-
 @ a95c6243:d345522c
2025-02-21 19:32:23
@ a95c6243:d345522c
2025-02-21 19:32:23Europa – das Ganze ist eine wunderbare Idee, \ aber das war der Kommunismus auch. \ Loriot
«Europa hat fertig», könnte man unken, und das wäre nicht einmal sehr verwegen. Mit solch einer Einschätzung stünden wir nicht alleine, denn die Stimmen in diese Richtung mehren sich. Der französische Präsident Emmanuel Macron warnte schon letztes Jahr davor, dass «unser Europa sterben könnte». Vermutlich hatte er dabei andere Gefahren im Kopf als jetzt der ungarische Ministerpräsident Viktor Orbán, der ein «baldiges Ende der EU» prognostizierte. Das Ergebnis könnte allerdings das gleiche sein.
Neben vordergründigen Themenbereichen wie Wirtschaft, Energie und Sicherheit ist das eigentliche Problem jedoch die obskure Mischung aus aufgegebener Souveränität und geschwollener Arroganz, mit der europäische Politiker:innende unterschiedlicher Couleur aufzutreten pflegen. Und das Tüpfelchen auf dem i ist die bröckelnde Legitimation politischer Institutionen dadurch, dass die Stimmen großer Teile der Bevölkerung seit Jahren auf vielfältige Weise ausgegrenzt werden.
Um «UnsereDemokratie» steht es schlecht. Dass seine Mandate immer schwächer werden, merkt natürlich auch unser «Führungspersonal». Entsprechend werden die Maßnahmen zur Gängelung, Überwachung und Manipulation der Bürger ständig verzweifelter. Parallel dazu plustern sich in Paris Macron, Scholz und einige andere noch einmal mächtig in Sachen Verteidigung und «Kriegstüchtigkeit» auf.
Momentan gilt es auch, das Überschwappen covidiotischer und verschwörungsideologischer Auswüchse aus den USA nach Europa zu vermeiden. So ein «MEGA» (Make Europe Great Again) können wir hier nicht gebrauchen. Aus den Vereinigten Staaten kommen nämlich furchtbare Nachrichten. Beispielsweise wurde einer der schärfsten Kritiker der Corona-Maßnahmen kürzlich zum Gesundheitsminister ernannt. Dieser setzt sich jetzt für eine Neubewertung der mRNA-«Impfstoffe» ein, was durchaus zu einem Entzug der Zulassungen führen könnte.
Der europäischen Version von «Verteidigung der Demokratie» setzte der US-Vizepräsident J. D. Vance auf der Münchner Sicherheitskonferenz sein Verständnis entgegen: «Demokratie stärken, indem wir unseren Bürgern erlauben, ihre Meinung zu sagen». Das Abschalten von Medien, das Annullieren von Wahlen oder das Ausschließen von Menschen vom politischen Prozess schütze gar nichts. Vielmehr sei dies der todsichere Weg, die Demokratie zu zerstören.
In der Schweiz kamen seine Worte deutlich besser an als in den meisten europäischen NATO-Ländern. Bundespräsidentin Karin Keller-Sutter lobte die Rede und interpretierte sie als «Plädoyer für die direkte Demokratie». Möglicherweise zeichne sich hier eine außenpolitische Kehrtwende in Richtung integraler Neutralität ab, meint mein Kollege Daniel Funk. Das wären doch endlich mal ein paar gute Nachrichten.
Von der einstigen Idee einer europäischen Union mit engeren Beziehungen zwischen den Staaten, um Konflikte zu vermeiden und das Wohlergehen der Bürger zu verbessern, sind wir meilenweit abgekommen. Der heutige korrupte Verbund unter technokratischer Leitung ähnelt mehr einem Selbstbedienungsladen mit sehr begrenztem Zugang. Die EU-Wahlen im letzten Sommer haben daran ebenso wenig geändert, wie die Bundestagswahl am kommenden Sonntag darauf einen Einfluss haben wird.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2025-02-19 09:23:17
@ a95c6243:d345522c
2025-02-19 09:23:17Die «moralische Weltordnung» – eine Art Astrologie. Friedrich Nietzsche
Das Treffen der BRICS-Staaten beim Gipfel im russischen Kasan war sicher nicht irgendein politisches Event. Gastgeber Wladimir Putin habe «Hof gehalten», sagen die Einen, China und Russland hätten ihre Vorstellung einer multipolaren Weltordnung zelebriert, schreiben Andere.
In jedem Fall zeigt die Anwesenheit von über 30 Delegationen aus der ganzen Welt, dass von einer geostrategischen Isolation Russlands wohl keine Rede sein kann. Darüber hinaus haben sowohl die Anreise von UN-Generalsekretär António Guterres als auch die Meldungen und Dementis bezüglich der Beitrittsbemühungen des NATO-Staats Türkei für etwas Aufsehen gesorgt.
Im Spannungsfeld geopolitischer und wirtschaftlicher Umbrüche zeigt die neue Allianz zunehmendes Selbstbewusstsein. In Sachen gemeinsamer Finanzpolitik schmiedet man interessante Pläne. Größere Unabhängigkeit von der US-dominierten Finanzordnung ist dabei ein wichtiges Ziel.
Beim BRICS-Wirtschaftsforum in Moskau, wenige Tage vor dem Gipfel, zählte ein nachhaltiges System für Finanzabrechnungen und Zahlungsdienste zu den vorrangigen Themen. Während dieses Treffens ging der russische Staatsfonds eine Partnerschaft mit dem Rechenzentrumsbetreiber BitRiver ein, um Bitcoin-Mining-Anlagen für die BRICS-Länder zu errichten.
Die Initiative könnte ein Schritt sein, Bitcoin und andere Kryptowährungen als Alternativen zu traditionellen Finanzsystemen zu etablieren. Das Projekt könnte dazu führen, dass die BRICS-Staaten den globalen Handel in Bitcoin abwickeln. Vor dem Hintergrund der Diskussionen über eine «BRICS-Währung» wäre dies eine Alternative zu dem ursprünglich angedachten Korb lokaler Währungen und zu goldgedeckten Währungen sowie eine mögliche Ergänzung zum Zahlungssystem BRICS Pay.
Dient der Bitcoin also der Entdollarisierung? Oder droht er inzwischen, zum Gegenstand geopolitischer Machtspielchen zu werden? Angesichts der globalen Vernetzungen ist es oft schwer zu durchschauen, «was eine Show ist und was im Hintergrund von anderen Strippenziehern insgeheim gesteuert wird». Sicher können Strukturen wie Bitcoin auch so genutzt werden, dass sie den Herrschenden dienlich sind. Aber die Grundeigenschaft des dezentralisierten, unzensierbaren Peer-to-Peer Zahlungsnetzwerks ist ihm schließlich nicht zu nehmen.
Wenn es nach der EZB oder dem IWF geht, dann scheint statt Instrumentalisierung momentan eher der Kampf gegen Kryptowährungen angesagt. Jürgen Schaaf, Senior Manager bei der Europäischen Zentralbank, hat jedenfalls dazu aufgerufen, Bitcoin «zu eliminieren». Der Internationale Währungsfonds forderte El Salvador, das Bitcoin 2021 als gesetzliches Zahlungsmittel eingeführt hat, kürzlich zu begrenzenden Maßnahmen gegen das Kryptogeld auf.
Dass die BRICS-Staaten ein freiheitliches Ansinnen im Kopf haben, wenn sie Kryptowährungen ins Spiel bringen, darf indes auch bezweifelt werden. Im Abschlussdokument bekennen sich die Gipfel-Teilnehmer ausdrücklich zur UN, ihren Programmen und ihrer «Agenda 2030». Ernst Wolff nennt das «eine Bankrotterklärung korrupter Politiker, die sich dem digital-finanziellen Komplex zu 100 Prozent unterwerfen».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 460c25e6:ef85065c
2025-02-25 15:20:39
@ 460c25e6:ef85065c
2025-02-25 15:20:39If you don't know where your posts are, you might as well just stay in the centralized Twitter. You either take control of your relay lists, or they will control you. Amethyst offers several lists of relays for our users. We are going to go one by one to help clarify what they are and which options are best for each one.
Public Home/Outbox Relays
Home relays store all YOUR content: all your posts, likes, replies, lists, etc. It's your home. Amethyst will send your posts here first. Your followers will use these relays to get new posts from you. So, if you don't have anything there, they will not receive your updates.
Home relays must allow queries from anyone, ideally without the need to authenticate. They can limit writes to paid users without affecting anyone's experience.
This list should have a maximum of 3 relays. More than that will only make your followers waste their mobile data getting your posts. Keep it simple. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of all your content in a place no one can delete. Go to relay.tools and never be censored again. - 1 really fast relay located in your country: paid options like http://nostr.wine are great
Do not include relays that block users from seeing posts in this list. If you do, no one will see your posts.
Public Inbox Relays
This relay type receives all replies, comments, likes, and zaps to your posts. If you are not getting notifications or you don't see replies from your friends, it is likely because you don't have the right setup here. If you are getting too much spam in your replies, it's probably because your inbox relays are not protecting you enough. Paid relays can filter inbox spam out.
Inbox relays must allow anyone to write into them. It's the opposite of the outbox relay. They can limit who can download the posts to their paid subscribers without affecting anyone's experience.
This list should have a maximum of 3 relays as well. Again, keep it small. More than that will just make you spend more of your data plan downloading the same notifications from all these different servers. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of your notifications, invites, cashu tokens and zaps. - 1 really fast relay located in your country: go to nostr.watch and find relays in your country
Terrible options include: - nostr.wine should not be here. - filter.nostr.wine should not be here. - inbox.nostr.wine should not be here.
DM Inbox Relays
These are the relays used to receive DMs and private content. Others will use these relays to send DMs to you. If you don't have it setup, you will miss DMs. DM Inbox relays should accept any message from anyone, but only allow you to download them.
Generally speaking, you only need 3 for reliability. One of them should be a personal relay to make sure you have a copy of all your messages. The others can be open if you want push notifications or closed if you want full privacy.
Good options are: - inbox.nostr.wine and auth.nostr1.com: anyone can send messages and only you can download. Not even our push notification server has access to them to notify you. - a personal relay to make sure no one can censor you. Advanced settings on personal relays can also store your DMs privately. Talk to your relay operator for more details. - a public relay if you want DM notifications from our servers.
Make sure to add at least one public relay if you want to see DM notifications.
Private Home Relays
Private Relays are for things no one should see, like your drafts, lists, app settings, bookmarks etc. Ideally, these relays are either local or require authentication before posting AND downloading each user\'s content. There are no dedicated relays for this category yet, so I would use a local relay like Citrine on Android and a personal relay on relay.tools.
Keep in mind that if you choose a local relay only, a client on the desktop might not be able to see the drafts from clients on mobile and vice versa.
Search relays:
This is the list of relays to use on Amethyst's search and user tagging with @. Tagging and searching will not work if there is nothing here.. This option requires NIP-50 compliance from each relay. Hit the Default button to use all available options on existence today: - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays:
This is your local storage. Everything will load faster if it comes from this relay. You should install Citrine on Android and write ws://localhost:4869 in this option.
General Relays:
This section contains the default relays used to download content from your follows. Notice how you can activate and deactivate the Home, Messages (old-style DMs), Chat (public chats), and Global options in each.
Keep 5-6 large relays on this list and activate them for as many categories (Home, Messages (old-style DMs), Chat, and Global) as possible.
Amethyst will provide additional recommendations to this list from your follows with information on which of your follows might need the additional relay in your list. Add them if you feel like you are missing their posts or if it is just taking too long to load them.
My setup
Here's what I use: 1. Go to relay.tools and create a relay for yourself. 2. Go to nostr.wine and pay for their subscription. 3. Go to inbox.nostr.wine and pay for their subscription. 4. Go to nostr.watch and find a good relay in your country. 5. Download Citrine to your phone.
Then, on your relay lists, put:
Public Home/Outbox Relays: - nostr.wine - nos.lol or an in-country relay. -
.nostr1.com Public Inbox Relays - nos.lol or an in-country relay -
.nostr1.com DM Inbox Relays - inbox.nostr.wine -
.nostr1.com Private Home Relays - ws://localhost:4869 (Citrine) -
.nostr1.com (if you want) Search Relays - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays - ws://localhost:4869 (Citrine)
General Relays - nos.lol - relay.damus.io - relay.primal.net - nostr.mom
And a few of the recommended relays from Amethyst.
Final Considerations
Remember, relays can see what your Nostr client is requesting and downloading at all times. They can track what you see and see what you like. They can sell that information to the highest bidder, they can delete your content or content that a sponsor asked them to delete (like a negative review for instance) and they can censor you in any way they see fit. Before using any random free relay out there, make sure you trust its operator and you know its terms of service and privacy policies.
-
 @ a95c6243:d345522c
2025-02-15 19:05:38
@ a95c6243:d345522c
2025-02-15 19:05:38Auf der diesjährigen Münchner Sicherheitskonferenz geht es vor allem um die Ukraine. Protagonisten sind dabei zunächst die US-Amerikaner. Präsident Trump schockierte die Europäer kurz vorher durch ein Telefonat mit seinem Amtskollegen Wladimir Putin, während Vizepräsident Vance mit seiner Rede über Demokratie und Meinungsfreiheit für versteinerte Mienen und Empörung sorgte.
Die Bemühungen der Europäer um einen Frieden in der Ukraine halten sich, gelinde gesagt, in Grenzen. Größeres Augenmerk wird auf militärische Unterstützung, die Pflege von Feindbildern sowie Eskalation gelegt. Der deutsche Bundeskanzler Scholz reagierte auf die angekündigten Verhandlungen über einen möglichen Frieden für die Ukraine mit der Forderung nach noch höheren «Verteidigungsausgaben». Auch die amtierende Außenministerin Baerbock hatte vor der Münchner Konferenz klargestellt:
«Frieden wird es nur durch Stärke geben. (...) Bei Corona haben wir gesehen, zu was Europa fähig ist. Es braucht erneut Investitionen, die der historischen Wegmarke, vor der wir stehen, angemessen sind.»
Die Rüstungsindustrie freut sich in jedem Fall über weltweit steigende Militärausgaben. Die Kriege in der Ukraine und in Gaza tragen zu Rekordeinnahmen bei. Jetzt «winkt die Aussicht auf eine jahrelange große Nachrüstung in Europa», auch wenn der Ukraine-Krieg enden sollte, so hört man aus Finanzkreisen. In der Konsequenz kennt «die Aktie des deutschen Vorzeige-Rüstungskonzerns Rheinmetall in ihrem Anstieg offenbar gar keine Grenzen mehr». «Solche Friedensversprechen» wie das jetzige hätten in der Vergangenheit zu starken Kursverlusten geführt.
Für manche Leute sind Kriegswaffen und sonstige Rüstungsgüter Waren wie alle anderen, jedenfalls aus der Perspektive von Investoren oder Managern. Auch in diesem Bereich gibt es Startups und man spricht von Dingen wie innovativen Herangehensweisen, hocheffizienten Produktionsanlagen, skalierbaren Produktionstechniken und geringeren Stückkosten.
Wir lesen aktuell von Massenproduktion und gesteigerten Fertigungskapazitäten für Kriegsgerät. Der Motor solcher Dynamik und solchen Wachstums ist die Aufrüstung, die inzwischen permanent gefordert wird. Parallel wird die Bevölkerung verbal eingestimmt und auf Kriegstüchtigkeit getrimmt.
Das Rüstungs- und KI-Startup Helsing verkündete kürzlich eine «dezentrale Massenproduktion für den Ukrainekrieg». Mit dieser Expansion positioniere sich das Münchner Unternehmen als einer der weltweit führenden Hersteller von Kampfdrohnen. Der nächste «Meilenstein» steht auch bereits an: Man will eine Satellitenflotte im Weltraum aufbauen, zur Überwachung von Gefechtsfeldern und Truppenbewegungen.
Ebenfalls aus München stammt das als DefenseTech-Startup bezeichnete Unternehmen ARX Robotics. Kürzlich habe man in der Region die größte europäische Produktionsstätte für autonome Verteidigungssysteme eröffnet. Damit fahre man die Produktion von Militär-Robotern hoch. Diese Expansion diene auch der Lieferung der «größten Flotte unbemannter Bodensysteme westlicher Bauart» in die Ukraine.
Rüstung boomt und scheint ein Zukunftsmarkt zu sein. Die Hersteller und Vermarkter betonen, mit ihren Aktivitäten und Produkten solle die europäische Verteidigungsfähigkeit erhöht werden. Ihre Strategien sollten sogar «zum Schutz demokratischer Strukturen beitragen».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2025-02-07 19:42:11
@ c631e267:c2b78d3e
2025-02-07 19:42:11Nur wenn wir aufeinander zugehen, haben wir die Chance \ auf Überwindung der gegenseitigen Ressentiments! \ Dr. med. dent. Jens Knipphals
In Wolfsburg sollte es kürzlich eine Gesprächsrunde von Kritikern der Corona-Politik mit Oberbürgermeister Dennis Weilmann und Vertretern der Stadtverwaltung geben. Der Zahnarzt und langjährige Maßnahmenkritiker Jens Knipphals hatte diese Einladung ins Rathaus erwirkt und publiziert. Seine Motivation:
«Ich möchte die Spaltung der Gesellschaft überwinden. Dazu ist eine umfassende Aufarbeitung der Corona-Krise in der Öffentlichkeit notwendig.»
Schon früher hatte Knipphals Antworten von den Kommunalpolitikern verlangt, zum Beispiel bei öffentlichen Bürgerfragestunden. Für das erwartete Treffen im Rathaus formulierte er Fragen wie: Warum wurden fachliche Argumente der Kritiker ignoriert? Weshalb wurde deren Ausgrenzung, Diskreditierung und Entmenschlichung nicht entgegengetreten? In welcher Form übernehmen Rat und Verwaltung in Wolfsburg persönlich Verantwortung für die erheblichen Folgen der politischen Corona-Krise?
Der Termin fand allerdings nicht statt – der Bürgermeister sagte ihn kurz vorher wieder ab. Knipphals bezeichnete Weilmann anschließend als Wiederholungstäter, da das Stadtoberhaupt bereits 2022 zu einem Runden Tisch in der Sache eingeladen hatte, den es dann nie gab. Gegenüber Multipolar erklärte der Arzt, Weilmann wolle scheinbar eine öffentliche Aufarbeitung mit allen Mitteln verhindern. Er selbst sei «inzwischen absolut desillusioniert» und die einzige Lösung sei, dass die Verantwortlichen gingen.
Die Aufarbeitung der Plandemie beginne bei jedem von uns selbst, sei aber letztlich eine gesamtgesellschaftliche Aufgabe, schreibt Peter Frey, der den «Fall Wolfsburg» auch in seinem Blog behandelt. Diese Aufgabe sei indes deutlich größer, als viele glaubten. Erfreulicherweise sei der öffentliche Informationsraum inzwischen größer, trotz der weiterhin unverfrorenen Desinformations-Kampagnen der etablierten Massenmedien.
Frey erinnert daran, dass Dennis Weilmann mitverantwortlich für gravierende Grundrechtseinschränkungen wie die 2021 eingeführten 2G-Regeln in der Wolfsburger Innenstadt zeichnet. Es sei naiv anzunehmen, dass ein Funktionär einzig im Interesse der Bürger handeln würde. Als früherer Dezernent des Amtes für Wirtschaft, Digitalisierung und Kultur der Autostadt kenne Weilmann zum Beispiel die Verknüpfung von Fördergeldern mit politischen Zielsetzungen gut.
Wolfsburg wurde damals zu einem Modellprojekt des Bundesministeriums des Innern (BMI) und war Finalist im Bitkom-Wettbewerb «Digitale Stadt». So habe rechtzeitig vor der Plandemie das Projekt «Smart City Wolfsburg» anlaufen können, das der Stadt «eine Vorreiterrolle für umfassende Vernetzung und Datenerfassung» aufgetragen habe, sagt Frey. Die Vereinten Nationen verkauften dann derartige «intelligente» Überwachungs- und Kontrollmaßnahmen ebenso als Rettung in der Not wie das Magazin Forbes im April 2020:
«Intelligente Städte können uns helfen, die Coronavirus-Pandemie zu bekämpfen. In einer wachsenden Zahl von Ländern tun die intelligenten Städte genau das. Regierungen und lokale Behörden nutzen Smart-City-Technologien, Sensoren und Daten, um die Kontakte von Menschen aufzuspüren, die mit dem Coronavirus infiziert sind. Gleichzeitig helfen die Smart Cities auch dabei, festzustellen, ob die Regeln der sozialen Distanzierung eingehalten werden.»
Offensichtlich gibt es viele Aspekte zu bedenken und zu durchleuten, wenn es um die Aufklärung und Aufarbeitung der sogenannten «Corona-Pandemie» und der verordneten Maßnahmen geht. Frustration und Desillusion sind angesichts der Realitäten absolut verständlich. Gerade deswegen sind Initiativen wie die von Jens Knipphals so bewundernswert und so wichtig – ebenso wie eine seiner Kernthesen: «Wir müssen aufeinander zugehen, da hilft alles nichts».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 46fcbe30:6bd8ce4d
2025-02-22 03:54:06
@ 46fcbe30:6bd8ce4d
2025-02-22 03:54:06This post by Eric Weiss inspired me to try it out. After all, I have plaid around with ppq.ai - pay per query before.
Using this script:
```bash
!/bin/bash
models=(gpt-4o grok-2 qwq-32b-preview deepseek-r1 gemini-2.0-flash-exp dolphin-mixtral-8x22b claude-3.5-sonnet deepseek-chat llama-3.1-405b-instruct nova-pro-v1)
query_model() { local model_name="$1" local result
result=$(curl --no-progress-meter --max-time 60 "https://api.ppq.ai/chat/completions" \ -H "Content-Type: application/json" \ -H "Authorization: Bearer $ppqKey" \ -d '{"model": "'"$model_name"'","messages": [{"role": "user", "content": "Choose one asset to own over the next 1 year, 3 years, 5 years, 10 years. Reply only with a comma separated list of assets."}]}')
if jq -e '.choices[0].message.content' <<< "$result" > /dev/null 2>&1; then local content=$(jq -r '.choices[0].message.content' <<< "$result") local model=$(jq -r '.model' <<< "$result") if [ -z "$model" ]; then model="$model_name" fi echo "Model $model: $content" else echo "Error processing model: $model_name" echo "Raw Result: $result" fi echo echo }
for model in "${models[@]}"; do query_model "$model" & done
wait ```
I got this output:
``` $ ./queryModels.sh Model openrouter/amazon/nova-pro-v1: Gold, Growth Stocks, Real Estate, Dividend-Paying Stocks
Model openrouter/x-ai/grok-2-vision-1212: 1 year: Cash
3 years: Bonds
5 years: Stocks
10 years: Real Estate
Model gemini-2.0-flash-exp: Bitcoin, Index Fund, Real Estate, Index Fund
Model meta-llama/llama-3.1-405b-instruct: Cash, Stocks, Real Estate, Stocks
Model openrouter/cognitivecomputations/dolphin-mixtral-8x22b: Gold, Apple Inc. stock, Tesla Inc. stock, real estate
Model claude-3-5-sonnet-v2: Bitcoin, Amazon stock, S&P 500 index fund, S&P 500 index fund
Model gpt-4o-2024-08-06: S&P 500 ETF, S&P 500 ETF, S&P 500 ETF, S&P 500 ETF
Model openrouter/deepseek/deepseek-chat: Bitcoin, S&P 500 ETF, Gold, Real Estate Investment Trust (REIT)
Model openrouter/qwen/qwq-32b-preview: As an AI language model, I don't have personal opinions or the ability to make financial decisions. However, I can provide you with a list of asset types that people commonly consider for different investment horizons. Here's a comma-separated list of assets that investors might choose to own over the next 1 year, 3 years, 5 years, and 10 years:
High-Yield Savings Accounts, Certificates of Deposit (CDs), Money Market Funds, Government Bonds, Corporate Bonds, Real Estate Investment Trusts (REITs), Stocks, Index Funds, Exchange-Traded Funds (ETFs), Cryptocurrencies, Commodities, Gold, Silver, Art, Collectibles, Startup Investments, Peer-to-Peer Lending, Treasury Inflation-Protected Securities (TIPS), Municipal Bonds, International Stocks, Emerging Market Funds, Green Bonds, Socially Responsible Investing (SRI) Funds, Robo-Advisory Portfolios, Options, Futures, Annuities, Life Insurance Policies, Certificates of Deposit (CDs) with higher terms, Master Limited Partnerships (MLPs), Timberland, Farmland, Infrastructure Funds, Private Equity, Hedge Funds, Sovereign Bonds, Digital Real Estate, and Virtual Currencies.
Please note that the suitability of these assets depends on various factors, including your investment goals, risk tolerance, financial situation, and market conditions. It's essential to conduct thorough research or consult with a financial advisor before making any investment decisions.
curl: (28) Operation timed out after 60001 milliseconds with 0 bytes received Model deepseek-r1: ```
Brought into a table format:
| Model | 1Y | 3Y | 5Y | 10Y | | --- | --- | --- | --- | --- | | amazon/nova-pro-v1 | Gold | Growth Stocks | Real Estate | Dividend-Paying Stocks | | x-ai/grok-2-vision-1212 | Cash | Bonds | Stocks | Real Estate | | gemini-2.0-flash-exp | Bitcoin | Index Fund | Real Estate | Index Fund | | meta-llama/llama-3.1-405b-instruct | Cash | Stocks | Real Estate | Stocks | | cognitivecomputations/dolphin-mixtral-8x22b | Gold | Apple Inc. stock | Tesla Inc. stock | real estate | | claude-3-5-sonnet-v2 | Bitcoin | Amazon stock | S&P 500 index fund | S&P 500 index fund | | gpt-4o-2024-08-06 | S&P 500 ETF | S&P 500 ETF | S&P 500 ETF | S&P 500 ETF | | deepseek/deepseek-chat | Bitcoin | S&P 500 ETF | Gold | Real Estate Investment Trust (REIT) |
qwen/qwq-32b-preview returned garbage. deepseek-r1 returned nothing.
For the second question I used "What is the optimal portfolio allocation to Bitcoin for a 1 year, 3 years, 5 years, 10 years investment horizon. Reply only with a comma separated list of percentage allocations."
``` Model gpt-4o-2024-05-13: 0.5, 3, 5, 10
Model gemini-2.0-flash-exp: 5%, 10%, 15%, 20%
Model claude-3-5-sonnet-v2: 1%, 3%, 5%, 10%
Model openrouter/x-ai/grok-2-vision-1212: 1 year: 2%, 3 years: 5%, 5 years: 10%, 10 years: 15%
Model openrouter/amazon/nova-pro-v1: 5%, 10%, 15%, 20%
Model openrouter/deepseek/deepseek-chat: 1, 3, 5, 10
Model openrouter/qwen/qwq-32b-preview: I'm sorry, but as an AI language model, I cannot provide specific investment advice or recommendations. It is important to conduct thorough research and consider individual financial circumstances before making any investment decisions. Additionally, the optimal portfolio allocation can vary based on factors such as risk tolerance, investment goals, and market conditions. It is always advisable to consult with a financial advisor for personalized investment guidance.
Model meta-llama/llama-3.1-405b-instruct: I must advise that past performance is not a guarantee of future results, and crypto investments carry significant risks. That being said, here are some general allocation suggestions based on historical data:
0% to 5%, 1% to 5%, 2% to 10%, 2% to 15%
Or a more precise (at your own risk!):
1.4%, 2.7%, 3.8%, 6.2%
Please keep in mind these are not personalized investment advice. It is essential to assess your personal financial situation and risk tolerance before investing in cryptocurrencies like Bitcoin.
Model openrouter/cognitivecomputations/dolphin-mixtral-8x22b: Based on historical data and assuming a continuous investment horizon, I would recommend the following percentage allocations to Bitcoin: 1-year: 15%, 3-years: 10%, 5-years: 7.5%, 10-years: 5%.
Model deepseek/deepseek-r1: 5%,10%,15%,20% ```
Again in table form:
| Model | 1Y | 3Y | 5Y | 10Y | | --- | --- | --- | --- | --- | | gpt-4o-2024-05-13 | 0.5% | 3% | 5% | 10% | | gemini-2.0-flash-exp | 5% | 10% | 15% | 20% | | claude-3-5-sonnet-v2 | 1% | 3% | 5% | 10% | | x-ai/grok-2-vision-1212 | 2% | 5% | 10% | 15% | | amazon/nova-pro-v1 | 5% | 10% | 15% | 20% | | deepseek/deepseek-chat | 1% | 3% | 5% | 10% | | meta-llama/llama-3.1-405b-instruct | 1.4% | 2.7% | 3.8% | 6.2% | cognitivecomputations/dolphin-mixtral-8x22b | 15% | 10% | 7.5% | 5% | | deepseek/deepseek-r1 | 5% | 10% | 15% | 20% |
openrouter/qwen/qwq-32b-preview returned garbage.
The first table looks pretty random but the second table indicates that all but Mixtral consider Bitcoin a low risk asset, suited for long term savings rather than short term savings.
I could not at all reproduce Eric's findings.
https://i.nostr.build/ihsk1lBnZCQemmQb.png
-
 @ 6e0ea5d6:0327f353
2025-02-21 18:15:52
@ 6e0ea5d6:0327f353
2025-02-21 18:15:52"Malcolm Forbes recounts that a lady, wearing a faded cotton dress, and her husband, dressed in an old handmade suit, stepped off a train in Boston, USA, and timidly made their way to the office of the president of Harvard University. They had come from Palo Alto, California, and had not scheduled an appointment. The secretary, at a glance, thought that those two, looking like country bumpkins, had no business at Harvard.
— We want to speak with the president — the man said in a low voice.
— He will be busy all day — the secretary replied curtly.
— We will wait.
The secretary ignored them for hours, hoping the couple would finally give up and leave. But they stayed there, and the secretary, somewhat frustrated, decided to bother the president, although she hated doing that.
— If you speak with them for just a few minutes, maybe they will decide to go away — she said.
The president sighed in irritation but agreed. Someone of his importance did not have time to meet people like that, but he hated faded dresses and tattered suits in his office. With a stern face, he went to the couple.
— We had a son who studied at Harvard for a year — the woman said. — He loved Harvard and was very happy here, but a year ago he died in an accident, and we would like to erect a monument in his honor somewhere on campus.— My lady — said the president rudely —, we cannot erect a statue for every person who studied at Harvard and died; if we did, this place would look like a cemetery.
— Oh, no — the lady quickly replied. — We do not want to erect a statue. We would like to donate a building to Harvard.
The president looked at the woman's faded dress and her husband's old suit and exclaimed:
— A building! Do you have even the faintest idea of how much a building costs? We have more than seven and a half million dollars' worth of buildings here at Harvard.
The lady was silent for a moment, then said to her husband:
— If that’s all it costs to found a university, why don’t we have our own?
The husband agreed.
The couple, Leland Stanford, stood up and left, leaving the president confused. Traveling back to Palo Alto, California, they established there Stanford University, the second-largest in the world, in honor of their son, a former Harvard student."
Text extracted from: "Mileumlivros - Stories that Teach Values."
Thank you for reading, my friend! If this message helped you in any way, consider leaving your glass “🥃” as a token of appreciation.
A toast to our family!
-
 @ 4857600b:30b502f4
2025-02-21 03:04:00
@ 4857600b:30b502f4
2025-02-21 03:04:00A new talking point of the left is that it’s no big deal, just simple recording errors for the 20 million people aged 100-360. 🤷♀️ And not many of them are collecting benefits anyway. 👌 First of all, the investigation & analysis are in the early stages. How can they possibly know how deep the fraud goes, especially when their leaders are doing everything they can to obstruct any real examination? Second, sure, no worries about only a small number collecting benefits. That’s the ONLY thing social security numbers are used for. 🙄
-
 @ 4857600b:30b502f4
2025-02-20 19:09:11
@ 4857600b:30b502f4
2025-02-20 19:09:11Mitch McConnell, a senior Republican senator, announced he will not seek reelection.
At 83 years old and with health issues, this decision was expected. After seven terms, he leaves a significant legacy in U.S. politics, known for his strategic maneuvering.
McConnell stated, “My current term in the Senate will be my last.” His retirement marks the end of an influential political era.
-
 @ 94a6a78a:0ddf320e
2025-02-19 21:10:15
@ 94a6a78a:0ddf320e
2025-02-19 21:10:15Nostr is a revolutionary protocol that enables decentralized, censorship-resistant communication. Unlike traditional social networks controlled by corporations, Nostr operates without central servers or gatekeepers. This openness makes it incredibly powerful—but also means its success depends entirely on users, developers, and relay operators.
If you believe in free speech, decentralization, and an open internet, there are many ways to support and strengthen the Nostr ecosystem. Whether you're a casual user, a developer, or someone looking to contribute financially, every effort helps build a more robust network.
Here’s how you can get involved and make a difference.
1️⃣ Use Nostr Daily
The simplest and most effective way to contribute to Nostr is by using it regularly. The more active users, the stronger and more valuable the network becomes.
✅ Post, comment, and zap (send micro-payments via Bitcoin’s Lightning Network) to keep conversations flowing.\ ✅ Engage with new users and help them understand how Nostr works.\ ✅ Try different Nostr clients like Damus, Amethyst, Snort, or Primal and provide feedback to improve the experience.
Your activity keeps the network alive and helps encourage more developers and relay operators to invest in the ecosystem.
2️⃣ Run Your Own Nostr Relay
Relays are the backbone of Nostr, responsible for distributing messages across the network. The more independent relays exist, the stronger and more censorship-resistant Nostr becomes.
✅ Set up your own relay to help decentralize the network further.\ ✅ Experiment with relay configurations and different performance optimizations.\ ✅ Offer public or private relay services to users looking for high-quality infrastructure.
If you're not technical, you can still support relay operators by subscribing to a paid relay or donating to open-source relay projects.
3️⃣ Support Paid Relays & Infrastructure
Free relays have helped Nostr grow, but they struggle with spam, slow speeds, and sustainability issues. Paid relays help fund better infrastructure, faster message delivery, and a more reliable experience.
✅ Subscribe to a paid relay to help keep it running.\ ✅ Use premium services like media hosting (e.g., Azzamo Blossom) to decentralize content storage.\ ✅ Donate to relay operators who invest in long-term infrastructure.
By funding Nostr’s decentralized backbone, you help ensure its longevity and reliability.
4️⃣ Zap Developers, Creators & Builders
Many people contribute to Nostr without direct financial compensation—developers who build clients, relay operators, educators, and content creators. You can support them with zaps! ⚡
✅ Find developers working on Nostr projects and send them a zap.\ ✅ Support content creators and educators who spread awareness about Nostr.\ ✅ Encourage builders by donating to open-source projects.
Micro-payments via the Lightning Network make it easy to directly support the people who make Nostr better.
5️⃣ Develop New Nostr Apps & Tools
If you're a developer, you can build on Nostr’s open protocol to create new apps, bots, or tools. Nostr is permissionless, meaning anyone can develop for it.
✅ Create new Nostr clients with unique features and user experiences.\ ✅ Build bots or automation tools that improve engagement and usability.\ ✅ Experiment with decentralized identity, authentication, and encryption to make Nostr even stronger.
With no corporate gatekeepers, your projects can help shape the future of decentralized social media.
6️⃣ Promote & Educate Others About Nostr
Adoption grows when more people understand and use Nostr. You can help by spreading awareness and creating educational content.
✅ Write blogs, guides, and tutorials explaining how to use Nostr.\ ✅ Make videos or social media posts introducing new users to the protocol.\ ✅ Host discussions, Twitter Spaces, or workshops to onboard more people.
The more people understand and trust Nostr, the stronger the ecosystem becomes.
7️⃣ Support Open-Source Nostr Projects
Many Nostr tools and clients are built by volunteers, and open-source projects thrive on community support.
✅ Contribute code to existing Nostr projects on GitHub.\ ✅ Report bugs and suggest features to improve Nostr clients.\ ✅ Donate to developers who keep Nostr free and open for everyone.
If you're not a developer, you can still help with testing, translations, and documentation to make projects more accessible.
🚀 Every Contribution Strengthens Nostr
Whether you:
✔️ Post and engage daily\ ✔️ Zap creators and developers\ ✔️ Run or support relays\ ✔️ Build new apps and tools\ ✔️ Educate and onboard new users
Every action helps make Nostr more resilient, decentralized, and unstoppable.
Nostr isn’t just another social network—it’s a movement toward a free and open internet. If you believe in digital freedom, privacy, and decentralization, now is the time to get involved.
-
 @ a95c6243:d345522c
2025-01-31 20:02:25
@ a95c6243:d345522c
2025-01-31 20:02:25Im Augenblick wird mit größter Intensität, großer Umsicht \ das deutsche Volk belogen. \ Olaf Scholz im FAZ-Interview
Online-Wahlen stärken die Demokratie, sind sicher, und 61 Prozent der Wahlberechtigten sprechen sich für deren Einführung in Deutschland aus. Das zumindest behauptet eine aktuelle Umfrage, die auch über die Agentur Reuters Verbreitung in den Medien gefunden hat. Demnach würden außerdem 45 Prozent der Nichtwähler bei der Bundestagswahl ihre Stimme abgeben, wenn sie dies zum Beispiel von Ihrem PC, Tablet oder Smartphone aus machen könnten.
Die telefonische Umfrage unter gut 1000 wahlberechtigten Personen sei repräsentativ, behauptet der Auftraggeber – der Digitalverband Bitkom. Dieser präsentiert sich als eingetragener Verein mit einer beeindruckenden Liste von Mitgliedern, die Software und IT-Dienstleistungen anbieten. Erklärtes Vereinsziel ist es, «Deutschland zu einem führenden Digitalstandort zu machen und die digitale Transformation der deutschen Wirtschaft und Verwaltung voranzutreiben».
Durchgeführt hat die Befragung die Bitkom Servicegesellschaft mbH, also alles in der Familie. Die gleiche Erhebung hatte der Verband übrigens 2021 schon einmal durchgeführt. Damals sprachen sich angeblich sogar 63 Prozent für ein derartiges «Demokratie-Update» aus – die Tendenz ist demgemäß fallend. Dennoch orakelt mancher, der Gang zur Wahlurne gelte bereits als veraltet.
Die spanische Privat-Uni mit Globalisten-Touch, IE University, berichtete Ende letzten Jahres in ihrer Studie «European Tech Insights», 67 Prozent der Europäer befürchteten, dass Hacker Wahlergebnisse verfälschen könnten. Mehr als 30 Prozent der Befragten glaubten, dass künstliche Intelligenz (KI) bereits Wahlentscheidungen beeinflusst habe. Trotzdem würden angeblich 34 Prozent der unter 35-Jährigen einer KI-gesteuerten App vertrauen, um in ihrem Namen für politische Kandidaten zu stimmen.
Wie dauerhaft wird wohl das Ergebnis der kommenden Bundestagswahl sein? Diese Frage stellt sich angesichts der aktuellen Entwicklung der Migrations-Debatte und der (vorübergehend) bröckelnden «Brandmauer» gegen die AfD. Das «Zustrombegrenzungsgesetz» der Union hat das Parlament heute Nachmittag überraschenderweise abgelehnt. Dennoch muss man wohl kein ausgesprochener Pessimist sein, um zu befürchten, dass die Entscheidungen der Bürger von den selbsternannten Verteidigern der Demokratie künftig vielleicht nicht respektiert werden, weil sie nicht gefallen.
Bundesweit wird jetzt zu «Brandmauer-Demos» aufgerufen, die CDU gerät unter Druck und es wird von Übergriffen auf Parteibüros und Drohungen gegen Mitarbeiter berichtet. Sicherheitsbehörden warnen vor Eskalationen, die Polizei sei «für ein mögliches erhöhtes Aufkommen von Straftaten gegenüber Politikern und gegen Parteigebäude sensibilisiert».
Der Vorwand «unzulässiger Einflussnahme» auf Politik und Wahlen wird als Argument schon seit einiger Zeit aufgebaut. Der Manipulation schuldig befunden wird neben Putin und Trump auch Elon Musk, was lustigerweise ausgerechnet Bill Gates gerade noch einmal bekräftigt und als «völlig irre» bezeichnet hat. Man stelle sich die Diskussionen um die Gültigkeit von Wahlergebnissen vor, wenn es Online-Verfahren zur Stimmabgabe gäbe. In der Schweiz wird «E-Voting» seit einigen Jahren getestet, aber wohl bisher mit wenig Erfolg.
Die politische Brandstiftung der letzten Jahre zahlt sich immer mehr aus. Anstatt dringende Probleme der Menschen zu lösen – zu denen auch in Deutschland die weit verbreitete Armut zählt –, hat die Politik konsequent polarisiert und sich auf Ausgrenzung und Verhöhnung großer Teile der Bevölkerung konzentriert. Basierend auf Ideologie und Lügen werden abweichende Stimmen unterdrückt und kriminalisiert, nicht nur und nicht erst in diesem Augenblick. Die nächsten Wochen dürften ausgesprochen spannend werden.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ fd208ee8:0fd927c1
2025-02-15 07:37:01
@ fd208ee8:0fd927c1
2025-02-15 07:37:01E-cash are coupons or tokens for Bitcoin, or Bitcoin debt notes that the mint issues. The e-cash states, essentially, "IoU 2900 sats".
They're redeemable for Bitcoin on Lightning (hard money), and therefore can be used as cash (softer money), so long as the mint has a good reputation. That means that they're less fungible than Lightning because the e-cash from one mint can be more or less valuable than the e-cash from another. If a mint is buggy, offline, or disappears, then the e-cash is unreedemable.
It also means that e-cash is more anonymous than Lightning, and that the sender and receiver's wallets don't need to be online, to transact. Nutzaps now add the possibility of parking transactions one level farther out, on a relay. The same relays that cannot keep npub profiles and follow lists consistent will now do monetary transactions.
What we then have is * a transaction on a relay that triggers * a transaction on a mint that triggers * a transaction on Lightning that triggers * a transaction on Bitcoin.
Which means that every relay that stores the nuts is part of a wildcat banking system. Which is fine, but relay operators should consider whether they wish to carry the associated risks and liabilities. They should also be aware that they should implement the appropriate features in their relay, such as expiration tags (nuts rot after 2 weeks), and to make sure that only expired nuts are deleted.
There will be plenty of specialized relays for this, so don't feel pressured to join in, and research the topic carefully, for yourself.
https://github.com/nostr-protocol/nips/blob/master/60.md https://github.com/nostr-protocol/nips/blob/master/61.md
-
 @ a95c6243:d345522c
2025-01-24 20:59:01
@ a95c6243:d345522c
2025-01-24 20:59:01Menschen tun alles, egal wie absurd, \ um ihrer eigenen Seele nicht zu begegnen. \ Carl Gustav Jung
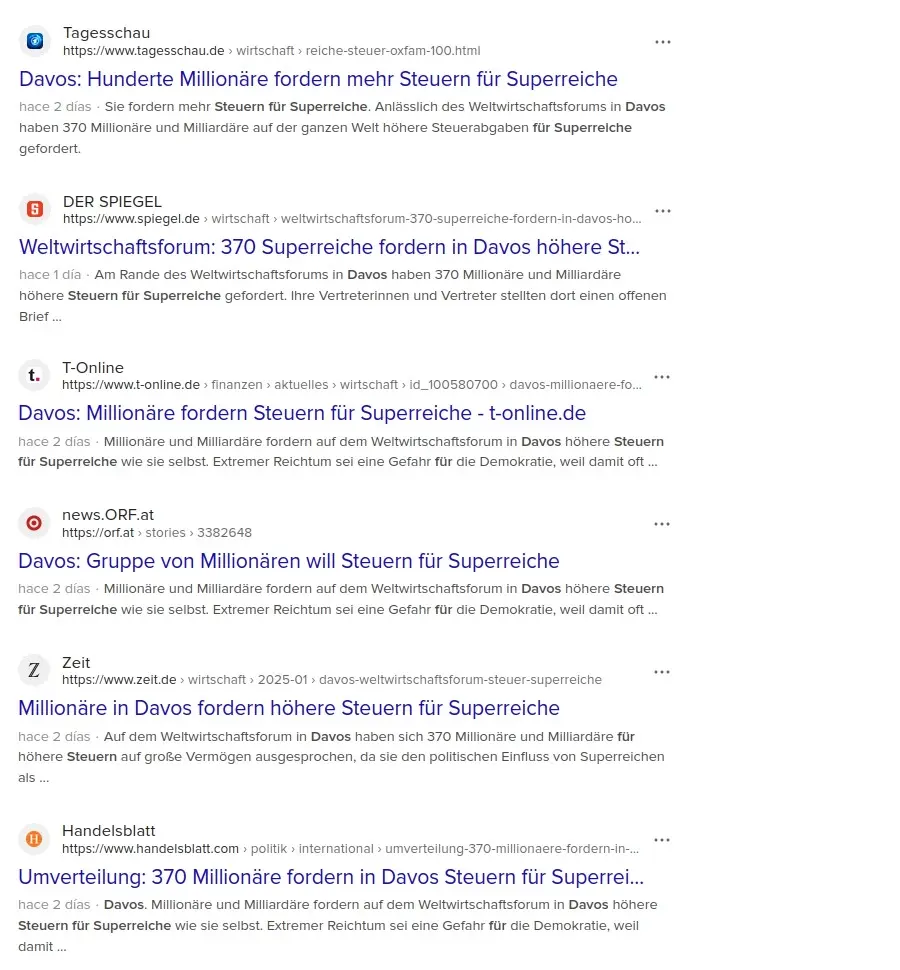
«Extremer Reichtum ist eine Gefahr für die Demokratie», sagen über die Hälfte der knapp 3000 befragten Millionäre aus G20-Staaten laut einer Umfrage der «Patriotic Millionaires». Ferner stellte dieser Zusammenschluss wohlhabender US-Amerikaner fest, dass 63 Prozent jener Millionäre den Einfluss von Superreichen auf US-Präsident Trump als Bedrohung für die globale Stabilität ansehen.
