-
 @ b8851a06:9b120ba1
2025-01-28 21:34:54
@ b8851a06:9b120ba1
2025-01-28 21:34:54Private property isn’t lines on dirt or fences of steel—it’s the crystallization of human sovereignty. Each boundary drawn is a silent declaration: This is where my will meets yours, where creation clashes against chaos. What we defend as “mine” or “yours” is no mere object but a metaphysical claim, a scaffold for the unfathomable complexity of voluntary exchange.
Markets breathe only when individuals anchor their choices in the inviolable. Without property, there is no negotiation—only force. No trade—only taking. The deed to land, the title to a car, the seed of an idea: these are not static things but frontiers of being, where human responsibility collides with the infinite permutations of value.
Austrian economics whispers what existentialism shouts: existence precedes essence. Property isn’t granted by systems; it’s asserted through action, defended through sacrifice, and sanctified through mutual recognition. A thing becomes “owned” only when a mind declares it so, and others—through reason or respect—refrain from crossing that unseen line.
Bitcoin? The purest ledger of this truth. A string of code, yes—but one that mirrors the unyielding logic of property itself: scarce, auditable, unconquerable. It doesn’t ask permission. It exists because sovereign minds choose it to.
Sigh. #nostr
I love #Bitcoin. -
 @ 599f67f7:21fb3ea9
2025-01-26 11:01:05
@ 599f67f7:21fb3ea9
2025-01-26 11:01:05¿Qué es Blossom?
nostr:nevent1qqspttj39n6ld4plhn4e2mq3utxpju93u4k7w33l3ehxyf0g9lh3f0qpzpmhxue69uhkummnw3ezuamfdejsygzenanl0hmkjnrq8fksvdhpt67xzrdh0h8agltwt5znsmvzr7e74ywgmr72
Blossom significa Blobs Simply Stored on Media Servers (Blobs Simplemente Almacenados en Servidores de Medios). Blobs son fragmentos de datos binarios, como archivos pero sin nombres. En lugar de nombres, se identifican por su hash sha256. La ventaja de usar hashes sha256 en lugar de nombres es que los hashes son IDs universales que se pueden calcular a partir del archivo mismo utilizando el algoritmo de hash sha256.
💡 archivo -> sha256 -> hash
Blossom es, por lo tanto, un conjunto de puntos finales HTTP que permiten a los usuarios almacenar y recuperar blobs almacenados en servidores utilizando su identidad nostr.
¿Por qué Blossom?
Como mencionamos hace un momento, al usar claves nostr como su identidad, Blossom permite que los datos sean "propiedad" del usuario. Esto simplifica enormemente la cuestión de "qué es spam" para el alojamiento de servidores. Por ejemplo, en nuestro Blossom solo permitimos cargas por miembros de la comunidad verificados que tengan un NIP-05 con nosotros.
Los usuarios pueden subir en múltiples servidores de blossom, por ejemplo, uno alojado por su comunidad, uno de pago, otro público y gratuito, para establecer redundancia de sus datos. Los blobs pueden ser espejados entre servidores de blossom, de manera similar a cómo los relays nostr pueden transmitir eventos entre sí. Esto mejora la resistencia a la censura de blossom.
A continuación se muestra una breve tabla de comparación entre torrents, Blossom y servidores CDN centralizados. (Suponiendo que hay muchos seeders para torrents y se utilizan múltiples servidores con Blossom).
| | Torrents | Blossom | CDN Centralizado | | --------------------------------------------------------------- | -------- | ------- | ---------------- | | Descentralizado | ✅ | ✅ | ❌ | | Resistencia a la censura | ✅ | ✅ | ❌ | | ¿Puedo usarlo para publicar fotos de gatitos en redes sociales? | ❌ | ✅ | ✅ |
¿Cómo funciona?
Blossom utiliza varios tipos de eventos nostr para comunicarse con el servidor de medios.
| kind | descripción | BUD | | ----- | ------------------------------- | ------------------------------------------------------------------ | | 24242 | Evento de autorización | BUD01 | | 10063 | Lista de Servidores de Usuarios | BUD03 |
kind:24242 - Autorización
Esto es esencialmente lo que ya describimos al usar claves nostr como IDs de usuario. En el evento, el usuario le dice al servidor que quiere subir o eliminar un archivo y lo firma con sus claves nostr. El servidor realiza algunas verificaciones en este evento y luego ejecuta el comando del usuario si todo parece estar bien.
kind:10063 - Lista de Servidores de Usuarios
Esto es utilizado por el usuario para anunciar a qué servidores de medios está subiendo. De esta manera, cuando el cliente ve esta lista, sabe dónde subir los archivos del usuario. También puede subir en múltiples servidores definidos en la lista para asegurar redundancia. En el lado de recuperación, si por alguna razón uno de los servidores en la lista del usuario está fuera de servicio, o el archivo ya no se puede encontrar allí, el cliente puede usar esta lista para intentar recuperar el archivo de otros servidores en la lista. Dado que los blobs se identifican por sus hashes, el mismo blob tendrá el mismo hash en cualquier servidor de medios. Todo lo que el cliente necesita hacer es cambiar la URL por la de un servidor diferente.
Ahora, además de los conceptos básicos de cómo funciona Blossom, también hay otros tipos de eventos que hacen que Blossom sea aún más interesante.
| kind | descripción | | ----- | --------------------- | | 30563 | Blossom Drives | | 36363 | Listado de Servidores | | 31963 | Reseña de Servidores |
kind:30563 - Blossom Drives
Este tipo de evento facilita la organización de blobs en carpetas, como estamos acostumbrados con los drives (piensa en Google Drive, iCloud, Proton Drive, etc.). El evento contiene información sobre la estructura de carpetas y los metadatos del drive.
kind:36363 y kind:31963 - Listado y Reseña
Estos tipos de eventos permiten a los usuarios descubrir y reseñar servidores de medios a través de nostr. kind:36363 es un listado de servidores que contiene la URL del servidor. kind:31963 es una reseña, donde los usuarios pueden calificar servidores.
¿Cómo lo uso?
Encuentra un servidor
Primero necesitarás elegir un servidor Blossom donde subirás tus archivos. Puedes navegar por los públicos en blossomservers.com. Algunos de ellos son de pago, otros pueden requerir que tus claves nostr estén en una lista blanca.
Luego, puedes ir a la URL de su servidor y probar a subir un archivo pequeño, como una foto. Si estás satisfecho con el servidor (es rápido y aún no te ha fallado), puedes agregarlo a tu Lista de Servidores de Usuarios. Cubriremos brevemente cómo hacer esto en noStrudel y Amethyst (pero solo necesitas hacer esto una vez, una vez que tu lista actualizada esté publicada, los clientes pueden simplemente recuperarla de nostr).
noStrudel
- Encuentra Relays en la barra lateral, luego elige Servidores de Medios.
- Agrega un servidor de medios, o mejor aún, varios.
- Publica tu lista de servidores. ✅
Amethyst
- En la barra lateral, encuentra Servidores multimedia.
- Bajo Servidores Blossom, agrega tus servidores de medios.
- Firma y publica. ✅
Ahora, cuando vayas a hacer una publicación y adjuntar una foto, por ejemplo, se subirá en tu servidor blossom.
⚠️ Ten en cuenta que debes suponer que los archivos que subas serán públicos. Aunque puedes proteger un archivo con contraseña, esto no ha sido auditado.
Blossom Drive
Como mencionamos anteriormente, podemos publicar eventos para organizar nuestros blobs en carpetas. Esto puede ser excelente para compartir archivos con tu equipo, o simplemente para mantener las cosas organizadas.
Para probarlo, ve a blossom.hzrd149.com (o nuestra instancia comunitaria en blossom.bitcointxoko.com) e inicia sesión con tu método preferido.
Puedes crear una nueva unidad y agregar blobs desde allí.
Bouquet
Si usas múltiples servidores para darte redundancia, Bouquet es una buena manera de obtener una visión general de todos tus archivos. Úsalo para subir y navegar por tus medios en diferentes servidores y sincronizar blobs entre ellos.
Cherry Tree
nostr:nevent1qvzqqqqqqypzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qyghwumn8ghj7mn0wd68ytnhd9hx2tcpzfmhxue69uhkummnw3e82efwvdhk6tcqyp3065hj9zellakecetfflkgudm5n6xcc9dnetfeacnq90y3yxa5z5gk2q6
Cherry Tree te permite dividir un archivo en fragmentos y luego subirlos en múltiples servidores blossom, y más tarde reensamblarlos en otro lugar.
Conclusión
Blossom aún está en desarrollo, pero ya hay muchas cosas interesantes que puedes hacer con él para hacerte a ti y a tu comunidad más soberanos. ¡Pruébalo!
Si deseas mantenerte al día sobre el desarrollo de Blossom, sigue a nostr:nprofile1qyghwumn8ghj7mn0wd68ytnhd9hx2tcpzfmhxue69uhkummnw3e82efwvdhk6tcqyqnxs90qeyssm73jf3kt5dtnk997ujw6ggy6j3t0jjzw2yrv6sy22ysu5ka y dale un gran zap por su excelente trabajo.
Referencias
-
 @ 29af23a9:842ef0c1
2025-01-24 09:28:37
@ 29af23a9:842ef0c1
2025-01-24 09:28:37A Indústria Pornográfica se caracteriza pelo investimento pesado de grandes empresários americanos, desde 2014.
Na década de 90, filmes pornográficos eram feitos às coxas. Era basicamente duas pessoas fazendo sexo amador e sendo gravadas. Não tinha roteiro, nem produção, não tinha maquiagem, nada disso. A distribuição era rudimentar, os assinantes tinham que sair de suas casas, ir até a locadora, sofrer todo tipo de constrangimento para assistir a um filme pornô.
No começo dos anos 2000, o serviço de Pay Per View fez o número de vendas de filmes eróticos (filme erótico é bem mais leve) crescer mas nada se compara com os sites de filmes pornográficos por assinatura.
Com o advento dos serviços de Streaming, os sites que vendem filmes por assinatura se estabeleceram no mercado como nunca foi visto na história.
Hoje, os Produtores usam produtos para esticar os vasos sanguíneos do pênis dos atores e dopam as atrizes para que elas aguentem horas de gravação (a Série Black Mirror fez uma crítica a isso no episódio 1 milhão de méritos de forma sutil).
Além de toda a produção em volta das cenas. Que são gravadas em 4K, para focar bem as partes íntimas dos atores. Quadros fechados, iluminação, tudo isso faz essa Indústria ser "Artística" uma vez que tudo ali é falso. Um filme da Produtora Vixen, por exemplo, onde jovens mulheres transam em mansões com seus empresários estimula o esteriótipo da mina padrão que chama seu chefe rico de "daddy" e seduz ele até ele trair a esposa.
Sites como xvídeos, pornHub e outros nada mais são do que sites que salvam filmes dessas produtoras e hospedam as cenas com anúncios e pop-ups. Alguns sites hospedam o filme inteiro "de graça".
Esse tipo de filme estimula qualquer homem heterosexual com menos de 30 anos, que não tem o córtex frontal de seu cérebro totalmente desenvolvido (segundo estudos só é completamente desenvolvido quando o homem chega aos 31 anos).
A arte Pornográfica faz alguns fantasiarem ter relação sexual com uma gostosa americana branquinha, até escraviza-los. Muitos não conseguem sair do vício e preferem a Ficção à sua esposa real. Então pare de se enganar e admita. A Pornografia faz mal para a saúde mental do homem.
Quem sonha em ter uma transa com Lana Rhodes, deve estar nesse estágio. Trata-se de uma atriz (pornstar) que ganhou muito dinheiro vendendo a ilusão da Arte Pornografica, como a Riley Reid que só gravava para grandes Produtoras. Ambas se arrependeram da carreira artística e agora tentam viver suas vidas como uma mulher comum.
As próprias atrizes se consideram artistas, como Mia Malkova, chegou a dizer que Pornografia é a vida dela, que é "Lindo e Sofisticado."
Mia Malkova inclusive faz questão de dizer que a industria não escravisa mulheres jovens. Trata-se de um negócio onde a mulher assina um contrato com uma produtora e recebe um cachê por isso. Diferente do discurso da Mia Khalifa em entrevista para a BBC, onde diz que as mulheres são exploradas por homens poderosos. Vai ela está confundindo o Conglomerado Vixen com a Rede Globo ou com a empresa do Harvey Weinstein.
Enfim, se você é um homem solteiro entre 18 e 40 anos que já consumiu ou que ainda consome pornografia, sabia que sofrerá consequências. Pois trata-se de "produções artísticas" da indústria audiovisual que altera os níveis de dopamina do seu cérebro, mudando a neuroplasticidade e diminuindo a massa cinzenta, deixando o homem com memória fraca, sem foco e com mente nebulosa.
Por que o Estado não proíbe/criminaliza a Pornografia se ela faz mal? E desde quando o Estado quer o nosso bem? Existem grandes empresarios que financiam essa indústria ajudando governos a manterem o povo viciado e assim alienado. É um pão e circo, só que muito mais viciante e maléfico. Eu costume dizer aos meus amigos que existem grandes empresários jvdeus que são donos de grandes Produtoras de filmes pornográficos como o Conglomerado Vixen. Então se eles assistem vídeos pirateados de filmes dessas produtoras, eles estão no colo do Judeu.
-
 @ f4db5270:3c74e0d0
2025-01-23 18:09:14
@ f4db5270:3c74e0d0
2025-01-23 18:09:14Hi Art lover! 🎨🫂💜 You may not know it yet but all of the following paintings are available in #Bitcoin on my website: https://isolabell.art/#shop
For info and prices write to me in DM and we will find a good deal! 🤝
 ON THE ROAD AGAIN
40x50cm, Oil on canvas
Completed January 23, 2025
ON THE ROAD AGAIN
40x50cm, Oil on canvas
Completed January 23, 2025
 SUN OF JANUARY
40x50cm, Oil on canvas
Completed January 14, 2025
SUN OF JANUARY
40x50cm, Oil on canvas
Completed January 14, 2025
 THE BLUE HOUR
40x50cm, Oil on canvas
Completed December 14, 2024
THE BLUE HOUR
40x50cm, Oil on canvas
Completed December 14, 2024
 LIKE A FRAGMENT OF ETERNITY
50x40cm, Oil on canvas
Completed December 01, 2024
LIKE A FRAGMENT OF ETERNITY
50x40cm, Oil on canvas
Completed December 01, 2024
 WHERE WINTER WHISPERS
50x40cm, Oil on canvas
Completed November 07, 2024
WHERE WINTER WHISPERS
50x40cm, Oil on canvas
Completed November 07, 2024
 L'ATTESA DI UN MOMENTO
40x40cm, Oil on canvas
Completed October 29, 2024
L'ATTESA DI UN MOMENTO
40x40cm, Oil on canvas
Completed October 29, 2024
 LE COSE CHE PENSANO
40x50cm, Oil on paper
Completed October 05, 2024
LE COSE CHE PENSANO
40x50cm, Oil on paper
Completed October 05, 2024
 TWILIGHT'S RIVER
50x40cm, Oil on canvas
Completed September 17, 2024
TWILIGHT'S RIVER
50x40cm, Oil on canvas
Completed September 17, 2024
 GOLD ON THE OCEAN
40x50cm, Oil on paper
Completed September 08, 2024
GOLD ON THE OCEAN
40x50cm, Oil on paper
Completed September 08, 2024
 SUSSURRI DI CIELO E MARE
50x40cm, Oil on paper
Completed September 05, 2024
SUSSURRI DI CIELO E MARE
50x40cm, Oil on paper
Completed September 05, 2024
 THE END OF A WONDERFUL WEEKEND
40x30cm, Oil on board
Completed August 12, 2024
THE END OF A WONDERFUL WEEKEND
40x30cm, Oil on board
Completed August 12, 2024
 FIAMME NEL CIELO
60x35cm, Oil on board
Completed July 28, 2024
FIAMME NEL CIELO
60x35cm, Oil on board
Completed July 28, 2024
 INIZIO D'ESTATE
50x40cm, Oil on cradled wood panel
Completed July 13, 2024
INIZIO D'ESTATE
50x40cm, Oil on cradled wood panel
Completed July 13, 2024
 OMBRE DELLA SERA
50x40cm, Oil on cradled wood panel
Completed June 16, 2024
OMBRE DELLA SERA
50x40cm, Oil on cradled wood panel
Completed June 16, 2024
 NEW ZEALAND SUNSET
80x60cm, Oil on canvas board
Completed May 28, 2024
NEW ZEALAND SUNSET
80x60cm, Oil on canvas board
Completed May 28, 2024
 VENICE
50x40cm, Oil on board
Completed May 4, 2024
VENICE
50x40cm, Oil on board
Completed May 4, 2024
 CORNWALL
50x40cm, Oil on board
Completed April 26, 2024
CORNWALL
50x40cm, Oil on board
Completed April 26, 2024
 DOCKS ON SUNSET
40x19,5cm, Oil on board
Completed March 14, 2024
DOCKS ON SUNSET
40x19,5cm, Oil on board
Completed March 14, 2024
 SOLITUDE
30x30cm, Oil on cradled wood panel
Completed March 2, 2024
SOLITUDE
30x30cm, Oil on cradled wood panel
Completed March 2, 2024
 LULLING WAVES
40x30cm, Oil on cradled wood panel
Completed January 14, 2024
LULLING WAVES
40x30cm, Oil on cradled wood panel
Completed January 14, 2024
 MULATTIERA IN AUTUNNO
30x30cm, Oil on cradled wood panel
MULATTIERA IN AUTUNNO
30x30cm, Oil on cradled wood panel
 TRAMONTO A KOS
40x40cm, oil on board canvas
TRAMONTO A KOS
40x40cm, oil on board canvas
 HIDDEN SMILE
40x40cm, oil on board
HIDDEN SMILE
40x40cm, oil on board
 INIZIO D'AUTUNNO
40x40cm, oil on canvas
INIZIO D'AUTUNNO
40x40cm, oil on canvas
 BOE NEL LAGO
30x30cm, oil on canvas board
BOE NEL LAGO
30x30cm, oil on canvas board
 BARCHE A RIPOSO
40x40cm, oil on canvas board
BARCHE A RIPOSO
40x40cm, oil on canvas board
 IL RISVEGLIO
30x40cm, oil on canvas board
IL RISVEGLIO
30x40cm, oil on canvas board
 LA QUIETE PRIMA DELLA TEMPESTA
30x40cm, oil on canvas board
LA QUIETE PRIMA DELLA TEMPESTA
30x40cm, oil on canvas board
 LAMPIONE SUL LAGO
30x30cm, oil on canvas board
LAMPIONE SUL LAGO
30x30cm, oil on canvas board
 DUE NELLA NEVE
60x25cm, oil on board
DUE NELLA NEVE
60x25cm, oil on board
 UNA CAREZZA
30x30cm, oil on canvas board
UNA CAREZZA
30x30cm, oil on canvas board
 REBEL WAVES
44x32cm, oil on canvas board
REBEL WAVES
44x32cm, oil on canvas board
 THE SCREAMING WAVE
40x30cm, oil on canvas board
THE SCREAMING WAVE
40x30cm, oil on canvas board
 "LA DONZELLETTA VIEN DALLA CAMPAGNA..."
30x40cm, oil on canvas board
"LA DONZELLETTA VIEN DALLA CAMPAGNA..."
30x40cm, oil on canvas board
 LIGHTHOUSE ON WHITE CLIFF
30x40cm, oil on canvas board
LIGHTHOUSE ON WHITE CLIFF
30x40cm, oil on canvas board -
 @ b17fccdf:b7211155
2025-01-21 18:33:28
@ b17fccdf:b7211155
2025-01-21 18:33:28
CHECK OUT at ~ > ramix.minibolt.info < ~
Main changes:
- Adapted to Raspberry Pi 5, with the possibility of using internal storage: a PCIe to M.2 adapter + SSD NVMe:
Connect directly to the board, remove the instability issues with the USB connection, and unlock the ability to enjoy higher transfer speeds**
- Based on Debian 12 (Raspberry Pi OS Bookworm - 64-bit).
- Updated all services that have been tested until now, to the latest version.
- Same as the MiniBolt guide, changed I2P, Fulcrum, and ThunderHub guides, to be part of the core guide.
- All UI & UX improvements in the MiniBolt guide are included.
- Fix some links and wrong command issues.
- Some existing guides have been improved to clarify the following steps.
Important notes:
- The RRSS will be the same as the MiniBolt original project (for now) | More info -> HERE <-
- The common resources like the Roadmap or Networkmap have been merged and will be used together | Check -> HERE <-
- The attempt to upgrade from Bullseye to Bookworm (RaspiBolt to RaMiX migration) has failed due to several difficult-to-resolve dependency conflicts, so unfortunately, there will be no dedicated migration guide and only the possibility to start from scratch ☹️
⚠️ Attention‼️-> This guide is in the WIP (work in progress) state and hasn't been completely tested yet. Many steps may be incorrect. Pay special attention to the "Status: Not tested on RaMiX" tag at the beginning of the guides. Be careful and act behind your responsibility.
For Raspberry Pi lovers!❤️🍓
Enjoy it RaMiXer!! 💜
By ⚡2FakTor⚡ for the plebs with love ❤️🫂
- Adapted to Raspberry Pi 5, with the possibility of using internal storage: a PCIe to M.2 adapter + SSD NVMe:
-
 @ 7f29628d:e160cccc
2025-01-07 11:50:30
@ 7f29628d:e160cccc
2025-01-07 11:50:30Der gut informierte Bürger denkt bei der Pandemie sofort an Intensivstationen, an die Bilder aus Bergamo und erinnert sich an die Berichterstattung damals – also muss es wohl ein Maximum gewesen sein. Manche Skeptiker behaupten jedoch das Gegenteil. Klarheit sollte ein Blick nach Wiesbaden, zum Statistischen Bundesamt, schaffen. Schließlich sitzen dort gut bezahlte Profis, die seit vielen Jahrzehnten die Sterbestatistik pflegen und veröffentlichen. Jeder Todesfall wird in Deutschland über die Standesämter exakt erfasst.
Doch die Überraschung: Das Statistische Bundesamt liefert uns auf diese einfache Frage zwei extrem unterschiedliche Antworten – ein Minimum und ein Maximum. Das Ergebnis hängt davon ab, wie tief man in die Veröffentlichungen des Bundesamtes eintaucht. Betrachtet man nur die Webseiten und Pressemitteilungen, erhält man den Eindruck eines Maximums. Schaut man jedoch etwas tiefer in die Tabellen und Rohdaten, zeigt sich plötzlich ein Minimum. Aber wie kann das sein? Beides gleichzeitig geht ja wohl kaum. Wer lügt hier – die Tabellen des Amtes oder die Pressemitteilungen? Gehen wir dieser Frage Schritt für Schritt auf den Grund.
2020: Ein historisches Maximum?
Schauen wir uns die vielen Hundert Veröffentlichungen des Statistischen Bundesamtes aus dieser Zeit an. Oder wir kürzen ab und fragen ChatGPT, da die KI auf diesen Daten trainiert wurde und das gesamte Material kennt. Die Frage an ChatGPT lautet also: Wie war das Sterbegeschehen im Jahr 2020 im Vergleich zu den Vorjahren?
ChatGPT antwortet: »Im Jahr 2020 war die Sterblichkeit in Deutschland höher als in den Jahren zuvor. Es gab eine Übersterblichkeit von etwa 982.000 Todesfällen, das sind rund 46.000 mehr als der Durchschnitt der Vorjahre (2016 bis 2019). Dieser Anstieg wurde überwiegend im Zusammenhang mit der COVID-19-Pandemie gesehen. Während die Sterbezahlen in den Vorjahren schwankten, war ein solch signifikanter Anstieg wie 2020 bisher nicht zu beobachten.«
Wir fragen konkreter: Ist es ein Fakt, dass wir eine so ernste Lage im Sterbegeschehen wie im Frühjahr 2020 noch nie erlebt haben?
ChatGPT bestätigt: »Ja, die COVID-19-Pandemie führte im Frühjahr 2020 zu einer außergewöhnlichen Situation im Sterbegeschehen in Deutschland. Die dramatische Übersterblichkeit, die ab der 13. Kalenderwoche auftrat, veranlasste das Statistische Bundesamt, besonders eindringliche Warnungen zu veröffentlichen. Der damalige Vizepräsident des Amtes und andere führende Stimmen wiesen öffentlich darauf hin, dass die Todesfallzahlen stark vom Durchschnitt abwichen. Diese klare Warnung richtete sich an die Öffentlichkeit und die Politik gleichermaßen. Die Medien berichteten intensiv über diese Warnungen, was das Bewusstsein für die Schwere der Pandemie erheblich schärfte. In den vergangenen Jahrzehnten hatte es keine vergleichbare Übersterblichkeit gegeben, die eine solch umfangreiche Kommunikation durch das Statistische Bundesamt erforderlich gemacht hätte.«
Ein gut informierter Zeitungsleser wird sich an dieser Stelle bestätigt fühlen: Ja, so war es damals. Ein Maximum im Sterbegeschehen – wegen der Pandemie. Oder etwa nicht?
2020: Ein historisches Minimum?
Tauchen wir in die Rohdaten des Statistischen Bundesamtes ein. Die Tabellen, die das Amt seit Jahrzehnten verlässlich veröffentlicht, nennen sich Sterbetafeln. Diese werden jährlich bereitgestellt und stehen auf der Website des Bundesamtes zum Download bereit. Ein erster Blick in die Sterbetafeln mag den Laien abschrecken, doch mit einer kurzen Erklärung wird alles verständlich. Wir gehen schrittweise vor.
Nehmen wir die Sterbetafel des Jahres 2017. Sie enthält zwei große Tabellen – eine für Männer und eine für Frauen. Jede Zeile der Tabelle steht für einen Jahrgang, zum Beispiel zeigt die Zeile 79 die Daten der 79-jährigen Männer. Besonders wichtig ist nun die zweite Spalte, in der der Wert 0,05 eingetragen ist. Das bedeutet, dass 5 Prozent der 79-jährigen Männer im Jahr 2017 verstorben sind. Das ist die wichtige Kennzahl. Wenn wir diesen exakten Wert, den man auch als Sterberate bezeichnet, nun in ein Säulendiagramm eintragen, erhalten wir eine leicht verständliche visuelle Darstellung (Grafik 1).

Es ist wichtig zu betonen, dass dieser Wert weder ein Schätzwert noch eine Modellrechnung oder Prognose ist, sondern ein exakter Messwert, basierend auf einer zuverlässigen Zählung. Sterberaten (für die Fachleute auch Sterbewahrscheinlichkeiten qx) sind seit Johann Peter Süßmilch (1707–1767) der Goldstandard der Sterbestatistik. Jeder Aktuar wird das bestätigen. Fügen wir nun die Sterberaten der 79-jährigen Männer aus den Jahren davor und danach hinzu, um das Gesamtbild zu sehen (Grafik 2). Und nun die entscheidende Frage: Zeigt das Jahr 2020 ein Maximum oder ein Minimum?

Ein kritischer Leser könnte vermuten, dass die 79-jährigen Männer eine Ausnahme darstellen und andere Jahrgänge im Jahr 2020 ein Maximum zeigen würden. Doch das trifft nicht zu. Kein einziger Jahrgang verzeichnete im Jahr 2020 ein Maximum. Im Gegenteil: Auch die 1-Jährigen, 2-Jährigen, 3-Jährigen, 9-Jährigen, 10-Jährigen, 15-Jährigen, 18-Jährigen und viele weitere männliche Jahrgänge hatten ihr Minimum im Jahr 2020. Dasselbe gilt bei den Frauen. Insgesamt hatten 31 Jahrgänge ihr Minimum im Jahr 2020. Wenn wir schließlich alle Jahrgänge in einer einzigen Grafik zusammenfassen, ergibt sich ein klares Bild: Das Minimum im Sterbegeschehen lag im Jahr 2020 (Grafik 3).

Ein kritischer Leser könnte nun wiederum vermuten, dass es innerhalb des Jahres 2020 möglicherweise starke Ausschläge nach oben bei einzelnen Jahrgängen gegeben haben könnte, die später durch Ausschläge nach unten ausgeglichen wurden – und dass diese Schwankungen in der jährlichen Übersicht nicht sichtbar sind. Doch auch das trifft nicht zu. Ein Blick auf die wöchentlichen Sterberaten zeigt, dass die ersten acht Monate der Pandemie keine nennenswerten Auffälligkeiten aufweisen. Es bleibt dabei: Die Rohdaten des Statistischen Bundesamtes bestätigen zweifelsfrei, dass die ersten acht Monate der Pandemie das historische Minimum im Sterbegeschehen darstellen. (Für die Fachleute sei angemerkt, dass im gleichen Zeitraum die Lebenserwartung die historischen Höchststände erreicht hatte – Grafik 4.)

So konstruierte das Amt aus einem Minimum ein Maximum:
Zur Erinnerung: Die Rohdaten des Statistischen Bundesamtes, die in den jährlichen Sterbetafeln zweifelsfrei dokumentiert sind, zeigen für das Jahr 2020 eindeutig ein Minimum im Sterbegeschehen. Aus diesen »in Stein gemeißelten« Zahlen ein Maximum zu »konstruieren«, ohne die Rohdaten selbst zu verändern, scheint auf den ersten Blick eine unlösbare Aufgabe. Jeder Student würde an einer solchen Herausforderung scheitern. Doch das Statistische Bundesamt hat einen kreativen Weg gefunden - ein Meisterstück gezielter Manipulation. In fünf Schritten zeigt sich, wie diese Täuschung der Öffentlichkeit umgesetzt wurde:
(1) Ignorieren der Sterberaten: Die präzisen, objektiven und leicht verständlichen Sterberaten aus den eigenen Sterbetafeln wurden konsequent ignoriert und verschwiegen. Diese Daten widersprachen dem gewünschten Narrativ und wurden daher gezielt ausgeklammert.
(2) Fokus auf absolute Todeszahlen: Die Aufmerksamkeit wurde stattdessen auf die absolute Zahl der Todesfälle gelenkt. Diese wirkt allein durch ihre schiere Größe dramatisch und emotionalisiert die Diskussion. Ein entscheidender Faktor wurde dabei ignoriert: Die absolute Zahl der Todesfälle steigt aufgrund der demografischen Entwicklung jedes Jahr an. Viele Menschen verstehen diesen Zusammenhang nicht und verbinden die steigenden Zahlen fälschlicherweise mit der vermeintlichen Pandemie.
(3) Einführung der Übersterblichkeit als neue Kennzahl: Erst ab Beginn der „Pandemie“ wurde die Kennzahl "Übersterblichkeit" eingeführt – und dies mit einer fragwürdigen Methode, die systematisch überhöhte Werte lieferte. Diese Kennzahl wurde regelmäßig, oft monatlich oder sogar wöchentlich, berechnet und diente als ständige Grundlage für alarmierende Schlagzeilen.
(4) Intensive Öffentlichkeitsarbeit: Durch eine breit angelegte Kampagne wurden die manipulativen Kennzahlen gezielt in den Fokus gerückt. Pressemitteilungen, Podcasts und öffentliche Auftritte konzentrierten sich fast ausschließlich auf die absoluten Todeszahlen und die Übersterblichkeit. Ziel war es, den Eindruck einer dramatischen Situation in der Öffentlichkeit zu verstärken.
(5) Bekämpfen kritischer Stimmen: Kritiker, die die Schwächen und manipulativen Aspekte dieser Methoden aufdeckten, wurden systematisch diskreditiert. Ihre Glaubwürdigkeit und Kompetenz wurden öffentlich infrage gestellt, um das sorgsam konstruierte Narrativ zu schützen.
Ohne diesen begleitenden Statistik-Betrug wäre das gesamte Pandemie-Theater meiner Meinung nach nicht möglich gewesen. Wer aus einem faktischen Minimum ein scheinbares Maximum "erschafft", handelt betrügerisch. Die Folgen dieses Betruges sind gravierend. Denken wir an die Angst, die in der Bevölkerung geschürt wurde – die Angst, bald sterben zu müssen. Denken wir an Masken, Abstandsregeln, isolierte ältere Menschen, Kinderimpfungen und all die Maßnahmen, die unter anderem auf diese falsche Statistik zurückgehen.
Wollen wir Bürger uns das gefallen lassen?
Wenn wir als Bürger zulassen, dass ein derart offensichtlicher und nachprüfbarer Täuschungsversuch ohne Konsequenzen bleibt, dann gefährdet das nicht nur die Integrität unserer Institutionen – es untergräbt das Fundament unserer Gesellschaft. In der DDR feierte man öffentlich Planerfüllung und Übererfüllung, während die Regale leer blieben. Damals wusste jeder: Statistik war ein Propagandainstrument. Niemand traute den Zahlen, die das Staatsfernsehen verkündete.
Während der Pandemie war es anders. Die Menschen vertrauten den Mitteilungen des Statistischen Bundesamtes und des RKI – blind. Die Enthüllungen durch den "RKI-Leak" haben gezeigt, dass auch das Robert-Koch-Institut nicht der Wissenschaft, sondern den Weisungen des Gesundheitsministers und militärischen Vorgaben folgte. Warum sollte es beim Statistischen Bundesamt anders gewesen sein? Diese Behörde ist dem Innenministerium unterstellt und somit ebenfalls weisungsgebunden.
Die Beweise für Täuschung liegen offen zutage. Es braucht keinen Whistleblower, keine geheimen Enthüllungen: Die Rohdaten des Statistischen Bundesamtes sprechen für sich. Sie sind öffentlich einsehbar – klar und unmissverständlich. Die Daten, die Tabellen, die Veröffentlichungen des Amtes selbst – sie sind die Anklageschrift. Sie zeigen, was wirklich war. Nicht mehr und nicht weniger.
Und wir? Was tun wir? Schweigen wir? Oder fordern wir endlich ein, was unser Recht ist? Wir Bürger dürfen das nicht hinnehmen. Es ist Zeit, unsere Behörden zur Rechenschaft zu ziehen. Diese Institutionen arbeiten nicht für sich – sie arbeiten für uns. Wir finanzieren sie, und wir haben das Recht, Transparenz und Verantwortung einzufordern. Manipulationen wie diese müssen aufgearbeitet werden und dürfen nie wieder geschehen. Die Strukturen, die solche Fehlentwicklungen in unseren Behörden ermöglicht haben, müssen offengelegt werden. Denn eine Demokratie lebt von Vertrauen – und Vertrauen muss verdient werden. Jeden Tag aufs Neue.
.
.
MARCEL BARZ, Jahrgang 1975, war Offizier der Bundeswehr und studierte Wirtschafts- und Organisationswissenschaften sowie Wirtschaftsinformatik. Er war Gründer und Geschäftsführer einer Softwarefirma, die sich auf Datenanalyse und Softwareentwicklung spezialisiert hatte. Im August 2021 veröffentlichte Barz den Videovortrag »Die Pandemie in den Rohdaten«, der über eine Million Aufrufe erzielte. Seitdem macht er als "Erbsenzähler" auf Widersprüche in amtlichen Statistiken aufmerksam.
-
 @ eac63075:b4988b48
2025-01-04 19:41:34
@ eac63075:b4988b48
2025-01-04 19:41:34Since its creation in 2009, Bitcoin has symbolized innovation and resilience. However, from time to time, alarmist narratives arise about emerging technologies that could "break" its security. Among these, quantum computing stands out as one of the most recurrent. But does quantum computing truly threaten Bitcoin? And more importantly, what is the community doing to ensure the protocol remains invulnerable?
The answer, contrary to sensationalist headlines, is reassuring: Bitcoin is secure, and the community is already preparing for a future where quantum computing becomes a practical reality. Let’s dive into this topic to understand why the concerns are exaggerated and how the development of BIP-360 demonstrates that Bitcoin is one step ahead.
What Is Quantum Computing, and Why Is Bitcoin Not Threatened?
Quantum computing leverages principles of quantum mechanics to perform calculations that, in theory, could exponentially surpass classical computers—and it has nothing to do with what so-called “quantum coaches” teach to scam the uninformed. One of the concerns is that this technology could compromise two key aspects of Bitcoin’s security:
- Wallets: These use elliptic curve algorithms (ECDSA) to protect private keys. A sufficiently powerful quantum computer could deduce a private key from its public key.
- Mining: This is based on the SHA-256 algorithm, which secures the consensus process. A quantum attack could, in theory, compromise the proof-of-work mechanism.
Understanding Quantum Computing’s Attack Priorities
While quantum computing is often presented as a threat to Bitcoin, not all parts of the network are equally vulnerable. Theoretical attacks would be prioritized based on two main factors: ease of execution and potential reward. This creates two categories of attacks:
1. Attacks on Wallets
Bitcoin wallets, secured by elliptic curve algorithms, would be the initial targets due to the relative vulnerability of their public keys, especially those already exposed on the blockchain. Two attack scenarios stand out:
-
Short-term attacks: These occur during the interval between sending a transaction and its inclusion in a block (approximately 10 minutes). A quantum computer could intercept the exposed public key and derive the corresponding private key to redirect funds by creating a transaction with higher fees.
-
Long-term attacks: These focus on old wallets whose public keys are permanently exposed. Wallets associated with Satoshi Nakamoto, for example, are especially vulnerable because they were created before the practice of using hashes to mask public keys.
We can infer a priority order for how such attacks might occur based on urgency and importance.
 Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)
Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)2. Attacks on Mining
Targeting the SHA-256 algorithm, which secures the mining process, would be the next objective. However, this is far more complex and requires a level of quantum computational power that is currently non-existent and far from realization. A successful attack would allow for the recalculation of all possible hashes to dominate the consensus process and potentially "mine" it instantly.
 Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin Attacks
Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin AttacksRecently, Narcelio asked me about a statement I made on Tubacast:
https://x.com/eddieoz/status/1868371296683511969
If an attack became a reality before Bitcoin was prepared, it would be necessary to define the last block prior to the attack and proceed from there using a new hashing algorithm. The solution would resemble the response to the infamous 2013 bug. It’s a fact that this would cause market panic, and Bitcoin's price would drop significantly, creating a potential opportunity for the well-informed.
Preferably, if developers could anticipate the threat and had time to work on a solution and build consensus before an attack, they would simply decide on a future block for the fork, which would then adopt the new algorithm. It might even rehash previous blocks (reaching consensus on them) to avoid potential reorganization through the re-mining of blocks using the old hash. (I often use the term "shielding" old transactions).
How Can Users Protect Themselves?
While quantum computing is still far from being a practical threat, some simple measures can already protect users against hypothetical scenarios:
- Avoid using exposed public keys: Ensure funds sent to old wallets are transferred to new ones that use public key hashes. This reduces the risk of long-term attacks.
- Use modern wallets: Opt for wallets compatible with SegWit or Taproot, which implement better security practices.
- Monitor security updates: Stay informed about updates from the Bitcoin community, such as the implementation of BIP-360, which will introduce quantum-resistant addresses.
- Do not reuse addresses: Every transaction should be associated with a new address to minimize the risk of repeated exposure of the same public key.
- Adopt secure backup practices: Create offline backups of private keys and seeds in secure locations, protected from unauthorized access.
BIP-360 and Bitcoin’s Preparation for the Future
Even though quantum computing is still beyond practical reach, the Bitcoin community is not standing still. A concrete example is BIP-360, a proposal that establishes the technical framework to make wallets resistant to quantum attacks.
BIP-360 addresses three main pillars:
- Introduction of quantum-resistant addresses: A new address format starting with "BC1R" will be used. These addresses will be compatible with post-quantum algorithms, ensuring that stored funds are protected from future attacks.
- Compatibility with the current ecosystem: The proposal allows users to transfer funds from old addresses to new ones without requiring drastic changes to the network infrastructure.
- Flexibility for future updates: BIP-360 does not limit the choice of specific algorithms. Instead, it serves as a foundation for implementing new post-quantum algorithms as technology evolves.
This proposal demonstrates how Bitcoin can adapt to emerging threats without compromising its decentralized structure.
Post-Quantum Algorithms: The Future of Bitcoin Cryptography
The community is exploring various algorithms to protect Bitcoin from quantum attacks. Among the most discussed are:
- Falcon: A solution combining smaller public keys with compact digital signatures. Although it has been tested in limited scenarios, it still faces scalability and performance challenges.
- Sphincs: Hash-based, this algorithm is renowned for its resilience, but its signatures can be extremely large, making it less efficient for networks like Bitcoin’s blockchain.
- Lamport: Created in 1977, it’s considered one of the earliest post-quantum security solutions. Despite its reliability, its gigantic public keys (16,000 bytes) make it impractical and costly for Bitcoin.
Two technologies show great promise and are well-regarded by the community:
- Lattice-Based Cryptography: Considered one of the most promising, it uses complex mathematical structures to create systems nearly immune to quantum computing. Its implementation is still in its early stages, but the community is optimistic.
- Supersingular Elliptic Curve Isogeny: These are very recent digital signature algorithms and require extensive study and testing before being ready for practical market use.
The final choice of algorithm will depend on factors such as efficiency, cost, and integration capability with the current system. Additionally, it is preferable that these algorithms are standardized before implementation, a process that may take up to 10 years.
Why Quantum Computing Is Far from Being a Threat
The alarmist narrative about quantum computing overlooks the technical and practical challenges that still need to be overcome. Among them:
- Insufficient number of qubits: Current quantum computers have only a few hundred qubits, whereas successful attacks would require millions.
- High error rate: Quantum stability remains a barrier to reliable large-scale operations.
- High costs: Building and operating large-scale quantum computers requires massive investments, limiting their use to scientific or specific applications.
Moreover, even if quantum computers make significant advancements, Bitcoin is already adapting to ensure its infrastructure is prepared to respond.
Conclusion: Bitcoin’s Secure Future
Despite advancements in quantum computing, the reality is that Bitcoin is far from being threatened. Its security is ensured not only by its robust architecture but also by the community’s constant efforts to anticipate and mitigate challenges.
The implementation of BIP-360 and the pursuit of post-quantum algorithms demonstrate that Bitcoin is not only resilient but also proactive. By adopting practical measures, such as using modern wallets and migrating to quantum-resistant addresses, users can further protect themselves against potential threats.
Bitcoin’s future is not at risk—it is being carefully shaped to withstand any emerging technology, including quantum computing.
-
 @ 6be5cc06:5259daf0
2024-12-29 19:54:14
@ 6be5cc06:5259daf0
2024-12-29 19:54:14Um dos padrões mais bem estabelecidos ao medir a opinião pública é que cada geração tende a seguir um caminho semelhante em termos de política e ideologia geral. Seus membros compartilham das mesmas experiências formativas, atingem os marcos importantes da vida ao mesmo tempo e convivem nos mesmos espaços. Então, como devemos entender os relatórios que mostram que a Geração Z é hiperprogressista em certos assuntos, mas surpreendentemente conservadora em outros?
A resposta, nas palavras de Alice Evans, pesquisadora visitante na Universidade de Stanford e uma das principais estudiosas do tema, é que os jovens de hoje estão passando por um grande divergência de gênero, com as jovens mulheres do primeiro grupo e os jovens homens do segundo. A Geração Z representa duas gerações, e não apenas uma.
Em países de todos os continentes, surgiu um distanciamento ideológico entre jovens homens e mulheres. Milhões de pessoas que compartilham das mesmas cidades, locais de trabalho, salas de aula e até casas, não veem mais as coisas da mesma maneira.
Nos Estados Unidos, os dados da Gallup mostram que, após décadas em que os sexos estavam distribuídos de forma relativamente equilibrada entre visões políticas liberais e conservadoras, as mulheres entre 18 e 30 anos são agora 30 pontos percentuais mais liberais do que os homens dessa faixa etária. Essa diferença surgiu em apenas seis anos.
A Alemanha também apresenta um distanciamento de 30 pontos entre homens jovens conservadores e mulheres jovens progressistas, e no Reino Unido, a diferença é de 25 pontos. Na Polônia, no ano passado, quase metade dos homens entre 18 e 21 anos apoiou o partido de extrema direita Confederation, em contraste com apenas um sexto das jovens mulheres dessa mesma idade.
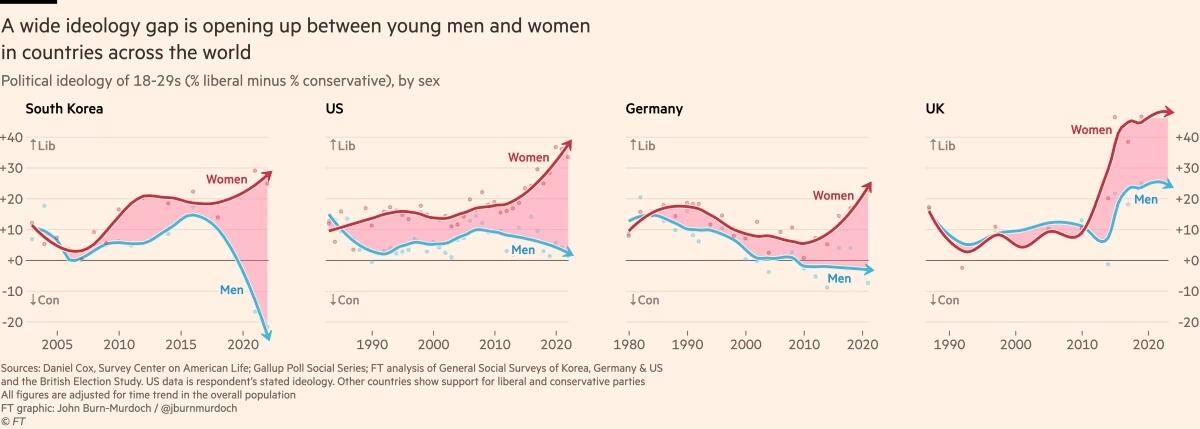
Fora do Ocidente, há divisões ainda mais acentuadas. Na Coreia do Sul, há um enorme abismo entre homens e mulheres jovens, e a situação é semelhante na China. Na África, a Tunísia apresenta o mesmo padrão. Vale notar que em todos os países essa divisão drástica ocorre principalmente entre a geração mais jovem, sendo muito menos pronunciada entre homens e mulheres na faixa dos 30 anos ou mais velhos.
O movimento # MeToo foi o principal estopim, trazendo à tona valores feministas intensos entre jovens mulheres que se sentiram empoderadas para denunciar injustiças de longa data. Esse estopim encontrou especialmente terreno fértil na Coreia do Sul, onde a desigualdade de gênero é bastante visível e a misoginia explícita é comum. (palavras da Financial Times, eu só traduzi)
Na eleição presidencial da Coreia do Sul em 2022, enquanto homens e mulheres mais velhos votaram de forma unificada, os jovens homens apoiaram fortemente o partido de direita People Power, enquanto as jovens mulheres apoiaram o partido liberal Democratic em números quase iguais e opostos.
A situação na Coreia é extrema, mas serve como um alerta para outros países sobre o que pode acontecer quando jovens homens e mulheres se distanciam. A sociedade está dividida, a taxa de casamento despencou e a taxa de natalidade caiu drasticamente, chegando a 0,78 filhos por mulher em 2022, o menor número no mundo todo.
Sete anos após a explosão inicial do movimento # MeToo, a divergência de gênero em atitudes tornou-se autossustentável.
Dados das pesquisas mostram que em muitos países, as diferenças ideológicas vão além dessa questão específica. A divisão progressista-conservadora sobre assédio sexual parece ter causado ou pelo menos faz parte de um alinhamento mais amplo, em que jovens homens e mulheres estão se organizando em grupos conservadores e liberais em outros assuntos.
Nos EUA, Reino Unido e Alemanha, as jovens mulheres agora adotam posturas mais liberais sobre temas como imigração e justiça racial, enquanto grupos etários mais velhos permanecem equilibrados. A tendência na maioria dos países tem sido de mulheres se inclinando mais para a esquerda, enquanto os homens permanecem estáveis. No entanto, há sinais de que os jovens homens estão se movendo para a direita na Alemanha, tornando-se mais críticos em relação à imigração e se aproximando do partido de extrema direita AfD nos últimos anos.
Seria fácil dizer que tudo isso é apenas uma fase passageira, mas os abismos ideológicos apenas crescem, e os dados mostram que as experiências políticas formativas das pessoas são difíceis de mudar. Tudo isso é agravado pelo fato de que o aumento dos smartphones e das redes sociais faz com que os jovens homens e mulheres agora vivam em espaços separados e tenham culturas distintas.
As opiniões dos jovens frequentemente são ignoradas devido à baixa participação política, mas essa mudança pode deixar consequências duradouras, impactando muito mais do que apenas os resultados das eleições.
Retirado de: https://www.ft.com/content/29fd9b5c-2f35-41bf-9d4c-994db4e12998
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ d61f3bc5:0da6ef4a
2025-02-12 16:57:44
@ d61f3bc5:0da6ef4a
2025-02-12 16:57:44Micropayments on the Internet have been theorized for decades. However, it wasn’t until the emergence of Nostr that we’ve finally seen them deployed at scale. Nostr is still in its infancy, yet we are already witnessing an explosion of apps built on top of this open protocol. And most of them are featuring zaps! With the recent Primal 2.1 release, Nostr developers now have the option to enhance the experience for their users by integrating a Nostr-powered bitcoin wallet.
There is no doubt that micropayments add a new dimension to consumer apps. The incumbents have realized this and are rushing to add payments to their closed platforms. It won't be long before apps that don’t include built-in payments feel dated or outright broken. The question is not if apps of the future will have built-in payments, but what kind of payments they will be. Given that open networks have a tendency to win, our bet is that apps of the future will be powered by Bitcoin. Let’s see how Primal can help.
Primal Wallet
Our vision for Primal Wallet is simple: deliver the smoothest transactional bitcoin wallet, endowed with expert Nostr skills. The wallet leverages Nostr’s open social graph as a de facto public lightning directory, while offering the highest level of user experience for Nostr’s rich content. For example, the user can scroll through the transaction list, select a zap, and drill straight into the conversation thread where the zap originated. The whole flow feels perfectly natural.
 Since we launched Primal Wallet in December 2023, the user response has been incredibly positive. People love the idea of being able to post something on Nostr, get zaps from plebs around the world, then buy a coffee or a meal with those sats - all from the same app.
Since we launched Primal Wallet in December 2023, the user response has been incredibly positive. People love the idea of being able to post something on Nostr, get zaps from plebs around the world, then buy a coffee or a meal with those sats - all from the same app. Having a bitcoin wallet with social skills resonated strongly with users, so Primal Wallet grew rapidly in popularity and usage. Since the launch, we have processed 1,338,460 transactions, with 238,916 just in the past month alone. This rivals some of the leading bitcoin wallets, and we are just getting started! We hear from many bitcoin OGs that they are using Primal Wallet as their transactional daily driver. Bullish.
All this is great, but something has been missing. Our users demanded the ability to connect Primal Wallet to other Nostr apps, so they can zap from anywhere in Nostr’s growing ecosystem.
Zapping from Any Nostr App
For an existing Primal user, connecting the wallet to a new Nostr app can now be done in two clicks. Let’s take a look at how this is done from Olas, one of the most exciting new apps on Nostr:
 Yes. Click, click. And you can start zapping!
Yes. Click, click. And you can start zapping! Such smooth integration of payments is not available in any competing technology stack. Tradfi, fintech, crypto, etc., have nothing on Bitcoin and Nostr. Two clicks and your external wallet is connected. I’ll give you a moment now to allow for this new reality to settle in.
Primal enables you to connect any number of external apps and manage them from wallet settings:
 Note that you can set your daily spend budget for each app or revoke its access at any time.
Note that you can set your daily spend budget for each app or revoke its access at any time. How This Works
So, what is this sorcery? How does it work under the hood?
Connecting Nostr apps to external wallets is accomplished via the Nostr Wallet Connect protocol. It utilizes Nostr’s public relay infrastructure to enable communication between apps and wallets. You can learn more about this protocol here, and access developer docs here.
The smooth, two-click connection setup UX is implemented through deep links between Primal and the external app. Here’s the deep link that the external app needs to call to invoke this feature:
nostrnwc+primal://connect?appicon=[icon_url]&appname=[app_name]&callback=[callback_string]After the user clicks “Create Wallet Connection” in Primal, the Primal app calls the deep link defined in the callback, and passes the NWC connection string. That's all that the external app needs to make the wallet connection.
What Comes Next?
The Nostr Wallet Connect protocol has been around for almost two years. Several bitcoin wallets implement it and many Nostr apps use it as their main way of enabling payments. What’s new with Primal 2.1 is the elevated user experience. Since Primal is a Nostr-powered wallet, it is aware of all the relevant metadata for each transaction: Nostr zaps, users, and the related events. Primal indexes the entire Nostr network, and now this is open to all Nostr apps that wish to integrate payments.
Nostr keeps expanding and getting better. Its openness enables us to build capabilities that lift all boats. The future is bright; I can’t wait to see how things evolve from here. 🍿🍿🍿
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ 4ba8e86d:89d32de4
2024-10-07 13:37:38
@ 4ba8e86d:89d32de4
2024-10-07 13:37:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável.
https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ 7e538978:a5987ab6
2024-10-02 13:57:31
@ 7e538978:a5987ab6
2024-10-02 13:57:31Chain Duel, a fast paced PvP game that takes inspiration from the classic snake game and supercharges it with Bitcoin’s Lightning Network. Imagine battling another player for dominance in a race to collect blocks, where the length of your chain isn’t just a visual cue. It represents real, staked satoshis. The player with the most Proof of Work wins, but it’s not just about gameplay; it’s about the seamless integration of the Lightning Network and real-time payments.
But how does Chain Duel manage these instant transactions with such efficiency? That’s where LNbits comes in. LNbits, an open-source wallet and payment infrastructure, handles all in-game payments making it easy for developers to focus on gameplay while LNbits takes care of everything from microtransactions to automated splits for developers and designers. In this article, we’ll dive deep into how Chain Duel leverages LNbits to streamline in-game payments and how other developers can take advantage of this powerful toolset to build the future of Lightning-powered gaming.
Let’s explore how LNbits transforms payment processing and why it’s quickly becoming a must-have for game developers working in the Bitcoin space.
Overview of Chain Duel
Chain Duel is a unique Lightning Network-inspired game that reimagines the classic snake game with a competitive twist, integrating real-time payments. Two players face off in real-time, racing to "catch" blocks and extend their chains. Each block added to the chain represents Proof of Work, and the player with the most Proof of Work wins the duel. The stakes are high, as the game represents satoshis (small units of Bitcoin) as points, with the winner taking home the prize.
The game is designed to be Lightning-native, meaning all payments within Chain Duel are processed through the Lightning Network. This ensures fast payments, reducing latency and making gameplay smooth. With additional features like practice mode, tournaments and highscores, Chain Duel creates an engaging and competitive environment for Bitcoin enthusiasts and gamers alike.

