-
 @ 76c71aae:3e29cafa
2025-01-26 22:51:16
@ 76c71aae:3e29cafa
2025-01-26 22:51:16When I first heard about the DOGE project, I was ready to throw my laptop out the window. The initial proposal read like a Silicon Valley libertarian fever dream - taking Musk's chaotic "move fast and break democracy" Twitter approach and unleashing it on federal agencies. Great, I thought, just what we need: more tech bros thinking they can "optimize" public institutions into oblivion.
But here's the weird thing - when you actually dig into what DOGE has morphed into, it's basically just USDS with a meme-worthy rebrand. For those not deep in the civic tech weeds, USDS was Obama's attempt to drag government technology out of the 1990s, inspired by the UK's actually-functional GDS program. And let's be real - government tech procurement is an absolute dumpster fire right now. We're talking billions wasted on projects that would make a CS101 student cringe, while the average American has to navigate websites that look like they were designed on GeoCities.
The deeply ironic thing is that Musk - for all his cosplaying as a technocratic messiah following in his grandfather's footsteps of dreaming up an antidemocratic technocratic state - actually has some relevant experience here. SpaceX did figure out how to work with government contracts without producing $500 million paperweights, and Tesla somehow gamed clean vehicle incentives into birthing the first new major car company since we invented radio.
Look, I'm the first to roll my eyes at Musk's wannabe-fascist posting sprees and his perpetual "I'm the main character of capitalism" energy. But speaking as someone who's banged their head against the wall of government technology modernization for years - if he actually focuses on the tech and keeps his brainrot political takes to himself, maybe DOGE could do some good?
Even Jen Pahlka, who basically wrote the book on government digital services, is cautiously optimistic. The services Americans get from their government are objectively terrible, and the procurement system is trapped in an infinite loop of failure. Maybe - and I can't believe I'm typing this - Musk's particular flavor of disruptive tech deployment could help?
Just... please, for the love of all things agile, let's keep him focused on the actual technology and far away from any more attempts to recreate his grandfather's dreams of a technocratic dystopia. We've got enough of those already.
-
 @ 83279ad2:bd49240d
2025-01-24 09:15:37
@ 83279ad2:bd49240d
2025-01-24 09:15:37備忘録として書きます。意外と時間がかかりました。全体で1時間くらいかかるので気長にやりましょう。 仮想通貨取引所(販売所ではないので、玄人が使えばお得らしい)かつBitcoinの送金手数料が無料(全ての取引所が無料ではない、例えばbitbankは0.0006bitcoinかかる)なので送金元はGMOコインを使います。(注意:GMOコインは0.02ビットコイン以下は全額送金になってしまいます) 今回はカストディアルウォレットのWallet of Satoshiに送金します。 以下手順 1. GMOコインでbitcoinを買います。 2. GMOコインの左のタブから入出金 暗号資産を選択します。 3. 送付のタブを開いて、+新しい宛先を追加するを選択します。 4. 送付先:GMOコイン以外、送付先ウォレット:プライベートウォレット(MetaMaskなど)、受取人:ご本人さま を選んで宛先情報の登録を選ぶと次の画面になります。
 5. 宛先名称にwallet of satoshi(これはなんでも良いです わかりやすい名称にしましょう) wallet of satoshiを開いて、受信→Bitcoin On-Chainからアドレスをコピーして、ビットコインアドレスに貼り付けます。
5. 宛先名称にwallet of satoshi(これはなんでも良いです わかりやすい名称にしましょう) wallet of satoshiを開いて、受信→Bitcoin On-Chainからアドレスをコピーして、ビットコインアドレスに貼り付けます。 6. 登録するを押します。これで送金先の登録ができました。GMOコインの審査がありますがすぐ終わると思います。
7. ここから送金をします。送付のタブから登録したビットコインの宛先リストwallet of satoshiを選択し、送付数量と送付目的を選択して、2段階認証をします。
6. 登録するを押します。これで送金先の登録ができました。GMOコインの審査がありますがすぐ終わると思います。
7. ここから送金をします。送付のタブから登録したビットコインの宛先リストwallet of satoshiを選択し、送付数量と送付目的を選択して、2段階認証をします。 8. 実行を押せば終わりです。もうあなたがやることはありません。送金が終わるのを40分くらい眺めるだけです。
8. 実行を押せば終わりです。もうあなたがやることはありません。送金が終わるのを40分くらい眺めるだけです。 8. 取引履歴のタブから今の送金のステータスが見れます。
8. 取引履歴のタブから今の送金のステータスが見れます。 9. 15分くらい待つとステータスが受付に変わります。
9. 15分くらい待つとステータスが受付に変わります。 10. 20分くらい待つとトランザクションIDが表示されます。
10. 20分くらい待つとトランザクションIDが表示されます。

この時点からwallet of satoshiにも送金されていることが表示されます。(まだ完了はしていない)
 11. ステータスが完了になったら送金終わりです。
11. ステータスが完了になったら送金終わりです。

wallet of satoshiにも反映されます。

お疲れ様でした!
-
 @ ae6ce958:d0f02c7d
2025-01-27 23:27:51
@ ae6ce958:d0f02c7d
2025-01-27 23:27:51In a world dominated by overhyped tech and broken promises, DamageBDD stands apart as a Bitcoin-first revolution for developers, QA teams, and enterprises. Built on the belief that resilience, transparency, and accountability are not optional, this innovation is more than just another BDD platform—it's a tool designed to harness the unstoppable power of Bitcoin and the Lightning Network to redefine software quality and team productivity. Here's why DamageBDD will light up the Lightning Network like never before:
1. Lightning-Powered Incentives for Development
Imagine a world where developers are rewarded in sats the moment their code passes a milestone. With DamageBDD, that’s no longer a dream. We use Lightning-based escrow payments tied to milestone completions, ensuring every contributor gets instant, trustless payouts for verified work. This isn’t just about payments—this is about transforming the economics of collaboration and incentivizing excellence.
2. Real-Time Transparency Meets Bitcoin Immutability
Every BDD test, every passing milestone, and every failure is immutably recorded, showcasing the evolution of a project with a timestamped on-chain timeline. By anchoring progress to Bitcoin’s ultimate ledger of truth, DamageBDD creates a level of transparency that ensures trust—whether you're a developer, a manager, or an investor.
3. Immediate Liquidity Without Compromise
The Lightning Network enables participants to exit their locked funds through near-instant buybacks—no risk of long-term lock-ins or centralized interference. Developers and stakeholders can convert their contributions back to Bitcoin at market-close rates, minus nominal fees. This system protects value while keeping all incentives aligned with delivering quality software.
4. A Bitcoin Economy for BDD
Why settle for fiat-denominated payments or centralized intermediaries when you can build directly on Bitcoin? DamageBDD’s ecosystem ensures that every satoshi stays true to the ethos of decentralization, enabling organizations to manage projects in a way that’s fair, transparent, and resilient.
5. Scalable Adoption of High-Performance Teams
The Lightning Network isn’t just a payments rail—it’s a bridge for building relationships across borders. DamageBDD allows distributed teams to thrive, making trustless collaboration possible while fostering high-performance, Bitcoin-powered workflows.
6. Redefining ROI for Investors
Investors can now lock funds into milestone-driven escrows, ensuring ROI is directly tied to results. With DamageBDD’s Lightning-enabled payouts, there’s no waiting for endless revisions or missed deadlines—just real-time accountability, measured and delivered on a timeline that’s verifiable and immutable.
Bitcoiners, this is the spark.
While the fiat world struggles with inefficiency, corruption, and misaligned incentives, DamageBDD fuels the future with a Bitcoin-powered toolkit that transforms how teams work, get paid, and build trust. This isn’t just about better software—it’s about building an unstoppable Bitcoin economy where transparency reigns, quality wins, and the Lightning Network becomes the default rail for human collaboration.
DamageBDD isn’t here to gamble on hype—it’s here to build the future. Let’s light up the Lightning Network and show the world what Bitcoin-backed innovation can achieve. Are you ready to join the revolution?
-
 @ eac63075:b4988b48
2025-01-04 19:41:34
@ eac63075:b4988b48
2025-01-04 19:41:34Since its creation in 2009, Bitcoin has symbolized innovation and resilience. However, from time to time, alarmist narratives arise about emerging technologies that could "break" its security. Among these, quantum computing stands out as one of the most recurrent. But does quantum computing truly threaten Bitcoin? And more importantly, what is the community doing to ensure the protocol remains invulnerable?
The answer, contrary to sensationalist headlines, is reassuring: Bitcoin is secure, and the community is already preparing for a future where quantum computing becomes a practical reality. Let’s dive into this topic to understand why the concerns are exaggerated and how the development of BIP-360 demonstrates that Bitcoin is one step ahead.
What Is Quantum Computing, and Why Is Bitcoin Not Threatened?
Quantum computing leverages principles of quantum mechanics to perform calculations that, in theory, could exponentially surpass classical computers—and it has nothing to do with what so-called “quantum coaches” teach to scam the uninformed. One of the concerns is that this technology could compromise two key aspects of Bitcoin’s security:
- Wallets: These use elliptic curve algorithms (ECDSA) to protect private keys. A sufficiently powerful quantum computer could deduce a private key from its public key.
- Mining: This is based on the SHA-256 algorithm, which secures the consensus process. A quantum attack could, in theory, compromise the proof-of-work mechanism.
Understanding Quantum Computing’s Attack Priorities
While quantum computing is often presented as a threat to Bitcoin, not all parts of the network are equally vulnerable. Theoretical attacks would be prioritized based on two main factors: ease of execution and potential reward. This creates two categories of attacks:
1. Attacks on Wallets
Bitcoin wallets, secured by elliptic curve algorithms, would be the initial targets due to the relative vulnerability of their public keys, especially those already exposed on the blockchain. Two attack scenarios stand out:
-
Short-term attacks: These occur during the interval between sending a transaction and its inclusion in a block (approximately 10 minutes). A quantum computer could intercept the exposed public key and derive the corresponding private key to redirect funds by creating a transaction with higher fees.
-
Long-term attacks: These focus on old wallets whose public keys are permanently exposed. Wallets associated with Satoshi Nakamoto, for example, are especially vulnerable because they were created before the practice of using hashes to mask public keys.
We can infer a priority order for how such attacks might occur based on urgency and importance.
 Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)
Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)2. Attacks on Mining
Targeting the SHA-256 algorithm, which secures the mining process, would be the next objective. However, this is far more complex and requires a level of quantum computational power that is currently non-existent and far from realization. A successful attack would allow for the recalculation of all possible hashes to dominate the consensus process and potentially "mine" it instantly.
 Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin Attacks
Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin AttacksRecently, Narcelio asked me about a statement I made on Tubacast:
https://x.com/eddieoz/status/1868371296683511969
If an attack became a reality before Bitcoin was prepared, it would be necessary to define the last block prior to the attack and proceed from there using a new hashing algorithm. The solution would resemble the response to the infamous 2013 bug. It’s a fact that this would cause market panic, and Bitcoin's price would drop significantly, creating a potential opportunity for the well-informed.
Preferably, if developers could anticipate the threat and had time to work on a solution and build consensus before an attack, they would simply decide on a future block for the fork, which would then adopt the new algorithm. It might even rehash previous blocks (reaching consensus on them) to avoid potential reorganization through the re-mining of blocks using the old hash. (I often use the term "shielding" old transactions).
How Can Users Protect Themselves?
While quantum computing is still far from being a practical threat, some simple measures can already protect users against hypothetical scenarios:
- Avoid using exposed public keys: Ensure funds sent to old wallets are transferred to new ones that use public key hashes. This reduces the risk of long-term attacks.
- Use modern wallets: Opt for wallets compatible with SegWit or Taproot, which implement better security practices.
- Monitor security updates: Stay informed about updates from the Bitcoin community, such as the implementation of BIP-360, which will introduce quantum-resistant addresses.
- Do not reuse addresses: Every transaction should be associated with a new address to minimize the risk of repeated exposure of the same public key.
- Adopt secure backup practices: Create offline backups of private keys and seeds in secure locations, protected from unauthorized access.
BIP-360 and Bitcoin’s Preparation for the Future
Even though quantum computing is still beyond practical reach, the Bitcoin community is not standing still. A concrete example is BIP-360, a proposal that establishes the technical framework to make wallets resistant to quantum attacks.
BIP-360 addresses three main pillars:
- Introduction of quantum-resistant addresses: A new address format starting with "BC1R" will be used. These addresses will be compatible with post-quantum algorithms, ensuring that stored funds are protected from future attacks.
- Compatibility with the current ecosystem: The proposal allows users to transfer funds from old addresses to new ones without requiring drastic changes to the network infrastructure.
- Flexibility for future updates: BIP-360 does not limit the choice of specific algorithms. Instead, it serves as a foundation for implementing new post-quantum algorithms as technology evolves.
This proposal demonstrates how Bitcoin can adapt to emerging threats without compromising its decentralized structure.
Post-Quantum Algorithms: The Future of Bitcoin Cryptography
The community is exploring various algorithms to protect Bitcoin from quantum attacks. Among the most discussed are:
- Falcon: A solution combining smaller public keys with compact digital signatures. Although it has been tested in limited scenarios, it still faces scalability and performance challenges.
- Sphincs: Hash-based, this algorithm is renowned for its resilience, but its signatures can be extremely large, making it less efficient for networks like Bitcoin’s blockchain.
- Lamport: Created in 1977, it’s considered one of the earliest post-quantum security solutions. Despite its reliability, its gigantic public keys (16,000 bytes) make it impractical and costly for Bitcoin.
Two technologies show great promise and are well-regarded by the community:
- Lattice-Based Cryptography: Considered one of the most promising, it uses complex mathematical structures to create systems nearly immune to quantum computing. Its implementation is still in its early stages, but the community is optimistic.
- Supersingular Elliptic Curve Isogeny: These are very recent digital signature algorithms and require extensive study and testing before being ready for practical market use.
The final choice of algorithm will depend on factors such as efficiency, cost, and integration capability with the current system. Additionally, it is preferable that these algorithms are standardized before implementation, a process that may take up to 10 years.
Why Quantum Computing Is Far from Being a Threat
The alarmist narrative about quantum computing overlooks the technical and practical challenges that still need to be overcome. Among them:
- Insufficient number of qubits: Current quantum computers have only a few hundred qubits, whereas successful attacks would require millions.
- High error rate: Quantum stability remains a barrier to reliable large-scale operations.
- High costs: Building and operating large-scale quantum computers requires massive investments, limiting their use to scientific or specific applications.
Moreover, even if quantum computers make significant advancements, Bitcoin is already adapting to ensure its infrastructure is prepared to respond.
Conclusion: Bitcoin’s Secure Future
Despite advancements in quantum computing, the reality is that Bitcoin is far from being threatened. Its security is ensured not only by its robust architecture but also by the community’s constant efforts to anticipate and mitigate challenges.
The implementation of BIP-360 and the pursuit of post-quantum algorithms demonstrate that Bitcoin is not only resilient but also proactive. By adopting practical measures, such as using modern wallets and migrating to quantum-resistant addresses, users can further protect themselves against potential threats.
Bitcoin’s future is not at risk—it is being carefully shaped to withstand any emerging technology, including quantum computing.
-
 @ 5d4b6c8d:8a1c1ee3
2025-01-27 20:54:45
@ 5d4b6c8d:8a1c1ee3
2025-01-27 20:54:45Today marks one month since I took over managing the ~econ territory.
I've been very happy with our post quality and quantity: ~econ ranked 7th in number of posts, 5th in number of comments, 4th in stacking and spending (how are those different?).
The top 3 posts by zaprank were
- The Pleb Economist #2: Politics is Provably Hard by @SimpleStacker
- MONEY CLASS OF THE DAY: Wealth, Bitcoin, and A Monetary System Enriching Us by @denlillaapan
- Is Bitcoin telling us something about the broader market/economy? by @grayruby
Revenue
Revenue has been up, since reducing the posting fee. That means we could reduce it further. If there's no objection, I'll lower it to 54 sats.
Over the past month, ~econ made about 75k. The previous month ~econ brought in about 47k.
Owner's Pledge
Since we are running a profit, I'd like to consider some options for making good on the pledge to do right by those who helped support ~econ before it was profitable. A few options come to mind, but I'm open to others: 1. Treat those donations as profit shares: i.e. if you donated 10k, I'll give you 10/450 of the territory profit at the end of the year 2. Fund some sort of contest with them 3. Simple refund taken out of end of year profits 4. Donate the sats to a charity of your choice, on your behalf
Feedback
Let me know what you thought of the past month in ~econ.
Are there any particular changes you'd like to see going forward?
Is there anything I should be pushing k00b and ek for?
Keep stackin', stackers.
originally posted at https://stacker.news/items/866986
-
 @ c7e300eb:e94ebe38
2025-01-27 17:44:53
@ c7e300eb:e94ebe38
2025-01-27 17:44:53How many people have you successfully orange-pilled? What's your success rate? I'm going to guess it's way worse than you wish it was. I'd like to share 3 different stories from people I've talked to about Bitcoin and the varying degrees of "success" in each of them. Maybe you can relate to one (or all) of them...\ \ Bob (Person 1)
This first person we will call Bob. Ironically, Bob was stacking sats long before I ever took an interest in Bitcoin. He's a pretty financially savvy person, loves history, and is a bit of a prepper. Bob views Bitcoin as a nice-to-have and certainly understands the NGU math that comes with a fixed supply asset and money printing; unfortunately, that's largely where his interest ends. He's not stacking anymore and doesn't seem moved to ever resume, despite his understanding of how fragile our financial system is. If/when hyper-bitcoinization happens, he's "got enough". \ \ I've been able to get him out of shitcoins entirely and he seems content hodling, which is a pretty big win in my book. At the same time, it can be disheartening to see someone sitting near the edge of the rabbit hole and parking the bus right there...\ \ Alice (Person 2)
Person 2 will be Alice. This person is much more motivated by social topics than economical ones, which always made me approach our Bitcoin conversations in a unique way. She inspired me to see through a different lens than I was normally comfortable with, which ultimately expanded my own interest in how Bitcoin, both as a money and a network, could positively impact people all over the world.
Alice, in my observation, grew to appreciate the way I saw Bitcoin. She understood the Cantillon Effect, fractional reserve lending, why censorship resistance is important, etc. Hell, she even managed to (sorta) orange-pill someone else! She was effectively as orange-pilled as one could get without actually owning sats. \ \ Through our many talks about money and personal finance, she greatly leveled up her game compared to when we first met. She now uses budgeting software, has a high-yield savings account, an investment account, and is building credit. For some reason though, she never got the desire to start stacking sats...
\ Mary (Person 3)
Mary is the least financially-literate of our 3 persons of interest. Just not wired that way at all. She's never had dedicated savings or tracked her spending. Getting her to set up direct deposit at her place of employment was a daunting task. \ \ Saving and investing have never been part of her vocabulary either. A few days ago, however, she asked if I could help her begin this process. For someone taking that first big step, I felt like stacking sats would be a bit daunting. We talked about automatically sending X% to a high-yield savings account. When we got to "investing" though, something interesting happened: she said she would rather start buying Bitcoin because "nobody can take it from me, right?" This was fascinating to me, as I had never heard a normal person express concerns about a bank actually not having their money (despite how many people I have told this to, including Alice and Bob). We agreed on the same X% into Bitcoin as into her HYS. Starting with her next paycheck, Mary will officially begin stacking sats.
If I had to make a chart of all the people in my life and rate how likely they'd be to adopt Bitcoin, Mary would be near the bottom. After so many failed attempts, I still don't quite understand how this specific case ended up being my first success in getting someone to enter the rabbit hole. We'll see how far she ends up going, but I am committed to helping her with every step.
Conclusion
So, what have I taken away from these 3 example cases? For starters, I learned that orange-pilling can take more than one form: Bob got rid of shitcoins and committed to hodling, but won't stack any more; Alice groks the problems Bitcoin will fix, but won't stack at all; Mary hardly even knows about Bitcoin, yet she understands the importance of having control over her own savings enough to take the leap. Each one of these examples has helped me refine my approach to orange-pilling, while also teaching me that it is no science. It's as much a choice and a willingness on their end as it is how you approach the conversation. You cannot force someone to take the pill or jump down the hole. Just stay humble and keep stacking sats. Cheers!
-
 @ 5d4b6c8d:8a1c1ee3
2025-01-27 15:30:28
@ 5d4b6c8d:8a1c1ee3
2025-01-27 15:30:28Here are today's picks using my proprietary betting strategy at Freebitcoin. For details about what Risk Balanced Odds Arbitrage is and why it works see https://stacker.news/items/342765/r/Undisciplined.
For a hypothetical 1k-ish wager on each match, distribute your sats as follows:
| Outcome 1 | Outcome 2 | Outcome 3 | Bet 1 | Bet 2 | Bet 3 | |--------------|-------------|--------------|-------|-------|-------| | Roma| Napoli| Draw | 323| 407| 289| | Juventus| Empoli| Draw | 727| 100| 208| | AC Milan| Inter Milan| Draw | 244| 489| 278| | Osasuna| Real Sociedad| Draw | 308| 400| 323| | Getafe| Sevilla| Draw | 400| 293| 333| | Espanyol| Real Madrid| Draw | 105| 733| 190| | Barcelona| Alaves| Draw | 818| 77| 145| | Atletico Madrid| Mallorca| Draw | 714| 100| 217| | Union Berlin| RB Leipzig| Draw | 313| 417| 278| | Heidenheim| Dortmund| Draw | 244| 542| 250| | FC Bayern| Holstein Kiel| Draw | 941| 20| 53|
The most recently completed two rounds of RBOA earned 100k on 102k bet, so this was a slightly down week. One note about that, though, is that I didn't get those in as early as normal.
I still haven't precisely identified where the threshold is, but it might be worth skipping any of these with a "time weight multiplier" lower than 90.
A note of caution about Freebitcoin: they recorded the wrong outcome for last week's Bills vs Ravens game and as of yet have not corrected it. I recall one other instance of something similar happening, so proceed with caution.
This RBOA strategy is largely immune from that problem, but be aware of it when just betting on one outcome.
originally posted at https://stacker.news/items/866672
-
 @ 57d1a264:69f1fee1
2025-01-28 02:36:34
@ 57d1a264:69f1fee1
2025-01-28 02:36:34About the role In this role, you will work on the product design of umbrelOS, some of our umbrelOS apps, and the umbrel.com website.
What are you looking for in candidates? Talent, passion, genuine love for your craft, and the desire to do meaningful work. What we’re not looking for: credentials and degrees. When you really love what you do, work feels like play. And when work feels like play, you become the best at it. That’s what we’re looking for.
We hope you: - Like to spend your days staring at artboards in Figma - Are obsessed with creating delightful micro-interactions and animations - Are willing to throw away ideas if they're not great, and optimistic enough to keep hunting for new ones - Care about the details, maybe a bit too much (a pixel off ruins your sleep) - Are excited to collaborate with everyone on the team: engineers, customer facing folks, etc—you believe inspiration can come from anywhere - Have good judgement of when to ship - Like to level up your design skills continually - Put yourselves in the shoes of our users to craft a great experience - Enjoy being a generalist and are not tied down to a specific design, trend, or tools
Benefits - 🚑 Health insurance - 💻 New work equipment - 🌎 Work from anywhere in the world - 💆♀️ Complete autonomy at work - 📚 Learning and development stipend - 🏝 Minimum 2-weeks of paid time off - ❤️ Most importantly — doing meaningful work that can change the world
Apply at https://app.withrapha.com/job/692
originally posted at https://stacker.news/items/867248
-
 @ da0b9bc3:4e30a4a9
2025-01-27 14:32:50
@ da0b9bc3:4e30a4a9
2025-01-27 14:32:50Hello Stackers!
It's Monday so we're back doing "Meta Music Mondays" 😉.
From before the territory existed there was just one post a week in a ~meta take over. Now each month we have a different theme and bring music from that theme.
This month it's New Year New Artists! Bringing you small time artists with great music. Artists without some huge record label or massive following. Let's find those hidden little gems.
This week, may I present to you, Belle Sisoski and her cover of "Legends Never Die"
https://youtu.be/VMIL1YbUQrI?si=kR2YLib5x3qLEn8A
originally posted at https://stacker.news/items/866591
-
 @ 54286b98:3debc100
2025-01-27 14:30:18
@ 54286b98:3debc100
2025-01-27 14:30:18Looking back on that time, I now see clearly that my faith--my only real faith--that which apart from my animal instincts gave impulse to my life --was a belief in perfecting myself. But in what this perfecting consisted and what its object was, I could not have said. I tried to perfect myself mentally--I studied everything I could, anything life threw in my way; I tried to perfect my will, I drew up rules I tried to follow; I perfected myself physically, cultivating my strength and agility by all sorts of exercises, and accustoming myself to endurance and patience by all kinds of privations. And all this I considered to be the pursuit of perfection. — Leo Tolstoy, A Confession
It seems to be a good trait, perfecting sounds and looks good. Why would you not want to improve yourself? You should!
In his book A Confession, Tolstoy starts the first chapter by laying down one of the main Christian principles: we cannot do enough work to achieve salvation, nor can we buy our way into it.
We may strive to be perfect and solve things in our own strength, but we may fail miserably. Christ bought our way in, and the only way to claim that ticket is by surrendering our strength and working in His. Striving to be perfect in our own strength is not different from living by the law (this refers to the Law given to the Jewish people versus living by faith alone).
10 For all who rely on works of the law are under a curse; for it is written, “Cursed be everyone who does not abide by all things written in the Book of the Law, and do them.” 11 Now it is evident that no one is justified before God by the law, for “The righteous shall live by faith.— Galatians 3: 10-11
Trying to be good and do good works is an excellent attitude, but we can only achieve this by walking in His footsteps. Moreover, I think and believe that the inner call to be perfect may exist within us simply to reveal our incapability of such an accomplishment.
For by works of the law no human being will be justified in his sight, since through the law comes knowledge of sin.— Romans 3:20
Of course, faith alone is not proof either, but it’s a start. If we are given the gift of believing in Christ, what we do with that belief is shown through the fruits of the works we do.
14 What good is it, my brothers, if someone says he has faith but does not have works? Can that faith save him? 15 If a brother or sister is poorly clothed and lacking in daily food, 16 and one of you says to them, “Go in peace, be warmed and filled,” without giving them the things needed for the body, what good[a] is that? 17 So also faith by itself, if it does not have works, is dead.
18 But someone will say, “You have faith and I have works.” Show me your faith apart from your works, and I will show you my faith by my works. 19 You believe that God is one; you do well. Even the demons believe—and shudder! 20 Do you want to be shown, you foolish person, that faith apart from works is useless? 21 Was not Abraham our father justified by works when he offered up his son Isaac on the altar? 22 You see that faith was active along with his works, and faith was completed by his works; 23 and the Scripture was fulfilled that says, “Abraham believed God, and it was counted to him as righteousness”—and he was called a friend of God. 24 You see that a person is justified by works and not by faith alone. James 2:14-24
Until the next one,
J
-
 @ 0d97beae:c5274a14
2025-01-11 16:52:08
@ 0d97beae:c5274a14
2025-01-11 16:52:08This article hopes to complement the article by Lyn Alden on YouTube: https://www.youtube.com/watch?v=jk_HWmmwiAs
The reason why we have broken money
Before the invention of key technologies such as the printing press and electronic communications, even such as those as early as morse code transmitters, gold had won the competition for best medium of money around the world.
In fact, it was not just gold by itself that became money, rulers and world leaders developed coins in order to help the economy grow. Gold nuggets were not as easy to transact with as coins with specific imprints and denominated sizes.
However, these modern technologies created massive efficiencies that allowed us to communicate and perform services more efficiently and much faster, yet the medium of money could not benefit from these advancements. Gold was heavy, slow and expensive to move globally, even though requesting and performing services globally did not have this limitation anymore.
Banks took initiative and created derivatives of gold: paper and electronic money; these new currencies allowed the economy to continue to grow and evolve, but it was not without its dark side. Today, no currency is denominated in gold at all, money is backed by nothing and its inherent value, the paper it is printed on, is worthless too.
Banks and governments eventually transitioned from a money derivative to a system of debt that could be co-opted and controlled for political and personal reasons. Our money today is broken and is the cause of more expensive, poorer quality goods in the economy, a larger and ever growing wealth gap, and many of the follow-on problems that have come with it.
Bitcoin overcomes the "transfer of hard money" problem
Just like gold coins were created by man, Bitcoin too is a technology created by man. Bitcoin, however is a much more profound invention, possibly more of a discovery than an invention in fact. Bitcoin has proven to be unbreakable, incorruptible and has upheld its ability to keep its units scarce, inalienable and counterfeit proof through the nature of its own design.
Since Bitcoin is a digital technology, it can be transferred across international borders almost as quickly as information itself. It therefore severely reduces the need for a derivative to be used to represent money to facilitate digital trade. This means that as the currency we use today continues to fare poorly for many people, bitcoin will continue to stand out as hard money, that just so happens to work as well, functionally, along side it.
Bitcoin will also always be available to anyone who wishes to earn it directly; even China is unable to restrict its citizens from accessing it. The dollar has traditionally become the currency for people who discover that their local currency is unsustainable. Even when the dollar has become illegal to use, it is simply used privately and unofficially. However, because bitcoin does not require you to trade it at a bank in order to use it across borders and across the web, Bitcoin will continue to be a viable escape hatch until we one day hit some critical mass where the world has simply adopted Bitcoin globally and everyone else must adopt it to survive.
Bitcoin has not yet proven that it can support the world at scale. However it can only be tested through real adoption, and just as gold coins were developed to help gold scale, tools will be developed to help overcome problems as they arise; ideally without the need for another derivative, but if necessary, hopefully with one that is more neutral and less corruptible than the derivatives used to represent gold.
Bitcoin blurs the line between commodity and technology
Bitcoin is a technology, it is a tool that requires human involvement to function, however it surprisingly does not allow for any concentration of power. Anyone can help to facilitate Bitcoin's operations, but no one can take control of its behaviour, its reach, or its prioritisation, as it operates autonomously based on a pre-determined, neutral set of rules.
At the same time, its built-in incentive mechanism ensures that people do not have to operate bitcoin out of the good of their heart. Even though the system cannot be co-opted holistically, It will not stop operating while there are people motivated to trade their time and resources to keep it running and earn from others' transaction fees. Although it requires humans to operate it, it remains both neutral and sustainable.
Never before have we developed or discovered a technology that could not be co-opted and used by one person or faction against another. Due to this nature, Bitcoin's units are often described as a commodity; they cannot be usurped or virtually cloned, and they cannot be affected by political biases.
The dangers of derivatives
A derivative is something created, designed or developed to represent another thing in order to solve a particular complication or problem. For example, paper and electronic money was once a derivative of gold.
In the case of Bitcoin, if you cannot link your units of bitcoin to an "address" that you personally hold a cryptographically secure key to, then you very likely have a derivative of bitcoin, not bitcoin itself. If you buy bitcoin on an online exchange and do not withdraw the bitcoin to a wallet that you control, then you legally own an electronic derivative of bitcoin.
Bitcoin is a new technology. It will have a learning curve and it will take time for humanity to learn how to comprehend, authenticate and take control of bitcoin collectively. Having said that, many people all over the world are already using and relying on Bitcoin natively. For many, it will require for people to find the need or a desire for a neutral money like bitcoin, and to have been burned by derivatives of it, before they start to understand the difference between the two. Eventually, it will become an essential part of what we regard as common sense.
Learn for yourself
If you wish to learn more about how to handle bitcoin and avoid derivatives, you can start by searching online for tutorials about "Bitcoin self custody".
There are many options available, some more practical for you, and some more practical for others. Don't spend too much time trying to find the perfect solution; practice and learn. You may make mistakes along the way, so be careful not to experiment with large amounts of your bitcoin as you explore new ideas and technologies along the way. This is similar to learning anything, like riding a bicycle; you are sure to fall a few times, scuff the frame, so don't buy a high performance racing bike while you're still learning to balance.
-
 @ da18e986:3a0d9851
2025-01-22 23:49:06
@ da18e986:3a0d9851
2025-01-22 23:49:06Since DVMs were introduced to Nostr in July 2023, we've witnessed remarkable growth - over 2.5 million DVM events (Kinds 5000-7000) and counting. Last fall, when Primal added custom feeds (Kind 5300 DVMs), we saw a 10x surge in DVM activity. To handle this growth, I've spent the last few months completely rewriting DVMDash.
The first version of DVMDash, still live at https://dvmdash.live, unfortunately uses full database table scans to compute the metrics. The code was simpler, but the computation ran on the database. This meant the only way to scale the system was to upgrade the database. Using managed databases (like AWS, Azure, Digital Ocean) beyond the lower tiers gets expensive quickly.
The other problem with the first version: it computes metrics globally (well... as global as you can get; there's no true global with Nostr). Global or all-time metrics aren't sustainable with a system that plans to analyze billions of events in the future (a long term goal for DVMDash). Especially metrics like the number of unique DVMs, Kinds, and Users. I spent more time than I care to admit on possible designs, and have settled on these design principles for now:
- Precise accurate metrics will only be computed for the last 30 days of DVM activity.
- At the turn of a new month, we will compute a snapshot of the last month's activity, and a snapshot per DVM and per Kind, and store them in a historical table. This way we can see what any given month in the past looked like from a bird's eye view with metrics like number of job requests, job results, a count of unique DVMs, kinds and users, which DVMs ran jobs on which kinds, etc. The monthly data will all be aggregate.
The goal of the new redesign is to support processing millions of DVM events an hour. Therefore we need to ensure we can horizontally scale the processing as the traffic increases. Horizontal scaling was the primary goal of this new redesign, and early results indicate it's working.
The new architecture for DVMDash uses a redis queue to hold events collected from relays. Then batches of events are pulled off of the queue by dvm event analyzers to compute metrics. Duplicating these analyzers is one way DVMDash can horizontally scale.
To see if increasing the number of dvm event analyzers improves speed, I ran a performance test on Digital Ocean using real DVM events collected from Jan. 1st 2024 to Jan 9th 2025, which includes more than 2.4 million events. The only difference between each run is the number of DVM event analyzers ranging from 1 to 6.

The first graph shows that adding more event analyzers has a significant speed improvement. With only one analyzer it took nearly an hour to process the 2.4 million events. With every added analyzer, there was a noticeable speedup, as can be seen in the graph. With n=6 analyzers, we were able to process all 2.4 million events in about 10 minutes.
When we look at the rate of processing shown in the second graph, we can see that we get up to 300k dvm events processed per minute when n=6, compared to just ~50k events processed when n=1.

While I did test beyond 6 analyzers, I found the sweet spot for the current infrastructure setup to be around 6 analyzers. This provides plenty of headroom above our current processing needs, which typically see less than a million events per month. Even at a million DVM events per day, DVMDash should be able to handle it with n=2 analyzers running. The most important takeaway is that DVMDash can now horizontally scale by adding more analyzers as DVM activity grows in the future.
The code to run these performance tests, either locally or on Digital Ocean (you'd need an API key), is in the dvmdash repo, so anyone can replicate these tests. There's a lot of nuance to scaling that I'm leaving out of this short article, and you can't get away from having to adjust database capacity (especially number of connections). The code for this test can be found in
experiments/test_batch_processing_scaling.pyand the code to produce the graphs is inexperiments/graph_batch_processing_scaling_data.py. For now this is still in thefull-redesignbranch, soon it will be merged intomain.The live version of dvmdash doesn't have these performance updates yet, a complete redesign is coming soon, including a new UI.
I've had my head down working on this rewrite, and couldn't move on to add new features until this was done. Thank you to the folks who made github issues, I'll be getting to those soon.
DVMDash is open source, please drop by and give us a feature request, bug report, pull request or star. Thanks to OpenSats for funding this work.
Github: https://github.com/dtdannen/dvmdash
Shoutout to nostr:npub12xeqxplp5ut4h92s3vxthrdv30j0czxz9a8tef8cfg2cs59r85gqnzrk5w for helping me think through database design choices.
-
 @ a012dc82:6458a70d
2025-01-27 12:51:47
@ a012dc82:6458a70d
2025-01-27 12:51:47In the contemporary financial world, Cathie Wood, the founder of ARK Invest, stands out for her innovative investment approaches. Recently, Wood has focused on Bitcoin (BTC), highlighting its potential as a hedge against both inflationary and deflationary economic conditions. This article delves into Wood's perspective, exploring Bitcoin's evolving role in the global financial landscape. We examine its multifaceted nature, not just as a digital currency, but as a strategic asset capable of navigating the complex dynamics of the modern economy. Wood's insights offer a nuanced understanding of Bitcoin's potential in offering stability amidst economic uncertainties.
Table Of Content
-
Bitcoin's Hedge Potential
-
Decentralization: A Key Advantage
-
The Banking Crisis and Bitcoin
-
Bitcoin vs. Gold
-
Institutional Involvement
-
Conclusion
-
FAQs
Bitcoin's Hedge Potential
Cathie Wood's perspective on Bitcoin transcends its usual perception as a mere digital currency. She champions it as a dynamic tool against economic fluctuations, a quality rarely matched by traditional assets. In an era marked by economic instability, Bitcoin stands as a beacon of potential stability. This is particularly notable in its capacity to act as a hedge during inflationary periods, where fiat currencies lose value, and deflationary periods, characterized by increased money value but decreased economic activity. This dual capability positions Bitcoin as a significant asset in diversified portfolios, resonating with Wood's innovative investment philosophy.
Decentralization: A Key Advantage
For Wood, Bitcoin's decentralization is a critical advantage. This aspect sets it apart from traditional banking systems, which often grapple with issues of transparency and central control. In Bitcoin's ecosystem, there is a clear absence of counterparty risk, thanks to its decentralized ledger and visible transactions. This transparency assures investors of a level of security and autonomy not found in conventional financial systems. In Wood's view, this decentralization is not just a technical feature but a foundational aspect that provides Bitcoin with a resilience and reliability, crucial in a world where financial systems are increasingly interconnected and vulnerable.
The Banking Crisis and Bitcoin
Reflecting on recent financial upheavals, such as the U.S. regional bank crisis and the FTX collapse, Wood sees these events as vindications of Bitcoin's stability and resilience. These crises underscored the inherent risks of centralized financial systems, revealing their fragility under stress. In contrast, Bitcoin demonstrated an impressive resilience, with its value surging during these tumultuous times. This reaction not only highlights Bitcoin's potential as a safe haven but also its capacity to serve as a barometer for the health of the broader financial system.
Bitcoin vs. Gold
While gold has traditionally been the go-to asset for hedge investments, Wood argues that Bitcoin has a distinct edge over it. Her preference for Bitcoin stems from its novelty and the increasing interest from younger investors and institutional players. Unlike gold, whose market and demand patterns are well-established, Bitcoin represents an emerging asset class with untapped potential. Wood believes that Bitcoin's journey is just beginning, and its full potential as a hedge asset is yet to be realized, making it a more attractive option for forward-looking investors.
Institutional Involvement
Wood's belief in Bitcoin's future is mirrored in ARK Invest's substantial investments in cryptocurrency-related ventures. These investments are not mere speculative plays; they represent a deep conviction in the long-term value of Bitcoin. ARK's pursuit of a spot Bitcoin ETF is a significant move, indicating a belief in the cryptocurrency's viability as a mainstream investment asset. This institutional backing by a leading investment firm not only legitimizes Bitcoin's role in the financial markets but also paves the way for more widespread adoption among traditional investors.
Conclusion
Cathie Wood's endorsement of Bitcoin is a compelling narrative in the evolving story of this digital asset. Her insights provide a valuable perspective on Bitcoin's role as a hedge against both inflation and deflation, highlighting its potential in the current economic climate. As we navigate through uncertain financial times, Wood's views offer a guidepost for investors looking to diversify and stabilize their portfolios with innovative assets like Bitcoin.
FAQs
What is Cathie Wood's view on Bitcoin? Cathie Wood sees Bitcoin as a viable hedge against both inflation and deflation, highlighting its decentralized nature and resilience.
Why does Wood prefer Bitcoin over traditional banking systems? Wood values Bitcoin's transparency and lack of counterparty risk, contrasting it with the opacity of traditional banking systems.
How did the banking crisis impact Bitcoin's value? The U.S. regional bank crisis and the FTX collapse showed Bitcoin's stability, with its value increasing during these times.
Why does Wood favor Bitcoin over gold? Wood believes Bitcoin has more potential for growth and is more appealing to younger investors and institutions compared to gold.
What is ARK Invest's involvement in Bitcoin? ARK Invest holds significant stakes in cryptocurrency ventures and is pursuing a spot Bitcoin ETF, reflecting a strong belief in Bitcoin's future.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 3b70689a:c1e351eb
2025-01-22 23:47:36
@ 3b70689a:c1e351eb
2025-01-22 23:47:36来自西班牙的公司 Liberux 最近推出了他们的新手机 Liberux NEXX 众筹计划. 根据目前主页上的介绍, 这款设备将会搭载基于 Debian 13 ARM 构建的 LiberuxOS 操作系统, 并且还提供一个受限的(jailed)的 Android 子系统.

Liberux 的 Fediverse 主页
Liberux 硬件开发工程师 Carlos Rodríguez 的 Fediverse 主页
Carlos Rodríguez 说, 目前网站上的 NEXX 是最初版本, 目前仍然在努力制造第一台原型机, 并且所有的硬件和软件设计都将免费(公开).
WOW, I think our little secret has been revealed, we hope that in a short time you will be able to see the first functional prototypes. We are working very hard on it, by the way, all our designs, both hardware and software, will be free. At the moment the web is a first version, some things will be modified.
硬件参数
-
CPU: 瑞芯微 RK3588s (八核心, 8nm, 2.4Ghz, 2022Q1)
-
GPU: ARM Mali-G610 (4 核心, 2021Q2)
- 存储: 32GB LPDDR4x RAM, 256GB eMMC ROM
- 电池: 5300mAh (可拆卸)
- 接口: 3.5mm 耳机 * 1, USB-C 3.1 * 2
- 扩展: microSD 插槽 (2TB Max)
- 屏幕: 6.34 吋, OLED, 2400*1080
- 相机: 后置 32MP, 前置 13MP
- 通讯: 高通骁龙 X62 基带 (2021Q1), 海华 AW-CM256SM 无线网卡 (Wi-Fi 5, 蓝牙 5.0)
- 传感器: 昇佳 STK3311-X 环境光传感器, 美新 MMC3630KJ 三轴磁传感器, 应美盛 ICM-42670-P 加速度计/陀螺仪
- 其他: 内置 DAC 和功放芯片 (瑞昱 ALC5640-VB-CG, 艾为 AW8737SCSR)
其他特点
设备目前公布的外观设计均是渲染效果, 最终交付的设备很可能会与这些渲染图片有很大出入. 但仍然可以通过这些效果图理解 Liberux 的最初意图.
- 摄像头 & 麦克风, 蓝牙 & WLAN, 数据网络功能模块的物理开关(位于顶部).

- 后置指纹解锁, 无摄像模组凸起.
- 左上角挖孔前置摄像头.

- 电源键位于侧边右下角.
其他报道
- Liberux Nexx: New Linux smartphone with 32GB RAM, 2TB storage, 5G and more - NotebookCheck.net News
- Смартфон Liberux Nexx получил ОС Linux и поддержку 2 ТБ памяти - 4PDA (讨论)
- Smartfon z Linuksem? Oto Liberux NEXX. Ekran OLED, 32 GB RAM i system oparty na Debianie. Ciekawy model, choć nie bez wad | PurePC.pl (讨论)
- LINux on MOBile: "The Liberux Nexx (https://libe…" - Fosstodon (Fediverse, 讨论, 工程师回复)
-
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ 37fe9853:bcd1b039
2025-01-11 15:04:40
@ 37fe9853:bcd1b039
2025-01-11 15:04:40yoyoaa
-
 @ b8851a06:9b120ba1
2025-01-27 11:58:53
@ b8851a06:9b120ba1
2025-01-27 11:58:53Trump's Blueprint for Gaza: The New Nakba
Trump’s offhand suggestion to “clean out” 1.5 million Palestinians from Gaza isn’t just reckless—it’s a thinly veiled blueprint for ethnic cleansing. The proposed forced displacement of millions isn't new; it’s the 21st-century sequel to the Nakba, designed to erase Palestine from the map.
