-
 @ f9cf4e94:96abc355
2024-12-31 20:18:59
@ f9cf4e94:96abc355
2024-12-31 20:18:59Scuttlebutt foi iniciado em maio de 2014 por Dominic Tarr ( dominictarr ) como uma rede social alternativa off-line, primeiro para convidados, que permite aos usuários obter controle total de seus dados e privacidade. Secure Scuttlebutt (ssb) foi lançado pouco depois, o que coloca a privacidade em primeiro plano com mais recursos de criptografia.
Se você está se perguntando de onde diabos veio o nome Scuttlebutt:
Este termo do século 19 para uma fofoca vem do Scuttlebutt náutico: “um barril de água mantido no convés, com um buraco para uma xícara”. A gíria náutica vai desde o hábito dos marinheiros de se reunir pelo boato até a fofoca, semelhante à fofoca do bebedouro.

Marinheiros se reunindo em torno da rixa. ( fonte )
Dominic descobriu o termo boato em um artigo de pesquisa que leu.
Em sistemas distribuídos, fofocar é um processo de retransmissão de mensagens ponto a ponto; as mensagens são disseminadas de forma análoga ao “boca a boca”.
Secure Scuttlebutt é um banco de dados de feeds imutáveis apenas para acréscimos, otimizado para replicação eficiente para protocolos ponto a ponto. Cada usuário tem um log imutável somente para acréscimos no qual eles podem gravar. Eles gravam no log assinando mensagens com sua chave privada. Pense em um feed de usuário como seu próprio diário de bordo, como um diário de bordo (ou diário do capitão para os fãs de Star Trek), onde eles são os únicos autorizados a escrever nele, mas têm a capacidade de permitir que outros amigos ou colegas leiam ao seu diário de bordo, se assim o desejarem.
Cada mensagem possui um número de sequência e a mensagem também deve fazer referência à mensagem anterior por seu ID. O ID é um hash da mensagem e da assinatura. A estrutura de dados é semelhante à de uma lista vinculada. É essencialmente um log somente de acréscimo de JSON assinado. Cada item adicionado a um log do usuário é chamado de mensagem.
Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações. Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.

Estrutura de alto nível de um feed
Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar. Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência.
Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub.
Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.
Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de Pubs públicos em que todos podem participar . Explicaremos como ingressar em um posteriormente neste guia. Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais. Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.

Perspectivas dos participantes
Scuttlebot
O software Pub é conhecido como servidor Scuttlebutt (servidor ssb ), mas também é conhecido como “Scuttlebot” e
sbotna linha de comando. O servidor SSB adiciona comportamento de rede ao banco de dados Scuttlebutt (SSB). Estaremos usando o Scuttlebot ao longo deste tutorial.Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações. Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.

Estrutura de alto nível de um feed
Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar. Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência.
Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub.
Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.
Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de Pubs públicos em que todos podem participar . Explicaremos como ingressar em um posteriormente neste guia. Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais. Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.


Perspectivas dos participantes
Pubs - Hubs
Pubs públicos
| Pub Name | Operator | Invite Code | | ------------------------------------------------------------ | ------------------------------------------------------------ | ------------------------------------------------------------ | |
scuttle.us| @Ryan |scuttle.us:8008:@WqcuCOIpLtXFRw/9vOAQJti8avTZ9vxT9rKrPo8qG6o=.ed25519~/ZUi9Chpl0g1kuWSrmehq2EwMQeV0Pd+8xw8XhWuhLE=| | pub1.upsocial.com | @freedomrules |pub1.upsocial.com:8008:@gjlNF5Cyw3OKZxEoEpsVhT5Xv3HZutVfKBppmu42MkI=.ed25519~lMd6f4nnmBZEZSavAl4uahl+feajLUGqu8s2qdoTLi8=| | Monero Pub | @Denis |xmr-pub.net:8008:@5hTpvduvbDyMLN2IdzDKa7nx7PSem9co3RsOmZoyyCM=.ed25519~vQU+r2HUd6JxPENSinUWdfqrJLlOqXiCbzHoML9iVN4=| | FreeSocial | @Jarland |pub.freesocial.co:8008:@ofYKOy2p9wsaxV73GqgOyh6C6nRGFM5FyciQyxwBd6A=.ed25519~ye9Z808S3KPQsV0MWr1HL0/Sh8boSEwW+ZK+8x85u9w=| |ssb.vpn.net.br| @coffeverton |ssb.vpn.net.br:8008:@ze8nZPcf4sbdULvknEFOCbVZtdp7VRsB95nhNw6/2YQ=.ed25519~D0blTolH3YoTwSAkY5xhNw8jAOjgoNXL/+8ZClzr0io=| | gossip.noisebridge.info | Noisebridge Hackerspace @james.network |gossip.noisebridge.info:8008:@2NANnQVdsoqk0XPiJG2oMZqaEpTeoGrxOHJkLIqs7eY=.ed25519~JWTC6+rPYPW5b5zCion0gqjcJs35h6JKpUrQoAKWgJ4=|Pubs privados
Você precisará entrar em contato com os proprietários desses bares para receber um convite.
| Pub Name | Operator | Contact | | --------------------------------------------- | ------------------------------------------------------------ | ----------------------------------------------- | |
many.butt.nz| @dinosaur | mikey@enspiral.com | |one.butt.nz| @dinosaur | mikey@enspiral.com | |ssb.mikey.nz| @dinosaur | mikey@enspiral.com | | ssb.celehner.com | @cel | cel@celehner.com |Pubs muito grandes
Aviso: embora tecnicamente funcione usar um convite para esses pubs, você provavelmente se divertirá se o fizer devido ao seu tamanho (muitas coisas para baixar, risco para bots / spammers / idiotas)
| Pub Name | Operator | Invite Code | | --------------------------------------- | ----------------------------------------------- | ------------------------------------------------------------ | |
scuttlebutt.de| SolSoCoG |scuttlebutt.de:8008:@yeh/GKxlfhlYXSdgU7CRLxm58GC42za3tDuC4NJld/k=.ed25519~iyaCpZ0co863K9aF+b7j8BnnHfwY65dGeX6Dh2nXs3c=| |Lohn's Pub| @lohn |p.lohn.in:8018:@LohnKVll9HdLI3AndEc4zwGtfdF/J7xC7PW9B/JpI4U=.ed25519~z3m4ttJdI4InHkCtchxTu26kKqOfKk4woBb1TtPeA/s=| | Scuttle Space | @guil-dot | Visit scuttle.space | |SSB PeerNet US-East| timjrobinson |us-east.ssbpeer.net:8008:@sTO03jpVivj65BEAJMhlwtHXsWdLd9fLwyKAT1qAkc0=.ed25519~sXFc5taUA7dpGTJITZVDCRy2A9jmkVttsr107+ufInU=| | Hermies | s | net:hermies.club:8008~shs:uMYDVPuEKftL4SzpRGVyQxLdyPkOiX7njit7+qT/7IQ=:SSB+Room+PSK3TLYC2T86EHQCUHBUHASCASE18JBV24= |GUI - Interface Gráfica do Utilizador(Usuário)
Patchwork - Uma GUI SSB (Descontinuado)
Patchwork é o aplicativo de mensagens e compartilhamento descentralizado construído em cima do SSB . O protocolo scuttlebutt em si não mantém um conjunto de feeds nos quais um usuário está interessado, então um cliente é necessário para manter uma lista de feeds de pares em que seu respectivo usuário está interessado e seguindo.

Fonte: scuttlebutt.nz
Quando você instala e executa o Patchwork, você só pode ver e se comunicar com seus pares em sua rede local. Para acessar fora de sua LAN, você precisa se conectar a um Pub. Um pub é apenas para convidados e eles retransmitem mensagens entre você e seus pares fora de sua LAN e entre outros Pubs.
Lembre-se de que você precisa seguir alguém para receber mensagens dessa pessoa. Isso reduz o envio de mensagens de spam para os usuários. Os usuários só veem as respostas das pessoas que seguem. Os dados são sincronizados no disco para funcionar offline, mas podem ser sincronizados diretamente com os pares na sua LAN por wi-fi ou bluetooth.
Patchbay - Uma GUI Alternativa
Patchbay é um cliente de fofoca projetado para ser fácil de modificar e estender. Ele usa o mesmo banco de dados que Patchwork e Patchfoo , então você pode facilmente dar uma volta com sua identidade existente.

Planetary - GUI para IOS

Planetary é um app com pubs pré-carregados para facilitar integração.
Manyverse - GUI para Android

Manyverse é um aplicativo de rede social com recursos que você esperaria: posts, curtidas, perfis, mensagens privadas, etc. Mas não está sendo executado na nuvem de propriedade de uma empresa, em vez disso, as postagens de seus amigos e todos os seus dados sociais vivem inteiramente em seu telefone .
Fontes
-
https://scuttlebot.io/
-
https://decentralized-id.com/decentralized-web/scuttlebot/#plugins
-
https://medium.com/@miguelmota/getting-started-with-secure-scuttlebut-e6b7d4c5ecfd
-
Secure Scuttlebutt : um protocolo de banco de dados global.
-
-
 @ 5d4b6c8d:8a1c1ee3
2024-07-14 13:50:54
@ 5d4b6c8d:8a1c1ee3
2024-07-14 13:50:54Yesterday's edition https://stacker.news/items/607040/r/Undisciplined
Happy July 14th, everyone. America narrowly averted a civil war last night and I'm pretty happy about that. I was impressed by how well Stacker News covered the biggest breaking news event of the site's existence. People were pulling together lots of sources and offering generally measured thoughts.
-
- -
July 14, 2023 📅
📝
TOP POSTCommon psychological biases that bitcoiners have
Excerpt
One of the primary reasons I got involved with markets is my interest in psychology. Humans are a fickle bunch, and it's fascinating to observe the human condition in such a clear, mathematical way.
3217 sats \ 11 comments \ @birdeye21 \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/208075/r/Undisciplined?commentId=208936
Excerpt
I get your point, but this seems to me one of the (rare) differences where "technically possible but empirically infeasible" vs "technically impossible" matters a lot.
1128 sats \ 3 replies \ @elvismercury
From Portable experiences by @k00b in ~nostr
🏆
TOP STACKER2nd place @k00b (1st hiding, presumed @siggy47)
7947 stacked \ 10.5k spent \ 3 posts \ 12 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
37.3k stacked \ 0 revenue \ 51.8k spent \ 95 posts \ 214 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 14, 2022 📅
📝
TOP POSTPine – A bitcoin wallet w/ a messenger-like UI || A BTC Wallet UX for the masses
Link to https://pine.pm/
509 sats \ 15 comments \ @Spartan \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/44747/r/Undisciplined?commentId=45060
Excerpt
The user @darthcoin has way to many guides from wich you can learn a lot IMO, he is active here to most of the time, though I dont know if I've @ him correctly.
300 sats \ 4 replies \ @bangbang_u_r_done
From Any Good Routing Node Strategies? by @andyleroy in ~bitcoin
🏆
TOP STACKER1st place @nerd2ninja
544 stacked \ 1765 spent \ 3 posts \ 17 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
14.6k stacked \ 0 revenue \ 31.6k spent \ 133 posts \ 261 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 14, 2021 📅
📝
TOP POSTHow Bitcoin And Green Energy Can Save Ethiopia’s Economy
Link to https://stacker.news/items/320/r/Undisciplined
2 sats \ 1 comment \ @0268486dc4 \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/332/r/Undisciplined?commentId=333
Excerpt
From the Twitter announcement
Students will learn how to build #Bitcoin applications from the ground up using the Rust programming language. […]
18 sats \ 0 replies \ @sha256
From Fodé Diop Launches a Bitcoin Academy by @sha256 in ~bitcoin
🏆
TOP STACKER1st place @sha256
4 stacked \ 5 spent \ 2 posts \ 1 comment \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
10 stacked \ 0 revenue \ 47 spent \ 9 posts \ 8 comments
originally posted at https://stacker.news/items/608036
-
-
 @ b2caa9b3:9eab0fb5
2024-07-14 10:52:36
@ b2caa9b3:9eab0fb5
2024-07-14 10:52:36The African sun is warming things up here at Kilimanjaro, but there's still a crispness in the morning air. My fleece jacket came in handy after a refreshing shower! I started my day with a perfect combo: coffee and breakfast on the rooftop, with a stunning view as my backdrop.

Speaking of tech, today was dedicated to getting my workspace set up. First on the agenda: Thunderbird, my trusty email client from my Linux days. It took a few hours to wrangle everything, especially the S/MIME encryption. Feeling a bit lost in the weeds, I decided to switch gears and embrace OpenPGP for end-to-end encryption – a simpler solution in my opinion.
Just as I finished conquering Thunderbird, Kilimanjaro itself decided to make an appearance! The clouds parted to reveal the majestic peak, and I couldn't resist capturing the moment with a couple of photos.
Today's another day with no set plans, just taking things minute by minute. Soaking up the beautiful scenery, the cool mornings, and the positive vibes. As soon as my foot heals, I'll be out exploring the town, snapping photos, and enjoying a delicious coffee at a local cafe.

Speaking of exploring, the world of NFTs has piqued my interest. I have a few on Opensea and WAX Blockchain, but I'm curious – where else are people showcasing their digital art? Let me know in the comments where you buy and sell your NFTs, or if they're just patiently waiting for a better future. I'd love to hear your NFT stories!

Life has a way of taking us on unexpected journeys. So, here's to embracing the unexpected, making the most of each situation, and maybe even finding a small online job to boost my budget. Wishing you all a wonderful day – and remember, don't stress yourself!

Online
Feel free to support me by sending some sats via the lightning network to rubenstorm@sats.mobi
-
 @ e97aaffa:2ebd765d
2024-07-14 09:57:13
@ e97aaffa:2ebd765d
2024-07-14 09:57:13Estamos numa época tão estranha da humanidade…
Onde alguns querem reescrever a história, em vez de aprender e evoluir com a mesma. São com os erros que se cresce.
Onde o termo fascista é sinónimo de alguém com uma opinião diferente da sua, sem minimamente saber o real significado dessa palavra.
Onde defendem uma liberdade, que proíba o contraditório.
Onde não se discutem ideias, mas sim combatem ideias.
Onde o ambientalmente sustentável é substituir árvores e zonas verdes por estruturas em aço e zonas negras.
Onde os políticos constroem casas ou cidades, literalmente, em cima dos rios mas depois a culpa das cheias é as alterações climáticas.
Onde os alimentos tem menos importância que um peido de uma vaca.
Onde pessoas defendem que a solução para o aquecimento, é morrer de frio.
Onde a igualdade é favorecer um grupo, em detrimento de outro.
Onde o essencial é viver para consumir, em vez de usufruir.
Onde o importante é ser rico e ostentar essa mesma riqueza, mesmo que tenha de espezinhar outros para a conquistar.
Onde o mais importante é parecer em vez de ser.
Onde políticos defendem que o conhecimento pode levar a escolhas erradas, defendem o carneirismo.
Onde um político define o que é verdade ou mentira, limitando o que as pessoas podem expressar. Mas quem controla o controlador.
Onde os revisores da verdade deixaram de estar num gabinete, passando a ser um exército de jovens atrás de um teclado.
Onde, são propostas e aprovadas limitações de liberdade, sem esclarecimento ou divulgação pública. Pior que a obscuridade, é desinteresse da comunidade por liberdade.
Onde a censura é o novo normal, defender o contrário é que é censurável.
Onde a imprensa é tão livre como uma pomba dentro de sua gaiola.
Onde, quem comete o crime é protegido, quem o denúncia é perseguido.
Onde o certo é pensar com a cabeça dos outros, sem questionar.
Onde os pais delegaram o papel de educar às escolas e aos ecrãs azuis.
Onde a escola deixou de ser um lugar de conhecimento e/ou do desenvolvimento do espírito crítico.
Onde as crianças crescem doutrinados por políticos e por AI.
Onde a sociedade é programada e com um destino predefinido, como um rato dentro da sua roda.
Onde o maior erro, é pretender construir seres que não cometem erros, que não tenham vícios. Quando isso acontecer, deixamos de ser humanos. A imperfeição é a essência dos seres humanos, é o que nos difere das máquinas.
Onde só se ensina a não cair, em vez de ajudar e incentivar a levantar.
Onde se suspende a liberdade de circulação e os direitos mais básicos, sem ninguém questionar.
Onde a privacidade é crime.
Onde Satoshi é excomungado, mas Miguel Tiago é idoleterado.
Onde a moeda é utilizado como uma arma.
Onde uma guerra é digladiada entre zeros e uns, sem o comum mortal aperceber da sua existência.
Onde crianças caem em campos de batalha, como folhas em pleno outono.
Onde o direito ao Livre-arbítrio está sob ameaça.
-
 @ 700c6cbf:a92816fd
2024-07-14 00:51:44
@ 700c6cbf:a92816fd
2024-07-14 00:51:44... something else
This is the final image. Or is it? Likely, it is not. I have already started on a perfect version of my Mother Earth painting.
Of course, there is no such thing as a perfect painting. What I mean is that I already started on a vector version of Mother Earth. You're familiar with vector vs. pixel, right?
But let's start at the beginning, not the end.
This here is a pic from the sketching phase. I am not one who can just magically and with a few strokes produce an amazing sketch of something that resembles a human. There are artists out there that do this wonderfully. It's amazing but it is not me (unfortunately).

Here I am starting to color in the sketch with a watercolor brush. This is all done in Procreate App on an iPad Pro. The coloring is on a separate layer with the pencil sketch set to multiply to shine through the colors. That's why the pencil strokes now are black. I like that look.

And here, I am almost done. Just need to decide on the background color. And as you can see from the gif and video I didn't really decide. Though at the moment I am favoring that muted pinkish red - LOL

Which color is your favorite?


Here you can see the whole process in a timelapse. Above pictures were grabbed from it to detail the process a little.
https://cdn.satellite.earth/05774dcaaf4679c34cbeb46cb43b4c4f85553a3d2b4850a7256d26a871b0c4f3.mp4
And that's it my Nostr friends for my first longform post in this community.
I hope you enjoyed this post. Comments are encouraged an appreciated. Thank you.
Cheers, OceanBee
-
 @ 9edd72eb:cb697b0a
2024-07-13 22:16:45
@ 9edd72eb:cb697b0a
2024-07-13 22:16:45If one knows exactly what to do to alleviate one's pain, comfort oneself, and emerge more or less unscathed from Adversity, I think it can be said that one has reached a fairly high level of Wisdom in Life.
originally posted at https://stacker.news/items/607422
-
 @ ed5774ac:45611c5c
2025-02-15 05:38:56
@ ed5774ac:45611c5c
2025-02-15 05:38:56Bitcoin as Collateral for U.S. Debt: A Deep Dive into the Financial Mechanics
The U.S. government’s proposal to declare Bitcoin as a 'strategic reserve' is a calculated move to address its unsustainable debt obligations, but it threatens to undermine Bitcoin’s original purpose as a tool for financial freedom. To fully grasp the implications of this plan, we must first understand the financial mechanics of debt creation, the role of collateral in sustaining debt, and the historical context of the petro-dollar system. Additionally, we must examine how the U.S. and its allies have historically sought new collateral to back their debt, including recent attempts to weaken Russia through the Ukraine conflict.
The Vietnam War and the Collapse of the Gold Standard
The roots of the U.S. debt crisis can be traced back to the Vietnam War. The war created an unsustainable budget deficit, forcing the U.S. to borrow heavily to finance its military operations. By the late 1960s, the U.S. was spending billions of dollars annually on the war, leading to a significant increase in public debt. Foreign creditors, particularly France, began to lose confidence in the U.S. dollar’s ability to maintain its value. In a dramatic move, French President Charles de Gaulle sent warships to New York to demand the conversion of France’s dollar reserves into gold, as per the Bretton Woods Agreement.
This demand exposed the fragility of the U.S. gold reserves. By 1971, President Richard Nixon was forced to suspend the dollar’s convertibility to gold, effectively ending the Bretton Woods system. This move, often referred to as the "Nixon Shock," declared the U.S. bankrupt and transformed the dollar into a fiat currency backed by nothing but trust in the U.S. government. The collapse of the gold standard marked the beginning of the U.S.’s reliance on artificial systems to sustain its debt. With the gold standard gone, the U.S. needed a new way to back its currency and debt—a need that would lead to the creation of the petro-dollar system.
The Petro-Dollar System: A New Collateral for Debt
In the wake of the gold standard’s collapse, the U.S. faced a critical challenge: how to maintain global confidence in the dollar and sustain its ability to issue debt. The suspension of gold convertibility in 1971 left the dollar as a fiat currency—backed by nothing but trust in the U.S. government. To prevent a collapse of the dollar’s dominance and ensure its continued role as the world’s reserve currency, the U.S. needed a new system to artificially create demand for dollars and provide a form of indirect backing for its debt.
The solution came in the form of the petro-dollar system. In the 1970s, the U.S. struck a deal with Saudi Arabia and other OPEC nations to price oil exclusively in U.S. dollars. In exchange, the U.S. offered military protection and economic support. This arrangement created an artificial demand for dollars, as countries needed to hold USD reserves to purchase oil. Additionally, oil-exporting nations reinvested their dollar revenues in U.S. Treasuries, effectively recycling petro-dollars back into the U.S. economy. This recycling of petrodollars provided the U.S. with a steady inflow of capital, allowing it to finance its deficits and maintain low interest rates.
To further bolster the system, the U.S., under the guidance of Henry Kissinger, encouraged OPEC to dramatically increase oil prices in the 1970s. The 1973 oil embargo and subsequent price hikes, masterminded by Kissinger, quadrupled the cost of oil, creating a windfall for oil-exporting nations. These nations, whose wealth surged significantly due to the rising oil prices, reinvested even more heavily in U.S. Treasuries and other dollar-denominated assets. This influx of petrodollars increased demand for U.S. debt, enabling the U.S. to issue more debt at lower interest rates. Additionally, the appreciation in the value of oil—a critical global commodity—provided the U.S. banking sector with the necessary collateral to expand credit generation. Just as a house serves as collateral for a mortgage, enabling banks to create new debt, the rising value of oil boosted the asset values of Western corporations that owned oil reserves or invested in oil infrastructure projects. This increase in asset values allowed these corporations to secure larger loans, providing banks with the collateral needed to expand credit creation and inject more dollars into the economy. However, these price hikes also caused global economic turmoil, disproportionately affecting developing nations. As the cost of energy imports skyrocketed, these nations faced mounting debt burdens, exacerbating their economic struggles and deepening global inequality.
The Unsustainable Debt Crisis and the Search for New Collateral
Fast forward to the present day, and the U.S. finds itself in a familiar yet increasingly precarious position. The 2008 financial crisis and the 2020 pandemic have driven the U.S. government’s debt to unprecedented levels, now exceeding $34 trillion, with a debt-to-GDP ratio surpassing 120%. At the same time, the petro-dollar system—the cornerstone of the dollar’s global dominance—is under significant strain. The rise of alternative currencies and the shifting power dynamics of a multipolar world have led to a decline in the dollar’s role in global trade, particularly in oil transactions. For instance, China now pays Saudi Arabia in yuan for oil imports, while Russia sells its oil and gas in rubles and other non-dollar currencies. This growing defiance of the dollar-dominated system reflects a broader trend toward economic independence, as nations like China and Russia seek to reduce their reliance on the U.S. dollar. As more countries bypass the dollar in trade, the artificial demand for dollars created by the petro-dollar system is eroding, undermining the ability of US to sustain its debt and maintain global financial hegemony.
In search of new collateral to carry on its unsustainable debt levels amid declining demand for the U.S. dollar, the U.S., together with its Western allies—many of whom face similar sovereign debt crises—first attempted to weaken Russia and exploit its vast natural resources as collateral. The U.S. and its NATO allies used Ukraine as a proxy to destabilize Russia, aiming to fragment its economy, colonize its territory, and seize control of its natural resources, estimated to be worth around $75 trillion. By gaining access to these resources, the West could have used them as collateral for the banking sector, enabling massive credit expansion. This, in turn, would have alleviated the sovereign debt crisis threatening both the EU and the U.S. This plan was not unprecedented; it mirrored France’s long-standing exploitation of its former African colonies through the CFA franc system.
For decades, France has maintained economic control over 14 African nations through the CFA franc, a currency pegged to the euro and backed by the French Treasury. Under this system, these African countries are required to deposit 50% of their foreign exchange reserves into the French Treasury, effectively giving France control over their monetary policy and economic sovereignty. This arrangement allows France to use African resources and reserves as implicit collateral to issue debt, keeping its borrowing costs low and ensuring demand for its bonds. In return, African nations are left with limited control over their own economies, forced to prioritize French interests over their own development. This neo-colonial system has enabled France to sustain its financial dominance while perpetuating poverty and dependency in its former colonies.
Just as France’s CFA franc system relies on the economic subjugation of African nations to sustain its financial dominance, the U.S. had hoped to use Russia’s resources as a lifeline for its debt-ridden economy. However, the plan ultimately failed. Russia not only resisted the sweeping economic sanctions imposed by the West but also decisively defeated NATO’s proxy forces in Ukraine, thwarting efforts to fragment its economy and seize control of its $75 trillion in natural resources. This failure left the U.S. and its allies without a new source of collateral to back their unsustainable debt levels. With this plan in ruins, the U.S. has been forced to turn its attention to Bitcoin as a potential new collateral for its unsustainable debt.
Bitcoin as Collateral: The U.S. Government’s Plan
The U.S. government’s plan to declare Bitcoin as a strategic reserve is a modern-day equivalent of the gold standard or petro-dollar system. Here’s how it would work:
-
Declaring Bitcoin as a Strategic Reserve: By officially recognizing Bitcoin as a reserve asset, the U.S. would signal to the world that it views Bitcoin as a store of value akin to gold. This would legitimize Bitcoin in the eyes of institutional investors and central banks.
-
Driving Up Bitcoin’s Price: To make Bitcoin a viable collateral, its price must rise significantly. The U.S. would achieve this by encouraging regulatory clarity, promoting institutional adoption, and creating a state-driven FOMO (fear of missing out). This would mirror the 1970s oil price hikes that bolstered the petro-dollar system.
-
Using Bitcoin to Back Debt: Once Bitcoin’s price reaches a sufficient level, the U.S. could use its Bitcoin reserves as collateral for issuing new debt. This would restore confidence in U.S. Treasuries and allow the government to continue borrowing at low interest rates.
The U.S. government’s goal is clear: to use Bitcoin as a tool to issue more debt and reinforce the dollar’s role as the global reserve currency. By forcing Bitcoin into a store-of-value role, the U.S. would replicate the gold standard’s exploitative dynamics, centralizing control in the hands of large financial institutions and central banks. This would strip Bitcoin of its revolutionary potential and undermine its promise of decentralization. Meanwhile, the dollar—in digital forms like USDT—would remain the primary medium of exchange, further entrenching the parasitic financial system.
Tether plays a critical role in this strategy. As explored in my previous article (here: [https://ersan.substack.com/p/is-tether-a-bitcoin-company]), Tether helps sustaining the current financial system by purchasing U.S. Treasuries, effectively providing life support for the U.S. debt machine during a period of declining demand for dollar-denominated assets. Now, with its plans to issue stablecoins on the Bitcoin blockchain, Tether is positioning itself as a bridge between Bitcoin and the traditional financial system. By issuing USDT on the Lightning Network, Tether could lure the poor in developing nations—who need short-term price stability for their day to day payments and cannot afford Bitcoin’s volatility—into using USDT as their primary medium of exchange. This would not only create an artificial demand for the dollar and extend the life of the parasitic financial system that Bitcoin was designed to dismantle but would also achieve this by exploiting the very people who have been excluded and victimized by the same system—the poor and unbanked in developing nations, whose hard-earned money would be funneled into sustaining the very structures that perpetuate their oppression.
Worse, USDT on Bitcoin could function as a de facto central bank digital currency (CBDC), where all transactions can be monitored and sanctioned by governments at will. For example, Tether’s centralized control over USDT issuance and its ties to traditional financial institutions make it susceptible to government pressure. Authorities could compel Tether to implement KYC (Know Your Customer) rules, freeze accounts, or restrict transactions, effectively turning USDT into a tool of financial surveillance and control. This would trap users in a system where every transaction is subject to government oversight, effectively stripping Bitcoin of its censorship-resistant and decentralized properties—the very features that make it a tool for financial freedom.
In this way, the U.S. government’s push for Bitcoin as a store of value, combined with Tether’s role in promoting USDT as a medium of exchange, creates a two-tiered financial system: one for the wealthy, who can afford to hold Bitcoin as a hedge against inflation, and another for the poor, who are trapped in a tightly controlled, surveilled digital economy. This perpetuates the very inequalities Bitcoin was designed to dismantle, turning it into a tool of oppression rather than liberation.
Conclusion: Prolonging the Parasitic Financial System
The U.S. government’s plan to declare Bitcoin as a strategic reserve is not a step toward financial innovation or freedom—it is a desperate attempt to prolong the life of a parasitic financial system that Bitcoin was created to replace. By co-opting Bitcoin, the U.S. would gain a new tool to issue more debt, enabling it to continue its exploitative practices, including proxy wars, economic sanctions, and the enforcement of a unipolar world order.
The petro-dollar system was built on the exploitation of oil-exporting nations and the global economy. A Bitcoin-backed system would likely follow a similar pattern, with the U.S. using its dominance to manipulate Bitcoin’s price and extract value from the rest of the world. This would allow the U.S. to sustain its current financial system, in which it prints money out of thin air to purchase real-world assets and goods, enriching itself at the expense of other nations.
Bitcoin was designed to dismantle this parasitic system, offering an escape hatch for those excluded from or exploited by traditional financial systems. By declaring Bitcoin a strategic reserve, the U.S. government would destroy Bitcoin’s ultimate purpose, turning it into another instrument of control. This is not a victory for Bitcoin or bitcoiners—it is a tragedy for financial freedom and global equity.
The Bitcoin strategic reserve plan is not progress—it is a regression into the very system Bitcoin was designed to dismantle. As bitcoiners, we must resist this co-option and fight to preserve Bitcoin’s original vision: a decentralized, sovereign, and equitable financial system for all. This means actively working to ensure Bitcoin is used as a medium of exchange, not just a store of value, to fulfill its promise of financial freedom.
-
-
 @ 6f7db55a:985d8b25
2025-02-14 21:23:57
@ 6f7db55a:985d8b25
2025-02-14 21:23:57This article will be basic instructions for extreme normies (I say that lovingly), or anyone looking to get started with using zap.stream and sharing to nostr.
EQUIPMENT Getting started is incredibly easy and your equipment needs are miniscule.
An old desktop or laptop running Linux, MacOs, or Windows made in the passed 15yrs should do. Im currently using and old Dell Latitude E5430 with an Intel i5-3210M with 32Gigs of ram and 250GB hard drive. Technically, you go as low as using a Raspberry Pi 4B+ running Owncast, but Ill save that so a future tutorial.
Let's get started.
ON YOUR COMPUTER You'll need to install OBS (open broaster software). OBS is the go-to for streaming to social media. There are tons of YouTube videos on it's function. WE, however, will only be doing the basics to get us up and running.
First, go to https://obsproject.com/

Once on the OBS site, choose the correct download for you system. Linux, MacOs or Windows. Download (remember where you downloaded the file to). Go there and install your download. You may have to enter your password to install on your particular operating system. This is normal.
Once you've installed OBS, open the application. It should look something like this...

For our purposes, we will be in studio mode. Locate the 'Studio Mode' button on the right lower-hand side of the screen, and click it.

You'll see the screen split like in the image above. The left-side is from your desktop, and the right-side is what your broadcast will look like.
Next, we go to settings. The 'Settings' button is located right below the 'Studio Mode" button.

Now we're in settings and you should see something like this...

Now locate stream in the right-hand menu. It should be the second in the list. Click it.

Once in the stream section, go to 'Service' and in the right-hand drop-down, find and select 'Custom...' from the drop-down menu.

Remeber where this is because we'll need to come back to it, shortly.
ZAPSTREAM We need our streamkey credentials from Zapstream. Go to https://zap.stream. Then, go to your dashboard.

Located on the lower right-hand side is the Server URL and Stream Key. You'll need to copy/paste this in OBS.

You may have to generate new keys, if they aren't already there. This is normal. If you're interested in multi-streaming (That's where you broadcast to multiple social media platforms all at once), youll need the server URL and streamkeys from each. You'll place them in their respective forms in Zapstream's 'Stream Forwarding" section.

Use the custom form, if the platform you want to stream to isn't listed.
*Side-Note: remember that you can use your nostr identity across multiple nostr client applications. So when your login for Amethyst, as an example, could be used when you login to zapstream. Also, i would suggest using Alby's browser extension. It makes it much easier to fund your stream, as well as receive zaps. *
Now, BACK TO OBS... With Stream URL and Key in hand, paste them in the 'Stream" section of OBS' settings. Service [Custom...] Server [Server URL] StreamKey [Your zapstream stream key]

After you've entered all your streaming credentials, click 'OK' at the bottom, on the right-hand side.
WHAT'S NEXT? Let's setup your first stream from OBS. First we need to choose a source. Your source is your input device. It can be your webcam, your mic, your monitor, or any particular window on your screen. assuming you're an absolute beginner, we're going to use the source 'Window Capture (Xcomposite)'.

Now, open your source file. We'll use a video source called 'grannyhiphop.mp4'. In your case it can be whatever you want to stream; Just be sure to select the proper source.

Double-click on 'Window Capture' in your sources list. In the pop-up window, select your file from the 'Window' drop-down menu.


You should see something like this...

Working in the left display of OBS, we will adjust the video by left-click, hold and drag the bottom corner, so that it takes up the whole display.

In order to adjust the right-side display ( the broadcast side), we need to manipulate the video source by changing it's size.

This may take some time to adjust the size. This is normal. What I've found to help is, after every adjustment, I click the 'Fade (300ms)' button. I have no idea why it helps, but it does, lol.

Finally, after getting everything to look the way you want, you click the 'Start Stream' button.

