-
 @ b8851a06:9b120ba1
2025-01-28 21:34:54
@ b8851a06:9b120ba1
2025-01-28 21:34:54Private property isn’t lines on dirt or fences of steel—it’s the crystallization of human sovereignty. Each boundary drawn is a silent declaration: This is where my will meets yours, where creation clashes against chaos. What we defend as “mine” or “yours” is no mere object but a metaphysical claim, a scaffold for the unfathomable complexity of voluntary exchange.
Markets breathe only when individuals anchor their choices in the inviolable. Without property, there is no negotiation—only force. No trade—only taking. The deed to land, the title to a car, the seed of an idea: these are not static things but frontiers of being, where human responsibility collides with the infinite permutations of value.
Austrian economics whispers what existentialism shouts: existence precedes essence. Property isn’t granted by systems; it’s asserted through action, defended through sacrifice, and sanctified through mutual recognition. A thing becomes “owned” only when a mind declares it so, and others—through reason or respect—refrain from crossing that unseen line.
Bitcoin? The purest ledger of this truth. A string of code, yes—but one that mirrors the unyielding logic of property itself: scarce, auditable, unconquerable. It doesn’t ask permission. It exists because sovereign minds choose it to.
Sigh. #nostr
I love #Bitcoin. -
 @ f4db5270:3c74e0d0
2025-01-23 18:09:14
@ f4db5270:3c74e0d0
2025-01-23 18:09:14Hi Art lover! 🎨🫂💜 You may not know it yet but all of the following paintings are available in #Bitcoin on my website: https://isolabell.art/#shop
For info and prices write to me in DM and we will find a good deal! 🤝
 ON THE ROAD AGAIN
40x50cm, Oil on canvas
Completed January 23, 2025
ON THE ROAD AGAIN
40x50cm, Oil on canvas
Completed January 23, 2025
 SUN OF JANUARY
40x50cm, Oil on canvas
Completed January 14, 2025
SUN OF JANUARY
40x50cm, Oil on canvas
Completed January 14, 2025
 THE BLUE HOUR
40x50cm, Oil on canvas
Completed December 14, 2024
THE BLUE HOUR
40x50cm, Oil on canvas
Completed December 14, 2024
 LIKE A FRAGMENT OF ETERNITY
50x40cm, Oil on canvas
Completed December 01, 2024
LIKE A FRAGMENT OF ETERNITY
50x40cm, Oil on canvas
Completed December 01, 2024
 WHERE WINTER WHISPERS
50x40cm, Oil on canvas
Completed November 07, 2024
WHERE WINTER WHISPERS
50x40cm, Oil on canvas
Completed November 07, 2024
 L'ATTESA DI UN MOMENTO
40x40cm, Oil on canvas
Completed October 29, 2024
L'ATTESA DI UN MOMENTO
40x40cm, Oil on canvas
Completed October 29, 2024
 LE COSE CHE PENSANO
40x50cm, Oil on paper
Completed October 05, 2024
LE COSE CHE PENSANO
40x50cm, Oil on paper
Completed October 05, 2024
 TWILIGHT'S RIVER
50x40cm, Oil on canvas
Completed September 17, 2024
TWILIGHT'S RIVER
50x40cm, Oil on canvas
Completed September 17, 2024
 GOLD ON THE OCEAN
40x50cm, Oil on paper
Completed September 08, 2024
GOLD ON THE OCEAN
40x50cm, Oil on paper
Completed September 08, 2024
 SUSSURRI DI CIELO E MARE
50x40cm, Oil on paper
Completed September 05, 2024
SUSSURRI DI CIELO E MARE
50x40cm, Oil on paper
Completed September 05, 2024
 THE END OF A WONDERFUL WEEKEND
40x30cm, Oil on board
Completed August 12, 2024
THE END OF A WONDERFUL WEEKEND
40x30cm, Oil on board
Completed August 12, 2024
 FIAMME NEL CIELO
60x35cm, Oil on board
Completed July 28, 2024
FIAMME NEL CIELO
60x35cm, Oil on board
Completed July 28, 2024
 INIZIO D'ESTATE
50x40cm, Oil on cradled wood panel
Completed July 13, 2024
INIZIO D'ESTATE
50x40cm, Oil on cradled wood panel
Completed July 13, 2024
 OMBRE DELLA SERA
50x40cm, Oil on cradled wood panel
Completed June 16, 2024
OMBRE DELLA SERA
50x40cm, Oil on cradled wood panel
Completed June 16, 2024
 NEW ZEALAND SUNSET
80x60cm, Oil on canvas board
Completed May 28, 2024
NEW ZEALAND SUNSET
80x60cm, Oil on canvas board
Completed May 28, 2024
 VENICE
50x40cm, Oil on board
Completed May 4, 2024
VENICE
50x40cm, Oil on board
Completed May 4, 2024
 CORNWALL
50x40cm, Oil on board
Completed April 26, 2024
CORNWALL
50x40cm, Oil on board
Completed April 26, 2024
 DOCKS ON SUNSET
40x19,5cm, Oil on board
Completed March 14, 2024
DOCKS ON SUNSET
40x19,5cm, Oil on board
Completed March 14, 2024
 SOLITUDE
30x30cm, Oil on cradled wood panel
Completed March 2, 2024
SOLITUDE
30x30cm, Oil on cradled wood panel
Completed March 2, 2024
 LULLING WAVES
40x30cm, Oil on cradled wood panel
Completed January 14, 2024
LULLING WAVES
40x30cm, Oil on cradled wood panel
Completed January 14, 2024
 MULATTIERA IN AUTUNNO
30x30cm, Oil on cradled wood panel
MULATTIERA IN AUTUNNO
30x30cm, Oil on cradled wood panel
 TRAMONTO A KOS
40x40cm, oil on board canvas
TRAMONTO A KOS
40x40cm, oil on board canvas
 HIDDEN SMILE
40x40cm, oil on board
HIDDEN SMILE
40x40cm, oil on board
 INIZIO D'AUTUNNO
40x40cm, oil on canvas
INIZIO D'AUTUNNO
40x40cm, oil on canvas
 BOE NEL LAGO
30x30cm, oil on canvas board
BOE NEL LAGO
30x30cm, oil on canvas board
 BARCHE A RIPOSO
40x40cm, oil on canvas board
BARCHE A RIPOSO
40x40cm, oil on canvas board
 IL RISVEGLIO
30x40cm, oil on canvas board
IL RISVEGLIO
30x40cm, oil on canvas board
 LA QUIETE PRIMA DELLA TEMPESTA
30x40cm, oil on canvas board
LA QUIETE PRIMA DELLA TEMPESTA
30x40cm, oil on canvas board
 LAMPIONE SUL LAGO
30x30cm, oil on canvas board
LAMPIONE SUL LAGO
30x30cm, oil on canvas board
 DUE NELLA NEVE
60x25cm, oil on board
DUE NELLA NEVE
60x25cm, oil on board
 UNA CAREZZA
30x30cm, oil on canvas board
UNA CAREZZA
30x30cm, oil on canvas board
 REBEL WAVES
44x32cm, oil on canvas board
REBEL WAVES
44x32cm, oil on canvas board
 THE SCREAMING WAVE
40x30cm, oil on canvas board
THE SCREAMING WAVE
40x30cm, oil on canvas board
 "LA DONZELLETTA VIEN DALLA CAMPAGNA..."
30x40cm, oil on canvas board
"LA DONZELLETTA VIEN DALLA CAMPAGNA..."
30x40cm, oil on canvas board
 LIGHTHOUSE ON WHITE CLIFF
30x40cm, oil on canvas board
LIGHTHOUSE ON WHITE CLIFF
30x40cm, oil on canvas board -
 @ 7f29628d:e160cccc
2025-01-07 11:50:30
@ 7f29628d:e160cccc
2025-01-07 11:50:30Der gut informierte Bürger denkt bei der Pandemie sofort an Intensivstationen, an die Bilder aus Bergamo und erinnert sich an die Berichterstattung damals – also muss es wohl ein Maximum gewesen sein. Manche Skeptiker behaupten jedoch das Gegenteil. Klarheit sollte ein Blick nach Wiesbaden, zum Statistischen Bundesamt, schaffen. Schließlich sitzen dort gut bezahlte Profis, die seit vielen Jahrzehnten die Sterbestatistik pflegen und veröffentlichen. Jeder Todesfall wird in Deutschland über die Standesämter exakt erfasst.
Doch die Überraschung: Das Statistische Bundesamt liefert uns auf diese einfache Frage zwei extrem unterschiedliche Antworten – ein Minimum und ein Maximum. Das Ergebnis hängt davon ab, wie tief man in die Veröffentlichungen des Bundesamtes eintaucht. Betrachtet man nur die Webseiten und Pressemitteilungen, erhält man den Eindruck eines Maximums. Schaut man jedoch etwas tiefer in die Tabellen und Rohdaten, zeigt sich plötzlich ein Minimum. Aber wie kann das sein? Beides gleichzeitig geht ja wohl kaum. Wer lügt hier – die Tabellen des Amtes oder die Pressemitteilungen? Gehen wir dieser Frage Schritt für Schritt auf den Grund.
2020: Ein historisches Maximum?
Schauen wir uns die vielen Hundert Veröffentlichungen des Statistischen Bundesamtes aus dieser Zeit an. Oder wir kürzen ab und fragen ChatGPT, da die KI auf diesen Daten trainiert wurde und das gesamte Material kennt. Die Frage an ChatGPT lautet also: Wie war das Sterbegeschehen im Jahr 2020 im Vergleich zu den Vorjahren?
ChatGPT antwortet: »Im Jahr 2020 war die Sterblichkeit in Deutschland höher als in den Jahren zuvor. Es gab eine Übersterblichkeit von etwa 982.000 Todesfällen, das sind rund 46.000 mehr als der Durchschnitt der Vorjahre (2016 bis 2019). Dieser Anstieg wurde überwiegend im Zusammenhang mit der COVID-19-Pandemie gesehen. Während die Sterbezahlen in den Vorjahren schwankten, war ein solch signifikanter Anstieg wie 2020 bisher nicht zu beobachten.«
Wir fragen konkreter: Ist es ein Fakt, dass wir eine so ernste Lage im Sterbegeschehen wie im Frühjahr 2020 noch nie erlebt haben?
ChatGPT bestätigt: »Ja, die COVID-19-Pandemie führte im Frühjahr 2020 zu einer außergewöhnlichen Situation im Sterbegeschehen in Deutschland. Die dramatische Übersterblichkeit, die ab der 13. Kalenderwoche auftrat, veranlasste das Statistische Bundesamt, besonders eindringliche Warnungen zu veröffentlichen. Der damalige Vizepräsident des Amtes und andere führende Stimmen wiesen öffentlich darauf hin, dass die Todesfallzahlen stark vom Durchschnitt abwichen. Diese klare Warnung richtete sich an die Öffentlichkeit und die Politik gleichermaßen. Die Medien berichteten intensiv über diese Warnungen, was das Bewusstsein für die Schwere der Pandemie erheblich schärfte. In den vergangenen Jahrzehnten hatte es keine vergleichbare Übersterblichkeit gegeben, die eine solch umfangreiche Kommunikation durch das Statistische Bundesamt erforderlich gemacht hätte.«
Ein gut informierter Zeitungsleser wird sich an dieser Stelle bestätigt fühlen: Ja, so war es damals. Ein Maximum im Sterbegeschehen – wegen der Pandemie. Oder etwa nicht?
2020: Ein historisches Minimum?
Tauchen wir in die Rohdaten des Statistischen Bundesamtes ein. Die Tabellen, die das Amt seit Jahrzehnten verlässlich veröffentlicht, nennen sich Sterbetafeln. Diese werden jährlich bereitgestellt und stehen auf der Website des Bundesamtes zum Download bereit. Ein erster Blick in die Sterbetafeln mag den Laien abschrecken, doch mit einer kurzen Erklärung wird alles verständlich. Wir gehen schrittweise vor.
Nehmen wir die Sterbetafel des Jahres 2017. Sie enthält zwei große Tabellen – eine für Männer und eine für Frauen. Jede Zeile der Tabelle steht für einen Jahrgang, zum Beispiel zeigt die Zeile 79 die Daten der 79-jährigen Männer. Besonders wichtig ist nun die zweite Spalte, in der der Wert 0,05 eingetragen ist. Das bedeutet, dass 5 Prozent der 79-jährigen Männer im Jahr 2017 verstorben sind. Das ist die wichtige Kennzahl. Wenn wir diesen exakten Wert, den man auch als Sterberate bezeichnet, nun in ein Säulendiagramm eintragen, erhalten wir eine leicht verständliche visuelle Darstellung (Grafik 1).

Es ist wichtig zu betonen, dass dieser Wert weder ein Schätzwert noch eine Modellrechnung oder Prognose ist, sondern ein exakter Messwert, basierend auf einer zuverlässigen Zählung. Sterberaten (für die Fachleute auch Sterbewahrscheinlichkeiten qx) sind seit Johann Peter Süßmilch (1707–1767) der Goldstandard der Sterbestatistik. Jeder Aktuar wird das bestätigen. Fügen wir nun die Sterberaten der 79-jährigen Männer aus den Jahren davor und danach hinzu, um das Gesamtbild zu sehen (Grafik 2). Und nun die entscheidende Frage: Zeigt das Jahr 2020 ein Maximum oder ein Minimum?

Ein kritischer Leser könnte vermuten, dass die 79-jährigen Männer eine Ausnahme darstellen und andere Jahrgänge im Jahr 2020 ein Maximum zeigen würden. Doch das trifft nicht zu. Kein einziger Jahrgang verzeichnete im Jahr 2020 ein Maximum. Im Gegenteil: Auch die 1-Jährigen, 2-Jährigen, 3-Jährigen, 9-Jährigen, 10-Jährigen, 15-Jährigen, 18-Jährigen und viele weitere männliche Jahrgänge hatten ihr Minimum im Jahr 2020. Dasselbe gilt bei den Frauen. Insgesamt hatten 31 Jahrgänge ihr Minimum im Jahr 2020. Wenn wir schließlich alle Jahrgänge in einer einzigen Grafik zusammenfassen, ergibt sich ein klares Bild: Das Minimum im Sterbegeschehen lag im Jahr 2020 (Grafik 3).

Ein kritischer Leser könnte nun wiederum vermuten, dass es innerhalb des Jahres 2020 möglicherweise starke Ausschläge nach oben bei einzelnen Jahrgängen gegeben haben könnte, die später durch Ausschläge nach unten ausgeglichen wurden – und dass diese Schwankungen in der jährlichen Übersicht nicht sichtbar sind. Doch auch das trifft nicht zu. Ein Blick auf die wöchentlichen Sterberaten zeigt, dass die ersten acht Monate der Pandemie keine nennenswerten Auffälligkeiten aufweisen. Es bleibt dabei: Die Rohdaten des Statistischen Bundesamtes bestätigen zweifelsfrei, dass die ersten acht Monate der Pandemie das historische Minimum im Sterbegeschehen darstellen. (Für die Fachleute sei angemerkt, dass im gleichen Zeitraum die Lebenserwartung die historischen Höchststände erreicht hatte – Grafik 4.)

So konstruierte das Amt aus einem Minimum ein Maximum:
Zur Erinnerung: Die Rohdaten des Statistischen Bundesamtes, die in den jährlichen Sterbetafeln zweifelsfrei dokumentiert sind, zeigen für das Jahr 2020 eindeutig ein Minimum im Sterbegeschehen. Aus diesen »in Stein gemeißelten« Zahlen ein Maximum zu »konstruieren«, ohne die Rohdaten selbst zu verändern, scheint auf den ersten Blick eine unlösbare Aufgabe. Jeder Student würde an einer solchen Herausforderung scheitern. Doch das Statistische Bundesamt hat einen kreativen Weg gefunden - ein Meisterstück gezielter Manipulation. In fünf Schritten zeigt sich, wie diese Täuschung der Öffentlichkeit umgesetzt wurde:
(1) Ignorieren der Sterberaten: Die präzisen, objektiven und leicht verständlichen Sterberaten aus den eigenen Sterbetafeln wurden konsequent ignoriert und verschwiegen. Diese Daten widersprachen dem gewünschten Narrativ und wurden daher gezielt ausgeklammert.
(2) Fokus auf absolute Todeszahlen: Die Aufmerksamkeit wurde stattdessen auf die absolute Zahl der Todesfälle gelenkt. Diese wirkt allein durch ihre schiere Größe dramatisch und emotionalisiert die Diskussion. Ein entscheidender Faktor wurde dabei ignoriert: Die absolute Zahl der Todesfälle steigt aufgrund der demografischen Entwicklung jedes Jahr an. Viele Menschen verstehen diesen Zusammenhang nicht und verbinden die steigenden Zahlen fälschlicherweise mit der vermeintlichen Pandemie.
(3) Einführung der Übersterblichkeit als neue Kennzahl: Erst ab Beginn der „Pandemie“ wurde die Kennzahl "Übersterblichkeit" eingeführt – und dies mit einer fragwürdigen Methode, die systematisch überhöhte Werte lieferte. Diese Kennzahl wurde regelmäßig, oft monatlich oder sogar wöchentlich, berechnet und diente als ständige Grundlage für alarmierende Schlagzeilen.
(4) Intensive Öffentlichkeitsarbeit: Durch eine breit angelegte Kampagne wurden die manipulativen Kennzahlen gezielt in den Fokus gerückt. Pressemitteilungen, Podcasts und öffentliche Auftritte konzentrierten sich fast ausschließlich auf die absoluten Todeszahlen und die Übersterblichkeit. Ziel war es, den Eindruck einer dramatischen Situation in der Öffentlichkeit zu verstärken.
(5) Bekämpfen kritischer Stimmen: Kritiker, die die Schwächen und manipulativen Aspekte dieser Methoden aufdeckten, wurden systematisch diskreditiert. Ihre Glaubwürdigkeit und Kompetenz wurden öffentlich infrage gestellt, um das sorgsam konstruierte Narrativ zu schützen.
Ohne diesen begleitenden Statistik-Betrug wäre das gesamte Pandemie-Theater meiner Meinung nach nicht möglich gewesen. Wer aus einem faktischen Minimum ein scheinbares Maximum "erschafft", handelt betrügerisch. Die Folgen dieses Betruges sind gravierend. Denken wir an die Angst, die in der Bevölkerung geschürt wurde – die Angst, bald sterben zu müssen. Denken wir an Masken, Abstandsregeln, isolierte ältere Menschen, Kinderimpfungen und all die Maßnahmen, die unter anderem auf diese falsche Statistik zurückgehen.
Wollen wir Bürger uns das gefallen lassen?
Wenn wir als Bürger zulassen, dass ein derart offensichtlicher und nachprüfbarer Täuschungsversuch ohne Konsequenzen bleibt, dann gefährdet das nicht nur die Integrität unserer Institutionen – es untergräbt das Fundament unserer Gesellschaft. In der DDR feierte man öffentlich Planerfüllung und Übererfüllung, während die Regale leer blieben. Damals wusste jeder: Statistik war ein Propagandainstrument. Niemand traute den Zahlen, die das Staatsfernsehen verkündete.
Während der Pandemie war es anders. Die Menschen vertrauten den Mitteilungen des Statistischen Bundesamtes und des RKI – blind. Die Enthüllungen durch den "RKI-Leak" haben gezeigt, dass auch das Robert-Koch-Institut nicht der Wissenschaft, sondern den Weisungen des Gesundheitsministers und militärischen Vorgaben folgte. Warum sollte es beim Statistischen Bundesamt anders gewesen sein? Diese Behörde ist dem Innenministerium unterstellt und somit ebenfalls weisungsgebunden.
Die Beweise für Täuschung liegen offen zutage. Es braucht keinen Whistleblower, keine geheimen Enthüllungen: Die Rohdaten des Statistischen Bundesamtes sprechen für sich. Sie sind öffentlich einsehbar – klar und unmissverständlich. Die Daten, die Tabellen, die Veröffentlichungen des Amtes selbst – sie sind die Anklageschrift. Sie zeigen, was wirklich war. Nicht mehr und nicht weniger.
Und wir? Was tun wir? Schweigen wir? Oder fordern wir endlich ein, was unser Recht ist? Wir Bürger dürfen das nicht hinnehmen. Es ist Zeit, unsere Behörden zur Rechenschaft zu ziehen. Diese Institutionen arbeiten nicht für sich – sie arbeiten für uns. Wir finanzieren sie, und wir haben das Recht, Transparenz und Verantwortung einzufordern. Manipulationen wie diese müssen aufgearbeitet werden und dürfen nie wieder geschehen. Die Strukturen, die solche Fehlentwicklungen in unseren Behörden ermöglicht haben, müssen offengelegt werden. Denn eine Demokratie lebt von Vertrauen – und Vertrauen muss verdient werden. Jeden Tag aufs Neue.
.
.
MARCEL BARZ, Jahrgang 1975, war Offizier der Bundeswehr und studierte Wirtschafts- und Organisationswissenschaften sowie Wirtschaftsinformatik. Er war Gründer und Geschäftsführer einer Softwarefirma, die sich auf Datenanalyse und Softwareentwicklung spezialisiert hatte. Im August 2021 veröffentlichte Barz den Videovortrag »Die Pandemie in den Rohdaten«, der über eine Million Aufrufe erzielte. Seitdem macht er als "Erbsenzähler" auf Widersprüche in amtlichen Statistiken aufmerksam.
-
 @ eac63075:b4988b48
2025-01-04 19:41:34
@ eac63075:b4988b48
2025-01-04 19:41:34Since its creation in 2009, Bitcoin has symbolized innovation and resilience. However, from time to time, alarmist narratives arise about emerging technologies that could "break" its security. Among these, quantum computing stands out as one of the most recurrent. But does quantum computing truly threaten Bitcoin? And more importantly, what is the community doing to ensure the protocol remains invulnerable?
The answer, contrary to sensationalist headlines, is reassuring: Bitcoin is secure, and the community is already preparing for a future where quantum computing becomes a practical reality. Let’s dive into this topic to understand why the concerns are exaggerated and how the development of BIP-360 demonstrates that Bitcoin is one step ahead.
What Is Quantum Computing, and Why Is Bitcoin Not Threatened?
Quantum computing leverages principles of quantum mechanics to perform calculations that, in theory, could exponentially surpass classical computers—and it has nothing to do with what so-called “quantum coaches” teach to scam the uninformed. One of the concerns is that this technology could compromise two key aspects of Bitcoin’s security:
- Wallets: These use elliptic curve algorithms (ECDSA) to protect private keys. A sufficiently powerful quantum computer could deduce a private key from its public key.
- Mining: This is based on the SHA-256 algorithm, which secures the consensus process. A quantum attack could, in theory, compromise the proof-of-work mechanism.
Understanding Quantum Computing’s Attack Priorities
While quantum computing is often presented as a threat to Bitcoin, not all parts of the network are equally vulnerable. Theoretical attacks would be prioritized based on two main factors: ease of execution and potential reward. This creates two categories of attacks:
1. Attacks on Wallets
Bitcoin wallets, secured by elliptic curve algorithms, would be the initial targets due to the relative vulnerability of their public keys, especially those already exposed on the blockchain. Two attack scenarios stand out:
-
Short-term attacks: These occur during the interval between sending a transaction and its inclusion in a block (approximately 10 minutes). A quantum computer could intercept the exposed public key and derive the corresponding private key to redirect funds by creating a transaction with higher fees.
-
Long-term attacks: These focus on old wallets whose public keys are permanently exposed. Wallets associated with Satoshi Nakamoto, for example, are especially vulnerable because they were created before the practice of using hashes to mask public keys.
We can infer a priority order for how such attacks might occur based on urgency and importance.
 Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)
Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)2. Attacks on Mining
Targeting the SHA-256 algorithm, which secures the mining process, would be the next objective. However, this is far more complex and requires a level of quantum computational power that is currently non-existent and far from realization. A successful attack would allow for the recalculation of all possible hashes to dominate the consensus process and potentially "mine" it instantly.
 Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin Attacks
Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin AttacksRecently, Narcelio asked me about a statement I made on Tubacast:
https://x.com/eddieoz/status/1868371296683511969
If an attack became a reality before Bitcoin was prepared, it would be necessary to define the last block prior to the attack and proceed from there using a new hashing algorithm. The solution would resemble the response to the infamous 2013 bug. It’s a fact that this would cause market panic, and Bitcoin's price would drop significantly, creating a potential opportunity for the well-informed.
Preferably, if developers could anticipate the threat and had time to work on a solution and build consensus before an attack, they would simply decide on a future block for the fork, which would then adopt the new algorithm. It might even rehash previous blocks (reaching consensus on them) to avoid potential reorganization through the re-mining of blocks using the old hash. (I often use the term "shielding" old transactions).
How Can Users Protect Themselves?
While quantum computing is still far from being a practical threat, some simple measures can already protect users against hypothetical scenarios:
- Avoid using exposed public keys: Ensure funds sent to old wallets are transferred to new ones that use public key hashes. This reduces the risk of long-term attacks.
- Use modern wallets: Opt for wallets compatible with SegWit or Taproot, which implement better security practices.
- Monitor security updates: Stay informed about updates from the Bitcoin community, such as the implementation of BIP-360, which will introduce quantum-resistant addresses.
- Do not reuse addresses: Every transaction should be associated with a new address to minimize the risk of repeated exposure of the same public key.
- Adopt secure backup practices: Create offline backups of private keys and seeds in secure locations, protected from unauthorized access.
BIP-360 and Bitcoin’s Preparation for the Future
Even though quantum computing is still beyond practical reach, the Bitcoin community is not standing still. A concrete example is BIP-360, a proposal that establishes the technical framework to make wallets resistant to quantum attacks.
BIP-360 addresses three main pillars:
- Introduction of quantum-resistant addresses: A new address format starting with "BC1R" will be used. These addresses will be compatible with post-quantum algorithms, ensuring that stored funds are protected from future attacks.
- Compatibility with the current ecosystem: The proposal allows users to transfer funds from old addresses to new ones without requiring drastic changes to the network infrastructure.
- Flexibility for future updates: BIP-360 does not limit the choice of specific algorithms. Instead, it serves as a foundation for implementing new post-quantum algorithms as technology evolves.
This proposal demonstrates how Bitcoin can adapt to emerging threats without compromising its decentralized structure.
Post-Quantum Algorithms: The Future of Bitcoin Cryptography
The community is exploring various algorithms to protect Bitcoin from quantum attacks. Among the most discussed are:
- Falcon: A solution combining smaller public keys with compact digital signatures. Although it has been tested in limited scenarios, it still faces scalability and performance challenges.
- Sphincs: Hash-based, this algorithm is renowned for its resilience, but its signatures can be extremely large, making it less efficient for networks like Bitcoin’s blockchain.
- Lamport: Created in 1977, it’s considered one of the earliest post-quantum security solutions. Despite its reliability, its gigantic public keys (16,000 bytes) make it impractical and costly for Bitcoin.
Two technologies show great promise and are well-regarded by the community:
- Lattice-Based Cryptography: Considered one of the most promising, it uses complex mathematical structures to create systems nearly immune to quantum computing. Its implementation is still in its early stages, but the community is optimistic.
- Supersingular Elliptic Curve Isogeny: These are very recent digital signature algorithms and require extensive study and testing before being ready for practical market use.
The final choice of algorithm will depend on factors such as efficiency, cost, and integration capability with the current system. Additionally, it is preferable that these algorithms are standardized before implementation, a process that may take up to 10 years.
Why Quantum Computing Is Far from Being a Threat
The alarmist narrative about quantum computing overlooks the technical and practical challenges that still need to be overcome. Among them:
- Insufficient number of qubits: Current quantum computers have only a few hundred qubits, whereas successful attacks would require millions.
- High error rate: Quantum stability remains a barrier to reliable large-scale operations.
- High costs: Building and operating large-scale quantum computers requires massive investments, limiting their use to scientific or specific applications.
Moreover, even if quantum computers make significant advancements, Bitcoin is already adapting to ensure its infrastructure is prepared to respond.
Conclusion: Bitcoin’s Secure Future
Despite advancements in quantum computing, the reality is that Bitcoin is far from being threatened. Its security is ensured not only by its robust architecture but also by the community’s constant efforts to anticipate and mitigate challenges.
The implementation of BIP-360 and the pursuit of post-quantum algorithms demonstrate that Bitcoin is not only resilient but also proactive. By adopting practical measures, such as using modern wallets and migrating to quantum-resistant addresses, users can further protect themselves against potential threats.
Bitcoin’s future is not at risk—it is being carefully shaped to withstand any emerging technology, including quantum computing.
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ 4ba8e86d:89d32de4
2024-10-07 13:37:38
@ 4ba8e86d:89d32de4
2024-10-07 13:37:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável.
https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ 5d4b6c8d:8a1c1ee3
2025-02-06 00:49:05
@ 5d4b6c8d:8a1c1ee3
2025-02-06 00:49:05Herbs and spices don't just taste great. Most of the time they're also great for you. - Spicier foods ironically are strongly anti-inflammatory and chronic inflammation is one of the major drivers of poor health - Roots, like turmeric/ginger/garlic/onion, are also strongly anti-inflammatory - Herbs, like parsley and oregano, are super high in vitamins K, C, beta carotene, folate, and others, as well as potassium, manganese, and other minerals. - Seeds, like cumin or coriander, are super mineral dense. - Sea salt (unrefined) has a broad array and excellent balance of minerals.
So, what's the health principle?
Eat tastier more flavorful food. It's tasty because it's good for us (shut up sugar!).
originally posted at https://stacker.news/items/877209
-
 @ 3b7fc823:e194354f
2025-02-06 00:19:45
@ 3b7fc823:e194354f
2025-02-06 00:19:45Your phone is not your friend. It is a filthy little snitch that tells anyone who asks where you are, what you are doing, and who you are doing it with. You can obscure and hide some things through the use of privacy respecting software like encrypted communication apps, Tor pathways using Orbot, or the base OS like Graphene but metadata and geolocation is still very loud and very present. It is built into the infrastructure of how cell phones work. Your phone is tracked at all times through every cell tower area you pass through logging your IMEI and by extension your phone number and identity. This data is logged and saved forever by companies who use and sell it for corporate surveillance and post Patriot Act give it to police and government agencies warrantlessly.
Fine, I will just turn it off then. Nice try, but unless the battery can be removed it still tracks you. You didn't think it was weird that Find My Phone still works even if the phone was off? Luddites are not off the hook. That dumb phone or flip phone is tracked just the same and since it will not run encrypted communications you are screaming out the content of every call or text and not just the metadata.
OK, I will get a burner phone or anonymous SIM card not tied to my identity. Better, but not bulletproof. This is great for use and toss but if you continue to use it multiple times, around other devices that are tied to you or your social network, or take it to your home, work, or any location associated with you then it will be doxxed. Once doxxed all past information associated with it becomes now linked to you.
Metadata, Profile, and Network Your network is very easily known and built up over time. Who are the contacts saved in your phone? Who do you interact with? Who do you call, text, email, DM, or follow on social networks? Who do you never contact but your geolocation overlaps with them often. Now look at all those contacts and who they have a network with. A giant spider web of connections. If by 7 degrees of Kevin Bacon you have a shady contact in your network then you may get more scrutiny than you may realize.
You are spilling metadata everywhere you go along with your geolocation. Time stamps, who you contacted, how long you talk to them, which app was used when, internet searches, map app searches, etc. People are creatures of habit and over time this metadata builds a pretty good profile on you. Phone becomes active around 7am when they wake up. Scans social media and news sites for usually 30 minutes. Assume they are taking a shower because the phone is on but not being used until 8am most weekdays. Travels to a coffee place on the corner most mornings and then goes to their place of work. Between 9:30 and 10:30 am they again scan social media and news sites for a solid 10 minutes, probably their bathroom schedule. During lunch they frequent these locations with these people. You get the point.
This profile, plus your geolocation history, plus your network paints a pretty complete picture on you. Surprisingly it is not what you do but when you do something different that gets attention. There was a big protest last night that we are not happy about. We already have a list of everyone who took their phones with them at that geolocation and timestamp. We run an algorithm looking for simple patterns. John is usually at a restaurant eating with friends during this time but strangely his phone was left at home and turned off during that time frame. Did anyone in his network go to the protest that we have already confirmed? Anyone in his network follow the protest Facebook page, or have a deviation from their usual pattern such as their phone being somewhere dormant when it is usually active during this time?
What can you do? You can choose to do nothing. You can just live your life with the awareness that you are being tracked and profiled, maybe work to limit how much metadata you are spilling out to the universe. If you are an activist, an oppressed minority, live in an oppressive regime, or your country suddenly becomes oppressive this might not be an option. Randomize or maintain your profile. This is hard but not impossible. Make your profile and habits so chaotic that any deviation is not a deviation. Most people cannot do this but if you are couch-surfing, going to different places constantly, new friends and new activities on the daily agent of chaos then maybe this is an option.
On the opposite extreme maybe you are a very regimented person so be aware of that and always stick to your routine. If you want to go to that protest but are usually home doom scrolling youtube during that time then set your phone to no sleep mode and set up to watch a long playlist of youtube videos left at home while you go to the protest.
Home phone only. Maybe you decide to have a home phone only, no not a landline, but an actual smart device that can utilize encrypted communications services but never leaves the house. This could potentially save you a lot of money on data plans, texts, and minutes if you don't buy a network plan and just use VOIP on your home WIFI. Or maybe you have a very minimal network plan and when you leave the house you either take it with you in a Faraday bag or have a secondary device that lives in a Faraday bag that only comes out for emergencies and to check in. Just be aware that the time in and out of the Faraday bag is part of your profile.
No Phone. You can have no phone whatsoever. This will not work for most people in the modern age but if you have an extreme risk profile then this might be the extreme option you need. How do you survive with no phone or only a home phone? Just some alternatives and some ideas. You can still buy WIFI only devices that have no network connection and / or stay in airplane mode. Old MP3 players for music and podcasts while on the go. Old phones that you can download maps to for navigation and use VOIP services in WIFI hotspots.
Emergency Communication and Go Bag Prepper culture has given us all sorts of bags: bug out bags, get home bags, never coming back bags, and go bags. I define go bags as very small, light weight, and compact bags or kits. They carry very minimal, bare necessary gear, and ideally are so small that you actually have it on you, in your purse or computer satchel or car all of the time. Emergency communication will be part of this. This is when the burner phone, purchased with cash out of town, and stored in a Faraday bag all the time shines. It has no connection to you and has no history of use. It is a have but hope to never use oh shit device. If you are the activist, the whistleblower, the oppressed that they could come after at any time, or the journalist that investigates corruption, organized crime, or terrorism then you need this.
-
 @ 7e538978:a5987ab6
2024-10-02 13:57:31
@ 7e538978:a5987ab6
2024-10-02 13:57:31Chain Duel, a fast paced PvP game that takes inspiration from the classic snake game and supercharges it with Bitcoin’s Lightning Network. Imagine battling another player for dominance in a race to collect blocks, where the length of your chain isn’t just a visual cue. It represents real, staked satoshis. The player with the most Proof of Work wins, but it’s not just about gameplay; it’s about the seamless integration of the Lightning Network and real-time payments.
But how does Chain Duel manage these instant transactions with such efficiency? That’s where LNbits comes in. LNbits, an open-source wallet and payment infrastructure, handles all in-game payments making it easy for developers to focus on gameplay while LNbits takes care of everything from microtransactions to automated splits for developers and designers. In this article, we’ll dive deep into how Chain Duel leverages LNbits to streamline in-game payments and how other developers can take advantage of this powerful toolset to build the future of Lightning-powered gaming.
Let’s explore how LNbits transforms payment processing and why it’s quickly becoming a must-have for game developers working in the Bitcoin space.
Overview of Chain Duel
Chain Duel is a unique Lightning Network-inspired game that reimagines the classic snake game with a competitive twist, integrating real-time payments. Two players face off in real-time, racing to "catch" blocks and extend their chains. Each block added to the chain represents Proof of Work, and the player with the most Proof of Work wins the duel. The stakes are high, as the game represents satoshis (small units of Bitcoin) as points, with the winner taking home the prize.
The game is designed to be Lightning-native, meaning all payments within Chain Duel are processed through the Lightning Network. This ensures fast payments, reducing latency and making gameplay smooth. With additional features like practice mode, tournaments and highscores, Chain Duel creates an engaging and competitive environment for Bitcoin enthusiasts and gamers alike.

One of the standout aspects of Chain Duel is its deeper integration with the Lightning Network even at a design level. For example, actual Bitcoin blocks can appear on screen during matches, offering bonus points when mined in sync with the game. The game’s current version, still in beta, has already drawn attention within the Bitcoin community, gaining momentum at conferences and with a growing user base through its social networks. With its innovative combination of gaming, the Lightning Network, and competitive play, Chain Duel offers a glimpse into the future of Lightning-based gaming.
How LNbits is Used in Chain Duel
Seamless Integration with LNbits
At the core of Chain Duel’s efficient payment processing is LNbits, which handles in-game transactions smoothly and reliably. Chain Duel uses the LNbits LNURL-pay and LNURL-withdraw extensions to manage payments and rewards between players. Before each match, players send satoshis using LNURL-pay, which generates a static QR code or link for making the payment. LNURL-pay allows users to attach a note to the payment, which Chain Duel creatively uses as a way to insert the player name in-game. The simplicity of LNURL-pay ensures that users can quickly and easily initiate games, with fresh invoices being issued for every game. When players win, LNURL-withdraw enables them to seamlessly pull their earnings from the game, providing a quick payout system.
These extensions make it easy for players to send and receive Bitcoin with minimal latency, fully leveraging the power of the Lightning Network for fast and low-cost payments. The flexibility of LNbits’ tools means that game developers don’t need to worry about building custom payment systems from scratch—they can rely on LNbits to handle all financial transactions with precision.
Lightning Tournaments
Chain Duel tournaments leverage LNbits and its LNURL extensions to create a seamless and efficient experience for players. In Chain Duel tournaments, LNbits plays a crucial role in managing the overall economics. LNbits facilitates the generation of LNURL QR codes that participants can scan to register quickly or withdraw their winnings. LNbits allows Chain Duel to automatically handle multiple registrations through LNURL-pay, enabling players to participate in the tournament without additional steps. The Lightning Network's speed ensures that these payments occur in real-time, reducing wait times and allowing for a smoother flow in-game.
Splitting Payments
LNbits further simplifies revenue-sharing within Chain Duel. This feature allows the game to automatically split the satoshis sent by players into different shares for the game’s developer, designer, and host. Each time a payment is made to join a match, LNbits is used to automattically pay each of the contributors, according to pre-defined rules. This automated process ensures that everyone involved in the development and running of the game gets their fair share without manual intervention or complex bookkeeping.
Nostr Integration
Chain Duel also integrates with Nostr, a decentralized protocol for social interactions. Players can join games using "Zaps", small tips or micropayments sent over the Lightning Network within the Nostr ecosystem. Through NIP-57, which enables Nostr clients to request Zap invoices, players can use LNURL-pay enabled Zaps to register in P2P matches, further enhancing the Chain Duel experience. By using Zaps as a way to register in-game, Chain Duel automates the process of fetching players' identity, creating a more competitive and social experience. Zaps are public on the Nostr network, further expanding Chain Duel's games social reach and community engagement.
Game and Payment Synchronization

