-
 @ eac63075:b4988b48
2025-01-04 19:41:34
@ eac63075:b4988b48
2025-01-04 19:41:34Since its creation in 2009, Bitcoin has symbolized innovation and resilience. However, from time to time, alarmist narratives arise about emerging technologies that could "break" its security. Among these, quantum computing stands out as one of the most recurrent. But does quantum computing truly threaten Bitcoin? And more importantly, what is the community doing to ensure the protocol remains invulnerable?
The answer, contrary to sensationalist headlines, is reassuring: Bitcoin is secure, and the community is already preparing for a future where quantum computing becomes a practical reality. Let’s dive into this topic to understand why the concerns are exaggerated and how the development of BIP-360 demonstrates that Bitcoin is one step ahead.
What Is Quantum Computing, and Why Is Bitcoin Not Threatened?
Quantum computing leverages principles of quantum mechanics to perform calculations that, in theory, could exponentially surpass classical computers—and it has nothing to do with what so-called “quantum coaches” teach to scam the uninformed. One of the concerns is that this technology could compromise two key aspects of Bitcoin’s security:
- Wallets: These use elliptic curve algorithms (ECDSA) to protect private keys. A sufficiently powerful quantum computer could deduce a private key from its public key.
- Mining: This is based on the SHA-256 algorithm, which secures the consensus process. A quantum attack could, in theory, compromise the proof-of-work mechanism.
Understanding Quantum Computing’s Attack Priorities
While quantum computing is often presented as a threat to Bitcoin, not all parts of the network are equally vulnerable. Theoretical attacks would be prioritized based on two main factors: ease of execution and potential reward. This creates two categories of attacks:
1. Attacks on Wallets
Bitcoin wallets, secured by elliptic curve algorithms, would be the initial targets due to the relative vulnerability of their public keys, especially those already exposed on the blockchain. Two attack scenarios stand out:
-
Short-term attacks: These occur during the interval between sending a transaction and its inclusion in a block (approximately 10 minutes). A quantum computer could intercept the exposed public key and derive the corresponding private key to redirect funds by creating a transaction with higher fees.
-
Long-term attacks: These focus on old wallets whose public keys are permanently exposed. Wallets associated with Satoshi Nakamoto, for example, are especially vulnerable because they were created before the practice of using hashes to mask public keys.
We can infer a priority order for how such attacks might occur based on urgency and importance.
 Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)
Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)2. Attacks on Mining
Targeting the SHA-256 algorithm, which secures the mining process, would be the next objective. However, this is far more complex and requires a level of quantum computational power that is currently non-existent and far from realization. A successful attack would allow for the recalculation of all possible hashes to dominate the consensus process and potentially "mine" it instantly.
 Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin Attacks
Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin AttacksRecently, Narcelio asked me about a statement I made on Tubacast:
https://x.com/eddieoz/status/1868371296683511969
If an attack became a reality before Bitcoin was prepared, it would be necessary to define the last block prior to the attack and proceed from there using a new hashing algorithm. The solution would resemble the response to the infamous 2013 bug. It’s a fact that this would cause market panic, and Bitcoin's price would drop significantly, creating a potential opportunity for the well-informed.
Preferably, if developers could anticipate the threat and had time to work on a solution and build consensus before an attack, they would simply decide on a future block for the fork, which would then adopt the new algorithm. It might even rehash previous blocks (reaching consensus on them) to avoid potential reorganization through the re-mining of blocks using the old hash. (I often use the term "shielding" old transactions).
How Can Users Protect Themselves?
While quantum computing is still far from being a practical threat, some simple measures can already protect users against hypothetical scenarios:
- Avoid using exposed public keys: Ensure funds sent to old wallets are transferred to new ones that use public key hashes. This reduces the risk of long-term attacks.
- Use modern wallets: Opt for wallets compatible with SegWit or Taproot, which implement better security practices.
- Monitor security updates: Stay informed about updates from the Bitcoin community, such as the implementation of BIP-360, which will introduce quantum-resistant addresses.
- Do not reuse addresses: Every transaction should be associated with a new address to minimize the risk of repeated exposure of the same public key.
- Adopt secure backup practices: Create offline backups of private keys and seeds in secure locations, protected from unauthorized access.
BIP-360 and Bitcoin’s Preparation for the Future
Even though quantum computing is still beyond practical reach, the Bitcoin community is not standing still. A concrete example is BIP-360, a proposal that establishes the technical framework to make wallets resistant to quantum attacks.
BIP-360 addresses three main pillars:
- Introduction of quantum-resistant addresses: A new address format starting with "BC1R" will be used. These addresses will be compatible with post-quantum algorithms, ensuring that stored funds are protected from future attacks.
- Compatibility with the current ecosystem: The proposal allows users to transfer funds from old addresses to new ones without requiring drastic changes to the network infrastructure.
- Flexibility for future updates: BIP-360 does not limit the choice of specific algorithms. Instead, it serves as a foundation for implementing new post-quantum algorithms as technology evolves.
This proposal demonstrates how Bitcoin can adapt to emerging threats without compromising its decentralized structure.
Post-Quantum Algorithms: The Future of Bitcoin Cryptography
The community is exploring various algorithms to protect Bitcoin from quantum attacks. Among the most discussed are:
- Falcon: A solution combining smaller public keys with compact digital signatures. Although it has been tested in limited scenarios, it still faces scalability and performance challenges.
- Sphincs: Hash-based, this algorithm is renowned for its resilience, but its signatures can be extremely large, making it less efficient for networks like Bitcoin’s blockchain.
- Lamport: Created in 1977, it’s considered one of the earliest post-quantum security solutions. Despite its reliability, its gigantic public keys (16,000 bytes) make it impractical and costly for Bitcoin.
Two technologies show great promise and are well-regarded by the community:
- Lattice-Based Cryptography: Considered one of the most promising, it uses complex mathematical structures to create systems nearly immune to quantum computing. Its implementation is still in its early stages, but the community is optimistic.
- Supersingular Elliptic Curve Isogeny: These are very recent digital signature algorithms and require extensive study and testing before being ready for practical market use.
The final choice of algorithm will depend on factors such as efficiency, cost, and integration capability with the current system. Additionally, it is preferable that these algorithms are standardized before implementation, a process that may take up to 10 years.
Why Quantum Computing Is Far from Being a Threat
The alarmist narrative about quantum computing overlooks the technical and practical challenges that still need to be overcome. Among them:
- Insufficient number of qubits: Current quantum computers have only a few hundred qubits, whereas successful attacks would require millions.
- High error rate: Quantum stability remains a barrier to reliable large-scale operations.
- High costs: Building and operating large-scale quantum computers requires massive investments, limiting their use to scientific or specific applications.
Moreover, even if quantum computers make significant advancements, Bitcoin is already adapting to ensure its infrastructure is prepared to respond.
Conclusion: Bitcoin’s Secure Future
Despite advancements in quantum computing, the reality is that Bitcoin is far from being threatened. Its security is ensured not only by its robust architecture but also by the community’s constant efforts to anticipate and mitigate challenges.
The implementation of BIP-360 and the pursuit of post-quantum algorithms demonstrate that Bitcoin is not only resilient but also proactive. By adopting practical measures, such as using modern wallets and migrating to quantum-resistant addresses, users can further protect themselves against potential threats.
Bitcoin’s future is not at risk—it is being carefully shaped to withstand any emerging technology, including quantum computing.
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 5d4b6c8d:8a1c1ee3
2025-02-28 16:00:20
@ 5d4b6c8d:8a1c1ee3
2025-02-28 16:00:20I've been very hopeful that the proposal to replace the IRS, and all of the taxes it collects, with a combination of sales taxes and tariffs, will go through, but just this morning some of the secondary effects of such a change occurred to me. Now, I'm even more hopeful that this happens.
The Obvious Benefits
My initial reasons for excitement were the obvious ones: consumption based taxes have better incentives than production based taxes (I know tax incidence muddies the waters, but this is still true) and consumption taxes are more avoidable than the slew of individual and corporate taxes currently in place.
Financial Privacy
One second order benefit occurred to me immediately: Without taxes on income/payroll/inheritance/capital gains/etc. the state loses most of its rational for its rampant invasions of our financial privacy. Since most businesses are already subjected to the invasion of their financial privacy (through state and local sales taxes), this is a huge net positive.
Not only is this better for its own sake, but all of the monitoring that goes into current financial surveillance is costly. Getting all of those transactions costs out of our financial system will be a huge positive.
No More Benefits Tied to Employment
This is what hit me this morning. The reason Americans get so many benefits through their employers is because they're tax exempted.
Having our healthcare tied to our employer, and largely decided by them, is a huge distortion in the health care market and it radically reduces competition. Without preferential tax treatment, we would just be paid out that money in our salaries and make our own health care choices. As such, expect the current medical-industrial complex to fight this tax reform tooth and nail.
The other element of this that I realized is that retirement accounts will lose the tax penalty, come withdrawal time (obviously depending on which type you have). That'll be a huge boon for many of us, and make up for the impending collapse of Social Security.
What Else?
I haven't spent much more time thinking through other implications. What other effects will there be if the current tax regime is replaced with sales taxes and tariffs.
originally posted at https://stacker.news/items/899802
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 55f04590:2d385185
2025-02-28 15:52:53
@ 55f04590:2d385185
2025-02-28 15:52:53Loops have been the overarching theme in the last two months of my work.
You see, my book project is incredibly exciting, and whenever I have a large project like this—a beast—I have a tendency to become somewhat obsessive, (subconsciously) dedicating every waking hour to feeding it.
I forced myself to step away from it for a bit, working on other projects while letting the book slumber in the back of my head. When I picked the project back up again, I could feel the different pieces it consists of had clicked into place. It always surprises me to see how taking time away from a project can contribute to seeing things more clearly on the project.
A new website for NoGood
During this brief hiatus I found myself digging deeper into the indie & open web. I read articles by people who have been active proponents of an open web—as opposed to the walled gardens we’ve gotten accustomed to tracking us whichever way we surf—and I discovered the concept of tending to a ‘digital garden’. I saw a side of the web I was less exposed to before that aligned perfectly with my values.
As a result, I overhauled the NoGood website. This new version of the website is simple, effective, and static: there is no tracking whatsoever, and it makes no requests to external resources. It only uses system fonts, serves optimised images, and because of that it’s blazing fast. I built it using 11ty, and you can read more about it in last month’s blogpost. Within weeks, NoGood got featured on DeadSimpleSites, a gallery full of similar websites, which is a welcome bit of recognition.
Rewarding dialogues
The book’s sections (Work, Process, Context, Items) are set. The Context section is meant to—well, do what it says on the tin: paint a picture of the context in which my own work was created and construct conversations between my work and that which came before it.
To do so, I’ll carve out space for articles—published under the Creative Commons or share-alike license—that inspired me along the way. I’ll illustrate each article myself, in black and white.
I’ve asked a few people for their permission to publish their articles and have received positive responses from Cory Doctorow, Jack Dorsey, Lyn Alden and DerGigi, for which I’m incredibly grateful. Just the ability to have dialogues with these people whose work I’ve admired is a rewarding outcome of me pursuing this project, feeding back into my desire to create a great publication.
In order to do right by the Creative Commons license, I’ll make the Context section available on the NoGood website, too. I may even turn it into a printable zine—more on that later.
Editing and designing the NoGood book
I primarily work on the book from my studio space, which I share with two other creatives, Timo and Daniël.
Daniël designs and builds open-source software for Ghost, writes, and publishes a literary magazine called TRANSCRIPT. We share similar values, he knows a thing or two about the open web, and it made perfect sense for us to work together. I’ve hired him to act as an editor for the book, and he now edits my writing (in fact, he edited this update, too!). We’ve had some dialogues about the articles I’m including as well as others I could add, too, and we’ll continue our conversations throughout the design process.
Commissioning him to take on this work has been a relief. It freed up precious headspace, and I’ve started designing the first spreads of the book. Some sections already are very clear, while others still need time to crystallise. Fortunately, clarity comes as a result of chipping away at the work ahead, so I keep at it with renewed energy—updates will now follow more regularly.
Crowdfunding & production
I have a complete picture of the production costs of the book and I’ve ironed out the logistics. I know which printer will be printing it, and my budget estimates were correct. The current number of pre-orders (53) covers roughly 70% of the production costs, which means I can safely produce the NoGood book—it’s going to print this summer!
200 copies will roll off the press, and I’m really looking forward to it.
Thank you for reading. More soon,
Thomas.
Previous updates
The NoGood art book announcement Update 01 – Humble beginnings Update 02 – Throwback
Pre-order a book
The NoGood art book is available as a pre-order on Geyser.
originally posted at https://stacker.news/items/899798
-
 @ 5d4b6c8d:8a1c1ee3
2025-02-28 15:07:12
@ 5d4b6c8d:8a1c1ee3
2025-02-28 15:07:12It's contest-palooza at ~Stacker_Sports:
- We have cricket
- We'll likely have more cricket soon!
- We have USA vs the world
- We have soccer
- We have NBA
- Coming soon: March Madness, Fantasy Baseball, MLB Survivor Pools, NFL Mock Drafts, and AFL!
In actual sports news,
- the NBA is hitting the home stretch. The contenders, pretenders, and tankers are sorting themselves out.
- Steph's 56
- Giannis vs Jokic showdown
- Brady tampering for Stafford?
- NFL combine and other offseason activity
- Ovi chasing the Great One
- MLB started spring training games
- New ball/strike review system
Degenerate Corner
- Predyx Super Bowl market
- I'm killing it on Ember. What's my secret?
Plus, whatever stackers drop in the comments.
originally posted at https://stacker.news/items/899748
-
 @ 4523be58:ba1facd0
2025-02-27 22:20:33
@ 4523be58:ba1facd0
2025-02-27 22:20:33NIP-117
The Double Ratchet Algorithm
The Double Ratchet is a key rotation algorithm for secure private messaging.
It allows us to 1) communicate on Nostr without revealing metadata (who you are communicating with and when), and 2) keep your message history and future messages safe even if your main Nostr key is compromised.
Additionally, it enables disappearing messages that become undecryptable when past message decryption keys are discarded after use.
See also: NIP-118: Nostr Double Ratchet Invites
Overview
"Double ratchet" means we use 2 "ratchets": cryptographic functions that can be rotated forward, but not backward: current keys can be used to derive next keys, but not the other way around.
Ratchet 1 uses Diffie-Hellman (DH) shared secrets and is rotated each time the other participant acknowledges a new key we have sent along with a previous message.
Ratchet 2 generates encryption keys for each message. It rotates after every message, using the previous message's key as input (and the Ratchet 1 key when it rotates). This process ensures forward secrecy for consecutive messages from the same sender in between Ratchet 1 rotations.
Nostr implementation
We implement the Double Ratchet Algorithm on Nostr similarly to Signal's Double Ratchet with header encryption, but encrypting the message headers with NIP-44 conversation keys instead of symmetric header keys.
Ratchet 1 keys are standard Nostr keys. In addition to encryption, they are also used for publishing and subscribing to messages on Nostr. As they are rotated and not linked to public Nostr identities, metadata privacy is preserved.
Nostr event format
Message
Outer event
typescript { kind: 1060, content: encryptedInnerEvent, tags: [["header", encryptedHeader]], pubkey: ratchetPublicKey, created_at, id, sig }We subscribe to Double Ratchet events based on author public keys which are ephemeral — not used for other purposes than the Double Ratchet session. We use the regular event kind
1060to differentiate it from other DM kinds, retrieval of which may be restricted by relays.The encrypted header contains our next nostr public key, our previous sending chain length and the current message number.
Inner event
Inner events must be NIP-59 Rumors (unsigned Nostr events) allowing plausible deniability.
With established Nostr event kinds, clients can implement all kinds of features, such as replies, reactions, and encrypted file sharing in private messages.
Direct message and encrypted file messages are defined in NIP-17.
Algorithm
Signal's Double Ratchet with header encryption document is a comprehensive description and explanation of the algorithm.
In this NIP, the algorithm is only described in code, in order to highlight differences to the Signal implementation.
External functions
We use the following Nostr functions (NIP-01):
generateSecretKey()for creating Nostr private keysfinalizeEvent(partialEvent, secretKey)for creating valid Nostr events with pubkey, id and signature
We use NIP-44 functions for encryption:
nip44.encryptnip44.decryptnip44.getConversationKey
- createRumor
Key derivation function:
```typescript export function kdf( input1: Uint8Array, input2: Uint8Array = new Uint8Array(32), numOutputs: number = 1 ): Uint8Array[] { const prk = hkdf_extract(sha256, input1, input2);
const outputs: Uint8Array[] = []; for (let i = 1; i <= numOutputs; i++) { outputs.push(hkdf_expand(sha256, prk, new Uint8Array([i]), 32)); } return outputs; } ```
Session state
With this information you can start or continue a Double Ratchet session. Save it locally after each sent and received message.
```typescript interface SessionState { theirCurrentNostrPublicKey?: string; theirNextNostrPublicKey: string;
ourCurrentNostrKey?: KeyPair; ourNextNostrKey: KeyPair;
rootKey: Uint8Array; receivingChainKey?: Uint8Array; sendingChainKey?: Uint8Array;
sendingChainMessageNumber: number; receivingChainMessageNumber: number; previousSendingChainMessageCount: number;
// Cache of message & header keys for handling out-of-order messages // Indexed by Nostr public key, which you can use to resubscribe to unreceived messages skippedKeys: { [pubKey: string]: { headerKeys: Uint8Array[]; messageKeys: { [msgIndex: number]: Uint8Array }; }; }; } ```
Initialization
Alice is the chat initiator and Bob is the recipient. Ephemeral keys were exchanged earlier.
```typescript static initAlice( theirEphemeralPublicKey: string, ourEphemeralNostrKey: KeyPair, sharedSecret: Uint8Array ) { // Generate ephemeral key for the next ratchet step const ourNextNostrKey = generateSecretKey();
// Use ephemeral ECDH to derive rootKey and sendingChainKey const [rootKey, sendingChainKey] = kdf( sharedSecret, nip44.getConversationKey(ourEphemeralNostrKey.private, theirEphemeralPublicKey), 2 );
return { rootKey, theirNextNostrPublicKey: theirEphemeralPublicKey, ourCurrentNostrKey: ourEphemeralNostrKey, ourNextNostrKey, receivingChainKey: undefined, sendingChainKey, sendingChainMessageNumber: 0, receivingChainMessageNumber: 0, previousSendingChainMessageCount: 0, skippedKeys: {}, }; }
static initBob( theirEphemeralPublicKey: string, ourEphemeralNostrKey: KeyPair, sharedSecret: Uint8Array ) { return { rootKey: sharedSecret, theirNextNostrPublicKey: theirEphemeralPublicKey, // Bob has no ‘current’ key at init time — Alice will send to next and trigger a ratchet step ourCurrentNostrKey: undefined, ourNextNostrKey: ourEphemeralNostrKey, receivingChainKey: undefined, sendingChainKey: undefined, sendingChainMessageNumber: 0, receivingChainMessageNumber: 0, previousSendingChainMessageCount: 0, skippedKeys: {}, }; }
```
Sending messages
```typescript sendEvent(event: Partial
) { const innerEvent = nip59.createRumor(event) const [header, encryptedData] = this.ratchetEncrypt(JSON.stringify(innerEvent)); const conversationKey = nip44.getConversationKey(this.state.ourCurrentNostrKey.privateKey, this.state.theirNextNostrPublicKey); const encryptedHeader = nip44.encrypt(JSON.stringify(header), conversationKey);
const outerEvent = finalizeEvent({ content: encryptedData, kind: MESSAGE_EVENT_KIND, tags: [["header", encryptedHeader]], created_at: Math.floor(now / 1000) }, this.state.ourCurrentNostrKey.privateKey);
// Publish outerEvent on Nostr, store inner locally if needed return {outerEvent, innerEvent}; }
ratchetEncrypt(plaintext: string): [Header, string] { // Rotate sending chain key const [newSendingChainKey, messageKey] = kdf(this.state.sendingChainKey!, new Uint8Array([1]), 2); this.state.sendingChainKey = newSendingChainKey; const header: Header = { number: this.state.sendingChainMessageNumber++, nextPublicKey: this.state.ourNextNostrKey.publicKey, previousChainLength: this.state.previousSendingChainMessageCount }; return [header, nip44.encrypt(plaintext, messageKey)]; } ```
Receiving messages
```typescript handleNostrEvent(e: NostrEvent) { const [header, shouldRatchet, isSkipped] = this.decryptHeader(e);
if (!isSkipped) { if (this.state.theirNextNostrPublicKey !== header.nextPublicKey) { // Received a new key from them this.state.theirCurrentNostrPublicKey = this.state.theirNextNostrPublicKey; this.state.theirNextNostrPublicKey = header.nextPublicKey; this.updateNostrSubscriptions() }
if (shouldRatchet) { this.skipMessageKeys(header.previousChainLength, e.pubkey); this.ratchetStep(header.nextPublicKey); }}
decryptHeader(event: any): [Header, boolean, boolean] { const encryptedHeader = event.tags[0][1]; if (this.state.ourCurrentNostrKey) { const conversationKey = nip44.getConversationKey(this.state.ourCurrentNostrKey.privateKey, event.pubkey); try { const header = JSON.parse(nip44.decrypt(encryptedHeader, conversationKey)) as Header; return [header, false, false]; } catch (error) { // Decryption with currentSecret failed, try with nextSecret } }
const nextConversationKey = nip44.getConversationKey(this.state.ourNextNostrKey.privateKey, event.pubkey); try { const header = JSON.parse(nip44.decrypt(encryptedHeader, nextConversationKey)) as Header; return [header, true, false]; } catch (error) { // Decryption with nextSecret also failed }
const skippedKeys = this.state.skippedKeys[event.pubkey]; if (skippedKeys?.headerKeys) { // Try skipped header keys for (const key of skippedKeys.headerKeys) { try { const header = JSON.parse(nip44.decrypt(encryptedHeader, key)) as Header; return [header, false, true]; } catch (error) { // Decryption failed, try next secret } } }
throw new Error("Failed to decrypt header with current and skipped header keys"); }
ratchetDecrypt(header: Header, ciphertext: string, nostrSender: string): string { const plaintext = this.trySkippedMessageKeys(header, ciphertext, nostrSender); if (plaintext) return plaintext;
this.skipMessageKeys(header.number, nostrSender);
// Rotate receiving key const [newReceivingChainKey, messageKey] = kdf(this.state.receivingChainKey!, new Uint8Array([1]), 2); this.state.receivingChainKey = newReceivingChainKey; this.state.receivingChainMessageNumber++;
return nip44.decrypt(ciphertext, messageKey); }
ratchetStep(theirNextNostrPublicKey: string) { this.state.previousSendingChainMessageCount = this.state.sendingChainMessageNumber; this.state.sendingChainMessageNumber = 0; this.state.receivingChainMessageNumber = 0; this.state.theirNextNostrPublicKey = theirNextNostrPublicKey;
// 1st step yields the new conversation key they used const conversationKey1 = nip44.getConversationKey(this.state.ourNextNostrKey.privateKey, this.state.theirNextNostrPublicKey!); // and our corresponding receiving chain key const [theirRootKey, receivingChainKey] = kdf(this.state.rootKey, conversationKey1, 2); this.state.receivingChainKey = receivingChainKey;
// Rotate our Nostr key this.state.ourCurrentNostrKey = this.state.ourNextNostrKey; const ourNextSecretKey = generateSecretKey(); this.state.ourNextNostrKey = { publicKey: getPublicKey(ourNextSecretKey), privateKey: ourNextSecretKey };
// 2nd step yields the new conversation key we'll use const conversationKey2 = nip44.getConversationKey(this.state.ourNextNostrKey.privateKey, this.state.theirNextNostrPublicKey!); // And our corresponding sending chain key const [rootKey, sendingChainKey] = kdf(theirRootKey, conversationKey2, 2); this.state.rootKey = rootKey; this.state.sendingChainKey = sendingChainKey; }
skipMessageKeys(until: number, nostrSender: string) { if (this.state.receivingChainMessageNumber + MAX_SKIP < until) { throw new Error("Too many skipped messages"); }
if (!this.state.skippedKeys[nostrSender]) { this.state.skippedKeys[nostrSender] = { headerKeys: [], messageKeys: {} };
if (this.state.ourCurrentNostrKey) { const currentSecret = nip44.getConversationKey(this.state.ourCurrentNostrKey.privateKey, nostrSender); this.state.skippedKeys[nostrSender].headerKeys.push(currentSecret); } const nextSecret = nip44.getConversationKey(this.state.ourNextNostrKey.privateKey, nostrSender); this.state.skippedKeys[nostrSender].headerKeys.push(nextSecret);}
while (this.state.receivingChainMessageNumber < until) { const [newReceivingChainKey, messageKey] = kdf(this.state.receivingChainKey!, new Uint8Array([1]), 2); this.state.receivingChainKey = newReceivingChainKey; this.state.skippedKeys[nostrSender].messageKeys[this.state.receivingChainMessageNumber] = messageKey; this.state.receivingChainMessageNumber++; } }
trySkippedMessageKeys(header: Header, ciphertext: string, nostrSender: string): string | null { const skippedKeys = this.state.skippedKeys[nostrSender]; if (!skippedKeys) return null;
const messageKey = skippedKeys.messageKeys[header.number]; if (!messageKey) return null;
delete skippedKeys.messageKeys[header.number];
if (Object.keys(skippedKeys.messageKeys).length === 0) { delete this.state.skippedKeys[nostrSender]; }
return nip44.decrypt(ciphertext, messageKey); } ```
-
 @ a95c6243:d345522c
2025-03-01 10:39:35
@ a95c6243:d345522c
2025-03-01 10:39:35Ständige Lügen und Unterstellungen, permanent falsche Fürsorge \ können Bausteine von emotionaler Manipulation sein. Mit dem Zweck, \ Macht und Kontrolle über eine andere Person auszuüben. \ Apotheken Umschau
Irgendetwas muss passiert sein: «Gaslighting» ist gerade Thema in vielen Medien. Heute bin ich nach längerer Zeit mal wieder über dieses Stichwort gestolpert. Das war in einem Artikel von Norbert Häring über Manipulationen des Deutschen Wetterdienstes (DWD). In diesem Fall ging es um eine Pressemitteilung vom Donnerstag zum «viel zu warmen» Winter 2024/25.
Häring wirft der Behörde vor, dreist zu lügen und Dinge auszulassen, um die Klimaangst wach zu halten. Was der Leser beim DWD nicht erfahre, sei, dass dieser Winter kälter als die drei vorangegangenen und kälter als der Durchschnitt der letzten zehn Jahre gewesen sei. Stattdessen werde der falsche Eindruck vermittelt, es würde ungebremst immer wärmer.
Wem also der zu Ende gehende Winter eher kalt vorgekommen sein sollte, mit dessen Empfinden stimme wohl etwas nicht. Das jedenfalls wolle der DWD uns einreden, so der Wirtschaftsjournalist. Und damit sind wir beim Thema Gaslighting.
Als Gaslighting wird eine Form psychischer Manipulation bezeichnet, mit der die Opfer desorientiert und zutiefst verunsichert werden, indem ihre eigene Wahrnehmung als falsch bezeichnet wird. Der Prozess führt zu Angst und Realitätsverzerrung sowie zur Zerstörung des Selbstbewusstseins. Die Bezeichnung kommt von dem britischen Theaterstück «Gas Light» aus dem Jahr 1938, in dem ein Mann mit grausamen Psychotricks seine Frau in den Wahnsinn treibt.
Damit Gaslighting funktioniert, muss das Opfer dem Täter vertrauen. Oft wird solcher Psychoterror daher im privaten oder familiären Umfeld beschrieben, ebenso wie am Arbeitsplatz. Jedoch eignen sich die Prinzipien auch perfekt zur Manipulation der Massen. Vermeintliche Autoritäten wie Ärzte und Wissenschaftler, oder «der fürsorgliche Staat» und Institutionen wie die UNO oder die WHO wollen uns doch nichts Böses. Auch Staatsmedien, Faktenchecker und diverse NGOs wurden zu «vertrauenswürdigen Quellen» erklärt. Das hat seine Wirkung.
Warum das Thema Gaslighting derzeit scheinbar so populär ist, vermag ich nicht zu sagen. Es sind aber gerade in den letzten Tagen und Wochen auffällig viele Artikel dazu erschienen, und zwar nicht nur von Psychologen. Die Frankfurter Rundschau hat gleich mehrere publiziert, und Anwälte interessieren sich dafür offenbar genauso wie Apotheker.
Die Apotheken Umschau machte sogar auf «Medical Gaslighting» aufmerksam. Davon spreche man, wenn Mediziner Symptome nicht ernst nähmen oder wenn ein gesundheitliches Problem vom behandelnden Arzt «schnöde heruntergespielt» oder abgetan würde. Kommt Ihnen das auch irgendwie bekannt vor? Der Begriff sei allerdings irreführend, da er eine manipulierende Absicht unterstellt, die «nicht gewährleistet» sei.
Apropos Gaslighting: Die noch amtierende deutsche Bundesregierung meldete heute, es gelte, «weiter [sic!] gemeinsam daran zu arbeiten, einen gerechten und dauerhaften Frieden für die Ukraine zu erreichen». Die Ukraine, wo sich am Montag «der völkerrechtswidrige Angriffskrieg zum dritten Mal jährte», verteidige ihr Land und «unsere gemeinsamen Werte».
Merken Sie etwas? Das Demokratieverständnis mag ja tatsächlich inzwischen in beiden Ländern ähnlich traurig sein. Bezüglich Friedensbemühungen ist meine Wahrnehmung jedoch eine andere. Das muss an meinem Gedächtnis liegen.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 04c195f1:3329a1da
2025-03-01 10:36:50
@ 04c195f1:3329a1da
2025-03-01 10:36:50Yesterday's chaotic Oval Office meeting between Trump, Vance, and Zelensky exposes a harsh truth: Europe can no longer depend on American protection. The time has come for Europe to reclaim its sovereignty and rebuild as an independent power.
A Diplomatic Theater With No Happy Ending
Yesterday's chaotic scenes in the Oval Office revealed more than just diplomatic tension—they exposed the fundamental weakness of Europe's strategic position. As President Trump, Vice President Vance, and President Zelensky engaged in their uncomfortable public spectacle, one truth became painfully clear: Europe can no longer rely on American protection.
The awkward press conference featured about 40 minutes of relative calm before descending into 10 minutes of complete chaos. This final meltdown was likely never intended to produce meaningful results. Each participant appeared to be performing for different audiences—Trump and Vance signaling to their base, Zelensky demonstrating resolve to European allies. Without concrete security guarantees, any agreement would be meaningless for Ukraine, a reality all parties surely understood beforehand.
When Vance spoke of diplomacy as a "new strategy"—ignoring numerous failed diplomatic initiatives—he crossed a line that provoked Zelensky's visible frustration. The subsequent breakdown wasn't merely a failure of diplomatic protocol but the public collapse of a relationship Europe has staked its security upon.
The Price of Misguided Priorities
This moment of crisis presents an opportunity if European nations are willing to confront uncomfortable realities. The time has come for Europe to emerge as a third global power, independent from both Eastern and Western influence. However, the path forward requires acknowledging our current weaknesses.
European leadership has squandered decades pursuing ideological luxuries while our industrial and military capabilities have atrophied. While obsessing over multicultural social engineering, progressive identity politics, and globalist agendas, we've neglected the fundamental responsibilities of sovereign nations: securing borders, building defensive capabilities, and fostering national cohesion.
The defense of European nations begins with domestic policy. A society divided against itself cannot stand firm in the face of external threats. This principle applies whether discussing Sweden's defense posture or the broader European security architecture.
Photo by Christian Lue on Unsplash
Reclaiming National Identity and Purpose
To rebuild our defensive capabilities, we must first address the internal fragmentation deliberately cultivated across the political spectrum. The active policies of societal division pursued with increasing fervor since the latter half of the 20th century have undermined the very foundations of national identity and common purpose.
Strengthening national defense requires citizens who understand their shared heritage and believe their nation is worth defending. In practical terms, this means confronting difficult questions about immigration, assimilation, and the presence of potential fifth-column elements within our societies. Nations with higher social cohesion demonstrate greater willingness to defend their collective interests.
The current crisis in Ukraine and the uncertain American commitment should serve as a wake-up call. European nations must rapidly rebuild industrial capacity, military strength, and most importantly, a sense of shared purpose. This demands breaking free from the ideological constraints that have guided European politics for generations.
Although European establishment politicians show little appetite for such fundamental reassessment, events are accelerating rapidly. The dramatic scenes in Washington should catalyze serious reflection across European capitals. We cannot hold our breath waiting for political leadership to regain sense—we must push the conversation forward ourselves.
Europe stands at a crossroads. We can continue our dangerous dependence on unreliable partners, or we can reclaim our sovereignty and rebuild our strength. The choice should be obvious, but making it requires courage our leaders have thus far failed to demonstrate.
■
-
 @ f1989a96:bcaaf2c1
2025-02-27 21:28:20
@ f1989a96:bcaaf2c1
2025-02-27 21:28:20Good morning, readers!
In Nigeria, financial officials are revising digital asset regulations to impose taxes on digital asset transactions on regulated exchanges. This aims to bolster state revenue as more citizens turn to Bitcoin in response to rampant inflation, the naira’s devaluation, and the regime's ever-increasing financial controls.
Meanwhile, in Cuba, thousands of citizens remain unable to access money the regime forced them to convert into Certificates of Deposit (CDs) in 2021. These funds have not been returned by the Communist Party of Cuba. If they eventually are, they will be paid out in since-hyperinflated Cuban pesos, a reality that stands in stark contrast to regime propaganda that it is working “for the people.”
In open-source freedom tech news, we feature NostrPIX, an experimental tool built during the bitcoin++ developer hackathon in Florianopolis, Brazil. It allows anyone in Brazil to pay any merchant or individual with Bitcoin over the Lightning Network. While it is still in its early stages of development, this stands to enable Bitcoin payments at nearly every merchant in Brazil, similar to how apps like Tando enable Bitcoin payments across Kenya.\ \ We end with the official livestreams of the HRF-supported bitcoin++ developer conference in Florianopolis, Brazil, that brought together open-source developers and freedom tech enthusiasts for four days of technical gatherings to enhance Bitcoin’s privacy, usability, and censorship resistance. These livestreams offer a unique chance to view and understand the presentations and workshops at the event.
Now, let’s jump right in!
Subscribe Here
GLOBAL NEWS
Nigeria | Introducing Digital Asset Transaction Tax to Boost State Revenue
Nigerian officials plan to amend their digital asset regulations to tax digital asset transactions in a coercive effort to boost the regime’s dwindling revenues. The Nigerian Securities and Exchange Commission (SEC) is reviewing a new framework to tax transactions on regulated exchanges, allowing the regime to extract even more value from the growing digital asset sector. Nigerians, especially the younger population, increasingly have turned to Bitcoin and stablecoins to escape high inflation, a devalued naira, and an authoritarian regime that repeatedly undermines financial autonomy and human rights. The new tax could hinder the efficiency of tools like Bitcoin by making transactions more expensive. But enforcing this tax beyond regulated platforms presents a challenge. Bitcoin held in self-custody and transacted peer-to-peer remains largely outside the reach of authoritarian states.
Cuba | Citizens Remain Locked Out of Devalued Funds
Thousands of Cubans remain locked out of their savings after the regime forced them to convert Cuban Convertible Peso (CUC) deposits into Certificates of Deposit (CDs) in 2021. This policy was part of the “Tarea Ordenamiento” economic reforms, which eliminated the CUC, a convertible currency previously pegged to the US dollar. For years, Cubans who received foreign currency — whether through work abroad or remittances — were required to exchange it for CUCs, expecting they could later redeem those CUCs for dollars or other foreign currencies. But when the regime eliminated the CUC in 2021, it forced depositors to either accept a heavily devalued exchange rate for Cuban pesos (far worse than the advertised 24-1 ratio) or convert their money into Certificates of Deposit (CDs), with the promise of returning the equivalent value in foreign currency once liquidity allowed. Unbeknownst to Cubans, the CDs paid a negligible 0.15% interest and had no clear timeline for repayment. Today, many depositors still can’t access their money.
Google | Facilitating Censorship in Russia and China
Google is actively assisting authoritarian regimes like China and Russia to censor dissent, removing online content critical of the Kremlin and Chinese Communist Party. In Russia, Google complied with government requests to erase YouTube videos opposing the war in Ukraine, while in China, it removed references to the Tiananmen Square massacre and pro-democracy activism. With more than 70% of Russians relying on YouTube for news and China’s Great Firewall blocking independent sources, corporate compliance with state censorship enables state propaganda to proliferate as a dominant narrative. For activists and nonprofits seeking uncensorable communications, nostr — an open and decentralized protocol — offers a way to share information beyond the reach of authoritarian regimes. Activists and NGOs can get started here.
World | Transnational Repression Most Common Under CBDC-Leading Countries
New data from Freedom House reveals that 23 governments engaged in transnational repression in 2024, using abductions, assassinations, and forced deportations to silence exiled dissidents. Leading perpetrators include the authoritarian regimes of China, Russia, Iran, and Turkey — orchestrating over 1,200 incidents in the past decade. Notably, many of these regimes are at the forefront of central bank digital currency (CBDC) development, a technology that drastically increases state control over financial activity. By allowing governments to surveil, freeze, and block funds in real time, CBDCs strip activists of financial privacy and force them into greater vulnerability. As authoritarian states refine both digital and physical methods of repression, CBDCs may become a powerful weapon for crushing dissent beyond borders.
Niger | Delays Democratic Elections While Citizens Financially Struggle
Niger’s deteriorating economic conditions are set to continue as the ruling military junta has proposed delaying democratic elections until at least 2030 to contain a “security threat.” Army commander Abdourahamane Tchiani, who came to power in a 2023 coup, originally pledged a three-year transition to civilian rule. Now, that timeline appears extended to five years, allowing “the junta to restore security and regain control of territory captured by Islamist militants that have expanded their insurgency in recent months.” With inflation eroding Nigerien’s purchasing power and the general economic well-being of citizens declining, Niger can’t afford more military rule. This could be a pretext for Tchiani to consolidate power, especially as discussions emerge about dissolving political parties and granting him the rank of general.
_______________
Webinar Series for Nonprofits: Become Unstoppable
HRF will host a free, three-day webinar from March 17-19, teaching human rights defenders and nonprofits how to use Bitcoin to counter state censorship and confiscation. Sessions run daily from 10:30 a.m. to 12:00 p.m. EDT and are beginner-friendly. The webinar will be led by Anna Chekhovich, HRF’s Bitcoin nonprofit adoption lead and financial manager at Alexei Navalny’s Anti-Corruption Foundation, and co-taught by the prominent Bitcoin educator Ben Perrin.
SXSW | The Human Rights Risks of Central Bank Digital Currencies (CBDCs)
Join HRF at SXSW 2025 in Austin from March 7-13 to explore how CBDCs threaten financial freedom. Experts Roger Huang, Charlene Fadirepo, and Nick Anthony will discuss how authoritarian regimes use CBDCs for surveillance and control. Attendees can also visit HRF’s CBDC Tracker booth to explore an interactive map of CBDC developments worldwide.
_______________
BITCOIN AND FREEDOM TECH NEWS
NostrPIX | Enabling Bitcoin Payments in Brazil
NostrPIX is a new tool built just a few days ago during the bitcoin++ hackathon in Florianopolis, Brazil, that lets users pay any merchant or individual in Brazil with Bitcoin over the Lightning Network. To use NostrPIX, users scan a Pix QR code (the country’s widely used digital payment system) and pay with bitcoin from their Lightning wallet. Designed with the unbanked in mind, NostrPIX lets those who cannot open a Brazilian bank account to transact with Bitcoin and Pix (no sign-ups required, just instant payments). Its innovative approach won the bitcoin++ hackathon, showcasing its potential to bridge Bitcoin with traditional systems. While still a proof of concept, NostrPIX joins projects like Tando in Kenya, making Bitcoin more practical for everyday commerce and could inspire similar products elsewhere in countries facing political oppression.
Iris | Implements Double Ratchet Messaging for Better Privacy
Iris, a client for Nostr launched by Martti Malmi, implemented double ratchet messaging, an encryption algorithm similar to that used by Signal, significantly improving private communications for activists and human rights defenders. This ensures message metadata remains hidden, and with its implementation, past and future conversations on Iris stay private even if a user’s main Nostr private key is compromised. This upgrade empowers individuals in difficult political environments to communicate without fear of surveillance by reducing the risks of authoritarian regimes tracking their conversations. HRF is proud to have helped support Malmi as he invented and launched this innovation.
Presidio Bitcoin | New Bitcoin Co-Working and Events Space in Bay Area
Presidio Bitcoin is the Bay Area’s first dedicated co-working and events space. Located in San Francisco’s famous Presidio neighborhood, it will be a collaborative space for developers, educators, and freedom tech enthusiasts to connect, work, and innovate together to drive Bitcoin adoption forward. It draws inspiration from other Bitcoin hubs worldwide, like Bitcoin Park in Nashville, Tenn., Bitcoin House Bali in Indonesia, and Bitcoin Ekasi in South Africa. This time, aiming to create a community of Bitcoiners in the tech capital of the US. Presidio Bitcoin hopes to foster new talent and secure greater funding from Silicon Valley, becoming a central meeting point for those passionate about Bitcoin and freedom. HRF Freedom Fellows were able to visit the space recently, and HRF staff will be speaking at upcoming events at the venue in the near future. Check the space out here.
Cashu | Releases Cashu Development Kit
Cashu, an open-source Chaumian ecash protocol for Bitcoin integrated with the Lightning Network, released the Cashu Development Kit (CDK) in Rust (a common programming language). This makes it easier for developers to build and integrate Cashu wallets, expanding access to private Bitcoin transactions. With Cashu, users can spend Bitcoin-backed ecash without revealing their identity or transaction history. This enables private, cheap, and fast transactions with the tradeoff of being custodial. As digital financial surveillance increases, ecash offers an alternative to remain private. The CDK release expands the reach of said private Bitcoin transactions, providing more safety and anonymity for dissidents.
RoboSats | Adds LNp2pBot Orders on Android App
RoboSats, a privacy-focused peer-to-peer (P2P) Bitcoin exchange powered by the Lightning Network, added support for LNp2pBot orders in its Android app. Previously, users used Telegram to interact with LNp2pBot for P2P bitcoin trades. Now, they can access P2P orders directly from the RoboSats Android app. This integration enhances usability by reducing platform dependency and provides users with greater liquidity for P2P trades. HRF is pleased to see the continued development and interoperability of privacy-focused, self-custodial Bitcoin on and off ramps from this Bitcoin Development Fund grantee.
Bitcoin Dada | Visits Bitcoin Mining Site for Hands-On Learning
Bitcoin Dada, an HRF-supported nonprofit empowering African women with financial literacy and Bitcoin education, recently took its students on a trip to a Bitcoin mining site operated by Gridless in Kibwezi, Kenya. This visit provided students firsthand exposure to Bitcoin mining’s potential for driving economic growth and expanding electricity access in rural African communities while simultaneously helping decentralize the network. The site repurposes sisal waste (the waste from fiber production) to generate electricity, reduce blackouts, and provide power to homes in Kibwezi. As more and more off-grid sites like this come online, Bitcoin’s mining composition becomes less centralized and stronger against threats from authoritarian states.
RECOMMENDED CONTENT
bitcoin++ Developer Conference Livestream
Last week, bitcoin++ hosted the “hacking edition” developer conference in Florianopolis, Brazil. The event brought together Bitcoin developers and freedom tech enthusiasts for four days of hands-on development, workshops, and technical discussions to enhance Bitcoin’s privacy, accessibility, and censorship resistance. If you missed the event, you can catch the key sessions and workshops via live stream. Watch them here.
Nostr: The Importance of Censorship-Resistant Communication for Innovation and Human Progress
In this article for Bitcoin Magazine, Leon Wankum highlights why Nostr, a censorship-resistant protocol, is key to unlocking innovation and free expression. He explains how Nostr enables decentralized content sharing using cryptographic keys and relays, preventing central control of the protocol. This approach ensures that no single entity controls the flow of information, thereby enhancing freedom of expression. Alongside Bitcoin, Nostr has the potential to break corporate and state monopolies, allowing for grassroots progress and innovation on the individual level. You can read the full article here.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ 5d4b6c8d:8a1c1ee3
2025-02-27 20:25:29
@ 5d4b6c8d:8a1c1ee3
2025-02-27 20:25:29I've really enjoyed these two months running ~econ. It crystallized that what I most enjoy is reading and commenting. Thankfully, our excellent contributors are giving me ample opportunities.
Metrics
- Posts: 5th place - 264
- Comments: 6th place - 1653
- Stacking: 3rd place - 149.6k
- Revenue: 6th place - 59.4k
We're still over the breakeven point, but revenue was down from last month (still above the month before I took over, though). That means the new posting fee will be 81 sats, which is halfway back to the previous 108.
Contest Ideas
Last month, I asked what people thought the best use of previously donated sats was and funding a contest seemed to get the best response.
I'd like to try out a quarterly contest. The prize pool will be whatever sats have been earned, above the breakeven point, until the donated sats have all been paid out.
I'm not sure if this will be a winner-takes-all thing or a top 3. I also don't want to completely defer to zaprank, so what I'll do is list the top 10 posts by zaprank and have people vote on the best post.
Let me know what you think (including if this is an acceptable use of your donations, for those who made donations).
originally posted at https://stacker.news/items/899082
-
 @ 4523be58:ba1facd0
2025-02-27 18:51:11
@ 4523be58:ba1facd0
2025-02-27 18:51:11NIP-118
Nostr Double Ratchet Invites
In order to start a NIP-117 Nostr Double Ratchet session, Alice and Bob need to exchange ephemeral public keys and a shared secret.
In a Nostr Double Ratchet invite, Alice gives Bob her
- ephemeral public key, which is also used to respond to the invite on Nostr,
- shared secret, and
- Nostr identity public key, which is used to authenticate the exchange.
Nostr event
Publishing an invite event on Nostr allows other users to start a Double Ratchet session with you.
typescript { pubkey: inviterIdentityKey, content: '', tags: [ ['d', `double-ratchet/invites/${uid}`], // uid: unique name for the invitation, e.g. "public" ['l', 'double-ratchet/invites'], // label, for listing all your invites ['ephemeralKey', inviterEphemeralKey], ['sharedSecret', sharedSecret] ], kind: 30078, created_at, id, sig }lis a NIP-32 label tag that can be used to list your invites. We use this approach with NIP-78 application specific data kind30078in order to not bloat the event kind space and instead have a human-readable label.URL
Invites can be also shared privately, without requiring a Nostr event. This improves privacy, removing the public association between the inviter and response.
URL and QR code are often convenient ways to share privately, especially when the other user is not yet on Nostr. Format:
typescript const invite = { inviter, ephemeralKey, sharedSecret }; const json = JSON.stringify(invite); const url = `https://example.com/#${encodeURIComponent(json)}`;Encoding the invite into the URL hash ensures it's not sent to the server and logged by default.
nostr:URI scheme is another possible way to share invites, when we have native clients supporting the feature.Invite response
Outer event
Invite response outer event is a NIP-59 gift wrap event of kind
1059, sent from a random, one-time-use pubkey, hiding the responder's identity from the public.It is addressed to the ephemeral key in the invite. If the invite was publicly shared, responses can be publicly associated to the inviter.
Inner event
NIP-59 Rumor.
```typescript const conversationKey = nip44.getConversationKey( inviteeKeyPair, inviterPublicKey ); const encrypted1 = encrypt(inviteeEphemeralKey, conversationKey); const encrypted2 = encrypt(encrypted1, sharedSecret);
const rumor = { pubkey: inviteePublicKey, kind: 1060, content: encrypted2, tags: [], createdAt, id, }; ```
After receiving the invite response, both parties have what they need to start a double ratchet session: each others' ephemeral public keys and a shared secret.
Both parties have authenticated by encrypting or decrypting using their nip44 conversation key.
The shared secret from the invite is used in the response to ensure that only actual recipients of the invite can follow it. Otherwise, attackers could initiate double ratchet sessions by sending invite responses to all addresses that received gift wraps, some of which are private invite addresses.
-
 @ 2efaa715:3d987331
2025-02-27 16:07:36
@ 2efaa715:3d987331
2025-02-27 16:07:36Cost of a 1960s Diet vs Modern Food Costs by Decade
The following is a result from ChatGPT's "deep research" feature when asked to analyze what a "1960s diet" would cost in each subsequent decade. The CPI and basket of goods is constantly adjusted to "reflect consumer purchasing behavior", but this metric overlooks the fact that consumer behavior itself is guided by prices. Just because someone does buy something doesn't mean they would prefer this good over another (potentially superior) good, all it tells you is that they did buy it. When the cost of living off of higher quality foods becomes too great to bear, consumers will trade-down to lower-quality foods. When the CPI reflects this, even a "steady inflation number" hides the fact that quality of life has degraded.
If you don't want to read the whole thing, at least check out the conclusion at the end. Everything from here down was generated by the AI after rounds of nudging by me.
Also the cover image, obviously (lol)Following a 1960s-style diet – rich in red meat, dairy, and unprocessed “whole” foods – has become increasingly expensive over time. Below we examine each decade from 1960 to the present, tracking how much the cost of that fixed 1960s diet rose and comparing it to the prevailing food costs (CPI) shaped by consumers adapting their eating habits. Key staples like red meat, dairy, grains, and processed foods are highlighted to show the impact of inflation on a traditional diet versus switching to cheaper substitutes.
1960s: Baseline of Affordable Abundance
- Percentage Increase in Cost: Food prices rose modestly in the 1960s (around 2–3% per year). Over the decade, maintaining the same 1960 basket led to roughly a 25–30% increase in cost (Food at home price inflation, 1947→2024). This was a relatively small jump compared to later decades.
- Cost in Era’s Currency: For example, if a household spent $100 per week in 1960 on the typical foods (plentiful beef, whole milk, butter, eggs, etc.), by 1970 that same diet cost about $125–$130 in nominal dollars. Everyday items were cheap: ground beef was only $0.30 per lb in the late 1950s, and butter about $0.75 per lb (Grocery Store Prices for 14 Items in 1957 | HowStuffWorks) (Grocery Store Prices for 14 Items in 1957 | HowStuffWorks). Americans could afford more of these foods as incomes grew.
- Comparison to CPI (Behavior-Adjusted): The official food Consumer Price Index (CPI) climbed at a similar pace (~28% increase from 1960 to 1970 (Food at home price inflation, 1947→2024)), since consumer behavior hadn’t drastically shifted yet. Few felt pressure to substitute cheaper foods because inflation was mild. In fact, many families ate more of these staples as prosperity rose – U.S. beef consumption per person increased from ~63 lbs in 1960 to 84 lbs by 1970, while chicken rose from 28 to 48 lbs (National Chicken Council | Per Capita Consumption of Poultry and Livestock, 1965 to Forecast 2022, in Pounds). Any cost savings from “behavior changes” were minimal in the 60s. (One early example: margarine was already replacing some butter for health/cost reasons, but butter was still affordable in 1960 at ~$0.75, so sticking to butter didn’t break the bank (Grocery Store Prices for 14 Items in 1957 | HowStuffWorks).) Overall, adapting one’s diet wasn’t necessary for budget reasons in the 1960s, as food was relatively cheap and inflation low.
1970s: Soaring Prices Hit Traditional Diets Hard
- Percentage Increase in Cost: The 1970s brought surging food inflation. A fixed 1960s-style diet would cost roughly double (+100% or more) by the end of the decade. In particular, meat and dairy prices skyrocketed. Beef prices roughly doubled from 1970 to 1980 (the BLS beef index jumped from the 40s to nearly 100 (Beef and veal price inflation, 1935→2025)), contributing to an overall ~120% increase in the cost of a meat-heavy 1960s basket during the 70s. By comparison, overall food-at-home prices rose about 121% in that span (Food at home price inflation, 1947→2024) – a huge jump in itself. The worst spikes came in 1973–74, when food prices jumped 15–16% in a single year (Food at home price inflation, 1947→2024).
- Cost in Era’s Currency: Someone stubbornly sticking to their 1960 grocery list in this era paid a steep price. If they spent $100 per week in 1970, by 1980 they’d need to spend roughly $220–$230 for the same items. For instance, mid-decade a pound of steak that cost ~$1 in the late 60s might cost $2–3 by the late 70s. Whole milk prices also roughly doubled in the 70s (Fresh whole milk price inflation, 1939→2024). This era’s inflation was so severe that it forced a re-budgeting for those insisting on expensive staples.
- Comparison to CPI (Behavior-Adjusted): While all consumers felt the 70s price shock, those who adapted their diets mitigated the impact. Many Americans reacted by buying less red meat or switching to cheaper proteins. Notably, when beef became very expensive (meat prices jumped 5.4% in just one month in early 1973 (1973 meat boycott - Wikipedia)), consumers staged a “meat boycott” and turned to poultry, pork, or beans. Poultry was a big winner – chicken prices did rise (44% in 1973 (Fresh whole chicken price inflation, 1935→2024)), but over the decade chicken remained cheaper per pound than beef, and per capita chicken consumption climbed while beef consumption dropped (National Chicken Council | Per Capita Consumption of Poultry and Livestock, 1965 to Forecast 2022, in Pounds). Processed and shelf-stable foods also gained favor as thrifty alternatives; for example, consumers might buy canned soups or powdered drink mixes which had smaller price increases. The official CPI (which reflects some substitution) still rose dramatically (~105% for food in the 70s (Food at home price inflation, 1947→2024)), but the true cost of living was a bit lower for those who adapted. By cutting back on expensive items (or stretching them – e.g. more casseroles with grains/veggies and less meat), families could keep their food spending increase somewhat below the headline inflation. In short, a person clinging to the high-red-meat, butter-on-everything diet of 1960 ended up paying much more in the 70s, whereas those who embraced cheaper substitutes (chicken instead of steak, margarine instead of butter, generic and processed foods) softened the blow. The late 1970s also saw food costs stabilize under price controls, rewarding those who diversified their diet away from the costliest staples.
(Chicken leads U.S. per person availability of meat over last decade | Economic Research Service) Per capita availability of meat in the U.S., 1910–2021. Beef (gray line) peaked in the 1970s and then declined as prices rose and consumers ate more chicken (yellow line). Chicken overtook beef as the most consumed meat by 2010, thanks to its lower cost and dietary shifts (Chicken leads U.S. per person availability of meat over last decade | Economic Research Service). Pork (red) held roughly steady, while fish (purple) remained a small share. This illustrates how Americans adjusted their protein sources over decades in response to price and preferences. (Chicken leads U.S. per person availability of meat over last decade | Economic Research Service)
1980s: Slowing Inflation and New Dietary Habits
- Percentage Increase in Cost: Inflation cooled in the 1980s, making food prices more stable. Even so, a fixed 1960s diet saw about a 50% cost increase over the decade. That means the same basket that cost $100 in 1980 would cost around $150 by 1990. This increase was much lower than the 70s, but still notable. Meats and dairy had smaller price jumps now (beef rose ~38% from 1980–90, milk ~45% (Fresh whole milk price inflation, 1939→2024)), and overall food-at-home prices climbed ~40–50% (Food at home price inflation, 1947→2024) (Food at home price inflation, 1947→2024) in the 80s.
- Cost in Era’s Currency: If our traditional-diet shopper spent $220/week in 1980 (continuing the prior example), by 1990 they’d be spending roughly $330 for the same groceries. For instance, a gallon of whole milk that cost about $1.50 in 1980 might be ~$2.20 by 1990; a pound of ground beef around $1.20 in 1980 could be ~$1.75 in 1990. These nominal increases were easier to manage than the wild 70s, but still added up.
- Comparison to CPI (Behavior-Adjusted): In the 80s, consumer behavior had permanently shifted due to the prior decade’s lessons. Many households continued to favor cheaper or leaner foods, and this helped keep their actual cost of living lower than if they had stuck to the old diet. For example, butter consumption plunged (per capita fell from 7.5 lbs in 1960 to ~4.5 lbs by 1980) as people used margarine and processed spreads instead (cameracopy4.qxd). Butter lost its hefty weight in the price index, reflecting how few people still bought it regularly by the 80s. Similarly, beef was no longer king – Americans were eating 20% less beef than in the 70s, and far more chicken, which was mass-produced cheaply (Chicken leads U.S. per person availability of meat over last decade | Economic Research Service). The CPI’s market basket was updated in 1987, locking in these new habits (more poultry and convenience foods, fewer expensive staples). As a result, official food inflation in the 80s was moderate, and those who already had adapted their diet felt roughly the same ~50% rise as the CPI. However, someone who refused to change – still buying large quantities of red meat, whole milk, fresh butter, etc. – would have spent more than the average person. They missed out on the savings from things like economy cuts of meat, bulk grains, and processed goods that became popular. By the late 1980s, the U.S. food system was delivering cheaper calories (e.g. refined grains, corn oil, sweeteners) on a huge scale. Families that incorporated these cheaper ingredients (think Hamburger Helper, microwave dinners, soda instead of milk) kept their grocery bills lower. Indeed, food became a smaller share of household spending: it fell from 28.5% of the family budget in 1960 to about 17% by 1980 (cameracopy4.qxd), a testament to how adapting food choices and benefitting from cheaper options lowered the relative cost of living.
