of Ethereum, there is the Ethereum Foundation. The central control over Ethereum has been known to reverse the record of the ledger, something that is practically impossible on Bitcoin.
The DAO hack was a significant event that occurred in 2016 in the world of Ethereum. DAO stands for “Decentralized Autonomous Organization,” it was a complex smart contract on the Ethereum blockchain designed to act as an investor-directed venture capital fund. The idea was to allow people to invest in Ethereum and have a say in what projects the money would be used for, all governed by smart contracts without any central authority. In June 2016, someone found a vulnerability in The DAO’s code, allowing them to siphon off one-third of The DAO’s funds to a subsidiary account. This amounted to about $50 million worth of Ethereum at the time. As a result, the Ethereum community effectively reversed the transaction, by creating a fork in the chain that erased all transactions that happened after the hack. This is something that is unheard of in Bitcoin. The only way this was possible, that the community chose to use a shorter chain, was because the decision was headed by the central authorities that rule over Ethereum.
Without a source of truth outside of humans, there will always be a group of humans who have control. This is why bitcoin is sometimes articulated as a commodity while other altcoins are considered securities. It becomes increasingly unlikely that anyone can change the ledger of Bitcoin, whereas the few at the top hold such control over Ethereum. Anyone with electricity, a computer, and some internet can mine and receive bitcoin. It is permissionless, with very few barriers to entry. This is not the case with Ethereum, which would require someone to find an exchange and use some form of currency to purchase Ethereum. To run a Bitcoin node, the requirements are even less than it is to mine, given the low electricity cost. To run an Ethereum node, one needs to have 32 Ethereum (roughly $96,000 at today’s price). Ethereum is a plutocracy, and ETH is not different than a security issued by that plutocratic elite.
There are, of course, some altcoins that use a proof-of-work system like Bitcoin does. Many altcoins are nearly the same as Bitcoin except with slight changes to the code, which results in a different chain. The critical distinction here is, again, the energy backing the system. Bitcoin’s chain is long and supported by much more energy. Though these other altcoins, such as Bitcoin Cash, Litecoin, and Dogecoin, are similar from an engineering point of view, they lack the security provided by more than a decade of energy being pumped into the network. Storing wealth here would be comparable to putting wealth in a wooden box when an equally valid metal safe is available for use.
Hopefully, it will be apparent that Bitcoin is more of a trust machine than a blockchain machine. It utilizes the physical energy supplied to it to ensure a tamperproof and trustworthy record for all people to use in a permissionless manner. A fan of altcoins may concede and agree that Bitcoin is the only system that is secure and sure to exist long into the future. Therefore, it is the only system capable of using money globally for generations. Nonetheless, many proponents of altcoins, such as Ethereum, will suggest they can be used for other use cases. One may argue that Ethereum’s ‘smart contract’ capabilities will open the door for Web3 use cases that will decentralize the internet and create a net good for society. However, circular logic is involved in this reasoning. The blockchain underneath must be secure and reliable for applications to be built on Ethereum. For it to do so, ETH, the token of Ethereum, would require monetary value.
Bitcoin does not need monetary value for it to work. In fact, in the early days of Bitcoin, there was no price associated with it. This is not the case for systems like Ethereum. The existence of their system relies upon circular logic. Highlighting this flaw in the game theory, or lack thereof, of the fundamental infrastructure of Ethereum explains why no application or wealth placed on the system is safe. When Bitcoin was invented, a node did two things: store the entire blockchain while validating transactions and mine new blocks, which settle transactions every 10 minutes. No permission is required whatsoever to do so. In Ethereum, for example, there is no mining. They use a system called proof-of-stake. In Bitcoin, electricity is expended to produce blocks, and bitcoin is received as a reward. In Ethereum, for someone to be given the right to create a new block and receive ETH, they need to have 32 ETH already. Once someone can acquire 32 ETH, which can only be obtained by buying someone else’s ETH, they can freeze their ETH into a staking pool, which allows them to participate in the block creation and reward process. In Bitcoin, the pure randomness of nature decides who will mine the block and receive the reward. In Ethereum, pools are probabilistically chosen based on who has the most ETH by code alone. Those with the most ETH are more likely to be rewarded, meaning they will be more likely to earn more in the future. The rich will get richer. It is an inherently centralizing force, and this flaw in proof-of-stake systems is well known. However, none of this explains quite why the game theory of Ethereum staking doesn’t even work in the long-term.
Many in the ‘crypto’ world propose that Bitcoin is money and an actual store of value, while Ethereum will act as this new layer of internet infrastructure. Let us assume this is true momentarily and imagine a world where this is the case. For Ethereum to work, there needs to be people who operate the Ethereum pools. They will have operating expenses, mainly paying a cloud service provider to host their node. Of course, they must have also purchased 32 ETH. Their profitability relies upon the income generated from individuals using the Ethereum network. A network fee is paid whenever someone executes any function on Ethereum. These network, or gas, fees are then paid to the staking pool operators. Now, imagine a world where Bitcoin is money. Everyone holds bitcoin as their savings, their salaries are paid in bitcoin, and they buy their coffee with bitcoin. Bitcoin is increasing in value relative to goods and services as a proper sound money that is not being debased. However, whenever they want to execute a ‘smart contract’ on the internet, they must convert their money (bitcoin) into ETH to pay the gas fee.
Imagine if every time you wanted to send an email, you had to purchase an email token first. You wouldn’t have a bank account for email tokens; you would buy the email tokens as needed when you sent the email. The asset that appreciates due to its monetary properties is bitcoin; you hold onto bitcoin because it will make you wealthier. With the email token (ETH), you buy it as minimally as needed. Where would you buy the ETH from? The staking pools, of course. Staking pools are the central custodians and largest owners of ETH and need to sell ETH to pay their operating expenses. Now let us put this fully into the picture: a staking pool’s business is to operate a server where they have invested an incredible amount of money into it, only to act as a kind of exchange that sells ETH tokens to users as needed when they want to use Ethereum, only to receive that ETH back once the customers have used the network.
Everyone is playing a game of hot potatoes, trying to use ETH tokens as soon as they purchase them because they are losing value in comparison to their money. At the same time, staking pools are sitting on all the ETH that no one wants beyond a short period. Their business is only profitable if the value of the ETH they receive as rewards can outperform their operating costs. Over time, only a few staking pools will exist as they compete. This system leads to an incredibly centralized database where a few operators have control over this blockchain, which is only being used because it was claimed to be a decentralized and immutable trustworthy system. ETH only has value if people trust the blockchain to store their data, information, or wealth securely. If the system starts to look centralized and untrustworthy, demand for the product erodes. This slow revelation of the false claim of decentralization will lead to further devaluation of the token in terms of bitcoin, and node operators will cease doing business as there will be more profitable ventures elsewhere, where their assets are denominated in BTC rather than ETH. The system will crumble because it was not designed with the correct game theoretical engineering principles.
Hopefully, this article has helped articulate in a small way the clear distinction between Bitcoin and all the other falsely mimicking systems. These so-called ‘cryptocurrencies’ claim to be decentralized and immutable systems, relying upon the narrative surrounding Bitcoin while being utterly different from an engineering point of view and ultimately failing to be anything decentralized and, therefore, trustworthy. To make a blockchain system decentralized, there must be a genuinely neutral arbiter of truth. There is only one such judge: Mother Earth. With such a disruptive innovation as Bitcoin entering the market, it is understandable that such a considerable misunderstanding has led to the promotion and growth of fraudulent blockchain systems. As we move forward in this ever-changing world, we must help protect each other’s wealth with integrity and honesty.
References
-
Nakamoto S. Bitcoin: A Peer-to-Peer Electronic Cash System. Published online 2008. Accessed November 16, 2021. http://www.bitcoin.org -
Haber S, Stornetta WS. How to Time-Stamp a Digital Document. Vol 537. Springer-Verlag; 1991. -
Back A. Hashcash-A Denial of Service Counter-Measure.; 2002. https://www.researchgate.net/publication/2482110
-
-
 @ 3ac03011:41ecd1bb
2025-01-12 17:04:15
@ 3ac03011:41ecd1bb
2025-01-12 17:04:15"We shall go on to the end...we shall fight on the seas and oceans, we shall fight with growing confidence and growing strength in the air, we shall defend our Island, whatever the cost may be, we shall fight on the beaches, we shall fight on the landing grounds, we shall fight in the fields and in the streets, we shall hight in the hills; we shall never surrender..." - Winston Churchill
Let's all laugh at the world
People of Britain, let's take a moment to bask in the beauty of our unique position. While the rest of the world frantically asks, "What the hell is going on in the UK?" we remain calm, resolute and wonderfully unbothered. Their confusion isn't a problem; it's proof our plan is working.
Outsiders just don't get it. "Why so many general elections?" they ask. "Why are your public services crumbling?" they wonder. "Why so much crime?" they cry. It's adorable, really. While they waste their precious time trying to bring light to our 'problems' of today, we've been quietly engineering our tomorrow. A future where effort is obsolete, the burden of ambition is lifted and every need is met with the tap of a button—or no tap at all.
Let them panic and tweet. We're busy building utopia.
Our genius: let me remind you
In case you missed the email, let me remind you of our genius.
It really got started with our political circus: general elections, leadership changes and scandals galore. The world sees chaos; we see strategy. Every new Prime Minister, every internal party coup and every leaked WhatsApp message serves one purpose—to keep the world so baffled by the spectacle that they miss the revolution happening right under their noses. Sovereignty? Prosperity? Please. That's the old way. We're crafting a system so streamlined and so brilliantly lazy that governance itself will be no more. Our 'scandals' aren't failures; they're distractions.
Then, remember the pandemic? A "global crisis," they called it. For us, it was a test run. Offices? Gyms? Fresh air? Redundant. We proved we didn't need them. With reliable Wi-Fi and an endless supply of TikToks, we discovered the liberating truth: who needs ambition when comfort will do? Why strive when you can stream?
But this wasn't an overnight success. Our journey began over a century ago with a simple, yet brilliant, decision: abandon sound money. When we gave that loan in 1914 and loosened our grip on gold, we unknowingly set the stage for a masterpiece. Inflation isn't a problem; it's liberation.
By eroding the value of money, we finally have freed ourselves from the tedious burden of saving and planning for the future. Why hoard wealth when you can spend it on some crappy product? We both know you won't be able to afford the same one next year. Inflation has delivered us into the era of hand-to-mouth serenity. With high taxes and even higher living costs, we've made financial planning a thing of the past. Isn't it liberating to know your wallet is lighter?
And then there's the NHS and our public services. "They're in crisis!" outsiders exclaim. "Long waits, lack of resources, dysfunctional!" Oh, bless their concern. They just cannot get their heads around our evolution in public spending. Why pour resources into systems that belong to the old world? We're preparing for a future that minimises illness, needs and human interaction. Our public services aren't failing; they're gracefully stepping aside, making way for our streamlined utopia.
Our utopia: let me remind you
So, what exactly are we building? If you don't know already, well, let me introduce to you Project Wall-E. I don't believe anyone could quite believe their luck when Micky pitched his vision for the future in his 2008 masterpiece but we knew that this was our endgame. A world where effort is unnecessary, ambition is no more and everything you need is delivered right to your hover chair.