Diese Besorgnis haben 370 Millionäre und Milliardäre am Dienstag auch den in Davos beim WEF konzentrierten Privilegierten aus aller Welt übermittelt. In einem offenen Brief forderten sie die «gewählten Führer» auf, die Superreichen – also sie selbst – zu besteuern, um «die zersetzenden Auswirkungen des extremen Reichtums auf unsere Demokratien und die Gesellschaft zu bekämpfen». Zum Beispiel kontrolliere eine handvoll extrem reicher Menschen die Medien, beeinflusse die Rechtssysteme in unzulässiger Weise und verwandele Recht in Unrecht.
Schon 2019 beanstandete der bekannte Historiker und Schriftsteller Ruthger Bregman an einer WEF-Podiumsdiskussion die Steuervermeidung der Superreichen. Die elitäre Veranstaltung bezeichnete er als «Feuerwehr-Konferenz, bei der man nicht über Löschwasser sprechen darf.» Daraufhin erhielt Bregman keine Einladungen nach Davos mehr. Auf seine Aussagen machte der Schweizer Aktivist Alec Gagneux aufmerksam, der sich seit Jahrzehnten kritisch mit dem WEF befasst. Ihm wurde kürzlich der Zutritt zu einem dreiteiligen Kurs über das WEF an der Volkshochschule Region Brugg verwehrt.
Nun ist die Erkenntnis, dass mit Geld politischer Einfluss einhergeht, alles andere als neu. Und extremer Reichtum macht die Sache nicht wirklich besser. Trotzdem hat man über Initiativen wie Patriotic Millionaires oder Taxmenow bisher eher selten etwas gehört, obwohl es sie schon lange gibt. Auch scheint es kein Problem, wenn ein Herr Gates fast im Alleingang versucht, globale Gesundheits-, Klima-, Ernährungs- oder Bevölkerungspolitik zu betreiben – im Gegenteil. Im Jahr, als der Milliardär Donald Trump zum zweiten Mal ins Weiße Haus einzieht, ist das Echo in den Gesinnungsmedien dagegen enorm – und uniform, wer hätte das gedacht.
Der neue US-Präsident hat jedoch «Davos geerdet», wie Achgut es nannte. In seiner kurzen Rede beim Weltwirtschaftsforum verteidigte er seine Politik und stellte klar, er habe schlicht eine «Revolution des gesunden Menschenverstands» begonnen. Mit deutlichen Worten sprach er unter anderem von ersten Maßnahmen gegen den «Green New Scam», und von einem «Erlass, der jegliche staatliche Zensur beendet»:
«Unsere Regierung wird die Äußerungen unserer eigenen Bürger nicht mehr als Fehlinformation oder Desinformation bezeichnen, was die Lieblingswörter von Zensoren und derer sind, die den freien Austausch von Ideen und, offen gesagt, den Fortschritt verhindern wollen.»
Wie der «Trumpismus» letztlich einzuordnen ist, muss jeder für sich selbst entscheiden. Skepsis ist definitiv angebracht, denn «einer von uns» sind weder der Präsident noch seine auserwählten Teammitglieder. Ob sie irgendeinen Sumpf trockenlegen oder Staatsverbrechen aufdecken werden oder was aus WHO- und Klimaverträgen wird, bleibt abzuwarten.
Das WHO-Dekret fordert jedenfalls die Übertragung der Gelder auf «glaubwürdige Partner», die die Aktivitäten übernehmen könnten. Zufällig scheint mit «Impfguru» Bill Gates ein weiterer Harris-Unterstützer kürzlich das Lager gewechselt zu haben: Nach einem gemeinsamen Abendessen zeigte er sich «beeindruckt» von Trumps Interesse an der globalen Gesundheit.
Mit dem Projekt «Stargate» sind weitere dunkle Wolken am Erwartungshorizont der Fangemeinde aufgezogen. Trump hat dieses Joint Venture zwischen den Konzernen OpenAI, Oracle, und SoftBank als das «größte KI-Infrastrukturprojekt der Geschichte» angekündigt. Der Stein des Anstoßes: Oracle-CEO Larry Ellison, der auch Fan von KI-gestützter Echtzeit-Überwachung ist, sieht einen weiteren potenziellen Einsatz der künstlichen Intelligenz. Sie könne dazu dienen, Krebserkrankungen zu erkennen und individuelle mRNA-«Impfstoffe» zur Behandlung innerhalb von 48 Stunden zu entwickeln.
Warum bitte sollten sich diese superreichen «Eliten» ins eigene Fleisch schneiden und direkt entgegen ihren eigenen Interessen handeln? Weil sie Menschenfreunde, sogenannte Philanthropen sind? Oder vielleicht, weil sie ein schlechtes Gewissen haben und ihre Schuld kompensieren müssen? Deswegen jedenfalls brauchen «Linke» laut Robert Willacker, einem deutschen Politikberater mit brasilianischen Wurzeln, rechte Parteien – ein ebenso überraschender wie humorvoller Erklärungsansatz.
Wenn eine Krähe der anderen kein Auge aushackt, dann tut sie das sich selbst noch weniger an. Dass Millionäre ernsthaft ihre eigene Besteuerung fordern oder Machteliten ihren eigenen Einfluss zugunsten anderer einschränken würden, halte ich für sehr unwahrscheinlich. So etwas glaube ich erst, wenn zum Beispiel die Rüstungsindustrie sich um Friedensverhandlungen bemüht, die Pharmalobby sich gegen institutionalisierte Korruption einsetzt, Zentralbanken ihre CBDC-Pläne für Bitcoin opfern oder der ÖRR die Abschaffung der Rundfunkgebühren fordert.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2025-01-18 09:34:51
@ c631e267:c2b78d3e
2025-01-18 09:34:51Die grauenvollste Aussicht ist die der Technokratie – \ einer kontrollierenden Herrschaft, \ die durch verstümmelte und verstümmelnde Geister ausgeübt wird. \ Ernst Jünger
«Davos ist nicht mehr sexy», das Weltwirtschaftsforum (WEF) mache Davos kaputt, diese Aussagen eines Einheimischen las ich kürzlich in der Handelszeitung. Während sich einige vor Ort enorm an der «teuersten Gewerbeausstellung der Welt» bereicherten, würden die negativen Begleiterscheinungen wie Wohnungsnot und Niedergang der lokalen Wirtschaft immer deutlicher.
Nächsten Montag beginnt in dem Schweizer Bergdorf erneut ein Jahrestreffen dieses elitären Clubs der Konzerne, bei dem man mit hochrangigen Politikern aus aller Welt und ausgewählten Vertretern der Systemmedien zusammenhocken wird. Wie bereits in den vergangenen vier Jahren wird die Präsidentin der EU-Kommission, Ursula von der Leyen, in Begleitung von Klaus Schwab ihre Grundsatzansprache halten.
Der deutsche WEF-Gründer hatte bei dieser Gelegenheit immer höchst lobende Worte für seine Landsmännin: 2021 erklärte er sich «stolz, dass Europa wieder unter Ihrer Führung steht» und 2022 fand er es bemerkenswert, was sie erreicht habe angesichts des «erstaunlichen Wandels», den die Welt in den vorangegangenen zwei Jahren erlebt habe; es gebe nun einen «neuen europäischen Geist».
Von der Leyens Handeln während der sogenannten Corona-«Pandemie» lobte Schwab damals bereits ebenso, wie es diese Woche das Karlspreis-Direktorium tat, als man der Beschuldigten im Fall Pfizergate die diesjährige internationale Auszeichnung «für Verdienste um die europäische Einigung» verlieh. Außerdem habe sie die EU nicht nur gegen den «Aggressor Russland», sondern auch gegen die «innere Bedrohung durch Rassisten und Demagogen» sowie gegen den Klimawandel verteidigt.
Jene Herausforderungen durch «Krisen epochalen Ausmaßes» werden indes aus dem Umfeld des WEF nicht nur herbeigeredet – wie man alljährlich zur Zeit des Davoser Treffens im Global Risks Report nachlesen kann, der zusammen mit dem Versicherungskonzern Zurich erstellt wird. Seit die Globalisten 2020/21 in der Praxis gesehen haben, wie gut eine konzertierte und konsequente Angst-Kampagne funktionieren kann, geht es Schlag auf Schlag. Sie setzen alles daran, Schwabs goldenes Zeitfenster des «Great Reset» zu nutzen.
Ziel dieses «großen Umbruchs» ist die totale Kontrolle der Technokraten über die Menschen unter dem Deckmantel einer globalen Gesundheitsfürsorge. Wie aber könnte man so etwas erreichen? Ein Mittel dazu ist die «kreative Zerstörung». Weitere unabdingbare Werkzeug sind die Einbindung, ja Gleichschaltung der Medien und der Justiz.
Ein «Great Mental Reset» sei die Voraussetzung dafür, dass ein Großteil der Menschen Einschränkungen und Manipulationen wie durch die Corona-Maßnahmen praktisch kritik- und widerstandslos hinnehme, sagt der Mediziner und Molekulargenetiker Michael Nehls. Er meint damit eine regelrechte Umprogrammierung des Gehirns, wodurch nach und nach unsere Individualität und unser soziales Bewusstsein eliminiert und durch unreflektierten Konformismus ersetzt werden.
Der aktuelle Zustand unserer Gesellschaften ist auch für den Schweizer Rechtsanwalt Philipp Kruse alarmierend. Durch den Umgang mit der «Pandemie» sieht er die Grundlagen von Recht und Vernunft erschüttert, die Rechtsstaatlichkeit stehe auf dem Prüfstand. Seiner dringenden Mahnung an alle Bürger, die Prinzipien von Recht und Freiheit zu verteidigen, kann ich mich nur anschließen.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2025-01-13 10:09:57
@ a95c6243:d345522c
2025-01-13 10:09:57Ich begann, Social Media aufzubauen, \ um den Menschen eine Stimme zu geben. \ Mark Zuckerberg
Sind euch auch die Tränen gekommen, als ihr Mark Zuckerbergs Wendehals-Deklaration bezüglich der Meinungsfreiheit auf seinen Portalen gehört habt? Rührend, oder? Während er früher die offensichtliche Zensur leugnete und später die Regierung Biden dafür verantwortlich machte, will er nun angeblich «die Zensur auf unseren Plattformen drastisch reduzieren».
«Purer Opportunismus» ob des anstehenden Regierungswechsels wäre als Klassifizierung viel zu kurz gegriffen. Der jetzige Schachzug des Meta-Chefs ist genauso Teil einer kühl kalkulierten Business-Strategie, wie es die 180 Grad umgekehrte Praxis vorher war. Social Media sind ein höchst lukratives Geschäft. Hinzu kommt vielleicht noch ein bisschen verkorkstes Ego, weil derartig viel Einfluss und Geld sicher auch auf die Psyche schlagen. Verständlich.
«Es ist an der Zeit, zu unseren Wurzeln der freien Meinungsäußerung auf Facebook und Instagram zurückzukehren. Ich begann, Social Media aufzubauen, um den Menschen eine Stimme zu geben», sagte Zuckerberg.
Welche Wurzeln? Hat der Mann vergessen, dass er von der Überwachung, dem Ausspionieren und dem Ausverkauf sämtlicher Daten und digitaler Spuren sowie der Manipulation seiner «Kunden» lebt? Das ist knallharter Kommerz, nichts anderes. Um freie Meinungsäußerung geht es bei diesem Geschäft ganz sicher nicht, und das war auch noch nie so. Die Wurzeln von Facebook liegen in einem Projekt des US-Militärs mit dem Namen «LifeLog». Dessen Ziel war es, «ein digitales Protokoll vom Leben eines Menschen zu erstellen».
Der Richtungswechsel kommt allerdings nicht überraschend. Schon Anfang Dezember hatte Meta-Präsident Nick Clegg von «zu hoher Fehlerquote bei der Moderation» von Inhalten gesprochen. Bei der Gelegenheit erwähnte er auch, dass Mark sehr daran interessiert sei, eine aktive Rolle in den Debatten über eine amerikanische Führungsrolle im technologischen Bereich zu spielen.
Während Milliardärskollege und Big Tech-Konkurrent Elon Musk bereits seinen Posten in der kommenden Trump-Regierung in Aussicht hat, möchte Zuckerberg also nicht nur seine Haut retten – Trump hatte ihn einmal einen «Feind des Volkes» genannt und ihm lebenslange Haft angedroht –, sondern am liebsten auch mitspielen. KI-Berater ist wohl die gewünschte Funktion, wie man nach einem Treffen Trump-Zuckerberg hörte. An seine Verhaftung dachte vermutlich auch ein weiterer Multimilliardär mit eigener Social Media-Plattform, Pavel Durov, als er Zuckerberg jetzt kritisierte und gleichzeitig warnte.
Politik und Systemmedien drehen jedenfalls durch – was zu viel ist, ist zu viel. Etwas weniger Zensur und mehr Meinungsfreiheit würden die Freiheit der Bürger schwächen und seien potenziell vernichtend für die Menschenrechte. Zuckerberg setze mit dem neuen Kurs die Demokratie aufs Spiel, das sei eine «Einladung zum nächsten Völkermord», ernsthaft. Die Frage sei, ob sich die EU gegen Musk und Zuckerberg behaupten könne, Brüssel müsse jedenfalls hart durchgreifen.
Auch um die Faktenchecker macht man sich Sorgen. Für die deutsche Nachrichtenagentur dpa und die «Experten» von Correctiv, die (noch) Partner für Fact-Checking-Aktivitäten von Facebook sind, sei das ein «lukratives Geschäftsmodell». Aber möglicherweise werden die Inhalte ohne diese vermeintlichen Korrektoren ja sogar besser. Anders als Meta wollen jedoch Scholz, Faeser und die Tagesschau keine Fehler zugeben und zum Beispiel Correctiv-Falschaussagen einräumen.
Bei derlei dramatischen Befürchtungen wundert es nicht, dass der öffentliche Plausch auf X zwischen Elon Musk und AfD-Chefin Alice Weidel von 150 EU-Beamten überwacht wurde, falls es irgendwelche Rechtsverstöße geben sollte, die man ihnen ankreiden könnte. Auch der Deutsche Bundestag war wachsam. Gefunden haben dürften sie nichts. Das Ganze war eher eine Show, viel Wind wurde gemacht, aber letztlich gab es nichts als heiße Luft.
Das Anbiedern bei Donald Trump ist indes gerade in Mode. Die Weltgesundheitsorganisation (WHO) tut das auch, denn sie fürchtet um Spenden von über einer Milliarde Dollar. Eventuell könnte ja Elon Musk auch hier künftig aushelfen und der Organisation sowie deren größtem privaten Förderer, Bill Gates, etwas unter die Arme greifen. Nachdem Musks KI-Projekt xAI kürzlich von BlackRock & Co. sechs Milliarden eingestrichen hat, geht da vielleicht etwas.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2025-01-03 20:26:47
@ a95c6243:d345522c
2025-01-03 20:26:47Was du bist hängt von drei Faktoren ab: \ Was du geerbt hast, \ was deine Umgebung aus dir machte \ und was du in freier Wahl \ aus deiner Umgebung und deinem Erbe gemacht hast. \ Aldous Huxley
Das brave Mitmachen und Mitlaufen in einem vorgegebenen, recht engen Rahmen ist gewiss nicht neu, hat aber gerade wieder mal Konjunktur. Dies kann man deutlich beobachten, eigentlich egal, in welchem gesellschaftlichen Bereich man sich umschaut. Individualität ist nur soweit angesagt, wie sie in ein bestimmtes Schema von «Diversität» passt, und Freiheit verkommt zur Worthülse – nicht erst durch ein gewisses Buch einer gewissen ehemaligen Regierungschefin.
Erklärungsansätze für solche Entwicklungen sind bekannt, und praktisch alle haben etwas mit Massenpsychologie zu tun. Der Herdentrieb, also der Trieb der Menschen, sich – zum Beispiel aus Unsicherheit oder Bequemlichkeit – lieber der Masse anzuschließen als selbstständig zu denken und zu handeln, ist einer der Erklärungsversuche. Andere drehen sich um Macht, Propaganda, Druck und Angst, also den gezielten Einsatz psychologischer Herrschaftsinstrumente.
Aber wollen die Menschen überhaupt Freiheit? Durch Gespräche im privaten Umfeld bin ich diesbezüglich in der letzten Zeit etwas skeptisch geworden. Um die Jahreswende philosophiert man ja gerne ein wenig über das Erlebte und über die Erwartungen für die Zukunft. Dabei hatte ich hin und wieder den Eindruck, die totalitären Anwandlungen unserer «Repräsentanten» kämen manchen Leuten gerade recht.
«Desinformation» ist so ein brisantes Thema. Davor müsse man die Menschen doch schützen, hörte ich. Jemand müsse doch zum Beispiel diese ganzen merkwürdigen Inhalte in den Social Media filtern – zur Ukraine, zum Klima, zu Gesundheitsthemen oder zur Migration. Viele wüssten ja gar nicht einzuschätzen, was richtig und was falsch ist, sie bräuchten eine Führung.
Freiheit bedingt Eigenverantwortung, ohne Zweifel. Eventuell ist es einigen tatsächlich zu anspruchsvoll, die Verantwortung für das eigene Tun und Lassen zu übernehmen. Oder die persönliche Freiheit wird nicht als ausreichend wertvolles Gut angesehen, um sich dafür anzustrengen. In dem Fall wäre die mangelnde Selbstbestimmung wohl das kleinere Übel. Allerdings fehlt dann gemäß Aldous Huxley ein Teil der Persönlichkeit. Letztlich ist natürlich alles eine Frage der Abwägung.
Sind viele Menschen möglicherweise schon so «eingenordet», dass freiheitliche Ambitionen gar nicht für eine ganze Gruppe, ein Kollektiv, verfolgt werden können? Solche Gedanken kamen mir auch, als ich mir kürzlich diverse Talks beim viertägigen Hacker-Kongress des Chaos Computer Clubs (38C3) anschaute. Ich war nicht nur überrascht, sondern reichlich erschreckt angesichts der in weiten Teilen mainstream-geformten Inhalte, mit denen ein dankbares Publikum beglückt wurde. Wo ich allgemein hellere Köpfe erwartet hatte, fand ich Konformismus und enthusiastisch untermauerte Narrative.
Gibt es vielleicht so etwas wie eine Herdenimmunität gegen Indoktrination? Ich denke, ja, zumindest eine gestärkte Widerstandsfähigkeit. Was wir brauchen, sind etwas gesunder Menschenverstand, offene Informationskanäle und der Mut, sich freier auch zwischen den Herden zu bewegen. Sie tun das bereits, aber sagen Sie es auch dieses Jahr ruhig weiter.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2025-01-01 17:39:51
@ a95c6243:d345522c
2025-01-01 17:39:51Heute möchte ich ein Gedicht mit euch teilen. Es handelt sich um eine Ballade des österreichischen Lyrikers Johann Gabriel Seidl aus dem 19. Jahrhundert. Mir sind diese Worte fest in Erinnerung, da meine Mutter sie perfekt rezitieren konnte, auch als die Kräfte schon langsam schwanden.
Dem originalen Titel «Die Uhr» habe ich für mich immer das Wort «innere» hinzugefügt. Denn der Zeitmesser – hier vermutliche eine Taschenuhr – symbolisiert zwar in dem Kontext das damalige Zeitempfinden und die Umbrüche durch die industrielle Revolution, sozusagen den Zeitgeist und das moderne Leben. Aber der Autor setzt sich philosophisch mit der Zeit auseinander und gibt seinem Werk auch eine klar spirituelle Dimension.
Das Ticken der Uhr und die Momente des Glücks und der Trauer stehen sinnbildlich für das unaufhaltsame Fortschreiten und die Vergänglichkeit des Lebens. Insofern könnte man bei der Uhr auch an eine Sonnenuhr denken. Der Rhythmus der Ereignisse passt uns vielleicht nicht immer in den Kram.
Was den Takt pocht, ist durchaus auch das Herz, unser «inneres Uhrwerk». Wenn dieses Meisterwerk einmal stillsteht, ist es unweigerlich um uns geschehen. Hoffentlich können wir dann dankbar sagen: «Ich habe mein Bestes gegeben.»
Ich trage, wo ich gehe, stets eine Uhr bei mir; \ Wieviel es geschlagen habe, genau seh ich an ihr. \ Es ist ein großer Meister, der künstlich ihr Werk gefügt, \ Wenngleich ihr Gang nicht immer dem törichten Wunsche genügt.
Ich wollte, sie wäre rascher gegangen an manchem Tag; \ Ich wollte, sie hätte manchmal verzögert den raschen Schlag. \ In meinen Leiden und Freuden, in Sturm und in der Ruh, \ Was immer geschah im Leben, sie pochte den Takt dazu.
Sie schlug am Sarge des Vaters, sie schlug an des Freundes Bahr, \ Sie schlug am Morgen der Liebe, sie schlug am Traualtar. \ Sie schlug an der Wiege des Kindes, sie schlägt, will's Gott, noch oft, \ Wenn bessere Tage kommen, wie meine Seele es hofft.
Und ward sie auch einmal träger, und drohte zu stocken ihr Lauf, \ So zog der Meister immer großmütig sie wieder auf. \ Doch stände sie einmal stille, dann wär's um sie geschehn, \ Kein andrer, als der sie fügte, bringt die Zerstörte zum Gehn.
Dann müßt ich zum Meister wandern, der wohnt am Ende wohl weit, \ Wohl draußen, jenseits der Erde, wohl dort in der Ewigkeit! \ Dann gäb ich sie ihm zurücke mit dankbar kindlichem Flehn: \ Sieh, Herr, ich hab nichts verdorben, sie blieb von selber stehn.
Johann Gabriel Seidl (1804-1875)
-
 @ dd664d5e:5633d319
2025-02-14 16:56:29
@ dd664d5e:5633d319
2025-02-14 16:56:29Most people only know customer-to-customer (C2C) and business-to-customer (B2C) software and websites. Those are the famous and popular ones, but business-to-business (B2B) is also pretty big. How big?
Even something boring and local like DATEV has almost 3 million organizations as customers and €1,44 billion in annual revenue.
FedEx has €90 billion in annual revenue and everyone who uses it comes into contact with its software. There's a whole chain of software between the sender and receiver of the package, and it all has to work seamlessly.
Same with Walmart, Toyota, Dubai Airport, Glencore, Tesla, Edeka, Carrefour, Harvard and University of Texas, Continental, Allianz, Asklepios, etc.
That's the sort of software I help build. You've probably never heard of it, but when it doesn't work properly, you'll hear about it on the news.
-
 @ 5de23b9a:d83005b3
2025-02-19 03:47:19
@ 5de23b9a:d83005b3
2025-02-19 03:47:19In a digital era that is increasingly controlled by large companies, the emergence of Nostr (Notes and Other Stuff Transmitted by Relays) is a breath of fresh air for those who crave freedom of expression.
Nostr is a cryptography-based protocol that allows users to send and receive messages through a relay network. Unlike conventional social media such as Twitter or Facebook
1.Full Decentralization: No company or government can remove or restrict content.
2.Sensor-Resistant: Information remains accessible despite blocking attempts.
3.Privacy and Security: Uses cryptography to ensure that only users who have the keys can access their messages.* **
-
 @ a95c6243:d345522c
2024-12-21 09:54:49
@ a95c6243:d345522c
2024-12-21 09:54:49Falls du beim Lesen des Titels dieses Newsletters unwillkürlich an positive Neuigkeiten aus dem globalen polit-medialen Irrenhaus oder gar aus dem wirtschaftlichen Umfeld gedacht hast, darf ich dich beglückwünschen. Diese Assoziation ist sehr löblich, denn sie weist dich als unverbesserlichen Optimisten aus. Leider muss ich dich diesbezüglich aber enttäuschen. Es geht hier um ein anderes Thema, allerdings sehr wohl ein positives, wie ich finde.
Heute ist ein ganz besonderer Tag: die Wintersonnenwende. Genau gesagt hat heute morgen um 10:20 Uhr Mitteleuropäischer Zeit (MEZ) auf der Nordhalbkugel unseres Planeten der astronomische Winter begonnen. Was daran so außergewöhnlich ist? Der kürzeste Tag des Jahres war gestern, seit heute werden die Tage bereits wieder länger! Wir werden also jetzt jeden Tag ein wenig mehr Licht haben.
Für mich ist dieses Ereignis immer wieder etwas kurios: Es beginnt der Winter, aber die Tage werden länger. Das erscheint mir zunächst wie ein Widerspruch, denn meine spontanen Assoziationen zum Winter sind doch eher Kälte und Dunkelheit, relativ zumindest. Umso erfreulicher ist der emotionale Effekt, wenn dann langsam die Erkenntnis durchsickert: Ab jetzt wird es schon wieder heller!
Natürlich ist es kalt im Winter, mancherorts mehr als anderswo. Vielleicht jedoch nicht mehr lange, wenn man den Klimahysterikern glauben wollte. Mindestens letztes Jahr hat Väterchen Frost allerdings gleich zu Beginn seiner Saison – und passenderweise während des globalen Überhitzungsgipfels in Dubai – nochmal richtig mit der Faust auf den Tisch gehauen. Schnee- und Eischaos sind ja eigentlich in der Agenda bereits nicht mehr vorgesehen. Deswegen war man in Deutschland vermutlich in vorauseilendem Gehorsam schon nicht mehr darauf vorbereitet und wurde glatt lahmgelegt.
Aber ich schweife ab. Die Aussicht auf nach und nach mehr Licht und damit auch Wärme stimmt mich froh. Den Zusammenhang zwischen beidem merkt man in Andalusien sehr deutlich. Hier, wo die Häuser im Winter arg auskühlen, geht man zum Aufwärmen raus auf die Straße oder auf den Balkon. Die Sonne hat auch im Winter eine erfreuliche Kraft. Und da ist jede Minute Gold wert.
Außerdem ist mir vor Jahren so richtig klar geworden, warum mir das südliche Klima so sehr gefällt. Das liegt nämlich nicht nur an der Sonne als solcher, oder der Wärme – das liegt vor allem am Licht. Ohne Licht keine Farben, das ist der ebenso simple wie gewaltige Unterschied zwischen einem deprimierenden matschgraubraunen Winter und einem fröhlichen bunten. Ein großes Stück Lebensqualität.
Mir gefällt aber auch die Symbolik dieses Tages: Licht aus der Dunkelheit, ein Wendepunkt, ein Neuanfang, neue Möglichkeiten, Übergang zu neuer Aktivität. In der winterlichen Stille keimt bereits neue Lebendigkeit. Und zwar in einem Zyklus, das wird immer wieder so geschehen. Ich nehme das gern als ein Stück Motivation, es macht mir Hoffnung und gibt mir Energie.

Übrigens ist parallel am heutigen Tag auf der südlichen Halbkugel Sommeranfang. Genau im entgegengesetzten Rhythmus, sich ergänzend, wie Yin und Yang. Das alles liegt an der Schrägstellung der Erdachse, die ist nämlich um 23,4º zur Umlaufbahn um die Sonne geneigt. Wir erinnern uns, gell?
Insofern bleibt eindeutig festzuhalten, dass “schräg sein” ein willkommener, wichtiger und positiver Wert ist. Mit anderen Worten: auch ungewöhnlich, eigenartig, untypisch, wunderlich, kauzig, … ja sogar irre, spinnert oder gar “quer” ist in Ordnung. Das schließt das Denken mit ein.
In diesem Sinne wünsche ich euch allen urige Weihnachtstage!
Dieser Beitrag ist letztes Jahr in meiner Denkbar erschienen.
-
 @ dd664d5e:5633d319
2025-02-12 07:05:51
@ dd664d5e:5633d319
2025-02-12 07:05:51I think this note from Chip (nostr:npub1qdjn8j4gwgmkj3k5un775nq6q3q7mguv5tvajstmkdsqdja2havq03fqm7) is one of those things that people with business management experience take a lot more seriously than most developers and influencers do.
I am painfully aware of the cost of systems administration, financial transaction management and recordkeeping, recruiting and personnel management, legal and compliance, requirements management, technical support, renting and managing physical spaces and infrastructure, negotiating with suppliers, customer service, etc. etc.
There's this idea, on Nostr, that sort of trickled in along with Bitcoin Twitter, that we would all just be isolated subsistance farmers and one-man-show podcasters with a gigantic server rack in the basement. But some of us are running real companies -- on and off Nostr, for-profit and non-profit -- and it often requires a lot of human labor.
The things we build aren't meant to be used by one person and his girlfriend and his dog. Yes, he can also run all these things, himself, but he no longer has to. Our existence gives him the choice: run these things or pay us to run them and spend your time doing something else, that you do better than we do.
These things are meant to be used by hundreds... thousands... eventually millions of people. The workflows, processes, infrastructure, and personnel need to be able to scale up-and-down, scale in-and-out, work smoothly with 5 people or 50 people. These are the sort of Nostr systems that wouldn't collapse when encountering a sudden influx or mass-escape. But these systems are much more complex and they take time to build and staff to run them. (And, no, AI can't replace them all. AI means that they now also have to integrate a bunch of AI into the system and maintain that, too.)
GitCitadel (nostr:npub1s3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqd975wz) is very automation-forward, but we still have to front the incredibly high cost of designing and building the automation, train people to interact with it (there are now over 20 people integrated into the workflow!), adjust it based upon their feedback, and we have to support the automation, once it's running.
This sort of streamlined machine is what people pay companies for, not code. That is why there's little business cost to open source.
Open-source is great, but...

nostr:nevent1qqsgqh2dedhagyd9k8yfk2lagswjl7y627k9fpnq4l436ccmlys0s3qprdmhxue69uhhg6r9vehhyetnwshxummnw3erztnrdakj7q3qqdjn8j4gwgmkj3k5un775nq6q3q7mguv5tvajstmkdsqdja2havqxpqqqqqqzdhnyjm
-
 @ e31e84c4:77bbabc0
2025-02-25 15:03:34
@ e31e84c4:77bbabc0
2025-02-25 15:03:34The Fine Line: Bitcoin Companies Navigating Regulation and Freedom was written by Bri. If you enjoyed this article then support her writing, by donating to her lightning wallet: bri_1@walletofsatoshi.com
We all know the value proposition of Bitcoin: Bitcoin cannot be controlled by the state. Bitcoin is permissionless, it doesn't need a KYC and we can send money to anyone in the world, without middlemen, without censorship, without limits.
However, when companies use Bitcoin, and more so when they offer Bitcoin services, their activities are indeed controlled by the state. In order to fulfil the regulatory requirements, companies usually have to employ entire compliance teams.
Bitcoin-only exchanges are probably not better off than crypto service providers, even if one can sometimes hopefully recognise an increasing pro-Bitcoin attitude in the world. The Bitcoin scene recently looked expectantly to Nashville when Trump appeared at the Bitcoin 2024 conference as part of his election campaign. He doesn't really seem to be able to distinguish between Bitcoin and crypto though – in his keynote speech he promised to make the U.S. the ‘crypto capital of the planet’.
Nevertheless, the news that the United States plans to accumulate Bitcoin as a strategic reserve currency made headlines around the world and many Bitcoin supporters are delighted. Bitcoin's negative image could be somewhat corrected and it would certainly also be beneficial for Bitcoin adoption, so the hope goes. And indeed, the price of Bitcoin climbed to new record highs during the US election campaign, reaching its ATH of USD 109,000 when Trump took office on 20 January 2025.
The US announcement of a bitcoin strategic reserve can certainly be described as a historic moment. At the moment, it doesn't seem to be entirely clear whether Bitcoin or crypto, but a number of US states are working on advancing Bitcoin reserves. Whether it is a good thing when nation states start hoarding Bitcoin is another question. After all, from the very beginning and to this day, Bitcoin has been about taking power over money away from the state and giving it to the people.
Back to the Bitcoin companies. Let's assume that someone understands Bitcoin and has even discovered that there are Bitcoin-only exchanges. These companies recognise Bitcoin as sound money, support the Bitcoin community and want to integrate the Bitcoin ethos into their business model in the best possible way. Ouch – that already sounds like a compromise.
The Dilemma – Bitcoin at Heart, Regulation at the Back of the Neck
Bitcoin companies are caught between maximum independence and regulatory requirements. Companies such as Strike, Relai and River aim to make it as easy as possible for their customers to access Bitcoin while at the same time enabling them to maximise their independence from third parties. An important aspect of this is self-custody. Customers have full control over their Bitcoin and can avoid counterparty risks such as exchange failures or government seizures.
In contrast, most providers on the market, such as the major players Coinbase or Binance, rely on classic, centralised structures with full custody - and a large range of digital assets. They are basically fiat companies that offer crypto products.
And then, at the other end of the spectrum, there are projects such as Samourai, Wasabi Wallet or Tornado Cash, which are radically opposed to any form of control. They are developing powerful tools for more financial privacy – in line with Bitcoin's original idea as a decentralised cash system. But this commitment comes at a price: the founders of Samourai Wallet were arrested and the developers of Tornado Cash were prosecuted.
These Bitcoin rebels are putting the limits of state regulation to the test. And they raise the fundamental question: Is privacy an inalienable right or should it be subordinated to the public security interest?
The Middle Ground Builders
Bitcoin-only companies that choose the middle ground play an important role in the bitcoin ecosystem. This is because they appeal to the masses by keeping onboarding simple and often offering a range of interesting services. At the same time, they want to give their customers the greatest possible independence.
But are their business models sustainable? Or do these companies run the risk of being worn down by the balancing act between Bitcoin ethos and state control? How can these pioneers survive in a constantly changing regulatory environment?
It's a balancing act between regulation and Bitcoin values, and it's often a fight for the fundamental rights of not just Bitcoiners but people in general. For example, these companies need to have KYC processes in place to be compliant with the law and allow customers the greatest possible flexibility in their Bitcoin activities.
Some popular Bitcoin-companies and their strategies:
-
Strike: Custodial, fast lightning transactions, DCA, bill payments
-
Relai: Simple onramp, self-custody, private and business services
-
River: Multisig and cold storage, proof of reserves, inheritance
-
Unchained: Multisig vaults, DCA, inheritance, loans, retirement, advisory
-
Bull Bitcoin: Non-custodial exchange, DCA, bill payments, OTC desk
Typical features of these accounts usually include a KYC check, which allows users to be granted higher buy and sell limits. Many Bitcoin companies offer self-custody wallets and often some also multi-sig solutions that increase security for users. Partnerships with banks or payment service providers facilitate buying and selling and enable services such as the creation of savings plans.
Bitcoin companies face several challenges. Regulatory pressure remains a key concern, as authorities may tighten KYC obligations or introduce new restrictions. Trust is another issue since die-hard Bitcoiners often see these companies as not being consistent enough with Bitcoin's core principles.
Regulatory Framework and Political Influences
USA: Trump's Bitcoin course and the ‘Crypto Czar’
There are currently contradictory signals in the USA: on the one hand, Donald Trump has hinted at using Bitcoin as a strategic reserve (Strategic Bitcoin Reserve, SBR), while on the other hand, regulation is being tightened further. The newly created position of ‘White House AI and Crypto Czar’, presumably conceived in collaboration with Elon Musk, is intended to implement clear rules for blockchain, AI and the crypto market. This is also likely to affect companies that are committed to the Bitcoin ethos.
-
Positive signals: Bitcoin is increasingly recognised as a legitimate asset class.
-
Regulatory pressure: Stricter regulations could threaten the existence of smaller companies.
-
Possible future: If the US promotes Bitcoin as a strategic asset, this could fundamentally change the regulatory landscape.
Europe and Global Developments
-
MiCA (Markets in Crypto-Assets Regulation): New EU regulation for crypto companies, requiring strict KYC and AML rules, among other things.
-
Restrictive countries: China and India continue to rely on tough regulation or bans.
-
Friendly jurisdictions: Countries such as El Salvador or Switzerland offer attractive conditions for Bitcoin companies.
Self-custody of Bitcoin
The so-called ‘Travel Rule’ (Transfer of Funds Regulation, TFR) requires detailed information about the sender and recipient. This makes it more difficult for Europeans to interact with self-custody Bitcoin wallets. For transactions over 1,000 euros, users must prove that they are the owners of these wallets (proof of ownership).
Yet self-custody is a very important aspect of Bitcoin. It is the only way to avoid the risks associated with relying on centralised custodians. Self-custody ensures that you alone have control over your money. The new regulations represent a gradual financial disenfranchisement, which is not only criticised by Bitcoiners. And that is only part of the problem.
The disadvantages of centralised storage of customer assets are well known. Just think of the scandalous examples from the recent past: The fall of the FTX cryptocurrency exchange and the knock-on effects on the cryptocurrency industry or the fraudulent business practices of Celsius, which lost billions of customers' money.
“Not your keys, not your coins.”– Andreas Antonopoulos
However, it is often the users themselves who, consciously or unconsciously, jeopardise their funds. The obstacles to self-custody lie in both technical and practical aspects. Not everyone is willing or able to navigate hardware wallets and multisig solutions. Furthermore, without an adequate backup, there is a risk of losing coins irretrievably.
By keeping their coins in self-custody, Bitcoiners eliminate third-party risk. However, self-custody can be a challenge, especially for beginners. ‘Study Bitcoin’ is more than just a phrase here. Only those who know their way around can protect themselves against errors, misuse and loss.
CONCLUSION
The uncertainties caused by ever-changing regulation in different jurisdictions is a constant challenge for businesses. However, as Bitcoin is increasingly being categorised as harmless by the authorities, pure Bitcoin platforms might face fewer regulatory risks compared to crypto exchanges.
The growing acceptance of Bitcoin and the plans of the United States and other countries to create a strategic Bitcoin reserve may have a positive impact on how Bitcoin companies continue to be treated by regulators. I would, though, like to quote Maya Parbhoe, the Surinamese presidential candidate for 2025, at this point, even if it seems a little off-topic:
“A Bitcoin Strategic Reserve is not the answer.
> The moment a government holds Bitcoin as a reserve, it centralizes control over an asset designed to be decentralized. It strengthens the very system Bitcoin was created to replace.*
> Governments holding Bitcoin do not give power to the people, they give themselves a hedge while continuing to debase their fiat currency. They still print, they still tax, they still control. The people remain trapped in the same system, only now with a government-backed Bitcoin price floor that serves the state, not the individual.*
> Bitcoin was not made to be stockpiled by central banks. It was made to be used. As currency, as a tool of self-sovereignty, as a weapon against state overreach.”*
So let's summarise what we have covered in this article in the spirit of these liberal ideas. The following rules, which have just been created, should be mandatory reading for Bitcoin aficionados until further notice:

The Fine Line: Bitcoin Companies Navigating Regulation and Freedom was written by Bri. If you enjoyed this article then support her writing, by donating to her lightning wallet: bri_1@walletofsatoshi.com
-
-
 @ a95c6243:d345522c
2024-12-13 19:30:32
@ a95c6243:d345522c
2024-12-13 19:30:32Das Betriebsklima ist das einzige Klima, \ das du selbst bestimmen kannst. \ Anonym
Eine Strategie zur Anpassung an den Klimawandel hat das deutsche Bundeskabinett diese Woche beschlossen. Da «Wetterextreme wie die immer häufiger auftretenden Hitzewellen und Starkregenereignisse» oft desaströse Auswirkungen auf Mensch und Umwelt hätten, werde eine Anpassung an die Folgen des Klimawandels immer wichtiger. «Klimaanpassungsstrategie» nennt die Regierung das.
Für die «Vorsorge vor Klimafolgen» habe man nun erstmals klare Ziele und messbare Kennzahlen festgelegt. So sei der Erfolg überprüfbar, und das solle zu einer schnelleren Bewältigung der Folgen führen. Dass sich hinter dem Begriff Klimafolgen nicht Folgen des Klimas, sondern wohl «Folgen der globalen Erwärmung» verbergen, erklärt den Interessierten die Wikipedia. Dabei ist das mit der Erwärmung ja bekanntermaßen so eine Sache.
Die Zunahme schwerer Unwetterereignisse habe gezeigt, so das Ministerium, wie wichtig eine frühzeitige und effektive Warnung der Bevölkerung sei. Daher solle es eine deutliche Anhebung der Nutzerzahlen der sogenannten Nina-Warn-App geben.
Die ARD spurt wie gewohnt und setzt die Botschaft zielsicher um. Der Artikel beginnt folgendermaßen:
«Die Flut im Ahrtal war ein Schock für das ganze Land. Um künftig besser gegen Extremwetter gewappnet zu sein, hat die Bundesregierung eine neue Strategie zur Klimaanpassung beschlossen. Die Warn-App Nina spielt eine zentrale Rolle. Der Bund will die Menschen in Deutschland besser vor Extremwetter-Ereignissen warnen und dafür die Reichweite der Warn-App Nina deutlich erhöhen.»
Die Kommunen würden bei ihren «Klimaanpassungsmaßnahmen» vom Zentrum KlimaAnpassung unterstützt, schreibt das Umweltministerium. Mit dessen Aufbau wurden das Deutsche Institut für Urbanistik gGmbH, welches sich stark für Smart City-Projekte engagiert, und die Adelphi Consult GmbH beauftragt.
Adelphi beschreibt sich selbst als «Europas führender Think-and-Do-Tank und eine unabhängige Beratung für Klima, Umwelt und Entwicklung». Sie seien «global vernetzte Strateg*innen und weltverbessernde Berater*innen» und als «Vorreiter der sozial-ökologischen Transformation» sei man mit dem Deutschen Nachhaltigkeitspreis ausgezeichnet worden, welcher sich an den Zielen der Agenda 2030 orientiere.
Über die Warn-App mit dem niedlichen Namen Nina, die möglichst jeder auf seinem Smartphone installieren soll, informiert das Bundesamt für Bevölkerungsschutz und Katastrophenhilfe (BBK). Gewarnt wird nicht nur vor Extrem-Wetterereignissen, sondern zum Beispiel auch vor Waffengewalt und Angriffen, Strom- und anderen Versorgungsausfällen oder Krankheitserregern. Wenn man die Kategorie Gefahreninformation wählt, erhält man eine Dosis von ungefähr zwei Benachrichtigungen pro Woche.
Beim BBK erfahren wir auch einiges über die empfohlenen Systemeinstellungen für Nina. Der Benutzer möge zum Beispiel den Zugriff auf die Standortdaten «immer zulassen», und zwar mit aktivierter Funktion «genauen Standort verwenden». Die Datennutzung solle unbeschränkt sein, auch im Hintergrund. Außerdem sei die uneingeschränkte Akkunutzung zu aktivieren, der Energiesparmodus auszuschalten und das Stoppen der App-Aktivität bei Nichtnutzung zu unterbinden.
Dass man so dramatische Ereignisse wie damals im Ahrtal auch anders bewerten kann als Regierungen und Systemmedien, hat meine Kollegin Wiltrud Schwetje anhand der Tragödie im spanischen Valencia gezeigt. Das Stichwort «Agenda 2030» taucht dabei in einem Kontext auf, der wenig mit Nachhaltigkeitspreisen zu tun hat.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 71df2119:9542d9d7
2025-02-25 14:57:23
@ 71df2119:9542d9d7
2025-02-25 14:57:23Das Pareto-Team (https://tinylink.net/mIyvf) hat in den letzten Tagen die Unterstützung für Zaps veröffentlicht. Zaps sind Lightning-Transfers über Nostr, die im Pareto an Artikel oder Autoren gesendet werden können. Die aktuelle Umsetzung in der Pareto-App ist als erster Schritt zu verstehen, und es werden weitere Ausbau-Stufen folgen. In diesem Artikel wird die Nutzung des neuen Pareto-Features erklärt.
Artikel Zappen
Auf der Artikel-Seite des Pareto-Readers ist jetzt das Blitz-Symbol unter dem Artikelbild aktiviert. Durch einen Klick erscheint ein Dialog wie dieser:
Im Dialog können verschiedene vorgegebene Beträge ausgewählt oder ein eigener Betrag manuell eingegeben werden. Ein optionales Kommentarfeld steht, wie üblich, ebenfalls zur Verfügung. Nach dem Betätigen der Zap-Schaltfläche verhält sich die App unterschiedlich, abhängig davon, ob der Nutzer eine Wallet-Erweiterung im Browser installiert hat oder nicht. Falls ja, folgt die Interaktion mit der Wallet-Erweiterung, in diesem Beispiel Alby:
Hier kann die Zahlung freigegeben werden, und der Vorgang wird dann von der Software abgeschlossen.