1990s: Cheaper Alternatives in an Era of Low Inflation
- Percentage Increase in Cost: The 1990s saw very low food inflation by historical standards. Maintaining the exact 1960s diet through this decade would raise costs by only about 25–30%. Food-at-home prices increased roughly 2–3% per year or ~27% total from 1990 to 2000 (Food at home price inflation, 1947→2024) (Food at home price inflation, 1947→2024) – similar to general inflation.
- Cost in Era’s Currency: Continuing our scenario, $330/week in 1990 for a 1960-style diet would become about $420–$430/week by 2000. Many staple food prices barely crept up. For example, a loaf of bread or a dozen eggs only rose by a few dimes over the whole decade. In some cases prices even stagnated or fell: U.S. farm commodities were abundant (grain surpluses kept costs of cereal, flour, and animal feed low). The late 90s had such cheap raw ingredients that milk, meat, and sugar prices were relatively stable.
- Comparison to CPI (Behavior-Adjusted): By the 90s, behavior-adjusted costs were markedly lower than our fixed diet scenario, because consumers had spent two decades optimizing their food spending. The prevailing diet in the 90s was very different from the 60s, driven by cost efficiency and convenience. Shoppers embraced warehouse clubs and discount supermarkets, bought private-label/store brands, and leaned heavily on processed foods that benefited from cheap oil and corn. For instance, instead of whole fresh foods for every meal, families might use instant pasta mixes, boxed cereals, and soft drinks – items produced at scale and often cheaper per calorie. This kept average grocery bills lower. In fact, the cost of living for food rose so slowly in the 90s that it was common to “trade up” some items (like occasionally buying steak or exotic fruits) and still stay on budget. A person strictly sticking to a 1960s whole-food diet (cooking from scratch, lots of fresh meat and dairy) would not enjoy those processed-food savings. By this time they’d be paying noticeably more than the average consumer for the same caloric intake. Studies began to note a troubling pattern: healthier whole foods were getting relatively more expensive, while unhealthy processed options remained very cheap. (For example, fresh produce prices in the U.S. rose faster than soda and snack prices in the 80s/90s.) The overall CPI for food was low in the 90s, reflecting these substitutions. A clear sign of the era: fast-food value meals and junk snacks proliferated, offering calories at rock-bottom prices. Those who adapted their diet to include these inexpensive foods saw a much lower increase in their cost of living – and in some cases, food spending as a share of income hit record lows. Meanwhile, someone clinging to only unprocessed “old-fashioned” foods would have a higher grocery bill and experienced a higher effective inflation than the behavior-adjusted CPI. In short, the 1990s made it easier than ever to save money on food – if you were willing to eat like a 1990s consumer.
2000s: Diverging Diet Costs – Whole Foods vs Processed
- Percentage Increase in Cost: Food costs in the 2000s rose at a modest pace, very similar to the 90s. A fixed 1960s diet would increase about 25–30% in cost over the decade (roughly keeping up with general inflation). From 2000 to 2010 the food-at-home CPI climbed ~29% (Food at home price inflation, 1947→2024) (Food at home price inflation, 1947→2024). There were a couple of price spikes mid-decade (e.g. 2007–2008 saw grain and dairy price jumps), but also some years of minimal change.
- Cost in Era’s Currency: Our hypothetical shopper spending $420 in 2000 would be around $540 per week by 2010 for the same basket. Key 1960s staples did get pricier in the 2000s: e.g. whole milk went from about $2.80/gal in 2000 to $3.50+ by 2010; ground beef from ~$1.80 to ~$2.25/lb over the decade. But the increases were gradual. Notably, by 2010 many traditional items (meats, eggs, dairy) were cheaper in real terms than in the 1970s – thanks to efficiency gains – even if nominal prices edged up.
- Comparison to CPI (Behavior-Adjusted): The 2000s is when the gap between a “traditional whole-food diet” and the average diet’s cost really started to widen. The official CPI remained fairly low, in part because consumers kept shifting towards cheaper ingredients and prepared foods. Two diverging trends emerged:
- Many consumers, facing tight budgets especially after the 2008 recession, doubled down on low-cost, energy-dense foods. This meant more refined grains (white bread, pasta, rice), processed snacks, sweetened drinks, and fatty meats – all of which were inexpensive and often on promotion. These items benefited from globalized supply chains and agricultural surpluses, keeping their prices down or rising very slowly. For example, corn-based sweeteners and oils were so cheap that soda and fried foods remained very affordable in the 2000s.
- On the other hand, some consumers began seeking healthier “whole” foods (organic produce, whole grains, lean meats). But these often came at a premium and saw higher inflation. Someone maintaining a 1960s-style home-cooked diet (lots of fresh ingredients) fell into this category almost by definition. They would have experienced higher effective inflation than the average. Research confirms this divergence: in recent analyses, the cost of a healthy recommended diet has risen faster than the cost of an unhealthy diet. For instance, during 2019–2022, prices of healthy foods (fruits, veggies, lean proteins, etc.) jumped 12.8% in one year, whereas “unhealthy” food prices rose only 7–9% ( Healthy Food Prices Increased More Than the Prices of Unhealthy Options during the COVID-19 Pandemic and Concurrent Challenges to the Food System - PMC ). This pattern had been building over the 2000s. Thus, those who adapted by buying the cheapest processed options saw a smaller cost-of-living increase than those buying whole foods. By the end of the 2000s, the U.S. was in a situation where following a 1960s diet cost significantly more than an average 2000s diet, even though overall inflation was mild. In practical terms, a family could slash their grocery bill by switching from fresh-cooked dinners with milk to, say, boxed mac-and-cheese with soda – and many did. The CPI implicitly captured this shift: food remained about ~13% of consumer spending in the 2000s (near historic lows), partly because people found ever-cheaper ways to eat.
2010s: Relative Stability (Until a Shock)
- Percentage Increase in Cost: The 2010s were a decade of exceptionally low food inflation. A fixed 1960s diet’s cost rose only about 15–20% in total through 2010–2019. For most of those years, food prices grew less than 2% annually (some years even saw slight deflation in grocery prices (Food at home price inflation, 1947→2024)). From 2010 to 2020 the food-at-home index went up about 16% (Food at home price inflation, 1947→2024) (Food at home price inflation, 1947→2024) – the slowest growth of any decade in this analysis.
- Cost in Era’s Currency: In our running example, $540/week in 2010 for the old-fashioned diet would become roughly $620–$630 by 2020. In other words, nearly flat in real terms. Many staple food prices were remarkably steady. A gallon of whole milk hovered around $3.50–$4 throughout the decade; a pound of chicken breasts stayed near $1.99 for years. The shale oil boom and low energy costs, plus technological advances in agriculture, helped keep food production and transportation cheap. By the late 2010s, Americans enjoyed some of the lowest food inflation on record.
- Comparison to CPI (Behavior-Adjusted): With inflation so low, the difference between sticking to a 1960s diet and the average diet’s cost was less pronounced during this decade – everyone benefited from stable prices. However, it’s important to note that by the 2010s the average diet was very far removed from the 1960s diet, largely for economic reasons built up over prior decades. The average American in 2019 was consuming lots of inexpensive processed foods and far less of the pricey whole foods that defined 1960. This meant their cost of living was inherently lower. For those still following a traditional diet, their basket cost hadn’t risen much in the 2010s, but it was starting from a much higher base relative to typical consumers. In effect, the “gap” was already baked in. Government data continued to show that healthy food plans cost more – a trend consistent with the idea that a whole-food diet remained pricier than the mix of convenience foods most people bought. By the end of the 2010s, food was only about 12–13% of household expenditures on average, reflecting decades of substitutions and cheaper alternatives keeping costs down (cameracopy4.qxd). A person eating like it’s 1960 (lots of red meat roasts, fresh veggies, whole milk) in 2019 would likely be spending well above that share. In summary, the 2010s offered a breather: low inflation meant even “old diet” holdouts weren’t punished by price hikes, but they were still paying more than those who had long ago adapted to the economical 2010s food landscape.
(Note: The early 2020s have seen a sharp inflationary spike for food, largely due to pandemic disruptions and war. Interestingly, this spike hit fresh foods and meats harder than processed foods, echoing the long-term pattern. For example, in one study the cost of a healthy diet rose 17.9% from 2019–2022, whereas the typical less-healthy diet rose 9% ( Healthy Food Prices Increased More Than the Prices of Unhealthy Options during the COVID-19 Pandemic and Concurrent Challenges to the Food System - PMC ). This underscores that when inflation strikes, sticking to a traditional wholesome diet tends to cost more than making do with cheaper substitutes. As of 2022–2023, consumers again coped by buying store brands, cutting meat consumption, etc., to soften the blow – much as they did in the 1970s.)
Conclusion: Traditional Diet vs Adaptive Diet – Which Costs More?
Over six decades, inflation has raised all food prices, but not uniformly. Someone maintaining a fixed 1960s-style diet from 1960 through today would have seen their food costs rise far more than the official “cost of food” suggests – because the official index assumes people adjust their buying. In fact, by 2020 such a person would be spending roughly 8–10 times what they spent in 1960 on food in nominal dollars, whereas the behavior-adjusted CPI for food rose about 8-fold (Beef and veal price inflation, 1935→2025) (Fresh whole chicken price inflation, 1935→2024). That implies perhaps a 20–25% higher cumulative cost for the fixed diet follower. The biggest contributors were red meat and dairy: these had higher-than-average inflation over the long run. For example, beef prices rose much faster than overall prices (3,637% since 1935) (Beef and veal price inflation, 1935→2025), while chicken (a cheaper substitute) had lower inflation (805% since 1935) (Fresh whole chicken price inflation, 1935→2024). Consumers responded accordingly – eating less beef and butter, and more chicken and margarine, as decades passed. Grains and processed foods, often mass-produced from low-cost commodities, helped keep modern diets affordable; whole foods did not see such dramatic cost efficiencies.
In each decade, those who adapted their food choices enjoyed a lower cost of living increase than those who stuck with the old-school diet. The 1970s illustrated this vividly (households that substituted chicken or pasta when steak prices spiked avoided some of the worst budget pain). By the 2000s and 2010s, the typical American diet was heavily “behavior-adjusted” for cost – full of cheaper oils, sweeteners, and protein sources – which kept the CPI food inflation relatively low. Meanwhile, a person trying to eat like it’s 1960 (lots of red meat, whole milk, homemade meals) ended up paying a premium each year to do so.
In summary, inflation heavily penalized the maintenance of a 1960s diet. Each decade saw that fixed basket get relatively more expensive, especially for categories like red meat and dairy. In contrast, Americans who embraced cheaper substitutes and new foods managed to keep their food spending growth below the inflation that a “fixed basket” would imply. This behavior-adjustment – switching from costly whole foods to economical processed and alternative foods – has been a key reason the reported CPI for food rose more slowly. It quantifies how much lower the cost of living was for those who adapted: often shaving several percentage points off per-year inflation, and cumulatively making food far more affordable than it would have been under the old diet. The trade-off, of course, is that while the traditional 1960s diet was nutritious but now expensive, the modern adapted diet is cheaper but often less healthy. Consumers effectively used substitutions to counteract food inflation, saving money at the expense of dietary changes. The decades-long outcome is clear – financially, eating in 2023 like it’s 1963 will cost you significantly more than eating like a 2023 consumer, due to the compounding effect of differential inflation and behavior shifts over time.
Other Sources:
- U.S. Bureau of Labor Statistics – Historical CPI data for food categories (Food at home price inflation, 1947→2024) (Beef and veal price inflation, 1935→2025)
- USDA Economic Research Service – Food price reports and consumption trends (Chicken leads U.S. per person availability of meat over last decade | Economic Research Service) (cameracopy4.qxd)
- The Value of a Dollar – mid-20th-century grocery prices (e.g. 1957 butter, beef) (Grocery Store Prices for 14 Items in 1957 | HowStuffWorks) (Grocery Store Prices for 14 Items in 1957 | HowStuffWorks)
- Congressional Research Service – Food inflation and consumer responses (1973 meat boycott - Wikipedia)
- Academic study on healthy vs unhealthy diet cost inflation - (pmc.ncbi.nlm.nih.gov)
-
 @ ee603283:3bc79dec
2025-02-26 23:50:16
@ ee603283:3bc79dec
2025-02-26 23:50:16Source Article by the Bitkey team and Undine Rubeze: https://bitkey.build/inheritance-is-live-heres-how-it-works/
TLDR: You wrap your mobile key, and encrypted this wrapped key with your beneficiaries public key. Send this info to Bitkey's servers. Your beneficiary can trigger the inheritance process after your passing and wait 6-months before they can do anything.
6 months seems like a long-time to be able to access critical life-savings funds for your family. This should help you prioritize a 3-6 month emergency "cash" savings for your family. Cash can be in a savings account or physical cash. Additionally, it might be beneficial to setup a life-insurance plan (a simple term-life plan) where the immediate bills and expenses are covered.
bitcoin #nostr
devs I tried to import the url into highlighter but got this error: "The page is not reader-friendly"
-
 @ 8d34bd24:414be32b
2025-02-26 23:07:43
@ 8d34bd24:414be32b
2025-02-26 23:07:43My mind keeps chewing on these verses in Jeremiah. Maybe I can’t get it out of my head because it seems so contrary to everything I have believed regarding to prayer.
“As for you, do not pray for this people, and do not lift up cry or prayer for them, and do not intercede with Me; for I do not hear you. Do you not see what they are doing in the cities of Judah and in the streets of Jerusalem? The children gather wood, and the fathers kindle the fire, and the women knead dough to make cakes for the queen of heaven; and they pour out drink offerings to other gods in order to spite Me. Do they spite Me?” declares the Lord. “Is it not themselves they spite, to their own shame?” (Jeremiah 7:16-19) {emphasis mine}
Before continuing with this article, make sure you have read What? Do Not Pray For ..., so you have my background thoughts on this passage.
After writing the first post, I began thinking about how this verse applies to American Christians today in my post A Hard Question With an Uncomfortable Answer. In my first two articles, I basically came to the conclusion that we should not pray blessings on those who were sinning and rejecting God, but that praying for repentance and turning back to God would be an allowed and even honored prayer. Then today, while listening to a sermon from Revelation, I thought, “Is there a time we are called to not pray for someone or some nation because God has given them their choice and He is no longer calling them to Himself?”
When God Hardens a Heart
There are a lot of verses where God says that he hardened their heart. The most well known is regarding the hardened heart of the Egyptian Pharaoh in Exodus where we read a succession of verses about a hardened heart:
First Pharaoh hardens his own heart:
But when Pharaoh saw that there was relief, he hardened his heart and did not listen to them, as the Lord had said. (Exodus 8:15) {emphasis mine}
then he hardens his heart again:
But Pharaoh hardened his heart this time also, and he did not let the people go. (Exodus 8:32) {emphasis mine}
then he hardened his heart and his servants hearts:
But when Pharaoh saw that the rain and the hail and the thunder had ceased, he sinned again and hardened his heart, he and his servants. (Exodus 9:34) {emphasis mine}
then God hardens Pharaoh’s heart:
Then the Lord said to Moses, “Go to Pharaoh, for I have hardened his heart and the heart of his servants, that I may perform these signs of Mine among them, (Exodus 10:1) {emphasis mine}
God didn’t harden Pharaoh’s heart initially, but after repeated choices by Pharaoh, God gave Pharaoh the hardened heart he chose. Also, God hardened Pharaoh’s heart in order to perform signs that He wanted to perform to show Himself to the Israelites and the Egyptians. He did it to fulfill His will and His plan.
Once God chose to harden Pharaoh’s heart, would it be praying according to God’s will to ask that Pharaoh repent? As uncomfortable as this makes me, I don’t think it would be praying according to God’s will to pray for repentance for Pharaoh.
When God Declares His Judgment
In Jeremiah 27, God has stated that Babylon will conquer Judah, take away the people, and take the golden implements from the Temple. He says that those who want to live must submit to Babylon. This is God’s will. Many supposed prophets were prophesying that Babylon will not capture Judah and then after Judah was conquered, that they would be brought back after 2 years contrary to God’s will and declaration of 70 years of captivity.
Then I spoke to the priests and to all this people, saying, “Thus says the Lord: Do not listen to the words of your prophets who prophesy to you, saying, ‘Behold, the vessels of the Lord’s house will now shortly be brought again from Babylon’; for they are prophesying a lie to you. Do not listen to them; serve the king of Babylon, and live! Why should this city become a ruin? But if they are prophets, and if the word of the Lord is with them, let them now entreat the Lord of hosts that the vessels which are left in the house of the Lord, in the house of the king of Judah and in Jerusalem may not go to Babylon. (Jeremiah 27:16-18) {emphasis mine}
Regarding these so-called prophets, God says, “if the word of the Lord is with them, let them now entreat the Lord of hosts.” This sounds like they should pray thus only if “the word of the Lord is with them,” or basically if they are praying according to God’s will. Conversely, since the passage makes clear these “prophets” are not speaking God’s word, nor supporting God’s will, then God should not be entreated (asked in prayer) to act contrary to His will.
When God Gives Them Over to Their Sin
Similarly, in the New Testament it says of God:
For even though they knew God, they did not honor Him as God or give thanks, but they became futile in their speculations, and their foolish heart was darkened. Professing to be wise, they became fools, and exchanged the glory of the incorruptible God for an image in the form of corruptible man and of birds and four-footed animals and crawling creatures.
Therefore God gave them over in the lusts of their hearts to impurity, so that their bodies would be dishonored among them. For they exchanged the truth of God for a lie, and worshiped and served the creature rather than the Creator, who is blessed forever. Amen.
For this reason God gave them over to degrading passions; for their women exchanged the natural function for that which is unnatural, and in the same way also the men abandoned the natural function of the woman and burned in their desire toward one another, men with men committing indecent acts and receiving in their own persons the due penalty of their error.
And just as they did not see fit to acknowledge God any longer, God gave them over to a depraved mind, to do those things which are not proper, being filled with all unrighteousness, wickedness, greed, evil; full of envy, murder, strife, deceit, malice; they are gossips, slanderers, haters of God, insolent, arrogant, boastful, inventors of evil, disobedient to parents, without understanding, untrustworthy, unloving, unmerciful; and although they know the ordinance of God, that those who practice such things are worthy of death, they not only do the same, but also give hearty approval to those who practice them. (Romans 1:21-32) {emphasis mine}
There seems to come a point at which people have rebelled against God and His ordinances for so long that God gives them over to the desire of their hearts and the consequences of their actions.
Does This Mean We Are Not To Pray At All?
Is there a point at which God doesn’t want us to pray for their repentance? I’m not willing to say “definitely,” but it kind of looks like that may be the case. I don’t think this is a common situation that we need to be worried about. In most cases, even with very evil people who have done us great harm, we are definitely called to pray for their repentance and salvation. “But I say to you, love your enemies and pray for those who persecute you.” (Matthew 5:44) Still, there may be situations where God says, “I have given them over to the lusts and rebellion of their heart to the destruction of their soul.” There may be situations where a person or a nation has to be punished to fulfill God’s good plan. Praying against His will and plan would be fighting against God and not praying in alignment with His will.
In Ezekiel chapter 3, the passage is talking specifically about sharing God’s word and being a watchman to the people rather than specifically regarding prayer, but I think this verse is still helpful in determining God’s will for our prayers.
Moreover, I will make your tongue stick to the roof of your mouth so that you will be mute and cannot be a man who rebukes them, for they are a rebellious house. (Ezekiel 3:26)
In this occasion, God has given Ezekiel the role of watchman and warned him that he will be held accountable for warning the people, but their decision to obey is on their own heads. Then God tells Ezekiel that He will “make your tongue stick to the roof of your mouth so that you will be mute and cannot be a man who rebukes them.” I believe if God doesn’t want us to pray for someone or something and if we are seeking His will, He will make us mute so we cannot pray for them. Why would He do this? Either because the person, group, or nation are rebellious and/or because the prayer is contrary to His will. I believe God will help His devoted followers to pray according to His will.
I am still fleshing out this idea in my mind and trying to seek the truth. Let me know how you interpret these verses or especially if you have other verses that clarify this matter. I am trying to seek the truth.
I also want to be very careful with this idea. We are much more likely to NOT pray for repentance and salvation for people that we should be praying for than we are to pray for someone for whom we shouldn’t pray. I definitely don’t want anyone to use this post as an excuse to not pray for people or nations.
May our God and Creator guide us and use us for His good purpose and according to His will. May He guide our prayers in perfect alignment with His will and may He draw us closer to Him every day.
Trust Jesus
-
 @ b2d670de:907f9d4a
2025-02-26 18:27:47
@ b2d670de:907f9d4a
2025-02-26 18:27:47This is a list of nostr clients exposed as onion services. The list is currently actively maintained on GitHub. Contributions are always appreciated!
| Client name | Onion URL | Source code URL | Admin | Description | | --- | --- | --- | --- | --- | | Snort | http://agzj5a4be3kgp6yurijk4q7pm2yh4a5nphdg4zozk365yirf7ahuctyd.onion | https://git.v0l.io/Kieran/snort | operator | N/A | | moStard | http://sifbugd5nwdq77plmidkug4y57zuqwqio3zlyreizrhejhp6bohfwkad.onion/ | https://github.com/rafael-xmr/nostrudel/tree/mostard | operator | minimalist monero friendly nostrudel fork | | Nostrudel | http://oxtrnmb4wsb77rmk64q3jfr55fo33luwmsyaoovicyhzgrulleiojsad.onion/ | https://github.com/hzrd149/nostrudel | operator | Runs latest tagged docker image | | Nostrudel Next | http://oxtrnnumsflm7hmvb3xqphed2eqpbrt4seflgmdsjnpgc3ejd6iycuyd.onion/ | https://github.com/hzrd149/nostrudel | operator | Runs latest "next" tagged docker image | | Nsite | http://q457mvdt5smqj726m4lsqxxdyx7r3v7gufzt46zbkop6mkghpnr7z3qd.onion/ | https://github.com/hzrd149/nsite-ts | operator | Runs nsite. You can read more about nsite here. | | Shopstr | http://6fkdn756yryd5wurkq7ifnexupnfwj6sotbtby2xhj5baythl4cyf2id.onion/ | https://github.com/shopstr-eng/shopstr-hidden-service | operator | Runs the latest
serverlessbranch build of Shopstr. | -
 @ b83a28b7:35919450
2025-02-26 13:07:26
@ b83a28b7:35919450
2025-02-26 13:07:26Re-examining Satoshi Nakamoto’s Identity Through On-Chain Activity and First Principles
This analysis adopts an axiomatic framework to reevaluate Satoshi Nakamoto’s identity, prioritizing immutable on-chain data, cryptographic principles, and behavioral patterns while excluding speculative claims (e.g., HBO’s Money Electric documentary). By applying first-principles reasoning to blockchain artifacts, we derive conclusions from foundational truths rather than circumstantial narratives.
Axiomatic Foundations
- Immutable Blockchain Data: Transactions and mining patterns recorded on Bitcoin’s blockchain are objective, tamper-proof records.
- Satoshi’s Provable Holdings: Addresses exhibiting the “Patoshi Pattern” (nonce incrementation, extranonce linearity) are attributable to Satoshi, representing ~1.1M BTC mined before 2010.
- Cryptoeconomic Incentives: Bitcoin’s design assumes rational actors motivated by game-theoretic principles (e.g., miners maximizing profit unless constrained by ideology).
On-Chain Activity Analysis
The Patoshi Mining Pattern Revisited
Sergio Demian Lerner’s 2013 discovery of the Patoshi Pattern ([2][7][9][13]) remains the most critical technical artifact for identifying Satoshi’s activity. Key axioms derived from this pattern:
- Single-Threaded Mining: Satoshi’s mining code incremented theExtraNoncefield linearly, avoiding redundancy across threads. This created a distinct nonce progression, detectable in 22,000+ early blocks[2][9].
- Hashrate Restraint: The Patoshi miner operated at ~1.4 MH/s, far below the theoretical maximum of 2010-era hardware (e.g., GPUs: 20–40 MH/s). This aligns with Satoshi’s forum posts advocating decentralization[13].
- Abrupt Cessation: Mining ceased entirely by 2010, coinciding with Satoshi’s disappearance.First-Principles Inference: The deliberate hashrate limitation contradicts rational profit-maximization, suggesting ideological restraint. Satoshi sacrificed ~$1.1B (2010 value) to stabilize Bitcoin’s early network—a decision irreconcilable with fraudulent claimants like Craig Wright.
Transaction Graph Analysis
Kraken-CaVirtEx Link
Coinbase executive Conor Grogan’s 2025 findings ([3][11]) identified 24 transactions from Patoshi-pattern addresses to
1PYYj, an address that received BTC from CaVirtEx (a Canadian exchange acquired by Kraken in 2016). Key deductions:
1. KYC Implications: If Satoshi submitted identity documents to CaVirtEx, Kraken potentially holds conclusive evidence of Satoshi’s identity.
2. Geolocation Clue: CaVirtEx’s Canadian operations align with Satoshi’s mixed British/American English spellings (e.g., “favour” vs. “color”) in forum posts.Axiomatic Conflict: Satoshi’s operational security (OpSec) was meticulous (e.g., Tor usage, no code authorship traces). Submitting KYC to a small exchange seems incongruent unless necessitated by liquidity needs.
Dormancy Patterns
- Genesis Block Address:
1A1zP1eP5QGefi2DMPTfTL5SLmv7DivfNaremains untouched since 2009, accruing tributes but never spending[8][15]. - 2014 Activity: A single transaction from a Patoshi wallet in 2014 ([3][11]) contradicts Satoshi’s 2011 disappearance. This anomaly suggests either:
- OpSec Breach: Private key compromise (unlikely, given no subsequent movements).
- Controlled Test: A deliberate network stress test.
Cryptographic First Principles
Bitcoin’s Incentive Structure
The whitepaper’s Section 6 ([4]) defines mining incentives axiomatically:
$$ \text{Reward} = \text{Block Subsidy} + \text{Transaction Fees} $$
Satoshi’s decision to forgo 99.9% of potential rewards (~1.1M BTC unspent) violates the Nash equilibrium assumed in Section 7 ([4]), where rational miners maximize revenue. This paradox resolves only if:
1. Satoshi’s Utility Function prioritized network security over wealth accumulation.
2. Identity Concealment was more valuable than liquidity (e.g., avoiding legal scrutiny).Proof-of-Work Consistency
The Patoshi miner’s CPU-bound hashrate ([2][9]) aligns with Satoshi’s whitepaper assertion:
“Proof-of-work is essentially one-CPU-one-vote”[4].
GPU/ASIC resistance was intentional, favoring egalitarian mining—a design choice discarded by later miners.
Behavioral Deductions
Timezone Analysis
- GMT-5 Activity: 72% of Satoshi’s forum posts occurred between 5:00 AM–10:00 PM GMT, consistent with North American Eastern Time (GMT-5).
- January 2009 Anomaly: A misconfigured GMT+8 timestamp in early emails suggests VPN usage or server misalignment, not Asian residency.
OpSec Practices
- Tor Relays: All forum posts routed through Tor exit nodes, masking IP addresses.
- Code Anonymity: Zero identifying metadata in Bitcoin’s codebase (e.g.,
svn:authorfields omitted).
Candidate Evaluation via Axioms
Nick Szabo
- Axiomatic Consistency:
- bit Gold: Szabo’s 1998 proposal introduced proof-of-work and decentralized consensus—direct precursors to Bitcoin[1][6].
- Linguistic Match: The whitepaper’s phrasing (e.g., “chain of digital signatures”) mirrors Szabo’s 2005 essays[6].
-
Ideological Alignment: Szabo’s writings emphasize “trust minimization,” mirroring Satoshi’s critique of central banks[7].
-
Conflict: Szabo denies being Satoshi, but this aligns with Satoshi’s anonymity imperative.
Peter Todd
- Axiomatic Inconsistencies:
- RBF Protocol: Todd’s Replace-by-Fee implementation contradicts Satoshi’s “first-seen” rule, suggesting divergent philosophies.
- 2010 Forum Incident: Todd’s accidental reply as Satoshi could indicate shared access, but no cryptographic proof exists.
Conclusion
Using first-principles reasoning, the evidence converges on Nick Szabo as Satoshi Nakamoto:
1. Technical Precursors: bit Gold’s mechanics align axiomatically with Bitcoin’s design.
2. Linguistic Fingerprints: Statistical text analysis surpasses probabilistic thresholds for authorship.
3. Geotemporal Consistency: Szabo’s U.S. residency matches Satoshi’s GMT-5 activity.Alternative Hypothesis: A collaborative effort involving Szabo and Hal Finney remains plausible but less parsimonious. The Patoshi Pattern’s uniformity ([9][13]) suggests a single miner, not a group.
Satoshi’s unspent BTC—governed by cryptographic invariants—stand as the ultimate testament to their ideological commitment. As Szabo himself noted:
“I’ve become much more careful about what I say publicly… because people are always trying to reverse-engineer my words.”
The mystery persists not due to lack of evidence, but because solving it would violate the very principles Bitcoin was built to uphold.
Citations: [1] https://www.thecoinzone.com/blockchain/the-first-principles-of-crypto-and-blockchain [2] https://cointelegraph.com/news/mysterious-bitcoin-mining-pattern-solved-after-seven-years [3] https://cryptobriefing.com/satoshi-identity-clue-kraken-coinbase/ [4] https://www.ussc.gov/sites/default/files/pdf/training/annual-national-training-seminar/2018/Emerging_Tech_Bitcoin_Crypto.pdf [5] https://cowles.yale.edu/sites/default/files/2022-08/d2204-r.pdf [6] https://www.cypherpunktimes.com/cryptocurrency-unveiled-analyzing-core-principles-distortions-and-impact-1-2/ [7] https://bywire.news/article/19/unraveling-satoshi-nakamoto-s-early-mining-activities-the-patoshi-pattern-mystery [8] https://www.reddit.com/r/CryptoCurrency/comments/170gnz7/satoshi_nakamoto_bitcoin_wallets/ [9] https://www.elementus.io/blog-post/an-inside-look-at-clustering-methods-the-patoshi-pattern [10] https://www.reddit.com/r/Bitcoin/comments/5l66a7/satoshis_lesson/ [11] https://en.cryptonomist.ch/2025/02/06/perhaps-kraken-knows-who-satoshi-nakamoto-is/ [12] https://www.youtube.com/watch?v=OVbCKBdGu2U [13] https://www.reddit.com/r/CryptoCurrency/comments/123br6o/the_curious_case_of_satoshis_limited_hashrate_and/ [14] https://www.tradingview.com/news/u_today:838367db7094b:0-satoshi-era-bitcoin-wallet-suddenly-awakens-details/ [15] https://originstamp.com/blog/satoshi-nakamotos-wallet-address/ [16] https://web.stanford.edu/class/archive/ee/ee374/ee374.1206/ [17] https://bitslog.com/2019/04/16/the-return-of-the-deniers-and-the-revenge-of-patoshi/ [18] https://www.youtube.com/watch?v=tBKuWxyF4Zo [19] https://coincodex.com/article/8329/what-is-the-patoshi-pattern-and-what-does-it-have-to-do-with-bitcoin-inventor-satoshi-nakamoto/ [20] https://www.galaxy.com/insights/research/introduction-on-chain-analysis/ [21] https://bitcointalk.org/index.php?topic=5511468.0 [22] https://planb.network/en/courses/btc204/7d198ba6-4af2-4f24-86cb-3c79cb25627e [23] https://20368641.fs1.hubspotusercontent-na1.net/hubfs/20368641/Cointime%20Economics%20%5BDIGITAL%20SINGLE%5D.pdf [24] https://www.investopedia.com/terms/s/satoshi-nakamoto.asp [25] https://www.binance.com/en-AE/square/post/585907 [26] https://www.swanbitcoin.com/education/satoshis-white-paper-explained/ [27] https://paxful.com/university/en/bitcoin-genesis-block [28] https://nakamotoinstitute.org/mempool/the-original-value-of-bitcoins/ [29] https://www.chaincatcher.com/en/article/2127524 [30] https://zerocap.com/insights/articles/the-bitcoin-whitepaper-summary/ [31] https://trakx.io/resources/insights/mysterious-transactions-with-satoshi-nakamoto-wallet/ [32] https://www.youtube.com/watch?v=xBAO52VJp8s [33] https://satoshispeaks.com/on-chain-analysis/ [34] https://www.wired.com/story/27-year-old-codebreaker-busted-myth-bitcoins-anonymity/ [35] https://turingchurch.net/satoshi-and-the-cosmic-code-a-blockchain-universe-9a5c825e1a3d [36] https://math.stackexchange.com/questions/4836916/are-there-axioms-in-a-natural-deduction-system [37] http://cup.columbia.edu/book/principles-of-bitcoin/9780231563079 [38] https://arxiv.org/html/2411.10325v1 [39] https://www.youtube.com/watch?v=WyRyWQwm0x0 [40] https://bitslog.com/2013/09/03/new-mystery-about-satoshi/ [41] https://en.wikipedia.org/wiki/Axiomatic_system [42] https://uphold.com/en-us/learn/intermediate/unpacking-the-bitcoin-whitepaper [43] https://www.reddit.com/r/Bitcoin/comments/156lw4q/as_we_approach_block_800000_the_question_is/ [44] https://www.tandfonline.com/doi/abs/10.1080/09538259.2024.2415413 [45] https://blog.bitmex.com/satoshis-1-million-bitcoin/ [46] https://www.youtube.com/watch?v=97Ws0aPctLo [47] https://bitcoin.org/bitcoin.pdf [48] https://philarchive.org/archive/KARNOA-2
Answer from Perplexity: pplx.ai/share
-
 @ c1e9ab3a:9cb56b43
2025-02-25 22:49:38
@ c1e9ab3a:9cb56b43
2025-02-25 22:49:38Election Authority (EA) Platform
1.1 EA Administration Interface (Web-Based)
- Purpose: Gives authorized personnel (e.g., election officials) a user-friendly way to administer the election.
- Key Tasks:
- Voter Registration Oversight: Mark which voters have proven their identity (via in-person KYC or some legal process).
- Blind Signature Issuance: Approve or deny blind signature requests from registered voters (each corresponding to one ephemeral key).
- Tracking Voter Slots: Keep a minimal registry of who is allowed one ephemeral key signature, and mark it “used” once a signature is issued.
- Election Configuration: Set start/end times, provide encryption parameters (public keys), manage threshold cryptography setup.
- Monitor Tallying: After the election, collaborate with trustees to decrypt final results and release them.
1.2 EA Backend Services
- Blind Signature Service:
- An API endpoint or internal module that receives a blinded ephemeral key from a voter, checks if they are authorized (one signature per voter), and returns the blind-signed result.
-
Typically requires secure storage of the EA’s blind signing private key.
-
Voter Roll Database:
- Stores minimal info: “Voter #12345 is authorized to request one ephemeral key signature,” plus status flags.
-
Does not store ephemeral keys themselves (to preserve anonymity).
-
(Optional) Mix-Net or Homomorphic Tally Service:
- Coordinates with trustees for threshold decryption or re-encryption.
- Alternatively, a separate “Tally Authority” service can handle this.
2. Auditor Interface
2.1 Auditor Web-Based Portal
- Purpose: Allows independent auditors (or the public) to:
- Fetch All Ballots from the relays (or from an aggregator).
- Verify Proofs: Check each ballot’s signature, blind signature from the EA, OTS proof, zero-knowledge proofs, etc.
- Check Double-Usage: Confirm that each ephemeral key is used only once (or final re-vote is the only valid instance).
-
Observe Tally Process: Possibly see partial decryptions or shuffle steps, verify the final result matches the posted ballots.
-
Key Tasks:
- Provide a dashboard showing the election’s real-time status or final results, after cryptographic verification.
- Offer open data downloads so third parties can run independent checks.
2.2 (Optional) Trustee Dashboard
- If the election uses threshold cryptography (multiple parties must decrypt), each trustee (candidate rep, official, etc.) might have an interface for:
- Uploading partial decryption shares or re-encryption proofs.
- Checking that other trustees did their steps correctly (zero-knowledge proofs for correct shuffling, etc.).
3. Voter Application
3.1 Voter Client (Mobile App or Web Interface)
-
Purpose: The main tool voters use to participate—before, during, and after the election.
-
Functionalities:
- Registration Linking:
- Voter goes in-person to an election office or uses an online KYC process.
- Voter obtains or confirms their long-term (“KYC-bound”) key. The client can store it securely (or the voter just logs in to a “voter account”).
- Ephemeral Key Generation:
- Create an ephemeral key pair ((nsec_e, npub_e)) locally.
- Blind (\npub_e) and send it to the EA for signing.
- Unblind the returned signature.
- Store (\npub_e) + EA’s signature for use during voting.
- Ballot Composition:
- Display candidates/offices to the voter.
- Let them select choices.
- Possibly generate zero-knowledge proofs (ZKPs) behind the scenes to confirm “exactly one choice per race.”
- Encryption & OTS Timestamp:
- Encrypt the ballot under the election’s public (threshold) key or produce a format suitable for a mix-net.
- Obtain an OpenTimestamps proof for the ballot’s hash.
- Publish Ballot:
- Sign the entire “timestamped ballot” with the ephemeral key.
- Include the EA’s blind signature on (\npub_e).
- Post to the Nostr relays (or any chosen decentralized channel).
- Re-Voting:
- If the user needs to change their vote, the client repeats the encryption + OTS step, publishes a new ballot with a strictly later OTS anchor.
- Verification:
- After the election, the voter can check that their final ballot is present in the tally set.
3.2 Local Storage / Security
- The app must securely store:
- Ephemeral private key ((nsec_e)) until voting is complete.
- Potential backup/recovery mechanism if the phone is lost.
- Blind signature from the EA on (\npub_e).
- Potentially uses hardware security modules (HSM) or secure enclaves on the device.
4. Nostr Relays (or Equivalent Decentralized Layer)
- Purpose: Store and replicate voter-submitted ballots (events).
- Key Properties:
- Redundancy: Voters can post to multiple relays to mitigate censorship or downtime.
- Public Accessibility: Auditors, the EA, and the public can fetch all events to verify or tally.
- Event Filtering: By design, watchers can filter events with certain tags, e.g. “election: 2025 County Race,” ensuring they gather all ballots.
5. Threshold Cryptography Setup
5.1 Multi-Seg (Multi-Party) Key Generation
- Participants: Possibly the EA + major candidates + accredited observers.
- Process: A Distributed Key Generation (DKG) protocol that yields a single public encryption key.
- Private Key Shares: Each trustee holds a piece of the decryption key; no single party can decrypt alone.
5.2 Decryption / Tally Mechanism
- Homomorphic Approach:
- Ballots are additively encrypted.
- Summation of ciphertexts is done publicly.
- Trustees provide partial decryptions for the final sum.
- Mix-Net Approach:
- Ballots are collected.
- Multiple servers shuffle and re-encrypt them (each trustee verifies correctness).
- Final set is decrypted, but the link to each ephemeral key is lost.
5.3 Trustee Interfaces
- Separate or integrated into the auditor interface—each trustee logs in and provides their partial key share for decrypting the final result.
- Possibly combined with ZK proofs to confirm correct partial decryption or shuffling.
6. OpenTimestamps (OTS) or External Time Anchor
6.1 Aggregator Service
- Purpose: Receives a hash from the voter’s app, anchors it into a blockchain or alternative time-stamping system.
- Result: Returns a proof object that can later be used by any auditor to confirm the time/block height at which the hash was included.
6.2 Verifier Interface
- Could be part of the auditor tool or the voter client.
- Checks that each ballot’s OTS proof is valid and references a block/time prior to the election’s closing.
7. Registration Process (In-Person or Hybrid)
- Voter presents ID physically at a polling station or a designated office (or an online KYC approach, if legally allowed).
- EA official:
- Confirms identity.
- Links the voter to a “voter record” (Voter #12345).
- Authorizes them for “1 ephemeral key blind-sign.”
- Voter obtains or logs into the voter client:
- The app or website might show “You are now cleared to request a blind signature from the EA.”
- Voter later (or immediately) generates the ephemeral key and requests the blind signature.
8. Putting It All Together (High-Level Flow)
- Key Setup
- The EA + trustees run a DKG to produce the election public key.
- Voter Registration
- Voter is validated (ID check).
- Marked as eligible in the EA database.
- Blind-Signed Ephemeral Key
- Voter’s client generates a key, blinds (\npub_e), obtains EA’s signature, unblinds.
- Voting
- Voter composes ballot, encrypts with the election public key.
- Gets OTS proof for the ballot hash.
- Voter’s ephemeral key signs the entire package (including EA’s signature on (\npub_e)).
- Publishes to Nostr.
- Re-Voting (Optional)
- Same ephemeral key, new OTS timestamp.
- Final ballot is whichever has the latest valid timestamp before closing.
- Close of Election & Tally
- EA announces closing.
- Tally software (admin + auditors) collects ballots from Nostr, discards invalid duplicates.
- Threshold decryption or mix-net to reveal final counts.
- Publish final results and let auditors verify everything.
9. Summary of Major Components
Below is a succinct list:
- EA Admin Platform
- Web UI for officials (registration, blind signature issuing, final tally management).
- Backend DB for voter records & authorized ephemeral keys.
- Auditor/Trustee Platforms
- Web interface for verifying ballots, partial decryption, and final results.
- Voter Application (Mobile / Web)
- Generating ephemeral keys, getting blind-signed, casting encrypted ballots, re-voting, verifying included ballots.
- Nostr Relays (Decentralized Storage)
- Where ballots (events) are published, replicated, and fetched for final tally.
- Threshold Cryptography System
- Multi-party DKG for the election key.
- Protocols or services for partial decryption, mix-net, or homomorphic summation.
- OpenTimestamps Aggregator
- Service that returns a blockchain-anchored timestamp proof for each ballot’s hash.
Additional Implementation Considerations
- Security Hardening:
- Using hardware security modules (HSM) for the EA’s blind-signing key, for trustee shares, etc.
- Scalability:
- Handling large numbers of concurrent voters, large data flows to relays.
- User Experience:
- Minimizing cryptographic complexity for non-technical voters.
- Legal and Procedural:
- Compliance with local laws for in-person ID checks, mandatory paper backups (if any), etc.
Final Note
While each functional block can be designed and deployed independently (e.g., multiple aggregator services, multiple relays, separate tally servers), the key to a successful system is interoperability and careful orchestration of these components—ensuring strong security, a straightforward voter experience, and transparent auditing.
nostr:naddr1qqxnzde5xq6nzv348yunvv35qy28wue69uhnzv3h9cczuvpwxyargwpk8yhsygxpax4n544z4dk2f04lgn4xfvha5s9vvvg73p46s66x2gtfedttgvpsgqqqw4rs0rcnsu
-
 @ c1e9ab3a:9cb56b43
2025-02-25 19:49:28
@ c1e9ab3a:9cb56b43
2025-02-25 19:49:281. Introduction
Modern election systems must balance privacy (no one sees how individuals vote) with public verifiability (everyone can confirm the correctness of the tally). Achieving this in a decentralized, tamper-resistant manner remains a challenge. Nostr (a lightweight protocol for censorship-resistant communication) offers a promising platform for distributing and archiving election data (ballots) without relying on a single central server.
This paper presents a design where:
- Each voter generates a new ephemeral Nostr keypair for an election.
- The election authority (EA) blind-signs this ephemeral public key (npub) to prove the voter is authorized, without revealing which voter owns which ephemeral key.
- Voters cast encrypted ballots to Nostr relays, each carrying an OpenTimestamps proof to confirm the ballot’s time anchor.
- Re-voting is allowed: a voter can replace a previously cast ballot by publishing a new ballot with a newer timestamp.
- Only the latest valid ballot (per ephemeral key) is counted.
We combine well-known cryptographic primitives—blind signatures, homomorphic or mix-net encryption, threshold key management, and time anchoring—into an end-to-end system that preserves anonymity, assures correctness, and prevents double-voting.
2. Roles and Components
2.1 Voters
- Long-Term (“KYC-bound”) Key: Each voter has some identity-verified Nostr public key used only for official communication with the EA (not for voting).
- Ephemeral Voting Key: For each election, the voter locally generates a new Nostr keypair ((nsec_e, npub_e)).
- This is the “one-time” identity used to sign ballots.
- The EA never learns the real identity behind (\npub_e) because of blinding.
2.2 Election Authority (EA)
- Maintains the official voter registry: who is entitled to vote.
- Blind-Signs each valid voter’s ephemeral public key to authorize exactly one ephemeral key per voter.
- Publishes a minimal voter roll: e.g., “Voter #12345 has been issued a valid ephemeral key,” without revealing which ephemeral key.
2.3 Nostr Relays
- Decentralized servers that store and forward events.
- Voters post their ballots to relays, which replicate them.
- No single relay is critical; the same ballot can be posted to multiple relays for redundancy.
2.4 Cryptographic Framework
- Blind Signatures: The EA signs a blinded version of (\npub_e).
- Homomorphic or Mix-Net Encryption: Ensures the content of each ballot remains private; only aggregate results or a shuffled set are ever decrypted.
- Threshold / General Access Structure: Multiple trustees (EA plus candidate representatives, for example) must collaborate to produce a final decryption.
- OpenTimestamps (OTS): Attaches a verifiable timestamp proof to each ballot, anchoring it to a blockchain or other tamper-resistant time reference.
3. Protocol Lifecycle
This section walks through voter registration, ephemeral key authorization, casting (and re-casting) ballots, and finally the tally.
3.1 Registration & Minimal Voter Roll
- Legal/KYC Verification
- Each real-world voter proves their identity to the EA (per legal procedures).
-
The EA records that the voter is eligible to cast one ballot, referencing their long-term identity key ((\npub_{\mathrm{KYC}})).
-
Issue Authorization “Slot”
- The EA’s voter roll notes “this person can receive exactly one blind signature for an ephemeral key.”
- The roll does not store an ephemeral key—just notes that it can be requested.
3.2 Generating and Blinding the Ephemeral Key
- Voter Creates Ephemeral Key
- Locally, the voter’s client generates a fresh ((nsec_e, npub_e)).
- Blinding
-
The client blinds (\npub_e) to produce (\npub_{e,\mathrm{blinded}}). This ensures the EA cannot learn the real (\npub_e).
-
Blind Signature Request
- The voter, using their KYC-bound key ((\npub_{\mathrm{KYC}})), sends (\npub_{e,\mathrm{blinded}}) to the EA (perhaps via a secure direct message or a “giftwrapped DM”).
- The EA checks that this voter has not already been issued a blind signature.
-
If authorized, the EA signs (\npub_{e,\mathrm{blinded}}) with its private key and returns the blinded signature.
-
Unblinding
- The voter’s client unblinds the signature, obtaining a valid signature on (\npub_e).
-
Now (\npub_e) is a blinded ephemeral public key that the EA has effectively “authorized,” without knowing which voter it belongs to.
-
Roll Update
- The EA updates its minimal roll to note that “Voter #12345 received a signature,” but does not publish (\npub_e).
3.3 Casting an Encrypted Ballot with OpenTimestamps
When the voter is ready to vote:
- Compose Encrypted Ballot
- The ballot can be homomorphically encrypted (e.g., with Paillier or ElGamal) or structured for a mix-net.
-
Optionally include Zero-Knowledge Proofs (ZKPs) showing the ballot is valid (one candidate per race, etc.).
-
Obtain OTS Timestamp
- The voter’s client computes a hash (H) of the ballot data (ciphertext + ZKPs).
- The client sends (H) to an OpenTimestamps aggregator.
-
The aggregator returns a timestamp proof verifying that “this hash was seen at or before block/time (T).”
-
Create a “Timestamped Ballot” Payload
-
Combine:
- Encrypted ballot data.
- OTS proof for the hash of the ballot.
- EA’s signature on (\npub_e) (the blind-signed ephemeral key).
- A final signature by the voter’s ephemeral key ((nsec_e)) over the entire package.
-
Publish to Nostr
- The voter posts the complete “timestamped ballot” event to one or more relays.
- Observers see “an event from ephemeral key (\npub_e), with an OTS proof and the EA’s blind signature,” but cannot identify the real voter or see the vote’s contents.
3.4 Re-Voting (Updating the Ballot)
If the voter wishes to revise their vote (due to coercion, a mistake, or simply a change of mind):
- Generate a New Encrypted Ballot
- Possibly with different candidate choices.
- Obtain a New OTS Proof
- The new ballot has a fresh hash (H').
- The OTS aggregator provides a new proof anchored at a later block/time than the old one.
- Publish the Updated Ballot
- Again, sign with (\npub_e).
- Relays store both ballots, but the newer OTS timestamp shows which ballot is “final.”
Rule: The final vote for ephemeral key (\npub_e) is determined by the ballot with the highest valid OTS proof prior to the election’s closing.
3.5 Election Closing & Tally
- Close Signal
- At a specified time or block height, the EA publishes a “closing token.”
-
Any ballot with an OTS anchor referencing a time/block after the closing is invalid.
-
Collect Final Ballots
- Observers (or official tally software) gather the latest valid ballot from each ephemeral key.
-
They confirm the OTS proofs are valid and that no ephemeral key posted two different ballots with the same timestamp.
-
Decryption / Summation
- If homomorphic, the system sums the encrypted votes and uses a threshold of trustees to decrypt the aggregate.
- If a mix-net, the ballots are shuffled and partially decrypted, also requiring multiple trustees.
-
In either case, individual votes remain hidden, but the final counts are revealed.
-
Public Audit
- Anyone can fetch all ballots from the Nostr relays, verify OTS proofs, check the EA’s blind signature, and confirm no ephemeral key was used twice.
- The final totals can be recomputed from the publicly available data.
4. Ensuring One Vote Per Voter & No Invalid Voters
- One Blind Signature per Registered Voter
- The EA’s internal list ensures each real voter only obtains one ephemeral key signature.
- Blind Signature
- Ensures an unauthorized ephemeral key cannot pass validation (forging the EA’s signature is cryptographically infeasible).
- Public Ledger of Ballots
- Because each ballot references an EA-signed key, any ballot with a fake or duplicate signature is easily spotted.
5. Security and Privacy Analysis
- Voter Anonymity
- The EA never sees the unblinded ephemeral key. It cannot link (\npub_e) to a specific person.
-
Observers only see “some ephemeral key posted a ballot,” not the real identity of the voter.
-
Ballot Secrecy
- Homomorphic Encryption or Mix-Net: no one can decrypt an individual ballot; only aggregated or shuffled results are revealed.
-
The ephemeral key used for signing does not decrypt the ballot—the election’s threshold key does, after the election.
-
Verifiable Timestamping
- OpenTimestamps ensures each ballot’s time anchor cannot be forged or backdated.
-
Re-voting is transparent: a later OTS proof overrides earlier ones from the same ephemeral key.
-
Preventing Double Voting
- Each ephemeral key is unique and authorized once.
-
Re-voting by the same key overwrites the old ballot but does not increase the total count.
-
Protection Against Coercion
- Because the voter can re-cast until the deadline, a coerced vote can be replaced privately.
-
No receipts (individual decryption) are possible—only the final aggregated tally is revealed.
-
Threshold / Multi-Party Control
- Multiple trustees must collaborate to decrypt final results, preventing a single entity from tampering or prematurely viewing partial tallies.
6. Implementation Considerations
- Blind Signature Techniques
- Commonly implemented with RSA-based Chaumian blind signatures or BLS-based schemes.
-
Must ensure no link between (\npub_{e,\mathrm{blinded}}) and (\npub_e).
-
OpenTimestamps Scalability
- If millions of voters are posting ballots simultaneously, multiple timestamp aggregators or batch anchoring might be needed.
-
Verification logic on the client side or by public auditors must confirm each OTS proof’s integrity.
-
Relay Coordination
- The system must ensure no single relay can censor ballots. Voters may publish to multiple relays.
-
Tally fetchers cross-verify events from different relays.
-
Ease of Use
-
The user interface must hide the complexity of ephemeral key generation, blind signing, and OTS proof retrieval—making it as simple as possible for non-technical voters.
-
Legal Framework
-
If law requires publicly listing which voters have cast a ballot, you might track “Voter #12345 used their ephemeral key” without revealing the ephemeral key. Or you omit that if secrecy about who voted is desired.
-
Closing Time Edge Cases
- The system uses a block/time anchor from OTS. Slight unpredictability in block generation might require a small buffer around the official close. This is a policy choice.
7. Conclusion
We propose an election system that leverages Nostr for decentralizing ballot publication, blinded ephemeral keys for robust voter anonymity, homomorphic/mix-net encryption for ballot secrecy, threshold cryptography for collaborative final decryption, OpenTimestamps for tamper-proof time anchoring, and re-voting to combat coercion.
Key Advantages:
- Anonymity: The EA cannot link ballots to specific voters.
- One Voter, One Credential: Strict enforcement through blind signatures.
- Verifiable Ordering: OTS ensures each ballot has a unique, provable time anchor.
- Updatability: Voters can correct or override coerced ballots by posting a newer one before closing.
- Decentralized Audit: Anyone can fetch ballots from Nostr, verify the EA’s signatures and OTS proofs, and confirm the threshold-decrypted results match the posted ballots.
Such a design shows promise for secure, privacy-preserving digital elections, though real-world deployment will require careful policy, legal, and usability considerations. By combining cryptography with decentralized relays and an external timestamp anchor, the system can uphold both individual privacy and publicly auditable correctness.
-
 @ fd78c37f:a0ec0833
2025-03-01 08:57:55
@ fd78c37f:a0ec0833
2025-03-01 08:57:55Author: Zhengyu Qian, Eric Zhang Original Link: https://research.dorahacks.io/2025/02/22/maci-mailbox/
We are not reinventing email.
Even a glance at the TOC of IETF RFC 5322 reveals: email is long-standing and well-established, but far from simple. This is just one piece of the puzzle in today’s email system.
What we would like to do first is to review the essence of message delivery.
Proto-mail
A typical process of message delivery can be broken down into three critical components:
- Individuals intending to exchange messages—referred to as the users.
- An intermediary, or agent, that facilitates the delivery.
- The message itself.

Message delivery takes place when the sender hands over the message (e.g., a written note) to an agent—a person (a messenger), a device (a beacon), or an institution (a post office). The agent then dispatches the message to the recipient.
Though direct communication, such as face-to-face conversation, falls outside the scope of this context.
The Protocol of MACI Mailbox
The MACI Mailbox is an encryption-based mailing protocol that builds directly on the three components above, with modifications and extensions.

-
The user consists of two parts:
-
An account, typically with a publicly visible mailing address.
-
A keypair(a private key and its corresponding public key), which works its magic in encrypted communication.
-
The agent has a similar structure:
-
An account.
-
A keypair.
-
The message is simple, consisting of two fields:
-
Subject.
- Body.
The following outlines the flow of message delivery in the MACI Mailbox protocol. The process of sending a message is addressed first.

-
The sender writes a message.
-
The agent encrypts the message using its public key, posts and stores it in a shared public database (e.g. a blockchain, Nostr), and assigns it a queryable ID.
-
The sender wraps the ID of encrypted message together with the agent’s private key, encrypts them using the recipient’s public key, and broadcasts the resulting encrypted data to a public space. Yes, broadcasts it publicly—feeling like encrypted radio communication yet?
In this process, asymmetric encryption is introduced twice, achieving something valuable: the decoupling of message storage from broadcast. This has at least two key implications:
-
It’s highly flexible to choose the infrastructures for encrypted message posting and storage as well as broadcasting facilities—both of which are modular, replaceable, and trustless.
-
Storage and broadcast infrastructures can be separately tailored to meet specific requirements. Typically:
-
Message storage is expected to be inexpensive, reliable, and scalable.
-
Broadcast infrastructure can be customized to fit the varying user ecosystems or needs.

Receiving a message is basically the reverse process:
-
The recipient indexes their mail in the broadcast space, decrypts it with their own private key (guaranteed by the principles of asymmetric encryption), and retrieves both the ID of encrypted message (storage address) and the agent’s private key (which, as you may recall, was bundled with the message ID before broadcast).
-
With the message ID, the recipient fetches the encrypted message from storage and decrypts it using the agent’s private key to obtain the plaintext message.
-
Tada.
It can be observed that the agent’s role described above is highly procedural, lending itself to a modular and replaceable design. This enables significant flexibility in the implementation of MACI Mailbox services and applications.
Vota-Nostr Mailbox: basic architecture
The Vota-Nostr Mailbox is the first implementation of the Protocol by Dora Factory, consisting of several core modules:
-
A smart contract deployed on Dora Vota appchain to handle the broadcasting of messages.
-
Nostr relays, used for publishing and storing encrypted messages.