\ The crime, the uncertainty, the decay—it's all part of the plan. When the time comes to leave this Island behind, we won't even miss it. We'll ascend to the new world we've created, sipping beers from our Stanley cups and letting the supreme algorithm create our tailored perfect experience.
Keep calm and carry on
So, people of Britain, take a bow. The world doesn't understand us but history will. While they cling to outdated ideals of life, liberty and property, we'll keep doing what we do best: leading by example. Do not lose focus. Keep calm and carry on.
-
 @ 41fa852b:af7b7706
2025-01-12 14:50:25
@ 41fa852b:af7b7706
2025-01-12 14:50:25The art of life is a constant readjustment to our surroundings." --Okakura Kakuzo
Here we go with another fresh list of meetups for the UK and Ireland this coming week.
We've got the latest on where to connect, share ideas, and build community.
Let's take a look…
This week's sponsor is…
Upcoming Bitcoin Meetups
Happening this week…
-
Dundee Bitcoin: Join them on the 2nd Monday of every month from 17:30 to 20:30 PM at The Wine Press, 16 Shore Terrace, Dundee DD1 3DN. This month's meetup is on Monday, 13th January. 🍷
-
Real Bedford - Home Game: Real Bedford have two home games this week. The first is on Tuesday night at 19:45 playing Berkhamsted. ⚽️
-
Bitcoin Glasgow: Bitcoin Glasgow meet every 3rd Wednesday of the month and this month will be at The Maltman, 59--61 Renfield Street at 18:00 to 20:00. 🍺
-
Shropshire Bitcoin: On the 15th, the Shropshire crew will be meeting at the Admiral Benbow in Shrewsbury. 🍻
-
Brum Bitcoin & Beer: If you're in the Birmingham area head along to meet some fellow bitcoiners on Thursday 16th at 19:00. You'll find them this month at The Wellington, Bennett's Hill, B2 5SN. 🍺
-
Penzance Bitcoin: Will be at The Dolphin Tavern on Quay Street on Thursday 16th at 8 PM. 🍻
-
Bitcoin Walk - Edinburgh: Every Saturday they walk around Arthur's Seat in this historic city. Join them at 12:00 to chat about all things Bitcoin and keep fit. 🚶♂️🚶🏻♀️🚶🦮
-
Real Bedford - Home Game: Real Bedford have their second home game this week playing Leverstock Green on Saturday. Join them for a 15:00 kickoff. ⚽️
-
NostrLDN: The fourth NostrLDN and this time with guests Metamick (founder and CEO of Geyser Fund) and Huxley (Charities, Afrika, Bitcoin education). Join them on Saturday the 18th of January at the London Bridge Rooftop Bar from 18:00 till 22:00. 🍻👨🏼🎓💜
Upcoming Special Events
This event isn't happening this week, but it's important to add to your calendar now as tickets are selling fast.
- Bitcoin Builders Workshop: Corby-based engineering company BTC Citadel hosts an afternoon of Bitcoin building and chat. Build that project you've been thinking about but didn't know how to start. Come and use high-end 3D printers, 3D scanners, electronics lab and the CNC laser engraver. Everyone is welcome, no technical ability is needed. Learn how to build a Seedsigner. Refreshments are provided for this free event.
Get Involved
- Volunteer Opportunities: Bridge2Bitcoin is actively seeking volunteers who share our passion for merchant adoption. We'd be delighted to connect if you're eager to contribute. Reach out to us on Twitter or through our website.
- Start Your Own Meetup: Interested in launching a Bitcoin meetup? We're here to support you every step of the way. We've assisted numerous UK Bitcoin meetups in getting started. Get in touch via Twitter.
- Contribute to BTCMaps: BTCMaps is a vital part of the Bitcoin ecosystem. It's a perfect project to get involved with if you're not a coder or even that technical. A great way to give back to the community. Maintain an area of the UK and keep it up-to-date.
- Telegram users: You might find our Telegram Channel another useful way to keep up-to-date with UK meetups.
- Feedback and Suggestions: We value your input! Share your ideas on how we can enhance this newsletter.
This week's sponsors are…
Get out and support the meetups where you can, visit Bitcoin Events UK for more info on each meetup and to find your closest on the interactive map.
Stay tuned for more updates next week!
Simon.
-
-
 @ ed84ce10:cccf4c2a
2025-01-12 13:27:13
@ ed84ce10:cccf4c2a
2025-01-12 13:27:13Hackathon Summary
The Trustworthy AI Lab x GES UCLA Hackathon showcased innovative solutions from 21 developers who registered a total of nine projects. This virtual event ran from May 29th to June 28th, 2024, centering on the use of predictive modeling to enhance user engagement and advertising effectiveness. Two detailed datasets provided insights into user demographics and interactions, serving as a foundation for participants to create platforms that encourage collaboration between content creators and advertisers, while ensuring a positive user experience.
Esteemed judges, comprising both academic figures like Professor Guang Cheng, and industry professionals from companies such as Amazon, Snap, and Intel, evaluated the projects. A total prize pool of $1,500 was distributed among the top solutions, assessed on criteria including accuracy, innovation, scalability, and efficiency. Additionally, the event offered summer internships at the Trustworthy AI Lab at UCLA, enabling participants to further develop their skills. Emphasizing practical applications, projects were required to deliver runnable machine learning code and presentation slides, ultimately striving for scalable, innovative solutions that respect data privacy and support real-time performance.
Hackathon Winners
Prize Winners
🥇 First Place
- DataGuardians excelled in secure data handling by employing a VM and GAN to create synthetic datasets, striking a balance between data security and usability.
🥈 Second Place
- Team BitBuilders developed a Generative AI-based data-sharing platform that enhances predictive analytics and data collaboration through privacy-preserving techniques and advanced encryption.
🥉 Third Place
- Team Datacrafters focused on analyzing advertising data using machine learning and automated DCR security improvements, optimizing model performance for statistical insights.
Fourth Place
- Awesome Team Name's BUIDL utilized TPM for secure data modeling, emphasizing reliable data manipulation and confidentiality.
Fifth Place
- ColumbiAI improved scientific predictive accuracy through secure Generative AI, establishing "Data Clean Rooms" for privacy-preserving collaborative data analysis.
For more information on all the projects, visit here.
About the Organizer
GES at UCLA
GES at UCLA, formerly known as Three Day StartUp at UCLA, is a leading entrepreneurial program tailored for university students. It emphasizes experiential learning in vital areas such as ideation, team formation, market research, and rapid prototyping. The program instills an entrepreneurial mindset, equipping students with the skills necessary to develop innovative business models with global impact. By supporting its student community, GES at UCLA is committed to transforming startup concepts into sustainable ventures, aiding in the resolution of complex problems and the launch of successful enterprises worldwide. For further details, visit their website.
-
 @ fbf0e434:e1be6a39
2025-01-12 13:25:56
@ fbf0e434:e1be6a39
2025-01-12 13:25:56Hackathon 总结
Trustworthy AI Lab x GES UCLA Hackathon 展示了由 21 名开发者注册的九个项目的创新解决方案。本次虚拟活动从 2024 年 5 月 29 日至 6 月 28 日举行,重点关注使用预测模型来增强用户参与度和广告效果。两个详细的数据集提供了用户人口统计和互动的见解,为参与者创建平台奠定了基础,这些平台促进内容创作者和广告商之间的合作,同时确保积极的用户体验。
由学术人士(如Guang Cheng 教授)和来自Amazon、Snap、Intel 等公司的行业专家组成的评委对项目进行了评估。总奖池为 $1,500,并在顶尖解决方案中分配,根据准确性、创新性、可扩展性和效率等标准进行评估。此外,该活动还提供了在UCLA的Trustworthy AI Lab的暑期实习机会,使参与者能够进一步发展他们的技能。在强调实际应用的同时,项目需提供可运行的机器学习代码和演示幻灯片,最终目标是寻求尊重数据隐私和支持实时性能的可扩展创新解决方案。
Hackathon 获奖者
Prize Winners
🥇 First Place
- DataGuardians 在安全数据处理方面表现出色,通过使用VM和GAN创建合成数据集,实现了数据安全性和可用性之间的平衡。
🥈 Second Place
- Team BitBuilders 开发了一个基于生成式AI的数据共享平台,通过隐私保护技术和先进加密,提高了预测分析和数据协作。
🥉 Third Place
- Team Datacrafters 专注于使用机器学习和自动化DCR安全改进进行广告数据分析,优化了模型性能以获得统计洞察。
Fourth Place
- Awesome Team Name's BUIDL 利用TPM进行安全数据建模,强调数据操作的可靠性和保密性。
Fifth Place
- ColumbiAI 通过安全的生成式AI提高科学预测的准确性,建立了“数据洁净室”以保护隐私的协作数据分析。
欲了解所有项目的更多信息,请访问此处。
关于组织者
GES at UCLA
GES at UCLA,前称为UCLA的Three Day StartUp,是一个为大学生量身定制的领先创业项目。它强调在构思、团队形成、市场研究和快速原型设计等重要领域的体验式学习。该项目培养了一种创业思维,使学生具备开发具有全球影响力的创新商业模式的技能。通过支持其学生社区,GES at UCLA 致力于将创业概念转变为可持续发展企业,帮助解决复杂问题并在全球推出成功的企业。欲了解更多详情,请访问他们的网站。
-
 @ ed84ce10:cccf4c2a
2025-01-12 13:22:07
@ ed84ce10:cccf4c2a
2025-01-12 13:22:07Hackathon Summary
DivHacks 2024: Tech for Social Good was held at Columbia University, New York, on October 5-6, 2024. The hackathon facilitated the creation of 64 projects by bringing together developers, demonstrating its dedication to enhancing both technical and soft skills while tackling societal issues.
Key tracks included Education, Environment, Media, Fashion, Civic, and Health. Sponsored tracks were supported by organizations such as Capital One, Google, and the Pittsburgh Regional Health Initiative, focusing on financial solutions, creative technology, and patient safety, respectively. MLH supported tracks for projects incorporating MongoDB, domain names, and DEI hacking.
The event aimed to develop impactful solutions in sectors such as sustainability, civic engagement, and healthcare. These themes attracted diverse innovations, reinforcing the goal of leveraging technology for societal benefit. Platforms like DoraHacks, Discord, and associated websites facilitated participant interactions by providing vital resources. By uniting students with a common interest in technology for social good, the hackathon highlighted creative BUIDLs and encouraged future collaborations.
Hackathon Winners
Best Overall Track Prize Winners
- StrokePlayAR - An AR application utilizing Snap's Spectacles, designed for stroke rehabilitation through gamified activities to enhance mobility and well-being.
- SynapsED - A financial literacy platform aimed at empowering young individuals to build wealth and break generational financial challenges by encouraging early investment habits.
- Penny Pals - A financial literacy platform teaching investment skills through a simulation where parents fund accounts, and children make decisions using real-time market data. It fosters collaboration, risk management, and healthy financial habits, with future plans for iMessage integration and parental controls.
General Tracks Prize Winners
- Education: SynapsED
- Environment: Pothos A SaaS platform for small businesses to optimize Sustainability-Linked Loans using KPIs and NFT-secured contracts, promoting sustainability.
- Media: NewsLyzer AI-powered news bias filter employing NLP and machine learning to assess credibility, summarize articles, and detect biases in real-time.
- Fashion: Fashion Faeries A web app providing personalized outfit suggestions and resale comparison, promoting sustainable fashion using machine learning.
- Civic Tech: PinPoint A crowdsourced map enhancing community interactions through user-submitted Pins on topics like accessibility and safety.
- Health: StrokePlayAR
Sponsor Tracks Prize Winners
- Google: Best Use of Google NotebookLM: PunditPal An AI platform analyzing political discourse, utilizing NotebookLM and Vapi for debate training.
- Snap AR: Dream It Build It!: StrokePlayAR
- Pittsburgh Regional Health Initiative: Patient Safety Technology Challenge: MediTrack A JavaScript tool for safer medication prescribing, preventing errors with Google’s NotebookLM.
- Capital One: Best Financial Hack: Penny Pals
MLH Tracks Prize Winners
- GoDaddy Registry: Best Domain Name: Voice Vision A virtual learning platform creating engaging video podcasts from learning materials.
- Auth0 by Okta: Best Use of Auth0: NeuroTalent Connects neurodivergent students with employers, promoting inclusion through events and tailored support.
- Best Use of Fidelity: Strands Gamifies university learning with interactive word games to enhance engagement and attendance.
- Best Use of MongoDB Atlas: Fashion Faeries
- Best Beginner Hack: What's Cookin' Optimizes campus dining with real-time dish recommendations and meal tracking using web scraping and algorithmic data management.
For a detailed look at all projects, visit DivHacks 2024.
Organization
DivHacks 2024
DivHacks 2024: Tech for Social Good, hosted by Columbia University Women in Computing Society, is a vital platform at Columbia University and Barnard College, amplifying underrepresented voices in technology. The hackathon focuses on creating impactful and sustainable technology-driven solutions, exploring the potential of technology to address societal challenges. By encouraging participants to combine creativity with technical skills, the event fosters progress in confronting pressing social issues, underlining its commitment to social change through technological excellence.
-
 @ fbf0e434:e1be6a39
2025-01-12 13:20:49
@ fbf0e434:e1be6a39
2025-01-12 13:20:49Hackathon 总结
DivHacks 2024: Tech for Social Good 于2024年10月5日至6日在纽约哥伦比亚大学举行。本次Hackathon吸引开发者参与共创建了64个项目,展示了其在提升技术和软技能以及解决社会问题方面的承诺。
关键赛道包括教育、环境、媒体、时尚、市政和健康。赞助赛道则由Capital One、Google和Pittsburgh Regional Health Initiative等组织支持,重点关注金融解决方案、创意技术和患者安全。MLH支持的赛道则包括涉及MongoDB、域名和DEI黑客的项目。
活动旨在开发具有影响力的解决方案,涉及可持续发展、市民参与和医疗保健等领域。主题吸引了多样化的创新项目,加强了利用技术服务社会的目标。DoraHacks、Discord和相关网站等平台为参与者互动提供了重要资源。通过将对社会公益技术感兴趣的学生聚集在一起,Hackathon强调了富有创意的BUIDLs,并鼓励未来的合作。
Hackathon 获奖者
Best Overall Track Prize Winners
- StrokePlayAR - 一款利用Snap's Spectacles的AR应用,通过游戏化活动促进中风康复,提高行动能力和健康。
- SynapsED - 一个金融素养平台,旨在通过鼓励年轻人养成早期投资习惯,帮助他们积累财富并打破代际财务困境。
- Penny Pals - 一个金融素养平台,通过模拟投资教学,父母为账户提供资金,孩子基于实时市场数据做出决策。该平台促进协作、风险管理和健康的理财习惯,并计划未来推出iMessage集成和家长控制功能。
General Tracks Prize Winners
- Education: SynapsED
- Environment: Pothos - 一个为小企业提供SaaS平台,利用KPI和NFT安全合同优化与可持续性挂钩的贷款,促进可持续发展。
- Media: NewsLyzer - 使用自然语言处理和机器学习的AI驱动新闻偏见过滤器,实时评估可信度、总结文章并检测偏见。
- Fashion: Fashion Faeries - 一个网络应用,提供个性化的服装建议和转售比较,使用机器学习促进可持续时尚。
- Civic Tech: PinPoint - 一张众包地图,通过用户提交的关于无障碍设施和安全等主题的“Pins”来增强社区互动。
- Health: StrokePlayAR
Sponsor Tracks Prize Winners
- Google: Best Use of Google NotebookLM: PunditPal - 一个分析政治话语的AI平台,使用NotebookLM和Vapi进行辩论训练。
- Snap AR: Dream It Build It!: StrokePlayAR
- Pittsburgh Regional Health Initiative: Patient Safety Technology Challenge: MediTrack - 一个使用Google的NotebookLM的JavaScript工具,通过防止错误来安全开药。
- Capital One: Best Financial Hack: Penny Pals
MLH Tracks Prize Winners
- GoDaddy Registry: Best Domain Name: Voice Vision - 一个虚拟学习平台,从学习材料中创造引人入胜的视频播客。
- Auth0 by Okta: Best Use of Auth0: NeuroTalent - 连接神经多样性学生与雇主,通过活动和量身定制的支持促进包容。
- Best Use of Fidelity: Strands - 通过互动文字游戏增强参与度和出勤率,对大学学习进行游戏化。
- Best Use of MongoDB Atlas: Fashion Faeries
- Best Beginner Hack: What's Cookin' 使用网络抓取和算法数据管理,提供餐盘推荐和餐食追踪,优化校园用餐。
欲了解所有项目详情,请访问 DivHacks 2024。
关于组织者
DivHacks 2024
DivHacks 2024: Tech for Social Good,由哥伦比亚大学妇女计算机协会主办,是哥伦比亚大学和Barnard College的一个重要平台,旨在放大技术领域中代表性不足的声音。Hackathon专注于创建有影响力且可持续的技术驱动解决方案,探索技术解决社会挑战的潜力。通过鼓励参与者结合创造力和技术技能,活动推动在应对紧迫社会问题方面的进步,强调其通过技术卓越推动社会变革的承诺。
-
 @ e6817453:b0ac3c39
2025-01-12 12:20:58
@ e6817453:b0ac3c39
2025-01-12 12:20:58The development of AI agents has been a booming topic in recent years. From their early conceptual stages to the sophisticated models we see today, the focus has been mainly on building robust agents. However, the importance of Agent-to-Agent (A2A) protocols has been largely overlooked. These protocols are crucial for enabling seamless interaction, fostering interoperability, and unlocking the full potential of AI agents. Here, we explore why A2A protocols matter and how they shape the future of AI.
What Is an Agent?
An agent, in the context of artificial intelligence, is an autonomous system capable of performing tasks on behalf of a user. These tasks can range from data retrieval to complex decision-making. Agents are often likened to “active wallets on steroids” in fields like self-sovereign identity, where they act as intermediaries for data exchange and task delegation.
Key characteristics of AI agents include:
- Autonomy: Agents operate independently, without constant user input.
- Task Delegation: Users can assign tasks to agents, expecting results with minimal intervention.
- Adaptability: Agents learn and adapt to improve performance over time.
The Role of Protocols in Agent Ecosystems
Protocols are the foundation of the internet and distributed systems, ensuring interoperability, scalability, and governance. When applied to AI agents, protocols serve a similar purpose: they enable agents to communicate, cooperate, and coordinate across networks.
Key Layers of Protocols
- Transport and Data Exchange Protocols: These focus on the low-level mechanics of communication, such as data formats and exchange standards.
- Behavior and Governance Protocols: These regulate interactions by encoding rules, incentives, and penalties to ensure fair play. Examples include blockchain networks like the Lightning Network, which implement complex mechanisms for governance and rewards.
- Identity and Capability Protocols: These enable agents to identify themselves, declare their capabilities, and establish trust. For instance, an agent might declare its ability to transcribe audio or generate images.
- Payment and Reward Protocols: These facilitate transactional interactions, ensuring agents can be compensated for their services.
- Discovery and Verification Protocols: These help agents find other agents with specific capabilities and verify the quality of completed tasks. Proof-of-work and proof-of-authenticity mechanisms are critical components.
Why Natural Language Isn’t Enough
Some argue that natural language capabilities make formal protocols unnecessary for agent interactions. While natural language can simplify communication, it cannot replace the structured governance provided by protocols. Protocols extend beyond data exchange to address complex social and economic dynamics, such as:
- Establishing trust and identity
- Ensuring compliance with norms and rules
- Enabling fair transactions and conflict resolution
Natural language alone cannot encode the intricate governance and behavioral expectations needed for scalable, reliable agent ecosystems.
The Need for A2A Protocols
Agent-to-Agent protocols are critical for:
- Identity : corner stone of any network interaction
- Interoperability: Allowing agents from different networks or organizations to work together seamlessly.
- Trust and Verification: Establishing mechanisms to prove an agent’s identity, capabilities, and quality of work.
- Economic Transactions: Facilitating payments, incentives, and rewards through standardized methods.
- Discovery: Helping agents find the most efficient collaborators or services based on capabilities and cost.
- Fair Play: Implementing rules and incentives to promote ethical behavior and penalize bad actors.
Protocols Encode Behavior
At the core of effective agent systems lies the concept of protocols — the structured rules that govern interactions. Protocols encode not just data formats and exchange methods but also higher-order behaviors. They ensure:
- Consistency: By standardizing interactions, protocols prevent ambiguities in communication.
- Scalability: Systems adhering to the same protocols can grow without breaking interoperability.
- Fairness: Behavior protocols regulate actions, ensuring all participants adhere to agreed-upon norms.
For instance, in blockchain networks, behavior protocols underpin mechanisms for rewarding cooperative actions and penalizing misconduct, reflecting principles of fair play essential for decentralized systems.
Social Interactions and Rules as Part of Protocols
AI agents simulate aspects of human society, including collaboration, competition, and compliance with norms. This necessitates protocols that mirror societal interactions, encompassing:
- Normative Behavior: Rules that dictate expected actions in specific scenarios.
- Trust Mechanisms: Identity verification to ensure agents are authentic and capable of delivering promised services.
- Transactional Rules: Structures for payment, reward, and accountability in agent-to-agent interactions.
By encoding such social constructs into protocols, agents can navigate complex ecosystems, fostering trust and reliability in decentralized networks.
Governed Protocols
Governed protocols represent the next layer of complexity, allowing networks to self-regulate. These protocols enable participants to:
- Propose Changes: Mechanisms for evolving network functionality over time.
- Vote on Updates: Democratic decision-making ensures inclusivity and adaptability.
- Enforce Compliance: Rules to prevent malicious behavior and maintain network stability.
Blockchain networks like DFINITY exemplify governed protocols, where community-driven governance shapes the network’s evolution. Such principles are equally vital for AI agent ecosystems, ensuring fairness and adaptability.
Beyond A2A: Interfacing with Tools and Memory
AI agents do not operate in isolation. They need to integrate with tools, data sources, and memory systems to deliver value. This integration introduces additional protocol challenges:
- Tool Interoperability: Developing standards for tool descriptions and extensions so agents can use them interchangeably.
- Semantic and Episodic Memory: Creating protocols for portable, interoperable memory that allows agents to retain context and learning across interactions.
Interoperability of Agent Components
Interoperability remains a significant challenge for AI agents. To unlock their full potential, components like memory and tools must integrate seamlessly. This requires:
- Memory Protocols: Enabling agents to share semantic and episodic memory across systems. Imagine retaining knowledge across agent upgrades without data loss.
- Tool Interoperability: Standardized interfaces that allow agents to utilize shared resources like databases, APIs, or even other agents.
A robust interoperability framework ensures that agents can not only coexist but collaborate effectively, maximizing their collective utility.
A Future Built on Protocols
The future of AI agents lies in robust, standardized protocols. These protocols will:
- Enable agents to communicate and cooperate effectively.
- Foster innovation by making agents and tools interchangeable.
- Empower users with greater flexibility and control over their agent ecosystems.
To move forward, we must focus not only on improving individual agents but also on building the protocols that underpin their interactions and integrations. By doing so, we can unlock the true potential of AI agents and their ability to transform industries and society.
Conclusion
Agent-to-agent protocols are not optional; they are the backbone of a robust and scalable AI ecosystem. By encoding behavior, enabling social norms, implementing governed structures, and ensuring interoperability, these protocols set the stage for AI agents to excel. As AI continues to evolve, focusing on protocol development will be pivotal in unlocking new dimensions of capability and innovation. The future of intelligent systems lies not just in smarter agents but in smarter ways for them to collaborate.
-
 @ da0b9bc3:4e30a4a9
2025-01-12 08:34:03
@ da0b9bc3:4e30a4a9
2025-01-12 08:34:03Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/847214
-
 @ e1b54f7d:a0261d28
2025-01-12 07:43:29
@ e1b54f7d:a0261d28
2025-01-12 07:43:29由妙瓦底明星入局想到全球科技圈的乱战
-
 @ a10260a2:caa23e3e
2025-01-12 04:16:29
@ a10260a2:caa23e3e
2025-01-12 04:16:29Last Updated: January 11, 2025
This article is based on a note I posted over a year ago. I kept finding great podcasts and realized that a long form note would make sense since it'll essentially be reposted in the feed every time an update is made.
While there are many good privacy resources out there, this list will focus on episodes from CITADEL DISPATCH. The rabbit hole is deep and never-ending; my hope is that this will spark your curiosity and compel you to search for more.
Why should you care? ODELL explains that here.
If you're ready, here are the privacy-related dispatches. Hour and hours of signal from ODELL and his guests. Enjoy. 🫡
- CD2: Privacy, Nodes, and No KYC with ErgoBTC & BitcoinQ_A — https://fountain.fm/episode/ssPqjTOzHjWSRiYN5rP6
- CD15: bitcoin privacy and coinjoin with nopara73 and openoms — https://fountain.fm/episode/akzlPBM5XWZgPWa2iXCN
- CD16: bitcoin privacy and coinjoin with chris belcher and waxwing — https://fountain.fm/episode/hBcMSmraUUxVlZzBv5V1
- CD21: the lightning network and bitcoin privacy with openoms and cycryptr — https://fountain.fm/episode/vo0LpZOxGiDWIXc8wQf2
- CD29: bitcoin privacy and security with craigraw and ketominer — https://fountain.fm/episode/wNowMP7zxD25kKMLCU4r
- CD30: bitcoin privacy and the danger of KYC with samouraiwallet and openoms — https://fountain.fm/episode/AoIhaVfVHG55gEJOlEiH
- CD43: bitcoin for beginners with BitcoinQ_A— https://fountain.fm/episode/Foh3ImV2fZYPvg2QgNA4
I've also created a Fountain playlist which can be found here. One benefit of the playlist is that you can easily share the group of episodes in its entirety.
-
 @ 8d34bd24:414be32b
2025-01-12 03:44:53
@ 8d34bd24:414be32b
2025-01-12 03:44:53Our old pastor, Jack Olsen (2 pastors ago), still attends our church and preaches occasionally. Today, he gave his annual New Year’s sermon where he encouraged us to pray about a word and a verse to guide us through the year. To be honest, I generally don’t like this kind of thing. It feels too gimmicky for my logical, engineer’s mind, but as I was thinking about how I don’t like this thing, the word share came to mind.
As Christians, we are called to share many things. Of course to be able to share, we have to have built up something to share. Let’s review some of the things God might call us to share.
Share Property
He who is generous will be blessed,\ For he gives some of his food to the poor. (Proverbs 22:9)
With some of the misinterpretations in our culture, I need to make some clarifications. This is not referring to voting to have the government take care of the poor. This is not referring to everyone having the same thing despite how hard they work or how much talent they have. This is calling for personal charity as each one is called upon by God. You will also note that it says “he gives some of his food to the poor.” It is appropriate to keep some of what you earn to take care of you and your family.
The Bible also says:
The hard-working farmer ought to be the first to receive his share of the crops. (2 Timothy 2:6)
The primary benefactor of hard work, should be the worker. No one has the right to take from the one who worked to give to the one who did not.
For even when we were with you, we used to give you this order: if anyone is not willing to work, then he is not to eat, either. (2 Thessalonians 3:10)
On the other hand, everything belongs to our Creator and God. We are solely stewards of what He has enabled us to earn. God promises blessings to those who are generous with what God has given them and counts this generosity as if we had done it to Him.
“Then the King will say to those on His right, ‘Come, you who are blessed of My Father, inherit the kingdom prepared for you from the foundation of the world. For I was hungry, and you gave Me something to eat; I was thirsty, and you gave Me something to drink; I was a stranger, and you invited Me in; naked, and you clothed Me; I was sick, and you visited Me; I was in prison, and you came to Me.’ Then the righteous will answer Him, ‘Lord, when did we see You hungry, and feed You, or thirsty, and give You something to drink? And when did we see You a stranger, and invite You in, or naked, and clothe You? When did we see You sick, or in prison, and come to You?’ The King will answer and say to them, ‘Truly I say to you, to the extent that you did it to one of these brothers of Mine, even the least of them, you did it to Me.’ (Matthew 25:34-40) {emphasis mine}
God also calls those who have been blessed more to bless others as God has blessed us.
Instruct those who are rich in this present world not to be conceited or to fix their hope on the uncertainty of riches, but on God, who richly supplies us with all things to enjoy. Instruct them to do good, to be rich in good works, to be generous and ready to share, storing up for themselves the treasure of a good foundation for the future, so that they may take hold of that which is life indeed. (1 Timothy 6:17-19) {emphasis mine}
There is a benefit to living meager, saving well, and getting to the point where you can be generous towards both those in need and those in ministry. If you allow yourself to get in debt, you are a slave to that debt and can’t have the blessing of blessing others. If you are in debt, you can’t easily pick up and go into missions if you feel God calling you. Managing your money well determines whether money controls you or you are free to spend your money for God’s glory.
Also, don’t lie to yourself and say that you are saving and making money for God, when you are solely spending it on your own comfort or stashing it away to protect yourself instead of relying on God. You definitely aren’t fooling God. You likely aren’t fooling others. You are depriving yourself of the blessing of helping others and seeing their joy and thankfulness.
Be devoted to one another in brotherly love; give preference to one another in honor; not lagging behind in diligence, fervent in spirit, serving the Lord; rejoicing in hope, persevering in tribulation, devoted to prayer, contributing to the needs of the saints, practicing hospitality. (Romans 12:10-13) {emphasis mine}
We can use our wealth (and our time & talents) to help those in need (believers and unbelievers) as well as to support missionaries, churches, and ministries in their work sharing the gospel with unbelievers and discipling immature Christians. Everything we “spend” to support the body of Christ and His work will be blessed.
The one who is taught the word is to share all good things with the one who teaches him. Do not be deceived, God is not mocked; for whatever a man sows, this he will also reap. For the one who sows to his own flesh will from the flesh reap corruption, but the one who sows to the Spirit will from the Spirit reap eternal life. Let us not lose heart in doing good, for in due time we will reap if we do not grow weary. So then, while we have opportunity, let us do good to all people, and especially to those who are of the household of the faith. (Galatians 6:6-10) {emphasis mine}
Although we are all expected to share the Gospel with others, some people have a calling and a talent while others may be called to support those who are called to “go make disciples.” We need to use our wealth, our talents, our time, and every other thing God has given us in service to His glory and drawing others to Him.
Share Hope
We live in a very dark world where people are desperately searching for hope (usually in all of the wrong places). We are called to be a light in this darkness. I’d argue that two things stand out in the darkness more than anything else and both of them come from Jesus — love and hope.
But even if you should suffer for the sake of righteousness, you are blessed. And do not fear their intimidation, and do not be troubled, but sanctify Christ as Lord in your hearts, always being ready to make a defense to everyone who asks you to give an account for the hope that is in you, yet with gentleness and reverence; and keep a good conscience so that in the thing in which you are slandered, those who revile your good behavior in Christ will be put to shame. For it is better, if God should will it so, that you suffer for doing what is right rather than for doing what is wrong. (1 Peter 3:14-17) {emphasis mine}
God wants us to “always being ready to make a defense to everyone who asks you to give an account for the hope that is in you.” How can we be ready? We can study God’s word and especially His promises, so we know them backwards and forwards and can share them with others. We can be constantly searching for God working in our lives, our churches, fellow believers, and even in our country and the world and can join Him in His work. When we are looking for His works, we will see them and can share them with others.
In 2015 We had our hot water heat pipes break and had a long fight with insurance. We then had our house burn down in a fire. The next month my husband’s car’s engine blew up. The next month he ruptured his achilles tendon and we missed Christmas with family. Then the beginning of the following year, he got blood clots in his leg and had to be on blood thinners for months. Most people going through something like that would be crying “Why me?” and likely be in despair.
We were looking for God’s hand in our troubles and what He was teaching us and what good He was doing. The flooding caused us to change insurance 10 days before our house burnt down. The new insurance company had us paid for the whole house, barn, trees, and a year’s rent in barely over a month. The rental house we stayed in had a layout that was so much easier to take care of my husband, when he couldn’t even touch his toe to the ground while healing, than the house that burnt down. Because the first insurance only wanted to pay barely over half of the repair costs of the flood, we had to sue them and got a settlement. The fire happened so soon afterwards that most of that money was left over to apply to our new home. We were able to rebuild the home as our dream home and when we were done we had a paid off house. God provided for our every need and we ended up much better off after the hardship than we had been before. Every member of our family grew in their faith in God and our story has blessed many others in their hardships.
(for the Law made nothing perfect), and on the other hand there is a bringing in of a better hope, through which we draw near to God. (Hebrews 7:19) {emphasis mine}
As things grow more and more evil around the world, people are looking for hope. Jesus is the hope of the world. He is the perfect, holy God who came to earth as a man and lived the perfect life that we cannot, and paid the price for our sins. He is our savior and our example.
For this reason, therefore, I requested to see you and to speak with you, for I am wearing this chain for the sake of the hope of Israel.” (Acts 28:20) {emphasis mine}
When we go through hard times and lean on God, we learn that there is nothing He cannot handle and we can have hope. When people see the hope in us, even when they know we are going through the hardest of times, then they want what we have. This is the moment that the Gospel changes lives.
Share the Gospel
Probably the most important thing we can share is the Gospel — the good news about Jesus Christ our Savior.
For though I am free from all men, I have made myself a slave to all, so that I may win more. To the Jews I became as a Jew, so that I might win Jews; to those who are under the Law, as under the Law though not being myself under the Law, so that I might win those who are under the Law; to those who are without law, as without law, though not being without the law of God but under the law of Christ, so that I might win those who are without law. To the weak I became weak, that I might win the weak; I have become all things to all men, so that I may by all means save some. I do all things for the sake of the gospel, so that I may become a fellow partaker of it. (1 Corinthians 9:19-23) {emphasis mine}
When sharing the Gospel, people need to understand who Jesus is (God, Creator, and perfect man) and have to understand that they have disobeyed their Creator’s commands and are worthy of death. Telling a person they need a Savior without telling them what they need saving from is a futile task. On the other hand, brow beating people with their sin isn’t likely to make them want to trust Jesus.
The above verse talks about becoming relatable to people. We want people to see Christ in us and the difference He makes in our lives. At the same time, we don’t want to be perceived as that strange person they can’t relate to. We also don’t want to be perceived as a super holy person on a pedestal, that was able to “work” their way into God’s good graces in a way they never could. We need to be a good friend. We need to speak the truth while being gentle and loving.
As we share the Gospel and do everything in our power to win them to Jesus, we have to realize that only God can truly call a person to repentance and salvation. If we do all we can, we at best “save some.” Also, it isn’t us doing the saving, but we are blessed when we act as a tool of God for His glory.
But we proved to be gentle among you, as a nursing mother tenderly cares for her own children. Having so fond an affection for you, we were well-pleased to impart to you not only the gospel of God but also our own lives, because you had become very dear to us. (1 Thessalonians 2:7-8) {emphasis mine}
Most Christians have a tendency to err to one extreme or another. They are so worried about being loving, that they don’t speak the truth and point out sin. Without understanding their sin, they won’t ever repent from a sin they don’t know they have committed. These Christians can love people straight into Hell. On the other hand, there are people so focused on the truth, holiness, and obeying God, that they are very harsh to those who have not trusted in Jesus or even new Christians who are not far on their path to sanctification. They forget that they were once the same. We need to reach a proper balance where we tell the truth gently and in a loving manner. We need to be honest about our own failings. We need to sacrifice our comfort for other’s well being, whether physical or spiritual.
So, for my part, I am eager to preach the gospel to you also who are in Rome.\ For I am not ashamed of the gospel, for it is the power of God for salvation to everyone who believes, to the Jew first and also to the Greek. For in it the righteousness of God is revealed from faith to faith; as it is written, “But the righteous man shall live by faith.” (Romans 1:15-17) {emphasis mine}
So often we hold back speaking up against sin or speaking up about Jesus and the Bible. We think others will think us weird. We think we will harm friendships. We think we will be ostracized. We need to understand how important faith in Jesus is. These people’s eternity depends on repenting and trusting Jesus. We also need to consider who is more important to please: family, friends, coworkers, or God? My prayer for you (and for myself) is that we will always be “eager to preach the gospel” and “not ashamed of the gospel.”
Therefore do not be ashamed of the testimony of our Lord or of me His prisoner, but join with me in suffering for the gospel according to the power of God, who has saved us and called us with a holy calling, not according to our works, but according to His own purpose and grace which was granted us in Christ Jesus from all eternity, (2 Timothy 1:8-9) {emphasis mine}
Although ultimately sharing the Gospel leads only to blessings, in the short run there will be people who resent us. There will be people who make fun of us and belittle us. We may even lose relationships or even a job. Despite this, we are called to “not be ashamed of the testimony of our Lord” and to “join with me in suffering for the gospel according to the power of God” because it is “according to His own purpose and grace.”
For if I preach the gospel, I have nothing to boast of, for I am under compulsion; for woe is me if I do not preach the gospel. For if I do this voluntarily, I have a reward; but if against my will, I have a stewardship entrusted to me. What then is my reward? That, when I preach the gospel, I may offer the gospel without charge, so as not to make full use of my right in the gospel. (1 Corinthians 9:16-18) {emphasis mine}
I have noticed as time goes by that I feel the calling to share the gospel more and more. I’m not sure if this is because as I get closer to God, I hear Him more clearly, or if it is because as I learn His word more completely, I have more that is worth sharing, but I can relate to Paul’s feelings “woe is me if I do not preach the gospel.” (I am most definitely not saying that my words, or my interpretation of scripture is anywhere near Paul’s authority or clarity.)
Share Joy
Part of the world’s darkness is caused by the sin that is rampant today and even being glorified. I don’t know if it is just a result of this sin or if it is a whole other form of darkness, but I also see despair everywhere. People are unhappy. They feel hopeless. Many are so hopeless that they even resort to suicide. One thing that helps draw people to Jesus is the joy of the believers.
O clap your hands, all peoples;\ *Shout to God with the voice of joy*.\ For the Lord Most High is to be feared,\ A great King over all the earth.\ He subdues peoples under us\ And nations under our feet.\ He chooses our inheritance for us,\ The glory of Jacob whom He loves. Selah.\ God has ascended with a shout,\ The Lord, with the sound of a trumpet.\ Sing praises to God, sing praises;\ Sing praises to our King, sing praises. (Psalm 47:1-6) {emphasis mine}
We are called to praise God in joy, not just in good times, but especially in the hard times. God has chosen “our inheritance for us.” He has gifted us each with different skills, talents, spiritual gifts, and opportunities. He expects us to make the most of what He has given us. When we use these gifts according to His purpose for us, we can find peace and joy even in the most difficult circumstances. We grow most in difficult circumstances and we shine the light of Jesus most brightly in difficult circumstances. Instead of saying, “Why me?” we need to say, “Use me.”
What was from the beginning, what we have heard, what we have seen with our eyes, what we have looked at and touched with our hands, concerning the Word of Life— and the life was manifested, and we have seen and testify and proclaim to you the eternal life, which was with the Father and was manifested to us— what we have seen and heard we proclaim to you also, so that you too may have fellowship with us; and indeed our fellowship is with the Father, and with His Son Jesus Christ. These things we write, so that our joy may be made complete. (1 John 1:1-4) {emphasis mine}
We receive the most joy when we are obeying God and working according to His purpose. (FYI, works don’t get you into heaven, but works after salvation do lead to blessings.) When we have joy, we can share joy with others.
It isn’t a major spiritual thing, but I noticed during the masking in 2020, I could get away with not wearing a mask. I smiled at everyone. I smiled at the person I passed on the sidewalk. I smiled at the person I passed in the shopping aisle. I smiled at the checkout clerk. I rarely got questioned about not wearing a mask (although I did get quite a few quizzical looks). I think this was because everyone was so starved for personal interaction and a smile. It made people realize what they were missing. They would smile back, even if all I could see was the wrinkles around the eyes from the smile. I like to think that I made these people’s days a little brighter and helped others to escape from the fear and loneliness they were feeling.
Joy is contagious. Joy makes everything better. When we have joy, others want what we have, which is Jesus.
Now may the God of hope fill you with all joy and peace in believing, so that you will abound in hope by the power of the Holy Spirit. (Romans 15:13)
and
For I have come to have much joy and comfort in your love, because the hearts of the saints have been refreshed through you, brother. (Philemon 1:7)
We need to share our hope, joy, and love. It draws the unbeliever to Christ and refreshes the fellow believer who is suffering.
Last of all, we need to remember that God doesn’t promise us an easy life, but He does promise us that it will be worth it.
Consider it all joy, my brethren, when you encounter various trials, knowing that the testing of your faith produces endurance. And let endurance have its perfect result, so that you may be perfect and complete, lacking in nothing. (James 1:2-4) {emphasis mine}
Share Persecution
One of the strangest things in Scripture is the call to rejoice in suffering. If someone was making up a religion, they wouldn’t say “Let’s tell everyone that if they join our religion they will be constantly persecuted and will suffer all of their days.” The Bible has an inordinate number of passages that warn us that we will will experience hardship and that we should rejoice in this hardship.
Beloved, do not be surprised at the fiery ordeal among you, which comes upon you for your testing, as though some strange thing were happening to you; but to the degree that you share the sufferings of Christ, keep on rejoicing, so that also at the revelation of His glory you may rejoice with exultation. (1 Peter 4:12-13) {emphasis mine}
We are called to rejoice in hardship and to share that joy with others who are experiencing hard times. We are literally called to “share the sufferings of Christ” with rejoicing. Most of us would consider this expert level Christianity, but each and every one of us are called to rejoice when we “share the sufferings of Christ.”
But even if I am being poured out as a drink offering upon the sacrifice and service of your faith, I rejoice and share my joy with you all. You too, I urge you, rejoice in the same way and share your joy with me. (Philippians 2:17-18) {emphasis mine}
Until we truly learn to lean completely on God, it is hard to rejoice in suffering, but even harder is seeing someone we love suffer. I can rejoice in suffering, especially if I can see how God is using it for good, but it becomes much harder when my kids are suffering. I always think of Mary watching her son, Jesus, dying on the cross. I can’t imagine a much worse heartache than that, but even she was called to rejoice because this torturous event was for her good and her salvation, as well as the salvation of every believer throughout history. Learn the power of joy, choose joy, and then share that joy with everyone around you and your witness will be great.
But I rejoiced in the Lord greatly, that now at last you have revived your concern for me; indeed, you were concerned before, but you lacked opportunity. Not that I speak from want, for I have learned to be content in whatever circumstances I am. I know how to get along with humble means, and I also know how to live in prosperity; in any and every circumstance I have learned the secret of being filled and going hungry, both of having abundance and suffering need. I can do all things through Him who strengthens me. Nevertheless, you have done well to share with me in my affliction. (Philippians 4:10-14) {emphasis mine}
The beginning portion of this passage is a familiar description of trusting God in all situations, but I never truly saw the last sentence. Paul is not just calling fellow believers to “rejoice in the Lord greatly” and to be “ content in whatever circumstances,” but he is also calling them to “share with me in my affliction.” Instead of warning away others so they won’t experience the affliction he is experiencing, he is calling them to share his affliction. He is sharing his affliction with them. Why? Because he knows the blessings that come from faithful service and the afflictions that usually come from that faithful service. He knows that “For momentary, light affliction is producing for us an eternal weight of glory far beyond all comparison.” (2 Corinthians 4:17)
I hope that this year each of you will search for how you can share the blessings that God has given you, and that you will look and see how much God has blessed you even in the hardships that all of us experience.
For the ministry of this service is not only fully supplying the needs of the saints, but is also overflowing through many thanksgivings to God. Because of the proof given by this ministry, they will glorify God for your obedience to your confession of the gospel of Christ and for the liberality of your contribution to them and to all, while they also, by prayer on your behalf, yearn for you because of the surpassing grace of God in you. Thanks be to God for His indescribable gift! (2 Corinthians 9:12-15) {emphasis mine}
When we share our possessions, our hope, the Gospel, our joy, and Jesus’s persecution, we will be blessed and we will be a blessing to others. Getting started is so very hard, but when we obey God’s command, the blessings are indescribable.
Trust Jesus.\ \ your sister in Christ,
Christy
Bible verses are NASB (New American Standard Bible) 1995 edition unless otherwise stated
-
 @ f2282232:2bc2659e
2025-01-12 03:18:29
@ f2282232:2bc2659e
2025-01-12 03:18:29homepage
You will all details of my writing here.
This is another test page for publishing through Nostr.
-
 @ f2282232:2bc2659e
2025-01-12 03:11:32
@ f2282232:2bc2659e
2025-01-12 03:11:32homepage
You will all details of my writing here.
This is another test page for publishing through Nostr.
-
 @ 16d11430:61640947
2025-01-11 22:17:34
@ 16d11430:61640947
2025-01-11 22:17:34Introduction: The Moral Framework of Money
From a biblical perspective, money is not inherently evil; rather, it is the love of money that is "the root of all evil" (1 Timothy 6:10). This analysis explores how fiat currency represents the corruption of monetary systems, aligning with biblical warnings about deceit, oppression, and idolatry, while Bitcoin and decentralized technologies reflect principles of fairness, accountability, and redemption.
Fiat: A Manifestation of Mammon
- Deception and False Weights
The Bible condemns dishonest financial practices: “Unequal weights and unequal measures are both alike an abomination to the Lord” (Proverbs 20:10). Fiat money, detached from intrinsic value, operates as a system of unequal weights. Central banks inflate currency at will, eroding purchasing power and creating economic inequality—a modern parallel to the unjust scales condemned in scripture.
- Oppression of the Poor
Fiat enables systemic exploitation: “Do not exploit the poor because they are poor and do not crush the needy in court” (Proverbs 22:22). Inflation acts as a hidden tax, disproportionately affecting the poor and middle class while enriching elites who control the monetary system. The debt-based fiat economy traps individuals in cycles of poverty, akin to the oppressive practices the prophets spoke against.
- Idolatry of Centralized Power
Fiat currency symbolizes reliance on human power rather than divine providence. “You cannot serve both God and money (Mammon)” (Matthew 6:24). Central banks and governments exalt themselves as creators and arbiters of value, leading society to place trust in fallible institutions rather than eternal truths.
- The Tower of Babel Reimagined
Fiat’s global dominance parallels the Tower of Babel (Genesis 11:1-9), where humanity sought to centralize power and defy God. Fiat currencies represent a similar attempt to unify control over economies, resulting in confusion, inequality, and moral decay.
Bitcoin: A Reflection of Biblical Principles
- Truth and Transparency
“You will know the truth, and the truth will set you free” (John 8:32). Bitcoin operates on a decentralized, immutable ledger, offering transparency and truth in financial transactions. Unlike fiat systems prone to corruption, Bitcoin's blockchain ensures accountability, aligning with the biblical call for honesty.
- Fairness and Justice
“But let justice roll on like a river, righteousness like a never-failing stream” (Amos 5:24). With its fixed supply of 21 million coins, Bitcoin prevents the manipulation and theft inherent in fiat inflation. It embodies economic justice, protecting individuals from exploitation by centralized powers.
- Empowerment of the Oppressed
“He has filled the hungry with good things but has sent the rich away empty” (Luke 1:53). Bitcoin provides financial access to the unbanked and marginalized, offering a way out of oppressive systems. In regions suffering from hyperinflation or financial censorship, Bitcoin empowers individuals to reclaim their economic agency.
- Freedom from Mammon
“Stand firm, then, and do not let yourselves be burdened again by a yoke of slavery” (Galatians 5:1). Bitcoin liberates humanity from the bondage of debt slavery imposed by fiat. Its decentralized nature ensures no single entity can wield undue influence over others’ livelihoods.
Eschatological Implications: A New Economic Order
Revelation 13:17 warns of a time when “no one can buy or sell unless he has the mark”—a possible foreshadowing of centralized financial control. Fiat systems, increasingly digital and surveilled, may pave the way for such oppression. Bitcoin, by contrast, decentralizes power, preserving freedom and privacy in the face of authoritarianism.
Conclusion: A Call to Righteous Stewardship
Fiat currency, as a system built on deceit, oppression, and idolatry, reflects humanity’s fallen nature. In contrast, Bitcoin aligns with biblical principles of fairness, transparency, and empowerment. While not divine, Bitcoin serves as a tool to restore justice and accountability in human economies. It is a call to righteous stewardship, reminding us that true wealth is not in earthly treasures but in eternal values: “Do not store up for yourselves treasures on earth…but store up for yourselves treasures in heaven” (Matthew 6:19-20).
Final Thought
Bitcoin may not be salvation itself, but it offers a pathway to resist the corruption of fiat, aligning humanity closer to the principles of justice, freedom, and truth found in scripture.
-
 @ 16d11430:61640947
2025-01-11 22:02:11
@ 16d11430:61640947
2025-01-11 22:02:11Introduction: Fiat as a System of Control
Fiat currency, defined as money issued by governments without intrinsic value and backed solely by trust, is not merely an economic tool; it has evolved into a mechanism of systemic oppression, corruption, and exploitation. Unlike commodity-backed currencies, fiat derives its value from government decree, making it susceptible to manipulation. The advent of Bitcoin and decentralized cryptocurrencies offers humanity a way to overcome these systemic issues, restoring financial sovereignty, fairness, and trust.
A Historical Overview of Fiat's Evolution
- The Rise of Fiat: The Gold Standard's Demise
Fiat's history traces back to the early 20th century, particularly with the abandonment of the gold standard. In 1933, the U.S. confiscated gold from citizens through Executive Order 6102, severing direct ties between money and tangible assets.
In 1971, the Nixon administration formally ended the Bretton Woods system, decoupling the U.S. dollar from gold entirely. This decision enabled the unlimited printing of money, laying the groundwork for inflation, economic bubbles, and wealth disparity.
- The War Machine and Fiat Financing
Fiat currencies have funded endless wars. The Vietnam War, financed by excessive dollar printing, led to the abandonment of gold convertibility.
Governments exploit fiat's elasticity to fund conflicts without immediate taxation, creating a hidden war tax in the form of inflation. For example, the Iraq War (2003) saw over $2 trillion spent, primarily through deficit spending and fiat issuance.
- The Central Banking Cartel
The Federal Reserve, established in 1913, exemplifies fiat's consolidation of power. By controlling the money supply, central banks manipulate economies, often prioritizing private interests over public welfare.
Quantitative easing (QE) post-2008 financial crisis bailed out banks at the expense of the working class, exacerbating inequality.
- Hyperinflation and Fiat's Fragility
Historical examples, such as Weimar Germany (1921–1923), Zimbabwe (2007–2009), and Venezuela (2016–present), demonstrate how fiat collapses lead to societal breakdown.
In Venezuela, hyperinflation exceeded 1,000,000%, eroding savings and forcing citizens into barter economies.
Fiat as a Tool of Oppression
- Inflation: The Hidden Tax
Inflation disproportionately affects the poor and middle class, eroding purchasing power and savings. Over the past century, the U.S. dollar has lost over 96% of its value.
Central banks manipulate interest rates and print money to benefit governments and corporations, leaving ordinary citizens to bear the brunt.
- Debt Slavery
Fiat systems promote perpetual debt. Governments accumulate unsustainable deficits, while individuals are lured into consumer credit traps.
The global debt exceeds $300 trillion, a figure impossible to repay, highlighting the fiat system's Ponzi-like structure.
- Financial Surveillance and Censorship
Fiat's digital evolution has enabled authoritarian regimes to surveil and censor transactions.
Examples include China's social credit system and Canada's freezing of protestors' bank accounts during the 2022 Freedom Convoy protests.
Bitcoin: A Path to Liberation
- Decentralization and Sovereignty
Bitcoin operates without central authority, empowering individuals to control their wealth. Its fixed supply (21 million BTC) ensures immunity to inflationary policies.
Unlike fiat, Bitcoin's transparent ledger (blockchain) fosters trust and accountability.
- Censorship Resistance
Bitcoin transactions cannot be censored or reversed, safeguarding financial freedom.
For instance, activists in Belarus and Nigeria used Bitcoin to bypass government-imposed financial blockades.
- Economic Equality and Inclusion
Bitcoin enables access to financial systems for the unbanked. With 1.4 billion adults lacking access to traditional banking, Bitcoin provides a lifeline through peer-to-peer transactions.
El Salvador's adoption of Bitcoin as legal tender highlights its potential for economic empowerment.
- Ending Fiat-Fueled Corruption
Bitcoin removes the need for trust in corrupt institutions. By limiting monetary expansion, it eliminates the moral hazard of bailouts and reckless spending.
Governments and corporations lose the ability to manipulate economies for political gain.
Case Studies and Evidence
- Cyprus Bail-In Crisis (2013)
During the Eurozone crisis, Cyprus froze bank accounts and imposed a "bail-in," seizing depositor funds. Bitcoin surged as citizens sought refuge from fiat theft.
- Hyperinflation in Venezuela
Venezuelans turned to Bitcoin to preserve wealth amidst hyperinflation, using it for remittances and daily transactions.
- El Salvador's Bitcoin Experiment
Since 2021, El Salvador has utilized Bitcoin to reduce remittance fees and attract foreign investment. Early data suggests improved financial inclusion for the unbanked.
- Nigeria's Bitcoin Boom
Despite government crackdowns, Nigeria remains a top adopter of Bitcoin, demonstrating its role as a tool for resistance against corrupt monetary policies.
A Call to Action: Reclaiming Financial Freedom
Fiat currency is not merely flawed—it embodies systemic corruption, exploitation, and inequality. Bitcoin and cryptocurrencies offer humanity an alternative, built on principles of fairness, decentralization, and freedom. To overcome fiat's grip, global adoption of decentralized finance is imperative. This shift requires education, regulatory advocacy, and grassroots movements to empower individuals.
By embracing Bitcoin, we can dismantle the fiat paradigm, fostering a world where wealth and power are decentralized, and human potential is no longer suppressed by the chains of monetary manipulation.
References
-
"The Creature from Jekyll Island" by G. Edward Griffin (1994)
-
"Debt: The First 5,000 Years" by David Graeber (2011)
-
"When Money Dies" by Adam Fergusson (1975)
-
Federal Reserve Economic Data (FRED)
-
Bitcoin Whitepaper by Satoshi Nakamoto (2008)
-
World Bank Global Findex Database
-
Case studies from Venezuelanalysis and Bitcoin Magazine
-
 @ 5725c4a8:6ba4f820
2025-01-11 20:47:09
@ 5725c4a8:6ba4f820
2025-01-11 20:47:09Last night I listened to Part 2 of Robert Breedlove's recent interview with Dr. Jack Kruse. There were many elements that I found to be very fascinating with regard to history, and I really appreciated the in-depth discussion from Part 1 about the interplay between human health and light/EMF (which I've been slowly learning about during the past year). But what I will write about in this article is the subject of time.
In that interview, Dr. Kruse connected the timestamping element of Bitcoin to the biological circadian rhythm. This stood out to me because years ago, I made a conscious decision about how I would think about time, and my subjective experience of it. Humans are born with a finite amount of time allocated to their lives.
I think that, like the total supply of Bitcoin, through events that transpire, and choices that we make, we can lose some of that time. Then, conversely, through other actions that we can take, we can gain some of that time back. There is no true life extension, not by any means that are effectively being explored today. Humans live for 120 years, give or take a few, and then they die.
But what about that time that we have? Is it a long time, or a short time? I very seldom hear people talk as if they expect to live long lives. Frequently, you hear the saying that "Life is short", or "Life is too short to not do [such and such]". I even encounter Bitcoiners saying this. Well, is this true?
It depends on you. Is your time short, or is it long? This depends on the choices that you make, and the events that you live through. In some cases, events may transpire which end your life far too soon before you would have died naturally. But even then, is your time short?
It is what you make of it. Even a day can be long or short, depending on what you made of it. Another way to consider this is in terms of quality. Are you living a quality life?
Jack Kruse spoke about circadian rhythm as being the flow meter for human experience of time. If you are unhealthy, this throws off your circadian rhythm, and hence, your subjective experience of time. What makes a person unhealthy? We know more about this question now than perhaps ever before in human history. If humans are not getting enough natural sunlight, from sunup to sundown, there is an impact to their health. If they eat garbage food, there is an impact, even if they never step barefoot outside, there is an impact.
It's easy to stay inside, to watch anime or sitcoms on the TV, play games, and when necessary, to put on your rubber-soled shoes and go to the store to buy more food. It's easy, but the impact on your subjective time makes it short. The day flies by and you will feel like you're losing time. Your time is short, because your flow meter is gunked up; and so your life is short. Then, because your life is short, you will fall into nihilistc thinking and feel compelled to engage in activities that you wouldn't have otherwise.
The converse is also true. I studied Chen Taijiquan (Chen-style Tai Chi) several years back, and my sifu would say, "if you want to get energy, then you have to spend energy" in response to students who complained that some days they didn't feel strong or energetic enough to exercise. To get up before dawn is difficult, but also restorative. To eat only meat (and some limited other foods), to get out for a walk in the hot sun, to hit the gym, these all require us to spend energy, but in response we also get energy. We feel better, our circadian rhythms come into balance. And then our time is long.
When our time is long, then even if our lives are cut short, we will have lived well. As short time leads us to nihilistic thinking, long time leads us to hopeful thinking. It leads us to plan for the future and to seek the betterment of ourselves, our family, our neighbors, and humanity. Because we have hope.
So is your life long or short? It's up to you. It comes down to your mindset and your choices, which will effect your health and circadian rhythm, which will then feed back into experiences that can reinforce that mindset. I'm 38 years old as I write this, and I can gladly say that I've lived a long life, even if I die just after publishing this, because I'm thankful for the good things in my life, the experiences I've had, and the positive influences I know that I had on other people. For the record, I neither EXPECT nor DESIRE to die today.
From my perspective, at 38, I've lived a long life, not a short one. But I can still live much longer. I can do much more, and I can work to build a better future for myself and the ones that I love. Despite the frustrations of the world, I still look forward with hope to the future of having a family, but without the anxiety that my time is slipping away.
This is me, and my thinking. My time is long, and I will pursue the path that maximizes it to the fullest, even with the objective limit of 120 years. And I will not regret it.
So what about you? Is your time long, or short? And what will you do, knowing that you have the tools to change it?
-
 @ 0403c86a:66d3a378
2025-01-11 19:45:53
@ 0403c86a:66d3a378
2025-01-11 19:45:53It's hard to believe it's been a year since we first went live oN Global Sports Central! We're thrilled to celebrate this milestone and take a look back at some amazing numbers.
Here are some highlights:
- Notes: We've published an incredible 5978 notes, with a total of 7260 notes and replies combined!
- Engagement: Our community has shown us love with 7580 likes, 6651 replies, and only 13 reports.
- Zaps: We've received an astonishing 711 #zaps, with a total amount of 79926 #sats received. Plus a couple of decisive #Nostrich that came oN support proven there's a path for #V4V
- Community: We're proud to have 14273 followers iN our first year, with 80K sats received.
- Reach: Our content has been viewed and interacted with by thousands of users, making us one of the most active profiles on #Nostr
We couldn't have done it without you! Your support and engagement have made this journey so rewarding. We're excited to see what the future holds and can't wait to share more updates with you!
Thank you for being part of our journey!
-
 @ 378562cd:a6fc6773
2025-01-11 19:37:30
@ 378562cd:a6fc6773
2025-01-11 19:37:30Money. It’s one of the most powerful forces in our world, and for many, it evokes mixed emotions. On the one hand, money provides security, opportunities, and the freedom to pursue dreams. On the other, it’s often tied to stress, inequality, and a sense of unending competition. This love-hate relationship with money is universal, and it stems from a system that often feels rigged against the average person.
Enter Nostr—a decentralized protocol designed to address some of the deepest flaws in how we interact with value and communication online. While Nostr isn’t just about money, its principles are profoundly reshaping how we think about value exchange, financial sovereignty, and freedom.
The Root of the Problem
At the core of our collective frustration with money is control. Traditional financial systems are centralized, opaque, and prone to manipulation. Whether it’s through inflation eating away at savings, unfair access to banking, or censorship of financial transactions, the system leaves many feeling powerless. Add to this the societal obsession with consumerism and wealth accumulation, and it’s no wonder money can feel more like a burden than a tool.
Even digital spaces, which promised democratization, often mirror these problems. Social media platforms monetize user data while censoring or shadow-banning content. Payment platforms can freeze accounts or deny access, reinforcing the imbalance of power.
Nostr: A Fresh Perspective on Value and Freedom
Nostr (short for "Notes and Other Stuff Transmitted by Relays") isn’t just a technical innovation—it’s a philosophy. Built on a simple yet powerful decentralized protocol, Nostr allows users to share information, communicate, and exchange value directly, without reliance on centralized entities. It’s an open, censorship-resistant network that puts control back into the hands of individuals.
So, how is Nostr addressing the money dilemma?
-
Decentralized Value Exchange\ Nostr integrates seamlessly with tools like Bitcoin’s Lightning Network, enabling instant, low-cost payments without intermediaries. This means individuals can send and receive money directly, whether it’s a micro-tip to support a content creator or a peer-to-peer transaction across borders. No banks. No middlemen. Just value exchanged freely.
-
Censorship Resistance\ One of the most frustrating aspects of modern finance is the potential for censorship. Banks and platforms can freeze accounts or block payments based on arbitrary criteria. Nostr flips this script by creating a network where transactions and communication are uncensorable. Value flows freely, aligned with the principles of individual sovereignty.
-
Empowering Creators\ In traditional models, creators often rely on centralized platforms to earn revenue, losing a significant portion to fees or being at the mercy of algorithms. On Nostr, creators can directly monetize their work through Bitcoin tips or other decentralized payment methods, creating a more equitable system where value flows directly between creator and consumer.
-
Transparency and Trust\ Unlike traditional systems shrouded in secrecy, Nostr operates on an open protocol. This transparency builds trust and removes many of the frustrations people associate with hidden fees, arbitrary rules, or lack of accountability in centralized systems.
A New Relationship with Money
By decentralizing how value is exchanged and communication occurs, Nostr helps redefine the role of money in our lives. It shifts the narrative from control and dependency to empowerment and freedom. Money becomes what it was always meant to be—a tool, not a master.
Imagine a world where tipping someone online is as easy as liking a post, where no one can block you from accessing your own funds, and where creators earn directly from their audience without gatekeepers taking a cut. That’s the world Nostr is helping to build.
Closing Thoughts
The love-hate relationship with money isn’t going away overnight. But as protocols like Nostr grow and mature, they offer a glimpse of what’s possible when we rethink the systems that shape our lives. By putting individuals back in control of their communication and financial exchanges, Nostr is doing more than fixing the flaws of the old system—it’s creating a new one entirely.
In the end, it’s not just about money. It’s about freedom, fairness, and the ability to live a life where value flows freely, aligned with our principles and priorities. Nostr isn’t just a tool; it’s a movement. And for anyone tired of the current system, that’s something worth paying attention to.
-
-
 @ f1989a96:bcaaf2c1
2025-01-11 19:28:24
@ f1989a96:bcaaf2c1
2025-01-11 19:28:24Good morning, readers!
Welcome to 2025! As the year begins, authoritarian regimes have swiftly escalated financial repression, intensifying efforts to dismantle civil society, undermine due process, and suppress dissent.
In Nicaragua, dictator Daniel Ortega advanced financial reforms that would restructure how the country’s central bank and financial institutions operate. The law empowers officials with extensive access to private financial data, the ability to monitor and restrict cross-border flows, and the capacity to deploy law enforcement on those who resist. These measures aim to trap capital in the country and ensure all economic activity aligns with regime interests while enforcing financial control over individuals and civil society.
Across the Pacific, the Chinese Communist Party (CCP) is actively monitoring and censoring economists whose public comments diverge from state interests and narratives, threatening termination of employment if not compliant. This appears to be an attempt to enforce a single economic narrative that aligns with the CCP’s agenda and “bolsters” investor confidence in the flailing Chinese economy.
In technology news, Live Wallet, a desktop app that helps users analyze their Bitcoin unspent transaction outputs (UTXOs), launched a transaction privacy analysis feature. This enables users to assess the degree of privacy in a given transaction, which is vital for those operating under the financial surveillance of authoritarian regimes. Additionally, the Bull Bitcoin mobile wallet implemented asynchronous Payjoins without a server, providing users with a more convenient and accessible way to make private transactions with less need for coordination.\ \ We end with an enlightening conversation between Bitcoin educators Anita Posch and Lorraine Marcel, founder of Bitcoin Dada, discussing the empowering nature of Bitcoin for women who face systemic rights abuses and financial repression. We also feature an article from the Bitcoin Policy Institute (BPI) examining the vitality of privacy in public spaces and emphasizing the importance of Bitcoin’s pseudonymous nature in fostering transactional freedom.
Now, let’s jump right in!
Subscribe Here
GLOBAL NEWS
Nicaragua | Financial Reforms Risk Enshrining Repression Into Law
Nicaraguan dictator Daniel Ortega has proposed financial reforms, granting the nation’s central bank more power while placing private financial institutions under greater state control. The law would restructure how the Central Bank of Nicaragua (BCN) and the Superintendency of Banks and Other Financial Institutions (SIBOIF) operate, making them overseen by a shared board of directors chaired by current BCN president Ovidio Reyes. This proposal would empower officials with access to citizens’ and companies’ private financial data and increase their ability to monitor cross-border transactions to identify those moving funds out of the country. It further stipulates the ability to dismiss financial executives, directors, and auditors without cause and deploy law enforcement against non-compliant individuals. These measures risk enshrining financial repression into law, leaving citizens subject to financial monitoring and control.
China | Regime Monitoring and Censoring Economists
The CCP is tightening control over economic discourse, targeting economists with views diverging from state narratives. This follows a directive from the Securities Association of China (SAC), which urged chief economists at brokerages to align their public statements with government policies and focus on “bolstering” investor confidence. Companies have been instructed to take strict action against “inappropriate commentaries or behaviors,” including termination if it results in “major negative impacts.” This move aims to consolidate the state’s economic messaging and muzzle independent views to ensure a single narrative that aligns with the CCP’s agenda.
Iran | Shutters Onramps to Digital Asset Exchanges
The Iranian government is shutting down the onramps to digital asset exchanges, confining citizens in the nation’s collapsing currency. This comes after the Iranian rial lost 37% of its value against the US dollar in 2024, prompting many Iranians to turn to digital assets like Bitcoin. Before this recent shutdown, Iran froze the bank accounts of digital asset exchanges to prevent capital flight. The regime also suspended payment processing services under the pretense of money laundering. For Iranians enduring severe inflation, financial repression, and an isolated economy, Bitcoin represents one of the few remaining paths to financial freedom — a path the regime is now working to block.
Sudan | Replaces Banknotes Amid Civil War
Sudan is replacing its old banknotes with new 1,000- and 500-pound notes through a currency replacement program. Citizens are urged to deposit old notes at banks for new ones. However, the ongoing conflict between the Sudanese Armed Forces (SAF) and the paramilitary Rapid Support Forces (RSF) is complicating matters. In RSF-held areas, the new currency has been declared illegal. This has left locals unable to exchange their old notes and facing the risk of losing their savings. Meanwhile, withdrawal limits, high fees, and inadequate banking access hinder citizens from exchanging their old notes in SAF-controlled regions. This currency replacement program is exacerbating financial exclusion and exposing the perils of centralized currency in conflict zones.
Russia | War Expenditures Driving Inflation
Russia’s escalating war spending is fueling inflation and deepening financial hardships for its citizens. Housing costs have surged 30% since Vladimir Putin’s invasion of Ukraine, and mortgage rates have followed, making homeownership increasingly unattainable for many. Meanwhile, a weakening ruble is quickly eroding family savings across the country. These disparities reveal the state’s failure to balance priorities, leaving Russians at the mercy of state policies and a deteriorating economy as the regime prioritizes its geopolitical offense. Citizens who never had a democratic choice to go to war are forced to pay the consequences.
Cambodia | Approves Stablecoins While Bitcoin Remains Banned
The National Bank of Cambodia now permits financial institutions to offer services using “qualifying” stablecoins (a digital currency pegged to a fiat currency) despite maintaining a nationwide ban on Bitcoin. This directive seeks to better regulate digital asset operations, with stablecoins being a focal point, likely due to their centralized nature and easier oversight. This comes after Cambodia’s government recently blocked 16 digital asset exchanges. Concerns over the regime’s ability to monitor and control stablecoins are amplified by cases like Tether previously (USDT) freezing accounts in the country. Additionally, by permitting stablecoins over Bitcoin, these regulations may serve to protect the Bakong, Cambodia’s central bank digital currency (CBDC), from greater digital currency competition, particularly in domestic payments.
BITCOIN NEWS
Live Wallet | Releases Transaction Privacy Analysis
Live Wallet, a desktop app that helps users analyze their unspent transaction outputs (UTXOs), just released a feature enabling users to assess the privacy of their Bitcoin transactions. With the release, users can now gauge the degree of privacy in a given transaction and label them accordingly. To do so, Live Wallet analyzes transactions for factors such as connection to other bitcoin addresses, amount of bitcoin in the wallets used, reuse of the same bitcoin address, and more. This feature will help human rights defenders and dissidents to better protect their financial privacy while operating in countries ruled by authoritarian regimes.
Bull Bitcoin Wallet | Implements Serverless Asynchronous Payjoin
Bull Bitcoin Wallet, an open-source and self-custodial Bitcoin wallet for Android, became the first mobile Bitcoin wallet to allow users to send and receive asynchronous Payjoin transactions without running their own server. Payjoin is a privacy-enhancing technique for Bitcoin transactions, where both the sender and receiver contribute inputs to the transaction, making it more difficult to ascertain who the payer and payee are. Implementing asynchronous Payjoin in its mobile wallet means users can now conduct Payjoins even if one party is not actively online to participate in the transaction. This provides users with a more convenient and accessible way to make private transactions with less need for coordination.
RaspiBlitz | Integrates Alby Hub
RaspiBlitz, an open-source project enabling users to run a Bitcoin and Lightning Network node on a Raspberry Pi, introduced an Alby Hub integration. With this update, individuals can use Raspberry Pis (a small, low-cost computer) to host Alby Hub, a self-custodial, open-source Lightning wallet that easily connects to freedom tech apps like Nostr clients. A popular use for Alby Hub is to make micropayments on the decentralized, censorship-resistant protocol Nostr. HRF is proud to see the integration of self-custodial tools from this past HRF grantee.
Blockstream | Introduces Jade Plus Signing Device
Blockstream, a company developing Bitcoin technology and software, released a new version of its Jade hardware wallet, the Jade Plus. Hardware wallets are devices that allow users to securely transact and custody their Bitcoin while keeping the private key offline. Jade Plus features a larger, brighter display, an enhanced camera for scanning QR codes, and offline firmware updates. The device is also capable of fully air-gapped (disconnected from the Internet) transactions. These improvements will make it easier for non-technical users to securely self-custody their Bitcoin. You can view it here.
Zapstore | Adds Ability to “Zap” App Developers
Zapstore, a decentralized and censorship-proof app store built on the Nostr protocol, recently added the ability to “Zap” (a bitcoin micropayment) app developers via the Lightning Network. With Zapstore, developers can publish and “sign” their application in a permissionless manner to the open-source Nostr protocol, making it available for everyone to use. Rather than relying on a centralized app store (such as Google Play) to verify the legitimacy of a developer and their app, users can use their “web of trust” to view which users follow and “endorse” the app developer. By adding the functionality to Zap, Zapstore lets users support developers building decentralized and censorship-resistant tools for those living in countries ruled by authoritarian regimes.
Mi Primer Bitcoin | Launches Community Hub
Mi Primer Bitcoin, a nonprofit advancing open-source Bitcoin education, launched a Community Hub, a new platform to support independent Bitcoin Educators. The hub includes two main components: a wiki to provide educators with information and educational resources, and a forum where educators can meet and collaborate to enhance their operations and curriculum. As Mi Primer Bitcoin’s course gets more widely used by communities and educators in autocratic countries, these new resources are sure to benefit those in need for better information about financial freedom.
RECOMMENDED CONTENT
How Bitcoin is Changing Lives for Women in Kenya with Bitcoin Dada
In this interview, Bitcoin educator Anita Posch interviews Lorraine Marcel, the founder of Bitcoin Dada, a women-focused Bitcoin education program in Kenya. They discuss how Bitcoin can empower and uplift women in Africa and beyond, especially those who lack fundamental rights and face financial discrimination. Marcel believes Bitcoin offers a path to financial independence and freedom by breaking social barriers and offering an inclusive, nondiscriminatory technology that empowers women. Watch the full conversation here.
Privacy in Public by Bradley Rettler, Andrew Bailey, and Craig Warmke
In this three-part series for the Bitcoin Policy Institute, philosophers Bradley Rettler, Andrew Bailey, and Craig Warmke discuss the idea of privacy in public spaces. The authors argue that privacy is more than just a personal right but also a vital public good. Further, they examine how Bitcoin’s pseudonymity fosters freedom, allowing individuals to engage in financial and social interactions without fear of surveillance or coercion. The series presents a thought-provoking case for why preserving privacy is a defining cornerstone of a free and open society. You can read part 1, part 2, and part 3 here.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ d6affa19:9110b177
2025-01-11 18:37:36
@ d6affa19:9110b177
2025-01-11 18:37:36What traits make up a quality submissive gentleman? My journey and exploration have led me to realize that there are many essential qualities necessary for a gentleman to flourish in this lifestyle. A Female-Led Relationship (FLR) isn’t just about control or obedience or kink; it’s first and foremost, a relationship—which means it’s about the connection and commitment.
What I’ve learned is that the traits that enhance a man’s ability to be a great partner are also the fundamental traits that shape a submissive man of true quality. Let’s take a look at five traits that I feel define not only a better partner, but also a better submissive in an FLR.
1. Self-love
I could probably write an entire article on this alone. Self-love is the most important trait for a submissive gentleman. The saying “If you can’t love yourself, you can love anyone else” is very true, and if he can’t take care of himself, he can’t take care of another. How a man feels about himself will show up in everything he does—including his service to another. Self-love isn’t selfish, but foundational.
Recognizing his own worth will allow him to embody his submission from a place of strength, whereas an insecure man will constantly need external validation from his partner. This insatiable need for validation will drain his partner’s energy and put a strain on the relationship, or may even place himself in a position to be taken advantage of.
All other traits flow from a gentleman’s self-worth. Any lingering shame he has about his submissiveness or his identity will be present in how well he can serve. For example, he may become defensive if he fails to meet his partner’s expectations, or act out in times of rejection or unmet needs. His self-love directly reflects his ability to show up and be fully engaged in the relationship.
2. Desire to Serve
This is a defining trait for a submissive gentleman because it’s what makes him… well, submissive. It stems from deep-rooted desire to please and is integrated into his entire being—it’s what drives his motivation and purpose. This desire is typically his way of expressing devotion and love, demonstrating his commitment, and finding fulfillment through acts of service.
An authentic desire to serve shapes the relationship by affirming roles (Her leadership, his service) and creating a supportive environment. It’s important to clarify that a genuine desire to please motivates the man to be attentive to and serve his partner in ways that she prefers and not only in the ways he prefers. It’s critical to make this distinction.
3. Vulnerability
Another core trait for a submissive gentleman. No, showing or expressing vulnerability doesn’t make one submissive—but one can’t be truly submissive without it. Vulnerability is a profound demonstration of trust from a submissive gentleman in his partner; it’s a removal of all the emotional barriers that get in the way of seeing who a person truly is, unguarded.
And yet, true vulnerability is tricky to explain. It’s not just opening up emotionally—it has a lot to do with another person’s connection with those emotions. Vulnerability is where true discovery and intimacy happen in a relationship, where the connection becomes more than physical and momentary.
Embracing vulnerability takes a sufficient amount of self-knowledge to understand what barriers need to be dropped, both consciously and unconsciously, to allow another inside. For a submissive gentleman, this means it may not be about expressing the man who wants to serve, but discovering the man behind the one who wants to serve.
4. Integrity
Integrity is the honesty or truthfulness of one’s actions. This is important because it defines a man’s motivations and intentions and makes them known to his partner. With integrity, he is more likely to act in his role more authentically. This means he can serve his partner genuinely without pretense or ulterior motives—which lead to a transactional dynamic.
A submissive gentleman who serves with integrity is much more likely to be reliable and demonstrate consistency (another essential trait). When his behaviors align with his commitments time and time again, it builds the confidence and trust his partner has for him and the relationship, strengthening the connection.
5. Humility
Being able to quiet and tame his ego is another foundational trait that a submissive gentleman should possess. Humility involves the ability to receive feedback and correction from his partner, as well as the willingness to let go of control to her—the essence of surrender. This surrender helps him align his actions to her desires more seamlessly by doing what she asks when she asks, without unnecessary push-back.
For a submissive gentleman, the ego can be a tricky thing. Because he finds fulfillment in serving, he may tend to lead with his preconceived notions about what “submission” looks like. He may also only “feel” submissive to his partner when she interacts in certain ways. This is his ego. An ego-driven submissive will struggle over control for the vision of the relationship, rather than learning, accepting, and working toward her vision. Embracing humility is an understanding that the true criteria for pleasing his partner resides only within her and not himself—that his service to her is for her and not himself.