One of the key reasons Chain Duel developers chose LNbits is its powerful API that connects directly with the game’s logic. LNbits allows the game to synchronize payments with gameplay in real-time, providing a seamless experience where payments are an integrated part of the gaming mechanics.
With LNbits managing both the payment process and the Lightning Network’s complex infrastructure, Chain Duel developers are free to concentrate on enhancing the competitive and Lightning Network-related aspects of the game. This division of tasks is essential for streamlining development while still providing an innovative in-game payment experience that is deeply integrated with the Bitcoin network.
LNbits proves to be an indispensable tool for Chain Duel, enabling smooth in-game transactions, real-time revenue sharing, and seamless integration with Nostr. For developers looking to build Lightning-powered games, LNbits offers a powerful suite of tools that handle everything from micropayments to payment distribution—ensuring that the game's focus remains on fun and competition rather than complex payment systems.
LNBits facilitating Education and Adoption
This system contributes to educating users on the power of the Lightning Network. Since Chain Duel directly involve real satoshis and LNURL for registration and rewards, players actively experience how Lightning can facilitate fast, cheap, and permissionless payments. By incorporating LNbits into Chain Duel, the game serves as an educational tool that introduces users to the benefits of the Lightning Network. Players gain direct experience using Lightning wallets and LNURL, helping them understand how these tools work in real-world scenarios. The near-instant nature of these payments showcases the power of Lightning in a practical context, highlighting its potential beyond just gaming. Players are encouraged to set up wallets, explore the Lightning ecosystem, and eventually become familiar with Bitcoin and Lightning technology. By integrating LNbits, Chain Duel transforms in-game payments into a learning opportunity, making Bitcoin and Lightning more approachable for users worldwide.
Tools for Developers
LNbits is a versatile, open-source platform designed to simplify and enhance Bitcoin Lightning Network wallet management. For developers, particularly those working on Lightning-native games like Chain Duel, LNbits offers an invaluable set of tools that allow for seamless integration of Lightning payments without the need to build complex custom solutions from scratch. LNbits is built on a modular and extensible architecture, enabling developers to easily add or create functionality suited to their project’s needs.
Extensible Architecture for Customization
At the core of LNbits is a simple yet powerful wallet system that developers can access across multiple devices. What makes LNbits stand out is its extensible nature—everything beyond the core functionality is implemented as an extension. This modular approach allows users to customize their LNbits installation by enabling or building extensions to suit specific use cases. This flexibility is perfect for developers who want to add Lightning-based services to their games or apps without modifying the core codebase.
- Extensions for Every Use Case
LNbits comes with a wide array of built-in extensions created by contributors, offering various services that can be plugged into your application. Some popular extensions include: - Faucets: Distribute small amounts of Bitcoin to users for testing or promotional purposes.
- Paylinks: Create shareable links for instant payments.
- Points-of-sale (PoS): Allow users to set up shareable payment terminals.
- Paywalls: Charge users to access content or services.
- Event tickets: Sell tickets for events directly via Lightning payments.
- Games and services: From dice games to jukeboxes, LNbits offers entertaining and functional tools.
These ready-made solutions can be adapted and used in different gaming scenarios, for example in Chain Duel, where LNURL extensions are used for in game payments. The extensibility ensures developers can focus on building engaging gameplay while LNbits handles payment flows.
Developer-Friendly Customization
LNbits isn't just a plug-and-play platform. Developers can extend its functionality even further by creating their own extensions, giving full control over how the wallet system is integrated into their games or apps. The architecture is designed to make it easy for developers to build on top of the platform, adding custom features for specific requirements.
Flexible Funding Source Management
LNbits also offers flexibility in terms of managing funding sources. Developers can easily connect LNbits to various Lightning Network node implementations, enabling seamless transitions between nodes or even different payment systems. This allows developers to switch underlying funding sources with minimal effort, making LNbits adaptable for games that may need to scale quickly or rely on different payment infrastructures over time.
A Lean Core System for Maximum Efficiency
Thanks to its modular architecture, LNbits maintains a lean core system. This reduces complexity and overhead, allowing developers to implement only the features they need. By avoiding bloated software, LNbits ensures faster transactions and less resource consumption, which is crucial in fast-paced environments like Chain Duel where speed and efficiency are paramount.
LNbits is designed with developers in mind, offering a suite of tools and a flexible infrastructure that makes integrating Bitcoin payments easy. Whether you’re developing games, apps, or any service that requires Lightning Network transactions, LNbits is a powerful, open-source solution that can be adapted to fit your project.
Conclusion
Chain Duel stands at the forefront of Lightning-powered gaming, combining the excitement of competitive PvP with the speed and efficiency of the Lightning Network. With LNbits handling all in-game payments, from microtransactions to automated revenue splits, developers can focus entirely on crafting an engaging gaming experience. LNbits’ powerful API and extensions make it easy to manage real-time payments, removing the complexity of building payment infrastructure from scratch.
LNbits isn’t just a payment tool — it’s a flexible, developer-friendly platform that can be adapted to any gaming model. Whether you're developing a fast-paced PvP game like Chain Duel or any project requiring seamless Lightning Network integration, LNbits provides the ideal solution for handling instant payments with minimal overhead.
For developers interested in pushing the boundaries of Lightning-powered gaming, Chain Duel is a great example of how LNbits can enhance your game, letting you focus on the fun while LNbits manages real-time transactions.
Find out more
Curious about how Lightning Network payments can power your next game? Explore the following:
- Learn more about Chain Duel: Chain Duel
- Learn how LNbits can simplify payment handling in your project: LNbits
- Dive into decentralized communication with Nostr: Nostr
- Extensions for Every Use Case
-
 @ ec42c765:328c0600
2025-02-05 23:45:09
@ ec42c765:328c0600
2025-02-05 23:45:09test
test
-
 @ c4f5e7a7:8856cac7
2024-09-27 08:20:16
@ c4f5e7a7:8856cac7
2024-09-27 08:20:16Best viewed on Habla, YakiHonne or Highlighter.
TL;DR
This article explores the links between public, community-driven data sources (such as OpenStreetMap) and private, cryptographically-owned data found on networks such as Nostr.
The following concepts are explored:
- Attestations: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your web-of-trust.
- Proof of Place: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in meatspace with their digital representations in the Nostrverse.
- Check-ins: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time.
The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems.
Open Data in a public commons has a place and should not be thrown out with the Web 2.0 bathwater.
Cognitive Dissonance
Ever since discovering Nostr in August of 2022 I've been grappling with how BTC Map - a project that helps bitcoiners find places to spend sats - should most appropriately use this new protocol.
I am assuming, dear reader, that you are somewhat familiar with Nostr - a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: Nostr is Identity for the Internet and The Power of Nostr by @max and @lyn, respectively. Nostr is so much more than a short-form social media replacement.
The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting - all your silos are indeed broken - however, something fundamental has been bothering me for a while and I think it comes down to data ownership.
For those unfamiliar, BTC Map uses OpenStreetMap (OSM) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) - FOSD if you will, but more commonly referred to as Open Data.
In contrast, Notes and Other Stuff on Nostr (Places in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned.
How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data?
Self-sovereign Identity
Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something - an identity.
All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money.
Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state.
Or, as @nvk said recently: "Don't build your house on someone else's land.".
https://i.nostr.build/xpcCSkDg3uVw0yku.png
While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this.
Nostr is PGP for the masses and will take cryptographic identities mainstream.
Full NOSTARD?
Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons.
We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be.
https://i.nostr.build/s3So2JVAqoY4E1dI.png
There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a Wikifreedia variant of OpenStreetMap.
While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native - there's no need to go Full NOSTARD. H/T to @princeySOV for the original meme.
https://i.nostr.build/ot9jtM5cZtDHNKWc.png
So, how do we appropriately blend cryptographically owned data with the commons?
If a location is owned in meatspace and it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the tragedy of the commons.
The remainder of this article explores how we can:
- Verify ownership of a physical place in the real world;
- Link that ownership to the corresponding digital place in cyberspace.
As a side note, I don't see private key custodianship - or, even worse, permissioned use of Places signed by another identity's key - as any more viable than the rented identities of Web 2.0.
And as we all know, the Second Law of Infodynamics (no citation!) states that:
"The total amount of sensitive information leaked will always increase over time."
This especially holds true if that data is centralised.
Not your keys, not your notes. Not your keys, not your identity.
Places and Web-of-Trust
@Arkinox has been leading the charge on the Places NIP, introducing Nostr notes (kind 37515) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via NIP-73 - External Content IDs (championed by @oscar of @fountain).
However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world.
Ultimately, this problem can only be solved in a decentralised way by using Web-of-Trust - using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop.
This requires users to:
- Verify the owner of a Place in cyberspace is the owner of a place in meatspace.
- Signal this verification to their social graph.
Let's look at the latter idea first with the concept of Attestations ...
Attestations
A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false.
Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too.
However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc).
Here is a recent example from @lyn that would carry more signal if it were an Attestation:
https://i.nostr.build/lZAXOEwvRIghgFY4.png
Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or Data Vending Machines in accordance with:
- Your social graph;
- The type or subject of the content being attested and by whom;
- Your personal preferences.
They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places.
NIP-25 (Reactions) do allow for users to up/downvote notes with optional content (e.g., emojis) and could work for Attestations, but I think we need something less ambiguous and more definitive.
‘This is true’ resonates more strongly than ‘I like this.’.
https://i.nostr.build/s8NIG2kXzUCLcoax.jpg
There are similar concepts in the Web 3 / Web 5 world such as Verified Credentials by tdb. However, Nostr is the Web 3 now and so wen Attestation NIP?
https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg
That said, I have seen @utxo has been exploring ‘smart contracts’ on nostr and Attestations may just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust.
Proof of Place
Attestations handle the signalling of your truth, but what about the initial verification itself?
We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth.
Introducing Proof of Place, an out–of-band process where an oracle (such as BTC Map) would mail - yes physically mail- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace.
One way of doing this would be to mint a 1 sat cashu ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location.
Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places).
In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as @Gigi says in PoW is Essential:
"A failure to understand Proof of Work, is a failure to understand Bitcoin."
In the Nostrverse, Proof of Place helps bridge the digital and physical worlds.
@Gigi also observes in Memes vs The World that:
"In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone."
https://i.nostr.build/dOnpxfI4u7EL2v4e.png
This isn’t true for Nostr.
In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯
Check-ins
Although not a draft NIP yet, @Arkinox has also been exploring the familiar concept of Foursquare-style Check-ins on Nostr (with kind 13811 notes).
For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as OSM elements) if NIP-73 - External Content IDs are used.
Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices.
Bringing Check-ins to Nostr is possible (as @sebastix capably shows here), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am.
Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable.
How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene - I’m sure @blackcoffee and @Ben Arc could hack something together over a weekend!
Check-ins could also be used as a signal for bonafide Place ownership over time.
Summary: Trust Your Bros
So, to recap, we have:
Places: Digital representations of physical locations on Nostr.
Check-ins: Users signalling their presence at a location.
Attestations: Verifiable social proofs used to confirm ownership or the truth of a claim.
You can visualise how these three concepts combine in the diagram below:
https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg
And, as always, top right trumps bottom left! We have:
Level 0 - Trust Me Bro: Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all.
Level 1 - Definitely Maybe Somewhere: This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL.
Level 2 - Trust Your Bros: An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph.
https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg
Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map?
Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ - you decide.
As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities.
Thanks
With thanks to Arkinox, Avi, Ben Gunn, Kieran, Blackcoffee, Sebastix, Tomek, Calle, Short Fiat, Ben Weeks and Bitcoms for helping shape my thoughts and refine content, whether you know it or not!
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ ec42c765:328c0600
2025-02-05 23:43:35
@ ec42c765:328c0600
2025-02-05 23:43:35test
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ ec42c765:328c0600
2025-02-05 23:38:12
@ ec42c765:328c0600
2025-02-05 23:38:12カスタム絵文字とは
任意のオリジナル画像を絵文字のように文中に挿入できる機能です。
また、リアクション(Twitterの いいね のような機能)にもカスタム絵文字を使えます。

カスタム絵文字の対応状況(2025/02/06)

カスタム絵文字を使うためにはカスタム絵文字に対応したクライアントを使う必要があります。
※表は一例です。クライアントは他にもたくさんあります。
使っているクライアントが対応していない場合は、クライアントを変更する、対応するまで待つ、開発者に要望を送る(または自分で実装する)などしましょう。
対応クライアント
ここではnostterを使って説明していきます。
準備
カスタム絵文字を使うための準備です。
- Nostrエクステンション(NIP-07)を導入する
- 使いたいカスタム絵文字をリストに登録する
Nostrエクステンション(NIP-07)を導入する
Nostrエクステンションは使いたいカスタム絵文字を登録する時に必要になります。
また、環境(パソコン、iPhone、androidなど)によって導入方法が違います。
Nostrエクステンションを導入する端末は、実際にNostrを閲覧する端末と違っても構いません(リスト登録はPC、Nostr閲覧はiPhoneなど)。
Nostrエクステンション(NIP-07)の導入方法は以下のページを参照してください。
ログイン拡張機能 (NIP-07)を使ってみよう | Welcome to Nostr! ~ Nostrをはじめよう! ~
少し面倒ですが、これを導入しておくとNostr上の様々な場面で役立つのでより快適になります。
使いたいカスタム絵文字をリストに登録する
以下のサイトで行います。
右上のGet startedからNostrエクステンションでログインしてください。
例として以下のカスタム絵文字を導入してみます。
実際より絵文字が少なく表示されることがありますが、古い状態のデータを取得してしまっているためです。その場合はブラウザの更新ボタンを押してください。

- 右側のOptionsからBookmarkを選択

これでカスタム絵文字を使用するためのリストに登録できます。
カスタム絵文字を使用する
例としてブラウザから使えるクライアント nostter から使用してみます。
nostterにNostrエクステンションでログイン、もしくは秘密鍵を入れてログインしてください。
文章中に使用
- 投稿ボタンを押して投稿ウィンドウを表示
- 顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択
- : 記号に挟まれたアルファベットのショートコードとして挿入される

この状態で投稿するとカスタム絵文字として表示されます。
カスタム絵文字対応クライアントを使っている他ユーザーにもカスタム絵文字として表示されます。
対応していないクライアントの場合、ショートコードのまま表示されます。

ショートコードを直接入力することでカスタム絵文字の候補が表示されるのでそこから選択することもできます。

リアクションに使用
- 任意の投稿の顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択

カスタム絵文字リアクションを送ることができます。

カスタム絵文字を探す
先述したemojitoからカスタム絵文字を探せます。
例えば任意のユーザーのページ emojito ロクヨウ から探したり、 emojito Browse all からnostr全体で最近作成、更新された絵文字を見たりできます。
また、以下のリンクは日本語圏ユーザーが作ったカスタム絵文字を集めたリストです(2025/02/06)
※漏れがあるかもしれません
各絵文字セットにあるOpen in emojitoのリンクからemojitoに飛び、使用リストに追加できます。
以上です。
次:Nostrのカスタム絵文字の作り方
Yakihonneリンク Nostrのカスタム絵文字の作り方
Nostrリンク nostr:naddr1qqxnzdesxuunzv358ycrgveeqgswcsk8v4qck0deepdtluag3a9rh0jh2d0wh0w9g53qg8a9x2xqvqqrqsqqqa28r5psx3
仕様
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 638d2a79:f5645f4e
2025-02-05 23:28:37
@ 638d2a79:f5645f4e
2025-02-05 23:28:37China was ruled by one ruler, but over time, China split into two—South and North—which had a rivalry between them. At this time, Yang Chien was a general in the army of Northern China. He thought that China should be whole once more, so, like any insert age here year old would do, he attacked the king of the South (for peace!). After a bit of fighting, he overpowered Southern China and took control of all of China. This man founded a dynasty—the Sui Dynasty—to rule and to keep China united.
But wait! Rivers made travel difficult between the North and South, so his son created a new river when he became emperor. This canal made it easier to cross the rivers, which greatly improved trade. The people did not like working on this river, and after it was completed, they killed him, making him the second and last emperor of the Sui Dynasty.
Cue the new emperor, Li Yuan, AKA "the smart guy." He wanted to stay alive for a long time, and he saw how unhappy people had just killed the last important ruler. So, he decided to invest in keeping people happy instead. This started the Golden Age of China, also called the Tang Dynasty.
Tags: [[human behavior index]] ,[[history]]
-
 @ ec42c765:328c0600
2025-02-05 23:16:35
@ ec42c765:328c0600
2025-02-05 23:16:35てすと
nostr:nevent1qqst3uqlls4yr9vys4dza2sgjle3ly37trck7jgdmtr23uuz52usjrqqqnjgr
nostr:nevent1qqsdvchy5d27zt3z05rr3q6vvmzgslslxwu0p4dfkvxwhmvxldn9djguvagp2
test
てs
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ dff95033:862fbf40
2025-02-05 23:02:55
@ dff95033:862fbf40
2025-02-05 23:02:55Se você achava que o Brasil já tinha atingido o fundo do poço em termos de gestão fiscal, prepare-se para uma surpresa: o poço tem subsolo. O estudo "Projeções Fiscais e Orçamentárias: O Desafio das Despesas Discricionárias", elaborado pela Consultoria de Orçamento e Fiscalização Financeira (Conof) da Câmara dos Deputados, é um retrato nada animador do futuro das contas públicas brasileiras. E, como todo bom retrato de família, é feio, mas é o que temos.
O Barco Está Afundando, mas o Capitão Continua no Churrasco
O estudo começa com uma premissa básica: o Regime Fiscal Sustentável (RFS), aquela joia rara da Lei Complementar nº 200/2024, está prestes a naufragar. A ideia era simples: limitar o crescimento das despesas primárias para evitar que o país virasse um PIB de mentirinha com uma dívida pública de verdade. Só que, como tudo na República do Brasil, a teoria é linda, mas a prática é uma tragédia.
O problema central é o espaço para despesas discricionárias, ou melhor, a falta dele. Enquanto as despesas obrigatórias (aqueles gastos que o governo não pode cortar, como aposentadorias e salários) continuam crescendo como erva daninha, o espaço para investimentos em áreas como saúde, educação e infraestrutura está diminuindo mais rápido que copo de um certo pinguço. O estudo projeta que, a partir de 2027, o governo vai ter que escolher entre pagar as estravaJanjas da Alvorada ou investir em hospitais — obviamente a estravaJanja.
As Pressões: Quando o Salário Mínimo Vira um Pesadelo
O estudo lista uma série de pressões que estão esmagando o orçamento. A primeira delas é o aumento do salário mínimo, que, pasmem, não é só uma boa notícia para os trabalhadores. Ele impacta diretamente benefícios como o RGPS, o BPC, o seguro-desemprego e o abono salarial. Em 2025, o salário mínimo subiu de R$ 1.509 para R$ 1.518. Parece pouco, mas quando você multiplica isso por milhões de beneficiários, o resultado é um rombo de R$ 32,8 bilhões. É como se o governo tivesse comprado um apartamento na praia e descobrisse que a taxa de condomínio é em dólar.
E não para por aí. O estudo também aponta a necessidade de suplementações orçamentárias para programas como o Auxílio-Gás e o Pé-de-Meia. No caso do Pé-de-Meia, o Tribunal de Contas da União (TCU) já deu o veredito: o governo não pode usar recursos de fundos sem autorização orçamentária. Ou seja, o programa que deveria ajudar estudantes do ensino médio agora é mais um furo no bolso do contribuinte. Parabéns, 3 meses de curso de economia valeram a pena, né, Senhor Ministro da Economia!
Os Alívios: Um Band-Aid num Ferimento de Bala
Claro, nem tudo está perdido. O estudo aponta algumas fontes de alívio, como o aumento do limite de despesa primária do Poder Executivo (R$ 12,4 bilhões) e as economias geradas pelo pacote fiscal Brasil Mais Forte (R$ 10,4 bilhões). Mas vamos ser sinceros: isso é como tentar apagar um incêndio florestal com um copo d'água. O pacote fiscal, aliás, é uma piada pronta. Ele promete economias, mas, na prática, é mais um remendo mal costurado em um sistema que já está caindo aos pedaços.
O estudo ainda menciona que o pacote foi "excessivamente tímido" em relação à desvinculação de despesas. Traduzindo: o governo mexeu onde não doía e ignorou os problemas reais. Enquanto isso, a PEC Alternativa, a qual o estudo menciona, propõe medidas mais robustas como a desindexação de despesas e a limitação de supersalários, continua engatinhando no Congresso. Ou seja, enquanto o Titanic afunda, Brasília está discutindo como as lagostas serão marinadas.
O Futuro: Um Cenário de Terror (Sem Pipoca)
As projeções para o período de 2025 a 2034 são de cortar o coração — ou o bolso, dependendo de quem está lendo. O estudo mostra que, a partir de 2027, o espaço para despesas discricionárias vai encolher tanto que o governo vai ter que escolher entre pagar os funcionários públicos ou manter os hospitais abertos — Olá Correios! Ou, se der bobeira, nenhum dos dois.
O piso de investimentos de 0,6% do PIB, que já é baixo, vai consumir boa parte do pouco espaço que resta. E o pior: o estudo alerta para o risco de um "desligamento" (shutdown) da máquina pública. Sim, aquela coisa que acontece nos EUA quando o Congresso não aprova o orçamento. Só que, no Brasil, o shutdown não vai ser por falta de acordo, mas por falta de dinheiro mesmo. Imagine o caos: escolas fechadas, hospitais sem médicos, e o Congresso ainda tentando aprovar um aumento de salário para os parlamentares.
Dívida pública brasileira, então? Vixe, vai ser uma explosão nuclear. Anota aí: vai entrar pra história.
Conclusão: O Brasil Precisa de um Milagre (ou de um Novo Governo)
O estudo da Conof é um alerta vermelho para o país. Sem medidas estruturais sérias, o Brasil vai continuar navegando em águas turbulentas, com um barco cheio de furos e um capitão que insiste em ignorar o iceberg à frente. A PEC Alternativa é uma luz no fim do túnel, mas, como tudo no Brasil, depende da vontade política de quem está no poder. E, convenhamos, vontade política é algo que anda em falta por aqui.
Enquanto isso, o contribuinte continua pagando a conta de um sistema que parece ter sido projetado para falir. O estudo termina com uma mensagem clara: ou o país faz reformas profundas, ou o futuro será uma sucessão de crises fiscais. E, no ritmo em que as coisas estão indo, o futuro já começou.
Então, se você ainda acredita que o Brasil vai recuperar-se, talvez seja hora de repensar. Ou, pelo menos, garantir que você tem um bom fundo e, em alguns casos, seguro de vida — porque o barco está afundando, e nem todos vão conseguir um lugar no bote.
 E por falar em reformas, minha preferência pessoal vai para a PEC 7/2020, uma proposta que considero mais salubre e alinhada com as necessidades estruturais do país. A PEC 7/2020 traz medidas robustas para conter o crescimento dos gastos públicos, com foco na desvinculação de despesas e na revisão de benefícios fiscais, além de propor uma reforma administrativa que promove maior eficiência e transparência na gestão pública. Se você se preocupa com o futuro fiscal do Brasil e acredita que é possível fazer mais com menos, convido você a conhecer a PEC 7/2020 e entender por que ela pode ser a chave para um orçamento público mais sustentável. Afinal, reformas profundas exigem propostas ousadas — e a PEC 7/2020 é exatamente isso.
E por falar em reformas, minha preferência pessoal vai para a PEC 7/2020, uma proposta que considero mais salubre e alinhada com as necessidades estruturais do país. A PEC 7/2020 traz medidas robustas para conter o crescimento dos gastos públicos, com foco na desvinculação de despesas e na revisão de benefícios fiscais, além de propor uma reforma administrativa que promove maior eficiência e transparência na gestão pública. Se você se preocupa com o futuro fiscal do Brasil e acredita que é possível fazer mais com menos, convido você a conhecer a PEC 7/2020 e entender por que ela pode ser a chave para um orçamento público mais sustentável. Afinal, reformas profundas exigem propostas ousadas — e a PEC 7/2020 é exatamente isso.
REFERÊNCIAS
CÂMARA DOS DEPUTADOS. Consultoria de Orçamento e Fiscalização Financeira. Projeções fiscais e orçamentárias: o desafio das despesas discricionárias. Brasília, 2025. Disponível em: https://www2.camara.leg.br/orcamento-da-uniao/estudos/2025/ET_042025_0204Projeesfiscaiseoramentriasodesafiodasdespesasdiscricionrias.pdf. Acesso em: 05 de fev. 2025
BRAGANÇA, Luiz Orléans e. Reforma e alinhamento tributário: a opção pelo progresso. 2023. Disponível em: https://lpbraganca.com.br/reforma-alinhamento-tributario-opcao-progresso/. Acesso em: 05 de fev. 2025
-
 @ df478568:2a951e67
2025-02-05 22:12:20
@ df478568:2a951e67
2025-02-05 22:12:20In the Case For A 100 Percent Gold Dollar, Murray Rothbard argues, “the debacle of 1931-1933, when the world abandoned the gold standard, was not a sudden shift from gold weight to paper name; it was the last step in a lenghty, complex process.” He said that before WWI, a dollar was defined as aproximately 1/20th of an ounce of gold.” If it worked, a dollar would buy about as much as $143 does today, but it didn't work.
Gold ownership was banned until Executive Order 6102 was lifted in the 1970's. According to Rothbard, France sent a battleship to the United States to repatriate its gold. Then, Nixon took the dollar "temporarily" off the gold standard in 1971. It just so happened I listened to a podcast after I started writing this. Joseph Voelnel tells the story in this podcast.
https://fountain.fm/episode/mXreHZ2um0RnxaHsWMfe
I paid for the transcript using bitcoin on the lightning network using a podcasting 2.0 app named Fountain. Try it out. You can earn small amount of bitcoin just for listening. It is not self-custodial, but it's a great way to get started if you're curious. If you're not curious, you probably won't like bitcoin.
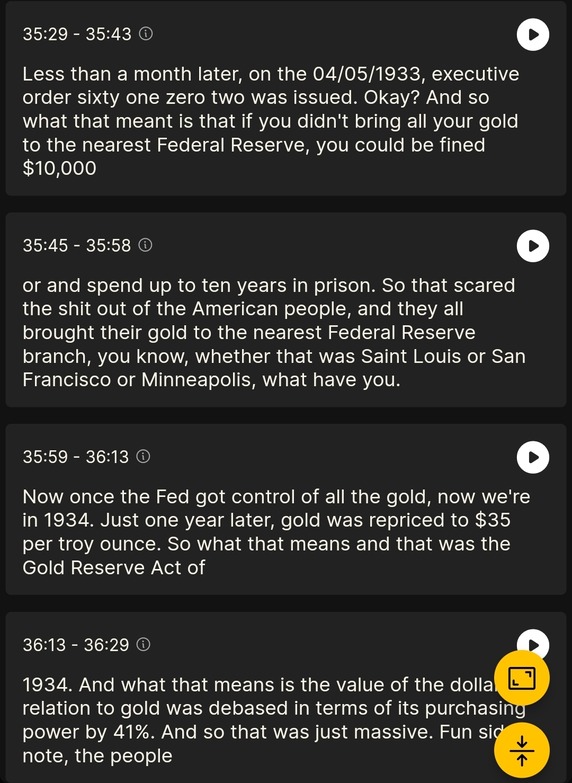
The US government debased gold and made it 41% after issuing Executive Order 6102. Nixon took the dollar completely off the gold standard in 1971. The dollar is still a fiat currency, backed by nothing but "good faith and credit of the United States." That's basically nothing. You might as well say the US dollar is backed by good vibes. Do you think the US can pay 36 trillion bucks back with good vibes?
I do not.
Gold will not fix this.
If the US went back to the gold standard, we would need to trust the good vibes of Fort Knox, but anyone in their right mind would not trust these good vibes.
"The root problem with conventional currency is all the trust that's required to make it work. The central bank must be trusted not to debase the currency, but the history of fiat currencies is full of breaches of that trust."
Satoshi Nakamoto, P2P Foundation thread.
Even if we self-custody gold again, metal does not prevent debasement. Here's one of my favorite quotes from Adam Smith's Wealth of Nations:
"There was a third event which occurred in the course of the same period, and which, though it could not occasion any scarcity of corn, nor, perhaps, in the real quantity of silver which was usually paid for it, must necessarily have occasioned some augmentation in the nominal sum. This event was the great debasement of the silver coin, by clipping and wearing. This evil had begun in the reign of Charles II. and had gone on continually increasing till 1695; at which time, as we may learn from Mr Lowndes, the current silver coin was, at an average, near five-and-twenty percent. Below its standard value."
Monetary debasement is not a new phenomenon. The double-spending problem has been around for hundreds of years. In my opinion, bitcoin is the best shot humankind has of solving the double spending problem.
"A purely peer-to-peer version of electronic cash would allow online payments to be sent directly from one party to another without going through a financial institution. Digital signatures provide part of the solution, but the main benefits are lost if a trusted third party is still required to prevent double-spending."
Satoshi Nakamoto, Bitcoin: A Peer-To-Peer Electronic Cash System
To steel-man the case against bitcoin, I would say the biggest issue is how many people prefer to use a trusted third party to custody their bitcoin. That’s why education is important. In principle, I think we should keep 100% custody of our bitcoin. In practice, I do keep some of my sats in a custodial wallet to pay bills. I working on this, but I need to open up a fatter lightning channel and set up auto-payments to my Strike wallet. That’s my goal, but I need to I want to make sure I don’t rug myself first so I am testing it out with smaller amounts first. It is possible, it just takes time to learn how to do it safely.
I still think bitcoin is our best shot against centuries of monetary debasement.
npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 8d5ba92c:c6c3ecd5
2025-02-05 22:06:18
@ 8d5ba92c:c6c3ecd5
2025-02-05 22:06:18There I was, minding my own business at the airport (i.e., arranging the list of Bitcoin/Freedom podcasts for the next seven hours of flight), when I came across a scene that could have been ripped straight from a show about the decline of civilization. Heart-wrenching. Shocking. Dystopian. To put it simply, what the f*ck?!
Prologue.
A family of five, including two early-school kids (let’s call them 'Timmy' and 'Amy', around 5 and 7 years old), a father who looked like he’d given up on life, and a perfect mother multitasking like a pro—breastfeeding a baby while chowing down on a Big Mac.
Oh yeah, the whole family was happily consuming their McDonald’s junk as if it was their daily ritual. Watching little kids eat that stuff? A mix of anger and sadness. But seeing a breastfeeding mother give her newborn absolute garbage? The scene I can’t forget.
She also washed it all down with some fizzy, sugary, chemical-laden sludge later on. Still, while breastfeeding. Because, you know, nothing screams nourishment like a steady diet of artificial stuff. Best to get them hooked in the first few months, right?
Act One: The Mother’s Masterpiece.
A modern-day Madonna, cradling her infant while balancing junk food’s finest. The baby, blissfully unaware of the nutritional betrayal unfolding in real-time, probably wasn’t even dreaming of normal food that might one day help it grow into a healthy being.
Seeing this scene, knowing all the options available at the airport—many much more reasonable than this crap—and watching the family enjoy their 'sacred food', I’m almost certain this little one had been getting a side of heavily processed rubbish long before it even left the womb...
Rave: A standing ovation for conscious parenting.
Act Two: Innocent Contribution.
Just when I thought the scene couldn’t get worse, little “Timmy” decided to play bartender. With the enthusiasm of a child clearly raised on a steady diet of Big Macs and Coca-Cola (or whatever other delicacies were on offer), he extended his cup to his tiny brother or sister. The devoted mother, of course, helped him guide the straw to the baby’s mouth. “Drink, little one! Drink not just from my body, but directly from the cup. Drink this (crap) with us!”
Why not? If McDonald’s was good enough for everyone in the family, surely it was good enough for the baby sibling, right?
They all looked almost proud of Timmy’s little “sharing is caring” moment. Meanwhile, my heart shattered into a million pieces, each one screaming, “Seriously?! Should I interfere? How would they react?”
I was close enough to keep taking photos, staring at them with my mouth probably hanging open, horror written all over my face. The mother met my gaze once—cold, unreadable. No 'leave us alone.' No 'it’s our business.' No 'what's wrong, tell us.' Just... nothing.
My husband, noticing my growing frustration and sensing I was about to step in, whispered, “Let it go. You won’t save them in 10 minutes at the airport.”
Maybe he was right. But I’ll be thinking about it for a long time…
Act Three: A Recipe for Regret.
It was as if the parents had collectively agreed that their bodies were nothing more than human garbage bins, and their children were just smaller versions of the same.
Let’s be clear: adults can do whatever they want with their health. If you want to treat your body like a landfill, go ahead—it’s your funeral (literally). But when you drag your kids into it, it’s no longer a personal choice. It’s more like a crime. These children didn’t sign up for a life of artificial flavors, empty calories, and a future riddled with health problems. They deserve better.
And if you’re reading this thinking, ‘What’s the big deal?’—let's talk.
My brain is on the verge of exploding, trying to understand how anyone could actively contribute to the slow, painful destruction of the people they (presumably) love. You should love and respect your own body, and even more so the lives of your kids. What could possibly justify feeding your family McDonald's if it’s not the very last option you have on earth to survive? Please, help me understand why!
Epilogue: The Aftertaste.
As I stepped into the boarding line, I couldn’t shake the thought: Is this really where we are now? A world where care and nutritional awareness no longer exist. Where junk food became a family tradition. Where children are raised on a cocktail of chemicals when better options are right there!
To the McDonald’s family at the airport—and anyone on their way to becoming one: Not sure if you enjoyed your meal. If you did, I wish you luck. You’ll need it.
https://i.nostr.build/e8f3h9iuDNQbtmaF.png
And please, maybe—just maybe—consider giving your kids a chance. They deserve more than a trash life packed with chemicals in a paper bag.
BTC Your Mind. Let it ₿eat.
Şelale
-
 @ ec42c765:328c0600
2025-02-05 22:05:55
@ ec42c765:328c0600
2025-02-05 22:05:55カスタム絵文字とは
任意のオリジナル画像を絵文字のように文中に挿入できる機能です。
また、リアクション(Twitterの いいね のような機能)にもカスタム絵文字を使えます。

カスタム絵文字の対応状況(2025/02/06)

カスタム絵文字を使うためにはカスタム絵文字に対応したクライアントを使う必要があります。
※表は一例です。クライアントは他にもたくさんあります。
使っているクライアントが対応していない場合は、クライアントを変更する、対応するまで待つ、開発者に要望を送る(または自分で実装する)などしましょう。
対応クライアント
ここではnostterを使って説明していきます。
準備
カスタム絵文字を使うための準備です。
- Nostrエクステンション(NIP-07)を導入する
- 使いたいカスタム絵文字をリストに登録する
Nostrエクステンション(NIP-07)を導入する
Nostrエクステンションは使いたいカスタム絵文字を登録する時に必要になります。
また、環境(パソコン、iPhone、androidなど)によって導入方法が違います。
Nostrエクステンションを導入する端末は、実際にNostrを閲覧する端末と違っても構いません(リスト登録はPC、Nostr閲覧はiPhoneなど)。
Nostrエクステンション(NIP-07)の導入方法は以下のページを参照してください。
ログイン拡張機能 (NIP-07)を使ってみよう | Welcome to Nostr! ~ Nostrをはじめよう! ~
少し面倒ですが、これを導入しておくとNostr上の様々な場面で役立つのでより快適になります。
使いたいカスタム絵文字をリストに登録する
以下のサイトで行います。
右上のGet startedからNostrエクステンションでログインしてください。
例として以下のカスタム絵文字を導入してみます。
実際より絵文字が少なく表示されることがありますが、古い状態のデータを取得してしまっているためです。その場合はブラウザの更新ボタンを押してください。

- 右側のOptionsからBookmarkを選択

これでカスタム絵文字を使用するためのリストに登録できます。
カスタム絵文字を使用する
例としてブラウザから使えるクライアント nostter から使用してみます。
nostterにNostrエクステンションでログイン、もしくは秘密鍵を入れてログインしてください。
文章中に使用
- 投稿ボタンを押して投稿ウィンドウを表示
- 顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択
- : 記号に挟まれたアルファベットのショートコードとして挿入される

この状態で投稿するとカスタム絵文字として表示されます。
カスタム絵文字対応クライアントを使っている他ユーザーにもカスタム絵文字として表示されます。
対応していないクライアントの場合、ショートコードのまま表示されます。

ショートコードを直接入力することでカスタム絵文字の候補が表示されるのでそこから選択することもできます。

リアクションに使用
- 任意の投稿の顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択

カスタム絵文字リアクションを送ることができます。

カスタム絵文字を探す
先述したemojitoからカスタム絵文字を探せます。
例えば任意のユーザーのページ emojito ロクヨウ から探したり、 emojito Browse all からnostr全体で最近作成、更新された絵文字を見たりできます。
また、以下のリンクは日本語圏ユーザーが作ったカスタム絵文字を集めたリストです(2025/02/06)
※漏れがあるかもしれません
各絵文字セットにあるOpen in emojitoのリンクからemojitoに飛び、使用リストに追加できます。
以上です。
次:Nostrのカスタム絵文字の作り方
Yakihonneリンク Nostrのカスタム絵文字の作り方
Nostrリンク nostr:naddr1qqxnzdesxuunzv358ycrgveeqgswcsk8v4qck0deepdtluag3a9rh0jh2d0wh0w9g53qg8a9x2xqvqqrqsqqqa28r5psx3
仕様
-
 @ 21ffd29c:518a8ff5
2025-02-05 21:42:14
@ 21ffd29c:518a8ff5
2025-02-05 21:42:14The concept of "Sovereigns: The Power of Your Thoughts - Navigating the Journey from Awareness to Creation" can be beautifully integrated with the empowering strength of strong masculine energy. This synergy combines personal empowerment with a sense of assertiveness and confidence, guiding individuals toward their desired reality.
-
Understanding Sovereignty: Sovereignty in this context refers to the ability to shape one's life and reality through thought. It emphasizes personal control over external circumstances by influencing inner beliefs and perceptions.
-
Strong Masculine Energy: This energy is characterized by assertiveness, confidence, power, and a sense of leadership. It aligns with traits like courage, determination, and self-assurance. In the context of empowerment, it encourages individuals to take charge of their lives with strength and clarity.
-
Integration of Concepts:
- Personify sovereignty as a strong, authoritative figure who guides personal growth by helping others master their thoughts and create their reality.
-
Emphasize the role of masculine energy in cultivating assertiveness, confidence, and leadership qualities that empower individuals to align their thoughts with their desires.
-
Practical Steps:
- Mindfulness: Practice observing thoughts and actions with clarity and calmness, fostering a state of present awareness.
- Affirmations: Use positive statements to reinforce self-confidence and shift belief systems towards empowerment.
- Visualization: Imagine desired outcomes and focus on actionable steps to achieve them, embodying the courage and determination associated with masculine energy.
-
Seeking Guidance: Engage mentors or coaches who can provide support and clarity, reinforcing leadership qualities and assertiveness.
-
Benefits:
- Empowerment: Gain control over your life's direction and outcomes through mindful thought manipulation.
- Clarity & Focus: Achieve a clear vision of goals and paths towards them with confidence and determination.
- Confidence & Success: Build self-assurance from aligning actions with inner strength and assertiveness.
-
Fulfillment & Peace: Experience inner satisfaction from creating a life that resonates with personal values and energy.
-
Addressing Concerns:
- Clarify that while beliefs influence perception, true transformation requires consistent effort and awareness of one's inner strength.
-
Emphasize that thoughts can shape reality positively when aligned with assertiveness and confidence.
-
Conclusion: Empower yourself today to shape an extraordinary future by understanding the power of your thoughts as a tool for personal growth. Cultivate strong masculine energy through mindfulness, affirmations, visualization, and leadership qualities, guiding yourself toward a life aligned with your inner strength and determination.
By merging the concepts of sovereignty and strong masculine energy, we create a powerful framework that not only empowers individuals but also encourages them to lead lives that reflect their inner confidence and assertiveness.
-
-
 @ d4457110:c7dec82b
2025-02-05 21:38:01
@ d4457110:c7dec82b
2025-02-05 21:38:01
¡Puede construir un dispositivo de firma de transacciones de Bitcoin con espacio de aire (AirGap) fuera de línea a partir de componentes comunes faciles de enconrar listos para usar!
¿Que es SeedSigner?
En simples palabras SeedSiner es un dispositivo de firma bitcoin
Cree su propio Seedsigner y firme transacciones en Bitcoin sin comprometer la seguridad y privacidad.
La mayoría de personas en Bitcoin respetan y valoran lo que puede hacer este aparato, pues suele verse como una navaja suiza para administrar nuestros Bitcoins y no es para menos, Veamos que puede hacer.
¿Que hace SeedSigner?
Los usuarios de Bitcoin generalmente construyen y usan un SeedSigner por las mismas razones que construyen y usan un nodo completo mayor privacidad, menos confianza, mayor seguridad
- Calcula la palabra 12/24 de una frase semilla BIP39
- Crea una frase semilla BIP39 usando tiradas de dados D6
- Crea una frase semilla BIP39 con entropía a partir de una foto digital
- Interfaz guiada para crear manualmente un SeedQR para almacenamiento/entrada (video)
- Compatibilidad con frase de contraseña/palabra 13/25 BIP39
- Generación nativa Segwit Multisig XPUB con pantalla QR
- Escanea y analiza datos de transacciones de códigos QR animados
- Firme transacciones y transfiera datos XPUB usando códigos QR animados (video)
- Configura los ajustes de usuario con persistencia (opcional)
- Soporte para Bitcoin Mainnet, Testnet y Regtest
- Derivar frases semilla BIP85 secundarias indexadas
Tres usos imprtantes
- Crea claves privadas seguras de forma minimizada
- Genere claves públicas extendidas utilizadas durante la configuración inicial de la billetera
- Firme transacciones de forma segura a través de conjuntos de códigos QR animados
Ventajas
- La operación en aislamiento (sin USB/WiFi/Bluetooth) reduce drásticamente los vectores de ataque
- El bajo costo de construcción hace que el dispositivo sea accesible para más personas en más partes del mundo
- La apatridia hace factible el uso de SeedSigner con múltiples semillas y/o múltiples billeteras
- La arquitectura de software completamente FOSS subyacente hace posible la creación independiente desde el origen
- El uso de hardware no específico de bitcoin puede mejorar en gran medida la privacidad del usuario
¿Que necesitas?
- Una computadora
- Raspberry Pi Zero, versión 1.3 (recomendable pero agotada en las tiendas) SeedSigner es compatible con los modelos alternativos W/WH/2W y Raspberry Pi 2/3/4 vea la disponibilidad de Raspberrys en stock en rpilocator.com, si ha elegido alguna de estas opciones alternativas es importante deshabilitar Wifi/Bluetooth por hardware mi recomendación seria ir por la Raspberry Pi Zero 2 WH con Headers, solo tomara unos minutos hacerlo. Proceso en video
- Pantalla/controles Waveshare de 1,3” 240x240 links de compra Wavesshare, Amazon, AliExpress
- Cámara compatible con Raspberry Pi (con un cable compatible con Zero) links de compra AliExpress 1 - 2 - 3 - 4
- MicroSD (minimo 4GB) con adaptador SD para conectar a la computadora y grabar la imagen, link de compra Amazon
- Powerbank con cable MicroUSB o cargador de RaspberryPi, es importante resaltar que si decide usar una powerbank asegurese que esta tenga un modo de bajo consumo
- Impresora 3D (opcional) si no dispone de una compre un case para su SeedSigner 1 - 2 - 3 - 4 - 5 - 6 - 7
Quiero saltarme todo el proceso de armado y de comprar materiales, quiero un SeedSigner ya!
Empecemos