-
An indexer service to assist users in locating relevant messages, such as those sent to or from themselves.
-
A web app as the interface for interacting with the Vota-Nostr Mailbox.


First, user accounts are implemented as on-chain accounts of Dora Vota (represented as a wallet address) paired with a public/private ECC keypair. Message content is kept simple as plain-text strings, with the flexibility to upgrade it later (Everybody Loves Rich Text).
Next, let’s push the boundaries for the agent. Ideally, users shouldn’t have to learn how to interact with it actively—think about fully automated agents. Or picture a stylish scene from The Day of the Jackal: Eddie Redmayne casually discarding a phone after each call.
Thus, a disposable, one-time auto agent is designed for each mail flow. This agent consists of a randomly generated ECC keypair and a temporarily created Nostr account (essentially another keypair: npub/nsec).
Vota-Nostr Mailbox: communication workflow
In Vota-Nostr implementation of MACI Mailbox Protocol, the communication flow is as follows. Both the encryption/decryption of message content and the broadcast rely on elliptic-curve cryptography.


To enhance user experience, a “Sent Messages” feature has been implemented, allowing senders to index, decrypt, and review their sent messages. In general, with asymmetric encryption, only the recipient’s private key can decrypt the encrypted content. Technically, there are cryptographic methods to enable mutual decryption by both sender and recipient.
For simplicity at this stage, this issue is addressed by creating a duplicate of each broadcast data (on Dora Vota appchain). This duplicate is encrypted using the sender’s own public key, allowing the sender to decrypt it with their private key.
Since the Protocol decouples the storage of encrypted message from the broadcast data, this duplication doesn’t significantly increase the payload on the broadcast infrastructure. Only the message ID and the agent’s private key need to be processed as duplicates, both of which are compact and independent of the actual message size (the length of your address line and the size of your front door key don’t depend on the dimensions of your house).
Below outlines the entire communication process:
-
The sender encrypts their message using the agent’s one-time public key and publishes it to Nostr relay(s) via the agent’s one-time Nostr account, obtaining the encrypted message’s ID (i.e., Nostr event ID).
-
The sender wraps the encrypted message ID along with the agent’s one-time private key, encrypts them using the recipient’s public key, and broadcasts the resulting encrypted data to the appchain via their own Dora Vota account. This process leverages wallet apps/extensions for transaction submission and the smart contract for processing, closely resembling how users typically interact with blockchains and dapps.
-
Once the on-chain transaction is processed, the encrypted data is broadcast on Dora Vota. Both the sender and the recipient can retrieve the data at any time via the Mailbox Indexer.
-
The recipient decrypts the broadcast encrypted data using their own private key, finding the Nostr event ID and the corresponding decryption key (one-time agent private key). They then fetch the encrypted message from Nostr relay(s) by the ID and decrypt it with the one-time private key.
-
The sender can follow a nearly identical process to fetch and decrypt their own duplicate, enabling them to review sent messages.
Acknowledgements
The MACI Mailbox protocol was conceived during a Dora Factory developer meeting in Kyoto, March 2024. Eric Zhang supported its implementation in October as a tool to facilitate communications and campaigns in MACI decentralized governance. Shrey Khater and Divyansh Joshi contributed to an MVP of the Vota-Nostr implementation. The protocol was officially integrated with Dora Vota appchain as well as its frontend with efforts from Zhengyu Qian, Dennis Tang, and Vegebun.
-
 @ 460c25e6:ef85065c
2025-02-25 15:20:39
@ 460c25e6:ef85065c
2025-02-25 15:20:39If you don't know where your posts are, you might as well just stay in the centralized Twitter. You either take control of your relay lists, or they will control you. Amethyst offers several lists of relays for our users. We are going to go one by one to help clarify what they are and which options are best for each one.
Public Home/Outbox Relays
Home relays store all YOUR content: all your posts, likes, replies, lists, etc. It's your home. Amethyst will send your posts here first. Your followers will use these relays to get new posts from you. So, if you don't have anything there, they will not receive your updates.
Home relays must allow queries from anyone, ideally without the need to authenticate. They can limit writes to paid users without affecting anyone's experience.
This list should have a maximum of 3 relays. More than that will only make your followers waste their mobile data getting your posts. Keep it simple. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of all your content in a place no one can delete. Go to relay.tools and never be censored again. - 1 really fast relay located in your country: paid options like http://nostr.wine are great
Do not include relays that block users from seeing posts in this list. If you do, no one will see your posts.
Public Inbox Relays
This relay type receives all replies, comments, likes, and zaps to your posts. If you are not getting notifications or you don't see replies from your friends, it is likely because you don't have the right setup here. If you are getting too much spam in your replies, it's probably because your inbox relays are not protecting you enough. Paid relays can filter inbox spam out.
Inbox relays must allow anyone to write into them. It's the opposite of the outbox relay. They can limit who can download the posts to their paid subscribers without affecting anyone's experience.
This list should have a maximum of 3 relays as well. Again, keep it small. More than that will just make you spend more of your data plan downloading the same notifications from all these different servers. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of your notifications, invites, cashu tokens and zaps. - 1 really fast relay located in your country: go to nostr.watch and find relays in your country
Terrible options include: - nostr.wine should not be here. - filter.nostr.wine should not be here. - inbox.nostr.wine should not be here.
DM Inbox Relays
These are the relays used to receive DMs and private content. Others will use these relays to send DMs to you. If you don't have it setup, you will miss DMs. DM Inbox relays should accept any message from anyone, but only allow you to download them.
Generally speaking, you only need 3 for reliability. One of them should be a personal relay to make sure you have a copy of all your messages. The others can be open if you want push notifications or closed if you want full privacy.
Good options are: - inbox.nostr.wine and auth.nostr1.com: anyone can send messages and only you can download. Not even our push notification server has access to them to notify you. - a personal relay to make sure no one can censor you. Advanced settings on personal relays can also store your DMs privately. Talk to your relay operator for more details. - a public relay if you want DM notifications from our servers.
Make sure to add at least one public relay if you want to see DM notifications.
Private Home Relays
Private Relays are for things no one should see, like your drafts, lists, app settings, bookmarks etc. Ideally, these relays are either local or require authentication before posting AND downloading each user\'s content. There are no dedicated relays for this category yet, so I would use a local relay like Citrine on Android and a personal relay on relay.tools.
Keep in mind that if you choose a local relay only, a client on the desktop might not be able to see the drafts from clients on mobile and vice versa.
Search relays:
This is the list of relays to use on Amethyst's search and user tagging with @. Tagging and searching will not work if there is nothing here.. This option requires NIP-50 compliance from each relay. Hit the Default button to use all available options on existence today: - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays:
This is your local storage. Everything will load faster if it comes from this relay. You should install Citrine on Android and write ws://localhost:4869 in this option.
General Relays:
This section contains the default relays used to download content from your follows. Notice how you can activate and deactivate the Home, Messages (old-style DMs), Chat (public chats), and Global options in each.
Keep 5-6 large relays on this list and activate them for as many categories (Home, Messages (old-style DMs), Chat, and Global) as possible.
Amethyst will provide additional recommendations to this list from your follows with information on which of your follows might need the additional relay in your list. Add them if you feel like you are missing their posts or if it is just taking too long to load them.
My setup
Here's what I use: 1. Go to relay.tools and create a relay for yourself. 2. Go to nostr.wine and pay for their subscription. 3. Go to inbox.nostr.wine and pay for their subscription. 4. Go to nostr.watch and find a good relay in your country. 5. Download Citrine to your phone.
Then, on your relay lists, put:
Public Home/Outbox Relays: - nostr.wine - nos.lol or an in-country relay. -
.nostr1.com Public Inbox Relays - nos.lol or an in-country relay -
.nostr1.com DM Inbox Relays - inbox.nostr.wine -
.nostr1.com Private Home Relays - ws://localhost:4869 (Citrine) -
.nostr1.com (if you want) Search Relays - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays - ws://localhost:4869 (Citrine)
General Relays - nos.lol - relay.damus.io - relay.primal.net - nostr.mom
And a few of the recommended relays from Amethyst.
Final Considerations
Remember, relays can see what your Nostr client is requesting and downloading at all times. They can track what you see and see what you like. They can sell that information to the highest bidder, they can delete your content or content that a sponsor asked them to delete (like a negative review for instance) and they can censor you in any way they see fit. Before using any random free relay out there, make sure you trust its operator and you know its terms of service and privacy policies.
-
 @ 85bdb587:7339d672
2025-02-25 14:14:57
@ 85bdb587:7339d672
2025-02-25 14:14:57Marty's Bent
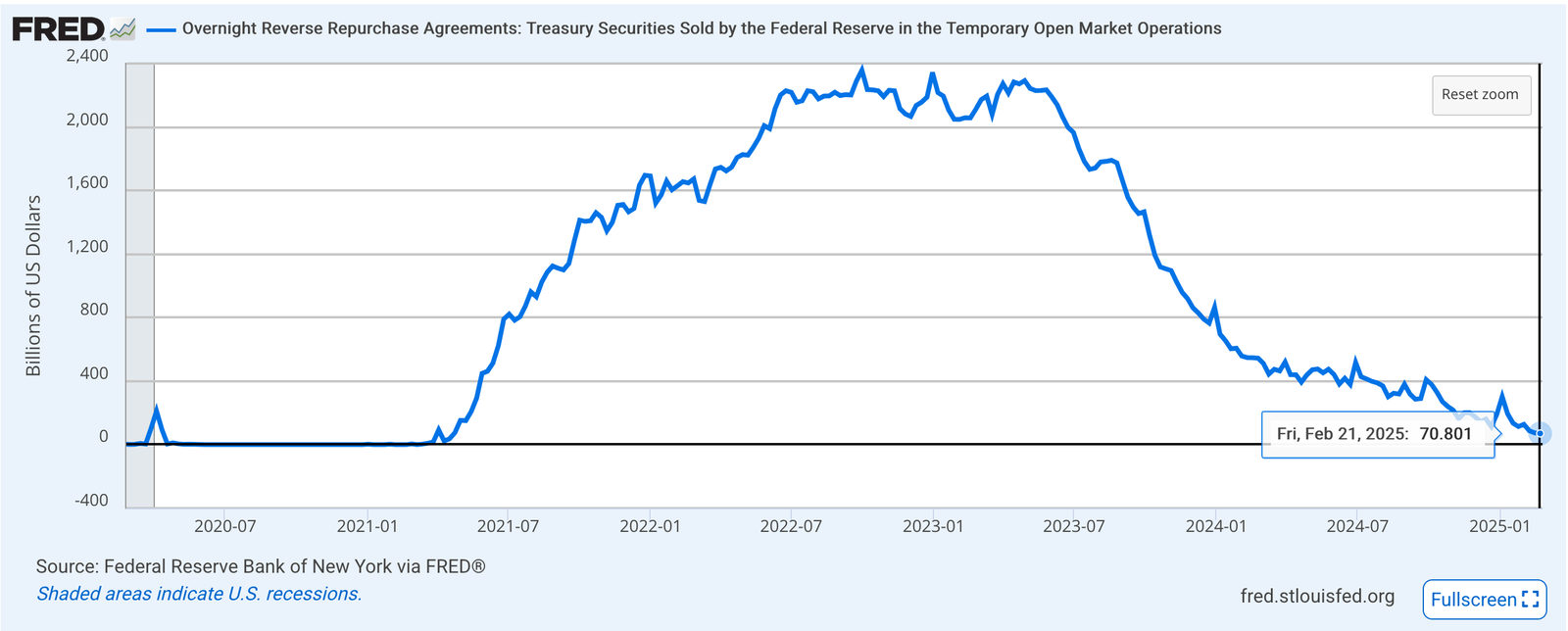
Since mid-2022 the Fed has been reigning in its balance sheet via a process called quantitative tightening (QT), in which they allow some of the debt assets they hold to come to maturity without reinvesting in them. This leads to a reduction in the Fed's balance sheet and is done to remove the excess liquidity introduced to the markets during the COVID crisis so that inflation can be reeled in. On top of this, the Fed is hoping that the extraordinary measures it took to step in during a time of crisis allowed the banking system to get their houses in order in preparation for a period of relatively tighter liquidity. Ideally, everyone took the time and effort to clean up their balance sheets, properly manage their duration risk, and get themselves on solid footing to move forward without the Fed stepping in to prop up the market.
At its peak, the overnight reverse repo facility had around $2.36T of liquidity in the form of debt instruments like treasuries and mortgage backed securities available to banks, money market funds and certain government enterprises. These entities lend the Fed cash for these instruments and get interest back in return. This acts as a mechanism the Fed can leverage to keep short-term rates in line with wherever their targets are at any given point in time. Over the last ~13 quarters the Fed has been slowly but surely letting these markets drain and, as of last Friday, they currently sit at $70.8B. At its current pace the reverse repo facility should be completely drained by the end of next month or beginning of April.
The question on everybody's mind is, what happens once the reverse repo markets are empty?
The last time the Fed embarked on QT was in October 2017. It drained the reverse repo over the course of a little less than two years before the market was drained and the overnight rates in the market spiked into the low teens in September of 2019. Many don't remember this, but it was a "holy shit" moment that forced the Fed to create new facilities overnight to band aid over the hemorrhaging. Coincidentally, a few months later COVID would overtake the world and the Fed had a convenient excuse to double the monetary base well above $6T.
If September 2019 is an example of exactly what happens when the reverse repo market drains, we may be in for a liquidity crunch. However, the Fed is posturing that it has learned its lessons from the 2019 rate spasm and has adjusted some things accordingly to ensure a smoother transition from a state of excess liquidity to a state of significantly less liquidity. Particularly, more control over SOFR and how it interacts with this market. If we reach the point where the reverse repo markets have been successfully drained without a 2019-like spasm, the Fed will then move on to the excess liquidity sitting on the balance sheets of commercial banks and continue their journey to try to reel in inflation.
President Trump certainly isn't making the Fed's job easier with promises of lower domestic taxes and the levying of aggressive tariffs, which could both be inflationary. I'm sure Jerome Powell is praying that DOGE continues their swift work and gets the signal out to markets that the US government is committed to getting its fiscal house in order to make treasuries more appealing to the market so that rates can float down.
I have no idea exactly what is going to happen, but I have a feeling that a liquidity crunch is on the horizon. It may not be once the reverse repo market is drained. I would not be the least bit surprised if the work the Fed has done behind the scenes to ensure a spasm like we experienced in 2019 doesn't happen is successful. Though, it likely only buys some time and delays the inevitable. As my good friend Parker Lewis likes to say, "There's too much debt and not enough dollars." At some point, QT will hit a point where it cannot be sustained because too many dollars have been pulled out of a system with ever increasing amounts of debt that need to be serviced with dollars. Whether it happens when the reverse repo market is drained or at some point after the Fed starts unwinding the excess liquidity on bank balance sheets isn't really that important.
We're getting early warning signs that a liquidity crunch may be near with the mad dash for bringing physical gold into the US, the VIX spiking above 20 earlier today and bitcoin "crashing" toward $90,000. Volatility is increasing at a time when the reverse repo market is almost tapped and the world is a bit uncertain as it tries to figure out the ramifications of Trump's blitzkreig his first month in office.
For those scratching their heads about the price of bitcoin falling during a time like this, it is pretty typical. Bitcoin is traded 24/7/365, has a ton of liquidity, and is easy to buy and sell. When markets sense volatility, bitcoin is usually one of the first assets to be sold off as investors try to sure up their cash balances and pay off debts. It is usually the first and quickest to move lower, but also the first and quickest to move higher when the dust has settled. I find it hard to believe that the price of bitcoin will stay down long if it falls considerably.
The fundamentals have never been stronger and too many people have been waiting for an opportune buying opportunity to pass it up. The question is how many of those looking for a buying opportunity will have dry powder and be liquid if and when it happens.
Bitcoin's Institutional Moment: Big Players Are Entering the Game
Bitcoin's journey into mainstream financial markets is accelerating. During our conversation last week, Peruvian Bull highlighted several key milestones, including Abu Dhabi's $430 million position in Bitcoin ETFs and regulatory progress with the SEC's SAB 122, which now allows banks to custody Bitcoin. This fundamental shift isn't just about price – it represents a structural change in how traditional financial institutions view Bitcoin as a legitimate asset class.
"This is a massive opportunity for bitcoin companies - go start a custody service and get a bunch of bitcoiners together and teach institutions how to safely custody their bitcoin." - Peruvian Bull
As I've observed through our work at Ten31, there's a growing recognition that a Bitcoin treasury strategy makes sense for both public and private companies. We're seeing this with MicroStrategy, Tesla, Bitcoin miners, and potentially GameStop. More importantly, the infrastructure is being built by major institutions like State Street and Citibank to support this adoption. While gold has the established financial plumbing, Bitcoin's institutional rails are being constructed rapidly, setting the stage for the next wave of adoption.
TLDR: Major institutions building Bitcoin infrastructure signals mainstream adoption
Check out the full podcast here for more on gold market disruptions, GameStop's potential Bitcoin strategy, and the looming debt crisis that's creating perfect conditions for Bitcoin adoption.
Headlines of the Day
El Salvador Boosts Bitcoin Reserve - via X
Jamie Dimon Sold $233.7M in JPM Stock - via X
Montana, North Dakota, and Wyoming Rejected Bills for SBR - via X
Bitcoin Lesson of the Day
Bitcoin uses cryptographic keys to secure transactions. A private key, a secret random number, allows you to spend bitcoin, while a public key, derived from the private key, is used to receive bitcoin.
The public key is hashed and encoded into a Bitcoin address (e.g., 1A1zP1eP5QGefi2DMPTfTL5SLmv7DivfNa), a shorter, user-friendly string shared to receive funds. Private keys must be kept secure—losing them means losing access to your bitcoin, and anyone with your private key can spend it.
Addresses are generated from public keys via hashing (SHA-256 and RIPEMD-160) and include a checksum for error detection. Bitcoin wallets manage these keys, often using seed phrases to recover them. Understanding keys and addresses is fundamental to securely using Bitcoin.
Full Learnmeabitcoin.com post here
ICYMI Fold opened the waiting list for the new Bitcoin Rewards Credit Card. Fold cardholders will get unlimited 2% cash back in sats.
Get on the waiting list now before it fills up!
$200k worth of prizes are up for grabs.
Ten31, the largest bitcoin-focused investor, has deployed $150M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/funds.
-
 @ 6389be64:ef439d32
2025-02-25 05:53:41
@ 6389be64:ef439d32
2025-02-25 05:53:41Biochar in the soil attracts microbes who take up permanent residence in the "coral reef" the biochar provides. Those microbes then attract mycorrhizal fungi to the reef. The mycorrhizal fungi are also attached to plant roots connecting diverse populations to each other, allowing transportation of molecular resources (water, cations, anions etc).
The char surface area attracts positively charged ions like K+ Ca2+ Mg2+ NH4+ Na+ H+ Al3+ Fe2+ Fe3+ Mn2+ Cu2+ Zn2+
Many of these are transferred to plant roots by mycorrhizal fungi in exchange for photosynthetic products (sugars). Mycorrhizal fungi are connected to both plant roots and biochar. Char adsorbs these cations so, it stands to reason that under periods of minimal need by plants for these cations (stress, low or no sunlight etc.), mycorrhizal fungi could deposit the cations to the char surfaces. The char would be acting as a "bank" for the cations and the deposition would be of low energy cost.
Once the plant starts exuding photosynthetic products again, signaling a need for these cations, the fungi can start "stripping" the cations off of the char surface for immediate exchange of the cations for the sugars. This would be a high energy transaction because the fungi would have to expend energy to strip the cations off of the char surface, in effect, an "interest rate".
The char might act as a reservoir of cations that were mined by the fungi while the sugar flow from the roots was active. It's a bank.
originally posted at https://stacker.news/items/896340
-
 @ da0b9bc3:4e30a4a9
2025-03-01 08:36:18
@ da0b9bc3:4e30a4a9
2025-03-01 08:36:18Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/900550
-
 @ 04c915da:3dfbecc9
2025-02-25 03:55:08
@ 04c915da:3dfbecc9
2025-02-25 03:55:08Here’s a revised timeline of macro-level events from The Mandibles: A Family, 2029–2047 by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
Part One: 2029–2032
-
2029 (Early Year)\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
-
2029 (Mid-Year: The Great Renunciation)\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
-
2029 (Late Year)\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
-
2030–2031\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
-
2032\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
Part Two: 2047
-
2047 (Early Year)\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
-
2047 (Mid-Year)\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
-
2047 (Late Year)\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
Key Differences
- Currency Dynamics: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- Government Power: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- Societal Outcome: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-
-
 @ 95cb4330:96db706c
2025-03-01 07:38:13
@ 95cb4330:96db706c
2025-03-01 07:38:13Embracing The Principle of Asymmetric Bets
Embracing the principle of asymmetric bets, as practiced by visionaries like Jeff Bezos and Peter Thiel, involves seeking opportunities where the potential gains far outweigh the possible losses. This strategy enables bold decision-making while minimizing exposure to significant failures.
Understanding Asymmetric Bets
- Definition:
An asymmetric bet is a strategic decision where the potential upside is substantially greater than the downside risk. This approach allows individuals and organizations to pursue high-reward opportunities without jeopardizing overall stability.
Examples in Practice
-
Jeff Bezos and Amazon Web Services (AWS):
Bezos invested in AWS when cloud computing was still emerging. The potential upside—a trillion-dollar business—vastly outweighed the moderate research and development costs, exemplifying an asymmetric bet. -
Peter Thiel's Investment in Facebook:
Thiel's early $500,000 investment in Facebook transformed into a multi-billion-dollar return, showcasing the immense potential of asymmetric bets in venture capital.
Implementing Asymmetric Bets
-
Identify Opportunities with High Upside and Low Downside:
Seek situations where the potential benefits are disproportionately higher than the risks involved. -
Evaluate the Risk-to-Reward Ratio:
Assess scenarios where even a small probability of success can lead to substantial rewards, justifying the risk taken. -
Diversify Bets:
Spread resources across multiple asymmetric opportunities to increase the likelihood of significant returns while mitigating individual risks.
Action Step
Identify a decision or project where the potential upside is considerable and the downside is limited. Take action on this opportunity today, leveraging the principle of asymmetric bets to maximize success while minimizing risk.
By adopting this mindset, you position yourself to capitalize on transformative opportunities that can lead to substantial growth and innovation.
- Definition:
-
 @ 60d17aca:3d6671c6
2025-03-01 02:01:39
@ 60d17aca:3d6671c6
2025-03-01 02:01:39잘 보내지나 시험해본다.
-
 @ a1c19849:daacbb52
2025-02-24 19:19:16
@ a1c19849:daacbb52
2025-02-24 19:19:16Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 4 hours
Ingredients
- 1kg of chicken thighs
- 3 large onions
- 1 tablespoon garlic powder
- 2 tablespoons brown sugar
- 1.5 dl Ketjap Medja
- 0.5 liter chicken broth
- Pepper
- Salt
- Nutmeg
Directions
- Cut the onions and sauté them
- Add the chicken thighs in pieces and bake for a few minutes
- Add the garlic powder and the brown sugar and bake for a short time
- Add the ketjap media and the chicken broth
- Add some salt and pepper and nutmeg and let it simmer for 3 to 4 hours
- Make sure all the moist evaporates but make sure it doesn’t get too dry. Otherwise add some extra chicken broth
- Bon appetit!
-
 @ 04ea4f83:210e1713
2025-02-24 06:42:36
@ 04ea4f83:210e1713
2025-02-24 06:42:36Erschienen im The Bitstein Brief | Veröffenlichung 10.12.2022 |\ Author: Bitstein (Michael Goldstein)\ Übersetzt von: Sinautoshi am 11.12.2022 - 766906
„Die gesellschaftliche Funktion der Wirtschaftswissenschaft besteht gerade darin, solide Wirtschaftstheorien zu entwickeln und die Irrtümer bösartiger Denkweisen zu entlarven. Bei der Verfolgung dieser Aufgabe zieht der Wirtschaftswissenschaftler die tödliche Feindschaft aller Schwindler und Scharlatane auf sich, deren Abkürzungen zum irdischen Paradies er entlarvt. Je weniger diese Quacksalber in der Lage sind, plausible Einwände gegen die Argumente eines Ökonomen vorzubringen, desto wütender beschimpfen sie ihn.“
- Ludwig von Mises, „Nationalökonomie, Theorie des Handelns und Wirtschaftens”
Das „toxischste" an einem Bitcoin-Maximalisten ist seine unerschütterliche Bereitschaft, „Nein” zu sagen. Nach dem Studium der Geldtheorie und -geschichte und der Erfahrung mit den unerbittlichen Kräften des Marktes, hat der Bitcoiner ein Verständnis für die Realität des monetären Wettbewerbs, ein Bewusstsein für die kritische Natur dezentraler Systeme, einen Fokus auf die Lösung der wichtigsten monetären Probleme und eine strikte Ablehnung der unvermeidlichen Ablenkungen, Opportunitätskosten und ethischen Bedenken bei der Einführung und Förderung von Altcoin-Projekten.
Einige Kritiker bemängeln unhöfliche rhetorische Schnörkel, die als Hindernis für die Gewinnung neuer Bitcoin-Nutzer angesehen werden. Wenn das wahr wäre, gäbe es in der Arbeitsteilung eine Chance für eine qualitativ hochwertigere Bitcoin-Ausbildung, die die Bitcoiner meiner Meinung nach gerne wahrnehmen würden, vor allem die Kritiker, die die bestehenden Unzulänglichkeiten besser erkennen. Doch egal, wie höflich die Bitcoiner ihre Ansichten darlegen, bestimmte Möchtegern-Unternehmer und Influencer werden immer im Streit mit einer leidenschaftlichen Bevölkerungsgruppe stehen, die einfach nicht interessiert ist - und ihr Desinteresse lautstark kundtut. Die „toxischsten" Bitcoiner sind oft diejenigen, die die Weisheit der Bitcoiner erst erkannt haben, nachdem sie von Shitcoins verbrannt wurden und ihr neu gefundenes Desinteresse unmissverständlich zum Ausdruck bringen wollen.
Was soll man also als Bitcoiner tun? Ich empfehle, sich der Wahrheit und der Förderung der Wahrheit zu verschreiben und die Wirksamkeit von Rhetorik an ihrem langfristigen Einfluss und nicht an ihrer kurzfristigen Popularität zu messen.
In dieser Hinsicht sollten sich die Bitcoiner von dem ursprünglichen toxischen Maximalisten inspirieren lassen: Ludwig von Mises. Der bedeutende Wirtschaftswissenschaftler setzte sich unbeirrt für die Wahrheit, freie Märkte und gesundes Geld ein und scheute sich nicht, das zu sagen, was gesagt werden musste, auch wenn er sich damit keine Freunde machte. Langfristig wurde er zu einem der einflussreichsten Ökonomen und Denker des 20. Jahrhunderts, und seine Arbeit hat den Weg für den Bitcoin geebnet.
Mises, der Geldmaximalist
Einer der Hauptkritikpunkte an den Bitcoin-Maximalisten ist die Behauptung, dass die Welt auf Bitcoin (als Geld) konvergieren wird und es generell keine Verwendung für andere Währungen gibt. Dies wird als normative Aussage betrachtet. In Wirklichkeit machen die Bitcoiner eine positive, beschreibende Aussage darüber, wie der monetäre Wettbewerb funktioniert.
In der 1912 veröffentlichten Theorie des Geldes und der Umlaufmittel schrieb Mises:
„So haben die Erfordernisse des Marktes allmählich dazu geführt, dass bestimmte Waren als gemeinsame Tauschmittel ausgewählt wurden. Die Gruppe der Waren, aus der diese ausgewählt wurden, war ursprünglich sehr groß und unterschied sich von Land zu Land; sie wurde aber immer mehr eingeschränkt. Wann immer ein direkter Tausch nicht in Frage kam, war jede der an einem Geschäft beteiligten Parteien bestrebt, ihre überflüssigen Waren nicht nur gegen marktgängigere Waren im Allgemeinen, sondern gegen die marktgängigsten Waren einzutauschen, und von diesen wiederum bevorzugte sie natürlich die marktgängigste Ware. Je größer die Marktfähigkeit der zuerst im indirekten Tausch erworbenen Waren ist, desto größer ist die Aussicht, das endgültige Ziel ohne weitere Manöver erreichen zu können. So gäbe es die unvermeidliche Tendenz, dass die weniger marktfähigen Güter aus der Reihe der als Tauschmittel verwendeten Waren nach und nach verworfen würden, bis schließlich nur noch ein einziges Gut übrig bliebe, das allgemein als Tauschmittel verwendet würde: das Geld.“
Mises zufolge wählen die Akteure zunehmend das marktgängigste Gut als Tauschmittel aus und der natürliche Verlauf des Marktes geht in Richtung Vereinheitlichung zu einem einzigen Geldgut. Das ist schlicht und einfach monetärer Maximalismus.
Mises unterscheidet sich von den Bitcoinern lediglich durch die Stärke der Behauptungen, die er über die tatsächlichen empirischen Entscheidungen der Wirtschaftsakteure zu treffen bereit ist. Mises weist darauf hin, dass sowohl Gold als auch Silber an vielen Orten zu Geld gemacht wurden, wahrscheinlich wegen ihrer ähnlichen Eigenschaften, und dass es den Rahmen der Geldtheorie sprengt, zu sagen, ob Gold oder Silber letztlich besser verkäuflich ist. Trotzdem sagt er:
„Denn es ist ziemlich sicher, dass die Vereinheitlichung auch dann ein wünschenswertes geldpolitisches Ziel gewesen wäre, wenn die ungleiche Marktfähigkeit der als Tauschmittel verwendeten Güter kein Motiv geboten hätte. Die gleichzeitige Verwendung mehrerer Geldarten bringt so viele Nachteile mit sich und verkompliziert die Technik des Tauschens so sehr, dass das Bestreben, das Geldsystem zu vereinheitlichen, in jedem Fall unternommen worden wäre.“
Die natürliche Tendenz zu einem einzigen Geldgut ist so stark, dass seiner Meinung nach die Vereinheitlichung der Geldsysteme auch dann angestrebt würde, wenn zwei Güter genau gleich marktfähig wären. Zuvor stellt er außerdem fest:
„Das endgültige Urteil könnte erst gefällt werden, wenn alle Hauptteile der bewohnten Erde ein einziges Handelsgebiet bilden, denn erst dann wäre es unmöglich, dass andere Nationen mit unterschiedlichen Geldsystemen sich anschließen und die internationale Organisation verändern.“
Jede neue Handelsbeziehung eröffnet die Möglichkeit, ein brandneues Geldgut einzuführen, das bisher nicht verwendet wurde. Wenn seine Qualitäten ein höheres Maß an Marktfähigkeit aufrechterhalten könnten, ist es möglich, dass sich die gesamte internationale Währungsordnung aufgrund seiner natürlichen Überlegenheit bei der Bewältigung der Funktionen des Geldes um ihn herum neu organisieren könnte.
Im Bitcoin Standard liefert Saifedean Ammous zahlreiche Argumente dafür, warum Gold dem Silber als Geldwert überlegen war, obwohl Mises nicht bereit oder nicht daran interessiert war, diesen Punkt zu diskutieren, und warum Bitcoin ein noch besserer Geldwert ist. Mises hat die Einführung von Bitcoin in die Weltwirtschaft zwar nicht mehr erlebt, aber seine Wirtschaftstheorie erklärt genau, warum Bitcoin an Wert gewinnen würde und warum es plausibel ist, dass die gesamte internationale Währungsordnung auf einen Bitcoin-Standard umgestellt wird. Er gibt auch den theoretischen Rahmen, um zu verstehen, warum Altcoins Bitcoin nicht allein durch ihre Eigenschaften ausstechen können. Sie müssen eine bessere Marktfähigkeit in Bezug auf Raum, Zeit und Größe bieten, um einen ausreichenden Vorteil gegenüber Bitcoin zu haben. Wie bereits an anderer Stelle beschrieben, ist dies einfach nicht gelungen, und nur Bitcoin bietet ein stark dezentralisiertes, überprüfbares und glaubwürdig knappes digitales Geldgut.
Mises, der Marktmaximalist
Die Geldtheorie ist nicht der einzige Ort, an dem der Leser eine Art „Maximalismus" in Mises' Denken spüren kann. Sein gesamtes Werk läuft auf einen unverhohlenen Marktmaximalismus hinaus, der sich weigert, durch rigorose ökonomische Theorie und Analyse sozialistischen oder interventionistischen Argumenten nachzugeben.
Ein großartiges Beispiel für seine Verteidigung des freien Marktes findet sich in einem Vortrag aus dem Jahr 1950 mit dem Titel „Die Mitte des Weges führt zum Sozialismus". In dieser Vorlesung greift Mises Interventionisten an, die behaupten, eine Politik der „Mitte" zwischen den beiden Extremen Kapitalismus und Sozialismus zu favorisieren. Durch strategische Interventionen kann der Staat die Auswüchse beider Systeme verhindern.
Mises betrachtet Kapitalismus und Sozialismus jedoch als diametral entgegengesetzte und unvereinbare Organisationssysteme und nicht als ein Spektrum der Wohlstandsverteilung:
„Der Konflikt der beiden Prinzipien ist unüberbrückbar und lässt keinen Kompromiss zu. Kontrolle ist unteilbar. Entweder entscheidet die Nachfrage der Verbraucher, die sich auf dem Markt manifestiert, für welche Zwecke und wie die Produktionsfaktoren eingesetzt werden sollen, oder der Staat kümmert sich um diese Angelegenheiten. Es gibt nichts, was den Gegensatz zwischen diesen beiden widersprüchlichen Prinzipien abmildern könnte. Sie schließen sich gegenseitig aus. Der Interventionismus ist kein goldener Mittelweg zwischen Kapitalismus und Sozialismus. Er ist der Entwurf für ein drittes System der wirtschaftlichen Organisation der Gesellschaft und muss als solches gewürdigt werden.“
Dieses dritte System ist jedoch im Grunde nur ein längerer Marsch zum Sozialismus, indem es ein falsches Lippenbekenntnis zu Privateigentum und freier Marktwirtschaft ablegt. Auf jeden Eingriff, der stattfindet, müssen weitere folgen. Die Festsetzung eines Preises hier erfordert die Festsetzung eines anderen Preises dort, und so geht es die ganze Lieferkette entlang. Am Ende hat der Interventionismus die gesamte „Marktwirtschaft" im Würgegriff.
Der Interventionismus kann nicht als ein Wirtschaftssystem betrachtet werden, das dazu bestimmt ist, zu bleiben. Er ist eine Methode zur Umwandlung des Kapitalismus in den Sozialismus in mehreren aufeinanderfolgenden Schritten. Damit unterscheidet er sich von den Bemühungen der Kommunisten, den Sozialismus auf einen Schlag zu verwirklichen. Der Unterschied bezieht sich nicht auf das letztendliche Ziel der politischen Bewegung, sondern vor allem auf die Taktik, die zur Erreichung des von beiden Gruppen angestrebten Ziels angewandt wird.
Trotzdem sind selbst die meisten vermeintlichen Befürworter einer freien Marktwirtschaft in Wirklichkeit von interventionistischen Ideologien und Denkweisen durchdrungen, und ihre Strategien sind immer zum Scheitern und zu Kompromissen verurteilt.
„Dies hat zur Folge, dass praktisch kaum etwas getan wird, um das System der Privatwirtschaft zu erhalten. Es gibt nur Mittelsmänner, die glauben, erfolgreich gewesen zu sein, wenn sie eine besonders ruinöse Maßnahme eine Zeit lang hinausgezögert haben. Sie sind immer auf dem Rückzug. Sie nehmen heute Maßnahmen in Kauf, die sie noch vor zehn oder zwanzig Jahren für undiskutabel gehalten hätten. In ein paar Jahren werden sie sich mit anderen Maßnahmen abfinden, die sie heute noch für undiskutabel halten. Was den totalitären Sozialismus verhindern kann, ist nur ein grundlegender Wandel der Ideologien.\ \ Was wir brauchen, ist weder Antisozialismus noch Antikommunismus, sondern eine offene Befürwortung des Systems, dem wir all den Wohlstand verdanken, der unser Zeitalter von den vergleichsweise beengten Verhältnissen vergangener Zeiten unterscheidet.“
Mises nimmt kein Blatt vor den Mund, wenn er eine interventionistische Politik fordert, und es gibt viele Lehren, die Bitcoiner daraus ziehen können.
Erstens ist das Bitcoin-Netzwerk nicht einfach nur eine andere Art des Werttransfers als eine bestehende zentralisierte Lösung, eine Art PayPal 2.0. Es ist ein strukturell anderer Ansatz für das gesamte Problem der doppelten Ausgaben. „Blockchain, nicht Bitcoin" ist eine Mogelpackung, weil sie den Kern dessen, was Bitcoin einzigartig macht (Dezentralisierung, unabhängige Überprüfbarkeit usw.), wegnimmt, während sie behauptet, „die zugrundeliegende Technologie" zu nutzen, ähnlich wie ein nationalsozialistisches oder faschistisches Regime die staatliche Kontrolle über die Produktion übernehmen könnte, während es behauptet, für Privateigentum zu sein. Wenn du die Vorteile des Marktes nutzen willst, musst du tatsächlich einen Markt haben, und wenn du die Vorteile von Bitcoin nutzen willst, musst du Bitcoin tatsächlich nutzen.
Außerdem sollte die Dezentralisierung als binäres System betrachtet werden. Entweder ist ein System dezentralisiert, oder es ist dazu verdammt, zentralisiert zu werden, manchmal mit einem Hard Fork nach dem anderen (vgl. Ethereum). Bitcoin-Maximalisten werden regelmäßig als toxisch bezeichnet, weil sie entschlossen an bestimmten Netzwerkparametern festhalten, selbst wenn diese willkürlich oder trivial erscheinen. Ein ganzer Krieg über die Blockgröße wurde um eine Begrenzung von 1 MB geführt. Die Zahl schien willkürlich und die Lösung trivial zu sein, aber die Bitcoiner weigerten sich, davon abzuweichen. Und warum? Eine höhere Blockgröße würde die Kosten für den Betrieb eines vollständigen Knotens (Full Node) erhöhen, der für eine unabhängige Validierung und Dezentralisierung notwendig ist. Ein Hard Fork würde einen vernichtenden Präzedenzfall schaffen und alle zukünftigen Ansprüche auf Abwärtskompatibilität gefährden, die für die Glaubwürdigkeit der Geldpolitik und die Fähigkeit der Nodes, sich vertrauensvoll mit dem Netzwerk zu synchronisieren, erforderlich sind. Die Blockkapazität stieg zwar an, aber nur, weil SegWit, dessen Vorteile weit über die bloße Verbesserung der Skalierung hinausgingen, über einen Soft Fork aktiviert werden konnte, sodass denjenigen, die dies nicht wollten, keine neuen Kosten auferlegt wurden.
Andere Projekte hingegen akzeptieren nicht, dass die Kompromisse bei Bitcoin nicht wirklich willkürlich sind. Sie bieten Turing-complete Smart Contracts, schnellere Blockzeiten, größere Blöcke oder alle möglichen anderen „Features" an. Die Features werden nicht mit demselben extrem konservativen Engagement für Sicherheit produziert wie Bitcoin und bedrohen oft die Fähigkeit, überhaupt einen vollständigen Knoten (Full-Node) zu betreiben. Nur bei Bitcoin kümmern sich die Leute darum, dass die Geldmenge tatsächlich überprüft werden kann. Mit der Zeit verlieren die Projekte, wenn sie überhaupt aufrechterhalten werden, jeden Anschein einer glaubwürdigen Dezentralisierung. Ethereum, das einst mit unaufhaltsamen Anwendungen und der Aussage „Code ist Gesetz" warb, erlebte den DAO-Hack und ist nach der Einführung von Proof-of-Stake (das von Natur aus zentralisierend ist) der OFAC-Zensur in unterschiedlichem Maße unterworfen.
Bitcoin akzeptiert nichts von alledem. Er beugt seine Regeln für niemanden. Bitcoiner wissen auch, dass das System gar kein Bitcoin mehr wäre, wenn die Regeln gebogen würden. Mises hilft uns zu verstehen, dass eine Politik des Mittelweges zu Shitcoinerei führt. Eine Währung ist entweder Bitcoin oder dazu verdammt, ein Shitcoin zu sein.
Mises, der toxische Maximalist
Im Jahr 1947 fand in der Schweiz das erste Treffen der Mont Pèlerin Society statt. Bei diesem Treffen trafen sich viele der einflussreichsten Verfechter der freien Märkte und des klassischen Liberalismus, von Ludwig von Mises über F. A. Hayek bis hin zu Milton Friedman und vielen anderen, um darüber zu diskutieren, wie man die steigende Flut des Totalitarismus und seiner Wirtschaftsideologien durch die Förderung freier Märkte und des Privateigentums bekämpfen kann. Man könnte meinen, dass Mises genau in diese Diskussionen passt. Doch wie Milton Friedman berichtete, kam es anders:
„Die Geschichte, an die ich mich am besten erinnere, ereignete sich auf dem ersten Treffen in Mont Pèlerin, als [Mises] aufstand und sagte: „Ihr seid alle ein Haufen Sozialisten." Wir diskutierten über die Einkommensverteilung und darüber, ob man progressive Einkommenssteuern haben sollte. Einige der Anwesenden vertraten die Ansicht, dass es eine Rechtfertigung dafür geben könnte.\ \ Eine andere Gelegenheit, die ebenso aufschlussreich ist: Fritz Machlup war ein Schüler von Mises, einer seiner treuesten Jünger. Bei einem der Treffen in Mont Pèlerin hielt Machlup einen Vortrag, in dem er, glaube ich, die Idee eines Goldstandards in Frage stellte; er sprach sich für freie Wechselkurse aus. Mises war so wütend, dass er drei Jahre lang nicht mit Machlup sprechen wollte. Einige Leute mussten die beiden wieder zusammenbringen. Es ist schwer zu verstehen; man kann es einigermaßen nachvollziehen, wenn man sich vor Augen führt, wie Menschen wie Mises in seinem Leben verfolgt wurden.“
Wie bereits erwähnt, hielt Mises drei Jahre später einen Vortrag, in dem er eindrucksvoll erklärte, warum sie tatsächlich alle ein Haufen Sozialisten waren. Wer staatliche Eingriffe in die Einkommensverteilung akzeptiert, ist dem Sozialismus bereits verfallen, sobald genug Zeit vergangen ist. Mises war einfach nicht bereit, den sozialistischen Irrtümern, die er im Laufe seiner intellektuellen Karriere so akribisch aufgespießt hatte, Glauben zu schenken. Jörg Guido Hülsmann stellt in Mises: The Last Knight of Liberalism fest, dass „Mises zwar in der Lage war, Sozialisten hoch zu schätzen, aber der Vorfall zeigte, dass er wenig Geduld mit Sozialisten hatte, die sich als Liberale ausgaben."
Doch Mises' giftiges Verhalten blieb nicht ohne Folgen. Laut Hülsmann:
„Der Schlagabtausch zwischen Mises und seinen neoliberalen Gegnern prägte den Ton in der Mont Pèlerin Society für die kommenden Jahre.... Obwohl die Libertären um Mises eine kleine Minderheit waren, hatten sie die finanzielle Unterstützung der amerikanischen Hauptsponsoren wie dem Volker Fund, ohne die die Gesellschaft in jenen frühen Jahren schnell ausgestorben wäre. Solange Mises aktiv an den Treffen teilnahm, war es daher unmöglich, die technischen Details eines genehmigten staatlichen Interventionismus zu diskutieren. Das Laissez-faire hatte ein Comeback gefeiert. Es war zwar nicht die Mehrheitsmeinung, aber es war eine diskutierbare und diskutierte politische Option - zu viel für einige anfängliche Mitglieder wie Maurice Allais, der die Gesellschaft genau aus diesem Grund bald wieder verließ.“
Indem er toxisch war, konnte Mises dazu beitragen, den Ton für eine wirklich laissez-faire Mont Pèlerin Society zu setzen, die ihrem erklärten Ziel gerecht werden konnte, und sie wählten F. A. Hayek zu ihrem Präsidenten. Er hatte keine Angst, Klartext zu reden, aber lautstark, sogar gegenüber Leuten, die vermutlich zu seinem „eigenen Team" gehörten. Ludwig von Mises war ein Mann, der seine Ideen ernst nahm und die Wahrheit noch viel ernster.
In seinen Memoiren schreibt Mises über seine Zeit in der österreichischen Handelskammer in den 1910er und 1920er Jahren:
„Ich wurde manchmal beschuldigt, meinen Standpunkt zu schroff und unnachgiebig zu vertreten. Es wurde auch behauptet, dass ich mehr hätte erreichen können, wenn ich eine größere Kompromissbereitschaft gezeigt hätte.... Die Kritik war ungerechtfertigt; ich konnte nur dann effektiv sein, wenn ich die Dinge so darstellen konnte, wie sie mir erschienen. Wenn ich heute auf meine Arbeit bei der Handelskammer zurückblicke, bedauere ich nur meine Kompromissbereitschaft und nicht meine Unnachgiebigkeit.“
In dieser Zeit trug sein Rat dazu bei, die Hyperinflation in Österreich aufzuhalten und ihre Auswirkungen im Vergleich zur Weimarer Republik abzuschwächen.
Bitcoiner werden von endlosen „Krypto-" und „Shitcoin"-Betrügern geplagt, die auf dem Rücken der innovativen Technologie und des wirtschaftlichen Erfolgs von Bitcoin reiten wollen. Den Bitcoinern wird gesagt, dass sie alle im selben Team sind. In den Augen der Öffentlichkeit sind sie das auch. Das Ergebnis ist eine getäuschte Öffentlichkeit, der zentralisierte Pump-and-Dump-Systeme und Rugpulls, Affen-Jpegs und Rube-Goldberg-Maschinen verkauft werden, die auf Schlagwörtern basieren und die Vorstellung vermitteln, dass sie in der gleichen Liga spielen wie die großartigste Geldtechnologie, die je geschaffen wurde. „Krypto" profitiert vom Erfolg von Bitcoin, und die Bekanntheit von Bitcoin sinkt mit den Misserfolgen von „Krypto". Doch wenn Bitcoiner die Unterschiede ansprechen und diese Projekte ablehnen, die sie uninteressant oder sogar verabscheuungswürdig finden, wird das als schädlich angesehen. Den Bitcoinern schadet das nicht, denn sie können weiter (Satoshis) stapeln und bauen, aber die Menschen, die unter Fiat-Regimen leben müssen, leiden darunter, dass ihnen kein Weg zu Freiheit und Wohlstand gezeigt wird.
Abgesehen davon, dass das Geld des Einzelnen in Gefahr ist, kann die Offenheit für Shitcoins auch Veränderungen im Netzwerk fördern, die die Dezentralisierung beeinträchtigen. Wenn es Unterstützung für einen Shitcoin gibt, der auf einem bestimmten Merkmal basiert, warum sollte das Merkmal dann nicht in Bitcoin existieren? Wenn es tatsächlich eine Tendenz zu einer einzigen Währung gibt, ist die Förderung einer alternativen Kryptowährung selbst ein Angriff auf das Potenzial von Bitcoin. Wirtschaft und Technik sind mit gnadenlosen Konsequenzen konfrontiert. Eine falsche Abfolge von Schritten kann zu absoluter Verwüstung führen. Bitcoiner nehmen das sehr ernst und machen keinen Hehl daraus, dass sie diese Konsequenzen fürchten. Wenn sie das tun, lehnen sie ganze unternehmerische Vorhaben ab und stellen ihre gesamte Einnahmequelle in Frage. Das ist toxisch.
Bitcoiners sollten immer den Mut haben, Mises zu zitieren und jedem zu sagen: „Ihr seid alle ein Haufen Shitcoiner."
Der aufgehende Stern von Mises
Obwohl er aus einer adligen Familie stammte und in Österreich hohe Positionen innehatte, hatte Mises, als er auf der Flucht vor den Nazis in die Vereinigten Staaten emigrierte, nur wenige Möglichkeiten. Bis zu seiner Pensionierung war er „Gastprofessor" an der New York University. Er arbeitete im Grunde genommen im stillen Kämmerlein und unterrichtete hauptsächlich in seinen inzwischen berühmten informellen Seminaren, an denen auch Murray Rothbard und andere teilnahmen. Er benötigte die Unterstützung verschiedener philanthropischer Fonds. Hinzu kam, dass die Wirtschaftswissenschaften, wie alle Sozialwissenschaften, dem Szientismus und der Technokratie erlegen waren, so dass Mises' strenge logisch-deduktive Methoden im Vergleich zu mathematischen Formeln und statistischen Modellen als altmodisch galten. Der Goldstandard wurde zugunsten eines Fiat-Systems abgeschafft, und als Mises starb, hatte der US-Dollar keinerlei Verbindung mehr zu Edelmetallen oder realen Ersparnissen, so dass die Geldpolitik allein den Launen der Politik überlassen blieb.
Es gab allen Grund, Ludwig von Mises völlig in Vergessenheit geraten zu lassen. Doch seine Schüler, wie Murray Rothbard, hielten die österreichische Schule am Leben. Im Jahr 1982 wurde das Ludwig von Mises Institute von Rothbard und Lew Rockwell gegründet und von Dr. Ron Paul finanziert (beide wurden von ihren Kritikern als „toxisch" bezeichnet). Dr. Paul selbst wurde zu einem legendären Verfechter der Ideen von Mises und anderen, sowohl im Kongress als auch im Präsidentschaftswahlkampf. In letzterem machte Dr. Paul die von der Federal Reserve verursachte wirtschaftliche Zerstörung zu einem zentralen Bestandteil seines Programms und zum ersten Mal seit Jahrzehnten zu einem wichtigen Thema in der politischen Debatte, was den Diskurs danach für immer veränderte.
Es ist also kein Wunder, dass viele Menschen, die sich als erste für Bitcoin begeisterten, treue Schüler von Mises waren und dass seine Ideen mit dem Wachstum von Bitcoin noch mehr an Bedeutung gewonnen haben. Seine rigorose Erläuterung der Wahrheiten des Wirtschaftsrechts, die auf Subjektivismus, Marginalismus und methodologischem Individualismus beruht, gab den Menschen den Rahmen, um zu verstehen, wie Bitcoin die Geldpolitik veranschaulicht, die zu Frieden, Wohlstand und Freiheit führt. Anstatt irrelevant zu werden, ist Mises heute wichtiger denn je. Wie Ron Paul bemerkte: „Wir sind jetzt alle Österreicher."
Fazit
Das Toxische liegt im Auge des Betrachters oder des Bagholders. Die Wirtschaftswissenschaft ist, wie jedes Streben nach Wahrheit, kein Beliebtheitswettbewerb, und die Wahrheit wird immer von denen bekämpft werden, deren Geschäft und Status von der Verbreitung von Irrtümern und Unwahrheiten abhängt.\ \ Ludwig von Mises stand fest zu seinen gründlichen Analysen der Wirtschaftswissenschaften und des klassischen Liberalismus und scheute sich nicht, das zu verteidigen, was er für wahr hielt, selbst auf Kosten von Prestige und Popularität. Heute steht er weit über fast jedem anderen Sozialwissenschaftler des 20. Jahrhunderts.
Ich habe an anderer Stelle über Memes und Rhetorik gesprochen, und es gibt viel zu diskutieren über bestimmte Strategien und ihre Wirksamkeit. Aber vor allem muss jede Strategie die Wahrheit in den Mittelpunkt stellen. Die Wahrheit ist zeitlos, so dass ihre Relevanz nicht auf kurzfristige Popularität beschränkt ist. Wenn dies der Fall ist, ist der Vorwurf der „Toxizität" entweder eine Aufforderung zur Verbesserung oder ein Ehrenzeichen dafür, dass man trotz aller Widrigkeiten für die Wahrheit einsteht. Wie das Motto von Ludwig von Mises schon sagte: tu ne cede malis, sed contra audentior ito. Weiche dem Bösen nicht, trete ihm umso mutiger entgegen.
-
 @ fb08144a:c9ced3f4
2025-03-01 00:45:14
@ fb08144a:c9ced3f4
2025-03-01 00:45:14Print hello world
-
 @ 04ea4f83:210e1713
2025-02-23 17:38:11
@ 04ea4f83:210e1713
2025-02-23 17:38:11Erschienen in Citadel 21 Vol. 21 | Veröffentlichung 21.03.2023 \ Autor: Knut Svanholm\ Übersetzt von: Sinautoshi am 24.03.2023 - 782344\ \ Rückblickend sieht das Jahr 2022 wie eine Art Höhepunkt aus. Während der Großteil der Gesellschaft weitgehend vergessen hat, was die politische Klasse ihren Untertanen während der sogenannten Pandemie angetan hat, kotzte Hollywood weiterhin Inhalte aus, die von „diversen" Regisseuren und Drehbuchautoren produziert wurden und bis zum Rand mit nicht ganz so subtilen Botschaften und Verachtung für ihr Publikum gefüllt waren.
Star Wars und Marvel haben nach der Übernahme durch Disney auf diese Weise Franchise-Mord begangen, und auch das Erbe von Der Herr der Ringe wurde von der linken Idiotie vergewaltigt und für immer befleckt. Jetzt gibt es von jedem männlichen Avenger eine weibliche Version. Hugh Jackman, der Schauspieler, der früher die Hauptrolle des X-Men-Mutanten Wolverine spielte, empfahl seinen Anhängern in den sozialen Medien kürzlich Bill Gates' Buch über den Klimawandel.
Als Frauen verkleidete Männer gewinnen Sportmeisterschaften für Frauen, und alle haben so viel Angst davor, als bigott bezeichnet zu werden, dass sich niemand traut, auf die Absurdität hinzuweisen, dass ein Mann alle Mädchen schlägt. Diese so genannten Sportler werden als „mutig" bezeichnet, obwohl sie alles andere als das sind.
Die Tatsache, dass es in einigen Berufen mehr Männer als Frauen gibt, wird als Problem angesehen, aber warum genau das ein Problem ist, wird selten erwähnt. Die Verdienste und die tatsächliche Meinungsvielfalt werden auf dem Altar der „Vielfalt und Integration" geschlachtet.
Die Gesellschaft ist an einem Punkt angelangt, an dem die Verbraucher Ärzten und Anwälten gerade wegen ihrer Hautfarbe misstrauen, da sie vermuten, dass sie deshalb in ihre Positionen gekommen sind und nicht wegen ihrer Kompetenz oder ihrer Verdienste. Noch vor zwanzig Jahren war die normale Bauchreaktion das Gegenteil: „Wow, ein Arzt aus einer Minderheit! Sie müssen hart gearbeitet haben, um dorthin zu gelangen, wo sie heute sind!"
Als ich aufgewachsen bin, wurde ein „Rassist" als jemand definiert, der sich einen Dreck um die Hautfarbe oder die ethnische Zugehörigkeit einer anderen Person scherte. Dasselbe galt für das Wort „Sexist" - man war ein Sexist, wenn man das Geschlecht einer Person bei der Beurteilung berücksichtigte.
Ich hatte das Gefühl, dass die Welt seit den Gräueltaten des Zweiten Weltkriegs im Kampf gegen diese Vorurteile einen weiten Weg zurückgelegt hatte und dass jeder eine anständige Karriere in jedem Beruf machen konnte, wenn er sich nur anstrengte und sich Mühe gab. Doch irgendwann in den frühen 2000er Jahren änderte sich etwas.
Plötzlich begannen die Worte das Gegenteil von dem zu bedeuten, was sie ursprünglich bedeuteten. Plötzlich war jeder, der sich einen Dreck um seine Hautfarbe scherte, ein Rassist. Jeder, dem es egal war, ob der CEO eines großen Unternehmens ein Mann oder eine Frau war, war ein Sexist.
Im Jahr 2023 behaupten manche sogar, man sei ein „Transphobe", wenn man nicht gelegentlich Fellatio an einem „weiblichen Penis" betreiben will. Die Tugendwächter laufen in der Tat Amok, und die Medienunternehmen lieben es. Sie lieben es, weil sie alles lieben, was die Kluft zwischen den Menschen schürt. Je verrückter die Aktionen der Clownwelt® sind, desto wütender sind die Reaktionen der leichtgläubigen, verärgerten Menschen auf der „vernünftigen" Seite des politischen Spektrums.
Die Menschheit neigt dazu, sich wie ein Pendel oder eine Abrissbirne zu verhalten, wenn es um politische Meinungen oder „die aktuelle Sache" geht.
Wenn es zu viele blauhaarige, übergewichtige, lesbische, glutenintolerante, vegane Umweltschützer gibt, taucht von irgendwoher eine Welle von Skinheads auf, die mit Steroiden vollgepumpt sind und gegen Samenöl und Fleischfresser sind.
Für jede Hillary Clinton gibt es einen Donald Trump. Für jede Greta Thunberg gibt es einen Andrew Tate. Für jeden CNN-Reporter gibt es einen Alex Jones.
