-
 @ eac63075:b4988b48
2025-01-04 19:41:34
@ eac63075:b4988b48
2025-01-04 19:41:34Since its creation in 2009, Bitcoin has symbolized innovation and resilience. However, from time to time, alarmist narratives arise about emerging technologies that could "break" its security. Among these, quantum computing stands out as one of the most recurrent. But does quantum computing truly threaten Bitcoin? And more importantly, what is the community doing to ensure the protocol remains invulnerable?
The answer, contrary to sensationalist headlines, is reassuring: Bitcoin is secure, and the community is already preparing for a future where quantum computing becomes a practical reality. Let’s dive into this topic to understand why the concerns are exaggerated and how the development of BIP-360 demonstrates that Bitcoin is one step ahead.
What Is Quantum Computing, and Why Is Bitcoin Not Threatened?
Quantum computing leverages principles of quantum mechanics to perform calculations that, in theory, could exponentially surpass classical computers—and it has nothing to do with what so-called “quantum coaches” teach to scam the uninformed. One of the concerns is that this technology could compromise two key aspects of Bitcoin’s security:
- Wallets: These use elliptic curve algorithms (ECDSA) to protect private keys. A sufficiently powerful quantum computer could deduce a private key from its public key.
- Mining: This is based on the SHA-256 algorithm, which secures the consensus process. A quantum attack could, in theory, compromise the proof-of-work mechanism.
Understanding Quantum Computing’s Attack Priorities
While quantum computing is often presented as a threat to Bitcoin, not all parts of the network are equally vulnerable. Theoretical attacks would be prioritized based on two main factors: ease of execution and potential reward. This creates two categories of attacks:
1. Attacks on Wallets
Bitcoin wallets, secured by elliptic curve algorithms, would be the initial targets due to the relative vulnerability of their public keys, especially those already exposed on the blockchain. Two attack scenarios stand out:
-
Short-term attacks: These occur during the interval between sending a transaction and its inclusion in a block (approximately 10 minutes). A quantum computer could intercept the exposed public key and derive the corresponding private key to redirect funds by creating a transaction with higher fees.
-
Long-term attacks: These focus on old wallets whose public keys are permanently exposed. Wallets associated with Satoshi Nakamoto, for example, are especially vulnerable because they were created before the practice of using hashes to mask public keys.
We can infer a priority order for how such attacks might occur based on urgency and importance.
 Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)
Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)2. Attacks on Mining
Targeting the SHA-256 algorithm, which secures the mining process, would be the next objective. However, this is far more complex and requires a level of quantum computational power that is currently non-existent and far from realization. A successful attack would allow for the recalculation of all possible hashes to dominate the consensus process and potentially "mine" it instantly.
 Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin Attacks
Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin AttacksRecently, Narcelio asked me about a statement I made on Tubacast:
https://x.com/eddieoz/status/1868371296683511969
If an attack became a reality before Bitcoin was prepared, it would be necessary to define the last block prior to the attack and proceed from there using a new hashing algorithm. The solution would resemble the response to the infamous 2013 bug. It’s a fact that this would cause market panic, and Bitcoin's price would drop significantly, creating a potential opportunity for the well-informed.
Preferably, if developers could anticipate the threat and had time to work on a solution and build consensus before an attack, they would simply decide on a future block for the fork, which would then adopt the new algorithm. It might even rehash previous blocks (reaching consensus on them) to avoid potential reorganization through the re-mining of blocks using the old hash. (I often use the term "shielding" old transactions).
How Can Users Protect Themselves?
While quantum computing is still far from being a practical threat, some simple measures can already protect users against hypothetical scenarios:
- Avoid using exposed public keys: Ensure funds sent to old wallets are transferred to new ones that use public key hashes. This reduces the risk of long-term attacks.
- Use modern wallets: Opt for wallets compatible with SegWit or Taproot, which implement better security practices.
- Monitor security updates: Stay informed about updates from the Bitcoin community, such as the implementation of BIP-360, which will introduce quantum-resistant addresses.
- Do not reuse addresses: Every transaction should be associated with a new address to minimize the risk of repeated exposure of the same public key.
- Adopt secure backup practices: Create offline backups of private keys and seeds in secure locations, protected from unauthorized access.
BIP-360 and Bitcoin’s Preparation for the Future
Even though quantum computing is still beyond practical reach, the Bitcoin community is not standing still. A concrete example is BIP-360, a proposal that establishes the technical framework to make wallets resistant to quantum attacks.
BIP-360 addresses three main pillars:
- Introduction of quantum-resistant addresses: A new address format starting with "BC1R" will be used. These addresses will be compatible with post-quantum algorithms, ensuring that stored funds are protected from future attacks.
- Compatibility with the current ecosystem: The proposal allows users to transfer funds from old addresses to new ones without requiring drastic changes to the network infrastructure.
- Flexibility for future updates: BIP-360 does not limit the choice of specific algorithms. Instead, it serves as a foundation for implementing new post-quantum algorithms as technology evolves.
This proposal demonstrates how Bitcoin can adapt to emerging threats without compromising its decentralized structure.
Post-Quantum Algorithms: The Future of Bitcoin Cryptography
The community is exploring various algorithms to protect Bitcoin from quantum attacks. Among the most discussed are:
- Falcon: A solution combining smaller public keys with compact digital signatures. Although it has been tested in limited scenarios, it still faces scalability and performance challenges.
- Sphincs: Hash-based, this algorithm is renowned for its resilience, but its signatures can be extremely large, making it less efficient for networks like Bitcoin’s blockchain.
- Lamport: Created in 1977, it’s considered one of the earliest post-quantum security solutions. Despite its reliability, its gigantic public keys (16,000 bytes) make it impractical and costly for Bitcoin.
Two technologies show great promise and are well-regarded by the community:
- Lattice-Based Cryptography: Considered one of the most promising, it uses complex mathematical structures to create systems nearly immune to quantum computing. Its implementation is still in its early stages, but the community is optimistic.
- Supersingular Elliptic Curve Isogeny: These are very recent digital signature algorithms and require extensive study and testing before being ready for practical market use.
The final choice of algorithm will depend on factors such as efficiency, cost, and integration capability with the current system. Additionally, it is preferable that these algorithms are standardized before implementation, a process that may take up to 10 years.
Why Quantum Computing Is Far from Being a Threat
The alarmist narrative about quantum computing overlooks the technical and practical challenges that still need to be overcome. Among them:
- Insufficient number of qubits: Current quantum computers have only a few hundred qubits, whereas successful attacks would require millions.
- High error rate: Quantum stability remains a barrier to reliable large-scale operations.
- High costs: Building and operating large-scale quantum computers requires massive investments, limiting their use to scientific or specific applications.
Moreover, even if quantum computers make significant advancements, Bitcoin is already adapting to ensure its infrastructure is prepared to respond.
Conclusion: Bitcoin’s Secure Future
Despite advancements in quantum computing, the reality is that Bitcoin is far from being threatened. Its security is ensured not only by its robust architecture but also by the community’s constant efforts to anticipate and mitigate challenges.
The implementation of BIP-360 and the pursuit of post-quantum algorithms demonstrate that Bitcoin is not only resilient but also proactive. By adopting practical measures, such as using modern wallets and migrating to quantum-resistant addresses, users can further protect themselves against potential threats.
Bitcoin’s future is not at risk—it is being carefully shaped to withstand any emerging technology, including quantum computing.
-
 @ 20e17dd0:2ae504d7
2025-02-01 21:14:41
@ 20e17dd0:2ae504d7
2025-02-01 21:14:411. Hardware Selection
It is important to select adequately the hardware that will be used to build your Node. The Node will be running 24h /7 days and will countain your lightning channels. It is important to use high quality hardware and spend the extra dollars for it.
At the time of building my Node, there was a shortage of Raspberry Pi and I was looking for an optimal alternative. I have decided to go ahead and purchase a used Mac Mini (late 2012).
It is recommended NOT to purchase a Mac Mini newer than 2012 (i.e 2014 and up) because Apple started to solder the RAM to the Logic Board after 2012. The Mac Mini Late 2012 is the last model that is fully customizable with SSD and RAM upgrades.
Here is the list of hardware that will be used in this build:
- 2 x 8G DDR3L Sodim 1600Mhz 1.35V
- 1 x Mac Mini (Late 2012) 2.5Ghz
- 1 x Samsung Evo 870 1Tb SSD ^
^ Note: As discussed earlier, it is important to select hardware of quality. I had initially purchased a low cost 2Tb SSD but it failed while trying to download the Bitcoin blockchain.
2. Hardware Upgrade
To facilitate the upgrade of the hardware, you will need the proper tools to remove some T6 & T8 screws.
Here are the steps to dismount the few components of the Mac Mini to upgrade the hardware:
- Unplug the Mac Mini.
- Turn it upside down with the black cover facing up.
-
Put your thumbs in the 2 grooves of the cover and turn the piece counterclockwise.

-
Remove the cover.
- Remove 3 x T6 screws holding the fan.

- Lift the fan and disconnect the connector by pulling gently straight up the wires.
- Remove 1x T6 screw at the bottom of the shroud (black plastic piece on the left of the fan).

-
Remove the shroud by holding the top right part with your fingers and turning it clockwise.

-
Remove 4 x T8 screws of the grill WIFI cover.

- The top of the grill is mounted under the Mac Mini case. Lift gently the bottom of the grill and pull towards yourself to remove the grill.
- Move the grill aside, you do not have to disconnect the WIFI sensor, just be careful.
2.1 Upgrading the RAM
The RAM is visible and accessible from the moment you remove the cover. Simply release each RAM by releasing the clips on the side. Once disengaged, the RAM will spring in a 45-degree angle. Remove it and put back the upgraded RAM at a 45 degree angle and push it down for it to clip.
2.2 Upgrading the SSD
It is important to note that the Mac Mini has 2 SSD bay. They are referred to as the “upper bay” and “lower bay”. Since we have flipped the Mac Mini upside down to remove the bottom cover, the “upper bay” is located under the “lower bay”.
The “upper bay” is mounted with an expansion kit that holds the SSD in position whereas the “lower bay” SSD is simply resting on top of the “upper bay” SSD.
One important aspect is that the connecting cables for the “lower bay” and “upper bay” SSD are not the same. The “upper bay” SSD connects on the logic board on the right and the “lower bay” SSD cable connects on the left. Removing the “upper bay” SSD requires removing the logic board therefore requires more work. It is recommended to install the new SSD in the “lower” bay. Here are the 2 scenarios:
1.Your Mac Mini has already a Hard Drive installed in the “lower” bay. In that case insert a credit card under the HD and gently pry it upwards. You will be able to slide it out of the bay. The reason to pry it gently is because since there is no “upper” bay drive, The HD is being held in the air by 2 screws on the side that are aligned in 2 holes in the Mac Mini case. Once the HD is removed, transfer the connecting cable and the 2 screws to the new SSD. To put back the new SSD, it is easier to rotate the Mac Mini 90 degree and have the mounting holes at the bottom and use the gravity to get the 2 mounting screws in the holes. After, connect the connector to the logic board.
- Your Mac Mini has already a Hard Drive installed in the “upper bay”? Leave it there, you do not need mounting screws, but you need a new connecting cable. You will have to buy a “lower bay connector”. Once installed on the SSD, slide the SSD on top of the original one. The connector will plug on the logic board on the left of the “upper bay” SSD connector.
A good preparation would be to go in “Disk Utility” menu on MacOS and search for “upper” or “lower” position before starting to disassemble.
Reassemble everything and you are done.
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ b17fccdf:b7211155
2025-02-01 18:41:27
@ b17fccdf:b7211155
2025-02-01 18:41:27Next new resources about the MiniBolt guide have been released:
- 🆕 Roadmap: LINK
- 🆕 Dynamic Network map: LINK
- 🆕 Nostr community: LINK < ~ REMOVE the "[]" symbols from the URL (naddr...) to access
- 🆕 Linktr FOSS (UC) by Gzuuus: LINK
- 🆕 Donate webpage: 🚾 Clearnet LINK || 🧅 Onion LINK
- 🆕 Contact email: hello@minibolt.info
Enjoy it MiniBolter! 💙
-
 @ 1cb14ab3:95d52462
2025-02-04 22:17:27
@ 1cb14ab3:95d52462
2025-02-04 22:17:27Chef's notes
Credit to The Yummy Life. Go show them love below: https://www.theyummylife.com/Pickled_Jalapeno_Peppers
Details
- ⏲️ Prep time: 1 hour
- 🍳 Cook time: 20 mins
- 🍽️ Servings: 4 mason jars (pint)
Ingredients
- 2 lbs. jalapenos
- 2-1/4 cups vinegar (white distilled, apple cider, or a combination of the two)
- 2-1/4 cups water
- 2 tablespoons sugar or honey (optional)
- ADD TO EACH PINT JAR
- 1/2 teaspoon kosher salt
- 1/2 teaspoon whole black pepper corns
- 1/4 teaspoon whole cumin seeds
- 1/4 teaspoon whole coriander seeds
- 1 bay leaf
- 1 whole garlic clove, peeled
- 1/8 teaspoon Pickle Crisp granules (optional)
Directions
- Slice 1/2 pound jalapenos into 1/8" rounds, discarding stem ends.
- Prepare the jars: Wash 4 pint jars and lids in hot sudsy water, then keep them warm.
- Prepare the pickling liquid: Combine 1/2 cup plus 1 tablespoon vinegar, 1/2 cup plus 1 tablespoon water, and 1-1/2 teaspoons sugar or honey (optional) in a 2 quart pan, heating until just before boiling.
- Fill the jars: Add jalapeno slices to each jar, pressing them down and packing them in compactly, then pour the hot pickling liquid into each jar, leaving 1/2" head space.
- Process and store: Allow jars to cool to room temperature, then store them in the refrigerator or can them using standard USDA water process canning procedures, following storage guidelines for refrigerator or canned pickled peppers.
-
 @ 1cb14ab3:95d52462
2025-02-04 21:42:24
@ 1cb14ab3:95d52462
2025-02-04 21:42:24Chef's notes
Classic beef n' broccoli. Easy to make and dank to eat.
Details
- ⏲️ Prep time: 20 mins
- 🍳 Cook time: 10 mins.
Ingredients
- 1 lb top sirloin steak, thinly sliced
- ¼ cup low sodium soy sauce
- 2 teaspoons cornstarch
- 1 tablespoon dark brown sugar
- 2 tablespoons fresh ginger, minced
- 1 tablespoon oil
- 1 head broccoli, cut into 1-inch (2 ½ cm) florets
- ½ cup water
- 3 cloves garlic, minced
- ¼ teaspoon red pepper flakes, optional
- 1 teaspoon toasted sesame oil
Directions
- In a medium bowl, mix together the sirloin steak, soy sauce, cornstarch, brown sugar, and ginger until the meat is evenly covered in the marinade. Set aside to marinate for 20 minutes.
- Heat the oil in a large skillet or wok over medium-high heat. Dump in the meat and marinade and sear each side until golden brown. Transfer the meat to a clean bowl and set aside.
- Place the broccoli into the hot skillet and sauté until the broccoli has just started to brown, about 1 minute. Pour the water into the skillet and immediately cover with a lid. Let it steam for 2 minutes, until the broccoli has softened.
- Remove the lid and toss in the garlic, red pepper flakes, and sesame oil. Sauté until the garlic becomes fragrant, about 30 seconds.
- Add the steak back into the pan and stir to combine. Remove from heat and serve on a bed of brown rice.
-
 @ a95c6243:d345522c
2025-01-31 20:02:25
@ a95c6243:d345522c
2025-01-31 20:02:25Im Augenblick wird mit größter Intensität, großer Umsicht \ das deutsche Volk belogen. \ Olaf Scholz im FAZ-Interview
Online-Wahlen stärken die Demokratie, sind sicher, und 61 Prozent der Wahlberechtigten sprechen sich für deren Einführung in Deutschland aus. Das zumindest behauptet eine aktuelle Umfrage, die auch über die Agentur Reuters Verbreitung in den Medien gefunden hat. Demnach würden außerdem 45 Prozent der Nichtwähler bei der Bundestagswahl ihre Stimme abgeben, wenn sie dies zum Beispiel von Ihrem PC, Tablet oder Smartphone aus machen könnten.
Die telefonische Umfrage unter gut 1000 wahlberechtigten Personen sei repräsentativ, behauptet der Auftraggeber – der Digitalverband Bitkom. Dieser präsentiert sich als eingetragener Verein mit einer beeindruckenden Liste von Mitgliedern, die Software und IT-Dienstleistungen anbieten. Erklärtes Vereinsziel ist es, «Deutschland zu einem führenden Digitalstandort zu machen und die digitale Transformation der deutschen Wirtschaft und Verwaltung voranzutreiben».
Durchgeführt hat die Befragung die Bitkom Servicegesellschaft mbH, also alles in der Familie. Die gleiche Erhebung hatte der Verband übrigens 2021 schon einmal durchgeführt. Damals sprachen sich angeblich sogar 63 Prozent für ein derartiges «Demokratie-Update» aus – die Tendenz ist demgemäß fallend. Dennoch orakelt mancher, der Gang zur Wahlurne gelte bereits als veraltet.
Die spanische Privat-Uni mit Globalisten-Touch, IE University, berichtete Ende letzten Jahres in ihrer Studie «European Tech Insights», 67 Prozent der Europäer befürchteten, dass Hacker Wahlergebnisse verfälschen könnten. Mehr als 30 Prozent der Befragten glaubten, dass künstliche Intelligenz (KI) bereits Wahlentscheidungen beeinflusst habe. Trotzdem würden angeblich 34 Prozent der unter 35-Jährigen einer KI-gesteuerten App vertrauen, um in ihrem Namen für politische Kandidaten zu stimmen.
Wie dauerhaft wird wohl das Ergebnis der kommenden Bundestagswahl sein? Diese Frage stellt sich angesichts der aktuellen Entwicklung der Migrations-Debatte und der (vorübergehend) bröckelnden «Brandmauer» gegen die AfD. Das «Zustrombegrenzungsgesetz» der Union hat das Parlament heute Nachmittag überraschenderweise abgelehnt. Dennoch muss man wohl kein ausgesprochener Pessimist sein, um zu befürchten, dass die Entscheidungen der Bürger von den selbsternannten Verteidigern der Demokratie künftig vielleicht nicht respektiert werden, weil sie nicht gefallen.
Bundesweit wird jetzt zu «Brandmauer-Demos» aufgerufen, die CDU gerät unter Druck und es wird von Übergriffen auf Parteibüros und Drohungen gegen Mitarbeiter berichtet. Sicherheitsbehörden warnen vor Eskalationen, die Polizei sei «für ein mögliches erhöhtes Aufkommen von Straftaten gegenüber Politikern und gegen Parteigebäude sensibilisiert».
Der Vorwand «unzulässiger Einflussnahme» auf Politik und Wahlen wird als Argument schon seit einiger Zeit aufgebaut. Der Manipulation schuldig befunden wird neben Putin und Trump auch Elon Musk, was lustigerweise ausgerechnet Bill Gates gerade noch einmal bekräftigt und als «völlig irre» bezeichnet hat. Man stelle sich die Diskussionen um die Gültigkeit von Wahlergebnissen vor, wenn es Online-Verfahren zur Stimmabgabe gäbe. In der Schweiz wird «E-Voting» seit einigen Jahren getestet, aber wohl bisher mit wenig Erfolg.
Die politische Brandstiftung der letzten Jahre zahlt sich immer mehr aus. Anstatt dringende Probleme der Menschen zu lösen – zu denen auch in Deutschland die weit verbreitete Armut zählt –, hat die Politik konsequent polarisiert und sich auf Ausgrenzung und Verhöhnung großer Teile der Bevölkerung konzentriert. Basierend auf Ideologie und Lügen werden abweichende Stimmen unterdrückt und kriminalisiert, nicht nur und nicht erst in diesem Augenblick. Die nächsten Wochen dürften ausgesprochen spannend werden.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2025-01-24 20:59:01
@ a95c6243:d345522c
2025-01-24 20:59:01Menschen tun alles, egal wie absurd, \ um ihrer eigenen Seele nicht zu begegnen. \ Carl Gustav Jung
«Extremer Reichtum ist eine Gefahr für die Demokratie», sagen über die Hälfte der knapp 3000 befragten Millionäre aus G20-Staaten laut einer Umfrage der «Patriotic Millionaires». Ferner stellte dieser Zusammenschluss wohlhabender US-Amerikaner fest, dass 63 Prozent jener Millionäre den Einfluss von Superreichen auf US-Präsident Trump als Bedrohung für die globale Stabilität ansehen.
Diese Besorgnis haben 370 Millionäre und Milliardäre am Dienstag auch den in Davos beim WEF konzentrierten Privilegierten aus aller Welt übermittelt. In einem offenen Brief forderten sie die «gewählten Führer» auf, die Superreichen – also sie selbst – zu besteuern, um «die zersetzenden Auswirkungen des extremen Reichtums auf unsere Demokratien und die Gesellschaft zu bekämpfen». Zum Beispiel kontrolliere eine handvoll extrem reicher Menschen die Medien, beeinflusse die Rechtssysteme in unzulässiger Weise und verwandele Recht in Unrecht.
Schon 2019 beanstandete der bekannte Historiker und Schriftsteller Ruthger Bregman an einer WEF-Podiumsdiskussion die Steuervermeidung der Superreichen. Die elitäre Veranstaltung bezeichnete er als «Feuerwehr-Konferenz, bei der man nicht über Löschwasser sprechen darf.» Daraufhin erhielt Bregman keine Einladungen nach Davos mehr. Auf seine Aussagen machte der Schweizer Aktivist Alec Gagneux aufmerksam, der sich seit Jahrzehnten kritisch mit dem WEF befasst. Ihm wurde kürzlich der Zutritt zu einem dreiteiligen Kurs über das WEF an der Volkshochschule Region Brugg verwehrt.
Nun ist die Erkenntnis, dass mit Geld politischer Einfluss einhergeht, alles andere als neu. Und extremer Reichtum macht die Sache nicht wirklich besser. Trotzdem hat man über Initiativen wie Patriotic Millionaires oder Taxmenow bisher eher selten etwas gehört, obwohl es sie schon lange gibt. Auch scheint es kein Problem, wenn ein Herr Gates fast im Alleingang versucht, globale Gesundheits-, Klima-, Ernährungs- oder Bevölkerungspolitik zu betreiben – im Gegenteil. Im Jahr, als der Milliardär Donald Trump zum zweiten Mal ins Weiße Haus einzieht, ist das Echo in den Gesinnungsmedien dagegen enorm – und uniform, wer hätte das gedacht.
Der neue US-Präsident hat jedoch «Davos geerdet», wie Achgut es nannte. In seiner kurzen Rede beim Weltwirtschaftsforum verteidigte er seine Politik und stellte klar, er habe schlicht eine «Revolution des gesunden Menschenverstands» begonnen. Mit deutlichen Worten sprach er unter anderem von ersten Maßnahmen gegen den «Green New Scam», und von einem «Erlass, der jegliche staatliche Zensur beendet»:
«Unsere Regierung wird die Äußerungen unserer eigenen Bürger nicht mehr als Fehlinformation oder Desinformation bezeichnen, was die Lieblingswörter von Zensoren und derer sind, die den freien Austausch von Ideen und, offen gesagt, den Fortschritt verhindern wollen.»
Wie der «Trumpismus» letztlich einzuordnen ist, muss jeder für sich selbst entscheiden. Skepsis ist definitiv angebracht, denn «einer von uns» sind weder der Präsident noch seine auserwählten Teammitglieder. Ob sie irgendeinen Sumpf trockenlegen oder Staatsverbrechen aufdecken werden oder was aus WHO- und Klimaverträgen wird, bleibt abzuwarten.
Das WHO-Dekret fordert jedenfalls die Übertragung der Gelder auf «glaubwürdige Partner», die die Aktivitäten übernehmen könnten. Zufällig scheint mit «Impfguru» Bill Gates ein weiterer Harris-Unterstützer kürzlich das Lager gewechselt zu haben: Nach einem gemeinsamen Abendessen zeigte er sich «beeindruckt» von Trumps Interesse an der globalen Gesundheit.
Mit dem Projekt «Stargate» sind weitere dunkle Wolken am Erwartungshorizont der Fangemeinde aufgezogen. Trump hat dieses Joint Venture zwischen den Konzernen OpenAI, Oracle, und SoftBank als das «größte KI-Infrastrukturprojekt der Geschichte» angekündigt. Der Stein des Anstoßes: Oracle-CEO Larry Ellison, der auch Fan von KI-gestützter Echtzeit-Überwachung ist, sieht einen weiteren potenziellen Einsatz der künstlichen Intelligenz. Sie könne dazu dienen, Krebserkrankungen zu erkennen und individuelle mRNA-«Impfstoffe» zur Behandlung innerhalb von 48 Stunden zu entwickeln.
Warum bitte sollten sich diese superreichen «Eliten» ins eigene Fleisch schneiden und direkt entgegen ihren eigenen Interessen handeln? Weil sie Menschenfreunde, sogenannte Philanthropen sind? Oder vielleicht, weil sie ein schlechtes Gewissen haben und ihre Schuld kompensieren müssen? Deswegen jedenfalls brauchen «Linke» laut Robert Willacker, einem deutschen Politikberater mit brasilianischen Wurzeln, rechte Parteien – ein ebenso überraschender wie humorvoller Erklärungsansatz.
Wenn eine Krähe der anderen kein Auge aushackt, dann tut sie das sich selbst noch weniger an. Dass Millionäre ernsthaft ihre eigene Besteuerung fordern oder Machteliten ihren eigenen Einfluss zugunsten anderer einschränken würden, halte ich für sehr unwahrscheinlich. So etwas glaube ich erst, wenn zum Beispiel die Rüstungsindustrie sich um Friedensverhandlungen bemüht, die Pharmalobby sich gegen institutionalisierte Korruption einsetzt, Zentralbanken ihre CBDC-Pläne für Bitcoin opfern oder der ÖRR die Abschaffung der Rundfunkgebühren fordert.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 21ffd29c:518a8ff5
2025-02-04 21:12:15
@ 21ffd29c:518a8ff5
2025-02-04 21:12:15- What Are Homestead Chickens?
Homestead chickens are domesticated fowl kept by homeowners to provide eggs and companionship. They play a vital role in the homestead ecosystem.
Why Water is Essential in Cold Weather - Hydration Basics:
Chickens don't drink much water naturally but need it for hydration, especially during cold weather when metabolic rates increase. - Environmental Factors:
Cold weather can lead to ice buildup on water sources. Chickens benefit from having access to fresh water year-round.Maintaining Accessible Water Sources - Shallow Troughs:
Use shallow troughs instead of deep containers to minimize ice formation and ensure constant water supply. - Automatic Feeders:
Consider installing automatic feeders for convenience, especially in unpredictable weather conditions. - Multiple Water Sources:
Provide multiple water sources to prevent competition and ensure all chickens have access.Preventing Ice Buildup - Floating Shallow Troughs:
Opt for troughs that sit above the ground to avoid ice buildup. Ensure they're placed where they can't freeze completely. - Regular Checks:
Inspect water sources regularly to remove ice and debris, maintaining accessibility for chickens.Best Practices for Watering Chickens - Waterers Designed for Cold Weather:
Use waterers made of stainless steel or plastic that can withstand cold temperatures. - Seasonal Adjustments:
During extreme cold spells, supplement with a small amount of fresh water to aid in drinking.Conclusion - Key Takeaways:
Providing proper water is crucial for the health and well-being of homestead chickens during cold weather. Maintaining accessible, shallow water sources prevents issues like ice buildup and ensures hydration.Final Thoughts - Sustainability Considerations:
While chickens don't drink much, ensuring they have water supports their overall health and sustainability efforts. - Environmental Impact:
Thoughtful water management can reduce water usage, promoting eco-friendly practices on the homestead. - What Are Homestead Chickens?
-
 @ bf6e4fe1:46d21f26
2025-01-31 01:51:03
@ bf6e4fe1:46d21f26
2025-01-31 01:51:03{"title":"test","content":"test"}
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ c631e267:c2b78d3e
2025-01-18 09:34:51
@ c631e267:c2b78d3e
2025-01-18 09:34:51Die grauenvollste Aussicht ist die der Technokratie – \ einer kontrollierenden Herrschaft, \ die durch verstümmelte und verstümmelnde Geister ausgeübt wird. \ Ernst Jünger
«Davos ist nicht mehr sexy», das Weltwirtschaftsforum (WEF) mache Davos kaputt, diese Aussagen eines Einheimischen las ich kürzlich in der Handelszeitung. Während sich einige vor Ort enorm an der «teuersten Gewerbeausstellung der Welt» bereicherten, würden die negativen Begleiterscheinungen wie Wohnungsnot und Niedergang der lokalen Wirtschaft immer deutlicher.
Nächsten Montag beginnt in dem Schweizer Bergdorf erneut ein Jahrestreffen dieses elitären Clubs der Konzerne, bei dem man mit hochrangigen Politikern aus aller Welt und ausgewählten Vertretern der Systemmedien zusammenhocken wird. Wie bereits in den vergangenen vier Jahren wird die Präsidentin der EU-Kommission, Ursula von der Leyen, in Begleitung von Klaus Schwab ihre Grundsatzansprache halten.
Der deutsche WEF-Gründer hatte bei dieser Gelegenheit immer höchst lobende Worte für seine Landsmännin: 2021 erklärte er sich «stolz, dass Europa wieder unter Ihrer Führung steht» und 2022 fand er es bemerkenswert, was sie erreicht habe angesichts des «erstaunlichen Wandels», den die Welt in den vorangegangenen zwei Jahren erlebt habe; es gebe nun einen «neuen europäischen Geist».
Von der Leyens Handeln während der sogenannten Corona-«Pandemie» lobte Schwab damals bereits ebenso, wie es diese Woche das Karlspreis-Direktorium tat, als man der Beschuldigten im Fall Pfizergate die diesjährige internationale Auszeichnung «für Verdienste um die europäische Einigung» verlieh. Außerdem habe sie die EU nicht nur gegen den «Aggressor Russland», sondern auch gegen die «innere Bedrohung durch Rassisten und Demagogen» sowie gegen den Klimawandel verteidigt.
Jene Herausforderungen durch «Krisen epochalen Ausmaßes» werden indes aus dem Umfeld des WEF nicht nur herbeigeredet – wie man alljährlich zur Zeit des Davoser Treffens im Global Risks Report nachlesen kann, der zusammen mit dem Versicherungskonzern Zurich erstellt wird. Seit die Globalisten 2020/21 in der Praxis gesehen haben, wie gut eine konzertierte und konsequente Angst-Kampagne funktionieren kann, geht es Schlag auf Schlag. Sie setzen alles daran, Schwabs goldenes Zeitfenster des «Great Reset» zu nutzen.
Ziel dieses «großen Umbruchs» ist die totale Kontrolle der Technokraten über die Menschen unter dem Deckmantel einer globalen Gesundheitsfürsorge. Wie aber könnte man so etwas erreichen? Ein Mittel dazu ist die «kreative Zerstörung». Weitere unabdingbare Werkzeug sind die Einbindung, ja Gleichschaltung der Medien und der Justiz.
Ein «Great Mental Reset» sei die Voraussetzung dafür, dass ein Großteil der Menschen Einschränkungen und Manipulationen wie durch die Corona-Maßnahmen praktisch kritik- und widerstandslos hinnehme, sagt der Mediziner und Molekulargenetiker Michael Nehls. Er meint damit eine regelrechte Umprogrammierung des Gehirns, wodurch nach und nach unsere Individualität und unser soziales Bewusstsein eliminiert und durch unreflektierten Konformismus ersetzt werden.
Der aktuelle Zustand unserer Gesellschaften ist auch für den Schweizer Rechtsanwalt Philipp Kruse alarmierend. Durch den Umgang mit der «Pandemie» sieht er die Grundlagen von Recht und Vernunft erschüttert, die Rechtsstaatlichkeit stehe auf dem Prüfstand. Seiner dringenden Mahnung an alle Bürger, die Prinzipien von Recht und Freiheit zu verteidigen, kann ich mich nur anschließen.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 1cb14ab3:95d52462
2025-02-04 18:40:56
@ 1cb14ab3:95d52462
2025-02-04 18:40:56What is it?
I stumbled upon the Elgato Stream Deck while aimlessly browsing the web, and I was instantly intrigued. But one question kept nagging me—how would I use this, and why do I even need it?
I don’t stream.
At first glance, it seemed like just another gadget to clutter my already cramped desk in my tiny Shanghai apartment. But curiosity got the best of me. After some research, I decided to give it a shot and see what all the hype was about.
And wow—was that hype justified.
This isn’t a deep-dive review covering every feature (there are plenty of those online). Instead, I want to share some of the workflows I’ve set up and hopefully get you thinking about the endless possibilities you could create with a Stream Deck.
If you’re someone who loves making computer tasks easier but struggles to remember keyboard shortcuts beyond Ctrl + V, this little device might just change the way you work.
Launching Apps and Websites

I won’t lie—my favorite use for the Stream Deck is the sheer convenience of pressing a button and instantly launching what I need.
Want to watch YouTube? Button.
Open Photoshop? Button.
Play a game? Button.
Check Bitcoin prices? Those are always on the display.


Sure, it’s a small thing, but the speed and ease of launching apps or navigating to websites make a surprising difference. What used to be a few clicks and keystrokes is now a single tap.
After using the Stream Deck for a while, my laptop feels... clunky. I’ve genuinely noticed an increase in my productivity and focus.
Custom Application Profiles
One of the most powerful features of the Stream Deck is its ability to switch profiles based on the application you’re using.
This means that every time you switch programs, the buttons automatically adjust to show relevant shortcuts and commands. It’s a game-changer for software with hundreds of keyboard shortcuts, making multitasking seamless.
I’ll admit—setting up custom profiles can be a bit time-consuming. The good news? You don’t have to start from scratch. There are tons of downloadable third-party profiles for popular programs like Illustrator, Photoshop, Final Cut Pro, DaVinci Resolve, Microsoft Office, and Ableton.

If your favorite app doesn’t have a pre-made profile, you can always build your own. It takes some effort, but once it's set up, the workflow improvements are worth it.
Music and Audio Control

I use an audio interface for lossless wired playback and external microphone support. The Stream Deck makes switching between my computer’s default mic and my studio mic effortless—no more digging through system preferences.
Even if you don’t use external audio gear, the Stream Deck still has plenty of value for music lovers.

It integrates with Apple Music and Spotify, letting you control playback, skip tracks, like songs, and add them to playlists—all without switching apps. Elgato is constantly adding new third-party integrations, which gives the device even more longevity.
Lighting and Smart Home Control
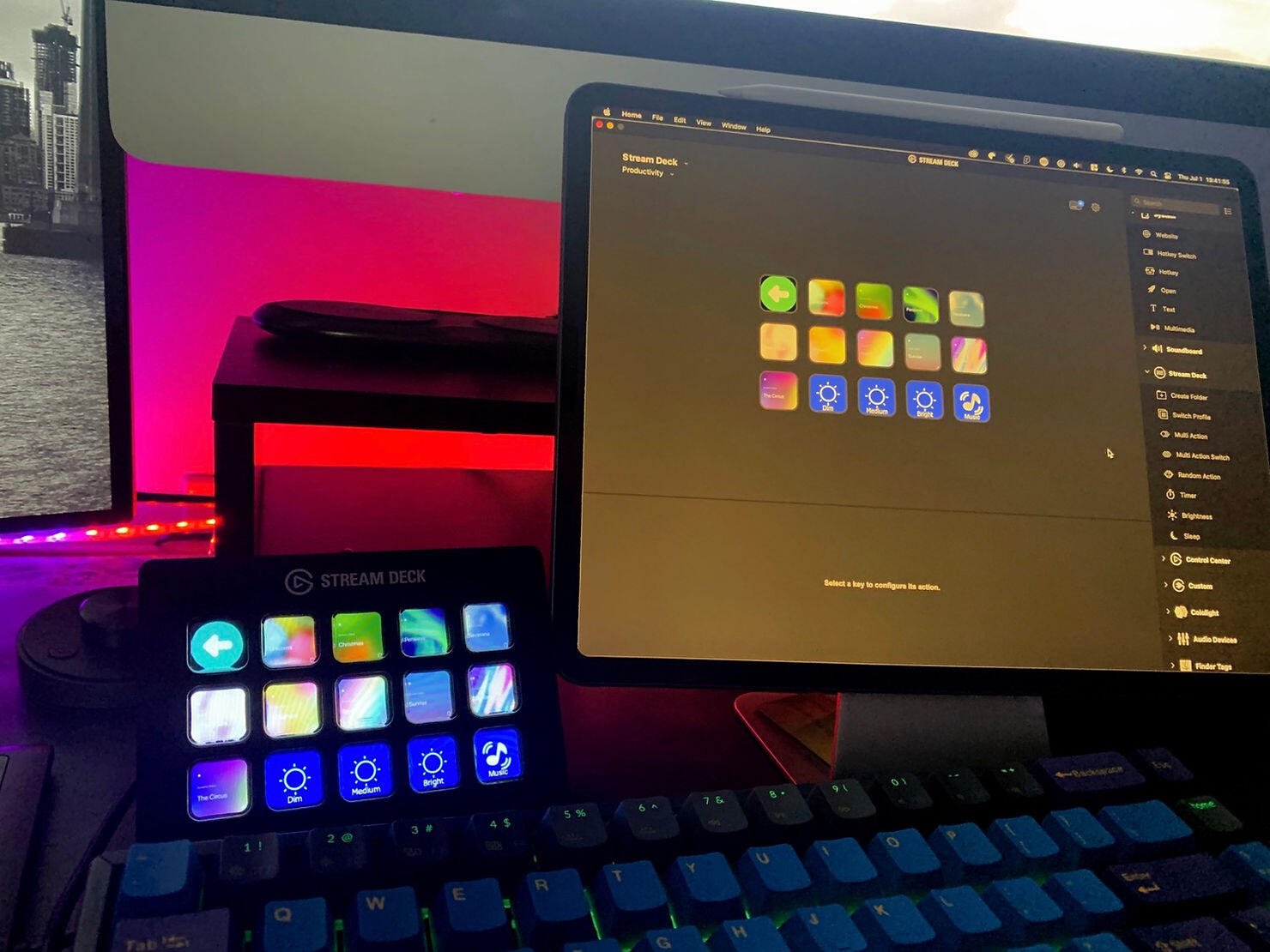
If you have smart home devices, the Stream Deck can act as a command center. It integrates with platforms like Philips Hue, LIFX, Nanoleaf, and IFTTT, letting you control lights, scenes, and colors with a single tap.
Want to set the mood for gaming, reading, or watching a movie? Done.
You can even use it to trigger other smart devices, like cameras, thermostats, or speakers, using IFTTT applets. The possibilities here are endless.
Finder and Document Shortcuts
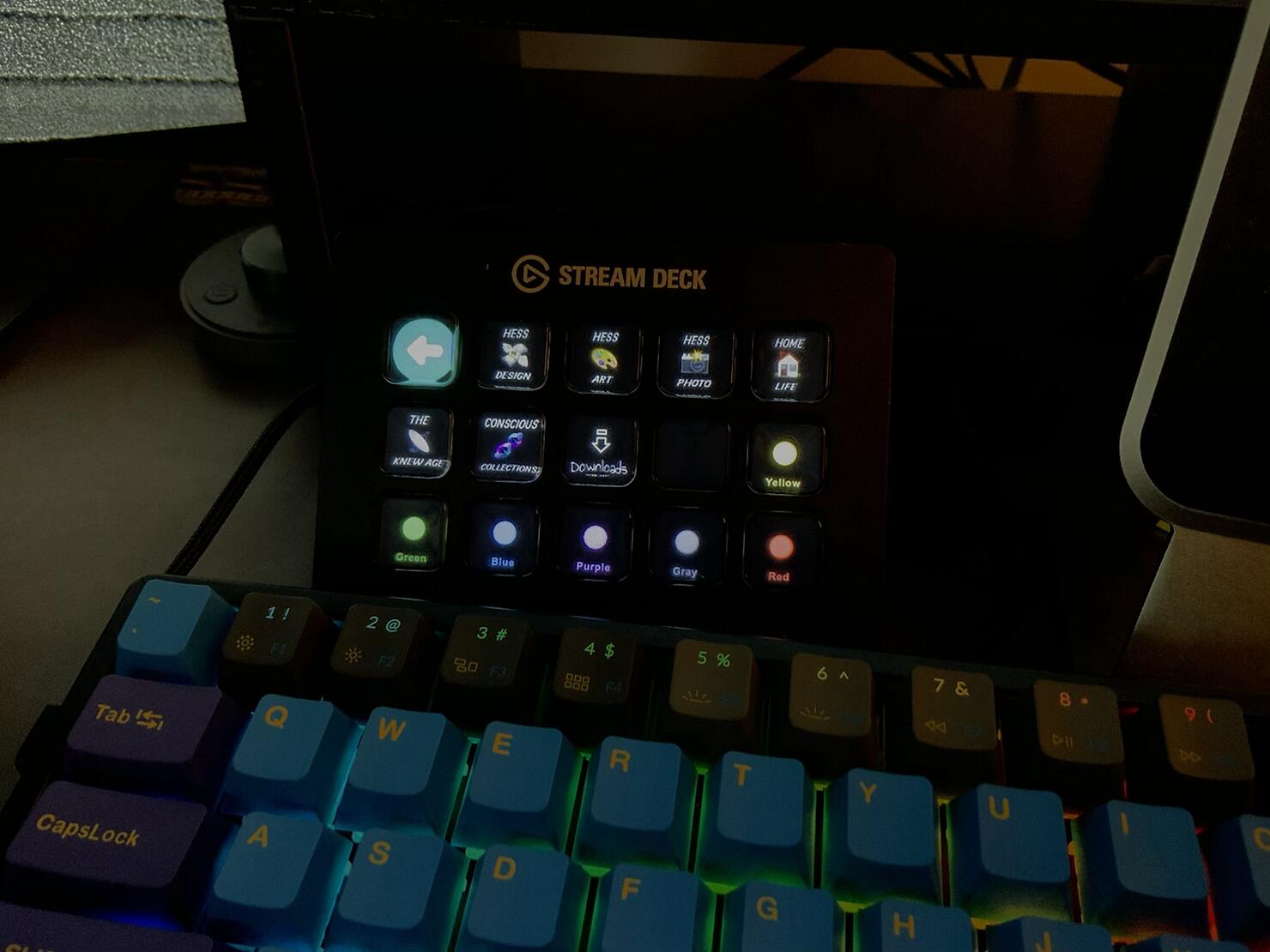
One of the most unexpectedly useful features for me has been quick access to folders and files.
I’ve set up buttons for my most frequently used folders—Downloads, Desktop, and Documents—so I can access them instantly. I’ve also created buttons for specific files like spreadsheets and PDFs, so I don’t have to dig through folders to find them.
It sounds simple, but when juggling multiple projects, these little time-savers add up fast.
Final Thoughts
The Elgato Stream Deck is a surprisingly versatile tool that enhances productivity, creativity, and entertainment. Whether you’re launching apps, controlling music, managing smart devices, or creating complex workflows, it streamlines everyday tasks in a way that’s hard to go back from.
At first, I thought it was just for streamers. Now? I can’t imagine working without it.
I hope this post gives you some ideas on how to make the most of a Stream Deck. If you have any questions or thoughts, drop a comment below.
Thanks for reading!
Feel free to support me by grabbing one through my affiliate link below:
More from Hes
Originally published in 2022. All images are credit of Hes, but you are free to download and use for any purpose. If you find joy from my art, please feel free to send a zap. Enjoy life on a Bitcoin standard.
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ a95c6243:d345522c
2025-01-13 10:09:57
@ a95c6243:d345522c
2025-01-13 10:09:57Ich begann, Social Media aufzubauen, \ um den Menschen eine Stimme zu geben. \ Mark Zuckerberg
Sind euch auch die Tränen gekommen, als ihr Mark Zuckerbergs Wendehals-Deklaration bezüglich der Meinungsfreiheit auf seinen Portalen gehört habt? Rührend, oder? Während er früher die offensichtliche Zensur leugnete und später die Regierung Biden dafür verantwortlich machte, will er nun angeblich «die Zensur auf unseren Plattformen drastisch reduzieren».
«Purer Opportunismus» ob des anstehenden Regierungswechsels wäre als Klassifizierung viel zu kurz gegriffen. Der jetzige Schachzug des Meta-Chefs ist genauso Teil einer kühl kalkulierten Business-Strategie, wie es die 180 Grad umgekehrte Praxis vorher war. Social Media sind ein höchst lukratives Geschäft. Hinzu kommt vielleicht noch ein bisschen verkorkstes Ego, weil derartig viel Einfluss und Geld sicher auch auf die Psyche schlagen. Verständlich.
«Es ist an der Zeit, zu unseren Wurzeln der freien Meinungsäußerung auf Facebook und Instagram zurückzukehren. Ich begann, Social Media aufzubauen, um den Menschen eine Stimme zu geben», sagte Zuckerberg.
Welche Wurzeln? Hat der Mann vergessen, dass er von der Überwachung, dem Ausspionieren und dem Ausverkauf sämtlicher Daten und digitaler Spuren sowie der Manipulation seiner «Kunden» lebt? Das ist knallharter Kommerz, nichts anderes. Um freie Meinungsäußerung geht es bei diesem Geschäft ganz sicher nicht, und das war auch noch nie so. Die Wurzeln von Facebook liegen in einem Projekt des US-Militärs mit dem Namen «LifeLog». Dessen Ziel war es, «ein digitales Protokoll vom Leben eines Menschen zu erstellen».
Der Richtungswechsel kommt allerdings nicht überraschend. Schon Anfang Dezember hatte Meta-Präsident Nick Clegg von «zu hoher Fehlerquote bei der Moderation» von Inhalten gesprochen. Bei der Gelegenheit erwähnte er auch, dass Mark sehr daran interessiert sei, eine aktive Rolle in den Debatten über eine amerikanische Führungsrolle im technologischen Bereich zu spielen.
Während Milliardärskollege und Big Tech-Konkurrent Elon Musk bereits seinen Posten in der kommenden Trump-Regierung in Aussicht hat, möchte Zuckerberg also nicht nur seine Haut retten – Trump hatte ihn einmal einen «Feind des Volkes» genannt und ihm lebenslange Haft angedroht –, sondern am liebsten auch mitspielen. KI-Berater ist wohl die gewünschte Funktion, wie man nach einem Treffen Trump-Zuckerberg hörte. An seine Verhaftung dachte vermutlich auch ein weiterer Multimilliardär mit eigener Social Media-Plattform, Pavel Durov, als er Zuckerberg jetzt kritisierte und gleichzeitig warnte.
Politik und Systemmedien drehen jedenfalls durch – was zu viel ist, ist zu viel. Etwas weniger Zensur und mehr Meinungsfreiheit würden die Freiheit der Bürger schwächen und seien potenziell vernichtend für die Menschenrechte. Zuckerberg setze mit dem neuen Kurs die Demokratie aufs Spiel, das sei eine «Einladung zum nächsten Völkermord», ernsthaft. Die Frage sei, ob sich die EU gegen Musk und Zuckerberg behaupten könne, Brüssel müsse jedenfalls hart durchgreifen.
Auch um die Faktenchecker macht man sich Sorgen. Für die deutsche Nachrichtenagentur dpa und die «Experten» von Correctiv, die (noch) Partner für Fact-Checking-Aktivitäten von Facebook sind, sei das ein «lukratives Geschäftsmodell». Aber möglicherweise werden die Inhalte ohne diese vermeintlichen Korrektoren ja sogar besser. Anders als Meta wollen jedoch Scholz, Faeser und die Tagesschau keine Fehler zugeben und zum Beispiel Correctiv-Falschaussagen einräumen.
Bei derlei dramatischen Befürchtungen wundert es nicht, dass der öffentliche Plausch auf X zwischen Elon Musk und AfD-Chefin Alice Weidel von 150 EU-Beamten überwacht wurde, falls es irgendwelche Rechtsverstöße geben sollte, die man ihnen ankreiden könnte. Auch der Deutsche Bundestag war wachsam. Gefunden haben dürften sie nichts. Das Ganze war eher eine Show, viel Wind wurde gemacht, aber letztlich gab es nichts als heiße Luft.
Das Anbiedern bei Donald Trump ist indes gerade in Mode. Die Weltgesundheitsorganisation (WHO) tut das auch, denn sie fürchtet um Spenden von über einer Milliarde Dollar. Eventuell könnte ja Elon Musk auch hier künftig aushelfen und der Organisation sowie deren größtem privaten Förderer, Bill Gates, etwas unter die Arme greifen. Nachdem Musks KI-Projekt xAI kürzlich von BlackRock & Co. sechs Milliarden eingestrichen hat, geht da vielleicht etwas.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ b8851a06:9b120ba1
2025-01-28 21:34:54
@ b8851a06:9b120ba1
2025-01-28 21:34:54Private property isn’t lines on dirt or fences of steel—it’s the crystallization of human sovereignty. Each boundary drawn is a silent declaration: This is where my will meets yours, where creation clashes against chaos. What we defend as “mine” or “yours” is no mere object but a metaphysical claim, a scaffold for the unfathomable complexity of voluntary exchange.
Markets breathe only when individuals anchor their choices in the inviolable. Without property, there is no negotiation—only force. No trade—only taking. The deed to land, the title to a car, the seed of an idea: these are not static things but frontiers of being, where human responsibility collides with the infinite permutations of value.
Austrian economics whispers what existentialism shouts: existence precedes essence. Property isn’t granted by systems; it’s asserted through action, defended through sacrifice, and sanctified through mutual recognition. A thing becomes “owned” only when a mind declares it so, and others—through reason or respect—refrain from crossing that unseen line.
Bitcoin? The purest ledger of this truth. A string of code, yes—but one that mirrors the unyielding logic of property itself: scarce, auditable, unconquerable. It doesn’t ask permission. It exists because sovereign minds choose it to.
Sigh. #nostr
I love #Bitcoin. -
 @ a95c6243:d345522c
2025-01-03 20:26:47
@ a95c6243:d345522c
2025-01-03 20:26:47Was du bist hängt von drei Faktoren ab: \ Was du geerbt hast, \ was deine Umgebung aus dir machte \ und was du in freier Wahl \ aus deiner Umgebung und deinem Erbe gemacht hast. \ Aldous Huxley
Das brave Mitmachen und Mitlaufen in einem vorgegebenen, recht engen Rahmen ist gewiss nicht neu, hat aber gerade wieder mal Konjunktur. Dies kann man deutlich beobachten, eigentlich egal, in welchem gesellschaftlichen Bereich man sich umschaut. Individualität ist nur soweit angesagt, wie sie in ein bestimmtes Schema von «Diversität» passt, und Freiheit verkommt zur Worthülse – nicht erst durch ein gewisses Buch einer gewissen ehemaligen Regierungschefin.
Erklärungsansätze für solche Entwicklungen sind bekannt, und praktisch alle haben etwas mit Massenpsychologie zu tun. Der Herdentrieb, also der Trieb der Menschen, sich – zum Beispiel aus Unsicherheit oder Bequemlichkeit – lieber der Masse anzuschließen als selbstständig zu denken und zu handeln, ist einer der Erklärungsversuche. Andere drehen sich um Macht, Propaganda, Druck und Angst, also den gezielten Einsatz psychologischer Herrschaftsinstrumente.
Aber wollen die Menschen überhaupt Freiheit? Durch Gespräche im privaten Umfeld bin ich diesbezüglich in der letzten Zeit etwas skeptisch geworden. Um die Jahreswende philosophiert man ja gerne ein wenig über das Erlebte und über die Erwartungen für die Zukunft. Dabei hatte ich hin und wieder den Eindruck, die totalitären Anwandlungen unserer «Repräsentanten» kämen manchen Leuten gerade recht.
«Desinformation» ist so ein brisantes Thema. Davor müsse man die Menschen doch schützen, hörte ich. Jemand müsse doch zum Beispiel diese ganzen merkwürdigen Inhalte in den Social Media filtern – zur Ukraine, zum Klima, zu Gesundheitsthemen oder zur Migration. Viele wüssten ja gar nicht einzuschätzen, was richtig und was falsch ist, sie bräuchten eine Führung.
Freiheit bedingt Eigenverantwortung, ohne Zweifel. Eventuell ist es einigen tatsächlich zu anspruchsvoll, die Verantwortung für das eigene Tun und Lassen zu übernehmen. Oder die persönliche Freiheit wird nicht als ausreichend wertvolles Gut angesehen, um sich dafür anzustrengen. In dem Fall wäre die mangelnde Selbstbestimmung wohl das kleinere Übel. Allerdings fehlt dann gemäß Aldous Huxley ein Teil der Persönlichkeit. Letztlich ist natürlich alles eine Frage der Abwägung.
Sind viele Menschen möglicherweise schon so «eingenordet», dass freiheitliche Ambitionen gar nicht für eine ganze Gruppe, ein Kollektiv, verfolgt werden können? Solche Gedanken kamen mir auch, als ich mir kürzlich diverse Talks beim viertägigen Hacker-Kongress des Chaos Computer Clubs (38C3) anschaute. Ich war nicht nur überrascht, sondern reichlich erschreckt angesichts der in weiten Teilen mainstream-geformten Inhalte, mit denen ein dankbares Publikum beglückt wurde. Wo ich allgemein hellere Köpfe erwartet hatte, fand ich Konformismus und enthusiastisch untermauerte Narrative.
Gibt es vielleicht so etwas wie eine Herdenimmunität gegen Indoktrination? Ich denke, ja, zumindest eine gestärkte Widerstandsfähigkeit. Was wir brauchen, sind etwas gesunder Menschenverstand, offene Informationskanäle und der Mut, sich freier auch zwischen den Herden zu bewegen. Sie tun das bereits, aber sagen Sie es auch dieses Jahr ruhig weiter.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2025-01-01 17:39:51
@ a95c6243:d345522c
2025-01-01 17:39:51Heute möchte ich ein Gedicht mit euch teilen. Es handelt sich um eine Ballade des österreichischen Lyrikers Johann Gabriel Seidl aus dem 19. Jahrhundert. Mir sind diese Worte fest in Erinnerung, da meine Mutter sie perfekt rezitieren konnte, auch als die Kräfte schon langsam schwanden.
Dem originalen Titel «Die Uhr» habe ich für mich immer das Wort «innere» hinzugefügt. Denn der Zeitmesser – hier vermutliche eine Taschenuhr – symbolisiert zwar in dem Kontext das damalige Zeitempfinden und die Umbrüche durch die industrielle Revolution, sozusagen den Zeitgeist und das moderne Leben. Aber der Autor setzt sich philosophisch mit der Zeit auseinander und gibt seinem Werk auch eine klar spirituelle Dimension.
Das Ticken der Uhr und die Momente des Glücks und der Trauer stehen sinnbildlich für das unaufhaltsame Fortschreiten und die Vergänglichkeit des Lebens. Insofern könnte man bei der Uhr auch an eine Sonnenuhr denken. Der Rhythmus der Ereignisse passt uns vielleicht nicht immer in den Kram.
Was den Takt pocht, ist durchaus auch das Herz, unser «inneres Uhrwerk». Wenn dieses Meisterwerk einmal stillsteht, ist es unweigerlich um uns geschehen. Hoffentlich können wir dann dankbar sagen: «Ich habe mein Bestes gegeben.»
Ich trage, wo ich gehe, stets eine Uhr bei mir; \ Wieviel es geschlagen habe, genau seh ich an ihr. \ Es ist ein großer Meister, der künstlich ihr Werk gefügt, \ Wenngleich ihr Gang nicht immer dem törichten Wunsche genügt.
Ich wollte, sie wäre rascher gegangen an manchem Tag; \ Ich wollte, sie hätte manchmal verzögert den raschen Schlag. \ In meinen Leiden und Freuden, in Sturm und in der Ruh, \ Was immer geschah im Leben, sie pochte den Takt dazu.
Sie schlug am Sarge des Vaters, sie schlug an des Freundes Bahr, \ Sie schlug am Morgen der Liebe, sie schlug am Traualtar. \ Sie schlug an der Wiege des Kindes, sie schlägt, will's Gott, noch oft, \ Wenn bessere Tage kommen, wie meine Seele es hofft.
Und ward sie auch einmal träger, und drohte zu stocken ihr Lauf, \ So zog der Meister immer großmütig sie wieder auf. \ Doch stände sie einmal stille, dann wär's um sie geschehn, \ Kein andrer, als der sie fügte, bringt die Zerstörte zum Gehn.
Dann müßt ich zum Meister wandern, der wohnt am Ende wohl weit, \ Wohl draußen, jenseits der Erde, wohl dort in der Ewigkeit! \ Dann gäb ich sie ihm zurücke mit dankbar kindlichem Flehn: \ Sieh, Herr, ich hab nichts verdorben, sie blieb von selber stehn.
Johann Gabriel Seidl (1804-1875)
-
 @ a95c6243:d345522c
2024-12-21 09:54:49
@ a95c6243:d345522c
2024-12-21 09:54:49Falls du beim Lesen des Titels dieses Newsletters unwillkürlich an positive Neuigkeiten aus dem globalen polit-medialen Irrenhaus oder gar aus dem wirtschaftlichen Umfeld gedacht hast, darf ich dich beglückwünschen. Diese Assoziation ist sehr löblich, denn sie weist dich als unverbesserlichen Optimisten aus. Leider muss ich dich diesbezüglich aber enttäuschen. Es geht hier um ein anderes Thema, allerdings sehr wohl ein positives, wie ich finde.
Heute ist ein ganz besonderer Tag: die Wintersonnenwende. Genau gesagt hat heute morgen um 10:20 Uhr Mitteleuropäischer Zeit (MEZ) auf der Nordhalbkugel unseres Planeten der astronomische Winter begonnen. Was daran so außergewöhnlich ist? Der kürzeste Tag des Jahres war gestern, seit heute werden die Tage bereits wieder länger! Wir werden also jetzt jeden Tag ein wenig mehr Licht haben.
Für mich ist dieses Ereignis immer wieder etwas kurios: Es beginnt der Winter, aber die Tage werden länger. Das erscheint mir zunächst wie ein Widerspruch, denn meine spontanen Assoziationen zum Winter sind doch eher Kälte und Dunkelheit, relativ zumindest. Umso erfreulicher ist der emotionale Effekt, wenn dann langsam die Erkenntnis durchsickert: Ab jetzt wird es schon wieder heller!
Natürlich ist es kalt im Winter, mancherorts mehr als anderswo. Vielleicht jedoch nicht mehr lange, wenn man den Klimahysterikern glauben wollte. Mindestens letztes Jahr hat Väterchen Frost allerdings gleich zu Beginn seiner Saison – und passenderweise während des globalen Überhitzungsgipfels in Dubai – nochmal richtig mit der Faust auf den Tisch gehauen. Schnee- und Eischaos sind ja eigentlich in der Agenda bereits nicht mehr vorgesehen. Deswegen war man in Deutschland vermutlich in vorauseilendem Gehorsam schon nicht mehr darauf vorbereitet und wurde glatt lahmgelegt.
Aber ich schweife ab. Die Aussicht auf nach und nach mehr Licht und damit auch Wärme stimmt mich froh. Den Zusammenhang zwischen beidem merkt man in Andalusien sehr deutlich. Hier, wo die Häuser im Winter arg auskühlen, geht man zum Aufwärmen raus auf die Straße oder auf den Balkon. Die Sonne hat auch im Winter eine erfreuliche Kraft. Und da ist jede Minute Gold wert.
Außerdem ist mir vor Jahren so richtig klar geworden, warum mir das südliche Klima so sehr gefällt. Das liegt nämlich nicht nur an der Sonne als solcher, oder der Wärme – das liegt vor allem am Licht. Ohne Licht keine Farben, das ist der ebenso simple wie gewaltige Unterschied zwischen einem deprimierenden matschgraubraunen Winter und einem fröhlichen bunten. Ein großes Stück Lebensqualität.
Mir gefällt aber auch die Symbolik dieses Tages: Licht aus der Dunkelheit, ein Wendepunkt, ein Neuanfang, neue Möglichkeiten, Übergang zu neuer Aktivität. In der winterlichen Stille keimt bereits neue Lebendigkeit. Und zwar in einem Zyklus, das wird immer wieder so geschehen. Ich nehme das gern als ein Stück Motivation, es macht mir Hoffnung und gibt mir Energie.