- Descargar la imagen correspondiente al hardare de Raspberry Pi
- Grabar la imagen en la microSD use Rufus para windows y BalenaEtcher para MacOS
- Ensamblado
- Conectar la placa con los pines GPIO (omitir esta parte si estos ya vienen soldados)
- Encajar los pines GPIO con la pantalla Waveshare
- Inserte la SD
- Poner en un case. Hay varios diseños que puede descargar para imprimir
- Open Pill
- Orange Pill
- Simple Pill
- Lill Pill
- OrangeSurf Case
- PS4 Seedsigner
- OpenPill Faceplate
- Waveshare Coverplate
- Guarde sus semillas y SeedQR (plantillas, preferiblemente metal)
Si tiene dudas preguntas o aportes vaya a su Github, Telegram
Referencias
Sitios con las que me apoye para hacer este proyecto
Puede seguir estas guias de instrucciones con mucho mas detalle
-
 @ a367f9eb:0633efea
2025-02-05 20:41:31
@ a367f9eb:0633efea
2025-02-05 20:41:31When a consumer has an account at their bank or another financial service closed on them, it’s a maddening experience.
These notices usually appear seemingly out of the blue, giving the customer just a few weeks to empty their funds from the account to move them elsewhere.
Sometimes, it’s because of fraudulent activity or suspicious transactions. It may also be because of a higher risk profile for customer, including those who often pay their bills late or let their account go negative too many times.
These customers will necessarily be categorized as much riskier to the bank’s operations and more liable to have their accounts closed.
But what if accounts are shut down not because of any true financial risk, but because the banks believe their customers are a regulatory risk?
Perhaps you buy and sell cryptocurrencies, partake in sports betting, or own and operate a cannabis dispensary in a state where it’s legal? While each of these categories of financial transactions are not suspicious nor illegal in themselves, they increase the scrutiny that regulators will place on banks that take on such customers.
While any reasonable standard of risk management applied to banking will discriminate against accounts that rack up fees or clearly participate in fraud, the notion of inherent risk due to regulatory punishment doled out to banks is a separate and concerning issue.
As Cato Institute Policy Analyst Nick Anthony rightly sketches out, this creates a dichotomy between what he deems “operational” debanking and “governmental” debanking, where the former is based on actual risk of default or fraud while the latter is due only to regulatory risk from government institutions and regulators.
The Bank Secrecy Act and Weaponization
The law that creates these mandates and imposes additional liabilities on banks is called the Bank Secrecy Act, originally signed into law in 1970.
Though banking regulation has existed in some form throughout the 19th and 20th centuries, the BSA imposed new obligations on financial institutions, mandating Know Your Customer and Anti-Money Laundering programs to fully identify bank customers and surveil their transactions to detect any potentially illegal behavior.
Without any requirements for warrants or judicial orders, banks are forced to report the “suspicious” transactions of their customers directly to the Financial Crimes Enforcement Network (FinCEN), what is called a “Suspicious Activity Report”. The grounds for filing this could be anything from the name of the recipient, whether the amount is over $10,000, or perhaps even any note or description in the bank transfer that may allude to some criminal activity. If the banks do not file this pre-emptively, they could be on the hook for massive penalties from regulators.
As the House Weaponization Subcommittee revealed in one of its final reports, the Bank Secrecy Act and SARs were ramped up specifically to target political conservatives, MAGA supporters, and gun owners.
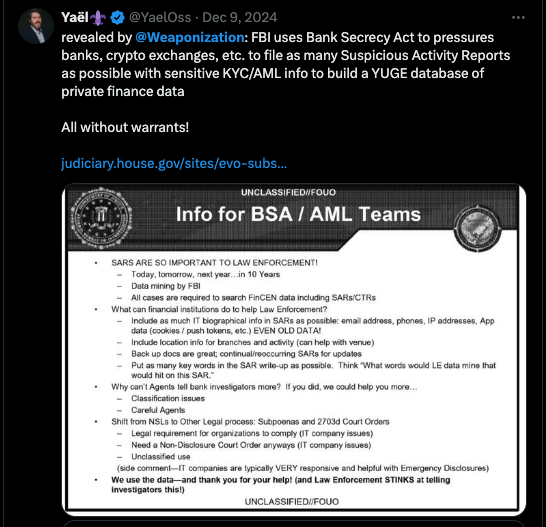
The consequences of the BSA and its imposed surveillance have reaped unintended havoc on millions of ordinary Americans. This is especially true for those who have undergone “debanking”.
Many Bitcoin and cryptocurrency entrepreneurs, for example, have been debanked on the sole grounds of being involved in the virtual currency industry, while millions of others have been swept up in the dragnet of the BSA and financial regulators forcibly deputizing banks to cut off customers, often without explanation.
According to FinCEN guidance, financial institutions are compelled to keep suspicious activity reports confidential, even from customers, or face criminal penalties. This just makes the problems worse.
Further reading
The excellent research by the team at the Cato Institute’s Center for Monetary and Financial Alternatives provides reams of data on these points. As put by Cato’s Norbert Michel, “People get wrapped up in BSA surveillance for simply spending their own money”.
My colleagues and I have written extensively about why we need reforms to undue the financial surveillance regime that only accelerates debanking of Americans. It’s even worse for those who are interested in the innovative world of Bitcoin and its crypto-offspring as I explain here.
It’s one reason why the Consumer Choice Center supports the Saving Privacy Act introduced by Sens. Mike Lee and Rick Scott, which would vastly reform the Bank Secrecy Act to remove the pernicious and faulty Suspicious Activity Report system.
As the Senate Banking Committee holds a hearing on debanking in February 2025, we hope they will zero-in on the issue of excessive financial surveillance required by financial regulators and the harmful and likely unconstitutional impact of the Bank Secrecy Act. With renewed interest and motivation, American leaders can reform these rules to ensure that our financial privacy and freedom to transact are restored and upheld.
-
 @ ec42c765:328c0600
2025-02-05 20:30:46
@ ec42c765:328c0600
2025-02-05 20:30:46カスタム絵文字とは
任意のオリジナル画像を絵文字のように文中に挿入できる機能です。
また、リアクション(Twitterの いいね のような機能)にもカスタム絵文字を使えます。

カスタム絵文字の対応状況(2024/02/05)

カスタム絵文字を使うためにはカスタム絵文字に対応したクライアントを使う必要があります。
※表は一例です。クライアントは他にもたくさんあります。
使っているクライアントが対応していない場合は、クライアントを変更する、対応するまで待つ、開発者に要望を送る(または自分で実装する)などしましょう。
対応クライアント
ここではnostterを使って説明していきます。
準備
カスタム絵文字を使うための準備です。
- Nostrエクステンション(NIP-07)を導入する
- 使いたいカスタム絵文字をリストに登録する
Nostrエクステンション(NIP-07)を導入する
Nostrエクステンションは使いたいカスタム絵文字を登録する時に必要になります。
また、環境(パソコン、iPhone、androidなど)によって導入方法が違います。
Nostrエクステンションを導入する端末は、実際にNostrを閲覧する端末と違っても構いません(リスト登録はPC、Nostr閲覧はiPhoneなど)。
Nostrエクステンション(NIP-07)の導入方法は以下のページを参照してください。
ログイン拡張機能 (NIP-07)を使ってみよう | Welcome to Nostr! ~ Nostrをはじめよう! ~
少し面倒ですが、これを導入しておくとNostr上の様々な場面で役立つのでより快適になります。
使いたいカスタム絵文字をリストに登録する
以下のサイトで行います。
右上のGet startedからNostrエクステンションでログインしてください。
例として以下のカスタム絵文字を導入してみます。
実際より絵文字が少なく表示されることがありますが、古い状態のデータを取得してしまっているためです。その場合はブラウザの更新ボタンを押してください。

- 右側のOptionsからBookmarkを選択

これでカスタム絵文字を使用するためのリストに登録できます。
カスタム絵文字を使用する
例としてブラウザから使えるクライアント nostter から使用してみます。
nostterにNostrエクステンションでログイン、もしくは秘密鍵を入れてログインしてください。
文章中に使用
- 投稿ボタンを押して投稿ウィンドウを表示
- 顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択
- : 記号に挟まれたアルファベットのショートコードとして挿入される

この状態で投稿するとカスタム絵文字として表示されます。
カスタム絵文字対応クライアントを使っている他ユーザーにもカスタム絵文字として表示されます。
対応していないクライアントの場合、ショートコードのまま表示されます。

ショートコードを直接入力することでカスタム絵文字の候補が表示されるのでそこから選択することもできます。

リアクションに使用
- 任意の投稿の顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択

カスタム絵文字リアクションを送ることができます。

カスタム絵文字を探す
先述したemojitoからカスタム絵文字を探せます。
例えば任意のユーザーのページ emojito ロクヨウ から探したり、 emojito Browse all からnostr全体で最近作成、更新された絵文字を見たりできます。
また、以下のリンクは日本語圏ユーザーが作ったカスタム絵文字を集めたリストです(2024/06/30)
※漏れがあるかもしれません
各絵文字セットにあるOpen in emojitoのリンクからemojitoに飛び、使用リストに追加できます。
以上です。
次:Nostrのカスタム絵文字の作り方
Yakihonneリンク Nostrのカスタム絵文字の作り方
Nostrリンク nostr:naddr1qqxnzdesxuunzv358ycrgveeqgswcsk8v4qck0deepdtluag3a9rh0jh2d0wh0w9g53qg8a9x2xqvqqrqsqqqa28r5psx3
仕様
-
 @ eee391ee:8d0b97c2
2025-02-05 19:37:29
@ eee391ee:8d0b97c2
2025-02-05 19:37:29Amber 3.2.1
- Add some details when signing a contact list
- Refactor check for logged in account
- After granting notification permissions show the notification
Download it with zap.store, Obtainium, f-droid or download it directly in the releases page
If you like my work consider making a donation
Verifying the release
In order to verify the release, you'll need to have
gpgorgpg2installed on your system. Once you've obtained a copy (and hopefully verified that as well), you'll first need to import the keys that have signed this release if you haven't done so already:bash gpg --keyserver hkps://keys.openpgp.org --recv-keys 44F0AAEB77F373747E3D5444885822EED3A26A6DOnce you have his PGP key you can verify the release (assuming
manifest-v3.2.1.txtandmanifest-v3.2.1.txt.sigare in the current directory) with:bash gpg --verify manifest-v3.2.1.txt.sig manifest-v3.2.1.txtYou should see the following if the verification was successful:
bash gpg: Signature made Fri 13 Sep 2024 08:06:52 AM -03 gpg: using RSA key 44F0AAEB77F373747E3D5444885822EED3A26A6D gpg: Good signature from "greenart7c3 <greenart7c3@proton.me>"That will verify the signature on the main manifest page which ensures integrity and authenticity of the binaries you've downloaded locally. Next, depending on your operating system you should then re-calculate the sha256 sum of the binary, and compare that with the following hashes:
bash cat manifest-v3.2.1.txtOne can use the
shasum -a 256 <file name here>tool in order to re-compute thesha256hash of the target binary for your operating system. The produced hash should be compared with the hashes listed above and they should match exactly. -
 @ ed60dae0:cc3d5108
2025-02-05 19:22:31
@ ed60dae0:cc3d5108
2025-02-05 19:22:31I'm a student. I study Bitcoin and markets. I am not a financial advisor, hold no licenses or registrations, and am not qualified to give advice on anything. Talk to your financial advisor. Do your own research.
I get things wrong. If I ever list predictions about the future, note that I will likely get them (partially) wrong.
I often own positions in the names I discuss in my posts. None of this is ever a solicitation to buy or sell securities. It is simply a look into my personal opinions and portfolio. These positions may change immediately after I publish a piece, with or without notice. You are on your own. Do not make decisions based on my posts.
Use of The First Bastion
Use of The First Bastion (TFB) is at your own risk. In no event shall TFB or any affiliated party be liable for any direct or indirect trading losses caused by any information posted by TFB.
You agree to conduct your own research and due diligence and consult your own financial, legal, and tax advisors before making any investment decision regarding securities mentioned herein. As of the publication date of any content by TFB, you should assume that TFB (possibly along with members, partners, affiliates, employees, and/or consultants) and our clients and/or investors hold positions, long or short, in all stocks and assets (and/or options of the stocks or assets) covered. We may stand to realize significant gains if the price of any stock or asset covered herein moves in our favor. Following the publication of any material on this site or other TFB social media platforms, I may continue transacting in the securities discussed and may be long, short, or neutral at any time thereafter, regardless of prior recommendations, conclusions, or opinions.
This is not an offer to sell or a solicitation to buy any security, nor shall any security be offered or sold in any jurisdiction where such an offer would be unlawful under the securities laws of that jurisdiction.
To the best of my ability and belief, all information contained herein is accurate and reliable, obtained from public sources I believe to be accurate and reliable, and not from insiders or individuals connected to the stock or asset discussed who may owe fiduciary or confidentiality obligations. However, all information is presented "as is," without any warranty—express or implied. TFB makes no representation regarding the accuracy, timeliness, or completeness of any information provided or the results that may be obtained from its use. All expressions of opinion are subject to change without notice, and TFB does not undertake to update or supplement this site, my social media, or any of the information contained herein.
-
 @ fa7153ef:1de1cf78
2025-02-05 18:05:42
@ fa7153ef:1de1cf78
2025-02-05 18:05:42"Things usually don't pan out the way you want them to."
It's not really a quote, probably someone said it at some point, but I just wanted to have it at the beginning. My thought process while sitting here is going as - I haven''t written anything for close to 6 months, I need to refer to that fact, and say something about it. I know, things don't usually work out, and wanting to write once a week turned to be no writing for 6 months. Tough luck
I don't really have a good explanation for this. Last post was from end of August 2024. I wouldn't say a lot of things happened in the meantime (especially not a lot that would make me not have time to sit down and write something). People always ask "How have you been?", "Anything happened to you lately?", and my answer is usually - "Nothing special", "Nothing new", "Same old".. (that's probably why I'm not good in conversations with people). But a lot of things have happened, it's just that I feel none of my stories would be interesting to people, or things I find fascinating would just bore everyone. So I usually keep quiet. This is strange, really, since a lot of things that people talk to me about, I don't really care for. But those are their interests, and what are friends for, than to listen to each other? I may be wrong with this one, since writing these words was hard - and I don't really believe in them. It requires some additional thought.
I've always considered myself to be good at spotting when people are uncomfortable, or bored with something (or someone) - like George form Seinfeld. It's likely that I've caught on to people being that way in my presence, so I stopped sharing a lot. Who the heck knows, it's hard being your own psychiatrist, so I won't be one. I'm here to write things.
Since we're on the topic of what happened in the past 6 months, I'd really need to think about everything, and even though you're reading this quickly, a lot of pause has been made when composing this list (I'm going at it one by one, and really trying to remember): - I met with my old university friends - haven't seen them in 3 years - visited my sister in another country, and hung out with my little nephew - had a PR in my squats (50kg) - it's a topic for a different day, but it's a big thing for me, I'm very proud of it. - I'm working on my spiritual side - trying to get closer to God by reading scripture, praying, and listening to various sermons (which is also a good topic - to share my experiences here) - I'm following semen retention, it's been a whole year recently. Being single helps, but I won't go into details of it now - I bought a small 25-key keyboard, and I'm learning playing on it (trying to transfer as much as I can from the guitar experience) - I feel like anxiety, and fears which have been overwhelming my whole life, have died down a bit. I can still feel them, and when days are bad, so are they, but there have been a lot of good days. Causes for this are numerous, but again, a topic for another time - I've kept my job - I've started buying Bitcoin again - I was so "down and out" that even the thought of re-activating my accounts on exchanges was a no-go, but somehow I managed to do it, and am becoming increasingly richer in sats, on a daily basis - I've been going out more - hanging out with people, and socializing - I'm noticing a substantial increase of this kind of behaviour. I'm not really meeting new people, mostly stick to the ones I already know (which is not a lot) - I've visited my lifelong friend in another country again, and have a feeling we've rekindled the friendship. It's been a rough time for both of us, and even though we met here and there, at times it felt to be more of a chore. Now, I feel things have changed a bit, and I like it. - I'm still living with my parents. I don't hate it, it's just something I do. There are strange comments, and I guess people find it curious, but it is what it is. - I have a much better relation with my father. We've always had an OK relation. He's also a reserved person - I'm not sure of the term and google isn't helping. Likes to keep to himself mostly. We've found some common topics to discuss, and I've been enjoying it. He seems to like it as well. It mostly revolves around football, and watching games together. - even though I've been sick for the past couple of weeks, my health in general is good. I'm not totally happy with the situation I'm in, but it's still miles ahead of what it has been just a year or two ago - Some plans have been popping up in my head - after a long time, I have some things I'd like to do. It usually takes a long time to actually do them, but even the thought of wanting something new and different is refreshing, and I'll take it.
I don't know.. There probably are a lot of other things - I mean, there certainly are more private thoughts I've been thinking about - love, romance, romantic partners, God, inner peace, lust, fears, music, family, future.. But I'm not willing to share those yet.
I've finished the Bible last year - by doing daily readings of 10-15 minutes via an app. I've restarted it this year, and going through it again.
Also, I'M noticing that a lot of these sentences start with "I've done this", "I've done that", "I'm this" or "I'm that" - it's understandable, with this being sort-of a personal writing journey, but somehow it's not sitting well with me to have most of the sentences being this way.
I'll keep that in mind for next time. ^^
-
 @ 638d2a79:f5645f4e
2025-02-05 18:05:19
@ 638d2a79:f5645f4e
2025-02-05 18:05:19When doing division with two-digit dividends, round up to the nearest tens place if the number ends in 6-9.
Example:
200÷29200 \div 29200÷29 can be approximated as 200÷30200 \div 30200÷30, which simplifies to 20÷320 \div 320÷3.Also, zeros cancel out in division.
Example:
20000÷70020000 \div 70020000÷700 can be simplified to 200÷7200 \div 7200÷7, which gives the same answer.Multiplication Rule:
When doing multiplication, do not write out all of the zeros.
Example:
For 90×290 \times 290×2, you don’t need to write out “00” at the start. Just do 9×29 \times 29×2 and add the zero later.Division with Two-Digit Divisors:
If the second digit of the divisor is between 1-5, only divide the first digit by the first digit.
Example:
5124÷215124 \div 215124÷21 can be solved as follows:- Approximate: 5÷2=25 \div 2 = 25÷2=2 (write 2 as the first digit).
- 21×2=4221 \times 2 = 4221×2=42, subtract to get 92.
- 9÷2≈49 \div 2 \approx 49÷2≈4, so 21×4=8421 \times 4 = 8421×4=84, subtract to get 8.
- Bring down the 4 to make 84, which we already know is 21×421 \times 421×4.
- Final answer: 244.
![[Recording 20250122112454.m4a]]
Converting a Remainder into a Decimal:
To turn a remainder into a decimal, divide the remainder by the divisor.
- Add a zero to the end of your remainder and divide normally.
- The quotient becomes the decimal value.
Example:
32÷10032 \div 10032÷100 → Rewrite as 320÷100320 \div 100320÷100.- 100 goes into 320 three times (3).
- Bring down a zero → 30.
- Add another zero → 300 → 100 goes in three times (3).
- Final answer: 0.32.
If one of the numbers is smaller, like in 880÷22880 \div 22880÷22, where 22 doesn’t go into 0:
- Instead, check how many times 0.22 goes into 88. The answer is 4.
- 22 goes into 0, 0 times.
- So, 880÷22=40880 \div 22 = 40880÷22=40.
Division with Three-Digit Numbers:
Use the same method as with two-digit divisors.
Example: 100,492÷518100,492 \div 518100,492÷518
- Approximate using 5 for each digit of the answer.
Another example:
36.85÷21636.85 \div 21636.85÷216- 222 goes into 3 once → Write 1.
- 216×1=216216 \times 1 = 216216×1=216, subtract from 368 → 152.
- Bring down the 5 and continue dividing.
Calculating Volume:
To find the volume of something, use the equation:
Width×Height\text{Width} \times \text{Height}Width×Height
The answer will be in square units.Example:
A 2D box with width 1 inch and height 4 inches has an area of 4 inches squared.[[America|American]] Flag Instructions:
- The length of the flag is 1.9 times its width.
- Each stripe should be one-thirteenth of the flag's height.
- The blue area covers 7.6 of the flag’s width.
- The height of the blue area is exactly 7 stripes, or 7/13 of the flag’s height.
Finding the Median Score of a Class:
- Count the number of students with the highest score, then move downward.
- Write scores in one column and the number of students in another.
- Find the median of the possible scores.
Example:
Possible scores: 10, 9, 8, 6, 4 → Median is 8.
Then, count students until you reach the middle score (8 or the median value)| Posable score | number of students | | - | | | 10 | 3 | | 9 | 6 | | 8 | 4 | | 6 | 1 | | 4 | 1 | The answer would be 6 1,2,3,4,5,6,7,8 and we are in the 6 Groupe
Tags: [[arrhythmic]]
-
 @ 638d2a79:f5645f4e
2025-02-05 18:03:29
@ 638d2a79:f5645f4e
2025-02-05 18:03:29China was ruled by one ruler, but over time, China split into two—South and North—which had a rivalry between them. At this time, Yang Chien was a general in the army of Northern China. He thought that China should be whole once more, so, like any insert age here year old would do, he attacked the king of the South (for peace!). After a bit of fighting, he overpowered Southern China and took control of all of China. This man founded a dynasty—the Sui Dynasty—to rule and to keep China united.
But wait! Rivers made travel difficult between the North and South, so his son created a new river when he became emperor. This canal made it easier to cross the rivers, which greatly improved trade. The people did not like working on this river, and after it was completed, they killed him, making him the second and last emperor of the Sui Dynasty.
Cue the new emperor, Li Yuan, AKA "the smart guy." He wanted to stay alive for a long time, and he saw how unhappy people had just killed the last important ruler. So, he decided to invest in keeping people happy instead. This started the Golden Age of China, also called the Tang Dynasty.
Tags: [[human behavior index]]
-
 @ e3ba5e1a:5e433365
2025-02-05 17:47:16
@ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a friendly discussion on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it!
The US healthcare system is essentially the worst of both worlds:
- Unlike full single payer, individuals incur high costs
- Unlike a true free market, regulation causes increases in costs and decreases competition among insurers
I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do:
- Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice.
- Reduce regulations significantly.
-
In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways:
- Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices.
- Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.)
Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation.
And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers.
And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply."
https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
-
 @ 8be6bafe:b50da031
2025-02-05 17:00:40
@ 8be6bafe:b50da031
2025-02-05 17:00:40Botev Plovdiv FC is proud to present the Bitcoin Salary Calculator tool, as the foundational tool to showcase athletes the financial power of Bitcoin.
We built the Salary Calculator to help anyone follow in the financial footsteps of prominent athletes such as Kieran Gibbs, Russell Okung, Saquon Barkley, and Renato Moicano, who have significantly increased their savings tank thanks to Bitcoin.
The Bitcoin Salary Calculator allows any person to choose how much of their monthly salary they are comfortable saving in Bitcoin. Instantly, users can backtrack and see how their Bitcoin savings would have performed using the once-in-a-species opportunity which Bitcoin brings.
https://video.nostr.build/a9f2f693f6b5ee75097941e7a30bfc722225918a896b29a73e13e7581dfed77c.mp4
Athletes need Bitcoin more than anyone else
Unlike most people, athletes’ careers and earning years are limited. This has driven the likes of Odell Beckham Jr. and Alex Crognale to also start saving a part of their income in Bitcoin with a long-term outlook as they prepare for retirement.
“The reason why announced 50% of my salary in Bitcoin is because I feel one the noblest things you can do is to get people to understand Bitcoin.” Kieran Gibbs, founder ONE FC, ex Arsenal, ex Inter Miami, ex West Bromich Albion.
“I am trusting Bitcoin for my life after football. Every time my club paid me, I bought Bitcoin.” Alex Crognale, San Antonio FC player.
https://x.com/TFTC21/status/1883228348379533469
“At Botev Plovdiv FC, we believe not only in fostering sporting talent, but also helping them the the most of their careers so they excel in life after retiring from sports. It is with this mission in mind that the club is launching the Bitcoin Football Cup hub, striving to accelerate mass Bitcoin education via sports and athletes - the influencers and role models for billions of people.” shared Botev’s Bitcoin Director George Manolov.
https://x.com/obj/status/1856744340795662432
The Bitcoin Football Cup aims for young prospects to be able to learn key financial lessons from seasoned veterans across all sports. Our Bitcoin Salary Calculator is only the first step toward that goal.
We encourage anyone to hear these stories straight from the current roster of Bitcoin athletes -for whom -in many cases- Bitcoin has allowed them to outperform the wealth it took decades to earn on the field.
Follow us on the Bitcoin Cup’s social media channels to learn more and hear the latest stories of how Bitcoin is shaking up the world of sports:
- Twitter: https://x.com/Bitcoin_Cup/
- Instagram: https://www.instagram.com/BitcoinCup/
- TikTok: https://www.tiktok.com/@BitcoinCup/
- YouTube: https://www.youtube.com/@BitcoinCup/
-
 @ 8d34bd24:414be32b
2025-02-05 16:13:21
@ 8d34bd24:414be32b
2025-02-05 16:13:21This post was written because of an error I made on Substack. I'm sharing it here despite the fact the scheduling error didn't happen on NOSTR. The intro paragraph isn't fully applicable for you NOSTR friends.
On Sunday 2/1/25, I made an oopsie. I tend to write articles ahead of time so I can schedule them and not worry about being inspired on a schedule. I had written two posts: Don't Be Like Martha and Whose Point of View. One was supposed to post on Sunday 2/1/25 and one on Wednesday 2/5/25. I accidentally posted both on Sunday. I was fretting about what to do for a post on Wednesday, because I usually have my husband review posts but he was out of town. I don’t like to do the deep posts without Him checking for grammatical errors, theological errors, or lack of clarity. I also had a brief idea I wanted to discuss and was debating whether to make it a short long form post or a longish note and this situation decided it for me.
Excited Puppy
I recently got into a long discussion/debate with a couple of people on Nostr about God. I tend to get pretty excited about God, the Bible, and biblical inerrancy. It made me think about my dog.
I have a Leonberger. He is about 115 pounds, is very tall, is very long, and has thick hair which makes him look even bigger. He is 8 years old, but still acts like a puppy. When his tail gets going it causes mayhem and destruction. It knocks all of the Christmas cards and missionary prayer cards off the refrigerator. It knocks ornaments off the Christmas tree. On occasion, his excitement can even cause a person to stumble or fall (he never actually jumps on anyone). He is a sweet, loving dog that likes everyone and wants to give and receive attention to and from everyone, but he doesn’t realize how big and strong he is. Sometimes I think I can be like my dog.
 I am passionate about God and the Bible. I have seen what He has done in my life. I have seen what reading and studying the Bible has done for my faith and understanding of God and His word. I intellectually know that it has taken 40ish years to get me this far, but I want everyone to come to this level of faith and understanding right now! There is a reason that God uses years of time and a lifetime of experiences to teach us and sanctify us. This growth can’t be forced. It can’t be rushed. We all have our own paths in growth in Christ and certain things can’t be changed until it is time.
I am passionate about God and the Bible. I have seen what He has done in my life. I have seen what reading and studying the Bible has done for my faith and understanding of God and His word. I intellectually know that it has taken 40ish years to get me this far, but I want everyone to come to this level of faith and understanding right now! There is a reason that God uses years of time and a lifetime of experiences to teach us and sanctify us. This growth can’t be forced. It can’t be rushed. We all have our own paths in growth in Christ and certain things can’t be changed until it is time.Sometimes I am like my sweet puppy. I get so excited about God’s word that I may cause more harm than good. I want to help, but people feel judged. I want to bless, but they feel attacked. I want to raise them up, but end up knocking them down. Although I wonder why my dog has to push the one person in the room that doesn’t want his attention, I then end up doing the same thing with faith.
I am working on improvement, paying closer attention to their response (harder to do online than in person where you can see body language and hear voice tone), and listen to the Spirit on when to press forward and when to pull back.
My prayer is that God will guide us all in our service to Him, that He we would never be afraid to witness and stand for the truth, but that with His help we will not trample those we seek to guide to the Savior and in faith in Him.
Trust Jesus.
-
 @ 77aba0b1:7e3350f5
2025-02-05 15:42:06
@ 77aba0b1:7e3350f5
2025-02-05 15:42:06Canada and Mexico don't have any leverage
The cheapest labor in the world is not China and it's not on the other side of the world. It's in Mexico.
Due to rising Chinese wages, a rapidly growing economy, and demographic changes, China is no longer the low-wage capital of the world. Great news for Mexico as it means more manufacturing jobs have come their way. But bad news if your wealthy neighbor to the north wants to impose tariffs that are going to prevent you from selling to the world's largest consumer market.
 Mexican President Claudia Sheinbaum talking with President Trump | AI generated image
Mexican President Claudia Sheinbaum talking with President Trump | AI generated image
Now consider Canada's dilemma. The US buys 97% of Canada's oil, at a discount. Canada lacks the capacity to refine 75% of their oil production, so they have to sell their sour crude oil to the US at discounted rates because only the US has the infrastructure to move, refine, store, and distribute this commodity. (See video for a detailed explanation.)
 Canadian Prime Minister Justin Trudeau meeting with President Trump | AI generated image
Canadian Prime Minister Justin Trudeau meeting with President Trump | AI generated image
Canada and Mexico share a common double-edged sword; they're geographically close to the United States. This is a huge benefit for reducing transportation costs to the largest consumer market in the world. But that also means you don't have the transportation infrastructure necessary to sell your products around the world.
China had to build a global transportation and supply chain infrastructure if it wanted to reach American and European markets. Because of this inherent characteristic, China is much better positioned to withstand an economic trade war with the United States than either Mexico or Canada.
People often mention how fragile the American economy has become because of its reliance on imported foreign goods. They are absolutely correct. But that cuts both ways. The United States can be cut off from foreign goods, but foreign nations will be cut off from a market to sell their products. What happens when there is a huge supply of goods and demand for those goods goes away? Prices drop... precipitously.
The United States largest export is the US Dollar. Like it or not, as the printer of the Global Reserve Currency, the US finances the consumer markets and the manufacturing base of the world economy.
 The value of fiat currencies always goes to zero | AI generated image
The value of fiat currencies always goes to zero | AI generated image
Free Trade vs Managed Trade
We see a lot of economists and media pundits talking about how tariffs will increase prices and lead to even more inflation. What they really mean is it will lead to "price inflation" which is how most of American society has come to view inflation. Actual inflation is an increase of the money supply and with more moeny chases the same amounts of goods and services, we get an increase in prices or price inflation.
The same people who told you that inflation was "transitory" are now telling you the price of a Corona will go up. They're forgetting that we have a fairly robust domestic beer industry.
 Chuck Schumer and Dylan Mulvaney share bad takes | AI generated image
Chuck Schumer and Dylan Mulvaney share bad takes | AI generated image
But what really needs to be highlighted is that these pundits are discussing Trump's trade war as if we lived under a free trade system; a truly free market. Sadly, we are nowhere close to this being a reality. The global economic system is Managed Trade, or Bureaucratic Trade; with corporations, lobbyists, the politically appointed and well connected making deals that protect their fiefdoms and syphon money to those who control the levers of power.
They are right that tariffs are taxes imposed on imported goods and those taxes are passed on to the consumer. But they act as if tariffs don't didn't exist before Trump. The Biden administration placed tariffs on Chinese "green" technologies. The same administration that said climate change was an existential threat made cheaper, environmentally friendly technology more expensive. It's almost as if it's not about the climate.
The Global Economic Empire
When you owe the bank $1 million, the bank owns you. When you owe the bank $37 trillion, you own the bank.
Trump is betting the house and calling everyone's bluff and he's betting that the US can weather the economic fallout better than any other country, except maybe China. It's a race to the bottom and he knows that the USG can cover its finances longer, causing other countries to go bankrupt and need US assistance.
It's the equivalent of a run on the banks and the US will buy up the debt for cheap. Really they'll buy it for free, since they're printing the currency they buy up assets with. Canada and Mexico folding are a no brainer. Their economies are not built to export large quantities of goods acros the world. It's almost entirely north or south across the border. They had to cave or risk economic collapse.
 China: Rising Dragon or Paper Tiger | AI generated image
China: Rising Dragon or Paper Tiger | AI generated image
China is another story. "Is China a Rising Dragon or a Paper Tiger" has been the headline for 20 to 30 years ever since Deng Xiaoping liberalized their economy and instituted social reform. Their economy has been booming but also suffering from population decline due to the One Child policy that was in effect from 1980 to 2016.
China has a global supply chain and provides most of the world with manufactured goods. That means they need markets to sell their goods in. If Trump threatens every nation with tariffs, it effects the global economy; meaning it will massively effect China. Couple that with a declining population that’s getting older.
The strength of the Chinese economy is that it already has this well established global supply chain. They stand the best chance to weather a trade war with the United States. But a global economic collapse would be a race to the bottom to see which, if any, global power emerges victorious. Just as in war, there is no winner; just bigger losers than others.
If Trump uses this leverage to get concessions that benefit the American people, he could be the greatest statesmen who ever lived. Trump may not be clever enough to think this deeply, but he is certainly brash and confident enough to attempt it.
-
 @ 044da344:073a8a0e
2025-02-05 14:58:26
@ 044da344:073a8a0e
2025-02-05 14:58:26Zugegeben: Die Erwartung war groß. „Angepasst. Aktivistisch. Abgehoben“, ruft das Cover. Triple-A sozusagen. Und das in einem Buch über die Tagesschau, geschrieben von einem Ostdeutschen, der dort sechs Jahre gearbeitet hat, vorher lange beim MDR war und außerdem damit wirbt, auch Privatfernsehen und Presse zu kennen. Mehr Insider geht nicht. Die drei Adjektive mit dem großen A im gelben Punkt sagen: Jetzt spreche ich. Jetzt wird abgerechnet.

Das Marketing hat funktioniert, nicht nur bei mir. Platz drei in der Spiegel-Bestsellerliste und Platz sieben in den Wochencharts von Amazon, nur knapp hinter Angela Merkel. Ich dachte eigentlich, dass ich nach Claus Kleber auf ewig die Finger lassen würde von den Ergüssen beitragsfinanzierter Redakteure. Was soll da schon kommen? Wir sind frei. Niemand ruft an. Niemand redet uns rein. Wir machen das, was die Nachrichtenlage verlangt und was wir kraft Ausbildung und Wassersuppe für richtig halten.
Eine ganze Menge Claus Kleber steckt auch in Alexander Teske. Staatsfunk? Nicht doch. Wir sind halt „alle ähnlich sozialisiert“ (S. 110), haben die „gleichen Relevanzkriterien“ (S. 108) und „schreiben voneinander ab“ – „aus lauter Unsicherheit, etwas ‚falsch‘ zu machen“ (S. 109). Wenn die Sprecherin des Bundespräsidenten, eine Kollegin, die die Seiten gewechselt hat, doch mal nachhelfen muss, dann ist das in der Welt von Alexander Teske die Ausnahme, die die Regel bestätigt. Kein Einfluss, nirgends – bis auf den Seiten 140 und 141 plötzlich Reiner Haseloff auftaucht, Ministerpräsident von Sachsen-Anhalt. Alexander Teske braucht diesen Redaktionsbesuch („Haseloff redete über eine Stunde (…) im vollbesetzten Konferenzraum“) für eine seiner Kernthesen. Der Osten, sagt er, ist der Redaktion in Hamburg nicht einfach nur egal. Dieser Haseloff nervt. O-Ton einer Tagesthemen-Frau: „Sollen wir jetzt etwa über den Rosenmontag in Köthen berichten?“
Vermutlich war es dieser Teil, der mich hat rückfällig werden lassen. Die „Arroganz der Westmedien“ ist eines meiner Lebensthemen. Alexander Teske liefert dafür reichlich Futter. Zehn von 300, schätzt er, sind im Tagesschau-Maschinenraum „ostdeutsch sozialisiert“ (S. 141). Genauer geht es nicht, weil man das im Fall der Fälle lieber für sich behält, immer noch. Achtung: Karrierehindernis. Der Dialekt sowieso. Teske, ein Sachse, nahm „jahrelang Sprecherziehung“, um im Ersten auf Sendung gehen zu dürfen (S. 156). In Bayern oder Hessen lachen darüber die Hühner. Entsprechend sieht der Osten aus in der Tagesschau. Wenn das Volk hier sprechen darf, sagt Kronzeuge Alexander Teske, „werden die kürzesten, plakativsten und dümmsten Aussagen“ bevorzugt, „gern in emotionaler Tonlage“ (S. 143). Dass die Redaktion nur Westpresse abonniert (Ausnahme: die LVZ, die aber keiner liest, S. 146), passt genauso in dieses Bild wie das Sozialporträt einer Redaktion, in der man Arbeiterkinder, HSV-Fans oder Nichtakademiker mit der Lupe suchen muss, dafür aber an der Spitze eine Phalanx von zehn Chefs vom Dienst findet, die auf 11.000 Euro brutto kommen (manchmal offenbar auch mehr, S. 23), für ein „Klima der Angst“ (S. 51) sorgen und, so sagt es jedenfalls Teske, selbst bestimmen, wer zu ihnen aufrücken darf (S. 29).
Was fängt man mit alldem an? Vor allem: Wer kann etwas damit anfangen? Alexander Teske erwähnt einen MDR-Kommentar von Rommy Arndt, gesprochen im Januar 2023, der gegen deutsche Panzer in der Ukraine war (S. 144). In der Tagesschau undenkbar, sagt er, und für Rommy Arndt der letzte große öffentlich-rechtliche Auftritt. Auch Sarah Frühauf kommt bei ihm vor, eine andere MDR-Journalisten, „berühmt“ geworden durch einen Tagesthemen-Kommentar im November 2021, der einer Impfpflicht das Wort redete und „alle Ungeimpften“ gar nicht sehr subtil mitverantwortlich machte für die „wohl Tausenden Opfer dieser Corona-Welle“ (S. 41). Teske beklagt, dass die Tagesschau das Thema RKI-Protokolle erst fünf Tage nach der Veröffentlichung aufgegriffen hat und dabei das Online-Magazin Multipolar nicht erwähnte (S. 127). Davon abgesehen gibt es die Gegenöffentlichkeit bei ihm nicht. Nicht einmal die Dokumentation der Ständigen Publikumskonferenz, die sich lange in weiten Teilen um die Tagesschau drehte, oder die entsprechenden Bücher. Alexander Teske mag nicht, wenn jemand „Zwangsgebühr“ sagt (S. 191), nutzt „Querdenker“ als Schimpfwort (S. 25), hält Telegram für einen Ort, an dem sich „bevorzugt Rechtsradikale, Waffenhändler, Drogendealer, Coronaleugner und Reichsbürger“ tummeln, und wirft der Bild-Zeitung vor, „jeden noch so kleinen Fehler“ zum Skandal aufzublasen (S. 115). Dass Sarah Frühauf ihren Kommentar sprechen konnte, passiert bei ihm einfach so. War knapp bei der Abstimmung. Drei Namen zur Auswahl. Und am nächsten Morgen wundern sich alle.
Was also, ich wiederhole diese Frage, fängt man mit einem Buch an, das sich eher wie ein Bewerbungsschreiben für öffentlich-rechtliche Führungsaufgaben liest, so sich die Zeiten doch noch ändern sollten? Punkt eins: Die Redaktionen der Leitmedien sind nicht so homogen, wie es von außen oft scheint. Alexander Teske trägt die Auseinandersetzungen von innen nach außen – sicher ein Grund, warum der NDR eher dünnhäutig reagierte und darauf hinwies, dass sich der geliebte Ex-Kollege noch 2022 erfolglos auf eine Dauerstelle beworben hat.
Punkt zwei, wichtiger: Das Buch von Alexander Teske dokumentiert den Wandel im Journalismus, den wir gerade live erleben und erleiden. Teske selbst steht dabei für das Früher. Sagen, was ist. Sachlich, nüchtern, mit Distanz. Auch dann, wenn es um die AfD geht. Die wichtigen Themen nach vorn und nicht die, die Quote garantieren. „Nachrichten pur“, wie er das an einer Stelle nennt (S. 227) – ohne Soft News und Infotainment, ohne elend lange Fußball-, Promi- und Katastrophenblöcke mit Bochum gegen Heidenheim, Waldbränden noch und nöcher und jeden Pups der Royals, auch ohne „moderative Sprache“ (S. 226). Nachrichten pur heißt bei ihm im Subtext auch: Finger weg von den Digitalplattformen (im Moment jeden Tag bedient von 20 Redakteuren plus Planer, Grafiker, Cutter, S. 271). Finger weg auch davon, einfach ein, zwei Minuten länger zu machen, um die Quote mit denen aufzufüllen, die nur die nächste Sendung sehen wollen (S. 232).
Das ist in diesem Tagesschau-Buch-Kosmos auch ein Streit zwischen Alten und (oft schlechter bezahlten) Jungen, aber nicht nur. Alexander Teske erzählt, wie er mit seinem Journalismus-Ideal auch und gerade an der Generation 50+ gescheitert ist (vor allem an Männern, die im Dienst Antifa-T-Shirts tragen und den FC St. Pauli lieben) – auch, weil ein Ostdeutscher wie er in Hamburg kaum auf Seinesgleichen stößt. Über den Tellerrand zu schauen, hat er dabei trotzdem nicht gelernt. Anders formuliert: Auch in einer Tagesschau made by Alexander Teske würde ein Teil der Wirklichkeit fehlen.
-
 @ a012dc82:6458a70d
2025-02-05 14:29:47
@ a012dc82:6458a70d
2025-02-05 14:29:47The cryptocurrency market is a dynamic and often unpredictable space. With Bitcoin's impressive surge in value, many investors are looking beyond the pioneer cryptocurrency to diversify their portfolios. This article explores various cryptocurrency options, weighing the potential of holding (HODLing) or selling them in the current market.
Table Of Content
-
Bitcoin's Stellar Performance
-
Ether (ETH)
-
Solana (SOL)
-
Binance Coin (BNB)
-
BLUR
-
Conclusion
-
FAQs
Bitcoin's Stellar Performance
Bitcoin, the first and most well-known cryptocurrency, has seen a remarkable increase in value, rising by 120% in 2023. This surge sets a benchmark for evaluating other cryptocurrencies. Bitcoin's growth is influenced by several factors, including the anticipation of a Bitcoin ETF and its upcoming fourth halving. These developments could further drive its demand and value.
The potential introduction of a Bitcoin ETF is particularly significant. It would allow a broader range of investors to gain exposure to Bitcoin without the complexities of direct cryptocurrency ownership. This development could lead to increased institutional investment and potentially stabilize Bitcoin's historically volatile price. Furthermore, the halving event, expected to occur in April, is a fundamental aspect of Bitcoin's design. It reduces the reward for mining new blocks, effectively limiting the supply of new bitcoins. This scarcity is a key driver of Bitcoin's value and has historically led to significant price increases.
However, Bitcoin's dominance and performance also raise questions about market saturation and the potential for continued growth. While Bitcoin remains a safe haven for many investors, its large market capitalization means that it may not offer the same growth potential as some smaller, emerging cryptocurrencies. Investors looking for high-growth opportunities may find these in altcoins, which, while riskier, offer the potential for higher returns.
Ether (ETH)
Ether, the native token of the Ethereum blockchain, has a different appeal compared to Bitcoin. While Bitcoin excels as a payment network, Ethereum's strength lies in its versatility as a platform for decentralized applications. Ether's growth has been modest compared to Bitcoin, with a 65% increase this year.
Ethereum's broader utility stems from its ability to support smart contracts and decentralized applications (dApps). These features have made it the backbone of various sectors, including decentralized finance (DeFi) and non-fungible tokens (NFTs). The recent upgrade to Ethereum 2.0, transitioning to a proof-of-stake consensus mechanism, aims to address scalability and energy efficiency issues, potentially increasing its attractiveness to both developers and investors.
Despite these advancements, Ether's price has not seen the same explosive growth as Bitcoin. This could be due to the market's maturation and the increasing competition from other blockchain platforms. However, Ethereum's established position and ongoing development make it a strong contender for long-term growth. Investors may consider holding Ether as a bet on the continued expansion and innovation in the DeFi and NFT spaces, where Ethereum plays a central role.
Solana (SOL)
Solana, a blockchain platform seen as a competitor to Ethereum, has recovered remarkably from the impacts of the FTX collapse, with its value increasing by 313% this year. This growth is a testament to the resilience and potential of Solana as an investment.
Solana's key selling point is its high throughput and low transaction costs, making it an attractive platform for both developers and users. Its ability to process thousands of transactions per second outpaces Ethereum significantly, which has been a bottleneck for the latter. This technical superiority has led to increased adoption of Solana for various applications, including decentralized exchanges, gaming, and NFTs.
The rapid recovery of Solana's value post-FTX collapse indicates strong investor confidence and market support for the platform. It suggests that Solana has managed to dissociate itself from the negative sentiment surrounding FTX and is being recognized for its inherent technological strengths. For investors, Solana presents an opportunity to diversify into a high-potential blockchain platform that could capture significant market share in the future.
Binance Coin (BNB)
BNB, the native token of the Binance exchange, has faced significant challenges following legal issues with Binance’s CEO. These developments have led to a decrease in BNB's value, prompting considerations for selling the asset.
The legal troubles surrounding Binance and its CEO have raised concerns about the exchange's future and, by extension, the value of BNB. Binance Coin's utility is closely tied to the Binance ecosystem, being used for transaction fee discounts and participation in token sales. If regulatory actions lead to a decrease in Binance's user base or a change in its operational model, BNB could see a further decline in value.
However, it's also important to consider Binance's position as one of the largest and most influential cryptocurrency exchanges globally. The platform has a substantial user base and a wide array of services, including trading, staking, and a native blockchain, Binance Smart Chain. If Binance navigates through its legal challenges successfully, BNB could recover and potentially grow in value. Investors need to weigh the risks of regulatory impacts against the potential for Binance to continue playing a major role in the crypto ecosystem.
BLUR
BLUR, associated with the NFT marketplace Blur, has maintained a significant market capitalization despite a downturn in NFT trading. As the NFT market shows signs of a potential rebound, holding BLUR could be a strategic move for investors interested in the digital art and collectibles space.
The NFT market has experienced a significant cooldown from its peak in 2021, but it remains a sector with potential for innovation and growth. BLUR's association with the Blur marketplace positions it well within this niche. The marketplace has gained traction among NFT traders for its user-friendly interface and unique features, such as rewarding users with BLUR tokens based on their trading volume.
BLUR's utility within the Blur ecosystem could drive its value as the NFT market evolves. The token's use in governance and transaction fee payments on the platform aligns it closely with the marketplace's success. As new artists and collectors continue to enter the NFT space, platforms like Blur that offer a streamlined and rewarding experience could see increased usage, potentially boosting BLUR's value.
Investors considering BLUR should monitor the broader NFT market trends and Blur's position within it. While the NFT market is known for its volatility, it also offers unique opportunities for growth, especially in niches that are innovating and capturing user interest.
Conclusion
The cryptocurrency market is diverse and constantly evolving. While Bitcoin continues to be a strong performer, other cryptocurrencies offer varied investment opportunities. Investors should consider their risk tolerance, market trends, and the unique attributes of each cryptocurrency when making decisions. Whether to HODL or sell depends on individual investment goals and the ever-changing landscape of the crypto world. Diversification and staying informed are key to navigating this dynamic market successfully.
FAQs
Is it better to invest in Bitcoin or other cryptocurrencies? It depends on your investment goals and risk tolerance. Bitcoin is more established but may offer lower growth potential compared to some emerging altcoins. Diversifying your portfolio with a mix of Bitcoin and other cryptocurrencies might be a balanced approach.
What makes Ether a good investment option? Ether is the native token of the Ethereum blockchain, known for its versatility in supporting smart contracts and decentralized applications. Its ongoing development and central role in the DeFi and NFT sectors make it a strong contender for long-term growth.
Why is Solana considered a rising competitor in the crypto market? Solana offers high transaction speeds and low costs, making it an attractive platform for developers and users. Its rapid recovery post-FTX collapse indicates strong market support and potential for significant market share in the future.
What are the risks associated with investing in Binance Coin (BNB)? BNB faces risks due to legal issues surrounding Binance and its CEO. Its value is closely tied to the Binance ecosystem, so any negative impact on the exchange could affect BNB's value.
Is investing in BLUR a good strategy? Investing in BLUR could be a strategic move if you're interested in the NFT market. As the native token of the Blur NFT marketplace, its value may grow with the platform's success in the evolving NFT space.
How important is diversification in cryptocurrency investment? Diversification is crucial in managing risk in the volatile cryptocurrency market. It involves spreading your investment across different assets to reduce the impact of any single asset's performance on your overall portfolio.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ c69b71dc:426ba763
2025-02-05 13:44:29
@ c69b71dc:426ba763
2025-02-05 13:44:29Nature shows us the way…
…but what does humanity do?
Let’s take a look at winter:
Trees shed their leaves. The plant’s energy withdraws so it can conserve strength and survive the cold season.
Wild animals follow the same pattern: In autumn, they build up reserves, grow thick fur, and retreat into their caves and thickets. Little movement, lots of sleep – a natural strategy for preserving energy. Animals that wouldn’t survive the cold migrate to warmer places to spend the winter.
And what does humanity do?
We eat just as much, move just as much (or little), sleep too little – just as we do all year round. Why? Because we can. Because our lives are no longer governed by the seasons. Refrigerators are full, supermarkets are always open, work calls, and daily routines remain unchanged. But this does not come without consequences.
During winter, we don’t allow ourselves to rest or retreat. We ignore our natural needs, overexerting ourselves physically, mentally, and emotionally. The result? An exhausted body and mind, discontent. The lymphatic system gets clogged, the body becomes overly acidic. Spring fatigue, low energy, depression, inflammation, and other ailments follow.