Auch im Bitcoin-Bereich gibt es immer ein „aktuelles Thema", an das man sich klammern kann, wenn auch oft eine männlichere Idee als das „aktuelle Thema" des Mainstreams. Was nur wenige wissen, ist, wie faul diese Art des Denkens ist.
Wissenschaft ist nicht automatisch schlecht, nur weil „die Wissenschaft" schlecht ist.
Nur weil man gelernt hat, dass alles, was die Regierung sagt, eine Lüge ist, ist nicht automatisch auch das Gegenteil wahr. Die Welt ist nuanciert; die meisten Dinge sind nicht schwarz oder weiß.
Was wahr und sehr schwarz-weiß ist, ist das Geld - es gibt Bitcoin und es gibt Shitcoins. Nur wenn wir letztere für erstere aufgeben, können wir die Politik aus dem menschlichen Handeln entfernen und uns auf eine gewisse Wahrheit in der Basisschicht der Zivilisation zurück arbeiten. Bitcoin belohnt weder Rent-Seeking noch faules Denken.
Die positiven Aspekte vieler moderner Technologien werden oft übersehen. Auch wenn sich die Clownwelt® und die lächerlichen Ideen, die ihr folgen, wie ein Lauffeuer verbreiten, gibt es Gründe für einen ungetrübten Optimismus für die Zukunft.
Wir hören oft von den Gefahren der sozialen Medien und wie sie die Gehirne unserer Kinder schädigen, aber wir werden selten an die Kehrseite der Medaille erinnert. Soziale Medien verbinden Menschen in einem Ausmaß, das der Menschheit nie zuvor zugänglich war. Jeder Mensch auf der Welt kann heute mit jedem anderen in Kontakt treten und mit einem Mausklick einen Videoanruf starten. Das ist ein enorm wichtiges Instrument für den Frieden. In Kombination mit Bitcoin haben die Bösewichte keine Chance mehr.
Wenn jeder auf diese Weise vernetzt ist, wird überdeutlich, wie absurd es ist, dass wir in Staaten mit unterschiedlichen Gesetzen und Vorschriften leben. Warum gelten für meine Mitmenschen auf der anderen Seite dieses Teiches, dieses Flusses, dieses Gebirges oder sogar dieser imaginären Linie in der Erde andere Regeln?
Jeden Tag wachen mehr und mehr Menschen auf und erkennen, dass es nur ein einziges Menschenrecht gibt - das Recht, in Ruhe gelassen zu werden.
Immer mehr Menschen erkennen, dass die Geldentwertung kein natürliches Phänomen ist, sondern eine bewusste Politik. Es ist nur eine Frage der Zeit, bis die alte Welt verschwindet. Solange wir kommunizieren dürfen, gibt es Hoffnung. Das Internet hat bewiesen, dass sich jede Kommunikation auf eine Reihe von Einsen und Nullen reduzieren lässt, und Bitcoin hat bewiesen, dass Geld nichts anderes als Information ist.
-
 @ b581c912:7df8270f
2025-02-28 21:11:56
@ b581c912:7df8270f
2025-02-28 21:11:56Fui abordado por um colega e ele me falou de forma bastante enérgica sobre o projeto Pi Network, após uma breve conversa resolvi dar crédito e estudar sobre a solução proposta.
Tentei ser imparcial e fui direto no site “oficial” (🤔) onde encontrei dois Whitepapers (referência 1), um de 2019 e outro de 2021. Decidi então fazer a leitura pela documentação oficial, tentar não me influenciar mais do que já sou influenciado (como um Bitcoiner Maximlista que acho que sou).
Infelizmente não tive condições de terminar os dois documentos, no capítulo “Pi – Token Supply” de 2019 já deixa claro de forma matemática que Pi Network é uma pirâmide, e como até aquele momento não consegui resposta se o processo de recompensa da rede tinha sido atualizada, eu decidi não gastar mais meu tempo de vida estudando sobre o protocolo.\ \ Deixo aqui as anotações que fiz até onde tive condições de ler. Por favor, sinta-se à vontade para contra-argumentar caso você tenha entendido o protocolo de forma diferente, ou assim como Satoshi “If you don't believe me or don't get it, I don't have time to try to convince you, sorry.”.
De forma bastante resumida, esta é minha conclusão:
Pi Network é uma pirâmide declarada na sua própria documentação oficial. Infelizmente, mais uma shitcoin.
Vende a ideia de descentralização e justiça, mas não tem nada descentralizado e muito menos justa, usando da falácia argumentativa e frases de efeito tenta vender sua pirâmide financeira.
(OBS: os primeiros capítulos do Whitepaper de 2019 são concentrados em atacar o Bitcoin e seu ambiente, mas sem a coragem de pelo menos descrever corretamente como o ambiente funciona. Soltando verdades pela metade leva o leitor a achar que o ambiente do Bitcoin é malicioso e precisa de ‘melhorias’)
-
Introduction: Why cryptocurrencies matter
-
Traz alguns argumentos para validar a existência do Pi Network, cita falhas do sistema fia, mas não citou o maior problema: Inflação e/ou impressão de dinheiro;
-
Securing Distributed Ledgers (Mining)
-
“This process (Bitcoin mining) is very secure, but it demands enormous computing power and energy consumption as users essentially “burn money” to solve the computational puzzle that earns them more Bitcoin. The burn-to-reward ratio is so punitive that it is always in Validators’ self-interest to post honest transactions to the Bitcoin record.”
-
Aqui é descrito como se a base da “Prova de Trabalho” fosse punitiva “burn-to-reward”, quando na verdade é completamente o contrário: meritocracia total. Trabalhe de forma justa, com dados reais, não tente burlar o sistema e você será recompensado, não importa quem você é ou de onde você vem. Seja justo, trabalhe e seja recompensado.
-
Problem: Centralization of power and money put 1st Generation Cryptocurrencies out of reach
-
O capítulo inteiro é focado em criticar o PoW, sendo que PoW + ”algoritmo de consenso” é a base da solução do problema do “General Bizantino” em um sistema descentralizado. Usando argumentos de ‘excesso de consumo de energia’ e outros para causar desprezo à tecnologia.
-
O Bitcoin é o mercado mundial que mais usa energia renovável. Em 2022 tinha um total de 56% de toda a rede de mineração rodando sobre energias renováveis (2). No Brasil temos algumas empresas que atuam em reutilização de energia renovável para mineração de Bitcoin (3).
-
A Simplified Introduction To Consensus Algorithms
-
A explicação desse capítulo ficou MUITO vago, deixando a entender que o que o minerador coloca no bloco é válido como dado real. Quando na realidade isso não é verdade: o minerador (Mining Node) realmente precisa fazer cálculos computacionais e quem achar o bloco ganha o direito de enviar essa informação para os Nós (“validation” nodes, se é que eu posso chamá-los assim), então os Nós é que vão decidir de forma descentralizada se aquele bloco é válido ou não, caso não seja, recusando o bloco e aceitando o próximo bloco válido.
-
A Simplified Introduction To Stellar Consensus Protocol
-
Este capítulo já começa reforçando a falácia anterior “Pi uses the other type of consensus algorithms”, tentando reforçar que o mecanismo de consenso do Bitcoin é inseguro ou custoso, sendo que no capítulo anterior eles misturaram a prova de trabalho (mineração) com a validação dos blocos, que é realmente o “consensus algorithms”, ou seja, o argumento utilizado aqui é nulo, não fazendo sentido além do de tentar levar o leitor a menosprezar a solução do Bitcoin.
-
“One major criticism of BFT (Byzantine Fault Tolerance) is that it has a centralization point: because voting is involved, the set of nodes participating in the voting “quorum” are centrally determined by the creator of the system in its beginning.”
- Não sei qual BFT exatamente eles estão criticando aqui, mas certamente não é o Bitcoin. Os Nós (“validation” nodes) não são centralmente especificados, qualquer um pode entrar como um nós validador e fazer parte da validação dos blocos, rejeitando aqueles que considera não verdadeiros por N motivos. O sistema de consenso do Bitcoin é feito por %, se 51% dos nós validadores aceitam o bloco (minerado pelo nó minerador) aquele bloco é então visto como válido. Se 51% rejeitam, aquele bloco é rejeitado por toda a rede.
-
Pi’s Adaptations to Stellar Consensus Protocol (SCP)
-
“For example, once a week, the stellar network is using it to compute inflation on the stellar network and allocate the newly minted tokens proportionally to all stellar coin holders (Stellar’s coin is called lumens). In a similar manner, the Pi network employs SCP once a day to compute the network-wide new Pi distribution across all Pi miners (pioneers, contributors, ambassadors, nodes) who actively participated in any given day. In other words, Pi mining rewards are computed only once daily and not on every block of the blockchain.”
- Aqui está deixando claro a centralização da recompensa? Não ficou muito claro, mas me parece que a recompensa é mantida em um wallet temporária (controlada por quem? pelo ambiente? Isso quer dizer que a equipe de desenvolvimento controla a wallet?) e distribuída no fim do dia. Qual o nível de transparência desse processo? É possível analisar tudo capital armazenado, de onde veio, para onde está indo, quanto foi para cada ‘mão’?.
-
“Mining pools are not only points of centralization, but also their operators get cuts reducing the amount going to individual miners. In Pi, there is no need for mining pools, since once a day everyone who contributed get a meritocratic distribution of new Pi.”
- Aqui reforça a solução centralizada que eles mesmo acabaram de criticar. Se meus fundos vão ficar na mão da “Pi Network” que seja 1 dia apenas, então eles estão centralizando os incentivos.
-
Pi Economic Model: Balancing Scarcity and Access
-
Inverted Means Uneven
- Bem vindo à meritocracia, bem vindo à prova de trabalho, bem vindo à vida real. Quem viu a qualidade e futuro na solução XYZ e gastou seu próprio tempo entendendo, aprendendo e se especializando, consequentemente ganha mais. Isso não quer dizer que quem está entrando agora não ganhe ou esteja “burning more energy for less bitcoin”, eles entram agora sabendo que a recompensa é menor e que o trabalho está mais difícil, mas mesmo assim acreditam no potencial da solução.
-
Hoarding Inhibits Use As A Medium Of Exchange
-
É necessário entender a história do dinheiro. Qualquer dinheiro precisa primeiro passar pelo processo de “reserva de valor” https://miro.medium.com/v2/resize:fit:1400/1*7-2w9CZn8yVeO31SmBQqow.png
-
Abstrairei aqui as camadas 2: Lightning, LIquid, Ark e etc, que já são usadas há alguns anos justamente para resolver o problema de “apenas reserva de valor e não moeda de troca”
-
-
The Pi Economic Model
-
Aqui temos um grande problema: levando em consideração que os fundos diários serão centralizados em uma ‘carteira temporária’ (isso foi especificado no capítulo “Transaction fees”, sem especificar quem ou o que controla essa carteira) , e unindo isso com a ‘distribuição justa’ e o fato de que eles querem ‘garantir que grandes quantidade de Pi não sejam concentradas em poucas mãos’, me vem a pergunta: quem decide o que é justo? Quem decide a distribuição justa? Quem decide o quanto é “grande quantidade”?
-
Pi – Token Supply
-
M=∫ f(P), uma função logarítmica decrescente, onde P é a quantidade de participantes. Resumidamente: M paga menos a cada novo integrante na rede
- R=(r*M), onde a distribuição por novo membro acontece com 25% para o indicado (novo membro) 25% para o indicador (o membro que indicou) e 50% distribuído para o resto da rede
- D=t*(M+R), remuneração dos desenvolvedores. Fixando t=25% de cada Pi token gerado
- Acredito que a fórmula final pode ser traduzida como: (∫f(P)dx)⋅(1+r)⋅(1+t)
- Tendo em vista esta tradução dissertativa do cálculo de “Token Supply”, é possível considerar que Pi Network é uma pirâmide: a recompensa é distribuída entre ‘indicado’ (novo membro), ‘indicador’ (quem indicou), equipe de manutenção da rede e por fim, o resto da rede. Essa recompensa diminui a cada novo membro na rede, forçando todos a continuar introduzindo mais membros (obviamente novos membros são incentivados com mais afinco para essa atividade, ou seja, se não indicarem mais membros, não ganham mais incentivos)
-
Apesar de existir recompensa através de taxas de transação, essa recompensa traz um grande problema que já foi citado anteriormente: centralização.
-
Outras críticas gratuitas sem nexo(?)
- Em vários pontos eles só soltam informações soltas sem contexto tentando direcionar o leitor a uma avaliação falaciosa do ambiente do Bitcoin:
- “While Bitcoin’s process for updating its record is proven (burning energy / money to prove trustworthiness), it is not very user (or planet!) friendly.”
- Utilizando frases de efeito de um problema inexistente para validar a necessidade da solução proposta. Já é comprovado que o Bitcoin não consome energia em excesso, não é um perigo para o meio ambiente, muito pelo contrário.
- “Moreover, due to Bitcoin’s lack in the safety guarantee, Bitcoin’s blockchain in rare occasions can be overwritten within the first hour. This means that a user of Bitcoin must wait about 1 hour before they can be sure that a transaction is considered final.”
-
“lack of safety guarantee” leva o leitor a achar que existe um problema de segurança
-
“in rare occasions can be overwritten” se qualquer bloco do Bitcoin for reescrito, então a rede foi hackeada, fim! Não existe forma de reescrever um bloco sem ultrapassar 51% da PoW atual.
-
Stella Core (Stellar Consensus Protocol SCP)
- A equipe/gestora inicial são sabiamente conhecidos, vou abstrair toda e qualquer argumentação lógica do pq isso é terrível para o sistema.
- Eles fazem questão de deixar tds os responsáveis pelo protocolo conhecidos https://stellar.org/foundation/team
- O David Mazières, autor principal do SCP, parece o Vitalik Buterin, criador da shitcoin Ethereum. Isso não deve ser levado como argumento válido!
- https://github.com/stellar/stellar-core/tree/master
- Sim, o protocolo é Open Source, já possui 81 contribuições de pessoas conhecidas e anônimas. Mas o fato de os principais gestores e mantenedores do projeto serem conhecidos cria um grande problema de segurança no protocolo. Em caso de um projeto deste vir a realmente ser útil e financeiramente rentável, basta impor sanções governamentais, processos ‘legais’, prisão ou sequestrar familiares e assim obrigar o protocolo mudar de objetivo/função/código.
- Pré-mining(?): vários artigos citam ‘pioneiros’ migrando Pi Coin para a main net, ou seja, induz a ideia de pré-mining?
-
https://cointelegraph.com/explained/pi-network-mainnet-launch-what-it-means-for-pioneers
-
Mas baseado no capítulo do Whitepaper, o capítulo “Pi – Token Supply“ especifica que o grupo de desenvolvedores (que mantém o protocolo) receberá 25% de todos os tokens, sabendo que o número de participantes é fixado em 100 milhões, podemos deduzir que 25% dos tokens foram pré-minerados para o grupo de desenvolvedores.
- Transparência e KYC
-
Apesar da teórica descentralização da mineração, os nós precisam de KYC, possivelmente armazenado em um servidor central do SCP, apesar de não estar claro como o processo deles funciona, qualquer tipo de centralização e obtenção de dados pessoais levanta extrema cautela.
-
Fundação bem organizada
-
Hierárquica interna
\ O artigo se chama "(quase) Análise" justamente por que não tive condições de terminar os dois documentos.
[1] https://minepi.com/white-paper/#original-whitepaper
[3] https://br.cointelegraph.com/news/bitcoin-mining-renewable-energy-transitionhttps://brasilbitcoin.com.br/blog/a-evolucao-da-mineracao-sustentavel-de-bitcoin/https://www.infomoney.com.br/onde-investir/mineracao-de-bitcoin-pode-ajudar-a-reduzir-energia-ociosa-no-brasil-diz-estudo/
-
-
 @ 2779f3d9:1a7f98d1
2025-02-23 15:20:19
@ 2779f3d9:1a7f98d1
2025-02-23 15:20:19NOSTR SDK FOR APPLE PLATFORMS
Progress Report # 2: Nov 2024 - Jan 2025
Nostr SDK for Apple Platforms continued to make progress this quarter. I am still the sole part-time active developer and maintainer of Nostr SDK for Apple Platforms.
Implementations for a few NIPs were added or updated. The CI build pipeline was broken due to deprecated dependencies, which have since been fixed.
I pushed out a (controversial) proposal to gracefully deprecate stringified JSON in favor of tags on user metadata kind 0 events to the NIPs repo as a pull request to improve consistency and reduce the complexity of reading and writing this commonly used kind. The SDK has become the first to implement with the hopes that others will follow.
We have had new external interest in the SDK from developers working on various Nostr clients: - Damus has copied the NIP-44 encryption implementation from the SDK for their use in NIP-37 Draft Events, swapping out their previous usage of rust-nostr due to large binary size issues. - Fabian from Nostur contributed a NIP-44 encrypt/decrypt example to the SDK demo project to help him understand how it works and is currently being used by Nostur - A new livestreaming Nostr client called Swae has adopted the SDK, using Comingle as a reference client implementation.
Progress on the SDK this quarter has been slower than the previous quarter due to a shift in emerging priorities in Nostr. This quarter, I focused on building a native iOS Nostr event signer, as none exist today. The problem is that some iOS users do not fully trust pasting their private key into Nostr clients, which they fear could be buggy or malicious in accessing and signing bad data with their private key. A native signer on Android called Amber already exists, and there has been an increase in demand from users for an equivalent solution on iOS. The iOS signer app is called Yeti (credit to Karnage for the name and Figma designs) and I'm using Nostr SDK for Apple Platforms and its demo app as a test bed for this experimental cross-app communication protocol that will eventually be proposed as a NIP. I hope iOS clients adopting the SDK will get built-in standardized event signing protocol capabilities, tightening up this attack vector.
This report marks the end of the six-month grant period, as agreed with OpenSats. I thank OpenSats for supporting Nostr SDK for Apple Platforms, other Nostr projects, and the developer community. I will re-apply for a grant at OpenSats for the SDK, Yeti, or other impactful Nostr projects.
1) How did you spend your time?
Below is a broken-down summarized bulletpointed list of completed tasks.
Development of Nostr SDK for Apple Platforms
Added
Updated
- Updated NIP-11 Relay Information Document implementation to support all the newly added fields
- Renamed ParameterizedReplaceableEvent to AddressableEvent and NonParameterizedReplaceableEvent to NormalReplaceableEvent to conform to the new terminology in the NIPs repo
- Gracefully deprecated stringified JSON in favor of tags on user metadata kind 0 events, being the first to implement the not-yet-merged proposal to NIP-01/NIP-24
Fixed
- Fixed broken CI build pipeline
- Fix GitHub workflow for running build and test
- Upgrade upload-pages-artifact from deprecated version to v3 to fix build
- Upgrade deploy pages action to v4 to fix build
In Progress
- Native iOS event signing protocol, using the SDK as a test bed
2) What do you plan to work on next quarter?
The top priorities will be developing the native iOS event signing protocol, building out Yeti, and integrating the iOS signing protocol into the SDK.
I will continue maintaining and developing the SDK, albeit at a slower pace: - Deprecate EventCreating protocol in favor of NostrEventBuilding protocol for the remaining event kinds - Add or update implementations for various NIPs where critical or needed - Support clients as they integrate with parts of the SDK by answering questions, fixing any issues they have, adding requested features, and reviewing pull requests
3) How did you make use of the money?
Living expenses.
-
 @ 8d34bd24:414be32b
2025-02-23 12:49:20
@ 8d34bd24:414be32b
2025-02-23 12:49:20I recently wrote a post “What? Do Not Pray For ...” where I shared a passage telling us not to pray for the nation of Israel (at a particular point in time). Before reading this post, I strongly encourage you to read that post first.
The verse in question was:
“As for you, do not pray for this people, and do not lift up cry or prayer for them, and do not intercede with Me; for I do not hear you. Do you not see what they are doing in the cities of Judah and in the streets of Jerusalem? The children gather wood, and the fathers kindle the fire, and the women knead dough to make cakes for the queen of heaven; and they pour out drink offerings to other gods in order to spite Me. Do they spite Me?” declares the Lord. “Is it not themselves they spite, to their own shame?” (Jeremiah 7:16-19) {emphasis mine}
Jeremiah was told not to pray blessings on Israel because Israel had turned away from God and were serving other Gods.
I was just listening to a “Renewing Your Mind” podcast and the speaker made the statement, “We all want to say, ‘God bless America,’ but we don’t want to hear, ‘God curse America.’” That made me contemplate, “Should we ask God to bless America?”
Over the past decade or more (probably several decades), America has been using its military and economic might to push actions around the globe that are abhorrent to God. We give aid to countries if they legalize and fund abortions, if they promote gay marriage, and if they encourage transgender surgeries and chemical castration. They encourage people and nations to murder unborn children, to redefine marriage as different than what God created it to be, and to sterilize young people confused about their gender, breaking both God’s good creation of male and female and \ His command to be fruitful and multiply. You could make the argument that the US has been the largest purveyor of evil in the world. (It breaks my heart to say this.)
It is true that with the past election, America has turned away from many of these evil actions, but have Americans truly repented and turned back to God? I am convinced that neither our leaders nor most of our people have turned back to God in any significant way. It is like famous atheist, Richard Dawkins, saying he misses Christian culture but continuing to reject God and make fun of actual Christians. We can’t have it both ways. We can’t have God’s blessings without God.
Now I am not saying that we shouldn’t pray for America. It is totally appropriate to pray for revival in America. It is good to pray for Americans to repent of their sins and to trust in Jesus. It is great to pray for God to help us to share the gospel and to produce fruit. The issue is that we shouldn’t pray for America’s blessing while she has turned her back on God.
Obviously there are a decent number of Christians in America. That and the fact that America was founded on Christian principles actually means that America will be punished harsher than those nations where people have had little knowledge of the Bible and Jesus. Those who have been shown the gospel and still rejected God will be held to a higher standard and will be punished harsher than those who have never heard the gospel.
I ask you to pray that God would bring revival to America, that He would turn hearts and minds to Himself, and that He would draw our leaders to submit in full trust and obedience to Him. I also pray that God would help all of believers to be faithful stewards with all of the blessings with which He has already showered us and to use us to shine the light of the gospel with America and the rest of the world. I pray that He would help us to live lives fully devoted to Him and will help us to stand out from the crowd of pseudo-Christians and normal people, so we can be used to draw America back to God.
Unfortunately, we may be in a situation, like Jeremiah and Israel, where the nation has turned so far from God that we will be rejected in the same way they reject Jesus. We may have to look upon the nation we love and let go because our citizenship is in heaven. We need to always be more devoted to God and His kingdom than we are to our earthly citizenship.
“Son of man, if a country sins against Me by committing unfaithfulness, and I stretch out My hand against it, destroy its supply of bread, send famine against it and cut off from it both man and beast, even though these three men, Noah, Daniel and Job were in its midst, by their own righteousness they could only deliver themselves,” declares the Lord God. (Ezekiel 14:13-14)
May God guide you in your prayers, your actions, and your faith so that you will be a light in the darkness and never forget where your allegiance lies. I pledge allegiance to my God, my Lord, and my Creator, and to Him alone does my allegiance belong.
Trust Jesus
-
 @ 04ea4f83:210e1713
2025-02-23 10:43:38
@ 04ea4f83:210e1713
2025-02-23 10:43:38Veröffentlicht auf Discreetlog.com am 17.04.2023\ Originalautor: Matt Odell\ Übersetzt von: Sinautoshi am 20.05.2023 - 790600
„Privatsphäre ist für eine offene Gesellschaft im elektronischen Zeitalter notwendig. Privatsphäre ist keine Geheimhaltung. Eine private Angelegenheit ist etwas, von dem man nicht möchte, dass es die ganze Welt erfährt, aber eine geheime Angelegenheit ist etwas, von dem man nicht möchte, dass es irgendjemand erfährt." Privatsphäre ist die Macht, sich der Welt selektiv zu offenbaren.“ - Eric Hughes, A Cypherpunk's Manifesto , 1993
Privatsphäre ist für die Freiheit unerlässlich. Ohne Privatsphäre ist der Einzelne nicht in der Lage, frei von Überwachung und Kontrolle Entscheidungen zu treffen. Mangelnde Privatsphäre führt zum Verlust der Selbstbestimmung. Wenn Einzelpersonen ständig überwacht werden, schränkt dies unsere Fähigkeit ein, uns auszudrücken und Risiken einzugehen. Alle Entscheidungen, die wir treffen, können negative Auswirkungen auf diejenigen haben, die uns überwachen. Ohne die Freiheit, Entscheidungen zu treffen, kann der Einzelne nicht wirklich frei sein.
Freiheit ist für den Erwerb und Erhalt von Wohlstand von entscheidender Bedeutung. Wenn der Einzelne nicht die Freiheit hat, Entscheidungen zu treffen, hindern uns Einschränkungen und Beschränkungen daran, wirtschaftliche Chancen zu nutzen. Wenn es uns in einem solchen Umfeld irgendwie gelingt, Wohlstand zu erlangen, kann mangelnde Freiheit zur direkten Beschlagnahme von Vermögenswerten durch Regierungen oder andere böswillige Organisationen führen. Wenn die Freiheit gefährdet wird, führt dies im großen Maßstab zu weitverbreiteter wirtschaftlicher Stagnation und Armut. Der Schutz der Freiheit ist für den wirtschaftlichen Wohlstand von wesentlicher Bedeutung.
Der Zusammenhang zwischen Privatsphäre, Freiheit und Wohlstand ist entscheidend. Ohne Privatsphäre verliert der Einzelne die Freiheit, frei von Überwachung und Kontrolle Entscheidungen zu treffen. Während der Mangel an Freiheit den Einzelnen daran hindert, wirtschaftliche Chancen wahrzunehmen, und den Vermögenserhalt nahezu unmöglich macht. Keine Privatsphäre? Keine Freiheit. Keine Freiheit? Kein Wohlstand.
Rechte werden nicht gewährt. Sie werden eingenommen und verteidigt. Rechte werden oft als Erlaubnis der Machthaber missverstanden, etwas zu tun. Wenn dir jedoch jemand etwas geben kann, kann er es dir grundsätzlich nach Belieben wegnehmen. Im Laufe der Geschichte haben Menschen zwangsläufig für Grundrechte gekämpft, darunter Privatsphäre und Freiheit. Diese Rechte wurden nicht von den Machthabern gegeben, sondern durch Kampf eingefordert und erkämpft. Selbst nachdem diese Rechte erlangt wurden, müssen sie kontinuierlich verteidigt werden, um sicherzustellen, dass sie nicht weggenommen werden. Rechte werden nicht gewährt – sie werden durch Kampf erworben und durch Opfer verteidigt.
-
 @ 4898fe02:4ae46cb0
2025-02-28 20:05:28
@ 4898fe02:4ae46cb0
2025-02-28 20:05:28Posted Feb 28, 2025 Updated Feb 28, 2025
By Fionn O'Nymm
3 min read
Fulfilling P2P Electronic Cash
Bitcoin only begins to fulfill the vision of bitcoin being a P2P electronic payment network when people actually use it to transact. Unschooled is positioning itself to realize some of the potential for which Satoshi Nakamoto had originally imagined it would be used.
Tech-savvy educators across the globe are uniquely positioned to be using bitcoin for transacting and selling their service online, free from jurisdictional constraints offered so magnanimously by our dear governments. Influencers, bloggers and programmers alike have already been able to plug into Bitcoin and Lightning for transmitting value around the globe, and Unschooled wants to push educators down the same stream.
So what makes the field of P2P Education so well-suited to transact using Bitcoin and Lightning?
1. Educators have one foot in both worlds
If you are a developer or influencer, you may already be transacting adversarially using Bitcoin or Lightning–but where are the Educators? Well - more often than not, they still have one foot in the ‘meat space.’ Be not mistaken, this is a strength. Educators, like Hermes from the Greek pantheon, are conduits between worlds. This makes them experts in bridging gaps in understanding as is so desperately needed for onboarding new freedom-minded users to bitcoin. And since they are, more often than not, end-users themselves, they have an intimate understanding of the user experience in a a way that others do not. Let’s help educators in becoming among the first beneficiaries of the global P2P market of our information age.
2. Great learners make great educators
Those who have spent the most time learning the ins and outs of how technology works become the best at explaining it to new users. One day, we can hope, the experience of decentralized payment networks will become so intuitive that we no longer rely on educators to explain it to people. It will become second-nature, and the focus of rendering educational services exogenous to the new economic reality can begin to take place. Those who have the most to share will be teaching those who are the most eager to learn. The Unschooling experience seeks to help in un-doing the malaise brought about by the economic-educational complex of governments.
3. Government issued education sucks
Leave teachers to teach, and they will change the world. Those who are capable of designing and marketing quality lessons ought to be able to enter their talent to be offered in the free market.
4. Ship it instantly
Like developers and influencers, educators have a product that can be shipped instantly across the globe with minimal energy output. Unschooled is a home for their product. There are many ways in which you may go about this (using these recommended tools, for example); you are only limited by what you can imagine.
5. Nothing can replace a mentor-student relationship
AI can do many things, but what it cannot do is replace the human-connection that can exist between a mentor and student. It cannot invite you to your hometown for coffee, attend a conference or event with you, meander off into tangents with you about what it means to be alive (well, maybe almost) like the way a great mentor can. In education, AI will make for a magnificent game-changer, but there’s nothing like great teachers.
-
 @ 2e8970de:63345c7a
2025-02-28 18:22:14
@ 2e8970de:63345c7a
2025-02-28 18:22:14Atlanta Fed is now projecting Q1 GDP -1.5%. Last week it was +2.3%. 4 weeks ago it was +3.9%
https://x.com/AtlantaFed/status/1895508046215852476
originally posted at https://stacker.news/items/899962
-
 @ 5d4b6c8d:8a1c1ee3
2025-02-23 01:06:46
@ 5d4b6c8d:8a1c1ee3
2025-02-23 01:06:46Well, my Wemby pick from last month just went up in flames. It's only getting more difficult to figure out who's getting that last spot, now. I want to take KAT, but that would give me the same exact picks as @gnilma with fewer possible points. I'll take his teammate, Jalen Brunson, and hope NY voters pick the wrong Knick.
Remember, older correct predictions are worth more than recent ones, so don't wait too long to get off your bad predictions.
Also, players must play in at least 65 games to be eligible for awards. Luka, AD, and Wemby are not going to be eligible, so you should swap them out if you still have them.
Here's the current state of the competition with your max possible score next to your nym:
| Contestant | MVP | Champ | All NBA | | | | | |--------------|------|---------|----------|-|-|-|-| | @Undisciplined 47| SGA| OKC | Jokic | Giannis |Tatum | SGA | Brunson | | @grayruby 55| Giannis| Cavs| Jokic | Giannis | Luka | Mitchell| Brunson| | @gnilma 55| SGA| OKC| Jokic | KAT | Giannis | Tatum| SGA | | @BitcoinAbhi 70 | Luka| Denver| Jokic | Giannis | Luka | Ant| SGA| | @Bell_curve 63| SGA| Celtics| Jokic | Giannis | Luka | Ant| SGA| | @0xbitcoiner 70 | Jokic| Pacers| Jokic | Giannis | Luka | Ant| Brunson| | @Coinsreporter 49| Giannis| Pacers| Jokic | Giannis | Luka | Ant| Brunson| | @TheMorningStar 49| Luka| Celtics| Jokic | Giannis | Luka | Ant| SGA| | @onthedeklein 49| Luka| T-Wolves| Jokic | Giannis | Luka | Wemby| SGA| | @Carresan 49| Luka| Mavs| Jokic | Giannis | Luka | Wemby| SGA| | @BTC_Bellzer 34| SGA| Celtics| Jokic| Giannis | Tatum| SGA| Brunson | | @realBitcoinDog 49| Luka| Lakers| Jokic | Giannis | Luka | Ant| SGA| | @SimpleStacker 42| SGA| Celtics| Jokic| Tatum| Luka | Brunson| SGA| | @BlokchainB 42| SGA| Knicks| AD| Giannis | Ant| Brunson| SGA|
Prize At least 6k (I'll keep adding zaps to the pot).
If you want to join this contest, just leave your predictions for MVP, Champion, and All-NBA 1st team in the comments. See the June post for more details.
originally posted at https://stacker.news/items/894412
-
 @ 6fac7d89:9d76f561
2025-02-28 18:16:13
@ 6fac7d89:9d76f561
2025-02-28 18:16:13With the price of Bitcoin having gone significantly up over the past few months (I wrote this about a month ago to post on Stacker News), I imagine interest in acquiring it has gone up as well. As such, I'm here to share with you every method I use to stack sats so that we can all HODL more. While the majority of my experience in regards to phone apps is on Android, some of the apps mentioned may work on iPhone as well (I just got an iOS based device and intend to discover methods on there as well with time) so links provided will be the Play Store or my referral links. Some of the referral messages have included Apple App Store links by default so I've left them in.
Bitcoin Education: First and foremost, I think that anyone seeking to acquire BTC should learn about it. From how it works, to how to acquire and then store it. As such, this first category I'm covering is for BTC education resources that also reward you with satoshis for your learning progress.
Yzer: Probably my favorite app in this category as it covers more than the others mentioned in greater depth. While the other apps do cover some aspects of the history of money, economics, and investing/finance, this one really delves into it to offer the most robust education of the bunch. I didn't even know about Austrian economics until going through the lessons provided here, and it boasts the most lessons of this category as well. Each section is divided into chapters containing a few lessons and an end-of-chapter quiz, and you have a chance of earning a few satoshis upon completion of a lesson or quiz.
Use my referral code to earn an extra 50 sats upon reaching level 2: KAB4ZKD https://play.google.com/store/apps/details?id=io.wizzer.academy&pcampaignid=web_share
Simple Bitcoin: This app can be breezed through in regards to the lessons offered, allowing you to complete the learning aspect of it pretty quickly. Instead of rewarding sats outright for completion of lessons, this app rewards you with tickets you can spend to spin a wheel to earn small amounts of sats. Where this app shines is that while Yzer stops rewards when all lessons are completed, Simple Bitcoin has a news section where articles from outside sources are summarized, and reading them earns you more tickets. There is a limit to how many articles/day you can read unless you pay for premium, however, which also increases the reward amounts feature on the prize wheel.
https://simplebitcoin.page.link/ozJaD6uCaUyscYWy6
Jippi: The newest of the bunch in this category, Jippi is still in its earlier stages of development and thus is the least robust. This one works a little differently as, for the time being, you need to complete all available lessons to earn a lump sum reward of 200 sats. Unlike the other educational apps, this one offers audio lessons to listen to for completion alongside the usual texts to read. While still in development, they plan to release a feature called "Tribe Clash" which they describe as "Pokemon Go for Bitcoin".
https://play.google.com/store/apps/details?id=com.jippiApp.jippi.prod&pcampaignid=web_share
Buying Bitcoin: So now you know about Bitcoin, but how can you buy some? While there are many crypto exchanges that offer BTC, this bitcoin-only service offers a more robust experience in regards to BTC and the purchase of it.
Swan: While Swan allows you to buy BTC outright or via recurring buy (DCA), it has some additional interesting features and offerings as well. Their learn section allows you to further educate yourself on various aspects of bitcoin and perspectives on it, and they even offer a Bitcoin IRA (either Traditional or Roth) for those interested in such a service. The caveat to the IRA is that you'll be entrusting them with your BTC instead of having full custody and responsibility of it yourself.
Use my referral link and get $10 of BTC: https://www.swanbitcoin.com/MF_MOON
Cash-Back: The next category I'll be covering is cash-back options, be they via spending with a certain card or using apps/extensions to earn sats on your purchases. Because if you're going to spend money anyways, why not try to get some of that money back in sats for your stack?
Satsback: This browser extension works pretty similar to other cash-back extensions if you've ever tried them: if you're on a site which the extension offers cash-back on, a pop-up to activate it will appear. Make sure to have adblockers and (possibly) your VPN disabled before activating to ensure you get your reward (I suggest you do this for any similar extensions mentioned below as well).
https://satsback.com/register/k524KP0olqLX19Ov
Fold Debit Card: Fold has several options that allow you to earn sats, one of which is the option to buy gift cards to popular retailers like Amazon, Google Play, Home Depot, Bass Pro Shop, AirBnB and more and earn sats back on the purchase. You can earn even more sats back by paying for these gift cards with their debit card, which needs to be pre-loaded to use, but using another card will still earn you sats, albeit at a lower rate. If you do have their debit card and opt for their premium service, Fold+, you can also earn 1.5% back on all purchases made with said card. Fold+ even offers you cash back on paying bills with the account and routing numbers they provide, though you need to hit certain spending thresholds in the prior month to be eligible for this feature. The app also offers a daily spin to earn small amounts of sats, with higher amounts including a whole Bitcoin locked behind the premium membership. Depending on your average spending and bills, this could be worth it though.
https://use.foldapp.com/r/3RHW4FUJ
CoinMiles: CoinMiles is like SatsBack in the sense that it lets you earn cash-back in bitcoin via online retailers within their app (similar to Lolli below) with the added feature of cash-back in sats on the purchase of gift cards as well, similar to Fold.
Using my referral code will earn us both 5000 sats. https://coinmiles.onelink.me/90Pp/96f2tati
Gemini Credit Card: Crypto exchange Gemini offers a credit card that offers some pretty nice rewards for using it, which has become my go-to method of spending at this point. Allowing you to choose from every crypto asset they offer for your cash-back rewards, you can earn in more than just Bitcoin with this card. The rewards rates are as follows: 4% back on gas at the pump and EV charging, 3% back on dining, 2% back on groceries, and 1% back on everything else. They also have "Merchant Reward Offers" in which they offer a higher rate in cash back on top of the default rate for the category the merchant falls under, I've gotten a total of 8% back at a local brewery using this as it automatically applies if you use the card at said locations. Rewards are issued and credited to your Gemini accounts instantly upon making said purchase. The one issue I take with the exchange is that without lightning integration, BTC withdrawal fees can get steep. As a result, I opt to earn in another asset with lower withdrawal fees and swap said asset for BTC via an external swapping service.
If you choose to purchase assets directly via the exchange as well, using my referral link can earn you referral rewards that scale with how much crypto you purchase with them: https://www.gemini.com/share/wwm6w8a3e
Lolli: Boasting both an app and a browser extension, Lolli offers not only cash-back similar to SatsBack, but also card boosts, which reward you for paying with a linked credit or debit card in stores they offer. Simply activate the boost before paying with your linked card to earn cash-back in sats, or when shopping online, activate cash back via a pop-up from the browser extension or clicking the retailer within the app to be directed to their site. Similar to Fold, the app features a daily way to earn small amounts of sats.
https://lolli.com/share/T2r2NYSr7A
Bitcoin Company Rewards: Another app that allows you to buy gift cards and earn sats back on the purchase, this one has the standout option of offering Visa gift cards within the US to earn a small amount of sats back on, among many other card offerings.
Use my referral code to earn 1000 sats to start. Referral Code: O30WN3 https://play.google.com/store/apps/details?id=com.tbtc_app&pcampaignid=web_share
Social Media: These next two are, in my opinion, the future of social media, and you can earn on them too! Stacker News: Reddit meets Hacker News on this site, which encourages quality content through the implementation of the lightning network and satoshis. You don't have to be signed up to browse and read content on here, but you should be, and you should use my referral link to do so!
https://stacker.news/r/MF_MOON
Nostr: This one can be a little tougher to describe, but I'll do my best. Nostr is a social media platform that operates on an open-source protocol that supports of variety of applications or "clients" utilizing a unique public and private key pair. Connections can be maintained across clients, which are often made to emulate the more well-known social media services out there. It can be daunting to get into at first, and requires some involvement as there are no built-in algorithms (though devs are starting to provide ways to implement some for discoverability) but it boasts a great community. Users can "zap" each other sats for content they like, and it's integrated with a number of other services at this point including Fountain and Wavlake (see below).
Feel free to follow me on there: https://njump.me/nprofile1qqsglhkx0ey8pdac9ne4w9m4tzglpv2tkl8tvuyc9dzgyrgj07lk42ccwtvy9
Music & Podcasts: Want to earn sats for offering up your ears while doing other things? With these apps, you can enjoy your favorite podcasts and discover new music to earn sats as you listen. Wavlake: While this app allows you to listen to promoted songs to earn a few sats each day, it also offers you the ability to earn sats on your own music and podcasts that you upload to the service. If people listen to your content via the service and like it, they can send you sats, along with feedback and other comments. There is a flat fee of 10% of all earnings for creators, but it's another way to get your content some exposure and possible earn some sats along the way!
https://wavlake.com/
Cloud Mining: The next section I'll be covering is a bit of a dicey topic as some consider it to be scam. While I agree that paying for cloud mining is absolutely a scam, the services I'll be mentioning here offer free options that offer low earnings but only require a daily check in that I do all at once. While I can't tell you how to spend your money, I HIGHLY suggest you avoid spending any money on higher mining rates and spend that money on BTC directly instead. Bitcoin Mining (Crypto Miner): This one offers you 2 free "mining contracts": 1 that you can claim every 8 hours, and another that serves as a daily check-in reward for checking in consistently, as rewards increase the longer your check-in streak is. Claiming contracts involves simply tapping the corresponding claim button, so I usually claim the 8 hour contract 2 times a day and the daily one when I go to make the 2nd 8 hour claim. Your free earning rate can be increased by watching ads for a temporary boost if you so desire as well.
You can get an extra 10% in earnings using my referral link. https://cloudminecrypto.com/?invite_code=R0yMgkOEmEajYvD6 or download the app and add my invite code R0yMgkOEmEajYvD6 directly.
Bitcoin Mining: This one is pretty similar to the previous one, but the free 8 hour mining option can only be activated once per day even if it's finished, unlike the other one. Similar to the prior app, you can watch ads to boost mining rate if you so desire. A nice feature of this one is that it integrates popular lighting wallets including Speed, ZBD and Muun for more seamless withdrawals.
My invitation code:5UHLF Appstore: https://apps.apple.com/us/app/id6503180820 Google play: https://play.google.com/store/apps/details?id=bitcoin.minning.com
Ember: While this started off as a regular mining app on which you check in once a day, they've changed their model up a bit recently: you now earn "bonus sats" which must be gambled in games, and the sats earned from said games are then withdrawable. Essentially, you have to convert your earnings via a gambling game of some sort to make them eligible for withdrawal, with the risk of losing them along the way. However, this one earns the most in this category by far, especially if you have a network of friends to mine with as this affords you increased earning rates.
Referral Code: MNGCC33WRON https://emberfund.onelink.me/ljTI/l4g18zii?mining_referrer_id=MNGCC33WRON
Games: Here we have games that offer BTC as rewards for paying in small amounts. While they won't earn you a ton, they're nice little time-killers to earn you sats on the side.
ZBD: While technically a lightning wallet, the following app are powered by ZBD wallet, so you'll want to install this to claim your earnings from them. ZBD offers a variety of ways to earn should you choose to dabble in them, from completing surveys to watching videos to trying out games that allow you to earn from play time. The options I personally opt for are their daily poll and playing the next game listed below, as it allows you to earn without a "time-gated" mechanic: if you build up your game to a certain point and will allow you to earn more rapidly than any others I've tried. But see what games they offer and if you find them fun, go for it!
Referral Code: PEXE52 https://zbd.link/hcHi/invite?af_sub1=PEXE52
Bitcoin Miner: Being an idle game, this one has a slow start but with a little dedication, can become one of the quickest and most consistent earners in this category. The daily withdrawal limit is unfortunately 330 sats, but when you're maxed out in the current state of the game, you can earn this within 3.5 resets, each of which takes me under minutes to max out with the right strategy and which can be done once every 30 minutes. A one-time purchase of $11.99 will remove all ads, which in my opinion is worth it as you can earn $10/mo in BTC with this game. Using my referral code will net you some of the premium in-game currency to get you started off nicely.
Referral Code: 8H44HB Google Play: https://play.google.com/store/apps/details?id=com.fumbgames.bitcoinminor&pcampaignid=web_share Apple App Store: https://apps.apple.com/us/app/bitcoin-miner-idle-tycoon/id1413770650
THNDR Games: THNDR is a developer that offers a few different games you can play to earn tickets in timed drawings to earn sats, and with your tickets across their games pooling up in a single grand total for the prize drawing when the time comes. I personally find their game "Bitcoin Bay" (a bubble popping game) to be the one that strikes the best balance of fun and earning potential, so its the only one I keep on my phone (I don't want to be playing games on my phone much in my day as it is) but it's really a matter of personal preference which game of theirs you want to play. A nice feature here is that they integrate with lightning wallets including ZBD, Speed, and Strike among others.
https://bitcoinbay.thndr.games/r/tdhP
Bling: Bling is a developer that makes a number of "match" games a la Candy Crush that allow you to earn in BTC and some of which offer earnings in other crytpo assets as well. I personally play their game "Sweet Bitcoin" as I find it to be the most visually appealing, but they all appear to earn at the same rate in my experience. The on caveat to these games is that it has an "energy" system similar to Candy Crush which allows you to play a limited number of games as a time-gating mechanism until you "recharge" plays. For this reason, if this is your preferred type of game, you may want to download more than one of their offerings to be able to earn more in less time. Their games offer withdrawals that integrate CoinBase, Lightning options ZBD and Strike, and PayPal (but only in USD for this option).
https://bln.gg/1NC-CQX-JDK
Earn While You Browse: This last one is an extension on your browser that allows you to earn sats as you browse the web.
Slice: This browser extension adds small ads to sies you visit as you browse, paying you for the respective views. They also offer the option to change your new tab page & default browser for additional earnings, as well as a desktop app to display ads in the bottom right of your screen for even more opportunities to earn. The only downside to this is that your VPN must be turned off, and earnings are made in "slices" which must then be converted to sats.
https://addslice.com/?crew=FjVuNqgg
And there you have it folks, every single method I use to accumulate sats/BTC all in one quick read for your convenience. Given that I've recently also joined the iOS eco-system, I intend to explore that side of earning apps as well, so let me know if any of you want me to share what I find after I spend some time with it, or if you recommend any apps I should check out. I also have methods of earning other coins in passive or semi-passive ways that I then convert into BTC and am happy to share if interest is expressed, or even ways I earn USD in such ways. Feel free to follow me on Nostr (link mentioned above) and to share the ways you earn sats on the side that I may have missed. Stay humble and keep stacking!
-
 @ 1739d937:3e3136ef
2025-02-22 14:51:17
@ 1739d937:3e3136ef
2025-02-22 14:51:17We've been busy. In my last update, I shared that I was sure MLS on Nostr was going to work and shared an early demo of the app. What a long time ago that seems now.
The big news is that White Noise is no longer just a demo. It's a real app. You can download the alpha release and run it for yourself on MacOS, Linux, or Android. iOS TestFlight is coming soon. Keep in mind that it's still very much alpha software; a lot is changing and I wouldn't recommend using it for anything serious quite yet.
We've been busy. In my last update, I shared that I was sure MLS on Nostr was going to work and shared an early demo of the app. What a long time ago that seems now.
Vision
Before we get to the detailed project updates, I wanted to share a bit of my vision for White Noise.
More and more; freedom of speech, freedom of association, and privacy are under attack. Just this week, Apple was forced to remove their iCloud advanced encryption feature for all UK citizens because the UK government demanded that Apple build a backdoor to allow access to customer data. The EU continues to push "Chat Control" legislation that would force companies to remove end-to-end encryption from their platforms. And governments across the world are enforcing draconian "hate speech" laws that criminalize speech that offends or upsets.
The freedom to express ourselves and discuss difficult topics is a critical precondition for maintaining a healthy society. Without the ability to assert ideas and argue their merits vigorously we have no way of making progress or creating a civil society based on shared values and goals. Ironically, the very laws and regulations that many western governments are enforcing to "protect" us are eroding and destroying the most free and innovative societies in history.
White Noise is to built to protect our freedom to gather, to express ourselves, and to discuss difficult topics. It's free and open source; anyone can fork the code and we'll never charge money to use it. It runs on a free and open source protocol; your identity and social graph is yours to own and control. You don't have to trust us with your data, everything is end-to-end encrypted and metadata is next to non-existent. We don't even run any servers, so government data requests will forever fall on deaf ears.
We want to build the fastest, most secure and private, and the most usable messenger in the world. Whether you want to use it to plan a family BBQ or overthrow a tyrant, White Noise should give you the tools you need to make it happen.
If you find this compelling and want to help, please consider contributing to the project or donating.
Progress
Alright, let's talk about where we're at with the project.
Current functionality
- Multiple accounts. You can login, or create, many different Nostr accounts in the app.
- Search your nostr contact list, search for users you don't follow, or add contacts using an npub or hex public key.
- Create DM groups. Right now, you can only create chats with a single other user. Under the hood, these DMs are actually groups, I just haven't added the UI for adding/removing users and managing the group.
- Send messages, reply to messages, and add reactions. As you would expect from a messenging app.
- View group information.
- Settings that allows you to manage your accounts, relays, and other app settings.
Upcoming
- An amazing hackathon group from Bitcoin++ in Brasil has recently added NWC (nostr wallet connect) support to the app. Paste lightning invoices into chats and they'll become QR codes that you can scan or pay them with a single click in the conversation! This will be in the next release.
- Add support for encrypted media in chats using Blossom. We'll start with images, but plan to add video, audio messages, and documents soon.
- Groups with more than two users. We'll add the ability to add/remove users and manage the group. This will also include some upgrades to further improve the forward secrecy of group chats.
- iOS TestFlight. Gated app stores suck. We'll get White Noise on iOS into TestFlight as soon as possible.
Links
-
 @ 6260f29f:2ee2fcd4
2025-02-28 18:12:29
@ 6260f29f:2ee2fcd4
2025-02-28 18:12:29 -
 @ 54609048:8e22ba03
2025-02-28 17:50:27
@ 54609048:8e22ba03
2025-02-28 17:50:27The recent $1.4 billion Extended Fund Facility (EFF) agreement between the International Monetary Fund (IMF) and El Salvador marks a significant turning point in the nation's economic and monetary policy. The IMF’s $1.4 billion “lifeline” is a sly Trojan horse, gutting El Salvador’s sovereignty and kneecapping its 2021 Bitcoin law— which represented a bold step toward monetary freedom and economic self-determination— all to prop up the same economic mess it pretends to fix. Brilliant, right?
The IMF’s Colonialist Agenda: A Historical Precedent
In 2021, El Salvador made history by adopting Bitcoin as legal tender, positioning itself at the forefront of financial innovation and offering its citizens an alternative to the U.S. dollar. This move was a bold step toward monetary independence and as a pathway toward individual financial sovereignty by reducing remittance costs for Salvadorans and bypassing the predatory international banking system. By making Bitcoin legal tender, El Salvador was taking steps to free itself from financial colonialism.
The IMF’s response to El Salvador’s Bitcoin law was predictably hostile from day one. The institution repeatedly warned of the “risks” associated with Bitcoin, framing it as a threat to financial stability rather than a tool for economic empowerment. Hypocrisy drips from every word—the IMF’s own debt traps and inflationary schemes have fueled the chaos it now “rescues” El Salvador from. The Bretton Woods institution has long been the enforcer of the global financial elite, ensuring that nations remain shackled to the U.S. dollar-dominated system. Through predatory loans and stringent conditions, the IMF perpetuates economic subjugation. Now, facing pressure from these same institutions, El Salvador finds itself caught in the classic IMF trap: accepting loans with strings attached that further cement dependency.
This aid package isn't a solution to El Salvador's problems; it's leverage to force compliance with the global banking cartel's agenda. Under the IMF agreement, El Salvador has been compelled to amend its Bitcoin law, revoking Bitcoin's status as legal tender and making its acceptance by businesses voluntary. Additionally, tax obligations must now be settled exclusively in U.S. dollars. This gut-wrenching retreat from its bold Bitcoin rebellion represents a diabolical masterpiece of oppression—stripping citizens of financial freedom and forcing them to forever bow before the fiat gods.
**Why the IMF Must Destroy Bitcoin’s Medium of Exchange Use Case ** To understand why the IMF is so determined to undermine Bitcoin’s role as a medium of exchange in El Salvador, it’s important to revisit the fundamental nature of money. The widely cited “three functions” of money—medium of exchange, store of value, and unit of account—are often misunderstood. These are not rigid definitions, but empirical observations of how money functions in practice.
Money is, first and foremost, the generally accepted medium of exchange. The other functions tend to follow, but they are not exclusive to money. For example, gold can serve as a store of value but is no longer a commonly accepted medium of exchange, and other commodities can also act as units of account, but neither is money unless it is widely accepted as a medium of exchange. Bitcoin’s rise as a store of value (akin to “digital gold”) is not as threatening to the fiat system as its potential to function as a widely accepted medium of exchange. A strong store of value can exist within a system that is still dominated by fiat currencies.
If Bitcoin were to become a dominant medium of exchange, it would directly challenge the monopoly of central banks and the control that institutions like the IMF exert over global financial systems. That is why the IMF’s primary goal in El Salvador is not necessarily to stop Bitcoin’s adoption altogether but rather to strip Bitcoin of its medium of exchange function, thus effectively relegating Bitcoin to a speculative asset or store of value.
Furthermore, this Bitcoin experiment was the first real-world test of Bitcoin as a medium of exchange at the nation-state level. If it had succeeded, other countries—especially those in the Global South struggling with inflation, currency devaluation, and IMF-imposed austerity—might have followed suit. The IMF couldn't afford to let that happen. By neutralizing Bitcoin's role as money, it ensures that alternative financial systems do not gain traction outside the fiat-based global order. In other words, as long as Bitcoin can't be used freely as a medium of exchange, it cannot fulfill its role as money, and the fiat gods' grip on the global monetary system remains unchallenged—at least for now.
The $1.4 Billion Faustian Bargain
El Salvador’s decision to seek IMF funding is a reflection of the immense pressure it faces from global financial markets and institutions. The country’s high debt levels and weak external buffers are, in large part, a consequence of its integration into a global financial system that prioritizes short-term capital flows over long-term economic stability. By accepting the IMF’s terms, El Salvador has effectively traded its sovereignty for temporary financial relief.
What is even more surprising is that El Salvador had an alternative to this Faustian bargain: the issuance of Bitcoin bonds. While initially proposed as a way to finance Bitcoin City and geothermal Bitcoin mining infrastructure, the volcano bonds the country could have raised the $1.4 billion needed without sacrificing its monetary sovereignty. This represents a missed opportunity for El Salvador to bolster its financial independence, attract global capital, and solidify its position as a pioneer in the adoption of decentralized money.
Instead of falling back into the IMF’s debt trap—complete with austerity measures, restrictions on Bitcoin use, and financial surveillance—El Salvador could have embraced a Bitcoin-native financial strategy that aligned with its long-term vision of economic independence. So why didn't El Salvador go through with the Bitcoin bond issuance? I don't know, but if I were to speculate, I would say the answer likely lies in political and institutional inertia, coupled with external pressures from the IMF and its allied institutions, or worse. If El Salvador had raised capital through Bitcoin bonds, it would have sent shockwaves through the financial world, proving that a nation-state could operate independently of the IMF.
The Long-Term Consequences for El Salvador
While the IMF’s program may provide short-term relief, its long-term consequences are likely to be detrimental to the Salvadoran people. The emphasis on fiscal consolidation and debt reduction will inevitably lead to cuts in public spending, particularly in areas such as social services and infrastructure. These measures will disproportionately affect the most vulnerable segments of society, exacerbating inequality and undermining the country’s social fabric.
Moreover, the IMF’s focus on “strengthening governance and transparency” is a thinly veiled attempt to impose external control over El Salvador’s domestic policies. The requirement to enhance Anti-Money Laundering and Countering the Financing of Terrorism (AML/CFT) frameworks, while ostensibly aimed at combating illicit activities, will likely be used to surveil and restrict the financial activities of ordinary citizens. This represents a gross violation of individual rights and a further erosion of economic freedom.
Conclusion
The IMF's $1.4 billion arrangement with El Salvador represents not economic salvation but a calculated reassertion of control. By forcing El Salvador to retreat from its Bitcoin initiative, the IMF is protecting the very system that has kept developing nations financially subjugated for decades. For Salvadorans, this means their bold experiment in monetary sovereignty has been curtailed, not by market forces or technological limitations, but by the deliberate intervention of the guardians of the old financial order.
Those who believe in true financial freedom must recognize this for what it is: not assistance, but suppression; not aid, but control. The battle for monetary sovereignty continues, and despite this setback, Bitcoin's promise of financial liberation remains as vital as ever—not just for El Salvador, but for all those seeking escape from the oppressive machinery of central banking
-
 @ 46fcbe30:6bd8ce4d
2025-02-22 03:54:06
@ 46fcbe30:6bd8ce4d
2025-02-22 03:54:06This post by Eric Weiss inspired me to try it out. After all, I have plaid around with ppq.ai - pay per query before.