Übrigens ist parallel am heutigen Tag auf der südlichen Halbkugel Sommeranfang. Genau im entgegengesetzten Rhythmus, sich ergänzend, wie Yin und Yang. Das alles liegt an der Schrägstellung der Erdachse, die ist nämlich um 23,4º zur Umlaufbahn um die Sonne geneigt. Wir erinnern uns, gell?
Insofern bleibt eindeutig festzuhalten, dass “schräg sein” ein willkommener, wichtiger und positiver Wert ist. Mit anderen Worten: auch ungewöhnlich, eigenartig, untypisch, wunderlich, kauzig, … ja sogar irre, spinnert oder gar “quer” ist in Ordnung. Das schließt das Denken mit ein.
In diesem Sinne wünsche ich euch allen urige Weihnachtstage!
Dieser Beitrag ist letztes Jahr in meiner Denkbar erschienen.
-
 @ 59c2e15a:d25e6e8d
2025-01-27 02:29:42
@ 59c2e15a:d25e6e8d
2025-01-27 02:29:42Note: I originally wrote these essays on bitcoin and yoga in 2022 after completing my yoga teacher training and going deep down the bitcoin rabbit hole. I then published them to my Ghost blog in 2023. I decided to repost them here on Nostr to start 2025 to further spread the wisdom and timelessness that bitcoin and yoga share. I split my original essay into seven parts, and I will add an eighth comparing yoga and Nostr. I hope you enjoy part one - namaste!
Part I: Bitcoin and Yoga Shared Values
Part II: Mythical/Mystical Origins
Part III: Evolution of Money and Yoga
Part IV: Ashtanga Yoga - The Eight Limbs of Yoga (limbs 1-2)
Part V: Ashtanga Yoga - The Eight Limbs of Yoga (limbs 3-8)
Part VI: Bitcoin is Dharma
Part VII: Himalayan Kriya Yoga
Introduction
With each passing day, month, and year, it feels as though our human civilization is becoming more dysfunctional, untethered, and unsustainable. Individuals are working harder, longer hours, yet most remain stuck in place, goals farther from reach. We live in a world where many have outsourced the most critical task that has enabled humans to prosper – critical thinking. I challenge each one of you to remove preconceived notions you might have about Bitcoin or Yoga before reading this series. I invite you to enter with an open mind. Think for yourself – you are welcome to agree or disagree with the information and arguments I put forth.
I also encourage you to go beyond thinking – feel. Use your intuition to understand if the way you’re living your day-to-day life feels good to you, or if you have sense, an inner knowing that something is off with our society today – that there can be a better way. If you open your heart and mind to receiving new information, there is potential to motivate yourself to change your thoughts and behaviors for more aligned action towards individual sovereignty. Every individual can choose freedom and independence. Yet it has become increasingly difficult to live a life of freedom due to the fiat system of inflation and the many distractions that keep us from going inward. After deep study and reflection, I believe bitcoin and yoga both provide the individual control over their own life journey, and frameworks to understand our connection to self and others.
I'm excited to share what I have found in my own personal experience, and hope to spark curiosity within you to follow your passion. This writing is intended for anyone seeking tools to lead a life of freedom, make positive changes and deepen your understanding of self. In addition, it is written for yogis who want to learn about bitcoin, bitcoiners who want to learn more about yoga, and anyone who is interested in a fundamental understanding of these topics that I believe contain the potential to transform your life.
Part I: Bitcoin and Yoga Shared Values
Bitcoin and yoga share many fundamental values with one another and provide deep wisdom on guiding individuals towards living better and more meaningful lives. Ultimately bitcoin and yoga share the goal of individual liberation, freedom from suffering, and a deep inner, lasting peace in Being. In yoga, this state is called moksha or samadhi. I believe everyone has a true essence, an inner being that knows what is best. However, our external environment and our own conscious mind push us away from this serenity, leading to regrets about the past or anxieties about the future. This perspective of linear time and our own individual stories and identity damage our ability to stay present in the Now, leading to endless distractions. In similar ways, bitcoin and yoga provide us insight for an individual’s path to inner peace, as well as for humanity’s path to collective peace and prosperity.
Energy
At the most elemental level, energy is the force underlying both bitcoin and yoga. Energy is the universal currency of life. We would not exist without energy. We require physical energy to fuel our cells and bodies to perform essential tasks like breathing, circulation, digestion, and movement. We perceive many forms of energy such as light or sound waves, yet there are many energy wavelengths we are not able to or are not trained to perceive.
Bitcoin is powered by physical energy in the real world in a process that secures the network and unlocks new bitcoin for distribution, a process commonly referred to as mining. Interestingly, 100 years ago, Henry Ford pushed for an energy-linked currency measured in kilowatt hours that could bring peace after a brutal World War, as seen in the New York Tribune headline and article December 4, 1921: ‘Ford Would Replace Gold with Energy Currency and Stop Wars’ (i). It took another century, but mankind has finally developed a digitally-native currency tied to the physical world through energy expenditure – bitcoin.
Yoga is similarly rooted in energy that individuals tap into through breathwork, physical movement and meditations practices. This life-force energy is known in Sanskrit as prana. Prana is not bound by time or space, and it flows through individuals in over 72,000 nadis, or channels. There are three main nadis - the first is ida, our left side body which corresponds to the feminine, receiving energy, or the moon. On the right side is pingala, relating to our masculine, giving energy, or the sun. The central nadi runs through our shushumna, linking our seven main energetic centers, known as chakras. These chakras run from the base of the tail bone, up through the spine and the top of the head. Each chakra has a name, a color and key characteristics that can often become blocked through negative emotion, trauma or stress in the body. Different yogic practices target these energy centers to unlock what is stuck and enable energy to more freely flow through us in an open exchange with the earth and out the universe. This energy is ever-present; one need only to tap into this energy, feel it and utilize it for the strengthening of one’s inner being that then radiates outwards on others in your life. The energetic experience and upward surge can also be referred to as kundalini energy, a creative power of divine feminine energy that originates in the muladara chakra at the base of the spine.
 Depiction of our chakras and nadis (image source)
Depiction of our chakras and nadis (image source)Proof of Work
In both Bitcoin and Yoga, "proof of work" is required to operate, practice and move forwards. In the Bitcoin network as described in the original white paper, miners contribute tangible energy towards running a hashing algorithm on a computer – SHA256 – to earn the right to add the next block to the blockchain and collect both the coinbase and transaction fee reward (ii). The work is difficult to produce but easy to validate by others. Miners are collecting all of the valid peer-to-peer transactions being propagated to the network and establishing them as truth into the distributed ledger. The rules in bitcoin’s code incentivize honest behavior from miners through unforgeable costliness – if a miner were to lie about any of the transactions it includes in a block, independent nodes in the network would reject the block, and the miner would have lost all the real resources it expended to solve the proof of work calculation.
 Example of an ASIC - a specialized computer solely dedicated to mining bitcoin.
Example of an ASIC - a specialized computer solely dedicated to mining bitcoin.In yoga, dedicated work is needed to learn the asanas, postures, and practice for oneself; you won’t just be able to go upside down or flow through sun salutations without first learning proper alignment and breathing techniques. An individual needs to conscious decision to work on a daily yoga practice that requires energy to flow. There are several ways to work on your yoga practice beyond physical movement; these include bhakti yoga (devotion/prayer), jnana yoga (study/wisdom), karma yoga(selfless action) and raja yoga (ashtanga). Raja yoga includes ashtanga, the eight limbs or paths of yoga that Patanjali detailed \~2000 years ago that we will explore in more depth in part IV. These ancient margas (paths) and subsequent development of these ancient teachings provides individual with ample opportunity to dedicate and work towards individual enlightenment.
Decentralization
Next, there are no external barriers preventing an individual from participating in Bitcoin or yoga. Bitcoin does not discriminate and can be accessed by anyone around the world. Yoga provides a way of life full of mindfulness and appreciation. The only barriers are internal blockages, or unwillingness to ask questions, learn and take responsibility for oneself and state of being. Therefore, Bitcoin and yoga can both be defined as decentralized. There are no centralized gatekeepers preventing one from accessing the Bitcoin network or using bitcoin as money; anyone can spin up a node, download a wallet or mine bitcoin. There are over 16,000 nodes geographically distributed around the world voluntarily running the bitcoin core software code establishing the payment network, validating transactions and storing the entire transaction history of bitcoin (iii). It costs as little as a few hundred dollars and requires less than 600 gigabytes of storage to run a node – in 2023 you can find mobile phones with that much storage. No one can prevent you from sending a peer-to-peer transaction or storing your own wealth with 12 words in your head – you need only decide to take true freedom into your own hands and learn how to do so (iv). The common maxim is “don’t trust, verify”. You don’t need someone else’s permission to participate in bitcoin or trust anyone else (eg, banks) to hold your wealth.
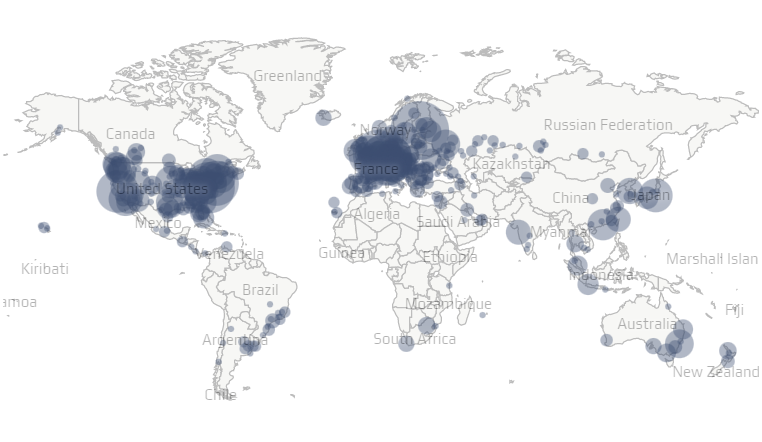 Geographic distribution of reachable bitcoin nodes (source: bitnodes)
Geographic distribution of reachable bitcoin nodes (source: bitnodes)Similarly, no one can stop an individual from practicing yoga, learning yogic philosophy or connecting with one’s truest self and inner guru. Anyone can choose to follow the path of yoga, focus on ones breath or develop a strong asana practice. There are many different ways to learn and interact with yoga, with experienced teachers willing to share their lessons to students all over the world. One need to simply find yoga studio, enroll in a teacher training or and engage with a teacher to experience yoga for themselves. Yoga looks and feels different depending on what country you are in or in which lineage you are being taught. Tapping into these profound lessons, as fundamental as controlling ones own breath, requires only an individual desire and the conscious decision to act. There’s no CEO or central authority dictating how Bitcoin or yoga has to be. Individuals have the freedom to express themselves voluntarily guided by frameworks we will dive into deeper.
Low Time Preference
Another core value that bitcoin and yoga share is low time preference. In Austrian economics, time preference refers to individual decision making. An individual with a low time preference makes decisions with greater consideration of the future, quieting immediate cravings and desires to pursue a higher goal (v). In bitcoin and money, lower time preference decisions include putting off consumption to save value for the future. Unfortunately, our fiat (by government decree) system induces individuals to make high time preference decisions, heightening consumerism and poor habits today that we see rampant in our society. There is a disincentive to save, as inflation of the money supply leads to debasing value of the dollar and other fiat currencies, decreasing individuals purchasing power of cash they hold onto and don’t spend soon. For example, the purchasing power of your dollar today will be cut in half over the next decade at current levels of inflation. In many ways, bitcoin is time, described brilliantly by Gigi, as it creates a decentralized clock that establishes consensus with each block (vi).
In contrast, the hard cap supply of 21 million bitcoin enables individuals to save with the knowledge that governments and central banks will not be able to debase their hard-earned value. This allows for one to plan with greater certainty, making investments that have a longer payoff period rather than chasing quick, material gains. Likewise in yoga, developing your own practice will not bear fruit right away; it takes discipline and time to continuously improve and strive towards a better future self. For example, in modern Ashtanga yoga taught by Pattabhi Jois, there is a set sequence of asanas that one studies and repeats each practice. It may even take months to have find the right alignment of body and breath for a single pose! The hours-long sequence requires dedication to practice and learn. The dedicated yogi understands that wholehearted commitment today will pay off for one’s mental, physical and spiritual health in the years to come. The ability to develop a calm mind can also be beneficial when people don’t initially understand or are intimidated by bitcoin. This approach can also enable you to stay grounded and discover the signal through the noise when learning about bitcoin.
 Sequence of asanas in Jois' Ashtanga Yoga (image source)
Sequence of asanas in Jois' Ashtanga Yoga (image source)Union
Yoga comes from the Sanskrit word “yuj”, which means ‘to join’ or ‘to unite’. Yoga represents the union of the mind, body, and soul of an individual. Yoga provides a pathway to individual sovereignty through disciplined practice and purpose. Yoga unites an individual internally and to one’s community, fostering connectedness and support (vii). Similarly, bitcoin provides a pathway to individual sovereignty in many ways. Bitcoin empowers the individual authority with property rights over one’s value, which in turn frees individuals from outside control (government or otherwise). Bitcoin’s technology enables one to hold their own wealth and life’s energy in a self-custodial fashion. Bitcoin is money that can be stored forever and transmitted through space at the speed of light on layer two via the Lightning Network.
Bitcoin is an open economic network with the potential to unite eight billion people together in a way our current unfair and fragmented financial system could never do. In many countries, a majority of people are unbanked, while intermediaries take a cut of the value to transfer slow, legacy payments like Western Union. While tens of millions people around the world have so far interacted with bitcoin – we are still early – similar to the internet of the mid-nineties. Bitcoin eliminates counter party risk associated with non-bearer assets, such as fiat currency (e.g., dollars, euros, yen). Bitcoin’s supply schedule is set and eliminates inflation time theft that fiat currency wages on individuals, which leads to anxiety and depression or feelings of hopelessness. Fiat is money enforced by the monopoly on violence that modern nation states grip tightly.
In contrast, bitcoin and yoga empower the individual to remove the shackles and embrace personal responsibility to improve ones life. Bitcoin and yoga also connect people directly to each other and tap into truth, ones inner being, bringing peace in the present and ultimately offer hope for a better future for each person, your community, and the world. Bitcoin and yoga have the power to unite humanity in love.
In the next section, we will explore both yoga and bitcoin's mystical and mythical origins.
Note: Bitcoin with a capital "B" generally refers to the protocol/network; bitcoin with a lower case "b" refers to the money/currency.
References:
i. Redman, Jamie, How Henry Ford Envisaged Bitcoin 100 Years Ago — A Unique 'Energy Currency' That Could 'Stop Wars', News.Bitcoin.Com, October 11, 2021 <https://news.bitcoin.com/how-henry-ford-envisaged-bitcoin-100-years-ago-a-unique-energy-currency-that-could-stop-wars/>
ii. Nakomoto, Satoshi, Bitcoin: A Peer-to-Peer Electronic Cash System, bitcoin.org, October 31, 2008 <https://bitcoin.org/bitcoin.pdf>
iii. https://bitnodes.io/
iv. Hall, Stephen, What is a bitcoin seed phrase and how does it work? Unchained.com. December 17, 2021 <https://unchained.com/blog/what-is-a-bitcoin-seed-phrase/>
v. Ammous, Saifedean, Making Time Preference Low Again, The Bitcoin Times, Austrian Edition (V). November 8, 2022 <https://bitcointimes.io/making-time-preference-low-again/>
vi. Gigi, Bitcoin is Time, dergigi.com. Jan 14,2021 <https://dergigi.com/2021/01/14/bitcoin-is-time/>
vii. 200 hour yoga teacher training. House of Om, Bali, Indonesia. <https://houseofom.com/>
-
 @ a95c6243:d345522c
2024-12-13 19:30:32
@ a95c6243:d345522c
2024-12-13 19:30:32Das Betriebsklima ist das einzige Klima, \ das du selbst bestimmen kannst. \ Anonym
Eine Strategie zur Anpassung an den Klimawandel hat das deutsche Bundeskabinett diese Woche beschlossen. Da «Wetterextreme wie die immer häufiger auftretenden Hitzewellen und Starkregenereignisse» oft desaströse Auswirkungen auf Mensch und Umwelt hätten, werde eine Anpassung an die Folgen des Klimawandels immer wichtiger. «Klimaanpassungsstrategie» nennt die Regierung das.
Für die «Vorsorge vor Klimafolgen» habe man nun erstmals klare Ziele und messbare Kennzahlen festgelegt. So sei der Erfolg überprüfbar, und das solle zu einer schnelleren Bewältigung der Folgen führen. Dass sich hinter dem Begriff Klimafolgen nicht Folgen des Klimas, sondern wohl «Folgen der globalen Erwärmung» verbergen, erklärt den Interessierten die Wikipedia. Dabei ist das mit der Erwärmung ja bekanntermaßen so eine Sache.
Die Zunahme schwerer Unwetterereignisse habe gezeigt, so das Ministerium, wie wichtig eine frühzeitige und effektive Warnung der Bevölkerung sei. Daher solle es eine deutliche Anhebung der Nutzerzahlen der sogenannten Nina-Warn-App geben.
Die ARD spurt wie gewohnt und setzt die Botschaft zielsicher um. Der Artikel beginnt folgendermaßen:
«Die Flut im Ahrtal war ein Schock für das ganze Land. Um künftig besser gegen Extremwetter gewappnet zu sein, hat die Bundesregierung eine neue Strategie zur Klimaanpassung beschlossen. Die Warn-App Nina spielt eine zentrale Rolle. Der Bund will die Menschen in Deutschland besser vor Extremwetter-Ereignissen warnen und dafür die Reichweite der Warn-App Nina deutlich erhöhen.»
Die Kommunen würden bei ihren «Klimaanpassungsmaßnahmen» vom Zentrum KlimaAnpassung unterstützt, schreibt das Umweltministerium. Mit dessen Aufbau wurden das Deutsche Institut für Urbanistik gGmbH, welches sich stark für Smart City-Projekte engagiert, und die Adelphi Consult GmbH beauftragt.
Adelphi beschreibt sich selbst als «Europas führender Think-and-Do-Tank und eine unabhängige Beratung für Klima, Umwelt und Entwicklung». Sie seien «global vernetzte Strateg*innen und weltverbessernde Berater*innen» und als «Vorreiter der sozial-ökologischen Transformation» sei man mit dem Deutschen Nachhaltigkeitspreis ausgezeichnet worden, welcher sich an den Zielen der Agenda 2030 orientiere.
Über die Warn-App mit dem niedlichen Namen Nina, die möglichst jeder auf seinem Smartphone installieren soll, informiert das Bundesamt für Bevölkerungsschutz und Katastrophenhilfe (BBK). Gewarnt wird nicht nur vor Extrem-Wetterereignissen, sondern zum Beispiel auch vor Waffengewalt und Angriffen, Strom- und anderen Versorgungsausfällen oder Krankheitserregern. Wenn man die Kategorie Gefahreninformation wählt, erhält man eine Dosis von ungefähr zwei Benachrichtigungen pro Woche.
Beim BBK erfahren wir auch einiges über die empfohlenen Systemeinstellungen für Nina. Der Benutzer möge zum Beispiel den Zugriff auf die Standortdaten «immer zulassen», und zwar mit aktivierter Funktion «genauen Standort verwenden». Die Datennutzung solle unbeschränkt sein, auch im Hintergrund. Außerdem sei die uneingeschränkte Akkunutzung zu aktivieren, der Energiesparmodus auszuschalten und das Stoppen der App-Aktivität bei Nichtnutzung zu unterbinden.
Dass man so dramatische Ereignisse wie damals im Ahrtal auch anders bewerten kann als Regierungen und Systemmedien, hat meine Kollegin Wiltrud Schwetje anhand der Tragödie im spanischen Valencia gezeigt. Das Stichwort «Agenda 2030» taucht dabei in einem Kontext auf, der wenig mit Nachhaltigkeitspreisen zu tun hat.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 1ec45473:d38df139
2025-01-25 20:15:01
@ 1ec45473:d38df139
2025-01-25 20:15:01Preston Pysh posted this event this morning:

Behind the scenes, the nostr event looks like this:
Event = { "id":"a6fa7e1a73ce70c6fb01584a0519fd29788e59d9980402584e7a0af92cf0474a", "pubkey":"85080d3bad70ccdcd7f74c29a44f55bb85cbcd3dd0cbb957da1d215bdb931204", "created_at":1724494504, "kind":1, "tags":[ [ "p", "6c237d8b3b120251c38c230c06d9e48f0d3017657c5b65c8c36112eb15c52aeb", "", "mention" ], [ "p", "77ec966fcd64f901152cad5dc7731c7c831fe22e02e3ae99ff14637e5a48ef9c", "", "mention" ], [ "p", "c1fc7771f5fa418fd3ac49221a18f19b42ccb7a663da8f04cbbf6c08c80d20b1", "", "mention" ], [ "p", "50d94fc2d8580c682b071a542f8b1e31a200b0508bab95a33bef0855df281d63", "", "mention" ], [ "p", "20d88bae0c38e6407279e6a83350a931e714f0135e013ea4a1b14f936b7fead5", "", "mention" ], [ "p", "273e7880d38d39a7fb238efcf8957a1b5b27e819127a8483e975416a0a90f8d2", "", "mention" ], [ "t", "BH2024" ] ], "content":"Awesome Freedom Panel with...", "sig":"2b64e461cd9f5a7aa8abbcbcfd953536f10a334b631a352cd4124e8e187c71aad08be9aefb6a68e5c060e676d06b61c553e821286ea42489f9e7e7107a1bf79a" }In nostr, all events have this form, so once you become familiar with the nostr event structure, things become pretty easy.
Look at the "tags" key. There are six "p" tags (pubkey) and one "t" tag (hashtag).
The p tags are public keys of people that are mentioned in the note. The t tags are for hashtags in the note.
It is common when working with NOSTR that you have to extract out certain tags. Here are some examples of how to do that with what are called JavaScript Array Methods:
Find the first "p" tag element:
``` Event.tags.find(item => item[0] === 'p')
[ 'p', '6c237d8b3b120251c38c230c06d9e48f0d3017657c5b65c8c36112eb15c52aeb', '', 'mention' ]
```
Same, but just return the pubkey":
``` Event.tags.find(item => item[0] === 'p')[1]
'6c237d8b3b120251c38c230c06d9e48f0d3017657c5b65c8c36112eb15c52aeb'
```
Filter the array so I only get "p" tags:
``` Event.tags.filter(item => item[0] === 'p')
[ [ 'p', '6c237d8b3b120251c38c230c06d9e48f0d3017657c5b65c8c36112eb15c52aeb', '', 'mention' ], [ 'p', '77ec966fcd64f901152cad5dc7731c7c831fe22e02e3ae99ff14637e5a48ef9c', '', 'mention' ], [ 'p', 'c1fc7771f5fa418fd3ac49221a18f19b42ccb7a663da8f04cbbf6c08c80d20b1', '', 'mention' ], [ 'p', '50d94fc2d8580c682b071a542f8b1e31a200b0508bab95a33bef0855df281d63', '', 'mention' ], [ 'p', '20d88bae0c38e6407279e6a83350a931e714f0135e013ea4a1b14f936b7fead5', '', 'mention' ], [ 'p', '273e7880d38d39a7fb238efcf8957a1b5b27e819127a8483e975416a0a90f8d2', '', 'mention' ] ]
```
Return an array with only the pubkeys in the "p" tags:
``` Event.tags.filter(item => item[0] === 'p').map(item => item[1])
[ '6c237d8b3b120251c38c230c06d9e48f0d3017657c5b65c8c36112eb15c52aeb', '77ec966fcd64f901152cad5dc7731c7c831fe22e02e3ae99ff14637e5a48ef9c', 'c1fc7771f5fa418fd3ac49221a18f19b42ccb7a663da8f04cbbf6c08c80d20b1', '50d94fc2d8580c682b071a542f8b1e31a200b0508bab95a33bef0855df281d63', '20d88bae0c38e6407279e6a83350a931e714f0135e013ea4a1b14f936b7fead5', '273e7880d38d39a7fb238efcf8957a1b5b27e819127a8483e975416a0a90f8d2' ]
```
-
 @ 1e566682:60493eed
2025-02-04 18:05:06
@ 1e566682:60493eed
2025-02-04 18:05:06بازار ارزهای دیجیتال بهزودی شاهد یک تغییر مهم خواهد بود. طبق گزارش اخیر منتشرشده در فوربز، بیتکوین و سایر ارزهای دیجیتال در آستانه یک "زلزله قیمتی" قرار دارند که به دلیل تغییرات نظارتی و تصمیمات کلان اقتصادی در ایالات متحده شکل میگیرد. کارشناسان پیشبینی میکنند که این تغییرات میتوانند نوسانات شدیدی در ارزش داراییهای دیجیتال ایجاد کنند و بازار را تحت تأثیر قرار دهند.
دلایل اصلی این زلزله قیمتی
- سیاستهای جدید نظارتی و قانونی
دولت آمریکا به دنبال وضع مقررات سختگیرانهتری برای نظارت بر ارزهای دیجیتال است. کمیسیون بورس و اوراق بهادار ایالات متحده و سایر نهادهای نظارتی در حال بررسی اقداماتی برای محدود کردن برخی فعالیتهای مرتبط با ارزهای دیجیتال هستند. این مقررات میتواند شامل نظارت دقیقتر بر صرافیهای ارز دیجیتال، سختگیری در فرآیندهای ضدپولشویی و احراز هویت مشتریان باشد.
- تغییرات مالیاتی و تأثیر آن بر سرمایهگذاران
دولت ایالات متحده در حال بررسی اصلاحات مالیاتی است که میتواند تأثیر قابلتوجهی بر سرمایهگذاران ارزهای دیجیتال بگذارد. مالیات بر سود حاصل از معاملات ارزهای دیجیتال میتواند افزایش یابد و سرمایهگذاران را به اتخاذ استراتژیهای جدید معاملاتی وادار کند. این مسئله ممکن است موجب کاهش حجم معاملات و افزایش نوسانات قیمتی شود.
- سیاستهای پولی فدرال رزرو
فدرال رزرو (بانک مرکزی آمریکا) نقش مهمی در تعیین نرخ بهره و سیاستهای مالی دارد. اگر نرخ بهره افزایش یابد، سرمایهگذاران ممکن است تمایل بیشتری به سرمایهگذاری در داراییهای کمریسک مانند اوراق قرضه دولتی داشته باشند و سرمایههای خود را از بازار ارزهای دیجیتال خارج کنند. این امر میتواند منجر به کاهش قیمت بیتکوین و سایر رمزارزها شود.
- افزایش پذیرش سازمانی و واکنش بازار
در حالی که قوانین سختگیرانه میتوانند فشار نزولی بر قیمتها وارد کنند، افزایش پذیرش بیتکوین توسط شرکتهای بزرگ و موسسات مالی میتواند از کاهش شدید قیمتها جلوگیری کند. بسیاری از شرکتها همچنان به پذیرش رمزارزها بهعنوان یک روش پرداخت ادامه میدهند و برخی بانکهای بزرگ نیز وارد بازار رمزارز شدهاند که این موضوع میتواند روند کلی بازار را تغییر دهد.
تأثیرات احتمالی بر قیمت بیتکوین و سایر ارزهای دیجیتال
با در نظر گرفتن این عوامل، دو سناریوی اصلی برای آینده قیمت بیتکوین و بازار رمزارزها وجود دارد:
-
سناریوی نزولی: اگر مقررات سختگیرانه اجرایی شوند و نرخ بهره افزایش یابد، ممکن است بیتکوین و سایر رمزارزها با کاهش قیمت مواجه شوند. در این شرایط، سرمایهگذاران خرد و سازمانی ممکن است با خروج از بازار، نوسانات شدیدتری را رقم بزنند.
-
سناریوی صعودی: در صورتی که افزایش پذیرش بیتکوین در میان موسسات مالی ادامه یابد و قوانین بهطور متعادل اجرا شوند، احتمال دارد که بیتکوین بتواند سطح حمایتی خود را حفظ کرده و در بلندمدت به رشد خود ادامه دهد.
جمعبندی: سرمایهگذاران باید چه کار کنند؟
با توجه به این شرایط، سرمایهگذاران ارزهای دیجیتال باید با دقت تحولات نظارتی و اقتصادی را دنبال کنند. مدیریت ریسک، تنوعبخشی به سبد سرمایهگذاری و در نظر گرفتن چشمانداز بلندمدت میتواند از ضررهای احتمالی جلوگیری کند.
این زلزله قیمتی ممکن است بازار رمزارزها را به شدت متزلزل کند، اما همانطور که در گذشته نیز دیدهایم، بازار ارزهای دیجیتال بارها از بحرانهای مشابه عبور کرده و به رشد خود ادامه داده است. باید دید که در نهایت این تغییرات چگونه شکل خواهند گرفت و چه تأثیری بر آینده بیتکوین و سایر ارزهای دیجیتال خواهند گذاشت.
-
 @ 8d34bd24:414be32b
2025-02-04 17:55:30
@ 8d34bd24:414be32b
2025-02-04 17:55:30So many of our problems are due to our point of view. The closer our point of view gets to God, the more peace and joy we will feel.
Too often we look at God as the big, bad killjoy. We resent when He tells us all the “fun” things we aren’t supposed to do and when He tells us to do difficult things like submit to God, submit to husbands, submit to authorities. Too many people focus on the “do nots,” and don’t like the idea of anyone telling them what to do. They then do their own thing, which they think will make them happy. Unfortunately, this leads to the opposite.
God is our Creator. He created us for a purpose within the rest of His creation.
For we are His workmanship, created in Christ Jesus for good works, which God prepared beforehand so that we would walk in them. (Ephesians 2:10)
When we are doing His will we will find peace and joy. When we fight Him on what we should and should not be doing, we feel frustration, depression, and even despair. Our constant seeking of things to make us happy is actually our innate desire for God and to fulfill His will. Unfortunately, we frequently don’t see the truth and avoid the one thing that will give us peace because it is hard, inconvenient, and doesn’t lead to what we think we want right now.
God wants what is best for us. He also thinks eternally. He doesn’t think in the here and now, like we do. Just as a parent makes decisions for his/her child based on knowledge of what will be better for them in the long term (saving vs spending, healthy food vs junk food, etc.), God makes decisions for us based on what will best prepare us for eternity with Him. Frequently that looks much different than what we think we want. Frequently that even includes hardship and pain because we are much more likely to grow in faith, strength, and holiness during hardship than we do during comfort. We need to understand that God knows best and that He never makes a mistake.
Trust in the Lord with all your heart\ And do not lean on your own understanding.\ In all your ways acknowledge Him,\ And He will make your paths straight.\ Do not be wise in your own eyes;\ Fear the Lord and turn away from evil.\ It will be healing to your body\ And refreshment to your bones. (Proverbs 3:5-8)
Nothing happens on earth without God allowing it. Just as Satan had to ask permission to persecute Job, in the same way nobody can cause believers harm without God allowing it for His purpose, which is usually related to helping them to put their full trust in Him.
Remember the former things long past,\ For I am God, and there is no other;\ I am God, and there is no one like Me,\ Declaring the end from the beginning,\ And from ancient times things which have not been done,\ Saying, ‘My purpose will be established,\ And I will accomplish all My good pleasure’; (Isaiah 46:9-10)
So often I focus on how awesome, powerful, and holy our God is. He is also the most tender, loving, caring, personal father God. Read Psalm 139. The God of the Bible is not a distant clock maker who set the world in motion and let it go about without His care. He is personally involved in everything that happens and in the life of every person on earth, but especially in the life of those who trust in Him.
O Lord, You have searched me and known me.\ You know when I sit down and when I rise up;\ You understand my thought from afar.\ You scrutinize my path and my lying down,\ *And are intimately acquainted with all my ways.\ Even before there is a word on my tongue,\ Behold, O Lord, You know it all.*\ You have enclosed me behind and before,\ And laid Your hand upon me.\ Such knowledge is too wonderful for me;\ It is too high, I cannot attain to it.\ Where can I go from Your Spirit?\ Or where can I flee from Your presence?\ If I ascend to heaven, You are there;\ If I make my bed in Sheol, behold, You are there.\ If I take the wings of the dawn,\ If I dwell in the remotest part of the sea,\ *Even there Your hand will lead me*,\ And Your right hand will lay hold of me.\ If I say, “Surely the darkness will overwhelm me,\ And the light around me will be night,”\ Even the darkness is not dark to You,\ And the night is as bright as the day.\ Darkness and light are alike to You.\ For You formed my inward parts;\ You wove me in my mother’s womb.\ I will give thanks to You, for I am fearfully and wonderfully made;\ Wonderful are Your works,\ And my soul knows it very well.\ My frame was not hidden from You,\ When I was made in secret,\ And skillfully wrought in the depths of the earth;\ Your eyes have seen my unformed substance;\ And in Your book were all written\ The days that were ordained for me,\ When as yet there was not one of them.\ How precious also are Your thoughts to me, O God!\ How vast is the sum of them!\ If I should count them, they would outnumber the sand.\ When I awake, I am still with You.\ O that You would slay the wicked, O God;\ Depart from me, therefore, men of bloodshed.\ For they speak against You wickedly,\ And Your enemies take Your name in vain.\ Do I not hate those who hate You, O Lord?\ And do I not loathe those who rise up against You?\ I hate them with the utmost hatred;|\ They have become my enemies.\ **Search me, O God, and know my heart;\ Try me and know my anxious thoughts;\ And see if there be any hurtful way in me,\ And lead me in the everlasting way. (Psalm 139) {emphasis mine}
What is one of the greatest desires of our hearts? Isn’t it to be truly known and loved for who we are?
O Lord, You have searched me and known me.\ You know when I sit down and when I rise up;\ You understand my thought from afar. (Psalm 139:1-2)
How amazing is it that the Creator of the universe knows you personally and cares for you among all of creation?
Even before there is a word on my tongue,\ Behold, O Lord, You know it all. (Psalm 139:4)
He knows our every action, our every thought, and our every feeling before we do.
Such knowledge is too wonderful for me;\ It is too high, I cannot attain to it. (Psalm 139:6)
We cannot fully understand how much our Creator cares for us and how carefully God guides us in our every path. We usually can’t see what is for our best. We usually can’t see what great work God is working in us. We usually can’t comprehend how great is His love, knowledge, and plan.
Even there Your hand will lead me,\ And Your right hand will lay hold of me. (Psalm 139:10)
It doesn’t matter how difficult a situation we have gotten into. It doesn’t matter how powerful our adversaries are. It doesn’t matter how weak we are. God is always there guiding us and protecting us. Just as God allowed Job to go through difficulty as part of God’s plan for Job and for us, He did not allow Job to be killed. He was guided through the worst of situations and led to ultimate blessing.
Your eyes have seen my unformed substance;\ And in Your book were all written\ The days that were ordained for me,\ When as yet there was not one of them. (Psalm 139:16)
God knew us and had a plan for us before He even created the universe. He knew every day we would live before we were conceived. We can’t surprise Him and He will be guiding us every day of our lives, especially those who have trusted Him as savior.
How precious also are Your thoughts to me, O God!\ How vast is the sum of them! (Psalm 139:17)
We are precious to God and He should be precious to us because of all He has done for us.
Search me, O God, and know my heart;\ Try me and know my anxious thoughts;\ And see if there be any hurtful way in me,\ And lead me in the everlasting way. (Psalm 139:23-24)
This should be our prayer. We should ask for Him to bring are faults to our minds so we can repent and we should ask for Him to lead us in His “everlasting way.” We should admit that our Father God knows best and submit to His will. Everything goes so much smoother when we aren’t fighting our God. Even when He leads us through hardship, being in His will makes all of the difference in the world.
I pray that you will put your trust in our loving Creator and that you will submit to His will. I pray that you will understand that His ways are better even when you don’t understand the why. I pray that you will humbly submit to His will and be used to further the Kingdom for His glory and your blessing.
Trust Jesus.
FYI, Psalm 139 is also one of the best passages on why all believers should oppose abortion. In God’s universe there are no accidents and there are no unwanted babies. Every person ever conceived had a purpose in God’s plan. Every person ever conceived is valuable and made in the image of God. God values all human life and so should we.
-
 @ a95c6243:d345522c
2024-12-06 18:21:15
@ a95c6243:d345522c
2024-12-06 18:21:15Die Ungerechtigkeit ist uns nur in dem Falle angenehm,\ dass wir Vorteile aus ihr ziehen;\ in jedem andern hegt man den Wunsch,\ dass der Unschuldige in Schutz genommen werde.\ Jean-Jacques Rousseau
Politiker beteuern jederzeit, nur das Beste für die Bevölkerung zu wollen – nicht von ihr. Auch die zahlreichen unsäglichen «Corona-Maßnahmen» waren angeblich zu unserem Schutz notwendig, vor allem wegen der «besonders vulnerablen Personen». Daher mussten alle möglichen Restriktionen zwangsweise und unter Umgehung der Parlamente verordnet werden.
Inzwischen hat sich immer deutlicher herausgestellt, dass viele jener «Schutzmaßnahmen» den gegenteiligen Effekt hatten, sie haben den Menschen und den Gesellschaften enorm geschadet. Nicht nur haben die experimentellen Geninjektionen – wie erwartet – massive Nebenwirkungen, sondern Maskentragen schadet der Psyche und der Entwicklung (nicht nur unserer Kinder) und «Lockdowns und Zensur haben Menschen getötet».
Eine der wichtigsten Waffen unserer «Beschützer» ist die Spaltung der Gesellschaft. Die tiefen Gräben, die Politiker, Lobbyisten und Leitmedien praktisch weltweit ausgehoben haben, funktionieren leider nahezu in Perfektion. Von ihren persönlichen Erfahrungen als Kritikerin der Maßnahmen berichtete kürzlich eine Schweizerin im Interview mit Transition News. Sie sei schwer enttäuscht und verspüre bis heute eine Hemmschwelle und ein seltsames Unwohlsein im Umgang mit «Geimpften».
Menschen, die aufrichtig andere schützen wollten, werden von einer eindeutig politischen Justiz verfolgt, verhaftet und angeklagt. Dazu zählen viele Ärzte, darunter Heinrich Habig, Bianca Witzschel und Walter Weber. Über den aktuell laufenden Prozess gegen Dr. Weber hat Transition News mehrfach berichtet (z.B. hier und hier). Auch der Selbstschutz durch Verweigerung der Zwangs-Covid-«Impfung» bewahrt nicht vor dem Knast, wie Bundeswehrsoldaten wie Alexander Bittner erfahren mussten.
Die eigentlich Kriminellen schützen sich derweil erfolgreich selber, nämlich vor der Verantwortung. Die «Impf»-Kampagne war «das größte Verbrechen gegen die Menschheit». Trotzdem stellt man sich in den USA gerade die Frage, ob der scheidende Präsident Joe Biden nach seinem Sohn Hunter möglicherweise auch Anthony Fauci begnadigen wird – in diesem Fall sogar präventiv. Gibt es überhaupt noch einen Rest Glaubwürdigkeit, den Biden verspielen könnte?
Der Gedanke, den ehemaligen wissenschaftlichen Chefberater des US-Präsidenten und Direktor des National Institute of Allergy and Infectious Diseases (NIAID) vorsorglich mit einem Schutzschild zu versehen, dürfte mit der vergangenen Präsidentschaftswahl zu tun haben. Gleich mehrere Personalentscheidungen des designierten Präsidenten Donald Trump lassen Leute wie Fauci erneut in den Fokus rücken.
Das Buch «The Real Anthony Fauci» des nominierten US-Gesundheitsministers Robert F. Kennedy Jr. erschien 2021 und dreht sich um die Machenschaften der Pharma-Lobby in der öffentlichen Gesundheit. Das Vorwort zur rumänischen Ausgabe des Buches schrieb übrigens Călin Georgescu, der Überraschungssieger der ersten Wahlrunde der aktuellen Präsidentschaftswahlen in Rumänien. Vielleicht erklärt diese Verbindung einen Teil der Panik im Wertewesten.
In Rumänien selber gab es gerade einen Paukenschlag: Das bisherige Ergebnis wurde heute durch das Verfassungsgericht annuliert und die für Sonntag angesetzte Stichwahl kurzfristig abgesagt – wegen angeblicher «aggressiver russischer Einmischung». Thomas Oysmüller merkt dazu an, damit sei jetzt in der EU das Tabu gebrochen, Wahlen zu verbieten, bevor sie etwas ändern können.
Unsere Empörung angesichts der Historie von Maßnahmen, die die Falschen beschützen und für die meisten von Nachteil sind, müsste enorm sein. Die Frage ist, was wir damit machen. Wir sollten nach vorne schauen und unsere Energie clever einsetzen. Abgesehen von der Umgehung von jeglichem «Schutz vor Desinformation und Hassrede» (sprich: Zensur) wird es unsere wichtigste Aufgabe sein, Gräben zu überwinden.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2024-11-29 19:45:43
@ a95c6243:d345522c
2024-11-29 19:45:43Konsum ist Therapie.
Wolfgang JoopUmweltbewusstes Verhalten und verantwortungsvoller Konsum zeugen durchaus von einer wünschenswerten Einstellung. Ob man deswegen allerdings einen grünen statt eines schwarzen Freitags braucht, darf getrost bezweifelt werden – zumal es sich um manipulatorische Konzepte handelt. Wie in der politischen Landschaft sind auch hier die Etiketten irgendwas zwischen nichtssagend und trügerisch.
Heute ist also wieder mal «Black Friday», falls Sie es noch nicht mitbekommen haben sollten. Eigentlich haben wir ja eher schon eine ganze «Black Week», der dann oft auch noch ein «Cyber Monday» folgt. Die Werbebranche wird nicht müde, immer neue Anlässe zu erfinden oder zu importieren, um uns zum Konsumieren zu bewegen. Und sie ist damit sehr erfolgreich.
Warum fallen wir auf derartige Werbetricks herein und kaufen im Zweifelsfall Dinge oder Mengen, die wir sicher nicht brauchen? Pure Psychologie, würde ich sagen. Rabattschilder triggern etwas in uns, was den Verstand in Stand-by versetzt. Zusätzlich beeinflussen uns alle möglichen emotionalen Reize und animieren uns zum Schnäppchenkauf.
Gedankenlosigkeit und Maßlosigkeit können besonders bei der Ernährung zu ernsten Problemen führen. Erst kürzlich hat mir ein Bekannter nach einer USA-Reise erzählt, dass es dort offenbar nicht unüblich ist, schon zum ausgiebigen Frühstück in einem Restaurant wenigstens einen Liter Cola zu trinken. Gerne auch mehr, um das Gratis-Nachfüllen des Bechers auszunutzen.
Kritik am schwarzen Freitag und dem unnötigen Konsum kommt oft von Umweltschützern. Neben Ressourcenverschwendung, hohem Energieverbrauch und wachsenden Müllbergen durch eine zunehmende Wegwerfmentalität kommt dabei in der Regel auch die «Klimakrise» auf den Tisch.
Die EU-Kommission lancierte 2015 den Begriff «Green Friday» im Kontext der überarbeiteten Rechtsvorschriften zur Kennzeichnung der Energieeffizienz von Elektrogeräten. Sie nutzte die Gelegenheit kurz vor dem damaligen schwarzen Freitag und vor der UN-Klimakonferenz COP21, bei der das Pariser Abkommen unterzeichnet werden sollte.
Heute wird ein grüner Freitag oft im Zusammenhang mit der Forderung nach «nachhaltigem Konsum» benutzt. Derweil ist die Europäische Union schon weit in ihr Geschäftsmodell des «Green New Deal» verstrickt. In ihrer Propaganda zum Klimawandel verspricht sie tatsächlich «Unterstützung der Menschen und Regionen, die von immer häufigeren Extremwetter-Ereignissen betroffen sind». Was wohl die Menschen in der Region um Valencia dazu sagen?
Ganz im Sinne des Great Reset propagierten die Vereinten Nationen seit Ende 2020 eine «grüne Erholung von Covid-19, um den Klimawandel zu verlangsamen». Der UN-Umweltbericht sah in dem Jahr einen Schwerpunkt auf dem Verbraucherverhalten. Änderungen des Konsumverhaltens des Einzelnen könnten dazu beitragen, den Klimaschutz zu stärken, hieß es dort.
Der Begriff «Schwarzer Freitag» wurde in den USA nicht erstmals für Einkäufe nach Thanksgiving verwendet – wie oft angenommen –, sondern für eine Finanzkrise. Jedoch nicht für den Börsencrash von 1929, sondern bereits für den Zusammenbruch des US-Goldmarktes im September 1869. Seitdem mussten die Menschen weltweit so einige schwarze Tage erleben.
Kürzlich sind die britischen Aufsichtsbehörden weiter von ihrer Zurückhaltung nach dem letzten großen Finanzcrash von 2008 abgerückt. Sie haben Regeln für den Bankensektor gelockert, womit sie «verantwortungsvolle Risikobereitschaft» unterstützen wollen. Man würde sicher zu schwarz sehen, wenn man hier ein grünes Wunder befürchten würde.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2024-11-08 20:02:32
@ a95c6243:d345522c
2024-11-08 20:02:32Und plötzlich weißt du:
Es ist Zeit, etwas Neues zu beginnen
und dem Zauber des Anfangs zu vertrauen.
Meister EckhartSchwarz, rot, gold leuchtet es im Kopf des Newsletters der deutschen Bundesregierung, der mir freitags ins Postfach flattert. Rot, gelb und grün werden daneben sicher noch lange vielzitierte Farben sein, auch wenn diese nie geleuchtet haben. Die Ampel hat sich gerade selber den Stecker gezogen – und hinterlässt einen wirtschaftlichen und gesellschaftlichen Trümmerhaufen.
Mit einem bemerkenswerten Timing hat die deutsche Regierungskoalition am Tag des «Comebacks» von Donald Trump in den USA endlich ihr Scheitern besiegelt. Während der eine seinen Sieg bei den Präsidentschaftswahlen feierte, erwachten die anderen jäh aus ihrer Selbsthypnose rund um Harris-Hype und Trump-Panik – mit teils erschreckenden Auswüchsen. Seit Mittwoch werden die Geschicke Deutschlands nun von einer rot-grünen Minderheitsregierung «geleitet» und man steuert auf Neuwahlen zu.
Das Kindergarten-Gehabe um zwei konkurrierende Wirtschaftsgipfel letzte Woche war bereits bezeichnend. In einem Strategiepapier gestand Finanzminister Lindner außerdem den «Absturz Deutschlands» ein und offenbarte, dass die wirtschaftlichen Probleme teilweise von der Ampel-Politik «vorsätzlich herbeigeführt» worden seien.
Lindner und weitere FDP-Minister wurden also vom Bundeskanzler entlassen. Verkehrs- und Digitalminister Wissing trat flugs aus der FDP aus; deshalb darf er nicht nur im Amt bleiben, sondern hat zusätzlich noch das Justizministerium übernommen. Und mit Jörg Kukies habe Scholz «seinen Lieblingsbock zum Obergärtner», sprich: Finanzminister befördert, meint Norbert Häring.
Es gebe keine Vertrauensbasis für die weitere Zusammenarbeit mit der FDP, hatte der Kanzler erklärt, Lindner habe zu oft sein Vertrauen gebrochen. Am 15. Januar 2025 werde er daher im Bundestag die Vertrauensfrage stellen, was ggf. den Weg für vorgezogene Neuwahlen freimachen würde.
Apropos Vertrauen: Über die Hälfte der Bundesbürger glauben, dass sie ihre Meinung nicht frei sagen können. Das ging erst kürzlich aus dem diesjährigen «Freiheitsindex» hervor, einer Studie, die die Wechselwirkung zwischen Berichterstattung der Medien und subjektivem Freiheitsempfinden der Bürger misst. «Beim Vertrauen in Staat und Medien zerreißt es uns gerade», kommentierte dies der Leiter des Schweizer Unternehmens Media Tenor, das die Untersuchung zusammen mit dem Institut für Demoskopie Allensbach durchführt.
«Die absolute Mehrheit hat absolut die Nase voll», titelte die Bild angesichts des «Ampel-Showdowns». Die Mehrheit wolle Neuwahlen und die Grünen sollten zuerst gehen, lasen wir dort.
Dass «Insolvenzminister» Robert Habeck heute seine Kandidatur für das Kanzleramt verkündet hat, kann nur als Teil der politmedialen Realitätsverweigerung verstanden werden. Wer allerdings denke, schlimmer als in Zeiten der Ampel könne es nicht mehr werden, sei reichlich optimistisch, schrieb Uwe Froschauer bei Manova. Und er kenne Friedrich Merz schlecht, der sich schon jetzt rhetorisch auf seine Rolle als oberster Feldherr Deutschlands vorbereite.
Was also tun? Der Schweizer Verein «Losdemokratie» will eine Volksinitiative lancieren, um die Bestimmung von Parlamentsmitgliedern per Los einzuführen. Das Losverfahren sorge für mehr Demokratie, denn als Alternative zum Wahlverfahren garantiere es eine breitere Beteiligung und repräsentativere Parlamente. Ob das ein Weg ist, sei dahingestellt.
In jedem Fall wird es notwendig sein, unsere Bemühungen um Freiheit und Selbstbestimmung zu verstärken. Mehr Unabhängigkeit von staatlichen und zentralen Institutionen – also die Suche nach dezentralen Lösungsansätzen – gehört dabei sicher zu den Möglichkeiten. Das gilt sowohl für jede/n Einzelne/n als auch für Entitäten wie die alternativen Medien.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2024-10-26 12:21:50
@ a95c6243:d345522c
2024-10-26 12:21:50Es ist besser, ein Licht zu entzünden, als auf die Dunkelheit zu schimpfen. Konfuzius
Die Bemühungen um Aufarbeitung der sogenannten Corona-Pandemie, um Aufklärung der Hintergründe, Benennung von Verantwortlichkeiten und das Ziehen von Konsequenzen sind durchaus nicht eingeschlafen. Das Interesse daran ist unter den gegebenen Umständen vielleicht nicht sonderlich groß, aber es ist vorhanden.
Der sächsische Landtag hat gestern die Einsetzung eines Untersuchungsausschusses zur Corona-Politik beschlossen. In einer Sondersitzung erhielt ein entsprechender Antrag der AfD-Fraktion die ausreichende Zustimmung, auch von einigen Abgeordneten des BSW.
In den Niederlanden wird Bill Gates vor Gericht erscheinen müssen. Sieben durch die Covid-«Impfstoffe» geschädigte Personen hatten Klage eingereicht. Sie werfen unter anderem Gates, Pfizer-Chef Bourla und dem niederländischen Staat vor, sie hätten gewusst, dass diese Präparate weder sicher noch wirksam sind.
Mit den mRNA-«Impfstoffen» von Pfizer/BioNTech befasst sich auch ein neues Buch. Darin werden die Erkenntnisse von Ärzten und Wissenschaftlern aus der Analyse interner Dokumente über die klinischen Studien der Covid-Injektion präsentiert. Es handelt sich um jene in den USA freigeklagten Papiere, die die Arzneimittelbehörde (Food and Drug Administration, FDA) 75 Jahre unter Verschluss halten wollte.
Ebenfalls Wissenschaftler und Ärzte, aber auch andere Experten organisieren als Verbundnetzwerk Corona-Solution kostenfreie Online-Konferenzen. Ihr Ziel ist es, «wissenschaftlich, demokratisch und friedlich» über Impfstoffe und Behandlungsprotokolle gegen SARS-CoV-2 aufzuklären und die Diskriminierung von Ungeimpften zu stoppen. Gestern fand eine weitere Konferenz statt. Ihr Thema: «Corona und modRNA: Von Toten, Lebenden und Physik lernen».
Aufgrund des Digital Services Acts (DSA) der Europäischen Union sei das Risiko groß, dass ihre Arbeit als «Fake-News» bezeichnet würde, so das Netzwerk. Staatlich unerwünschte wissenschaftliche Aufklärung müsse sich passende Kanäle zur Veröffentlichung suchen. Ihre Live-Streams seien deshalb zum Beispiel nicht auf YouTube zu finden.
Der vielfältige Einsatz für Aufklärung und Aufarbeitung wird sich nicht stummschalten lassen. Nicht einmal der Zensurmeister der EU, Deutschland, wird so etwas erreichen. Die frisch aktivierten «Trusted Flagger» dürften allerdings künftige Siege beim «Denunzianten-Wettbewerb» im Kontext des DSA zusätzlich absichern.
Wo sind die Grenzen der Meinungsfreiheit? Sicher gibt es sie. Aber die ideologische Gleichstellung von illegalen mit unerwünschten Äußerungen verfolgt offensichtlich eher das Ziel, ein derart elementares demokratisches Grundrecht möglichst weitgehend auszuhebeln. Vorwürfe wie «Hassrede», «Delegitimierung des Staates» oder «Volksverhetzung» werden heute inflationär verwendet, um Systemkritik zu unterbinden. Gegen solche Bestrebungen gilt es, sich zu wehren.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2024-10-23 20:26:10
@ c631e267:c2b78d3e
2024-10-23 20:26:10Herzlichen Glückwunsch zum dritten Geburtstag, liebe Denk Bar! Wieso zum dritten? Das war doch 2022 und jetzt sind wir im Jahr 2024, oder? Ja, das ist schon richtig, aber bei Geburtstagen erinnere ich mich immer auch an meinen Vater, und der behauptete oft, der erste sei ja schließlich der Tag der Geburt selber und den müsse man natürlich mitzählen. Wo er recht hat, hat er nunmal recht. Konsequenterweise wird also heute dieser Blog an seinem dritten Geburtstag zwei Jahre alt.
Das ist ein Grund zum Feiern, wie ich finde. Einerseits ganz einfach, weil es dafür gar nicht genug Gründe geben kann. «Das Leben sind zwei Tage», lautet ein gängiger Ausdruck hier in Andalusien. In der Tat könnte es so sein, auch wenn wir uns im Alltag oft genug von der Routine vereinnahmen lassen.
Seit dem Start der Denk Bar vor zwei Jahren ist unglaublich viel passiert. Ebenso wie die zweieinhalb Jahre davor, und all jenes war letztlich auch der Auslöser dafür, dass ich begann, öffentlich zu schreiben. Damals notierte ich:
«Seit einigen Jahren erscheint unser öffentliches Umfeld immer fragwürdiger, widersprüchlicher und manchmal schier unglaublich - jede Menge Anlass für eigene Recherchen und Gedanken, ganz einfach mit einer Portion gesundem Menschenverstand.»
Wir erleben den sogenannten «großen Umbruch», einen globalen Coup, den skrupellose Egoisten clever eingefädelt haben und seit ein paar Jahren knallhart – aber nett verpackt – durchziehen, um buchstäblich alles nach ihrem Gusto umzukrempeln. Die Gelegenheit ist ja angeblich günstig und muss genutzt werden.
Nie hätte ich mir träumen lassen, dass ich so etwas jemals miterleben müsste. Die Bosheit, mit der ganz offensichtlich gegen die eigene Bevölkerung gearbeitet wird, war früher für mich unvorstellbar. Mein (Rest-) Vertrauen in alle möglichen Bereiche wie Politik, Wissenschaft, Justiz, Medien oder Kirche ist praktisch komplett zerstört. Einen «inneren Totalschaden» hatte ich mal für unsere Gesellschaften diagnostiziert.
Was mich vielleicht am meisten erschreckt, ist zum einen das Niveau der Gleichschaltung, das weltweit erreicht werden konnte, und zum anderen die praktisch totale Spaltung der Gesellschaft. Haben wir das tatsächlich mit uns machen lassen?? Unfassbar! Aber das Werkzeug «Angst» ist sehr mächtig und funktioniert bis heute.
Zum Glück passieren auch positive Dinge und neue Perspektiven öffnen sich. Für viele Menschen waren und sind die Entwicklungen der letzten Jahre ein Augenöffner. Sie sehen «Querdenken» als das, was es ist: eine Tugend.
Auch die immer ernsteren Zensurbemühungen sind letztlich nur ein Zeichen der Schwäche, wo Argumente fehlen. Sie werden nicht verhindern, dass wir unsere Meinung äußern, unbequeme Fragen stellen und dass die Wahrheit peu à peu ans Licht kommt. Es gibt immer Mittel und Wege, auch für uns.
Danke, dass du diesen Weg mit mir weitergehst!
-
 @ b17fccdf:b7211155
2025-01-21 18:39:47
@ b17fccdf:b7211155
2025-01-21 18:39:47~ > Check out the steps to get this ~ > HERE < ~
Note: for different reasons, it is recommended choosing Option 1: DoT & DNSSEC using systemd-resolved, but you could want to use Option 2, choose behind your criteria, both are valid to achieve the same objective.
Some more changes were released recently in other places of the MiniBolt guide, check the full release notes:
Full release notes
~ > Static IP & custom DNS servers bonus guide:
- Adds custom DNS server suggestions.
- Adds different steps to check the changes after configurations.
- Deleted some unnecessary steps.
- Fix some nits.
~ > Modifications on Configuration (
bitcoin.conf) of Bitcoin Core:- Replace proxy value parameter to use UNIX domain socket (
proxy=unix:/run/tor/socks) | (recently enabled on Bitcoin Core v28). - Replace
startupnotify=chmod g+r /home/bitcoin/.bitcoin/.cookietorpccookieperms=groupBitcoin Core PR. - Adds another special bind address to listen to incoming connections from Tor (
bind=127.0.0.1=onion) | (recently changed on Bitcoin Core v28). - Modified systemd service to improve the startup and shutdown process.
Note: remember to restart Bitcoin Core and reload the systemd with
sudo systemctl daemon-reloadto apply changes.
~ > Delete unnecessary parameters of the systemd service of Lightning client.
Note: remember to reload the systemd with
sudo systemctl daemon-reloadto apply changes.
~ > Others:
- New i2pd webconsole section.
- Adds a new "Validation" subsection to the guides to clarify when checks begin.
- New "Use the Tor proxy from another device" section.
- Adds Electrs compatible with Testnet4 on Testnet bonus guide.
- Adds how to build a Guard/Middle relay section on "Tor services: bridges & relays" bonus guide.
- Adds Extras (optional) section to "Tor services: bridges & relays" bonus guide with different utilities like install Nyx, how to "Limit bandwidth" and others.
- Changed Electrs ports to enable simultaneous mode with Fulcrum.
- Updated aliases list to include news additions in line with updates.
- Updated the Networkmap resource to include news additions in line with updates and migrate to a dynamic visual mode.
- Reorganized some menu items and sections to improve the UX and make more sense in the face of the future.
- Restructure and rename the "Tor obfs4 bridge" bonus guide to "Tor services: bridges & relays" and modify it to run the obfs4bridge, relays, and the master, in separate instances.
- Hidden NYM mixnet and Sparrow server bonus guides from the menus due to disuse or poor performance. Note: it will continue to be maintained later if the situation changes due to the development of the associated software.
- Bump version of various services.
~ > Coming soon...
- Enable DNSSEC for your domain using Cloudflare + Namecheap.
- Enable DoH on:
- Desktop/Android browser (Windows/Linux).
- OS: Windows 11 // Linux (Completed ✅)
- Router.
- Enable DoT on:
- Android OS.
- OS: Windows 11 // Linux (Completed ✅) with DNSSEC verification included.
- Router.
Enjoy it MiniBolter!💙
-
 @ a95c6243:d345522c
2024-10-19 08:58:08
@ a95c6243:d345522c
2024-10-19 08:58:08Ein Lämmchen löschte an einem Bache seinen Durst. Fern von ihm, aber näher der Quelle, tat ein Wolf das gleiche. Kaum erblickte er das Lämmchen, so schrie er:
"Warum trübst du mir das Wasser, das ich trinken will?"
"Wie wäre das möglich", erwiderte schüchtern das Lämmchen, "ich stehe hier unten und du so weit oben; das Wasser fließt ja von dir zu mir; glaube mir, es kam mir nie in den Sinn, dir etwas Böses zu tun!"
"Ei, sieh doch! Du machst es gerade, wie dein Vater vor sechs Monaten; ich erinnere mich noch sehr wohl, daß auch du dabei warst, aber glücklich entkamst, als ich ihm für sein Schmähen das Fell abzog!"
"Ach, Herr!" flehte das zitternde Lämmchen, "ich bin ja erst vier Wochen alt und kannte meinen Vater gar nicht, so lange ist er schon tot; wie soll ich denn für ihn büßen."
"Du Unverschämter!" so endigt der Wolf mit erheuchelter Wut, indem er die Zähne fletschte. "Tot oder nicht tot, weiß ich doch, daß euer ganzes Geschlecht mich hasset, und dafür muß ich mich rächen."
Ohne weitere Umstände zu machen, zerriß er das Lämmchen und verschlang es.
Das Gewissen regt sich selbst bei dem größten Bösewichte; er sucht doch nach Vorwand, um dasselbe damit bei Begehung seiner Schlechtigkeiten zu beschwichtigen.
Quelle: https://eden.one/fabeln-aesop-das-lamm-und-der-wolf
-
 @ b17fccdf:b7211155
2025-01-21 18:30:13
@ b17fccdf:b7211155
2025-01-21 18:30:13~ > Available at: https://minibolt.info
~> It builds on a personal computer with x86/amd64 architecture processors.
~> It is based on the popular RaspiBolt v3 guide.
Those are some of the most relevant changes:
- Changed OS from Raspberry Pi OS Lite (64-bits) to Ubuntu Server LTS (Long term support) 64-bit PC (AMD64).
- Changed binaries and signatures of the programs to adapt them to x86/amd64 architecture.
- Deleted unnecessary tools and steps, and added others according to this case of use.
- Some useful authentication logs and monitoring commands were added in the security section.
- Added some interesting parameters in the settings of some services to activate and take advantage of new features.
- Changed I2P, Fulcrum, and ThunderHub guides, to be part of the core guide.
- Added exclusive optimization section of services for slow devices.
~ > Complete release notes of the MiniBolt v1: https://github.com/twofaktor/minibolt/releases/tag/1.0.
~ > Feel free to contribute to the source code on GitHub by opening issues, pull requests or discussions.
Created by ⚡2 FakTor⚡
-
 @ b17fccdf:b7211155
2025-01-21 18:22:51
@ b17fccdf:b7211155
2025-01-21 18:22:51😱 Did you recently find this signature verification error when you tried to update your MiniBolt repositories with ->
sudo apt update? 💥🚨👇
🔧 Don't worry, that's because Tor renewed its signing key since it expired last 07/15, just renew your keyring by following the next steps to solve this problem:
~ > CLICK HERE < ~
Enjoy it MiniBolter!💙
-
 @ 91bea5cd:1df4451c
2025-02-04 17:24:50
@ 91bea5cd:1df4451c
2025-02-04 17:24:50Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\000\000\000\000\000\000'; output TEXT = '';
unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ```
ULID TO UUID
```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ```
UUID to ULID
```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ```
Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars;END; $$ LANGUAGE plpgsql; ```
Exemplo de USO
```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ```
Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-
 @ e97aaffa:2ebd765d
2025-02-04 16:58:18
@ e97aaffa:2ebd765d
2025-02-04 16:58:18Será que neste ciclo teremos turistas no #Bitcoin? Nos últimos meses tenho me debruçado muito sobre este assunto, mas não consigo chegar a uma conclusão.
Antes de mais, o que são turistas? Os turistas são aqueles que compram Bitcoin alimentados pelo FOMO, com a ganância de enriquecer rapidamente. Não tem o mínimo conhecimento do Bitcoin, nem tem interesse em conhecer, só estão pelo dinheiro.
Com a entrada dos turistas, o preço do Bitcoin começa a valorizar exponencialmente, é a segunda fase da bullrun, acontece sempre após o halving e após superar o anterior ATH. Com o novo ATH começa a surgir as notícias nas televisões e jornais, o mainstream acorda. Só que a quantidade de turistas é de tal maneira elevada, muito superior à dos holders. Este desequilíbrio entre forças de curto prazo(turistas) e do longo prazo(holders), gera forte volatilidade. Quanto maior o desequilíbrio, maior a volatilidade. A avalanche de turistas, faz o preço disparar e quanto mais sobe, mais turistas atrai.
Só que o movimento não dura para sempre, a esperança dos turistas de enriquecer rápido, desvanece e rapidamente se transforma numa desilusão, na sua grande maioria entra em pânico, assim que o preço começa a corrigir, vendendo em prejuízo. Sendo responsável pelas gigantes correções, superiores a 70%.
Este é o meu 4° ciclo, eu noto que este está a ser completamente diferente. Nos anteriores, os turistas entravam pelo Bitcoin, mas desta vez está a acontecer uma mudança. Devido ao elevado marketcap do Bitcoin, este já não permite valorização exponenciais num curto espaço de tempo, estes turistas que procuram multiplicar o seu dinheiro por 10x, 100x ou 1000x, estão a ir directamente para as shitcoins ou memecoins. Estas valorização pornograficas, só acontecerá em meia dúzia, mas o grande problema é que existem milhões de memecoins, é como encontrar uma agulha num palheiro. É o verdadeiro casino e os turistas procuram isto.
Só que neste ciclo, a maior parte dos novos inflows estão a ser através do institucional, sobretudo pelos ETFs. Só que tem um perfil não diferente dos turistas, têm conhecimento de mercados financeiros tradicionais, são muito mais racionais, têm um conhecimento mínimo do Bitcoin. Não têm as mãos de diamante como os holders, mas também não são mãos de alface como os turistas. É um perfil de investidor intermédio. Poderá vender uma pequena parte do Bitcoin, para retirar uma parte do seu investimento inicial, mas tem um pensamento mais de médio-longo prazo.
Com isto, existe um maior equilíbrio entre os que pensam a curto prazo e os que pensam a longo prazo. Até ao momento, eu tenho a sensação que os turistas já não procuram o Bitcoin, ou são muito poucos.
O afastamento dos turistas é bom ou mau? A meu ver é bom, é verdade que deixamos de ter aquelas enormes explosões no preço para cima, mas também acredito que as correções também serão muito menores. Em suma, uma redução na volatilidade do Bitcoin. Mas essa redução na volatilidade, vai trazer um novo público, aquele que não é especulador, que apenas quer preservar o seu património, o real valor do Bitcoin, que pensa a longo prazo.
Estes turistas que procuram o 100x, com uma pura ganância, vão passar muitas noites sem dormir e na sua maioria vão perder muito dinheiro, vão acabar por receber uma dura lição de vida. Alguns vão finalmente compreender que Bitcoin é diferente, e que os 2x é suficiente para a sua vida.
A redução de turistas não afeta só o Bitcoin, mas também afeta o mercado das altcoins e das memecoins. Nos ciclos anteriores, os turistas entravam pelo Bitcoin mas depois rodavam o capital para as altcoins, gerando a chamada altseason. Se neste ciclo, os turistas descartam o Bitcoin, consequentemente a rotação será muito menor, possivelmente não haverá altseason.
Mas isto é apenas a minha convicção, só o tempo dirá, se os turistas trocaram o Bitcoin, pelo casino das memecoins.
-
 @ b17fccdf:b7211155
2025-01-21 17:58:35
@ b17fccdf:b7211155
2025-01-21 17:58:35The router reserves the IP address of the device for a time after going out, but if the device goes out some time, the next time that the device starts, the router could assign a different IP and you could lose access to your node. To avoid this, you need to set a static IP to your MiniBolt.
~ > In addition, you can customize your DNS servers to improve your privacy, normally your ISP, gives you the router with its own DNS servers set by default, and this does that you expose all of your navigation trackings to your ISP, affecting seriously your privacy.
~ > This bonus guide includes all of the necessary steps to get this and is available ~ > HERE < ~

Enjoy it MiniBolter! 💙
-
 @ b17fccdf:b7211155
2025-01-21 17:47:28
@ b17fccdf:b7211155
2025-01-21 17:47:28Link to the bonus guide ~ > HERE < ~
Some sections of the guide:
- Generate SSH keys
- Import SSH pubkey
- Connect to the MiniBolt node using SSH keys
- Disable password login
- Disable admin password request
Some shortcuts to the Extra sections:
Enjoy it MiniBolter! 💙
-
 @ b17fccdf:b7211155
2025-01-21 17:29:54
@ b17fccdf:b7211155
2025-01-21 17:29:54Some sections inside of the guide:
- Set up Dynamic DNS
- Wireguard VPN server & client side configurations
- Install & configure the WireGuard VPN Client on a mobile phone
- Configure additional servers & clients
- Use your router’s DDNS preconfigured provider
- Port forwarding on NAT/PAT router
Link to the bonus guide HERE
Enjoy it MiniBolter! 💙
-
 @ b17fccdf:b7211155
2025-01-21 17:19:12
@ b17fccdf:b7211155
2025-01-21 17:19:12Do you want to use a different disk to store data (blockchain and other databases) independently of the disk of the system?
A step-by-step guide using a secondary disk to store the data (blockchain and other databases) independently of the disk of the system and using the Ubuntu Server guided installation.
What's changed
- Rebuilt the Ubuntu Server installation guide based on this bonus guide added.
- Added GIFs to improve the illustration of the steps to follow.
- Case 1: during the Ubuntu server guided installation.
- Case 2: build it after system installation (by command line).
~ > Link to the bonus guide HERE
Enjoy it MiniBolter! 💙
-
 @ b17fccdf:b7211155
2025-01-21 17:07:47
@ b17fccdf:b7211155
2025-01-21 17:07:47 -
 @ 554ab6fe:c6cbc27e
2025-02-04 15:56:29
@ 554ab6fe:c6cbc27e
2025-02-04 15:56:29Modern life, despite all our technology, can still feel challenging. Many of us work very long hours to make ends meet, burdened by stress that can dramatically affect our health. The internet provides us with a wealth of helpful knowledge but also bombards us with headlines that can make us uneasy about the state of the world. In short, life can feel very stressful. Sometimes, leaving it all behind and becoming a monk may seem like a perfect way to escape it all. Though this may work for some, this is simply not a practical thing to do for many of us. Many of us are here to stay. However, even though the stressful nature of society will not change for a very long time, it is possible to reorient one's perspective so that it feels less stressful. In other words, rather than needing to go to a temple to become a monk, one can learn to bring the monk mind here.
It can be challenging to know where to begin to generate a positive outlook on life. So many people try to give advice, yet there never seems to be a "one size fits all" approach. We attempt to solve our outlooks by rationalizing the situation in a more positive way. Indeed, this can be useful for some, but not all. Furthermore, different people require different rationalizations. Regardless of advice, some are still stuck wondering how to have a better outlook on life. There is, of course, another method of perspective, and that is through non-judgment and simple acceptance.
Mindfulness meditation is a method of training the mind to become calmer and more at peace. In the scientific community, meditation is defined as a method of self-regulation of attention to the present moment, involving adopting a particular orientation toward one's experiences characterized by curiosity, openness, acceptance, and non-judgmental (Bishop et al., 2004). The benefits of meditation are many; however, much more research is required to understand its benefits and mechanisms better. The most well-documented benefit of mindfulness meditation is its ability to alleviate stress and anxiety (Greeson et al., 2018; Petterson & Olson, 2017; Querstret et al., 2020). The method by which this occurs is still reasonably unclear, yet many researchers have developed psychological and physiological theories. Furthermore, meditation reduces stress and anxiety while also creating resilience (Chin et al., 2019; Hwang et al., 2018). So, not only does it seem to be a curative treatment, but a preventative one as well. Understanding how meditation creates stress resilience is crucial to understand why meditation is so beneficial to health—the lessons provided in the research share profound philosophical lessons for us to bear in mind.
When studying meditation and its effects on the mind and body, it is essential to take a neuroscientific and psychological approach. The neuroscientific approach is valuable in both providing evidence that meditation impacts the body and sheds light on the mechanisms of action. A psychological perspective is also critical because it evaluates the mental schemas' effect on the body to better understand how the reader can practice this at home and in their daily lives. Both points of view will be discussed below.
Amygdala and ACC connectivity
The two brain areas that seem to be highly related to the process of resilience toward stress induced by mindfulness meditation are the amygdala and the anterior cingulate cortex (ACC).
The amygdala is found medial to the brain's temporal lobe and plays a vital role in emotional regulation and attention (Desbordes et al., 2012). For this reason, numerous studies have shown to be heavily involved in the experience of stress (Britton, 2006; Hölzel et al., 2009; Rubinow et al., 2016). It also influences the body in response to stress. For example, the amygdala regulates blood pressure in response to stressful stimuli (Saha, 2005).
The role of the ACC is seemingly more complex than the amygdala. In general, it is involved in executing responses regarding incoming interoceptive signals (signals from within the body) (Craig, 2002). For this reason, it connects to the motor cortex of the brain (Craig, 2002). On this same note, the anterior portion of the amygdala, the more executive region, has been associated with regulating endocrine functions, conditioned learning responses, expressing internal states vocally, and maternal-infant interactions (Devinsky et al., 1995). The ACC is related mainly to the processing of internal stimuli, associating it with the practice of mindfulness meditation. Less clear is how it relates to the amygdala and resilience to stress.
The neuroscientific observations of stress resilience are found within the connectivity between the amygdala and the ACC. In a randomized control trial involving a 3-day intensive mindfulness meditation program, researchers found that reduced stress following the practice was marked by decreased communication between the amygdala and the ACC (Taren et al., 2014). The study also noted reduced communication between the amygdala and ACC lessened HPA-axis activation (Taren et al., 2014). The HPA-axis is responsible for releasing hormones such as cortisol, which is a common biomarker for the activation of stress. This study is not alone in observing signs that mindfulness meditation reduces cortisol (Hoge et al., 2018). This is strong evidence that meditation induces physical changes within the brain, promoting resilience to biological responses to stress. The question is, how does this occur mentally, and how can we put this into practice?
Important Techniques within Meditation
The discussion and research surrounding how meditation leads to physical changes in the brain and body are complex and poorly understood. The appreciation for science in the west is new, and there is much research to be done. The author's current opinion is that meditation involves both physical and mental mechanisms that lead to some of its practical health benefits. Regarding resilience, a randomized control trial also observed that the resilience created was both physical and mental (Hoge et al., 2018). Though the exact mechanism is not fully understood, there has been an effort to gain insight applicable to modern-day life.
The research involving the mechanism at which meditation generates resilience towards stress is often pursued from a psychological point of view. To pursue this question, experiments involve different groups of people who are asked to perform similar tasks but differ in mental schemas practiced. The observed differences in health results indicate specific meditation techniques that are so helpful in generating resilience. For example, a randomized control trial in 2018 involved sending a group of participants to a temple (Hwang et al., 2018). One group was asked to participate in meditation sessions, while another group was asked to simply relax during this time at a peaceful place. The purpose was to discern whether or not the relaxing aspect of meditation was sufficient to produce resilience to stress or if something else was causing the change. The results found that both groups showed short-term benefits, but only the meditators had prolonged resilience towards stress months after the experiment. The results indicate that there was a mental practice involved through meditation that promoted stress resilience. A randomized control trial in 2019 expanded on this investigation by having one group of meditators purely practice the focused attention on the present, while the other group focused on the present while also cultivating a perspective of acceptance to all incoming stimuli (Chin et al., 2019). This study found that those who practiced a non-judgmental awareness showed a more significant reduction of stress than the attention group and the non-meditators, suggesting that the non-judgmental awareness of the present moment and experience was an essential aspect of stress resilience. Others have produced a similar theory on why meditation seems to be a healthy therapeutic method for those suffering from PTSD (Thompson & Waltz, 2010). The significance of these findings is not only crucial for those who have a meditation practice but anyone in general.
Be Non-Judgmental
A key aspect of meditation practice is to be mindful and aware of the present experience and interpret all thoughts, experiences, and stimuli in an accepting and non-judgemental manner. Not only is this important within the philosophical teachings, but it is a core aspect of how meditation works from a scientific point of view. This has profound implications for the importance of how we generate personal narratives. In meditation, one learns to let go of every incoming experience, no matter how tempting it is to value that thought or feeling. This is perhaps why the amygdala and ACC are involved. The amygdala is involved in emotions and stress, and the ACC is involved in "doing something about it." In meditation, no matter the feeling, thought, or stressor, one must cultivate an attitude of acceptance. One must simply continue sitting and focusing on the present. There is no evaluation, no judgment, simply acceptance.
This article began with the idea that one can become resilient to stress and experience less of it by simply reorienting their perspective of modern stressors. It was also stated that there is seemingly no one answer for everyone. This may be because people often try to generate rational or schemas to help people think about events differently. This article argues a different approach: don't think, just accept, let go, and move on. This is easier said than done, of course, and by no means are the benefits of meditation best articulated through argument. It is best to be experienced first hand.
Nonetheless, we are heavily burdened by the values we give to thoughts related to the stressors of modern-day life. We cannot avoid the stressors, but we can change their power over us. Removing their meaning and value removes their power and influence.
References
Bishop, S. R., Lau, M., Shapiro, S., Carlson, L., Anderson, N. D., Carmody, J., Segal, Z. v., Abbey, S., Speca, M., Velting, D., & Devins, G. (2004). Mindfulness: A Proposed Operational Definition. Clinical Psychology: Science and Practice, 11(3), 230–241. https://doi.org/10.1093/clipsy.bph077
Britton, W. B. (2006). Meditation and Depression.
Chin, B., Lindsay, E. K., Greco, C. M., Brown, K. W., Smyth, J. M., Wright, A. G. C., & Creswell, J. D. (2019). Psychological mechanisms driving stress resilience in mindfulness training: A randomized controlled trial. Health Psychology, 38(8), 759–768. https://doi.org/10.1037/hea0000763
Craig, A. D. (2002). How do you feel? Nature Review. https://doi.org/10.1177/1359105308095062
Desbordes, G., Negi, L. T., Pace, T. W. W., Alan Wallace, B., Raison, C. L., & Schwartz, E. L. (2012). Effects of mindful-attention and compassion meditation training on amygdala response to emotional stimuli in an ordinary, Nonmeditative State. Frontiers in Human Neuroscience, 6(OCTOBER 2012), 292. https://doi.org/10.3389/fnhum.2012.00292
Devinsky, O., Morrell, M. J., & Vogt, B. A. (1995). Contributions of anterior cingulate cortex to behaviour. Brain, 118(1), 279–306. https://doi.org/10.1093/BRAIN/118.1.279
Greeson, J. M., Zarrin, H., Smoski, M. J., Brantley, J. G., Lynch, T. R., Webber, D. M., Hall, M. H., Suarez, E. C., & Wolever, R. Q. (2018). Mindfulness Meditation Targets Transdiagnostic Symptoms Implicated in Stress-Related Disorders: Understanding Relationships between Changes in Mindfulness, Sleep Quality, and Physical Symptoms. Evidence-Based Complementary and Alternative Medicine, 2018. https://doi.org/10.1155/2018/4505191
Hoge, E. A., Bui, E., Palitz, S. A., Schwarz, N. R., Owens, M. E., Johnston, J. M., Pollack, M. H., & Simon, N. M. (2018). The effect of mindfulness meditation training on biological acute stress responses in generalized anxiety disorder. Psychiatry Research, 262(May 2016), 328–332. https://doi.org/10.1016/j.psychres.2017.01.006
Hölzel, B. K., Carmody, J., Evans, K. C., Hoge, E. A., Dusek, J. A., Morgan, L., Pitman, R. K., & Lazar, S. W. (2009). Stress reduction correlates with structural changes in the amygdala. Social Cognitive and Affective Neuroscience, 5(1), 11–17. https://doi.org/10.1093/scan/nsp034
Hwang, W. J., Lee, T. Y., Lim, K. O., Bae, D., Kwak, S., Park, H. Y., & Kwon, J. S. (2018). The effects of four days of intensive mindfulness meditation training (Templestay program) on resilience to stress: A randomized controlled trial. Psychology, Health and Medicine, 23(5), 497–504. https://doi.org/10.1080/13548506.2017.1363400
Petterson, H., & Olson, B. L. (2017). Effects of mindfulness-based interventions in high school and college athletes for reducing stress and injury, and improving quality of life. Journal of Sport Rehabilitation, 26(6), 578–587. https://doi.org/10.1123/jsr.2016-0047
Querstret, D., Morison, L., Dickinson, S., Cropley, M., & John, M. (2020). Mindfulness-based stress reduction and mindfulness-based cognitive therapy for psychological health and well-being in nonclinical samples: A systematic review and meta-analysis. International Journal of Stress Management, 27(4), 394–411. https://doi.org/10.1037/str0000165
Rubinow, M. J., Mahajan, G., May, W., Overholser, J. C., Jurjus, G. J., Dieter, L., Herbst, N., Steffens, D. C., Miguel-Hidalgo, J. J., Rajkowska, G., & Stockmeier, C. A. (2016). Basolateral amygdala volume and cell numbers in major depressive disorder: a postmortem stereological study. Brain Structure and Function, 221(1), 171–184. https://doi.org/10.1007/s00429-014-0900-z
Saha, S. (2005). ROLE OF THE CENTRAL NUCLEUS OF THE AMYGDALA IN THE CONTROL OF BLOOD PRESSURE: DESCENDING PATHWAYS TO MEDULLARY CARDIOVASCULAR NUCLEI. Clinical and Experimental Pharmacology and Physiology, 32(5–6), 450–456. https://doi.org/10.1111/j.1440-1681.2005.04210.x
Taren, A. A., Gianaros, P. J., Greco, C. M., Lindsay, E. K., Fairgrieve, A., Brown, K. W., Rosen, R. K., Ferris, J. L., Julson, E., Marsland, A. L., Bursley, J. K., Ramsburg, J., & Creswell, J. D. (2014). Mindfulness meditation training alters stress-related amygdala resting state functional connectivity: A randomized controlled trial. Social Cognitive and Affective Neuroscience, 10(12), 1758–1768. https://doi.org/10.1093/scan/nsv066
Thompson, B. L., & Waltz, J. (2010). Mindfulness and experiential avoidance as predictors of posttraumatic stress disorder avoidance symptom severity. Journal of Anxiety Disorders, 24(4), 409–415. https://doi.org/10.1016/j.janxdis.2010.02.005
-
 @ b17fccdf:b7211155
2025-01-21 16:56:24
@ b17fccdf:b7211155
2025-01-21 16:56:24It turns out that Ubuntu Linux installations of Ubuntu 23.04, 22.04.3 LTS, and installs done since April 2023 that accepted the Snap version update haven't been following Ubuntu's own recommended security best practices for their security pocket configuration for packages.
A new Subiquity release was issued to fix this problem while those on affected Ubuntu systems already installed are recommended to manually edit their
/etc/apt/sources.listfile.If you didn't install MiniBolt recently, you are affected by this bug, and we need to fix that manually if not we want to install all since cero. Anyway, if you installed Minibolt recently, we recommend you review that.
Follow these easy steps to review and fix this:
- Edit the
sources-listfile:
sudo nano /etc/apt/sources.list- Search now for every line that includes '-security' (without quotes) (normally at the end of the file) and change the URL to --> http://security.ubuntu.com/ubuntu
~ > For example, from http://es.archive.ubuntu.com/ubuntu (or the extension corresponding to your country) to --> http://security.ubuntu.com/ubuntu
~> Real case, Spain location, before fix:
``` deb http://es.archive.ubuntu.com/ubuntu jammy-security main restricted
deb-src http://es.archive.ubuntu.com/ubuntu jammy-security main restricted
deb http://es.archive.ubuntu.com/ubuntu jammy-security universe
deb-src http://es.archive.ubuntu.com/ubuntu jammy-security universe
deb http://es.archive.ubuntu.com/ubuntu jammy-security multiverse
deb-src http://es.archive.ubuntu.com/ubuntu jammy-security multiverse
```
After fix:
``` deb http://security.ubuntu.com/ubuntu jammy-security main restricted
deb-src http://es.archive.ubuntu.com/ubuntu jammy-security main restricted
deb http://security.ubuntu.com/ubuntu jammy-security universe
deb-src http://es.archive.ubuntu.com/ubuntu jammy-security universe
deb http://security.ubuntu.com/ubuntu jammy-security multiverse
deb-src http://es.archive.ubuntu.com/ubuntu jammy-security multiverse
```
Save and exit
Note: If you have already these lines changed, you are not affected by this bug, and is not necessary to do anything. Simply exit the editor by doing Ctrl-X
- Finally, type the next command to refresh the repository pointers:
sudo apt update- And optionally take the opportunity to update the system by doing:
sudo apt full-upgradeMore context:
- https://wiki.ubuntu.com/SecurityTeam/FAQ#What_repositories_and_pockets_should_I_use_to_make_sure_my_systems_are_up_to_date.3F
- https://bugs.launchpad.net/subiquity/+bug/2033977
- https://www.phoronix.com/news/Ubuntu-Security-Pocket-Issue
- Edit the
-
 @ b17fccdf:b7211155
2025-01-21 16:49:27
@ b17fccdf:b7211155
2025-01-21 16:49:27What's changed
- New method for Bitcoin Core signature check, click ~ >HERE< ~
- GitHub repo of Bitcoin Core release attestations (Guix), click ~ >HERE< ~
History:
~ > PR that caused the broken and obsolescence of the old signature verification process, click ~ >HERE< ~
~ > New GitHub folder of Bitcoin Core repo that stores the signatures, click ~ >HERE< ~
Thanks to nostr:npub1gzuushllat7pet0ccv9yuhygvc8ldeyhrgxuwg744dn5khnpk3gs3ea5ds for building the command that made magic possible 🧙♂️🧡
Enjoy it MiniBolter! 💙
-
 @ a012dc82:6458a70d
2025-02-04 15:49:10
@ a012dc82:6458a70d
2025-02-04 15:49:10Bitcoin halving is a cornerstone event in the cryptocurrency landscape, occurring approximately every four years, or after every 210,000 blocks are mined. This event is significant because it marks a reduction in the reward that miners receive for adding new blocks to the Bitcoin blockchain, effectively halving the rate at which new bitcoins are generated. The concept of halving is embedded in Bitcoin's protocol by Satoshi Nakamoto, its mysterious creator, as a measure to mimic the scarcity and deflationary characteristics of precious metals like gold. This mechanism is crucial in controlling the supply of Bitcoin, ensuring that it remains finite and valuable. As the next halving event draws near, it's not just miners who are impacted; the entire cryptocurrency market, including investors and enthusiasts, keenly anticipates the potential outcomes. Historically, halving events have been associated with increased market activity, price volatility, and heightened public interest in Bitcoin. The event is seen as a moment of transformation for Bitcoin, where the dynamics of supply and demand are altered, potentially leading to significant shifts in its market value.
Table Of Content
-
Understanding the Hash Rate Surge
-
Implications of the Rising Hash Rate
-
The Halving Event: What to Expect
-
Preparing for the Halving
-
Conclusion
-
FAQs
Understanding the Hash Rate Surge
What is Hash Rate?
The hash rate, in the context of Bitcoin, refers to the total computational power being used to mine and process transactions on the blockchain. It's a vital metric that reflects the health and security of the network. A higher hash rate means that more computational resources are being dedicated to maintaining the network, making it more robust against potential attacks. The hash rate is measured in hashes per second (H/s), and with advancements in mining technology, the network has seen this rate reach exahash levels (1 EH/s = 1 quintillion hashes per second). This metric is crucial for miners, as it affects their chances of solving the mathematical puzzles required to mine new blocks and earn rewards. It also indicates the level of competition among miners, as a higher hash rate suggests more participants or more powerful mining equipment in the network.
Record-Breaking Levels
The Bitcoin network's hash rate has recently hit an all-time high, reaching a staggering 491 exahashes per second (EH/s). This surge is indicative of the growing strength and security of the network. Such a high hash rate means that the network is more resilient than ever to potential attacks, such as the 51% attack, where a single entity could potentially gain control over the majority of the network's mining power. This level of security is crucial, especially as Bitcoin continues to gain mainstream acceptance and attract significant institutional investment. The record-breaking hash rate also reflects the increasing global interest in Bitcoin mining. It suggests that despite the high costs associated with mining - including specialized hardware and significant electricity consumption - miners are still heavily investing in this activity. This investment is not just in terms of money but also in research and development of more efficient mining technologies, which could further drive up the hash rate.
Implications of the Rising Hash Rate
Enhanced Network Security
The surge in Bitcoin's hash rate is a positive development for the network's security. A higher hash rate means that it becomes exponentially more difficult for a malicious actor to orchestrate an attack on the network. This security is paramount for a system that handles billions of dollars worth of transactions. The decentralized nature of Bitcoin relies heavily on the integrity of its blockchain, which is maintained by this collective computational effort. As the hash rate increases, the confidence in the network's security also grows, which is crucial for both individual users and institutional investors. This enhanced security is particularly important in the context of the upcoming halving event, as it ensures the stability and reliability of the network during a period of significant change.
Increased Mining Difficulty
With the rise in hash rate comes an increase in the difficulty of mining Bitcoin. The Bitcoin network is designed to adjust the difficulty of mining new blocks approximately every two weeks to ensure that the time between blocks remains around 10 minutes. As more computational power joins the network, the difficulty increases, making it harder for individual miners to solve the cryptographic puzzles required to mine new blocks. This increase in difficulty can have several implications for miners. Smaller miners or those with less efficient equipment may find it increasingly difficult to compete with larger mining operations that have access to more powerful and efficient technology. This could lead to a consolidation in the mining industry, where only the most efficient operations can survive. Additionally, as the difficulty increases, the profitability of mining can decrease, especially if the price of Bitcoin does not increase proportionally. Miners must constantly evaluate their operations' efficiency and electricity costs to ensure continued profitability.
Energy Consumption Concerns
The rising hash rate of the Bitcoin network has brought renewed attention to the issue of energy consumption in Bitcoin mining. The process of mining Bitcoin is energy-intensive, as it requires a significant amount of computational power. As the hash rate increases, so does the total energy consumption of the network. This has led to concerns about the environmental impact of Bitcoin mining, especially in regions where electricity is generated from fossil fuels. The debate around Bitcoin's energy consumption is complex. On one hand, proponents argue that much of the energy used for Bitcoin mining comes from renewable sources, and the industry drives innovation in energy efficiency. On the other hand, critics point out that the overall energy consumption is still substantial and could be directed towards other, more productive uses. This debate is likely to continue as the network grows and the hash rate increases, especially in the context of global concerns about climate change and sustainable energy practices.
The Halving Event: What to Expect
Reward Reduction
The upcoming Bitcoin halving event is a scheduled reduction in the rewards that miners receive for verifying and adding new transactions to the blockchain. This halving reduces the number of new bitcoins created and earned by miners with each new block from 6.25 bitcoins to 3.125 bitcoins. This event occurs every 210,000 blocks, or approximately every four years, and is a fundamental part of Bitcoin's economic model. The halving is designed to mimic the extraction of precious resources, becoming progressively harder and less rewarding over time. This mechanism ensures that the total supply of Bitcoin will never exceed 21 million coins, making Bitcoin a deflationary asset. The halving event is significant because it affects the economics of Bitcoin mining. With the reward halving, the revenue for miners is effectively cut in half overnight. This can lead to a shakeout in the mining industry, as less efficient miners may no longer be profitable and could be forced to shut down their operations.
Market Impact
Historically, Bitcoin halving events have been followed by significant price increases. This pattern has led to a common perception that halving events are bullish for Bitcoin's price. The rationale behind this is simple: as the rate of new supply of Bitcoin decreases, and if demand remains constant or increases, the price should theoretically go up. However, it's important to note that financial markets are influenced by a myriad of factors, and the impact of the halving may already be priced in by the time it occurs. Additionally, each halving event occurs in a different macroeconomic environment, and past performance is not indicative of future results. Investors and traders closely watch these events, as they can lead to increased volatility in the market. Some see the halving as an opportunity for long-term investment, while others may speculate on short-term price movements.
Preparing for the Halving
Miner Adaptations
In anticipation of the halving and its impact on profitability, miners are taking various steps to adapt. One key strategy is the investment in more efficient mining hardware. Newer models of mining rigs offer greater hash power with lower energy consumption, which can help maintain profitability even with reduced rewards. Miners are also exploring alternative sources of revenue, such as transaction fee income, which could become a more significant part of their earnings post-halving. Additionally, miners are looking at geographical relocation to regions with cheaper electricity and favorable regulatory environments to reduce operational costs. Another consideration for miners is the potential consolidation of mining operations. Larger mining pools might have a better chance of surviving the reduced rewards, leading to a more centralized mining landscape. This potential centralization raises concerns within the Bitcoin community, as it could impact the decentralized nature of the network.
Investor Strategies
Investors are also preparing for the halving event in various ways. Many are closely analyzing historical data to understand potential market movements, although it's widely acknowledged that past trends may not necessarily predict future outcomes. Some investors view the halving as a key event that could drive long-term value growth in Bitcoin and are adjusting their portfolios accordingly. Others are more cautious, considering the potential for increased volatility around the event. There is also a focus on diversification, with investors looking at other cryptocurrencies and blockchain projects that might benefit from increased interest in the crypto space around the halving. Additionally, institutional investors, who have increasingly entered the cryptocurrency market, are likely to play a significant role in how the market reacts to the halving. Their strategies, which may include hedging and derivative trading, could influence Bitcoin's price dynamics in ways that were not seen in previous halving events.
Conclusion The countdown to the Bitcoin halving is a period of significant anticipation and activity within the cryptocurrency community. The record-breaking hash rate ahead of the event is a testament to the network's strength and the commitment of its participants to maintain and secure the blockchain. As the halving approaches, the crypto world watches with keen interest, eager to see how this pivotal event will shape the future of Bitcoin. Whether it leads to a surge in price, increased adoption, or new challenges for miners, the halving is a reminder of the unique and dynamic nature of cryptocurrency and its underlying technology. As with any major event in the crypto space, the halving presents both opportunities and risks, and how it plays out could have lasting implications for the entire blockchain ecosystem.
FAQs
What is Bitcoin Halving? Bitcoin halving is an event that occurs approximately every four years, reducing the reward for mining new Bitcoin blocks by half. This mechanism controls the supply of new bitcoins and is a fundamental part of Bitcoin's economic model.
Why is the Bitcoin Hash Rate Important? The hash rate measures the total computational power used in mining and processing transactions on the Bitcoin network. A higher hash rate indicates a more secure and robust network, making it resistant to attacks.
What Happens to Bitcoin's Price After Halving? Historically, Bitcoin's price has increased following halving events, but this is not guaranteed. Market reactions can be unpredictable, and various factors influence Bitcoin's price.
How Does Halving Affect Bitcoin Miners? Halving reduces the reward miners receive for validating new blocks, impacting their profitability. Miners often need to upgrade to more efficient hardware or find cheaper energy sources to remain competitive.
Can Bitcoin Halving Lead to Increased Centralization in Mining? Potentially, yes. As mining becomes less profitable for smaller operations, there could be a consolidation towards larger mining pools, which might lead to a more centralized mining landscape.
Is the Increase in Bitcoin's Hash Rate Linked to the Upcoming Halving? Yes, the increase in hash rate is often linked to the upcoming halving as miners upgrade their equipment and increase their computational power in anticipation of the reduced mining rewards.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ b17fccdf:b7211155
2025-01-21 16:40:01
@ b17fccdf:b7211155
2025-01-21 16:40:01Important notice to MiniBolt node runners:
~ > It turns out that the I2P devs have opened an issue on the Bitcoin Core GitHub repo commenting that because they gave the option to enable the
notransit=trueparameter in the official documentation:[...] If you prefer not to relay any public I2P traffic and only allow I2P traffic from programs connecting through the SAM proxy, e.g. Bitcoin Core, you can set the no transit option to true [...] are having a heavy load on the I2P network since last December 19. Also comment that it is advisable to share as much bandwidth and transit tunnels as we can, to increase anonymity with coverage traffic, by contributing more to the I2p network than we consume.
So they ask that we deactivate that option that you use activated. With all this, he already updated the "Privacy" section by removing that setting.
The steps to delete this configuration once we have already configured it, are the following:
- With the "admin" user, stop i2pd:
sudo systemctl stop i2pd- Comment line 93 with "#" at the beginning of it (notransit = true), save and exit
sudo nano /var/lib/i2pd/i2pd.conf --line numbers- Start i2pd again:
sudo systemctl start i2pd- And that's it, you could take a look at Bitcoin Core to see that it has detected i2pd running again after the reboot with:
tail --lines 500 -f /home/bitcoin/.bitcoin/debug.log~ > If you don't see that I2P is up in Bitcoin Core after the restart,
sudo systemctl restart bitcoindand look again at the logs of the same.
More info in the rollback commit, see ~> HERE < ~
-
 @ b17fccdf:b7211155
2025-01-21 16:15:51
@ b17fccdf:b7211155
2025-01-21 16:15:51What's changed
A bonus guide to get a quick overview of the system status with the most relevant data about the services on the main guide.
➕Additional extra sections (optional) to:
- Show on login
- Get the channel.db size of an old LND bbolt database backend
- Use MobaXterm compatibility version
🔧 GitHub PR related: https://github.com/minibolt-guide/minibolt/pull/97
Σ Dedicated GitHub repository: https://github.com/minibolt-guide/system_overview
🫂Acknowledgments
This is a fork of the minibolt_info repository, the main developer of this project is rmnscb, a member of the MiniBolt community, all the merits go to him. Thank you for your contribution 🧡🫂
-> CLICK HERE <- to go to the bonus guide
Enjoy it MiniBolter! 💙
-
 @ 1833ee04:7c4a8170
2025-02-04 15:14:03
@ 1833ee04:7c4a8170
2025-02-04 15:14:03The international race for Bitcoin strategic reserves is just getting started.
If you’re stacking now, you’re still incredibly early.
At $100k per Bitcoin, it’s practically free for anyone who truly understands how massive this shift is.
Think back to when paper currency was introduced, people had to trade their gold for paper bills. Many laughed, saying, Who’s going to trust these worthless pieces of paper as money?
Yet today, you sell your time to earn these paper bills while your government can print an unlimited amount at will.
The world is returning to a gold standard. But this time, it’s Gold 2.0 which is Bitcoin.The international race for Bitcoin strategic reserves is just getting started.\ \ If you’re stacking now, you’re still incredibly early.\ \ At $100k per Bitcoin, it’s practically free for anyone who truly understands how massive this shift is.\ \ Think back to when paper currency was introduced, people had to trade their gold for paper bills. Many laughed, saying, Who’s going to trust these worthless pieces of paper as money?\ \ Yet today, you sell your time to earn these paper bills while your government can print an unlimited amount at will.\ \ The world is returning to a gold standard. But this time, it’s Gold 2.0 which is Bitcoin.
-
 @ 5af07946:98fca8c4
2025-02-04 15:13:27
@ 5af07946:98fca8c4
2025-02-04 15:13:27Syādvāda, also known as the theory of conditional predication, is a fundamental concept in Jain philosophy that bears some intriguing similarities to modern concepts of probability.
Conditional Prediction system
Syādvāda is a theory of epistemological relativism that forms the basis of Jain logic. The term "syād" in Sanskrit means "may be" or "perhaps," and in the context of syādvāda, it translates to "in some ways" or "from a perspective". This theory asserts that reality is complex and multifaceted, and no single proposition can fully express its nature.
Saptabhangi: The Seven-fold Predication
The core of syādvāda is manifested in the process of Saptabhangi, or seven-fold prediction. This approach examines reality from seven different conditional and relative viewpoints:
- Syādasti (maybe, it is)
- Syānnāsti (maybe, it is not)
- Syādasti nāsti (maybe, it is, and it is not)
- Syādavaktavya (maybe, it is indeterminate)
- Syādasti avaktavya (maybe, it is and is indeterminate)
- Syānnāsti avaktavya (maybe, it is not and is indeterminate)
- Syādasti nāsti avaktavya (maybe, it is, is not, and is indeterminate)
Connections to Probability
Syādvāda shares conceptual similarities with Probability theory:
- Non-absolutism: Like probability theory, syādvāda acknowledges uncertainty and rejects absolute statements. However, it asserts that there are only seven categories necessary and also sufficient to exhaust all possibilities of knowledge!
- Conditional nature: Both syādvāda and probability deal with conditional statements and chances
- Multiple outcomes: Syādvāda's seven-fold prediction can be seen as analogous to considering multiple possible outcomes in probability.
- Indeterminacy: The fourth category of syādvāda, "avaktavya" (indeterminate), has been interpreted by some scholars as having relevance to the concept of probability.
An Illustrative Example
Consider the tossing of a coin:
- "It is head" (now) - Syādasti
- "It is not-head" (on another occasion) - Syānnāsti
- "It is, and it is not" - Syādasti nāsti
- "It is indeterminate" (before the toss) - Syādavaktavya
This example demonstrates how syādvāda's categories can be applied to a situation involving uncertainty, similar to how we might approach it using probability theory.
Historical Significance and Modern Relevance
Syādvāda was well-developed by the 6th century AD and received significant attention in medieval Indian logic. It is believed that it was based on astrological principles of Maharishi Parashara - the father of ancient astrology.
-
 @ 6be5cc06:5259daf0
2025-01-18 02:11:43
@ 6be5cc06:5259daf0
2025-01-18 02:11:43- Not your keys, not your coins
Se você não tem as chaves privadas do seu Bitcoin, ele não é realmente seu. Deixar seus BTCs em exchanges ou carteiras controladas por terceiros significa confiar neles e assumir o risco de perder seus fundos.
- HODL - Não venda
O Bitcoin é uma reserva de valor a longo prazo e potencialmente o dinheiro do futuro. Não se desespere com as flutuações de preço; mantenha seus BTCs, pois o histórico se mostra favorável.
- Stay humble - Não saia falando que você tem BTC
Manter discrição sobre seu patrimônio é uma questão de segurança e humildade. Falar demais pode atrair curiosos, oportunistas ou outras ameaças.
- Don't trust, verify
No Bitcoin, confie no protocolo, não em pessoas. Sempre que possível, verifique por conta própria, seja transações, códigos ou informações.
- Reject altcoins
As altcoins podem parecer promissoras, mas frequentemente são distrações ou apostas arriscadas. Foque no Bitcoin, que já provou ser sólido e resistente.
- Stack sats - DCA
Empilhe satoshis consistentemente, utilizando a estratégia de DCA (Dollar Cost Averaging), comprando regularmente independentemente do preço. Isso reduz o risco de tentar "acertar o mercado".
- Reject the ego
Não aposte contra o Bitcoin. Aqueles que subestimaram sua força ou estabilidade, perderam.
- Keep learning
Nunca pare de estudar sobre Bitcoin, economia e a tecnologia por trás dele. Quanto mais você entende, mais confiança terá em sua decisão.
- Help beginners
O Bitcoin pode ser complicado para quem está começando. Compartilhe seus conhecimentos com paciência para fortalecer a comunidade.
- Don't push it
Cada pessoa tem seu próprio tempo para entender e entrar no mundo do Bitcoin. Forçar alguém pode ser contraproducente; dê direcionamento e deixe o tempo agir.
-
 @ 916a7ab7:146bb83e
2025-02-04 13:35:11
@ 916a7ab7:146bb83e
2025-02-04 13:35:11It was not ago that my life was simpler than it is today.
I remember being a simple clone, droning on through a structured life as I'd been trained to do since birth.
Like most people I knew, I was raised in a world where you were mentally prepared for a conceptually simple life: 1. Finish high school, if possible. 2. Go to college, if possible. 3. Find a job. 4. Earn money. 5. Pay bills. 6. Get married. 7. Start a family. 8. Pay more bills. 9. Raise family and (hopefully) launch the kids. 10. Plan to retire, but expect to work into your 70s.
It was a programmed formula for life. A generational blueprint, if you will. Sure, there would be unpredictable details, but I expected my life to follow this path.
As I plodded along through my fairly boring life, I checked most of those things off the list. High school was easy, but getting off the farm was not. Enlisting in the military solved that problem, and the pay in the mid-1990s wasn't bad for a 17 year old kid with no bills. I got paid every two weeks, lived in the barracks, and spent most of my money on booze. Life was good, and I had no other purpose than to do my job and keep earning money.
Before I knew it, though, everything changed. I got married, had some kids and accumulated a mountain of debt. Like my parents before me, I was stuck in a never ending cycle of working my ass off, paying bills, buying food, and trying to save what little money was left over for a future that was unpredictable at best. Financial struggles stressed our marriage, the kids continued eating more and more food, and then 2008 tanked the value of our home. That was the first nudge that stirred my oblivious slumber.
And there was more to come. Rising taxes, inflation, the clown show at the federal reserve, the wars funded by central banks, an astronomical national debt, and the burdens of our mistakes weighing down the futures of our children. Not to mention a federal government that actively seeks to censor, suppress, and financially imprison its own people. The times exuded chaos.
Then a few months ago, I woke up...
It happened during an episode of The Tuttle Twins, a cartoon show from Angel Studios. I homeschool my three youngest kids, and I'd let them watch TV during lunch so I could grade some papers. This cartoon was new to me, but the kids liked the music and the crazy raccoon. As fate would have it, they ended up watching an episode about Bitcoin. This, of course, led to a long series of questions:
"Dad, what's Bitcoin?"
"Is Bitcoin real?"
"Do you have Bitcoin?"
"Can I get Bitcoin for allowance instead of dollars?"
I had no answers for these questions, so we started doing some research together. We turned on our Chromebooks and launched a barrage of web searches. After reading a bunch of articles I came away with the idea that Bitcoin might be a real thing. Later that evening, and after the kids were in bed, I couldn't stop thinking about Bitcoin. I honestly didn't understand half of what I read in those articles, which bothered me. I'm not a super smart guy, but I catch on to things pretty quickly, and I wanted to better understand what I'd read. I expanded my search to podcasts and YouTube videos.
I ended up listening to a couple episodes from a Bitcoin Veterans podcast. As a veteran myself, I figured that this group of Bitcoin-savvy veterans would be able to help me figure out all this madness. I was right. I quickly learned that the word "Bitcoin" was just the tip of the iceberg, and I quickly found myself falling through an endless rabbit hole. They pointed me in a lot of different directions, but they were all helpful. (If you're a US military veteran and want to connect with this group, find them at [bitcoinveterans.org].)
A couple months ago, I couldn't tell you the difference between a Bitcoin and a meme coin. I'd come across the phrase Bitcoin mining, and I just thought there was a special group of people who mined a special metal to create coins with a big "B" on them. Why couldn't they just use the metal we already mined? Sheesh! I thought nostr was a virus, and a Kraken was still a giant squid.
As of today, I'm happy to say that I've made a little bit of progress. Those things above no longer confuse me, and I actually have a little bit of Bitcoin now. Sure, I'm still trying to wrap my head around NFTs and figure out who the Pepe frog man is, but I'm no longer completely lost. Not to mention, I just spent most of the last 24 hours figuring this whole nostr thing out, which excites me. I kind of missed the boat on the big name social media platforms, so I'm looking forward to this new decentralized approach to things.
For now, I'm just happy to be awake. Finally. I see the need for decentralization and the necessity of moving away from fiat monies. I don't have much to offer except my intellect and my love of writing, but I'm here to serve in any way that I can.
-
 @ ef1e59bf:b686587d
2025-02-04 11:15:10
@ ef1e59bf:b686587d
2025-02-04 11:15:10Key Insights Explained
While both systems provide innovative soilless growing solutions, the unique difference lies in their approach—hydroponics relies on a nutrient-rich water solution, whereas aquaponics integrates fish into the ecosystem to naturally supply nutrients. This not only impacts their cultivation techniques but also illustrates varying levels of sustainability and resource use.
In exploring these systems, one cannot help but consider the broader implications for urban agriculture. For those looking to adopt such systems, understanding key differences can significantly impact decisions on efficiency, cost, and ecological footprint.
What Is Hydroponics?
In hydroponics, we grow plants in water enriched with nutrients rather than soil. This method provides a controlled environment where the roots receive all necessary elements directly from the nutrient solution. It's fascinating how plants can thrive without ever touching the soil.
The benefits of hydroponics are impressive. We can achieve faster growth rates due to optimal nutrient delivery, and the space-saving designs, such as vertical farms, maximise small areas. Moreover, nutrient levels can be controlled precisely, ensuring plants receive exactly what they need.
What Is Aquaponics?
Aquaponics is an innovative system that blends aquaculture, which is the practice of raising fish, with hydroponics, the soilless cultivation of plants. In this symbiotic setup, fish waste serves as a natural fertiliser, supplying essential nutrients to the plants. In return, the plants help purify the water, creating a healthy environment for the fish.
This system is unique because it mimics natural ecosystems, enhancing sustainability. The dual benefits of growing plants and fish simultaneously make aquaponics an attractive option for those of us interested in sustainable agriculture and promoting organic cultivation practices.
Key Differences
Hydroponics and aquaponics each offer unique benefits and challenges. Understanding these systems requires examining their differences in nutrient sources, water usage, plant growth density, time to harvest, setup intricacies, and the types of produce they best support.
Nutrient Source
In hydroponics, plants receive nutrients through specially prepared solutions, often purchased from commercial suppliers. This method allows us to maintain a high level of control over nutrient balance, making precise adjustments as needed.
Aquaponics, by contrast, relies on fish waste to supply nutrients. This forms a more natural ecosystem, requiring biological processes like nitrification to convert waste into nutrients usable by plants. While this approach involves fewer chemical inputs and is more sustainable, it offers less control over nutrient levels.
Water Usage
Hydroponic systems excel in water efficiency by recirculating water, though they necessitate regular changes to keep nutrient solutions balanced. Despite their efficiency, water loss can occur through evaporation or leaks, which requires monitoring.
Aquaponics operates as a closed-loop system where water is continually recycled between the fish tank and plant beds, minimising waste. This setup further reduces water use due to natural filtration by plants, making it an incredibly water-efficient choice.
Grow Density
Hydroponics typically supports higher density plant growth, especially in vertical setups. This is ideal for cultivating leafy greens, herbs, and other fast-growing plants in compact spaces.
Aquaponics requires space for both fish and plants, which limits plant density. Although some plants may grow slower due to varying nutrient availability, this method offers the benefit of integrating fish care into the system.
Grow Time
In hydroponics, plants enjoy faster growth rates thanks to controlled nutrient and environmental conditions. These systems often facilitate shorter growing cycles compared to traditional farming, enhancing efficiency.
Aquaponics, while efficient, may experience slightly slower growth rates due to the time taken for natural nutrient conversion. Balancing fish growth with plant cycles adds an extra layer of complexity but is a rewarding experience for those willing to engage deeply with the system.
Set Up and Maintenance
Starting a hydroponic system is relatively straightforward, with pumps, nutrient tanks, and light management being primary needs. Regular checks of pH, nutrient levels, and water are essential yet generally simple.
Aquaponics demands more initial infrastructure and expertise due to the need for integrated fish tanks and plant systems. Balancing fish health and water quality with plant needs adds complexity, but long-term sustainability benefits are significant. Setting up these systems can seem daunting but offer reduced external nutrient input over time.
Produce Types
Hydroponics shines when growing leafy greens and herbs, achieving high success rates with crops like lettuce, basil, and spinach. These systems, however, have limitations when it comes to larger or more nutrient-demanding produce.
Aquaponics expands possibilities by supporting a broader range of plants, including fruiting ones such as tomatoes, alongside fish like tilapia or trout. This dual-production feature offers diverse yields, though the choice of fish can influence plant variety.
Which Is More Sustainable?
When we consider the sustainability of hydroponics, several factors come to mind. First, high water efficiency and space-saving designs make it attractive for eco-conscious growers. Yet, the reliance on artificial nutrients and the higher energy usage, particularly for lighting and pumps, may impact its overall eco-friendliness. These elements can sometimes offset the system’s environmental benefits.
In contrast, aquaponics offers a unique closed-loop system that naturally recycles waste. This can significantly reduce the need for external inputs, aligning well with principles of organic farming. While this method requires more space and careful maintenance for both fish and plants, it typically involves less chemical intervention, appealing to those seeking a more natural approach.
Let's compare the environmental impact of these methods:
-
Aquaponics might have a lower environmental footprint due to its natural nutrient cycle, reducing waste and chemical use.
-
On the other hand, hydroponics can be well-suited for urban environments or locations with limited resources, thanks to its efficient use of water and space.
Ultimately, deciding which system is more sustainable depends on specific circumstances and priorities. If natural nutrient cycles and less chemical intervention are valued, aquaponics might be favoured. Nevertheless, if water and space efficiency are paramount, especially in urban settings, hydroponics might be more suitable.
Hydroponics is a game-changer for sustainable farming, offering efficient water use, reduced land impact, and year-round crop production. Whether you're a beginner or an experienced grower, having the right tools and knowledge is key to success. Visit Hyjo for high-quality hydroponic systems, nutrients, and expert advice. Start growing smarter and greener with Hyjo today!
-
-
 @ 66675158:1b644430
2025-01-16 20:44:33
@ 66675158:1b644430
2025-01-16 20:44:33Before the time of Utensils, people lived in genuine harmony. They gathered in markets to trade freely, built homes where they pleased, and traveled without papers or permissions. Communities solved their own problems through discussion and agreement. When disputes arose, wise elders would help find solutions that satisfied all. Children learned from their parents or chose mentors from among the skilled craftspeople.
In those days, gold changed hands freely for goods and services. Each person kept what they earned. Communities would voluntarily pool resources for shared needs - wells, bridges, and roads. Those who had more would often help those with less, not by decree but by choice.
Neighbors knew each other's names. Doors were left unlocked. Children played in the streets until sunset. Gardens grew wherever people planted them. Merchants traveled between towns without inspections. Healers practiced their craft freely, sharing knowledge openly.
Then came the Utensils.
In our land, Aldrich found the Silver Spoon. In the East, Emperor Chen discovered the Jade Chopsticks. The Norse kingdoms united under the Golden Fork. The desert peoples followed the Bronze Ladle.
Each Utensil, their holders claimed, granted divine wisdom to rule. Each promised protection and prosperity in exchange for obedience.
The changes came slowly at first. The Spoon Holder requested a share of each harvest to store for hard times. The Chopstick Emperor required homes to be built in specific ways to prevent fires. The Fork King demanded that travelers carry documents proving their loyalty.
At first, the Utensils did bring some genuine improvements. The Spoon Holder's collectors used part of their harvest share to help villages during droughts. The Chopstick Emperor's building codes truly did reduce fires. The Fork King's road patrols deterred the few bandits who had troubled merchants. The Bronze Ladle's water management systems helped farms flourish in the desert.
The early years saw stone roads replace dirt paths, connecting villages more efficiently than before. Granaries were built with better designs, preserving food longer. Some diseases decreased as the Chopstick Emperor's cleanliness codes spread. The Fork Kingdom's standardized weights and measures did make trade easier.
The Spoon Holder soon declared that carrying gold was dangerous and inefficient. They introduced sacred paper notes, "backed by the Silver Spoon's power." At first, you could trade these notes back for gold, but gradually this right vanished.
Scholars wrote lengthy memos about the divine wisdom of the Utensils, creating complex theories about why ordinary people couldn't possibly understand how to live without direction. They advised the Holders and were rewarded with special privileges, comfortable positions, and influence.
When anyone questioned this system, the Utensil Holders and their Experts would ask: "But who would build the roads without us? Who would help the poor? Who would protect you?" They spoke as if humans had never cooperated or helped each other before the Utensils came, and many began to believe it.
People grumbled but accepted. After all, the Utensils shone with otherworldly power.
Some remembered these early benefits when questioning the growing restrictions. "Remember how the Spoon Holder's men helped during the great flood?" they would say. "Surely they have our best interests at heart." The Utensil Holders carefully nurtured these memories, even as their power grew far beyond such humble beginnings.
More rules followed. The Spoon Holder's men began watching the roads, collecting portions from merchants. The Chopstick Guards enforced strict codes about proper behavior. The Fork Watchers kept lists of who attended the mandatory gatherings.
Children were taught the sacred histories of their Utensils. The Spoon's light blessed the worthy. The Chopsticks maintained harmony. The Fork brought strength. The Ladle provided guidance.
When people remembered the old freedoms, the Utensil Holders reminded them of the chaos before - though few could actually recall any chaos.
But surely there must have been chaos, or why would the Utensils have come?
The Utensil Holders began to eye each other's territories. How dare the Fork King claim his metal was superior? How could the Chopstick Emperor suggest jade held more wisdom than silver? The Ladle Holder's bronze was clearly inferior to all!
The Utensil Holders pointed to their achievements - the roads, the granaries, the safer towns - as proof of their divine right to rule. They spoke of how they had unified squabbling villages, standardized laws, and created order. Few noticed how these very achievements had required less and less input from the people themselves.
Wars erupted. Armies marched under banners bearing their sacred Utensils. Men died believing their Utensil was the one true source of authority. Villages burned as soldiers searched for heretics who might secretly worship foreign Utensils.
The Utensil Holders demanded more from their people - more food, more gold, more obedience. They placed watchers in every village. They required written permission for travel between towns. They forbade more than three people from gathering without a Guardian present.
"It's for protection," they said, holding their Utensils high. "How can you doubt the sacred silver?"
And indeed, their guards did stop some thieves, their inspectors did prevent some fraud, their builders did create some useful works. But these benefits came with an ever-increasing price in freedom, until the cost far exceeded any advantage. Yet by then, most people could no longer imagine providing these services for themselves, as their ancestors had done.
Towns built walls, not against invaders but to control who could enter and leave. The Utensil Holders required everyone to wear markers showing their village of origin. They appointed observers in every community to report suspicious behavior - like speaking of the time before Utensils.
Children were taken to special houses to learn proper reverence for their Utensil. Families who taught the old ways disappeared in the night. The Holders declared certain words forbidden, certain thoughts dangerous, certain memories treasonous.
Now, centuries later, the Utensils rule absolutely. People bow when the sacred implements pass by. They inform on neighbors who question the Utensils' power. They offer their children to serve in the Utensil temples.
The latest marvel was Utensil Technology - enchanted mirrors and crystals that watched people's movements, recorded their words, and tracked their trades. "Only criminals fear being watched," the Holders proclaimed, as their surveillance spread into every home and market. The crystals even allowed them to freeze people's paper money if they spoke against the Utensils.
The Utensil Holders formed special partnerships with the largest merchant guilds. These favored merchants received special permissions, protection from smaller competitors, and access to the new paper money first. In return, they helped enforce the Holders' rules and collected information about their customers. Small traders and craftsmen found themselves crushed between these powerful allies.
The latest decree requires all newborns to be blessed by touching their foreheads to their realm's sacred Utensil, marking them forever as its property. Parents compete for earlier blessing times, believing this shows greater devotion.
The wars continue. The Fork Kingdoms battle the Chopstick Empire. The Ladle Realms raid the Spoon Holdings. Each believes their Utensil must rule all.
And in quiet corners, in hidden places, a few elders still whisper stories of the time before - when humans lived without Utensils telling them how to live. But fewer remember with each passing year. After all, who could imagine a world without the guidance of sacred silverware?
-
 @ 3eacaa76:bac66fe4
2025-01-15 16:25:13
@ 3eacaa76:bac66fe4
2025-01-15 16:25:13Few days back this track get on Top of list on #wavlake. It's nice , but not a point. at all.
The message is clear. like Real Talk should be !
We know, specialy on #nostr, that solutions are available. However, the world is not yet aware of them.
100% of the donations for this remix will be sent to my friend Yusef who is on the ground and has been providing food, water, and shelter for children in Gaza even before or the psyop with October 07 took a place. Israel has enforced a blockade on Gaza for over decade. And Just past year completly destroyed 90% of land. Like to the ground , no schools , no hospitals ... hard to find anything what surrvived those daily airstrikes without 1h of pause since 350 days. WTF
It's heartbreaking to see children dying daily in houreds and the lack of action from the public and authorities of other nations. The statistics are alarming, and it's essential to address this issue and find ways to make progress. it's crucial to raise awareness and take action to prevent further tragedies. Let's remember that every child's life is precious and deserves our attention and support.
In most apocaliptic condition , where is-real controling all money supply (check lastest news about banknotes in there) , the #Bitcoin is one and only solution can help them in daily bases. It was helping them before with great succes. Why you ask ? becuse even if they close all platforms You can still send them some sats.
How fookin cool is that !!
I know it doesn't sound funny.
Those People pushed to the limit , now they have a tool that fulfills exactly what was created for A Peer-to-Peer Electronic Cash System.
No Middle man .``` On the middle is only a finger whitch WE the PEOPLE can give to those Scumbagz in Goverments and Banks, Full stop.
```
Many people are only recently realizing the truth about Gaza being an open-air prison from like 75 years. Not 3, not 5 or even 20 ..... but seventy five fookin years.
This music mix was created to share the truth and provoke to critical thinking, which has been lacking for the past decade. and even more.
I wonder why we can watch live streams of the ongoing genocide in 4K HD and stil be silent. not all but many.
Why are we surprised that normies don't understand Bitcoin and still use fiat shit currency? Whitch is fudament of All war crimes. We should ask ourselves.
Our own ignorance and the banking system are the cancers of this world.
If we lose Palestine, we will lose much more than we think.
You will be next - One way or another
Thank you for your support, not for me but for those in need who can gain hope from our efforts.
Respect to you all.