BACK TO ZAPSTREAM Now, we go back to zapstream to check to see if our stream is up. It may take a few moments to update. You may even need to refresh the page. This is normal.
 STREAMS UP!!!
STREAMS UP!!!A few things, in closing. You'll notice that your dashbooard has changed. It'll show current stream time, how much time you have left (according to your funding source), who's zapped you with how much theyve zapped, the ability to post a note about your stream (to both nostr and twitter), and it shows your chatbox with your listeners. There are also a raid feature, stream settings (where you can title & tag your stream). You can 'topup' your funding for your stream. As well as, see your current balance.
You did a great and If you ever need more help, just use the tag #asknostr in your note. There are alway nostriches willing to help.
STAY AWESOME!!!
npub: nostr:npub1rsvhkyk2nnsyzkmsuaq9h9ms7rkxhn8mtxejkca2l4pvkfpwzepql3vmtf
-
 @ 6f170f27:711e26dd
2024-07-13 18:16:58
@ 6f170f27:711e26dd
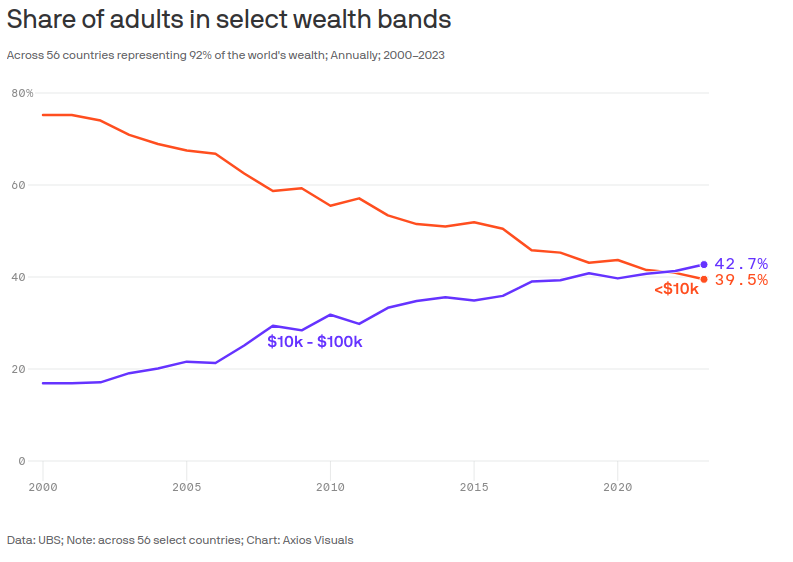
2024-07-13 18:16:58This century has known a stunning decrease in global income inequality, bringing it down to levels not seen in well over a century. That's the conclusion that Branko Milanovic, one of the world's foremost inequality researchers, comes to in an important essay for Foreign Affairs.
https://www.axios.com/2024/07/11/world-income-inequality-ubs-wealth-report
https://www.axios.com/2023/06/14/global-economic-inequality
originally posted at https://stacker.news/items/607318
-
 @ 5d4b6c8d:8a1c1ee3
2024-07-13 12:44:32
@ 5d4b6c8d:8a1c1ee3
2024-07-13 12:44:32Yesterday's edition https://stacker.news/items/605773/r/Undisciplined
We have a confessional from a professional shitcoiner, today. That's fun.
-
- -
July 13, 2023 📅
📝
TOP POSTValidating Lightning Signer - AMA
Excerpt
VLS is a nifty piece of software that helps boost the security of the Bitcoin Lightning Network. 🛡️
11k sats \ 33 comments \ @devrandom \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/208442/r/Undisciplined?commentId=208454
Excerpt
Ever bought a computer or cell phone? Why? Why not wait until your money is worth more later compared to the price of that cell phone?
1441 sats \ 7 replies \ @02674f045a
From Opinion: Why BTC can't become the reserve currency by @0xBTC in ~bitcoin
🏆
TOP STACKER1st place @k00b
5838 stacked \ 7855 spent \ 3 posts \ 19 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
27k stacked \ 0 revenue \ 40.6k spent \ 108 posts \ 281 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 13, 2022 📅
📝
TOP POSTAny Good Routing Node Strategies?
Excerpt
For people who have/are running nodes, are there any strategies that have been most effective for you for earning routing fees? From my very limited routing experience so far it seems there are a few main questions:
1232 sats \ 33 comments \ @andyleroy \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/44747/r/Undisciplined?commentId=44755
Excerpt
Obligatory not a node routing expert, but this guy is a good follow: https://mobile.twitter.com/cold_sats
276 sats \ 1 reply \ @Cornleone
From Any Good Routing Node Strategies? by @andyleroy in ~bitcoin
🏆
TOP STACKER1st place @k00b
37.3k stacked \ 15.2k spent \ 1 post \ 29 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
27.4k stacked \ 0 revenue \ 34.7k spent \ 117 posts \ 279 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 13, 2021 📅
📝
TOP POSTI joined a shitcoin project full time couple of months ago
Excerpt
I though it would be exciting and fun. But I think I'm wasting my time.
3 sats \ 9 comments \ @03785de7ab \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/306/r/Undisciplined?commentId=316
Excerpt
There are many companies working with Bitcoin but it's not their main focus. I did implement Bitgo sevices for one e-wallet provider but that was it. What I'm looking for is a project which build useful things for user with current Bitcoin features, […]
2 sats \ 1 reply \ @03785de7ab
From I joined a shitcoin project full time couple of months ago by @03785de7ab in ~bitcoin
🏆
TOP STACKERNo top stacker
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
37 stacked \ 0 revenue \ 60 spent \ 6 posts \ 10 comments
originally posted at https://stacker.news/items/607040
-
-
 @ b8851a06:9b120ba1
2025-01-28 21:34:54
@ b8851a06:9b120ba1
2025-01-28 21:34:54Private property isn’t lines on dirt or fences of steel—it’s the crystallization of human sovereignty. Each boundary drawn is a silent declaration: This is where my will meets yours, where creation clashes against chaos. What we defend as “mine” or “yours” is no mere object but a metaphysical claim, a scaffold for the unfathomable complexity of voluntary exchange.
Markets breathe only when individuals anchor their choices in the inviolable. Without property, there is no negotiation—only force. No trade—only taking. The deed to land, the title to a car, the seed of an idea: these are not static things but frontiers of being, where human responsibility collides with the infinite permutations of value.
Austrian economics whispers what existentialism shouts: existence precedes essence. Property isn’t granted by systems; it’s asserted through action, defended through sacrifice, and sanctified through mutual recognition. A thing becomes “owned” only when a mind declares it so, and others—through reason or respect—refrain from crossing that unseen line.
Bitcoin? The purest ledger of this truth. A string of code, yes—but one that mirrors the unyielding logic of property itself: scarce, auditable, unconquerable. It doesn’t ask permission. It exists because sovereign minds choose it to.
Sigh. #nostr
I love #Bitcoin. -
 @ f4db5270:3c74e0d0
2025-01-23 18:09:14
@ f4db5270:3c74e0d0
2025-01-23 18:09:14Hi Art lover! 🎨🫂💜 You may not know it yet but all of the following paintings are available in #Bitcoin on my website: https://isolabell.art/#shop
For info and prices write to me in DM and we will find a good deal! 🤝
 ON THE ROAD AGAIN
40x50cm, Oil on canvas
Completed January 23, 2025
ON THE ROAD AGAIN
40x50cm, Oil on canvas
Completed January 23, 2025
 SUN OF JANUARY
40x50cm, Oil on canvas
Completed January 14, 2025
SUN OF JANUARY
40x50cm, Oil on canvas
Completed January 14, 2025
 THE BLUE HOUR
40x50cm, Oil on canvas
Completed December 14, 2024
THE BLUE HOUR
40x50cm, Oil on canvas
Completed December 14, 2024
 LIKE A FRAGMENT OF ETERNITY
50x40cm, Oil on canvas
Completed December 01, 2024
LIKE A FRAGMENT OF ETERNITY
50x40cm, Oil on canvas
Completed December 01, 2024
 WHERE WINTER WHISPERS
50x40cm, Oil on canvas
Completed November 07, 2024
WHERE WINTER WHISPERS
50x40cm, Oil on canvas
Completed November 07, 2024
 L'ATTESA DI UN MOMENTO
40x40cm, Oil on canvas
Completed October 29, 2024
L'ATTESA DI UN MOMENTO
40x40cm, Oil on canvas
Completed October 29, 2024
 LE COSE CHE PENSANO
40x50cm, Oil on paper
Completed October 05, 2024
LE COSE CHE PENSANO
40x50cm, Oil on paper
Completed October 05, 2024
 TWILIGHT'S RIVER
50x40cm, Oil on canvas
Completed September 17, 2024
TWILIGHT'S RIVER
50x40cm, Oil on canvas
Completed September 17, 2024
 GOLD ON THE OCEAN
40x50cm, Oil on paper
Completed September 08, 2024
GOLD ON THE OCEAN
40x50cm, Oil on paper
Completed September 08, 2024
 SUSSURRI DI CIELO E MARE
50x40cm, Oil on paper
Completed September 05, 2024
SUSSURRI DI CIELO E MARE
50x40cm, Oil on paper
Completed September 05, 2024
 THE END OF A WONDERFUL WEEKEND
40x30cm, Oil on board
Completed August 12, 2024
THE END OF A WONDERFUL WEEKEND
40x30cm, Oil on board
Completed August 12, 2024
 FIAMME NEL CIELO
60x35cm, Oil on board
Completed July 28, 2024
FIAMME NEL CIELO
60x35cm, Oil on board
Completed July 28, 2024
 INIZIO D'ESTATE
50x40cm, Oil on cradled wood panel
Completed July 13, 2024
INIZIO D'ESTATE
50x40cm, Oil on cradled wood panel
Completed July 13, 2024
 OMBRE DELLA SERA
50x40cm, Oil on cradled wood panel
Completed June 16, 2024
OMBRE DELLA SERA
50x40cm, Oil on cradled wood panel
Completed June 16, 2024
 NEW ZEALAND SUNSET
80x60cm, Oil on canvas board
Completed May 28, 2024
NEW ZEALAND SUNSET
80x60cm, Oil on canvas board
Completed May 28, 2024
 VENICE
50x40cm, Oil on board
Completed May 4, 2024
VENICE
50x40cm, Oil on board
Completed May 4, 2024
 CORNWALL
50x40cm, Oil on board
Completed April 26, 2024
CORNWALL
50x40cm, Oil on board
Completed April 26, 2024
 DOCKS ON SUNSET
40x19,5cm, Oil on board
Completed March 14, 2024
DOCKS ON SUNSET
40x19,5cm, Oil on board
Completed March 14, 2024
 SOLITUDE
30x30cm, Oil on cradled wood panel
Completed March 2, 2024
SOLITUDE
30x30cm, Oil on cradled wood panel
Completed March 2, 2024
 LULLING WAVES
40x30cm, Oil on cradled wood panel
Completed January 14, 2024
LULLING WAVES
40x30cm, Oil on cradled wood panel
Completed January 14, 2024
 MULATTIERA IN AUTUNNO
30x30cm, Oil on cradled wood panel
MULATTIERA IN AUTUNNO
30x30cm, Oil on cradled wood panel
 TRAMONTO A KOS
40x40cm, oil on board canvas
TRAMONTO A KOS
40x40cm, oil on board canvas
 HIDDEN SMILE
40x40cm, oil on board
HIDDEN SMILE
40x40cm, oil on board
 INIZIO D'AUTUNNO
40x40cm, oil on canvas
INIZIO D'AUTUNNO
40x40cm, oil on canvas
 BOE NEL LAGO
30x30cm, oil on canvas board
BOE NEL LAGO
30x30cm, oil on canvas board
 BARCHE A RIPOSO
40x40cm, oil on canvas board
BARCHE A RIPOSO
40x40cm, oil on canvas board
 IL RISVEGLIO
30x40cm, oil on canvas board
IL RISVEGLIO
30x40cm, oil on canvas board
 LA QUIETE PRIMA DELLA TEMPESTA
30x40cm, oil on canvas board
LA QUIETE PRIMA DELLA TEMPESTA
30x40cm, oil on canvas board
 LAMPIONE SUL LAGO
30x30cm, oil on canvas board
LAMPIONE SUL LAGO
30x30cm, oil on canvas board
 DUE NELLA NEVE
60x25cm, oil on board
DUE NELLA NEVE
60x25cm, oil on board
 UNA CAREZZA
30x30cm, oil on canvas board
UNA CAREZZA
30x30cm, oil on canvas board
 REBEL WAVES
44x32cm, oil on canvas board
REBEL WAVES
44x32cm, oil on canvas board
 THE SCREAMING WAVE
40x30cm, oil on canvas board
THE SCREAMING WAVE
40x30cm, oil on canvas board
 "LA DONZELLETTA VIEN DALLA CAMPAGNA..."
30x40cm, oil on canvas board
"LA DONZELLETTA VIEN DALLA CAMPAGNA..."
30x40cm, oil on canvas board
 LIGHTHOUSE ON WHITE CLIFF
30x40cm, oil on canvas board
LIGHTHOUSE ON WHITE CLIFF
30x40cm, oil on canvas board -
 @ b2caa9b3:9eab0fb5
2024-07-13 12:01:35
@ b2caa9b3:9eab0fb5
2024-07-13 12:01:35I woke up in my dorm this morning to the sound of rain – a rarity in Africa, but a common occurrence here around Mount Kilimanjaro. The climate is much like a European summer, with comfortable temperatures ranging from 18 to 30 degrees Celsius. Unlike the rest of Africa, this region receives more rainfall, creating a lush and scenic environment.

After a quick shower, I stepped out onto the balcony to find myself greeted by a chilly rain. Not ideal weather for exploring, but it did present a different perspective of the majestic Kilimanjaro. The mountain, often shrouded in clouds, occasionally peeks through, and on a clear day, might even be bathed in sunshine. From this vantage point, it's hard to imagine the countless hikers making their way up its slopes.
Did you know that Kilimanjaro, Africa's tallest mountain and a dormant volcano, once held a unique title? Back in 1910, during the German Empire, it was considered the empire's highest peak. While Mount Everest holds the title of the world's highest mountain overall, Kilimanjaro takes the crown for the tallest freestanding mountain – any higher peak is likely part of a mountain range or group.
Gazing at Kilimanjaro, I'm struck by its history – a single, towering volcano, once a part of the German Empire. Traces of that era linger in Moshi, with some colonial-era buildings, some in disrepair, others beautifully restored. Arusha, another nearby town, boasts an impressive art gallery and a fascinating National Museum. This museum, housed in a former German fort, offers a glimpse into the past. One particularly intriguing resident is a giant tortoise, discovered by German colonists as a hatchling in Kilimanjaro National Park. This living relic has witnessed a century of change, a silent observer of a bygone era.

Today promises to be a relaxing one. I'll spend time soaking up the views from the rooftop, hoping to catch a glimpse of Kilimanjaro in all its glory. On a more practical note, I'm also on the hunt for a remote job to help with some financial constraints. Finding the right opportunity seems to be a bit more challenging than anticipated.
As I wrap up this post, the weather has taken a turn for the better. The rain has stopped, the temperature has risen, and the sun is beginning to peek through the clouds. Here's to a wonderful day for everyone – enjoy yours!
(P.S. Be sure to check out the photos – one captures Kilimanjaro from yesterday evening, the other is a picture of me with the giant tortoise from my previous trip here in December 2022).
Online
Feel free to support me by sending some sats via the lightning network to rubenstorm@sats.mobi
-
 @ 7f29628d:e160cccc
2025-01-07 11:50:30
@ 7f29628d:e160cccc
2025-01-07 11:50:30Der gut informierte Bürger denkt bei der Pandemie sofort an Intensivstationen, an die Bilder aus Bergamo und erinnert sich an die Berichterstattung damals – also muss es wohl ein Maximum gewesen sein. Manche Skeptiker behaupten jedoch das Gegenteil. Klarheit sollte ein Blick nach Wiesbaden, zum Statistischen Bundesamt, schaffen. Schließlich sitzen dort gut bezahlte Profis, die seit vielen Jahrzehnten die Sterbestatistik pflegen und veröffentlichen. Jeder Todesfall wird in Deutschland über die Standesämter exakt erfasst.
Doch die Überraschung: Das Statistische Bundesamt liefert uns auf diese einfache Frage zwei extrem unterschiedliche Antworten – ein Minimum und ein Maximum. Das Ergebnis hängt davon ab, wie tief man in die Veröffentlichungen des Bundesamtes eintaucht. Betrachtet man nur die Webseiten und Pressemitteilungen, erhält man den Eindruck eines Maximums. Schaut man jedoch etwas tiefer in die Tabellen und Rohdaten, zeigt sich plötzlich ein Minimum. Aber wie kann das sein? Beides gleichzeitig geht ja wohl kaum. Wer lügt hier – die Tabellen des Amtes oder die Pressemitteilungen? Gehen wir dieser Frage Schritt für Schritt auf den Grund.
2020: Ein historisches Maximum?
Schauen wir uns die vielen Hundert Veröffentlichungen des Statistischen Bundesamtes aus dieser Zeit an. Oder wir kürzen ab und fragen ChatGPT, da die KI auf diesen Daten trainiert wurde und das gesamte Material kennt. Die Frage an ChatGPT lautet also: Wie war das Sterbegeschehen im Jahr 2020 im Vergleich zu den Vorjahren?
ChatGPT antwortet: »Im Jahr 2020 war die Sterblichkeit in Deutschland höher als in den Jahren zuvor. Es gab eine Übersterblichkeit von etwa 982.000 Todesfällen, das sind rund 46.000 mehr als der Durchschnitt der Vorjahre (2016 bis 2019). Dieser Anstieg wurde überwiegend im Zusammenhang mit der COVID-19-Pandemie gesehen. Während die Sterbezahlen in den Vorjahren schwankten, war ein solch signifikanter Anstieg wie 2020 bisher nicht zu beobachten.«
Wir fragen konkreter: Ist es ein Fakt, dass wir eine so ernste Lage im Sterbegeschehen wie im Frühjahr 2020 noch nie erlebt haben?
ChatGPT bestätigt: »Ja, die COVID-19-Pandemie führte im Frühjahr 2020 zu einer außergewöhnlichen Situation im Sterbegeschehen in Deutschland. Die dramatische Übersterblichkeit, die ab der 13. Kalenderwoche auftrat, veranlasste das Statistische Bundesamt, besonders eindringliche Warnungen zu veröffentlichen. Der damalige Vizepräsident des Amtes und andere führende Stimmen wiesen öffentlich darauf hin, dass die Todesfallzahlen stark vom Durchschnitt abwichen. Diese klare Warnung richtete sich an die Öffentlichkeit und die Politik gleichermaßen. Die Medien berichteten intensiv über diese Warnungen, was das Bewusstsein für die Schwere der Pandemie erheblich schärfte. In den vergangenen Jahrzehnten hatte es keine vergleichbare Übersterblichkeit gegeben, die eine solch umfangreiche Kommunikation durch das Statistische Bundesamt erforderlich gemacht hätte.«
Ein gut informierter Zeitungsleser wird sich an dieser Stelle bestätigt fühlen: Ja, so war es damals. Ein Maximum im Sterbegeschehen – wegen der Pandemie. Oder etwa nicht?
2020: Ein historisches Minimum?
Tauchen wir in die Rohdaten des Statistischen Bundesamtes ein. Die Tabellen, die das Amt seit Jahrzehnten verlässlich veröffentlicht, nennen sich Sterbetafeln. Diese werden jährlich bereitgestellt und stehen auf der Website des Bundesamtes zum Download bereit. Ein erster Blick in die Sterbetafeln mag den Laien abschrecken, doch mit einer kurzen Erklärung wird alles verständlich. Wir gehen schrittweise vor.
Nehmen wir die Sterbetafel des Jahres 2017. Sie enthält zwei große Tabellen – eine für Männer und eine für Frauen. Jede Zeile der Tabelle steht für einen Jahrgang, zum Beispiel zeigt die Zeile 79 die Daten der 79-jährigen Männer. Besonders wichtig ist nun die zweite Spalte, in der der Wert 0,05 eingetragen ist. Das bedeutet, dass 5 Prozent der 79-jährigen Männer im Jahr 2017 verstorben sind. Das ist die wichtige Kennzahl. Wenn wir diesen exakten Wert, den man auch als Sterberate bezeichnet, nun in ein Säulendiagramm eintragen, erhalten wir eine leicht verständliche visuelle Darstellung (Grafik 1).

Es ist wichtig zu betonen, dass dieser Wert weder ein Schätzwert noch eine Modellrechnung oder Prognose ist, sondern ein exakter Messwert, basierend auf einer zuverlässigen Zählung. Sterberaten (für die Fachleute auch Sterbewahrscheinlichkeiten qx) sind seit Johann Peter Süßmilch (1707–1767) der Goldstandard der Sterbestatistik. Jeder Aktuar wird das bestätigen. Fügen wir nun die Sterberaten der 79-jährigen Männer aus den Jahren davor und danach hinzu, um das Gesamtbild zu sehen (Grafik 2). Und nun die entscheidende Frage: Zeigt das Jahr 2020 ein Maximum oder ein Minimum?

Ein kritischer Leser könnte vermuten, dass die 79-jährigen Männer eine Ausnahme darstellen und andere Jahrgänge im Jahr 2020 ein Maximum zeigen würden. Doch das trifft nicht zu. Kein einziger Jahrgang verzeichnete im Jahr 2020 ein Maximum. Im Gegenteil: Auch die 1-Jährigen, 2-Jährigen, 3-Jährigen, 9-Jährigen, 10-Jährigen, 15-Jährigen, 18-Jährigen und viele weitere männliche Jahrgänge hatten ihr Minimum im Jahr 2020. Dasselbe gilt bei den Frauen. Insgesamt hatten 31 Jahrgänge ihr Minimum im Jahr 2020. Wenn wir schließlich alle Jahrgänge in einer einzigen Grafik zusammenfassen, ergibt sich ein klares Bild: Das Minimum im Sterbegeschehen lag im Jahr 2020 (Grafik 3).

Ein kritischer Leser könnte nun wiederum vermuten, dass es innerhalb des Jahres 2020 möglicherweise starke Ausschläge nach oben bei einzelnen Jahrgängen gegeben haben könnte, die später durch Ausschläge nach unten ausgeglichen wurden – und dass diese Schwankungen in der jährlichen Übersicht nicht sichtbar sind. Doch auch das trifft nicht zu. Ein Blick auf die wöchentlichen Sterberaten zeigt, dass die ersten acht Monate der Pandemie keine nennenswerten Auffälligkeiten aufweisen. Es bleibt dabei: Die Rohdaten des Statistischen Bundesamtes bestätigen zweifelsfrei, dass die ersten acht Monate der Pandemie das historische Minimum im Sterbegeschehen darstellen. (Für die Fachleute sei angemerkt, dass im gleichen Zeitraum die Lebenserwartung die historischen Höchststände erreicht hatte – Grafik 4.)

So konstruierte das Amt aus einem Minimum ein Maximum:
Zur Erinnerung: Die Rohdaten des Statistischen Bundesamtes, die in den jährlichen Sterbetafeln zweifelsfrei dokumentiert sind, zeigen für das Jahr 2020 eindeutig ein Minimum im Sterbegeschehen. Aus diesen »in Stein gemeißelten« Zahlen ein Maximum zu »konstruieren«, ohne die Rohdaten selbst zu verändern, scheint auf den ersten Blick eine unlösbare Aufgabe. Jeder Student würde an einer solchen Herausforderung scheitern. Doch das Statistische Bundesamt hat einen kreativen Weg gefunden - ein Meisterstück gezielter Manipulation. In fünf Schritten zeigt sich, wie diese Täuschung der Öffentlichkeit umgesetzt wurde:
(1) Ignorieren der Sterberaten: Die präzisen, objektiven und leicht verständlichen Sterberaten aus den eigenen Sterbetafeln wurden konsequent ignoriert und verschwiegen. Diese Daten widersprachen dem gewünschten Narrativ und wurden daher gezielt ausgeklammert.
(2) Fokus auf absolute Todeszahlen: Die Aufmerksamkeit wurde stattdessen auf die absolute Zahl der Todesfälle gelenkt. Diese wirkt allein durch ihre schiere Größe dramatisch und emotionalisiert die Diskussion. Ein entscheidender Faktor wurde dabei ignoriert: Die absolute Zahl der Todesfälle steigt aufgrund der demografischen Entwicklung jedes Jahr an. Viele Menschen verstehen diesen Zusammenhang nicht und verbinden die steigenden Zahlen fälschlicherweise mit der vermeintlichen Pandemie.
(3) Einführung der Übersterblichkeit als neue Kennzahl: Erst ab Beginn der „Pandemie“ wurde die Kennzahl "Übersterblichkeit" eingeführt – und dies mit einer fragwürdigen Methode, die systematisch überhöhte Werte lieferte. Diese Kennzahl wurde regelmäßig, oft monatlich oder sogar wöchentlich, berechnet und diente als ständige Grundlage für alarmierende Schlagzeilen.
(4) Intensive Öffentlichkeitsarbeit: Durch eine breit angelegte Kampagne wurden die manipulativen Kennzahlen gezielt in den Fokus gerückt. Pressemitteilungen, Podcasts und öffentliche Auftritte konzentrierten sich fast ausschließlich auf die absoluten Todeszahlen und die Übersterblichkeit. Ziel war es, den Eindruck einer dramatischen Situation in der Öffentlichkeit zu verstärken.
(5) Bekämpfen kritischer Stimmen: Kritiker, die die Schwächen und manipulativen Aspekte dieser Methoden aufdeckten, wurden systematisch diskreditiert. Ihre Glaubwürdigkeit und Kompetenz wurden öffentlich infrage gestellt, um das sorgsam konstruierte Narrativ zu schützen.
Ohne diesen begleitenden Statistik-Betrug wäre das gesamte Pandemie-Theater meiner Meinung nach nicht möglich gewesen. Wer aus einem faktischen Minimum ein scheinbares Maximum "erschafft", handelt betrügerisch. Die Folgen dieses Betruges sind gravierend. Denken wir an die Angst, die in der Bevölkerung geschürt wurde – die Angst, bald sterben zu müssen. Denken wir an Masken, Abstandsregeln, isolierte ältere Menschen, Kinderimpfungen und all die Maßnahmen, die unter anderem auf diese falsche Statistik zurückgehen.
Wollen wir Bürger uns das gefallen lassen?
Wenn wir als Bürger zulassen, dass ein derart offensichtlicher und nachprüfbarer Täuschungsversuch ohne Konsequenzen bleibt, dann gefährdet das nicht nur die Integrität unserer Institutionen – es untergräbt das Fundament unserer Gesellschaft. In der DDR feierte man öffentlich Planerfüllung und Übererfüllung, während die Regale leer blieben. Damals wusste jeder: Statistik war ein Propagandainstrument. Niemand traute den Zahlen, die das Staatsfernsehen verkündete.
Während der Pandemie war es anders. Die Menschen vertrauten den Mitteilungen des Statistischen Bundesamtes und des RKI – blind. Die Enthüllungen durch den "RKI-Leak" haben gezeigt, dass auch das Robert-Koch-Institut nicht der Wissenschaft, sondern den Weisungen des Gesundheitsministers und militärischen Vorgaben folgte. Warum sollte es beim Statistischen Bundesamt anders gewesen sein? Diese Behörde ist dem Innenministerium unterstellt und somit ebenfalls weisungsgebunden.
Die Beweise für Täuschung liegen offen zutage. Es braucht keinen Whistleblower, keine geheimen Enthüllungen: Die Rohdaten des Statistischen Bundesamtes sprechen für sich. Sie sind öffentlich einsehbar – klar und unmissverständlich. Die Daten, die Tabellen, die Veröffentlichungen des Amtes selbst – sie sind die Anklageschrift. Sie zeigen, was wirklich war. Nicht mehr und nicht weniger.
Und wir? Was tun wir? Schweigen wir? Oder fordern wir endlich ein, was unser Recht ist? Wir Bürger dürfen das nicht hinnehmen. Es ist Zeit, unsere Behörden zur Rechenschaft zu ziehen. Diese Institutionen arbeiten nicht für sich – sie arbeiten für uns. Wir finanzieren sie, und wir haben das Recht, Transparenz und Verantwortung einzufordern. Manipulationen wie diese müssen aufgearbeitet werden und dürfen nie wieder geschehen. Die Strukturen, die solche Fehlentwicklungen in unseren Behörden ermöglicht haben, müssen offengelegt werden. Denn eine Demokratie lebt von Vertrauen – und Vertrauen muss verdient werden. Jeden Tag aufs Neue.
.
.
MARCEL BARZ, Jahrgang 1975, war Offizier der Bundeswehr und studierte Wirtschafts- und Organisationswissenschaften sowie Wirtschaftsinformatik. Er war Gründer und Geschäftsführer einer Softwarefirma, die sich auf Datenanalyse und Softwareentwicklung spezialisiert hatte. Im August 2021 veröffentlichte Barz den Videovortrag »Die Pandemie in den Rohdaten«, der über eine Million Aufrufe erzielte. Seitdem macht er als "Erbsenzähler" auf Widersprüche in amtlichen Statistiken aufmerksam.
-
 @ 1f9e547c:8af216ed
2024-07-13 07:37:05
@ 1f9e547c:8af216ed
2024-07-13 07:37:05Opinion about Bitcoin Wallet Crypto Ethereum (android)
For archival purposes
Atomic Wallet suffers hack on June 2023
Sources
Atomic Wallet users have been left wanting more answers, despite the decentralized wallet provider finally releasing a full “event statement” about the June exploit — which some estimate has run up to $100 million in losses.
In a June 20 blog post — the first major update from the firm since the June 3 exploit — Atomic Wallet claimed there have been no new confirmed cases after initial reports of the hack.
Atomic Wallet Was Breached by North Korean Hackers: Elliptic
Atomic Wallet users might have fallen victim to Lazarus, the infamous North Korean hacking group, said blockchain intelligence firm Elliptic in a blog post on Tuesday.
Early Saturday morning, the team behind Atomic, a non-custodial crypto wallet, announced that some users were compromised and lost the funds from their wallets. According to the company, the number of incidents did not exceed 1% of "monthly active users." The announcement followed multiple reports on Reddit from users complaining their wallets had been drained.
WalletScrutiny #nostrOpinion
-
 @ eac63075:b4988b48
2025-01-04 19:41:34
@ eac63075:b4988b48
2025-01-04 19:41:34Since its creation in 2009, Bitcoin has symbolized innovation and resilience. However, from time to time, alarmist narratives arise about emerging technologies that could "break" its security. Among these, quantum computing stands out as one of the most recurrent. But does quantum computing truly threaten Bitcoin? And more importantly, what is the community doing to ensure the protocol remains invulnerable?
The answer, contrary to sensationalist headlines, is reassuring: Bitcoin is secure, and the community is already preparing for a future where quantum computing becomes a practical reality. Let’s dive into this topic to understand why the concerns are exaggerated and how the development of BIP-360 demonstrates that Bitcoin is one step ahead.
What Is Quantum Computing, and Why Is Bitcoin Not Threatened?
Quantum computing leverages principles of quantum mechanics to perform calculations that, in theory, could exponentially surpass classical computers—and it has nothing to do with what so-called “quantum coaches” teach to scam the uninformed. One of the concerns is that this technology could compromise two key aspects of Bitcoin’s security:
- Wallets: These use elliptic curve algorithms (ECDSA) to protect private keys. A sufficiently powerful quantum computer could deduce a private key from its public key.
- Mining: This is based on the SHA-256 algorithm, which secures the consensus process. A quantum attack could, in theory, compromise the proof-of-work mechanism.
Understanding Quantum Computing’s Attack Priorities
While quantum computing is often presented as a threat to Bitcoin, not all parts of the network are equally vulnerable. Theoretical attacks would be prioritized based on two main factors: ease of execution and potential reward. This creates two categories of attacks:
1. Attacks on Wallets
Bitcoin wallets, secured by elliptic curve algorithms, would be the initial targets due to the relative vulnerability of their public keys, especially those already exposed on the blockchain. Two attack scenarios stand out:
-
Short-term attacks: These occur during the interval between sending a transaction and its inclusion in a block (approximately 10 minutes). A quantum computer could intercept the exposed public key and derive the corresponding private key to redirect funds by creating a transaction with higher fees.
-
Long-term attacks: These focus on old wallets whose public keys are permanently exposed. Wallets associated with Satoshi Nakamoto, for example, are especially vulnerable because they were created before the practice of using hashes to mask public keys.
We can infer a priority order for how such attacks might occur based on urgency and importance.
 Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)
Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)2. Attacks on Mining
Targeting the SHA-256 algorithm, which secures the mining process, would be the next objective. However, this is far more complex and requires a level of quantum computational power that is currently non-existent and far from realization. A successful attack would allow for the recalculation of all possible hashes to dominate the consensus process and potentially "mine" it instantly.
 Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin Attacks
Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin AttacksRecently, Narcelio asked me about a statement I made on Tubacast:
https://x.com/eddieoz/status/1868371296683511969
If an attack became a reality before Bitcoin was prepared, it would be necessary to define the last block prior to the attack and proceed from there using a new hashing algorithm. The solution would resemble the response to the infamous 2013 bug. It’s a fact that this would cause market panic, and Bitcoin's price would drop significantly, creating a potential opportunity for the well-informed.
Preferably, if developers could anticipate the threat and had time to work on a solution and build consensus before an attack, they would simply decide on a future block for the fork, which would then adopt the new algorithm. It might even rehash previous blocks (reaching consensus on them) to avoid potential reorganization through the re-mining of blocks using the old hash. (I often use the term "shielding" old transactions).
How Can Users Protect Themselves?
While quantum computing is still far from being a practical threat, some simple measures can already protect users against hypothetical scenarios:
- Avoid using exposed public keys: Ensure funds sent to old wallets are transferred to new ones that use public key hashes. This reduces the risk of long-term attacks.
- Use modern wallets: Opt for wallets compatible with SegWit or Taproot, which implement better security practices.
- Monitor security updates: Stay informed about updates from the Bitcoin community, such as the implementation of BIP-360, which will introduce quantum-resistant addresses.
- Do not reuse addresses: Every transaction should be associated with a new address to minimize the risk of repeated exposure of the same public key.
- Adopt secure backup practices: Create offline backups of private keys and seeds in secure locations, protected from unauthorized access.
BIP-360 and Bitcoin’s Preparation for the Future
Even though quantum computing is still beyond practical reach, the Bitcoin community is not standing still. A concrete example is BIP-360, a proposal that establishes the technical framework to make wallets resistant to quantum attacks.
BIP-360 addresses three main pillars:
- Introduction of quantum-resistant addresses: A new address format starting with "BC1R" will be used. These addresses will be compatible with post-quantum algorithms, ensuring that stored funds are protected from future attacks.
- Compatibility with the current ecosystem: The proposal allows users to transfer funds from old addresses to new ones without requiring drastic changes to the network infrastructure.
- Flexibility for future updates: BIP-360 does not limit the choice of specific algorithms. Instead, it serves as a foundation for implementing new post-quantum algorithms as technology evolves.
This proposal demonstrates how Bitcoin can adapt to emerging threats without compromising its decentralized structure.
Post-Quantum Algorithms: The Future of Bitcoin Cryptography
The community is exploring various algorithms to protect Bitcoin from quantum attacks. Among the most discussed are:
- Falcon: A solution combining smaller public keys with compact digital signatures. Although it has been tested in limited scenarios, it still faces scalability and performance challenges.
- Sphincs: Hash-based, this algorithm is renowned for its resilience, but its signatures can be extremely large, making it less efficient for networks like Bitcoin’s blockchain.
- Lamport: Created in 1977, it’s considered one of the earliest post-quantum security solutions. Despite its reliability, its gigantic public keys (16,000 bytes) make it impractical and costly for Bitcoin.
Two technologies show great promise and are well-regarded by the community:
- Lattice-Based Cryptography: Considered one of the most promising, it uses complex mathematical structures to create systems nearly immune to quantum computing. Its implementation is still in its early stages, but the community is optimistic.
- Supersingular Elliptic Curve Isogeny: These are very recent digital signature algorithms and require extensive study and testing before being ready for practical market use.
The final choice of algorithm will depend on factors such as efficiency, cost, and integration capability with the current system. Additionally, it is preferable that these algorithms are standardized before implementation, a process that may take up to 10 years.
Why Quantum Computing Is Far from Being a Threat
The alarmist narrative about quantum computing overlooks the technical and practical challenges that still need to be overcome. Among them:
- Insufficient number of qubits: Current quantum computers have only a few hundred qubits, whereas successful attacks would require millions.
- High error rate: Quantum stability remains a barrier to reliable large-scale operations.
- High costs: Building and operating large-scale quantum computers requires massive investments, limiting their use to scientific or specific applications.
Moreover, even if quantum computers make significant advancements, Bitcoin is already adapting to ensure its infrastructure is prepared to respond.
Conclusion: Bitcoin’s Secure Future
Despite advancements in quantum computing, the reality is that Bitcoin is far from being threatened. Its security is ensured not only by its robust architecture but also by the community’s constant efforts to anticipate and mitigate challenges.
The implementation of BIP-360 and the pursuit of post-quantum algorithms demonstrate that Bitcoin is not only resilient but also proactive. By adopting practical measures, such as using modern wallets and migrating to quantum-resistant addresses, users can further protect themselves against potential threats.
Bitcoin’s future is not at risk—it is being carefully shaped to withstand any emerging technology, including quantum computing.
-
 @ 502ab02a:a2860397
2024-07-13 02:14:11
@ 502ab02a:a2860397
2024-07-13 02:14:11Anna Britt Agnsäter ผู้อุทิศชีวิตให้โภชนาการ แต่โดนโลกบูลลีเพราะอเมริกา?
โลกรับรู้ว่า คุณ Anna Britt Agnsäter (ขอเรียกสั้นๆว่า ป้าแอน) เป็นผู้ที่นำเสนอ ปิรามิดอาหาร คนแรกของโลก และเป็นแบบจำลองที่ทาง USDA นำไปพัฒนาปรับใช้แล้วนำมาเป็น แบบที่ใช้สื่อสารกับคนทั้งโลก ในเรื่องของการกำหนด ประเภทอาหารที่ควรกิน ในช่วงปี 1992-2005 ซึ่งในบทความที่แล้วผมได้เขียนว่า ปิรามิดเวอร์ชั่นที่ป้าแอนคิด กับ ที่อเมริกาเอาไปปรับใช้เป็นคนละตัวกัน แต่โลกทั้งโลกก็บูลลีป้าเอนว่า เป็นสาเหตุของการทำลายสุขภาพคนทั้งโลก ทั้งๆที่ไม่ได้เป็นนักวิทยาศาสตร์ ผมก็เป็นคนนึงที่เคยคิดแบบนั้นครับ และเคยอุทานในใจเบาๆว่า แกเป็นใครนะทำไมถึงนำเสนออะไรแบบนี้มาทำร้ายคนทั้งโลก???
นานวันเข้า ความคิดอีกฝั่งของผมก็บอกมาว่า ประโยคข้างบนเป็นคำบ่นหรือคำถาม
นั่นสิ!!!!! ถ้ามันเป็นคำถาม มันจะทำให้เราได้รู้จักตัวตนป้าแอนและเข้าใจว่าแกได้ทำอะไรลงไปนะ มันควรเป็นคำถามมากกว่าคำบ่น นั่นเลยเป็นเหตุผลที่ทำให้ผมเริ่มขุดเรื่องป้าแอน Anna Britt Agnsäter มากที่สุดเท่าที่จะทำได้ พร้อมที่จะอ่านกันแล้วใช่ไหมครับ
Anna Britt Agnsäter เกิดเมื่อปี 1915 ที่เมือง Älmhult ประเทศสวีเดน (นอกเรื่องนิดนึง เมืองนี้คือเมืองที่ให้กำเนิด IKEA ที่เรารู้จักกันดีเรื่องเฟอร์นิเจอร์ ที่นี่มีพิพิธภัณฑ์อิเกีย ซึ่งปรับปรุงมาจากโกดังแห่งแรกของเขาด้วยครับ) เรียกได้ว่า เกิดในช่วงสงครามโลกครั้งที่1 พอดีเลยครับ
ป้าแอน จบการศึกษาที่โรงเรียนสตรี ในเมือง Ystad ก่อนจะเข้ารับการฝึกสอนเพื่อเป็นครูสอนวิทยาศาสตร์ในครัวเรือน (rural domestic science teacher) ในช่วงปี 1930 ที่โรงเรียนวิทยาศาสตร์ในครัวเรือนในชนบทชื่อว่า Rimforsa ก่อนจะได้รับวุฒิการศึกษาการสอนวิทยาศาสตร์ในครัวเรือนในชนบทในปี 1939 จาก Kvinnliga medborgarskola (civic women’s school) จนกระทั่ง ปี 1943 ถึง 1945 เธอได้เดินทางไปทั่ว Norrland (พื้นที่ภาคเหนือของสวีเดน) โดยได้รับเงินสนับสนุนจาก Kooperativa Förbund (เรียกสั้นๆว่า KF หรือ สมาคมสหกรณ์ ก่อตั้งขึ้นในปี 1899 โดยสหกรณ์ผู้บริโภคในท้องถิ่น 41 แห่ง เป็นผู้นำด้านการค้าปลีกในสวีเดนโดยพัฒนารูปแบบร้านค้าใหม่และใหญ่ขึ้น และเป็นหนึ่งในกลุ่มธุรกิจหลักในสแกนดิเนเวีย ในสมัยนี้คำว่าสหกรณ์อาจจะดูเชยๆ แต่ต้องเข้าใจครับว่ายุคนั้นคือความก้าวหน้ามากๆ และต้องมีความรู้รอบด้านทั้งวิทยาศาสตร์ เศรษฐกิจ การเมือง) เพื่อบรรยายให้คนหนุ่มสาวและแม่บ้านฟังเกี่ยวกับวิธีรับมือกับเสบียงที่มีจำกัดในช่วงสงครามที่ตึงเครียด เนื่องจากอยู่ในภาวะสงครามโลกครั้งที่2