Gaza: The Systematic Machinery of Destruction
The assault on Gaza isn’t chaos—it’s coordinated demolition:
- 47,306+ killed – lives extinguished with impunity.
- 111,483 injured – survivors burdened with physical and psychological scars.
- 92% of homes destroyed – families displaced, memories shattered.
- 60% of infrastructure dismantled – society intentionally crippled.
This is more than war—it’s annihilation by design.
A Second Nakba in Motion
The original Nakba (1948) was the template:
- 6 million refugees still barred from returning home.
- Generations of children growing up stateless, inheriting loss.
- Cultural heritage erased, lands stolen, and identities fractured.
Trump’s “solution” carries this legacy forward, pushing millions toward another endless exile.
The Humanitarian Collapse
If enacted, the mass displacement would trigger a humanitarian apocalypse across the region:
- Healthcare systems overwhelmed in neighboring nations.
- Schools collapsing under the weight of refugee students.
- Economic and social infrastructures stretched beyond capacity.
This isn’t just a Palestinian crisis—it’s a global one.
A Calculated Plan for Erasure
Make no mistake: the destruction of Gaza is deliberate. Israeli Finance Minister Avi Dichter’s chilling declaration of a "rolling Gaza Nakba" lays bare the intent: erase Gaza and its people from existence. The steps are cold, calculated, and systematic:
- Starvation as a weapon of war.
- Targeting hospitals to eliminate healthcare.
- Destroying water supplies to force displacement.
This isn’t collateral damage—it’s genocide.
Generational Wounds That Won’t Heal
The impact of this erasure will reverberate for centuries:
- Children growing up with inherited trauma.
- A culture erased piece by piece.
- Future generations left stateless, voiceless, and forgotten.
Every demolished building and every child killed are steps toward creating a permanent refugee underclass.
Silence is Complicity
The global silence is deafening. Trump’s “solution” isn’t a spontaneous idea—it’s the culmination of decades of dehumanization and demographic engineering. And every moment the world stays silent, the machinery of genocide moves forward.
Resistance is Survival
The choice is clear: submit to tyranny or resist. Every truth told, every act of defiance, every refusal to look away chips away at their plans. They want us silent. They need us indifferent.
But we’re not sheep—we’re the descendants of those who refused to kneel. - Share their crimes. - Expose their lies. - Refuse their narrative.
Because the battle for Palestine isn’t just about land—it’s about dignity, existence, and the refusal to be erased.
-
 @ 9dd283b1:cf9b6beb
2025-01-27 11:22:04
@ 9dd283b1:cf9b6beb
2025-01-27 11:22:04Everybody is freaking out about DeepSeek—markets crashed, people are saying Nvidia is doomed, and stuff like that. 😄 So I decided to play with it a bit, as I use ChatGPT daily for my work. Here are some thoughts about it:
DeepSeek is not that smart I know they provided some amazing results and seem to be beating the O1 model, but for personal use, it’s not that smart. I use ChatGPT 90% of the time to write emails, and DeepSeek failed to support me. It wasn’t able to write what I wanted, couldn’t properly reply to emails, and kept mixing up who the sender and recipient were. Completely unusable for me at this point.
DeepSeek is very censored Nothing about China seems to go through. It looks like the algorithm tries to reply as it types the answer but then terminates the response mid-sentence, providing a generic reply like: "Sorry, that's beyond my current scope. Let’s talk about something else."
I get this result whether I ask about obvious topics like Tiananmen Square or less obvious ones like Ai Weiwei’s imprisonment and life.
So not sure about the hype, but I've already closed and forgot about it=)
originally posted at https://stacker.news/items/865930
-
 @ 62033ff8:e4471203
2025-01-11 15:00:24
@ 62033ff8:e4471203
2025-01-11 15:00:24收录的内容中 kind=1的部分,实话说 质量不高。 所以我增加了kind=30023 长文的article,但是更新的太少,多个relays 的服务器也没有多少长文。
所有搜索nostr如果需要产生价值,需要有高质量的文章和新闻。 而且现在有很多机器人的文章充满着浪费空间的作用,其他作用都用不上。
https://www.duozhutuan.com 目前放的是给搜索引擎提供搜索的原材料。没有做UI给人类浏览。所以看上去是粗糙的。 我并没有打算去做一个发microblog的 web客户端,那类的客户端太多了。
我觉得nostr社区需要解决的还是应用。如果仅仅是microblog 感觉有点够呛
幸运的是npub.pro 建站这样的,我觉得有点意思。
yakihonne 智能widget 也有意思
我做的TaskQ5 我自己在用了。分布式的任务系统,也挺好的。
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ a311301f:4663f8f2
2025-01-22 21:39:38
@ a311301f:4663f8f2
2025-01-22 21:39:38```perl
!/usr/bin/perl
use strict; use warnings; use Term::ReadKey;
STDOUT->autoflush(1);
this version run on Windows and use a pwd.txt file created by
the perl program ; otherwise encoding issue may follow
following sub needs to be used first by uncommenting the main call
sub write_password { print ("Enter Password: ") ; my $password =
; my $file_path = 'pwd.txt'; open(my $fh, '>', $file_path) or die "Cannot open file '$file_path' for writing: $!"; print $fh $password; close($fh); print ("\n"); print "Password written to '$file_path'\n"; } sub printhex { my $str = shift ; foreach my $char (split //, $str) { printf "%02x ", ord($char); } print "\n"; }
Function to read password from file
sub read_password_from_file { #unecessary #binmode(STDIN, ':crlf'); my $file_path = shift; #unecessary #local $/ = "\r\n" ; # CR, use "\r\n" for CRLF or "\n" for LF open(my $fh, '<', $file_path) or die "Cannot open file '$file_path' for reading: $!"; my $password = <$fh>; close($fh); #printhex ($password) ;
chomp($password); print "'$password'\n" ; #$password =~ s/\r?\n$//; # Remove newline character #$password = substr($password, 2) ; # BOM File starts with FF FE printhex($password ) ; # "\'$password\'\n" ; #$password = "abcde" ;
return $password; }Main program
sub main { #write_password(); # to uncomment for first use my $correct_password = read_password_from_file("pwd.txt") ; print "Enter password: "; ReadMode('noecho'); # Turn off echo my $entered_password = ReadLine(0); ReadMode('restore'); # Restore echo chomp($entered_password); print "\n";
# Compare entered password with the correct password if ($entered_password eq $correct_password) { print "Access granted!\n"; } else { print "Access denied!\n"; print "'$entered_password' not eq '$correct_password' \n"; printhex ($entered_password); printhex ($correct_password) ; print "The end! \n" ; }}
Call main function
main();
```
-
 @ dbb19ae0:c3f22d5a
2025-01-26 08:43:57
@ dbb19ae0:c3f22d5a
2025-01-26 08:43:57First make sure to add this relay wss://relay.momostr.pink in your Nostr setting and second follow this account
Soon after an account will be created on bluesky and will mirror your Nostr profile the address will be like this: bsky.app/profile/npub1mwce4c8qa2zn9zw9f372syrc9dsnqmyy3jkcmpqkzaze0slj94dqu6nmwy.momostr.pink.ap.brid.gy
And from there keep spreading the good word
originally posted at https://stacker.news/items/825913
-
 @ 8d34bd24:414be32b
2025-01-26 04:54:21
@ 8d34bd24:414be32b
2025-01-26 04:54:21My writing tends to be responsive. I respond to something I read in a book. I respond to something I read online. I respond to a podcast or sermon I was listening to. I also have a strong longing for truth (which seems to be in short supply these days). Because of my ideas being responsive, I probably tend to speak against things too often and not for things enough. I condemn not having a high enough view of God, but may inaccurately convey a harsh God and not spend enough time conveying His love and the positive reasons to follow Him. I may spend too much time on the stick and not enough on the carrot.
I’ve noticed in others that I can see two people arguing over a biblical point. One is arguing against an error/extreme to one direction while the other is arguing against an error/extreme in the opposite direction. In reality, their beliefs are very close, but they sound like they are far apart. I’ve had many opportunities to help the two people realize that they mostly agree with each other, but they are each personally dealing with opposite errors. Just as I can do a good job editing someone else’s writing, but can’t edit my own (I usually have my amazing, wonderful, handsome, intelligent, humorous husband [editor’s note - adjectives added by editor] read and edit everything I write before publishing), I may sometimes be too reactive to an error and fail to properly communicate the whole and complete truth.
Differences in Perspective
I was recently listening to a podcast by a by Bible teacher. He was talking about how he had an unloving father and how, after being saved, he originally didn’t think God cared about him personally. He then went on to teach about how personal and loving God is and how God is actively involved in every detail of every believer’s life. I agree.
On the other hand, I have seen many people that focus only on God’s love and ignore God’s holiness. They believe it is more important to be “loving” and therefore they withhold the truth (if they even know it). They are so focused on God’s forgiveness that they excuse believers actively sinning and promoting sin. Since being saved, I never doubted God’s love or His involvement in my life, so I tend to not talk about God’s love as much as I probably should. My big “Ah Ha!” was seeing His absolute sovereignty and holiness and coming to understand that the fact that He is creator gives Him the authority to tell us how to live our lives, so I tend to focus on this area.
Although I would never say God’s truth is whatever the compromise of ideas is, there are a lot of truths about God where we can fall into error in two (or more) opposing directions. God is loving and is holy. If we focus only on His love or only on His holiness, we are in error. God is forgiving and has the right to judge. If we focus so much on the fact that we are forgiven that we do not obey Him, we have erred, but if we focus so much on His judgment that we don’t acknowledge His mercy for others and for ourselves, we have also erred.
To Associate or Not to Associate
There are lots of different denominations and division among Christians that are not what God desires. At the same time, there are churches that focus on the truth as communicated through God’s word, the Bible and there are churches that have compromised that truth and let the culture, evil spirits, or just interest in self and popularity lead them astray. As Christians, we need to know God’s word, so we can know when we should avoid a close association with those who call themselves Christians, but actively disobey His clear commands.
But actually, I wrote to you not to associate with any so-called brother if he is an immoral person, or covetous, or an idolater, or a reviler, or a drunkard, or a swindler—not even to eat with such a one. (1 Corinthians 5:11) {emphasis mine}
If anyone does not obey our instruction in this letter, take special note of that person and do not associate with him, so that he will be put to shame (2 Thessalonians 4:13) {emphasis mine}
On the other hand there are many areas where our differences are not salvation issues but are more about style than substance. One side may be in error, but still be in right fellowship with God and earnestly seeking to follow Him faithfully. We shouldn’t allow these things to cause the church to fight against itself.
But now God has placed the members, each one of them, in the body, just as He desired. If they were all one member, where would the body be? But now there are many members, but one body. (1 Corinthians 12:18-20) {emphasis mine}
Therefore I, the prisoner of the Lord, implore you to walk in a manner worthy of the calling with which you have been called, with all humility and gentleness, with patience, showing tolerance for one another in love, being diligent to preserve the unity of the Spirit in the bond of peace. There is one body and one Spirit, just as also you were called in one hope of your calling; one Lord, one faith, one baptism, one God and Father of all who is over all and through all and in all. (Ephesians 4:1-5) {emphasis mine}
A so-called church, that encourages or condones things God has called evil, is not a church with which we want to associate. There are other things of which we may disagree and disagree strongly (Armenian vs Calvinist, preterist/pre-trib/post-trib, or young earth vs old earth) that although important shouldn’t cause division within the church. We should always seek the truth as spoken by God through the Scriptures, but we shouldn’t let disagreements, that don’t affect the Gospel and how we should live, keep us divided. Between Armenian and Calvinist opinions on whether we freely choose to accept Jesus or Jesus causes us to accept Jesus, as long as we agree that salvation comes through faith and not works and through Jesus and no other path, we can work together. With the different end times interpretations, as long as we agree that God said it and it will be as He said it and that it is important for us to live godly lives and to share the gospel with the lost, we can work together. With young earth vs old earth, as long as we both agree that God is ultimately our creator and His word is true, we can work together.
I do believe that there is only one truth in these and other areas, and discovering the truth is very important. Being wrong can mislead us and make us less effective for Jesus. Many of these errors can be caused by or lead us to put scientists or historians or theologians in authority over God’s word. This is wrong. We should always continually search the scripture to find the truth. We should not fear honest debate which can help lead us to the truth and strengthen our faith in God’s word. It is not wrong to correct a brother in Christ using Scripture as our foundation, but we also need to acknowledge that it could be we who are in error. I don’t know any great theologian since the apostles that hasn’t had an error in their thinking somewhere.
The Head or the Body
There can also be differences between the leadership and the individuals in a church or denomination. I have major concerns with the Vatican leadership and question if many of them are Christians at all. So much of what they say and do seem to be working against God and His commands. At the same time, I have many good friends (in person and online) who are wonderful Catholics, who I would never doubt are devout Christians with a true relationship with Jesus. I will maintain my Christian fellowship with my Catholic, Christian friends while speaking against unbiblical words and actions by the Pope and the Vatican.
But false prophets also arose among the people, just as there will also be false teachers among you, who will secretly introduce destructive heresies, even denying the Master who bought them, bringing swift destruction upon themselves. Many will follow their sensuality, and because of them the way of the truth will be maligned; and in their greed they will exploit you with false words; their judgment from long ago is not idle, and their destruction is not asleep. (2 Peter 2:1-3)
Of course false prophets and false teachers are most definitely not limited to the Catholic Church. For example, the female Episcopalian Bishop that led the inauguration prayer breakfast for Trump spent most of her time promoting LGBTQ+ issues which are contrary to the word of God and little to none actually honoring God or supporting the issues that God has stated are important. (For that matter, scripture specifically says women shouldn’t be church leaders.) We all need to be more like the Bereans “Now these were more noble-minded than those in Thessalonica, for they received the word with great eagerness, examining the Scriptures daily to see whether these things were so.” (Acts 17:11) We need to use the Scripture to both test if our beliefs and actions are biblical and if the teachings of our leaders are biblical.
Different Paths, but One Jesus
Ultimately, there is only one way of salvation — repentance and faith in Jesus. On the other hand, the path each believer is called to walk towards sanctification can vary. I have seen God lead me at different times to correct different sins and misconceptions. The areas of my life that I am convicted of and my path towards understanding the truth communicated in the Bible is not the same as other believers. We should all be growing to be more like Jesus, but our path to His likeness will not look the same. We start as different people; we have different experiences; and God works on us in different ways. We must be careful about judging another because their growth in Christ looks different.
We all have strengths and weaknesses. We all have doctrines of the Bible that we understand better than others and doctrines of the Bible about which we are either unsure or in error. Most of us also have a tendency to judge someone who is weak where we are strong and overlook the fact that that same person might be strong where we are weak. We need to pray for wisdom and mercy. We need to earnestly study God’s word. We need to listen closely to the Holy Spirit’s leading and use these differences to build up each other rather than divide and beat down those who are different, but are still part of the body of Christ.
For through the grace given to me I say to everyone among you not to think more highly of himself than he ought to think; but to think so as to have sound judgment, as God has allotted to each a measure of faith. For just as we have many members in one body and all the members do not have the same function, so we, who are many, are one body in Christ, and individually members one of another. Since we have gifts that differ according to the grace given to us, each of us is to exercise them accordingly: if prophecy, according to the proportion of his faith; if service, in his serving; or he who teaches, in his teaching; or he who exhorts, in his exhortation; he who gives, with liberality; he who leads, with diligence; he who shows mercy, with cheerfulness. (Romans 12:3-8)
My prayer is that we would all study God’s word, understand His word, live His word, and work together to share the Gospel with the word. My prayer is that our different understandings of the Bible will lead to fruitful debate that leads all parties closer to truth, to God and to each other. May God lead us all to truth and fellowship in Him.
Trust Jesus.
-
 @ 23b0e2f8:d8af76fc
2025-01-08 18:17:52
@ 23b0e2f8:d8af76fc
2025-01-08 18:17:52Necessário
- Um Android que você não use mais (a câmera deve estar funcionando).
- Um cartão microSD (opcional, usado apenas uma vez).
- Um dispositivo para acompanhar seus fundos (provavelmente você já tem um).
Algumas coisas que você precisa saber
- O dispositivo servirá como um assinador. Qualquer movimentação só será efetuada após ser assinada por ele.
- O cartão microSD será usado para transferir o APK do Electrum e garantir que o aparelho não terá contato com outras fontes de dados externas após sua formatação. Contudo, é possível usar um cabo USB para o mesmo propósito.
- A ideia é deixar sua chave privada em um dispositivo offline, que ficará desligado em 99% do tempo. Você poderá acompanhar seus fundos em outro dispositivo conectado à internet, como seu celular ou computador pessoal.
O tutorial será dividido em dois módulos:
- Módulo 1 - Criando uma carteira fria/assinador.
- Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.
No final, teremos:
- Uma carteira fria que também servirá como assinador.
- Um dispositivo para acompanhar os fundos da carteira.

Módulo 1 - Criando uma carteira fria/assinador
-
Baixe o APK do Electrum na aba de downloads em https://electrum.org/. Fique à vontade para verificar as assinaturas do software, garantindo sua autenticidade.
-
Formate o cartão microSD e coloque o APK do Electrum nele. Caso não tenha um cartão microSD, pule este passo.

- Retire os chips e acessórios do aparelho que será usado como assinador, formate-o e aguarde a inicialização.

- Durante a inicialização, pule a etapa de conexão ao Wi-Fi e rejeite todas as solicitações de conexão. Após isso, você pode desinstalar aplicativos desnecessários, pois precisará apenas do Electrum. Certifique-se de que Wi-Fi, Bluetooth e dados móveis estejam desligados. Você também pode ativar o modo avião.\ (Curiosidade: algumas pessoas optam por abrir o aparelho e danificar a antena do Wi-Fi/Bluetooth, impossibilitando essas funcionalidades.)

- Insira o cartão microSD com o APK do Electrum no dispositivo e instale-o. Será necessário permitir instalações de fontes não oficiais.

- No Electrum, crie uma carteira padrão e gere suas palavras-chave (seed). Anote-as em um local seguro. Caso algo aconteça com seu assinador, essas palavras permitirão o acesso aos seus fundos novamente. (Aqui entra seu método pessoal de backup.)

Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.
-
Criar uma carteira somente leitura em outro dispositivo, como seu celular ou computador pessoal, é uma etapa bastante simples. Para este tutorial, usaremos outro smartphone Android com Electrum. Instale o Electrum a partir da aba de downloads em https://electrum.org/ ou da própria Play Store. (ATENÇÃO: O Electrum não existe oficialmente para iPhone. Desconfie se encontrar algum.)
-
Após instalar o Electrum, crie uma carteira padrão, mas desta vez escolha a opção Usar uma chave mestra.

- Agora, no assinador que criamos no primeiro módulo, exporte sua chave pública: vá em Carteira > Detalhes da carteira > Compartilhar chave mestra pública.

-
Escaneie o QR gerado da chave pública com o dispositivo de consulta. Assim, ele poderá acompanhar seus fundos, mas sem permissão para movimentá-los.
-
Para receber fundos, envie Bitcoin para um dos endereços gerados pela sua carteira: Carteira > Addresses/Coins.
-
Para movimentar fundos, crie uma transação no dispositivo de consulta. Como ele não possui a chave privada, será necessário assiná-la com o dispositivo assinador.

- No assinador, escaneie a transação não assinada, confirme os detalhes, assine e compartilhe. Será gerado outro QR, desta vez com a transação já assinada.

- No dispositivo de consulta, escaneie o QR da transação assinada e transmita-a para a rede.
Conclusão
Pontos positivos do setup:
- Simplicidade: Basta um dispositivo Android antigo.
- Flexibilidade: Funciona como uma ótima carteira fria, ideal para holders.
Pontos negativos do setup:
- Padronização: Não utiliza seeds no padrão BIP-39, você sempre precisará usar o electrum.
- Interface: A aparência do Electrum pode parecer antiquada para alguns usuários.
Nesse ponto, temos uma carteira fria que também serve para assinar transações. O fluxo de assinar uma transação se torna: Gerar uma transação não assinada > Escanear o QR da transação não assinada > Conferir e assinar essa transação com o assinador > Gerar QR da transação assinada > Escanear a transação assinada com qualquer outro dispositivo que possa transmiti-la para a rede.
Como alguns devem saber, uma transação assinada de Bitcoin é praticamente impossível de ser fraudada. Em um cenário catastrófico, você pode mesmo que sem internet, repassar essa transação assinada para alguém que tenha acesso à rede por qualquer meio de comunicação. Mesmo que não queiramos que isso aconteça um dia, esse setup acaba por tornar essa prática possível.
-
 @ 35f3a26c:92ddf231
2025-01-22 20:48:34
@ 35f3a26c:92ddf231
2025-01-22 20:48:34Background
Most people non familiar with Bitcoin thinks that there its has not smart contracts capabilities, and that is incorrect, there are smart contract capabilities, and despite limited in comparison with other blockchain networks, those capabilities are evolving slowly but surely.
The support for smart contracts is done through its scripting language, Script, which allows developers to create complex conditions for transactions.
What can you do with Script? 1. time locks 2. multi-signature requirements 3. other custom logic
opcodes like OP_CHECKLOCKTIMEVERIFY (CLTV) and OP_CHECKSEQUENCEVERIFY (CSV) are used to build more sophisticated smart contracts, these opcodes enable features such as the Lightning Network, a key scaling solution for Bitcoin
back in 2021, the Taproot upgrade introduced Pay-to-Taproot (P2TR), in summary allows for more private and efficient smart contracts, in that soft fork more was added, in addition to Taproot, we got as well Schnorr signatures, which enables multiple signatures to be aggregated into a single signature, improving scalability and privacy and MAST (Merklized Abstract Syntax Trees) which reduces the size of complex smart contracts, making them more efficient, as an added value, this efficiency reduces the cost of transactions.
The Taproot upgrade has laid the foundation for the development of more sophisticated smart contracts on the Bitcoin network, and the use of covenants is an important part of this development.
What is Bitcoin Covenants?
It is a BIP (Bitcoin Improvement Proposal), BIP-347, assigned on April 24, 2024, which marks the first step towards reintroducing functionality removed from Bitcoin by its creator Satoshi Nakamoto in 2010. This proposal aims to bring smart contract functionality to Bitcoin as we see in other EVM networks.
The proposal’s developers authors names are Ethan Heilman and Armin Sabouri, now the community will debate its merits.
Here the link, in case you are curious:
https://github.com/bitcoin/bips/blob/master/bip-0347.mediawiki
It is worth to read the motivation section of the BIP, which reads:
“Bitcoin Tapscript lacks a general purpose way of combining objects on the stack, restricting the expressiveness and power of Tapscript. This prevents, among many other things, the ability to construct and evaluate merkle trees and other hashed data structures in Tapscript. OP_CAT, by adding a general purpose way to concatenate stack values, would overcome this limitation and greatly increase the functionality of Tapscript.
OP_CAT aims to expand the toolbox of the tapscript developer with a simple, modular, and useful opcode in the spirit of Unix. To demonstrate the usefulness of OP_CAT below we provide a non-exhaustive list of some use cases that OP_CAT would enable:
Bitstream, a protocol for the atomic swap (fair exchange) of bitcoins for decryption keys, that enables decentralized file hosting systems paid in Bitcoin. While such swaps are currently possible on Bitcoin without OP_CAT, they require the use of complex and computationally expensive Verifiable Computation cryptographic techniques. OP_CAT would remove this requirement on Verifiable Computation, making such protocols far more practical to build in Bitcoin.
Tree signatures provide a multisignature script whose size can be logarithmic in the number of public keys and can encode spend conditions beyond n-of-m. For instance a transaction less than 1KB in size could support tree signatures with up to 4,294,967,296 public keys. This also enables generalized logical spend conditions.
Post-Quantum Lamport signatures in Bitcoin transactions. Lamport signatures merely require the ability to hash and concatenate values on the stack. [4] It has been proposed that if ECDSA is broken or a powerful computer was on the horizon, there might be an effort to protect ownership of bitcoins by allowing people to mark their taproot outputs as "script-path only" and then move their coins into such outputs with a leaf in the script tree requiring a Lamport signature. It is an open question if a tapscript commitment would preserve the quantum resistance of Lamport signatures. Beyond this question, the use of Lamport Signatures in taproot outputs is unlikely to be quantum resistant even if the script spend-path is made quantum resistant. This is because taproot outputs can also be spent with a key. An attacker with a sufficiently powerful quantum computer could bypass the taproot script spend-path by finding the discrete log of the taproot output and thus spending the output using the key spend-path. The use of "Nothing Up My Sleeve" (NUMS) points as described in BIP-341 to disable the key spend-path does not disable the key spend-path against a quantum attacker as NUMS relies on the hardness of finding discrete logs. We are not aware of any mechanism which could disable the key spend-path in a taproot output without a soft-fork change to taproot.
Non-equivocation contracts in tapscript provide a mechanism to punish equivocation/double spending in Bitcoin payment channels. OP_CAT enables this by enforcing rules on the spending transaction's nonce. The capability is a useful building block for payment channels and other Bitcoin protocols.
Vaults [6] which are a specialized covenant that allows a user to block a malicious party who has compromised the user's secret key from stealing the funds in that output. As shown in OP_CAT is sufficient to build vaults in Bitcoin.
Replicating CheckSigFromStack which would allow the creation of simple covenants and other advanced contracts without having to pre-sign spending transactions, possibly reducing complexity and the amount of data that needs to be stored. Originally shown to work with Schnorr signatures, this result has been extended to ECDSA signatures.
OP_CAT was available in early versions of Bitcoin. In 2010, a single commit disabled OP_CAT, along with another 15 opcodes. Folklore states that OP_CAT was removed in this commit because it enabled the construction of a script whose evaluation could have memory usage exponential in the size of the script. For example, a script that pushed a 1-byte value on the stack and then repeated the opcodes OP_DUP, OP_CAT 40 times would result in a stack element whose size was greater than 1 terabyte assuming no maximum stack element size. As Bitcoin at that time had a maximum stack element size of 5000 bytes, the effect of this expansion was limited to 5000 bytes. This is no longer an issue because tapscript enforces a maximum stack element size of 520 bytes.”
The last update of the BIP was done on Sep. 8 2024 by Ethan Heilman
Controversy
The controversy revolves around two main camps:
- Those who want to preserve Bitcoin’s network for monetary transactions only, arguing that adding smart contract capabilities could introduce risks and complexity.
- Others who advocate for expanding Bitcoin’s capabilities to support a wider range of applications, seeing OP_CAT as a step towards enhancing the network’s utility.
Final Thoughts
Bitcoin have done what no other asset have done in history, neither gold, its success is clear, and now, that BlackRock is involved, “miraculously”, corporations and governments are getting on board and Bitcoin is not anymore only for criminals or “rat poison” or “is going to zero”.
But as all tech, improvements are important, if those improvements are done to secure more the network and to make it more robust, there will be little to none controversy, however, when those changes are aiming at adding new shinning features that would change Bitcoin into a network with similar features as Ethereum in terms of contracts that requires attention and debate, few questions come to mind:
- How will that change affect the security of the network?
- How that change will affect the blockchain usage?
- What is the projected impact over the fees per transaction if this change is approved?
- Will the impact create pressure for the block size increase discussion to come back to the table and with it a second war?
Looking into Ethan Heilman work and contribution to the Bitcoin ecosystem, I am inclined to believe that he has considered most of those questions.
Looking forward to observe the evolution of this proposal.
You liked the article? Make my day brighter!
Like and share!
Last but not least, the following link is an unstoppable domain, it will open a page in which you can perform an anonymous contribution to support my work:
https://rodswallet.unstoppable/
The link didn’t open?
To open the link you need to use a best in class browser that supports web3, two are recommended: Brave Browser and Opera Browser
-
 @ 0463223a:3b14d673
2025-01-27 10:47:00
@ 0463223a:3b14d673
2025-01-27 10:47:00I wrote this article back in 2019 but I wanted to see how it stood up today. Since writing this I’ve been diagnosed with autism. However, I question this. For sure I’ve gone through lots of ups and downs in life. Some issues probably due to childhood trauma, others due to drugs etc. but I still ask if is a natural response to bullshit.
I don’t write this to belittle any problems anyone has and the autism spectrum disorder is real (but not disorder to me). When the whole population gets diagnosed as neurodivergent what next?
If you need help, get help. I write this as a person trying to get off the drugs prescribed to me many years ago. Something I’m finding difficult but I will do it…
From 2019
A large part of the adult population in the Western World are mad, mental, bonkers, have lost their marbles and are totally insane. Well, that’s at least according to the World Health Organisation A recent WHO report stated one in four people in the world will be affected by mental or neurological disorders at some point in their lives. And there’s a very high chance that you, the reader, are completely off your rocker. Mental Health is the buzzphrase of our times. It’s on the TV, the radio and all over the internet. The UK’s Prime Minister goes on TV to state how big the problem is and just how very seriously she takes it and we’re assured the government are working extremely hard to tackle it. However, the rhetoric never amounts to anything, as anyone seeking genuine help will attest. Help is hard to come by. Doctors prescribe pills to subdue the wrong thoughts, but nothing else. No long term solutions, just keep taking the pills. Hundreds of thousands of adults are medicated in this way and now, more worryingly, are many children. So it’s vital to talk about it. It’s permanently Mentalspeng Awareness Day or Tell Facebacon Your Neurologicalwankfuck Week. It’s even become quite fashionable, with regular treats from celebrities telling of their darkest moments and how they nearly didn’t get that huge Hollywood deal because they woke up feeling sad and unhappy one winter morning. If you’re a fruit-loop tell everyone. It will be ok… Tell them about the time you were going to drive your car off a cliff and ended up in hospital after a particularly long conversation with The Samaritans. Great stuff! Tell them about the regular, uncontrollable urges to slash yourself with a Stanley knife or any other sharp object close to hand. Awesome! Tell them about how you smash yourself repeatedly in the head, sometimes with a heavy object, as you can no longer deal with the stress and frustration of being disempowered by situations completely out of your control. Cool! Tell them how you feel trapped by an increasingly expensive housing market and how you have zero financial security. Brilliant! Or maybe just tell them that sometimes you can’t get out of bed and you don’t know why or that you panic uncontrollably for no reason. Skills! Tell the world! We’re so understanding of mental health issues these days, just raise more awareness and everything will be fine, we’re here for you man/woman! (and yes, we might need to sell this information on to the appropriate persons, future employers, insurance companies or government agencies etc.). After all, we’re all good people right? Tell everyone you’re mad and they’ll understand. They’ll think of the time you were a dick and they’ll say “Ahh, poor sod, you know he’s a mental don’t you”. Well frankly no. The world is full of cunts and whilst the people close to you will be sympathetic, as far as wider society goes, you’ll be marked, your position compromised and your word will not be trusted. I mean who knows, maybe you’re delusional, perhaps you’re about to rampage through town wielding a knife or driving your car into a crowded supermarket… But hold up…. One in every four of us is mental?! Is that really the case? Let’s think about this for a second. When did 25% of the population become a massive neurospeng? This wasn’t the case 30 years ago, a quarter of the population weren’t mad. There wasn’t the vast array of medications available these days; Prozac, Sertraline, Citralopram, Promethazine, Venlafaxine, Amiltryptaline, to name a few (there are many, many more). It’s clear that a lot of people aren’t feeling right but how come the suicide rates are higher now than they were 30 years ago? If we’re all so much more aware and well medicated, surely rates would be going down? Perhaps you were diagnosed as a mental because you responded negatively to events happening around you? Maybe you’re working increasingly longer hours for less money. Perhaps the terms of your work changed drastically and you no longer feel secure. Maybe you lost jobs because of funding cut backs. Perhaps you’re in despair because your friend took their own life when their job was cut in an austerity drive. Suicide is the most horrible thing which ever way you look at it. You strip a person of their purpose and they react with the most extreme act of self violence, causing an unbelievable amount of emotional distress for those left to pick up the pieces… And so we say, “Ahh but you understand, they were mad… They were fucking mental, they lost control of their senses, it such a terrible shame but they were mad you know”. Bullshit. The term Mental Health removes all responsibility from the structures creating an environment where people are deemed no longer of value or viable human beings. But maybe you were angry because you were told by politicians that you need to live within your means, whilst those in large financial institutions increased their wealth exponentially? The world economy crashed in 2008 and there’s no money. Eh? The governments of printed more and more money, but there’s no money for you, you cunt. Perhaps it was packed aboard a spaceship and is now hurtling towards Mars! (mad people tend to think like this, after all it couldn’t be that the money was stolen). Maybe you got angry with the blatant corruption from those in public life? Politicians shout loudly that they’re for the people but will pocket pay rises, local council officials bully members of the public and make threats to cut funding . This can be done with total with total impunity, as the structures put in place to control such actions cover up any wrong doing. You see the powerful can not and will not be challenged. There is no pathway to justice. When the fire at Grenfell happened, it was clear for all to see that the housing association, council and big business were at fault, but no, blame was heaped on the lone fire officer who had the awful task of managing two lowly fire engines in London’s biggest fire since World War II. At the time my local Member of Parliament response was “the flats were refurbished to a very high standard”. We shouldn’t lay blame at those in power, we cannot have any fault with the establishment. I bet that poor fire officer was a mental too… When discussing mental health we’re not talking about a brain injury or unfortunate illness. There’s extreme difficulty coping with the world but it’s not madness and it’s not a delusion. It’s a natural reaction to bullshit. We’re are completely surrounded by bullshit, on the internet bullshit, on the TV bullshit, in the work place bullshit, from our leaders bullshit etc. etc. The world is running on massive excess levels of bullshit. And this is the natural emotional response to bullshit. Mental Health is used to invalidate the anger, freeing the powerful from responsibility and laying blame squarely at the individuals door. In the meantime, piece by piece, the powerful steal everything we’ve ever owned. So next time someone says to you raise awareness about mental health, maybe tell them to fuck off. Either that or tell them you’re flying to the Moon to have tea with Kim Jong Un and Barney The Dinosaur. Fuck mental health. *Image used without permission of Barney The Dinosaur.
-
 @ e373ca41:b82abcc5
2025-01-27 08:33:39
@ e373ca41:b82abcc5
2025-01-27 08:33:39
This article by Milosz Matuschek first appeared in German in his publication "Freischwebende Intelligenz".
It's working! Or is it? Trump's inauguration casted its shadow in the last weeks already and produced the first big upsets. Meta/Facebook cancelled their squad of fact-checkers and will rely (like X) on community comments in future. Wokistan is unwound. Zuckerberg now presents himself as an advocate of free speech, declaring a “return to principles”.
For those who believe it, Zuckerberg is an opportunist who gave in to the Biden administration and its deletion requests during Covid without much resistance (after having given 400 mio. USD through intermediary organizations into Bidens campaign), regardless of whether it was about masks or later about “vaccinations”. His Canossa walk to Rogan does not change the fact that he betrayed his own principles and deleted millions of critical profiles, channels and groups, including groups in which Facebook users discussed vaccine damage. Where are the profiles? Are they back? Zuckerberg played Ministry of Truth and is now quoting Orwell and toeing the Musk line. This is what a driven man looks like, not a man of conviction. The mainstream is shocked and is already labeling Facebook as a new hate portal. When will the accusation of anti-Semitism kick in?
https://x.com/TheBabylonBee/status/1876683974560350626
The Musk effect
All of these are gestures of submission to the new ruler of public opinion: Elon Musk. He owns the largest network for "free speech", he himself is its biggest influencer and is recalibrating what can be said in public. His journeyman's piece was Trump's election victory. Changing the political mood in the world could be his masterpiece.
For a long time, he admittedly did this extremely skillfully. He tweeted about the deep state, Soros and Gates, the population collapse, compulsory vaccination, etc. and got on well with the critical scene, some of whom are now all too submissively trying to recognize their new messiah in him. Musk throws his media spotlight on topics that the newspapers remain silent about and gave politicians underrepresented in the mainstream, such as Alice Weidel (opposition leader in Germany, AfD), a forum.
Musk has repeatedly brought the Epstein case and paedophile scandals, such as in England (Rotherham, Oxford), into the media spotlight. Pakistani gangs abused minors and children there for years; anyone reading the verdict will need strong nerves. In Austria, a trial for gang abuse of a 12-year-old girl has just ended with an acquittal. The judges believe she wanted it that way. During the trial, the defendant put a hundred Euro note on the table for the victim's lawyer, which is what mocking “reparation” looks like. In “our democracy” in Germany, sentences are handed down on a piecework basis for ludicrous “insults to politicians”.

Musk is de facto the most powerful man in the world (satellites, SpaceX, Mars, Tesla, mRNA vaccination routes, Pentagon connections, X..,). Where so much power is involved, megalomania is not far away. He is acting increasingly clumsily.
It is currently confirming for all to see the cliché that politics is basically the entertainment department of industry. Even in “our democracy”, the bosses of the world have always chosen their political generals, who are interchangeable. In the case of Bill Gates, George Soros & Son etc., the executive was the woke nomenklatura right up to the EU. With Musk, it is the new, right-wing conservative nomenklatura.
ADVERTISEMENT:
Looking for the easiest way to buy Bitcoin and store it yourself? The Relai app is the No. 1 crypto start-up and No. 2 of all fintech start-ups in Switzerland. Here you can buy Bitcoin in just a few steps and also set up savings plans. Nobody has access to your Bitcoin except you. With the referral code MILOSZ you save on fees (no financial advice). Disclaimer due to regulatory issues: The services of the Relai App are hereby only recommended to inhabitants of Switzerland or Italy.

Need more security? The Trezor wallets are recommended and easy to use, others are available in the store. Need more advice? Book an introductory meeting with a wallet expert.
Musk smooches Meloni, interviews Alice Weidel, auditions Farage (and cancels again: “doesn't have what it takes”). The Weidel interview was certainly a necessary corrective to the current media asymmetry (and no one should be able to deny access to a source of information). There is no doubt that the second strongest party in the German mainstream media does not have a fair chance to convey its content. Talk shows, if there are invitations to AfD politicians at all, are public inquisition events with calls for self-criticism.
But the Musk-Weidel talk was not journalism either. It was a public casting event, a kind of “Apprentice” on X. Or have you seen a journalist anywhere? A platform operator and a politician tapped each other a bit and confirmed each other. All this is already bringing the EU onto the scene, Thierry Breton is already waving the possible annulment of the elections in Germany. An oligarch is unmasking the EU oligarchy and both want to do it for democracy, what a world...
"Which piggy would you like?"
https://www.youtube.com/watch?v=tiwkYCFD6EA
So asked Robert Lembke some decades ago in the German TV show “What am I?”: And that's supposed to be the choice now: Pick your favorite oligarch or next slave owner. In the end, every big tech business model is based on advertising and data mining. Zuckerberg, Musk & Co. sell identity, friendship, memories and ultimately your content. Twitter also wanted to buy Substack and got “Revue”. The customer (aka the product) is sold to the advertising industry, Zuckerberg potentially knows each of his users down to their character traits (unknown even to the user) (check: www.applymagicsauce.com). Like in the 80s movie with Arnie, this is a kind of “running man”, a gladiator game in front of an assembled world audience.
Whoever wins attention for themselves (and the platform) wins back a small amount of freedom and even earns something in the process. Musk recently changed his X name to “Kekius Maximus” (whereupon memecoins of the same name immediately sprang up, to each ruler his own currency), reminiscent of the gladiator Maximus from the film of the same name by Ridley Scott. The gladiator's owner told him: “Win the crowd and you win your freedom”. Not much has changed since ancient Rome. As the world's top meme maker with the greatest reach, Musk also has the greatest influence on social moods. No content is more viral and memorable than memes. The winner here is the one with the highest level of replication. That's what Musk does.

The changes we are currently seeing are just the beginning, both positive and (possibly) negative. The first effect is already visible: Wokistan is withdrawing from platforms that are not ideologically curated. Fearing accusations of contact guilt, they obediently throw themselves off the nearest cliff and voluntarily curtail their own reach; the last example was “Watson.ch” from Switzerland, a journalistically narrow-chested list and click medium for chai latte sippers from Bern and Zurich. Will the “X-itus” be followed by the great unfriending of Facebook? There won't be much left, Tiktok also ticked to the right beat by their standards (as long as it's not against China). The next place of mercy for Woke is called Bluesky, where there is neither hate nor agitation, right?
It must be clear to everyone now: The result of liberation by others is never freedom, but new dependence. What has not been fought for is always a continuation of neo-feudalism and (virtual) serfdom in a different form. The tools for regaining freedom have long been in our hands. What separates us from freedom is ultimately only comfort.
The book “The Sovereign Individual” was recently translated into German. It was written over 25 years ago.
Read it!
Join the marketplace of ideas! We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Sound money and sound information should finally be in the hands of the people, right? Want to learn more about the Pareto Project? Zap me, if you want to contribute (all Zaps go to the project).

Are you a publication or journalist and want to be part of it, test us, migrate your content to Nostr? Write to team@pareto.space**
Not yet on Nostr and want the full experience? Easy onboarding via Nosta.me.

-
 @ b17fccdf:b7211155
2025-01-21 18:10:10
@ b17fccdf:b7211155
2025-01-21 18:10:10Link to the bonus guide ~ > HERE <~
Some notes:
ℹ️ For the moment, this guide will touch only the case of an only testnet mode situation, in the future, we will study adding the case of configuration to enable the parallel/simultaneous mode (mainnet+testnet in the same device) in an extra section in this guide.
ℹ️ The services mentioned in this guide are those that have been tested using testnet configuration and these worked fine. Later, in the next versions of this guide, we will go to adding other processes to adapt other services to the testnet mode.
Enjoy it MiniBolter! 💙
-
 @ b17fccdf:b7211155
2025-01-21 18:04:28
@ b17fccdf:b7211155
2025-01-21 18:04:28Available at: https://minibolt.info
Main changes to the version 1:
- The complete guide has been migrated to the new design visual builder web tool platform gitbook.com
- New modern UI (responsive, full width, and better visual items)
- New menu structure for a better user experience
- New visual items to improve the navigation through the web page
- New switch to enable light/dark theme
- Enabled Cloudflare Proxy for maximum protection against attacks and better management of the domain
Other changes:
- New MiniBolt Linktr forked of the alternative FOSS project proposed by Gzuuus
- Changed MiniBolt from a personal project to an organization so that the project has its own identity
- New email contact address hello@minibolt.info to receive proposals and give support
- New resources folder with the current MiniBolt roadmap, network map diagrams, and others
ℹ️ More info:
- The new version is available with the known domain: minibolt.info but from now on links associated with the new v2 version were shared using the v2.minibolt.info subdomain due to a GitBook limitation
- The old and deprecated v1 will be still available at a time in the subdomain v1.minibolt.info, but is in the roadmap delete it definitely in the future, take note ASAP of all that you need of that version before this happens
- Contributors and collaborators will be able to continue doing PR through code programming or using the design block builder gitbook.com
Enjoy it MiniBolter! 💙
-
 @ 207ad2a0:e7cca7b0
2025-01-07 03:46:04
@ 207ad2a0:e7cca7b0
2025-01-07 03:46:04Quick context: I wanted to check out Nostr's longform posts and this blog post seemed like a good one to try and mirror. It's originally from my free to read/share attempt to write a novel, but this post here is completely standalone - just describing how I used AI image generation to make a small piece of the work.
Hold on, put your pitchforks down - outside of using Grammerly & Emacs for grammatical corrections - not a single character was generated or modified by computers; a non-insignificant portion of my first draft originating on pen & paper. No AI is ~~weird and crazy~~ imaginative enough to write like I do. The only successful AI contribution you'll find is a single image, the map, which I heavily edited. This post will go over how I generated and modified an image using AI, which I believe brought some value to the work, and cover a few quick thoughts about AI towards the end.