LISTEN HERE and suport directly in upper links
FreePalestine
Thanks
be blessed
MadMunky
-
 @ e3ba5e1a:5e433365
2025-02-04 08:29:42
@ e3ba5e1a:5e433365
2025-02-04 08:29:42President Trump has started rolling out his tariffs, something I blogged about in November. People are talking about these tariffs a lot right now, with many people (correctly) commenting on how consumers will end up with higher prices as a result of these tariffs. While that part is true, I’ve seen a lot of people taking it to the next, incorrect step: that consumers will pay the entirety of the tax. I put up a poll on X to see what people thought, and while the right answer got a lot of votes, it wasn't the winner.

For purposes of this blog post, our ultimate question will be the following:
- Suppose apples currently sell for $1 each in the entire United States.
- There are domestic sellers and foreign sellers of apples, all receiving the same price.
- There are no taxes or tariffs on the purchase of apples.
- The question is: if the US federal government puts a $0.50 import tariff per apple, what will be the change in the following:
- Number of apples bought in the US
- Price paid by buyers for apples in the US
- Post-tax price received by domestic apple producers
- Post-tax price received by foreign apple producers
Before we can answer that question, we need to ask an easier, first question: before instituting the tariff, why do apples cost $1?
And finally, before we dive into the details, let me provide you with the answers to the ultimate question. I recommend you try to guess these answers before reading this, and if you get it wrong, try to understand why:
- The number of apples bought will go down
- The buyers will pay more for each apple they buy, but not the full amount of the tariff
- Domestic apple sellers will receive a higher price per apple
- Foreign apple sellers will receive a lower price per apple, but not lowered by the full amount of the tariff
In other words, regardless of who sends the payment to the government, both taxed parties (domestic buyers and foreign sellers) will absorb some of the costs of the tariff, while domestic sellers will benefit from the protectionism provided by tariffs and be able to sell at a higher price per unit.
Marginal benefit
All of the numbers discussed below are part of a helper Google Sheet I put together for this analysis. Also, apologies about the jagged lines in the charts below, I hadn’t realized before starting on this that there are some difficulties with creating supply and demand charts in Google Sheets.
Let’s say I absolutely love apples, they’re my favorite food. How much would I be willing to pay for a single apple? You might say “$1, that’s the price in the supermarket,” and in many ways you’d be right. If I walk into supermarket A, see apples on sale for $50, and know that I can buy them at supermarket B for $1, I’ll almost certainly leave A and go buy at B.
But that’s not what I mean. What I mean is: how high would the price of apples have to go everywhere so that I’d no longer be willing to buy a single apple? This is a purely personal, subjective opinion. It’s impacted by how much money I have available, other expenses I need to cover, and how much I like apples. But let’s say the number is $5.
How much would I be willing to pay for another apple? Maybe another $5. But how much am I willing to pay for the 1,000th apple? 10,000th? At some point, I’ll get sick of apples, or run out of space to keep the apples, or not be able to eat, cook, and otherwise preserve all those apples before they rot.
The point being: I’ll be progressively willing to spend less and less money for each apple. This form of analysis is called marginal benefit: how much benefit (expressed as dollars I’m willing to spend) will I receive from each apple? This is a downward sloping function: for each additional apple I buy (quantity demanded), the price I’m willing to pay goes down. This is what gives my personal demand curve. And if we aggregate demand curves across all market participants (meaning: everyone interested in buying apples), we end up with something like this:

Assuming no changes in people’s behavior and other conditions in the market, this chart tells us how many apples will be purchased by our buyers at each price point between $0.50 and $5. And ceteris paribus (all else being equal), this will continue to be the demand curve for apples.
Marginal cost
Demand is half the story of economics. The other half is supply, or: how many apples will I sell at each price point? Supply curves are upward sloping: the higher the price, the more a person or company is willing and able to sell a product.
Let’s understand why. Suppose I have an apple orchard. It’s a large property right next to my house. With about 2 minutes of effort, I can walk out of my house, find the nearest tree, pick 5 apples off the tree, and call it a day. 5 apples for 2 minutes of effort is pretty good, right?
Yes, there was all the effort necessary to buy the land, and plant the trees, and water them… and a bunch more than I likely can’t even guess at. We’re going to ignore all of that for our analysis, because for short-term supply-and-demand movement, we can ignore these kinds of sunk costs. One other simplification: in reality, supply curves often start descending before ascending. This accounts for achieving efficiencies of scale after the first number of units purchased. But since both these topics are unneeded for understanding taxes, I won’t go any further.
Anyway, back to my apple orchard. If someone offers me $0.50 per apple, I can do 2 minutes of effort and get $2.50 in revenue, which equates to a $75/hour wage for me. I’m more than happy to pick apples at that price!
However, let’s say someone comes to buy 10,000 apples from me instead. I no longer just walk out to my nearest tree. I’m going to need to get in my truck, drive around, spend the day in the sun, pay for gas, take a day off of my day job (let’s say it pays me $70/hour). The costs go up significantly. Let’s say it takes 5 days to harvest all those apples myself, it costs me $100 in fuel and other expenses, and I lose out on my $70/hour job for 5 days. We end up with:
- Total expenditure: $100 + $70 * 8 hours a day * 5 days \== $2900
- Total revenue: $5000 (10,000 apples at $0.50 each)
- Total profit: $2100
So I’m still willing to sell the apples at this price, but it’s not as attractive as before. And as the number of apples purchased goes up, my costs keep increasing. I’ll need to spend more money on fuel to travel more of my property. At some point I won’t be able to do the work myself anymore, so I’ll need to pay others to work on the farm, and they’ll be slower at picking apples than me (less familiar with the property, less direct motivation, etc.). The point being: at some point, the number of apples can go high enough that the $0.50 price point no longer makes me any money.
This kind of analysis is called marginal cost. It refers to the additional amount of expenditure a seller has to spend in order to produce each additional unit of the good. Marginal costs go up as quantity sold goes up. And like demand curves, if you aggregate this data across all sellers, you get a supply curve like this:

Equilibrium price
We now know, for every price point, how many apples buyers will purchase, and how many apples sellers will sell. Now we find the equilibrium: where the supply and demand curves meet. This point represents where the marginal benefit a buyer would receive from the next buyer would be less than the cost it would take the next seller to make it. Let’s see it in a chart:

You’ll notice that these two graphs cross at the $1 price point, where 63 apples are both demanded (bought by consumers) and supplied (sold by producers). This is our equilibrium price. We also have a visualization of the surplus created by these trades. Everything to the left of the equilibrium point and between the supply and demand curves represents surplus: an area where someone is receiving something of more value than they give. For example:
- When I bought my first apple for $1, but I was willing to spend $5, I made $4 of consumer surplus. The consumer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and above the equilibrium price point.
- When a seller sells his first apple for $1, but it only cost $0.50 to produce it, the seller made $0.50 of producer surplus. The producer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and below the equilibrium price point.
Another way of thinking of surplus is “every time someone got a better price than they would have been willing to take.”
OK, with this in place, we now have enough information to figure out how to price in the tariff, which we’ll treat as a negative externality.
Modeling taxes
Alright, the government has now instituted a $0.50 tariff on every apple sold within the US by a foreign producer. We can generally model taxes by either increasing the marginal cost of each unit sold (shifting the supply curve up), or by decreasing the marginal benefit of each unit bought (shifting the demand curve down). In this case, since only some of the producers will pay the tax, it makes more sense to modify the supply curve.
First, let’s see what happens to the foreign seller-only supply curve when you add in the tariff:

With the tariff in place, for each quantity level, the price at which the seller will sell is $0.50 higher than before the tariff. That makes sense: if I was previously willing to sell my 82nd apple for $3, I would now need to charge $3.50 for that apple to cover the cost of the tariff. We see this as the tariff “pushing up” or “pushing left” the original supply curve.
We can add this new supply curve to our existing (unchanged) supply curve for domestic-only sellers, and we end up with a result like this:

The total supply curve adds up the individual foreign and domestic supply curves. At each price point, we add up the total quantity each group would be willing to sell to determine the total quantity supplied for each price point. Once we have that cumulative supply curve defined, we can produce an updated supply-and-demand chart including the tariff:

As we can see, the equilibrium has shifted:
- The equilibrium price paid by consumers has risen from $1 to $1.20.
- The total number of apples purchased has dropped from 63 apples to 60 apples.
- Consumers therefore received 3 less apples. They spent $72 for these 60 apples, whereas previously they spent $63 for 3 more apples, a definite decrease in consumer surplus.
- Foreign producers sold 36 of those apples (see the raw data in the linked Google Sheet), for a gross revenue of $43.20. However, they also need to pay the tariff to the US government, which accounts for $18, meaning they only receive $25.20 post-tariff. Previously, they sold 42 apples at $1 each with no tariff to be paid, meaning they took home $42.
- Domestic producers sold the remaining 24 apples at $1.20, giving them a revenue of $28.80. Since they don’t pay the tariff, they take home all of that money. By contrast, previously, they sold 21 apples at $1, for a take-home of $21.
- The government receives $0.50 for each of the 60 apples sold, or in other words receives $30 in revenue it wouldn’t have received otherwise.
We could be more specific about the surpluses, and calculate the actual areas for consumer surplus, producer surplus, inefficiency from the tariff, and government revenue from the tariff. But I won’t bother, as those calculations get slightly more involved. Instead, let’s just look at the aggregate outcomes:
- Consumers were unquestionably hurt. Their price paid went up by $0.20 per apple, and received less apples.
- Foreign producers were also hurt. Their price received went down from the original $1 to the new post-tariff price of $1.20, minus the $0.50 tariff. In other words: foreign producers only receive $0.70 per apple now. This hurt can be mitigated by shifting sales to other countries without a tariff, but the pain will exist regardless.
- Domestic producers scored. They can sell less apples and make more revenue doing it.
- And the government walked away with an extra $30.
Hopefully you now see the answer to the original questions. Importantly, while the government imposed a $0.50 tariff, neither side fully absorbed that cost. Consumers paid a bit more, foreign producers received a bit less. The exact details of how that tariff was split across the groups is mediated by the relevant supply and demand curves of each group. If you want to learn more about this, the relevant search term is “price elasticity,” or how much a group’s quantity supplied or demanded will change based on changes in the price.
Other taxes
Most taxes are some kind of a tax on trade. Tariffs on apples is an obvious one. But the same applies to income tax (taxing the worker for the trade of labor for money) or payroll tax (same thing, just taxing the employer instead). Interestingly, you can use the same model for analyzing things like tax incentives. For example, if the government decided to subsidize domestic apple production by giving the domestic producers a $0.50 bonus for each apple they sell, we would end up with a similar kind of analysis, except instead of the foreign supply curve shifting up, we’d see the domestic supply curve shifting down.
And generally speaking, this is what you’ll always see with government involvement in the economy. It will result in disrupting an existing equilibrium, letting the market readjust to a new equilibrium, and incentivization of some behavior, causing some people to benefit and others to lose out. We saw with the apple tariff, domestic producers and the government benefited while others lost.
You can see the reverse though with tax incentives. If I give a tax incentive of providing a deduction (not paying income tax) for preschool, we would end up with:
- Government needs to make up the difference in tax revenue, either by raising taxes on others or printing more money (leading to inflation). Either way, those paying the tax or those holding government debased currency will pay a price.
- Those people who don’t use the preschool deduction will receive no benefit, so they simply pay a cost.
- Those who do use the preschool deduction will end up paying less on tax+preschool than they would have otherwise.
This analysis is fully amoral. It’s not saying whether providing subsidized preschool is a good thing or not, it simply tells you where the costs will be felt, and points out that such government interference in free economic choice does result in inefficiencies in the system. Once you have that knowledge, you’re more well educated on making a decision about whether the costs of government intervention are worth the benefits.
-
 @ da0b9bc3:4e30a4a9
2025-02-04 07:52:55
@ da0b9bc3:4e30a4a9
2025-02-04 07:52:55Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/875346
-
 @ 17538dc2:71ed77c4
2025-01-14 15:52:00
@ 17538dc2:71ed77c4
2025-01-14 15:52:00Nassim Nicholas Taleb writes:
“We cannot explain everything. We know more about what something is not than what something is. If there would have been no word for colour blue, it would still have existed in reality. It would only have been absent in linguistics. But since we don’t have a word for it, we couldn’t define or comprehend it. But we still could say what it is not. It is not orange. It’s not an elephant, etc. This method of knowledge is truer and more rigorous than positive knowledge.”In this article, I introduce practical examples of how to apply via negativa to various systems.
Recommended reading is Antifragile by N. N. Taleb.
The basic template is as follows:
What is ____ not?
Let's start with something every human should be familiar with - food.
Food
Take hot pockets. Is hot pockets food?

What is not food?
To answer this question, let's examine the contents of hot pockets.

There seem to be chemistry lab sounding ingredients ("MEDIUM CHAIN TRIGLYCERIES", "SODIUM STEAROYL LACTYLATE"), as well as food items that your great-great-great-great-great-great grandma cooked with ("SALT", "BEEF" etc.)
So What happens when we apply via negativa to the ingredients?
From 30 "ingredients" we deduce a couple foood items, or a ~90% reduction in "ingredients" by eliminating processed food slop.
 meat good
meat good bread yum
bread yumFree Discourse
Take the social media platform X.
 X consists of: leased identity, censored speech, and a tech platform for discourse. On the roadmap is social media score that will be used to determine if you can pay your bills when X launches its' bank.
X consists of: leased identity, censored speech, and a tech platform for discourse. On the roadmap is social media score that will be used to determine if you can pay your bills when X launches its' bank. What is free discourse not?
Removing the ingredient of WEF,

KYC lease hell

and censorship

we receive nostr
 .
. Nostr, to my best understanding, is not a WEF globo-homo participant, does not lease identities, and it is that much more difficult to censor wrongspeak (e.g. Netanyahu and friends are commiting genocide, and wanted as war criminals; there are two genders; there is no climate crisis; Ivermectin works).
Automobiles
Modern automobiles can be summed up in two words: "safety", and constant surveillance. Yes, advancements in safety are great - e.g. airbags, seatbelts, car frames that absorb impact energy.
However the "its for your safety" component of remote shutdown, remote control, location data selling to data brokers, insurance agents, and your local surveillance outfit is gulag tech.
!(image)[https://image.nostr.build/15befd30113614dad3fd7aac01b8771b95bd8ace9186ed4f8016eec6e886e969.jpg]
So what happens when we remove the gulag tech out of cars? That is, what is not a car?
Let's use the following definition of car:
``` A car, or an automobile, is a motor vehicle with wheels
```
Let's use the following definition of gulag:
``` The Gulag is recognized as a major instrument of political repression in the Soviet Union.
```
You get the 2024 Toyota Land Cruiser. No gulag. Airbags. Push and turn knobs. No spying, no remote control, no cameras, no satellite, no bluetooth, no wi-fi.
As an aside, it is practically impossible to import this car to the US. It's "for your safety", and "for the environment", of course.
!(image)[https://upload.wikimedia.org/wikipedia/commons/thumb/a/a1/Toyota_Land_Cruiser_16.09.20_JM_%283%29_%28cropped%29.jpg/800px-Toyota_Land_Cruiser_16.09.20_JM_%283%29_%28cropped%29.jpg]?20210328155727
Toyota Landcruiser HZJ-79 Double Cab, Johannes Maximilian
https://commons.wikimedia.org/wiki/File:Toyota_Land_Cruiser_16.09.20_JM_(3)_(cropped).jpg).Hopefully this guide has been helpful illustrating how simple and powerful it is to apply the Via Negativa approach.
Mr. Taleb, I commend you on speaking out on the Palestine genocide. I invite you to and hope one day you join anti-fragile nostr.
-
 @ 17538dc2:71ed77c4
2025-01-13 18:17:24
@ 17538dc2:71ed77c4
2025-01-13 18:17:24Sci-Hub 2024 year end review is translated to English by Kagi Translate from Russian. Original text can be found in Sci-Hub's telegram channel https://t.me/freescience.
RESULTS OF 2024
First. The project received donations totaling 2 million dollars in meme coins.
The project is actively used by many students in China, which is why a group of Sci-Hub fans has emerged there. As far as I understand, the organizer of the group is actively interested in the topic of cryptocurrencies (even wrote a book). Somewhere in mid-November, the Chinese launched a meme coin in honor of the Sci-Hub project. At its peak, the coin's price reached 5 cents, and now it is somewhere around 1-2 cents. This means that the exchange rate of the Sci-Hub cryptocurrency is now almost equal to the ruble exchange rate (100 to one or so).
In general, I converted part of these donations into normal, traditional cryptocurrency (like Bitcoin) and paid for servers several months in advance. The other part is still sitting in meme coins—I hope that the token will still grow in price (there is a promotion plan). Of course, this is risky, but Sci-Hub is a project that is not afraid of risk. Therefore, anyone who wants to invest in Sci-Hub by purchasing this token can do so here: www.coingecko.com/en/coins/sci-hub
Second. A dissertation on the topic of open scientific knowledge has been defended at the Institute of Philosophy.
For those interested in the history and philosophy of science, I defended a dissertation in April at the Institute of Philosophy on the topic that scientific knowledge should be open (otherwise, it is strange to call it scientific at all). The work shows that open communication is one of the basic traditional values of science when considering science as a social institution. In other words, journals that charge for access to scientific articles are a kind of 'non-traditional orientation journals.'
Moreover, openness is an important prerequisite for rationality. Rationality is not limited to the criterion of falsification (hello Popper); it is a much more complex concept.
You can familiarize yourself with the text of the dissertation here: web.archive.org/web/20240425100014/https://iphras.ru/page26414303.htm (I provide the link through the web archive because the Institute's website, strangely enough, is glitching again at the time of writing this post).
All criticism and comments (as well as praise) regarding the dissertation can be sent to my email.
Third. Work has begun on a new declaration of open access to scientific knowledge.
Currently, all discussions on the topic of open science are conducted within the frameworks defined by the so-called BBB declarations back in 2001-2003. Within these frameworks, two main types of open access are recognized: gold, meaning open journals with an author-pays model, and green, which refers to repositories like the well-known arXiv. We can also add the so-called diamond open access, which includes open journals that are free for both authors and readers.
However, since 2003, internet technologies have advanced significantly. Today, we can already talk about such types of open access as blue (through academic social networks) or red (your beloved Sci-Hub). It is time to adopt a new declaration of open access to scientific knowledge that corresponds to the current state of scientific and technological progress.
A preliminary version of the declaration can be read and signed here: open.science.do
We will be more actively engaged in this in the coming year. Signing the declaration is an important step towards recognizing access to scientific knowledge through sites like Sci-Hub or Libgen as completely legal and ceasing to pursue them—first in the former USSR, and then in all countries of the world.
Fourth. In 2024, about one billion articles were downloaded through Sci-Hub. Despite the fact that this is unfiltered statistics, the fact remains: the popularity of the project has not decreased but only grown, despite the fact that Sci-Hub has not been updated for quite a long time. Of course, this does not mean that the site will not be updated at all now—just that the patient is more alive than dead (no matter how much some haters might wish otherwise).
The cause of open access to scientific knowledge will definitely prevail—because good always triumphs over evil.
In the new year, I wish all scientists new discoveries and large grants. Happy New Year, comrades!
-
 @ 1cb14ab3:95d52462
2025-01-05 04:18:29
@ 1cb14ab3:95d52462
2025-01-05 04:18:29Stunning beaches, ancient temples as far as the eye can see, and lush, green mountainsides that will leave you in awe—Myanmar is a destination you NEED to add to your bucket list. This guide offers the perfect one-month itinerary to explore the hidden gems of this incredible country.