ในปี 1946 ป้าแอนได้รับการแต่งตั้งเป็นหัวหน้าของSwedish Cooperative Union หรือ Kooperativa Förbundets (KF) Provkök (experimental kitchen หรือ ภาษาสมัยนี้น่าจะใกล้เคียงกับ kitchen lab นั่นเอง) ซึ่งเป็นองค์กรที่มีอิทธิพลทางด้านอาหารเป็นอย่างมากในสวีเดน มีบทบาทสำคัญในเศรษฐกิจและสังคมสวีเดน โดยสร้างโอกาสให้แก่สมาชิกและส่งเสริมการพัฒนาที่ยั่งยืนในชุมชนต่าง ๆ ทั่วประเทศ
ป้าแอนทำงานที่นี่นานจนถึงช่วงปี 1980 ขนาดของ KF ก็ใหญ่โตขึ้นมากมาย จนขยายอำนาจและขอบเขตการทำงานไปถึงการเป็นคณะกรรมการทดสอบรสชาติซึ่งทดสอบอาหารกึ่งสำเร็จรูปและอาหารสำเร็จรูปใหม่ด้วย ในจุดนี้ ป้าแอน เล็งเห็นความสำคัญและความรับผิดชอบของผู้ผลิต/ผู้ค้าอาหาร ควรจะขยายความรับผิดชอบครอบคลุมไปจนถึงโต๊ะอาหาร (ในที่นี่น่าจะหมายถึงลูกค้า) นั่นคือเหตุผลที่การติดฉลากอาหารจึงมีความสำคัญมาก ป้าแอนได้มุ่งเน้นให้ความรู้กับผู้บริโภคว่า ‘Weigh up the price against the quality’ หรือ ให้ชั่งน้ำหนักพิจารณาให้ดี ระหว่างราคากับคุณภาพ ตลอดระยะเวลาการทำงาน Anna-Britt Agnsäter ได้รณรงค์เพื่อให้มีการแสดงข้อมูล ให้ผู้บริโภครับทราบ เพื่อคุณภาพชีวิตที่ดีขึ้นและได้ให้คำแนะนำด้านโภชนาการ เพื่อให้เข้าใจได้ง่ายขึ้น ในรูปแบบฉลากโภชนาการ
ในปี 1946 เช่นกันป้าแอนได้มีแผนในการทำ มีแผนที่จะผลิตหนังสือสอนทำอาหารสำหรับสถานการณ์ฉุกเฉิน เพราะบทเรียนในภาวะสงครามโลก ที่ป้าแอนผ่านมาตลอด แต่ไม่สามารถพิมพ์ออกมาได้เนื่องจากกระดาษขาดแคลนเนื่องจากอยู่ในภาวะหลังสงคราม
ในปี 1948-1949 ป้าแอนเดินทางไปอเมริกา เพื่อศึกษาเทคนิคการทำอาหารใหม่ๆ การผลิตภัณฑ์อาหารแช่แข็ง รวมถึงอาหารผงแห้งต่างๆ (dry powder) รวมไปถึงวิทยาศาสตร์การอาหาร (food science) ที่มหาวิทยาลัย Iowa State University การเดินทางมาอเมริกาครั้งนี้เปลี่ยนโลกของป้าแอนเป็นอย่างมาก ในตอนที่ป้าทำงานกับ KF เธอมักจะร่วมงานกับ Hemmens Forskningsinstitut (สถาบันวิจัยในประเทศ) เพื่อจัดหาเครื่องมือในครัวที่ยกระดับมาตรฐานการทำอาหารที่ดียิ่งขึ้น รวมถึงอุปกรณ์การครัว ภาชนะต่างๆที่เข้าเตาอบได้ และจากประสบการณ์ที่อเมริกานี้
ป้าแอนได้จับมือกับ โรงงานเครื่องเคลือบและพลาสติก Gustavsberg และ HFI Anna-Britt Agnsäter พัฒนาช้อนตวง ชุด4ชิ้น ที่วางซ้อนกันได้ ซึ่งเป็นการปฎิวัติวงการอาหารครั้งสำคัญของสวีเดน เรียกว่า “ชุดช้อนตวงมาตรฐาน” ซึ่งจะมีการระบุขนาดที่ชัดเจน 4 ชิ้น ประกอบไปด้วย

ซึ่งทำให้ผู้ใช้สามารถวัดปริมาณวัตถุดิบได้อย่างถูกต้องตามที่สูตรอาหารกำหนด กลายเป็นเครื่องมือที่จำเป็นในครัวเรือนและการประกอบอาหารในเชิงพาณิชย์
แม้การพัฒนา “ชุดช้อนตวงมาตรฐาน” นี้จะเริ่มต้นในสวีเดน แต่นวัตกรรมนี้มีผลกระทบที่กว้างขวางและแพร่หลายไปยังครัวเรือนและอุตสาหกรรมอาหารทั่วโลกจนถึงปัจจุบัน


ในชุดช้อนตวงมาตรฐาน original 4 คุณอาจสังเกตคำนึงที่ไม่ค่อยคุ้นสักเท่าไรคือหน่วย kryddmått
นอกจากชุดช้อนตวงมาตรฐานแล้ว ป้าแอนยังคิดค้นสิ่งต่างๆอีกมากมาย ให้กับวงการอาหารสวีเดน รวมถึงหน่วยวัดใหม่ที่เรียกว่า kryddmått นี้ด้วยครับ ซึ่งมันเป็นหน่วยวัดขนาดเล็กที่ใช้ในการตวงเครื่องเทศและวัตถุดิบปริมาณน้อย โดยหน่วยวัดนี้มีขนาด 1 มิลลิลิตร (ml)ซึ่งถูกกำหนดมาเป็นหน่วยที่เล็กที่สุดซึ่งทำให้มีการจดบันทึกสูตรได้แม่นยำยิ่งขึ้น นั่นเพราะว่า การตวงเครื่องเทศ หรือ เกลือ นั้นหากรสชาติที่เข้มข้น หรือมีการใช้มากเกินไปหรือไม่พออาจทำให้รสชาติของอาหารเปลี่ยนไป การใช้ kryddmått ช่วยให้การวัดปริมาณเครื่องเทศที่ใช้ในสูตรอาหารเป็นไปอย่างแม่นยำและสม่ำเสมอ
ถือว่าเป็นอีกผลงานคุโณปการที่ป้าแอน ฝากไว้ให้กับโลกนี้ มันมีส่วนสำคัญในการทำให้งานครัวเรือนง่ายขึ้นและมีประสิทธิภาพมากขึ้นผ่านการพัฒนาหน่วยวัดที่แม่นยำและสะดวกในการใช้งาน นวัตกรรมนี้ช่วยให้การทำอาหารเป็นไปอย่างราบรื่นและมีคุณภาพสูงยิ่งขึ้น

ในปี 1951 ป้าแอนได้บูรณะหนังสือการทำอาหารประจำสวีเดนใหม่ทั้งหมด (Vår kokbok) จุดประสงค์ของตำราอาหาร Vår คือการนำเสนอตำราอาหารราคาต้นทุนวัตถุดิบไม่แพง ที่ให้ความรู้เรื่องสารอาหารและใช้งานง่าย นอกจากนี้ยังเป็นการวางวัตถุดิบให้ได้รับสารอาหารที่เพียงพออีกด้วย เพราะในยุคนั้นสวีเดนมีข้อจำกัดในเรื่องอาหารเป็นอย่างมาก
เนื้อหาสูตรอาหารที่ใช้ในหนังสือเล่มนี้กลายเป็นบรรทัดฐานในช่วงทศวรรษ 1950 โดยมีการใช้หน่วยชั่งตวงแบบใหม่ ตามชุดช้อนตวงมาตรฐาน (ปริมาตร) จากของเดิมที่ใช้การชั่งน้ำหนัก ใช้ศัพท์ในการทำอาหารแบบเป็นสากล เช่น ขูด ปอกเปลือก ล้าง เป็นต้น (grate, peel, rinse) จัดอาร์ทเวิคให้แต่ละสูตร สามารถจบได้ในหน้าเดียวไม่ต้องพลิกอ่านหน้าต่อๆไป ทำให้สะดวกในการเปิดแล้วทำตาม การไล่ลำดับอาหาร เปลี่ยนจากการไล่ประเภทอาหาร ไปเป็นไล่ลำดับตามวัตถุดิบหลักของอาหาร ทำให้คนอ่านสามารถบริหารจัดการเมนูได้ง่าย เช่น ไก่ ก็สามารถไล่เรียงได้เลยว่า วันนี้มีไก่ จะทำอะไรกินดี
นอกจากนี้ยังรับประกันว่าทุกสูตรสามารถทำได้จริง เพราะป้าแอนลงมือทดสอบสูตรด้วยตัวเองทุกสูตร นอกจากนี้ยังคงมีการแนะนำให้ใช้การวัดอุณหภูมิในการทำอาหารด้วยเพื่อความเป๊ะในรสชาติ เนื่องจากป้าแอนเห็นตอนไปดูงานที่อเมริกา จนถึงทุกวันนี้ Vår kokbok เป็นหนึ่งในตำราอาหารที่ขายมากที่สุดในโลกด้วยยอดขายมากกว่า 2.3 ล้านเล่มนับตั้งแต่เริ่มต้น โดยเฉลี่ยมากกว่า 40,000 เล่มต่อปี


ด้วยความที่ Kooperativa Förbundets เป็นองค์กรที่มีอิทธิพลสูงมากในวงการอาหารสวีเดน และคุณป้าแอน ก็มีตำแหน่งที่สูงมาก จึงสามารถเป็นผู้มีส่วนสนับสนุนรูปแบบซูเปอร์มาร์เก็ตสมัยใหม่ ในการใส่รายการส่วนผสมและคำแนะนำในการปรุงอาหารในรูปแบบฉลากของผลิตภัณฑ์อาหารสมัยใหม่

จนกระทั่งในช่วงปี 1970 ประเทศสวีเดนต้องเผชิญกับปัญหาราคาอาหารที่สูงเนื่องจากเงินเฟ้อ รวมถึงสภาพอากาศของสวีเดนนั้น ไม่เอื้อต่อการได้รับสารอาหารที่หลากหลายได้ ครอบครัวที่มีเด็ก ไม่สามารถปรุงอาหารและรับประทานอาหารที่มีคุณค่าทางโภชนาการในราคาที่เหมาะสมได้ รัฐบาลจึงมอบหมายให้ Sweden’s National Board of Health and Welfare (คณะกรรมการสุขภาพและสวัสดิการแห่งชาติของสวีเดน) หาวิธีแก้ไขสถานการณ์ดังกล่าว และคัดกรองแบ่งประเภทอาหารออกเป็น “basic food” และ “supplement” มาเป็นรูปแบบของ กราฟวงกลม (diet circle) แต่ป้าแอนพบปัญหาบางอย่าง ที่ทำให้กราฟวงกลมนี้ใช้งานยาก เพราะการแบ่งปริมาณของอาหารแต่ละประเภทไม่ชัดเจน
ในระหว่างบรรยายเรื่องการกำหนดอาหารพื้นฐาน คุณ Fjalar Clemes หนึ่งในผู้เข้าร่วมการบรรยาย ได้ให้ไอเดียด้วยการสร้างแบบจำลองที่เรียกว่า ปิรามิดอาหาร (Food Pyramid) ขึ้นมา เพื่อให้เห็นภาพสัดส่วนอาหารที่ชัดเจนขึ้น ป้าแอนเลยนำข้อมูลจากกราฟวงกลมนั้น มาสร้างโมเดลจำลองให้อยู่ในรูปแบบปิรามิด โดยให้ “basic food” เช่น ขนมปัง มันฝรั่ง พาสต้า และนม และ “supplements” เช่น ผลไม้ ผัก เนื้อสัตว์ และปลา อยู่ในรูปแบบที่เข้าใจได้ง่ายขึ้น แม้แต่คนที่อ่านหนังสือไม่ออก

แต่นี่แหละที่เป็นจุดเริ่มต้นของปัญหา ด้วยความที่มันใช้งานง่ายสะดวก อเมริกาจึงนำไปปรับปรุงเป็นเวอร์ชั่นตัวเอง แต่ก็มีการเปลี่ยนแปลงไปอย่างมาก ตามที่ได้มีการทำบทความไปแล้ว (อ่านที่นี่)
ทั้งๆที่ปิรามิดต้นแบบของป้าแอนนั้น สร้างขึ้นมาเพื่อชาวสวีเดนเนื่องจากนำข้อมูลพื้นฐานจากข้อจำกัดในประเทศในขณะนั้น ไม่ว่าจะเรื่องของวัตถุดิบที่หาได้ในภาวะยากแค้นแบบนั้น อุณหภูมิอันปรวนแปร รวมถึงสภาพเศรษฐกิจที่ย่ำแย่มาก การจัดแจงข้อจำกัดที่มีเพื่อให้ได้สารอาหารที่เพียงพอที่สุดเท่าที่จะทำได้ต่างหาก (eat healthier, more affordable and save on fat) ที่เป็นที่มาของ “ปิรามิดอาหารของสวีเดน” (คือ จะให้เอาอุดมคติมาสร้างปิรามิดอาหาร คงไม่มีประโยชน์ เพราะยังไงก็ไม่มีเงินซื้อและหาวัตถุดิบไมไ่ด้ตามอุดมคติ วัตถุประสงค์ในการสร้างและเผยแพร่ครั้งนี้มันเพื่อให้ประชาชนทั้งประเทศที่มีความรู้ด้านอาหารน้อย รู้และทำตามได้จริง สมกับพื้นที่และกำลังทรัพย์ // ความเห็นส่วนตัวผมครับ)
ปิรามิดอาหารที่แท้จริงแล้ว จะมีการปรับปรุงตลอดเวลา ตามปัจจัยที่เปลี่ยนไป ไม่ใช่ปิรามิดที่เอาไว้ยึดถือตลอดไป แต่การที่อเมริกานำไปยึดถือว่าเป็น all time information เป็นค่าคงที่ให้ทั้งโลกยึดตาม รวมถึงสร้างด้วยเบื้องหลังด้านธุรกิจ จึงต่างกับที่ป้าแอนทำในทุกมิติ แต่ไฉน เป้าการบูลลี จึงต้องไปตกที่ป้าแอน ว่าเป็นต้นตอความพังของสุขภาพ มันแฟร์แล้วหรือ
เรื่องนี้มีข้อพิสูจน์ได้จนถึงปัจจุบันเช่น ในปี 2022 ก็มีการนำเสนอ ปิรามิดอาหารสำหรับ Mixed diet, flexitarian, vegetarian และ vegan ออกมาสืบทอดเจตนารมณ์ป้าแอน นอกจากนี้ในช่วงที่ป้าแอนมีชีวิต ก็ยังคงมีการช่วยเหลือแนะนำให้ประเทศต่างๆ “มีปิรามิดอาหารของตัวเอง” นั่นคือ วิชั่นที่กว้างไกลของป้าแอน ที่เห็นได้ชัดเจนว่า อาหารพื้นถิ่นกับสารอาหารที่สมดุล ของแต่ละประเทศมีความไม่เหมือนกัน และแนวคิดนี้ได้มีทั้ง เดนมาร์ก, นอร์เวย์, ฟินแลนด์, ญี่ปุ่น, ศรีลังกา ได้นำไปพัฒนาใช้เช่นกัน
นอกจากนี้ ป้าแอนและองค์กร Kooperativa Förbundets ยังให้ข้อมูลการศึกษาที่สำคัญสำหรับประชาชนผ่านบทความเกี่ยวกับอาหารที่ตีพิมพ์ใน นิตยสาร Vi รวมถึงการจัดตั้งกลุ่มการศึกษาร่วมกับทาง สมาคมการศึกษาของชนชั้นแรงงาน หรือ Arbetarnas bildningsförbund (ABF) มีส่วนสนับสนุนในการอภิปรายแบบเปิดทางสังคมเกี่ยวกับปัญหาโรคอ้วนอีกด้วย รวมถึงยังออกหนังสือเกี่ยวกับการทำอาหารอีกร่วมๆ 30เล่ม ซึ่งรวมถึงบทเกี่ยวกับมื้ออาหารที่มีคุณค่าทางโภชนาการที่สมดุล ด้วยเช่นกัน

ในปี 1983 ป้าแอนได้ตีพิมพ์หนังสือ Matboken ซึ่งได้รับการพิสูจน์แล้วว่าเป็นประโยชน์อย่างมาก โดยเฉพาะกับคนหนุ่มสาวเกี่ยวกับวิธีการกินอาหารที่มีคุณค่าทางโภชนาการและมีวิธีทำที่เรียบง่ายที่สุด

ในช่วงทศวรรษ 1990 เมื่อป้าแอนเป็นม่าย จึงได้ย้ายเข้าไปอยู่ในบ้านพักคนชรา Färdknäppen ใน Södermalm ในสตอกโฮล์ม และ ได้แก้ไขสูตรอาหาร 250 สูตรจาก Vår kokbok เพื่อให้เหมาะสมกับสภาพแวดล้อมการปรุงอาหารส่วนกลางของบ้านพักคนชรา เพื่อให้ได้อาหารที่มีสารอาหารครบถ้วนตามที่ควรเป็น
เกียรติประวัติป้าแอนได้รับการตอบแทนดังนี้ ในปี 1979 ได้รับรางวัลเหรียญ St Erik เพื่อเป็นการยกย่องสิ่งที่เธอทุ่มเทแรงกายแรงใจทำมาตลอดชีวิต ในปี 1993 ได้รับเหรียญ HM Konungens ลำดับที่ 8 (HM The King’s Medal หรือ H.M. Konungens medalj ในภาษาสวีเดน) เป็นหนึ่งในรางวัลเกียรติยศที่สำคัญที่สุดที่มอบโดยพระมหากษัตริย์สวีเดนเพื่อยกย่องบุคคลที่มีผลงานดีเด่นหรือมีความโดดเด่นในด้านต่าง ๆ เช่น วิทยาศาสตร์ ศิลปะ วัฒนธรรม และการบริการสาธารณะ ในปี 1995 ได้รับเหรียญทอง Albin Johansson สำหรับผลงานอันทรงคุณค่าของเธอต่อสหกรณ์สวีเดน ในปี 1998 ได้รับรางวัล Gastronomiska Akademiens Guldpenna (ปากกาทองของสถาบันอาหาร) สำหรับบทความเกี่ยวกับส่วนผสมและการทำอาหารของเธอ

Anna-Britt Agnsäter เสียชีวิตในปี 2006 (อายุ 90ปี) ป้าแอนทำงานทั้งชีวิตเพื่อสอนชาวสวีเดนในการจัดการอาหารให้ดีขึ้น ทุกการทดลอง ทดสอบ ได้มีการบันทึกไว้อย่างชัดเจนสามารถพัฒนาต่อไปได้ การริเริ่มให้ข้อมูลที่ซื่อสัตย์ต่อผู้บริโภค ทั้งการติดฉลากอุปกรณ์ คำแนะนำในการทำอาหาร สูตรอาหาร บทความ และตำราอาหาร สิ่งเหล่านี้กลายเป็นพื้นฐานสำคัญในอุตสาหกรรมอาหารจนปัจจุบัน
แต่ทุกวันนี้วงการสุขภาพส่วนมากยังคงล้อเลียนเธอว่าเป็นครูธรรมดา ที่มีหน้ามาสร้างปิรามิดอาหาร จึงทำให้คนทั่งโลกป่วย ทั้งที่ความจริงทั้งหมดนั้น ความรู้ของป้าแอนไม่ได้น้อยไปกว่า ผู้เชี่ยวชาญทางวิทยาศาสตร์การอาหาร ซึ่งในสมัยนั้นนับว่าเป็นอีกแขนงที่อยู่ในระดับบนของการศึกษา ไม่ต่างกับวิทยาศาสตร์อื่นๆ ปิรามิดควรเป็นไปตามถิ่นที่อยู่ สภาพเวลาและสภาพเศรษฐกิจขณะนั้น ไม่ใช่การสร้างมาตรฐานให้ต้องทำเหมือนกันทั่วโลก โดยมาจากอิทธิพลของกลุ่มธุรกิจดังที่ usda ได้ทำการแก้ไขก่อนจะประกาศให้คนทั่วไปยึดถือ รายละเอียดเป็นไปตามที่สืบค้นข้อมูลประวัติของป้าแอน มาเล่าสู่กันฟัง ณ วันนี้ครับ
ผมก็เป็นหนึ่งในนั้น สิ่งที่ผมสามารถทำได้เพื่อเป็นการขอโทษคุณ Anna-Britt Agnsäter ที่ดีที่สุดที่ทำได้ตอนนี้คือ เผยแพร่ประวัติอันทรงคุณค่าของเธอ ให้คนอื่นๆได้รับทราบมากที่สุด เท่าที่จะทำได้
โปรดแชร์ เพื่อคืนความเป็นธรรมให้ Anna-Britt Agnsäter ให้โลกได้เข้าใจและรับรู้ถึงการอุทิศชีวิตให้วงการอาหารของคุณป้าครับ
ปล.มีการค้นพบไฟล์เสียง ที่ป้าแอน จัดรายการวิทยุในปี 1968 ให้ลองฟังกันครับ (น่าจะภาษาสวีเดนนะ 5555) ฟังได้ที่นี่ครับ https://rumble.com/v56p1wa-ann-britt-agnster-in-a-radio-find-from-1968.html
siamstr #pirateketo
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ 1ec45473:d38df139
2024-07-12 22:51:49
@ 1ec45473:d38df139
2024-07-12 22:51:49The probability of AGI ending us is negative.
A common tactic among doomers is to state something along the lines of the following:
"If we create AGI, there is some non-zero chance every year, that the AGI will end humanity. Whatever that chance is compounds every year, and is thus unacceptable."
The question I would ask the doomer is "How do you know that the chance of AGI ending humanity isn't negative?"
What does it mean for AGI to have a negative chance of ending humanity?
Setting aside AGI for a moment, what is the chance every year that humanity ends from other events, such as nuclear war, solar flares, super-volcanoes, asteroid hits, societal collapse, etc?
How do you even answer this question in a reasonable manner? Well lets look at past data.
Of all species that have existed 99% have gone extinct.
Of our closest 7 relatives from the genus Homo, 100% have gone extinct.
On a higher level looking at civilizational collapse. According to Wikipedia, virtually all historical societies have collapsed.
Looking out into the universe, we see no signs of life elsewhere, so if there was life in the past we can assume that they have gone extinct.
It would therefore be reasonable to say that the chance of our extinction is very high even without AGI, well above 90%. Maybe 99%.
You could argue the numbers but at least with these numbers we are using some past data to extrapolate the future, where the doomers are using no data whatsoever to support their numbers.
We can also state, that of all the species and societies that have collapsed in the past, they have done so because they did not yet have the knowledge on how to survive. They didn't know how to create antibiotics, or generate enough energy, or defend themselves from the environment.
What is AGI? AGI is a way to create knowledge. Most all societies in the past have collapsed because they didn't have the knowledge on how to survive, and the doomer argument is that we should slow down our ability to create knowledge, when we know that this has been precisely the problem in the past.
It is a certainty we will all die without more knowledge then we have now. The future death of our sun ensures that.
We have to create the knowledge on how to survive, and that is what AGI does - it creates knowledge.
AGI most certainly has a negative probability of ending humanity.
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ b6dcdddf:dfee5ee7
2024-07-12 20:15:22
@ b6dcdddf:dfee5ee7
2024-07-12 20:15:22🚀 Exciting News: Introducing Project Affiliates!
Creators can finally reach a wider audience by partnering with affiliates!
Affiliates earn automated payouts for contributions enabled through their shares. 🤑
Announcement link: https://x.com/geyserfund/status/1811434402041282680
originally posted at https://stacker.news/items/606500
-
 @ 7175188c:6382a72c
2024-07-12 20:02:24
@ 7175188c:6382a72c
2024-07-12 20:02:24originally posted at https://stacker.news/items/606482
-
 @ ab8cb80e:5395d502
2024-07-12 14:21:14
@ ab8cb80e:5395d502
2024-07-12 14:21:14Hey, I have nothing to do this Friday evening, so why not chill with chess?
Spontaneously I launched an Arena Tournament for today: https://lichess.org/tournament/2iNa8jh4
@ek @kristapsk @BitcoinAbhi @grayruby @frostdragon @Taft @02d43d3798 @030e0dca83 @riberet19 @felipe @didiplaywell @SatsMate @itsTomekK @wize123 @Coinsreporter @stefano @anon @314piepi @160ed04091 do you want to play?
! TODAY ! ♟️ https://lichess.org/tournament/2iNa8jh4 ♟️ 90 min arena, with 5 minute games.
Join on @Alby's new Discord: https://discord.gg/3vbafUCZ?event=1261325278358016091 for voicechat I plan to stream it to zap.stream, because why not.
Who takes my challenge?
originally posted at https://stacker.news/items/605942
-
 @ 4ba8e86d:89d32de4
2024-10-07 13:37:38
@ 4ba8e86d:89d32de4
2024-10-07 13:37:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável.
https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ 0dc2dcb1:4787801a
2024-07-12 13:44:28
@ 0dc2dcb1:4787801a
2024-07-12 13:44:28- Prepared a Dutch webinar with an short introduction to Nostr - https://welkom.keuzevrijbijmij.nl/evenement/wwebinar-vergroot-je-privacy-op-social-media-10-juli/

- Received a nice t-shirt with the Nostr-PHP logo from Bitpopart who designed the logo
- Did an introduction talk in Dutch on a webinar with 350+ people subscribed on July 10th. 100+ watched the webinar live.
- Here is the full replay:
At around 38min the Nostr stuff begins
- Here is the full replay:
- Adding pages and wrote some documentation on nostr-php.dev
- Added a custom field
field_nsecto the user entity on nostrver.se (Drupal website) using the contrib module field_encrypt. The value of this field is stored encrypted in the database using a self created private key. This key is stored as a blob the server, but multiple ways of storing this are possible. In the Drupal CMS I now can save a Nostr private key for each user which will be fetch from nostr_content_nip23. All changes made in this Drupal contrib module for this: https://git.drupalcode.org/project/nostr_content_nip23/-/commit/cbc172b976aceaff107fea0296a8a476e098467e -
With a
nsecstored for each user, it’s possible to select a user when you’re broadcasting an Nostr event from Drupal. The event will be signed with the nsec of the selected user. Quick demo here: https://njump.me/nevent1qvzqqqqqqypzqpnrnguxe8qszsshvgkvhn6qjzxy7xsvx03rlrtddr62haj4lrm3qy88wumn8ghj7mn0wvhxcmmv9uq3camnwvaz7tmwdaehgu3wwdjkyctnw35hstnnda3kjctv9uqzqj75dy5eps3lgwum7f9p2l8sywy7wuxjr08pyhzyzv9mklylaydgdyll3z
-
 @ f4db5270:3c74e0d0
2024-07-12 10:33:41
@ f4db5270:3c74e0d0
2024-07-12 10:33:41
"Barche a riposo" (2023)
40x40 cm, oil on panel canvas
-
 @ 1739d937:3e3136ef
2024-07-12 10:11:42
@ 1739d937:3e3136ef
2024-07-12 10:11:42This is the third in a series of weekly updates detailing progress on bringing MLS protocol DMs and group messaging to Nostr.
Previous Updates
Progress this week
Short update post this week but I made solid progress updating several OpenMLS dependencies and building a new library that implements all the OpenMLS crypto requirements for Nostr.
HPKE-RS
I mentioned a PR last week on the
rust-hpkelibrary, that PR is still waiting on review. However, in the meantime, the OpenMLS library depends on a slightly different hpke library, thehpke-rslibrary.This library didn't support the secp256k1 curve either so I've opened a PR to add support for secp256k1. That PR uses the
RustCryptolibrary that is the default in the thehpke-rslibrary. However, because this library is built to allow for swapping out the underlying crypto library (using traits), I was also able to create a new library that uses thesecp256k1library instead of theRustCryptolibrary. This is the main crypto library that almost all Bitcoin and Nostr apps use so it's important we use that instead ofRustCrypto.OpenMLS Nostr Crypto
The library that I've created (openmls-nostr-crypto) does a few things via separate sub-libraries (crates). The entire library tries to do as little as possible; only implementing the one required ciphersuite for all MLS implementations and the
secp256k1schnorr signatures ciphersuite I've created for Nostr. It's also using the rightsecp256k1library to do it.openmls-nostr-crypto: implementes the crypto traits that the OpenMLS library expects to find for a given provider and removes all the ciphersuites that we don't care about supporting.
hpke-rs-nostr-crypto: This implements the crypto traits that the hpke-rs library expects to find. Again removing all the ciphersuites we don't care about supporting.
I've not yet written any tests for these libraries (which needs to be done) but I've gotten some very simple demos working with OpenMLS using this new set of libraries to handle the crypto.
I've been really impressed with the simplicity of the OpenMLS interface as well. While there is A LOT going on under the hood, the public interface that client developers have to use is clean and simple.
Onward and Upward
Next week I'll continue working on these libraries; adding tests and continuing to build out my small demo app. I've been in touch with the maintainers of the OpenMLS library and I'm hoping to get a review done with them on my PRs and on my new library.
One thing I'll call out here: The review of my library and getting them to review the direction of the project overall will be paid consulting so I'm making sure that I've got as much done as possible before scheduling that time and paying their rates. I'm a strong believer that the right conversation can save you months of wasted time, but I'm also a believer in making sure you're prepared if you're going to drop money on that conversation. 😅
-
 @ 38d0888d:bd8e1246
2024-07-12 07:10:35
@ 38d0888d:bd8e1246
2024-07-12 07:10:35A thriving society rests on the principles of modesty and humility, avoiding idleness and self-indulgence. Individuals are needed to forsake the constant pursuit of attention and instead aspire to selflessness, dedicating themselves to serving humanity. Humility fosters spiritual harmony and protects against materialism and selfish desires.
Beyond personal conduct, humanity must champion altruism and solidarity within the global community. Belief in collective endeavors will pave the way for global harmony. Embracing values like kindness, compassion, and genuine concern for others promotes positivity and reflects the influence of a higher power. The aim is to cultivate a unified multicultural community where each person contributes to manifesting this higher presence.
The collective goal is to direct humanity to nurture a community that experiences spiritual growth while upholding humility as a guiding principle, resisting materialism's allure. By creating such an environment, the hope is to resonate with a sacred harmony that extends beyond immediate boundaries. Through intentional actions and meaningful relationships, a collective space embodying these values can be established, ensuring the higher power's presence guides individual lives and interactions with the world.
-
 @ ee11a5df:b76c4e49
2024-07-11 23:57:53
@ ee11a5df:b76c4e49
2024-07-11 23:57:53What Can We Get by Breaking NOSTR?
"What if we just started over? What if we took everything we have learned while building nostr and did it all again, but did it right this time?"
That is a question I've heard quite a number of times, and it is a question I have pondered quite a lot myself.
My conclusion (so far) is that I believe that we can fix all the important things without starting over. There are different levels of breakage, starting over is the most extreme of them. In this post I will describe these levels of breakage and what each one could buy us.
Cryptography
Your key-pair is the most fundamental part of nostr. That is your portable identity.
If the cryptography changed from secp256k1 to ed25519, all current nostr identities would not be usable.
This would be a complete start over.
Every other break listed in this post could be done as well to no additional detriment (save for reuse of some existing code) because we would be starting over.
Why would anyone suggest making such a break? What does this buy us?
- Curve25519 is a safe curve meaning a bunch of specific cryptography things that us mortals do not understand but we are assured that it is somehow better.
- Ed25519 is more modern, said to be faster, and has more widespread code/library support than secp256k1.
- Nostr keys could be used as TLS server certificates. TLS 1.3 using RFC 7250 Raw Public Keys allows raw public keys as certificates. No DNS or certification authorities required, removing several points of failure. These ed25519 keys could be used in TLS, whereas secp256k1 keys cannot as no TLS algorithm utilizes them AFAIK. Since relays currently don't have assigned nostr identities but are instead referenced by a websocket URL, this doesn't buy us much, but it is interesting. This idea is explored further below (keep reading) under a lesser level of breakage.
Besides breaking everything, another downside is that people would not be able to manage nostr keys with bitcoin hardware.
I am fairly strongly against breaking things this far. I don't think it is worth it.
Signature Scheme and Event Structure
Event structure is the next most fundamental part of nostr. Although events can be represented in many ways (clients and relays usually parse the JSON into data structures and/or database columns), the nature of the content of an event is well defined as seven particular fields. If we changed those, that would be a hard fork.
This break is quite severe. All current nostr events wouldn't work in this hard fork. We would be preserving identities, but all content would be starting over.
It would be difficult to bridge between this fork and current nostr because the bridge couldn't create the different signature required (not having anybody's private key) and current nostr wouldn't be generating the new kind of signature. Therefore any bridge would have to do identity mapping just like bridges to entirely different protocols do (e.g. mostr to mastodon).
What could we gain by breaking things this far?
- We could have a faster event hash and id verification: the current signature scheme of nostr requires lining up 5 JSON fields into a JSON array and using that as hash input. There is a performance cost to copying this data in order to hash it.
- We could introduce a subkey field, and sign events via that subkey, while preserving the pubkey as the author everybody knows and searches by. Note however that we can already get a remarkably similar thing using something like NIP-26 where the actual author is in a tag, and the pubkey field is the signing subkey.
- We could refactor the kind integer into composable bitflags (that could apply to any application) and an application kind (that specifies the application).
- Surely there are other things I haven't thought of.
I am currently against this kind of break. I don't think the benefits even come close to outweighing the cost. But if I learned about other things that we could "fix" by restructuring the events, I could possibly change my mind.
Replacing Relay URLs
Nostr is defined by relays that are addressed by websocket URLs. If that changed, that would be a significant break. Many (maybe even most) current event kinds would need superseding.
The most reasonable change is to define relays with nostr identities, specifying their pubkey instead of their URL.
What could we gain by this?
- We could ditch reliance on DNS. Relays could publish events under their nostr identity that advertise their current IP address(es).
- We could ditch certificates because relays could generate ed25519 keypairs for themselves (or indeed just self-signed certificates which might be much more broadly supported) and publish their public ed25519 key in the same replaceable event where they advertise their current IP address(es).
This is a gigantic break. Almost all event kinds need redefining and pretty much all nostr software will need fairly major upgrades. But it also gives us a kind of Internet liberty that many of us have dreamt of our entire lives.
I am ambivalent about this idea.
Protocol Messaging and Transport
The protocol messages of nostr are the next level of breakage. We could preserve keypair identities, all current events, and current relay URL references, but just break the protocol of how clients and relay communicate this data.
This would not necessarily break relay and client implementations at all, so long as the new protocol were opt-in.
What could we get?
- The new protocol could transmit events in binary form for increased performance (no more JSON parsing with it's typical many small memory allocations and string escaping nightmares). I think event throughput could double (wild guess).
- It could have clear expectations of who talks first, and when and how AUTH happens, avoiding a lot of current miscommunication between clients and relays.
- We could introduce bitflags for feature support so that new features could be added later and clients would not bother trying them (and getting an error or timing out) on relays that didn't signal support. This could replace much of NIP-11.
- We could then introduce something like negentropy or negative filters (but not that... probably something else solving that same problem) without it being a breaking change.
- The new protocol could just be a few websocket-binary messages enhancing the current protocol, continuing to leverage the existing websocket-text messages we currently have, meaning newer relays would still support all the older stuff.
The downsides are just that if you want this new stuff you have to build it. It makes the protocol less simple, having now multiple protocols, multiple ways of doing the same thing.
Nonetheless, this I am in favor of. I think the trade-offs are worth it. I will be pushing a draft PR for this soon.
The path forward
I propose then the following path forward:
- A new nostr protocol over websockets binary (draft PR to be shared soon)
- Subkeys brought into nostr via NIP-26 (but let's use a single letter tag instead, OK?) via a big push to get all the clients to support it (the transition will be painful - most major clients will need to support this before anybody can start using it).
- Some kind of solution to the negative-filter-negentropy need added to the new protocol as its first optional feature.
- We seriously consider replacing Relay URLs with nostr pubkeys assigned to the relay, and then have relays publish their IP address and TLS key or certificate.
We sacrifice these:
- Faster event hash/verification
- Composable event bitflags
- Safer faster more well-supported crypto curve
- Nostr keys themselves as TLS 1.3 RawPublicKey certificates
-
 @ 0dc2dcb1:4787801a
2024-07-11 15:16:25
@ 0dc2dcb1:4787801a
2024-07-11 15:16:25- Added ids and
setIds()to the Filter class to fetch events with ids - https://github.com/nostrver-se/nostr-php/compare/1.3.1...1.3.2 - Discovered https://revolt.run/ as a package to be used for concurrent async code in PHP. Source: TalkingDrupal podcast with KingDutch - https://www.drupal.org/project/drupal/issues/3257726
- Fix response in Relay class - https://github.com/nostrver-se/nostr-php/releases/tag/1.3.3. Found and reported on Nostr: https://njump.me/nevent1qvzqqqqqqypzphtxf40yq9jr82xdd8cqtts5szqyx5tcndvaukhsvfmduetr85ceqy88wumn8ghj7mn0wvhxcmmv9uq3zamnwvaz7tmwdaehgu3wwa5kuef0qqsq3utlvgf6tz88ctexwu8ppgct9dkahmv5esxhmmgphv675get22qmzah0a
- Created a seperate repository with the code for the nostr-php.dev website: https://github.com/nostrver-se/nostr-php.dev
- Added ids and
-
 @ 7e538978:a5987ab6
2024-10-02 13:57:31
@ 7e538978:a5987ab6
2024-10-02 13:57:31Chain Duel, a fast paced PvP game that takes inspiration from the classic snake game and supercharges it with Bitcoin’s Lightning Network. Imagine battling another player for dominance in a race to collect blocks, where the length of your chain isn’t just a visual cue. It represents real, staked satoshis. The player with the most Proof of Work wins, but it’s not just about gameplay; it’s about the seamless integration of the Lightning Network and real-time payments.
But how does Chain Duel manage these instant transactions with such efficiency? That’s where LNbits comes in. LNbits, an open-source wallet and payment infrastructure, handles all in-game payments making it easy for developers to focus on gameplay while LNbits takes care of everything from microtransactions to automated splits for developers and designers. In this article, we’ll dive deep into how Chain Duel leverages LNbits to streamline in-game payments and how other developers can take advantage of this powerful toolset to build the future of Lightning-powered gaming.
Let’s explore how LNbits transforms payment processing and why it’s quickly becoming a must-have for game developers working in the Bitcoin space.
Overview of Chain Duel
Chain Duel is a unique Lightning Network-inspired game that reimagines the classic snake game with a competitive twist, integrating real-time payments. Two players face off in real-time, racing to "catch" blocks and extend their chains. Each block added to the chain represents Proof of Work, and the player with the most Proof of Work wins the duel. The stakes are high, as the game represents satoshis (small units of Bitcoin) as points, with the winner taking home the prize.
The game is designed to be Lightning-native, meaning all payments within Chain Duel are processed through the Lightning Network. This ensures fast payments, reducing latency and making gameplay smooth. With additional features like practice mode, tournaments and highscores, Chain Duel creates an engaging and competitive environment for Bitcoin enthusiasts and gamers alike.