One of the standout aspects of Chain Duel is its deeper integration with the Lightning Network even at a design level. For example, actual Bitcoin blocks can appear on screen during matches, offering bonus points when mined in sync with the game. The game’s current version, still in beta, has already drawn attention within the Bitcoin community, gaining momentum at conferences and with a growing user base through its social networks. With its innovative combination of gaming, the Lightning Network, and competitive play, Chain Duel offers a glimpse into the future of Lightning-based gaming.
How LNbits is Used in Chain Duel
Seamless Integration with LNbits
At the core of Chain Duel’s efficient payment processing is LNbits, which handles in-game transactions smoothly and reliably. Chain Duel uses the LNbits LNURL-pay and LNURL-withdraw extensions to manage payments and rewards between players. Before each match, players send satoshis using LNURL-pay, which generates a static QR code or link for making the payment. LNURL-pay allows users to attach a note to the payment, which Chain Duel creatively uses as a way to insert the player name in-game. The simplicity of LNURL-pay ensures that users can quickly and easily initiate games, with fresh invoices being issued for every game. When players win, LNURL-withdraw enables them to seamlessly pull their earnings from the game, providing a quick payout system.
These extensions make it easy for players to send and receive Bitcoin with minimal latency, fully leveraging the power of the Lightning Network for fast and low-cost payments. The flexibility of LNbits’ tools means that game developers don’t need to worry about building custom payment systems from scratch—they can rely on LNbits to handle all financial transactions with precision.
Lightning Tournaments
Chain Duel tournaments leverage LNbits and its LNURL extensions to create a seamless and efficient experience for players. In Chain Duel tournaments, LNbits plays a crucial role in managing the overall economics. LNbits facilitates the generation of LNURL QR codes that participants can scan to register quickly or withdraw their winnings. LNbits allows Chain Duel to automatically handle multiple registrations through LNURL-pay, enabling players to participate in the tournament without additional steps. The Lightning Network's speed ensures that these payments occur in real-time, reducing wait times and allowing for a smoother flow in-game.
Splitting Payments
LNbits further simplifies revenue-sharing within Chain Duel. This feature allows the game to automatically split the satoshis sent by players into different shares for the game’s developer, designer, and host. Each time a payment is made to join a match, LNbits is used to automattically pay each of the contributors, according to pre-defined rules. This automated process ensures that everyone involved in the development and running of the game gets their fair share without manual intervention or complex bookkeeping.
Nostr Integration
Chain Duel also integrates with Nostr, a decentralized protocol for social interactions. Players can join games using "Zaps", small tips or micropayments sent over the Lightning Network within the Nostr ecosystem. Through NIP-57, which enables Nostr clients to request Zap invoices, players can use LNURL-pay enabled Zaps to register in P2P matches, further enhancing the Chain Duel experience. By using Zaps as a way to register in-game, Chain Duel automates the process of fetching players' identity, creating a more competitive and social experience. Zaps are public on the Nostr network, further expanding Chain Duel's games social reach and community engagement.
Game and Payment Synchronization

One of the key reasons Chain Duel developers chose LNbits is its powerful API that connects directly with the game’s logic. LNbits allows the game to synchronize payments with gameplay in real-time, providing a seamless experience where payments are an integrated part of the gaming mechanics.
With LNbits managing both the payment process and the Lightning Network’s complex infrastructure, Chain Duel developers are free to concentrate on enhancing the competitive and Lightning Network-related aspects of the game. This division of tasks is essential for streamlining development while still providing an innovative in-game payment experience that is deeply integrated with the Bitcoin network.
LNbits proves to be an indispensable tool for Chain Duel, enabling smooth in-game transactions, real-time revenue sharing, and seamless integration with Nostr. For developers looking to build Lightning-powered games, LNbits offers a powerful suite of tools that handle everything from micropayments to payment distribution—ensuring that the game's focus remains on fun and competition rather than complex payment systems.
LNBits facilitating Education and Adoption
This system contributes to educating users on the power of the Lightning Network. Since Chain Duel directly involve real satoshis and LNURL for registration and rewards, players actively experience how Lightning can facilitate fast, cheap, and permissionless payments. By incorporating LNbits into Chain Duel, the game serves as an educational tool that introduces users to the benefits of the Lightning Network. Players gain direct experience using Lightning wallets and LNURL, helping them understand how these tools work in real-world scenarios. The near-instant nature of these payments showcases the power of Lightning in a practical context, highlighting its potential beyond just gaming. Players are encouraged to set up wallets, explore the Lightning ecosystem, and eventually become familiar with Bitcoin and Lightning technology. By integrating LNbits, Chain Duel transforms in-game payments into a learning opportunity, making Bitcoin and Lightning more approachable for users worldwide.
Tools for Developers
LNbits is a versatile, open-source platform designed to simplify and enhance Bitcoin Lightning Network wallet management. For developers, particularly those working on Lightning-native games like Chain Duel, LNbits offers an invaluable set of tools that allow for seamless integration of Lightning payments without the need to build complex custom solutions from scratch. LNbits is built on a modular and extensible architecture, enabling developers to easily add or create functionality suited to their project’s needs.
Extensible Architecture for Customization
At the core of LNbits is a simple yet powerful wallet system that developers can access across multiple devices. What makes LNbits stand out is its extensible nature—everything beyond the core functionality is implemented as an extension. This modular approach allows users to customize their LNbits installation by enabling or building extensions to suit specific use cases. This flexibility is perfect for developers who want to add Lightning-based services to their games or apps without modifying the core codebase.
- Extensions for Every Use Case
LNbits comes with a wide array of built-in extensions created by contributors, offering various services that can be plugged into your application. Some popular extensions include: - Faucets: Distribute small amounts of Bitcoin to users for testing or promotional purposes.
- Paylinks: Create shareable links for instant payments.
- Points-of-sale (PoS): Allow users to set up shareable payment terminals.
- Paywalls: Charge users to access content or services.
- Event tickets: Sell tickets for events directly via Lightning payments.
- Games and services: From dice games to jukeboxes, LNbits offers entertaining and functional tools.
These ready-made solutions can be adapted and used in different gaming scenarios, for example in Chain Duel, where LNURL extensions are used for in game payments. The extensibility ensures developers can focus on building engaging gameplay while LNbits handles payment flows.
Developer-Friendly Customization
LNbits isn't just a plug-and-play platform. Developers can extend its functionality even further by creating their own extensions, giving full control over how the wallet system is integrated into their games or apps. The architecture is designed to make it easy for developers to build on top of the platform, adding custom features for specific requirements.
Flexible Funding Source Management
LNbits also offers flexibility in terms of managing funding sources. Developers can easily connect LNbits to various Lightning Network node implementations, enabling seamless transitions between nodes or even different payment systems. This allows developers to switch underlying funding sources with minimal effort, making LNbits adaptable for games that may need to scale quickly or rely on different payment infrastructures over time.
A Lean Core System for Maximum Efficiency
Thanks to its modular architecture, LNbits maintains a lean core system. This reduces complexity and overhead, allowing developers to implement only the features they need. By avoiding bloated software, LNbits ensures faster transactions and less resource consumption, which is crucial in fast-paced environments like Chain Duel where speed and efficiency are paramount.
LNbits is designed with developers in mind, offering a suite of tools and a flexible infrastructure that makes integrating Bitcoin payments easy. Whether you’re developing games, apps, or any service that requires Lightning Network transactions, LNbits is a powerful, open-source solution that can be adapted to fit your project.
Conclusion
Chain Duel stands at the forefront of Lightning-powered gaming, combining the excitement of competitive PvP with the speed and efficiency of the Lightning Network. With LNbits handling all in-game payments, from microtransactions to automated revenue splits, developers can focus entirely on crafting an engaging gaming experience. LNbits’ powerful API and extensions make it easy to manage real-time payments, removing the complexity of building payment infrastructure from scratch.
LNbits isn’t just a payment tool — it’s a flexible, developer-friendly platform that can be adapted to any gaming model. Whether you're developing a fast-paced PvP game like Chain Duel or any project requiring seamless Lightning Network integration, LNbits provides the ideal solution for handling instant payments with minimal overhead.
For developers interested in pushing the boundaries of Lightning-powered gaming, Chain Duel is a great example of how LNbits can enhance your game, letting you focus on the fun while LNbits manages real-time transactions.
Find out more
Curious about how Lightning Network payments can power your next game? Explore the following:
- Learn more about Chain Duel: Chain Duel
- Learn how LNbits can simplify payment handling in your project: LNbits
- Dive into decentralized communication with Nostr: Nostr
- Extensions for Every Use Case
-
 @ 85bdb587:7339d672
2025-02-12 15:24:11
@ 85bdb587:7339d672
2025-02-12 15:24:11Chart of the Day
While this is a bitcoin focused rag, I think it is important for any of you who read this to begin paying attention to gold markets if you haven't already. There has been an ongoing exodus of physical gold from London vaults and a rapid acceleration of gold being moved to the three biggest vaults in the United States in recent weeks. More gold has flooded into the US vaults over the first two months of this year than at the peak of the flight to safety during the beginning of the COVID lock downs.
This is particularly perplexing considering the fact that equities are flat or up on the year, depending on the index you like to follow. Gold outperformed the S&P 500 significantly in 2024 and its momentum hasn't slowed down a bit in 2025 as the precious metal consistently hits new all time highs. The current correlation to the S&P 500 has only happened two times in history; right now and October of 2007.
Institutional investors and nation states are piling into gold at an unprecedented pace. This signals that they are preparing for something to break. The catalysts for the exodus of gold from London to the US and from paper gold to physical gold are fears over Trump's tariffs, institutions and governments preparing for a potential monetary reset, and fears of a looming liquidity crisis as liquidity in the reverse repo market dries up. Uncertainty and chaos rule the day and we are witnessing a flight to safety.
Many of you are probably asking, "Why isn't bitcoin moving?!" That's a good question. Considering everything mentioned above one would think that bitcoin would be on the move toward new all time highs as well. Having been following bitcoin for twelve years your Uncle Marty has developed some pattern recognition when it comes to this market. Upward bitcoin price movements typically happen in a staircase fashion. Meaning that it trends up and to the right over the long-run with quick bursts to higher levels followed by small corrections and consolidation periods. If I had to guess, we are currently in a consolidation period that should come to an end at some point in the next few months. In recent years, gold has moved higher first and bitcoin has followed. Typically outperforming gold significantly. I find it hard to believe that this relationship is going to end any time soon. Especially considering the geopolitical and economic backdrop.
Luke Gromen Warns Bitcoin Holders: Historical Currency Revaluations Show Speed Matters
During my recent conversation with Luke Gromen, he raised a sobering point about the velocity of monetary regime changes. Drawing from historical examples, including a Ukrainian family who saw their savings devalue from "five cars to one month's groceries" over a single weekend, Luke emphasized that Americans are uniquely blind to how quickly these transitions can occur. The current stress in our financial system - from Treasury market dynamics to global trade tensions - suggests we're approaching a similar inflection point.
*"What if they do it on Friday night like they did with Trump coin and you wake up and gold's up 1,000% by the time you're up on Saturday morning, what are you going to do? You're going to sell your bonds and buy gold on Saturday?"* - Luke Gromen
This warning shouldn't be taken lightly. Those waiting for clear signals before acquiring bitcoin may find themselves locked out of the transition entirely. Luke's analysis suggests that rather than a gradual shift, we're more likely to see a compressed timeframe where major monetary changes happen over days or weeks, not months or years. The recent Trump coin phenomenon, while different in nature, demonstrates how quickly markets can move when sentiment shifts dramatically.
TLDR: Major monetary changes happen fast - don't wait to stack sats.
Check out the full podcast here for more on DeepSeek's impact on AI markets, Colombia's trade negotiations, and Scott Percent's three arrows for economic reform.
Headlines of the Day
U.S. Faces $1.67B Annual Cost Spike on Single Bond Rollover - via X
BlackRock: Bitcoin is Monetary Hedge, Ethereum is Tech Play - via X
Lummis: SBR Could Slash U.S. Debt by 50% in Two Decades - via X
Fold Launches Bitcoin Rewards Visa Credit Card - via Business Wire
Obscura VPN launches with a MacOS product - via nobsbitcoin.com
Bitcoin Lesson of the Day
The SegWit (Segregated Witness) upgrade in August 2017 made two key changes to Bitcoin. First, it moved transaction signatures to a separate part of the data, fixing "transaction malleability" by preventing nodes from modifying transaction IDs. Second, it increased effective block capacity by introducing "weight units" that gave signature data a 75% discount, allowing blocks to grow from 1MB to about 1.8MB.
As a "soft fork," SegWit remained compatible with older Bitcoin software. The upgrade activated at block 481,824 after 95% of miners signaled support. This approach allowed Bitcoin to increase capacity and fix technical issues while maintaining network compatibility.
ICYMI Fold opened the waiting list for the new Bitcoin Rewards Credit Card. Fold cardholders will get unlimited 2% cash back in sats.
Get on the waiting list now before it fills up!
$200k worth of prizes are up for grabs . The Fold Bitcoin Rewards Credit Card waitlist is live!
Ten31, the largest bitcoin-focused investor, has deployed $150M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/funds.
Subscribe to our YouTube channels and follow us on Nostr and X:
-
 @ c4f5e7a7:8856cac7
2024-09-27 08:20:16
@ c4f5e7a7:8856cac7
2024-09-27 08:20:16Best viewed on Habla, YakiHonne or Highlighter.
TL;DR
This article explores the links between public, community-driven data sources (such as OpenStreetMap) and private, cryptographically-owned data found on networks such as Nostr.
The following concepts are explored:
- Attestations: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your web-of-trust.
- Proof of Place: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in meatspace with their digital representations in the Nostrverse.
- Check-ins: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time.
The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems.
Open Data in a public commons has a place and should not be thrown out with the Web 2.0 bathwater.
Cognitive Dissonance
Ever since discovering Nostr in August of 2022 I've been grappling with how BTC Map - a project that helps bitcoiners find places to spend sats - should most appropriately use this new protocol.
I am assuming, dear reader, that you are somewhat familiar with Nostr - a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: Nostr is Identity for the Internet and The Power of Nostr by @max and @lyn, respectively. Nostr is so much more than a short-form social media replacement.
The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting - all your silos are indeed broken - however, something fundamental has been bothering me for a while and I think it comes down to data ownership.
For those unfamiliar, BTC Map uses OpenStreetMap (OSM) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) - FOSD if you will, but more commonly referred to as Open Data.
In contrast, Notes and Other Stuff on Nostr (Places in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned.
How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data?
Self-sovereign Identity
Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something - an identity.
All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money.
Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state.
Or, as @nvk said recently: "Don't build your house on someone else's land.".
https://i.nostr.build/xpcCSkDg3uVw0yku.png
While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this.
Nostr is PGP for the masses and will take cryptographic identities mainstream.
Full NOSTARD?
Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons.
We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be.
https://i.nostr.build/s3So2JVAqoY4E1dI.png
There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a Wikifreedia variant of OpenStreetMap.
While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native - there's no need to go Full NOSTARD. H/T to @princeySOV for the original meme.
https://i.nostr.build/ot9jtM5cZtDHNKWc.png
So, how do we appropriately blend cryptographically owned data with the commons?
If a location is owned in meatspace and it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the tragedy of the commons.
The remainder of this article explores how we can:
- Verify ownership of a physical place in the real world;
- Link that ownership to the corresponding digital place in cyberspace.
As a side note, I don't see private key custodianship - or, even worse, permissioned use of Places signed by another identity's key - as any more viable than the rented identities of Web 2.0.
And as we all know, the Second Law of Infodynamics (no citation!) states that:
"The total amount of sensitive information leaked will always increase over time."
This especially holds true if that data is centralised.
Not your keys, not your notes. Not your keys, not your identity.
Places and Web-of-Trust
@Arkinox has been leading the charge on the Places NIP, introducing Nostr notes (kind 37515) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via NIP-73 - External Content IDs (championed by @oscar of @fountain).
However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world.
Ultimately, this problem can only be solved in a decentralised way by using Web-of-Trust - using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop.
This requires users to:
- Verify the owner of a Place in cyberspace is the owner of a place in meatspace.
- Signal this verification to their social graph.
Let's look at the latter idea first with the concept of Attestations ...
Attestations
A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false.
Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too.
However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc).
Here is a recent example from @lyn that would carry more signal if it were an Attestation:
https://i.nostr.build/lZAXOEwvRIghgFY4.png
Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or Data Vending Machines in accordance with:
- Your social graph;
- The type or subject of the content being attested and by whom;
- Your personal preferences.
They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places.
NIP-25 (Reactions) do allow for users to up/downvote notes with optional content (e.g., emojis) and could work for Attestations, but I think we need something less ambiguous and more definitive.
‘This is true’ resonates more strongly than ‘I like this.’.
https://i.nostr.build/s8NIG2kXzUCLcoax.jpg
There are similar concepts in the Web 3 / Web 5 world such as Verified Credentials by tdb. However, Nostr is the Web 3 now and so wen Attestation NIP?
https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg
That said, I have seen @utxo has been exploring ‘smart contracts’ on nostr and Attestations may just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust.
Proof of Place
Attestations handle the signalling of your truth, but what about the initial verification itself?
We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth.
Introducing Proof of Place, an out–of-band process where an oracle (such as BTC Map) would mail - yes physically mail- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace.
One way of doing this would be to mint a 1 sat cashu ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location.
Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places).
In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as @Gigi says in PoW is Essential:
"A failure to understand Proof of Work, is a failure to understand Bitcoin."
In the Nostrverse, Proof of Place helps bridge the digital and physical worlds.
@Gigi also observes in Memes vs The World that:
"In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone."
https://i.nostr.build/dOnpxfI4u7EL2v4e.png
This isn’t true for Nostr.
In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯
Check-ins
Although not a draft NIP yet, @Arkinox has also been exploring the familiar concept of Foursquare-style Check-ins on Nostr (with kind 13811 notes).
For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as OSM elements) if NIP-73 - External Content IDs are used.
Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices.
Bringing Check-ins to Nostr is possible (as @sebastix capably shows here), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am.
Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable.
How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene - I’m sure @blackcoffee and @Ben Arc could hack something together over a weekend!
Check-ins could also be used as a signal for bonafide Place ownership over time.
Summary: Trust Your Bros
So, to recap, we have:
Places: Digital representations of physical locations on Nostr.
Check-ins: Users signalling their presence at a location.
Attestations: Verifiable social proofs used to confirm ownership or the truth of a claim.
You can visualise how these three concepts combine in the diagram below:
https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg
And, as always, top right trumps bottom left! We have:
Level 0 - Trust Me Bro: Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all.
Level 1 - Definitely Maybe Somewhere: This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL.
Level 2 - Trust Your Bros: An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph.
https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg
Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map?
Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ - you decide.
As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities.
Thanks
With thanks to Arkinox, Avi, Ben Gunn, Kieran, Blackcoffee, Sebastix, Tomek, Calle, Short Fiat, Ben Weeks and Bitcoms for helping shape my thoughts and refine content, whether you know it or not!
-
 @ 94a6a78a:0ddf320e
2025-02-12 15:05:48
@ 94a6a78a:0ddf320e
2025-02-12 15:05:48Azzamo is more than just a relay provider—it’s a high-performance network designed to make Nostr faster, smoother, and more reliable for everyone. Whether you're posting notes, zapping sats, sharing media, or sending DMs, Azzamo keeps your Nostr experience seamless and efficient.
Nostr is unstoppable, but not all relays are the same. Some are slow, unreliable, or disappear overnight, while others get overloaded, making message delivery inconsistent. Azzamo is built differently—offering fast, stable, and globally distributed relays to ensure low-latency, high-speed connections, no matter where you are.
🌍 Premium Relays for Maximum Performance
Azzamo Premium Relays are optimized for speed, reliability, and uptime, available exclusively to Premium users:
📡 Azzamo Premium Relays:
- Europe:
wss://relay.azzamo.net - America:
wss://us.azzamo.net - Asia:
wss://asia.azzamo.net
Add Azzamo Premium Time to unlock unlimited, high-speed access across these global relays.
🔗 Get Premium: azzamo.net/premium
🆓 Freemium Relays – Free for Everyone
Azzamo believes in keeping Nostr open and accessible to all. That’s why we offer free relays for everyone, with no rate limits for Premium members
📡 Freemium Relays:
- Free Relay:
wss://nostr.azzamo.net– Open to all. - Inbox Relay:
wss://inbox.azzamo.net– Reliable for DMs & group messages.
By offering both free and premium options, Azzamo ensures that anyone can use Nostr, while also funding the infrastructure that keeps it running smoothly.
🛡️ Minimal Moderation, Maximum Transparency
Nostr is about free speech, but that doesn’t mean zero moderation. Azzamo follows a minimal moderation policy to keep relays functional and spam-free while maintaining transparency in enforcement.\ \ 🚫 Spam & network abuse\ 🚫 Illegal content (CSAM, fraud, malware, scams)\ 🚫 Impersonation & identity abuse
We also maintain a public Ban API for transparent moderation decisions.
📖 More on our Ban API: azzamo.net/introducing-the-azzamo-ban-api
🚀 Get Started with Azzamo Relays Today!
🔗 Connect now:\ 📡
wss://nostr.azzamo.net(Freemium Free Relay)\ 📬wss://inbox.azzamo.net(Freemium Inbox Relay)\ 📡wss://relay.azzamo.net(Premium Europe Relay)\ 📡wss://us.azzamo.net(Premium Americas Relay)\ 📡wss://asia.azzamo.net(Premium Asia Relay)Nostr is growing fast. Make sure your relays can keep up. 🚀
azzamo #grownostr #nostr #relay #relays #premiumrelay #paidrelay
- Europe:
-
 @ c4b5369a:b812dbd6
2025-02-12 12:23:40
@ c4b5369a:b812dbd6
2025-02-12 12:23:40
Unidirectional payment channels revisited
Nodeless lightning - Reduce ecash mints custodial risk
Sats N Facts
The nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx unconference has just wrapped up. And what a blast it was. In the heart of northern Thailand, developers, researchers, content creators and more, came together to share ideas on how Bitcoin, Nostr and other free protocols are being used everyday to liberate people.
Not only were stories shared from different community leaders on how embracing bitcoin has empowered them and their communities, but a big goal of the unconference was to bring bitcoin engineers and developers from various domains together in one room, unstructured, chaotic, and let them do their thing.
At first, I thought not having a schedule might be boring, but oh boy was I wrong. There was so much stuff going on, it was hard to choose which session I would have to miss!
Luke's Spillman channel proposal
One of the sessions I definitely did not want to miss, was nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac s proposal
Ecash mints funded with Spillman channels: The ultimate nodeless Lightning wallet
.
In true unconference fashion, he announced in the main room that the session was about to start, and that the people that are interested should meet him in the whiteboard corner in 10 minutes. The corner was packed, and Luke explained his proposal.
What's a "Spillman channel"?
Essentially when we are talking about Spillman channels, what is meant are unidirectional payment channels (or CLTV-style channels). An unidirectional payment channel means, only one party can send payments, but not receive, and the other party can only receive, but not send. They also expire after a predetermined amount of time, and must be closed.

At first glance, this might look kinda stupid. After all, we have Poon-Dryja channels that are powering the lightning network. They are bi-directional, do not expire, and can be used to shuffle coins back and forth theorethically an unlimited amount of times.
So, why bother with this stupid one-way channel?
Simplicity is king
People that have worked with lightning channels can sing you a song about complexity, state handling and risks about the current state of bidirectional payment channels. Essentially, There are a lot of requirements on both channel parties when it comes to Liveness (being online) and also state handling (continuous backups).
 In some cases, especially when in the context of end-users wanting to perform payments on their mobile phone, they would appreciate it if there was not so much complexity and overhead involved.
In some cases, especially when in the context of end-users wanting to perform payments on their mobile phone, they would appreciate it if there was not so much complexity and overhead involved. The gist of the idea is to combine unidirectional channels and ecash mints to achieve the following:
A self custodial unidirectional payment channel to an ecash mint, massively reducing the senders liveness and state handling requirements when compared to a lightning channel. Sending payments through the mint will be done through swapping some of the channel balance for ecash tokens. At this point, the user is trusting the mint to honor the redemption of these tokens, while the remaining channel balance remains in self custody. This gives them better controll over their funds than just holding their entire balance custodied in the mint. The ecash tokens can then be redeemed to pay a lightning invoice, just the same as it is done now with normal cashu mints.

So this channel, that has no liveness or state management requirements for the sender, and must have a pre-defined close time, seems to be a perfect fit for the following usecase:
- A
senderreceives his salary once a month. He opens a channel that is valid for one month. - The
senderthen can do his daily spending over this channel. He only trusts themintwith the amount for the current outgoing payment while it is swapped for ecash, waiting for redemption. - If the
sendermust receive funds (a refund for example), he can do so into themintscustody, by receiving ecash. He can spend his ecash funds first when doing his next payment, to reduce his custodial exposure. - When the channel expires, or runs out of funds, the
mintcloses the channel.
From a consumer perspective, that just want to receive his salary and make frequent payments afterwards, this usecase seems to make a lot of sense. Obviously from a merchants perspective on the other hand, such a channel doesn't really work. But that's fine, it's not the problem we're trying to solve here.
What do you think of this idea? Be sure to let me know in the comments!
In the next article, we will dive into how such a system can be implemented today, using Bitcoin, Cashu and Lightning. We will also discover how the system can be improved, to make channels non-expiring (A collaborative idea between nostr:npub148jz5r9xujcjpqygk69yl4jqwjqmzgrqly26plktfjy8g4t7xaysj9xhgp and nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac born at nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx ).
So stay tuned!
- A
-
 @ c2827524:5f45b2f7
2025-02-12 12:22:11
@ c2827524:5f45b2f7
2025-02-12 12:22:11L’animo umano

Una delle entità più belle che esistono e che, a mio parere, rendono ancor più meraviglioso questo mondo, è l’animo degli esseri umani. È un cocktail fatto di sentimenti, intenzioni, azioni e logica. Quelli che preferisco sono gli animi gentili. Le azioni e le intenzioni devono convergere verso la delicatezza, senza una sbavatura, per essere gentili e io adoro la gentilezza, la riconosco al volo, forse perché non sono delicata. Per niente.
L’animo è forse uno dei più grandi segreti dell’umanità: in genere perché lo si tiene sempre privato, come è anche logico che sia.
C’è un solo fattore che fa rivelare l’animo alle persone, loro malgrado: uno stress test estremo.
Dal febbraio del 2020, lo stress test si è tramutato in un organismo multidimensionale, uscendo dalla fantasia distopica di George Orwell e – loro malgrado – tutti hanno dovuto manifestare l’animo segreto.
Fateci caso: è con il covid-1984 che avete scoperto la vera natura di amici, parenti, sconosciuti o conoscenti.
Stato di eccezione

La distopia non è mica fuoriuscita da un laboratorio di Wuhan, che ha infettato un pangolino, che ha infettato una papera, che al mercato mio padre comprò. Ha origini molto più antiche.
Profondi conoscitori dell’animo umano, in grado di prevedere le reazioni delle masse di fronte ad ogni tipo di evento, potrebbero progettare modelli catastrofici e predeterminare con una precisione disarmante la risposta delle persone comuni. Ad esempio di fronte alla probabilità che quattro aerei impazziscano nei cieli americani di una splendida mattina di settembre, oppure guardando i corpi smembrati di un attentato compiuto da una qualunque “sigla” islamica.
Infine, potrebbero decidere come e quando dare una sferzata finale allo stress test, ad esempio con il pangolino. O era il pipistrello?
È la «forma legale di ciò che non può avere forma legale», più in generale lo spirito disumano dei governanti di oggi, la consuetudine della guerra preventiva, la quale impone con forza che «lo stato di eccezione tende sempre più a presentarsi come il paradigma di governo dominante della politica contemporanea».
Così analizza magistralmente Giorgio Agamben nel II° volume della raccolta Homo Sacer, intitolato per l’appunto Stato di Eccezione.
Stato indegno

Gli esseri umani, fondamentalmente miti e pacifici, tendono a condurre vite “normali” in ogni condizione ambientale.
Un’unica variabile tende ad interferire per cambiare la condizione ambientale: la politica dello stato. E lo fa in maniera sempre negativa.
Lo stato crea emergenze, per poi sbattere il suo (piccolissimo) pene sul tavolo e imporre con forza la soluzione, che tenderà puntualmente a facilitare la propria vita rendendo impossibile quella dei ~~cittadini~~ sudditi.
Le disuguaglianze create hanno poi il solo scopo di mettere esseri miti e pacifici (ma sotto costante pressione) gli uni contro gli altri.
Pensateci: da quanti decenni siete sotto la pressione di una «forma legale di ciò che non può avere forma legale»? Sentendo il Marchese del Grillo «Io so’ io, voi siete un cazzo», probabilmente è qualche secolo che questo stato indegno esiste.
Vera natura o Nuda vita?

Il fatto, poi, che lo stato indegno venga accettato senza fiatare, fa parte di quella serie di reazioni delle masse e che i profondi conoscitori dell’animo umano sfruttano per mantenere il potere.
Si passa poi alle peggiori angherie che lo stato indegno e i suoi agenti perpetrano nei confronti dei ~~cittadini~~ sudditi, alle estreme disparità tra ~~cittadini~~ sudditi e i “servitori” dello stato, chiamati così perché servono lo stato indegno e non i ~~cittadini~~ sudditi.
Prima di arrivare alla sferzata finale dello stress test, persone miti e pacifiche hanno subito così tanti torti da non saperli più contare, ormai fanno parte della normalità. La loro esistenza è ormai ridotta a quello che Walter Benjamin prima e Giorgio Agamben poi definiscono la Nuda Vita, mettendo in analogia i sudditi con i detenuti di Guantanamo, giuridicamente innominabili e inclassificabili, ovvero «oggetto di una pura signoria di fatto».
Il sontuoso master

Nello stato di eccezione in cui viviamo da almeno 50 anni, a parte pochi dotati di un immenso spirito di osservazione (e i profondi conoscitori al potere, chiaro), nessuno di noi ha mai avuto veramente il piacere di conoscere la reale natura delle persone con cui abbiamo scelto di circondarci.
Magari c’era quel “piccolo tarlo”, quella “vocina” che ci ha fatto preferire alcuni piuttosto che altri, ma alla fine ha sempre prevalso l’attitudine mite e pacifica, che ha messo a tacere quella vocina.
covid-1984 ha il merito di aver messo a nudo tutti: vittime e carnefici. Si tratta verosimilmente di un sontuoso master che svelerà la vera natura di ognuno, nessuno escluso. Ahinoi, il master è decennale e siamo appena all'inizio del V° anno accademico.
Istruzioni, prima ancora che l’istruzione

Se c’è un consiglio che mi sento di dare a chi è ancora molto giovane, è proprio quello di non mettere mai a tacere quella “vocina”, per nessun motivo, seppure plausibile. Anche senza rovinare i rapporti, ma l’animo umano va sempre indagato, si deve fare chiarezza sulla vera natura delle persone con cui si decide di fare un percorso di vita.
La scoperta porterà ad evitare tutti quei “servitori” dello stato di cose indegno di essere definito umano. I compliant, gli asserviti, quelli senza spina dorsale o, peggio, che hanno un interesse personale a mantenere lo status quo devono essere evitati a tutti i costi.
È oltremodo doloroso, ma va fatto. Questi indegni devono essere isolati al più presto, in maniera da renderli innocui. Sono loro il vero esercito dello stato indegno, disposti a combattere qualunque guerra pur di rimediare un piccolissimo quanto ridicolo privilegio.
Oggi, i tempi in cui questo esercito si abbassava a tanto per il classico piatto di lenticchie riscaldate, sono un lontanissimo ricordo. covid-1984 ha ulteriormente abbattuto lo standard: ora gli indegni fiancheggiano qualsiasi assurdità in cambio di un piatto di lenticchie rimasticate dalla signoria di fatto.
L’unico risultato possibile è che l'infame stato rafforza il suo potere di controllo e rosicherà uno alla volta i (pochi) diritti e la libertà di chiunque.
Ecco perché bisogna spuntare le armi di questo spregevole stato di cose colpendo l’anello debole, isolandolo. Debole perché non ci crede (nello stato) ma agisce asservito solo per quel piatto di lenticchie (quelle rimasticate e sputate).
La prima volta che si incontrano, la vocina vi metterà di fronte alla sensazione di essere ai limiti di uno scontro frontale: capire da che parte andrà il rivale, per buttarsi in quella opposta ed evitare così uno schianto fatale.
Fatelo: buttatevi dall’altra parte. E scegliete la parte giusta.
-
 @ 7460b7fd:4fc4e74b
2024-09-05 08:37:48
@ 7460b7fd:4fc4e74b
2024-09-05 08:37:48请看2014年王兴的一场思维碰撞,视频27分钟开始
最后,一个当时无法解决的点:丢失
-
 @ 575a8227:065bba95
2025-02-12 10:57:10
@ 575a8227:065bba95
2025-02-12 10:57:10https://www.youtube.com/watch?v=SiV7UhoiZM8
Hola nostr, El reciente podcast de lunaticoin con Salinas ha puesto sobre la mesa una reflexión profunda sobre el llamado "fondo estratégico Bitcoin" de Trump, revelando una paradoja que merece nuestra atención.
Pensemos en el camino que hemos recorrido como individuos en el ecosistema Bitcoin. Durante años, cada uno de nosotros ha trabajado incansablemente, ahorrando con determinación para adquirir Bitcoin con dinero real, fruto de nuestro esfuerzo diario. En ese trayecto, hemos enfrentado críticas constantes: que si Bitcoin solo servía para actividades ilícitas, que si era un esquema Ponzi, que si carecía de valor intrínseco.
Ahora, en 2025, presenciamos un giro narrativo sorprendente. Los mismos que demonizaron Bitcoin proponen crear un "fondo estratégico", ¿y cómo planean financiarlo? Con la misma herramienta contra la que Bitcoin nació para protegernos: la impresión infinita de dinero fiat. Pretenden adquirir con papel sin respaldo lo que a tantos nos ha costado años de esfuerzo y convicción conseguir.
La comunidad Bitcoin se ha construido desde abajo, con personas que creyeron en el proyecto cuando pocos lo hacían, que mantuvieron sus convicciones en los momentos más difíciles, que construyeron infraestructura y educaron a otros. Somos nosotros, no los oportunistas de última hora, quienes hemos llevado Bitcoin hasta donde está hoy.
La propuesta actual representa una doble expropiación: primero devalúan nuestros ahorros mediante la inflación, y luego utilizan ese mismo dinero devaluado para intentar acaparar Bitcoin. Es un mecanismo que perpetúa exactamente aquello contra lo que Bitcoin fue creado para luchar.
Bitcoin nació como una herramienta de libertad financiera para el individuo, no como un instrumento más de control centralizado. Cada día que pasa, se hace más evidente que ningún político, independientemente de su retórica, representa los valores fundamentales de Bitcoin.
En estos momentos, mantener nuestros sats no es solo una decisión financiera, es una declaración de principios.
HODL 🟠₿
-
 @ b60c3e76:c9d0f46e
2024-05-15 10:08:47
@ b60c3e76:c9d0f46e
2024-05-15 10:08:47KRIS menjamin semua golongan masyarakat mendapatkan perlakuan sama dari rumah sakit, baik pelayanan medis maupun nonmedis.
Demi memberikan peningkatan kualitas layanan kesehatan kepada masyarakat, pemerintah baru saja mengeluarkan Peraturan Presiden (Perpres) nomor 59 tahun 2024 tentang Jaminan Kesehatan. Melalui perpres itu, Presiden Joko Widodo (Jokowi) telah menghapus perbedaan kelas layanan 1, 2, dan 3 dalam Badan Penyelenggara Jaminan Sosial atau BPJS Kesehatan.
Layanan berbasis kelas itu diganti dengan KRIS (Kelas Rawat Inap Standar). Berkaitan dengan lahirnya Perpres 59/2024 tentang Perubahan Ketiga atas Perpres 82/2018 tentang Jaminan Kesehatan, Presiden Joko Widodo telah memerintahkan seluruh rumah sakit yang bekerja sama dengan BPJS Kesehatan melaksanakannya.
Kebijakan baru itu mulai berlaku per 8 Mei 2024 dan paling lambat 30 Juni 2025. Dalam jangka waktu tersebut, rumah sakit dapat menyelenggarakan sebagian atau seluruh pelayanan rawat inap berdasarkan KRIS sesuai dengan kemampuan rumah sakit.
Lantas apa yang menjadi pembeda dari sisi layanan dengan layanan rawat inap sesuai Perpres 59/2024? Dahulu sistem layanan rawat BPJS Kesehatan dibagi berdasarkan kelas yang dibagi masing-masing kelas 1, 2, dan 3. Namun, melalui perpres, layanan kepada masyarakat tidak dibedakan lagi.
Pelayanan rawat inap yang diatur dalam perpres itu--dikenal dengan nama KRIS—menjadi sistem baru yang digunakan dalam pelayanan rawat inap BPJS Kesehatan di rumah sakit-rumah sakit. Dengan KRIS, semua golongan masyarakat akan mendapatkan perlakuan yang sama dari rumah sakit, baik dalam hal pelayanan medis maupun nonmedis.
Dengan lahirnya Perpres 59/2024, tarif iuran BPJS Kesehatan pun juga akan berubah. Hanya saja, dalam Perpres itu belum dicantumkan secara rinci ihwal besar iuran yang baru. Besaran iuran baru BPJS Kesehatan itu sesuai rencana baru ditetapkan pada 1 Juli 2025.
“Penetapan manfaat, tarif, dan iuran sebagaimana dimaksud ditetapkan paling lambat tanggal 1 Juli 2025,” tulis aturan tersebut, dikutip Senin (13/5/2024).
Itu artinya, iuran BPJS Kesehatan saat ini masih sama seperti sebelumnya, yakni sesuai dengan kelas yang dipilih. Namun perpres itu tetap berlaku sembari menanti lahirnya peraturan lanjutan dari perpres tersebut.
Kesiapan Rumah Sakit
Berkaitan dengan lahirnya kebijakan layanan kesehatan tanpa dibedakan kelas lagi, Kementerian Kesehatan (Kemenkes) menegaskan mayoritas rumah sakit di Indonesia siap untuk menjalankan layanan KRIS untuk pasien BPJS Kesehatan.
Kesiapan itu diungkapkan oleh Dirjen Pelayanan Kesehatan Kemenkes Azhar Jaya. “Survei kesiapan RS terkait KRIS sudah dilakukan pada 2.988 rumah sakit dan yang sudah siap menjawab isian 12 kriteria ada sebanyak 2.233 rumah sakit,” ujar Azhar.
Sebagai informasi, KRIS adalah pengganti layanan Kelas 1, 2, dan 3 BPJS Kesehatan yang bertujuan untuk memberikan layanan kesehatan secara merata tanpa melihat besaran iurannya.
Melalui KRIS, rumah sakit perlu menyiapkan sarana dan prasarana sesuai dengan 12 kriteria kelas rawat inap standar secara bertahap. Apa saja ke-12 kriteria KRIS itu?
Sesuai bunyi Pasal 46A Perpres 59/2024, disyaratkan kriteria fasilitas perawatan dan pelayanan rawat inap KRIS meliputi komponen bangunan yang digunakan tidak boleh memiliki tingkat porositas yang tinggi serta terdapat ventilasi udara dan kelengkapan tidur.
Demikian pula soal pencahayaan ruangan. Perpres itu juga mengatur pencahayaan ruangan buatan mengikuti kriteria standar 250 lux untuk penerangan dan 50 lux untuk pencahayaan tidur, temperature ruangan 20--26 derajat celcius.
Tidak hanya itu, layanan rawat inap berdasarkan perpres itu mensyaratkan fasilitas layanan yang membagi ruang rawat berdasarkan jenis kelamin pasien, anak atau dewasa, serta penyakit infeksi atau noninfeksi.
Selain itu, kriteria lainnya adalah keharusan bagi penyedia layanan untuk mempertimbangkan kepadatan ruang rawat dan kualitas tempat tidur, penyediaan tirai atau partisi antartempat tidur, kamar mandi dalam ruangan rawat inap yang memenuhi standar aksesibilitas, dan menyediakan outlet oksigen.
Selain itu, kelengkapan tempat tidur berupa adanya dua kotak kontak dan nurse call pada setiap tempat tidur dan adanya nakas per tempat tidur. Kepadatan ruang rawat inap maksimal empat tempat tidur dengan jarak antara tepi tempat tidur minimal 1,5 meter.
Tirai/partisi dengan rel dibenamkan menempel di plafon atau menggantung. Kamar mandi dalam ruang rawat inap serta kamar mandi sesuai dengan standar aksesibilitas dan outlet oksigen.
Azhar menjamin, Kemenkes akan menjalankan hal tersebut sesuai dengan tupoksi yang ada. “Tentu saja kami akan bekerja sama dengan BPJS Kesehatan dalam implementasi dan pengawasannya di lapangan,” ujar Azhar.
Berkaitan dengan perpres jaminan kesehatan itu, Direktur Utama BPJS Kesehatan Ghufron Mukti menilai, perpres tersebut berorientasi pada penyeragaman kelas rawat inap yang mengacu pada 12 kriteria. "Bahwa perawatan ada kelas rawat inap standar dengan 12 kriteria, untuk peserta BPJS, maka sebagaimana sumpah dokter tidak boleh dibedakan pemberian pelayan medis atas dasar suku, agama, status sosial atau beda iurannya," ujarnya.
Jika ada peserta ingin dirawat pada kelas yang lebih tinggi, kata Ghufron, maka diperbolehkan selama hal itu dipengaruhi situasi nonmedis. Hal itu disebutkan dalam Pasal 51 Perpres Jaminan Kesehatan diatur ketentuan naik kelas perawatan.
Menurut pasal tersebut, naik kelas perawatan dilakukan dengan cara mengikuti asuransi kesehatan tambahan atau membayar selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya yang harus dibayar akibat peningkatan pelayanan.
Selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya pelayanan dapat dibayar oleh peserta bersangkutan, pemberi kerja, atau asuransi kesehatan tambahan.
Ghufron Mukti juga mengimbau pengelola rumah sakit tidak mengurangi jumlah tempat tidur perawatan pasien dalam upaya memenuhi kriteria KRIS. "Pesan saya jangan dikurangi akses dengan mengurangi jumlah tempat tidur. Pertahankan jumlah tempat tidur dan penuhi persyaratannya dengan 12 kriteria tersebut," tegas Ghufron.
Penulis: Firman Hidranto Redaktur: Ratna Nuraini/Elvira Inda Sari Sumber: Indonesia.go.id
-
 @ 266815e0:6cd408a5
2024-05-09 17:23:28
@ 266815e0:6cd408a5
2024-05-09 17:23:28Lot of people are starting to talk about building a web-of-trust and how nostr can or is already being used as such
We all know about using the kind:3 following lists as a simple WoT that can be used to filter out spam. but as we all know it does not really signal "trust", its mostly just "I find your content interesting"
But what about real "trust"... well its kind of multi-denominational, I could trust that your a good developer or a good journalist but still not trust you enough to invite you over to my house. There are some interesting and clever solutions proposed for quantifying "trust" in a digital sense but I'm not going to get into that here. I want to talk about something that I have not see anyone discuss yet.
How is the web-of-trust maintained? or more precisely how do you expect users to update the digital representation of the "trust" of other users?
Its all well and good to think of how a user would create that "trust" of another user when discovering them for the first time. They would click the "follow" button, or maybe even rate them on a few topics with a 1/5 star system But how will a user remove that trust? how will they update it if things change and they trust them less?
If our goal is to model "trust" in a digital sense then we NEED a way for the data to stay up-to-date and as accurate as possible. otherwise whats the use? If we don't have a friction-less way to update or remove the digital representation of "trust" then we will end up with a WoT that continuously grows and everyone is rated 10/10
In the case of nostr kind:3 following lists. its pretty easy to see how these would get updated. If someone posts something I dislike or I notice I'm getting board of their content. then I just unfollow them. An important part here is that I'm not thinking "I should update my trust score of this user" but instead "I'm no longer interested, I don't want to see this anymore"
But that is probably the easiest "trust" to update. because most of us on social media spend some time curating our feed and we are used to doing it. But what about the more obscure "trust" scores? whats the regular mechanism by which a user would update the "honestly" score of another user?
In the real world its easy, when I stop trusting someone I simply stop associating with them. there isn't any button or switch I need to update. I simply don't talk to them anymore, its friction-less But in the digital realm I would have to remove or update that trust. in other words its an action I need to take instead of an action I'm not doing. and actions take energy.
So how do we reflect something in the digital world that takes no-energy and is almost subconscious in the real world?
TLDR; webs-of-trust are not just about scoring other users once. you must keep the score up-to-date
-
 @ 266815e0:6cd408a5
2024-04-22 22:20:47
@ 266815e0:6cd408a5
2024-04-22 22:20:47While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent
I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS
There were a few things I learned from all these conversations:
- All the existing solutions have one thing in common. A universal ID of some kind for files
- HTTP is still good. we don't have to throw the baby out with the bath water
- nostr could fix this... somehow
Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...
An Identity system
An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files
This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)
What is blossom?
Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id
What are Blobs?
blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names
Instead blobs have a sha256 hash (like
b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553) as an IDThese IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can get a files sha256 hash on linux using:
sha256sum bitcoin.pdf)How do the servers work?
Blossom servers expose four endpoints to let clients and users upload and manage blobs
GET /<sha256>(optional file.ext)PUT /uploadAuthentication: Signed nostr event- Returns a blob descriptor
GET /list/<pubkey>- Returns an array of blob descriptors
Authentication(optional): Signed nostr eventDELETE /<sha256>Authentication: Signed nostr event
What is Blossom Drive?
Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs
What are Drives
Drives are just nostr events (kind
30563) that store a map of blobs and what filename they should have along with some extra metadataAn example drive event would be
json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at
If your interested, the full event definition is at github.com/hzrd149/blossom-drive
Getting started
Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started
1. Open the app
Open https://blossom.hzrd149.com
2. Login using extension

You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an
ncryptsecpassword protected private key - ansecunprotected private key (please don't) - bunker:// URI from nsecbunker3. Add a blossom server

Right now
https://cdn.satellite.earthis the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript github.com/hzrd149/blossom-server4. Start uploading your files
NOTE: All files upload to blossom drive are public by default. DO NOT upload private files

5. Manage files

Encrypted drives
There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify

Whats next?
I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything
also all the images in this article are stored in one of my blossom drives here
nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ 8d5ba92c:c6c3ecd5
2025-02-12 09:48:19
@ 8d5ba92c:c6c3ecd5
2025-02-12 09:48:19Keeping up with everything happening in Bitcoin isn’t easy, even if you’ve been around for a while. The pace is relentless: stream of events, discussions, projects, and updates, not to mention the noise on social media...
One of the most efficient options to expand your knowledge and truly connect with people actively working in the space is through direct interactions, whether they’re happening at large conferences or smaller, semi-official meetups. But let’s be honest: finding all meaningful events can be a mess.
Take, for example, the ''BTC Events Map,’ which already lists over 550 Bitcoin-only gatherings worldwide. This simple but very useful resource, put together by Satlantis, can help many of us plan our trips throughout the year. However, if you don’t know about its existence and rely solely on a search engine—whether Google or Brave—you’ll likely end up frustrated (and unfortunately missing many great opportunities to meet with others and learn).
Search for '[bitcoin events],' and you’ll get a mix of irrelevant crypto, fintech, and Web3 results, with Bitcoin-related stuff buried somewhere in the middle, if at all.. Well, it’s really tough to find what you’re actually looking for.
That’s why word of mouth and trusted communities are so important. Sometimes, the best way to hear about an event is directly from people you know.
One of those that flew under my radar was SatsNFacts. It wasn’t listed on many typical event aggregators or any big news-promo sites. It mostly spread peer-to-peer and through the main channels on Nostr.
I was ‘lucky’ enough to hear about it just in time to plan the trip from Europe to Thailand. Now, I’d like to briefly share my experience with you—everything that, in my opinion, made this event truly stand out.
A Journey to Southeast Asia...
Approximately 10,176 kilometers, 14 hours of travel, and finally three days spent at SatsNFacts—"Thailand’s first Bitcoin Technical Unconference”.
The event ran from February 8 to 10 in Chiang Mai (the largest city in northern Thailand). Held at Weave Artisan Society, a 700 sq.m venue that used to be an ice factory, it smoothly combined pleasant outdoors with an industrial-style, two-floor indoor area, creating a unique and very practical setup.
Where Builders and Artists Collide
While its was billed as a “Technical Unconference,” in practice it nicely connected the developer-based ecosystem with different aspects of culture and art.
Each day, from 10 am to 6 pm, the agenda—shaped directly by attendees—was packed with various presentations, group chats, learning session, hackathons, and actionable workshops.
With many options available (around 10-20 topics per day), I couldn’t attend everything, but here are a few more technical sessions I joined and found especially worthwhile:
- Liana Workshop (long-term security, recovery, and inheritance),
- TollGates (streaming sats for internet access),
- Open Vault (enterprise wallet interface),
- Yaki Honne (decentralized media),
- Nostr Proxies (Epoxy, WebSocket and relay monetization).
- Silent payments (simplified payment experiences without compromising privacy).
As mentioned earlier, SatsNFacts wasn’t just about Bitcoin tech. Some topics focused on community aspects as well. Two discussions I joined highlighted Bitcoin adoption ⚡ in for example Bali and Thailand, showing how sound money, integrity, and consistent work can solve real problems in these regions. Impressive stuff! Here you can learn more:
- HuaiPhueng on Geyser + "Bitcoin City" (their short video ).
- Bitcoin Indonesia & Bitcoin House Bali (all in one on GitHub )
Now, the art gallery, to continue with less technical aspects of SatsNFacts 🎨
This nicely-organized space located on the ground floor, near cozy coworking and networking spots, was for me a real gem. Indeed, adding a creative vibe to the entire event.
Around 30 unique works from local and international artists were on display, all inspired by themes of freedom and privacy. Though I don’t see myself as a typical 'artist', I was honored to have some of my own pieces exhibited there as well (a short video 👇).
One of the highlights was meeting local Thai artists, especially Siritravelsketch, who travelled six hours by train just one way to attend two days of the event.
Her stunning paintings, created using just a bamboo stick and ink, are deeply inspired by Thai architecture and culture. While some of her pre-prepared pieces hung in the gallery, she also painted a few new works on the spot during her visit.
Truly spectacular!