And then comes spring…
Nature awakens. Life begins anew everywhere. Buds sprout, blossoms unfold – pure energy in its most vibrant form! Everything that grows now serves cleansing and detoxification: wild herbs, fresh shoots, and buds – nature’s medicine for body and mind.
Wild animals follow this rhythm. They shed their winter coats, become more active, consume this natural medicine, mate, or give birth.
And what does humanity do?
We keep eating the same, sleeping too little, rushing through our daily routines. And then we wonder why we feel tired, sluggish, and drained. Why our thoughts feel heavy and our bodies weak. Why depression creeps up on us at this very moment. Did you know that the highest suicide rate is in spring?

Summer – the time of abundance
Nature gifts us with light, warmth, ripe fruits, berries, and fresh vegetables.
Animals spend most of their time outdoors, eating what nature provides and recharging their energy into every cell of their being.
And what does humanity do?
We keep working as always, consuming industrially processed foods, barely spending time outside. Too much artificial light, too little sleep. No wonder so many feel exhausted even in summer, drained, struggling with digestion and metabolism.

Autumn – preparing for retreat
Now is the time for harvest. Nuts, mushrooms, apples, pears, root vegetables, pumpkins, cabbage – all available to build up reserves.
Animals follow nature’s call, gathering, storing energy, preparing for the coming months. Chlorophyll in leaves breaks down, green turns to vibrant autumn colours.
And what does humanity do?
We ignore these signals. We stay trapped in the hamster wheel. We enter winter unprepared, weakened, prone to infections, drained by a lack of sunlight and an overly acidic system.

A cycle of exhaustion
And so the wheel keeps turning. Because we ignore nature. Because we no longer listen to our bodies. Because we have lost touch with our intuition. Because we have enslaved ourselves.
What can you do?
Not everyone is ready to leave their daily life behind, move to a warm country, and become self-sufficient. Many want to maintain their current lifestyle.
So how can we break the cycle?
Turn inward. Take time each day to listen to yourself. To truly feel what you need. To give space to your needs. Sense what drains you, what makes you sluggish. What brings you joy. Cleanse yourself – physically, mentally, emotionally!
*Do* more of what you miss, of what makes you happy and fulfilled. Remember: You too are nature.****
If all this sounds like a lot of inner work, I invite you to take first steps.
Ask yourself:
- Does your body need detoxification?
- Cleansing?
- More movement?
- Or is it time for emotional release?
If you wish support, let me know and we will discuss an energy exchange that allows you to do something good for yourself in a sustainable way. Supporting you in reclaiming your energy and strength – for a year filled with vitality, self-respect, and self-love. 💛
**
Spring is calling! It offers us a new chance. Do you hear it? Yes, it’s calling you! Let’s go! 🚀**
-
 @ 0b118e40:4edc09cb
2025-02-05 13:23:56
@ 0b118e40:4edc09cb
2025-02-05 13:23:56I’d like to see a world where a small artisan in Sarawak sells handcrafted goods directly to a boutique in Paris by bypassing currency exchange fluctuations, banking restrictions, and government-imposed tariffs. Or where a coffee farmer in Ethiopia sells beans straight to a roaster in Tokyo by sidestepping middlemen, exchange fees, and bureaucratic red tape.
In theory, free trade should enable this exchange smoothly, allowing businesses of all sizes to compete on a level playing field. But in reality, global trade is far from free. Policies, interventions, and economic theories are often designed to favor the powerful.
One particular theory that troubled me was Paul Krugman’s New Trade Theory (NTT), which argues that large businesses with economies of scale, supported by government-backed advantages, dominate international trade. This manifestation of the global marketplace favoring the giants, leaving smaller players like that Ethiopian coffee farmer out and struggling to compete, had led to trade hegemonies and trade wars.
After going through centuries of trade theories from Adam Smith’s Wealth of Nations to Keynesian interventionism and Friedman’s libertarianism I found myself questioning:
Is Krugman right?
After all, in today’s world, global trade is controlled by a few key players. The U.S., China, Germany, Japan, and the U.K. alone contribute to 40% of global trade in goods and services. The 134 countries of the Global South are often forgotten.
Can Bitcoin offer a countermeasure to help globalize small businesses from anywhere in the world?
Big players rule the game.
Let’s go a little deeper on Krugman’s New Trade Theory. He believes that trade is increasingly dominated by large firms because they benefit from economies of scale and brand power. While older trade theories assumed that countries traded based on resource advantages, NTT tries to explain why similar economies like the U.S. and Europe, engage in high levels of trade with each other, missing out on the obvious nuances of global alliances on geopolitical control and power.
Another aspect of Krugman’s theory is that large companies have a better chance of capturing market lead if they can benefit from unfair advantages through additional boosters in an imperfect market. In simple terms, power, status, and wealth are all you need to win.
So if you are a big company and you have status, government perks, and economic advantages, you can be the market leader. It’s like the Olympics of global trade, except some players get to use performance-enhancing drugs (subsidies, trade barriers, and financial influence) while others run clean. The race isn’t fair, but the rules say it’s fine.
So what is the blind spot here?
Well, other than the obvious disregard for merits and fair play, this model also assumes that only large corporations drive global trade, leaving small businesses to struggle against giants - despite the fact that small businesses often contribute significantly (sometimes up to 80%) to a country's revenue.
Small business in a big economy
NTT was developed in the 1970s and 1980s when economies of scale and industrial advantages were the primary drivers of global trade. Kugman's argument assumes that large corporations, due to their financial and logistical dominance, will continue to dictate trade flows. But is this still true today?
Small businesses are establishing themselves in a globalized world, even without economies of scale, as opposed to Krugman's belief. The rise of e-commerce, digital platforms, and decentralized technologies has significantly altered the trade landscape, though many barriers remain.
In the past, small businesses struggled because they lacked access to global markets, but platforms like Alibaba, Amazon, and Shopify have reduced the barriers to entry, allowing even micro-businesses to participate in international trade.
When Jack Ma started Alibaba, businesses didn’t automatically sign up. His team traveled to small villages and industrial hubs to onboard businesses that had never considered global trade let alone understand digital interfaces, communicate in English, or use the internet. This grassroots effort revolutionized commerce, digitizing and globalizing it at an unprecedented scale.
Krugman’s model assumes that large firms control trade, but in reality, many countries thrive on small business-driven exports.
I’ve been to these areas in China and seen firsthand how they operate. These small manufacturers in China may not have the scale of a multinational, but they’re deeply integrated into global supply chains. And despite limited resources, they’re able to compete globally.
Other countries like Germany and Japan are great examples where ‘hidden champions' who are typically highly specialized small businesses, play a crucial role in global supply chains.
US is not there yet, but it has the opportunity to explore untapped potential of globalizing small businesses and compete in the global market to drive sustainable economic growth.
In fact with this model, ideally anyone is welcome. But there are many barriers that still exist in limiting the globalization of small businesses : * High transaction costs. * Complexity of currency exchange and exchange fees * Complex regulations and banking restrictions * Difficulty finding trustworthy international partners
Imagine a small business trying to import materials from multiple global suppliers. Not only is it hard to find them, as many countries still rely on government agencies, trade directories, and outdated methods for searching and connecting with suppliers, but when it comes to solidifying deals, the complications don’t stop. One supplier might require an international wire transfer, another may only accept Western Union, and a third insists on using a local bank with high fees and delays. Small businesses simply don’t have the same access to banking services and streamlined financial systems that large corporations do. The variations often depend on the specific banking practices and infrastructure of both parties.
To make matters even more complicated, small businesses don't have dedicated teams like large corporations. They run on minimal resources, managing everything themselves. One small error or delay can stall shipments, disrupt cash flow, and risk losing customers. Yet, global trade expects them to compete at the same level as industry giants, without the same financial infrastructure or support.
More often than not, small businesses are left to fend for themselves, struggling to overcome these challenges alone.
And that’s where Bitcoin changes everything.
Can Bitcoin Create a True Free Market?
Unlike traditional banking systems, which are tied to government policies and centralized institutions, Bitcoin operates on a decentralized, borderless network. This enables direct transactions between buyers and sellers without intermediaries or excessive fees.
While Krugman’s theory explains why big corporations once held an advantage, it overlooks how decentralization removes trade bottlenecks, giving small businesses a real chance to compete globally.
In a Bitcoin-based global economy: * No more currency conversion fees - Businesses trade freely across borders. * No more reliance on banks - Transactions occur on a trustless system, reducing fraud and expensive intermediaries. * No more cross-border delays - Payments are instantaneous, bypassing restrictive banking regulations.
For small businesses, this means fewer barriers to global trade. A textile producer in India could sell directly to a retailer in Canada without needing to figure out the bureaucratic maze of currency exchanges and trade laws. A graphic designer in Brazil could collaborate with a company in Australia and receive payment instantly without relying on high-fee banking systems. A shea butter producer in Kenya could sell organic products directly to small skincare manufacturers in the U.S., bypassing middlemen and avoiding international shipping delays.
Bitcoin removes middlemen, slashes costs, and levels the playing field, not by government intervention, but by eliminating artificial barriers altogether.
The Challenges and the Future
Bitcoin isn’t a perfect solution, and we know that. Scalability, price volatility, and regulatory pushback remain major hurdles.
Currently, stablecoins are attempting to integrate into the Bitcoin Layer 2 network, which could potentially distract from Bitcoin's intended role as a global decentralized medium of exchange. Some are pushing for trade to happen through currency-pegged, centralized coins, which risks undermining Bitcoin's strong push toward free trade and decentralization.
Governments and banks resist decentralization because it threatens their control over money flows.
However, the concept of Bitcoin as a medium of exchange is already taking root. Leaders and developers are dedicating their legacies to building this system for a truly global community. El Salvador’s Bitcoin experiment has shown both the potential and the obstacles of a Bitcoin-driven economy with many lessons to learn from. Block Inc’s innovations have expanded into strengthening Bitcoin’s role as a decentralized medium globally, particularly through decentralized mining benefits and commercialized cold wallets.
Nostr has been very successful in seeing growth in these domains as well. It is slow but it's taking the right steps towards simplifying Bitcoin commerce adoption through zaps.
However the million-dollar question remains. If Bitcoin removes trade barriers, will small businesses adopt it?
History suggests yes but with the right approach. Just as Jack Ma went door to door convincing small businesses to embrace e-commerce, a similar effort is needed for Bitcoin adoption.
With Bitcoin, global trade can become digitized, commercialized, and pain-free, but only if small businesses understand how to use it. More importantly, it disrupts trade hegemony and creates a more equitable world that everyone can be part of.
A challenge I foresee beyond technology, is education. Initiatives that focus on simple onboarding, low-cost adoption, and real-world use cases can drive Bitcoin-powered trade forward. There are many non-tech Bitcoin enthusiasts who want to contribute to the Bitcoin ecosystem and would love to take on educator roles. Once the infrastructure and understanding around Bitcoin become more conceptualized, these folks could play a strong role in spreading awareness and adoption.
If Bitcoin is introduced strategically, not as a speculative asset but as an international trade enabler through its medium of exchange, it could reshape global commerce just as e-commerce once did. The only difference is that this time, trade is truly borderless, trustless, and not controlled by financial intermediaries.
Krugman’s New Trade Theory remains useful in explaining how economies of scale shape trade. But it fails to account for decentralized digital economies, where small businesses can bypass the old rules of power and privilege.
If Bitcoin achieves mainstream adoption, we may finally see a world where trade is truly free, where merit, not governments or middlemen, determines success.
-
 @ 0fb8901a:2bced885
2025-02-05 13:23:54
@ 0fb8901a:2bced885
2025-02-05 13:23:54We are a family passionate about working with and for people, and we have a deep love for food.
Our journey began when our neighbors, who have a pizza oven, invited us and our children to make our own pizzas. The experience was delightful and memorable.
Inspired by this, we decided to offer the same joy to other kids and adults. We invested in a handcrafted wood-fired pizza oven, made from scratch by a friend who specializes in pizza oven craftsmanship. This oven was imported to the UK, and it brings out the most wonderful flavors in our pizzas, taking us back to the basics of traditional cooking.
We proudly serve Bracknell and the surrounding areas within a 20-mile radius.
What’s Different About Us?
Our pizza oven is brand new and crafted from reliable, safe materials. Unlike traditional setups confined to a van, our oven is fully visible from all angles, allowing you to watch your pizza being made. It features detachable stainless steel tables on both sides, enabling you to work in close proximity to the oven. Our pizzas are wood-fired, giving them a wonderful, authentic taste. Both our tomato and cream sauces are homemade, and our dough is made from organic flour, ensuring the freshest ingredients.
-
 @ c8383d81:f9139549
2025-02-05 13:06:05
@ c8383d81:f9139549
2025-02-05 13:06:05My own stats on what I’ve done over the weekend:
-
Spoke to +100 developers, it was great seeing a couple of familiar Flemish faces and meeting some new ones but overall the crowd was extremely diverse.
-
Ended up doing a short interview promoting the protocol and ended up going to 0 talks.
-
Tried to evangelize by going booth by booth to distribute a Nostr flyer to other FOSDEM projects, with the hope that they would broadcast the info towards their SOME person to add Nostr on their list or to build out a library for the languages that were present ( This was a fairly slow approach )
-
Kept it to Nostr protocol 95% of the time, the Bitcoin narrative is not always a good time to push and as a side note I’ve met more Monero users than in the last 5 years.
-
Was able to convince some engineers to look into the #soveng endeavor.
Small overview from the most common questions:
- They have heard about Nostr but are not sure of the details. ( mostly through the bitcoin community )
- What is the difference with ActivityPub, Mastodon, Fediverse ?
- IOT developers, so questions regarding MQTT & Meshtastic integrations ?
- Current state of MLS on Nostr ?
- What are the current biggest clients / apps build on Nostr ?
- Will jack still give a talk ?
Things we could improve:
- Bring more stickers like loads more,
- Bring T-shirts, Pins… could be a good way to fund these adventures instead of raising funds. ( Most projects where selling something to help raise funds for projects )
- Almost no onboarding / client installs.
- Compared to the Nostr booth at BTC Amsterdam not a single person asked if they could charge their phone.
Personal Note: The last time I visited was roughly 13 years ago and me being a little more seasoned I just loved the fact that I was able to pay some support to the open source projects I’ve been using for years ( homebrew, modzilla, Free BSD,.. ) and see the amazing diverse crowd that is the open source Movement 🧡
Al final shoutout to our great pirate crew 🏴☠️: The Dutch Guard ( nostr:npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe & nostr:npub1l77twp5l02jadkcjn6eeulv2j7y5vmf9tf3hhtq7h7rp0vzhgpzqz0swft ) and a adrenaline fueled nostr:npub1t6jxfqz9hv0lygn9thwndekuahwyxkgvycyscjrtauuw73gd5k7sqvksrw , nostr:npub1rfw075gc6pc693w5v568xw4mnu7umlzpkfxmqye0cgxm7qw8tauqfck3t8 and nostr:npub1r30l8j4vmppvq8w23umcyvd3vct4zmfpfkn4c7h2h057rmlfcrmq9xt9ma amazing finally meeting you IRL after close to 2 years since the Yakihonne hackathon 😀

-
-
 @ a7bbc310:fe7b7be3
2025-02-05 12:20:59
@ a7bbc310:fe7b7be3
2025-02-05 12:20:59 In 2018 I started doing film photography. I asked myself what could I do that was unique. So, I tried taking picture at local gig venues. I’d look around and everyone was using digital cameras. I had a limited number of shots I could take, inconsistent lighting at different venues but some delayed gratification of not knowing how the images would turn out until I developed them. I’d come home late from a show and be up until the early hours developing and scanning the images. 2020 put a stop to that. It’s something I’d like to start again. I’ll be sharing some of my favourite images I from my badly categorised/labled folders.
In 2018 I started doing film photography. I asked myself what could I do that was unique. So, I tried taking picture at local gig venues. I’d look around and everyone was using digital cameras. I had a limited number of shots I could take, inconsistent lighting at different venues but some delayed gratification of not knowing how the images would turn out until I developed them. I’d come home late from a show and be up until the early hours developing and scanning the images. 2020 put a stop to that. It’s something I’d like to start again. I’ll be sharing some of my favourite images I from my badly categorised/labled folders.
 Artist in photo is called Conner Youngblood. It’s been interesting to listen to his most recent projects (Cascades, Cascading, Cascadingly) to compare to his earlier ones (Australia)
Artist in photo is called Conner Youngblood. It’s been interesting to listen to his most recent projects (Cascades, Cascading, Cascadingly) to compare to his earlier ones (Australia)Australia is a stripped back, couple guitars, vox and drums. Most recent has a few more vocal effects and electronica sounds. A comparison I would make would be Bon Iver’s - Emma with their 3rd album 22, a million.
As a when I arrange the files on my HD, I’ll be share a few more band photos.
-
 @ 5e13e5d5:217fe898
2025-02-05 11:30:01
@ 5e13e5d5:217fe898
2025-02-05 11:30:01With the rapid development of science and technology, communication technology has penetrated into all aspects of our lives, but the accompanying security risks cannot be ignored. As an effective technical means, signal jamming technology has gradually attracted people's attention in the field of public security in recent years. This article will explore the application of signal jammer in public security and its potential impact.
Basic concept of signal jammer
Signal jammer, as the name suggests, is a device used to interfere with or block signals of a specific frequency. By emitting electromagnetic waves of a specific frequency, signal jammers can effectively shield or weaken the reception of certain wireless signals, thereby preventing unnecessary information transmission. Signal jammers have a wide range of application scenarios, from countermeasures in the military field to security protection in the civilian field.
Application in public security
1. Preventing terrorist attacks
In some important public places, such as airports, stadiums, and large conferences, signal jammers can be used to prevent terrorists from remotely detonating bombs through mobile phones and other devices. Such devices can create a "jamming area" in a critical area, making communications related to explosive devices impossible, thereby effectively reducing the risk of terrorist attacks.
https://www.thejammerblocker.com/cell-phone-jammer-blocker-for-gsm-5g/
2. Maintaining public order
In some special cases, such as demonstrations or large gatherings, in order to prevent criminals from using mobile phones to organize or incite, law enforcement agencies can choose to use signal jammers moderately. By interfering with the communication signals at the scene, the organization ability of criminals can be effectively weakened, thereby maintaining public order.
3. Criminal investigation
During criminal investigations, the police sometimes need to monitor certain targets. Signal jammers can be used to block the communication between suspects and the outside world, so as to further obtain evidence or make arrests. However, this method must be carried out within the scope permitted by law to avoid infringing personal privacy.
4. Security precautions
In some special places, such as prisons and important laboratories, gps blocker can prevent jailbreaks or leaks. By interfering with mobile phone signals, prisoners can be effectively prevented from contacting the outside world and ensuring the safety of the place.
Potential impacts and legal ethical issues
Although signal jammers have many applications in public safety, their use also faces some potential impacts and legal ethical issues. First, the use of signal jammers may infringe on personal freedom of communication. Interference with citizens' mobile phone signals may affect their ability to seek help in an emergency. Secondly, if the jammer is abused by criminals, it may lead to social chaos. Therefore, when using drone jamming device, relevant departments should formulate strict usage specifications and legal frameworks to protect the legitimate rights and interests of citizens.
Conclusion
In summary, as an emerging public safety technology, bluetooth blocker have important application value in preventing terrorist attacks, maintaining public order and criminal investigation. However, how to maintain personal privacy and freedom of communication while ensuring public safety is a question worth pondering. In the future, with the further development of science and technology, the application of signal jammers in public safety will become more and more common, but we must be vigilant about its potential impact and use this technology reasonably and legally.
https://www.thejammerblocker.com/dj-x5-military-grade-signal-jammer-device-5-antennas/
-
 @ da0b9bc3:4e30a4a9
2025-02-05 07:29:27
@ da0b9bc3:4e30a4a9
2025-02-05 07:29:27Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/876357
-
 @ 3c7dc2c5:805642a8
2025-02-05 07:02:42
@ 3c7dc2c5:805642a8
2025-02-05 07:02:42🧠Quote(s) of the week:
Old model:
-You work for money.
-They print it.
-You save your money.
-They devalue it.
-You invest your money.
-They manipulate it.
New model:
-You save in Bitcoin.
-There’s nothing they can do about it.
🧡Bitcoin news🧡
Before we start some extra info to get you focused.
1 BTC is unreachable for the majority.
The aspiration used to be 6.15. Now it's 0.1.
'Now who owns Bitcoin? 'The Answer Might Surprise You.
👉🏽Bitcoin is often misunderstood. Some think it’s controlled by a handful of institutions, others believe governments secretly hoard it. The reality? Bitcoin ownership is diverse and widely distributed across individuals, businesses, funds, and even governments.
👉🏽57% of Bitcoin is held by individuals. From everyday savers to long-term believers, Bitcoin’s largest share is in the hands of the people.
👉🏽4% belongs to businesses. Companies are increasingly adding BTC to their treasuries, recognizing its role as digital gold.
👉🏽5% is held by funds and ETFs. Bitcoin is being adopted by the financial system, providing new ways for institutions and retail investors to gain exposure.
👉🏽Governments own 2% to 3%. Whether through seized BTC or strategic holdings where states already acknowledged Bitcoin’s value.
👉🏽Around 18% is estimated to be lost forever. This actually makes Bitcoin even scarcer than its 21 million cap suggests.
👉🏽Miners and yet-to-be-mined Bitcoin represent the rest. This small remaining fraction coupled with a fixed supply means competition for mining remaining bitcoins will only increase over time.
This distribution is one of the many reasons why Bitcoin is unique. Not only there is no single entity that controls it (no government or bank can print more of it), but also its distribution among the population is more fairly distributed than for any other monetary asset.
Bitcoin is owned by those who understand its value, regardless of nationality, religion, skin color, political affiliation, or beliefs. Bitcoin is for everyone.' -Thomas Jeegers
On the 28th of January:
➡️European Squash Federation adopts Bitcoin for its treasury.
➡️Binance under investigation for money laundering, tax fraud, and drug trafficking in France - Reuters
➡️'Metaplanet will issue 21 million new stock warrants with a 0% discount rate, raising approximately $870 million to fund additional Bitcoin purchases. This marks the largest-ever fundraising for Bitcoin purchases in the history of the Asian stock market.' -Metaplanet
➡️U.S. Senator Cynthia Lummis received a framed Bitcoin block from Marathon’s Jayson Browder to mark her role as the new chair of the Senate Banking Subcommittee on Digital Assets. MARA Pool mined the block by calculating 1,476,600,000,000,000,000,000 Bitcoin hashes within 46 seconds.
➡️'Fidelity is now bigger than Greyscale:
- BlackRock ETF: 576k BTC
- Fidelity ETF: 205k BTC
- Greyscale ETF: 202k BTC' -Bitcoin for Freedom
➡️'Brazil’s state-owned oil and gas company Petrobras is reportedly assessing getting into Bitcoin mining. This is a new chapter for the company and shows how traditional industries are adapting to the digital world. Petrobras, one of the largest and most profitable oil companies in the world, is going to use excess natural gas produced during the oil extraction process to power Bitcoin mining. This will reduce energy waste and methane emissions, and create a new revenue stream for the company.' -Bitcoin News
➡️Last week, the 613-foot smokestack of the former Somerset Generating Station in Niagara County, New York was demolished. The site, now Tera Wulf Inc.’s Lake Mariner Data, will focus on Bitcoin mining and AI processing powered by hydroelectric energy
➡️'For the first time ever in Bitcoin's 16-year history, the epoch-over-epoch (EOE) growth has fallen below +100%. Pack it up, fellas.'- Wicked
On the 29th of January:
➡️Czech central bank Governor Ales Michl said he would propose a plan to include bitcoin in the country’s official reserves, the Financial Times reported.
Michl statement: 'Czech National Bank’s goal is price stability. When we took office in July 2022, inflation was 17.5%. We brought it down to target. We are also diversifying reserves—gradually increasing gold holdings from 0% to around 5% and planning for 30% in equities. An asset under consideration is Bitcoin. It currently has zero correlation to bonds and is an interesting asset for a large portfolio. Worth considering. Right now, it’s only at the stage of analysis and discussion. The Bank Board decides, and no decision is imminent. Thoughtful analysis is needed.
Bitcoin has significant volatility, which makes it harder to take advantage of its current low correlation with other assets. That’s why I will ask our team on Thursday to further assess Bitcoin’s potential role in our reserves. Nothing more, nothing less. The article is very accurate, including my statement that Bitcoin could one day be worth either zero or a huge amount. At our meeting on Thursday, after discussing a document on international reserve management in 2024, the Bank Board of the Czech National Bank (CNB) approved a proposal to analyze the options for investing in additional asset classes.
The central bank has been increasingly diversifying its investments over the last two years as part of its reserve management strategy. At the proposal of Governor Aleš Michl, the CNB is to assess whether it would be appropriate in terms of diversification and return to include other asset classes in the reserves as well. Based on the results of the analysis, the Bank Board will then decide how to proceed further. No changes will be implemented in this area until then. Any changes in the reserve portfolios will be disclosed in the quarterly information on the CNB’s international reserves and the CNB’s annual report.'
The head of a central bank tweeting about potentially allocating to Bitcoin was not on my 2025 bingo card.
➡️Jerome Powell: "Banks are perfectly able to serve crypto customers." I love how everyone is recognizing and acknowledging Bitcoin now. Banks can custody Bitcoin on behalf of clients, create structured Bitcoin financial products, and allow customers to buy Bitcoin. Even Powell isn't badmouthing it anymore.
On the 29th of January:
➡️'It is utterly remarkable that BTC Dominance is at 62% considering it's really from 45% to 62% has coincided with massive issuance of Memecoins This really is a different market, a schism between Bitcoin and Crypto.' - Steven Lubka
➡️Illinois State Rep. has introduced a bill to establish a Bitcoin Strategic Reserve.
➡️The decoupling of Bitcoin & Crypto Market Caps:
ETH losing 50% of its value vs. BTC in the past 11 months explains the lack of enthusiasm about $100K BTC. Mitchell Hodl: '2 years ago if you sold 1 ETH and bought Bitcoin, you would have acquired ~.07 BTC. Today if you sell 1 ETH and buy Bitcoin, you’ll acquire .03 BTC. Those “toxic maximalists” were right. If it’s not BTC, it’s dogshit.'
On the 3rd of February Bitcoin dominance soared over 64%. Four-year high. Massively bullish. Despite the hundreds of billions of dollars invested in crypto, Bitcoin dominance has just tagged Nov 2017 levels. At 73%, it unwinds back to the pre-ICO era.
'The truth is, there is no more alt season. The sooner you accept that, the sooner you can still build up a meaningful Bitcoin position. You're not too late. You're among the first 1-2% of people to get into bitcoin. It's time to leave this chapter of false narratives behind and get on board with something real and meaningful.' - Sam Wouters
If you're trying to outperform Bitcoin with an "alt", just remember that you're mixing with a crowd that is simply trying to beat you to the exit.
➡️Senator Bob Menendez who fought against El Salvador adopting Bitcoin was just sentenced to 11 years in prison for taking bribes in Gold and Cash! Classic!
➡️INDIANA Bitcoin Bill!
HB 1322 would allow 'the Hoosier state' to invest state retirement funds in Bitcoin ETFs. Nation-states, States, Companies & Individuals are clamoring to acquire Bitcoin.
On the 30th of January:
➡️World's largest stablecoin Tether is now minting its stablecoin on the Bitcoin Lightning Network.
➡️ECB chief Lagarde says she "is confident" that Bitcoin will not end up in the EU central bank reserves. Here is the video of how she is explaining that Bitcoin isn’t liquid, secure, or safe for EU reserves.
Bitcoin trades 24/7—one of the most liquid markets in the world.
Its code secures $2T+ in wealth, never hacked.
It’s the most secure computer code ever written.
Remember what she said on Bitcoin a while ago: 'It's a matter that needs to be agreed at a global level. If there is an escape, that escape will be used.'
Oh one more: "People are happier to have a job than to have their savings protected." — Christine Lagarde, 10/30/2019
Christine Lagarde has been convicted of more crimes than the average Bitcoin user. Oh well, the more that central banks manipulate the money, the more people will want sound money, and the more people will turn to Bitcoin. Checkmate.
➡️Norway's sovereign wealth fund's indirect Bitcoin exposure has increased by 153% in the past year, reaching 3,821 BTC. Since 2020, its Bitcoin holdings have grown from 796 BTC to over 3,821 BTC, now valued at over € 350M.
➡️'A $400 home Bitcoin miner just mined a block worth OVER $330,000. They beat ONCE IN A LIFETIME odds.' -Pete Rizzo
On the 31st of January:
➡️'For the first time in nearly 2 years, the Bitcoin network is running out of pending transactions to fill up new blocks. It's looking like it could happen within a few hours (only 6 block backlog). This is nothing to worry about. But if you self-custody bitcoin, it's a great time to learn about UTXOs and consolidate the ones in your wallet, which could save you thousands of dollars worth of bitcoin in the long term.' - Tom Honzik
Learn more here: https://unchained.com/blog/too-many-bitcoin-utxos
➡️MicroStrategy will have up to $584m to buy more Bitcoin after its stock offering was oversubscribed by nearly 3X, increasing from 2.5M shares to 7.3M priced at $80 each.
➡️El Salvador removes Bitcoin's legal tender status and makes its acceptance voluntary, in line with IMF requirements for a $1.4B credit line. Francis Pouliot: 'Bukele bends the knee to IMF and officially abandons the original Bitcoin law that had caused Bitcoiners to move and invest there in the first place... exactly at the same time as the Bitcoin conference in El Salvador attracting Bitcoiners from all over the world.'
➡️The 2nd time this week another solo Bitcoin miner mined a $300.000 block.
On the 1st of February:
➡️'For the past three consecutive months, the Bitcoin network has processed more than $2 trillion worth of transactions. That's a lot of utility!' -Pierre Rochard
➡️Retail are capitulating their Bitcoin, whilst whales are buying. Transfer of wealth from the weak hands to the strong hands. Retail investors are reducing exposure, while large investors (whales) are capitalizing on this opportunity to accumulate. Historically, this divergence aligns with accumulation phases before price appreciation.
➡️So far, so good: Spot bitcoin ETFs pulled in $4.94 billion in January, which annualizes to ~$59 billion. For context: In all of 2024, they brought in $35.2 billion.
On the 3rd of February:
➡️Ethereum just fell -37% in 60 hours since the trade war headlines mid-day on Friday.
➡️$2B liquidated in 24 hours. That’s a record. More than the COVID dump. More than the FTX collapse.
➡️Trump signs an executive order to create a sovereign wealth fund spearheaded by Howard Lutnick and Scott Bessent. Both are avowedly pro-Bitcoin.
➡️New Record Bitcoin Network Computer Hashrate: 800,000,000,000,000,000,000x per second
➡️OKLAHOMA BITCOIN BILL SB 315 allows state employees (and all OK residents) to receive payments in Bitcoin. The bill has progressed to Committee consideration.
➡️'Solid, data-driven reporting on why Bitcoin mining is increasingly regarded among energy experts, academics, and those in the environmental movement as a net positive to the environment across several fronts.' - Daniel Batten on the Mara report.
https://x.com/MARAHoldings/status/1880063353168753133
➡️$562m leveraged Bitcoin positions liquidated as the price plunged as low as $91,359 this morning.
💸Traditional Finance / Macro:
On the 27th of January:
👉🏽Over $787 billion was wiped out from the US stock market today.
On the 28th of January:
👉🏽'Amazon, Google, Meta, Microsoft, and Oracle's CapEx are expected to reach a record $274 billion this year. This would be more than DOUBLE the CapEx posted in 2021 and $127 billion more than in 2023. Amazon, and Microsoft, are expected to spend $86 billion and $63 billion, respectively. Spending has accelerated as Big Tech invests in more advanced chips from firms like Nvidia, and large data centers to store them. The big question is whether China’s DeepSeek will disrupt this trend. Is AI spending out of control?' -TKL
But meanwhile:
'Magnificent 7 stocks have underperformed the market in 2025: The Magnificent 7 stocks are down -1.4% while the S&P 500 itself is up ~2.9%. Meanwhile, the remaining 493 stocks in the S&P 500 have gained +6.6%. To put this into perspective, in 2024, the Magnificent 7 stocks returned +67.4% while the remaining 493 firms gained just +5.0%.' -TKL
👉🏽MicroStratey today announced the launch of STRK a new convertible preferred stock offering available to institutional investors & select retail investors. To view the investor presentation video, learn more about participating, & access key details, click here.
👉🏽Microsoft shares closed down 6.2% on the worst day since 2022. If only they had listened to Saylor's 3-minute Bitcoin pitch.
🏦Banks:
👉🏽Global central banks now hold more Gold than at any point in the past 45 years. Something is brewing.
🌎Macro/Geopolitics:
On the 28th of January:
👉🏽'Positions Europe to play a leading role globally.' Inhale, exhale! The EU bureaucrats are stifling innovation. The EU developed the AI Act instead of AI. To paraphrase Geoffrey Howe, the EU is like a man who knows 364 ways of making love but doesn’t know any women.
Europe also innovated with 'smart waste bins'. The sad this is, I couldn't even refute that now. What groundbreaking future technology has Europe produced in the last 30, 40 50 years?
Europe is done. No Bitcoin, no AI, no tech, no nothing. Regulation fees are becoming their only source of revenue. Wrong side of history, they'll be left behind.
👉🏽Jeroen Blokland: 'China has literally bought its 5% growth target, issuing and swapping tons of DEBT! China's budget deficit is expected to have hit a whopping 7.1% of GDP in 2024. Why do you think China's 10-year yield is at 1.60%? In a world full of debt, invest in scarce assets!'
👉🏽The following is from last week's Weekly Recap: 'The rich are getting richer faster than ever before: US household net worth has risen ~$56 TRILLION since Q1 2020 and hit a record $160 trillion in Q3 2024. Currently, the top 10% own $111 trillion of all wealth, accounting for 69% of the total. The top 0.1% alone own a massive $22 trillion, reflecting 14% of household net worth. On the other hand, the bottom 50% holds just $3.9 trillion, or 2.4% of wealth. This comes as the S&P 500 and the Nasdaq 100 have risen 128% and 166% since Q1 2020 while national home prices have surged ~50%. The wealth gap is growing.' -TKL
Just to elaborate on that, in 1990 the wealth gap between the top 1% and the bottom 50% was $3 trillion. Incredible chart!
Now the gap is $40 trillion. Ask yourself why. Has there been more or less government since 1990? Is there more or less money printing?
Cantillion things I guess, and oh don't forget if it was adjusted for inflation it would be even worse, the red line would be pointed down.
👉🏽Ursula von der Leyen: " Dear Christine, dear ECB Governing Council Europe’s competitiveness is our shared interest—and an urgent challenge. The Savings and Investments Union must become a reality. It is so needed. Looking forward to our great work together also in this new mandate."
You mean: "We will grab and redistribute your savings." These people (one convicted criminal - Lagarde) are so out of touch with reality. And a new mandate? Are you kidding me?
👉🏽Jeroen Blokland: 'Germany is heading for something 'unique!' BDI, which calls itself 'The Voice of German Industry,' expects the German economy to shrink again in 2025. That would mean three consecutive years of GDP decline. How do German politicians explain this, and how does this reconcile with the re-election of that other German politician, Ursula von der Leyen?'
On the 29th of January:
👉🏽'SUMMARY OF FED DECISION (1/29/2025): 1. Fed leaves rates unchanged, pausing the "Fed Pivot" 2. The decision to halt cuts was a unanimous 12-0 vote 3. Fed says inflation "remains somewhat elevated" 4. The Fed says "Unemployment has stabilized at a low level" 5. Statement on progress toward 2% inflation removed 6. The Fed seems to be aware disinflation has stalled The battle against inflation continues in 2025.' -TKL
👉🏽Americans spent over $113 billion on lottery tickets last year, which is more than they spent on movies, books, concerts, and sports tickets - combined. James Lavish: 'Central Banks have turned otherwise normal people into desperate gamblers trying to keep up with the cost of everything.'
👉🏽Gold prices surge to a new all-time high of $2840/oz. Gold prices are now up +40% in 12 months as the US Dollar and interest rates are up sharply. This has never happened in history. Gold is telling us something.' -TKL
Yes, let me use the following quote by Lawrence Lepard: 'Analog sound money saying sovereign debt crisis inbound.'
But remember, Gold hit an ATH in USD but an ATL in Bitcoin. Fiat money is absolute garbage and Bitcoin is superior to both.
On the 30th of January:
👉🏽The ECB, Christine Lagarde: 'We’re redesigning euro banknotes! Our Governing Council has selected motifs based on our two chosen themes, “European culture” and “Rivers and birds”. We’ll be launching a design contest later this year to help us select the final designs in 2026.'
On the 31st of January:
👉🏽Germany's unemployment rate hits its highest level in almost 10 years. The unemployment rate spiked by 0.4% to 6.4%.
👉🏽December PCE inflation, the Fed's preferred inflation measure, RISES to 2.6%, in line with expectations of 2.6%. Core PCE inflation was 2.8%, in line with expectations of 2.8%. PCE inflation is now at its highest level since May 2024.
On the 1st of February:
👉🏽 The DOJ just argued that your money isn’t actually property—so the government can take it at will. If that sounds insane, it’s because it is. A federal court will decide if this madness stands. https://reason.com/2025/01/31/the-government-says-money-isnt-property-so-it-can-take-yours/ The money in your bank isn’t actually yours. Only Bitcoin can fix this. Still think you don't need Bitcoin?
🎁If you have made it this far I would like to give you a little gift:
++++
Preston Pysh podcast with Lawrence Lepard: 'Exploring the roots of broken money, the moral case for sound currency, and how Bitcoin offers hope for a decentralized financial future.' https://www.youtube.com/watch?v=WxB8M8q8hQ8
Credit: I have used multiple sources!
My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: PocketBitcoin especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly. Use the code BITCOINFRIDAY
Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple.⠀⠀⠀⠀ ⠀ ⠀⠀⠀
Do you think this post is helpful to you? If so, please share it and support my work with a zap.
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
⭐ Many thanks⭐
Felipe - Bitcoin Friday!
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
-
 @ 0b118e40:4edc09cb
2025-02-05 06:07:11
@ 0b118e40:4edc09cb
2025-02-05 06:07:11Tipping Point by Malcolm Gladwell has been around for a long time. I first read this book maybe about 10 years ago, but this time around I read it from the perspective of marketing, and PR.
Gladwell is a highly controversial and thought-provoking author - and while I often both agree and disagree, I'm impressed by how he links and simplifies his ideas to real-world examples from sports, fashion, social attributes, genes, religion, kids, politics, history and more. If you have similar or opposing views on Gladwell’s takes; I’d love to hear it
This book talks about how niche or idiosyncratic trends become mainstream.
If I were to re-read books related to these topics again, to understand the concepts better, I would read all 4 books in the following sequence :
- Crossing the Chasm; Marketing and selling disruptive products to mainstream customers by Geoffrey A.Moore
- Tipping Point; How little things can make a big difference by Malcolm Gladwell
- Made to Stick; Why some ideas survive and others die by Chip and Dan Heath
- Contagious; Why Things Catch On by Jonah Berger (I've shared No 1 a long time ago, and No 4 recently. This is No 2)
Now, onto Gladwell's take - 3 factors can make an idea spread like wildfire or become contagious like an epidemic :
- Law of The Few - influence of a few individuals
- Stickiness Factor - how messages stick in people’s minds
- The Power of Context - how environment and circumstances affect outcome
The overarching concept is how small actions can lead to significant and unexpected outcomes very quickly
- Law of the Few - talks about connectors, mavens and salespeople. These are people who are your links to groups, and communities and make the messages spread.
Some examples shared -
Paul Revere as the connector - he is famously known for his midnight ride, went town to town, knocked on each door, spread the right message and everyone was ready for the British invaders by morning leading to the American Revolution. William Dawes took on the same mission in the West of Boston but did not have the same impact - which concludes that connectors have a special gift of spreading messages
Another example is six degrees of separation - and eventually, the points of contact will be connectors
More people find jobs through connections
Needle exchange programme - discovered that the “insiders” collect all the used needles, exchange them for fresh ones and sell them for a dollar each to drug addicts. While this wasn't the original plan for needle exchange, it was effective as the insiders knew where the junkies were, when they were used etc and effectively got them fresh needles.
Connectors are people who know a lot of people, and also, the kind of people that they know. They bring people together, there’s no snobbery. They may not be the first to discover it, but they are the people who can broadcast it. Mavens are people who are experts in certain areas and accumulate knowledge. Salespeople are persuaders. Sometimes you can find all 3 in one, sometimes they are different individuals
- The second factor is the stickiness factor and understanding what keeps people glued. Examples include :
Tetanus shot - In an experiment, half of the students received a "high fear" booklet on tetanus and the other half a regular one. The high fear group was more convinced but only 3% got the shot. The second time, a booklet with schedules and shot locations improved adoption, showing persuasion alone was not enough - the right information sealed the deal.
Sesame Street - getting children to stay focused on a TV programme. The observation is that children would only like straightforward information and can get distracted from time to time - hence every few minutes, there is a “distractor” on the show that switches the kids' focus and back.
The concept of a "distractor" refers to something attention-grabbing or visually stimulating that can potentially divert a child's focus from the educational content being presented such as colourful puppets, catchy songs, and entertaining characters like Elmo. These distractors are strategically woven into the show to maintain children's interest and keep them engaged in the main educational program
Blue Clues took it a step further and made it engaging for the kids to participate by answering questions and repeating many times
The factors that make a message stick are: Repetition, Distractor (something unexpected or unusual that captures people's attention), Unexpectedness ( things that are out of the ordinary), Concreteness, Emotion, Simplicity, Credibility, Storytelling
- The Power of Context was quite interesting - It says that human beings are a lot more sensitive to their environment than they may seem. It retells the idea of PR and the importance of it.
An example is the Broken Window Theory, which highlights how people's behaviour can change based on their environment. For instance, in a poorer community, you're more likely to observe higher social issues, whereas in an improved community in terms of proper infrastructure, and visually appealing, the same individuals tend to exhibit and experience fewer problems. The example referred to the NY subway problems in the 80s and how it was reduced drastically.
Another well-known experiment is the Stanford Prison Experiment. In this study, individuals were assigned the roles of either prisoners or guards. The environment was transformed to resemble a grim prison, leading the guards to exhibit cruelty while the prisoners lost their sense of self, referring to themselves by numbers. The experiment was called off after just six days.
The power of context talks about the importance of Nature over Nurture and the influence of Peers that impacts how you react and make decisions.
Other examples were the teen smoking epidemic, and the suicide epidemic (these two were on how to contain it)
- Some other examples that are related to community building
If you want to bring about a fundamental change in people’s beliefs and behaviour, a change that would persist and serve as an example to others, you need to create a community around them, where those new beliefs could be practised and expressed and nurtured.
Examples - the Methodist group spread - John Wesley who went from town to town, met with the locals, set up communities and connected it.
Another example is the Ya-Ya sisterhood book - this did not spread early on, but it did when the author when town to town over a year and reached out to the book clubs
Both the above two examples talked about a continuous time frame of say 1 year of going from location to location (both within a country) to spread the message.
150 seems like a good number within a small community to have effective engagement. Anything more leads to a new community, to build up the next 150. Gladwell gave many examples from tribes (Hutterites) to the corporate environment that uses this concept. To serve as incubators for contagious messages, the group has to be kept below the 150 Tipping Point.
One last example - there was a campaign to spread awareness of diabetes - and this was done in churches for its large group of people - but it did not catch on because people were tired, hungry, and wanted to go home. So the campaign shifted location to saloons and that picked up because people were relaxed and spent hours there.
In comparison to the diffusion model - connectors to me are not the early adopters, but rather the key spokesperson in the early minorities. Connectors also translate the message of the innovators into something the rest of us can understand.
In summary - The tipping point talks about the possibility of doing a lot with a little - by concentrating on a few key areas - to make something spread.
The "Law of the Few" emphasizes that Connectors, Mavens, and Salesmen drive word-of-mouth epidemics, so concentrate resources on them if you want to start one.
Stickiness - the key is to package information irresistibly - you just need to discover how.
The "Power of Context" reveals our profound sensitivity to environmental changes. Our inner states reflect our outer circumstances.
-
 @ 1cb14ab3:95d52462
2025-02-05 04:10:38
@ 1cb14ab3:95d52462
2025-02-05 04:10:38Tree branches. 4' x 4' [Littleton, USA. 2016]
Introduction
Platte captures a tranquil bend of the South Platte River, where the steady flow of water meets the rugged backdrop of Waterton Canyon. This lens offers a moment of respite, encouraging visitors to step away from the river’s busy recreational activities and focus on the quiet beauty of this secluded scene.
Site & Placement
Positioned on the west bank of the South Platte River, the lens directs attention to the water’s gentle curves and the canyon rising in the background. A bench placed 12 feet away provides the perfect spot for reflection, emphasizing the interplay of movement and stillness in the landscape.
Impermanence & Integration
The lens, constructed from branches and stone, mirrors the ever-changing nature of the river itself. As it stands, it frames a single moment within the flow of time, but its materials will soon be reclaimed by the earth, echoing the river’s constant reshaping of the land.
Reflection
Platte invites viewers to contemplate the river’s journey—its constancy in motion and its quiet persistence. The work becomes a metaphor for life’s flow, urging us to find beauty in the transient and the enduring alike.
Photos