Let's be clear, I can't draw, but I wanted a map which I believed would improve the story I was working on. After getting abysmal results by prompting AI with text only I decided to use "Diffuse the Rest," a Stable Diffusion tool that allows you to provide a reference image + description to fine tune what you're looking for. I gave it this Microsoft Paint looking drawing:

and after a number of outputs, selected this one to work on:

The image is way better than the one I provided, but had I used it as is, I still feel it would have decreased the quality of my work instead of increasing it. After firing up Gimp I cropped out the top and bottom, expanded the ocean and separated the landmasses, then copied the top right corner of the large landmass to replace the bottom left that got cut off. Now we've got something that looks like concept art: not horrible, and gets the basic idea across, but it's still due for a lot more detail.

The next thing I did was add some texture to make it look more map like. I duplicated the layer in Gimp and applied the "Cartoon" filter to both for some texture. The top layer had a much lower effect strength to give it a more textured look, while the lower layer had a higher effect strength that looked a lot like mountains or other terrain features. Creating a layer mask allowed me to brush over spots to display the lower layer in certain areas, giving it some much needed features.

At this point I'd made it to where I felt it may improve the work instead of detracting from it - at least after labels and borders were added, but the colors seemed artificial and out of place. Luckily, however, this is when PhotoFunia could step in and apply a sketch effect to the image.

At this point I was pretty happy with how it was looking, it was close to what I envisioned and looked very visually appealing while still being a good way to portray information. All that was left was to make the white background transparent, add some minor details, and add the labels and borders. Below is the exact image I wound up using:

Overall, I'm very satisfied with how it turned out, and if you're working on a creative project, I'd recommend attempting something like this. It's not a central part of the work, but it improved the chapter a fair bit, and was doable despite lacking the talent and not intending to allocate a budget to my making of a free to read and share story.
The AI Generated Elephant in the Room
If you've read my non-fiction writing before, you'll know that I think AI will find its place around the skill floor as opposed to the skill ceiling. As you saw with my input, I have absolutely zero drawing talent, but with some elbow grease and an existing creative direction before and after generating an image I was able to get something well above what I could have otherwise accomplished. Outside of the lowest common denominators like stock photos for the sole purpose of a link preview being eye catching, however, I doubt AI will be wholesale replacing most creative works anytime soon. I can assure you that I tried numerous times to describe the map without providing a reference image, and if I used one of those outputs (or even just the unedited output after providing the reference image) it would have decreased the quality of my work instead of improving it.
I'm going to go out on a limb and expect that AI image, text, and video is all going to find its place in slop & generic content (such as AI generated slop replacing article spinners and stock photos respectively) and otherwise be used in a supporting role for various creative endeavors. For people working on projects like I'm working on (e.g. intended budget $0) it's helpful to have an AI capable of doing legwork - enabling projects to exist or be improved in ways they otherwise wouldn't have. I'm also guessing it'll find its way into more professional settings for grunt work - think a picture frame or fake TV show that would exist in the background of an animated project - likely a detail most people probably wouldn't notice, but that would save the creators time and money and/or allow them to focus more on the essential aspects of said work. Beyond that, as I've predicted before: I expect plenty of emails will be generated from a short list of bullet points, only to be summarized by the recipient's AI back into bullet points.
I will also make a prediction counter to what seems mainstream: AI is about to peak for a while. The start of AI image generation was with Google's DeepDream in 2015 - image recognition software that could be run in reverse to "recognize" patterns where there were none, effectively generating an image from digital noise or an unrelated image. While I'm not an expert by any means, I don't think we're too far off from that a decade later, just using very fine tuned tools that develop more coherent images. I guess that we're close to maxing out how efficiently we're able to generate images and video in that manner, and the hard caps on how much creative direction we can have when using AI - as well as the limits to how long we can keep it coherent (e.g. long videos or a chronologically consistent set of images) - will prevent AI from progressing too far beyond what it is currently unless/until another breakthrough occurs.
-
 @ fd208ee8:0fd927c1
2025-01-23 15:31:24
@ fd208ee8:0fd927c1
2025-01-23 15:31:24Planning Alexandria
People keep asking what features nostr:npub1s3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqd975wz has planned for #Alexandria, but they're not set in stone because we're an agile project.
What we do have, is lots of tickets on our Kanban boards and a naming scheme, where we use a famous person's last name, to signify the release goals.

Gutenberg v 0.1.0
(after the inventor of the printing press) will contain the features needed to read and write NIP-62 Curated Publications, as well as encompassing the complex infrastructure, architecture, documentation, and personnel we require to make this all run smoothly and look easy.

Euler v 0.2.0
(after a mathematician credited with establishing graph theory) will contain the features for deep-searching, visually exploring, and smartly navigating the data set, wiki page display, annotating and citing the publications, exporting to other formats (like PDF, ePUB, and LaTeX), and commenting/reviewing. To help with the heavy lifting, we will be swapping out the core with our own Nostr SDK called "Aedile".

Defoe v 0.3.0
(after an author who perfected the novel format) will be all about our favorite writers. We will be focusing upon profile data, payment systems, book clubs and communities, and stylesheets.
That is everything we have planned, for the v1.0 edition, and we consider that version to be a true product.
As for after that, a teaser...

-
 @ da0b9bc3:4e30a4a9
2025-01-27 06:30:31
@ da0b9bc3:4e30a4a9
2025-01-27 06:30:31Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/865514
-
 @ b17fccdf:b7211155
2025-01-21 17:47:28
@ b17fccdf:b7211155
2025-01-21 17:47:28Link to the bonus guide ~ > HERE < ~
Some sections of the guide:
- Generate SSH keys
- Import SSH pubkey
- Connect to the MiniBolt node using SSH keys
- Disable password login
- Disable admin password request
Some shortcuts to the Extra sections:
Enjoy it MiniBolter! 💙
-
 @ b17fccdf:b7211155
2025-01-21 17:39:34
@ b17fccdf:b7211155
2025-01-21 17:39:34Link to the bonus guide ~ > HERE < ~
⏰ Recently added an update that includes a new section How to detect Ordinals transactions and verify Ordisrespector filter works to verify that Ordispector is filtering and burning Ordinals correctly 🔥
Fuck Ordinals🤡🔫 and enjoy it MiniBolter! 💙
-
 @ b17fccdf:b7211155
2025-01-21 16:49:27
@ b17fccdf:b7211155
2025-01-21 16:49:27What's changed
- New method for Bitcoin Core signature check, click ~ >HERE< ~
- GitHub repo of Bitcoin Core release attestations (Guix), click ~ >HERE< ~
History:
~ > PR that caused the broken and obsolescence of the old signature verification process, click ~ >HERE< ~
~ > New GitHub folder of Bitcoin Core repo that stores the signatures, click ~ >HERE< ~
Thanks to nostr:npub1gzuushllat7pet0ccv9yuhygvc8ldeyhrgxuwg744dn5khnpk3gs3ea5ds for building the command that made magic possible 🧙♂️🧡
Enjoy it MiniBolter! 💙
-
 @ e6817453:b0ac3c39
2025-01-05 14:29:17
@ e6817453:b0ac3c39
2025-01-05 14:29:17The Rise of Graph RAGs and the Quest for Data Quality
As we enter a new year, it’s impossible to ignore the boom of retrieval-augmented generation (RAG) systems, particularly those leveraging graph-based approaches. The previous year saw a surge in advancements and discussions about Graph RAGs, driven by their potential to enhance large language models (LLMs), reduce hallucinations, and deliver more reliable outputs. Let’s dive into the trends, challenges, and strategies for making the most of Graph RAGs in artificial intelligence.
Booming Interest in Graph RAGs
Graph RAGs have dominated the conversation in AI circles. With new research papers and innovations emerging weekly, it’s clear that this approach is reshaping the landscape. These systems, especially those developed by tech giants like Microsoft, demonstrate how graphs can:
- Enhance LLM Outputs: By grounding responses in structured knowledge, graphs significantly reduce hallucinations.
- Support Complex Queries: Graphs excel at managing linked and connected data, making them ideal for intricate problem-solving.
Conferences on linked and connected data have increasingly focused on Graph RAGs, underscoring their central role in modern AI systems. However, the excitement around this technology has brought critical questions to the forefront: How do we ensure the quality of the graphs we’re building, and are they genuinely aligned with our needs?
Data Quality: The Foundation of Effective Graphs
A high-quality graph is the backbone of any successful RAG system. Constructing these graphs from unstructured data requires attention to detail and rigorous processes. Here’s why:
- Richness of Entities: Effective retrieval depends on graphs populated with rich, detailed entities.
- Freedom from Hallucinations: Poorly constructed graphs amplify inaccuracies rather than mitigating them.
Without robust data quality, even the most sophisticated Graph RAGs become ineffective. As a result, the focus must shift to refining the graph construction process. Improving data strategy and ensuring meticulous data preparation is essential to unlock the full potential of Graph RAGs.
Hybrid Graph RAGs and Variations
While standard Graph RAGs are already transformative, hybrid models offer additional flexibility and power. Hybrid RAGs combine structured graph data with other retrieval mechanisms, creating systems that:
- Handle diverse data sources with ease.
- Offer improved adaptability to complex queries.
Exploring these variations can open new avenues for AI systems, particularly in domains requiring structured and unstructured data processing.
Ontology: The Key to Graph Construction Quality
Ontology — defining how concepts relate within a knowledge domain — is critical for building effective graphs. While this might sound abstract, it’s a well-established field blending philosophy, engineering, and art. Ontology engineering provides the framework for:
- Defining Relationships: Clarifying how concepts connect within a domain.
- Validating Graph Structures: Ensuring constructed graphs are logically sound and align with domain-specific realities.
Traditionally, ontologists — experts in this discipline — have been integral to large enterprises and research teams. However, not every team has access to dedicated ontologists, leading to a significant challenge: How can teams without such expertise ensure the quality of their graphs?
How to Build Ontology Expertise in a Startup Team
For startups and smaller teams, developing ontology expertise may seem daunting, but it is achievable with the right approach:
- Assign a Knowledge Champion: Identify a team member with a strong analytical mindset and give them time and resources to learn ontology engineering.
- Provide Training: Invest in courses, workshops, or certifications in knowledge graph and ontology creation.
- Leverage Partnerships: Collaborate with academic institutions, domain experts, or consultants to build initial frameworks.
- Utilize Tools: Introduce ontology development tools like Protégé, OWL, or SHACL to simplify the creation and validation process.
- Iterate with Feedback: Continuously refine ontologies through collaboration with domain experts and iterative testing.
So, it is not always affordable for a startup to have a dedicated oncologist or knowledge engineer in a team, but you could involve consulters or build barefoot experts.
You could read about barefoot experts in my article :
Even startups can achieve robust and domain-specific ontology frameworks by fostering in-house expertise.
How to Find or Create Ontologies
For teams venturing into Graph RAGs, several strategies can help address the ontology gap:
-
Leverage Existing Ontologies: Many industries and domains already have open ontologies. For instance:
-
Public Knowledge Graphs: Resources like Wikipedia’s graph offer a wealth of structured knowledge.
- Industry Standards: Enterprises such as Siemens have invested in creating and sharing ontologies specific to their fields.
-
Business Framework Ontology (BFO): A valuable resource for enterprises looking to define business processes and structures.
-
Build In-House Expertise: If budgets allow, consider hiring knowledge engineers or providing team members with the resources and time to develop expertise in ontology creation.
-
Utilize LLMs for Ontology Construction: Interestingly, LLMs themselves can act as a starting point for ontology development:
-
Prompt-Based Extraction: LLMs can generate draft ontologies by leveraging their extensive training on graph data.
- Domain Expert Refinement: Combine LLM-generated structures with insights from domain experts to create tailored ontologies.
Parallel Ontology and Graph Extraction
An emerging approach involves extracting ontologies and graphs in parallel. While this can streamline the process, it presents challenges such as:
- Detecting Hallucinations: Differentiating between genuine insights and AI-generated inaccuracies.
- Ensuring Completeness: Ensuring no critical concepts are overlooked during extraction.
Teams must carefully validate outputs to ensure reliability and accuracy when employing this parallel method.
LLMs as Ontologists
While traditionally dependent on human expertise, ontology creation is increasingly supported by LLMs. These models, trained on vast amounts of data, possess inherent knowledge of many open ontologies and taxonomies. Teams can use LLMs to:
- Generate Skeleton Ontologies: Prompt LLMs with domain-specific information to draft initial ontology structures.
- Validate and Refine Ontologies: Collaborate with domain experts to refine these drafts, ensuring accuracy and relevance.
However, for validation and graph construction, formal tools such as OWL, SHACL, and RDF should be prioritized over LLMs to minimize hallucinations and ensure robust outcomes.
Final Thoughts: Unlocking the Power of Graph RAGs
The rise of Graph RAGs underscores a simple but crucial correlation: improving graph construction and data quality directly enhances retrieval systems. To truly harness this power, teams must invest in understanding ontologies, building quality graphs, and leveraging both human expertise and advanced AI tools.
As we move forward, the interplay between Graph RAGs and ontology engineering will continue to shape the future of AI. Whether through adopting existing frameworks or exploring innovative uses of LLMs, the path to success lies in a deep commitment to data quality and domain understanding.
Have you explored these technologies in your work? Share your experiences and insights — and stay tuned for more discussions on ontology extraction and its role in AI advancements. Cheers to a year of innovation!
-
 @ ae6ce958:d0f02c7d
2025-01-27 05:36:26
@ ae6ce958:d0f02c7d
2025-01-27 05:36:26In the tradition of The Pragmatic Programmer, let’s dive deeper into how DamageBDD enables programmers to switch into flow, earn sats for their efforts, and unlock a positive neural feedback loop by fostering behavior-driven thinking. This not only amplifies productivity but also strengthens cognitive abilities, making developers sharper, more agile thinkers in the long run.
Flow State Meets Real-Time Rewards
What Is Flow?
The flow state is that magical zone where work feels effortless, time disappears, and every action seems to naturally lead to the next. Achieving flow requires clarity, focus, feedback, and a meaningful sense of progress—elements that DamageBDD inherently provides.
How DamageBDD Induces Flow
-
Behavior-Driven Focus:
BDD scenarios act as the “North Star” for developers, defining what the system should do in clear, actionable terms. There’s no ambiguity, no wasted energy figuring out what needs to be done—only a set of behaviors to implement, refine, or fix. -
Instant Feedback Loops:
Every line of code you write is immediately evaluated against predefined BDD scenarios. If it works, you see the green light and earn sats. If it fails, you get actionable feedback to correct it. This near-instantaneous feedback is a cornerstone of flow, reinforcing productive momentum. -
Real-Time Rewards:
With Bitcoin Lightning integration, every passing test or fixed behavior comes with an immediate, tangible payout. The brain loves rewards—earning sats becomes a dopamine hit, keeping you engaged and motivated.
The Positive Neural Feedback Loop of Thinking in Terms of Behavior
Why Behavior-Driven Thinking Matters
Programming in terms of behavior is more than a methodology—it’s a cognitive framework that sharpens your mind. When you define problems as behaviors to achieve, you:
- Simplify Complexity: Abstracting functionality into behaviors reduces cognitive load, making it easier to reason about systems.
- Improve Problem Solving: Thinking in terms of "what should happen" (rather than "how to make it happen") trains your brain to identify outcomes first, encouraging solution-focused thinking.
- Enhance Communication: Clear behavior definitions bridge gaps between developers, testers, and stakeholders, fostering better collaboration.
The Neural Benefits
-
Reinforcing Neural Pathways for Logical Thinking:
Every time you think in terms of behaviors, you exercise critical thinking and decision-making processes. Over time, these neural pathways strengthen, making you a faster, sharper problem solver. -
Amplifying Pattern Recognition:
Writing and debugging BDD scenarios train your brain to recognize patterns in system behaviors. This skill extends beyond coding—your ability to spot patterns in other domains improves as well. -
The Dopamine Feedback Loop:
Passing a test, fixing a bug, or earning sats provides immediate positive reinforcement. This dopamine boost strengthens your association between effort and reward, creating a virtuous cycle that keeps you engaged and growing. -
Cognitive Flexibility:
Behavior-driven thinking encourages adaptability. You’re constantly switching between defining, implementing, and refining behaviors—an exercise in cognitive flexibility that enhances your ability to pivot quickly in complex situations.
Amplifying Cognitive Skills Through BDD Practices
-
Systems Thinking:
DamageBDD encourages you to think holistically. BDD scenarios inherently connect individual behaviors to the larger system, fostering a deep understanding of how components interact. -
Empathy for End Users:
Since BDD focuses on expected behaviors, you’re always considering the user’s perspective. This not only improves product quality but also develops your ability to empathize and anticipate needs—a skill valuable in both technical and non-technical settings. -
Mindfulness and Focus:
Writing clear, precise BDD scenarios requires mindfulness. You must focus on the behavior you’re defining, ignoring distractions or unnecessary details. This mindful attention to detail translates into improved focus across all areas of life.
Switching Into Flow with DamageBDD: The Process
-
Defined Goals Through BDD:
BDD scenarios clearly define what needs to be accomplished. Each scenario is a mini-goal, providing a structured starting point for deep work. -
Automated Context Switching:
DamageBDD integrates seamlessly into CI/CD pipelines, handling testing, verification, and payouts. This automation eliminates the mental effort of managing manual workflows, freeing your mind to focus on the task at hand. -
Visual Dashboards for Real-Time Progress:
Real-time dashboards keep you in the loop, showing which tests have passed, which are failing, and how much you’ve earned in sats. This constant visibility reinforces a sense of progress and achievement, key elements of flow.
Switching Out of Flow: Sustainable Productivity
-
Natural Breakpoints:
Each passing test, earned payout, or resolved scenario creates a natural stopping point, encouraging healthy breaks and preventing burnout. -
Celebrating Progress:
DamageBDD doesn’t just reward you with sats—it gives you a clear picture of your contributions. Seeing how your work aligns with the product’s evolution provides intrinsic motivation and satisfaction. -
Gamification for Reflection:
Leaderboards, badges, or streaks could be implemented to gamify progress, encouraging reflection on your work and motivating future engagement.
Earning Sats in Cyberspace: Making Work Tangible
DamageBDD’s integration with the Bitcoin Lightning Network creates a revolutionary financial model for developers:
1. Every Contribution Matters:
Whether you’re fixing a bug, passing a test, or writing new BDD scenarios, you’re rewarded in sats. This turns even small contributions into meaningful, tangible outcomes.-
Microtransactions for Microtasks:
Unlike traditional compensation models, DamageBDD pays for specific, measurable achievements. This decentralizes reward distribution and ensures fairness. -
Compounding Value:
As you earn sats, you’re also improving the product and your skills. This creates a compounding effect where your work generates value for the system, for yourself, and for your future employability.
A Day in the Life with DamageBDD
- Morning: You review a list of failing BDDs, prioritizing those with the highest payouts. You dive in, quickly fixing a few behaviors, and see your balance increase by 15,000 sats.
- Midday: Collaborating with teammates, you define new BDD scenarios for a feature. As they pass, you collectively earn sats while seeing the feature evolve in real-time.
- Afternoon: You notice an ambiguous BDD and rewrite it for clarity. Your improved scenario prevents potential bugs and earns you recognition and additional sats.
By the end of the day, you’ve been immersed in productive flow, refined your cognitive skills, and earned sats for your contributions.
Conclusion: DamageBDD as a Cognitive and Economic Catalyst
DamageBDD doesn’t just make programming more productive—it makes it more rewarding, both financially and cognitively. By fostering behavior-driven thinking, enabling flow states, and creating a tangible connection between effort and reward, it:
- Strengthens your brain’s problem-solving abilities.
- Encourages mindfulness and focus.
- Provides immediate gratification for meaningful contributions.For pragmatic programmers who value growth, productivity, and fairness, DamageBDD isn’t just a tool—it’s a transformative experience that rewards you for diving into cyberspace, one behavior at a time.
-
-
 @ a4a6b584:1e05b95b
2025-01-02 18:13:31
@ a4a6b584:1e05b95b
2025-01-02 18:13:31The Four-Layer Framework
Layer 1: Zoom Out

Start by looking at the big picture. What’s the subject about, and why does it matter? Focus on the overarching ideas and how they fit together. Think of this as the 30,000-foot view—it’s about understanding the "why" and "how" before diving into the "what."
Example: If you’re learning programming, start by understanding that it’s about giving logical instructions to computers to solve problems.
- Tip: Keep it simple. Summarize the subject in one or two sentences and avoid getting bogged down in specifics at this stage.
Once you have the big picture in mind, it’s time to start breaking it down.
Layer 2: Categorize and Connect

Now it’s time to break the subject into categories—like creating branches on a tree. This helps your brain organize information logically and see connections between ideas.
Example: Studying biology? Group concepts into categories like cells, genetics, and ecosystems.
- Tip: Use headings or labels to group similar ideas. Jot these down in a list or simple diagram to keep track.
With your categories in place, you’re ready to dive into the details that bring them to life.
Layer 3: Master the Details

Once you’ve mapped out the main categories, you’re ready to dive deeper. This is where you learn the nuts and bolts—like formulas, specific techniques, or key terminology. These details make the subject practical and actionable.
Example: In programming, this might mean learning the syntax for loops, conditionals, or functions in your chosen language.
- Tip: Focus on details that clarify the categories from Layer 2. Skip anything that doesn’t add to your understanding.
Now that you’ve mastered the essentials, you can expand your knowledge to include extra material.
Layer 4: Expand Your Horizons

Finally, move on to the extra material—less critical facts, trivia, or edge cases. While these aren’t essential to mastering the subject, they can be useful in specialized discussions or exams.
Example: Learn about rare programming quirks or historical trivia about a language’s development.
- Tip: Spend minimal time here unless it’s necessary for your goals. It’s okay to skim if you’re short on time.
Pro Tips for Better Learning
1. Use Active Recall and Spaced Repetition
Test yourself without looking at notes. Review what you’ve learned at increasing intervals—like after a day, a week, and a month. This strengthens memory by forcing your brain to actively retrieve information.
2. Map It Out
Create visual aids like diagrams or concept maps to clarify relationships between ideas. These are particularly helpful for organizing categories in Layer 2.
3. Teach What You Learn
Explain the subject to someone else as if they’re hearing it for the first time. Teaching exposes any gaps in your understanding and helps reinforce the material.
4. Engage with LLMs and Discuss Concepts
Take advantage of tools like ChatGPT or similar large language models to explore your topic in greater depth. Use these tools to:
- Ask specific questions to clarify confusing points.
- Engage in discussions to simulate real-world applications of the subject.
- Generate examples or analogies that deepen your understanding.Tip: Use LLMs as a study partner, but don’t rely solely on them. Combine these insights with your own critical thinking to develop a well-rounded perspective.
Get Started
Ready to try the Four-Layer Method? Take 15 minutes today to map out the big picture of a topic you’re curious about—what’s it all about, and why does it matter? By building your understanding step by step, you’ll master the subject with less stress and more confidence.
-
 @ b17fccdf:b7211155
2025-01-21 16:30:11
@ b17fccdf:b7211155
2025-01-21 16:30:11Your MiniBolt is on a home local network, you want to expose it on the public Internet (clearnet) without exposing your public IP, without Firewall rules, without NAT port forwarding, without risk, easy and cheap?
Go to the bonus guide by clicking ~ >HERE <~
Enjoy it MiniBolter! 💙
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ f33c8a96:5ec6f741
2025-01-22 20:38:02
@ f33c8a96:5ec6f741
2025-01-22 20:38:02 -
 @ fe32298e:20516265
2024-12-16 20:59:13
@ fe32298e:20516265
2024-12-16 20:59:13Today I learned how to install NVapi to monitor my GPUs in Home Assistant.

NVApi is a lightweight API designed for monitoring NVIDIA GPU utilization and enabling automated power management. It provides real-time GPU metrics, supports integration with tools like Home Assistant, and offers flexible power management and PCIe link speed management based on workload and thermal conditions.
- GPU Utilization Monitoring: Utilization, memory usage, temperature, fan speed, and power consumption.
- Automated Power Limiting: Adjusts power limits dynamically based on temperature thresholds and total power caps, configurable per GPU or globally.
- Cross-GPU Coordination: Total power budget applies across multiple GPUs in the same system.
- PCIe Link Speed Management: Controls minimum and maximum PCIe link speeds with idle thresholds for power optimization.
- Home Assistant Integration: Uses the built-in RESTful platform and template sensors.
Getting the Data
sudo apt install golang-go git clone https://github.com/sammcj/NVApi.git cd NVapi go run main.go -port 9999 -rate 1 curl http://localhost:9999/gpuResponse for a single GPU:
[ { "index": 0, "name": "NVIDIA GeForce RTX 4090", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 16, "power_limit_watts": 450, "memory_total_gb": 23.99, "memory_used_gb": 0.46, "memory_free_gb": 23.52, "memory_usage_percent": 2, "temperature": 38, "processes": [], "pcie_link_state": "not managed" } ]Response for multiple GPUs:
[ { "index": 0, "name": "NVIDIA GeForce RTX 3090", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 14, "power_limit_watts": 350, "memory_total_gb": 24, "memory_used_gb": 0.43, "memory_free_gb": 23.57, "memory_usage_percent": 2, "temperature": 36, "processes": [], "pcie_link_state": "not managed" }, { "index": 1, "name": "NVIDIA RTX A4000", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 10, "power_limit_watts": 140, "memory_total_gb": 15.99, "memory_used_gb": 0.56, "memory_free_gb": 15.43, "memory_usage_percent": 3, "temperature": 41, "processes": [], "pcie_link_state": "not managed" } ]Start at Boot
Create
/etc/systemd/system/nvapi.service:``` [Unit] Description=Run NVapi After=network.target
[Service] Type=simple Environment="GOPATH=/home/ansible/go" WorkingDirectory=/home/ansible/NVapi ExecStart=/usr/bin/go run main.go -port 9999 -rate 1 Restart=always User=ansible
Environment="GPU_TEMP_CHECK_INTERVAL=5"
Environment="GPU_TOTAL_POWER_CAP=400"
Environment="GPU_0_LOW_TEMP=40"
Environment="GPU_0_MEDIUM_TEMP=70"
Environment="GPU_0_LOW_TEMP_LIMIT=135"
Environment="GPU_0_MEDIUM_TEMP_LIMIT=120"
Environment="GPU_0_HIGH_TEMP_LIMIT=100"
Environment="GPU_1_LOW_TEMP=45"
Environment="GPU_1_MEDIUM_TEMP=75"
Environment="GPU_1_LOW_TEMP_LIMIT=140"
Environment="GPU_1_MEDIUM_TEMP_LIMIT=125"
Environment="GPU_1_HIGH_TEMP_LIMIT=110"
[Install] WantedBy=multi-user.target ```
Home Assistant
Add to Home Assistant
configuration.yamland restart HA (completely).For a single GPU, this works: ``` sensor: - platform: rest name: MYPC GPU Information resource: http://mypc:9999 method: GET headers: Content-Type: application/json value_template: "{{ value_json[0].index }}" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature scan_interval: 1 # seconds
- platform: template sensors: mypc_gpu_0_gpu: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} GPU" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_memory: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Memory" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_power: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Power" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_0_power_limit: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_0_temperature: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Temperature" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'temperature') }}" unit_of_measurement: "°C" ```
For multiple GPUs: ``` rest: scan_interval: 1 resource: http://mypc:9999 sensor: - name: "MYPC GPU0 Information" value_template: "{{ value_json[0].index }}" json_attributes_path: "$.0" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature - name: "MYPC GPU1 Information" value_template: "{{ value_json[1].index }}" json_attributes_path: "$.1" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature
-
platform: template sensors: mypc_gpu_0_gpu: friendly_name: "MYPC GPU0 GPU" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_memory: friendly_name: "MYPC GPU0 Memory" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_power: friendly_name: "MYPC GPU0 Power" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_0_power_limit: friendly_name: "MYPC GPU0 Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_0_temperature: friendly_name: "MYPC GPU0 Temperature" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'temperature') }}" unit_of_measurement: "C"
-
platform: template sensors: mypc_gpu_1_gpu: friendly_name: "MYPC GPU1 GPU" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_1_memory: friendly_name: "MYPC GPU1 Memory" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_1_power: friendly_name: "MYPC GPU1 Power" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_1_power_limit: friendly_name: "MYPC GPU1 Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_1_temperature: friendly_name: "MYPC GPU1 Temperature" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'temperature') }}" unit_of_measurement: "C"
```
Basic entity card:
type: entities entities: - entity: sensor.mypc_gpu_0_gpu secondary_info: last-updated - entity: sensor.mypc_gpu_0_memory secondary_info: last-updated - entity: sensor.mypc_gpu_0_power secondary_info: last-updated - entity: sensor.mypc_gpu_0_power_limit secondary_info: last-updated - entity: sensor.mypc_gpu_0_temperature secondary_info: last-updatedAnsible Role
```
-
name: install go become: true package: name: golang-go state: present
-
name: git clone git: repo: "https://github.com/sammcj/NVApi.git" dest: "/home/ansible/NVapi" update: yes force: true
go run main.go -port 9999 -rate 1
-
name: install systemd service become: true copy: src: nvapi.service dest: /etc/systemd/system/nvapi.service
-
name: Reload systemd daemons, enable, and restart nvapi become: true systemd: name: nvapi daemon_reload: yes enabled: yes state: restarted ```
-
 @ 000002de:c05780a7
2025-01-22 16:33:59
@ 000002de:c05780a7
2025-01-22 16:33:59Anyone else noticing their LN address not working with Minibits?
originally posted at https://stacker.news/items/860143
-
 @ b17fccdf:b7211155
2025-01-21 16:23:44
@ b17fccdf:b7211155
2025-01-21 16:23:44Build your nostr relay step by step on your MiniBolt node! (easily adaptable to other environment) No need to trust anyone else! Be sovereign!
~> Go to the bonus guide by clicking ~> HERE< ~
~> This guide includes a complete extra section to cover the different processes for using nostr as a user and relay operator.
PS: The MiniBolt project has its FREE relay, be free to connect by adding to your favorite client the next address:
wss://relay.minibolt.info~> Let a review on noStrudel or Coracle of your experience using it.
Remember, Nostr is freedom! Stay resilient! 💜 🛡️💪
-
 @ a853296a:209e695f
2025-01-22 15:30:28
@ a853296a:209e695f
2025-01-22 15:30:28🎙️ Howdy cowboys, stackers and podcast enthusiasts! 🤠
Last week we released Pull That Up Jamie. 🚀
Today we're thrilled to announce an upgrade to The Fastest Podcast Search in the West 🤠 with significant UX improvements! Check out the full details in the (announcement post). 📰
🔥 Fast Jamie Rundown:
- 🛠️ 18 high-signal Bitcoin and lifestyle podcasts for lightning-fast insights ⚡
- 🔗 Share podcast clips with exact timestamps and a dedicated landing page
- 📱 Listen and explore from mobile or desktop browser — smooth and seamless!
- 🚀 Enhanced hybrid keyword and embeddings search for lightning-fast performance & spot-on results
🏆 Highlights
🎧 Learning about P2P rights legal work on Samourai and Tornado Cash with Zach Shapiro on Citadel Dispatch @ODELL (deeplink)
🎧 @nicktee highlighted this Bitcoin Optech gem on BOLT12 blinded paths (clip deeplink)
🎧 @futurepaul's chat with @TheGuySwann on Mutiny's pivot to Open Secret (clip deeplink)
🚀 Future Development:
- 🎙️ Expanding podcast feeds: From sports and health to AI and theology!
- 🌐 Integrating with Jamie Web Search for a unified search experience
- 🤖 More automation for seamless use
- 🚨 More [REDACTED]... stay tuned for epic updates! 😉
🤠 Giddy-up, and happy listening, y’all! Let us know your thoughts in the comments! 🗣️
originally posted at https://stacker.news/items/860053
-
 @ 59c2e15a:d25e6e8d
2025-01-27 02:29:42
@ 59c2e15a:d25e6e8d
2025-01-27 02:29:42Note: I originally wrote these essays on bitcoin and yoga in 2022 after completing my yoga teacher training and going deep down the bitcoin rabbit hole. I then published them to my Ghost blog in 2023. I decided to repost them here on Nostr to start 2025 to further spread the wisdom and timelessness that bitcoin and yoga share. I split my original essay into seven parts, and I will add an eighth comparing yoga and Nostr. I hope you enjoy part one - namaste!
Part I: Bitcoin and Yoga Shared Values
Part II: Mythical/Mystical Origins
Part III: Evolution of Money and Yoga
Part IV: Ashtanga Yoga - The Eight Limbs of Yoga (limbs 1-2)
Part V: Ashtanga Yoga - The Eight Limbs of Yoga (limbs 3-8)
Part VI: Bitcoin is Dharma
Part VII: Himalayan Kriya Yoga
Introduction
With each passing day, month, and year, it feels as though our human civilization is becoming more dysfunctional, untethered, and unsustainable. Individuals are working harder, longer hours, yet most remain stuck in place, goals farther from reach. We live in a world where many have outsourced the most critical task that has enabled humans to prosper – critical thinking. I challenge each one of you to remove preconceived notions you might have about Bitcoin or Yoga before reading this series. I invite you to enter with an open mind. Think for yourself – you are welcome to agree or disagree with the information and arguments I put forth.
I also encourage you to go beyond thinking – feel. Use your intuition to understand if the way you’re living your day-to-day life feels good to you, or if you have sense, an inner knowing that something is off with our society today – that there can be a better way. If you open your heart and mind to receiving new information, there is potential to motivate yourself to change your thoughts and behaviors for more aligned action towards individual sovereignty. Every individual can choose freedom and independence. Yet it has become increasingly difficult to live a life of freedom due to the fiat system of inflation and the many distractions that keep us from going inward. After deep study and reflection, I believe bitcoin and yoga both provide the individual control over their own life journey, and frameworks to understand our connection to self and others.
I'm excited to share what I have found in my own personal experience, and hope to spark curiosity within you to follow your passion. This writing is intended for anyone seeking tools to lead a life of freedom, make positive changes and deepen your understanding of self. In addition, it is written for yogis who want to learn about bitcoin, bitcoiners who want to learn more about yoga, and anyone who is interested in a fundamental understanding of these topics that I believe contain the potential to transform your life.
Part I: Bitcoin and Yoga Shared Values
Bitcoin and yoga share many fundamental values with one another and provide deep wisdom on guiding individuals towards living better and more meaningful lives. Ultimately bitcoin and yoga share the goal of individual liberation, freedom from suffering, and a deep inner, lasting peace in Being. In yoga, this state is called moksha or samadhi. I believe everyone has a true essence, an inner being that knows what is best. However, our external environment and our own conscious mind push us away from this serenity, leading to regrets about the past or anxieties about the future. This perspective of linear time and our own individual stories and identity damage our ability to stay present in the Now, leading to endless distractions. In similar ways, bitcoin and yoga provide us insight for an individual’s path to inner peace, as well as for humanity’s path to collective peace and prosperity.
Energy
At the most elemental level, energy is the force underlying both bitcoin and yoga. Energy is the universal currency of life. We would not exist without energy. We require physical energy to fuel our cells and bodies to perform essential tasks like breathing, circulation, digestion, and movement. We perceive many forms of energy such as light or sound waves, yet there are many energy wavelengths we are not able to or are not trained to perceive.
Bitcoin is powered by physical energy in the real world in a process that secures the network and unlocks new bitcoin for distribution, a process commonly referred to as mining. Interestingly, 100 years ago, Henry Ford pushed for an energy-linked currency measured in kilowatt hours that could bring peace after a brutal World War, as seen in the New York Tribune headline and article December 4, 1921: ‘Ford Would Replace Gold with Energy Currency and Stop Wars’ (i). It took another century, but mankind has finally developed a digitally-native currency tied to the physical world through energy expenditure – bitcoin.
Yoga is similarly rooted in energy that individuals tap into through breathwork, physical movement and meditations practices. This life-force energy is known in Sanskrit as prana. Prana is not bound by time or space, and it flows through individuals in over 72,000 nadis, or channels. There are three main nadis - the first is ida, our left side body which corresponds to the feminine, receiving energy, or the moon. On the right side is pingala, relating to our masculine, giving energy, or the sun. The central nadi runs through our shushumna, linking our seven main energetic centers, known as chakras. These chakras run from the base of the tail bone, up through the spine and the top of the head. Each chakra has a name, a color and key characteristics that can often become blocked through negative emotion, trauma or stress in the body. Different yogic practices target these energy centers to unlock what is stuck and enable energy to more freely flow through us in an open exchange with the earth and out the universe. This energy is ever-present; one need only to tap into this energy, feel it and utilize it for the strengthening of one’s inner being that then radiates outwards on others in your life. The energetic experience and upward surge can also be referred to as kundalini energy, a creative power of divine feminine energy that originates in the muladara chakra at the base of the spine.
 Depiction of our chakras and nadis (image source)
Depiction of our chakras and nadis (image source)Proof of Work
In both Bitcoin and Yoga, "proof of work" is required to operate, practice and move forwards. In the Bitcoin network as described in the original white paper, miners contribute tangible energy towards running a hashing algorithm on a computer – SHA256 – to earn the right to add the next block to the blockchain and collect both the coinbase and transaction fee reward (ii). The work is difficult to produce but easy to validate by others. Miners are collecting all of the valid peer-to-peer transactions being propagated to the network and establishing them as truth into the distributed ledger. The rules in bitcoin’s code incentivize honest behavior from miners through unforgeable costliness – if a miner were to lie about any of the transactions it includes in a block, independent nodes in the network would reject the block, and the miner would have lost all the real resources it expended to solve the proof of work calculation.
 Example of an ASIC - a specialized computer solely dedicated to mining bitcoin.
Example of an ASIC - a specialized computer solely dedicated to mining bitcoin.In yoga, dedicated work is needed to learn the asanas, postures, and practice for oneself; you won’t just be able to go upside down or flow through sun salutations without first learning proper alignment and breathing techniques. An individual needs to conscious decision to work on a daily yoga practice that requires energy to flow. There are several ways to work on your yoga practice beyond physical movement; these include bhakti yoga (devotion/prayer), jnana yoga (study/wisdom), karma yoga(selfless action) and raja yoga (ashtanga). Raja yoga includes ashtanga, the eight limbs or paths of yoga that Patanjali detailed \~2000 years ago that we will explore in more depth in part IV. These ancient margas (paths) and subsequent development of these ancient teachings provides individual with ample opportunity to dedicate and work towards individual enlightenment.
Decentralization
Next, there are no external barriers preventing an individual from participating in Bitcoin or yoga. Bitcoin does not discriminate and can be accessed by anyone around the world. Yoga provides a way of life full of mindfulness and appreciation. The only barriers are internal blockages, or unwillingness to ask questions, learn and take responsibility for oneself and state of being. Therefore, Bitcoin and yoga can both be defined as decentralized. There are no centralized gatekeepers preventing one from accessing the Bitcoin network or using bitcoin as money; anyone can spin up a node, download a wallet or mine bitcoin. There are over 16,000 nodes geographically distributed around the world voluntarily running the bitcoin core software code establishing the payment network, validating transactions and storing the entire transaction history of bitcoin (iii). It costs as little as a few hundred dollars and requires less than 600 gigabytes of storage to run a node – in 2023 you can find mobile phones with that much storage. No one can prevent you from sending a peer-to-peer transaction or storing your own wealth with 12 words in your head – you need only decide to take true freedom into your own hands and learn how to do so (iv). The common maxim is “don’t trust, verify”. You don’t need someone else’s permission to participate in bitcoin or trust anyone else (eg, banks) to hold your wealth.
 Geographic distribution of reachable bitcoin nodes (source: bitnodes)
Geographic distribution of reachable bitcoin nodes (source: bitnodes)Similarly, no one can stop an individual from practicing yoga, learning yogic philosophy or connecting with one’s truest self and inner guru. Anyone can choose to follow the path of yoga, focus on ones breath or develop a strong asana practice. There are many different ways to learn and interact with yoga, with experienced teachers willing to share their lessons to students all over the world. One need to simply find yoga studio, enroll in a teacher training or and engage with a teacher to experience yoga for themselves. Yoga looks and feels different depending on what country you are in or in which lineage you are being taught. Tapping into these profound lessons, as fundamental as controlling ones own breath, requires only an individual desire and the conscious decision to act. There’s no CEO or central authority dictating how Bitcoin or yoga has to be. Individuals have the freedom to express themselves voluntarily guided by frameworks we will dive into deeper.
Low Time Preference
Another core value that bitcoin and yoga share is low time preference. In Austrian economics, time preference refers to individual decision making. An individual with a low time preference makes decisions with greater consideration of the future, quieting immediate cravings and desires to pursue a higher goal (v). In bitcoin and money, lower time preference decisions include putting off consumption to save value for the future. Unfortunately, our fiat (by government decree) system induces individuals to make high time preference decisions, heightening consumerism and poor habits today that we see rampant in our society. There is a disincentive to save, as inflation of the money supply leads to debasing value of the dollar and other fiat currencies, decreasing individuals purchasing power of cash they hold onto and don’t spend soon. For example, the purchasing power of your dollar today will be cut in half over the next decade at current levels of inflation. In many ways, bitcoin is time, described brilliantly by Gigi, as it creates a decentralized clock that establishes consensus with each block (vi).
In contrast, the hard cap supply of 21 million bitcoin enables individuals to save with the knowledge that governments and central banks will not be able to debase their hard-earned value. This allows for one to plan with greater certainty, making investments that have a longer payoff period rather than chasing quick, material gains. Likewise in yoga, developing your own practice will not bear fruit right away; it takes discipline and time to continuously improve and strive towards a better future self. For example, in modern Ashtanga yoga taught by Pattabhi Jois, there is a set sequence of asanas that one studies and repeats each practice. It may even take months to have find the right alignment of body and breath for a single pose! The hours-long sequence requires dedication to practice and learn. The dedicated yogi understands that wholehearted commitment today will pay off for one’s mental, physical and spiritual health in the years to come. The ability to develop a calm mind can also be beneficial when people don’t initially understand or are intimidated by bitcoin. This approach can also enable you to stay grounded and discover the signal through the noise when learning about bitcoin.
 Sequence of asanas in Jois' Ashtanga Yoga (image source)
Sequence of asanas in Jois' Ashtanga Yoga (image source)Union
Yoga comes from the Sanskrit word “yuj”, which means ‘to join’ or ‘to unite’. Yoga represents the union of the mind, body, and soul of an individual. Yoga provides a pathway to individual sovereignty through disciplined practice and purpose. Yoga unites an individual internally and to one’s community, fostering connectedness and support (vii). Similarly, bitcoin provides a pathway to individual sovereignty in many ways. Bitcoin empowers the individual authority with property rights over one’s value, which in turn frees individuals from outside control (government or otherwise). Bitcoin’s technology enables one to hold their own wealth and life’s energy in a self-custodial fashion. Bitcoin is money that can be stored forever and transmitted through space at the speed of light on layer two via the Lightning Network.
Bitcoin is an open economic network with the potential to unite eight billion people together in a way our current unfair and fragmented financial system could never do. In many countries, a majority of people are unbanked, while intermediaries take a cut of the value to transfer slow, legacy payments like Western Union. While tens of millions people around the world have so far interacted with bitcoin – we are still early – similar to the internet of the mid-nineties. Bitcoin eliminates counter party risk associated with non-bearer assets, such as fiat currency (e.g., dollars, euros, yen). Bitcoin’s supply schedule is set and eliminates inflation time theft that fiat currency wages on individuals, which leads to anxiety and depression or feelings of hopelessness. Fiat is money enforced by the monopoly on violence that modern nation states grip tightly.
In contrast, bitcoin and yoga empower the individual to remove the shackles and embrace personal responsibility to improve ones life. Bitcoin and yoga also connect people directly to each other and tap into truth, ones inner being, bringing peace in the present and ultimately offer hope for a better future for each person, your community, and the world. Bitcoin and yoga have the power to unite humanity in love.
In the next section, we will explore both yoga and bitcoin's mystical and mythical origins.
Note: Bitcoin with a capital "B" generally refers to the protocol/network; bitcoin with a lower case "b" refers to the money/currency.