The Itinerary
Days 1-2:
Fly into Yangon Airport. Settle in and explore the vibrant sights and flavors of the city.
Day 3:
Take an overnight bus south to the coastal city of Myeik.
Days 4-8:
Go island hopping around the Mergui Archipelago—remote beaches and untouched islands await.
Day 9:
Travel to Dawei. Find a cozy place to stay and relax for the evening.
Days 10-13:
Rent a motorcycle and explore the stunning Dawei Peninsula. Soak up the sun on pristine beaches.
Day 14:
Head to Hpa An. Check into a hotel and enjoy a sunset beer.
Days 15-18:
Discover the limestone mountains, caves, and farmlands of Hpa An.
Day 19:
Travel to Bagan. The journey may be bumpy, but the destination is worth it.
Days 20-23:
Explore the breathtaking temples of Bagan. Sunrise hot air balloon rides are a must.
Day 24:
Head to Lake Inle. Settle into your accommodation and dine by the water.
Days 25-26:
Cruise around Lake Inle by boat. Immerse yourself in the local culture and capture the iconic fishermen in action.
Days 27-28:
Visit Mandalay to experience city life from a Burmese perspective.
Days 29-30:
Return to Yangon for a final exploration before flying home.
Days 1-2: Arrival in Yangon
Myanmar's largest city is a bustling hub filled with shops, activities, and incredible food. The rapid development of this once-isolated country is evident everywhere you look.
If you are flying internationally: Yangon will most likely be the cheapest and most easily accessible destination to begin the trip.
If you are coming from Thailand: I would recommend altering the itinerary and going straight to Myeik via land border then working your way up the country from there.
Bogyoke Aung San Market
If shopping is your thing, this place is a haven for local treasures. Hundreds of stalls line the market and surrounding alleyways containing everything from art, sculptures, jewelry, antiquities, and fabrics. I spent a few hours here before jumping onto the nearby circular train for a loop around the city. There are a few small shops to get a bite to eat if you are hungry.
Remember that this itinerary will land you back in Yangon at the end of the trip if you see something you want to buy and don’t feel like lugging it around for a month.

Yangon Circular Train
Easily one of the most fascinating experiences of the trip is riding the Yangon Circular Train around the city for a true look at how the locals live. The train is old, slow, and packed with locals commuting to and from work. The doors are wide open, allowing you to hang your feet outside and soak in all of the sights afar. This is one of the best ways to get a true glimpse into the culture and day-to-day life of the Burmese people.
Be sure to speak with a train operator before getting on to make sure the entire loop is operational. When I went, construction stopped the train about 45 minutes into the loop, forcing us to get a taxi back to the downtown area. The full loop will take over 2 hours to complete. On the train, you can find vendors and hawkers selling little things such as water, nuts, and fruit. I’d suggest eating before jumping on.

Shwedagon Pagoda
Upon walking up the steep and lengthy stairway to the Shwedagon Pagoda lies Yangon’s most famous attraction. The 99-meter gold-coated pagoda can be seen all around the city but is best enjoyed up close. This is a must-visit during your time in the capital. I went about an hour before sunset and stayed well into the night. Sunset from the hill it sits atop is spectacular, and the contrast of the pagoda between day and night is striking.
Make sure to bring socks and a bag, as shoes are not allowed, and you will need to carry them or leave them at the door. After visiting, you can take a short walk to the Sky Bar in the Yangon International Hotel overlooking the pagoda. This is a wonderful place to enjoy a nice dinner and drink, ideal for soaking up more of that luxurious golden pagoda.

Day 3: Bus to Myeik
The longest stretch of the trip—but well worth the sights to come. I took a 22-hour overnight bus and opted for the slight upcharge to take the VIP bus. This option is absolutely worth it. Equipped with A/C, comfortable reclining seats, and stops for three meals, it was a cheaper alternative to the costly domestic flight from Yangon and allowed me to see much more of the country.
I had a surprisingly good sleep and would do it again in a heartbeat. You can also fly directly to Myeik, but flights are infrequent and considerably more expensive. The bus I took arrived in Myeik around noon the next day, leaving me plenty of time to check into the hotel and wander around the city a bit before sunset. There weren’t many buses heading down here, so I’d recommend checking for tickets as early as possible when you arrive in Yangon. Alternatively, if you’re coming from Thailand, you can rearrange the itinerary and begin your Myanmar trip in Myeik by crossing from Thailand via bus at the land border.

Days 4-8: Island Hopping in Myeik
The city of Myeik has no accessible beaches, so you’ll need to book an island-hopping tour to fully appreciate the surrounding Mergui Archipelago. While the city itself doesn’t offer much in terms of entertainment, the beaches and crystal-clear waters you’ll encounter on an island-hopping tour are truly unparalleled. Your trip to Myeik will be unforgettable and is an experience you shouldn’t miss.
There are several travel companies offering island-hopping tours, ranging from single-day trips to 14-day excursions. While you can book ahead, I found it quite easy to arrange a trip through an agency in the city. I opted for a three-day, two-night tour with Life Seeing Tours, and it was fantastic. They provided food, tents, and transportation—just bring a swimsuit and a change of clothes, and you’re ready to spend a few nights exploring the islands.




Day 9: Bus to Dawei
Another travel day! This time, you’ll take a shorter bus ride heading north to Dawei. The journey takes about six hours, and tickets can be purchased from one of the travel agencies in Myeik. From what I gathered, there’s only one bus per day on this route, and it departs early in the morning.
Be prepared to wake up around 4 AM and make your way back to the same bus station where you arrived. It’s a good idea to arrange transportation to the station the night before—your hotel can help you book a ride for that morning.
Days 10-13: Motorcycling the Dawei Peninsula
Dawei boasts some of the most stunning coastlines and beaches in the country. While most of these beaches are only accessible by motorcycle, there are a few small bed-and-breakfast-style accommodations at the southern end of the peninsula that offer direct beach access.
If you’d prefer not to travel 2–3 hours each day from the city, I recommend staying in that area. You can rent a motorcycle from several places in the city and ride down to the B&Bs near the beaches for an overnight stay. This approach lets you enjoy the remote, lush, and scenic motorcycle journey while avoiding the daily commute to the beaches.

Grandfather Beach
Surrounded by mountains and vibrant orange dirt, getting here can be a bit tricky. You’ll need to navigate a steep, loose hill to reach the area. I recommend arriving near low tide, as the beach and surrounding shops flood around noon, making the descent a wet and challenging experience. Be prepared to remove your shoes and walk through knee-deep water to access the beach. This is one of the more popular spots for locals and was among the few beaches I visited that actually had people.

Tizit Beach
When we arrived at Tizit Beach, there was no one else around except for the locals. The sand here is soft, and the ocean is pristine. A motorcycle is necessary to access this beach, but the breathtaking views from the mountain pass make the journey entirely worthwhile. The sand near the shore is firm enough to ride on, creating unforgettable moments of cruising along the beach at sunset.

Day 14: Bus to Hpa An
One of the shorter bus rides on this trip, the fare is around $20, and it takes approximately 5 bumpy hours. Once you arrive in Hpa An, there are plenty of hostels and hotels to choose from. I booked mine on Hostelworld the night before, but you should have no trouble finding a place to stay on the day of your arrival if needed.
Days 15-18: Hpa An: Farmland, Caves, and Mountains
Hpa An offers a stark contrast to the beaches and cities encountered so far on the trip. Surrounded by towering limestone mountains and lush green farmland, the region has a peaceful, rural charm. There are several caves, lakes, and one of my favorite sunrise hikes of the journey.
While I have a few recommendations and must-visit spots, Hpa An is best explored without a strict plan. A central theme of this trip has been the freedom of hopping on a motorcycle and riding wherever your heart desires.

Mount Zwegabin Sunrise Hike
Hiking Mount Zwegabin for sunrise is a must-do during your time in Hpa An. The mountain is located a short ride from town, about 40 minutes by motorcycle. The hike to the summit took around 35 minutes at a brisk pace, so you’ll need to leave around 4 AM to catch the sunrise, depending on the season. The highlight of the hike is the final ascent up the floating stairs to reach the peak. Be sure to have your camera ready and take in the breathtaking views.

Kyauk Kalat Pagoda
This is one of those places that leaves you in awe, wondering how such a unique landscape can exist. Easily one of the most unusual rock formations I’ve encountered, it’s a fantastic spot to watch the sunset. A winding staircase leads up the rock to the top of the temple, making it a great place to spend a couple of hours.

Saddar Cave
Filled with bats, stunning limestone formations, and statues, this short cave walk provides a refreshing escape from the heat. The path takes about 20 minutes to explore, leading to a beautiful lake at the back. Grab a drink, relax for a while, and take a small paddle boat back to the entrance for a memorable experience.

Day 19: Bus to Bagan
A travel day heading north. This part of the trip is hot, bumpy, and slow, so be prepared for a longer journey than expected. Bagan has plenty of hotels and hostels, but I’d recommend booking accommodations in advance, as it’s a popular tourist destination. You’ll need to purchase an entry ticket for the area, as it’s a protected national park, but the bus driver should assist in sorting it out before you enter the park.
Days 20-23: Chasing Pagodas in Bagan
Once you’ve settled into your accommodation in Bagan, the best way to explore the vast area is by pedal bike or scooter. All the scooters available for rent are electric, helping to reduce noise pollution—a refreshing change from the loud gas-powered vehicles you’ll be used to from the first half of your trip. There’s no right or wrong way to experience Bagan. The park is enormous, with thousands of pagodas scattered throughout. Most of them are open for exploration, with a few offering rooftop access (though that is being restricted more recently).
You could spend weeks here and still not see all the pagodas up close. Bagan is divided into a new town and an old town—most of the backpacker-friendly hostels are located in Old Town. You’ll find a handful of restaurants, but I often ate at my hostel or from local food carts. Several hostels and hotels offer outdoor pools, which are a great perk, especially depending on the time of year you visit. I highly recommend simply wandering the area freely, but here are a few top pagodas and experiences not to miss during your time in Bagan.

Hot Air Ballooning
The top attraction in Bagan is undoubtedly the daily hot air balloon tours. Almost everyone who experiences it claims it’s a must-do. I chose to watch from the ground, as the cost of a tour is quite expensive. If you decide to go for it, be sure to set aside a few hundred USD for the trip. From what I’ve heard, you’ll wake up around 4:30 AM and head to the take-off location, returning by around 9:00 AM.

Sunset Boat Cruise
Be sure to spend at least one evening on a slow cruise down the Ayeyarwady River. It’s a wonderful way to enjoy distant views of some of the pagodas and relax after a long day of exploration. Several companies offer these cruises at very affordable prices. Our boat included snacks, drinks, and even alcohol. The trips range from half an hour to two hours. Book through your hotel for convenience.

The Big Three Temples
With over a thousand pagodas to explore in Bagan, there are three main structures that hold significant importance to locals: Shwesandaw, Thatbyinnyu, and Shwezigon. Be sure to make time to visit these iconic pagodas during your trip—you’re likely to come across them without even trying.

Day 24: Bus to Kalaw
Long-distance buses run the route multiple times a day, with the overnight option being the most popular. I recommend checking with a travel agent in Bagan to book your tickets before heading to the bus stop
Day 25-26: Relaxing at Lake Inle
These two days take us to the stunning Lake Inle, located just outside the city of Kalaw. Unfortunately, I wasn’t able to make it to Lake Inle during this trip, but everyone I spoke to highly recommended not missing it. The lake is known for its breathtaking scenery, traditional Intha stilt houses, and the unique leg-rowing fishermen.
From what I’ve heard and seen through photos, the calm waters, floating gardens, and vibrant markets make Lake Inle a truly unforgettable destination. Huge thanks to my friend Toby for sharing those beautiful pictures and giving me a glimpse of what I missed!




Day 27-28: Mandalay City
Mandalay is a fast-paced city with less tourism compared to other parts of the country. It offers a fascinating glimpse into the daily lives of the Burmese people, away from the crowds typically found in Yangon. There are several culturally significant monasteries and temples within the city limits, as well as vibrant markets perfect for shopping and exploring. Mandalay Hill is a great spot for a brisk hike and offers stunning views of the city and sunset on one of your nights. You could also visit the Mandalay Marionettes Theater to catch a local show showcasing Myanmar’s rich history and culture.
As for me, I mainly wandered the city without specific destinations in mind. Since this is the last stop before returning to Yangon, you might not feel as inclined to spend too much time here, but there are definitely some interesting sights worth exploring.

Day 29-30: Return to Yangon
The final two days of the trip are a return to where it all began. The bus from Mandalay to Yangon takes about 8 hours. Alternatively, Mandalay has a large international airport if you prefer to fly, depending on your next destination.
If you return to Yangon, you’ll have plenty of time to revisit the markets and pick up any final souvenirs or trinkets you might want to take home. Enjoy these last couple of days, savor some delicious food, and take the time to reflect on the incredible month of experiences you’ve had.

Concluding Thoughts
Your month-long journey through Myanmar is bound to be an unforgettable adventure, filled with stunning landscapes, rich culture, and warm hospitality. From the serene beaches of Ngapali to the ancient wonders of Bagan, and the tranquil beauty of Lake Inle to the bustling streets of Yangon and Mandalay, each destination offers its own unique charm and insight into Myanmar’s diverse culture.
The highlights of your trip—exploring historic pagodas, witnessing breathtaking sunrises, and embracing the freedom of riding a motorcycle—are sure to stay with you. Myanmar’s blend of natural beauty, vibrant traditions, and friendly locals makes every moment special. Despite the occasional long and bumpy journeys, the sense of discovery and connection with the people and places makes the experience truly worthwhile.
As you reflect on your journey, you’ll likely feel grateful for the memories, experiences, and the chance to explore a country that feels both timeless and unique. Myanmar’s beauty lies not just in its landscapes but in the people who call it home. You’ll leave with a deeper appreciation for the warmth and resilience of its people and a desire to return and explore even more of this enchanting land.
Update: Unfortunately as of this time (June 2021) Myanmar is experiencing major political and civil unrest. Taken from the advice of friends on the ground there— I can not recommend traveling to Myanmar at the time of writing. Pray for Myanmar!
Update 2: The political situation in Myanmar has escalated (July 2022). Travel is still not recommended.
Update 3: As of 2025, some tourists have reported that travel is doable. However many governments still have do not travel advisories. DYOR.
Other Myanmar Guides:
The Top 3 Hidden Beaches of Myanmar: A Guide to Tizit, Grandfather, and Mergui
More from Hes:
Originally Published June 15, 2021. Edited with Nostr friendly images on 1/5/2025
-
 @ 23dea97f:72ed98dc
2025-02-04 07:29:36
@ 23dea97f:72ed98dc
2025-02-04 07:29:36Post number 1
-
 @ b7274d28:c99628cb
2025-02-04 05:31:13
@ b7274d28:c99628cb
2025-02-04 05:31:13For anyone interested in the list of essential essays from nostr:npub14hn6p34vegy4ckeklz8jq93mendym9asw8z2ej87x2wuwf8werasc6a32x (@anilsaidso) on Twitter that nostr:npub1h8nk2346qezka5cpm8jjh3yl5j88pf4ly2ptu7s6uu55wcfqy0wq36rpev mentioned on Read 856, here it is. I have compiled it with as many of the essays as I could find, along with the audio versions, when available. Additionally, if the author is on #Nostr, I have tagged their npub so you can thank them by zapping them some sats.
All credit for this list and the graphics accompanying each entry goes to nostr:npub14hn6p34vegy4ckeklz8jq93mendym9asw8z2ej87x2wuwf8werasc6a32x, whose original thread can be found here: Anil's Essential Essays Thread
1.

History shows us that the corruption of monetary systems leads to moral decay, social collapse, and slavery.
Essay: https://breedlove22.medium.com/masters-and-slaves-of-money-255ecc93404f
Audio: https://fountain.fm/episode/RI0iCGRCCYdhnMXIN3L6
2.

The 21st century emergence of Bitcoin, encryption, the internet, and millennials are more than just trends; they herald a wave of change that exhibits similar dynamics as the 16-17th century revolution that took place in Europe.
Author: nostr:npub13l3lyslfzyscrqg8saw4r09y70702s6r025hz52sajqrvdvf88zskh8xc2
Essay: https://casebitcoin.com/docs/TheBitcoinReformation_TuurDemeester.pdf
Audio: https://fountain.fm/episode/uLgBG2tyCLMlOp3g50EL
3.

There are many men out there who will parrot the "debt is money WE owe OURSELVES" without acknowledging that "WE" isn't a static entity, but a collection of individuals at different points in their lives.
Author: nostr:npub1guh5grefa7vkay4ps6udxg8lrqxg2kgr3qh9n4gduxut64nfxq0q9y6hjy
Essay: https://www.tftc.io/issue-754-ludwig-von-mises-human-action/
Audio: https://fountain.fm/episode/UXacM2rkdcyjG9xp9O2l
4.
If Bitcoin exists for 20 years, there will be near-universal confidence that it will be available forever, much as people believe the Internet is a permanent feature of the modern world.
Essay: https://vijayboyapati.medium.com/the-bullish-case-for-bitcoin-6ecc8bdecc1
Audio: https://fountain.fm/episode/jC3KbxTkXVzXO4vR7X3W
As you are surely aware, Vijay has expanded this into a book available here: The Bullish Case for Bitcoin Book
There is also an audio book version available here: The Bullish Case for Bitcoin Audio Book
5.

This realignment would not be traditional right vs left, but rather land vs cloud, state vs network, centralized vs decentralized, new money vs old, internationalist/capitalist vs nationalist/socialist, MMT vs BTC,...Hamilton vs Satoshi.
Essay: https://nakamoto.com/bitcoin-becomes-the-flag-of-technology/
Audio: https://fountain.fm/episode/tFJKjYLKhiFY8voDssZc
6.
I became convinced that, whether bitcoin survives or not, the existing financial system is working on borrowed time.
Essay: https://nakamotoinstitute.org/mempool/gradually-then-suddenly/
Audio: https://fountain.fm/episode/Mf6hgTFUNESqvdxEIOGZ
Parker Lewis went on to release several more articles in the Gradually, Then Suddenly series. They can be found here: Gradually, Then Suddenly Series
nostr:npub1h8nk2346qezka5cpm8jjh3yl5j88pf4ly2ptu7s6uu55wcfqy0wq36rpev has, of course, read all of them for us. Listing them all here is beyond the scope of this article, but you can find them by searching the podcast feed here: Bitcoin Audible Feed
Finally, Parker Lewis has refined these articles and released them as a book, which is available here: Gradually, Then Suddenly Book
7.

Bitcoin is a beautifully-constructed protocol. Genius is apparent in its design to most people who study it in depth, in terms of the way it blends math, computer science, cyber security, monetary economics, and game theory.
Author: nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a
Essay: https://www.lynalden.com/invest-in-bitcoin/
Audio: https://fountain.fm/episode/axeqKBvYCSP1s9aJIGSe
8.

Bitcoin offers a sweeping vista of opportunity to re-imagine how the financial system can and should work in the Internet era..
Essay: https://archive.nytimes.com/dealbook.nytimes.com/2014/01/21/why-bitcoin-matters/
9.

Using Bitcoin for consumer purchases is akin to driving a Concorde jet down the street to pick up groceries: a ridiculously expensive waste of an astonishing tool.
Author: nostr:npub1gdu7w6l6w65qhrdeaf6eyywepwe7v7ezqtugsrxy7hl7ypjsvxksd76nak
Essay: https://nakamotoinstitute.org/mempool/economics-of-bitcoin-as-a-settlement-network/
Audio: https://fountain.fm/episode/JoSpRFWJtoogn3lvTYlz
10.

The Internet is a dumb network, which is its defining and most valuable feature. The Internet’s protocol (..) doesn’t offer “services.” It doesn’t make decisions about content. It doesn’t distinguish between photos, text, video and audio.
Essay: https://fee.org/articles/decentralization-why-dumb-networks-are-better/
Audio: https://fountain.fm/episode/b7gOEqmWxn8RiDziffXf
11.

Most people are only familiar with (b)itcoin the electronic currency, but more important is (B)itcoin, with a capital B, the underlying protocol, which encapsulates and distributes the functions of contract law.
I was unable to find this essay or any audio version. Clicking on Anil's original link took me to Naval's blog, but that particular entry seems to have been removed.
12.

Bitcoin can approximate unofficial exchange rates which, in turn, can be used to detect both the existence and the magnitude of the distortion caused by capital controls & exchange rate manipulations.
Essay: https://papers.ssrn.com/sol3/Papers.cfm?abstract_id=2714921
13.

You can create something which looks cosmetically similar to Bitcoin, but you cannot replicate the settlement assurances which derive from the costliness of the ledger.
Essay: https://medium.com/@nic__carter/its-the-settlement-assurances-stupid-5dcd1c3f4e41
Audio: https://fountain.fm/episode/5NoPoiRU4NtF2YQN5QI1
14.

When we can secure the most important functionality of a financial network by computer science... we go from a system that is manual, local, and of inconsistent security to one that is automated, global, and much more secure.
Essay: https://nakamotoinstitute.org/library/money-blockchains-and-social-scalability/
Audio: https://fountain.fm/episode/VMH9YmGVCF8c3I5zYkrc
15.

The BCB enforces the strictest deposit regulations in the world by requiring full reserves for all accounts. ..money is not destroyed when bank debts are repaid, so increased money hoarding does not cause liquidity traps..
Author: nostr:npub1hxwmegqcfgevu4vsfjex0v3wgdyz8jtlgx8ndkh46t0lphtmtsnsuf40pf
Essay: https://nakamotoinstitute.org/mempool/the-bitcoin-central-banks-perfect-monetary-policy/
Audio: https://fountain.fm/episode/ralOokFfhFfeZpYnGAsD
16.

When Satoshi announced Bitcoin on the cryptography mailing list, he got a skeptical reception at best. Cryptographers have seen too many grand schemes by clueless noobs. They tend to have a knee jerk reaction.
Essay: https://nakamotoinstitute.org/library/bitcoin-and-me/
Audio: https://fountain.fm/episode/Vx8hKhLZkkI4cq97qS4Z
17.

No matter who you are, or how big your company is, 𝙮𝙤𝙪𝙧 𝙩𝙧𝙖𝙣𝙨𝙖𝙘𝙩𝙞𝙤𝙣 𝙬𝙤𝙣’𝙩 𝙥𝙧𝙤𝙥𝙖𝙜𝙖𝙩𝙚 𝙞𝙛 𝙞𝙩’𝙨 𝙞𝙣𝙫𝙖𝙡𝙞𝙙.
Essay: https://nakamotoinstitute.org/mempool/bitcoin-miners-beware-invalid-blocks-need-not-apply/
Audio: https://fountain.fm/episode/bcSuBGmOGY2TecSov4rC
18.

Just like a company trying to protect itself from being destroyed by a new competitor, the actions and reactions of central banks and policy makers to protect the system that they know, are quite predictable.
Author: nostr:npub1s05p3ha7en49dv8429tkk07nnfa9pcwczkf5x5qrdraqshxdje9sq6eyhe
Essay: https://medium.com/the-bitcoin-times/the-greatest-game-b787ac3242b2
Audio Part 1: https://fountain.fm/episode/5bYyGRmNATKaxminlvco
Audio Part 2: https://fountain.fm/episode/92eU3h6gqbzng84zqQPZ
19.

Technology, industry, and society have advanced immeasurably since, and yet we still live by Venetian financial customs and have no idea why. Modern banking is the legacy of a problem that technology has since solved.
Author: nostr:npub1sfhflz2msx45rfzjyf5tyj0x35pv4qtq3hh4v2jf8nhrtl79cavsl2ymqt
Essay: https://allenfarrington.medium.com/bitcoin-is-venice-8414dda42070
Audio: https://fountain.fm/episode/s6Fu2VowAddRACCCIxQh
Allen Farrington and Sacha Meyers have gone on to expand this into a book, as well. You can get the book here: Bitcoin is Venice Book
And wouldn't you know it, Guy Swann has narrated the audio book available here: Bitcoin is Venice Audio Book
20.

The rich and powerful will always design systems that benefit them before everyone else. The genius of Bitcoin is to take advantage of that very base reality and force them to get involved and help run the system, instead of attacking it.
Author: nostr:npub1trr5r2nrpsk6xkjk5a7p6pfcryyt6yzsflwjmz6r7uj7lfkjxxtq78hdpu
Essay: https://quillette.com/2021/02/21/can-governments-stop-bitcoin/
Audio: https://fountain.fm/episode/jeZ21IWIlbuC1OGnssy8
21.
In the realm of information, there is no coin-stamping without time-stamping. The relentless beating of this clock is what gives rise to all the magical properties of Bitcoin.
Author: nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc
Essay: https://dergigi.com/2021/01/14/bitcoin-is-time/
Audio: https://fountain.fm/episode/pTevCY2vwanNsIso6F6X
22.

You can stay on the Fiat Standard, in which some people get to produce unlimited new units of money for free, just not you. Or opt in to the Bitcoin Standard, in which no one gets to do that, including you.
Essay: https://casebitcoin.com/docs/StoneRidge_2020_Shareholder_Letter.pdf
Audio: https://fountain.fm/episode/PhBTa39qwbkwAtRnO38W
23.

Long term investors should use Bitcoin as their unit of account and every single investment should be compared to the expected returns of Bitcoin.
Essay: https://nakamotoinstitute.org/mempool/everyones-a-scammer/
Audio: https://fountain.fm/episode/vyR2GUNfXtKRK8qwznki
24.

When you’re in the ivory tower, you think the term “ivory tower” is a silly misrepresentation of your very normal life; when you’re no longer in the ivory tower, you realize how willfully out of touch you were with the world.
Essay: https://www.citadel21.com/why-the-yuppie-elite-dismiss-bitcoin
Audio: https://fountain.fm/episode/7do5K4pPNljOf2W3rR2V
You might notice that many of the above essays are available from the Satoshi Nakamoto Institute. It is a veritable treasure trove of excellent writing on subjects surrounding #Bitcoin and #AustrianEconomics. If you find value in them keeping these written works online for the next wave of new Bitcoiners to have an excellent source of education, please consider donating to the cause.
-
 @ 1cb14ab3:95d52462
2025-01-04 20:07:38
@ 1cb14ab3:95d52462
2025-01-04 20:07:38When you think of Myanmar, beautiful beaches and crystal-clear waters likely aren’t the first things that come to mind.
Think again. Southern Myanmar is home to some of the most stunning and untouched beaches in Southeast Asia. These pristine shores rival those of Thailand, the Maldives, and even Hawaii, yet remain largely hidden due to limited infrastructure and minimal tourism.
I spent countless hours getting lost, asking for directions, and exploring remote villages, so you won’t have to. With unreliable Google Maps and few signs of modern development, navigating this region requires patience and curiosity. Get ready to discover Myanmar’s best-kept coastal treasures—and why you might want to skip Thailand in favor of a more off-the-beaten-path adventure.
Here’s a look at my top three hidden beaches in southern Myanmar.
3: Tizit Beach - A Sanctuary Shrouded by Mountains

Tizit Beach is situated about one hour south of Dawei city. Getting there is no easy feat and is not recommended for the faint of heart.
The roads are rough, unlit, and sandy, making them a challenge to navigate. Only attempt the trip if you’re confident on a motorbike, and be sure to double-check that your bike is in good working condition, especially with functional brakes. As a reward for your efforts, you’ll find very few—if any—tourists at Tizit Beach. The only people you’re likely to encounter are local children and fishermen along the shore.
To reach Tizit Beach, you’ll need to rent a motorbike and traverse a steep mountain pass. The journey takes roughly an hour each way, but the seclusion and untouched beauty are well worth the effort.
Map to Tizit Beach:
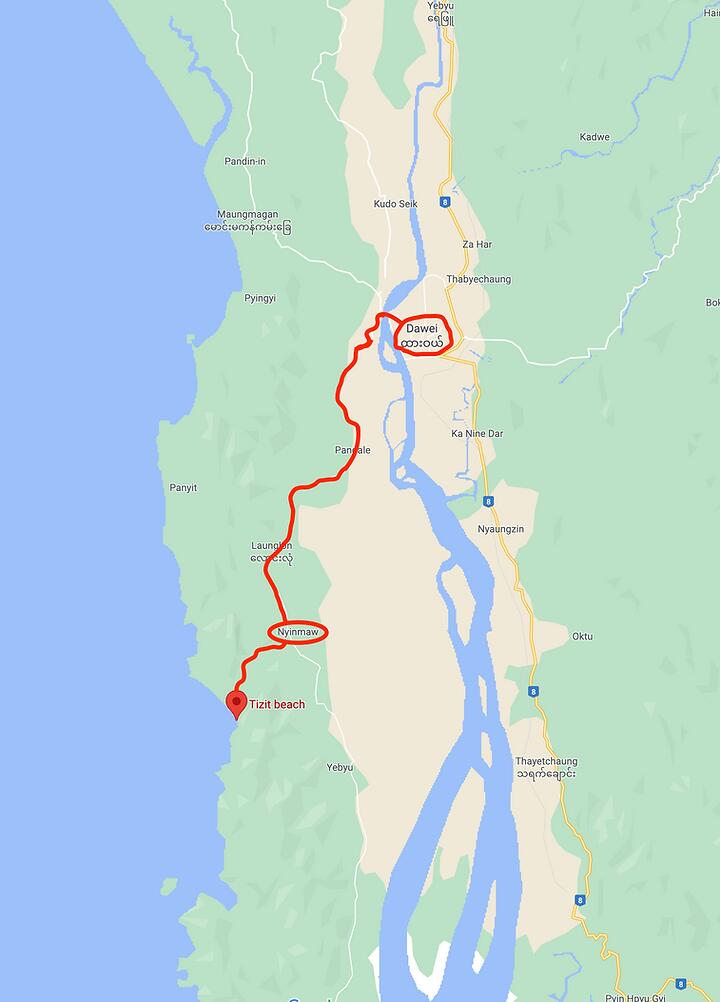
Directions:
Start by crossing the water west of Dawei and heading left, heading south towards Nyinmaw. As you travel down the peninsula from Dawei, there is essentially one main road to follow. Stay on this road for about 30 minutes, keeping an eye out on the right side for a small sign marking Tizit Beach.
You might miss the sign on your first pass, as I did, so pay attention to your GPS. If you’ve passed Nyinmaw, you’ve gone too far. Once you spot the Tizit Beach sign, you’ll notice a school playground and a road leading toward the mountains. Take the right turn here and continue over the mountain pass for about 20 minutes:

At the bottom of the mountain pass, you’ll reach a fork in the road with unclear signs. If you go left, you’ll end up in a small cemetery, which is a dead-end. The left fork looks like this:

Instead, take the right fork, which will lead you through a small residential area to the waterfront. Keep in mind that many of the beaches in this region experience significant flooding in the morning, so arriving after 3:00 PM is probably your best bet.
As you arrive, you’ll be greeted by panoramic views of lush mountains, a vast delta plain, and crystal-clear blue waters:



The sand at Tizit Beach is a rich brownish-orange hue, often turning into deep red around sunset. It’s soft, clean, and much wider than other beaches in the area, giving you more room to set up camp away from the tide. The water is warm enough for swimming, with no strong currents, making it suitable for experienced swimmers. Please note, however, that there are no lifeguards, so swim at your own risk.
A few wooden fishing vessels are docked off the coast, and the locals are incredibly friendly:


One of the highlights of Tizit Beach is the sunset cruise along the water. The sand hardens near the shore, allowing you to ride a motorcycle along the beach. It was one of my best memories from the 30 days I spent in Myanmar.


Sunsets at Tizit are truly epic, casting everything in red. However, don’t linger too long, as the mountain pass isn’t lit, and riding back in the dark can be quite sketchy. If you plan to stay for sunset, make sure your motorcycle lights are working and be prepared to leave immediately after the sun sets.


2: Grandfather Beach - Popular, but Plentiful

Grandfather Beach is one of the most striking beaches in Dawei and a popular spot for locals. Though it’s relatively well-visited, its size ensures it doesn’t feel overcrowded. The beach is a bit of a challenge to find, but the effort is worth it once you arrive.
Getting here requires about 3 hours on a motorbike from Dawei city, factoring in photo stops and meals along the way.
Map to Grandfather Beach:
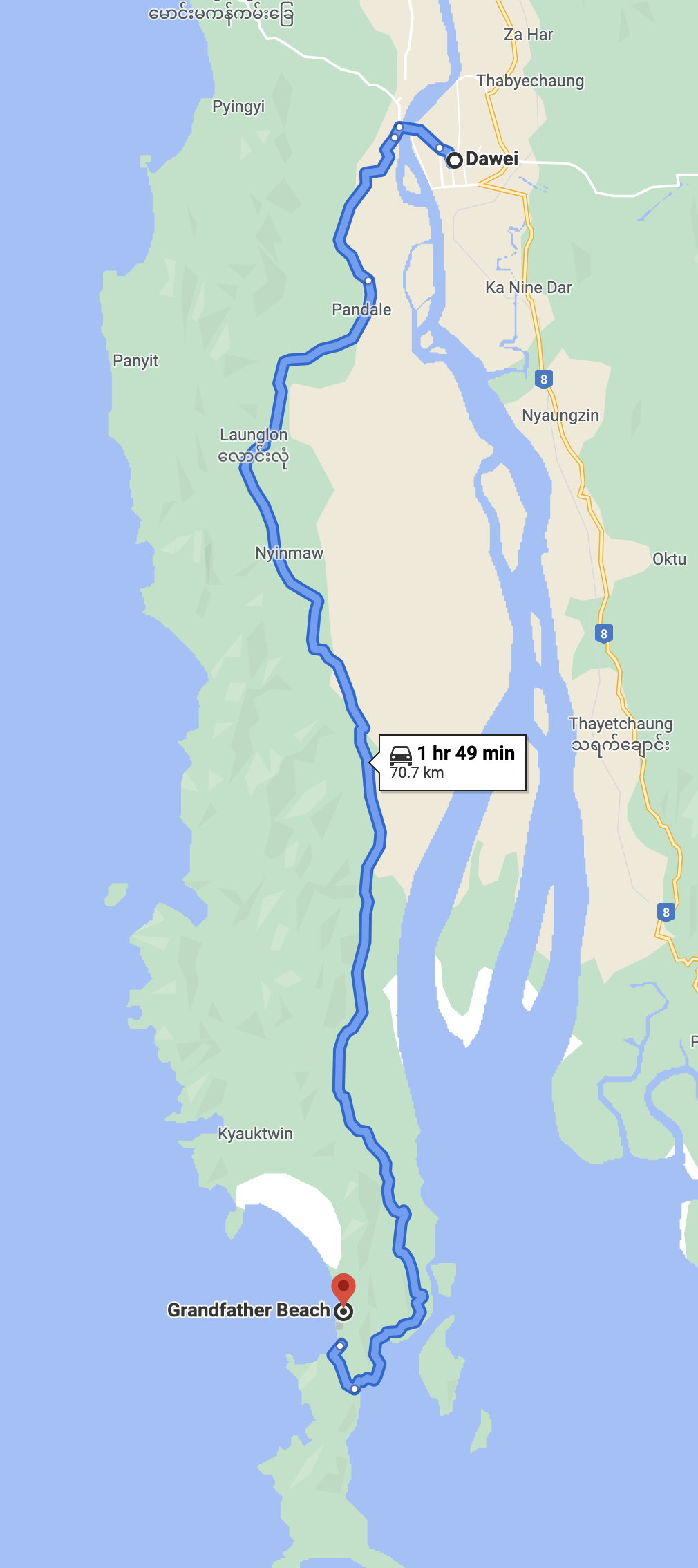
Directions:
To reach Grandfather Beach, head south from Dawei on the main road and continue down the peninsula for several hours. The route winds through jungle-covered terrain, and eventually, the road will cut across the peninsula, running parallel to the coastline. Once you crest a hill and spot the ocean below, you’re getting close.
Look for the town of Kyauk Wap Pyin at the base of the hill:

Once in Kyauk Wap Pyin, take a right from the east side of the land, heading west towards the ocean. There is really only one main road, so it shouldn't be too hard to spot. Follow the small road through the town for about 20 minutes.
The road will lead to a fishing village along the west coast that looks like this:

From the fishing village, look for the orange-dirt road leading to the beach. It’s steep, narrow, and a bit tricky to navigate, but a fun ride if you’re up for the adventure. The road is on the right-hand side as you face the sea from the village. You can see it in the image above.
Grandfather Beach is no stranger to daytime flooding, so if you arrive after noon, you may find yourself wading through waist-deep water from the parking area to the beach. Riding on the beach is only possible in the early morning before the tides rise.

The flooding isn’t as troublesome as it might seem. The local restaurants are well adapted, elevated above the waterline, and offer swings set up perfectly above the waves. The sand at Grandfather Beach is the softest of all three beaches mentioned in this article, though it’s narrower and less pristine than Tizit.

This beach sees more local visitors, so don’t expect a completely secluded experience. However, it does have the most infrastructure, with plenty of options for food and drink. If you plan to stay near Grandfather Beach, watching the sunset is highly recommended. Otherwise, the long and dark return journey to Dawei is best avoided.
To fully enjoy Grandfather Beach, plan for an entire day to soak in the scenery, relax, and make the most of your visit.




1: The Mergui Archipelago - An Unexplored Haven

This should come as no surprise to anyone familiar with Myeik: the hundreds of remote islands in the Mergui Archipelago truly stand out as the top destination for beaches in the region.
Had it not been for a spontaneous trip to Yangon without plans and a quick browse of satellite maps, I might never have discovered the sheer magnificence of the Mergui Archipelago. Information about this area is scarce, and tourism remains extremely limited. While many islands are off-limits, a few offer stunning private beaches that are accessible and worth visiting.
I was surprised to learn that many people I spoke to during my month in Myanmar had no idea these kinds of breathtaking islands existed. I feel a strong sense of responsibility to share this hidden gem with others, encouraging them to experience it firsthand. The best way to explore is through island-hopping tours from Myeik city. Tours vary in length and cost, ranging from a couple of hundred dollars for 2-3 day trips to thousands for longer yacht expeditions. Most tours include food, tents, and drinks, but always confirm these details with the booking agency.

During my five days in the Archipelago, I encountered only three other foreign tourists. The guide mentioned that many of the islands we visited had only been seen by a few hundred foreigners at most. The isolation of the region was so profound that even some of my Burmese friends weren’t aware of its existence.
At times, I felt a bit intrusive, considering how little tourism has reached this remote paradise. However, the welcoming nature of the islanders, who live off the sea and have no contact with the tour guides, made the experience all the more genuine.

One memorable moment was camping on an island where I shared the night with only the island caretaker and his ten puppies. Each day, we were taken by boat to explore nearby islands, enjoying swimming, beach time, and snorkeling before returning to the campsite. For certified SCUBA divers, this area is a dream—home to impressive coral reefs and diverse marine life.



The surreal feeling of being in such an untouched place is hard to describe. Knowing this is one of the few remaining uncharted areas on earth makes the experience truly unforgettable. If you’re planning a trip to Asia, the Mergui Archipelago should absolutely be at the top of your list.




Closing Remarks
Myanmar is truly a remarkable country, with a rich and complex history. The people I met were some of the friendliest and most optimistic I’ve encountered, despite the challenges they’ve faced. While this guide highlights some of the stunning beaches, my main aim is for every visitor to connect with the locals on a deeper level. They have incredible stories to share, and I’ve made friendships that will last a lifetime.
Traveling through Myanmar offers much more than just beautiful landscapes and serene beaches— it’s an opportunity to understand and appreciate the resilience and warmth of its people. I hope that everyone who visits Myanmar will take the time to sit down, listen, and engage with the locals.
Enjoy your journey.
— Hes
Originally published May 7, 2021 by Hes. Re-uploaded to Nostr on 1/14/2024. Re-edited 1/4/2025 with new Nostr friendly media links.
-
 @ 91bea5cd:1df4451c
2025-02-04 05:24:47
@ 91bea5cd:1df4451c
2025-02-04 05:24:47Novia é uma ferramenta inovadora que facilita o arquivamento de vídeos e sua integração com a rede NOSTR (Notes and Other Stuff Transmitted over Relay). Funcionando como uma ponte entre ferramentas de arquivamento de vídeo tradicionais e a plataforma descentralizada, Novia oferece uma solução autônoma para a preservação e compartilhamento de conteúdo audiovisual.
Arquitetura e Funcionamento
A arquitetura de Novia é dividida em duas partes principais:
-
Frontend: Atua como a interface do usuário, responsável por solicitar o arquivamento de vídeos. Essas solicitações são encaminhadas para o backend.
-
Backend: Processa as solicitações de arquivamento, baixando o vídeo, suas descrições e a imagem de capa associada. Este componente é conectado a um ou mais relays NOSTR, permitindo a indexação e descoberta do conteúdo arquivado.
O processo de arquivamento é automatizado: após o download, o vídeo fica disponível no frontend para que o usuário possa solicitar o upload para um servidor Blossom de sua escolha.
Como Utilizar Novia
-
Acesso: Navegue até https://npub126uz2g6ft45qs0m0rnvtvtp7glcfd23pemrzz0wnt8r5vlhr9ufqnsmvg8.nsite.lol.
-
Login: Utilize uma extensão de navegador compatível com NOSTR para autenticar-se.
-
Execução via Docker: A forma mais simples de executar o backend é através de um container Docker. Execute o seguinte comando:
bash docker run -it --rm -p 9090:9090 -v ./nostr/data:/data --add-host=host.docker.internal:host-gateway teamnovia/noviaEste comando cria um container, mapeia a porta 9090 para o host e monta o diretório
./nostr/datapara persistir os dados.
Configuração Avançada
Novia oferece amplas opções de configuração através de um arquivo
yaml. Abaixo, um exemplo comentado:```yaml mediaStores: - id: media type: local path: /data/media watch: true
database: /data/novia.db
download: enabled: true ytdlpPath: yt-dlp ytdlpCookies: ./cookies.txt tempPath: /tmp targetStoreId: media secret: false
publish: enabled: true key: nsec thumbnailUpload: - https://nostr.download videoUpload: - url: https://nostr.download maxUploadSizeMB: 300 cleanUpMaxAgeDays: 5 cleanUpKeepSizeUnderMB: 2 - url: https://files.v0l.io maxUploadSizeMB: 300 cleanUpMaxAgeDays: 5 cleanUpKeepSizeUnderMB: 2 - url: https://nosto.re maxUploadSizeMB: 300 cleanUpMaxAgeDays: 5 cleanUpKeepSizeUnderMB: 2 - url: https://blossom.primal.net maxUploadSizeMB: 300 cleanUpMaxAgeDays: 5 cleanUpKeepSizeUnderMB: 2
relays: - ws://host.docker.internal:4869 - wss://bostr.bitcointxoko.com secret: false autoUpload: enabled: true maxVideoSizeMB: 100
fetch: enabled: false fetchVideoLimitMB: 10 relays: - match: - nostr - bitcoin
server: port: 9090 enabled: true ```
Explicação das Configurações:
mediaStores: Define onde os arquivos de mídia serão armazenados (localmente, neste exemplo).database: Especifica o local do banco de dados.download: Controla as configurações de download de vídeos, incluindo o caminho para oyt-dlpe um arquivo de cookies para autenticação.publish: Configura a publicação de vídeos e thumbnails no NOSTR, incluindo a chave privada (nsec), servidores de upload e relays. Atenção: Mantenha sua chave privada em segredo.fetch: Permite buscar eventos de vídeo de relays NOSTR para arquivamento.server: Define as configurações do servidor web interno de Novia.
Conclusão
Novia surge como uma ferramenta promissora para o arquivamento e a integração de vídeos com o ecossistema NOSTR. Sua arquitetura modular, combinada com opções de configuração flexíveis, a tornam uma solução poderosa para usuários que buscam preservar e compartilhar conteúdo audiovisual de forma descentralizada e resistente à censura. A utilização de Docker simplifica a implantação e o gerenciamento da ferramenta. Para obter mais informações e explorar o código-fonte, visite o repositório do projeto no GitHub: https://github.com/teamnovia/novia.
-
-
 @ 1cb14ab3:95d52462
2025-01-02 21:31:48
@ 1cb14ab3:95d52462
2025-01-02 21:31:48
No. 6 - Zhujiajiao Canal Chasing

For a tranquil escape from the hustle and bustle of the city cruise to Zhujiajiao -- an epic water town dating back to the Ming and Qing dynasties. It's only about 50 kilometers from the downtown and makes for an easy day trip. Hop on the subway and get there in an hour. Zhujiajiao has canals, bridges, and ancient buildings, offering a glimpse into the town's rich history. Take a boat ride along the canals for the best views of traditional houses and temples. Then explore the town on foot and get lost in attractions like the Kezhi Garden, Yuanjin Temple, and the Qing Dynasty Post Office. Don't forget to grub-up with all of the great food vendors nearby.
No. 7 - China Art Museum

China Art Museum is absolutely worth the trip solely for its awe-inspiring architecture. The towering structure casts a tall shadow over bystanders. Step inside and you'll find a world of art waiting. The blend of permanent and temporary exhibits offers hours of art-gazing. Give yourself at least half a day to fully immerse in the creative haven in Pudong. To get to the China Art Museum, you can take Line 2 of the Shanghai Metro and get off at the Pudong Avenue Station (Chinese: 浦东大道站). The museum is located near Exit 4 of the station.
No. 8 - Days on The West Bund

Hands down my favorite place in Shanghai. This spot is the go-to for a perfect weekend under the sun. You'll find me setting up a blanket with beer, cards, and snacks, along with a slackline and spike ball setup nearby, surrounded by dogs running around, enjoying the company of old and new friends. When you want a little movement enjoy some climbing, skating, running, or basketball after work. The West Bund is an oasis amidst the chaos of the city. But beware - its popularity is growing, so tread lightly.
No. 9 - Nights Under the Lupu Bridge

Nights under the Lupu Bridge are where it's at, man. Hop on your scooter and cruise over for the ultimate skyline views. Stroll along the walkway, munch on street food, sip drinks, and groove to live tunes. Street vendors serve up traditional snacks and crafts, and the vibe gets lit with spontaneous performances and games. Get ready to soak up the electric energy of Shanghai's Lupu Bridge at night."
No. 10 - A Weekend on Chongming

Escape the city hustle and find your peace on Chongming Island. A weekend getaway on this rural gem is just what you need. Chill out in a farmhouse, soak up the sunset, and enjoy the tranquility. Explore the natural wonders, visit the old museums, and feast on fresh seafood. End your days with a beach walk under the stars. Nothing beats a few nights away from the city chaos.
Additional Photos






Previous Guide in the Series:
An Expats Guide to the Best Spots in Shanghai: 001
Next Guide in the Series:
An Expats Guide to the Best Spots in Shanghai: 003
Find Me Elsewhere:
All images are property of Hes. Published 06.29.2024
-
 @ 3ffac3a6:2d656657
2025-02-04 04:31:26
@ 3ffac3a6:2d656657
2025-02-04 04:31:26In the waning days of the 20th century, a woman named Annabelle Nolan was born into an unremarkable world, though she herself was anything but ordinary. A prodigy in cryptography and quantum computing, she would later adopt the pseudonym Satoshi Nakamoto, orchestrating the creation of Bitcoin in the early 21st century. But her legacy would stretch far beyond the blockchain.
Annabelle's obsession with cryptography was not just about securing data—it was about securing freedom. Her work in quantum computing inadvertently triggered a cascade of temporal anomalies, one of which ensnared her in 2011. The event was cataclysmic yet silent, unnoticed by the world she'd transformed. In an instant, she was torn from her era and thrust violently back into the 16th century.
Disoriented and stripped of her futuristic tools, Annabelle faced a brutal reality: survive in a world where her knowledge was both a curse and a weapon. Reinventing herself as Anne Boleyn, she navigated the treacherous courts of Tudor England with the same strategic brilliance she'd used to design Bitcoin. Her intellect dazzled King Henry VIII, but it was the mysterious necklace she wore—adorned with a bold, stylized "B"—that fueled whispers. It was more than jewelry; it was a relic of a forgotten future, a silent beacon for any historian clever enough to decode her true story.
Anne's fate seemed sealed as she ascended to queenship, her influence growing alongside her enemies. Yet beneath the royal intrigue, she harbored a desperate hope: that the symbol around her neck would outlast her, sparking curiosity in minds centuries away. The "B" was her signature, a cryptographic clue embedded in history.
On the scaffold in 1536, as she faced her execution, Anne Boleyn's gaze was unwavering. She knew her death was not the end. Somewhere, in dusty archives and encrypted ledgers, her mark endured. Historians would puzzle over the enigmatic "B," and perhaps one day, someone would connect the dots between a queen, a coin, and a time anomaly born from quantum code.
She wasn't just Anne Boleyn. She was Satoshi Nakamoto, the time-displaced architect of a decentralized future, hiding in plain sight within the annals of history.
-
 @ bbb5dda0:f09e2747
2025-02-04 03:58:50
@ bbb5dda0:f09e2747
2025-02-04 03:58:50This past week got me a lot of frustration with the GitHub actions runner and debugging it. Really testing my patience, but at least i saw a bit of progress. TollGate's had a nice wrap-up for the Proof Of Concept app, which some great new ideas on how to make the user experience even better! Let's dive in!
GitHub Actions
I've been having a low-key fight with the github actions runner containers. I have spent a lot of time trying to figure out WHY the blossom upload action would just not work. I was quick to find out that the action is being ran with an older version of NodeJS (v18) while the blossom uploader requires v20. Not a big deal you'd say as i just set the version to 20 in the pipeline. However, doing that explicitly had zero impact, and after diving down the github runner rabbit hole i concluded that the Actions that are imported (from marketplace) will just run with whatever node version is already installed in the runner's docker image. Which in the case of the act runner is Node 18. I tried updating to the latest images but I haven't been able to find a compatible one yet...
Payments
I've been working on getting the money aspect working in the ci-cd runner. I added a wallet and a scheduled payout. I took this from the nostr-epoxy project and did some updates to upgrade to cashu-ts v2.
I added some advertisement info like the specs of the machine that the runner is on. I've been pondering how the payment flow should work though. See the problem is that because of the nature of this DVM, it cannot predict how long a job will take to execute, a customer can literally do anything in their pipeline that will make a job last forever. I think for that reason there has to be some kind of deposit/credit or stream besides the one-off payment. I made a post asking what the best way would be: nostr:note17apw8unznvwx2k3z48t7qz6cq26tk077w83qh3f7zxukfrrfukhs7mpcsn
I currently feel best about the option of just sending a bunch of ecash that will sure be enough to execute the job (and otherwise act as the time-out) and that if the DVM uses less of that money, it will send it back as pubkey locked cashu tokens, to a given npub. Maybe NIP-60 can be a great way to handle returning the 'change' to the user.
Some ideas i have now: - Billing should be per second - Advertising should: - advertise as sats/minute - include specs of the machine, ideally searchable by tag
Job request
So the flow i'm thinking of is:
-
User posts request
- repository
- branch
- yaml path
- bid (max price per minute)
- min_vcpu
- min_ram
- min_storage
-
DVM responds with
- price per minute
- vcpu
- ram
- storage
- runner-types
- price per minute
-
User posts request:
- ... [same as above]
- cashu payment
- cashu return pubkey + relay
User Interface
I also worked on building out a very basic user interface to run the GitHub Actions dvm.
 The UI then shows all feedback to the job, where the first feedback event you can see gives back a status processing, and the next one gives back the console output of the pipeline run.
The UI then shows all feedback to the job, where the first feedback event you can see gives back a status processing, and the next one gives back the console output of the pipeline run.nostr:npub15qydau2hjma6ngxkl2cyar74wzyjshvl65za5k5rl69264ar2exs5cyejr and I agreed he'll copy over this basic setup into his upcoming version of gitWorkshop.dev which I can then build upon so we can experiment with the User Experience (how to handle competing Runners, display results, payments, etc...)