I also had the chance to reconnect with Satoshi Builds, who made many great sketches during this event, and with BitPopArt, a Dutch artist who, just like me, chosen a nomadic lifestyle yet has been clearly considering Thailand his 'second home' as well for several years now. By the way, ✍️ here's his short summary of the event, focusing more on the artistic side of SatsNFacts: "Art exhibition in Chiang Mai ".
All in all, spending my time in many meaningful conversations and seeing so many deep artworks in one place filled me with hope and positive energy. THANK YOU, EVERYONE!
https://v.nostr.build/Fy7J510ZaNyMktIX.mp4
(*** presented artworks by for example: Agi Choote, Samhain, Zed Erwan, Existing Sprinkles, AZA 21m , BitPopArt .)
Mr. Rabbit in Thailand...
Monday, the final evening, and SatsNFacts got one more item on its agenda rooted in creative expression and independent art.
Representing Bitcoin FilmFest (a grassroots project created by an amazing group of freedom fighters and activists 🐇🧡), since I was the only one from our team in Thailand, in one of the rooms upstairs, I put together a mini cinematic experience.
Seven trailers and eleven shorts, including for example:
-
NO MORE INFLATION, HUMMINGBIRD, PARALLEL SPACE, UNBANKABLE, THE LEGEND OF LANDI (🎬 some of the trailers).
-
BITCOIN A NEW HOPE, SATOSHI NAKAMOTO - THE CREATOR OF BITCOIN, MAXIS CLUB SHOW - CHAPTER ONE, THE GREATEST HEIST IN HISTORY, HODL, THE ANATOMY OF BITCOIN – GENESIS BLOCK (📺 some of the presented shorts)
With around 10-15 participants, the response was positive, and we ended up spending an extra 10-maybe-20 minutes discussing the challenges and opportunities in Bitcoin-powered filmmaking, as well as the upcoming edition of BFF25 (the annual festival we're organizing this May in Warsaw, Poland).
https://i.nostr.build/RE3mKJacw5vB23V6.png
Substance Over Hype.
SatsNFacts made a solid reminder that Bitcoin events can help build a truly sovereign future while bringing together developers and artistic souls alike.
The mix of technical depth and creative energy—free from the shiny gossip that floods many social channels—made it a truly meaningful experience.
SatsNFacts set a high standard, and I hope to see more events like it in the future. More unconferences, more cultural and community-driven gatherings.
Here's to more signal, less noise!!!
Big congrats to everyone who made the first SatsNFacts happen 👏 Respect especially to the organizers! You pulled off something truly special!
BTC Your Mind. Let it Beat.... Şela
-
 @ 57d1a264:69f1fee1
2025-02-12 09:32:53
@ 57d1a264:69f1fee1
2025-02-12 09:32:53 -
 @ 0fe1a615:c70a7ba5
2025-02-12 09:22:11
@ 0fe1a615:c70a7ba5
2025-02-12 09:22:11华为手表3000多元,其中的血压计功能可能只占不到300元左右。如果用医保个人账户全额购买华为手表,似乎不太妥当。 如果产品可以通过花费极少的成本,来增加某项医疗功能,从而实现医保报销。这就相当于打开了一个口子,那么以后很多测心率的产品是否也都可以医保报销呢? 举个简单的例子,比如可乐。轻度低血糖病人在中午时,喝几口可乐,可以有效缓解低血糖症状。那以后可不可以用医保个人账户报销可乐呢? 网上有些人提到医保个人账户的资金,是自己的,可以购买华为手表,可以自由支配。鄙以为不然。保险的本来意义在于大家集资救助那些需要大额资金救助的人群,而不是给自己用的。按照上述观点,那么企业给你交的社保,不是也应该算到个人账户吗?其实可以这么理解,现在将个人账户和统筹账户分开,只是医保的一个过渡阶段,按照理论上来讲,以后应该是只需要统筹账户来实现全民共济,而不应该存在个人账户。 如果医保可以全额购买智能手表,这么自由的话,其实个人根本没必要交钱到医保个人账户,而只需要企业交到统筹即可。 故我认为,医保目录为智能手表开口子,实在是荒唐至极,此举既假公济私,又动摇了医保共济的根基,实在不可取。 因此,我建议,就算想照顾到国内企业,提振销量,可以设定报销比例。比如智能手表的血压功能只能占到300元,与市面上血压计价格差不多,那么医保就只能报销300元。再比如可乐含糖成分有效缓解低血糖,那么可以按照糖分比例,可能只有几角钱或者更低,来进行报销。 望三思而行。
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 21a37315:affe6e25
2025-02-12 07:55:24
@ 21a37315:affe6e25
2025-02-12 07:55:24Bond Back Guarantee Cleaning: Get Your Full Deposit Back with Ease!
Moving out of a rental property can be stressful, especially when it comes to ensuring you get your bond back. One of the biggest reasons tenants lose part of their deposit is due to cleaning issues. That’s where Bond Back Guarantee Cleaning comes in—offering a hassle-free solution to meet the landlord’s expectations and secure your deposit.
What is Bond Back Guarantee Cleaning? Bond back cleaning is a professional deep-cleaning service that ensures your rental property meets the cleanliness standards required by landlords or property managers. A bond back guarantee means the cleaning service is so thorough that if the landlord is not satisfied, the company will return to fix any issues at no extra cost.
Why is Bond Cleaning Important? When vacating a rental, your bond (security deposit) is held by the landlord or real estate agency. If the property is not returned in the same condition as when you moved in (excluding normal wear and tear), deductions will be made from your bond. A professional bond cleaning service helps prevent this by covering all essential areas:
✅ Deep carpet and floor cleaning ✅ Kitchen degreasing and appliance cleaning ✅ Bathroom scrubbing and sanitization ✅ Wall and skirting board washing ✅ Window and glass polishing ✅ Dusting and cobweb removal
Benefits of Hiring a Bond Back Guarantee Cleaning Service 100% Bond Refund Assurance – With a guarantee, you can be confident that your cleaning meets the required standards. Time & Stress Saver – Moving is already a big task; let professionals handle the cleaning. Meets Real Estate Requirements – Experts know what property managers look for in an exit clean. Affordable & Cost-Effective – Losing your bond can cost more than hiring a cleaning service. How to Choose the Right Bond Back Cleaning Service? ✔️ Check for a written bond back guarantee ✔️ Look for customer reviews and ratings ✔️ Ensure they cover a full checklist of cleaning tasks ✔️ Ask about their re-cleaning policy Final Thoughts A Bond Back Guarantee Cleaning service is an investment in peace of mind. With professionals ensuring your rental is spotless, you can move out stress-free, knowing your full bond refund is secured.
Need reliable bond cleaning? Contact us today for a guaranteed spotless exit!
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ d360efec:14907b5f
2025-02-12 07:37:43
@ d360efec:14907b5f
2025-02-12 07:37:43

Bitcoin (BTCUSDT) กำลังอยู่ในช่วงหัวเลี้ยวหัวต่อ แม้ว่าแนวโน้มหลักในระยะกลางถึงยาว (TF Day & 4H) จะยังคงเป็นขาขึ้นที่แข็งแกร่ง แต่ในระยะสั้นมาก (TF15) กลับแสดงสัญญาณของความอ่อนแอและการปรับฐานลงมาอย่างรวดเร็ว
แนวโน้ม: * TF Day: ขาขึ้น (Uptrend) แข็งแกร่ง – ราคาอยู่เหนือ EMA 50 และ EMA 200, โครงสร้างราคาเป็น Higher Highs (HH) และ Higher Lows (HL) อย่างต่อเนื่อง * TF4H: ขาขึ้น (Uptrend) ชัดเจน – ราคาอยู่เหนือ EMA, มีการพักตัวลงมา (Pullback) แต่ยังไม่เสียโครงสร้างขาขึ้น * TF15: ขาลง (Downtrend) ระยะสั้นมาก – ราคาหลุด EMA และแนวรับย่อย, โครงสร้างราคาเริ่มเป็น Lower Highs (LH) และ Lower Lows (LL)
โครงสร้างราคา (SMC): * TF Day: ยืนยันแนวโน้มขาขึ้น (HH, HL, BOS) * TF4H: ยืนยันแนวโน้มขาขึ้น (HH, HL, BOS), มี Equal Highs (EQH) ที่เป็นแนวต้าน * TF15: บ่งบอกถึงแนวโน้มขาลงระยะสั้น (BOS ด้านล่าง, LH, LL), มี EQH เป็นแนวต้าน
Money Flow (LuxAlgo): * TF Day: Money Flow: โดยรวมเป็นสีเขียว แสดงถึงแรงซื้อที่ยังคงมีอิทธิพลเหนือกว่า แต่ก็มีแท่งสีแดงแทรกบ้าง บ่งบอกถึงการขายทำกำไรในบางช่วง * TF4H: Money Flow: โดยรวมเป็นสีเขียว แต่เริ่มมีแท่งสีเขียวสั้นลง และมีแท่งสีแดงยาวขึ้น แสดงว่าแรงซื้อเริ่มอ่อนแรงลง และมีแรงขายเข้ามา * TF15: Money Flow: สีแดงมีอิทธิพลเหนือกว่าสีเขียวอย่างชัดเจน และแท่งสีแดงค่อนข้างยาว แสดงถึงแรงขายที่แข็งแกร่ง
EMA (Exponential Moving Average): * TF Day & 4H: EMA 50 & 200 เป็นแนวรับสำคัญ * TF15: EMA 50 & 200 กลายเป็นแนวต้าน หลังจากราคาหลุดลงมา
แนวรับ-แนวต้านสำคัญ: | Timeframe | แนวรับ | แนวต้าน | |---|---|---| | Day | EMA 50, EMA 200, บริเวณ 96,000-98,000 (Volume Profile), 85,724.7 | 109,998.9 (High เดิม) | | 4H | EMA 50, EMA 200, บริเวณ 96,000-98,000 (Volume Profile, Equilibrium), 89,037.0 | 109,998.9 (EQH, High เดิม) | | 15m | 95,200 (Low ล่าสุด), 94,707.4 (Low ก่อนหน้า) | EMA 50, EMA 200, บริเวณ 96,000, 96,807.8, 97,000-97,200 |
กลยุทธ์ (BTCUSDT): * Wait & See (ทางเลือกที่ดีที่สุดในตอนนี้): * เนื่องจาก TF15 ขัดแย้งกับ TF Day & 4H อย่างชัดเจน การ "รอ" ให้ตลาดเฉลยทิศทางที่ชัดเจนกว่านี้ เป็นทางเลือกที่ปลอดภัยที่สุด * สังเกตพฤติกรรมราคา (Price Action) บริเวณแนวรับ-แนวต้านใน TF15 * Buy on Dip (Day, 4H) - ต้องระมัดระวังอย่างสูง: * สำหรับนักลงทุนระยะกลาง-ยาว ที่เชื่อมั่นในแนวโน้มขาขึ้น * เงื่อนไข: ต้องรอสัญญาณการกลับตัวของราคาใน TF15 ก่อน เช่น * การ Breakout แนวต้านย่อยๆ พร้อม Volume * การเปลี่ยน Money Flow (LuxAlgo) เป็นสีเขียว (ถ้ามี) * การเกิด Bullish Candlestick Patterns * จุดเข้า: บริเวณ EMA 50/200 ของ TF Day หรือ 4H, หรือบริเวณแนวรับอื่นๆ ที่มีนัยสำคัญ * Stop Loss: ต่ำกว่า Low ล่าสุดของ TF15 หรือต่ำกว่าแนวรับที่เข้าซื้อ * Short (15, ความเสี่ยงสูงมาก): * สำหรับนักเก็งกำไรระยะสั้น ที่รับความเสี่ยงได้สูง * เงื่อนไข: ราคาไม่สามารถกลับขึ้นไปยืนเหนือ EMA ของ TF15 ได้ * จุดเข้า: บริเวณ EMA ของ TF15 หรือแนวต้านอื่นๆ * Stop Loss: เหนือ High ล่าสุดของ TF15 หรือเหนือแนวต้านที่เข้า Short
คำแนะนำ: * ความขัดแย้งของ Timeframes: การที่ TF15 ขัดแย้งกับ TF Day & 4H เป็นสิ่งที่ต้องระวังอย่างมาก * Volume: การ Breakout หรือ Breakdown ใดๆ ควรมี Volume สนับสนุน เพื่อยืนยันความน่าเชื่อถือ * Risk Management: สำคัญที่สุด ไม่ว่าจะเลือกกลยุทธ์ใด ต้องมีการบริหารความเสี่ยงที่ดี (ตั้ง Stop Loss, ไม่ Overtrade) * ข่าวสาร: ติดตามข่าวสารที่อาจส่งผลกระทบต่อราคา Bitcoin
สรุป: สถานการณ์ของ BTCUSDT ตอนนี้ค่อนข้างซับซ้อนและมีความเสี่ยงสูง การ "รอ" อาจเป็นทางเลือกที่ดีที่สุดสำหรับนักลงทุนส่วนใหญ่ จนกว่าจะเห็นสัญญาณที่ชัดเจนมากขึ้นค่ะ
Disclaimer: การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ dd664d5e:5633d319
2025-02-12 07:05:51
@ dd664d5e:5633d319
2025-02-12 07:05:51I think this note from Chip (nostr:npub1qdjn8j4gwgmkj3k5un775nq6q3q7mguv5tvajstmkdsqdja2havq03fqm7) is one of those things that people with business management experience take a lot more seriously than most developers and influencers do.
I am painfully aware of the cost of systems administration, financial transaction management and recordkeeping, recruiting and personnel management, legal and compliance, requirements management, technical support, renting and managing physical spaces and infrastructure, negotiating with suppliers, customer service, etc. etc.
There's this idea, on Nostr, that sort of trickled in along with Bitcoin Twitter, that we would all just be isolated subsistance farmers and one-man-show podcasters with a gigantic server rack in the basement. But some of us are running real companies -- on and off Nostr, for-profit and non-profit -- and it often requires a lot of human labor.
The things we build aren't meant to be used by one person and his girlfriend and his dog. Yes, he can also run all these things, himself, but he no longer has to. Our existence gives him the choice: run these things or pay us to run them and spend your time doing something else, that you do better than we do.
These things are meant to be used by hundreds... thousands... eventually millions of people. The workflows, processes, infrastructure, and personnel need to be able to scale up-and-down, scale in-and-out, work smoothly with 5 people or 50 people. These are the sort of Nostr systems that wouldn't collapse when encountering a sudden influx or mass-escape. But these systems are much more complex and they take time to build and staff to run them. (And, no, AI can't replace them all. AI means that they now also have to integrate a bunch of AI into the system and maintain that, too.)
GitCitadel (nostr:npub1s3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqd975wz) is very automation-forward, but we still have to front the incredibly high cost of designing and building the automation, train people to interact with it (there are now over 20 people integrated into the workflow!), adjust it based upon their feedback, and we have to support the automation, once it's running.
This sort of streamlined machine is what people pay companies for, not code. That is why there's little business cost to open source.
Open-source is great, but...

nostr:nevent1qqsgqh2dedhagyd9k8yfk2lagswjl7y627k9fpnq4l436ccmlys0s3qprdmhxue69uhhg6r9vehhyetnwshxummnw3erztnrdakj7q3qqdjn8j4gwgmkj3k5un775nq6q3q7mguv5tvajstmkdsqdja2havqxpqqqqqqzdhnyjm
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ da0b9bc3:4e30a4a9
2025-02-12 06:27:16
@ da0b9bc3:4e30a4a9
2025-02-12 06:27:16Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/883472
-
 @ 502ab02a:a2860397
2025-02-12 05:53:52
@ 502ab02a:a2860397
2025-02-12 05:53:52เนื่องด้วยทางสมาคมเบาหวานแห่งประเทศไทยฯ ได้มีการผลิตหนังสือ หลักการและแนวปฏิบัติเพื่อการดูแลโรคเบาหวานให้เข้าสู่ระยะสงบ ฉบับพิมพ์ครั้งแรก 1 มีนาคม 2568 ออกมาเป็นที่เรียบร้อยครับ และได้มีการจัดทำในรูปแบบ ebook เอาไว้ด้วย โหลดได้ตาม link ด้านล่างนี้ครับ
https://siripun.com/wp-content/uploads/2025/02/2025-2-12-Diabetes-Remission-in-Thailand.pdf
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ d2e97f73:ea9a4d1b
2023-04-11 19:36:53
@ d2e97f73:ea9a4d1b
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 57d1a264:69f1fee1
2025-02-12 05:31:13
@ 57d1a264:69f1fee1
2025-02-12 05:31:13 -
 @ d360efec:14907b5f
2025-02-12 05:26:39
@ d360efec:14907b5f
2025-02-12 05:26:39ภาพรวม LUNCUSDT (OKX):
LUNCUSDT กำลังพยายามฟื้นตัวจากแนวโน้มขาลงระยะยาว แต่ยังคงมีความผันผวนและมีความเสี่ยงสูง แนวโน้มระยะกลางถึงยาว (TF Day & 4H) เริ่มมีสัญญาณบวกของการกลับตัวเป็นขาขึ้น (Early Uptrend) หลังจากราคา Breakout EMA 50 ใน TF Day และเกิด Golden Cross อย่างไรก็ตาม ในระยะสั้นมาก (TF15) กลับแสดงถึงความอ่อนแอและมีการปรับฐานลงมา


แนวโน้ม:
- TF Day: เริ่มเป็นขาขึ้น (Early Uptrend) – ราคา Breakout EMA 50 และเกิด Golden Cross, Money Flow เป็นบวก
- TF4H: เริ่มเป็นขาขึ้น (Early Uptrend) – ราคา Breakout EMA 50, มีการพักตัวลงมาทดสอบ EMA 50, Money Flow เริ่มไม่แน่นอน
- TF15: แกว่งตัวออกข้าง (Sideways) หลังจากร่วงลง – ราคาอยู่ใต้ EMA, โครงสร้างราคาเป็น Lower Highs/Lows, Money Flow เป็นลบ
โครงสร้างราคา (SMC):
- TF Day: มี Break of Structure (BOS) ด้านบน, เริ่มเห็น Higher Highs (HH) และ Higher Lows (HL)
- TF4H: มี BOS ด้านบน, เริ่มเห็น HH/HL (แต่ไม่ชัดเจน), มี Equal Highs (EQH) และ Equal Lows (EQL)
- TF15: มี BOS ด้านล่าง, มี Change of Character (CHoCH) ทั้งบนและล่าง, เริ่มเห็น Lower Highs (LH) และ Lower Lows (LL)
Money Flow (LuxAlgo):
- TF Day: แรงซื้อแข็งแกร่ง (ไม่มีภาพ แต่จากการวิเคราะห์ก่อนหน้า)
- TF4H: แรงซื้อและแรงขายพอๆ กัน, เริ่มมีแรงขายเข้ามา
- TF15: แรงขายมีมากกว่าแรงซื้อ
EMA (Exponential Moving Average):
- TF Day: EMA 50 & 200 เป็นแนวรับ
- TF4H: EMA 50 เป็นแนวรับที่กำลังถูกทดสอบ, EMA 200 เป็นแนวต้าน
- TF15: EMA 50 & 200 กลายเป็นแนวต้าน
แนวรับ-แนวต้านสำคัญ:
| Timeframe | แนวรับ | แนวต้าน | | :-------- | :------------------------------------------------------------------------ | :------------------------------------------------------------------------------------------- | | Day | EMA 50 (0.00010000), EMA 200 (0.00008000), 0.00006000-0.00007000 | 0.00017953 (High ล่าสุด), 0.00014000 (Volume Profile) | | 4H | EMA 50 (ประมาณ 0.00007000), 0.00006000-0.00007000, Equilibrium | EMA 200 (0.00008000), 0.00008132, 0.00010000-0.00012000 (EQH) | | 15m | 0.00007300 (EQL, Volume Profile) | EMA 50, EMA 200, 0.00007531 (EQH), 0.00007636 (EQH, High ก่อนหน้า) |
กลยุทธ์ (LUNCUSDT):
- Wait & See (ทางเลือกที่ดีที่สุด):
- เนื่องจาก TF15 ขัดแย้งกับ TF Day & 4H และ TF4H ก็เริ่มแสดงสัญญาณอ่อนแรง การ "รอ" ให้ตลาดแสดงทิศทางที่ชัดเจนกว่านี้ จะเป็นทางเลือกที่ปลอดภัยที่สุด
- สังเกตพฤติกรรมราคา (Price Action) บริเวณแนวรับ-แนวต้านใน TF15 และ TF4H
- Buy on Dip (Day, 4H) - ความเสี่ยงสูงมาก ต้องระมัดระวังเป็นพิเศษ:
- สำหรับนักลงทุนระยะกลาง-ยาว ที่เชื่อมั่นในการกลับตัวของ LUNC (แต่ต้องยอมรับความเสี่ยงได้สูงมาก)
- เงื่อนไข: ต้องรอสัญญาณการกลับตัวของราคาใน TF15 ก่อน เช่น
- การ Breakout แนวต้านย่อยๆ พร้อม Volume
- การเปลี่ยน Money Flow (LuxAlgo) เป็นสีเขียว
- การเกิด Bullish Candlestick Patterns
- จุดเข้า (Day): EMA 50 (0.00010000), EMA 200 (0.00008000) ต้องดู TF15 ประกอบ
- จุดเข้า (4H): EMA 50 (ประมาณ 0.00007000) ต้องดู TF15 ประกอบ
- Stop Loss: ต่ำกว่า Low ล่าสุดของ TF15 หรือต่ำกว่าแนวรับที่เข้าซื้อ
- Short (15, ความเสี่ยงสูงมาก):
- สำหรับนักเก็งกำไรระยะสั้น ที่รับความเสี่ยงได้สูงมาก
- เงื่อนไข: ราคาไม่สามารถกลับขึ้นไปยืนเหนือ EMA ของ TF15 ได้
- จุดเข้า: บริเวณ EMA ของ TF15 หรือแนวต้านอื่นๆ
- Stop Loss: เหนือ High ล่าสุดของ TF15 หรือเหนือแนวต้านที่เข้า Short
คำแนะนำ (เน้นย้ำ):
- ความขัดแย้งของ Timeframes: สถานการณ์ของ LUNCUSDT ตอนนี้มีความขัดแย้งกันสูงมากระหว่าง Timeframes และมีความเสี่ยงสูงกว่า XRP และ BTC
- Money Flow: Money Flow ใน TF15 เป็นลบ และใน TF4H ก็เริ่มไม่แน่นอน
- LUNC เป็นเหรียญ High Risk: มีความผันผวนสูงมาก และอาจมีการเปลี่ยนแปลงอย่างรวดเร็ว
- ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด: รอสัญญาณที่ชัดเจนกว่านี้ หรือเลือกเทรดเหรียญอื่นที่มีความเสี่ยงน้อยกว่า
- Risk Management: สำคัญที่สุด ไม่ว่าจะเลือกกลยุทธ์ใด ต้องมีการบริหารความเสี่ยงที่ดี (ตั้ง Stop Loss, ไม่ Overtrade, กระจายความเสี่ยง)
สรุป: LUNCUSDT กำลังอยู่ในช่วงเวลาที่ยากลำบากและมีความเสี่ยงสูงมาก การตัดสินใจที่ผิดพลาดอาจนำไปสู่การขาดทุนได้ ควรพิจารณาอย่างรอบคอบก่อนเข้าเทรดทุกครั้ง และ "รอ" อาจเป็นทางเลือกที่ดีที่สุดสำหรับนักลงทุนส่วนใหญ่ค่ะ
Disclaimer: การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
-
 @ 16d11430:61640947
2025-02-12 04:41:43
@ 16d11430:61640947
2025-02-12 04:41:43In the world of monetary systems, there exists a fundamental divide: Bitcoin, rooted in thermodynamic energy expenditure, and fiat, which is conjured into existence without cost. This contrast is not merely economic but thermodynamic and absolute, and it exposes why fiat cannot compete with Bitcoin in the long run.
Fiat is an illusion, a monetary system unbacked by real work, while Bitcoin is a pure manifestation of the first law of thermodynamics—an asset where value is directly tied to the energy required to produce it. The battle between fiat and Bitcoin is thus not just one of finance but one of physics, where only one system is bound by the immutable laws of energy conservation, entropy, and work.
- The First Law of Thermodynamics: Fiat Violates Conservation of Energy
The first law of thermodynamics states that energy cannot be created or destroyed, only transformed.
Bitcoin respects this law: Every single Bitcoin that exists was mined through proof-of-work, meaning that its existence required real-world energy expenditure. The hash power securing Bitcoin is derived from electricity converted into computational work, which is then permanently recorded on an immutable ledger.
Fiat violates this law: Central banks create fiat money out of nothing. There is no energy backing it, no transformation of work into value—only arbitrary decree (hence the term "fiat"). Governments increase the supply at will, diluting purchasing power without consuming energy.
By ignoring the fundamental rule of energy conservation, fiat is not a real asset—it is a transient system of control masquerading as money.
- The Second Law of Thermodynamics: Fiat Is a High-Entropy System
The second law of thermodynamics states that entropy (disorder) in a system always increases unless energy is applied to maintain order.
Bitcoin is a low-entropy system: Its supply is mathematically fixed at 21 million coins, and mining difficulty adjusts dynamically, ensuring that equilibrium is maintained. No single actor can distort the system without expending equivalent energy. The network remains in a steady state of thermodynamic balance.
Fiat is a high-entropy system: Governments print money without work, inflating the supply and injecting systemic disorder into the economy. This inflation acts as monetary heat death, where the increasing supply dissipates value across holders while concentrating purchasing power in those who print it. Fiat money is in a constant state of decay, requiring increasing levels of control (interest rate manipulation, debt issuance, taxation) just to delay collapse.
As entropy increases, fiat systems require exponentially more intervention to function, but Bitcoin remains in a natural thermodynamic equilibrium, immune to external interference.
- Proof-of-Work vs. Proof-of-Authority: Energy vs. Deception
In physics, all work requires energy. Any system that attempts to extract value without work is an illusion. Bitcoin and fiat represent these two competing paradigms:
Bitcoin = Proof of Work: Every coin is mined through energy expenditure. Value is tied to the energy needed to produce it. No energy, no Bitcoin. It is the only monetary system in human history that ties value to thermodynamic reality.
Fiat = Proof of Authority: Money is created by decree, without cost. A handful of central planners determine supply, creating purchasing power without exerting work. Fiat is a perpetual thermodynamic imbalance, kept afloat only by coercion.
The two systems cannot coexist indefinitely because one follows the laws of physics while the other fights against them. Fiat’s reliance on arbitrary issuance is unsustainable, whereas Bitcoin, bound by the laws of energy, will persist.
- The Cost of Securing the System: Bitcoin vs. Fiat Enforcement
All monetary systems require energy to maintain security and function. Here’s how Bitcoin and fiat compare:
Bitcoin’s security budget = Thermodynamic work
Mining requires energy input.
Network security grows as more work is performed.
The system self-regulates through difficulty adjustments.
No external authority is required.
Fiat’s security budget = Bureaucracy, coercion, and war
Central banks manipulate money supply.
Governments enforce fiat’s value through taxation and legal mandates.
Military and police power are needed to uphold fiat supremacy.
The cost of maintaining fiat rises exponentially as the system destabilizes.
Bitcoin is secured by laws of physics, while fiat is secured by laws of men, enforced through control structures that demand increasingly inefficient energy expenditure. In the long run, this makes fiat unsustainable, as no amount of coercion can outmatch the absolute authority of thermodynamic principles.
- The Final Thermodynamic Death of Fiat
Fiat is trapped in a paradox:
-
Printing money (entropy injection) devalues it, requiring further interventions to maintain purchasing power.
-
Raising interest rates or reducing money supply (attempting order) leads to economic contraction, creating social instability.
-
Fiat collapses when the cost of enforcing order exceeds the energy available to maintain it.
Bitcoin has no such issue. Its value is rooted in absolute energy conservation and cannot be manipulated without equivalent work.
As fiat systems degrade, they will require exponentially increasing amounts of energy to sustain themselves—energy they do not have. Bitcoin, on the other hand, will continue its natural thermodynamic process: converting energy into an immutable store of value.
Conclusion: The Laws of Physics Are Final
Fiat’s fate is sealed because it is in conflict with the fundamental laws of thermodynamics:
-
It violates energy conservation by printing money from nothing.
-
It succumbs to entropy by requiring more intervention as disorder grows.
-
It lacks a proof-of-work foundation, meaning its value is arbitrary.
-
Its security model is based on force, which demands increasing energy inputs.
Bitcoin, by contrast, is aligned perfectly with energy conservation and entropy minimization. It is a low-entropy monetary system that cannot be inflated, corrupted, or debased. It is the thermodynamic apex of monetary evolution.
Fiat is an unstable system destined to fail because it defies the laws of physics. Bitcoin is the natural state of money because it follows them. The contest is not one of ideology but of reality—fiat will collapse, and Bitcoin will remain, as dictated by the immutable laws of thermodynamics.
-
 @ d360efec:14907b5f
2025-02-12 04:39:09
@ d360efec:14907b5f
2025-02-12 04:39:09ภาพรวม XRPUSDT :
XRPUSDT กำลังอยู่ในช่วงหัวเลี้ยวหัวต่อ คล้ายกับ BTC แต่มีความอ่อนแอกว่าเล็กน้อย แนวโน้มระยะกลางถึงยาว (TF Day & 4H) เริ่มมีสัญญาณบวกของการเป็นขาขึ้น (Early Uptrend) แต่ในระยะสั้นมาก (TF15) กลับแสดงถึงความอ่อนแอและมีการปรับฐานลงมา


แนวโน้ม:
- TF Day: เริ่มเป็นขาขึ้น (Early Uptrend) – ราคา Breakout EMA 50 ขึ้นมาได้, Money Flow เป็นบวก
- TF4H: เริ่มเป็นขาขึ้น (Early Uptrend) – ราคา Breakout EMA 50, มีการพักตัวลงมาทดสอบ EMA 50, Money Flow เริ่มอ่อนแรง
- TF15: แกว่งตัวลง (Sideways Down) – ราคาหลุด EMA, โครงสร้างราคาเป็น Lower Highs/Lows, Money Flow เป็นลบ
โครงสร้างราคา (SMC):
- TF Day: มี Break of Structure (BOS) ด้านบน, เริ่มเห็น Higher Highs (HH) และ Higher Lows (HL)
- TF4H: มี BOS ด้านบน, เริ่มเห็น HH/HL (แต่ไม่ชัดเจน), มี Equal Highs (EQH) และ Equal Lows (EQL)
- TF15: มี BOS ด้านล่าง, มี Change of Character (CHoCH) ทั้งบนและล่าง, เริ่มเห็น Lower Highs (LH) และ Lower Lows (LL)
Money Flow (LuxAlgo):
- TF Day: แรงซื้อแข็งแกร่ง
- TF4H: แรงซื้อเริ่มอ่อนแรงลง, มีแรงขายเข้ามา
- TF15: แรงขายมีมากกว่าแรงซื้อ
EMA (Exponential Moving Average):
- TF Day: EMA 50 & 200 เป็นแนวรับ
- TF4H: EMA 50 เป็นแนวรับที่กำลังถูกทดสอบ, EMA 200 เป็นแนวรับถัดไป
- TF15: EMA 50 & 200 กลายเป็นแนวต้าน
แนวรับ-แนวต้านสำคัญ:
| Timeframe | แนวรับ | แนวต้าน | | :-------- | :------------------------------------------------------------------------ | :-------------------------------------------------------------------- | | Day | EMA 50 (1.56), EMA 200 (1.08), Low ก่อนหน้า | 2.4450 (High ล่าสุด), 3.00-3.20 (EQH), 3.4049 | | 4H | EMA 50 (ประมาณ 2.20), EMA 200, 2.10-2.20 (EQL), 1.7820 | 2.4427, 2.3987, 3.00-3.20 (EQH), 3.4049 | | 15m | 2.38 (EQL, Volume Profile), 2.3274 | EMA 50, EMA 200, 2.4196, Equilibrium (2.44), 2.44-2.48 (EQH) |
กลยุทธ์ (XRPUSDT):
- Wait & See (ทางเลือกที่ดีที่สุด):
- เนื่องจาก TF15 ขัดแย้งกับ TF Day & 4H อย่างชัดเจน และ TF4H ก็เริ่มแสดงสัญญาณอ่อนแรง การ "รอ" ให้ตลาดแสดงทิศทางที่ชัดเจนกว่านี้ จะเป็นทางเลือกที่ปลอดภัยที่สุด
- สังเกตพฤติกรรมราคา (Price Action) บริเวณแนวรับ-แนวต้านใน TF15 และ TF4H
- Buy on Dip (Day, 4H) - ความเสี่ยงสูงมาก ต้องระมัดระวังเป็นพิเศษ:
- สำหรับนักลงทุนระยะกลาง-ยาว ที่เชื่อมั่นในแนวโน้มขาขึ้น (แต่ต้องยอมรับความเสี่ยงได้สูง)
- เงื่อนไข: ต้องรอสัญญาณการกลับตัวของราคาใน TF15 ก่อน เช่น
- การ Breakout แนวต้านย่อยๆ พร้อม Volume
- การเปลี่ยน Money Flow (LuxAlgo) เป็นสีเขียว
- การเกิด Bullish Candlestick Patterns
- จุดเข้า (Day): EMA 50 (1.56), EMA 200 (1.08) ต้องดู TF15 ประกอบ
- จุดเข้า (4H): EMA 50 (2.20), บริเวณ EQL (2.10-2.20) ต้องดู TF15 ประกอบ
- Stop Loss: ต่ำกว่า Low ล่าสุดของ TF15 หรือต่ำกว่าแนวรับที่เข้าซื้อ
- Short (15, ความเสี่ยงสูงมาก):
- สำหรับนักเก็งกำไรระยะสั้น ที่รับความเสี่ยงได้สูงมาก
- เงื่อนไข: ราคาไม่สามารถกลับขึ้นไปยืนเหนือ EMA ของ TF15 ได้
- จุดเข้า: บริเวณ EMA ของ TF15 หรือแนวต้านอื่นๆ
- Stop Loss: เหนือ High ล่าสุดของ TF15 หรือเหนือแนวต้านที่เข้า Short
คำแนะนำ (เน้นย้ำ):
- ความขัดแย้งของ Timeframes: สถานการณ์ของ XRPUSDT ตอนนี้มีความขัดแย้งกันสูงมากระหว่าง Timeframes
- Money Flow: Money Flow ใน TF15 เป็นลบ และใน TF4H ก็เริ่มอ่อนแรง
- EMA 50 (TF4H): เป็นจุดชี้ชะตา ถ้าหลุด แนวโน้มขาขึ้นระยะกลางอาจเสีย
- ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด: รอสัญญาณที่ชัดเจนกว่านี้ หรือเลือกเทรดเหรียญอื่นที่มีความเสี่ยงน้อยกว่า
สรุป: XRPUSDT กำลังอยู่ในช่วงเวลาที่ยากลำบากและมีความเสี่ยงสูง การตัดสินใจที่ผิดพลาดอาจนำไปสู่การขาดทุนได้ ควรพิจารณาอย่างรอบคอบก่อนเข้าเทรดทุกครั้งค่ะ
Disclaimer: การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
-
 @ d360efec:14907b5f
2025-02-12 03:42:09
@ d360efec:14907b5f
2025-02-12 03:42:09บทที่ 1: การเดินทางของนักเวทย์สาว ข้าคือ อาเรีย นักเวทย์ฝึกหัดผู้เดินทางมาจากดินแดนอันไกลโพ้น ข้าได้ยินเรื่องราวของอาณาจักรไทย ที่ซึ่งมีปัญหาเกี่ยวกับ "แรงงานเงา" ซึ่งเป็นกลุ่มคนจากอีกดินแดนหนึ่งที่เข้ามาทำงานในอาณาจักรแห่งนี้ ข้าตัดสินใจที่จะเดินทางมายังอาณาจักรไทย เพื่อศึกษาเรื่องราวเหล่านี้ และหาทางแก้ไขปัญหา

บทที่ 2: การพบปะกับผู้คน เมื่อข้ามาถึงอาณาจักรไทย ข้าได้พบกับผู้คนมากมาย ทั้งชาวไทยและชาวพม่า ข้าได้ฟังเรื่องราวของพวกเขา ทั้งความยากลำบากในการทำงาน การถูกกดขี่ค่าแรง และความหวังที่จะมีชีวิตที่ดีขึ้น ข้าได้เห็นถึงความขยันและอดทนของพวกเขา แต่ก็มีความขัดแย้งและความเข้าใจผิดเกิดขึ้นระหว่างคนทั้งสองกลุ่ม

บทที่ 3: การไขปริศนา ข้าเริ่มสืบหาความจริงเกี่ยวกับเรื่องราวเหล่านี้ และได้พบว่ามีกลุ่มคนบางกลุ่มที่ต้องการใช้ประโยชน์จากแรงงานเงาม โดยการกดขี่ค่าแรงและแสวงหาผลประโยชน์ ข้ายังได้เรียนรู้ว่าอาณาจักรไทยกำลังเผชิญกับปัญหาการขาดแคลนแรงงาน และจำเป็นต้องพึ่งพาแรงงานเงา

บทที่ 4: การตัดสินใจ ข้าได้คิดทบทวนเรื่องราวทั้งหมด และตัดสินใจที่จะใช้เวทย์มนตร์ของข้า เพื่อช่วยเหลือผู้คนเหล่านั้น ข้าต้องการที่จะสร้างความเข้าใจและความเท่าเทียมกันระหว่างคนทุกกลุ่ม และทำให้อาณาจักรไทยเป็นสถานที่ที่ทุกคนสามารถอยู่ร่วมกันได้อย่างมีความสุข

บทที่ 5: การผจญภัย การเดินทางของข้ายังไม่จบสิ้น ข้ายังคงต้องเผชิญกับอุปสรรคและความท้าทายอีกมากมาย แต่ข้าเชื่อมั่นว่าด้วยความมุ่งมั่นและความพยายามของข้า ข้าจะสามารถสร้างความเปลี่ยนแปลงให้กับอาณาจักรไทยแห่งนี้ได้