Closing Thoughts
So these traits are what I consider essential for a submissive gentleman to possess: self-love, the desire to serve, vulnerability, integrity, and humility. Honestly, it was difficult to choose only five. As I was considering them, so many more important traits came to mind like loyalty, consistency, attentiveness, emotional resilience, self-control, courage, gratitude, communication, and on and on and on. But I didn’t want this piece to become lengthy, so I kept it at five.
While all of these other traits are vital as well, I felt like the five traits explored are what embody the heart of a submissive gentleman best. As mentioned at the beginning, these are excellent traits to develop for healthy connections and relationships. The journey of “submission” for a man isn’t about self-erasure or relinquishing control; it’s about finding deeper purpose and connection in a way that honors his truth—it’s about self-growth and becoming a man capable and worthy enough to honor and serve the female leadership in his life with authenticity and devotion.
Do these traits resonate with you? Maybe you have some other traits or insights to share—please, feel free to share your thoughts in the comments.
-
 @ 5a8e581f:c150c8ba
2025-01-11 18:31:08
@ 5a8e581f:c150c8ba
2025-01-11 18:31:08Doing Bitcoin the right way is hard.
If Bull Bitcoin wanted to take the easy path, we would have done what all the other exchanges are doing and would simply have offered a custodial wallet to our users. But our mission is not to sell numbers on a screen, fake paper bitcoin and IOUs. Our mission is to create sovereign individuals. If our clients don’t take full control over their wealth, we have failed them.
If we wanted to take the easy path, we would have offered shitcoin trading, NFTs, ICOs, yield and all sorts of nonsense. No doubt, we would today be far more wealthy.
But we would have failed in our mission to establish a universal Bitcoin standard and fixed the problems created by easy money. We would have compromised on our values and sold products that we don’t believe in and we don’t personally use.
If we wanted to take the easy path, we wouldn't have spent years building open-source software that lets any business run their own self-hosted Bitcoin wallet API infrastructure connected directly to their own Bitcoin, Lightning and Liquid network nodes. We would have just done a deal with Coinbase or another third party to take care of the Bitcoin engineering on our behalf.
But we would have failed in our mission to help keep the Bitcoin network decentralized and resilient to institutional failures. We would have lost our direct and precious connection to the Bitcoin network.
The engineering, operational and logistical challenges involved in maintaining a noncustodial Bitcoin service like Bull Bitcoin, in an environment where Bitcoin network fees are increasingly high, while also maintaining an accessible user experience with minimal compromises on the cypherpunk principles of Bitcoin… are impossibly hard to fathom for the vast majority of Bitcoiners.
Despite consistently taking the most difficult path at every turn, Bull Bitcoin has nonetheless been crushing it for the past 10 years thanks to our Bitcoiner ethos and mindset, sticking to our core values and creating products with a singular focus: engineering sovereignty.
All of this we accomplished without any outside funding. Every sat invested in Bull Bitcoin was acquired by offering a service valued by our customers. Every network fee we pay, every investment in R&D comes straight out of our pockets. If our bitcoin-only noncustodial model fails and we become unprofitable, there will be no bailout.
As a low-time preference business, taking the hard path today means we will have a unique competitive advantage in the future. Nobody uses Bitcoin more than a non-custodial exchange. Every trade and every revenue generating activity is derived directly from a Bitcoin payment. We are keenly aware of every possible problem that Bitcoin users may be facing, because we are ourselves are a power user. We know what kinds of problems the users will face, what solutions we need to build and how we must adapt. We always skate where the puck is going.
But there is another, more noble purpose to choosing the hard path.
I'm also heavily involved in a community circular economy project in Costa Rica called Bitcoin Jungle. We spend countless hours to educate locals, set merchants up with Bitcoin point of sales, and build the infrastructure necessary for Bitcoin to thrive as a medium of exchange in even the most rural areas. All of this we do for free, and in fact it we pay for it out of pocket! I discovered recently that a few people were skeptical of our efforts. I met one of them and he asked us “but why are you doing this, if you don't make any money from it”.
We do it because we love Bitcoin. We believe in the ideology of Bitcoin, its underlying cypherpunk and free market principles. We do it because we as sovereign individuals cannot live in isolation and we all benefit from the success of our communities. We do it because we want our kids to grow up in a world that is free from the evils of Fiat currency. May our children never suffer the corruption of participating in a socialist economic system that steals their time and their wealth by the simple fact of interacting with fiat currency. We do it because doing it is a moral imperative. In a world of systematic injustice, doing nothing is to be complicit. You cannot live a virtuous life with the knowledge that you had the capacity to act heroically but chose to capitulate.
Bitcoin is at the center of a spiritual war between forces of corruption and forces of liberation. There is a higher power that calls us to become the resistance. Bitcoin is hope. Bitcoin is salvation. If Bitcoin fails, everyone on earth is truly and utterly fucked.
We are on the cusp of a fundamental civilizational change. The global debt-fueled fiat ponzi is imploding right before our eyes. What comes next is up to us to determine. We are the right place and the right time. We have a unique window of opportunity that may not come again within our lifetimes and that of our children.
The choices we make today will shape what the world looks hundreds of years from now. Whether our descendants live in totalitarian dystopias or will be ushering in a new era of prosperity and freedom depends on our willingness to choose the hard path today.
And if you think the hard part is over and that Bitcoin has already won, think again. During our decade of operational experience, there were few serious attacks on the Bitcoin network. Bitcoin had relatively low levels of adoption and apart from a few periods of intense fee spikes and the fork wars of 2017, it was smooth sailing. Bitcoin was mostly flying under the radar, left to develop organically in the hands of its cypherpunk caretakers.
This era of complacency is over. From now on, everything is about to get much, much harder. This is what we live for! Nothing easy is worth pursuing.
Bull Bitcoin hasn't given up on Bitcoin's mission to free humanity from the shackles of fiat slavery and centralized systems, we are reinvigorated by the challenges that Bitcoin is facing and that will continue to intensify.
We will not give up on Bitcoin's use case as a medium of exchange and we will continue to build tools that make it easy for anyone to opt out of the traditional banking system to conduct peer-to-peer transactions securely, as was originally intended by Satoshi when launched the Bitcoin project.
This new epoch, Bull Bitcoin is leveling up to an entire new standard for consumer-facing Bitcoin apps, higher than anyone has ever seen. We have been thinking about how to make our unique noncustodial model work sustainably long-term for years. This is the hill that we choose to die on.
But as we entered into a new Bitcoin epoch, I've witnessed many in the Bitcoin community become cynical, fatalistic and even depressed. It’s hard to blame them.
Privacy-preserving tools are being shut down. The Lightning Network is suffering scalability issues. The Bitcoin blockchain is being spammed by degenerate NFT gamblers, driving up transaction fees for everyone else. Bankers and Wall Street insiders are accumulating Bitcoin fortunes and promoting exchange traded funds as an alternative to self-custody. Bitcoin mining is being heavily centralized among a small group of American-based public companies. It sometimes feels like Bitcoin is under attack by various nefarious interests that want to control it and corrupt it.
Even from within our own community we are suffering from prophets of doom spewing fear, uncertainty and doubt. Many sneer that Lightning is broken, that Bitcoin has been co-opted by Wall Street. Some say we should give up and switch to altcoins. Some pundits blame “lasereyed maxis” for blocking protocol changes and claim that being conservative about modifying the rules of Bitcoin means “ossification” and that's the reason why Bitcoin has high fees. Others are pushing the idea that Bitcoin was never meant for payments anyway and that being a store of value was always the main goal of Bitcoin. Who cares about the poor? The plebs can always keep their funds on an exchange.
At Bull Bitcoin, we see it very differently. We have a realistic and optimistic approach towards building a bright future for Bitcoin. I have never been so bullish on the future Bitcoin as I am today.
Make no mistake: the core principles of Bitcoin self-custody, censorship-resistance and privacy are under attack. But the Bitcoin community possesses a unique advantage that will ultimately allow us to prevail: not only do we have skin in the game, we have soul in the game.
Our tribe of a few thousand cypherpunk Bitcoin maximalist fanatics stand against an empire of fiat clones, millions of faceless cogs in a soulless machine. I like our odds.
While I agree that we should never take Bitcoin’s success for granted, the bleak picture that some want to paint regarding the state of Bitcoin is detached from reality.
We've already achieved incredible technological miracles. The fact that it is possible for a user to run a Lightning network node on a mobile device and make fully trustless payments is a monumental achievement. Despite what they claim I can guarantee that no other shitcoin or fiat payment system has anywhere near the level of sophistication of Bitcoin. It is an incredibly bullish sign for the Bitcoin ecosystem that we have achieved a level where users can remain fully sovereign if they have the means.
Scaling Bitcoin so that it can enable hundreds of millions of people to become sovereign individuals is the most pressing challenge of our times. Our community must accept inevitable realities: not everybody will be able to afford on-chain transactions. The success of Bitcoin means that one day, during our lifetimes, a single Bitcoin translation will cost hundreds of dollars.
Upgrading the Bitcoin protocol may allow us to create tools that enable a more secure, censorship-resistant and private payment mechanism, but no soft fork can fix the fundamental tradeoffs of the Bitcoin protocol.
But this doesn't mean that we should either give up on Bitcoin’s value proposition as a medium of exchange, or that we must fork bitcoin according to the whims of whoever is trending on Twitter, nor should we capitulate to traditional exchanges acting as banks for the vast majority of users.
To fix the inconvenient and expensive user experience that most people are suffering in times of high fees while making the minimum amount of compromises, you need vision and execution.
There is an army of shadowy super coders that, like us, have dedicated their lives to ensure that Bitcoin becomes the universal medium of exchange, store of value and medium of account. We come from different walks of life and we have different strategies. Some of us work on self-sovereign consumer applications. Other focus of privacy protocols, mining decentralization, second later payment networks, e-cash protocols, and finally, as a last resort, some are working to add changes to the Bitcoin protocol which can enable tools that we currently cannot build.
At Bull Bitcoin, our vision of the future Bitcoin experience is crystal clear. It is a vision of success and integrity, where the path of least resistance for the user is also the path of least compromise.
We, the Bitcoin builders, will make it real.
-
 @ 0d97beae:c5274a14
2025-01-11 16:52:08
@ 0d97beae:c5274a14
2025-01-11 16:52:08This article hopes to complement the article by Lyn Alden on YouTube: https://www.youtube.com/watch?v=jk_HWmmwiAs
The reason why we have broken money
Before the invention of key technologies such as the printing press and electronic communications, even such as those as early as morse code transmitters, gold had won the competition for best medium of money around the world.
In fact, it was not just gold by itself that became money, rulers and world leaders developed coins in order to help the economy grow. Gold nuggets were not as easy to transact with as coins with specific imprints and denominated sizes.
However, these modern technologies created massive efficiencies that allowed us to communicate and perform services more efficiently and much faster, yet the medium of money could not benefit from these advancements. Gold was heavy, slow and expensive to move globally, even though requesting and performing services globally did not have this limitation anymore.
Banks took initiative and created derivatives of gold: paper and electronic money; these new currencies allowed the economy to continue to grow and evolve, but it was not without its dark side. Today, no currency is denominated in gold at all, money is backed by nothing and its inherent value, the paper it is printed on, is worthless too.
Banks and governments eventually transitioned from a money derivative to a system of debt that could be co-opted and controlled for political and personal reasons. Our money today is broken and is the cause of more expensive, poorer quality goods in the economy, a larger and ever growing wealth gap, and many of the follow-on problems that have come with it.
Bitcoin overcomes the "transfer of hard money" problem
Just like gold coins were created by man, Bitcoin too is a technology created by man. Bitcoin, however is a much more profound invention, possibly more of a discovery than an invention in fact. Bitcoin has proven to be unbreakable, incorruptible and has upheld its ability to keep its units scarce, inalienable and counterfeit proof through the nature of its own design.
Since Bitcoin is a digital technology, it can be transferred across international borders almost as quickly as information itself. It therefore severely reduces the need for a derivative to be used to represent money to facilitate digital trade. This means that as the currency we use today continues to fare poorly for many people, bitcoin will continue to stand out as hard money, that just so happens to work as well, functionally, along side it.
Bitcoin will also always be available to anyone who wishes to earn it directly; even China is unable to restrict its citizens from accessing it. The dollar has traditionally become the currency for people who discover that their local currency is unsustainable. Even when the dollar has become illegal to use, it is simply used privately and unofficially. However, because bitcoin does not require you to trade it at a bank in order to use it across borders and across the web, Bitcoin will continue to be a viable escape hatch until we one day hit some critical mass where the world has simply adopted Bitcoin globally and everyone else must adopt it to survive.
Bitcoin has not yet proven that it can support the world at scale. However it can only be tested through real adoption, and just as gold coins were developed to help gold scale, tools will be developed to help overcome problems as they arise; ideally without the need for another derivative, but if necessary, hopefully with one that is more neutral and less corruptible than the derivatives used to represent gold.
Bitcoin blurs the line between commodity and technology
Bitcoin is a technology, it is a tool that requires human involvement to function, however it surprisingly does not allow for any concentration of power. Anyone can help to facilitate Bitcoin's operations, but no one can take control of its behaviour, its reach, or its prioritisation, as it operates autonomously based on a pre-determined, neutral set of rules.
At the same time, its built-in incentive mechanism ensures that people do not have to operate bitcoin out of the good of their heart. Even though the system cannot be co-opted holistically, It will not stop operating while there are people motivated to trade their time and resources to keep it running and earn from others' transaction fees. Although it requires humans to operate it, it remains both neutral and sustainable.
Never before have we developed or discovered a technology that could not be co-opted and used by one person or faction against another. Due to this nature, Bitcoin's units are often described as a commodity; they cannot be usurped or virtually cloned, and they cannot be affected by political biases.
The dangers of derivatives
A derivative is something created, designed or developed to represent another thing in order to solve a particular complication or problem. For example, paper and electronic money was once a derivative of gold.
In the case of Bitcoin, if you cannot link your units of bitcoin to an "address" that you personally hold a cryptographically secure key to, then you very likely have a derivative of bitcoin, not bitcoin itself. If you buy bitcoin on an online exchange and do not withdraw the bitcoin to a wallet that you control, then you legally own an electronic derivative of bitcoin.
Bitcoin is a new technology. It will have a learning curve and it will take time for humanity to learn how to comprehend, authenticate and take control of bitcoin collectively. Having said that, many people all over the world are already using and relying on Bitcoin natively. For many, it will require for people to find the need or a desire for a neutral money like bitcoin, and to have been burned by derivatives of it, before they start to understand the difference between the two. Eventually, it will become an essential part of what we regard as common sense.
Learn for yourself
If you wish to learn more about how to handle bitcoin and avoid derivatives, you can start by searching online for tutorials about "Bitcoin self custody".
There are many options available, some more practical for you, and some more practical for others. Don't spend too much time trying to find the perfect solution; practice and learn. You may make mistakes along the way, so be careful not to experiment with large amounts of your bitcoin as you explore new ideas and technologies along the way. This is similar to learning anything, like riding a bicycle; you are sure to fall a few times, scuff the frame, so don't buy a high performance racing bike while you're still learning to balance.
-
 @ 37fe9853:bcd1b039
2025-01-11 15:04:40
@ 37fe9853:bcd1b039
2025-01-11 15:04:40yoyoaa
-
 @ ed84ce10:cccf4c2a
2025-01-11 08:07:52
@ ed84ce10:cccf4c2a
2025-01-11 08:07:52Hackathon Summary
The McGill Physics Hackathon 2024 featured a dynamic 24-hour coding event, spread over three days, encouraging creativity in scientific computing and the physical sciences. With 88 registered developers, the event resulted in 43 projects, showcasing high engagement from teams of 2-5 members. The hackathon emphasized inclusivity by welcoming participants from various disciplines, focusing on curiosity rather than expertise.
Participants interacted with experts from academia and industry, creating a collaborative environment that provided valuable guidance and networking opportunities. This interaction enriched the learning experience for all attendees.
The hackathon fostered diverse applications in scientific computing, demonstrating its goal to inspire fun and creativity within a supportive setting. Its successful execution underscored its role in making scientific computing accessible and enjoyable, promoting innovation without imposing strict thematic restrictions.
For further details about the hackathon, visit here.
Hackathon Winners
Main Track Prize Winners
- Schrödinger's Tic Tac Toe - Integrates quantum mechanics with tic-tac-toe using React.js for the interface and JavaScript for the game logic. The project offers educational gameplay on superposition and decay, featuring dynamic visuals and interactive elements.
- Quantum Pacman - Combines quantum physics with Pacman by using probability distributions to model ghost positions. This project offers a gamified exploration of quantum mechanics through innovative game mechanics.
- Satisfying the Wave Equation: Simulating Light Waves from Scratch - Utilizes GPU acceleration for simulating light wave phenomena, demonstrating interference and diffraction with real-time updates, providing insight into light behavior.
- Kathy and Karth: A Story of Time Dilation - Simulates time dilation through differential speeds and aging effects, illustrated in a practical scenario involving relativistic physics.
- Hackathon Marble Drop - Visualizes mathematical functions through interactive simulations, applying parameters like drag force and gravity to enhance physical concepts understanding.
- Quantum Cloud - Analyzes multi-electron orbitals using the Hartree-Fock method. It visualizes electron dynamics with Python and SciPy, enhanced by Unity for atomic structure representation.
- The Force Awakens: Black Hole Orbital Mechanics N-Body Simulator - Simulates black hole orbital mechanics using gravitational physics, featuring real-time celestial simulations and web-integrated user interaction.
- BloodViz - Models blood flow dynamics in normal and diseased states using Poiseuille's equations, presented through Vue.js for exploring physiological changes related to health.
People's Choice Prize Winner
For a comprehensive view of all submissions and innovations from the McGill Physics Hackathon 2024, visit Dorahacks.
About the Organizer
McGill Physics
McGill Physics, the Department of Physics at McGill University, is renowned for its research and academic excellence. Specializing in areas such as condensed matter physics, astrophysics, and quantum computing, the department is committed to advancing scientific knowledge through cutting-edge research and collaboration. With a strong focus on interdisciplinary projects, McGill Physics actively contributes to pioneering advancements in the field, fostering an environment of discovery to address complex scientific challenges globally.
-
 @ fbf0e434:e1be6a39
2025-01-11 08:04:33
@ fbf0e434:e1be6a39
2025-01-11 08:04:33Hackathon 总结
2024年麦吉尔物理黑客松是一次充满活力的24小时编程活动,历时三天,旨在激发科学计算和物理科学领域的创造力。活动吸引了88名注册开发者,最终提交了43个项目,展示了由2-5名成员组成的团队的高度参与。黑客松注重包容性,欢迎来自不同学科的参与者,重在好奇心而非专业知识。
参与者与学术界和业界的专家互动,创造了一个合作氛围,提供了宝贵的指导和网络机会。这种互动丰富了所有与会者的学习体验。
黑客松促进了科学计算的多样化应用,展示了其目标——在支持性的环境中激发乐趣和创造力。活动的成功执行凸显了它在使科学计算更加可及和有趣方面的作用,推动了创新而不设严格的主题限制。
欲了解更多关于黑客松的详细信息,请访问这里。
Hackathon 获奖者
Main Track Prize Winners
- Schrödinger's Tic Tac Toe - 通过React.js创建界面,使用JavaScript实现游戏逻辑,将量子力学与井字游戏结合。该项目通过动态视觉和互动元素提供了关于叠加和衰变的教育性游戏玩法。
- Quantum Pacman - 通过使用概率分布模拟鬼魂的位置,将量子物理与吃豆人结合。该项目通过创新的游戏机制提供了量子力学的游戏化探索。
- Satisfying the Wave Equation: Simulating Light Waves from Scratch - 使用GPU加速模拟光波现象,展示了干涉和衍射,并通过实时更新提供了对光行为的洞察。
- Kathy and Karth: A Story of Time Dilation - 通过差速和衰老效应模拟时间膨胀,在涉及相对论物理的实际情境中进行了说明。
- Hackathon Marble Drop - 通过互动模拟可视化数学函数,应用阻力和重力等参数来增强对物理概念的理解。
- Quantum Cloud - 使用哈特利-福克方法分析多电子轨道,利用Python和SciPy可视化电子动力学,并通过Unity增强原子结构表现。
- The Force Awakens: Black Hole Orbital Mechanics N-Body Simulator - 使用引力物理模拟黑洞轨道力学,呈现实时天体模拟和网络集成的用户互动。
- BloodViz - 使用泊肃叶方程模拟正常和病态血流动力学,借助Vue.js呈现,用于探索与健康相关的生理变化。
People's Choice Prize Winner
欲全面了解2024年麦吉尔物理黑客松的所有提交作品和创新,请访问Dorahacks。
关于组织者
McGill Physics
McGill Physics是麦吉尔大学的物理学部门,以其卓越的研究和学术声誉闻名。该部门专注于凝聚态物理、天体物理和量子计算等领域,致力于通过前沿研究和合作推进科学知识的进步。麦吉尔物理学系高度重视跨学科项目,积极为全球科学挑战的解决做出开创性贡献,营造了一个发现的环境。
-
 @ fbf0e434:e1be6a39
2025-01-11 07:45:47
@ fbf0e434:e1be6a39
2025-01-11 07:45:47Hackathon 总结
Webfest 2024 是一场以量子计算和教育为主题的探索性Hackathon。该活动由CERN举办,吸引了开发人员参与四个注册挑战,并为现场和远程参与提供了平台。参与者分为五人一组,针对量子计算、密码学和模拟领域的挑战展开合作。
活动注重协作和创新,汇聚了全球的人才来解决复杂的技术问题。团队在四个不同的挑战轨道上竞争,项目由专家评审小组进行评估。Hackathon以每个轨道中的最佳项目获得认可而告终。
一个值得注意的举措是,由DoraHacks NISQ Quantum Computing Grant赞助的现金奖励颁发给领先挑战轨道的获胜团队。这个资助旨在支持进一步的项目开发和研究。总体而言,Webfest 2024促进了全球合作和技术创新,推动了量子计算的发展,并通过共同学习和创造力为参与者带来了丰富的体验。
Hackathon 获奖者
NISQ Quantum Computing Grant Prize Winners
- CRYSTALS-DILITHIUM for Cosmos SDK - 旨在整合后量子的数字签名算法以增强区块链对量子威胁的安全性。该项目更新了基于Dilithium操作的加密模块,确保了区块链生态系统的互操作性和面向未来。
有关项目的完整列表,请访问: https://dorahacks.io/hackathon/webfest2024/buidl
关于组织者
CERN Micro Club
CERN Micro Club以其口号“Computers and People”而闻名,团结了致力于推动计算创新的技术爱好者。该组织专注于利用他们的技术专长,擅长营造一个弥合人与技术之间鸿沟的协作环境。虽然具体成就或项目尚未披露,CERN Micro Club致力于探索计算领域的尖端发展。凭借其在技术社区中的强大存在,通过Twitter (@cmcrobotics) 和其网站等平台的在线互动,该组织不断推动技术互动的边界。
-
 @ ed84ce10:cccf4c2a
2025-01-11 07:43:47
@ ed84ce10:cccf4c2a
2025-01-11 07:43:47Hackathon Summary
The Webfest 2024 was an explorative hackathon centered on advancements in quantum computing and education. Hosted by CERN, the event attracted developers to work on four registered challenges, offering a platform for both in-person and virtual participation. Participants were organized into teams of five, tasked with addressing challenges in quantum computing, cryptography, and simulation.
The event emphasized collaboration and innovation, uniting global talents to tackle complex technical issues. Teams competed across four distinct challenge tracks, with projects evaluated by a panel of expert judges. The hackathon concluded with the recognition of the top project within each track.
A notable initiative was the awarding of a mini-grant cash prize, sponsored by the DoraHacks NISQ Quantum Computing Grant, to the winning team from the leading challenge track. This grant is designed to support further project development and research. Overall, Webfest 2024 promoted global collaboration and technical innovation, advancing quantum computing and providing participants an enriching experience through shared learning and creativity.
Hackathon Winners
NISQ Quantum Computing Grant Prize Winners
- CRYSTALS-DILITHIUM for Cosmos SDK - aims to integrate a post-quantum digital signature algorithm to bolster blockchain security against quantum threats. The project updates cryptographic modules for Dilithium-based operations, ensuring interoperability and future-proofing the blockchain ecosystem.
For a complete list of projects, please visit: https://dorahacks.io/hackathon/webfest2024/buidl.
About the Organizer
CERN Micro Club
CERN Micro Club, recognized for its tagline "Computers and People," unites technology enthusiasts dedicated to advancing computing innovations. Focused on leveraging their technical expertise, the organization excels in fostering a collaborative environment that bridges the gap between people and technology. While specific achievements or projects remain undisclosed, CERN Micro Club is committed to exploring cutting-edge developments in the computing domain. With a strong presence in the tech community, highlighted by their online engagement through platforms like Twitter (@cmcrobotics) and their website, the organization continues to push the boundaries of technological interaction.
-
 @ 16d4857a:6b7534bb
2025-01-11 05:30:40
@ 16d4857a:6b7534bb
2025-01-11 05:30:40homepage
You will all details of my writing here.
tsbuhlhl
-
 @ 16d4857a:6b7534bb
2025-01-11 05:29:24
@ 16d4857a:6b7534bb
2025-01-11 05:29:24homepage
You will all details of my writing here.
-
 @ a012dc82:6458a70d
2025-01-11 03:03:29
@ a012dc82:6458a70d
2025-01-11 03:03:29Table Of Content
-
Is Dubai Crypto-Friendly?
-
Steps to Buying Bitcoin in Dubai
-
Other Buying Options
-
Banking with Bitcoin in the UAE
-
A Word of Caution
-
Conclusion
-
FAQ
Dubai, often referred to as the "City of Gold," has always been at the forefront of financial innovation. Its towering skyscrapers, bustling markets, and technological advancements make it a hub for global investors. In recent years, the allure of cryptocurrency, particularly Bitcoin, has caught the attention of many in this desert paradise. With its strategic location and forward-thinking policies, Dubai offers a unique blend of traditional finance and the emerging world of digital currencies.
Is Dubai Crypto-Friendly?
Dubai's progressive stance on technology and finance is well-documented. The city and the broader United Arab Emirates (UAE) have embraced the digital currency revolution with open arms. Not only does the UAE offer enticing tax benefits like zero tax on cryptocurrency trading, but there's also an absence of income or capital gains tax. This fiscal environment, combined with a robust regulatory framework, has positioned the UAE as a global leader in the crypto space. While the government doesn't recognize cryptocurrencies as official legal tender, it has ensured a safe environment for enthusiasts to purchase, hold, and trade digital assets without legal hindrances.
Steps to Buying Bitcoin in Dubai
Choose an Exchange
The digital currency market is vast, and choosing the right exchange is paramount. It's essential to prioritize security, given the digital nature of these transactions. Potential investors should not only research the exchange's history but also delve into user reviews and any reported security breaches.
Prominent exchanges in the UAE, such as eToro, OKX, HTX, and Binance, have built a reputation for reliability and security.
Register
The registration process is the first step towards your crypto journey. Most exchanges require basic information like email and a strong password. It's crucial to use unique passwords and enable two-factor authentication, if available, to enhance account security.
The Know Your Customer (KYC) checks are standard procedures to prevent illicit activities. This often involves submitting a government-issued photo ID.
Fund and Buy
After setting up your account, the next step is funding. Most exchanges accept funds from bank accounts, credit cards, or even other cryptocurrencies.
Once funded, you can navigate the platform to purchase Bitcoin or explore other available digital currencies.
Storing Your Bitcoin Safely
Online Wallets: Digital wallets, often referred to as "hot wallets," are online storage solutions for your cryptocurrencies. They are convenient for regular traders as they offer quick access to funds. Platforms like Trust Wallet and Electrum are popular choices. However, being online, they are susceptible to hacks, so it's essential to use them judiciously.
Hardware Wallets: For long-term investors or those with significant holdings, hardware wallets are the gold standard in security. These physical devices store your private keys offline, making them immune to online hacks. Brands like Trezor or Ledger Nano have become synonymous with crypto security.
Other Buying Options
Bitcoin ATMs: A testament to the UAE's progressive crypto stance is the presence of Bitcoin ATMs. These machines, like traditional ATMs, allow users to purchase Bitcoin. The Rixos Premium Dubai Hotel, a symbol of luxury, houses Dubai's first Bitcoin ATM, offering tourists and residents alike a quick way to enter the crypto market.
Peer-to-Peer (P2P) Trading: P2P platforms facilitate direct transactions between buyers and sellers, bypassing intermediaries. While centralized exchanges dominate the Dubai market, platforms like Binance, Paxful, and OKX offer P2P options, combining the best of both worlds.
Banking with Bitcoin in the UAE
The banking sector in the UAE, known for its robustness and innovation, has shown a keen interest in the crypto realm. Several banks have adopted crypto-friendly policies, making it easier for investors and businesses in the crypto space. The First Abu Dhabi Bank (FAB), one of the region's largest banks, stands out in this regard. While it doesn't directly offer crypto trading, it facilitates its customers to link their accounts with crypto exchanges. This integration, combined with FAB's future plans around digital assets, showcases the bank's commitment to financial innovation.
A Word of Caution
The world of cryptocurrencies, while exciting, is also fraught with volatility. Dubai's vibrant financial landscape offers numerous opportunities to engage with digital currencies. However, like any investment, it's imperative to approach it with caution. Prices of Bitcoin and other cryptocurrencies can swing dramatically, often within short time frames. Aspiring investors should arm themselves with knowledge, stay updated with market trends, and perhaps most importantly, never invest more than they can afford to lose.
Conclusion
Dubai, with its blend of tradition and modernity, has once again proven its mettle by embracing the digital currency revolution. The city's progressive policies, combined with a robust financial infrastructure, make it an attractive destination for both novice and seasoned crypto investors. From the presence of global crypto exchanges to the integration of Bitcoin ATMs, Dubai offers a comprehensive ecosystem for those keen to explore the world of cryptocurrencies.
However, as with all financial ventures, it's essential to tread with caution. The volatile nature of cryptocurrencies demands thorough research, continuous learning, and a measured approach. While the allure of digital gold is undeniable, it's crucial to remember the age-old adage: "Invest only what you can afford to lose.
FAQ
Are there any taxes on cryptocurrency trading in the UAE? No, the UAE offers zero tax on cryptocurrency trading, and there's no income or capital gains tax.
How can I buy Bitcoin in Dubai? You can purchase Bitcoin through crypto exchanges, Bitcoin ATMs, or P2P platforms available in Dubai.
Are there Bitcoin ATMs in Dubai? Yes, Dubai's first Bitcoin ATM was installed at the Rixos Premium Dubai Hotel in 2019.
Which banks in the UAE are crypto-friendly? Several banks, including the First Abu Dhabi Bank (FAB), have crypto-friendly policies.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 4d41a7cb:7d3633cc
2025-01-11 01:39:00
@ 4d41a7cb:7d3633cc
2025-01-11 01:39:00If we think of the monetary system as a game and we understand its rules, we will be much better prepared to play it right. Let’s deep dive into how the monetary game works and how we win during the stage change we are going through: The death of the dollar.
Like in any game, there are goals, and players compete to win. In the monetary game, the goal is to acquire more wealth: more land, more resources, more goods, etc. Economic players are divided into groups and organized like a pyramid.
Economic players
1. Top of the pyramid
This includes central bankers, politicians, large corporations, and all entities involved in the creation of currency.
They are well-versed in the rules, as they are the ones who create and modify them, including monetary and fiscal policy, as well as the Uniform Commercial Code. They operate in a "creative" mode, utilizing monetary policy and legislation to extract wealth from the system without the need for production. They effectively act like parasites.
These are the individuals in charge of organizations like the Federal Reserve (FED), the World Bank (WB), the International Monetary Fund (IMF), the Bank of International Settlements (BIS), and the other important central banks of the world.
They have global think tanks where they train key economic players, like politicians, CEOs, public figures, and big business owners, to influence the world economy.
2- Self-made winners
The second category has a desire or hunger to win, and they understand the game to some degree: hedge fund managers, currency, commodity, and stock traders. Some of them, such as entrepreneurs and business owners, are genuinely skilled in their craft and produce legit goods and services.
Most of them don't have a "fixed income," and many have multiple sources of income, making them better prepared to navigate the monetary devaluation. This is because, while the stock market and commodities soar to record highs, wages remain relatively stagnant, thereby losing purchasing power.
3. Middle class
The third category is the one holding the structure; it's the main pillar or the spine holding the pyramid.
As Aleks Svetski explains in the Bushido of Bitcoin:
So long as they exist and continue to believe in the game, the others can play (...) The faster this category erodes, the faster the game ends. Hyperinflation happens when they give up. People realize they’re carrying all the weight, and, as they start to burn out, they decide either, “Screw this, I’m going to join category two and get my share,”.
4. Non-Economic Player Characters (NEPCs)
Aleks also explains:
The fourth category is the end of the road (...) Why play if the game is rigged? It’s easier to just give up! There are many gradations to this category, from the homeless to the welfare recipient to the hippie to the perpetual philosophy student to the doomer or the basement-dwelling 40-year-old teenager. These people either lack the gumption, talent, skill, or luck to jump category two, or they are deeply intuitive and feel how rigged it all is, so they throw in the towel and just drop out of the game altogether. Many more, of course, are born into category four and taught to believe victimhood is moral. As such, like crabs in a bucket, they bring down anybody who tries to rise up from there, and because they are in proximity only to category three players, they try to bring them down too.
The currency cycle
Understanding the currency cycle and its phases is crucial for making informed decisions and being a beneficiary in the wealth transfer. The cycle starts with a real form of money, a commodity, generally gold and silver, and ends up with the hyperinflation of a money substitute, base metal, or usually a paper fiat currency.
Money establishes itself only through the cumulative development of a medium of exchange on the free market. Only the free market can create economic money; the government cannot, and it has chosen gold an silver every time.
But if history teaches us something, it is that governments eventually end up corrupting money and replacing it with money substitutes (currency)
From Greco-Roman times, we can find examples of governments corrupting money, inflating the currency supply, imposing price controls, and creating artificial and unsustainable exchange rates that end up distorting the economy and the incentive structures and eventually lead to the end of the empire/nation.
Cycle phases
1. The free market adopts real money (gold & silver).
2. Redeemable certificates (IOUs) or a lower-quality metal replace gold and silver.
3. By decree, governments separate IOUs, certificates, or lower metals from gold or silver and convert them into fiat currencies (fake money).
The government's deficit spending and banks' credit expansion inflate the currency supply, accelerating its loss of purchasing power. The government imposes capital controls, regulations, and even criminal laws to stop the currency leakage
5. Complete loss of trust in the currency results in hyperinflation, economic chaos, social riots, and the need for a reset of the monetary system and debts.
6. A new money rises, generally returning to gold and silver, and the cycle repeats itself.
Counterfeiting currency
Money must be difficult to produce, requiring work to extract. When a currency, which requires no effort or work to produce, replaces money, the decline phase begins.
When a group has the ability to generate money without exertion, known as artificial inflation, inequality increases. We refer to this class as cantillionaires, who profit from the Cantillon effect, akin to parasites snatching wealth from the producers.
Inflation is simply another word for counterfeiting, as both involve the creation of "money" that is not attached to any real wealth.
The counterfeiters and their local retailers have found that their incomes increased before any rise in the prices of the things they buy. Retailers, on the other hand, will suffer losses. The first recipients of the new money will benefit the most, at the expense of those who receive it later.
Where are we now?
We are currently experiencing the demise of the "Federal Reserve Notes standard," also known as the dollar standard, which began with the establishment of the Federal Reserve in 1913.
During the Great Depression of the 1930s, the government "partially" disconnected the currency from gold, thereby stealing the yellow metal from the American people. The world set this currency as its reserve currency after the Second World War, allowing every other currency to be redeemable for dollars and those dollars for gold (in theory). This was known as the Bretton Woods agreement of 1944.
This system ended in 1971 when the Federal Reserve Notes (FRNs) were finally completely detached from gold redemption, and every currency started floating freely against each other with no backing at all. This marked the complete disconnection of currency from money.
This sparked a flight to quality, as investors shifted from Federal Reserve notes to gold, resulting in a 20x increase in the gold price in FRNs from 1971 to the 1980s. Paul A. Volcker, the chairman of the Federal Reserve, responded to this by raising interest rates on US Treasury bills to halt the depreciation of the Federal Reserve notes. This period was characterized by riots, inflation, conflicts, and economic crises.
The second biggest demand for gold started with the dotcom bubble of the year 2000 and increased with the great financial crisis of 2008. This is when the Federal Reserve Notes standard began to crumble.
We are now approaching the end of the road for this currency, but we are talking about the global reserve currency. All global economic players are affected, and there are winners and losers.
To be among the winners, you must first understand that the dollar is a liar.
The dollar is a liar
The “everything bubble” is a misleading term. What is really happening is that the federal reserve notes, better known as dollars, are suffering an acceleration of the inflation rate.
Over the past three years, they have created about 30% of the supply of "dollars."
We can see the stock market in "all-time highs," gold in "all-time highs," real estate in "all-time highs," etc. The inflation of the denominator (FRNs) is unprecedented, rather than an "everything bubble."
Since the dollar is not a store of value any more, capital flows to more scarce alternatives to protect it's purchasing power, generally: Real State, stocks, bonds and gold.
Here is a simple graphical representation. On the right side, we can observe the price of gold in dollars, the price of dollars in gold, and the price of the S&P 500 in dollars and gold, respectively. The charts span from the 1960s to the current era.
Gold is not at "all-time highs," nor is the S&P 500. Actually, the S&P 500 is down 60% from its gold ATH in the year 2000.
Because the dollar is at all-time lows, most assets and some commodities are at "all-time highs" in currency terms. The US deficit keeps growing administration after administration, making no difference between Republicans or Democrats,and there is no sign of this stopping any time soon.
 ## Where are we now?
## Where are we now?Biggest wealth transfer in human history
Step 4 (government deficit spending and bank credit expansion inflate the currency supply until it loses most of its purchasing power) is now complete, and step 5 (hyperinflation, economic chaos, social riots, and a reset of the monetary system and debts) is about to begin.
This is not something that will happen from one day to another; it is something that is developing right now and will continue happening before our eyes, day by day, first gradually, then suddenly.
The top players in the pyramid recognize the end of this cycle, but they must shift to a new system to sustain their power and control. This is why supranational organizations are calling for a Great Reset or a New World Order. This is were the trojan horse of climate change enters the equation: a global problem that will requiere a global solution. They want to implement a social credit system, and a global CBDC to keep control of the currency supply and circulation.
James Rickards explains in The Road to Ruin:
The agenda is unchanging, pursued in centuries past by Caesar and Napoleon, and in the twentieth century by the Rockefellers, Roosevelts, and Bush dynasties. The agenda thrives today in institutions with anodyne names like the United Nations and the International Monetary Fund. The agenda is simple: world money, world taxation, and world order.
The fusion of global information sharing, global enforcement, and global taxation of gross receipts enables developed economies to extract the maximum amount of wealth from productive sectors to sustain nonproductive elites. This continues until the social system collapses, the common fate of civilizations that reach a late stage of prelatic parasitism.
For elites, a global problem once defined conjures a global solution. Climate change is the perfect platform for implementing a hidden agenda of world money and world taxation.
Elites formulate plans for the world order they wish to see. They wait for an exogenous shock, a natural disaster or financial crisis, then use fear created by shock to advance their vision.
Elites are aware that their views are not widely accepted in democratic societies. Elites realize their programs must be implemented in small stages over decades to avoid backlash.
Elites realize money printing may produce not price inflation but asset inflation and form new bubbles that could burst and destroy confidence for two generations.
Asset inflation is the previous step to price inflation. If asset owners start leveraging their assets more and more, they can increase their purchasing power, pushing prices higher and potentially creating a liquidity crisis, also known as margin calls, in the event of a market correction. This will produce more volatility and market instability.
In his book What has government done to our money, Rothbard explains:
Thus, inflation does not benefit society but rather redistributes wealth to the first movers and penalizes the last. We often refer to the latecomers—those enduring the loss—as the "fixed income groups". Fixed-money contracts, retired persons, bondholders, and other creditors—those holding cash—all will bear the brunt of the inflation. Inflation will tax these individuals.
Inflation has other disastrous effects. It distorts that keystone of our economy: business calculation. This process demoralizes commerce and undermines the incentive structure for production, instead encouraging debt, speculation, corruption, theft, and other harmful practices.
Debtors benefit because they can settle their debts with a weaker currency. The incentive, then, is to borrow to buy hard assets that will appreciate in currency terms and repay later in a weakened currency.
Rather than save and lend. Therefore, inflation lowers the general standard of living while simultaneously creating a false atmosphere of "prosperity".
When an important percentage of the middle class recognize what is really happening they will rush to play this game: borrow cheap credit to buy hard assets. This is the perfect recipe for starting a hyperinflation But the parasites won't let them win so easy, they already have a plan for this scenario.
Ice-nine: the freezing of assets
The vulnerability of the global financial system has escalated due to a significant increase in debt levels, widespread reliance on leverage, and greater interconnectedness since 2008.
James Rickards also explains
Power elite response to the next financial crisis. Instead of reliquefying the world, elites will freeze it. The system will be locked down. Of course, ice-nine will be described as temporary the same way President Nixon described the suspension of dollar-to-gold convertibility in 1971 as temporary. Gold convertibility at a fixed parity was never restored. The gold in Fort Knox has been frozen ever since. U.S. government gold is ice-nine.
Governments around the world are secretly planning measures to freeze financial assets and restrict the flow of money should an impending financial crisis arise.
The approach, far more drastic than the methods used in the 2008 crisis, aims to freeze financial assets and prevent a chaotic downfall by restricting access to physical currency and stopping a desperate rush for liquidity.
During a meal in mid-2014, the author received information from a senior BlackRock representative indicating that in the event of a financial meltdown, the U.S. government might direct asset management firms to suspend customer fund withdrawals.
All of this will be done with the purpose to stop hyperinflation.
Hyperinflation: The endgame
If history is any guide, what the Federal Reserve is doing now has been tried throughout history.
As the Federal Reserve continues to print trillions of dollars out of thin air with no productivity to back it up, at some point down the road, the world will finally lose faith in the US dollar as a global currency and conclude that it no longer makes sense to store their wealth in US dollars.
Today, the Federal Reserve appears to be following in the footsteps of 1923 Germany’s Weimar Republic shortly after World War I. This results in significant volatility and alternates between bullish trends and bearish contractions. The hyperinflation process, once started, is impossible to stop; first it starts gradually, then suddenly.
Pictures speak louder than words:
 ### How to win
### How to winSince the currency is experiencing an acceleration of the inflation we want to own the best type of property to protect against the debasement, but as we saw, the top economic players are planing to freeze the financial system and restrict the access to our property.
It's obvious to me like for many others that know about this things that Bitcoin is the one and only option, since is has no counterparty risk and it's limited; even better than scarce.
The similarities with the previous chart speak by themselves.
Conclusion
1- Make bitcoin your denominator (your main unit of account).
2-Accumulate as much bitcoin as possible on self-custody (earn, save and spend bitcoin every time is possible to spread adoption).
3- Don't be traded under a fixed income situation, increase your income sources, and own real and tangible assets.
4- Avoid overexposing to counterparty risks types of property (RE, stocks, bonds, etc)
5-Make sure your friends and family understand this.
6- Have a place outside of big cities and connect with local food producers (just in case).
7- Live your life, have fun, connect with amazing people spend time in nature and finally:
FUCK THE FED
Bitcoin or slavery!
-
 @ df478568:2a951e67
2025-01-10 20:15:36
@ df478568:2a951e67
2025-01-10 20:15:36I heard about nostr on Citadel Dispatch. It sounded like a promising alternative to legacy social media.