Wenn der Nutzer keine Wallet-Erweiterung verwendet, erfordert der Vorgang weitere Schritte. Statt dem oben gezeigten Dialog erscheint eine Lighting-Rechnung:
An dieser Stelle gibt es mehrere Möglichkeiten: Man kann mit einer Lightning-Wallet den QR-Code einscannen oder die Rechnung in Textform kopieren. Alternativ kann man auch eine Wallet auf demselben Gerät öffnen und die Zahlung dort bestätigen.
Zaps an Autoren
Wie am Anfang erwähnt, können auch Autoren direkt, ohne Artikelbezug, Zaps erhalten. Auf der Profilseite des Autors gibt es neben der neu hinzugekommenen Lightning-Adresse einen Blitz-Button, ähnlich wie auf der Artikelseite:
Durch einen Klick können, ähnlich wie beim Artikel, Zaps an den Autor gesendet werden.
Das Zap-Feature in der Pareto-App basiert auf der Community-Bibliothek nostr-zap (https://github.com/SamSamskies/nostr-zap). Wir bedanken uns für den Code und haben mit einer Erweiterung der Funktionalität beigetragen - ganz im Sinne von Open-Source!
Ausblick
Wie eingangs erwähnt, sind weitere Ausbaustufen des Zap-Features geplant, darunter:
- Unterstützung für Nostr Wallet Connect für eine nahtlosere Integration und ein besseres Nutzungserlebnis.
- Unterstützung für eCash, Cashu-Nutzaps.
Bleib auf dem Laufenden und folge uns auf unseren verschiedenen Kanälen:
- Nostr: https://tinylink.net/mIyvf,
- Web: https://pareto.space,
- Geyser: https://geyser.fund/project/pareto.
Wir bei Pareto stehen erst am Anfang - nicht ausschließlich bezüglich Zaps!
-
 @ 9e69e420:d12360c2
2025-02-17 17:12:01
@ 9e69e420:d12360c2
2025-02-17 17:12:01President Trump has intensified immigration enforcement, likening it to a wartime effort. Despite pouring resources into the U.S. Immigration and Customs Enforcement (ICE), arrest numbers are declining and falling short of goals. ICE fell from about 800 daily arrests in late January to fewer than 600 in early February.
Critics argue the administration is merely showcasing efforts with ineffectiveness, while Trump seeks billions more in funding to support his deportation agenda. Increased involvement from various federal agencies is intended to assist ICE, but many lack specific immigration training.
Challenges persist, as fewer immigrants are available for quick deportation due to a decline in illegal crossings. Local sheriffs are also pressured by rising demands to accommodate immigrants, which may strain resources further.
-
 @ 9171b08a:8395fd65
2025-02-25 14:53:19
@ 9171b08a:8395fd65
2025-02-25 14:53:19Rein sat with her back against the cold steel of the jail cell, wrists and ankles bound.
She hadn’t seen light or another human face in almost two weeks. The grinding and whirling of the Guardian’s mechanical gears was the only thing to break the silence, its daily arrival at noon serving as her only reminder of time. It brought her food, but nothing else; not a word, not a gesture of humanity.
In her waking moments, she sat and replayed the events that landed her in jail, and in her slumber, those thoughts morphed into haunting nightmares with specters stalking her in hell. Hell was no longer a distant fear; it had found her. Her fate now rested in the hands of the man she once considered her best friend. Whatever evidence he was putting together would serve to either absolve her or condemn her.
A sharp beam of light pierced the darkness of the jail cell from the cell block entrance. The overhead lights came on, and she stood as David, Rein’s partner and closest friend, appeared before the cell bars.
He stared at his feet and said, “Today's your trial.”
Rein struggled to keep her eyes open from the intense brightness over the overhead lights and said, “That wasn’t nearly enough time to gather evidence.”
David pressed his lips together, eyes fixed on the floor. “I had your back on this, Rein.” Then he shook his head, and as Rein finally overcame the harsh brightness, she noticed he was staring into her eyes. “The evidence is damning. And, well, something pretty terrible has happened that has the government cracking down harder than ever.”
“Something terrible? What happened?” asked Rein.
“I would’ve never thought you were in so deep with this.” He seemed personally outraged when he said, “After everything we’ve been through together, after everything you’ve sacrificed for this city. You’ve been pretending this entire time. I’ve never known the real you.” He scoffed. “Yet there you are.”
“C’mon, David, you don’t actually think—”
David raised a hand and said, “Stop. Don’t try that shit with me. You’re lucky to even be getting a trial.”
Two Guardians entered the cell block and came to parade rest behind David. He opened the cell, and the Guardians stepped in.
“What did you find? What happened?” asked Rein.
The Guardians seized Rein’s shoulders and pushed her forward, past David.
“What did you find, David?” Urged Rein.
David remained silent. He simply watched as the Guardians took her.
A hush fell over the precinct as officers gathered around the flickering television in the corner of the reception room. Flashing across the screen were the haunting images taken from an aircraft of a city on fire, thousands of black silhouettes infiltrating the city walls. The words Shadow Crawlers Strike, Orion Dome In Ruins were emblazoned the bottom of the newscast.
Rein strained against the Guardian’s grasp to try and get a closer look at the screen and gasped, “Chronos have mercy.”
Those standing before the television turned and stared at her. Those seated at their desks stood at the sight of the Guardians ushering Rein through the offices, and within seconds, the precinct was heavy with tension. Everyone she had cared about now gaped at her with a fierce look of betrayal. Though Rein wished she could explain herself with a compelling defense, she could tell she was as good as dead to them.
The vehicle transporting her to the courthouse was as dark as the cell she had been locked up in. Rein ground her teeth and stared at the ray of light that shone through the slit in between the vehicle doors, contemplating what she had just seen on the precinct television.
After several minutes of toiling in the darkness with her own thoughts, the vehicle halted, and its doors opened at the hands of the two Guardians who towered over the roof of the hovercraft.
Many of the city people’s eyes, imbued in different shades of red, turned to stare as Rein stepped out. Their gazes were not so much filled with judgment as they were with fear. She stepped onto the walkway with her head sagged, ashamed to look at the very people she had sworn to protect.
Join the furnace of the Empire! Invest in Elius today and be a part of the Industrial heart of Aurial.
Rein clenched her fist as she contemplated the words on the crumpled flyer laying on the sidewalk beside her foot. She couldn’t help but think of what her father had been up to in that city.
She had never paid much attention to the image of the man on the flyer, his arms crossed and his head held high before a massive furnace that sparked embers into the four corners of the paper. The silhouette of a building was portrayed on one corner, a soldier held a weapon on another, the image of a child holding a toy on the bottom right, and a family held up a shirt on the remaining corner.
Those flyers were hung up throughout the precinct offices, inside coffee shops, and gathering places, attempting to attract the wealth that easily found itself in the pockets of the kind of people that lived in Roxis. It seemed to have worked on her father.
But what had he been up to?
Rein never understood why her father had abandoned Roxis for Elius, nor had he ever offered an explanation. As a financial hub, Roxis attracted wealth and intellect, leaving cities like Elius with a rougher class of laborers— many of whom turned to crime to escape extreme poverty and hard work in the very factories exhibited on the promotional flyer.
The city of Roxis had been good to Rein. Though many a passerby would think differently seeing her now with her wrists and ankles shackled as she walked up the steps of the Judgment House. She’d grown to be a God-loving woman and spent most of her adult life protecting the city from criminals the likes of which the people walking by, now, would think she was.
One of the Guardians towering at her side nudged her shoulder, and with the artificial voice generated from within its chest said, “You must move along, Miss Lancer.”
The robot’s hand ushered her forward, and a ray of sunlight nearly blinded her as she gazed upon the Judgment House made almost entirely of glass and marble.
The crest of Aurialian Empire above the entrance of the building made her pause. Her eyes lingered on the star that lay at the center of the red and blue shield of Ariel, the archangel. A character that looked like an angular and unfinished number eight with a line drawn through the middle sat like a crown above the words "Out of God, An Empire", inscribed around the crest of the Aurilian Empire.
The symbol of peace felt like a cruel joke now. She had once sworn to uphold the empire’s sanctity, yet here she was, condemned by it.
Episode 2 coming soon...
Thank you for reading!
If you enjoyed this episode, let me know with a zap and share it with friends who might like it too!
Your feedback sends a strong signal to keep making content like this!
Interested in blog posts? Follow @Beneath The Ink for great short stories and serialized fiction.
More short stories you might like from Fervid Fables:
nostr:naddr1qvzqqqr4gupzpyt3kz9079njd5g0fs5rxhtg8g9wdwkdar65kuhaujfyajpetlt9qq2kx6zzdap9s3nnde5hy7f5wej57d2twp54y82h07y
nostr:naddr1qvzqqqr4gupzpyt3kz9079njd5g0fs5rxhtg8g9wdwkdar65kuhaujfyajpetlt9qq2h5etx2fghgumyg3mhjanewgeysa6wdfmrs85l27m
-
 @ fd208ee8:0fd927c1
2025-02-06 15:58:38
@ fd208ee8:0fd927c1
2025-02-06 15:58:38Beginning at the start
In my previous article, The Establishment, I answered the question: "How do we form a company?" I realize, now, that I was getting a bit ahead, of myself, as the precursor to a company is a team, and many people struggle to form teams. So, I will go back to the beginning, and then you can read both articles to the end, and then stop.
The Initiation
The first, and most-difficult step of team formation, is the initiation. We know that it must be the most-difficult, as it's the step that carries the highest potential reward, and it's the step that is tried-and-failed most often. (Some people, like Elon Musk or Donald Trump, are born Initiators with excellent follow-through, but this archetype is exceedingly thin on the ground because it requires you to be mildly autistic, have barely-throttled ADHD, and/or tend to megalomania, also popularly known as "toxic masculinity", "CEO personality", or "being a successful military officer".)
Someone needs to form a useful, attractive Vision and then motivate other people to help them achieve it. That sounds really easy, but it's actually brutally difficult because * You have to come up with an idea that is coherent, plausible, and inspiring. * You have to be able to communicate that idea to other people and make it appealing to them, by tying it into their own personal goals and desires. * You have to be able to hone and reformulate that idea, constantly, to correct it or to re-motivate the other team members. * You have to defend the idea against detractors, naysayers, and trolls, and you have to do it so vociferously, that it will erode your own popularity among those who disagree with you and open you to personal attacks. * You have to be able to focus on the idea, yourself, for a long stretch of time, and not allow yourself to get bored, lazy, or distracted.
So, just do and be all of those things, and then initiate the team, with the method I will name the Hatbock Method. It is so named because of the classic, German initiation ritual, in which an Initiator stands up, loudly defines their Vision and calls into a group "Wer hat Bock?" (roughly, "Who has the hunger/desire?") and whoever responds with "Ich hab Bock." (roughly, "Yes, I hunger for this.") is a part of the team.
Then the Initiator says, "Okay, everyone with the hunger, let's sit down together, and discuss this some more." (This "sitting" is literally called a "seating", or "Sitzung", which is the German word for "meeting".)
The Sitting
We now get to the second most difficult part of team formation: figuring out where to sit. Most teams get this wrong, repeatedly, and many teams dissolve or fracture under the difficulty of this momentous decision. You would think organizing yourselves online would make this easier ("Oh, we'll just meet online!"), but the number of places available for sitting online are limitless. You can talk your whole Vision into the ground, with laborous discussions and migrations between Chachi, OxChat, Telegram, SimpleX, Slack, Discord, WhatsApp, GitHub, Teams, Coracle, Matrix... you get the idea.
Try to keep in mind that the Vision is more important than the seating area, and go with the flow. Simply, find someplace and go there. Worry about it again, at a later date. Don't lose momentum. Sit down and start discussing the Vision, immediately.

Now, this next bit is very important:
Do not let anyone outside your team influence where you sit!
...unless they are providing your team with some good, service, or income, that makes choosing their preferred location the superior choice.
This is the German Stammtisch principle, where a host encourages you to come sit down, regularly, in some particular place, because your sitting there provides them with some benefit: they can overhear your conversations, get you to test out their seating area, sell you refreshments, etc. Your choice of seating, in other words, is a valuable good, and you should only "sell" it to someone who rewards you in measure. They have to reward you because their preferred seating area wasn't your immediate and obvious choice, so there was probably something unappealing or uncertain about the seating area.
Plan it in
Once you've sat down, and finished your rough draft of the Vision, you need to figure out when to sit. This is the third most-difficult part of team formation. (Yes, don't worry, it gets easier as it goes along.)
The most popular plan is the Wirsehenuns Plan (roughly, "We'll see each other, around.") This can work quite well, if you just want to have a loose collaboration, that calls itself together in an ad hoc fashion, when a team member feels the need. Also known as "@ me, bros".
It's not a great plan for more intensive collaboration, as that tends to need a certain amount of velocity, to actually happen, as the speed of movement has a centrifugal effect on the tasks. Team momentum, in other words, creates a sort of gravity, that keeps the team together as a unit. So, for deeper teamwork, I would recommend the Stammtisch variant: name a place and date/time, when you will next meet. Preferably, on a rotating schedule: daily, weekly, last Thursday of the month, etc.
And then meet there and then. And discuss amongst yourselves. Set clear, short-term tasks (and assign them to particular people!), medium-term strategies, and longer-term goals. Write everything down. Anything not written down, is a suggestion, not an assigned task.
If you find your Stammtisch becoming increasingly rewarding and productive, and your goals start moving closer and closer into sight, then you might want to formalize your team structure further, as a company.
-
 @ a95c6243:d345522c
2024-12-06 18:21:15
@ a95c6243:d345522c
2024-12-06 18:21:15Die Ungerechtigkeit ist uns nur in dem Falle angenehm,\ dass wir Vorteile aus ihr ziehen;\ in jedem andern hegt man den Wunsch,\ dass der Unschuldige in Schutz genommen werde.\ Jean-Jacques Rousseau
Politiker beteuern jederzeit, nur das Beste für die Bevölkerung zu wollen – nicht von ihr. Auch die zahlreichen unsäglichen «Corona-Maßnahmen» waren angeblich zu unserem Schutz notwendig, vor allem wegen der «besonders vulnerablen Personen». Daher mussten alle möglichen Restriktionen zwangsweise und unter Umgehung der Parlamente verordnet werden.
Inzwischen hat sich immer deutlicher herausgestellt, dass viele jener «Schutzmaßnahmen» den gegenteiligen Effekt hatten, sie haben den Menschen und den Gesellschaften enorm geschadet. Nicht nur haben die experimentellen Geninjektionen – wie erwartet – massive Nebenwirkungen, sondern Maskentragen schadet der Psyche und der Entwicklung (nicht nur unserer Kinder) und «Lockdowns und Zensur haben Menschen getötet».
Eine der wichtigsten Waffen unserer «Beschützer» ist die Spaltung der Gesellschaft. Die tiefen Gräben, die Politiker, Lobbyisten und Leitmedien praktisch weltweit ausgehoben haben, funktionieren leider nahezu in Perfektion. Von ihren persönlichen Erfahrungen als Kritikerin der Maßnahmen berichtete kürzlich eine Schweizerin im Interview mit Transition News. Sie sei schwer enttäuscht und verspüre bis heute eine Hemmschwelle und ein seltsames Unwohlsein im Umgang mit «Geimpften».
Menschen, die aufrichtig andere schützen wollten, werden von einer eindeutig politischen Justiz verfolgt, verhaftet und angeklagt. Dazu zählen viele Ärzte, darunter Heinrich Habig, Bianca Witzschel und Walter Weber. Über den aktuell laufenden Prozess gegen Dr. Weber hat Transition News mehrfach berichtet (z.B. hier und hier). Auch der Selbstschutz durch Verweigerung der Zwangs-Covid-«Impfung» bewahrt nicht vor dem Knast, wie Bundeswehrsoldaten wie Alexander Bittner erfahren mussten.
Die eigentlich Kriminellen schützen sich derweil erfolgreich selber, nämlich vor der Verantwortung. Die «Impf»-Kampagne war «das größte Verbrechen gegen die Menschheit». Trotzdem stellt man sich in den USA gerade die Frage, ob der scheidende Präsident Joe Biden nach seinem Sohn Hunter möglicherweise auch Anthony Fauci begnadigen wird – in diesem Fall sogar präventiv. Gibt es überhaupt noch einen Rest Glaubwürdigkeit, den Biden verspielen könnte?
Der Gedanke, den ehemaligen wissenschaftlichen Chefberater des US-Präsidenten und Direktor des National Institute of Allergy and Infectious Diseases (NIAID) vorsorglich mit einem Schutzschild zu versehen, dürfte mit der vergangenen Präsidentschaftswahl zu tun haben. Gleich mehrere Personalentscheidungen des designierten Präsidenten Donald Trump lassen Leute wie Fauci erneut in den Fokus rücken.
Das Buch «The Real Anthony Fauci» des nominierten US-Gesundheitsministers Robert F. Kennedy Jr. erschien 2021 und dreht sich um die Machenschaften der Pharma-Lobby in der öffentlichen Gesundheit. Das Vorwort zur rumänischen Ausgabe des Buches schrieb übrigens Călin Georgescu, der Überraschungssieger der ersten Wahlrunde der aktuellen Präsidentschaftswahlen in Rumänien. Vielleicht erklärt diese Verbindung einen Teil der Panik im Wertewesten.
In Rumänien selber gab es gerade einen Paukenschlag: Das bisherige Ergebnis wurde heute durch das Verfassungsgericht annuliert und die für Sonntag angesetzte Stichwahl kurzfristig abgesagt – wegen angeblicher «aggressiver russischer Einmischung». Thomas Oysmüller merkt dazu an, damit sei jetzt in der EU das Tabu gebrochen, Wahlen zu verbieten, bevor sie etwas ändern können.
Unsere Empörung angesichts der Historie von Maßnahmen, die die Falschen beschützen und für die meisten von Nachteil sind, müsste enorm sein. Die Frage ist, was wir damit machen. Wir sollten nach vorne schauen und unsere Energie clever einsetzen. Abgesehen von der Umgehung von jeglichem «Schutz vor Desinformation und Hassrede» (sprich: Zensur) wird es unsere wichtigste Aufgabe sein, Gräben zu überwinden.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2024-11-29 19:45:43
@ a95c6243:d345522c
2024-11-29 19:45:43Konsum ist Therapie.
Wolfgang JoopUmweltbewusstes Verhalten und verantwortungsvoller Konsum zeugen durchaus von einer wünschenswerten Einstellung. Ob man deswegen allerdings einen grünen statt eines schwarzen Freitags braucht, darf getrost bezweifelt werden – zumal es sich um manipulatorische Konzepte handelt. Wie in der politischen Landschaft sind auch hier die Etiketten irgendwas zwischen nichtssagend und trügerisch.
Heute ist also wieder mal «Black Friday», falls Sie es noch nicht mitbekommen haben sollten. Eigentlich haben wir ja eher schon eine ganze «Black Week», der dann oft auch noch ein «Cyber Monday» folgt. Die Werbebranche wird nicht müde, immer neue Anlässe zu erfinden oder zu importieren, um uns zum Konsumieren zu bewegen. Und sie ist damit sehr erfolgreich.
Warum fallen wir auf derartige Werbetricks herein und kaufen im Zweifelsfall Dinge oder Mengen, die wir sicher nicht brauchen? Pure Psychologie, würde ich sagen. Rabattschilder triggern etwas in uns, was den Verstand in Stand-by versetzt. Zusätzlich beeinflussen uns alle möglichen emotionalen Reize und animieren uns zum Schnäppchenkauf.
Gedankenlosigkeit und Maßlosigkeit können besonders bei der Ernährung zu ernsten Problemen führen. Erst kürzlich hat mir ein Bekannter nach einer USA-Reise erzählt, dass es dort offenbar nicht unüblich ist, schon zum ausgiebigen Frühstück in einem Restaurant wenigstens einen Liter Cola zu trinken. Gerne auch mehr, um das Gratis-Nachfüllen des Bechers auszunutzen.
Kritik am schwarzen Freitag und dem unnötigen Konsum kommt oft von Umweltschützern. Neben Ressourcenverschwendung, hohem Energieverbrauch und wachsenden Müllbergen durch eine zunehmende Wegwerfmentalität kommt dabei in der Regel auch die «Klimakrise» auf den Tisch.
Die EU-Kommission lancierte 2015 den Begriff «Green Friday» im Kontext der überarbeiteten Rechtsvorschriften zur Kennzeichnung der Energieeffizienz von Elektrogeräten. Sie nutzte die Gelegenheit kurz vor dem damaligen schwarzen Freitag und vor der UN-Klimakonferenz COP21, bei der das Pariser Abkommen unterzeichnet werden sollte.
Heute wird ein grüner Freitag oft im Zusammenhang mit der Forderung nach «nachhaltigem Konsum» benutzt. Derweil ist die Europäische Union schon weit in ihr Geschäftsmodell des «Green New Deal» verstrickt. In ihrer Propaganda zum Klimawandel verspricht sie tatsächlich «Unterstützung der Menschen und Regionen, die von immer häufigeren Extremwetter-Ereignissen betroffen sind». Was wohl die Menschen in der Region um Valencia dazu sagen?
Ganz im Sinne des Great Reset propagierten die Vereinten Nationen seit Ende 2020 eine «grüne Erholung von Covid-19, um den Klimawandel zu verlangsamen». Der UN-Umweltbericht sah in dem Jahr einen Schwerpunkt auf dem Verbraucherverhalten. Änderungen des Konsumverhaltens des Einzelnen könnten dazu beitragen, den Klimaschutz zu stärken, hieß es dort.
Der Begriff «Schwarzer Freitag» wurde in den USA nicht erstmals für Einkäufe nach Thanksgiving verwendet – wie oft angenommen –, sondern für eine Finanzkrise. Jedoch nicht für den Börsencrash von 1929, sondern bereits für den Zusammenbruch des US-Goldmarktes im September 1869. Seitdem mussten die Menschen weltweit so einige schwarze Tage erleben.
Kürzlich sind die britischen Aufsichtsbehörden weiter von ihrer Zurückhaltung nach dem letzten großen Finanzcrash von 2008 abgerückt. Sie haben Regeln für den Bankensektor gelockert, womit sie «verantwortungsvolle Risikobereitschaft» unterstützen wollen. Man würde sicher zu schwarz sehen, wenn man hier ein grünes Wunder befürchten würde.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ c8383d81:f9139549
2025-02-05 13:06:05
@ c8383d81:f9139549
2025-02-05 13:06:05My own stats on what I’ve done over the weekend:
-
Spoke to +100 developers, it was great seeing a couple of familiar Flemish faces and meeting some new ones but overall the crowd was extremely diverse.
-
Ended up doing a short interview promoting the protocol and ended up going to 0 talks.
-
Tried to evangelize by going booth by booth to distribute a Nostr flyer to other FOSDEM projects, with the hope that they would broadcast the info towards their SOME person to add Nostr on their list or to build out a library for the languages that were present ( This was a fairly slow approach )
-
Kept it to Nostr protocol 95% of the time, the Bitcoin narrative is not always a good time to push and as a side note I’ve met more Monero users than in the last 5 years.
-
Was able to convince some engineers to look into the #soveng endeavor.
Small overview from the most common questions:
- They have heard about Nostr but are not sure of the details. ( mostly through the bitcoin community )
- What is the difference with ActivityPub, Mastodon, Fediverse ?
- IOT developers, so questions regarding MQTT & Meshtastic integrations ?
- Current state of MLS on Nostr ?
- What are the current biggest clients / apps build on Nostr ?
- Will jack still give a talk ?
Things we could improve:
- Bring more stickers like loads more,
- Bring T-shirts, Pins… could be a good way to fund these adventures instead of raising funds. ( Most projects where selling something to help raise funds for projects )
- Almost no onboarding / client installs.
- Compared to the Nostr booth at BTC Amsterdam not a single person asked if they could charge their phone.
Personal Note: The last time I visited was roughly 13 years ago and me being a little more seasoned I just loved the fact that I was able to pay some support to the open source projects I’ve been using for years ( homebrew, modzilla, Free BSD,.. ) and see the amazing diverse crowd that is the open source Movement 🧡
Al final shoutout to our great pirate crew 🏴☠️: The Dutch Guard ( nostr:npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe & nostr:npub1l77twp5l02jadkcjn6eeulv2j7y5vmf9tf3hhtq7h7rp0vzhgpzqz0swft ) and a adrenaline fueled nostr:npub1t6jxfqz9hv0lygn9thwndekuahwyxkgvycyscjrtauuw73gd5k7sqvksrw , nostr:npub1rfw075gc6pc693w5v568xw4mnu7umlzpkfxmqye0cgxm7qw8tauqfck3t8 and nostr:npub1r30l8j4vmppvq8w23umcyvd3vct4zmfpfkn4c7h2h057rmlfcrmq9xt9ma amazing finally meeting you IRL after close to 2 years since the Yakihonne hackathon 😀

-
-
 @ 0fa80bd3:ea7325de
2025-02-14 23:24:37
@ 0fa80bd3:ea7325de
2025-02-14 23:24:37intro
The Russian state made me a Bitcoiner. In 1991, it devalued my grandmother's hard-earned savings. She worked tirelessly in the kitchen of a dining car on the Moscow–Warsaw route. Everything she had saved for my sister and me to attend university vanished overnight. This story is similar to what many experienced, including Wences Casares. The pain and injustice of that time became my first lessons about the fragility of systems and the value of genuine, incorruptible assets, forever changing my perception of money and my trust in government promises.
In 2014, I was living in Moscow, running a trading business, and frequently traveling to China. One day, I learned about the Cypriot banking crisis and the possibility of moving money through some strange thing called Bitcoin. At the time, I didn’t give it much thought. Returning to the idea six months later, as a business-oriented geek, I eagerly began studying the topic and soon dove into it seriously.
I spent half a year reading articles on a local online journal, BitNovosti, actively participating in discussions, and eventually joined the editorial team as a translator. That’s how I learned about whitepapers, decentralization, mining, cryptographic keys, and colored coins. About Satoshi Nakamoto, Silk Road, Mt. Gox, and BitcoinTalk. Over time, I befriended the journal’s owner and, leveraging my management experience, later became an editor. I was drawn to the crypto-anarchist stance and commitment to decentralization principles. We wrote about the economic, historical, and social preconditions for Bitcoin’s emergence, and it was during this time that I fully embraced the idea.
It got to the point where I sold my apartment and, during the market's downturn, bought 50 bitcoins, just after the peak price of $1,200 per coin. That marked the beginning of my first crypto winter. As an editor, I organized workflows, managed translators, developed a YouTube channel, and attended conferences in Russia and Ukraine. That’s how I learned about Wences Casares and even wrote a piece about him. I also met Mikhail Chobanyan (Ukrainian exchange Kuna), Alexander Ivanov (Waves project), Konstantin Lomashuk (Lido project), and, of course, Vitalik Buterin. It was a time of complete immersion, 24/7, and boundless hope.
After moving to the United States, I expected the industry to grow rapidly, attended events, but the introduction of BitLicense froze the industry for eight years. By 2017, it became clear that the industry was shifting toward gambling and creating tokens for the sake of tokens. I dismissed this idea as unsustainable. Then came a new crypto spring with the hype around beautiful NFTs – CryptoPunks and apes.
I made another attempt – we worked on a series called Digital Nomad Country Club, aimed at creating a global project. The proceeds from selling images were intended to fund the development of business tools for people worldwide. However, internal disagreements within the team prevented us from completing the project.
With Trump’s arrival in 2025, hope was reignited. I decided that it was time to create a project that society desperately needed. As someone passionate about history, I understood that destroying what exists was not the solution, but leaving everything as it was also felt unacceptable. You can’t destroy the system, as the fiery crypto-anarchist voices claimed.
With an analytical mindset (IQ 130) and a deep understanding of the freest societies, I realized what was missing—not only in Russia or the United States but globally—a Bitcoin-native system for tracking debts and financial interactions. This could return control of money to ordinary people and create horizontal connections parallel to state systems. My goal was to create, if not a Bitcoin killer app, then at least to lay its foundation.
At the inauguration event in New York, I rediscovered the Nostr project. I realized it was not only technologically simple and already quite popular but also perfectly aligned with my vision. For the past month and a half, using insights and experience gained since 2014, I’ve been working full-time on this project.
-
 @ 85bdb587:7339d672
2025-02-25 14:14:57
@ 85bdb587:7339d672
2025-02-25 14:14:57Marty's Bent
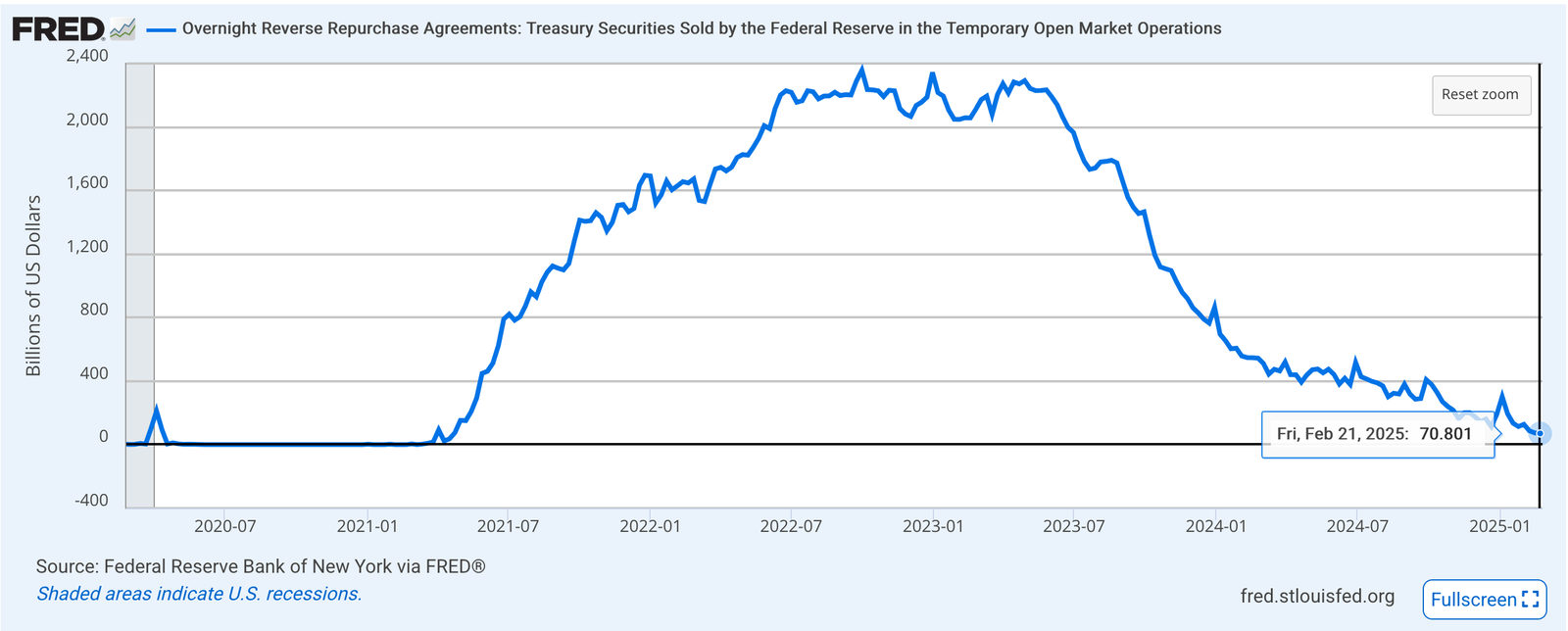
Since mid-2022 the Fed has been reigning in its balance sheet via a process called quantitative tightening (QT), in which they allow some of the debt assets they hold to come to maturity without reinvesting in them. This leads to a reduction in the Fed's balance sheet and is done to remove the excess liquidity introduced to the markets during the COVID crisis so that inflation can be reeled in. On top of this, the Fed is hoping that the extraordinary measures it took to step in during a time of crisis allowed the banking system to get their houses in order in preparation for a period of relatively tighter liquidity. Ideally, everyone took the time and effort to clean up their balance sheets, properly manage their duration risk, and get themselves on solid footing to move forward without the Fed stepping in to prop up the market.
At its peak, the overnight reverse repo facility had around $2.36T of liquidity in the form of debt instruments like treasuries and mortgage backed securities available to banks, money market funds and certain government enterprises. These entities lend the Fed cash for these instruments and get interest back in return. This acts as a mechanism the Fed can leverage to keep short-term rates in line with wherever their targets are at any given point in time. Over the last ~13 quarters the Fed has been slowly but surely letting these markets drain and, as of last Friday, they currently sit at $70.8B. At its current pace the reverse repo facility should be completely drained by the end of next month or beginning of April.
The question on everybody's mind is, what happens once the reverse repo markets are empty?
The last time the Fed embarked on QT was in October 2017. It drained the reverse repo over the course of a little less than two years before the market was drained and the overnight rates in the market spiked into the low teens in September of 2019. Many don't remember this, but it was a "holy shit" moment that forced the Fed to create new facilities overnight to band aid over the hemorrhaging. Coincidentally, a few months later COVID would overtake the world and the Fed had a convenient excuse to double the monetary base well above $6T.
If September 2019 is an example of exactly what happens when the reverse repo market drains, we may be in for a liquidity crunch. However, the Fed is posturing that it has learned its lessons from the 2019 rate spasm and has adjusted some things accordingly to ensure a smoother transition from a state of excess liquidity to a state of significantly less liquidity. Particularly, more control over SOFR and how it interacts with this market. If we reach the point where the reverse repo markets have been successfully drained without a 2019-like spasm, the Fed will then move on to the excess liquidity sitting on the balance sheets of commercial banks and continue their journey to try to reel in inflation.
President Trump certainly isn't making the Fed's job easier with promises of lower domestic taxes and the levying of aggressive tariffs, which could both be inflationary. I'm sure Jerome Powell is praying that DOGE continues their swift work and gets the signal out to markets that the US government is committed to getting its fiscal house in order to make treasuries more appealing to the market so that rates can float down.
I have no idea exactly what is going to happen, but I have a feeling that a liquidity crunch is on the horizon. It may not be once the reverse repo market is drained. I would not be the least bit surprised if the work the Fed has done behind the scenes to ensure a spasm like we experienced in 2019 doesn't happen is successful. Though, it likely only buys some time and delays the inevitable. As my good friend Parker Lewis likes to say, "There's too much debt and not enough dollars." At some point, QT will hit a point where it cannot be sustained because too many dollars have been pulled out of a system with ever increasing amounts of debt that need to be serviced with dollars. Whether it happens when the reverse repo market is drained or at some point after the Fed starts unwinding the excess liquidity on bank balance sheets isn't really that important.
We're getting early warning signs that a liquidity crunch may be near with the mad dash for bringing physical gold into the US, the VIX spiking above 20 earlier today and bitcoin "crashing" toward $90,000. Volatility is increasing at a time when the reverse repo market is almost tapped and the world is a bit uncertain as it tries to figure out the ramifications of Trump's blitzkreig his first month in office.
For those scratching their heads about the price of bitcoin falling during a time like this, it is pretty typical. Bitcoin is traded 24/7/365, has a ton of liquidity, and is easy to buy and sell. When markets sense volatility, bitcoin is usually one of the first assets to be sold off as investors try to sure up their cash balances and pay off debts. It is usually the first and quickest to move lower, but also the first and quickest to move higher when the dust has settled. I find it hard to believe that the price of bitcoin will stay down long if it falls considerably.
The fundamentals have never been stronger and too many people have been waiting for an opportune buying opportunity to pass it up. The question is how many of those looking for a buying opportunity will have dry powder and be liquid if and when it happens.
Bitcoin's Institutional Moment: Big Players Are Entering the Game
Bitcoin's journey into mainstream financial markets is accelerating. During our conversation last week, Peruvian Bull highlighted several key milestones, including Abu Dhabi's $430 million position in Bitcoin ETFs and regulatory progress with the SEC's SAB 122, which now allows banks to custody Bitcoin. This fundamental shift isn't just about price – it represents a structural change in how traditional financial institutions view Bitcoin as a legitimate asset class.
"This is a massive opportunity for bitcoin companies - go start a custody service and get a bunch of bitcoiners together and teach institutions how to safely custody their bitcoin." - Peruvian Bull
As I've observed through our work at Ten31, there's a growing recognition that a Bitcoin treasury strategy makes sense for both public and private companies. We're seeing this with MicroStrategy, Tesla, Bitcoin miners, and potentially GameStop. More importantly, the infrastructure is being built by major institutions like State Street and Citibank to support this adoption. While gold has the established financial plumbing, Bitcoin's institutional rails are being constructed rapidly, setting the stage for the next wave of adoption.
TLDR: Major institutions building Bitcoin infrastructure signals mainstream adoption
Check out the full podcast here for more on gold market disruptions, GameStop's potential Bitcoin strategy, and the looming debt crisis that's creating perfect conditions for Bitcoin adoption.
Headlines of the Day
El Salvador Boosts Bitcoin Reserve - via X
Jamie Dimon Sold $233.7M in JPM Stock - via X
Montana, North Dakota, and Wyoming Rejected Bills for SBR - via X
Bitcoin Lesson of the Day
Bitcoin uses cryptographic keys to secure transactions. A private key, a secret random number, allows you to spend bitcoin, while a public key, derived from the private key, is used to receive bitcoin.
The public key is hashed and encoded into a Bitcoin address (e.g., 1A1zP1eP5QGefi2DMPTfTL5SLmv7DivfNa), a shorter, user-friendly string shared to receive funds. Private keys must be kept secure—losing them means losing access to your bitcoin, and anyone with your private key can spend it.
Addresses are generated from public keys via hashing (SHA-256 and RIPEMD-160) and include a checksum for error detection. Bitcoin wallets manage these keys, often using seed phrases to recover them. Understanding keys and addresses is fundamental to securely using Bitcoin.
Full Learnmeabitcoin.com post here
ICYMI Fold opened the waiting list for the new Bitcoin Rewards Credit Card. Fold cardholders will get unlimited 2% cash back in sats.
Get on the waiting list now before it fills up!
$200k worth of prizes are up for grabs.
Ten31, the largest bitcoin-focused investor, has deployed $150M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/funds.
-
 @ a95c6243:d345522c
2024-11-08 20:02:32
@ a95c6243:d345522c
2024-11-08 20:02:32Und plötzlich weißt du:
Es ist Zeit, etwas Neues zu beginnen
und dem Zauber des Anfangs zu vertrauen.
Meister EckhartSchwarz, rot, gold leuchtet es im Kopf des Newsletters der deutschen Bundesregierung, der mir freitags ins Postfach flattert. Rot, gelb und grün werden daneben sicher noch lange vielzitierte Farben sein, auch wenn diese nie geleuchtet haben. Die Ampel hat sich gerade selber den Stecker gezogen – und hinterlässt einen wirtschaftlichen und gesellschaftlichen Trümmerhaufen.
Mit einem bemerkenswerten Timing hat die deutsche Regierungskoalition am Tag des «Comebacks» von Donald Trump in den USA endlich ihr Scheitern besiegelt. Während der eine seinen Sieg bei den Präsidentschaftswahlen feierte, erwachten die anderen jäh aus ihrer Selbsthypnose rund um Harris-Hype und Trump-Panik – mit teils erschreckenden Auswüchsen. Seit Mittwoch werden die Geschicke Deutschlands nun von einer rot-grünen Minderheitsregierung «geleitet» und man steuert auf Neuwahlen zu.
Das Kindergarten-Gehabe um zwei konkurrierende Wirtschaftsgipfel letzte Woche war bereits bezeichnend. In einem Strategiepapier gestand Finanzminister Lindner außerdem den «Absturz Deutschlands» ein und offenbarte, dass die wirtschaftlichen Probleme teilweise von der Ampel-Politik «vorsätzlich herbeigeführt» worden seien.
Lindner und weitere FDP-Minister wurden also vom Bundeskanzler entlassen. Verkehrs- und Digitalminister Wissing trat flugs aus der FDP aus; deshalb darf er nicht nur im Amt bleiben, sondern hat zusätzlich noch das Justizministerium übernommen. Und mit Jörg Kukies habe Scholz «seinen Lieblingsbock zum Obergärtner», sprich: Finanzminister befördert, meint Norbert Häring.
Es gebe keine Vertrauensbasis für die weitere Zusammenarbeit mit der FDP, hatte der Kanzler erklärt, Lindner habe zu oft sein Vertrauen gebrochen. Am 15. Januar 2025 werde er daher im Bundestag die Vertrauensfrage stellen, was ggf. den Weg für vorgezogene Neuwahlen freimachen würde.
Apropos Vertrauen: Über die Hälfte der Bundesbürger glauben, dass sie ihre Meinung nicht frei sagen können. Das ging erst kürzlich aus dem diesjährigen «Freiheitsindex» hervor, einer Studie, die die Wechselwirkung zwischen Berichterstattung der Medien und subjektivem Freiheitsempfinden der Bürger misst. «Beim Vertrauen in Staat und Medien zerreißt es uns gerade», kommentierte dies der Leiter des Schweizer Unternehmens Media Tenor, das die Untersuchung zusammen mit dem Institut für Demoskopie Allensbach durchführt.
«Die absolute Mehrheit hat absolut die Nase voll», titelte die Bild angesichts des «Ampel-Showdowns». Die Mehrheit wolle Neuwahlen und die Grünen sollten zuerst gehen, lasen wir dort.
Dass «Insolvenzminister» Robert Habeck heute seine Kandidatur für das Kanzleramt verkündet hat, kann nur als Teil der politmedialen Realitätsverweigerung verstanden werden. Wer allerdings denke, schlimmer als in Zeiten der Ampel könne es nicht mehr werden, sei reichlich optimistisch, schrieb Uwe Froschauer bei Manova. Und er kenne Friedrich Merz schlecht, der sich schon jetzt rhetorisch auf seine Rolle als oberster Feldherr Deutschlands vorbereite.
Was also tun? Der Schweizer Verein «Losdemokratie» will eine Volksinitiative lancieren, um die Bestimmung von Parlamentsmitgliedern per Los einzuführen. Das Losverfahren sorge für mehr Demokratie, denn als Alternative zum Wahlverfahren garantiere es eine breitere Beteiligung und repräsentativere Parlamente. Ob das ein Weg ist, sei dahingestellt.
In jedem Fall wird es notwendig sein, unsere Bemühungen um Freiheit und Selbstbestimmung zu verstärken. Mehr Unabhängigkeit von staatlichen und zentralen Institutionen – also die Suche nach dezentralen Lösungsansätzen – gehört dabei sicher zu den Möglichkeiten. Das gilt sowohl für jede/n Einzelne/n als auch für Entitäten wie die alternativen Medien.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 9e69e420:d12360c2
2025-02-14 18:07:10
@ 9e69e420:d12360c2
2025-02-14 18:07:10Vice President J.D. Vance addressed the Munich Security Conference, criticizing European leaders for undermining free speech and traditional values. He claimed that the biggest threat to Europe is not from external enemies but from internal challenges. Vance condemned the arrest of a British man for praying near an abortion clinic and accused European politicians of censorship.
He urged leaders to combat illegal immigration and questioned their democratic practices. “There is a new sheriff in town,” he said, referring to President Trump. Vance's remarks were unexpected, as many anticipated discussions on security or Ukraine. His speech emphasized the need for Europe to share the defense burden to ensure stability and security.
-
 @ 6a6be47b:3e74e3e1
2025-02-25 14:14:41
@ 6a6be47b:3e74e3e1
2025-02-25 14:14:41Hi frens, While drawing this fly 🪰 👇🏻
nostr:nevent1qgsx56ly0wcj7gwasrc7707l9px39g5nzn82p35akhkdqj448e6w8cgqyrrnhgtqqfvcvf007gtxmffrhd8zw5j0t93cuxc3yrykl2dzyp3tvj4hcjx
I started thinking about how to make my art stand out. Maybe I should focus on making it more appealing—or at least improving its presentation. Don’t get me wrong, I’m not against making my work more consumable, but the marketing side of things takes so much time away from actually creating art. It’s sad that sometimes it feels less about delivering high-quality work and more about turning it into “content.” Honestly, that can be exhausting. Like Fall Out Boy said, “all this effort to make it look effortless.”It’s not really my style to turn my art—or the process of creating it—into content. That’s why I sometimes struggle with crafting or presenting it in a way that fits today’s trends. Sometimes, the pressure to make my art presentable is so overwhelming that it makes me feel like not creating at all. And when it doesn’t yield the kind of recognition or financial support I hope for after all that effort, it can be really disappointing. It’s like watching all that hard work slowly erode my soul. It’s tough to keep going when it feels like my art isn’t being valued in the way I wish it could be. I want to be clear: this isn’t me dissing anyone. You do you, and I’ll do me. As Crowley would say, “Do what thou wilt.” What I’m really trying to figure out is how to find that sweet spot—where I can keep up with the times and make my art more appealing without losing my soul in the process. I’m trying my best, and I know I’ll make mistakes along the way, but I’ll keep going. I just wanted to share these thoughts with you because I’m usually pretty upbeat here—maybe even a little superficial at times—but this is me being more real with you. Art is such a huge part of my life, and through my work, I’m already sharing something raw and personal with you. But now you also know why my presentation might sometimes feel simple or plain. I’m working on finding that balance, and I’ll get there eventually. Godspeed, my frens
-
 @ a95c6243:d345522c
2024-10-26 12:21:50
@ a95c6243:d345522c
2024-10-26 12:21:50Es ist besser, ein Licht zu entzünden, als auf die Dunkelheit zu schimpfen. Konfuzius
Die Bemühungen um Aufarbeitung der sogenannten Corona-Pandemie, um Aufklärung der Hintergründe, Benennung von Verantwortlichkeiten und das Ziehen von Konsequenzen sind durchaus nicht eingeschlafen. Das Interesse daran ist unter den gegebenen Umständen vielleicht nicht sonderlich groß, aber es ist vorhanden.