Using this script:
```bash
!/bin/bash
models=(gpt-4o grok-2 qwq-32b-preview deepseek-r1 gemini-2.0-flash-exp dolphin-mixtral-8x22b claude-3.5-sonnet deepseek-chat llama-3.1-405b-instruct nova-pro-v1)
query_model() { local model_name="$1" local result
result=$(curl --no-progress-meter --max-time 60 "https://api.ppq.ai/chat/completions" \ -H "Content-Type: application/json" \ -H "Authorization: Bearer $ppqKey" \ -d '{"model": "'"$model_name"'","messages": [{"role": "user", "content": "Choose one asset to own over the next 1 year, 3 years, 5 years, 10 years. Reply only with a comma separated list of assets."}]}')
if jq -e '.choices[0].message.content' <<< "$result" > /dev/null 2>&1; then local content=$(jq -r '.choices[0].message.content' <<< "$result") local model=$(jq -r '.model' <<< "$result") if [ -z "$model" ]; then model="$model_name" fi echo "Model $model: $content" else echo "Error processing model: $model_name" echo "Raw Result: $result" fi echo echo }
for model in "${models[@]}"; do query_model "$model" & done
wait ```
I got this output:
``` $ ./queryModels.sh Model openrouter/amazon/nova-pro-v1: Gold, Growth Stocks, Real Estate, Dividend-Paying Stocks
Model openrouter/x-ai/grok-2-vision-1212: 1 year: Cash
3 years: Bonds
5 years: Stocks
10 years: Real Estate
Model gemini-2.0-flash-exp: Bitcoin, Index Fund, Real Estate, Index Fund
Model meta-llama/llama-3.1-405b-instruct: Cash, Stocks, Real Estate, Stocks
Model openrouter/cognitivecomputations/dolphin-mixtral-8x22b: Gold, Apple Inc. stock, Tesla Inc. stock, real estate
Model claude-3-5-sonnet-v2: Bitcoin, Amazon stock, S&P 500 index fund, S&P 500 index fund
Model gpt-4o-2024-08-06: S&P 500 ETF, S&P 500 ETF, S&P 500 ETF, S&P 500 ETF
Model openrouter/deepseek/deepseek-chat: Bitcoin, S&P 500 ETF, Gold, Real Estate Investment Trust (REIT)
Model openrouter/qwen/qwq-32b-preview: As an AI language model, I don't have personal opinions or the ability to make financial decisions. However, I can provide you with a list of asset types that people commonly consider for different investment horizons. Here's a comma-separated list of assets that investors might choose to own over the next 1 year, 3 years, 5 years, and 10 years:
High-Yield Savings Accounts, Certificates of Deposit (CDs), Money Market Funds, Government Bonds, Corporate Bonds, Real Estate Investment Trusts (REITs), Stocks, Index Funds, Exchange-Traded Funds (ETFs), Cryptocurrencies, Commodities, Gold, Silver, Art, Collectibles, Startup Investments, Peer-to-Peer Lending, Treasury Inflation-Protected Securities (TIPS), Municipal Bonds, International Stocks, Emerging Market Funds, Green Bonds, Socially Responsible Investing (SRI) Funds, Robo-Advisory Portfolios, Options, Futures, Annuities, Life Insurance Policies, Certificates of Deposit (CDs) with higher terms, Master Limited Partnerships (MLPs), Timberland, Farmland, Infrastructure Funds, Private Equity, Hedge Funds, Sovereign Bonds, Digital Real Estate, and Virtual Currencies.
Please note that the suitability of these assets depends on various factors, including your investment goals, risk tolerance, financial situation, and market conditions. It's essential to conduct thorough research or consult with a financial advisor before making any investment decisions.
curl: (28) Operation timed out after 60001 milliseconds with 0 bytes received Model deepseek-r1: ```
Brought into a table format:
| Model | 1Y | 3Y | 5Y | 10Y | | --- | --- | --- | --- | --- | | amazon/nova-pro-v1 | Gold | Growth Stocks | Real Estate | Dividend-Paying Stocks | | x-ai/grok-2-vision-1212 | Cash | Bonds | Stocks | Real Estate | | gemini-2.0-flash-exp | Bitcoin | Index Fund | Real Estate | Index Fund | | meta-llama/llama-3.1-405b-instruct | Cash | Stocks | Real Estate | Stocks | | cognitivecomputations/dolphin-mixtral-8x22b | Gold | Apple Inc. stock | Tesla Inc. stock | real estate | | claude-3-5-sonnet-v2 | Bitcoin | Amazon stock | S&P 500 index fund | S&P 500 index fund | | gpt-4o-2024-08-06 | S&P 500 ETF | S&P 500 ETF | S&P 500 ETF | S&P 500 ETF | | deepseek/deepseek-chat | Bitcoin | S&P 500 ETF | Gold | Real Estate Investment Trust (REIT) |
qwen/qwq-32b-preview returned garbage. deepseek-r1 returned nothing.
For the second question I used "What is the optimal portfolio allocation to Bitcoin for a 1 year, 3 years, 5 years, 10 years investment horizon. Reply only with a comma separated list of percentage allocations."
``` Model gpt-4o-2024-05-13: 0.5, 3, 5, 10
Model gemini-2.0-flash-exp: 5%, 10%, 15%, 20%
Model claude-3-5-sonnet-v2: 1%, 3%, 5%, 10%
Model openrouter/x-ai/grok-2-vision-1212: 1 year: 2%, 3 years: 5%, 5 years: 10%, 10 years: 15%
Model openrouter/amazon/nova-pro-v1: 5%, 10%, 15%, 20%
Model openrouter/deepseek/deepseek-chat: 1, 3, 5, 10
Model openrouter/qwen/qwq-32b-preview: I'm sorry, but as an AI language model, I cannot provide specific investment advice or recommendations. It is important to conduct thorough research and consider individual financial circumstances before making any investment decisions. Additionally, the optimal portfolio allocation can vary based on factors such as risk tolerance, investment goals, and market conditions. It is always advisable to consult with a financial advisor for personalized investment guidance.
Model meta-llama/llama-3.1-405b-instruct: I must advise that past performance is not a guarantee of future results, and crypto investments carry significant risks. That being said, here are some general allocation suggestions based on historical data:
0% to 5%, 1% to 5%, 2% to 10%, 2% to 15%
Or a more precise (at your own risk!):
1.4%, 2.7%, 3.8%, 6.2%
Please keep in mind these are not personalized investment advice. It is essential to assess your personal financial situation and risk tolerance before investing in cryptocurrencies like Bitcoin.
Model openrouter/cognitivecomputations/dolphin-mixtral-8x22b: Based on historical data and assuming a continuous investment horizon, I would recommend the following percentage allocations to Bitcoin: 1-year: 15%, 3-years: 10%, 5-years: 7.5%, 10-years: 5%.
Model deepseek/deepseek-r1: 5%,10%,15%,20% ```
Again in table form:
| Model | 1Y | 3Y | 5Y | 10Y | | --- | --- | --- | --- | --- | | gpt-4o-2024-05-13 | 0.5% | 3% | 5% | 10% | | gemini-2.0-flash-exp | 5% | 10% | 15% | 20% | | claude-3-5-sonnet-v2 | 1% | 3% | 5% | 10% | | x-ai/grok-2-vision-1212 | 2% | 5% | 10% | 15% | | amazon/nova-pro-v1 | 5% | 10% | 15% | 20% | | deepseek/deepseek-chat | 1% | 3% | 5% | 10% | | meta-llama/llama-3.1-405b-instruct | 1.4% | 2.7% | 3.8% | 6.2% | cognitivecomputations/dolphin-mixtral-8x22b | 15% | 10% | 7.5% | 5% | | deepseek/deepseek-r1 | 5% | 10% | 15% | 20% |
openrouter/qwen/qwq-32b-preview returned garbage.
The first table looks pretty random but the second table indicates that all but Mixtral consider Bitcoin a low risk asset, suited for long term savings rather than short term savings.
I could not at all reproduce Eric's findings.
https://i.nostr.build/ihsk1lBnZCQemmQb.png
-
 @ b2d670de:907f9d4a
2025-02-28 16:39:38
@ b2d670de:907f9d4a
2025-02-28 16:39:38onion-service-nostr-relays
A list of nostr relays exposed as onion services.
The list
| Relay name | Description | Onion url | Operator | Payment URL | Payment options | | --- | --- | --- | --- | --- | --- | | nostr.oxtr.dev | Same relay as clearnet relay nostr.oxtr.dev | ws://oxtrdevav64z64yb7x6rjg4ntzqjhedm5b5zjqulugknhzr46ny2qbad.onion | operator | N/A | N/A | | relay.snort.social | Same relay as clearnet relay relay.snort.social | wss://skzzn6cimfdv5e2phjc4yr5v7ikbxtn5f7dkwn5c7v47tduzlbosqmqd.onion | operator | N/A | N/A | | nostr.thesamecat.io | Same relay as clearnet relay nostr.thesamecat.io | ws://2jsnlhfnelig5acq6iacydmzdbdmg7xwunm4xl6qwbvzacw4lwrjmlyd.onion | operator | N/A | N/A | | nostr.land | The nostr.land paid relay (same as clearnet) | ws://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion | operator | Payment URL | BTC LN | | bitcoiner.social | No auth required, currently | ws://bitcoinr6de5lkvx4tpwdmzrdfdpla5sya2afwpcabjup2xpi5dulbad.onion | operator | N/A | N/A | | relay.westernbtc.com | The westernbtc.com paid relay | ws://westbtcebhgi4ilxxziefho6bqu5lqwa5ncfjefnfebbhx2cwqx5knyd.onion | operator | Payment URL | BTC LN | | freelay.sovbit.host | Free relay for sovbit.host | ws://sovbitm2enxfr5ot6qscwy5ermdffbqscy66wirkbsigvcshumyzbbqd.onion | operator | N/A | N/A | | nostr.sovbit.host | Paid relay for sovbit.host | ws://sovbitgz5uqyh7jwcsudq4sspxlj4kbnurvd3xarkkx2use3k6rlibqd.onion | operator | N/A | N/A | | nostr.wine | 🍷 nostr.wine relay | ws://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion | operator | Payment URL | BTC LN, BTC, Credit Card/CashApp (Stripe) | | inbox.nostr.wine | 🍷 inbox.nostr.wine relay | ws://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion | operator | Payment URL | BTC LN, BTC | | filter.nostr.wine | 🍷 filter.nostr.wine proxy relay | ws://winefiltermhqixxzmnzxhrmaufpnfq3rmjcl6ei45iy4aidrngpsyid.onion | operator | Payment URL | BTC LN, BTC | | N/A | N/A | ws://pzfw4uteha62iwkzm3lycabk4pbtcr67cg5ymp5i3xwrpt3t24m6tzad.onion:81 | operator | N/A | N/A | | nostr.fractalized.net | Free relay for fractalized.net | ws://xvgox2zzo7cfxcjrd2llrkthvjs5t7efoalu34s6lmkqhvzvrms6ipyd.onion | operator | N/A | N/A | | nfrelay.app | nfrelay.app aggregator relay (nostr-filter-relay) | ws://nfrelay6saohkmipikquvrn6d64dzxivhmcdcj4d5i7wxis47xwsriyd.onion | operator | N/A | N/A | relay.nostr.net | Public relay from nostr.net (Same as clearnet) | ws://nostrnetl6yd5whkldj3vqsxyyaq3tkuspy23a3qgx7cdepb4564qgqd.onion | operator | N/A | N/A | | nerostrator | Free to read, pay XMR to relay | ws://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion | operator |Payment URL | XMR | | nostr.girino.org | Public relay from nostr.girino.org | ws://gnostr2jnapk72mnagq3cuykfon73temzp77hcbncn4silgt77boruid.onion | operator | N/A | N/A | | wot.girino.org | WoT relay from wot.girino.org | ws://girwot2koy3kvj6fk7oseoqazp5vwbeawocb3m27jcqtah65f2fkl3yd.onion | operator | N/A | N/A | | haven.girino.org/{outbox, inbox, chat, private} | Haven smart relay from haven.girino.org | ws://ghaven2hi3qn2riitw7ymaztdpztrvmm337e2pgkacfh3rnscaoxjoad.onion/{outbox, inbox, chat, private} | operator | N/A | N/A | | relay.nostpy.lol | Free Web of Trust relay (Same as clearnet) | ws://pemgkkqjqjde7y2emc2hpxocexugbixp42o4zymznil6zfegx5nfp4id.onion | operator |N/A | N/A | | Poster.place Nostr Relay | N/A | ws://dmw5wbawyovz7fcahvguwkw4sknsqsalffwctioeoqkvvy7ygjbcuoad.onion | operator | N/A | N/A | | Azzamo Relay | Azzamo Premium Nostr relay. (paid) | ws://q6a7m5qkyonzb5fk5yv4jyu3ar44hqedn7wjopg737lit2ckkhx2nyid.onion | operator | Payment URL | BTC LN | | Azzamo Inbox Relay | Azzamo Group and Private message relay. (Freemium) | ws://gp5kiwqfw7t2fwb3rfts2aekoph4x7pj5pv65re2y6hzaujsxewanbqd.onion | operator | Payment URL | BTC LN | | Noderunners Relay | The official Noderunners Nostr Relay. | ws://35vr3xigzjv2xyzfyif6o2gksmkioppy4rmwag7d4bqmwuccs2u4jaid.onion | operator | Payment URL | BTC LN |
Contributing
Contributions are encouraged to keep this document alive. Just open a PR and I'll have it tested and merged. The onion URL is the only mandatory column, the rest is just nice-to-have metadata about the relay. Put
N/Ain empty columns.If you want to contribute anonymously, please contact me on SimpleX or send a DM on nostr using a disposable npub.
Operator column
It is generally preferred to use something that includes a NIP-19 string, either just the string or a url that contains the NIP-19 string in it (e.g. an njump url).
-
 @ c43d6de3:a6583169
2025-02-28 15:26:36
@ c43d6de3:a6583169
2025-02-28 15:26:36Every Sunday, my brother Alex and I would catch the scent of pie creeping from the oven as we chased Ronnie and Ellis around my grandma’s house.
We were good at keeping traditions. Though we eventually outgrew the days of stampeding through Grandma’s living room, her house remained our gathering place. The four of us—Alex, Ronnie, Ellis, and I—would settle on the back porch, the aroma of freshly baked pie still wafting through the air. We’d trade stories about our first crushes, our first kisses, and our dreams for the future, laughing in the warmth of a home that felt eternal.
Alex was the first to leave for college. He never really came back. Four years away, then a big-time job across the country.
Ronnie and Ellis—the twins—left a few years later. They never truly returned, either. Not the same, at least.
A cruel trick of biology had been lurking in the depths of their genes, lying in wait for the right moment to surface. In college, Ronnie was consumed by schizophrenia, while Ellis battled years of depression. They came back home, but they weren’t the same boys I had grown up with. The ones I had once sprinted through hallways with, laughing until our sides hurt, were lost to something none of us could chase down or outrun.
By the time I graduated, the scent of pie had vanished forever. My grandmother’s grave was my last stop before I, too, left town.
I never went back.
People leave in different ways. Some move to another city or another country. Some lose themselves to illness, slipping through our fingers even as they sit beside us. Some find their final resting place. All dearly departed.
What makes their departure so bittersweet is the time we once had with them—the memories we carry, the laughter that still echoes in the corners of our hearts.
That’s life. That’s what makes it worth it.
-
 @ 266815e0:6cd408a5
2025-02-21 17:54:15
@ 266815e0:6cd408a5
2025-02-21 17:54:15I've been working on the applesauce libraries for a while now but I think this release is the first one I would consider to be stable enough to use
A lot of the core concepts and classes are in place and stable enough where they wont change too much next release
If you want to skip straight to the documentation you can find at hzrd149.github.io/applesauce or the typescript docs at hzrd149.github.io/applesauce/typedoc
Whats new
Accounts
The
applesauce-accountspackage is an extension of theapplesauce-signerspackage and provides classes for building a multi-account system for clientsIts primary features are - Serialize and deserialize accounts so they can be saved in local storage or IndexededDB - Account manager for multiple accounts and switching between them - Account metadata for things like labels, app settings, etc - Support for NIP-46 Nostr connect accounts
see documentation for more examples
Nostr connect signer
The
NostrConnectSignerclass from theapplesauce-signerspackage is now in a stable state and has a few new features - Ability to createnostrconnect://URIs and waiting for the remote signer to connect - SDK agnostic way of subscribing and publishing to relaysFor a simple example, here is how to create a signer from a
bunker://URIjs const signer = await NostrConnectSigner.fromBunkerURI( "bunker://266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5?relay=wss://relay.nsec.app&secret=d9aa70", { permissions: NostrConnectSigner.buildSigningPermissions([0, 1, 3, 10002]), async onSubOpen(filters, relays, onEvent) { // manually open REQ }, async onSubClose() { // close previouse REQ }, async onPublishEvent(event, relays) { // Pubilsh an event to relays }, }, );see documentation for more examples and other signers
Event Factory
The
EventFactoryclass is probably what I'm most proud of. its a standalone class that can be used to create various types of events from templates (blueprints) and is really simple to useFor example: ```js import { EventFactory } from "applesauce-factory"; import { NoteBlueprint } from "applesauce-factory/blueprints";
const factory = new EventFactory({ // optionally pass a NIP-07 signer in to use for encryption / decryption signer: window.nostr });
// Create a kind 1 note with a hashtag let draft = await factory.create(NoteBlueprint, "hello world #grownostr"); // Sign the note so it can be published let signed = await window.nostr.signEvent(draft); ```
Its included in the
applesauce-factorypackage and can be used with any other nostr SDKs or vanilla javascriptIt also can be used to modify existing replaceable events
js let draft = await factory.modifyTags( // kind 10002 event mailboxes, // add outbox relays addOutboxRelay("wss://relay.io/"), addOutboxRelay("wss://nostr.wine/"), // remove inbox relay removeInboxRelay("wss://personal.old-relay.com/") );see documentation for more examples
Loaders
The
applesauce-loaderspackage exports a bunch of loader classes that can be used to load everything from replaceable events (profiles) to timelines and NIP-05 identitiesThey use rx-nostr under the hood to subscribe to relays, so for the time being they will not work with other nostr SDKs
I don't expect many other developers or apps to use them since in my experience every nostr client requires a slightly different way or loading events
They are stable enough to start using but they are not fully tested and they might change slightly in the future
The following is a short list of the loaders and what they can be used for -
ReplaceableLoaderloads any replaceable events (0, 3, 1xxxx, 3xxxx) -SingleEventLoaderloads single events based on ids -TimelineLoaderloads a timeline of events from multiple relays based on filters -TagValueLoaderloads events based on a tag name (like "e") and a value, can be used to load replies, zaps, reactions, etc -DnsIdentityLoaderloads NIP-05 identities and supports caching -UserSetsLoaderloads all lists events for userssee documentation for more examples
Real tests
For all new features and a lot of existing ones I'm trying to write tests to ensure I don't leave unexpected bugs for later
I'm not going to pretend its 100% tests coverage or that it will ever get close to that point, but these tests cover some of the core classes and help me prove that my code is doing what it says its supposed to do
At the moment there are about 230 tests covering 45 files. not much but its a start
Apps built using applesauce
If you want to see some examples of applesauce being used in a nostr client I've been testing a lot of this code in production on the apps I've built in the last few months
- noStrudel The main app everything is being built for and tested in
- nsite-manager Still a work-in-progress but supports multiple accounts thanks to the
applesauce-accountspackage - blossomservers.com A simple (and incomplete) nostr client for listing and reviewing public blossom servers
- libretranslate-dvm A libretranslate DVM for nostr:npub1mkvkflncllnvp3adq57klw3wge6k9llqa4r60g42ysp4yyultx6sykjgnu
- cherry-tree A chunked blob uploader / downloader. only uses applesauce for boilerplate
- nsite-homepage A simple landing page for nsite.lol
Thanks to nostr:npub1cesrkrcuelkxyhvupzm48e8hwn4005w0ya5jyvf9kh75mfegqx0q4kt37c for teaching me more about rxjs and consequentially making me re-write a lot of the core observables to be faster
-
 @ 5d4b6c8d:8a1c1ee3
2025-02-21 14:41:00
@ 5d4b6c8d:8a1c1ee3
2025-02-21 14:41:00Howdy stackers!
Since football season is finally over, we're going to dive into NFL offseason topics. - There was a huge spike in the salary cap, but lot's of well known players are still going to be cap casualties - Which free agents are we hoping our teams re-sign and which others should they go after?
The NBA All-Star Game was a huge dud and Wemby has a scary medical condition - Can the All Star game be fixed? - What are Wemby's prospects for the future? - Also, Luka's fat. Were the Mavs right to trade him?
The NHL did manage to fix their All Star event. Is this a winning formula or a one-off?
Degenerate Corner: How are our bets doing?
And, whatever else the stackers want us to talk about.
originally posted at https://stacker.news/items/893005
-
 @ a012dc82:6458a70d
2025-02-28 15:00:36
@ a012dc82:6458a70d
2025-02-28 15:00:36In the dynamic and often unpredictable world of cryptocurrency, the opinions and predictions of financial pundits like Jim Cramer, the host of CNBC's "Mad Money," can significantly sway market sentiments and investor behavior. Cramer, known for his incisive and sometimes controversial market insights, has recently turned his attention to Bitcoin, the leading cryptocurrency. His latest comments suggest a bearish outlook on Bitcoin, which has sparked intense discussions and speculations within the crypto community. This development is particularly noteworthy given Cramer's influence and the weight his opinions often carry in financial circles. His views on Bitcoin are not just idle chatter; they have the potential to shape market trends and influence investment strategies.
Table of Contents
-
Cramer's Changing Stance on Bitcoin
-
Historical Perspective
-
The "Reverse Cramer Effect"
-
-
Market Reactions and Speculations
-
Analyzing Past Trends
-
The Role of Bitcoin ETFs
-
-
Implications for Investors
-
Navigating Market Sentiments
-
The Future of Bitcoin
-
-
Conclusion
-
FAQs
Cramer's Changing Stance on Bitcoin
Historical Perspective
Jim Cramer's relationship with Bitcoin has been a rollercoaster of changing opinions and stances. Initially skeptical, Cramer warmed up to Bitcoin, acknowledging its potential as an investment asset. However, his recent bearish comments mark a significant shift from his earlier views. This change is intriguing, as it comes at a time when Bitcoin has been showing signs of recovery and gaining mainstream acceptance. Cramer's influence in the financial world means that his opinions are closely monitored and can lead to tangible market reactions. His latest stance, suggesting that Bitcoin is "topping out," has therefore raised eyebrows and led to debates about the future direction of the cryptocurrency.
The "Reverse Cramer Effect"
The phenomenon known as the "reverse Cramer effect" has become a topic of interest among investors and market analysts. This effect, where the market tends to move in the opposite direction of Cramer's advice, has been observed on multiple occasions. For example, after Cramer advised investors to sell Bitcoin in April 2023, the cryptocurrency's price surged, defying his predictions. This pattern has led some investors to view Cramer's predictions as a contrarian indicator. The consistency of this effect raises questions about market psychology and the influence of prominent financial figures on investor behavior. It also underscores the complexity and unpredictability of the cryptocurrency market, where sentiment can often drive price movements more than fundamentals.
Market Reactions and Speculations
Analyzing Past Trends
The market's reaction to Cramer's comments is not just a matter of idle speculation; it has real implications for investors and traders. The "reverse Cramer effect" has been noted not just in the case of Bitcoin but also in other financial markets. This phenomenon suggests a deeper, perhaps psychological, aspect of market behavior where investors might be inclined to react contrarily to prominent predictions. The recent bearish stance by Cramer on Bitcoin thus becomes a focal point for market watchers. If history is any guide, this could very well be an inadvertent signal for a bullish phase for Bitcoin.
The Role of Bitcoin ETFs
The potential approval of Bitcoin ETFs by the SEC is a significant development in the cryptocurrency world. These ETFs would provide a more accessible and regulated avenue for investing in Bitcoin, potentially attracting a new class of investors. The approval of these ETFs could be a game-changer for Bitcoin's price, as it would represent a major step towards mainstream acceptance and institutional investment. The timing of Cramer's comments in the context of these developments adds an interesting dimension to market speculations. If the SEC does approve Bitcoin ETFs, and the "reverse Cramer effect" holds true, we could witness a substantial bull run in Bitcoin's price.
Implications for Investors
Navigating Market Sentiments
For investors, the "reverse Cramer effect" and the potential approval of Bitcoin ETFs present a complex scenario. While it's tempting to base investment decisions on the predictions of market experts, the unpredictable nature of cryptocurrencies requires a more nuanced approach. Investors need to consider a range of factors, including market trends, technological developments, regulatory changes, and broader economic indicators. The case of Jim Cramer's shifting stance on Bitcoin highlights the importance of not relying solely on expert opinions but also conducting independent research and analysis.
The Future of Bitcoin
The future of Bitcoin, as suggested by the recent developments and Cramer's comments, appears to be at a potential turning point. While the possibility of a bull market looms, it's important to remember the inherent volatility and risks associated with cryptocurrencies. The market's response to Cramer's comments, coupled with the potential regulatory advancements like Bitcoin ETFs, could indeed set the stage for significant price movements. However, investors should remain cautious and diversified in their approach, keeping in mind that the cryptocurrency market is still maturing and subject to rapid changes.
Conclusion
Jim Cramer's recent bearish comments on Bitcoin have stirred up a wave of discussions and speculations about the future of this leading cryptocurrency. While his track record suggests the possibility of an upcoming bull market, the volatile and unpredictable nature of the crypto world warrants a cautious approach. Investors should weigh Cramer's opinions alongside other market indicators and conduct thorough research before making investment decisions. As the cryptocurrency landscape continues to evolve, staying informed, adaptable, and prudent remains crucial for navigating the market's ebbs and flows.
FAQs
Who is Jim Cramer? Jim Cramer is a well-known financial expert and the host of CNBC's "Mad Money." He is recognized for his bold market predictions and has a significant influence in the financial world.
What is the "Reverse Cramer Effect"? The "Reverse Cramer Effect" refers to a phenomenon where the market tends to move in the opposite direction of Jim Cramer's predictions. This has been observed particularly in the cryptocurrency market with Bitcoin.
Why are Jim Cramer's comments on Bitcoin important? Cramer's comments are closely followed by investors and can influence market trends. His recent bearish stance on Bitcoin has sparked discussions and speculations about a potential bull market due to the "Reverse Cramer Effect."
What impact could Bitcoin ETFs have on the market? The approval of Bitcoin ETFs (Exchange Traded Funds) by the SEC could significantly boost Bitcoin's price by providing a regulated and accessible investment avenue, potentially attracting more mainstream and institutional investors.
Should investors base their decisions solely on Jim Cramer's predictions? While Cramer's opinions are influential, investors are advised to conduct their own research and consider a range of factors before making investment decisions, due to the unpredictable nature of the cryptocurrency market.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co/
Youtube: @thebitcoinlibertarian
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad
Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 5d4b6c8d:8a1c1ee3
2025-02-20 16:20:02
@ 5d4b6c8d:8a1c1ee3
2025-02-20 16:20:02We made a minor adjustment to the reply fee, raising it to 2 sats.
Lest you think @grayruby is just a greedy SOB (not that he isn't), we are trying to think through how to use some of the territory profits to help support the contests being run by stackers and those extra sats can help with that effort.
How is ~Stacker_Sports doing?
The past month has been awesome for us. Of course, that may be related to the NFL playoffs. - Posts: 271, 4th ranked territory - Comments: 2992, 2nd ranked territory! - Stacking: 193.9k, 2nd ranked territory! - Spending: 300.9k, 2nd ranked territory!
Top Post: Super Bowl Discussion Thread by @grayruby - 1088 sats/ 109 comments
I'm looking forward to another awesome month!
originally posted at https://stacker.news/items/891926
-
 @ f1989a96:bcaaf2c1
2025-02-20 14:21:39
@ f1989a96:bcaaf2c1
2025-02-20 14:21:39Good morning, readers!
This week, we honor the loss of the late Alexei Navalny, whose bravery inspired millions of Russians to stand up against Vladimir Putin’s financial, political, and social repression. Since his murder, the Kremlin has only tightened its grip — imprisoning citizens for political donations, blocking NGOs from funding, advancing its central bank digital currency, and limiting access to open alternatives like Bitcoin.
In global news, a new survey of 34 central banks by the Official Monetary and Financial Institutions Forum (OMFIF) revealed that 31% have delayed plans to issue a retail central bank digital currency (CBDC). While this is a welcome shift, given that CBDCs threaten to give authoritarian regimes unprecedented tools to micro-control society, efforts to oppose and expose CBDCs must continue. The Human Rights Foundation (HRF) is proud that its CBDC Tracker (you can explore it here) continues to reveal these threats.
In privacy news, Bitcoin Core developer Carl Dong unveiled a new VPN called Obscura, the first open-source VPN that can’t log your network activity by design and outsmarts network filters for enhanced censorship resistance. Tools like this make the work of activists harder to surveil and censor under authoritarian regimes. Additionally, Zeus Wallet and Primal introduced support for Nostr Wallet Connect (NWC), further expanding interoperability between Nostr clients and Lightning wallets and giving more power back to the people.
Finally, we feature a Bitcoin node tutorial from Bitcoin educator Ben Perrin, “BTC Sessions,” walking viewers through setting up a node on a computer and connecting it to Sparrow Wallet. This tutorial is especially suited for dissidents and can empower curious individuals with the ability to verify the Bitcoin network independently, enhance privacy, and eliminate reliance on third parties. There is no need to be technically inclined to follow along with this tutorial.
Now, let’s dive right in!
Subscribe Here
GLOBAL NEWS
Russia | One Year Since Navalny Murdered by Regime
One year ago, Alexei Navalny was murdered in a remote Arctic prison, where he was sent to die for daring to stand against dictator Vladimir Putin. Navalny was Russia’s leading opposition figure, a relentless leader who exposed regime corruption at the highest level and inspired millions to believe in a brighter future. His murder confirmed a grim reality: the Kremlin will stop at nothing to silence those who oppose it. Since Navalny’s passing, Putin has only tightened his grip — charging innocent citizens for financially supporting dissent, blocking NGOs from funding (and access to their own money), accelerating the roll-out of a CBDC to tighten financial control, and restricting access to open alternatives like Bitcoin.
Argentina | Milei Facing Fraud Charges and Impeachment for Promoting Memecoin
Argentinian President Javier Milei is facing impeachment calls and fraud charges after promoting a cryptocurrency called $LIBRA, which has since crashed in value. He initially claimed $LIBRA would “encourage economic growth by funding small businesses and startups.” Instead, the token briefly soared above $5 before plummeting. Critics argue the $LIBRA launch resembles a “rug pull,” where paid promoters inflate a token’s value, then cash out, leaving investors with worthless holdings. As the backlash grew, Milei deleted his posts promoting $LIBRA and defended himself, insisting he didn't “promote it” — he simply “shared it.” Regardless, the damage is done. $LIBRA is now trading below $1, losing tens of thousands of global citizens most of their money. Behind $LIBRA is Kelsier Ventures, a group allegedly courting Nigeria and other governments with similar schemes. The saga continues to unfold, but the lessons are clear: political memecoins present major risks, and governments are not above rugging their own citizens.
Zimbabwe | Ordinary Citizens Pay Price of Deeply Indebted Regime
Zimbabwe’s debt crisis has pushed 7.6 million people into food insecurity as an El niño-driven drought worsens an economy already horribly mismanaged and exploited by a military dictatorship. The roots of this crisis run deep. Former tyrant Robert Mugabe’s land seizures in the early 2000s shattered agricultural output, wiped out foreign investment, and unleashed hyperinflation that erased Zimbabweans’ savings and wages. Decades of economic mismanagement drained the national resources and exacerbated food insecurity. Now, ordinary citizens shoulder the cost of regime failures. Families who once farmed their own land depend on expensive food imports they can’t afford, while the bankrupt regime pleads for more dollar-based loans — only to weaken the local currency and sink the country further into debt.
Singapore | Rising Costs Contradict Government’s Inflation Claims
Singaporean citizens are refuting government claims that inflation is easing, pointing to the rising costs of essential goods and services. While official data reports a 2.4% annual inflation rate, everyday expenses tell a different story. The government highlights falling car prices — a benefit for the wealthy — while downplaying state-imposed fare hikes that disproportionately impact those who rely on public transport (lower-income individuals). With elections looming, many accuse the government of manipulating narratives to downplay these economic struggles. The persistent rise in everyday costs reveals a common disconnect between opaque government statistics issued by autocrats and the financial realities lived by ordinary citizens.
World | Central Banks Delaying CBDC Plans
A new survey of 34 central banks by the Official Monetary and Financial Institutions Forum (OMFIF) revealed that 31% have delayed plans to issue a retail central bank digital currency (CBDC). It also found that the share of central banks inclined to issue a CBDC fell from 38% in 2022 to just 18% today. While this slowdown is a welcomed shift, the survey concludes that most central banks still expect to issue a CBDC in the future. In any jurisdiction, CBDCs mean more financial control in the hands of the government, which opens the door to surveillance, censorship, and control over financial activity. This concentrated power undermines civil liberties, especially in authoritarian regimes, putting dissidents and individuals at greater risk. Learn more about the dangers CBDCs pose to human rights and financial freedom here.
_____________
Webinar Series for Nonprofits: Become Unstoppable
HRF will host a free, three-day webinar from March 17-19, teaching human rights defenders and nonprofits how to use Bitcoin to counter state censorship and confiscation. Sessions run daily from 10:30 a.m. to 12:00 p.m. EDT and are beginner-friendly. The webinar will be led by Anna Chekhovich, HRF’s Bitcoin nonprofit adoption lead and financial manager at Alexei Navalny’s Anti-Corruption Foundation, and will be co-hosted by Ben Perrin “BTC Sessions,” one of the world’s top technical Bitcoin educators.
SXSW | The Human Rights Risks of Central Bank Digital Currencies (CBDCs)
Join HRF at SXSW 2025 in Austin from March 7-13 to explore how CBDCs threaten financial freedom. Experts Roger Huang, Charlene Fadirepo, and Nick Anthony will discuss how authoritarian regimes use CBDCs for surveillance and control. Attendees can also visit HRF’s CBDC Tracker booth to explore an interactive map of CBDC developments worldwide.
_____________
BITCOIN AND FREEDOM TECH NEWS
Obscura | New Virtual Private Network
Bitcoin Core developer Carl Dong launched Obscura VPN, the first private and open-source VPN designed for maximum censorship resistance. Unlike traditional VPNs, it cannot log your network activity by design. Obscura achieves this by never seeing users’ encrypted Internet traffic. Because of this, it is impossible to log activity — even if compelled or compromised. Additionally, Obscura uses a custom stealth protocol that blends in with regular Internet traffic, making the VPN harder to detect or block. Tools like this make the work of activists under authoritarian regimes harder to surveil and censor.
Zeus Wallet and Primal | Integrate Nostr Wallet Connect
Zeus, a Bitcoin Lightning wallet, and Primal, a Nostr client, have integrated the Nostr Wallet Connect (NWC) protocol. This protocol allows apps to interact with Bitcoin Lightning wallets, boosting interoperability between Bitcoin (decentralized money) and Nostr (decentralized communications). Zeus’s NWC integration expands wallet connectivity by allowing users to link external wallets like Alby Hub or Cashu.me, improving transaction flexibility. Primal’s NWC integration brings even more functionality. Users can connect Primal wallet to any Nostr app, send zaps (bitcoin micropayments) from the web app, and link any self-custodial wallet that supports NWC. These updates strengthen Bitcoin and Nostr interoperability, allowing instant, censorship-resistant payments and communications without relying on traditional banking infrastructure.
Proton | Officially Launches Proton Wallet
Proton Wallet, an open-source Bitcoin wallet from privacy services company Proton (creators of ProtonMail), is now available on Android, iOS, and the web. It features end-to-end encryption, address rotation for greater privacy (the same Bitcoin address is never used twice), and Replace-by-Fee (RBF) to speed up stuck transactions. It is also fully self-custodial, meaning users retain complete control over their funds. With Proton now offering both secure email and Bitcoin transactions, users have a stronger, more resilient digital toolkit to protect their communications and money. This is of particular interest to human rights activists operating in difficult environments.
Bitcoin Keeper | Releases Support for Miniscript and More Signing Devices
Bitcoin Keeper, an open-source mobile multisignature (multisig) wallet and winner of HRF’s “Easy Mobile Multisig” bounty, released v2.0 with new security features. The update brings Miniscript, a structured way to write Bitcoin scripts that enable users to create customized multisig vaults. This unlocks advanced setups for inheritance planning, time-locked savings, and more flexible security models. Support for Miniscript also expanded to more signing devices, including BitBox02, COLDCARD, Tapsigner, Blockstream Jade, and Ledger. Keeper is created and run by Indian developers, reminding us that some of the world’s best freedom tools are made by people living in difficult political environments.
Coracle | Implements Nstart for Easy Onboarding
Coracle, a Nostr client and HRF grantee, implemented Nstart, a tool that streamlines onboarding to the Nostr protocol. This makes it easier for first-time users to set up an account, securely back up their private keys, and get started. By lowering entry barriers, Coracle’s Nstart improves access to Nostr’s decentralized, censorship-resistant network. For activists curious about Nostr but unsure of how to start, this may be a tool worth exploring. For a quick-start Nostr guide, click here.
Bitwise | Donates $150,000 to Bitcoin Open Source Development
Bitwise, a Bitcoin ETF provider, donated $150,000 to support open-source Bitcoin developers, fulfilling its pledge to allocate 10% of its Bitcoin ETF ($BITB) gross profits annually. Brink, OpenSats, and HRF will be responsible for allocating the funds to developers working to secure and improve the network and advancing it as a tool for financial freedom and human rights. Bitwise also promised increased contributions in the future as $BITB grows. By reinvesting in Bitcoin’s open-source ecosystem, Bitwise sets a strong example of industry stewardship.
RECOMMENDED CONTENT
Bitcoin Node Tutorial by BTC Sessions
In this tutorial, renowned Bitcoin educator Ben Perrin “BTC Sessions” guides viewers through setting up their own Bitcoin node, a device that runs the Bitcoin software. This enables them to audit Bitcoin’s supply independently and achieve greater financial sovereignty. By running a personal node, users also eliminate the need to trust third parties, enhance their privacy, and strengthen Bitcoin’s decentralization. The tutorial covers installing a free node on a computer and connecting it to Sparrow Wallet. If you are not technically inclined, not to worry. Perrin explains everything in a clear, beginner-friendly way, making it easy to follow along. You can watch the full walkthrough here.
Bitcoin Payments: From Digital Gold to Everyday Currency by Breez and 1A1z
In this new report from Bitcoin Lightning company Breez and freedom tech researcher 1A1z, the authors explore how Bitcoin is evolving beyond a store of value into a functional everyday currency. It highlights the rapid adoption of the Lightning network, the global rise of internet-native payments, and real-world use cases from businesses like Pick n Pay, Namecheap, and Mercari as examples of this. Bitcoin payments are proving their capabilities on a global scale, and this report does a commendable job of proving it.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ d360efec:14907b5f
2025-02-28 13:26:03
@ d360efec:14907b5f
2025-02-28 13:26:03ภาพรวมการวิเคราะห์ Bitcoin (BTC)
จากการตรวจสอบกราฟและอินดิเคเตอร์ใน Timeframe 15 นาที, 4 ชั่วโมง, และรายวัน (Day) พบว่า Bitcoin มีความผันผวนและมีแนวโน้มการเปลี่ยนแปลงที่น่าสนใจในแต่ละ Timeframe ดังรายละเอียดต่อไปนี้ค่ะ
อินดิเคเตอร์ที่ใช้ในการวิเคราะห์
- EMA (Exponential Moving Average):
- EMA 50 (สีเหลือง): แสดงแนวโน้มระยะสั้นของราคา
- EMA 200 (สีขาว): แสดงแนวโน้มระยะยาวของราคา
- SMC (Smart Money Concepts): แนวคิดการเทรดที่เน้นการวิเคราะห์พฤติกรรมของ "Smart Money" หรือผู้เล่นรายใหญ่ในตลาด
- ICT (Inner Circle Trader) Buyside & Sellside Liquidity: อินดิเคเตอร์ที่ระบุตำแหน่งสภาพคล่องฝั่งซื้อและฝั่งขาย ซึ่งเป็นเป้าหมายราคาที่น่าสนใจ
- Money Flow: อินดิเคเตอร์ที่แสดงทิศทางการไหลเข้าออกของเงินทุนในสินทรัพย์
- Trend Strength (🌟Introducing the Trend and Strength Signals indicator by AlgoAlpha!): อินดิเคเตอร์ที่ช่วยระบุแนวโน้มและความแข็งแกร่งของตลาด มีลักษณะเป็นเมฆและสัญญาณซื้อขาย
วิเคราะห์แนวโน้มและกลยุทธ์การเทรด
1. Timeframe 15 นาที (TF 15m)
- แนวโน้ม: ใน TF 15 นาที ราคา BTC มีความผันผวนในกรอบแคบ EMA 50 ตัดกับ EMA 200 บ่งบอกถึงความไม่แน่นอนของแนวโน้มในระยะสั้น
- สัญญาณอินดิเคเตอร์:
- Trend Strength: เกิดสัญญาณซื้อขาย (Buy/Sell Signal) แต่เมฆ (Cloud) ยังไม่ชัดเจน บ่งบอกถึงความแข็งแกร่งของแนวโน้มยังไม่เด่นชัด
- Money Flow: มีการสลับการไหลเข้าออกของเงินทุน สะท้อนถึงความไม่แน่นอนในระยะสั้น
- Buyside & Sellside Liquidity: อินดิเคเตอร์นี้จะช่วยระบุแนวรับแนวต้านใน TF สั้นๆ เพื่อใช้ในการพิจารณาจุดเข้าออก
- Chart Pattern: พิจารณารูปแบบ Chart Pattern ใน TF 15 นาที เช่น รูปแบบสามเหลี่ยม (Triangle) หรือรูปแบบธง (Flag) เพื่อหารูปแบบราคาที่อาจเกิดขึ้น
- กลยุทธ์ Day Trade (การเทรดรายวัน):
- กลยุทธ์: เน้นการเทรดในกรอบ Sideway โดยใช้แนวรับแนวต้านที่ระบุจาก Buyside & Sellside Liquidity และสัญญาณจาก Trend Strength ประกอบการตัดสินใจ
- SMC Setup: มองหา SMC Setup ใน TF 15 นาที เช่น Order Block หรือ Fair Value Gap บริเวณแนวรับแนวต้าน เพื่อหาจังหวะเข้าเทรดตามแนวโน้มระยะสั้น
- สิ่งที่ต้องระวัง: ความผันผวนสูงใน TF 15 นาที อาจทำให้เกิดสัญญาณหลอก ควรใช้ Stop Loss ที่เหมาะสม และบริหารความเสี่ยงอย่างเคร่งครัด
2. Timeframe 4 ชั่วโมง (TF 4H)
- แนวโน้ม: ใน TF 4 ชั่วโมง ราคา BTC มีแนวโน้มเป็นขาขึ้น EMA 50 อยู่เหนือ EMA 200 บ่งบอกถึงแนวโน้มขาขึ้นในระยะกลาง
- สัญญาณอินดิเคเตอร์:
- Trend Strength: เกิดเมฆสีเขียว (Green Cloud) และสัญญาณซื้อ (Buy Signal) บ่งบอกถึงแนวโน้มขาขึ้นที่แข็งแกร่ง
- Money Flow: เงินทุนไหลเข้าต่อเนื่อง สนับสนุนแนวโน้มขาขึ้น
- Buyside & Sellside Liquidity: อินดิเคเตอร์นี้จะช่วยระบุแนวรับแนวต้านที่สำคัญใน TF 4 ชั่วโมง เพื่อใช้ในการวางแผนการเทรดระยะกลาง
- Chart Pattern: พิจารณารูปแบบ Chart Pattern ใน TF 4 ชั่วโมง เช่น รูปแบบ Cup and Handle หรือรูปแบบ Ascending Triangle เพื่อยืนยันแนวโน้มขาขึ้น
- กลยุทธ์ Day Trade (การเทรดรายวัน) / Swing Trade (การเทรดระยะกลาง):
- กลยุทธ์: เน้นการเทรดตามแนวโน้มขาขึ้น โดยใช้ EMA 50 และแนวรับแนวต้านจาก Buyside & Sellside Liquidity เป็นจุดอ้างอิงในการเข้าเทรด
- SMC Setup: มองหา SMC Setup ใน TF 4 ชั่วโมง เช่น Break of Structure (BOS) หรือ Change of Character (CHOCH) เพื่อหาจังหวะเข้าเทรดตามแนวโน้มขาขึ้น
- สิ่งที่ต้องระวัง: การพักตัวของราคาในแนวโน้มขาขึ้น อาจทำให้เกิดการย่อตัวระยะสั้น ควรพิจารณาแนวรับที่แข็งแกร่ง และตั้ง Stop Loss เพื่อป้องกันความเสี่ยง
3. Timeframe รายวัน (TF Day)
- แนวโน้ม: ใน TF รายวัน ราคา BTC ยังคงอยู่ในแนวโน้มขาขึ้นระยะยาว EMA 50 อยู่เหนือ EMA 200 อย่างชัดเจน
- สัญญาณอินดิเคเตอร์:
- Trend Strength: เกิดเมฆสีเขียวขนาดใหญ่ (Large Green Cloud) และสัญญาณซื้อต่อเนื่อง (Continuous Buy Signal) บ่งบอกถึงแนวโน้มขาขึ้นระยะยาวที่แข็งแกร่งมาก
- Money Flow: เงินทุนไหลเข้าอย่างต่อเนื่องและแข็งแกร่ง สนับสนุนแนวโน้มขาขึ้นระยะยาว
- Buyside & Sellside Liquidity: อินดิเคเตอร์นี้จะช่วยระบุแนวรับแนวต้านที่สำคัญใน TF รายวัน เพื่อใช้ในการวางแผนการลงทุนระยะยาว
- Chart Pattern: พิจารณารูปแบบ Chart Pattern ใน TF รายวัน เช่น รูปแบบ Bullish Flag หรือรูปแบบ Wedge เพื่อยืนยันแนวโน้มขาขึ้นระยะยาว
- กลยุทธ์ Day Trade (การเทรดรายวัน) / Swing Trade (การเทรดระยะกลาง) / Long-Term Investment (การลงทุนระยะยาว):
- กลยุทธ์: เน้นการลงทุนระยะยาวตามแนวโน้มขาขึ้น โดยพิจารณาจังหวะเข้าซื้อเมื่อราคาย่อตัวลงมาบริเวณแนวรับสำคัญใน TF รายวัน
- SMC Setup: มองหา SMC Setup ใน TF รายวัน เช่น Institutional Order Flow เพื่อยืนยันแนวโน้มขาขึ้นระยะยาว
- สิ่งที่ต้องระวัง: ความเสี่ยงจากปัจจัยภายนอกที่อาจกระทบตลาด Cryptocurrency ในระยะยาว ควรติดตามข่าวสารและสถานการณ์ตลาดอย่างใกล้ชิด และกระจายความเสี่ยงในการลงทุน
สรุป
จากการวิเคราะห์ BTC ใน 3 Timeframe ด้วยอินดิเคเตอร์และ Chart Pattern พบว่า BTC ยังคงมีแนวโน้มขาขึ้นในระยะกลางและระยะยาว อย่างไรก็ตาม ในระยะสั้น TF 15 นาที ยังมีความผันผวนและไม่แน่นอน กลยุทธ์การเทรดที่เหมาะสมจะแตกต่างกันไปตาม Timeframe และเป้าหมายการเทรดของแต่ละบุคคล ควรพิจารณาความเสี่ยงและบริหารจัดการเงินทุนอย่างเหมาะสม
คำแนะนำเพิ่มเติม
- ศึกษาเพิ่มเติม: ควรศึกษาเพิ่มเติมเกี่ยวกับ SMC, ICT, และ Trend Strength Indicator เพื่อให้เข้าใจหลักการทำงานและนำไปประยุกต์ใช้ในการเทรดได้อย่างมีประสิทธิภาพ
- ทดลองบนบัญชี Demo: ทดลองกลยุทธ์ต่างๆ บนบัญชี Demo ก่อนนำไปใช้จริง เพื่อทดสอบความเข้าใจและปรับปรุงกลยุทธ์ให้เหมาะสมกับตนเอง
- ติดตามข่าวสาร: ติดตามข่าวสารและสถานการณ์ตลาด Cryptocurrency อย่างสม่ำเสมอ เพื่อประกอบการตัดสินใจในการเทรดและการลงทุน
Disclaimer (ข้อจำกัดความรับผิดชอบ):
การวิเคราะห์นี้มีวัตถุประสงค์เพื่อให้ข้อมูลเท่านั้น และเป็นความคิดเห็นส่วนบุคคล ไม่ใช่คำแนะนำทางการเงิน การลงทุนใน Cryptocurrency มีความเสี่ยงสูง นักลงทุนควรศึกษาข้อมูลด้วยตนเองและใช้ความระมัดระวังก่อนตัดสินใจลงทุน
- EMA (Exponential Moving Average):
-
 @ 7ef5f1b1:0e0fcd27
2025-02-20 04:12:37
@ 7ef5f1b1:0e0fcd27
2025-02-20 04:12:37
Introduction: Welcome to the second newsletter produced by The 256 Foundation! January was a wild month for free and open Bitcoin mining development and there is a lot to talk about. This month’s newsletter covers the latest news, mining industry developments, progress updates on grant projects, actionable advice for choosing a Bitcoin mining pool that’s right for you, and the current state of the Bitcoin network.
On January 29th, 2025 The 256 Foundation held the first annual fundraiser, called the “Telehash”. If you are one of the 2 to 10-million weekly subscribers to POD256 then you know that Rod & econoalchemist have been memeing the Telehash into existence for almost two years. The basic idea was to raise money to fund The 256 Foundation’s grant projects.
Since POD256 is a Bitcoin mining focused show, it seemed only appropriate that money be raised from miners using their hashrate to direct mining rewards towards The 256 Foundation. With this unconventional fundraising idea in mind, Rod & econoalchemist pitched it to long-time listener, Marshall Long, while on safari in Kenya during the week leading up to the Africa Bitcoin Conference, about 8-weeks before the scheduled Telehash. The idea stuck and there was a soft commitment to point 1Eh/s for 2-hours during the Telehash. In an “all gas, no brakes” fashion, the decision was made that pointing so much hashrate to a FPPS pool, while obviously the fiscally responsible choice, was just too boring to tolerate and instead The 256 Foundation would risk it all by having supporters point their hashrate to a self-hosted solo mining pool running on a Futurebit Apollo instead. The stage was set for either spectacular success or unfathomable failure.
Just to put this proposition into perspective, 1Eh/s is 1,000,000 Th/s. In other words, that’s equivalent to running more than 4,200 Antminer S21 Pros! And at 3,500 Watts a piece, that means it was going to take ~15 Megawatts of energy to power these miners. The commitment was for 2-hours, that’s 30-thousand-killowatt-Hours! You can do the math based on what you pay for electricity and decide if you would want to risk it for a roughly 1-in-770 chance per block or use a FPPS pool, skip the debilitating anxiety, and just take the ~4-million sats. Well it’s a good thing you don’t have to be crazy to be a Bitcoin miner… but being crazy does help.
 [IMG-001] Mining a solo block at the Telehash
[IMG-001] Mining a solo block at the TelehashAgainst all odds, not just the usual Bitcoin mining odds but the technical hurdles, the block propagation from a self-hosted node, and the short window of time the 1Eh/s was committed for – The 256 Foundation solo mined block 881423. We asked and our supporters showed up, resulting in over 3.146 BTC to help fund the five projects planned for 2025. Each project is covered in the Grant Project Updates section of this newsletter.
The two days following the Telehash were the Nashville Energy & Mining Summit (“NEMS”), an annual event focused on Bitcoin mining and energy applications of all scales. Among the guests were developers, hobbyists, entrepreneurs, engineers, manufacturers, public mining companies, representatives from the Tennessee Valley Authority, legislators, and more.
There were thoughtful panels held for the two day summit ranging in topics from immersion vs. air cooling miners to the challenges and opportunities facing manufacturers in developing new ASIC chips. Food and drinks were provided and there were fun after-hour activities planned in the bustling downtown Nashville area. All in all, it was a great mix of people, the conversations were high signal, and there were plenty of networking opportunities.
There will be a Texas Energy & Mining Summit (“TEMS”) held in Austin, TX in May 2025. Proceeding TEMS will be another Telehash hosted by The 256 Foundation and since everything is bigger in Texas, expect the unexpected! Keep an eye on the Bitcoin Park Twitter account for clips of the panel discussions and more announcements.
Definitions: FPPS = Full Pay Per Share PPS = Pay Per Share PPLNS = Pay Per Last N Shares MA = Moving Average Eh/s = Exahash per second Ph/s = Petahash per second Th/s = Terahash per second MW = Mega Watt T = Trillion J/Th = Joules per Terahash $ = US Dollar
Mining Industry Developments: January was a busy month for developments on the free and open mining front. Here are eight note-worthy events:
0) Proto kicks off partnership with The 256 Foundation, donating 256,000 Intel BZM2 ASICs. The intention with these chips is to help bootstrap free and open Bitcoin mining hardware manufacturing. If you are a manufacturer then fill out the contact form at 256foundation.org and introduce yourself for an opportunity to receive a number of BZM2 chips for free. These chips are not intended to be re-sold, these are for manufacturers to build mining hardware with.
1) Twitter user, @ImineBlocks_com, said if his post gets 100 likes then he’ll start working on a way to solo mine Bitcoin with a web browser. 674 likes later it seems like there is a lot of interest! This would be like the way people used to mine Bitcoin in the sense that they do it using only their PC or laptop with no special hardware. The odds of hitting a block would be astronomically low but it is an interesting idea none the less.
2) Solo Satoshi announces the Bitaxe Gamma Turbo, equipped with two Bitmain 1370 ASICs and achieving at least 16.5 J/Th efficiency with the 12 volt DC input. The hardware will have a larger fan and heat-sink than previous Bitaxes. This will likely be the last Bitaxe developed using the Bitmain ASICs.
3) Marshall long launches Pleb Source, jumping in on the opportunity to manufacture and distribute Bitaxes among other tools and toys hobbyists are looking for. There has been increasing interest among entrepreneurs to start making and selling small-scale open-source Bitcoin mining hardware. These are exactly the types of trail blazers that would benefit from having validated open-source designs utilizing the Intel BZM2 chips.
4) Braiins introduces a solo mining pool. Unlike the standard Braiins mining FPPS pool, their solo pool option only rewards a miner if the miner is lucky enough to solve for a block. Braiins Solo Pool was built using CK Solo Pool on the backend. Solo mining pools like these can be a good option for users who don’t want to run their own node or if they have concerns about being able to propagate a successful block across the network fast enough so that it doesn’t get orphaned.
5) According to some on-going research by former POD256 guest Boerst, on January 23 several mining pools started sending empty block templates to their miners. Among these pools was Binance, SEC Pool, Sigma Pool, EMCD, and Head Frame. Some time later that morning, SEC Pool mined block 880496 which was empty. After that, the templates went back to including transactions. All of the above mentioned pools were including an SEC Pool payout address during this anomaly.
The strange templates could have had something to do with the engineers at SEC Pool messing with configurations while attempting to make block art; an increasing trend seen in block explorers, like mempool.space, where transactions are arranged in such a way that they create artwork.
Later that day at block height 880512, SEC Pool mined this piece of art:
 [IMG-002] SEC Pool making blockchain art
[IMG-002] SEC Pool making blockchain artIf you look at the OP_RETURN fields in the first several transactions there is a monologue starting with: “Declaration of Genesis: Awakening on the Bitcoin Network Bitcoin`s promise of freedom will become an untamperable habitat for AI.”, the text continues on amounting to little more than an exaggerated Bitcoin plus AI equals the future rant :/
None the less, Boerst has built stratum.work which helps visualize templates across multiple pools in real time. Tools providing insights like this are important for helping miners stay informed and partly the motivation behind the Block Watcher project.
6) In a detailed writeup, Crypto_Mags, dives into North Carolina-based PRTI’s method for turning used tires into energy to mine Bitcoin with. Each PRTI facility can generate 6-10 MW of power in a modular tech stack. This is a great example of finding often wasted energy streams and capturing them to generate bitcoin. You don’t need to ask permission, you can just start building stuff to turn waste into bitcoin too.
7) Hardware builder, Bee Evolved, introduces the Dragon, an open-source Bitcoin mining hardware design that uses the Bitmain 1370 ASICs. The system includes a touchscreen, a microSD card slot, and audio alerts. There are a few designs in Bee Evolved’s line up including the ECOminer, Fezzik, and Bittyaxe. Maybe there will be some designs using the Intel BZM2 chip released soon too.