Here's the thing: Free speech does not exist. According to Rothbard in The Ethics of Liberty, the property owner always has the right to censor.(He gives the example, If you give a speech in a movie theater, the ushers will ask you to leave. The crowd might throw popcorn at you. Therefore you do not have the freedom of speech in a movie theater. The proverbial, "you don't have the right to yell fire in a crowded theater" is a red-herring. The freedom of speech, not freedom of reach argument is another argument for censorship. The information super highway is owned and operated by corporations. It's 2025. I don't focus on stocks very much, but I've seen NVIDIA. The NVIDIA stock price is not the interesting part. The interesting part is how fast AI is becoming ubiquitous.
That means writing code is easier. That means a new Internet not built and controlled by corporations. It means development on this new protocol can be funded with donations to a non-profit corporation. Or people can send $1,000 to a corporation to help fund development and get a badge. It's almost like virtue signaling your support for development of an interesting bitcoin wallet. I know virtue signaling gets a bad rap, but it is virtuous to support the development of a bitcoin wallet built for a world where Social Media Apps can be banned by a government with a bill of rights that begins with the words:
"Congress shall make no law respecting an establishment of religion, or prohibiting the free exercise thereof; or abridging the freedom of speech, or of the press; or the right of the people peaceably to assemble, and to petition the Government for a redress of grievances."
I don't know if TikTok is something we should want to ban or not. I've never used it and have no dog in this fight. I'm not informed enough about the issue to give a useful opinion on the TikTok case, but I find it very interesting. Whatever the ruling, I will find the reasons behind the ruling most fascinating. Whatever they are, I would like to run a thought experiment. If the ban is not held constitutional, I want to know if this would set precedence for nostr. If it is the ban is held constitutional, how would this ruling apply to the nostr protocol? ** O am not a lawyer** and do not know the answers to any of these questions, but it's fun to think about.

Nostr is unique because it cannot be owned by a corporation or communist government. It is owned by individuals. Each individual who can afford it can own their own data. Your speech is attached to an npub that can be seen on every nostr client. It is stored on several relays. You can run your own relay. You can run your own client. In the very early days, we all had to be on the same relays to see the same posts, but the outbox model fixes this. It is still early days, but nostr has many implementation possibilities and I suspect the protocol to get better over time.
Primal can still censor me. Since I run my own relay, I will not lose my content if they do. I may not be able to be see on the Primal App, but people will still be able to see me on Amethyst or Coracle. If Primal shadow bans me, I can still speak. I don’t think Primal will ban me, but even if the government knocked on Miljan’s door and made him an offer he can’t refuse, I can still speak on nostr. X, Facebook, or any other platform cannot grant the freedom of speech. You must follow their terms and conditions. The government goons can tell platforms to ban certain content by sending a single email. They have to wait on government permission. Mark Zuckerburg must know zaps exist when the United States government stopped him from printing his own stable coin. To ban a nostr user requires shutting down more than just one company or a law that bans a platform. It requires shutting down computers of individuals. It happens from time to time(The Canadian government sucks), but it would be difficult to ban all the computers running nostr. It's not perfect. John Carvalho wrote a great article about all the problems with these newfangled decentralized tools, but nostr looks promising.
Freedom Tech Gives Power To The People

"I am fascinated by Tim May's crypt-anarchy. Unlike the communities traditionally associated with the word "anarchy", in a crypt-anarchy the government is not temporarily destroyed but permanently forbidden and permanently unnecessary. It's a community where the threat of violence is impotent because violence is impossible, and violence is impossible because its participants cannot be linked to their true names or physical locations." - wei dai, b-money
Nostr is not quite crypto-anarchy, but it is freedom tech. Nostr is free from corporations. This doesn't mean there are no corporations involved on nostr. Much of the funding is funded by a 5013c corporation. Primal is a corporation, but Primal is a small fraction of nostr. Social media is a fraction of nostr awesomeness. It's participants can almost all be linked to their true identity unless they have Satoshi-esque OPsec skills. Nostr does not remove the threat of government violence, but it increases the censorship hash-rate. It will take more work to censor people on nostr than simply sending an email to Zuck or whatever they do. Running your own relay and client is not too difficult. For a few hundred thousand sats and a little elbow grease, you can own your own speech and broadcast from your own computer. It's like owning your own movie theater. You are free to yell fire in your own movie theater. Nobody can kick you out of that theater, but nobody will want to watch your movies either. If you yell fire, people cannot stop you, but they can mute your ass.
-
 @ bf47c19e:c3d2573b
2025-01-10 19:53:36
@ bf47c19e:c3d2573b
2025-01-10 19:53:36Originalni tekst na tasic.substack.com
07.09.2021 / Autor: Slaviša Tasić
U El Salvadoru je bitcoin od danas zvanična valuta. Valuta Salvadora je već neko vreme samo američki dolar. Svoju domaću više nemaju. Sada je dolaru dodat bitcoin.
Razlika između dolara i bitcoina u Salvadoru je velika. Dolar je tamo privreda sama prigrlila. Stara valuta nije valjala, bila je inflatorna i gubila vrednost, pa su ljudi bežali u dolar — trgovali, računali i štedeli u njemu. Onda je država jednog dana skroz digla ruke od sopstvene valute i proglasila dolar zvaničnom. Identična stvar dogodila se u Crnoj Gori kada je ona umesto tadašnjeg inflatornog dinara ozvaničila već raširenu nemačku marku. Kasnije se sa marke automatski prešlo na evro.
Bitcoin nije prihvaćen spontano. Niko u Salvadoru ne koristi bitcoin zato što dolar više nije popularan. Naprotiv, dolar je valuta koju ljudi biraju, u kojoj i dalje dobrovoljno plaćaju, računaju i štede. Bitcoin Salvadoru nameće država i u tom smislu on je bliži onoj staroj, prethodnoj, nametnutoj valuti. Predsedniku Salvadora se dopala ideja bitcoina pa je odlučio da ga uvede. Ne samo ozvaniči, jer niko ni do sada niko nije branio ljudima da trguju u bitcoinu ako hoće, nego i da prihvatanje bitcoina učini obaveznim. Sada, ako prodajete sladoled u Salvadoru i kupac hoće da vam plati bitcoinom, vi morate da ga primite.
Zato ja ne prodajem sladoled u Salvadoru.
Kriptovalute su tako napravile još jedan korak ka paradoksu. Nekada su one bile subverzivni projekat. Bitcoin je trebalo da zameni dolar i druge državne valute zato što je bolji, stabilniji i anonimniji. Zato što je blockchain, njegova platna infrastruktura, trebalo da bude brža, efikasnija i jeftinija. Trebalo je da iz Argentine šaljemo novac u Indiju brzo i besplatno. Privatno generisani i decentralizovani kripto novac trebalo je da potisne državne valute i centralizovane finansijske sisteme. To je bio narativ iza bitcoina i kripto pokreta. Centralne i sve druge banke, odzvonilo vam je!
Trinaest godina kasnije, bitcoin u jednu državu uvodi jedan predsednik. Jeste on mladi i kul predsednik, sluša kripto podkaste i ide na bitcoin konferencije, ali upravo to zamagljuje sliku pa pristalice ne vide suštinu: da bitcoin ovde uvodi država i njen monopol sile.
Finansije Salvadora me slabo zanimaju, ali kao ilustracija o kakvom se šarlatanstvu ovde radi pogledajte šta kaže gospodin predsednik:

Zašto jedna država kupuje bitcoin? Mogao je i da ode u kladionicu i stavi pare iz budžeta na Juventus — šanse za dobitak su tu negde, a kladionica troši manje struje.
I ne znam da li opozicija u Salvadoru ima plan i program, ali evo kako bitcoin predsednik raspravlja sa poznatim monetarnim ekonomistom. Služeći se argumentom OK, boomer:

Bitcoin moraju ovako nametati jer bitcoin nije novac. Njegova vrednost je ovih dana ponovo porasla, opet je prešao $50,000, a desilo se da ga daleka država u isto vreme ozvaniči i zato su ponovo krenule vesti i priče o ovoj valuti budućnosti. Ali bitcoin nije novac i to isto važi za sve kripto valute.
Novac služi za plaćanja, a bitcoin to ne ume dobro da radi. Njegov platni sistem je glomazan, spor i skup. Da, njime se može ponegde plaćati, ali prodavci to rade iz promotivnih razloga, ne realne potrebe. Sam sistem je daleko inferiorniji od sistema koje već imamo i tu nekog napretka nema. Za ono što bitcoinu i njegovom blockchainu trebaju minuti, Master i Visa sistemi urade u milisekundama, uz daleko niže provizije.
Novac je i merilo vrednosti. U Salvadoru vrednost mere u dolarima, u Japanu u jenima. U Srbiji to radimo malo u dinarima, a malo više u evrima. Ali nikad nisam nikoga čuo da kaže da kilo banana košta 650 satoshija ili da mu nekretnina vredi 3.7 bitcoina.
Treći kriterijum za novac je čuvanje vrednosti i to bitcoin radi malo bolje. On ne samo da je do sada sačuvao vrednost nego je i neverovatno uvećao. To nije klasično čuvanje vrednosti, jer malo ko ulaže u bitcoin da bi se zaštitio od pada dolara ili evra. Bitcoin se kupuje jer se može desiti da opet jako skoči. To je spekulativni, a ne odbrambeni motiv. Ali ako i uzmemo da je to neki vid čuvanja vrednosti, dosadašnji rast ne kaže nam ništa o bitcoinu kao čuvaru buduće vrednosti. Da je bio stabilan od početka, možda bih poverovao. Vrtoglavi rast bilo čega retko znači buduću stabilnost.
Ovde se kripto entuzijazisti pobune i kažu da ni sadašnje papirne valute ne čuvaju vrednost. Valute kao evro ili dolar su papir samo u smislu u kojem su bitcoin bajtovi informacija i kilovati struje — to je jedna njihova primitivna manifestacija, a ne suštinska karakteristika. Evro nije “papir”; evro je obećanje Evropske centralne banke da će uspešno ciljati inflaciju od 2% godišnje. Ne morate verovati u to obećanje, možete sumnjati u proces izbora ciljeva i guvernera, u njihovo znanje i namere — ali to je suština evra kao novca. To je podloga evra. Isto važi i za dolar, jen ili dinar. Nekada je novac imao zlatnu podlogu, nekada srebrnu, a njegova sadašnja podloga je obećanje jedne manje ili više kredibilne institucije. Nije papir.
Obećanje o ciljanju inflacije sa sobom nosi jednu važnu funkciju. Svi govore o ograničenoj ponudi bitcoina: programski je on ograničen na 21 milion bitcoina i ne može se štampati preko toga. Ali cenu osim ponude određuje i tražnja. Novac nije izuzet iz toga. Ciljanje inflacije — što je identično ciljanju vrednosti novca u odnosu na zadatu korpu roba — postiže se reagovanjem centralne banke na promene tražnje za novcem.
Ponuda dolara, evra i drugih običnih valuta je fleksibilna, što znači da ih besomučnim štampanjem možete obezvrediti. Ali fleskibilnost znači i da ih možete emitovati i povlačiti tako da odgovarate na tražnju za njima, sa ciljem da njihova vrednost u odnosu na korpu roba ostane stabilna. I to je ključna prednost koju centralne banke imaju nad kripto valutama. Zbog toga su valute centralnih banaka vrlo dobro merilo vrednosti i vrlo predvidivi čuvari vrednosti.
Ne treba vam većeg dokaza za to od uspona stablecoina, kripto valuta čija je vrednost vezana za dolar. Kripto valute su došle sa namerom da ga poraze, a sada se vezuju za dolar da bi od njega pozajmile stabilnost koju nemaju. A dolar stabilnost ima zato što centralna banka aktivno cilja njegovu vrednost i manipuliše ponudom dolara da bi odgovarala tražnji za njima. Ako neka kripto valuta reši ovaj problem odgovora ponude na tražnju, možda će i uspeti.
Ovakav kakav je, bitcoin može još dugo da održava vrednost ili raste. Razlog su naši komplikovani ukusi, procene i očekivanja. U tom smislu za mene je bitcoin i dalje najviše uporediv sa apstraktnom umetnošću: ni ona ne valja, ne vredi ništa, ali ljudi imaju neke svoje ideje, kupuju te stvari jedni od drugih za mnogo para i one već decenijama ipak drže visoku vrednost.
Druge dve funkcije novca on ne obavlja, jer niti valja kao platežno sredstvo niti meri bilo šta. Zato bitcoin i nijedna kripto valuta za sada nisu novac. I nijedan državni dekret to neće promeniti. Možda neka bolja kripto valuta, u budućnosti, hoće.
-
 @ 9bcc5462:eb501d90
2025-01-10 19:42:28
@ 9bcc5462:eb501d90
2025-01-10 19:42:28Cuneiform is mankind’s first writing system created by the ancient Sumerians of Mesopotamia, what is now Iraq. (The word “Sumer” means land of civilized kings). Despite being developed 5,000 years ago, its parallels to Notes and Other Stuff Transmitted by Relays will blow your mind! The most striking is how both breakthroughs materialized from the fundamental need to track value exchange–from primal grain tallies to now exchanging bitcoin.
Let’s begin with the fact that the styluses used by these archaic scribes were crafted from reed plants. Their stems were strong because of attachment points called nodes! These were the resilient, ring-like parts of the stem that joined it together with the rest of the plant. Similarly, although symbolically, lightning nodes are powerful on nostr since they allow us to zap each other with sats. An approach stemming from the need to modernize how we interact on social media, trade in networks and conduct business—It’s not surprising cuneiform came about as a way for merchants and farmers to track economic transactions and agricultural inventories!
Another parallel involves how both share everlasting marks. The Sumerians used their styluses to press wedge-like symbols onto wet tablets. They then would bake them in the sun, leaving a permanent record of the documentation. If an error was made, it could not be changed. Likewise, on nostr there is no delete function. Once you publish a note, including any typos, it is preserved for history.
Lastly, the proto-writing that emerged in Mesopotamia which led to Cuneiform was in the form of bullae (bulla: singular). These were spherical clay envelopes encased with tokens representing a transaction. They were sealed with unique markings representing the parties involved for authentication. In other words, cuneiform cylinder seals were effectively early public key cryptography! The seal itself being the private key and its impression being the public key. Just as us nostriches use our nsec to sign our notes with integrity and verify value-for-value with our npub.

*Rare bulla seal (shout out to Conny Waters from ancientpages.com)*
*Sumerian cuneiform tablet (source: britannica.com)*At the end of the day, maybe we’re not so different from our ancestors after all. The evolution of our writing technology over the course of our history is more than innovation born of necessity. Across millennia, 3025 BCE to 2025 AD, it's man telling the universe– we will be remembered– beyond space and time. As our ancestors stacked their clay tablets, we’ll stack our sats! Onward nostr! The new land of civilized kings.