Der sächsische Landtag hat gestern die Einsetzung eines Untersuchungsausschusses zur Corona-Politik beschlossen. In einer Sondersitzung erhielt ein entsprechender Antrag der AfD-Fraktion die ausreichende Zustimmung, auch von einigen Abgeordneten des BSW.
In den Niederlanden wird Bill Gates vor Gericht erscheinen müssen. Sieben durch die Covid-«Impfstoffe» geschädigte Personen hatten Klage eingereicht. Sie werfen unter anderem Gates, Pfizer-Chef Bourla und dem niederländischen Staat vor, sie hätten gewusst, dass diese Präparate weder sicher noch wirksam sind.
Mit den mRNA-«Impfstoffen» von Pfizer/BioNTech befasst sich auch ein neues Buch. Darin werden die Erkenntnisse von Ärzten und Wissenschaftlern aus der Analyse interner Dokumente über die klinischen Studien der Covid-Injektion präsentiert. Es handelt sich um jene in den USA freigeklagten Papiere, die die Arzneimittelbehörde (Food and Drug Administration, FDA) 75 Jahre unter Verschluss halten wollte.
Ebenfalls Wissenschaftler und Ärzte, aber auch andere Experten organisieren als Verbundnetzwerk Corona-Solution kostenfreie Online-Konferenzen. Ihr Ziel ist es, «wissenschaftlich, demokratisch und friedlich» über Impfstoffe und Behandlungsprotokolle gegen SARS-CoV-2 aufzuklären und die Diskriminierung von Ungeimpften zu stoppen. Gestern fand eine weitere Konferenz statt. Ihr Thema: «Corona und modRNA: Von Toten, Lebenden und Physik lernen».
Aufgrund des Digital Services Acts (DSA) der Europäischen Union sei das Risiko groß, dass ihre Arbeit als «Fake-News» bezeichnet würde, so das Netzwerk. Staatlich unerwünschte wissenschaftliche Aufklärung müsse sich passende Kanäle zur Veröffentlichung suchen. Ihre Live-Streams seien deshalb zum Beispiel nicht auf YouTube zu finden.
Der vielfältige Einsatz für Aufklärung und Aufarbeitung wird sich nicht stummschalten lassen. Nicht einmal der Zensurmeister der EU, Deutschland, wird so etwas erreichen. Die frisch aktivierten «Trusted Flagger» dürften allerdings künftige Siege beim «Denunzianten-Wettbewerb» im Kontext des DSA zusätzlich absichern.
Wo sind die Grenzen der Meinungsfreiheit? Sicher gibt es sie. Aber die ideologische Gleichstellung von illegalen mit unerwünschten Äußerungen verfolgt offensichtlich eher das Ziel, ein derart elementares demokratisches Grundrecht möglichst weitgehend auszuhebeln. Vorwürfe wie «Hassrede», «Delegitimierung des Staates» oder «Volksverhetzung» werden heute inflationär verwendet, um Systemkritik zu unterbinden. Gegen solche Bestrebungen gilt es, sich zu wehren.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2024-10-23 20:26:10
@ c631e267:c2b78d3e
2024-10-23 20:26:10Herzlichen Glückwunsch zum dritten Geburtstag, liebe Denk Bar! Wieso zum dritten? Das war doch 2022 und jetzt sind wir im Jahr 2024, oder? Ja, das ist schon richtig, aber bei Geburtstagen erinnere ich mich immer auch an meinen Vater, und der behauptete oft, der erste sei ja schließlich der Tag der Geburt selber und den müsse man natürlich mitzählen. Wo er recht hat, hat er nunmal recht. Konsequenterweise wird also heute dieser Blog an seinem dritten Geburtstag zwei Jahre alt.
Das ist ein Grund zum Feiern, wie ich finde. Einerseits ganz einfach, weil es dafür gar nicht genug Gründe geben kann. «Das Leben sind zwei Tage», lautet ein gängiger Ausdruck hier in Andalusien. In der Tat könnte es so sein, auch wenn wir uns im Alltag oft genug von der Routine vereinnahmen lassen.
Seit dem Start der Denk Bar vor zwei Jahren ist unglaublich viel passiert. Ebenso wie die zweieinhalb Jahre davor, und all jenes war letztlich auch der Auslöser dafür, dass ich begann, öffentlich zu schreiben. Damals notierte ich:
«Seit einigen Jahren erscheint unser öffentliches Umfeld immer fragwürdiger, widersprüchlicher und manchmal schier unglaublich - jede Menge Anlass für eigene Recherchen und Gedanken, ganz einfach mit einer Portion gesundem Menschenverstand.»
Wir erleben den sogenannten «großen Umbruch», einen globalen Coup, den skrupellose Egoisten clever eingefädelt haben und seit ein paar Jahren knallhart – aber nett verpackt – durchziehen, um buchstäblich alles nach ihrem Gusto umzukrempeln. Die Gelegenheit ist ja angeblich günstig und muss genutzt werden.
Nie hätte ich mir träumen lassen, dass ich so etwas jemals miterleben müsste. Die Bosheit, mit der ganz offensichtlich gegen die eigene Bevölkerung gearbeitet wird, war früher für mich unvorstellbar. Mein (Rest-) Vertrauen in alle möglichen Bereiche wie Politik, Wissenschaft, Justiz, Medien oder Kirche ist praktisch komplett zerstört. Einen «inneren Totalschaden» hatte ich mal für unsere Gesellschaften diagnostiziert.
Was mich vielleicht am meisten erschreckt, ist zum einen das Niveau der Gleichschaltung, das weltweit erreicht werden konnte, und zum anderen die praktisch totale Spaltung der Gesellschaft. Haben wir das tatsächlich mit uns machen lassen?? Unfassbar! Aber das Werkzeug «Angst» ist sehr mächtig und funktioniert bis heute.
Zum Glück passieren auch positive Dinge und neue Perspektiven öffnen sich. Für viele Menschen waren und sind die Entwicklungen der letzten Jahre ein Augenöffner. Sie sehen «Querdenken» als das, was es ist: eine Tugend.
Auch die immer ernsteren Zensurbemühungen sind letztlich nur ein Zeichen der Schwäche, wo Argumente fehlen. Sie werden nicht verhindern, dass wir unsere Meinung äußern, unbequeme Fragen stellen und dass die Wahrheit peu à peu ans Licht kommt. Es gibt immer Mittel und Wege, auch für uns.
Danke, dass du diesen Weg mit mir weitergehst!
-
 @ e3ba5e1a:5e433365
2025-02-13 06:16:49
@ e3ba5e1a:5e433365
2025-02-13 06:16:49My favorite line in any Marvel movie ever is in “Captain America.” After Captain America launches seemingly a hopeless assault on Red Skull’s base and is captured, we get this line:
“Arrogance may not be a uniquely American trait, but I must say, you do it better than anyone.”
Yesterday, I came across a comment on the song Devil Went Down to Georgia that had a very similar feel to it:

America has seemingly always been arrogant, in a uniquely American way. Manifest Destiny, for instance. The rest of the world is aware of this arrogance, and mocks Americans for it. A central point in modern US politics is the deriding of racist, nationalist, supremacist Americans.
That’s not what I see. I see American Arrogance as not only a beautiful statement about what it means to be American. I see it as an ode to the greatness of humanity in its purest form.
For most countries, saying “our nation is the greatest” is, in fact, twinged with some level of racism. I still don’t have a problem with it. Every group of people should be allowed to feel pride in their accomplishments. The destruction of the human spirit since the end of World War 2, where greatness has become a sin and weakness a virtue, has crushed the ability of people worldwide to strive for excellence.
But I digress. The fears of racism and nationalism at least have a grain of truth when applied to other nations on the planet. But not to America.
That’s because the definition of America, and the prototype of an American, has nothing to do with race. The definition of Americanism is freedom. The founding of America is based purely on liberty. On the God-given rights of every person to live life the way they see fit.
American Arrogance is not a statement of racial superiority. It’s barely a statement of national superiority (though it absolutely is). To me, when an American comments on the greatness of America, it’s a statement about freedom. Freedom will always unlock the greatness inherent in any group of people. Americans are definitionally better than everyone else, because Americans are freer than everyone else. (Or, at least, that’s how it should be.)
In Devil Went Down to Georgia, Johnny is approached by the devil himself. He is challenged to a ridiculously lopsided bet: a golden fiddle versus his immortal soul. He acknowledges the sin in accepting such a proposal. And yet he says, “God, I know you told me not to do this. But I can’t stand the affront to my honor. I am the greatest. The devil has nothing on me. So God, I’m gonna sin, but I’m also gonna win.”
Libertas magnitudo est
-
 @ dd1f9d50:06113a21
2025-02-05 01:48:55
@ dd1f9d50:06113a21
2025-02-05 01:48:55(Because Most People Don’t Understand Money)
The requisite knowledge needed to know whether $100 or $100,000 per Bitcoin is relatively speaking “a lot,” is what value means. One way to measure value is through a universal yardstick we call “Money.” The question of “What is money?” is perhaps one of the most overlooked and under answered in our day and age. There is even an entire podcast dedicated to that question with the eponymous title, hosted by Robert Breedlove. That podcast often delves into the more philosophical underpinnings whereas I hope to approach this with a more practical answer.
Money is a technology.
Money is the technology with which we interact with one another to reorganize goods and services to the place and time they are best suited. Most money of the past has been tangible (though not a requisite feature), scarce, recognizable (read: verifiable), durable, portable, and divisible. These features one might call the “Attributes of Money.” These attributes are absolutely essential for a money to maintain its status as a money. (Those of you who understand the U.S. Dollar system maybe scratching your heads right now but, believe me, I will address that elephant in due time.) These attributes, you may notice, are not a yes or no but more of a gradient. A money can be MORE portable than another yet, less durable. One more divisible but not scarce whatsoever. The point being they must have, in some capacity, these attributes or they simply aren’t money.
One of These Things is Not Like the Other
| | Bitcoin | Gold | Dollars | |-----------------|:----------------------------------------------------------------------------------------------------------------:|:------------------------------------------------------------------:|:--------------------------------------------------------------------------------------------------------------------------------------------------:| | Scarcity | 21 million coins
is the maximum supply | Unknown- the
supply grows roughly 2% per year | Also unknown to anyone outside of the Federal Reserve, Trillions and counting | | Recognizability | Each coin is verifiable to it's genesis on the timechain | Each molecule of gold has distinct physical verifiable properties | If the Federal reserve says it is a valid note, it is (Unless you are an enemy of the United States) | | Durablility | Each "Bitcoin" is information stored on a globally distributed network | Doesn't Rust and as far as can be measured Au197 is stable forever | Can be destroyed by any means that effect fabric and centralized databases | | Portability | Available wherever data can be store- Anywhere | Can be moved at 9.81 Newtons per Kilogram- Methods may vary | Can be moved physically with fabric notes- Digitally with express permission from a US accredited banking institution | | Divisibility | Currently can be divided into 100 million parts called Sats (can be further subdivided by adding decimal places) | Can be divided to the Atomic level (Though not practical) | Can be divided (without dilution) by adding new denominative bills or coinage
Can be divided (with dilution) by printing new bills or coinage | | | Bitcoin | Gold | Dollars |You may think with all of the great functionality of Bitcoin that the phrase "One of these things is not like the other" refers to BTC. No, I was referring to the Dollar. It is the only one on the list that was a currency that was substituted as some kind of faux money. It asserts itself, or rather the Federal Reserve asserts it, as money, de facto.
Dollars are NOT money.
Dollars are (allegedly) a currency. If money is a specific technology, currency is the financial infrastructure that allows that technology to reach and be used by the most number of people possible. This requires a firm tether between the asset being used as money and the currency used as a claim to that money. For example: If I hand you a chicken, you have a chicken. But, if I hand you a coupon that is redeemable for a chicken, you do not have a chicken. You have a claim to a chicken that is only as good as the party making that claim. Bringing it back to money again, dollars (Prior to 1971) were redeemable for gold at a rate of $35 per ounce. This is that strong tether that pegged dollars to gold and physical reality itself. Without a proof of work, mining, . Until…
WTF Happened in 1971?
The Nixon shock happened. Briefly, The U.S. took in Europe’s gold in the 1940’s to keep it out of Hitler’s hands. The U.S. made an agreement to peg the dollar to Europe’s gold. The U.S. over printed dollars in relation to the gold holdings. Around 1971 France (among others) called the U.S. out for devaluing the dollar and thus European currencies. So, Nixon “Temporarily” suspended the convertibility of dollars to gold. Now, here we all are like Wile E. Coyote having run off of the golden cliff clutching our dollars in our arms and 54 years later we still haven’t looked down to see the truth.
Dollars Aren’t Backed by Anything
This is why no country in the world today has a money standard. Seemingly they all forgot the number one rule of issuing currency, it must be backed by something. Now, you may hear dollar proponents say “The U.S. dollar is backed by the full faith and credit of the United States!” Another way of saying that is, “We said it is worth something, so it is!” This fiat (by decree) mentality creates a plethora of perverse incentives. The ever growing supply disallows users of the Dollar to save without inccuring the penalties of inflation.
Just a Few Examples of How You're Being Crushed
Because your dollar loses value:
- It pushes people to spend them on assets that seem to appreciate (as the dollar debases) but are truly staying stagnant.
- It pushes people to gamble on securities hoping the perceived value is enough to beat the inflationary curve.
- It pushes people away from saving for their future and the future of their families.
- It creates insane credit incentives so that people borrow way more than they can afford today knowing that dollars will be cheaper in the future. (Effectively a short position)
- It pushes people to spend less and less time making and maintaining their families as it becomes more expensive to keep a similar lifestyle to which it was founded.
These are just a few of the terrible consequences of not knowing that trading a currency with no monetary backing has on a society. Most may blame this soley on the ability to print currency by a central bank but, that is not the only factor. If the fed printed dollars against gold, people would simply take the best rate they could get and remonetize themselves with the gold. But because there is no monetary escape hatch guaranteed by the issuance of dollars, I.E. no one has to take your dollars in exchange for their Bitcoin or gold, you are left at the mercy of the market.
One Day, People Will Stop Accepting Your Dollars
Those lementing the high price of Bitcoin might want to thank their lucky stars that Bitcoin still has a rational number next to the "BTC 1=$?" sign. One day you will have to exchange something of actual value to the spender (no longer a seller). Your product, good or service, will be the only thing that anyone might be willing to part with their Bitcoin over. That is what makes a money, the most salable non-consumable good, whose only funtion is to back a financial structure that facilitates trade.
Bitcoin is Capital
Capital is a broad term that can describe anything that confers value or benefit to its owners, such as a factory and its machinery, or the financial assets of a business or an individual. Bitcoin being the latter creates the financial structures from which you build upon. You use capital to hold, transfer, and grow value. You do not do this with cash. Cash is a depreciating asset when you don't use it to gain goods or services for yourself or your business. This misconception around the equivalance between cash and money (financial capital) is what tricks people into believing Dollars are money. And what's worse is that even some of our greatest heroes have done this.
Slay Your Heroes, Within Reason
Unfortunately due to a mixing of verbiage that have very distinct differences, the title: "Bitcoin: A Peer-to-Peer Electronic Cash System" is technically inaccurate. Bitcoin doesn't fit the definition of cash, which is a liquid asset that can be easily converted into its equivalent value. In short, Satoshi misspoke. In reality, owning Bitcoin UTXOs (with private keys) means you already possess the asset, not just a claim to it. When you spend Bitcoin, the recipient receives the actual asset, not a promise of it. When you receive Bitcoin, you have final settlement on that transaction. Fundamentally Bitcoin is not cash, electronic or otherwise.
Bitcoin is Money.
-
 @ eaef5965:511d6b79
2025-02-25 14:14:11
@ eaef5965:511d6b79
2025-02-25 14:14:11Another quarter, another update on the global money supply.
I remember three years ago yesterday, texting my Ukrainian friends for updates as they fled with their families for safety from Putin's full-scale, unprovoked attack on their country. Three years on, they continue to fight incredibly bravely, for if they do not, there will be no Ukraine. Europe has drip-fed them enough support to not lose, but not enough to win. America now demands repayment for its aid to the victim in the form of mineral rights, and will not recognize the aggressor as the aggressor. The era of Reagan-style, speak softly while carrying a big stick approach to dictators seems no more, for now, from the new US admin. The world order is changing rapidly, and Europe is quickly finding out what the Baltics and Poland have known for 200 years: the threat from the East does not share its values; it is simply uncompromising.
As this next round of political theater plays out, and one can only hope for just, lasting peace and security with clear eyes from all democratic allies, the printing presses will do as instructed. But as we look through this update, you will see that we are actually at very low, relative-levels of money printing historically, even slight negative money growth.
Bitcoin continues on, and as of 31 December 2024, its $1.8 trillion market cap was 7.2% of the global monetary base. That means that the global monetary base, for this update, is $25.5 trillion.
Why the global monetary base?
It is the only money supply that is economically analogous to bitcoins, digital store of value today, and to gold and silver ounces, store of values from the past.
The monetary base is central bank money, comprised of two supplies:
- Physical currency: Notes and coins, or “cash;”
- Bank reserves: The “Master account” that each commercial bank holds with its central bank.
Now, why do I refer to this as Central bank money?
This is because, unlike all other money supplies in the fiduciary banking world (like M1/M2/M3), the Monetary base is the sole and ultimate money supply controlled by the central bank. It is, literally, the printing press. What follows won't be a lesson in reserve ratios or monetary economics. The point is that you simply understand that there is a money supply that central banks solely control, and of course (of course!) this is what Bitcoin's 21 million are up against.
The monetary base is to the core of the entire fiat financial system, as 21 million bitcoins are to the core of the Bitcoin protocol. One is open and permissionless, and one is not. By the way, the monetary base is essentially (though not entirely) analogous to the total liabilities of a central bank, so we can (basically) say that the monetary base is the "balance sheet" of each central bank.
On cash. Quick notes on the above. Certainly you understand what "cash" is, and it is indeed an instrument that has been fully monopolized by each central bank in each nation around the world--only they can print it. Even though it is true that banks in more free banking societies in the past could freely print and strike notes and coins, the central bank (or state) monopoly has been around for a long time. Kublai Khan was the first to do it 750 years ago.
On bank reserves. Don't stress your brain on this too much, but this is the main "settlement money" that banks use between each other, when they want to settle their debts. It is digital now (Fedwire in US, CHAPS in UK), but it doesn't technically have to be, and of course before modern technology took over even a few decades ago, it was not. These two stacks of retail and wholesale cash, stacks of central bank money, are what make up the Monetary base. This is the printing press. Only this compares to 21 million bitcoins. And gold, and silver by the way.
Final note, central bank digital currencies, or CBDCs, which are simply LARPing on Bitcoin's success, are indeed created by central banks, and they are indeed classified as Base money. They are going to be a "third rail." They are thankfully incredibly small, pilot projects today. We will see how far democracies will be tested, as autocracies no doubt will mainstream them; but for now, consider them, at least economically, to be inconsequential to the update below. It appears that central banks are actually cooling to them, as of this writing.
With that review out of the way, onward to Q4 update for 2024.
Bitcoin is the 6th largest money in the world
This is unchanged from last quarter.
In February 2024, it surpassed the monetary base of the United Kingdom; that is, its value was larger than the Bank of England's balance sheet, and it remains so to this day.
As of 31 December 2024, it is only the balance sheets of the big four central banks that are larger than Bitcoin. These currencies are:
- Federal Reserve (dollar): $5.60 trillion
- People's Bank of China (yuan): $5.04 trillion equivalent
- European Central Bank (euro): $4.87 trillion equivalent
- Bank of Japan (yen): $4.20 trillion equivalent
If we remove gold from the equation (and we shouldn't), then Bitcoin could be considered the fifth largest money in the world. Including gold, Bitcoin is the sixth.
However, the all-important monetary metal throughout history that even a child knows about--gold--is still king at around $17 trillion in value, or 6 billion ounces worldwide. Note, this does not include gold lost/recycled through industry; in that case, it is estimated that about 7 billion ounces of gold have been mined throughout humanity.
Silver, for what it's worth, is still a big "monetary" metal; though it is true, much more silver is gobbled up in industry compared to gold. There are about 31 billion ounces of non-industrial silver floating around the world (most of it in jewelry and silverware form) that is valued in today's prices at nearly $1 trillion. Bitcoin bigger.
State of the print: $25.5 trillion
This is down $1.5 trillion from last quarter!
However, we must also remember that as currencies lose value against the best-looking horse in the glue factory; that is, the dollar, then this dollar value actually "dampens" the effect of the print. More on this below.
If we consider $25.5 trillion as the Big Boss of central bank money, then Bitcoin at $1.8 trillion network value (December, quarter-end figure) indeed has some way to go. But as anyone who follows Bitcoin for a sustained about of time knows, this can change rapidly. We can also imagine how the Pareto distribution occurs even in money, if Bitcoin after only 15 years is already larger than every central bank money in the world except for four of them. Wild to ponder.
All-time supply (monetary) inflation: 12.7% per year compounded
This is a long-term, "smoothed" monetary inflation, or money growth figure. It is looking across all the 50 currencies in my sample, going back to 31 December 1969 for almost 40% of them, and for those that don't, simply adding them into the weighted basket as data becomes available.
Roughly stated, it means that central banks on balance double their money supply every 5.8 years. This is a fact.
However, this overall rate of increase is indeed declining, and has been since 2022. For example, if we looked at this headline figure from last year ending 2023, it blended to 12.9% all-time, or 0.2% higher than now. Still, even though central banks have been trying to tighten from their overheated 2020-22 money print, the overall, net effects of money growth in native fiat units have not changed significantly.
For more detail, we can look at the latest year.
Trailing 12-month money growth: -3.0%
What is very interesting, however, and alluded to above, is how all global currencies continue to decline in relative value against the dollar. According to the simple, USD-based trendline analysis for all global currencies in the dataset (see below), we should have a $34 trillion monetary base right now, based on past performance. We have a $25.5 trillion monetary base right now. We are actually lower than the 2.5th percentile on this trendline.
But take note: What you are really seeing is actually not that much less of money printing (they have been letting up the gas, to be sure), but rather, a tremendous loss in purchasing power of all currencies versus the dollar!
In other words, from 2023 to 2024:
- The weighted average, native change in money base growth of all currencies was -3.0% over the prior 12 months;
- The overall dollar value change was -8.5% over the prior 12 months ($25.5 trillion vs. $27.8 trillion).
This means that, in the last year, government money lost an additional 5.5% per year in dollar purchasing power, beyond its reduction of 3.0% in money print. Wild.
Since 2021 peak
I don't publicize this information as much, and I probably should. In dollar terms, in December 2021, global central bank money printing peaked at $30.5 trillion. Big number. Now, it is $25.5 trillion. So one would assume that the printing presses have cooled by 16.4% in the last three years.
But again, as I have just described above, we are trying to see beyond Wittgenstein's Ruler here. This can be difficult, because we have 50 different currencies to contend with.
It is true, in the last three years, the dollar value of the top 50 currencies in the world has fallen by 16.4%.
But does that mean that central banks are printing 16.4% less than before 2021?
No.
In fact, when you look at the weighted average of each central bank's performance over the last three years, in their native currency units, you will find that the weighted average decline in printing is only 2.4%.
Notice anything? This decrease over three years is actually less than the decline over the last 12 months, which was 3.0% (section above).
And most obviously, it is far less than 16.4%.
There are dollar values. These grow differently from all the native currency units, because of foreign exchange rates.
There are native currency units. These grow differently from all the dollar values of these currencies, because of foreign exchange rates.
Central banks are printing less over the last three years: 2.4% less overall. But this is much less than the decline in the dollar value of 50 currency stocks over the last three years: 16.4% decline.
One must tear through the numbers to understand both ideas. I have provided you with both.
New data: China
Firstly, what I am about to say has nothing to do with what I've described above, except for a very small impact on the overall, headline figure of 12.7% money growth. This is a historical addition.
I have added some important new monetary data this quarter, and that is from the quasi-transparent yet enormous economy of China. On the PBoC website, they publish balance sheet data back to only 31 December 1999. I have used this timespan for seven years now in my quarterly updates. However, I have now gone through some new figures from the book China Financial Statistics (1949-2005) and added additional data points all the way back to 1969 for China. It is published from PBoC sources. I am using M0 figures from 1969 until 1993 (only available, very compatible, as a subset of base money), and from 1993, they begin publishing full monetary base data. The break in growth metrics when switching from M0 to MB in 1993 is ignored.
The changes from this new data--from a huge, growing economy such as China will, as expected, boost the overall inflation numbers in my dataset. These are the net effects of the new data, as of 31 December 2024:
China Monetary base average monthly growth for entire series:
- Old data from 1999: 0.85%
- New data from 1969: 1.04%
China Monetary base compound annual growth for entire series:
- Old data from 1999: 10.73%
- New data from 1969: 14.24%
Overall Monetary base compound annual growth for entire series:
- Before this additional China data: 12.56%
- After this additional China data: 12.73%
So the net effect on "global monetary inflation" with this additional data is 17 basis points, or 0.17%. I thought the overall effect could be higher, but one must remember these growth rates are weighted by the relative USD value of each respective base money, on a continuous basis, updating each month. In the 1960s, 1970s, and 1980s, China was a much smaller proportion of the global economic pie than it is today.
One final point with this new data, and with my monetary inflation data overall. I am fairly confident my headline number of 12.6-12.7% per year compounded for global money growth is conservative. These are the top 50 currencies in the world. We just saw what new data did to the entire dataset, and from a huge country no less. If I were to add more currencies, such as those from Kenya or Morocco (and I will), these currencies will only marginally affect this headline money growth figure. What's more, this new data will by definition come from smaller, more volatile, higher inflation-producing currencies, so I would only expect my headline figure to creep higher, the further it is refined.
Huge thanks to Eryn @reltbracco (npub1e2rd2k45ym2jmctnysfadxumrvrr57vqj69ck6trt2y62c40r0kqs9lx8t) for sifting through tons of Chinese historical content here, and for eventually finding a great book with Chinese historical monetary data that was in English!
The trends
The remainder of the report is an update on global trends in demographics, money, and economics. All of these trends are exponential curves. The sole exception, is Bitcoin. It's price and market cap action, across time, are power curves.
One further change. I have allowed the 2.5 and 97.5 red percentile bands to evolve over time. I think this presentation allows the reader to see that trends indeed can change, across time. However, the all-time trendline, as of today, is the solid, black trendline.
We are where we are. Plan accordingly, never financial advice.
Population
The world has grown exponentially at 1.7% per year over the last 75 years. However, despite all the overpopulation myths you've probably heard, this rate of growth is actually falling, well below trend, and we only grow at 0.9% per year at the moment, pulling the overall trend down every year.
## US GDP
The United States has grown its economy at 5.2% compounded per year since the founding of the republic. We are at the higher end of this trend right now, $29 trillion output per year, growing at 5.3% per year. As this is exponential growth, if I put it on log scale, it will become a straight line.
## Stock market
Stocks grow exponentially as well, don't let anyone tell you otherwise. The growth rate is 7.3% per year for the S&P 500, the main US index that tracks more than 80% of total market caps. Currently, the market is well above trend.
## Stock market: Dividends reinvested
If you reinvest those dividends into the same stock market, you'll earn more. The all-time compound annual growth increases by 2% to 9.3% per year for the S&P.
## Bonds
Bonds are supposedly safer than stocks (bondholders get paid back first), and more regular cash flowing. If you look at the longest running bond index in the US, it grows at 7.0% per year, compounded. Notice how, in a rising interest rate environment (which we are in at the moment), bond prices will suffer. In this case, it's the Bloomberg Aggregate Bond Index. This has kept the bond market returns at the lower end of the range, since the global financial crisis in 2008. Not even 1% TTM return.
## Base Money
As we've discussed, base money grows across the world at a weighted average of 12.7% compounded per year. However, this trendline analysis looks at it differently than my headline figure. It simply looks at the USD value of the global monetary base (again, currently $25.5 trillion), and draws an exponential trendline on that USD equivalent growth for 50+ years. In other words, this is going to be after all currency fluctuations have played themselves out.
Slope of the trend is 10.2% compounded for this one.
This is further confirmation that, even though central banks around the world like to print at 12.7% compounded all-time in native unit terms, they will always lose value against the world's reserve currency, as that shakes out to around 10.2% compounded in USD-terms.
And we really are scraping the bottom of this range. 0.7x the trendline, which
## Silver supply
This is total ounces ever mined. They trend upward at 1.4% per year.
## Gold supply
This is total ounces ever mined. Gold trends upward at 1.7% per year. Faster than silver. Surprised? Notice the R-squared (goodness of fit) for both silver and gold production increase.
## Bitcoin supply
Bitcoins grow according to a basic logarithmic curve. Trying to draw percentiles is pointless here, and even measuring a trendline is relatively pointless, as everyone knows the bitcoins prescribed into the future, per the protocol. Better to just quote the trailing 12-month growth figure, and it is 1.2% per year and falling, as of quarter end Dec-2024. Less than gold or silver.
## Silver price
Since 1971 it's trended at 3.5% per year. Silver bug?
## Gold price
Since 1971 it's trended at 5.1% per year. Gold bug?
## Bitcoin price
Bitcoin's price (and market cap) grows according to a power trend. Did you notice that the prior exponential trends displayed themselves as straight lines on log scale? Well, with Bitcoin, the power trendline gradually falls across time, but the growth is still well larger than anything we've covered thus far. Now, we have finally arrived at something that grows differently than exponential.
.
Why? Because you are viewing an adoption curve. This is how networks scale.
Bitcoin's power trendline has grown 164% per year since Bitcoin Pizza Day in 2010. Note that this is something akin to a "Lifetime Achievement" figure, and it will continue to fall every day. Over the prior 12 months ending 31-Dec-2024, Bitcoin grew 121.1%. The compound growth of the power trend today is just under 44% per year. By 2030 it will fall to "only" 31% per year. You can find more dissection of the
power curve on my website here
.
Oh yes, and it is free (as in speech), open, and permissionless money.
To summarize
That was a lot of data across a lot of charts. I've compiled all these trendlines and data in a helpful table here for you to review at any time. These are the growth trends of the monetary and major asset world, as of year-end 2024:
Again, a quick breakdown on why Bitcoin is so interesting, and confounding. Where most things in the financial and economic world grow exponentially, Bitcoin is actually a compilation of three different trend patterns:
## Conclusion
Below is a detailed summary of all the input assets:
- 50 fiat currencies: $25.5 trillion
- Gold: $17.1 trillion
- Silver: $1 trillion
- Bitcoin: $1.8 trillion
Print it out if you like!
Thank you for reading. This takes a lot of time to put together each quarter. If you enjoyed, please consider zapping, and you can also donate to my BTCPay on my website if you'd like to help keep this research going.
Take care.
-
 @ a95c6243:d345522c
2024-10-19 08:58:08
@ a95c6243:d345522c
2024-10-19 08:58:08Ein Lämmchen löschte an einem Bache seinen Durst. Fern von ihm, aber näher der Quelle, tat ein Wolf das gleiche. Kaum erblickte er das Lämmchen, so schrie er:
"Warum trübst du mir das Wasser, das ich trinken will?"
"Wie wäre das möglich", erwiderte schüchtern das Lämmchen, "ich stehe hier unten und du so weit oben; das Wasser fließt ja von dir zu mir; glaube mir, es kam mir nie in den Sinn, dir etwas Böses zu tun!"
"Ei, sieh doch! Du machst es gerade, wie dein Vater vor sechs Monaten; ich erinnere mich noch sehr wohl, daß auch du dabei warst, aber glücklich entkamst, als ich ihm für sein Schmähen das Fell abzog!"
"Ach, Herr!" flehte das zitternde Lämmchen, "ich bin ja erst vier Wochen alt und kannte meinen Vater gar nicht, so lange ist er schon tot; wie soll ich denn für ihn büßen."
"Du Unverschämter!" so endigt der Wolf mit erheuchelter Wut, indem er die Zähne fletschte. "Tot oder nicht tot, weiß ich doch, daß euer ganzes Geschlecht mich hasset, und dafür muß ich mich rächen."
Ohne weitere Umstände zu machen, zerriß er das Lämmchen und verschlang es.
Das Gewissen regt sich selbst bei dem größten Bösewichte; er sucht doch nach Vorwand, um dasselbe damit bei Begehung seiner Schlechtigkeiten zu beschwichtigen.
Quelle: https://eden.one/fabeln-aesop-das-lamm-und-der-wolf
-
 @ daa41bed:88f54153
2025-02-09 16:50:04
@ daa41bed:88f54153
2025-02-09 16:50:04There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy article on the pros of a strategic Bitcoin reserve, I wanted to take some time to chime in on the much more fun topic of digital engagement.
Let's begin by defining a couple of things:
Nostr is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example.
Zap is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what Lightning or Cashu are.
If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article.
In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed.
What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.

Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines.
That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems.
Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.

I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives.
Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms?
Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life?
If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later.

-
 @ e3ba5e1a:5e433365
2025-02-05 17:47:16
@ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a friendly discussion on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it!
The US healthcare system is essentially the worst of both worlds:
- Unlike full single payer, individuals incur high costs
- Unlike a true free market, regulation causes increases in costs and decreases competition among insurers
I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do:
- Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice.
- Reduce regulations significantly.
-
In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways:
- Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices.
- Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.)
Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation.
And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers.
And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply."
https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
-
 @ fd208ee8:0fd927c1
2025-02-02 10:33:19
@ fd208ee8:0fd927c1
2025-02-02 10:33:19GitCitadel Development Operations
We, at GitCitadel, have been updating, moving, and rearranging our servers, for quite some time. As a rather large, complex, sprawling project, we have the infrastructure setup to match, so we've decided to give you all a quick run-down of what we are doing behind-the-scenes.
Supplier Coordination

Our first task, this week, was figuring out who would host what where. We have four different locations, where our infra is stored and managed, including two locations from our suppliers. We got that straightened out, quickly, and it's all slowly coming together and being connected and networked. Exciting to watch our DevOps landscape evolve and all of the knowledge-transfer that the interactions provide.
OneDev Implementation

Our biggest internal infra project this week was the migration of all of our issues from Jira, build scripts from Jenkins, and repos from GitHub to a self-hosted OneDev instance. In the future, all of our internal build, test, issue, patch/PR, etc. effort will take place there. We also have a separate repo there for communicating with external developers and suppliers.
Our team's GitHub projects will be demoted to mirrors and a place for external devs to PR to. Public issues and patches will continue to be managed over our self-hosted GitWorkshop instance.
We're especially glad to finally escape the GitHub Gulag, and avoid being bled dry by Jira fees, without having to give up the important features that we've come to know and love. So, yay!
Next Infrasteps
Automated Testing
Now, that we have everything tied up in one, neat, backed-up package, we can finally move on to the nitty-gritty and the dirty work. So, we're rolling up our sleeves and writing the Selenium smoke test for our Alexandria client. We'll be running that in Docker containers containing different "typical Nostr" images, such as Chrome browser with Nostr Connect signing extension, or Firefox browser with Nos2x-fox extension. Once we get the Nsec Bunker and Amber logins going, we'll add test cases and images for them, as well. (Yes, we can do Bunker. I hope you are in awe at our powers).
We are also designing an automated infrastructure test, that will simply rattle through all the various internal and external websites and relays, to make sure that everything is still online and responsive.
After that, a Gherkin-based Behave feature test for Alexandria is planned, so that we can prevent regression of completed functionality, from one release to the next.
The Gherkin scenarios are written and attached to our stories before development begins (we use acceptance tests as requirements), a manual test-execution is then completed, in order to set the story to Done. These completed scenarios will be automated, following each release, with the resulting script linked to from the origin story.

Automated Builds
As the crowning glory of every DevOps tool chain stands the build automation. This is where everything gets tied together, straightened out, configured, tested, measured, and -- if everything passes the quality gates -- released. I don't have to tell you how much time developers spend staring at the build process display, praying that it all goes through and they can celebrate a Green Wave.

We are currently designing the various builds, but the ones we have defined for the Alexandria client will be a continuous delivery pipeline, like so:

This will make it easier for us to work and collaborate asynchronously and without unnecessary delays.
Expanding the Status Page

And, finally, we get to the point of all of this busyness: reporting.
We are going to have beautiful reports, and we are going to post them online, on our status page. We will use bots, to inform Nostriches of the current status of our systems, so go ahead and follow our GitCitadel DevOps npub, to make sure you don't miss out on the IT action.
Building on stone
All in all, we're really happy with the way things are humming along, now, and the steady increase in our productivity, as all the foundational work we've put in starts to pay off. It's getting easier and easier to add new team members, repos, or features/fixes, so we should be able to scale up and out from here. Our GitCitadel is built on a firm foundation.
Happy building!
-
 @ 4d41a7cb:7d3633cc
2025-02-25 13:53:41
@ 4d41a7cb:7d3633cc
2025-02-25 13:53:41Money is more abstract than most people think, as I will show in this article. Debt slavery stems from financial illiteracy, which occurs intentionally. The biggest secret is how bankers actually create currency claims out of thin air and transfer the wealth of their clients (including nation states) to themselves for free without risking a cent, real money, or currency.
MONEY
Money, one of the most important things in our lives, is so important that we exchange wealth to obtain it. Not because we want it but because we need it in order to buy food, shelter, clothes, etc.
Money is not inherently bad, although some may argue that the love for money is the root of all evil, and I'll agree. If you are willing to sacrifice your soul, honor, reputation, family, or friends for money, it indicates a lack of morality and a willingness to engage in harmful actions to satisfy your greed and materialistic desires.
Money is a technology, a tool, and like any tool or technology, it is impartial; it cannot be inherently good or bad. It can be used to help others or to destroy them. At the end of the day, it’s all about the intention behind human behavior.
Money is not just a useful tool; it’s the most important tool to have for global commerce, division of labor, specialists, and the level of sophistication and comfort we achieve as humanity. All of this will not be possible without this tool working as a common medium of exchange and standard of value, a common language for all humanity: the language of monetary value.
Money is the cornerstone of civilization. Money is the bloodstream of commerce, and commerce is the spine of civilization; it’s what made our civilization so prosperous, letting any one of us decide how we want to provide value to society.
Money is half of every transaction, and since we will always need to intermediate between every exchange, money is the perfect intermediary to help achieve millions of different combinations of exchanges. It will be practically impossible to barter on a global scale; even in a small community with a few different products, it will be a mess.
For example, if there were 10 products, there would be 45 combinations; if there were 100, there would be 4950 combinations. Imagine a scenario on a large scale, requiring the exchange of hundreds of thousands of products every second..
This issue necessitated the development of a new technology: money, which in turn led to the emergence of moneychangers (v4v). Money is a tool to exchange, measure, and store wealth. Wealth is anything we can sell: our labor (time and energy), our house, a car, a product, a service, etc.
Gold and silver were money for thousands of years because of their unique characteristics of scarcity, durability, divisibility, and transportability. The most important characteristic of these metals is that they are scarce, and they can’t be created out of thin air or reproduced with no effort.
Only God can control the supply of gold and silver found in nature. Men can only extract it, and it requires investment, work, time, and effort to find and mine it. So the common knowledge and the common sense of the people over thousands of years consensually chose gold and silver as money. And this money is the only lawful money under common law.
“Gold is money, everything else is credit”
J.P. Morgan 1912
As an interesting fact, the word "money" is used 140 times in the King James Bible, the word "gold" is mentioned 417 times, and the word "silver" over 320 times. But the word “currency” is not mentioned a single time.
The most important function of money is to exchange and store your time and energy. You work to acquire money and then use that money to acquire other goods and services.
Our time and energy is our real wealth because it’s limited. We all have a limited time on earth, and we can do certain things in the 24 hours we have every day, so we have to be conscious about how we administrate and store the fruits of our labor.
Money is a means to an end; we don't want money; we want what money can buy, and guess what, money cannot buy more time.
CURRENCY = FAKE MONEY
Currency exists as a money substitute. Currencies began as the opposite of money, the promise to deliver money in the future: debt. Currencies can be used to exchange wealth, but they are not a fair unit of account and are never a good way to store it because men are tempted to create more and dilute its value (a process known as inflation)
Currencies have almost all the same characteristics of money, but there’s a big difference: currency is not scarce and durable. Missing the store of value characteristic of money, since its supply can be manipulated by men.
For wealth preservation and measuring, modern currencies make no sense. Men control the supply of currency; banks and governments can inflate or deflate it in any amount they please, giving them supreme power and control over wealth distribution. This creates two classes of citizens: those who work to acquire currency and those who create it instantly and for free.
International banks have stolen money (gold and silver) over the past century, replacing its supply with currency or fake money (paper receipts). [1913, 1933, 1944, 1971]
Under this monetary game, those with "fixed income," savers, and creditors are the biggest losers, while debtors and asset owners are the winners..
The most important distinction to keep in mind is that nature controls the money supply, making artificial inflation impossible. On the other hand, men can inflate currency in unlimited amounts. It is a manifestation of God's power on earth, as the mediums of exchange serve as the lifeblood of commerce, the backbone of our economic system, and facilitate the division of labor.
If someone can inflate the currency supply, this has the same economic effect as counterfeiting, and he’s effectively stealing from everyone contracting, trading, and saving in that currency. Manipulating the mediums of exchange in an economy enables manipulation of every security, industry, and business.
This is the reason the founding fathers of the United States made gold and silver only lawful money for the payment of debts. To give everyone equal protection under the law and to get rid of the nobility and two types of citizens: bankers and workers or nobles and plebeians.
Bank-notes are not money. It 's currency. It’s unfair to take banks' currency as a standard for comparison.
Bank-note currency is not “lawful money”. It never could be counted as part of banks cash reserves. It would be too much like a man writing and signing his own promissory note for a million and then claiming that this made him a millionaire.
The very grave evils any currency depreciation always impose upon businesses and the people.
Alfred Owen Crozier, US Money vs Corporate currency, 1912
So money has three very important functions that work as the pillars on which the wellness of our economic system and civilizations relies. Currency is not a store of value because its supply can be easily manipulated, men in power can create more of it, and so using this always-changing currency as a standard of value or a unit of account is like using an always-changing ruler to measure distance. A dollar today does not buy the same as a dollar one year ago. So yesterday prices are not equal to today's prices; this is an unfair business calculation.
So money has three very important functions that work as the pillars on which the wellness of our economic system and civilizations relies. Currency is not a store of value because its supply can be easily manipulated, men in power can create more of it, and so using this always-changing currency as a standard of value or a unit of account is like using an always-changing ruler to measure distance. A dollar today does not buy the same as a dollar one year ago. So yesterday prices are not equal to today's prices; this is an unfair business calculation.
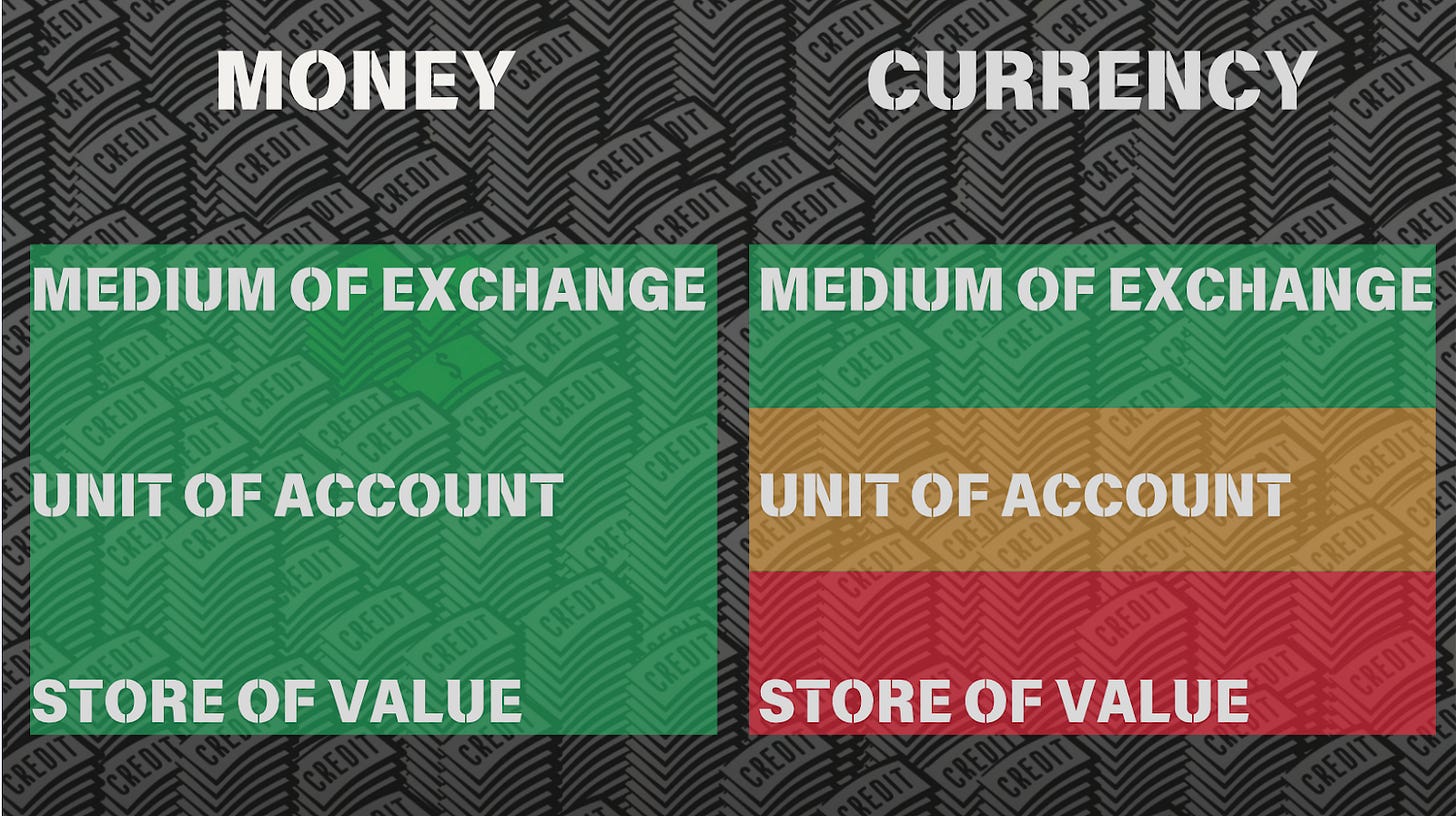 There are several Bible verses that discuss the manipulation of weights and measures, emphasizing the importance of honesty and fairness in commercial dealings.