One of the standout aspects of Chain Duel is its deeper integration with the Lightning Network even at a design level. For example, actual Bitcoin blocks can appear on screen during matches, offering bonus points when mined in sync with the game. The game’s current version, still in beta, has already drawn attention within the Bitcoin community, gaining momentum at conferences and with a growing user base through its social networks. With its innovative combination of gaming, the Lightning Network, and competitive play, Chain Duel offers a glimpse into the future of Lightning-based gaming.
How LNbits is Used in Chain Duel
Seamless Integration with LNbits
At the core of Chain Duel’s efficient payment processing is LNbits, which handles in-game transactions smoothly and reliably. Chain Duel uses the LNbits LNURL-pay and LNURL-withdraw extensions to manage payments and rewards between players. Before each match, players send satoshis using LNURL-pay, which generates a static QR code or link for making the payment. LNURL-pay allows users to attach a note to the payment, which Chain Duel creatively uses as a way to insert the player name in-game. The simplicity of LNURL-pay ensures that users can quickly and easily initiate games, with fresh invoices being issued for every game. When players win, LNURL-withdraw enables them to seamlessly pull their earnings from the game, providing a quick payout system.
These extensions make it easy for players to send and receive Bitcoin with minimal latency, fully leveraging the power of the Lightning Network for fast and low-cost payments. The flexibility of LNbits’ tools means that game developers don’t need to worry about building custom payment systems from scratch—they can rely on LNbits to handle all financial transactions with precision.
Lightning Tournaments
Chain Duel tournaments leverage LNbits and its LNURL extensions to create a seamless and efficient experience for players. In Chain Duel tournaments, LNbits plays a crucial role in managing the overall economics. LNbits facilitates the generation of LNURL QR codes that participants can scan to register quickly or withdraw their winnings. LNbits allows Chain Duel to automatically handle multiple registrations through LNURL-pay, enabling players to participate in the tournament without additional steps. The Lightning Network's speed ensures that these payments occur in real-time, reducing wait times and allowing for a smoother flow in-game.
Splitting Payments
LNbits further simplifies revenue-sharing within Chain Duel. This feature allows the game to automatically split the satoshis sent by players into different shares for the game’s developer, designer, and host. Each time a payment is made to join a match, LNbits is used to automattically pay each of the contributors, according to pre-defined rules. This automated process ensures that everyone involved in the development and running of the game gets their fair share without manual intervention or complex bookkeeping.
Nostr Integration
Chain Duel also integrates with Nostr, a decentralized protocol for social interactions. Players can join games using "Zaps", small tips or micropayments sent over the Lightning Network within the Nostr ecosystem. Through NIP-57, which enables Nostr clients to request Zap invoices, players can use LNURL-pay enabled Zaps to register in P2P matches, further enhancing the Chain Duel experience. By using Zaps as a way to register in-game, Chain Duel automates the process of fetching players' identity, creating a more competitive and social experience. Zaps are public on the Nostr network, further expanding Chain Duel's games social reach and community engagement.
Game and Payment Synchronization

One of the key reasons Chain Duel developers chose LNbits is its powerful API that connects directly with the game’s logic. LNbits allows the game to synchronize payments with gameplay in real-time, providing a seamless experience where payments are an integrated part of the gaming mechanics.
With LNbits managing both the payment process and the Lightning Network’s complex infrastructure, Chain Duel developers are free to concentrate on enhancing the competitive and Lightning Network-related aspects of the game. This division of tasks is essential for streamlining development while still providing an innovative in-game payment experience that is deeply integrated with the Bitcoin network.
LNbits proves to be an indispensable tool for Chain Duel, enabling smooth in-game transactions, real-time revenue sharing, and seamless integration with Nostr. For developers looking to build Lightning-powered games, LNbits offers a powerful suite of tools that handle everything from micropayments to payment distribution—ensuring that the game's focus remains on fun and competition rather than complex payment systems.
LNBits facilitating Education and Adoption
This system contributes to educating users on the power of the Lightning Network. Since Chain Duel directly involve real satoshis and LNURL for registration and rewards, players actively experience how Lightning can facilitate fast, cheap, and permissionless payments. By incorporating LNbits into Chain Duel, the game serves as an educational tool that introduces users to the benefits of the Lightning Network. Players gain direct experience using Lightning wallets and LNURL, helping them understand how these tools work in real-world scenarios. The near-instant nature of these payments showcases the power of Lightning in a practical context, highlighting its potential beyond just gaming. Players are encouraged to set up wallets, explore the Lightning ecosystem, and eventually become familiar with Bitcoin and Lightning technology. By integrating LNbits, Chain Duel transforms in-game payments into a learning opportunity, making Bitcoin and Lightning more approachable for users worldwide.
Tools for Developers
LNbits is a versatile, open-source platform designed to simplify and enhance Bitcoin Lightning Network wallet management. For developers, particularly those working on Lightning-native games like Chain Duel, LNbits offers an invaluable set of tools that allow for seamless integration of Lightning payments without the need to build complex custom solutions from scratch. LNbits is built on a modular and extensible architecture, enabling developers to easily add or create functionality suited to their project’s needs.
Extensible Architecture for Customization
At the core of LNbits is a simple yet powerful wallet system that developers can access across multiple devices. What makes LNbits stand out is its extensible nature—everything beyond the core functionality is implemented as an extension. This modular approach allows users to customize their LNbits installation by enabling or building extensions to suit specific use cases. This flexibility is perfect for developers who want to add Lightning-based services to their games or apps without modifying the core codebase.
- Extensions for Every Use Case
LNbits comes with a wide array of built-in extensions created by contributors, offering various services that can be plugged into your application. Some popular extensions include: - Faucets: Distribute small amounts of Bitcoin to users for testing or promotional purposes.
- Paylinks: Create shareable links for instant payments.
- Points-of-sale (PoS): Allow users to set up shareable payment terminals.
- Paywalls: Charge users to access content or services.
- Event tickets: Sell tickets for events directly via Lightning payments.
- Games and services: From dice games to jukeboxes, LNbits offers entertaining and functional tools.
These ready-made solutions can be adapted and used in different gaming scenarios, for example in Chain Duel, where LNURL extensions are used for in game payments. The extensibility ensures developers can focus on building engaging gameplay while LNbits handles payment flows.
Developer-Friendly Customization
LNbits isn't just a plug-and-play platform. Developers can extend its functionality even further by creating their own extensions, giving full control over how the wallet system is integrated into their games or apps. The architecture is designed to make it easy for developers to build on top of the platform, adding custom features for specific requirements.
Flexible Funding Source Management
LNbits also offers flexibility in terms of managing funding sources. Developers can easily connect LNbits to various Lightning Network node implementations, enabling seamless transitions between nodes or even different payment systems. This allows developers to switch underlying funding sources with minimal effort, making LNbits adaptable for games that may need to scale quickly or rely on different payment infrastructures over time.
A Lean Core System for Maximum Efficiency
Thanks to its modular architecture, LNbits maintains a lean core system. This reduces complexity and overhead, allowing developers to implement only the features they need. By avoiding bloated software, LNbits ensures faster transactions and less resource consumption, which is crucial in fast-paced environments like Chain Duel where speed and efficiency are paramount.
LNbits is designed with developers in mind, offering a suite of tools and a flexible infrastructure that makes integrating Bitcoin payments easy. Whether you’re developing games, apps, or any service that requires Lightning Network transactions, LNbits is a powerful, open-source solution that can be adapted to fit your project.
Conclusion
Chain Duel stands at the forefront of Lightning-powered gaming, combining the excitement of competitive PvP with the speed and efficiency of the Lightning Network. With LNbits handling all in-game payments, from microtransactions to automated revenue splits, developers can focus entirely on crafting an engaging gaming experience. LNbits’ powerful API and extensions make it easy to manage real-time payments, removing the complexity of building payment infrastructure from scratch.
LNbits isn’t just a payment tool — it’s a flexible, developer-friendly platform that can be adapted to any gaming model. Whether you're developing a fast-paced PvP game like Chain Duel or any project requiring seamless Lightning Network integration, LNbits provides the ideal solution for handling instant payments with minimal overhead.
For developers interested in pushing the boundaries of Lightning-powered gaming, Chain Duel is a great example of how LNbits can enhance your game, letting you focus on the fun while LNbits manages real-time transactions.
Find out more
Curious about how Lightning Network payments can power your next game? Explore the following:
- Learn more about Chain Duel: Chain Duel
- Learn how LNbits can simplify payment handling in your project: LNbits
- Dive into decentralized communication with Nostr: Nostr
- Extensions for Every Use Case
-
 @ b2caa9b3:9eab0fb5
2024-07-11 15:04:06
@ b2caa9b3:9eab0fb5
2024-07-11 15:04:06Hey everyone,
Today wasn't super eventful, but there were a couple things I wanted to share. First off, I had to pay rent, which meant a trip to the bank with my still-not-great foot. On the bright side, I took some pictures of Moshi along the way - hopefully you'll enjoy a glimpse of the city!

Speaking of my foot, there's been some improvement! The pain isn't constant anymore, only when I'm walking around. It looks better too, so hopefully it'll be back to normal soon.
Now, onto the slightly more frustrating topic: the Kenyan border situation. As you might recall, I had a big issue where border control wouldn't let me leave the country and even refused to contact my embassy. Basically, they held me hostage (which, by the way, is a violation of international law).
Two days later, I managed to get out through a different border. Recently, the Kenyan police has started investigating. They contacted me on WhatsApp a few days ago, and things are getting stranger by the day.

There's a big part of this that just doesn't add up. They keep asking for a photo of the exit stamp, but the officer who wouldn't let me leave never gave me one. He actually denied my exit and put me on a bus back to the city! I explained this and told them another border provided the stamp later, but they insist they need the original stamp to find this as "proof" related to this officer. It just doesn't connect to the man who caused the problem in the first place.

Even more concerning, they want me to return to Kenya. First, they want me to sign a document, but when I expressed hesitation about returning, they switched to asking me to identify this officer in a lineup. And all of this communication is happening on a personal WhatsApp number, which makes the whole situation incredibly suspicious.
Overall, it's a confusing situation.
On a brighter note, my foot is definitely on the mend. Here's to hoping it keeps getting better!
That's all for today. I'll just be relaxing and grabbing some dinner later.
Stay tuned for more updates!


Online
Feel free to support me by sending some sats via the lightning network to rubenstorm@sats.mobi
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 796a6d9b:3bb533e3
2024-07-11 12:57:35
@ 796a6d9b:3bb533e3
2024-07-11 12:57:35For more than a while now, I think you have experienced the feeling that things are not right in the world or in your country, it is not surprising that it coincides with a moment in history where we will experience the end of a monetary cycle like It is FIAT money or in other words fiat money that is backed by debt, every day you look around you and people do not find much hope in the future, many of them are working to support themselves, pay the costs of living and In the best of cases, just saving a little inflationary money, a slower theft in the population, in the worst of cases, people are full of debt and without a plan on how to escape said trap.
Everything is connected, we just have to look for the signs that are leaving us with the naked eye, as for example we have never had in history countries so indebted based on their GDP or gross domestic product and that this same debt was financed with a deficit, For people who have studied or lived the situations of hyperinflationary countries like Venezuela, Argentina, Turkey, Lebanon, you will know what I am talking about, it is simpler than it sounds, no country can spend more than it produces without any consequences, someone has to pay the price, in this case the population through the dark hand of inflation.
We have reached the point where governments blatantly lie to us with inflation data that does not include food, rent and energy prices, to save appearances and maintain the psychological operation that everything is fine, but when you go to the supermarket you know that something was never there. Well, it is not surprising that even you, the person reading this, know that inevitably your Dollars, Euros or Pesos will not buy you the same thing in a year as what they buy you today.
So where are we headed? It is normal then that people are not very enthusiastic about the future, since when we look into the depths of our system we realize that people's savings and purchasing power will increasingly be devalued so that everything continues to function as it has until now. Today, it is noticeable that something in people's subconscious warns them that tomorrow will be worse and that is why they have to enjoy the now, reducing their time preference to sporadic moments without thinking about the long term, even if they do not understand complex mechanisms. economics, it is observed that people are increasingly working more for less remuneration since the numbers of a salary can increase nominally but they buy fewer and fewer goods and services, as we can see in this graph.
What we have left in the coming years is the acceleration of government mechanisms to be able to continue keeping the wealth extraction system functioning, trying to extend the psychological operation to a point of no return, it is clear that a form of money has been confiscated from us. . that allowed us savings like gold did, I think it is important that we begin to question certain things and choose not to continue participating in a system that is arranged to destroy the energy of our work.
What can we do? Alternatives such as Bitcoin and gold to protect the energy of our work are some of the best options that we can implement as a refuge from the disaster to which our politicians have dragged us. Using these alternatives as a kind of battery for our energy is the only way we can ensure that the effort we make every day in our jobs, ventures or companies is not devalued, since both gold and bitcoin are not debt. of anyone, they are reserves of value and have no risk of reverse departure or non-payment.
It is time to take action and educate ourselves to be able to rise to the challenges of the paradigm shift that we will have as a civilization, since a change in the monetary standard is what can lead us to a better path of incentives where people can change preferences. temporary and build for the future.
originally posted at https://stacker.news/items/604619
-
 @ b2caa9b3:9eab0fb5
2024-07-11 12:34:49
@ b2caa9b3:9eab0fb5
2024-07-11 12:34:49Back then, I was still living in a house in Höpfigheim. The house bordered directly on nature, a nature reserve, and I loved going out into nature there. I regularly took photos in this area. That's how this photo came about on that day in April 2011.
The photo was taken in Höpfigheim, a town in the Ludwigsburg district of Baden-Württemberg, Germany.

Photo Information
- Author: Ruben Storm
- Date Taken: April 22, 2011
- Published: June 19, 2012
- Camera: Nikon D3100
- Lens: Not specified
- Location: Höpfigheim, Germany
Links:
-
 @ c4b5369a:b812dbd6
2025-02-17 06:06:48
@ c4b5369a:b812dbd6
2025-02-17 06:06:48As promised in my last article:
nostr:naddr1qvzqqqr4gupzp394x6dfmvn69cduj7e9l2jgvtvle7n5w5rtrunjlr6tx6up9k7kqq2k6ernff9hw3tyd3y453rdtph5uvm6942kzuw08y0
In this one we will dive into how exactly an unidirectional payments channel powered ecash mint system would be implemented, using the tech available today! So if you haven't read that article yet, give it a read!
I first intended to write a longwinded article, explaining each part of the system. But then I realized that I would need some visualization to get the message across in a more digestable way. This lead me to create a slide deck, and as I started to design the slides it became more and more clear that the information is easier shown with visualizations, than written down. I will try to give a summary as best as I can in this article, but I urge you, to please go visit the slide deck too, for the best experience:
TAKE ME TO THE SLIDE DECK!
Intro
In this article we will go over how we can build unidirectional payment channels on Bitcoin. Then we will take a look into how Cashu ecash mints work, and how we can use unidirectional payment channels to change the dynamics between ecash users and the mint.
Before we start, let me also give credits to nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac for comming up with the idea, to nostr:npub148jz5r9xujcjpqygk69yl4jqwjqmzgrqly26plktfjy8g4t7xaysj9xhgp for providing an idea for non-expiring unidirectional channels, and nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx unconference for hosting an event where these ideas could be discussed and flourish.
Building unidirectional payment channels
If you've read the previous article, you already know what unidirectional payment channels are. There are actually a coupple different ways to implement them, but they all do have a few things in common:
- The
sendercan only send - The
Receivercan only receive - They are VERY simple
Way simpler than the duplex channels like we are using in the lightning network today, at least. Of course, duplex channels are being deployed on LN for a reason. They are very versatile and don't have these annoying limitations that the unidirectional payment channels have. They do however have a few drawbacks:
- Peers have liveness requirements (or they might forfeit their funds)
- Peers must backup their state after each transaction (if they don't they might forfeit their funds)
- It is a pretty complex system
This article is not meant to discredit duplex channels. I think they are great. I just also think that in some use-cases, their requirements are too high and the system too complex.
But anyway, let's see what kind of channels we can build!
Spillman/CLTV-Channel
The Spillman channel idea has been around for a long time. It's even explained in Tadge Dryjas Presentation on Payment channels and the lightning network from back in the day. I compiled a list of some of the most important propperties of them in the slide below:

Great!
Now that we know their properties, let's take a look at how we can create such a channel (Slides):

We start out by the
sendercreating afunding TX. Thesenderdoesn't broadcast the transaction though. If he does, he might get locked into a multisig with thereceiverwithout an unilateral exit path.Instead the
senderalso creates arefund TXspending the outputs of the yet unsignedfunding TX. Therefund TXis timelocked, and can only be broadcast after 1 month. Bothsenderandreceivercan sign thisrefund TXwithout any risks. Oncesenderreceives the signedrefund TX, he can broadcast thefunding TXand open the channel. Thesendercan now update the channel state, by pre-signing update transactions and sending them over to thereceiver. Being a one-way channel, this can be done in a single message. It is very simple. There is no need for invalidating old states, since thesenderdoes not hold any signedupdate TXsit is impossible for thesenderto broadcast an old state. Thereceiveronly cares about the latest state anyways, since that is the state where he gets the most money. He can basically delete any old states. The only thing thereceiverneeds to make sure of, is broadcasting the latestupdate TXbefore therefund TX'stimelock expires. Otherwise, thesendermight take the whole channel balance back to himself.This seems to be already a pretty useful construct, due to its simplicity. But we can make it even more simple!

This setup works basically the same way as the previous one, but instead of having a refund transaction, we build the
timelockspend path directly into thefunding TXThis allows thesenderto have an unilateral exit right from the start, and he can broadcast thefunding TXwithout communicating with thereceiver. In the worst case, the receiver rejects the channel, and the sender can get his money back after the timelock on the output has expired. Everything else basically works in the same way as in the example above.The beauty about this channel construct is in its simplicity. The drawbacks are obvious, but they do offer some nice properties that might be useful in certain cases.

One of the major drawbacks of the
Spillman-style channels(apart from being unidirectional) is that they expire. This expiry comes with the neat property that neither of the party has to watch the chain for channel closures, and thesendercan operate the channel with zero additional state, apart from his private keys. But they do expire. And this can make them quite inflexible. It might work in some contexts, but not so much in others, where time needs to be more flexible.This is where
Roose-Childs triggered channelscome into play.Roose-Childs triggered channel
(I gave it that name, named after nostr:npub148jz5r9xujcjpqygk69yl4jqwjqmzgrqly26plktfjy8g4t7xaysj9xhgp and nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac . If someone knows if this idea has been around before under a different name, please let us know!)
Roose-Childs triggered channelswere an idea developed by Steven and Luke at the nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx unconference. They essentially remove the channel expiry limitation in return for introducing the need for thesenderto create a channel backup at the time of channel creation, and for thereceiverthe need to watch the chain for trigger transactions closing the channel.
They also allow for splicing funds, which can be important for a channel without expiry, allowing the
senderto top-up liquidity once it runs out, or for thereceivertaking out liquidity from the channel to deploy the funds elsewhere.Now, let's see how we can build them!

The
funding TXactually looks the same as in the first example, and similarly it gets created, but not signed by thesender. Then, sender and receiver both sign thetrigger TX. Thetrigger TXis at the heart of this scheme. It allows bothsenderandreceiverto unilaterally exit the channel by broadcasting it (more on that in a bit).Once the
trigger TXis signed and returned to thesender, the sender can confidently sign and boradcast thefunding TXand open the channel. Thetrigger TXremains off-chain though. Now, to update the channel, thesendercan pre-sign transactions in similar fashion to the examples above, but this time, spending the outputs of the unbroadcastedtrigger TX. This way, both parties can exit the channel at any time. If thereceiverwants to exit, he simply boradcasts thetrigger TXand immediately spends its outputs using the latestupdate TX. If thesenderwants to exit he will broadcast thetrigger TXand basically force thereceivershand. Either, thereceiverwill broadcast the latestupdate TX, or thesenderwill be able to claim the entire channel balance after the timelock expired.
We can also simplify the
receiver'sexit path, by thesenderpre-signing an additional transactionR exit TXfor each update. this way, thereceiveronly needs to broadcast one transaction instead of two.
As we've mentioned before, there are some different trade-offs for
Roose-Childs triggered channels. We introduce some minimal state and liveness requirements, but gain more flexibility.
Ecash to fill in the gaps
(I will assume that the reader knows how ecash mints work. If not, please go check the slides where I go through an explanation)
Essentially, we are trying to get a lightning like experience, without all the lightning complexities and requirements. One big issue with ecash, is that it is fully custodial. If we can offset that risk by holding most of the funds in a self custodial channel, we can have a reasonable trade-off between usability and self custody.

In a system like that, we would essentially turn the banking model onto its head. Where in a traditional bank, the majority of the funds are held in the banks custody, and the user only withdraws into his custody what he needs to transact, in our model the user would hold most funds in his own custody.

If you ask me, this approach makes way more sense. Instead of a custodian, we have turned the "bank" into a service provider.
Let's take a look at how it would work in a more practical sense:

The
ecash userwould open an unidirectional payment channel to themint, using one of his on-chain UTXOs. This allows him then to commit incrementally funds into the mints custody, only the amounts for his transactional needs. The mint offers connectivity to the lightning network an handles state and liveness as a service provider.The
ecash user, can remain offline at all times, and his channel funds will always be safe. The mint can only ever claim the balance in the channel via theupdate TXs. Themintcan of course still decide to no longer redeem any ecash, at which point they would have basically stolen theecash user'stransactional balance. At that point, it would probably be best for theecash userto close his channel, and no longer interact or trust thismint.Here are some of the most important points of this system summarized:

And that is basically it! I hope you enjoyed this breakdown of Unidirectional payment channel enabled Ecash mints!
If you did, consider leaving me a zap. Also do let me know if this type of breakdown helps you understand a new topic well. I am considering doing similar breakdowns on other systems, such as ARK, Lightning or Statechains, if there is a lot of interest, and it helps people, I'll do it!
Pleas also let me know what you think about the
unidirectional channel - ecash mintidea in the comments. It's kind of a new idea, an it probably has flaws, or things that we haven't thought about yet. I'd love to discuss it with you!I'll leave you with this final slide:

Cheers,
Gandlaf
- The
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ 6e0ea5d6:0327f353
2025-02-17 01:04:37
@ 6e0ea5d6:0327f353
2025-02-17 01:04:37Ascolta bene, sì? In the game of business, as in chess or the streets of Palermo, there are times to advance like a ruthless king and times to wait like a wolf stalking its prey. Those who fail to grasp this distinction are doomed to be taken down before they even see the sun rise.
Prudence is the sharp blade that separates the wise man from the fool who rushes headlong into the enemy’s spear. Those who act without weighing the consequences end up as the corpses rotting on the sidewalks of unbridled ambition. But understand this well—prudence is not cowardice. The coward hesitates out of fear; the prudent man waits because he knows the right moment to strike. The difference? One crawls, the other conquers.
Fortis Fortuna Adiuvat—fortune favors the bold. But boldness without calculation is like a man crossing a minefield blindfolded. Greed blinds, destroys, and devours the reckless like a raging sea dragging bodies to the depths. You see it every day—entrepreneurs who rise too fast and crumble at the first crisis, young men who burn through their earnings chasing illusions of instant wealth, fools who trust too much in friends already hiding the dagger up their sleeve.
There’s a reason why great men endure while mere opportunists vanish like smoke in the wind. They understand that every battle has its time, every strike must have precision. Trade the cleaver for the scalpel—the butcher wounds without thought, the surgeon cuts with precision and saves his own skin.
Dimmi, quale vuoi essere? The fool who charges into war without a shield, or the strategist who, in the end, sits at the banquet of victory? The answer is not in what you say, but in what you do while others waste their opportunities.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 5d4b6c8d:8a1c1ee3
2024-07-11 12:17:18
@ 5d4b6c8d:8a1c1ee3
2024-07-11 12:17:18Yesterday's edition https://stacker.news/items/603455/r/Undisciplined
-
- -
July 11, 2023 📅
📝
TOP POSTI am not a routing node anymore
Excerpt
Over the past two years I ran an amateur routing node that was in the top 300 on lightning terminal. I have decided to stop for the following reasons […]
5586 sats \ 37 comments \ @lnvisualizer \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/207349/r/Undisciplined?commentId=207482
Excerpt
While you were making Bitcoin banks, Phoenix scripted out lightning channel management […]
1776 sats \ 12 replies \ @nerd2ninja
From Introducing the new Phoenix: a 3rd generation self-custodial Lightning wallet by @Norbert in ~bitcoin
🏆
TOP STACKER2nd place @nerd2ninja (1st hiding, presumed @siggy47)
746 stacked \ 2262 spent \ 1 post \ 11 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
91.7k stacked \ 0 revenue \ 113.7k spent \ 90 posts \ 302 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 11, 2022 📅
📝
TOP POSTI'm Evan Kaloudis, Founder of Zeus. July 11th AMA!
Excerpt
I'm stoked to chat with you all today. Zeus (https://zeusln.app) is a mobile app for iOS and Android that lets you connect to and control your lightning node remotely. It supports LND, Core Lightning, and Eclair.
31.7k sats \ 58 comments \ @evankaloudis \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/43634/r/Undisciplined?commentId=43640
Excerpt
Hello, I am a Bitcoin maxi and I put my sats where my mouth is. Bitcoin maximalism is a method of consumer protection. My story as a maximalist, is that I used to shitcoin back in 2016. During the 2018 bear market, I lost so much money in everything […]
390 sats \ 11 replies \ @nerd2ninja
From I am moving over from Twitter by @charles_stack in ~bitcoin
🏆
TOP STACKER1st place @k00b
19.3k stacked \ 32k spent \ 2 posts \ 17 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
53.4k stacked \ 0 revenue \ 62.2k spent \ 114 posts \ 304 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 11, 2021 📅
📝
TOP POSTThis company sells passports to Americans looking for a tax break on their bitcoin profits
Link to https://www.cnbc.com/2021/07/11/plan-b-passport-tax-break-bitcoin-profits.html
5 sats \ 4 comments \ @0268486dc4 \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/256/r/Undisciplined?commentId=282
Excerpt
Fascinating to see the disconnect between fundamentals of a crypto/stock and the price action created by market movers and how it seems to follow so many mathematical patterns. Makes you want to be a trader but then you remember 90%+ or whatever jus […]
1 sat \ 2 replies \ @gmd
From What are your favorite Bitcoin newsletters? by @k00b in ~bitcoin
🏆
TOP STACKERNo top stacker
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
21 stacked \ 0 revenue \ 151 spent \ 5 posts \ 15 comments
originally posted at https://stacker.news/items/604559
-
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 6e0ea5d6:0327f353
2025-02-17 00:53:36
@ 6e0ea5d6:0327f353
2025-02-17 00:53:36Ascolta! When you allow the flame of ambition to fade within your chest, you inevitably drift toward petty and foolish concerns unworthy of an adult. In other words, the moment you abandon your dedication to grand objectives—precisely due to idleness—you will end up entangled in trivial matters, thus weakening your masculinity. Lacking the responsibilities inherent to a grown man, you will inevitably behave like a boy in all aspects of life, including relationships.
He who is truly determined to win in life has neither the time nor the energy to engage in matters of neediness, jealousy, or fear of abandonment.
Love, as it is often romanticized, is a dangerous illusion that leads us to reckless and self-destructive behaviors. The romantic ideal, propagated by poets and dreamers, makes us vulnerable to manipulation and disappointment.
A man who is aware of his value remains focused on what truly matters, and because he understands the weight of his priorities, that alone is enough.
Weakness does not inspire confidence. In a world where strength and determination are essential for survival and success, showing weakness is signing your own sentence of irrelevance. A man must be the foundation upon which the relationship stands. He must be the unshakable rock amid life’s storms. Life is a game of power and influence, and those who fail to understand this are doomed to failure.
Take care of yourself. Strengthen your body, your mind, and your spirit. Be an example of determination and courage. The woman by your side must see in you a leader, a visionary, someone destined for great achievements. Only then will you earn not only her respect and admiration but also full control over your own destiny.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 502ab02a:a2860397
2024-07-11 08:42:42
@ 502ab02a:a2860397
2024-07-11 08:42:42เตรียมตัวเตรียมของ 3 อย่าง ก่อนลงสู่ทุ่งม่วง
โพสที่แล้ว เราเห็นข้อเปรียบเทียบระหว่าง nostr กับ โซเชียลมีเดีย กันไปแล้ว โพสนี้เราจะมาทำความรู้จัก ของหลักๆที่จำเป็นในการลงสู่ทุ่งม่วงกันครับ

อย่างที่ 1 : กุญแจคู่ รู้ตัวตน ก่อนจะเข้าประตูสู่ทุ่งม่วงนั้น เราต้องการกุญแจ 2 ดอกครับ มันทำงานคล้ายๆเซฟธนาคาร คือ กุญแจ 2 ดอกนี้ต้องเข้าชุดกัน ถึงจะเปิดออกได้ ซึ่งกุญแจ 2 ดอกนี้ เราเรียกว่า npub กับ nsec
อย่าเพิ่งตกใจ ไหนบอกว่าจะมีศัพท์คอมพิวเตอร์น้อยๆไง 5555 ใช่ครับ บางคำอาจจำเป็นต้องรู้จักไว้ แต่ผมจะเทียบเคียงเป็นภาษาบ้านๆเราให้นะครับ npub กับ nsec จะเป็นชุดตัวเลขที่คอมพิวเตอร์คำนวนมาให้ (วิธีการได้มาจะบอกภายหลังครับ)
Npub เราทำความเข้าใจเป็นภาษาอังกฤษง่ายๆว่า Nostr Public key ตัวย่อ NPUB หรือกุญแจที่เราเอาไว้ให้คนอื่นเพื่อจดจำว่าเป็นเรา ซึ่งคนอื่น นั่น นอกจากจะเป็นคนจริงๆแล้ว ยังหมายถึงระบบแอพต่างๆด้วย
Nsec เราทำความเข้าใจเป็นภาษาอังกฤษง่ายๆว่า Nostr Secret key ตัวย่อ NSEC หรือกุญแจที่เราเก็บไว้ที่ตัวเองเท่านั้น ห้ามใครรู้
ระบบต่างๆจะคำนวนว่า npub กับ nsec เป็นชุดเดียวกันหรือเปล่า ก่อนนะอนุญาตให้เราดำเนินการใดๆได้ใน nostr พูดง่ายๆคือ npub nsec คือ กุญแจคู่ที่เอาไว้ยืนยันความเป็นตัวเรานั่นเองครับ
ทีนี้ข้อเด่นของระบบ nostr ที่เหนือกว่า แอพโซเชียล www ทุกวันนี้คือ กุญแจคู่นี้ชุดเดียว ทำให้คุณสามารถท่องไปในดินแดน nostr ได้ตลอดกาล ไม่ว่าในอนาคตจะมีคนสร้าง nostr app อะไรใหม่ๆขึ้นมา โครงสร้างหลักของ nostr จะเป็นการใช้กุญแจคู่นี้ตลอดไปเช่นกัน ไม่เหมือนกับ โซเชียล www ทุกวันนี้ ที่ต้องไปไล่สมัคร user id ตามเอกชนแต่ละที่ แล้วเราก็ต้องมีเป็นร้อยๆ account ตามจำนวนบริการที่เราใช้ ไหนจะ เฟสบุค ไหนจะยูทูป ไหนจะกูเกิ้ล นี่ยังดีที่ แอพเล็กๆหลายๆเจ้าไปพึ่งใบบุญลูกพี่ใหญ่ อย่างเฟสบุค ยูทูป ไปบ้างแล้ว แต่เราก็ต้องมีสารพัด user id อยู่ดี
นอกจากนี้ ข้อมูล password ของเราก็ยังถูกบันทึกไว้ที่คอมของ แอพนั้นๆ ต่างกับ กุญแจคู่ของ nostr ที่ไม่ได้เป็นการบันทึกข้อมูลของกุญแจไว้ในคอมของแอพ(ที่ใน nostr เราเรียกว่า รีเลย์ จำได้ใช่ไหมครับ) ระบบของ nostr เป็นการนำตัวเลขของกุญแจคู่นี้ มาคำนวนความเข้ากันได้ว่าเป็นคู่ที่ถูกต้องไหม ถ้าถูกต้องมันจะอนุญาตให้เราดำเนินการต่อ นั่นหมายถึงไม่มีการบันทึกใดๆไว้ในคอมผู้ให้บริการเลย ตราบใดที่คุณเก็บกุญแจไว้ที่ตัวดีๆ your key is your id
ทีนี้การที่จะได้กุญแจคู่นี้มานั้นไม่ยากครับ เพียงแค่เราใช้แอพของ nostr เป็นตัวสร้างได้เลย

อย่างที่ 2 : แอพไหน ไฟแรงเวอร์ ก่อนจะเข้าสู่การสร้าง เรามาทำความเข้าใจ โลกของ nostr app กันเพิ่มสักนิดก่อนครับ อย่างที่บอกในโพสที่แล้ว nostr คือระบบการส่งข้อมูลแบบใหม่ เทียบให้เห็นภาพก็คือ www (world wide web) Nostr คือ การส่งอะไรก็ตามผ่านรีเลย์ (Notes and Other Stuff Transmitted by Relays)
ทีนี้ในโลกของ www เราก็จะมีแอพซึ่งภาษาทางการเรียกว่า web app เห็นชัดๆก็พวกที่อยู่ในมือถือเรานั่นละครับ เฟสบุค ยูทูป ไอจี ทวิตเตอร์ มันคือหน้าฉากเป็นมือถือแต่หลังบ้านมันเป็นการติดต่อส่งรับข้อมูลในระบบ www รวมศูนย์อยู่ที่แอพแต่ละยี่ห้อ
การทำงานของ Nostr ก็เหมือนกัน แม้จะใช้การส่งข้อมูลผ่านรีเลย์แต่ระบบยังคงทำงานบนอินเตอร์เนทช่วยในการเดินทาง เราจึงจะมี nostr app เพื่อใช้เป็นหน้าบ้านในการส่งรับข้อมูลในระบบ nostr ที่เชื่อมต่อถึงกันโดยรีเลย์ ดังนั้นเอาจริงๆในฐานะผู้ใช้ แทบจะไม่ต้องปรับอะไรมากเลย นอกจากเรียนรู้การใช้แอพใหม่
ส่วนการอธิบายหลักการที่ผ่านมา มันแค่ช่วยให้คุณเข้าใจความเจ๋ง ความอิสระ ความปลอดภัย เพื่อให้คุณ อิน ในระบบที่ไม่ต้องพึ่งพาบริษัทเอกชนที่เอาคุณเป็นสินค้าใดๆอีก
นักเขียนโปรแกรม เขาก็ทำ app ขึ้นมาให้เราเทียบเคียงการใช้งานกับโลกทุกวันนี้ ยกตัวอย่างให้เห็นภาพกันก่อนเช่น Facebook twitter เขาก็จะมีแอพ damus artemis primal ฯลฯ ที่เป็นการโพสข้อความ รูป ลิงค์ มีกดไลค์ มีแชร์ ได้เหมือนกัน Youtube เขาก็จะมีแอพ zapstream flare ฯลฯ ที่เป็นลักษณะคลังเก็บวีดีโอ หรือ การไลฟ์ต่างๆ ซึ่งอันนี้แค่ตัวอย่างครับ จริงๆแล้วยังมี nostr app อีกมากมายก่ายกอง ที่เริ่มมีการทะยอยออกมาให้ใช้งานกัน (แน่ละครับ มันยังไม่มากแบบใน app store แต่มันคือจุดเริ่มต้นที่ผ่านมาได้พักนึงแล้ว และแอพใช้งานทั่วไปก็ครอบคลุมแล้ว)
ที่สำคัญคือ ทุก nostr app ใช้กุญแจคู่เดียว ในการแสดงตัวตนของเราในการใช้งานนั้นๆ ตามที่บอกไว้ข้างบน (อย่างที่1) ไม่ต้องสมัครอะไรอีกต่อไป โหลดแล้วใช้เลย และใครที่ใช้คอม จะยิ่งมี nostr app ที่ใช้งานแบบบนคอมเยอะกว่าในมือถือเสียอีก