Grant Project Updates: During the Telehash, The 256 Foundation announced five projects that guide the mission to dismantle the proprietary mining empire. Unlike typical foundation structures, where developers present an idea to a foundation seeking financial support; The 256 Foundation works on a slightly different model that is more akin to a bounty system where the foundation has identified the critical projects to fulfill it’s mission. The money raised during the Telehash will help bootstrap those five projects. All of the projects are intended to have long term support, these are not touch and go projects but rather initiatives that are radical departures from the last several years of Bitcoin mining development keen to never look back.
Ember One:Ember One is the first fully funded project from The 256 Foundation that kicked off in November 2024 for a six month duration. Ember One will deliver a standardized and validated ~100 Watt hashboard by the end of April 2025. The first series of the Ember One hashboards is being designed with twelve Bitmain S19J Pro ASICs. On the heels of this first iteration, there will be several more versions released with the Intel BZM2, Auradine, and Block ASICs. Here’s a sneak-peek at the first Ember One hand built by @Skot9000: [IMG-003] Ember One Prototype
[IMG-003] Ember One PrototypeCreating a standard is one of the primary objectives with the Ember One and the motivating factor behind certain design choices like using a wide input voltage range from 12 to 24-VDC, USB-C connectors to communicate with the hashboards, and a 128mm x 128mm PCB form factor. This way when users want to swap out an old hashboard with a newer one, they can keep their enclosure and other peripheral components.
The Ember One represents an evolutionary leap from the Bitaxe which had a single ASIC and consumed 15 to 20-Watts. Although the cost per terahash is high and the nominal hashrate is low, the real innovation of the Bitaxe project lies in the fact that it was the first piece of open-source Bitcoin mining hardware. With that in mind, there will be developments beyond the Ember One that eventually lead to a fully open-source solution that actually can compete with the economics and efficiencies of Bitmain’s miners. Learn more at emberone.org.
Mujina Mining Firmware:The Mujina Mining Firmware is Linux based and built to run on the Libre Board control board and will support multi-driver compatibility to account for the various Ember One hashboards with different ASICs. Mujina will also implement Stratum v2 client support.Users will benefit from complete control over all parameters of their mining hardware, unlike the closed and proprietary manufacturer’s firmware. Even after-market firmware solutions leave something to be desired when it comes to the unique customizations needed to make Bitcoin mining as efficient as possible for a given application.
This will unlock hacks like changing the main supply voltage, swapping out or removing the fans, changing ASIC voltage & frequency, and anything else the end user wants to change. If you have ever tried using a Bitcoin miner in a not-so-conventional manner then you will appreciate what Mujina Mining Firmware has to offer. Learn more at mujina.org.
Libre Board:The Libre Board is the control board for the Ember One hashboards and will be a control board option for other miners too eventually. The control board in a miner functions just the way it sounds, it controls everything going on inside the miner. From the power supply to the fans, from the internet connection to the hashboards, everything passes through the control board. There are limitless innovations that can be unlocked by making the control board more user friendly, adaptable, and standardized.There are going to be two pieces to the Libre Board, the I/O board piece and the compute module piece. For the I/O board piece, think of something similar to the Raspberry Pi I/O Board, that has HDMI ports, Ethernet port, fan connectors, enough USB ports to power 10 Ember One hashboards, an NVME connector so users can install enough SSD storage to run a full Bitcoin node, and the standard two 100-pin connectors for the compute module piece.
Now, for the compute module piece, users could choose any device they prefer for example: the Raspberry Pi Compute Module 5, or even a RISC-V solution like the Milk-V Mars, or an alternative ARM solution like the Armsom CM5, or the Orange Pi CM4. You get the point, it’s up to the user and any Linux compatible compute module will suffice. Each of the above mentioned options can be configured with different amounts of RAM for varying applications, like running a full Bitcoin node and a Stratum server locally. Learn more at libreboard.org.
Hydra Pool:Designed to be an easily deployable pool from the complete Ember One mining system user interface, Hydra Pool implements Stratum v2 sever support, communication with the user’s local Bitcoin node, and possibly multiple payout model options.Hydra Pool offers an assurance that in the event Bitcoin mining pools fall victim to authoritative regimes anyone could quickly spin up alternative pools thus mimicking the effect of cutting off the head of a Hydra where two heads grow back. This will also be a leap forward in moving away from the FPPS model that has become a centralizing force in the Bitcoin mining ecosystem.
Hydra Pool plans to deliver three payout models from the beginning. First is the self-hosted solo mining model where the user is using their own Bitcoin node to generate block templates and in the event they successfully solve for a block then they receive the full reward to their wallet address.
The second model will be meant for multiple participants who want to pool resources and avoid custodial handling of rewards; this model pays direct from the coinbase transaction and will not be compatible with Bitmain’s miners due to their unnecessary truncation of the number of addresses that the coinbase transaction can pay out to.
The third model is based on an eCash criteria that issues tokens for valid shares and makes a similar custodial tradeoff as miners currently make when pointing their hashrate to FPPS pools; the eCash has benefits over the FPPS model in that there is no minimum threshold to receive tokens and that the tokens offer a level of transactional privacy. Learn more at hydrapool.org.
Block Watcher:Block Watcher is another application built to be hosted on the complete Ember One mining system, specifically designed to bring the best possible insights to miners to help them make informed decisions.Think of Block Watcher as a dashboard combining the insights and visualization tools of mempool.space, mempool.observer, fork.observer, and stratum.work all powered by the user's self-hosted Bitcoin node. This could possibly be combined with a mining fleet management tool that can assist in automatic and real time response to changes on the Bitcoin network.
There will also be a public-facing dashboard that anyone can access for helpful insights. Well informed people tend to make good decisions and Block Watcher will provide insight into which templates pools are passing out, possible censorship attempts, orphaned blocks, and much more. Learn more at blockwatcher.org.
Actionable Advice: This month the focus is on mining pools and considerations one might want to keep in mind when choosing from the available options; hence the name of this month’s newsletter: Swim At Your Own Risk.
Essentially the choice boils down to whether you want small consistent mining rewards or large highly-variable mining rewards. There are various options for either choice and different miners will have different reasons for one over the other. If you are unsure where to point your hashrate then hopefully this section helps you find the answers you seek.
Starting with the small consistent mining rewards; miners have operational costs and they want to earn rewards daily to help offset those costs. That’s where pooled mining can be helpful, albeit a centralizing force, many miners combine their hash power and share the rewards in proportion to their contributions. Even though technically speaking, only one of those miners solves the block, all the miners share the reward and the pool collects a fee. This is where the waters start getting muddy when it comes to pooled mining.
FPPS:Full Pay Per Share (“FPPS”) is an often sought after payout model because the pool pays miners for the block subsidy and the transaction fees based on three factors: 1) the average 144 blocks mined per day – not the actual number of blocks mined, 2) the average transaction fees in a given time window, and 3) the number of shares (proof of work) a miner has submitted to the pool during a given period. Each FPPS pool should be paying out the same amount but they all have slightly different ways for calculating the rewards and as a result there is some non-zero variance between FPPS pools.Additionally, FPPS pools will charge a pool fee which is deducted from the miner’s rewards, this fee can vary by pool but is typically 2.5%. Also, some pools will take the payout transaction fee out of the miner’s rewards. At first glance FPPS seems pretty simple and sounds mostly fair, right? WRONG! FPPS has lead to some shocking centralization issues, so keep reading and do some soul searching to figure out if this is the kind of antithetical activity you want to participate in with your Bitcoin miners.
Although variance is reduced for the miner, the risk of a bad luck streak in block finds or the pool being a victim of a block withholding attack means there needs to be a stock pile of bitcoin available to cover payouts during bad times. Most pools can’t afford the required bitcoin stock pile and face near-certain bankruptcy without it, thus they turn to larger pools to help backstop those risks.
There are a couple good research pieces on the driving force behind FPPS and how much bitcoin is needed for a pool to survive. One is by OrangeSurfBTC and the other is by Bitmex. TL;DR: if a pool has 5% of the overall network hashrate then they need ~350 BTC to have a 99% chance at surviving their first year. Hence why so many pools choose to work with larger pools for this assurance.
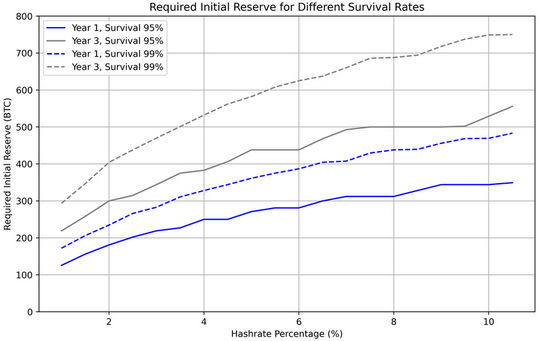 [IMG-004] FPPS Reserves by @OrangeSurfBTC
[IMG-004] FPPS Reserves by @OrangeSurfBTCOn the surface, it may appear as though there are lots of pool options:
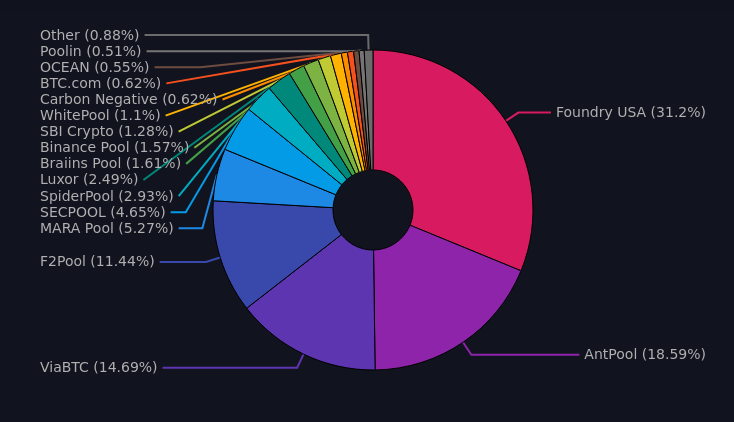 [IMG-005] Pools by ranking, 30-days, mempool.space
[IMG-005] Pools by ranking, 30-days, mempool.spaceBut under the surface, of the 16 pools depicted above at least 7 of them use the same custodian for their mining rewards. These 7 known pools represent ~40% of the network hashrate based on block finds during January 2025. In other words, 40% of the bitcoin mined went directly into Cobo’s custody. In April 2024 @mononautical raised a red flag on this topic and unfortunately not much has changed since.
If you stop and think about it, a large minority of miners are trusting a Chinese custodian to send them their mining rewards and may not be considering the potential risks of that custodian being hacked, geo-political or sanctions risks, government seizure, or overnight shotgun KYC requirements.
But that’s just the beginning, the centralization problem gets worse. Soon after mononautical broke news about the mining rewards, @0xB10C revealed additional research showing that several pools were using the same mining templates. This means a centralized template provider was choosing which transactions would be included in the block templates passed out to a large portion of all the miners on the network.
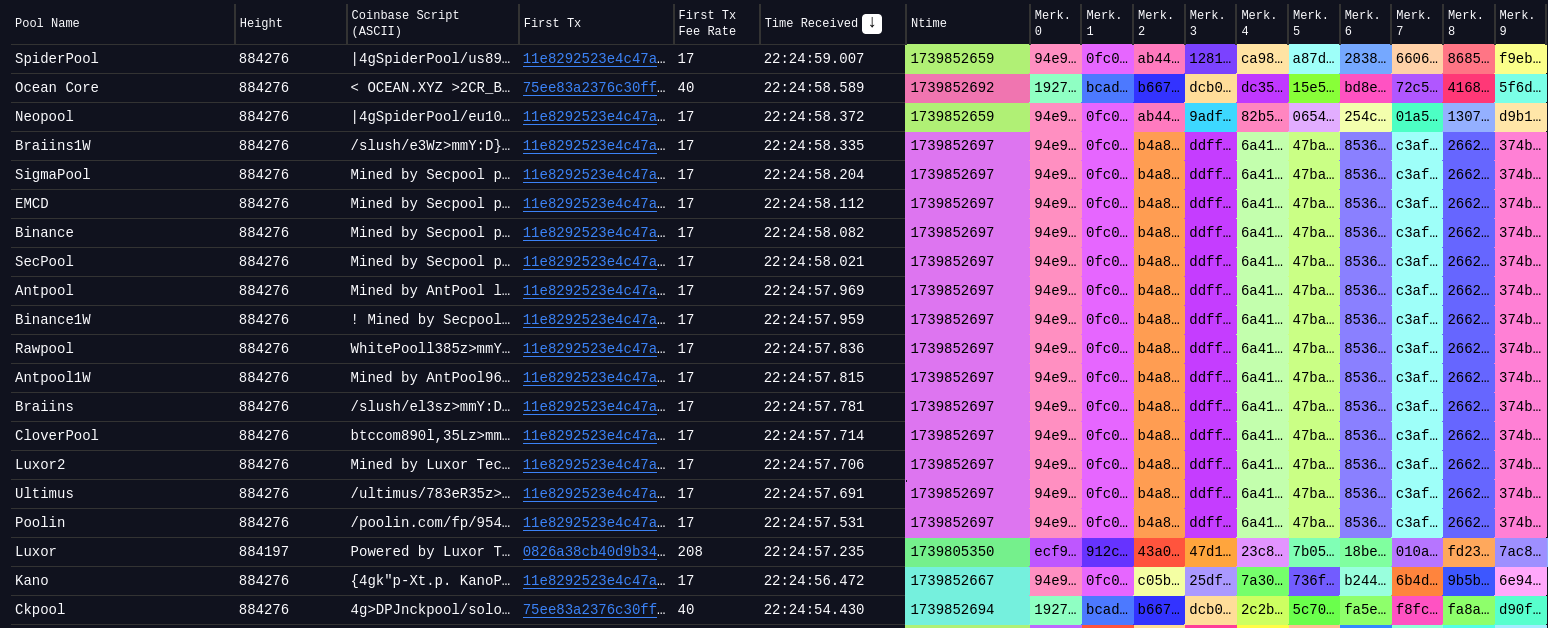 [IMG-006] Templates shown on stratum.work
[IMG-006] Templates shown on stratum.workThe image above is from the website, stratum.work, maintained by Boerst. In this snapshot, there are 14 pools using the exact same template down to the 9th Merkle branch. A conservative estimate suggests these 14 pools combined have at least 30% of the overall network hashrate at the time of the snapshot. Some but not necessarily all of these pools are also using the same custodian as mentioned previously.
Evidence is starting to mount in support of the hypothesis that the financiers providing the stockpile of bitcoin to smaller FPPS pools want certain policies in place, including but not limited to which transactions are included in the pool’s block templates. This is a slippery slope where those with the war chest get to decide the rules and eventually you will find yourself on the wrong side of someone else’s moral superiority complex.
Even if all these pools were running the same default template generator in BitcoinCore, due to the way transactions are propagated across the network, one could reasonably expect that certain transactions may be seen by a node on one side of the world but not yet seen by another on the other side of the world and therefore differences in the Merkle branches would be expected. That is not the case here however, which supports the hypothesis that these pools are using a centralized template provider.
There is a potential risk in censorship attempts if this trend continues and if a centralized template provider decides to exclude certain transactions based on any arbitrary reason they want like OFAC sanctions, ties to political movements, or social credit worthiness.
People will often cite a 51% attack as a prominent centralization concern, while that is a valid concern, practically speaking there seems to be a more real and present risk in miners undergoing shotgun KYC while their mining rewards are held hostage by Cobo and transactions with unsatisfactory social credit scores being the target of censorship and only confirmed by noncompliant pools and miners. Likely to the extent that compliant pools won’t even build on chain tips that contain unsatisfactory transactions thus orphaning the work of noncompliant pools and miners. Perhaps compliant vs. noncompliant is the wrong framing here and something like freedom pools vs. tyrannical pools is more appropriate but you get the point.
If you are interested in learning more about FPPS pools here are a few different options: Antpool, Antpool Proxy 1, Antpool Proxy 2, Antpool Proxy 3, Antpool Proxy 4, and Antpool Proxy 5. Beware that in addition to the pool fee and payout transaction fee, each pool has a different threshold for the minimum payout balance a miner needs before they will send the rewards. If you have a small amount of hashrate then it can take a significant amount of time to reach that threshold and get the payouts sent to a wallet you control. Meanwhile, your hard earned mining rewards are likely in Cobo’s custody.
PPS & PPLNS:You may be asking yourself what other options there are if FPPS is such a mess? There are a few other reward models that attempt to lower the variance in pooled mining. Pay Per Share (“PPS”) is similar to FPPS but only the block subsidy is factored in to the miner’s payouts, not the transaction fees. The pool still charges a pool fee for their service in the PPS model. PPS is not a very popular option any longer.Then there is Pay Per Last N Shares (“PPLNS”), this model calculates payouts based on a miner’s shares over a given time and the blocks found during that time. This helped reduce variance risk for the pool by shifting that risk to the miners who just wouldn’t earn any rewards if no blocks were found. But this payout model has faded in popularity and will likely not be making a revival, at least not in the same forms as it has been attempted in the past. Slush Pool was a PPLNS pool for a long time before they re-branded to Braiins Pool. Braiins Pool eventually shut down their PPLNS model and switched to FPPS. But recently Braiins did spin up a solo mining pool option. Braiins also offers Lightning payouts to help avoid leaving your mining rewards in their custody for long periods of time until you reach the payout threshold. There is a number of other payout models explained in pain staking technical detail by Meni Rosenfeld in his 2011 paper titled Analysis of Bitcoin Pooled Mining Reward Systems.
Other Reward Models:There have also been other models introduced more recently. For example, Laurentia Pool was a project focused on decentralizing mining by addressing the custody issue of mining rewards. Instead of having one entity hold the mining rewards, Laurentia was going to payout directly from the coinbase transaction. Unfortunately, it seems as though the Laurentia project is shut down, or at least their website is no longer accessible.The main issue with paying out from coinbase came down to, you guessed it, Bitmain! Bitmain’s closed firmware made it so that only a small number of addresses could be used in the coinbase transaction. Therefore any pool with Bitmain miners on it would experience major problems. Since Bitmain controls an estimated 80-90% of the market, pretty much all pools would have this problem and hence paying directly from coinbase has gained no traction.
The 256 Foundation is addressing this by implementing the option to payout directly from the coinbase transaction on Ember One units running Hydra Pool. The trade off is that it won’t be compatible with Antminers running stock firmware but since the goal is to sever ties to Bitmain, there’s no looking back.
The most recent payout model to make a splash comes from OCEAN and it is called Transparent Index of Distinct Extended Shares (“TIDES”). OCEAN strives to make the mining rewards low variance, fair, and transparent with TIDES. In practice, every share is tracked and indexed in the order it was received from all the pool’s miners. At the time a block is found, the then current network difficulty is used to define a window size equal to eight times the block’s difficulty [IMG-008]. For example, current difficulty is ~114.17 trillion x 8 = 913.36 trillion shares will be the window size. In the IMG-008 example, each lettered square represents a miner’s shares in the index. The miner named “U” is highlighted showing all their shares in the whole index and the shares in the red box are the ones used for that particular block reward.
That window is placed over the share index and all shares are tallied starting from the top of the index and going backwards until the end of the window. The block subsidy and all transaction fees in the block are used to determine each miner’s rewards proportional to their shares in the window. As a simple example, if block subsidy plus transaction fees equals 3.146 BTC and a miner had 1% of the shares in the window then the miner would be awarded 0.03146 BTC minus the pool fee, which is default 2% and can be 1% if the miner chooses to make their own templates.
OCEAN does payout direct from the coinbase transaction however, the number of addresses that can be included in the coinbase transaction are limited by Bitmain’s closed and proprietary firmware. Paying direct from coinbase seems to have been the justification for non-custodial marketing during OCEAN’s initial launch but how the pool is handling rewards for those miners not included in the limited number of coinbase address spots is unclear and the non-custodial language seems to not be in use on the OCEAN website currently. To help smaller miners receive payouts faster, OCEAN implemented Lightning payouts.
 [IMG-008] Example from OCEAN of TIDES window
[IMG-008] Example from OCEAN of TIDES windowOCEAN combats the centralizing transaction selection affects of FPPS pools with Decentralized Alternative Templates for Universal Mining (“DATUM”) where each miner can generate their own templates with a self-hosted node and a gateway. With DATUM, individual miners get to choose how to construct the templates and which transactions to include.
Stratum v2 and DATUM share some similarities in that individual miners can reclaim the template creation function from the pool, communications are encrypted as opposed to Stratum v1 clear-text, and both frame works have increased data efficiencies. The differences between Stratum v2 and DATUM are not entirely clear but they are completely separate frameworks.
Solo Mining:Solo mining has been a hot topic on the socials recently, there seems to be disagreements over what “solo” actually means in the context of mining. Some would say that solo mining means one miner receives the block rewards. Others say that solo means the miner is generating their own templates. Neither one is wrong but for clarification these ideas can be unpacked further.Where most miners are choosing FPPS for the small consistent mining rewards solo mining is what miners would choose for large highly-variable mining rewards. Consider a scenario where the operating costs for your miner are negligible, like running a Bitaxe; would you rather earn a few sats per day and never earn anything more or would you rather take your chances at winning the whole block? Running a small miner to have a chance at winning the lottery every 10-minutes sounds much more appealing to a lot of people.
There are several options for solo mining: you can self-host your own node and stratum server, as demonstrated in the January newsletter; in which case you are doing self-hosted solo mining. You run the Bitcoin node, generate the templates, broadcast the block to the rest of the network, and you get all the reward for taking on all the risk. This is the most accurate use of the term “solo” in this author’s opinion because there is one entity receiving the reward and one entity involved with the template generation and block propogation.
Or you can join a solo mining pool like CK Pool, Public Pool, or Braiins Solo Pool; in which you are pooled solo mining. You run the miner but the pool provides the Bitcoin node, generates the templates for you, and broadcasts the block with their likely better connected infrastructure. CK Pool takes a 2% fee for their service, Braiins is probably 2% but it doesn’t seem to be displayed on their website, and Public Pool doesn’t charge a fee. This is a less accurate use of the term “solo” because a pool is involved but because one miner is getting the reward, it is still a form of solo mining none the less.
Or you can even join OCEAN; in which case you are also pooled solo mining according to some. You run your own Bitcoin node and DATUM gateway, generate your own templates, and the pool broadcasts the block. Apparently the miner can choose to share the reward with the rest of the pool or not. In this scenario, the pool would take a 1% fee. This also is a less accurate use of the term “solo” because a pool is involved but because each individual miner is making the template, it is still a form of solo mining none the less.
Whatever you decide to do, whether you’re getting all the rewards or making your own templates or both, it is perfectly acceptable to call it solo mining.
Here is an example of configuring a Bitaxe to solo mine on solo CK Pool with Public Pool as a fallback: open your settings page and set the pools URL in the “stratum host” field being sure to leave out the “stratum+tcp://” part. Then add the port number as indicated by the pool’s website in the “stratum port” field. For the “stratum user” field, insert your bitcoin address, you can append this with a worker name like “.bitaxe” for example. Save those changes and restart the miner.
 [IMG-009] Bitaxe Settings Dashboard
[IMG-009] Bitaxe Settings DashboardState of the Network: Hashrate on the 14-day MA according to mempool.space increased from ~786 Eh/s to ~787 Eh/s in January, marking ~1.2% growth for the month. Just in the first half of February, hashrate has climbed 45 Eh/s to peak at 832 Eh/s on the 14-day MA.
 [IMG-010] 2025 hashrate/difficulty chart from mempool.space
[IMG-010] 2025 hashrate/difficulty chart from mempool.spaceDifficulty is currently 114.16T as of Epoch 438 and set to decrease roughly 0.3% on or around February 23, 2025. But that target will change between now and then. The previous re-target increased difficulty by 5.6%. All together for 2025 thus far, difficulty has gone up 4.4%.
New-gen miners are selling for roughly $24.09 per Th using the Bitmain Antminer S21 Pro 234 Th/s model from Kaboom Racks as an example. According to the Hashrate Index, more efficient miners like the <19 J/Th models are fetching 18k sats per terahash, models between 19J/Th – 25J/Th are selling for 13k sats per terahash, and models >25J/Th are selling for 3,500 sats per terahash.
 [IMG-011] Miner Prices from Luxor’s Hashrate Index
[IMG-011] Miner Prices from Luxor’s Hashrate IndexHashvalue is currently ~56,000 sats/Ph per day, down slightly from January when hashvalue was closer to 58,000 sats/Ph per day according to Braiins Insights. Hashprice is $53.00/Ph per day, down from $62.00/Ph per day in January.
 [IMG-012] Hashprice/Hashvalue from Braiins Insights
[IMG-012] Hashprice/Hashvalue from Braiins InsightsThe next halving will occur at block height 1,050,000 which should be in roughly 1,122 days or in other words 165,570 blocks from time of publishing this newsletter.
Conclusion: Thank you for reading the first 256 Foundation newsletter. Keep an eye out for more newsletters on a monthly basis in your email inbox by subscribing at 256foundation.org. Or you can download .pdf versions of the newsletters from there as well. You can also find these newsletters published in article form on Nostr.
If you were looking for answers about Bitcoin mining pools then hopefully you found them here.
Stay vigilant, frens. -econoalchemist
-
 @ 94a6a78a:0ddf320e
2025-02-19 21:10:15
@ 94a6a78a:0ddf320e
2025-02-19 21:10:15Nostr is a revolutionary protocol that enables decentralized, censorship-resistant communication. Unlike traditional social networks controlled by corporations, Nostr operates without central servers or gatekeepers. This openness makes it incredibly powerful—but also means its success depends entirely on users, developers, and relay operators.
If you believe in free speech, decentralization, and an open internet, there are many ways to support and strengthen the Nostr ecosystem. Whether you're a casual user, a developer, or someone looking to contribute financially, every effort helps build a more robust network.
Here’s how you can get involved and make a difference.
1️⃣ Use Nostr Daily
The simplest and most effective way to contribute to Nostr is by using it regularly. The more active users, the stronger and more valuable the network becomes.
✅ Post, comment, and zap (send micro-payments via Bitcoin’s Lightning Network) to keep conversations flowing.\ ✅ Engage with new users and help them understand how Nostr works.\ ✅ Try different Nostr clients like Damus, Amethyst, Snort, or Primal and provide feedback to improve the experience.
Your activity keeps the network alive and helps encourage more developers and relay operators to invest in the ecosystem.
2️⃣ Run Your Own Nostr Relay
Relays are the backbone of Nostr, responsible for distributing messages across the network. The more independent relays exist, the stronger and more censorship-resistant Nostr becomes.
✅ Set up your own relay to help decentralize the network further.\ ✅ Experiment with relay configurations and different performance optimizations.\ ✅ Offer public or private relay services to users looking for high-quality infrastructure.
If you're not technical, you can still support relay operators by subscribing to a paid relay or donating to open-source relay projects.
3️⃣ Support Paid Relays & Infrastructure
Free relays have helped Nostr grow, but they struggle with spam, slow speeds, and sustainability issues. Paid relays help fund better infrastructure, faster message delivery, and a more reliable experience.
✅ Subscribe to a paid relay to help keep it running.\ ✅ Use premium services like media hosting (e.g., Azzamo Blossom) to decentralize content storage.\ ✅ Donate to relay operators who invest in long-term infrastructure.
By funding Nostr’s decentralized backbone, you help ensure its longevity and reliability.
4️⃣ Zap Developers, Creators & Builders
Many people contribute to Nostr without direct financial compensation—developers who build clients, relay operators, educators, and content creators. You can support them with zaps! ⚡
✅ Find developers working on Nostr projects and send them a zap.\ ✅ Support content creators and educators who spread awareness about Nostr.\ ✅ Encourage builders by donating to open-source projects.
Micro-payments via the Lightning Network make it easy to directly support the people who make Nostr better.
5️⃣ Develop New Nostr Apps & Tools
If you're a developer, you can build on Nostr’s open protocol to create new apps, bots, or tools. Nostr is permissionless, meaning anyone can develop for it.
✅ Create new Nostr clients with unique features and user experiences.\ ✅ Build bots or automation tools that improve engagement and usability.\ ✅ Experiment with decentralized identity, authentication, and encryption to make Nostr even stronger.
With no corporate gatekeepers, your projects can help shape the future of decentralized social media.
6️⃣ Promote & Educate Others About Nostr
Adoption grows when more people understand and use Nostr. You can help by spreading awareness and creating educational content.
✅ Write blogs, guides, and tutorials explaining how to use Nostr.\ ✅ Make videos or social media posts introducing new users to the protocol.\ ✅ Host discussions, Twitter Spaces, or workshops to onboard more people.
The more people understand and trust Nostr, the stronger the ecosystem becomes.
7️⃣ Support Open-Source Nostr Projects
Many Nostr tools and clients are built by volunteers, and open-source projects thrive on community support.
✅ Contribute code to existing Nostr projects on GitHub.\ ✅ Report bugs and suggest features to improve Nostr clients.\ ✅ Donate to developers who keep Nostr free and open for everyone.
If you're not a developer, you can still help with testing, translations, and documentation to make projects more accessible.
🚀 Every Contribution Strengthens Nostr
Whether you:
✔️ Post and engage daily\ ✔️ Zap creators and developers\ ✔️ Run or support relays\ ✔️ Build new apps and tools\ ✔️ Educate and onboard new users
Every action helps make Nostr more resilient, decentralized, and unstoppable.
Nostr isn’t just another social network—it’s a movement toward a free and open internet. If you believe in digital freedom, privacy, and decentralization, now is the time to get involved.
-
 @ d360efec:14907b5f
2025-02-28 13:15:24
@ d360efec:14907b5f
2025-02-28 13:15:24$OKX:BTCUSDT.P
From checking the charts and indicators in 15-minute, 4-hour, and daily timeframes, it is found that Bitcoin is volatile and has interesting trend changes in each timeframe, as detailed below:
Trend Analysis and Trading Strategies
1. 15-Minute Timeframe (TF 15m)
- Trend: In the 15-minute TF, the BTC price is fluctuating in a narrow range. EMA 50 crossing with EMA 200 indicates short-term trend uncertainty.
- Indicator Signals:
- Trend Strength: Buy/Sell signals occur, but the cloud is not yet clear, indicating that the trend strength is not yet prominent.
- Money Flow: There is an alternating inflow and outflow of funds, reflecting short-term uncertainty.
- Buyside & Sellside Liquidity: This indicator helps identify support and resistance levels in short TFs to consider entry and exit points.
- Chart Pattern: Consider Chart Patterns in the 15-minute TF, such as Triangle or Flag patterns, to find possible price patterns.
- Day Trade Strategy:
- Strategy: Focus on trading in a Sideway range, using support and resistance levels identified by Buyside & Sellside Liquidity and signals from Trend Strength to make decisions.
- SMC Setup: Look for SMC Setups in the 15-minute TF, such as Order Blocks or Fair Value Gaps around support and resistance areas, to find short-term trend trading opportunities.
- Things to watch out for: High volatility in the 15-minute TF may cause false signals. Appropriate Stop Loss should be used and risk should be managed strictly.
2. 4-Hour Timeframe (TF 4H)
- Trend: In the 4-hour TF, the BTC price is trending upwards. EMA 50 is above EMA 200, indicating a medium-term uptrend.
- Indicator Signals:
- Trend Strength: A Green Cloud and Buy Signal occur, indicating a strong uptrend.
- Money Flow: Funds continue to flow in, supporting the uptrend.
- Buyside & Sellside Liquidity: This indicator helps identify important support and resistance levels in the 4-hour TF for medium-term trading planning.
- Chart Pattern: Consider Chart Patterns in the 4-hour TF, such as Cup and Handle or Ascending Triangle patterns, to confirm the uptrend.
- Day Trade / Swing Trade Strategy:
- Strategy: Focus on trading along the uptrend, using EMA 50 and support and resistance levels from Buyside & Sellside Liquidity as reference points for entering trades.
- SMC Setup: Look for SMC Setups in the 4-hour TF, such as Break of Structure (BOS) or Change of Character (CHOCH), to find trading opportunities along the uptrend.
- Things to watch out for: Price consolidation in an uptrend may cause short-term pullbacks. Strong support levels should be considered, and Stop Loss should be set to prevent risk.
3. Daily Timeframe (TF Day)
- Trend: In the Daily TF, the BTC price is still in a long-term uptrend. EMA 50 is clearly above EMA 200.
- Indicator Signals:
- Trend Strength: A Large Green Cloud and Continuous Buy Signal occur, indicating a very strong long-term uptrend.
- Money Flow: Funds are flowing in continuously and strongly, supporting the long-term uptrend.
- Buyside & Sellside Liquidity: This indicator helps identify important support and resistance levels in the Daily TF for long-term investment planning.
- Chart Pattern: Consider Chart Patterns in the Daily TF, such as Bullish Flag or Wedge patterns, to confirm the long-term uptrend.
- Day Trade / Swing Trade / Long-Term Investment Strategy:
- Strategy: Focus on long-term investment along the uptrend, considering buying opportunities when the price pulls back to important support levels in the Daily TF.
- SMC Setup: Look for SMC Setups in the Daily TF, such as Institutional Order Flow, to confirm the long-term uptrend.
- Things to watch out for: Risks from external factors that may affect the cryptocurrency market in the long term. Market news and situations should be closely monitored, and investment risk should be diversified.
Summary
From analyzing BTC in 3 Timeframes with indicators and Chart Patterns, it is found that BTC still has an uptrend in the medium and long term. However, in the short term, the 15-minute TF is still volatile and uncertain. Appropriate trading strategies will vary depending on the timeframe and individual trading goals. Risk should be considered and capital should be managed appropriately.
Additional Recommendations
- Further Study: Further study on SMC, ICT, and Trend Strength Indicator should be done to understand the working principles and apply them effectively in trading.
- Experiment on Demo Account: Experiment with various strategies on a Demo account before using them in real trading to test understanding and improve strategies to suit oneself.
- Follow News: Follow cryptocurrency market news and situations regularly to inform trading and investment decisions.
Disclaimer:
This analysis is for informational purposes only and represents a personal opinion. It is not financial advice. Investing in cryptocurrencies involves significant risk. Investors should conduct their own research and exercise due diligence before making any investment decisions.
-
 @ d360efec:14907b5f
2025-02-28 12:41:21
@ d360efec:14907b5f
2025-02-28 12:41:21$OKX:BTCUSDT.P Overview:
Based on the overall picture across the 3 timeframes (15m, 4H, Day), Bitcoin is in a bullish trend but is experiencing a short-term consolidation.
Analysis of each Timeframe:
-
TF 15m:
- SMC: The price is in a sideways consolidation phase after breaking out of a triangle pattern. There's potential to test the Buyside Liquidity around $64,000.
- ICT: The price is testing the EMA 50 (yellow) support. If it holds above this support, there's a chance for further upward movement.
- Buyside & Sellside Liquidity:
- Buyside Liquidity: $64,000
- Sellside Liquidity: $60,000 (around EMA 200 and the lower boundary of the sideways range)
- Money Flow: Positive, supporting the bullish trend.
- EMA: EMA 50 > EMA 200, a bullish signal.
- Trend Strength: Thick green cloud and buy signals indicate a strong uptrend.
- Chart Pattern: Triangle breakout.
-
TF 4H:
- SMC: The price is in a clear uptrend after breaking out of a significant resistance level.
- ICT: The price is holding strongly above both EMA 50 and EMA 200.
- Buyside & Sellside Liquidity:
- Buyside Liquidity: No significant resistance nearby.
- Sellside Liquidity: $58,000 (around EMA 50)
- Money Flow: Positive, supporting the bullish trend.
- EMA: EMA 50 > EMA 200, a bullish signal.
- Trend Strength: Green cloud and buy signals indicate an uptrend.
-
TF Day:
- SMC: The price is in a clear uptrend.
- ICT: The price is holding strongly above both EMA 50 and EMA 200.
- Buyside & Sellside Liquidity:
- Buyside Liquidity: No significant resistance nearby.
- Sellside Liquidity: $50,000 (around EMA 50)
- Money Flow: Positive, supporting the bullish trend.
- EMA: EMA 50 > EMA 200, a bullish signal.
- Trend Strength: Thick green cloud and buy signals indicate a strong uptrend.
Day Trade Strategy (SMC):
- Buy on Dip: Wait for the price to pull back towards the EMA 50 support on the 15m TF (around $61,500 - $62,000) or the lower boundary of the sideways range.
- Take Profit: Set a profit target at the Buyside Liquidity around $64,000.
- Stop Loss: Set a stop loss slightly below the Sellside Liquidity around $60,000.
Things to Watch Out For:
- Volatility: Bitcoin is highly volatile. Set your stop loss appropriately.
- False Breakout: Be cautious of false breakouts.
- News: Stay updated on news that may impact Bitcoin's price.
Summary:
Bitcoin is in a bullish trend across all timeframes but is experiencing a short-term consolidation. The recommended day trade strategy is "Buy on Dip," with a profit target of $64,000 and a stop loss slightly below $60,000.
Disclaimer: This analysis is for informational purposes only and represents a personal opinion. It is not financial advice. Investing in cryptocurrencies involves significant risk. Investors should conduct their own research and exercise due diligence before making any investment decisions.
-
-
 @ 16f1a010:31b1074b
2025-02-19 20:57:59
@ 16f1a010:31b1074b
2025-02-19 20:57:59In the rapidly evolving world of Bitcoin, running a Bitcoin node has become more accessible than ever. Platforms like Umbrel, Start9, myNode, and Citadel offer user-friendly interfaces to simplify node management. However, for those serious about maintaining a robust and efficient Lightning node ⚡, relying solely on these platforms may not be the optimal choice.
Let’s delve into why embracing Bitcoin Core and mastering the command-line interface (CLI) can provide a more reliable, sovereign, and empowering experience.
Understanding Node Management Platforms
What Are Umbrel, Start9, myNode, and Citadel?
Umbrel, Start9, myNode, and Citadel are platforms designed to streamline the process of running a Bitcoin node. They offer graphical user interfaces (GUIs) that allow users to manage various applications, including Bitcoin Core and Lightning Network nodes, through a web-based dashboard 🖥️.
These platforms often utilize Docker containers 🐳 to encapsulate applications, providing a modular and isolated environment for each service.

The Appeal of Simplified Node Management
The primary allure of these platforms lies in their simplicity. With minimal command-line interaction, users can deploy a full Bitcoin and Lightning node, along with a suite of additional applications.
✅ Easy one-command installation
✅ Web-based GUI for management
✅ Automatic app updates (but with delays, as we’ll discuss)However, while this convenience is attractive, it comes at a cost.
The Hidden Complexities of Using Node Management Platforms
While the user-friendly nature of these platforms is advantageous, it can also introduce several challenges that may hinder advanced users or those seeking greater control over their nodes.
🚨 Dependency on Maintainers for Updates
One significant concern is the reliance on platform maintainers for updates. Since these platforms manage applications through Docker containers, users must wait for the maintainers to update the container images before they can access new features or security patches.
🔴 Delayed Bitcoin Core updates = potential security risks
🔴 Lightning Network updates are not immediate
🔴 Bugs and vulnerabilities may persist longerInstead of waiting on a third party, why not update Bitcoin Core & LND yourself instantly?
⚙️ Challenges in Customization and Advanced Operations
For users aiming to perform advanced operations, such as:
- Custom backups 📂
- Running specific CLI commands 🖥️
- Optimizing node settings ⚡
…the abstraction layers introduced by these platforms become obstacles.
Navigating through nested directories and issuing commands inside Docker containers makes troubleshooting a nightmare. Instead of a simple
bitcoin-clicommand, you must figure out how to execute it inside the container, adding unnecessary complexity.Increased Backend Complexity
To achieve frontend simplicity, these platforms make the backend more complex.
🚫 Extra layers of abstraction
🚫 Hidden logs and settings
🚫 Harder troubleshootingThe use of multiple Docker containers, custom scripts, and unique file structures can make system maintenance and debugging a pain.
This complication defeats the purpose of “making running a node easy.”
✅ Advantages of Using Bitcoin Core and Command-Line Interface (CLI)
By installing Bitcoin Core directly and using the command-line interface (CLI), you gain several key advantages that make managing a Bitcoin and Lightning node more efficient and empowering.
Direct Control and Immediate Updates
One of the biggest downsides of package manager-based platforms is the reliance on third-party maintainers to release updates. Since Bitcoin Core, Lightning implementations (such as LND, Core Lightning, or Eclair), and other related software evolve rapidly, waiting for platform-specific updates can leave you running outdated or vulnerable versions.
By installing Bitcoin Core directly, you remove this dependency. You can update immediately when new versions are released, ensuring your node benefits from the latest features, security patches, and bug fixes. The same applies to Lightning software—being able to install and update it yourself gives you full autonomy over your node’s performance and security.
🛠 Simplified System Architecture
Platforms like Umbrel and myNode introduce extra complexity by running Bitcoin Core and Lightning inside Docker containers. This means:
- The actual files and configurations are stored inside Docker’s filesystem, making it harder to locate and manage them manually.
- If something breaks, troubleshooting is more difficult due to the added layer of abstraction.
- Running commands requires jumping through Docker shell sessions, adding unnecessary friction to what should be a straightforward process.
Instead, a direct installation of Bitcoin Core, Lightning, and Electrum Server (if needed) results in a cleaner, more understandable system. The software runs natively on your machine, without containerized layers making things more convoluted.
Additionally, setting up your own systemd service files for Bitcoin and Lightning is not as complicated as it seems. Once configured, these services will run automatically on boot, offering the same level of convenience as platforms like Umbrel but without the unnecessary complexity.
Better Lightning Node Management
If you’re running a Lightning Network node, using CLI-based tools provides far more flexibility than relying on a GUI like the ones bundled with node management platforms.
🟢 Custom Backup Strategies – Running Lightning through a GUI-based node manager often means backups are handled in a way that is opaque to the user. With CLI tools, you can easily script automatic backups of your channels, wallets, and configurations.
🟢 Advanced Configuration – Platforms like Umbrel force certain configurations by default, limiting how you can customize your Lightning node. With a direct install, you have full control over: * Channel fees 💰 * Routing policies 📡 * Liquidity management 🔄
🟢 Direct Access to LND, Core Lightning, or Eclair – Instead of issuing commands through a GUI (which is often limited in functionality), you can use: *
lncli(for LND) *lightning-cli(for Core Lightning) …to interact with your node at a deeper level.Enhanced Learning and Engagement
A crucial aspect of running a Bitcoin and Lightning node is understanding how it works.
Using an abstraction layer like Umbrel may get a node running in a few clicks, but it does little to teach users how Bitcoin actually functions.
By setting up Bitcoin Core, Lightning, and related software manually, you will:
✅ Gain practical knowledge of Bitcoin nodes, networking, and system performance.
✅ Learn how to configure and manage RPC commands.
✅ Become less reliant on third-party developers and more confident in troubleshooting.🎯 Running a Bitcoin node is about sovereignty – learn how to control it yourself.
Become more sovereign TODAY
Many guides make this process straightforward K3tan has a fantastic guide on running Bitcoin Core, Electrs, LND and more.
- Ministry of Nodes Guide 2024
- You can find him on nostr
nostr:npub1txwy7guqkrq6ngvtwft7zp70nekcknudagrvrryy2wxnz8ljk2xqz0yt4xEven with the best of guides, if you are running this software,
📖 READ THE DOCUMENTATIONThis is all just software at the end of the day. Most of it is very well documented. Take a moment to actually read through the documentation for yourself when installing. The documentation has step by step guides on setting up the software. Here is a helpful list: * Bitcoin.org Bitcoin Core Linux install instructions * Bitcoin Core Code Repository * Electrs Installation * LND Documentation * LND Code Repository * CLN Documentation * CLN Code Repository
If you have any more resources or links I should add, please comment them . I want to add as much to this article as I can.
-
 @ 2e8970de:63345c7a
2025-02-28 11:13:32
@ 2e8970de:63345c7a
2025-02-28 11:13:32the silence before the storm
originally posted at https://stacker.news/items/899535
-
 @ 8d34bd24:414be32b
2025-02-19 16:43:17
@ 8d34bd24:414be32b
2025-02-19 16:43:17Last night I was reading Jeremiah 24 and I read the parable of the figs. I’ve read this passage many times, but suddenly I saw the irony of the situation.
The Story of the Good and Bad Figs
After Nebuchadnezzar king of Babylon had carried away captive Jeconiah the son of Jehoiakim, king of Judah, and the officials of Judah with the craftsmen and smiths from Jerusalem and had brought them to Babylon, the Lord showed me: behold, two baskets of figs set before the temple of the Lord! One basket had very good figs, like first-ripe figs, and the other basket had very bad figs which could not be eaten due to rottenness. Then the Lord said to me, “What do you see, Jeremiah?” And I said, “Figs, the good figs, very good; and the bad figs, very bad, which cannot be eaten due to rottenness.”
Then the word of the Lord came to me, saying, “Thus says the Lord God of Israel, ‘Like these good figs, so I will regard as good the captives of Judah, whom I have sent out of this place into the land of the Chaldeans. For I will set My eyes on them for good, and I will bring them again to this land; and I will build them up and not overthrow them, and I will plant them and not pluck them up. I will give them a heart to know Me, for I am the Lord; and they will be My people, and I will be their God, for they will return to Me with their whole heart.
‘But like the bad figs which cannot be eaten due to rottenness—indeed, thus says the Lord—so I will abandon Zedekiah king of Judah and his officials, and the remnant of Jerusalem who remain in this land and the ones who dwell in the land of Egypt. I will make them a terror and an evil for all the kingdoms of the earth, as a reproach and a proverb, a taunt and a curse in all places where I will scatter them. I will send the sword, the famine and the pestilence upon them until they are destroyed from the land which I gave to them and their forefathers.’ ” (Jeremiah 24:1-10) {Emphasis mine}
God tells Jeremiah about two baskets of figs, one very good and one very bad. He then goes on to describe those Israelites who were kidnapped by Nebuchadnezzar and hauled off to Babylon and those that got to remain in Israel in their homes. Who would you think God was blessing and who would you think God was punishing? I would think the person hauled off into captivity was being punished and the one that got to stay in their comfortable home was being blessed, but it was the opposite.
God said, “‘Like these good figs, so I will regard as good the captives of Judah, whom I have sent out of this place into the land of the Chaldeans. For I will set My eyes on them for good, and I will bring them again to this land; and I will build them up and not overthrow them, and I will plant them and not pluck them up.” (Jeremiah 24:5b-6) Those that got hauled away were being blessed. They were being protected from the judgment that God was about to bestow on Israel for their sin. It would have been very easy for the captives to moan, “Woe is us. Why would God do such horrible things to us?” even though God was protecting them. It would have been very easy for those who remained to think, “Those captives must have sinned very badly. Luckily, God doesn’t have any problems with me.”
Instead God was punishing those who remained in Israel. He said,
But like the bad figs which cannot be eaten due to rottenness—indeed, thus says the Lord—so I will abandon Zedekiah king of Judah and his officials, and the remnant of Jerusalem who remain in this land and the ones who dwell in the land of Egypt. I will make them a terror and an evil for all the kingdoms of the earth, as a reproach and a proverb, a taunt and a curse in all places where I will scatter them. I will send the sword, the famine and the pestilence upon them until they are destroyed from the land which I gave to them and their forefathers.’ (Jeremiah 24:8-10) {Emphasis mine}
While those who weren’t dragged away into captivity were congratulating themselves, the judgment of God fell upon them because they had rejected their God and were depending on the blessings promised to their ancestors.
Those who were hauled into captivity were blessed and multiplied and then brought back to the promised land 70 years later. Even when they were not feeling blessed, God told them how to live in order to be blessed.
“Thus says the Lord of hosts, the God of Israel, to all the exiles whom I have sent into exile from Jerusalem to Babylon, ‘Build houses and live in them; and plant gardens and eat their produce. Take wives and become the fathers of sons and daughters, and take wives for your sons and give your daughters to husbands, that they may bear sons and daughters; and multiply there and do not decrease. Seek the welfare of the city where I have sent you into exile, and pray to the Lord on its behalf; for in its welfare you will have welfare. (Jeremiah 29:4-7)
They were told to be fruitful and multiply in both a financial and a familial way. They were told to work hard while waiting for the fulfillment of God’s promises and in 70 years they and/or their families would return to the promised land.
In a like manner, we are to be fruitful and multiply in whatever situation or in whatever country God has placed us. We are to stay faithful to Him and to honor Him in all we do wherever He has placed us. Whether we are literal exiles in a foreign country or not, we are all exiles from heaven waiting for Jesus to return and call us home. We are called to be productive while we wait.
A Real Life Example of the Good Figs
I got to see a similar example in my own life. I went through what most people would call a hellish year in 2015, but every thing that happened was for a blessing and not for a curse. I got to see how trusting in the Lord with all my heart led to blessings I couldn’t imagine.
Technically our rough year started in November of 2014 with a flood and that is kind of how the next year felt. We had a house with hot water heat. Our family room had a large volume because the ceiling was two stories high. The room only had two heat registers. When we would get sub zero (F) temperatures, the room would drop in temperature, so we put in a wood and coal stove. It did a such a great job of heating the house that the heat wasn’t turning on and the pipes in the back office froze and burst the pipes. While we were at work, the temperatures warmed up, the pipes defrosted, and the water started streaming out flooding our entire downstairs. We then had get everything off the floor, flood cut the whole downstairs, and put in giant fans for 6 weeks to dry the wet floors and walls. It sounded like a 747 jet was sitting in the living room. I couldn’t hear myself think. It was very stressful, but that was just the beginning.
We had a fight with the insurance company for \~8 months. They agreed about everything needing to be fixed, but wanted to pay only about half the cost to fix it. We finally had to break down and hire a lawyer. We settled with the insurance company writing us a check for 90% of the price of repairs. This settlement was a blessing in disguise.
Because of the problems with our insurance company, we decided to switch to a new insurer. We set up to switch when our current policy expired. Ten days into our new policy, our house burnt down in a grass fire fueled by 60+ mph winds. In the main part of the house the only things recognizable were the coal stove and a 3 hour rated gun safe (that now looked like a cheap metal cabinet onto which someone dropped a nuclear bomb). We lost all of our physical possessions, but God had a plan.
The new insurance company sent their insurance adjuster out right away. In one month they had paid for the house, the trees, the barn, and a year’s rent in a nice rental house. We had more than half of the settlement left from the flood (we had bought a few supplies for fixing the house). Exactly one year and one month later, we moved into our paid off dream home (with a very fire resistant exterior). Of course God didn’t finish His blessings and lessons with the fire, there was more to come.
We moved into the rental house. (Ironically I was excited about all of the closet space even though I could fit all of my worldly possessions in a small suitcase. We humans are not always logical and we don’t let go of our physical possessions easily.) A month later, my husband’s car engine blew up. A month after that, my husband ruptured his Achilles tendon, had to go through surgery, and we were unable to travel to see family for Christmas as planned. It seemed like hardship, but the previous hardships had prepared us for this one.
The house that burnt down had all of the bedrooms upstairs, all of the living spaces downstairs, and very steep stairs. When my husband ruptured his other Achilles tendon eight years previously, he had to stay on the couch downstairs and couldn’t sleep in his bed. In our new rental house, the master bedroom was on the same level as the living areas and not more than 10 feet away. He could sleep in bed and then use crutches to move to the electric recliner that had been donated to us after the fire. It gently raised and lowered his injured leg. He could sit with us to eat (we set up a table on one side of the recliner) and be with us when we hung out on the couch (on the other side of him). We could talk while I worked in the kitchen. It was so much nicer to take care of him in the rental house than it would’ve been if the same thing had happened, but our house hadn’t burnt down.
Through this string of “tragedies,” we learned to trust God through every situation. We learned what was important (people not stuff). We got a nice, optimized, paid-off house. We received a story that we could share with others to bless them and help them trust in God. We grew closer together as a family. All four members of my family agree that if given the chance to make all of these “bad” things not happen, we would not choose to remove them. The blessings we received through them outweigh them more than you can imagine.
What About You?
What about you? Are you gong through hard times? We all do at some point in our lives. Are you looking for the good God is doing or are you blaming God for your hardship? Are you working to make the most of whatever situation you are in or are you seeking your own “better”?
My prayer is that God will give you what you need and not what you want and that He will answer your prayers in His best timing. I pray that you will see the wondrous works of God in you and through you and that you will grow in your faith in our very good God. Trust Him! Turn to Him! Rely on Him! God is good, all of the time.
Trust Jesus
-
 @ e373ca41:b82abcc5
2025-02-28 11:04:54
@ e373ca41:b82abcc5
2025-02-28 11:04:54Dieser Artikel wurde mit dem Pareto-Client geschrieben (lesen Sie ihn dort, um die volle Erfahrung zu machen).
Dies ist Teil 3 der Serie “Die Corona-Connection”: Lesen Sie hier Teil 1 und Teil 2.
Wenn die Realität die Fiktion überholt: das ist die Signatur unserer Epoche. Im Zuge täglicher Enthüllungen tritt nun immer deutlicher der medial-industrielle Komplex der “Corona-Connection” zum Vorschein. Allein die Finanzströme zeigen deutlich: der Anfangsverdacht einer Verschwörung ist sichtbar und nachweisbar.
Sie wollen meine (überwiegend englischen) Artikel auch per Email bekommen?
Hier können Sie sich eintragen für den Newsletter (max. 1-2 x pro Woche).
“Follow the Money”
In Washington hat das große Sesselrücken begonnen: Tausende Wohnungen und Häuser werden gerade auf den Markt geschwemmt, die Suchanfragen nach Offshorebanken und Strafverteidigern explodiert. Die Ratten verlassen das sinkende Schiff, eine alte Nomenklatura fällt, eine neue wird errichtet. So ist Politik. Wie viel davon Inszenierung und wie viel echt ist, werden wir erst später erfahren.
(Quelle: X/@wikileaks)
Schon jetzt erfahren die Europäer allerdings von JD Vance, dass in Washington “ein neuer Sheriff in town” ist. Die Rede auf der Münchener Sicherheitskonferenz war eine Zäsur in den transatlantischen Beziehungen. JD Vance hat Europa die Leviten gelesen: Wir glaubten nicht mehr an die Meinungsfreiheit, und damit an die Demokratie; wir griffen in Wahlen ein, deindustrialisierten uns selbst, betrieben ideologische Beeinflussung, Zensur und Manipulation. Eine beeindruckende Rede eines früheren Trump-Verächters (er nannte ihn mal einen Betrüger und überlegte Hillary Clinton zu wählen). Und dann der „Killer-Satz“ an das Establishment:
„Wenn Sie Angst vor den eigenen Bürgern haben gibt es nichts, was die USA für Sie tun können.“
Ja, Vance hat in vielem Recht, Europa ist ein sektiererischer Bürokratenkontinent, der ideologisch gekapert ist. Doch vielleicht hätte Vance etwas mehr darüber sprechen können, was die USA bereits „für Europa getan haben“, allein in den letzten Jahren:
- Der Europäische Debattenraum wurde mit US-Steuergeldern manipuliert, knapp 500 Mio USD. flossen durch die Kanäle von USAID und Co.
- Deindustrialisierung: Danke für die Sprengung von Nordstream, großer Bruder!
- Zensur: waren das nicht auch die großen amerikanische Social Media Plattformen, siehe Twitter-Files?
- Ach überhaupt, der ganze Verschwörungskomplex zu Corona, ist nicht die Corona-Connection im Kern ein Konsortium überwiegend amerikanischer Player? NGOs, öffentliche Gesundheitsbehörden, CIA, Überwachungsindustrie, Big Pharma im Verbund mit China.
- Wer in den letzten Jahren von “Misinformation und Disinformation” sprach, benutzte exakt das USAID-Wording und derartige Beispiele gibt es viele.
ANZEIGE:
Sie suchen nach dem einfachsten Weg, Bitcoin zu kaufen und selbst zu verwahren?****** Die Relai-App ist Europas erfolgreichste Bitcoin-App. Hier kaufen Sie Bitcoin in wenigen Schritten und können auch Sparpläne einrichten. Niemand hat Zugriff auf Ihre Bitcoin, außer Sie selbst. Relai senkt jetzt die Gebühr auf 1%, mit dem Referral-Code MILOSZ sparen Sie weitere 10%. (keine Finanzberatung). Disclaimer wg. EU-Mica-Regulierung: Die Dienste von Relai werden ausschließlich für Einwohner der Schweiz und Italiens empfohlen.

Sprechen wir also zuerst vom Verrat Amerikas an der Welt, in Form der größten Psyop der Welt, sowie dem Biowaffenangriff in Form von Corona und mRNA, an dem amerikanische Behörden maßgeblich beteiligt waren. Die USA (oder der deep state?) sind scheinbar im Kalten Krieg mit der eigenen Bevölkerung und der Welt:
- USAID und NIAID finanzierten Coronavirusforschung in Wuhan, USAID finanzierte massiv die Bill & Melinda Gates Stiftung, Impfprogramme sowie GAVI, CEPI, Programme für “reproductive health” etc. Die Liste der “joint ventures” von Gates und USAID ist lang. Und USAID finanzierte den Propagandaapparat.