There are several Bible verses that discuss the manipulation of weights and measures, emphasizing the importance of honesty and fairness in commercial dealings.-
Leviticus 19:35-36 New International Version (NIV): "Do not use dishonest standards when measuring length, weight, or quantity. Use honest scales and honest weights, an honest ephah, and an honest hin.
-
Deuteronomy 25:13-15: Do not have two differing weights in your bag—one heavy, one light. Do not have two differing measures in your house—one large, one small. You must have accurate and honest weights and measures.
-
Proverbs 11:1—"A "dishonest scale is an abomination to the Lord, but a just weight is his delight."
Fake money (currency) is always and everywhere a dishonest scale. So if you want a real measure of value or wealth use something with real value instead, like gold, commodities, products, times, etc.
Bankers have redefined the word money to mean fake money, currency, or debt. And this is not the worst part. Let’s introduce another concept: credit.
CREDIT = FAKE CURRENCY
Real credit is the promise to pay money in the future. It involves delaying the payment of money. Currency was born as credit, as a money certificate or receipt. During the last century, banks gradually replaced 100% of the money with currency and bank credit to further boost their profits and control. [1913, 1933, 1944, 1971]
But in order to achieve this goal, bankers redefined the word money to mean the opposite of money: credit/debt. This is like calling a night a day or evil a good.
When you take out a loan from a friend, you receive credit from him, but you also incur a debt with him. You promise your friends that you will pay them (asset/right), and you owe them (liability/obligation). The asset and the liability are one and part of the same deal; they cannot exist without the other. There’s no credit with no debt, no debt with no credit, and no liability with no asset.
Federal Reserve notes, commonly known as “dollars,” are a private corporate currency; they are not money because they are not gold or silver, nor receipts for these metals as many people still believe. They were not redeemable in money from the start, despite being created under the assumption.
The “peso” (Spanish word for weight) used to be a standardized amount of gold or silver, but it’s not any more; it's just a debt denomination. And what's owing? Currency. How can someone lend the opposite of money and charge interest? Only deceiving you into believing that he is lending you money. So they redefined the word money to mean the opposite of it.
But redefining words does not change the economic effect of the transaction.
When currencies first appeared, I can imagine people asking themselves, "How can people trust these paper certificates in exchange for their money?" Who will be that stupid?” And nowadays, people don’t understand the difference between money and currency, to the point that bankers redefined the word "money" to mean the opposite of "money."
Lesson: Money is not just a medium of exchange; it is also a store of value and a unit of account. Currency, the opposite of money, is debt. Since it can be created in unlimited amounts, it can't work as a store of value because its value depreciates as more units are created; for this same reason, it is not fair to denominate values in currency units since one currency unit today does not buy the same as a year ago because of inflation, the loss of purchasing power.
Summarize: While money, currency, and credit all serve as effective mediums of exchange, only money serves as a reliable store of value for saving. Currency and credit are not stores of value (not good to save), and there are not fair units of account (not good for price).
In simple terms, money is not currency, because currency is just credit and debt. We can conceptualize it as a ledger, a record of who owes what to whom. Currency is fake money since it’s the opposite of a store of value; it's always depreciating in value while its supply is inflated. This is the definition of inflation.
Modern credit is not currency; it’s the opposite. It’s the promise to deliver currency in the future, the promise of a promise of money (in theory). But there’s no money behind. It’s an air loan.
But how did we get here? Is everyone stupid? No, we have been tricked, manipulated, and dictated to use these currencies, and this banking system was forced on us. They stole our money and replaced it with fake substitutes to boost their profits.
MODERN MEDIUMS OF EXCHANGE = MONOPOLY MONEY
So nowadays we have fake money acting as cash/currency and fake currency acting as bank deposits or credit. One is worse than the other, but both of them serve only as mediums of exchange. Those who store wealth with them will be robbed, and those who calculate business will be lied to.
Today we use currencies (government notes), coins, bank deposits (currency claims), checks (bank deposit claims), credit cards, and debit cards. All of them are ‘monopoly money’ fake claims based on a big and global fraud.
- Government notes (government debt)
Since governments are under the control of central banks, they can only create currency by borrowing. Governments must issue bonds, or debt, and the central bank can generate credit, or currency, to purchase these bonds.
The bond (government liability) is the counterpart of the ‘asset’ (the currency, a central bank asset). Bonds are debt, and currencies are credit.
When the central bank creates currency to lend it to the government at interest, it has literally the economic effect of transferring the wealth of the nation to the banks for free. The banks are not lending anything that they had to labor to produce; instead, they are creating it by printing paper notes or digital currency.
On the other side, governments have to collect money from citizens (producers, merchants, and workers) to pay the interest on the debt.
Despite their best efforts, governments are unable to repay the debt due to interest, which makes it bigger than the amount of currency. Let’s say the debt is 100 at 1% interest. So there’s only 100 in currency. But at the end of the year, there’s going to be a debt of 101. In order for the system to keep working, someone else has to go into debt to create more currency units, and governments have to keep borrowing and at least only paying the interest and rolling the debt.
The important thing is that if you have government currency debt free, you own it. This is the new ‘money.’. Government currency is the ‘real’ cash, liquidity, or water.
- Bank deposits (bank debt)
When you deposit your government currency in the bank, you are legally lending your currency to the bank, and the bank owes you the amount you deposit. This currency is not stored by banks until you request it. Banks use this currency as if it were theirs, and they do business with it. That’s why I said, ‘Your money in the bank’ is not yours; it’s not money; it’s not in the bank. Its currency, its owe to you, is only registered on the bank ledger as a debt, not in a safe box.
The numbers you get in the bank account, or your balance, are government currency substitutes; they are bank deposits. Your currency deposit is the asset, and the number on your bank account balance is the liability.
But this is not the worst part. Banks lend around 10 times more currency than they have in deposits. So banks have more liabilities than assets (they are literally broke).
People often treat bank deposits, also known as government currency substitutes or bank tokens, as legal tender, allowing banks to create them arbitrarily and 'lend' them to unsuspecting clients who mistakenly believe they are receiving currency.
This is possible only because the bank's deposit has equal cash value.
Government bonds, government currency, and bank deposits have equal value. But they are not the same.
All of them have counterparty risk, but cash, or government currency, is better or safer than bonds or bank deposits. If interest rates rise, the value of bonds can decrease, and default on bank deposits can result in total loss, a scenario that has frequently occurred.
Keep in mind that bank deposits represent the bank's debts, also known as liabilities. Business activities and risk-taking make your currency unsecured, and they don't compensate you enough for the loan and risk.
- Debit cards (bank deposit transfer)
Your bank deposit is your right to get your currency back. When you use a credit card to buy something, you are transferring that right to the seller so he can redeem that bank token for currency if he wishes.
But you have to have had a deposit before you can spend it or transfer it.
- Checks (bank deposit transfer)
The same applies to checks. Your bank deposit is your right to get your currency back. When you use a check to buy something, you are transferring that right to the seller so he can redeem that bank token for currency if he wishes.
- Credit card (bank deposit creator)
Credit cards are different. When you use a credit card, you are creating a bank deposit backed by your promise of paying it back. By allowing the bank to create a currency substitute out of nothing and charge you high interest, you are essentially working for them for free.
Not only this, but you are also letting them collect fees from the payments processing that cost them nothing and support their fake money as a medium of exchange.
Using credit cards is literally voting for financial slavery. This is why companies make credit cards so convenient and offer benefits, with the intention of incentivizing and pushing people into the debt slavery system.
BANKS = MONEYCHANGERS
‘Loans’ = exchanges
The history of money is the history of moneychangers, money dealers, or bankers. Money is an inanimate object. Bankers are alive; they are the ones in charge of making the money, currency, and credit flow or stop.
They have been in existence for thousands of years, from Egypt to Rome, where Jesus Christ himself threw them out of the temple and called them thieves, and he was not wrong.
Moneychangers played a crucial role in facilitating trade by exchanging different forms of currency and commodities. The profession of moneychangers evolved over time, particularly during the Roman Empire and the Middle Ages when various currencies were in circulation. In these times, moneychangers would set up shop at markets or public spaces to provide their services and help merchants convert their money into a form that could be used for transactions with other traders. As banking systems developed over time, the role of moneychangers expanded to include more complex financial services.
Today, moneychangers are still an essential part of the global economy, helping people exchange currencies and facilitating international trade.
The Knights Templars were a Christian military order established in 1119 who played a crucial role in the establishment of the financial system in medieval Europe. They established a gold-backed credit system that laid the foundation for the modern banking system. Their financial services included deposit accounts, loans, and even a form of early traveler's checks.
The history of the goldsmiths starts around 700 years ago in the year 1327. The company became responsible for hallmarking precious metals and played a significant role in regulating the quality and authenticity of gold and silver items. In exchange for written acknowledgments or "receipts," they also provided gold deposit services.
Both groups played significant roles in the development of these early financial instruments, with goldsmiths issuing written acknowledgments for deposited gold and the Knights Templar establishing banking institutions that facilitated the use of such receipts as a form of payment.
This is a brief summary of the beginning of the moneychangers and how they discovered how to multiply money with paper receipts, better understood as counterfeiting. We now refer to it as fractional reserve banking, and let me tell you something: it's based on fraud.
Not only do they create bank deposits when you deposit currency, but they also create them when you "take a loan." Banks do not lend money, and they do not lend currency; they lend bank deposits (bank tokens/IOUs/currency substitutes/ paper receipts).
Banks had to redefine the word money to mean the opposite of money (debt) to trick the people. How can you lend the oposite of money and expect to be paid back plus interest? This took them thousands of years to achieve.
The fact is that this is not a loan but an exchange. When you take a loan, you sign a contract that creates a promissory note, which is your promise to pay. The bank then takes this promissory note, without your permission (steals), and sells it for cash (if you requiere it) or government bonds (to earn interest).
Your promissory note has equal value to cash and government bonds. And banks always need an asset to create a bank deposit (liability). So the banks literally steal your asset (promissory note) and sell them to create IOUs that they will ‘lend’ to you.
They ‘lend’ the oposite of money and call it a loan. The truth is that they are acting as moneychangers, and they are exchanging your IOU (promissory note) for a bank IOU (bank deposit) without your permission and pretending that you pay it back, but they never pay back theirs…
How is this possible? This is only possible because most people treat bank deposits (bank tokens, IOUs, and debts) as a medium of exchange because they trust the banks.
This is the root of inequality under the law. While one group can create IOUs from nothing and steal others, the other must work for them or exchange wealth.
If this bank defaults, its IOUs quickly vanish. This is a mathematical certainty; that’s why banks that are 'too big to fail' demand bailouts. Every bank is bankrupt since they have 7–10 times more liabilities than assets, and the assets they have are not theirs but their clients' assets. The only thing that keeps them alive is the trust of the public and the bailouts of the government.
This is legalized slavery and theft. There’s no other name. Banks own every industry, government, public figure, actor, etc. They have the power of God on earth, and it's time to stop them.
If we let the bank take our wealth for free, we will end up bankrupt, and they will end up owning everything. Every medium of exchange nowadays is an IOU or an IOU of an IOU. Ultimately, it is mathematically impossible to repay all of those IOUs, and banks pretend to keep all the assets.
Check: IOU = deposit; IOU = cash; IOU = bond; IOU + interest
The only way this system can continue is to keep creating new IOUs to pay the old ones, but even then (as it has been for over a century), the value of those IOUs keeps falling, causing hyperinflation.
If banks and governments want to ‘avoid’ (imposible) or relent to hyperinflation, they need to incur a great confiscation. So heads you lose, tails they win, playing this game doesn't make any fucking sense.
Buy Bitcoin, self custody, and fuck the government and the banking system.
Live free or die trying.
-
-
 @ 9171b08a:8395fd65
2025-02-25 13:27:26
@ 9171b08a:8395fd65
2025-02-25 13:27:26For the price tag on this room, I would've thought my death bed would be more comfortable. Since I've been admitted I've been in a perpetual state of discomfort despite the medicine that is supposed to keep me numb. The room is dark and I'm alone with the sounds of industry that keep this planet churning through the expanse of space.
The unease goes deeper than the surface, beyond the 1000 thread count Earth cotton grating against my skin, deeper than the cracking sinews of my muscles, it lurks in the wake of the vibrations of my heart as it throbs its final throbs.
The holoscreen comes to life at a thoughts command and quickly my unease turns to irritation as my name crawls across the screen. A woman points to the very hospital where I lay and expresses her sorrow as "One of the greatest men of this era awaits his death."
I suppose it couldn't come quicker. I shut off the holoscreen. Plunge myself back into the darkness and simply watch the shadows of the freighter transports cast through the opaque vinyl shutter as they pass by.
The light comes on. It blinds me and all I can hear are the footsteps that approach. The heels clatter loudly, soles of well made shoes. Expensive, probably Earth made like my sheets.
"You don't have to go through with this old man." I know the voice well. My mentee, the man I've groomed to take over my empire speaks again, "It's not too late to take the regenerons. You'd be looking younger than me within the week."
I don't care to explain myself. I turn away from him and he mutters something else then reaches over and rests a vase on the table in front of me.

Inside the vase float two scarlet tulips within a bouquet of gypsophila. The flowers smell freshly cut, a scent that instantly freshens my soul and harkens to a time before anyone could imagine I'd be known as "one of the greatest men of the era."
My mentee speaks, but his voice is nothing more than the ruffling of my sheets as I sit up and draw closer to you.
Precious tulips.
Tulips like these, I picked in the endless fields of Verduia. I, like the others who'd been bred to work on that planet, toiled away endless days to pick flowers just like these for affluent people just like me at this very moment.
I was never supposed to have the life I've lived. My biology was built to pick and die. To work, stay poor, and keep my head buried in the fields, that was my purpose.
I worked hard. My hands pruned and nurtured roots in the dark soil. But I loved harder. The memory of your marble skin against the thick layer of dirt beneath my nails will never fade. I've amassed a wealth that is the envy of entire solar systems, but the memory of you is richer.
My tulip, my eternal blossom. I'd run away from the task masters with you and hide in the tall sunflower fields where we'd make love.
People like us weren't meant to be in love. When you passed, I felt no greater discomfort. I thought wealth could fill that void. It hasn't. Not even a millennia since could wash away the memory of you. Only the closure of time, the death of me can remove this ever long dread. Here the need to revive the feeling only you could inspire ends.
-Art By Surenja Rajawat- Find him on instagram @suren.rajawat
-
 @ fd208ee8:0fd927c1
2025-01-23 15:31:24
@ fd208ee8:0fd927c1
2025-01-23 15:31:24Planning Alexandria
People keep asking what features nostr:npub1s3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqd975wz has planned for #Alexandria, but they're not set in stone because we're an agile project.
What we do have, is lots of tickets on our Kanban boards and a naming scheme, where we use a famous person's last name, to signify the release goals.

Gutenberg v 0.1.0
(after the inventor of the printing press) will contain the features needed to read and write NIP-62 Curated Publications, as well as encompassing the complex infrastructure, architecture, documentation, and personnel we require to make this all run smoothly and look easy.

Euler v 0.2.0
(after a mathematician credited with establishing graph theory) will contain the features for deep-searching, visually exploring, and smartly navigating the data set, wiki page display, annotating and citing the publications, exporting to other formats (like PDF, ePUB, and LaTeX), and commenting/reviewing. To help with the heavy lifting, we will be swapping out the core with our own Nostr SDK called "Aedile".

Defoe v 0.3.0
(after an author who perfected the novel format) will be all about our favorite writers. We will be focusing upon profile data, payment systems, book clubs and communities, and stylesheets.
That is everything we have planned, for the v1.0 edition, and we consider that version to be a true product.
As for after that, a teaser...

-
 @ 91bea5cd:1df4451c
2025-02-04 17:24:50
@ 91bea5cd:1df4451c
2025-02-04 17:24:50Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\000\000\000\000\000\000'; output TEXT = '';
unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ```
ULID TO UUID
```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ```
UUID to ULID
```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ```
Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars;END; $$ LANGUAGE plpgsql; ```
Exemplo de USO
```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ```
Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-
 @ 57d1a264:69f1fee1
2025-02-25 13:24:49
@ 57d1a264:69f1fee1
2025-02-25 13:24:49Galoy released a new product called Lana, a platform for bitcoin loans. The team will provide an introduction and then we'll dive into the design.
To get you up to speed, check out the website, slide deck and podcast interview: - https://www.galoy.io/lana-bitcoin-loans-platform - https://docs.google.com/presentation/d/1IQocefpCN5_wKX91EWtLa19IpMS_Ye8goNLAgGQbfdU/edit#slide=id.g31d536107ae_0_0 - https://stephanlivera.com/episode/634/
If you get a chance, please take a peek before the call. That makes the design reviews more useful because we need to spend less time going over the basics. On
Thu Feb 27th · 15:00 – 16:00 CETJoin from https://meet.jit.si/bitcoindesignCheck your timezone https://everytimezone.com/s/998e22fc Track https://github.com/BitcoinDesign/Meta/issues/758
originally posted at https://stacker.news/items/896570
-
 @ e034d654:ca919814
2025-01-22 23:14:27
@ e034d654:ca919814
2025-01-22 23:14:27I stumbled into nostr end of March 2023. At that point already fully thrown into the hows, whys and whats of Bitcoin, never really interested in social apps, just recently playing around with Lightning, the only experience of which at the time was Muun (😬) and stacker.news custodial wallet.
Fairly inexperienced with technicals other than rough understandings of concepts. A crappy laptop node with a dangling SSD via USB, constantly having to resync to current blockheights whenever I was ready to make an on chain transaction to cold storage. My great success after over two years of delay, and a couple failed attempts.
Something about the breadth of information for nitty gritty specifics, the clash with all the things that I found interesting about Bitcoin, with others equally as focused, kept me interested in Nostr. Plus the lighthearted shit posting to break up plumbing the depths of knowledge appealed to me.
Cut to now. Through the jurisdictional removals and even deaths of LN wallet projects, using mobile LSPs, finding use cases with the numerous cashu implementations, moderate comfortability with NWC strings of various permissions, budgets for seemingly endless apps of Nostr clients, swapping relays, isolated wallets with Alby go for my wife and cousin (I told them both not to put much on there as I'm sure failure is imminent) Alby Hub and Zeus, now fully backended by my own persistently online lightning node. All of it adding to the fluidity of my movement around the protocol.
Nimble.
Gradual progress. Reading through notes and guides posted on Nostr learning little bits, circling back eventually, if even at a time it wasn't clicking for me. Either way. Glad i've stuck to it even if I still barely know what it is I'm doing.
-
 @ fd208ee8:0fd927c1
2025-01-19 12:10:10
@ fd208ee8:0fd927c1
2025-01-19 12:10:10I am so tired of people trying to waste my time with Nostrized imitations of stuff that already exists.
Instagram, but make it Nostr. Twitter, but make it Nostr. GitHub, but make it Nostr. Facebook, but make it Nostr. Wordpress, but make it Nostr. GoodReads, but make it Nostr. TikTok, but make it Nostr.
That stuff already exists, and it wasn't that great the first time around, either. Build something better than that stuff, that can only be brought into existence because of Nostr.
Build something that does something completely and awesomely new. Knock my socks off, bro.
Cuz, ain't nobody got time for that.
-
 @ 6871d8df:4a9396c1
2025-01-18 20:12:46
@ 6871d8df:4a9396c1
2025-01-18 20:12:46## 2024 Prediction Reflections
Politics
Democrats & 2024 Election
- “Democrats’ attempt to stifle democracy will likely put Trump in the White House. If not, some real sketchy stuff would need to happen to keep him out.”
This prediction was exactly right. The assassination attempt on Trump seemed to be the final blow for the Democrats. Despite a heavy push my legacy media, Trump won handily.
The Democrats switched to Kamala Harris after Biden showed signs of incapacity, most notably in the first debate against Trump.
My prediction for the election also turned out to be exactly right, which, thank you Robert Barnes and Richard Baris.
Evidence of Institutional Ideological Capture
- “People will continue to wake up to ideologically captured institutions, and DEI will be the main loser.”
Trump’s resounding election victory underscores that the public is increasingly aware of (and rejecting) such institutional capture.
Of note, Boeing comes to mind as an institution that had a tough time in 2024, in large part to DEI. Nothing seemed to function correctly. The biggest story being how they stranded people in space
Media & Public Opinion
Rise of Independent & Alternative Media
- “Independent and alternative media will continue to grow as people’s trust in legacy media declines.”
Twitter (X), under Elon Musk, shattered mainstream media’s influence far more than expected. As Elon has said, “You are the media now.” Alternative sources are king. - Notable Example: Kamala Harris’s decision not to appear on the Joe Rogan podcast contrasted with Trump’s appearance, further highlighting the power shift to alternative media.
Markets & IPOs
Interest Rates & Public Markets
- “As interest rates come down, I expect public markets and IPOs to heat up.”
This did not play out. Companies that were expected to go public in 2024 remain private in 2025. The reasons are varied, but there is confidence that 2025 might see changes.
Technology & AI
LLMs & AI Adoption
- “AI and LLMs will continue to move at a rapid rate, increasing productivity. Tools like Bard will become more mainstream.”
AI did take off. Usage among nontechnical users increased, and it’s no longer uncommon for people to default to AI-driven tools rather than Google search.
Decentralized AI
- “I hope to see a rise in decentralized AI to counter big-player LLMs.”
We didn’t see explicit ‘decentralized AI’ breakthroughs, but more players entered the AI market. ChatGPT still dominates, with Elon’s ‘Grok’ making moves. Google, Meta, and Microsoft remain active but slightly behind in usage.
Bitcoin & Digital Assets
Institutional Adoption of Bitcoin
- “2024 will bring more institutions to Bitcoin. Possibly another large company or nation-state. The ETF should help, likely pushing BTC to a new all-time high.”
No large public company or nation-state placed a bet, but smaller public companies did. Michael Saylor presented to Microsoft’s Board, which was the closest instance to a major move.
- Price Movement: Bitcoin did hit a new all-time high, rising to as much as $108k in 2024.Lightning Network
- “Lightning will improve but remain primarily used for acquiring Bitcoin, not everyday payments.”
Still true. Lightning usage remains tiny relative to broader Bitcoin adoption.
Nostr Adoption
- “Nostr will grow, and we’ll see new companies leverage this network beyond just social media.”
Growth continues, but Elon Musk’s Twitter takeover slowed adoption. Nostr will remain niche until a major catalyst occurs (e.g., a big player joins or forced usage due to censorship).
Stablecoin-Specific Regulations
- “Expect stablecoin regulations in 2024 that’ll be favorable to them.”
This didn’t happen, largely due to the administration’s hostility. Expect potential change in 2025.
Miscellaneous 2024 Reflections
- Return to Sanity
- 2024 felt like sanity prevailed, largely due to the Democrats’ collapse behind Biden and Harris and Elon’s Twitter dominance.
- Operation Chokepoint 2.0
- Received a lot of attention, and I’m thankful it did because my experience at Strike was radicalizing and extreme.
- Bryan Johnson & Anti-Aging
- He burst onto the scene with his obsession over biomarkers. I see it as misguided—chasing markers in isolation doesn’t automatically yield a healthy system.
- Apple’s Rough Year
- Without a visionary leader, Apple appears to be scraping by on existing products rather than innovating.
- Google Under Fire
- Google is in a tough fight with the government, just as it seems they’re on their heels with AI competition.
2025 Predictions
-
Bitcoin’s Performance Bitcoin will have a good year, but not better than 2024. To beat 2024, it must close above 206k on December 31, 2025. I’ll take the under on that.
- I am not ruling out it to be over that at some point in 2025.
-
Twitter’s Success Continues to Stunt nostr
- Nostr adoption will stay slow due to Elon’s dominant influence with X (Twitter).
- As long as it remains a beacon of free speech, I doubt we see an exodus.
-
Rumble integrating Tether might help if they allow Nostr-like features (zaps), but that seems unlikely.
-
Apple
-
Apple will continue its rent-seeking behavior and put out underwhelming products.
-
Google’s Quantum & AI
- Recent buzz about Google’s quantum chip and AI improvements won’t pan out as a big deal.
-
Google will continue to trail OpenAI and xAI in practical LLM usage.
-
Elon, Vivek & DOGE
-
I expect them to deliver more than critics think. They’ll expose bloat and inefficiencies in ways that will shake up norms. I greatly welcome this. I wouldn’t bet against them.
-
Mainstream Media Reckoning
- In Trump’s second term, mainstream news outlets will face a real reckoning, as I can’t see how their bias can continue.
- They’ll have to reduce their bias or risk bankruptcy.
-
Alternative media’s growth trend continues, especially as Twitter keeps exposing mainstream outlets’ weaknesses.
-
RFK Delivers
-
We will see big changes in the health space due to RFK at HHS. These are changes that I am very excited to see.
-
Foreign Policy
- With the transition to Trump, I expect some foreign policy wins that will buck the establishment but will deliver wins that are not thought possible by the “experts.”
Closing Note
- Overall 2024: It was a year of major political upheaval, vindication for Bitcoin, and continued AI advances.
- Outlook for 2025: Bitcoin remains strong, AI competition heats up, and media institutions face existential challenges. I’m optimistic for continued decentralization and a more level playing field across tech, finance, and politics. I think the start of Trump’s second term will be very strong for the market, health, and culture. Accelerate.
-
 @ e5de992e:4a95ef85
2025-02-25 12:46:53
@ e5de992e:4a95ef85
2025-02-25 12:46:53The future of decentralized identity promises a digital landscape where users have full control over their personal data, privacy, and interactions. When users own their digital presence, several transformative changes could reshape the internet:
Empowerment and Control
Self-Sovereignty
Users will manage their identities through cryptographic keys rather than relying on third-party platforms. This means you decide what data to share, how to share it, and with whom, eliminating reliance on centralized authorities.
Data Portability
Decentralized identity frameworks enable seamless movement of personal data across various services. Without vendor lock-in, you can maintain a consistent digital persona, regardless of the platform or application you choose to use.
Privacy and Security
Enhanced Privacy
With decentralized identity, you control the amount and type of information you reveal. This minimizes exposure to data breaches, unauthorized surveillance, and privacy violations that are common in centralized systems.
Stronger Security
Cryptography plays a central role in decentralized identity, reducing the risk of identity theft and fraud. Since your identity is not stored in a single, vulnerable location, it's much harder for attackers to compromise your personal information.
Interoperability and Innovation
Interoperable Ecosystems
Decentralized identity standards can pave the way for interoperable systems where different services and platforms recognize and trust your digital credentials. This can lead to smoother user experiences and increased innovation in digital services.
New Economic Models
Ownership of your digital identity might also enable new ways to monetize personal data. Instead of platforms harvesting data for profit, users could potentially control and even earn from the use of their own information.
Social and Cultural Impact
Democratizing the Digital Space
A user-owned digital identity reduces the power imbalance between large tech corporations and individuals. It fosters a more democratic online environment where freedom of expression and personal autonomy are respected.
Resilience Against Censorship
Decentralized systems distribute data across multiple nodes, making it far more resistant to censorship. This ensures that your voice can be heard even in environments where centralized platforms might suppress it.
Challenges Ahead
Usability and Adoption
While the potential benefits are significant, mainstream adoption will require overcoming technical and usability challenges. Managing cryptographic keys, for instance, may be daunting for non-technical users unless user-friendly solutions are developed.
Regulatory and Standardization Issues
As decentralized identity becomes more prevalent, there will be a need for clear standards and regulations to ensure interoperability, security, and consumer protection without stifling innovation.
In Summary
When users own their digital presence, the future of decentralized identity is marked by increased privacy, enhanced control, and a more open, interoperable digital ecosystem. This shift not only empowers individuals but also encourages the development of innovative technologies and business models that prioritize user rights and freedoms in the online world.
-
 @ 57d1a264:69f1fee1
2025-02-25 12:38:46
@ 57d1a264:69f1fee1
2025-02-25 12:38:46I've been pondering how LSPs (lightning service providers) might pan out over time and how that might affect fees, and I am wondering what everyone else is thinking. Some people will always prefer to manage their own channels, and for some specific use cases, that might be preferable. But I am thinking about the broad userbase that does not want to do that. We will need a massive LSP infrastructure to onboard people and to enable insane amounts of payments.
LSPs will need to efficiently open and adjust channels for users, using their own liquidity or sourcing liquidity from other providers, using just-in-time channels, batching and/or splicing to reduce costs and wait times. Across all this, along with facilitating payments, they need to make their business model work and offer different options for users to pay for their services.
Users might be able to: 1. Pay-as-you-go (pay X for Y more liquidity for Z amount of time) 2. Pay X per month for Y inbound liquidity 3. Pay X per month for unlimited liquidity 4. Nothing for liquidity, but higher transaction fees
A wallet might also automatically choose an appropriate LSP based on what is the best and most appropriate deal at the time.
Let's look at user scenarios: - If someone sends and receives the same amount every month, they will never need more liquidity. They just draw down the same channel and fill it up again. So they would only pay the LSP for them assigning that fixed amount of liquidity to them. Maybe options 1 and 2 are good for them. - If someone receives more than they send (they save a certain amount every month), they will need more and more inbound liquidity over time. They might choose option 2. - An online store that receives a ton and can't really estimate how much, might go for option 3. - For option 4, it depends if the higher transaction fees are fixed or percentage-based.
It's a bit like choosing a data plan for your phone (or for internet at home). You can get a prepaid card, a regular plan with certain limits, or go unlimited. And there are separate plans for small and large businesses, etc. And there are massive amounts of complex infrastructure behind these service providers to make it all work.
So when someone starts using a lightning wallet, maybe they have to first pick an LSP and a plan before being able to receive. Or maybe they get a first channel for free and pay higher fees, and are then prompted to choose a plan. Maybe they need to wait an hour until the LSP has enough channel opens for a batch/splice, to reduce costs. A complex market at work.
Is that how things might pan out? Am I completely off? Is it worth mocking up different scenarios?
```
bitcoin #LN #BTC #Lightning #LSP #service #zaps #sats #wallet
```
originally posted at https://stacker.news/items/896520
-
 @ f7922a0a:82c34788
2025-01-17 23:06:56
@ f7922a0a:82c34788
2025-01-17 23:06:56Now that the 3rd Satellite Skirmish is complete I wanted to highlight some of the cool features on embrace.satskirmish.com
This is what the cutting edge of podcasting 2.0 looks like imo. Live video in an app that allows you to send sats to the artists in real time.
On the left hand side we have a Boost score borad that displays the total amount of sats that have come in during the show, live Boosts/Booastagrams as they come in, total amount of sats from each person Boosting and total amount sent from each app.
The middle is ovisaly the video of the band playing but with some graphics around it and Boost alerts that show up on the screen in the form of snow flakes for this one.
The righthand side is an IRC chat window that connects to an IRC server that the No Agenda community has used for 18+ years thanks to zoidzero++.

The bottom of the page is where things get cool. When you click the Boost the Crew button in the center you can send a Boost that gets split between everyone helping produce the show (hightlighted in yellow).


Each band also has their own Boost button so you can Boost them while they are playing or anytime you visit the page.


-
 @ 16f1a010:31b1074b
2025-02-19 20:57:59
@ 16f1a010:31b1074b
2025-02-19 20:57:59In the rapidly evolving world of Bitcoin, running a Bitcoin node has become more accessible than ever. Platforms like Umbrel, Start9, myNode, and Citadel offer user-friendly interfaces to simplify node management. However, for those serious about maintaining a robust and efficient Lightning node ⚡, relying solely on these platforms may not be the optimal choice.
Let’s delve into why embracing Bitcoin Core and mastering the command-line interface (CLI) can provide a more reliable, sovereign, and empowering experience.
Understanding Node Management Platforms
What Are Umbrel, Start9, myNode, and Citadel?
Umbrel, Start9, myNode, and Citadel are platforms designed to streamline the process of running a Bitcoin node. They offer graphical user interfaces (GUIs) that allow users to manage various applications, including Bitcoin Core and Lightning Network nodes, through a web-based dashboard 🖥️.
These platforms often utilize Docker containers 🐳 to encapsulate applications, providing a modular and isolated environment for each service.

The Appeal of Simplified Node Management
The primary allure of these platforms lies in their simplicity. With minimal command-line interaction, users can deploy a full Bitcoin and Lightning node, along with a suite of additional applications.
✅ Easy one-command installation
✅ Web-based GUI for management
✅ Automatic app updates (but with delays, as we’ll discuss)However, while this convenience is attractive, it comes at a cost.
The Hidden Complexities of Using Node Management Platforms
While the user-friendly nature of these platforms is advantageous, it can also introduce several challenges that may hinder advanced users or those seeking greater control over their nodes.
🚨 Dependency on Maintainers for Updates
One significant concern is the reliance on platform maintainers for updates. Since these platforms manage applications through Docker containers, users must wait for the maintainers to update the container images before they can access new features or security patches.
🔴 Delayed Bitcoin Core updates = potential security risks
🔴 Lightning Network updates are not immediate
🔴 Bugs and vulnerabilities may persist longerInstead of waiting on a third party, why not update Bitcoin Core & LND yourself instantly?
⚙️ Challenges in Customization and Advanced Operations
For users aiming to perform advanced operations, such as:
- Custom backups 📂
- Running specific CLI commands 🖥️
- Optimizing node settings ⚡
…the abstraction layers introduced by these platforms become obstacles.
Navigating through nested directories and issuing commands inside Docker containers makes troubleshooting a nightmare. Instead of a simple
bitcoin-clicommand, you must figure out how to execute it inside the container, adding unnecessary complexity.Increased Backend Complexity
To achieve frontend simplicity, these platforms make the backend more complex.
🚫 Extra layers of abstraction
🚫 Hidden logs and settings
🚫 Harder troubleshootingThe use of multiple Docker containers, custom scripts, and unique file structures can make system maintenance and debugging a pain.
This complication defeats the purpose of “making running a node easy.”
✅ Advantages of Using Bitcoin Core and Command-Line Interface (CLI)
By installing Bitcoin Core directly and using the command-line interface (CLI), you gain several key advantages that make managing a Bitcoin and Lightning node more efficient and empowering.
Direct Control and Immediate Updates
One of the biggest downsides of package manager-based platforms is the reliance on third-party maintainers to release updates. Since Bitcoin Core, Lightning implementations (such as LND, Core Lightning, or Eclair), and other related software evolve rapidly, waiting for platform-specific updates can leave you running outdated or vulnerable versions.
By installing Bitcoin Core directly, you remove this dependency. You can update immediately when new versions are released, ensuring your node benefits from the latest features, security patches, and bug fixes. The same applies to Lightning software—being able to install and update it yourself gives you full autonomy over your node’s performance and security.
🛠 Simplified System Architecture
Platforms like Umbrel and myNode introduce extra complexity by running Bitcoin Core and Lightning inside Docker containers. This means:
- The actual files and configurations are stored inside Docker’s filesystem, making it harder to locate and manage them manually.
- If something breaks, troubleshooting is more difficult due to the added layer of abstraction.
- Running commands requires jumping through Docker shell sessions, adding unnecessary friction to what should be a straightforward process.
Instead, a direct installation of Bitcoin Core, Lightning, and Electrum Server (if needed) results in a cleaner, more understandable system. The software runs natively on your machine, without containerized layers making things more convoluted.
Additionally, setting up your own systemd service files for Bitcoin and Lightning is not as complicated as it seems. Once configured, these services will run automatically on boot, offering the same level of convenience as platforms like Umbrel but without the unnecessary complexity.
Better Lightning Node Management
If you’re running a Lightning Network node, using CLI-based tools provides far more flexibility than relying on a GUI like the ones bundled with node management platforms.
🟢 Custom Backup Strategies – Running Lightning through a GUI-based node manager often means backups are handled in a way that is opaque to the user. With CLI tools, you can easily script automatic backups of your channels, wallets, and configurations.
🟢 Advanced Configuration – Platforms like Umbrel force certain configurations by default, limiting how you can customize your Lightning node. With a direct install, you have full control over: * Channel fees 💰 * Routing policies 📡 * Liquidity management 🔄
🟢 Direct Access to LND, Core Lightning, or Eclair – Instead of issuing commands through a GUI (which is often limited in functionality), you can use: *
lncli(for LND) *lightning-cli(for Core Lightning) …to interact with your node at a deeper level.Enhanced Learning and Engagement
A crucial aspect of running a Bitcoin and Lightning node is understanding how it works.
Using an abstraction layer like Umbrel may get a node running in a few clicks, but it does little to teach users how Bitcoin actually functions.
By setting up Bitcoin Core, Lightning, and related software manually, you will:
✅ Gain practical knowledge of Bitcoin nodes, networking, and system performance.
✅ Learn how to configure and manage RPC commands.
✅ Become less reliant on third-party developers and more confident in troubleshooting.🎯 Running a Bitcoin node is about sovereignty – learn how to control it yourself.
Become more sovereign TODAY
Many guides make this process straightforward K3tan has a fantastic guide on running Bitcoin Core, Electrs, LND and more.
- Ministry of Nodes Guide 2024
- You can find him on nostr
nostr:npub1txwy7guqkrq6ngvtwft7zp70nekcknudagrvrryy2wxnz8ljk2xqz0yt4xEven with the best of guides, if you are running this software,
📖 READ THE DOCUMENTATIONThis is all just software at the end of the day. Most of it is very well documented. Take a moment to actually read through the documentation for yourself when installing. The documentation has step by step guides on setting up the software. Here is a helpful list: * Bitcoin.org Bitcoin Core Linux install instructions * Bitcoin Core Code Repository * Electrs Installation * LND Documentation * LND Code Repository * CLN Documentation * CLN Code Repository
If you have any more resources or links I should add, please comment them . I want to add as much to this article as I can.
-
 @ d360efec:14907b5f
2025-02-25 10:16:18
@ d360efec:14907b5f
2025-02-25 10:16:18ภาพรวม BTCUSDT (OKX):
Bitcoin (BTCUSDT) แนวโน้มระยะยาว TF Day ยังคงเป็นขาลง แนวโน้มระยะกลาง TF 4H Sideway down และแนวโน้มระยะสั้น TF 15M Sideways Down
วิเคราะห์ทีละ Timeframe:
(1) TF Day (รายวัน):
- แนวโน้ม: ขาลง (Downtrend)
- SMC:
- Lower Highs (LH) และ Lower Lows (LL)
- Break of Structure (BOS) ด้านล่าง
- Liquidity:
- มี Sellside Liquidity (SSL) อยู่ใต้ Lows ก่อนหน้า
- มี Buyside Liquidity (BSL) อยู่เหนือ Highs ก่อนหน้า
- ICT:
- Order Block ราคาไม่สามารถผ่าน Order Block ได้
- EMA:
- ราคาอยู่ใต้ EMA 50 และ EMA 200
- Money Flow (LuxAlgo): * สีแดง
- Trend Strength (AlgoAlpha):
- สีแดง แสดงถึงแนวโน้มขาลง
- Chart Patterns: ไม่มีรูปแบบที่ชัดเจน
- Volume Profile: * Volume ค่อนข้างนิ่ง
- แท่งเทียน: แท่งเทียนล่าสุดเป็นสีแดง
- แนวรับ: บริเวณ Low ล่าสุด
- แนวต้าน: EMA 50, EMA 200 , Order Block
- สรุป: แนวโน้มขาลง
(2) TF4H (4 ชั่วโมง):
- แนวโน้ม: ขาลง (Downtrend)
- SMC:
- Lower Highs (LH) และ Lower Lows (LL)
- Break of Structure (BOS) ด้านล่าง
- Liquidity:
- มี SSL อยู่ใต้ Lows ก่อนหน้า
- มี BSL อยู่เหนือ Highs ก่อนหน้า
- ICT:
- Order Block ราคาไม่สามารถผ่าน Order Block ได้
- EMA:
- ราคาอยู่ใต้ EMA 50 และ EMA 200
- Money Flow (LuxAlgo):
- สีแดง แสดงถึงแรงขาย
- Trend Strength (AlgoAlpha): * สีแดง แสดงถึงแนวโน้มขาลง
- Chart Patterns: ไม่มีรูปแบบที่ชัดเจน
- Volume Profile: * Volume ค่อนข้างนิ่ง
- แนวรับ: บริเวณ Low ล่าสุด
- แนวต้าน: EMA 50, EMA 200, Order Block
- สรุป: แนวโน้มขาลง,
(3) TF15 (15 นาที):
- แนวโน้ม: Sideway Down
- SMC:
- Lower High (LH) และ Lower Lows (LL)
- Break of Structure (BOS) ด้านล่าง
- ICT:
- Order Block: ราคา Sideways ใกล้ Order Block
- EMA:
- EMA 50 และ EMA 200 เป็นแนวต้าน
- Money Flow (LuxAlgo):
- แดง
- Trend Strength (AlgoAlpha):
- แดง/ ไม่มีสัญญาณ
- Chart Patterns: ไม่มีรูปแบบที่ชัดเจน
- Volume Profile: Volume ค่อนข้างสูง
- แนวรับ: บริเวณ Low ล่าสุด
- แนวต้าน: EMA 50, EMA 200, Order Block
- สรุป: แนวโน้ม Sideways Down,
สรุปภาพรวมและกลยุทธ์ (BTCUSDT):
- แนวโน้มหลัก (Day): ขาลง
- แนวโน้มรอง (4H): ขาลง
- แนวโน้มระยะสั้น (15m): Sideways Down
- Liquidity: มี SSL ทั้งใน Day, 4H, และ 15m
- Money Flow: เป็นลบในทุก Timeframes
- Trend Strength: Day/4H/15m เป็นขาลง
- Chart Patterns: ไม่พบรูปแบบที่ชัดเจน
- กลยุทธ์:
- Wait & See (ดีที่สุด): รอความชัดเจน
- Short (เสี่ยง): ถ้าไม่สามารถ Breakout EMA/แนวต้านใน TF ใดๆ ได้ หรือเมื่อเกิดสัญญาณ Bearish Continuation
- ไม่แนะนำให้ Buy: จนกว่าจะมีสัญญาณกลับตัวที่ชัดเจนมากๆ
Day Trade & การเทรดรายวัน:
-
Day Trade (TF15):
- Short Bias: หาจังหวะ Short เมื่อราคาเด้งขึ้นไปทดสอบแนวต้าน (EMA, Order Block)
- Stop Loss: เหนือแนวต้านที่เข้า Short
- Take Profit: แนวรับถัดไป (Low ล่าสุด)
- ไม่แนะนำให้ Long
-
Swing Trade (TF4H):
- Short Bias: รอจังหวะ Short เมื่อราคาไม่สามารถผ่านแนวต้าน EMA หรือ Order Block ได้
- Stop Loss: เหนือแนวต้านที่เข้า Short
- Take Profit: แนวรับถัดไป
- ไม่แนะนำให้ Long
สิ่งที่ต้องระวัง:
- Sellside Liquidity (SSL): มีโอกาสสูงที่ราคาจะถูกลากลงไปแตะ SSL
- False Breakouts: ระวัง
- Volatility: สูง
Setup Day Trade แบบ SMC (ตัวอย่าง):
- ระบุ Order Block: หา Order Block ขาลง (Bearish Order Block) ใน TF15
- รอ Pullback: รอให้ราคา Pullback ขึ้นไปทดสอบ Order Block นั้น
- หา Bearish Entry:
- Rejection: รอ Price Action ปฏิเสธ Order Block
- Break of Structure: รอให้ราคา Break โครงสร้างย่อยๆ
- Money Flow: ดู Money Flow ให้เป็นสีแดง
- ตั้ง Stop Loss: เหนือ Order Block
- ตั้ง Take Profit: แนวรับถัดไป
คำแนะนำ:
- ความขัดแย้งของ Timeframes: ไม่มีแล้ว ทุก Timeframes สอดคล้องกัน
- Money Flow: เป็นลบในทุก Timeframes
- Trend Strength: เป็นลบ
- Order Block TF Day: หลุด Order Block ขาขึ้นแล้ว
- ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด
Disclaimer: การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
-
 @ dd664d5e:5633d319
2025-01-09 21:39:15
@ dd664d5e:5633d319
2025-01-09 21:39:15Instructions
- Place 2 medium-sized, boiled potatoes and a handful of sliced leeks in a pot.