บทสรุป
เรื่องราวของอาเรีย นักเวทย์สาวผู้เดินทางมาเพื่อแก้ไขปัญหาแรงงานเงาในอาณาจักรไทย เป็นเรื่องราวที่สะท้อนให้เห็นถึงปัญหาที่เกิดขึ้นในสังคมของเรา การกดขี่ค่าแรง การแบ่งแยกชนชั้น และการแสวงหาผลประโยชน์จากผู้อื่น
เราทุกคนสามารถเป็นเหมือนอาเรียได้ โดยการลุกขึ้นมาต่อสู้เพื่อความถูกต้องและความเท่าเทียมกัน และสร้างสังคมที่ทุกคนสามารถอยู่ร่วมกันได้อย่างมีความสุข
-
 @ d058ffb7:70ed2330
2025-02-12 02:25:09
@ d058ffb7:70ed2330
2025-02-12 02:25:09Afin de profiter de tous les bienfaits du bitcoin, il est recommandé d'en prendre le réel contrôle, qui ese résume à posséder ses propres clés privés. Pour se faire, on doit utilise un portefeuille bitcoin.
À l'opposé, il y a les solutions de type "gardien de valeur" (ou "custodial"), tel que Coinbase, Binance ou ShakePay, pour lesquels vous n'avez que "des bitcoin sur papier".
Une portefeuille bitcoin doit au minimum permettre de : * Générer des clés privés, principalement via le concept de 12 | 24 mots secrets. * À partir de cette clé privée, dériver les clés publiques (ou "adresse bitcoin") * Signer et diffuser de nouvelles transactions * Afficher le solde des bitcoins
Pour la majorité des cas d'utilisation, des applications mobiles sont suffisantes. Il y en a plusieurs dont l'offre de service peut différer.
Pour profiter d'un maximum de fonctionnalités, il est avantageux d'utiliser un logiciel complet, sur PC, qui peut se connecter à son propre nœud ou utiliser un nœud public. Le logiciel Sparrow Wallet est souvent cité comme exemple puisqu'il est complet, convivial et open-source. Ce guide sert de point de départ pour apprendre à l'utiliser.
Téléchargement
À partir du site officiel, téléchargez la version qui correspond à votre système d'exploitation (Windows, Mac ou Linux).
Avertissement : le bitcoin et les cryptomonnaies en général sont des cibles de choix pour les fraudeurs. Vérifiez bien d'être sur le bon site (par exemple, en se fiant à son concepteur @craigraw) et évitez les sites commandités par les moteurs de recherche.
Vérification du logiciel
Cette étape est facultative mais pour éviter les attaques de type "man-in-the-middle", où un fraudeur va remplacer la version officielle par une version frauduleuse, il est recommandé de vérifier l'exactitude intégrale du code, via une "stratégie PGP" (Pretty good privacy).
Depuis peu, cette étape est seulement nécessaire pour le premier téléchargement de Sparrow Wallet puisque le logiciel offre une nouvelle fonctionnalité de validation simplifiée, expliquée sur la page de téléchargement. Pour la façon traditionnelle, les étapes détaillées sont disponible sur cette même page.
Installation
Sur Windows, vous n'avez qu'à télécharger le fichier .exe et à l'exécuter.
Connexion à un nœud public
Si vous lisez le présent guide, il est probable que vous ne mainteniez pas un nœud bitcoin local. Sparrow Wallet offre la possibilité de se connecter à un nœud public, via une liste d'adresses préfiltrées, disponible dans les paramètres de connexion.
Création d'un nouveau portefeuille bitcoin
Pour un premier portefeuille, un portefeuille de type native segwit est adéquat. Ce type est un compromis entre les adresses legacy et le nouveau protocole taproot. Il vous permet déjà de profiter d'économies sur les frais de transactions.
Vous pouvez appliquer les changements pour créer un nouveau portefeuille, puis choisir le mode de création de la clé privée. L'utilisation de plusieurs mots, via BIP39, est la stratégie la plus répandue et qui a faite ces preuves.
Vous pouvez choisir d'ajouter une passphrase, que vous pouvez choisir et qui joue le rôle de mot supplémentaire. Il est essentiel de le connaitre pour pouvoir signer des transactions ou encore restaurer votre portefeuille.
Vous devez ensuite prendre ces mots en note car il vous sera demander de les réinscrire pour les valider.
Une fois vos mots confirmés, vous pouvez confirmer la valeur par défaut pour le chemin de dérivation, puis appliquer les changements. Enfin, vous pourrez ajouter un mot de passe au besoin.
Recevoir des bitcoin
Avant d'envoyer des bitcoin, vous devez en avoir déjà reçu dans votre portefeuille. Pour cela, vous pouvez cliquer sur "Receive" pour afficher la prochaine adresse inutilisée. Pour des raisons de sécurité et de confidentialité, il est recommandé de toujours utiliser une adresse différente. Dans la section "Transactions", vous verrez plutôt toutes les adresses disponibles, incluant celles utilisées pour le change. Vous pouvez alors utiliser ces adresses dans l'application ou il y a les fonds.
Envoyer des bitcoin
Maintenant que vous avez des bitcoin, vous pouvez voir votre solde dans la section "Transactions". Si vous allez dans la section "Send", vous pourrez créer une nouvelle transaction. Pour les intrants à cette transaction, Sparrow Wallet peut choisir en fonction de l'efficience (coûts) ou de la confidentialité. La section "UTXO", qui exposent vos transactions non dépensées, permet un contrôle manuel des intrants à une transaction.
Une fois créée, la transaction devra être signée (avec votre clé privée), puis diffusée (broadcaster) sur le réseau.
Explorer la chaîne
Vous ne voyez toujours pas votre transaction ? Vous êtes curieux de voir ce qu'il se passe sur le réseau bitcoin. Alors allez jetez un coup d'oeil à mempool.space. Dans la boîte de recherche, vous pouvez y coller votre transaction ou votre adresse et confirmer l'état de la transaction. Vous pouvez également valider que votre portefeuille est à jour y en comparant la hauteur (ou numéro de bloc).
Restaurer un portefeuille
Vous avez trouver 12 mots et voulez tester si ça cache quelque chose ? Perdu votre cellulaire avec votre application mobile mais vous avez vos 12 mots ? Il est alors possible de restaurer un portefeuille en utilisant la fonctionnalité de création mentionnée plus haut. Cette fois-ci, plutôt que de les générer automatiquement, vous n'avez qu'à saisir les mots pris en note et le passphrase s'il y a lieu. Il est prudent de considérer ce portefeuille comme étant corrompue ou comme ayant fuité et d'en créer un nouveau puis d'y transférer les fonds.
Avec ces instructions, vous devriez avoir la fondation nécessaire pour faire vos premières transactions sécuritairement. Dans les prochains guide, vous verrez comment utiliser une Coldcard, soit une portefeuille physique qui permet de créer la clé privée hors-connexion, ainsi qu'un OpenDime, une clé à usage unique.
Si vous avez des commentaires, vous pouvez m'écrire sur X (anciennement Twitter) @lekingfu ou par courriel au bitcoin@lekingfu.com.
-
 @ 3b7fc823:e194354f
2025-02-12 02:20:27
@ 3b7fc823:e194354f
2025-02-12 02:20:27I fought with making this work for two days before I finally figured out that I made a simple SQL format mistake. I asked chatGPT to write a tutorial on how to do it based on what I did and the work I did with it. Sharing it in case anyone finds it useful.
Enabling Persistent Memory in Open WebUI with Ollama
This tutorial will guide you through the process of enabling persistent memory for your AI models running locally with Ollama and Open WebUI on Debian Linux. By the end of this guide, your AI will be able to remember the last 20 conversations you’ve had with it.
Prerequisites
- Debian Linux system
- Ollama installed and configured
- Open WebUI installed and running
Step 1: Setting Up the Database for Persistent Memory
We'll use SQLite to store conversation history.
1.1 Create
conversation_memory.pyNavigate to your Open WebUI backend directory and create a new file called
conversation_memory.py.bash cd /home/your_username/Documents/open-webui-0.5.10/backend nano conversation_memory.pyPaste the following code into
conversation_memory.py:```python import sqlite3 import os
Set DB_FILE to the absolute path of memory.db in the same directory as this script
DB_FILE = "/home/your_username/Documents/open-webui-0.5.10/backend/memory.db"
def init_db(): """Create database table if it doesn't exist""" conn = sqlite3.connect(DB_FILE) c = conn.cursor() c.execute(""" CREATE TABLE IF NOT EXISTS memory ( id INTEGER PRIMARY KEY AUTOINCREMENT, user TEXT, ai TEXT ) """) conn.commit() conn.close()
def save_conversation(user_input, ai_response): """Save a conversation entry to the database and maintain only the last 20 entries.""" try: conn = sqlite3.connect(DB_FILE) c = conn.cursor() c.execute("INSERT INTO memory (user, ai) VALUES (?, ?)", (user_input, ai_response)) c.execute(""" DELETE FROM memory WHERE id NOT IN ( SELECT id FROM memory ORDER BY id DESC LIMIT 20 ) """) conn.commit() conn.close() print(f"Successfully saved: User - {user_input}, AI - {ai_response}") except Exception as e: print(f"Error saving conversation: {e}")
def get_last_conversations(limit=5): """Retrieve the last 'limit' number of conversations""" try: conn = sqlite3.connect(DB_FILE) c = conn.cursor() c.execute("SELECT user, ai FROM memory ORDER BY id DESC LIMIT ?", (limit,)) conversations = c.fetchall() conn.close() return conversations except Exception as e: print(f"Error retrieving conversations: {e}") return []
Initialize the database when this script is run
init_db() ```
Step 2: Integrating Memory into Open WebUI Middleware
We'll modify the Open WebUI middleware to save and retrieve conversations.
2.1 Edit
middleware.pyOpen the
middleware.pyfile for editing:bash nano middleware.py2.2 Import Memory Functions
At the top of the file, import the memory functions:
python from conversation_memory import save_conversation, get_last_conversations2.3 Retrieve and Append Conversation History
Locate the function responsible for processing chat payloads. Add the following code to retrieve and append the last 20 conversations:
```python
Retrieve past conversations (e.g., last 20 messages)
conversation_history = get_last_conversations(limit=20)
Format past conversations as context
history_text = "\n".join([f"User: {conv[0]}\nAI: {conv[1]}" for conv in conversation_history])
Append conversation history to the current user message
user_message = get_last_user_message(form_data["messages"]) if history_text: combined_message = f"Previous conversation:\n{history_text}\n\nNew message:\nUser: {user_message}" else: combined_message = f"User: {user_message}"
Update the last user message with combined history
form_data["messages"][-1]["content"] = combined_message ```
2.4 Save New Conversations
Ensure that new conversations are saved after the AI generates a response. Add the following code where the AI response is handled:
```python
Extract AI response content
if isinstance(ai_response, dict) and "choices" in ai_response: ai_response_content = ai_response["choices"][0]["message"]["content"] else: ai_response_content = ""
Save the new conversation
if ai_response_content.strip(): save_conversation(user_message, ai_response_content) ```
Step 3: Testing Persistent Memory
3.1 Run the Script to Test Saving
Run
conversation_memory.pyto ensure it's saving data correctly:bash python3 /home/your_username/Documents/open-webui-0.5.10/backend/conversation_memory.py3.2 Query the Database to Verify Data
Use SQLite to check if conversations are being saved:
bash sqlite3 /home/your_username/Documents/open-webui-0.5.10/backend/memory.db sqlite> SELECT * FROM memory;You should see your test conversations listed.
Step 4: Final Verification in Open WebUI
- Restart the Open WebUI server to apply changes.
- Start a conversation with the AI.
- After several interactions, verify if the AI references past conversations.
- Query
memory.dbagain to ensure new conversations are being saved:
bash sqlite3 /home/your_username/Documents/open-webui-0.5.10/backend/memory.db sqlite> SELECT * FROM memory;
Conclusion
You’ve successfully enabled persistent memory for your AI models running with Ollama and Open WebUI! The AI will now remember the last 20 conversations, creating a more dynamic and personalized user experience.
Feel free to adjust the memory limit or expand the functionality as needed. Happy coding!
Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero
82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1
-
 @ b83a28b7:35919450
2025-02-12 01:51:50
@ b83a28b7:35919450
2025-02-12 01:51:50The traditional product development lifecycle is undergoing a profound transformation. Powered by AI tools evolving at a scarcely believable pace, 2025 promises to revolutionize how we conceive, build, and iterate on products, offering unprecedented efficiency and innovation.
In this post, I'm going to lay out how the seven traditional stages of the PDLC can be accelerated by 5-10x with existing tools.
It's worth pointing out that these capabilities I'm listing are current as of February 11 2025. It is very possible that these all get upended by something even better by March or April!
1. Ideation and Market Research
The first phase of product development is supercharged by AI's ability to analyze vast datasets and identify trends. Tools like AlphaSense and Google Gemini 2.0 can sift through financial reports, social media chatter, and market analyses to distill actionable insights in a fraction of the time it would take human researchers. This AI-augmented ideation process doesn't replace human creativity but amplifies it, allowing teams to explore a broader range of possibilities and make data-driven decisions from the outset.
[Note, I'm not even touching on OpenAI's Deep Research Model that was released last week, which from all the initial reaction, will likely be a massive improvement on the models above]
2. Requirements Gathering and User Story Generation
AI models like Tara AI and Claude 3.5 Sonnet excel at translating abstract business objectives into detailed user stories and technical specifications. These tools can analyze workflows, integrate with existing systems, and generate comprehensive requirements documents. While AI streamlines this process, product managers still play a crucial (but perhaps diminishing over the next few years) role in refining and validating these AI-generated outputs, ensuring alignment with business goals and human needs.
3. Design and Prototyping
The design phase is revolutionized by tools like Adobe Firefly and Neurons Predict AI. These AI systems can generate high-fidelity prototypes based on text prompts and even simulate user behavior to optimize UI/UX designs. Human designers remain essential, infusing prototypes with creativity and emotional resonance that AI alone cannot provide.
4. Development and Implementation
AI coding assistants like GitHub Copilot X and Claude 3.5 Sonnet, and more recently, DeepSeek R1 and o3-mini, are transforming the development process. These tools can generate code, assist with debugging, and accelerate development workflows. However, human developers are still crucial for overseeing critical logic, ensuring security compliance, and making high-level architectural decisions.
5. Quality Assurance
AI-driven QA tools like ACCELQ Autopilot and Appvance IQ automate test case creation, execution, and maintenance. These systems can adapt to application changes in real-time, significantly reducing the manual effort required in testing. Human QA engineers focus on validating critical test cases and ensuring overall product reliability.
6. Deployment
Deployment is streamlined with AI-powered tools like Harness CI/CD and AWS SageMaker. These systems automate deployment pipelines and use machine learning to detect potential failures proactively. Human DevOps teams oversee these processes, ensuring smooth rollouts and managing any unforeseen issues.
7. Post-Launch Monitoring and Iteration
AI excels in post-launch monitoring, with tools like Arize AI and Weights & Biases providing real-time insights and actionable analytics. These systems can detect usage patterns, identify areas for improvement, and even suggest optimizations. Product teams use these AI-generated insights to prioritize updates and guide the product's evolution.
By leveraging AI throughout the product development lifecycle, teams can dramatically reduce time-to-market while maintaining or even improving product quality. This AI-driven approach doesn't eliminate the need for human expertise but rather enhances it, allowing teams to focus on higher-level strategic decisions and creative problem-solving.
The future of product development lies in this symbiosis between human ingenuity and AI capabilities. As these AI tools continue to evolve, we can expect even greater efficiencies and innovations in the PDLC, ultimately leading to better products that more closely align with user needs and market demands.
-
 @ 3b7fc823:e194354f
2025-02-12 01:15:49
@ 3b7fc823:e194354f
2025-02-12 01:15:49We are constantly surrounded by technologies that claim to enhance our experiences but often come at the cost of our privacy. Think about it – every time you visit a website, cookies are being dropped like breadcrumbs, tracking your every move without you even knowing.
How Tech Companies Collect Your Data: The Spy Next Door
-
Cookies: These tiny files are placed on your device as soon as you visit a site. They follow you around the web, creating a digital trail that companies use to learn about your habits and interests.
-
Tracking Pixels: Like cookies, these are invisible tags that track your actions across different websites. Imagine someone following you wherever you go online – that's what tracking pixels do.
-
Behavioral Targeting: This is when companies analyze your browsing history to serve you ads tailored to your interests. It's like knowing what you like and then bombarding you with it, whether you like it or not.
-
Data Brokers: These middlemen collect data from various sources and sell it on to the highest bidder. Your information could be used for marketing, insurance, or even political purposes – without your consent!
-
Third-Party trackers: Apps and websites you visit may share your data with other companies, creating a web of surveillance that's hard to escape.
What They Do with Your Data
Once companies have your data, they can use it for targeted advertising, profile building, and even political manipulation. Think about the Cambridge Analytica scandal... Your data isn't just used to make your experience better; it's being sold and exploited in ways you probably never imagined.
How to Stop Them: Empower Yourself
-
Use Privacy-Friendly Browsers: Tools like Brave or Firefox with enhanced tracking protection can block trackers and cookies, giving you control over what data is collected.
-
Block Trackers and Cookies: Browser extensions that allow you to block these elements are available for free, providing an added layer of privacy.
-
Minimize Data Usage: When using apps or websites, avoid granting unnecessary permissions that could lead to data collection.
-
Delete Unused Apps: Regularly delete apps and services that are no longer needed to stop data collection from inactive accounts.
-
Read Privacy Policies: Before accepting terms of service or privacy policies, read through them to understand what data will be collected and how it will be used.
-
Use Incognito or Private Browsing Modes: These modes often block cookies and trackers, offering an additional way to reduce data collection. But remember that Google was still tracking you on Chrome regardless, so your mileage may vary.
-
Limit Device Usage: Avoid using personal devices for sensitive activities when privacy is a concern.
-
Use Tor: Yes it's slower, yes some sites won't work. It's more private and you using helps disquise traffic giving protection for others that might need it more than you do.
Why It Matters: The Domino Effect
The data collected today isn't just for ads; it's used in decision-making processes that can affect your life. From insurance rates to job opportunities, your data can influence significant aspects of your existence. Imagine a world where your information is bought and sold without your consent – it's time to take control.
Your Data, Your Choice
Your data is being collected and sold without your consent, and the time to act is now. By understanding how data collection works and taking steps to protect yourself, you can reclaim control over your privacy. Remember, you're not just a user – you're the owner of your information. It's time to stand up for your rights and demand transparency from the companies that claim to serve you.
Don't Let Corporate Spies Steal Your Privacy
Your data is valuable, and it's being harvested without your knowledge. Take action today by educating yourself and others about the importance of privacy. Together, we can create a world where privacy is respected and protected, not exploited for profit.
Join the movement to fight against corporate surveillance and protect your right to privacy. Your information is too important to leave in the hands of those who don't have your consent. It's time to take a stand – your digital life depends on it.
Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero
82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1
-
-
 @ 9e69e420:d12360c2
2025-02-12 01:07:41
@ 9e69e420:d12360c2
2025-02-12 01:07:41Scientists at the University of Oxford have made a significant advancement in teleportation. They successfully beamed data between two quantum computers over a distance of more than six feet. By using light particles, they created a shared quantum link, allowing both devices to function as one.
This achievement addresses issues in building scalable quantum computers, enabling smaller devices to work together instead of needing a massive machine. The team accomplished this using quantum gates, vital for quantum computing tasks. As lead researcher Dougal Main noted, "By carefully tailoring these interactions, we can perform logical quantum gates."
Such breakthroughs could pave the way for a 'quantum internet' capable of secure communication and data processing.
-
 @ 9673b322:1b75ee9e
2025-02-11 21:40:18
@ 9673b322:1b75ee9e
2025-02-11 21:40:18This is a sub heading
Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.
- Test bullet point
- test teste
- test
sdfasdfasdfasdfadf
The standard Lorem Ipsum passage, used since the 1500s
"Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum."
Section 1.10.32 of "de Finibus Bonorum et Malorum", written by Cicero in 45 BC
"Sed ut perspiciatis unde omnis iste natus error sit voluptatem accusantium doloremque laudantium, totam rem aperiam, eaque ipsa quae ab illo inventore veritatis et quasi architecto beatae vitae dicta sunt explicabo. Nemo enim ipsam voluptatem quia voluptas sit aspernatur aut odit aut fugit, sed quia consequuntur magni dolores eos qui ratione voluptatem sequi nesciunt. Neque porro quisquam est, qui dolorem ipsum quia dolor sit amet, consectetur, adipisci velit, sed quia non numquam eius modi tempora incidunt ut labore et dolore magnam aliquam quaerat voluptatem. Ut enim ad minima veniam, quis nostrum exercitationem ullam corporis suscipit laboriosam, nisi ut aliquid ex ea commodi consequatur? Quis autem vel eum iure reprehenderit qui in ea voluptate velit esse quam nihil molestiae consequatur, vel illum qui dolorem eum fugiat quo voluptas nulla pariatur?"
1914 translation by H. Rackham
"But I must explain to you how all this mistaken idea of denouncing pleasure and praising pain was born and I will give you a complete account of the system, and expound the actual teachings of the great explorer of the truth, the master-builder of human happiness. No one rejects, dislikes, or avoids pleasure itself, because it is pleasure, but because those who do not know how to pursue pleasure rationally encounter consequences that are extremely painful. Nor again is there anyone who loves or pursues or desires to obtain pain of itself, because it is pain, but because occasionally circumstances occur in which toil and pain can procure him some great pleasure. To take a trivial example, which of us ever undertakes laborious physical exercise, except to obtain some advantage from it? But who has any right to find fault with a man who chooses to enjoy a pleasure that has no annoying consequences, or one who avoids a pain that produces no resultant pleasure?"
Section 1.10.33 of "de Finibus Bonorum et Malorum", written by Cicero in 45 BC
"At vero eos et accusamus et iusto odio dignissimos ducimus qui blanditiis praesentium voluptatum deleniti atque corrupti quos dolores et quas molestias excepturi sint occaecati cupiditate non provident, similique sunt in culpa qui officia deserunt mollitia animi, id est laborum et dolorum fuga. Et harum quidem rerum facilis est et expedita distinctio. Nam libero tempore, cum soluta nobis est eligendi optio cumque nihil impedit quo minus id quod maxime placeat facere possimus, omnis voluptas assumenda est, omnis dolor repellendus. Temporibus autem quibusdam et aut officiis debitis aut rerum necessitatibus saepe eveniet ut et voluptates repudiandae sint et molestiae non recusandae. Itaque earum rerum hic tenetur a sapiente delectus, ut aut reiciendis voluptatibus maiores alias consequatur aut perferendis doloribus asperiores repellat."


-
 @ 9673b322:1b75ee9e
2025-02-11 21:31:32
@ 9673b322:1b75ee9e
2025-02-11 21:31:32This is a sub heading
Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.
- Test bullet point
- test teste
- test
sdfasdfasdfasdfadf
The standard Lorem Ipsum passage, used since the 1500s
"Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum."
Section 1.10.32 of "de Finibus Bonorum et Malorum", written by Cicero in 45 BC
"Sed ut perspiciatis unde omnis iste natus error sit voluptatem accusantium doloremque laudantium, totam rem aperiam, eaque ipsa quae ab illo inventore veritatis et quasi architecto beatae vitae dicta sunt explicabo. Nemo enim ipsam voluptatem quia voluptas sit aspernatur aut odit aut fugit, sed quia consequuntur magni dolores eos qui ratione voluptatem sequi nesciunt. Neque porro quisquam est, qui dolorem ipsum quia dolor sit amet, consectetur, adipisci velit, sed quia non numquam eius modi tempora incidunt ut labore et dolore magnam aliquam quaerat voluptatem. Ut enim ad minima veniam, quis nostrum exercitationem ullam corporis suscipit laboriosam, nisi ut aliquid ex ea commodi consequatur? Quis autem vel eum iure reprehenderit qui in ea voluptate velit esse quam nihil molestiae consequatur, vel illum qui dolorem eum fugiat quo voluptas nulla pariatur?"
1914 translation by H. Rackham
"But I must explain to you how all this mistaken idea of denouncing pleasure and praising pain was born and I will give you a complete account of the system, and expound the actual teachings of the great explorer of the truth, the master-builder of human happiness. No one rejects, dislikes, or avoids pleasure itself, because it is pleasure, but because those who do not know how to pursue pleasure rationally encounter consequences that are extremely painful. Nor again is there anyone who loves or pursues or desires to obtain pain of itself, because it is pain, but because occasionally circumstances occur in which toil and pain can procure him some great pleasure. To take a trivial example, which of us ever undertakes laborious physical exercise, except to obtain some advantage from it? But who has any right to find fault with a man who chooses to enjoy a pleasure that has no annoying consequences, or one who avoids a pain that produces no resultant pleasure?"
Section 1.10.33 of "de Finibus Bonorum et Malorum", written by Cicero in 45 BC
"At vero eos et accusamus et iusto odio dignissimos ducimus qui blanditiis praesentium voluptatum deleniti atque corrupti quos dolores et quas molestias excepturi sint occaecati cupiditate non provident, similique sunt in culpa qui officia deserunt mollitia animi, id est laborum et dolorum fuga. Et harum quidem rerum facilis est et expedita distinctio. Nam libero tempore, cum soluta nobis est eligendi optio cumque nihil impedit quo minus id quod maxime placeat facere possimus, omnis voluptas assumenda est, omnis dolor repellendus. Temporibus autem quibusdam et aut officiis debitis aut rerum necessitatibus saepe eveniet ut et voluptates repudiandae sint et molestiae non recusandae. Itaque earum rerum hic tenetur a sapiente delectus, ut aut reiciendis voluptatibus maiores alias consequatur aut perferendis doloribus asperiores repellat."
https://media.geekiam.systems/624f3a63-b25e-4a04-9207-7e3b1ced80da.png https://media.geekiam.systems/04f60be2-9bdf-4e29-9115-d0249789247a.png https://media.geekiam.systems/ef4b507b-2457-4f3a-b458-6841ce408fd1.png
-
 @ 9673b322:1b75ee9e
2025-02-11 21:28:21
@ 9673b322:1b75ee9e
2025-02-11 21:28:21This is a sub heading
Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.
- Test bullet point
- test teste
- test
sdfasdfasdfasdfadf
The standard Lorem Ipsum passage, used since the 1500s
"Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum."
Section 1.10.32 of "de Finibus Bonorum et Malorum", written by Cicero in 45 BC
"Sed ut perspiciatis unde omnis iste natus error sit voluptatem accusantium doloremque laudantium, totam rem aperiam, eaque ipsa quae ab illo inventore veritatis et quasi architecto beatae vitae dicta sunt explicabo. Nemo enim ipsam voluptatem quia voluptas sit aspernatur aut odit aut fugit, sed quia consequuntur magni dolores eos qui ratione voluptatem sequi nesciunt. Neque porro quisquam est, qui dolorem ipsum quia dolor sit amet, consectetur, adipisci velit, sed quia non numquam eius modi tempora incidunt ut labore et dolore magnam aliquam quaerat voluptatem. Ut enim ad minima veniam, quis nostrum exercitationem ullam corporis suscipit laboriosam, nisi ut aliquid ex ea commodi consequatur? Quis autem vel eum iure reprehenderit qui in ea voluptate velit esse quam nihil molestiae consequatur, vel illum qui dolorem eum fugiat quo voluptas nulla pariatur?"
1914 translation by H. Rackham
"But I must explain to you how all this mistaken idea of denouncing pleasure and praising pain was born and I will give you a complete account of the system, and expound the actual teachings of the great explorer of the truth, the master-builder of human happiness. No one rejects, dislikes, or avoids pleasure itself, because it is pleasure, but because those who do not know how to pursue pleasure rationally encounter consequences that are extremely painful. Nor again is there anyone who loves or pursues or desires to obtain pain of itself, because it is pain, but because occasionally circumstances occur in which toil and pain can procure him some great pleasure. To take a trivial example, which of us ever undertakes laborious physical exercise, except to obtain some advantage from it? But who has any right to find fault with a man who chooses to enjoy a pleasure that has no annoying consequences, or one who avoids a pain that produces no resultant pleasure?"
Section 1.10.33 of "de Finibus Bonorum et Malorum", written by Cicero in 45 BC
"At vero eos et accusamus et iusto odio dignissimos ducimus qui blanditiis praesentium voluptatum deleniti atque corrupti quos dolores et quas molestias excepturi sint occaecati cupiditate non provident, similique sunt in culpa qui officia deserunt mollitia animi, id est laborum et dolorum fuga. Et harum quidem rerum facilis est et expedita distinctio. Nam libero tempore, cum soluta nobis est eligendi optio cumque nihil impedit quo minus id quod maxime placeat facere possimus, omnis voluptas assumenda est, omnis dolor repellendus. Temporibus autem quibusdam et aut officiis debitis aut rerum necessitatibus saepe eveniet ut et voluptates repudiandae sint et molestiae non recusandae. Itaque earum rerum hic tenetur a sapiente delectus, ut aut reiciendis voluptatibus maiores alias consequatur aut perferendis doloribus asperiores repellat."
https://media.geekiam.systems/34f99b84-cf8e-4cbc-aaee-d04f0436ba7e.pnghttps://media.geekiam.systems/2d24f1fe-d394-4477-a402-b5d708098b5f.pnghttps://media.geekiam.systems/4f40f1a9-7ec3-49e3-bf0a-c9825b351442.png
-
 @ 9673b322:1b75ee9e
2025-02-11 21:01:42
@ 9673b322:1b75ee9e
2025-02-11 21:01:42This is a sub heading
Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.
- Test bullet point
- test teste
- test
sdfasdfasdfasdfadf
The standard Lorem Ipsum passage, used since the 1500s
"Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum."
Section 1.10.32 of "de Finibus Bonorum et Malorum", written by Cicero in 45 BC
"Sed ut perspiciatis unde omnis iste natus error sit voluptatem accusantium doloremque laudantium, totam rem aperiam, eaque ipsa quae ab illo inventore veritatis et quasi architecto beatae vitae dicta sunt explicabo. Nemo enim ipsam voluptatem quia voluptas sit aspernatur aut odit aut fugit, sed quia consequuntur magni dolores eos qui ratione voluptatem sequi nesciunt. Neque porro quisquam est, qui dolorem ipsum quia dolor sit amet, consectetur, adipisci velit, sed quia non numquam eius modi tempora incidunt ut labore et dolore magnam aliquam quaerat voluptatem. Ut enim ad minima veniam, quis nostrum exercitationem ullam corporis suscipit laboriosam, nisi ut aliquid ex ea commodi consequatur? Quis autem vel eum iure reprehenderit qui in ea voluptate velit esse quam nihil molestiae consequatur, vel illum qui dolorem eum fugiat quo voluptas nulla pariatur?"
1914 translation by H. Rackham
"But I must explain to you how all this mistaken idea of denouncing pleasure and praising pain was born and I will give you a complete account of the system, and expound the actual teachings of the great explorer of the truth, the master-builder of human happiness. No one rejects, dislikes, or avoids pleasure itself, because it is pleasure, but because those who do not know how to pursue pleasure rationally encounter consequences that are extremely painful. Nor again is there anyone who loves or pursues or desires to obtain pain of itself, because it is pain, but because occasionally circumstances occur in which toil and pain can procure him some great pleasure. To take a trivial example, which of us ever undertakes laborious physical exercise, except to obtain some advantage from it? But who has any right to find fault with a man who chooses to enjoy a pleasure that has no annoying consequences, or one who avoids a pain that produces no resultant pleasure?"
Section 1.10.33 of "de Finibus Bonorum et Malorum", written by Cicero in 45 BC
"At vero eos et accusamus et iusto odio dignissimos ducimus qui blanditiis praesentium voluptatum deleniti atque corrupti quos dolores et quas molestias excepturi sint occaecati cupiditate non provident, similique sunt in culpa qui officia deserunt mollitia animi, id est laborum et dolorum fuga. Et harum quidem rerum facilis est et expedita distinctio. Nam libero tempore, cum soluta nobis est eligendi optio cumque nihil impedit quo minus id quod maxime placeat facere possimus, omnis voluptas assumenda est, omnis dolor repellendus. Temporibus autem quibusdam et aut officiis debitis aut rerum necessitatibus saepe eveniet ut et voluptates repudiandae sint et molestiae non recusandae. Itaque earum rerum hic tenetur a sapiente delectus, ut aut reiciendis voluptatibus maiores alias consequatur aut perferendis doloribus asperiores repellat."
![[https://media.geekiam.systems/206d4e36-e1cf-4e4e-9f41-471732828966.png]]![[https://media.geekiam.systems/7ad5b2c8-546c-4626-93ab-dce7d9453011.png]]![[https://media.geekiam.systems/99941110-2d79-4904-a82c-21d1ede67cde.png]]![[https://media.geekiam.systems/9483fec1-85ce-49b8-99d3-e2600d760ace.png]]
-
 @ 9673b322:1b75ee9e
2025-02-11 20:51:04
@ 9673b322:1b75ee9e
2025-02-11 20:51:04This is a sub heading
Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.
- Test bullet point
- test teste
- test
sdfasdfasdfasdfadf
The standard Lorem Ipsum passage, used since the 1500s
"Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum."
Section 1.10.32 of "de Finibus Bonorum et Malorum", written by Cicero in 45 BC
"Sed ut perspiciatis unde omnis iste natus error sit voluptatem accusantium doloremque laudantium, totam rem aperiam, eaque ipsa quae ab illo inventore veritatis et quasi architecto beatae vitae dicta sunt explicabo. Nemo enim ipsam voluptatem quia voluptas sit aspernatur aut odit aut fugit, sed quia consequuntur magni dolores eos qui ratione voluptatem sequi nesciunt. Neque porro quisquam est, qui dolorem ipsum quia dolor sit amet, consectetur, adipisci velit, sed quia non numquam eius modi tempora incidunt ut labore et dolore magnam aliquam quaerat voluptatem. Ut enim ad minima veniam, quis nostrum exercitationem ullam corporis suscipit laboriosam, nisi ut aliquid ex ea commodi consequatur? Quis autem vel eum iure reprehenderit qui in ea voluptate velit esse quam nihil molestiae consequatur, vel illum qui dolorem eum fugiat quo voluptas nulla pariatur?"
1914 translation by H. Rackham
"But I must explain to you how all this mistaken idea of denouncing pleasure and praising pain was born and I will give you a complete account of the system, and expound the actual teachings of the great explorer of the truth, the master-builder of human happiness. No one rejects, dislikes, or avoids pleasure itself, because it is pleasure, but because those who do not know how to pursue pleasure rationally encounter consequences that are extremely painful. Nor again is there anyone who loves or pursues or desires to obtain pain of itself, because it is pain, but because occasionally circumstances occur in which toil and pain can procure him some great pleasure. To take a trivial example, which of us ever undertakes laborious physical exercise, except to obtain some advantage from it? But who has any right to find fault with a man who chooses to enjoy a pleasure that has no annoying consequences, or one who avoids a pain that produces no resultant pleasure?"
Section 1.10.33 of "de Finibus Bonorum et Malorum", written by Cicero in 45 BC
"At vero eos et accusamus et iusto odio dignissimos ducimus qui blanditiis praesentium voluptatum deleniti atque corrupti quos dolores et quas molestias excepturi sint occaecati cupiditate non provident, similique sunt in culpa qui officia deserunt mollitia animi, id est laborum et dolorum fuga. Et harum quidem rerum facilis est et expedita distinctio. Nam libero tempore, cum soluta nobis est eligendi optio cumque nihil impedit quo minus id quod maxime placeat facere possimus, omnis voluptas assumenda est, omnis dolor repellendus. Temporibus autem quibusdam et aut officiis debitis aut rerum necessitatibus saepe eveniet ut et voluptates repudiandae sint et molestiae non recusandae. Itaque earum rerum hic tenetur a sapiente delectus, ut aut reiciendis voluptatibus maiores alias consequatur aut perferendis doloribus asperiores repellat."
![[api-design-patterns.png]]![[rust-header.png]]
-
 @ 3c7dc2c5:805642a8
2025-02-11 20:50:34
@ 3c7dc2c5:805642a8
2025-02-11 20:50:34🧠Quote(s) of the week:
You conflate maximalism with close-mindedness because you believe money is a 'collective hallucination' instead of an emergent solution to a coordination problem. Anilsaidso
'DOGE finding waste and fraud? Don’t miss the forest for the trees: Any money system that does not fix a unit of currency to a unit of energy is functionally fraudulent, because if a currency is not tied to energy, then creating fiat currency functionally means creating energy by govt fiat, which is a violation of physics, which is fraud.
Once you are in a system that pretends it can create energy by printing currency, it is just a question of “How much fraud occurs until the system collapses?”
You will know the end of that system is near when debt gets high, rates rise, & yet the price of energy-linked neutral assets like gold & BTC rise with rates (instead of falling), as free markets scramble out of printed currency & debt into actual energy linked assets, which is happening - rates up, & yet see gold and BTC.)' - Luke Gromen
🧡Bitcoin news🧡
On the 4th of February:
➡️El Salvador bought another 11 Bitcoin worth over $1.1 million for their strategic Bitcoin reserve.
➡️'Someone just moved 50 Bitcoin worth $5 MILLION that they mined 15 years ago They HODL'ed from $0.10 to $100k. Legend.' - Pete Rizzo
➡️Bitcoin funding rates turn negative — a very rare signal historically followed by massive price surges. Buckle up.
➡️Coinbase urges US to remove barriers for banks to provide Bitcoin and crypto services - BBG
➡️'Forbes recently covered how Bitcoin mining is fast-tracking millions of Ethiopians out of energy poverty. 100% renewable + economically benefitting the country No other technology has been able to do this. Ever.' Daniel Batten / Forbes
➡️President Trump's Crypto Czar David Sacks had a press conference on this day. Here are some notes:
• “will be heavy on Bitcoin and timelines.”
• “Discussion of Sovereign Wealth Fund.”
• “Timelines laid out as to proposed legislation (Lummis) and BSR.”
• “Yes, I expect there to be ‘America First’ rhetoric with SWF and crypto.”
• “reiterating, no $XRP”
Ergo a lot of word salad and not something juuuggggge was happening.
➡️President Bukele Offers To Jail Roger Ver in El Salvador. Bukele: "El Salvador prisons have big cell blocks. It's the perfect place for him" If you don’t get the joke, Study Bitcoin's history in detail. I will give you a hint. Book: The Blocksize War!
➡️'Semler Scientific acquired 871 Bitcoins for $88.5 million and has generated a BTC Yield of 152% since July 1, 2024. Now holding 3,192 bitcoin. Just getting started.' - Eric Semler
On the 5th of February:
➡️Bitcoin on track to hit $1.5m by 2030 - Ark Invest
On the 6th of February:
➡️Czech President signed a law removing the capital gains tax on #Bitcoin after 3+ years of holding. Sovereign game theory intensifies. Tick tock, next block! Meanwhile the ECB. 'The ECB just published an interview with Reuters where they contemplate a risk assessment of current FX swap lines if another central bank held Bitcoin reserves. They are literally trying to hinder the Czech National Bank from buying Bitcoin. Bitcoin is winning.' - Andre Dragosch
➡️Former PayPal President: Sell Gold Reserves to Buy Bitcoin "We're the number 1 holder of gold. If you think of Bitcoin as a better version of gold, why not rebalance a portion of that reserve to Bitcoin? There's a lot more growth in Bitcoin in the coming decades."
➡️Whales are buying Bitcoin like never seen before. Billionaires are stacking Bitcoin, front-running governments, pubco’s, and plebs.
➡️IOWA BITCOIN RESERVE BILL HF 246 would allow investment of 5% of public monies in digital assets of $750b+ market cap (i.e. Bitcoin)
➡️Eric Balchunas: Trump to launch "Bitcoin Plus" ETF.
➡️'The power is so cheap in the north of Norway now that the hydropower plants are considering dumping their water in the sea. We need more Bitcoin mining.' -Jaran Mellerud
Great explanation on the topic: https://x.com/GoldIRAChannel/status/1887718777338667369
➡️Great report by Breeze. https://breez.technology/report/
'Bitcoin isn't "just" digital gold, it's an everyday currency. 650M+people reached on Lightning Businesses real-world impact Growing ecosystem driving adoption New use cases unlocked.' - Breeze
Breeze is one of, if not, my favorite self-custodial Lightning Bitcoin payments app.
On the 7th of February:
➡️Utah pulls ahead in the race to create a Strategic Bitcoin Reserve. Utah’s HB230 just became the first state Bitcoin reserve bill to clear a chamber vote, passing the House and heading to the Senate.
➡️ If any public companies are wondering whether Bitcoin is the solution… here’s your answer: Metaplanet’s market cap has been 100X’d (3.50 0%)since adopting Bitcoin as a treasury asset less than one year ago.
➡️Maryland State Delegate Caylin Young introduces the "Strategic Bitcoin Reserve Act of Maryland".
➡️MISSOURI FILES 2ND Bitcoin reserve bill that includes: - 5 YR HODL requirement - State must accept BTC payments - No cap on how much the state can buy 1st bill SB614 is currently in the Senate!
➡️Rep. TJ Roberts introduces a bill to invest up to 10% of state funds in Bitcoin for Kentucky.
➡️BlackRock boosts its stake in MicroStrategy to 5%, now holding 11.2M shares, up from 4.09% in September. Next to that, BlackRock holds $140m in IBIT - their Bitcoin ETF. Per their 13F SEC filing today. Up from $92m in November 2024.
➡️ Tornado Cash founder Alexey Pertsev has been released from prison. Pertsev was found guilty of money laundering in 2024. He is currently preparing an appeal. https://decrypt.co/304723/tornado-cash-developer-alexey-perstev-leaving-prison
On the 8th of February:
➡️Florida is the latest state to introduce a Strategic Bitcoin Reserve. Republican Senator Joe Gruters has introduced a bill proposing the investment of part of the state’s funds in Bitcoin to counter rising inflation.
➡️'FTX will repay 98% of creditors on February 18th. Creditors will receive a total of 119% of their funds lost in US dollar terms on November 11th, 2022. This is the equivalent of only 20% in Bitcoin terms. This is a lesson in self-custody.' -The Bitcoin Therapist
Just a quick reminder: 'Over 5 million Bitcoins are gone. Forever. No keys. No recovery. No second chance. - Satoshi’s wallet: 1M BTC, untouched - Mt. Gox hack: 744K BTC, - Lost key & wallets: ~3.7M BTC - James Howells’ hard drive: 8K BTC, buried Do people even grasp Bitcoin’s scarcity?'- Eli Nagar
➡️MONTANA BITCOIN RESERVE BILL
MT House Bill 429 would authorize up to $50m invested into 'digital assets over $750b market cap' i.e. Bitcoin, by July 15, 2025.
19 States want Bitcoin in their reserves so far, and 27 states are all pro-Bitcoin and Digital Asset Bills. It's just crazy to me what's happening. A few years ago, I couldn't even imagine it would go this fast. Hello, game theory!
➡️PNC, the 8th largest U.S. bank with $325 billion in AUM, has disclosed $67 million in Bitcoin exposure through its 13F filing with the SEC.
On the 9th of February:
➡️Hong Kong officially recognizes Bitcoin as proof of capital for residency applications.
➡️That’s 815,000,000,000,000,000,000 hashes per second securing the world’s largest permissionless monetary network Bitcoin’s hashrate sets a new record high above 810 EH.
➡️University of Austin to buy $5m Bitcoin. "We don’t want to be left behind," says CIO of the university fund.
On the 10th of February:
➡️'Priced in Bitcoin the S&P 500 looks like a meme coin rug pull.' -CarlBMenger
➡️Valid point by Bit Harington: 'It takes years for Bitcoin to finally leave a new 10X price zone and start looking for the next 10X. $1K lasted ~3.5 years. $10K also 3 years. It seems logical to assume that the $100K price zone will also last several years; One of the reasons I don't believe in $1M this cycle.'
➡️Another solo miner has mined an entire Bitcoin block worth $ 300,000. Just sensational.
➡️Michael Saylor's STRATEGY just bought another 7,633 Bitcoin worth $742 million. 'Strategy has added 7,633 Bitcoin to its holdings for ~$742.4 million at an average price of $97,255 per Bitcoin, bringing its total Bitcoin stack to 478,740 BTC. Acquired for ~$31.1 billion at an average of $65,033 per Bitcoin, the company's Bitcoin yield stands at a 4.1% YTD in 2025.' - Saylor
➡️Japan to scrap ban on Bitcoin ETFs and cut taxes on crypto-assets from 55% down to 20%.
💸Traditional Finance / Macro:
On the 3rd of February:
👉🏽'Nvidia stock, falls over -5% at the open as markets react to the beginning of the trade war. The stock is currently down -26% from its all-time high.' - TKL
👉🏽Microsoft shares closed down 6.2% on the worst day since 2022. If only they had listened to Saylor's 3-minute Bitcoin pitch.
On the 4th of February:
👉🏽Alphabet stock, falls over -7% after reporting Q4 2024 earnings.
🏦Banks:
👉🏽Global central banks now hold more Gold than at any point in the past 45 years. Something is brewing. (see for more info in the segment below - on the 9th of February)
🌎Macro/Geopolitics:
Recently I found something interesting.
'Another fantastic open-source dataset is the Global Datahub at Georgetown University. It covers a wide range of topics including:
Geopolitics: Data on military spending, UN voting patterns, indicators of freedom and democracy, trade restrictions, social unrest, property rights, and demographic trends. Trade and Production: Information on trade, energy balances, GDP per capita, and trade patterns.
External Accounts: Current account balances, foreign investment flows, real exchange rates, international reserves, and remittances. Public Finance: Public sector deficits, composition of public debt, country risk, and trends in public spending.
Monetary and Financial: Inflation rates, monetary policy interest rates, exchange rate regimes, availability of credit, corporate bond rates, and amortizations of public and corporate debt.
Other Topics: Data on digital infrastructure, environmental sustainability, and progress toward achieving the United Nations' Sustainable Development Goals (SDGs).'
https://globallacdatahub.com/index.html
And none of this wonder data is disaggregated!
On the 4th of February:
👉🏽Germany has become kind of a tutorial in self-immolation. Really! Germany has cut its offshore wind generation capacity target from 50 gigawatts by 2035 to 40 gigawatts by 2034 due to crowded seas causing a "wake effect" that reduces output. The reduced capacity and delays in grid connections may hinder Germany's offshore wind ambitions, including its 2045 goal of 70 gigawatts. Stupidity has no limits. Really… self-inflicted harm…the idiocy of closing nuclear plants.
👉🏽'Local authorities in the UK have spent £141 million of taxpayer money on services for migrants such as PlayStations, yoga and circus skills classes, driving and DJ lessons' — Telegraph Money well spent! And then people wonder why all these people are coming to the West.
On the 5th of February
👉🏽 The Federal Reserve's Reverse Repo Facility hit its lowest inventory in 1,385 days, today. Ergo: The US is borrowing so much debt to fund deficit spending that the RRP has been DEPLETED to a 1,385-day low. Do you know what's coming? QE & money printing will start aggressively when this drains to 0. They may have 10 different names for it but it’s coming.
On the 6th of February:
👉🏽 Secretary of State Marco Rubio just deemed that only 294 USAID staffers are necessary out of 14,000. The entire agency will be imminently reduced from 14,000 to 294 employees. This has to be the biggest mass firing yet.
On the 7th of February:
👉🏽Indian Rupee falling off the cliff as it plunges to its weakest level against the U.S. Dollar in HISTORY!
👉🏽'30 years ago each major US corporation used to have an equivalent in Germany or France, today their competitors are in Asia and Europe is on a happy path into irrelevance. Overregulation, lack of Innovation, and left redistribution mindset have their price. Will it ever change?' -Michael A. Arouet
A shame how Europe, once the epicenter of the Industrial Revolution has self-sabotaged into near irrelevancy. Just to give you one comparison, the total valuation of all European companies combined is already smaller than the 2 biggest US companies. Yikes!
👉🏽United Kingdom's leftist government orders Apple to create a back door allowing access to encrypted data stored by Apple users worldwide in its cloud — WaPo
👉🏽The US consumers expect 4.3% inflation during the next 12 months, UP a massive 1.0 percentage point from January. The 4.3% is the highest since November 2023. 4.3%, the highest since November 2023. This marks a 1.7 percentage point jump over the last 3 months, the largest surge since February 2020.
Moreover, 5-10-year inflation expectations rose to 3.3%, the highest since June 2008, and the estimates were above 3.2%. Meanwhile, consumer sentiment fell to 67.8 points in February, the lowest in 3 months. Inflation is still a major issue. How will Trump and Bessent deal with that side of the trade tariffs?
Meanwhile, one year from now Democrats expect hyperinflation, and Republicans expect deflation.
This chart is hilarious because it just tells you: “If your brain uses politics it's not rational!”
👉🏽There it is: 600K lower across all of 2024, and even more downward revisions coming next February' - ZeroHedge
https://www.zerohedge.com/economics/tomorrows-jobs-report-will-finally-capture-surge-illegal-aliens-lead-another-negative
Oh by the way, in just January, 1 MILLION immigrants (legal and illegal) gained a job. Meanwhile, native-born Americans gained just 8,000. All net jobs gains post-Covid are immigrants. This is why they opened the border.
To make it even more funnier. The December jobs report has been revised HIGHER, showing 307,000 jobs added for the month, up from 256,000. That's the strongest job number since March 2024. Let's wait a couple of months if this still holds. I kinda don't believe job reports anymore, especially after the last 4 years and revisions.
👉🏽Sam Callahan: 'On Wednesday, the Government Accountability Office published its annual report to Congress on the nation's fiscal health and it didn't sugarcoat things.' full report: https://www.gao.gov/assets/gao-25-107714.pdf
👉🏽Argentina will have an inflation of 23.2% in 2025, according to the REM published by the BCRA For January they expect month over month of of 2.3%, and they predict that in April monthly inflation will break through the 2% barrier. In 2027 Argentina should have single-digit annual inflation again, something that has not happened since 2006.
Progress under Milei, but let's see if he can manage it. There's still room for improvement.
👉🏽'The UK Labour Government has ordered Apple to create a backdoor in iCloud allowing security services to access your private information. Keir Starmer wants to see your messages. Scary times we live in.' - Basil the Great What is the point of GDPR again?
👉🏽'MASSIVE OPEN AI DATA BREACH? 20 MILLION ACCOUNTS ALLEGEDLY HACKED! A hacker claims to have stolen login details—including emails and passwords—for 20 million OpenAI accounts and is selling them on the dark web. OpenAI says it’s investigating but insists there’s no evidence of a system breach—yet. Cybersecurity experts warn this could lead to identity theft, phishing scams, and even AI-powered cyberattacks.' - Mario Nawfal
Although this breach is yet to be verified by OpenAI, anyone using the tool should update their passwords and credentials, as a precaution. If you haven’t already, switch on multi-factor authentication within OpenAI’s settings, as this should give you another layer of protection even if your password has been compromised.
On the 8th of February:
👉🏽USAID:
'USAID has pushed nearly half a billion dollars ($472.6m) through a secretive US government-financed NGO, "Internews Network" (IN), which has “worked with” 4,291 media outlets, producing in one year 4,799 hours of broadcasts reaching up to 778 million people and "training” over 9000 journalists (2023 figures). IN has also supported social media censorship initiatives.' -WikiLeaks Source: https://x.com/wikileaks/status/1888072129327083979
'USAID sent $40M to a coronavirus scientist at the Wuhan Institute of Virology who became patient zero of COVID-19.' - Financelot
'Bill Gates’ vaccine organization ‘GAVI’ was awarded $4,880,000,000.00 from USAID. Nearly $5 BILLION in taxpayer money to a single organization Two grants are still active; the 4B dollar grant ends Aug 2030. No wonder Gates is speaking out against DOGE dismantling USAID.' - Lindsay Penney
👉🏽Great breakdown of the US deficit by 'Infra':
We are currently running a ~$2.1 trillion deficit. To balance the budget would require cutting about $2T in spending It won’t be possible without significant legislation and the resulting contraction in GDP would be worse than the GFC
Here’s the math:
-Current GDP is $29T, 3Q24 growth at 2.8%
-GDP grew by $1.5T from 1Q23->1Q24
-Current government spending as a % of GDP is 36%
-Current government spending is ~$7.5T (on budget)
-Current tax receipts are 20% of GDP (~$5.5T)
-Current deficit is ~$2T'
Great write-up, full thread: https://x.com/infraa_/status/1888021955686842760
Govt wastes 100% of our tax dollars on bankrupt entitlement programs, forever wars, corporate & social welfare, and other bullshit. Just look at the USAID bit. Nothing stops this train folks. Nothing! Got Bitcoin?
On the 9th of February:
👉🏽It’s estimated that the federal government loses $233 Billion to $521 Billion annually to fraud. Although I don't think fraud is the right word, laundering and corruption fit better.
Half $1 trillion for 40 years equals 20 trillion. So instead of having a $36 trillion deficit, we would have a $16 trillion deficit if our government didn’t steal our money. Again this is not something I made up or found on a sketchy website, here you have the source: https://www.gao.gov/products/gao-24-105833
The U.S. Government Accountability Office.
Just to give you another example of how fucked up the government operates. This statement is from a 2018 report: The Pentagon spent $1 billion to audit its 2018 financials, and it failed the audit! $1 BILLION!!
Ever heard of anyone spending 1 billion just to audit their financials? The audacity.
👉🏽Gold just hit $2900 for the first time in history. Gold's new all-time high above $2900 as a global physical shortage is about to surpass Covid levels.
'London's Gold Shortage: A Symptom Of Global Economic Anxiety' -ZeroHedge Source: https://www.zerohedge.com/precious-metals/londons-gold-shortage-symptom-global-economic-anxiety
The above statement perfectly matches the collapse in the FEDs Overnight Repo facility chart.
No One Trusts each other's Collateral globally. When the collateral calls come (and they ARE coming) paper coupons ain't gonna cut it.
The big institutions know something we don’t. March 2020 pattern.
🎁If you have made it this far I would like to give you a little gift:
Preston Pysh and Luke Gromen discuss Bitcoin’s Lightning Network, Tether’s USDT integration, and the impact on global payments and traditional banking infrastructure. https://www.youtube.com/watch?v=w8JXdYmllZ4
Credit: I have used multiple sources!
My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: PocketBitcoin especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly.
Use the code SE3997
Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple. ⠀⠀⠀⠀ ⠀ ⠀⠀⠀
Do you think this post is helpful to you? If so, please share it and support my work with a zap.
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
⭐ Many thanks⭐
Felipe - Bitcoin Friday!
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
-
 @ 9673b322:1b75ee9e
2025-02-11 20:30:43
@ 9673b322:1b75ee9e
2025-02-11 20:30:43This is a sub heading
Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.
- Test bullet point
- test teste
- test
sdfasdfasdfasdfadf
The standard Lorem Ipsum passage, used since the 1500s
"Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum."
Section 1.10.32 of "de Finibus Bonorum et Malorum", written by Cicero in 45 BC
"Sed ut perspiciatis unde omnis iste natus error sit voluptatem accusantium doloremque laudantium, totam rem aperiam, eaque ipsa quae ab illo inventore veritatis et quasi architecto beatae vitae dicta sunt explicabo. Nemo enim ipsam voluptatem quia voluptas sit aspernatur aut odit aut fugit, sed quia consequuntur magni dolores eos qui ratione voluptatem sequi nesciunt. Neque porro quisquam est, qui dolorem ipsum quia dolor sit amet, consectetur, adipisci velit, sed quia non numquam eius modi tempora incidunt ut labore et dolore magnam aliquam quaerat voluptatem. Ut enim ad minima veniam, quis nostrum exercitationem ullam corporis suscipit laboriosam, nisi ut aliquid ex ea commodi consequatur? Quis autem vel eum iure reprehenderit qui in ea voluptate velit esse quam nihil molestiae consequatur, vel illum qui dolorem eum fugiat quo voluptas nulla pariatur?"
1914 translation by H. Rackham
"But I must explain to you how all this mistaken idea of denouncing pleasure and praising pain was born and I will give you a complete account of the system, and expound the actual teachings of the great explorer of the truth, the master-builder of human happiness. No one rejects, dislikes, or avoids pleasure itself, because it is pleasure, but because those who do not know how to pursue pleasure rationally encounter consequences that are extremely painful. Nor again is there anyone who loves or pursues or desires to obtain pain of itself, because it is pain, but because occasionally circumstances occur in which toil and pain can procure him some great pleasure. To take a trivial example, which of us ever undertakes laborious physical exercise, except to obtain some advantage from it? But who has any right to find fault with a man who chooses to enjoy a pleasure that has no annoying consequences, or one who avoids a pain that produces no resultant pleasure?"
Section 1.10.33 of "de Finibus Bonorum et Malorum", written by Cicero in 45 BC
"At vero eos et accusamus et iusto odio dignissimos ducimus qui blanditiis praesentium voluptatum deleniti atque corrupti quos dolores et quas molestias excepturi sint occaecati cupiditate non provident, similique sunt in culpa qui officia deserunt mollitia animi, id est laborum et dolorum fuga. Et harum quidem rerum facilis est et expedita distinctio. Nam libero tempore, cum soluta nobis est eligendi optio cumque nihil impedit quo minus id quod maxime placeat facere possimus, omnis voluptas assumenda est, omnis dolor repellendus. Temporibus autem quibusdam et aut officiis debitis aut rerum necessitatibus saepe eveniet ut et voluptates repudiandae sint et molestiae non recusandae. Itaque earum rerum hic tenetur a sapiente delectus, ut aut reiciendis voluptatibus maiores alias consequatur aut perferendis doloribus asperiores repellat."
![[api-design-patterns.png]]![[rust-header.png]]
-
 @ ae61640c:4ab8f91b
2025-02-11 19:58:08
@ ae61640c:4ab8f91b
2025-02-11 19:58:08Проверка

-
 @ 9673b322:1b75ee9e
2025-02-11 19:55:37
@ 9673b322:1b75ee9e
2025-02-11 19:55:37This is an example of test blog post, to be published via the obstrlish plugin.
This is a sub heading
Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.
- Test bullet point
- test teste
- test
sdfasdfasdfasdfadf
The standard Lorem Ipsum passage, used since the 1500s
"Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum."
Section 1.10.32 of "de Finibus Bonorum et Malorum", written by Cicero in 45 BC
"Sed ut perspiciatis unde omnis iste natus error sit voluptatem accusantium doloremque laudantium, totam rem aperiam, eaque ipsa quae ab illo inventore veritatis et quasi architecto beatae vitae dicta sunt explicabo. Nemo enim ipsam voluptatem quia voluptas sit aspernatur aut odit aut fugit, sed quia consequuntur magni dolores eos qui ratione voluptatem sequi nesciunt. Neque porro quisquam est, qui dolorem ipsum quia dolor sit amet, consectetur, adipisci velit, sed quia non numquam eius modi tempora incidunt ut labore et dolore magnam aliquam quaerat voluptatem. Ut enim ad minima veniam, quis nostrum exercitationem ullam corporis suscipit laboriosam, nisi ut aliquid ex ea commodi consequatur? Quis autem vel eum iure reprehenderit qui in ea voluptate velit esse quam nihil molestiae consequatur, vel illum qui dolorem eum fugiat quo voluptas nulla pariatur?"
1914 translation by H. Rackham
"But I must explain to you how all this mistaken idea of denouncing pleasure and praising pain was born and I will give you a complete account of the system, and expound the actual teachings of the great explorer of the truth, the master-builder of human happiness. No one rejects, dislikes, or avoids pleasure itself, because it is pleasure, but because those who do not know how to pursue pleasure rationally encounter consequences that are extremely painful. Nor again is there anyone who loves or pursues or desires to obtain pain of itself, because it is pain, but because occasionally circumstances occur in which toil and pain can procure him some great pleasure. To take a trivial example, which of us ever undertakes laborious physical exercise, except to obtain some advantage from it? But who has any right to find fault with a man who chooses to enjoy a pleasure that has no annoying consequences, or one who avoids a pain that produces no resultant pleasure?"
Section 1.10.33 of "de Finibus Bonorum et Malorum", written by Cicero in 45 BC
"At vero eos et accusamus et iusto odio dignissimos ducimus qui blanditiis praesentium voluptatum deleniti atque corrupti quos dolores et quas molestias excepturi sint occaecati cupiditate non provident, similique sunt in culpa qui officia deserunt mollitia animi, id est laborum et dolorum fuga. Et harum quidem rerum facilis est et expedita distinctio. Nam libero tempore, cum soluta nobis est eligendi optio cumque nihil impedit quo minus id quod maxime placeat facere possimus, omnis voluptas assumenda est, omnis dolor repellendus. Temporibus autem quibusdam et aut officiis debitis aut rerum necessitatibus saepe eveniet ut et voluptates repudiandae sint et molestiae non recusandae. Itaque earum rerum hic tenetur a sapiente delectus, ut aut reiciendis voluptatibus maiores alias consequatur aut perferendis doloribus asperiores repellat."
![[api-design-patterns.png]]
-
 @ cc448f8b:a1ad47db
2025-02-11 19:16:32
@ cc448f8b:a1ad47db
2025-02-11 19:16:32Introduction
This is a long standing family favorite. If you like blueberries, I think you'll love it! You could substitute other fruit fillings but it rocks with the blueberries.
Ingredients
- 1/2 lb soft butter
- 2 cups sugar
- 2 cups flour
- 4 eggs
- 1 t vanilla
- 1 t baking powder
- 1 can blueberry pie filling (or equivalent amount of home made filling)
Directions
- Preheat oven to 350 F
- Cream butter and sugar together.
- Add eggs, vanilla, flour and baking power and mix together.
- Pour half of the batter in a 13 x 9 pan (batter will be thick) and spread to the edge of the pan.
- Spread pie filling on top of batter
- Spread the other half of batter on top of pie filling. The top layer is hard to spread, just do the best you can and it usually comes out OK.
- Bake at 350 for 55 min.
Let cool, cut into squares and cover with plastic wrap then serve anytime in the next several days.
-
 @ b8a9df82:6ab5cbbd
2025-02-11 18:42:35
@ b8a9df82:6ab5cbbd
2025-02-11 18:42:35The last three weeks have felt like a dream—one I don’t want to wake up from. But here I am, on my last day in El Zonte, sitting by the ocean, doing what I love most: watching the waves roll in, surfers gliding across them, some catching them effortlessly, others tumbling but always getting back up. It’s a blessing to be here, soaking in the tranquility, reflecting on the past few weeks while finally sitting down to write about this incredible journey.
Reflecting on this experience, I realize how few people get to live something like this, and I am deeply grateful. Living by the ocean has always been a dream of mine, and these last few weeks have been nothing short of magical. The thought of saying goodbye? Not something I want to entertain. In a world where you can be anything, be kind, be grateful, and cherish the little things—the laughter, the small victories, the unexpected moments of pure joy.