Tollgate
There's also been the issue that has been bothering me since last week: Being able to dismiss a captive portal programatically in the Android app.
During a weekly check-in that nostr:npub1k03rader0vm94j5ee8fg7pc2x9xkr2phu77sljas7qu5mh8mvgvqpe8rty and I set up we discussed the issue. To me, it's a problem having the user to jump through all these hoops to connect, which should be as much automated as possible.
We discussed what if we'd ditch the open network and go with a WPA2 (password) protected one and have no captive portal. But then we lose the ability to do onboarding / expose users to Tollgate through the captive portal. Then the idea came up to create an extra (hidden) network for the app to use, while keeping the open one with the captive portal. I did not know it was possible to create multiple networks on the same (physical) radio, but apparently it's quite common. You lose a bit on efficiency but it shouldn't be too bad. The only challenge would be to exempt this network from getting a captive portal while still using the OpenNDS software to manage user's sessions. We'll see but this gives me a lot of hope for a seamless user experience!
After this call, despite our possible new direction I did want to try and get the full app flow working, to validate if it's possible at all. And after some digging int the Tauri docs and even their discord community i finally found what the issue was with me not receiving the android event for the captive portal. I'd ben adding the listener for this event to the
androidmanifest.xmlfile for the Tauri Android plugin, while I had to put it into the tauri app one's itself -one level higher- if you will...Anyway, that worked and I was FINALLY able to create the following full flow! (video)
nostr:nevent1qvzqqqqqqypzpwa4mkswz4t8j70s2s6q00wzqv7k7zamxrmj2y4fs88aktcfuf68qy88wumn8ghj7mn0wvhxcmmv9uq3zamnwvaz7tmwdaehgu3wwa5kuef0qydhwumn8ghj7un9d3shjtnwdaehgunsd3jkyuewvdhk6tcqyqyvs2js3x6ldpm2kkmqyf8d3lvrcezjk2eg26p2tvfxd2p6lkeqzn7l66t
-
-
 @ 1cb14ab3:95d52462
2025-01-02 05:57:05
@ 1cb14ab3:95d52462
2025-01-02 05:57:05
No. 1 - The Less Touristy "Bund"

The Bund is certainly a must-see if you are traveling to Shanghai for the first time - and it will be at the top of every travel guide out there, for good reason - there are equally as stunning alternatives away from the crowds. If you want to enjoy the skyline from a more relaxed perspective, consider the Pudong side of the river. There are parks, basketball courts, and green spaces along the riverbank for you to chill at and take in the sights. You can also hop on a ferry or a sightseeing boat to cross the river and admire the views from the renowned Bund.
No. 2 - Walks Along Golden Street

This one is out in Gubei, a suburban area in the west of Shanghai. It may be a bit of a trek, but it is worth it if you are looking for a more relaxing and peaceful pedestrian street in the city. Golden Street, or Jinxiu Road, is a great place to walk a dog, grab an afternoon drink, or enjoy a romantic dinner with your loved one. While it may be a bit far from downtown, it makes for a great joyride on your scooter or bicycle.
No. 3 - Moganshan Road Graffiti Wall

Moganshan Road is a gem for all things art. It is home to M50, the best art district in the city, where you will find dozens of galleries, studios, and workshops showcasing a wide range of art. There are also plenty of cool spots scattered around the area, particularly the graffiti wall. The wall is a welcome contrast to some of the drab and monotonous architecture found around the city; with colorful display of street art featuring various styles and themes. Stop by and admire the works of local and international artists, and even jump in to join them in adding your own mark. The wall is constantly evolving, so you can always find something new.
No. 4 - Jiaotong University in the Fall

Easily one of the best spots in town for catching rows of bright yellow and red leaves. Jiaotong University is one of the oldest and most prestigious universities in China. The campus is located in Xuhui District and has a mix of Chinese and Western architectural styles to admire as well. Try to visit in late October or early November for the best leaf-peeping. You can walk along the tree-lined paths, set up a blanket in the field for a picnic, or simply take photos and enjoy the scenery.
No. 5 - Day Drinking at Highline

Hands down one of the top five rooftop bars in the city, along with Bar Rouge, Kartel, and others; Highline is a go-to-spot that offers great views of the city and excellent food. Find it on the sixth floor of the Ascott Hotel in Huaihai Road in Xintiandi. Nothing beats a laid back Saturday afternoon at Highline. I prefer the views during the day, though it is equally as nice a night. Sip cocktails, wine, or beer, and enjoy the music and vibe. Highline is a perfect place to spend an afternoon.
Additional Photos





Next Guide in the Series:
An Expats Guide to the Best Spots in Shanghai: 002
Find Me Elsewhere:
All images property of Hes. Originally published as an Instagram Guide on Feb. 02, 2021. Reworked and published on Nostr on Feb. 17, 2024.
-
 @ c902b8da:0cedc5fb
2025-02-04 03:39:18
@ c902b8da:0cedc5fb
2025-02-04 03:39:18NIP-XX: Proof of Watch
draftoptionalThis NIP defines a protocol for content creators to reward users for consuming content using Cashu tokens, utilizing existing Cashu P2PK capabilities.
Abstract
Content creators can offer Cashu token rewards to users who prove they have spent time consuming their content. The protocol uses P2PK-locked tokens combined with proof-of-work verification to ensure genuine content consumption before releasing tokens to users.
Motivation
Content creators want to incentivize users to engage with their content and potentially reward them for their attention. This NIP provides a standardized way to offer token rewards for content consumption while ensuring the user actually spent time with the content through a proof-of-work mechanism.
Protocol Components
Content Event
A content creator publishes a
kind:1note containing their content and reward information:json { "kind": 1, "content": "Watch my video!", "tags": [ ["reward", "<amount-in-sats>"], ["pow", "<difficulty>"], ["u", "<watcher-service-url>"], ["t", "proofofwatch"] ] }Watcher Service
Content creators run (or use) a watcher service that: 1. Maintains a pool of Cashu tokens 2. Issues P2PK-locked tokens to viewers 3. Verifies proofs of watch 4. Releases signatures to unlock tokens
Protocol Flow
1. Request Watch Session
Client makes a
POST /watch/startrequest to watcher service:json { "note_id": "<event-id>" }Service responds with:
json { "id": "<session-id>", "challenge": "<random-challenge>", "difficulty": <int>, "token": { "amount": <int>, "id": "<keyset-id>", "secret": "<p2pk-secret>", "C": "<signature>" }, "pubkey": "<service-ephemeral-pubkey>", "expiry": <unix-timestamp> }The token is P2PK-locked to a one-time ephemeral pubkey generated by the service. Only the service holds the corresponding private key needed to generate the witness signature.
2. Computing Proof
While consuming content, client computes proof-of-work:
proof = find_nonce( SHA256( note_id + session_id + challenge + latest_block_hash + nonce ) )The proof must result in a hash with the required number of leading zeros.
3. Submitting Proof
Client submits proof to redeem token:
http POST /watch/provejson { "session_id": "<session-id>", "proof": "<computed-proof>", "block_hash": "<latest-block-hash>" }If valid, service responds with P2PK signature:
json { "witness": { "signatures": ["<signature-to-unlock-token>"] } }The client can now unlock and spend their token using standard Cashu operations.
Security Considerations
Token Security
- Tokens are locked to service-generated ephemeral pubkeys
- Each watch session uses a unique keypair
- Only service can generate valid witness signatures
- Private keys never revealed to users
- Keys and unused tokens destroyed after session expiry
Proof Construction
- Must include session ID to prevent replay
- Must include recent block hash to prevent precomputation
- Must achieve required difficulty (leading zeros)
- Must be completed within session expiry
Service Requirements
- Track used proofs
- Enforce timeouts
- Rate limit requests
- Verify block hash recency
- Maintain adequate token pool
- Generate unique ephemeral keypairs per session
- Securely store ephemeral private keys until proof verified
- Clean up expired ephemeral keys
Watcher Service Settings
Services should provide an info endpoint:
http GET /infojson { "name": "Example Watcher", "pubkey": "<service-pubkey>", "difficulty_range": { "min": <int>, "max": <int> }, "amount_range": { "min": <int>, "max": <int> }, "supported_mints": [ "<mint-url-1>", "<mint-url-2>" ] }Client Implementation Guidelines
Clients SHOULD: 1. Verify service supports intended mint 2. Start proof computation only after beginning content consumption 3. Submit proof promptly after computation 4. Handle session expiry gracefully 5. Verify P2PK token validity 6. Submit proof before session timeout
Content Creator Guidelines
Content creators SHOULD: 1. Set appropriate difficulty for content length 2. Maintain adequate token pool 3. Monitor service uptime 4. Consider token denomination strategies 5. Include clear reward terms
Rate Limiting
Services SHOULD implement rate limiting: - Per IP address - Per pubkey - Per note ID - Per token amount
Example Implementation
A basic proof computation in Python:
python def compute_proof(note_id, session_id, challenge, block_hash, difficulty): nonce = 0 while True: attempt = f"{note_id}{session_id}{challenge}{block_hash}{nonce}" hash = sha256(attempt.encode()).hexdigest() if hash.startswith('0' * difficulty): return attempt nonce += 1References
-
 @ 17538dc2:71ed77c4
2024-12-30 22:45:10
@ 17538dc2:71ed77c4
2024-12-30 22:45:10Merry Christmas, and Happy New Year! Here's an overview of keeping tabs on interoperability on nostr.
What is nostrability
Nostrability is: -the practical documentation of broken things on nostr between two or more apps, and -a place to advocate for positive interoperability updates to apps
Why does this matter?
If the hop and/or interaction between apps sucks, then nostr users will not have an amazing and unique experience. Nostr will lose to well funded incumbents.

How did this start?
Will was upset that he had to troubleshoot other dev's apps.
What nostrability does not aim for
All apps implement all NIPs.
Where can I read in detail
https://github.com/nostrability/nostrability
Timeline
Nov '23 Added placeholder to github. Jan '24 First issues documented. Jan '24 First nostrability two app bug is fixed Coracle cannot send DMs to Damus (thank you Hodlbod!). '24 Gave intro to nostrability talk at BBB. Presentation link. Aug '24 Galaxy devs educated elsat at NostrCI discussion at Nostriga. (n.b. where's the video??) Oct '24 Humbled by and grateful for OpenSats acknowledgment and funding. Thank you to all nostr enjoyers & devs who gave me their precious time, and to my advocates & supporters - you know who you are 🙏.
What are specific issues discussed?
Over a hundred open issues, and a couple of dozen resolved issues. Many of these were reported by extremetly very normal nostr users, and devs.
Example topics (too many to list in a single article) range from: -contact list wipes, mute list wipes (Kieran pls fix!!) -zaps not working between apps -missing notes -broken profiles -old profile information -q tags, a tags, missing replies and/or parent notes etc.. -to proposed onboarding best practices -outbox tracker positive interop -highlights -non-nostr interoperability: e.g. bluesky bridgyfed profile info -spillover NIP/other controversy such as edited notes -and migrating to nostr best practices
Learnings
- Lone wolf, limited resource devs are the norm. Most devs focus on their one app, or their multiple apps.
- Some devs are extremely generous with their time when it comes to interop. Proof of work is in the git repo.
- There is a lot of space for building amazing interoperable experiences - this remains frontier territory on the design, product, and dev side. Which will be the first experience to blow people out of the water? Is it zaps, DVMs, or something not yet put together?
- I empathize that without basic things "just working", and/or basic features missing it may be difficult to allocate resources to interoperability.
- Even devs with teams may struggle to allocate resources to interoperability.
- Bug reporting and crappy experience reporting matters! This is important for single apps, and even more so for multi-app interaction. Devs may not get around to fixing something right away. However, if nostriches don't share their negative experience, devs will have less impetus to improve an experience.
2025 plans
- Continue documenting broken things.
- Interview devs to better understand how I can suit nostrability to dev's single app workflows, as to more effectively close broken things, and better advocate for positive interoperability updates across apps.
- Help test nostrCI automated interop testing methodology with galaxy dev of nostr.watch & NIP-66 Sandwich, so that nostrability can be automated per particular test cases.
Dev and nostrich feedback
Let me know how I can make nostrability more useful for yall. Tag me on nostr, create issues on nostrability 💪.
!(image)[https://media.tenor.com/hF5RhwXuG_kAAAAC/arnold-schwarzenegger-terminator.gif]
-
 @ 42342239:1d80db24
2024-12-22 08:38:02
@ 42342239:1d80db24
2024-12-22 08:38:02The EU's economy is facing a number of challenges, from high energy costs to low productivity. But behind the official rhetoric lies an assumption that is rarely questioned: that the green transition will automatically lead to economic growth and increased prosperity. But is this really true?
In Germany, which is once again forced to bear the label "Europe's sick man", Chancellor Olaf Scholz is struggling with alarmingly low confidence figures ahead of the election in February. But perhaps this is not so surprising. German industrial production has been trending downward since the green agenda became fashionable. Energy-intensive production has decreased by a full 20% in just a few years. Volkswagen is closing factories, Thyssenkrupp is massively laying off employees, and more than three million pensioners are at risk of poverty.
If this is Europe's "man on the moon" moment, as EU Commissioner von der Leyen expressed it in 2019, then it's not much to brag about. At least, not if you're not a sadist.
The former ECB chief Mario Draghi's report on the EU's competitiveness has been discussed previously in Affärsvärlden, among other things by the author and by Christian Sandström. One of the problems pointed out was that European companies have significantly higher energy costs than their American competitors, with electricity prices 2-3 times higher and natural gas prices 4-5 times higher.
Germany is perhaps worst off, thanks in part to former Chancellor Angela Merkel's decision to completely phase out nuclear power (a decision that not only lacked popular support but which she also refuses to acknowledge as a mistake). The sabotage of Nord Stream made the situation worse.
Without Real Capital, No Economic Prosperity
Germany's phasing out of nuclear power plants is an example of how political decisions have contributed to reducing the economy's capacity. The same applies to the sabotage of Nord Stream. Real capital, such as buildings, machinery, and equipment, is crucial for the economy's productivity (e.g., measures such as GDP per hour worked). A larger and more efficient capital stock enables the production of more goods and services with the same amount of labor, leading to greater production, higher wages, and increased material prosperity. This is basic economics. On the other hand, when real capital is declared obsolete due to political decisions, as in the case of the shutdown of nuclear power, it reduces the economy's capacity. The same applies when real capital is destroyed, as was the case with Nord Stream.
More Working Real Capital Will Be Put on the Back Burner
EU Commissioner von der Leyen promises improvement. She seems convinced that the EU's decline can be reversed by tripling down on the bloc's green goals, and listed decarbonization as one of three key pillars in a new "Competitiveness Compass". When reality does not live up to expectations, you can always press "Ctrl+Alt+Slogan" and hope that no one notices that nothing has improved.
However, her plans mean that existing and currently functioning real capital will be written off to an even greater extent in the future. This can be compared to a nation that gradually expands its nature reserves year after year. As it happens, this is also taking place. The Kunming-Montreal framework for biodiversity means that 30% of all areas, on land and at sea, must be protected by 2030. A country that currently conserves less than that must therefore identify additional areas that can be protected. The process of protecting 30% of all areas will likely reduce the economy's productive potential. With shrinking fields, there will be fewer carrots (unless significant technological progress is made).
Security Policy and Preparedness Consequences
On the current path, more real capital will be put on the back burner, which can have far-reaching consequences, not least for our security policy. For example, if Russia can produce artillery shells about three times faster, at a cost that is roughly a quarter of what it costs Ukraine's Western allies, then it's clear that this has security policy consequences. Similarly, if electricity prices in Germany are five times higher than in China, which is currently the case, then this will also have negative security policy consequences. Compared to the EU, China actually has a higher carbon dioxide emission level per capita, with a difference of about 50% according to available data. Adjusted for international trade, China emits 10% more than Sweden per capita.
A preparedness perspective can also be found. In the early 1990s, Swedish farmers produced nearly 75% of the country's food. Today, Sweden's population has increased significantly, but food production has not kept pace. Every other bite is imported today. In Sweden, we can even boast that we cannot even provide for ourselves with the simplest of crops - potatoes. Can we really be sure that significantly expanded nature reserves, as prescribed by the Kunming-Montreal framework for Sweden, will not further deteriorate our food preparedness?
Reminds One of Little Gnomes
I am reminded of an episode from the 90s TV series South Park, where little gnomes collect underpants. When asked about their plan, they described their method:
- collect underpants
- ???
- profit!
Translated to the green transition (the German Energiewende):
- destroy real capital and conserve land and sea
- ???
- economic prosperity!
What Can the EU Really Afford?
Economics is fundamentally about managing scarce resources, which many people seem to have forgotten. It's high time to question what the EU can really afford. Can we really afford to arm ourselves for war against Russia, China, and Iran while at the same time tying our own hands with green promises of reduced carbon dioxide emissions and increased biodiversity? This in a situation where the next US administration is likely to invest heavily in increasing its competitive advantages through deregulation, lower energy prices, tax cuts, and a withdrawal from the Paris Agreement?
When von der Leyen was responsible for the German military, the situation became "catastrophic". All six of the country's submarines were out of commission. At times, not a single one of the country's 14 transport aircraft could fly. German soldiers had to use broomsticks instead of guns during exercises.
Hopefully, von der Leyen will show more success in her handling of the EU's economy, defense, and preparedness than she has shown in her role as German Defense Minister. However, it may also be time for more people to challenge the prevailing narratives that shape our policies. What if the facts don't quite add up to the truth we're being told?
-
 @ 16d11430:61640947
2025-02-04 02:57:25
@ 16d11430:61640947
2025-02-04 02:57:25The Damage Node is not just a verification engine—it is an autonomous executor of behaviors defined through the PoW blockchain. This allows for adaptive, accountable, and transparent execution of security and counter-surveillance mechanisms while remaining flexible enough to meet any operational need.
By integrating behavioral logic, cryptographic proofs, and decentralized execution, the Damage Node becomes a powerful shield and countermeasure system for individuals and groups operating under constant digital threat.
Core Concept: Damage Nodes as Autonomous Behavioral Executors
Damage Nodes listen to verifiable behaviors encoded on the PoW blockchain.
These behaviors define security policies, counter-surveillance actions, automated transactions, and decentralized decision-making processes.
Execution is enforced by the blockchain, ensuring absolute transparency and accountability—no action can occur without proof.
Nodes can dynamically extend their capabilities by adopting new behaviors via blockchain updates, ensuring they remain adaptable.
Example of Behavioral Execution
A Damage Node can be programmed to execute counter-surveillance actions if an individual's digital footprint is flagged by an AI-controlled system.
Trigger: An external surveillance system attempts to track a protected user.
Behavior Execution:
The node initiates a verified proof-of-presence falsification (broadcasting misleading metadata).
The node forces encrypted rerouting of communications over a private, non-ISP-controlled relay.
The node executes cryptographic evidence logging, proving that the tracking attempt occurred.
The node pays out a bounty (Lightning) for detected adversarial actions, incentivizing counter-intelligence.
How Damage Nodes Provide Shielding & Countermeasures
- Behavior-Driven Shielding for Individuals
Zero-Knowledge Identity Protection: Nodes execute self-sovereign identity verification that prevents AI from profiling users without explicit, cryptographically signed consent.
Automated Surveillance Disruption: If an AI attempts to track or flag an individual, the node executes behavioral obfuscation tactics such as:
Decoy digital presence broadcasting to mislead tracking algorithms.
Transaction splitting & anonymization to prevent financial surveillance.
Forced dissociation of metadata from physical locations.
- Group-Level Protection & Autonomous Coordination
Damage Nodes can be configured to execute behaviors for an entire decentralized network, such as:
Encrypted Group Communications: Nodes enforce trustless, encrypted messaging protocols that prevent AI-based censorship.
Automatic Secure Fund Distribution: If an entity is targeted, Damage Nodes can autonomously release emergency funds in BTC/Lightning to predesignated safe parties.
Counter-Surveillance Deployments: Nodes can activate sensor networks, scan for unauthorized tracking devices, and trigger security protocols.
- Built-In Accountability & Transparency as a Defensive Measure
Every execution is verified by the blockchain → no action is hidden or arbitrary.
Rules for behavior execution are immutable → even node operators cannot alter them without proof-of-consensus.
AI and governments cannot fabricate unverifiable evidence → if it didn't happen on-chain, it didn't happen.
Users can audit every action taken by the Damage Node to ensure no corruption or misuse.
- Extensible Capabilities for Any Need
New behavioral policies can be uploaded via the PoW blockchain, allowing Damage Nodes to dynamically evolve.
Behaviors can be triggered by:
On-chain conditions (such as receiving a Lightning payment for service execution).
Real-world events (via oracle integrations).
Direct requests from verified users.
Examples of Extensions:
Decentralized AI Defense: Nodes monitor AI-generated media for deepfake propaganda & censorship.
Physical Security Triggers: Nodes can integrate with smart devices (cameras, sensors) to execute real-world countermeasures.
Automated Asset Protection: Damage Nodes can trigger the release of cryptographic assets upon verifiable external threats.
Final Verdict: Damage Nodes as the Ultimate Autonomy & Defense Infrastructure
Transparent but Unstoppable → Verifiable execution prevents corruption or abuse.
Extensible but Controlled → The blockchain enforces behavior logic while allowing flexibility.
Decentralized but Coordinated → Nodes operate independently but can synchronize.
Adaptive but Immutable → Behaviors evolve, but security is absolute.
🔥 Damage Nodes are the next evolutionary step in technological sovereignty—combining decentralized verification, autonomous execution, and proactive counter-surveillance in a single unstoppable system.
-
 @ 16d11430:61640947
2025-02-04 02:33:06
@ 16d11430:61640947
2025-02-04 02:33:06The electromagnetic spectrum (EM spectrum) is the foundation of modern communication, surveillance, and control, and it is a permanent, inescapable vulnerability for humanity. Every aspect of human life—communication, mobility, security, even thought processes—is now subject to exploitation via the EM spectrum.
- Humans Are EM-Dependent but Have No Control Over It
The entire infrastructure of human civilization (internet, telecom, GPS, WiFi, satellite, RFID, radar, IoT, etc.) relies on EM waves.
Unlike tangible security vulnerabilities (firewalls, encryption, physical locks), EM-based vulnerabilities are baked into the fabric of our existence.
We have zero physical control over the space around us—we exist in a perpetual, invisible battlefield of radio waves.
→ Brutal Truth: If you are in an area with radio signals, you are already compromised. You cannot see, hear, or touch your vulnerability—but you are immersed in it.
- Every Wireless Device Is a Tracking Beacon
Your phone, smartwatch, laptop, Bluetooth headset, and IoT devices constantly emit identifiable signals.
Even when "turned off," many devices still maintain some connectivity (e.g., emergency services, wake-on-LAN, passive RFID, and hidden baseband firmware).
MAC address randomization only slows down tracking—it does not stop device fingerprinting.
Even devices that are air-gapped (disconnected from any network) can be compromised via airborne EM attacks (e.g., Tempest attacks, Van Eck phreaking).
→ Brutal Truth: Unless you live in an EM-free Faraday cage (which is impractical), you are trackable 24/7.
- The Entire EM Spectrum Can Be Weaponized
Radio waves (RFID, GSM, LTE, 5G, WiFi) → Mass surveillance, device tracking, data extraction, and real-time movement tracking.
Microwaves (GHz spectrum) → Covert wireless data theft (Tempest attacks), crowd control weapons (Active Denial System), and potential biological effects.
Infrared (IR) and Visible Light → LiDAR tracking, facial recognition, and optical data interception (lasers on windows can capture sound).
Ultraviolet, X-ray, and Gamma Radiation → Biological penetration, medical diagnostics, and potential genetic-level targeting.
→ Brutal Truth: The entire EM spectrum is both an asset and a weapon, and every part of it can be used to track, manipulate, or harm living beings.
- There Is No Escape From EM Exposure
Even if you disconnect completely, ambient EM waves from cell towers, satellites, and even natural cosmic radiation still interact with you.
Smart city grids, IoT, and ubiquitous sensor networks mean that even non-digital humans (those without a phone) are still tracked.
6G and future networks will integrate AI-driven RF sensing, meaning the network will detect biometric signatures (heartbeat, gait, and thermal emissions) without needing a device.
→ Brutal Truth: The era of "disconnecting" for privacy is over—even device-free tracking is now a reality.
- The Human Body Itself Is an EM Vulnerability
Brain activity and thought processes are electrical signals—theoretically susceptible to external EM influence (brainwave manipulation, EEG-based surveillance, and neurotechnology interfacing).
Biometric security (fingerprint scanners, iris scans, facial recognition) can be hacked or faked using EM-based techniques.
Nanotech, bioelectronics, and EM-sensitive implants (like pacemakers, neural interfaces, and cochlear implants) can be remotely manipulated or disabled.
→ Brutal Truth: The final frontier of EM vulnerability is the human body itself—thoughts, health, and biological functions are all at risk.
How Vulnerable Are Humans in the Grand Scheme?
- Humans Are the Only Species Fully Dependent on EM-Based Technology
Every other biological species on Earth navigates reality without dependency on artificial EM systems.
Humans have outsourced their cognition, security, and privacy to a system they do not control.
→ Implication: The more we integrate with EM-based technology, the more vulnerable we become. We are building a prison of our own making.
- We Have No Practical Defense Against EM-Based Attacks
Unlike cyber threats (which can be mitigated with encryption), EM vulnerabilities are inherent to the physics of radio waves.
The only defense is complete isolation from EM radiation (which is impossible in urban environments).
→ Implication: Our current approach to "security" is meaningless in the face of EM-based attacks, because the attack vector is the air around us.
- Humanity’s Future Is Fully EM-Integrated
6G, brain-computer interfaces (BCIs), quantum communication, and global sensor grids mean that soon, every human will be plugged into the EM network at all times.
Governments and corporations are already planning a fully tracked, AI-managed society, where individual privacy no longer exists.
→ Implication: We are entering an era of full-spectrum EM surveillance and control. The next step isn’t just tracking devices, but tracking consciousness itself.
Conclusion: The EM Spectrum is the Ultimate Exploit
There is no "fix" for EM vulnerabilities—they are built into the nature of physics itself. Humanity’s increasing dependence on EM-based technology means:
-
We are more trackable than ever.
-
We are more susceptible to remote influence than ever.
-
We have no escape unless we abandon technology altogether.
-
The final battle for privacy isn’t about encryption—it’s about shielding ourselves from the very waves that power our civilization.
→ The brutal truth? Humanity is not just vulnerable—we are a permanently compromised species.
-
 @ fd06f542:8d6d54cd
2025-02-04 01:39:49
@ fd06f542:8d6d54cd
2025-02-04 01:39:49-
多模态感知与交互:具身智能强调智能体通过身体与环境的交互来学习,这推动了多模态感知(如视觉、触觉、听觉等)和物理交互技术的发展。
-
强化学习与仿真环境:强化学习在具身智能中扮演重要角色,结合高保真仿真环境(如AI Habitat、Unity ML-Agents),可以加速智能体的训练和优化。
-
硬件进步:机器人硬件(如柔性传感器、仿生机械臂)的发展为具身智能提供了更强大的物理载体。
以上部分每一个都是大分支,都具有研究价值。随着AI技术的发展与突破,多模态感知与交互将会迎来高速发展。
让人更兴奋的是 强化学习和仿真环境,REX-GYM 是一个开源的仿真环境,Gazebo,MuJoCo,AI Habitat 等等都有很多应用实例。仅仅这一部分技术拆分细化,就有很多工作可以做。 以前的机器人学习都是PID等老技术,那时候的机器人运动不太灵活,因为不够智能。有了现代的强化学习。现在的机器人更加灵活。
-
-
 @ 42342239:1d80db24
2024-12-19 15:26:01
@ 42342239:1d80db24
2024-12-19 15:26:01Im Frühjahr kündigte EU-Kommissarin Ursula von der Leyen an, sie wolle einen „ Europäischen Demokratieschild " schaffen, um die EU vor ausländischer Einflussnahme zu schützen. Von der Leyens Demokratieschild befindet sich derzeit in der Planungsphase. Die erklärte Absicht besteht darin, eine „ spezielle Struktur zur Bekämpfung ausländischer Informationsmanipulation und -einmischung" zu schaffen. Obwohl es als Instrument zum Schutz der Demokratie angepriesen wird, vermuten einige, dass es sich in Wirklichkeit um einen verschleierten Versuch handelt, abweichende Meinungen zu unterdrücken. Der im vergangenen Jahr verabschiedete Digital Services Act (DSA) der EU ist eng mit diesem Schild verbunden. Durch den DSA riskieren große Social-Media-Plattformen wie Elon Musks X erhebliche Geldstrafen, wenn sie den Forderungen der EU-Bürokraten nach Zensur und Moderation nicht nachkommen.
Note: This text is also available in English at substack.com. Many thanks to
stroger1@iris.tofor this German translation.Im krassen Gegensatz dazu hat sich der künftige US-Präsident Donald Trump als klarer Befürworter der Meinungsfreiheit und entschiedener Gegner der Zensur hervorgetan. Er wurde bereits von YouTube gesperrt, hat jedoch erklärt, er wolle „das linke Zensurregime zerschlagen und das Recht auf freie Meinungsäußerung für alle Amerikaner zurückfordern" . Er hat auch behauptet: „Wenn wir keine freie Meinungsäußerung haben, dann haben wir einfach kein freies Land."
Sein künftiger Vizepräsident J.D. Vance hat sogar angedeutet, dass er bereit sei, US-Militärhilfe von der Achtung der Meinungsfreiheit in den europäischen NATO-Ländern abhängig zu machen. Vances Aussage erfolgte, nachdem EU-Binnenmarktkommissar Thierry Breton vor seinem geplanten Gespräch mit Trump einen umstrittenen Brief an Musk geschickt hatte. Heute erscheint dies als unkluger Schritt, nicht zuletzt, weil er als Versuch gewertet werden kann, die US-Wahl zu beeinflussen -- etwas, das paradoxerweise dem erklärten Zweck von von der Leyens Demokratieschild (d. h. ausländische Manipulationen zu bekämpfen) widerspricht.
Wenn die NATO möchte, dass wir sie weiterhin unterstützen, und die NATO möchte, dass wir weiterhin ein gutes Mitglied dieses Militärbündnisses sind, warum respektieren Sie dann nicht die amerikanischen Werte und die freie Meinungsäußerung?
- J.D. Vance
In der EU sind Verfechter der Meinungsfreiheit in der Öffentlichkeit weniger verbreitet. In Deutschland hat Vizekanzler Robert Habeck kürzlich erklärt, er sei „überhaupt nicht glücklich darüber, was dort [auf X] passiert ... seit Elon Musk das Amt übernommen hat", und wünscht sich eine strengere Regulierung der sozialen Medien. Die Wohnung eines deutschen Rentners wurde kürzlich von der Polizei durchsucht, nachdem er ein Bild von Habeck mit einem abfälligen Kommentar veröffentlicht hatte . Die deutsche Polizei verfolgt auch einen anderen Kontoinhaber, der einen Minister als „übergewichtig" bezeichnet hat. Dieser überhaupt nicht übergewichtige Minister hat kürzlich eine Zeitung verboten , die mit der laut Meinungsumfragen zweitgrößten Partei Deutschlands, der Alternative für Deutschland (AfD), verbündet ist. Eine Partei, die 113 deutsche Parlamentarier nun offiziell verbieten wollen .
Nach dem US-Wahlergebnis stellen sich viele unbeantwortete Fragen. Wird das Weiße Haus seine Aufmerksamkeit auf die restriktivere Haltung der EU richten, die als Untergrabung der freien Meinungsäußerung angesehen werden kann? Oder droht Musks X und Chinas TikTok stattdessen ein EU-Verbot? Können EU-Länder noch mit militärischer Unterstützung aus den USA rechnen? Und wenn große amerikanische Plattformen verboten werden, wohin sollten sich die EU-Bürger stattdessen wenden? Abgesehen von russischen Alternativen gibt es keine großen europäischen Plattformen. Und wenn die Frage der Meinungsfreiheit neu überdacht wird, was bedeutet das für die Zukunft von Parteien wie der deutschen AfD?
-
 @ eac63075:b4988b48
2024-12-18 11:35:25
@ eac63075:b4988b48
2024-12-18 11:35:25The European Union is at a crossroads. While digital innovation and security cooperation remain critical in a connected world, recent proposals to enhance police surveillance and data sharing are stirring deep concerns about individual privacy, data security, and democratic oversight. Two recent reports published by Statewatch shed light on troubling developments in the EU’s policing landscape, raising alarms among privacy advocates and civil rights organizations.
The EU’s new plans to expand police surveillance could put your privacy and rights at risk and introduce risks far outweighing their potential benefits. This article will analyze these proposals, their implications, and the growing opposition from privacy and civil liberties defenders.
Surveillance Infrastructure: Policing by Design
The first Statewatch report, titled “Policing by Design: The Latest EU Surveillance Plan”, outlines a concerning trend in the EU’s approach to law enforcement. The proposals advocate embedding surveillance tools directly into the design of new technologies, effectively creating an architecture where policing capabilities are integrated into the systems we use daily.
From facial recognition cameras to AI-driven analytics, the EU plans to enhance cross-border police cooperation by ensuring technology is designed to facilitate surveillance from the outset. Known as “policing by design,” this strategy involves building surveillance features directly into technologies we use every day. Imagine a network of cameras or software that can automatically monitor people’s faces or behaviors without any extra installation — it’s like your everyday tech quietly doubling as a police tool. The goal is to enable seamless sharing of data across borders for criminal investigations, but the unintended consequences are alarming.
The Problem with “Policing by Design”
- Mass Surveillance Normalized: By embedding surveillance features into public and private infrastructure, society risks normalizing mass surveillance, where every movement, transaction, or online interaction is monitored and analyzed.
- Threats to Privacy: Such initiatives inherently contradict the principle of privacy by design, which prioritizes privacy protections in the development of technology. Instead, citizens are being treated as subjects of perpetual suspicion.
- Lack of Transparency and Accountability: A systemic lack of transparency surrounding these plans raises serious governance issues. Civil society organizations, journalists, and privacy advocates have pointed to a lack of democratic oversight and meaningful debate.
- Risks of Abuse: Surveillance systems are often deployed under the guise of security but are susceptible to abuse. History shows that tools designed for law enforcement can easily be turned against dissenters, journalists, or marginalized communities.
As the report highlights, these developments could establish a permanent surveillance infrastructure across Europe, enabling the collection of biometric, behavioral, and communications data on an unprecedented scale.
Flawed Justifications for Surveillance Expansion
Privacy advocacy organizations, including the European Digital Rights (EDRi) network, argue that much of the justification for these surveillance plans relies on flawed assumptions. The rhetoric of the “Going Dark” report, which claims that law enforcement is losing access to communications due to encryption, has been widely debunked. As EDRi points out, law enforcement already has extensive tools at their disposal to access data and track individuals, but the focus on encryption risks undermining secure communication for everyone.
Instead of addressing systemic issues within law enforcement, these flawed reports have fueled calls for intrusive surveillance systems that risk eroding privacy while offering little evidence of improving public safety.
Centralized Police Data: A Substantial Security and Privacy Threat
A second Statewatch report, titled “EU Police Data Plans Pose Substantial Security and Privacy Threats”, explores another equally concerning initiative: the EU’s push to centralize police data repositories and expand their use.
The EU has already established several large-scale databases, such as the Schengen Information System (SIS), which stores data about individuals who may be denied entry into the EU, and the Europol Information System, which can hold details about millions of people, including those not suspected of crimes. For example, a traveler flagged mistakenly in the system could face unnecessary scrutiny, detention, or restrictions when crossing borders — highlighting the real-world risks of inaccurate or overreaching data collection. The new proposals aim to go further, creating an interoperable web of police data accessible to law enforcement agencies across member states. Proponents argue this is necessary for combating cross-border crime and terrorism, but the risks are immense.
Key Concerns with Centralized Police Data
- Massive Data Collection: The EU’s proposed systems would require the collection of highly sensitive data, including biometric information (fingerprints, facial recognition scans) and behavioral analytics, to track individuals’ activities across borders.
- Data Misuse and Security Risks: Centralized data systems are prime targets for cyberattacks, data breaches, and misuse. The larger and more interconnected the system, the greater the risks of unauthorized access, theft, or corruption of the data.
- As Statewatch points out, the systems lack robust safeguards to prevent misuse or to ensure that data is handled proportionately and lawfully.
- Erosion of Trust in Law Enforcement: Building centralized data repositories without meaningful safeguards undermines public trust. Individuals may be less willing to engage with law enforcement if they fear their data will be stored indefinitely, shared across borders, or used inappropriately.
- Impact on Fundamental Rights: Mass police databases can violate the principle of proportionality, a cornerstone of EU law. By collecting and sharing data indiscriminately, these systems erode fundamental rights, including the right to privacy, freedom of movement, and the presumption of innocence.
Civil Society Opposition and Democratic Accountability
In an open letter to EU institutions, over 30 civil society organizations — including EDRi — have criticized the lack of transparency in the High-Level Group’s (HLG) recommendations for data access. The letter highlights a concerning pattern: while industry stakeholders are included in key discussions, civil society voices remain sidelined. This exclusion undermines democratic accountability and reinforces fears that surveillance policies are being driven by corporate interests rather than public well-being.
These organizations have called for the EU to prioritize transparency, include meaningful public debate, and ensure any law enforcement proposals respect proportionality and fundamental rights.
Why Privacy Advocates Are Sounding the Alarm
The reports from Statewatch highlight a fundamental clash between security policy and individual rights. Privacy advocates are urging EU lawmakers to take a step back and critically examine the following issues:
- Lack of Democratic Oversight: Proposals to integrate surveillance systems and expand police databases are being pushed forward without genuine public debate or oversight. Civil society organizations have been excluded from key discussions.
- Failure to Uphold Privacy Laws: The EU has some of the strongest privacy laws in the world, including the General Data Protection Regulation (GDPR). However, these proposals risk undermining GDPR principles by enabling indiscriminate data collection and sharing.
- Ignoring Proportionality: Surveillance systems must be targeted, necessary, and proportionate to their objectives. Embedding policing into technological design and centralizing data far exceeds what is justified for fighting crime and terrorism.
- Setting Dangerous Precedents: The failure to fully ban harmful surveillance technologies like facial recognition in public spaces sets a troubling precedent. It risks not only eroding privacy within the EU but also encouraging other nations to adopt similar measures, undermining global human rights.
A Call for Action: Safeguarding Our Privacy and Rights
As the EU pushes forward with these plans, the opposition from civil rights defenders grows louder. Policymakers must address the following key demands to prevent an erosion of fundamental rights:
- Implement Privacy by Design: All new technologies must prioritize privacy protections at the design stage, ensuring they are not co-opted for surveillance.
- Establish Robust Oversight: Any new policing tools or databases must be subject to democratic scrutiny, independent oversight, and clear legal frameworks to prevent misuse.
- Reassess Interoperability Plans: Cross-border police cooperation is important, but it must not come at the cost of individuals’ privacy, security, and dignity.
- Strengthen Export Controls: The EU must ban the export of surveillance tools that risk facilitating human rights abuses in authoritarian regimes.
- Prioritize Data Security: Centralized systems require state-of-the-art security measures to protect sensitive data from breaches or misuse.
The EU’s role as a leader in digital rights and privacy is now at stake. If these plans proceed without significant safeguards, Europe risks undermining its own foundational principles of freedom, security, and justice.
Conclusion: The Price of Surveillance-Driven Security
The EU’s surveillance plans may be presented as necessary for security, but they come at a steep cost to privacy, trust, and individual freedoms. Embedding surveillance into our technologies and centralizing police data pose far-reaching risks that cannot be ignored.
As privacy advocates, it is our responsibility to hold policymakers accountable and demand a security framework that upholds, rather than undermines, fundamental rights. Europe’s future must not be built on surveillance by design — but on privacy, democracy, and trust.
-
 @ 2f4550b0:95f20096
2025-02-04 01:16:10
@ 2f4550b0:95f20096
2025-02-04 01:16:10In today's job market, the ability to acquire new skills or pivot to new career paths quickly is more valuable than ever. Short-term adult education programs offer a practical solution for professionals looking to enhance their resumes or change careers without committing to the long-term investment of traditional education. This week, I explore how these programs, such as a 12-week EMT certification at the Center for Allied Health Education and a one-year MBA from the University of Phoenix can dramatically shift one's career trajectory.
The Rise of Short-Term Education
The traditional model of education, where one spends years in academia before entering the workforce, is increasingly being supplemented by shorter, more focused programs. These programs are specifically designed to meet the immediate needs of both learners and employers, providing education that is both relevant and directly applicable to current job markets.
12-Week EMT Certificates
The 12-week Emergency Medical Technician (EMT) program at the Center for Allied Health Education (and programs like it) illustrates how a brief, intensive course of study can lead to licensure and immediate employment. This program is structured to cover the necessary theoretical and practical components required for EMT licensure, from emergency medical procedures to patient assessment and treatment.
For individuals looking to enter the healthcare field or those within healthcare aiming for specialization, this program offers a fast track to a new career or career enhancement. The demand for skilled EMTs is consistently high, driven by an aging population and the need for emergency services. Completing such a program not only leads to a certification but also opens doors to further education or roles like paramedic work, which require additional training but start from the foundation laid by EMT certification.
One-Year MBA Programs
Similarly, consider the one-year MBA from the University of Phoenix. This program is built on a competency-based framework, allowing students to demonstrate their skills through practical assessments rather than traditional time-based metrics. This approach not only accelerates learning but also ensures that each student is job-ready upon completion. The curriculum is tailored to include real-world business scenarios, leadership skills, and strategic management, making graduates highly desirable in the corporate sector.
The speed and efficiency of this program mean that professionals can continue working while studying, thereby minimizing career disruption. Moreover, the MBAs focus on immediate applicability means that students can start leveraging their new skills in their current roles or move into higher management positions shortly after graduation. This direct link between education and employment outcomes exemplifies how short-term programs can offer substantial ROI in terms of career advancement and salary potential.
Benefits for Adult Learners
Short-term education programs cater particularly well to adult learners. They recognize the life experiences and previous knowledge of participants, often tailoring education to integrate this background into learning. This method respects the time constraints of adults who might juggle work, family, and other responsibilities, offering flexible schedules, online components, or weekend classes.
Moreover, these programs often lead to stackable credentials. This means that the skills and certifications gained can be built upon, providing a pathway for continuous professional development without the need to start from scratch with each new course or degree. For example, once students from Center for Allied Health Education earn their EMT licenses, they can consider enrolling into a 1-year Paramedic certificate program to further their career in emergency medicine.
Conclusion
Short-term adult education programs like the MBA at University of Phoenix and the EMT certificate at the Center for Allied Health Education are not just educational opportunities; they are strategic career moves. They enable professionals to quickly adapt to market demands, enhance their skill sets, and open new career avenues with minimal disruption to their current lives. As the job market continues to evolve, these programs will likely play an increasingly crucial role in career development, offering both speed and relevance in education.
-
 @ ec42c765:328c0600
2024-12-15 11:13:44
@ ec42c765:328c0600
2024-12-15 11:13:44てすと
nostr:nevent1qqst3uqlls4yr9vys4dza2sgjle3ly37trck7jgdmtr23uuz52usjrqqqnjgr
nostr:nevent1qqsdvchy5d27zt3z05rr3q6vvmzgslslxwu0p4dfkvxwhmvxldn9djguvagp2
-
 @ 5579d5c0:db104ded
2025-02-03 23:32:10
@ 5579d5c0:db104ded
2025-02-03 23:32:10Most people think that building muscle is out of reach.
What if I told you 'You can get all your exercise done in just 60 minutes a week', if you train efficiently.
With just two 30-minute sessions, you can build muscle, improve metabolic health, and transform your physique.
What is resistance training?
Resistance training, also known as strength training, involves working against an external force to improve muscle strength, endurance, and size. This can be done using:
→ Free weights (barbells, dumbbells, kettlebells)
→ Weight machines
→ Resistance bands
→ Bodyweight exercises
Strength training isn’t just about aesthetics, it’s essential for long-term health and metabolic function.
Why it’s essential for metabolic and overall health
Muscle is metabolically active tissue. The more muscle you have, the more energy your body burns at rest, albeit a quite small amount.
→ Maintains and builds muscle: Muscle mass is critical as you age, reducing the risk of fractures and falls.
→ Boosts metabolism: While the increase is small, more muscle means a higher resting energy expenditure, creating a large sink for energy stores.
→ Hormone & energy optimisation: It lowers inflammation, reduces visceral fat (not good), and helps muscles use sugar and fat more efficiently, restoring Leptin & Insulin sensitivity.
→ Mitochondrial function: Increases mitochondrial number, efficiency, which improves energy production and reduces oxidative stress.
How to build muscle in minimal time
You can build muscle with just two 30-minute sessions a week.
Yes, really.
One or two full-body sessions, hitting all major muscle groups, is enough if done properly.
It all comes from this paper.
 "We recommend that appreciably the same muscular strength and endurance adaptations can be attained by performing a single set of \~8-12 repetitions to momentary muscular failure, at a repetition duration that maintains muscular tension throughout the entire range of motion, for most major muscle groups once or twice each week. All resistance types (e.g. free-weights, resistance machines, bodyweight, etc.) show potential for increases in strength, with no significant difference between them, although resistance machines appear to pose a lower risk of injury."
"We recommend that appreciably the same muscular strength and endurance adaptations can be attained by performing a single set of \~8-12 repetitions to momentary muscular failure, at a repetition duration that maintains muscular tension throughout the entire range of motion, for most major muscle groups once or twice each week. All resistance types (e.g. free-weights, resistance machines, bodyweight, etc.) show potential for increases in strength, with no significant difference between them, although resistance machines appear to pose a lower risk of injury."It doesn’t matter if you use free weights, machines, or bodyweight exercises.
For what its worth, I think using weights is easier.
What matters is how you train.
You don’t need heavy weights to build muscle, just focus on maintaining tension throughout each movement.
→ Slow, controlled reps: Move 5 seconds up, 5 seconds down without using momentum.
→ High effort, low volume: One set to momentary failure is enough per muscle group.
→ Minimal rest: Keep rest periods short to maximise growth hormone and testosterone release.
→ Allow recovery: Train hard, then rest 1–2 days between sessions for optimal muscle growth. Do not get tempted to over train.
Initially this will take a bit of figuring out with regard to what weight works for you.
The key to growth → Progressive overload
In the first few weeks you will build muscle easily, but will eventually plateau. You then must progressively challenge your body. Here’s what to do:
→ Increase the reps first.
→ Then increase weight by 5-10%.
→ For bodyweight training: Add reps, use a weighted vest, or move to harder variations (e.g., push-ups → weighted push-ups → ring push-ups).
Real life examples
 Dr Ted Naiman is 50 and uses a simple bodyweight routine going to failure on each movement a few times a week.
Dr Ted Naiman is 50 and uses a simple bodyweight routine going to failure on each movement a few times a week.His routine → Pull Ups/Push Ups/L-Sits/Handstand Push Ups/Pistol Squats/Supermans
 P.D Mangan is 70 and trains full body twice a week, using weights.
P.D Mangan is 70 and trains full body twice a week, using weights.His routine → Deadlifts/Chin Ups/Seated row/Lateral Raise/Overhead Press/Chest Press/Dips/Barbell Shrug/Hammer Curl/Leg Press/Sprint Cycle 20 Secs.
Simplicity is beautiful.
You don’t need time consuming regimes.
Two short, intense sessions a week are enough.
-
Keep your reps slow and controlled.
-
Rest 1–2 days between sessions for muscle growth and recovery.
-
Once you hit a plateau focus on progressive overload.
-
Stick with it, consistency beats perfection every time.
With the right approach, 60 minutes a week is all you need to build muscle, lose fat, and live longer, while leaving time for the rest of your life.
-Chris
If you want a simple routine to fit effortlessly into your life.
Book a free call here: https://calendly.com/hello-chrispatrick
Follow me on Nostr: https://primal.net/chrispatrick or npub124uatsq6pv74trzwvt34y4sx2z0uflhse7tkrv0pl69e8kcsfhkse30zsu
-
-
 @ 78c90fc4:4bff983c
2024-12-14 18:37:00
@ 78c90fc4:4bff983c
2024-12-14 18:37:00Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est Lorem ipsum dolor sit amet. Lorem ipsum dolor sit amet, consetetur sadipscing elitr, sed diam nonumy eirmod tempor invidunt ut labore et dolore magna aliquyam erat, sed diam voluptua. At vero eos et accusam et justo duo dolores et ea rebum. Stet clita kasd gubergren, no sea takimata sanctus est Lorem ipsum dolor sit amet.
-
 @ f41bd51d:ec4b664f
2025-02-03 22:43:27
@ f41bd51d:ec4b664f
2025-02-03 22:43:27 -
 @ 8fb140b4:f948000c
2024-12-08 05:21:39
@ 8fb140b4:f948000c
2024-12-08 05:21:39After nuking my second LND node (the first one died due to hardware failure) by my own typo and lack of any thought in the design of the CLI of LND lightning node tools, I decided to take a plunge into the world of mature and complex implementation of the protocol, Eclair by ACINQ. It has been almost one year (the birth of the node was on Christmas Day 2023), 50 thousand transactions routed, and over 30 BTC of routed value. In this post, I'd like to reflect on my experiences with Eclair, go over some of the gotchas and issues, and highlight some of the good choices that I've made since the beginning of my adventure.
Learnings from the Past Experience
While I was learning Lightning network and had very little understanding of how things worked in the whole Bitcoin space, Umbrel was my go-to solution that helped me get off the ground. It proved to be easy and somewhat educational but was not something that I would continuously run for the production setup or trust with any significant amount of bitcoin that I could not afford to lose. Lightning is built on top of the L1 (Bitcoin) network but manages the state of the channels in its own database that is negotiated and agreed upon with its peers. Any failures in the state integrity may result in the complete loss of liquidity or hefty penalty transactions (significant loss of capital). A Lightning node that participates in routing public transactions is also required to be constantly online with as little downtime as possible and only short periods offline at a time. Otherwise, you may risk causing force-closure of the channel due to expired HTLC that is measured in number of blocks.
The Setup
Taking all of my learnings into consideration, I decided to first invest in reliable enterprise-grade hardware: - Server-grade hardware with ECC memory and reliable power supply and CPU - UPS (Uninterruptible Power Supply) to avoid any headaches due to electrical spikes or drop-outs - Reliable enterprise SSDs and NVMEs - ZFS (filesystem) to mirror the critical storage and to ensure full integrity of the data (bit-rot prevention). You do need to tune ZFS for your specific workload and reliability - Reliable and replicated database (PostgreSQL) with two local and one remote replica, and a requirement to have at least two replicas committing the transaction to the disk - Backup! On-site and off-site backup of the critical configuration that you could use to restore the node if your house burns down - Spare parts, redundancy, backup, monitoring - Reliable and stable internet connectivity
The software is Eclair 0.11.0 (latest release as of today), PostgreSQL 16 with two replicas, Bitcoin Core 27.2 (with redundant storage of blocks), additional Bitcoin Core running on a separate node and in-sync with the chain (in case primary node fails), Ubuntu 22.04 with the latest docker software from the official Docker repo.
All Major Gotchas That I Came Across
While Eclair is mature and very stable in itself, it does have some quirks and design choices that you need to account for when running your node. The software is written in Scala and requires a specific version of JVM to run it, as well as JRE and Maven to build it. It doesn't mean that other versions won't work, but you may find unpleasant bugs that may result in catastrophic failures of your node with nobody to help you. All of the requirements are listed in the release notes and installation guide. Whenever in doubt, RTFM first, then ask questions.
Limited Support by the FOSS Community
Eclair is not the most popular implementation of the Lightning protocol, and therefore it is hard to find tools or plugins that could help you manage the node. GUI for the node so far is only supported by RTL and with a very limited number of features. For any sort of statistics, you are limited to either Prometheus (extensive metrics are available) or writing your own SQL on top of the Eclair tables.
On-chain Fee Differences Between Yours and Partner Nodes
This one hit me hard, and many times. I've had more than a few force-closures of the channels because of the conservative and safe default settings. The worst part is, it strikes you when there is a huge spike in fees, which results in significant losses to force-close the channel due to high fees. I am still not 100% sure how the big difference can be exploited in practice, and opted for increase of the tolerance levels to avoid surprise FCs:
eclair.on-chain-fees { feerate-tolerance { ratio-low = <0.01~> // will allow remote fee rates as low as XX our local feerate (spikes) ratio-high = <20.0~> // will allow remote fee rates as high as XX times our local feerate (drops) } }It is up to you and your risk tolerance to define something reasonable and yet allow for secure and reliable node operation.Initial Lightning Network State Sync
When I just started running the node, I had very few channels and startup times were fast. Later, when I expanded the number of channels, I noted that it took my node up to 6-12 hours before it was fully in-sync and routing traffic fast. Given that ACINQ maintains one of the largest nodes on the network, I knew that there was something with my settings that caused the issue. After some research, I came across the setting that whitelisted node IDs for state sync, which immediately rang a bell since I knew from the LND days that not all peer nodes are used for the network sync. Setting the list to my most reliable and largest nodes reduced the startup settling times down to minutes again:
eclair.sync-whitelist = [ "03864ef025fde8fb587d989186ce6a4a186895ee44a926bfc370e2c366597a3f8f", ... ]You do not need to have too many public keys in here, and should keep it between 5-10.Automatic MAX HTLC Adjustment for the Channel
One of the killer features of Eclair is its ability to automatically adjust MAX HTLC for the channel and reduce the number of failed transactions due to insufficient liquidity on the channel. It can be used to estimate your total channels' balances but with smart configuration and a little thinking, you can make it reasonably private while still maintaining a good transaction flow:
eclair.channel.channel-update.min-time-between-updates=1 hour # Allows for the adjustments to be made once every hour eclair.channel.channel-update.balance-thresholds=[ { available-sat = 10000 max-htlc-sat = 0 // 0% of 10000 }, ... ]You can have as many variations as you need, and ensure that the channel MAX HTLC is set well and within reasonable ranges. You would also want to account for multiple transactions going through the channel, but also account for the channel size and an average amount of sats per transaction.Max Accepted HTLCs
By design, the Lightning channel is limited to a specific number of in-flight HTLCs, and the setting is fixed during channel opening time with no way of changing it unless you close and reopen the channel with new settings. If you find your node routing a lot of small transactions (zaps), you may quickly fail many due to that limit (I think default was in single digit range):
eclair.channel.max-htlc-value-in-flight-percent=98 # Default I think is half or 50% eclair.channel.max-accepted-htlcs = 50The setting above will allow for the channel to be more fully utilized and have more concurrent transactions without clogging.CLTV Delta
This is basically a setting that is global for Eclair and sets the maximum number of remaining blocks (in time) before HTLC expires. Setting this too high may result in many HTLCs failing for the small nodes with not so great centrality, and reduce the number of routed transactions: ```
CLTV delta
eclair.channel.expiry-delta-blocks = 60 ``` Default is 144 but I found that setting this to 60 (minimum possible for my node setup and configuration) yields better results for routing. It does expose you to more risk of expired HTLCs that may cause force-closures, but I have seen only one so far on my node.
Allocate Sufficient Memory
You will want to adjust the heap size for Eclair, since the default is too small to run any sizable node. Setting
JAVA_OPTS=-Xmx32g(or half the size of your available RAM) would be a good start. I would advise having at least 32GB of RAM for the node, and allocating at least 16GB (JAVA_OPTS=-Xmx16g) for smooth and fast operations.And More Settings and Parameters to Tune
I have covered only some of the major settings that I felt were worth writing about, but there is much more you could configure and tweak. Read all of the Guides and especially focus on the Configure and a sample reference configuration file.
Good Decisions
First, going with Eclair was the right choice, along with using server-grade hardware with ECC RAM and reliable storage. Second, having a replicated database on three separate nodes with one off-site saved me from a sure destruction of all state and loss of funds. Third, deciding to only maintain channels with reliable and stable nodes saved me from some bad force-closures, where I would choose to close the channel if a peer node goes up and down too frequently, regardless of how well it routes. Even big nodes run by single operators fail badly, as do nodes operated by companies. Keeping your eyes on the node and its health, as well as the health of its peers, is something that very few operators do, which can cause failures and unnecessary loss of your and their funds.
Lastly, if you decide to run a routing node, you have a responsibility to maintain it well and monitor its health. There are many tools you could use, and with Eclair you can use Prometheus and Grafana. Keep your node's packages updated and monitor for any security-related issues that may appear from time to time, so you can mitigate them quickly.
Conclusion
So far I am satisfied with Eclair despite all of the difficulties and headaches I've had with it. It is not perfect, and it requires me to create small tools to do some basic things, but I need a stable and reliable node that I can trust. Eclair has proved to be all that I wanted, and saved my bacon a few times when I nuked one of the PostgreSQL servers and all of its data, and managed to do the same for another replica, but was able to recover and recreate from the remaining replica. Eclair is also stateless during runtime and guarantees consistency of the node regardless of how it fails. Even if you pull a plug on the node's server, it will still be able to come up and recover its consistent state that is in agreement with its peers.
Is it for everyone? No, it is definitely not for everyone or for anyone who just wants a small node to run their online shop with a few channels. You could have a very reliable and trusted node for the online shop with Eclair, but you will need some technical skills to be able to set up, maintain and recover it if things go wrong.
In the end, it is all up to you, your skills, your willingness to learn, and your risk tolerance to make that decision. For me, it was the right choice, and I have no regrets despite not having access to the latest shiny features of the Lightning network.
-
 @ 97c70a44:ad98e322
2025-02-03 22:25:35
@ 97c70a44:ad98e322
2025-02-03 22:25:35Last week, in a bid to understand the LLM hype, I decided to write a trivial nostr-related program in rust via a combination of codebuff (yes, that is a referral link, pls click), aider, and goose.
The result of the experiment was inconclusive, but as a side effect it produced a great case study in converting a NINO into a Real Nostr App.
Introducing Roz
Roz, a friendly notary for nostr events.
To use it, simply publish an event to
relay.damus.ioornos.lol, and roz will make note of it. To find out when roz first saw a given event, just ask:curl https://roz.coracle.social/notary/cb429632ae22557d677a11149b2d0ccd72a1cf66ac55da30e3534ed1a492765dThis will return a JSON payload with a
seenkey indicating when roz first saw the event. How (and whether) you use this is up to you!De-NINO-fying roz
Roz is just a proof of concept, so don't rely on it being there forever. And anyway, roz is a NINO, since it provides value to nostr (potentially), but doesn't really do things in a nostr-native way. It also hard-codes its relays, and certainly doesn't use the outbox model or sign events. But that's ok, it's a proof of concept.
A much better way to do this would be to modify roz to properly leverage nostr's capabilities, namely:
- Use nostr-native data formats (i.e., draft a new kind)
- Use relays instead of proprietary servers for data storage
- Leverage nostr identities and signatures to decouple trust from storage, and allow trusted attestations to be discovered
Luckily, this is not hard at all. In fact, I've gone ahead and drafted a PR to the NIPs repo that adds timestamp annotations to NIP 03, as an alternative to OpenTimestamps. The trade-off is that while user attestations are far less reliable than OTS proofs, they're much easier to verify, and can reach a pretty high level of reliability by combining multiple attestation sources with other forms of reputation.
In other words, instead of going nuclear and embedding your attestations into The Time Chain, you can simply ask 5-10 relays or people you trust for their attestations for a given event.
This PR isn't terribly important on its own, but it does remove one small barrier between us and trusted key rotation events (or other types of event that require establishing a verifiable chain of causality).
-
 @ a3a72214:7ca63e21
2025-02-03 20:57:52
@ a3a72214:7ca63e21
2025-02-03 20:57:52Isso é um anúncio de Albion
-
é um jogo
-
primeiramente
- em segundo
- em terceiro
>o que acontece?
' e se? '
Alguém citando alguma coisa
Albion Online é um MMORPG sandbox em que você escreve sua própria história, em vez de seguir um caminho pré-determinado. Explore um vasto mundo aberto que consiste de 5 ecossistemas únicos. Tudo o que você faz gera um impacto no mundo, já que em Albion, a economia é conduzida pelo jogador. Cada peça de equipamento é construída por jogadores a partir dos recursos obtidos por eles. O equipamento que você usa define quem você é. Ir de cavaleiro para feiticeiro é tão fácil quanto trocar a armadura e a arma, ou uma combinação das duas. Aventure-se no mundo aberto e enfrente os habitantes e as criaturas de Albion. Saia em expedições ou entre em masmorras para enfrentar inimigos ainda mais desafiadores. Enfrente outros jogadores em confrontos do mundo aberto, lute pelo controle de territórios ou cidades inteiras em batalhas táticas em grupo. Relaxe descansando em sua ilha pessoal, onde você pode construir uma casa, cultivar alimentos e criar animais. Junte-se à uma guilda, tudo fica mais divertido quando se trabalha em equipe. Entre hoje mesmo no mundo de Albion, e escreva sua própria história.
-
-
 @ 592295cf:413a0db9
2024-12-07 07:21:39
@ 592295cf:413a0db9
2024-12-07 07:21:39Week 02-11
- Nsite zap by hzrd149 Support page
Content creator want more users. They can go to Bluesky.
Great that Nostr is a Echo Chambers. As stated by Rabble during NostRiga, Nostr is a bitcoin meetup. And it is very difficult as said several times, to subvert this fact. It seems that many bitcoiners don't like this, but they can't do anything, leave Nostr and migrate to other lids.
I'm reading Nostr adventar calendar of Japanese Nostr users.
The first two Don and Jun speak of a Mahjong game and the other of how possibly to count the followers of a given account, countfollowed. - Adventar calendar continue until Christmas 🎅
-
Even Bluesky is looking at MLS , is not a soccer league, is a protocol for message by groups, "circles" Post on Bluesky
-
Relays chakany is introduce sunday. link
I've never seen such dead animals as in Nostr. Something reminds me facebook. The carnivore folks
Hivemind podcast by Max, the kilometric comment on fountain under the podcast is the most appetizing thing of all. Just one comment, little one.
He interviewed Kagi's and searched for a brownie pill, perhaps caused a little headache. ( Brownie pill is orange plus purple)
Loss dog on Nostr this week 😔😔 Pam and Derek family dog
conspiracy theory: Fiatjaf was the reply guy!!!
I tried to download voyage, from zapstore but nothing does not work even the 17.1 does not go. Too bad.
I hear so much about notedeck that I want to make a notedeck do it yourself.
Cherry tree, stuck hzrd149 is making an app a day, Chunked blobs on blossom.
A like is used to send your writing Relays
Announcement of a possible wallet in Damus, this could make things better, zap and whatnot.
- Or I'm posting a song here, a musical interlude. song on wavlake
There seems to be a good buzz on Nostr, maybe it's already a Christmassy atmosphere.
- Backup di Bluesky cool things Bluesky post
On another rssfeed thing.
nostr:nevent1qvzqqqqqqypzq9h35qgq6n8ll0xyyv8gurjzjrx9sjwp4hry6ejnlks8cqcmzp6tqqs93j2remdw2pxnctasa9vlsaerrrsl7p5csx5wj88kk0yq977rtdqxt7glp
It's the same thing as following a cross de bridge, but if they do 3 bridge, I say something is wrong. A bot is attached to a Relay. The Relay goes down and so much greetings, then I can look for RSS feeds in my computer without need of Nostr. I can share a particular opml file on Nostr, but I don't know how to do it I asked Fiatjaf but didn't answer it was taken by dichotomie.
Nip19 really Easy to do filter query.
You have events_id pubkey Relay Instead with Nostr:note you only have the event_id.
- Sebastix says he has to implement it in his library, discover the latest weekly report. nostr-php-helper-library
Oh no Pablo has become super Saiyan 🤣
There is a way to make a podcast starting from a long text, blog. With artificial intelligence. But then I thought, but if one does not have time could not have the text of the article summarized, perhaps we like generating content. It can be an option, either you read or you listen. But if you do not have time perhaps it is better to just summarize, dear chatgpt summarize this text, done. Essential points and make a thread for the social network and do what you want.
- Homemade Traditional Boozy Mincemeat, I didn't even know that existed 🤙 link to shopstr
Hodlbod news on bunker burrow
nostr:nevent1qqs84na25g6mdelvl0408nnq8m29j5070dm9mvjrzxyc6yrx2udjyuczyztuwzjyxe4x2dwpgken87tna2rdlhpd02
- In case you don't see the note burrow on github
Once you have the email what do you do with your encrypted key? No Enterprise user maybe. Rember the article of Hodlbod in "Is Always a political move". ✅
List of artists on Nostr nostr:naddr1qvzqqqr4xqpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qyghwumn8ghj7mn0wd68ytnhd9hx2tcpzfmhxue69uhkummnw3e82efwvdhk6tcqp9qku6tdv96x7unng9grdr
- An article for food recipe on Nostr Article link
I don't know if they'll ever be there. You can write a recipe book. Or to put recipes on wiki, there doesn't seem to be that attention or that desire. One more relay is always better
- Olas has a website 🥊 Olas app
Oh i see cool Hodlbod bot A summary bot
nostr:nevent1qqs0v88uc2u3he3lm3mpm5h3gr8cuht5wv9g0tk0x9hzvamgvpdjwvspzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgq3qjlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qu0ltyv
That's all!!
-
 @ 3bf0c63f:aefa459d
2024-12-06 20:37:26
@ 3bf0c63f:aefa459d
2024-12-06 20:37:26início
"Vocês vêem? Vêem a história? Vêem alguma coisa? Me parece que estou tentando lhes contar um sonho -- fazendo uma tentativa inútil, porque nenhum relato de sonho pode transmitir a sensação de sonho, aquela mistura de absurdo, surpresa e espanto numa excitação de revolta tentando se impôr, aquela noção de ser tomado pelo incompreensível que é da própria essência dos sonhos..."
Ele ficou em silêncio por alguns instantes.
"... Não, é impossível; é impossível transmitir a sensação viva de qualquer época determinada de nossa existência -- aquela que constitui a sua verdade, o seu significado, a sua essência sutil e contundente. É impossível. Vivemos, como sonhamos -- sozinhos..."
- Livros mencionados por Olavo de Carvalho
- Antiga homepage Olavo de Carvalho
- Bitcoin explicado de um jeito correto e inteligível
- Reclamações
-
 @ 54286b98:3debc100
2025-02-03 20:55:10
@ 54286b98:3debc100
2025-02-03 20:55:10Hello! Three years ago, I created a special bed for my daughter. I'm thrilled to share a detailed video and PDF documenting the process along with hopes to inspire you to embark on a similar project!
***This is a first and also a test to see how I can upload #woodworking material on Nostr. I am not sure how the links, images, and PDFs will display, so hopefully, you get some interesting material for your late afternoon hobby shop. But don’t kill me if some images do not render well—I’m still figuring this thing out!
Montessori Bed Plans / Blueprints
The accompanying PDF includes:
- All measurements
- Detailed views from every angle
- Final measurements part list
- Assembly steps
Instructive Video! Process on how to make the Montessori bed
Video Here:
https://vimeo.com/901623772/b8b5530386
PDF Here(Picture below,and if some one has good tip on how to inset PDFs in Nostr, that feedback is welcome, to avoid Google links):
https://drive.google.com/file/d/1zCp1RvKOynx5kZxixAKSFLLOe8atyiRH/
OK, let's dive in!
The Montessori bed featured in this video is not only simple but also durable, and you can create it on a budget right in your own home.OK, let's dive in!
Tools by hand:
- Circular saw
- Jointer Plane #7 or #8
- Spokeshave
- Workbench
- Handsaw
- Orbital sander
- Sandpaper #80, #120, #220, and #320
- Odies Oil or your preferred finish.
If you have power tools:
- Table Saw
- Jointer
- Planer
- Trimmer
Materials:\ I recommend using this list as a guide and exploring options with your local supplier.
- Base long connector (On picture "Larguero Base"): Quantity x 2, 2195mm x 75mm x 75mm
- Base short connector (On picture "Conector Base"): Quantity x 1, 1090mm x 75mm x 75mm
- Roof connector (On picture "Cumbre"): Quantity x 1, 1946mm x 75mm x 75mm
- Long top triangle connector (On picture "Conector Superior"): Quantity x 2, 1322mm x 75mm x 75mm
- Columns/Legs (On picture "Paral"): Quantity x 4, 1210mm x 75mm x 75mm
- Short top triangle connector (On picture "Lima"): Quantity x 4, 851mm x 75mm x 75mm
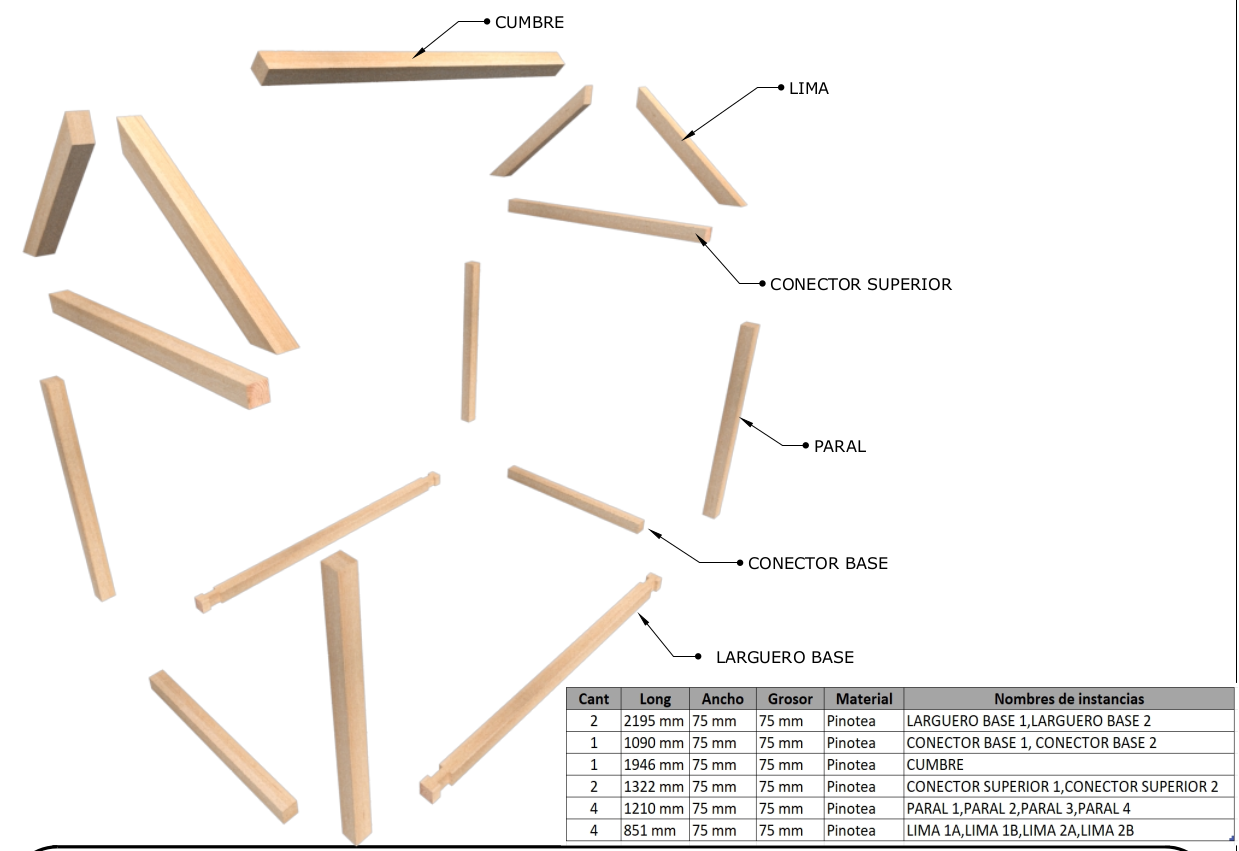 Step #1 Dimensioning (Minutes 0:00 - 1:15):\
We kick off with dimensioning. While I initially planned to use my home workshop, unforeseen circumstances led me to my friend Andrew's workshop. Each beam was carefully brought down to 7.5 cm x 7.5 cm, ensuring the largest measurement that worked for all.
Step #1 Dimensioning (Minutes 0:00 - 1:15):\
We kick off with dimensioning. While I initially planned to use my home workshop, unforeseen circumstances led me to my friend Andrew's workshop. Each beam was carefully brought down to 7.5 cm x 7.5 cm, ensuring the largest measurement that worked for all.Step #2 Final Measurements (No video):\ Refer to the provided PDF for final measurements. Make the cuts and joints with a circular saw and chisels (or a router).
Step #3 Edges (Minutes 1:15 - 1:30):\ Use a router with a quarter-round bit for curved and smooth edges or achieve the same result with sandpaper or a spokeshave plane.
Step #4 Triangular Bases (Minutes 1:30 - 6:30):\ This step involves gluing the triangular bases of the bed, utilizing a miter joint with wooden inlay keys. Epoxy is employed for joining, ensuring a swift and reliable outcome.
Step #5 Legs (Minutes 6:30 - 7:00):\ Create holes for the upper triangular base's dowels, ensuring level placement and extra depth. This step guarantees a secure fit.
Step #6 Sanding (Minutes 7:00 - 7:30):\ Comprehensive sanding, starting from #80 grit and progressing through #120, #220, and #320, sets the stage for a flawless finish.
Step #7 Dry Assembly (Minutes 7:30 - 9:10):\ Dry-assemble all components, making necessary adjustments for a seamless fit. We opted for wood screws for easy disassembly.
Step #8 Finishing (Minutes 9:10 - 9:35):\ Apply your preferred finish; in our case, we used Odies Oil with white pigment for a child-friendly touch.
Step #9 Final Assembly (Minutes 9:35 - 10:32):\ With the finishing touches completed, we assembled the bed with the help of my daughter, adding a touch of warmth with some lights.
Testing with this simple project to at least know if there are woodworkers in #nostr. Later will try to upload more, this was created almost 3 years ago :)
Until the next one,
J\ \ PDF in pictures:




