References:
i. Redman, Jamie, How Henry Ford Envisaged Bitcoin 100 Years Ago — A Unique 'Energy Currency' That Could 'Stop Wars', News.Bitcoin.Com, October 11, 2021 <https://news.bitcoin.com/how-henry-ford-envisaged-bitcoin-100-years-ago-a-unique-energy-currency-that-could-stop-wars/>
ii. Nakomoto, Satoshi, Bitcoin: A Peer-to-Peer Electronic Cash System, bitcoin.org, October 31, 2008 <https://bitcoin.org/bitcoin.pdf>
iii. https://bitnodes.io/
iv. Hall, Stephen, What is a bitcoin seed phrase and how does it work? Unchained.com. December 17, 2021 <https://unchained.com/blog/what-is-a-bitcoin-seed-phrase/>
v. Ammous, Saifedean, Making Time Preference Low Again, The Bitcoin Times, Austrian Edition (V). November 8, 2022 <https://bitcointimes.io/making-time-preference-low-again/>
vi. Gigi, Bitcoin is Time, dergigi.com. Jan 14,2021 <https://dergigi.com/2021/01/14/bitcoin-is-time/>
vii. 200 hour yoga teacher training. House of Om, Bali, Indonesia. <https://houseofom.com/>
-
 @ c1e6505c:02b3157e
2025-01-20 19:44:05
@ c1e6505c:02b3157e
2025-01-20 19:44:05There’s a tension between nature’s rhythms and human ambition, especially in winter. As Earth meanders to its furthest point from the sun, our social and economic engines paradoxically accelerate - driven by holidays, deadlines, and the relentless pursuit of being productive. Yet nature offers a contrasting wisdom in its deliberate deceleration, encouraging us to slow down and reflect.
 Seasonal cycles are not arbitrary patterns but interconnected signals within a web of biological, environmental, and economic systems. *Their foundation lies in light itself — the building block of existence, essentially matter in a slowed-down state. This act of deceleration doesn’t just create physical substance; it provides structure, clarity, and form.* Meandering through these seasonal changes isn’t a passive drift - it’s an opportunity to realign. Slowing down, like nature does, creates space to step back from the busyness of society and technology. It allows us to reflect on where we are, re-ground ourselves, and act with greater intention. In this pause, we rediscover the creative power of slowness: the ability to lay foundations, see clearly, and prepare for growth when the time is right. Seasons are more than a backdrop — they are guides. They remind us that slowing down isn’t stagnation but essential groundwork. Winter’s invitation to pause and meander is not only natural; it’s necessary for balance, perspective, and creating something enduring.
Seasonal cycles are not arbitrary patterns but interconnected signals within a web of biological, environmental, and economic systems. *Their foundation lies in light itself — the building block of existence, essentially matter in a slowed-down state. This act of deceleration doesn’t just create physical substance; it provides structure, clarity, and form.* Meandering through these seasonal changes isn’t a passive drift - it’s an opportunity to realign. Slowing down, like nature does, creates space to step back from the busyness of society and technology. It allows us to reflect on where we are, re-ground ourselves, and act with greater intention. In this pause, we rediscover the creative power of slowness: the ability to lay foundations, see clearly, and prepare for growth when the time is right. Seasons are more than a backdrop — they are guides. They remind us that slowing down isn’t stagnation but essential groundwork. Winter’s invitation to pause and meander is not only natural; it’s necessary for balance, perspective, and creating something enduring. 







 *All photographs are taken around where I live in South Carolina* ***I shoot with a Leica M262, and edit in Lightroom + Dehancer*** [***Use “PictureRoom” for 10% off Dehancer Film***](https://www.dehancer.com/shop/pslr/film) If you’ve made it this far, thank you for taking the time to view my work - I appreciate it. Please contact me if you would like to purchase any of my prints.
*All photographs are taken around where I live in South Carolina* ***I shoot with a Leica M262, and edit in Lightroom + Dehancer*** [***Use “PictureRoom” for 10% off Dehancer Film***](https://www.dehancer.com/shop/pslr/film) If you’ve made it this far, thank you for taking the time to view my work - I appreciate it. Please contact me if you would like to purchase any of my prints. -
 @ 6f6b50bb:a848e5a1
2024-12-15 15:09:52
@ 6f6b50bb:a848e5a1
2024-12-15 15:09:52Che cosa significherebbe trattare l'IA come uno strumento invece che come una persona?
Dall’avvio di ChatGPT, le esplorazioni in due direzioni hanno preso velocità.
La prima direzione riguarda le capacità tecniche. Quanto grande possiamo addestrare un modello? Quanto bene può rispondere alle domande del SAT? Con quanta efficienza possiamo distribuirlo?
La seconda direzione riguarda il design dell’interazione. Come comunichiamo con un modello? Come possiamo usarlo per un lavoro utile? Quale metafora usiamo per ragionare su di esso?
La prima direzione è ampiamente seguita e enormemente finanziata, e per una buona ragione: i progressi nelle capacità tecniche sono alla base di ogni possibile applicazione. Ma la seconda è altrettanto cruciale per il campo e ha enormi incognite. Siamo solo a pochi anni dall’inizio dell’era dei grandi modelli. Quali sono le probabilità che abbiamo già capito i modi migliori per usarli?
Propongo una nuova modalità di interazione, in cui i modelli svolgano il ruolo di applicazioni informatiche (ad esempio app per telefoni): fornendo un’interfaccia grafica, interpretando gli input degli utenti e aggiornando il loro stato. In questa modalità, invece di essere un “agente” che utilizza un computer per conto dell’essere umano, l’IA può fornire un ambiente informatico più ricco e potente che possiamo utilizzare.
Metafore per l’interazione
Al centro di un’interazione c’è una metafora che guida le aspettative di un utente su un sistema. I primi giorni dell’informatica hanno preso metafore come “scrivanie”, “macchine da scrivere”, “fogli di calcolo” e “lettere” e le hanno trasformate in equivalenti digitali, permettendo all’utente di ragionare sul loro comportamento. Puoi lasciare qualcosa sulla tua scrivania e tornare a prenderlo; hai bisogno di un indirizzo per inviare una lettera. Man mano che abbiamo sviluppato una conoscenza culturale di questi dispositivi, la necessità di queste particolari metafore è scomparsa, e con esse i design di interfaccia skeumorfici che le rafforzavano. Come un cestino o una matita, un computer è ora una metafora di se stesso.
La metafora dominante per i grandi modelli oggi è modello-come-persona. Questa è una metafora efficace perché le persone hanno capacità estese che conosciamo intuitivamente. Implica che possiamo avere una conversazione con un modello e porgli domande; che il modello possa collaborare con noi su un documento o un pezzo di codice; che possiamo assegnargli un compito da svolgere da solo e che tornerà quando sarà finito.
Tuttavia, trattare un modello come una persona limita profondamente il nostro modo di pensare all’interazione con esso. Le interazioni umane sono intrinsecamente lente e lineari, limitate dalla larghezza di banda e dalla natura a turni della comunicazione verbale. Come abbiamo tutti sperimentato, comunicare idee complesse in una conversazione è difficile e dispersivo. Quando vogliamo precisione, ci rivolgiamo invece a strumenti, utilizzando manipolazioni dirette e interfacce visive ad alta larghezza di banda per creare diagrammi, scrivere codice e progettare modelli CAD. Poiché concepiamo i modelli come persone, li utilizziamo attraverso conversazioni lente, anche se sono perfettamente in grado di accettare input diretti e rapidi e di produrre risultati visivi. Le metafore che utilizziamo limitano le esperienze che costruiamo, e la metafora modello-come-persona ci impedisce di esplorare il pieno potenziale dei grandi modelli.
Per molti casi d’uso, e specialmente per il lavoro produttivo, credo che il futuro risieda in un’altra metafora: modello-come-computer.
Usare un’IA come un computer
Sotto la metafora modello-come-computer, interagiremo con i grandi modelli seguendo le intuizioni che abbiamo sulle applicazioni informatiche (sia su desktop, tablet o telefono). Nota che ciò non significa che il modello sarà un’app tradizionale più di quanto il desktop di Windows fosse una scrivania letterale. “Applicazione informatica” sarà un modo per un modello di rappresentarsi a noi. Invece di agire come una persona, il modello agirà come un computer.
Agire come un computer significa produrre un’interfaccia grafica. Al posto del flusso lineare di testo in stile telescrivente fornito da ChatGPT, un sistema modello-come-computer genererà qualcosa che somiglia all’interfaccia di un’applicazione moderna: pulsanti, cursori, schede, immagini, grafici e tutto il resto. Questo affronta limitazioni chiave dell’interfaccia di chat standard modello-come-persona:
-
Scoperta. Un buon strumento suggerisce i suoi usi. Quando l’unica interfaccia è una casella di testo vuota, spetta all’utente capire cosa fare e comprendere i limiti del sistema. La barra laterale Modifica in Lightroom è un ottimo modo per imparare l’editing fotografico perché non si limita a dirti cosa può fare questa applicazione con una foto, ma cosa potresti voler fare. Allo stesso modo, un’interfaccia modello-come-computer per DALL-E potrebbe mostrare nuove possibilità per le tue generazioni di immagini.
-
Efficienza. La manipolazione diretta è più rapida che scrivere una richiesta a parole. Per continuare l’esempio di Lightroom, sarebbe impensabile modificare una foto dicendo a una persona quali cursori spostare e di quanto. Ci vorrebbe un giorno intero per chiedere un’esposizione leggermente più bassa e una vibranza leggermente più alta, solo per vedere come apparirebbe. Nella metafora modello-come-computer, il modello può creare strumenti che ti permettono di comunicare ciò che vuoi più efficientemente e quindi di fare le cose più rapidamente.
A differenza di un’app tradizionale, questa interfaccia grafica è generata dal modello su richiesta. Questo significa che ogni parte dell’interfaccia che vedi è rilevante per ciò che stai facendo in quel momento, inclusi i contenuti specifici del tuo lavoro. Significa anche che, se desideri un’interfaccia più ampia o diversa, puoi semplicemente richiederla. Potresti chiedere a DALL-E di produrre alcuni preset modificabili per le sue impostazioni ispirati da famosi artisti di schizzi. Quando clicchi sul preset Leonardo da Vinci, imposta i cursori per disegni prospettici altamente dettagliati in inchiostro nero. Se clicchi su Charles Schulz, seleziona fumetti tecnicolor 2D a basso dettaglio.
Una bicicletta della mente proteiforme
La metafora modello-come-persona ha una curiosa tendenza a creare distanza tra l’utente e il modello, rispecchiando il divario di comunicazione tra due persone che può essere ridotto ma mai completamente colmato. A causa della difficoltà e del costo di comunicare a parole, le persone tendono a suddividere i compiti tra loro in blocchi grandi e il più indipendenti possibile. Le interfacce modello-come-persona seguono questo schema: non vale la pena dire a un modello di aggiungere un return statement alla tua funzione quando è più veloce scriverlo da solo. Con il sovraccarico della comunicazione, i sistemi modello-come-persona sono più utili quando possono fare un intero blocco di lavoro da soli. Fanno le cose per te.
Questo contrasta con il modo in cui interagiamo con i computer o altri strumenti. Gli strumenti producono feedback visivi in tempo reale e sono controllati attraverso manipolazioni dirette. Hanno un overhead comunicativo così basso che non è necessario specificare un blocco di lavoro indipendente. Ha più senso mantenere l’umano nel loop e dirigere lo strumento momento per momento. Come stivali delle sette leghe, gli strumenti ti permettono di andare più lontano a ogni passo, ma sei ancora tu a fare il lavoro. Ti permettono di fare le cose più velocemente.
Considera il compito di costruire un sito web usando un grande modello. Con le interfacce di oggi, potresti trattare il modello come un appaltatore o un collaboratore. Cercheresti di scrivere a parole il più possibile su come vuoi che il sito appaia, cosa vuoi che dica e quali funzionalità vuoi che abbia. Il modello genererebbe una prima bozza, tu la eseguirai e poi fornirai un feedback. “Fai il logo un po’ più grande”, diresti, e “centra quella prima immagine principale”, e “deve esserci un pulsante di login nell’intestazione”. Per ottenere esattamente ciò che vuoi, invierai una lista molto lunga di richieste sempre più minuziose.
Un’interazione alternativa modello-come-computer sarebbe diversa: invece di costruire il sito web, il modello genererebbe un’interfaccia per te per costruirlo, dove ogni input dell’utente a quell’interfaccia interroga il grande modello sotto il cofano. Forse quando descrivi le tue necessità creerebbe un’interfaccia con una barra laterale e una finestra di anteprima. All’inizio la barra laterale contiene solo alcuni schizzi di layout che puoi scegliere come punto di partenza. Puoi cliccare su ciascuno di essi, e il modello scrive l’HTML per una pagina web usando quel layout e lo visualizza nella finestra di anteprima. Ora che hai una pagina su cui lavorare, la barra laterale guadagna opzioni aggiuntive che influenzano la pagina globalmente, come accoppiamenti di font e schemi di colore. L’anteprima funge da editor WYSIWYG, permettendoti di afferrare elementi e spostarli, modificarne i contenuti, ecc. A supportare tutto ciò è il modello, che vede queste azioni dell’utente e riscrive la pagina per corrispondere ai cambiamenti effettuati. Poiché il modello può generare un’interfaccia per aiutare te e lui a comunicare più efficientemente, puoi esercitare più controllo sul prodotto finale in meno tempo.
La metafora modello-come-computer ci incoraggia a pensare al modello come a uno strumento con cui interagire in tempo reale piuttosto che a un collaboratore a cui assegnare compiti. Invece di sostituire un tirocinante o un tutor, può essere una sorta di bicicletta proteiforme per la mente, una che è sempre costruita su misura esattamente per te e il terreno che intendi attraversare.
Un nuovo paradigma per l’informatica?
I modelli che possono generare interfacce su richiesta sono una frontiera completamente nuova nell’informatica. Potrebbero essere un paradigma del tutto nuovo, con il modo in cui cortocircuitano il modello di applicazione esistente. Dare agli utenti finali il potere di creare e modificare app al volo cambia fondamentalmente il modo in cui interagiamo con i computer. Al posto di una singola applicazione statica costruita da uno sviluppatore, un modello genererà un’applicazione su misura per l’utente e le sue esigenze immediate. Al posto della logica aziendale implementata nel codice, il modello interpreterà gli input dell’utente e aggiornerà l’interfaccia utente. È persino possibile che questo tipo di interfaccia generativa sostituisca completamente il sistema operativo, generando e gestendo interfacce e finestre al volo secondo necessità.
All’inizio, l’interfaccia generativa sarà un giocattolo, utile solo per l’esplorazione creativa e poche altre applicazioni di nicchia. Dopotutto, nessuno vorrebbe un’app di posta elettronica che occasionalmente invia email al tuo ex e mente sulla tua casella di posta. Ma gradualmente i modelli miglioreranno. Anche mentre si spingeranno ulteriormente nello spazio di esperienze completamente nuove, diventeranno lentamente abbastanza affidabili da essere utilizzati per un lavoro reale.
Piccoli pezzi di questo futuro esistono già. Anni fa Jonas Degrave ha dimostrato che ChatGPT poteva fare una buona simulazione di una riga di comando Linux. Allo stesso modo, websim.ai utilizza un LLM per generare siti web su richiesta mentre li navighi. Oasis, GameNGen e DIAMOND addestrano modelli video condizionati sull’azione su singoli videogiochi, permettendoti di giocare ad esempio a Doom dentro un grande modello. E Genie 2 genera videogiochi giocabili da prompt testuali. L’interfaccia generativa potrebbe ancora sembrare un’idea folle, ma non è così folle.
Ci sono enormi domande aperte su come apparirà tutto questo. Dove sarà inizialmente utile l’interfaccia generativa? Come condivideremo e distribuiremo le esperienze che creiamo collaborando con il modello, se esistono solo come contesto di un grande modello? Vorremmo davvero farlo? Quali nuovi tipi di esperienze saranno possibili? Come funzionerà tutto questo in pratica? I modelli genereranno interfacce come codice o produrranno direttamente pixel grezzi?
Non conosco ancora queste risposte. Dovremo sperimentare e scoprirlo!Che cosa significherebbe trattare l'IA come uno strumento invece che come una persona?
Dall’avvio di ChatGPT, le esplorazioni in due direzioni hanno preso velocità.
La prima direzione riguarda le capacità tecniche. Quanto grande possiamo addestrare un modello? Quanto bene può rispondere alle domande del SAT? Con quanta efficienza possiamo distribuirlo?
La seconda direzione riguarda il design dell’interazione. Come comunichiamo con un modello? Come possiamo usarlo per un lavoro utile? Quale metafora usiamo per ragionare su di esso?
La prima direzione è ampiamente seguita e enormemente finanziata, e per una buona ragione: i progressi nelle capacità tecniche sono alla base di ogni possibile applicazione. Ma la seconda è altrettanto cruciale per il campo e ha enormi incognite. Siamo solo a pochi anni dall’inizio dell’era dei grandi modelli. Quali sono le probabilità che abbiamo già capito i modi migliori per usarli?
Propongo una nuova modalità di interazione, in cui i modelli svolgano il ruolo di applicazioni informatiche (ad esempio app per telefoni): fornendo un’interfaccia grafica, interpretando gli input degli utenti e aggiornando il loro stato. In questa modalità, invece di essere un “agente” che utilizza un computer per conto dell’essere umano, l’IA può fornire un ambiente informatico più ricco e potente che possiamo utilizzare.
Metafore per l’interazione
Al centro di un’interazione c’è una metafora che guida le aspettative di un utente su un sistema. I primi giorni dell’informatica hanno preso metafore come “scrivanie”, “macchine da scrivere”, “fogli di calcolo” e “lettere” e le hanno trasformate in equivalenti digitali, permettendo all’utente di ragionare sul loro comportamento. Puoi lasciare qualcosa sulla tua scrivania e tornare a prenderlo; hai bisogno di un indirizzo per inviare una lettera. Man mano che abbiamo sviluppato una conoscenza culturale di questi dispositivi, la necessità di queste particolari metafore è scomparsa, e con esse i design di interfaccia skeumorfici che le rafforzavano. Come un cestino o una matita, un computer è ora una metafora di se stesso.
La metafora dominante per i grandi modelli oggi è modello-come-persona. Questa è una metafora efficace perché le persone hanno capacità estese che conosciamo intuitivamente. Implica che possiamo avere una conversazione con un modello e porgli domande; che il modello possa collaborare con noi su un documento o un pezzo di codice; che possiamo assegnargli un compito da svolgere da solo e che tornerà quando sarà finito.
Tuttavia, trattare un modello come una persona limita profondamente il nostro modo di pensare all’interazione con esso. Le interazioni umane sono intrinsecamente lente e lineari, limitate dalla larghezza di banda e dalla natura a turni della comunicazione verbale. Come abbiamo tutti sperimentato, comunicare idee complesse in una conversazione è difficile e dispersivo. Quando vogliamo precisione, ci rivolgiamo invece a strumenti, utilizzando manipolazioni dirette e interfacce visive ad alta larghezza di banda per creare diagrammi, scrivere codice e progettare modelli CAD. Poiché concepiamo i modelli come persone, li utilizziamo attraverso conversazioni lente, anche se sono perfettamente in grado di accettare input diretti e rapidi e di produrre risultati visivi. Le metafore che utilizziamo limitano le esperienze che costruiamo, e la metafora modello-come-persona ci impedisce di esplorare il pieno potenziale dei grandi modelli.
Per molti casi d’uso, e specialmente per il lavoro produttivo, credo che il futuro risieda in un’altra metafora: modello-come-computer.
Usare un’IA come un computer
Sotto la metafora modello-come-computer, interagiremo con i grandi modelli seguendo le intuizioni che abbiamo sulle applicazioni informatiche (sia su desktop, tablet o telefono). Nota che ciò non significa che il modello sarà un’app tradizionale più di quanto il desktop di Windows fosse una scrivania letterale. “Applicazione informatica” sarà un modo per un modello di rappresentarsi a noi. Invece di agire come una persona, il modello agirà come un computer.
Agire come un computer significa produrre un’interfaccia grafica. Al posto del flusso lineare di testo in stile telescrivente fornito da ChatGPT, un sistema modello-come-computer genererà qualcosa che somiglia all’interfaccia di un’applicazione moderna: pulsanti, cursori, schede, immagini, grafici e tutto il resto. Questo affronta limitazioni chiave dell’interfaccia di chat standard modello-come-persona:
Scoperta. Un buon strumento suggerisce i suoi usi. Quando l’unica interfaccia è una casella di testo vuota, spetta all’utente capire cosa fare e comprendere i limiti del sistema. La barra laterale Modifica in Lightroom è un ottimo modo per imparare l’editing fotografico perché non si limita a dirti cosa può fare questa applicazione con una foto, ma cosa potresti voler fare. Allo stesso modo, un’interfaccia modello-come-computer per DALL-E potrebbe mostrare nuove possibilità per le tue generazioni di immagini.
Efficienza. La manipolazione diretta è più rapida che scrivere una richiesta a parole. Per continuare l’esempio di Lightroom, sarebbe impensabile modificare una foto dicendo a una persona quali cursori spostare e di quanto. Ci vorrebbe un giorno intero per chiedere un’esposizione leggermente più bassa e una vibranza leggermente più alta, solo per vedere come apparirebbe. Nella metafora modello-come-computer, il modello può creare strumenti che ti permettono di comunicare ciò che vuoi più efficientemente e quindi di fare le cose più rapidamente.
A differenza di un’app tradizionale, questa interfaccia grafica è generata dal modello su richiesta. Questo significa che ogni parte dell’interfaccia che vedi è rilevante per ciò che stai facendo in quel momento, inclusi i contenuti specifici del tuo lavoro. Significa anche che, se desideri un’interfaccia più ampia o diversa, puoi semplicemente richiederla. Potresti chiedere a DALL-E di produrre alcuni preset modificabili per le sue impostazioni ispirati da famosi artisti di schizzi. Quando clicchi sul preset Leonardo da Vinci, imposta i cursori per disegni prospettici altamente dettagliati in inchiostro nero. Se clicchi su Charles Schulz, seleziona fumetti tecnicolor 2D a basso dettaglio.
Una bicicletta della mente proteiforme
La metafora modello-come-persona ha una curiosa tendenza a creare distanza tra l’utente e il modello, rispecchiando il divario di comunicazione tra due persone che può essere ridotto ma mai completamente colmato. A causa della difficoltà e del costo di comunicare a parole, le persone tendono a suddividere i compiti tra loro in blocchi grandi e il più indipendenti possibile. Le interfacce modello-come-persona seguono questo schema: non vale la pena dire a un modello di aggiungere un return statement alla tua funzione quando è più veloce scriverlo da solo. Con il sovraccarico della comunicazione, i sistemi modello-come-persona sono più utili quando possono fare un intero blocco di lavoro da soli. Fanno le cose per te.
Questo contrasta con il modo in cui interagiamo con i computer o altri strumenti. Gli strumenti producono feedback visivi in tempo reale e sono controllati attraverso manipolazioni dirette. Hanno un overhead comunicativo così basso che non è necessario specificare un blocco di lavoro indipendente. Ha più senso mantenere l’umano nel loop e dirigere lo strumento momento per momento. Come stivali delle sette leghe, gli strumenti ti permettono di andare più lontano a ogni passo, ma sei ancora tu a fare il lavoro. Ti permettono di fare le cose più velocemente.
Considera il compito di costruire un sito web usando un grande modello. Con le interfacce di oggi, potresti trattare il modello come un appaltatore o un collaboratore. Cercheresti di scrivere a parole il più possibile su come vuoi che il sito appaia, cosa vuoi che dica e quali funzionalità vuoi che abbia. Il modello genererebbe una prima bozza, tu la eseguirai e poi fornirai un feedback. “Fai il logo un po’ più grande”, diresti, e “centra quella prima immagine principale”, e “deve esserci un pulsante di login nell’intestazione”. Per ottenere esattamente ciò che vuoi, invierai una lista molto lunga di richieste sempre più minuziose.
Un’interazione alternativa modello-come-computer sarebbe diversa: invece di costruire il sito web, il modello genererebbe un’interfaccia per te per costruirlo, dove ogni input dell’utente a quell’interfaccia interroga il grande modello sotto il cofano. Forse quando descrivi le tue necessità creerebbe un’interfaccia con una barra laterale e una finestra di anteprima. All’inizio la barra laterale contiene solo alcuni schizzi di layout che puoi scegliere come punto di partenza. Puoi cliccare su ciascuno di essi, e il modello scrive l’HTML per una pagina web usando quel layout e lo visualizza nella finestra di anteprima. Ora che hai una pagina su cui lavorare, la barra laterale guadagna opzioni aggiuntive che influenzano la pagina globalmente, come accoppiamenti di font e schemi di colore. L’anteprima funge da editor WYSIWYG, permettendoti di afferrare elementi e spostarli, modificarne i contenuti, ecc. A supportare tutto ciò è il modello, che vede queste azioni dell’utente e riscrive la pagina per corrispondere ai cambiamenti effettuati. Poiché il modello può generare un’interfaccia per aiutare te e lui a comunicare più efficientemente, puoi esercitare più controllo sul prodotto finale in meno tempo.
La metafora modello-come-computer ci incoraggia a pensare al modello come a uno strumento con cui interagire in tempo reale piuttosto che a un collaboratore a cui assegnare compiti. Invece di sostituire un tirocinante o un tutor, può essere una sorta di bicicletta proteiforme per la mente, una che è sempre costruita su misura esattamente per te e il terreno che intendi attraversare.
Un nuovo paradigma per l’informatica?
I modelli che possono generare interfacce su richiesta sono una frontiera completamente nuova nell’informatica. Potrebbero essere un paradigma del tutto nuovo, con il modo in cui cortocircuitano il modello di applicazione esistente. Dare agli utenti finali il potere di creare e modificare app al volo cambia fondamentalmente il modo in cui interagiamo con i computer. Al posto di una singola applicazione statica costruita da uno sviluppatore, un modello genererà un’applicazione su misura per l’utente e le sue esigenze immediate. Al posto della logica aziendale implementata nel codice, il modello interpreterà gli input dell’utente e aggiornerà l’interfaccia utente. È persino possibile che questo tipo di interfaccia generativa sostituisca completamente il sistema operativo, generando e gestendo interfacce e finestre al volo secondo necessità.
All’inizio, l’interfaccia generativa sarà un giocattolo, utile solo per l’esplorazione creativa e poche altre applicazioni di nicchia. Dopotutto, nessuno vorrebbe un’app di posta elettronica che occasionalmente invia email al tuo ex e mente sulla tua casella di posta. Ma gradualmente i modelli miglioreranno. Anche mentre si spingeranno ulteriormente nello spazio di esperienze completamente nuove, diventeranno lentamente abbastanza affidabili da essere utilizzati per un lavoro reale.
Piccoli pezzi di questo futuro esistono già. Anni fa Jonas Degrave ha dimostrato che ChatGPT poteva fare una buona simulazione di una riga di comando Linux. Allo stesso modo, websim.ai utilizza un LLM per generare siti web su richiesta mentre li navighi. Oasis, GameNGen e DIAMOND addestrano modelli video condizionati sull’azione su singoli videogiochi, permettendoti di giocare ad esempio a Doom dentro un grande modello. E Genie 2 genera videogiochi giocabili da prompt testuali. L’interfaccia generativa potrebbe ancora sembrare un’idea folle, ma non è così folle.
Ci sono enormi domande aperte su come apparirà tutto questo. Dove sarà inizialmente utile l’interfaccia generativa? Come condivideremo e distribuiremo le esperienze che creiamo collaborando con il modello, se esistono solo come contesto di un grande modello? Vorremmo davvero farlo? Quali nuovi tipi di esperienze saranno possibili? Come funzionerà tutto questo in pratica? I modelli genereranno interfacce come codice o produrranno direttamente pixel grezzi?
Non conosco ancora queste risposte. Dovremo sperimentare e scoprirlo!
Tradotto da:\ https://willwhitney.com/computing-inside-ai.htmlhttps://willwhitney.com/computing-inside-ai.html
-
-
 @ 783850fd:77511d32
2025-01-20 13:22:54
@ 783850fd:77511d32
2025-01-20 13:22:54I'm thinking about buying a small house or a plot of land in Morocco and living there. The amount I am willing to pay for this would be $10 000 - 30 000. How much might I liquidate into their fiat (MAD) bank account with a month or so without them freezing my account and god only knows what worse things them doing to me. I use robosats and never exceed the amount of 950 euro when selling Bitcoin. I have all my wealth in Bitcoin, no history of income over the last 5 years, no filing tax returns too. I am from the EU, residing in Spain. How has your experience with Morocco been? Can one open a bank account in Morocco without having a residence there?
originally posted at https://stacker.news/items/857178
-
 @ e6817453:b0ac3c39
2024-12-07 15:06:43
@ e6817453:b0ac3c39
2024-12-07 15:06:43I started a long series of articles about how to model different types of knowledge graphs in the relational model, which makes on-device memory models for AI agents possible.
We model-directed graphs
Also, graphs of entities
We even model hypergraphs
Last time, we discussed why classical triple and simple knowledge graphs are insufficient for AI agents and complex memory, especially in the domain of time-aware or multi-model knowledge.
So why do we need metagraphs, and what kind of challenge could they help us to solve?
- complex and nested event and temporal context and temporal relations as edges
- multi-mode and multilingual knowledge
- human-like memory for AI agents that has multiple contexts and relations between knowledge in neuron-like networks
MetaGraphs
A meta graph is a concept that extends the idea of a graph by allowing edges to become graphs. Meta Edges connect a set of nodes, which could also be subgraphs. So, at some level, node and edge are pretty similar in properties but act in different roles in a different context.
Also, in some cases, edges could be referenced as nodes.
This approach enables the representation of more complex relationships and hierarchies than a traditional graph structure allows. Let’s break down each term to understand better metagraphs and how they differ from hypergraphs and graphs.Graph Basics
- A standard graph has a set of nodes (or vertices) and edges (connections between nodes).
- Edges are generally simple and typically represent a binary relationship between two nodes.
- For instance, an edge in a social network graph might indicate a “friend” relationship between two people (nodes).
Hypergraph
- A hypergraph extends the concept of an edge by allowing it to connect any number of nodes, not just two.
- Each connection, called a hyperedge, can link multiple nodes.
- This feature allows hypergraphs to model more complex relationships involving multiple entities simultaneously. For example, a hyperedge in a hypergraph could represent a project team, connecting all team members in a single relation.
- Despite its flexibility, a hypergraph doesn’t capture hierarchical or nested structures; it only generalizes the number of connections in an edge.
Metagraph
- A metagraph allows the edges to be graphs themselves. This means each edge can contain its own nodes and edges, creating nested, hierarchical structures.
- In a meta graph, an edge could represent a relationship defined by a graph. For instance, a meta graph could represent a network of organizations where each organization’s structure (departments and connections) is represented by its own internal graph and treated as an edge in the larger meta graph.
- This recursive structure allows metagraphs to model complex data with multiple layers of abstraction. They can capture multi-node relationships (as in hypergraphs) and detailed, structured information about each relationship.
Named Graphs and Graph of Graphs
As you can notice, the structure of a metagraph is quite complex and could be complex to model in relational and classical RDF setups. It could create a challenge of luck of tools and software solutions for your problem.
If you need to model nested graphs, you could use a much simpler model of Named graphs, which could take you quite far.
The concept of the named graph came from the RDF community, which needed to group some sets of triples. In this way, you form subgraphs inside an existing graph. You could refer to the subgraph as a regular node. This setup simplifies complex graphs, introduces hierarchies, and even adds features and properties of hypergraphs while keeping a directed nature.
It looks complex, but it is not so hard to model it with a slight modification of a directed graph.
So, the node could host graphs inside. Let's reflect this fact with a location for a node. If a node belongs to a main graph, we could set the location to null or introduce a main node . it is up to you
Nodes could have edges to nodes in different subgraphs. This structure allows any kind of nesting graphs. Edges stay location-free
Meta Graphs in Relational Model
Let’s try to make several attempts to model different meta-graphs with some constraints.
Directed Metagraph where edges are not used as nodes and could not contain subgraphs

In this case, the edge always points to two sets of nodes. This introduces an overhead of creating a node set for a single node. In this model, we can model empty node sets that could require application-level constraints to prevent such cases.
Directed Metagraph where edges are not used as nodes and could contain subgraphs

Adding a node set that could model a subgraph located in an edge is easy but could be separate from in-vertex or out-vert.
I also do not see a direct need to include subgraphs to a node, as we could just use a node set interchangeably, but it still could be a case.Directed Metagraph where edges are used as nodes and could contain subgraphs
As you can notice, we operate all the time with node sets. We could simply allow the extension node set to elements set that include node and edge IDs, but in this case, we need to use uuid or any other strategy to differentiate node IDs from edge IDs. In this case, we have a collision of ephemeral edges or ephemeral nodes when we want to change the role and purpose of the node as an edge or vice versa.

A full-scale metagraph model is way too complex for a relational database.
So we need a better model.Now, we have more flexibility but loose structural constraints. We cannot show that the element should have one vertex, one vertex, or both. This type of constraint has been moved to the application level. Also, the crucial question is about query and retrieval needs.
Any meta-graph model should be more focused on domain and needs and should be used in raw form. We did it for a pure theoretical purpose. -
 @ 5d4b6c8d:8a1c1ee3
2025-01-26 23:17:10
@ 5d4b6c8d:8a1c1ee3
2025-01-26 23:17:10I'm finally moving on from Luka, who won't even be eligible for these awards, with how much time he's missed. While I'm at it, I'll also move off of Ant, who just isn't looking like the guy we expected to see this season. Tatum is an easy enough All NBA replacement, but I have not idea who's going to get the final spot, so I picked Wemby, who I at least think the media will be eager to vote for.
I made sure to record @grayruby's switch from the Pacers to the Magic. Boy, that is not aging well.
Remember, older correct predictions are worth more than younger ones, so don't wait too long to get off your bad predictions.
Here's the current state of the competition with your max possible score next to your nym:
| Contestant | MVP | Champ | All NBA | | | | | |--------------|------|---------|----------|-|-|-|-| | @Undisciplined 48| SGA| OKC | Jokic | Giannis | Wemby| Tatum| SGA | | @grayruby 65| Giannis| Magic| Jokic | Giannis | Luka | Mitchell| Brunson| | @gnilma 62| SGA| OKC| Jokic | Giannis| Tatum | Luka | SGA| | @BitcoinAbhi 70 | Luka| Denver| Jokic | Giannis | Luka | Ant| SGA| | @Bell_curve 70 | Luka| Celtics| Jokic | Giannis | Luka | Ant| SGA| | @0xbitcoiner 70 | Jokic| Pacers| Jokic | Giannis | Luka | Ant| Brunson| | @Coinsreporter 49| Giannis| Pacers| Jokic | Giannis | Luka | Ant| Brunson| | @TheMorningStar 49| Luka| Celtics| Jokic | Giannis | Luka | Ant| SGA| | @onthedeklein 49| Luka| T-Wolves| Jokic | Giannis | Luka | Wemby| SGA| | @Carresan 49| Luka| Mavs| Jokic | Giannis | Luka | Wemby| SGA| | @BTC_Bellzer 49| Luka| Celtics| Embiid| Giannis | Luka | Tatum| SGA| | @realBitcoinDog 49| Luka| Lakers| Jokic | Giannis | Luka | Ant| SGA| | @SimpleStacker 42| SGA| Celtics| Jokic| Tatum| Luka | Brunson| SGA| | @BlokchainB 42| SGA| Knicks| AD| Giannis | Ant| Brunson| SGA|
Prize At least 5k (I'll keep adding zaps to the pot).
If you want to join this contest, just leave your predictions for MVP, Champion, and All-NBA 1st team in the comments. See the June post for more details.
originally posted at https://stacker.news/items/865017
-
 @ 000002de:c05780a7
2025-01-21 21:29:39
@ 000002de:c05780a7
2025-01-21 21:29:39The Bellamy salute is a palm-out salute created by James B. Upham as the gesture that was to accompany the Pledge of Allegiance of the United States of America, whose text had been written by Francis Bellamy. It was also known as the "flag salute" during the period when it was used with the Pledge of Allegiance. Bellamy promoted the salute and it came to be associated with his name. Both the Pledge and its salute originated in 1892. It was also known as the "flag salute" during the period when it was used with the Pledge of Allegiance. Bellamy promoted the salute and it came to be associated with his name. Both the Pledge and its salute originated in 1892. Later, during the 1920s and 1930s, Italian fascists and Nazi Germans adopted a salute which was very similar, attributed to the Roman salute, a gesture that was popularly believed to have been used in ancient Rome.[1] This resulted in controversy over the use of the Bellamy salute in the United States. It was officially replaced by the hand-over-heart salute when Congress amended the Flag Code on December 22, 1942.
originally posted at https://stacker.news/items/859191
-
 @ e6817453:b0ac3c39
2024-12-07 15:03:06
@ e6817453:b0ac3c39
2024-12-07 15:03:06Hey folks! Today, let’s dive into the intriguing world of neurosymbolic approaches, retrieval-augmented generation (RAG), and personal knowledge graphs (PKGs). Together, these concepts hold much potential for bringing true reasoning capabilities to large language models (LLMs). So, let’s break down how symbolic logic, knowledge graphs, and modern AI can come together to empower future AI systems to reason like humans.
The Neurosymbolic Approach: What It Means ?
Neurosymbolic AI combines two historically separate streams of artificial intelligence: symbolic reasoning and neural networks. Symbolic AI uses formal logic to process knowledge, similar to how we might solve problems or deduce information. On the other hand, neural networks, like those underlying GPT-4, focus on learning patterns from vast amounts of data — they are probabilistic statistical models that excel in generating human-like language and recognizing patterns but often lack deep, explicit reasoning.
While GPT-4 can produce impressive text, it’s still not very effective at reasoning in a truly logical way. Its foundation, transformers, allows it to excel in pattern recognition, but the models struggle with reasoning because, at their core, they rely on statistical probabilities rather than true symbolic logic. This is where neurosymbolic methods and knowledge graphs come in.
Symbolic Calculations and the Early Vision of AI
If we take a step back to the 1950s, the vision for artificial intelligence was very different. Early AI research was all about symbolic reasoning — where computers could perform logical calculations to derive new knowledge from a given set of rules and facts. Languages like Lisp emerged to support this vision, enabling programs to represent data and code as interchangeable symbols. Lisp was designed to be homoiconic, meaning it treated code as manipulatable data, making it capable of self-modification — a huge leap towards AI systems that could, in theory, understand and modify their own operations.
Lisp: The Earlier AI-Language
Lisp, short for “LISt Processor,” was developed by John McCarthy in 1958, and it became the cornerstone of early AI research. Lisp’s power lay in its flexibility and its use of symbolic expressions, which allowed developers to create programs that could manipulate symbols in ways that were very close to human reasoning. One of the most groundbreaking features of Lisp was its ability to treat code as data, known as homoiconicity, which meant that Lisp programs could introspect and transform themselves dynamically. This ability to adapt and modify its own structure gave Lisp an edge in tasks that required a form of self-awareness, which was key in the early days of AI when researchers were exploring what it meant for machines to “think.”
Lisp was not just a programming language—it represented the vision for artificial intelligence, where machines could evolve their understanding and rewrite their own programming. This idea formed the conceptual basis for many of the self-modifying and adaptive algorithms that are still explored today in AI research. Despite its decline in mainstream programming, Lisp’s influence can still be seen in the concepts used in modern machine learning and symbolic AI approaches.
Prolog: Formal Logic and Deductive Reasoning
In the 1970s, Prolog was developed—a language focused on formal logic and deductive reasoning. Unlike Lisp, based on lambda calculus, Prolog operates on formal logic rules, allowing it to perform deductive reasoning and solve logical puzzles. This made Prolog an ideal candidate for expert systems that needed to follow a sequence of logical steps, such as medical diagnostics or strategic planning.
Prolog, like Lisp, allowed symbols to be represented, understood, and used in calculations, creating another homoiconic language that allows reasoning. Prolog’s strength lies in its rule-based structure, which is well-suited for tasks that require logical inference and backtracking. These features made it a powerful tool for expert systems and AI research in the 1970s and 1980s.
The language is declarative in nature, meaning that you define the problem, and Prolog figures out how to solve it. By using formal logic and setting constraints, Prolog systems can derive conclusions from known facts, making it highly effective in fields requiring explicit logical frameworks, such as legal reasoning, diagnostics, and natural language understanding. These symbolic approaches were later overshadowed during the AI winter — but the ideas never really disappeared. They just evolved.
Solvers and Their Role in Complementing LLMs
One of the most powerful features of Prolog and similar logic-based systems is their use of solvers. Solvers are mechanisms that can take a set of rules and constraints and automatically find solutions that satisfy these conditions. This capability is incredibly useful when combined with LLMs, which excel at generating human-like language but need help with logical consistency and structured reasoning.
For instance, imagine a scenario where an LLM needs to answer a question involving multiple logical steps or a complex query that requires deducing facts from various pieces of information. In this case, a solver can derive valid conclusions based on a given set of logical rules, providing structured answers that the LLM can then articulate in natural language. This allows the LLM to retrieve information and ensure the logical integrity of its responses, leading to much more robust answers.
Solvers are also ideal for handling constraint satisfaction problems — situations where multiple conditions must be met simultaneously. In practical applications, this could include scheduling tasks, generating optimal recommendations, or even diagnosing issues where a set of symptoms must match possible diagnoses. Prolog’s solver capabilities and LLM’s natural language processing power can make these systems highly effective at providing intelligent, rule-compliant responses that traditional LLMs would struggle to produce alone.
By integrating neurosymbolic methods that utilize solvers, we can provide LLMs with a form of deductive reasoning that is missing from pure deep-learning approaches. This combination has the potential to significantly improve the quality of outputs for use-cases that require explicit, structured problem-solving, from legal queries to scientific research and beyond. Solvers give LLMs the backbone they need to not just generate answers but to do so in a way that respects logical rigor and complex constraints.
Graph of Rules for Enhanced Reasoning
Another powerful concept that complements LLMs is using a graph of rules. A graph of rules is essentially a structured collection of logical rules that interconnect in a network-like structure, defining how various entities and their relationships interact. This structured network allows for complex reasoning and information retrieval, as well as the ability to model intricate relationships between different pieces of knowledge.
In a graph of rules, each node represents a rule, and the edges define relationships between those rules — such as dependencies or causal links. This structure can be used to enhance LLM capabilities by providing them with a formal set of rules and relationships to follow, which improves logical consistency and reasoning depth. When an LLM encounters a problem or a question that requires multiple logical steps, it can traverse this graph of rules to generate an answer that is not only linguistically fluent but also logically robust.
For example, in a healthcare application, a graph of rules might include nodes for medical symptoms, possible diagnoses, and recommended treatments. When an LLM receives a query regarding a patient’s symptoms, it can use the graph to traverse from symptoms to potential diagnoses and then to treatment options, ensuring that the response is coherent and medically sound. The graph of rules guides reasoning, enabling LLMs to handle complex, multi-step questions that involve chains of reasoning, rather than merely generating surface-level responses.
Graphs of rules also enable modular reasoning, where different sets of rules can be activated based on the context or the type of question being asked. This modularity is crucial for creating adaptive AI systems that can apply specific sets of logical frameworks to distinct problem domains, thereby greatly enhancing their versatility. The combination of neural fluency with rule-based structure gives LLMs the ability to conduct more advanced reasoning, ultimately making them more reliable and effective in domains where accuracy and logical consistency are critical.
By implementing a graph of rules, LLMs are empowered to perform deductive reasoning alongside their generative capabilities, creating responses that are not only compelling but also logically aligned with the structured knowledge available in the system. This further enhances their potential applications in fields such as law, engineering, finance, and scientific research — domains where logical consistency is as important as linguistic coherence.
Enhancing LLMs with Symbolic Reasoning
Now, with LLMs like GPT-4 being mainstream, there is an emerging need to add real reasoning capabilities to them. This is where neurosymbolic approaches shine. Instead of pitting neural networks against symbolic reasoning, these methods combine the best of both worlds. The neural aspect provides language fluency and recognition of complex patterns, while the symbolic side offers real reasoning power through formal logic and rule-based frameworks.