- Fill the pot with water or vegetable broth, to cover the potatoes twice over.
- Add a splash of white wine, if you like, and some bouillon powder, if you went with water instead of broth.

- Bring the soup to a boil and then simmer for 15 minutes.
- Puree the soup, in the pot, with a hand mixer. It shouldn't be completely smooth, when you're done, but rather have small bits and pieces of the veggies floating around.

- Bring the soup to a boil, again, and stir in one container (200-250 mL) of heavy cream.
- Thicken the soup, as needed, and then simmer for 5 more minutes.
- Garnish with croutons and veggies (here I used sliced green onions and radishes) and serve.

Guten Appetit!
- Place 2 medium-sized, boiled potatoes and a handful of sliced leeks in a pot.
-
 @ 91bea5cd:1df4451c
2025-02-04 17:15:57
@ 91bea5cd:1df4451c
2025-02-04 17:15:57Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\000\000\000\000\000\000'; output TEXT = '';
unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ```
ULID TO UUID
```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ```
UUID to ULID
```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ```
Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars;END; $$ LANGUAGE plpgsql; ```
Exemplo de USO
```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ```
Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-
 @ 7ed7d5c3:6927e200
2025-01-08 17:10:00
@ 7ed7d5c3:6927e200
2025-01-08 17:10:00Can't decide if the terrible book you just read is a 1 or 1.5 star book? Look no further than this chart. Was it Shit or just Bad? Was that movie you watched Very Good or just Decent? How many things out there are really Life Changing?
Finally, a rating scale for humans. Use it for anything in your life that needs a rating out of 5 stars.
Rating / Description
0.5 – The worst 1.0 – Shit 1.5 – Bad 2.0 – Eh 2.5 – Entertaining, but not great 3.0 – Neutral 3.5 – Alright 4.0 – Decent 4.5 – Very good 5.0 – Life Changing
P.S. Do not use it to rate your wife's cooking. The author is not liable for any damages.
-
 @ d360efec:14907b5f
2025-02-25 09:12:44
@ d360efec:14907b5f
2025-02-25 09:12:44$OKX:BTCUSDT.P
Overall Assessment:
Bitcoin (BTCUSDT) on OKX is currently showing a bearish trend across all analyzed timeframes (Daily, 4-Hour, and 15-Minute). While the long-term trend (Daily) was technically an uptrend, it has significantly weakened and broken key support levels, including a major bullish Order Block and the 50-period EMA. The 4-hour and 15-minute charts confirm the downtrend. This analysis focuses on identifying potential areas of Smart Money activity (liquidity pools and order blocks), assessing trend strength, and looking for any emerging chart patterns.
Detailed Analysis by Timeframe:
(1) TF Day (Daily):
- Trend: Downtrend
- SMC (Smart Money Concepts):
- The Higher Highs (HH) and Higher Lows (HL) structure is broken.
- Prior Breaks of Structure (BOS) to the upside, but now a significant and deep pullback/reversal is underway.
- Liquidity:
- Sellside Liquidity (SSL): Significant SSL rests below previous lows in the 85,000 - 90,000 range.
- Buyside Liquidity (BSL): BSL is present above the all-time high.
- ICT (Inner Circle Trader Concepts):
- Order Block: The price has broken below the prior bullish Order Block. This is a major bearish signal.
- FVG: No significant Fair Value Gap is apparent at the current price level.
- EMA (Exponential Moving Average):
- Price is below the 50-period EMA (yellow).
- The 200-period EMA (white) is the next major support level.
- Money Flow (LuxAlgo):
- A long red bar indicates strong and sustained selling pressure.
- Trend Strength (AlgoAlpha):
- Red cloud, indicating a downtrend. No buy/sell signals are present.
- Chart Patterns: No readily identifiable chart patterns are dominant.
- Volume Profile: Relatively low volume.
- Candlesticks: Recent candlesticks are red, confirming selling pressure.
- Support: EMA 200, 85,000-90,000 (SSL area).
- Resistance: EMA 50, Previous All-Time High.
- Summary: The Daily chart has shifted to a downtrend. The break below the Order Block and 50 EMA, combined with negative Money Flow and Trend Strength, are all strong bearish signals.
(2) TF4H (4-Hour):
- Trend: Downtrend.
- SMC:
- Lower Highs (LH) and Lower Lows (LL).
- BOS to the downside.
- Liquidity:
- SSL: Below previous lows.
- BSL: Above previous highs.
- ICT:
- Order Block: The price was rejected by a bearish Order Block.
- EMA:
- Price is below both the 50-period and 200-period EMAs (bearish).
- Money Flow (LuxAlgo):
- Predominantly red, confirming selling pressure.
- Trend Strength (AlgoAlpha):
- Red cloud, confirming downtrend.
- Chart Patterns: No readily identifiable chart patterns.
- Volume Profile: Relatively steady volume.
- Support: Recent lows.
- Resistance: EMA 50, EMA 200, Order Block.
- Summary: The 4-hour chart is in a confirmed downtrend. Money Flow and Trend Strength are bearish.
(3) TF15 (15-Minute):
* Trend: Downtrend / Sideways Down * SMC: * Lower Highs (LH) and Lower Lows (LL). * BOS to the downside. * ICT: * Order Block price is near to a bearish Order Block. * EMA: * The 50-period and 200-period EMAs are acting as resistance. * Money Flow (LuxAlgo): * Red * Trend Strength (AlgoAlpha): * Red/No signals * Chart Patterns: None * Volume Profile: * Relatively High Volume * Support: Recent lows. * Resistance: EMA 50, EMA 200, Order Block. * Summary: The 15-minute chart is clearly bearish, with price action, EMAs, and Money Flow all confirming the downtrend.
Overall Strategy and Recommendations (BTCUSDT):
- Primary Trend (Day): Downtrend
- Secondary Trend (4H): Downtrend.
- Short-Term Trend (15m): Downtrend/ Sideways Down.
- Liquidity: Significant SSL zones exist below the current price on all timeframes.
- Money Flow: Negative on all timeframes.
- Trend Strength: Bearish on Day,4H and 15m.
-
Chart Patterns: None identified.
-
Strategies:
- Wait & See (Best Option): The strong bearish momentum on all shorter timeframes.
-
Short (High Risk): This aligns with the 4H and 15m downtrends.
- Entry: On rallies towards resistance levels (EMAs on 15m/4H, previous support levels that have turned into resistance, Order Blocks).
- Stop Loss: Above recent highs on the chosen timeframe, or above a key resistance level.
- Target: The next support levels (recent lows on 15m, then potentially the SSL zones on the 4H and Daily charts).
-
Buy (Extremely High Risk - NOT Recommended): Do not attempt to buy until there are very strong and consistent bullish reversal signals across all timeframes.
Key Recommendations:
- Conflicting Timeframes: The conflict is resolved toward the downside. The Daily is weakening significantly.
- Money Flow: Consistently negative across all timeframes, a major bearish factor.
- Trend Strength: Bearish on Day,4h and 15m.
- Daily Order Block: The break of the bullish Order Block on the Daily chart is a significant bearish development.
- Sellside Liquidity (SSL): Be aware that Smart Money may target the SSL zones below. This increases the risk of stop-loss hunting.
- Risk Management: Due to the high uncertainty and volatility, strict risk management is absolutely critical. Use tight stop-losses, do not overtrade, and be prepared for rapid price swings.
- Volume: Confirm any breakout or breakdown with volume.
Day Trading and Intraday Trading Strategies:
-
Day Trade (TF15 focus):
- Short Bias: Given the current 15m downtrend and negative Money Flow, the higher probability is to look for shorting opportunities.
- Entry: Look for price to rally to resistance levels (EMAs, Order Blocks, previous support levels that have become resistance) and then show signs of rejection (bearish candlestick patterns, increasing volume on the downside).
- Stop Loss: Place a stop-loss order above the resistance level where you enter the short position.
- Take Profit: Target the next support level (recent lows).
- Avoid Long positions until there's a clear and confirmed bullish reversal on the 15m chart (break above EMAs, positive Money Flow, bullish market structure).
- Short Bias: Given the current 15m downtrend and negative Money Flow, the higher probability is to look for shorting opportunities.
-
Swing Trade (TF4H focus):
- Short Bias: The 4H chart is in a downtrend.
- Entry: Wait for price to rally to resistance levels (EMAs, Order Blocks) and show signs of rejection.
- Stop Loss: Above the resistance level where you enter the short position.
- Take Profit: Target the next support levels (e.g., the 200 EMA on the Daily chart, SSL zones).
- Avoid Long positions until there's a clear and confirmed bullish reversal on the 4H chart.
- Short Bias: The 4H chart is in a downtrend.
SMC Day Trade Setup Example (TF15 - Bearish):
- Identify Bearish Order Block: Locate a bearish Order Block on the TF15 chart (a bullish candle before a strong downward move).
- Wait for Pullback: Wait for the price to pull back up to test the Order Block (this may or may not happen).
- Bearish Entry:
- Rejection: Look for price action to reject the Order Block (e.g., a pin bar, engulfing pattern, or other bearish candlestick pattern).
- Break of Structure: Look for a break of a minor support level on a lower timeframe (e.g., 1-minute or 5-minute) after the price tests the Order Block. This confirms weakening bullish momentum.
- Money Flow: Confirm that Money Flow remains negative (red).
- Stop Loss: Place a stop-loss order above the Order Block.
- Take Profit: Target the next support level (e.g., recent lows) or a bullish Order Block on a higher timeframe.
In conclusion, BTCUSDT is currently in a high-risk, bearish environment. The "Wait & See" approach is strongly recommended for most traders. Shorting is the higher-probability trade at this moment, but only for experienced traders who can manage risk extremely effectively. Buying is not recommended at this time.
Disclaimer: This analysis is for informational purposes only and represents a personal opinion. It is not financial advice. Investing in cryptocurrencies involves significant risk. Investors should conduct their own research and exercise due diligence before making any investment decisions.
-
 @ 57d1a264:69f1fee1
2025-02-25 07:28:18
@ 57d1a264:69f1fee1
2025-02-25 07:28:18
@Voltage team will be building a simple implementation of a Lightning gated API service using a Voltage LND Node and the L402 protocol.
📅 Thursday, February 27th 4:00 PM CDT
📷 Live on Voltage Discord, on X, or on YouTube. - discord.gg/EN93fDfQ - https://x.com/voltage_cloud/status/1892938201980919985 - https://www.youtube.com/@voltage_cloud
originally posted at https://stacker.news/items/896373
-
 @ dd664d5e:5633d319
2025-01-07 19:57:14
@ dd664d5e:5633d319
2025-01-07 19:57:14Hodling Bitcoin does not make you a capitalist
I've noticed that Bitcoin-mindedness seems to lead some people to communistic thinking because it's a hard-limited form of capital. Marx, like most Bitcoiners, heavily discounted the possibility of economic growth or transformation changing the economy enough to undermine some minority's control of some form of capital.
What few today understand, is that many of the Dirty Capitalists of Marx's era actually agreed with him; they were just disdainful of labor and worried that the workers finding out that Marxism is correct about the nature of capitalism would cause unrest. They were the original HFSP crowd.
This was the basic idea, that Marx had, and that many Bitcoiners would agree with:
Capital is strictly limited and the people that control it can keep labor from attaining any, except when their labor is necessary.
And, as we know, automation will make human labor increasingly unnecessary.
The math doesn't check out

That underlies all of the calculations of "Well, if I just grab this Bitcoin wallet and hodl for twenty years, then it will grow in value to equal half of everything in existence and then I can just buy up half the planet and rule over everyone like a god."
This is economic nonsense because it assumes that: 1) the value of all things remains static over time, 2) purchasing something with money gives you ownership of it, 3) people will always use that specific money (or any money, at all!) for all transactions, 4) there is no such thing as opportunity cost, 5) people will always value money more than any other thing, and therefore be willing to always trade it for anything else, 6) humans are passive, defenseless, and easy to rule over, 7) someone who is preoccupied with hodling an asset steadily and sharply rising in price would ever be emotionally ready to part with it.
All monies can die.
People use money for everything because it is easy, fast and cheap. If money becomes too precious or scarce, they will simply switch to using other things (as we saw with gold). Humans replace tools that aren't working well, with those that work better, and money is just another tool. Bitcoin is more divisible than gold, but that won't matter, if enough of it is held by too few.
This is why there's a natural cap on the price of a money and why human productivity in the here and now is not irrelevant or in vain.
-
 @ dd664d5e:5633d319
2025-01-06 20:36:17
@ dd664d5e:5633d319
2025-01-06 20:36:17Ingredients
- 1 kg of pork roast with rind, such as shoulder or a lean belly
- 1 bottle of beer, light or dark
- chopped German-style mirepoix (best combination, for this recipe, includes celery root, carrot, red onion, and leeks)
- salt, pepper, nutmeg
- 1 diced garlic clove
Directions
- Spread the vegetables on the bottom of the roasting pan.
- Pour half the beer over the roast. (Drink the other half.)
- Season the meat, to taste.
- Roast the meat at 180 °C, until done (depends upon the weight of the roast).
- Remove the meat from the oven, and wrap in aluminum foil.
- Pour 2-3 cups of water into the roasting pan.
- Pour/scrape everything from the pan into a sieve over a sauce pot.
- Press the vegetables against the sieve, with the back of a spoon, to ensure that you get all that good dripping flavor into the sauce.
- Defat the sauce with a grease separator, then pour it back into the pot.
- Thicken the sauce, slightly (it should remain slightly watery, and not turn into a gravy), according to your usual method.
- Open the foil and slice the roast.
- Serve with the sauce.








-
 @ a42048d7:26886c32
2025-01-04 22:32:52
@ a42048d7:26886c32
2025-01-04 22:32:52OP_CAT, Coffee, and keeping an open mind to Bitcoin soft forks by an 80 IQ BTC Maxi Pleb
TLDR: CAT is both low risk and low appeal to the broader non-dev BTC community. I don’t care and you shouldn’t either. If I am an 80 IQ HODL pleb or a company that caters to that group, can you please give me 2-4 fifth grade level coherent english sentences that explain why I should support CAT? I’m still waiting… CTV or LNHANCE on the other hand have broad appeal.
Five years ago in the office we got a fancy $6,000 coffee maker. It was hooked up to wifi, showed TV on a giant screen, and could make every type of coffee/milkshake you could think of. I was captivated… for about 1 day. After trying a few times I realized almost all the drinks it made were of low quality. The wifi connection actually ended up just being annoying. Half the time I wanted a coffee, only had a 5 minute break, and the machine displayed some inscrutable error. I went back to the proverbial grind un-caffeinated and frustrated wishing we had the old reliable boring coffee maker back. I also found myself only coming back to the 2 drinks I really cared about, espresso and maybe an occasional cappuccino. It was “cool” that new machine could make over 60 different drinks, but when I sat back and thought about it all I really needed or wanted were a few key options that I used constantly. Especially as those extra bells and whistles seemed to be the usual suspect in the coffee machine constantly breaking. I would’ve loved them upgrading from burnt starbucks coffee beans to a local specialty roaster, that would’ve greatly enhanced my daily coffee. Echoing this realization, my coffee setup at home became a simple machine that could only make espresso and a hand crank coffee bean grinder. Still have them years later and they work great. They’re robust and fit exactly what I wanted with no nonsense that created more headache than everyday value. As you probably suspected, this is a loose comparison to OP_CAT. I’ve listened to podcast after podcast, read blog after blog, and sat through every CAT pitch I could find. I genuinely tried to approach with an open mind. However, ultimately what every pro OP_CAT argument boils down to is that there is no simple left curve elevator pitch a pleb will understand or care about. “But we can get this really cool ZK Rollup and have infinite DEFI bridging to altcoin chains! Look we sort of did it on this other altcoin chain.” And they did, they aren’t lying. They have live software on a shitcoin chain like ETH or SOL that does some modest volume. But the story quickly falls apart in the face of a few basic left curve questions: “Why should I, as an 80 IQ left curve BTC maxi give a shit?” “Does this enhance my everyday experience holding and using BTC?” “Why do you have a non-BTC token for your rollup/sidechain/glorified multisig that is totally centralized?” “Why is there only a hard to understand often ill-defined path to de-centralization? Why isn’t it just already decentralized?” “What is a clear use case that the typical non-technical everyday BTC holder can understand and rally behind?” “Why should I care about bridging to ETH, SOL, or whatever shitcoin chain? I only want BTC and don’t want to participate in all that shitcoin bullshit. Bitcoin is a store of value and money to me and it doesn’t help with those use cases in a clear direct way. It sounds like it maybe, kinda, sorta does help with a lot of caveats, ifs, and steps that I struggle to understand.” Sorry yeah I know, that one got a little personal. I’ll try to do better going forward guys.
ZK proofs or other Pro-CAT arguments, are undoubtedly cool and do factually enable potential cool new stuff. It just happens to all be stuff that sounds complex, esoteric, and unappealing to an 80 IQ HODL pleb - let alone a miner, ETF investor, or exchange exec. I don’t mean to say ZK or other tech has no potential and that we won’t eventually move there, but just to say that it’s not in the cards as currently dealt.
I really went out trying to keep an open mind and steelman the case for CAT. I came back firmly believing:
1 Support is deep in the developer community, but nonexistent everywhere else. I have yet to find a single person that supports CAT who is not a dev or working at or sponsored by a company that stands to directly profit from something CAT enables. Which is fine, but I reserve the right to be skeptical of your direct incentive. I acknowledge rough consensus is very hard to judge, and am open to changing my mind on this over time but feel this is a currently accurate assessment.
2 To get a soft fork you need rough consensus. Most people in that potential consensus are not highly technical developers. They care mostly or exclusively about BTC’s store of value use case. No one has yet articulated a clear compelling store of value enhancing use case that they can understand and care about. Without pull demand from potential users and paying customers, CAT will inevitably stall.
3 Lots of factually inaccurate FUD has been thrown at CAT. People saw the Taproot Wizards or shitcoiners pushing CAT, and immediately dismiss CAT as an evil psyop without any real consideration for its technical merits. Frankly most people just hate Udi and say “Fuck CAT” based solely on that. Maybe not fair, but true.
4 CAT is low risk, and it is not a catastrophe waiting to happen. Anything bad it potentially enables is enabled in such an inefficient and/or use hostile way that it is highly unlikely to pose any issues to Bitcoin. CAT’s technical risk is low and this is consistently proven by other chains enabling CAT and having no issues with it, such as Liquid.
5 Lots of people who have no idea wtf they are talking about falsely claim CAT is the apocalypse without any ability whatsoever to explain why. Imho you are no better than Udi and the shitcoiners if you are willing to lie about CAT just because you dislike them. We as the BTC community need the ability to have a rational discussion on technical merits, and not to devolve into a cult of personality based political battle. The question should be, “Is CAT good or bad and why?” and not “I just hate Udi, therefore its a no from me dog.”
Summarizing CAT using TradFi language: those pushing CAT have technology in search of a problem and no clear product market fit. They are pushing their technology to an apathetic audience. Pushers of CAT are not pulled forward by customer demand. In the tech world these are some of the quintessential red flags that every good investor knows mean you need to sit this one out.
CTV or LNHANCE on the other hand are soft fork proposals that have clear use cases you can quickly explain to a broad swathe of the Bitcoin ecosystem: “Hey HOLD pleb, worried about losing your coins? Wouldn’t it be nice to have a simple vault that reduces the chances your coins are lost or stolen? Let’s make self custody and BTC’s store of value use case strictly better, specifically without enabling any shitcoin-ery.” “Hey Blackrock, Van Eck, ARK, Franklin Templeton, and every ETF investor - it would really suck if Coinbase lost all your Bitcoin and that ETF went to zero, right? What it we could create vaults to make that Bitcoin more secure?” “Like Lightning but find it hard to use self-custodially? Let’s make Lightning better, easier, and more scalable with fewer onchain transactions and lower fees.” “Tried or seen the ARK demos yet? They have real working code even without covenants. With covenants we get big ARK volumes and scaling while also making it easier.”
Signing off: See the difference? I, an 80 IQ pleb, can steelman multiple use cases for CTV/LNHANCE that have broad appeal. I have yet to see any such case for CAT, and until then I don’t think it’ll go anywhere.
*Pro-CAT Sources I’ve digested and would encourage others to consider: https://en.bitcoin.it/wiki/Covenants_support https://www.youtube.com/watch?v=no_Nj-MX53w https://www.youtube.com/watch?v=_yp4eYK9S6M
Pro-CTV/LNHANCE sources to consider which have CLEAR use cases with widespead appeal: https://github.com/jamesob/simple-ctv-vault https://github.com/stutxo/op_ctv_payment_pool https://lnhance.org/ https://bitcoinmagazine.com/technical/how-ctv-can-help-scale-bitcoin
-
 @ a4a6b584:1e05b95b
2025-01-02 18:13:31
@ a4a6b584:1e05b95b
2025-01-02 18:13:31The Four-Layer Framework
Layer 1: Zoom Out

Start by looking at the big picture. What’s the subject about, and why does it matter? Focus on the overarching ideas and how they fit together. Think of this as the 30,000-foot view—it’s about understanding the "why" and "how" before diving into the "what."
Example: If you’re learning programming, start by understanding that it’s about giving logical instructions to computers to solve problems.
- Tip: Keep it simple. Summarize the subject in one or two sentences and avoid getting bogged down in specifics at this stage.
Once you have the big picture in mind, it’s time to start breaking it down.
Layer 2: Categorize and Connect

Now it’s time to break the subject into categories—like creating branches on a tree. This helps your brain organize information logically and see connections between ideas.
Example: Studying biology? Group concepts into categories like cells, genetics, and ecosystems.
- Tip: Use headings or labels to group similar ideas. Jot these down in a list or simple diagram to keep track.
With your categories in place, you’re ready to dive into the details that bring them to life.
Layer 3: Master the Details

Once you’ve mapped out the main categories, you’re ready to dive deeper. This is where you learn the nuts and bolts—like formulas, specific techniques, or key terminology. These details make the subject practical and actionable.
Example: In programming, this might mean learning the syntax for loops, conditionals, or functions in your chosen language.
- Tip: Focus on details that clarify the categories from Layer 2. Skip anything that doesn’t add to your understanding.
Now that you’ve mastered the essentials, you can expand your knowledge to include extra material.
Layer 4: Expand Your Horizons

Finally, move on to the extra material—less critical facts, trivia, or edge cases. While these aren’t essential to mastering the subject, they can be useful in specialized discussions or exams.
Example: Learn about rare programming quirks or historical trivia about a language’s development.
- Tip: Spend minimal time here unless it’s necessary for your goals. It’s okay to skim if you’re short on time.
Pro Tips for Better Learning
1. Use Active Recall and Spaced Repetition
Test yourself without looking at notes. Review what you’ve learned at increasing intervals—like after a day, a week, and a month. This strengthens memory by forcing your brain to actively retrieve information.
2. Map It Out
Create visual aids like diagrams or concept maps to clarify relationships between ideas. These are particularly helpful for organizing categories in Layer 2.
3. Teach What You Learn
Explain the subject to someone else as if they’re hearing it for the first time. Teaching exposes any gaps in your understanding and helps reinforce the material.
4. Engage with LLMs and Discuss Concepts
Take advantage of tools like ChatGPT or similar large language models to explore your topic in greater depth. Use these tools to:
- Ask specific questions to clarify confusing points.
- Engage in discussions to simulate real-world applications of the subject.
- Generate examples or analogies that deepen your understanding.Tip: Use LLMs as a study partner, but don’t rely solely on them. Combine these insights with your own critical thinking to develop a well-rounded perspective.
Get Started
Ready to try the Four-Layer Method? Take 15 minutes today to map out the big picture of a topic you’re curious about—what’s it all about, and why does it matter? By building your understanding step by step, you’ll master the subject with less stress and more confidence.
-
 @ 8da249fe:ecc00e09
2025-02-25 01:08:49
@ 8da249fe:ecc00e09
2025-02-25 01:08:49Existem diversas corretoras onde você pode comprar e vender bitcoins e outras moedas. O ideal é sempre escolher empresas idoneas e com boa fama, para isso, antes de ir comprando bitcoin conheça pessoas que usam estas corretoras, veja os depoimentos destas pessoas sobre esta plataforma, isso é bem básico e serve para qualquer coisa.
Geralmente estas exchanges (corretoras) exigem alguns dados pessoais, ou seja, são fontes de bitcoin por KYC. Para pessoas que querem ter bitcoin sem seus dados registrados é necessário a compra peer-to-peer, que é a compra direta por pessoas sem a uma "instituição financeira" mediando a transação.
Dica número 1 : Nunca deixe seus bitcoins armazenados em corretoras.

Apesar do bitcoin ainda não ter nenhum tipo de regulamentação, as corretoras por serem consideradas "instituições financeiras" são reguladas pelo Sistema Financeiro Nacional, sendo vulneráveis as decisões governamentais.
Além disso, as corretoras por movimentarem grandes quantidades de dinheiro, estão vulneráveis ataques hackears que são frequentementes.
Dica número 2: Sempre deposite seus bitcoins em carteiras

As carteiras são locais de armazenamento seguros e alguns tipos com as cold Wallet não há gestão dos seus fundos por intermediários, logo a responsabilidade pelo seu dinheiro é totalmente sua.
Sempre importante guardar e ter uma boa organização quanto as senhas de acesso, pois uma vez que perde não há nenhuma forma de recuperá-la.
Algo que o economista Fernando Roxo fala no YT que concordo plenamente ,é , que não se deve deixar todos os ovos numa cesta só. O que aplico no universo bitcoin que não se deve colocar todos os seus bitcoin em apenas uma carteira. É muito importante dificultar o máximo para os criminosos roubarem, por isso devem ter várias carteiras.
Dica número 3: Entenda que Bitcoin não é investimento, e sim uma solução econômica.

Não desista do bitcoin , só porque ele ocila de valor. O bitcoin não é um investimento a onde se aplica e você tem um lucro. O bitcoin é uma solução em decorrência da desonestidade dos governos que imprimem moedas sem valor agregado.
Este conhecimento é extremamente importante para que não se iluda com promessa de ficar milionário ou algo do tipo. O bitcoin é uma moeda segura que tem o intuito de proteger o mercado financeiro em decorrência da má fé de estados, e também uma arma contra governos.
Dica número 4 : Ajude a comunidade, comercialize em bitcoin.
Quer você seja consumidor ou produtor, faça com que seus fundos estejam em bitcoin. Apesar de estamos engatinhando no mercado há muitas iniciativas como o Bitrefill, maquininhas e software para movimentações em bitcoin que tem facilitado as transações.
Dica número 5: Conheça os termos técnico sobre este universo.
Fique sempre atualizados com os termos da comunidade com KYC, cold wallet, hot wallet, fiat ... Assim você poderá seu um "agente" pró bitcoin e ajudar pessoas simples a entrarem neste universo e ter sua auto custódia e estarem imunes aos desgovernos.
-
 @ 79998141:0f8f1901
2025-01-02 05:04:56
@ 79998141:0f8f1901
2025-01-02 05:04:56Happy new year, Anon.
Thanks for tuning in to whatever this long form post will be. I hope to make these more regular, like journal entries as we travel through "real life" and the Nostrverse together. If I'm making time for this reflective writing, then things are going as planned.
2024 was a wildly transformative year for me for many reasons... there's no way I can possibly fit all of them here. They're not all related to Bitcoin and Nostr- I've got a beautiful life outside of all that which has its own independent arc. My wife and I celebrated 7 years of marriage together, stronger than ever (don't believe that "itch" bullshit). We let go of some negative relationships and embraced some positive ones. We cut some bad habits, and we made some good habits. We worked, we traveled, we saw family, and we partied.
But damn, these two technologies have become a huge part of my life. God willing, this trend will continue until they've both eclipsed my professional capacity through our startup, Conduit BTC.
This was the year I was truly orange pilled. Until late 2023, I had traded (quite profitably) Bitcoin, "crypto", stocks, options, prediction markets and whatever else I could get my hands on that felt undervalued. I did this all in my spare time, grinding out a little financial freedom while I hustled at my fiat ventures to support my little family. I wasn't a true believer- just an opportunist with a knack for spotting where and when a crowd might flock to next. That was right up until I ran face first into Lyn Alden's book "Broken Money".
Something about Lyn's engineer/macro-finance inspired prose clicked with me, lock and key. Total one way function. By the end of the book my laser eyes had burned a hole in my bedroom ceiling. I was all in- and acted accordingly both with my capital and my attention. It wasn't long before I discovered Nostr and dove in here too, falling deep into my current orange and purple polyamorous love affair.
"If you know the enemy and know yourself, you need not fear the result of a hundred battles."
Despite the passion, through studying Bitcoin's criticisms (from the likes of Mike Green and Nassim Taleb) I found a hole in the utopian plot: none of this works without Bitcoin actually being used as money. Worldwide transactions must skyrocket demand for blockspace to keep the network secure/stable for the long term. Besides, if everyday folks aren't using Bitcoin as money then we haven't done shit to make the world a better place. In that world, we've only replaced old masters with new ones. Fuck that.
Whatever I did in this space needed to increase the usage of Bitcoin as money. Simple. This was bigger than passion, this was purpose. I knew that come hell or high water I would dedicate myself to this mission.
Lucky for me I found a partner and best friend in @aceaspades to go on this adventure with. I'm infinitely grateful for him. He's an incredible man who also happens to be an insanely creative and talented software developer. We'd tried for years to find the right project to focus on together, experimenting with all kinds of new techy ideas as they came across our field. Nothing had ever captured our attention like this. This was different. By March of 2024 we had formed a company and gotten to work iterating on how we could leverage these beautiful protocols and open-source tech to create something that served our mission. This is @ConduitBTC.
I've done well in my fiat career executing plans downstream of someone else's creative vision. I've learned the ins and outs of an established ecosystem and found ways to profit from it. I take plans developed by others, compete to win contracts to build them, and execute on them in a cashflow-positive way. I'm bringing this no bullshit blue collar skillset with me to the Nostrverse whether they like it or not.
The adventure we're embarking on now is totally different though. We're charting a new course - totally creative, highly intuitive and extremely speculative towards a future that doesn't exist yet. There are few established norms. The potential is vast but unknown. We're diving into a strange quest to sell a map to an imaginary place and to simultaneously architect its creation (alongside all the amazing builders here doing the same thing). This is insanely exciting to me.
We're barely getting started but a lot has been invested under the surface which will show itself in 2025. We'll be sharing updates in a proper post on @ConduitBTC soon.
As for my personal 2025 resolutions, here they are: - zero alcohol for the entire year (did this in 2019 and had a great year, it's time for a rerun) - more focused presence in the moment: especially with my wife - more self care and prioritized mental/physical health - this includes daily: naps, prayer, self hypnosis or meditation, sweat, and stretching/massaging (overworked in 2024 with a fiat 9-5, a board/advisor role in a fiat business I have equity in, and my newfound passion here. Two serious burn out episodes experienced this year - zero is the only acceptable number of burnouts for long term health and success.) - related to the above: get Conduit some mission-aligned funding partners and leave my fiat 9-5. Grow the Conduit team (have put in a serious amount of my personal capital already to get this going, which will show fruit in the new year... but I am not an island) - more authentic and thoughtful posts on Nostr, with a solid amount of shitposting and organic home grown memes to balance it out... more zaps, more geniune connections and interactions with the curious forward thinking people on here - more IRL Nostr/Bitcoin events - more laughter, more jokes
Enough for now. Cheers to you and yours Anon, may 2025 bring you the magic you've been dreaming of.
-
 @ ed5774ac:45611c5c
2025-02-15 05:38:56
@ ed5774ac:45611c5c
2025-02-15 05:38:56Bitcoin as Collateral for U.S. Debt: A Deep Dive into the Financial Mechanics
The U.S. government’s proposal to declare Bitcoin as a 'strategic reserve' is a calculated move to address its unsustainable debt obligations, but it threatens to undermine Bitcoin’s original purpose as a tool for financial freedom. To fully grasp the implications of this plan, we must first understand the financial mechanics of debt creation, the role of collateral in sustaining debt, and the historical context of the petro-dollar system. Additionally, we must examine how the U.S. and its allies have historically sought new collateral to back their debt, including recent attempts to weaken Russia through the Ukraine conflict.
The Vietnam War and the Collapse of the Gold Standard
The roots of the U.S. debt crisis can be traced back to the Vietnam War. The war created an unsustainable budget deficit, forcing the U.S. to borrow heavily to finance its military operations. By the late 1960s, the U.S. was spending billions of dollars annually on the war, leading to a significant increase in public debt. Foreign creditors, particularly France, began to lose confidence in the U.S. dollar’s ability to maintain its value. In a dramatic move, French President Charles de Gaulle sent warships to New York to demand the conversion of France’s dollar reserves into gold, as per the Bretton Woods Agreement.
This demand exposed the fragility of the U.S. gold reserves. By 1971, President Richard Nixon was forced to suspend the dollar’s convertibility to gold, effectively ending the Bretton Woods system. This move, often referred to as the "Nixon Shock," declared the U.S. bankrupt and transformed the dollar into a fiat currency backed by nothing but trust in the U.S. government. The collapse of the gold standard marked the beginning of the U.S.’s reliance on artificial systems to sustain its debt. With the gold standard gone, the U.S. needed a new way to back its currency and debt—a need that would lead to the creation of the petro-dollar system.
The Petro-Dollar System: A New Collateral for Debt
In the wake of the gold standard’s collapse, the U.S. faced a critical challenge: how to maintain global confidence in the dollar and sustain its ability to issue debt. The suspension of gold convertibility in 1971 left the dollar as a fiat currency—backed by nothing but trust in the U.S. government. To prevent a collapse of the dollar’s dominance and ensure its continued role as the world’s reserve currency, the U.S. needed a new system to artificially create demand for dollars and provide a form of indirect backing for its debt.
The solution came in the form of the petro-dollar system. In the 1970s, the U.S. struck a deal with Saudi Arabia and other OPEC nations to price oil exclusively in U.S. dollars. In exchange, the U.S. offered military protection and economic support. This arrangement created an artificial demand for dollars, as countries needed to hold USD reserves to purchase oil. Additionally, oil-exporting nations reinvested their dollar revenues in U.S. Treasuries, effectively recycling petro-dollars back into the U.S. economy. This recycling of petrodollars provided the U.S. with a steady inflow of capital, allowing it to finance its deficits and maintain low interest rates.
To further bolster the system, the U.S., under the guidance of Henry Kissinger, encouraged OPEC to dramatically increase oil prices in the 1970s. The 1973 oil embargo and subsequent price hikes, masterminded by Kissinger, quadrupled the cost of oil, creating a windfall for oil-exporting nations. These nations, whose wealth surged significantly due to the rising oil prices, reinvested even more heavily in U.S. Treasuries and other dollar-denominated assets. This influx of petrodollars increased demand for U.S. debt, enabling the U.S. to issue more debt at lower interest rates. Additionally, the appreciation in the value of oil—a critical global commodity—provided the U.S. banking sector with the necessary collateral to expand credit generation. Just as a house serves as collateral for a mortgage, enabling banks to create new debt, the rising value of oil boosted the asset values of Western corporations that owned oil reserves or invested in oil infrastructure projects. This increase in asset values allowed these corporations to secure larger loans, providing banks with the collateral needed to expand credit creation and inject more dollars into the economy. However, these price hikes also caused global economic turmoil, disproportionately affecting developing nations. As the cost of energy imports skyrocketed, these nations faced mounting debt burdens, exacerbating their economic struggles and deepening global inequality.
The Unsustainable Debt Crisis and the Search for New Collateral
Fast forward to the present day, and the U.S. finds itself in a familiar yet increasingly precarious position. The 2008 financial crisis and the 2020 pandemic have driven the U.S. government’s debt to unprecedented levels, now exceeding $34 trillion, with a debt-to-GDP ratio surpassing 120%. At the same time, the petro-dollar system—the cornerstone of the dollar’s global dominance—is under significant strain. The rise of alternative currencies and the shifting power dynamics of a multipolar world have led to a decline in the dollar’s role in global trade, particularly in oil transactions. For instance, China now pays Saudi Arabia in yuan for oil imports, while Russia sells its oil and gas in rubles and other non-dollar currencies. This growing defiance of the dollar-dominated system reflects a broader trend toward economic independence, as nations like China and Russia seek to reduce their reliance on the U.S. dollar. As more countries bypass the dollar in trade, the artificial demand for dollars created by the petro-dollar system is eroding, undermining the ability of US to sustain its debt and maintain global financial hegemony.
In search of new collateral to carry on its unsustainable debt levels amid declining demand for the U.S. dollar, the U.S., together with its Western allies—many of whom face similar sovereign debt crises—first attempted to weaken Russia and exploit its vast natural resources as collateral. The U.S. and its NATO allies used Ukraine as a proxy to destabilize Russia, aiming to fragment its economy, colonize its territory, and seize control of its natural resources, estimated to be worth around $75 trillion. By gaining access to these resources, the West could have used them as collateral for the banking sector, enabling massive credit expansion. This, in turn, would have alleviated the sovereign debt crisis threatening both the EU and the U.S. This plan was not unprecedented; it mirrored France’s long-standing exploitation of its former African colonies through the CFA franc system.
For decades, France has maintained economic control over 14 African nations through the CFA franc, a currency pegged to the euro and backed by the French Treasury. Under this system, these African countries are required to deposit 50% of their foreign exchange reserves into the French Treasury, effectively giving France control over their monetary policy and economic sovereignty. This arrangement allows France to use African resources and reserves as implicit collateral to issue debt, keeping its borrowing costs low and ensuring demand for its bonds. In return, African nations are left with limited control over their own economies, forced to prioritize French interests over their own development. This neo-colonial system has enabled France to sustain its financial dominance while perpetuating poverty and dependency in its former colonies.
Just as France’s CFA franc system relies on the economic subjugation of African nations to sustain its financial dominance, the U.S. had hoped to use Russia’s resources as a lifeline for its debt-ridden economy. However, the plan ultimately failed. Russia not only resisted the sweeping economic sanctions imposed by the West but also decisively defeated NATO’s proxy forces in Ukraine, thwarting efforts to fragment its economy and seize control of its $75 trillion in natural resources. This failure left the U.S. and its allies without a new source of collateral to back their unsustainable debt levels. With this plan in ruins, the U.S. has been forced to turn its attention to Bitcoin as a potential new collateral for its unsustainable debt.
Bitcoin as Collateral: The U.S. Government’s Plan
The U.S. government’s plan to declare Bitcoin as a strategic reserve is a modern-day equivalent of the gold standard or petro-dollar system. Here’s how it would work:
-
Declaring Bitcoin as a Strategic Reserve: By officially recognizing Bitcoin as a reserve asset, the U.S. would signal to the world that it views Bitcoin as a store of value akin to gold. This would legitimize Bitcoin in the eyes of institutional investors and central banks.
-
Driving Up Bitcoin’s Price: To make Bitcoin a viable collateral, its price must rise significantly. The U.S. would achieve this by encouraging regulatory clarity, promoting institutional adoption, and creating a state-driven FOMO (fear of missing out). This would mirror the 1970s oil price hikes that bolstered the petro-dollar system.
-
Using Bitcoin to Back Debt: Once Bitcoin’s price reaches a sufficient level, the U.S. could use its Bitcoin reserves as collateral for issuing new debt. This would restore confidence in U.S. Treasuries and allow the government to continue borrowing at low interest rates.
The U.S. government’s goal is clear: to use Bitcoin as a tool to issue more debt and reinforce the dollar’s role as the global reserve currency. By forcing Bitcoin into a store-of-value role, the U.S. would replicate the gold standard’s exploitative dynamics, centralizing control in the hands of large financial institutions and central banks. This would strip Bitcoin of its revolutionary potential and undermine its promise of decentralization. Meanwhile, the dollar—in digital forms like USDT—would remain the primary medium of exchange, further entrenching the parasitic financial system.
Tether plays a critical role in this strategy. As explored in my previous article (here: [https://ersan.substack.com/p/is-tether-a-bitcoin-company]), Tether helps sustaining the current financial system by purchasing U.S. Treasuries, effectively providing life support for the U.S. debt machine during a period of declining demand for dollar-denominated assets. Now, with its plans to issue stablecoins on the Bitcoin blockchain, Tether is positioning itself as a bridge between Bitcoin and the traditional financial system. By issuing USDT on the Lightning Network, Tether could lure the poor in developing nations—who need short-term price stability for their day to day payments and cannot afford Bitcoin’s volatility—into using USDT as their primary medium of exchange. This would not only create an artificial demand for the dollar and extend the life of the parasitic financial system that Bitcoin was designed to dismantle but would also achieve this by exploiting the very people who have been excluded and victimized by the same system—the poor and unbanked in developing nations, whose hard-earned money would be funneled into sustaining the very structures that perpetuate their oppression.
Worse, USDT on Bitcoin could function as a de facto central bank digital currency (CBDC), where all transactions can be monitored and sanctioned by governments at will. For example, Tether’s centralized control over USDT issuance and its ties to traditional financial institutions make it susceptible to government pressure. Authorities could compel Tether to implement KYC (Know Your Customer) rules, freeze accounts, or restrict transactions, effectively turning USDT into a tool of financial surveillance and control. This would trap users in a system where every transaction is subject to government oversight, effectively stripping Bitcoin of its censorship-resistant and decentralized properties—the very features that make it a tool for financial freedom.
In this way, the U.S. government’s push for Bitcoin as a store of value, combined with Tether’s role in promoting USDT as a medium of exchange, creates a two-tiered financial system: one for the wealthy, who can afford to hold Bitcoin as a hedge against inflation, and another for the poor, who are trapped in a tightly controlled, surveilled digital economy. This perpetuates the very inequalities Bitcoin was designed to dismantle, turning it into a tool of oppression rather than liberation.
Conclusion: Prolonging the Parasitic Financial System
The U.S. government’s plan to declare Bitcoin as a strategic reserve is not a step toward financial innovation or freedom—it is a desperate attempt to prolong the life of a parasitic financial system that Bitcoin was created to replace. By co-opting Bitcoin, the U.S. would gain a new tool to issue more debt, enabling it to continue its exploitative practices, including proxy wars, economic sanctions, and the enforcement of a unipolar world order.
The petro-dollar system was built on the exploitation of oil-exporting nations and the global economy. A Bitcoin-backed system would likely follow a similar pattern, with the U.S. using its dominance to manipulate Bitcoin’s price and extract value from the rest of the world. This would allow the U.S. to sustain its current financial system, in which it prints money out of thin air to purchase real-world assets and goods, enriching itself at the expense of other nations.
Bitcoin was designed to dismantle this parasitic system, offering an escape hatch for those excluded from or exploited by traditional financial systems. By declaring Bitcoin a strategic reserve, the U.S. government would destroy Bitcoin’s ultimate purpose, turning it into another instrument of control. This is not a victory for Bitcoin or bitcoiners—it is a tragedy for financial freedom and global equity.
The Bitcoin strategic reserve plan is not progress—it is a regression into the very system Bitcoin was designed to dismantle. As bitcoiners, we must resist this co-option and fight to preserve Bitcoin’s original vision: a decentralized, sovereign, and equitable financial system for all. This means actively working to ensure Bitcoin is used as a medium of exchange, not just a store of value, to fulfill its promise of financial freedom.
-
-
 @ dd664d5e:5633d319
2024-12-29 20:29:03
@ dd664d5e:5633d319
2024-12-29 20:29:03The paparazzi are we

One of the things that bothers me about social media, in general, is that it gives celebrities an air of approachability, that they don't actually offer.
Theoretically, a celebrity could respond to any one of the dozens or even hundreds of people asking them questions or lodging complaints or singing their praises, but they usually only respond very selectively and leave everyone else just sitting there, as a living monument to the ReplyGuy.
And, as a wise man once said, ReplyGuy is a hoe.
Death of a ReplyGuy
This is usually because of time and energy restrictions, but also due to distaste, disdain, or indifference. Regardless of motivation, it is simply the nature of things, when a larger number of people are clamboring for the attention of some particular person.
Ooh, ooh! Can I have the next question?! Would you please address my bug? May I have a microsecond of your time?

Social media (and I include GitHub in this category) ups this game considerably, and potentially turns it all into a dangerous psychological torture, by making us all preoccupied with people who don't interact with us. The most irrational of groupies because we are forever making almost-contact with our stars.
If we can see them talking to one person, we're supposed to feel like they've spoken with all of us. But they haven't. They spoke with someone else, and we were allowed to watch. No different than on television, except that we might be disappointed and eager to return the next day, to renew our futile attempt.
The same intoxicating feeling that playing the lottery elicits. Everyone is a potential winner, but there is only one jackpot. Come back next week. Buy another ticket. This next time, is your time. Promise.