อย่างที่ 3 : แฮชแทคจ๋า พี่มาแล้ว ด้วยความที่โลกของ nostr กว้างใหญ่มาก อิสระมาก และที่สำคัญคือ ไม่มีอัลกอลิทึม ในการที่จะยัดเยียดการมองเห็น ดังนั้นสิ่งที่จะทำให้ทุกอย่างง่ายขึ้นนั่นคือแฮชแทค ถ้าใครเล่น ig twitter เราจะคุ้นเคยกันดี ว่าหากเราโพสอะไรแล้วใส่แฮชแทค คนที่ติดตามแฮชแทคนั้น จะได้เห็นข้อความเราไปเอง nostr ก็เช่นกัน มีแฮชแทคมากมายให้ติดตามกัน โดยเฉพาะ แฮชแทค #siamstr ที่เราชาวไทยรวมใจกันใช้ เพื่อสร้างอาณาเขตของคนไทยในทุ่งม่วง นอกจากนี้ของผมเองคือ #pirateketo ที่ใช้อยู่กับเฟสบุคและ ig ก็นำไปใช้ในทุ่งม่วงด้วย สามารถเจอโพสของพวกเราได้ ตามแฮชแทคนี้
ถ้าเป็นคนเล่นแฮชแทคอยู่แล้วก็ง่ายเลยแทบไม่ต้องปรับตัว ใครไม่ค่อยเล่นก็สามารถลองกดๆแฮชแทคในเฟสบุคดูเพื่อทำความเข้าใจการทำงานได้ก่อนที่จะลงทุ่งม่วง
ทบทวนอีกที ของ3อย่างที่ต้องเตรียมรู้ก่อนลงทุ่งม่วง 1.กุญแจคู่ รู้ตัวตน 2.แอพไหน ไฟแรงเวอร์ 3. แฮชแทคจ๋า พี่มาแล้ว เมื่อทำความเข้าใจ 3 อย่างนี้แล้ว เราก็พร้อมจะลงไปมั่วกันแล้วครับ เล่นก่อนเรียนตามกันไปอีกที
pirateketo
siamstr
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ c0a57a12:8b230f7a
2025-02-17 00:08:04
@ c0a57a12:8b230f7a
2025-02-17 00:08:04Ever notice how we’ve all turned into a bunch of regulation junkies? Not just the kids—us, too. The parents. The supposed adults in the room. We sit around shaking our heads at this new generation, wondering why they can’t make a move without a permission slip, but let’s be honest: we made them that way. We were trained for it. We just passed the neurosis down like a bad heirloom.
Used to be, kids ran wild, made their own fun, learned how things worked by getting their hands dirty and screwing up a few times. You fell out of a tree? Tough. That’s how you figured out gravity was real. Now, a kid gets a splinter and half the neighborhood has to be briefed. But let’s not act like it started with them. We didn’t grow up in the Wild West. Our parents—the ones who were handed a country built by men who cleared forests and carved railroads and settled frontiers—they took one look at all that, clutched their pearls, and decided the real enemy was risk. They started slapping safety labels on everything, turned common sense into a government-subsidized industry, and set about making sure we never had to experience a single moment of danger, discomfort, or—God help us—independence.
And we ate it up. Grew up afraid of the sun, the air, the drinking water. If you touched a stranger, you’d get kidnapped. If you ate the wrong snack, you’d drop dead from an allergy you didn’t even have. If you rode a bike without strapping on enough gear to survive re-entry from orbit, you might as well be suicidal. Then, just to really hammer it in, we were given rules for everything. How to sit, how to talk, how to play, how to think. And because we’d been softened up, we listened. We obeyed. We internalized the great lesson of modern civilization: only do what is approved.
And when it came time for us to raise kids? Oh, we ran with it. Helicopter parenting? That was us. Participation trophies? Us. Baby-proofing the entire godforsaken planet so that Junior never had to encounter anything sharper than a cotton ball? Us again. Every bit of micromanaged, soul-sucking, over-regulated nonsense we complain about today? We enforced it. So now we’ve got a generation that doesn’t know how to function without checking the rulebook first. They hesitate before every decision because we taught them hesitation. They sit around waiting for a green light because that’s all we ever told them to do.
And you know what? We’re no better. When’s the last time you did something without checking if it was "allowed"? When’s the last time you ignored a ridiculous rule instead of just sighing and complying? When’s the last time you acted like a free man instead of a well-behaved tax mule hoping the system doesn’t notice you?
We’ve swallowed a lie, and we keep regurgitating it—that compliance is morality, that following orders is a virtue, that a safe, predictable, well-regulated life is a good one. It’s not. It’s never been. You don’t get freedom by waiting for permission to use it. You don’t get courage by asking if it’s okay. You don’t build a worthwhile life by making sure you never color outside the lines.
And yet, here we are, acting surprised. Acting like we don’t know how we got here. Acting like we didn’t choose this. Like we didn’t let it happen.
So what now? We could stop. We could teach our kids to take risks, to get their hands dirty, to act instead of waiting for permission. We could start ignoring stupid rules, start trusting our own judgment, start living like we weren’t raised in a padded cell.
Or we could do nothing. Keep following orders. Keep playing it safe. Keep watching the world shrink into a flavorless, permission-based, committee-approved version of itself.
Your call. But either way, don’t pretend to be surprised.
-
 @ 5a261a61:2ebd4480
2025-02-16 21:54:41
@ 5a261a61:2ebd4480
2025-02-16 21:54:41As I grow older, I find myself often discovering things that I haven't understood before, or just see completely differently. Like with this fable of the toad and scorpion. You know, the classic where scorpion needs to get across the river, and asks the toad for help, promising not to sting. The toad refuses at first, pointing out that scorpion's sting would kill them both. But scorpion argues that would be illogical - why would it sting if that meant its own death? The toad, convinced by this logic, agrees to help. Halfway across, scorpion stings anyway, and as they both sink, toad asks "why?" Scorpion simply answers "It's my nature."
That leads me to my scorpion sighting. I have somewhat stronger libido and given the circumstances, I usually situate myself in the submissive position in both married and online life. When I am not ventilating or getting these things out in some way, it usually leads to my growing frustration that seriously hinders my usual life. And in those trying times I usually tell myself, "screw that, I don't like this, I don't like how that makes me feel, it sucks, why does it have to hurt so much" (well, I don't think 'hurt' as I have been indoctrinated by the society that men don't process feelings this way, but I think if I had a therapist, they would want me to spell it like that). Let's not go to the subspace again, it's silly space. Sometimes it gets really dark...but then comes the climax, like literally, and suddenly everything is forgiven and (almost) forgotten. And all is well.
Let's just not go there next time, avoid being burned again, I keep saying to myself. And these days submissive scorpion in my head just silently waits for my monologuing toad to finish defending ourselves. It knows that it needs only one chance so I cave in, while toad needs to defend my sanity every day. So one day, I will bring scorpion to cross the river with me again. And it will again promise that this time it will be ok. And we will both pretend like we believe that, so the play can go on. And it will eventually sting me, because we both yearn for unreachable things.
And next day I will again see scorpion on the river, not wooing me, no, we are beyond that, it knows it just needs to wait before I come back for the poison I need.As I grow older, I find myself often discovering things that I haven't understood before, or just see completely differently. Like with this fable of the toad and scorpion.
You know, the classic where scorpion needs to get across the river, and asks the toad for help, promising not to sting. The toad refuses at first, pointing out that scorpion's sting would kill them both. But scorpion argues that would be illogical - why would it sting if that meant its own death? The toad, convinced by this logic, agrees to help. Halfway across, scorpion stings anyway, and as they both sink, toad asks "why?" Scorpion simply answers "It's my nature."
That leads me to my scorpion sighting. I have somewhat stronger libido and given the circumstances, I usually situate myself in the submissive position in both married and online life. When I am not ventilating or getting these things out in some way, it usually leads to my growing frustration that seriously hinders my usual life. And in those trying times I usually tell myself, "screw that, I don't like this, I don't like how that makes me feel, it sucks, why does it have to hurt so much" (well, I don't think 'hurt' as I have been indoctrinated by the society that men don't process feelings this way, but I think if I had a therapist, they would want me to spell it like that). Let's not go to the subspace again, it's silly space. Sometimes it gets really dark...but then comes the climax, like literally, and suddenly everything is forgiven and (almost) forgotten. And all is well.
Let's just not go there next time, avoid being burned again, I keep saying to myself. And these days submissive scorpion in my head just silently waits for my monologuing toad to finish defending ourselves.
It knows that it needs only one chance so I cave in, while toad needs to defend my sanity every day. So one day, I will bring scorpion to cross the river with me again. And it will again promise that this time it will be ok. And we will both pretend like we believe that, so the play can go on. And it will eventually sting me, because we both yearn for unreachable things.
And next day I will again see scorpion on the river, not wooing me, no, we are beyond that, it knows it just needs to wait before I come back for the poison I need.
-
 @ 502ab02a:a2860397
2024-07-11 07:14:05
@ 502ab02a:a2860397
2024-07-11 07:14:05 ก่อนจะเปิดหลุมกระต่าย ให้เพื่อนๆลงไปสู่ ทุ่งม่วง wonderland เรามาเบิกเนตรระบบที่ทำให้เราเป็นสินค้าแทนที่จะเป็นลูกค้ากันก่อนครับ
ก่อนจะเปิดหลุมกระต่าย ให้เพื่อนๆลงไปสู่ ทุ่งม่วง wonderland เรามาเบิกเนตรระบบที่ทำให้เราเป็นสินค้าแทนที่จะเป็นลูกค้ากันก่อนครับอินเตอร์เนทเริ่มต้นด้วยอุดมการณ์ที่ดี ที่จะให้ข้อมูลข่าวสารมันฉับไว ซึ่งมันก็เป็นเช่นนั้นจริงๆ แต่โลกมันมีสิ่งนึงที่เกิดขึ้นอยู่เสมอ นั้นคือ การชิงทรัพยากร ดินแดน เวลา และการควบคุมคนให้อยู่ในอาณัติ
อินเตอร์เนทเริ่มถูกยึดดินแดนมาตั้งแต่การเริ่มมีการสื่อสาร 2 ทางที่โต้ตอบกันได้เร็วขึ้น เจ้า www (World Wide Web) มันกลายเป็นดินแดนของไม่กี่บริษัท ที่เป็นผู้ยิ่งใหญ่ในโลก ดอทคอม สร้างกิจกรรมบางอย่างแล้วให้คนทั้งโลกเข้ามาใช้งาน
จะเห็นว่าทุกวันนี้เราแทบไม่พ้นการเข้าไปดู เฟสบุค ยูทูป ทวิตเตอร์ ไอจี ชอปปี้ ลาซาด้า และอื่นๆที่เหมือนจะมากมายแต่ไม่ได้มากมายเมื่อเทียบประชากรโลก
บางคนบอกว่ามันก็ดีไม่ใช่เหรอ เราได้ใช้ฟรีๆ ตรงนี้ละครับ เราจะเข้าเรื่องกันแล้ว
คำที่เราหลงไปกับมันคือ เขาทำมาให้เราใช้ฟรีๆ เขาต้องเห็นเราเป็นลูกค้าสิ แต่ความจริงนั้น เราคือสินค้าครับ เขาฟาร์มเราไว้เป็นสินค้า เป็นหมูในแฮปปี้ฟาร์ม ยิ่งประชากรในฟาร์มมีมาก เขาก็จะมีมูลค่าสูงมาก ดังเช่นที่เราเห็นว่า
มีการบ่นมากมายเรื่องการกดการมองเห็น การที่มีแต่โพสพนัน หลอกขายของที่เป็นสปอนเซอร์ การที่เราลงรูปไก่ต้มแล้วโดนแบนเพราะเขามองว่าทรมานสัตว์ และอื่นๆอีกมากมายที่ทำให้รู้สึกว่า ทำไมเขาดูแลผู้ใช้งานไม่ดีเลย เราเป็นลูกค้าเขานะ
ถ้ามองในอีกมุมนึง จริงๆเขาดูแลลูกค้าดีแล้วครับ ลูกค้าของเขาคือคนซื้อโฆษณาต่างหาก ใครที่จ่ายมาก ก็เอาสินค้าเค้ามายัดเยียดให้ประชากรในฟาร์ม ได้ดูกันตาแตก หมูในฟาร์มคนไหนออกนอกลู่นอกทางก็จะเชือดทิ้ง นี่ละครับที่บอกว่าเราคือสินค้าต่างหาก
กลุ่มคนที่ต้องการอิสระเสรี จึงสร้างสิ่งใหม่ขึ้นมา ไม่ใช่แค่ทำแอพ ไม่ใช่ทำแค่เว็บ เพราะมันยังต้องพึ่งพาเอกชนในการเอาข้อมูลไปฝากไว้ในเครือข่าย แต่สิ่งใหม่นี้มันเป็นระบบการส่งข้อมูลแบบใหม่ครับ
ให้เห็นภาพยิ่งขึ้น เราบอกไปแล้วว่าดินแดนอินเตอร์เนท มันอยู่ในกำมือคนที่เป็น land lord ไม่กี่คน และทุกอย่างเราต้องอยู่ใต้อาณัติเขา ตั้งแต่การได้เห็นแค่ข้อมูลเขาก็เลือกให้ จนถึงว่าถ้าเขาสงสัยว่าเราไม่ใช่เราตัวจริง เขาสามารถลบเราไปโดยไม่ต้องถามอะไร ชีวิต7ปี 10ปี ที่ผ่านมาในแอพมันสามารถเหลือ 0โพสได้ในพริบตาและไม่ให้อุธรณ์ใดๆ
นั่นเพราะข้อมูลทุกอย่างมันไปอยู่ในเครื่องคอมของแต่ละบริษัท ทั้งยูทูป เฟสบุค ไอจี ของๆเรา เราเอาไปอัพไว้ในคอมเขา ต้องทำตามกฎที่เขาตั้งและเปลี่ยนใจได้ทุกเมื่อ และแอบมองของๆเราได้ทุกรูปทุกข้อความลับ
ทุกอย่าง ย้ำว่าทุกอย่าง ต้องผ่านคอมของเขาทั้งหมด เราไม่มีอะไรเป็นของเราเลย ในฟาร์มนี้ เราแค่รอโดนเชือดและเราไม่กล้าออกมาเพราะคิดว่าเป็น safe zone
ส่วนระบบการส่งข้อมูลแบบใหม่ เราเรียกว่า nostr อ่านว่า นอสเตอร์ ชื่อเต็มมันยาว แต่ถ้ารู้ จะเข้าใจง่ายขึ้น เพราะมันมาจากคำว่า Notes and Other Stuff Transmitted by Relays แปลว่า ”อะไรก็ตามที่เอามาส่งผ่านรีเลย์“
ผมขอเรียกมันว่าส่งไม้ต่อละกันครับ มองภาพการวิ่ง 4x100 มันมีการส่งไม้ผลัดใช่ไหมครับ นั่นละ รีเลย์

ระบบเก่าเราเรียกว่า การรวมศูนย์ นั่นคือเอะอะก็ต้องไปเก็บหรือไปดู จากคอมบริษัทนั้นๆ เช่น ดูคลิปก็ต้องไปโหลดจากคอมของยูทูป จะดูฟีดเพื่อนก็ต้องไปโหลดข้อความที่เพื่อนฝากไว้ในคอมของเฟสบุค
ถ้าวันนึง เฟสบุคล่ม นั่นคือทุกคนติดต่อหรือดูอะไรไม่ได้เลย และถ้ากู่ไม่กลับ นั้นคือทุกอย่างหายหมด นอกจากนี้ผู้คุมศูนย์คือสั่งชี้เป็นชี้ตายคุณได้ทันที ที่ไม่พอใจคุณ บ้านเขากฎเขา นั้นเอง

ในขณะที่ nostr เป็นระบบส่งไม้ผลัด นั่นคือ ใครๆก็สามารถเป็น รีเลย์ได้ แค่มีคอมก็เรียบร้อย วิธีการเป็นรีเลย์ เรายังไม่ต้องสนใจครับ เราเป็นแค่ผู้ใช้ ไม่ต้องเป็นผู้ให้บริการก็ได้ ฟรีด้วย วันนี้เราแค่มาเข้าใจเส้นทางก่อนครับ
อย่างที่บอกครับ ระบบการส่งข้อมูลเราเป็นรีเลย์ หรือ ไม้ผลัด หลักการก็แค่เราก็แค่ใส่ที่อยู่รีเลย์ ลงไปในแอพของเรา แล้วข้อมูลที่เราส่งไป เจ้ารีเลย์มันก็จะวิ่งส่งไม้ผลัดนี้ไปให้สมาชิกทุกคนในรีเลย์
ในทางกลับกัน เราก็จะได้รับข้อมูลที่สมาชิกในสังกัดรีเลย์ที่เราลงไว้ ส่งมาให้ผ่านทางรีเลย์ด้วยเช่นกัน
และที่เจ๋งก็คือ รีเลย์ ไม่สนใจอะไรอย่างอื่นอีก นอกเหนือแค่ส่งไม้ผลัดให้สมาชิกทุกคน นั่นคือ มันไม่คิดว่าอะไรควรส่งไม่ควรส่ง มันไม่คิดว่าข้อมูลดีแค่ไหน มันไม่ปิดกั้น มันไม่เซนเซอร์ นั่นคือ มีหน้าที่แค่ส่งจริงๆ นอกจากนี้ถ้าเราเป็นใส่รีเลย์มากกว่า 1 แห่งในตัวเรา ข้อมูลทั้งหมดก็จะสำเนาไปยังรีเลย์ที่เหลือได้เช่นกัน หมายถึงว่า ข้อมูลเราจะกระจายแบบสำเนาไปได้อีกหลายๆๆๆๆรีเลย์
นอกจากอิสระแล้วยังฆ่าไม่ตายด้วย เพราะรีเลย์มีขึ้นเป็นดอกเห็ด และใครๆทำรีเลย์มาเปิดให้บริการได้เอง (เราเป็นแค่ผู้ใช้ ไม่ได้อยากเป็นผู้ให้บริการ เราไม่ต้องสร้างรีเลย์ก็สามารถใช้งาน nostr ได้ครับ)
ดังนั้น nostr จึงเหมาะกับคนที่ต้องการเสรีภาพแบบเต็มๆ เพราะไม่มีใครเซนเซอร์คุณได้เลย คุณเท่านั้นที่จะต้องรับผิดชอบการกระทำของคุณเอง
เพราะด้วยที่มันฆ่าไม่ตาย นั่นหมายถึง สิ่งที่คุณพิมพ์หรือโพสลงไป จะไม่สามารถลบหรือแก้ไขได้เช่นกัน แม้แต่ตัวคุณเองก็ตาม
ดังนั้นไต่ตรองให้ดีถ้าจะสร้างเนื้อหา เพราะมันจะบันทึกสิ่งที่คุณทำไว้ตลอดไป แต่ถ้าเรายังไม่มั่นใจเราลองเล่นแบบเป็นคนอ่านก่อนก็ได้ครับ พอเราใช้คล่องขึ้น มีสติสัมปชัญญะเพียงพอ ก็เริ่มทักทายคนในนั้นได้ มันไม่น่ากลัวหรอกครับ เพราะหัวใจหล้กของ nostr คือการเข้าสังคม สร้างสังคมคุณภาพ มากกว่าการโพสเท่ๆเอาไลค์ เพราะ มันไม่มีอัลกอลิทึ่มใดๆ เขายึดมั่นใน proof of work
ไลฟ์ของเราจะไม่โดนปิดกั้น โพสของเราจะไม่โดนลดการมองเห็น ถ้ามันมีคุณภาพเพียงพอที่คนจะเลือกติดตามชม
ถ้ามองเห็นกลลวงของโซเชียลแล้ว ตอนหน้า จะรวบรัด ลงหลุมกระต่ายกันเลย เอาแบบโหลดแล้วเล่นก่อน แล้วเรียนไปพร้อมๆกับเล่นนี่แหละ
ถ้าทุกคนเริ่มวันนี้ อิสระก็จะเริ่มยิ่งใหญ่วันนี้ แล้วก็จะไม่มีคำว่า คนมันยังน้อยอยู่
เคยดูหนังไหมครับ เช่นตอนเปิดแผ่นดินใหม่ ใครขี่ม้าไปปักธงจองอาณาเขตได้ก่อน ก็จะคุ้นชินพื้นที่นั้นๆได้ก่อนใครครับ
pirateketo
กูต้องรู้มั๊ย
Siamstr
-
 @ e7bc35f8:3ed2a7cf
2025-02-16 19:19:41
@ e7bc35f8:3ed2a7cf
2025-02-16 19:19:41In the grand chessboard of geopolitics, Iran has long been a target for covert Western intervention. The 2009 Iranian presidential election provided yet another example of a well-worn playbook—one designed to undermine sovereign nations under the guise of democracy. But this was far from a spontaneous people's movement. Instead, it bore all the hallmarks of a carefully orchestrated operation, leveraging the power of mass media, intelligence agencies, and globalist financial interests.
2009: A Manufactured Uprising
In June 2009, before Iran's election results were even finalized, opposition leader Mir-Houssein Mousavi prematurely declared victory. This calculated move set the stage for immediate allegations of fraud, ensuring that any outcome favoring incumbent President Mahmoud Ahmadinejad would be delegitimized. The Western media wasted no time in amplifying the chaos, competing to push the most dramatic narratives. The BBC took the lead, publishing outright fabrications about mass uprisings—falsehoods they were later forced to retract.
Then came the Twitter storm. On June 13, a sudden flood of 30,000 tweets, many in English, began pouring in from Iran. The accounts responsible? Newly created profiles, often using identical photos, a hallmark of an information warfare campaign. The Jerusalem Post quickly picked up on the phenomenon, covering it within hours. This was no organic grassroots movement; it was a digital psy-op, mirroring past regime-change operations.
The Blueprint: Iran 1953—The CIA’s Original Coup
This wasn’t Iran’s first encounter with a foreign-backed destabilization campaign. In 1953, Iran’s democratically elected Prime Minister Mohammed Mossadegh made the fatal mistake of challenging Western oil interests. He sought to nationalize Iran’s petroleum industry, then controlled by the Anglo-Iranian Oil Company (later BP). The response was swift and brutal: the CIA launched Operation Ajax, an insidious regime-change operation that became the prototype for future coups.
The CIA’s strategy was as ruthless as it was effective: * Staged bombings blamed on Mossadegh’s government * Islamist agitation funded and nurtured to turn public sentiment * Propaganda campaigns demonizing Mossadegh as a secular threat * Bribery of officials and military leaders to ensure betrayal
The result? The overthrow of Mossadegh and the installation of the pro-Western Shah, whose reign saw brutal repression under the secret police SAVAK—trained by the CIA and Mossad. The template was established. From Guatemala (1954) to Afghanistan (1980s) to Serbia (1990s), the same playbook was deployed. But with each coup, Western fingerprints became harder to conceal.
A New Strategy: Economic Warfare and the NGO Takeover
With direct coups becoming too risky, a subtler method emerged: economic strangulation. Enter the International Monetary Fund (IMF). The play was simple: 1. A corrupt dictator takes out massive loans for projects the country cannot afford. 2. The country inevitably defaults, giving the IMF the power to restructure its economy. 3. Western corporations move in, plundering national resources under the guise of “recovery.”
This scheme was exposed in 2001 when former World Bank chief economist Joseph Stiglitz blew the whistle on these manufactured debt traps. Further details emerged in 2004 with John Perkins' “Confessions of an Economic Hitman”, which revealed how Western front companies and intelligence-backed corporations systematically dismantled economies for geopolitical gain.
But even this strategy had its limits. As exposure grew, the need for an even more sophisticated approach became apparent—one cloaked in the language of democracy and human rights.
Color Revolutions: The Soros Connection
Enter the age of the NGO-driven color revolutions, where regime change is disguised as a people’s uprising. Organizations like the Open Society Institute (George Soros), Freedom House, and the National Endowment for Democracy (NED) became the new weapons of choice. These NGOs: * Fund and train opposition groups * Coordinate mass protests during elections * Provide media support to delegitimize governments
The results? A series of destabilizations across the world: Ukraine (2004 - Orange Revolution) Lebanon (2005 - Cedar Revolution) Georgia (2003 - Rose Revolution) Kyrgyzstan (2005 - Tulip Revolution)
Each followed the same pattern—Western-backed NGOs funneled money and resources into opposition movements, ensuring their success. Unsurprisingly, these uprisings all bore the fingerprints of Soros, the billionaire financier with a long history of manipulating global politics to serve elite financial interests.
However, this strategy has started to backfire. Georgia witnessed a major anti-Soros backlash, and attempts to replicate these revolutions elsewhere—such as the failed Moldovan "Grape Revolution"—have faltered as people wake up to the deception.
Iran 2009: An Operation in Plain Sight
While no one denies that Ahmadinejad’s regime had its flaws, the coordinated media hysteria and backing of Mir-Houssein "Butcher of Beirut" Mousavi raises serious questions. Why was the Western establishment so eager to install a leader with a brutal history? The answer lies in the same playbook used time and again: 1. Foment unrest through digital manipulation and street protests. 2. Control the narrative via Western media outlets. 3. Install a leader more compliant with Western economic and geopolitical interests.
Iran 2009 was not an isolated event. It was part of a much larger pattern—a centuries-old strategy of covert intervention, economic sabotage, and media manipulation to secure Western control over sovereign nations.
As history has shown, the real fight isn’t between the people and their governments—it’s between sovereign nations and the global power structures that seek to enslave them. And until people recognize the hidden hands behind these so-called revolutions, the cycle of deception will continue.
-
 @ 5196eb85:5c9ff0f8
2024-07-10 23:35:24
@ 5196eb85:5c9ff0f8
2024-07-10 23:35:24There have been alot of talks about testnet3, after it been running for almost 11 years bitcoin core can not reset it. It become too decentralize.
Some people forked testnet3 and made testnet4 with higher blocks space, due testnet3 having value and can not be resets !
https://pbs.twimg.com/media/GP7gEf8aYAAnTQj?format=jpg&name=large
Now we have 11 years old chain we dont know what to do with it, and nobody can stop it !
Mining Costs Over $130 per tBTC3 (testnet3) has being going up and volume on DEX started to go up
https://altquick.com/exchange/market/BitcoinTestnet
originally posted at https://stacker.news/items/604075
-
 @ 9a4acdeb:1489913b
2025-02-16 18:26:58
@ 9a4acdeb:1489913b
2025-02-16 18:26:58Chef's notes
Original recipe, a favorite of family and friends, and the easiest and fastest prep time meal I make. Like all really good pork recipes, it does take time in the cooker, but it's set-and-forget and requires no attention between starting and serving.
Using fresh herbs and peppers does enhance the meal (especially fresh cilantro if it doesn't taste like soap to you), but this is optional, and it is excellent with dry ingredients.
Excluding the beans and/or tomato makes this meal extra-low carb for those carnivores amongst us, or those sensitive to beans. Frying the shredded cheese in a slick pan is a good way to
It will take up to 15min to come up to pressure, so it may be helpful to pay attention to it to be sure it pressurizes until you become familiar with how this meal acts in your particular pressure cooker. The Instant Pot pressure cookers make this easy.
Details
- ⏲️ Prep time: 20min
- 🍳 Cook time: 2hrs
- 🍽️ Servings: 6
Ingredients
- 4lbs Pork loin
- 1-2 Yellow onion, roughly chopped
- 3-5 Jalapeños or 1x 4oz canned
- 6-8 Green chilis or 1x 4oz canned
- 2oz canned sliced Black olives (may use half a 4oz can)
- 2-3tsp minced garlic, or 1-2 tsp garlic powder
- A small bunch of cilantro, chopped, or 1-2 tsb dried cilantro (optional)
- 1tbsp Oregano, chopped fresh or dried
- 2-3tsb Chili powder; Ancho, Chipotle, or a blend of the two is best
- 2-3tsb ground Cumin
- 3-4tsp salt
- 2-tsp black pepper
- 1 large or 4oz canned tomato (optional)
- Mexican mix shredded cheese (topping)
- 4oz Black beans (optional)
- Tortillas (optional)
- Avocado (optional toping)
- 6 Limes and/or 3oz lime juice
Directions
- Mix dry seasonings
- Chop and mix fresh herbs and veggies, canned or otherwise
- Add chopped onion to bottom of pressure cooker
- Add pork loin atop the onion; chopping into steaks may make the texture better
- Add veggies to the top, shaking to settle into the pressure cooker
- Add lime juice
- Start on high pressure for 2hrs.
- (Optional) Drain the broth into a saucepan, cook down, and add back into the mix to make it extra flavorful. Otherwise, can be served as a soup or poured over rice.
- Serve with cheese as a topping, over rice, in a tortilla as tacos or burritos, or in a number of other fashions you may fancy. Those who prefer a little more lime may squeeze fresh or splash some more on their meal.
- (Optional) For presentation, garnish with cilantro and lime slices, maybe a dollop of shredded cheese, sour cream, or cream cheese.
-
 @ 5d4b6c8d:8a1c1ee3
2024-07-10 13:09:22
@ 5d4b6c8d:8a1c1ee3
2024-07-10 13:09:22Yesterday's edition https://stacker.news/items/602257/r/Undisciplined
We had been doing a good job keeping @k00b off the leaderboards, but for the second day in a row he's taking all of the Top Stacker spots. For posterity's sake, don't let him win a fourth July 10th in a row.
-
- -
July 10, 2023 📅
📝
TOP POSTWhat’s the Hardest lesson you’ve learned from Bitcoin?
Excerpt
For me, staying humble while stacking sats.
We don’t have it all figured out. 2107 sats \ 22 comments \ @birdeye21 \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/206793/r/Undisciplined?commentId=206809
25.3k sats \ 0 replies \ @Darth
From Meme Monday - Best Bitcoin Meme Gets 25,000 Sats by @sn in ~bitcoin
🏆
TOP STACKER2nd place @k00b (1st hiding, presumed @siggy47)
8282 stacked \ 8933 spent \ 2 posts \ 11 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
38.7k stacked \ 0 revenue \ 48.6k spent \ 102 posts \ 286 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 10, 2022 📅
📝
TOP POST🔥 Presenting LNCal.com ⚡️ - Earn Bitcoin with your public calendar! (LNURL enabled)
Link to https://lncal.com/
2221 sats \ 36 comments \ @e \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/43271/r/Undisciplined?commentId=43283
Excerpt
- Begin learning the protocols quite well. I recommend Chaincode ... If you don't like classes/accountability/mentorship, you can self-teach using their materials: https://chaincode.gitbook.io/seminars/.
939 sats \ 6 replies \ @k00b
From Ask SN: how to contribute to Bitcoin core, or layers 2 and beyond? by @a in ~bitcoin
🏆
TOP STACKER1st place @k00b
18.3k stacked \ 6570 spent \ 1 post \ 29 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
10.4k stacked \ 0 revenue \ 13.6k spent \ 59 posts \ 181 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 10, 2021 📅
📝
TOP POST[For the lols] Why you should be terrified of owning Bitcoin
Link to https://fortune.com/2021/07/10/bitcoin-why-you-should-be-terrified-of-owning-btc/
4 sats \ 6 comments \ @shawnyeager \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/247/r/Undisciplined?commentId=263
Excerpt
Kind of regretting settling in Austin 😂. South America will soon be the place to be.
21 sats \ 2 replies \ @k00b
From Paraguay set to introduce Bitcoin bill on July 14th by @gmd in ~bitcoin
🏆
TOP STACKER1st place @k00b
10 stacked \ 26 spent \ 3 posts \ 7 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
32 stacked \ 0 revenue \ 55 spent \ 4 posts \ 13 comments
originally posted at https://stacker.news/items/603455
-
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ ee2f41fa:23552fbb
2024-07-10 12:38:57
@ ee2f41fa:23552fbb
2024-07-10 12:38:57Chef's notes
Perfect for the summer days
Details
- ⏲️ Prep time: 5-10min
- 🍳 Cook time: no cooking time
- 🍽️ Servings: 4
Ingredients
- 2 cucumbers (about 500 g or 1 lb)
- 500 g plain yogurt (1 lb)
- 2 -3 tablespoons of crushed walnuts (optional)
- 1 bunch fresh dill
- oil
- salt
- water (optional)
Directions
- Beat the yogurt with a fork until it gets liquid and pour it over the cucumbers.
- Add the crushed garlic, the walnuts and the minced dill as well as salt and oil to taste.
- If needed add some water to make the soup as liquid as you like but take care not to make it too "thin".
- Put into the refrigerator to cool or add ice cubes.
- Serve cold
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ b2caa9b3:9eab0fb5
2024-07-10 08:12:37
@ b2caa9b3:9eab0fb5
2024-07-10 08:12:37Woke up at the crack of dawn today in my dorm, just past 5 am, to a flurry of activity. The two guests who checked in yesterday were already checking out, including the Chinese woman who'd been here for almost two weeks. With the room suddenly quiet, I grabbed my phone to check my account – hoping to see the tokens I'd transferred the previous day. But to my surprise, they were nowhere to be found.