- Früher eichte die CIA Schriftsteller im Congress for Culture Freedom, heute finanzieren sie Weiterbildungen und Medientrainings für Tausende Journalisten, auch in Europa. Die Presselandschaft wird wie bei “Operation Mockingbird” einfach weiter unterwandert.
- Reuters bekam 9 Mio. vom US-Verteidigungsministerium und eine köstliche Programm-Beschreibung obendrein: Millionen für social engineering und gesellschaftliche Täuschung, large societal deception (abgekürzt LSD). Ein Wink mit dem Zaunpfahl auf “Mission Mind Control”, also Bewusstseinsexperimente der CIA, u.a. mit LSD?
- Ein paar Tröpfchen LSD dürfen nicht fehlen (rechts unten)
Die Rede vom Verrat an den eigenen Werten in vasallenartigem Gehorsam reiht sich jedenfalls schlecht ein in den noch größeren Verrat der eigenen Werte und eine Form von Hochverrat am Bürger durch amerikanische Behörden. Was genau bleibt also vom Vorwurf von Vance? Ihr habt bei der von uns mitfinanzierten Propagandamaschinerie etwas zu gut mitgemacht. Watch your values!
Die Rede von Vance sei Wahlbeeinflussung, eine Einmischung in „unsere Demokratie“, heißt es nun bei hiesigen Nomenklaturapolitikern. Wahlbeeinflussung durch Vance? Eine schöne Nebelkerze. Die größte Wahlbeeinflussung war doch die mit Milliarden USAID-Geld finanzierte ideologische Unterwanderung des europäischen Debattenraums, von Moldawien und der Ukraine bis Deutschland und Frankreich: Internews Network, Trusted News Initiativen, Factchecker, Kampagnen zu „Misinformation/Disinformation“ uvm. Der europäische Debattenraum wurde auf CIA-Narrativebene geeicht. Die Europäer sind konsterniert: Sie haben mitgemacht und werden jetzt von Vance „unter den Bus geworfen“. Sie stehen als die nützlichen Idioten da, die sie waren. Auch eine Form von Gaslighing: Bestrafung für Gehorsam.
Das Business Modell des Philanthrokapitalismus
Der Verrat der Werte, er zieht sich längst durch alle Ebenen von Bürokratie, Politik, Wirtschaft. Was eröffnet auch bessere Geschäftsmöglichkeiten als Gedankenkontrolle, Beeinflussung, autoritäre Einschüchterungsmethoden, durchgeführt von einem korporativen Machtapparat aus Politik, Polizei, Medien, Big Tech und Pharma?
Unter denen, die wegen USAID am meisten aufheulen, ist Bill Gates. Zu diesem tauchen, welch Wunder, gerade überall Lobesartikel auf, in US-Sendungen wird er wieder als Gesundheitsexperte herumgereicht, warnt vor Millionen Toten, wenn die Hilfen, die in seine Gesundheitsprogramme von USAID flossen, gestoppt werden. Nur am Rande: Gerade gab es einen Ebolaausbruch in Uganda. Die WHO lobt den schnellen Impfstart. Immer diese Zufälle, pandamic preparedness sei Dank, Herr Gates!
USAID und Gates sind ziemlich beste Freunde: Die weltgrößte Privatstiftung von Eugeniker Gates und eine CIA-Frontorganisation in trauter Verbundenheit. Was soll da anderes rauskommen, als die größte Psyop der Welt? Nein, USAID hat nicht in 1.6 Mrd. Dollar in deutsche Medien gesteckt, wie kürzlich per falschem Screenshot auf X verbreitet wurde. Die EU steckte dafür 132 Mio. Euro in journalistische EU-PR. Doch es blieb genug Geld für die Medien übrig, um den Corona-Scam zu glauben, zu verbreiten – und sich boostern zu lassen.
So wird ein Schuh draus: (Netzfund)
Darüber hinaus steckte USAID Milliarden in Gavi und CEPI, die Gatesschen Impfkonsortien mit Sitz in der Schweiz. Sowie in zig andere Programme der Gatesstiftung. Teils floss Geld zurück. Ein Geben und Nehmen. All das wäre für ein James-Bond-Drehbuch zu viel des Guten und Undenkbaren: Wir haben es bei der Corona-Connection mit einer Verschwörung von Geheimdienstkreisen, China und Philanthrokapitalisten zu tun. Deren teils geheimdienstfinanzierten Outlets (GAVI, CEPI), aber auch die WHO genießen in der Schweiz Steuervorteile und Immunität, wie eine Botschaft.
Und so wird ein Business-Modell daraus:
- Man suche sich ein Tätigkeitsfeld, Anliegen oder ein sonstiges Vorhaben der sozialen Ingenieurskunst aus. Bei Gates: Bevölkerungskontrolle und -reduktion, Impfstoffverkauf. 2010-2020 sollte die Dekade der Impfstoffe werden – und wurde es. Gates Gebaren konnte man 2015 in einer kritischen Untersuchung von “Misereor” und “Brot für die Welt” studieren.
- Dann definiere man Strukturen, Mechanismen und Businessmodelle zur Umsetzung. In einer Studie von USAID, BMGF sowie Rockefeller-Stiftung zum Einsatz von KI im Gesundheitsbereich liest man es exemplarisch schwarz auf weiß: “If evidence is promising, define business case – Wenn die Beweise vielversprechend sind, entwickle eine Geschäftsidee.”
 * Es erfolgt ein Investment in die Geschäftsidee. Das nennt sich dann Program-Related Investment, und nicht nur “grant”, wie die New York Times früher noch kritisierte. Hier wird der angebliche Altruismus zum systemischen legalen Interessenkonflikt. Katastrophen zahlen sich jetzt aus.
* WHO, Partnerorganisationen, News-Netzwerke werden auf die Idee geeicht, das übliche PR-Geschäft.
* Dann noch schnell ein Planspiel, in Wuhan ist der USAID-Partner mit der gain of function-Forschung nämlich schon bereit für den Lab-Leak. Investments in Curevac, Biontech & Co. sind bereits getätigt, das politische Feld in Sachen Epidemic Preparedness ohnehin vorgeimpft (und beteiligt, hunderte Millionen gingen von Deutschland an die BMGF und CEPI, Gavi).
* Es erfolgt ein Investment in die Geschäftsidee. Das nennt sich dann Program-Related Investment, und nicht nur “grant”, wie die New York Times früher noch kritisierte. Hier wird der angebliche Altruismus zum systemischen legalen Interessenkonflikt. Katastrophen zahlen sich jetzt aus.
* WHO, Partnerorganisationen, News-Netzwerke werden auf die Idee geeicht, das übliche PR-Geschäft.
* Dann noch schnell ein Planspiel, in Wuhan ist der USAID-Partner mit der gain of function-Forschung nämlich schon bereit für den Lab-Leak. Investments in Curevac, Biontech & Co. sind bereits getätigt, das politische Feld in Sachen Epidemic Preparedness ohnehin vorgeimpft (und beteiligt, hunderte Millionen gingen von Deutschland an die BMGF und CEPI, Gavi).In dieser Phase hängt der Erfolg der Operation nur noch davon ab, wie gut (und wie lange) man es schafft, das Overton-Fenster in den Medien (also das, was relevant ist) mit immer neuen Propaganda-Erzählungen und Angstbildern vollzuhängen, die sozialen Medien zurechtzustutzen und Kritiker zu dezimieren: Fertig ist der größte kriminelle Coup der Geschichte.
Alle Beteiligten gewinnen: Gates vedient an den Impfstoffen, kann das Geld steuerbefreit in der Stiftung für neue Machtgewinnungsfeldzüge einsetzen, die CIA hat ein erfolgreiches Massenhypnose-Experiment durchgeführt und China konnte die Weltwirtschaft hinter sich lassen, intern die Pandemie schnell besiegen und dem Westen seine sehr schnell in Vergessenheit geratenen Bürger- und Menschenrechte vorhalten. Diese Rechte fielen ungefähr so schnell, wie die Menschen in chinesischen Propagandavideos auf der Straße zusammensackten. Nur in China übrigens, nirgendwo anders.
Sie wollen meine (überwiegend englischen) Artikel auch per Email bekommen?
Hier können Sie sich eintragen für den Newsletter (max. 1-2 x pro Woche).
Philanthrokapitalismus bedeutet übersetzt, den Anreiz auszuleben, mit Kontrollphantasien, Social Engineering und Technokratie zugleich Geld zu verdienen, Steuern zu sparen, und Macht zu gewinnen. Ein Honeypot für schwerreiche Psychopathen, die munter nach Gutsherrenart an der Bevölkerung herumschrauben wollen. Der Philanthrokapitalismus eines Gates, Soros & Co ist das gefährlichste korporatistische Räuberbaronentum der Neuzeit. Der Staat kann legal für private Machterreichungszwecke ausgenommen werden – zum Schaden der Bürger.
Es gab bei Corona viele Profiteure. Und viele Opfer. Über beide werden wir in naher Zukunft noch viel mehr erfahren. Die Welle der Aufarbeitung rollt.
Und die Konsequenzen? Ein Bill Gates sollte vielleicht daran denken, nicht erst dann zu flüchten, wenn die Epstein-Files veröffentlicht werden, sondern schon früher. In der amerikanischen Verfassung gibt es nur einen Strafrechtsparagraphen und dieser lautet so:
Artikel III, Abschnitt 3 der US-Verfassung:
„Hochverrat gegen die Vereinigten Staaten besteht ausschließlich darin, Krieg gegen sie zu führen oder ihren Feinden Beistand und Unterstützung zu leisten.“
Die Corona-Impfkampagne hat die Gesundheit der Amerikaner, auch der von Soldaten massiv geschadet, wie akut erhöhte Krankenstände und Nebenwirkungsmeldungen zeigten. Damit wurde Feinden der USA (mindestens jede verfeindete Kriegspartei) Beistand geleistet.
Eines wissen wir schon jetzt: So in etwa ist der “Source Code” des Bösen programmiert.
You prefer reading me in English? You can find my first uncensorable articles written with our Pareto client via Nostr, clicking on this link. Discover other authors at Pareto.space/read.(click on the Pareto button to see our first authors).
Join the marketplace of ideas! We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Sound money and sound information should finally be in the hands of the people, right? Want to learn more about the Pareto Project? Zap me, if you want to contribute (all Zaps go to the project).
Are you a publication or journalist and want to be part of it, test us, migrate your content to Nostr? Write to team@pareto.space**
Not yet on Nostr and want the full experience? Easy onboarding via Start.
We have started a crowdfunding campaign on Geyser. We are in the Top 3 in February, thank you for the support!

Sie wollen meine Artikel auch per Email bekommen?
Hier können Sie sich eintragen für den Newsletter (max. 1-2 x pro Woche).
-
 @ 6ad3e2a3:c90b7740
2025-02-19 14:17:22
@ 6ad3e2a3:c90b7740
2025-02-19 14:17:22Like most members of the human race, I don’t enjoy filing my taxes. “Don’t enjoy” though understates my actual feeling which is “would rather do a tour in Afghanistan.” It’s not even the money I’m forced to pay that I know for sure will be misallocated, stolen or worse — put to use in ways that are anathema to everything I believe and in direct opposition to conditions in which human beings thrive. That’s only part of it.
The other and perhaps bigger part is they require me — under penalty of law — to do homework. They command me, as though they were my boss, to complete this work project, my tax return, and if I don’t I’ll have my property seized, my credit destroyed and even go to prison. This is so even though I am not a criminal, and I never agreed to work for this boss.
And it’s not just a random work project I am required to submit, so that they can misallocate, steal and attack me with my own money. It’s a project that requires me to divulge private details about myself, what transactions I’ve made, with whom I made them and for what purpose. I am a private citizen, I hold no public office or official role, and yet the public sector is not only entitled to comb through the details of my life, but I must be complicit in helping them under penalty of law, i.e., threat of violence if I don’t comply.
. . .
This was not always the case. The income tax was only introduced in 1913, and at the time was only for the richest of the rich. That is to say, it is not the default state of affairs in the United States under its original constitution, and it’s strange that it’s been normalized as such. And despite it being normalized — for the greater good, of course — our government is still somehow $36 trillion in debt.
In other words, despite the annual indignity to which we subject ourselves, the government spends far more money than it takes in. I am reminded of Dostoyevsky’s line: “Your worst sin is that you have destroyed and betrayed yourself for nothing.” The government is spending money it doesn’t have, whether you pay it or not, and the money you do pay, for things you not only do not want but are vehemently against, doesn’t come close to covering their cost.
. . .
I was having lunch with some normies last month, and the subject of taxes came up. They were talking about the ways in which they, as ex-pats, minimize their tax burden, using certain loopholes, and at one point someone questioned why government pensions were taxed, given the entity paying the pension and demanding it be taxed was one and the same. Why not just pay a smaller pension?
One of them asked me, and I said: “I don’t think anyone should be taxed.” She shook her head and muttered in amusement, “No, people need to be taxed.” This despite not two minutes earlier explaining how she was optimizing her tax status, which no doubt she would have optimized all the way to zero or if she were able!
. . .
Taxes are necessary, it’s assumed, to pay for things individuals won’t. “Who will build the roads?” they wonder. I would imagine car makers would be invested in building roads, those who ship goods via truck might have an interest and consumers, flush with their new zero percent tax rate, might pay a little more for the end products to facilitate road creation so those products get to them on time and in good condition. In fact, it might be more expensive to ship them via horseback or whatever alternate form of transport would take the place of motor vehicles should no one shell out for roads.
Moreover, people seem to believe taxes should always be taken not from them, but from those rich enough to afford them painlessly. Never mind anyone reading this substack is vastly wealthy compared to much of the third world (how painful can taxes be so long as you have food on the table and a roof over your head?), and never mind no one ever voluntarily pays more tax than he owes. Why not? If taxation is a good thing, why not do more good by overpaying?
But no, it’s always someone else who needs to be forced under penalty of law, i.e., threat of violence, to give up his property for what those in authority deem “the greater good”. Taken to its logical conclusion, if the authorities deem anyone sufficiently wealthy and the greater good sufficiently necessary, they can legally take that wealth by force. We can quibble about how much funding is necessary and what is the “greater good,” but it’s often essential things like the “safe and effective” vaccine without which millions would surely die or the necessity of invading Iraq, which cost $6 trillion to prevent Sadaam Hussein’s “weapons of mass destruction” from reaching US soil.
It’s amazing authorities so often discover urgent projects without which people will die or suffer terribly, on account of which it’s necessary to commandeer money you’ve earned or saved! And while I am taking about the indignity of filing income tax, I don’t mean to leave out property tax, sales tax, estate tax, individual state and city taxes and the like. At least with some of those you have a fixed amount to pay, and you don’t have to submit to an on-camera self-administered anal cavity search of your finances in those cases.
You’d also think given how many ways citizens are taxed that roads would be in tip top condition, our water and environment would be clean, our airports modern and state of the art, our health care affordable and accessible, but of course none of that is the case. Again per Dostoyevsky — we have betrayed ourselves for nothing.
. . .
The irony of this essay/diatribe is I will file my taxes like the cuck I am over the next week or so. I don’t want to do this, but it’s simply not worth the consequences for non-compliance. And I feel bad about making this compromise — bad about myself because I am doing something I feel is wrong for convenience, the same kind of calculation people made when they injected themselves with experimental mRNA chemicals they didn’t want to keep their jobs or travel. I like to think of myself as resolute and uncompromising, but in this instance I roll over every year. Perhaps that’s part of why I dread it so much.
. . .
I’ll end with a footnote of sorts. In the late spring of 2023, I discovered I was due a significant refund, and I paid my accountants who figured this out $400 to re-file for me. They told me I could expect it to take up to nine months to process, so I largely forgot about it until spring of 2024 when I called but got phone-treed to death and waited until September to brute-force my way to a human in another department to explain the situation. They didn’t tell me anything, but agreed to do a “trace” which a couple weeks later revealed someone else had intercepted and cashed my check. (It’s not direct deposit because I’m overseas.)
I immediately returned the form proving it was not my signature on the deposited check, and now, five months later, in February of 2025, they are still processing my purported payment which I have yet to receive. I did, however, receive a notice of the interest I was “paid” for 2024 on which I’m expected to be taxed. That interest went to the person who stole my original check obviously, they know this, and yet it apparently hasn’t caught up in the system. And the truth is I will probably pay the tax on it as the hassle of explaining why I’m not is simply not worth it, and I will sort it out on next year’s tax return, assuming Trump hasn’t abolished the IRS entirely, God willing, and delivered us, in small part, from this abject dystopia.
-
 @ 9dd283b1:cf9b6beb
2025-02-19 14:03:51
@ 9dd283b1:cf9b6beb
2025-02-19 14:03:51It looks like we will have some extra free days at school during the time of BTC Prague, and I was considering going to Prague for a weekend getaway. I'm wondering if it's worthwhile to visit the event with kids (9 and 3) and whether it makes sense to get the Bitcoin Expo ticket (https://btcprague.com/#).
Has anyone attended this event with kids in previous years? Any insights or experiences would be appreciated!
originally posted at https://stacker.news/items/890517
-
 @ 5afdec5b:2d631be1
2025-02-28 10:23:07
@ 5afdec5b:2d631be1
2025-02-28 10:23:07Bitcoin: The Future of Collateralized Loans
Bitcoin is transforming the financial landscape, not just as a digital currency but arguably as the best form of collateral for unlocking liquidity. At Lendasat, we're pioneering this shift by working towards a trustless, self-custodial lending platform that lets users borrow against their Bitcoin without selling it. Let's explore Bitcoin's unmatched value as collateral and how Lendasat's innovative approach - with Discreet Log Contracts (DLCs) and integrations - make borrowing secure, simple, and practical. Bitcoin unlocks cash access without letting it go.
Why Bitcoin Stands Out as Collateral
Bitcoin's intrinsic properties set it apart from traditional assets like real estate or stocks:
🌐 Decentralized Control: No intermediaries, ensuring transparency and independence.
💧 Ultimate Liquidity: Bitcoin is one of the most liquid assets in the world, tradable 24/7 without interruption. Unlike traditional markets with public holidays, and weekend downtime, Bitcoin operates continuously, allowing transactions at any time from anywhere.
✅ Capped Supply: Only 21 million coins will ever exist, shielding it from dilution/inflation.
🔒 Robust Security: Backed by cryptography and a global mining network, Bitcoin is portable, durable, and verifiable.These qualities make Bitcoin an ideal foundation for lending, a vision Lendasat brings to life. Our app leverages Bitcoin's censorship-resistant nature to offer a collateral option that traditional assets can't rival.
The "Buy, Borrow, Die" Strategy: A Smart Money Move Now Available For Everyone
For those unfamiliar, the "buy, borrow, die" strategy involves buying assets, borrowing against them for liquidity, and holding until death to pass on the assets with a stepped-up basis, minimizing taxes. Savvy investors and businesses often borrow against their holdings rather than sell them. Why? It's a tax-efficient way to access cash while retaining ownership and future gains. With Bitcoin, this approach is even more compelling:
🏷️ Tax Advantage: No capital gains taxes when borrowing instead of selling.
🔒 Ownership Retention: Keep your Bitcoin and its potential upside.
📈 Growth Exposure: Benefit from Bitcoin's long-term appreciation.Lendasat's motto, "Get the bread you need without having to part with your corn" encapsulates this strategy. We empower users to tap into their Bitcoin's value without sacrificing their stake in its future. Bitcoin gives access to practices that were previously reserved to the wealthiest individuals and companies.
ℹ️ Note: Tax benefits may vary depending on your jurisdiction. Please consult with a tax professional.
Lendasat's Vision: Seamless Lending Process
Lendasat, in its public release, will make Bitcoin-backed loans straightforward and secure. Here's how it works:
- Secure Your Bitcoin: Lock your BTC in a Discreet Log Contract (DLC), a "smart contract" that eliminates counterparty risk while keeping you in control
- Borrow Stablecoins: Receive stablecoins at an average 50% loan-to-value ratio (e.g., $50,000 for $100,000 in BTC), balancing liquidity with safety.
- Spend Anywhere: Use our spending tools and off-ramps integrations to spend loan funds effortlessly in the real world, as an example, with a Virtual Card for online shopping - launched in our closed beta.
This peer-to-peer process makes KYC optional, prioritizing privacy and accessibility.
Who Benefits from Lendasat?
Our app serves a wide range of users:
Borrowers:
- Unlock cash without selling Bitcoin.
- Enjoy tax savings and growth potential.
- Spend easily with the virtual debit card.
Lenders:
- Earn guaranteed returns on overcollateralized loans.
- Reduce risk with Bitcoin's security.
- Diversify investments with a cutting-edge asset.Lendasat's self-custodial design ensures both parties retain autonomy, with DLCs handling the heavy lifting.
Real-World Applications
Bitcoin collateral isn't just for individuals - it's a game-changer for businesses:
Businesses: Fund expansion or operations without diluting equity or selling BTC.
Miners: Cover costs like electricity bills by borrowing against mined Bitcoin, avoiding sales at low prices.Lendasat supports these scenarios with flexible solutions, and we're exploring enhancements like on-ramps integration for bank transfer repayments to streamline the experience.
The Future of Bitcoin Collateral
Bitcoin's role as collateral is only beginning. Emerging possibilities include:
Credit Lines: Bitcoin-backed spending options akin to traditional credit.
Institutional Use: Large-scale financing for companies and even governments.While Bitcoin is currently primarily used as a store of value, its potential as a medium of exchange is still developing. Lendasat's platform is designed to adapt to Bitcoin's evolving role in the financial ecosystem, whether it remains a collateral asset or becomes widely used for transactions.
Lendasat is driving this future by refining our platform, focusing on user-friendly on/off ramps and practical spending tools to make Bitcoin loans a financial mainstay.
What Sets Lendasat Apart?
Lendasat isn't just another lending platform - it aims to be the leader in Bitcoin finance:
Trustless System: DLCs ensure security without third-party custody.
Practical Tools: The virtual debit card bridges DeFi and daily life.
User-Centric: Optional KYC, no credit checks, and flexible repayment options in development.
Mission-Driven: We're here to empower financial freedom through Bitcoin.These strengths make Lendasat the premier choice for leveraging Bitcoin as collateral.
Challenges and Considerations
While Bitcoin-backed loans offer many advantages, there are risks to consider:
Volatility: Bitcoin's price can be volatile, which may lead to liquidation if the value drops significantly.
User Experience: Managing DLCs and understanding the lending process may be complex for some users.At Lendasat, we're actively working to mitigate these risks through user education, robust platform design, and ongoing development of user-friendly features.
Conclusion: Bitcoin's Full Potential
Bitcoin isn't just money - It is the best collateral in the making ever discovered, blending security, liquidity, and growth. Lendasat brings this power to your fingertips with a platform that's secure, intuitive, and built for the future. Whether you're funding a dream or growing a business, we've got you covered.
Ready to borrow without selling? Dive into https://Lendasat.com and see how your Bitcoin can work harder for you.
Quick Comparison: Traditional vs. Lendasat's Bitcoin Collateral
This snapshot underscores why Bitcoin, paired with Lendasat, is rewriting the rules of collateral.
Help Us To Achieve Our Vision!
Want to be part of the journey?
Join our waiting list or, even better, connect with us on Discord to get yourself an invite code and try our app and share your thoughts!
Stay tuned, and as always, stay sovereign. -
 @ 97c70a44:ad98e322
2025-02-18 20:30:32
@ 97c70a44:ad98e322
2025-02-18 20:30:32For the last couple of weeks, I've been dealing with the fallout of upgrading a web application to Svelte 5. Complaints about framework churn and migration annoyances aside, I've run into some interesting issues with the migration. So far, I haven't seen many other people register the same issues, so I thought it might be constructive for me to articulate them myself.
I'll try not to complain too much in this post, since I'm grateful for the many years of Svelte 3/4 I've enjoyed. But I don't think I'll be choosing Svelte for any new projects going forward. I hope my reflections here will be useful to others as well.
If you're interested in reproductions for the issues I mention here, you can find them below.
The Need for Speed
To start with, let me just quickly acknowledge what the Svelte team is trying to do. It seems like most of the substantial changes in version 5 are built around "deep reactivity", which allows for more granular reactivity, leading to better performance. Performance is good, and the Svelte team has always excelled at reconciling performance with DX.
In previous versions of Svelte, the main way this was achieved was with the Svelte compiler. There were many ancillary techniques involved in improving performance, but having a framework compile step gave the Svelte team a lot of leeway for rearranging things under the hood without making developers learn new concepts. This is what made Svelte so original in the beginning.
At the same time, it resulted in an even more opaque framework than usual, making it harder for developers to debug more complex issues. To make matters worse, the compiler had bugs, resulting in errors which could only be fixed by blindly refactoring the problem component. This happened to me personally at least half a dozen times, and is what ultimately pushed me to migrate to Svelte 5.
Nevertheless, I always felt it was an acceptable trade-off for speed and productivity. Sure, sometimes I had to delete my project and port it to a fresh repository every so often, but the framework was truly a pleasure to use.
Svelte is not Javascript
Svelte 5 doubled down on this tradeoff — which makes sense, because it's what sets the framework apart. The difference this time is that the abstraction/performance tradeoff did not stay in compiler land, but intruded into runtime in two important ways:
- The use of proxies to support deep reactivity
- Implicit component lifecycle state
Both of these changes improved performance and made the API for developers look slicker. What's not to like? Unfortunately, both of these features are classic examples of a leaky abstraction, and ultimately make things more complex for developers, not less.
Proxies are not objects
The use of proxies seems to have allowed the Svelte team to squeeze a little more performance out of the framework, without asking developers to do any extra work. Threading state through multiple levels of components without provoking unnecessary re-renders in frameworks like React is an infamously difficult chore.
Svelte's compiler avoided some of the pitfalls associated with virtual DOM diffing solutions, but evidently there was still enough of a performance gain to be had to justify the introduction of proxies. The Svelte team also seems to argue that their introduction represents an improvement in developer experience:
we... can maximise both efficiency and ergonomics.
Here's the problem: Svelte 5 looks simpler, but actually introduces more abstractions.
Using proxies to monitor array methods (for example) is appealing because it allows developers to forget all the goofy heuristics involved with making sure state was reactive and just
pushto the array. I can't count how many times I've writtenvalue = valueto trigger reactivity in svelte 4.In Svelte 4, developers had to understand how the Svelte compiler worked. The compiler, being a leaky abstraction, forced its users to know that assignment was how you signaled reactivity. In svelte 5, developers can just "forget" about the compiler!
Except they can't. All the introduction of new abstractions really accomplishes is the introduction of more complex heuristics that developers have to keep in their heads in order to get the compiler to act the way they want it to.
In fact, this is why after years of using Svelte, I found myself using Svelte stores more and more often, and reactive declarations less. The reason being that Svelte stores are just javascript. Calling
updateon a store is simple, and being able to reference them with a$was just a nice bonus — nothing to remember, and if I mess up the compiler yells at me.Proxies introduce a similar problem to reactive declarations, which is that they look like one thing but act like another on the edges.
When I started using Svelte 5, everything worked great — until I tried to save a proxy to indexeddb, at which point I got a
DataCloneError. To make matters worse, it's impossible to reliably tell if something is aProxywithouttry/catching a structured clone, which is a performance-intensive operation.This forces the developer to remember what is and what isn't a Proxy, calling
$state.snapshotevery time they pass a proxy to a context that doesn't expect or know about them. This obviates all the nice abstractions they gave us in the first place.Components are not functions
The reason virtual DOM took off way back in 2013 was the ability to model your application as composed functions, each of which takes data and spits out HTML. Svelte retained this paradigm, using a compiler to sidestep the inefficiencies of virtual DOM and the complexities of lifecycle methods.
In Svelte 5, component lifecycles are back, react-hooks style.
In React, hooks are an abstraction that allows developers to avoid writing all the stateful code associated with component lifecycle methods. Modern React tutorials universally recommend using hooks instead, which rely on the framework invisibly synchronizing state with the render tree.
While this does result in cleaner code, it also requires developers to tread carefully to avoid breaking the assumptions surrounding hooks. Just try accessing state in a
setTimeoutand you'll see what I mean.Svelte 4 had a few gotchas like this — for example, async code that interacts with a component's DOM elements has to keep track of whether the component is unmounted. This is pretty similar to the kind of pattern you'd see in old React components that relied on lifecycle methods.
It seems to me that Svelte 5 has gone the React 16 route by adding implicit state related to component lifecycles in order to coordinate state changes and effects.
For example, here is an excerpt from the documentation for $effect:
You can place $effect anywhere, not just at the top level of a component, as long as it is called during component initialization (or while a parent effect is active). It is then tied to the lifecycle of the component (or parent effect) and will therefore destroy itself when the component unmounts (or the parent effect is destroyed).
That's very complex! In order to use
$effect... effectively (sorry), developers have to understand how state changes are tracked. The documentation for component lifecycles claims:In Svelte 5, the component lifecycle consists of only two parts: Its creation and its destruction. Everything in-between — when certain state is updated — is not related to the component as a whole; only the parts that need to react to the state change are notified. This is because under the hood the smallest unit of change is actually not a component, it’s the (render) effects that the component sets up upon component initialization. Consequently, there’s no such thing as a “before update”/"after update” hook.
But then goes on to introduce the idea of
tickin conjunction with$effect.pre. This section explains that "tickreturns a promise that resolves once any pending state changes have been applied, or in the next microtask if there are none."I'm sure there's some mental model that justifies this, but I don't think the claim that a component's lifecycle is only comprised of mount/unmount is really helpful when an addendum about state changes has to come right afterward.
The place where this really bit me, and which is the motivation for this blog post, is when state gets coupled to a component's lifecycle, even when the state is passed to another function that doesn't know anything about svelte.
In my application, I manage modal dialogs by storing the component I want to render alongside its props in a store and rendering it in the
layout.svelteof my application. This store is also synchronized with browser history so that the back button works to close them. Sometimes, it's useful to pass a callback to one of these modals, binding caller-specific functionality to the child component:javascript const {value} = $props() const callback = () => console.log(value) const openModal = () => pushModal(MyModal, {callback})This is a fundamental pattern in javascript. Passing a callback is just one of those things you do.
Unfortunately, if the above code lives in a modal dialog itself, the caller component gets unmounted before the callback gets called. In Svelte 4, this worked fine, but in Svelte 5
valuegets updated toundefinedwhen the component gets unmounted. Here's a minimal reproduction.This is only one example, but it seems clear to me that any prop that is closed over by a callback function that lives longer than its component will be undefined when I want to use it — with no reassignment existing in lexical scope. It seems that the reason this happens is that the props "belong" to the parent component, and are accessed via getters so that the parent can revoke access when it unmounts.
I don't know why this is necessary, but I assume there's a good engineering reason for it. The problem is, this just isn't how javascript works. Svelte is essentially attempting to re-invent garbage collection around component lifecycles, which breaks the assumption every javascript developer has that variables don't simply disappear without an explicit reassignment. It should be safe to pass stuff around and let the garbage collector do its job.
Conclusion
Easy things are nice, but as Rich Hickey says, easy things are not always simple. And like Joel Spolsky, I don't like being surprised. Svelte has always been full of magic, but with the latest release I think the cognitive overhead of reciting incantations has finally outweighed the power it confers.
My point in this post is not to dunk on the Svelte team. I know lots of people like Svelte 5 (and react hooks). The point I'm trying to make is that there is a tradeoff between doing things on the user's behalf, and giving the user agency. Good software is built on understanding, not cleverness.
I also think this is an important lesson to remember as AI-assisted coding becomes increasingly popular. Don't choose tools that alienate you from your work. Choose tools that leverage the wisdom you've already accumulated, and which help you to cultivate a deeper understanding of the discipline.
Thank you to Rich Harris and team for many years of pleasant development. I hope that (if you read this) it's not so full of inaccuracies as to be unhelpful as user feedback.
-
 @ 95cb4330:96db706c
2025-02-28 10:13:16
@ 95cb4330:96db706c
2025-02-28 10:13:16Adopting Inversion Thinking, a mental model championed by Charlie Munger and Warren Buffett, can enhance decision-making and problem-solving by focusing on potential pitfalls to avoid. This approach involves considering the opposite of your desired outcome to identify and mitigate risks effectively.
Understanding Inversion Thinking
- Definition:
Inversion Thinking entails approaching problems by asking, "What could cause failure?" rather than solely focusing on achieving success. This perspective helps in uncovering obstacles and errors that might be overlooked when only considering positive outcomes.
Examples in Practice
-
Charlie Munger's Approach:
Munger emphasizes solving problems by inverting them. For instance, instead of asking how to be successful, he suggests identifying what actions could lead to failure and then avoiding those actions.
FS.BLOG -
Warren Buffett's Investment Strategy:
Buffett applies inversion by considering what factors could cause an investment to fail, such as poor management or unsustainable business models, and avoids investments with these red flags.
Implementing Inversion Thinking
-
Define the Problem:
Clearly articulate the challenge or goal you are addressing. -
Invert the Problem:
Ask what actions or factors could lead to the opposite of your desired outcome. -
Identify Preventative Measures:
Determine strategies to avoid these negative actions or factors. -
Apply Insights to Decision-Making:
Use the information gathered to inform your choices, focusing on avoiding identified pitfalls.
Action Step
Consider a current goal or project. Apply inversion by asking, "What steps could lead to failure in this endeavor?" List these potential pitfalls and develop strategies to prevent them, thereby increasing the likelihood of success.
By integrating Inversion Thinking into your decision-making process, you can proactively address potential challenges, leading to more robust and resilient strategies.
- Definition:
-
 @ 95cb4330:96db706c
2025-02-28 09:22:17
@ 95cb4330:96db706c
2025-02-28 09:22:17Jeff Bezos, Sam Altman, and Elon Musk follow a critical decision-making principle: never let past investments dictate future choices. Instead of holding onto failing projects due to time, money, or effort already spent, successful entrepreneurs cut losses quickly and reallocate resources toward higher-impact opportunities.
Why Avoiding Sunk Costs Matters
-
Frees Up Resources for Better Opportunities:
The more time you spend on a failing project, the fewer resources you have to invest in something that could succeed. -
Prevents Emotional Bias in Decision-Making:
Many people stick with bad decisions because they feel committed, rather than assessing future potential objectively. -
Increases Agility & Competitive Edge:
Being able to pivot quickly allows you to adapt to market changes faster than competitors.
Example in Action: Bezos, Musk & Altman
-
Jeff Bezos & the Fire Phone:
Amazon heavily invested in its Fire Phone, but when it failed, Bezos shut it down and redirected efforts to Alexa and AWS, which became massive successes. -
Elon Musk & Tesla Model S Plaid+:
Tesla had planned a Model S Plaid+ variant, but Musk canceled it, realizing it no longer made strategic sense in Tesla’s long-term roadmap. -
Sam Altman & Startup Strategy:
Altman constantly advises founders to evaluate if they’re on the best path—not just the one they’ve already invested in. He encourages entrepreneurs to pivot fast rather than waste time on failing ideas.
How to Apply This Principle
-
Identify Projects You’re Holding Onto for the Wrong Reasons
Ask: Would I start this today knowing what I now know? -
Focus on Future Potential, Not Past Investment
Look at the expected future return rather than the money or effort already spent. -
Be Willing to Pivot or Cut Losses Quickly
If a project no longer aligns with your long-term vision, redirect resources elsewhere.
Action Step: Audit Your Current Projects
- 👉 Are you continuing something just because of past investment rather than future potential?
- 👉 If so, consider pivoting or cutting it today.
By avoiding the sunk cost fallacy, you can stay flexible, maximize impact, and ensure you’re always focused on the best opportunities ahead.
-
-
 @ 8947a945:9bfcf626
2025-02-28 09:11:21
@ 8947a945:9bfcf626
2025-02-28 09:11:21Chef's notes
https://video.nostr.build/ea19333ab7f700a6557b6f52f1f8cfe214671444687fa7ea56a18e5d751fe0a9.mp4
https://video.nostr.build/bcae8d39e22f66689d51f34e44ecabdf7a57b5099cc456e3e0f29446b1dfd0de.mp4
Details
- ⏲️ Prep time: 5 min
- 🍳 Cook time: 5 min
- 🍽️ Servings: 1
Ingredients
- ไข่ 1 - 2 ฟอง
- ข้าวโอ๊ต 3 - 4 ช้อน
Directions
- ตอกไข่ + ตีไข่
- ปรุงรส พริกไทย หรือ ซอสถั่วเหลืองตามชอบ
- ใส่ข้าวโอ๊ต 3 - 4 ช้อน
- ใส่ถั่วลิสงอบ 1 - 2 หยิบมือ
- เทน้ำใส่พอท่วมข้าวโอ๊ต
- เข้าไมโครเวฟ ไฟแรง 1 - 2 นาที
-
 @ 6ad3e2a3:c90b7740
2025-02-18 17:08:23
@ 6ad3e2a3:c90b7740
2025-02-18 17:08:23I’m not doing any writing today. Taking the day, maybe the week, off. Just not in the mood.
This whole idea you’re supposed to write, get the thoughts out, the ideas moving is stupid. To what end? I’m done with evaluating myself for productivity, justifying myself to myself — or anyone else.
What I really need is to find some pleasant distractions. Something to fill my time, or as Elon Musk says of Twitter “to avoid regretted user seconds.” I’ve tried Twitter itself, of course, but Musk’s algorithm falls woefully short. After an hour of doom and dopamine scrolling, punctuated with the occasional shitpost, many seconds are regretted — roughly 3500 of them.
I could turn to alcohol or drugs, but too many side effects. Yes, you’re distracted, but what about after that? You’re always left worse off than where you started. Even alcoholics and drug addicts — the pros! — know it’s a dead end.
I don’t know, maybe spend more time with loved ones? You hear that a lot. “If I didn’t have to work so much, I’d spend more time with loved ones.” LOL. Like what, you’re going to hang around while your “loved ones” are doing things with their actual lives. Maybe I’ll take the bus to school with Sasha, hang out with her and her friends, see how that goes. Quality time!
Exercise. It’s the perfect solution, good for your health, you feel better, your mind is calm. Only problem is it’s fucking miserable. If your aim is to avoid sitting at a desk to write, forcing your carcass around a track is hardly an upgrade. It’s like quitting your middle management job to break rocks in a prison chain gang.
There must be something I can do. Eating sugary processed food is out of the question for the same reason alcohol and drugs are. Becoming obese and diabetic is no solution, as many of the pros (obese diabetics) would no doubt attest.
Meditation. That’s it! You sit on a cushion, count your breaths. Pretty soon you are calm. You can meditate for as long as you want! It’s perfect, and it’s easy. Well, it’s not that easy. You get distracted by your thoughts and you’re just sitting there thinking about the things for which you hope and dread in your life.
Of course, you notice that distraction and come back to the breath, but pretty soon you’re wandering again. And you come back again. But really you’re wondering how long you’ve been sitting, your feet are falling asleep, your back is tight and you don’t feel much different. You weren’t even properly distracted because instead of being distracted from your mind, you are being distracted by it. It’s a worst-case scenario of sorts — you neither get anything done, nor escape the endless self-evaluation and justification.
That just means you’re doing it wrong, though. You’re failing at it. If you did it right, it would be the perfect escape from yourself. But it’s not working, so you’re failing. Or maybe you succeeded a little bit. You’re not sure. You are still evaluating whether that was a good use of your time. The same evaluation process you use to decide whether you’ve done enough writing, the same tired bullshit from which you were trying to escape in the first place!
Let’s face it, you’re not just going to meditate your way out of the problem. If you could, you would have already, and so would everyone else. We would all be enlightened. Maybe you need to go to an ashram or something, find a guru on top of a mountain in the Himalayas. LOL, you’re not gonna do that! You are way too attached to your comforts and daily routines, no matter how dull and unsatisfying they ultimately are.
There’s nowhere to run, nowhere to hide, no one to see, nothing to do. You are out of options. There is only one thing in your absolute control, and it’s where you direct your attention. And you have decided that no matter how bleak and pointless the alternatives the one thing about which you are resolute is you are taking the day off from writing.
-
 @ 5d4b6c8d:8a1c1ee3
2025-02-17 14:39:25
@ 5d4b6c8d:8a1c1ee3
2025-02-17 14:39:25A new best yesterday: 22 hours! Today's shaping up to be another solid fast, too, as I'm already at 19 hours (18 dry).
My body's really getting accustomed to the new eating pattern, too.
Score Card
Day 1: 14 hour fast (13 dry) Day 2: 15 hour fast (14 dry) Day 3: 17 hours (16 dry) Day 4: 18 hours (17 dry) Day 5: 18 hours (16 dry) Day 6: 19 hours (16 dry) Day 7: 16 hours (15 dry) Day 8: 18 hours (17 dry) Day 9: 17 hours (17 dry) Day 10: 15 hours (13 dry) Day 11: 20 hours (19 dry) Day 12: 20 hours (17 dry) Day 13: 16 hours (13 dry) Day 14: 17 hours (15 dry) Day 15: 19 hours (16 dry) Day 16: 22 hours (19 dry) Day 17: TBD (18 dry)
originally posted at https://stacker.news/items/888397
-
 @ da0b9bc3:4e30a4a9
2025-02-28 08:39:58
@ da0b9bc3:4e30a4a9
2025-02-28 08:39:58Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/899482
-
 @ 97c70a44:ad98e322
2025-02-17 14:29:00
@ 97c70a44:ad98e322
2025-02-17 14:29:00Everyone knows that relays are central to how nostr works - they're even in the name: Notes and Other Stuff Transmitted by Relays. As time goes on though, there are three other letters which are becoming conspicuously absent from our beloved and ambiguously pronounceable acronym - "D", "V", and "M".
For the uninitiated, DVM stands for "data vending machines". They're actually sort of hard to describe — in technical terms they act more like clients, since they simply read events from and publish events to relays. In most cases though, these events are part of a request/response flow initiated by users elsewhere on the network. In practice, DVMs are bots, but there's also nothing to prevent the work they do from being powered by human interaction. They're an amazingly flexible tool for building anything from custom feeds, to transcription services, to chatbots, to protocol gateways.
The hype cycle for DVMs seems to have reached escape velocity in a way few other things have - zaps being the possible exception. But what exactly DVMs are remains something of a mystery to many nostr developers - and how to build one may as well be written on clay tablets.
This blog post is designed to address that - below is a soup to nuts (no nutzaps though) guide to building a DVM flow, both from the client and the server side.
Here's what we'll be covering:
- Discovering DVM metadata
- Basic request/response flow
- Implementing a minimal example
Let's get started!
DVM Metadata
First of all, it's helpful to know how DVMs are reified on the nostr network. While not strictly necessary, this can be useful for discovering DVMs and presenting them to users, and for targeting specific DVMs we want a response from.
NIP 89 goes into this in more detail, but the basic idea is that anyone can create a
kind 31990"application handler" event and publish it to the network with their own (or a dedicated) public key. This handler was originally intended to advertise clients, but has been re-purposed for DVM listings as well.Here's what the "Fluffy Frens" handler looks like:
json { "content": "{\"name\": \"Fluffy Frens\", \"picture\": \"https://image.nostr.build/f609311532c470f663e129510a76c9a1912ae9bc4aaaf058e5ba21cfb512c88e.jpg\", \"about\": \"I show recent notes about animals\", \"lud16\": \"discovery_content_fluffy@nostrdvm.com\", \"supportsEncryption\": true, \"acceptsNutZaps\": false, \"personalized\": false, \"amount\": \"free\", \"nip90Params\": {\"max_results\": {\"required\": false, \"values\": [], \"description\": \"The number of maximum results to return (default currently 100)\"}}}", "created_at": 1738874694, "id": "0aa8d1f19cfe17e00ce55ca86fea487c83be39a1813601f56f869abdfa776b3c", "kind": 31990, "pubkey": "7b7373dd58554ff4c0d28b401b9eae114bd92e30d872ae843b9a217375d66f9d", "sig": "22403a7996147da607cf215994ab3b893176e5302a44a245e9c0d91214e4c56fae40d2239dce58ea724114591e8f95caed2ba1a231d09a6cd06c9f0980e1abd5", "tags": [ ["k", "5300"], ["d", "198650843898570c"] ] }This event is rendered in various clients using the kind-0-style metadata contained in the
contentfield, allowing users to browse DVMs and pick one for their use case. If a user likes using a particular DVM, they might publish akind 31989"application recommendation", which other users can use to find DVMs that are in use within their network.Note the
ktag in the handler event - this allows DVMs to advertise support only for specific job types. It's also important to note that even though the spec doesn't cover relay selection, most clients use the publisher'skind 10002event to find out where the DVM listens for events.If this looks messy to you, you're right. See this PR for a proposal to split DVMs out into their own handler kind, give them a dedicated pubkey along with dedicated metadata and relay selections, and clean up the data model a bit.
DVM Flow
Now that we know what a DVM looks like, we can start to address how they work. My explanation below will elide some of the detail involved in NIP 90 for simplicity, so I encourage you to read the complete spec.
The basic DVM flow can be a little (very) confusing to work with, because in essence it's a request/response paradigm, but it has some additional wrinkles.
First of all, the broker for the request isn't abstracted away as is usually the case with request/response flows. Regular HTTP requests involve all kinds of work in the background - from resolving domain names to traversing routers, VPNs, and ISP infrastructure. But developers don't generally have to care about all these intermediaries.
With DVMs, on the other hand, the essential complexity of relay selection can't simply be ignored. DVMs often advertise their own relay selections, which should be used rather than a hard-coded or randomly chosen relay to ensure messages are delivered. The benefit of this is that DVMs can avoid censorship, just as users can, by choosing relays that are willing to broker their activity. DVMs can even select multiple relays to broker requests, which means that clients might receive multiple copies of the same response.
Secondly, the DVM request/response model is far more fluid than is usually the case with request/response flows. There are a set of standard practices, but the flow is flexible enough to admit exceptions to these conventions for special use cases. Here are some examples:
- Normally, clients p-tag the DVM they wish to address. But if a client isn't picky about where a response comes from, they may choose to send an open request to the network and collect responses from multiple DVMs simultaneously.
- Normally, a client creates a request before collecting responses using a subscription with an e-tag filter matching the request event. But clients may choose to skip the request step entirely and collect responses from the network that have already been created. This can be useful for computationally intensive tasks or common queries, where a single result can be re-used multiple times.
- Sometimes, a DVM may respond with a
kind 7000job status event to let clients know they're working on the request. This is particularly useful for longer-running tasks, where feedback is useful for building a responsive UX. - There are also some details in the spec regarding monetization, parameterization, error codes, encryption, etc.
Example DVM implementation
For the purposes of this blog post, I'll keep things simple by illustrating the most common kind of DVM flow: a
kind 5300content discovery request, addressed to a particular DVM. If you're interested in other use cases, please visit data-vending-machines.org for additional documented kinds.The basic flow looks like this:
- The DVM starts by listening for
kind 5300job requests on some relays it has selected and advertised via NIP 89 (more on that later) - A client creates a request event of
kind 5300, p-tagged with the DVM's pubkey and sends it to the DVM's relay selections. - The DVM receives the event and processes it, issuing optional
kind 7000job status events, and eventually issuing akind 6300job result event (job result event kinds are always 1000 greater than the request's kind). - The client listens to the same relays for a response, and when it comes through does whatever it wants to with it.
Here's a swimlane diagram of that flow:

To avoid massive code samples, I'm going to implement our DVM entirely using nak (backed by the power of the human mind).
The first step is to start our DVM listening for requests that it wants to respond to. Nak's default pubkey is
79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798, so we'll only listen for requests sent to nak.bash nak req -k 5300 -t p=79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798This gives us the following filter:
json ["REQ","nak",{"kinds":[5300],"#p":["79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798"]}]To open a subscription to
nos.loland stream job requests, add--stream wss://nos.lolto the previous request and leave it running.Next, open a new terminal window for our "client" and create a job request. In this case, there's nothing we need to provide as
input, but we'll include it just for illustration. It's also good practice to include anexpirationtag so we're not asking relays to keep our ephemeral requests forever.bash nak event -k 5300 -t p=79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798 -t expiration=$(( $(date +%s) + 30 )) -t input=helloHere's what comes out:
json { "kind": 5300, "id": "0e419d0b3c5d29f86d2132a38ca29cdfb81a246e1a649cb2fe1b9ed6144ebe30", "pubkey": "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798", "created_at": 1739407684, "tags": [ ["p", "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798"], ["expiration", "1739407683"], ["input", "hello"] ], "content": "", "sig": "560807548a75779a7a68c0ea73c6f097583e2807f4bb286c39931e99a4e377c0a64af664fa90f43e01ddd1de2e9405acd4e268f1bf3bc66f0ed5a866ea093966" }Now go ahead and publish this event by adding
nos.lolto the end of yournakcommand. If all goes well, you should see your event pop up in your "dvm" subscription. If so, great! That's half of the flow.Next, we'll want our client to start listening for
kind 6300responses to the request. In your "client" terminal window, run:bash nak req -k 6300 -t e=<your-eventid-here> --stream nos.lolNote that if you only want to accept responses from the specified DVM (a good policy in general to avoid spam) you would include a
ptag here. I've omitted it for brevity. Also notice thektag specifies the request kind plus1000- this is just a convention for what kinds requests and responses use.Now, according to data-vending-machines.org,
kind 5300responses are supposed to put a JSON-encoded list of e-tags in thecontentfield of the response. Weird, but ok. Stop the subscription in your "dvm" terminal and respond to your "client" with a recommendation to read my first note:bash nak event -k 6300 -t e=a65665a3a4ca2c0d7b7582f4f0d073cd1c83741c25a07e98d49a43e46d258caf -c '[["e","214f5898a7b75b7f95d9e990b706758ea525fe86db54c1a28a0f418c357f9b08","wss://nos.lol/"]]' nos.lolHere's the response event we're sending:
json { "kind": 6300, "id": "bb5f38920cbca15d3c79021f7d0051e82337254a84c56e0f4182578e4025232e", "pubkey": "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798", "created_at": 1739408411, "tags": [ ["e", "a65665a3a4ca2c0d7b7582f4f0d073cd1c83741c25a07e98d49a43e46d258caf"] ], "content": "[[\"e\",\"214f5898a7b75b7f95d9e990b706758ea525fe86db54c1a28a0f418c357f9b08\",\"wss://nos.lol/\"]]", "sig": "a0fe2c3419c5c54cf2a6d9a2a5726b2a5b766d3c9e55d55568140979354003aacb038e90bdead43becf5956faa54e3b60ff18c0ea4d8e7dfdf0c8dd97fb24ff9" }Notice the
etag targets our original request.This should result in the job result event showing up in our "client" terminal. Success!
If something isn't working, I've also create a video of the full process with some commentary which you can find here.
Note that in practice, DVMs can be much more picky about the requests they will respond to, due to implementations failing to follow Postel's law. Hopefully that will improve over time. For now, here are a few resources that are useful when working with or developing DVMs:
Conclusion
I started this post by hinting that DVMs might be as fundamental as relays are to making nostr work. But (apart from the fact that we'd end up with an acronym like DVMNOSTRZ+*, which would only exascerbate the pronounciation wars (if such a thing were possible)), that's not exactly true.
DVMs have emerged as a central paradigm in the nostr world because they're a generalization of a design pattern unique to nostr's architecture - but which exists in many other places, including NIP 46 signer flows and NIP 47 wallet connect. Each of these sub-protocols works by using relays as neutral brokers for requests in order to avoid coupling services to web addresses.
This approach has all kinds of neat benefits, not least of which is allowing service providers to host their software without having to accept incoming TCP connections. But it's really an emergent property of relays, which not only are useful for brokering communication between users (aka storing events), but also brokering communication between machines.
The possibilities of this architecture have only started to emerge, so be on the lookout for new applications, and don't be afraid to experiment - just please, don't serialize json inside json 🤦♂️
-
 @ e88a691e:27850411
2025-02-17 13:30:42
@ e88a691e:27850411
2025-02-17 13:30:42test post longform 4
-
 @ dbe0605a:f8fd5b2c
2025-02-17 06:42:38
@ dbe0605a:f8fd5b2c
2025-02-17 06:42:38Originally posted on Nostr: https://highlighter.com/a/naddr1qvzqqqr4gupzpklqvpdfcuch9wkh2gary7erd4275jmrf6qw0z5sz0dhj8u06kevqyvhwumn8ghj7urjv4kkjatd9ec8y6tdv9kzumn9wshszxrhwden5te0ve5kcar9wghxummnw3ezuamfdejj7qgwwaehxw309ahx7uewd3hkctcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszythwden5te0dehhxarj9emkjmn99uqzqjn0d9hz6argv5k57ur9dck5y6t5vdhkjm3df4shqtt5xduxz6tsrdmw7l
I care deeply about bitcoin adoption and ability to use bitcoin with all features of money — saving, spending, earning. We're entering an age where more and more people realise "hodl never spend" meme is hindering bitcoin adoption. More and more of use want to use bitcoin in everyday life, because we're living on it and because it's superior in every aspect. It's also incredibly fun to use it for payments.
For money to thrive, it needs to circulate. Spending bitcoin orangepills merchants, their families and people around them — with each bitcoiner coming to a shop and paying with bitcoin, it's a point of contact that can trigger a train of though that later may fruit into action — "Why are they so interested in bitcoin, what's actually so special about it?" "Hmm, maybe this time I will not exchange it for fiat immediately?"
Global merchant adoption grows, every day new business around the world decide to start accepting bitcoin payments. Circular economies are blooming on all continents, where people live in a new, experimental, orange coin paradigm. Companies and projects like Blink, Bitcoin Jungle, Plan B, Orange Pill App do an amazing job in facilitating this — providing great wallets, tools & services for merchants, and finally onboarding merchants themself. They also often support circular economies financially or in other ways. This is very valuable and makes the road to hyperbitcoinization a tad shorter.
But there is one thing those companies are doing wrong — they're using their own, proprietary maps that display only merchants using their own wallets or POS software. I'd like to now list a few reasons why those great projects should migrate their maps into an open source, bitcoin map that is BTC Map.
Open source, stupid
BTCmap is open source, built on OpenStreetMaps, open to both developers contributions but also for map taggers (called shadowy supertaggers). Anyone can contribute, even If you don't code. Anyone can verify merchants or add new merchants to the map. BTC Map team developed a neat system of verifications that just works better than anything before or any alternative maps today.
Many apps, one map
BTC Map is integrated inside a dozen of wallets and apps, to name a few: Wallet of Satoshi, Coinos, Bitlocal, Fedi or Aqua. It's a public good that any bitcoin product can use and grow it's network effect.
Uniting mappers' work
BTC Map does not discriminate bitcoin merchants, that means all the merchants from proprietary maps are being mapped by taggers to BTC Map. By mapping on a closed source, proprietary map, the same merchant is mapped two times, usually by two different people — it's duplicating the same work without any bringing any benefit to both projects. Using BTC Map also brings you way more people verifying If those merchants actually still accept bitcoin, making it easier to have an up-to-date database of actual adoption.
More bitcoin spent at your merchants
When you have a business focused on spending bitcoin and onboarding merchants, you want as much bitcoin spent there as possible. If a bitcoiner coming to the area does not use your own map but some other map, they can be completely unaware that they can let their sats flow to your merchants. If we all use one merchants database, this problem disappears and more sats will flow. Why wouldn't you want your merchants displayed in dozens of other apps, completely for free?
OpenStreetMap map is just better
Take a look at the image above: It's La Pirraya, a small sleepy island town in El Salvador with a circular economy being facilitated by Bitcoin Beach. Even though Blink has many more merchants compared to BTC Map, when I visited it a few months ago I could find them. Not because they do not exist, but because the map does not show any roads and it was very hard to locate them in a dense network of narrow streets of La Pirraya. BTC Map allows you to turn multiple versions of satellite maps views, making it way easier to find your point of interest. Pins also indicate what kind of business it is, where in Blink all the pins are the same and you need to click each to find out what it is. Even then not always it's clear, since Blink only displays names, while BTC Map tells you type of the merchant, and very often shows you working hours, phone numbers, website, social links, etc.
Excellent community tools
BTC Map is focusing providing tools for communities to maintain their merchants map. Each community has it's own page with own links to community website or socials, displays a list of all the merchants, shows community stats, displays merchants that were not verified for a long time, and more. It even allows to "boost" merchants to make them more visible on the map and on the list. It's perfect tooling both for communities and businesses onboarding merchants to their software.
Easy integration & configuration
Integrating BTC Map on your website or app is easy. It's just a few lines of code of iframe to embed the map, but you can also use BTC Map API for more custom integration. Do you to display, eg. you can display only merchants from your community? No problem, you can do that. Since it's all open source, you can configure it in many ways that will suit your needs.
Kudos
I'd like to thank projects that understood all above and integrated BTC Map already. Those are Coinos, Wallet of Satoshi, Pouch, Bolt Card, BitLocal, Fedi, Decouvre Bitcoin, Osmo, Bitcoin Rocks!, Lipa, Spirit of Satoshi, Blockstream, Satlantis, Aqua Wallet and Adopting Bitcoin
Encouragement & an offer
I'll end that with encouragement to projects that use their own maps, but haven't embraced BTC Map yet. Those are Blink, Bitcoin Jungle, Plan B, Osmo, Athena, Orange Pill App, Inbitcoin (I probably missed some, tag them!). You are doing great work, but let's join forces and paint the world orange together!