Mexico—a country I was always warned about. "It’s dangerous," they said. "Drugs, crime, food poisoning, even kidnappings. A woman shouldn’t travel there alone." But despite the fear-mongering, after almost three months in South America, I was craving the ocean, and I kept hearing about Mexico’s stunning beaches. A little spoiler: I did see the beach… but it rained almost every day, and my toes barely touched the water.
With three options on the table—Tulum, Holbox, or Isla Mujeres—the decision wasn’t too hard. There was a crazy woman trying to Bitcoinize an entire island, and I had to see that for myself.
Just 13 kilometers off the coast of Cancún, Isla Mujeres is a tiny Caribbean paradise—perfect for unwinding and recharging. The island is wonderfully walkable, which I love. No need for a car. I even went for a few runs, and with the island stretching just 7 km in length, I got to explore its hidden oceanfront gems in no time.
But let’s talk about the journey. Arriving in Cancún after a long, exhausting flight, I was hit by chaos at the airport. Dozens of people aggressively offering rides, each one claiming to be a cab driver—it was a nightmare. Not speaking Spanish made things even harder, but thankfully, I wasn’t alone. After dodging the taxi mafia, getting stopped by the military for a random checkpoint (because, you know, legal taxis are apparently a thing to be double-checked), and making a pit stop in Cancún, we finally reached Isla Mujeres—greeted by storms and rain. But none of that mattered. I was here. I was at the ocean. And I was excited.
We stayed at Mayakita, a beautiful villa-style co-living space where you share the common areas—kitchen, coworking space, and outdoor lounges—but still have your own private room, bathroom, and balcony. Oh, and did I mention there’s a Jacuzzi? Absolute win.
The Mayakita team is even building a gym, which is a relief because the local options on the island were… let’s just say, unusable. Picture a tiny, overcrowded room packed with sweaty bodies, zero space between machines, and a never-ending queue for every piece of equipment. Nope. Not for me.
But the real highlight? The incredible restaurant attached to the villas. The food was an explosion of flavors—true mouthgasm territory. And, of course, you could pay for everything in Bitcoin.

To my surprise, I ended up staying with @nostr:npub1aftmyhm62lrp6lwsha3yzyjy5kqdvuy7g23qg28a8q0cnmudv0ds0sdcke the woman leading the Bitcoin adoption movement on the island. That’s when the craziness really started. The villa next door was booked by a couple of Bitcoiners, and as soon as they found out we had arrived, one of them knocked on our door. A warm smile, a little dog in his arms, and a simple, "Hey, need anything? Food? Help? A bottle opener?"
That’s what I love about this community. The energy, the kindness, the openness—it’s next level. You won’t get that at a typical resort, where people keep to themselves. Here? Instant bonding.
We spent the week exploring the island, asking every restaurant and shop if they accepted Bitcoin. If they didn’t? We walked away. Thanks to Isabella’s hard work, some businesses already do, and one of the highlights? Paying for a tattoo in Bitcoin.
One downside, though—transportation. Even though the island is walkable, taxis and golf carts are available for rent. But renting a golf cart for a week? A whopping $1,000! Insane. Luckily, Isabella had a tiny tuk-tuk, so she packed a few of us into the back and drove us around. No lights, barely any air, and a very bumpy ride. Did we survive? Yes. Would I do it again? Debatable. But hey, it was an experience!

Waking up every morning to the ocean was pure magic. The food? Unbelievable. The freshness of the vegetables, fruit, and fish—something you just don’t get in Germany. Even though I had the most expensive lunch of my life (let’s just say we spent way too much on ceviche and a main course), it was worth every cent.
This week taught me something valuable: You don’t need to be in the Bitcoin space for years to make an impact. I get it—long-time Bitcoiners might find it frustrating that adoption seems "easier" now. But I wouldn’t call myself a Bitcoiner just yet. I still have so much to learn. There were moments when I had no clue what people were talking about, even after all those private lessons, hours of talking how a lightening network works, what a hash is and that your 12 - 24 words, the so called private key is actually the master key that can generate an entire tree of private keys. But I’m incredibly lucky to be surrounded by people who are patient, willing to share their knowledge, and never get tired of explaining things again and again.
If I had to sum up this week in one phrase, it would be ridiculously beautiful and painfully peaceful.
If you love what Isabella is doing and want to support her work, consider sending her some sats.
All pictures taken by @nostr:npub1ygzsm5m9ndtgch9n22cwsx2clwvxhk2pqvdfp36t5lmdyjqvz84qkca2m5
-
 @ 2198da8d:23a73c4e
2025-02-11 18:15:27
@ 2198da8d:23a73c4e
2025-02-11 18:15:27Recovery and relaxation in the fast world today are important for general health. Whether you want to reduce your muscle tension as an athlete or fitness enthusiast, these two can do the trick: the body massage roller and the aqua bike. These have been established tools not only in helping in recovery but also in improving circulation, flexibility, and fitness in general. Let's learn more about them and how to integrate them into your life.
Body massage roller: the last breakthrough in muscle recovery
A body massage roller is just a simple device that is to be used by people for unwinding the muscles, increasing their flexibility, and enhancing blood flow. Using foam rollers, spiky balls, or vibrating rollers falls under a self-massage technique known as myofascial release; it breaks the muscle knots, which decreases the soreness caused by it.
The Perks of having a Body Massager Roller on your side,
- Relieve Your Muscle Tension – The stress on the massage roller will melt away soreness and stiffness through muscles.
-
Flexible – Regular sessions with a massager roller enable muscles to maintain flexibility, causing movements to occur more fluid with fewer injuries than expected.
-
Good Circulation Boosts – Its rolling action propels blood that carries oxygenation and nutrients required for faster rehabilitation.
-
Relieves Stress and Fatigue - The massaging effects of the roller increase its value as an addition to your wellness regimen.
-
Improves Performance —Whether an athletic performer or just a casual gym enthusiast, using a massage roller can help prepare your muscles for optimal performance.
How to Use a Body Massage Roller Effectively
1. Pre-Workout: Roll the major muscle groups like legs, back, and shoulders to activate circulation. 2. Post-Workout: Use it post-exercise to relieve muscle stiffness and promote faster recovery. 3. Daily Use: Include it in your routine for relaxation and stress relief.
Aqua Bike: The Future of Low-Impact Fitness
An aqua bike is a really revolutionary piece of fitness equipment designed to combine water resistance with a cycling workout, usually done inside a pool, providing a very low-impact yet high-intensity exercise regardless of the levels of fitness and health. That is why a person recovering from an injury as well as searching for a challenge can be particularly interested in doing an aqua bike.
An Aqua Bike has the following benefits:
- Joint-Friendly Workout- As water reduces the impact on the joints, it is for those with arthritis or are recovering from injuries.
- Improves Cardiovascular Health – Cycling in water increases the heart rate but the safety of the joints is maintained.
- Engagement of Muscles – It increases the chances of getting stronger muscles compared to normal cycling in the water due to the natural resistance in water.
- Burns more calories- Water resistance intensifies workout and thus burns more calories.
- Reduces Muscle Soreness – It automatically massages the muscles, hence reduces post-workout soreness.
- Improves Lymphatic Drainage – The pressure from the hydrostatic effect of water can remove toxins in the body and reduce swelling.
How to Add Aquabiking into Your Training
- Warm-up: Begin with slow pedaling to get accustomed to the resistance of the water.
- Cardio Session: Increase resistance and effect by pedaling rapidly or adding resistance from pool currents.
- Strength Session: Include intervals of sprinting and slow cruising to target different muscle groups involved in exercises.
- Cool Down: Slower pedaling and some stretching help muscles relax and recover.
Body Massage Roller: Combine this with an Aqua Bike for Maximum Benefit
This would be a very effective recovery and fitness tool as the combination of the body massage roller and aqua bike brings outstanding results. Here is how you can combine them:
- Pre-Workout Use massage roller to warm up the muscles before heading into an aqua bike.
- Workout: Aqua biking workout for 30–45 minutes for full body conditioning.
- Finish the workout with a massage roller for the release of muscle tightness and faster recovery.
Conclusion
The body massage roller and aqua bike are a couple of excellent tools for enhancing muscle recovery, your fitness, and general wellness. Be it to obtain low-impact cardio workouts or to help ease muscle tension, these tools can offer a practical solution for you. Integrate them into your fitness routine and achieve better flexibility, improved circulation, and faster recovery of your muscles toward a healthier and more active lifestyle.
-
 @ 000002de:c05780a7
2025-02-11 17:53:51
@ 000002de:c05780a7
2025-02-11 17:53:51Please don't take offense to this if you believe in the moral rightness of the existence of the modern state. I don't mean it as a slur, its just the best way to describe the opposite of an anarchist or voluntarist, people that believe in a voluntary society without an artificial monopoly on the use of violence.
I think the fact that many bitcoiners value liberty to some degree and often tend to be libertarian in their views, it is easy to assume we are all opposed to the state. My time in bitcoin circles has shown that to be false. Sure there is a much higher proportion of anti-state people in bitcoin than in the normal population, but we are not the majority. That's the sense I get at least.
Bitcoin's lure is far more broad than liberty and self sovereignty. The number of people that value these things for others is incredibly small. They exist but its a tiny number. Most people are NPCs. Some are just asleep. Others are on journeys of discovery and maybe they can be reached.
Since Trump won the election in the US I have noticed many articles trying to throw cold water on the people happy about his win and the changes he's been making over the past few weeks. I think a big mistake many are making is assuming these people have been seduced by Trump. Maybe that's true but I don't think most of these people were opposed to the state before Trump. Trump is just a different animal. A bull in a china shop doing some things many people have wanted for decades. He's not ideological, moral, or principled.
Like the left these bitcoiners just want their way. They want big daddy government to make the world in the way they want it to be. Its a journey. I wasn't born with all the ideas I now hold. I don't think its persuasive or smart to assume your fellow bitcoiners are like you in their views on the state. They probably are much closer to traditional conservatives than anarchists.
With all that said, I think far too few people seek to find common ground with others. I may not seem to value this on SN but let me assure you that in person I very much seek common ground with those around me.
Some of you need to hear this. We will never have a society where everyone agrees on anywhere near to everything. Sure, some things like murder are pretty agreed upon but I bet you are thinking of examples of disagreements on how to handle it.
So keep that in mind. Bitcoin isn't going to turn everyone into a mirror image of your beliefs. Stay humble. We need the people around us. We don't need millions of clones.
originally posted at https://stacker.news/items/882903
-
 @ a012dc82:6458a70d
2025-02-11 17:18:57
@ a012dc82:6458a70d
2025-02-11 17:18:57As the calendar flips to 2024, the financial world's spotlight remains firmly on Bitcoin. This digital currency, once a niche interest, has burgeoned into a major financial asset, challenging traditional investment paradigms. After a staggering 150% rally in 2023, outperforming stalwarts like the S&P 500, gold, and the U.S. dollar, Bitcoin has stirred a mix of excitement and skepticism. Investors, analysts, and enthusiasts are now keenly debating what the future holds for this pioneering cryptocurrency. Will the upward trajectory continue, or is a correction imminent? This article aims to dissect the various factors and indicators that could influence Bitcoin's journey through 2024, offering insights into its potential growth or pitfalls.
Table Of Content
-
Understanding the Current Landscape
-
Key Indicators for 2024
-
The Halving Event: A Catalyst for Change
-
Global Economic Factors
-
Technological Advancements and Adoption
-
Challenges and Risks
-
Conclusion
-
FAQs
-
Analyzing Bitcoin's Potential for 2024
Understanding the Current Landscape
The story of Bitcoin in 2023 is one of resilience and resurgence. Following a tumultuous period marked by regulatory uncertainties and market skepticism, Bitcoin's impressive rally has been a testament to its growing acceptance and maturation as an asset class. This resurgence is underpinned by several key developments: increasing institutional investment, which has lent credibility and stability; advancements in blockchain technology, enhancing Bitcoin's utility and efficiency; and a broader recognition of Bitcoin as a viable digital alternative to traditional safe-haven assets like gold. Moreover, the socio-economic landscape, characterized by inflationary pressures and a search for non-traditional investment havens, has further fueled Bitcoin's appeal. However, this landscape is complex and ever-evolving, with regulatory shifts, technological advancements, and global economic trends continuously reshaping the narrative.
Key Indicators for 2024
Puell Multiple
The Puell Multiple, a sophisticated yet insightful metric, currently paints a promising picture for Bitcoin. Standing at 1.53, it indicates a balanced valuation – not too hot, not too cold. This equilibrium is significant, considering the historical context where extremes in this metric have often signaled impending market shifts. A value above four typically heralds a peak, signaling overheating, while a dip below 0.5 has often been a precursor to market bottoms, indicating undervaluation. The current reading suggests a potential for steady, sustainable growth, devoid of the speculative frenzy that has characterized previous cycles.
MVRV Z-Score
The MVRV Z-Score, another critical indicator, echoes a similar sentiment. With a current score of 1.6, it implies that Bitcoin is neither in the throes of overvaluation nor languishing in undervaluation. This metric, by comparing market capitalization with realized value, offers a nuanced view of Bitcoin's market position. Historically, extreme values in this score have been reliable harbingers of market tops and bottoms. The current moderate score suggests that Bitcoin may have room for growth, absent the speculative bubbles that have led to volatile boom-and-bust cycles in the past.
Mayer Multiple
The Mayer Multiple, currently at 1.404, offers a perspective on Bitcoin's price relative to its historical performance. This indicator, by comparing the current market price to the 200-day simple moving average, helps identify potential overbought or oversold conditions. A value above 2.4 has historically indicated overbought conditions, often leading to corrections, while a value below 0.5 suggests oversold conditions, presenting potential buying opportunities. The current Mayer Multiple suggests that Bitcoin is trading at a healthy level above its long-term average, indicating that there's potential for further growth before it enters overbought territory.
The Halving Event: A Catalyst for Change
The upcoming Bitcoin halving event in March 2024 is poised to be a pivotal moment. This event, which occurs approximately every four years, reduces the reward for mining new Bitcoin blocks by half. Historically, halving events have been significant market catalysts, often leading to substantial price increases in the following months. The rationale is straightforward: a reduction in the rate of new Bitcoin creation leads to a decrease in supply. If demand remains constant or increases, this supply squeeze can lead to higher prices. However, the halving is more than just a supply-side story. It also attracts media attention and investor interest, potentially drawing new participants into the Bitcoin market. The anticipation and speculation surrounding the halving can create a self-fulfilling prophecy, driving prices up. However, it's important to note that past performance is not indicative of future results, and the market dynamics surrounding each halving are unique.
Global Economic Factors
The trajectory of Bitcoin in 2024 will also be heavily influenced by the broader global economic environment. Factors such as inflation rates, monetary policies of major central banks, and geopolitical tensions play a significant role in shaping investor sentiment towards risk assets, including cryptocurrencies. In an environment where traditional currencies are devalued due to inflation or economic instability, Bitcoin could gain further traction as a digital store of value. Conversely, a tightening of monetary policy, leading to higher interest rates, could dampen investor appetite for riskier assets like Bitcoin. Additionally, geopolitical events that create uncertainty in traditional markets could either drive investors towards safe-haven assets like gold and potentially Bitcoin or lead to a broader risk-off sentiment, adversely affecting all risk assets, including cryptocurrencies.
Technological Advancements and Adoption
The ongoing development and adoption of Bitcoin and blockchain technology will be crucial determinants of Bitcoin's value in 2024. The evolution of the Lightning Network, which promises faster and cheaper transactions, could significantly enhance Bitcoin's utility as a medium of exchange. This, in turn, could broaden its appeal beyond just a store of value, potentially attracting a new wave of users and investors. Furthermore, the integration of Bitcoin into more mainstream financial services and the continued growth of the decentralized finance (DeFi) sector could provide additional use cases and increase its value proposition. However, technological advancements are not without risks. Issues such as network scalability, security vulnerabilities, and the environmental impact of Bitcoin mining continue to be areas of concern that could influence public perception and regulatory scrutiny.
Challenges and Risks
Despite the optimistic outlook based on current indicators, the path ahead for Bitcoin is fraught with uncertainties and risks. Regulatory developments remain a wildcard. Governments and financial regulators around the world are still grappling with how to best regulate cryptocurrencies. Stricter regulations, or even outright bans in certain jurisdictions, could impact Bitcoin's accessibility and attractiveness. Additionally, the inherent volatility of Bitcoin remains a significant concern. While this volatility can present opportunities for high returns, it also poses substantial risks for investors, particularly those who are not well-versed in the cryptocurrency market. Moreover, the technological landscape of cryptocurrencies is rapidly evolving, and Bitcoin faces competition from newer, potentially more technologically advanced cryptocurrencies. This competition could impact Bitcoin's market dominance and investor sentiment.
Conclusion
As we look towards 2024, the journey of Bitcoin continues to be an intriguing blend of potential and unpredictability. The indicators and factors discussed in this article suggest a cautiously optimistic outlook for Bitcoin. However, it is crucial for investors and enthusiasts to remain vigilant and informed, considering both the opportunities and the risks involved. The evolution of Bitcoin is not just a financial story; it's a technological and socio-economic narrative that continues to unfold in fascinating and often unexpected ways. The coming year promises to be another chapter in this ongoing saga, as Bitcoin navigates the complex interplay of market dynamics, technological advancements, and global economic trends.
FAQs
What is the significance of the Bitcoin halving event in 2024? The Bitcoin halving, expected in March 2024, is a pivotal event where the reward for mining new Bitcoin blocks is halved. Historically, this has led to a reduction in supply and often a subsequent increase in price, attracting significant investor attention.
How do economic factors influence Bitcoin's value? Global economic factors such as inflation rates, monetary policies, and geopolitical tensions can significantly impact Bitcoin's value. Inflation or economic instability can enhance Bitcoin's appeal as a digital store of value, while tighter monetary policies might reduce the appetite for riskier assets like Bitcoin.
What are the key indicators to watch for Bitcoin in 2024? Key indicators include the Puell Multiple, MVRV Z-Score, and Mayer Multiple. These metrics provide insights into Bitcoin's valuation, market capitalization, and comparison to historical performance, helping gauge its potential growth or correction.
How does technological advancement affect Bitcoin? Technological advancements, like improvements in the Lightning Network, enhance Bitcoin's utility and efficiency. This can broaden its use cases, potentially increasing its value. However, technological risks and competition from other cryptocurrencies also play a role.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 000002de:c05780a7
2025-02-11 17:09:02
@ 000002de:c05780a7
2025-02-11 17:09:02Have you ever tried to explain the political factions in the US to a curious young person? If you haven't you might not realize how little sense they make. This is only becoming more evident with the radical changes the current admin are making.
I have to say I'm enjoy being a spectator of it all. When I was a kid the dems were called liberals and they called themselves liberals. The republicans didn't always call themselves conservatives but over the years that has become more of the case.
These days with a new admin that is hardly conservative, the left is losing their mind because of the new admin's strategy for reforming the executive branch. When I listen to them they sound a lot like conservatives. Talking about how long this thing or that thing has been in place. How these kids are being given power. Its all rather funny and hypocritical to me.
Conservatives typically don't like change but they seem to like the new approach in Washington. I would argue what is going on is NOT conservative. Its actually pretty radical. I have long thought that the conservative movement was a joke. What are they conserving? They seem to never get the core problems and how deep the rot goes. They seem to be stuck in some nostalgic dream of a time that never existed. A perpetual 20 years ago time that never existed. When education was great and morals were more to their liking.
Michael Malice said it best I think, "Conservatives are progressives going the speed limit".
The dems typically call themselves progressive now which is also a bad descriptor. They seem to be bigger moralists than their opponents. Rather than progressing towards a bright future, blazing a new trail they seem to want to try to old meritless ideas of old men like Marx. Their answers to every problem are centralizing power and giving more of your freedoms away. This is hardly a progressive or new idea. Its an old idea. One of a strong state that controls more of your life. Its hardly liberal either.
I don't have new terms that work and even if I did good luck changing them :)
Just one man's observation.
originally posted at https://stacker.news/items/882858
-
 @ 527b02f7:b0ed5fd2
2025-02-11 16:17:50
@ 527b02f7:b0ed5fd2
2025-02-11 16:17:50Después de un tiempo sin escribir, he decidido retomar el blog con un enfoque más amplio. Seguiré compartiendo contenidos sobre póker, mental game y pot-limit omaha, pero también quiero adentrarme en otros temas que me despiertan curiosidad y que he explorado a fondo últimamente: Bitcoin, inteligencia artificial, finanzas, productividad…
Espero que las nuevas entradas que tengo previstas publicar te resulten interesantes y que puedan inspirarte, ayudarte a reflexionar o simplemente ofrecerte una lectura amena. Hoy quiero comenzar con un tema que me apasiona particularmente: Bitcoin.
Cuando alguien afirma que "Bitcoin no sirve para nada" o que no tiene valor intrínseco, está sugiriendo que todos los casos de uso documentados de Bitcoin carecen de valor. Pero ¿es realmente así? Este artículo se inspira en una brillante contestación de X (Twitter) de Daniel Batten, donde refuta esta afirmación enumerando 19 casos concretos donde Bitcoin ya está marcando una diferencia tangible. Desde proyectos de sostenibilidad energética en África hasta la inclusión financiera para millones de personas, los ejemplos abundan.
Antes de abordar estos casos, es importante explorar una pregunta clave: ¿Qué entendemos por "valor"?
El valor: una perspectiva subjetiva
El concepto de valor, lejos de ser una cualidad objetiva e intrínseca de los objetos, es una construcción subjetiva que depende del contexto, la percepción individual y las circunstancias específicas de cada persona. Esta afirmación, que puede parecer intuitiva en lo cotidiano, tiene profundas implicaciones filosóficas y prácticas que han sido objeto de debate desde la antigüedad hasta nuestros días.
En términos filosóficos, podemos remontarnos a la escuela estoica, que sostenía que no son los eventos ni los objetos los que tienen valor en sí mismos, sino las opiniones que formamos sobre ellos. Epicteto, por ejemplo, afirmaba:
“No son las cosas las que nos perturban, sino las opiniones que tenemos sobre ellas.”
Este principio encapsula la idea de que el valor no reside en los objetos, sino en la forma en que interactuamos emocional y racionalmente con ellos.
Desde una perspectiva económica, esta noción de subjetividad se formaliza en la teoría del valor subjetivo, desarrollada por economistas como Carl Menger durante la revolución marginalista. Según esta teoría, el valor de un bien no depende de sus características intrínsecas, sino de la utilidad percibida que ofrece al individuo en un momento dado.

El valor que asociamos de un activo viene determinado por varias características. La utilidad es una de ellas, pero no es la única, ya que si esa fuera la única, el aire que respiramos sería el activo más valioso. El problema es que, al no ser escaso, su valor percibido no es alto. Por ejemplo, un vaso de agua puede ser trivial en una ciudad con acceso a agua potable, pero se convierte en un objeto de valor incalculable para alguien que atraviesa un desierto. Por tanto, un bien debe ser no solo útil, sino también escaso para tener un alto valor.
Esto subraya que el valor es dinámico y depende tanto del contexto como de las necesidades y deseos del individuo.
En el caso de tecnologías como Bitcoin, este principio es aún más evidente. Para un habitante de una economía estable, con acceso a servicios financieros modernos, Bitcoin puede parecer un experimento especulativo o una moda pasajera. Sin embargo, para alguien en una región afectada por la hiperinflación o excluida del sistema bancario, puede representar una herramienta crucial para preservar sus ahorros y participar en la economía global.
Esto nos lleva a la conclusión de que el valor no puede ser medido universalmente ni reducido a una fórmula fija. Depende de quién lo perciba, bajo qué circunstancias y con qué expectativas.
Así, el valor es un reflejo de nuestra humanidad: una mezcla de subjetividad, contexto y significado que le conferimos a las cosas. Entender esto no solo nos ayuda a apreciar la diversidad de perspectivas, sino también a cuestionar nuestras propias suposiciones sobre lo que consideramos valioso.
El oro, por ejemplo, es el activo con mayor valor en términos de capitalización de mercado, estimado en aproximadamente 16.3 trillones de dólares. Aunque su utilidad práctica es limitada —principalmente en adornos ornamentales, como la joyería, y en algunas aplicaciones tecnológicas por su alta conductividad y resistencia a la corrosión—, no alimenta a nadie, ni genera energía. Sin embargo, sus propiedades y aceptación universal a lo largo de los siglos, le han otorgado un estatus especial. El oro es fácilmente reconocible, divisible y difícil de producir, lo que lo convierte en un bien apreciado y valioso. No obstante, presenta ciertos inconvenientes, como la dificultad para transportarlo, verificar su autenticidad y su vulnerabilidad a la confiscación. Además, aunque su tasa de inflación es baja, cada año se extrae nuevo oro y su producción puede aumentar si la demanda así lo requiere.

De manera similar, el arte puede ser invaluable para algunos y un objeto sin sentido para otros. ¿Cómo explicamos que una pintura contemporánea o una escultura de un artista moderno pueda valer millones para algunos y carecer de valor para otros? Es la percepción subjetiva de las personas, y su escasez, lo que determina el valor, no una cualidad objetiva inherente a la obra.

El valor de los bienes inmuebles no está determinado únicamente por sus propiedades (metros, calidades) si no que está profundamente ligado a la escasez. Un apartamento en primera línea de playa tiene un valor elevado porque existe una cantidad limitada de espacio en estas zonas, lo que lo convierte en un bien escaso y no replicable. De manera similar, los inmuebles más preciados en las ciudades suelen encontrarse donde hay mayor infraestructura, oportunidades de negocio y servicios. En cambio, un inmueble en mitad de la nada, aunque tenga las mismas dimensiones, calidades y número de habitaciones que otro inmueble en una ubicación privilegiada, no es escaso ni está rodeado de servicios o infraestructura, lo que reduce significativamente su valor percibido. A mayor demanda del inmueble y menor oferta del mismo, mayor será su valor en el mercado.

Por otro lado, el valor de las acciones de una empresa está relacionado con su capacidad de aportar soluciones a problemas reales y generar beneficios. Una empresa crea valor porque satisface una demanda en el mercado, mejora la vida de las personas y, en consecuencia, genera ingresos y flujos de caja positivos. Este valor intrínseco se refleja en el precio de las acciones, que no solo capturan el rendimiento financiero actual de la empresa, sino también las expectativas de su crecimiento futuro y su capacidad de seguir generando beneficios.

Las monedas fiduciarias, como el dólar o el euro, son efectivas para realizar transacciones gracias a su red de aceptación global y su estabilidad de precio en el corto plazo. Sin embargo, estas monedas pierden valor de forma predecible y gradual, (debido a la continua creación de nuevas unidades por parte de los bancos centrales), lo cual las hace adecuadas como medio de intercambio, pero no como reserva de riqueza a largo plazo. Una inflación anual del 2% implica que en 50 años habrás perdido el 100% del poder adquisitivo de tu capital. Y esto aplica a las monedas más estables del mundo; si hablamos de monedas con tasas de inflación más altas, la pérdida es aún mayor. Además, la inflación real, en términos de la pérdida de capacidad de compra, suele ser significativamente superior al 2% anual, ya que el incremento de la masa monetaria es mayor al 2%.

Esto hace que el capital fluya hacia otros tipos de activos, mencionados anteriormente, con el objetivo de preservar su valor a lo largo del tiempo. Acciones, bonos del tesoro, bienes inmuebles, arte y oro son algunos de los activos que absorben gran parte del capital global, actualmente estimado en unos 450 trillones de dólares (trillones con T).


Bitcoin no puede encuadrarse en el marco de los activos tradicionales, ya que se trata de un tipo de activo nuevo, el primer activo real digital. Esta nueva clase de activo permite transferir y almacenar valor en el tiempo, sin necesidad de confianza en terceros ni de intermediarios, de manera segura.
A diferencia de los activos tradicionales, Bitcoin no está sujeto a la inflación monetaria, la intervención de gobiernos o el riesgo de contraparte que afectan a divisas y otros activos. Su naturaleza descentralizada y deflacionaria lo convierte en una forma de preservación de valor que supera los desafíos de los activos convencionales, ofreciendo seguridad y autonomía sin precedentes.
El verdadero cambio de paradigma que plantea Bitcoin es que, como tecnología, permite preservar el capital a lo largo del tiempo de una manera sin precedentes. Con mínimos costes de mantenimiento y absoluta seguridad, Bitcoin ofrece una alternativa que supera las limitaciones históricas de preservar riqueza. Hasta ahora, preservar el capital o la riqueza a lo largo del tiempo no era posible debido a la naturaleza inflacionaria de los métodos de preservación de capital utilizados hasta el siglo XX. Los métodos tradicionales del mundo analógico, como los activos financieros, el arte, los bienes inmuebles, las acciones, los bonos del tesoro o los metales preciosos, padecen de distintos defectos que los hacen susceptibles a la inflación y presentan riesgos significativos, como el riesgo de contraparte.
Como activo de reserva de valor, Bitcoin proporciona una serie de beneficios y ofrece una serie de características novedosas y muy interesantes, si lo comparamos con otros activos que se han usado históricamente para tal uso:
Beneficios
- Sin impuestos
- Sin tráfico
- Sin inquilinos
- Sin disputas legales
- Sin problemas
- Sin alcalde o gobierno local
- Sin dependencia del clima
- Sin corrosión
- Sin regulador
Características
- Invisible
- Indestructible
- Inmortal
- Teletransportable
- Programable
- Divisible
- Fungible
- Configurable
Bitcoin representa una nueva forma de preservar valor que no depende de la confianza en intermediarios, ya que está protegida de la devaluación por su naturaleza deflacionaria (nadie puede crear más unidades arbitrariamente) y está respaldada por la energía utilizada en su proceso de minería.

Esta energía asegura la red y garantiza la seguridad de las transacciones, haciendo que el valor de Bitcoin esté protegido por un recurso tangible y difícil de replicar. Se trata de una solución específicamente diseñada para resolver el problema de la pérdida de capital a lo largo del tiempo. Estas características hacen que Bitcoin sea una opción única y potente en el ámbito de la preservación de riqueza, una solución que no ha existido hasta ahora.
Al ser un avance tecnológico y un activo intangible, muchas personas no logran entender la trascendencia del significado de Bitcoin. No se debe a una falta de capacidad intelectual, sino a que lo están analizando desde una perspectiva equivocada o con un enfoque anticuado. Intentar agruparlo con otros activos tradicionales impide apreciar su verdadero significado y las implicaciones de primer, segundo y tercer orden que conlleva este descubrimiento.

Bitcoin como revolución tecnológica
Bitcoin no es una moneda digital; es una tecnología disruptiva. Para comprender su impacto, podríamos usar la analogía de la pólvora, popularizada por Álvaro D. María:
"Bitcoin viene a redefinir el derecho de propiedad, es a las finanzas lo que la pólvora fue a las batallas."
En sus inicios, la pólvora fue vista como un experimento curioso, sin aplicaciones reales para quienes no comprendían su potencial. Pero una vez que su poder transformador se hizo evidente, cambió las reglas del juego para siempre. Lo mismo está sucediendo con Bitcoin.
Álvaro D. María utiliza la analogía de la pólvora para ilustrar cómo Bitcoin está revolucionando el sistema financiero. Al igual que la pólvora transformó la guerra, alterando para siempre el equilibrio de poder y permitiendo nuevas tácticas y estrategias, Bitcoin está haciendo lo mismo con el dinero. La pólvora eliminó las barreras tradicionales de poder basadas en la fuerza física, mientras que Bitcoin está eliminando la necesidad de depender de intermediarios y de las estructuras centralizadas que han dominado el sistema financiero durante siglos.

Bitcoin democratiza el acceso a una reserva de valor, permite transferencias de capital sin restricciones y redefine el concepto de confianza en las transacciones financieras. Por ejemplo, al eliminar la necesidad de intermediarios como los bancos, Bitcoin permite que personas de cualquier parte del mundo transfieran valor directamente entre sí, sin depender de una institución centralizada que garantice la transacción. De la misma forma que la pólvora permitió a pequeños ejércitos vencer a grandes potencias, Bitcoin permite a individuos tomar el control de su propia riqueza, sin necesidad de confiar en bancos o gobiernos.
Esta revolución tecnológica está apenas comenzando, y su potencial para reconfigurar el panorama económico mundial es tan profundo como lo fue la pólvora para la historia de la humanidad.
Si quieres escuchar la opinión de Álvaro D. María directamente de sus propias palabras, te recomiendo que veas esta entrevista que puedes ver en YouTube:
https://www.youtube.com/watch?v=6Yefg_g-iXg&t=945s
Desmontando el argumento de la inutilidad
A continuación, repasamos algunos ejemplos concretos que muestran por qué decir que Bitcoin "no sirve para nada" es ignorar su impacto en el mundo real.
*Al final del artículo tienes enlaces a las noticias reales de todos y cada uno de los casos que expongo a continuación
1. Energía y sostenibilidad
Bitcoin está ayudando a aprovechar recursos energéticos que, de otro modo, se desperdiciarían. Por ejemplo, en Bután, la minería de Bitcoin utiliza energía hidroeléctrica sobrante, acelerando la independencia energética de la región.
En África, proyectos de minería impulsan la construcción de infraestructuras energéticas en aldeas aisladas, proporcionando electricidad a comunidades que antes no tenían acceso.
2. Inclusión financiera
Más de 2 mil millones de personas en el mundo no tienen acceso a servicios bancarios. Bitcoin está cambiando eso al ofrecer una alternativa que no requiere permisos ni documentación.
En Afganistán, miles de mujeres utilizan Bitcoin para esquivar la discriminación financiera y acceder a sus propios ahorros. En países como Venezuela o Argentina, donde la hiperinflación erosiona los ahorros, Bitcoin actúa como una salvaguarda.
3. Soberanía económica y justicia global
Catorce países africanos aún sufren los efectos de una colonización financiera ejercida a través del franco CFA. Bitcoin ofrece una vía para lograr la independencia económica, permitiendo a estas naciones gestionar su riqueza sin interferencias externas.
Además, los refugiados de guerra encuentran en Bitcoin un medio seguro para recibir ayuda económica directamente, sin depender de sistemas que podrían bloquear los fondos.
4. Innovación ambiental
Bitcoin no solo reduce la dependencia de energías fósiles, sino que también mitiga las emisiones de metano al reutilizar gas quemado o ventilado para generar energía. Esto ha llevado a proyectos que, en conjunto, reducen más emisiones que el mayor proyecto de captura de carbono del mundo.
5. Bitcoin como Capital Digital
Bitcoin es más que una moneda digital; es una revolución en cómo entendemos y preservamos el valor.
Satoshi Nakamoto descubrió un método para transferir y almacenar valor sin la necesidad de un intermediario de confianza, lo cual es un logro monumental en la historia del dinero. Bitcoin representa la transformación de nuestro capital, pasando de activos financieros y físicos a activos digitales.
Este nuevo tipo de activo digital no está sujeto a los riesgos financieros de las divisas, acciones o bonos, ni a los riesgos físicos que afectan a los bienes inmuebles o propiedades. Bitcoin es, esencialmente, capital digital: un activo seguro y descentralizado que proporciona una alternativa sin precedentes para almacenar valor de manera efectiva, sin la intervención de terceros y sin las restricciones propias de los sistemas financieros tradicionales.
Esto es algo que el mercado está descubriendo y que ha estado mostrando al mundo durante sus primeros años de vida.

Bitcoin no es un test de inteligencia, es un test de ego
Negar la utilidad de Bitcoin a pesar de la evidencia puede reflejar una falta de comprensión o una resistencia natural al cambio más que una evaluación crítica. A menudo, la adopción de nuevas tecnologías no depende de su perfección, sino de nuestra disposición a comprender y aceptar su impacto.
A Bitcoin le es indiferente que creas o no en él; no tiene en cuenta si lo valoras o no. La red seguirá creciendo y generando bloques a un ritmo constante de aproximadamente 10 minutos por bloque, independientemente de su valor en términos de moneda fiduciaria. Mientras tanto, el mundo y el mercado irán descubriendo, poco a poco, su propuesta de valor.
La verdadera cuestión no es si Bitcoin tiene valor hoy, sino si estamos preparados para adaptarnos al cambio monumental que representa. Aquellos que comprendan esta transformación a tiempo podrán beneficiarse de la misma, mientras que los que la ignoren se enfrentarán a una realidad en la que Bitcoin ya es parte fundamental del sistema económico global.
A continuación tienes todos los casos de uso citados en el tweet y los enlaces a los artículos correspondientes:
- Ayudar a traer abundancia energética a 1800 aldeanos africanos no tiene valor.
https://t.co/bgOaasQeUG - Enviar ayuda a miles de refugiados de guerra es inútil.
https://t.co/WKD4FNPGlq - Desarrollar independencia energética en Bután es inútil.
https://t.co/fKBkfEKDea - Proteger Parques Nacionales en África es inútil.
https://t.co/455ChX6f9P - Ayudar a 19,4 millones de mujeres afganas a evitar la discriminación financiera estatal es inútil.
https://t.co/GsClHWJn7H - Establecer la soberanía económica de 14 naciones africanas que aún sufren colonización financiera francesa es inútil.
https://t.co/s18NsVHKKT - Crear una alternativa a un sistema monetario que prolonga guerras, aumenta brechas de riqueza, rescata banqueros pero no protege a empleados ni pequeñas empresas es inútil.
https://t.co/T6D7yoGZdz - Ofrecer servicios bancarios a 2 mil millones de personas no bancarizadas es inútil. https://t.co/T4mjBZ8oRo
- Proveer un sistema financiero más difícil de usar para el lavado de dinero que las monedas fiat es inútil.
https://t.co/CLghbaZfU5 - Evitar represalias financieras por liderar campañas humanitarias en naciones autocráticas donde viven 5,7 mil millones de personas es inútil.
https://t.co/2KM9kuAUQp - Ofrecer a 250 millones de personas en países con hiperinflación una forma de evitar la erosión del 50% o más de sus ahorros anuales es inútil.
https://t.co/7Yu7IpSSpd - Permitir a las personas en naciones en desarrollo recibir remesas sin retrasos ni altas comisiones es inútil.
https://t.co/NWTeMOLUny - Tener un depósito de valor seguro, sin permisos, descentralizado, disponible 24/7 y con suministro monetario fijo es inútil.
https://t.co/J75wOAXWzS - Lograr ser la industria más sustentablemente alimentada del mundo es inútil.
https://twitter.com/DSBatten/status/1670320573480833025 - Acelerar la transición a energías renovables haciéndolas más rentables es inútil.
https://t.co/4SCHxTMRBu - Reducir más emisiones de vertederos que el mayor proyecto de captura de carbono del mundo es inútil.
https://t.co/5IysyKbWrg - Desarrollar un sistema financiero con significativamente menos emisiones que el sistema bancario es inútil.
https://t.co/RIiW2jx63R
https://twitter.com/DSBatten/status/1671336675497349121 - Conservar gas natural perdido, ventilado o quemado a través de la minería de Bitcoin, evitando contaminación por metano.
https://t.co/EZ1kjBz4Pt - Mejorar la estabilidad de la red eléctrica.
https://t.co/c5rny2m66V
-
 @ 316ede27:a512e056
2025-02-11 15:33:26
@ 316ede27:a512e056
2025-02-11 15:33:26hi
-
 @ d57360cb:4fe7d935
2025-02-11 14:09:51
@ d57360cb:4fe7d935
2025-02-11 14:09:51Disbelief in oneself
Theres a scene near the opening of the movie where Terence Fletcher (JK Simmons) is yelling at one of his trombone players about being out of tune. He’s asks him ‘Do you think you’re out of tune?’ The player nervous and shook by Fletcher puts his head down and says yes. Fletcher proceeds to yelling in his face and kicking him out.
The funny thing about this scene is that the trombone player wasn’t actually out of tune, it was someone else. What Fletcher is looking for in his world class band are individuals who believe in themselves. The scene had nothing to do with being out of tune with the instrument but more so being out of tune with yourself. The trombone players every action is motivated by the energy of fear.
I believe Fletcher’s character represents the world and critics they are harsh, they don’t care about your feelings, they will attack you and if you lack belief you’ll give up and stop short or worse won’t even begin the journey at all.
The harshest critic can sometimes be oneself as displayed by the trombone player. His belief is so low Fletchers words act as reinforcement to his already low view of himself. In this way Fletcher acts a mirror to his students.
Belief in oneself
Another scene i’d like to highlight is the exact opposite of the trombone scene. Near the end of the film Andrew Nieman (Miles Teller) is late for the bands show and he barges into the room a few minutes before the start. Irate, Fletcher attacks him for being late and tells him he’s losing his spot to another drummer. This is a test on Andrew to see how he reacts, will he crumble and fall like the trombone player?
Andrews response displays an individual with unwavering belief in his abilities he tells fletcher in essence ‘fuck off its my part’. No matter how much Fletcher attacks his skill and character, Andrew doesn’t care he’s willing to stand on his ability and not let the noise bother him.
This scene to me symbolizes the epitome of confidence. Throughout the movie Fletcher is downplaying Andrew and his skill. He tells him he’s not good enough, his skills aren’t sharp. What he was doing wasn’t pushing Andrew to practice more and get better, he was pushing him to believe in his own power and greatness.
“Our deepest fear is not that we are inadequate. Our deepest fear is that we are powerful beyond measure”.
Links to the clips
Trombone clip: https://www.youtube.com/watch?v=e0yL-avlEsg
Andrew loses spot clip: https://www.youtube.com/watch?v=5OxTIpMSkpw
-
 @ c69b71dc:426ba763
2025-02-11 14:07:34
@ c69b71dc:426ba763
2025-02-11 14:07:34The Power of Words...
...Shaping a Compassionate Future
This morning I woke up with this thought:
> If we were more mindful of our choice of words, we would immediately need to change the following: Schools would no longer have classes and classifications, but only Communities!
This would make a huge difference in terms of togetherness, well-being, and caring for one another. 🙌🏼
Language shapes reality
Words influence how we see the world and ourselves. When we replace terms like "classes" or "grades" with "community" and "development," it changes our entire way of thinking about education and coexistence. For example, in companies, we often talk about "teams" instead of "departments." This unconsciously fosters unity, cooperation, and a sense of belonging on equal terms.
Community instead of competition
In school, work, and everyday life, we often evaluate, compare, and classify. But what if we focused on cooperation and synergies instead of competition? In some schools, there are no grades anymore, just individual feedback – this takes away the performance pressure and strengthens intrinsic motivation.
Appreciation instead of categorization
Putting people in "boxes" – whether through grading systems, social classes, or job titles – often creates separation rather than connection. Instead of labeling people as "successful" or "failed," we could ask: "What are their strengths? How can we support each other?" Mindful language in everyday life We could also reflect on our word choices in daily life: Instead of "problem" → "challenge" Instead of "failure" → "learning opportunity" Instead of "mistake" → "experience"
School as a mirror of society
How we learn to interact with each other in school shapes our behavior in society. When children grow up in communities instead of class systems, they learn that cooperation and empathy are more important than competition. There are so-called democratic schools where there are no grade levels – children learn from each other across ages. Students support each other by sharing knowledge and helping each other. Teachers are seen as coaches, not as "all-knowing" authority figures. They too are human and can learn from the children. Many teachers want to give children something that will help them in life.
However, the rigid old school system dictates what must be taught and when, often disregarding the individual interests of the children. This stifles passions – in both the children and the teachers. Instead, teachers could act as inspiring sparks, igniting curiosity and enthusiasm for learning.
**A history teacher once said to me on the phone, when discussing my son who didn’t want to read printed Wikipedia sheets: "If there is no spark in the child, the teacher can’t ignite anything." **
This sentence frustrated me, because it shows that this teacher had long since lost his own spark! Children always have a spark. Always!
A day without evaluations
What if we consciously refrained from evaluating others for one day – whether through grades, criticism, or labels? Instead of saying to a friend, "You made a mistake," we could say, "That was an interesting experience – what did you learn from it?" Instead of saying, "That wasn’t good," we could ask, "How could it be done differently or better?" Instead of grading children in school, we could tell them what they did well and where they can still grow. Instead of getting upset about a difficult customer, we could feel empathy for their situation.
Mindful language as the key to change
**If we are more mindful with our language – also with how we speak to ourselves – we can shape a society where people meet each other with compassion. **
Words are vibrations that shape reality. Chosen consciously, they can create a world based on connection, growth, and love. It is up to us to start this change within ourselves – and carry it into the world.Thank you for reading 🕊️

-
 @ 54286b98:3debc100
2025-02-11 11:33:38
@ 54286b98:3debc100
2025-02-11 11:33:38We correct because we care.\ And when others correct us, it’s a reminder: We’re cared for.
“No calm ocean makes a skilled sailor,” they say. Yet we often prize safety more than the process that actually makes us skillful—able to navigate life’s oceans securely. We want the result: expertise, confidence, calm at the helm. But we’re often reluctant to embrace the very process that shapes us.
Trials and life’s tests aren’t pleasant, but maybe we should see them through our Father’s eyes. How else can we possibly grow? If not by trials, then how? Any parent knows we don’t just learn by hearing; we are stubborn beings who truly learn after experiencing.
It’s in those small, fear-fueled moments—realizing you could have fallen off a cliff, been hit by a car, or lost your career over a careless comment—that your senses awaken to very real consequences. Hopefully, that flash of adrenaline is enough to teach a lesson. But often, more often than we’d like to admit, it isn’t.
God’s parenting style is fascinating; He’s patient beyond measure. He can handle our insecurities and weaknesses for a very long time. Even when our earthly parents may have given up on us, He won't. Either we walk away from His lessons, or we keep facing the same challenges meant to shape us—making us whole, maturing us in our faith—until we finally learn and pass the test.
Paraphrasing the message of James chapter 1: “Count it all joy, pure joy, when you face trials. If you don’t understand why you’re going through what you’re going through, ask God for wisdom—He will give it to you.”
During your high, victorious moments, remember: you’ll be tested again. Take heart—because the end goal is a more resilient and confident version of you, anchored in God rather than in yourself.
During your low moments—when everything feels painfully hard—remember that you have a Father’s hand guiding you, never leaving you alone.
You’ve got this…in God.\ Until the next one,\ J
Legacy website article and email subscription here.\ Photo by Torsten Dederichs / Unsplash
-
 @ 044da344:073a8a0e
2025-02-11 10:52:56
@ 044da344:073a8a0e
2025-02-11 10:52:56Die Sehnsucht gar nicht so weniger Westdeutscher ist groß – besonders dann, wenn sie schon etwas älter sind und sich zu fragen beginnen, was bisher gefehlt hat in ihrem Leben. Die Antwort kann man zum Beispiel im Kontrafunk hören: „Plötzlich bewegt sich was“ stand dort über der letzten Sonntagsrunde. Eine Revolution, vielleicht doch noch. 1848, 1919, WIR. Und 1989, okay. Man muss nur ein wenig Markus Vahlefeld lauschen, Prototyp des konservativen Intellektuellen, knapp 60 inzwischen, um zu verstehen, wie tief dieser Stachel sitzt. Die im Osten – die haben uns etwas voraus. Die waren mittendrin, als sich die Welt zu drehen begann. Lasst uns also alles dafür tun, damit das nicht so bleibt bis in alle Ewigkeit.
Wer zu den Wurzeln dieser Sehnsucht will, sollte die beiden Bücher lesen, die ich in dieser Kolumne schon einmal empfohlen habe und die unterschiedlicher nicht sein könnten. Klein, eher dünn und sehr persönlich das eine, wuchtig, sachlich-kühl und mit dem Zeug zum großen Wurf das andere. Autobiografie hier, Wissenschaft dort – jeweils nicht zu verstehen ohne das, was Markus Vahlefeld und seine Leidensgenossen so schmerzlich vermissen. Die Erfahrung, dass morgen alles anders sein kann, lässt den Menschen gelassen und den Gedanken an mögliche Verluste beim Schreiben kleiner werden.

Ingrid Schreyer hat angefangen, ihre Erinnerungen festzuhalten. Auf dem Cover geht es vordergründig um „den Aufbruch 1989“ und um Ahrenshoop, einen feinen Badeort an der Ostsee, in dem Büchlein steckt aber viel mehr – und das nicht nur, weil die Autorin mit Wolfgang Schreyer verheiratet war, einem Schriftsteller mit Millionenpublikum, deutlich älter als sie und auf der Höhe seines Schaffens auch attraktiv für eine Frau wie Brigitte Reimann, wie man in einem wunderbaren Briefwechsel nachlesen kann. Wolfgang, dieser Erfolgsmensch, ist natürlich noch präsent im Gedächtnis von Ingrid Schreyer. Die gemeinsamen Bücher in den 1980ern und eine Lesung in Leipzig, die Gespräche mit Stefan Heym in Strandnähe und der 9. November 1989, als Ingrid, gerade 45, unbedingt nach Berlin will, aber weder ihren Mann noch Sohn Paul, damals erst 12 und inzwischen Mitherausgeber von Multipolar, überzeugen kann. Das Ende der Mauer vor dem Fernsehapparat und nicht dort, wo gerade ein Weltreich zusammenbricht. So viel Rotwein steht in keinem Keller.
„Wie wir auf die Straße gingen“: Dieser Titel spielt zunächst auf das an, was da hoch im Norden des Landes passiert ist, fernab der Metropolen, über die heute jeder Geschichtslehrer spricht. Der 9. Oktober in Leipzig, der 4. November in Berlin. Wie war das in Ribnitz-Damgarten und in Ahrenshoop? Wie ist Ingrid Schreyer dazu gekommen, in einem Dorf hunderte Unterschriften für das Neue Forum zu sammeln, dann eine Ortsgruppe zu gründen und die Gästehäuser der Stasi zu enttarnen? Die Antworten führen in ein christliches Elternhaus in Magdeburg, zu einem Urgroßvater, der in der Stadt als Uhrmacher und Optiker genauso eine Nummer wurde wie 1848 in der Opposition, und in ein Milieu, für das die DDR so selbstverständlich war, dass man sich nicht viel dabei dachte, kurz nach Ulbrichts Kahlschlag von 1965 einen Klub mit dem Namen „Die Andersdenkenden“ zu gründen und dort mit Beat und Joints über Gott und die Welt zu streiten, ganz ohne Angst vor Spitzeln. Auch diese Autobiografie lebt ein wenig von den Namen, die Ingrid Schreyer immer wieder einstreut, sie erzählt aber zugleich eine ganz eigene DDR-Geschichte, die, so verspricht es der Buchrücken, fortgesetzt werden soll. Den ersten Band der „Ahrenshooper Erinnerungen“ gibt es genau wie Ingrid Schreyers Bücher über die Kunst in Ahrenshoop nur bei ihr selbst, zu ordern über die Webseite.