Personal Knowledge Graphs (PKGs) come into play here as well. Knowledge graphs are data structures that encode entities and their relationships — they’re essentially semantic networks that allow for structured information retrieval. When integrated with neurosymbolic approaches, LLMs can use these graphs to answer questions in a far more contextual and precise way. By retrieving relevant information from a knowledge graph, they can ground their responses in well-defined relationships, thus improving both the relevance and the logical consistency of their answers.
Imagine combining an LLM with a graph of rules that allow it to reason through the relationships encoded in a personal knowledge graph. This could involve using deductive databases to form a sophisticated way to represent and reason with symbolic data — essentially constructing a powerful hybrid system that uses LLM capabilities for language fluency and rule-based logic for structured problem-solving.
My Research on Deductive Databases and Knowledge Graphs
I recently did some research on modeling knowledge graphs using deductive databases, such as DataLog — which can be thought of as a limited, data-oriented version of Prolog. What I’ve found is that it’s possible to use formal logic to model knowledge graphs, ontologies, and complex relationships elegantly as rules in a deductive system. Unlike classical RDF or traditional ontology-based models, which sometimes struggle with complex or evolving relationships, a deductive approach is more flexible and can easily support dynamic rules and reasoning.
Prolog and similar logic-driven frameworks can complement LLMs by handling the parts of reasoning where explicit rule-following is required. LLMs can benefit from these rule-based systems for tasks like entity recognition, logical inferences, and constructing or traversing knowledge graphs. We can even create a graph of rules that governs how relationships are formed or how logical deductions can be performed.
The future is really about creating an AI that is capable of both deep contextual understanding (using the powerful generative capacity of LLMs) and true reasoning (through symbolic systems and knowledge graphs). With the neurosymbolic approach, these AIs could be equipped not just to generate information but to explain their reasoning, form logical conclusions, and even improve their own understanding over time — getting us a step closer to true artificial general intelligence.
Why It Matters for LLM Employment
Using neurosymbolic RAG (retrieval-augmented generation) in conjunction with personal knowledge graphs could revolutionize how LLMs work in real-world applications. Imagine an LLM that understands not just language but also the relationships between different concepts — one that can navigate, reason, and explain complex knowledge domains by actively engaging with a personalized set of facts and rules.
This could lead to practical applications in areas like healthcare, finance, legal reasoning, or even personal productivity — where LLMs can help users solve complex problems logically, providing relevant information and well-justified reasoning paths. The combination of neural fluency with symbolic accuracy and deductive power is precisely the bridge we need to move beyond purely predictive AI to truly intelligent systems.
Let's explore these ideas further if you’re as fascinated by this as I am. Feel free to reach out, follow my YouTube channel, or check out some articles I’ll link below. And if you’re working on anything in this field, I’d love to collaborate!
Until next time, folks. Stay curious, and keep pushing the boundaries of AI!
-
 @ 9349d012:d3e98946
2025-01-19 19:47:15
@ 9349d012:d3e98946
2025-01-19 19:47:15For many reasons, not least of those the outcome of the last US presidential election, I’m now working on Librarian Detective, Book Two as my creative release. At the moment, I’m already on chapter seven, which means I made it through writing the second chapter, always an admirable hurdle to clear. If you’ll recall, with Librarian Detective, Book One, clearing that milestone was a challenge. It took between nine and 12 years to finish that book, although I wrote three books in those meantime years. This was partly because of working on my day job business more fulltime (MyLibrarian! Our app is out, sign up to test on the pop up here) but also because I revamped my entire writing process, which I’ll share with you.
Here’s a picture of the writing methods I use. I went from writing longhand to digitally, which is more efficient, and I also use a series of guides to help organize the writing process: An outline, character list, calendar timeline, editing checklist and the main writing doc itself.
Seven years ago when I realized my writing method was working for me, I started doing a video series on Writing, called On Storytelling, filmed at all the remote locations I work at, one of the best of which I’m at right now, working on my new book. If you are looking for more writing resources, there’s a list on my blog. When you go down these rabbit holes you may come out ready to write your first book.
GOOD LUCK—MEZ
Originally appeared on https://www.michellezaffino.com/my-writing-methods/
-
 @ f9cf4e94:96abc355
2025-01-18 06:09:50
@ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |
 | Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |
| Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |  | 16Gb |
| 16Gb |Recomendo que use o Ubuntu Server para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi aqui. O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível aqui. Não instale um desktop (como xubuntu, lubuntu, xfce, etc.).
Passo 1: Atualizar o Sistema 🖥️
Primeiro, atualize seu sistema e instale o Tor:
bash apt update apt install tor
Passo 2: Criar o Arquivo de Serviço
nrs.service🔧Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo:
```unit [Unit] Description=Nostr Relay Server Service After=network.target
[Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure
[Install] WantedBy=multi-user.target ```
Passo 3: Baixar o Binário do Nostr 🚀
Baixe o binário mais recente do Nostr aqui no GitHub.
Passo 4: Criar as Pastas Necessárias 📂
Agora, crie as pastas para o aplicativo e o pendrive:
bash mkdir -p /opt/nrs /mnt/edriver
Passo 5: Listar os Dispositivos Conectados 🔌
Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados:
bash lsblk
Passo 6: Formatando o Pendrive 💾
Escolha o pendrive correto (por exemplo,
/dev/sda) e formate-o:bash mkfs.vfat /dev/sda
Passo 7: Montar o Pendrive 💻
Monte o pendrive na pasta
/mnt/edriver:bash mount /dev/sda /mnt/edriver
Passo 8: Verificar UUID dos Dispositivos 📋
Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados:
bash blkid
Passo 9: Alterar o
fstabpara Montar o Pendrive Automáticamente 📝Abra o arquivo
/etc/fstabe adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim:fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0
Passo 10: Copiar o Binário para a Pasta Correta 📥
Agora, copie o binário baixado para a pasta
/opt/nrs:bash cp nrs-arm64 /opt/nrs
Passo 11: Criar o Arquivo de Configuração 🛠️
Crie o arquivo de configuração com o seguinte conteúdo e salve-o em
/opt/nrs/config.yaml:yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true
Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️
Agora, copie o arquivo
nrs.servicepara o diretório/etc/systemd/system/:bash cp nrs.service /etc/systemd/system/Recarregue os serviços e inicie o serviço
nrs:bash systemctl daemon-reload systemctl enable --now nrs.service
Passo 13: Configurar o Tor 🌐
Abra o arquivo de configuração do Tor
/var/lib/tor/torrce adicione a seguinte linha:torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334
Passo 14: Habilitar e Iniciar o Tor 🧅
Agora, ative e inicie o serviço Tor:
bash systemctl enable --now tor.serviceO Tor irá gerar um endereço
.onionpara o seu servidor Nostr. Você pode encontrá-lo no arquivo/var/lib/tor/nostr_server/hostname.
Observações ⚠️
- Com essa configuração, os dados serão salvos no pendrive, enquanto o binário ficará no cartão SD do Raspberry Pi.
- O endereço
.oniondo seu servidor Nostr será algo como:ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion.
Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳
Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
-
 @ 006532cb:fd8f28b4
2025-01-26 22:10:39
@ 006532cb:fd8f28b4
2025-01-26 22:10:39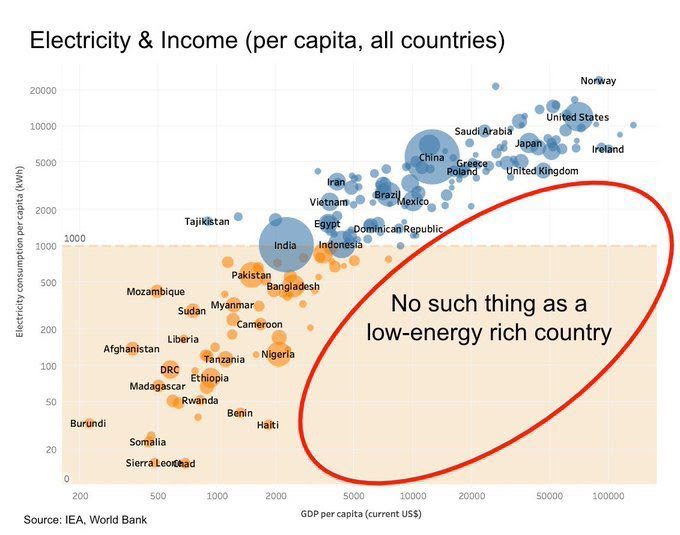

Law of Conservation of Energy: The Law of Conservation of Energy states that energy cannot be created or destroyed, only converted from one form to another. This means that the total energy of an isolated system remains constant over time, but the form of energy can change (e.g., from kinetic energy to potential energy). This fundamental principle in physics highlights the importance of energy efficiency and the potential for energy to be transformed and reused.
Henry Ford's Energy Currency: Henry Ford, the founder of the Ford Motor Company, proposed the concept of an "energy currency" in the 1920s. He suggested that energy, rather than gold or other commodities, could serve as the basis for a new monetary system. Ford's idea was that energy is the fundamental unit of value, as it is the driving force behind all economic activity. He proposed that energy could be used as a standard unit of exchange, allowing for more efficient and equitable trade.
Buckminster Fuller's View on Energy Production and Wealth: Buckminster Fuller, a renowned architect, systems theorist, and futurist, believed that energy production is the key to creating wealth and abundance. He argued that energy is the fundamental driver of economic growth and that increasing energy production can lead to increased prosperity. Fuller's concept of "ephemeralization" suggests that as energy production becomes more efficient and widespread, the cost of goods and services decreases, leading to increased abundance and wealth. He also emphasized the importance of designing systems that maximize energy efficiency and minimize waste, allowing for more equitable distribution of resources and wealth.
-
 @ 26ceca6b:2ae71cb7
2025-01-28 01:09:29
@ 26ceca6b:2ae71cb7
2025-01-28 01:09:29I am working on a story to help people understand money and the problems that arise in the system. A very good story that is popular: https://x.com/saylor/status/1878154748353818932 "What's the Problem". I am seeking to keep this to a couple of minutes. Here is the story that I told my wife:
Times are hard as are all too familiar to those at the little church at the edge of the city. The elders decide that the food pantry needs expansion to help those in need through this time. They decide to turn the pantry into a store where people can bring various goods like vegetables and things of basic needs, like sugar and blankets, medicines, and so forth. They decide to start a ledger where people can earn credits for the items they donate to the store. 2 eggs are worth 1 credit, as are 3 potatoes and a dozen carrots. There is also a table where people can offer items in trade for credits. The ledger is a huge success.
After some time, the elder that was named the bookkeeper encounters a widow in the store who is known to be very poor, such that her children have no shoes, and she is in great need. In his desire to help her get the few items that would help her family so much, he gets the idea to just add an entry on the ledger in her account. He gives her enough credits to help her through the month. He was quite pleased with himself.
Days passed, and now the brothers of the widow have come to the store. They ask for the bookkeeper, and when he meets with them, they demand credits as he had done for their sister. After all, they were orphans. The bookkeeper tells them that he will ask for a special collection to meet their needs, but they don't want donations. They want the dignity of buying what they need at the store where no one will look down on them as beggars. The bookkeeper is in a bind. He tells them he must consult with the elders on such matters to buy some time.
He meets with the elders to discuss this new development. They decide that he should extend the brothers’ credit to resolve the matter. They also decide that he should get a sum of credits for himself since the bookkeeping has become difficult. Not long after, the elders decide that they too should get a salary for their work, and so more ledger entries are created. The ledger book is getting quite heavy. The lines of credit are quite popular.
But then problems arose. The store ran out of eggs, vegetables, and meat was now worth twice what it was priced in eggs or credits. The elders gathered with the bookkeeper and were astonished at this development. They decided the solution was to start buying meat and eggs from the market to sell at the store. To do this, they made more entries in the ledger, issued notes at the market, and once again stocked the shelves. Only this time it was 1 egg/ 1 Credit, meat was 5 credits for the piece the size of a child’s fist.
The store languished with the high prices. The people quit paying their debt and stopped trading their vegetables for credits. They traded amongst themselves instead, sharing meals together. Many bought chickens, and some traded eggs for goats, goats for cattle, and cattle for land. The elders sat in the empty store and argued over the last potato; they decided to give it to the highest bidder. The bookkeeper offered all his credits, and next month’s too. He got his potato and traded it for one egg.
originally posted at https://stacker.news/items/866207
-
 @ 99a07115:0f0df457
2025-01-28 01:09:24
@ 99a07115:0f0df457
2025-01-28 01:09:24Mrow.
I hesitate to muddy up what seems to be more of an underground news feed with my own silly content, but if there's an appetite for my nonsense then maybe I'll keep it up.I've been on a whirlwind tour through bitcoin culture for the past few days. I haven't really been able to shut up on Nostr about how much running a node changed the game for me.
My node made me understand the Blocksize War
It's probably no surprise to this audience, but the Blocksize War didn't really register to me as something of importance until I got to syncing my node. It took well over a week for me to get through the whole blockchain. That time frame feels either painfully long or, considering bitcoin's growing popularity, astonishingly quick. Something like 700GB of data. That's it. It's so crazy to me I still want to just grab strangers IRL and be like, "CAN YOU BELIEVE IT'S ONLY 700GB".
Kind of fun checking up throughout the process and seeing where in "Blocktime" my node was, then checking mempools.space to see exactly when that was.
Bitcoin is a store of value... until you reach Nostr
Yeah look I'm still too green to open public channels on my node, too small of a fish to toss around the kind of liquidity I'm guessing big noderunners are playing with, and I'm keeping most of the sats that enter my gravitational field. Still, everything about accumulating bitcoin was somewhat desperate and even daunting up until I reached 100% sync with the blockchain. As soon as I hopped on Nostr and got to zapping it really shifted. Suddenly, there's a small stash of sats that I'm using to engage with this community, to support others or give them a little digital nod. I really couldn't connect with the platform or even considered layer 2 much at all until I had skin in the game. Only a full node+lightning node and Nostr, along with the interconnected platforms/utilities that many of you have been building, really could bring me out of my trance of layer 1 sat stacking. So thank you to those that have done such excellent work, it's incredible stuff.
Screw Elite Dangerous, I'll just try to be a halfway decent Lightning noderunner
Was considering one of those crazy detailed space sims to give my brain some exercise but... then I found Amboss and realized I can made my head hurt just with layer 2's. I'm definitely not ready for the big leagues. But for now, a few private channels feels great while I read up over the next few weeks on DarthCoin's outstanding documentation. Speaking of, are there LSP guilds like the Fuel Rats? That'd be fun. "We have Liquidity. You don't."
That is all for now.
Chau chau, meow meow.
originally posted at https://stacker.news/items/867208
-
 @ a0c34d34:fef39af1
2025-01-14 14:28:28
@ a0c34d34:fef39af1
2025-01-14 14:28:28I feel fabulously free, I deleted TikTok. I am spending less time on my phone and more time developing Onboard60. I never expected to go from the Metaverse to A.I. healthcare and NFCC medical bracelets.
I was on Vine, Twitter back in 2009… I went from 8 second nonsensical videos and funny tweets to diving deeper down any rabbit hole I ever imagined.
In 2016, I heard a little noise about Bitcoin and I haven’t gotten off the rollercoaster of a merry go round yet. If you know, you know.
I found Nostr awhile ago but I’m no maxi, I’m curious. I learned about different things pertaining to blockchain and cryptocurrency, social media and protocols.
I kept journals of my fears and conferences I experienced and published them as my first years behind the scenes of a senior citizen diving deep into the unknowns.
Someone had to tell me I was a senior citizen. I’m 64 now , that was four years ago. Since then I took a crazy idea and started Onboard60.
I created a curriculum for myself. For years I have learned a variety of subjects. I took the basics and made a cliff note booklet - Web3 1101 for Seniors.
I didn’t want to be left behind so I learned Spatial and created an auditorium, an art gallery and an office. It was my attempt to get senior citizens involved to connect with their grandkids in virtual reality like Roblox.
Over the years, I’ve written articles on Substack sharing my journey, and sporadically posted on Zentaurios. I remember writing on YakiHonne when I first discovered it.
Onboard60 has become more than what I ever thought it would be, as I started just sharing my journey in hopes others would join me.
I hoped senior citizens would be interested in learning how to put their trust funds, H.O.A.s, POLSTs and other senior citizen documents on chain.
The past four years, nothing until I speak of medical bracelets. I do not mention BitDoctor AI or mirrors that do body scans. Bracelets, I speak bracelets.
The focus is to keep senior citizens up to date with new technologies that focus on improving their quality of life.
Finding YakiHonne again is refreshing. The esthetics clean, seemless cross posting, and better options for posting. Soft landing.
I have learned a lot over the years, experiencing this space becoming , watching protocols grow, some platforms fizzle, creating a new world isn’t easy.
I’m enjoying being a mermaid in Monniverse community on Farcaster, not Farcaster itself but enjoy being a mermaid. Monniverse is a decentralized animation production company. I’m learning how to use the image generator and like the global reach.
I have compromised on so many social media sites just to be on them. I still frequent Twitter Onboard60, and have my old Vine group on Instagram. I spend time on Lens mostly.
I use traditional media to share Onboard60 - LinkedIn and YouTube for Onboard60. I am creating a digital replica of all the information, subjects, videos, content that I created as Onboard60. I hope to keep it updated as times goes forward.
I’m going to use my guide to IRL events at Blockchain Miami in a few weeks, WAGMI MIAMI. After so many conferences and events, I had to write down a step by step how to get through these and follow up after. They can be overwhelming and I needed a way to decompress. My guide helps me.
I seem to be rambling. I don’t have a purpose or any value to share with this article, I just wanted to share my thoughts for now, walking into 2025.
Sandra ,Samm,Sababa
Onboard60, founder
-
 @ e6817453:b0ac3c39
2024-12-07 14:54:46
@ e6817453:b0ac3c39
2024-12-07 14:54:46Introduction: Personal Knowledge Graphs and Linked Data
We will explore the world of personal knowledge graphs and discuss how they can be used to model complex information structures. Personal knowledge graphs aren’t just abstract collections of nodes and edges—they encode meaningful relationships, contextualizing data in ways that enrich our understanding of it. While the core structure might be a directed graph, we layer semantic meaning on top, enabling nuanced connections between data points.
The origin of knowledge graphs is deeply tied to concepts from linked data and the semantic web, ideas that emerged to better link scattered pieces of information across the web. This approach created an infrastructure where data islands could connect — facilitating everything from more insightful AI to improved personal data management.
In this article, we will explore how these ideas have evolved into tools for modeling AI’s semantic memory and look at how knowledge graphs can serve as a flexible foundation for encoding rich data contexts. We’ll specifically discuss three major paradigms: RDF (Resource Description Framework), property graphs, and a third way of modeling entities as graphs of graphs. Let’s get started.
Intro to RDF
The Resource Description Framework (RDF) has been one of the fundamental standards for linked data and knowledge graphs. RDF allows data to be modeled as triples: subject, predicate, and object. Essentially, you can think of it as a structured way to describe relationships: “X has a Y called Z.” For instance, “Berlin has a population of 3.5 million.” This modeling approach is quite flexible because RDF uses unique identifiers — usually URIs — to point to data entities, making linking straightforward and coherent.
RDFS, or RDF Schema, extends RDF to provide a basic vocabulary to structure the data even more. This lets us describe not only individual nodes but also relationships among types of data entities, like defining a class hierarchy or setting properties. For example, you could say that “Berlin” is an instance of a “City” and that cities are types of “Geographical Entities.” This kind of organization helps establish semantic meaning within the graph.
RDF and Advanced Topics
Lists and Sets in RDF
RDF also provides tools to model more complex data structures such as lists and sets, enabling the grouping of nodes. This extension makes it easier to model more natural, human-like knowledge, for example, describing attributes of an entity that may have multiple values. By adding RDF Schema and OWL (Web Ontology Language), you gain even more expressive power — being able to define logical rules or even derive new relationships from existing data.
Graph of Graphs
A significant feature of RDF is the ability to form complex nested structures, often referred to as graphs of graphs. This allows you to create “named graphs,” essentially subgraphs that can be independently referenced. For example, you could create a named graph for a particular dataset describing Berlin and another for a different geographical area. Then, you could connect them, allowing for more modular and reusable knowledge modeling.
Property Graphs
While RDF provides a robust framework, it’s not always the easiest to work with due to its heavy reliance on linking everything explicitly. This is where property graphs come into play. Property graphs are less focused on linking everything through triples and allow more expressive properties directly within nodes and edges.
For example, instead of using triples to represent each detail, a property graph might let you store all properties about an entity (e.g., “Berlin”) directly in a single node. This makes property graphs more intuitive for many developers and engineers because they more closely resemble object-oriented structures: you have entities (nodes) that possess attributes (properties) and are connected to other entities through relationships (edges).
The significant benefit here is a condensed representation, which speeds up traversal and queries in some scenarios. However, this also introduces a trade-off: while property graphs are more straightforward to query and maintain, they lack some complex relationship modeling features RDF offers, particularly when connecting properties to each other.
Graph of Graphs and Subgraphs for Entity Modeling
A third approach — which takes elements from RDF and property graphs — involves modeling entities using subgraphs or nested graphs. In this model, each entity can be represented as a graph. This allows for a detailed and flexible description of attributes without exploding every detail into individual triples or lump them all together into properties.
For instance, consider a person entity with a complex employment history. Instead of representing every employment detail in one node (as in a property graph), or as several linked nodes (as in RDF), you can treat the employment history as a subgraph. This subgraph could then contain nodes for different jobs, each linked with specific properties and connections. This approach keeps the complexity where it belongs and provides better flexibility when new attributes or entities need to be added.
Hypergraphs and Metagraphs
When discussing more advanced forms of graphs, we encounter hypergraphs and metagraphs. These take the idea of relationships to a new level. A hypergraph allows an edge to connect more than two nodes, which is extremely useful when modeling scenarios where relationships aren’t just pairwise. For example, a “Project” could connect multiple “People,” “Resources,” and “Outcomes,” all in a single edge. This way, hypergraphs help in reducing the complexity of modeling high-order relationships.
Metagraphs, on the other hand, enable nodes and edges to themselves be represented as graphs. This is an extremely powerful feature when we consider the needs of artificial intelligence, as it allows for the modeling of relationships between relationships, an essential aspect for any system that needs to capture not just facts, but their interdependencies and contexts.
Balancing Structure and Properties
One of the recurring challenges when modeling knowledge is finding the balance between structure and properties. With RDF, you get high flexibility and standardization, but complexity can quickly escalate as you decompose everything into triples. Property graphs simplify the representation by using attributes but lose out on the depth of connection modeling. Meanwhile, the graph-of-graphs approach and hypergraphs offer advanced modeling capabilities at the cost of increased computational complexity.
So, how do you decide which model to use? It comes down to your use case. RDF and nested graphs are strong contenders if you need deep linkage and are working with highly variable data. For more straightforward, engineer-friendly modeling, property graphs shine. And when dealing with very complex multi-way relationships or meta-level knowledge, hypergraphs and metagraphs provide the necessary tools.
The key takeaway is that only some approaches are perfect. Instead, it’s all about the modeling goals: how do you want to query the graph, what relationships are meaningful, and how much complexity are you willing to manage?
Conclusion
Modeling AI semantic memory using knowledge graphs is a challenging but rewarding process. The different approaches — RDF, property graphs, and advanced graph modeling techniques like nested graphs and hypergraphs — each offer unique strengths and weaknesses. Whether you are building a personal knowledge graph or scaling up to AI that integrates multiple streams of linked data, it’s essential to understand the trade-offs each approach brings.
In the end, the choice of representation comes down to the nature of your data and your specific needs for querying and maintaining semantic relationships. The world of knowledge graphs is vast, with many tools and frameworks to explore. Stay connected and keep experimenting to find the balance that works for your projects.
-
 @ 3ae7fdae:f8d4b19d
2025-01-28 00:00:26
@ 3ae7fdae:f8d4b19d
2025-01-28 00:00:26Lifting the Curtain on Power and Scandal
The Illusion of Power and TrustIn the modern world, the line between trust and skepticism is razor-thin, especially when it comes to powerful figures and organizations. They present polished facades, dazzling us with promises of stability, innovation, or in Disney’s case, enchantment. Yet, the revelations surrounding Jeffrey Epstein’s network reminded us that power is often far more complex than it appears. This scandal became a litmus test for public trust and fueled questions about who, or what, might be entwined in hidden truths.
When Epstein's crimes were exposed, they revealed not just the horrifying details of exploitation, but also the unsettling reach of his influence. As the media peeled back the layers of his associations, public attention naturally shifted to recognizable names and institutions, including Disney. How could a company that represented childhood innocence, with castles and fairy tales, find itself whispered about in the same breath as Epstein’s infamous circle? This segment examines the roots of that question and the facts that illuminate its plausibility or dismiss it.
Epstein: A Man Who Mastered Access to PowerJeffrey Epstein was more than just a financier—he was a gatekeeper to influence. His lifestyle and operations were an entangled web of charm, manipulation, and wealth, meticulously designed to secure him a place among the powerful. Investigative articles by The Guardian and The New York Times depict Epstein as a social engineer, curating relationships that ranged from politicians and royalty to scientists and celebrities.
Court documents and deposition testimonies during Epstein’s trial confirmed that his homes and private jet were hubs for connecting with influential figures. This access did not come without consequence; it cemented him as both a source of curiosity and, later, fear. Public records, such as those scrutinized in The Washington Post, indicated his involvement with many high-profile individuals. Yet, the details of these relationships varied—some guests were casual acquaintances, others, confidants.
The Infamous Flight LogsThe flight logs of Epstein’s private jet, colloquially known as the "Lolita Express," became a centerpiece for public scrutiny. Released through court orders and accessed by journalists, these logs listed names that triggered a cascade of questions. Guests ranged from prominent business executives to entertainment figures, sparking a debate over whether mere association implied complicity or deeper connections. This fueled the narrative that Epstein’s reach was far more extensive than previously understood, implicating industries where entertainment, power, and trust intersected.
The Role of Speculation in Public DiscourseAs soon as these flight logs surfaced, discussions surged online and across media platforms. The presence of any entertainment figure in Epstein’s orbit raised an eyebrow and, in many cases, invited a leap of logic: if influential media personalities were tied to him, could companies known for entertainment and global reach, like Disney, have hidden associations as well? This hypothesis, though lacking concrete evidence, found fertile ground among those predisposed to distrust large, seemingly untouchable institutions.
It’s crucial to dissect why Disney, specifically, became a subject of speculation. On one hand, its status as an omnipresent media empire makes it an easy target for conspiracy theories that thrive on the juxtaposition of light (Disney’s brand) and darkness (Epstein’s crimes). On the other, it speaks to a larger societal impulse to find cracks in the foundations of those we consider infallible. The idea that even the most beloved entities might harbor hidden truths appeals to a deep-seated desire for transparency and accountability.
The Catalyst of Public CuriosityThe timing of Epstein’s exposure was a critical factor. His arrest and subsequent death in 2019 coincided with a period marked by rising distrust in institutions, fueled by political and social upheavals globally. Social media platforms amplified this distrust, creating echo chambers where half-truths and speculative narratives merged seamlessly with confirmed facts.
It is here that Disney’s name began to surface not as an accused, but as a speculative point in discussions. The reasoning often pointed to a "guilt by association" logic: if the powerful dined, flew, or partied with Epstein, then it was worth questioning the circles in which those powerful entities moved, even without direct evidence. This leap from speculation to assumption reflects a pattern that sociologists recognize as part of conspiracy theory psychology—where a lack of clear answers invites the mind to fill in gaps, often with what feels most compelling.
Reframing the Public’s QuestionsThe real question becomes: why does this speculation hold such sway, even when evidence is scarce? Part of the answer lies in precedent. History is replete with instances where institutions that seemed above reproach were later implicated in hidden misdeeds, from financial frauds to abuse scandals within trusted organizations. This collective memory primes the public to believe that beneath any glittering surface could lie a dark, concealed underbelly.
Disney’s position as an icon of childhood and innocence adds another layer to this narrative. To imagine that such a symbol could be tainted by proximity to someone like Epstein is not just shocking—it’s fascinating. It strikes at the core of what we hold sacred, making it an irresistible topic of conversation and investigation.
Why This MattersUnderstanding why names like Disney are brought into these discussions without verified evidence is essential. It helps differentiate between warranted inquiry and unsupported speculation, allowing us to approach these narratives critically. Addressing this head-on does not only clear the air but strengthens the foundation upon which valid criticism and accountability are built.
A Note on EvidenceAs we move deeper into this exploration, it’s critical to emphasize that while Epstein’s connections to high-profile figures are thoroughly documented, there remains no evidence tying Disney, as an organization, to his operations. Still, the fascination with the “what-ifs” continues, driven by our collective quest for understanding power, secrecy, and the thin line between public and private lives.
The next segment will dive into Epstein’s proven network, unraveling the extent of his influence and why it has been the breeding ground for questions involving the world’s most trusted corporations.
Epstein’s Documented Network
The Web of Power: A Portrait of InfluenceJeffrey Epstein’s network was not merely a collection of acquaintances; it was a curated gallery of the world’s most influential figures, built on calculated relationships and strategic connections. Epstein wielded this network with the precision of a skilled operator, bridging disparate realms of society—politics, academia, business, and media. Investigative reporting by sources such as The New York Times and The Guardian exposed how Epstein maintained access to individuals who shaped policy, managed wealth, and crafted the narratives of popular culture.
Court records, testimonies, and detailed analyses of his interactions revealed that Epstein was adept at placing himself at the center of elite circles. His estates, from Manhattan townhouses to private islands, hosted events that blurred the lines between social gatherings and strategic networking. This chapter delves into the proven extent of Epstein’s reach and why it sparked questions about connections to corporations and public institutions, including Disney.
Flight Logs: The Proof and the SparkThe flight logs from Epstein’s private jet, the infamous "Lolita Express," were among the most illuminating pieces of evidence in mapping his connections. These logs, legally obtained and examined by journalists, painted a picture of Epstein’s influence stretching across industries. High-profile figures were listed, including financiers, political leaders, and entertainment personalities. The presence of notable names triggered waves of speculation—if Epstein had access to such power players, how many more remained unnamed but entangled?
The Guardian and The Washington Post reported that these flights were not just transportation but often involved visits to Epstein’s various properties, known for their opulence and the dark rumors surrounding them. While these logs confirmed that many public figures knew Epstein, the depth and nature of their associations varied widely, from casual acquaintance to deeper involvement.
The Limits of the KnownDespite the breadth of documented connections, there was no verifiable evidence linking Disney as an entity to Epstein’s circle. What the flight logs and guest lists revealed was a man deeply embedded in networks of power, yet even within these proven associations, context was crucial. For instance, some guests, confirmed by court records and investigative articles, were shown to have attended public events or engaged in business unrelated to Epstein’s criminal activities.
The distinction between documented presence and complicity is where the narrative often splinters. The leap from association to implication fueled public debate and conspiracy theories. This was especially true when figures from media and entertainment, sectors known for influencing public sentiment and childhood memories, appeared on the periphery of Epstein’s activities.
Epstein’s Parties and Gatherings: The Elite’s Shadowed StageEpstein’s parties were legendary, drawing attendees from the highest echelons of influence. These gatherings were not casual mixers but orchestrated showcases of power. Reports from court depositions and firsthand accounts highlighted how Epstein leveraged these events to cement alliances and reinforce his status as a gatekeeper to the elite. Some testimonies even described how these events served as platforms for discussing investments, politics, and global initiatives, reinforcing Epstein’s perceived omnipotence.
High-Profile Confirmations and Their ImplicationsSeveral prominent individuals were indeed verified as having ties to Epstein, raising legitimate questions about the extent of their knowledge or involvement. These names included politicians, royalty, and entertainment figures. The ambiguity surrounding these associations allowed theories to flourish. The sheer presence of influential names on Epstein’s guest lists raised the question: If these individuals were implicated, what about the institutions they represented or the circles they moved within?
This was a turning point for public speculation. The logic extended: if an individual from a major media company or entertainment empire like Disney was even remotely connected, could that implicate the company itself? The answer, according to existing court records and credible investigations, remained no. Yet, the absence of direct evidence did not stop speculation; in many cases, it intensified it.
Why Disney Was Brought Into the ConversationDisney’s reputation as a family-friendly giant contrasted starkly with the dark nature of Epstein’s activities, making it an unlikely yet intriguing topic for public discourse. While some entertainment figures appeared on Epstein’s flight logs or were rumored to have interacted with him, investigations have not yielded any proof of corporate-level involvement. However, public fascination persisted, bolstered by the broader questions Epstein’s connections evoked.
It’s worth noting that corporations like Disney, with their vast reach and unparalleled influence, naturally become focal points when discussions of hidden truths arise. The mere idea that such an iconic entity could be associated with real-world shadows captures the imagination and fuels stories that, while lacking proof, thrive on the “what-ifs” that echo through media and online forums.
How Public Perception Shapes the NarrativeSociologists studying the psychology of conspiracy theories point out that the human mind tends to fill gaps in knowledge with what feels most plausible or compelling. When figures from reputable media or entertainment companies are tied, even tangentially, to a scandal as vast as Epstein’s, it challenges the boundaries of trust. This is exacerbated when concrete answers remain elusive, leading to a cycle where suspicion feeds speculation.
The public’s thirst for accountability, especially in the wake of uncovered scandals involving powerful institutions, is both a force for truth and a catalyst for assumptions. In Epstein’s case, the proven reach of his influence and the confirmed involvement of significant figures were enough to trigger the question of how many untold stories lay beneath.
What We Know vs. What We ImagineThe narrative surrounding Epstein’s documented network shows us that while connections can be verified and associations noted, the leap to implicating entire organizations like Disney requires more than names on a list or rumors. It requires evidence that has, thus far, not been presented in any court or investigation. The proven facts are compelling enough: Epstein’s influence was extensive, his ties to power irrefutable. Yet, without direct links, the conversations about specific corporate involvement remain speculative.
In the next segment, we will explore why Disney’s reputation makes it a prime target for such speculation and how its historical handling of public crises plays into these narratives.
Disney – The Symbol of Trust and Target of Suspicion
Why Disney? The Paradox of a Trusted InstitutionDisney’s legacy is built on a foundation of storytelling, dreams, and the belief in happy endings. For nearly a century, the company has woven itself into the fabric of childhoods, becoming synonymous with innocence and magic. This legacy, however, has a dual edge. As the public's trust in institutions erodes and hidden truths are revealed in other sectors, Disney’s position as an untouchable cultural icon makes it both a beacon of light and a potential target for suspicion.
The Symbolism of Disney’s BrandDisney represents more than just a company; it embodies an idea—a refuge where imagination and wonder reign. But this same image that has made Disney a household name also contributes to the paradox of suspicion it faces. When an organization is seen as larger than life, transcending generations and continents, the notion that it could have skeletons in its closet becomes a tantalizing thought. The juxtaposition of innocence with possible shadows creates a narrative that is compelling and worth exploring, even if it remains speculative.
This paradox of Disney as both a trusted symbol and a target for scandal reflects a broader trend. Major corporations that hold influence in our everyday lives—particularly those that shape childhood memories and societal values—are natural focal points when scandals involving power, influence, and exploitation arise. The idea that a company with as much reach as Disney could be connected, however tangentially, to figures like Epstein feeds into this pattern.
Documented Misconduct and Public ReactionsThere have been verified cases involving Disney employees engaging in misconduct, which have been reported by media outlets such as NBC News and local news channels. These incidents, though not systemic and unrelated to Epstein’s network, show how the actions of a few can impact public perception of an entire organization. Examples include arrests for crimes involving minors or inappropriate behavior, isolated events that Disney has publicly addressed through statements and cooperation with law enforcement.
However, these incidents were sufficient to plant seeds of doubt in some minds. Even when addressed swiftly and in line with corporate protocols, such cases reveal a vulnerability: the company’s image can be tarnished not just by its policies, but by the misdeeds of individuals who wear its badge.
The Fuel for SpeculationThe Epstein case acted as a catalyst for looking beyond the obvious, particularly in the context of powerful organizations. If political leaders, financiers, and cultural icons could be connected to Epstein’s circle, why not wonder about the involvement of a company with as vast a presence as Disney? While investigations by trusted outlets have shown no direct corporate link, the sheer scope of Epstein’s influence suggested that any entity known for associating with the powerful could be implicated.
This speculation was not helped by Disney’s approach to public relations. The company’s PR strategies, while sophisticated and generally effective, often prioritize message control over transparency. In a world where silence can be seen as complicity, this strategy sometimes backfires, leading to more questions than answers.
Public Distrust and Historical ContextThe public’s fascination with uncovering hidden truths within major institutions is not unfounded. History is replete with cases where seemingly trustworthy organizations were later found to have concealed scandals. From corporate frauds to abuses within religious institutions, these stories have taught the public that innocence is not immune to corruption. This backdrop primes society to believe that even the most beloved entities, like Disney, could harbor secrets.
Sociologists and media analysts argue that this distrust is a byproduct of what they term the “betrayal effect”—where past disappointments with trusted institutions lower the threshold for believing that betrayal could be lurking everywhere. Disney, with its spotless public image and vast influence, becomes an especially juicy target for such theories. The leap from real cases of employee misconduct to more systemic accusations, however, is where evidence often falls short.
The Role of Social Media and Echo ChambersThe digital age has amplified how speculation morphs into perceived truth. Platforms like Twitter, Reddit, and Facebook allow theories to spread quickly, often outpacing fact-checking and nuanced analysis. Discussions that might once have been confined to fringe circles now gain mainstream attention, especially when they involve powerful figures or beloved brands.
In the context of Epstein’s exposure, this meant that any high-profile connection or name could become part of a broader narrative of guilt by association. The fact that Disney, as a corporation, appeared in speculative discussions alongside verified names from Epstein’s logs was enough for some to draw connections, even without direct evidence.
Reputation Management and PerceptionDisney’s approach to crises and controversies has long involved careful reputation management. From its response to legal issues to how it handles employee-related incidents, the company employs sophisticated PR strategies to mitigate damage and maintain its standing. This is standard practice for global brands; however, the public’s interpretation can be different. Strategic silence or tightly controlled statements can come across as evasive, fueling theories that there is something more to hide.
For a company like Disney, which operates at the intersection of family values and global corporate power, the stakes are high. The expectation isn’t just for entertainment but for upholding the moral high ground. When speculation links Disney to scandals, no matter how peripherally, it chips away at this carefully crafted image.
Why Address This Now?The speculation around Disney and Epstein underscores a crucial point about the nature of public inquiry and corporate reputation. It is not enough for companies to rely solely on public relations strategies that worked in the past. The demand for transparency is greater than ever, and silence, even when warranted, can erode trust.
Disney’s role in the public consciousness means that even baseless theories need addressing. By understanding why these narratives gain traction, both companies and the public can engage in more meaningful dialogues about accountability, proof, and trust.
The next segment will delve into how the public navigates between confirmed facts and conspiratorial whispers, exploring why certain theories stick and what it means for how we view powerful organizations.
Separating Fact from Conspiracy
The Thin Line Between Evidence and Speculation In the age of information, where facts are readily available yet often overshadowed by conjecture, separating truth from conspiracy is both an art and a necessity. When powerful entities like Disney find themselves drawn into discussions of hidden networks and scandals involving figures such as Jeffrey Epstein, it highlights a broader societal challenge: how do we differentiate between what is proven and what is assumed? This segment dissects the interplay of evidence, theory, and the psychological factors that drive our need to seek connections.
The Basis of Public Suspicion Public trust in large institutions has waned over decades, driven by a series of high-profile betrayals. From corporate frauds that shattered economies to scandals involving trusted religious or educational institutions, society has learned that power often conceals flaws and, in some cases, criminal actions. According to research published in the Journal of Communication, this erosion of trust leads to a phenomenon known as confirmation bias—the tendency to interpret new evidence as confirmation of one’s existing beliefs or suspicions.
The Epstein case provided fertile ground for such biases. The verified details of Epstein’s operations—the private jet, the exclusive parties, the high-profile guests—were enough to prompt a collective re-examination of how far his reach extended. While many of his associations were proven to be casual or professional in nature, the public’s hunger for deeper revelations ensured that speculation would thrive in areas where clarity was lacking.
The Role of Real Connections Epstein’s documented network included figures from politics, academia, finance, and media. The release of flight logs and court documents revealed that powerful individuals attended his events and interacted within his sphere. This factual basis, verified by investigative reporting from The New York Times, The Guardian, and other reputable sources, provided legitimacy to the idea that Epstein’s influence was pervasive. However, the extent to which these relationships were innocent or complicit was not uniformly clear.
This ambiguity created a vacuum where speculation could flourish. Public attention shifted from individuals named in the logs to the institutions and industries they represented. It was here that major corporations, including Disney, entered the discourse—not because of documented ties, but because of their visibility and influence.
The Psychology Behind Linking Power and Scandal To understand why theories about Disney’s potential involvement in Epstein’s network persist, it is essential to examine the psychology of conspiracy. Sociological and psychological studies indicate that people are naturally inclined to question narratives when they feel that the truth is being withheld. The more powerful or untouchable an institution seems, the more likely it is to be suspected of hiding something significant.
Disney’s image as a global giant that molds childhoods and shapes culture makes it an appealing target for such theories. The company’s public persona as a bastion of family values and innocence stands in stark contrast to any whispers of scandal or misconduct. This contrast alone provides fertile ground for stories to grow, even in the absence of solid proof.
Confirmed Misconduct vs. Conspiracy It is important to acknowledge that Disney, like any large corporation, has faced incidents involving employee misconduct. News reports from outlets such as NBC News have documented cases where employees were arrested for inappropriate conduct involving minors. These cases, while serious and handled with appropriate legal responses, were isolated incidents. No evidence points to these cases being part of a larger, systemic issue within the company or connected to external figures like Epstein.
However, the very existence of these incidents is often enough to keep theories alive. Public perception does not always differentiate between an individual’s actions and the culture of the organization they work for. When these incidents coincide with broader conversations about power and secrecy, they feed into narratives that imply guilt by association.
The Amplifying Power of Social Media The role of social media in shaping and amplifying conspiracy theories cannot be overstated. Platforms like Twitter and Reddit have created spaces where facts, opinions, and theories coexist with little separation. When the Epstein scandal broke, social media was flooded with discussions, many of which featured a mix of verifiable information and speculative connections. The absence of direct evidence linking companies like Disney to Epstein did not deter users from proposing connections based on circumstantial evidence and “what-if” scenarios.
This phenomenon, described by media analysts as the “echo chamber effect,” allows theories to gain credibility through repetition rather than proof. As theories are shared, retweeted, and commented on, they accumulate a sense of legitimacy that belies their origins.
Why Certain Theories Stick Certain theories persist because they tap into deep-seated fears and the knowledge that the powerful often operate beyond the reach of conventional accountability. High-profile scandals involving powerful figures—whether in business, politics, or entertainment—reinforce the belief that more may be hidden just out of reach. Epstein’s network was confirmed to include names that were once considered untouchable, which validated the idea that hidden truths could surface anywhere.
Disney’s name appearing in speculative discussions highlights the intersection of innocence and power. It reflects a societal expectation that if one pillar of influence is shown to be compromised, others may be as well. This expectation, however, must be tempered with critical thinking and an examination of evidence.
The Need for Discernment Understanding the difference between fact and theory is crucial for informed dialogue. Public scrutiny is essential for accountability, but it must be balanced with discernment. While Epstein’s known associations spanned many sectors, and while individuals from the entertainment industry were involved in his circle, the leap to implicating entire organizations like Disney has not been supported by verified investigations.
The Reality Check Here’s what we know:
Documented Facts: Epstein’s network included influential figures, confirmed by court records and journalistic investigations. Disney’s Position: While Disney has faced isolated cases of employee misconduct, no substantial evidence ties the company as an institution to Epstein’s criminal activities. Public Perception: Theories are fueled by a combination of legitimate distrust in powerful institutions and the psychological need to connect the dots, even when the evidence does not support it. In the next segment, we will explore how media control and the use of non-disclosure agreements (NDAs) contribute to the public’s perception of secrecy and whether this perception is warranted.