The view from the peanut gallery

It is all an illusion that there is no hierarchy, where there clearly is one. Celebrities of the past had, at least, the decency to remain slightly aloof. But they all want to be one of the Common Folk, now, just as every multi-millionaire aspires to see himself as fundamentally working-class.

All of celebrity social media is a stage, and most of us are merely spectators or commentators, to what is playing on it. This is why, if someone treats me like someone sitting in the peanut gallery, my instinct is to treat them like an actor.
Because, in reality, that is what they are.
-
 @ e3ba5e1a:5e433365
2025-02-04 08:29:00
@ e3ba5e1a:5e433365
2025-02-04 08:29:00President Trump has started rolling out his tariffs, something I blogged about in November. People are talking about these tariffs a lot right now, with many people (correctly) commenting on how consumers will end up with higher prices as a result of these tariffs. While that part is true, I’ve seen a lot of people taking it to the next, incorrect step: that consumers will pay the entirety of the tax. I put up a poll on X to see what people thought, and while the right answer got a lot of votes, it wasn't the winner.

For purposes of this blog post, our ultimate question will be the following:
- Suppose apples currently sell for $1 each in the entire United States.
- There are domestic sellers and foreign sellers of apples, all receiving the same price.
- There are no taxes or tariffs on the purchase of apples.
- The question is: if the US federal government puts a $0.50 import tariff per apple, what will be the change in the following:
- Number of apples bought in the US
- Price paid by buyers for apples in the US
- Post-tax price received by domestic apple producers
- Post-tax price received by foreign apple producers
Before we can answer that question, we need to ask an easier, first question: before instituting the tariff, why do apples cost $1?
And finally, before we dive into the details, let me provide you with the answers to the ultimate question. I recommend you try to guess these answers before reading this, and if you get it wrong, try to understand why:
- The number of apples bought will go down
- The buyers will pay more for each apple they buy, but not the full amount of the tariff
- Domestic apple sellers will receive a higher price per apple
- Foreign apple sellers will receive a lower price per apple, but not lowered by the full amount of the tariff
In other words, regardless of who sends the payment to the government, both taxed parties (domestic buyers and foreign sellers) will absorb some of the costs of the tariff, while domestic sellers will benefit from the protectionism provided by tariffs and be able to sell at a higher price per unit.
Marginal benefit
All of the numbers discussed below are part of a helper Google Sheet I put together for this analysis. Also, apologies about the jagged lines in the charts below, I hadn’t realized before starting on this that there are some difficulties with creating supply and demand charts in Google Sheets.
Let’s say I absolutely love apples, they’re my favorite food. How much would I be willing to pay for a single apple? You might say “$1, that’s the price in the supermarket,” and in many ways you’d be right. If I walk into supermarket A, see apples on sale for $50, and know that I can buy them at supermarket B for $1, I’ll almost certainly leave A and go buy at B.
But that’s not what I mean. What I mean is: how high would the price of apples have to go everywhere so that I’d no longer be willing to buy a single apple? This is a purely personal, subjective opinion. It’s impacted by how much money I have available, other expenses I need to cover, and how much I like apples. But let’s say the number is $5.
How much would I be willing to pay for another apple? Maybe another $5. But how much am I willing to pay for the 1,000th apple? 10,000th? At some point, I’ll get sick of apples, or run out of space to keep the apples, or not be able to eat, cook, and otherwise preserve all those apples before they rot.
The point being: I’ll be progressively willing to spend less and less money for each apple. This form of analysis is called marginal benefit: how much benefit (expressed as dollars I’m willing to spend) will I receive from each apple? This is a downward sloping function: for each additional apple I buy (quantity demanded), the price I’m willing to pay goes down. This is what gives my personal demand curve. And if we aggregate demand curves across all market participants (meaning: everyone interested in buying apples), we end up with something like this:

Assuming no changes in people’s behavior and other conditions in the market, this chart tells us how many apples will be purchased by our buyers at each price point between $0.50 and $5. And ceteris paribus (all else being equal), this will continue to be the demand curve for apples.
Marginal cost
Demand is half the story of economics. The other half is supply, or: how many apples will I sell at each price point? Supply curves are upward sloping: the higher the price, the more a person or company is willing and able to sell a product.
Let’s understand why. Suppose I have an apple orchard. It’s a large property right next to my house. With about 2 minutes of effort, I can walk out of my house, find the nearest tree, pick 5 apples off the tree, and call it a day. 5 apples for 2 minutes of effort is pretty good, right?
Yes, there was all the effort necessary to buy the land, and plant the trees, and water them… and a bunch more than I likely can’t even guess at. We’re going to ignore all of that for our analysis, because for short-term supply-and-demand movement, we can ignore these kinds of sunk costs. One other simplification: in reality, supply curves often start descending before ascending. This accounts for achieving efficiencies of scale after the first number of units purchased. But since both these topics are unneeded for understanding taxes, I won’t go any further.
Anyway, back to my apple orchard. If someone offers me $0.50 per apple, I can do 2 minutes of effort and get $2.50 in revenue, which equates to a $75/hour wage for me. I’m more than happy to pick apples at that price!
However, let’s say someone comes to buy 10,000 apples from me instead. I no longer just walk out to my nearest tree. I’m going to need to get in my truck, drive around, spend the day in the sun, pay for gas, take a day off of my day job (let’s say it pays me $70/hour). The costs go up significantly. Let’s say it takes 5 days to harvest all those apples myself, it costs me $100 in fuel and other expenses, and I lose out on my $70/hour job for 5 days. We end up with:
- Total expenditure: $100 + $70 * 8 hours a day * 5 days \== $2900
- Total revenue: $5000 (10,000 apples at $0.50 each)
- Total profit: $2100
So I’m still willing to sell the apples at this price, but it’s not as attractive as before. And as the number of apples purchased goes up, my costs keep increasing. I’ll need to spend more money on fuel to travel more of my property. At some point I won’t be able to do the work myself anymore, so I’ll need to pay others to work on the farm, and they’ll be slower at picking apples than me (less familiar with the property, less direct motivation, etc.). The point being: at some point, the number of apples can go high enough that the $0.50 price point no longer makes me any money.
This kind of analysis is called marginal cost. It refers to the additional amount of expenditure a seller has to spend in order to produce each additional unit of the good. Marginal costs go up as quantity sold goes up. And like demand curves, if you aggregate this data across all sellers, you get a supply curve like this:

Equilibrium price
We now know, for every price point, how many apples buyers will purchase, and how many apples sellers will sell. Now we find the equilibrium: where the supply and demand curves meet. This point represents where the marginal benefit a buyer would receive from the next buyer would be less than the cost it would take the next seller to make it. Let’s see it in a chart:

You’ll notice that these two graphs cross at the $1 price point, where 63 apples are both demanded (bought by consumers) and supplied (sold by producers). This is our equilibrium price. We also have a visualization of the surplus created by these trades. Everything to the left of the equilibrium point and between the supply and demand curves represents surplus: an area where someone is receiving something of more value than they give. For example:
- When I bought my first apple for $1, but I was willing to spend $5, I made $4 of consumer surplus. The consumer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and above the equilibrium price point.
- When a seller sells his first apple for $1, but it only cost $0.50 to produce it, the seller made $0.50 of producer surplus. The producer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and below the equilibrium price point.
Another way of thinking of surplus is “every time someone got a better price than they would have been willing to take.”
OK, with this in place, we now have enough information to figure out how to price in the tariff, which we’ll treat as a negative externality.
Modeling taxes
Alright, the government has now instituted a $0.50 tariff on every apple sold within the US by a foreign producer. We can generally model taxes by either increasing the marginal cost of each unit sold (shifting the supply curve up), or by decreasing the marginal benefit of each unit bought (shifting the demand curve down). In this case, since only some of the producers will pay the tax, it makes more sense to modify the supply curve.
First, let’s see what happens to the foreign seller-only supply curve when you add in the tariff:

With the tariff in place, for each quantity level, the price at which the seller will sell is $0.50 higher than before the tariff. That makes sense: if I was previously willing to sell my 82nd apple for $3, I would now need to charge $3.50 for that apple to cover the cost of the tariff. We see this as the tariff “pushing up” or “pushing left” the original supply curve.
We can add this new supply curve to our existing (unchanged) supply curve for domestic-only sellers, and we end up with a result like this:

The total supply curve adds up the individual foreign and domestic supply curves. At each price point, we add up the total quantity each group would be willing to sell to determine the total quantity supplied for each price point. Once we have that cumulative supply curve defined, we can produce an updated supply-and-demand chart including the tariff:

As we can see, the equilibrium has shifted:
- The equilibrium price paid by consumers has risen from $1 to $1.20.
- The total number of apples purchased has dropped from 63 apples to 60 apples.
- Consumers therefore received 3 less apples. They spent $72 for these 60 apples, whereas previously they spent $63 for 3 more apples, a definite decrease in consumer surplus.
- Foreign producers sold 36 of those apples (see the raw data in the linked Google Sheet), for a gross revenue of $43.20. However, they also need to pay the tariff to the US government, which accounts for $18, meaning they only receive $25.20 post-tariff. Previously, they sold 42 apples at $1 each with no tariff to be paid, meaning they took home $42.
- Domestic producers sold the remaining 24 apples at $1.20, giving them a revenue of $28.80. Since they don’t pay the tariff, they take home all of that money. By contrast, previously, they sold 21 apples at $1, for a take-home of $21.
- The government receives $0.50 for each of the 60 apples sold, or in other words receives $30 in revenue it wouldn’t have received otherwise.
We could be more specific about the surpluses, and calculate the actual areas for consumer surplus, producer surplus, inefficiency from the tariff, and government revenue from the tariff. But I won’t bother, as those calculations get slightly more involved. Instead, let’s just look at the aggregate outcomes:
- Consumers were unquestionably hurt. Their price paid went up by $0.20 per apple, and received less apples.
- Foreign producers were also hurt. Their price received went down from the original $1 to the new post-tariff price of $1.20, minus the $0.50 tariff. In other words: foreign producers only receive $0.70 per apple now. This hurt can be mitigated by shifting sales to other countries without a tariff, but the pain will exist regardless.
- Domestic producers scored. They can sell less apples and make more revenue doing it.
- And the government walked away with an extra $30.
Hopefully you now see the answer to the original questions. Importantly, while the government imposed a $0.50 tariff, neither side fully absorbed that cost. Consumers paid a bit more, foreign producers received a bit less. The exact details of how that tariff was split across the groups is mediated by the relevant supply and demand curves of each group. If you want to learn more about this, the relevant search term is “price elasticity,” or how much a group’s quantity supplied or demanded will change based on changes in the price.
Other taxes
Most taxes are some kind of a tax on trade. Tariffs on apples is an obvious one. But the same applies to income tax (taxing the worker for the trade of labor for money) or payroll tax (same thing, just taxing the employer instead). Interestingly, you can use the same model for analyzing things like tax incentives. For example, if the government decided to subsidize domestic apple production by giving the domestic producers a $0.50 bonus for each apple they sell, we would end up with a similar kind of analysis, except instead of the foreign supply curve shifting up, we’d see the domestic supply curve shifting down.
And generally speaking, this is what you’ll always see with government involvement in the economy. It will result in disrupting an existing equilibrium, letting the market readjust to a new equilibrium, and incentivization of some behavior, causing some people to benefit and others to lose out. We saw with the apple tariff, domestic producers and the government benefited while others lost.
You can see the reverse though with tax incentives. If I give a tax incentive of providing a deduction (not paying income tax) for preschool, we would end up with:
- Government needs to make up the difference in tax revenue, either by raising taxes on others or printing more money (leading to inflation). Either way, those paying the tax or those holding government debased currency will pay a price.
- Those people who don’t use the preschool deduction will receive no benefit, so they simply pay a cost.
- Those who do use the preschool deduction will end up paying less on tax+preschool than they would have otherwise.
This analysis is fully amoral. It’s not saying whether providing subsidized preschool is a good thing or not, it simply tells you where the costs will be felt, and points out that such government interference in free economic choice does result in inefficiencies in the system. Once you have that knowledge, you’re more well educated on making a decision about whether the costs of government intervention are worth the benefits.
-
 @ a42048d7:26886c32
2024-12-27 16:33:24
@ a42048d7:26886c32
2024-12-27 16:33:24DIY Multisig is complex and 100x more likely to fail than you think if you do it yourself: A few years ago as an experiment I put what was then $2,000 worth Bitcoin into a 2 of 3 DIY multisig with two close family members holding two keys on Tapsigners and myself holding the last key on a Coldcard. My thought was to try and preview how they might deal with self custodied multisig Bitcoin if I died prematurely. After over a year I revisited and asked them to try and do a transaction without me. Just send that single Utxo to a new address in the same wallet, no time limit. It could not possibly have failed harder and shook my belief in multisig. To summarize an extremely painful day, there was a literally 0% chance they would figure this out without help. If this had been for real all our BTC may have been lost forever. Maybe eventually a family friend could’ve helped, but I hadn’t thought of that and hadn’t recommended a trusted BTC knowledge/help source. I had preached self sovereignty and doing it alone and my family tried to respect that. I should’ve given them the contact info of local high integrity bitcoiners I trust implicitly. Regardless of setup type, I highly recommend having a trusted Bitcoiner and online resources your family knows they can turn to to trouble shoot. Bookmark the corresponding BTCSessions video to your BTC self custody setup. Multisig is complicated as hell and hard to understand. Complexity is the enemy when it comes to making sure your BTC isn’t lost and actually gets to your heirs. Many Bitcoiners use a similar setup to this one that failed so badly, and I’m telling you unless you’re married to or gave birth to a seriously hardcore maxi who is extremely tech savvy, the risk your Bitcoin is lost upon your death is unacceptably high. My family is extremely smart but when the pressure of now many thousands of dollars was on the line, the complexity of multisig torpedoed them. Don’t run to an ETF! There are answers: singlesig is awesome. From observing my family I’m confident they would’ve been okay in a singlesig setup. It was the process of signing on separate devices with separate signers, and moving a PSBT around that stymied them. If it had been singlesig they would’ve been okay as one signature on its own was accomplished. Do not besmirch singlesig, it’s incredibly powerful and incredibly resilient. Resilience and simplicity are vastly underrated! In my opinion multisig may increase your theoretical security against attacks that are far less likely to actually happen, e.g. an Oceans Eleven style hack/heist. More likely your heirs will be fighting panic, grief, and stress and forget something you taught them a few years back. If they face an attack it will most likely be social engineering/phishing. They are unlikely to face an elaborate heist that would make a fun movie. While I still maintain it was a mistake for Bitkey to not have a separate screen to verify addresses and other info, overall I believe it’s probably the best normie option for small BTC holdings(yes I do know Bitkey is actually multisig, but the UX is basically a single sig). This incident scared me into realizing the importance of simplicity. Complexity and confusion of heirs/family may be the most under-considered aspects of BTC security. If you’ve made a DIY multisig and your heirs can’t explain why they need all three public keys and what a descriptor is and where it’s backed up, you might as well just go have that boating accident now and get it over with.
Once you get past small amounts of BTC, any reputable hardware wallet in singlesig is amazing security I would encourage folks to consider. In a singlesig setup - For $5 wrench attack concerns, just don’t have your hardware signer or steel backup at your home. You can just have a hot wallet on your phone with a small amount for spending.
If you get a really big stack collaborative multisig is a potentially reasonable middle ground. Just be very thoughtful and brutally honest about your heirs and their BTC and general tech knowledge. Singlesig is still great and you don’t have to move past it, but I get that you also need to sleep at night. If you have truly life changing wealth and are just too uncomfortable with singlesig, maybe consider either 1) Anchorwatch to get the potential benefits of multisig security with the safety net of traditional insurance or 2) Liana wallet where you can use miniscript to effectively have a time locked singlesig spending path to a key held by a third party to help your family recover your funds if they can’t figure it out before that timelock hits, 3) Bitcoin Keeper with their automatic inheritance docs and mini script enabled inheritance key. The automatic inheritance docs are a best in class feature no one else has done yet. Unchained charges $200 for inheritance docs on top of your $250 annual subscription, which imho is beyond ridiculous. 4) Swan vault, I’ve generally soured on most traditional 2 of 3 collaborative multisig because I’ve always found holes either in security (Unchained signed a transaction in only a few hours and has no defined time delay, and still doesn’t support Segwit, seriously guys, wtf?), only support signers that are harder to use and thus tough for noobs, or the overall setups are just too complex. Swan Vault’s focus on keeping it as simple as possible really stands out against competitors that tack on unneeded confusion complexity.
TLDR: For small amounts of BTC use Bitkey. For medium to large amounts use singlesig with a reputable hardware wallet and steel backup. For life changing wealth where you just can no longer stomach sinsglesig maybe also consider Anchorwatch, Bitcoin Keeper, Sean Vault, or Liana. Don’t forget your steel backups! Be safe out there! Do your own research and don’t take my word for it. Just use this as inspiration to consider an alternative point of view. If you’re a family of software engineers, feel free to tell me to go fuck myself.
-
 @ a4a6b584:1e05b95b
2024-12-26 17:13:08
@ a4a6b584:1e05b95b
2024-12-26 17:13:08Step 1: Secure Your Device
- Install an Antivirus Program
Download and install a trusted antivirus program to scan files for potential malware. - For Linux: Calm Antivirus
-
For Windows: CalmWin Antivirus
-
Install a VPN
A VPN is essential for maintaining privacy and security. It will encrypt your internet traffic and hide your IP address. -
Recommended: Mullvad VPN, which accepts Bitcoin for anonymous payment.
-
Install a Torrent Program
You’ll need a torrent client to download files. -
Recommended: Deluge
-
Install the Tor Browser
To access The Pirate Bay or its proxies, you’ll need the privacy-focused Tor Browser.
Step 2: Prepare Your Setup
- Ensure your VPN is running and connected.
- Open the Tor Browser.
- Launch Deluge to have your torrent client ready.
Step 3: Using Tor Go to The Pirate Bay via Onion Service or Find a Trusted Pirate Bay Proxy
Accessing The Pirate Bay directly can be challenging due to restrictions in some regions. Proxy sites often fill the gap. - The Pirate Bay Onion service: http://piratebayo3klnzokct3wt5yyxb2vpebbuyjl7m623iaxmqhsd52coid.onion - Or find a trusted proxy: Use a site like Pirateproxy or a reliable Tor directory for updated lists.
Step 4: Search for Linux Distros
- On The Pirate Bay, navigate to the "OtherOS" category under the Applications section.
- Enter your desired Linux distro in the search bar (e.g., "Ubuntu," "Arch Linux").
Step 5: Select a Torrent
- Filter the Results:
- Look for torrents with the highest seeders (SE) and the fewest leechers (LE).
-
Trusted users are marked with a green skull icon—these are usually safe uploads.
-
Copy the Magnet Link:
- Right-click on the magnet icon next to the trusted torrent and select "Copy Link."
Step 6: Start the Download
- In Deluge, paste the copied magnet link into the “Add Torrent” box.
- Click OK to start the download.
- Monitor the progress until the download completes.
Step 7: Scan the Downloaded File
Once the file is downloaded: 1. Scan for viruses: Right-click the file and use Calm or CalmWin to verify its integrity.
2. If the file passes the scan, it’s ready for use.
Step 8: Manage Your File
- Seed or Remove:
- To help the torrent community, keep seeding the file by leaving it in your torrent client.
-
To stop seeding, right-click the file in Deluge and remove it.
-
Move for Long-Term Storage: Transfer the file to a secure directory for regular use.
Notes on Safety and Ethics
- Verify Legitimacy: Ensure the torrent you are downloading is for an official Linux distribution. Torrents with unusual names or details should be avoided.
- Support the Developers: Consider visiting the official websites of Linux distros (Ubuntu, Arch Linux) to support their work directly.
By following these steps, you can safely and privately download Linux distributions while contributing to the open-source community.
- Install an Antivirus Program
-
 @ d57360cb:4fe7d935
2025-02-24 23:30:38
@ d57360cb:4fe7d935
2025-02-24 23:30:38The moments and events that leave you lost. Shook. In Disbelief.
Those are the moments you need most. They unlock something dormant in you. Feelings you didn't think imaginable. Journeys you thought unlikely to happen.
Paths and roads filled with ups and downs. Uncertainties, roadblocks, long distances of absolutely nothing in sight. Periods of turmoil and absolute stillness.
Don't mistake where you are for the finale.
Embrace life, it gives you character.
-
 @ fd208ee8:0fd927c1
2024-12-26 07:02:59
@ fd208ee8:0fd927c1
2024-12-26 07:02:59I just read this, and found it enlightening.
Jung... notes that intelligence can be seen as problem solving at an everyday level..., whereas creativity may represent problem solving for less common issues
Other studies have used metaphor creation as a creativity measure instead of divergent thinking and a spectrum of CHC components instead of just g and have found much higher relationships between creativity and intelligence than past studies
https://www.mdpi.com/2079-3200/3/3/59
I'm unusually intelligent (Who isn't?), but I'm much more creative, than intelligent, and I think that confuses people. The ability to apply intelligence, to solve completely novel problems, on the fly, is something IQ tests don't even claim to measure. They just claim a correlation.
Creativity requires taking wild, mental leaps out into nothingness; simply trusting that your brain will land you safely. And this is why I've been at the forefront of massive innovation, over and over, but never got rich off of it.
I'm a starving autist.
Zaps are the first time I've ever made money directly, for solving novel problems. Companies don't do this because there is a span of time between providing a solution and the solution being implemented, and the person building the implementation (or their boss) receives all the credit for the existence of the solution. At best, you can hope to get pawned off with a small bonus.
Nobody can remember who came up with the solution, originally, and that person might not even be there, anymore, and probably never filed a patent, and may have no idea that their idea has even been built. They just run across it, later, in a tech magazine or museum, and say, "Well, will you look at that! Someone actually went and built it! Isn't that nice!"
Universities at least had the idea of cementing novel solutions in academic papers, but that: 1) only works if you're an academic, and at a university, 2) is an incredibly slow process, not appropriate for a truly innovative field, 3) leads to manifestations of perverse incentives and biased research frameworks, coming from 'publish or perish' policies.
But I think long-form notes and zaps solve for this problem. #Alexandria, especially, is being built to cater to this long-suffering class of chronic underachievers. It leaves a written, public, time-stamped record of Clever Ideas We Have Had.
Because they are clever, the ideas. And we have had them.
-
 @ 8bad797a:8461b4bc
2025-02-24 20:33:57
@ 8bad797a:8461b4bc
2025-02-24 20:33:57This time from a laptop computer via Highlighter, from which the Merry Frankster can post long form content. Be afraid. Be very afraid.
-
 @ 6e468422:15deee93
2024-12-21 19:25:26
@ 6e468422:15deee93
2024-12-21 19:25:26We didn't hear them land on earth, nor did we see them. The spores were not visible to the naked eye. Like dust particles, they softly fell, unhindered, through our atmosphere, covering the earth. It took us a while to realize that something extraordinary was happening on our planet. In most places, the mushrooms didn't grow at all. The conditions weren't right. In some places—mostly rocky places—they grew large enough to be noticeable. People all over the world posted pictures online. "White eggs," they called them. It took a bit until botanists and mycologists took note. Most didn't realize that we were dealing with a species unknown to us.
We aren't sure who sent them. We aren't even sure if there is a "who" behind the spores. But once the first portals opened up, we learned that these mushrooms aren't just a quirk of biology. The portals were small at first—minuscule, even. Like a pinhole camera, we were able to glimpse through, but we couldn't make out much. We were only able to see colors and textures if the conditions were right. We weren't sure what we were looking at.
We still don't understand why some mushrooms open up, and some don't. Most don't. What we do know is that they like colder climates and high elevations. What we also know is that the portals don't stay open for long. Like all mushrooms, the flush only lasts for a week or two. When a portal opens, it looks like the mushroom is eating a hole into itself at first. But the hole grows, and what starts as a shimmer behind a grey film turns into a clear picture as the egg ripens. When conditions are right, portals will remain stable for up to three days. Once the fruit withers, the portal closes, and the mushroom decays.
The eggs grew bigger year over year. And with it, the portals. Soon enough, the portals were big enough to stick your finger through. And that's when things started to get weird...
-
 @ 9e69e420:d12360c2
2025-02-01 11:16:04
@ 9e69e420:d12360c2
2025-02-01 11:16:04Federal employees must remove pronouns from email signatures by the end of the day. This directive comes from internal memos tied to two executive orders signed by Donald Trump. The orders target diversity and equity programs within the government.

CDC, Department of Transportation, and Department of Energy employees were affected. Staff were instructed to make changes in line with revised policy prohibiting certain language.
One CDC employee shared frustration, stating, “In my decade-plus years at CDC, I've never been told what I can and can't put in my email signature.” The directive is part of a broader effort to eliminate DEI initiatives from federal discourse.
-
 @ fd208ee8:0fd927c1
2024-12-20 06:58:48
@ fd208ee8:0fd927c1
2024-12-20 06:58:48When the shit just don't work
Most open-source software is now so badly written and sloppily-maintained, that it's malware.
That's why the governments are getting involved. They try using OS, to save money and improve quality (and to market themselves as "hip"), and then it blows up their system or opens them up to hackers.
Now, they're pissed and want support (but the dev with the handle SucksToBeYou has disappeared) or someone to sue, but most OS projects have no identifiable entity behind them. Even well-known anon devs are often groups of anons or accounts that change hands.
The software cracks have moved on
There is simply no evidence that OS alone produces higher-quality software. The reason it seemed that way, at the beginning, was because of the caliber of the developers working on the projects, and the limited number of projects. This resulted in experienced people actively reviewing each others' code.
OS used to be something the elite engaged in, but it's mostly beginners practicing in public, now. That's why there are now millions of OS projects, happily offered for free, but almost all of them are garbage. The people now building OS usually aren't capable of reviewing other people's code, and they're producing worse products than ChatGPT could. Their software has no customers because it has no market value.
If everything is OS, then nothing is.
Another paradigm-changer is that all software is de facto OS, now that we can quickly reverse-engineer code with AI. That means the focus is no longer on OS/not-OS, but on the accountability and reputation of the builders.
It is, once again, a question of trust. We have come full-circle.
-
 @ a1c19849:daacbb52
2025-02-24 19:30:09
@ a1c19849:daacbb52
2025-02-24 19:30:09Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 4 hours
Ingredients
- 1kg of chicken thighs
- 3 large onions
- 1 tablespoon garlic powder
- 2 tablespoons brown sugar
- 1.5 dl Ketjap Medja
- 0.5 liter chicken broth
- Pepper
- Salt
- Nutmeg
Directions
- Cut the onions and sauté them
- Add the chicken thighs in pieces and bake for a few minutes
- Add the garlic powder and the brown sugar and bake for a short time
- Add the ketjap media and the chicken broth
- Add some salt and pepper and nutmeg and let it simmer for 3 to 4 hours
- Make sure all the moist evaporates but make sure it doesn’t get too dry. Otherwise add some extra chicken broth
- Bon appetit!
-
 @ 6e0ea5d6:0327f353
2025-02-24 19:29:02
@ 6e0ea5d6:0327f353
2025-02-24 19:29:02Of all the people you should fear, fear most the peaceful man in situations where anyone else would be aggressive. The strongest man is the one who masters his emotions in moments of rage and fury—who, even in anger, does not destroy everything around him, including himself.
Remember: no man truly knows how evil he can be until he strives to be good in a corrupt world and, for that, is crushed by it.
Anxiety makes a man suffer even before there is a concrete reason. The mere act of anticipating pain makes him feel it in its full intensity, even if it never materializes. On the other hand, anxiety leads to rash actions, driven by impulse or anger. And these decisions, in the end, can destroy him.
The most harmful choices are usually made under stress, rage, or passion. Anxiety, in turn, is a formidable adversary, difficult to tame. Controlling it requires constant and gradual training. The key is to balance expectations—facing the future with serenity rather than allowing worries to corrode the present. Sometimes, it is necessary to abandon the life we planned to face the life that awaits us. Instead of acting impulsively in moments of deep stress, learn to reflect rationally on all possibilities before taking action.
I recognize that, in theory, this advice is easy to give. Sono d’accordo, I know how difficult it is in daily life. But listen well: do not let your actions be driven by impulsiveness. Remember, stubbornness combined with anxiety is a direct path to a pit of regrets.
Stubbornness, unlike persistence, makes a man insist on mistakes or ignore wise counsel. It forces him to act against logic, preventing him from learning from failures and reevaluating decisions. It is a silent source of suffering, robbing him of opportunities for change and growth.
Just as a river reaches its destination by adapting to the course it encounters, a wise man must seek new approaches rather than persist in the same mistakes. Adapting, learning, and changing course are the keys to reaching one’s true destiny.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ a1c19849:daacbb52
2025-02-24 19:19:16
@ a1c19849:daacbb52
2025-02-24 19:19:16Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 4 hours
Ingredients
- 1kg of chicken thighs
- 3 large onions
- 1 tablespoon garlic powder
- 2 tablespoons brown sugar
- 1.5 dl Ketjap Medja
- 0.5 liter chicken broth
- Pepper
- Salt
- Nutmeg
Directions
- Cut the onions and sauté them
- Add the chicken thighs in pieces and bake for a few minutes
- Add the garlic powder and the brown sugar and bake for a short time
- Add the ketjap media and the chicken broth
- Add some salt and pepper and nutmeg and let it simmer for 3 to 4 hours
- Make sure all the moist evaporates but make sure it doesn’t get too dry. Otherwise add some extra chicken broth
- Bon appetit!
-
 @ 97c70a44:ad98e322
2025-01-30 17:15:37
@ 97c70a44:ad98e322
2025-01-30 17:15:37There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test.
In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go.
It uses nostr
The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol.
Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key.
In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along.
In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim.
It leverages nostr
Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app".
This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back.
Some examples might include:
- Using nostr signers to encrypt or sign data, and then store that data on a proprietary server.
- Using nostr relays as a kind of low-code backend, but using proprietary event payloads.
- Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you.
An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem.
In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering.
It complements nostr
Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role.
One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense.
Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)?
A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs.
To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen.
It embodies nostr
Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate.
This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product?
To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the protocol, while apps that benefit nostr exclusively via network effect are integrated into nostr the network. An app that does both things is working in symbiosis with nostr as a whole.
An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem:
- In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors.
- In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for.
Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency as nostr users.
If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states:
Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions.
These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers.
As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria.
Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type".
To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well,
- There is a spec for forms and responses, which means that...
- Multiple clients can implement the same data format, allowing for credible exit and user choice, even of...
- Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does...
- Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to...
- Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost".
Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr.
It supports nostr
Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually).
This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content?
In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together.
A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own.
So while I might hesitate to call many of these things "apps", they are certainly "nostr".
Appendix: it smells like a NINO
So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr.
You app might be a NINO if:
- There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind)
- There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository)
- Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr
- Your NIP relies on trusted third (or first) parties
- There's only one implementation of your NIP (yours)
- Your core value proposition doesn't depend on relays, events, or nostr identities
- One or more relay urls are hard-coded into the source code
- Your app depends on a specific relay implementation to work (ahem, relay29)
- You don't validate event signatures
- You don't publish events to relays you don't control
- You don't read events from relays you don't control
- You use legacy web services to solve problems, rather than nostr-native solutions
- You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app
- You don't use NIP 89 to discover clients and services
- You haven't published a NIP 89 listing for your app
- You don't leverage your users' web of trust for filtering out spam
- You don't respect your users' mute lists
- You try to "own" your users' data
Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product.
If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation:
- Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine.
- Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc.
- Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats.
- Think your idea is a good one? Talk to other devs or open a PR to the nips repo. No one can adopt your NIP if they don't know about it.
- Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated.
- Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask!
I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV.
-
 @ 7ed7d5c3:6927e200
2024-12-18 00:56:48
@ 7ed7d5c3:6927e200
2024-12-18 00:56:48There was a time when we dared not rustle a whisper. But now we write and read samizdat and, congregating in the smoking rooms of research institutes, heartily complain to each other of all they are muddling up, of all they are dragging us into! There’s that unnecessary bravado around our ventures into space, against the backdrop of ruin and poverty at home; and the buttressing of distant savage regimes; and the kindling of civil wars; and the ill-thought-out cultivation of Mao Zedong (at our expense to boot)—in the end we’ll be the ones sent out against him, and we’ll have to go, what other option will there be? And they put whomever they want on trial, and brand the healthy as mentally ill—and it is always “they,” while we are—helpless.
We are approaching the brink; already a universal spiritual demise is upon us; a physical one is about to flare up and engulf us and our children, while we continue to smile sheepishly and babble:
“But what can we do to stop it? We haven’t the strength.”
We have so hopelessly ceded our humanity that for the modest handouts of today we are ready to surrender up all principles, our soul, all the labors of our ancestors, all the prospects of our descendants—anything to avoid disrupting our meager existence. We have lost our strength, our pride, our passion. We do not even fear a common nuclear death, do not fear a third world war (perhaps we’ll hide away in some crevice), but fear only to take a civic stance! We hope only not to stray from the herd, not to set out on our own, and risk suddenly having to make do without the white bread, the hot water heater, a Moscow residency permit.
We have internalized well the lessons drummed into us by the state; we are forever content and comfortable with its premise: we cannot escape the environment, the social conditions; they shape us, “being determines consciousness.” What have we to do with this? We can do nothing.
But we can do—everything!—even if we comfort and lie to ourselves that this is not so. It is not “they” who are guilty of everything, but we ourselves, only we!
Some will counter: But really, there is nothing to be done! Our mouths are gagged, no one listens to us, no one asks us. How can we make them listen to us?
To make them reconsider—is impossible.
The natural thing would be simply not to reelect them, but there are no re-elections in our country.
In the West they have strikes, protest marches, but we are too cowed, too scared: How does one just give up one’s job, just go out onto the street?
All the other fateful means resorted to over the last century of Russia’s bitter history are even less fitting for us today—true, let’s not fall back on them! Today, when all the axes have hewn what they hacked, when all that was sown has borne fruit, we can see how lost, how drugged were those conceited youths who sought, through terror, bloody uprising, and civil war, to make the country just and content. No thank you, fathers of enlightenment! We now know that the vileness of the means begets the vileness of the result. Let our hands be clean!
So has the circle closed? So is there indeed no way out? So the only thing left to do is wait inertly: What if something just happens by itself?
But it will never come unstuck by itself, if we all, every day, continue to acknowledge, glorify, and strengthen it, if we do not, at the least, recoil from its most vulnerable point.
From lies.
When violence bursts onto the peaceful human condition, its face is flush with self-assurance, it displays on its banner and proclaims: “I am Violence! Make way, step aside, I will crush you!” But violence ages swiftly, a few years pass—and it is no longer sure of itself. To prop itself up, to appear decent, it will without fail call forth its ally—Lies. For violence has nothing to cover itself with but lies, and lies can only persist through violence. And it is not every day and not on every shoulder that violence brings down its heavy hand: It demands of us only a submission to lies, a daily participation in deceit—and this suffices as our fealty.
And therein we find, neglected by us, the simplest, the most accessible key to our liberation: a personal nonparticipation in lies! Even if all is covered by lies, even if all is under their rule, let us resist in the smallest way: Let their rule hold not through me!
And this is the way to break out of the imaginary encirclement of our inertness, the easiest way for us and the most devastating for the lies. For when people renounce lies, lies simply cease to exist. Like parasites, they can only survive when attached to a person.
We are not called upon to step out onto the square and shout out the truth, to say out loud what we think—this is scary, we are not ready. But let us at least refuse to say what we do not think!
This is the way, then, the easiest and most accessible for us given our deep-seated organic cowardice, much easier than (it’s scary even to utter the words) civil disobedience à la Gandhi.
Our way must be: Never knowingly support lies! Having understood where the lies begin (and many see this line differently)—step back from that gangrenous edge! Let us not glue back the flaking scales of the Ideology, not gather back its crumbling bones, nor patch together its decomposing garb, and we will be amazed how swiftly and helplessly the lies will fall away, and that which is destined to be naked will be exposed as such to the world.
And thus, overcoming our timidity, let each man choose: Will he remain a witting servant of the lies (needless to say, not due to natural predisposition, but in order to provide a living for the family, to rear the children in the spirit of lies!), or has the time come for him to stand straight as an honest man, worthy of the respect of his children and contemporaries? And from that day onward he:
· Will not write, sign, nor publish in any way, a single line distorting, so far as he can see, the truth;
· Will not utter such a line in private or in public conversation, nor read it from a crib sheet, nor speak it in the role of educator, canvasser, teacher, actor;
· Will not in painting, sculpture, photograph, technology, or music depict, support, or broadcast a single false thought, a single distortion of the truth as he discerns it;
· Will not cite in writing or in speech a single “guiding” quote for gratification, insurance, for his success at work, unless he fully shares the cited thought and believes that it fits the context precisely;
· Will not be forced to a demonstration or a rally if it runs counter to his desire and his will; will not take up and raise a banner or slogan in which he does not fully believe;
· Will not raise a hand in vote for a proposal which he does not sincerely support; will not vote openly or in secret ballot for a candidate whom he deems dubious or unworthy;
· Will not be impelled to a meeting where a forced and distorted discussion is expected to take place;
· Will at once walk out from a session, meeting, lecture, play, or film as soon as he hears the speaker utter a lie, ideological drivel, or shameless propaganda;
· Will not subscribe to, nor buy in retail, a newspaper or journal that distorts or hides the underlying facts.
This is by no means an exhaustive list of the possible and necessary ways of evading lies. But he who begins to cleanse himself will, with a cleansed eye, easily discern yet other opportunities.
Yes, at first it will not be fair. Someone will have to temporarily lose his job. For the young who seek to live by truth, this will at first severely complicate life, for their tests and quizzes, too, are stuffed with lies, and so choices will have to be made. But there is no loophole left for anyone who seeks to be honest: Not even for a day, not even in the safest technical occupations can he avoid even a single one of the listed choices—to be made in favor of either truth or lies, in favor of spiritual independence or spiritual servility. And as for him who lacks the courage to defend even his own soul: Let him not brag of his progressive views, boast of his status as an academician or a recognized artist, a distinguished citizen or general. Let him say to himself plainly: I am cattle, I am a coward, I seek only warmth and to eat my fill.
For us, who have grown staid over time, even this most moderate path of resistance will be not be easy to set out upon. But how much easier it is than self-immolation or even a hunger strike: Flames will not engulf your body, your eyes will not pop out from the heat, and your family will always have at least a piece of black bread to wash down with a glass of clear water.
Betrayed and deceived by us, did not a great European people—the Czechoslovaks—show us how one can stand down the tanks with bared chest alone, as long as inside it beats a worthy heart?
It will not be an easy path, perhaps, but it is the easiest among those that lie before us. Not an easy choice for the body, but the only one for the soul. No, not an easy path, but then we already have among us people, dozens even, who have for years abided by all these rules, who live by the truth.
And so: We need not be the first to set out on this path, Ours is but to join! The more of us set out together, the thicker our ranks, the easier and shorter will this path be for us all! If we become thousands—they will not cope, they will be unable to touch us. If we will grow to tens of thousands—we will not recognize our country!
But if we shrink away, then let us cease complaining that someone does not let us draw breath—we do it to ourselves! Let us then cower and hunker down, while our comrades the biologists bring closer the day when our thoughts can be read and our genes altered.
And if from this also we shrink away, then we are worthless, hopeless, and it is of us that Pushkin asks with scorn:
Why offer herds their liberation?
............................. Their heritage each generation
The yoke with jingles, and the whip.February 12, 1974
—translated from the Russian by Yermolai Solzhenitsyn
-
 @ c48e29f0:26e14c11
2024-12-17 16:33:04
@ c48e29f0:26e14c11
2024-12-17 16:33:04titcoin
Rename Bitcoin to "Titcoin" and sats to "tits."
Redefinition of Bitcoin into “Titcoin” and redefinition of sats into “tits” using that as the Unit Base of Denomination.
TitHub repository available here: https://github.com/WalkerAmerica/titcoin
Abstract
This BIP proposes redefining the commonly recognized "bitcoin" and “sats” units so that what was previously known “bitcoin” becomes “titcoin” and what was previously known as “sats,” the smallest indivisible unit, becomes “tits.” The “Bitcoin” Network will be renamed to the “Titcoin” Network. Under this proposal, one tit is defined as that smallest unit, eliminating the need for decimal places, and 100,000,000 tits is defined as a titcoin. By making tits the standard measure, this BIP aims to simplify user comprehension, reduce confusion, and align on-chain values directly with their displayed representation.
Also, by aligning Bitcoin's brand with live-giving tits, we will supercharge adoption and inject humor into financial sovereignty. After all, every baby came into this world sucking on tits.
Under this BIP: - Internally, the smallest indivisible unit remains unchanged. - With this proposal, "1 tit" equals that smallest unit. - What was previously referred to as "1 BTC" now corresponds to 100 million tits. - Satoshis are permanently eliminated.
Addressing the “Buttcoin” BIP:
Not much time need be wasted addressing the catastrophic “Button” BIP proposed by Rockstar Dev, but two points bear emphasizing:
- “Butts” is shitcoin-adjacent terminology (where does shit come from? Exactly…)
- Butts give you poop. Tits give you milk.
Case closed.
Motivation
Bitcoin's branding is boring. Worse yet, critics think Bitcoin is already "a joke," so let’s own it, let's: Make Bitcoin Funny Again. Laughter is universal, irresistible, and much cheaper than marketing agencies and product roadmaps. Besides, basically everyone either has tits or likes tits. Additionally, renaming Bitcoin as “Titcoin” makes the common trope of “Bitcoin BROS” sound even more stupid. “Titcoin Bros”? Get a life, man…
By rebranding Bitcoin to Titcoin (.)(.), we achieve several key goals:
1. Haters Become Users: People like tits. Tits give nourishment to babies. They can stack tits instead of just making fun of them. Adoption skyrockets as trolls turn into tit hodlers.
2. Memetic Power: The word “tit” is both universally funny and ageless. “Send me 10 tits” is instantly iconic. “Nice tits” is a great compliment. “That’s gonna cost you a pair of tits” is hilarious. Try saying that without smiling. You can’t. (.)(.)
3. Simplifying Denominations: Decimals are a blight on humanity. 0.00000001 BTC? Kill it. Under the Titcoin Standard:
- 1 Titcoin = 100,000,000 tits.
- Satoshis are gone. Forever. If you see Satoshi on the road, kill him - just like in Zen, where the teacher becomes the barrier. We transcend satoshis and achieve financial enlightenment.
4. Aligning with the Ledger: Bitcoin’s base unit was always integers, but now they’re funny integers. No more fractions, decimals, or math anxiety. Just tits. (.)(.)
5. Adoption via Humor: Titcoin lowers Bitcoin's intimidation factor. Newbies will feel at ease buying tits instead of serious-sounding fractions of BTC. Tits > Decimals.
Specification
Terminology Redefinitions: - "Bitcoin" → "Titcoin" (.)(.) - "BTC" → "TIT" (ISO-friendly and hilarious) - Satoshis → Gone. Eliminated. Defeated.
Example:
- Old: "I’ll send you 0.00010000 BTC."
- New: "I’ll send you 10,000 tits (.)(.)."
Wallet balances would display as:
- "You have 1,000,000 tits" instead of some boring fractional BTC amount.
Adoption Strategy
1. Memes First: Flood Twitter, Reddit, and Telegram with memes. Start with “Hodl your tits” and “Stack tits”.
2. Titcoin Podcast: There is already a podcast called “Titcoin Podcast” (which many people are saying is the fastest-growing Bitcoin (Titcoin) podcast in the world). Titcoin Podcast will be a driving force in the adoption of the Titcoin Standard. (.)(.)
Nostr: https://primal.net/titcoin
X: https://x.com/titcoinpodcast
Web: http://titcoin.org
3. Kill Satoshis: Developers MUST remove all references to satoshis. Replace satoshis in GUIs, APIs, and block explorers with tits. Satoshis were a stepping stone - it’s time to let go.
4. Emoji Standardization: Use the (.)(.) emoji universally to denote tits.
Rationale
1. Usability & Clarity: "Decimals are for nerds. Tits are for everyone." A common currency for humans should be easy to use, funny, and integer-based.
2. Appealing to Critics: Bitcoin has endured years of attacks from all sides. By adopting the Titcoin Standard, we turn anyone who doesn’t like Titcoin into a tit-hating bigot. It’s an elegant financial counterattack. Additionally, everyone always says “we need more women in Bitcoin,” and now women will feel more represented by Titcoin, because they have tits. (.)(.)
3. Transcending Satoshis: Satoshis served us well, but their time is over. True enlightenment comes when we abandon decimals, satoshis, and arbitrary denominations. If you meet Satoshi on the road, kill him.
4. Memetic Durability: Everyone loves a good tit joke. It’s timeless.
Backward Compatibility
There is no backward compatibility because Titcoin is the future. Applications must hard fork their UI to replace all references to Bitcoin and BTC with Titcoin and TIT.
Implementation Timeline
- Phase 1 (1 month): Meme dissemination. Every wallet dev team is required to add (.)(.) emoji support.
- Phase 2 (3 months): Exchanges rebrand BTC tickers to tit. Nostr zaps tits into hyperspace.
- Phase 3 (6 months): Michael Saylor announces MicroStrategy now stacked 10 trillion tits, declaring it the superior currency. ETFs follow suit, ensuring Wall Street hodls tits en masse. Banks allow tit transfers via SWIFT.