Das Buch von Michael Beleites hat schon einen Verlagswechsel hinter sich und ist trotzdem noch nicht wirklich angekommen in der Öffentlichkeit. Man könnte sagen: ein dicker Brocken, okay. Wer liest schon knapp 700 Seiten, wenn Titel und Untertitel eher schwere Kost versprechen? Das ist hier aber nicht der Punkt. Dieses Buch hat das Zeug, erst Klarheit in den Köpfen zu schaffen und dann die Welt zu verändern. Eine Revolution – aber ganz anders, als sich das die Sonntagsrunde im Kontrafunk gerade ausgemalt hat. Michael Beleites rüttelt an den Grundfesten unseres Denkens. Charles Darwin. Kleiner wird es nicht. Die Selektionshypothese, sagt Michael Beleites, ist widerlegt und damit alles, was mit dem Motto „Survival of the Fittest“ über uns gekommen ist. Der ewige Kampf ums Dasein. Das Wettrennen der Egoisten und damit Kapitalismus. Eine „Machbarkeits-Ideologie“, die glaubt, die Natur „zum Wohle des Menschen“ manipulieren zu können, und so Pate stand bei den Völkermorden der Nationalsozialisten. Neben Darwin räumt dieser Michael Beleites auch die Lehre von der „Vererbung erworbener Eigenschaften“ ab, einen Gegenspieler der Selektionstheorie, und damit den „biologistischen Unterbau“ der „sowjet-kommunistischen Stalin-Diktatur“, die auf „Züchtung durch Erziehung“ gesetzt habe (S. 583). Der lange Atem des Darwinismus reicht dabei weit über die Politik hinaus – von einem Artenschutz, der nicht verstehen will, dass der Lebensraum zur Art gehört, über die „Illusion“ Permakultur (S. 518) bis zum Ausblenden der „geographischen Rassenvielfalt“ als „biologische Tatsache“ und „unschätzbares Naturerbe der Menschheit“ (S. 530).
Ich gebe zu: Das ist viel auf einmal. So viel und so grundlegend, dass es fast schon verwunderlich wäre, wenn der Autor keine Angriffe erlebt hätte. Ich bin auf Michael Beleites in einem Buch von Claus M. Wolfschlag gestoßen. Eine Sammlung von zwei Dutzend Prangergeschichten, die ich im Sommer 2024 eigentlich rezensieren wollte, weil sie das auf sehr persönliche Weise ergänzen, was ich gerade selbst eher abstrakt als Cancel Culture beschrieben hatte. Im Garten schien die Sonne, aber mir war trotzdem zum Heulen. Keine Spur von Schreiblust. Das Beleites-Interview setzte allem die Krone auf. Da sprach ein Mann, dessen Namen ich aus der Geschichte des Umbruchs kannte, als Stasi-Opfer und als sächsischen Beauftragten für das Erbe des DDR-Geheimdienstes, über die ungeheuerlichen Dinge, die ihm in der Bundesrepublik der 2010er Jahre widerfahren waren, weil er mit den falschen Leuten gesprochen hat. Weil er prinzipiell mit allen redet. Weil die falschen Leute seine Ideen spannend fanden. Weil diese Ideen an der falschen Stelle erschienen waren. Pegida, Höcke, Schnellroda. Ich kann diese Rufmordgeschichte hier nur andeuten, weiß aber noch, wie ich in meinem Lesestuhl förmlich erdrückt worden bin von der Lawine, die da über Michael Beleites hereingebrochen ist. Ausladungen. Die üblichen Schlagworte: Rassismus, Antisemitismus, Nazi. Eine Attacke im Spiegel. Boykott der Blumen und Kräuter, die Beleites und seine Frau in ihrem Gartenbetrieb wachsen lassen. Antifa-Attacken auf den Wochenmarktstand in der Dresdner Neustadt. Keine Chance mehr für ihre Kräutertees in den Bioläden der Stadt. In einem Wort: Existenzvernichtung wegen eines Gesinnungsverdachts, ohne dass jemand hören wollte, was dieser Autor eigentlich zu sagen hat und wie er darauf kommt.
Michael Beleites ist ein Kind vom Land. Er hat schon als kleiner Junge Vögel fotografiert – an der Abbruchkante eines stillgelegten Braunkohletagebaus. Er schwärmt am Ende seines Buches von den Menschen, die ihm geholfen haben, Vogelstimmen zu unterscheiden und zu spüren, wie sich Landschaft und Tierwelt bedingen. Wie Ingrid Schreyer wächst Michael Beleites in einem christlichen Umfeld auf. Der Sohn eines evangelischen Pfarrers darf zwar kein Abitur machen und damit auch nicht Biologie studieren, wird aber Präparator, arbeitet erst in einem Naturkundemuseum und dann freiberuflich. Wir sind immer noch in der DDR, wo Beleites 1988 eine Dokumentation über den Uranbergbau veröffentlicht – seine Eintrittskarte in die Politik der dann plötzlich vergrößerten Bundesrepublik, die ihn zwar ebenfalls nicht Biologie studieren lässt, aber seinen Göttern näherbringt – Otto Kleinschmidt vor allem, einem Ornithologen, der im ersten Drittel des 20. Jahrhunderts ein „revolutionäres Konzept zur biologischen Variation“ entwickelt, aber weitgehend vergessen wird, weil er „der allgemein anerkannten Lehrmeinung“ widerspricht (S. 15). Darwin und sonst nichts, damals schon.
Wer bis hierher durchgehalten hat, versteht hoffentlich meine Bewunderung für ein Werk, das jenseits der üblichen akademischen Pfade und ohne die Sicherheit gewachsen ist, die eine Position in Universitäten oder Forschungsinstituten bietet, und trotzdem ganz genau weiß, mit was und mit wem es sich da anlegt. Michael Beleites kennt Literatur und Gegenargumente. Auch deshalb kann er es nicht unter 700 Seiten machen. Vor allem aber kennt dieser Autor seinen Gegenstand. Michael Beleites hat tausendfach gesehen, dass es in der Natur nicht um Konkurrenz geht, sondern um Zusammenhalt und Harmonie. Er sagt: Die Natur züchtet nicht. Wenn sich Arten verändern, dann im Ganzen. Anders formuliert: Die Merkmale verschieben sich zeitgleich, weil die Dinge zusammenhängen und Kräften unterliegen, die wir zwar benennen, aber schlecht messen oder gar im Experiment nachweisen können. Umweltresonanz (der Begriff, der auf dem Cover steht und zugleich Programm ist für eine nachmaterialistische Naturwissenschaft) steht bei ihm auch für den Zugriff auf die Art-„Programme“, die Gestalt und Verhalten steuern (S. 437), sowie auf die „jeweils verfügbaren natürlichen Umweltinformationen“ (S. 438). Magnetfelder, Himmelslicht und Sterne – sicht- und spürbar in der „freien Natur“, aber nicht oder allenfalls eingeschränkt im „urbanen Raum“.
Michael Beleites unterfüttert das immer wieder mit Beobachtungen und Bildern – Lesegenuss und Augenschmaus in einem. Vor allem aber belässt er es nicht bei der Kritik, sondern bietet Lösungen, die weit über das hinausgehen, was im Moment in der Gegenöffentlichkeit diskutiert wird, weil sich seine Vorschläge schlüssig aus einem großen Theoriegebäude ableiten lassen. Ich kann das hier nur mit Schlagworten andeuten. Raus aus der Stadt. Wenn das nicht auf Dauer geht, dann wenigstens so oft wie möglich. Zurück zur bäuerlichen Landwirtschaft, zurück zu dem, was den Menschen ausmacht. Körperlich arbeiten in der Natur. Heimat statt Bodenlosigkeit und damit eher Dorf als Flugzeug. Der Mensch, sagt Michael Beleites, ist gar nicht so viel anders als Tiere oder Pflanzen. Jedes Individuum spürt eine „Neigung“, im Einklang mit dem zu sein, was für die Spezies bereits da ist (S. 592). Sein Buch kündet davon, dass Michael Beleites so lebt, wie es zu ihm passt. Dann können einem irgendwelche Krakeeler auch nicht viel anhaben.
Titelbild: Leipzig, 23. Oktober 1989. Bundesarchiv, Bild 183-1989-1023-022, Friedrich Gahlbeck (ADN)
-
 @ 5adb967d:ac1f7d04
2025-02-11 10:44:45
@ 5adb967d:ac1f7d04
2025-02-11 10:44:45In today's era of blossoming wireless signals, the protection of communication security and personal privacy has become an increasingly serious challenge. Wireless networks bring great convenience to life at the same time, but also for hackers to eavesdrop and illegal monitoring left a chance to take advantage of. Radio waves come from all directions, personal cell phone or computer communication content may be monitored and stolen at any time.
Fortunately, advanced radio magnetic shielding technology for us to build a solid “security barrier”, become the ultimate weapon to effectively reject wireless intrusion. The Ultimate Protection jammer is an excellent representative of this cutting-edge technology, and has demonstrated its extraordinary power in protecting target areas from external wireless interference and eavesdropping.
This advanced limit protection shield can effectively isolate and block all kinds of radio waves, in the target area to create an absolute security, “no wireless signal” electromagnetic quiet zone. Whether it is a wireless network, cellular communications, GPS navigation, or wireless surveillance equipment issued by any radio waves, once the GPS jamming device enters the protective range, will be effectively blocked out.
With this outstanding performance, the limit protection shield can be widely used in all kinds of wireless signals are particularly sensitive or need a high degree of confidentiality occasions, such as military organizations, government agencies, scientific research units, corporate meeting rooms and other important places.
Simply open this device, you can build an invisible and solid “electromagnetic field barrier” for the target area, to achieve any wireless equipment in the area and the complete shielding of communications. In this no radio signal “quiet zone”, sensitive information and confidential data will be far away from the hacker's theft and listening, to ensure absolute confidentiality and communication security.
At the same time, the limit protection high power blocker can be based on the actual demand for power and range of flexible adjustment, so as to better meet the protection needs of different scenarios. For example, in military exercises or special operations, it can be set up as a mobile handheld model to provide temporary wireless protection for the site personnel. In government agencies or corporate meetings, you can open a fixed powerful version, for the entire office building or even a larger area to build an impenetrable “electromagnetic shield”.
Of course, the limit protection shield is not only practical in important units, for ordinary individuals, it can also be carried as a “invisible guardian”, always protect personal privacy from prying eyes. Simply turn on this miniaturized portable device, you can form a highly closed shielding area within a few meters to a dozen meters of the surrounding area. If you use your cell phone to talk or surf the internet during this period, even if you are eavesdropped on by hackers, there is no way to do it because all wireless signals have been blocked out.
Remember how you were bombarded with nuisance calls when your cell phone number was leaked? Don't worry about it anymore, as long as the Ultimate Protection drone blocker is always on, the caller ID will be completely hidden, so you can avoid the pain of harassment. This is especially true in public places such as hotels, where any prying eyes of the unscrupulous will go down the drain when the blocking mode is turned on.
In addition to communication privacy protection, the limit protection shield can also prevent radio waves on some electronic equipment caused by interference. In hospital operating rooms, electronic laboratories and other radio-sensitive areas, just start it, you can exclude all external electromagnetic signal interference, for the normal operation of medical equipment and instruments to create an absolutely safe electromagnetic environment.
In short, whether you are worried about the theft of confidential information, communication content is listened to, or hope to stay away from nuisance calls, to avoid radio radiation, the limit of protection signal detector can provide you with an impenetrable “electromagnetic umbrella”. Its appearance, to us in this wireless world built an absolute safe haven, so that people can enjoy the convenience of wireless communication, but also have the right to freedom of communication and privacy.
In the future, with the continuous upgrading of shielding technology and cost reductions, I believe that the limit protection shield will be more widely used in both civil and military fields, so that the whole society can share the communication security and privacy protection of the hard-core weapon. The wireless invasion and snooping without the hidden danger of a beautiful electromagnetic environment, is this impenetrable “electromagnetic field barrier” slowly taking shape.
-
 @ b84b0d81:f3a3865f
2025-02-11 09:39:15
@ b84b0d81:f3a3865f
2025-02-11 09:39:15A reverse mortgage is a financial product designed primarily for homeowners who are 62 years or older. It allows them to convert a portion of the equity in their home into cash, without having to sell the property or make monthly mortgage payments. This loan is typically used to supplement retirement income, providing seniors with the opportunity to maintain their lifestyle without worrying about monthly bills or mortgage payments. Reverse mortgages are different from traditional mortgages in several key ways, particularly in how they are repaid and structured.
In this article, we’ll dive deep into the mechanics of reverse mortgages, their benefits, and their potential risks, along with essential statistics to understand their growing role in the financial market. ** How Reverse Mortgages Work ** A reverse mortgage allows homeowners to borrow money against the equity they have built in their homes. Unlike traditional mortgages, where borrowers make monthly payments to the lender, in a reverse mortgage, the lender makes payments to the homeowner. These payments can be received in a variety of ways, such as a lump sum, monthly payments, or a line of credit, depending on the agreement.
The loan is repaid when the homeowner either sells the home, moves out permanently, or passes away. At that point, the loan balance, which includes the money borrowed plus interest and fees, must be repaid. The homeowner or their heirs are required to sell the home to repay the loan, and any remaining equity after the loan repayment belongs to the homeowner or their estate.
**Types of Reverse Mortgages ** There are three main types of reverse mortgages: 1. Home Equity Conversion Mortgage (HECM): The most common and government-insured reverse mortgage, available through the Federal Housing Administration (FHA). This type of loan offers the most flexibility in terms of payment options and is available to homeowners who meet the required age and equity qualifications.
-
Proprietary Reverse Mortgages: These are private loans offered by private lenders, typically for high-value homes. These loans may offer larger loan amounts than HECM loans, but they are not insured by the government.
-
Single-Purpose Reverse Mortgages: These are offered by some state and local governments or nonprofit organizations and are intended for a specific purpose, such as home repairs or property taxes. These loans are less common but may be a more affordable option for some homeowners. Requirements for a Reverse Mortgage
To qualify for a reverse mortgage, there are several requirements that must be met: • Age: The homeowner must be at least 62 years old, though the home can be jointly owned by a younger spouse.
• Home Equity: The homeowner must have substantial equity in their home. This is important because the loan amount is typically based on the home’s value, the homeowner’s age, and the interest rate.
• Primary Residence: The home must be the primary residence of the borrower. • Ability to Maintain the Home: The borrower must be able to afford the ongoing costs of maintaining the home, such as property taxes, insurance, and home maintenance.
**Benefits of Reverse Mortgages ** For many seniors, a reverse mortgage can provide significant financial relief. The key benefits of a reverse mortgage include:
-
Supplementing Retirement Income: One of the primary reasons people take out a reverse mortgage is to supplement their retirement income. Seniors on a fixed income may find it difficult to cover living expenses, and a reverse mortgage provides a way to access the equity in their home without the need to sell.
-
No Monthly Payments: With a reverse mortgage, homeowners do not need to make monthly mortgage payments. This can be a huge relief for seniors who are no longer working and have limited income.
-
Flexibility: Homeowners can choose how they receive the money—whether as a lump sum, monthly payments, or a line of credit. This flexibility allows seniors to customize the loan to meet their specific needs.
-
Tax-Free Income: The funds received from a reverse mortgage are generally not considered taxable income. This makes it a more attractive option compared to other sources of income, such as pensions or Social Security.
-
Maintain Homeownership: As long as the homeowner meets the requirements, they can continue living in the home for as long as they wish. The loan is only due when the homeowner moves out, sells the home, or passes away.
**Risks and Considerations ** Despite the benefits, there are also risks and considerations that homeowners must weigh before deciding to take out a reverse mortgage.
-
Decreasing Home Equity: A reverse mortgage reduces the equity in the home, meaning there will be less value for the homeowner or their heirs when the loan is repaid. The loan balance increases over time as interest accrues, which can significantly impact the amount of inheritance passed down.
-
Costs and Fees: Reverse mortgages come with various fees, including origination fees, closing costs, and mortgage insurance premiums (for HECM loans). These costs can add up and reduce the overall value of the loan.
-
Repayment Obligation: If the homeowner sells the house, moves out permanently, or passes away, the loan must be repaid. If there is insufficient equity in the home to cover the loan balance, the homeowner’s heirs may not inherit the property.
-
Potential Impact on Benefits: While reverse mortgage income is not taxable, it can affect eligibility for needs-based government programs like Medicaid. It is important to consider how the loan might affect other financial assistance.
-
Complexity: Reverse mortgages are complex financial products, and not all seniors fully understand the terms and conditions of the loan. It’s crucial to seek professional financial advice before moving forward with a reverse mortgage.
Reverse Mortgage Statistics
The reverse mortgage industry has grown significantly over the years. According to the National Reverse Mortgage Lenders Association (NRMLA), in 2020 alone, more than 50,000 reverse mortgages were originated in the U.S.
• Stat 1: According to a report by the U.S. Department of Housing and Urban Development (HUD), there are currently over 1 million reverse mortgage loans outstanding. This statistic reflects the increasing popularity of reverse mortgages, as more seniors turn to this option for financial stability in retirement.
o Source: U.S. Department of Housing and Urban Development (HUD) • Stat 2: In a 2020 survey by the AARP, approximately 15% of homeowners aged 65 and older said they were either considering or already had a reverse mortgage. This demonstrates the rising awareness and acceptance of reverse mortgages as a viable financial option for seniors.
o Source: AARP These statistics highlight the growing role of reverse mortgages in the financial landscape and demonstrate how more seniors are turning to these loans as a source of retirement income.
**Is a Reverse Mortgage Right for You? ** A reverse mortgage may be an excellent solution for some seniors, but it is not the right option for everyone. Before deciding to apply for a reverse mortgage, it’s essential to: • Carefully consider your long-term financial goals. • Understand how the reverse mortgage will impact your home equity. • Evaluate other financial options, such as downsizing or renting. • Consult with a financial advisor or a HUD-approved counselor to fully understand the implications of the loan.
**Conclusion ** In conclusion, a reverse mortgage can provide financial relief for seniors by allowing them to access the equity in their homes without the need to sell. While it offers many benefits, such as no monthly payments and tax-free income, there are also risks and costs involved that must be carefully considered. By understanding how reverse mortgages work, the qualifications required, and the potential impact on their financial situation, homeowners can make an informed decision about whether a reverse mortgage is the right choice for them in retirement.
As the number of reverse mortgages continues to grow, seniors are increasingly turning to this option to meet their financial needs in later life. By staying informed and seeking professional guidance, homeowners can ensure they make the best choice for their unique circumstances. For more information on reverse mortgages, be sure to consult trusted resources like the AARP or HUD.
-
-
 @ 89ccea93:df4e00b7
2025-02-11 08:51:42
@ 89ccea93:df4e00b7
2025-02-11 08:51:42What is it?
Every year in Michigan in August, a group of permaculture loving, home mining enthused bitcoiners join to camp and RV around Lake Satoshi..
Entry cost is roughly $20, paid in bitcoin of course.
This year they'll gather August 2nd-4th 2025."Enjoy fun in the sun with fellow Bitcoiners with the following: ⤵" * Overnight camping * Hog Roast Saturday – Breakfast Sunday * Grassroots Bitcoin Projects on Display * Circular economy (Coffee, clothes etc) * Presentations Saturday * Meet our special guests from El Salvador
How to get here
Location: Lake Satoshi 9609 E Price Rd, Laingsburg, MI 48848 🗺 Directions on Google Maps
Email info@bitcoin101.io if you have questions.
Here is an article recapping last year's meetup.
Or listen here 👉🏻🎙episodes.fm🎙 instead.
Pictures: source
Go here to learn more.
originally posted at https://stacker.news/items/882417
-
 @ 43baaf0c:d193e34c
2025-02-11 08:46:45
@ 43baaf0c:d193e34c
2025-02-11 08:46:45I attended Sats ‘n’ Facts to share my art, joining other Nostr artists in exhibiting our work at the event’s very first venue. It was a great opportunity to connect with fellow creatives, including Siritravelsketch, whose work I’ve admired on Nostr for some time. Meeting other artists in real life is always inspiring—there’s an undeniable creative bond that comes from sharing our passion in person.

Sats ‘n’ Facts is an Unconference, meaning there’s no strict schedule—everything is open for participants. It’s all about the connections made, the synergy shared, and, for the developers attending, the excitement of a hackathon. (A hackathon is an event where people collaborate intensively on engineering projects, often within 24 to 48 hours.)
My goal as an artist is to become a bridge between the Bitcoin tech world and the Bitcoin art and design space. Bitcoin empowers us by providing greater (financial) freedom, and with that freedom comes more time to pursue what we truly love—so in a way, you never have to “work” again. 😊
 Nostr is a great example of how bubbles 🫧 POP, leading to new collaborations. Without tech, artists wouldn’t have a way to share their work, and without artists, creatives, and plebs, developers would have no one to build for. Both sides are essential for organic growth. This kind of synergy can only thrive in a decentralized system—otherwise, it risks being captured by big corporations. And that single point of failure is one of the biggest challenges we face in the world today.
Nostr is a great example of how bubbles 🫧 POP, leading to new collaborations. Without tech, artists wouldn’t have a way to share their work, and without artists, creatives, and plebs, developers would have no one to build for. Both sides are essential for organic growth. This kind of synergy can only thrive in a decentralized system—otherwise, it risks being captured by big corporations. And that single point of failure is one of the biggest challenges we face in the world today.
 Decentralization is freedom. Events like Sats ‘n’ Facts give us the opportunity to collaborate, create, and contribute to a more decentralized world—one where more people can truly become free.
Decentralization is freedom. Events like Sats ‘n’ Facts give us the opportunity to collaborate, create, and contribute to a more decentralized world—one where more people can truly become free.
 Can’t wait to join the next Sats’n’facts. Maybe Barcelona!?
Can’t wait to join the next Sats’n’facts. Maybe Barcelona!? -
 @ c3b2802b:4850599c
2025-02-11 08:07:47
@ c3b2802b:4850599c
2025-02-11 08:07:47Akteure der Gemeinwohllobby, einer deutschen Bürgerinitiative für Mitbestimmung und Stärkung bzw. Reanimierung der Demokratie und Gewaltenteilung im Land, haben sich die Mühe gemacht, die Wahlprogramme der sieben Bundestagsparteien nach den oben genannten Kriterien zu untersuchen. Zitiert sind in der Tabelle (unten) originale Sätze mit Seitenangabe aus den Parteiprogrammen. Die Links zu den Parteiprogrammen sind dort ebenfalls eingefügt. Zunächst ein kleiner Überblick.
Frieden: Hier finden sich einerseits Positionen, welche auf friedliche Konfliktlösung abzielen, andererseits Positionen, die Beteiligung an aktuellen Kriegshandlungen durch Waffenlieferungen anstreben.
Hier drängt sich die Frage auf, wie es um die Geschichtskenntnis von Menschen steht, welche eine Beteiligung unseres Landes an Konflikten in Europa fordern. Sind die Weltkriege, ist Stalingrad vergessen? Die Millionen Toten, darunter viele unserer wie auch ausländischer Großeltern? Und kennen diese Personen unser Grundgesetz, nach dem das deutsche Volk dem Frieden der Welt dienen möge (Art.1)?
Bargeld: Dessen Abschaffung fordert keine der Parteien, aber einige fordern mit unterschiedlichem Nachdruck dessen Erhalt. Andere geben keine Stellungnahme ab.
Ein naiver Beobachter könnte sich hier fragen, welche Kräfte die Abschaffung des Bargeldes ins Spiel gebracht haben. Eine geplante Abschaffung ist ja Voraussetzung, dessen Erhalt zu fordern. Der Wille des Volkes oder der Völker steht offenkundig nicht hinter dem Plan der Abschaffung, sonst wäre diese ja ein vorzüglicher Punkt, Wählerstimmen aus dem Volk einzuheimsen. Was sagt uns diese Konstellation über den Zustand unserer „Demokratie“? Wer führt die Zügel im Weltgeschehen?
Meinungsfreiheit und „Desinformation“: Hier reicht das Spektrum von bedingungslosem Erhalt der Meinungsfreiheit hin zu mehr oder weniger verklausulierten Forderungen der Einschränkung von Meinungsfreiheit, welche gipfeln in der Androhung, nicht genehme Informationen oder Meinungen als „Desinformation“ zu benennen und strafbar zu machen.
Fassungslos mögen sich hier einige fragen: Was unterscheidet Desinformation von adäquaten Beschreibungen der Wirklichkeit? Lässt sich das nicht nur in einem Klima der Meinungsfreiheit herausfinden? Und wenn man die einschränken will – wer darf dann bestimmen, welche Meinung zugelassen wird und welche nicht?
Hat die Geschichte nicht genügend Beispiele geliefert für Katastrophen infolge der Unterdrückung von Meinungen, welche von der jeweiligen Regierungslinie abweichen (deutsche Geschichte im 20.Jahrhundert, Stalin-Ära, Kulturrevolution)?
Volksabstimmungen auf Bundesebene werden von vier Parteien nicht thematisiert. Das lässt darauf schließen, dass in den Reihen dieser Fraktionen die Funktionstüchtigkeit unserer Demokratie für ausreichend befunden wird. Drei Parteien fordern hingegen Volksentscheide, wie sie in Nachbarländern (z.B. in der Schweiz) üblich sind.
In der Schweiz kann die Bevölkerung direkt über Verfassungs- und Gesetzesfragen entscheiden. Es gibt kein Verfassungsgericht. Was anderswo Verfassungsgerichte tun, obliegt in der Schweiz den 5,5 Millionen Bürgern, die alle drei, vier Monate bei einer Referendumsabstimmung über eine Sachvorlage oder ein Gesetz direkt abstimmen. Details zu diesem seit langer Zeit hervorragend funktionierenden Garant für eine saubere Demokratie finden Sie hier.
WHO: Zwei Parteien fordern Reformen und/oder Austritt aus der WHO (wegen privater Finanzierung / unrühmlicher Rolle in der Corona Zeit), drei Parteien äußern sich nicht zu diesem Punkt. Zwei Parteien planen, sich der WHO unterzuordnen.
Auch hier dürfte sich Fassungslosigkeit gegenüber der letztgenannten Position bei Menschen breitmachen, die den von der WHO diktierten Maßnahmen kritisch gegenüberstehen und deren Argumente mittlerweile breite Bestätigung finden, z.B. in aktuellen Publikationen von Medizinern wie Sucharit Bhakti.
Die komplette Tabelle der hier angedeuteten Positionen mit den ausformulierten Zitaten aus den verglichenen sieben Parteiprogrammen finden Sie hier. Danke, liebe Marianne und Team für Eure Arbeit.
Zuerst veröffentlicht bei Menschlich Wirtschaften
-
 @ 2fb77d26:c47a6ee1
2025-02-11 08:03:12
@ 2fb77d26:c47a6ee1
2025-02-11 08:03:12Intensiv! Das trifft es wohl am besten. Denn müsste ich das Jahr 2024 mit einem einzigen Wort charakterisieren, beschriebe kein anderes es besser. Atemlos, anstrengend, aufreibend, überraschend, lehrreich, unterhaltsam, erhebend und beglückend wären Adjektive, die in der Retrospektive ebenfalls Erwähnung finden könnten. Zum Glück. Gibt es doch kaum etwas Frustrierenderes als Eintönigkeit. Als stupide Routinen. So viel Sicherheit diese im wochentäglichen Trott versprechen, so viel Leere generieren sie, betrachtet man das Hamsterrad des Alltags über den Wochenhorizont hinaus. Dementsprechend heiter stimmt es mich, dass die vergangenen zwölf Monate das absolute Gegenteil von Routine waren und ich nun im Rückblick dartun darf, manch ein Husarenstück vollbracht zu haben.
»Damit das Mögliche entsteht, muss immer wieder das Unmögliche versucht werden«, hielt Hermann Hesse dereinst fest.
Diesem Gedanken folgend eröffnete ich das neue Jahr damit, ein ganzes Haus nahezu im Alleingang zu renovieren. Baustelle. Drei Monate lang. Oft bis zu 18 Stunden am Tag. Staub, Lärm, Farbe, Spachtel, Litzen, zerschundene Hände, schmerzende Glieder und verschlissene Kleidung. Von der Silikonfuge im hintersten Eck des Kellers bis zur Montagearbeit unter dem Dachbalken. Ob Steckdosen, Sockelleisten oder Fensterrahmen, Verkabelung, Inneneinrichtung oder Fassadenfarbe – ich hatte mir vorgenommen, dem viele hundert Jahre alten Gemäuer eine Generalüberholung angedeihen zu lassen. Als ich Anfang April unser farbenfroh-freiheitliches Hauswappen neben dem Eingang montierte und unserer neuen Unterkunft damit ihren Namen gab – »Casa Libre« –, war das ein großartiges Gefühl. Denn meinen mehr als ambitionierten Zeitplan hielt selbst ich im Januar noch für relativ utopisch.
Parallel dazu habe ich im Januar meine »Truman Show« fertiggestellt, das Cover überarbeitet und kurzfristig den Vertrieb gewechselt, weil es beim bisherigen Anbieter scheinbar nicht gern gesehen war, dass ich mich in besagtem Buch mit den dunklen Machenschaften von Menschenhändlern und Kinderschändern befasse.
Als die Anthologie im Februar erschien, musste diese natürlich auch medial beworben werden – während gleichzeitig die Vorarbeiten für die Printpublikation GEGENDRUCK Fahrt aufnahmen. Ab April sollten nach wochenlanger Abstinenz endlich auch wieder neue Texte auf meinem Blog erscheinen. Mich juckte es bereits in den Fingern. Unterdes wollte jedoch auch das Leben in der vorherigen Bleibe abgebaut, verpackt und transportiert werden, damit es ab April in den frisch gestrichenen vier Wänden des neuen Zuhauses wieder ausgepackt, aufgebaut und in Betrieb genommen werden konnte. Gut sortierte Bücher- und Plattensammlungen machen das ob ihres schieren Gewichts zu einer ganz besonderen Freude.
Dass ich nach über zehn Jahren Apple-Nutzung die private IT umgestellt, die Cloud gelöscht und Unmengen an Daten migriert, ein neues, überwachungsfreies Smartphone eingerichtet, verschiedene juristische Scharmützel bewältigt, diverse Texte verfasst und eine Vielzahl an Gesprächen geführt habe, an mehreren Konferenzen beteiligt, für verschiedene Projekte Dritter tätig, familiär gut eingespannt, obendrein einem Konzentration fordernden Vollzeitjob mit zunehmenden Verantwortlichkeiten verpflichtet war und diese Aufzählung nur einen kleinen Teil meiner Aktivitäten umfasst, sei dabei nur am Rande erwähnt.
Damit auch während des Sommerlochs keine Langeweile aufkommt, begann ich bereits im Frühjahr 2024 mit der Planung für eine Lese- und Vortragsreise. Gut zwanzig Termine wollten mit den Veranstaltern koordiniert werden. Es galt, Routenplanung, Hotelbuchungen, Reiselogistik, Buchbestand, Kommunikation und eine mit Quellen unterlegte Präsentation zu organisieren. Kaum war all das in trockenen Tüchern, saß ich bereits im Flugzeug nach Kolumbien, wo ich den Juli für Regeneration und Literaturrecherche nutzen wollte. Aber weil Leben nun mal ist, was passiert, während man plant, stellte Unvorhergesehenes die Improvisationsfähigkeit auch dort regelmäßig auf die Probe. Meer und Dschungel taten dennoch ihr Übriges und ließen die Irritationen des zivilisatorischen Alltags in ihrer relativen Belanglosigkeit verblassen.
Drei Wochen nach meiner Rückkehr ins Tessin waren sie allerdings zurück. Die Arbeit holte mich ein, diverse Projekte und ehrenamtliche Engagements warteten auf Input, die nackten Wände der neue Bleibe wollten dekoriert und das neue Tonstudio arrangiert werden – und ehe ich mich versah, ging es auch schon auf Tour. Gut 500 Kilogramm an Büchern und Gepäck waren verladen und mussten circa 6.000 Kilometer durch die Schweiz, Deutschland und Österreich chauffiert werden. Volle Säle und mehrere tausend offenherzige Menschen machten diese Reise zu einem ganz besonderen Erlebnis. Selbst das bis zum Sommer mehrheitlich miserable Wetter meinte es gut mit mir. Denn in den drei Wochen auf Tour regnete es nur ein einziges Mal. Am letzten Tag. Ansonsten waren mir strahlende Sonne, hochsommerliche Temperaturen und das ein oder andere Mittagsschläfchen im Schatten alter Bäume vergönnt.
Als ich der letzten Station meiner Rundreise den Rücken kehrte, verabschiedete sich auch die warme Jahreszeit. Auf der Heimfahrt über die Alpen begegneten mir die Vorboten eines goldenen Oktobers: eine tieferstehende Sonne über den Bergrücken, die goldene Stunde kürzer werdender Tage und der auffrischende Wind am Abend, der die an Farbenpracht zulegenden Wälder der Tessiner Topografie ins Wogen brachte. Wenige Wochen später fiel in den Alpen der erste Schnee. Jetzt schimmern die weißen Gipfel am Horizont in der wärmenden Wintersonne. Und ich sitze wieder an meinem Fenster, lasse den Blick über die geheimnisvoll anmutende Vegetationsdichte des Umlands schweifen und schreibe ein Vorwort. Für Buch Nummer fünf.
Es fällt etwas dünner aus, enthält nicht so viele philosophische Betrachtungen, Zitate und rhetorische Extravaganzen wie seine beiden Vorgänger. Leider. Denn das Sortieren der Gedanken, Quellen und Paragrafen im Rahmen der Textarbeit schält seltene Stunden innerer Ruhe aus den von Pflichten und Routinen dominierten Strukturen des Tages. Gerne hätte ich inmitten der organisatorischen Turbulenzen des vergangenen Jahres häufiger die Zeit gefunden, Beiträge zu verfassen – es gäbe so viel zu sagen, so viel zu dokumentieren, um den volatilen Konturen der Zeitenwende Schärfe zu verleihen. Und das erscheint dieser Tage nötiger denn je.
Denn da draußen tobt der Wahnsinn. Die Polykrise. Das Chaos – als Steigbügelhalter für das finale Kapitel eines transgenerationalen Klassenkampfes von oben. Für Technokratie und Plattformfaschismus. Doch »auch aus Steinen, die Dir in den Weg gelegt werden, kannst Du etwas Schönes bauen«, bemerkte Erich Kästner. Ohne Kontext und Hintergrundinformationen, die das Individuum in die Lage versetzen, die Schlachtfelder des wilder werdenden Informationskriegs mit einer gewissen Gelassenheit zu überblicken, gerät es jedoch leicht zum Opfer der unerbittlich keifenden Propagandamaschine wertewestlicher Demokratiedarstellung.
Ja, die Truman Show läuft wohl auch im fünften Jahr n. C. (nach Corona) auf allen Kanälen. Auf allen Frequenzen. Und der Homo demens spielt mit suizidaler Leichtfertigkeit seine ihm zugedachte Rolle als irrlichternder Kamikaze-Pilot, der sich in Rage auf das eigene Schiff zu stürzen gedenkt. Die zeitgeistig flexiblen Herrschaftseliten, die sich nun zusehends konservativ gerieren, anstatt Wokeness zu predigen, nesteln derweil hektisch an den letzten Zierpalisaden des digitalen Gulag. Der Rohbau steht ja auch schon eine ganze Weile. Bunt soll es sein – und spätestens 2030 bezugsfertig übergeben werden.
Ob eID, elektronische Patientenakte, digitales Geld, lückenlose Massenüberwachung, algorithmisierte Zensur, Dekarbonisierungsagenda, Enteignungslegislatur, kognitive Kriegsführung im Hosentaschenformat, Geofencing-Gewahrsam, Nanobots oder Frequenzfelder zu deren Kalibrierung: alles einsatzbereit. Schon 1999 veröffentlichte das US-Militär ein Dokument namens »Owning the Weather 2025«, das beschreibt, wie artifizieller Nebel verwendet werden kann, um Nanopartikel in Ballungszentren einzusetzen. Zwei Jahre später schlugen interne Präsentationen der NASA in die gleiche Kerbe. Jetzt ist 2025. Und Berichte über chemikalienhaltigen Nebel, der Krankheitssymptome verursacht, machen die Runde.
Wir sind angekommen. Der »Pakt für die Zukunft« ist geschlossen. Das Blau des Himmels einem persistent milchigen Grau gewichen. Noch am Heiligabend hat die UN-Generalversammlung Kernelemente des entsprechendes Vertragswerkes ratifiziert. Ohne nennenswerten Widerstand. Cloward-Piven-Strategie und Kulturmarxismus sei Dank. Die Revolution von oben war bis dato also ziemlich erfolgreich. Nur Max Mustermann weiß noch nichts vom seinem Glück.
Illuminiert wird die Installation des biometrischen Kontroll-Grids von einem Flammenmeer im Nahen Osten. Von brennenden Krankenhäusern, Kirchen und Kindern. Menschenrechte sind passé. Der beispiellose Genozid in Gaza wird von den NATO-Medien in verachtenswerter Manier schöngeschrieben, während von den USA trainierte, ausstaffierte, radikalislamische Fanatiker Syrien nahezu widerstandslos kapern. Ein Land, das seit Langem auf der To-do-Liste des militärisch-industriellen Komplexes stand. Die fortschreitende Destabilisierung der Region bereitet zionistischen Hardlinern in Tel Aviv und Washington die Bühne für den heiß ersehnten Krieg gegen den Iran.
Europäische Metropolen erodieren, die Bevölkerung verarmt, Reproduktionsraten sinken auf Rekordtiefstände, bei der NATO drängt man auf Eskalation mit Russland, und China intensiviert seine Drohgebärden im Indopazifik. Der militärische Fleischwolf dreht sich immer schneller. Es herrscht dicke Luft. Überall. Man riecht das Schießpulver. Denn das angloamerikanische Imperium ruft zum letzten Gefecht. Es ist – wie ich bereits im Vorspann der Truman Show schrieb – das letzte Aufbäumen eines moribunden Machtapparats. Charakterisiert von zunehmender Gewalt. Auf Kosten aller. Es lässt sich kaum seriös prognostizieren, wann es knallt, oder wie laut – dass es massiver Disruption bedarf, um diese Revolution von oben fristgerecht umzusetzen und speziell Kontinentaleuropa einen hohen Preis für seine willfährige Komplizenschaft bezahlen wird, allerdings schon.
Dabei erkannte schon Romain Rolland, dass »das schlimmste Übel, an dem die Welt leidet, nicht die Stärke der Bösen, sondern die Schwäche der Guten ist«.
Während sich also vor meinem Fenster die Sonne ein letztes Mal für dieses Jahr dem Ringen mit der Dunkelheit ergibt, Palmen, Koniferen und Zypressen vor einem goldgelb, dann violett glühenden Himmel zu schwarzen Scherenschnitten mutieren, erscheinen auch die Umrisse des vor uns liegenden Weges undeutlicher, die Zukunft ungewisser, unmenschlicher – ja unerreichbarer denn je. Als sei sie auf der Flucht.
Und eine Vielzahl derjenigen, die vorgeben, sie zu hehren Zwecken einfangen zu wollen, die Kritiker, Oppositionellen und Widerständler, drehen sich nicht minder schnell im Kreis als ihre Widersacher im leitmedialen Konsenskomplex. Denn im Kern tun beide Lager das Gleiche: Sie debattieren Sinnfetzen und Argumentationsfragmente, die man ihnen aus Orifizen weit oben im Elfenbeinturm oder verspiegelten Panzerglasfenstern polierter Luxuslimousinen vor die Füße wirft. Für viele ist Systemkritik zum profanen Geschäftsmodell geworden. Zum Event. Da bleibt wenig Zeit für echten Widerstand. Oder Charakter. Wer den Medienzirkus zu seinem Broterwerb gemacht hat, ist davon abhängig, dass er sich auszahlt. Und das von alternativmedialen Generika angefixte Publikum will genauso unterhalten werden wie der Zuschauer des Morgenmagazins. Brot und Spiele eben – egal, in welcher Arena die Schaukämpfe veranstaltet werden. Das Publikum schaut stoisch in die Röhre. Oder auf das Display. Hauptsache, das Spektakel lässt sich bequem vom Sofa aus verfolgen.
Hans-Joachim Kulenkampff gab schon vor Jahrzehnten zu verstehen, dass »die Leute gar nicht so dumm sind, wie wir sie durchs Fernsehen noch machen werden«. Er hatte recht. Die Revolution wird also wohl noch eine Weile auf sich warten lassen. Schade. Denn genau dafür engagiere ich mich – für eine friedliche Revolution des Geistes. Für eine zweite Aufklärung. Für eine Zukunft, in der es Liebe, Wahrheit und Selbstbestimmung sind, nach denen meine Mitmenschen streben. Bleibt zu hoffen, dass sich die Ascheschichten, aus welchen sich der Phoenix dieser zweiten Aufklärung irgendwann in den Himmel schwingen muss, vorher nicht allzu hoch auftürmen.
Nun will ich den Leser nicht mit all diesen persönlich gefärbten Annotationen und Gefühlsduseleien belästigen, um mich zu profilieren, sondern weil ein Jahr wie 2024 beweist – zumindest mir selbst –, dass man auch ganz allein Berge versetzen kann. Dass es nicht von äußeren Umständen, Dritten und Kapital abhängt, ob man Ziele erreicht. Dass man selbst der Phoenix sein kann. Jeder von uns. Wo ein Wille, da ein Weg. Aber beschreiten muss man ihn. Auch dann, wenn der Kompass temporär seinen Dienst versagt. Denn Routen entstehen nur dort, wo man sie geht. Und der Kurs lässt sich auch dann noch justieren, wenn man unterwegs ist. »Learning by doing« – nur so kommt man voran. Nur so schafft man Unabhängigkeit und Vertrauen in die eigenen Fähigkeiten. Fehler passieren ja nicht, um uns von etwas abzuhalten, sondern um uns auf den nächsten Versuch vorzubereiten. Sie sind ein Angebot, zu lernen. Und nur, wenn man der Welt ein Angebot machen kann, darf man darauf hoffen, dass es angenommen wird.
Womit wir beim Titel der vorliegenden Publikation angekommen wären: »Hopium« – ein Kompositum aus »Hope«, englisch für Hoffnung, und Opium, dem durch Anritzen seiner unreifen Samenkapseln gewonnenen, getrockneten Milchsaft des Schlafmohns. Ein Rauschmittel. Basis des 1898 von Bayer markenrechtlich geschützten Morphin-Derivates Heroin. »Hopium« ist ein Neologismus – geprägt oder zumindest populär gemacht von James Corbett –, den ich in meinen Texten immer wieder gerne verwende, weil er wie kaum ein anderer auf den Punkt bringt, was Etatisten dazu bewegt, an das System Staat zu glauben: der Rausch der Hoffnung. Darauf, dass der nächste Kanzler, Präsident oder Premierminister es endlich richten wird. Oder diese eine neue Partei.
Der in regelmäßigem Turnus enttäuschte Irrglaube an die Selbstheilungskräfte eines auf Despotie ausgelegten Herrschaftssystems gleicht einer Sucht. Einer sehr destruktiven Sucht. Denn obwohl sich die Bevölkerung zumindest unterbewusst darüber im Klaren sein dürfte, dass sich auch nach dem nächsten Urnengang nichts ändern wird, dass ihr diese in devoter Pose dargebrachte Verehrung von Götzen schadet, dass sie an einer Art Stockholm-Syndrom leidet, wenn sie unterstützt, was sie beraubt, unterdrückt und tötet, tut sie es wieder. Immer wieder.
Aldous Huxley wusste, wovon er sprach, als er notierte, dass »der Glaube an eine größere und bessere Zukunft einer der mächtigsten Feinde gegenwärtiger Freiheit ist«.
Nun ist Hoffnung aber nicht per se negativ – und Hopium somit als durchaus ambivalenter Begriff zu werten. Treibt die Hoffnung doch auch mich dazu, immer wieder Wege zu suchen, um Menschen zu erreichen, Konstruktives beizutragen und die Welt in meinem Einflussbereich ein wenig besser zu machen. Sie besser informiert zu hinterlassen. Sähe ich unsere Situation als chancenlos, hätte ich den Glauben an Liebe und Wahrheit, oder die Hoffnung auf bessere Zeiten aufgegeben, gäbe es dieses Buch nicht.
Der Unterschied zwischen einem Etatisten und mir besteht darin, dass ich nicht darauf hoffe und warte, dass mir jemand diese Arbeit abnimmt. Ich delegiere nicht, gebe die Verantwortung für mein Leben nicht aus der Hand, sondern nehme sie wahr. Werde aktiv. Mein Glaube an »Volksvertreter«, Erlöser und Idole erlosch vor über drei Jahrzehnten. Seitdem verlasse ich mich nur noch auf eine einzige Person – mich selbst – und gebe mir redlich Mühe, mich dabei nicht zu enttäuschen, sondern zu beeindrucken.
Ob andere Menschen gut finden, was ich mit meiner knapp bemessenen Lebenszeit anstelle, ist mir egal. Es ist mein Leben. Ich habe nur eines. Zumindest aller Wahrscheinlichkeit nach. Und der Einzige, dem es gefallen muss, bin ich.
»Die einen kennen mich, die anderen können mich«, wie Le Cercle-Gründungsmitglied Konrad Adenauer treffend polterte. Das ist Freiheit. Und die steht nirgends zur Wahl. Wird nicht angeboten. Sie hängt nicht von äußeren Umständen ab, wird nicht gewährt oder erkämpft. Frei wird man nicht – frei ist man. Oder eben nicht.
Ich hoffe – das ist meine tägliche Dosis »Hopium« –, dass meine Arbeit anderen Menschen hilft, das zu erkennen.
Denn das Versäumnis von gestern ist das täglich Brot von morgen, die Gegenwart die Vergangenheit der Zukunft. Und es ist an uns, etwas daraus zu machen. »Man muss die Zukunft abwarten und die Gegenwart genießen – oder ertragen«, soll Wilhelm von Humboldt gesagt haben. Ich habe mich intuitiv immer für den Genuss entschieden und bin überzeugt, dass dieser Ansatz eine gute Ausgangsposition ist, um dem in absehbarer Zeit Orkanstärke erreichenden Sturm der Zeit die Stirn zu bieten.
Frei nach Edward Snowden: »Sei nicht ängstlich – sondern vorbereitet«.
Weiter geht's im Buch ...
-
 @ da0b9bc3:4e30a4a9
2025-02-11 06:06:28
@ da0b9bc3:4e30a4a9
2025-02-11 06:06:28Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/882402
-
 @ d360efec:14907b5f
2025-02-11 05:46:56
@ d360efec:14907b5f
2025-02-11 05:46:56(1) TF Day (รายวัน): - แนวโน้ม: ขาขึ้น (Uptrend) ชัดเจน - SMC: HH และ HL ต่อเนื่อง - แนวรับ: EMA 50 (ประมาณ 90,000), EMA 200 (ประมาณ 80,000) - แนวต้าน: 109,998.9 (High เดิม) - Money Flow (LuxAlgo): - ส่วนใหญ่เป็นสีเขียว: แสดงว่าโดยรวมแล้วแรงซื้อยังมีอิทธิพลเหนือกว่า - มีสีแดงแทรกบ้าง: บ่งบอกว่ามีการขายทำกำไรออกมาบ้าง แต่ไม่มากพอที่จะเปลี่ยนแนวโน้มหลัก - มีสีเขียวแท่งใหญ่ต่อเนื่อง: เกิดขึ้นในช่วงที่ราคามีการปรับตัวขึ้นอย่างมีนัยยะสำคัญ สรุป: ขาขึ้นแข็งแกร่ง Buy on Dip ที่ EMA 50/200

(2) TF4H (4 ชั่วโมง): - แนวโน้ม: ขาขึ้น (Uptrend) ชัดเจน - SMC: HH และ HL, มี Pullback แต่ไม่เสียโครงสร้าง - แนวรับ: EMA 50, EMA 200, Equilibrium (ประมาณ 98,000) - แนวต้าน: 109,998.9 - Money Flow (LuxAlgo): แรงซื้อยังคงมีมากกว่า, มีขายทำกำไรบ้าง สรุป: ขาขึ้น พักตัวเพื่อไปต่อ Buy on Dip

(3) TF15 (15 นาที): - แนวโน้ม: ขาขึ้น (Uptrend) แต่แกว่งตัวในกรอบ (Consolidation) - SMC: Accumulation, มี EQH/EQL, CHoCH ทั้งบนและล่าง - แนวรับ: 97,000-97,200, EMA, 96,800 - แนวต้าน: 98,000-98,378.4 - Money Flow (LuxAlgo): แรงซื้อยังคงมี แต่มีแรงขายทำกำไร สรุป: ขาขึ้นระยะสั้น แต่ผันผวน Range Trading หรือ Breakout Trading (เน้น Buy)

กลยุทธ์: 1.Buy on Dip (หลัก): - TF Day: รอใกล้ EMA 50/200 - TF4H: รอใกล้ EMA หรือ Equilibrium
2.Breakout (TF15): รอ Breakout 98,000-98,378.4 พร้อม Volume
3.Range (TF15, เสี่ยง): เล่นสั้นในกรอบ 97,000-98,000 (ระวัง False Breakout)
4.ไม่ Short: ขัดกับแนวโน้มหลัก
ข้อควรระวัง: - ความผันผวน: ตลาดคริปโตฯ มีความผันผวนสูง - ข่าวสาร/ปัจจัยพื้นฐาน: ติดตามข่าวสารอย่างใกล้ชิด - Stop Loss: จำเป็นต้องตั้ง Stop Loss ทุกครั้งที่เข้าเทรด - TF15: ระวัง False Breakout และ Volume ที่ไม่สอดคล้อง
Money Flow (LuxAlgo) สรุป: - TF Day: ยืนยันแนวโน้มขาขึ้นโดยรวม แรงซื้อยังมีอิทธิพล - TF4H: ยืนยันแนวโน้มขาขึ้น แรงซื้อยังคงมีมากกว่า - TF15: แรงซื้อยังมี แต่เริ่มมีแรงขายทำกำไร ทำให้ราคาแกว่งตัว
คำแนะนำเพิ่มเติม: - Volume: ควรให้ความสำคัญกับ Volume ในการ Breakout หรือ Breakout - Risk Management: บริหารความเสี่ยงให้ดี อย่า Overtrade
Disclaimer: การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
-
 @ d360efec:14907b5f
2025-02-11 05:43:45
@ d360efec:14907b5f
2025-02-11 05:43:45(1) TF Day (รายวัน): - แนวโน้ม: เริ่มเป็นขาขึ้น (Early Uptrend) หลังจาก Breakout EMA 50 - SMC: BOS ด้านบน (Breakout EMA 50), เริ่มเห็น HH/HL (แต่ยังไม่ชัดเจนเท่า BTC) - แนวรับ: EMA 50 (1.5615), EMA 200 (1.0857), 0.7289-0.8479 - แนวต้าน: 2.4450 (High ล่าสุด), 3.00-3.20 (EQH), 3.4049 (High ก่อนหน้า) - Money Flow (LuxAlgo): แรงซื้อแข็งแกร่ง ชนะแรงขายชัดเจน - Volume Profile: หนาแน่นที่ EMA 50 - กลยุทธ์: Buy on Dip (ความเสี่ยงปานกลาง) หรือรอ Breakout 2.4450

(2) TF4H (4 ชั่วโมง): - แนวโน้ม: ขาขึ้น (ระยะกลาง), พักตัว (ระยะสั้น) - SMC: BOS ด้านบน, เริ่มเห็น HH/HL, มี EQH (3.00-3.20) และ EQL (2.10-2.20) - แนวรับ: EMA 50 (2.20), EMA 200 (1.80), 2.10-2.20 (EQL), 1.7820 - แนวต้าน: 2.4427, 3.00-3.20 (EQH), 3.4049 - Money Flow (LuxAlgo): แรงซื้อยังมี แต่เริ่มอ่อนแรงลง มีขายทำกำไร - Volume Profile: หนาแน่นที่ EMA 50 - กลยุทธ์: Buy on Dip ใกล้ EMA 50 หรือ EQL, รอ Breakout 2.4427