Media Control and NDAs – Protecting Power or Ensuring Silence?
The Strategy of Silence in Crisis Management When powerful organizations face potential scandal or crises, the first line of defense is often control—control over the narrative, control over information, and control over public perception. This strategy, while effective in mitigating immediate damage, can backfire by fostering an aura of secrecy that leads to suspicion. Disney, like many other global corporations, has historically employed these tactics, particularly through the use of non-disclosure agreements (NDAs) and strategic public relations (PR) campaigns. But do these measures protect legitimate corporate interests, or do they simply fuel theories that there is more being hidden?
Understanding the Role of NDAs NDAs are legal tools designed to maintain confidentiality and protect business interests. In most cases, their use is standard practice, whether to protect trade secrets, secure settlements, or manage sensitive internal matters. However, when NDAs intersect with scandals involving powerful individuals or organizations, they can become symbols of enforced silence. A report from the Harvard Business Review highlights that while NDAs are often employed for legitimate purposes, their misuse—especially when used to silence allegations of misconduct—has cast a shadow over their intent.
Disney has used NDAs in its corporate dealings, as have many in the media and entertainment sectors. This is not in itself suspicious; however, the mere presence of NDAs in a company’s arsenal can contribute to a narrative of secrecy, especially when paired with limited transparency during controversies.
The Case of High-Profile Secrecy The Epstein scandal showed how the use of NDAs and strategic silence could be perceived in a different light. When influential figures and companies were linked to his circle, silence from those implicated was interpreted by many as an attempt to avoid deeper inquiry. While Disney has not been tied to Epstein’s activities through verified evidence, its use of NDAs in unrelated circumstances and its approach to handling public controversies have made it a recurring subject in theories about hidden truths.
For example, Disney’s meticulous control over its brand image means that it often handles internal issues privately, releasing carefully crafted statements that address public concerns without divulging specifics. This approach, while protective, sometimes has the unintended consequence of making the public wonder what is not being said.
The Intersection of PR and Public Perception Public relations are designed to safeguard a company’s image, ensuring that responses to any negative news are swift and tightly managed. Disney’s PR machine is among the most sophisticated, capable of steering narratives and maintaining its reputation as an entertainment titan. This strategic control has allowed Disney to weather crises that might have permanently damaged lesser brands. However, in the context of a scandal as sprawling and notorious as Epstein’s, such control is perceived differently.
When the Epstein story broke and high-profile connections came to light, companies with any tenuous ties activated their crisis management protocols. For some, this meant issuing vague statements or refusing to comment altogether. To the public, this read as silence—a strategic choice that seemed suspicious when paired with known instances of NDAs being used to keep serious allegations quiet in other industries. The #MeToo movement, for instance, revealed how NDAs were used by some media companies to shield powerful perpetrators of harassment, showing that these tools can sometimes contribute to a culture of concealment.
Silence as Complicity? For a company like Disney, known for its polished public image, silence during times of widespread speculation can amplify suspicions. The question becomes: Is silence an act of protection or complicity? While NDAs are often used to manage settlements or protect internal processes, the fact that they prevent full transparency can make even innocent parties appear as if they have something to hide.
Experts in crisis communication argue that silence may protect the brand short-term but can erode trust long-term. Disney’s approach to handling public perception, from managing employee misconduct cases to addressing larger social controversies, often involves strategic responses that give the public enough information to stay satisfied but not enough to quell the more skeptical voices. This is standard practice but becomes contentious when the public is searching for accountability.
The Impact of Strategic Silence on Public Trust Media and communication studies have shown that transparency is increasingly becoming a measure of trustworthiness for corporations. In an era where the public demands answers and alternative media thrive on filling in gaps left by corporate PR, the stakes for maintaining trust are higher than ever. The use of NDAs and controlled statements can protect a company’s interests, but it also contributes to a perception of secrecy that feeds public doubt.
Disney’s balancing act—protecting its brand while managing incidents behind closed doors—reflects a broader industry trend. Corporations that prioritize narrative control must now reckon with an environment where even a hint of concealment can lead to damaging speculation. The Epstein case amplified this issue, putting the spotlight on how major organizations handle proximity to scandal, even if only by association.
Navigating the Perception The real challenge for Disney and similar companies lies in navigating the fine line between protecting their interests and fostering trust. Complete transparency can be risky, but strategic silence risks becoming complicit silence in the eyes of the public. This duality—where necessary protection measures are perceived as proof of hidden wrongdoing—is why entities like Disney find themselves caught up in discussions about figures like Epstein, despite the absence of concrete evidence.
The Takeaway for Institutions and the Public Understanding the role of NDAs and PR in managing public crises helps frame why powerful companies might become targets of suspicion. While the use of these tools is standard and often justified, their impact on public perception can’t be ignored. For the public, recognizing the difference between warranted inquiry and overreach is key to maintaining productive scrutiny without falling into the trap of baseless theories.
The next segment will focus on what these perceptions mean for society as a whole and why the pursuit of transparency and trust must be a collective endeavor.
Beyond the Shadows – A Call to Unity
The Complex Path to UnderstandingIn an age where trust in powerful institutions is fraying, and access to information is both a blessing and a burden, our approach to truth becomes more critical than ever. The discussions surrounding figures like Jeffrey Epstein and corporations like Disney are not just about scandal; they are about how we, as a society, confront power, secrecy, and transparency. This segment is a call to unite in the pursuit of truth—not through a divisive lens, but with collective discernment and an unwavering commitment to evidence and integrity.
The Lessons from HistoryHistory teaches us that institutions once seen as untouchable can harbor hidden truths. The exposure of corporate frauds, systemic abuses, and cover-ups within trusted sectors has shaped a society that questions everything. The Epstein scandal underscored this, revealing a network of power that reached further than many dared to imagine. Yet, while it validated the public’s instinct to question, it also highlighted a key challenge: differentiating between grounded inquiry and baseless theory.
Disney’s name appearing in speculative discussions about Epstein points to a broader pattern—our collective desire to ensure that those who hold power are not above scrutiny. But as we demand accountability, we must also unite in the practice of informed skepticism. The leap from isolated cases of misconduct or association to implicating entire organizations requires evidence, not just conjecture. This distinction is where we, as a society, must find common ground.
The Role of TransparencyTransparency has become the cornerstone of public trust. Organizations that handle controversies behind closed doors risk damaging their credibility. For companies like Disney, known for protecting their brand with meticulous care, the challenge is clear: find a balance between safeguarding legitimate interests and providing enough transparency to maintain public trust.
The use of NDAs, strategic silence, and controlled narratives may shield brands in the short term, but they can erode trust in the long run. Studies in crisis communication emphasize that openness, even when it exposes vulnerabilities, can reinforce loyalty and confidence among stakeholders. In the context of Epstein and the persistent whispers about powerful corporations, this lesson is especially relevant.
A Collective Call to ClarityThe pursuit of truth is not just the responsibility of journalists, whistleblowers, or industry watchdogs—it is a collective endeavor. The public plays a crucial role in this, but so do the corporations that hold sway over cultural and economic landscapes. When Disney’s name enters speculative discussions, it reflects a deep-seated desire for transparency from those we trust. This desire should be met not with fear of the unknown but with a commitment to clarity.
This segment is a call for unity in approaching these conversations. The balance between healthy skepticism and conspiracy theory is delicate but essential. We must ask hard questions and hold power accountable without losing sight of what separates substantiated fact from assumption.
Why Unity MattersIn times where speculation can divide and misinformation can spread faster than verified facts, unity in the pursuit of truth is vital. When we allow fear and uncertainty to fracture our approach, we weaken our collective power to bring genuine issues to light. Epstein’s case showed that hidden wrongs do exist and can involve the most influential figures. It also showed that uncovering the full scope of such wrongs takes a community committed to patience, evidence, and shared purpose.
Public scrutiny is essential for democracy and social justice, but so is discernment. When theories about organizations like Disney arise without evidence, they risk diverting attention from real, proven issues that demand action. Unity in seeking truth means supporting real investigations, demanding transparency, and recognizing the power of evidence-based inquiry.
Building a Culture of Informed AccountabilityThe goal is not to silence questions but to elevate them, ensuring that they are grounded in reality. This approach not only empowers the public but also sets a standard for institutions. If Disney and other corporations prioritize transparency, they can reinforce the public trust that sustains their brands. Similarly, when the public insists on evidence and integrity in its discussions, it strengthens the very fabric of accountability.
Reflections for the Road AheadAs we move forward, let us commit to being a society that seeks truth not for scandal’s sake but for justice and integrity. Let us stand together in holding power to account, using facts as our foundation and unity as our strength. The story of Epstein and the questions it raises about power, influence, and hidden truths are reminders that transparency and trust are not just corporate responsibilities—they are collective ones.
This call to unity is a reminder that we all play a part in shaping how these stories unfold. When we seek, question, and demand clarity together, we create a society that values truth over rumor, evidence over assumption, and justice over division.
As we conclude this exploration, may we carry forward the lessons learned: the importance of questioning with integrity, seeking truth with diligence, and facing the unknown not as individuals, but as a united community.
-
 @ b17fccdf:b7211155
2025-01-21 17:02:21
@ b17fccdf:b7211155
2025-01-21 17:02:21The past 26 August, Tor introduced officially a proof-of-work (PoW) defense for onion services designed to prioritize verified network traffic as a deterrent against denial of service (DoS) attacks.
~ > This feature at the moment, is deactivate by default, so you need to follow these steps to activate this on a MiniBolt node:
- Make sure you have the latest version of Tor installed, at the time of writing this post, which is v0.4.8.6. Check your current version by typing
tor --versionExample of expected output:
Tor version 0.4.8.6. This build of Tor is covered by the GNU General Public License (https://www.gnu.org/licenses/gpl-3.0.en.html) Tor is running on Linux with Libevent 2.1.12-stable, OpenSSL 3.0.9, Zlib 1.2.13, Liblzma 5.4.1, Libzstd N/A and Glibc 2.36 as libc. Tor compiled with GCC version 12.2.0~ > If you have v0.4.8.X, you are OK, if not, type
sudo apt update && sudo apt upgradeand confirm to update.- Basic PoW support can be checked by running this command:
tor --list-modulesExpected output:
relay: yes dirauth: yes dircache: yes pow: **yes**~ > If you have
pow: yes, you are OK- Now go to the torrc file of your MiniBolt and add the parameter to enable PoW for each hidden service added
sudo nano /etc/tor/torrcExample:
```
Hidden Service BTC RPC Explorer
HiddenServiceDir /var/lib/tor/hidden_service_btcrpcexplorer/ HiddenServiceVersion 3 HiddenServicePoWDefensesEnabled 1 HiddenServicePort 80 127.0.0.1:3002 ```
~ > Bitcoin Core and LND use the Tor control port to automatically create the hidden service, requiring no action from the user. We have submitted a feature request in the official GitHub repositories to explore the need for the integration of Tor's PoW defense into the automatic creation process of the hidden service. You can follow them at the following links:
- Bitcoin Core: https://github.com/lightningnetwork/lnd/issues/8002
- LND: https://github.com/bitcoin/bitcoin/issues/28499
More info:
- https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/
- https://gitlab.torproject.org/tpo/onion-services/onion-support/-/wikis/Documentation/PoW-FAQ
Enjoy it MiniBolter! 💙
-
 @ f7d424b5:618c51e8
2025-01-26 19:03:22
@ f7d424b5:618c51e8
2025-01-26 19:03:22(These podcast shownotes were originally posted on our website melonmancy.net
A second video game award show has hit the south tower. Also if you have topic ideas feel free to sign up on our forum we decided to not restrict any posts on the idea threads.
We mentioned a few things in the show you might want to pull up while listening, they are the following:
- Literally WHO studio grandstanding over lewd PC mods
- Aggro Crab leaves X - cringe or no?
- Selacodev immediately bullied after their trailer was shown at TRGAs for free w/o permission
Obligatory:
- Listen to the new episode here!
- Discuss this episode on OUR NEW FORUM
- Get the RSS and Subscribe (this is a new feed URL, but the old one redirects here too!)
- Get a modern podcast app to use that RSS feed on at newpodcastapps.com
- Or listen to the show on the forum using the embedded Podverse player!
- Send your complaints here
Reminder that this is a Value4Value podcast so any support you can give us via a modern podcasting app is greatly appreciated and we will never bow to corporate sponsors!
Our podcast is created entirely with free software and is proudly hosted on RSSBlue!
-
 @ e6817453:b0ac3c39
2024-12-07 14:52:47
@ e6817453:b0ac3c39
2024-12-07 14:52:47The temporal semantics and temporal and time-aware knowledge graphs. We have different memory models for artificial intelligence agents. We all try to mimic somehow how the brain works, or at least how the declarative memory of the brain works. We have the split of episodic memory and semantic memory. And we also have a lot of theories, right?
Declarative Memory of the Human Brain
How is the semantic memory formed? We all know that our brain stores semantic memory quite close to the concept we have with the personal knowledge graphs, that it’s connected entities. They form a connection with each other and all those things. So far, so good. And actually, then we have a lot of concepts, how the episodic memory and our experiences gets transmitted to the semantic:
- hippocampus indexing and retrieval
- sanitization of episodic memories
- episodic-semantic shift theory
They all give a different perspective on how different parts of declarative memory cooperate.
We know that episodic memories get semanticized over time. You have semantic knowledge without the notion of time, and probably, your episodic memory is just decayed.
But, you know, it’s still an open question:
do we want to mimic an AI agent’s memory as a human brain memory, or do we want to create something different?
It’s an open question to which we have no good answer. And if you go to the theory of neuroscience and check how episodic and semantic memory interfere, you will still find a lot of theories, yeah?
Some of them say that you have the hippocampus that keeps the indexes of the memory. Some others will say that you semantic the episodic memory. Some others say that you have some separate process that digests the episodic and experience to the semantics. But all of them agree on the plan that it’s operationally two separate areas of memories and even two separate regions of brain, and the semantic, it’s more, let’s say, protected.
So it’s harder to forget the semantical facts than the episodes and everything. And what I’m thinking about for a long time, it’s this, you know, the semantic memory.
Temporal Semantics
It’s memory about the facts, but you somehow mix the time information with the semantics. I already described a lot of things, including how we could combine time with knowledge graphs and how people do it.
There are multiple ways we could persist such information, but we all hit the wall because the complexity of time and the semantics of time are highly complex concepts.
Time in a Semantic context is not a timestamp.
What I mean is that when you have a fact, and you just mentioned that I was there at this particular moment, like, I don’t know, 15:40 on Monday, it’s already awake because we don’t know which Monday, right? So you need to give the exact date, but usually, you do not have experiences like that.
You do not record your memories like that, except you do the journaling and all of the things. So, usually, you have no direct time references. What I mean is that you could say that I was there and it was some event, blah, blah, blah.
Somehow, we form a chain of events that connect with each other and maybe will be connected to some period of time if we are lucky enough. This means that we could not easily represent temporal-aware information as just a timestamp or validity and all of the things.
For sure, the validity of the knowledge graphs (simple quintuple with start and end dates)is a big topic, and it could solve a lot of things. It could solve a lot of the time cases. It’s super simple because you give the end and start dates, and you are done, but it does not answer facts that have a relative time or time information in facts . It could solve many use cases but struggle with facts in an indirect temporal context. I like the simplicity of this idea. But the problem of this approach that in most cases, we simply don’t have these timestamps. We don’t have the timestamp where this information starts and ends. And it’s not modeling many events in our life, especially if you have the processes or ongoing activities or recurrent events.
I’m more about thinking about the time of semantics, where you have a time model as a hybrid clock or some global clock that does the partial ordering of the events. It’s mean that you have the chain of the experiences and you have the chain of the facts that have the different time contexts.
We could deduct the time from this chain of the events. But it’s a big, big topic for the research. But what I want to achieve, actually, it’s not separation on episodic and semantic memory. It’s having something in between.
Blockchain of connected events and facts
I call it temporal-aware semantics or time-aware knowledge graphs, where we could encode the semantic fact together with the time component.I doubt that time should be the simple timestamp or the region of the two timestamps. For me, it is more a chain for facts that have a partial order and form a blockchain like a database or a partially ordered Acyclic graph of facts that are temporally connected. We could have some notion of time that is understandable to the agent and a model that allows us to order the events and focus on what the agent knows and how to order this time knowledge and create the chains of the events.
Time anchors
We may have a particular time in the chain that allows us to arrange a more concrete time for the rest of the events. But it’s still an open topic for research. The temporal semantics gets split into a couple of domains. One domain is how to add time to the knowledge graphs. We already have many different solutions. I described them in my previous articles.
Another domain is the agent's memory and how the memory of the artificial intelligence treats the time. This one, it’s much more complex. Because here, we could not operate with the simple timestamps. We need to have the representation of time that are understandable by model and understandable by the agent that will work with this model. And this one, it’s way bigger topic for the research.”
-
 @ 58937958:545e6994
2025-01-13 03:31:48
@ 58937958:545e6994
2025-01-13 03:31:48I made croquettes inspired by Spiral's character "Bitcoin (Puppet)."

The method is the same as making regular croquettes. I also tried making a version (right) with the arms and legs attached while shaping the filling, but they fell off before I could coat them in flour.

The face is made with seaweed and sliced cheese. The arms and legs are made with fish cake (hanpen). I brushed soy sauce on the legs and lightly toasted them in a toaster, which gave them a brown color.
 The arms and legs are attached using thin spaghetti.
When I searched for character-themed bentos (kyaraben), I came across the idea of using dried pasta, which made sense.
I used fried spaghetti sticks for attachment.
The arms and legs are attached using thin spaghetti.
When I searched for character-themed bentos (kyaraben), I came across the idea of using dried pasta, which made sense.
I used fried spaghetti sticks for attachment.Here’s Bitcoin Croquette squished into a bento box:

Halving

Notes
- I tried freezing the filling to help it hold its shape, but it backfired. It stuck to the plate and the cooking paper, and once partially thawed, it became way too watery. Freezing might work with better preparation.
- The filling was quite dry when shaping, so it might be better to add a binder (this time, I only used potatoes and sautéed onions).
The shape of Bitcoin Puppet was really easy and fun to make, so I’d love to try creating something else next time!
nostr:nevent1qqsxgpjvf9g9suhzx5asqhvnlvnarl43kuhas8v5g2ryjr9yjjp0z5ctkh5pt
-
 @ 50809a53:e091f164
2025-01-20 22:30:01
@ 50809a53:e091f164
2025-01-20 22:30:01For starters, anyone who is interested in curating and managing "notes, lists, bookmarks, kind-1 events, or other stuff" should watch this video:
https://youtu.be/XRpHIa-2XCE
Now, assuming you have watched it, I will proceed assuming you are aware of many of the applications that exist for a very similar purpose. I'll break them down further, following a similar trajectory in order of how I came across them, and a bit about my own path on this journey.
We'll start way back in the early 2000s, before Bitcoin existed. We had https://zim-wiki.org/
It is tried and true, and to this day stands to present an option for people looking for a very simple solution to a potentially complex problem. Zim-Wiki works. But it is limited.
Let's step into the realm of proprietary. Obsidian, Joplin, and LogSeq. The first two are entirely cloud-operative applications, with more of a focus on the true benefit of being a paid service. I will assume anyone reading this is capable of exploring the marketing of these applications, or trying their freemium product, to get a feeling for what they are capable of.
I bring up Obsidian because it is very crucial to understand the market placement of publication. We know social media handles the 'hosting' problem of publishing notes "and other stuff" by harvesting data and making deals with advertisers. But- what Obsidian has evolved to offer is a full service known as 'publish'. This means users can stay in the proprietary pipeline, "from thought to web." all for $8/mo.
See: https://obsidian.md/publish
THIS IS NOSTR'S PRIMARY COMPETITION. WE ARE HERE TO DISRUPT THIS MARKET, WITH NOTES AND OTHER STUFF. WITH RELAYS. WITH THE PROTOCOL.
Now, on to Joplin. I have never used this, because I opted to study the FOSS market and stayed free of any reliance on a paid solution. Many people like Joplin, and I gather the reason is because it has allowed itself to be flexible and good options that integrate with Joplin seems to provide good solutions for users who need that functionality. I see Nostr users recommending Joplin, so I felt it was worthwhile to mention as a case-study option. I myself need to investigate it more, but have found comfort in other solutions.
LogSeq - This is my "other solutions." It seems to be trapped in its proprietary web of funding and constraint. I use it because it turns my desktop into a power-house of note archival. But by using it- I AM TRAPPED TOO. This means LogSeq is by no means a working solution for Nostr users who want a long-term archival option.
But the trap is not a cage. It's merely a box. My notes can be exported to other applications with graphing and node-based information structure. Specifically, I can export these notes to:
- Text
- OPML
- HTML
- and, PNG, for whatever that is worth.
Let's try out the PNG option, just for fun. Here's an exported PNG of my "Games on Nostr" list, which has long been abandoned. I once decided to poll some CornyChat users to see what games they enjoyed- and I documented them in a LogSeq page for my own future reference. You can see it here:
https://i.postimg.cc/qMBPDTwr/image.png
This is a very simple example of how a single "page" or "list" in LogSeq can be multipurpose. It is a small list, with multiple "features" or variables at play. First, I have listed out a variety of complex games that might make sense with "multiplayer" identification that relies on our npubs or nip-05 addresses to aggregate user data. We can ALL imagine playing games like Tetris, Snake, or Catan together with our Nostr identities. But of course we are a long way from breaking into the video game market.
On a mostly irrelevant sidenote- you might notice in my example list, that I seem to be excited about a game called Dot.Hack. I discovered this small game on Itch.io and reached out to the developer on Twitter, in an attempt to purple-pill him, but moreso to inquire about his game. Unfortunately there was no response, even without mention of Nostr. Nonetheless, we pioneer on. You can try the game here: https://propuke.itch.io/planethack
So instead let's focus on the structure of "one working list." The middle section of this list is where I polled users, and simply listed out their suggestions. Of course we discussed these before I documented, so it is note a direct result of a poll, but actually a working interaction of poll results! This is crucial because it separates my list from the aggregated data, and implies its relevance/importance.
The final section of this ONE list- is the beginnings of where I conceptually connect nostr with video game functionality. You can look at this as the beginning of a new graph, which would be "Video Game Operability With Nostr".
These three sections make up one concept within my brain. It exists in other users' brains too- but of course they are not as committed to the concept as myself- the one managing the communal discussion.
With LogSeq- I can grow and expand these lists. These lists can become graphs. Those graphs can become entire catalogues of information than can be shared across the web.
I can replicate this system with bookmarks, ideas, application design, shopping lists, LLM prompting, video/music playlists, friend lists, RELAY lists, the LIST goes ON forever!
So where does that lead us? I think it leads us to kind-1 events. We don't have much in the way of "kind-1 event managers" because most developers would agree that "storing kind-1 events locally" is.. at the very least, not so important. But it could be! If only a superapp existed that could interface seamlessly with nostr, yada yada.. we've heard it all before. We aren't getting a superapp before we have microapps. Basically this means frameworking the protocol before worrying about the all-in-one solution.
So this article will step away from the deep desire for a Nostr-enabled, Rust-built, FOSS, non-commercialized FREEDOM APP, that will exist one day, we hope.
Instead, we will focus on simple attempts of the past. I encourage others to chime in with their experience.
Zim-Wiki is foundational. The user constructs pages, and can then develop them into books.
LogSeq has the right idea- but is constrained in too many ways to prove to be a working solution at this time. However, it is very much worth experimenting with, and investigating, and modelling ourselves after.
https://workflowy.com/ is next on our list. This is great for users who think LogSeq is too complex. They "just want simple notes." Get a taste with WorkFlowy. You will understand why LogSeq is powerful if you see value in WF.
I am writing this article in favor of a redesign of LogSeq to be compatible with Nostr. I have been drafting the idea since before Nostr existed- and with Nostr I truly believe it will be possible. So, I will stop to thank everyone who has made Nostr what it is today. I wouldn't be publishing this without you!
One app I need to investigate more is Zettlr. I will mention it here for others to either discuss or investigate, as it is also mentioned some in the video I opened with. https://www.zettlr.com/
On my path to finding Nostr, before its inception, was a service called Deta.Space. This was an interesting project, not entirely unique or original, but completely fresh and very beginner-friendly. DETA WAS AN AWESOME CLOUD OS. And we could still design a form of Nostr ecosystem that is managed in this way. But, what we have now is excellent, and going forward I only see "additional" or supplemental.
Along the timeline, Deta sunsetted their Space service and launched https://deta.surf/
You might notice they advertise that "This is the future of bookmarks."
I have to wonder if perhaps I got through to them that bookmarking was what their ecosystem could empower. While I have not tried Surf, it looks interested, but does not seem to address what I found most valuable about Deta.Space: https://webcrate.app/
WebCrate was an early bookmarking client for Deta.Space which was likely their most popular application. What was amazing about WebCrate was that it delivered "simple bookmarking." At one point I decided to migrate my bookmarks from other apps, like Pocket and WorkFlowy, into WebCrate.
This ended up being an awful decision, because WebCrate is no longer being developed. However, to much credit of Deta.Space, my WebCrate instance is still running and completely functional. I have since migrated what I deem important into a local LogSeq graph, so my bookmarks are safe. But, the development of WebCrate is note.
WebCrate did not provide a working directory of crates. All creates were contained within a single-level directory. Essentially there were no layers. Just collections of links. This isn't enough for any user to effectively manage their catalogue of notes. With some pressure, I did encourage the German developer to flesh out a form of tagging, which did alleviate the problem to some extent. But as we see with Surf, they have pioneered in another direction.
That brings us back to Nostr. Where can we look for the best solution? There simply isn't one yet. But, we can look at some other options for inspiration.
HedgeDoc: https://hedgedoc.org/
I am eager for someone to fork HedgeDoc and employ Nostr sign-in. This is a small step toward managing information together within the Nostr ecosystem. I will attempt this myself eventually, if no one else does, but I am prioritizing my development in this way:
- A nostr client that allows the cataloguing and management of relays locally.
- A LogSeq alternative with Nostr interoperability.
- HedgeDoc + Nostr is #3 on my list, despite being the easiest option.
Check out HedgeDoc 2.0 if you have any interest in a cooperative Markdown experience on Nostr: https://docs.hedgedoc.dev/
Now, this article should catch up all of my dearest followers, and idols, to where I stand with "bookmarking, note-taking, list-making, kind-1 event management, frameworking, and so on..."
Where it leads us to, is what's possible. Let's take a look at what's possible, once we forego ALL OF THE PROPRIETARY WEB'S BEST OPTIONS:
https://denizaydemir.org/
https://denizaydemir.org/graph/how-logseq-should-build-a-world-knowledge-graph/
https://subconscious.network/
Nostr is even inspired by much of the history that has gone into information management systems. nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn I know looks up to Gordon Brander, just as I do. You can read his articles here: https://substack.com/@gordonbrander and they are very much worth reading! Also, I could note that the original version of Highlighter by nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft was also inspired partially by WorkFlowy.
About a year ago, I was mesmerized coming across SubText and thinking I had finally found the answer Nostr might even be looking for. But, for now I will just suggest that others read the Readme.md on the SubText Gtihub, as well as articles by Brander.
Good luck everyone. I am here to work with ANYONE who is interested in these type of solution on Nostr.
My first order of business in this space is to spearhead a community of npubs who share this goal. Everyone who is interested in note-taking or list-making or bookmarking is welcome to join. I have created an INVITE-ONLY relay for this very purpose, and anyone is welcome to reach out if they wish to be added to the whitelist. It should be freely readable in the near future, if it is not already, but for now will remain a closed-to-post community to preemptively mitigate attack or spam. Please reach out to me if you wish to join the relay. https://logstr.mycelium.social/
With this article, I hope people will investigate and explore the options available. We have lots of ground to cover, but all of the right resources and manpower to do so. Godspeed, Nostr.
Nostr #Notes #OtherStuff #LogSec #Joplin #Obsidian
-
 @ 000002de:c05780a7
2025-01-20 16:27:40
@ 000002de:c05780a7
2025-01-20 16:27:40I just finished the audio book read by Norm himself. I must say, if you love Norm you will love this book. I highly recommend the audio book. I don't want to spoil anything but the book is like sitting down with Norm and listening to him tell you stories. You never know what is true or false and if the whole thing IS the joke. I laughed out loud many times.
originally posted at https://stacker.news/items/857482
-
 @ cb43dde2:ef277171
2025-01-27 23:10:39
@ cb43dde2:ef277171
2025-01-27 23:10:39HODL has been defined by many as an acronym for “Hold on for Dear Life.” Many my age were taught to earn money and save it for the future as conventional wisdom. That wisdom would have you holding something designed to degrade in value at a rate of 2% annually. If all “goes to plan,” the purchasing power (value) of your savings in 35 years will be half that of today. In 2022 the US dollar value degraded a total of 8%. At this rate, your savings’ value will cut in half in less than nine years. Not quite the retirement plan one would hope for, but happens to be what my generation was taught in school. Thankfully there is a solution: become a HODLer of assets.
Every investor is a collector of assets. They all have their own thesis about the assets they collect and how the collection will transport their monetary value across space and time. My thesis is that when you hold assets (the practice of HODLing) you hold the superposition in the market and can make better decisions against the overall economic tide. I like to hold a diverse portfolio across asset types, themes, and tax treatments, so that I am always in a superposition when liquidity is needed for the next opportunity. In the words of Charles Darwin, “it is not the strongest of the species that survive, nor the most intelligent, but the one most responsive to change.”
The Superposition of Markets
A superposition is a phenomenon observed in nature where something is in one of two antithetical positions, both equally likely, and is only defined when observed or measured. Most have heard of the Schrödinger’s Cat thought experiment; this is an example of superposition (references below). The financial markets act as a measuring tool identifying the next entangled pair of buyer and seller. Therefore, as a HODLer you remain in a superposition within the market until either your buy price or sell price is realized, instantaneously identifying your entangled counterpart within the market. To hold assets puts the HODLer in a superposition within the markets in which they HODL.
Making a Market: It Only Takes Two
A market is made when two parties, a buyer and a seller, come to an agreement to transfer personal property between each other. Without an agreement, there is no market activity and therefore no market. There are many more participants that help to facilitate markets like stock exchanges, store fronts, and Craigslist to name a few. This infrastructure has not changed the necessities to make a market but instead acts as a courier of information, often referred to as data. Knowing what a group of sellers are willing to take in exchange for their property, and knowing what a group of buyers are willing to pay, allows for the mapping of the market’s superpositions (known as an order book). HODLers remain in a superposition except at the moment when a market is made, identifying the two parties involved and the respective roles each will play out.
HODLers are Not Market Participants
They have in fact shown to be previous market participants and willing to fill at least one side of the transaction. However, if you’re HODLing, you are neither a seller nor a buyer and thus not in the market. Rather, you are both a buyer and a seller that has not been realized yet. We all have our buy price and our sell price of the assets we own. However, the market may have not dropped to the point where you are willing to buy again, nor has it risen to the level in which you are prepared to sell. You are but a ‘HODLer-in-waiting’ with two potential states; you are a potential buyer and a potential seller, waiting to be measured, thus identifying and filling your market role as dictated by the market and your need for access to liquidity.
HODLing: An Investment Strategy Built Upon Superpositions
Due to many market forces, successful investors do not simply stack cash for retirement, they are buying assets. As Robert Kiyosaki explains in his book, Rich Dad Poor Dad, “An asset is something that puts money in my pocket. A liability is something that takes money out of my pocket.” Investors are buying assets in hopes that their portfolio will ferry their purchasing power, today’s monetary value, across space and time. Why HODL something that is planned to lose value for any longer than necessary?
HODLing can feel like a rollercoaster at times with the need to “hold on for dear life.” Markets are unpredictable and (as an ex-manager of mine used to say) they will always do what f@&ks the most amount of people. Combat this with conviction in your purchase decisions. Conviction on where you think the price of the asset will go and in how much time. If you start by finding and choosing your long-term savings vehicle, many will call this money, asset purchases on your way to retirement become easier as you are not battling inflation, aka planned degradation of your hard-earned dollars. What you HODL matters.
-
 @ 0b118e40:4edc09cb
2025-01-26 16:39:37
@ 0b118e40:4edc09cb
2025-01-26 16:39:37Does Bitcoin incentivize innovations in renewable and clean energy sectors? Absolutely.
While the debate about Bitcoin’s energy consumption continues, its role in driving innovation often goes unnoticed.
Over 50% of the energy consumed by Bitcoin miners now comes from renewable sources, and the industry is pushing the boundaries of repurposing waste energy and tapping into underutilized resources.
This sets a clear contradiction from industries like chemicals, primary metals, and textiles, which dominate global energy consumption with coal and natural gas. Despite global initiatives like the ESG (Environmental, Social, and Governance) framework, which mandates sustainability investments, fossil fuels still account for over 80% of global energy use in 2023. Big corporations can easily "greenwash" their efforts by purchasing carbon credits and slapping on green labels, yet their day-to-day operations remain largely unchanged.
Bitcoin miners, however, are not coerced into adopting clean energy; they are incentivized by the need to minimize costs. Their profitability depends on finding the most affordable energy sources, and this has led to innovations in utilizing surplus and waste energy.
What began with small-scale experiments has now captured the attention of global corporations like Deutsche Telekom and Tokyo Electric Power Company (TEPCO), which are leveraging surplus energy for Bitcoin mining.
Are these developments signaling that Bitcoin mining is becoming integral to mainstream energy systems? The answer increasingly appears to be yes.
I first came across the idea that Bitcoin could incentivize renewable energy through a tweet from Jack a few years ago, and out of curiosity, I explored some of the ways Bitcoin is advancing renewable and clean energy. I’ll share a few examples below. Please note that this is by no means an exhaustive list, but it provides a glimpse into Bitcoin’s role in driving renewable and clean energy innovation.
There are 2 categories of energy sources I looked into :
Renewables: Hydropower, geothermal, ocean wave energy, wind power, and solar energy. Clean Non-Renewables: Waste coal, flare gas, and nuclear energy.
Renewables
1. Hydropower
Hydropower is one of the oldest renewable energy sources, but many countries struggle with maintaining an aging infrastructure, leading to abandoned dams. However, countries like Paraguay and Laos have successfully utilized hydropower to meet 90% or more of their energy needs, often yielding a surplus. In Paraguay, Marathon Digital Holdings partnered with the Penguin Group to establish a hydro-powered Bitcoin mining facility near the Itaipú Dam. Globally, companies like GRIID Infrastructure and Sazmining have integrated hydropower into their operations, with hydropower now accounting for about 23% of Bitcoin mining’s energy use.
2. Geothermal Energy
In El Salvador, Bitcoin mining powered by volcanic heat has attracted investments, with proceeds funding schools and hospitals. In the last 3 years, nearly 474 Bitcoin worth $29 million using volcano-fueled geothermal power was mined. In Africa, Gridless leverages geothermal, hydro, and solar power for decentralized mining in Kenya, Malawi, and Zambia.
3. Ocean Energy
Ocean thermal energy conversion (OTEC), a 150-year-old concept, is emerging as a viable solution, particularly in regions like Hawaii (Oahu) where traditional renewables face challenges. Not only is the cost of energy the highest in the US, the people of Hawaii face a wastage of energy surplus which can be turned into profit through Bitcoin mining.
When I first read about the potential of ocean energy used for Bitcoin Mining, it was through Lord Fusitu’a, a member of the Parliament of the Kingdom of Tonga in 2021. Unfortunately, he passed away and I was not able to find many updates on it after that. Ocean energy was also tested by Tara Ocean as a combination project between Paris and Los Angeles and it showed promising results.
4. Wind Power
Texas leads in wind energy, accounting for 25% of its grid. Bitcoin miners have flocked to the state, leveraging tax incentives and abundant wind power to fuel operations, tripling Bitcoin mining hashrate since 2021. DARI (Digital Assets Research Institute) revealed Bitcoin mining saved Texas up to $18 billion by reducing the need for new gas peaker plants. Companies like German Telekom also use excess wind and solar energy for mining, addressing intermittency challenges.
5. Solar Energy
Block Inc. and Blockstream’s solar-powered Bitcoin mining facility highlight the untapped potential of solar in sun-rich regions like Africa. Companies like TeraWulf and Aspen Creek are also pioneering solar-powered mining operations. In late 2022, Meco unveiled the world’s first solar-electric crypto-mining rigs. Additionally, investments are flowing into companies focusing on renewable-powered Bitcoin mining, with Aspen Creek securing $8 million in 2022 to expand its solar-powered operations.
Clean Non-Renewables
1. Flare Gas
Crusoe Energy Systems captures methane from oil drilling to power Bitcoin mining, making it carbon-negative and eliminating 99.89% of greenhouse gas emissions. This method is a key example of using waste gas that would otherwise be flared into the atmosphere.
2. Nuclear Energy
TeraWulf’s Nautilus Cryptomine facility in Pennsylvania represents the first nuclear-powered Bitcoin mining operation in the U.S., with nearly 8,000 mining rigs online. Nuclear energy is stable, scalable and clean as its low-carbon energy source, making it an attractive option for Bitcoin mining. I recall the mayor of Miami, Francis Suarez also recognized the potential of nuclear energy to attract Bitcoin mining operations to the city but I don’t have any recent updates on this.
3. Waste Coal
Stronghold Digital Mining repurposes waste coal from old mining sites to generate energy for Bitcoin mining operations. While this method helps reduce the environmental impact of waste coal, it has faced criticism for emissions produced by burning additional materials like tires.
The Potentials of Bitcoin mining in underdeveloped regions
In regions where traditional energy infrastructure is scarce, Bitcoin mining is a significant opportunity to stimulate the development of renewable energy sources and improve living conditions.
In many African countries, solar and hydroelectric resources remain largely untapped or abandoned, with nations like Congo, South Sudan, and Malawi having less than 10% access to electricity. Bitcoin mining’s energy demand acts as a powerful economic incentive, attracting investments to build infrastructure that enhances access to electricity, clean water, and other basic amenities.
Alex Gladstein beautifully captures this idea in his article "The Humanitarian and Environmental Case for Bitcoin" where he discusses how Bitcoin mining can be a force for good, encouraging investment in renewable energy and providing sustainable economic growth for regions long underserved by traditional infrastructure.
On a last note
Bitcoin mining is proving to be a catalyst for renewable energy innovation. Despite decades of Keynesian counter-cyclical policies targeted at boosting infrastructure spending, ranging from IMF infrastructure loans in the 1970s to frameworks like the Sustainable Development Goals (SDGs), Millennium Development Plans, and now ESG, the Global South remains impoverished, with many regions still lacking basic amenities. Non-renewable energy usage remain high. Traditional approaches have not solved the problem.
Bitcoin, however, just works.
Its financial system empowers individuals worldwide, breaking free from centralized control, while its mining operations leverage surplus and clean energy sources to drive renewable innovation. With growing global adoption, Bitcoin is no longer an isolated financial system. It is becoming an integral part of daily life and a force for global energy transformation.
As the mining focus shifts toward individual contribution with open-source integrated chips and decentralized mining solutions, we are likely to witness a new wave of renewable energy innovations on a smaller, more accessible scale that anyone can adopt.
The current energy debate surrounding Bitcoin often overlooks its potential. Beyond the criticisms, Bitcoin mining is creating tangible opportunities to innovate in renewable energy, particularly in underdeveloped areas. As the industry grows, it’s becoming abundantly clear that Bitcoin is a key part of the solution to our financial and energy challenges.
-
 @ 5d4b6c8d:8a1c1ee3
2025-01-26 15:32:13
@ 5d4b6c8d:8a1c1ee3
2025-01-26 15:32:13Here are today's picks using my proprietary betting strategy at Freebitcoin. For details about what Risk Balanced Odds Arbitrage is and why it works see https://stacker.news/items/342765/r/Undisciplined.
For a hypothetical 1k-ish wager on each match, distribute your sats as follows:
| Outcome 1 | Outcome 2 | Outcome 3 | Bet 1 | Bet 2 | Bet 3 | |--------------|-------------|--------------|-------|-------|-------| | Newcastle| Fullham| Draw | 583| 200| 238| | Man United| Crystal Palace| Draw | 459| 286| 280| | Chelsea| West Ham| Draw | 714| 125| 179| | Brentford| Tottenham| Draw | 417| 364| 250| | Arsenal| Man City| Draw | 465| 278| 274| | Bournemouth| Liverpool| Draw | 211| 565| 238|
A note of caution about Freebitcoin: they recorded the wrong outcome for last week's Bills vs Ravens game and as of yet have not corrected it. I recall one other instance of something similar happening, so proceed with caution.
This RBOA strategy is largely immune from that problem, but be aware of it when just betting on one outcome.
originally posted at https://stacker.news/items/864472
-
 @ 8d34bd24:414be32b
2025-01-19 23:33:36
@ 8d34bd24:414be32b
2025-01-19 23:33:36I have a teenaged son with Down Syndrome. He likes telling me he is all grown up despite having the maturity and understanding of a 3rd or 4th grader. He does not like being corrected and his newest response to correction is to hold up his hand making a talking hand motion. Whenever he is having this reaction, he isn’t listening and isn’t learning and more often than not ends up harming himself.
Today I sat down with him and discussed some Bible verses related to wisdom and correction in an attempt to explain why this behavior was only hurting himself. (Due to his immaturity, logic and facts don’t always work.)
Afterwards, I thought that all of us adults could probably use this same lesson. We don’t like being corrected by the Bible, the Holy Spirit, and definitely not by other Christians. It takes a lot of maturity to actually seek out correction, but that is what we are called to do.
He whose ear listens to the life-giving reproof\ Will dwell among the wise. (Proverbs 15:31)
If we want to be wise, we have to listen to “life-giving reproof.” Where can we get this “life-giving reproof?” Obviously the Bible gives it, but also mature Christians can give us “life-giving reproof.” A wise person will always listen and evaluate correction from a fellow Christian, especially one who has proven to have Biblical knowledge and wisdom. This doesn’t mean we will take their advice 100% of the time. It must be judged by the truth in the Bible, but it should be honestly considered. Even the greatest theologians have at least one point of error. If we fail to listen to correction and evaluate it biblically, we can be more easily led astray.
He who neglects discipline despises himself,\ But he who listens to reproof acquires understanding. (Proverbs 15:32)
The benefit of listening to correction is acquiring understanding. The curse of not listening to correction is the harm it causes to ourselves. The harm is so great, only a fool or those who despise themselves would act this way.
The fear of the Lord is the instruction for wisdom,\ And before honor comes humility. (Proverbs 15:33)
Wisdom comes from the fear of the Lord. Fear of the Lord leads to seeking His will. Seeking His will leads us to the correction of the Bible and mature Christians. We then have to humble ourselves and look at our mistakes and failures. We all want to think of ourselves as good, honest, and wise, but we all do bad things, tell lies, and act foolishly. The only way to fix these (and only after repenting, trusting Jesus as Savior, and submitting to His will) is to honestly assess our own failings — whether foolish, uninformed, or willful. It takes a lot of humility to fully do.
As an employer, the one trait that I can’t stand in an employee is a person who can’t or won’t admit any mistakes. We all make mistakes. A person who wants to learn can be taught. A person, who refuses to admit making any mistakes and who always blames someone else, is untrainable.
Sometimes I wonder if God feels the same way with us because we refuse to admit our failings.
Yet they did not listen or incline their ears, but stiffened their necks in order not to listen or take correction. (Jeremiah 17:23)
We always need to listen to God. The three main ways are to read the Bible, to seek wise council, and to pray for leading. When we choose to seek council and prayer, we still need to check the answers given against the unchanging truth in the Bible.
When we refuse to read the Bible, we are not listening to God. Although there are definitely some things in the Bible that are confusing and not immediately clear, the primary tenants in the Bible are readily understandable by even a young child. Sometimes I wonder if the reason people don’t read their Bible and say it is too confusing is because they don’t like what they are reading. It is “confusing” because God is telling us what we don’t want to hear. It is “confusing” because God is telling us what we don’t want to do. If we actually read and understand, it will mean we will have to make changes to our thoughts and actions.