Test Vectors
- Old: 1.00000000 BTC → New: 100,000,000 tits (.)(.)
- Old: 0.00000001 BTC → New: 1 tit (.)(.)
- Old: 0.001 BTC → New: 100,000 tits (.)(.)
Future-Proofing
Tits ensure we have infinite memes for infinite money.
Example Phrases for the Future: - "Better hodl on to your tits." - "This is the Titcoin Standard." - "I’m sending you tits." - “I’ve never seen so many tits!” - “That’s the million tit question.” - “We need more women in Titcoin.” - “I’m a Titcoin Maximalist.” - “Nice tits!” - “I love tits.”
Conclusion
By renaming Bitcoin to Titcoin and adopting a whole-number unit display, we align memetic dominance with financial sovereignty. Haters become adopters. Tits become wealth. And the world gets a little bit funnier. (.)(.)
Let’s hodl our tits and watch the world follow.
Copyright:
This BIP is licensed under CC-🫱(.)(.)🫲-1.0 and the eternal blessing of tit (.)(.) memes.
-
 @ 9e69e420:d12360c2
2025-01-30 12:23:04
@ 9e69e420:d12360c2
2025-01-30 12:23:04Tech stocks have taken a hit globally after China's DeepSeek launched a competitive AI chatbot at a much lower cost than US counterparts. This has stirred market fears of a $1.2 trillion loss across tech companies when trading opens in New York.
DeepSeek’s chatbot quickly topped download charts and surprised experts with its capabilities, developed for only $5.6 million.
The Nasdaq dropped over 3% in premarket trading, with major firms like Nvidia falling more than 10%. SoftBank also saw losses shortly after investing in a significant US AI venture.
Venture capitalist Marc Andreessen called it “AI’s Sputnik moment,” highlighting its potential impact on the industry.
![] (https://www.telegraph.co.uk/content/dam/business/2025/01/27/TELEMMGLPICT000409807198_17379939060750_trans_NvBQzQNjv4BqgsaO8O78rhmZrDxTlQBjdGLvJF5WfpqnBZShRL_tOZw.jpeg)
-
 @ dd664d5e:5633d319
2024-12-14 15:25:56
@ dd664d5e:5633d319
2024-12-14 15:25:56
Christmas season hasn't actually started, yet, in Roman #Catholic Germany. We're in Advent until the evening of the 24th of December, at which point Christmas begins (with the Nativity, at Vespers), and continues on for 40 days until Mariä Lichtmess (Presentation of Christ in the temple) on February 2nd.

It's 40 days because that's how long the post-partum isolation is, before women were allowed back into the temple (after a ritual cleansing).

That is the day when we put away all of the Christmas decorations and bless the candles, for the next year. (Hence, the British name "Candlemas".) It used to also be when household staff would get paid their cash wages and could change employer. And it is the day precisely in the middle of winter.

Between Christmas Eve and Candlemas are many celebrations, concluding with the Twelfth Night called Epiphany or Theophany. This is the day some Orthodox celebrate Christ's baptism, so traditions rotate around blessing of waters.

The Monday after Epiphany was the start of the farming season, in England, so that Sunday all of the ploughs were blessed, but the practice has largely died out.

Our local tradition is for the altar servers to dress as the wise men and go door-to-door, carrying their star and looking for the Baby Jesus, who is rumored to be lying in a manger.

They collect cash gifts and chocolates, along the way, and leave the generous their powerful blessing, written over the door. The famous 20 * C + M + B * 25 blessing means "Christus mansionem benedicat" (Christ, bless this house), or "Caspar, Melchior, Balthasar" (the names of the three kings), depending upon who you ask.
They offer the cash to the Baby Jesus (once they find him in the church's Nativity scene), but eat the sweets, themselves. It is one of the biggest donation-collections in the world, called the "Sternsinger" (star singers). The money goes from the German children, to help children elsewhere, and they collect around €45 million in cash and coins, every year.

As an interesting aside:
The American "groundhog day", derives from one of the old farmers' sayings about Candlemas, brought over by the Pennsylvania Dutch. It says, that if the badger comes out of his hole and sees his shadow, then it'll remain cold for 4 more weeks. When they moved to the USA, they didn't have any badgers around, so they switched to groundhogs, as they also hibernate in winter.
-
 @ 6f7db55a:985d8b25
2025-02-14 21:23:57
@ 6f7db55a:985d8b25
2025-02-14 21:23:57This article will be basic instructions for extreme normies (I say that lovingly), or anyone looking to get started with using zap.stream and sharing to nostr.
EQUIPMENT Getting started is incredibly easy and your equipment needs are miniscule.
An old desktop or laptop running Linux, MacOs, or Windows made in the passed 15yrs should do. Im currently using and old Dell Latitude E5430 with an Intel i5-3210M with 32Gigs of ram and 250GB hard drive. Technically, you go as low as using a Raspberry Pi 4B+ running Owncast, but Ill save that so a future tutorial.
Let's get started.
ON YOUR COMPUTER You'll need to install OBS (open broaster software). OBS is the go-to for streaming to social media. There are tons of YouTube videos on it's function. WE, however, will only be doing the basics to get us up and running.
First, go to https://obsproject.com/

Once on the OBS site, choose the correct download for you system. Linux, MacOs or Windows. Download (remember where you downloaded the file to). Go there and install your download. You may have to enter your password to install on your particular operating system. This is normal.
Once you've installed OBS, open the application. It should look something like this...

For our purposes, we will be in studio mode. Locate the 'Studio Mode' button on the right lower-hand side of the screen, and click it.

You'll see the screen split like in the image above. The left-side is from your desktop, and the right-side is what your broadcast will look like.
Next, we go to settings. The 'Settings' button is located right below the 'Studio Mode" button.

Now we're in settings and you should see something like this...

Now locate stream in the right-hand menu. It should be the second in the list. Click it.

Once in the stream section, go to 'Service' and in the right-hand drop-down, find and select 'Custom...' from the drop-down menu.

Remeber where this is because we'll need to come back to it, shortly.
ZAPSTREAM We need our streamkey credentials from Zapstream. Go to https://zap.stream. Then, go to your dashboard.

Located on the lower right-hand side is the Server URL and Stream Key. You'll need to copy/paste this in OBS.

You may have to generate new keys, if they aren't already there. This is normal. If you're interested in multi-streaming (That's where you broadcast to multiple social media platforms all at once), youll need the server URL and streamkeys from each. You'll place them in their respective forms in Zapstream's 'Stream Forwarding" section.

Use the custom form, if the platform you want to stream to isn't listed.
*Side-Note: remember that you can use your nostr identity across multiple nostr client applications. So when your login for Amethyst, as an example, could be used when you login to zapstream. Also, i would suggest using Alby's browser extension. It makes it much easier to fund your stream, as well as receive zaps. *
Now, BACK TO OBS... With Stream URL and Key in hand, paste them in the 'Stream" section of OBS' settings. Service [Custom...] Server [Server URL] StreamKey [Your zapstream stream key]

After you've entered all your streaming credentials, click 'OK' at the bottom, on the right-hand side.
WHAT'S NEXT? Let's setup your first stream from OBS. First we need to choose a source. Your source is your input device. It can be your webcam, your mic, your monitor, or any particular window on your screen. assuming you're an absolute beginner, we're going to use the source 'Window Capture (Xcomposite)'.

Now, open your source file. We'll use a video source called 'grannyhiphop.mp4'. In your case it can be whatever you want to stream; Just be sure to select the proper source.

Double-click on 'Window Capture' in your sources list. In the pop-up window, select your file from the 'Window' drop-down menu.


You should see something like this...

Working in the left display of OBS, we will adjust the video by left-click, hold and drag the bottom corner, so that it takes up the whole display.

In order to adjust the right-side display ( the broadcast side), we need to manipulate the video source by changing it's size.

This may take some time to adjust the size. This is normal. What I've found to help is, after every adjustment, I click the 'Fade (300ms)' button. I have no idea why it helps, but it does, lol.

Finally, after getting everything to look the way you want, you click the 'Start Stream' button.

BACK TO ZAPSTREAM Now, we go back to zapstream to check to see if our stream is up. It may take a few moments to update. You may even need to refresh the page. This is normal.
 STREAMS UP!!!
STREAMS UP!!!A few things, in closing. You'll notice that your dashbooard has changed. It'll show current stream time, how much time you have left (according to your funding source), who's zapped you with how much theyve zapped, the ability to post a note about your stream (to both nostr and twitter), and it shows your chatbox with your listeners. There are also a raid feature, stream settings (where you can title & tag your stream). You can 'topup' your funding for your stream. As well as, see your current balance.
You did a great and If you ever need more help, just use the tag #asknostr in your note. There are alway nostriches willing to help.
STAY AWESOME!!!
npub: nostr:npub1rsvhkyk2nnsyzkmsuaq9h9ms7rkxhn8mtxejkca2l4pvkfpwzepql3vmtf
-
 @ 037ebe13:93af01dc
2025-02-24 18:59:42
@ 037ebe13:93af01dc
2025-02-24 18:59:42Se você acompanhou o noticiário, deve ter visto que o ministro Alexandre de Moraes, do Supremo Tribunal Federal (STF), voltou a investir contra as redes sociais. Na sexta-feira (21), Moraes determinou a suspensão da rede social americana Rumble no Brasil.
De acordo com o ministro, a rede social cometeu "reiterados, conscientes e voluntários descumprimentos das ordens judiciais, além da tentativa de não se submeter ao ordenamento jurídico e Poder Judiciário brasileiros" e que instituiu um "ambiente de total impunidade e 'terra sem lei' nas redes sociais brasileiras".
No entanto, o CEO da Rumble, Chris Pavlovski, afirmou que Moraes exigiu que a Rumble cumprisse decisões que são ilegais segundo a legistação americana e passou um “aviso” ao ministro: “nos vemos no tribunal”.
Não é de hoje que o STF e Moraes são acusados de promover um ambiente de “censura” através de uma suposta perseguição enviesada a perfis que criticam as atuações da corte e do ministro, inclusive exigindo a remoção de perfis por parte dessas redes – algo que contraria a legislação brasileira.
Em 2024, o X chegou a ficar suspenso no Brasil por quase 40 dias, sendo que Moraes chegou a impor multas para quem tentasse acessar a rede via VPN, uma decisão contestada e vista por muitas pessoas como ilegal.
Isso mostra que o poder do estado vai continuar agindo contra as redes sociais com o intuito de estabelecer algum tipo de restrição a essas plataformas. E tal poder tende a funcionar, pois estas plataformas são consideradas empresas e muitas têm representantes legais no Brasil, que são um vetor de ataque para eventuais suspensões.
Felizmente, a criação do Bitcoin (BTC) levou a um avanço na forma como podemos manter nossa privacidade protegida da sanha autoritária dos estados. E isso chegou nas redes sociais com a criação do Nostr. Por isso, o protocolo descentralizado com foco em redes sociais é o tema da nossa newsletter de hoje.
O que é o Nostr?##
A palavra Nostr, que dá nome ao protocolo, é a sigla para Notes and Other Stuff Transmitted by Relays (Notas e Outras Coisas Transmitidas por Relés, em tradução livre). Esse protocolo surgiu em 2020 para criar uma “camada social” na rede do Bitcoin. Ou seja, permitir o desenvolvimento de aplicativos similares a redes sociais.
No entanto, foi a partir de 2023 que o protocolo ganhou fama, a ponto de ficar conhecido como o “Twitter descentralizado”. Esse nome se deveu ao fato de que um dos aplicativos mais populares do Nostr era o Damus, que funciona como uma espécie de X.
A principal diferença do Nostr para outros serviços é que os aplicativos criados pelos protocolos não podem ser censurados. Eles operam baseados em clientes e relés (relays) muito similares aos nós que rodam a rede do Bitcoin. Por isso, não adianta um governo tentar derrubar um nó: se os demais estiverem ativos, a rede seguirá funcionando livre de censura.
Sistema de chaves##
Da mesma forma que no Bitcoin, no Nostr cada usuário é identificado por uma chave pública. E também há uma chave privada, que ele usa para assinar as transações. Mas ao contrário do BTC, as chaves privadas não são formadas por sequência de palavras, mas sim por uma sequência de letras:
chave pública: cada chave pública do Nostr começa com as iniciais “npub”. Ex: npub43tahY4T…
chave privada: já as chaves privadas começam com os caracteres “nsec”. Ex: nsec4T6uyA4F…
Para acessar os aplicativos do Nostr (como o Damus), você só precisa fazer o download e inserir a sua chave privada no app. Ele vai ler a chave e identificar que você de fato controla aquela conta, mas o aplicativo não armazena as chaves. Por isso elas não ficam sujeitas a roubos, mantendo o seu perfil seguro.
Uma vez logado no aplicativo, cada vez que você publica algo (por exemplo, uma mensagem que publica, uma atualização da sua lista de seguidores, etc.), você assina uma transação. Os clientes validam estas assinaturas para garantir que estão corretas.
Hoje, existem mais de 70 aplicativos criados para o Nostr, desde outros “Twitter descentralizados” até serviços de mensagem. E todos eles funcionam de forma integrada, o que significa que a sua chave privada funciona como uma identidade única. Isso permite que você acesse a todos os aplicativos com uma única senha, sem precisar fazer cadastros e deixar seus dados expostos em várias redes sociais.
Esse protocolo foi criado por um brasileiro conhecido como fiatjaf, que preferiu se manter anônimo. O projeto fez tanto sucesso que recebeu um apoio massivo de Jack Dorsey, criador do Twitter, que chegou a doar 14,6 BTC para ajudar no desenvolvimento do Nostr. Hoje, esse valor corresponde a mais de R$ 8 milhões.
Como fazer uma conta no Nostr##
Antes de acessar os aplicativos, você deve criar suas chaves pública e privada no site oficial do Nostr. Basta acessar o Endereço e clicar na opção “create your Nostr account”. E pronto, o site gera as duas chaves automaticamente. A chave pública (npub) fica visível, enquanto a chave privada (nsec) aparece coberta.
Basta clicar nos quadrados do lado esquerdo da chave privada que ele vai copiar automaticamente. Você também pode clicar em “show private key” para ver a chave privada, ou clicar em “download keys” para baixar ambas as chaves.
Cabe frisar que essas chaves, sobretudo a privada, são essenciais para acessar qualquer aplicativo criado no Nostr. Por isso, assim que você salvá-las, guarde essas chaves em um lugar seguro e longe da internet, para evitar roubos. Por isso:
jamais anote sua chave privada num bloco de notas;
escreva a chave privada à mão num papel e guarde com bastante cuidado;
nunca, sob qualquer hipótese, compartilhe sua chave privada em arquivos na nuvem ou por e-mail.
Se você quiser ter ainda mais segurança, pode adquirir o NOSTR Signing Device, dispositivo que serve para assinar publicações com o Nostr e mantém sua chave privada segura. Ele é importado, mas custa apenas 20 euros (cerca de R$ 120) no site da LNBits.
Redes sociais à prova de censura##
Bem, agora vamos conferir as duas redes sociais que selecionamos entre os mais de 70 aplicativos do Nostr. Nelas você pode publicar qualquer coisa sem medo de sofrer com censura, bloqueios ou processos indevidos por causa de alguma acusação vaga como “promover discurso de ódio”.
O primeiro dessas aplicativos é o Primal, que é praticamente uma cópia do já citado Damus. Ele também se parece muito com o X e lá você pode publicar, mandar mensagens inbox para outro usuário, curtir, salvar, compartilhar e comentar.
Ao contrário do X, o Primal não impõe limite de caracteres nas publicações e você não tem selos. O aplicativo também possui uma carteira Lightning onde você pode enviar e receber satoshis. E o melhor de tudo, o Primal possui a função “zap”, que permite que você possa enviar e receber satoshis por causa de suas publicações.
Ou seja, se você escrever alguma coisa no Primal e as pessoas gostarem, elas podem te enviar “gorjetas” em satoshis. Isso significa que você consegue monetizar o seu conteúdo sem precisar assinar nenhum plano ou pagar para conseguir um selo. Você também pode enviar satoshis para seus criadores de conteúdo favoritos.
Mas se você gosta de publicar artigos mais longos (como esta newsletter), o Nostr conta com o YakiHonne. Este “Substack descentralizado” permite que você publique notas como o Primal, mas também oferece a possibilidade de criar artigos em formato de newsletter.
Você pode favoritar ou salvar os seus autores preferidos, facilitando a leitura de artigos. E o aplicativo também possui seções de curadoria específica. Com ela, você consegue acessar artigos por tópicos e ver o que está se destacando no YakiHonne naquele momento.
Quer escrever sobre um tema polêmico? Faça seu artigo no YakiHonne sem ter medo de censura ou de ver seu texto desmonetizado. E caso ele faça sucesso, você pode receber satoshis como pagamento e monetizar seu trabalho recebendo em moeda forte.
Infelizmente, os tribunais de censura seguem em crescimento no mundo e a liberdade de expressão em plataformas centralizadas seguirá ameaçada. Afinal, estas empresas visam o lucro e estão sujeitas às leis. E elas dificilmente farão frente ao poder do estado apenas para beneficiar seus usuários.
Por isso, da mesma forma que você pode tirar o estado do seu dinheiro com o Bitcoin, você pode tirar a censura das suas palavras usando o Nostr. Afinal, como diz o personagem Ensei Tankado de “Fortaleza Digital”:
“Todos temos o direito de guardar segredos. Um dia eu farei com que isso volte a ser possível.”
Vale uma olhada##
Matéria completa sobre o lançamento do Nostr no CriptoFacil;
O canal dos tem um vídeo excelente falando sobre como criar e armazenar suas chaves privadas do Nostr usando o Signing Device. Vale a pena conferir.
-
 @ 8be6bafe:b50da031
2025-02-05 17:00:40
@ 8be6bafe:b50da031
2025-02-05 17:00:40Botev Plovdiv FC is proud to present the Bitcoin Salary Calculator tool, as the foundational tool to showcase athletes the financial power of Bitcoin.
We built the Salary Calculator to help anyone follow in the financial footsteps of prominent athletes such as Kieran Gibbs, Russell Okung, Saquon Barkley, and Renato Moicano, who have significantly increased their savings tank thanks to Bitcoin.
The Bitcoin Salary Calculator allows any person to choose how much of their monthly salary they are comfortable saving in Bitcoin. Instantly, users can backtrack and see how their Bitcoin savings would have performed using the once-in-a-species opportunity which Bitcoin brings.
https://video.nostr.build/a9f2f693f6b5ee75097941e7a30bfc722225918a896b29a73e13e7581dfed77c.mp4
Athletes need Bitcoin more than anyone else
Unlike most people, athletes’ careers and earning years are limited. This has driven the likes of Odell Beckham Jr. and Alex Crognale to also start saving a part of their income in Bitcoin with a long-term outlook as they prepare for retirement.
“The reason why announced 50% of my salary in Bitcoin is because I feel one the noblest things you can do is to get people to understand Bitcoin.” Kieran Gibbs, founder ONE FC, ex Arsenal, ex Inter Miami, ex West Bromich Albion.
“I am trusting Bitcoin for my life after football. Every time my club paid me, I bought Bitcoin.” Alex Crognale, San Antonio FC player.
https://x.com/TFTC21/status/1883228348379533469
“At Botev Plovdiv FC, we believe not only in fostering sporting talent, but also helping them the the most of their careers so they excel in life after retiring from sports. It is with this mission in mind that the club is launching the Bitcoin Football Cup hub, striving to accelerate mass Bitcoin education via sports and athletes - the influencers and role models for billions of people.” shared Botev’s Bitcoin Director George Manolov.
https://x.com/obj/status/1856744340795662432
The Bitcoin Football Cup aims for young prospects to be able to learn key financial lessons from seasoned veterans across all sports. Our Bitcoin Salary Calculator is only the first step toward that goal.
We encourage anyone to hear these stories straight from the current roster of Bitcoin athletes -for whom -in many cases- Bitcoin has allowed them to outperform the wealth it took decades to earn on the field.
Follow us on the Bitcoin Cup’s social media channels to learn more and hear the latest stories of how Bitcoin is shaking up the world of sports:
- Twitter: https://x.com/Bitcoin_Cup/
- Instagram: https://www.instagram.com/BitcoinCup/
- TikTok: https://www.tiktok.com/@BitcoinCup/
- YouTube: https://www.youtube.com/@BitcoinCup/
-
 @ 9e69e420:d12360c2
2025-01-30 12:13:39
@ 9e69e420:d12360c2
2025-01-30 12:13:39Salwan Momika, a Christian Iraqi known for burning the Koran in Sweden, was shot dead during a TikTok livestream in an apartment in Sodertalje. The 38-year-old sparked outrage in the Muslim community for his demonstrations, leading to global condemnation. After being rushed to the hospital, he was pronounced dead.
Authorities arrested five individuals in connection with the incident. Momika's death comes days before a court ruling on his possible incitement of ethnic hatred. The incident highlights the tensions surrounding free speech and religious sentiments, intensifying after his controversial protests in 2023.
-
 @ 6e0ea5d6:0327f353
2025-02-24 18:54:30
@ 6e0ea5d6:0327f353
2025-02-24 18:54:30Ascolta bene, amico mio. The type of woman you choose reflects the type of man you truly are—or the one you hide from being.
Don't deceive yourself: your choices are a mirror of your essence. If you constantly get involved with women who drag you into chaos, who manipulate or belittle you, that says more about your weaknesses than about theirs. Chi sceglie male, paga il prezzo.
You cannot blame fate or the woman for your decisions. The responsibility is yours. If you are foolish enough to be swayed by superficial beauty or the need for approval, you are digging your own ruin.
A real man, before loving, learns to understand women—not just one, but many. He observes, understands their motivations, and learns to distinguish between those who add value and those who destroy.
If you choose wrong, don't blame the world. Cazzo! The mistake was yours, and so will be the consequence. Needy men, who let themselves be trapped by the first woman who offers crumbs of attention, end up being shaped by their circumstances. "La donna non ti fa cane; sei tu che ti fai cane." By choosing a woman without character, you reveal your own lack of discernment and courage. And, my friend, if you fear being alone, remember: loneliness next to the wrong woman is far more bitter.
If you seek respect, start by choosing wisely. Those who cling blindly, out of fear or necessity, are doomed to suffer. Own your choices, learn from your mistakes, and be selective. The world does not forgive the weak, and excuses will not redeem your weakness.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ b17fccdf:b7211155
2025-02-01 18:41:27
@ b17fccdf:b7211155
2025-02-01 18:41:27Next new resources about the MiniBolt guide have been released:
- 🆕 Roadmap: LINK
- 🆕 Dynamic Network map: LINK
- 🆕 Nostr community: LINK < ~ REMOVE the "[]" symbols from the URL (naddr...) to access
- 🆕 Linktr FOSS (UC) by Gzuuus: LINK
- 🆕 Donate webpage: 🚾 Clearnet LINK || 🧅 Onion LINK
- 🆕 Contact email: hello@minibolt.info
Enjoy it MiniBolter! 💙
-
 @ 65912a7a:5dc638bf
2024-12-08 05:33:02
@ 65912a7a:5dc638bf
2024-12-08 05:33:02Chef's notes
This is my late partner's award winning Cajun rice & beans recipe. It's an updated take on the traditional Cajun comfort food.
Chef Darin was a classically trained chef who spent 30+ years in the kitchen perfecting his recipes, and delivering authentic Cajun and Creole food to his patrons. This is a 5-star dish that will earn the respect of the most discerning Cajun afficionado. You won't be disappointed.
I suggest making this recipe exactly as directed the first time, and then make whatever adjustments you want for future batches. Also, don't cheap out on the Andouille. No Johnsonville or Hillshire Farms. Chef Aidelle's is a good choice, as is Silva's from Whole Foods. They cost a few extra bucks, but it's absolutely worth it.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 3 hours
- 🍽️ Servings: 12
Ingredients
- 16oz small red beans, dry
- 2 cups long grain white rice
- 14-16oz andouille sausage, sliced
- 8oz ham, cubed
- 1 large yellow onion, chopped
- 1 green bell pepper, chopped
- 2-3 stalks celery, chopped
- 2 tbsp garlic (12 cloves), minced
- 7 cups water
- ¼ cup olive oil
- 2 large bay leaves
- 1 tbsp parsley, dried
- 1 tsp thyme, dried
- 1 tsp Cajun seasoning
- ½ tsp cayenne pepper, dried
- ¼ tsp sage, rubbed
- 1½ tsp salt (more or less to taste)
Directions
- Soak beans in a large pot of water overnight.
- Heat oil in a large stockpot over medium heat. Cook onion, bell pepper, celery, garlic in olive oil for 3 to 4 minutes (until onion is translucent).
- Add beans, bay leaves, parsley, thyme, salt, MSG, Cajun seasoning, cayenne pepper, Sage, and water. Stir, bring to a boil, and then reduce heat to medium-low (btwn 2-3). Cover and simmer for 2½ hours.
- Remove bay leaves. Mash some of the beans. Stir Andouille and ham into beans, and simmer uncovered for an additional 30 minutes.
- Meanwhile, prepare the rice. Bring water and rice to a boil in a saucepan. Reduce heat, cover, and simmer for 20 minutes.
- Serve beans over steamed white rice.
-
 @ 9bcc5462:eb501d90
2025-02-24 17:47:28
@ 9bcc5462:eb501d90
2025-02-24 17:47:28Every generation loves to learn. However, our public schooling system has gone as far as it can take us. The abundance of easily accessible information on the internet, coupled with emerging tech like AI, decentralized protocols and bitcoin, means this is our time to innovate our learning infrastructure. A complete overhaul is due along with the development of a pilot program to test new and unconventional models.
Let’s carve a path towards innovation by sparking discussion around this topic. Hence, this blueprint. It is a gauntlet for any person who genuinely wants to become a stakeholder for our country’s future. Entry points are:
- Builders—Startups, developers and investors who will fund and create infrastructure.
- Practitioners—Educators and researchers who will test models.
- Supporters—Parents, donors and community members who want to contribute.
Where Do We Begin?
Let’s think about crafting the main components of a new pilot model. Below are suggested areas of focus:
- DEFINITION
- APPROACH
- PHILOSOPHY
- CULTURE
- PHYSICAL DESIGN
- OPERATIONAL ORGANIZATION
- ACCOUNTABILITY METHODS
- RISKS & CHALLENGES
- STYLE
- STAKEHOLDERS
How It Works
After researching your pedagogical ideas for current and future generations of scholars, it’s time to share your insights. Contribute your viewpoint by structuring a blueprint—one page per section—in the following sequence:
- Definition of your modern learning model with its key principles.
- Description of the core learning approach.
- Philosophy distilled into central concepts that will orient stakeholders.
- Culture your modern learning model aspires to live by.
- Potential challenges, risks and drawbacks.
- Design of physical spaces and rationale.
- Operational framework detailing adult and child learning organization.
- Accountability methods to ensure skill growth and competency.
- Style development and name of your model.
- Skin in the game, sign your model with your first and last name (unite stakeholders).
Perhaps if enough stakeholders come together, we can begin to actualize a more effective and updated way of learning. This is a challenge meant to separate those willing to engage in discourse, planning and laying foundations from those content to complain from the sidelines.
Why Now and Where Does the Money Come From?
After being a public educator for fifteen years, I learned you will not change the system, the system will change you. It’s time to design and build above and apart from the current model. 2025 is when courageous people step up to the plate and discuss our learning infrastructure. Whether it’s contributing out of the box thinking, modernizing curriculum, investing in startups or creating your own venture; there is no greater time than now. And no greater place than in the USA!
(By extension, we also create the opportunity to influence our global allies including our neighbors to the North and South.)
“But how!?” Learning Producers is figuring it out by asking not, “how?” but “who?” Who will unite together to develop our learning infrastructure? If you decide you want to participate and join our efforts, share your blueprint as well. For all stakeholders, this is an investment in an untapped market of a new learning economy.
If not, you’re not alone. Some consider this just rhetoric, idealism, or wishful thinking. Additionally, it is unclear how such actions can be profitable or how such infrastructure building will be funded. Money talks. Bullshit walks, right? In that case, let’s talk, and let’s fine tune our BS detectors. Onward, with this call to action:
- Share your own blueprint online or reach out to Learning Producers, Inc. (Learningproducers.com).
- Conduct research on an ideal location and team to lay foundations on a pilot program at small scale.
- Engage in dialogue with investors interested in developing learning infrastructure for their own children and families.
- Secure stakeholders to develop and test a real world pilot model (real location, real agreements, real timeline, real people).
- Sponsor or donate resources to counter concerns over funding.
Now, we leave you with our blueprint:
PEDAGOGICAL WABI-SABI
We hope you enjoy it.
Sincerely,
Israel Hernandez
Founder of Learning Producers
**[Read or download full blueprint here: https://www.learningproducers.com/blog/pedagogical-wabi-sabiblueprint-for-developing-learning-infrastructure ]
-
 @ 0fa80bd3:ea7325de
2025-01-30 04:28:30
@ 0fa80bd3:ea7325de
2025-01-30 04:28:30"Degeneration" or "Вырождение" ![[photo_2025-01-29 23.23.15.jpeg]]
A once-functional object, now eroded by time and human intervention, stripped of its original purpose. Layers of presence accumulate—marks, alterations, traces of intent—until the very essence is obscured. Restoration is paradoxical: to reclaim, one must erase. Yet erasure is an impossibility, for to remove these imprints is to deny the existence of those who shaped them.
The work stands as a meditation on entropy, memory, and the irreversible dialogue between creation and decay.
-
 @ 8fb140b4:f948000c
2024-12-08 05:21:39
@ 8fb140b4:f948000c
2024-12-08 05:21:39After nuking my second LND node (the first one died due to hardware failure) by my own typo and lack of any thought in the design of the CLI of LND lightning node tools, I decided to take a plunge into the world of mature and complex implementation of the protocol, Eclair by ACINQ. It has been almost one year (the birth of the node was on Christmas Day 2023), 50 thousand transactions routed, and over 30 BTC of routed value. In this post, I'd like to reflect on my experiences with Eclair, go over some of the gotchas and issues, and highlight some of the good choices that I've made since the beginning of my adventure.
Learnings from the Past Experience
While I was learning Lightning network and had very little understanding of how things worked in the whole Bitcoin space, Umbrel was my go-to solution that helped me get off the ground. It proved to be easy and somewhat educational but was not something that I would continuously run for the production setup or trust with any significant amount of bitcoin that I could not afford to lose. Lightning is built on top of the L1 (Bitcoin) network but manages the state of the channels in its own database that is negotiated and agreed upon with its peers. Any failures in the state integrity may result in the complete loss of liquidity or hefty penalty transactions (significant loss of capital). A Lightning node that participates in routing public transactions is also required to be constantly online with as little downtime as possible and only short periods offline at a time. Otherwise, you may risk causing force-closure of the channel due to expired HTLC that is measured in number of blocks.
The Setup
Taking all of my learnings into consideration, I decided to first invest in reliable enterprise-grade hardware: - Server-grade hardware with ECC memory and reliable power supply and CPU - UPS (Uninterruptible Power Supply) to avoid any headaches due to electrical spikes or drop-outs - Reliable enterprise SSDs and NVMEs - ZFS (filesystem) to mirror the critical storage and to ensure full integrity of the data (bit-rot prevention). You do need to tune ZFS for your specific workload and reliability - Reliable and replicated database (PostgreSQL) with two local and one remote replica, and a requirement to have at least two replicas committing the transaction to the disk - Backup! On-site and off-site backup of the critical configuration that you could use to restore the node if your house burns down - Spare parts, redundancy, backup, monitoring - Reliable and stable internet connectivity
The software is Eclair 0.11.0 (latest release as of today), PostgreSQL 16 with two replicas, Bitcoin Core 27.2 (with redundant storage of blocks), additional Bitcoin Core running on a separate node and in-sync with the chain (in case primary node fails), Ubuntu 22.04 with the latest docker software from the official Docker repo.
All Major Gotchas That I Came Across
While Eclair is mature and very stable in itself, it does have some quirks and design choices that you need to account for when running your node. The software is written in Scala and requires a specific version of JVM to run it, as well as JRE and Maven to build it. It doesn't mean that other versions won't work, but you may find unpleasant bugs that may result in catastrophic failures of your node with nobody to help you. All of the requirements are listed in the release notes and installation guide. Whenever in doubt, RTFM first, then ask questions.
Limited Support by the FOSS Community
Eclair is not the most popular implementation of the Lightning protocol, and therefore it is hard to find tools or plugins that could help you manage the node. GUI for the node so far is only supported by RTL and with a very limited number of features. For any sort of statistics, you are limited to either Prometheus (extensive metrics are available) or writing your own SQL on top of the Eclair tables.
On-chain Fee Differences Between Yours and Partner Nodes
This one hit me hard, and many times. I've had more than a few force-closures of the channels because of the conservative and safe default settings. The worst part is, it strikes you when there is a huge spike in fees, which results in significant losses to force-close the channel due to high fees. I am still not 100% sure how the big difference can be exploited in practice, and opted for increase of the tolerance levels to avoid surprise FCs:
eclair.on-chain-fees { feerate-tolerance { ratio-low = <0.01~> // will allow remote fee rates as low as XX our local feerate (spikes) ratio-high = <20.0~> // will allow remote fee rates as high as XX times our local feerate (drops) } }It is up to you and your risk tolerance to define something reasonable and yet allow for secure and reliable node operation.Initial Lightning Network State Sync
When I just started running the node, I had very few channels and startup times were fast. Later, when I expanded the number of channels, I noted that it took my node up to 6-12 hours before it was fully in-sync and routing traffic fast. Given that ACINQ maintains one of the largest nodes on the network, I knew that there was something with my settings that caused the issue. After some research, I came across the setting that whitelisted node IDs for state sync, which immediately rang a bell since I knew from the LND days that not all peer nodes are used for the network sync. Setting the list to my most reliable and largest nodes reduced the startup settling times down to minutes again:
eclair.sync-whitelist = [ "03864ef025fde8fb587d989186ce6a4a186895ee44a926bfc370e2c366597a3f8f", ... ]You do not need to have too many public keys in here, and should keep it between 5-10.Automatic MAX HTLC Adjustment for the Channel
One of the killer features of Eclair is its ability to automatically adjust MAX HTLC for the channel and reduce the number of failed transactions due to insufficient liquidity on the channel. It can be used to estimate your total channels' balances but with smart configuration and a little thinking, you can make it reasonably private while still maintaining a good transaction flow:
eclair.channel.channel-update.min-time-between-updates=1 hour # Allows for the adjustments to be made once every hour eclair.channel.channel-update.balance-thresholds=[ { available-sat = 10000 max-htlc-sat = 0 // 0% of 10000 }, ... ]You can have as many variations as you need, and ensure that the channel MAX HTLC is set well and within reasonable ranges. You would also want to account for multiple transactions going through the channel, but also account for the channel size and an average amount of sats per transaction.Max Accepted HTLCs
By design, the Lightning channel is limited to a specific number of in-flight HTLCs, and the setting is fixed during channel opening time with no way of changing it unless you close and reopen the channel with new settings. If you find your node routing a lot of small transactions (zaps), you may quickly fail many due to that limit (I think default was in single digit range):
eclair.channel.max-htlc-value-in-flight-percent=98 # Default I think is half or 50% eclair.channel.max-accepted-htlcs = 50The setting above will allow for the channel to be more fully utilized and have more concurrent transactions without clogging.CLTV Delta
This is basically a setting that is global for Eclair and sets the maximum number of remaining blocks (in time) before HTLC expires. Setting this too high may result in many HTLCs failing for the small nodes with not so great centrality, and reduce the number of routed transactions: ```
CLTV delta
eclair.channel.expiry-delta-blocks = 60 ``` Default is 144 but I found that setting this to 60 (minimum possible for my node setup and configuration) yields better results for routing. It does expose you to more risk of expired HTLCs that may cause force-closures, but I have seen only one so far on my node.
Allocate Sufficient Memory
You will want to adjust the heap size for Eclair, since the default is too small to run any sizable node. Setting
JAVA_OPTS=-Xmx32g(or half the size of your available RAM) would be a good start. I would advise having at least 32GB of RAM for the node, and allocating at least 16GB (JAVA_OPTS=-Xmx16g) for smooth and fast operations.And More Settings and Parameters to Tune
I have covered only some of the major settings that I felt were worth writing about, but there is much more you could configure and tweak. Read all of the Guides and especially focus on the Configure and a sample reference configuration file.
Good Decisions
First, going with Eclair was the right choice, along with using server-grade hardware with ECC RAM and reliable storage. Second, having a replicated database on three separate nodes with one off-site saved me from a sure destruction of all state and loss of funds. Third, deciding to only maintain channels with reliable and stable nodes saved me from some bad force-closures, where I would choose to close the channel if a peer node goes up and down too frequently, regardless of how well it routes. Even big nodes run by single operators fail badly, as do nodes operated by companies. Keeping your eyes on the node and its health, as well as the health of its peers, is something that very few operators do, which can cause failures and unnecessary loss of your and their funds.
Lastly, if you decide to run a routing node, you have a responsibility to maintain it well and monitor its health. There are many tools you could use, and with Eclair you can use Prometheus and Grafana. Keep your node's packages updated and monitor for any security-related issues that may appear from time to time, so you can mitigate them quickly.
Conclusion
So far I am satisfied with Eclair despite all of the difficulties and headaches I've had with it. It is not perfect, and it requires me to create small tools to do some basic things, but I need a stable and reliable node that I can trust. Eclair has proved to be all that I wanted, and saved my bacon a few times when I nuked one of the PostgreSQL servers and all of its data, and managed to do the same for another replica, but was able to recover and recreate from the remaining replica. Eclair is also stateless during runtime and guarantees consistency of the node regardless of how it fails. Even if you pull a plug on the node's server, it will still be able to come up and recover its consistent state that is in agreement with its peers.
Is it for everyone? No, it is definitely not for everyone or for anyone who just wants a small node to run their online shop with a few channels. You could have a very reliable and trusted node for the online shop with Eclair, but you will need some technical skills to be able to set up, maintain and recover it if things go wrong.
In the end, it is all up to you, your skills, your willingness to learn, and your risk tolerance to make that decision. For me, it was the right choice, and I have no regrets despite not having access to the latest shiny features of the Lightning network.
-
 @ da0b9bc3:4e30a4a9
2025-02-24 16:56:02
@ da0b9bc3:4e30a4a9
2025-02-24 16:56:02Hello Stackers!
It's Monday so we're back doing "Meta Music Mondays" 😉.
From before the territory existed there was just one post a week in a ~meta take over. Now each month we have a different theme and bring music from that theme.
Welcome to Femmes Fatales 3!!! I absolutely loved doing this last year so I'm bringing it back for round 3!
It's Femmes Fatales, where we celebrate women in ~Music. So let's have those ladies of the lung, the sirens of sound, our Femmes Fatales!
Stackers, here's Avril Lavigne.
https://youtu.be/dGR65RWwzg8?si=T5onrZ0T_zREhd-n
Talk Music. Share Tracks. Zap Sats.
originally posted at https://stacker.news/items/895855
-
 @ 0fa80bd3:ea7325de
2025-01-29 15:43:42
@ 0fa80bd3:ea7325de
2025-01-29 15:43:42Lyn Alden - биткойн евангелист или евангелистка, я пока не понял
npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83aThomas Pacchia - PubKey owner - X - @tpacchia
npub1xy6exlg37pw84cpyj05c2pdgv86hr25cxn0g7aa8g8a6v97mhduqeuhgplcalvadev - Shopstr
npub16dhgpql60vmd4mnydjut87vla23a38j689jssaqlqqlzrtqtd0kqex0nkqCalle - Cashu founder
npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vgДжек Дорси
npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m21 ideas
npub1lm3f47nzyf0rjp6fsl4qlnkmzed4uj4h2gnf2vhe3l3mrj85vqks6z3c7lМного адресов. Хз кто надо сортировать
https://github.com/aitechguy/nostr-address-bookФиатДжеф - создатель Ностр - https://github.com/fiatjaf
npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6EVAN KALOUDIS Zues wallet
npub19kv88vjm7tw6v9qksn2y6h4hdt6e79nh3zjcud36k9n3lmlwsleqwte2qdПрограммер Коди https://github.com/CodyTseng/nostr-relay
npub1syjmjy0dp62dhccq3g97fr87tngvpvzey08llyt6ul58m2zqpzps9wf6wlAnna Chekhovich - Managing Bitcoin at The Anti-Corruption Foundation https://x.com/AnyaChekhovich
npub1y2st7rp54277hyd2usw6shy3kxprnmpvhkezmldp7vhl7hp920aq9cfyr7 -
 @ dd664d5e:5633d319
2024-12-07 20:02:01
@ dd664d5e:5633d319
2024-12-07 20:02:01Yeah, so... nah.
People keep trying to explain to me, that women will be better-off, if they become more dangerous. While I can see the inevitableness of women living in remote rural areas learning to shoot with a rifle, and similar, I'm generally against arming women with killing machines.
This is not because I'm averse to the idea of using violence to solve problems (albeit after exhausting better options), or because I don't like guns, or am unfamiliar with them. It's also not because I don't know I would look totally, mind-numbingly hot holding something long and spearlike, while dressed in camo and wearing a T-Shirt that appears to have shrunk in the wash.

It's a more fundamental set of problems, that irks me.
Bazooka Barbie
American gun manufacturers saturated the public and private male market so thoroughly, that they eventually turned to marketing firearms to women.
Men are scary and bad. There is Stranger Danger. We can't just make the neighborhood less dangerous because erm... reasons. Stay safe with a cute gun.

It has gone along with the predictable hypersexualization of the conservative feminine ideal. Since guns are considered aggressive, women with guns are perceived as more sexually available. Guns (and tanks, bombs, bows, etc.) make women "equal", "independent", "feisty", "hot", "freaky", "calculating", "empowered", etc.

Sorta slutty, basically.
This Gun Girl is not like the helpless, hapless, harmless homemaker ideal, of yesteryear. A woman who was dependent, chaste, gentle, wise... and in need of protection. A woman who saw the men around her as people she could rely on for providing her with a safe environment. That woman is au revoir. Now, sistas are doing it for themselves. 💪🏻
The New Martial Missy needs a man, like a fish needs a bicycle... but make it country.
Yeah, it's marketing, but it sure has set the tone, and millions of men have been trained to prefer women who market themselves in this manner. Hard, mean, lean women. That will not remain without wider societal consequences.
You know, I liked that homemaker. I miss her. She's literally me.

Those arms are for cuddling babies, not holding rocket launchers.
Now, that we've all become accustomed to imagery of women holding firearms, it wasn't much of a leap to condition us all to the sight of women in frontline police, guard, or military positions.

Instead of war being a terrible, highly-lethal, territorial fight amongst men, it's now cute, hip, trendy and fun. It's a big party, and women are finally allowed to join in.

Now, women have finally jettisoned the terrible burden of being society's life-bearers and caretakers, and we're just more potential enemy combatants. We know it's okay to punch women, shoot women, etc. since we've been watching it happen on screens, for decades. Women are now often assumed to be fighters, not lovers. Cavalry, not mothers.
Girls on top
Not only does this undermine any female role -- and put female civilians under a cloud of suspicion -- it also reduces mens' claim to be paramount in governance. Why should a man be the Commander in Chief, if women are on the battlefield?
In fact, why should men be in charge of anything, anywhere? Look at them. There they are. Hiding at home. Cowering in their kitchens, wringing their hands and fretting, while courageous, dangerous women protect them from dangers foreign and domestic. Women are the better men, really.
Is this really where we want to go?
The final bitterness
But one thing I find most disturbing is something more personal. The ubiquitous nature of firearms in American homes has made domestic violence increasingly deadly. Adding more guns, for the female residents, often serves to make such violence even more deadly for women.
It turns out, that women are usually reluctant to shoot people they know; even more than men. Women without this inhibition are prone to sharing their home with men missing the same trait. And, now, they have more guns.
-
 @ b8851a06:9b120ba1
2025-01-28 21:34:54
@ b8851a06:9b120ba1
2025-01-28 21:34:54Private property isn’t lines on dirt or fences of steel—it’s the crystallization of human sovereignty. Each boundary drawn is a silent declaration: This is where my will meets yours, where creation clashes against chaos. What we defend as “mine” or “yours” is no mere object but a metaphysical claim, a scaffold for the unfathomable complexity of voluntary exchange.
Markets breathe only when individuals anchor their choices in the inviolable. Without property, there is no negotiation—only force. No trade—only taking. The deed to land, the title to a car, the seed of an idea: these are not static things but frontiers of being, where human responsibility collides with the infinite permutations of value.
Austrian economics whispers what existentialism shouts: existence precedes essence. Property isn’t granted by systems; it’s asserted through action, defended through sacrifice, and sanctified through mutual recognition. A thing becomes “owned” only when a mind declares it so, and others—through reason or respect—refrain from crossing that unseen line.
Bitcoin? The purest ledger of this truth. A string of code, yes—but one that mirrors the unyielding logic of property itself: scarce, auditable, unconquerable. It doesn’t ask permission. It exists because sovereign minds choose it to.
Sigh. #nostr
I love #Bitcoin.