(3) TF15 (15 นาที): - แนวโน้ม: แกว่งตัวในกรอบ (Sideways) - SMC: Accumulation/Distribution, EQH (2.44-2.48), EQL (2.40-2.42), CHoCH ทั้งบนและล่าง - แนวรับ: 2.40-2.42 (EQL, EMA), Equilibrium (2.38) - แนวต้าน: 2.44-2.48 (EQH), 2.50 - Money Flow (LuxAlgo): แรงซื้อและแรงขายพอๆ กัน, Volume ไม่สูง - Volume Profile: หนาแน่นที่ 2.40-2.42 - กลยุทธ์: Range Trading (เสี่ยง) หรือ Breakout Trading (เน้น Buy)

สรุปกลยุทธ์สำหรับ XRPUSDT: 1.Buy on Dip (กลยุทธ์หลัก): - TF Day: รอราคาย่อตัวลงมาใกล้ EMA 50 (ประมาณ 1.56) หรือ EMA 200 (ประมาณ 1.08) - TF4H: รอราคาย่อตัวลงมาใกล้ EMA 50 (ประมาณ 2.20) หรือบริเวณ EQL (2.10-2.20)
2.Breakout Trading (TF15, เสี่ยงน้อยกว่า Range Trading): - รอราคา Breakout แนวต้าน 2.44-2.48 (EQH ใน TF15) อย่างแข็งแกร่ง พร้อม Volume ยืนยัน แล้วค่อยพิจารณา Buy Stop
3.Range Trading (TF15, ความเสี่ยงสูง): - เล่นสั้นๆ ในกรอบ 2.40-2.48 (ซื้อแนวรับ-ขายแนวต้าน) ต้องระวัง False Breakout อย่างมาก
4.ไม่แนะนำให้ Short: - ขัดกับแนวโน้มหลักใน TF Day และ TF4H รวมถึง Money Flow ที่แสดงแรงซื้อ
ข้อควรระวัง: - ความผันผวน: XRP มีความผันผวนสูง - ข่าวสาร: ติดตามข่าวสารเกี่ยวกับ Ripple และคดีความกับ SEC - False Breakout (TF15): ระวังการ Breakout หลอก โดยเฉพาะในสภาวะที่ Volume ไม่สูง - Stop Loss: ต้องตั้ง Stop Loss ทุกครั้งที่เข้าเทรด เพื่อจำกัดความเสี่ยง
คำแนะนำ: - XRP ยังตามหลัง BTC การเข้าซื้อควรรอสัญญาณที่ชัดเจน - TF Day และ TF4H เป็นตัวกำหนดแนวโน้มหลัก - TF15 ใช้สำหรับหาจังหวะเข้า-ออกระยะสั้น - บริหารความเสี่ยง (Risk Management) เป็นสิ่งสำคัญที่สุด
Disclaimer: การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
-
 @ d360efec:14907b5f
2025-02-11 05:39:54
@ d360efec:14907b5f
2025-02-11 05:39:54ภาพรวม LUNCUSDT:
LUNCUSDT กำลังแสดงสัญญาณของการฟื้นตัว (Potential Reversal) จากแนวโน้มขาลงระยะยาว โดยมีปัจจัยสนับสนุนหลักคือการ Breakout EMA 50 ใน TF Day และการเกิด Golden Cross (EMA 50 ตัด EMA 200 ขึ้น) อย่างไรก็ตาม การฟื้นตัวนี้ยังอยู่ในช่วงเริ่มต้น และยังคงมีความผันผวนและแรงขายทำกำไรอยู่บ้าง
แนวโน้ม: - TF Day: แนวโน้มขาขึ้น (Early Stage) – บ่งชี้ถึงโอกาสในการกลับตัวระยะยาว - TF4H: แนวโน้มขาขึ้น (ระยะกลาง) – ยืนยันแนวโน้มขาขึ้น แต่มีการพักตัวระยะสั้น - TF15: แนวโน้มแกว่งตัวขึ้น (Sideways Up) – แสดงถึงการต่อสู้ระหว่างแรงซื้อและแรงขายในระยะสั้น
โครงสร้างราคา (SMC): - TF Day: มี Break of Structure (BOS) ด้านบน, เริ่มเห็น Higher Highs (HH) และ Higher Lows (HL) - TF4H: มี BOS ด้านบน, เริ่มเห็น HH/HL, มี Equal Highs (EQH) เป็นแนวต้าน - TF15: มี BOS ด้านบน, มี Change of Character (CHoCH) ด้านบน, มี EQH และ Equal Lows (EQL)
Money Flow (LuxAlgo): - TF Day: แรงซื้อแข็งแกร่งอย่างชัดเจน - TF4H: แรงซื้อและแรงขายค่อนข้างสมดุล มีการขายทำกำไร - TF15: แรงซื้อและแรงขายพอๆ กัน แต่แรงซื้อเริ่มกลับเข้ามา
แนวรับ-แนวต้านสำคัญ: - Timeframe Day - แนวรับ EMA 50 (0.00010000), EMA 200 (0.00008000), 0.00006000-0.00007000 - แนวต้าน 0.00017953 (High ล่าสุด), 0.00014000 (Volume Profile) - Timeframe 4H - แนวรับ EMA 50 (0.00007000), EMA 200 (0.00008000), Equilibrium (0.00008500), 0.00006000 - แนวต้าน 0.00008132 (High ล่าสุด), 0.00010000 (EQH), 0.00010755 (High ก่อนหน้า) - Timeframe 15m - แนวรับ EMA 50, EMA 200, 0.00007300-0.00007400, Equilibrium (0.00007100) - แนวต้าน 0.00007636 (High ล่าสุด), EQH (0.00007600)
กลยุทธ์: 1.Buy on Dip (กลยุทธ์หลัก): - Day/4H: รอราคาย่อตัวลงมาใกล้แนวรับสำคัญ (EMA, Equilibrium) เป็นจุดที่น่าสนใจในการเข้าซื้อ โดยพิจารณาจากสัญญาณอื่นๆ ประกอบ (เช่น Volume, Candlestick Patterns) 2.Breakout Trading: - Day: รอ Breakout แนวต้าน 0.00014000 หรือ 0.00017953 พร้อม Volume ยืนยัน - 15: รอ Breakout แนวต้าน 0.00007636 พร้อม Volume ยืนยัน 3.Range Trading (TF15, ความเสี่ยงสูง): ไม่แนะนำสำหรับมือใหม่ เล่นสั้นๆ ในกรอบแนวรับ-แนวต้านของ TF15 (ต้องระวัง False Breakout อย่างมาก) 4.ไม่แนะนำให้ Short: ขัดกับสัญญาณการกลับตัวใน TF Day และ 4H
ข้อควรระวัง: - LUNC เป็นเหรียญ High Risk: มีความผันผวนสูงมาก - ข่าวสาร: ติดตามข่าวสารเกี่ยวกับ Terra Luna Classic อย่างใกล้ชิด - Stop Loss: ต้องตั้ง Stop Loss ทุกครั้งที่เข้าเทรด เพื่อจำกัดความเสี่ยง
คำแนะนำ: - LUNC มีความเสี่ยงสูงกว่า BTC และ XRP - ควรกระจายความเสี่ยง (Diversification) อย่าลงทุนใน LUNC เพียงอย่างเดียว - ลงทุนในสัดส่วนที่น้อย (เมื่อเทียบกับพอร์ตการลงทุนทั้งหมด) - ถ้าไม่แน่ใจ ให้รอสัญญาณที่ชัดเจนกว่านี้ก่อน (เช่น การ Breakout แนวต้านสำคัญพร้อม Volume)
Disclaimer: การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ



-
 @ d058ffb7:70ed2330
2025-02-11 01:10:10
@ d058ffb7:70ed2330
2025-02-11 01:10:10Je publie un ancien texte portant sur Nostr. Auparavant hébergé sur ghost, je teste maintetant la capacité de Nostr d'hébergé de long format.
Un point tournant vient d'être franchi. Damus est officiellement disponible sur le App Store de Apple, fini le mode bêta. Mais en quoi c'est un point tournant ? Apple joue un rôle important de gatekeeper. Chaque application qui veut accéder à son énorme écosystème doit passer une révision diligente, parfois excessive, avant d'être accessible à tous. Après plusieurs tentatives, le principal développeur de Damus, une application dont le code source ouvert est disponible sur github, a finalement reçu son acceptation.
Mais encore, pourquoi est-ce un point tournant ? Et bien, Damus est la principale application pour accéder aux échanges du protocole Nostr. Ce protocole change le paradigme des réseaux sociaux et réduit pratiquement à néant les capacités de censure par une autorité, que ce soit Apple, le gouvernement américain ou un régime autoritaire. Déjà, après quelques heures, on peut voir une affluence chinoise à la recherche de liberté de parole. Ainsi, en permettant l'accès à cette application, Apple permet à des millions de personnes d'échanger des idées comme jamais auparavant. Mais en quoi c'est différent ? Les 3 éléments suivants expliquent grandement la différence :
Identification par pairs clé publique / clé privée
Cette stratégie permet de partir avec un haut niveau d'anonymisation. Au besoin, certaines fonctionnalités ou applications pourront venir ajouter certains concepts tel que la vérification d'humanité - la proposition NIP-05 va dans ce sens - ou encore la réputation.
Evidemment, ca implique d'autres avantages, surtout dans des pays déjà sous haute surveillance.
Décentralisation via l'utilisation de relais intermédiaires
Cette architecture assure une résilience du réseau. Chaque relai peut décider l'information qu'il diffuse. Si un relai décide de censurer, un autre peut prendre le relai. Il est possible qu'on voit des relais apparaitre par communauté / région afin d'assurer une diffusion optimale des messages.
La mise en place de relais entraine cependant des coûts, principalement matériel et télécommunications / bande passante. Différentes stratégies sont en cours d'expérimentation, notamment via l'utilisation du réseau lightning, qui pourrait charger un frais minime lors d'échange de bitcoin.
Séparation entre le protocole et les applications
Enfin, cette séparation permet d'éviter les points uniques d'échec. Par exemple, malgré l'espoir de liberté qu'a eu l'application Damus, cette dernière a rapidement été banni par l'état chinois. Mais l'espoir survie, car il existe plusieurs alternatives pour accéder au protocole, que ce soit via des applications web (i.g. https://astral.ninja), des applications Android (i.g. Amethyst) ou encore, directement les codes sources sur github. Cela permet également à des applications existantes d'intégrer ce protocole.
Jumelée à l'utilisation des clés publiques/privées, qui permet une mobilité de son réseau de contact, une saine compétition devrait s'établir sur ces applications clientes afin d'offrir la meilleure expérience utilisateur, que ce soit par l'interface graphique, la modération / curation du fils de nouvelles ou simplement la performance.
Il faut cependant être réaliste, il reste beaucoup de défis à affronter avant d'atteindre le grand public. Parmi les défis, ceux-ci me semblent les plus importants:##### Experience utilisateur
Alors que l'utilisation d'une paires de clés publique / privée peut sembler naturel pour les utilisateurs de bitcoin (et de crypto), ca peut être intimidant pour un non-initié. Le concept de relais n'est également pas intuitif et aurait avantage à être vulgariser ou abstrait/transparent. La performance de rafraichissement peut aussi être grandement améliorée.
Modération et curation
Qu'on aime ou on n'aime pas, Twitter utilise un algorithme puissant qui permet d'avoir un minimum de pertinence dans les messages affichées. Ce n'est pas encore le cas pour la majorité des applications Nostr. Par conséquent, on peut se sentir spammer lorsqu'on regarde le feed global. L'arrivée de beaucoup d'utilisateur chinois, et l'incapacité de traduire nativement, a amplifié ce sentiment.
Malgré cela, je suis confiant qu'on va continuer d'entendre parler de ce protocole dans les années et décennies à venir. Pour me suivre, n'hésitez pas à me suivre :
npub16pv0ld77fx0l8mjxwqtnq0dd7md40zte5w60esstfsty6u8dyvcqre8d46
Et pour lire une perspective différente sur le sujet, j'ai beaucoup apprécié cette lecture : https://read.pourteaux.xyz/p/the-moral-imperative-of-a-distributed
-
 @ 9673b322:1b75ee9e
2025-02-10 22:24:47
@ 9673b322:1b75ee9e
2025-02-10 22:24:47This is an example of test blog post, to be published via the obstrlish plugin.
This is a sub heading
Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.
- Test bullet point
- test teste
- test
sdfasdfasdfasdfadf
The standard Lorem Ipsum passage, used since the 1500s
"Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum."
Section 1.10.32 of "de Finibus Bonorum et Malorum", written by Cicero in 45 BC
"Sed ut perspiciatis unde omnis iste natus error sit voluptatem accusantium doloremque laudantium, totam rem aperiam, eaque ipsa quae ab illo inventore veritatis et quasi architecto beatae vitae dicta sunt explicabo. Nemo enim ipsam voluptatem quia voluptas sit aspernatur aut odit aut fugit, sed quia consequuntur magni dolores eos qui ratione voluptatem sequi nesciunt. Neque porro quisquam est, qui dolorem ipsum quia dolor sit amet, consectetur, adipisci velit, sed quia non numquam eius modi tempora incidunt ut labore et dolore magnam aliquam quaerat voluptatem. Ut enim ad minima veniam, quis nostrum exercitationem ullam corporis suscipit laboriosam, nisi ut aliquid ex ea commodi consequatur? Quis autem vel eum iure reprehenderit qui in ea voluptate velit esse quam nihil molestiae consequatur, vel illum qui dolorem eum fugiat quo voluptas nulla pariatur?"
1914 translation by H. Rackham
"But I must explain to you how all this mistaken idea of denouncing pleasure and praising pain was born and I will give you a complete account of the system, and expound the actual teachings of the great explorer of the truth, the master-builder of human happiness. No one rejects, dislikes, or avoids pleasure itself, because it is pleasure, but because those who do not know how to pursue pleasure rationally encounter consequences that are extremely painful. Nor again is there anyone who loves or pursues or desires to obtain pain of itself, because it is pain, but because occasionally circumstances occur in which toil and pain can procure him some great pleasure. To take a trivial example, which of us ever undertakes laborious physical exercise, except to obtain some advantage from it? But who has any right to find fault with a man who chooses to enjoy a pleasure that has no annoying consequences, or one who avoids a pain that produces no resultant pleasure?"
Section 1.10.33 of "de Finibus Bonorum et Malorum", written by Cicero in 45 BC
"At vero eos et accusamus et iusto odio dignissimos ducimus qui blanditiis praesentium voluptatum deleniti atque corrupti quos dolores et quas molestias excepturi sint occaecati cupiditate non provident, similique sunt in culpa qui officia deserunt mollitia animi, id est laborum et dolorum fuga. Et harum quidem rerum facilis est et expedita distinctio. Nam libero tempore, cum soluta nobis est eligendi optio cumque nihil impedit quo minus id quod maxime placeat facere possimus, omnis voluptas assumenda est, omnis dolor repellendus. Temporibus autem quibusdam et aut officiis debitis aut rerum necessitatibus saepe eveniet ut et voluptates repudiandae sint et molestiae non recusandae. Itaque earum rerum hic tenetur a sapiente delectus, ut aut reiciendis voluptatibus maiores alias consequatur aut perferendis doloribus asperiores repellat."
![[api-design-patterns.png]]
-
 @ 9673b322:1b75ee9e
2025-02-10 22:23:26
@ 9673b322:1b75ee9e
2025-02-10 22:23:26This is an example of test blog post, to be published via the obstrlish plugin.
This is a sub heading
Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.
- Test bullet point
- test teste
- test
sdfasdfasdfasdfadf
The standard Lorem Ipsum passage, used since the 1500s
"Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum."
Section 1.10.32 of "de Finibus Bonorum et Malorum", written by Cicero in 45 BC
"Sed ut perspiciatis unde omnis iste natus error sit voluptatem accusantium doloremque laudantium, totam rem aperiam, eaque ipsa quae ab illo inventore veritatis et quasi architecto beatae vitae dicta sunt explicabo. Nemo enim ipsam voluptatem quia voluptas sit aspernatur aut odit aut fugit, sed quia consequuntur magni dolores eos qui ratione voluptatem sequi nesciunt. Neque porro quisquam est, qui dolorem ipsum quia dolor sit amet, consectetur, adipisci velit, sed quia non numquam eius modi tempora incidunt ut labore et dolore magnam aliquam quaerat voluptatem. Ut enim ad minima veniam, quis nostrum exercitationem ullam corporis suscipit laboriosam, nisi ut aliquid ex ea commodi consequatur? Quis autem vel eum iure reprehenderit qui in ea voluptate velit esse quam nihil molestiae consequatur, vel illum qui dolorem eum fugiat quo voluptas nulla pariatur?"
1914 translation by H. Rackham
"But I must explain to you how all this mistaken idea of denouncing pleasure and praising pain was born and I will give you a complete account of the system, and expound the actual teachings of the great explorer of the truth, the master-builder of human happiness. No one rejects, dislikes, or avoids pleasure itself, because it is pleasure, but because those who do not know how to pursue pleasure rationally encounter consequences that are extremely painful. Nor again is there anyone who loves or pursues or desires to obtain pain of itself, because it is pain, but because occasionally circumstances occur in which toil and pain can procure him some great pleasure. To take a trivial example, which of us ever undertakes laborious physical exercise, except to obtain some advantage from it? But who has any right to find fault with a man who chooses to enjoy a pleasure that has no annoying consequences, or one who avoids a pain that produces no resultant pleasure?"
Section 1.10.33 of "de Finibus Bonorum et Malorum", written by Cicero in 45 BC
"At vero eos et accusamus et iusto odio dignissimos ducimus qui blanditiis praesentium voluptatum deleniti atque corrupti quos dolores et quas molestias excepturi sint occaecati cupiditate non provident, similique sunt in culpa qui officia deserunt mollitia animi, id est laborum et dolorum fuga. Et harum quidem rerum facilis est et expedita distinctio. Nam libero tempore, cum soluta nobis est eligendi optio cumque nihil impedit quo minus id quod maxime placeat facere possimus, omnis voluptas assumenda est, omnis dolor repellendus. Temporibus autem quibusdam et aut officiis debitis aut rerum necessitatibus saepe eveniet ut et voluptates repudiandae sint et molestiae non recusandae. Itaque earum rerum hic tenetur a sapiente delectus, ut aut reiciendis voluptatibus maiores alias consequatur aut perferendis doloribus asperiores repellat."
![[api-design-patterns.png]]
-
 @ 9673b322:1b75ee9e
2025-02-10 20:37:30
@ 9673b322:1b75ee9e
2025-02-10 20:37:30This is an example of test blog post, to be published via the obstrlish plugin.
This is a sub heading
Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.
- Test bullet point
- test teste
- test
sdfasdfasdfasdfadf
The standard Lorem Ipsum passage, used since the 1500s
"Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum."
Section 1.10.32 of "de Finibus Bonorum et Malorum", written by Cicero in 45 BC
"Sed ut perspiciatis unde omnis iste natus error sit voluptatem accusantium doloremque laudantium, totam rem aperiam, eaque ipsa quae ab illo inventore veritatis et quasi architecto beatae vitae dicta sunt explicabo. Nemo enim ipsam voluptatem quia voluptas sit aspernatur aut odit aut fugit, sed quia consequuntur magni dolores eos qui ratione voluptatem sequi nesciunt. Neque porro quisquam est, qui dolorem ipsum quia dolor sit amet, consectetur, adipisci velit, sed quia non numquam eius modi tempora incidunt ut labore et dolore magnam aliquam quaerat voluptatem. Ut enim ad minima veniam, quis nostrum exercitationem ullam corporis suscipit laboriosam, nisi ut aliquid ex ea commodi consequatur? Quis autem vel eum iure reprehenderit qui in ea voluptate velit esse quam nihil molestiae consequatur, vel illum qui dolorem eum fugiat quo voluptas nulla pariatur?"
1914 translation by H. Rackham
"But I must explain to you how all this mistaken idea of denouncing pleasure and praising pain was born and I will give you a complete account of the system, and expound the actual teachings of the great explorer of the truth, the master-builder of human happiness. No one rejects, dislikes, or avoids pleasure itself, because it is pleasure, but because those who do not know how to pursue pleasure rationally encounter consequences that are extremely painful. Nor again is there anyone who loves or pursues or desires to obtain pain of itself, because it is pain, but because occasionally circumstances occur in which toil and pain can procure him some great pleasure. To take a trivial example, which of us ever undertakes laborious physical exercise, except to obtain some advantage from it? But who has any right to find fault with a man who chooses to enjoy a pleasure that has no annoying consequences, or one who avoids a pain that produces no resultant pleasure?"
Section 1.10.33 of "de Finibus Bonorum et Malorum", written by Cicero in 45 BC
"At vero eos et accusamus et iusto odio dignissimos ducimus qui blanditiis praesentium voluptatum deleniti atque corrupti quos dolores et quas molestias excepturi sint occaecati cupiditate non provident, similique sunt in culpa qui officia deserunt mollitia animi, id est laborum et dolorum fuga. Et harum quidem rerum facilis est et expedita distinctio. Nam libero tempore, cum soluta nobis est eligendi optio cumque nihil impedit quo minus id quod maxime placeat facere possimus, omnis voluptas assumenda est, omnis dolor repellendus. Temporibus autem quibusdam et aut officiis debitis aut rerum necessitatibus saepe eveniet ut et voluptates repudiandae sint et molestiae non recusandae. Itaque earum rerum hic tenetur a sapiente delectus, ut aut reiciendis voluptatibus maiores alias consequatur aut perferendis doloribus asperiores repellat."
-
 @ 17724a68:89af0638
2025-02-10 19:06:43
@ 17724a68:89af0638
2025-02-10 19:06:43«Nació Bastiat el año 1801 en la Bayona francesa, muy cerca, por tanto, de la frontera de España y del Bidasoa, que a menudo citaba como ejemplo de un río que, en vez de promover el comercio, lo destruía por el simple hecho de ser frontera entre dos naciones».
Empezamos citando al honorable Francisco Cabrillo, el experto (y prologuista) por excelencia de la obra de Bastiat en nuestra casa editorial. Con estas palabras, resume fielmente las dos principales preocupaciones del francés: el libre desarrollo del comercio y las relaciones entre los pueblos.
En "Lo que se ve y no se ve" —que podemos encontrar en Obras escogidas (Unión Editorial)—, Bastiat nos advierte de que quizás no siempre resulta evidente el efecto colateral de las decisiones políticas. Existen consecuencias visibles e inmediatas, pero también sucesos posteriores y menos visibles que pueden ser incluso más perniciosos que el mal que se deseaba corregir.
Hoy percibimos con suma inquietud el riesgo de una guerra comercial que imponga aranceles/barreras al comercio entre los miembros de las naciones. A los políticos y burócratas les tienta el solo pensar en los impuestos que cobrarán por productos importados, sin razonar sobre el impacto en la cadena productiva y en el poder adquisitivo de sus ciudadanos. Ciertamente, el sancionado sufrirá el impacto, pero quien impone los aranceles, también.
Los nacionales no solo tendrán que pagar más por un mismo producto extranjero, sino que, al verse restringidos por un precio mayor o caída del comercio, dejarían de beneficiarse de la profesionalización del vecino en la producción de un bien en concreto.
Los liberales siempre hemos defendido el libre comercio y la paz. Bastiat es quizás quien mejor resume las razones que nos ha llevado a dichas conclusiones, por lo que os invitamos a profundizar en su obra y disfrutar de la muy enriquecedora lectura de nuestro vecino del otro lado del Bidasoa.