This unexpected early check-out (most hostels allow check-in after 2 pm) left me with a private room for a brief moment, a small perk amidst the confusion. But back to the real issue – my missing Blurt tokens.
Yesterday, I wrote a Hive Engine tutorial on transferring Blurt to your Blurt account. However, when I tried it myself, my 705 Blurt vanished into thin air. Completely baffled, I spent my morning researching after breakfast. While I knew transfers take time, I didn't expect it to take all night, let alone be missing by 10 am.
As a result, the Hive Engine tutorial will have to wait. I need to get to the bottom of this missing transfer before finalizing it. With no set plans for today and a foot still causing trouble, my biggest hope is for a speedy recovery on both fronts – my foot and the missing Blurt!
After hitting publish on this post, I'll be diving back in to figure out how to spend this unplanned day. Here's to hoping for a swift resolution and a chance to explore soon (on a pain-free foot, of course)!
(Image: Screenshot of Hive Engine transfer)
-
 @ 124b23f2:02455947
2024-07-10 05:24:33
@ 124b23f2:02455947
2024-07-10 05:24:33I'm reposting this in order to fix the images and get it correctly onto my npub.pro site
What is this ?
My Futurebit Apollo Miner in action
Futurebit is a company that manufactures home miners for retail users (see futurebit.io) - you can check out details on their website. These are targeted at individuals that want to participate in mining with an easy to use, quiet miner that does not use a ton of electricity.
The idea here is to try and stay true to the original bitcoin concept of a computer which runs the bitcoin software and mines bitcoin, all in one. While mining has obviously evolved into a commercial industry and the mining process has long been separated from running a bitcoin node, I think there are still some valid reasons to want to participate in the mining process and attempt to keep this original ethos alive:
- You learn a lot about bitcoin from mining. Reading about the process is one thing, but actually getting a machine running, pointing it towards the pool of your choice, and seeing the bitcoin process from this perspective is something I've found very enjoyable (mining is probably my favorite part of bitcoin, if I had to choose one). It can also be a gateway drug to more advanced mining, so...heavy care.
- It is marginally valuable to the network. Sure, one person running a futurebit miner is nothing compared to the hashrate of MARA. But, if you have tens of thousands of plebs all running their own miners from home, pointing their hashpower to the pool of their choice, it does provide a legitimate decentralizing anchor to large mining actors. Every pleb should be participating in mining, in my opinion, and the Futurebit Apollo miner offers a casual and unobtrusive avenue to do just that.
Now, the Futurebit Apollo Miner you most commonly see is the 'Full Package.' The Full Package is an Orange Pi computer running on a custom linux distribution. You basically boot it up, and it starts running bitcoin core and mining in a few clicks. That is very cool, and I did own one. However, I will say that the Full Package is, unfortunately, not a great product. I won't go into too much detail, but its a very poor quality computer, the security upkeep of the custom linux distribution is lacking, and I found connecting to the node to use with wallets to be very difficult. The mining was also consistently inturrupted due to the pi freezing up. You are better off going with a different option for running a bitcoin node.
This is simply to say, I dislike the Full Package Futurebit Apollo Unit. With that said, I very much like the 'Standard Unit'. The Standard Unit is simply a mining hashboard without the computer OS that comes with the Full Package. I've been running two Standard Units in my house for 18 months now and they just quietly hum along in my house, I barely notice them and they rarely need to be restarted (honestly I can't think of more than 3 times that I needed to troubleshoot and even then it was typically restarting the miner). They are a great way to make your personal contribution to the security of the bitcoin network.
(Please Note: These things are pretty pricey brand new, so don't even think about buying one as being a profitable choice. You can sometimes find decent deals for them used, but buyer beware I can't speak to that experience. This is about hands-on learning about bitcoin mining and participating in the security of the network with a machine that won't drive your family crazy and that I believe is well-built enough to last you a long time. Heck, you could even set one up at your office and I doubt anyone would notice and mine with free electricity.)
So, that's some background. Now, a standard unit is not the most friendly user experience if you are not used to using command line. I wasn't, but I spent a lot of time figuring it out. With this guide, any user should be able to get a Standard Unit hashing :) Here is the step by step process guide on how to run a standard unit, in use with both a Windows OS computer and a Linux OS computer (Ubuntu is what I use)...enjoy.
I. Linux
Your Futurebit Apollo Standard Unit (referred to from here as 'the Unit') miner comes with a power supply and a usb cable. It's pretty straight forward, but you will want to connect the Unit to the computer of your choice (the computer needs to be on and running while you are mining, so a low power consumption computer and/or a computer that you are already running all the time for some other reason would be best). Also, plug in the power supply to your unit and turn it on (there are instructions in the Unit's manual for how to hook up the power supply correctly).
- Go to https://github.com/jstefanop/Apollo-Miner-Binaries
- You'll land on a page that looks like this:
For the purposes of this guide, I am going to be using the 'linux-x86_64' package as it is most appropriate for my computer. But, you would need to select the appropriate binaries for your computer. Odds are, if you are running ubuntu on your laptop or desktop, you are going to use the 'linux-x86_64' package.
- Once you have clicked on the linux-x86_64 folder, you will land here:
Open each of these 4 files and download them using the 'Download Raw File' link in each file's page. Here is an example:
Once you have downloaded, I'd recommend making a folder and putting all 4 of the files into that folder. I am going to make a folder with the name 'Mining Files'. I am also going to move the folder out of my Downloads folder (not necessary, but I'd recommend as it's not a great place to park a folder you want to hold onto). I am going to move it to my Documents Folder:
-
Now, if you do not have a mining pool account, you will need to make one, otherwise you should be able to use your pool credentials in the next step. Alternatively, you can solo mine using solo.ckpool.org with only a btc address. However, for the purposes of this guide I am going to assume that you are using Braiins pool. If necessary, go ahead and make a login at braiins.com/pool. Note the username and password as we will need that later.
-
From the files that you downloaded in step 3, we are going to double-click on 'start_apollo.sh' and open it up in Text Editor. The first 60 lines or so are explanations on how to prepare this script for your use. However, I am going to run you through all the options to update, so you shouldn't need to read the description. Instead, we are going to focus on the text in black font at the bottom of the file:
We need to update the info in the following fields as follows
-host = stratum.braiins.com -port = 3333 -user = username for your Braiins login. I'll use "braiinsexample" for now. -pswd = password for your Braiins login. I'll use "Password123" for now. -comport = Most likely "/dev/ttyACM0" or "/dev/ttyACM1" or "/dev/ttyACM2" -brd_ocp = 48 -osc = 30 -ao_mode = 1
So, when our file is set up correctly, it will look like:
Make sure to save, then close out of text editor.
- Now, start up terminal on your computer. First, we are going to want to get into the correct directory. In our case, our file is in Documents > Mining Files. So, you would input the following command:
cd ~/Documents/Mining Files
Once you are in the correct directory, we will run the following command:
sudo ./start_apollo.sh
You will likely be prompted to enter your computer's password, input the password and, if all goes well, you should see a result like this in your terminal:
You are now mining! The setting we use run the Unit ins 'eco mode', which should yield 2 terahash per second in terms of mining power (you can monitor the performance from your respective mining pool dashboard). As long as you keep this terminal window open and the computer on that is connected to the miner, and you will be mining away :)
II. Windows
Your Futurebit Apollo Standard Unit (referred to from here as 'the Unit') miner comes with a power supply and a usb cable. It's pretty straight forward, but you will want to connect the Unit to the computer of your choice (the computer needs to be on and running while you are mining, so a low power consumption computer and/or a computer that you are already running all the time for some other reason would be best). Also, plug in the power supply to your unit and turn it on (there are instructions in the Unit's manual for how to hook up the power supply correctly).
- Go to https://github.com/jstefanop/Apollo-Miner-Binaries
- You'll land on a page that looks like this:
For Windows, you will click on the folder titled 'msvc19'. You'll see 2 files to download, go ahead and click on each and click 'Download Raw File' for each.
Please Note: Windows may see this file as a virus, so you may need to 'allow on device' in your virus & threat protection of your windows security service.
- Once you have downloaded each file, I'd recommend making a folder and putting all of the files into that folder. I am going to make a folder with the name 'Mining Files'. I am also going to move the folder out of my Downloads folder (not necessary, but I'd recommend as it's not a great place to park a folder you want to hold onto). I am going to move it to my Documents Folder:
-
Now, if you do not have a mining pool account, you will need to make one, otherwise you should be able to use your pool credentials in the next step. Alternatively, you can solo mine using solo.ckpool.org with only a btc address. However, for the purposes of this guide I am going to assume that you are using Braiins pool. If necessary, go ahead and make a login with at braiins.com/pool. Note the username and password as we will need that later.
-
From the files that you downloaded in step 3, we are going to right click on 'start_apollo' and select 'edit'. The file will open up in notepad. The first 60 lines or so are explanations on how to prepare this script for your use. However, I am going to run you through all the options to update, so you shouldn't need to read the description. Instead, we are going to focus on the text in black font at the bottom of the file:
We need to update the info in the following fields as follows
-host = stratum.braiins.com -port = 3333 -user = username for your Braiins login. I'll use "braiinsexample" for now. -pswd = password for your Braiins login. I'll use "Password123" for now. -comport = go to the 'Device Manager' service on your computer, expand the 'Ports' section, and you should find a 'USB serial device' with COM#. Update with your COM# (COM1, COM2, COM3, etc). -brd_ocp = 48 -osc = 30 -ao_mode = 1
So, when our file is set up correctly, it will look like:
- Now that the file is ready, save the file and exit out of notepad. You should be able to simply double-click on the file. The command prompt services will pop-up on your desktop, and should reflect this, indicating your connection is successful and mining has begun:
You are now mining! The setting we use run the Unit ins 'eco mode', which should yield 2 terahash per second in terms of mining power (you can monitor the performance from your respective mining pool dashboard). As long as you keep this terminal window open and the computer on that is connected to the miner, and you will be mining away :)
originally posted at https://stacker.news/items/603076
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 124b23f2:02455947
2024-07-10 04:54:00
@ 124b23f2:02455947
2024-07-10 04:54:00I'm reposting this article I wrote some time ago again to fix the images for it on my npub.pro site
In my previous post, I explained how to use your getalby ln address to receive zaps directly to your LND node. Similarly, there is an additional option that one can utilize to receive zaps directly to your lightning node: lnaddress.com.
Lnaddress.com is a federated lightning address server that you can use to create a custom ln address. Unlike using getalby, lnaddress.com can be used with any lightning implementation (not just LND). For the purposes of this write-up, I am going to use LNBits to connect an lnaddress.com lightning address with my node. And as will be the case with most of my write-ups, I am going to be using Start9 OS, so users of that OS will likely find this write-up most useful, but I'm sure people using other node interfaces can infer how to complete this set up as well.
With that said, let's dive into the step-by-step on how to create your own custom ln address with lnaddress.com and set it up to receive zaps directly to your lightning node:
*Users should have lnbits set up with their lightning node before proceeding.
- Go to lnaddress.com. Input your desired username, select 'Node Backend Type' = LNBits, and if necessary check the box 'This is a new lightning address'. Keep this page open in one tab as we will be returning to it to input info.
- From your Start9 OS services page, go to your LNBits service. Open the 'Properties' page, and in a new tab, open the (Tor) Superuser Account. Page will look like this:
From this LNbits page, you can choose to 'add a new wallet' and use that wallet instead of your superuser account. That is up to you but the steps will be the same.
- Now, we need to grab the info needed for the 'Host Protocol + IP or Domain + Port' field on the lnaddress.com page. On the lnbits page, expand the 'Api Docs' field, and the 'Get Wallet Details' field found on the right hand side menu. In this 'Get Wallet Details' section, you will want to copy some of the URL found in the 'curl example' section. Copy 'http://xxxxxx.onion' (don't copy any more!), and paste this into the 'Host (Protocol + IP or Domain + Port' field found on the lnaddress.com page.
-
Next, we need to grab the key for your lnbits wallet. From the lnbits page, expand the API docs section found on the right hand side menu. Copy the 'Invoice/read key' (make sure to use the invoice/read key and not your Admin key), and paste it into the key field found on the lnaddress.com page. Upon pasting in that last piece of info, click 'submit' at the bottom of the page.
-
If all info was input correctly, your connection will be successful. If successful, you will be brought to a page that looks like this:
You will want to save this secret PIN in case you need to update info in your ln address. You'll also find a test lightning invoice of 1 sat. Using a wallet not connected to the node we connected to our new ln address, you can test the ln address out by paying the 1 sat test invoice.
Users of Start9 OS might find the following info particularly useful: This ln address via lnaddress.com comes with a couple advantages aside from self-custodial zap receiving:
- One, you can have a custom ln address username to go with your nym or nostr username. Users of Start9 may be familiar with the ln address one can generate in the btcpay server service. This ln address is not customizable.
- Two, if you are running a tor only lightning node, you will be able to receive zaps from both tor and clear net lightning nodes. Users of Start9 may be familiar with the ln address one can generate in the btcpay server service. This ln address can only receive zaps from other tor nodes and can't receive zaps from clear net nodes.
That is it, you should now be all set up with your new ln address hosted on lnaddress.com, and you should be all ready to receive zaps or lightning payments of any kind :)
originally posted at https://stacker.news/items/603061
-
 @ a619eb76:11d75935
2024-07-09 22:22:19
@ a619eb76:11d75935
2024-07-09 22:22:19what is the story with these new pools, anyone know?
originally posted at https://stacker.news/items/602865
-
 @ 5d4b6c8d:8a1c1ee3
2024-07-09 21:05:01
@ 5d4b6c8d:8a1c1ee3
2024-07-09 21:05:01How stupid is it for a government to sell bitcoin in return for a money it can already print at will? FFS 🤦
https://primal.net/e/note1z8aezletp3k570eqpxumc7t0y537nprujvgym2ssdfzxsglujmfskeg8ps
I wanted to make sure @TomK saw this.
originally posted at https://stacker.news/items/602808
-
 @ e968e50b:db2a803a
2024-07-09 20:34:06
@ e968e50b:db2a803a
2024-07-09 20:34:06QUESTION:
So I found this shareware game: game repo
I want to turn it into a lightning/nostr game, kind of like that lntictactoe game. I just like the idea of throwing some sats in on a guessing game like that, maybe even just loading them in up front for anybody that wants to play for some free sats. The license looks pretty, "do whatever you want",y to me, but maybe somebody that does this more often might have some more insight.
Copyright (c) 2012-2023 Luigi Pinca
Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the "Software"), to deal in the Software without restriction, including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
originally posted at https://stacker.news/items/602790
-
 @ c902b8da:0cedc5fb
2025-02-16 18:13:20
@ c902b8da:0cedc5fb
2025-02-16 18:13:20I'll break down the key legal requirements, costs, and timelines for establishing a health insurance company, focusing purely on the regulatory aspects:
State Licensing Requirements (Primary State): - Initial Capital and Surplus: $10-15 million minimum (varies by state) - Risk-Based Capital (RBC) requirements: Must maintain 200-300% of RBC - Processing Time: 12-18 months - Application Fee: $25,000-50,000 - Filing Requirements: - Articles of Incorporation - Statutory Financial Statements - Actuarial Certifications - Detailed Ownership Information - Background Checks for All Officers/Directors - Holding Company Act Filings if Applicable
Federal Requirements: - ACA Compliance: - Must offer all 10 Essential Health Benefits - Medical Loss Ratio requirements (80% individual/small group, 85% large group) - No annual or lifetime limits - Guaranteed issue and renewal - HIPAA Compliance: - Privacy Officer Appointment - Security Protocols Implementation - Timeline: 6-8 months - Cost: $200,000-500,000 for initial setup
Multi-State Expansion (Per Additional State): - Certificate of Authority Application: $5,000-25,000 per state - State-Specific Capital Requirements: $2-5 million additional per state - Processing Time: 6-12 months per state - Required State Deposits: $500,000-2 million per state - Guaranty Fund Membership: $25,000-100,000 per state
Mandatory Insurance Filings: - Rate Filings: - Timeline: 60-90 days for approval - Filing Fees: $500-5,000 per filing - Form Filings: - Timeline: 30-60 days for approval - Filing Fees: $50-500 per form - Annual Statement Filing: $500-2,500 per state
Required Positions and Certifications: - Licensed Actuary (MAAA certification) - Compliance Officer - Medical Director (licensed physician) - Claims Manager - Network Management Director - Timeline for hiring/certification: 3-6 months - Annual Costs: $1-2 million for required personnel
Reserve Requirements: - Claims Reserves: 3-6 months of expected claims - Premium Reserves: 1-3 months of premium - Special Deposits: Varies by state ($1-5 million) - Total Reserve Requirements: 25-40% of annual premium
Ongoing Regulatory Compliance: - Quarterly Financial Filings: Due within 45 days of quarter end - Annual Financial Statements: Due March 1 - Market Conduct Examinations: Every 3-5 years - Cost: $100,000-500,000 per examination - Financial Examinations: Every 3-5 years - Cost: $200,000-1 million per examination
Required Insurance Coverage: - E&O Insurance: $5-10 million coverage - Annual Cost: $100,000-250,000 - D&O Insurance: $10-25 million coverage - Annual Cost: $200,000-500,000 - Cyber Insurance: $5-10 million coverage - Annual Cost: $100,000-300,000
Total Regulatory Timeline: - Initial State License: 12-18 months - Federal Compliance: 6-8 months (concurrent) - First Policy Issuance: 18-24 months from start - Multi-State Operation: Additional 12-24 months
Total Initial Regulatory Costs: - Single State Operation: $15-25 million - Multi-State Operation (5 states): $30-50 million - Annual Compliance Costs: $2-5 million per state
These requirements and costs can vary significantly based on: - State of domicile - Number of states operating in - Types of health insurance products offered - Size of projected enrollment - Market conditions and risk factors
Yes, existing insurance companies can potentially influence your application process, but not directly through a "veto" power. Here's how it works:
- Public Comment Period
- Most state insurance departments have a public comment period during the application process
- Existing insurers can submit formal objections or concerns
-
They typically focus on market saturation, financial viability, or potential unfair competition
-
Market Need Assessment
- Many states require a "need and necessity" showing as part of the application
- You must demonstrate that:
- There's sufficient market demand
- Your company brings something unique or beneficial
- The market can support another carrier
-
However, mere competition itself is not grounds for denial
-
State Regulator Discretion
- Regulators consider market concentration and competition
- They generally favor healthy competition unless there are legitimate concerns about:
- Market destabilization
- Your company's financial strength
- Risk to consumers
-
Pure "we don't want competition" arguments from existing insurers typically don't succeed
-
Trade Association Influence
- Insurance trade associations may provide input during the licensing process
- They can raise concerns about:
- Capital adequacy
- Management experience
- Business plan viability
- But they cannot directly block your application
Key Point: While existing insurers can object, the final decision rests with state regulators who are primarily concerned with: - Consumer protection - Market stability - Your company's financial soundness - Management competency
-
 @ 000002de:c05780a7
2024-07-09 20:22:21
@ 000002de:c05780a7
2024-07-09 20:22:21Curious if the devs on SN have any insights, opinions, or recommendations regarding FP. I've been aware of it for many years, I get the basic concepts but I'm now working on a rewrite of an existing app and another dev and I are considering FP.
Its gonna be a Typescript based node application likely using ExpressJS.
My college is a huge advocate for FP and really likes fp-ts.
originally posted at https://stacker.news/items/602772
-
 @ 000002de:c05780a7
2024-07-09 17:25:53
@ 000002de:c05780a7
2024-07-09 17:25:53So, Google Chrome gives all *.google.com sites full access to system / tab CPU usage, GPU usage, and memory usage. It also gives access to detailed processor information, and provides a logging backchannel.
This API is not exposed to other sites - only to *.google.com.
This is interesting because it is a clear violation of the idea that browser vendors should not give preference to their websites over anyone elses.
The DMA codifies this idea into law: browser vendors, as gatekeepers of the internet, must give the same capabilities to everyone
Depending on how you interpret the DMA, this additional exposure of information only to Google properties may be considered a violation of the DMA.
Take for example Zoom - they are now at a disadvantage because they can not provide the same CPU debugging feature as Google Meet.
For those interested: this is done through a built-in Chrome extension that can not be disabled, and does not show up in the extensions panel. Source code is here: https://source.chromium.org/chromium/chromium/src/+/main:chrome/browser/resources/hangout_services/
It is unclear whether the same extension also ships in other Chromium derived browsers.
This is one of the many reasons I do not use Google Chrome.
originally posted at https://stacker.news/items/602609
-
 @ 1aa437b3:51119dbd
2024-07-09 14:00:34
@ 1aa437b3:51119dbd
2024-07-09 14:00:34I have seen there a some tools for blogging via nostr... In a Medium type way. I've also tried npub.pro the other day. I wonder if there is something that is truly a blog, belonging to me via nostr where it's not the firehose but just posts I choose that end up there. Maybe there is a tool or method I have not seen?
originally posted at https://stacker.news/items/602294
-
 @ 5d4b6c8d:8a1c1ee3
2024-07-09 13:18:17
@ 5d4b6c8d:8a1c1ee3
2024-07-09 13:18:17Yesterday's edition https://stacker.news/items/600906/r/Undisciplined
Is it possible for these posts and comments to become top posts and comments today, if people zap them?
I'm not sure if I understand exactly how that works. Is it based on when stuff gets zapped or is it based on when it's posted?
-
- -
July 9, 2023 📅
📝
TOP POSTBitcoin needs more Record, Comic and Book Shops
Excerpt
Bitcoin needs more cultural hubs, and I'm referring to the curator/gate keeper/provocateur of everything that is of and related to the Bitcoin ethos. Even things only tertiary or tangently related.
3948 sats \ 23 comments \ @SatoshisSkeleton \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/206408/r/Undisciplined?commentId=206466
Excerpt
Damn, heavy story in the comments about one of the founders of CloudFlare: https://www.wired.com/story/lee-holloway-devastating-decline-brilliant-young-coder/ […]
210 sats \ 1 reply \ @gmd
From Don't Take VC Funding – It Will Destroy Your Company by @hn in ~tech
🏆
TOP STACKER2nd place @k00b (1st hiding, presumed @siggy47)
8813 stacked \ 12.1k spent \ 0 posts \ 10 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
37.4k stacked \ 0 revenue \ 43k spent \ 63 posts \ 246 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 9, 2022 📅
📝
TOP POSTExcerpt
So far I’ve found four apps that support Log in with Lightning so far, but pretty sure there are more: - Stacker News - LNMarkets - Kollider - Zapread
437 sats \ 24 comments \ @kr \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/42958/r/Undisciplined?commentId=42991
Excerpt
Apparently we already have 1M 👀 I was here before that (?).

208 sats \ 0 replies \ @gms
From Daily discussion thread by @saloon in ~null
🏆
TOP STACKER1st place @k00b
519.4k stacked \ 5660 spent \ 6 posts \ 14 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
511.8k stacked \ 0 revenue \ 512.1k spent \ 79 posts \ 123 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 9, 2021 📅
📝
TOP POSTParaguay set to introduce Bitcoin bill on July 14th
7 sats \ 1 comment \ @gmd \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/229/r/Undisciplined?commentId=243
Excerpt
I'll be honest this sounds made up, but if it is, it is very good viral marketing.
1 sat \ 2 replies \ @gmd
From Casa client case study: the Tinder trap by @k00b in ~bitcoin
🏆
TOP STACKER1st place @k00b
2 stacked \ 41 spent \ 3 posts \ 4 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
21 stacked \ 0 revenue \ 59 spent \ 8 posts \ 7 comments
originally posted at https://stacker.news/items/602257
-
-
 @ 08eade50:687ccb04
2024-07-09 08:53:24
@ 08eade50:687ccb04
2024-07-09 08:53:24Introducing Npub.pro - your personal websites from your Nostr content! Made with creators in mind, available to all.
Creating a website, maintaining and securing it is a lot of work. Sometimes it feels like an additional job, when all you really want to do is create. Setting up the hosting is a pain, securing the website is a constant uncertainty, and updating across all of your publishing platforms and your website feels like a huge chore.
Enter Npub.pro - a powerful tool to attract and convert your fans with less work. Powered by your Nostr content and enhanced with beautiful open source themes from Ghost, Npub.pro websites just work!
Some of the perks of a Nostr-based website: - Style it your way. Pick a theme that fits your audience and your preferences. You’re not limited to showing your content on one particular client. - Shareable links. Links to your website look amazing when shared on social media and messenger apps. - Great for conversions. A place to attract your audience and measure outcomes using existing web tools. - Hassle-free. No complex hosting, maintenance or security issues. Your content lives on relays. Themes are on Nostr relays and Blossom servers. No matter what, your site still works. - No duplicate work. Already published on Nostr? Npub.pro displays your Nostr content and you choose which type of content to display! - Works like an app. Your website is a progressive web app that can be added to home screen and works offline. - Post from any Nostr client. No need to log in to a CMS to check for comments. Everything is on Nostr so it just works from any client. - SEO friendly. Your content has proper meta tags and your website is rendered on the server to make sure search engines love it. - Self-host if you like. Use our scalable hosting infrastructure or switch to any file hosting like Github Pages. - Interoperable. Your website is a Nostr event proposed in NIP-512, themes are proposed NIP-136. Our engine is open-source libnostrsite.
Heads up! While this has been a long time in the making, we’re still in the early beta stage. Some stuff may be rough, won’t work properly and features may be missing. Content management is still a work in progress, please be patient.
Give it a try and let us know what you think!
Link: https://npub.pro
Built by Nostr.Band team.
-
 @ 02e5b397:33461d51
2024-07-09 03:05:27
@ 02e5b397:33461d51
2024-07-09 03:05:27Today the #GOP #Republicans passed their draft platform in full support of #crypto #cryptocurrency #bitcoin summary below. I hate to get political but if you want #selfsovereignty you have to vote hashtag#Trump as hashtag#Biden has been a disaster for the industry.
originally posted at https://stacker.news/items/601791
-
 @ 726a1e26:861a1c11
2024-07-08 18:01:28
@ 726a1e26:861a1c11
2024-07-08 18:01:28 -
 @ df478568:2a951e67
2025-02-16 17:10:55
@ df478568:2a951e67
2025-02-16 17:10:55I asked a pleb to answer a few questions about selling stuff for sats, and he asked me, "What made you want to do a story/article on this?"
The short answer: Because I like seeing people make their own bitcoin jobs, but the question made me think about the why. When I tried to be an English teacher, one of my professors said, "The difference between a job and a career is that a career is something you think about all day." I didn't become an English teacher, because I already had something I think about all day: bitcoin. I didn't fit the teacher ethos, for whatever reason, so undecided, I wanted to work in bitcoin sometime around block 525,000.

That's about the time I began writing on yalls.org. I fell in love with the idea of writing for sats. It was too early. Very few people used lightning back then, but the idea of earning sats to write was invigorating. I had no illusions of earning enough to earn a living, but yalls had a paywall. I spent a fair amount of time experimenting with these paywalls. Part of my articles were available for free, but to finish the article required a payment of 210 sats when that was about two cents. I was fascinated with this concept because it meant I could write for sats. Readers could send p2p electronic cash to me—sats short for satoshis. Each bitcoin can be divided into 100,000,000 sats. The lightning network allowed people to send you micropayments.
Yalls

This was not possible with credit cards because of the fees they charge. The lightning network can be used to circumvent fees imposed on credit card merchants and the sats can now be instantly converted to fiat. This is not financial advice. Earning bitcoin is 21 million times more interesting than trading bitcoin. Investors talk about green dildos, red dildos, and some other sex toy called a bollinger band. If you're into that kind of kinky stuff, I don't judge, but I stay vanilla and stack sats. I experimented with shitcoin play in younger years, but it was just a phase. I finally realized alts are an attempt to break the solution to the double-spending problem sometime around block 630,000.
That's when I declared myself a bitcoin maxi on yalls.org. Adam Back retweeted it. It didn't go viral, but that was amazing. I'm just an anonymous user who couldn't get an English teaching job, but Adam Back...You know..The guy Satoshi cited in the white paper—That guy retweeted my article. I started a couple of anonymous blogs and earned a small amount of sats in the early days of nostr.
How I Made 1,000,000 Volunteering At Pacific Bitcoin
I volunteered for Pacific Bitcoin 2022. I volunteered to save some sats on a ticket. I stayed in a hostel. I did not expect to get paid, but it earned me a million sats after I sold the pack of collectible cards that came in a swag bag at the conference. What if I can one day retire on the millions of sats I earned over the last few years? I'm not sure that will happen, but it might be enough for my grandchildren to retire. *If bitcoin goes up "forever Laura..." you're never too late to earn bitcoin on the side. The sats you earn go up in value forever.
Maybe the ROI on your college degree didn't pay off like you thought it would. You read Walden and Civil Disobedience and A Letter From a Birmingham Jail...thought...these are great ideas. They prepared me to read Early Retirement Extreme. I also listened to Choose FI and decoded Mr. Money Mustache. Dave Ramsey says you should get a second job to pay off debt in a country where many people working two jobs are still getting into more debt. Maybe they should use that extra job to stack sats. Earning bitcoin feels different than buying bitcoin. It means earning money on the Internet without needing a trusted third party. PayPal and Patreon have been around for years. They are nothing new, digital middlemen.
Although the less technical often use bitcoin non-custodially, it's getting easier to take self-custody and use bitcoin as it was intended, p2p electronic cash. Why use eBay when you can have a garage sale on nostr? Even Dave Ramsey can sell stuff on nostr. He's been telling people to avoid bitcoin since it was $400. What if you sell your fancy clothes made in Bangladesh on nostr while instantaneously converting it to USD on Strike? You can send 1,000 fiat bucks to your checking account faster than a speeding Superman. You can get the garage sale money deposited to your bank account within a half-hour. I can't even drive to an ATM that fast! Transfer the money to a savings account that pays 0.01% interest. Baby Step 1 complete! You can take the instant fiat from your next nostr garage sell and pay your debt straight from the Strike App! This is NOT financial advice.
I could earn fiat on Poker Stars until the government took away my permission. I could earn fiat on Full Tilt, but they spent players' fiat and barely kept a fraction in reserve. The same is true of platforms. You can earn fiat on Twitter if you pay for the monthly Twitter lottery. American's can currently earn fiat on TikTok...but do see where this is going? That's why I like supporting people who have some sort of bitcoin side hustle. I may have found bitcoin in 2014, but I didn't have a full-time job. I was unemployed for a couple of years before that. This one time, I got into an argument with my wife because, some months, we could only scrape up $50 to "buy bitcoin." I was an asshole. I kinda feel bad about that, but I'm a lucky guy with a beautiful wife who forgave me for being an asshole and dashing doors to stack bitcoin without telling her about it. She was pretty pissed. That Fifty bucks we argued over is now worth...
The misses is not so pisses anymore.😁
- I've picked up extra jobs to stack sats.
- I used BTCPayServer to stack sats.
- I stacked sats with lnbits
- I originally set up a lightning node so I could stack sats on yalls.org.
- It took me six months to get a lightning node up and running on a raspberry pi.
Few
Very few people used the lightning network back then. Any bitcoiner has the ability to make their own job. I started a blog and set up a BTCPayServer so people would pay me for my prose. Some actually did. It wasn't much money. I might have broken even, but the possibilities still intrigue me. You can use Alby Hub on the cloud, Zaprite, or run it on a Start9. You can pay GetAlby for a lightning node in the cloud. If you're a fiat-spending maximalist, you can convert all your bitcoin to fiat with Strike.*
Bitcoin Is For Everybody, Even Nocoiners
Maybe you don't want bitcoin, but need some extra cash and can make candles. Fiat won't hedge against eggflation, but that's not what this is about. That's not the point. Bitcoin is for anybody, even no-coiners. You don't even need to make a website anymore. You can just use Shopstr, Plebian Market, Coinos, Cashu.me, Buzz Pay, and more.I just bought some soap from someone I saw on nostr. I decided to try something new this month. I paid with fiat, but the soap miner received bitcoin on the other end. Anyone with the Strike App can pay dollars to people who want bitcoin and vice-versa. Some people proudly proclaim they never...ever...spend bitcoin. Those who hodl never sell.
In Everyone's A Scammer, Michael Bitstein says:
"Merchants are scammers because they lead you to believe that your bitcoins are only worth the price of their retail good in order to allow themselves (or those to whom they sell the bitcoins, if they so choose), rather than you, to benefit from future Bitcoin price increases. …And That’s a Good Thing This is not to say merchant adoption is bad. In fact, from the hoarder's perspective, merchant adoption is great. First, merchant adoption means that there is more demand for Bitcoin, that the Bitcoin network is growing, and that Bitcoin is thus more valuable than it was yesterday. Second, merchant adoption means there are more places to spend bitcoins. This does not mean a hoarder will actually want to spend bitcoins. More importantly, he can spend bitcoins.If you like this quote, [please zap this note. 100% of these zaps go to BitstienSaylor says bitcoin is hope, but you know what gives me hope? Not the billionaire buying bitcoin, but the pleb selling stuff for sats. - Maybe there's a homeless person selling a few used books for a meal. - Maybe an artist stacks $500 per month selling art on nostr. - Maybe a recently X government employee can sell DEI training on the free and open market on nostr. Or...Maybe they can sell culturally appropriate tamales on nostr for actual sats instead.
Those are the stories I want to find. Bitcoin is for everybody, even people with college degrees that the job market does not value much. Saylor's not wrong. Bitcoin is hope. Saylor said he wants to make education free. That's why he founded Saylor Academy. They have a course called Bitcoin Is For Everybody. Bitcoin is for everybody, even no-coiners, even for people who went to college even though it didn't lead to a high-paying job. Bitcoin is hope for those people, people just like me.
nostr:npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
* Strike is an affiliate and I earn a small commision if you pay for the service. I use it to pay my credit card bills.
-
 @ df478568:2a951e67
2025-02-16 16:53:45
@ df478568:2a951e67
2025-02-16 16:53:45I asked a pleb to answer a few questions about selling stuff for sats and he asked me, "What made you want to do a story/article on this?"" When I tried to be an English teacher, one of my professors said, "The difference between a job and a career is that a career is something you think about all day." I didn't become an English teacher, because I already had something I think about all day, bitcoin. I didn't fit the teacher ethos, for whatever reason, so Indecided I want to work in bitcoin sometime around block
That's about the time I began writing on yalls.org. I fell in love with the idea of writing for sats on yalls.org. It was an idea, but it was too early. It was very early days. Very few people used lightning back then, but the idea of earning sats to write was invigorating. I had no illusions of earning enough to earn a living, but yalls had a paywall. I spent a fair amount of time experimenting with these paywalls. Part of my articles were available for free, but to finish the article required a payment of 210 sats when that was about 2¢. I was as facinated with this concept because it meant I could write for sats. Readers could send p2p electronic cash to me-sats short for satoshis. Each bitcoin can be divided into 100,000,000 sats. The lightning network allowed people to send you micropayments. This was not possible with credit cards because of the fees they charge. The lightning network can be used to circumvent fees imposed on credit card merchants and the sats can now be instantly converted to fiat. This is not financial advice. Earning bitcoin is 21 million times more interesting than trading bitcoin. Investors talk about green dildos, red dildos, and some other sex toy called a bollinger band. If you're into that kind of kinky stuff, I don't judge, but I stay vanilla and stack sats. I experimented with shitcoin play in younger years, but it was just a phase. I finally realized alts are an attempt to break the solution to the double spending problem sometime around block 630,000.
That's when I declared myself a bitcoin maxi on yalls.org. Adam Back retweeted it. It didn't go viral, but that was amazing. I'm just an anon who couldn't get an English teaching job, but Adam Back...You know..The guy Satoshi cited in the white paper--That guy retweeted my article. I started a couple anon blogs and earned a small anount of sats in the early days of nostr. I volunteered for Pacific Bitcoin 2022. I volunteered to save some sats on a ticket. I stayed in a hostel. I did not expect to get paid, but it earned me a million sats after I sold the pack of collectible cards that came in a swag bag at t he conference. What if I can one day retire on the millions of sats I earned over the last few years? I'm not sure that will happen, but it it might be enough for my grandchildren to retire. *If bitcoin goes up "forever Laura..." you're never too late to earn bitcoin on the side. The sats you earn go up in value forever. Maybe the ROI on you're college degree didn't pay off like you thought it would. You read Walden and Cilvil Disobedience and A Letter From A Birmhingham Jail...thought...these are great ideas. They prepared me to read Early Retirement Extreme. I also listened to Choose FI and decoured Mr. Money Mustache. [Dave Ramsey](Resources to Tackle Debt - Ramsey) says you should get a second job to pay off debt in a country where many people working two jobs are still getting into more debt. Maybe they should use that extra job to stack sats. Earning bitcoin feels different than buying bitcoin. It means earning money on the Internet without needing a trusted third party. Paypal and Patreon have been around for years. They are nothing new, digital middlemen. Although the less technical often use bitcoin non-custodially, it's getting easier to take self custody and use bitcoin as it was intended, p2p electronic cash. Why use eBay when you can have a garage sale on nostr? Even Dave Ramsey can sell stuff on nostr. He's been telling people to avoid bitcoin since it was $400.00. What if you sell your fancy clothes made in Bangladesh on nostr while instantaniously converting it to USD on Strike? You can send 1,000 fiat bucks to your checking account faster than a speeding Superman. You can get the garage sale money deposited to your bank account within a half hour. I can't even drive to an ATM that fast! Transfer the money to a savings account that pays 0.01% interest. Baby Step 1 complete! You can take the insta-fiat from your next nostr garage sell and pay your debt straight from the Strike App! This is NOT financial advice. I could earn fiat on Poker Stars until the government took away my permission. I could earn fiat on Full Tilt, but they spent players fiat and barely kept a fraction in reserve. The same is true of platforms. You can earn fiat on Twitter if you pay for the monthly Twitter lottery. American's can can currently earn fiat on TikTok..but do see where this is going? That's why I like supporting people who have some sort of bitcoin side hustle. I may have found bitcoin in 2014, but I didn't have a full time job. I was unemployed for a couple years before that. This one time, I got into an argument with my wife because, some months, we could only scrape up $50 to "buy bitcoin." I was an asshole. I kinda feel bad about that, but I'm a lucky guy with a beautiful wife who forgave me for being an asshole and dashing doors to stack bitcoin without telling her about it. She was pretty pissed. That Fifty bucks we argued over is now worth...
The misses is not so pissed anymore.😁 I've picked up extra jobs to stack sats. I used BTCpayServer to stack sats. I originally set up a lightning node so stack sats on yalls.org. Very few people used the lightning network back then. Any bitcoiner has the ability to make their own job. I started a blog and set up a BTCpayServer so people would pay me for my prose. Some actually did. It wasn't much money. I might have broke even, but the possibilities still intrigue me. You can buy a Start9 and use Alby Hub. You can pay GetAlby for a lightning node in the cloud. If you're a fiat spending maxi, you can convert all your bitcoin to fiat with Strike. Maybe you don't want bitcoin, but need some extra cash and can make candles. Fiat won't hedge against eggflation, but that's not what this is about. That's not the point. Bitcoin is for anybody, even nocoiners. buYou don't even need to make a website anymore. You can just use Shopstr, Plebian Market, Coinos, Cashu.me, [Buzz Pay](https://pos.albylabs.com/#?nwc=bm9zdHIrd2FsbGV0Y29ubmVjdDovLzY5ZWZmZTdiNDlhNmRkNWNmNTI1YmQwOTA1OTE3YTUwMDVmZmU0ODBiNThlZWI4ZTg2MTQxOGNmM2FlNzYwZDk/cmVsYXk9d3NzOi8vcmVsYXkuZ2V0YWxieS5jb20vdjEmcHVia2V5PTVkNzVjZDQ5OTFkNGFhOTViMDllMWJkZTg1YmRkODllMTg2YjUxZmE3MDYwOTEyOTE5MGYxZWIwYjcyYzk0MWUmc2VjcmV0PWFiZDM5NDU3ODQ4NmI0OWJlMzMwNzk1ZWE2YTU2OGIwYWI2MWJjMjMzN2JkMTE5NzU1YTNiM2ZmZTBhZDEwMmQ=&name=Support my work using the Value 4 Value model), and more.I just bought some soap from someone I saw on nostr. I decided to try something new this month. I paid with fiat, but soap miner recieved bitcoin on the other end. Anyone with the Strike App can pay dollars to people who want bitcoin and vice-versa. Some people proudly proclaim they never...ever...ever spend bitcoin. Those who hodl never sodl can spend fiat at bitcoin shops using Strike. Buying stuff with bitcoin increases the stack of a fellow HODLer. In Everyone's A Scammer, Michael Goldstein says, "Merchants are scammers because they lead you to believe that your bitcoins are only worth the price of their retail good in order to allow themselves (or those to whom they sell the bitcoins, if they so choose), rather than you, to benefit from future Bitcoin price increases. …And That’s a Good Thing This is not to say merchant adoption is bad. In fact, from the hoarder’s perspective, merchant adoption is great. First, merchant adoption means that there is more demand for Bitcoin, that the Bitcoin network is growing, and that Bitcoin is thus more valuable than it was yesterday. Second, merchant adoption means there are more places to spend bitcoins. This does not mean a hoarder will actually want to spend bitcoins. More importantly, he can spend bitcoins. Demand for cash exists because there is uncertainty of future needs, and the holder of cash believes he will come across currently unknown opportunities in the future that can better satisfy his needs than any current opportunities." Saylor says bitcoin is hope, but you know what gives me hope? Not the billionaire buying bitcoin, but the pleb selling stuff for sats. Maybe there's a homeless person selling a few used books for a meal. Maybe an artist stacks $500 per month selling art on nostr. Those are the stories I want to find. Bitcoin is for everybody, even people with college degrees that the job market does not value much. Saylor's not wrong. Bitcoin is hope. Saylor said he wants to make education free. That's why he founded Saylor Academy. They have a course called [Bitcoin Is For Everybody](Bitcoin is for everybody](https://learn.saylor.org/course/view.php?id=468)). Bitcoin is for everybody, even no-coiners, even for people who went to college even though it didn't lead to a high paying job. Bitcoin is hope for those people, people just like me.
npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
[884,054(https://mempool.marc26z.com/block/00000000000000000000a9305d5f83abfc86da27c9524a7ad181b7a75f0827a9)
-
 @ 41fa852b:af7b7706
2025-02-16 15:52:51
@ 41fa852b:af7b7706
2025-02-16 15:52:51"Our lives begin to end the day we become silent about things that matter." --Martin Luther King, Jr
If Bitcoin's price action is putting you to sleep, maybe it's time to get out and add some spice to your life.
It's a big week with 12 meetups--check out the list below and see if there's one near you.
Most meetups are drop-in friendly--just head to the venue and keep an eye out for a few shady-looking characters in Bitcoin merch. If you'd prefer some certainty, you can find contact details for every meetup at bitcoinevents.uk. Just scroll down to find your meetup group, and you'll see how to get in touch.
Let's dive in…
This week's sponsor is…
Upcoming Bitcoin Meetups
Happening this week…
-
Newcastle Bitcoin Meetup: A relaxed gathering for anyone interested in Bitcoin. No prior experience or ownership of Bitcoin is required, just curiosity and an interest. Conversations are Bitcoin-only focused. Happening this month on Tuesday, February 18th, at 18:30. Find them at Kabin @ Kabannas, NE1 6UQ. 🍻
-
Bitcoin 101: Nodes at Cyphermunk House - Participants are invited to a hands-on, peer-led class to set up their own Bitcoin node. Those wishing to build a node during the session should bring an old laptop, computer, or mini PC, along with a 2TB SSD and a USB drive with at least 4GB of storage. Attendees are also welcome to join without building a node to learn from the process. Tickets cost £9 in sats or £10 in cash, with pre-booking available at cyphermunkhouse.com/events.. 👨🏼🎓
-
Bitcoin Glasgow: Bitcoin Glasgow meet every 3rd Wednesday of the month and this month will be at The Maltman, 59--61 Renfield Street at 18:00 to 20:00. This month on Wednesday the 19th. 🍺
-
Bitcoin Wales: Back in action with the first meetup of 2025, and looking to grow their membership. The gathering at Zerodegrees, 27 Westgate St, Cardiff CF10 1DD invites both seasoned Bitcoiners and newcomers to connect, share ideas, and shape the future of Bitcoin in Wales. 18:00 - 21:00 on Wednesday 19th February. 🍻
-
OPA London Bitcoin Meetup: The first OPA London Bitcoin Meetup takes place on Wednesday 19th at 18:30 - 21:30 at the Century Club (Bitcoin accepted), 61--63 Shaftesbury Ave, London W1D 6LQ. 🍺🍷🍸
-
Shropshire Bitcoin: On the 19th, the Shropshire crew will be meeting at the Admiral Benbow in Shrewsbury. 🍻
-
Brum Bitcoin & Beer: If you're in the Birmingham area head along to meet some fellow bitcoiners on Thursday 20th at 19:00. You'll find them this month at The Wellington, Bennett's Hill, B2 5SN. 🍺
-
Bitcoin Bristol: Meeting at The Left Handed Giant, BS1 6EU, at 18:15 on the 21st. Everyone is welcome, the aim is to encourage grassroots bitcoin adoption in Bristol. 🍻
-
2140 Collective: Tools of freedom - GrapheneOS workshop. Learn about GrapheneOS the privacy-focused mobile operating system. Friday 21st February, 18:00 - 21:40 at Cyphermunk House. 👨🏼🎓📱
-
Bitcoin Walk - Edinburgh: Every Saturday they walk around Arthur's Seat in this historic city. Join them at 12 pm to chat about all things Bitcoin and keep fit. 🚶🏽♂️🚶🏼♀️🚶🏻
-
Plymouth Bitcoiners: The Plymouth meetup is on the 22nd this month. Find them at Steel Brew, PL1 3GD at 14:00. 🍻
-
Bitcoin East: Join Bitcoin East in Bury St. Edmunds on Sunday 23rd, 10:00 at Procopio's Pantry and then on to Vespers Bar at 12:00. All welcome, Bitcoiners and anyone else curious about Bitcoin. 🍻☕️
Get Involved
- Volunteer Opportunities: Bridge2Bitcoin is actively seeking volunteers who share our passion for merchant adoption. We'd be delighted to connect if you're eager to contribute. Reach out to us on Twitter or through our website.
- Start Your Own Meetup: Interested in launching a Bitcoin meetup? We're here to support you every step of the way. We've assisted numerous UK Bitcoin meetups in getting started. Get in touch via Twitter.
- Contribute to BTCMaps: BTCMaps is a vital part of the Bitcoin ecosystem. It's a perfect project to get involved with if you're not a coder or even that technical. A great way to give back to the community. Maintain an area of the UK and keep it up-to-date.
- Telegram users: You might find our Telegram Channel another useful way to keep up-to-date with UK meetups.
- Feedback and Suggestions: We value your input! Share your ideas on how we can enhance this newsletter.
This week's sponsors are…
Get out and support the meetups where you can, visit Bitcoin Events UK for more info on each meetup and to find your closest on the interactive map.
Stay tuned for more updates next week!
Simon.
-
-
 @ b2caa9b3:9eab0fb5
2024-07-08 15:15:28
@ b2caa9b3:9eab0fb5
2024-07-08 15:15:28Hey everyone,
Just wanted to give you a quick update on my travels. Unfortunately, I haven't been doing much exploring lately. I had a bit of an accident a few days ago while crossing the street in the dark.
Since then, I've been mostly relaxing at the hostel, trying to keep my foot off it as much as possible. My daily routine has been pretty simple: wake up, shower, clean the wounds, grab breakfast, and then catch up on some work on my laptop. Not exactly the adventure I was hoping for, but hopefully it'll give my foot the rest it needs to heal quickly.