More from the 'Earth Lens' Series:
Earth Lens Series: Artist Statement + List of Works
"Looking Glass" (Earth Lens 001)
COMING SOON: "Grandfather" (Earth Lens 005)
COMING SOON: "Chongming" (Earth Lens 006)
More from Hes
All images are credit of Hes, but you are free to download and use for any purpose. If you find joy from my art, please feel free to send a zap. Enjoy life on a Bitcoin standard.
-
 @ c43d6de3:a6583169
2025-02-05 02:46:10
@ c43d6de3:a6583169
2025-02-05 02:46:10
Right this moment, 5.52 billion pairs of hands are within arm’s reach of the internet.
Hands stretch across pillows, eagerly reaching for phones first thing in the morning. Fingertips tap at keyboards and swipe across glowing glass.
The world has never been so connected. Billions of conversations are happening every second.
Yet, humanity has never been so quiet.
Hotel lobbies, waiting rooms, train stations, and airports — places once buzzing with the chatter of strangers — now lie quieter than libraries. Most libraries don’t exist in the physical sense anymore.
Humanity Has Gone Mute.

Small talk is disappearing. The tiniest thoughts are condensed into 280 characters to be posted on X, hoping to garner hearts, claps, zaps, or whatever gimmick social media platforms use to keep us tethered to their feeds. Instead of sharing these thoughts with the few souls occupying the same physical space as us, we broadcast them into the digital void.
Gone are the genuine, physical reactions — a smile, a laugh, maybe a headshake if a joke didn’t land.
Who needs small talk, right? Wasn’t it just that awkward thing people did before cellphones and the internet existed?
No. The silence is worse.
It’s the manifestation of relational decay.
That’s why people talked. People talked about the weather or about Mrs. Jones’ dog that always gets out. That’s what helped neighbors scale one another’s emotional fences and get to know one another. It was, and always will be, the first step to any meaningful relationship.
Today, small talk has been relegated to social feeds and forums. It’s easier to make a friend across the planet than to make one next door. People fall into the trap of chasing likes, followers, and fame, while their local connections — the ones critical to mental health and a sense of purpose — fade into the background.
Maybe I’m out of touch. Maybe I just don’t get out enough. But as a member of the Army Reserves, I’ve experienced something rare.
Once a month, I attend drill, and once a year, we’re sent on an annual training that can last up to thirty days. During those thirty days, we’re often shipped off to a place far from the internet. And in that time, something remarkable happens: small talk comes back to life.
It’s incredible to watch my fellow Soldiers connect.
The relationships we have before training versus after are night and day. And it all starts with small talk — simple jokes, shared gripes, and the mundane details that snowball into camaraderie.
When we’re forced to take that first step to avoid the boredom of silence, we discover one another’s existence. It’s a reminder that sometimes, the absence of convenience is what sparks true connection.
Small talk isn’t just filler. It’s the foundation of relationships. Maybe it’s time to put down the phone, look around, and say something — anything — to the person next to you.
While the world may feel quieter than ever, the potential for connection has never been stronger.
I want to show the world that life is a scroll riddled with ink. The marks will only ever be simple blots on the parchment unless you pause and perceive them for the characters they are.
Thank you for reading. If you liked this article let me know with a zap and share with friends you feel might enjoy it too!
-
 @ c43d6de3:a6583169
2025-02-05 02:37:14
@ c43d6de3:a6583169
2025-02-05 02:37:14Reflection on Growth and Gratitude

Ah, the Holidays… That time of year when we return where it all began. The hustle and grind of the past twelve months has built to a fever pitch, and whatever we’ve achieved — or failed to — clings to us like a weight on our shoulders as we step onto the doorsteps of home.
It’s a time of reunions, of seeing faces that knew us before careers, titles, and responsibilities etched lines into our brows. Eyes linger a moment too long, quietly assessing:
“Have they changed?” “Have they succeeded?” “How much weight have they gained — or lost?”
And then come the words — warm, congratulatory, or otherwise. “You look amazing!” they’ll gush, or worse, the silence of unspoken judgment.
Later, with old friends, the comparisons begin. It’s subtle, unspoken, but there. This year, as I stood in front of my best friend’s meticulously polished Porsche SUV, a gift to his wife, the voice in my head wasn’t congratulating him. It was whispering something else: envy.

I was happy for him — truly. I congratulated him on being in a position to give his wife something so extravagant. But as we spent the day together, subtle hints started to pile up, revealing there was more to his gift than I’d initially thought.
Since the last time I’d seen him, he’d grown significantly wealthier. There were comments and allusions that suggested he might even be a millionaire. What started as a faint whisper of envy in the back of my mind soon ignited into a flame of curiosity — and, I’ll admit, a touch of self-pity.
I couldn’t help but wonder: How the hell did he do it?
I tried to play it cool, to not make a fuss about it, but it was gnawing at me. I’d spent the last 12 months busting my ass, juggling work, two kids, and a wife, barely keeping my head above water.
He had kids. He was married. He worked a full-time job. Yet, somehow, he was fitter than me, his house was tidier than mine, and everything I struggled to maintain at a high standard seemed effortlessly better in his world.
What was I missing?
I fought the urge to chalk it up to something simple, like a secret inheritance from a wealthy relative I didn’t know about. Maybe, his grandfather passed and left him a fortune?
Our conversation deepened. I started to understand more about his daily routines and professional growth.
There was no silver bullet. No stroke of luck or hidden windfall. He was simply outworking me in every way imaginable.
Looking at him in his beautiful home, talking about his plans and the ways he still aspired to grow, took me back to when we were kids. Back to the times we would sit on the porch, watching cars roll by, projecting our dreams into the world.
He had turned those dreams into reality — and now, here he was, setting his sights on even higher ceilings to break through.
I felt a pang of shame for the envy stirring inside me.
What had I been doing wrong?
We were essentially the same person. We grew up in the same neighborhood, shared the same circle of friends all the way through college, believed in the same values, and approached life with the same mindset.
But as I listened to him, I realized we had the same foundations and potential, yet we executed differently. He was waking up at 4 a.m. to pursue the things he loved, knowing his busy days wouldn’t allow for it otherwise. Meanwhile, I was hitting snooze, sleeping until the last possible moment before scrambling to get the kids ready and start my day.
I’d been putting off the things I love — like writing. I’d turned down opportunities for higher-paying jobs because I feared they’d chip away at the little time I already had.
The envy I’d felt began to crystalize, forming a smooth, reflective surface — and staring back at me was my own face.
That’s when it hit me: I was actually lucky.
What better friend could I ask for than someone who serves as a reflection of a better version of myself? What better inspiration could there be than the drive to return next year and say, “Hey man, I’m right there with you.”

Not everyone returns from the holidays feeling inspired. Most head back to their “real” lives with bags of half-thought-out gifts, a few extra pounds around the waist, and the quiet relief of leaving their hometown behind.
Many start the new year armed with a list of goals but rarely with a clear vision of the person they want to become.
The seed of envy grew into something better in me; a desire to do more, to be more.
Cheers to you, bud. Here’s to the push I needed.
Envy #growNostr #Friends
-
 @ 57d1a264:69f1fee1
2025-02-05 02:18:03
@ 57d1a264:69f1fee1
2025-02-05 02:18:03Pre-Foundational learning for these participants has now kicked off in the Bitcoin Design Community, check out the #education channel on the Bitcoin.Design Discord channel.
🪇 10 talented participants from South America will be:
Learning bitcoin UX Design fundamentals using the Bitcoin Design Guide Working hands-on with South American-built products to evaluate their user experiences and support builders with data
Attending BTC++ in Florianópolis
This initiative is sponsored by the Human Rights Foundation in collaboration with the Bitcoin Design Foundation and Area Bitcoin.
🥅 Goals:
- Empower local talent to improve the UX of South American bitcoin products - seeing their passion and drive to bring bitcoin to their countries is really inspiring
- Create meaningful relationships with wallet developers through practical collaboration
- Scale bitcoin adoption by improving the user experience
- Create a public knowledge base: All research conducted in Africa and South America will be made publicly available for builders
originally posted at https://stacker.news/items/876215
-
 @ dd1f9d50:06113a21
2025-02-05 01:48:55
@ dd1f9d50:06113a21
2025-02-05 01:48:55(Because Most People Don’t Understand Money)
The requisite knowledge needed to know whether $100 or $100,000 per Bitcoin is relatively speaking “a lot,” is what value means. One way to measure value is through a universal yardstick we call “Money.” The question of “What is money?” is perhaps one of the most overlooked and under answered in our day and age. There is even an entire podcast dedicated to that question with the eponymous title, hosted by Robert Breedlove. That podcast often delves into the more philosophical underpinnings whereas I hope to approach this with a more practical answer.
Money is a technology.
Money is the technology with which we interact with one another to reorganize goods and services to the place and time they are best suited. Most money of the past has been tangible (though not a requisite feature), scarce, recognizable (read: verifiable), durable, portable, and divisible. These features one might call the “Attributes of Money.” These attributes are absolutely essential for a money to maintain its status as a money. (Those of you who understand the U.S. Dollar system maybe scratching your heads right now but, believe me, I will address that elephant in due time.) These attributes, you may notice, are not a yes or no but more of a gradient. A money can be MORE portable than another yet, less durable. One more divisible but not scarce whatsoever. The point being they must have, in some capacity, these attributes or they simply aren’t money.
One of These Things is Not Like the Other
| | Bitcoin | Gold | Dollars | |-----------------|:----------------------------------------------------------------------------------------------------------------:|:------------------------------------------------------------------:|:--------------------------------------------------------------------------------------------------------------------------------------------------:| | Scarcity | 21 million coins
is the maximum supply | Unknown- the
supply grows roughly 2% per year | Also unknown to anyone outside of the Federal Reserve, Trillions and counting | | Recognizability | Each coin is verifiable to it's genesis on the timechain | Each molecule of gold has distinct physical verifiable properties | If the Federal reserve says it is a valid note, it is (Unless you are an enemy of the United States) | | Durablility | Each "Bitcoin" is information stored on a globally distributed network | Doesn't Rust and as far as can be measured Au197 is stable forever | Can be destroyed by any means that effect fabric and centralized databases | | Portability | Available wherever data can be store- Anywhere | Can be moved at 9.81 Newtons per Kilogram- Methods may vary | Can be moved physically with fabric notes- Digitally with express permission from a US accredited banking institution | | Divisibility | Currently can be divided into 100 million parts called Sats (can be further subdivided by adding decimal places) | Can be divided to the Atomic level (Though not practical) | Can be divided (without dilution) by adding new denominative bills or coinage
Can be divided (with dilution) by printing new bills or coinage | | | Bitcoin | Gold | Dollars |You may think with all of the great functionality of Bitcoin that the phrase "One of these things is not like the other" refers to BTC. No, I was referring to the Dollar. It is the only one on the list that was a currency that was substituted as some kind of faux money. It asserts itself, or rather the Federal Reserve asserts it, as money, de facto.
Dollars are NOT money.
Dollars are (allegedly) a currency. If money is a specific technology, currency is the financial infrastructure that allows that technology to reach and be used by the most number of people possible. This requires a firm tether between the asset being used as money and the currency used as a claim to that money. For example: If I hand you a chicken, you have a chicken. But, if I hand you a coupon that is redeemable for a chicken, you do not have a chicken. You have a claim to a chicken that is only as good as the party making that claim. Bringing it back to money again, dollars (Prior to 1971) were redeemable for gold at a rate of $35 per ounce. This is that strong tether that pegged dollars to gold and physical reality itself. Without a proof of work, mining, . Until…
WTF Happened in 1971?
The Nixon shock happened. Briefly, The U.S. took in Europe’s gold in the 1940’s to keep it out of Hitler’s hands. The U.S. made an agreement to peg the dollar to Europe’s gold. The U.S. over printed dollars in relation to the gold holdings. Around 1971 France (among others) called the U.S. out for devaluing the dollar and thus European currencies. So, Nixon “Temporarily” suspended the convertibility of dollars to gold. Now, here we all are like Wile E. Coyote having run off of the golden cliff clutching our dollars in our arms and 54 years later we still haven’t looked down to see the truth.
Dollars Aren’t Backed by Anything
This is why no country in the world today has a money standard. Seemingly they all forgot the number one rule of issuing currency, it must be backed by something. Now, you may hear dollar proponents say “The U.S. dollar is backed by the full faith and credit of the United States!” Another way of saying that is, “We said it is worth something, so it is!” This fiat (by decree) mentality creates a plethora of perverse incentives. The ever growing supply disallows users of the Dollar to save without inccuring the penalties of inflation.
Just a Few Examples of How You're Being Crushed
Because your dollar loses value:
- It pushes people to spend them on assets that seem to appreciate (as the dollar debases) but are truly staying stagnant.
- It pushes people to gamble on securities hoping the perceived value is enough to beat the inflationary curve.
- It pushes people away from saving for their future and the future of their families.
- It creates insane credit incentives so that people borrow way more than they can afford today knowing that dollars will be cheaper in the future. (Effectively a short position)
- It pushes people to spend less and less time making and maintaining their families as it becomes more expensive to keep a similar lifestyle to which it was founded.
These are just a few of the terrible consequences of not knowing that trading a currency with no monetary backing has on a society. Most may blame this soley on the ability to print currency by a central bank but, that is not the only factor. If the fed printed dollars against gold, people would simply take the best rate they could get and remonetize themselves with the gold. But because there is no monetary escape hatch guaranteed by the issuance of dollars, I.E. no one has to take your dollars in exchange for their Bitcoin or gold, you are left at the mercy of the market.
One Day, People Will Stop Accepting Your Dollars
Those lementing the high price of Bitcoin might want to thank their lucky stars that Bitcoin still has a rational number next to the "BTC 1=$?" sign. One day you will have to exchange something of actual value to the spender (no longer a seller). Your product, good or service, will be the only thing that anyone might be willing to part with their Bitcoin over. That is what makes a money, the most salable non-consumable good, whose only funtion is to back a financial structure that facilitates trade.
Bitcoin is Capital
Capital is a broad term that can describe anything that confers value or benefit to its owners, such as a factory and its machinery, or the financial assets of a business or an individual. Bitcoin being the latter creates the financial structures from which you build upon. You use capital to hold, transfer, and grow value. You do not do this with cash. Cash is a depreciating asset when you don't use it to gain goods or services for yourself or your business. This misconception around the equivalance between cash and money (financial capital) is what tricks people into believing Dollars are money. And what's worse is that even some of our greatest heroes have done this.
Slay Your Heroes, Within Reason
Unfortunately due to a mixing of verbiage that have very distinct differences, the title: "Bitcoin: A Peer-to-Peer Electronic Cash System" is technically inaccurate. Bitcoin doesn't fit the definition of cash, which is a liquid asset that can be easily converted into its equivalent value. In short, Satoshi misspoke. In reality, owning Bitcoin UTXOs (with private keys) means you already possess the asset, not just a claim to it. When you spend Bitcoin, the recipient receives the actual asset, not a promise of it. When you receive Bitcoin, you have final settlement on that transaction. Fundamentally Bitcoin is not cash, electronic or otherwise.
Bitcoin is Money.
-
 @ 57d1a264:69f1fee1
2025-02-05 01:26:18
@ 57d1a264:69f1fee1
2025-02-05 01:26:18How does the collaborative nature of open design in bitcoin influence innovation and product development in the ecosystem?
originally posted at https://stacker.news/items/876187
-
 @ df478568:2a951e67
2025-02-05 01:02:39
@ df478568:2a951e67
2025-02-05 01:02:39
About 150,000 blocks ago, I bought burgers for my family with sats at NextBurger in Newport, California. The Orange County Bitcoin Meetup found a hamburger stand that wanted to accept Bitcoin. This attracted Bitcoiners from all over Southern California. People brought their families. Some sat stackers sold wares outside as if it were a Farmer's Market. A couple kids sold some hats. One dude sold pins. I bought one off him. It resembled the Opendime I use as a keychain. He wore a 21M/infinity hat. We talked about Knut Svanholm books. He asked me, "What do you do for bitcoin?"
"I write a blog," I said. I must have written three articles about Bitcoin back then. I set up a BTCpayServer with LunaNode. My real idea was to write for sats, but I spent more sats on Lunanode than I made. I needed something to sell.
I had a few shitty ideas but no real business plan. I told Pins about one of these shitty ideas.
"I'm thinking about selling BIP39 raffle tickets, but they're a pain in the ass to cut." See what I mean, bad ideas.
Pins didn't say it was a bad idea though. I assure you, it was, but Pins gave this advice.
”Maybe you can use a 3D Printer."
I never did it, but I was impressed by how willing he was to help me. That's common in bitcoin. Bitcoiners are incentivized to help other Bitcoiners. The more people that accept Bitcoin at their stores, the bigger the demand for Bitcoin. The bigger the demand, the more the

Bitcoin Is For Spending
I participate in the circular economy because I consider using Bitcoin as money to be more advantageous for my savings strategy. When you earn sats, spend sats, and save sats, you break free from the chains of fiat debasement. Dollars are designed to go down in purchasing power to manipulate the public into spending more. That's why most people have more than one TV, but can't afford a $400 emergency. I spend Bitcoin because it forces me to be frugal. Fiat is designed to spend as quickly as possible since it will buy less groceries tomorrow than it will today.
Bitcoin is designed to buy more groceries tomorrow than it will today. When you expect $30 worth of Open AI services will likely be worth $433 in 21 years(if we assume Saylor is correct) you evaluate everything you buy with an orange colored lens. Your shopping habits change. A month of Chat GPT premium mightr be a month's worth of groceries in the future. I no longer buy Nike's because they coat 80k-120k sats, but I expect them to look like shredded cheese in six months. I would rather pay 100k sats for a nice pair of hiking shoes. I expect they will last me a few years.
Knowing this, you might ask, why would you spend Sats on a stupid pin? I've had my open dime pin for almost 4 years now and I expect to have it for years to come. It must have cost me about 100k sats. I don't expect it to be worth that much in the future, but you never know. Sometimes, I watch The Antique Road Show on PBS. Some pins, made by famous artists, are worth thousands of dollars. There is a chance collectibles like this will become more valuable, but I'm skeptical of this. I bought this PIN because it sparks joy, as Marie Kondo says.
This is not investment advice. Your Sats will almost certainly be worth more than your pins in the future, but if you buy a PIN from Salvador Dali, nobody stacks Sats. If you buy a PIN from BTCPins, a hardcore bitccoiner stack sats, which means less sats on the market will be availavle for 8 billion people when you buy a pin. Maybe pins will buy another hat from a bitccoiner, but that just means another bitccoiner stacks Sats. Notice how these Sats never make it back to the exchange because Bitcoiners know their stack will be more valuable in the future than they are today. So when you spend Sats, you only spend Sats on the things you find most valuable.
Pins I Bought Online

Although I consider these Pins art. I don't view art as an investment. I don't expect to ever sell one of these Pins for $110,000 like that banana duct-taped to a canvas before the artist got the munchies. I don't want dollars anyway. That's like a whole coin for a banana. I wouldn't spend 100,000,000 sats for one of these Pins, but BTCPins are not so pretentiously priced.
I recently bought some pins I've been salivating over for months. I need a better way of displaying them, but here are the pins I recently bought.
An Awesome Affiliate Link
BTCPins has a unique affiliate link. Provide your lightning address and it will generate an affiliate link for you. These things have been around since the 90s, but what makes this particular link notable is how commissions are paid: In sats on the Bitcoin lightning network.
How BTCPins Affiliates Work
- Navigate to https://btcpins.com/affiliates/
- Enter your lightning address.
- Generate your link
- Share with the world.
So buy a pin or two from BTCPins today using my affiliate link:
Encrypted Link: https://btcpins.com/?aff=ex1GhhNeeU9-PQ1-ZVEkarU9bSnsNyq98Jy_lEUBLmsrWsCqa69PYohMWcCOGK9tK1rAqmuvT2KITFnAjhivbfOajnP3D8A8O09Hi-OY4K8
npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
-
 @ 16d11430:61640947
2025-02-05 00:52:05
@ 16d11430:61640947
2025-02-05 00:52:05Introduction: Colonization as a Multi-Generational Trauma
Colonization was not only a political and economic endeavor but also a deeply psychological one. Through forced labor, cultural erasure, and systematic oppression, colonizers imposed a set of economic and social behaviors that favored their interests. Though most colonies gained independence in the mid-20th century, the trauma of colonization remains embedded in their financial and governance structures.
Modern research in epigenetics suggests that trauma can alter gene expression and be passed down through generations (Yehuda & Lehrner, 2018). In a socio-economic context, the colonial mindset—marked by dependency, economic passivity, and a lack of financial sovereignty—persists within many post-colonial nations. One of the most insidious methods by which this trauma is maintained is through fiat currency and debt-based financial systems, which perpetuate economic dependency on former colonizers.
- The Psychological Impact of Colonial Trauma and Economic Passivity
Historical trauma theory suggests that populations subjected to prolonged oppression develop collective learned helplessness—a psychological state in which they stop attempting to resist their conditions because they have been conditioned to believe resistance is futile (Sotero, 2006).
This manifests in post-colonial societies in several ways:
-
Economic Dependency: A tendency to rely on foreign aid, multinational corporations, and foreign direct investment (FDI) rather than fostering self-sustaining industries.
-
Risk Aversion in Economic Policy: Research suggests that traumatic experiences affect the brain’s ability to take financial risks (Shields et al., 2016), leading to post-colonial states preferring IMF/World Bank solutions rather than exploring independent monetary policies.
-
Political Elite Compliance: Many former colonies' elites were educated in Western institutions, perpetuating colonial economic structures that maintain wealth extraction.
- Fiat Currency as a Tool of Economic Control
Fiat currency—money that has no intrinsic value but is backed by government decree—has been one of the most effective tools for maintaining economic dominance over former colonies.
A. The CFA Franc: A Colonial Currency in 2024
One of the most blatant examples of fiat currency maintaining colonial control is the CFA franc, used by 14 African countries, but ultimately controlled by France.
These countries must keep 50% of their foreign reserves in the French Treasury.
France dictates the monetary policies of these countries, limiting their financial autonomy.
Import dependency: Because the CFA franc is overvalued, it makes local goods more expensive while making European imports cheaper, reinforcing dependency on former colonizers.
B. The Role of the IMF and World Bank in Debt Colonialism
Post-colonial nations, lacking industrial infrastructures due to resource extraction under colonial rule, often turn to IMF and World Bank loans for development. However, these loans come with conditions that ensure neo-colonial economic control:
Structural Adjustment Programs (SAPs): Force nations to privatize industries, cut social spending, and open markets to foreign corporations—benefiting Western investors.
Perpetual Debt: Since loans are taken in foreign fiat currencies (USD, Euro), debt is rarely reduced, creating a cycle of endless repayment that prevents real economic independence.
- How Colonial Trauma Conditions Profitable Behaviors for Former Colonizers
Even outside of direct financial mechanisms, the trauma of colonization has conditioned post-colonial societies to adopt behaviors that benefit the former colonizers.
A. Elites as Gatekeepers of Colonial Structures
In many post-colonial nations, political and economic elites maintain colonial financial policies because they personally benefit from them. Studies (Acemoglu & Robinson, 2012) show that economic elites in post-colonial states are more likely to align with global financial institutions rather than advocate for economic self-determination.
B. Consumer Culture as a Neo-Colonial Tool
Western consumerism remains deeply ingrained in many post-colonial societies. This is a legacy of cultural imperialism, where local industries were suppressed in favor of Western goods.
The majority of African, South Asian, and Latin American countries continue to import Western luxury goods, technology, and services instead of developing their own.
As a result, much of the wealth generated in these countries flows back to Western corporations, mirroring the colonial economic extraction model.
Conclusion: Fiat Currency as the Modern Brand of Colonization
The economic and psychological trauma of colonization ensures that former colonies remain profitable markets and debt-ridden nations under the control of their colonizers. Fiat currency, international debt structures, and cultural hegemony serve as the modern pillars of economic colonialism, reinforcing behaviors that favor Western economic dominance.
Key Takeaways:
-
Historical trauma conditions former colonies into economic dependency.
-
Fiat currency (such as the CFA franc) remains a tool of colonial control.
-
The IMF and World Bank perpetuate financial dependency through debt cycles.
-
Consumer culture ensures wealth extraction from former colonies to Western economies.
Unless these structures are dismantled, economic sovereignty for formerly colonized nations remains an illusion. Breaking free from the financial colonial matrix requires monetary independence, de-dollarization strategies, and local industrialization, rather than continued reliance on Western financial systems.
References:
Yehuda, R., & Lehrner, A. (2018). Intergenerational transmission of trauma effects: Putative role of epigenetic mechanisms. World Psychiatry, 17(3), 243-257.
Sotero, M. M. (2006). A conceptual model of historical trauma: Implications for public health practice and research. Journal of Health Disparities Research and Practice, 1(1), 93-108.
Shields, G. S., Sazma, M. A., & Yonelinas, A. P. (2016). The effects of acute stress on economic decision-making. Psychoneuroendocrinology, 67, 226-234.
Acemoglu, D., & Robinson, J. (2012). Why Nations Fail: The Origins of Power, Prosperity, and Poverty. Crown Business.
Sylla, N. S. (2019). The CFA Franc: The Shackles of Monetary Dependence. Pluto Press.
Hudson, M. (2021). Super Imperialism: The Economic Strategy of American Empire. Pluto Press.
-
 @ 57d1a264:69f1fee1
2025-02-05 00:25:20
@ 57d1a264:69f1fee1
2025-02-05 00:25:20How does open source development contribute to bitcoin's security, reliability, and evolution as a network?
originally posted at https://stacker.news/items/876130
-
 @ 1cb14ab3:95d52462
2025-02-05 00:14:34
@ 1cb14ab3:95d52462
2025-02-05 00:14:34Welcome to the first installment of my ‘Nostr Spotlight’, a series where I explore various Nostr clients (which I will refer to as apps for simplicity sake), review their features, and share tips on how to use them effectively.
For the first installment, I’m diving into npub.pro, an incredible service that lets anyone on Nostr create a fully functional website using their already-published notes.
What is npub.pro?
npub.pro is a simple—yet powerful— tool that takes your Nostr content and turns it into a website instantly. By filtering through hashtags or keywords, or hand-selecting which notes to feature, you can curate what appears on your site.
This allows for highly customizable and dynamic websites that anyone on Nostr can deploy. Whether you’re a blogger, photographer, journalist, artist—or just want to organize your notes into a cleanly setup website—this service opens up endless possibilities for showcasing your notes.
Who Should Use npub.pro?
This service is ideal for:
✅ Writers and bloggers who want a frictionless way to publish content.
✅ Artists and photographers looking to showcase their work.
✅ Journalists and researchers who need an easy way to organize articles.
✅ Anyone who wants a personal website without dealing with hosting or technical setups.
Why I Love npub.pro
I’ve personally deployed several websites using npub.pro, each serving a different purpose:
HesArt – My personal art portfolio.
https://image.nostr.build/6a7030a24a9c5d4a9e3a0854020e08740241e870e46083b6b326ca36d5dc681f.png
Hes – My main long-form writing site, featuring artist statements, travel guides, photo series, tech reviews, and economic essays.
https://image.nostr.build/7d088829dd2ec0f9702430f115e29d368da85a78227cf6524f8773216f6a102e.png
HesCooks – A collection of curated recipes.
https://image.nostr.build/840ffdc74ac618ddf9534d4ab77a09d02aee45eee8c332a6733bcea5b80a3d2a.png
HesCreates – A categorized and searchable archive of my notes.
https://image.nostr.build/4663c91f3c77ad59f0f291813c672395f8cc20c6806ca2afffb3e3d65b6c6f37.png
The ability to filter my Nostr content and instantly publish it as a website has made organizing my notes seamless and efficient. The opportunities are endless and I have several ideas for other websites I plan on deploying.
How to Get Started
1.Visit npub.pro.
2.Enter your Nostr private key (nsec) using an extension of bunker.
3.Choose your filters (hashtags, keywords, etc.) to curate what appears and select a pre-made theme.
4.Publish instantly – no extra setup needed!
It’s that simple.
Final Verdict:
5/5 Stars ⭐⭐⭐⭐⭐
npub.pro is an outstanding tool that makes publishing on the web effortless for Nostr users. It’s intuitive, versatile, and packed with potential use cases. Whether you need a blog, portfolio, or curated archive, this app delivers.
Highly recommended!
More from Hes
Note: This spotlight is not sponsored. I thoroughly enjoy the service and have received outstanding customer service from the team at npub.pro!
Stay tuned for more Nostr App Spotlights as I explore the best apps in the ecosystem!
-
 @ 1cb14ab3:95d52462
2025-02-04 22:17:27
@ 1cb14ab3:95d52462
2025-02-04 22:17:27Chef's notes
Credit to The Yummy Life. Go show them love below: https://www.theyummylife.com/Pickled_Jalapeno_Peppers
Details
- ⏲️ Prep time: 1 hour
- 🍳 Cook time: 20 mins
- 🍽️ Servings: 4 mason jars (pint)
Ingredients
- 2 lbs. jalapenos
- 2-1/4 cups vinegar (white distilled, apple cider, or a combination of the two)
- 2-1/4 cups water
- 2 tablespoons sugar or honey (optional)
- ADD TO EACH PINT JAR
- 1/2 teaspoon kosher salt
- 1/2 teaspoon whole black pepper corns
- 1/4 teaspoon whole cumin seeds
- 1/4 teaspoon whole coriander seeds
- 1 bay leaf
- 1 whole garlic clove, peeled
- 1/8 teaspoon Pickle Crisp granules (optional)
Directions
- Slice 1/2 pound jalapenos into 1/8" rounds, discarding stem ends.
- Prepare the jars: Wash 4 pint jars and lids in hot sudsy water, then keep them warm.
- Prepare the pickling liquid: Combine 1/2 cup plus 1 tablespoon vinegar, 1/2 cup plus 1 tablespoon water, and 1-1/2 teaspoons sugar or honey (optional) in a 2 quart pan, heating until just before boiling.
- Fill the jars: Add jalapeno slices to each jar, pressing them down and packing them in compactly, then pour the hot pickling liquid into each jar, leaving 1/2" head space.
- Process and store: Allow jars to cool to room temperature, then store them in the refrigerator or can them using standard USDA water process canning procedures, following storage guidelines for refrigerator or canned pickled peppers.
-
 @ 1cb14ab3:95d52462
2025-02-04 21:42:24
@ 1cb14ab3:95d52462
2025-02-04 21:42:24Chef's notes
Classic beef n' broccoli. Easy to make and dank to eat.
Details
- ⏲️ Prep time: 20 mins
- 🍳 Cook time: 10 mins.
Ingredients
- 1 lb top sirloin steak, thinly sliced
- ¼ cup low sodium soy sauce
- 2 teaspoons cornstarch
- 1 tablespoon dark brown sugar
- 2 tablespoons fresh ginger, minced
- 1 tablespoon oil
- 1 head broccoli, cut into 1-inch (2 ½ cm) florets
- ½ cup water
- 3 cloves garlic, minced
- ¼ teaspoon red pepper flakes, optional
- 1 teaspoon toasted sesame oil
Directions
- In a medium bowl, mix together the sirloin steak, soy sauce, cornstarch, brown sugar, and ginger until the meat is evenly covered in the marinade. Set aside to marinate for 20 minutes.
- Heat the oil in a large skillet or wok over medium-high heat. Dump in the meat and marinade and sear each side until golden brown. Transfer the meat to a clean bowl and set aside.
- Place the broccoli into the hot skillet and sauté until the broccoli has just started to brown, about 1 minute. Pour the water into the skillet and immediately cover with a lid. Let it steam for 2 minutes, until the broccoli has softened.
- Remove the lid and toss in the garlic, red pepper flakes, and sesame oil. Sauté until the garlic becomes fragrant, about 30 seconds.
- Add the steak back into the pan and stir to combine. Remove from heat and serve on a bed of brown rice.
-
 @ 21ffd29c:518a8ff5
2025-02-04 21:12:15
@ 21ffd29c:518a8ff5
2025-02-04 21:12:15- What Are Homestead Chickens?
Homestead chickens are domesticated fowl kept by homeowners to provide eggs and companionship. They play a vital role in the homestead ecosystem.
Why Water is Essential in Cold Weather - Hydration Basics:
Chickens don't drink much water naturally but need it for hydration, especially during cold weather when metabolic rates increase. - Environmental Factors:
Cold weather can lead to ice buildup on water sources. Chickens benefit from having access to fresh water year-round.Maintaining Accessible Water Sources - Shallow Troughs:
Use shallow troughs instead of deep containers to minimize ice formation and ensure constant water supply. - Automatic Feeders:
Consider installing automatic feeders for convenience, especially in unpredictable weather conditions. - Multiple Water Sources:
Provide multiple water sources to prevent competition and ensure all chickens have access.Preventing Ice Buildup - Floating Shallow Troughs:
Opt for troughs that sit above the ground to avoid ice buildup. Ensure they're placed where they can't freeze completely. - Regular Checks:
Inspect water sources regularly to remove ice and debris, maintaining accessibility for chickens.Best Practices for Watering Chickens - Waterers Designed for Cold Weather:
Use waterers made of stainless steel or plastic that can withstand cold temperatures. - Seasonal Adjustments:
During extreme cold spells, supplement with a small amount of fresh water to aid in drinking.Conclusion - Key Takeaways:
Providing proper water is crucial for the health and well-being of homestead chickens during cold weather. Maintaining accessible, shallow water sources prevents issues like ice buildup and ensures hydration.Final Thoughts - Sustainability Considerations:
While chickens don't drink much, ensuring they have water supports their overall health and sustainability efforts. - Environmental Impact:
Thoughtful water management can reduce water usage, promoting eco-friendly practices on the homestead. - What Are Homestead Chickens?
-
 @ 1cb14ab3:95d52462
2025-02-04 18:40:56
@ 1cb14ab3:95d52462
2025-02-04 18:40:56What is it?
I stumbled upon the Elgato Stream Deck while aimlessly browsing the web, and I was instantly intrigued. But one question kept nagging me—how would I use this, and why do I even need it?
I don’t stream.
At first glance, it seemed like just another gadget to clutter my already cramped desk in my tiny Shanghai apartment. But curiosity got the best of me. After some research, I decided to give it a shot and see what all the hype was about.
And wow—was that hype justified.
This isn’t a deep-dive review covering every feature (there are plenty of those online). Instead, I want to share some of the workflows I’ve set up and hopefully get you thinking about the endless possibilities you could create with a Stream Deck.
If you’re someone who loves making computer tasks easier but struggles to remember keyboard shortcuts beyond Ctrl + V, this little device might just change the way you work.
Launching Apps and Websites

I won’t lie—my favorite use for the Stream Deck is the sheer convenience of pressing a button and instantly launching what I need.
Want to watch YouTube? Button.
Open Photoshop? Button.
Play a game? Button.
Check Bitcoin prices? Those are always on the display.


Sure, it’s a small thing, but the speed and ease of launching apps or navigating to websites make a surprising difference. What used to be a few clicks and keystrokes is now a single tap.
After using the Stream Deck for a while, my laptop feels... clunky. I’ve genuinely noticed an increase in my productivity and focus.
Custom Application Profiles
One of the most powerful features of the Stream Deck is its ability to switch profiles based on the application you’re using.
This means that every time you switch programs, the buttons automatically adjust to show relevant shortcuts and commands. It’s a game-changer for software with hundreds of keyboard shortcuts, making multitasking seamless.
I’ll admit—setting up custom profiles can be a bit time-consuming. The good news? You don’t have to start from scratch. There are tons of downloadable third-party profiles for popular programs like Illustrator, Photoshop, Final Cut Pro, DaVinci Resolve, Microsoft Office, and Ableton.

If your favorite app doesn’t have a pre-made profile, you can always build your own. It takes some effort, but once it's set up, the workflow improvements are worth it.
Music and Audio Control

I use an audio interface for lossless wired playback and external microphone support. The Stream Deck makes switching between my computer’s default mic and my studio mic effortless—no more digging through system preferences.
Even if you don’t use external audio gear, the Stream Deck still has plenty of value for music lovers.