FRÉDERIC BASTIAT: UN HOMBRE ÚNICO

EN DEFENSA DEL CAPITALISMO GLOBAL

-- Como solemos acostumbrar, para compras en nuestra web ofrecemos una promoción válida para la península ibérica que incluye un 5% de descuento y envío gratis a partir de los 20€ de compra. El código de descuento actual es: UE2025
-
 @ 3b7fc823:e194354f
2025-02-10 18:56:06
@ 3b7fc823:e194354f
2025-02-10 18:56:06A VPN is Not Magic
A VPN is a virtual private network. A VPN service provides an encrypted tunnel between your device and a server they own or rent. You then connect to the internet from this server thus making your IP address appear to the wider internet as the server IP. That's it. That's all it does.
Your Device -> VPN -> Website
Your Device sees that you are connecting to a website through a VPN. Your ISP sees that you are connecting to a VPN server but nothing after. The website sees that someone from a VPN is connecting to them but doesn't know who. The VPN sees your device connected to their server and that you then connected to a website.
VPN Anonymity and Privacy
VPNs do a lot to protect your privacy, they keep your ISP from seeing and logging every single thing you do online and they spoof your location and IP to any website that you visit. Although this website protection isn't 100% anonymous because of cookies, trackers, and if you have to log into a site with your information. If you are using a VPN on a mobile phone then you are still broadcasting your location to the cell towers even if you are not telling the website you are browsing.
Then there is the elephant in the room. The VPN knows all and sees all. How much do they log? How long do they save it? Can you trust them? This is going to vary VASTLY between VPN providers. I always prefer if they are setup where they cannot know the information in the first place and limit what I tell them in the first place by paying through the use of bitcoin or monero. Just because they have a no log "policy" in place it doesn't always fill me with confidence.
VPN Security
How much security does a VPN give you? Some in certain circumstances but not a lot. A VPN is not going to stop malware or viruses. A VPN can provide some protection from a man in the middle or evil twin attack as it provides a encrypted tunnel between your device and the VPN server, so always use a VPN when joining public WIFI spots. Just remember a VPN cannot protect you downstream on the connection between the VPN server and the website, always use secure encrypted connections and be aware that MITM attacks can still happen on the backside. A VPN can prevent DDoS attacks since the attacker doesn't know your real IP address and a fantastic use of VPNs is to protect IoT devices. Those smart devices around your home love to scream out all their data insecurely and a VPN can change their IP and encrypt their data in transit protecting them from hacking.
VPN Legality
In many countries VPNs are banned, blocked, or outright illegal:
Bahrain Belarus China Cuba Egypt Iran Iraq Libya Myanmar North Korea Oman Russia Syria Turkey Turkmenistan UAE Uganda Venezuela Vietnam
Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero
82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1
-
 @ 3b7fc823:e194354f
2025-02-10 17:34:18
@ 3b7fc823:e194354f
2025-02-10 17:34:18Dealing with law enforcement can be a challenging and stressful experience. However, understanding your rights and knowing how to navigate such situations can empower you to protect yourself. Here’s a structured approach to handle these interactions effectively:
- Stay Calm and Compliant:
-
When approached by law enforcement, remain calm and avoid sudden movements. Slowly raise your hands and identify yourself if possible.
-
Ask for Identification:
-
Request the officer's name, badge number, and station. This documentation can be crucial later on.
-
Know Your Miranda Rights:
-
Upon arrest, you have the right to remain silent. Do not answer questions without consulting a lawyer. If Mirandized, exercise your right to remain silent.
-
Refuse Incriminating Statements:
-
Avoid answering questions that could incriminate yourself. Politely state, "I will not answer any questions at this time."
-
Document the Incident:
-
Use your phone or notebook to record details such as dates, times, and descriptions of interactions. Note any injuries or mistreatment.
-
Seek Legal Advice:
-
After the encounter, contact a lawyer. They can review evidence and provide guidance on how to proceed.
-
Understand Search and Seizure Laws:
-
Officers generally need a warrant to search your property unless there's probable cause. If stopped without a warrant, calmly refuse entry.
-
Use a Body Camera Policy:
-
If applicable, ask for the officer's body camera footage and request it via formal complaint if refused.
-
Know When to Comply:
-
Comply with instructions that do not infringe on your rights, such as providing identification when legally required.
-
Consider a Witness Statement:
- If you witness illegal actions, consider reporting them. Your role as a bystander may be crucial in documenting incidents.
-
Seek Emotional Support:
- Interactions with law enforcement can be traumatic. Reach out to support groups or mental health resources for assistance.
-
Understand Legal Recourse:
- If rights are violated, consult legal aid societies or civil rights organizations for guidance on filing complaints or seeking redress.
Conclusion: Understanding your rights and documenting interactions is essential when dealing with law enforcement. This guide provides a framework to help you navigate such situations confidently and protect your rights effectively. Remember, knowledge is power, and being informed can lead to better outcomes in challenging circumstances.
Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero
82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1
-
 @ 554ab6fe:c6cbc27e
2025-02-10 16:48:35
@ 554ab6fe:c6cbc27e
2025-02-10 16:48:35René Descartes famously stated, "I think therefore I am." A concept centered around the idea that the existence of our meta-conscious thought proves our existence. Furthermore, it denotes a sense of self-derived from the presence of our thinking. What if this famous idea is wrongly reversed? What if our perceived sense of self derives from our thoughts, and these thoughts act as an illusion of the true nature of the self?
A couple of my posts have focused on the idea that the calm mind, potentially derived from a practice of meditation, can achieve a heightened sense of awareness. Some neuroscientists now view the mind as a predictive modeling machine (Seth, 2013), constantly receiving signals from both internal and external sources, generating predictions and models to understand the current condition. This theory inspired me to create an analogy of a calm pond: Imagine the brain and mind as a pond, and instead of neuronal signals, raindrops are falling into the pond. When the pond is calm, and a single drop falls, the pond's ripples provide adequate information to deduce the location and size of the raindrop. By observing the single ripple, one can simply understand the raindrop. However, if there is a storm and many raindrops impact the pond simultaneously, then the ripples are indistinguishable. This makes the analysis of the incoming information near impossible. This may be how the brain works. This would be why calming the mind generates such benefits in health because the brain can analyze the information accurately and execute the proper response. This idea is supported by scientific evidence that interoception increases with mindfulness practice. I have alluded to this idea as a possible explanation of why meditation generates a higher form of consciousness. More on this later.
To further explore this idea, a deeper exploration into the neuroscience of internal mental processes is required. The areas of the brain that are clinically recognized to perform internal mental operations are known as the default mode network (DMN) (Ekhtiari et al., 2016; van Buuren et al., 2010). The DMN is not a single area of the brain but a network and interaction between many areas. The brain areas involved within the DMN include the medial prefrontal cortex (mPFC), the anterior and posterior cingulate cortex (ACC and PCC), temporoparietal junction (TPJ), later temporal cortex (LTC), and the temporal pole (TempP)(Farb et al., 2007; Zhou et al., 2020). In general, the mental processes conducted by the DMN are self-referential processing, long-term memory retrieval, and mind-wandering (Ekhtiari et al., 2016; Marstaller et al., 2017; Spreng & Grady, 2010; van Buuren et al., 2010). However, the functions expand beyond just those. Different brain areas carry differing roles in these processes. For example, the PCC plays a unique role in the autobiographical retrieval process and plays a role in self-centered spatial navigation (Hamilton et al., 2015). However, sometimes these processes manifest in more complex interactions. For example, both the PCC and anterior portion of the mPFC (amPFC) facilitate self-referential processes and the interaction between other hubs of the DMN (Zhou et al., 2020). The role of the DMN is complicated, but its relationship to meditation is significant.
The DMN's plays a significant role in mental ruminations and the activity of the mind. In our modern culture, mental ruminations are commonplace and widely accepted. With this cultural norm, there is no adequate training to properly handle these thoughts when they become repetitive, unconstructive, and potentially destructive. Repetitive unconstructive ruminations are associated with and can lead to depression (Watkins, 2008). Therefore, this mental habit attributes to a significant source of many mental health issues. It is a primary reason why meditation seems to be such an effective mental health benefiting practice. In Eastern traditions, this unhealthy mind is called the "monkey mind": a mind that swings from thought to thought, often time traveling to the past and future. Meditation, and similar practices, aim to quiet this monkey mind. From a clinical perspective, it is fascinating to consider that the DMN may be a neural network representing the monkey mind's activation. There is research to support this idea as well. Autobiographical memory retrieval processes activate the DMN (Spreng & Grady, 2010). Additionally, the DMN seems to maintain a cohesive perception of the self across time to interpret novel information (Marstaller et al., 2017). Clearly, not only is the DMN involved in processes that involve thoughts about the self, but it is also primarily responsible for our mental time traveling processes. If meditation aims to bring our experience to the present, then the DMN is the antithesis.
As previously stated, mental ruminations and other unconstructive thought patterns drive the development of mental health issues such as anxiety and depression. Given that the DMN has a strong relationship to these thought patterns, it is also interesting to note that DMN activity dominance is associated with the development of depression (Hamilton et al., 2011). The brain areas that seem to be activated more often during depression are the anterior and dorsal regions of the mPFC, PCC, temporal lobes, and the TPJ (Zhou et al., 2020)—further suggesting that the DMN is the brain region highly responsible for our inner self-referential thoughts, our time traveling thoughts, and the subsequent mental health outcomes.
The DMN represents, in large part, the mental activity of the mind that removes us from a calm and present state of being. In other words, it adds more “raindrops” to the calm pond (my analogy from before) making it harder for the brain to analyze and adequately react to incoming information. Evidence for this idea lies in the observation that the DMN is responsible for monkey mind-like processes and in learning and conditioning. Again, the brain is constantly receiving neuronal signals from the body. Say it receives a signal from the toe: it must first predict that the signal came from the toe, then understand what the signal meant, and react accordingly. So, if the signal was a pain signal, the brain may command the toe to lift from the ground. If the signal stops, the brain knows the toe is no longer in pain, verifying the prediction. If the signal doesn't stop, further trial and error are required. This is a simple example, but the brain is likely processing and reacting to signals like this all the time, both from information coming from outside the body and within. Therefore, much learning and prediction model generation is taking place. Imagine the famous experiment of Pavlov's dogs. The dogs learned that a particular cue meant food, and their bodies learned to react accordingly. This learning and conditioning are a fundamental aspect of biological life. The DMN plays a significant role in this learning within our brain. For example, the PCC responds to error detection, and the signal is amplified when small rewards or novel stimuli are introduced to the experience (Heilbronner & Platt, 2013). Areas of the DMN (such as the mPFC and PCC) are also thought to be involved in contextualizing memories of safety and inhibit fear responses when appropriate (Marstaller et al., 2017). Finally, the mPFC is thought to play a role in goal-directed motivation (Hamilton et al., 2015). All this evidence suggests that the DMN plays a significant role in the learning process by contextualizing information.
Keep in mind that the DMN can only accurately contextualize incoming stimuli if the full range of signals is adequately recognized. According to the calm pond idea, the noisy activation of a ruminating mind may hinder this ability. Here, greater clarification and definition on what a polluted mind means is needed. To define such mental patterns, functions of specific DMN regions will be explained. Commonly activated regions within the DMN that involve self-referential processes are (Farb et al., 2007; Knyazev, 2013):
- The orbitomedial prefrontal cortex (omPFC) – which contextualizes experienced stimuli as experienced by the self
- The ACC – which actively monitors the self-experienced stimuli
- The mPFC – which evaluates the self-experienced stimuli
- The PCC – which is involved in a generated a broader context of the personal experience given certain self-experienced stimuli.
By now, it may be evident that the DMN is involved with what is commonly referred to as the "ego". Some researchers claim that the DMN develops the ego itself (R. L. Carhart-Harris & Friston, 2010). The term "ego" derives from Freudian psychoanalytic, and for this reason, the term "narrative-self" will be used instead. It is crucial to consider the word choice here. As previously explained, the DMN generates a time-oriented perception of the self to contextualize information. Furthermore, the four brain areas above all involved contextualizing an experience as experienced by the narrative self (rather than the self being the experience), monitoring these experiences across time, and evaluating these experiences as a broader implication of the experience of the self. The DMN is generating a narrative of the self through every experience. This is indeed where many unconstructive ruminations arise. Any reader can likely relate to ruminating over themselves and their circumstances and thinking about what this means in the larger context of their lives, worth, purpose, etc. This is the monkey mind. This is the DMN.
So, the real question becomes: what effect does the strong presence of a narrative-self have on our broader experience and health? Does a strong presence of the narrative-self influence the body's interoceptive abilities and ability to properly analyze and predict incoming stimuli? This is a complex and challenging question, but evidence suggests that this is indeed the case. In a fantastic study by Farb and others in 2007, fMRIs were used to monitor brain activity in those who did and did not practice mindfulness meditation (Farb et al., 2007). In this study, a distinction was made between narrative focus and experiential focus. For eight weeks, those who underwent mindfulness meditation training were taught to practice experiential focus, which involves having present centered awareness of all thoughts, feelings, and experiences in a non-judgmental manner. Narrative focus was defined as judging experiences and trying to figure out what those stimuli meant. Brain scans were performed on both trained and untrained participants during both focus styles. For both groups, narrative focus increased activation of the mPFC and PCC as expected. During experiential focus, both groups reduced mPFC activity, but only the meditation trained group increased activation of the insula. This is incredible because the insula is highly involved in interoception and the sensations of internal physical states (Fox et al., 2014; Mehling et al., 2012). This study by Farb and others suggests a functional difference between the narrative-self and an experiential-self and shows how the quieting of the narrative-self increases interoceptive abilities and enhances the brains' ability to analyze incoming stimuli properly. Not to mention, this study shows how this skill can be trained.
So far, we have seen how the DMN is involved in the generation of the narrative-self and how this influences our ability to analyze the signals coming from the body. The next reasonable question is to what extent can this be changed? And what are the implications of such change? As was previously shown in the mentioning of the study by Farb and others in 2007, mindfulness meditation appears to be capable of changing DMN activity. This is not the only study to suggest this. Another study showed that meditation decreased mPFC activity in DMN regions, such as the TPJ and PCC (Scheibner et al., 2017). It has also been shown that the neurotransmitter GABA reduces DMN activity, and both yoga and meditation have been implicated in the release of GABA (Guglietti et al., 2013; Hu et al., 2013; Streeter et al., 2018). The release of GABA release is also modulated by the vagus nerve, providing evidence of the possible mechanism at which meditation inhibits DMN activity (Hu et al., 2013; Keute et al., 2018; Streeter et al., 2018). Through these studies, it seems evident that meditation decreases DMN activity. In what ways is this significant? Firstly, it provides more explanation as to why meditation seems capable of alleviating depression. Similarly, it offers more evidence for how meditation increases interoceptive awareness (de Jong et al., 2016; Farb et al., 2010; Hanley et al., 2017). The increase in interoception suggests that the brain is more adequately processing not only the internal environment more adequately, but presumably the outside environment as well. Reality in general is being more accurately understood. It is possible that this also implicates a broader understanding of how meditation can alter consciousness and allowing monks, yogis, and the like to achieve nirvana/samadhi/enlightenment, or whatever you prefer to call such a state of altered consciousnesses. Perhaps this experience of altered consciousness is a more accurate interpretation of reality, produced by enhanced interoception and exteroception.
The subject of altered consciousness is perhaps best explored through brain changes induced by another technique commonly used in a spiritual manner: psychedelics. The famous studies from Johns Hopkins University using psilocybin found that this drug causes a spiritual experience often described as a sense of unity of all things that transcend space and time (Griffiths et al., 2006, 2008). Many participants rate this experience as one of the most significant spiritual experiences of their life (Griffiths et al., 2006). These experiences were often described with an experienced loss sense of self and an altered form of consciousness (Griffiths et al., 2008). It is not hard to imagine that this experience seems very similar to that of a trained monk or yogi, who learn to let go of their narrative-self and gain a sense of oneness with all things. This connection is further verified by the observation that psilocybin decreases the activity of the ACC, PCC, and mPFC (Robin L. Carhart-Harris et al., 2012). Ayahuasca, another psychedelic drug used in spiritual rituals by the indigenous peoples of the Amazon, also has been shown to have similar effects (Palhano-Fontes et al., 2015). Additionally, LSD has been shown to do the same (Speth et al., 2016). Suppose both psychedelic drugs and meditative practice decrease the same DMN, which generates the narrative-self. In that case, both methods likely lead one to the same place: an experience beyond time and space, where one is present with a profound sense of unity with everything.
This, to me, is a profound idea. It suggests that quieting the mind, or calming the “pond”, improves mental, physical, and spiritual health. It provides one with a perception full of compassion, peace, and love. It not only can make the individual healthier, but so too the community and planet. It is extraordinary evidence that improving the self is the greatest means of improving the world around us. Not to mention, it provides a simple means of liberating oneself from the struggle and hardship of life. Perhaps it is not life that is hard on us, but ourselves, by allowing the narrative-mind to take hold of our reality, rather than letting a purer form of consciousness dominate our perceptions. This is the pursuit, and meditation techniques are the practice.
References
Carhart-Harris, R. L., & Friston, K. J. (2010). The default-mode, ego-functions and free-energy: A neurobiological account of Freudian ideas. Brain, 133(4), 1265–1283. https://doi.org/10.1093/brain/awq010
Carhart-Harris, Robin L., Erritzoe, D., Williams, T., Stone, J. M., Reed, L. J., Colasanti, A., Tyacke, R. J., Leech, R., Malizia, A. L., Murphy, K., Hobden, P., Evans, J., Feilding, A., Wise, R. G., & Nutt, D. J. (2012). Neural correlates of the psychedelic state as determined by fMRI studies with psilocybin. Proceedings of the National Academy of Sciences of the United States of America, 109(6), 2138–2143. https://doi.org/10.1073/pnas.1119598109
de Jong, M., Lazar, S. W., Hug, K., Mehling, W. E., Hölzel, B. K., Sack, A. T., Peeters, F., Ashih, H., Mischoulon, D., & Gard, T. (2016). Effects of mindfulness-based cognitive therapy on body awareness in patients with chronic pain and comorbid depression. Frontiers in Psychology, 7(JUN). https://doi.org/10.3389/fpsyg.2016.00967
Ekhtiari, H., Nasseri, P., Yavari, F., Mokri, A., & Monterosso, J. (2016). Neuroscience of drug craving for addiction medicine: From circuits to therapies. In Progress in Brain Research (Vol. 223, pp. 115–141). Elsevier B.V. https://doi.org/10.1016/bs.pbr.2015.10.002
Farb, N. A. S., Anderson, A. K., Mayberg, H., Bean, J., McKeon, D., & Segal, Z. v. (2010). Minding One's Emotions: Mindfulness Training Alters the Neural Expression of Sadness. Emotion, 10(1), 25–33. https://doi.org/10.1037/a0017151
Farb, N. A. S., Segal, Z. v., Mayberg, H., Bean, J., Mckeon, D., Fatima, Z., & Anderson, A. K. (2007). Attending to the present: Mindfulness meditation reveals distinct neural modes of self-reference. Social Cognitive and Affective Neuroscience, 2(4), 313–322. https://doi.org/10.1093/scan/nsm030
Fox, K. C. R., Nijeboer, S., Dixon, M. L., Floman, J. L., Ellamil, M., Rumak, S. P., Sedlmeier, P., & Christoff, K. (2014). Is meditation associated with altered brain structure? A systematic review and meta-analysis of morphometric neuroimaging in meditation practitioners. Neuroscience and Biobehavioral Reviews, 43, 48–73. https://doi.org/10.1016/j.neubiorev.2014.03.016
Griffiths, R. R., Richards, W. A., Johnson, M. W., McCann, U. D., & Jesse, R. (2008). Mystical-type experiences occasioned by psilocybin mediate the attribution of personal meaning and spiritual significance 14 months later. Journal of Psychopharmacology, 22(6), 621–632. https://doi.org/10.1177/0269881108094300
Griffiths, R. R., Richards, W. A., McCann, U., & Jesse, R. (2006). Psilocybin can occasion mystical-type experiences having substantial and sustained personal meaning and spiritual significance. Psychopharmacology, 187(3), 268–283. https://doi.org/10.1007/s00213-006-0457-5
Guglietti, C. L., Daskalakis, Z. J., Radhu, N., Fitzgerald, P. B., & Ritvo, P. (2013). Meditation-related increases in GABAB modulated cortical inhibition. Brain Stimulation, 6(3), 397–402. https://doi.org/10.1016/j.brs.2012.08.005
Hamilton, J. P., Farmer, M., Fogelman, P., & Gotlib, I. H. (2015). Depressive Rumination, the Default-Mode Network, and the Dark Matter of Clinical Neuroscience. In Biological Psychiatry (Vol. 78, Issue 4, pp. 224–230). Elsevier USA. https://doi.org/10.1016/j.biopsych.2015.02.020
Hamilton, J. P., Furman, D. J., Chang, C., Thomason, M. E., Dennis, E., & Gotlib, I. H. (2011). Default-mode and task-positive network activity in major depressive disorder: Implications for adaptive and maladaptive rumination. Biological Psychiatry, 70(4), 327–333. https://doi.org/10.1016/j.biopsych.2011.02.003
Hanley, A. W., Mehling, W. E., & Garland, E. L. (2017). Holding the body in mind: Interoceptive awareness, dispositional mindfulness and psychological well-being. Journal of Psychosomatic Research, 99, 13–20. https://doi.org/10.1016/j.jpsychores.2017.05.014
Heilbronner, S. R., & Platt, M. L. (2013). Causal evidence of performance monitoring by neurons in posterior cingulate cortex during learning. Neuron, 80(6), 1384–1391. https://doi.org/10.1016/j.neuron.2013.09.028
Hu, Y., Chen, X., Gu, H., & Yang, Y. (2013). Resting-state glutamate and GABA concentrations predict task-induced deactivation in the default mode network. Journal of Neuroscience, 33(47), 18566–18573. https://doi.org/10.1523/JNEUROSCI.1973-13.2013
Keute, M., Ruhnau, P., Heinze, H. J., & Zaehle, T. (2018). Behavioral and electrophysiological evidence for GABAergic modulation through transcutaneous vagus nerve stimulation. Clinical Neurophysiology, 129(9), 1789–1795. https://doi.org/10.1016/j.clinph.2018.05.026
Knyazev, G. G. (2013). EEG correlates of self-referential processing. Frontiers in Human Neuroscience, 7(MAY), 1–14. https://doi.org/10.3389/fnhum.2013.00264
Marstaller, L., Burianová, H., & Reutens, D. C. (2017). Adaptive contextualization: A new role for the default mode network in affective learning. Human Brain Mapping, 38(2), 1082–1091. https://doi.org/10.1002/hbm.23442
Mehling, W. E., Price, C., Daubenmier, J. J., Acree, M., Bartmess, E., & Stewart, A. (2012). The Multidimensional Assessment of Interoceptive Awareness (MAIA). PLoS ONE, 7(11). https://doi.org/10.1371/journal.pone.0048230
Palhano-Fontes, F., Andrade, K. C., Tofoli, L. F., Jose, A. C. S., Crippa, A. S., Hallak, J. E. C., Ribeiro, S., & de Araujo, D. B. (2015). The psychedelic state induced by Ayahuasca modulates the activity and connectivity of the Default Mode Network. PLoS ONE, 10(2), 1–13. https://doi.org/10.1371/journal.pone.0118143
Scheibner, H. J., Bogler, C., Gleich, T., Haynes, J. D., & Bermpohl, F. (2017). Internal and external attention and the default mode network. NeuroImage, 148(January), 381–389. https://doi.org/10.1016/j.neuroimage.2017.01.044
Seth, A. K. (2013). Interoceptive inference, emotion, and the embodied self. Trends in Cognitive Sciences, 17(11), 565–573. https://doi.org/10.1016/j.tics.2013.09.007
Speth, J., Speth, C., Kaelen, M., Schloerscheidt, A. M., Feilding, A., Nutt, D. J., & Carhart-Harris, R. L. (2016). Decreased mental time travel to the past correlates with default-mode network disintegration under lysergic acid diethylamide. Journal of Psychopharmacology, 30(4), 344–353. https://doi.org/10.1177/0269881116628430
Spreng, R. N., & Grady, C. L. (2010). Patterns of brain activity supporting autobiographical memory, prospection, and theory of mind, and their relationship to the default mode network. Journal of Cognitive Neuroscience, 22(6), 1112–1123. https://doi.org/10.1162/jocn.2009.21282
Streeter, C., Gerbarg, P. L., Nielsen, G. H., Brown, R. P., Jensen, J. E., Silveri, M., & Streeter, C. C. (2018). Effects of Yoga on Thalamic Gamma-Aminobutyric Acid, Mood and Depression: Analysis of Two Randomized Controlled Trials. Neuropsychiatry, 8(6), 1923–1939. https://doi.org/10.4172/Neuropsychiatry.1000535
van Buuren, M., Gladwin, T. E., Zandbelt, B. B., Kahn, R. S., & Vink, M. (2010). Reduced functional coupling in the default-mode network during self-referential processing. Human Brain Mapping, 31(8), 1117–1127. https://doi.org/10.1002/hbm.20920
Watkins, E. R. (2008). Constructive and unconstructive repetitive thought. Psychological Bulletin, 134(2), 163–206. https://doi.org/10.1037/0033-2909.134.2.163
Zhou, H. X., Chen, X., Shen, Y. Q., Li, L., Chen, N. X., Zhu, Z. C., Castellanos, F. X., & Yan, C. G. (2020). Rumination and the default mode network: Meta-analysis of brain imaging studies and implications for depression. In NeuroImage (Vol. 206, p. 116287). Academic Press Inc. https://doi.org/10.1016/j.neuroimage.2019.116287
-
 @ 6bae33c8:607272e8
2025-02-10 15:27:25
@ 6bae33c8:607272e8
2025-02-10 15:27:25I didn’t realize how much I had missed a good old fashioned Super Bowl blowout. I wasn’t even gonna bet the game, but over the last couple days, I got an Eagles vibe. There was too much, “The refs won’t let the Chiefs lose”, and Patrick Mahomes and Taylor Swift, and other noise, and yet the line didn’t budge. It was obvious the Eagles were the sharper side, and they had the league’s best defense, which usually correlates to overperformance of the spread in Super Bowls, sometimes massive overperformance.
But it wasn’t any one thing — just an overall dawning on me that the Eagles were probably the right side. I didn’t feel that strongly about it, even so, and decided I’d just bet Saquon Barkley for MVP, get 3:1 or so if the Eagles won. So I texted someone in the states to place the bet for me, and best he could offer was +175! That’s a terrible value for a RB to win MVP! A few minutes later Tim Schuler offered to bet me $50, give me the Eagles +1, and I obliged him. After that, I texted my friend back to put $500 on the Eagles +1 for me.
Of course, I didn’t stay up all night to watch — after losing 1K on the Falcons (who were up 28-3 in the third quarter at 3 am) eight years ago, never again. So I caught the 40-minute version this morning. What a great game! The Eagles dominated from start to finish. The defensive line got after Mahomes on every play. And while the Chiefs sold out to stop Barkley, Jalen Hurts ran wild on them.
I’m sure I would have enjoyed a Chiefs blowout less, but the beauty of a blowout is it settles things. There’s no looking back at a bad call, a dropped pass or a fumble and wondering what might have been. Close games have drama, but they are more or less arbitrary. I mean I get it, the guy made the throw at the time with the game on the line, but maybe also he just got the cheap roughing the passer call or the ticky tack PI. When the Giants won the Super Bowl on Scott Norwood’s miss, I didn’t have the same sense of satisfaction I did when they blew out John Elway’s Broncos five years earlier. Yes, they won, but it might as well have been on a coin flip.
I grew up on blowouts in the ‘80s — Raiders-Redskins, 49ers-Dolphins, Pats-Bears, Giants-Broncos, Redskins-Broncos — only the Bengals managed to keep Super Bowl losses close (Congratulations Jeff Erickson!) This was before replay reviews and all the lawyering about what is and isn’t a completed catch. The last fucking thing you wanted was some controversy about who really outplayed whom. So it was nice to win some easy money and not to have to worry about refs or fumbles or untimely drops for a change.
-
I wanted Saquon to win MVP, but he drew the attention of the KC defense, is one of the best I’ve ever seen in blitz pickup and still had 97 yards from scrimmage. One of the all-time great years from an all-time great back. (He broke Terrell Davis’ record for the most yardage, regular season and playoffs, too, albeit in two extra games.)
-
Hurts threw the one bad pick under pressure, but it served as a good punt, and otherwise had a near perfect game. Only four other incomplete passes, 72 yards and a score on the ground. He was an easy MVP call.
-
I was a little worried about shaky Jake Elliott, but he drilled all four of his field goals, three of them twice!, due to penalties.
-
Patrick Mahomes padded his stats in garbage time, but he got crushed. An elite defense that gets home with four is the way you kill the GOATS. The Giants did it to Tom Brady twice.
-
Xavier Worthy had a nice garbage-time stat-padding game, but he was the only one. DeAndre Hopkins had a bad drop, though they got him a garbage-time feel-good TD, basically a participation trophy.
-
Congrats to Lane Johnson, Brandon Graham, Elliott and long-snapper Rick Lovato — the only four players in NFL history to defeat both Tom Brady and Mahomes in Super Bowls.
-
The only negative is I lost my $50 four-teams bet with Erickson. I had the Chiefs, Bills, Lions and Ravens, he had the field. But I directed Schuler to pay him, which is good, because I cancelled Paypal for their retarded foray into free-speech policing, and now I don’t have to figure out a workaround.
-
-
 @ 3b7fc823:e194354f
2025-02-10 13:13:25
@ 3b7fc823:e194354f
2025-02-10 13:13:25Alright, let’s get one thing straight: you’re scrolling through your phone, shopping online, maybe even working from home. But here’s the thing – someone might be watching. Not in the creepy stalker way, but in the “is that company really needing my data?” kind of way. That’s where a Virtual Private Network (VPN) comes in, saving you from the prying eyes of marketers, governments, and even your own internet provider.
What Does a VPN Do?
A VPN creates a secure, encrypted connection between your device and a VPN server. This allows you to browse the internet anonymously, keeping your online activities private from your Internet Service Provider (ISP), network administrators, and even hackers. When you connect to a VPN, your internet traffic is routed through an intermediary server, making it difficult for anyone to track your online movements.
Why You Need a VPN: Privacy edition
- Hiding Your IP Address
Every time you jump online, your device gets an IP address, like a digital ID. If you don’t use a VPN, everyone can see this ID, making it easy for advertisers and governments to track your every move.
-
[X ] Myth: A VPN hides my IP address from everyone.
-
[X] Reality: A VPN hides your IP address only from the websites you visit and your ISP. Your internet service provider still knows you're using a VPN, but they won't be able to see what sites you're visiting. Your VPN knows what sites you are visiting and may know who you are as well.
-
Bypassing Censorship
Ever tried accessing something that’s blocked in your country? A VPN can help you bypass those restrictions, letting you watch the latest shows, access social media, or even download books without getting flagged as a troublemaker.
- Protecting Your Data
When you connect to public Wi-Fi – like at a café or airport – you’re basically handing over your data on a silver platter. A VPN encrypts this data, so even if someone intercepts it, they can’t decode it. Think of it as adding an extra layer of security.
- Avoiding Surveillance
Companies and governments love collecting data. From what you search to who you talk to, there’s a lot of stuff that’s none of their business. A VPN ensures that only you know where you’ve been online.
- Safeguarding Your Personal and Professional Life
Whether you’re working from home or just shopping for a present, a VPN keeps your activities private. It’s like having a secure safe for all your online stuff, so no one can snoop.
- Stopping Targeted Ads
Companies track your browsing habits to send you ads that follow you around the internet. A VPN breaks this cycle, making sure those creepy “you might like” ads stop following you around.
- No Logs Policy
Some VPNs keep records of your activity, which means they could be handed over if the government comes knocking. But with a no-logs policy, nothing is stored – they promise ;)
- The Dark Side of Free VPNs
Before you jump into using a free VPN, think twice. Free services often come with a catch: they might sell your data to advertisers or even track your activity themselves. It’s like getting a free hotdog at a gas station – it sounds great, but you’ll probably regret it later.
How to Use a VPN (Because You’re Not a Tech Wizard)
- Choose the Right Provider
Go for a reputable service that offers strong encryption and a no-logs policy. Look for options with a kill switch, which stops any data from being leaked if the connection drops. I prefer ones you can pay annoymously but that may be overkill for most people.
- Download and Install
Once you pick a provider, download the app to your device. It’s not rocket science, but it does require a bit more than just opening an email.
- Set It Up
Most VPNs have user-friendly interfaces. Just click “Connect” and you’re good to go. You might need to enter your login details or use a password from your provider.
The Final Word Using a VPN isn’t about being a hacker or someone with something to hide. It’s about respecting your privacy and having control over what you share online. In today’s world, where companies and governments are constantly getting more creative about how they collect data, it’s practically a requirement if you want to stay ahead of the curve.
So there you have it – the secret life of your internet. With a VPN, you’re not just protecting yourself; you’re making sure that your digital footprint is as small as possible. Whether you’re at home or on the go, a VPN gives you the freedom to surf, shop, and work without anyone watching your every move.
And hey, if you’re still not convinced, just think about it this way: imagine your internet connection as a crowded public space. Without a VPN, everyone’s staring at you. With one, you’re wearing a mask, and no one’s the wiser.
Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero
82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1
-
 @ da0b9bc3:4e30a4a9
2025-02-10 12:51:46
@ da0b9bc3:4e30a4a9
2025-02-10 12:51:46Hello Stackers!
It's Monday so we're back doing "Meta Music Mondays" 😉.
From before the territory existed there was just one post a week in a ~meta take over. Now each month we have a different theme and bring music from that theme.
Welcome to Femmes Fatales 3!!!
I absolutely loved doing this last year so I'm bringing it back for round 3!
It's Femmes Fatales, where we celebrate women in ~Music. So let's have those ladies of the lung, the sirens of sound, our Femmes Fatales!
https://youtu.be/ya69LUa1E_w?si=cM6yCALsPpp9L3Sc
I recently got introduced to these ladies. Their music is fantastic, they're really talented musicians. They are:
Lilith: The vocalist. Lamia: The lead guitarist. Nixe: The bassist. Abrahel: The drummer.
Their identity is meant to be a mystery, so let's keep it that way.
These Nuns can make Noise!!
Let's go!
Talk Music. Share Tracks. Zap Sats.
originally posted at https://stacker.news/items/881416
-
 @ 78c90fc4:4bff983c
2025-02-10 12:08:13
@ 78c90fc4:4bff983c
2025-02-10 12:08:13“Die Welt wird von ganz anderen Personen regiert als diejenigen es sich vorstellen, die nicht hinter den Kulissen stehen.”
Benjamin Disraeli, zweimaliger britischer Premierminister und Romanautor.
Quelle:
https://www.unz.com/article/the-disraeli-enigma/\ \ Als 1853 der Krimkrieg zwischen Russland und dem Osmanischen Reich ausbrach, wurde das Osmanische Reich vom Vereinigten Königreich und Frankreich gerettet. Zwanzig Jahre später zog Zar Alexander II. als Beschützer der unterdrückten serbischen und bulgarischen Christen erneut gegen die Osmanen in den Krieg. Als die Russen vor den Toren Konstantinopels/Istanbuls standen, waren die Osmanen gezwungen, die Schaffung der autonomen Fürstentümer Bulgarien, Serbien und Rumänien durch den Vertrag von San Stefano zu akzeptieren. Die Briten waren mit diesem Vertrag unzufrieden und beriefen zusammen mit Österreich-Ungarn den Berliner Kongress (1878) ein, der ihn aufhob. Russische Eroberungen wurden zurückgenommen, Armenien und Bulgarien wurden größtenteils an das Osmanische Reich zurückgegeben und der Balkan wurde in heterogene und konfliktreiche Staaten aufgeteilt. Diese „Balkanisierung“ löste nationalistische Ressentiments aus, die den Ersten Weltkrieg auslösen sollten.
\ Das Hauptziel des Berliner Vertrags bestand darin, das zu retten, was von einem schwächelnden Osmanischen Reich zu retten war, um der panslawistischen Expansion Russlands entgegenzuwirken. England, das stets eifersüchtig auf seine Vormachtstellung zur See bedacht war, wollte verhindern, dass Russland näher an den Bosporus heranrückte. Die Briten erhielten das Recht, Zypern als Marinestützpunkt zu nutzen und gleichzeitig den Suezkanal zu überwachen. Dies war der Beginn des „Great Game“ Großbritanniens um die Kolonialherrschaft in Asien und die Eindämmung Russlands, was insbesondere zur Schaffung Afghanistans als Pufferstaat führte.
\ Es gibt verschiedene Möglichkeiten, diesen Abschnitt der Geschichte zu interpretieren, der den Keim für alle Tragödien des 20. Jahrhunderts („das jüdische Jahrhundert“ laut Yuri Slezkine) in sich trägt.[1]\ Yuri Slezkine, The Jewish Century, Princeton University Press, 2004.
\ Es gibt unterschiedliche Ansichten darüber, welche Kräfte die Geschichte in dieser entscheidenden Zeit geprägt haben. Aber letztendlich wird Geschichte von Menschen gemacht, und sie kann nur verstanden werden, wenn man die Hauptakteure und ihre Motive identifiziert: Man kann den Vietnamkrieg einfach nicht verstehen, ohne sich mit der Denkweise von Johnson oder Kissinger auseinanderzusetzen. Unter den Anstiftern des Berliner Vertrags sticht ein Name besonders hervor: Benjamin Disraeli (1804–1881), Premierminister unter Königin Victoria von 1868 bis 1869 und erneut von 1874 bis 1880. Disraeli war auch der Mann, der 1875 die Übernahme des Suezkanals durch England ermöglichte, und zwar durch die Finanzierung seines Freundes Lionel de Rothschild, dem Sohn von Nathan Mayer – eine Operation, die die Kontrolle der Rothschilds über die Bank of England festigte.
\ Disraeli ist ein sehr interessanter Fall, da er sowohl ein bedeutender britischer Staatsmann während der globalen Hegemonie Großbritanniens als auch ein Romanautor war, der seine fiktiven Figuren dazu benutzte, seine ehrlichen Gedanken zu äußern, während er eine Art „glaubhafte Abstreitbarkeit“ (Sidonia spricht, nicht ich!) aufrechterhielt. Wir haben daher die einzigartige Gelegenheit, die wahren Motive des Mannes in der Politik zwischen den Zeilen zu lesen. Stellen Sie sich vor, Kissinger hätte Romane geschrieben, in denen ein Jude die Hauptfigur ist, der die Außen- und Militärpolitik des Imperiums vorantrieb und gleichzeitig ein enger Freund des reichsten jüdischen Bankiers war.\ \
Disraeli wird als der wahre Erfinder des Britischen Empires bezeichnet, da er es war, der Königin Victoria durch das Parlament mit dem Royal Titles Act von 1876 zur Kaiserin von Indien ernennen ließ (das obere Bild ist eine Karikatur, die Disraeli als Hausierer zeigt, der der Königin die Kaiserkrone überreicht).
Disraeli war, wie bereits erwähnt, die Hauptinspiration für den Berliner Kongress. Darüber hinaus war Disraeli ein Vorläufer des Zionismus, der versuchte, die „Wiederherstellung Israels“ auf die Tagesordnung des Berliner Kongresses zu setzen, in der Hoffnung, den Sultan Abdul Hamid davon zu überzeugen, Palästina als autonome Provinz zu gewähren. Der Sultan lehnte das Angebot ab, das wahrscheinlich das Versprechen finanzieller Unterstützung für seine zusammenbrechende Wirtschaft beinhaltete – wie auch Herzls Angebot im Jahr 1902, das ebenfalls abgelehnt wurde.\ \ Der Zionismus war Disraelis uralter Traum: Nach einer Reise in den Nahen Osten im Alter von sechsundzwanzig Jahren veröffentlichte er seinen ersten Roman, Die wundersame Geschichte des Alroy, und ließ seinen Helden, einen einflussreichen Juden des Mittelalters, sagen: „Mein Wunsch ist eine nationale Existenz, die wir nicht haben. Mein Wunsch ist das Land der Verheißung und Jerusalem und der Tempel, alles, was wir eingebüßt haben, wonach wir uns gesehnt haben, wofür wir gekämpft haben, unser schönes Land, unser heiliges Glaubensbekenntnis, unsere einfachen Sitten und unsere alten Bräuche.“\ Disraeli schrieb diese Zeilen noch vor den Anfängen der biblischen Archäologie; erst 1841 veröffentlichte Edward Robinson seine Biblical Researches in Palestine. Die ersten Ausgrabungen des von Königin Victoria geförderten Palestine Exploration Fund begannen 1867. Wohlhabende britische Juden hatten sich jedoch schon lange zuvor für Palästina interessiert. Disraelis Interesse wurde durch seinen Nachbarn und vierzigjährigen Freund Moses Montefiore beeinflusst, der Judith Cohen, die Schwägerin von Nathan Rothschild, heiratete. Nach einer Reise nach Palästina im Jahr 1827 widmete Montefiore seine immensen Ressourcen der Unterstützung seiner Glaubensgenossen im Heiligen Land, indem er Land kaufte und Häuser baute.
\ Sowohl Montefiore als auch Disraeli waren sephardischer Herkunft. Disraeli stammte aus einer Familie portugiesischer Marranen, die in Venedig zum Judentum konvertierten. Sein Großvater war 1748 nach London gezogen. Benjamin wurde im Alter von dreizehn Jahren getauft, als sein Vater Isaac D'Israeli zusammen mit seiner ganzen Familie zum anglikanischen Christentum konvertierte. Isaac D'Israeli ist der Autor eines Buches mit dem Titel The Genius of Judaism(in Anlehnung an Chateaubriands Le Génie du Christianisme), in dem er die einzigartigen Eigenschaften des jüdischen Volkes verherrlicht, aber die talmudischen Rabbiner dafür verantwortlich macht, dass sie „den nationalen Geist ihres Volkes versiegeln“ und „die Einfachheit ihres antiken Glaubens korrumpieren“. Wie für viele andere Juden dieser Zeit war die Konversion für D'Israeli rein opportunistisch: Bis zum Beginn des 19. Jahrhunderts blieben Verwaltungskarrieren für Juden verschlossen. Ein Gesetz von 1740 hatte ihre Einbürgerung erlaubt, aber es hatte Volksaufstände provoziert und wurde 1753 aufgehoben. Viele einflussreiche Juden, wie der Stadtbankier Sampson Gideon, entschieden sich dann für eine nominelle Konversion ihrer Kinder.[2]\ Cecil Roth, A History of the Marranos (1932), Meridian Books, 1959, S. 148.\ \ Etwa zur gleichen Zeit wie Disraeli konvertierte Heinrich Heine (1797–1856) zum Luthertum (während einer seiner Brüder zum Katholizismus konvertierte, um Offizier in Österreich zu werden, und ein anderer zur Orthodoxie, um als Arzt in Russland zu dienen). Heine betrachtete die Taufe als „Eintrittskarte in die europäische Zivilisation“. Er beklagte sich jedoch darüber, dass er von den Deutschen immer noch als Jude angesehen wurde, und zog es daher vor, in Frankreich zu leben, wo er als Deutscher angesehen wurde. Nur wenige Jahre nach seiner Konversion zeigten seine Schriften eine sehr negative Einstellung gegenüber dem Christentum, das er als „düstere, blutrünstige Religion für Kriminelle“ bezeichnete, die die Sinnlichkeit unterdrücke. Am Ende seines Lebens bereute er seine Taufe, die ihm nichts gebracht hatte, und erklärte in seinem letzten Buch Romanzero: „Ich mache kein Geheimnis aus meinem Judentum, zu dem ich nicht zurückgekehrt bin, weil ich es nicht verlassen habe.“[3]\ Zitiert in Kevin MacDonald, Separation and Its Discontents: Toward an Evolutionary Theory of Anti-Semitism, Praeger, 1998, kindle 2013, l. 4732–4877.
\ Genau wie bei den portugiesischen Marranen im 15. Jahrhundert verstärkte die Taufe bei den europäischen Juden des 19. Jahrhunderts ein nicht-religiöses, rassisches Verständnis des Judentums. Disraeli bezeichnete sich selbst als „Anglikaner jüdischer Abstammung“.
\ Für Hannah Arendt ist Disraeli ein „Rassenfanatiker“, der in seinem ersten Roman Alroy (1833) „einen Plan für ein jüdisches Reich entwickelte, in dem Juden als streng getrennte Klasse herrschen würden“. In seinem anderen Roman Coningsby „entfaltete er einen fantastischen Plan, nach dem jüdisches Geld den Aufstieg und Fall von Höfen und Reichen beherrscht und in der Diplomatie die Oberhand hat“. Diese Idee „wurde zum Dreh- und Angelpunkt seiner politischen Philosophie“.[4]\ Hannah Arendt, The Origins of Totalitarianism, Band 1: Antisemitism, Meridian Books, 1958, S. 309–310.\ Dies ist eine ziemlich fantastische Anschuldigung, die die meisten Biografen Disraelis nicht bestätigen würden. Sie ist jedoch wahrscheinlich richtig. Aber wir müssen genau auf Disraelis eigene Stimme hören, die durch Sidonia zum Ausdruck kommt, die Figur, die in drei seiner Romane vorkommt: Coningsby (1844), Sybil (1845) und Tancred (1847).
In Sidonias Worten spürt man den Groll gegen die Nation, in die er sich zu integrieren versuchte:\ Kann es etwas Absurderes geben, als dass eine Nation sich an eine Einzelperson wendet, um ihren Kredit, ihre Existenz als Imperium und ihren Komfort als Volk zu erhalten; und diese Einzelperson, der ihre Gesetze die stolzesten Rechte der Staatsbürgerschaft, das Privileg, in ihrem Senat zu sitzen und Land zu besitzen, verweigern; denn obwohl ich unbesonnen genug war, mehrere Ländereien zu kaufen, bin ich der Meinung, dass ein Engländer hebräischen Glaubens nach dem geltenden Recht Englands keinen Boden besitzen kann.
\ Da es einem Juden nicht möglich ist, sich durch Landbesitz in die britische Aristokratie zu integrieren, selbst wenn er zum örtlichen Glauben konvertiert, was sollte ein Jude tun, außer durch die Macht des Geldes aufzusteigen? Wie Heine spürte auch Disraeli die Heuchelei der Christen, die es den Juden übel nahmen, dass sie keine Christen waren, sie aber weiterhin als Juden behandelten, wenn sie konvertierten, und es insgeheim sogar vorzogen, dass sie Juden blieben.
\ Laut Disraelis Biografen Robert Blake ist Sidonia „eine Kreuzung zwischen Lionel de Rothschild und Disraeli selbst“. Er stammt von einer Adelsfamilie aus Aragon ab, zu deren herausragenden Mitgliedern ein Erzbischof und ein Großinquisitor gehörten, die beide heimlich dem Judentum ihrer Väter anhingen. Sidonias Vater, wie auch Lionel de Rothschilds Vater, „machte während der Napoleonischen Kriege ein großes Vermögen mit Militärverträgen und der Versorgung der verschiedenen Armeen“. Nachdem er sich in London niedergelassen hatte, „setzte er alles, was er besaß, auf die Waterloo-Anleihe; und das Ereignis machte ihn zu einem der größten Kapitalisten Europas.“ Seit seinem siebzehnten Lebensjahr besuchte Sidonia die Fürstenhöfe der Schuldner seines Vaters und lernte die Geheimnisse der Macht kennen. „Die geheime Geschichte der Welt war sein Zeitvertreib. Es bereitete ihm großes Vergnügen, die verborgenen Motive mit den öffentlichen Vorwänden der Transaktionen zu kontrastieren.“ Disraeli selbst war laut Robert Blake „von Verschwörungen besessen“.[5]\ Robert Blake, Disraeli (1966), Faber Finds, 2010, S. 202.
\ Sidonia ist von seiner Rasse begeistert: „Alles ist Rasse – es gibt keine andere Wahrheit.“ Er weigert sich, eine Nichtjüdin zu heiraten, weil, so der Erzähler, „keine irdische Überlegung ihn jemals dazu veranlassen würde, die Reinheit der Rasse zu beeinträchtigen, auf die er stolz ist.“ Mit „Rasse“ meinte Disraeli Blutsverwandtschaft. In seinem letzten Roman Endymion (1880) schrieb er:\ Kein Mensch wird das Prinzip der Rasse gleichgültig behandeln. Es ist der Schlüssel zur Geschichte, und der Grund, warum die Geschichte oft so verwirrend ist, liegt darin, dass sie von Männern geschrieben wurde, die dieses Prinzip und all das damit verbundene Wissen nicht kennen ... Sprache und Religion machen keine Rasse aus – es gibt nur eine Sache, die eine Rasse ausmacht, und das ist Blut.\ Sidonia erzählt seinem Schützling Coningsby in Coningsby oder die neue Generation, dass die Verfolgung durch christliche Nationen die jüdische Nation niemals zerschlagen könnte.
\ Tatsache ist, dass man eine reine Rasse der kaukasischen Organisation nicht vernichten kann. Es ist eine physiologische Tatsache; ein einfaches Naturgesetz, das ägyptische und assyrische Könige, römische Kaiser und christliche Inquisitoren verblüfft hat. Keine Strafgesetze, keine körperlichen Folterungen können bewirken, dass eine überlegene Rasse in einer unterlegenen aufgehen oder von ihr vernichtet werden sollte. Die gemischten verfolgenden Rassen verschwinden, die reine verfolgte Rasse bleibt bestehen. Und im Moment, trotz Jahrhunderten oder gar Jahrzehnten der Erniedrigung, übt der jüdische Geist einen enormen Einfluss auf die Angelegenheiten Europas aus. Ich spreche nicht von ihren Gesetzen, denen Sie immer noch gehorchen; von ihrer Literatur, mit der Ihr Geist gesättigt ist, sondern vom lebendigen hebräischen Intellekt. Sie beobachten nie eine große intellektuelle Bewegung in Europa, an der die Juden nicht in hohem Maße beteiligt sind.\ Wo auch immer er reiste, fügte Sidonia hinzu, sah er jüdische Berater hinter Monarchen und Staatsoberhäuptern.
„Sie sehen also, mein lieber Coningsby, dass die Welt von ganz anderen Persönlichkeiten regiert wird, als diejenigen, die nicht hinter den Kulissen stehen, sich vorstellen können.“
In einem Sachbuch (Lord George Bentinck: A Political Biography, 1852) schrieb Disraeli:\ [Juden] sind ein lebendiger und der eindrucksvollste Beweis für die Falschheit dieser verderblichen Doktrin der Neuzeit, der natürlichen Gleichheit der Menschen. ... die natürliche Gleichheit der Menschen, die heute in Mode ist und die Form einer kosmopolitischen Bruderschaft annimmt, ist ein Prinzip, das, wenn man danach handeln könnte, die großen Rassen zersetzen und den ganzen Genius der Welt zerstören würde. ... Die angeborene Tendenz der jüdischen Rasse, die zu Recht stolz auf ihr Blut ist, ist gegen die Doktrin der Gleichheit der Menschen.[6]\ Benjamin Disraeli, Lord George Bentinck, Archibald, 1852 (archive.org), S. 496.
\ Disraeli ist eindeutig auf derselben Wellenlänge wie Moses Hess, Herzls geistiger Vater, der, nachdem er Marx (einen weiteren nominellen Konvertiten) beeinflusst hatte, zu dem Schluss kam, dass „der Rassenkrieg wichtiger ist als der Klassenkampf“ (Rom und Jerusalem, 1862). Ein gutes Beispiel für dialektische politische Manipulation ist, dass Hess Marx weiterhin heimlich unterstützte und auf dessen Bitte hin nach dem Generalkongress der Internationale in Basel (5.–12. September 1869) Verleumdungen gegen Bakunin veröffentlichte, in denen er Bakunin beschuldigte, ein Agent provocateur der russischen Regierung zu sein und „im Interesse des Panslawismus“ zu arbeiten.[7]\ Bakunins Antwort auf Französisch, „Aux citoyens rédacteurs du Réveil“, finden Sie auf Wikisource.org.\ Es ist interessant zu sehen, dass ein anderer Proto-Zionist wie Disraeli den russischen Interessen zutiefst feindlich gesinnt war.\ \ Was war Disraelis Motivation hinter der Außenpolitik, die er dem britischen Empire vermittelte? Glaubte er, dass es die offensichtliche Bestimmung der Briten sei, die Welt zu erobern? Oder sah er das britische Empire als Instrument für die überlegene Bestimmung der jüdischen Nation, wenn er sich daran erinnerte, wie Esra und Nehemia in biblischen Zeiten die Außenpolitik der Perser ausgenutzt hatten? Indem er den Suezkanal (der zwischen 1859 und 1869 von den Franzosen gegraben wurde) mit den britischen Interessen in Verbindung brachte, wollte er einfach nur die Franzosen übertrumpfen, oder legte er damit den Grundstein für das zukünftige Bündnis zwischen Israel und dem angloamerikanischen Empire? Da die Briten nun einmal den Suezkanal besaßen, mussten sie ihn verteidigen, und wie ginge das besser als mit einer befreundeten jüdischen autonomen Regierung in der Nähe in Palästina? Genau das war es, was Chaim Weizmann dreißig Jahre später den Briten schmackhaft machen wollte: „Das jüdische Palästina wäre ein Schutz für England, insbesondere in Bezug auf den Suezkanal.“[8]\ Chaim Weizmann, Trial and Error, Harper & Brothers, 1949, S. 192.
\ Und als die Israelis 1956 mit britischer und französischer Unterstützung in den Sinai einmarschierten, taten sie dies, indem sie Großbritannien erneut versprachen, die Kontrolle über den von Nasser verstaatlichten Kanal an Großbritannien zurückzugeben.
\ Disraelis Russophobie, zu der er Königin Victoria bekehrte, und seine Verteidigung der Türken, deren Massaker an den Serben und Bulgaren allgemein bekannt waren, führten zu Theorien über eine jüdische Verschwörung. William Ewart Gladstone, ein langjähriger Gegner Disraelis und selbst mehrmals Premierminister (1868–1874, 1880–1885, 1886 und 1892–1894), erklärte, dass Disraeli „die britische Außenpolitik als Geisel seiner jüdischen Sympathien nahm und mehr daran interessiert war, die Leiden der Juden in Russland und der Türkei zu lindern, als an britischen Interessen“. Die Zeitung „The Truth“ vom 22. November 1877 spielte auf die Vertrautheit Disraelis mit den Rothschilds an und vermutete „eine stillschweigende Verschwörung ... seitens einer beträchtlichen Anzahl von Anglo-Hebräern, um uns im Namen der Türken in einen Krieg zu ziehen“. Es wurde außerdem daran erinnert, dass Disraeli in einer Rede vor dem britischen Unterhaus im Jahr 1847 die Zulassung von Juden zu wählbaren Ämtern gefordert hatte, mit der Begründung, dass „der jüdische Geist einen enormen Einfluss auf die Angelegenheiten Europas ausübt“.[9]\ Stanley Weintraub, Disraeli: A Biography, Hamish Hamilton, 1993, S. 579, 547.
\ Die Königin stand, wie ein Großteil der britischen Aristokratie, bereits unter dem Bann einer modischen Theorie, die den Angelsachsen einen israelitischen Ursprung zuschrieb. Diese Theorie war erstmals zur Zeit Oliver Cromwells aufgetaucht und wurde 1840 von Pastor John Wilson in seinen Vorlesungen über das alte Israel und den israelitischen Ursprung der modernen Nationen Europas sowie 1870 von Edward Hine in The English Nation Identified with the Lost Israel neu aufgelegt. In diesem Werk erfahren wir, dass das Wort „Saxon“ von „Isaac's sons“ (Söhne Isaaks) abgeleitet ist. Diese lächerliche Theorie lieferte eine billige biblische Rechtfertigung für den britischen Kolonialismus und sogar für den Völkermord an den kolonisierten Völkern (neue Kanaaniter) durch das britische Empire (neues Israel).[10]\ André Pichot, Aux origines des théories raciales, de la Bible à Darwin, Flammarion, 2008, S. 124–143, 319.
\ Königin Victoria war glücklich, glauben zu können, dass ihre edle Abstammung auf König David zurückging, und ließ ihre Söhne beschneiden, ein Brauch, der bis heute fortbesteht. Es mag etwas Wahres an dem Gefühl der britischen Elite für ihr Judentum liegen, denn im 16. und 17. Jahrhundert hatten viele Ehen reiche jüdische Familien mit der alten, verarmten Landaristokratie vereint, so dass nach Hilaire Bellocs Schätzung „mit Beginn des 20. Jahrhunderts diejenigen der großen territorialen englischen Familien, in denen es kein jüdisches Blut gab, die Ausnahme waren“.[11]\ Hilaire Belloc, The Jews, Constable & Co., 1922 (archive.org), S. 223.
\ Die Begeisterung der Königin für das Judentum hatte aber auch viel mit dem Einfluss Disraelis zu tun, der einmal gegenüber einem Freund damit prahlte: „Jeder mag Schmeichelei, und wenn es um das Königshaus geht, sollte man sie mit einer Kelle auftragen.“[12]\ Stanley Weintraub, Disraeli: A Biography, Hamish Hamilton, 1993, S. 579, 547.
\ Der Fall Disraeli ist aufschlussreich, weil die Frage, die er aufwirft, dieselbe ist wie die Frage, die heute geopolitische Analysten in Bezug auf die Beziehung zwischen den Vereinigten Staaten und Israel spaltet: Wer führt wen an der Nase herum? Ist Israel der Brückenkopf der Vereinigten Staaten im Nahen Osten oder sind die Vereinigten Staaten, wie Zbigniew Brzezinski einmal sagte, der „dumme Esel“ Israels? Die Beantwortung dieser Frage für das Jahrhundert vor dem Zweiten Weltkrieg (als „Israel“ das internationale Judentum bedeutete) hilft bei der Beantwortung derselben Frage heute, da die symbiotische Beziehung zwischen Israel und dem Imperium erheblich gewachsen ist.
\ Die Antwort hängt vom Standpunkt des Betrachters ab. Die Zionisten haben natürlich ein Interesse daran, die Ansicht zu fördern, dass Israel den angloamerikanischen Interessen dient und nicht umgekehrt. Disraeli argumentierte vor dem britischen Parlament, dass ein jüdisches Palästina im Interesse des britischen Kolonialismus sei. Aber jüdische Zionisten haben die Dinge schon immer aus der anderen Perspektive betrachtet, und man kann kaum glauben, dass Disraeli ihre Ansicht nicht insgeheim teilte. Wenn der Held seines Romans Tancred (1847), ein Jude, der wie Disraeli zum Lord ernannt wurde, das britische Empire mit folgenden Worten verherrlicht: „Wir wollen die Welt erobern, angeführt von Engeln, um die Menschheit unter göttlicher Herrschaft glücklich zu machen“, wer verbirgt sich hinter diesem zweideutigen „wir“? Ist es dasselbe doppeldeutige „wir“, das die PNAC-Neokonservativen benutzten, um Amerika in Kriege zum Wohle Israels zu verwickeln?
\ Wenn ein britischer Jude wie Disraeli zu den Briten „wir“ sagte, war dies eine strategische Zweideutigkeit. Er traf damit den patriotischen Nerv der angelsächsischen Elite, die den gemeinsamen Glauben an die Mission des britischen Empires teilte, die Welt zu zivilisieren – Menschen wie Lord Salisbury, Mitglied von Cecil Rhodes' Round Table, der sich für eine Weltregierung durch die „britische Rasse“ einsetzte.[13]\ Carroll Quigley, The Anglo-American Establishment, From Rhodes to Cliveden (1949), Books In Focus, 1981.
\ Der britische Imperialismus und der zionistische Nationalismus wurden etwa zur gleichen Zeit geboren wie die Zwillinge Esau und Jakob und sind seit ihrer Geburt eng miteinander verflochten. Zwei Überlegungen helfen jedoch, ihre wahre Beziehung zu verstehen. Erstens reichen die ideologischen Wurzeln des Britischen Empires nicht weiter zurück als bis ins 17. Jahrhundert, während die des Zionismus mehr als zwei Jahrtausende zurückreichen. Zweitens starb das Britische Empire nach dem Ersten Weltkrieg, während der Zionismus aufblühte. Aus diesen beiden Gründen ist die Theorie, dass der Zionismus ein Nebenprodukt des britischen Imperialismus ist (nennen wir sie die Chomsky-Theorie), nicht haltbar.
\ Um die wahre Beziehung zwischen Zion und Albion zu Disraelis Zeiten zu verstehen, muss man die Macht der Rothschild-Dynastie über die britische Politik richtig einschätzen. Ohne die Rothschilds hätte Großbritannien nie die Kontrolle über den Suezkanal erlangt, der den Grundstein des britischen Empires im Nahen Osten bildete. Die Rothschilds selbst kandidierten nicht für ein politisches Amt, heirateten jedoch manchmal in eine solche Familie ein: Lord Archibald Primrose, 1886 und von 1892 bis 1894 Außenminister und 1894–1895 Premierminister, war der Schwiegersohn von Mayer Amschel de Rothschild.\ Es ist bemerkenswert, dass Theodor Herzl den zukünftigen jüdischen Staat als „aristokratische Republik“ mit „dem ersten Prinzen Rothschild“ an der Spitze sah. In einer langen Tirade in seinem Tagebuch ermahnte er die Rothschilds, ihre bösen Seelen zu erlösen, indem sie den Zionismus statt Kriege finanzierten:\ Ich weiß nicht, ob alle Regierungen bereits erkennen, welche internationale Bedrohung Ihr Weltreich darstellt. Ohne Sie können keine Kriege geführt werden, und wenn Frieden geschlossen werden soll, sind die Menschen umso mehr auf Sie angewiesen. Für das Jahr 1895 wurden die Militärausgaben der fünf Großmächte auf vier Milliarden Francs geschätzt, und ihre tatsächliche militärische Stärke in Friedenszeiten auf 2.800.000 Mann. Und diese Streitkräfte, die in der Geschichte ihresgleichen suchen, kommandieren Sie finanziell, ungeachtet der widerstreitenden Wünsche der Nationen. ... Und Ihr verfluchter Reichtum wächst immer noch. ... Aber wenn Sie sich uns anschließen, ... werden wir unseren ersten gewählten Herrscher aus Ihrem Haus nehmen. Das ist das leuchtende Leuchtfeuer, das wir auf die Spitze des fertigen Eiffelturms Ihres Vermögens setzen werden. In der Geschichte wird es so aussehen, als wäre das der Zweck des gesamten Bauwerks gewesen.[14]\ \ The Complete Diaries of Theodor Herzl, edited by Raphael Patai, Herzl Press & Thomas Yoseloff, 1960, vol. 1, pp. 163–170.\ Wie Richard Wagner jedoch einmal sagte (Judaism in Music, 1850), zogen es die Rothschilds vor, „die Juden der Könige“ zu bleiben, anstatt „die Könige der Juden“ zu sein.\ \ Wenn die Zeit für die Gründung des jüdischen Staates zu Disraelis Zeiten noch nicht reif war, dann vor allem deshalb, weil die Juden in Russland sich von Palästina ebenso wenig angezogen fühlten wie die Juden in Europa; sie wussten kaum, wo es lag. Erst kürzlich von Zar Alexander II. emanzipiert, strebten sie lediglich eine Auswanderung nach Europa oder in die Vereinigten Staaten an. Erst nach der Ermordung von Zar Alexander II. im Jahr 1881 (einen Monat vor Disraelis Tod) wurden einige von ihnen durch die Pogrome für Leon Pinskers proto-zionistischen Aufruf von 1882 empfänglich: „Wir müssen uns ein für alle Mal mit dem Gedanken abfinden, dass die anderen Nationen uns aufgrund ihres angeborenen natürlichen Antagonismus für immer ablehnen werden.“[15]\ Benzion Netanyahu, The Founding Fathers of Zionism, Balfour Books, 2012, Kindle l. 761-775.
\ Ebenfalls im Jahr 1881 begann Baron Edmond de Rothschild vom Pariser Zweig, unter der Schirmherrschaft seiner Palestine Jewish Colonization Association (PICA) Land in Palästina zu kaufen und die Ansiedlung jüdischer Siedler zu finanzieren, insbesondere in Tel Aviv. Die meisten bestehenden internationalen jüdischen Organisationen, wie B'nai B'rith (gegründet 1843 in New York) oder die Alliance Israélite Universelle (gegründet 1860 in Paris), waren jedoch der Meinung, dass Israel als verstreute Nation gut zurechtkäme und keine Pläne für Palästina habe.\ Dies änderte sich während des Ersten Weltkriegs, als ein äußerst effizientes Netzwerk aufgebaut wurde, das beide Seiten des Atlantiks verband.[16]\ Alison Weir, Against Our Better Judgment: The Hidden History of How the U.S. Was Used to Create Israel, 2014, Kindle l. 387-475.
\ Theodor Herz konzentrierte seine diplomatischen Bemühungen zunächst auf Deutschland, aber in England begannen sich die Dinge vielversprechend zu entwickeln („Der Schwerpunkt hat sich nach England verlagert“, schrieb er 1895 in sein Tagebuch), was zum Teil der Rekrutierung von Israel Zangwill zu verdanken war, der laut Benzion Netanyahu „der erste war, der in den oberen Kreisen der britischen Politik direkt über den Zionismus sprach“, insbesondere mit Lloyd George, „einem engen Bekannten Zangwills von Beginn seiner zionistischen Tätigkeit bis zu seinem Lebensende“.[17]\ Netanyahu, The Founding Fathers of Zionism, l. 2536-59.
\ Erinnern wir uns daran, dass Zangwill der erfolgreiche Autor von The Melting Pot war, einem Theaterstück, das Mischehen für Amerikaner pries. Hier besteht kein Widerspruch, denn „die gemischten verfolgten Rassen verschwinden, die reine verfolgte Rasse bleibt bestehen“, wie Sidonia sagte.\ \ Die Bedeutung von Disraelis geopolitischen Manövern wird von Historikern der Zionisten selten anerkannt, da sie oberflächlich betrachtet nicht den Weg für die Gründung des jüdischen Staates geebnet zu haben scheinen. Tatsächlich bildeten sie jedoch das unsichtbare Fundament, auf dem Herzl und Zangwill aufbauten. Und diese unsichtbare Kontinuität zeugt von der erstaunlichen generationsübergreifenden Beharrlichkeit des jüdischen Volkes, das sein jahrtausendealtes, selbsternanntes Schicksal Generation für Generation vorantreibt. Ja, es ist wirklich bewundernswert, wenn auch verheerend für die westliche Zivilisation, die durch zweitausend Jahre Christentum ahnungslos und ihres eigenen Sinns für Blut beraubt wurde. Wie der zionistische Autor Jakob Klatzkin einmal in der Zeitschrift „Der Jude“, 1916, schrieb:\ Wir bilden in uns selbst eine geschlossene juristische und geschäftliche Körperschaft. Eine starke Mauer, die wir errichtet haben, trennt uns von den Menschen in den Ländern, in denen wir leben – und hinter dieser Mauer befindet sich ein jüdischer Staat.[18]
Zitiert in Robert Edward Edmondson, The Jewish System Indicted by the Documentary Record, 1937 (archive.org), S. 15.\ \ Anmerkungen\ [1] Yuri Slezkine, The Jewish Century, Princeton University Press, 2004.\ [2] Cecil Roth, A History of the Marranos (1932), Meridian Books, 1959, S. 148.\ [3] Zitiert in Kevin MacDonald, Separation and Its Discontents: Toward an Evolutionary Theory of Anti-Semitism, Praeger, 1998, kindle 2013, l. 4732–4877.\ [4] Hannah Arendt, The Origins of Totalitarianism, Band 1: Antisemitism, Meridian Books, 1958, S. 309–310.\ [5] Robert Blake, Disraeli (1966), Faber Finds, 2010, S. 202.\ [6] Benjamin Disraeli, Lord George Bentinck, Archibald, 1852 (archive.org), S. 496.\ [7] Bakunins Antwort auf Französisch, „Aux citoyens rédacteurs du Réveil“, auf Wikisource.org.\ [8] Chaim Weizmann, Trial and Error, Harper & Brothers, 1949, S. 192.\ [9] Stanley Weintraub, Disraeli: A Biography, Hamish Hamilton, 1993, S. 579, 547.\ [10] André Pichot, Aux origines des théories raciales, de la Bible à Darwin, Flammarion, 2008, S. 124–143, 319.\ [11] Hilaire Belloc, The Jews, Constable & Co., 1922 (archive.org), S. 223.\ [12] Stanley Weintraub, Disraeli: A Biography, Hamish Hamilton, 1993, S. 579, 547.\ [13] Carroll Quigley, The Anglo-American Establishment, From Rhodes to Cliveden (1949), Books In Focus, 1981.\ [14] The Complete Diaries of Theodor Herzl, edited by Raphael Patai, Herzl Press & Thomas Yoseloff, 1960, vol. 1, pp. 163–170.\ [15] Benzion Netanyahu, The Founding Fathers of Zionism, Balfour Books, 2012, Kindle-Ausgabe, S. 761–775.\ [16] Alison Weir, Against Our Better Judgment: The Hidden History of How the U.S. Was Used to Create Israel, 2014, Kindle-Ausgabe, S. 387–475.\ [17] Netanyahu, The Founding Fathers of Zionism, S. 2536-59.\ [18] Zitiert in Robert Edward Edmondson, The Jewish System Indicted by the Documentary Record, 1937 (archive.org), S. 15.
-
 @ 7e19a1dd:ea50ba3b
2025-02-10 11:16:42
@ 7e19a1dd:ea50ba3b
2025-02-10 11:16:42Air compressors are workhorses across industries, from manufacturing plants to auto repair shops. However, keeping them running smoothly requires regular maintenance, which can be a time-consuming and costly chore. That’s where air compressor filters come into play. These simple yet vital components can help extend the life of your compressor while saving you money and headaches down the line.
What Do Air Compressor Filters Actually Do?
Air compressors suck in air from their surroundings, and that air isn’t always clean. It can carry dirt, moisture, and even tiny particles that can damage your compressor's internal parts. Filters act as the gatekeepers, trapping contaminants before they wreak havoc.
Without a good filter, dirt and debris can clog valves and reduce efficiency. Even worse, it can lead to costly repairs—or worse, a full-blown breakdown. Filters also remove moisture, preventing rust and corrosion in your compressor and connected equipment.
Less Maintenance, More Savings
Regular maintenance on an air compressor is inevitable, but filters significantly cut down the frequency of those tune-ups. Clean air means fewer clogs and less wear and tear on moving parts. As a result, you’ll need fewer repairs and part replacements over time.
And let’s not forget energy efficiency. When an air compressor operates with clean air, it doesn’t have to work as hard. This reduced workload translates into lower energy bills. Over time, this can add up to significant savings.
Filters Protect Your Investment
Air compressors aren’t cheap, and replacing one can feel like a punch to the wallet. Using high-quality air compressor filters protects your investment by keeping the equipment running at peak performance. Think of it like regularly changing your car’s oil. It’s a small, affordable step that prevents big problems later.
Save Time and Effort
No one enjoys unscheduled downtime, especially when deadlines are looming. A well-maintained compressor equipped with a proper filter is far less likely to break down unexpectedly. That means fewer interruptions and more time to focus on your work. And here’s another bonus: replacing filters is quick and easy. Compared to the hours it can take to clean or repair a compressor, swapping out a filter is a breeze.
Choosing the Right Filter
Not all filters are created equal. Make sure you choose one that matches your compressor’s specifications. If you’re unsure, check your user manual or ask a professional. Investing in a high-quality filter might cost a little more upfront, but it will pay off in the long run.
Final Thoughts
Air compressor filters are a small but mighty tool in keeping your equipment running smoothly. They cut down on maintenance, protect your compressor, and save you both time and money. By making filters a regular part of your maintenance routine, you’ll not only extend the life of your compressor but also improve its efficiency. That’s a win-win for your wallet and your workflow. So, the next time you fire up your air compressor, make sure its filter is up to the task. You’ll thank yourself later!
-
 @ 31da2214:af2508e2
2025-02-10 10:08:06
@ 31da2214:af2508e2
2025-02-10 10:08:06A global privacy nightmare is unfolding. The UK government secretly ordered Apple to backdoor encrypted iCloud storage worldwide—but Apple is legally forbidden from revealing this order, or they face criminal charges. This affects 2 BILLION USERS.
Here’s the full story & why it’s part of a much bigger power grab. 🧵👇 [Thread by @sayerjigmi on Thread Reader App]
1) The UK's Secret Order to Backdoor Encryption 🔓
Under the UK’s Investigatory Powers Act (IPA) 2016, Apple was served a Technical Capability Notice (TCN)—forcing them to create a backdoor for encrypted iCloud data.
This is not limited to UK users. It applies worldwide, meaning your private files are at risk, no matter where you live.
🔗 @macworld report
2) Apple’s Legal Gag Order 🤐
Apple is legally forbidden from revealing this order. If Apple even acknowledges that the UK issued this demand, they could face criminal charges.
This is a secret government order with global consequences.
3) A Global Threat to Encryption 🌍
This isn’t just about the UK (although they are leading the charge in threatening citizens in OTHER countries for violating BRITISH censorship laws!).
If Apple complies, every government in the world will demand the same access—from the US to China to authoritarian regimes.
End-to-end encryption would be effectively dead.
4) Apple’s Dilemma: Comply or Withdraw? 🚪
Apple has two choices:
- Comply & weaken encryption globally.
- Refuse & withdraw services from the UK.WhatsApp & Signal faced similar threats last year and vowed to leave the UK rather than compromise security. Will Apple do the same?
🚨 Watch the heated discussion between Damian Collins, director of CCDH (architect of the UK Online Safety Bill), and Signal’s CEO: YouTube Link
5) Why This Matters: Encryption Protects Everything 🔐
- Encryption protects financial data, health records, personal security (e.g., where you live or work), and private conversations.
- Governments always say they need backdoors for national security—but history shows they’re used for mass surveillance.
- Once a backdoor exists, hackers, rogue employees, and other governments WILL find it.
6) The UK’s War on Encryption 🛡️
The UK is trying to dominate the global surveillance & censorship landscape.
While the US, Canada, Australia, and New Zealand have supported strong encryption to mitigate cyber threats, the UK stands alone in its war on encryption.
7) The Free Speech Crackdown 🗣️
This isn’t just about encryption—it’s about control. Governments worldwide are criminalizing dissent and censoring free speech, using tech companies as their enforcement arms.
🔗 GreenMedInfo Report
8) The Global Censorship Agenda 🌐
This ties into the UK’s broader, GLOBALLY ORCHESTRATED censorship agenda:
- The Online Safety Bill criminalizes encrypted messaging & forces platforms to scan private messages.
- The Digital Services Act (EU) gives governments the power to shut down online content they don’t like.
- Leaked US-UK documents show direct coordination between UK intelligence & the Biden administration to censor online speech.
9) The Architects of Speech Policing: CCDH 🕵️♂️
The Center for Countering Digital Hate (CCDH)—a UK intelligence-backed group—has been a driving force behind global censorship.
They were caught:
- Running “black ops” to suppress RFK Jr.’s presidential campaign.
- Leading the "Kill Musk’s Twitter" directive, trying to shut down free speech on X.
- Labeling 12 private US citizens as the “Disinformation Dozen” to justify mass censorship.
🔗 Reclaim the Net Investigation
10) The Pattern is Clear: Surveillance + Censorship 🔍
1️⃣ Governments create "safety" laws to justify surveillance.
2️⃣ They pressure tech companies to enforce censorship.
3️⃣ Once encrypted services are gone, nothing is private anymore.This is the biggest attack on digital freedom in history.
11) What Can We Do? 💪
- Support companies that refuse to build backdoors (Signal, ProtonMail, etc.).
- Push for legislation that protects encryption & free speech.
- Stay informed & spread awareness—governments count on secrecy to push these policies through.
- Follow and support privacy and internet freedom organizations such as:
- @G_W_Forum
- @FFO_Freedom
- @ReclaimTheNetHQ
12) The Ultimate Power Grab: Controlling All Digital Communication 📱
If Apple caves, every other platform will be forced to follow.
📌 The UK’s Global Playbook:
- A backdoor to encryption (Investigatory Powers Act).
- A government-linked censorship network (CCDH).
- A speech-policing framework that extends worldwide (Online Safety Bill).This is a global effort to control what people can say, share, and store privately.
13) The Final Stand: Will You Comply or Resist? ⚔️🚨
They want total control—your speech, your privacy, your elections. This is the defining battle of our time.
🇬🇧 UK’s war on encryption = Global censorship blueprint.
🗳️ Election meddling + speech policing = A hijacked democracy.📢 Digital freedom is human freedom.
Stand up. Speak out. Fight back. 🏴☠️🔥
Full thread preserved by Thread Reader App.
-
 @ 42342239:1d80db24
2025-02-10 08:16:32
@ 42342239:1d80db24
2025-02-10 08:16:32The risks associated with cryptocurrencies have recently received attention in the media, where e.g. the Swedish Financial Supervisory Authority warns of the high volatility and risk of investments in crypto. Within the EU, as usual, significant efforts are being made to expand the already extensive regulatory framework. Meanwhile, in the US, there has been a marked turnaround. Even the presidential family has launched their own cryptocurrencies, resulting in criticism from industry experts .
Important perspectives, however, are conspicuous by their absence in the conversation.
Iain McGilchrist, a British psychiatrist and philosopher, has introduced the hemispheric hypothesis (a theory about how the brain's two hemispheres function). The left hemisphere is more detail- and control-oriented, while the right hemisphere is more holistic. A society dominated by the left hemisphere, such as our own according to McGilchrist , "would see it as its task to control everything maximally and would have a paranoid feeling that we need to have surveillance cameras everywhere...".
During a speech at the World Economic Forum, President Trump recently stated that conservatives complain about big banks, such as Bank of America, not allowing them to conduct business within the bank. Critics argue that the American banking system has been used to persecute political opponents, both during Obama's and Biden's terms. Under Obama, 'Operation Chokepoint' was introduced to limit certain businesses' access to banking services. A subcommittee in the Senate now wants to eradicate this phenomenon.
More and more people are discovering that their money is not always under their control. Non-profit associations and congregations are not allowed to open bank accounts. Sometimes they are even thrown out as bank customers. Others may report being subjected to lengthy interrogations by the bank about what they intend to do with their money, even when they just want to transfer funds between their own accounts. Rejected churches are met with silence, while a bank account is (still!) necessary to fully operate in society.
When leading economists at the International Monetary Fund (IMF) argue that a cashless society can threaten fundamental rights , including property rights, when churches are refused bank accounts in what is described as "a threat to civil society" and when regulations still fail to combat organised crime , is it not reasonable to wonder if we are on the right path?
With cash, people can pay freely without intermediaries, which constitutes a form of financial freedom. The notes you hold in your hand are your own. Cryptocurrencies, such as Bitcoin, offer a similar possibility: an electronic, peer-to-peer cash system (person to person).
A society dominated by the left hemisphere results in a pathological need for control, according to McGilchrist. A more holistic perspective, taking into account the right hemisphere, would acknowledge that too much control can be detrimental, that property rights are a fundamental right, and that financial freedom is a human right. Do these perspectives not deserve more attention?