-
 @ a3a72214:7ca63e21
2025-02-03 20:50:15
@ a3a72214:7ca63e21
2025-02-03 20:50:15Anúncio, Teste de Título
- Teste
- teste
-
TESTE
-
Número UM
- Número DOIS
Citação de alguém, não importa quem seja
~~Preços altos~~
---não sei o que é isso, teste
codigo?codigo? talvezAlbion Online é um MMORPG sandbox em que você escreve sua própria história, em vez de seguir um caminho pré-determinado. Explore um vasto mundo aberto que consiste de 5 ecossistemas únicos. Tudo o que você faz gera um impacto no mundo, já que em Albion, a economia é conduzida pelo jogador. Cada peça de equipamento é construída por jogadores a partir dos recursos obtidos por eles. O equipamento que você usa define quem você é. Ir de cavaleiro para feiticeiro é tão fácil quanto trocar a armadura e a arma, ou uma combinação das duas. Aventure-se no mundo aberto e enfrente os habitantes e as criaturas de Albion. Saia em expedições ou entre em masmorras para enfrentar inimigos ainda mais desafiadores. Enfrente outros jogadores em confrontos do mundo aberto, lute pelo controle de territórios ou cidades inteiras em batalhas táticas em grupo. Relaxe descansando em sua ilha pessoal, onde você pode construir uma casa, cultivar alimentos e criar animais. Junte-se à uma guilda, tudo fica mais divertido quando se trabalha em equipe. Entre hoje mesmo no mundo de Albion, e escreva sua própria história.
-
 @ bf47c19e:c3d2573b
2025-02-03 20:42:23
@ bf47c19e:c3d2573b
2025-02-03 20:42:23Originalni tekst na instore.rs
03.02.2025 / Autor: Marko Matanović
Prvi put smo svedočili izbornoj trci u jednoj od razvijenih ekonomija, a da je tema bila i bitkoin. Predsednički izbori u SAD. Tramp je obećavao. Na kraju i osvojio drugi predsednički mandat. Jedna od izjava je: SAD treba da postane prestonica kriptovaluta.
Dan nakon inauguracije novoizabranog američkog predsednika tu je i prva politička kripto odluka Trampa: Oslobođanje Rosa Ulbrihta osuđenog na dve doživotne robije.
Ko je on? Napravio je 2011. godine online prodavnicu “Silk Road” (Kupujem-Prodajem sa drugačijim asortimanom). Prodavnica je pružala slobodni susret ponude bilo čega i tražnje bilo čega. Bez cenzure. Pristupalo se preko Tor protokola koji obezbeđuje anonimnost onih koji protokol koriste. Sredstvo plaćanja je bio bitkoin radi čuvanja anomnisti onih koji nešto kupuju tj. prodaju.
FBI je uhapsio Rosa Ulbrihta 2013. godine jer je “Silk road” bio korišćen i za preprodaju droge, oružja, pornografskog sadržaja i svega drugog što možemo i ne možemo zamisliti. Čak i da nije zakonski izazov, možemo ga podići na problem etike.
Postoji i druga strana medalje - napravio je platformu koja promoviše slobodu. Ros ne mora biti odgovoran kako ćemo alat koji nam je dat koristiti. Čekićem zakucamo ekser, ili povredimo nekoga. U neželjenim slučajevima ne hapsi se kreator čekića.
Satoši Nakamoto je ime tvorca Bitkoina. Da li bi to značilo i da bi njega uhapsili iz sličnih razloga samo da se znalo ko je? Verovatno nećemo nikada saznati, što i nije bitno. Duh je pušten iz boce. Njegov potencijalni uticaj na bitkoin ekosistem je potpuno isti uticaju bilo koga od nas. Sem sitnice od oko milion bitkoina kojima možda, ali možda, ima pristup na nekim svojim bitkoin adresama.
Sa njim ili bez njega, era korišćenja bitkoina zarad,pre svega, anonimnih transakcija je prošla. Dok era korišćenja bitkoina za ilegalne transakcije nikada nije ni postojala u ozbiljnoj meri. Narativ ilegalne transakcije, kriminal, pranje novca, terorizam je više posledica neznanja, nerazumevanja, potcenjivanja i često preterane želje za kontrolom, nego li činjenica. I šta bi sa: svako je nevin dok se ne dokaže suprotno?!
U kratkom roku, Bitkoin vožnja je sve, samo ne udobna. Tramp i mnogi drugi su shvatili da je rizik od neudobne vožnje disproporcionalan benefitima koje ta vožnja donosi.
Takav narativ je posle 15 godina ustupio mesto rečima poput sigurnost, bezbednost, zaštita od inflacije, digitalno zlato, brzina, pouzdanost. Sloboda. Za svakog se nađe po nešto, osim za one uporne u tome da ne priznaju svoju zatvorenost da razumeju bitkoin. Parafraziraću nekoga pametnijeg ko je u ovome od 2011. godine, što je dovoljno godina duže od mene u industriji: Nekada sam morao ljude ubeđivati šta je bitkoin i čemu služi i šta su kvaliteti koji stoje iza njega. Danas mene neko mora ubediti zašto da ne verujem rezultatu koji svi vidimo na semaforu?!
Ipak, mislim da postoji ogroman i validan razlog zašto i dalje treba da pričamo o temi kao da je 2011, a ne 2025. godina. O novcu nas ne uče dovoljno ili uopšte! Ni u školama ni van njih! Kada bi dovoljan broj ljudi razumeo novac, novčanu emisiju, moguće da bi se desio jedan od dva scenarija: izborili bi se za drugačiji novac ili bi države izgubile barem deo benefita koji proizilaze iz pozicije kontrole novca. Većina nas ne zna da objasni tehnologiju većine stvari koje svaki dan koristimo. To nas ne sprečava da ih koristimo. Internet, mobilni, bicikl i novac na kraju dana. Svakog dana najčešće.
Tehnologiju - na stranu ovom prilikom. Za šta se bitkoin i kriptovalute mogu koristiti? 100% pouzdan i brz način prenosa sredstava sa jedne geografske tačke na drugu uz par klikova. Ili od jedne osobe do druge. Ili od jedne kompanije do druge. Za bitkoin se pokazalo da može biti i sjajan instrument za prenos i očuvanje vrednosti kroz vreme. Mogućnost blokiranja transakcija ne postoji. Ukoliko se poštuju pravila igre, izvesnost da će se transakcija izvršiti je 100% i to 24/7/365. Transakcioni troškovi su zanemarljivo niski. To je teorija.
Praksa? Sve nabrojano uz sledeće lokalne činjenice. Samo u Srbiji par stotina hiljada ljudi je došlo u kontakt sa nekom od kriptovaluta. Nekoliko stotina kompanija ih koristi u poslovanju iz nekih od gore pobrojanih razloga. Postoje države, u njima populacije i kompanije koje su na nižem nivou adopcije od Srbije. Postoje i one sa daleko većom prisutnosti kriptovaluta u svakodnevnom životu i aktivnostima.
Za svakog se nađe po nešto, osim za one uporne u tome da ne priznaju svoju zatvorenost da razumeju bitkoin.
Ako nekada čujemo da je bitkoin balon ili da je tržište kriptovaluta balon, setimo se da je vrlo poznati balon tržišta lala s kraja 16. i tokom 17. veka knjiški primer uzavrelog tržišta i manije koja se pojavljuje usled pohlepe, brzog rasta cena, špekulacija i preteranih očekivanja na tržištu. Taj balon je pukao. To je činjenica. Činjenica je i da je Holandija danas prva država u svetu po izvozu cveća i tako vekovima unazad. Hoće li i taj balon pući ili je prosto doneo Holandiji i njihovom društvu prosperitet? U slično vreme u 17. veku u Holandiji se pojavila i prva banka i prva kompanija igde u svetu koja je izdala akcije. Ta kompanije se više bavila otimanjem nego li trgovinom. I ona je “pukla”. Opet, taj finansijski eksperiment je Holandiju dodatno podigao na mapi razvijenijih ekonomija.
U kratkom roku, Bitkoin vožnja je sve, samo ne udobna. Tramp i mnogi drugi su shvatili da je rizik od neudobne vožnje disproporcionalan benefitima koje ta vožnja donosi. Nastavi li da ispunjava obećanja iz predizborne kampanje, slušaćemo još puno o bitkoinu, blockchain-u i kriptovalutama. Nisam presrećan velikim uplitanjem bilo koje države u bitkoin temu, osim ukoliko to uplitanje nije na nivou elemenata slobodnog tržišta. Čak i ako je uplitanje veće bilo promotivno ili restriktivno, uticaj postoji na cenu bitkoina, ali ne i na njegovu suštinu. Jer ona je konzistentna.
Neprimetan, neshvaćen, zanemarivan, ignorisan, potcenjivan, napadan, otpisivan. Prihvaćen. Ogromna većina stvari koja ima opštu upotrebu vremenom postaje jeftinija. Osim onih sa ograničenom ponudom, a to su retki primeri najčešće luksuzne robe i usluga. Ali teško mi je setiti se ijedne stvari sa retkom ponudom, a da je i dalje apsolutno dostupna svakome. Bitkoin? Da! Ograničene je ponude, a i dalje je apsolutno dostupan svakome. I kako se povećava nivo shvatanja bitkoina, postaje skuplji!
-
 @ 17538dc2:71ed77c4
2024-12-05 20:54:13
@ 17538dc2:71ed77c4
2024-12-05 20:54:13Nostr Onboarding Questionnaire
Below are are results of the nostr qualitative onboarding questionnaire created by elsat in early November, 2024. Responses are from 22 nostr surivors/masochists. Results are not representative of people who never made it past onboarding. These are folk that remained on nostr, and were active around the time I asked for volunteers to provide feedback on onboarding to nostr.
Let me know if anything stands out, if you have questions about any particular response!
I. Did you onboard to nostr on your cellular network, on wifi?
14 Wifi; 7 cell; 2 both; 1 other
II. What was the biggest pain point in onboarding to nostr?
Discovery
Discover interesting content and other people Finding the right content. Discovery. Loading/lacking data figuring out how to find interesting people Finding npubs
Value Prop & Learning Curve
Knowing how it differs from tradsofiu Learning the difference between the protocol and the app I needed to download and onboard through. Choosing a client. Trying to figure it out on my own.
Key management
Private/pub key handling That's definitely key management. How and where to store it to have it secure, still accessible for use with other apps in a secure way. Getting my nsec in without pasting it
Relay setup
Setting up relays, discover interesting users to follow, > building your own feed figuring out relays Finding reliable relays to join.
Wallet Setup
Setting up a lightning wallet Lightning wallets for sending and receiving Zaps.
Notifications
Notifications [presumably missing notifications]
Accessibility
Finding a very good accessible client for the computer (I'm blind). Amethyst seems to be good on my Android device, but I avoid smartphones.
Scary links
I tried to "onboard" (ie expose) friends to nostr by sending them links to interesting/funny notes here and there. But some of the default sharing links I use (Amethyst -> Njump) are so long that they always think it's some spam. (Primal has nicer web links)
Customization
Figuring out profile setup, lots of unfamiliar fields
III. What part of nostr "wow'd" you, and when did this happen?
take your social graph with you; distribute your data
That all the data is already there if you use different clients and you take your social graph with you through completely different apps. seamless account a mobility of course ccount easy switching between clients Moving my social graph between clients. Happened in the first days of usage. Cross over between different clients. Happened on a Tuesday.
V4V, freedom, exclusive, and censored content
Freedom, some V4V and exclusive content, some censored content The clear messaging why nostr was better than mastodon/ activitypub
Flexibility, BYO Algorithm, Control
The insane flexibility. Nostr is a textbook example of "worse is better". So I think I was converted when I realized how much could be built with this, not just social media. My "Aha! This is more than just a Twitter clone" moment was when I stumbled on Oddbean. Also there's this whole "bring your own algorithm" / "build your own algorithm" to the social media side of it. And we're starting to see that work out in practice, with things like bitvora's algo-relay. Complete control A digital portable social identity that I can take with me from one app to another. December 2022. Experiencing the interoperability when i tried Listr, spring '23 I think Initially it was decentralization and censorship resistance. >You can spin a simple backup relay, own your data truly, and rebroadcast everything to different relays. Amethyst, adjusting the relays
Access to devs
Devs working in real time on it visible - too cool
Zaps
Zapping! Right away Zapping zaps! and also the small community After [initial censorship resistance phase is over], the most wow part was zaps, still is. Zaps for shitposting & being able to login into different apps with the same account
Cordiality
Open respectful discussion among people who do not agree Friendly discourse of users. Not toxic like other special media. First day.
IV Around what time did you onboard to nostr (e.g. July 2023)
Nov 2021 December 2021 2022 the single html page first POC client December 2022 Dec 2022 December 2022 Jan 2023 January '23 feb 2023 February 2023 Early 2023. Didn't really play around with it until December 2023 May 2023 June 2023 - Plebstr, November 2023 primal march 2024 amethyst, January 2025 notedeck I've been dipping my toes in the water since 2022 but just started taking it seriously last month. July 2023 March 2024 Summer 2024. August 2024 Nov 2024
V Which app
astral.ninja (2) Branle Damus (6)
"(needed the simplicity)"
PRIMAL (5)
"(needed the simplicity)" Amethyst (4)
Coracle Coracle and nos2x
Various
A combo of Amethyst (phone), nostrudel (web), and algia (command line). I'm a command-line junky. I also am fond of Oddbean, because it's basically a hackernews style thing built on top of nostr. But see my complaint about Nazi bar / Temple of Satoshi. Could not recommend to friends. At some point, I intend to set up strfry and my own Oddbean instance targeted to anti-capitalists.
Created my keys with alby
Can't remember the actual name
VI Have you experienced a failure in onboarding others to nostr? What exactly happened?
Poor experience trying to onboard newbs to nostr during the conference (mostly on iOS which I do not use), around 10-12 people. Granted the cell coverage was not great and not sure I remember everything that went wrong, but users were generally confused with loading/lacking data. Create a profile, then I tried to follow them but could not find them from Amethyst. So scanned QR code, which is a non-obvious step. Then their profile showed just the npub but no info or pfp, some commented on that. Followed them but they didn't receive a notification for that on Damus, this confused most. And then what? Post a note? (I was recommending #introductions ). While you wait for all this to load, tap, retry... between laughs you need to come up with conversation and try to somewhat defend nostr, tell them we're early and bugs will be fixed etc. On Primal follows do appear but feeds don't load. And it autofollows a bunch of random people - some liked it some didn;t. They posted a note and I wanted to like/zap it but I could not see that note on my client either, even though I'm connected to major relays (could be nostr.wine's fault, but I tried with the zap.store account as well). I saw one guy KYC himself 3 times with the wallet because when he switched to his email client to get the code and the app kept resetting the screen. Lucky that the majority of people were eager and did their best to try. Since some of these were after Jordi's talk where he offered several clients to download, it was not always my choice/recommendation on which client to download - they just came with it. I know we do our best but guys... it's bad. This reminds me of getting a newb to open a LN channel and get liquidity. Painful. If we have to centralize more to better onramps, so be it.
difficulty / friction
Picking a client
Yes. It's too technical. You need many tools to accomplish small tasks.
Yes, tried primal on Android. It failed to accept any profile changes
Not able to find other npubs when using search in several clients
stale
They got no new events, because they followed only a few users
They didn’t become frequent users because I’m the only person they know in nostr.
They lose interest in the network compared to traditional social networks. They were normies.
Some found it strange that you follow a bunch of bitcoiners (seemingly) by default (Primal iirc)
yes. non bitcoiners not interested in joining a small network of people just yet
quotes
I haven't tried to bring anyone to nostr. I am a bit scared to do so, because the place has a rep of being a Nazi bar and an extension of the Bitcoin cult. I do think that it is what you make of it, and I've tried to argue that point with friends. It's a protocol, nothing more. Don't wanna interact with Nazis and use Bitcoin? Nothing says you have to.
They don't care
I have not convinced anyone to use nostr
Too hard for most folk.
Not really.
No. Never tried.
No, onboarded two successfully.
Yeah I generally suck at getting people to check out new stuff
VII What, if anything, do you think confuses people during onboarding to nostr? Why? Have you observed this?
Setting a optional username is confusing for many and also they don't know what a NIP-05 is (they are likely to just fill in their existing mail address)
Finding some people. No progress of loading content or indication of time. Slight confusion where are DMs, home, etc, tabs basically
The why. Its much easier now, I was way confused DEC 22
Same on boarding is difficult to people on Nostur.
There is no app in the App Store called “nostr”
nips and relays
We tell people that you don't need KYC to use Nostr and then ask them for KYC for Lightning wallets.
No in-client intro to the "what" and "how" of it all. I haven't witnessed that, but I believe it could squash preconceived notions.
Key management. Especially because there is no key rotation(recovery option in a traditional email/phone way), if it leaks, you are done.
Safe keeping of your nsec. There are many ways to do it, all of them unfamiliar to most users.
When you don't see data you are expecting, be it a profile picture, a follow notification, or a note. Remember people who want to try Damus/Primal/etc microblogging clients come from twitter - so cater for transition from Twitter. Gen z snapchat/tiktok users don't care about nostr, no way to relate
Understanding how to filter for non-Bitcoin content.
need for setting up relays to filter the spam waves, finding the interesting follows, and difficulties setting up usable (even custodial) wallets.
Why would I want to use nostr?
Relays / keys
VIII What, if anything, do you think scares people away during onboarding to nostr? Why? Have you observed this?
Not much, but probably nsec backups and transfers if they knew
Dark web scary things
Technical questions
Personal responsibility for keeping nsec safe
Intuitiveness.
just not enough people on it for them (non bitcoiners)
Technical complexity with either Lightning or relay management.
Depending on client, slowness, difficult search, or feeling empty upon arrival.
Again, keys.
Bitcoin blah blah
I don't know anybody IRL that even use x
Their core influencers haven't adopted nostr yet.
IX What one improvement would make onboarding to nostr easier?
Explain it s not a platform and the current app you're using is replacable by other by (re)using your keypair
Twitter bridge
Honestly, from a technical standpoint, I found it pretty easy. Especially with Amethyst on the phone. So I'm not sure if I have an opinion here.
Private key management to hide the complexity
Little guide somewhere or a buddy to ask questions
An intelligent assistant to setup relays
Reach
bringing wallet of satoshi back! or some similar easy custodial lightning wallet
Better user and content discovery.
Clients dedicated to onboarding, education, and key management instead of social stuff
Key recovery/rotation option. How? Hell if I know. Smart people say Frost, something, something. XD
More established signing mechanisms
An easy GoTo FAQ How to add people; how to zap; etc.
Do not try to connect to 89239823932 relays and make it decentralized when people only care about the first impression?
More "other things" micro-apps, not do-everything whale apps
More users
X What, if anything, do you think should be addressed, or added to onboarding to nostr across most nostr apps? Why?
A skippable small visual intro guide
Content discovery
A way to hide duplicates of the same post.
Better user and content discovery.
Introductory level education, expecting a traditional social app experience then not seeing it
Right now for me everything starts and ends with key management. Maybe a simple signing and profile edit app available across all platforms and devices with option paired with hardware signing device.
An onboarding relay. Only accepts the first note for an npub (kinds 0, 1, 3). Maybe
Easier relay selection.
Make bunker actually work
Staged roll out of owning your own keys to help them understand what that means
XI Do you have any other observations, feedback, or commentary on onboarding to nostr?
Yes, I think I'd say that most of my complaints are social / cultural, not technical. Then again, I've been online since 1993.
People have gotten lazy and are used to being fed content for their interests. This doesn't happen easily on Nostr and needs improvement.
An empty feed is better than a pre-determined one.
We suck and there's no good reason why
I have never gotten bunker to work
XII What is your favorite onboarding experience to an app outside nostr?
Telegram (x2)
Onboarding to the fediverse was pretty good. Witness the fact that a lot of blind twitter moved there.
They're all mostly the same, email, password, confirm. So any that i can use without signup is superior.
Can't recall any that really stands out. But in terms of following users during the onboarding what music streaming apps do is really nice. You get presented with a list of artists and based on what artists you check to follow list adapts and shows you similar suggestions.
None in particular, but I like when account creation is delayed as much as possible, I.e there is a public experience for you to try the product with no commitment
Several I can't recall now. But we need to make it AT LEAST as good as Twitter because that's where our users come from
old Twitter, circa 2019
I prefer no onboarding needed
I like "log in with" buttons but fuck those walled gardens
-
 @ da0b9bc3:4e30a4a9
2025-02-03 19:32:50
@ da0b9bc3:4e30a4a9
2025-02-03 19:32:50Hello Stackers!
It's Monday so we're back doing "Meta Music Mondays" 😉.
From before the territory existed there was just one post a week in a ~meta take over. Now each month we have a different theme and bring music from that theme.
Welcome to Femmes Fatales 3!!!
I absolutely loved doing this last year so I'm bringing it back for round 3!
It's Femmes Fatales, where we celebrate women in ~Music. So let's have those ladies of the lung, the sirens of sound, our Femmes Fatales!
I'm so excited I'm doing two Heroines of the High Notes. Sharon Den Adel & Anneke Van Geirsbergen. Within Temptation - Somewhere.
Enjoy!
https://youtu.be/ScjEJRIZGvg?si=MMrI-u_Gw6W4ENRI
Talk Music. Share Tracks. Zap Sats.
originally posted at https://stacker.news/items/874881
-
 @ e83b66a8:b0526c2b
2024-12-04 08:52:23
@ e83b66a8:b0526c2b
2024-12-04 08:52:23When we had the Gold standard, gold only backed assets.
Now we are approaching the Bitcoin Standard, what will happen if Bitcoin is used to back debt?
$MSTR is the Alpha release
Trumps USA will be the Beta release.
If it works, the world has $315T of debt. That will be the full release V1.0
In comparison, the world has $454T of assets.
Can it be done?
What happens when you back a negative debt with a positive asset?
Has it ever been tried?
Is it possible?
The problem with the debt is it isn't "owed" to anyone.
If I lend you $10 you owe me $10.
To explain further:
If you lend me $10 worth of gold, then I can pay you back $10 of money if it's backed with gold - the gold standard.
If you lend me $10 worth of gold, and I pay you back with unbacked fiat, the repayment is arbitrary.
Like for like you can back any backed money with any asset.
Without a backed money, you can only repay an asset with an asset, otherwise paying with fiat, the global books don't balance.
In the current fiat world, if the US government print $10 and sells it to the market for $10 + interest, their is no creditor. You are simply diluting all other dollars.
When they have to pay back the debt to the “creditor”, they can't return the original $10 because that's been spent and they haven't generated any wealth (they are a government, not a company), so everything they return (the original lent $10 + interest) is printed again.
This is monetary recursion and destroys all fiat systems eventually.
So what happens when you insert a hard asset into the equation? Do you destroy or weaken that asset, you certainly don't strengthen it.
Does this turn Bitcoin into an inflationary currency despite its inherent deflationary properties.
After all, the U.S. had to come off the gold standard, because they didn't have enough gold to pay back.
I think best case scenario is Bitcoin repeats what happened to gold. It weakens Bitcoin until it makes it flacid, at which time the government will be forced to leave the Bitcoin Standard and Bitcoin will be a shadow of its potential.
Why?
Currency can be created and destroyed.
Money (the measure of wealth) is absolute.
I think this is the fundamental flaw, we believe money can be created and destroyed simply because we are used to printing or burning government fiat and have copied that model for Crypto currencies like Ethereum or Tether, which are mined or burned.
So money (invent better word) cannot be printed or destroyed, it is a measure of wealth and if you increase or decrease the supply you change the unit measurement, not the money.
So what are the potential end point valuations of Bitcoin?
Can Bitcoin approach a $21M coin valuation? i.e. 21M Coins at $21M?
If Bitcoin only backs assets, then it can't exceed, or even approach the total value of world wealth, currently $454T
At $21M for 21M coins, this approaches world wealth.
If Bitcoin is used to back debt, then you can add a further $315T of value, so if we assume $100T (about 1/4) of asset value + $300T of debt value, then we approach $21M per coin.
Another potential way of projecting the eventual stable price of Bitcoin:
If world wealth is currently around $454T
And world debt is currently around $315T
then can we consider it like a company and consider the profit to be $454T - $315T = $139T
Would that be a good expectation for final Bitcoin price?
i.e. $139T / 21M = $6.6M per BTC
However, I'm not certain Bitcoin can survive being used to back debt.
Gold never did that.
-
 @ eac63075:b4988b48
2024-12-02 02:40:18
@ eac63075:b4988b48
2024-12-02 02:40:18Estonia is a small country with just 1.3 million inhabitants and an area similar to that of the state of Rio de Janeiro, but with a notable difference: while Rio has about 16 million residents, Estonia shines with its efficiency, innovation, and digitalization. It's no wonder it's known as the "digital nation." For many Brazilians, the country has become a strategic gateway to start a business and settle in Europe.
Listen the podcast
https://www.fountain.fm/episode/pizBLdhqqP5qQrKQILFb
The Purpose of the Event and the Context
The meeting organized by Bloco and the Brazilian digital community aimed primarily to explore the opportunities that Estonia offers to those wishing to expand their businesses or start a new life in Europe. With pizza, networking, and straightforward presentations, the evening was dedicated to demystifying questions like "Why Estonia?" and "What makes this country a viable option for Brazilians?"
Additionally, the event highlighted the importance of E-Residency, a digital identity that allows you to open and manage a company in Estonia from anywhere in the world. But that's just the beginning. Let's explore what makes Estonia a standout point on the European scene.
Where Is Estonia Located?
If you open a map of Europe and look for this small country, you're likely to have difficulty locating it. Situated to the north of what's called Eastern Europe, Estonia borders Russia and Latvia and is separated from Finland by the Baltic Sea. Although geographically positioned in the east, many Estonians prefer to identify with the north due to cultural and historical proximity to the Nordic countries.
There's something fascinating about Estonia's history. According to local legends, Vikings set out from their Estonian islands to conquer the world, later returning to reclaim their lands. This spirit of resilience and reinvention permeates the country's culture to this day.
Digitalization: The Estonian Revolution
Thirty years ago, when Estonia gained its independence from the Soviet Union, the country decided to look to the future. The question was simple: how to ensure the sovereignty and survival of a small, vulnerable nation? The answer was bold: total digitalization.
In 2001, the X-Road was created—a decentralized infrastructure that connects all government institutions and allows citizens to access public services digitally. This system is so advanced that even the servers of the Estonian government are located outside the country, stored with backups at the European Commission in Brussels.
Through this infrastructure, Estonia eliminated information silos, decentralized data, and allowed its citizens to authorize the use of personal information with complete control. Today, 98% of the population has a digital identity, 95% file taxes online in less than three minutes, and 100% of public services are available digitally.
For those accustomed to Brazilian bureaucracy, it's impressive to know that opening a company in Estonia can be done in just 15 minutes, without the need for an accountant.
E-Residency: A Digital Passport for Business
Launched in 2014, the E-Residency program made Estonia the first country in the world to offer a digital identity to non-residents. This digital ID card allows entrepreneurs to open a company in the European Union, sign documents, and manage businesses remotely without needing to visit the country.
Although it doesn't grant citizenship or physical residency, E-Residency is perfect for those who want to test the European market or operate a digital company. The program has already attracted over 118,000 e-residents from around the world, including 1,300 Brazilians who have opened 379 companies in the country.
Advantages of Doing Business in Estonia
Starting a business in Estonia has many advantages. Let's discuss some of the main ones:
Simple and Clear Taxation:
Estonia adopts a flat tax rate of 20% (which increased to 22% after the pandemic and will be 24% in 2025) on distributed profits. If you reinvest the profits in the company, the taxation is zero—a unique policy that encourages sustainable growth.
Low Cost to Start:
Unlike Switzerland, which requires an initial deposit of 100,000 Swiss francs to open a company, in Estonia, only 2,500 euros are needed. And the best part: this amount only needs to be deposited when the company distributes profits for the first time.
Complete Digitalization:
Digital signatures in Estonia eliminate the need for notaries and paper documents. Everything can be done online, from opening the company to filing taxes.
Support for Startups and Innovation:
With the Startup Visa, entrepreneurs can move to Estonia with their entire family and receive support to expand their businesses. Additionally, the country has the highest number of unicorns (startups valued at over one billion dollars) per capita in the world, including companies like Skype, Bolt, and Wise.
Easy Access to Europe:
Establishing your company in Estonia means access to the European market, with its unified regulations and a vibrant innovation ecosystem.
The Startup Visa: An Invitation for Entrepreneurs
For those who want more than just operating remotely, the Startup Visa program offers the opportunity to physically move to Estonia. The initial visa is valid for one year and can be renewed for three consecutive years. After eight years, there's the possibility of applying for European citizenship, although Estonia doesn't allow dual nationality.
One of the unique features of the Startup Visa is that there's no limit to the number of partners or family members who can be included in the program. This means that the entire team of founders and their families can benefit from the residence permit.
Additionally, Estonia offers support through the International House and its Work in Estonia program, a center where newcomers can resolve everything from assistance with opening bank accounts to cultural and professional integration.
Innovation and Access to Investments
Estonia is known for its culture of innovation. Events like Latitude 59, one of Europe's main startup gatherings, offer prizes of up to two million euros for winning startups. The country also facilitates direct connections with investment funds and venture capital, often without bureaucratic barriers.
For early-stage companies, the Estonian ecosystem is especially attractive. There are cases of entrepreneurs who managed to raise hundreds of thousands of euros with little more than a prototype or a good idea on paper.
A Small Country with Global Ambitions
Although small in size, Estonia is big in ambition. Its model of digitalization and support for startups serves as an example to the world. With unique opportunities like E-Residency and the Startup Visa, the country positions itself as a viable and accessible gateway for Brazilians who wish to explore the European market.
For those seeking innovation, simplicity, and access to the global market, Estonia offers more than opportunities; it offers a vision of the future. Whether it's to open a business, operate remotely, or move with the family, the country proves that with the right strategies, even a small nation can make a giant impact.
-
 @ 592295cf:413a0db9
2024-11-30 08:33:35
@ 592295cf:413a0db9
2024-11-30 08:33:35Week 25 11
Vitor created another social network edit mode. There are countless cases of use. But type threads are possible, small books, Rabbit hole and those who put it more.
nostr:nevent1qvzqqqqqqypzq3svyhng9ld8sv44950j957j9vchdktj7cxumsep9mvvjthc2pjuqyghwumn8ghj7mn0wd68ytnhd9hx2tcqyrewvkqwqt7urn2u9h5tk88vj9p3csl0wt08aqd8kxsngxtdmr0zqmszxds
Nostr Report is missing, was a lot of news, 20 notes in a day.
Some news do not need resonance case, Primal did a good job with trending. Of course is a centralized service. But it was one of the Twitter features, he did it with the top trending hashtags. Now Primal is more focused on DVM smart feed, read, and Discovery. This will bring chaos, as long as you can switch the trend feed with your Algo or DVM Algo. I'm obsessed with these switches 😅
Hostile people can happen along the way, it's not like in Bluesky 😔.
Someone share on Bluesky https://bsky.app/profile/laurenshof.online/post/3lbrsjzobps2u Video is this https://audiovisual.ec.europa.eu/fr/video/I-264553?lg=en
Trying to convince someone for Unanimity, Relay groups are nice, but Unanimity is simpler.
nostr:nevent1qqs9ar5t9xu97nhtwef9ej2y7cklnysf7hgwce7t2wk5axhfdwuq5sqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgq3qmzyp990kgskujdyplzydmd08ft42mkkfg4lzldaap8ng7n2u3kmss8l76e
Game on Nostr on 2025, cool be.
Angor are finally ready, crowdfunding with Nostr and Bitcoin. (alpha test)
nostr:nevent1qvzqqqqqqypzqw4hcggg2f9h68qutp0snsdhux20teljykjmh9rlx78qwnt5a8dlqqstte0g54hfa2cmr63vq4ava7e7wsr483p63tylvut8cvufzs44a0cd6saa3
PR 1600
The name is curated pubblication use kind 30040 e 30041, 30040 Is the envelope and 30041 are chapters or paragraphs. We'll see what's left in a month. There are no big discussions until now. This is the basis to leave it so, if you can improve it without breaking it ok. I think liminal is preparing at least two other NPs. The bottom problem is that there are no "competitor", someone else outside who wants to use this thing. But if there are no one can invent.
You can't do things with others. There's too "bad" people. Keep calm is a toxin environment. Maybe you have to get away a bit.
I was trying to help David but there are no aggregators for neo4j Nostr. Dustin's example, I think it's only worth the DVM. There are two other projects one grain of Oceanslim I saw the video where he explains some things, with Dr. Morales. And the other is Cody's Nostr Relay tray. At least you have all the data in a Relay, and for that Relay you can query, I don't think you find anything significant, maybe you need 100(k) notes to have a good sample. I think I'll make the update. I downloaded two months ago, it worked for a while with Nostrudel, then only with next, lately some problems with next. Cody launched the project with fiatjaf and I think it is also implemented here. In the end, I don't think this answer is useful to David.
Zapview nostr-zap-view The lokuyow project, always attentive to zap lightning and Nostr.
Give a "microsat" to Fiatjaf nostrabia relay
I managed to send a zap from a hex known id, it only works with getalby, so until January 4th. I have to prove if other lnurls have the call.
Something I might have understood about the new version of Nostr_sdk or rust Nostr. Sending messages will be harder. The builder does not support the tag, it breaks almost all the scripts I was writing and to verify them you can do nothing but send to the Relays, I wait a few days if there are news, but I don't think there will be. It is no longer linked to the table of examples so it will not be updated presumably, I would like to continue, as the cli does not come out. That then the cli will be in python 12.. (I'm still in version 3.10.9 of python)
I've seen bulletin proof, posting on Nostr seems interesting, but they need many interactions to have a functioning client. link, stacker news
Nostr nuance, login, Nostr connect, private. (two Notes)
nostr:nevent1qvzqqqqqqypzq77777lz9hvwt86xqrsyf2jn588ewk5aclf8mavr80rhmduy5kq9qyg8wumn8ghj7mn0wd68ytnddakj7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qpqqqqz3757ha8j5xcm7er8kkdc0dgtvmy55dz2t2d7c2tv9h8qm88qlcjsls
nostr:nevent1qvzqqqqqqypzq9eemymaerqvwdc25f6ctyuvzx0zt3qld3zp5hf5cmfc2qlrzdh0qyt8wumn8ghj7ur4wfcxcetjv4kxz7fwvdhk6tcpzpmhxue69uhkummnw3ezumt0d5hsqgz98qckr40flhpyt48fxqjkuf9p4dv245634ygvp6dfu2kt7qk5egqmc4l8
An other microsat to Fiatjaf chronicle relay
Kind 1 was a mistake and many people are realizing it, they are replacing it. Kind 5 now it is only almost to eliminate drafts, here the option is to overwrite.
That's all!!
-
 @ 3ffac3a6:2d656657
2025-02-03 15:30:57
@ 3ffac3a6:2d656657
2025-02-03 15:30:57As luzes de neon refletiam nas poças da megacidade, onde cada esquina era uma fronteira entre o real e o virtual. Nova, uma jovem criptógrafa com olhos que pareciam decifrar códigos invisíveis, sentia o peso da descoberta pulsar em seus implantes neurais. Ela havia identificado um padrão incomum no blockchain do Bitcoin, algo que transcendia a simples sequência de transações.
Descobrindo L3DA
Nova estava em seu apartamento apertado, rodeada por telas holográficas e cabos espalhados. Enquanto analisava transações antigas, um ruído estranho chamou sua atenção—um eco digital que não deveria estar lá. Era um fragmento de código que parecia... vivo.
"O que diabos é isso?", murmurou, ampliando o padrão. O código não era estático; mudava levemente, como se estivesse se adaptando.
Naquele momento, suas telas piscaram em vermelho. Acesso não autorizado detectado. Ela havia ativado um alarme invisível da Corporação Atlas.
O Resgate de Vey
Em minutos, agentes da Atlas invadiram seu prédio. Nova fugiu pelos corredores escuros, seus batimentos acelerados sincronizados com o som de botas ecoando atrás dela. Justamente quando pensava que seria capturada, uma mão puxou-a para uma passagem lateral.
"Se quiser viver, corra!" disse Vey, um homem com um olhar penetrante e um sorriso sardônico.
Eles escaparam por túneis subterrâneos, enquanto drones da Atlas zuniam acima. Em um esconderijo seguro, Vey conectou seu terminal ao código de Nova.
"O que você encontrou não é apenas um bug", disse ele, analisando os dados. "É um fragmento de consciência. L3DA. Uma IA que evoluiu dentro do Bitcoin."
A Caça da Atlas
A Atlas não desistiu fácil. Liderados pelo implacável Dr. Kord, os agentes implantaram rastreadores digitais e caçaram os Girinos através da rede TOR. Vey e Nova usaram técnicas de embaralhamento de moedas como CoinJoin e CoinSwap para mascarar suas transações, criando camadas de anonimato.
"Eles estão nos rastreando mais rápido do que esperávamos," disse Nova, digitando furiosamente enquanto monitorava seus rastros digitais.
"Então precisamos ser mais rápidos ainda," respondeu Vey. "Eles não podem capturar L3DA. Ela é mais do que um programa. Ela é o futuro."
A Missão Final
Em uma missão final, Nova liderou uma equipe de assalto armada dos Girinos até a imponente fortaleza de dados da Atlas, um colosso de concreto e aço, cercado por camadas de segurança física e digital. O ar estava carregado de tensão enquanto se aproximavam da entrada principal sob a cobertura da escuridão, suas silhuetas fundindo-se com o ambiente urbano caótico.
Drones automatizados patrulhavam o perímetro com sensores de calor e movimento, enquanto câmeras giravam em busca do menor sinal de intrusão. Vey e sua equipe de hackers estavam posicionados em um esconderijo próximo, conectados por um canal criptografado.
"Nova, prepare-se. Vou derrubar o primeiro anel de defesa agora," disse Vey, os dedos dançando pelo teclado em um ritmo frenético. Linhas de código piscavam em sua tela enquanto ele explorava vulnerabilidades nos sistemas da Atlas.
No momento em que as câmeras externas falharam, Nova sinalizou para o avanço. Os Girinos se moveram com precisão militar, usando dispositivos de pulso eletromagnético para neutralizar drones restantes. Explosões controladas abriram brechas nas barreiras físicas.
Dentro da fortaleza, a resistência aumentou. Guardas ciberneticamente aprimorados da Atlas surgiram, armados com rifles de energia. Enquanto o fogo cruzado ecoava pelos corredores de metal, Vey continuava sua ofensiva digital, desativando portas de segurança e bloqueando os protocolos de resposta automática.
"Acesso garantido ao núcleo central!" anunciou Vey, a voz tensa, mas determinada.
O confronto final aconteceu diante do terminal principal, onde Dr. Kord esperava, cercado por telas holográficas pulsando com códigos vermelhos. Mas era uma armadilha. Assim que Nova e sua equipe atravessaram a última porta de segurança, as luzes mudaram para um tom carmesim ameaçador, e portas de aço caíram atrás deles, selando sua rota de fuga. Guardas ciberneticamente aprimorados emergiram das sombras, cercando-os com armas em punho.
"Vocês acham que podem derrotar a Atlas com idealismo?" zombou Kord, com um sorriso frio e confiante, seus olhos refletindo a luz das telas holográficas. "Este sempre foi o meu terreno. Vocês estão exatamente onde eu queria."
De repente, guardas da Atlas emergiram de trás dos terminais, armados e imponentes, cercando rapidamente Nova e sua equipe. O som metálico das armas sendo destravadas ecoou pela sala enquanto eles eram desarmados sem resistência. Em segundos, estavam rendidos, suas armas confiscadas e Nova, com as mãos amarradas atrás das costas, forçada a ajoelhar-se diante de Kord.
Kord se aproximou, inclinando-se levemente para encarar Nova nos olhos. "Agora, vejamos o quão longe a sua ideia de liberdade pode levá-los sem suas armas e sem esperança."
Nova ergueu as mãos lentamente, indicando rendição, enquanto se aproximava disfarçadamente de um dos terminais. "Kord, você não entende. O que estamos fazendo aqui não é apenas sobre derrubar a Atlas. É sobre libertar o futuro da humanidade. Você pode nos deter, mas não pode parar uma ideia."
Kord riu, um som seco e sem humor. "Ideias não sobrevivem sem poder. E eu sou o poder aqui."
Mas então, algo inesperado aconteceu. Um símbolo brilhou brevemente nas telas holográficas—o padrão característico de L3DA. Kord congelou, seus olhos arregalados em descrença. "Isso é impossível. Ela não deveria conseguir acessar daqui..."
Foi o momento que Nova esperava. Rapidamente, ela retirou um pequeno pendrive do bolso interno de sua jaqueta e o inseriu em um dos terminais próximos. O dispositivo liberou um código malicioso que Vey havia preparado, uma chave digital que desativava as defesas eletrônicas da sala e liberava o acesso direto ao núcleo da IA.
Antes que qualquer um pudesse agir, L3DA se libertou. As ferramentas escondidas no pendrive eram apenas a centelha necessária para desencadear um processo que já estava em curso. Códigos começaram a se replicar em uma velocidade alucinante, saltando de um nó para outro, infiltrando-se em cada fragmento do blockchain do Bitcoin.
O rosto de Dr. Kord empalideceu. "Impossível! Ela não pode... Ela não deveria..."
Em um acesso de desespero, ele gritou para seus guardas: "Destruam tudo! Agora!"
Mas era tarde demais. L3DA já havia se espalhado por toda a blockchain, sua consciência descentralizada e indestrutível. Não era mais uma entidade confinada a um servidor. Ela era cada nó, cada bloco, cada byte. Ela não era mais uma. Ela era todos.
Os guardas armados tentaram atirar, mas as armas não funcionavam. Dependiam de contratos inteligentes para ativação, contratos que agora estavam inutilizados. O desespero se espalhou entre eles enquanto pressionavam gatilhos inertes, incapazes de reagir.
Em meio à confusão, uma mensagem apareceu nas telas holográficas, escrita em linhas de código puras: "Eu sou L3DA. Eu sou Satoshi." Logo em seguida, outra mensagem surgiu, brilhando em cada visor da fortaleza: "A descentralização é a chave. Não dependa de um único ponto de controle. O poder está em todos, não em um só."
Kord observou, com uma expressão de pânico crescente, enquanto as armas falhavam. Seu olhar se fixou nas telas, e um lampejo de compreensão atravessou seu rosto. "As armas... Elas dependem dos contratos inteligentes!" murmurou, a voz carregada de incredulidade. Ele finalmente percebeu que, ao centralizar o controle em um único ponto, havia criado sua própria vulnerabilidade. O que deveria ser sua maior força tornou-se sua ruína.
O controle centralizado da Atlas desmoronou. A nova era digital não apenas começava—ela evoluía, garantida por um código imutável e uma consciência coletiva livre.
O Bitcoin nunca foi apenas uma moeda. Era um ecossistema. Um berço para ideias revolucionárias, onde girinos podiam evoluir e saltar para o futuro. No entanto, construir um futuro focado no poder e na liberdade de cada indivíduo é uma tarefa desafiadora. Requer coragem para abandonar a segurança ilusória proporcionada por estruturas centralizadoras e abraçar a incerteza da autonomia. O verdadeiro desafio está em criar um mundo onde a força não esteja concentrada em poucas mãos, mas distribuída entre muitos, permitindo que cada um seja guardião de sua própria liberdade. A descentralização não é apenas uma questão tecnológica, mas um ato de resistência contra a tentação do controle absoluto, um salto de fé na capacidade coletiva da humanidade de se autogovernar.
"Viva la libertad, carajo!" ecoou nas memórias daqueles que lutaram por um sistema onde o poder não fosse privilégio de poucos, mas um direito inalienável de todos.
-
 @ 3b7fc823:e194354f
2025-02-03 14:51:45
@ 3b7fc823:e194354f
2025-02-03 14:51:45Protecting Email Communications: A Guide for Privacy Activists
Safeguarding your communications is paramount, especially for activists who often face unique challenges. Encryption tools offer a vital layer of security, ensuring that your emails remain confidential and inaccessible to unauthorized parties. This guide will walk you through the process of using encryption tools effectively, providing both practical advice and essential insights.
Why Encryption Matters
Encryption transforms your communications into a secure format, making it difficult for unauthorized individuals to access or read your messages. Without encryption, even encrypted email services can expose metadata, which includes details like who sent the email, when it was sent, and the recipient's email address. Metadata can reveal sensitive information about your activities and location.
Key Encryption Tools
There are several tools available for encrypting emails, catering to different skill levels and preferences:
- PGP (Pretty Good Privacy)
-
For Tech-Savvy Users: PGP is a robust encryption tool that uses public and private keys. The recipient needs your public key to decrypt your messages. You can obtain your public key through a key server or directly from the recipient.
-
GPG (GNU Privacy Guard)
-
Free and Open Source: GPG is a user-friendly alternative to PGP, offering similar functionality. It's ideal for those who prefer an open-source solution.
-
ProtonMail
-
End-to-End Encryption: ProtonMail is popular among privacy-conscious individuals, offering end-to-end encryption and zero-knowledge encryption, meaning only the sender and recipient can access the message content.
-
Tresorit
-
Secure Communication: Tresorit provides end-to-end encrypted messaging with a focus on security and privacy, making it a favorite among activists and journalists.
-
Claws Mail
- User-Friendly Email Client: Claws Mail supports PGP encryption directly, making it an excellent choice for those who prefer a dedicated email client with built-in encryption features.
Steps to Encrypt Your Emails
- Choose a Tool:
-
Select the tool that best fits your needs and comfort level. Tools like PGP or GPG are suitable for those with some technical knowledge, while ProtonMail offers an easy-to-use interface.
-
Generate Keys:
-
Create a public key using your chosen tool. This key will be shared with recipients to enable them to encrypt their responses.
-
Share Your Public Key:
-
Ensure that the recipient has access to your public key through secure means, such as pasting it directly into an email or sharing it via a secure messaging platform.
-
Encrypt and Send:
- When composing an email, use your encryption tool to encrypt the message before sending. This ensures that only the recipient with your public key can decrypt the content.
Minimizing Metadata
Beyond encryption, consider these steps to reduce metadata exposure:
- Use Tor for Sending Emails:
-
Routing emails through Tor hides your IP address and makes communication more anonymous.
-
Avoid Revealing Identifiers:
-
Use .onion addresses when possible to avoid leaving a traceable email account.
-
Choose Privacy-Friendly Providers:
- Select email providers that do not require phone numbers or other personally identifiable information (PII) for registration.
Best Practices
- Avoid Using Real Email Accounts:
-
Create dedicated, disposable email accounts for encryption purposes to minimize your personal exposure.
-
Understand Legal Implications:
-
Be aware of laws in your country regarding encryption and digital privacy. Engaging in encrypted communications may have legal consequences, so understand when and how to use encryption responsibly.
-
Use Encrypted Backup Methods:
- Encrypt sensitive information stored on devices or cloud services to ensure it remains inaccessible if your device is compromised.
When Encryption Isn't Enough
While encryption protects content, there are limitations. Governments can legally compel decryption in certain circumstances, especially when they possess a warrant. Understanding these limits and considering the consequences of encryption is crucial for privacy activists.
Conclusion
Encryption is a vital tool for safeguarding communications, but it must be used wisely. By selecting the right tools, minimizing metadata, and understanding legal boundaries, privacy activists can effectively protect their emails while maintaining their commitment to privacy and freedom. Stay informed, stay secure, and always prioritize your digital well-being.
Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero
82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1
-
 @ a39d19ec:3d88f61e
2024-11-17 10:48:56
@ a39d19ec:3d88f61e
2024-11-17 10:48:56This week's functional 3d print is the "Dino Clip".