It integrates with Apple Music and Spotify, letting you control playback, skip tracks, like songs, and add them to playlists—all without switching apps. Elgato is constantly adding new third-party integrations, which gives the device even more longevity.
Lighting and Smart Home Control
If you have smart home devices, the Stream Deck can act as a command center. It integrates with platforms like Philips Hue, LIFX, Nanoleaf, and IFTTT, letting you control lights, scenes, and colors with a single tap.
Want to set the mood for gaming, reading, or watching a movie? Done.
You can even use it to trigger other smart devices, like cameras, thermostats, or speakers, using IFTTT applets. The possibilities here are endless.
Finder and Document Shortcuts
One of the most unexpectedly useful features for me has been quick access to folders and files.
I’ve set up buttons for my most frequently used folders—Downloads, Desktop, and Documents—so I can access them instantly. I’ve also created buttons for specific files like spreadsheets and PDFs, so I don’t have to dig through folders to find them.
It sounds simple, but when juggling multiple projects, these little time-savers add up fast.
Final Thoughts
The Elgato Stream Deck is a surprisingly versatile tool that enhances productivity, creativity, and entertainment. Whether you’re launching apps, controlling music, managing smart devices, or creating complex workflows, it streamlines everyday tasks in a way that’s hard to go back from.
At first, I thought it was just for streamers. Now? I can’t imagine working without it.
I hope this post gives you some ideas on how to make the most of a Stream Deck. If you have any questions or thoughts, drop a comment below.
Thanks for reading!
Feel free to support me by grabbing one through my affiliate link below:
More from Hes
Originally published in 2022. All images are credit of Hes, but you are free to download and use for any purpose. If you find joy from my art, please feel free to send a zap. Enjoy life on a Bitcoin standard.
-
 @ 1e566682:60493eed
2025-02-04 18:05:06
@ 1e566682:60493eed
2025-02-04 18:05:06بازار ارزهای دیجیتال بهزودی شاهد یک تغییر مهم خواهد بود. طبق گزارش اخیر منتشرشده در فوربز، بیتکوین و سایر ارزهای دیجیتال در آستانه یک "زلزله قیمتی" قرار دارند که به دلیل تغییرات نظارتی و تصمیمات کلان اقتصادی در ایالات متحده شکل میگیرد. کارشناسان پیشبینی میکنند که این تغییرات میتوانند نوسانات شدیدی در ارزش داراییهای دیجیتال ایجاد کنند و بازار را تحت تأثیر قرار دهند.
دلایل اصلی این زلزله قیمتی
- سیاستهای جدید نظارتی و قانونی
دولت آمریکا به دنبال وضع مقررات سختگیرانهتری برای نظارت بر ارزهای دیجیتال است. کمیسیون بورس و اوراق بهادار ایالات متحده و سایر نهادهای نظارتی در حال بررسی اقداماتی برای محدود کردن برخی فعالیتهای مرتبط با ارزهای دیجیتال هستند. این مقررات میتواند شامل نظارت دقیقتر بر صرافیهای ارز دیجیتال، سختگیری در فرآیندهای ضدپولشویی و احراز هویت مشتریان باشد.
- تغییرات مالیاتی و تأثیر آن بر سرمایهگذاران
دولت ایالات متحده در حال بررسی اصلاحات مالیاتی است که میتواند تأثیر قابلتوجهی بر سرمایهگذاران ارزهای دیجیتال بگذارد. مالیات بر سود حاصل از معاملات ارزهای دیجیتال میتواند افزایش یابد و سرمایهگذاران را به اتخاذ استراتژیهای جدید معاملاتی وادار کند. این مسئله ممکن است موجب کاهش حجم معاملات و افزایش نوسانات قیمتی شود.
- سیاستهای پولی فدرال رزرو
فدرال رزرو (بانک مرکزی آمریکا) نقش مهمی در تعیین نرخ بهره و سیاستهای مالی دارد. اگر نرخ بهره افزایش یابد، سرمایهگذاران ممکن است تمایل بیشتری به سرمایهگذاری در داراییهای کمریسک مانند اوراق قرضه دولتی داشته باشند و سرمایههای خود را از بازار ارزهای دیجیتال خارج کنند. این امر میتواند منجر به کاهش قیمت بیتکوین و سایر رمزارزها شود.
- افزایش پذیرش سازمانی و واکنش بازار
در حالی که قوانین سختگیرانه میتوانند فشار نزولی بر قیمتها وارد کنند، افزایش پذیرش بیتکوین توسط شرکتهای بزرگ و موسسات مالی میتواند از کاهش شدید قیمتها جلوگیری کند. بسیاری از شرکتها همچنان به پذیرش رمزارزها بهعنوان یک روش پرداخت ادامه میدهند و برخی بانکهای بزرگ نیز وارد بازار رمزارز شدهاند که این موضوع میتواند روند کلی بازار را تغییر دهد.
تأثیرات احتمالی بر قیمت بیتکوین و سایر ارزهای دیجیتال
با در نظر گرفتن این عوامل، دو سناریوی اصلی برای آینده قیمت بیتکوین و بازار رمزارزها وجود دارد:
-
سناریوی نزولی: اگر مقررات سختگیرانه اجرایی شوند و نرخ بهره افزایش یابد، ممکن است بیتکوین و سایر رمزارزها با کاهش قیمت مواجه شوند. در این شرایط، سرمایهگذاران خرد و سازمانی ممکن است با خروج از بازار، نوسانات شدیدتری را رقم بزنند.
-
سناریوی صعودی: در صورتی که افزایش پذیرش بیتکوین در میان موسسات مالی ادامه یابد و قوانین بهطور متعادل اجرا شوند، احتمال دارد که بیتکوین بتواند سطح حمایتی خود را حفظ کرده و در بلندمدت به رشد خود ادامه دهد.
جمعبندی: سرمایهگذاران باید چه کار کنند؟
با توجه به این شرایط، سرمایهگذاران ارزهای دیجیتال باید با دقت تحولات نظارتی و اقتصادی را دنبال کنند. مدیریت ریسک، تنوعبخشی به سبد سرمایهگذاری و در نظر گرفتن چشمانداز بلندمدت میتواند از ضررهای احتمالی جلوگیری کند.
این زلزله قیمتی ممکن است بازار رمزارزها را به شدت متزلزل کند، اما همانطور که در گذشته نیز دیدهایم، بازار ارزهای دیجیتال بارها از بحرانهای مشابه عبور کرده و به رشد خود ادامه داده است. باید دید که در نهایت این تغییرات چگونه شکل خواهند گرفت و چه تأثیری بر آینده بیتکوین و سایر ارزهای دیجیتال خواهند گذاشت.
-
 @ 8d34bd24:414be32b
2025-02-04 17:55:30
@ 8d34bd24:414be32b
2025-02-04 17:55:30So many of our problems are due to our point of view. The closer our point of view gets to God, the more peace and joy we will feel.
Too often we look at God as the big, bad killjoy. We resent when He tells us all the “fun” things we aren’t supposed to do and when He tells us to do difficult things like submit to God, submit to husbands, submit to authorities. Too many people focus on the “do nots,” and don’t like the idea of anyone telling them what to do. They then do their own thing, which they think will make them happy. Unfortunately, this leads to the opposite.
God is our Creator. He created us for a purpose within the rest of His creation.
For we are His workmanship, created in Christ Jesus for good works, which God prepared beforehand so that we would walk in them. (Ephesians 2:10)
When we are doing His will we will find peace and joy. When we fight Him on what we should and should not be doing, we feel frustration, depression, and even despair. Our constant seeking of things to make us happy is actually our innate desire for God and to fulfill His will. Unfortunately, we frequently don’t see the truth and avoid the one thing that will give us peace because it is hard, inconvenient, and doesn’t lead to what we think we want right now.
God wants what is best for us. He also thinks eternally. He doesn’t think in the here and now, like we do. Just as a parent makes decisions for his/her child based on knowledge of what will be better for them in the long term (saving vs spending, healthy food vs junk food, etc.), God makes decisions for us based on what will best prepare us for eternity with Him. Frequently that looks much different than what we think we want. Frequently that even includes hardship and pain because we are much more likely to grow in faith, strength, and holiness during hardship than we do during comfort. We need to understand that God knows best and that He never makes a mistake.
Trust in the Lord with all your heart\ And do not lean on your own understanding.\ In all your ways acknowledge Him,\ And He will make your paths straight.\ Do not be wise in your own eyes;\ Fear the Lord and turn away from evil.\ It will be healing to your body\ And refreshment to your bones. (Proverbs 3:5-8)
Nothing happens on earth without God allowing it. Just as Satan had to ask permission to persecute Job, in the same way nobody can cause believers harm without God allowing it for His purpose, which is usually related to helping them to put their full trust in Him.
Remember the former things long past,\ For I am God, and there is no other;\ I am God, and there is no one like Me,\ Declaring the end from the beginning,\ And from ancient times things which have not been done,\ Saying, ‘My purpose will be established,\ And I will accomplish all My good pleasure’; (Isaiah 46:9-10)
So often I focus on how awesome, powerful, and holy our God is. He is also the most tender, loving, caring, personal father God. Read Psalm 139. The God of the Bible is not a distant clock maker who set the world in motion and let it go about without His care. He is personally involved in everything that happens and in the life of every person on earth, but especially in the life of those who trust in Him.
O Lord, You have searched me and known me.\ You know when I sit down and when I rise up;\ You understand my thought from afar.\ You scrutinize my path and my lying down,\ *And are intimately acquainted with all my ways.\ Even before there is a word on my tongue,\ Behold, O Lord, You know it all.*\ You have enclosed me behind and before,\ And laid Your hand upon me.\ Such knowledge is too wonderful for me;\ It is too high, I cannot attain to it.\ Where can I go from Your Spirit?\ Or where can I flee from Your presence?\ If I ascend to heaven, You are there;\ If I make my bed in Sheol, behold, You are there.\ If I take the wings of the dawn,\ If I dwell in the remotest part of the sea,\ *Even there Your hand will lead me*,\ And Your right hand will lay hold of me.\ If I say, “Surely the darkness will overwhelm me,\ And the light around me will be night,”\ Even the darkness is not dark to You,\ And the night is as bright as the day.\ Darkness and light are alike to You.\ For You formed my inward parts;\ You wove me in my mother’s womb.\ I will give thanks to You, for I am fearfully and wonderfully made;\ Wonderful are Your works,\ And my soul knows it very well.\ My frame was not hidden from You,\ When I was made in secret,\ And skillfully wrought in the depths of the earth;\ Your eyes have seen my unformed substance;\ And in Your book were all written\ The days that were ordained for me,\ When as yet there was not one of them.\ How precious also are Your thoughts to me, O God!\ How vast is the sum of them!\ If I should count them, they would outnumber the sand.\ When I awake, I am still with You.\ O that You would slay the wicked, O God;\ Depart from me, therefore, men of bloodshed.\ For they speak against You wickedly,\ And Your enemies take Your name in vain.\ Do I not hate those who hate You, O Lord?\ And do I not loathe those who rise up against You?\ I hate them with the utmost hatred;|\ They have become my enemies.\ **Search me, O God, and know my heart;\ Try me and know my anxious thoughts;\ And see if there be any hurtful way in me,\ And lead me in the everlasting way. (Psalm 139) {emphasis mine}
What is one of the greatest desires of our hearts? Isn’t it to be truly known and loved for who we are?
O Lord, You have searched me and known me.\ You know when I sit down and when I rise up;\ You understand my thought from afar. (Psalm 139:1-2)
How amazing is it that the Creator of the universe knows you personally and cares for you among all of creation?
Even before there is a word on my tongue,\ Behold, O Lord, You know it all. (Psalm 139:4)
He knows our every action, our every thought, and our every feeling before we do.
Such knowledge is too wonderful for me;\ It is too high, I cannot attain to it. (Psalm 139:6)
We cannot fully understand how much our Creator cares for us and how carefully God guides us in our every path. We usually can’t see what is for our best. We usually can’t see what great work God is working in us. We usually can’t comprehend how great is His love, knowledge, and plan.
Even there Your hand will lead me,\ And Your right hand will lay hold of me. (Psalm 139:10)
It doesn’t matter how difficult a situation we have gotten into. It doesn’t matter how powerful our adversaries are. It doesn’t matter how weak we are. God is always there guiding us and protecting us. Just as God allowed Job to go through difficulty as part of God’s plan for Job and for us, He did not allow Job to be killed. He was guided through the worst of situations and led to ultimate blessing.
Your eyes have seen my unformed substance;\ And in Your book were all written\ The days that were ordained for me,\ When as yet there was not one of them. (Psalm 139:16)
God knew us and had a plan for us before He even created the universe. He knew every day we would live before we were conceived. We can’t surprise Him and He will be guiding us every day of our lives, especially those who have trusted Him as savior.
How precious also are Your thoughts to me, O God!\ How vast is the sum of them! (Psalm 139:17)
We are precious to God and He should be precious to us because of all He has done for us.
Search me, O God, and know my heart;\ Try me and know my anxious thoughts;\ And see if there be any hurtful way in me,\ And lead me in the everlasting way. (Psalm 139:23-24)
This should be our prayer. We should ask for Him to bring are faults to our minds so we can repent and we should ask for Him to lead us in His “everlasting way.” We should admit that our Father God knows best and submit to His will. Everything goes so much smoother when we aren’t fighting our God. Even when He leads us through hardship, being in His will makes all of the difference in the world.
I pray that you will put your trust in our loving Creator and that you will submit to His will. I pray that you will understand that His ways are better even when you don’t understand the why. I pray that you will humbly submit to His will and be used to further the Kingdom for His glory and your blessing.
Trust Jesus.
FYI, Psalm 139 is also one of the best passages on why all believers should oppose abortion. In God’s universe there are no accidents and there are no unwanted babies. Every person ever conceived had a purpose in God’s plan. Every person ever conceived is valuable and made in the image of God. God values all human life and so should we.
-
 @ 91bea5cd:1df4451c
2025-02-04 17:24:50
@ 91bea5cd:1df4451c
2025-02-04 17:24:50Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\000\000\000\000\000\000'; output TEXT = '';
unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ```
ULID TO UUID
```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ```
UUID to ULID
```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ```
Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars;END; $$ LANGUAGE plpgsql; ```
Exemplo de USO
```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ```
Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-
 @ e97aaffa:2ebd765d
2025-02-04 16:58:18
@ e97aaffa:2ebd765d
2025-02-04 16:58:18Será que neste ciclo teremos turistas no #Bitcoin? Nos últimos meses tenho me debruçado muito sobre este assunto, mas não consigo chegar a uma conclusão.
Antes de mais, o que são turistas? Os turistas são aqueles que compram Bitcoin alimentados pelo FOMO, com a ganância de enriquecer rapidamente. Não tem o mínimo conhecimento do Bitcoin, nem tem interesse em conhecer, só estão pelo dinheiro.
Com a entrada dos turistas, o preço do Bitcoin começa a valorizar exponencialmente, é a segunda fase da bullrun, acontece sempre após o halving e após superar o anterior ATH. Com o novo ATH começa a surgir as notícias nas televisões e jornais, o mainstream acorda. Só que a quantidade de turistas é de tal maneira elevada, muito superior à dos holders. Este desequilíbrio entre forças de curto prazo(turistas) e do longo prazo(holders), gera forte volatilidade. Quanto maior o desequilíbrio, maior a volatilidade. A avalanche de turistas, faz o preço disparar e quanto mais sobe, mais turistas atrai.
Só que o movimento não dura para sempre, a esperança dos turistas de enriquecer rápido, desvanece e rapidamente se transforma numa desilusão, na sua grande maioria entra em pânico, assim que o preço começa a corrigir, vendendo em prejuízo. Sendo responsável pelas gigantes correções, superiores a 70%.
Este é o meu 4° ciclo, eu noto que este está a ser completamente diferente. Nos anteriores, os turistas entravam pelo Bitcoin, mas desta vez está a acontecer uma mudança. Devido ao elevado marketcap do Bitcoin, este já não permite valorização exponenciais num curto espaço de tempo, estes turistas que procuram multiplicar o seu dinheiro por 10x, 100x ou 1000x, estão a ir directamente para as shitcoins ou memecoins. Estas valorização pornograficas, só acontecerá em meia dúzia, mas o grande problema é que existem milhões de memecoins, é como encontrar uma agulha num palheiro. É o verdadeiro casino e os turistas procuram isto.
Só que neste ciclo, a maior parte dos novos inflows estão a ser através do institucional, sobretudo pelos ETFs. Só que tem um perfil não diferente dos turistas, têm conhecimento de mercados financeiros tradicionais, são muito mais racionais, têm um conhecimento mínimo do Bitcoin. Não têm as mãos de diamante como os holders, mas também não são mãos de alface como os turistas. É um perfil de investidor intermédio. Poderá vender uma pequena parte do Bitcoin, para retirar uma parte do seu investimento inicial, mas tem um pensamento mais de médio-longo prazo.
Com isto, existe um maior equilíbrio entre os que pensam a curto prazo e os que pensam a longo prazo. Até ao momento, eu tenho a sensação que os turistas já não procuram o Bitcoin, ou são muito poucos.
O afastamento dos turistas é bom ou mau? A meu ver é bom, é verdade que deixamos de ter aquelas enormes explosões no preço para cima, mas também acredito que as correções também serão muito menores. Em suma, uma redução na volatilidade do Bitcoin. Mas essa redução na volatilidade, vai trazer um novo público, aquele que não é especulador, que apenas quer preservar o seu património, o real valor do Bitcoin, que pensa a longo prazo.
Estes turistas que procuram o 100x, com uma pura ganância, vão passar muitas noites sem dormir e na sua maioria vão perder muito dinheiro, vão acabar por receber uma dura lição de vida. Alguns vão finalmente compreender que Bitcoin é diferente, e que os 2x é suficiente para a sua vida.
A redução de turistas não afeta só o Bitcoin, mas também afeta o mercado das altcoins e das memecoins. Nos ciclos anteriores, os turistas entravam pelo Bitcoin mas depois rodavam o capital para as altcoins, gerando a chamada altseason. Se neste ciclo, os turistas descartam o Bitcoin, consequentemente a rotação será muito menor, possivelmente não haverá altseason.
Mas isto é apenas a minha convicção, só o tempo dirá, se os turistas trocaram o Bitcoin, pelo casino das memecoins.
-
 @ 554ab6fe:c6cbc27e
2025-02-04 15:56:29
@ 554ab6fe:c6cbc27e
2025-02-04 15:56:29Modern life, despite all our technology, can still feel challenging. Many of us work very long hours to make ends meet, burdened by stress that can dramatically affect our health. The internet provides us with a wealth of helpful knowledge but also bombards us with headlines that can make us uneasy about the state of the world. In short, life can feel very stressful. Sometimes, leaving it all behind and becoming a monk may seem like a perfect way to escape it all. Though this may work for some, this is simply not a practical thing to do for many of us. Many of us are here to stay. However, even though the stressful nature of society will not change for a very long time, it is possible to reorient one's perspective so that it feels less stressful. In other words, rather than needing to go to a temple to become a monk, one can learn to bring the monk mind here.
It can be challenging to know where to begin to generate a positive outlook on life. So many people try to give advice, yet there never seems to be a "one size fits all" approach. We attempt to solve our outlooks by rationalizing the situation in a more positive way. Indeed, this can be useful for some, but not all. Furthermore, different people require different rationalizations. Regardless of advice, some are still stuck wondering how to have a better outlook on life. There is, of course, another method of perspective, and that is through non-judgment and simple acceptance.
Mindfulness meditation is a method of training the mind to become calmer and more at peace. In the scientific community, meditation is defined as a method of self-regulation of attention to the present moment, involving adopting a particular orientation toward one's experiences characterized by curiosity, openness, acceptance, and non-judgmental (Bishop et al., 2004). The benefits of meditation are many; however, much more research is required to understand its benefits and mechanisms better. The most well-documented benefit of mindfulness meditation is its ability to alleviate stress and anxiety (Greeson et al., 2018; Petterson & Olson, 2017; Querstret et al., 2020). The method by which this occurs is still reasonably unclear, yet many researchers have developed psychological and physiological theories. Furthermore, meditation reduces stress and anxiety while also creating resilience (Chin et al., 2019; Hwang et al., 2018). So, not only does it seem to be a curative treatment, but a preventative one as well. Understanding how meditation creates stress resilience is crucial to understand why meditation is so beneficial to health—the lessons provided in the research share profound philosophical lessons for us to bear in mind.
When studying meditation and its effects on the mind and body, it is essential to take a neuroscientific and psychological approach. The neuroscientific approach is valuable in both providing evidence that meditation impacts the body and sheds light on the mechanisms of action. A psychological perspective is also critical because it evaluates the mental schemas' effect on the body to better understand how the reader can practice this at home and in their daily lives. Both points of view will be discussed below.
Amygdala and ACC connectivity
The two brain areas that seem to be highly related to the process of resilience toward stress induced by mindfulness meditation are the amygdala and the anterior cingulate cortex (ACC).
The amygdala is found medial to the brain's temporal lobe and plays a vital role in emotional regulation and attention (Desbordes et al., 2012). For this reason, numerous studies have shown to be heavily involved in the experience of stress (Britton, 2006; Hölzel et al., 2009; Rubinow et al., 2016). It also influences the body in response to stress. For example, the amygdala regulates blood pressure in response to stressful stimuli (Saha, 2005).
The role of the ACC is seemingly more complex than the amygdala. In general, it is involved in executing responses regarding incoming interoceptive signals (signals from within the body) (Craig, 2002). For this reason, it connects to the motor cortex of the brain (Craig, 2002). On this same note, the anterior portion of the amygdala, the more executive region, has been associated with regulating endocrine functions, conditioned learning responses, expressing internal states vocally, and maternal-infant interactions (Devinsky et al., 1995). The ACC is related mainly to the processing of internal stimuli, associating it with the practice of mindfulness meditation. Less clear is how it relates to the amygdala and resilience to stress.
The neuroscientific observations of stress resilience are found within the connectivity between the amygdala and the ACC. In a randomized control trial involving a 3-day intensive mindfulness meditation program, researchers found that reduced stress following the practice was marked by decreased communication between the amygdala and the ACC (Taren et al., 2014). The study also noted reduced communication between the amygdala and ACC lessened HPA-axis activation (Taren et al., 2014). The HPA-axis is responsible for releasing hormones such as cortisol, which is a common biomarker for the activation of stress. This study is not alone in observing signs that mindfulness meditation reduces cortisol (Hoge et al., 2018). This is strong evidence that meditation induces physical changes within the brain, promoting resilience to biological responses to stress. The question is, how does this occur mentally, and how can we put this into practice?
Important Techniques within Meditation
The discussion and research surrounding how meditation leads to physical changes in the brain and body are complex and poorly understood. The appreciation for science in the west is new, and there is much research to be done. The author's current opinion is that meditation involves both physical and mental mechanisms that lead to some of its practical health benefits. Regarding resilience, a randomized control trial also observed that the resilience created was both physical and mental (Hoge et al., 2018). Though the exact mechanism is not fully understood, there has been an effort to gain insight applicable to modern-day life.
The research involving the mechanism at which meditation generates resilience towards stress is often pursued from a psychological point of view. To pursue this question, experiments involve different groups of people who are asked to perform similar tasks but differ in mental schemas practiced. The observed differences in health results indicate specific meditation techniques that are so helpful in generating resilience. For example, a randomized control trial in 2018 involved sending a group of participants to a temple (Hwang et al., 2018). One group was asked to participate in meditation sessions, while another group was asked to simply relax during this time at a peaceful place. The purpose was to discern whether or not the relaxing aspect of meditation was sufficient to produce resilience to stress or if something else was causing the change. The results found that both groups showed short-term benefits, but only the meditators had prolonged resilience towards stress months after the experiment. The results indicate that there was a mental practice involved through meditation that promoted stress resilience. A randomized control trial in 2019 expanded on this investigation by having one group of meditators purely practice the focused attention on the present, while the other group focused on the present while also cultivating a perspective of acceptance to all incoming stimuli (Chin et al., 2019). This study found that those who practiced a non-judgmental awareness showed a more significant reduction of stress than the attention group and the non-meditators, suggesting that the non-judgmental awareness of the present moment and experience was an essential aspect of stress resilience. Others have produced a similar theory on why meditation seems to be a healthy therapeutic method for those suffering from PTSD (Thompson & Waltz, 2010). The significance of these findings is not only crucial for those who have a meditation practice but anyone in general.
Be Non-Judgmental
A key aspect of meditation practice is to be mindful and aware of the present experience and interpret all thoughts, experiences, and stimuli in an accepting and non-judgemental manner. Not only is this important within the philosophical teachings, but it is a core aspect of how meditation works from a scientific point of view. This has profound implications for the importance of how we generate personal narratives. In meditation, one learns to let go of every incoming experience, no matter how tempting it is to value that thought or feeling. This is perhaps why the amygdala and ACC are involved. The amygdala is involved in emotions and stress, and the ACC is involved in "doing something about it." In meditation, no matter the feeling, thought, or stressor, one must cultivate an attitude of acceptance. One must simply continue sitting and focusing on the present. There is no evaluation, no judgment, simply acceptance.
This article began with the idea that one can become resilient to stress and experience less of it by simply reorienting their perspective of modern stressors. It was also stated that there is seemingly no one answer for everyone. This may be because people often try to generate rational or schemas to help people think about events differently. This article argues a different approach: don't think, just accept, let go, and move on. This is easier said than done, of course, and by no means are the benefits of meditation best articulated through argument. It is best to be experienced first hand.
Nonetheless, we are heavily burdened by the values we give to thoughts related to the stressors of modern-day life. We cannot avoid the stressors, but we can change their power over us. Removing their meaning and value removes their power and influence.
References
Bishop, S. R., Lau, M., Shapiro, S., Carlson, L., Anderson, N. D., Carmody, J., Segal, Z. v., Abbey, S., Speca, M., Velting, D., & Devins, G. (2004). Mindfulness: A Proposed Operational Definition. Clinical Psychology: Science and Practice, 11(3), 230–241. https://doi.org/10.1093/clipsy.bph077
Britton, W. B. (2006). Meditation and Depression.
Chin, B., Lindsay, E. K., Greco, C. M., Brown, K. W., Smyth, J. M., Wright, A. G. C., & Creswell, J. D. (2019). Psychological mechanisms driving stress resilience in mindfulness training: A randomized controlled trial. Health Psychology, 38(8), 759–768. https://doi.org/10.1037/hea0000763
Craig, A. D. (2002). How do you feel? Nature Review. https://doi.org/10.1177/1359105308095062
Desbordes, G., Negi, L. T., Pace, T. W. W., Alan Wallace, B., Raison, C. L., & Schwartz, E. L. (2012). Effects of mindful-attention and compassion meditation training on amygdala response to emotional stimuli in an ordinary, Nonmeditative State. Frontiers in Human Neuroscience, 6(OCTOBER 2012), 292. https://doi.org/10.3389/fnhum.2012.00292
Devinsky, O., Morrell, M. J., & Vogt, B. A. (1995). Contributions of anterior cingulate cortex to behaviour. Brain, 118(1), 279–306. https://doi.org/10.1093/BRAIN/118.1.279
Greeson, J. M., Zarrin, H., Smoski, M. J., Brantley, J. G., Lynch, T. R., Webber, D. M., Hall, M. H., Suarez, E. C., & Wolever, R. Q. (2018). Mindfulness Meditation Targets Transdiagnostic Symptoms Implicated in Stress-Related Disorders: Understanding Relationships between Changes in Mindfulness, Sleep Quality, and Physical Symptoms. Evidence-Based Complementary and Alternative Medicine, 2018. https://doi.org/10.1155/2018/4505191
Hoge, E. A., Bui, E., Palitz, S. A., Schwarz, N. R., Owens, M. E., Johnston, J. M., Pollack, M. H., & Simon, N. M. (2018). The effect of mindfulness meditation training on biological acute stress responses in generalized anxiety disorder. Psychiatry Research, 262(May 2016), 328–332. https://doi.org/10.1016/j.psychres.2017.01.006
Hölzel, B. K., Carmody, J., Evans, K. C., Hoge, E. A., Dusek, J. A., Morgan, L., Pitman, R. K., & Lazar, S. W. (2009). Stress reduction correlates with structural changes in the amygdala. Social Cognitive and Affective Neuroscience, 5(1), 11–17. https://doi.org/10.1093/scan/nsp034
Hwang, W. J., Lee, T. Y., Lim, K. O., Bae, D., Kwak, S., Park, H. Y., & Kwon, J. S. (2018). The effects of four days of intensive mindfulness meditation training (Templestay program) on resilience to stress: A randomized controlled trial. Psychology, Health and Medicine, 23(5), 497–504. https://doi.org/10.1080/13548506.2017.1363400
Petterson, H., & Olson, B. L. (2017). Effects of mindfulness-based interventions in high school and college athletes for reducing stress and injury, and improving quality of life. Journal of Sport Rehabilitation, 26(6), 578–587. https://doi.org/10.1123/jsr.2016-0047
Querstret, D., Morison, L., Dickinson, S., Cropley, M., & John, M. (2020). Mindfulness-based stress reduction and mindfulness-based cognitive therapy for psychological health and well-being in nonclinical samples: A systematic review and meta-analysis. International Journal of Stress Management, 27(4), 394–411. https://doi.org/10.1037/str0000165
Rubinow, M. J., Mahajan, G., May, W., Overholser, J. C., Jurjus, G. J., Dieter, L., Herbst, N., Steffens, D. C., Miguel-Hidalgo, J. J., Rajkowska, G., & Stockmeier, C. A. (2016). Basolateral amygdala volume and cell numbers in major depressive disorder: a postmortem stereological study. Brain Structure and Function, 221(1), 171–184. https://doi.org/10.1007/s00429-014-0900-z
Saha, S. (2005). ROLE OF THE CENTRAL NUCLEUS OF THE AMYGDALA IN THE CONTROL OF BLOOD PRESSURE: DESCENDING PATHWAYS TO MEDULLARY CARDIOVASCULAR NUCLEI. Clinical and Experimental Pharmacology and Physiology, 32(5–6), 450–456. https://doi.org/10.1111/j.1440-1681.2005.04210.x
Taren, A. A., Gianaros, P. J., Greco, C. M., Lindsay, E. K., Fairgrieve, A., Brown, K. W., Rosen, R. K., Ferris, J. L., Julson, E., Marsland, A. L., Bursley, J. K., Ramsburg, J., & Creswell, J. D. (2014). Mindfulness meditation training alters stress-related amygdala resting state functional connectivity: A randomized controlled trial. Social Cognitive and Affective Neuroscience, 10(12), 1758–1768. https://doi.org/10.1093/scan/nsv066
Thompson, B. L., & Waltz, J. (2010). Mindfulness and experiential avoidance as predictors of posttraumatic stress disorder avoidance symptom severity. Journal of Anxiety Disorders, 24(4), 409–415. https://doi.org/10.1016/j.janxdis.2010.02.005
-
 @ a012dc82:6458a70d
2025-02-04 15:49:10
@ a012dc82:6458a70d
2025-02-04 15:49:10Bitcoin halving is a cornerstone event in the cryptocurrency landscape, occurring approximately every four years, or after every 210,000 blocks are mined. This event is significant because it marks a reduction in the reward that miners receive for adding new blocks to the Bitcoin blockchain, effectively halving the rate at which new bitcoins are generated. The concept of halving is embedded in Bitcoin's protocol by Satoshi Nakamoto, its mysterious creator, as a measure to mimic the scarcity and deflationary characteristics of precious metals like gold. This mechanism is crucial in controlling the supply of Bitcoin, ensuring that it remains finite and valuable. As the next halving event draws near, it's not just miners who are impacted; the entire cryptocurrency market, including investors and enthusiasts, keenly anticipates the potential outcomes. Historically, halving events have been associated with increased market activity, price volatility, and heightened public interest in Bitcoin. The event is seen as a moment of transformation for Bitcoin, where the dynamics of supply and demand are altered, potentially leading to significant shifts in its market value.
Table Of Content
-
Understanding the Hash Rate Surge
-
Implications of the Rising Hash Rate
-
The Halving Event: What to Expect
-
Preparing for the Halving
-
Conclusion
-
FAQs
Understanding the Hash Rate Surge
What is Hash Rate?
The hash rate, in the context of Bitcoin, refers to the total computational power being used to mine and process transactions on the blockchain. It's a vital metric that reflects the health and security of the network. A higher hash rate means that more computational resources are being dedicated to maintaining the network, making it more robust against potential attacks. The hash rate is measured in hashes per second (H/s), and with advancements in mining technology, the network has seen this rate reach exahash levels (1 EH/s = 1 quintillion hashes per second). This metric is crucial for miners, as it affects their chances of solving the mathematical puzzles required to mine new blocks and earn rewards. It also indicates the level of competition among miners, as a higher hash rate suggests more participants or more powerful mining equipment in the network.
Record-Breaking Levels
The Bitcoin network's hash rate has recently hit an all-time high, reaching a staggering 491 exahashes per second (EH/s). This surge is indicative of the growing strength and security of the network. Such a high hash rate means that the network is more resilient than ever to potential attacks, such as the 51% attack, where a single entity could potentially gain control over the majority of the network's mining power. This level of security is crucial, especially as Bitcoin continues to gain mainstream acceptance and attract significant institutional investment. The record-breaking hash rate also reflects the increasing global interest in Bitcoin mining. It suggests that despite the high costs associated with mining - including specialized hardware and significant electricity consumption - miners are still heavily investing in this activity. This investment is not just in terms of money but also in research and development of more efficient mining technologies, which could further drive up the hash rate.
Implications of the Rising Hash Rate
Enhanced Network Security
The surge in Bitcoin's hash rate is a positive development for the network's security. A higher hash rate means that it becomes exponentially more difficult for a malicious actor to orchestrate an attack on the network. This security is paramount for a system that handles billions of dollars worth of transactions. The decentralized nature of Bitcoin relies heavily on the integrity of its blockchain, which is maintained by this collective computational effort. As the hash rate increases, the confidence in the network's security also grows, which is crucial for both individual users and institutional investors. This enhanced security is particularly important in the context of the upcoming halving event, as it ensures the stability and reliability of the network during a period of significant change.
Increased Mining Difficulty
With the rise in hash rate comes an increase in the difficulty of mining Bitcoin. The Bitcoin network is designed to adjust the difficulty of mining new blocks approximately every two weeks to ensure that the time between blocks remains around 10 minutes. As more computational power joins the network, the difficulty increases, making it harder for individual miners to solve the cryptographic puzzles required to mine new blocks. This increase in difficulty can have several implications for miners. Smaller miners or those with less efficient equipment may find it increasingly difficult to compete with larger mining operations that have access to more powerful and efficient technology. This could lead to a consolidation in the mining industry, where only the most efficient operations can survive. Additionally, as the difficulty increases, the profitability of mining can decrease, especially if the price of Bitcoin does not increase proportionally. Miners must constantly evaluate their operations' efficiency and electricity costs to ensure continued profitability.
Energy Consumption Concerns
The rising hash rate of the Bitcoin network has brought renewed attention to the issue of energy consumption in Bitcoin mining. The process of mining Bitcoin is energy-intensive, as it requires a significant amount of computational power. As the hash rate increases, so does the total energy consumption of the network. This has led to concerns about the environmental impact of Bitcoin mining, especially in regions where electricity is generated from fossil fuels. The debate around Bitcoin's energy consumption is complex. On one hand, proponents argue that much of the energy used for Bitcoin mining comes from renewable sources, and the industry drives innovation in energy efficiency. On the other hand, critics point out that the overall energy consumption is still substantial and could be directed towards other, more productive uses. This debate is likely to continue as the network grows and the hash rate increases, especially in the context of global concerns about climate change and sustainable energy practices.
The Halving Event: What to Expect
Reward Reduction
The upcoming Bitcoin halving event is a scheduled reduction in the rewards that miners receive for verifying and adding new transactions to the blockchain. This halving reduces the number of new bitcoins created and earned by miners with each new block from 6.25 bitcoins to 3.125 bitcoins. This event occurs every 210,000 blocks, or approximately every four years, and is a fundamental part of Bitcoin's economic model. The halving is designed to mimic the extraction of precious resources, becoming progressively harder and less rewarding over time. This mechanism ensures that the total supply of Bitcoin will never exceed 21 million coins, making Bitcoin a deflationary asset. The halving event is significant because it affects the economics of Bitcoin mining. With the reward halving, the revenue for miners is effectively cut in half overnight. This can lead to a shakeout in the mining industry, as less efficient miners may no longer be profitable and could be forced to shut down their operations.
Market Impact
Historically, Bitcoin halving events have been followed by significant price increases. This pattern has led to a common perception that halving events are bullish for Bitcoin's price. The rationale behind this is simple: as the rate of new supply of Bitcoin decreases, and if demand remains constant or increases, the price should theoretically go up. However, it's important to note that financial markets are influenced by a myriad of factors, and the impact of the halving may already be priced in by the time it occurs. Additionally, each halving event occurs in a different macroeconomic environment, and past performance is not indicative of future results. Investors and traders closely watch these events, as they can lead to increased volatility in the market. Some see the halving as an opportunity for long-term investment, while others may speculate on short-term price movements.
Preparing for the Halving
Miner Adaptations
In anticipation of the halving and its impact on profitability, miners are taking various steps to adapt. One key strategy is the investment in more efficient mining hardware. Newer models of mining rigs offer greater hash power with lower energy consumption, which can help maintain profitability even with reduced rewards. Miners are also exploring alternative sources of revenue, such as transaction fee income, which could become a more significant part of their earnings post-halving. Additionally, miners are looking at geographical relocation to regions with cheaper electricity and favorable regulatory environments to reduce operational costs. Another consideration for miners is the potential consolidation of mining operations. Larger mining pools might have a better chance of surviving the reduced rewards, leading to a more centralized mining landscape. This potential centralization raises concerns within the Bitcoin community, as it could impact the decentralized nature of the network.
Investor Strategies
Investors are also preparing for the halving event in various ways. Many are closely analyzing historical data to understand potential market movements, although it's widely acknowledged that past trends may not necessarily predict future outcomes. Some investors view the halving as a key event that could drive long-term value growth in Bitcoin and are adjusting their portfolios accordingly. Others are more cautious, considering the potential for increased volatility around the event. There is also a focus on diversification, with investors looking at other cryptocurrencies and blockchain projects that might benefit from increased interest in the crypto space around the halving. Additionally, institutional investors, who have increasingly entered the cryptocurrency market, are likely to play a significant role in how the market reacts to the halving. Their strategies, which may include hedging and derivative trading, could influence Bitcoin's price dynamics in ways that were not seen in previous halving events.
Conclusion The countdown to the Bitcoin halving is a period of significant anticipation and activity within the cryptocurrency community. The record-breaking hash rate ahead of the event is a testament to the network's strength and the commitment of its participants to maintain and secure the blockchain. As the halving approaches, the crypto world watches with keen interest, eager to see how this pivotal event will shape the future of Bitcoin. Whether it leads to a surge in price, increased adoption, or new challenges for miners, the halving is a reminder of the unique and dynamic nature of cryptocurrency and its underlying technology. As with any major event in the crypto space, the halving presents both opportunities and risks, and how it plays out could have lasting implications for the entire blockchain ecosystem.
FAQs
What is Bitcoin Halving? Bitcoin halving is an event that occurs approximately every four years, reducing the reward for mining new Bitcoin blocks by half. This mechanism controls the supply of new bitcoins and is a fundamental part of Bitcoin's economic model.
Why is the Bitcoin Hash Rate Important? The hash rate measures the total computational power used in mining and processing transactions on the Bitcoin network. A higher hash rate indicates a more secure and robust network, making it resistant to attacks.
What Happens to Bitcoin's Price After Halving? Historically, Bitcoin's price has increased following halving events, but this is not guaranteed. Market reactions can be unpredictable, and various factors influence Bitcoin's price.
How Does Halving Affect Bitcoin Miners? Halving reduces the reward miners receive for validating new blocks, impacting their profitability. Miners often need to upgrade to more efficient hardware or find cheaper energy sources to remain competitive.
Can Bitcoin Halving Lead to Increased Centralization in Mining? Potentially, yes. As mining becomes less profitable for smaller operations, there could be a consolidation towards larger mining pools, which might lead to a more centralized mining landscape.
Is the Increase in Bitcoin's Hash Rate Linked to the Upcoming Halving? Yes, the increase in hash rate is often linked to the upcoming halving as miners upgrade their equipment and increase their computational power in anticipation of the reduced mining rewards.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 1833ee04:7c4a8170
2025-02-04 15:14:03
@ 1833ee04:7c4a8170
2025-02-04 15:14:03The international race for Bitcoin strategic reserves is just getting started.
If you’re stacking now, you’re still incredibly early.
At $100k per Bitcoin, it’s practically free for anyone who truly understands how massive this shift is.
Think back to when paper currency was introduced, people had to trade their gold for paper bills. Many laughed, saying, Who’s going to trust these worthless pieces of paper as money?
Yet today, you sell your time to earn these paper bills while your government can print an unlimited amount at will.
The world is returning to a gold standard. But this time, it’s Gold 2.0 which is Bitcoin.The international race for Bitcoin strategic reserves is just getting started.\ \ If you’re stacking now, you’re still incredibly early.\ \ At $100k per Bitcoin, it’s practically free for anyone who truly understands how massive this shift is.\ \ Think back to when paper currency was introduced, people had to trade their gold for paper bills. Many laughed, saying, Who’s going to trust these worthless pieces of paper as money?\ \ Yet today, you sell your time to earn these paper bills while your government can print an unlimited amount at will.\ \ The world is returning to a gold standard. But this time, it’s Gold 2.0 which is Bitcoin.
-
 @ 5af07946:98fca8c4
2025-02-04 15:13:27