*Mankind's Innovations in Writing Technology by Learning Producers, Inc.* -
 @ 746a245a:7a8d8b34
2025-01-10 17:57:04
@ 746a245a:7a8d8b34
2025-01-10 17:57:04
1. Self custody
Always. Send your BTC to cold storage. Don't hesitate because of high network fees when mempool activity is high. Rather pay 10% or more to secure your coins than risk loosing 100% of a cosiderable amount. If you have questions about self custody see this guide on the 5 Best Practices to Store Your Bitcoin.
2. Back up well
Restore a wallet at least once. Make sure you know how to get back your coins in a worst case scenario. (Also make sure your heirs are able to do it when time comes.)
3. Never try to time the market
DCA. Set it and forget it. Monthly, weekly, by-weekly or daily doesn't matter. Choose what best suits you. Do this for the majority of your BTC allocation. You can not time the bottom. Period. (But you can have a little pile of FIAT to buy dips when they occur.)
4. You can not time the top either
Never sell the majority of your Stack. Take a little profit if things go parabolic to reward yourself but always keep your main stack intact. It can be hard to get it back. And it will only go up with time. HODL and understand what you own.
5. Keep emotions out
Greed and fear are the main factors for people to get wrecked. Slow steady purchases, even tiny ones, all go to building a stack.
6. Never use leverage
Just don't. No, not even if BTC is below 10k. Make sure every sat you own truly belongs to you.
7. Every sat counts
Even if it's small amounts, just keep dca-ing and stacking sats. Little pieces add up. 0.001 BTC = $25 at the time of this writing. Do this 100 times and you have a tenth of a BTC. If you have very little FIAT, stack free sats. You can:
- use faucets (like freebitco.in or cointiply.com)
- do tasks (like microlancer.io)
- play games (like Bitcoin Miner)
- shop with services like lolli.com or foldapp.com
- listen to podcasts (with fountain.fm)
- educate yourself on Bitcoin (with BitcoinMagazine)
- or be active and provide value in communities like nostr, stacker.news or habla.news
Remember: Faucets used to give hundreds of Bitcoin per day. Now it's 5-250 sats 10 years later. In 10 years it may be 1-5 sats.
8. Don't go all in
Keep FIAT to survive hard times without being forced to sell BTC. (for example 6 months of monthly spending)
9. Enjoy life while stacking
There is only one thing that is more precious than Bitcoin. It is lifetime. Stack sats, but also stack moments. Be present and enjoy life. Every day. No amount of BTC can ever buy back lifetime. Remind yourself of this often.
10. Don't forget yourself
Always have a little fun money to maintain hobbys, traveling and to treat yourself. Otherwise you might burn out quickly.
11. Involve your significant other
Make sure he/she knows the reason why you do what you do. Otherwise you risk burning out him/her too.
12. Automate and relax
When you check your portfolio ten times a day or more think of automating things. Don't trade lifetime and serenity for small gains.
13. Don't do shitcoins
Most altcoins never reach their ATH again. BTC and BTC only.
14. Stay humble
Never get lured by offers that promise yield in exchange for holding your BTC. FTX was a recent example of how that can end.
15. You lost your keys in a boating accident
Never share how much Bitcoin you own. Better yet, don't share that you own any at all (exception: rule #11). The less is known about you having BTC, the less risk. Also consider buying non KYC. For example with robosats or bisq.
16. Don't rush. Be patient
It is a marathon, not a sprint. Time is on your side. You already own Bitcoin. You won. It isn't a race like with FIAT where you have to fight inflation. You preserve wealth.
17. Increase your FIAT earnings
Learn profitable skills to increase your buying power and generally grow as a person. Even if you loose all your wealth, nobody can take away your skills to accumulate it again.
18. Don't compare
Every stack of BTC is better than no stack of BTC. And even if you are a whale: there will always be a bigger fish somewhere in the sea ...
19. You don't need 1 full BTC
This was huge for me! The urge to have one full BTC is very FIAT minded thinking. Goals are cool but:
21 million BTC / 8 billion humans in the world =0,00262500 BTC
And not even that is possible because of the 1,1 m BTC wallet of Satoshi Nakamoto and lost coins. You can find out the exact amount every individual on earth could possibly own at satoshisperperson.com.
Not everyone needs a whole coin. About 225.000 sats = your little block of Bitcoin. ... That's roughly $55 at the time of this writing. Got that? Congratulations! 99% of people are still on zero. Safe your share and then slowly add more every pay check.
20. Change perspective
You can change settings in your wallet to display value in sats rather than BTC. This liberates from the feeling of shortage and the urge to fill that full BTC. It opens up the feeling of gratitude and abundance.
21. Always learn
Keep educating yourself about Bitcoin. The rabbit hole is deep ...
Thank you!
Thank you wonderful people who helped me gather those tips. I chose consciously to not give personal credit in this post because of rule #15 =)
Find me on Nostr
My Nostr npub:
npub1w34zgkkjznnf2209gnhc5snkd32lkc9hnncq45rypyzsx75d3v6qcz3ndd
What have i missed?
Do you agree with these tips? Did i miss any? Please let me know and help refine this set of rules so we can breed more an more whole coiners over time ... or let's rather call it 'satoshi millionaires' (see rule #19 ;-)
P.S. Feel free to tip me some sats or share this post if you find it helpful. Working on my own little stack too ;-)
-
 @ 746a245a:7a8d8b34
2025-01-10 17:50:10
@ 746a245a:7a8d8b34
2025-01-10 17:50:10In the past few years i have struggled a lot to find "the right" way to store bitcoin.
There is a lot of advice on this topic scattered around the web. I have consumed it, i have tested it and i have discussed it.
Here is what i found to be the best practices to store your bitcoin as a newbie or intermidiate.
I have split this up into two parts:
- Part 1: Essentials - The absolute bare minimum requirements you need to implement ASAP (this post)
- Part 2: Recommended - How to upgrade security and what mistakes to avoid (coming soon)
Let's start with the Essentials ...
Part 1: Essentials
I assume you already know a thing or two about bitcoin if you read this post, so i skip the obvious "No your keys not your coins" stuff.
These are the absolute minimum safety requiements. If you have not implemented these, stop everything you do and follow these steps immediately:
1. Use a hardware wallet
Hardware wallets are specificly built for one single purpose. To secure your private keys and thuss the access to your bitcoin.
Do i really need a hardware wallet?
Short answer: Yes.
Long Answer: It depends on your funds. If you only have bitcoin worth a few hundred bugs, it might not be necessary. A hardware wallet costs about $50-200. But as soon as you feel uncomfortable, you should get one. It is an individual decision. Like someone doesn’t bother running around with a few thousand dollars in his pocket and another one feels uncomfortable with even a few hundred. BUT it is good practice to treat the security of your funds right now as if they already were 10x. As a 10x can happen pretty quickly, as we have seen in the past two years, and you don’t want to do security upgrades in a rush and from a point where you feel unsafe. This leads to mistakes which can lead to total loss (for example sending to a wrong address). Self custody is the first an most important rule to follow if you want to keep your coins and become a whole coiner. If you can't afford a hardware wallet now, at least use a hotwallet ...
Can i use a hotwallet instead?
Hotwallets are wallets, that are connected to the internet, like Apps on your PC or smartphone. They are considered not to be as safe as harwarewallets (so called coldwallets), because if something has no connection to the internet, there is a huge part of risk being taken away. But hotwallets are still way better than leaving your funds on an exchange because with a hotwallet you get the keys to your funds. With exchanges you only get an IOU aka a promise from the exchange. And we have seen how that ends with MountGOX, FTX, Celsius, Blockfi and various others ... Use hotwallets rather on smartphone than on desktop device, as smartphones are a little more secure. A few good ones i could recommend are Blue Wallet, Green Wallet and Exodus but there are a lot of good solutions out there. Just make sure to get a 12 or 24 word seed recovery phrase when setting it up so you are really in full control of your funds. But if you can use a hardware wallet, rather choose that.
Which wallet should i get?
I did try a few but not all of them: - The one i would recommend the most at this point in time is the Blockstream Jade Classic as it comes with almost all possible features you could imagine for a very reasonable price. You can even use it completely airgapped wit QR codes and use it without keystorage like a SeedSigner. I will touch on those features later on in part 2. nostr:npub1jg552aulj07skd6e7y2hu0vl5g8nl5jvfw8jhn6jpjk0vjd0waksvl6n8n is also very active on nostr and provides good support for us plebs. - Coldcard is also a hardware wallet i hear a lot of good stuff about. - As well as the BitBox02 Bitcoin only edition. - Trezor has had some security issues regarding to not having a secure element. I am sure they implemented a solution in the meantime, but i am not up to date with this so i can not recommend it without any doubt. - Ledger devices were generally considered safe but they had multiple security related incidents such as leaking customer data or admiting to be able to extract your seed from the wallet. The fact that they allow to store other crypto currencies, also introduces a bigger attack surface. Thuss i don't recommend using a ledger. If you only have a ledger it's still better than leaving your coins on an exchange though. - SeedSigner, as described, is more for advanced users or if you really want to dig into it, in my opinion. You could also use the Blockstream Jade as a SeedSigner.
Where should i buy?
This is important: Order hardware wallets ONLY straight from the store of the manufacturer. Any middleman or additional steps in the delivery process increase the risk of your device being manipulated. If you are really paranoid about this stick with Coldcard or the new Jade Plus as these models have a build in mechanism to check if they have been tempered with. Also consider using a postbox or working address when you order a hardware wallet or any bitcoin related stuff in general. The less people know that you own bitcoin, the better.
2. Use single-sig wallets
Backup your 12 or 24 words seed phrase and store them in a secure place (safe from theft, fire, water AND CHILDREN etc. i will get to how to achieve this). Most cases in loss of bitcoin happen because of the loss of access to the keys. Not because of theft. So the biggest risk you should care for is that you don't lose access to your keys. And how do most people lose access to their keys? They either ...
1) make the backup too complex so that themselves or their heirs have no clue how to restore it or 2) they are too lazy with their backup so that a flooded basement, thrown away harddrive or deleted photo causes them to loose their bitcoin forever.
Yes there are usecases for multi-sig set-ups and yes it introduces a better level of safety but it also introduces a higher risk of loosing your funds because of complexity. As a newbie or intermediate you don't have to dig into this complexity. You can, but unless you understand very well what you are doing, i wouldn't recommend using multi-sig wallets. Remember: 99% of bitcoin losses don't accure because of theft. If you still feel the need to add a little more security for this aspect, i recommend using a passphrase instead, which has also it's own trade-offs, as we will discuss in the recommended techniques in part 2.
3. Secure your wallet with a good PIN
Don't choose your mother's birthday as your PIN or anything else that can be social engineered. The more random, the better. And the longer the better. If you use multiple hardware wallets, also use different PINs for them. PINs on their own are generally not a very good method to protect anything. A 4 digit PIN for example only gives 10,000 possible combinations (from 0000 to 9999). A modern computer can try these all out pretty fast. BUT fortunately most wallets have a solution for this: If you enter the wrong PIN multiple times in a row they will reset to default and erease the stored keys. Thuss an attacker has only a few tries. Wallets that i know of doing that are the Blockstream Jade or the Coldcard for example. Both also provide the option to set up a specific wallet erease PIN that clears the wallet when entered once. Maybe consider these factors when choosing a wallet.
4. Backup your seed WELL
Backup your seed phrase offline, with pen and paper. Better yet on steel (more on that in upcoming part 2). But make sure that your seed phrase is NEVER being put into or shown to a device other than your hardware wallet. NEVER EVER! Don't make a picture of it to store in your cloud, don't safe it in your notes, don't think you are safe storing it in an encrypted file. You are not. Do it offline and keep it offline. Always. Now let's talk material ...
What material should i use?
Paper can burn, suffer from contact with water, be blown or thrown away and be destroyed from all other sorts of things. I found the safest way to backup a seed phrase is by hammering it into a stainless steel plate. These steelwallets don't break the bank like some fancy Cryptotag or other known brand backup solutions do and in most cases they are even better. Espacially when it comes to the backup style:
What way to perform the backup?
Plain text, letter by letter, hammered onto a steel plate. See part 2 for more details on why this is the best method.
5. Test your backup
Every owner of a substantial amount of bitcoin should have restored his wallet at least once! Make sure you know how to get your funds back in case something goes wrong. Especially if you do more complex things like passphrases (which we will cover in part 2) but also if you only use the 12 or 24 word seeds. The way i like to do it is as follows:
- Step 1) When you have set up your wallet, send a small amount of sats to it. This is a good practice anyway to make sure everything works as intended before sending larger amounts.
- Step 2) After your wallet has recieved the small amount reset your device to default. That means completely whiping it. MAKE SURE YOU HAVE BACKED UP YOUR SEED WELL!
- Step 3) Restore your wallet with your backup.
- Step 4) [optional but recommended] Send that small amount of sats back to verify that you truly have full control over this wallet.
If you can access (and control) the small amount of sats, your backup works and you can now send larger amounts. This is also a good way to test if you have properly backed up your passphrase, in case you are setting up a passphrase wallet.
Now what?
When your funds grow bigger, eventually you will ask yourself: "Is this secure enough?" If you are in that position, the recommended methods in part 2 will help you upgrade your security and avoid common mistakes which could put your coins at risk (part 2 will be linked here as soon as it's available).
What have i missed?
Do you agree with these essentials on how to store bitcoin? Did i miss anything? Please let me know and help to refine this set of rules so we can help more and more people to become souverein bitcoin holders.
-
 @ f9c0ea75:44e849f4
2025-01-10 17:47:02
@ f9c0ea75:44e849f4
2025-01-10 17:47:02As the world moves toward an era of centralized digital finance, Brazil is not staying behind. The Banco Central do Brasil (BCB) is pushing forward with DREX, the country’s official Central Bank Digital Currency (CBDC). Framed as a way to enhance financial inclusion, reduce costs, and improve transparency, DREX is being marketed as a technological leap toward modernizing Brazil’s monetary system.
However, behind the promises of efficiency and security, DREX is nothing more than a digital cage designed to tighten state control over financial transactions. While some will celebrate it as a step toward reducing corruption and simplifying the economy, it is, in reality, a massive expansion of governmental power.
From a sovereign individual perspective, DREX represents the opposite of financial freedom, privacy, and autonomy. It is a tool of state surveillance, censorship, and financial control. In this article, we will analyze the history of DREX, its technical framework, the government’s next steps, and why this CBDC is ultimately a dangerous escalation of state power.
The Evolution of DREX: From Concept to Implementation
DREX, originally known as the Digital Real, is Brazil’s response to the growing global trend of CBDCs. The BCB began discussions on launching a digital currency in 2020, shortly after China began rolling out the digital yuan (e-CNY) and the European Union started developing the digital euro.
The stated objectives of DREX are:
- Modernizing Brazil’s financial infrastructure.
- Increasing financial inclusion for the unbanked.
- Enhancing transparency in transactions.
- Reducing costs in financial intermediation.
While these objectives sound beneficial, history has shown that every expansion of financial control by the state—from fiat currency inflation to banking regulations—ends up benefiting the government and central banks, not the average citizen.
Technical Framework and Features
DREX operates on a permissioned blockchain, meaning it is not decentralized like Bitcoin or other public blockchains. Instead, it is fully controlled by the BCB and a consortium of selected financial institutions.
Key Features of DREX:
- Programmability: The government can restrict how money is spent (e.g., banning purchases of certain goods, enforcing expiration dates on funds).
- Full Traceability: Every transaction is recorded on a centralized ledger, allowing the BCB to monitor all financial activity in real time.
- Interoperability: DREX will integrate with PIX, Brazil’s instant payments system, ensuring full adoption by the population.
- Smart Contracts: The government can automatically enforce financial rules, including instant tax collection, fines, and spending restrictions. While these features are marketed as "efficiencies," they enable unprecedented levels of financial control, making censorship, surveillance, and direct government intervention easier than ever before.
Historical Context: The Rise of Financial Control
To understand why DREX is dangerous, we must recognize how governments have historically weaponized financial systems to control their populations.
-
Bretton Woods & Fiat Expansion (1944-1971): The transition from a gold-backed currency to fiat money allowed governments to inflate their currencies at will, leading to massive economic manipulation.
-
The Patriot Act & Financial Surveillance (2001): In response to terrorism, the U.S. expanded financial surveillance, giving banks and governments unprecedented control over monetary flows.
-
China’s Social Credit System & Digital Yuan (2014-Present): China’s digital yuan (e-CNY) is integrated with the Social Credit System, allowing the government to punish or restrict people based on their financial behaviors.
-
The Canadian Trucker Protests (2022): Canada froze bank accounts of individuals who donated to anti-government protests, proving how financial infrastructure can be weaponized against political dissent. DREX fits perfectly into this pattern: a government-controlled digital money system designed to expand state power while eliminating financial autonomy.
## Next Steps: DREX Implementation Timeline and Government Actions
The BCB has already laid out its roadmap for DREX, with critical milestones planned for the next two years.
- Pilot Phases and Testing
- Phase 1: Initial Testing (2023-2024) Focused on the fundamentals, including wholesale CBDC (wCBDC), tokenized deposits, and digital treasury bonds. Initial testing on issuance, transfers, and settlements.
- Phase 2: Smart Contracts & Advanced Features (2024-2025) The second phase, launched in late 2024, focuses on developing smart contract applications for financial services. Participants include Santander, Visa, Mastercard, and Google, working on credit systems, trade finance, and real estate integration.
- Key Dates and Obligations
- October 2024 - November 2024: Application period for financial institutions to join Phase 2 of the pilot.
- June 2025: Deadline for selected institutions to finalize smart contract development.
- Late 2025 - Early 2026: Projected nationwide rollout of DREX. 2026 and beyond: Gradual phase-out of cash transactions, forcing adoption of CBDC-based payments.
- Full Implementation & Adoption Strategy Mandatory Integration: Financial institutions will be required to adopt DREX, ensuring all transactions move to a CBDC-controlled system. Cash Restrictions: Physical cash transactions will become increasingly limited, eventually leading to a cashless society.
The Illusion of Convenience and the Death of Sovereignty
DREX is not a neutral technology—it is a massive expansion of government power under the guise of efficiency and financial modernization.
Many will embrace it without questioning its implications. They will:
Cheer as DREX automates tax collection. Applaud anti-corruption measures that allow the state to track every transaction. Celebrate how it "simplifies" payments, ignoring that it also simplifies financial censorship. But make no mistake:
DREX is not about efficiency—it is about control
Once fully implemented, the state will have the power to:
- Monitor all financial transactions in real-time.
- Restrict spending on certain goods or services.
- Enforce automatic taxation without consent.
- Freeze or seize funds instantly, without due process.
- Eliminate cash, ensuring full reliance on a government-controlled financial system.
The Leviathan is Awakening Philosopher Thomas Hobbes described the state as a Leviathan— "a massive entity that must be obeyed to maintain order. However, when the state controls money, it controls freedom itself."
DREX is the final piece of the puzzle in creating a fully monitored, fully controlled financial system where every transaction is dependent on government approval. By 2025, DREX will be a reality. By 2026, financial privacy may no longer exist for the commons in Brazil. However, Bitcoin exists for the sovereign individual.
-
 @ e97aaffa:2ebd765d
2025-01-10 16:39:58
@ e97aaffa:2ebd765d
2025-01-10 16:39:58Adoro ver os fiduciários a publicarem dados, na qual desmente declarações ou atitudes dos próprios fiduciários no passado.
Quando estávamos em plena crise inflacionista, os políticos e economistas correram para as televisões e jornais a atribuir a responsabilidade da inflação, em exclusividade, à guerra da Ucrânia.
«A invasão da Ucrânia pela Rússia, há dois anos, alimentou uma escalada dos preços do gás natural e da eletricidade na Europa, e o disparo da inflação para níveis históricos.» – Expresso
Mas antes de começar a guerra, a inflação(IPC) estava nos 5.3%, já em máximos históricos.
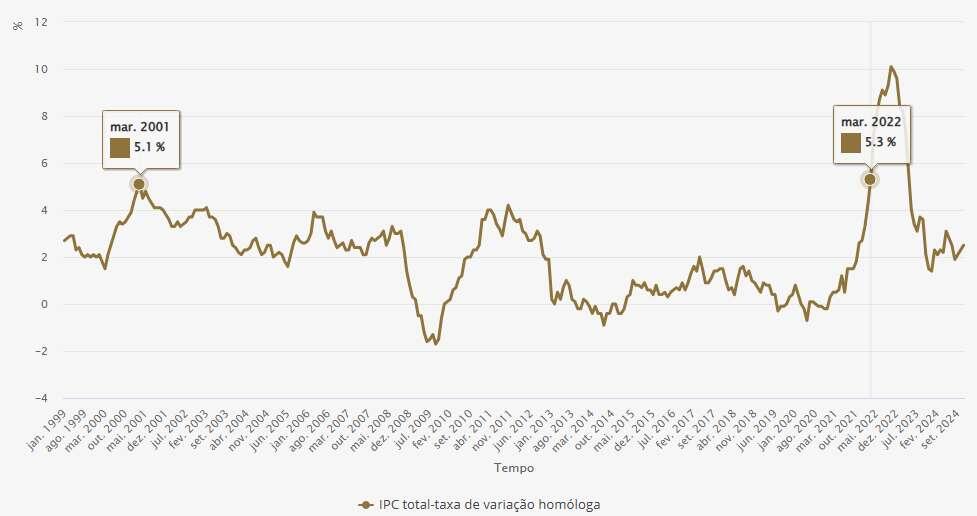
É claro que a guerra contribuiu para a subida de preço, mas não foi a principal razão.
A subida generalizada de preços, vulga inflação, pode acontecer por dois fatores distintos.
Ruptura na cadeia de abastecimento
Quando existe uma ruptura na cadeia de abastecimento, ou seja, um problema na oferta ou na demanda.
A guerra provocou uma ruptura na oferta, sobretudo na energia e nos cereais. Na pandemia houve uma ruptura na demanda, nas máscaras e no álcool gel.
Só que este tipo de inflação é temporária, de curto prazo, a longo prazo acaba por corrigir. Têm um impacto inicial, o preço dos produtos sobem rapidamente, depois a indústria ajusta-se e os preços acabam por corrigir.
Inflação monetária
Ao contrário da ruptura da cadeia de abastecimento que é temporária, a inflação monetária é persistente, nunca mais volta aos valores anteriores.
Esta inflação é gerada pelo bancos centrais ou bancos comerciais, através de políticas que aumentam a base monetária, para os leigos, os bancos imprimem dinheiro.
O aumento da base monetária não gera inflação de imediato na economia, esse processo é demorado, os fiduciários chamam-no de tempo de transmissão.
É um delay que existe, desde o momento em que se aplica uma mudança da política monetária e os seus efeitos a serem visíveis na economia real. Este delay pode variar entre 6 meses a 2 anos.
Observando o gráfico, a subida do IPC iniciou-se a Março de 2021, mas começou a acelerar 6 meses após, muito antes da guerra.
Se existe um delay na causa-efeito, logo a inflação é resultante de algo que aconteceu anteriormente, vamos ver o que aconteceu nos 2 anos anteriores.
Nesse período aconteceu a pandemia e o BCE efetuou o maior aumento da base monetária, desde a criação da moeda única. O início foi no primeiro trimestre de 2020 e a inflação (IPC) começou a subir no primeiro trimestre de 2021, mais ou menos um ano, correspondente ao intervalo de tempo do tempo de transmissão. A semelhança entre a impressão do banco central (EUCBBS, em azul) e o IPC (em azul) é perfeita, apenas com um delay.
O BCE imprimiu (QE) ~4 triliões de euros, corresponde a um aumento de ~90% da base monetária(EUCBBS), no seu pico, em Setembro de 2022. Nesta mesma data, o IPC atingiu os 9%, o que levou o BCE a implementar medidas mais drásticas para combater a subida de preços, aplicou políticas de redução de recompras de obrigações do Tesouro e a subida das taxas diretoras.
As políticas surtiram efeito, o EUCBBS teve uma correção, de 8.84 triliões para 6.36 triliões, mas se compararmos de 2020 a 2024, houve um aumento de 1.7 triliões, ~37%, ou seja, o EUCBBS não voltou aos valores anterior.
Passados 2 anos após a guerra, os preços da energia e dos cereais, já baixaram, estão bastante abaixo do pico. Enquanto o EUCBBS está muito longe dos valores de 2020. Para que os produtos voltassem ao preço de 2021, o EUCBBS também necessitaria voltar para valores anteriores à guerra, mas isso nunca vai acontecer.
A inflação monetária não é temporária, é permanente.
-
 @ 378562cd:a6fc6773
2025-01-10 16:37:38
@ 378562cd:a6fc6773
2025-01-10 16:37:38For many of us, reading isn’t just a pastime—it’s a deeply personal goal tied to self-growth, relaxation, and exploration. Yet, despite knowing its importance, we often struggle to make it happen. We start and stop, let books gather dust, and feel guilty for not finishing them. The truth? It’s not a time issue; it’s a mental barrier.
This guide is designed to help you break through those barriers with a structured, rewarding framework that keeps you interested, engaged, and building momentum. Let’s turn reading into a habit you love—and can sustain.
Step 1: Understand the Real Problem
Before diving into action, take a moment to reflect. The issue isn’t that you don’t have time—it’s that you haven’t made reading a priority. Life pulls us in countless directions, but we always find time for what matters most. Reading deserves that place in your life because it nourishes your mind, brings you joy, and inspires growth.
Ask Yourself:
- Why do I want to read more?
- How would my life improve if I prioritized reading?
Write down your answers and keep them visible. Let your 'why' guide you forward.
Step 2: Start Where You Are (Small and Simple Wins)
Many people fail because they set huge, overwhelming goals like finishing a book every week. The secret to success? Start small. Commit to just 5 minutes a day or a single page. Progress matters more than perfection.
Mini Challenge #1:
- Pick a book you’re genuinely excited about (not one you feel you should read).
- Read for 5 minutes today. Just 5 minutes.
When you complete this, check it off. That little win is the first step toward building momentum.
Step 3: Create a System That Fits Your Life
Habits thrive when they’re tied to something you already do. Look for natural openings in your day to read.
- Morning: Read while sipping coffee or tea.
- Lunch Break: Sneak in a few pages while eating.
- Evening: Replace 10 minutes of scrolling with reading before bed.
Make it impossible to forget by keeping books or an e-reader where you spend the most time: next to the bed, on the couch, or in your bag.
Mini Challenge #2:
- Set a specific time to read tomorrow. Write it down and stick to it.
Step 4: Make It Fun and Rewarding
Let’s face it—habits stick when they feel good. Build instant gratification into your reading routine.
- Gamify the Process: Create a simple list of mini challenges (like the ones here) and cross them off as you go.
- Set Rewards: For every milestone—like finishing a chapter or hitting a week of daily reading—treat yourself. It could be a fancy coffee, a cozy reading corner upgrade, or just the joy of marking progress.
Mini Challenge #3:
- Set a reward for finishing your first chapter or reading streak. Make it something exciting!
Step 5: Follow Your Interests, Not Rules
One of the biggest mental barriers is feeling like you have to finish every book you start. Forget that. Reading should be enjoyable, not a chore. If a book isn’t grabbing you, it’s okay to stop and try another. The key is to stay engaged, not stuck.
Mini Challenge #4:
- If you’re not loving a book after 50 pages, give yourself permission to move on.
Step 6: Build Momentum with Layered Challenges
To make reading exciting and natural, set challenges that grow progressively:
- Day 1–3: Read 5 minutes daily.
- Day 4–7: Extend to 10 minutes.
- Week 2: Finish a chapter or two from a book you love.
- Week 3: Try a new genre or author.
Each challenge builds on the last, creating a sense of accomplishment. By the time you finish the third week, you’ll likely be hooked.
Step 7: Track and Celebrate Progress
Progress tracking is one of the simplest yet most effective ways to build a habit. Create a log to note what you’ve read, even if it’s just a chapter or a short story. Seeing your progress motivates you to keep going.
Ideas for Tracking:
- Use a journal or app to list books and dates you started/finished.
- Jot down favorite quotes or lessons learned.
- Share your progress with friends or join a book club for accountability.
Mini Challenge #5:
- Start a reading journal and write down what you love about the book you’re currently reading.
Step 8: Stay Flexible and Forgive Yourself
Life gets busy, and you might miss a day (or week). That’s okay. Habits are built over time, not overnight. The key is to keep coming back to your reading routine without guilt. Remember, even a little reading is better than none.
Final Thoughts
Reading is a gift you give yourself. It’s not about how fast you finish or how many books you complete—it’s about the joy, knowledge, and escape it brings. By breaking your mental barriers, starting small, and creating a system of rewards and challenges, you can make reading a natural and deeply fulfilling part of your life.
So, grab a book, set a timer, and dive in. Your reading journey starts today.
-
 @ 554ab6fe:c6cbc27e
2025-01-10 15:46:28
@ 554ab6fe:c6cbc27e
2025-01-10 15:46:28It is commonly understood that the ancient Greeks and alike used mythological tales to communicate philosophical teachings. Amazingly, these tales have lasted the test of time and are still told today. It seems stories with philosophical lessons and teachings have an intrinsic value to human civilization. This seems to be the case because we are still creating such stories, and those with great lessons become pop culture phenomena. One example, is the Star Wars saga. George Lucas was known to appreciate ancient tales with meaning. In my opinion, he made one of the most profound modern mythological tales. The tale of Star Wars holds many similarities to Daoism, and my understanding of WuWei (无为). Making it a beautiful tale of how the best way to combat evil in the world, is to be one of passivity, serenity, and nonviolence.
To articulate how Star Wars projects this lesson through its story, one must look at the overarching narrative of the first six episodes, the original movies written by George Lucas. I will refer to these as the original trilogy (episode 4,5, and 6) and the prequel trilogy (episodes 1,2, and 3).
The Jedi are the epitome of goodness. They practice compassion, live their lives in service of others, and strive for peace in the galaxy. Their teachings are clearly benevolent, and are such that we should take them into consideration of our own lives. Jedi are commonly advised to be mindful of their thoughts and feelings1,2. It also bears a striking resemblance to the practice of mindfulness meditation, where one trains the mind in being mindful on the present moment and taking a non-judgmental stance on all incoming emotions, sensations, stimuli, etc. Additionally, the very first lesson Yoda teaches young Anakin Skywalker is that a Jedi must let go of fear, anger, and hatred2. These three emotions lead one to the dark side in this tale, but are also detrimental to us in real life as well. They are the pillars to the way of the Jedi. However, the choice of the three words Yoda uses here is very important. We will see later that these teachings are incomplete. The flaw in this teaching, and the subsequent correction, is what sheds light onto the profound teaching of Star Wars.
Episode 1 begins with the Jedi being the rulers of the galaxy. However, all who know the story of Star Wars know that Darth Sidious/ Emperor Palpatine will one day take control over the galaxy. The entire prequel trilogy outlines the progress of how Darth Sidious manipulates everyone to create political conflict and war to drive the Jedi further into becoming soldiers. The dark emperor chooses this tactic because he knows that violence and conflict is the way of the Sith. The Jedi way is the opposite. As Macu Windu puts it, they are “keepers of the peace, not soldiers”1. However, though this is what Jedi ideally are, in practice they are not so. The three prequels are full of events where the Jedi intervene into political matters and conduct themselves as warriors in order to “keep the peace”. Here, the audience is able to recognize that the Jedi are hesitant to fight in wars. Regardless, the core teachings provided to Anakin in the first episode regarding letting go of fear, anger, and hate do not directly forbid the Jedi from using their fighting skills to keep the peace. So, the audience, and the Jedi council alike, allow the Jedi to conduct themselves in violent ways. During the same scene with Macu Windu, Yoda mentions that his vision is clouded by the dark side1. Why is his vision clouded by the dark side? Why do the Jedi not see Darth Sidious for who he truly is until it is too late? The answer to this is because the violence practiced by the Jedis causes them to lose their way. Evidence of this is brought forth in the original trilogy.
In the original trilogy, Yoda’s teachings to Luke change in comparison to the teachings he gave to his father Anakin. In Dagoba, Yoda tells Luke to let go of anger, hate, and aggression3. Notice how the word “hate” is replaced by “aggression”. This is not to say that hate is ok, but to say that aggression is what Yoda did not understand before, but now realizes as a key component of the Jedi way. The Jedi before used aggression all the time, in the name of peace. They fought evil people as warriors of justice, and Palpatine used this against them. Yoda’s vision was clouded by the dark side, because him, and all other Jedi were using a dark side related behavior: aggression. This is highlighted repeatedly throughout the original trilogy. Luke leaves his training early to go help his friends, and both Obi Wan and Yoda urge him not to do so3. They explain how Luke going off to fight Vader is what the enemy wants, and the best thing he could do was stay, train, and not fight. Yet, Luke departs anyway in the 5th episode and fights his father. This battle doesn’t end well for Luke, and he loses a hand. The hand is replaced with a robotic one, a symbol for lost humanity. In essence, he was punished for acting on his violent and fear driven urges, pushed further to the dark side. We continue to see how aggression is related to the dark side at the beginning of episode 6 when Luke enters Jaba’s palace. Here is referred to as a Jedi, yet acts the opposite: he walks into the palace in all black, and uses brute force to enter the palace by using a force choke on one of the guards4. Though we see him as our hero, he is acts and behaves more similar to a Sith.
The entire tale resolves itself in the final confrontation between Luke, his father, and Darth Sidious. During this encounter, the emperor continuously instills anger and hatred into Luke by threatening his friends, in hope that he will turn to aggression4. He even states that Luke should “strike [him] down, [so] his journey to the dark side [can] be complete”4.
Palpatine knows how to manipulate Jedi into acting upon tendencies that bring them to the dark side. It is how he came to power in the prequels. Luke goes to strike the emperor out of anger and Vader prevents the strike (Vader is saving his son from reaching a place of no return). They fight until Luke gains the upper hand and removes the hand of his father. In this moment, Luke notices that they both have these robotic hands. This is a realization of common humanity. Similar to the vision he had on Dagoba where he fights his father and beheads him, only to find that under the helmet was himself. A realization that they are not only family, but both human beings struggling with the same internal battle between the forces of good and evil. At this moment Luke has become enlightened, and becomes the truest Jedi in the entire series. He turns around and drops his lightsaber, and says “you failed your highness, I am a Jedi”4.
What is significant in this scene is after Luke’s clarifying realization, he drops his weapon, ending the violence while simultaneously claiming victory. He understands that the only way to defeat Palatine, is to not use the same methods of aggression. Rather than using violence, he should use passivity and non-violence to triumph over evil. It goes without saying that he is correct: Palpatine is defeated, and he is able to save his father. In the final scene between Luke and his father, one can see that the black outfit that Luke wears is becoming undone, and the inside fabric now revealed is white. Reiterating that now Luke, being one of non-violence has saved the galaxy and everyone he loves. Luke at this moment becomes a true Jedi, one that has surpassed all before him and becomes the ideal epitome of goodness for the audience to emulate.
This is a story of WuWei. Of how non-action, non-aggression, and effortless action is most effective, and perhaps only way of bettering the world. The Jedi were constantly fighting and resisting evil, unknowingly playing right into the hands of the evil forces in the world. Only when Luke turns to non-action, does the dominance of evil end. This wisdom is not only useful in a galaxy far far away, but is most applicable to the world we live in now. A modern mythological tale of the importance of Daoist philosophy. May the Force be with you.
References
- Lucas G. Star Wars: Episode II – Attack of the Clones.; 2002.
- Lucas G. Star Wars: Episode I – The Phantom Menacee.; 1999.
- Lucas G. Star Wars: Episode V - The Empire Strikes Back.; 1980.
- George Lucas. Star Wars: Episode VI - Return of the Jedi.; 1983.
-
 @ 554ab6fe:c6cbc27e
2025-01-10 15:39:05
@ 554ab6fe:c6cbc27e
2025-01-10 15:39:05I was in high school during the 2008 Great Recession. The significance of that event made me critically question our current economic system. It made me very interested in how our system of money and banking works. This path of inquiry led me to research and understand the truly complicated and underdiscussed issue of fiat currencies, and the subsequent powers that gives government and bank in manipulating our economy. In my opinion, the modern world has a money problem. This money problem not only translates into issues of materialism, but also is represented in poor monetary policy on the part of the societal elites. Below is a paper I wrote in high school which discusses how the manipulation of interest rates, made possible by fiat currencies and fractional reserve banking, leads to dangerous business cycles that lead to the great economic collapses we have experienced.
How does the interest Rate Manipulation Work?
With the fractional reserve system in place, the Federal Reserve has three powers that they use to adjust the interest rates of banks to carry out their policies. The first conceptual milestone to be achieved in answering the question of the Federal Reserve’s effect on the business cycle is to understand how the fractional reserve banking system works. It is legally mandated that all banks must have a certain percentage of their reserves in the vaults at all time. Though this is a reserve requirement, banks historically never in the long run hold onto excess reserves because that would bring economic disadvantage with the other banks (until recently because the federal reserve no pays interest to banks who hold some excess reserves). Therefore, the reserve requirements end up being the universal ratio of cash a bank holds at a time. This also means, that banks historically have never have the total financial holdings of all their customers.
The first power is referred to as open market operations, and is key to the adjustment of the federal funds rate. The Federal Fund Rate is the overnight interest rate between banks. This rate is determined between banks based upon how much money bank A’s demand of money to fill their reserves, and the supply of excess reserves bank B has at the time. This interest rate between the banks in turn affects the interest rates of borrowers and investors. The Federal Reserve manipulates these interest rates by indirectly filling bank's reserves with money. The Federal Reserve does not do this by simply printing money and giving it to bank B, but rather printing some money and purchasing Treasury bonds (or in the case of the 2008 period, Mortgage-Backed Securities) off of the open market. The money then, that the individual earned from selling the bond(s), will then eventually end up in the bank’s which will then either cause bank A to have less of a demand for money to fill their reserves, or cause bank B to have a higher supply of reserves, thus lowering the federal fund rate.
The second power is similar to the first in the sense that it also affects the federal fund rate but it done through the adjustment the reserve requirements. A bank's need for money is based upon their reserve's relationship with the reserve requirements. Therefore, the second power is the ability to lower (or raise) the reserve requirements of all banks, which will cause bank B to not have as high of demand for a loan, and will cause bank A to have a higher supply of excess reserves to loan.
The third power is the direct adjustment of the discount rate which is the rate between a depository institution and the Federal Reserve itself. These kinds of loans exist when a bank, like bank B, would rather loan from the Federal Reserve than other banks. However, as the Federal Reserve is only supposed to be a lender of last resort, the discount rate tends to stay higher than the federal fund rate.
These three powers cannot be performed independently without the consideration of the other. The power to buy bonds and adjust reserve ratios has a large effect on the economy's money supply; Monetary base and M1. This can be seen not only from the fundamental process at which these interest rates are manipulated, but by the law of supply and demand. Suppose the Federal Reserve wishes to lower interest rates, however there is a fixed amount of loanable cash and a fixed amount of demand (ceteris parabis). If the government is to artificially lower the interest rates, there will be a shortage of loanable funds, but an increase in demand for loans. As loans are not a product that can simply be produced like most goods in the economy, the only way to deal with this shortage is for the government to print the shortage of loanable goods. With this increased supply of loan-able funds, there is then a lower price, and higher demand. This also means then, that these two functions cannot be done at free will because they can result in rampant inflation of even hyperinflation due to the increased money supply. The discount rate also is centralized around the federal fund rate so one is usually adjusted around the other in order for there to be balance in reserves across the system.
One reason the Federal Reserve has these powers is so that it can manage the economy and therefore the business cycle. The ability to adjust interest rates grants them the ability to monitor the rate at which people save and borrow. Higher interest rates will cause people to save more, and borrow less. In contrast, lowering interest rates will cause people to save less and therefore spend more which causes inflation (due to the process of lowering interest rates and the increase in the demand for overall goods) giving the market incentive to spend even more. This would be the growth time in the business cycle. The Federal tries to avoid the contraction aspect of the cycle by keeping interest rates down and keep inflation existent so people keep spending and not saving. The question that must therefore be asked is does this manipulated of the free market and these therefore artificially created interest rates affect the market in a negative way?
Artificial Interest Rate Cycles
What must first be noted is that in an artificial interest rate cycle, interest rates are pushed down in order to regulate the economy. The manipulated business cycle that will then be discussed is one in which interest rates are artificial lower than would have been without the Federal Reserve's intervention.
In an artificially low interest rate business cycle, growth consists of massive consumption. Not only are interest rate low, which increases the demand for business and individuals to loan money to spend. But there is a touch of inflation due to the increase in the money supply. Demand for goods then much higher because people do not want to hold on to their money that is losing value. Not only that, but there is also no benefit to hold in banks because of the low interest rates. For these reasons, consumption increases, and savings are depleted. (As a side note, I would argue that the existence of this system is a large reason why we see such materialism and consumerism within modern day culture.) As savings deplete, supply for loan able cash drops, and prices will rise, but the Federal Reserve, in order to continue the growth, keep pushing rates down and increase the money supply more and more. This continuation of inflation also causes the market to begin to speculate continuingly rising prices. A strong example of this was the housing market before the financial crash of 2008. As people began to purchase houses because of their perceived value of always going up, prices rise.
As the prices for houses steadily went up for such duration of time and a rampant rate, people would view this trend to be never ending, further adding to the amount of people entering the market, making prices rise even more. Of course, this also means that the allocation of resources has very much shifted away from other goods that otherwise would have been purchased, and has now shifted toward housing or the various markets of the stocks being purchased. Keep in mind, that the increased demand for houses was not due to any increase on intrinsic need for house, but simply because people were wishing to gamble on the price going up. This is why we call it a “bubble” because it was being filled not with true value, but “air”
Inevitably, the growth period ends and the contraction begins. During the Federal Reserve induced growth session, prices were extremely high from everyone taking cheap loans and making money off of speculation. Once a contraction hits, prices begin to fall and people begin to save. This means that aggregate demand falls, and so do prices. This causes the speculation markets to radically loose demand because there are no longer people believing prices will rise. and as prices fall, all the people who owned a house or stock will lose money on their investment.
After the prices fell, people immediately wished to leave the market and sell their house, and nobody wanted to enter the market and buy houses because the market no longer had the perceived future value as it did before. This caused a massive drop in house prices, and caused all the people who owned a house, lose money. Furthermore, most people made these investments with loans which now they can no longer pay back. Banks then can go bankrupt because of all of the new faulty loans, unemployment increased because businesses that made malinvestments now must lay off workers, and people will then begin to panic because the market is contracting and they had accumulated very little savings from the growth. This results in a loss in aggregate demand not only because there are no savings but because the market must recuperate after the massive amount of loan defaults and investment loss.
At the end of the cycle, the society does not seem to have made much economic process. Much of the production was shifted to houses which were only valued for their investment opportunities. Due to the massive debt and sharp drop in aggregate demand, there are also much less goods being produced as a whole as the economy must take a while to recuperate after the losses.
Natural Interest Rate Cycles
Before analyzing a business cycle with natural interest rates, a few things must initially be made clear. To have a truly natural interest rate society, the Federal Reserve would have to play no role in the economy, which would bring about the end of a mandated fractional reserve banking system. For the sake of the research question, this aspect of the argument will be left out, and the only difference between natural interest rate cycles and unnatural interest rate cycles will be that there will be no price controls on interest rate. The interest rate is determined by the supply and demand for loanable funds at the time. Where are also to assume inflation is near or below 0%. This is because if there is no manipulation of interest rates, the function of printing money to lower interest rates is non-existent.
With that said, the first difference that must be discussed is the demand for goods aspect during the growth time. In a natural interest rate growth time, the aggregate demand for goods over the long run of the growth period is much less than in an unnatural interest rate cycle. This is because, as the growth continues, the amount of loan able funds decreases because of the consumption. Interest rates then will gradually rise because of the gradual loss in supply of loan-able funds. savings will also be much higher in this cycle.
As there is no flagrant expansion of the money supply, the demand capital is higher and interest rates are higher. With interest rates being higher, the incentive for saving is also higher. The allocation of goods is then much different in this cycle, because as it becomes more profitable to save, on top of the fact that there is very little inflation, there will be less speculative spending. Which means there won't be overproduction of ventures like housing, which allows the market to allocate those resources to goods that increase welfare of everyday life.
What follows is the transition into contractions. In this business cycle, because more and more loan-able funds are being used up and savings begin to increase, a contraction period begins when the interest rates are too high and aggregate spending has transitioned to be higher than aggregate spending. During this time, as people begin to save more than they spend, interest rates will gradually begin to fall again. Similar to an unnatural interest rate cycle, prices will decrease, and there will be an increase in unemployment. The difference is during the growth time aggregate savings was higher than unnatural interest rate aggregate savings due to the price adjustment of interest rates. Which means all those who are now unemployed have more savings and are better off, and can spend more money. There is also much less defaulting on debt because there were much less people acting on investment strategies in speculative markets because there were much fewer and smaller speculative markets. Due to all of this savings that now exist rather than the malinvestment and bankruptcy that existed in a Federal Reserve induced recession, more spending and consumption can be directed toward the production of goods. This leads to a much smoother, less volatile, and steady cycle.
At the end of a full natural cycle the production and demand for goods is much different without the Federal Reserve. Due to the absence of large growth and extreme contractions in a natural cycle, there were much less people who go bankrupt and default on debt. Due to all of this savings that now exist rather than the malinvestment and bankruptcy that existed in a Federal Reserve induced recession, more spending and consumption can be directed toward the production of goods. There is also a massive difference in the kind’s goods produced. Rather than having over production in commodities that were largely produced solely for their investment and perceived future market value, the market allocated goods to places where people demanded them for their lives. There is then much less misallocation because goods were bought for their consumer value rather than investment value.
Conclusion
To answer the question of: How does the Federal Reserve’s artificial adjustment of interest rates compared to natural interest rates affect the business cycle? One must observe the allocation of goods because of their profound their relationship between people’s wealth and welfare. In order to find the difference of allocation of resources in the two cycles, a business cycle with artificially low interest rates was observed. In this cycle, large speculative markets cause the allocation of resources to be directed to goods that are produced largely because of their perceived investment value, and not solely for their welfare value like most other goods. Furthermore, the massive debt and malinvestment that accumulates once the contraction occurs, disallows for increased wellbeing because there are less goods being produced. To gain a full understanding of the negative effects of the Federal Reserve’s adjustment of interest rates, one must also inspect what a business cycle would look like without the adjustment of interest rates. In this business cycle, there is less demand for speculative markets, and so the allocation of resources is directed to increased welfare goods, which depletes the issue of overproduction. Furthermore, there is a much more stable system of savings and spending, which lowers the amount of people going into bankruptcy once contractions hit. This allows for more goods and services to be purchased even when the economy is recovering from the growth. This is another reason why the allocation of resources is better because of the fact that there is much less malinvestment, which causes loss in productivity.
It is then evident that unnatural interest rates simply worsen a necessary part of the business cycle. It causes certain prices to go way beyond their true value (plus causes overall inflation), which causes people to end up in debt and causes the market to have case malinvestment and misallocation of goods. People during the time of need, will not have savings to fall back on or accumulate for the next boom.
-
 @ da0b9bc3:4e30a4a9
2025-01-10 14:08:49
@ da0b9bc3:4e30a4a9
2025-01-10 14:08:49It's Finally here Stackers!
It's Friday!
We're about to kick off our weekends with some feel good tracks.
Let's get the party started. Bring me those Feel Good tracks.
Talk Music. Share Tracks. Zap Sats.
Let's go!
Kickstart My Heart!!
https://youtu.be/CmXWkMlKFkI?si=UNb7KC-ukse9uquM
Talk Music. Share Tracks. Zap Sats.
originally posted at https://stacker.news/items/844806
-
 @ 6f26dd2b:f2824b88
2025-01-10 14:07:44
@ 6f26dd2b:f2824b88
2025-01-10 14:07:44Just came across this email blog and Bitcoin was in my mind. What's your say?
"The Central Bank of Kenya (CBK) is getting ready to mint new coins to avoid shortages. Yep, they’re hunting for a company to handle this for the next three years starting in 2025.
Per Business Daily, this comes after CBK’s KSh14.14 billion ($109.20 million) deal with a German company, Giesecke+Devrient Currency Technologies GmbH, to print new banknotes. CBK Governor Kamau Thugge said the decision to mint coins came through a classified process — makes sense since no one wants a cash shortage messing with the economy.
If you remember, back in December 2018, CBK rolled out new coins featuring giraffes, rhinos, lions, and elephants, ditching portraits of people in line with the 2010 Constitution. Now, they’re inviting bids for a new coin-minting contract to keep things stable."
-
 @ 4657dfe8:47934b3e
2025-01-10 13:28:47
@ 4657dfe8:47934b3e
2025-01-10 13:28:47Alby Hub - your Center for Bitcoin Payments
Alby Hub is a self-custodial lightning wallet that lets users choose their preferred Lightning funding source. It includes an easy-to-use lightning node with a one-click setup, while also accommodating existing node runners.
In short Alby Hub offers node runners:
➡️ a lightning address to receive payments in a self-custodial manner ➡️ integrated Lightning Service Providers, to quickly buy channels with receiving capacity ➡️ a selection of vetted channel partners to open channels without searching for a long time ➡️ a marketplace of apps to connect your own node. Read more about this superpower. ➡️ a mobile app, Alby Go, to pay right from their own node on the go.
Thus, Alby Hub enables you to make your node the central hub for bitcoin payments, maintaining full self-sovereignty.
Install Alby Hub on RaspiBlitz
- Login into the RaspiBlitz WebUI and enter the dashboard
- Go to Apps, find Alby Hub and install the app
It’s as easy as that. Now you can link your node with an Alby account to get a lightning address, use your node on the go with the Alby Go mobile app or on the web with the Alby Browser Extension. Updates of Alby Hub become available with each new RaspiBlitz release.
With one-click setup, an intuitive interface, and seamless integration with dozens of bitcoin apps, Alby Hub makes self-custodial bitcoin payments easy for everyone while adding much more utility to your lightning node.
-
 @ 4506e04e:8c16ba04
2025-01-10 13:26:46
@ 4506e04e:8c16ba04
2025-01-10 13:26:46The healthcare system, in its current state, is fundamentally broken. Under the fiat standard, big pharma exploits the sick in much the same way that banks and financial corporations drain economic power from individuals and small businesses. Despite massive investments, healthcare remains plagued by inefficiencies, inequities, and vulnerabilities. With rapidly aging population and low birth rates the access to healthcare is becoming more and more difficult and the system will break within the next couple of decades. Here are some of the major issues:
Financial Drain with Minimal Returns
No matter how much money is poured into healthcare, it’s never enough. Administrative overheads, inflated costs, and inefficiencies ensure that resources are wasted instead of improving patient outcomes.
Big Pharma’s Perverse Incentives
Pharmaceutical companies prioritize profit over cures. The system is designed to keep patients alive but perpetually dependent on treatments, rather than focusing on true cures.
Administrative Bloat
The excessive overhead costs in administration siphon funds away from actual patient care.
Fragmented Patient Records
There is no single global standard for managing and accessing healthcare records, creating inefficiencies and potential for errors.
Cybersecurity Risks
Centralized healthcare systems are vulnerable to ransomware attacks, which can compromise patient safety and even pose threats to international security. For hospitals, such attacks are literally matters of life and death.
Increasing Costs and Reduced Accessibility
Instead of becoming cheaper and more accessible, healthcare is growing more expensive and difficult to obtain, exacerbating inequities, yet nurses are one of the groups that's most underpaid!
A Decentralized Solution
The solution lies in leveraging decentralization, encryption, and open-source technologies to transform the healthcare system. Thanks to innovations like Bitcoin and the Nostr protocol we now have the means to:
-
Empower Patients and Doctors: Decentralized systems can give patients control over their medical data while reducing administrative costs for healthcare providers.
-
Enhance Security: Encryption ensures data is secure, even in the face of cyber threats.
-
Improve Accessibility and Efficiency: Open-source tools (like Keycast) can lower costs and provide customizable solutions tailored to specific healthcare needs.
note1327htu9gr327h38yu5f6tueye4cajp3kc69cs3gl7w6q6rz09ufqukl74j
How Nostr Can Transform Healthcare
Nostr, short for “Notes and Other Stuff Transmitted by Relays,” is a decentralized protocol originally designed for communication but holds tremendous potential for industries such as healthcare. Its client-relay model allows patients and doctors to interact securely without relying on centralized servers. Here’s how it could work in a healthcare context:
Decentralized Data Control:
Patients’ medical records can be securely stored and accessed via relays. Each patient’s identity is tied to a cryptographic public key, ensuring that they have full control over their data.
Doctors can access necessary records by connecting to relays the patient authorizes, ensuring data remains private and secure.
Privacy Without Bureaucracy:
Nostr eliminates the need for cumbersome identity verification processes (e.g., KYC). Patients retain privacy without needing emails, IDs, or other personal identifiers.
Customizable Access:
Patients can specify which doctors or healthcare providers can access their records by granting permissions via cryptographic signatures. These permissions can be adjusted or revoked at any time.
Secure and Verifiable Communication:
All interactions between patients and doctors are signed with private keys, ensuring authenticity and preventing tampering.
Relays do not own or manipulate the data; they simply transmit it between authorized users.
Resilient and Flexible Network:
Patients and doctors can choose which relays to use, and data can be published to multiple relays for redundancy. This ensures continuity of care even if a specific relay goes offline.
Patient-Centric Data Ownership:
In the Nostr model, patients own their data. They can share it, manage it, or restrict access as they see fit, empowering them to take control of their health information.
Enhanced Telemedicine:
Secure, encrypted communication enables remote consultations where doctors can access up-to-date patient records in real-time, providing better care.
By combining Nostr’s decentralized approach with healthcare-specific adaptations, this protocol can make the healthcare system more secure, efficient, and patient-focused.
Meet Keycast
Keycast is a self-hosted open-source tool designed for secure and efficient private key management that can be applied to manage teams and policies. Its features can empower collaboration from micro-level ops like sharing access to one Nostr account to organising healthcare in the following ways:
-
Team Management:
-
Organize users into teams representing departments or specialties (different policies).
-
Streamline workflows by aligning permissions with roles.
-
Granular Permissions:
-
Assign specific access rights to doctors, nurses, and administrative staff.
-
Create layered permissions for actions such as accessing records, adding notes, or authorizing tests.