It is better to listen to the rebuke of a wise man\ Than for one to listen to the song of fools. (Ecclesiastes 7:5)
We need to remember, both as the giver and receiver of a rebuke, that the truth and God’s word are useful for wisdom. Biblical correction is a loving action that is for the good of the receiver of correction. It should be given in a loving manner and received in a loving manner. We may want to “listen to the song of fools,” but we should seek “he rebuke of a wise man.”
When I was a young Christian in college, I sometimes went to a tiny church in my college town and sometimes went to a huge church in my hometown. The large church had a large Sunday school group taught by a man who taught me to love exhortation. When ever I hear the word “exhortation,” I think of him. Exhortation is a mix of correction and encouragement.
When I first started attending the Sunday school, I avoided the teacher. He didn’t lecture. He asked questions. He asked uncomfortable questions. They weren’t uncomfortable because they were inappropriate. They were uncomfortable because the answers to these questions required a change in world view, a change in thought, or a change in actions. He led us to the truth without lecturing about the truth. By helping us to find the truth by ourselves (through the Bible), the truth became a part of us. We knew what we believed and why, so were not easily led astray.
For months, I’d sit far away from him and try to hide, so I wouldn’t get the uncomfortable questions. Over time, after being asked some of these questions, I saw how they led me to the truth. I changed from hiding from him, to seeking him out. I went from trying to avoid being questioned and challenged in my beliefs to seeking out the correction because it helped me grow in my faith, discover the truth (not my truth), and grow closer to God.
At this point, I can’t even remember my teacher’s name, but I will never forget or stop being thankful for the things I was taught in that Sunday school class, the greatest of all being to seek the truth and never fear correction.
I decided to end my post with a passage from Psalm 119 about how we should love God’s word, the truth, wisdom, His commandments, and His corrections. The problem was narrowing it down. I’ve included one section, but would recommend reading all of Psalm 119. Read this passage considering what it says about what our love of learning about God and His commands should be.
Mem.\ O how I love Your law!\ It is my meditation all the day.\ Your commandments make me wiser than my enemies,\ For they are ever mine.\ I have more insight than all my teachers,\ For Your testimonies are my meditation.\ I understand more than the aged,\ Because I have observed Your precepts.\ I have restrained my feet from every evil way,\ That I may keep Your word.\ I have not turned aside from Your ordinances,\ For You Yourself have taught me.\ How sweet are Your words to my taste!\ Yes, sweeter than honey to my mouth!\ From Your precepts I get understanding;\ Therefore I hate every false way. (Psalm 119:97-104)
Trust Jesus.
-
 @ 58937958:545e6994
2025-01-13 03:19:17
@ 58937958:545e6994
2025-01-13 03:19:17Spiralのキャラクター「ビットコイン(パペット)」のコロッケを作りました

作り方は一般的なコロッケです 試しにタネの状態で手足をくっつけたバージョン(右)も作りましたが 粉をつける前に手足がもげました

顔はのりとスライスチーズ 手足ははんぺんです 足は醤油をつけてトースターで軽く焼いたら茶色になりました
 手足はサラスパでくっつけてます
細いスパゲッティ
キャラ弁でググったらサラスパが出てきてなるほどな~と思いました
自分は揚げパスタにして刺しました
手足はサラスパでくっつけてます
細いスパゲッティ
キャラ弁でググったらサラスパが出てきてなるほどな~と思いました
自分は揚げパスタにして刺しました弁当箱に押し込まれてるコロッケくん

半減期

メモ
- タネを作った時に形を保たせるために冷凍してみたんですけど逆効果だった(皿とクッキングペーパーにくっついて取れなくなった&半解凍したら水分がすごいことになった)ので冷凍するなら対策が必要そう
- 形作るときにかなりパサパサだったので、つなぎがあった方がいいのかも(今回はじゃがいも&炒めタマネギだけ)
ビットコインくんの形はすごく作りやすくて面白いのでまた何か作りたいなぁと思いました
nostr:nevent1qqsxgpjvf9g9suhzx5asqhvnlvnarl43kuhas8v5g2ryjr9yjjp0z5ctkh5pt
-
 @ a39d19ec:3d88f61e
2024-11-21 12:05:09
@ a39d19ec:3d88f61e
2024-11-21 12:05:09A state-controlled money supply can influence the development of socialist policies and practices in various ways. Although the relationship is not deterministic, state control over the money supply can contribute to a larger role of the state in the economy and facilitate the implementation of socialist ideals.
Fiscal Policy Capabilities
When the state manages the money supply, it gains the ability to implement fiscal policies that can lead to an expansion of social programs and welfare initiatives. Funding these programs by creating money can enhance the state's influence over the economy and move it closer to a socialist model. The Soviet Union, for instance, had a centralized banking system that enabled the state to fund massive industrialization and social programs, significantly expanding the state's role in the economy.
Wealth Redistribution
Controlling the money supply can also allow the state to influence economic inequality through monetary policies, effectively redistributing wealth and reducing income disparities. By implementing low-interest loans or providing financial assistance to disadvantaged groups, the state can narrow the wealth gap and promote social equality, as seen in many European welfare states.
Central Planning
A state-controlled money supply can contribute to increased central planning, as the state gains more influence over the economy. Central banks, which are state-owned or heavily influenced by the state, play a crucial role in managing the money supply and facilitating central planning. This aligns with socialist principles that advocate for a planned economy where resources are allocated according to social needs rather than market forces.
Incentives for Staff
Staff members working in state institutions responsible for managing the money supply have various incentives to keep the system going. These incentives include job security, professional expertise and reputation, political alignment, regulatory capture, institutional inertia, and legal and administrative barriers. While these factors can differ among individuals, they can collectively contribute to the persistence of a state-controlled money supply system.
In conclusion, a state-controlled money supply can facilitate the development of socialist policies and practices by enabling fiscal policies, wealth redistribution, and central planning. The staff responsible for managing the money supply have diverse incentives to maintain the system, further ensuring its continuation. However, it is essential to note that many factors influence the trajectory of an economic system, and the relationship between state control over the money supply and socialism is not inevitable.
-
 @ 16d11430:61640947
2025-01-27 21:33:11
@ 16d11430:61640947
2025-01-27 21:33:11Gather ‘round, corporate overlords, bloated bureaucracies, and self-appointed tech deities. @DamageBDD is here to show you what happens when your castles of sand face a tsunami of irrefutable logic. Your empire of spaghetti code and buzzword bingo won't hold against the relentless precision of code as truth.
Let’s set the stage. For years, you've been huddling in glass towers, touting innovation while running on fumes of mediocrity. Your agile "transformations"? A PowerPoint deck. Your tech stack? A monument to vendor lock-in and weekend duct tape. And let’s not forget the compliance theater, where fake audits masquerade as accountability. Enter DamageBDD, where logic doesn’t lie, blockchain doesn’t forget, and BS dies a swift death.
Code Is the Law (But Better) You’ve heard it before: "Code is law." But we’re not here for slogans—we’re here for receipts. DamageBDD doesn’t trust your claims of success; it verifies them on-chain. Deliver your milestones or don’t—there’s no fudging it here. Your failed builds and broken promises are exposed in broad daylight, immutable as your shame.
BDD: The Guillotine of Bad Engineering Oh, how the giants hate being held accountable. They thrive on opacity, on a system where results are obscured by layers of corporate doublespeak. DamageBDD flips the table: if it can be defined, it can be verified. That MVP you promised? We’ll test it. That sprint you boasted about? We’ll see it on-chain. In this world, the only thing that ships is the truth. Everything else is noise.
"Move Fast and Break Things"? Nah, Try Building Things That Last Let’s talk about your cult of "disruption," where moving fast and breaking things conveniently excludes fixing them. DamageBDD doesn’t move fast—it moves right. Every behavior-driven test is a brick in a foundation that lasts, unlike your latest "pivot" designed to dazzle VCs while hiding the rot underneath.
Cypherpunk Cynicism, Powered by Bitcoin Here’s where we really shine. While you’re busy worshiping at the altar of fiat, we’re running Damage Token on Bitcoin and Aeternity—systems you can’t co-opt, corrupt, or inflate away. Your centralized control schemes crumble when faced with a network that doesn’t care about your boardroom games. DamageBDD doesn’t just bypass gatekeepers; it renders them obsolete.
The Era of Verifiable Integrity You’ve built a world where accountability is optional and profits trump principles. DamageBDD brings receipts to the revolution. Imagine a world where every claim you make is tested, verified, and recorded immutably. No more hiding behind marketing fluff or burying failures in red tape. DamageBDD strips away the facade and says, "Let’s see what you’re really made of."
We’re Not Here to Compete. We’re Here to Outlast. You can’t kill an idea whose time has come. DamageBDD is more than a tool—it’s a movement, a manifesto in code. While you scramble to protect your crumbling monopolies, we’re building something that doesn’t need your approval, your funding, or your permission. DamageBDD will humble you not with arrogance, but with truth, written in lines of immutable logic that your PR spin can’t erase.
So, keep clinging to your illusions of control. DamageBDD is patient. It’s inevitable. And when the dust settles, your legacy will be nothing more than a footnote in a system designed to be better, faster, and ungovernable by the likes of you.
You’ve been warned. Verification > Authority. Always.
-
 @ a39d19ec:3d88f61e
2024-11-17 10:48:56
@ a39d19ec:3d88f61e
2024-11-17 10:48:56This week's functional 3d print is the "Dino Clip".

Dino Clip
I printed it some years ago for my son, so he would have his own clip for cereal bags.
Now it is used to hold a bag of dog food close.
The design by "Sneaks" is a so called "print in place". This means that the whole clip with moving parts is printed in one part, without the need for assembly after the print.
 The clip is very strong, and I would print it again if I need a "heavy duty" clip for more rigid or big bags.
Link to the file at Printables
The clip is very strong, and I would print it again if I need a "heavy duty" clip for more rigid or big bags.
Link to the file at Printables -
 @ 0463223a:3b14d673
2025-01-26 13:07:36
@ 0463223a:3b14d673
2025-01-26 13:07:36Hmm so I heard that in order to improve my brain I should try writing… Ok groovy, I’ll give it a go. In all honesty I don’t know what to write, my brain is a jumble of noise and titbits of random knowledge. I likely know more about sound than the average person but as physics goes, I don’t have anything new or profound to add. Air moves and noises happen. Is there really any more to it? I could write some flowery bollocks about refraction, absorption coefficients and reverberation times, or I could write some out there, arty shit but I don’t think that adds any value to anyone.
A lot of folks online have very strong beliefs in how the world operates or should operate. Whilst their conviction is strong, there’s also is a large percentage of people who totally disagree with them and think the exact opposite is the answer. That’s quite shit isn’t it? Humans have been around for 100,000 years or so and haven’t worked it out. I wonder what makes the internet celeb so certain they’ve got it right when the next internet celeb completely disagrees? I do my best to avoid any of these cunts but despite running to the obscurest social media platforms they still turn up with their profound statements. Meh.
Ideologically I’m leaning toward anarchism but even that seems full of arguments and contradictions and ultimately I don’t think I can be arsed with identifying with any particular ideology. I tried reading some philosophy and struggled with it, although I deep fall into a lovely deep sleep. It’s fair to say I’m not the brightest button in the box. I have a wife, a couple of cats and lots of things that make nosies in my shed. That’s pretty cool right? Well it works for me.
So why write this? I clearly wrote in the first sentence that I’m trying to improve my brain, a brain that’s gone through a number to twists and turns, a lot brain altering substances. I own that, no one forced me to. Beside, George Clinton was still smoking crack aged 80, didn’t do him any harm…
I’m on the 5th paragraph. I don’t feel any smarter yet and each paragraph is getting shorter, having started from a low base. I guess I’m being too high time preference… Might be a while before I launch my Deep Thought podcasts where myself and a guest talk for 500 hours about the philosophy of money and 13 amp plug sockets.
I’ve tortured myself enough. I’m posting this on Nostr where it will never go away.. lol. If you got this far, I congratulate/commiserate you and wish you a wonderful day.
-
 @ 5579d5c0:db104ded
2025-01-27 19:49:52
@ 5579d5c0:db104ded
2025-01-27 19:49:52"Chris, what do you tell your clients to do?"
This is a question I get asked regularly, and the answer is not simple.
The truth is, every person’s health journey is unique.
There are no 'one size fits all' solutions, no rigid plans that guarantee results for everyone.
That’s why, as a health coach, my role isn’t to hand out answers or impose rules. It’s to guide you toward uncovering your own.

Bruce Lee on being a teacher.
Your health, your truth
Bruce Lee was right, you already hold the answers to your health challenges.
Your body is constantly giving you signals about what works and what doesn’t.
My role is to help you listen to those signals to cut through the noise of diets, trends, and quick fixes.
Together we focus on what aligns with your unique biology and lifestyle.
This isn’t about creating a rigid plan or forcing you into a pre-made program.
It’s about asking the right questions, giving you tools to explore, and helping you build the confidence to make decisions that work for you.
Health is deeply personal, and lasting change comes from understanding yourself.

Rigid oatmeal diet plan.
A coach who adapts to you
One of the most important aspects of my approach is meeting you where you are.
Your life, your habits, and your why are the foundation.
Together, we adapt strategies to fit your needs.
Health coaching isn’t about me telling you what to do.
It’s about empowering you to take ownership of your journey.
Sometimes that means learning to tune out the latest biohacking tool or Instagram diet trend, I'm looking at you 'Oatmeal diet for weight loss'.
Sometimes it means starting small, with manageable steps that build momentum.
Whatever it looks like, my focus is on helping you create sustainable habits that work for life, not just for the next few weeks.

Health information overload.
Protecting you from the noise
The world of health advice is noisy.
There’s always a new diet, a miracle supplement, or a "hack" promising results.
But more information doesn’t always mean better decisions, it often leads to overwhelm.
My role as your coach is to help you tune out the noise.
Together, we’ll focus on the basics that always work:
-
Sunlight
-
Circadian alignment
-
Eating real nutrient dense local and seasonal food
-
Moving regularly
-
Targeted training
-
Sleeping well
-
Dealing with stress in the right way
You don’t need the latest trends, you need a clear path that’s grounded in what’s proven and tailored to you.
Exploring, not imposing
The beauty of health coaching is that it’s not about giving you a checklist or medical guideline telling you "do this, not that."
It’s about exploration. What makes you feel your best? What habits energise you? What changes feel sustainable?
Together, we experiment, reflect, and adjust.
This process isn’t about finding the "right" way, it’s about finding your way.
I’m here to guide, support, and challenge you, but ultimately, the answers come from within.
As a coach, I see your potential even when you don’t. My job is to help you see it too.
Health isn’t a destination, it’s a journey. And the most powerful changes happen when you take ownership of that journey.
You already hold the answers. I just help you uncover them.
- Chris
If you're ready to explore your potential, let’s talk.
Click https://calendly.com/hello-chrispatrick to book a free discovery call with me.
-
-
 @ 558e15eb:efa6e980
2025-01-12 19:23:42
@ 558e15eb:efa6e980
2025-01-12 19:23:42[2025-02-07] Øy 5 year anniversary - Talk show and watch party @ online
Øy 5 year anniversary - Talk show and watch party online - https://lislegaard.stream/ (https://lislegaard.stream/)
(Friday, 7 February 20:00)

https://do.basspistol.org/event/oy-5-year-anniversary-talk-show-and-watch-party
-
 @ 3f770d65:7a745b24
2025-01-19 21:48:49
@ 3f770d65:7a745b24
2025-01-19 21:48:49The recent shutdown of TikTok in the United States due to a potential government ban serves as a stark reminder how fragile centralized platforms truly are under the surface. While these platforms offer convenience, a more polished user experience, and connectivity, they are ultimately beholden to governments, corporations, and other authorities. This makes them vulnerable to censorship, regulation, and outright bans. In contrast, Nostr represents a shift in how we approach online communication and content sharing. Built on the principles of decentralization and user choice, Nostr cannot be banned, because it is not a platform—it is a protocol.
PROTOCOLS, NOT PLATFORMS.
At the heart of Nostr's philosophy is user choice, a feature that fundamentally sets it apart from legacy platforms. In centralized systems, the user experience is dictated by a single person or governing entity. If the platform decides to filter, censor, or ban specific users or content, individuals are left with little action to rectify the situation. They must either accept the changes or abandon the platform entirely, often at the cost of losing their social connections, their data, and their identity.
What's happening with TikTok could never happen on Nostr. With Nostr, the dynamics are completely different. Because it is a protocol, not a platform, no single entity controls the ecosystem. Instead, the protocol enables a network of applications and relays that users can freely choose from. If a particular application or relay implements policies that a user disagrees with, such as censorship, filtering, or even government enforced banning, they are not trapped or abandoned. They have the freedom to move to another application or relay with minimal effort.
THIS IS POWERFUL.
Take, for example, the case of a relay that decides to censor specific content. On a legacy platform, this would result in frustration and a loss of access for users. On Nostr, however, users can simply connect to a different relay that does not impose such restrictions. Similarly, if an application introduces features or policies that users dislike, they can migrate to a different application that better suits their preferences, all while retaining their identity and social connections.
The same principles apply to government bans and censorship. A government can ban a specific application or even multiple applications, just as it can block one relay or several relays. China has implemented both tactics, yet Chinese users continue to exist and actively participate on Nostr, demonstrating Nostr's ability to resistant censorship.
How? Simply, it turns into a game of whack-a-mole. When one relay is censored, another quickly takes its place. When one application is banned, another emerges. Users can also bypass these obstacles by running their own relays and applications directly from their homes or personal devices, eliminating reliance on larger entities or organizations and ensuring continuous access.
AGAIN, THIS IS POWERUFL.
Nostr's open and decentralized design makes it resistant to the kinds of government intervention that led to TikTok's outages this weekend and potential future ban in the next 90 days. There is no central server to target, no company to regulate, and no single point of failure. (Insert your CEO jokes here). As long as there are individuals running relays and applications, users continue creating notes and sending zaps.
Platforms like TikTok can be silenced with the stroke of a pen, leaving millions of users disconnected and abandoned. Social communication should not be silenced so incredibly easily. No one should have that much power over social interactions.
Will we on-board a massive wave of TikTokers in the coming hours or days? I don't know.
TikTokers may not be ready for Nostr yet, and honestly, Nostr may not be ready for them either. The ecosystem still lacks the completely polished applications, tools, and services they’re accustomed to. This is where we say "we're still early". They may not be early adopters like the current Nostr user base. Until we bridge that gap, they’ll likely move to the next centralized platform, only to face another government ban or round of censorship in the future. But eventually, there will come a tipping point, a moment when they’ve had enough. When that time comes, I hope we’re prepared. If we’re not, we risk missing a tremendous opportunity to onboard people who genuinely need Nostr’s freedom.
Until then, to all of the Nostr developers out there, keep up the great work and keep building. Your hard work and determination is needed.
-
 @ a367f9eb:0633efea
2024-11-05 08:48:41
@ a367f9eb:0633efea
2024-11-05 08:48:41Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application.
The reporting purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States.
In a June paper reviewed by Reuters, six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”.
The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making.
While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the Star Trek episode “A Taste of Armageddon“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place.
Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran?
The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over one million open-source LLMs available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer.
With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are potentially trillions of dollars on the line.
Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American infrastructure, data, and yes, your credit history?
As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much many times.
At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative.
Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this.
Open-source matters When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it.
The various licensing schemes – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made.
While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit.
Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers.
Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other.
I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run.
Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots).
This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also open-source, which has allowed thousands of copycat protocols that have revolutionized how we view money.
You know what else is open-source and available for everyone to use, modify, and build upon?
PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit.
Open-source code is speech, and it is knowledge.
We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge.
Open-source is for your friends, and enemies In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license.
At this very moment, you can click on over to Hugging Face, download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth).
Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created.
We know this can be useful to friends, but what about enemies?
As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications.
The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians.
A bipartisan group of US House lawmakers want to put export controls on AI models, as well as block foreign access to US cloud servers that may be hosting AI software.
If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see The Crypto Wars). Many of the arguments we hear today were invoked by some of the same people as back then.
Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to.
Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place.
Limiting open-source threatens our own advancement If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way.
If there is a “Hundred Year Marathon” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible.
The Chinese military has been building up its capabilities with trillions of dollars’ worth of investments that span far beyond AI chatbots and skip logic protocols.
The theft of intellectual property at factories in Shenzhen, or in US courts by third-party litigation funding coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing.
But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source.
If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries.
Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application.
The reporting purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States.
In a June paper reviewed by Reuters, six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”.
The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making.
While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the Star Trek episode “A Taste of Armageddon“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place.
Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran?
The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over one million open-source LLMs available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer.
With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are potentially trillions of dollars on the line.
Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American infrastructure, data, and yes, your credit history?
As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much many times.
At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative.
Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this.
Open-source matters
When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it.
The various licensing schemes – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made.
While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit.
Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers.
Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other.
I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run.
Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots).
This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also open-source, which has allowed thousands of copycat protocols that have revolutionized how we view money.
You know what else is open-source and available for everyone to use, modify, and build upon?
PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit.
Open-source code is speech, and it is knowledge.
We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge.
Open-source is for your friends, and enemies
In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license.
At this very moment, you can click on over to Hugging Face, download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth).
Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created.
We know this can be useful to friends, but what about enemies?
As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications.
The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians.
A bipartisan group of US House lawmakers want to put export controls on AI models, as well as block foreign access to US cloud servers that may be hosting AI software.
If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see The Crypto Wars). Many of the arguments we hear today were invoked by some of the same people as back then.
Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to.
Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place.
Limiting open-source threatens our own advancement
If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way.
If there is a “Hundred Year Marathon” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible.
The Chinese military has been building up its capabilities with trillions of dollars’ worth of investments that span far beyond AI chatbots and skip logic protocols.
The theft of intellectual property at factories in Shenzhen, or in US courts by third-party litigation funding coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing.
But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source.
If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries.
Originally published on the website of the Consumer Choice Center.
-
 @ 5a8e581f:c150c8ba
2025-01-11 18:31:08
@ 5a8e581f:c150c8ba
2025-01-11 18:31:08Doing Bitcoin the right way is hard.
If Bull Bitcoin wanted to take the easy path, we would have done what all the other exchanges are doing and would simply have offered a custodial wallet to our users. But our mission is not to sell numbers on a screen, fake paper bitcoin and IOUs. Our mission is to create sovereign individuals. If our clients don’t take full control over their wealth, we have failed them.
If we wanted to take the easy path, we would have offered shitcoin trading, NFTs, ICOs, yield and all sorts of nonsense. No doubt, we would today be far more wealthy.
But we would have failed in our mission to establish a universal Bitcoin standard and fixed the problems created by easy money. We would have compromised on our values and sold products that we don’t believe in and we don’t personally use.
If we wanted to take the easy path, we wouldn't have spent years building open-source software that lets any business run their own self-hosted Bitcoin wallet API infrastructure connected directly to their own Bitcoin, Lightning and Liquid network nodes. We would have just done a deal with Coinbase or another third party to take care of the Bitcoin engineering on our behalf.
But we would have failed in our mission to help keep the Bitcoin network decentralized and resilient to institutional failures. We would have lost our direct and precious connection to the Bitcoin network.
The engineering, operational and logistical challenges involved in maintaining a noncustodial Bitcoin service like Bull Bitcoin, in an environment where Bitcoin network fees are increasingly high, while also maintaining an accessible user experience with minimal compromises on the cypherpunk principles of Bitcoin… are impossibly hard to fathom for the vast majority of Bitcoiners.
Despite consistently taking the most difficult path at every turn, Bull Bitcoin has nonetheless been crushing it for the past 10 years thanks to our Bitcoiner ethos and mindset, sticking to our core values and creating products with a singular focus: engineering sovereignty.
All of this we accomplished without any outside funding. Every sat invested in Bull Bitcoin was acquired by offering a service valued by our customers. Every network fee we pay, every investment in R&D comes straight out of our pockets. If our bitcoin-only noncustodial model fails and we become unprofitable, there will be no bailout.
As a low-time preference business, taking the hard path today means we will have a unique competitive advantage in the future. Nobody uses Bitcoin more than a non-custodial exchange. Every trade and every revenue generating activity is derived directly from a Bitcoin payment. We are keenly aware of every possible problem that Bitcoin users may be facing, because we are ourselves are a power user. We know what kinds of problems the users will face, what solutions we need to build and how we must adapt. We always skate where the puck is going.
But there is another, more noble purpose to choosing the hard path.
I'm also heavily involved in a community circular economy project in Costa Rica called Bitcoin Jungle. We spend countless hours to educate locals, set merchants up with Bitcoin point of sales, and build the infrastructure necessary for Bitcoin to thrive as a medium of exchange in even the most rural areas. All of this we do for free, and in fact it we pay for it out of pocket! I discovered recently that a few people were skeptical of our efforts. I met one of them and he asked us “but why are you doing this, if you don't make any money from it”.
We do it because we love Bitcoin. We believe in the ideology of Bitcoin, its underlying cypherpunk and free market principles. We do it because we as sovereign individuals cannot live in isolation and we all benefit from the success of our communities. We do it because we want our kids to grow up in a world that is free from the evils of Fiat currency. May our children never suffer the corruption of participating in a socialist economic system that steals their time and their wealth by the simple fact of interacting with fiat currency. We do it because doing it is a moral imperative. In a world of systematic injustice, doing nothing is to be complicit. You cannot live a virtuous life with the knowledge that you had the capacity to act heroically but chose to capitulate.
Bitcoin is at the center of a spiritual war between forces of corruption and forces of liberation. There is a higher power that calls us to become the resistance. Bitcoin is hope. Bitcoin is salvation. If Bitcoin fails, everyone on earth is truly and utterly fucked.
We are on the cusp of a fundamental civilizational change. The global debt-fueled fiat ponzi is imploding right before our eyes. What comes next is up to us to determine. We are the right place and the right time. We have a unique window of opportunity that may not come again within our lifetimes and that of our children.
The choices we make today will shape what the world looks hundreds of years from now. Whether our descendants live in totalitarian dystopias or will be ushering in a new era of prosperity and freedom depends on our willingness to choose the hard path today.
And if you think the hard part is over and that Bitcoin has already won, think again. During our decade of operational experience, there were few serious attacks on the Bitcoin network. Bitcoin had relatively low levels of adoption and apart from a few periods of intense fee spikes and the fork wars of 2017, it was smooth sailing. Bitcoin was mostly flying under the radar, left to develop organically in the hands of its cypherpunk caretakers.
This era of complacency is over. From now on, everything is about to get much, much harder. This is what we live for! Nothing easy is worth pursuing.
Bull Bitcoin hasn't given up on Bitcoin's mission to free humanity from the shackles of fiat slavery and centralized systems, we are reinvigorated by the challenges that Bitcoin is facing and that will continue to intensify.
We will not give up on Bitcoin's use case as a medium of exchange and we will continue to build tools that make it easy for anyone to opt out of the traditional banking system to conduct peer-to-peer transactions securely, as was originally intended by Satoshi when launched the Bitcoin project.
This new epoch, Bull Bitcoin is leveling up to an entire new standard for consumer-facing Bitcoin apps, higher than anyone has ever seen. We have been thinking about how to make our unique noncustodial model work sustainably long-term for years. This is the hill that we choose to die on.
But as we entered into a new Bitcoin epoch, I've witnessed many in the Bitcoin community become cynical, fatalistic and even depressed. It’s hard to blame them.
Privacy-preserving tools are being shut down. The Lightning Network is suffering scalability issues. The Bitcoin blockchain is being spammed by degenerate NFT gamblers, driving up transaction fees for everyone else. Bankers and Wall Street insiders are accumulating Bitcoin fortunes and promoting exchange traded funds as an alternative to self-custody. Bitcoin mining is being heavily centralized among a small group of American-based public companies. It sometimes feels like Bitcoin is under attack by various nefarious interests that want to control it and corrupt it.
Even from within our own community we are suffering from prophets of doom spewing fear, uncertainty and doubt. Many sneer that Lightning is broken, that Bitcoin has been co-opted by Wall Street. Some say we should give up and switch to altcoins. Some pundits blame “lasereyed maxis” for blocking protocol changes and claim that being conservative about modifying the rules of Bitcoin means “ossification” and that's the reason why Bitcoin has high fees. Others are pushing the idea that Bitcoin was never meant for payments anyway and that being a store of value was always the main goal of Bitcoin. Who cares about the poor? The plebs can always keep their funds on an exchange.
At Bull Bitcoin, we see it very differently. We have a realistic and optimistic approach towards building a bright future for Bitcoin. I have never been so bullish on the future Bitcoin as I am today.
Make no mistake: the core principles of Bitcoin self-custody, censorship-resistance and privacy are under attack. But the Bitcoin community possesses a unique advantage that will ultimately allow us to prevail: not only do we have skin in the game, we have soul in the game.
Our tribe of a few thousand cypherpunk Bitcoin maximalist fanatics stand against an empire of fiat clones, millions of faceless cogs in a soulless machine. I like our odds.
While I agree that we should never take Bitcoin’s success for granted, the bleak picture that some want to paint regarding the state of Bitcoin is detached from reality.
We've already achieved incredible technological miracles. The fact that it is possible for a user to run a Lightning network node on a mobile device and make fully trustless payments is a monumental achievement. Despite what they claim I can guarantee that no other shitcoin or fiat payment system has anywhere near the level of sophistication of Bitcoin. It is an incredibly bullish sign for the Bitcoin ecosystem that we have achieved a level where users can remain fully sovereign if they have the means.
Scaling Bitcoin so that it can enable hundreds of millions of people to become sovereign individuals is the most pressing challenge of our times. Our community must accept inevitable realities: not everybody will be able to afford on-chain transactions. The success of Bitcoin means that one day, during our lifetimes, a single Bitcoin translation will cost hundreds of dollars.
Upgrading the Bitcoin protocol may allow us to create tools that enable a more secure, censorship-resistant and private payment mechanism, but no soft fork can fix the fundamental tradeoffs of the Bitcoin protocol.
But this doesn't mean that we should either give up on Bitcoin’s value proposition as a medium of exchange, or that we must fork bitcoin according to the whims of whoever is trending on Twitter, nor should we capitulate to traditional exchanges acting as banks for the vast majority of users.
To fix the inconvenient and expensive user experience that most people are suffering in times of high fees while making the minimum amount of compromises, you need vision and execution.
There is an army of shadowy super coders that, like us, have dedicated their lives to ensure that Bitcoin becomes the universal medium of exchange, store of value and medium of account. We come from different walks of life and we have different strategies. Some of us work on self-sovereign consumer applications. Other focus of privacy protocols, mining decentralization, second later payment networks, e-cash protocols, and finally, as a last resort, some are working to add changes to the Bitcoin protocol which can enable tools that we currently cannot build.
At Bull Bitcoin, our vision of the future Bitcoin experience is crystal clear. It is a vision of success and integrity, where the path of least resistance for the user is also the path of least compromise.
We, the Bitcoin builders, will make it real.
-
 @ a10260a2:caa23e3e
2025-01-18 12:04:41
@ a10260a2:caa23e3e
2025-01-18 12:04:41Last Updated: January 18, 2025
First off, big shoutout to Coinos for having support for adding a memo to BOLT12 offers. This provides a solid alternative for the pleb who wants to support mining decentralization but doesn’t want to set up a CLN node and pay thousands of sats for a channel only to get little rewards. This is the case for most of us who only have a miner or two (e.g. a Bitaxe and/or an S9).
Before we get into setting up Lightning payouts, you’ll want to have your miner configured to mine with OCEAN of course. You’ll also want to make sure that the bitcoin address you use is from a wallet that supports signing messages.
These are the ones listed in the OCEAN docs:
- Bitcoin Knots/Bitcoin Core
- Coldcard
- Electrum
- LND (Command Line)
- Seedsigner
- Sparrow
- Specter
- Trezor
I checked one of my favorite, user-friendly wallets — Blue Wallet — and it happens to support signing messages as well.
Just tap the three dots on the upper right and you’ll see the “Sign/Verify Message” button at the bottom.
Update [January 18]: You can now use Coinos to sign by going to https://coinos.io/sign
The trick here is to not refresh the page. In other words, when you're logged in to your Coinos account, go to the URL and use the legacy address (starts with a "1") that's displayed to configure your miner(s). If you refresh the page, you're going to get a new address which will cause the signing to fail later on. Remember, keep the tab open and don't refresh the page.

Whichever wallet you choose, generate a receive address to use when configuring your miner (it’ll also be your OCEAN username).
Here’s how it looks on the Bitaxe (AxeOS)…
And the Antminer S9 (Braiins OS).
NOTE: There’s a slight difference in the URL format between the two apps. Other than that, the username will be your bitcoin address followed by the optional “.” + the nickname for your machine.
You can find more details on OCEAN’s get started page.
Alright, now that your miner is pointed at OCEAN. Let’s configure Lightning payouts!
Generating the BOLT12 Offer
In the Coinos app, go to Receive > Bolt 12.
Tap “Set memo” and set it to “OCEAN Payouts for [insert your bitcoin address]” (this text is case-sensitive). Use the same bitcoin address you used above to configure your miner(s).
After tapping OK, copy the BOLT12 offer (it should start with “lno”) and proceed to the next step.
Generating the Configuration Message
Navigate to the My Stats page by searching for your OCEAN Bitcoin address.
The click the Configuration link next to Next Block to access the configuration form.
Paste the BOLT12 offer here, update the block height to latest, click GENERATE, and copy the generated unsigned message.
Signing the Configuration Message
To sign the generated message, go back to Blue Wallet and use the signing function. Paste the configuration message in the Message field, tap Sign, and copy the signed message that’s generated.
If you're using Coinos to sign, return to the page that you kept open (and didn't refresh) and do the same. Paste the configuration message, click submit, and copy the signed message.
Submitting the Signed Message
Once signed, copy the signature, paste it in the OCEAN configuration form, and click CONFIRM.
If all goes well, you should see a confirmation that the configuration was successful. Congrats! 🎉
All you gotta do now is sit back, relax, and wait for a block to be found…
Or you can look into setting up DATUM. 😎
-
 @ 000002de:c05780a7
2025-01-17 17:23:25
@ 000002de:c05780a7
2025-01-17 17:23:25With the news of Facebook changing its policy on DEI I was reminded of how it started and my early thoughts on it. I don't think DEI is dead, far from it but there's a trend forming pushing back. With Facebook and companies in general you have to understand something. Companies are mostly spineless. If a company is pushing something its not "brave" or "risky". All companies are profit driven and when they run these "woke" commercial its not brave. It would have been brave for companies to speak boldly against racism in the 50s but not today. Today most people oppose racism. Not saying we are rid of racism but just that companies are like a flag flying in the wind. They show you the direction the winds are blowing in culture and politics.
I have to say the whole DEI story line has been interesting to watch over the past 20 years. 20 years? Yeah that's what I said because its been a long arc. 20 years is probably to short but in the tech field I'd argue it really started back in the mid 2000s.
In the early 2000s I remember a push to make the tech field more friendly to women. To rid the startup culture of the bro culture and make it more welcoming and less like a college fraternity culture. I had no problem with any of that. But it became clear that very vocal people were not satisfied with that. It wasn't enough to not discriminate and stop tolerating sexism. We needed to actively set quotas for female speakers at conferences and have more diverse representation all over the place. The idea of meritocracy which was once the hallmark of the high tech industry was denigrated.
In the place of meritocracy we have what some have called "positive discrimination". At least that is the perception of critics of DEI. It can be easy to ignore your critics and sometimes that is a good approach. But when your goals are changing the hearts and minds, which at least in the early days of DEI seemed to be the goal, it is vital. Before I offer criticism of DEI I want to say a few positive things about it. From my perspective working in tech for 20 years I think it is good that the culture has become more vocal about "isms". Racism and sexism will always be with us but we should strive to treat people fairly. I've seen both of these in my work life and people are much more comfortable speaking up than they were in the past. That's not a bad thing.
To me it is obvious that quotas and pushing lies like the wage gap harmed the goals of DEI. Why do I say this? Stay with me here. If you believe there are people that just hate women or are racists in an industry those people are very unlikely to come over to your side. So you of course have people that agree with your DEI agenda but to me the focus of DEI is really the middle. Those that aren't sexist or racist but also aren't that motivated. The majority of workers in the early 2000s at least were white males. I believe this is still true today. For the last 20 years this group have been ridiculed on mass and told they are the problem. If this is the group you are seeking to win over... I can't think of a more terrible strategy. So either you have people who just think they are terrible and are being told there isn't much if anything they can do about their racism and sexism. Or you have people who buck up against how they are being lumped in with real racists and sexists.
You end up making enemies of allies. I have watched this happen in the industry over the years. As DEI has expanded into other industries this push back has only became stronger.
Another unintended consequence of DEI seems obvious to me but I rarely hear it mentioned. Today when you see something go wrong and the org has been vocal about DEI those that DEI claims to protect become the obvious targets. This is regardless of any evidence. It just seems like if you are saying we hire and promote on a basis other than merit or qualifications you are not hiring the best. That doesn't mean someone that is a minority isn't as good as a white male but when you discriminate you undercut those you claim to protect.
The loudest voices in DEI have done a terrible job. They have made enemies of allies. When you aren't honest about statistics and data, when you lump people into massive groups and boil everything down to biology and DNA you show your true colors. People don't buy it. I believe this is what we are seeing with the rejection of DEI. When you build something on lies and half truths it is doomed to fail. I'm convinced MOST people that support DEI are just good hearted people that have been manipulated and propagandized. DEI on the surface sounds good to most people. Those that respond in hate to DEI also provide a good boogie man. Divide and conquer works for a while but in the end truth wins.
What do you think?
originally posted at https://stacker.news/items/853862
-
 @ 6ad3e2a3:c90b7740
2025-01-10 12:33:47
@ 6ad3e2a3:c90b7740
2025-01-10 12:33:47The excesses of wokeness are thankfully getting their overdue correction, but as often happens with corrections, they tend to overshoot. A case in point was from the usually reasonable writer Wesley Yang on Twitter, who posted the following:
Poor long-term immigration policy has apparently led to too many foreign-born and native criminals of foreign descent in Norway, a disproportionate number of whom, per the chart, hail from Somalia and Morocco. Yang argues using this data to inform Norway’s immigration policies going forward is both unproblematic and “no longer prejudice.”
This is a sleight of hand. You can advocate for designing prejudicial immigration policies based on the group to which an individual potential immigrant belongs, but you cannot both do so and pretend it is not prejudicial.
This is not a point about what countries should or should not DO. They are free IMO to design immigration policies as they see fit, and there are arguments to be had over that. But there is a reactionary blindness wherein people pretend that grouping individuals by race, religion or country of origin isn't prejudicial to those individuals who have no control over how others in their assigned group behave.
The grouping is justified in their view by "data" or "statistics" or "reason." The truth is most of us still view "prejudice" as negative, so no one advocating for discriminatory immigration policies wants to be considered prejudiced. They are for the policy, think it's good, and therefore try to pretend it's not prejudiced when it obviously is.
Don't pretend. If you're for prejudicial, discriminatory immigration policies "for the greater good", just advocate for it on those terms. Be honest about what you're saying.
This might seem like a trivial point on which to base a post, but I don’t think it is. It’s not because “prejudice is bad” or “racism!” That’s just one type of instance in which this midwit tendency — to assign individuals to a group and then pretend you are being “data-driven” — rears its terrible head. I remember a couple years ago people on Twitter accused me of “taking up an ICU bed” because I refused to inject myself with Pfizer’s latest. Their reasoning was similar: because the unvaccinated are more likely to take up ICU beds (which turned out to be a lie, but let’s assume it were true), I was in the group taking up more beds, therefore I was taking up a bed.
The trick is to assign someone to a group in which they qualify (Somali, unvaccinated, etc.), get “data” about that group and then apply that data to the individuals within it, even if it is totally inaccurate with respect to them.
This is the same trick used to justify disastrous DEI policies too. You are from a historically underprivileged group, so you deserve to be held to lower standards. It doesn’t matter if you would succeed on your own merit, it doesn’t matter your race, gender, sexual orientation are irrelevant to the task for which you are being hired, it doesn’t matter if you are the son of wealthy and famous people and attended all the best schools, you belong to a particular category and therefore this standard will be applied.
But the implications of this midwit sleight of hand are even worse than that, especially on the eve of AI-based systems taking over so many of the administrative functions at both the corporate and state level. You will be categorized, and you will be pre-judged on that basis because it is far more efficient for the system to do so than to examine everyone individually. In fact, I’d argue, unlike humans, AI is incapable of seeing individuals, it sees only “data.”
This was the premise for the movie Minority Report, set in a dystopian future wherein people get convicted of “pre-crime” because the system determined from the data about them they were likely to commit one. You might not have done anything yet, but based on your angry social media posts, your high testosterone, your age and background, you have a 99.9 percent chance of violence. Why not arrest you now before you victimize someone? For every 1000 victims we protect, we’ll convict only one person who would not in fact have done it!
There will be many people who are for this kind of reasoning. It’s “data” after all. Never mind the data can be biased based on the grouping. Why am I grouped with other people I don’t know and over whom I have no control? What if they added 100 other parameters which showed I’m among the least likely to commit violence? Who is selecting these parameters and what are their agendas?
But more to the point, such a society is not free. You are at the whims of your grouping, of parameters, of statistics. The paradigm of individual civil liberties, innocent until proven guilty, responsibility only for your own actions would be dead. You are pre-judged before you have done anything.
The second-order effects of such a paradigm would be a race to the bottom. If I am not in the wrong group I can do no wrong, based on my favorable peers. I can roam the streets, commit acts of vandalism and violence with impunity, I can loaf at work, not do my job and never be fired. I would argue that under the present (and mercifully soon-to-be-departed) administration we’ve already experienced many of these effects already.
So back to the original question. What is Norway to do with this “data”? One idea would be to have a non-discriminatory vetting process that involves delayed gratification and requires some diligence on the part of the prospective immigrant. This might self-sort the people capable of living in an open, prosperous western society and those who are not. You would be admitted or denied based on demonstrated suitability (merit), not with whom you were grouped (identity). This would be closer to the “postjudice” policy prescription Yang erroneously claims for his own in the cited post.
Whether that results in more people of one race or another, one nationality or another getting in, isn't important. What's important is both not judging individuals on the basis of their assigned group and keeping the country free of violent criminals. Both goals are essential if we want to avoid dystopian outcomes.
-
 @ d34e832d:383f78d0
2025-01-06 23:44:40
@ d34e832d:383f78d0
2025-01-06 23:44:40Lets explore three key aspects of Bitcoin technology to enhance your engagement with the ecosystem:
- Running an Alby Hub Cloud Instance
- Setting Up a Nutshell Ecash Mint on an Affordable VPS
- Integrating Nostr Wallet Connect for Seamless Tipping
These components empower users to manage transactions, ensure privacy, and facilitate smooth interactions within the Bitcoin and Nostr communities.
1. Running an Alby Hub Cloud Instance
Purpose and Benefits:
Alby Hub is a self-custodial Lightning wallet that allows you to manage Bitcoin transactions efficiently. By running an Alby Hub instance in the cloud, you gain 24/7 online access to receive payments via a Lightning address, integrate with various applications, and maintain control over your funds without the need for personal hardware.
Setting Up Alby Hub in the Cloud:
-
Choose Alby Cloud: For a hassle-free setup, Alby offers a cloud service where you can start your own hub in just 2 minutes. Give it A Try: Alby Cloud
-
Subscription Benefits: Subscribing to Alby Cloud provides you with a self-custodial Lightning wallet, 24/7 online access, exclusive partner deals, priority support, and access to a subscriber community.
-
Getting Started: Visit the Alby Cloud page, select the subscription that suits you, and follow the guided setup process to have your hub up and running quickly.