@ 5af07946:98fca8c4
2025-02-04 15:13:27Syādvāda, also known as the theory of conditional predication, is a fundamental concept in Jain philosophy that bears some intriguing similarities to modern concepts of probability.
Conditional Prediction system
Syādvāda is a theory of epistemological relativism that forms the basis of Jain logic. The term "syād" in Sanskrit means "may be" or "perhaps," and in the context of syādvāda, it translates to "in some ways" or "from a perspective". This theory asserts that reality is complex and multifaceted, and no single proposition can fully express its nature.
Saptabhangi: The Seven-fold Predication
The core of syādvāda is manifested in the process of Saptabhangi, or seven-fold prediction. This approach examines reality from seven different conditional and relative viewpoints:
- Syādasti (maybe, it is)
- Syānnāsti (maybe, it is not)
- Syādasti nāsti (maybe, it is, and it is not)
- Syādavaktavya (maybe, it is indeterminate)
- Syādasti avaktavya (maybe, it is and is indeterminate)
- Syānnāsti avaktavya (maybe, it is not and is indeterminate)
- Syādasti nāsti avaktavya (maybe, it is, is not, and is indeterminate)
Connections to Probability
Syādvāda shares conceptual similarities with Probability theory:
- Non-absolutism: Like probability theory, syādvāda acknowledges uncertainty and rejects absolute statements. However, it asserts that there are only seven categories necessary and also sufficient to exhaust all possibilities of knowledge!
- Conditional nature: Both syādvāda and probability deal with conditional statements and chances
- Multiple outcomes: Syādvāda's seven-fold prediction can be seen as analogous to considering multiple possible outcomes in probability.
- Indeterminacy: The fourth category of syādvāda, "avaktavya" (indeterminate), has been interpreted by some scholars as having relevance to the concept of probability.
An Illustrative Example
Consider the tossing of a coin:
- "It is head" (now) - Syādasti
- "It is not-head" (on another occasion) - Syānnāsti
- "It is, and it is not" - Syādasti nāsti
- "It is indeterminate" (before the toss) - Syādavaktavya
This example demonstrates how syādvāda's categories can be applied to a situation involving uncertainty, similar to how we might approach it using probability theory.
Historical Significance and Modern Relevance
Syādvāda was well-developed by the 6th century AD and received significant attention in medieval Indian logic. It is believed that it was based on astrological principles of Maharishi Parashara - the father of ancient astrology.
-
 @ 916a7ab7:146bb83e
2025-02-04 13:35:11
@ 916a7ab7:146bb83e
2025-02-04 13:35:11It was not ago that my life was simpler than it is today.
I remember being a simple clone, droning on through a structured life as I'd been trained to do since birth.
Like most people I knew, I was raised in a world where you were mentally prepared for a conceptually simple life: 1. Finish high school, if possible. 2. Go to college, if possible. 3. Find a job. 4. Earn money. 5. Pay bills. 6. Get married. 7. Start a family. 8. Pay more bills. 9. Raise family and (hopefully) launch the kids. 10. Plan to retire, but expect to work into your 70s.
It was a programmed formula for life. A generational blueprint, if you will. Sure, there would be unpredictable details, but I expected my life to follow this path.
As I plodded along through my fairly boring life, I checked most of those things off the list. High school was easy, but getting off the farm was not. Enlisting in the military solved that problem, and the pay in the mid-1990s wasn't bad for a 17 year old kid with no bills. I got paid every two weeks, lived in the barracks, and spent most of my money on booze. Life was good, and I had no other purpose than to do my job and keep earning money.
Before I knew it, though, everything changed. I got married, had some kids and accumulated a mountain of debt. Like my parents before me, I was stuck in a never ending cycle of working my ass off, paying bills, buying food, and trying to save what little money was left over for a future that was unpredictable at best. Financial struggles stressed our marriage, the kids continued eating more and more food, and then 2008 tanked the value of our home. That was the first nudge that stirred my oblivious slumber.
And there was more to come. Rising taxes, inflation, the clown show at the federal reserve, the wars funded by central banks, an astronomical national debt, and the burdens of our mistakes weighing down the futures of our children. Not to mention a federal government that actively seeks to censor, suppress, and financially imprison its own people. The times exuded chaos.
Then a few months ago, I woke up...
It happened during an episode of The Tuttle Twins, a cartoon show from Angel Studios. I homeschool my three youngest kids, and I'd let them watch TV during lunch so I could grade some papers. This cartoon was new to me, but the kids liked the music and the crazy raccoon. As fate would have it, they ended up watching an episode about Bitcoin. This, of course, led to a long series of questions:
"Dad, what's Bitcoin?"
"Is Bitcoin real?"
"Do you have Bitcoin?"
"Can I get Bitcoin for allowance instead of dollars?"
I had no answers for these questions, so we started doing some research together. We turned on our Chromebooks and launched a barrage of web searches. After reading a bunch of articles I came away with the idea that Bitcoin might be a real thing. Later that evening, and after the kids were in bed, I couldn't stop thinking about Bitcoin. I honestly didn't understand half of what I read in those articles, which bothered me. I'm not a super smart guy, but I catch on to things pretty quickly, and I wanted to better understand what I'd read. I expanded my search to podcasts and YouTube videos.
I ended up listening to a couple episodes from a Bitcoin Veterans podcast. As a veteran myself, I figured that this group of Bitcoin-savvy veterans would be able to help me figure out all this madness. I was right. I quickly learned that the word "Bitcoin" was just the tip of the iceberg, and I quickly found myself falling through an endless rabbit hole. They pointed me in a lot of different directions, but they were all helpful. (If you're a US military veteran and want to connect with this group, find them at [bitcoinveterans.org].)
A couple months ago, I couldn't tell you the difference between a Bitcoin and a meme coin. I'd come across the phrase Bitcoin mining, and I just thought there was a special group of people who mined a special metal to create coins with a big "B" on them. Why couldn't they just use the metal we already mined? Sheesh! I thought nostr was a virus, and a Kraken was still a giant squid.
As of today, I'm happy to say that I've made a little bit of progress. Those things above no longer confuse me, and I actually have a little bit of Bitcoin now. Sure, I'm still trying to wrap my head around NFTs and figure out who the Pepe frog man is, but I'm no longer completely lost. Not to mention, I just spent most of the last 24 hours figuring this whole nostr thing out, which excites me. I kind of missed the boat on the big name social media platforms, so I'm looking forward to this new decentralized approach to things.
For now, I'm just happy to be awake. Finally. I see the need for decentralization and the necessity of moving away from fiat monies. I don't have much to offer except my intellect and my love of writing, but I'm here to serve in any way that I can.
-
 @ ef1e59bf:b686587d
2025-02-04 11:15:10
@ ef1e59bf:b686587d
2025-02-04 11:15:10Key Insights Explained
While both systems provide innovative soilless growing solutions, the unique difference lies in their approach—hydroponics relies on a nutrient-rich water solution, whereas aquaponics integrates fish into the ecosystem to naturally supply nutrients. This not only impacts their cultivation techniques but also illustrates varying levels of sustainability and resource use.
In exploring these systems, one cannot help but consider the broader implications for urban agriculture. For those looking to adopt such systems, understanding key differences can significantly impact decisions on efficiency, cost, and ecological footprint.
What Is Hydroponics?
In hydroponics, we grow plants in water enriched with nutrients rather than soil. This method provides a controlled environment where the roots receive all necessary elements directly from the nutrient solution. It's fascinating how plants can thrive without ever touching the soil.
The benefits of hydroponics are impressive. We can achieve faster growth rates due to optimal nutrient delivery, and the space-saving designs, such as vertical farms, maximise small areas. Moreover, nutrient levels can be controlled precisely, ensuring plants receive exactly what they need.
What Is Aquaponics?
Aquaponics is an innovative system that blends aquaculture, which is the practice of raising fish, with hydroponics, the soilless cultivation of plants. In this symbiotic setup, fish waste serves as a natural fertiliser, supplying essential nutrients to the plants. In return, the plants help purify the water, creating a healthy environment for the fish.
This system is unique because it mimics natural ecosystems, enhancing sustainability. The dual benefits of growing plants and fish simultaneously make aquaponics an attractive option for those of us interested in sustainable agriculture and promoting organic cultivation practices.
Key Differences
Hydroponics and aquaponics each offer unique benefits and challenges. Understanding these systems requires examining their differences in nutrient sources, water usage, plant growth density, time to harvest, setup intricacies, and the types of produce they best support.
Nutrient Source
In hydroponics, plants receive nutrients through specially prepared solutions, often purchased from commercial suppliers. This method allows us to maintain a high level of control over nutrient balance, making precise adjustments as needed.
Aquaponics, by contrast, relies on fish waste to supply nutrients. This forms a more natural ecosystem, requiring biological processes like nitrification to convert waste into nutrients usable by plants. While this approach involves fewer chemical inputs and is more sustainable, it offers less control over nutrient levels.
Water Usage
Hydroponic systems excel in water efficiency by recirculating water, though they necessitate regular changes to keep nutrient solutions balanced. Despite their efficiency, water loss can occur through evaporation or leaks, which requires monitoring.
Aquaponics operates as a closed-loop system where water is continually recycled between the fish tank and plant beds, minimising waste. This setup further reduces water use due to natural filtration by plants, making it an incredibly water-efficient choice.
Grow Density
Hydroponics typically supports higher density plant growth, especially in vertical setups. This is ideal for cultivating leafy greens, herbs, and other fast-growing plants in compact spaces.
Aquaponics requires space for both fish and plants, which limits plant density. Although some plants may grow slower due to varying nutrient availability, this method offers the benefit of integrating fish care into the system.
Grow Time
In hydroponics, plants enjoy faster growth rates thanks to controlled nutrient and environmental conditions. These systems often facilitate shorter growing cycles compared to traditional farming, enhancing efficiency.
Aquaponics, while efficient, may experience slightly slower growth rates due to the time taken for natural nutrient conversion. Balancing fish growth with plant cycles adds an extra layer of complexity but is a rewarding experience for those willing to engage deeply with the system.
Set Up and Maintenance
Starting a hydroponic system is relatively straightforward, with pumps, nutrient tanks, and light management being primary needs. Regular checks of pH, nutrient levels, and water are essential yet generally simple.
Aquaponics demands more initial infrastructure and expertise due to the need for integrated fish tanks and plant systems. Balancing fish health and water quality with plant needs adds complexity, but long-term sustainability benefits are significant. Setting up these systems can seem daunting but offer reduced external nutrient input over time.
Produce Types
Hydroponics shines when growing leafy greens and herbs, achieving high success rates with crops like lettuce, basil, and spinach. These systems, however, have limitations when it comes to larger or more nutrient-demanding produce.
Aquaponics expands possibilities by supporting a broader range of plants, including fruiting ones such as tomatoes, alongside fish like tilapia or trout. This dual-production feature offers diverse yields, though the choice of fish can influence plant variety.
Which Is More Sustainable?
When we consider the sustainability of hydroponics, several factors come to mind. First, high water efficiency and space-saving designs make it attractive for eco-conscious growers. Yet, the reliance on artificial nutrients and the higher energy usage, particularly for lighting and pumps, may impact its overall eco-friendliness. These elements can sometimes offset the system’s environmental benefits.
In contrast, aquaponics offers a unique closed-loop system that naturally recycles waste. This can significantly reduce the need for external inputs, aligning well with principles of organic farming. While this method requires more space and careful maintenance for both fish and plants, it typically involves less chemical intervention, appealing to those seeking a more natural approach.
Let's compare the environmental impact of these methods:
-
Aquaponics might have a lower environmental footprint due to its natural nutrient cycle, reducing waste and chemical use.
-
On the other hand, hydroponics can be well-suited for urban environments or locations with limited resources, thanks to its efficient use of water and space.
Ultimately, deciding which system is more sustainable depends on specific circumstances and priorities. If natural nutrient cycles and less chemical intervention are valued, aquaponics might be favoured. Nevertheless, if water and space efficiency are paramount, especially in urban settings, hydroponics might be more suitable.
Hydroponics is a game-changer for sustainable farming, offering efficient water use, reduced land impact, and year-round crop production. Whether you're a beginner or an experienced grower, having the right tools and knowledge is key to success. Visit Hyjo for high-quality hydroponic systems, nutrients, and expert advice. Start growing smarter and greener with Hyjo today!
-
-
 @ e3ba5e1a:5e433365
2025-02-04 08:29:42
@ e3ba5e1a:5e433365
2025-02-04 08:29:42President Trump has started rolling out his tariffs, something I blogged about in November. People are talking about these tariffs a lot right now, with many people (correctly) commenting on how consumers will end up with higher prices as a result of these tariffs. While that part is true, I’ve seen a lot of people taking it to the next, incorrect step: that consumers will pay the entirety of the tax. I put up a poll on X to see what people thought, and while the right answer got a lot of votes, it wasn't the winner.

For purposes of this blog post, our ultimate question will be the following:
- Suppose apples currently sell for $1 each in the entire United States.
- There are domestic sellers and foreign sellers of apples, all receiving the same price.
- There are no taxes or tariffs on the purchase of apples.
- The question is: if the US federal government puts a $0.50 import tariff per apple, what will be the change in the following:
- Number of apples bought in the US
- Price paid by buyers for apples in the US
- Post-tax price received by domestic apple producers
- Post-tax price received by foreign apple producers
Before we can answer that question, we need to ask an easier, first question: before instituting the tariff, why do apples cost $1?
And finally, before we dive into the details, let me provide you with the answers to the ultimate question. I recommend you try to guess these answers before reading this, and if you get it wrong, try to understand why:
- The number of apples bought will go down
- The buyers will pay more for each apple they buy, but not the full amount of the tariff
- Domestic apple sellers will receive a higher price per apple
- Foreign apple sellers will receive a lower price per apple, but not lowered by the full amount of the tariff
In other words, regardless of who sends the payment to the government, both taxed parties (domestic buyers and foreign sellers) will absorb some of the costs of the tariff, while domestic sellers will benefit from the protectionism provided by tariffs and be able to sell at a higher price per unit.
Marginal benefit
All of the numbers discussed below are part of a helper Google Sheet I put together for this analysis. Also, apologies about the jagged lines in the charts below, I hadn’t realized before starting on this that there are some difficulties with creating supply and demand charts in Google Sheets.
Let’s say I absolutely love apples, they’re my favorite food. How much would I be willing to pay for a single apple? You might say “$1, that’s the price in the supermarket,” and in many ways you’d be right. If I walk into supermarket A, see apples on sale for $50, and know that I can buy them at supermarket B for $1, I’ll almost certainly leave A and go buy at B.
But that’s not what I mean. What I mean is: how high would the price of apples have to go everywhere so that I’d no longer be willing to buy a single apple? This is a purely personal, subjective opinion. It’s impacted by how much money I have available, other expenses I need to cover, and how much I like apples. But let’s say the number is $5.
How much would I be willing to pay for another apple? Maybe another $5. But how much am I willing to pay for the 1,000th apple? 10,000th? At some point, I’ll get sick of apples, or run out of space to keep the apples, or not be able to eat, cook, and otherwise preserve all those apples before they rot.
The point being: I’ll be progressively willing to spend less and less money for each apple. This form of analysis is called marginal benefit: how much benefit (expressed as dollars I’m willing to spend) will I receive from each apple? This is a downward sloping function: for each additional apple I buy (quantity demanded), the price I’m willing to pay goes down. This is what gives my personal demand curve. And if we aggregate demand curves across all market participants (meaning: everyone interested in buying apples), we end up with something like this:

Assuming no changes in people’s behavior and other conditions in the market, this chart tells us how many apples will be purchased by our buyers at each price point between $0.50 and $5. And ceteris paribus (all else being equal), this will continue to be the demand curve for apples.
Marginal cost
Demand is half the story of economics. The other half is supply, or: how many apples will I sell at each price point? Supply curves are upward sloping: the higher the price, the more a person or company is willing and able to sell a product.
Let’s understand why. Suppose I have an apple orchard. It’s a large property right next to my house. With about 2 minutes of effort, I can walk out of my house, find the nearest tree, pick 5 apples off the tree, and call it a day. 5 apples for 2 minutes of effort is pretty good, right?
Yes, there was all the effort necessary to buy the land, and plant the trees, and water them… and a bunch more than I likely can’t even guess at. We’re going to ignore all of that for our analysis, because for short-term supply-and-demand movement, we can ignore these kinds of sunk costs. One other simplification: in reality, supply curves often start descending before ascending. This accounts for achieving efficiencies of scale after the first number of units purchased. But since both these topics are unneeded for understanding taxes, I won’t go any further.
Anyway, back to my apple orchard. If someone offers me $0.50 per apple, I can do 2 minutes of effort and get $2.50 in revenue, which equates to a $75/hour wage for me. I’m more than happy to pick apples at that price!
However, let’s say someone comes to buy 10,000 apples from me instead. I no longer just walk out to my nearest tree. I’m going to need to get in my truck, drive around, spend the day in the sun, pay for gas, take a day off of my day job (let’s say it pays me $70/hour). The costs go up significantly. Let’s say it takes 5 days to harvest all those apples myself, it costs me $100 in fuel and other expenses, and I lose out on my $70/hour job for 5 days. We end up with:
- Total expenditure: $100 + $70 * 8 hours a day * 5 days \== $2900
- Total revenue: $5000 (10,000 apples at $0.50 each)
- Total profit: $2100
So I’m still willing to sell the apples at this price, but it’s not as attractive as before. And as the number of apples purchased goes up, my costs keep increasing. I’ll need to spend more money on fuel to travel more of my property. At some point I won’t be able to do the work myself anymore, so I’ll need to pay others to work on the farm, and they’ll be slower at picking apples than me (less familiar with the property, less direct motivation, etc.). The point being: at some point, the number of apples can go high enough that the $0.50 price point no longer makes me any money.
This kind of analysis is called marginal cost. It refers to the additional amount of expenditure a seller has to spend in order to produce each additional unit of the good. Marginal costs go up as quantity sold goes up. And like demand curves, if you aggregate this data across all sellers, you get a supply curve like this:

Equilibrium price
We now know, for every price point, how many apples buyers will purchase, and how many apples sellers will sell. Now we find the equilibrium: where the supply and demand curves meet. This point represents where the marginal benefit a buyer would receive from the next buyer would be less than the cost it would take the next seller to make it. Let’s see it in a chart:

You’ll notice that these two graphs cross at the $1 price point, where 63 apples are both demanded (bought by consumers) and supplied (sold by producers). This is our equilibrium price. We also have a visualization of the surplus created by these trades. Everything to the left of the equilibrium point and between the supply and demand curves represents surplus: an area where someone is receiving something of more value than they give. For example:
- When I bought my first apple for $1, but I was willing to spend $5, I made $4 of consumer surplus. The consumer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and above the equilibrium price point.
- When a seller sells his first apple for $1, but it only cost $0.50 to produce it, the seller made $0.50 of producer surplus. The producer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and below the equilibrium price point.
Another way of thinking of surplus is “every time someone got a better price than they would have been willing to take.”
OK, with this in place, we now have enough information to figure out how to price in the tariff, which we’ll treat as a negative externality.
Modeling taxes
Alright, the government has now instituted a $0.50 tariff on every apple sold within the US by a foreign producer. We can generally model taxes by either increasing the marginal cost of each unit sold (shifting the supply curve up), or by decreasing the marginal benefit of each unit bought (shifting the demand curve down). In this case, since only some of the producers will pay the tax, it makes more sense to modify the supply curve.
First, let’s see what happens to the foreign seller-only supply curve when you add in the tariff:

With the tariff in place, for each quantity level, the price at which the seller will sell is $0.50 higher than before the tariff. That makes sense: if I was previously willing to sell my 82nd apple for $3, I would now need to charge $3.50 for that apple to cover the cost of the tariff. We see this as the tariff “pushing up” or “pushing left” the original supply curve.
We can add this new supply curve to our existing (unchanged) supply curve for domestic-only sellers, and we end up with a result like this:

The total supply curve adds up the individual foreign and domestic supply curves. At each price point, we add up the total quantity each group would be willing to sell to determine the total quantity supplied for each price point. Once we have that cumulative supply curve defined, we can produce an updated supply-and-demand chart including the tariff:

As we can see, the equilibrium has shifted:
- The equilibrium price paid by consumers has risen from $1 to $1.20.
- The total number of apples purchased has dropped from 63 apples to 60 apples.
- Consumers therefore received 3 less apples. They spent $72 for these 60 apples, whereas previously they spent $63 for 3 more apples, a definite decrease in consumer surplus.
- Foreign producers sold 36 of those apples (see the raw data in the linked Google Sheet), for a gross revenue of $43.20. However, they also need to pay the tariff to the US government, which accounts for $18, meaning they only receive $25.20 post-tariff. Previously, they sold 42 apples at $1 each with no tariff to be paid, meaning they took home $42.
- Domestic producers sold the remaining 24 apples at $1.20, giving them a revenue of $28.80. Since they don’t pay the tariff, they take home all of that money. By contrast, previously, they sold 21 apples at $1, for a take-home of $21.
- The government receives $0.50 for each of the 60 apples sold, or in other words receives $30 in revenue it wouldn’t have received otherwise.
We could be more specific about the surpluses, and calculate the actual areas for consumer surplus, producer surplus, inefficiency from the tariff, and government revenue from the tariff. But I won’t bother, as those calculations get slightly more involved. Instead, let’s just look at the aggregate outcomes:
- Consumers were unquestionably hurt. Their price paid went up by $0.20 per apple, and received less apples.
- Foreign producers were also hurt. Their price received went down from the original $1 to the new post-tariff price of $1.20, minus the $0.50 tariff. In other words: foreign producers only receive $0.70 per apple now. This hurt can be mitigated by shifting sales to other countries without a tariff, but the pain will exist regardless.
- Domestic producers scored. They can sell less apples and make more revenue doing it.
- And the government walked away with an extra $30.
Hopefully you now see the answer to the original questions. Importantly, while the government imposed a $0.50 tariff, neither side fully absorbed that cost. Consumers paid a bit more, foreign producers received a bit less. The exact details of how that tariff was split across the groups is mediated by the relevant supply and demand curves of each group. If you want to learn more about this, the relevant search term is “price elasticity,” or how much a group’s quantity supplied or demanded will change based on changes in the price.
Other taxes
Most taxes are some kind of a tax on trade. Tariffs on apples is an obvious one. But the same applies to income tax (taxing the worker for the trade of labor for money) or payroll tax (same thing, just taxing the employer instead). Interestingly, you can use the same model for analyzing things like tax incentives. For example, if the government decided to subsidize domestic apple production by giving the domestic producers a $0.50 bonus for each apple they sell, we would end up with a similar kind of analysis, except instead of the foreign supply curve shifting up, we’d see the domestic supply curve shifting down.
And generally speaking, this is what you’ll always see with government involvement in the economy. It will result in disrupting an existing equilibrium, letting the market readjust to a new equilibrium, and incentivization of some behavior, causing some people to benefit and others to lose out. We saw with the apple tariff, domestic producers and the government benefited while others lost.
You can see the reverse though with tax incentives. If I give a tax incentive of providing a deduction (not paying income tax) for preschool, we would end up with:
- Government needs to make up the difference in tax revenue, either by raising taxes on others or printing more money (leading to inflation). Either way, those paying the tax or those holding government debased currency will pay a price.
- Those people who don’t use the preschool deduction will receive no benefit, so they simply pay a cost.
- Those who do use the preschool deduction will end up paying less on tax+preschool than they would have otherwise.
This analysis is fully amoral. It’s not saying whether providing subsidized preschool is a good thing or not, it simply tells you where the costs will be felt, and points out that such government interference in free economic choice does result in inefficiencies in the system. Once you have that knowledge, you’re more well educated on making a decision about whether the costs of government intervention are worth the benefits.
-
 @ da0b9bc3:4e30a4a9
2025-02-04 07:52:55
@ da0b9bc3:4e30a4a9
2025-02-04 07:52:55Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/875346
-
 @ 23dea97f:72ed98dc
2025-02-04 07:29:36
@ 23dea97f:72ed98dc
2025-02-04 07:29:36Post number 1
-
 @ b7274d28:c99628cb
2025-02-04 05:31:13
@ b7274d28:c99628cb
2025-02-04 05:31:13For anyone interested in the list of essential essays from nostr:npub14hn6p34vegy4ckeklz8jq93mendym9asw8z2ej87x2wuwf8werasc6a32x (@anilsaidso) on Twitter that nostr:npub1h8nk2346qezka5cpm8jjh3yl5j88pf4ly2ptu7s6uu55wcfqy0wq36rpev mentioned on Read 856, here it is. I have compiled it with as many of the essays as I could find, along with the audio versions, when available. Additionally, if the author is on #Nostr, I have tagged their npub so you can thank them by zapping them some sats.
All credit for this list and the graphics accompanying each entry goes to nostr:npub14hn6p34vegy4ckeklz8jq93mendym9asw8z2ej87x2wuwf8werasc6a32x, whose original thread can be found here: Anil's Essential Essays Thread
1.

History shows us that the corruption of monetary systems leads to moral decay, social collapse, and slavery.
Essay: https://breedlove22.medium.com/masters-and-slaves-of-money-255ecc93404f
Audio: https://fountain.fm/episode/RI0iCGRCCYdhnMXIN3L6
2.

The 21st century emergence of Bitcoin, encryption, the internet, and millennials are more than just trends; they herald a wave of change that exhibits similar dynamics as the 16-17th century revolution that took place in Europe.
Author: nostr:npub13l3lyslfzyscrqg8saw4r09y70702s6r025hz52sajqrvdvf88zskh8xc2
Essay: https://casebitcoin.com/docs/TheBitcoinReformation_TuurDemeester.pdf
Audio: https://fountain.fm/episode/uLgBG2tyCLMlOp3g50EL
3.

There are many men out there who will parrot the "debt is money WE owe OURSELVES" without acknowledging that "WE" isn't a static entity, but a collection of individuals at different points in their lives.
Author: nostr:npub1guh5grefa7vkay4ps6udxg8lrqxg2kgr3qh9n4gduxut64nfxq0q9y6hjy
Essay: https://www.tftc.io/issue-754-ludwig-von-mises-human-action/
Audio: https://fountain.fm/episode/UXacM2rkdcyjG9xp9O2l
4.
If Bitcoin exists for 20 years, there will be near-universal confidence that it will be available forever, much as people believe the Internet is a permanent feature of the modern world.
Essay: https://vijayboyapati.medium.com/the-bullish-case-for-bitcoin-6ecc8bdecc1
Audio: https://fountain.fm/episode/jC3KbxTkXVzXO4vR7X3W
As you are surely aware, Vijay has expanded this into a book available here: The Bullish Case for Bitcoin Book
There is also an audio book version available here: The Bullish Case for Bitcoin Audio Book
5.

This realignment would not be traditional right vs left, but rather land vs cloud, state vs network, centralized vs decentralized, new money vs old, internationalist/capitalist vs nationalist/socialist, MMT vs BTC,...Hamilton vs Satoshi.
Essay: https://nakamoto.com/bitcoin-becomes-the-flag-of-technology/
Audio: https://fountain.fm/episode/tFJKjYLKhiFY8voDssZc
6.
I became convinced that, whether bitcoin survives or not, the existing financial system is working on borrowed time.
Essay: https://nakamotoinstitute.org/mempool/gradually-then-suddenly/
Audio: https://fountain.fm/episode/Mf6hgTFUNESqvdxEIOGZ
Parker Lewis went on to release several more articles in the Gradually, Then Suddenly series. They can be found here: Gradually, Then Suddenly Series
nostr:npub1h8nk2346qezka5cpm8jjh3yl5j88pf4ly2ptu7s6uu55wcfqy0wq36rpev has, of course, read all of them for us. Listing them all here is beyond the scope of this article, but you can find them by searching the podcast feed here: Bitcoin Audible Feed
Finally, Parker Lewis has refined these articles and released them as a book, which is available here: Gradually, Then Suddenly Book
7.

Bitcoin is a beautifully-constructed protocol. Genius is apparent in its design to most people who study it in depth, in terms of the way it blends math, computer science, cyber security, monetary economics, and game theory.
Author: nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a
Essay: https://www.lynalden.com/invest-in-bitcoin/
Audio: https://fountain.fm/episode/axeqKBvYCSP1s9aJIGSe
8.

Bitcoin offers a sweeping vista of opportunity to re-imagine how the financial system can and should work in the Internet era..
Essay: https://archive.nytimes.com/dealbook.nytimes.com/2014/01/21/why-bitcoin-matters/
9.

Using Bitcoin for consumer purchases is akin to driving a Concorde jet down the street to pick up groceries: a ridiculously expensive waste of an astonishing tool.
Author: nostr:npub1gdu7w6l6w65qhrdeaf6eyywepwe7v7ezqtugsrxy7hl7ypjsvxksd76nak
Essay: https://nakamotoinstitute.org/mempool/economics-of-bitcoin-as-a-settlement-network/
Audio: https://fountain.fm/episode/JoSpRFWJtoogn3lvTYlz
10.

The Internet is a dumb network, which is its defining and most valuable feature. The Internet’s protocol (..) doesn’t offer “services.” It doesn’t make decisions about content. It doesn’t distinguish between photos, text, video and audio.
Essay: https://fee.org/articles/decentralization-why-dumb-networks-are-better/
Audio: https://fountain.fm/episode/b7gOEqmWxn8RiDziffXf
11.

Most people are only familiar with (b)itcoin the electronic currency, but more important is (B)itcoin, with a capital B, the underlying protocol, which encapsulates and distributes the functions of contract law.
I was unable to find this essay or any audio version. Clicking on Anil's original link took me to Naval's blog, but that particular entry seems to have been removed.
12.

Bitcoin can approximate unofficial exchange rates which, in turn, can be used to detect both the existence and the magnitude of the distortion caused by capital controls & exchange rate manipulations.
Essay: https://papers.ssrn.com/sol3/Papers.cfm?abstract_id=2714921
13.

You can create something which looks cosmetically similar to Bitcoin, but you cannot replicate the settlement assurances which derive from the costliness of the ledger.
Essay: https://medium.com/@nic__carter/its-the-settlement-assurances-stupid-5dcd1c3f4e41
Audio: https://fountain.fm/episode/5NoPoiRU4NtF2YQN5QI1
14.

When we can secure the most important functionality of a financial network by computer science... we go from a system that is manual, local, and of inconsistent security to one that is automated, global, and much more secure.
Essay: https://nakamotoinstitute.org/library/money-blockchains-and-social-scalability/
Audio: https://fountain.fm/episode/VMH9YmGVCF8c3I5zYkrc
15.

The BCB enforces the strictest deposit regulations in the world by requiring full reserves for all accounts. ..money is not destroyed when bank debts are repaid, so increased money hoarding does not cause liquidity traps..
Author: nostr:npub1hxwmegqcfgevu4vsfjex0v3wgdyz8jtlgx8ndkh46t0lphtmtsnsuf40pf
Essay: https://nakamotoinstitute.org/mempool/the-bitcoin-central-banks-perfect-monetary-policy/
Audio: https://fountain.fm/episode/ralOokFfhFfeZpYnGAsD
16.

When Satoshi announced Bitcoin on the cryptography mailing list, he got a skeptical reception at best. Cryptographers have seen too many grand schemes by clueless noobs. They tend to have a knee jerk reaction.
Essay: https://nakamotoinstitute.org/library/bitcoin-and-me/
Audio: https://fountain.fm/episode/Vx8hKhLZkkI4cq97qS4Z
17.

No matter who you are, or how big your company is, 𝙮𝙤𝙪𝙧 𝙩𝙧𝙖𝙣𝙨𝙖𝙘𝙩𝙞𝙤𝙣 𝙬𝙤𝙣’𝙩 𝙥𝙧𝙤𝙥𝙖𝙜𝙖𝙩𝙚 𝙞𝙛 𝙞𝙩’𝙨 𝙞𝙣𝙫𝙖𝙡𝙞𝙙.
Essay: https://nakamotoinstitute.org/mempool/bitcoin-miners-beware-invalid-blocks-need-not-apply/
Audio: https://fountain.fm/episode/bcSuBGmOGY2TecSov4rC
18.

Just like a company trying to protect itself from being destroyed by a new competitor, the actions and reactions of central banks and policy makers to protect the system that they know, are quite predictable.
Author: nostr:npub1s05p3ha7en49dv8429tkk07nnfa9pcwczkf5x5qrdraqshxdje9sq6eyhe
Essay: https://medium.com/the-bitcoin-times/the-greatest-game-b787ac3242b2
Audio Part 1: https://fountain.fm/episode/5bYyGRmNATKaxminlvco
Audio Part 2: https://fountain.fm/episode/92eU3h6gqbzng84zqQPZ
19.

Technology, industry, and society have advanced immeasurably since, and yet we still live by Venetian financial customs and have no idea why. Modern banking is the legacy of a problem that technology has since solved.
Author: nostr:npub1sfhflz2msx45rfzjyf5tyj0x35pv4qtq3hh4v2jf8nhrtl79cavsl2ymqt
Essay: https://allenfarrington.medium.com/bitcoin-is-venice-8414dda42070
Audio: https://fountain.fm/episode/s6Fu2VowAddRACCCIxQh
Allen Farrington and Sacha Meyers have gone on to expand this into a book, as well. You can get the book here: Bitcoin is Venice Book
And wouldn't you know it, Guy Swann has narrated the audio book available here: Bitcoin is Venice Audio Book
20.

The rich and powerful will always design systems that benefit them before everyone else. The genius of Bitcoin is to take advantage of that very base reality and force them to get involved and help run the system, instead of attacking it.
Author: nostr:npub1trr5r2nrpsk6xkjk5a7p6pfcryyt6yzsflwjmz6r7uj7lfkjxxtq78hdpu
Essay: https://quillette.com/2021/02/21/can-governments-stop-bitcoin/
Audio: https://fountain.fm/episode/jeZ21IWIlbuC1OGnssy8
21.
In the realm of information, there is no coin-stamping without time-stamping. The relentless beating of this clock is what gives rise to all the magical properties of Bitcoin.
Author: nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc
Essay: https://dergigi.com/2021/01/14/bitcoin-is-time/
Audio: https://fountain.fm/episode/pTevCY2vwanNsIso6F6X
22.

You can stay on the Fiat Standard, in which some people get to produce unlimited new units of money for free, just not you. Or opt in to the Bitcoin Standard, in which no one gets to do that, including you.
Essay: https://casebitcoin.com/docs/StoneRidge_2020_Shareholder_Letter.pdf
Audio: https://fountain.fm/episode/PhBTa39qwbkwAtRnO38W
23.

Long term investors should use Bitcoin as their unit of account and every single investment should be compared to the expected returns of Bitcoin.
Essay: https://nakamotoinstitute.org/mempool/everyones-a-scammer/
Audio: https://fountain.fm/episode/vyR2GUNfXtKRK8qwznki
24.

When you’re in the ivory tower, you think the term “ivory tower” is a silly misrepresentation of your very normal life; when you’re no longer in the ivory tower, you realize how willfully out of touch you were with the world.
Essay: https://www.citadel21.com/why-the-yuppie-elite-dismiss-bitcoin
Audio: https://fountain.fm/episode/7do5K4pPNljOf2W3rR2V
You might notice that many of the above essays are available from the Satoshi Nakamoto Institute. It is a veritable treasure trove of excellent writing on subjects surrounding #Bitcoin and #AustrianEconomics. If you find value in them keeping these written works online for the next wave of new Bitcoiners to have an excellent source of education, please consider donating to the cause.
-
 @ 91bea5cd:1df4451c
2025-02-04 05:24:47
@ 91bea5cd:1df4451c
2025-02-04 05:24:47Novia é uma ferramenta inovadora que facilita o arquivamento de vídeos e sua integração com a rede NOSTR (Notes and Other Stuff Transmitted over Relay). Funcionando como uma ponte entre ferramentas de arquivamento de vídeo tradicionais e a plataforma descentralizada, Novia oferece uma solução autônoma para a preservação e compartilhamento de conteúdo audiovisual.
Arquitetura e Funcionamento
A arquitetura de Novia é dividida em duas partes principais:
-
Frontend: Atua como a interface do usuário, responsável por solicitar o arquivamento de vídeos. Essas solicitações são encaminhadas para o backend.
-
Backend: Processa as solicitações de arquivamento, baixando o vídeo, suas descrições e a imagem de capa associada. Este componente é conectado a um ou mais relays NOSTR, permitindo a indexação e descoberta do conteúdo arquivado.
O processo de arquivamento é automatizado: após o download, o vídeo fica disponível no frontend para que o usuário possa solicitar o upload para um servidor Blossom de sua escolha.
Como Utilizar Novia
-
Acesso: Navegue até https://npub126uz2g6ft45qs0m0rnvtvtp7glcfd23pemrzz0wnt8r5vlhr9ufqnsmvg8.nsite.lol.
-
Login: Utilize uma extensão de navegador compatível com NOSTR para autenticar-se.
-
Execução via Docker: A forma mais simples de executar o backend é através de um container Docker. Execute o seguinte comando:
bash docker run -it --rm -p 9090:9090 -v ./nostr/data:/data --add-host=host.docker.internal:host-gateway teamnovia/noviaEste comando cria um container, mapeia a porta 9090 para o host e monta o diretório
./nostr/datapara persistir os dados.
Configuração Avançada
Novia oferece amplas opções de configuração através de um arquivo
yaml. Abaixo, um exemplo comentado:```yaml mediaStores: - id: media type: local path: /data/media watch: true
database: /data/novia.db
download: enabled: true ytdlpPath: yt-dlp ytdlpCookies: ./cookies.txt tempPath: /tmp targetStoreId: media secret: false
publish: enabled: true key: nsec thumbnailUpload: - https://nostr.download videoUpload: - url: https://nostr.download maxUploadSizeMB: 300 cleanUpMaxAgeDays: 5 cleanUpKeepSizeUnderMB: 2 - url: https://files.v0l.io maxUploadSizeMB: 300 cleanUpMaxAgeDays: 5 cleanUpKeepSizeUnderMB: 2 - url: https://nosto.re maxUploadSizeMB: 300 cleanUpMaxAgeDays: 5 cleanUpKeepSizeUnderMB: 2 - url: https://blossom.primal.net maxUploadSizeMB: 300 cleanUpMaxAgeDays: 5 cleanUpKeepSizeUnderMB: 2
relays: - ws://host.docker.internal:4869 - wss://bostr.bitcointxoko.com secret: false autoUpload: enabled: true maxVideoSizeMB: 100
fetch: enabled: false fetchVideoLimitMB: 10 relays: - match: - nostr - bitcoin
server: port: 9090 enabled: true ```
Explicação das Configurações:
mediaStores: Define onde os arquivos de mídia serão armazenados (localmente, neste exemplo).database: Especifica o local do banco de dados.download: Controla as configurações de download de vídeos, incluindo o caminho para oyt-dlpe um arquivo de cookies para autenticação.publish: Configura a publicação de vídeos e thumbnails no NOSTR, incluindo a chave privada (nsec), servidores de upload e relays. Atenção: Mantenha sua chave privada em segredo.fetch: Permite buscar eventos de vídeo de relays NOSTR para arquivamento.server: Define as configurações do servidor web interno de Novia.
Conclusão
Novia surge como uma ferramenta promissora para o arquivamento e a integração de vídeos com o ecossistema NOSTR. Sua arquitetura modular, combinada com opções de configuração flexíveis, a tornam uma solução poderosa para usuários que buscam preservar e compartilhar conteúdo audiovisual de forma descentralizada e resistente à censura. A utilização de Docker simplifica a implantação e o gerenciamento da ferramenta. Para obter mais informações e explorar o código-fonte, visite o repositório do projeto no GitHub: https://github.com/teamnovia/novia.
-
-
 @ 3ffac3a6:2d656657
2025-02-04 04:31:26
@ 3ffac3a6:2d656657
2025-02-04 04:31:26In the waning days of the 20th century, a woman named Annabelle Nolan was born into an unremarkable world, though she herself was anything but ordinary. A prodigy in cryptography and quantum computing, she would later adopt the pseudonym Satoshi Nakamoto, orchestrating the creation of Bitcoin in the early 21st century. But her legacy would stretch far beyond the blockchain.
Annabelle's obsession with cryptography was not just about securing data—it was about securing freedom. Her work in quantum computing inadvertently triggered a cascade of temporal anomalies, one of which ensnared her in 2011. The event was cataclysmic yet silent, unnoticed by the world she'd transformed. In an instant, she was torn from her era and thrust violently back into the 16th century.
Disoriented and stripped of her futuristic tools, Annabelle faced a brutal reality: survive in a world where her knowledge was both a curse and a weapon. Reinventing herself as Anne Boleyn, she navigated the treacherous courts of Tudor England with the same strategic brilliance she'd used to design Bitcoin. Her intellect dazzled King Henry VIII, but it was the mysterious necklace she wore—adorned with a bold, stylized "B"—that fueled whispers. It was more than jewelry; it was a relic of a forgotten future, a silent beacon for any historian clever enough to decode her true story.
Anne's fate seemed sealed as she ascended to queenship, her influence growing alongside her enemies. Yet beneath the royal intrigue, she harbored a desperate hope: that the symbol around her neck would outlast her, sparking curiosity in minds centuries away. The "B" was her signature, a cryptographic clue embedded in history.
On the scaffold in 1536, as she faced her execution, Anne Boleyn's gaze was unwavering. She knew her death was not the end. Somewhere, in dusty archives and encrypted ledgers, her mark endured. Historians would puzzle over the enigmatic "B," and perhaps one day, someone would connect the dots between a queen, a coin, and a time anomaly born from quantum code.
She wasn't just Anne Boleyn. She was Satoshi Nakamoto, the time-displaced architect of a decentralized future, hiding in plain sight within the annals of history.
-
 @ bbb5dda0:f09e2747
2025-02-04 03:58:50
@ bbb5dda0:f09e2747
2025-02-04 03:58:50This past week got me a lot of frustration with the GitHub actions runner and debugging it. Really testing my patience, but at least i saw a bit of progress. TollGate's had a nice wrap-up for the Proof Of Concept app, which some great new ideas on how to make the user experience even better! Let's dive in!
GitHub Actions