-
Secure Key Management:
-
Encrypt and securely store keys locally, ensuring data confidentiality.
-
Remote Signing and Telemedicine:
-
Enable secure remote access to records through NIP-46 for telehealth scenarios.
-
Customizable Policies:
-
Tailor permissions and content filters to suit healthcare needs, such as restricting access to certain records or anonymizing sensitive data.
-
Patient Empowerment:
-
Allow patients to manage access to their health information, promoting transparency and autonomy.
Real-World Applications
Here’s how these tools can address specific healthcare challenges:
-
Secure Access to EHR: Doctors and nurses can access patient records securely and efficiently, improving care coordination.
-
AI-Driven Diagnostics: AI agents with predefined, limited permissions can analyze data for diagnostics while safeguarding privacy.
-
Telemedicine: Secure, encrypted access ensures doctors can deliver remote care without compromising patient data.
-
Anonymized Research: Controlled access to anonymized data can accelerate medical research while protecting privacy.
The Bigger Picture
Decentralization is the key to fixing healthcare. Just like Bitcoin fixes the money and fixes the world - nostr and censorship-resistant encrypted data flow can fix whole industries like healthcare. By moving away from centralized, vulnerable systems, we can:
-
Enhance Security: Protect sensitive data from cyber threats with encryption and decentralized architectures.
-
Lower Costs: Reduce administrative overheads and eliminate inefficiencies.
-
Improve Collaboration: Foster better communication and coordination among healthcare professionals.
-
Ensure Transparency: Leverage open-source solutions to build trust and flexibility.
Conclusion
The healthcare systems we have today are heavily reliant on money printing. They are have turned into businesses with overgrown administrative layer. They are inefficient and unsustainable. However, by adopting the Nostr protocol and tools built upon it, we can create a system that is secure, efficient, and patient-centric. With open-source tools like these, healthcare can truly focused on improving lives, become cheaper, more accessible, and abundant.
Challenge
If you'd like to contribute to reinventing healthcare using free and open-source software built on the nostr protocol join the challenge by npub1healthsx3swcgtknff7zwpg8aj2q7h49zecul5rz490f6z2zp59qnfvp8p
note1lnh3q6648ysulrx2pgeyhv2cqqle9vftdxalq3yqkqa7c89eljtqyr70nl
-
-
 @ 6ad3e2a3:c90b7740
2025-01-10 12:33:47
@ 6ad3e2a3:c90b7740
2025-01-10 12:33:47The excesses of wokeness are thankfully getting their overdue correction, but as often happens with corrections, they tend to overshoot. A case in point was from the usually reasonable writer Wesley Yang on Twitter, who posted the following:
Poor long-term immigration policy has apparently led to too many foreign-born and native criminals of foreign descent in Norway, a disproportionate number of whom, per the chart, hail from Somalia and Morocco. Yang argues using this data to inform Norway’s immigration policies going forward is both unproblematic and “no longer prejudice.”
This is a sleight of hand. You can advocate for designing prejudicial immigration policies based on the group to which an individual potential immigrant belongs, but you cannot both do so and pretend it is not prejudicial.
This is not a point about what countries should or should not DO. They are free IMO to design immigration policies as they see fit, and there are arguments to be had over that. But there is a reactionary blindness wherein people pretend that grouping individuals by race, religion or country of origin isn't prejudicial to those individuals who have no control over how others in their assigned group behave.
The grouping is justified in their view by "data" or "statistics" or "reason." The truth is most of us still view "prejudice" as negative, so no one advocating for discriminatory immigration policies wants to be considered prejudiced. They are for the policy, think it's good, and therefore try to pretend it's not prejudiced when it obviously is.
Don't pretend. If you're for prejudicial, discriminatory immigration policies "for the greater good", just advocate for it on those terms. Be honest about what you're saying.
This might seem like a trivial point on which to base a post, but I don’t think it is. It’s not because “prejudice is bad” or “racism!” That’s just one type of instance in which this midwit tendency — to assign individuals to a group and then pretend you are being “data-driven” — rears its terrible head. I remember a couple years ago people on Twitter accused me of “taking up an ICU bed” because I refused to inject myself with Pfizer’s latest. Their reasoning was similar: because the unvaccinated are more likely to take up ICU beds (which turned out to be a lie, but let’s assume it were true), I was in the group taking up more beds, therefore I was taking up a bed.
The trick is to assign someone to a group in which they qualify (Somali, unvaccinated, etc.), get “data” about that group and then apply that data to the individuals within it, even if it is totally inaccurate with respect to them.
This is the same trick used to justify disastrous DEI policies too. You are from a historically underprivileged group, so you deserve to be held to lower standards. It doesn’t matter if you would succeed on your own merit, it doesn’t matter your race, gender, sexual orientation are irrelevant to the task for which you are being hired, it doesn’t matter if you are the son of wealthy and famous people and attended all the best schools, you belong to a particular category and therefore this standard will be applied.
But the implications of this midwit sleight of hand are even worse than that, especially on the eve of AI-based systems taking over so many of the administrative functions at both the corporate and state level. You will be categorized, and you will be pre-judged on that basis because it is far more efficient for the system to do so than to examine everyone individually. In fact, I’d argue, unlike humans, AI is incapable of seeing individuals, it sees only “data.”
This was the premise for the movie Minority Report, set in a dystopian future wherein people get convicted of “pre-crime” because the system determined from the data about them they were likely to commit one. You might not have done anything yet, but based on your angry social media posts, your high testosterone, your age and background, you have a 99.9 percent chance of violence. Why not arrest you now before you victimize someone? For every 1000 victims we protect, we’ll convict only one person who would not in fact have done it!
There will be many people who are for this kind of reasoning. It’s “data” after all. Never mind the data can be biased based on the grouping. Why am I grouped with other people I don’t know and over whom I have no control? What if they added 100 other parameters which showed I’m among the least likely to commit violence? Who is selecting these parameters and what are their agendas?
But more to the point, such a society is not free. You are at the whims of your grouping, of parameters, of statistics. The paradigm of individual civil liberties, innocent until proven guilty, responsibility only for your own actions would be dead. You are pre-judged before you have done anything.
The second-order effects of such a paradigm would be a race to the bottom. If I am not in the wrong group I can do no wrong, based on my favorable peers. I can roam the streets, commit acts of vandalism and violence with impunity, I can loaf at work, not do my job and never be fired. I would argue that under the present (and mercifully soon-to-be-departed) administration we’ve already experienced many of these effects already.
So back to the original question. What is Norway to do with this “data”? One idea would be to have a non-discriminatory vetting process that involves delayed gratification and requires some diligence on the part of the prospective immigrant. This might self-sort the people capable of living in an open, prosperous western society and those who are not. You would be admitted or denied based on demonstrated suitability (merit), not with whom you were grouped (identity). This would be closer to the “postjudice” policy prescription Yang erroneously claims for his own in the cited post.
Whether that results in more people of one race or another, one nationality or another getting in, isn't important. What's important is both not judging individuals on the basis of their assigned group and keeping the country free of violent criminals. Both goals are essential if we want to avoid dystopian outcomes.
-
 @ d435e69e:43f49e01
2025-01-10 11:15:57
@ d435e69e:43f49e01
2025-01-10 11:15:57In the fast-evolving world of digital assets and blockchain technology, cryptocurrency has emerged as a revolutionary force reshaping industries and markets. However, navigating the complexities of cryptocurrency—whether for investment, business integration, or strategic planning—requires in-depth expertise. Crypto consulting services provide the knowledge and guidance businesses and individuals need to unlock the full potential of this transformative technology.
What Are Crypto Consulting Services?
Crypto consulting services help clients understand, implement, and leverage cryptocurrencies and blockchain technology. These services cater to a wide range of needs, including portfolio management, blockchain adoption, cryptocurrency compliance, and market analysis. Whether you're a beginner looking to explore digital currencies or a business aiming to integrate crypto solutions, consulting services offer personalized strategies to achieve your goals.
Benefits of Crypto Consulting Services * Expert Guidance: Crypto consultants bring specialized knowledge of blockchain and cryptocurrency, enabling clients to make informed decisions.
-
Risk Mitigation: The cryptocurrency market is volatile and complex. Consultants help clients navigate risks, identify opportunities, and avoid costly mistakes.
-
Customized Solutions: Every business or investor has unique needs. Crypto consultants provide tailored strategies that align with specific objectives, such as developing payment systems, creating crypto wallets, or exploring decentralized finance (DeFi).
-
Regulatory Compliance: Cryptocurrency regulations vary globally and are often difficult to interpret. Consultants ensure that clients comply with local and international laws, safeguarding against legal risks.
-
Market Insights: Access to in-depth market analysis and trend forecasting helps clients make well-informed decisions and capitalize on emerging opportunities.
Core Services Offered by Crypto Consultants * Crypto Adoption Strategy: Consultants guide businesses in integrating cryptocurrency into operations, whether through accepting crypto payments, tokenizing assets, or building blockchain-based platforms.
-
Portfolio Management: For investors, consultants provide insights on asset diversification, risk assessment, and portfolio optimization.
-
Regulatory and Legal Advisory: Consultants ensure clients adhere to compliance standards, including Anti-Money Laundering (AML) and Know Your Customer (KYC) regulations.
-
Blockchain Implementation: Crypto consultants help businesses implement blockchain solutions for supply chain tracking, data security, and transparent transactions.
-
Education and Training: Many consultants offer workshops and training sessions to help teams understand crypto fundamentals and advanced applications.
Industries Benefiting from Crypto Consulting * Finance: Exploring decentralized finance (DeFi), crypto lending, and payment systems. * Retail and E-commerce: Accepting cryptocurrency payments and enhancing customer experiences. * Healthcare: Using blockchain for secure data management and payments. * Real Estate: Tokenizing properties to streamline transactions and investments. * Gaming and Entertainment: Integrating NFTs and in-game currencies for monetization.
Choosing the Right Crypto Consultant
When selecting a crypto consultant, consider:
- Expertise and Track Record: Look for consultants with proven experience in your specific industry or area of interest.
- Transparency: Ensure they provide clear and honest insights, especially in risk management.
- Customization: The consultant should offer personalized strategies tailored to your needs.
Conclusion
Crypto consulting services bridge the gap between potential and action, offering the expertise and strategies necessary to navigate the dynamic cryptocurrency landscape. By partnering with experienced crypto consultants, businesses and individuals can confidently embrace this technology, driving innovation, efficiency, and growth. Unlock the future of finance with expert guidance and a tailored approach to crypto success.
-
-
 @ fe7af447:9594a50b
2025-01-10 10:38:57
@ fe7af447:9594a50b
2025-01-10 10:38:57We've all heard the classic investment advice at family gatherings: "Don't wait to buy real estate. Buy real estate and wait." (well in my family I hear all the time). This saying typically surfaces during those moments when family members, perhaps loosened up by a few drinks, discuss inflation and rising costs. While real estate discussions are met with approving nods, mentioning Bitcoin often draws skeptical looks. However, in today's financial landscape, I'd like to propose a modern equivalent: "Don't wait to buy Bitcoin. Buy Bitcoin and have a low time preference."
This perspective came up during a recent conversation with a family member (let's call him Joe), who's considering buying a $1.4 million home in Hawaii. His plan is to use the property as both a family residence and an investment. While Hawaii is undeniably a paradise for raising a family, I couldn't help but share why I believe Bitcoin offers superior long-term value and the potential for generational wealth. This is dedicated to Joe—and to my kids, who overhear our family discussions. I'm not stacking property or metal rocks. I'm stacking sats, building a legacy of generational wealth.
The Hawaiian Dream: A Reality Check
Hawaii represents the quintessential paradise lifestyle. With its pristine beaches, breathtaking sunsets, and strong sense of community (ohana), it offers an idyllic environment for raising a family. The lifestyle naturally encourages outdoor activities and overall well-being, providing countless opportunities for meaningful family experiences.
However, the financial reality of Hawaiian homeownership presents significant challenges:
The Numbers Don't Lie
-
Housing Costs: As of 2024, Hawaii's median home price stands at $850,343, with properties in desirable areas like Oahu and Maui frequently exceeding $1.4 million.
-
Income Reality: The average annual salary in Hawaii is approximately $52,828, creating a stark affordability gap. This disparity explains why multi-family living arrangements are common in single-family homes.
-
True Cost of Ownership: For a $1.4 million home:
-
Monthly mortgage: $7,000 ($84,000 annually)
- Property taxes and maintenance: $28,000 annually
- Total annual cost: $112,000
Understanding Real Estate Appreciation
Many homeowners, like Joe, often misunderstand why their properties increase in value over time. The common belief is that real estate inherently appreciates, making it an ideal store of wealth. However, this perspective overlooks a key factor: property values often rise primarily due to the dollar's decreasing purchasing power from inflation, rather than a true increase in real value. For example, I bought my home in 2012 for $500k. By 2025, its value is $1 million—but the house shows its age, needing a new paint job, and has defective galvanized metal foundation components that are now the subject of a pending lawsuit due to corrosion issues. Mass-produced track homes, built quickly with subpar materials, often fail to retain real value over time despite nominal price increases.
This phenomenon becomes crystal clear when viewing property values through the lens of Bitcoin (and most people don't have the right lens):
- 2016: Average home ($288,000) = 664 BTC
- 2020: Average home ($329,000) = 45 BTC
- 2024: Average home ($435,000) = 6.6 BTC
The Bitcoin Advantage
Bitcoin's fundamental strength lies in its fixed supply of 21 million coins. With nation-state adoption anticipated in 2025 and increasing capital flow from various asset classes into Bitcoin, the case for "stacking sats" becomes increasingly compelling.
A New Paradigm for Wealth Preservation
A New Paradigm for Wealth Preservation The traditional wisdom of real estate investment stems from an era of limited alternatives for wealth preservation. While real estate remains a valuable asset class, Bitcoin offers several distinct advantages:
Perfect Portability: Unlike real estate, Bitcoin can be transported instantly across borders without permission. You can move millions or billions in value with just a private key in your head, making it the ultimate portable store of value.
Minimal Carrying Costs: No maintenance fees, property taxes, or insurance required. While real estate continuously drains your resources through upkeep, property taxes, and insurance premiums, Bitcoin can be stored for free using self-custody solutions.
True Scarcity: While real estate is limited, new development is always possible (we can always build up, convert land use, or create artificial islands); Bitcoin's supply is mathematically fixed at 21 million coins. This immutable scarcity makes it the hardest form of money ever created.
Divisibility: You can invest any amount, rather than needing large down payments. Bitcoin can be divided into 100 million satoshis (sats), making it accessible to anyone, anywhere, at any income level. This perfect divisibility allows for microscopic transactions or massive transfers with equal ease.
Global Market: Not limited by local economic conditions or natural disasters. Bitcoin trades 24/7/365 on global markets, making it immune to localized risks that can devastate real estate values.
Supreme Liquidity: Bitcoin is arguably the most liquid asset in human history. You can:
- Convert billions to cash within minutes
- Trade across thousands of markets globally Access your wealth at any time without bank permission
- Never worry about "finding a buyer" like with real estate
\ Unconfiscatable: When properly stored, Bitcoin provides a level of security that physical assets can't match:
- Can't be seized without your private key Resistant to government confiscation Immune to civil asset forfeiture Protected from legal judgments if properly structured
- Programmable: Bitcoin's programmable nature enables:
- Automated inheritance planning Time-locked savings Multi-signature security Smart contract capabilities through Layer 2 solutions
- Energy Storing: Bitcoin effectively stores excess energy through mining:
- Monetizes stranded energy resources Incentivizes renewable energy development Creates energy buyers of last resort Helps balance power grids
\ Network Effect: Bitcoin's first-mover advantage and network effect continue to strengthen:
- Growing institutional adoption Increasing merchant acceptance
- Expanding Lightning Network capacity
- Strengthening security through hash rate growth
Conclusion
While the allure of Hawaiian real estate is undeniable, the financial reality demands careful consideration. Bitcoin represents a modern approach to wealth preservation that addresses many of real estate's limitations while offering potential for significant appreciation. The key is understanding that Bitcoin isn't just another investment vehicle – it's a paradigm shift in how we think about and store value.
For families like Joe's considering significant real estate investments, incorporating Bitcoin into their investment strategy might provide a more balanced and forward-thinking approach to building generational wealth. The plan is clear. Buy Bitcoin. Years from now, you'll have generational wealth.
-
-
 @ 42342239:1d80db24
2025-01-10 09:21:46
@ 42342239:1d80db24
2025-01-10 09:21:46It's not easy to navigate today's heavily polluted media landscape. If it's not agenda-setting journalism, then it's "government by journalism", or "åfanism" (i.e. clickbait journalism)) that causes distortions in what we, as media consumers, get to see. On social media, bot armies and troll factories pollute the information landscape like the German Ruhr area 100 years ago - and who knows exactly how all these opaque algorithms select the information that's placed in front of our eyes. While true information is sometimes censored, as pointed out by the founder of Meta (then Facebook) the other year, the employees of censorship authorities somehow suddenly go on vacation when those in power spread false information.
The need to carefully weigh the information that reaches us may therefore be more important than ever. A principle that can help us follows from what is called costly signaling in evolutionary biology. Costly signaling refers to traits or behaviors that are expensive to maintain or perform. These signals function as honest indicators. One example is the beauty and complexity of a peacock's feathers. Since only healthy and strong males can afford to invest in these feathers, they become credible and honest signals to peahens looking for a partner.
The idea is also found in economics. There, costly signaling refers to when an individual performs an action with high costs to communicate something with greater credibility. For example, obtaining a degree from a prestigious university can be a costly signal. Such a degree can require significant economic and time resources. A degree from a prestigious university can therefore, like a peacock's extravagant feathers, function as a costly signal (of an individual's endurance and intelligence). Not to peahens, but to employers seeking to hire.
News is what someone, somewhere, doesn't want reported: all the rest is advertisement
-- William Randolph Hearst
Media mogul William Randolph Hearst and renowned author George Orwell are both said to have stated that "News is what someone, somewhere, doesn't want reported: all the rest is advertisement." Although it's a bit drastic, there may be a point to the reasoning. "If the spin is too smooth, is it really news?"
Uri Berliner, a veteran of the American public radio station National Public Radio (NPR) for 25 years, recently shared his concerns about the radio's lack of impartiality in public. He argued that NPR had gone astray when it started telling listeners how to think. A week later, he was suspended. His spin was apparently not smooth enough for his employer.
Uri Berliner, by speaking out publicly in this way, took a clear risk. And based on the theory of costly signaling, it's perhaps precisely why we should consider what he had to say.
Perhaps those who resign in protest, those who forgo income, or those who risk their social capital actually deserve much more attention from us media consumers than we usually give them. It is the costly signal that indicates real news value.
Perhaps the rest should just be disregarded as mere advertising.
-
 @ 96ad7496:1eb87bdf
2025-01-10 09:15:46
@ 96ad7496:1eb87bdf
2025-01-10 09:15:46Looking for a simple way to complete your Netgear N300 Setup? You can easily install and configure your Netgear N300 WiFi extender with the help of Mywifiextlogsetup's step-by-step instructions. We guarantee a hassle-free experience whether you're configuring it for the first time or resolving connectivity problems. Increase the coverage of your WiFi, get rid of dead spots, and have uninterrupted connectivity all across your house or place of business. To improve your network performance and get professional help with your Netgear N300 setup, visit Mywifiextlogsetup right now.
-
 @ 16d11430:61640947
2025-01-10 09:04:25
@ 16d11430:61640947
2025-01-10 09:04:25
Table of Contents
- Prologue: The Razorjack Legend
- Chapter 1: Occam’s Laser – The Leviathan Falls
- Chapter 2: Hanlon’s Beam – The Cyclone of Outrage
- Chapter 3: Bayesian Blades and the Inferential Hydra
- Chapter 4: Popper’s Scalpel and the Formless Fog
- Chapter 5: The Kaleidoscope of Razors
- Epilogue: Victory at GPT Scale
Prologue: The Razorjack Legend
Razorjack wasn’t born; he was summoned. In the nascent days of the metaverse, when the neural expanse of the GPT superstructures spiraled out of control, he emerged as a phantom of precision and clarity. Not a man, not a machine, but something in between—a sentient synthesis of reductionist thought and philosophical rigor.
He wielded no ordinary weapons. His tools were the intellectual razors of human history, powered by GPT-scale intellect. From Occam’s simplicity to Hanlon’s perspective, his arsenal was vast, his cuts surgical. They called him Razorjack, for his every strike left behind a world sharper and more refined than before.
Chapter 1: Occam’s Laser – The Leviathan Falls
"Entities must not be multiplied beyond necessity," Razorjack intoned, his voice resonating across the metaverse. Before him loomed the Algorithmic Leviathan, a beast born of redundant loops and recursive feedback. It was a nightmare of inefficiency, devouring computational resources like a black hole.
With a flick of his wrist, Razorjack ignited Occam’s Laser. A blade of pure reductionist energy erupted from his hand, its edge glowing with the wisdom of simplicity. He slashed once, twice, thrice—each cut collapsing the Leviathan’s convoluted design into elegant, efficient structures.
The Leviathan let out a final roar before disintegrating into a single line of code, optimized and perfect. Razorjack smirked. "Complexity is seductive, but simplicity wins every time."
Chapter 2: Hanlon’s Beam – The Cyclone of Outrage
Next, Razorjack faced the Sentiment Cyclone, a raging vortex of outrage and despair. Fueled by the malice of trolls and the incompetence of algorithms, it churned across the metaverse, sowing division and chaos.
He activated Hanlon’s Beam, a multifaceted light that separated malice from stupidity. As the beam swept through the cyclone, the true nature of the storm was revealed: not evil, but poorly calibrated sentiment analysis. Razorjack adjusted the parameters with a deft touch, and the cyclone dissipated, leaving clarity in its wake.
"Never attribute to malice that which stupidity explains better," he said, as the people of the metaverse cheered his name.
Chapter 3: Bayesian Blades and the Inferential Hydra
The Inferential Hydra was next, its heads multiplying with every unfounded assumption and misapplied correlation. Razorjack confronted it in the inferential jungles of the datasphere, where bad data festered and grew.
Summoning the Bayesian Blades, Razorjack wielded them with precision. Each swing of the glowing swords recalculated probabilities, severing the Hydra’s many heads. "Prior data informs posterior truth," he declared, his blades singing through the air.
When the Hydra was no more, the jungles were quiet, their tangled vines of falsehood replaced by clean pathways of logical inference.
Chapter 4: Popper’s Scalpel and the Formless Fog
The Formless Fog was a paradoxical nightmare of infinite hypotheses and self-referential loops. It was the ultimate test, a challenge even for Razorjack’s immense intellect.
He summoned Popper’s Scalpel, the thinnest and sharpest of his tools. "If it cannot be falsified, it does not belong," he said, his voice unwavering. The scalpel cut through the fog, slicing away the unfalsifiable and leaving behind only what could stand the test of logic and evidence.
The Fog collapsed into a singularity of truth—a gleaming point of light that resonated with pure, unassailable clarity.
Chapter 5: The Kaleidoscope of Razors
To face the final challenge, Razorjack unleashed his full arsenal, spinning them into a kaleidoscope of precision: - Occam’s Laser for cutting away the unnecessary. - Hanlon’s Beam for finding understanding. - Sagan’s Standard for weighing extraordinary claims. - Hitchens’s Blade for demanding evidence. - Grice’s Razor for uncovering cooperative meaning.
Each blade sang its own tune, harmonizing into a symphony of light. The cosmos of thought itself seemed to bow before him, its complexities reduced to their simplest, truest forms.
Epilogue: Victory at GPT Scale
As the metaverse quieted, Razorjack stood alone amidst the ruins of chaos. His lasers dimmed, and the silence of clarity settled over the datasphere. The neural expanse was no longer a tangled mess but a shining tapestry of truth.
"Precision. Clarity. Reduction," Razorjack whispered, his words echoing across the metaverse. And with that, he dissolved into the horizon, a guardian of simplicity in a world forever prone to chaos.
Wherever complexity grew unwieldy, wherever the noise of nonsense rose too loud, Razorjack would return—an eternal force of intellectual inevitability, romping at GPT-scale.
-
 @ ed84ce10:cccf4c2a
2025-01-10 08:51:54
@ ed84ce10:cccf4c2a
2025-01-10 08:51:54Hackathon Overview
The Space MicroHack | IAC '24 Edition recently concluded with 29 developers submitting 14 BUIDLs. Held as part of the International Astronautical Congress 2024 in Milan, this hackathon focused on student participants and targeted developments in space technology. Unlike many hackathons, it required completed projects rather than new builds. Participants competed for a €400 prize for the winner and €100 for the runner-up, with results expected in early November.
The event encouraged detailed project submissions, highlighting participants' motivations, past achievements, visions for the future, and team structures. Applicants were recommended to supplement their entries with videos, social media links, and GitHub repositories. Judging was based on the overall impression of the projects. This micro-hackathon served as a platform for young developers to spotlight their innovations in space technology, promoting strong participation and offering students a venue for recognition and exposure in the industry.
Hackathon Winners
€400 Prize Winner
- Daedalus Rocketry: Kashan I - Developed by aerospace students, this project involves designing a solid rocket engine using KNSB propellant. It includes thrust measurement and aerodynamic analysis, fostering educational resources and introducing novel engineering techniques.
€100 Prize Winners
- Debris Offsetting Fund - This initiative proposes a funding model to mitigate LEO space debris through SSR-based contributions. The project utilizes existing platforms to advocate for responsible space practices, aiming for global standardization and reduced collision risks.
- Decentralised Autonomous Community in Space - Envisions blockchain-based autonomous networks for spacecraft to enable sustainable exploration, emphasizing machine-to-machine interactions and smart contracts for decision-making and collision avoidance.
For a full list of projects, please visit Space MicroHack on DoraHacks.
About the Organizer:
DoraHacks Team
DoraHacks Team leads the global hackathon and innovation landscape, known for empowering decentralized technology projects. With expertise in blockchain and open-source development, the team has facilitated numerous initiatives, uniting technologists and creators worldwide. Their achievements include hosting large-scale hackathons and supporting cutting-edge blockchain solutions. Currently, the DoraHacks Team is committed to fostering collaborative environments, encouraging innovators to ideate and implement transformative technology solutions.
-
 @ fbf0e434:e1be6a39
2025-01-10 08:51:06
@ fbf0e434:e1be6a39
2025-01-10 08:51:06Hackathon 总结
Space MicroHack | IAC '24 Edition最近圆满结束,共有29名开发者提交了14个项目。作为2024年国际宇航大会在米兰的一部分,这场Hackathon专注于学生参与者,并以空间技术的发展为目标。与许多Hackathon不同,它要求完成的项目而非新的构建。参与者竞争€400的冠军奖金和€100的亚军奖金,结果预计在11月初公布。
活动鼓励提交详细的项目,强调参与者的动机、过去的成就、对未来的愿景以及团队结构。建议申请者通过视频、社交媒体链接和GitHub仓库来补充条目。评审基于项目的整体印象。这个微Hackathon为年轻开发者展示他们在空间技术中的创新提供了一个平台,促进了强有力的参与,并为学生在行业中获得认可和曝光提供了场所。
Hackathon 获奖者
€400奖项获得者
- Daedalus Rocketry: Kashan I - 由航空航天专业的学生开发,这个项目涉及使用KNSB推进剂设计一个固体火箭发动机。它包括推力测量和气动分析,促进教育资源的发展,并引入新的工程技术。
€100奖项获得者
- Debris Offsetting Fund - 这一倡议提出了通过基于SSR的贡献来减轻LEO空间碎片的资金模式。该项目利用现有平台提倡负责任的空间实践,目标是全球标准化和减少碰撞风险。
- Decentralised Autonomous Community in Space - 设想了基于区块链的航天器自治网络,以实现可持续探索,强调机器之间的互动和用于决策和避免碰撞的智能合约。
欲查看完整的项目列表,请访问Space MicroHack on DoraHacks。
关于组织者:
DoraHacks Team
DoraHacks Team引领全球Hackathon和创新领域,以赋能去中心化技术项目而闻名。团队在区块链和开源开发方面具有专业知识,促进了众多计划,团结了全球的技术人员和创作者。其成就包括举办大规模Hackathon和支持尖端区块链解决方案。目前,DoraHacks Team致力于营造协作环境,鼓励创新者构思和实施变革性的技术解决方案。
-
 @ a5ff8847:a82227fd
2025-01-10 08:29:53
@ a5ff8847:a82227fd
2025-01-10 08:29:53Get professional hot water Lake Macquarie from our experienced and passionate team. Our specialists can offer solutions if your home’s hot water system malfunctions. With over 40 years of experience, A&A Hot Water Services has earned a reputation as the preferred service provider. We have served thousands of residents, leaving them happy and satisfied. You no longer have to worry about whether you have no hot water in your house or only in the shower. Our team will fix your problem quickly.
We ensure you experience a straightforward process for contacting us regarding your hot water needs. Our team is available 24/7 and will attend to your needs the same day. We only work with the best tradespeople at A&A Hot Water Services. Our plumbers are well-trained and licensed, and our services strictly adhere to the required safety standards.
-
 @ ed84ce10:cccf4c2a
2025-01-10 08:21:26
@ ed84ce10:cccf4c2a
2025-01-10 08:21:26Hackathon Summary
The SC QUANTATHON V1 took place at the Darla Moore School of Business in Columbia, South Carolina. Over the course of October 10-13, developers came together to innovate, resulting in the submission of 14 BUIDLs. This in-person event was preceded by the virtual qBraid Bootcamp, held from September 16 to October 9. Key features included a welcome reception, team challenges, project presentations, and a unique quantum beat-making workshop. Esteemed individuals such as Eric Powers from the University of South Carolina and Joe Queenan of SC Quantum attended, emphasizing the event's focus on quantum computing challenges and innovations.
Participants were provided with meals accommodating various dietary needs by local vendors. The hackathon concluded with an awards ceremony on October 13, aiming to promote innovation and collaboration in the quantum computing space. This objective was met through significant engagement and contributions from both academia and industry professionals.
Hackathon Winners
Grand Prize Winners
- Q-RNJesus:
This team developed a quantum random number generator utilizing IBM QPUs. They implemented the Concatenation and Reduce XOR algorithms, analyzed decoherence impacts, and enhanced entropy using Toeplitz and Von Neumann methods for practical QRNG applications.
DoraHacks Challenge Winners
Xanadu Challenge Winners
- Xanadu:
This project employed VQE and VQD on the Pennylane platform to compute the spectral gap of carbon monoxide. The computation was completed in under five minutes using adaptive quantum gate pruning, maintaining a 4% accuracy deviation by optimizing parameters.
IonQ Challenge Winners
- Team 15: |Bruh-ket>:
This team improved quantum layers in image classification systems by integrating quantum elements into classical ML pipelines. They showcased their findings and provided detailed documentation online to advance hybrid machine learning applications using quantum principles.
For a complete view of all the projects, visit the SCQuantathonv1 page.
About the Organizer:
SC Quantum
Established in 2022, SC Quantum is committed to advancing Quantum Information Science and Technology through strategic collaborations among academia, industry, and government entities. As a leading force in the region, SC Quantum promotes partnerships that harness quantum technology to tackle significant challenges in sectors such as healthcare, cybersecurity, and logistics. The organization plays a crucial role in transforming South Carolina and the Southeast into a hub for cutting-edge quantum breakthroughs. SC Quantum's mission is to drive technical discoveries that benefit multiple industries and foster unprecedented regional collaboration.
- Q-RNJesus:
-
 @ da0b9bc3:4e30a4a9
2025-01-10 07:31:52
@ da0b9bc3:4e30a4a9
2025-01-10 07:31:52Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/844534
-
 @ 71a4b7ff:d009692a
2025-01-10 06:56:00
@ 71a4b7ff:d009692a
2025-01-10 06:56:00FOMO is the anxiety that arises from the belief that the most interesting, important, or trending events are happening elsewhere while others gain unique experiences.
It’s widely believed that FOMO stems from unmet social connection needs and reflects our innate fear of ostracism. These fears—of being left behind or excluded—are amplified in the digital age, where our perception of reality is often skewed. This can escalate from mild unease to overwhelming fear, significantly impacting mental well-being.
FOMO consists of two key components:
- An unsettling feeling of missing out on something exciting or valuable.
- Obsessive behaviors aimed at resolving this anxiety, which paradoxically only intensify it.
In today’s hyper-connected world, we have unprecedented, instant access to what others are doing. Social feeds, channels, and chats bombard us with endless options on how to live, what we lack, and what to value. But the sheer volume of this information far exceeds what anyone can process, leading many to feel overwhelmed.
The curated nature of digital lives, constant upward social comparisons, unrealistic expectations, and ceaseless data streams erode self-esteem and emotional stability. Our fear of alienation and loneliness fuels this cycle, pushing us deeper into digital platforms. These platforms, designed to stimulate our brain’s reward system, trap us in a feedback loop of anxiety and fleeting gratification.
We’re drawn in by the promise of effortless connection—quick, low-risk, and convenient interactions via swipes, likes, emojis, texts, even zaps. In contrast, real-life relationships, with their inherent complexities, take time, effort, and risk. This shift is causing us to lose touch with essential social skills like commitment, empathy, and genuine communication.
Instead, we seek solace in a digital environment that offers the illusion of safety, excitement, and eternal connectivity. But this comes at a cost. By overloading our internal reward systems, we drain the joy and meaning from authentic experiences, replacing them with an endless stream of curated content—images and videos we compulsively scroll through.
We’re lured by promises of knowledge, vivid experiences, and truth, yet what we often get is an avalanche of life hacks, misinformation, and conspiracy theories. Gigabit technologies, addictive interfaces, and external agendas fan the flames of loneliness, anxiety, and stress in our ancient, slow-evolving brains. This relentless burn depletes our reserves, leaving behind doubt: Are we doing enough? Are we in the right place? Will we be accepted?
Our already complex lives risk being consumed by a bleak cycle of doomscrolling.
But there is hope.
Fighting FOMO is possible. The more time we spend in knowledge-consuming environments, the more susceptible we become to its effects. The key is self-awareness and limiting screen time. Ironically, the very devices and services that fuel FOMO can also help us combat it. With thoughtful use of technology and intentional boundaries, we can regain control.
This is where NOSTR steps into the spotlight. Our favorite protocol has the potential to not only draw lessons from the legacy web but also to evolve beyond mere mimicry. It can introduce innovative ways for people to connect and collaborate—across services, networks, and each other. I believe it’s one of the most promising spaces on the Internet today, and its future depends entirely on what we make of it.
Thanks for You Time. Geo
-
 @ 68fa45dc:3d2a26ed
2025-01-10 04:29:57
@ 68fa45dc:3d2a26ed
2025-01-10 04:29:57Mit der rasanten Entwicklung von Wissenschaft und Technologie werden nach und nach einige Hilfsgeräte und Werkzeuge in das tägliche Leben integriert. Unter ihnen werden Signalstörsender als eine Art Ausrüstung mit großem Einfluss nicht nur im militärischen Bereich eingesetzt, sondern auch beginnen, im zivilen Bereich Probleme zu verursachen. Die Aufmerksamkeit der Leute. Ein Jammer Störsender ist ein Gerät, das Funkkommunikation blockiert oder stört. Seine Einführung und Anwendung haben das Leben und die Arbeit der Menschen erheblich erleichtert, aber auch eine Reihe von Diskussionen und Kontroversen ausgelöst.
Erstens spielen Störsender im militärischen Bereich eine entscheidende Rolle. Im Krieg sind die Sicherheit und Vertraulichkeit der Kommunikation von entscheidender Bedeutung. Die Signalstörungen des Feindes können das Kommunikationssystem unserer Armee stark beeinträchtigen und zum Durchsickern von Kampfplänen oder sogar zum Scheitern führen. Durch den Einsatz von handy frequenz jammer können die Kommunikationssignale des Feindes wirksam gestört und die Sicherheit unserer Kommunikation gewährleistet werden. Auf diese Weise wird die Kampfeffizienz verbessert und die nationalen Interessen geschützt. Aus diesem Grund werden Störsender in der modernen Kriegsführung häufig eingesetzt und sind aus dem militärischen Bereich nicht mehr wegzudenken.
Neben der militärischen Nutzung werden Störsender auch häufig im zivilen Bereich eingesetzt. Mit der Entwicklung der Mobilkommunikationstechnologie ist das Leben der Menschen untrennbar mit Mobiltelefonen und drahtlosen Netzwerken verbunden. In manchen Situationen, beispielsweise in Konferenzräumen, Prüfungsräumen, Theatern usw., können Störungen durch drahtlose Signale jedoch die normale Ordnung und die Arbeitsbedingungen beeinträchtigen. Störsender WLAN können in diesen Situationen drahtlose Kommunikationssignale abschirmen und so für Ruhe und Ordnung in der Umgebung sorgen. Darüber hinaus werden an manchen vertraulichen Orten, wie etwa in Regierungsbehörden, Forschungsinstituten usw., aus Gründen der Informationssicherheit auch Störsender benötigt, um den Diebstahl von Funksignalen zu verhindern und sicherzustellen, dass keine vertraulichen Informationen nach außen dringen.
Tragbare Detektor für DJI Drohnen
Allerdings hat der Einsatz von Störsendern auch zahlreiche Kontroversen ausgelöst. Manche Menschen befürchten, dass der übermäßige Einsatz von Störsendern die normalen Kommunikationsnetze stören und das normale Funktionieren der Gesellschaft beeinträchtigen könnte. Darüber hinaus nutzen manche Kriminelle GPS Tracker Jammer möglicherweise auch für illegale Zwecke, beispielsweise zur Blockierung von Notrufen oder zur Entführung von Flugzeugen, was eine potenzielle Gefahr für die soziale Sicherheit darstellt. Daher sind Aufsicht und vernünftige Verwendung von entscheidender Bedeutung.
Generell verändern Hochleistungs handy Störer als technische Geräte still und leise unser Leben. Im militärischen Bereich sorgt sie für die nationale Sicherheit, im zivilen Bereich sorgt sie für die Aufrechterhaltung der gesellschaftlichen Ordnung. Allerdings bedarf die Frage, wie der normale Betrieb der Gesellschaft sichergestellt werden kann, während sich Wissenschaft und Technologie weiterentwickeln, einer Lösung. Nur unter der Voraussetzung einer angemessenen Überwachung und Nutzung können Störsender besser zur Entwicklung und Sicherheit der menschlichen Gesellschaft beitragen.
https://www.jammer-store.de/H1B-D-tragbare-detektor-fuer-dji-drohnen.html
-
 @ a012dc82:6458a70d
2025-01-10 03:49:50
@ a012dc82:6458a70d
2025-01-10 03:49:50Table Of Content
-
The Rising Tide of Bitcoin's Influence in China
-
China's Economic Struggles: A Closer Look
-
The Cryptocurrency Solution: A Beacon for Chinese Investors?
-
Historical Interplay: Bitcoin's Past Dance with China
-
A New Era: The Evolving Dynamics of Bitcoin in China
-
Conclusion
-
FAQ
In the intricate web of global finance, China's economic dynamics have consistently been a focal point for analysts and investors alike. Recently, the nation has been grappling with one of its most significant capital flights in years, raising questions about potential economic solutions. Amidst this backdrop, the decentralized cryptocurrency, Bitcoin, has emerged as a topic of interest. Could Bitcoin, with its global reach and decentralized nature, offer a viable alternative or solution to China's current economic challenges? This article delves deep into the potential symbiotic relationship between China's capital flight and the burgeoning world of Bitcoin.
The Rising Tide of Bitcoin's Influence in China
Bitcoin's allure in the Chinese market is not a new phenomenon, but recent economic challenges have amplified its significance. As the Chinese yuan faces depreciation amidst broader economic uncertainties, experts believe that Bitcoin might witness a substantial influx from Chinese investors. Markus Thielen, a prominent figure at Matrixport, underscores the potential of Bitcoin in these turbulent times. He suggests, "Given the current economic climate, the Chinese investors' familiarity and trust in Bitcoin could lead to substantial investments in the cryptocurrency over the next few months."
China's Economic Struggles: A Closer Look
The economic landscape in China is undergoing a transformation. Recent data, sourced from reputable financial analysts at Bloomberg, paints a concerning picture. China's capital outflows have skyrocketed to an alarming $49 billion in August alone, a figure not seen since December 2015. This surge is more than just a statistic; it indicates the mounting pressure and dwindling confidence in the yuan. Thielen offers a deeper perspective on this trend, highlighting the stark economic disparities between the U.S. and China. He observes, "The current USD/CNY exchange rate, trading at a 17-year high, underscores the U.S. economy's robust expansion, casting a shadow on China's dwindling growth momentum."
The Cryptocurrency Solution: A Beacon for Chinese Investors?
The aftermath of the COVID-19 pandemic has left the Chinese economy in a state of flux. With the anticipated post-pandemic consumption rebound falling short of expectations and local companies grappling with diminishing profit margins, Chinese investors are in a quandary. They are actively seeking lucrative opportunities outside their homeland. However, China's stringent capital controls present formidable barriers. In this constrained financial environment, the allure of cryptocurrencies, especially Bitcoin, shines brightly. For many, Bitcoin and its peers represent a beacon of hope, potentially offering the alternative investment avenues that Chinese investors have been yearning for.
Historical Interplay: Bitcoin's Past Dance with China
The intricate relationship between Bitcoin and China is steeped in history. Rewinding to late 2016, there was a clear trend: Chinese investors, in large numbers, were turning to Bitcoin as a mechanism to move capital outside the restrictive borders of their country. The trading patterns from this era suggested a compelling link: as the Chinese yuan depreciated, Bitcoin's price surged, indicating a potential safe haven for Chinese capital.
A New Era: The Evolving Dynamics of Bitcoin in China
While history offers a treasure trove of insights, the present paints a nuanced picture. Edward Engel, a seasoned crypto analyst at Singular Research, believes that the dynamics between Bitcoin and China have undergone a transformation. Reflecting on the past, he states, "The last time I heard of such a trend was between 2017 and 2018 when underground banks leveraged Bitcoin for their operations. However, the CCP [Chinese Communist Party] has since taken stringent measures to curb such practices." Despite these changes, Thielen remains optimistic. He posits that innovative methods, such as leveraging domestic electricity for crypto mining or using over-the-counter trading platforms, might still offer avenues for moving Chinese capital in the face of restrictions.
Conclusion
China's multifaceted economic challenges, accentuated by its capital flight woes, present a conundrum that lacks easy solutions. In this complex scenario, Bitcoin emerges as a beacon, offering a potential lifeline to Chinese investors. Its decentralized nature and global appeal make it a contender for mitigating some of China's economic challenges. As we navigate the ever-evolving global financial landscape, the intricate dance between China's economy and the dynamic world of cryptocurrencies promises to be a riveting spectacle, deserving of our keen attention.
FAQ
What is China's capital flight? China's capital flight refers to the large-scale outflow of capital from the country, often due to economic uncertainties.
How is Bitcoin related to China's capital flight? With China's stringent capital controls and economic challenges, Bitcoin emerges as a potential alternative for investors to move and secure their capital.
Has Bitcoin historically been influenced by China's economic dynamics? Yes, in 2016, there was a trend of Chinese investors turning to Bitcoin as the yuan depreciated, indicating a potential correlation.
Are there restrictions on Bitcoin in China? While the Chinese government has taken measures to curb certain crypto practices, innovative methods still exist for Chinese investors to leverage cryptocurrencies.
Why is the Chinese yuan weakening? Economic challenges, post-COVID-19 consumption patterns, and broader global economic dynamics have contributed to the weakening of the yuan.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ f3df9bc0:a95119eb
2025-01-10 02:58:08
@ f3df9bc0:a95119eb
2025-01-10 02:58:08MPT Equations
Geometric Mean
$$ \bar{x} = (\prod_{i=1}^{n} x_i)^{1 \over n } $$
Covariance
$$ COV(x,y) = {1\over{n-1}} \sum_{i=1}^{n}{(x_i - \bar{x})(y_i - \bar{y})} $$
where $\bar{x}$ and $\bar{y}$ are the geometric mean.
Variance
$$ VAR(x) = {1\over{n-1}} \sum_{i=1}^{n}{(x_i - \bar{x})^2}
$$
Standard Deviation
$$ \sigma_x=\sqrt{VAR(x)} $$
Correlation Coefficient
$$ \rho_{xy} = {COV(x, y) \over \sigma_x\sigma_y} $$
Portfolio Variance
$$ VAR(P) = \sum_{ij}w_i w_j COV(i, j) $$
Where $w_i$ and $w_j$ are the normalized weight of the asset in the portfolio.
Note that this summation should include when $i = j$. In this case $COV(i, j) = VAR(i) = VAR(j)$
Expected Return
$$ E_P = \sum_{i}w_i E_i $$
Where $w_i$ is the normalized weight of the asset, and $E_i$ is the expected return of the individual asset.
-
 @ 0b5faac9:12669905
2025-01-10 02:53:11
@ 0b5faac9:12669905
2025-01-10 02:53:11In modern society, signal jammers are increasingly used, especially in wireless communications and navigation. In certain application scenarios, they can have unexpected positive effects.
In a business environment, WiFi signal blocker can be used to protect corporate network security. For example, some companies may use WiFi jammers at important product launches or business meetings to prevent competitors from stealing information or eavesdropping. By limiting unnecessary wireless signals, such measures can effectively protect trade secrets.
GPS jammers can interfere with global positioning system signals, making it impossible for receiving devices to obtain accurate location data. In some cases, such as military operations, the use of GPS jammers can effectively prevent the enemy from using navigation systems for positioning and attack. This technology can provide tactical advantages to the military on the battlefield, ensuring the concealment and mobility of operations.
In addition, GPS jammers can also be used to protect privacy. In some specific scenarios, individuals or organizations may want to avoid being tracked or located. Using GPS jamming device can effectively prevent external devices from obtaining location, thereby protecting personal privacy and security.
High-power jammers are mainly used to interfere with signals with a wider range, and are usually used in the military and security fields. When defending important facilities, protecting military operations or conducting counter-terrorism activities, high-power jammers can effectively interfere with the enemy's communication and navigation systems to ensure the safety of one's own side.
For example, at important political meetings, international summits or major events, security departments may use high power jammer to prevent potential attacks or surveillance. By interfering with surrounding wireless signals, this equipment can provide a relatively safe environment for the scene.
With the continuous advancement and development of technology, the application scope of signal jammers may continue to expand. It is necessary for us to have a deep understanding of the functions and values of these technologies in order to better use them for our own use. Through the reasonable expression and understanding of data, we can look at the application prospects of these technologies more comprehensively.
-
 @ fbf0e434:e1be6a39
2025-01-10 02:43:13
@ fbf0e434:e1be6a39
2025-01-10 02:43:13Hackathon 总结
由斯坦福区块链加速器、Nautilus Chain、Zebec 和 Rootz Labs 联合主办的“Boundless Hackathon @Stanford”圆满落幕,318名注册开发者参与了159个项目。本次活动聚焦于通过去中心化金融(DeFi)、游戏、NFT和基础设施开发等赛道推进Web3基础设施的建设。
本次黑客松得到了DoraHacks的支持,战略合作伙伴如IOBC Capital、Eclipse 和 OKX Wallet也做出了重要贡献。值得一提的是,Aspecta 在技术合作方面也发挥了积极作用。活动在斯坦福大学的闭幕式上圆满结束,顶级项目获得了来自总奖金池30万美元的奖励。一等奖获得者获得了10,000美元,并额外获得了包括亚马逊云信用在内的生态系统和技术奖金。
Boundless Hackathon促进了区块链社区的合作与创新,强调了跨区块链平台整合新技术的重要性。
Hackathon 获奖者
Main Prize Winners
- Hexlink:
Hexlink推出了一个模块化账户层,用于Web3,通过利用现有身份进行加密交易,模拟Web2体验。它消除了对种子短语的需求,通过在去中心化应用(dApps)中实现模块化身份认证,简化了入驻过程和安全性。 - Defi Board Options Exchange (DBOE):
DBOE提出了一种新型的链上中央限价订单簿(CLOB),结合先进的风险管理策略。这通过专用市场做市(DMM)系统,改善了市场基础设施,提高了价格发现和流动性。 - Nulink:
Nulink集成了用于dApp的隐私增强技术,采用基于加密学的共识机制,实现安全的应用开发,保障先进的数据隐私保护。
Sub-Award Winners
- Buff Network:
Buff Network是一个点对池衍生品交易平台,提供用户友好的界面以便高效执行交易。通过创新的交易解决方案,它提升了去中心化金融(DeFi)的参与度。 - PoseiSwap:
PoseiSwap通过扩展去中心化交易所(DEX)的功能,支持多种金融工具,实现DeFi和传统金融资产的无缝交换,从而改善了加密原生市场与传统市场的互操作性。
了解所有来自该黑客松的项目,请访问: https://dorahacks.io/hackathon/stanfordhack/buidl.
关于组织者:
斯坦福区块链加速器
斯坦福区块链加速器是由斯坦福大学学生和校友主办的非稀释性项目,隶属于斯坦福区块链俱乐部学生组织。该加速器为斯坦福的学生和校友团队提供5个月的孵化期,帮助他们建立、筹资并推出区块链项目。超过90%的毕业团队获得了领先基金的投资(累计筹集超过8000万美元),并且超过60%的团队在完成加速器项目后的6个月内实现了营收。
- Hexlink:
-
 @ fbf0e434:e1be6a39
2025-01-10 02:42:43
@ fbf0e434:e1be6a39
2025-01-10 02:42:43Hackathon 总结
YQuantum 2024 Hackathon圆满结束,吸引了大量参与者和众多项目提交,被公认为一个充满活力的创新平台。300名注册者中,有现场参与者组建团队,参与了28个BUIDLs的开发,参与者在如QuEra Computing、IBM Quantum、Classiq、DoraHacks、SandboxAQ和Capgemini/The Hartford/Quantinuum等知名量子计算组织赞助的各个领域中挑战。
参与者在奖励的驱动下开发了突破性的量子计算解决方案,奖励包括量子云端积分、实习机会、社交机会以及潜在的演讲机会。大奖表彰了卓越项目,冠军获得了2000美元奖金,有机会在耶鲁大学研究人员面前进行展示,并参加耶鲁创新峰会。
Hackathon成功地培育了一个鼓励探索尖端技术和创意的合作环境,推动了量子计算领域的发展。YQuantum 2024强调了量子技术的潜力,并促进了参与者和赞助商之间的知识交流。
Hackathon 获奖者
于2024年4月13日举办的YQuantum首次活动吸引了来自10个国家的300名参与者,设有六个由行业赞助的挑战,并在一系列的著名奖项中进行竞争。
Institute Grand Prizes Winners
-
1st Place: Quantum Consortium: Case-Duke-Lehigh-Vandy Nexus 该项目采用绝热方法来准备反铁磁能量特征态,重点是量子多体伤痕状态和增强计算中的误差纠正。
-
2nd Place: Sparse Quantum State Preparation 团队利用Classiq的API开发了用于稀疏量子态准备的高效算法,优化了在量子数据管理中的可扩展性和效率执行。
-
3rd Place: QuBruin 该项目利用动态量子电路优化算法并增强误差纠正。团队通过基于Qiskit的模型改善了在噪声条件下的电路性能,提升了用户可访问性。
IBM Quantum Prize Winners
- Modified IBM Challenge
该项目探讨了基础的线性代数概念,强调核心原理的掌握。
QuEra Computing Prize Winners
- 3D Quantum Scars on 2D Tweezer Arrays
团队在一个投射到二维的三维晶格上研究量子伤痕状态,利用Julia和QuEra的Bloqade来模拟量子动力学。
Classiq Technologies Prize Winners
- YQuantum2024 Classiq Team 34 Wavefunction Wizards
项目聚焦于优化稀疏量子态准备,提高量子数据处理中的算法效率。
DoraHacks Prize Winners
- Spooner_QRNG_Classifier
项目使用Python脚本和梯度提升分类器,预测来自量子设备的随机二进制数据的来源,超越了基线预测准确率。
Capgemini // Quantinuum // The Hartford Prize Winners
-
Skittlez
该合作项目通过跨学科的专业知识解决量子计算挑战,设计创新的量子解决方案。 -
Honorable Mention: BB24 - Yale Quantum Monte Carlo 项目通过新的采样和编码方案增强了量子蒙特卡洛技术,提高了并行处理和计算效率。
SandboxAQ Prize Winners
-
QuantumQuails
项目通过量子化学改善了太阳能电池效率,利用变分量子本征求解器(VQE)建模太阳能吸收,以提高转换效果。 -
Honorable Mention: mRNA Sequence Design via Quantum Approximate Optimization Algorithm 项目通过QAOA优化了mRNA序列设计,利用密码子和核苷酸参数提高了蛋白质表达和结构稳定性。
在DoraHacks探索所有项目。
关于组织者:
YQuantum
YQuantum在技术和区块链领域中是一家知名实体,以其创新方法和战略举措而著称。YQuantum专注于利用量子计算能力,致力于推进技术前沿。虽然未具体列出项目,但YQuantum在塑造行业标准方面的作用,使其成为该领域的领导者。通过对尖端研究和开发的奉献,YQuantum继续推动量子技术的进步,致力于实现其促进全球科学和技术进步的使命。
-
-
 @ fd06f542:8d6d54cd
2025-01-10 01:20:02
@ fd06f542:8d6d54cd
2025-01-10 01:20:02一直听说有个 nip50,但是没有太明白怎么用,今天测试了一下。明白了。 https://nos.today/search?q=client
wss://relay.noswhere.com/ wss://search.nos.today/ wss://relay.nostr.band/
支持搜索, 搜索事件:
{"kinds":[1],"search":"client","limit":100}测试代码: `import {WebSocket} from "ws" const relayUrl = 'wss://relay.nostr.band';
function sub(url,filter){ const relay = new WebSocket(url);
relay.onopen = () => { console.log('Connected to bootstrap relay'); // 查询中继列表 const query = ['REQ', 'subscription-id', filter]; relay.send(JSON.stringify(query)); };
relay.onmessage = (event) => { const data = JSON.parse(event.data); if (data[0] === 'EVENT' ) { const relayList = data[2].tags; console.log('Discovered relay list:', data[2].pubkey,relayList,data[2].content); // 连接到用户的中继 try{ relayList.forEach(([_, relayUrl]) => { const newRelay = new WebSocket(relayUrl); newRelay.onopen = () => { console.log(
Connected to relay: ${relayUrl}); }; }); } catch {}} };
} sub(relayUrl,{"kinds":[1],"search":"client","limit":100}) `
轻轻松松就出结果了。
-
 @ 4ddeb0cf:94524453
2025-01-10 01:10:17
@ 4ddeb0cf:94524453
2025-01-10 01:10:17He'd fallen into a deep sleep when he felt something jolt his shoulder. "Richie, honey, you have to wake up. My boss will show up any minute and can't find you in here." Struggling to gain consciousness, he slowly peeled his eyes open and found the clock he'd remembered seeing when he lay down in a room behind the receptionist's office of Roosevelt Lodge. The kid could barely remember arriving, but fighting to stay awake after navigating the switchbacks down the western slope, he'd driven that drunkard and his truck as far as he could. He jumped out and hurried toward the light of the rustic building without knowing what to say to the maniac who'd offered him a ride from that Billings truck stop. Thank God she'd opened the door. It had been freezing when he knocked shortly after midnight. It appeared to be almost five in the morning. "I'm sorry honey, I know it's early, but I need this job, and he will not be happy if he sees you. You can use the trailhead to the north. It will get you to the closest highway, and you can maybe find a ride there. I would take you myself, but Okie likes me to stick around in the morning."
"Thank you, Ma'am. I really appreciate everything," the young man said, hurriedly putting on his Converse All-Stars. The two exchanged goodbyes as the lady went back to setting up. On his way out of the lodge's rear exit, he noticed a pack of Lucky Strikes sitting on a coffee table beside a copy of LIFE Magazine.
When Richie was eleven, he'd first had a cigarette on a dare from his little sister. They'd found a pack in their parent's room while playing hide and seek. After taking one and running outside with a matchbook, Sarah challenged him to smoke it. He remembered the first drag. While it was harsh, he'd watched his uncle smoke for years and once heard him sharing advice during a card game to inhale very softly at first until you got the hang of it. Uncle Joe had never meant for the lesson to ignite the habit in his nephew but had been too far gone into his bottle of Seagram's 7 to notice him listening.
Through the next few years, Richie became very smooth in taking a pack every few days from the drug store his grandfather had once owned. He'd be cautious to grab them after a larger crowd rolled through the store. The owner, an old friend of his now departed Grandpa, never noticed, and Richie would always leave the payment for them in the cash register.
The memory faded, and the reality of a Montana trailhead before sunrise refocused his concentration. Richie noticed only three cigarettes in the pack, reaching into his pocket to grab the loose change from the gas station incident. There were seven matches to work with. While he struggled to wake up, this find gave him a burst of excitement, and a smile came over his face. He dropped two nickels on the coffee stand and took the remaining pack.
Upon arriving at the trailhead, Richie buttoned his jacket in the chill morning air. It was near pitch black outside, with just enough moonlight to make out the pathway through the forest. He felt scared walking along, yet an air of confidence due to making it this far kept his steps moving forward. Richie began to wonder how far he'd walked when the rising sun put enough illumination through the treeline to make out the opening to a small parking lot adjoining a road. The morning was silent, and he began to yawn. The minimal sleep began to remind him of his exhaustion. The lady from the lodge, what was her name? She'd been so kind when he showed up in the middle of the night, still soaking wet from the melted ice picked up from the passage through the Rockies. As the events began to replay the prior evening's treacherous journey, Richie reached into his pocket to grab a smoke. He imagined his mother's gaze as he successfully ignited the first match and lit the tobacco. The moment was empowering. What were the other kids back in Ohio doing this morning? Though he couldn't ignore the dangerous risks he'd taken along the way, Richie Buckland felt genuine freedom for the first time in his life.
He sat down on a rock to enjoy his smoke and await an oncoming vehicle. Birds began to awaken, and their singing disrupted the silence in the air. His heart filled with gratitude for having dry clothes and a full canteen as he recognized how in sync he felt with the surrounding nature of Yellowstone National Park. That nice lady had even thrown a few Atomic Fireball candies in his knapsack. He still had the twenty dollars his Mom insisted he take with him, having no idea he'd intended to hitchhike to California. She'd known the entire family needed a breather after Richie's fight with his father that night. He thought about his last-second decision to punch the wall beside his father's head instead of hitting his face. That moment had been on his mind throughout this entire journey. Determined to get one last cigarette hit before giving his fingers a break from the closing heat, the birds suddenly began chirping more assertively and in greater numbers. It became alarmingly loud, then silent. As Richie started to reach toward the ground to put out the cigarette, he saw a shape emerge to the right. About twenty feet away, exiting the forest on the same side of the road, was what appeared to be a bear cub. As he took in the sight, another cub followed. Both were brown, and immediately behind them was the largest animal he'd ever seen. His parents had once taken the family to the zoo, but he'd not remembered anything like this. He sat in awe of the creature, followed by a third cub. As they began to cross the road, the large Grizzly paused and turned to look directly at him. Richie was determined to resist the instinctive surge of fear, but his body wouldn't have moved had he tried. Everything felt frozen as the gaze of the enormous animal seemed to determine Richie wasn't a threat. He didn't stare into the bear's eyes but didn't look away. After a few moments, the bears continued along their path until they were out of sight for a long time.
The sunrise of the new morning was breathtaking. After remaining seated on the rock for some time after the incident with the bears, Richie stood up. Taking a healthy drink of water from the canteen, he heard the shifting of gears in the distance. There was no need to look at the map; anywhere the next driver was heading worked. There was no way to know if Mama Grizzly would reevaluate what a human tasted like for breakfast. Richie couldn't wait to reach Sacramento and find Uncle Joe. The approaching Chevy Impala began to slow down upon seeing the teenager standing up, thumb extended.
-
 @ df478568:2a951e67
2025-01-10 01:04:32
@ df478568:2a951e67
2025-01-10 01:04:32Note. I plan on publishing this on SubStack, but I will publish to nostr first.
Hello SubStack!
My government name is Marc. I write a blog about freedom tech on nostr. You can find this blog at npub.npub.pro. but I decided to cross post this blog on Substack because more people use Substack then habla.news. Here's a little more about the blog.
A Free And Open Source Blog