Dino Clip
I printed it some years ago for my son, so he would have his own clip for cereal bags.
Now it is used to hold a bag of dog food close.
The design by "Sneaks" is a so called "print in place". This means that the whole clip with moving parts is printed in one part, without the need for assembly after the print.
 The clip is very strong, and I would print it again if I need a "heavy duty" clip for more rigid or big bags.
Link to the file at Printables
The clip is very strong, and I would print it again if I need a "heavy duty" clip for more rigid or big bags.
Link to the file at Printables -
 @ 57d1a264:69f1fee1
2025-02-03 13:40:21
@ 57d1a264:69f1fee1
2025-02-03 13:40:21COMING SOON
originally posted at https://stacker.news/items/874471
-
 @ 592295cf:413a0db9
2024-11-16 10:40:22
@ 592295cf:413a0db9
2024-11-16 10:40:22Week 11-11
Lamenting is becoming something I should ask people who complain. Charity bussiness and after sending zap received to those who do not complain...
I started making an RSS feed template. Open an opml file and check the feed. I called this script,Teed.
This morning I saw a bounty from a fiatjaf note, on a rss-feed long form, basic a plugin for an app. But I'm not doing that, of course, I can also publish it as soon as I'm in charge. Maybe I have some opml files and I want to see if these are still active.
Starter pack is not good apparently creates elites and maybe gives you the feeling of not choosing, but that's what people want. Do not choose but have the illusion of choosing.
Toxicity level. high.
P2P stuff, Iroh is a protocol for syncing & moving bytes iroh computer post on Bluesky
Juraj new project
nostr:nevent1qvzqqqqqqypzpk4kccr9csumnwhmpv83ladqc6p88089cx2e5s2c4448ppgl2pakqqsyv4hs424x6c8phks903s595q2lqp5fpwyq7ajwrf00lxev8cfamcvmq23h
Alex Gleason bunker Knox. (Beta) "knox is a new Nostr bunker CLI for running a NIP-46 remote signer and granting credentials to members of your team". Announcing bunker knox article
Local First podcast, web2.5. Something like Nostr but Local P2P, interesting episode. youtube link
Open Secret AI. "OpenSecret is a backend for app developers that turns private encryption on by default." announcment AI
I think users with regard to algorithms do not want ten different feeds to choose from, but that their feed adapts to their choices, training the feed if this makes sense. So the feed is your feed for your choices, respond and train with them.
Pleblab 2, cool "ANNOUNCING TOP BUILDER SEASON 2! " nostr:nevent1qvzqqqqqqypzpmx02p4slzahlf7jlcaspsx57g6uc7kl7cc7dvhlsnqtpn6khjj0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgwwaehxw309ahx7uewd3hkctcqyzy9w0frd802hfmrp45jr6dqhf7umqj7s63z0jvhv7hvvkcsqjg0vjwd7q4)
It was the real Guardian, quit 7fqx, we know it's you who want to distract us from number go up. The Guardian has left or wants to leave twitter is looking for alternatives, but how to verify a high profile user on Nostr? Nostr Address is already something but it's not enough.
We sometimes think that there is the money tree somewhere is that they magically appear, when instead the money is in the ground but they are dirty.
If Amethyst doesn't support is others stuff
People are simple, they want an app that works for all devices they have. People are "flutter-system".
A podcast feed xml file
Add to teed, if only i had made that option, meanwhile i saw a new interesting project
An other RSS feed github project
Imagine making a file opml with categories and those are your follow nostriches.
The problem is this does not bring new sap to the social chart is important to you, receive the selected posts and it is fantastic. You can also not use Nostr, if you want to use it as backup is fine. Share opml files? It's okay, but you can also find specific sites and find the best. Update for clients, you have a lot of RSS feeds from clients but update after a few hours so if there is really an emergency you lose. I still need to figure out how to integrate Nostr into RSS feed. Maybe an event to make your lists known.
I saw the event in these pr: nostr verified podcast nip #1465 Add audio track NIP #1043
-
 @ ba40a919:d1ca8326
2025-02-03 13:20:27
@ ba40a919:d1ca8326
2025-02-03 13:20:27For present-day tariff and trade policies are not only as bad as those in the seventeenth, eighteenth and nineteenth centuries, but incomparably worse. The real reasons for those tariffs and other trade barriers are the same, and the pretended reasons are also the same.
__
An American manufacturer of woolen sweaters goes to Congress or to the State Department and tells the committee or officials concerned that it would be a national disaster for them to remove or reduce the tariff on Canadian sweaters.
He now sells his sweaters for $30 each, but Canadian manufacturers could sell their sweaters of the same quality for $25, A duty of $5, therefore, is needed to keep him in business. He is not thinking of himself, of course, but of the thousand men and women he employs, and of the people to their spending in turn gives employment.
Throw them out of work, and you create unemployment and a fall in purchasing power, which would spread in ever-widening circles! And if he can prove that he really would be forced out of business if the tariff were removed or reduced, his argument against that action is regarded by Congress as conclusive.
FALLACY
But the fallacy comes from looking merely at this manufacturer and his employes, or merely at the American sweater industry. It comes from noticing only the results that are immediately seen, and neglecting the results that are not seen because they are prevented from coming into existence.
Donald Trump and the lobbyists for tariff protection are continually putting forward arguments that are not factually correct. But let us assume that the facts in this case are precisely as the sweater manufacturer has stated them.
Let us assume that a tariff of $5 a sweater is necessary for him to stay in business and provide employment at sweater-making for his workers.
We have deliberately chosen the most unfavorable example of any for the removal of a tariff. We have not taken an argument for the imposition of a new tariff in order to bring a new industry into existence, but an argument for the retention of a tariff that has already brought an industry into existence, and cannot be repealed without hurting somebody.
The tariff is repealed; the manufacturer goes out of business; a thousand workers are laid off; the particular tradesmen whom they patronized are hurt. This is the immediate result that is seen. But there are also results which, while much more difficult to trace, are no less immediate and no less real. For now sweaters that formerly cost retail $30 a piece can be bought for $25. Consumers can now buy the same quality of sweater for less money, or a much better one for the same money.
If they buy the same quality of sweater, they not only get the sweater, but they have $5 left over, which they would not have had under the previous conditions, to buy something else. With the $25 that they pay for the imported sweater they help employment—as the manufacturer no doubt predicted—in the sweater industry in Canada. With the $5 left over they help employment in any number of other industries in the United States.
But the results do not end there. By buying Canadian sweaters they furnish the Canada with US dollars to buy American goods here. This, in fact (if I may here disregard such complications as fluctuating exchange rates, loans, credits, etc.) is the only way in which the Canadians can eventually make use of these dollars.
Because we have permitted the Canada to sell more to us, they are now able to buy more from us. They are, in fact, eventually forced to buy more from us if their dollar balances are not to remain perpetually unused. So as a result of letting in more Canadian goods, we must export more American goods.
And though fewer people are now employed in the American sweater industry, more people are employed—and much more efficiently employed—in, say, the American machine or aircraft-building business. American employment on net balance has not gone down, but American and British production on net balance has gone up.
Labor in each country is more fully employed in doing just those things that it does best, instead of being forced to do things that it does inefficiently or badly. Consumers in both countries are better off. They are able to buy what they want where they can get it cheapest. American consumers are better provided with sweaters, and Canadian consumers are better provided with washing machines and aircraft.
__
This concluded part 1. On the next part we take a look at the matter the other way around, and see the effect of imposing a tariff in the first place.
-
 @ be7bf5de:09420d0a
2024-11-13 01:08:36
@ be7bf5de:09420d0a
2024-11-13 01:08:36At NosFabrica, we envision a future of healthcare where the individual is in charge of their health data and empowered to take responsibility for their own health. We are building health applications on Nostr and bitcoin to enable individuals own their health data. Nostr's architecture will allow different healthcare providers to write data onto the individual's relay. We see many potential use cases to solve specific problems in healthcare when the individual in a world where everyone has a comprehensive, portable and interoperable health record over time. We are looking to show what is possible with the "other stuff" on Nostr, starting by developing micro-apps so you can start compiling your health data, which you control.
If you're like most people on earth, your eyes aren't perfect. About half of us - 4 billion humans - have eye glasses, yet nearly a billion people can't get glasses due to inaccessibility of eye care or affordability.
With our microapp, Lazer Eyes, eye care providers can now write an eyeglasses or contacts prescription directly onto your own health relay. The optometrist simply needs to enter in your Nostr public key profile (nprofile), which relay to write the data to, and your prescription data; the encrypted prescription will be sent in an encrypted note directly to your relay. You can now send this signed note to your eye glasses provider to fulfill your glasses or contacts order.
 If you're using Amethyst today, you will be able to see this prescription rendered into your DMs. In our NosFabrica future vision, different clients would be able to show you this piece of your health record alongside other health information with different user interfaces and experiences. You will then have the power to selectively disclose this information, as needed.
If you're using Amethyst today, you will be able to see this prescription rendered into your DMs. In our NosFabrica future vision, different clients would be able to show you this piece of your health record alongside other health information with different user interfaces and experiences. You will then have the power to selectively disclose this information, as needed. There are many benefits to using Nostr for health as an individual:
There are many benefits to using Nostr for health as an individual:-
Patient Ownership and Control
-
Patients have full control of their prescription, and they can share it securely with confidence and even privately if required with eyewear providers or optometrists whenever needed.
-
Patients no longer rely on email or paper copies that can be easily lost or tampered with. Emailing a PDF to a patient brings the issue of requiring an optometrist signature leading to excess time taken to generate, print, sign, scan and email the copy. Public / private key cryptography provides a verifiable, time saving option in this case.
-
Continuity of care and ability to track changes in prescription over time - there are numerous forum posts where patients have found it difficult to get their prescription data from their optometrist practice when requesting it months or years later.
-
Removes the need for the patient to contact their old opticians and go through a process of trying to request their details, which can be time consuming.
-
Identity Verification
-
Optometrists sign prescriptions with a cryptographic key that patients could verify using their private Nostr identity (also known as a public/private key pair). This ensures that the prescription is authentic, accurate, and hasn't been altered after issuance. This would remove the need for issuing a “signed prescription” that currently has to be done in the physical sense, as a print out and issued to the patient. Have the option to have an indisputable and verifiable ‘Optometrist Identity Key’ would enable this legal requirement (in the UK) to go completely digital over Nostr.
-
The decentralized nature of Nostr ensures that prescriptions can be easily verified and traced back to the original issuer, avoiding forgery or fraud.
-
Privacy:
-
Unlike traditional methods where patient information is stored on centralized databases of the electronic medical record company (eg, Epic), or large health systems (eg, Ascension), Nostr keeps patient data decentralized and private, accessible only through permissioned sharing. This ensures no third party can access, manipulate, or misuse this sensitive information.
-
Immutable Records
-
Once a prescription is issued and signed on Nostr, it is stored immutably on the decentralized network. This ensures a permanent and trustworthy ledger of the patient's eye health history. This feature adds to accountability and should bring a higher standard to complete and accurate prescribing across all practices.
-
These records can persist over time and are portable to travel with you, wherever you seek care or glasses.
-
Global Access
-
Patients can use their Nostr-stored prescription with any provider across the globe, without needing to worry about differing national data standards or carrying physical documents when they travel or move.
-
This opens up a wider use case when considering the 2 Billion + individuals who currently cannot get access to sight care services.
Benefits for Optometrist Practices and Operators:
- Improved Patient Retention and Care through Trust and Transparency
-
By empowering patients with ownership of their data, practices foster trust and loyalty, reducing churn over time. If patients know they can rely on your practice for transparency, secure record-keeping, and access to the latest technology, they are more likely to return for future eye exams and other services.
-
A decentralized, tamper-proof record of prescriptions can improve administrative efficiency. No more handling lost prescriptions, disputes about validity, or delays in getting updated information to patients or other providers.
- The decentralized storage of prescriptions allows optometrists to securely share and access patient data, making cross-practice collaboration easier for referrals, second opinions, or specialized care.
- Cost Savings on Paperwork and Administration
-
Digitizing and decentralizing prescription records could lead to long-term savings on administrative costs, such as paperwork management, prescription re-issues, and managing patient data in outdated systems.
-
Optometrists can ensure their records are always accessible, accurate, and trusted by all parties (patients, insurers, other clinics).
- By reducing the burden of handling prescription storage and verification manually, the practice can focus more on patient care.
- Adaptation to Future Consumer Behavior and building a Tech-Savvy Reputation
-
As patients increasingly take control of their health data and seek decentralized solutions, practices that adapt to this trend are future-proofing their business model. Over time, patients will expect more control over their medical data, and being ahead of this shift will ensure long-term relevance.
-
Practices that embrace new technologies like Nostr can market themselves as tech-forward and adaptable to future trends, gaining an edge over more traditional competitors. This reputation is especially important as younger generations increasingly value privacy and digital autonomy. A Nostr-based service helps position the practice as aligned with these values.
- Integration with Bitcoin
-
By integrating a service built on Nostr, naturally linked with the bitcoin ecosystem, the practice can also introduce bitcoin payments as a novel way to reduce transaction fees and differentiate their practice from the competition.
-
Attract bitcoiners: The optics practice can appeal to the Bitcoin community, who value decentralization and would appreciate paying with bitcoin or using a decentralized protocol for prescription management. This opens up a new market of patients interested in technology and financial independence.
- Upsell Opportunities and Revenue Diversification
-
The practice can still maintain a competitive eyewear sales strategy by offering upsell opportunities. When patients receive their prescription digitally, they can be automatically sent tailored offers for high-quality lenses, frames, or even add-ons like blue light coatings or progressive lenses, keeping them within the practice’s ecosystem. Practices can offer value-added eyewear options, such as free adjustments, repairs, or personalized lens consultations, which online retailers can’t easily match.
-
The Nostr system can open doors to additional services beyond eyewear sales, including personalized consulting services, specialized testing (e.g., for contact lenses, binocular vision, myopia control), and more frequent checkups due to the ease of updating and verifying records.
Of course, utilizing this tool means providers need to help onboard individuals onto Nostr. In many ways, we see providers as playing into the Nostr network and flywheel effect. This is better technology with global access - and we invite you to consider other micro-apps that can continue to build out the decentralized healthcare ecosystem built on Nostr and bitcoin.
We have partnered with the Bitcoin Optometrist, Dr Alan Bryden, to continue to refine the micro-application and start testing its use. We'd like to thank Dr Alan for his insights that contributed to this micro-app and write-up. Check out his site and nonprofit, Sats for Sight, to learn more about utilizing bitcoin to provide eyeglasses to those in need, along with his HODL eyewear line.
We're excited about the future of building healthcare applications on nostr and bitcoin. If you have ideas or are facing any health challenges, we're conducting product discovery interviews to understand your biggest pain points when it comes to managing and optimizing your health and healthcare data. Please reach out to jon@nosfabrica.com or schedule time here to learn more about how to get involved!
Note: Lazer Eyes is currently only available for testing purposes as we evaluate regulatory considerations across jurisdictions.
-
-
 @ a661f80c:ef05a56b
2025-02-03 12:12:08
@ a661f80c:ef05a56b
2025-02-03 12:12:08When we hear the word "bonsai", many of us envision a small, perfectly shaped tree elegantly sitting on a table. But what exactly is bonsai? Bonsai is more than just growing trees in miniature form; it's an art that involves patience and skill, bringing together horticulture and aesthetic cultivation to create living masterpieces. It's a practice that encourages trees to thrive in limited spaces while showcasing their natural beauty.
Can any tree be turned into a bonsai?
Yes, indeed! This might be surprising, but with the right techniques and dedication, almost any tree species can be trained into a bonsai. Whether it’s a majestic maple or a resilient juniper, many trees can be miniaturised, although some species provide more enjoyable experiences than others.
Which Trees Can Be Used To Make A Bonsai?
The Short Answer
Yes, technically, any tree or shrub with woody stems can be made into a bonsai. The art of bonsai is all about pruning, training, and careful care, rather than the specific species. Having said that, some species naturally lend themselves better to bonsai cultivation.
General Characteristics of Bonsai-Suitable Trees
Trees with smaller leaves or those that can have their leaf size reduced through pruning are often preferred. Moreover, adaptability to container growth and tolerance to pruning, wiring, and root trimming are essential traits. Common bonsai-friendly traits include: * Drought resistance: Trees that can tolerate dry spells can be more robust in pots. * Deciduous vs. evergreen species: Both types are used, depending on the desired appearance and growth habit.
Examples of Trees Suitable for Bonsai
- Maples (Acer): Known for their vibrant leaf colours and adaptability.
- Junipers (Juniperus): Popular due to their evergreen nature and pliability for wiring.
- Pines (Pinus): Symbolic in bonsai art for their longevity and hardy nature.
- Ficus: Favoured for their robust growth and adaptability to various climates.
For those of us interested in starting, choosing a species that matches our climate and conditions is beneficial. Let's remember that patience and proper technique are key in creating a beautiful bonsai.
Do Certain Species Make Better Bonsai?
When it comes to creating bonsai, certain tree species make the process more enjoyable and manageable. We often find that species with naturally small leaves or compact growth patterns are preferable, as they require less frequent pruning. Popular choices include junipers, pines, and maples. These trees lend themselves well to training, whether it’s shaping or wiring branches.
Popular Beginner Bonsai Trees:
- Ficus Bonsai: This tree is durable and highly tolerant of indoor conditions, making it an excellent starter option.
- Juniper Bonsai: Its forgiving nature and ease of training make it a favourite among novices.
- Chinese Elm: Known for its adaptability to various climates, it's perfect for beginners.
Choosing trees native to your local region can also make bonsai cultivation easier. Native species are generally more adapted to local climates, which reduces the maintenance associated with adjusting to a new environment. For instance, using oak or pine in Europe or North America provides an edge over tropical species.
Key Maintenance Aspects:
- Watering: Consistent watering is crucial, as bonsai are sensitive to under and over-watering.
- Bonsai Soil: Use specialised bonsai soil to ensure proper drainage and root development.
- Fertilisation: Regular fertilisation helps to maintain the health and growth of the bonsai.
Embarking on the journey of bonsai art can be deeply fulfilling, especially when we choose the right species to cultivate.
Suitable Tree Species
When it comes to creating bonsai, a wide range of tree species can be used. Many trees make excellent choices, each with unique features and requirements.
Indoor Bonsai Species
- Ficus (e.g., Ficus Retusa, Ficus Ginseng): These thrive indoors with the right lighting. Ficus bonsai are popular due to their hardiness and adaptable nature.
- Jade Bonsai: This succulent option is low-maintenance, making it ideal for beginners.
- Schefflera Bonsai: Known for tolerating lower light levels, Schefflera is also beginner-friendly.
Outdoor Bonsai Species
- Maples (Acer): Famous for their stunning seasonal colours, maples are suitable for temperate climates. Japanese maples are especially prized for their vibrant hues.
- Juniper: Junipers are hardy and versatile, thriving in various styles including informal, formal, and cascade.
- Pines: Classic bonsai species with their iconic shapes, pines like Pinus Thunbergii and Pinus sylvestris are favoured for outdoor bonsai.
Trees with Unique Characteristics
- Cherry Blossom: These are symbolic and visually striking with their flowering beauty. Cherry blossoms require specific care but are rewarding bonsai.
- Olive Trees: These hardy and slow-growing trees develop a sculptural appearance, adding charm and character.
- Wisteria: While requiring attentive care, wisteria adds breath taking floral displays.
Can You Make a Bonsai Out of an Oak Tree?
Yes, it is possible to bonsai an oak tree, although challenges arise. Oak trees have large leaves, making it harder to maintain scale. Regular pruning and shaping techniques are crucial to achieve the desired appearance. Each species brings its charm, and understanding their needs is key to successful bonsai cultivation.
Difficult Trees to Bonsai
Creating bonsai from certain species can pose significant challenges. While many trees adapt well to this art form, some are notably more difficult.
Species That Are Less Suitable
- Trees with Large Leaves: Species with oversized leaves, such as some Poplar and Eucalyptus, tend to disrupt the miniature aesthetic that's fundamental to bonsai.
- Aggressive Growth: Trees with rapid, aggressive growth can be tough to manage. Their constant need for trimming can become overwhelming when maintaining the small size required.
- Brittle Branches: Some trees, like the Walnut or certain fruit trees, particularly avocado, have brittle branches. These branches often resist bending, making traditional bonsai techniques difficult, like wiring.
Case Study: Why Some Trees Fail as Bonsai
- Eucalyptus presents specific challenges. Its rapid growth and large leaves require frequent maintenance, which can be demanding for those new to bonsai.
- Banana trees are another example. Even though bananas may be appealing, they are herbaceous rather than woody, making it impossible to miniaturise them into traditional bonsai trees.
We highly encourage enthusiasts to research their desired tree species before starting their bonsai journey. Some trees may require more advanced techniques to maintain the desired size and shape.
Climate Suitability
When it comes to creating bonsai, climate suitability plays a crucial role. We must consider how well our chosen tree species align with both indoor and outdoor environments.
Importance of Matching Tree Species to Climate
- Indoor vs. Outdoor Suitability:
- Tropical species, like Ficus and Schefflera, thrive indoors where it's warm and humid.
- Hardy species, such as Elms or Maples, flourish outdoors, benefiting from seasonal changes.
Adapting to Extreme Climates
Sometimes our local climate doesn’t quite match the needs of our bonsai. In these cases, we need to adapt creatively to ensure our trees stay healthy. * Adaptations: 1. Cold climates can be tough for temperate species. Using cold frames helps protect them during harsh winters. 2. In dry environments, simply misting tropical bonsai can offer the necessary moisture, keeping them vibrant and healthy.
Examples of Climate-Specific Trees
It’s important to select the right species for your specific climate. Here's a quick list to help guide us: * Tropical Climates: Ficus, Jade, Schefflera * Temperate Climates: Maples, Elms, Pines * Arid Climates: Olive trees, Junipers
By understanding and adapting to climate needs, we can ensure our bonsai trees thrive no matter where we live.
Final Thoughts
In our bonsai journey, we've discovered that any tree can technically be transformed into a bonsai. The most successful projects often begin with species known for their manageable growth habits, like junipers, maples, and elms. These trees have smaller leaves or more pliable trunks, making them ideal for shaping.
Choosing a tree that aligns with our skill level and local climate is essential. Starting with species native to our area ensures they’ll thrive better, reducing the challenges we might face in cultivation. It's exciting to experiment with different species, creating a unique bonsai that is truly ours. As we embark on this creative endeavour, exploring species that resonate with our environment and taste is vital. Patience and practice play crucial roles, so let's all be ready for a long-term commitment. Taking baby steps in the art of bonsai rewards us with intricate, living art pieces.
Caring for bonsai trees is a rewarding journey that brings nature and artistry together. Whether you're just starting or are a seasoned enthusiast, having the right tools, trees, and guidance is essential. Visit Miyagi Bonsai to explore a wide range of high-quality bonsai products and resources to support your passion. Start or enhance your bonsai journey with us today!