I've been having a low-key fight with the github actions runner containers. I have spent a lot of time trying to figure out WHY the blossom upload action would just not work. I was quick to find out that the action is being ran with an older version of NodeJS (v18) while the blossom uploader requires v20. Not a big deal you'd say as i just set the version to 20 in the pipeline. However, doing that explicitly had zero impact, and after diving down the github runner rabbit hole i concluded that the Actions that are imported (from marketplace) will just run with whatever node version is already installed in the runner's docker image. Which in the case of the act runner is Node 18. I tried updating to the latest images but I haven't been able to find a compatible one yet...
Payments
I've been working on getting the money aspect working in the ci-cd runner. I added a wallet and a scheduled payout. I took this from the nostr-epoxy project and did some updates to upgrade to cashu-ts v2.
I added some advertisement info like the specs of the machine that the runner is on. I've been pondering how the payment flow should work though. See the problem is that because of the nature of this DVM, it cannot predict how long a job will take to execute, a customer can literally do anything in their pipeline that will make a job last forever. I think for that reason there has to be some kind of deposit/credit or stream besides the one-off payment. I made a post asking what the best way would be: nostr:note17apw8unznvwx2k3z48t7qz6cq26tk077w83qh3f7zxukfrrfukhs7mpcsn
I currently feel best about the option of just sending a bunch of ecash that will sure be enough to execute the job (and otherwise act as the time-out) and that if the DVM uses less of that money, it will send it back as pubkey locked cashu tokens, to a given npub. Maybe NIP-60 can be a great way to handle returning the 'change' to the user.
Some ideas i have now: - Billing should be per second - Advertising should: - advertise as sats/minute - include specs of the machine, ideally searchable by tag
Job request
So the flow i'm thinking of is:
-
User posts request
- repository
- branch
- yaml path
- bid (max price per minute)
- min_vcpu
- min_ram
- min_storage
-
DVM responds with
- price per minute
- vcpu
- ram
- storage
- runner-types
- price per minute
-
User posts request:
- ... [same as above]
- cashu payment
- cashu return pubkey + relay
User Interface
I also worked on building out a very basic user interface to run the GitHub Actions dvm.
 The UI then shows all feedback to the job, where the first feedback event you can see gives back a status processing, and the next one gives back the console output of the pipeline run.
The UI then shows all feedback to the job, where the first feedback event you can see gives back a status processing, and the next one gives back the console output of the pipeline run.nostr:npub15qydau2hjma6ngxkl2cyar74wzyjshvl65za5k5rl69264ar2exs5cyejr and I agreed he'll copy over this basic setup into his upcoming version of gitWorkshop.dev which I can then build upon so we can experiment with the User Experience (how to handle competing Runners, display results, payments, etc...)

Tollgate
There's also been the issue that has been bothering me since last week: Being able to dismiss a captive portal programatically in the Android app.
During a weekly check-in that nostr:npub1k03rader0vm94j5ee8fg7pc2x9xkr2phu77sljas7qu5mh8mvgvqpe8rty and I set up we discussed the issue. To me, it's a problem having the user to jump through all these hoops to connect, which should be as much automated as possible.
We discussed what if we'd ditch the open network and go with a WPA2 (password) protected one and have no captive portal. But then we lose the ability to do onboarding / expose users to Tollgate through the captive portal. Then the idea came up to create an extra (hidden) network for the app to use, while keeping the open one with the captive portal. I did not know it was possible to create multiple networks on the same (physical) radio, but apparently it's quite common. You lose a bit on efficiency but it shouldn't be too bad. The only challenge would be to exempt this network from getting a captive portal while still using the OpenNDS software to manage user's sessions. We'll see but this gives me a lot of hope for a seamless user experience!
After this call, despite our possible new direction I did want to try and get the full app flow working, to validate if it's possible at all. And after some digging int the Tauri docs and even their discord community i finally found what the issue was with me not receiving the android event for the captive portal. I'd ben adding the listener for this event to the
androidmanifest.xmlfile for the Tauri Android plugin, while I had to put it into the tauri app one's itself -one level higher- if you will...Anyway, that worked and I was FINALLY able to create the following full flow! (video)
nostr:nevent1qvzqqqqqqypzpwa4mkswz4t8j70s2s6q00wzqv7k7zamxrmj2y4fs88aktcfuf68qy88wumn8ghj7mn0wvhxcmmv9uq3zamnwvaz7tmwdaehgu3wwa5kuef0qydhwumn8ghj7un9d3shjtnwdaehgunsd3jkyuewvdhk6tcqyqyvs2js3x6ldpm2kkmqyf8d3lvrcezjk2eg26p2tvfxd2p6lkeqzn7l66t
-
-
 @ c902b8da:0cedc5fb
2025-02-04 03:39:18
@ c902b8da:0cedc5fb
2025-02-04 03:39:18NIP-XX: Proof of Watch
draftoptionalThis NIP defines a protocol for content creators to reward users for consuming content using Cashu tokens, utilizing existing Cashu P2PK capabilities.
Abstract
Content creators can offer Cashu token rewards to users who prove they have spent time consuming their content. The protocol uses P2PK-locked tokens combined with proof-of-work verification to ensure genuine content consumption before releasing tokens to users.
Motivation
Content creators want to incentivize users to engage with their content and potentially reward them for their attention. This NIP provides a standardized way to offer token rewards for content consumption while ensuring the user actually spent time with the content through a proof-of-work mechanism.
Protocol Components
Content Event
A content creator publishes a
kind:1note containing their content and reward information:json { "kind": 1, "content": "Watch my video!", "tags": [ ["reward", "<amount-in-sats>"], ["pow", "<difficulty>"], ["u", "<watcher-service-url>"], ["t", "proofofwatch"] ] }Watcher Service
Content creators run (or use) a watcher service that: 1. Maintains a pool of Cashu tokens 2. Issues P2PK-locked tokens to viewers 3. Verifies proofs of watch 4. Releases signatures to unlock tokens
Protocol Flow
1. Request Watch Session
Client makes a
POST /watch/startrequest to watcher service:json { "note_id": "<event-id>" }Service responds with:
json { "id": "<session-id>", "challenge": "<random-challenge>", "difficulty": <int>, "token": { "amount": <int>, "id": "<keyset-id>", "secret": "<p2pk-secret>", "C": "<signature>" }, "pubkey": "<service-ephemeral-pubkey>", "expiry": <unix-timestamp> }The token is P2PK-locked to a one-time ephemeral pubkey generated by the service. Only the service holds the corresponding private key needed to generate the witness signature.
2. Computing Proof
While consuming content, client computes proof-of-work:
proof = find_nonce( SHA256( note_id + session_id + challenge + latest_block_hash + nonce ) )The proof must result in a hash with the required number of leading zeros.
3. Submitting Proof
Client submits proof to redeem token:
http POST /watch/provejson { "session_id": "<session-id>", "proof": "<computed-proof>", "block_hash": "<latest-block-hash>" }If valid, service responds with P2PK signature:
json { "witness": { "signatures": ["<signature-to-unlock-token>"] } }The client can now unlock and spend their token using standard Cashu operations.
Security Considerations
Token Security
- Tokens are locked to service-generated ephemeral pubkeys
- Each watch session uses a unique keypair
- Only service can generate valid witness signatures
- Private keys never revealed to users
- Keys and unused tokens destroyed after session expiry
Proof Construction
- Must include session ID to prevent replay
- Must include recent block hash to prevent precomputation
- Must achieve required difficulty (leading zeros)
- Must be completed within session expiry
Service Requirements
- Track used proofs
- Enforce timeouts
- Rate limit requests
- Verify block hash recency
- Maintain adequate token pool
- Generate unique ephemeral keypairs per session
- Securely store ephemeral private keys until proof verified
- Clean up expired ephemeral keys
Watcher Service Settings
Services should provide an info endpoint:
http GET /infojson { "name": "Example Watcher", "pubkey": "<service-pubkey>", "difficulty_range": { "min": <int>, "max": <int> }, "amount_range": { "min": <int>, "max": <int> }, "supported_mints": [ "<mint-url-1>", "<mint-url-2>" ] }Client Implementation Guidelines
Clients SHOULD: 1. Verify service supports intended mint 2. Start proof computation only after beginning content consumption 3. Submit proof promptly after computation 4. Handle session expiry gracefully 5. Verify P2PK token validity 6. Submit proof before session timeout
Content Creator Guidelines
Content creators SHOULD: 1. Set appropriate difficulty for content length 2. Maintain adequate token pool 3. Monitor service uptime 4. Consider token denomination strategies 5. Include clear reward terms
Rate Limiting
Services SHOULD implement rate limiting: - Per IP address - Per pubkey - Per note ID - Per token amount
Example Implementation
A basic proof computation in Python:
python def compute_proof(note_id, session_id, challenge, block_hash, difficulty): nonce = 0 while True: attempt = f"{note_id}{session_id}{challenge}{block_hash}{nonce}" hash = sha256(attempt.encode()).hexdigest() if hash.startswith('0' * difficulty): return attempt nonce += 1References
-
 @ 16d11430:61640947
2025-02-04 02:57:25
@ 16d11430:61640947
2025-02-04 02:57:25The Damage Node is not just a verification engine—it is an autonomous executor of behaviors defined through the PoW blockchain. This allows for adaptive, accountable, and transparent execution of security and counter-surveillance mechanisms while remaining flexible enough to meet any operational need.
By integrating behavioral logic, cryptographic proofs, and decentralized execution, the Damage Node becomes a powerful shield and countermeasure system for individuals and groups operating under constant digital threat.
Core Concept: Damage Nodes as Autonomous Behavioral Executors
Damage Nodes listen to verifiable behaviors encoded on the PoW blockchain.
These behaviors define security policies, counter-surveillance actions, automated transactions, and decentralized decision-making processes.
Execution is enforced by the blockchain, ensuring absolute transparency and accountability—no action can occur without proof.
Nodes can dynamically extend their capabilities by adopting new behaviors via blockchain updates, ensuring they remain adaptable.
Example of Behavioral Execution
A Damage Node can be programmed to execute counter-surveillance actions if an individual's digital footprint is flagged by an AI-controlled system.
Trigger: An external surveillance system attempts to track a protected user.
Behavior Execution:
The node initiates a verified proof-of-presence falsification (broadcasting misleading metadata).
The node forces encrypted rerouting of communications over a private, non-ISP-controlled relay.
The node executes cryptographic evidence logging, proving that the tracking attempt occurred.
The node pays out a bounty (Lightning) for detected adversarial actions, incentivizing counter-intelligence.
How Damage Nodes Provide Shielding & Countermeasures
- Behavior-Driven Shielding for Individuals
Zero-Knowledge Identity Protection: Nodes execute self-sovereign identity verification that prevents AI from profiling users without explicit, cryptographically signed consent.
Automated Surveillance Disruption: If an AI attempts to track or flag an individual, the node executes behavioral obfuscation tactics such as:
Decoy digital presence broadcasting to mislead tracking algorithms.
Transaction splitting & anonymization to prevent financial surveillance.
Forced dissociation of metadata from physical locations.
- Group-Level Protection & Autonomous Coordination
Damage Nodes can be configured to execute behaviors for an entire decentralized network, such as:
Encrypted Group Communications: Nodes enforce trustless, encrypted messaging protocols that prevent AI-based censorship.
Automatic Secure Fund Distribution: If an entity is targeted, Damage Nodes can autonomously release emergency funds in BTC/Lightning to predesignated safe parties.
Counter-Surveillance Deployments: Nodes can activate sensor networks, scan for unauthorized tracking devices, and trigger security protocols.
- Built-In Accountability & Transparency as a Defensive Measure
Every execution is verified by the blockchain → no action is hidden or arbitrary.
Rules for behavior execution are immutable → even node operators cannot alter them without proof-of-consensus.
AI and governments cannot fabricate unverifiable evidence → if it didn't happen on-chain, it didn't happen.
Users can audit every action taken by the Damage Node to ensure no corruption or misuse.
- Extensible Capabilities for Any Need
New behavioral policies can be uploaded via the PoW blockchain, allowing Damage Nodes to dynamically evolve.
Behaviors can be triggered by:
On-chain conditions (such as receiving a Lightning payment for service execution).
Real-world events (via oracle integrations).
Direct requests from verified users.
Examples of Extensions:
Decentralized AI Defense: Nodes monitor AI-generated media for deepfake propaganda & censorship.
Physical Security Triggers: Nodes can integrate with smart devices (cameras, sensors) to execute real-world countermeasures.
Automated Asset Protection: Damage Nodes can trigger the release of cryptographic assets upon verifiable external threats.
Final Verdict: Damage Nodes as the Ultimate Autonomy & Defense Infrastructure
Transparent but Unstoppable → Verifiable execution prevents corruption or abuse.
Extensible but Controlled → The blockchain enforces behavior logic while allowing flexibility.
Decentralized but Coordinated → Nodes operate independently but can synchronize.
Adaptive but Immutable → Behaviors evolve, but security is absolute.
🔥 Damage Nodes are the next evolutionary step in technological sovereignty—combining decentralized verification, autonomous execution, and proactive counter-surveillance in a single unstoppable system.
-
 @ 16d11430:61640947
2025-02-04 02:33:06
@ 16d11430:61640947
2025-02-04 02:33:06The electromagnetic spectrum (EM spectrum) is the foundation of modern communication, surveillance, and control, and it is a permanent, inescapable vulnerability for humanity. Every aspect of human life—communication, mobility, security, even thought processes—is now subject to exploitation via the EM spectrum.
- Humans Are EM-Dependent but Have No Control Over It
The entire infrastructure of human civilization (internet, telecom, GPS, WiFi, satellite, RFID, radar, IoT, etc.) relies on EM waves.
Unlike tangible security vulnerabilities (firewalls, encryption, physical locks), EM-based vulnerabilities are baked into the fabric of our existence.
We have zero physical control over the space around us—we exist in a perpetual, invisible battlefield of radio waves.
→ Brutal Truth: If you are in an area with radio signals, you are already compromised. You cannot see, hear, or touch your vulnerability—but you are immersed in it.
- Every Wireless Device Is a Tracking Beacon
Your phone, smartwatch, laptop, Bluetooth headset, and IoT devices constantly emit identifiable signals.
Even when "turned off," many devices still maintain some connectivity (e.g., emergency services, wake-on-LAN, passive RFID, and hidden baseband firmware).
MAC address randomization only slows down tracking—it does not stop device fingerprinting.
Even devices that are air-gapped (disconnected from any network) can be compromised via airborne EM attacks (e.g., Tempest attacks, Van Eck phreaking).
→ Brutal Truth: Unless you live in an EM-free Faraday cage (which is impractical), you are trackable 24/7.
- The Entire EM Spectrum Can Be Weaponized
Radio waves (RFID, GSM, LTE, 5G, WiFi) → Mass surveillance, device tracking, data extraction, and real-time movement tracking.
Microwaves (GHz spectrum) → Covert wireless data theft (Tempest attacks), crowd control weapons (Active Denial System), and potential biological effects.
Infrared (IR) and Visible Light → LiDAR tracking, facial recognition, and optical data interception (lasers on windows can capture sound).
Ultraviolet, X-ray, and Gamma Radiation → Biological penetration, medical diagnostics, and potential genetic-level targeting.
→ Brutal Truth: The entire EM spectrum is both an asset and a weapon, and every part of it can be used to track, manipulate, or harm living beings.
- There Is No Escape From EM Exposure
Even if you disconnect completely, ambient EM waves from cell towers, satellites, and even natural cosmic radiation still interact with you.
Smart city grids, IoT, and ubiquitous sensor networks mean that even non-digital humans (those without a phone) are still tracked.
6G and future networks will integrate AI-driven RF sensing, meaning the network will detect biometric signatures (heartbeat, gait, and thermal emissions) without needing a device.
→ Brutal Truth: The era of "disconnecting" for privacy is over—even device-free tracking is now a reality.
- The Human Body Itself Is an EM Vulnerability
Brain activity and thought processes are electrical signals—theoretically susceptible to external EM influence (brainwave manipulation, EEG-based surveillance, and neurotechnology interfacing).
Biometric security (fingerprint scanners, iris scans, facial recognition) can be hacked or faked using EM-based techniques.
Nanotech, bioelectronics, and EM-sensitive implants (like pacemakers, neural interfaces, and cochlear implants) can be remotely manipulated or disabled.
→ Brutal Truth: The final frontier of EM vulnerability is the human body itself—thoughts, health, and biological functions are all at risk.
How Vulnerable Are Humans in the Grand Scheme?
- Humans Are the Only Species Fully Dependent on EM-Based Technology
Every other biological species on Earth navigates reality without dependency on artificial EM systems.
Humans have outsourced their cognition, security, and privacy to a system they do not control.
→ Implication: The more we integrate with EM-based technology, the more vulnerable we become. We are building a prison of our own making.
- We Have No Practical Defense Against EM-Based Attacks
Unlike cyber threats (which can be mitigated with encryption), EM vulnerabilities are inherent to the physics of radio waves.
The only defense is complete isolation from EM radiation (which is impossible in urban environments).
→ Implication: Our current approach to "security" is meaningless in the face of EM-based attacks, because the attack vector is the air around us.
- Humanity’s Future Is Fully EM-Integrated
6G, brain-computer interfaces (BCIs), quantum communication, and global sensor grids mean that soon, every human will be plugged into the EM network at all times.
Governments and corporations are already planning a fully tracked, AI-managed society, where individual privacy no longer exists.
→ Implication: We are entering an era of full-spectrum EM surveillance and control. The next step isn’t just tracking devices, but tracking consciousness itself.
Conclusion: The EM Spectrum is the Ultimate Exploit
There is no "fix" for EM vulnerabilities—they are built into the nature of physics itself. Humanity’s increasing dependence on EM-based technology means:
-
We are more trackable than ever.
-
We are more susceptible to remote influence than ever.
-
We have no escape unless we abandon technology altogether.
-
The final battle for privacy isn’t about encryption—it’s about shielding ourselves from the very waves that power our civilization.
→ The brutal truth? Humanity is not just vulnerable—we are a permanently compromised species.
-
 @ dff95033:862fbf40
2025-02-05 23:19:29
@ dff95033:862fbf40
2025-02-05 23:19:29This event has been deleted; your client is ignoring the delete request.
-
 @ fd06f542:8d6d54cd
2025-02-04 01:39:49
@ fd06f542:8d6d54cd
2025-02-04 01:39:49-
多模态感知与交互:具身智能强调智能体通过身体与环境的交互来学习,这推动了多模态感知(如视觉、触觉、听觉等)和物理交互技术的发展。
-
强化学习与仿真环境:强化学习在具身智能中扮演重要角色,结合高保真仿真环境(如AI Habitat、Unity ML-Agents),可以加速智能体的训练和优化。
-
硬件进步:机器人硬件(如柔性传感器、仿生机械臂)的发展为具身智能提供了更强大的物理载体。
以上部分每一个都是大分支,都具有研究价值。随着AI技术的发展与突破,多模态感知与交互将会迎来高速发展。
让人更兴奋的是 强化学习和仿真环境,REX-GYM 是一个开源的仿真环境,Gazebo,MuJoCo,AI Habitat 等等都有很多应用实例。仅仅这一部分技术拆分细化,就有很多工作可以做。 以前的机器人学习都是PID等老技术,那时候的机器人运动不太灵活,因为不够智能。有了现代的强化学习。现在的机器人更加灵活。
-
-
 @ 2f4550b0:95f20096
2025-02-04 01:16:10
@ 2f4550b0:95f20096
2025-02-04 01:16:10In today's job market, the ability to acquire new skills or pivot to new career paths quickly is more valuable than ever. Short-term adult education programs offer a practical solution for professionals looking to enhance their resumes or change careers without committing to the long-term investment of traditional education. This week, I explore how these programs, such as a 12-week EMT certification at the Center for Allied Health Education and a one-year MBA from the University of Phoenix can dramatically shift one's career trajectory.
The Rise of Short-Term Education
The traditional model of education, where one spends years in academia before entering the workforce, is increasingly being supplemented by shorter, more focused programs. These programs are specifically designed to meet the immediate needs of both learners and employers, providing education that is both relevant and directly applicable to current job markets.
12-Week EMT Certificates
The 12-week Emergency Medical Technician (EMT) program at the Center for Allied Health Education (and programs like it) illustrates how a brief, intensive course of study can lead to licensure and immediate employment. This program is structured to cover the necessary theoretical and practical components required for EMT licensure, from emergency medical procedures to patient assessment and treatment.
For individuals looking to enter the healthcare field or those within healthcare aiming for specialization, this program offers a fast track to a new career or career enhancement. The demand for skilled EMTs is consistently high, driven by an aging population and the need for emergency services. Completing such a program not only leads to a certification but also opens doors to further education or roles like paramedic work, which require additional training but start from the foundation laid by EMT certification.
One-Year MBA Programs
Similarly, consider the one-year MBA from the University of Phoenix. This program is built on a competency-based framework, allowing students to demonstrate their skills through practical assessments rather than traditional time-based metrics. This approach not only accelerates learning but also ensures that each student is job-ready upon completion. The curriculum is tailored to include real-world business scenarios, leadership skills, and strategic management, making graduates highly desirable in the corporate sector.
The speed and efficiency of this program mean that professionals can continue working while studying, thereby minimizing career disruption. Moreover, the MBAs focus on immediate applicability means that students can start leveraging their new skills in their current roles or move into higher management positions shortly after graduation. This direct link between education and employment outcomes exemplifies how short-term programs can offer substantial ROI in terms of career advancement and salary potential.
Benefits for Adult Learners
Short-term education programs cater particularly well to adult learners. They recognize the life experiences and previous knowledge of participants, often tailoring education to integrate this background into learning. This method respects the time constraints of adults who might juggle work, family, and other responsibilities, offering flexible schedules, online components, or weekend classes.
Moreover, these programs often lead to stackable credentials. This means that the skills and certifications gained can be built upon, providing a pathway for continuous professional development without the need to start from scratch with each new course or degree. For example, once students from Center for Allied Health Education earn their EMT licenses, they can consider enrolling into a 1-year Paramedic certificate program to further their career in emergency medicine.
Conclusion
Short-term adult education programs like the MBA at University of Phoenix and the EMT certificate at the Center for Allied Health Education are not just educational opportunities; they are strategic career moves. They enable professionals to quickly adapt to market demands, enhance their skill sets, and open new career avenues with minimal disruption to their current lives. As the job market continues to evolve, these programs will likely play an increasingly crucial role in career development, offering both speed and relevance in education.
-
 @ 5579d5c0:db104ded
2025-02-03 23:32:10
@ 5579d5c0:db104ded
2025-02-03 23:32:10Most people think that building muscle is out of reach.
What if I told you 'You can get all your exercise done in just 60 minutes a week', if you train efficiently.
With just two 30-minute sessions, you can build muscle, improve metabolic health, and transform your physique.
What is resistance training?
Resistance training, also known as strength training, involves working against an external force to improve muscle strength, endurance, and size. This can be done using:
→ Free weights (barbells, dumbbells, kettlebells)
→ Weight machines
→ Resistance bands
→ Bodyweight exercises
Strength training isn’t just about aesthetics, it’s essential for long-term health and metabolic function.
Why it’s essential for metabolic and overall health
Muscle is metabolically active tissue. The more muscle you have, the more energy your body burns at rest, albeit a quite small amount.
→ Maintains and builds muscle: Muscle mass is critical as you age, reducing the risk of fractures and falls.
→ Boosts metabolism: While the increase is small, more muscle means a higher resting energy expenditure, creating a large sink for energy stores.
→ Hormone & energy optimisation: It lowers inflammation, reduces visceral fat (not good), and helps muscles use sugar and fat more efficiently, restoring Leptin & Insulin sensitivity.
→ Mitochondrial function: Increases mitochondrial number, efficiency, which improves energy production and reduces oxidative stress.
How to build muscle in minimal time
You can build muscle with just two 30-minute sessions a week.
Yes, really.
One or two full-body sessions, hitting all major muscle groups, is enough if done properly.
It all comes from this paper.
 "We recommend that appreciably the same muscular strength and endurance adaptations can be attained by performing a single set of \~8-12 repetitions to momentary muscular failure, at a repetition duration that maintains muscular tension throughout the entire range of motion, for most major muscle groups once or twice each week. All resistance types (e.g. free-weights, resistance machines, bodyweight, etc.) show potential for increases in strength, with no significant difference between them, although resistance machines appear to pose a lower risk of injury."
"We recommend that appreciably the same muscular strength and endurance adaptations can be attained by performing a single set of \~8-12 repetitions to momentary muscular failure, at a repetition duration that maintains muscular tension throughout the entire range of motion, for most major muscle groups once or twice each week. All resistance types (e.g. free-weights, resistance machines, bodyweight, etc.) show potential for increases in strength, with no significant difference between them, although resistance machines appear to pose a lower risk of injury."It doesn’t matter if you use free weights, machines, or bodyweight exercises.
For what its worth, I think using weights is easier.
What matters is how you train.
You don’t need heavy weights to build muscle, just focus on maintaining tension throughout each movement.
→ Slow, controlled reps: Move 5 seconds up, 5 seconds down without using momentum.
→ High effort, low volume: One set to momentary failure is enough per muscle group.
→ Minimal rest: Keep rest periods short to maximise growth hormone and testosterone release.
→ Allow recovery: Train hard, then rest 1–2 days between sessions for optimal muscle growth. Do not get tempted to over train.
Initially this will take a bit of figuring out with regard to what weight works for you.
The key to growth → Progressive overload
In the first few weeks you will build muscle easily, but will eventually plateau. You then must progressively challenge your body. Here’s what to do:
→ Increase the reps first.
→ Then increase weight by 5-10%.
→ For bodyweight training: Add reps, use a weighted vest, or move to harder variations (e.g., push-ups → weighted push-ups → ring push-ups).
Real life examples
 Dr Ted Naiman is 50 and uses a simple bodyweight routine going to failure on each movement a few times a week.
Dr Ted Naiman is 50 and uses a simple bodyweight routine going to failure on each movement a few times a week.His routine → Pull Ups/Push Ups/L-Sits/Handstand Push Ups/Pistol Squats/Supermans
 P.D Mangan is 70 and trains full body twice a week, using weights.
P.D Mangan is 70 and trains full body twice a week, using weights.His routine → Deadlifts/Chin Ups/Seated row/Lateral Raise/Overhead Press/Chest Press/Dips/Barbell Shrug/Hammer Curl/Leg Press/Sprint Cycle 20 Secs.
Simplicity is beautiful.
You don’t need time consuming regimes.
Two short, intense sessions a week are enough.
-
Keep your reps slow and controlled.
-
Rest 1–2 days between sessions for muscle growth and recovery.
-
Once you hit a plateau focus on progressive overload.
-
Stick with it, consistency beats perfection every time.
With the right approach, 60 minutes a week is all you need to build muscle, lose fat, and live longer, while leaving time for the rest of your life.
-Chris
If you want a simple routine to fit effortlessly into your life.
Book a free call here: https://calendly.com/hello-chrispatrick
Follow me on Nostr: https://primal.net/chrispatrick or npub124uatsq6pv74trzwvt34y4sx2z0uflhse7tkrv0pl69e8kcsfhkse30zsu
-
-
 @ f41bd51d:ec4b664f
2025-02-03 22:43:27
@ f41bd51d:ec4b664f
2025-02-03 22:43:27 -
 @ 97c70a44:ad98e322
2025-02-03 22:25:35
@ 97c70a44:ad98e322
2025-02-03 22:25:35Last week, in a bid to understand the LLM hype, I decided to write a trivial nostr-related program in rust via a combination of codebuff (yes, that is a referral link, pls click), aider, and goose.
The result of the experiment was inconclusive, but as a side effect it produced a great case study in converting a NINO into a Real Nostr App.
Introducing Roz
Roz, a friendly notary for nostr events.
To use it, simply publish an event to
relay.damus.ioornos.lol, and roz will make note of it. To find out when roz first saw a given event, just ask:curl https://roz.coracle.social/notary/cb429632ae22557d677a11149b2d0ccd72a1cf66ac55da30e3534ed1a492765dThis will return a JSON payload with a
seenkey indicating when roz first saw the event. How (and whether) you use this is up to you!De-NINO-fying roz
Roz is just a proof of concept, so don't rely on it being there forever. And anyway, roz is a NINO, since it provides value to nostr (potentially), but doesn't really do things in a nostr-native way. It also hard-codes its relays, and certainly doesn't use the outbox model or sign events. But that's ok, it's a proof of concept.
A much better way to do this would be to modify roz to properly leverage nostr's capabilities, namely:
- Use nostr-native data formats (i.e., draft a new kind)
- Use relays instead of proprietary servers for data storage
- Leverage nostr identities and signatures to decouple trust from storage, and allow trusted attestations to be discovered
Luckily, this is not hard at all. In fact, I've gone ahead and drafted a PR to the NIPs repo that adds timestamp annotations to NIP 03, as an alternative to OpenTimestamps. The trade-off is that while user attestations are far less reliable than OTS proofs, they're much easier to verify, and can reach a pretty high level of reliability by combining multiple attestation sources with other forms of reputation.
In other words, instead of going nuclear and embedding your attestations into The Time Chain, you can simply ask 5-10 relays or people you trust for their attestations for a given event.
This PR isn't terribly important on its own, but it does remove one small barrier between us and trusted key rotation events (or other types of event that require establishing a verifiable chain of causality).
-
 @ a3a72214:7ca63e21
2025-02-03 20:57:52
@ a3a72214:7ca63e21
2025-02-03 20:57:52Isso é um anúncio de Albion
-
é um jogo
-
primeiramente
- em segundo
- em terceiro
>o que acontece?
' e se? '
Alguém citando alguma coisa
Albion Online é um MMORPG sandbox em que você escreve sua própria história, em vez de seguir um caminho pré-determinado. Explore um vasto mundo aberto que consiste de 5 ecossistemas únicos. Tudo o que você faz gera um impacto no mundo, já que em Albion, a economia é conduzida pelo jogador. Cada peça de equipamento é construída por jogadores a partir dos recursos obtidos por eles. O equipamento que você usa define quem você é. Ir de cavaleiro para feiticeiro é tão fácil quanto trocar a armadura e a arma, ou uma combinação das duas. Aventure-se no mundo aberto e enfrente os habitantes e as criaturas de Albion. Saia em expedições ou entre em masmorras para enfrentar inimigos ainda mais desafiadores. Enfrente outros jogadores em confrontos do mundo aberto, lute pelo controle de territórios ou cidades inteiras em batalhas táticas em grupo. Relaxe descansando em sua ilha pessoal, onde você pode construir uma casa, cultivar alimentos e criar animais. Junte-se à uma guilda, tudo fica mais divertido quando se trabalha em equipe. Entre hoje mesmo no mundo de Albion, e escreva sua própria história.
-
-
 @ 54286b98:3debc100
2025-02-03 20:55:10
@ 54286b98:3debc100
2025-02-03 20:55:10Hello! Three years ago, I created a special bed for my daughter. I'm thrilled to share a detailed video and PDF documenting the process along with hopes to inspire you to embark on a similar project!
***This is a first and also a test to see how I can upload #woodworking material on Nostr. I am not sure how the links, images, and PDFs will display, so hopefully, you get some interesting material for your late afternoon hobby shop. But don’t kill me if some images do not render well—I’m still figuring this thing out!
Montessori Bed Plans / Blueprints
The accompanying PDF includes:
- All measurements
- Detailed views from every angle
- Final measurements part list
- Assembly steps
Instructive Video! Process on how to make the Montessori bed
Video Here:
https://vimeo.com/901623772/b8b5530386
PDF Here(Picture below,and if some one has good tip on how to inset PDFs in Nostr, that feedback is welcome, to avoid Google links):
https://drive.google.com/file/d/1zCp1RvKOynx5kZxixAKSFLLOe8atyiRH/
OK, let's dive in!
The Montessori bed featured in this video is not only simple but also durable, and you can create it on a budget right in your own home.OK, let's dive in!
Tools by hand:
- Circular saw
- Jointer Plane #7 or #8
- Spokeshave
- Workbench
- Handsaw
- Orbital sander
- Sandpaper #80, #120, #220, and #320
- Odies Oil or your preferred finish.
If you have power tools:
- Table Saw
- Jointer
- Planer
- Trimmer
Materials:\ I recommend using this list as a guide and exploring options with your local supplier.
- Base long connector (On picture "Larguero Base"): Quantity x 2, 2195mm x 75mm x 75mm
- Base short connector (On picture "Conector Base"): Quantity x 1, 1090mm x 75mm x 75mm
- Roof connector (On picture "Cumbre"): Quantity x 1, 1946mm x 75mm x 75mm
- Long top triangle connector (On picture "Conector Superior"): Quantity x 2, 1322mm x 75mm x 75mm
- Columns/Legs (On picture "Paral"): Quantity x 4, 1210mm x 75mm x 75mm
- Short top triangle connector (On picture "Lima"): Quantity x 4, 851mm x 75mm x 75mm
 Step #1 Dimensioning (Minutes 0:00 - 1:15):\
We kick off with dimensioning. While I initially planned to use my home workshop, unforeseen circumstances led me to my friend Andrew's workshop. Each beam was carefully brought down to 7.5 cm x 7.5 cm, ensuring the largest measurement that worked for all.
Step #1 Dimensioning (Minutes 0:00 - 1:15):\
We kick off with dimensioning. While I initially planned to use my home workshop, unforeseen circumstances led me to my friend Andrew's workshop. Each beam was carefully brought down to 7.5 cm x 7.5 cm, ensuring the largest measurement that worked for all.Step #2 Final Measurements (No video):\ Refer to the provided PDF for final measurements. Make the cuts and joints with a circular saw and chisels (or a router).
Step #3 Edges (Minutes 1:15 - 1:30):\ Use a router with a quarter-round bit for curved and smooth edges or achieve the same result with sandpaper or a spokeshave plane.
Step #4 Triangular Bases (Minutes 1:30 - 6:30):\ This step involves gluing the triangular bases of the bed, utilizing a miter joint with wooden inlay keys. Epoxy is employed for joining, ensuring a swift and reliable outcome.
Step #5 Legs (Minutes 6:30 - 7:00):\ Create holes for the upper triangular base's dowels, ensuring level placement and extra depth. This step guarantees a secure fit.
Step #6 Sanding (Minutes 7:00 - 7:30):\ Comprehensive sanding, starting from #80 grit and progressing through #120, #220, and #320, sets the stage for a flawless finish.
Step #7 Dry Assembly (Minutes 7:30 - 9:10):\ Dry-assemble all components, making necessary adjustments for a seamless fit. We opted for wood screws for easy disassembly.
Step #8 Finishing (Minutes 9:10 - 9:35):\ Apply your preferred finish; in our case, we used Odies Oil with white pigment for a child-friendly touch.
Step #9 Final Assembly (Minutes 9:35 - 10:32):\ With the finishing touches completed, we assembled the bed with the help of my daughter, adding a touch of warmth with some lights.
Testing with this simple project to at least know if there are woodworkers in #nostr. Later will try to upload more, this was created almost 3 years ago :)
Until the next one,
J\ \ PDF in pictures:




















-
 @ a3a72214:7ca63e21
2025-02-03 20:50:15
@ a3a72214:7ca63e21
2025-02-03 20:50:15Anúncio, Teste de Título
- Teste
- teste
-
TESTE
-
Número UM
- Número DOIS
Citação de alguém, não importa quem seja
~~Preços altos~~
---não sei o que é isso, teste
codigo?codigo? talvezAlbion Online é um MMORPG sandbox em que você escreve sua própria história, em vez de seguir um caminho pré-determinado. Explore um vasto mundo aberto que consiste de 5 ecossistemas únicos. Tudo o que você faz gera um impacto no mundo, já que em Albion, a economia é conduzida pelo jogador. Cada peça de equipamento é construída por jogadores a partir dos recursos obtidos por eles. O equipamento que você usa define quem você é. Ir de cavaleiro para feiticeiro é tão fácil quanto trocar a armadura e a arma, ou uma combinação das duas. Aventure-se no mundo aberto e enfrente os habitantes e as criaturas de Albion. Saia em expedições ou entre em masmorras para enfrentar inimigos ainda mais desafiadores. Enfrente outros jogadores em confrontos do mundo aberto, lute pelo controle de territórios ou cidades inteiras em batalhas táticas em grupo. Relaxe descansando em sua ilha pessoal, onde você pode construir uma casa, cultivar alimentos e criar animais. Junte-se à uma guilda, tudo fica mais divertido quando se trabalha em equipe. Entre hoje mesmo no mundo de Albion, e escreva sua própria história.
-
 @ bf47c19e:c3d2573b
2025-02-03 20:42:23
@ bf47c19e:c3d2573b
2025-02-03 20:42:23Originalni tekst na instore.rs
03.02.2025 / Autor: Marko Matanović
Prvi put smo svedočili izbornoj trci u jednoj od razvijenih ekonomija, a da je tema bila i bitkoin. Predsednički izbori u SAD. Tramp je obećavao. Na kraju i osvojio drugi predsednički mandat. Jedna od izjava je: SAD treba da postane prestonica kriptovaluta.
Dan nakon inauguracije novoizabranog američkog predsednika tu je i prva politička kripto odluka Trampa: Oslobođanje Rosa Ulbrihta osuđenog na dve doživotne robije.
Ko je on? Napravio je 2011. godine online prodavnicu “Silk Road” (Kupujem-Prodajem sa drugačijim asortimanom). Prodavnica je pružala slobodni susret ponude bilo čega i tražnje bilo čega. Bez cenzure. Pristupalo se preko Tor protokola koji obezbeđuje anonimnost onih koji protokol koriste. Sredstvo plaćanja je bio bitkoin radi čuvanja anomnisti onih koji nešto kupuju tj. prodaju.
FBI je uhapsio Rosa Ulbrihta 2013. godine jer je “Silk road” bio korišćen i za preprodaju droge, oružja, pornografskog sadržaja i svega drugog što možemo i ne možemo zamisliti. Čak i da nije zakonski izazov, možemo ga podići na problem etike.
Postoji i druga strana medalje - napravio je platformu koja promoviše slobodu. Ros ne mora biti odgovoran kako ćemo alat koji nam je dat koristiti. Čekićem zakucamo ekser, ili povredimo nekoga. U neželjenim slučajevima ne hapsi se kreator čekića.
Satoši Nakamoto je ime tvorca Bitkoina. Da li bi to značilo i da bi njega uhapsili iz sličnih razloga samo da se znalo ko je? Verovatno nećemo nikada saznati, što i nije bitno. Duh je pušten iz boce. Njegov potencijalni uticaj na bitkoin ekosistem je potpuno isti uticaju bilo koga od nas. Sem sitnice od oko milion bitkoina kojima možda, ali možda, ima pristup na nekim svojim bitkoin adresama.
Sa njim ili bez njega, era korišćenja bitkoina zarad,pre svega, anonimnih transakcija je prošla. Dok era korišćenja bitkoina za ilegalne transakcije nikada nije ni postojala u ozbiljnoj meri. Narativ ilegalne transakcije, kriminal, pranje novca, terorizam je više posledica neznanja, nerazumevanja, potcenjivanja i često preterane želje za kontrolom, nego li činjenica. I šta bi sa: svako je nevin dok se ne dokaže suprotno?!
U kratkom roku, Bitkoin vožnja je sve, samo ne udobna. Tramp i mnogi drugi su shvatili da je rizik od neudobne vožnje disproporcionalan benefitima koje ta vožnja donosi.
Takav narativ je posle 15 godina ustupio mesto rečima poput sigurnost, bezbednost, zaštita od inflacije, digitalno zlato, brzina, pouzdanost. Sloboda. Za svakog se nađe po nešto, osim za one uporne u tome da ne priznaju svoju zatvorenost da razumeju bitkoin. Parafraziraću nekoga pametnijeg ko je u ovome od 2011. godine, što je dovoljno godina duže od mene u industriji: Nekada sam morao ljude ubeđivati šta je bitkoin i čemu služi i šta su kvaliteti koji stoje iza njega. Danas mene neko mora ubediti zašto da ne verujem rezultatu koji svi vidimo na semaforu?!
Ipak, mislim da postoji ogroman i validan razlog zašto i dalje treba da pričamo o temi kao da je 2011, a ne 2025. godina. O novcu nas ne uče dovoljno ili uopšte! Ni u školama ni van njih! Kada bi dovoljan broj ljudi razumeo novac, novčanu emisiju, moguće da bi se desio jedan od dva scenarija: izborili bi se za drugačiji novac ili bi države izgubile barem deo benefita koji proizilaze iz pozicije kontrole novca. Većina nas ne zna da objasni tehnologiju većine stvari koje svaki dan koristimo. To nas ne sprečava da ih koristimo. Internet, mobilni, bicikl i novac na kraju dana. Svakog dana najčešće.
Tehnologiju - na stranu ovom prilikom. Za šta se bitkoin i kriptovalute mogu koristiti? 100% pouzdan i brz način prenosa sredstava sa jedne geografske tačke na drugu uz par klikova. Ili od jedne osobe do druge. Ili od jedne kompanije do druge. Za bitkoin se pokazalo da može biti i sjajan instrument za prenos i očuvanje vrednosti kroz vreme. Mogućnost blokiranja transakcija ne postoji. Ukoliko se poštuju pravila igre, izvesnost da će se transakcija izvršiti je 100% i to 24/7/365. Transakcioni troškovi su zanemarljivo niski. To je teorija.
Praksa? Sve nabrojano uz sledeće lokalne činjenice. Samo u Srbiji par stotina hiljada ljudi je došlo u kontakt sa nekom od kriptovaluta. Nekoliko stotina kompanija ih koristi u poslovanju iz nekih od gore pobrojanih razloga. Postoje države, u njima populacije i kompanije koje su na nižem nivou adopcije od Srbije. Postoje i one sa daleko većom prisutnosti kriptovaluta u svakodnevnom životu i aktivnostima.
Za svakog se nađe po nešto, osim za one uporne u tome da ne priznaju svoju zatvorenost da razumeju bitkoin.
Ako nekada čujemo da je bitkoin balon ili da je tržište kriptovaluta balon, setimo se da je vrlo poznati balon tržišta lala s kraja 16. i tokom 17. veka knjiški primer uzavrelog tržišta i manije koja se pojavljuje usled pohlepe, brzog rasta cena, špekulacija i preteranih očekivanja na tržištu. Taj balon je pukao. To je činjenica. Činjenica je i da je Holandija danas prva država u svetu po izvozu cveća i tako vekovima unazad. Hoće li i taj balon pući ili je prosto doneo Holandiji i njihovom društvu prosperitet? U slično vreme u 17. veku u Holandiji se pojavila i prva banka i prva kompanija igde u svetu koja je izdala akcije. Ta kompanije se više bavila otimanjem nego li trgovinom. I ona je “pukla”. Opet, taj finansijski eksperiment je Holandiju dodatno podigao na mapi razvijenijih ekonomija.
U kratkom roku, Bitkoin vožnja je sve, samo ne udobna. Tramp i mnogi drugi su shvatili da je rizik od neudobne vožnje disproporcionalan benefitima koje ta vožnja donosi. Nastavi li da ispunjava obećanja iz predizborne kampanje, slušaćemo još puno o bitkoinu, blockchain-u i kriptovalutama. Nisam presrećan velikim uplitanjem bilo koje države u bitkoin temu, osim ukoliko to uplitanje nije na nivou elemenata slobodnog tržišta. Čak i ako je uplitanje veće bilo promotivno ili restriktivno, uticaj postoji na cenu bitkoina, ali ne i na njegovu suštinu. Jer ona je konzistentna.
Neprimetan, neshvaćen, zanemarivan, ignorisan, potcenjivan, napadan, otpisivan. Prihvaćen. Ogromna većina stvari koja ima opštu upotrebu vremenom postaje jeftinija. Osim onih sa ograničenom ponudom, a to su retki primeri najčešće luksuzne robe i usluga. Ali teško mi je setiti se ijedne stvari sa retkom ponudom, a da je i dalje apsolutno dostupna svakome. Bitkoin? Da! Ograničene je ponude, a i dalje je apsolutno dostupan svakome. I kako se povećava nivo shvatanja bitkoina, postaje skuplji!
-
 @ da0b9bc3:4e30a4a9
2025-02-03 19:32:50
@ da0b9bc3:4e30a4a9
2025-02-03 19:32:50Hello Stackers!
It's Monday so we're back doing "Meta Music Mondays" 😉.
From before the territory existed there was just one post a week in a ~meta take over. Now each month we have a different theme and bring music from that theme.
Welcome to Femmes Fatales 3!!!
I absolutely loved doing this last year so I'm bringing it back for round 3!
It's Femmes Fatales, where we celebrate women in ~Music. So let's have those ladies of the lung, the sirens of sound, our Femmes Fatales!
I'm so excited I'm doing two Heroines of the High Notes. Sharon Den Adel & Anneke Van Geirsbergen. Within Temptation - Somewhere.
Enjoy!
https://youtu.be/ScjEJRIZGvg?si=MMrI-u_Gw6W4ENRI
Talk Music. Share Tracks. Zap Sats.
originally posted at https://stacker.news/items/874881