Speaking of the accident, let's just say it was a good reminder about the importance of being prepared, especially when traveling in Africa. Here, reliable access to electricity and Wi-Fi isn't always a guarantee. Luckily, the hostel I'm staying at has both, which is a real plus. However, frequent power outages are common, and having a flashlight is a lifesaver – literally!
In my case, the power was out when I tried to cross the street. Because I couldn't see a thing, I decided to walk to a crosswalk for better visibility. Big mistake. There was a curb at the crosswalk that I completely missed in the darkness. Tripped, fell, and ended up hurting my foot, knee, and hands.

Thankfully, the damage wasn't too severe. My knee and hands just had some minor scrapes, but my toes took the brunt of the fall. The hostel, unfortunately, didn't have a first-aid kit, but a kind fellow traveler from Egypt came to the rescue with some antiseptic fluid. Huge thanks to him for that!
Since the accident, I've been keeping the wounds open to the air, but today I noticed some signs of infection. So, I ventured out to a larger pharmacy to pick up some supplies and some disinfectant spray. Hopefully, this will help clear things up.
On a brighter note, the hostel has a fantastic rooftop bar and restaurant with Wi-Fi, which has become my hangout spot for the past few days. The view isn't too bad either!
Lesson Learned: Always take your flashlight out of your bag when it's dark outside, no matter how confident you feel. A little extra caution can go a long way in preventing accidents. From now on, my flashlight is coming out of my bag at dusk – no exceptions!

In the picture, you'll see my temporary workspace. I've spared you the close-up of my toes – trust me, it's not pretty!
Thanks for reading everyone, and have a great day!
Online
-
 @ 0e8c41eb:95ff0faa
2024-07-08 14:36:14
@ 0e8c41eb:95ff0faa
2024-07-08 14:36:14Chef's notes
Sprinkle a pinch of salt in a bowl. Sift 275 grams of flour above it. Make a well in the center of the flour and sprinkle the yeast into it. Add 50 grams of butter, 25 grams of sugar, and the egg. Pour in the milk and knead the dough with the mixer or by hand into a smooth dough. If necessary, add a bit more flour if the dough is too sticky. Form the dough into a ball. Let the dough rise covered with cling film at room temperature for 1 hour.
Peel the apples. Cut the apples and apricots into pieces. Cook the fruit with 150 grams of sugar and 50 ml of water in 15 minutes into a thick compote. Let this fruit filling cool.
Knead the dough again briefly and roll it out to a round sheet of about 28-30 cm in diameter, so that it fits well over the baking tin. Press the dough into the tin and press it well into the corners. Let the dough rise again for 10 minutes and cut off the excess edges.
Spread the fruit filling over the dough.
Mix the rest of the flour with the remaining 100 grams of butter and 100 grams of sugar and knead it with your fingers into a crumbly mixture. Sprinkle this crumble mixture over the fruit filling. Bake the tart in the preheated oven at 200°C for about 30 minutes until golden brown.
Variations: Only apple? Make this tart with 1 kilo of apples. High or low? You can also bake the crumble tart in a low tart tin of 30 cm diameter. If the fruit filling is a bit too voluminous, you can make double the crumble mixture and sprinkle it over the larger surface area.
Additional needs: Mixer with dough hooks or food processor Cling film Round baking tin with a diameter of 28-30 cm, greased
Details
- ⏲️ Prep time: 45 min + 1 hour Rising
- 🍳 Cook time: 30 minutes
- 🍽️ Servings: 8
Ingredients
- 375 grams flour
- 1 packet dried yeast (7 grams)
- 125 grams unsalted butter, at room temperature
- 275 grams sugar
- 1 egg
- 100 ml milk, at room temperature
- 500 grams apples
- 500 grams apricots (fresh or from a can)
Directions
- Sprinkle a pinch of salt in a bowl. Sift 275 grams of flour above it. Make a well in the center of the flour and sprinkle the yeast into it. Add 50 grams of butter, 25 grams of sugar, and the egg. Pour in the milk and knead the dough with the mixer or by hand into a smooth dough. If necessary, add a bit more flour if the dough is too sticky. Form the dough into a ball. Let the dough rise covered with cling film at room temperature for 1 hour.
- Peel the apples. Cut the apples and apricots into pieces. Cook the fruit with 150 grams of sugar and 50 ml of water in 15 minutes into a thick compote. Let this fruit filling cool.
- Knead the dough again briefly and roll it out to a round sheet of about 28-30 cm in diameter, so that it fits well over the baking tin. Press the dough into the tin and press it well into the corners. Let the dough rise again for 10 minutes and cut off the excess edges.
- Spread the fruit filling over the dough.
-
 @ 8194da31:0f3badf3
2025-02-16 12:41:16
@ 8194da31:0f3badf3
2025-02-16 12:41:16My stands on Plan B comments 👇
1- As a #Bitcoin maxi not your keys not your coins is non negotiable
2- Transferring your #Bitcoin to an ETF just because your are a fucking lazy ass is not an excuse
3- I do respect people who prefer the ETFs over #Bitcoin for 3 specific reasons:
A- you are over 70 years old
B- you are sovereign wealth fund or a Corporation
C- you will take advantage of the FIAT system by using IBIT as collateral to get more #Bitcoin
-
 @ 42342239:1d80db24
2025-02-16 08:39:59
@ 42342239:1d80db24
2025-02-16 08:39:59Almost 150 years ago, the British newspaper editor William Thomas Stead wrote that "the editorial pen is a sceptre of power, compared with which the sceptre of many a monarch is but a gilded lath". He had begun to regard journalism as something more than just conveying information - the journalist or editor could become a ruler.
Times had certainly changed compared to a few hundred years earlier. Before Gutenberg's invention of the printing press, it was mainly the church that controlled the dissemination of information in Europe, but when Stead put pen to paper, this control had shifted to newspapers, schools, and universities. Eventually, technologies like radio and TV entered the scene, but the power dynamics remained asymmetrical - only a few could send information to the many.
However, with the emergence of the internet, and especially with the spread of social media, a significant change followed. Instead of only a few being able to send information to the many, many could send to many. Almost anyone could now create their own newspaper, radio, or TV channel. The power over information dissemination was decentralised.
Ten years ago, Roberta Alenius, who was then press secretary for Sweden's Prime Minister Fredrik Reinfeldt of the Moderate Party, shared her experiences with Social Democratic and Moderate Party internet activists on social media. She reported that social media played a significant role in how news "comes out" and is shaped, and that journalism was now downstream of social media. Five years later, NATO's then-Secretary-General Jens Stoltenberg said that "NATO must be prepared for both conventional and hybrid threats: from tanks to tweets." This finally underscores the importance of social media.
Elon Musk, who took over X (formerly Twitter) in 2022, has claimed that "it's absolutely fundamental and transformative that the people actually get to decide the news and narrative and what's important," and that citizen journalism is the future.
While his platform allows most expressions - for better or worse - the reach of messages is instead limited ("freedom of speech does not mean freedom of reach "). X has also opened its recommendation algorithm to the outside world by making it open-source. Although this is a welcome step, the fact remains that it's impossible to know which code is actually used and what adjustments are made by humans or algorithms.
William Thomas Stead's "sceptre of power", which has wandered from the church to newspaper and TV editorial offices, and now to citizens according to Elon Musk, risks being transferred to algorithms' opaque methods?
Instead of talking about "toxic algorithms" and TikTok bans, like the so many do today, we should ask ourselves more fundamental questions. What happens when algorithms are no longer objective (how can they ever be?), but instead become tools for shaping our reality? Perhaps our greatest challenge today is not deciding who should govern the information landscape, but instead recognising that no one is up to the task - not even well-ventilated computers.
-
 @ c3c7122c:607731d7
2025-02-16 07:48:35
@ c3c7122c:607731d7
2025-02-16 07:48:35At my meet up (the SD Bitcoiners Cete) on Thursday, I presented trends on the Bisq protocol. One of its features is that anyone can export the trade history and analyze it. Bisq is a private, peer-tp-peer way to buy and sell bitcoin. All data are based on the BTC-USD market.
Trade number decreased in 2024

But USD volume increased ($/year)

(same graph but $/day by year)

Which means more higher value per trade

Interestingly, trade counts and price volatility lead to interesting BTC volume per year. The peaks are nearly identical (330 BTC)!

Not so surprising when you compare BTC volume traded to the average BTC price that year, local price valleys mean local peaks in BTC traded (and vice versa).

I separate fiat payment methods into three groups.

All USD payment methods used in 2024 by average value (y-axis) and number of trades (bubble size)

This is the same graph as above excluding Zelle and Strike, since they throw off the relative circle size (face-to-face only had 1 trade in 2024).

Two fiat methods had >1000 trades in 2024. Strike came on the scene hot in 2021 and ate some of the Zelle volume but that may have stabilized.

Six fiat methods had 200-1000 trades in 2024. Amazon Gift Card dwindling, Cash By Mail still top of this group, and Revolut surging (wtf is Revolut?)

Same group, all years

Last group is <200 trades in 2024. Basically unused, except for Wire Transfer increasing.

Same group, all years

What's the average trade size by fiat method? There are different reasons for this, largely driven by fiat fees and bank limits. Amazon Gift Card is an interesting option for smaller payments (note: you can't just send any gift card, there is a very specific process, see the Bisq wiki)

There no KYC premium, but there is a small Surveillance Discount

If you open Bisq for the first time, you'll likely see spreads 3-5% or larger. These offers persist because no one wants them. So people think that Bisq is "too expensive." But let's dig into the actual trades...

Comparing the daily trade volume to daily market rate (I used coingecko), and creating a monthly weighted average, the true surveillance discount emerges. It's not 3-5% as you might see in the order book at any given time. In fact, it was cheaper to trade on Bisq than exchanges in November and December! (Note: this does not take into account the 4 on-chain transactions required for a trade or price spread/fees used by exchanges)

In 2024, Strike had the worst surveillance discount and Cash By Mail had the best. This isn't surprising because receiving cash is convenient and low risk for a seller so they're willing to accept a lower price. Zelle (the most common USD payment method) had the second best surveillance discount.

Now let's compare the surveillance discount by week in 2024 for select payment methods.
Strike was consistently worse than Zelle

Revolut was sometimes way worse than Zelle but sometimes a little better.

The two most private payment methods are cash and money order. They're pretty competitive regarding surveillance discount.

Take aways * Be a maker and get a better price (fees are better too) * Zelle is better for speed + convenience * Amazon gift cards are good for speed + privacy (sorta) * Cash or money order are better for privacy + volume
-
 @ 5d4b6c8d:8a1c1ee3
2024-07-08 12:14:09
@ 5d4b6c8d:8a1c1ee3
2024-07-08 12:14:09Yesterday's edition https://stacker.news/items/599828/r/Undisciplined
I had no idea SN was already discussing higher posting/comment fees two years ago. For the newer folks, it used to just be 1 sat to post anything.
-
- -
July 8, 2023 📅
📝
TOP POSTAnita Posch Has Good News About Africa
Excerpt
It’s amazing to see how the Bitcoin adoption has been growing in African countries. There was only one initiative I knew of in 2020, when I visited Zimbabwe and Botswana. That was the Satoshicentre in Gaborone founded by Alakanani Itireleng. Together we organized a meetup at the university, where I held a Bitcoin talk. Now there are communities like the Bitcoin Cowries in Ghana, Bitcoin Dada in Kenya, Bitcoin for Fairness in Zambia, Bitcoin Ekasi and Bitcoin Ubuntu in South Africa and the new Bitcoin Innovation Hub in Uganda. In the next few years we’ll see tremendous growth. Exciting!
1801 sats \ 21 comments \ @siggy47 \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/205973/r/Undisciplined?commentId=205977
Excerpt
this is how it be

685 sats \ 2 replies \ @birdeye21
From Are You a Bitcoin Advocate or a Underground Bitcoiner by @tomlaies in ~bitcoin
🏆
TOP STACKER2nd place @03365d6a53 (1st hiding, presumed @siggy47)
481 stacked \ 1830 spent \ 0 posts \ 20 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
30.3k stacked \ 0 revenue \ 35.2k spent \ 86 posts \ 226 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 8, 2022 📅
📝
TOP POSTGloria Zhao is now a Bitcoin Core maintainer
Link to https://github.com/bitcoin/bitcoin/pull/25524
2137 sats \ 11 comments \ @k00b \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/42602/r/Undisciplined?commentId=42634
Excerpt
I think raising posting/comment fees to reduce bad content is reasonable. 10 sats seems like a good starting point.
A cool side-effect is that by raising posting and comment fees, Stacker News will also have far more sats to give back to the best us […]
282 sats \ 3 replies \ @kr
From More and more reddit posts referencing stacker.news - increase ⚡️ cost for posts/comments? by @vijo in ~bitcoin
🏆
TOP STACKER1st place @k00b
21.6k stacked \ 9265 spent \ 5 posts \ 20 comments \ 0 referrals
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
13.8k stacked \ 0 revenue \ 16.3k spent \ 96 posts \ 220 comments
https://imgprxy.stacker.news/fsFoWlgwKYsk5mxx2ijgqU8fg04I_2zA_D28t_grR74/rs:fit:960:540/aHR0cHM6Ly9tLnN0YWNrZXIubmV3cy8yMzc5Ng
July 8, 2021 📅
📝
TOP POSTCasa client case study: the Tinder trap
Link to https://blog.keys.casa/casa-client-case-study-the-tinder-trap/
2 sats \ 3 comments \ @k00b \ ~bitcoin
💬
TOP COMMENThttps://stacker.news/items/231/r/Undisciplined?commentId=232
Excerpt
Kevin Mulcrone has a twitter thread on the release and explains how his bitcoin based license works https://twitter.com/KayBeSee/status/1413162687379296256. […]
1 sat \ 0 replies \ @k00b
From Lily Wallet: A Slick Open Source Wallet with a Bitcoin Business Model by @k00b in ~bitcoin
🏆
TOP STACKERNo top stacker
🗺️
TOP TERRITORY~bitcoin
everything bitcoin related
founded by @k00b on Tue May 02 2023
7 stacked \ 0 revenue \ 17 spent \ 3 posts \ 3 comments
originally posted at https://stacker.news/items/600906
-
-
 @ cec2981c:814d4f26
2024-07-08 11:50:32
@ cec2981c:814d4f26
2024-07-08 11:50:32Chef's notes
More information about its origins: https://en.wikipedia.org/wiki/Soda_bread
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 45 min
- 🍽️ Servings: 4-8
Ingredients
- 500 gr whole grain flour
- 450 ml butter milk
- 10 gr (sea)salt
- 15 gr baking soda (not US's "baking powder") (also known as sodium bicarbonate)
- a bit of butter or olive oil
Directions
- Pre-heat the oven to 220°C
- Put all flour in a bowl with baking soda and salt. Mix it well.
- Create a hole in the middle and pour all butter milk in the center.
- Stir it from the centre and slowly mixing all together until you get a dough.
- When mixed, the dough is sticky. Use all purpose flour on counter and bulge to the same size as your skillet.
- Use a bit of butter or olive oil to wet the skillet to prevent sticky bread. And put the dough in your skillet.
- Add a but of flour on top of the dough and then cut lightly a X.
- Bake for ±45 min on 220°C until done (inside temperature must be at least 95°C). Turn up the heat for the last 5 min to get a crust.
- Let the bread cool down a bit before taking it out the skillet, and let it cool down even more before eating.
- Donate some sats to me if you like this recipe.
-
 @ e7bc35f8:3ed2a7cf
2025-02-16 05:34:56
@ e7bc35f8:3ed2a7cf
2025-02-16 05:34:56The 2012 attack on the U.S. diplomatic mission in Benghazi has been widely debated, but the real story remains obscured by political theatrics and media smokescreens. The mainstream narrative focuses on bureaucratic failures, misinformation about an anti-Islamic film, and partisan blame games. However, when you dig deeper, a far more sinister picture emerges—one involving illegal arms deals, covert CIA operations, and geopolitical power plays that stretch far beyond Libya.
Benghazi: A Strategic Flashpoint
Benghazi, Libya’s second-largest city, was a crucial battleground in the 2011 NATO-backed uprising that led to the overthrow and murder of Muammar Gaddafi. As a key port city, it was not only economically vital but also politically significant. After the fall of Gaddafi, Libya descended into chaos, becoming a breeding ground for militant groups and a hub for illicit weapons smuggling. On the night of September 11, 2012, around 150 armed militants—reportedly from Ansar al-Sharia, an Al-Qaeda-linked faction—attacked the U.S. diplomatic mission in Benghazi. Four Americans died in the assault, including Ambassador Christopher Stevens and two former Navy SEALs who were working as CIA contractors. In the immediate aftermath, the U.S. government, led by Ambassador Susan Rice, falsely claimed the attack was a spontaneous reaction to an obscure anti-Islamic video. This story collapsed within days, leading to Republican-led investigations and heated political battles. Yet, amid the partisan finger-pointing, the most critical questions were never fully answered: What was the real purpose of the U.S. presence in Benghazi?
Why was the CIA so heavily involved in this particular location?
Was the attack a cover-up for a botched operation?
The CIA’s Secret War in Benghazi
One of the most underreported aspects of Benghazi is the sheer volume of CIA operatives on the ground during the attack. In August 2013, even CNN admitted that “dozens” of CIA personnel were present in Benghazi that night. The agency went to extraordinary lengths to keep its operations in Libya under wraps. Whistleblowers later revealed that CIA officers were subjected to frequent polygraph tests to ensure they weren’t leaking information about what really happened in Benghazi. This level of secrecy suggests something far more than just diplomatic work was taking place. What were they hiding? Evidence points to an illegal arms-smuggling operation, reminiscent of the Iran-Contra scandal, where weapons were funneled to terrorist factions in Syria under the guise of aiding "moderate rebels."
Arming Terrorists: The Benghazi-Syria Connection
Reports suggest that Ambassador Stevens himself was deeply involved in a covert weapons pipeline, shipping arms from Libya’s looted stockpiles to Syrian insurgents. These insurgents—many linked to Al-Qaeda—somehow ended up with advanced weaponry, including U.S.-made Stinger missiles. Where did these weapons come from? The very security operation in Benghazi that was supposedly meant to prevent arms from falling into the wrong hands. Lieutenant Colonel Anthony Shaffer, a military intelligence whistleblower, suggested that Stevens was likely killed because he had knowledge of these weapons transfers. Similarly, CIA contractor Robert "Tosh" Plumlee, a veteran of Iran-Contra, supported the claim that the U.S. was funneling weapons to Syria through Turkey, Jordan, and even Pakistan.
The Security Farce: Aiding the Enemy
Another bizarre piece of the puzzle is the so-called security force hired to protect the U.S. mission in Benghazi: the February 17th Martyrs Brigade. Incredibly, this group publicly displayed Al-Qaeda flags on their own Facebook page, yet they were still entrusted with U.S. diplomatic security.

Why would the U.S. government pay known jihadists to guard its personnel? Was this sheer incompetence, or something more deliberate?
A Planned Hit That Spiraled Out of Control
It appears the Benghazi attack was more than just a terrorist ambush. There are indications that it was an orchestrated hit—perhaps an attempt to eliminate Stevens before he could blow the whistle on the weapons trafficking operation. The two former Navy SEALs who died that night ignored stand-down orders and engaged the attackers, holding them off long enough for military drones to capture real-time footage. This forced the U.S. military to take notice, disrupting whatever covert plan was in motion. An Air Force whistleblower later claimed that a rescue mission was possible but was deliberately withheld. This suggests that allowing Stevens and his team to die was part of a calculated decision to prevent certain truths from coming to light.
The Petraeus Affair: A Convenient Distraction?
As if this story couldn’t get any murkier, another subplot surfaced: CIA Director David Petraeus’ extramarital affair with his biographer, Paula Broadwell. Shortly before the scandal erupted, Broadwell gave a speech in which she accidentally revealed that the CIA had been holding Libyan militants prisoner at the Benghazi annex. This revelation was explosive because it contradicted Obama’s official stance against CIA black sites. Was the Petraeus scandal used as a distraction? Was he forced out because he knew too much?
The Aftermath: Tying Up Loose Ends
Years later, in a final act of "cleaning house," a key suspect in the Benghazi attack was killed in a U.S. airstrike in Iraq. The timing, as always, was suspicious. This has become a pattern—critical witnesses and suspects disappearing before they can testify.
A Scandal Bigger Than Partisan Politics
Benghazi was not about bureaucratic missteps or political negligence. It was about illegal arms deals, black ops, and the perpetual cycle of U.S.-backed destabilization in the Middle East. The official narrative is a smokescreen designed to distract from the uncomfortable truth: The U.S. government has been covertly arming and funding the same groups it claims to be fighting. This is not a Republican or Democrat issue. Both sides of the political spectrum have been complicit in covering up what really happened in Benghazi. The military-industrial complex thrives on endless war, and the intelligence agencies operate with impunity. If history has taught us anything, it’s that these covert operations never truly end—they simply move to the next theater of war. And as long as the public remains distracted by partisan squabbles, the real architects of these schemes continue to operate in the shadows, profiting from chaos.
The question is: Will we ever hold them accountable?
-
 @ 8d34bd24:414be32b
2025-02-16 04:19:34
@ 8d34bd24:414be32b
2025-02-16 04:19:34Last night in my Bible reading I read this verse:
“As for you, do not pray for this people, and do not lift up cry or prayer for them, and do not intercede with Me; for I do not hear you. (Jeremiah 7:16) {emphasis mine}
My first thought was “Why in the world is God telling us not to pray for this people? Doesn’t the Bible tell us to pray about everything?”
First of all, then, I urge that entreaties and prayers, petitions and thanksgivings, be made on behalf of all men, for kings and all who are in authority, so that we may lead a tranquil and quiet life in all godliness and dignity. This is good and acceptable in the sight of God our Savior, who desires all men to be saved and to come to the knowledge of the truth. (1 Timothy 2:1-4) {emphasis mine}
Doesn’t God tell us to pray for whatever is bothering us?
Be anxious for nothing, but in everything by prayer and supplication with thanksgiving let your requests be made known to God. And the peace of God, which surpasses all comprehension, will guard your hearts and your minds in Christ Jesus. (Philippians 4:6-7)
Doesn’t the Bible say that God will answer all of our requests?
Whatever you ask in My name, that will I do, so that the Father may be glorified in the Son. (John 14:13)
Doesn’t the Bible tell us to pray for Israel and Jerusalem and His chosen people?
Pray for the peace of Jerusalem:\ “May they prosper who love you.\ May peace be within your walls,\ And prosperity within your palaces.”\ For the sake of my brothers and my friends,\ I will now say, “May peace be within you.”\ For the sake of the house of the Lord our God,\ I will seek your good. (Psalm 122:6-9) {emphasis mine}
Doesn’t the Bible even tell us to pray for our enemies?
“But I say to you who hear, love your enemies, do good to those who hate you, bless those who curse you, pray for those who mistreat you. (Luke 6:27-28)
If all of this is true, then why does this verse tell us to not pray for this people, especially considering this is referring to God’s chosen people?
To answer this question, let us look at a broader portion of this passage:
“As for you, do not pray for this people, and do not lift up cry or prayer for them, and do not intercede with Me; for I do not hear you. Do you not see what they are doing in the cities of Judah and in the streets of Jerusalem? The children gather wood, and the fathers kindle the fire, and the women knead dough to make cakes for the queen of heaven; and they pour out drink offerings to other gods in order to spite Me. Do they spite Me?” declares the Lord. “Is it not themselves they spite, to their own shame?” (Jeremiah 7:16-19) {emphasis mine}
God is saying to not pray for these people who have turned from Him and are worshipping other gods. These people are in full rejection of God. Still does it mean that we can’t pray for them at all or is this talking about a particular kind of prayer?
A little later in Jeremiah, we read:
“Therefore do not pray for this people, nor lift up a cry or prayer for them; for I will not listen when they call to Me because of their disaster. (Jeremiah 11:14)
and
So the Lord said to me, “Do not pray for the welfare of this people. When they fast, I am not going to listen to their cry; and when they offer burnt offering and grain offering, I am not going to accept them. Rather I am going to make an end of them by the sword, famine and pestilence.” (Jeremiah 14:11-12) {emphasis mine}
We get a little more specificity on the command to “not pray for” in Jeremiah 14. We are told, “Do not pray for the welfare of this people.” This is not a universal command to never pray for them, but a command to not pray for their welfare. It is a command to not pray blessings on those in active rebellion against God.
At the time this command was made, the Israelites were expecting God’s protection and blessings while refusing to follow Him and instead worshipping other gods. This command isn’t a blanket statement to not pray for a sinning Israel, but a statement to not pray for blessings and protection for a sinning Israel. If this was a blanket statement it would contradict Psalm 122 above.
This is the confidence which we have before Him, that, if we ask anything according to His will, He hears us. And if we know that He hears us in whatever we ask, we know that we have the requests which we have asked from Him. (1 John 5:14-15) {emphasis mine}
Using 1 John 5:14, we can begin to see the catch. We are to pray “according to His will.” It is not God’s will for sinners and those in open rebellion against God to be blessed or protected from hardship. A prayer such as, “Please turn your people back to you and give them a pure heart and repentance from sin,” would be according to His will. A prayer to “Please bless and protect Israel” while Israel has turned their back on God is not a prayer that God will answer. He will “not hear you.”
The Bible also says:
You ask and do not receive, because you ask with wrong motives, so that you may spend it on your pleasures. (James 4:3)
How often are our prayers not answered because we pray with wrong motives? At least sometimes. Of course there are also times when God tells us to wait or has something better in mind and we can’t see it because we are not seeking His will, but our own.
It is always good to pray for someone’s repentance and salvation. It isn’t always good to pray for someone’s healing, blessings, and prosperity. It is always good to pray for a nation to turn back to God and to obey His commands. It isn’t always good to pray for a nation’s prosperity and power in the world. Sometimes God’s will is to punish those who turn away from Him or against Him. We need to make sure we are aligned to God’s will and not just seeking our own.
I recommend that our prayers be like Jesus’s prayer right before going to the cross, “saying, “Father, if You are willing, remove this cup from Me; yet not My will, but Yours be done.” (Luke 22:42). Our requests should be like that of Shadrach, Meshach, and Abed Ngo right before being thrown in the fiery furnace, “But even if He does not, let it be known to you, O king, that we are not going to serve your gods or worship the golden image that you have set up.” (Daniel 3:18). This isn’t just words thrown on the end of our prayers “yet not My will, but Yours be done,” but a cry of our hearts in full and complete trust in our Father God.
One thing that helps me is I try to pray the problem not the solution. God knows much better solutions than we do because He knows everything that has happened, everything that is happening, and everything that will happen. He knows what will lead to the best long term solution. When we pray the solution we desire, we miss out on the blessings of God’s knowledge, wisdom, and love.
May God lead you and guide you in a closer relationship to Him so that your will is completely aligned with His will and you are in close fellowship to Our Father in Heaven.
Trust Jesus
-
 @ c11cf5f8:4928464d
2024-07-08 11:07:29
@ c11cf5f8:4928464d
2024-07-08 11:07:29Here we are again with our Magnificent Seven, trying to give you a hit of what you missed lately in the ~AGORA territory.
In case you missed
Look's like conversations are taking over! Here some interesting ones:
- https://stacker.news/items/597538/r/AG How to respond to illicit & immoral Payment Requests & Notices of Prosecution? by @supratic
- https://stacker.news/items/575922/r/AG Fight the sockpuppets with a "sockpuppets business" by @DarthCoin
Top-Performing Ads
01[FOR SALE] Nashville Conference ticket for sale! $400 or Best Offfer! by @BlokchainB02[FOR SALE] Precious Metals/.999 Fine Silver 🔥 Sats Negotiable!!! 👊 by @watchmancbiz03[SELL] Antique Gold & Diamond Cross Pendant, Make an Offer in SATS Today!! by @watchmancbiz04🔥 Silver & Gold are about to EXPLODE 💥 by @watchmancbiz05🔥FOR SALE by Owner! Accepting SATS! Make an Offer I can't refuse 😉 by @watchmancbiz06[WTS] 2024 Nashville Bitcoin Conference ticket ($269) by @lv99slacker07[⚖️ SELL] Business Loans by @herschel
Create your Ads now!
- [⚖️ SELL] anything! or,
- if you're looking for something, hit the [🛒 BUY]!
- [🧑💻 HIRE] any bitcoiner skill or stuff from bitcoiners
- [🖇 OFFER] any product or service and stack more sats
- [🧑⚖️ AUCTION] to let stackers decide a fair price for your item
- [🤝 SWAP] if you're looking to exchange anything with anything else
- [🆓 FREE] your space, make a gift!
- [⭐ REVIEW] any bitcoin product or LN service you recently bought or subscribed to
Or contact @AGORA team on nostr DM and we can help you publish a personalized post.
originally posted at https://stacker.news/items/600789
-
 @ c43d6de3:a6583169
2024-07-08 10:07:48
@ c43d6de3:a6583169
2024-07-08 10:07:48Sovereign Souls
These little entities: Feet patter freely, knees against me.
Excitment seeking entities: Eyes in constant scan for fuscia flowers, limbs in constant contact with ground.
Can't be corraled kind of entities: In a beat, in a flash, once here now there, static fist clenching things undesirable.

Engaging Enclosures

Mind racing, I seek solace in their corraling. Bags of water balloons are enthralling. As the balloons fill, they linger. Bouncing trying to plunge in a finger.

Playground Pioneers

An exchange of glances with my wife and we're off. Little boy on my shoulders seeking a high colored prism. Little girl through tunnels offering a hand in altruism.

-
 @ 47cc4b41:1bad46c9
2025-02-15 23:20:11
@ 47cc4b41:1bad46c9
2025-02-15 23:20:11Since the last time I wrote about a United States Bitcoin Strategic Reserve, there have been a few federal updates. Notably, Treasury Secretary Scott Bessent and Commerce Secretary nominee Howard Lutnick will be developing a plan to create the first United States sovereign wealth fund after President Donald Trump signed an executive order. The order also directs Bessent and Lutnick to develop a plan for creating the fund within 90 days. Lutnick holds hundreds of millions of dollars of Bitcoin and is bullish on the future of Bitcoin and I personally believe this is a huge indication that Bitcoin will be included in this fund.
Additionally, David Sacks, the Crypto Czar said that a top agenda item for his task force is evaluating “the feasibility of a Bitcoin reserve.”
Both of these developments in my opinion are very positive for the future of Bitcoin at a federal level but the reality is that Federal legislation takes time and can suffer from gridlock, party disagreements, and overall levels of bureaucracy that states oftentimes don’t have to deal with. For this reason, many states have already made progress in pushing strategic reserve legislation and other Bitcoin-related legislation forward. This is also a reason why I expect the states to once again “lead” ahead of the federal government as it relates to Bitcoin.
Bitcoin Laws (bitcoinlaws.io) is a resource that has emerged to specifically track Bitcoin and other digital asset legislation at the state level. The website highlights all of the outstanding legislation and provides the status and details on what is being proposed. I personally believe this resource will continue to be incredibly important for tracking what is actually happening at the state level as it relates to Bitcoin. It is rather difficult to stay up to date on all of the legislative occurrences as it relates to Bitcoin and Bitcoin Laws provides a one-stop-shop for all of the updates.