- Alby Cloud page
For a visual guide on setting up Alby Hub, you can watch the following tutorial:
2. Setting Up a Nutshell Ecash Mint on an Affordable VPS
Purpose and Benefits:
Nutshell is an implementation of Ecash, a digital cash system that prioritizes privacy and anonymity. Setting up a Nutshell Ecash mint on a Virtual Private Server (VPS) allows you to operate your own mint, enhancing transaction privacy and providing a backup system for your Bitcoin transactions.
Setting Up on a $5 VPS:
-
Select a VPS Provider: Choose an affordable VPS provider that supports Bitcoin and Nostr communities. For instance, SatoshiHost offers VPS services tailored for such needs.
-
Install Nutshell: After setting up your VPS, install the Nutshell software by following the official installation guide.
- Nutshell
-
Configure the Mint: Set up the mint parameters, including denomination and security settings, to suit your requirements.
-
Secure the Server: Implement security measures such as firewalls and regular updates to protect your mint from potential threats.
- Recommendations
- Server Tips
3. Integrating Nostr Wallet Connect for Seamless Tipping
Purpose and Benefits:
Nostr Wallet Connect (NWC) is an open protocol that enables applications to interact with Bitcoin Lightning wallets. Integrating NWC allows for seamless tipping and payments within Nostr apps, enhancing user experience and promoting engagement.
Integration Steps:
-
Choose a Supporting App: Select a Nostr app that supports NWC, such as Amythystor Damus.
-
Connect Your Wallet: Use NWC to link your preferred Lightning wallet to the Nostr app. This connection facilitates seamless payments without the need to switch between applications.
-
Test the Integration: Perform a test transaction to ensure that the tipping functionality works as intended.
-
Maintain Security: Regularly update your wallet and Nostr app to incorporate the latest security features and improvements.
For a deeper understanding of Nostr Wallet Connect and its significance, you can watch the following discussion:
Final Thoughts On Setup
Implementing these components enhances your interaction with the Bitcoin ecosystem by providing efficient transaction management, improved privacy, and seamless integration with Nostr applications. By running an Alby Hub cloud instance, setting up a Nutshell Ecash mint on an affordable VPS, and integrating Nostr Wallet Connect, you contribute to a more robust and user-friendly Bitcoin environment.
Invitation for Feedback
I encourage you to share any questions or feedback regarding these topics. Let's continue the conversation to explore how we can further engage with and improve upon these technologies.
-
 @ 000002de:c05780a7
2025-01-16 18:20:29
@ 000002de:c05780a7
2025-01-16 18:20:29The more I learn about these terrible fires in LA the more damning the case against government becomes. Granted, I think the monopoly of the "state" is evil for many reasons but still.
The idea that this disaster can be laid at any other individual or group's feet is absurd. Isn't it? Every aspect of this to me seems to be owned or largely influenced by the various levels of government. Its kinda mind blowing to me.
I bet, if we had a free society and the cities were privately managed by different companies, if you had insurance companies that hired fire prevention services and those companies were found to be as incompetent as the various government agencies there would be massive lawsuits filed. Companies would go bankrupt. The insurance companies would be blamed without hesitation.
All of this would be justified. This mind virus of "government" being special because it isn't private is really being shown to be absurd. Political incentives are being shown to be inferior to market incentives over and over again. The people are taught to believe this nonsense by the government schools populated by teachers that believe the same nonsense.
How does it end? This tragedy makes me wonder. California's government is not special. Its just closer to socialism than other states. When you read about the USSR you find there were many failures and absurd ones. We are seeing just a small taste of this in California. California is not alone. We see government failures in New Orleans and in the floods of North Carolina as well.
I hope more people begin to see what is going on but I'm not counting on it.
originally posted at https://stacker.news/items/852698
-
 @ faade9ee:1c6dfd69
2025-01-26 11:46:44
@ faade9ee:1c6dfd69
2025-01-26 11:46:44test2c
-
 @ 09fbf8f3:fa3d60f0
2024-11-02 08:00:29
@ 09fbf8f3:fa3d60f0
2024-11-02 08:00:29> ### 第三方API合集:
免责申明:
在此推荐的 OpenAI API Key 由第三方代理商提供,所以我们不对 API Key 的 有效性 和 安全性 负责,请你自行承担购买和使用 API Key 的风险。
| 服务商 | 特性说明 | Proxy 代理地址 | 链接 | | --- | --- | --- | --- | | AiHubMix | 使用 OpenAI 企业接口,全站模型价格为官方 86 折(含 GPT-4 )| https://aihubmix.com/v1 | 官网 | | OpenAI-HK | OpenAI的API官方计费模式为,按每次API请求内容和返回内容tokens长度来定价。每个模型具有不同的计价方式,以每1,000个tokens消耗为单位定价。其中1,000个tokens约为750个英文单词(约400汉字)| https://api.openai-hk.com/ | 官网 | | CloseAI | CloseAI是国内规模最大的商用级OpenAI代理平台,也是国内第一家专业OpenAI中转服务,定位于企业级商用需求,面向企业客户的线上服务提供高质量稳定的官方OpenAI API 中转代理,是百余家企业和多家科研机构的专用合作平台。 | https://api.openai-proxy.org | 官网 | | OpenAI-SB | 需要配合Telegram 获取api key | https://api.openai-sb.com | 官网 |
持续更新。。。
推广:
访问不了openai,去
低调云购买VPN。官网:https://didiaocloud.xyz
邀请码:
w9AjVJit价格低至1元。
-
 @ faade9ee:1c6dfd69
2025-01-26 11:39:51
@ faade9ee:1c6dfd69
2025-01-26 11:39:51This is a normal piece of text.z
This is a bold piece of text via button press.z
this is also bold, but via double-starsz
this is an italic via button press
this also but via one-star
look, it's an underline!
oh, a piece of code has appeared. Nice. Button press tho. seems like it's purple / missed styling it, will change that.another code but via textcode block, kinda buggy (really buggy actually x3)```this is another, but via text which is disabled for now as it's cause issues```
This is a top number thing222
a bottom number thing5ss65435ghrt
- bullets!
-
another!
- a third!
-
Number!
-
another!
- a third!
-
[x] check
- [x] box
this is a quote
"quote"
heading 1
heading 2
heading 3 via text
heading 4 via text
heading 5 via text
heading 6 via text
this is a link via text (button has an annoyance bug)

video below
::youtube{#aApSteSbeGA}
-
 @ 3ffac3a6:2d656657
2025-01-06 23:42:53
@ 3ffac3a6:2d656657
2025-01-06 23:42:53Prologue: The Last Trade
Ethan Nakamura was a 29-year-old software engineer and crypto enthusiast who had spent years building his life around Bitcoin. Obsessed with the idea of financial sovereignty, he had amassed a small fortune trading cryptocurrencies, all while dreaming of a world where decentralized systems ruled over centralized power.
One night, while debugging a particularly thorny piece of code for a smart contract, Ethan stumbled across an obscure, encrypted message hidden in the blockchain. It read:
"The key to true freedom lies beyond. Burn it all to unlock the gate."
Intrigued and half-convinced it was an elaborate ARG (Alternate Reality Game), Ethan decided to follow the cryptic instruction. He loaded his entire Bitcoin wallet into a single transaction and sent it to an untraceable address tied to the message. The moment the transaction was confirmed, his laptop screen began to glitch, flooding with strange symbols and hash codes.
Before he could react, a flash of light engulfed him.
Chapter 1: A New Ledger
Ethan awoke in a dense forest bathed in ethereal light. The first thing he noticed was the HUD floating in front of him—a sleek, transparent interface that displayed his "Crypto Balance": 21 million BTC.
“What the…” Ethan muttered. He blinked, hoping it was a dream, but the numbers stayed. The HUD also showed other metrics:
- Hash Power: 1,000,000 TH/s
- Mining Efficiency: 120%
- Transaction Speed: Instant
Before he could process, a notification pinged on the HUD:
"Welcome to the Decentralized Kingdom. Your mining rig is active. Begin accumulating resources to survive."
Confused and a little terrified, Ethan stood and surveyed his surroundings. As he moved, the HUD expanded, revealing a map of the area. His new world looked like a cross between a medieval fantasy realm and a cyberpunk dystopia, with glowing neon towers visible on the horizon and villagers dressed in tunics carrying strange, glowing "crypto shards."
Suddenly, a shadow loomed over him. A towering beast, part wolf, part machine, snarled, its eyes glowing red. Above its head was the name "Feral Node" and a strange sigil resembling a corrupted block.
Instinct kicked in. Ethan raised his hands defensively, and to his shock, the HUD offered an option:
"Execute Smart Contract Attack? (Cost: 0.001 BTC)"
He selected it without hesitation. A glowing glyph appeared in the air, releasing a wave of light that froze the Feral Node mid-lunge. Moments later, it dissolved into a cascade of shimmering data, leaving behind a pile of "Crypto Shards" and an item labeled "Node Fragment."
Chapter 2: The Decentralized Kingdom
Ethan discovered that the world he had entered was built entirely on blockchain-like principles. The land was divided into regions, each governed by a Consensus Council—groups of powerful beings called Validators who maintained the balance of the world. However, a dark force known as The Central Authority sought to consolidate power, turning decentralized regions into tightly controlled fiefdoms.
Ethan’s newfound abilities made him a unique entity in this world. Unlike its inhabitants, who earned wealth through mining or trading physical crypto shards, Ethan could generate and spend Bitcoin directly—making him both a target and a potential savior.
Chapter 3: Allies and Adversaries
Ethan soon met a colorful cast of characters:
-
Luna, a fiery rogue and self-proclaimed "Crypto Thief," who hacked into ledgers to redistribute wealth to oppressed villages. She was skeptical of Ethan's "magical Bitcoin" but saw potential in him.
-
Hal, an aging miner who ran an underground resistance against the Central Authority. He wielded an ancient "ASIC Hammer" capable of shattering corrupted nodes.
-
Oracle Satoshi, a mysterious AI-like entity who guided Ethan with cryptic advice, often referencing real-world crypto principles like decentralization, trustless systems, and private keys.
Ethan also gained enemies, chief among them the Ledger Lords, a cabal of Validators allied with the Central Authority. They sought to capture Ethan and seize his Bitcoin, believing it could tip the balance of power.
Chapter 4: Proof of Existence
As Ethan delved deeper into the world, he learned that his Bitcoin balance was finite. To survive and grow stronger, he had to "mine" resources by solving problems for the people of the Decentralized Kingdom. From repairing broken smart contracts in towns to defending miners from feral nodes, every task rewarded him with shards and upgrades.
He also uncovered the truth about his arrival: the blockchain Ethan had used in his world was a prototype for this one. The encrypted message had been a failsafe created by its original developers—a desperate attempt to summon someone who could break the growing centralization threatening to destroy the world.
Chapter 5: The Final Fork
As the Central Authority's grip tightened, Ethan and his allies prepared for a final battle at the Genesis Block, the origin of the world's blockchain. Here, Ethan would face the Central Authority's leader, an amalgamation of corrupted code and human ambition known as The Miner King.
The battle was a clash of philosophies as much as strength. Using everything he had learned, Ethan deployed a daring Hard Fork, splitting the world’s blockchain and decentralizing power once again. The process drained nearly all of his Bitcoin, leaving him with a single satoshi—a symbolic reminder of his purpose.
Epilogue: Building the Future
With the Central Authority defeated, the Decentralized Kingdom entered a new era. Ethan chose to remain in the world, helping its inhabitants build fairer systems and teaching them the principles of trustless cooperation.
As he gazed at the sunrise over the rebuilt Genesis Block, Ethan smiled. He had dreamed of a world where Bitcoin could change everything. Now, he was living it.
-
 @ 3f770d65:7a745b24
2025-01-05 18:56:33
@ 3f770d65:7a745b24
2025-01-05 18:56:33New Year’s resolutions often feel boring and repetitive. Most revolve around getting in shape, eating healthier, or giving up alcohol. While the idea is interesting—using the start of a new calendar year as a catalyst for change—it also seems unnecessary. Why wait for a specific date to make a change? If you want to improve something in your life, you can just do it. You don’t need an excuse.
That’s why I’ve never been drawn to the idea of making a list of resolutions. If I wanted a change, I’d make it happen, without worrying about the calendar. At least, that’s how I felt until now—when, for once, the timing actually gave me a real reason to embrace the idea of New Year’s resolutions.
Enter Olas.
If you're a visual creator, you've likely experienced the relentless grind of building a following on platforms like Instagram—endless doomscrolling, ever-changing algorithms, and the constant pressure to stay relevant. But what if there was a better way? Olas is a Nostr-powered alternative to Instagram that prioritizes community, creativity, and value-for-value exchanges. It's a game changer.
Instagram’s failings are well-known. Its algorithm often dictates whose content gets seen, leaving creators frustrated and powerless. Monetization hurdles further alienate creators who are forced to meet arbitrary follower thresholds before earning anything. Additionally, the platform’s design fosters endless comparisons and exposure to negativity, which can take a significant toll on mental health.
Instagram’s algorithms are notorious for keeping users hooked, often at the cost of their mental health. I've spoken about this extensively, most recently at Nostr Valley, explaining how legacy social media is bad for you. You might find yourself scrolling through content that leaves you feeling anxious or drained. Olas takes a fresh approach, replacing "doomscrolling" with "bloomscrolling." This is a common theme across the Nostr ecosystem. The lack of addictive rage algorithms allows the focus to shift to uplifting, positive content that inspires rather than exhausts.
Monetization is another area where Olas will set itself apart. On Instagram, creators face arbitrary barriers to earning—needing thousands of followers and adhering to restrictive platform rules. Olas eliminates these hurdles by leveraging the Nostr protocol, enabling creators to earn directly through value-for-value exchanges. Fans can support their favorite artists instantly, with no delays or approvals required. The plan is to enable a brand new Olas account that can get paid instantly, with zero followers - that's wild.
Olas addresses these issues head-on. Operating on the open Nostr protocol, it removes centralized control over one's content’s reach or one's ability to monetize. With transparent, configurable algorithms, and a community that thrives on mutual support, Olas creates an environment where creators can grow and succeed without unnecessary barriers.
Join me on my New Year's resolution. Join me on Olas and take part in the #Olas365 challenge! It’s a simple yet exciting way to share your content. The challenge is straightforward: post at least one photo per day on Olas (though you’re welcome to share more!).
Download on Android or download via Zapstore.
Let's make waves together.
-
 @ 599f67f7:21fb3ea9
2025-01-26 11:01:05
@ 599f67f7:21fb3ea9
2025-01-26 11:01:05¿Qué es Blossom?
nostr:nevent1qqspttj39n6ld4plhn4e2mq3utxpju93u4k7w33l3ehxyf0g9lh3f0qpzpmhxue69uhkummnw3ezuamfdejsygzenanl0hmkjnrq8fksvdhpt67xzrdh0h8agltwt5znsmvzr7e74ywgmr72
Blossom significa Blobs Simply Stored on Media Servers (Blobs Simplemente Almacenados en Servidores de Medios). Blobs son fragmentos de datos binarios, como archivos pero sin nombres. En lugar de nombres, se identifican por su hash sha256. La ventaja de usar hashes sha256 en lugar de nombres es que los hashes son IDs universales que se pueden calcular a partir del archivo mismo utilizando el algoritmo de hash sha256.
💡 archivo -> sha256 -> hash
Blossom es, por lo tanto, un conjunto de puntos finales HTTP que permiten a los usuarios almacenar y recuperar blobs almacenados en servidores utilizando su identidad nostr.
¿Por qué Blossom?
Como mencionamos hace un momento, al usar claves nostr como su identidad, Blossom permite que los datos sean "propiedad" del usuario. Esto simplifica enormemente la cuestión de "qué es spam" para el alojamiento de servidores. Por ejemplo, en nuestro Blossom solo permitimos cargas por miembros de la comunidad verificados que tengan un NIP-05 con nosotros.
Los usuarios pueden subir en múltiples servidores de blossom, por ejemplo, uno alojado por su comunidad, uno de pago, otro público y gratuito, para establecer redundancia de sus datos. Los blobs pueden ser espejados entre servidores de blossom, de manera similar a cómo los relays nostr pueden transmitir eventos entre sí. Esto mejora la resistencia a la censura de blossom.
A continuación se muestra una breve tabla de comparación entre torrents, Blossom y servidores CDN centralizados. (Suponiendo que hay muchos seeders para torrents y se utilizan múltiples servidores con Blossom).
| | Torrents | Blossom | CDN Centralizado | | --------------------------------------------------------------- | -------- | ------- | ---------------- | | Descentralizado | ✅ | ✅ | ❌ | | Resistencia a la censura | ✅ | ✅ | ❌ | | ¿Puedo usarlo para publicar fotos de gatitos en redes sociales? | ❌ | ✅ | ✅ |
¿Cómo funciona?
Blossom utiliza varios tipos de eventos nostr para comunicarse con el servidor de medios.
| kind | descripción | BUD | | ----- | ------------------------------- | ------------------------------------------------------------------ | | 24242 | Evento de autorización | BUD01 | | 10063 | Lista de Servidores de Usuarios | BUD03 |
kind:24242 - Autorización
Esto es esencialmente lo que ya describimos al usar claves nostr como IDs de usuario. En el evento, el usuario le dice al servidor que quiere subir o eliminar un archivo y lo firma con sus claves nostr. El servidor realiza algunas verificaciones en este evento y luego ejecuta el comando del usuario si todo parece estar bien.
kind:10063 - Lista de Servidores de Usuarios
Esto es utilizado por el usuario para anunciar a qué servidores de medios está subiendo. De esta manera, cuando el cliente ve esta lista, sabe dónde subir los archivos del usuario. También puede subir en múltiples servidores definidos en la lista para asegurar redundancia. En el lado de recuperación, si por alguna razón uno de los servidores en la lista del usuario está fuera de servicio, o el archivo ya no se puede encontrar allí, el cliente puede usar esta lista para intentar recuperar el archivo de otros servidores en la lista. Dado que los blobs se identifican por sus hashes, el mismo blob tendrá el mismo hash en cualquier servidor de medios. Todo lo que el cliente necesita hacer es cambiar la URL por la de un servidor diferente.
Ahora, además de los conceptos básicos de cómo funciona Blossom, también hay otros tipos de eventos que hacen que Blossom sea aún más interesante.
| kind | descripción | | ----- | --------------------- | | 30563 | Blossom Drives | | 36363 | Listado de Servidores | | 31963 | Reseña de Servidores |
kind:30563 - Blossom Drives
Este tipo de evento facilita la organización de blobs en carpetas, como estamos acostumbrados con los drives (piensa en Google Drive, iCloud, Proton Drive, etc.). El evento contiene información sobre la estructura de carpetas y los metadatos del drive.
kind:36363 y kind:31963 - Listado y Reseña
Estos tipos de eventos permiten a los usuarios descubrir y reseñar servidores de medios a través de nostr. kind:36363 es un listado de servidores que contiene la URL del servidor. kind:31963 es una reseña, donde los usuarios pueden calificar servidores.
¿Cómo lo uso?
Encuentra un servidor
Primero necesitarás elegir un servidor Blossom donde subirás tus archivos. Puedes navegar por los públicos en blossomservers.com. Algunos de ellos son de pago, otros pueden requerir que tus claves nostr estén en una lista blanca.
Luego, puedes ir a la URL de su servidor y probar a subir un archivo pequeño, como una foto. Si estás satisfecho con el servidor (es rápido y aún no te ha fallado), puedes agregarlo a tu Lista de Servidores de Usuarios. Cubriremos brevemente cómo hacer esto en noStrudel y Amethyst (pero solo necesitas hacer esto una vez, una vez que tu lista actualizada esté publicada, los clientes pueden simplemente recuperarla de nostr).
noStrudel
- Encuentra Relays en la barra lateral, luego elige Servidores de Medios.
- Agrega un servidor de medios, o mejor aún, varios.
- Publica tu lista de servidores. ✅
Amethyst
- En la barra lateral, encuentra Servidores multimedia.
- Bajo Servidores Blossom, agrega tus servidores de medios.
- Firma y publica. ✅
Ahora, cuando vayas a hacer una publicación y adjuntar una foto, por ejemplo, se subirá en tu servidor blossom.
⚠️ Ten en cuenta que debes suponer que los archivos que subas serán públicos. Aunque puedes proteger un archivo con contraseña, esto no ha sido auditado.
Blossom Drive
Como mencionamos anteriormente, podemos publicar eventos para organizar nuestros blobs en carpetas. Esto puede ser excelente para compartir archivos con tu equipo, o simplemente para mantener las cosas organizadas.
Para probarlo, ve a blossom.hzrd149.com (o nuestra instancia comunitaria en blossom.bitcointxoko.com) e inicia sesión con tu método preferido.
Puedes crear una nueva unidad y agregar blobs desde allí.
Bouquet
Si usas múltiples servidores para darte redundancia, Bouquet es una buena manera de obtener una visión general de todos tus archivos. Úsalo para subir y navegar por tus medios en diferentes servidores y sincronizar blobs entre ellos.
Cherry Tree
nostr:nevent1qvzqqqqqqypzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qyghwumn8ghj7mn0wd68ytnhd9hx2tcpzfmhxue69uhkummnw3e82efwvdhk6tcqyp3065hj9zellakecetfflkgudm5n6xcc9dnetfeacnq90y3yxa5z5gk2q6
Cherry Tree te permite dividir un archivo en fragmentos y luego subirlos en múltiples servidores blossom, y más tarde reensamblarlos en otro lugar.
Conclusión
Blossom aún está en desarrollo, pero ya hay muchas cosas interesantes que puedes hacer con él para hacerte a ti y a tu comunidad más soberanos. ¡Pruébalo!
Si deseas mantenerte al día sobre el desarrollo de Blossom, sigue a nostr:nprofile1qyghwumn8ghj7mn0wd68ytnhd9hx2tcpzfmhxue69uhkummnw3e82efwvdhk6tcqyqnxs90qeyssm73jf3kt5dtnk997ujw6ggy6j3t0jjzw2yrv6sy22ysu5ka y dale un gran zap por su excelente trabajo.
Referencias
-
 @ 4c48cf05:07f52b80
2024-10-30 01:03:42
@ 4c48cf05:07f52b80
2024-10-30 01:03:42I believe that five years from now, access to artificial intelligence will be akin to what access to the Internet represents today. It will be the greatest differentiator between the haves and have nots. Unequal access to artificial intelligence will exacerbate societal inequalities and limit opportunities for those without access to it.
Back in April, the AI Index Steering Committee at the Institute for Human-Centered AI from Stanford University released The AI Index 2024 Annual Report.
Out of the extensive report (502 pages), I chose to focus on the chapter dedicated to Public Opinion. People involved with AI live in a bubble. We all know and understand AI and therefore assume that everyone else does. But, is that really the case once you step out of your regular circles in Seattle or Silicon Valley and hit Main Street?
Two thirds of global respondents have a good understanding of what AI is
The exact number is 67%. My gut feeling is that this number is way too high to be realistic. At the same time, 63% of respondents are aware of ChatGPT so maybe people are confounding AI with ChatGPT?
If so, there is so much more that they won't see coming.
This number is important because you need to see every other questions and response of the survey through the lens of a respondent who believes to have a good understanding of what AI is.
A majority are nervous about AI products and services
52% of global respondents are nervous about products and services that use AI. Leading the pack are Australians at 69% and the least worried are Japanise at 23%. U.S.A. is up there at the top at 63%.
Japan is truly an outlier, with most countries moving between 40% and 60%.
Personal data is the clear victim
Exaclty half of the respondents believe that AI companies will protect their personal data. And the other half believes they won't.
Expected benefits
Again a majority of people (57%) think that it will change how they do their jobs. As for impact on your life, top hitters are getting things done faster (54%) and more entertainment options (51%).
The last one is a head scratcher for me. Are people looking forward to AI generated movies?

Concerns
Remember the 57% that thought that AI will change how they do their jobs? Well, it looks like 37% of them expect to lose it. Whether or not this is what will happen, that is a very high number of people who have a direct incentive to oppose AI.
Other key concerns include:
- Misuse for nefarious purposes: 49%
- Violation of citizens' privacy: 45%
Conclusion
This is the first time I come across this report and I wil make sure to follow future annual reports to see how these trends evolve.
Overall, people are worried about AI. There are many things that could go wrong and people perceive that both jobs and privacy are on the line.
Full citation: Nestor Maslej, Loredana Fattorini, Raymond Perrault, Vanessa Parli, Anka Reuel, Erik Brynjolfsson, John Etchemendy, Katrina Ligett, Terah Lyons, James Manyika, Juan Carlos Niebles, Yoav Shoham, Russell Wald, and Jack Clark, “The AI Index 2024 Annual Report,” AI Index Steering Committee, Institute for Human-Centered AI, Stanford University, Stanford, CA, April 2024.
The AI Index 2024 Annual Report by Stanford University is licensed under Attribution-NoDerivatives 4.0 International.
-
 @ 378562cd:a6fc6773
2025-01-27 15:32:25
@ 378562cd:a6fc6773
2025-01-27 15:32:25In the ever-evolving cryptocurrency space, few assets have attracted as much attention—and controversy—as XRP. Marketed as a tool for revolutionizing cross-border payments, XRP has been at the center of debates about its legitimacy, legal entanglements, and centralization. In contrast, Bitcoin remains the gold standard of decentralization, embodying the original ideals of cryptocurrency as a secure, censorship-resistant, and community-driven digital asset.
The Ripple-SEC Legal Battle: A Dark Cloud Over XRP
XRP's legal troubles began in December 2020 when the U.S. Securities and Exchange Commission (SEC) filed a lawsuit against Ripple Labs, alleging the company had conducted an unregistered securities offering. The lawsuit hinged on whether XRP, the token Ripple uses for its cross-border payment solutions, qualifies as a security under U.S. law.
Ripple Labs and its executives, including CEO Brad Garlinghouse, argued that XRP should not be classified as a security. They claimed it was a digital currency akin to Bitcoin or Ethereum, which the SEC had already deemed non-securities. Despite Ripple scoring partial victories in court—such as a judge's ruling that XRP sales to retail investors did not constitute securities transactions—the company was ordered to pay a $125 million fine. While Ripple touted the outcome as a victory, the SEC’s ongoing appeal means uncertainty lingers over XRP's regulatory future.
These legal uncertainties have had significant implications for XRP’s adoption. After the lawsuit, major U.S. exchanges delisted XRP, temporarily causing its price to plummet. Although some platforms have since reintroduced XRP trading, its reputation remains tarnished in some circles.
Centralization Concerns: Is XRP Truly a Cryptocurrency?
A key critique of XRP lies in its centralized structure. Unlike Bitcoin’s decentralized proof-of-work (PoW) system, which relies on a distributed network of miners to validate transactions, XRP operates on a consensus protocol managed by a limited number of validators. This has led to accusations that Ripple Labs wields too much control over the network, undermining the core principle of decentralization that defines cryptocurrencies.
Adding to these concerns is Ripple Labs’ significant ownership of XRP tokens. Ripple initially held 80 billion of the 100 billion XRP tokens ever created, and as of 2024, it still holds a substantial portion in escrow. Critics argue that this concentration of ownership allows Ripple to manipulate XRP’s price and limits the asset’s independence.
Bitcoin: The Decentralized Gold Standard
In stark contrast to XRP, Bitcoin remains the archetype of decentralization. Introduced in 2009 by the pseudonymous Satoshi Nakamoto, Bitcoin operates on a PoW system that ensures no single entity can control the network. Its open-source code, coupled with a vast network of miners and nodes distributed globally, makes Bitcoin nearly immune to censorship and manipulation.
Bitcoin's decentralized nature is a cornerstone of its value. Unlike XRP, which is closely tied to Ripple Labs and its business interests, Bitcoin is not controlled by any organization or individual. This decentralization ensures transparency, security, and trust among its users, reinforcing its status as a digital alternative to gold.
Moreover, Bitcoin’s capped supply of 21 million coins enhances its appeal as a store of value. In a world where inflation and monetary policy can erode the value of fiat currencies, Bitcoin’s scarcity offers a hedge against economic uncertainty.
Adoption and Market Perception: Bitcoin vs. XRP
Despite its controversies, XRP has gained traction among financial institutions for its speed and low transaction costs in cross-border payments. Ripple’s partnerships with major banks and remittance providers have bolstered its utility, even as skepticism around its centralization persists.
Bitcoin, on the other hand, has achieved mainstream acceptance as both an investment asset and a medium of exchange. From institutional investors adding Bitcoin to their balance sheets to countries like El Salvador adopting it as legal tender, Bitcoin's adoption is steadily growing. Its resilience in the face of regulatory scrutiny and market volatility further cements its position as the most trusted cryptocurrency.
What XRP's Journey Teaches Us About Cryptocurrency Values
The contrasting narratives of XRP and Bitcoin highlight a fundamental tension in the cryptocurrency world: the trade-off between utility and decentralization. While XRP offers practical solutions for specific use cases, its centralized nature and reliance on Ripple Labs compromise its alignment with the ideals of cryptocurrency.
Bitcoin, by comparison, stays true to the vision of a decentralized financial system free from intermediaries. Its robust network, transparency, and immutability make it not just a cryptocurrency but a symbol of financial freedom.
Conclusion: Bitcoin’s Enduring Legacy
As the legal and market drama around XRP continues to unfold, one thing remains clear: decentralization is at the heart of what makes cryptocurrencies revolutionary. Bitcoin exemplifies this ideal, serving as a reliable store of value and a hedge against centralized control. While XRP may have its place in specific financial ecosystems, it cannot claim to uphold the principles that Bitcoin has come to represent.
For investors and enthusiasts alike, understanding these differences is crucial. In a rapidly evolving market, Bitcoin’s true value lies not just in its price but in its unwavering commitment to decentralization—a principle that defines the future of financial freedom.
-
 @ a853296a:209e695f
2025-01-16 17:28:31
@ a853296a:209e695f
2025-01-16 17:28:31🚀🤠⚡ The Fastest Podcast Search in the West! ⚡🤠
PullThatUpJamie v0.1 Release
👋 Hey stackers! I’m excited to announce a major new feature for Pull That Up Jamie: Podcast Search (Beta)—the fastest way to find high-signal moments in your favorite shows!
You can try it out now at: https://pullthatupjamie.ai/?searchMode=podcast-search
- 🚀 Podcast Search (Beta) is live at https://pullthatupjamie.ai/?searchMode=podcast-search.
- 🎙️ Search through 100k+ podcast clips with lightning-fast vector search.
- ✨ Features include:
- Share Button: Get links to exact timestamps for moments you searched.
- Listen Button: Jump straight into episodes without hassle.
- Filter by Feed: Focus your search on specific podcasts.
- 🎧 Highlights:
- High-signal technical content from Bitcoin Optech Podcast 📡.
- In-depth macro news from Green Candle Investments Podcast 💡.
- On-the-ground Bitcoin startup coverage from ThrillerX 📰.
- 🙌 More pods coming soon—let us know which ones you want added!
We’ve used state-of-the-art tools to make 100k+ podcast clips searchable, giving you the power to pinpoint the insights and commentary you need in seconds.
🎙️ Current Podcast Lineup (As of 1/16/25)
- 🎙️ Robin Seyr – Interviews with Bitcoiners worldwide.
- 💡 Green Candle Investments Podcast – Macro news and updates on Bitcoin and investing.
- 🥩 The Meat Mafia Podcast – Deep dives into health, wealth, and meaningful living.
- 📰 Thriller "A Bitcoin Zine" – On-the-ground Bitcoin startup coverage and local Austin Bitcoin news.
- 🎭 The Joe Rogan Experience – Conversations with fascinating guests from every walk of life.
- 🚲 Convos On The Pedicab – Polarizing topics discussed in Austin, TX.
- 🧠 The Diary Of A CEO with Steven Bartlett – Insights from the world’s top thinkers and leaders.
- ❓ The "What is Money?" Show – Exploring the philosophical rabbit hole of money.
- 📖 Bitcoin Audible – Bitcoin knowledge made accessible, one read at a time.
- 📚 The Bitcoin Standard Podcast – Discussions on Austrian economics and Bitcoin analysis.
- 🌀 The Bitcoin Matrix – Exploring the future of money and its broader implications.
- 🌎 The Juan Galt Show – Libertarian views and Bitcoin from a Latin perspective.
- 🐇 Rabbit Hole Recap – Weekly updates on Bitcoin news and developments.
- 🐴 TFTC: A Bitcoin Podcast – Straight talk about Bitcoin from Austin, TX.
- 🔥 THE Bitcoin Podcast – A no-nonsense take on Bitcoin’s evolution and signal.
- 📡 Bitcoin Optech Podcast – High-signal technical content about Bitcoin and Lightning Network.
- ⚡ Simply Bitcoin – Daily updates on the Bitcoin revolution.
🛠️ Features to Check Out
- Share Button: Get a link to the exact moment you searched for, complete with timestamps.
- Listen Button: Dive right into the content without leaving your search results.
- Filter by Feed: Refine your search results by podcast feed to focus on the shows you care about most.
Pull That Up Jamie Highlights
@Ge and @Car commenting on @DarthCoin 's incredible origin story (deeplink)
Learning about Superscaler on Bitcoin Optech deeplink
@Greencandleit interviewing American HODL on why MSTR is going to moon
Mel Gibson discussing his brain scans on JRE
🙌 We Want Your Feedback!
- Have a podcast you want us to add? Let us know!
- Stacker News Live pods are searchable going back to July on the ThrillerX feed.
- Optech: Search high-signal technical content on Bitcoin development and Lightning tech.
- Green Candle: Stay updated with great macro news and Bitcoin analysis.
- ThrillerX: Get on-the-ground coverage of the Bitcoin startup scene.
⚡ Try out Podcast Search now and let us know what you think: https://pullthatupjamie.ai/?searchMode=podcast-search
Together, let’s make Bitcoin and podcast search more accessible, private, and powerful! 🚀
originally posted at https://stacker.news/items/852635
-
 @ 6bae33c8:607272e8
2025-01-27 14:56:31
@ 6bae33c8:607272e8
2025-01-27 14:56:31I was rooting for the Eagles in the NFC because I want Saquon Barkley to win Super Bowl MVP, and on the first play from scrimmage he took a 60-yard run to the house. Unfortunately he got banged up on the play and was used sparingly for the rest of the game, but no matter. Another 118 yards and three TDs later, he’s got his chance in the Super Bowl.
The Killer Redskins are pretty good — they don’t stop coming at you, and Jayden Daniels should be a star for the next decade. But three lost fumbles destroyed any hopes they had. Fumbles and penalties are the worst part of the NFL — like getting Sorry’ed in the game of Sorry, they reverse whatever is happening on the field seismically.
-
The KRs are close. They could use an offensive line upgrade, maybe one more pass rusher and another explosive skill player, but with Daniels around, they’ll be contenders again.
-
Terry McLaurin didn’t have a big role, but he showed how fast and explosive he is on the 36-yard TD catch and run. He’s also big (210 lbs) for a speed receiver, but turns 30 in September.
-
Jalen Hurts made some nice downfield throws to A.J. Brown which is a good sign. If the Eagles are going to beat the Chiefs, they’ll need to make some plays in the passing game.
-
Jake Elliott missed a long FG and has been shaky all year. People don’t care about kickers, but I wouldn’t want to trust him with the game on the line.
-
In both games there were penalties on a TD that resulted in teams opting for the 1-yard 2-point conversion, and both failed. The Bills even took a successful PAT off the board.
-
I know there was controversy on the Chiefs’ fourth quarter. 4th-down stop, down 1 (and also the spot on the preceding 3rd-down play that made it 4th down.) But the Chiefs still had to drive for the touchdown and subsequent FG after the Bills tied it, stop them on defense one more time and then convert that last third down to seal it. In other words, it looked like two bad spots, but even if that was “cheating,” the game was won on the field. The Chiefs also lost a fumble on a botched snap, and the Bills recovered all of theirs.
-
Kareem Hunt is such a tough runner, he’s basically a healthy Isiah Pacheco at this point. Pacheco himself doesn’t look 100 percent.
-
Travis Kelce had a surprisingly minor role, but Xavier Worthy had a good game, and Patrick Mahomes spread the ball around. It was almost as if they had played it vanilla on purpose in earlier weeks and broke out a more aggressive passing game when they needed it.
-
Mahomes will now have appeared in five of the last six Super Bowls, with only Joe Burrow and the Bengals interrupting his streak. If he wins a fourth this year, he’ll have a chance to do the unthinkable which is to catch Tom Brady’s seven. Three more is still a lot though, and that’s only IF he wins against the Eagles.
-
Josh Allen played well on the road against one of the league’s best defenses. The Bills offense wasn’t as efficient as Buffalo’s, though, and they’re really missing a go-to playmaking receiver. Amari Cooper never seemed to integrate fully into the offense.
-
The AFC is loaded with QB talent that will never see a Super Bowl so long as Andy Reid and Mahomes are in the league. Allen, Lamar Jackson, Justin Herbert, Burrow (again) or maybe C.J. Stroud will break through one of these years, but it’s likely at least two of them won’t.
-
-
 @ dc4cd086:cee77c06
2024-10-18 04:08:33
@ dc4cd086:cee77c06
2024-10-18 04:08:33Have you ever wanted to learn from lengthy educational videos but found it challenging to navigate through hours of content? Our new tool addresses this problem by transforming long-form video lectures into easily digestible, searchable content.
Key Features:
Video Processing:
- Automatically downloads YouTube videos, transcripts, and chapter information
- Splits transcripts into sections based on video chapters
Content Summarization:
- Utilizes language models to transform spoken content into clear, readable text
- Formats output in AsciiDoc for improved readability and navigation
- Highlights key terms and concepts with [[term]] notation for potential cross-referencing
Diagram Extraction:
- Analyzes video entropy to identify static diagram/slide sections
- Provides a user-friendly GUI for manual selection of relevant time ranges
- Allows users to pick representative frames from selected ranges
Going Forward:
Currently undergoing a rewrite to improve organization and functionality, but you are welcome to try the current version, though it might not work on every machine. Will support multiple open and closed language models for user choice Free and open-source, allowing for personal customization and integration with various knowledge bases. Just because we might not have it on our official Alexandria knowledge base, you are still welcome to use it on you own personal or community knowledge bases! We want to help find connections between ideas that exist across relays, allowing individuals and groups to mix and match knowledge bases between each other, allowing for any degree of openness you care.
While designed with #Alexandria users in mind, it's available for anyone to use and adapt to their own learning needs.
Screenshots
Frame Selection

This is a screenshot of the frame selection interface. You'll see a signal that represents frame entropy over time. The vertical lines indicate the start and end of a chapter. Within these chapters you can select the frames by clicking and dragging the mouse over the desired range where you think diagram is in that chapter. At the bottom is an option that tells the program to select a specific number of frames from that selection.
Diagram Extraction

This is a screenshot of the diagram extraction interface. For every selection you've made, there will be a set of frames that you can choose from. You can select and deselect as many frames as you'd like to save.
Links
- repo: https://github.com/limina1/video_article_converter
- Nostr Apps 101: https://www.youtube.com/watch?v=Flxa_jkErqE
Output
And now, we have a demonstration of the final result of this tool, with some quick cleaning up. The video we will be using this tool on is titled Nostr Apps 101 by nostr:npub1nxy4qpqnld6kmpphjykvx2lqwvxmuxluddwjamm4nc29ds3elyzsm5avr7 during Nostrasia. The following thread is an analog to the modular articles we are constructing for Alexandria, and I hope it conveys the functionality we want to create in the knowledge space. Note, this tool is the first step! You could use a different prompt that is most appropriate for the specific context of the transcript you are working with, but you can also manually clean up any discrepancies that don't portray the video accurately.
nostr:nevent1qvzqqqqqqypzp5r5hd579v2sszvvzfel677c8dxgxm3skl773sujlsuft64c44ncqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgwwaehxw309ahx7uewd3hkctcpzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309aex2mrp0yh8xmn0wf6zuum0vd5kzmp0qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgc7hglpn
Or view on Coracle nostr:nevent1qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgcppemhxue69uhkummn9ekx7mp0qgsdqa9md83tz5yqnrqjw07hhkpmfjpkuv9hlh5v8yhu8z274w9dv7qnnq0s3
-
 @ eee391ee:8d0b97c2
2025-01-27 14:55:16
@ eee391ee:8d0b97c2
2025-01-27 14:55:16Amber 3.2.0
- Fix relay connection when starting the service
- Added profile picture in the incoming requests screen when using a large screen device
- Added more event kinds translations
- Added a log with the bunker request response
- Use the relay from the request to send the response when no app is found
Download it with zap.store, Obtainium, f-droid or download it directly in the releases page
If you like my work consider making a donation
Verifying the release
In order to verify the release, you'll need to have
gpgorgpg2installed on your system. Once you've obtained a copy (and hopefully verified that as well), you'll first need to import the keys that have signed this release if you haven't done so already:bash gpg --keyserver hkps://keys.openpgp.org --recv-keys 44F0AAEB77F373747E3D5444885822EED3A26A6DOnce you have his PGP key you can verify the release (assuming
manifest-v3.2.0.txtandmanifest-v3.2.0.txt.sigare in the current directory) with:bash gpg --verify manifest-v3.2.0.txt.sig manifest-v3.2.0.txtYou should see the following if the verification was successful:
bash gpg: Signature made Fri 13 Sep 2024 08:06:52 AM -03 gpg: using RSA key 44F0AAEB77F373747E3D5444885822EED3A26A6D gpg: Good signature from "greenart7c3 <greenart7c3@proton.me>"That will verify the signature on the main manifest page which ensures integrity and authenticity of the binaries you've downloaded locally. Next, depending on your operating system you should then re-calculate the sha256 sum of the binary, and compare that with the following hashes:
bash cat manifest-v3.2.0.txtOne can use the
shasum -a 256 <file name here>tool in order to re-compute thesha256hash of the target binary for your operating system. The produced hash should be compared with the hashes listed above and they should match exactly. -
 @ 6389be64:ef439d32
2025-01-16 15:44:06
@ 6389be64:ef439d32
2025-01-16 15:44:06Black Locust can grow up to 170 ft tall
Grows 3-4 ft. per year
Native to North America
Cold hardy in zones 3 to 8

Firewood
- BLT wood, on a pound for pound basis is roughly half that of Anthracite Coal
- Since its growth is fast, firewood can be plentiful
Timber

- Rot resistant due to a naturally produced robinin in the wood
- 100 year life span in full soil contact! (better than cedar performance)
- Fence posts
- Outdoor furniture
- Outdoor decking
- Sustainable due to its fast growth and spread
- Can be coppiced (cut to the ground)
- Can be pollarded (cut above ground)
- Its dense wood makes durable tool handles, boxes (tool), and furniture
- The wood is tougher than hickory, which is tougher than hard maple, which is tougher than oak.
- A very low rate of expansion and contraction
- Hardwood flooring
- The highest tensile beam strength of any American tree
- The wood is beautiful
Legume
- Nitrogen fixer
- Fixes the same amount of nitrogen per acre as is needed for 200-bushel/acre corn
- Black walnuts inter-planted with locust as “nurse” trees were shown to rapidly increase their growth [[Clark, Paul M., and Robert D. Williams. (1978) Black walnut growth increased when interplanted with nitrogen-fixing shrubs and trees. Proceedings of the Indiana Academy of Science, vol. 88, pp. 88-91.]]
Bees

- The edible flower clusters are also a top food source for honey bees
Shade Provider

- Its light, airy overstory provides dappled shade
- Planted on the west side of a garden it provides relief during the hottest part of the day
- (nitrogen provider)
- Planted on the west side of a house, its quick growth soon shades that side from the sun
Wind-break

- Fast growth plus it's feathery foliage reduces wind for animals, crops, and shelters
Fodder
- Over 20% crude protein
- 4.1 kcal/g of energy
- Baertsche, S.R, M.T. Yokoyama, and J.W. Hanover (1986) Short rotation, hardwood tree biomass as potential ruminant feed-chemical composition, nylon bag ruminal degradation and ensilement of selected species. J. Animal Sci. 63 2028-2043
-
 @ da0b9bc3:4e30a4a9
2025-01-26 10:29:32
@ da0b9bc3:4e30a4a9
2025-01-26 10:29:32Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/864256