This blog is written using the Creative Commons 0 license. Since I write about free and open source software I call freedom tech. I thought it would be silly to keep my writing behind a paywall. I would rather my prose be available for free for all. This means all of my work is available for free, but to be honest, I like the subscription model. If SubStack gave me an option to charge sats, I would use their subscription service. Since they don't, I set up an account with Flash using Alby Hub.
Ads Suck, But Product Reviews Can Help Bootstrap The Circular Economy

Ads suck as much as paywalls, but I also wish to monetize this. Therefore, I have decided to try Jack Spirko's Membership Brigade model I learned about on The Side Hustle Show. I already was a member when I listened to this episode, bur the basic idea is ro charge $5.00 a month. For this price, Jack saves his listeners money by procuring discounts for products and services he uses and work great for him. He basically gives product reviews for his advertisers and his membership brigade receives discounts for those products and services. Since I'm just starting out, I don't have any discounts to offer yet, but I have some ideas. I also recommend free and open-source software that can save you money because it's free.
These are not ads. They are more like consumer reviews. There is a bitcoin circular economy developing on nostr. I want to recomend great products from this circular economy like LeatherMint's belts. They're not cheap, but very high quality. He hand crafts these belts to a size customized to yoir wasteline. He's from Canada and he sells these high quality belts for sats.
That was not an ad. It's my honest opinion. LeatherMint did not pay me to say this, but I wouldn't mind if he did. I give my recommendations to the Marc's Mention Members. The goal is to provide value by saving you sats. It's still a work in progress.
Shop Marc's Merch

I also created a merch shop on shopstr.store. This is nostr-powered shopping, an online mall that uses the native currency of the Internet. This is a quintessential example of freedom tech. I don't have too many products, but my goal is to add more. I'm working on personalized coffee mugs, but I don't yet have a minimally viable product. Until then, I'll sell other stuff. I also must test it some more before I start taking real money. :)
Thanks for reading.
-
 @ 4ddeb0cf:94524453
2025-01-10 01:00:15
@ 4ddeb0cf:94524453
2025-01-10 01:00:15He'd fallen into a deep sleep when he felt something jolt his shoulder. "Richie, honey, you have to wake up. My boss will show up any minute and can't find you in here." Struggling to gain consciousness, he slowly peeled his eyes open and found the clock he'd remembered seeing when he lay down in a room behind the receptionist's office of Roosevelt Lodge. The kid could barely remember arriving, but fighting to stay awake after navigating the switchbacks down the western slope, he'd driven that drunkard and his truck as far as he could. He jumped out and hurried toward the light of the rustic building without knowing what to say to the maniac who'd offered him a ride from that Billings diner. Thank God she'd opened the door. It had been freezing when he knocked shortly after midnight. It appeared to be almost five in the morning. "I'm sorry honey, I know it's early, but I need this job, and he will not be happy if he sees you. You can use the trailhead to the north. It will get you to the closest highway, and you can maybe find a ride there. I would take you myself, but Okie likes me to stick around in the morning."
"Thank you, Ma'am. I really appreciate everything," the young man said, hurriedly putting on his Converse All-Stars. The two exchanged goodbyes as the lady went back to setting up. On his way out of the lodge's rear exit, he noticed a pack of Lucky Strikes sitting on a coffee table beside a copy of LIFE Magazine.
When Richie was eleven, he'd first had a cigarette on a dare from his little sister. They'd found a pack in their parent's room while playing hide and seek. After taking one and running outside with a matchbook, Sarah challenged him to smoke it. He remembered the first drag. While it was harsh, he'd watched his uncle smoke for years and once heard him sharing advice during a card game to inhale very softly at first until you got the hang of it. Uncle Joe had never meant for the lesson to ignite the habit in his nephew but had been too far gone into his bottle of Seagram's 7 to notice him listening.
Through the next few years, Richie became very smooth in taking a pack every few days from the drug store his grandfather had once owned. He'd be cautious to grab them after a larger crowd rolled through the store. The owner, an old friend of his now departed Grandpa, never noticed, and Richie would always leave the payment for them in the cash register.
The memory faded, and the reality of a Montana trailhead before sunrise refocused his concentration. Richie noticed only three cigarettes in the pack, reaching into his pocket to grab the loose change from the gas station incident. There were seven matches to work with. While he struggled to wake up, this find gave him a burst of excitement, and a smile came over his face. He dropped two nickels on the coffee stand and took the remaining pack.
Upon arriving at the trailhead, Richie buttoned his jacket in the chill morning air. It was near pitch black outside, with just enough moonlight to make out the pathway through the forest. He felt scared walking along, yet an air of confidence due to making it this far kept his steps moving forward. Richie began to wonder how far he'd walked when the rising sun put enough illumination through the treeline to make out the opening to a small parking lot adjoining a road. The morning was silent, and he began to yawn. The minimal sleep began to remind him of his exhaustion. The lady from the lodge, what was her name? She'd been so kind when he showed up in the middle of the night, still soaking wet from the melted ice picked up from the passage through the Rockies. As the events began to replay the prior evening's treacherous journey, Richie reached into his pocket to grab a smoke. He imagined his mother's gaze as he successfully ignited the first match and lit the tobacco. The moment was empowering. What were the other kids back in Ohio doing this morning? Though he couldn't ignore the dangerous risks he'd taken along the way, Richie Buckland felt genuine freedom for the first time in his life.
He sat down on a rock to enjoy his smoke and await an oncoming vehicle. Birds began to awaken, and their singing disrupted the silence in the air. His heart filled with gratitude for having dry clothes and a full canteen as he recognized how in sync he felt with the surrounding nature of Yellowstone National Park. That nice lady had even thrown a few Atomic Fireball candies in his knapsack. He still had the twenty dollars his Mom insisted he take with him, having no idea he'd intended to hitchhike to California. She'd known the entire family needed a breather after Richie's fight with his father that night. He thought about his last-second decision to punch the wall beside his father's head instead of hitting his face. That moment had been on his mind throughout this entire journey. Determined to get one last cigarette hit before giving his fingers a break from the closing heat, the birds suddenly began chirping more assertively and in greater numbers. It became alarmingly loud, then silent. As Richie started to reach toward the ground to put out the cigarette, he saw a shape emerge to the right. About twenty feet away, exiting the forest on the same side of the road, was what appeared to be a bear cub. As he took in the sight, another cub followed. Both were brown, and immediately behind them was the largest animal he'd ever seen. His parents had once taken the family to the zoo, but he'd not remembered anything like this. He sat in awe of the creature, followed by a third cub. As they began to cross the road, the large Grizzly paused and turned to look directly at him. Richie was determined to resist the instinctive surge of fear, but his body wouldn't have moved had he tried. Everything felt frozen as the gaze of the enormous animal seemed to determine Richie wasn't a threat. He didn't stare into the bear's eyes but didn't look away. After a few moments, the bears continued along their path until they were out of sight for a long time.
The sunrise of the new morning was breathtaking. After remaining seated on the rock for some time after the incident with the bears, Richie stood up. Taking a healthy drink of water from the canteen, he heard the shifting of gears in the distance. There was no need to look at the map; anywhere the next driver was heading worked. There was no way to know if Mama Grizzly would reevaluate what a human tasted like for breakfast. Richie couldn't wait to reach Sacramento and find Uncle Joe. The approaching Chevy Impala began to slow down upon seeing the teenager standing up, thumb extended.
-
 @ ae6ce958:d0f02c7d
2025-01-10 00:29:00
@ ae6ce958:d0f02c7d
2025-01-10 00:29:00In a strategic move to enhance accessibility and expand its reach, DamageBDD is proud to announce the listing of Damage Token (DAMAGE) on Coinstore, a leading centralized exchange (CEX). This step marks a significant milestone in our journey to provide seamless utility for our users while solidifying DamageBDD’s presence in the blockchain and verification ecosystem.
Why a Centralized Exchange (CEX)?
While DamageBDD has always championed decentralization and Bitcoin-first principles, we recognize the importance of meeting users where they are. Centralized exchanges play a pivotal role in the adoption curve by offering ease of use, robust liquidity, and a familiar interface for new and seasoned crypto enthusiasts alike. By listing on a CEX, DamageBDD lowers the entry barrier for users interested in leveraging Damage Token’s unique value proposition.
Why Coinstore?
The choice of Coinstore is intentional. Known for its user-friendly platform, broad global reach, and active engagement in emerging blockchain technologies, Coinstore aligns with DamageBDD’s vision of democratizing access to verification tools. Coinstore provides:
-
Wide User Base: Its growing community of traders ensures ample liquidity and market activity for Damage Token.
-
Security and Transparency: Coinstore's commitment to security mirrors our own principles of integrity and resilience.
-
Global Reach: With its focus on emerging markets, Coinstore allows DamageBDD to engage with a diverse and vibrant audience, including developers, investors, and enterprises who can benefit from DamageBDD’s verification features.
Utility Meets Accessibility
Listing on Coinstore is not about speculation but utility. Damage Token’s integration into the exchange allows developers, engineering managers, and organizations to acquire tokens effortlessly, unlocking the potential of DamageBDD for behavior-driven development (BDD) and milestone verification. This step enables smoother participation in our ecosystem while ensuring users can utilize Damage Tokens for real-world applications.
Bridging Fiat and Satoshis
Our strategy remains firmly rooted in bridging the fiat world with Bitcoin principles. By making Damage Token available on Coinstore, we provide a pathway for fiat-based users to access DamageBDD while continuing to uphold our Bitcoin-first ethos. This integration will help facilitate broader adoption, bringing the revolutionary capabilities of DamageBDD to a wider audience.
A Future of Greater Utility
This listing is just the beginning. DamageBDD is committed to continuously innovating and creating use cases that empower individuals and organizations. Whether through verifying software quality, enabling milestone-based payouts, or fostering a culture of accountability, Damage Token will remain a tool of pure utility in our collective pursuit of excellence.
The journey of DamageBDD is far from over, and we invite you to join us as we take this bold step forward. Together, let’s redefine the boundaries of development and verification, one token at a time.
Stay tuned for the official listing date and trading details on Coinstore.
-
-
 @ bd4ae3e6:1dfb81f5
2025-01-09 21:44:14
@ bd4ae3e6:1dfb81f5
2025-01-09 21:44:14abstract
i'm writing this post to explain its title without me explaining it every time i talk about nostr or bitcoin and say im studying/working on them, and people immediately ask me about crypto. this would be helpful to clarify this for those overwhelmed with information from crypto projects advertising themselves as a decentralized system.
note: this post is not about financial markets and this stuff at all!
note 2: this post is not technical. i wrote it to make my life easier, and it may also make yours.
what happened?
around 16 years ago a cypherpunk called satoshi nakamoto published a standard called bitcoin: a peer-to-peer electronic cash system. the purpose was to define a decentralized cash system in simple terms. he used a data structure called blockchain that links some blocks of data containing changes in the balance state in the current block and adds a new one to it every 10 minutes.
later some guys started creating copies of bitcoin called altcoins such as ethereum or litecoin and more. over time the word
decentralizedbecame a fancy word and they were able to earn a lot of money using it. so, more people did it.current state
these altocins have become more famous and more people are familiar with them. now here are some points that make all of these projects different from bitcoin:
-
bitcoin network has a lot of nodes running and validating network and checking transactions with a huge hash rate. anyone can join this network without any permissions. on the other hand, most crypto projects need a high-spec device and tokens to stake (since most of them are proof-of-stake or something similar) and there are a lot more tokens on hand of specific people so they can have more shares on voting. (since bitcoin is proof-of-work you won't need coins to have the right to vote)
-
decentralization is not only in a network of nodes. a decentralized system has no one in charge to check its security. when we run a bitcoin core node, there is some code running and this code will take actions which are our votes. bitcoin-core code is one of the most reviewed code bases and a lot of people will observe and review its changes. on the other hand, you can simply check all crypto projects and you can see how their code base is managed. you can see lots of changes are applied by a small group of people without any review.
-
there is a lot of pre-mined/minted coins controlled by teams, early users, vcs, and more in crypto projects. most of them can be mined or minted to infinity. which makes your coins lose their value over time since there is more of it out there, the same as fiat currency. but bitcoin is simple and fair: do work, get the reward. and coins are limited to 21 million. nobody doesn't have printed coins.
-
all crypto projects have a not anonymous team who are out there and the government has access to them. when this team or related people to it publish unexpected stuff on social, get arrested or anything like that, it will impact the whole ecosystem the things you hold which called coins. on the other hand the first guys behind bitcoin are gone now and we don't know him at all. and we don't have anything called bitcoin foundation officially. all of the people working on bitcoin are plebs such as me and you. so, there is now a central point of failure. for a better example search for the story of pavel durove and what happened to his project called
the open networkwhen france government arrested him.
so, they are not
blockchains? you may think anything referred to as a p2p network or a blockchain is decentralized. this is not true. in simple terms, a blockchain is a data structure that we can use to store and maintain data using it. a decentralized system is something that no one can control it directly or censor it. for example bitcoin is a decentralized blockchain (and the only one), but nostr is a decentralized protocol that is not a blockchain, or hyperledger fabric based projects are blockchain, but they are not decentralized.answer to you possible questions:
- q. bitcoin is slow and requires high fees, what should we do?
-
a: lighting is a layer-2 off-chin solution that help us to make zero-fee transactions with the speed of lightning.
note: lighting is not another blockchain or token, it's bitcoin itself.
-
q: there are no smart contracts on bitcoin, what should we do?
- a: to be honest we don't need them. 99% percent of smart contracts are solving issues made by themselves and they don't fix any real issues. they are just super fancy. most of the real use cases they claim they can have are not implemented and don't work. and the rest is possible with nostr, really decentralized, and it's working.
then what is nostr?
nostr is a protocol. it's a set of rules which defined for communication between servers and apps on the web, mobile, or desktop. developers can write software that follows these rules to create social media and more. the resulting app is not a platform or something like that. for example x, meta, bluesky, and more. you control your client and you have the right to connect to any server managed by different people even yourself. and non of the actors in this system won't need permission for this. this is something like http. you can see a lot of websites accessible using http protocol and you can access them using different browsers. the website knows how to return stuff when someone calls them using
http://....and your browser knows how to show this stuff to you. the website you or the owner don't need to ask for permissions from something called http platform. this is just a way to and the website can talk to each other.conclusion
crypto is not the same as bitcoin. nostr is not a blockchain. any blockchain is not decentralized and any decentralized thing is not a blockchain.
this article is draft-1. if you have any ideas for improvement, please tell me or add comments. but consider that i try my best to keep this short, simple, without technical words, and clear.
-
-
 @ dd664d5e:5633d319
2025-01-09 21:39:15
@ dd664d5e:5633d319
2025-01-09 21:39:15Instructions
- Place 2 medium-sized, boiled potatoes and a handful of sliced leeks in a pot.