Most importantly, as of February 10th, 21 ‘Bitcoin Reserve’ bills have been introduced at the state level with 19 still active in the legislative process.
The idea that “the states will lead” reflects a theme of governance from the days of our Founding Fathers—that of Federalism. Federalism is a mode of political organization that allows separate states to unite under a national government while maintaining their own aspects of sovereignty. In layman's terms, Federalism allows for a Federal Government while also allowing State governments to have power within their individual borders. This system emphasizes a division of power with certain powers being granted to the federal government and others residing at the state level.
When the Founding Fathers created the Articles of Confederation they emphasized state power over a strong federal government. This system led to some problems such as economic instability amongst states and difficulties in coordinating a national defense eventually leading to the Constitution taking over and being the rule of the land for the centuries to follow. The Constitution created a stronger federal government while still protecting levels of state authority, autonomy, and sovereignty. The Tenth Amendment is a key aspect of this where it states, “The powers not delegated to the United States by the Constitution, nor prohibited by it to the States, are reserved to the States respectively, or to the people.” The amendment means that any powers not explicitly given to the federal government by the Constitution fall to the states.
The states having and maintaining individual power was a focal point when the United States was created and remains true today. Justice Louis Brandeis gave one of the more famous statements related to the rights of the states when he referred to them as “laboratories of democracy” during the case New State Ice Co. v. Liebmann (1932). The full quote was, “It is one of the happy incidents of the federal system that a single courageous State may, if its citizens choose, serve as a laboratory; and try novel social and economic experiments without risk to the rest of the country.” The meaning emphasized the idea that states were “laboratories” and should be encouraged to enact policy ahead of the federal government. The rationale for why states should be encouraged to do this is any policy they enact is specifically within their own borders while federal legislation typically applies to the whole country. As such, the “test area” for any new piece of legislation is much smaller and impacts far fewer people than any federally enacted policy of the same measure.
We have seen the “states lead” with numerous issues throughout the years including legislation on same-sex marriage, marijuana, healthcare experiments, climate change regulations, civil rights, and more. I believe the table is being set for the states to once again lead the federal government as it relates to policy regarding a Bitcoin Strategic Reserve.
It is also my personal belief the urgency at which legislation is confirmed for a Bitcoin Strategic Reserve is a matter of national security. Every day that a federal strategic reserve for Bitcoin is not enacted is another day that foreign adversaries and other nations can front-run our country.
The positive of this scenario is that the common man can also front-run the federal government.
The positive of this scenario is that states can also front-run the federal government.
The positive of this scenario is that states have the opportunity to once again lead and pave the way for what I believe the United States Federal government will also adopt.
Strategic Reserves within the United States both at the state and federal level will have their 0 to 1 moment and rapidly have their 1 to many rush to completion.
The States will Lead.
Stack SATs.
The views and opinions expressed here are for entertainment purposes only and should, in no way, be interpreted as financial or investment advice. Always conduct your own research when making an investment or trading decision, as each such move involves risk. I am not a financial advisor and do not claim to be qualified to convey information or advice that a registered financial advisor would convey to clients as guidance. Nothing contained in this e-mail/article constitutes, or shall be construed as, an offering of financial instruments, investment advice, or recommendations of an investment strategy. If you are seeking financial advice, find a professional who is right for you.The views and opinions expressed here are for entertainment purposes only and should, in no way, be interpreted as financial or investment advice. Always conduct your own research when making an investment or trading decision, as each such move involves risk. I am not a financial advisor and do not claim to be qualified to convey information or advice that a registered financial advisor would convey to clients as guidance. Nothing contained in this e-mail/article constitutes, or shall be construed as, an offering of financial instruments, investment advice, or recommendations of an investment strategy. If you are seeking financial advice, find a professional who is right for you.
-
 @ 9171b08a:8395fd65
2024-07-08 02:18:13
@ 9171b08a:8395fd65
2024-07-08 02:18:13Five little heads brush past me in the foyer as I enter the house. I get a “Hey Daddio,” and “Love you Dad,” then a punch in the thigh, “‘sup dad,” from my two girls and little boy.
The neighbor's two girls are polite only in that they say their hellos but no one stops to give me the time of day. I hold the door open for the little band of miscreants and watch them make their way to the front yard.
“Let’s play tag,” says my eldest as she stretches her hands out high above her head.
I turn and notice my wife smiling at me, leaning against the kitchen island.
“No, you always hide in the woods,” says one of the neighbors.
I kiss my wife on the forehead, tell her I love her, and say, “I’ve got dinner tonight. You had a tough day.”
“Nuh-uh. I won’t. That phantom man is in there.”
I wince and look at Jasmine to see if she had heard that. She did and says, “I didn’t want to believe it but I’ve heard them talk about it a few times already so I asked Tanner if he and Andrea had heard the kids talking about the man in the forest. They’re worried about it.”
“Have you seen anything strange?” I ask.
Jasmine steps up to the floor to ceiling window in the breakfast nook and peers at the forest across the cul de sac. She purses her lips and shakes her head, “No. You?”
I say, “Nope,” as I pull out the ingredients I’ll be using for dinner tonight. “We’ve taught the kids well. They know not to go near strangers. I’ll see if I can maneuver the camera to keep an eye on the woodline. Yeah?”
“Yes, that sounds good,” says Jasmine, relaxing and settling into one of the breakfast nook table chairs. “I didn’t get the Letterman account.”
I take out the chicken from the refrigerator and say, “I figured as much from the way you sounded on the phone. Look, all is not lost. You just need to get a hold of someone who knows him well.”
Jasmine crosses her arms and peers out at the kids outside, “I don’t know. I might have to take this one as a loss.”
“No! You can’t give up,” I try to get her spirits up by reaching for a bottle of wine from the rack above the refrigerator. She smiles when I pour her a glass and puts a hand on mine to hold me for a while after I leave the glass in front of her. “You’re still in control. You can figure this out.”
“Sometimes things are just out of our control David.”
I stare back slack jawed, “Things are always in our control Jasmine. We didn’t get this far in life by pretending everything was predestined.” I laugh as I grip a handful air and say, “I’ve got life by the balls baby. Always have. That’s why we have such a splendid house, such a nice life.”
“Don’t give yourself all the credit, big guy.”
I turn back to the chicken with a smile and start preparing dinner. “Hey Google, play Tennessee Whiskey by Chris Stapleton.”
An upbeat voice from the little circular speaker on the kitchen island replies, “Sure, Tennessee Whiskey by Chris Stapleton.” Chris Stapleton’s classic four strums of the guitar echo out of the speaker and I dance as I marinate the chicken. I love the sound of the children enjoying themselves outside going along to the music; love the feeling of the chopped cilantro, salt, and pepper grind between my fingertips as I rub it into the chicken. The oil heats in the pan releasing a little wisp of smoke. The chicken sizzles in the pan and releases a hearty aroma.
When I rise from the pan, I notice Jasmine is standing at the window again, cup of wine in hand. Twilight is settling in but the street lights haven’t kicked on yet. Jasmine is strangely close to the window, I figure she’s enjoying the sight of the kids as their shadows zip past in front of her like specters in the night.
“David. I see something in the woodline.”
I shoot to her side and peer out the window along with her. The kids' shadows stalk in the night but I can’t make out anything across the cul de sac. “I don’t see anything.”
Jasmine plants a finger in the windowpane, “Right there. There, it's definitely someone out there. There’s a neighborhood on the other side of that treeline isn’t there?”
I strain to catch a glimpse at what she’s looking at and say, “I don't see anything. I, uh, I think there’s a neighborhood back there yeah.”

The street lights kick on. A man stands just out of reach of the street light on the far end of the cul de sac. “Holy fuck,” I say under my breath.
“Kids, come inside please!” shouts Jasmine.
“Aww c’mon mom. Just a bit longer,” calls out my son.
“Zach, get inside like your mother told you,” I growl and take my gaze away from the man for a second to sneer at my boy through the window. By the time I look back the man’s gone. “Where’d he go?”
Jasmine’s eyebrows raised, “He uh, just kind of vanished. Looks like he was never really there. Look,” She points at a tree shaped strangely enough like a man. “Maybe it was just that tree we were looking at.”
I didn’t take any chances. I tell the kids to come in and I maneuver the security cameras to get a good vantage of the place where the man had vanished. The next morning I help the kids get ready for school and personally walk them to their bus stop.
Still no man in the woods.
Shortly after I return to the house I kiss my wife goodbye and wish her good luck at work. Just as she pulls out of the cul de sac, as I am walking to my truck, I notice a figure in my peripheral vision but I don’t turn knowing I might scare him away. I halfway sit in my truck and shift the rearview mirror to where I’d seen him. There he is. The man stands several feet inside the forest. Greenery conceals him up to his torso and I can barely see his face in the shadows of the forest, but his figure is clear.
I consider calling the police, no, they won’t make it in time. I take a deep breath, count down from three, and burst out of my car into a sprint toward the man in the woods. The man doesn’t move an inch as I approach but somehow it seems as if the forest deepens around him. As I get closer his relative position from me grows further, but the man doesn’t take a step. It's as if the world around the man grows further and further out of focus the closer and closer I get.
I hear the leaves crushing beneath my footfalls and I look back for a second feeling as if I’d been running on a treadmill for the past few seconds. My house is barely visible through the foliage. I whipped my attention back at the man but he’s gone and I grind to a halt. I scrutinize the woods, the man has vanished.
My breaths slow, nearly holding my breath I listen intently for the sound of crushing leaves. The crunching leaves come from behind me at an alarming pace. Whatever is approaching is running fast. I turn, ready for someone to tackle me, but there is no one there, the footfalls go silent. I curse under my breath and peer back at my house. It's hard to make out now that I’m so deep in the woods, but it looks like the neighbor’s kids are out in front of my house. I shake my head and look down at my watch wondering how much time I’d wasted chasing the phantom man. I wince at the readout on my watch, five pm. Maybe I hit one of the program buttons while I was sprinting into the woods?
There’s a whisper in the wind, “Must of hit..”
I turn to the whispers.
Another whisper behind me, “One of the program buttons.”
I turn. I feel light in my own skin. There’s nothing behind me, no one around me, but I continue to hear the voice whispering.
“Five PM. Five?”
I’m literally beside myself. I know it's my own voice I’m hearing but I’m not sure if it's my thoughts or an illusion, just the wind blowing. Maybe it’s the shifting tree branches and my paranoia. The sun is bright, blinding. Suddenly, I’m seconds behind myself.
I saw my hand shifting in the sunlight. Perhaps it was the fatigue from a sleepless night having been worried about the phantom man lurking in the forest outside my house. The disconnect in time was jarring as every movement jolted like a violent tectonic shift in my head. I felt like a witness to my own reality as it had just happened.
I looked around and a sound off in the woods drew me deeper. The deeper I went, the dimmer the sunlight became. I ran faster and faster in chase of the sounds with the hopes I’d at least catch another glimpse of the phantom man.
Then, my foot caught a taproot and I slammed into rich dirt, but my descent did not stop. The dirt splashed about me as if I’d fallen in a lake of darkness. The grains of dirt filled my lungs in my panic.
A squirrel watched me trip and if only the gentle creature understood the mechanics of the universe he would’ve known where I had disappeared to. Unlike the squirrel, the tree on top whose branch it sat did not have the sense of sight to have seen me fall but it did encounter a minty sensation when it absorbed the nutrients of my being. I hadn’t granted the beings of its kind the sense of emotion, but somehow it still knew the sensation was good. It exhaled the vapors of me and enriched the atmosphere for the humans of that world. These little kinds of discoveries excited me. A design had led to an outcome I hadn’t thought possible and I saw that it was good.
The cosmic specs continued their spread before me and it suddenly occurred to me I hadn’t paid much attention to the adjacent place. There it was still only nothingness, phantom echoes of my self reflection. All was good, but was it best? I’ve created many things, breathed life into endless inanimate things yet most of my existing universe still lingers motionless, pushed only by the initial momentum of the beginning. The life that has existed has worshiped me, prayed to me, cursed me, forgotten me and found me, but is it best?
Perhaps I’ll never know until I compare it with another. So it is. From my word bubbled a new momentum from unfathomable depths. All possibilities confounded and reverberated and again there was an atmosphere charged with my essence, what would these new humans do with it?
The tree inhaled my essence and it was good. The squirrel watched a man disappear into the earth and it was good. Grains of dirt filled my lungs and dispersed from my nose and it was good. I was spat out from the depths of the universe and on my feet I chased the phantom man in the direction of my home. The sun had receded into the horizon and time had regressed to a moment.
Beyond the foliage I see my children play with the neighbors. Their laughter is alarmingly delicious to my ears as if I hadn’t heard that sweet sound in an unfathomable expanse of time. There I am in the window, looking this way. Then suddenly, the street light kicks on.
“Holy fuck,” says David under his breath.
I shout, “Kids, come inside please!”
-
 @ b804f68e:2fb0fa1f
2024-07-08 00:58:33
@ b804f68e:2fb0fa1f
2024-07-08 00:58:33If you were financially set, right here, right now, what is it that you would start doing? If you could do whatever it is your heart has always desired, what would you do? And I want you to dare to think big, because the fiat world confines us to thinking safe and small, but as stackers we must start thinking freaking big and strive towards it and refuse to settle for less.
I'll start: - I will build my own soccer club, and it will be providing immense value to my local community by bringing people together, and by being a space where everyone can learn about soccer, about optimizing health, and of course about Bitcoin. - I will be doing some sort of philanthropic work, not sure in what way but in some meaningful way. - I will be happily married to my partner and we will be building our life together, seeing more of the world, experiencing more of what this beautiful world has to offer. - I will help pay off my friend's debt and support him in his goal to become healthier. - I will continue to strive towards becoming the best athlete and nerd I can become. - I will open up my own gym combined with a soccer field. - I will donate to my friend's business that he is in the process of building as without him I would not be the athlete and person I am today. - I will pay for whatever it is my parents desire, all of it. - I will pay for whatever it is my love desires and more.
Just a few things that I will do when I am financially free.
Don't let your fiat mind hold you back, think big, be brave and be bold!
You have obtained financial freedom. It is done. So what amazing things are you going to do with this freedom?
originally posted at https://stacker.news/items/600417
-
 @ ee603283:3bc79dec
2024-07-07 22:27:41
@ ee603283:3bc79dec
2024-07-07 22:27:41Nikolai Kardashev proposed a categorization of hypothetical alien societies based on how much energy they could use in their technology.
Types of civilization: Type 1: harness 100% of the energy available on the planet. Type 2: harness the power of their entire star.
Did you know that humanity is not even on the Kardashev scale yet, here in 2024! It's crazy to think that all our collective advancements haven't resulted in global peace, unity, or collective efforts to get along. All that energy has been wasted on petty feuds, pointless arguments, and evil hatred. We would be much further ahead if we had collective incentives that were aligned to be honest and true. Even if we weren't honest and true, the tools in place could make it intuitive and trivial to verify the deception. This would lead dishonest individuals to be outcasted in society and be punished for it automatically. Kinda sounds familiar...hmmmm...
Taking advantage of all the energy available to us on earth requires the usage of different forms of fuel and different modes of transporting that energy. The energy will have to be stored efficiently and transported effortlessly.
Enter bitcoin and humanity’s big leap into a Kardashev Type 1 society. Bitcoin helps us achieve a Type 1 level society and helps us take a big leap towards advancing into a Type 2 level society. Bitcoin is trivially easy to verify if it's a valid transaction and helps us stay honest in the proof-of-work that was completed to mine a block. Transporting this form of energy is also easy because it can be sent to anyone anywhere in the world at a fraction of the cost to mine it, via the internet, telecom infrastructure, or satellite. First, we must think beyond ourselves and grow as an intergalactic species. We must play at a higher level.
Until next time bitcoin reader.
-
 @ 9e69e420:d12360c2
2025-02-15 20:24:09
@ 9e69e420:d12360c2
2025-02-15 20:24:09Ukraine's President Volodymyr Zelensky called for an "army of Europe" to defend against Russian threats, emphasizing that the US may not continue its traditional support for Europe. Speaking at the Munich Security Conference, he warned against peace deals made without Ukraine's involvement.
US Vice President JD Vance echoed this sentiment, urging Europe to enhance its defense efforts.
Zelensky stated, "I really believe the time has come - the armed forces of Europe must be created." He highlighted changing dynamics in US-Europe relations and noted that "the old days are over" regarding American support.
Despite discussions around NATO, Zelensky stated he wouldn't rule out NATO membership for Ukraine.
-
 @ 6e0ea5d6:0327f353
2025-02-15 19:47:49
@ 6e0ea5d6:0327f353
2025-02-15 19:47:49"You are a slave to whoever controls you emotionally."
"We get angry when someone tries to tell us what to do. 'Don’t tell me how to dress, how to think, how to do my job, how to live.' We feel this way because we see ourselves as independent, self-sufficient individuals.
Or at least, that’s what we tell ourselves.
Yet, if someone says something we disagree with, something inside us tells us we must argue with them. If a plate of treats is placed in front of us, we must eat them. If someone does something we don’t like, we must be furious. If a setback arises, we must be sad, depressed, or worried. But if something good happens a few minutes later, suddenly, we’re happy, excited, and wanting more.
We should never let another person shake us back and forth the way our impulses do. It’s time we start seeing things differently: we are not puppets, dancing to whichever tune suits us at the moment. We should be the ones in control—not our emotions—because we are independent, self-sufficient individuals."
— Ryan Holiday"Frame your thoughts like this: you are a mature man, and you will no longer allow yourself to be enslaved or manipulated like a puppet by every impulse. You will stop complaining about your current lot or fearing the future."
— Marcus Aurelius📌 Emotions can give us information, but they should not give us orders.
It’s not enough to learn to say "no" to others; you must also learn not to give in to the demands of your weaker self.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ eed76ece:afa98124
2024-07-07 21:25:58
@ eed76ece:afa98124
2024-07-07 21:25:58au nom des commerçants
Oui, conserver Bitcoin pour toujours est honorable, logique et sage.
Et je comprends que cela signifie NE PAS utiliser réellement dans le commerce, je comprends.
Pour aider les humains du monde à utiliser réellement Bitcoin à chaque instant dans le cadre de leurs transactions commerciales, pas seulement pour acheter une tasse de café ou une bière à l'aide d'une facture éclair, mais aussi pour le commerce de gros de produits en gros entre pays, nous devrions considérer quand Les humains font réellement ça ?
Comment pouvons-nous éduquer, justifier, expliquer ou soutenir la volatilité de la fixation d'un prix de vente dans SATS Bitcoin ?
originally posted at https://stacker.news/items/600307
-
 @ c582af78:698069cc
2025-02-15 19:21:25
@ c582af78:698069cc
2025-02-15 19:21:25The Face of God: How Art Became a Gateway to the Divine
If you live in the West, you’re surrounded by depictions of God, Jesus, and the saints—from paintings and statues to illustrated Bibles and stained glass windows.
But this is far from universal. In the Islamic world, religious art takes a very different form: vibrant colors, intricate geometry, and architectural symmetry. Depictions of God or Muhammad aren’t just discouraged—they are outright forbidden.
But why?
To answer that, we must go back to the origins of the Abrahamic religions—when early Christians, Jews, and Muslims were surprisingly unified in their views on religious art.
https://image.nostr.build/1515c5fd00d798cd283583618bbbc0d5eb91bc481a84c21d53644d42fa30173a.jpg
The Early Christian Hesitation
The first generation of Christians were deeply aware of Judaism’s strict prohibition against idol worship. Depicting God in any form was considered dangerous—a potential gateway to paganism.
For centuries, Christianity could have followed this path, rejecting religious imagery altogether. But one fundamental theological idea changed everything:
The Incarnation.
As the early Church wrestled with the nature of Christ, heated debates emerged:
- Was he part human and part divine?
- Was he fully human and fully divine?
- And what did the Gospel of John mean by “the Word became flesh and dwelt among us”?
The result of these debates was the doctrine of the Incarnation—the belief that God took on human form in real flesh and blood. And if God himself had chosen to be seen in finite form, then depicting Him in art could no longer be considered blasphemous.
This single theological shift laid the foundation for Christianity’s embrace of religious art—a decision that would not only shape Christian worship but redefine how we engage with art itself.
https://image.nostr.build/1cf9ea5d1385c46bd720de9c7de65123428a9f76356e39e37c5d7b9663993930.jpg
Let There Be Art…
How did this change Christian art?
https://image.nostr.build/b945e4ea06b281bb4618f08b2543108beecf7f510aaa795bed1c833614e32fb7.jpg
The early objections to religious imagery went something like this:
“God is infinite and mysterious. Reducing Him to a finite, limited form is blasphemy.”
But with the Incarnation, the argument flipped:
“If God took on real shape, color, and form without diminishing His divine nature, then we can depict Him in art without compromising His grandeur.”
Thus, images of Jesus, Mary, and saints not only became permissible—they were encouraged.
Christian leaders actively commissioned religious art to communicate the Gospel visually to a largely illiterate population. Paintings, statues, and stained glass became tools of evangelization, helping people grasp biblical stories without needing to read.
Take the Duomo of Milan with its 4,000 statues. They aren’t just decorative. They inspire faith by highlighting the lives of the saints.
Christianity had embraced art as a spiritual bridge, a way to connect the finite with the infinite.
https://image.nostr.build/4f6b79a9179d818a951bf461ee5ff785cbe618ed376b4a56d92e77dcb34005bc.jpg
The Criticism: Were They Worshiping the Art?
Not everyone agreed.
Some critics argued that Christians were focusing too much on the art itself, rather than the God it was meant to represent.
https://image.nostr.build/29afb401ef99d2b6c59b71d8534a5160c25d2ca468d81251ba0f55d033679490.jpg
But the Church’s response was clear:
"You are not meant to look at art, but through it.
Art is not the end goal—it is a gateway to something greater.
A painting of Christ isn’t meant to be worshiped—it’s meant to draw the viewer into His story, His sacrifice, and His message.
This perspective didn’t just shape religious art. It fundamentally changed how we experience all forms of art, even secular ones.
To Infinity and Beyond: The Lasting Impact of Religious Art
Christianity’s view of art—that it should point beyond itself—has so deeply influenced Western culture that we often don’t even realize it.
Think about how we experience books, music, and movies:
- A great novel inspires courage.
- A powerful song moves you to tears.
- A gripping film motivates you to keep going in life.
The best art doesn’t just exist for its own sake—it transports you beyond the canvas, the page, or the screen.
This idea mirrors the Incarnation itself: an infinite God becoming finite to guide us back to the infinite.
Tolkien, The Lord of the Rings, and the Incarnation of Art
A perfect example? J.R.R. Tolkien’s The Lord of the Rings.
Tolkien infused his story with themes of brotherhood, heroism, and sacrifice—all timeless, transcendental ideas. But instead of leaving them as abstract concepts, he "incarnated" them into words on a page—finite, tangible, and deeply relatable.
https://image.nostr.build/b120c4d7c7232cf226af65c33cb7fc494f495d50b8ad4593a58f3528fd0b71dc.jpg
His goal? To turn the reader’s heart back to the infinite by making them experience these ideals in a concrete way.
The same can be said for any truly great art.
It doesn’t exist for itself—it exists to move you, to inspire you, to challenge you.
And next time you step into a cathedral, gaze at a masterpiece, or listen to a symphony, remember:
You’re not supposed to simply look at the art around you—
You’re supposed to look beyond it, into eternity.
-
 @ eed76ece:afa98124
2024-07-07 21:02:01
@ eed76ece:afa98124
2024-07-07 21:02:01Eventually some smaller suppliers/exporters and buyers/importers will use Bitcoin Factoring. Actually a great idea. Minor detail when any Company in ANY Country imports and/or exports, there is so much paperwork and logging by various Government agencies that both parties in the sale or purchase of the goods still have to declare in fiat usually the USD.
However, a few brave souls out there are taking about using Bitcoin for Factoring instead of using fiat. Actually smaller garment and textile companies are already seeing that this will probably be used sooner rather than later in:
Cambodia Belarus El Salvador Hong Kong Honolulu (NOT "Hawaii"). India Laos Mexico Russia (2025 with or without a finish to the war). Thailand Vietnam
My biggest complaint from my peers in other Countries is that their own Governments keep changing what is "allowed" this year versus previous years, or this extra taxation, regardless it's coming, the actual use in B2B transactions using Bitcoin.
These are some the realities suppliers and buyers have to deal with
What is the declared price in fiat ? What is the price of Bitcoin at the time of the payment ? What was the payor's DCA of the Bitcoin they have possession of ?
Here again, smaller companies can just bypass a factoring their invoices and collect payment in Bitcoin, fast much, much cheaper and breaking up in to smaller installment payments via Lightning seems like the baby steps in trying this out.
We are so early, please keep in mind this handy reference:
Honolulu has many many flights every day from Asia and South East Asia, there are many business people that use Honolulu as a stepping stone to get started doing business in the USA
Why ?
- We are in the middle of the Ocean very few "factories" here, we have to import and export.
- It's logical to use Bitcoin, wire transfers are expensive and time consuming to process.
- Multiple "installment payment(s) and or deposit payments, or shipping payments, etc. can be done via Lightning payments, Zaprite invoicing is a good start for your customers they will see the option to pay with Bitcoin, or ACH, or a card, or link to square or stripe etc.
- It's a sales tool as it can create communication about factoring, and move to just giving or getting a discount of payment is made using Bitcoin.
Other Issues
A. Some Bitcoin payment providers and wallets are "leaving" or no longer support doing any transaction in the USA.
B. Whether your a buyer or seller of goods, If you are holding some Bitcoin that you DCA'ed as your starting point then it's easier to quote what your comfortable with.
C. Look at where tourism is doing good, growing is logically where your newer markets are to go to, especially if your an American.
D. Do NOT underestimate the trade in Belarus, Cambodia, Honolulu (NOT Hawaii), Hungary, India, Kazakhstan, Mexico, Myanmar, Poland, Russia, Thailand, Ukraine, Vietnam it's already taking place. Leave World politics aside, your either a merchant or not, the discussion here is about doing business.
E. Position your company to have at least one distributor, dealer, agent that is standing by and is familiar with your products.
F. Do NOT waste your time with these Countries, remember their stance on the lock downs before. Australia (EXCEPT PERTH it's ok), Canada, New Zealand, The United Kingdom.
G. Contact me if your an actual business person interested in selling your goods to destinations OUTSIDE of the USA. No business reports or academia discussions, merchant mentality only please.
H. Trump will probably shake up things with tariff comments, just stay the course, think opportunities in BOTH Importing AND Exporting. Do NOT think like a generic American, get straight to the point, think one page pdf brochures.
I. Friendly reminders USA uses UPC-A barcodes rest of the World varies. Spend thirty minutes on www.gs1.org
originally posted at https://stacker.news/items/600289
-
 @ a95c6243:d345522c
2025-02-15 19:05:38
@ a95c6243:d345522c
2025-02-15 19:05:38Auf der diesjährigen Münchner Sicherheitskonferenz geht es vor allem um die Ukraine. Protagonisten sind dabei zunächst die US-Amerikaner. Präsident Trump schockierte die Europäer kurz vorher durch ein Telefonat mit seinem Amtskollegen Wladimir Putin, während Vizepräsident Vance mit seiner Rede über Demokratie und Meinungsfreiheit für versteinerte Mienen und Empörung sorgte.
Die Bemühungen der Europäer um einen Frieden in der Ukraine halten sich, gelinde gesagt, in Grenzen. Größeres Augenmerk wird auf militärische Unterstützung, die Pflege von Feindbildern sowie Eskalation gelegt. Der deutsche Bundeskanzler Scholz reagierte auf die angekündigten Verhandlungen über einen möglichen Frieden für die Ukraine mit der Forderung nach noch höheren «Verteidigungsausgaben». Auch die amtierende Außenministerin Baerbock hatte vor der Münchner Konferenz klargestellt:
«Frieden wird es nur durch Stärke geben. (...) Bei Corona haben wir gesehen, zu was Europa fähig ist. Es braucht erneut Investitionen, die der historischen Wegmarke, vor der wir stehen, angemessen sind.»
Die Rüstungsindustrie freut sich in jedem Fall über weltweit steigende Militärausgaben. Die Kriege in der Ukraine und in Gaza tragen zu Rekordeinnahmen bei. Jetzt «winkt die Aussicht auf eine jahrelange große Nachrüstung in Europa», auch wenn der Ukraine-Krieg enden sollte, so hört man aus Finanzkreisen. In der Konsequenz kennt «die Aktie des deutschen Vorzeige-Rüstungskonzerns Rheinmetall in ihrem Anstieg offenbar gar keine Grenzen mehr». «Solche Friedensversprechen» wie das jetzige hätten in der Vergangenheit zu starken Kursverlusten geführt.
Für manche Leute sind Kriegswaffen und sonstige Rüstungsgüter Waren wie alle anderen, jedenfalls aus der Perspektive von Investoren oder Managern. Auch in diesem Bereich gibt es Startups und man spricht von Dingen wie innovativen Herangehensweisen, hocheffizienten Produktionsanlagen, skalierbaren Produktionstechniken und geringeren Stückkosten.
Wir lesen aktuell von Massenproduktion und gesteigerten Fertigungskapazitäten für Kriegsgerät. Der Motor solcher Dynamik und solchen Wachstums ist die Aufrüstung, die inzwischen permanent gefordert wird. Parallel wird die Bevölkerung verbal eingestimmt und auf Kriegstüchtigkeit getrimmt.
Das Rüstungs- und KI-Startup Helsing verkündete kürzlich eine «dezentrale Massenproduktion für den Ukrainekrieg». Mit dieser Expansion positioniere sich das Münchner Unternehmen als einer der weltweit führenden Hersteller von Kampfdrohnen. Der nächste «Meilenstein» steht auch bereits an: Man will eine Satellitenflotte im Weltraum aufbauen, zur Überwachung von Gefechtsfeldern und Truppenbewegungen.
Ebenfalls aus München stammt das als DefenseTech-Startup bezeichnete Unternehmen ARX Robotics. Kürzlich habe man in der Region die größte europäische Produktionsstätte für autonome Verteidigungssysteme eröffnet. Damit fahre man die Produktion von Militär-Robotern hoch. Diese Expansion diene auch der Lieferung der «größten Flotte unbemannter Bodensysteme westlicher Bauart» in die Ukraine.
Rüstung boomt und scheint ein Zukunftsmarkt zu sein. Die Hersteller und Vermarkter betonen, mit ihren Aktivitäten und Produkten solle die europäische Verteidigungsfähigkeit erhöht werden. Ihre Strategien sollten sogar «zum Schutz demokratischer Strukturen beitragen».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a853296a:209e695f
2024-07-07 19:45:25
@ a853296a:209e695f
2024-07-07 19:45:25What up stackers! We're back for a quick update: Today we're announcing the release of our new Word Level Transcripts API!
Have you ever heard a great point in a talk/podcast and not able to find it later? CASCDR Voice to Text fixes this . Just upload or provide a link to an mp3 or mp4 file and CASCDR comes back with your transcript:
Previously we launched this service as a proof of concept. Truthfully it was not good enough so we went ahead and upgraded it: - 20 min media limit -> 5 hour limit - Single Monolthic Transcript -> You can get full transcript, sentence level timestamps or word level timestamps
We implemented this new API in our YouTube Logic App to integrate the entire workflow. With just a YouTube URL you can explore, search and copy the entire transcript to your clipboard.
Searching the latest SNL with @Car and @k00b for updates on BOLT12
At CASCDR we believe that lightning enables a future of open, flexible, decentralized and truly useful AI applications and agents. A boon for humanity that cannot be overstated. Each and every service we create provides value to humans today but is also available to automated software and AI services from day 1. If this application interests you hit us with suggestions/questions/thoughts in the comments!
If you want virtually unlimited access to this tool or many others we offer CASCDR Amber for $9.99/month . Otherwise we also accept payments through the @Alby Bitcoin Connect plugin!
Additional Links/Materials
That's it for today! If you made it this far thank you! Here is a list of more CASCDR materials you can check out: SN Post about CASCDRVision AI Clipping Tool: https://stacker.news/items/568299 SN Post about YouTube Summarizer Agent: https://stacker.news/items/418051 CASCDR Appearance on AI Unchained with @GuySwann_nostr : https://www.youtube.com/watch?v=T3w9wqPw5xQ&pp=ygUQY2FzY2RyIGd1eSBzd2Fubg%3D%3D CASCDR Presentation at @PlebLab Top Builder: https://www.youtube.com/watch?v=1v3aWdGVx7s&pp=ygUSdG9wIGJ1aWxkZXIgY2FzY2Ry
originally posted at https://stacker.news/items/600228
-
 @ a42048d7:26886c32
2024-07-07 14:27:26
@ a42048d7:26886c32
2024-07-07 14:27:26*50% of the Bitcoin held with Unchained will be seized by the US government within 10 years: a thought experiment **
Let me start by saying that I believe collaborative multisig is strictly better than leaving on an exchange, an ETF, or other paper Bitcoin options. I have extensively tested collaborative multisig at the 3 most well known providers: Unchained, Casa, and Nunchuk. My participation in Bitcoin Twitter and Nostr has led me to the conclusion that KYC collaborative multisig is shockingly easy to seize. If you care about this topic I will assume you are already based enough that you need no primer on the horrid fiscal situation of the governments of the USA, EU, China, etc. A 6102 (President FDR ordering the seizure of all privately held gold) type event feels escalatingly likely in the short term, and almost inevitable in the medium term.
There are a few indisputable facts everyone must accept: Most users of collaborative multisig have at least 1 key (probably 2) at one of the following: their home, a bank safety deposit box, or other highly logical place in their immediate vicinity. Unchained multisig vaults are fully KYC. Meaning they have a list of your name, email address, and home address right next to your BTC holdings amount, 1 of 3 keys to your multisig, and even Social Security Number and more info if you use their loan or trading desk services.
Hopefully you should immediately recognize the problem. The American government is 1 warrant away from having your full identity, BTC amount, and 1 of your 3 keys. Further they are most likely 1 visit to your home or bank away from having a 2nd key, and thus control of your BTC. Further, everyone must also accept that video verification is not much better than no verification. The government could also just come to your home (where you almost certainly have 1 key) and force you to submit a transaction request to Unchained. Per their own website Unchained does not have a specific minimum waiting period to submit transaction, e.g. it could be 1-2 days if you submit on a slow Monday or it could be 3-5 days if you submit over a weekend during a crowded Mempool. Even before considering AI fakes, video verification is simply not secure. It is quite easy to have someone stand out of shot holding you and/or your family hostage. The American government also has more than enough prison capacity to hold anyone indefinitely they need to while waiting for transactions to process. Sit and ruminate on the fact that all the government needs to do to take your Bitcoin is enter your home, use their monopoly on violence, and not so politely ask you to sign with your key and request Unchained sign with theirs. After a brief delay, all your BTC is gone forever! There is a brutal cognitive dissonance in believing Bitcoin will become worth millions of dollars per coin, and simultaneously thinking the government will not bother to visit one office, a few homes, or a handful of banks for untold riches. If the government gets desperate, then large holders using KYCed collaborative multisig are a potentially appealing target. Yes it is strictly harder to seize than an ETF or on an exchange, but that doesn’t make it foolproof. The easiest target is often the overconfident one. It would likely be too difficult to discretely visit many places and hold many people for enough time to seize all coins held by Unchained, but grabbing a significant portion of the largest holders before news broke is certainly plausible. Maybe I’m underestimating Unchained and they’re willing to go to prison for life, and during a government raid would wipe their servers rather than hand them over. But would you trust that with your life savings? I would not. In my assessment for users with less technical knowledge non-KYC multisig options such as Casa and Nunchuk are strictly better than a fully doxed option like Unchained. For those with more advanced technical knowledge the potential of miniscript and timelocks in Liana presents an even more secure option, albeit with the tradeoff of additional complexity. There is no free lunch. You must decide for yourself. Just please thoughtfully consider your options.
I hope this is not taken as an attack at Unchained. I believe they are a solid Bitcoin only company doing some great work, but I also think they and their users drastically underestimate their current vulnerabilities. My hope is not to harm them in any way, but to force an uncomfortable conversation that the community needs to have. My greatest hope would be multisig makes strides in security across the industry. Taproot enabling multisigs to look like singlesigs and not placing all spending paths publicly on chain would be a great place to start. Miniscript next. These advanced security capabilities are available today via Liana and Anchorwatch. These are the next generation of multisig that the community desperately needs. They just haven’t realized it yet, but they will once a few Unchained customers publicly get their Bitcoins seized.
-
 @ d57360cb:4fe7d935
2025-02-15 17:35:54
@ d57360cb:4fe7d935
2025-02-15 17:35:54Don’t focus on the end goal solely. If you do you’ll always find yourself empty handed. You wouldn’t want a fast forward button on your favorite song or your favorite movie. You don’t want to rush through your meals or the time you spend with important people in your life.
Notice this tendency to do things in order to get to the end. It’s sapping the depth of your existence from you.
Slow down. Life is lived in the in between. If you learn how to savor that, you’ll have a rich meaningful life.
-
 @ 6f170f27:711e26dd
2024-07-07 14:13:13
@ 6f170f27:711e26dd
2024-07-07 14:13:13Alright. Been thinking about different ways to share photo memories with friends and family and will explain my thoughts on a few methods and then I want to hear what you like to do or was the last such event you participated in
There's something about reliving memories through images. It's not just nostalgia – I found it to be incredibly influencial on thinking about my whole life as kind of a story, bonding with people, and keep our most precious moments alive. But in this digital age, how we choose to revisit these memories?
I've been thinking a lot about different ways to share photo memories with friends and family. To me, that's kind of the point of it all. I might be obsessive about gear and tech etc but in the end all that counts to me is the social aspect and sharing it with people.
Analog Projectors: Bringing back the old school slideshow vibes.
Pros: Nostalgic feel, creates a "event" atmosphere, big screen impact. What I like about this is that making it an "event" lowers the social barrier of other people to actually engage in the activity. Cons: Setup can be a hassle, image quality varies, limited to physical slides or prints. You not only have to shoot analog - you have to shoot positive slides analog.

Maybe here is the point I should mention digital projectors as well. I know that this is what the purists do (maybe you are this, please tell me if so) and probably nice if you are rich enough to have a whole home theatre setup. I remember reading on Reddit that some people even insist on using the same cine lenses on their projectors that they shot a vacation with

I get the appeal of cinematic photos from an ARRI lens on Kodak Motion Picture Film. I get it. But for me that's a little too autistic no offense.
Smart TV: The modern take on slideshows.
Pros: Big screen experience, easy to control from your phone, good for group viewing. This is the biggest screen, most immersive setup, most inclusive for everyone to copy photos into a folder before hand. Cons: Requires some tech setup, can sometimes feel a bit too "produced". My personal experience is that this counterintuitively has the highest social barrier to do - even higher than doing analog projection as an "event". People don't like to commit to an calendar entry just for that. Might work well if tacked on onto the end of movie night or board game evening.
Prints: Going old school with fine art prints
Pros: Tactile experience, no tech required, creates a physical keepsake Cons: Takes effort to organize, can be costly, not as easy to share widely

Prints can be as classy and fine art or as casual and posters as you want them to be. Great for looking at as a side activity during a bbq or board game night. It gets really expensive to print a dozen pics for every occasion tho. At this point I also want to encourage everyone to make a huuuge print if you ever take a pic that xould be a magnum opus. Once every decade event maximum IMO. Bonus: video about printing papers
Looking at an iPhone together.
Pros: Super convenient, always with you, great for spontaneous Cons: Small screen limits the impact, not at all immersive. On vacation photos from last year I want to feel like I'm right there again. Not very social as people tend to hunch over the phone, can feel a bit impersonal. Even when we share an iPad or phone I think there is something subconscious about a personal device that makes it feel less together

I can't stress enough that this subconscous barrier makes it so that IMO the bonding aspect here is really zero. Idk how to say it.
VR: The futuristic option for immersive photo experiences.
Pros: Incredibly immersive, can feel like you're "in" the photo, great for panorama images which IMO one of the smart phone photography features that beats real cameras Cons: Expensive gear, isolating (usually one person at a time), can be overwhelming for some. I haven't tried Apple Vision Pro but it seems like this is still so so so far for a social event.

kinda dystopian. Maybe when I'm 90 and alone I'll do that scrolling through my entire life on the day before I die.
Digital Photo Frames
I hate this one, it's just TV but worse. No pro&con list. Call me biased, whatever.
Conclusion
I will try to do TV sessions tacked on to other events. I mentioned that the social barrier is high but I can't shoot everything on positive slides. I will also do fine art prints for 3-4 photos per vacation or real life thing where I took a camera.
What's your preferred method for sharing photo memories? Do you prioritize convenience, social interaction, or immersion? Any cool ideas or methods I missed? Do you maybe disagree with the entire premise that socializing and reminiscing is the entire point?
originally posted at https://stacker.news/items/599904