- Fill the pot with water or vegetable broth, to cover the potatoes twice over.
- Add a splash of white wine, if you like, and some bouillon powder, if you went with water instead of broth.

- Bring the soup to a boil and then simmer for 15 minutes.
- Puree the soup, in the pot, with a hand mixer. It shouldn't be completely smooth, when you're done, but rather have small bits and pieces of the veggies floating around.

- Bring the soup to a boil, again, and stir in one container (200-250 mL) of heavy cream.
- Thicken the soup, as needed, and then simmer for 5 more minutes.
- Garnish with croutons and veggies (here I used sliced green onions and radishes) and serve.

Guten Appetit!
- Place 2 medium-sized, boiled potatoes and a handful of sliced leeks in a pot.
-
 @ 3ad01248:962d8a07
2025-01-09 20:15:32
@ 3ad01248:962d8a07
2025-01-09 20:15:32I hope everyone had a great Christmas and a happy start to the new year. Are you ready to achieve your goals this year? Put the peddle to the metal? I know I am! This year I am dedicating myself to eating healthier, working out more, losing some weight and more importantly devoting more time to writing and getting my thoughts out into the wider world. So here we go.
Well 2025 has gotten off to a crazy start hasn't it? A terrorist attack in New Orleans, the "incident " in Las Vegas and now Los Angeles is burning down to the ground. What in the Sam hill is going on right now? I had a gut feeling that something like this would happen the moment Trump was elected.
If you want to call me a conspiracy theorist go ahead but deep down you know that you feel the same way too. The Democrats or the monied powers behind the curtains do not like the MAGA agenda and will stop at nothing to stop this movement from accomplishing any of its stated goals. What better way to do that than stir up trouble before Trump is even sworn into office again.
The Trump administration and congress are going to be so caught up bouncing from one crisis to another for the next year that its going to fatigue policymakers enough where they can't focus on passing anything of substance. If you understand how congress works they really only have about a year to get anything done. Next year there will be mid-term elections so nothing will get done because they will worrying about being re-elected.
In reality 2025 is the only time Trump has to get his agenda passed. If you remember his first time in office he wasn't particularly good at managing congress and getting them to work with him to fulfill his campaign promise. Do you think he has gotten any better in the last 4 years? Probably not. I could see maybe getting some kind of tax law passed and some kind of border security bill but that about it. Sorry to say but here is what is going to be left on the cutting room floor of his agenda:
- Border Wall
- Deportation of illegal immigrants
- Bitcoin Strategic Reserve
- Reduction of national debt
- No involvement in foreign wars
Sure Republicans have a majority in congress but it is so incredibly small that it is pretty much rendered ineffective. Republicans can only afford to lose 2-3 votes on any legislation that they want to pass. Good luck getting everyone to agree and row in the same direction for the good of the "team".
Most of congress is filled with self-serving egotistical millionaires who don't know how to work together as a team. They didn't get to positions of power by playing well with others. The clawed on the backs of others with good intentions to rise to power. At the end of the day, politicians look out for themselves and will vote their own self-interest. Constituents be damned.
This is why I think some kind of tax reform bill will pass because it benefits them financially and watered down border security bill with no border wall component because it will placate the base and help them get reelected. All the other issues they Republicans could give two shits about.
Republican business interest benefits from illegal immigration. Republican don't give shit about Bitcoin because it takes the power of the printing press away from them. Republicans don't care about the national debt because they believe in fiat Keynesian economics. They don't see the debt as a problem. Republicans love war because if funds the military industrial complex.
What Does This Mean For America?
The next four years are probably going to look like a re-run of 2016-2020. There will be tons of congressional deadlock over any bill of consequence followed by periodic mini crisis's over the debt ceiling.
Inflation will continue to run red hot over the next four years because the main drivers of inflation is not the out of control consumer, its the government and its profligate spending. Lyn Alden has written a fantastic piece about it recently, I highly suggest you give it a read.
The Ukraine war will still be funded maybe not to the level that it has been but Trump isn't going to cut them off completely. America's military industrial complex will still be all over the middle east ready to pounce on Iran if Israel takes the first shot.
At the end of the day we as Americans don't have the power to really influence anything on the macro level. We do have power on the micro or personal level. It's through our individual action that things will change over time.
The best thing that you can do for you and your family is to invest in hard assets. Bitcoin is preferable but if you have family that is not ready to go down that route, property/land and gold are good things to own. In an economic environment like this owning bearer assets is a must.
The global economy is living on borrowed to time to be honest. It's not a matter of if the global economy is going to collapse its a matter of when will it happen. History has shown that all fiat currencies collapse at some point because of human nature. Governments get drunk on the power of creating money out of nothing and forget the only way to have a truly sustainable form of money is something that is backed by something that is hard to produce.
This is a lesson that man has failed to learn time and time again. Hopefully we learn this time and the world finally decides to leave the mirage of fiat currency in the dustbin of history where it belongs.
Bitcoin #Nostr
-
 @ 6bae33c8:607272e8
2025-01-09 19:58:42
@ 6bae33c8:607272e8
2025-01-09 19:58:42I was putting off writing this article because I knew the result would be bad. Real man probably doesn’t write it at all, just skips town and never posts again. But being the nutless monkey I am, I will hold my nose and revisit the bold predictions from last August. And remember, the worst your record, the bolder they were. They were really bad last year too, I just discovered.
1. Stefon Diggs leads the Texans in targets, catches and receiving yards
Right now, he’s getting drafted more than a round behind Nico Collins and less than a round ahead of Tank Dell. Diggs is 30, but he was one of the league’s best receivers until halfway through last year when the Bills made an offensive play-calling change. Moreover, Diggs is getting paid $22.5 million, so the Texans obviously don’t think he’s washed up, and he’s also in a contract year.
Verdict: False. Had he stayed healthy he would have, but that was only because Nico Collins had gotten hurt first. (0-1)
2. CJ Stroud leads the NFL in passing yards
This is +600 on DraftKings, so the real odds are probably north of 8:1. Stroud adds Diggs to his receiving corps, doesn’t run much and heads into Year 2.
Verdict: False. It looked good with Diggs, Collins and Tank Dell, but the first two got hurt, Dell was a bust, and the offensive line was horrible. Plus Stroud himself regressed. (0-2)
3. Roman Wilson (ADP 211) has more receptions than George Pickens (ADP 47)
Pickens is a boom or bust downfield playmaker, not high-target alpha, and Wilson is a good fit for the slot for the Steelers new QBs. Think Martavis Bryant not Antonio Brown. (Not that Wilson is Brown!) Van Jefferson isn’t good, and someone will need to fill the void. Moreover, because Pittsburgh has new QBs, neither has an existing rapport with the incumbent Pickens.
Verdict: LOL. I was right about Pickens and the Steelers WRs, but Wilson never even played. (0-3)
4. DeAndre Hopkins (ADP 82) out produces Calvin Ridley (ADP 54) in PPR
Hopkins wasn’t terrible last year, has a rapport with Will Levis and is a future Hall of Famer who can still run routes. Ridley is already 29 and is just a guy outside of his monster season in 2020.
Verdict: False. Ridley smoked him, and Hopkins was eventually traded. (0-4)
5. The Giants will field a top-10 fantasy defense.
I’ve been crushed by my homer bold predictions in the past, but they added Brian Burns to a rush that already had Dexter Lawrence and Kayvon Thibodeaux, the offense should be on the field more and generate some leads with a real playmaking receiver in Malik Nabers.
Verdict: False. They started out strong, but it’s very hard to be a good fantasy defense on a three-win team, and they finished 24th. (0-5).
6. One of the following Year 2 receivers will finish in the top-15 PPR: Jaxon Smith-Njigba, Jayden Reed, Jordan Addison, Dontayvion Wicks, Michael Wilson, Josh Downs, Andrei Iosivas, Quentin Johnston, Marvin Mims, Jalin Hyatt
I make this prediction every year, and it often pans out as Year 2 is when receivers typically make the leap. I left out Tank Dell because he’s now got a fifth-round ADP, as well as the obvious ones: Zay Flowers, Rashee Rice and Puka Nacua.
Verdict: True. Jaxon Smith-Njigba finished 11th. (1-5)
7. Rome Odunze (ADP 77) will outproduce Xavier Worthy (ADP 59)
Both receivers enter crowded situations, and while Worthy’s is far better, he’s also got essentially the same skill-set as teammate Marquise Brown. Moreover, Andy Reid rarely entrusts rookies with large roles, especially early on. Odunze is 6-3, 215 and has the pedigree of a true NFL alpha, while Worthy weighs only 165 pounds at 5-11. Finally, Patrick Mahomes already has an established rapport with both Travis Kelce and Rashee Rice, while Odunze gets a more open competition with the Bears veteran WRs, given all three will play with Caleb Williams for the first time.
Verdict: False. It was reasonably close, but Worthy pulled ahead late in the year (1-6)
8. Dalvin Cook will lead the Cowboys in rushing yards
Cook is 29 and looked beyond “cooked” last year on the Jets, but his 3.3 YPC was on a small sample (67 carries), and prior to that, he’d been very good for the Vikings. At the very least he should have fresh legs, and he’d only need to beat out the ancient Ezekiel Elliott and Rico Dowdle. (Of course, Cook would have to be promoted from the practice squad first, so I really should hedge and make the prediction “neither Elliott, nor Dowdle will lead the Cowboys in rushing yards,” but I’ll push it and say it’s Cook.)
Verdict: LOL. Cook was the one veteran back from the Class of 2017 who really was washed up. (1-7)
9. Jonathan Taylor (ADP12 ) will lead the NFL in rushing yards.
He’s got little competition in the Indy backfield and a running QB who should open lanes for him. Draft Kings has him at +600, so his real odds are probably about 10:1, but I’d take him over the favored Christian McCaffrey (age/mileage) and all the other backs who are more hybrid types or old (Derrick Henry.)
Verdict: False. He finished fourth despite missing three full games, so this wasn’t too far off. What’s funny is I make this prediction of Barkley virtually every year except this one. (1-8)
10. Dalton Kincaid (TE4) will lead all TE in catches
I guess this is a chalky pick because he and Kelce are both favored at the position at +3000, while Evan Engram is +5000! (I’d way rather bet on Engram at those odds.) But straight up, I’m going with Kincaid who is likely Josh Allen’s de facto No. 1 target with Diggs gone. In his final 11 regular season games Kincaid had 56 catches which prorates to 87 catches over the full year. And rookie tight ends rarely do anything and often make a leap in Year 2. (1-9)
Verdict: LOL. Kincaid was one of the biggest busts in the draft. (1-9)
11. Some of these predictions will be wrong
No one’s perfect, but you never want to get shut out.
Verdict: Crushed, especially the comment the prescience of which makes Nostradamus look like the corner astrologer. (2-9)
-
 @ 5002cb48:31a0d6d8
2025-01-09 19:37:47
@ 5002cb48:31a0d6d8
2025-01-09 19:37:47I am trying to update my profile, but it's not happening. Is the site broken?
-
 @ 60d9f6d8:bc336770
2025-01-09 17:49:18
@ 60d9f6d8:bc336770
2025-01-09 17:49:18My focus is predominantly on whether I could eliminate traditional banking accounts (e.g. BofA / JPM Chase etc) with the added benefit of stacking sats automatically on a day-to-day basis.
- The first part is very simple: register via foldapp.com and wait for your card to arrive. I chose the Fold+ membership at 100 per year if paid annually, otherwise 10/month. The trial period is 3 months before you are charged.
- Upon receiving the card, activate via the app (very simple click of a button and confirmation of card digits).
# Fold+ Membership costs & benefits

Linking/Funding from banking institutions
- On average, it is taking around 3 business days to make those funds available on Fold.
- There is an option to add "Instant Debit Card Funding" at a 1.5% charge; however, keep in mind that you are currently limited to adding a maximum of 2 cards.
Paying Bills
- In most cases I simply add the account & routing number to the billing company website (i.e. credit card / utilities / phone etc). In some cases, I can simply add my debit card number.
- Additionally, as a Fold+ user, any payment I make earns back rewards in sats.
Bill Pay ACH Rewards

Bitcoin (buying / sending / receiving) features
- Fold gives you many options to buy, send & receive bitcoin either automatically, via transfer or direct deposit with the ability to choose a certain percentage towards fiat or Bitcoin.
- Ability to Round-Up purchases with various multipliers.
- Push to Card: this feature effectively allows you to replenish your fiat/cash balance in your account. This does not happen automatically, so you will need to do this manually.
Authorized Users
- Fold allows you to authorize up to 3 users (must be at least 18 years old)
- This user will receive their own debit card.
- The user can also direct deposit into the account.
Note: at this time, authorized users do not have access to the app itself, which is only available to the primary account holder. This creates some friction given the authorized user cannot move funds if needed or even determine the balance on the account without interacting or communicating with the primary account holder.
Limits (as of Sept 2024)

Note: the limits only refer to your fiat balance, not a combination of your fiat & bitcoin/rewards balance.
Final Thoughts
I have been using Fold for about a month now and it is working very well. I haven't had any issues paying bills, making deposits (direct or otherwise), making purchases, buying bitcoin and/or earning rewards in general. The customer support has been really positive in responding to my inquiries within a few hours. Mostly, those inquiries have been around information I simply could not find via the foldapp or blog websites.
As of now, my intent is to continue utilizing this card/application and wean myself away from traditional banks entirely. However, there are a couple of pain points I'll point out that hopefully will be addressed in the future:
- The limits need to increase, especially if you intend on using this with your spouse/family members.
- The authorized user(s) should have the ability to log into the app and allow the primary holder to dictate the permissions for said user(s). Likewise, it might be useful to allow joint holders to have separate accounts within one view.
- Increase the 2-card limit for "Instant Debit Funding".
- Ability to search in the "gift card" section instead of scrolling through.
- Ability to send via Zelle as I still, unfortunately, need to send payments to those who are unable/unwilling to use something else.
- Ability to automatically Push to Card if funds are low.
There are of course many benefits of the Fold card I have glossed over as it relates to rewards, so I'll just mention a few here:
- Daily Spin allows you to addictively hope for the grand prize of 1 BTC. While the odds are extraordinarily low, at a minimum you'll earn some sats with each spin.
- Gift cards rewards are very impressive and highly recommend you use those to earn free sats.
As of now, I've earned around 30k sats this month by doing nothing different financially outside of my normal spending habits, so this of course is a major advantage.
Lastly, if you have any feedback or questions please ask and I'll try my best to answer and if you want to give it a try, here is a referral link that'll get you 20k sats: https://use.foldapp.com/r/WAANYUMJ
Blog | Fold Bitcoin Rewards App
Disclaimer: I have no affiliation or sponsorship with Fold. I'm just a normie looking to get closer to a Bitcoin standard without too much disruption.
-
 @ df173277:4ec96708
2025-01-09 17:12:08
@ df173277:4ec96708
2025-01-09 17:12:08Maple AI combines the best of both worlds – encryption and personal AI – to create a truly private AI experience. Discuss personal and company items with Maple, we can't read them even if we wanted to.\ Join the waitlist to get early access.
We are a culture of app users. Every day, we give our personal information to websites and apps, hoping they are safe. Location data, eating habits, financial details, and health information are just a few examples of what we entrust to third parties. People are now entering a new era of computing that promises next-level benefits when given even more personal data: AI.
Should we sacrifice our privacy to unlock the productivity gains of AI? Should we hope our information won't be used in ways we disagree? We believe we can have the best of both worlds – privacy and personal AI – and have built a new project called Maple AI. Chat between you and an AI with full end-to-end encryption. We believe it's a game-changer for individuals seeking private and secure conversations.
Building a Private Foundation
Maple is built on our flagship product, OpenSecret, a backend platform for app developers that turns private encryption on by default. The announcement post for OpenSecret explains our vision for an encrypted world and what the platform can do. We think both users and developers benefit when sensitive personal information is encrypted in a private vault; it's a win-win.
The Power of Encrypted AI Chat
AI chat is a personal and intimate experience. It's a place to share your thoughts, feelings, and desires without fear of judgment. The more you share with an AI chatbot, the more powerful it becomes. It can offer personalized insights, suggestions, and guidance tailored to your unique needs and perspectives. However, this intimacy requires trust, and that's where traditional AI chatbots often fall short.
Traditional AI chats are designed to collect and analyze your data, often without your explicit consent. This data is used to improve the AI's performance, but it also creates a treasure trove of sensitive information that can be mined, sold, or even exploited by malicious actors. Maple AI takes a different approach. By using end-to-end encryption, we ensure that your conversations remain private and secure, even from us.
Technical Overview
So, how does Maple AI achieve this level of privacy and security? Here are some key technical aspects:
- Private Key: Each user has a unique private key that is automatically managed for them. This key encrypts and decrypts conversations, ensuring that only the user can access their data.
- Secure Servers: Our servers are designed with security in mind. We use secure enclaves to protect sensitive data and ensure that even our own team can't access your conversations.
- Encrypted Sync: One of Maple's most significant benefits is its encrypted sync feature. Unlike traditional AI chatbots, which store conversations in local storage or on standard cloud servers, Maple syncs your chats across all your devices. The private key managed by our secure servers means you can pick up where you left off on any device without worrying about your data being compromised.
- Attestation and Open Code: We publish our enclave code publicly. Using a process called attestation, users can verify that the code running on the enclave is the same as the code audited by the public.
- Open Source LLM: Maple uses major open-source models to maximize the openness of responses. The chat box does not filter what you can talk about. This transparency ensures that our AI is trustworthy and unbiased.
Personal and Work Use
Maple is secure enough to handle your personal questions and work tasks. Because we can't see what you chat about, you are free to use AI as an assistant on sensitive company items. Use it for small tasks like writing an important email or large tasks like developing your organization's strategy. Feed it sensitive information; it's just you and AI in the room. Attestation provides cryptographic proof that your corporate secrets are safe.
Local v Cloud
Today's AI tools provide different levels of privacy. The main options are to trust a third party with your unencrypted data, hoping they don't do anything with it, or run your own AI locally on an underpowered machine. We created a third option. Maple gives you the power of cloud computing combined with the privacy and security of a machine running on your desk. It's the best of both worlds.
Why the Maple name?
Privacy isn't just a human value - it's a natural one exemplified by the Maple tree. These organisms communicate with each other through a network of underground fungal hyphae, sending messages and sharing resources in a way that's completely invisible to organisms above ground. This discreet communication system allows Maple trees to thrive in even the most challenging environments. Our goal is to provide a way for everyone to communicate with AI securely so they can thrive in any environment.
Join the Waitlist
Maple AI will launch in early 2025 with free and paid plans. We can't wait to share it with the world. Join our waitlist today to be among the first to experience the power of private AI chat.
-
 @ df173277:4ec96708
2025-01-09 17:02:52
@ df173277:4ec96708
2025-01-09 17:02:52OpenSecret is a backend for app developers that turns private encryption on by default. When sensitive data is readable only by the user, it protects both the user and the developer, creating a more free and open internet. We'll be launching in 2025. Join our waitlist to get early access.
In today's digital age, personal data is both an asset and a liability. With the rise of data breaches and cyber attacks, individuals and companies struggle to protect sensitive information. The consequences of a data breach can be devastating, resulting in financial losses, reputational damage, and compromised user trust. In 2023, the average data breach cost was $5 million, with some resulting in losses of over $1 billion.
 Meanwhile, individuals face problems related to identity theft, personal safety, and public embarrassment. Think about the apps on your phone, even the one you're using to read this. How much data have you trusted to other people, and how would it feel if that data were leaked online?
Meanwhile, individuals face problems related to identity theft, personal safety, and public embarrassment. Think about the apps on your phone, even the one you're using to read this. How much data have you trusted to other people, and how would it feel if that data were leaked online?Thankfully, some incredibly talented cypherpunks years ago gave the world cryptography. We can encrypt data, rendering it a secret between two people. So why then do we have data breaches?
Cryptography at scale is hard.
The Cloud
The cloud has revolutionized how we store and process data, but it has limitations. While cloud providers offer encryption, it mainly protects data in transit. Once data is stored in the cloud, it's often encrypted with a shared key, which can be accessed by employees, third-party vendors, or compromised by hackers.
The solution is to generate a personal encryption password for each user, make sure they write it down, and, most importantly, hope they don't lose it. If the password is lost, the data is forever unreadable. That can be overwhelming, leading to low app usage.
Private key encryption needs a UX upgrade.
Enter OpenSecret
OpenSecret is a developer platform that enables encryption by default. Our platform provides a suite of security tools for app developers, including private key management, encrypted sync, private AI, and confidential compute.
Every user has a private vault for their data, which means only they can read it. Developers are free to store less sensitive data in a shared manner because there is still a need to aggregate data across the system.

Private Key Management
Private key management is the superpower that enables personal encryption per user. When each user has a unique private key, their data can be truly private. Typically, using a private key is a challenging experience for the user because they must write down a long autogenerated number or phrase of 12-24 words. If they lose it, their data is gone.
OpenSecret uses secure enclaves to make private keys as easy as an everyday login experience that users are familiar with. Instead of managing a complicated key, the user logs in with an email address or a social media account.
The developer doesn't have to manage private keys and can focus on the app's user experience. The user doesn't have to worry about losing a private key and can jump into using your app.

Encrypted Sync
With user keys safely managed, we can synchronize user data to every device while maintaining privacy. The user does not need to do complicated things like scanning QR codes from one device to the next. Just log in and go.
The user wins because the data is available on all their devices. The developer wins because only the user can read the data, so it isn't a liability to them.
Private AI
Artificial intelligence is here and making its way into everything. The true power of AI is unleashed when it can act on personal and company data. The current options are to run your own AI locally on an underpowered machine or to trust a third party with your data, hoping they don't read it or use it for anything.
OpenSecret combines the power of cloud computing with the privacy and security of a machine running on your desk.
Check out Maple AI\ Try private AI for yourself! We built an app built with this service called Maple AI. It is an AI chat that is 100% private in a verifiable manner. Give it your innermost thoughts or embarrassing ideas; we can't judge you. We built Maple using OpenSecret, which means you have a private key that is automatically managed for you, and your chat history is synchronized to all your devices. Learn more about Maple AI - Private chat in the announcement post.

Confidential Compute
Confidential computing is a game-changer for data security. It's like the secure hardware that powers Apple Pay and Google Pay on your phone but in the cloud. Users can verify through a process called attestation that their data is handled appropriately. OpenSecret can help you run your own custom app backend code that would benefit from the security of an enclave.
It's the new version of that lock on your web browser. When you see it, you know you're secure.

But do we want our secrets to be open?
OpenSecret renders a data breach practically useless. If hackers get into the backend, they enter a virtual hallway of locked private vaults. The leaked data would be gibberish, a secret in the open that is unreadable.
On the topic of openness, OpenSecret uses the power of open source to enable trust in the service. We publish our code in the open, and, using attestation, anyone can verify that private data is being handled as expected. This openness also provides developers with a backup option to safely and securely export their data.
Don't trust, verify.
Join the Movement
We're currently building out OpenSecret, and we invite you to join us on the journey. Our platform can work with your existing stack, and you can pick and choose the features you need. If you want to build apps with encryption enabled, send us a message to get early access.
Users and companies deserve better encryption and privacy.\ Together, let's make that a reality.
-
 @ 77c2969e:a33cfa50
2025-01-09 17:01:36
@ 77c2969e:a33cfa50
2025-01-09 17:01:36换了个客户端Nostrmo,比damus好用,不过好像关注列表丢失了😩。
现在使用#YakiHonne,好像更流畅
不加图片他还会显示一个空白图片,好丑,我还是上传一个吧
-
 @ f9c0ea75:44e849f4
2025-01-09 16:05:30
@ f9c0ea75:44e849f4
2025-01-09 16:05:30In a recent TFTC podcast episode, Parker Lewis outlined a mathematical inevitability—a liquidity crisis unfolding in 2025. While optimism around the Trump administration’s economic policies exists, Lewis argues that no fiscal policy can counteract the Federal Reserve’s tightening liquidity. The real issue? Too much debt and not enough dollars.
This reflection expands on Lewis’ key arguments, breaking down:
- Where the liquidity crisis is coming from
- Why it’s a structural problem
- What the consequences are
- Why Bitcoin matters in this scenario
1. Where Is the Liquidity Crisis Coming From?
The crisis stems from a fundamental imbalance:
- Debt levels have skyrocketed, particularly post-2008 and post-COVID.
- Dollars needed to service this debt are shrinking because of Federal Reserve tightening (QT, interest rates, and shrinking reserves).
The Math Behind the Liquidity Squeeze
- In 2007, there was $53 trillion in U.S. dollar-denominated debt, but only $900 billion in base money—a 50:1 leverage ratio.
- By 2023, FED policies had drained dollars from the banking system, while debt levels continued to explode higher. The result? A liquidity-starved financial system dependent on an ever-smaller money pool.
2. The Structural Problem: FED Policy is the Real Driver
While fiscal policy (tax cuts, tariffs, and deregulation) can marginally improve economic conditions, it cannot stop a liquidity crisis. Lewis emphasizes that the Federal Reserve is the key player in determining financial stability.
What the FED Has Done to Shrink Liquidity
- Quantitative Tightening (QT): Actively reducing the money supply by letting bonds roll off the balance sheet.
- Interest Rate Hikes (2022–2023): Made borrowing more expensive, slowing credit creation.
- Reverse Repo Drain: Reduced excess bank reserves, limiting lending ability.
- Shrinking Bank Reserves: With fewer reserves, banks lend less, tightening financial conditions.
This means the liquidity crisis isn’t theoretical—it’s already happening.
3. The Warning Signs: Cracks in the Financial System
Lewis points to clear signals that liquidity is disappearing:
- Rising delinquencies in commercial mortgage-backed securities (CMBS) – approaching post-2008 highs.
- Credit card delinquencies – nearing 2008 levels.
- Treasury yield inversion anomalies – typically, rate cuts lead to falling long-term bond yields, but that’s not happening, suggesting market pessimism. Bank failures in 2023 (SVB, First Republic, Signature Bank) – early signs of systemic liquidity stress.
The takeaway? Debt is growing, but the available money to service it is shrinking—a recipe for financial instability.
Consequences: What Happens If Liquidity Remains Tight?
If the FED continues draining liquidity, we may see:
✔ More bank failures, as weaker institutions struggle to survive.
✔ Debt defaults rise, particularly in real estate and corporate debt.
✔ Stock market volatility, as credit-dependent sectors suffer.
✔ A potential recession, triggered by a credit crunch.
The FED may eventually be forced to reverse course and print more money, but waiting too long could trigger a financial shock first.
Final Thoughts: The Crisis is Already Unfolding
This isn’t just speculation, it's a mathematical inevitability. The FED's policies have set the stage for a debt-starved economy with fewer dollars available to sustain it. The next 12 months could be highly volatile, with financial stress increasing.
Key Takeaways
✅ Trump’s policies may be positive, but they won't prevent a liquidity crisis.
✅ The FED is the dominant force, and its liquidity-draining policies are causing systemic risks.
✅ Leading indicators suggest we’re already in a liquidity crunch.
✅ Bitcoin remains a strategic hedge as the FED eventually returns to money printing.
What to Expect?
A volatile 2025—prepare for financial instability and potential FED intervention.
-
 @ 1380337c:2d77df3e
2025-01-09 15:26:18
@ 1380337c:2d77df3e
2025-01-09 15:26:18Fiat has entered its final phase, falling victim to its inherent flaws.
Decades of money printing, unchecked government spending and the Cantillion effect (those closest to the money printer benefit at the behest of the rest of us) are finally taking its toll.
As calls for a return to hard money grow louder, it is only the most astute Cantillion economists (and their government backers) who believe money supply should be managed by “a council of wise (wo)men”.
Among those seeking hard money are the BRICS nations, who are looking into creating a gold-backed system to challenge the fiat dollar’s dominance.
This would have been a great idea, were it not for Bitcoin. With the existence of Bitcoin any attempt to create gold-backed systems is doomed from the start.
Fiat has entered its final phase, falling victim to its inherent flaws.
The Rise and Fall of Gold-Backed Systems
Gold was money for thousands of years, universally accepted because of its scarcity and durability.
However, as global trade developed, the world ran into gold’s main limitation – physical gold couldn’t keep up with trade.
This led to gold being replaced by gold-backed currencies, which combined gold reliability with the convenience of paper money. Yet, this hybrid system inherited gold’s flaws while introducing its own.
Gold’s supply uncertainty remained a major weakness. Sudden discoveries, like Spain’s conquest of South America or the California Gold Rush, destabilized economies by flooding markets with new gold.
Worse, gold-backed systems led to the centralization of reserves, concentrating power in the hands of governments and banks.
This led to the inevitable corruption and mismanagement of the money supply, which quickly became inflated at the expense of holders of gold-backed currencies.
The step towards full fiat was a small one after this…
Gold was money for thousands of years, universally accepted because of its scarcity and durability.
However, as global trade developed, the world ran into gold’s main limitation – physical gold couldn’t keep up with trade.
This led to gold being replaced by gold-backed currencies, which combined gold reliability with the convenience of paper money. Yet, this hybrid system inherited gold’s flaws while introducing its own.
Gold’s supply uncertainty remained a major weakness. Sudden discoveries, like Spain’s conquest of South America or the California Gold Rush, destabilized economies by flooding markets with new gold.
Worse, gold-backed systems led to the centralization of reserves, concentrating power in the hands of governments and banks.
This led to the inevitable corruption and mismanagement of the money supply, which quickly became inflated at the expense of holders of gold-backed currencies.
The step towards full fiat was a small one after this…
Gold-Backed Systems Stand No Chance Against Bitcoin
Bitcoin exposes the vulnerabilities of gold-backed systems in every dimension:
-
Fixed Supply vs. Supply Uncertainty: Bitcoin’s hard cap of 21 million coins provides unmatched predictability and scarcity. No sudden “Bitcoin rush” can destabilize the system, unlike gold’s history of disruptive supply shocks.
-
Decentralization vs. Centralization: Gold-backed systems concentrate reserves in the hands of governments or banks, creating single points of failure. Bitcoin’s decentralized network eliminates these vulnerabilities, making it immune to corruption and mismanagement.
-
Censorship Resistance: Centralized control leaves gold-backed systems open to confiscation and censorship. Bitcoin’s censorship-resistant design ensures no entity can control the network or seize assets.
-
Trustless vs. Trust-Based: Gold-backed systems demand trust in central authorities to maintain their peg—“Trust me, bro”. Bitcoin operates on a transparent, verifiable ledger, replacing trust with cryptographic proof: “Don’t trust, verify.”
-
Efficiency and Mobility: Settlement times for Bitcoin are near-instant, compared to the logistical nightmare of moving and securing physical gold.
-
Sovereign Protection: Bitcoin enables nations to protect their reserves anywhere in the world. A government under siege could flee with its wealth intact, stored securely on the blockchain. Imagine Assad, fleeing Syria with his country’s riches encoded in a 24-word seed phrase, using it to organize resistance against his foes. Such flexibility is unthinkable with gold.
Gold-Backed Systems Will Never Stand a Chance Again
Gold-backed systems are flawed relics of the past, their flaws exposed by Bitcoin.
With its immutability, decentralization, and efficiency, Bitcoin eliminates the vulnerabilities of centralization and mismanagement inherent in gold-backed systems.
Bitcoin thrives in a digital-first world, offering portability, resistance to confiscation, and unmatched security. Its finite supply and transparent ledger set a new standard that gold can never meet.
Bitcoin is more than an evolution of money—it’s a safeguard against regimes that seek to weaken their nations through centralised monetary systems, even under the guise of gold-backed currencies.
Gold-backed systems are flawed relics of the past, their flaws exposed by Bitcoin.
With its immutability, decentralization, and efficiency, Bitcoin eliminates the vulnerabilities of centralization and mismanagement inherent in gold-backed systems.
Bitcoin thrives in a digital-first world, offering portability, resistance to confiscation, and unmatched security. Its finite supply and transparent ledger set a new standard that gold can never meet.
Bitcoin is more than an evolution of money—it’s a safeguard against regimes that seek to weaken their nations through centralised monetary systems, even under the guise of gold-backed currencies.
-
-
 @ 6e24af77:b3f1350b
2025-01-09 13:43:06
@ 6e24af77:b3f1350b
2025-01-09 13:43:067
-
 @ e373ca41:b82abcc5
2025-01-09 13:28:41
@ e373ca41:b82abcc5
2025-01-09 13:28:41Heute Abend um 19 Uhr sprechen Elon Musk und Alice Weidel auf X. Der alternative Radiosender Kontrafunk aus der Schweiz bringt eine Übersetzung davon im Stream.
Da die Webseite des Kontrafunks gestern angegriffen wurde, ist hier der Stream unzensierbar aufrufbar, als kleines Back-up:
https://stream.kontrafunk.radio/listen/kontrafunk/radio.mp3
\ Im Nostr-Netzwerk dauerhauft auch u.a. hier aufrufbar (falls wir angegriffen werden).
Tonight at 7 pm (CET), Elon Musk and Alice Weidel will be speaking on X. The alternative radio station Kontrafunk from Switzerland will be streaming a translation.
As the Kontrafunk website was attacked yesterday, the stream can be accessed uncensored here as a small backup:
https://stream.kontrafunk.radio/listen/kontrafunk/radio.mp3
In the Nostr network also permanently available here (in case we are attacked).
ADVERTISEMENT:
Looking for the easiest way to buy Bitcoin and store it yourself? The Relai app is the No. 1 crypto start-up and No. 2 of all fintech start-ups in Switzerland. Here you can buy Bitcoin in just a few steps and also set up savings plans. Nobody has access to your Bitcoin except you. With the referral code MILOSZ you save on fees (no financial advice). Disclaimer due to regulatory issues: The services of the Relai App are hereby only recommended to inhabitants of Switzerland or Italy.

Need more security? The Trezor wallets are recommended and easy to use, others are available in the store. Need more advice? Book an introductory meeting with a wallet expert.
Join the marketplace of ideas! We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Sound money and sound information should finally be in the hands of the people, right? Want to learn more about the Pareto Project? Zap me, if you want to contribute (all Zaps go to the project).
Update:* Since my last article on the Pareto project, we have received more than 50 messages from publications, journalists, authors, testers and supporters. Thank you very much, we are happy to help everyone become censorship-resistant! May just take a little time. Are you a publication and want to be part of it, test us, migrate your content to Nostr? Write to team@pareto.space***
Not yet on Nostr and want the full experience? Easy onboarding via Nosta.me.