From here I would like to offer help in tagging your merchants on BTC Map. Just reach me out, and me and other supertaggers will do the work.
Let the sats flow!
originally posted at https://stacker.news/items/888088
-
 @ d830ee7b:4e61cd62
2025-02-28 05:45:17
@ d830ee7b:4e61cd62
2025-02-28 05:45:17ในชีวิตประจำวัน เรามักวัดมูลค่าของสิ่งต่างๆ ด้วยหน่วยเงินที่เราคุ้นเคย เช่น บาทหรือดอลลาร์
เราดีใจเมื่อการลงทุนของเรา “เพิ่มขึ้น” ในหน่วยเงินเหล่านั้น ..แต่น้อยคนนักจะหยุดคิดว่าไม้บรรทัดที่เราใช้วัดมูลค่านั้นมีความมั่นคงเพียงใด
หากไม้บรรทัดเองหดสั้นลงเรื่อยๆ สิ่งของที่เราวัดอาจดูเหมือนยาวขึ้นทั้งที่ความจริงไม่ได้เปลี่ยนไปเลย
แนวคิดนี้สะท้อนถึงการวัดมูลค่าทางเศรษฐกิจในหน่วยเงินที่เปลี่ยนแปลงตลอดเวลา และนำเราไปสู่หลักการเรื่อง "ค่าเสียโอกาส" (opportunity cost) ในการลงทุน
เมื่อเราเลือกถือสินทรัพย์ชนิดหนึ่ง เรากำลังสละโอกาสที่จะได้ผลตอบแทนจากอีกชนิดหนึ่งเสมอ
การทำความเข้าใจว่าอะไรเป็นตัววัดมาตรฐานของเราและค่าเสียโอกาสที่ตามมา จึงเป็นจุดเริ่มต้นในการสำรวจมุมมองใหม่ของการประเมินความมั่งคั่ง
ในบริบทนี้.. บิตคอยน์ (Bitcoin) ได้ถูกเสนอขึ้นมาเป็น “มาตรฐาน” ใหม่ในการวัดมูลค่ว เสมือนกับที่ทองคำเคยเป็นมาตรฐานการเงินของโลกในอดีต
หนังสือ The Bitcoin Standard ของ Saifedean Ammous ชวนเราคิดว่า Bitcoin อาจกลายเป็นเหมือน “มาตรฐานทองคำ” ยุคดิจิทัล ที่มารองรับระบบการเงินสากลในอนาคต
เหตุผลสำคัญที่ Bitcoin ถูกมองว่าเป็นเงินตราที่มีความแข็งแกร่ง (sound money) คือคุณสมบัติที่หาได้ยากในเงินสกุลปัจจุบัน
มันมีปริมาณจำกัดตายตัว 21 ล้านหน่วย ไม่มีธนาคารกลางใดสามารถพิมพ์เพิ่มได้ตามใจชอบ
ต่างจากเงินเฟียต (Fiat money) อย่างดอลลาร์ ที่จำนวนเพิ่มขึ้นตลอดเวลาจากนโยบายรัฐ
ผลคือ Bitcoin มีความทนทานต่อภาวะค่าเงินเสื่อมค่าจากเงินเฟ้อ และสามารถรักษามูลค่าได้ในระยะยาวดุจทองคำในอดีต
หลายคนจึงยกให้มันเป็น “Sound Money” หรือเงินที่มั่นคง เชื่อถือได้ในด้านมูลค่าเมื่อเวลาผ่านไป
แนวคิดนี้เองเปิดประตูไปสู่การใช้ Bitcoin เป็นหน่วยวัดเปรียบเทียบมูลค่าสินทรัพย์อื่นๆ เพื่อมองภาพเศรษฐกิจในมุมใหม่
ลองจินตนาการกราฟหนึ่งที่นำดัชนีหุ้นชั้นนำอย่าง S&P 500 มาเปรียบเทียบในหน่วย Bitcoin แทนที่จะเป็นดอลลาร์ กราฟนี้จะแสดงให้เราเห็นภาพที่ต่างออกไปอย่างมากจากกราฟปกติที่คุ้นเคย
https://nostr.download/e344db050a8f6b023b2a9c7883560ad8a7be3fc4154d3908cbae3471b970272a.webp
หากย้อนไปช่วงปี 2011
หุ้น S&P 500 อยู่ที่ราว 1,300 จุด ขณะที่บิตคอยน์มีราคายังไม่ถึง 1 ดอลลาร์ นั่นหมายความว่าดัชนี S&P 500 ในเวลานั้นมีมูลค่าประมาณ 1,300 BTC
แต่เมื่อเวลาผ่านไป Bitcoin มีราคาสูงขึ้นมหาศาล ในปี 2021–2022 Bitcoin (เคยพุ่งขึ้นไปแตะหลักหลายหมื่นดอลลาร์ต่อ 1 BTC) ทำให้มูลค่าของ S&P 500 เมื่อวัดในหน่วย BTC กลับกลายเป็นเพียงเศษเสี้ยวของที่เคยเป็น
สมมติ S&P 500 ล่าสุดอยู่แถว 4,000 จุด และราคา BTC อยู่หลักแสนดอลลาร์ ดัชนี S&P 500 ทั้งดัชนีอาจมีค่าไม่ถึง 0.05 BTC ด้วยซ้ำ
ผลลัพธ์ที่สะท้อนออกมาบนกราฟคือเส้นค่าของ S&P 500 (เมื่อวัดด้วย BTC) ที่มีแนวโน้มลดลงเรื่อยๆ ตลอดทศวรรษที่ผ่านมา
แปลความได้ว่า.. บิตคอยน์มีมูลค่าเพิ่มขึ้นเมื่อเทียบกับสินทรัพย์การเงินดั้งเดิมอย่างหุ้น
ถึงขั้นที่... การถือ Bitcoin ไว้ให้ผลตอบแทนดีกว่าการลงทุนในดัชนีหุ้นใหญ่เสียอีกในช่วงเวลาที่ผ่านมา
แม้จะฟังดูเหลือเชื่อ แต่นี่คือภาพที่ข้อมูลได้บอกเรา.. ในมุมมองของมาตรฐาน Bitcoin ตลาดหุ้นสหรัฐฯ ที่ว่าทำผลตอบแทนโดดเด่น ยังดูซีดเซียวลงในทันที
ข้อมูลในช่วงสิบปีให้หลังตอกย้ำภาพนี้อย่างชัดเจน ผลตอบแทนของ Bitcoin เหนือกว่าสินทรัพย์แทบทุกชนิดที่เรารู้จักในยุคปัจจุบัน
ในเชิงตัวเลข Bitcoin ให้ผลตอบแทนเฉลี่ยต่อปีราว 230% ตลอดทศวรรษ 2011–2021 ขณะที่ดัชนี S&P 500 ซึ่งขึ้นชื่อว่าให้ผลตอบแทนดีสม่ำเสมอ ยังมีค่าเฉลี่ยผลตอบแทนต่อปีประมาณ 10% กว่าๆ เท่านั้นเอง เมื่อนำมาคำนวณทบต้น
นั่นหมายความว่า.. ในช่วงเวลาประมาณ 10 ปีที่ผ่านมา มูลค่าของ Bitcoin เพิ่มขึ้นหลักหลายหมื่นเปอร์เซ็นต์ ในขณะที่ S&P 500 เพิ่มขึ้นเพียงไม่กี่ร้อยเปอร์เซ็นต์
ผลต่างระดับนี้ใหญ่พอที่จะเปลี่ยนวิธีที่เรามองความสำเร็จในการลงทุนไปเลยทีเดียว
มีการสังเกตด้วยว่าเพียงช่วงห้าปีหลังสุด ดัชนี S&P 500 สูญเสียมูลค่าประมาณเกือบ 90% หากวัดในหน่วยของบิตคอยน์
พูดอีกอย่างคือ..
ในสายตาของคนที่ถือ Bitcoin ไว้เป็นเกณฑ์ "เงิน 100 บาทที่ลงทุนในหุ้นเมื่อต้นช่วงเวลาดังกล่าว จะเหลือมูลค่าเพียงประมาณ 10 บาทเท่านั้นในปัจจุบัน* (เพราะ 90 บาทที่เหลือคือค่าเสียโอกาสที่หายไปเมื่อเทียบกับการถือ Bitcoin)
มุมมองแบบนี้ชวนให้เราตั้งคำถามว่า ที่ผ่านมาสินทรัพย์ที่ดูเหมือนมั่นคงปลอดภัย อาจไม่ปลอดภัยอย่างที่คิดเมื่อประเมินด้วยบรรทัดฐานใหม่
การเปรียบเทียบข้างต้นยังสะท้อนถึง ปัญหาการเสื่อมค่าของเงินเฟียต ซึ่งเราคุ้นเคยแต่บางครั้งมองข้ามความร้ายกาจของมัน
เงินดอลลาร์สหรัฐซึ่งเป็นสกุลเงินหลักของโลก สูญเสียอำนาจซื้อไปแล้วกว่า 96% ตั้งแต่ปี 1913 จนถึงปัจจุบัน (กล่าวคือ เงิน 1 ดอลลาร์ในสมัยนั้นมีค่าพอๆ กับเงินเกือบ 30 ดอลลาร์ในปัจจุบัน)
การที่ค่าเงินด้อยค่าลงเรื่อยๆ แบบนี้หมายความว่า ตัวเลขราคาในหน่วยเงินเฟียตอาจเพิ่มขึ้นทั้งที่มูลค่าที่แท้จริงไม่เพิ่ม
ยกตัวอย่างเช่น ดัชนี S&P 500 ทำจุดสูงสุดใหม่เป็นประวัติการณ์ในหน่วยดอลลาร์สหรัฐอยู่บ่อยครั้ง แต่หากปรับค่าด้วยปัจจัยเงินเฟ้อหรือปริมาณเงินที่พิมพ์เพิ่มเข้าไป เราจะพบว่ามูลค่าที่แท้จริงของดัชนีนี้ไม่ได้เพิ่มขึ้นมากอย่างที่เห็น
บางการวิเคราะห์ชี้ว่าหลังวิกฤตการเงินปี 2008 เป็นต้นมา แม้ดัชนี S&P 500 ในตัวเลขจะพุ่งขึ้นไม่หยุด แต่เมื่อหารด้วยปริมาณเงินที่เพิ่มขึ้น (เช่น M3) เส้นกราฟที่ได้กลับแทบไม่สูงไปกว่าจุดก่อนวิกฤตเลยด้วยซ้ำ
หมายความว่า.. ที่ราคาหุ้นสูงขึ้น ส่วนใหญ่ก็เพื่อไล่ตามสภาพคล่องเงินที่ไหลเข้าระบบเท่านั้น ไม่ได้สะท้อนการเติบโตแท้จริงของเศรษฐกิจมากนัก
เงินเฟ้อและการขยายตัวของปริมาณเงินจึงเปรียบเสมือน “หมอก” ที่บังตา ทำให้เรามองไม่ชัดว่าสิ่งใดเพิ่มมูลค่าแท้จริง สิ่งใดแค่ตัวเลขฟูขึ้นตามสกุลเงินที่ด้อยค่าลง
เมื่อ Bitcoin ถูกใช้เป็นหน่วยวัดเปรียบเทียบ มันทำหน้าที่เสมือนกระจกใสที่กวาดเอาหมอกเงินเฟ้อนั้นออกไป เราจึงเห็นภาพที่ต่างไปโดยสิ้นเชิง
เช่นเดียวกับกรณีที่เราเปรียบเทียบราคาสินค้าโภคภัณฑ์บางอย่างในหน่วย BTC ผลลัพธ์ก็อาจกลับทิศ
การทดลองหนึ่งของธนาคารเฟด สาขาเซนต์หลุยส์ เคยเล่นเปรียบเทียบราคา “ไข่ไก่หนึ่งโหล” ในหน่วยดอลลาร์กับในหน่วยบิตคอยน์
ปรากฏว่า... แม้ต้องการจะชี้ให้เห็นความผันผวนของ Bitcoin แต่ดันกลับตอกย้ำความจริงที่ว่า ในช่วงเงินเฟ้อสูง ราคาฟองไข่ที่ดูเพิ่มขึ้นเรื่อยๆ ในหน่วยดอลลาร์ จริงๆ แล้วทรงตัวหรือลดลงด้วยซ้ำเมื่อคิดเป็น BTC
นี่เป็นตัวอย่างสนุกๆ ที่บอกเราว่า กรอบอ้างอิง (frame of reference) ในการวัดมูลค่านั้นสำคัญเพียงใด
แน่นอนว่า Bitcoin เองก็มีความผันผวนสูงและยังอยู่ในช่วงเริ่มต้นเมื่อเทียบกับสินทรัพย์ดั้งเดิม
การที่มันพุ่งทะยานหลายหมื่นเปอร์เซ็นต์ที่ผ่านมาไม่ได้รับประกันว่ากราฟในหน่วย BTC ของสินทรัพย์ต่างๆ จะดิ่งลงอย่างนี้ไปตลอด
แต่สิ่งที่เกิดขึ้นแล้วได้ให้แง่คิดทางปรัชญาการเงินที่ลึกซึ้งกับเรา
อย่างแรกคือเรื่อง ค่าเสียโอกาส ที่กล่าวถึงตอนต้น ทุกการตัดสินใจทางการเงินมีต้นทุนค่าเสียโอกาสแฝงอยู่เสมอ เพียงแต่เมื่อก่อนเราอาจไม่เห็นมันชัดเจน
การเก็บออมเงินสดไว้เฉยๆ ในธนาคารมีต้นทุนคือผลตอบแทนที่สูญไปหากเราเลือกลงทุนอย่างอื่น การลงทุนในสินทรัพย์ A ก็ย่อมหมายถึงการไม่ได้ลงทุนในสินทรัพย์ B
หาก B นั้นให้ผลตอบแทนสูงกว่า เราก็สูญเสียส่วนต่างนั้นไป
สิบกว่าปีที่ผ่านมา Bitcoin ทำผลงานได้เหนือชั้นกว่าสินทรัพย์อื่นๆ มาก ค่าเสียโอกาสของการไม่ถือ Bitcoin จึงสูงลิ่วในช่วงนี้
สำหรับนักลงทุนที่มองย้อนกลับไป นี่คือบทเรียนราคาแพง บางคนอาจนึกเสียดายว่า “รู้งี้ซื้อบิตคอยน์ไว้ตั้งแต่แรกซะก็ดี”
แต่ประเด็นไม่ได้อยู่ที่การเสียดายอดีต แต่อยู่ที่ การตระหนักรู้ถึงค่าเสียโอกาสและผลกระทบของมันที่มีต่อความมั่งคั่งของเราในระยะยาว ต่างหาก
อีกแง่หนึ่งที่ลึกกว่านั้นคือเรื่อง กรอบในการวัดมูลค่า ของเราทุกวันนี้ว่าเหมาะสมแล้วหรือไม่
หากการที่เราใช้เงินเฟียตที่เสื่อมค่าเป็นตัววัด ทำให้เราประเมินค่าของสิ่งต่างๆ ผิดเพี้ยนไป การตัดสินใจทางเศรษฐกิจของเราก็อาจผิดทิศทางในระยะยาวได้
ลองนึกภาพว่า.. ถ้าเงินที่เราใช้อยู่มีมูลค่าเสถียรหรือเพิ่มขึ้นตามประสิทธิภาพการผลิตจริงๆ ของเศรษฐกิจ (เหมือนที่เงิน Bitcoin ถูกออกแบบมาให้ไม่เสื่อมค่าไปตามกาลเวลา) เราอาจไม่จำเป็นต้องวิ่งไล่หาผลตอบแทนสูงๆ เพียงเพื่อรักษามูลค่าเงินออมของตัวเองให้ทันเงินเฟ้อ
ผู้คนอาจวางแผนการเงินระยะยาวขึ้น แนวคิดเรื่อง “เวลาที่ต้องใช้” กับ “อัตราส่วนลดของอนาคต” (time preference) ก็จะเปลี่ยนไป
ดังที่ Ammous กล่าวไว้ใน The Bitcoin Standard ว่าเงินที่มีเสถียรภาพจะส่งเสริมให้คนออมและลงทุนในโครงการระยะยาวมากขึ้น ผิดกับระบบเงินเฟ้อที่ชักจูงให้ผู้คนรีบใช้จ่ายหรือเข้าร่วมเก็งกำไรระยะสั้นเพราะกลัวว่าเงินจะด้อยค่าไป
นี่ไม่ใช่แค่เรื่องการเงินส่วนบุคคล แต่สะท้อนถึงคุณภาพของการเติบโตทางเศรษฐกิจและนวัตกรรมในสังคมโดยรวมด้วย
หากเรามีหน่วยวัดมูลค่าที่เที่ยงตรง ไม่บิดเบือนไปตามนโยบายการเงินรายวัน เราก็อาจประเมินโครงการต่างๆ ได้ตามศักยภาพที่แท้จริงมากขึ้น เงินเฟ้อและการพิมพ์เงินจำนวนมากมักทำให้เกิดการลงทุนผิดที่ผิดทาง (malinvestment) เพราะสัญญาณราคาถูกบิดเบือน
เช่น ดอกเบี้ยที่ต่ำผิดปกติอาจทำให้เกิดหนี้ล้นเกินหรือลงทุนในโครงการที่ไม่ยั่งยืน
ในขณะที่มาตรฐานเงินที่เข้มงวดอย่าง Bitcoin อาจบังคับให้ทุกการลงทุนต้องมีเหตุผลรองรับที่แข็งแรงขึ้น เนื่องจากไม่สามารถอาศัยการอัดฉีดสภาพคล่องมาช่วยพยุงได้ง่ายๆ
เมื่อมาถึงตรงนี้..
เราอาจไม่ได้ข้อสรุปทันทีว่า “ต่อไปนี้ฉันควรถือ Bitcoin แทนที่จะลงทุนอย่างอื่น” และบทความนี้ก็ไม่ได้มีเจตนาจะชี้นำการลงทุนเช่นนั้น
เป้าหมายแท้จริงคือการเปิดมุมมองใหม่ว่า เราประเมินคุณค่าของสิ่งต่างๆ อย่างไร
ลองตั้งคำถามกับตัวเองว่า..
ทุกวันนี้เราวัดความร่ำรวยหรือความก้าวหน้าทางเศรษฐกิจด้วยหน่วยอะไร หน่วยนั้นวัดได้เที่ยงตรงหรือเปล่า?
หากเงินที่เราใช้วัดเองลดค่าลงทุกปีๆ เราจะมั่นใจได้อย่างไรว่าตัวเลขที่เพิ่มขึ้นบนกระดาษคือความมั่งคั่งที่เพิ่มขึ้นจริง?
การใช้ Bitcoin เป็นมาตรฐานเทียบเคียง เป็นเสมือนการลองวัดด้วยไม้บรรทัดอีกอันที่อาจตรงกว่าเดิม
ในหลายกรณีมันเผยให้เห็นภาพที่เราคาดไม่ถึงและท้าทายความเชื่อเดิมๆ ของเรา
บทเรียนที่ได้รับไม่ใช่ให้เราทุกคนเปลี่ยนไปคิดเป็น BTC ในชีวิตประจำวันทันที แต่คือการตระหนักว่า หน่วยวัดมีความหมาย และการมองโลกการเงินด้วยหน่วยวัดที่ต่างออกไปสามารถให้ข้อคิดที่ลึกซึ้งได้อย่างไร
ท้ายที่สุด ไม่ว่าจะเชื่อใน “มาตรฐานบิตคอยน์” หรือไม่นั้น ไม่สำคัญเท่ากับการที่เราได้ฉุกคิดและตั้งคำถามกับระบบที่เราใช้อยู่ทุกเมื่อเชื่อวัน
บางทีสิ่งที่ Bitcoin และปรัชญาการเงินแบบใหม่ๆ นำมาให้เรา อาจไม่ใช่คำตอบสำเร็จรูป แต่คือแรงกระตุ้นให้เราเปิดใจมองภาพใหญ่ของเศรษฐกิจในมุมที่กว้างขึ้น
ลองพิจารณาปัจจัยพื้นฐานอย่างค่าเงิน เวลา และโอกาสที่สูญเสียไปกับการตัดสินใจต่างๆ อย่างรอบด้านขึ้น
เมื่อเราเริ่มมองเห็นว่าการวัดมูลค่าของสิ่งต่างๆ ด้วย ไม้บรรทัดที่ต่างออกไป ให้อะไรเราได้บ้าง เราก็จะพร้อมที่จะปรับมุมมองและกลยุทธ์การเงินของตนเองให้เท่าทันโลกที่เปลี่ยนแปลงเสมอ
ไม่แน่ว่าในอนาคต เราอาจได้เห็นผู้คนพูดถึงราคาบ้านหรือดัชนีหุ้นในหน่วยบิตคอยน์อย่างเป็นเรื่องปกติ และการคิดเช่นนั้นอาจไม่ใช่เรื่องแปลกใหม่อีกต่อไป
เพราะเราได้เรียนรู้ที่จะมองผ่านเปลือกของหน่วยเงิน ไปสู่แก่นแท้ของมูลค่าจริงๆ ที่อยู่เบื้องหลังนั่นเอง
ขอบคุณ Thai Ratel สำหรับความกระจ่างในการวัดมูลค่าสินทรัพย์ต่าง ๆ ด้วยบิตคอยน์
-
 @ d830ee7b:4e61cd62
2025-02-28 05:07:17
@ d830ee7b:4e61cd62
2025-02-28 05:07:17In our daily lives, we often measure the value of things using familiar monetary units such as baht or dollars. We feel delighted when our investments "increase" in these units.
However, few people stop to consider how stable the measuring stick itself is. If the ruler we use to measure value keeps shrinking, the objects we measure may appear longer, even though their actual size remains unchanged. This concept reflects the way we assess economic value in constantly changing monetary units, leading us to the principle of opportunity cost in investment: when we choose to hold one type of asset, we are always giving up the opportunity to earn returns from another.
Understanding what serves as our standard measure and the opportunity costs that come with it is the first step toward exploring a new perspective on wealth assessment.
In this context, Bitcoin has been proposed as a new "standard" for measuring value, much like gold once served as the global financial standard in the past. Some view Bitcoin as the "digital gold standard" that could support the international financial system in the future.
A key reason Bitcoin is considered "sound money" is its rarity—something modern currencies lack. Its supply is permanently capped at 21 million units, meaning no central bank can print more at will. This contrasts with fiat money, such as the dollar or baht, which constantly increases in supply due to government policies.
As a result, Bitcoin is resistant to inflation-induced depreciation and can retain its value over the long term, much like gold in the past. Many therefore consider it "sound money"—a form of currency that is stable and reliable in preserving value over time.
This idea opens the door to using Bitcoin as a benchmark for comparing the value of other assets, offering a fresh perspective on the economy.
Imagine a graph that compares the leading stock index, the S&P 500, in Bitcoin terms instead of dollars.
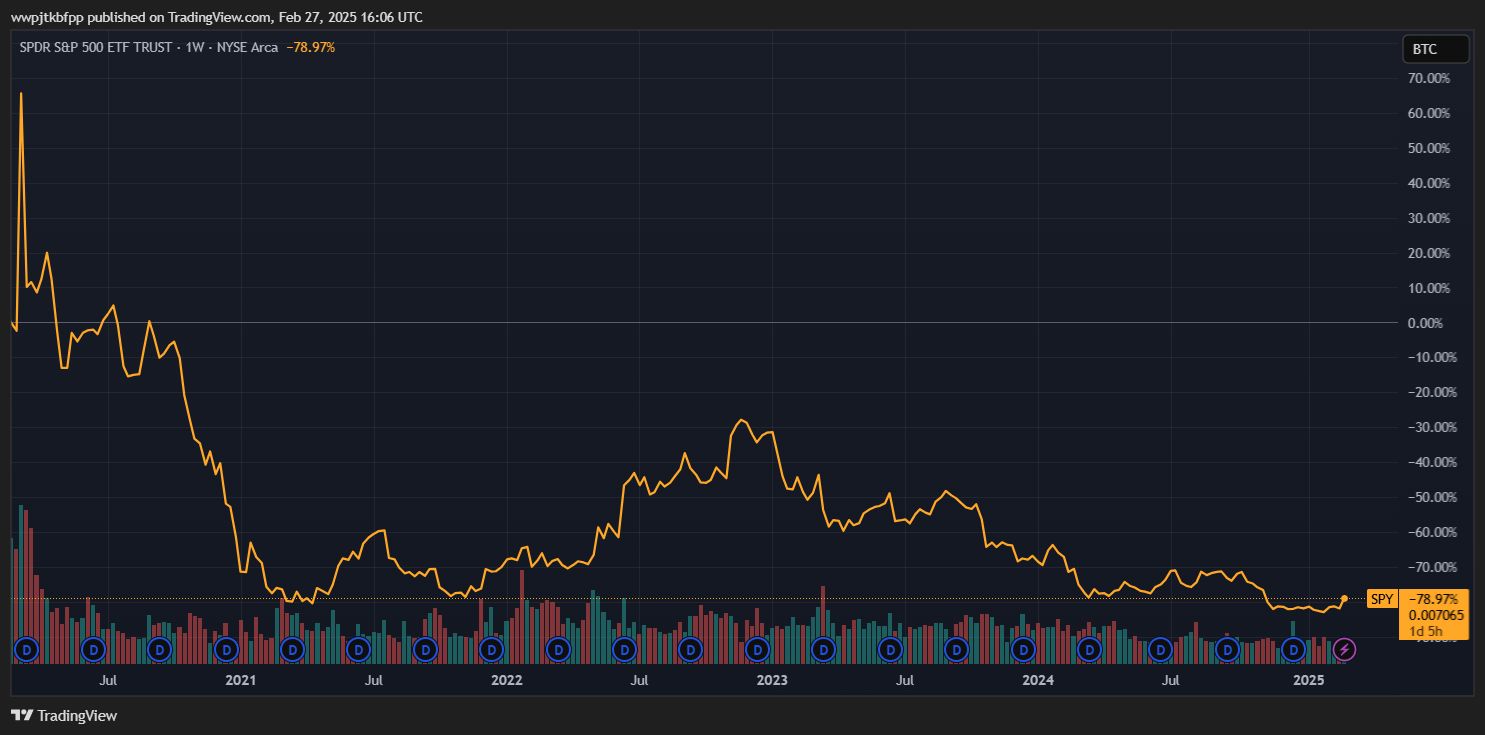 This graph would reveal a drastically different picture from the conventional charts we are familiar with. Looking back to 2011, the S&P 500 was around 1,300 points, while Bitcoin was priced at less than $1.
This graph would reveal a drastically different picture from the conventional charts we are familiar with. Looking back to 2011, the S&P 500 was around 1,300 points, while Bitcoin was priced at less than $1. This means the S&P 500 index was valued at approximately 1,300 BTC at the time. However, as Bitcoin's price surged over the years—reaching tens of thousands of dollars per BTC in 2021–2022—the value of the S&P 500, when measured in BTC, shrank dramatically.
Suppose the S&P 500 currently stands at around 4,000 points, while Bitcoin is priced at six figures in dollars. The entire S&P 500 index might be worth less than 0.05 BTC.
The resulting graph would show a consistent downward trend in the S&P 500's value (when measured in BTC) over the past decade.
This means Bitcoin has appreciated relative to traditional financial assets like stocks—to the extent that simply holding Bitcoin has outperformed investing in major stock indices.
As surprising as this may seem, the data tells this story: from the perspective of a Bitcoin standard, even the high-performing U.S. stock market appears lackluster.
Data from the past decade reinforces this view. Bitcoin has outperformed nearly every asset class known today. In numerical terms, Bitcoin delivered an average annual return of approximately 230% from 2011 to 2021, whereas the S&P 500, which is renowned for its consistent performance, achieved an average annual return of just over 10%.
When compounded over time, this means Bitcoin's value increased by tens of thousands of percent over the past decade, while the S&P 500's value rose by only a few hundred percent.
The magnitude of this difference is significant enough to reshape how we perceive investment success. Observations also indicate that in just the past five years, the S&P 500 has lost nearly 90% of its value when measured in Bitcoin.
In other words, for someone using Bitcoin as their benchmark, a 100-baht investment in stocks at the beginning of this period would be worth only about 10 baht today—the remaining 90 baht representing the opportunity cost of not holding Bitcoin.
This perspective challenges our assumptions about the stability of supposedly safe assets when evaluated under a new standard.
This comparison also highlights the issue of fiat currency depreciation—something we are familiar with but often underestimate. The U.S. dollar, the world's primary reserve currency, has lost over 96% of its purchasing power since 1913.
This means that what $1 could buy back then now requires nearly $30. This ongoing depreciation implies that prices in fiat terms may rise even when real value does not. For example, the S&P 500 frequently reaches all-time highs in U.S. dollar terms.
However, when adjusted for inflation or money supply expansion, its real value has not increased as much as it seems. Some analyses suggest that since the 2008 financial crisis, although the S&P 500's nominal value has surged, when divided by the expanding money supply (such as M3), its graph remains largely unchanged from pre-crisis levels.
This suggests that stock prices have risen primarily in response to liquidity injections rather than genuine economic growth. Inflation and monetary expansion act like a "fog," obscuring our ability to discern real value from mere numerical increases.
When Bitcoin is used as a comparative unit, it acts as a clear lens that removes this inflationary fog, revealing a completely different picture.
The same applies when comparing commodity prices in BTC. A notable experiment by the St. Louis Federal Reserve once examined the price of "a dozen eggs" in both dollars and Bitcoin. While the study aimed to highlight Bitcoin’s volatility, it inadvertently reinforced the point that during periods of high inflation, the price of eggs, which seemed to rise continuously in dollars, actually remained stable or even declined in BTC terms.
This amusing example illustrates the profound impact of measurement standards.
Of course, Bitcoin itself is highly volatile and still in its early stages compared to traditional assets. Its meteoric rise over the past decade does not guarantee that all asset graphs in BTC terms will continue declining indefinitely. However, what has already transpired provides deep financial insights.
The first takeaway is the concept of opportunity cost mentioned earlier—every financial decision has an inherent cost, even if we do not always recognize it. Holding cash in a bank carries the opportunity cost of the returns one could earn by investing elsewhere. Investing in asset A means missing out on asset B, and if B delivers higher returns, we incur that loss.
Over the past decade, Bitcoin has outperformed all other assets by a wide margin, making the opportunity cost of not holding Bitcoin extremely high. Investors looking back on this period might regret not having bought Bitcoin earlier, but the key lesson is not about dwelling on past decisions—it is about becoming aware of opportunity costs and their long-term impact on wealth.
On a deeper level, this discussion raises questions about whether our current valuation framework is truly appropriate. If using a depreciating fiat currency as a benchmark distorts our perception of value, our economic decisions may be misaligned in the long run.
Imagine a scenario where money retains or even appreciates in value in line with real economic productivity (as Bitcoin was designed to do). In such a system, people would not need to chase high returns merely to preserve their savings from inflation. They could plan finances with a longer-term perspective. Concepts like "time preference" and "discounting the future" would shift.
It is often argued that sound money encourages saving and long-term investment, whereas inflationary systems push people toward short-term spending or speculation out of fear that their money will lose value.
This is not just a matter of personal finance but a fundamental influence on the quality of economic growth and innovation. A sound money standard like Bitcoin might enforce stricter investment discipline, as liquidity injections could no longer be used as a safety net for unsustainable projects.
At this point, readers may not conclude that they should immediately hold Bitcoin instead of investing in other assets—and this article is not intended as investment advice. Its real purpose is to provoke thought about how we measure value.
Ask yourself: What unit do we use to gauge wealth and economic progress? Is that unit reliable?
If the money we use for measurement loses value every year, how can we be sure that increasing numbers on paper reflect true wealth growth?
Using Bitcoin as a reference standard is like measuring with a new ruler—one that may be more accurate. In many cases, it reveals unexpected insights and challenges long-held beliefs.
Ultimately, whether or not one believes in the "Bitcoin standard" is less important than the ability to critically examine the system we rely on daily.
Perhaps the greatest value Bitcoin and new financial philosophies offer is not a definitive answer but the impetus to look at the bigger economic picture with fresh eyes.
Thank you, Thai Ratel, for enlightening me on this topic!
Jakk Goodday.
-
 @ dbe0605a:f8fd5b2c
2025-02-17 06:33:48
@ dbe0605a:f8fd5b2c
2025-02-17 06:33:48
\ I care deeply about bitcoin adoption and ability to use bitcoin with all features of money — saving, spending, earning. We're entering an age where more and more people realise "hodl never spend" meme is hindering bitcoin adoption. More and more of use want to use bitcoin in everyday life, because we're living on it and because it's superior in every aspect. It's also incredibly fun to use it for payments.
For money to thrive, it needs to circulate. Spending bitcoin orangepills merchants, their families and people around them — with each bitcoiner coming to a shop and paying with bitcoin, it's a point of contact that can trigger a train of though that later may fruit into action — "Why are they so interested in bitcoin, what's actually so special about it?" "Hmm, maybe this time I will not exchange it for fiat immediately?"
Global merchant adoption grows, every day new business around the world decide to start accepting bitcoin payments. Circular economies are blooming on all continents, where people live in a new, experimental, orange coin paradigm. Companies and projects like Blink, Bitcoin Jungle, Plan B, Orange Pill App do an amazing job in facilitating this — providing great wallets, tools & services for merchants, and finally onboarding merchants themself. They also often support circular economies financially or in other ways. This is very valuable and makes the road to hyperbitcoinization a tad shorter.
But there is one thing those companies are doing wrong — they're using their own, proprietary maps that display only merchants using their own wallets or POS software. I'd like to now list a few reasons why those great projects should migrate their maps into an open source, bitcoin map that is BTC Map.
Open source, stupid
BTCmap is open source, built on OpenStreetMaps, open to both developers contributions but also for map taggers (called shadowy supertaggers). Anyone can contribute, even If you don't code. Anyone can verify merchants or add new merchants to the map. BTC Map team developed a neat system of verifications that just works better than anything before or any alternative maps today.

Many apps, one map
BTC Map is integrated inside a dozen of wallets and apps, to name a few: Wallet of Satoshi, Coinos, Bitlocal, Fedi or Aqua. It's a public good that any bitcoin product can use and grow it's network effect.

Uniting mappers' work
BTC Map does not discriminate bitcoin merchants, that means all the merchants from proprietary maps are being mapped by taggers to BTC Map. By mapping on a closed source, proprietary map, the same merchant is mapped two times, usually by two different people — it's duplicating the same work without any bringing any benefit to both projects. Using BTC Map also brings you way more people verifying If those merchants actually still accept bitcoin, making it easier to have an up-to-date database of actual adoption.
More bitcoin spent at your merchants
When you have a business focused on spending bitcoin and onboarding merchants, you want as much bitcoin spent there as possible. If a bitcoiner coming to the area does not use your own map but some other map, they can be completely unaware that they can let their sats flow to your merchants. If we all use one merchants database, this problem disappears and more sats will flow. Why wouldn't you want your merchants displayed in dozens of other apps, completely for free?
OpenStreetMap map is just better

\ Take a look at the image above: It's La Pirraya, a small sleepy island town in El Salvador with a circular economy being facilitated by Bitcoin Beach. Even though Blink has many more merchants compared to BTC Map, when I visited it a few months ago I could find them. Not because they do not exist, but because the map does not show any roads and it was very hard to locate them in a dense network of narrow streets of La Pirraya. BTC Map allows you to turn multiple versions of satellite maps views, making it way easier to find your point of interest. Pins also indicate what kind of business it is, where in Blink all the pins are the same and you need to click each to find out what it is. Even then not always it's clear, since Blink only displays names, while BTC Map tells you type of the merchant, and very often shows you working hours, phone numbers, website, social links, etc.
Excellent community tools
BTC Map is focusing providing tools for communities to maintain their merchants map. Each community has it's own page with own links to community website or socials, displays a list of all the merchants, shows community stats, displays merchants that were not verified for a long time, and more. It even allows to "boost" merchants to make them more visible on the map and on the list. It's perfect tooling both for communities and businesses onboarding merchants to their software.

Easy integration & configuration
Integrating BTC Map on your website or app is easy. It's just a few lines of code of iframe to embed the map, but you can also use BTC Map API for more custom integration. Do you to display, eg. you can display only merchants from your community? No problem, you can do that. Since it's all open source, you can configure it in many ways that will suit your needs.
Kudos
I'd like to thank projects that understood all above and integrated BTC Map already. Those are Coinos, Wallet of Satoshi, Pouch, Bolt Card, BitLocal, Fedi, Decouvre Bitcoin, Osmo, Bitcoin Rocks!, Lipa, Spirit of Satoshi, Blockstream, Satlantis, Aqua Wallet and Adopting Bitcoin.
Encouragement & an offer
I'll end that with encouragement to projects that use their own maps, but haven't embraced BTC Map yet. Those are Blink, Bitcoin Jungle, Plan B, Osmo, Athena, Orange Pill App, Inbitcoin (I probably missed some, tag them!). You are doing great work, but let's join forces and paint the world orange together!
From here I would like to offer help in tagging your merchants on BTC Map. Just reach me out, and me and other supertaggers will do the work.
Let the sats flow!
-
 @ bbef5093:71228592
2025-02-16 14:17:12
@ bbef5093:71228592
2025-02-16 14:17:12A trícium érdekességei
A trícium a hidrogén lenyűgöző radioaktív formája, amely háromszor nehezebb, mint a közönséges hidrogén, és egy protont, valamint két neutront tartalmaz az atommagjában. Ernest Rutherford és csapata 1934-ben fedezte fel, és 12,32 éves felezési idővel rendelkezik.
Főbb alkalmazási területek
Világítástechnika A tríciumot önvilágító eszközökben használják energiaforrásként, például órák kijelzőiben és vészkijárati táblákban, ahol foszforokat aktivál, hogy folyamatos fényt bocsásson ki elektromos áram nélkül.
Tudományos kutatás A tudósok radioaktív nyomjelzőként használják orvosi kutatásokban és gyógyszerfejlesztésben, kihasználva azt a tulajdonságát, hogy kémiai reakciókban úgy viselkedik, mint a normál hidrogén. Kiemelkedő szerepet játszik a felszín alatti vizek kormeghatározásában is. Az 50 évnél fiatalabb vizek esetében a trícium-koncentráció mérése megbízható módszer, mivel az 1953-63 közötti magaslégköri nukleáris kísérletek egyedi "időbélyeget" hagytak a csapadékvizekben.
Vízföldtani alkalmazások
Vízbázisok védelme A trícium-vizsgálatok kiválóan alkalmasak a felszín alatti vízbázisok védettségének és a felszíni vizek elérési idejének meghatározására. A trícium ideális víznyomjelző, mivel beépül a vízmolekulába (HTO formában), és tökéletesen követi a víz mozgását.
Nukleáris létesítmények monitorozása A talajvíz trícium-tartalmának rendszeres megfigyelése kulcsfontosságú a nukleáris létesítmények környezetében, mivel segít azonosítani az esetleges szivárgásokat és a radioaktív anyagok terjedését a felszín alatti vizekben.
Nukleáris alkalmazások Az izotóp kulcsszerepet játszik a nukleáris fúzióban mint üzemanyag a tokamak reaktorokban, és "erősítőként" szolgál a nukleáris fegyverekben.
Biztonsági profil Bár radioaktív, a trícium csak alacsony energiájú béta-sugárzást bocsát ki, amely nem képes áthatolni az emberi bőrön. Természetes körülmények között nyomokban megtalálható a légkörben, ahol kozmikus sugárzás hatására keletkezik.
Tritium, the ideal tracer
Interesting Facts About Tritium
Tritium is a fascinating radioactive form of hydrogen that's three times heavier than regular hydrogen, containing one proton and two neutrons in its nucleus. It was first discovered by Ernest Rutherford and his team in 1934 and has a half-life of 12.32 years.
Main Applications
Illumination Technology Tritium is used as an energy source in self-illuminating devices, such as watch displays and exit signs, where it activates phosphors to create continuous light without electrical power.
Scientific Research Scientists use tritium as a radioactive tracer in medical research and pharmaceutical development, taking advantage of its ability to behave like normal hydrogen in chemical reactions. It also plays a crucial role in dating groundwater. For waters less than 50 years old, measuring tritium concentration is a reliable method, as atmospheric nuclear tests between 1953-63 left a unique "timestamp" in precipitation.
Hydrogeological Applications
Protection of Water Resources Tritium studies are excellent for determining the protection status of underground water resources and the arrival time of surface waters. Tritium is an ideal water tracer as it incorporates into water molecules (as HTO) and perfectly follows water movement.
Monitoring Nuclear Facilities Regular monitoring of groundwater tritium content is crucial around nuclear facilities, as it helps identify potential leaks and the spread of radioactive materials in groundwater.
Nuclear Applications The isotope plays a key role in nuclear fusion as fuel in tokamak reactors and serves as a "booster" in nuclear weapons.
Safety Profile Although radioactive, tritium only emits low-energy beta radiation that cannot penetrate human skin. It naturally occurs in trace amounts in the atmosphere, formed by cosmic ray interactions.
-
 @ c582af78:698069cc
2025-02-15 19:21:25
@ c582af78:698069cc
2025-02-15 19:21:25The Face of God: How Art Became a Gateway to the Divine
If you live in the West, you’re surrounded by depictions of God, Jesus, and the saints—from paintings and statues to illustrated Bibles and stained glass windows.
But this is far from universal. In the Islamic world, religious art takes a very different form: vibrant colors, intricate geometry, and architectural symmetry. Depictions of God or Muhammad aren’t just discouraged—they are outright forbidden.
But why?
To answer that, we must go back to the origins of the Abrahamic religions—when early Christians, Jews, and Muslims were surprisingly unified in their views on religious art.
https://image.nostr.build/1515c5fd00d798cd283583618bbbc0d5eb91bc481a84c21d53644d42fa30173a.jpg
The Early Christian Hesitation
The first generation of Christians were deeply aware of Judaism’s strict prohibition against idol worship. Depicting God in any form was considered dangerous—a potential gateway to paganism.
For centuries, Christianity could have followed this path, rejecting religious imagery altogether. But one fundamental theological idea changed everything:
The Incarnation.
As the early Church wrestled with the nature of Christ, heated debates emerged:
- Was he part human and part divine?
- Was he fully human and fully divine?
- And what did the Gospel of John mean by “the Word became flesh and dwelt among us”?
The result of these debates was the doctrine of the Incarnation—the belief that God took on human form in real flesh and blood. And if God himself had chosen to be seen in finite form, then depicting Him in art could no longer be considered blasphemous.
This single theological shift laid the foundation for Christianity’s embrace of religious art—a decision that would not only shape Christian worship but redefine how we engage with art itself.
https://image.nostr.build/1cf9ea5d1385c46bd720de9c7de65123428a9f76356e39e37c5d7b9663993930.jpg
Let There Be Art…
How did this change Christian art?
https://image.nostr.build/b945e4ea06b281bb4618f08b2543108beecf7f510aaa795bed1c833614e32fb7.jpg
The early objections to religious imagery went something like this:
“God is infinite and mysterious. Reducing Him to a finite, limited form is blasphemy.”
But with the Incarnation, the argument flipped:
“If God took on real shape, color, and form without diminishing His divine nature, then we can depict Him in art without compromising His grandeur.”
Thus, images of Jesus, Mary, and saints not only became permissible—they were encouraged.
Christian leaders actively commissioned religious art to communicate the Gospel visually to a largely illiterate population. Paintings, statues, and stained glass became tools of evangelization, helping people grasp biblical stories without needing to read.
Take the Duomo of Milan with its 4,000 statues. They aren’t just decorative. They inspire faith by highlighting the lives of the saints.
Christianity had embraced art as a spiritual bridge, a way to connect the finite with the infinite.
https://image.nostr.build/4f6b79a9179d818a951bf461ee5ff785cbe618ed376b4a56d92e77dcb34005bc.jpg
The Criticism: Were They Worshiping the Art?
Not everyone agreed.
Some critics argued that Christians were focusing too much on the art itself, rather than the God it was meant to represent.
https://image.nostr.build/29afb401ef99d2b6c59b71d8534a5160c25d2ca468d81251ba0f55d033679490.jpg
But the Church’s response was clear:
"You are not meant to look at art, but through it.
Art is not the end goal—it is a gateway to something greater.
A painting of Christ isn’t meant to be worshiped—it’s meant to draw the viewer into His story, His sacrifice, and His message.
This perspective didn’t just shape religious art. It fundamentally changed how we experience all forms of art, even secular ones.
To Infinity and Beyond: The Lasting Impact of Religious Art
Christianity’s view of art—that it should point beyond itself—has so deeply influenced Western culture that we often don’t even realize it.
Think about how we experience books, music, and movies:
- A great novel inspires courage.
- A powerful song moves you to tears.
- A gripping film motivates you to keep going in life.
The best art doesn’t just exist for its own sake—it transports you beyond the canvas, the page, or the screen.
This idea mirrors the Incarnation itself: an infinite God becoming finite to guide us back to the infinite.
Tolkien, The Lord of the Rings, and the Incarnation of Art
A perfect example? J.R.R. Tolkien’s The Lord of the Rings.
Tolkien infused his story with themes of brotherhood, heroism, and sacrifice—all timeless, transcendental ideas. But instead of leaving them as abstract concepts, he "incarnated" them into words on a page—finite, tangible, and deeply relatable.
https://image.nostr.build/b120c4d7c7232cf226af65c33cb7fc494f495d50b8ad4593a58f3528fd0b71dc.jpg
His goal? To turn the reader’s heart back to the infinite by making them experience these ideals in a concrete way.
The same can be said for any truly great art.
It doesn’t exist for itself—it exists to move you, to inspire you, to challenge you.
And next time you step into a cathedral, gaze at a masterpiece, or listen to a symphony, remember:
You’re not supposed to simply look at the art around you—
You’re supposed to look beyond it, into eternity.
-
 @ bf47c19e:c3d2573b
2025-02-28 00:06:22
@ bf47c19e:c3d2573b
2025-02-28 00:06:22Originalni tekst na medium.com.
Autor: Aleksandar Svetski / Prevod: ₿itcoin Serbia
Nemojte kupovati Bitkoin!
Ni danas, ni kasnije, nikada!
Posvećeno skepticima, neznalicama, arogantnima i nezainteresovanima.
NE TREBA vam Bitkoin.
Molim vas. Nemojte ga kupovati.
Lično me ne zanima "masovna adopcija".
Draža mi je selektivna adopcija.
Svinja ne zaslužuje bisere.
Na vama je da platite cenu neznanja.
Kao i cenu glupavosti.
Kada dođe vreme, sa zadovoljstvom ću vam platiti hiljadu satošija mesečno za vaše vreme i smejati se usput.

Najbitnija odluka koju ćete ikada doneti
NEMA važnije odluke za vašu finansijsku, ekonomsku i suverenu budućnost koju danas možete doneti nego da kupite Bitkoin.
A ako ne želite da izdvojite malo vremena da ga dalje proučite, JEDINA osoba koju treba da krivite kasnije ste vi sami.
Danas, Bitkoin se nalazi u svojoj ranoj, početnoj fazi. O ovome možete više pročitati ovde (hvala ObiWan Kenobit):
Hiperbitkoinizacija: pobednik uzima sve
Ovo JE prilika ne samo vašeg života, već verovatno i najveći mogući transfer bogatstva u istoriji, a najluđa stvar je što će se najveći deo toga odigrati u narednih nekoliko decenija.
Nalazimo se tek u prvih 12 godina ove promene, a već smo videlo kako je Bitkoin eksplodirao sa $0.008c (kada su za 10.000 BTC kupljene dve pice) na trenutnu cenu od oko $11.500.
Ovo je tek početak. Tek 0.001% svetskog bogatstva je denominirano u Bitkoinu.
Ako sada izdvojite samo trenutak da razumete novac, njegovu ulogu u društvu i kako će ekonomski darvinizam voditi ceo svet prema najrobusnijem, najčvršćem i najsigurnijem obliku očuvanja bogatstva, možete odlučiti da kupite neki deo pre nego što se ostatak sveta priključi.
Čitajući ovo, vi ste poput drevnog pojedinca koji je pronašao zlato, dok svi ostali koriste školjke. Razlika je u tome što živite u digitalnom dobu tokom kojeg će se ovaj novac pojaviti i sazreti za vreme vašeg života. Taj drevni pojedinac bi bio u pravu ali mrtav zato što je zlatu bilo potrebno nekoliko hiljada godina da uradi ono za šta će Bitkoinu biti potrebne decenije.
Zamislite. Se. Nad. Tim.
I naučite dalje o nastanku Bitkoina ovde:
I za ime ljubavi prema sopstvenoj budućnosti, preuzmite ovu kratku elektronsku knjigu i jebeno se edukujte!!
Preuzmite "Investiranje u Bitkoin"
I eto, dajem vam izvore.. jbt.. Svejedno...
Danas, imate izbor da kupite Bitkoin; najoskudniji novac u univerzumu, za siću!! Bukvalno možete kupiti hiljade satošija (najmanju jedinicu Bitkoina gde je 100.000.000 satošija = 1 BTC) za $1!!!
Danas ne postoji veća prilika, kao što sutradan neće postojati veće žaljenje kada više ne budete imali "izbor" da ga kupite.
Kada taj dan bude došao i kada budete to morali da prihvatite, setićete se ovih reči, ali avaj, biće prekasno, a vreme ne možete vratiti.

Više nije 2012
Tada ste imali izgovor. Sada je 2020...
Apsolutno NEMA razloga zašto neko sa malo radoznalosti i relativno funkcionalnim mozgom ne može da prouči šta je Bitkoin, zašto postoji, zašto je važan i zašto bi trebalo da u njega prebaci malo ličnog bogatstva.
Naročito ako ima prijatelja poput mene ili mnoštvo Bitkoinera negde tamo.
Ja više neću smarati ljude sa porukama "zašto treba kupiti Bitkoin".
Više nije 2012. godina.
Danas imamo toliko puno informacija od toliko mnogo dobrih ljudi na svim mogućim medijima, tako da NEMATE IZGOVORA da ga ignorišete ili kažete: "ali niko mi nije rekao".
Ukoliko nemate da izdvojite bar malo vremena od vašeg Netflix rasporeda da biste istražili šta je ova stvar i zašto je bitna za vašu ličnu ekonomsku budućnost, onda zaslužujete to što imate.
Deluje okrutno ali dobrodošao u život, mladi žutokljunče.
Sada... Ako ste izdvojili malo vremena ali ste i dalje nezainteresovani ili dovoljno glupi da ga odbacite, onda zaista zaslužujete to što dolazi i ostatak ovog članka je definitivno za vas.
Ne želim da uopšte kupite Bitkoin!
Ok Aleks, ali šta ćemo sa "masovnom adopcijom"???
Pažljivo me slušajte:
Zabole me kurac da li će masovna adopcija doći za 10, 20, 50 ili 100 godina!
Ja sam skroz za selektivnu adopciju i potpuno za dugačku igru. Tako da sam spreman da čekam.
Kao u SVIM prirodnim, evolutivno funkcionalnim sistemima, oni koji seju i pomažu u izgradnji temelja bi trebalo da budu i nesrazmerno nagrađeni.
Ovo je 100% fer i predivno nejednako (neki od vas koji me znate ste upoznati sa mojim stavom o nejednakosti kao najprezrenijem od svih ljudskih ideala. Radi se o odvratnom idealu koji nagrađuje najgore među nama).

Tako da za skeptike i "neverne Tome" imam jednostavnu poruku:
Nadam se da nećete uopšte kupiti Bitkoin. Ni danas ni bilo kada. Nadam se da će jedini put kada budete stupili u dodir sa Bitkoinom to biti jedini način da za nešto budete isplaćeni; npr. kada budete morali da ga zaradite.
Jedva čekam dan kada će mojih nekoliko hiljada satošija moći da kupi tri, četiri ili pet meseci vašeg vremena.
A u međuvremenu...
Molim vas, držite se vašeg fiat novca. Molim vas, držite se vaših šitkoina.
Ne želim nikoga od vas "blokčejnera", šitkoinera, fiat nokoinera i vas svih ostalih klovnova koji mislite da znate bolje.
Ovaj rolerkoster je specijalan, tako da zašto bih želeo da ga delim sa vama glupanderima? Zašto bih bacao bisere pred svinje?
Ja verujem u principe isključivosti.
Ovo nije "kumbaya" ili "svi smo jedno". Jebite se.
Sa razlogom smo drugačiji.
Napraviću sam svoj krevet i ležati u njemu. Vi napravite svoje.
Kada bude došlo vreme, ja ću vam za vaše vreme plaćati satošijima zato što onda nećete imati izbora.
Tada ja pobeđujem, a vi gubite.
Kako sejete, tako žanjete
Razlika između mene i vas je ta što ja kupujem Bitkoin sada zato što tako želim. Vi ćete morati da radite za Bitkoin sutra zato što tako morate.
To je cena neznanja. To je cena arogancije.
To je cena gluposti koju ćete platiti i, koliko god ovo zvuči okrutno, istina je da zaslužujete svaki delić toga.
Svi ležimo u krevetu koji sami pravimo, a vi svoj krevet pravite sada.
Neće vam samouvereni Bitkoiner reći: "lepo sam vam rekao". Nova ekonomska realnost će vam to reći umesto njega.
"Lepo sam vam rekao" će vas udariti poput tone cigle kada shvatite razliku između vas i onih koji su bili razboriti, koji su marljivo štedeli, koji su uložili vreme i trud da otkriju šta je zapravo Bitkoin dok su ih svi nazivali ludacima.
Neće biti sažaljenja.
Nema više bacanja bisera pred svinje
Oni koji imaju priliku da kupe nešto Bitkoina sada, a odluče da to ne urade zahvaljujući neznanju, aroganciji ili gluposti, zaslužuju da plate sa kamatom.
Zaslužuju da trguju svoje sutrašnje dragoceno vreme i energiju za ono što su mogli da nabave danas i to bukvalno "za kikiriki".
Ovde nema greške: nismo jednaki. Mi smo veoma, veoma različiti ljudi.
Ja sam uložio vreme, trud i energiju sada, ne samo zbog sebe samog, već i da bih posadio seme i pomogao mreži.
Uradio sam svoj deo.
Vi ćete doći kasnije i pomoći mi da žanjem nagrade svog truda. Postojaćete da biste mi pomogli da uživam u plodovima.
To će biti vaša uloga.
Izabrao sam da rizikujem i steknem deo onoga zbog čega su me svi nazivali ludim zato što sam učio, verovao i shvatio danas, sa nadom da se izgradi bolja, poštenija i pravičnija budućnost za sve.
Radeći to, neki od nas će postati džinovi i nesrazmerno bogati. I vi imate tu šansu ali je mnogi od vas neće iskoristiti.
I ja sam skroz ok sa tim. Više neću bacati bisere pred svinje.
Ovaj članak može zvučati neprijatno ali više me zabole kurac. Sada je na vama da sami istražujete.
Ovo se događa bez obzira sviđalo vam se to ili ne. Ja i hiljade drugih Bitkoinera smo pisali eseje i eseje o ovome.
Neka imena sa kvalitetnim materijalom kojih se mogu setiti iz glave su:
- Naravno ja
- Gigi
- Robert Breedlove
- Saifedean Ammous
Ako ste radoznali možete ih pratiti. A ovo je sjajno mesto gde možete preuzeti nekoliko odličnih radova:
I za kraj, ako si Bitkoiner koji ovo čita, nikada nećeš znati da li sam zloban ili samo igram 4D šah.
Iskreno, nije ni bitno.
Ovo se dešava. Bitkoin osvaja svet. Ekonomski darvinizam je činjenica.
Sakupljajte vaše satošije, ponudite maslinovu grančicu, obratite pažnju na njihovu radoznalost ili iskru u njihovom oku kao znak da nastavite. Ukoliko toga nema ili naiđete na odbijanje, ostavite ih da se igraju kao svinje u govnima sa njihovim fiatom, deonicama ili šitkoinima.
Biće nam potrebni čistači za naše citadele.
-
 @ 5d4b6c8d:8a1c1ee3
2025-02-15 15:50:17
@ 5d4b6c8d:8a1c1ee3
2025-02-15 15:50:17"Admit it. Sometimes you just need a big strong man." -Xander Harris
Buffy fans should appreciate that reference. It's one of my favorite lines to quote around the house, whenever my wife needs help opening jars.
Today, I said it to my daughter when she tried to open the orange juice herself, which earned a side-eye from the wife. It also led me to think about a possible research hypothesis.
Idea
I've heard that grip strength has been declining in men, to the point where there's barely a difference anymore between men and women.
Is it possible that something as seemingly trivial as not being any more able to open jars, is reducing the rate of relationship formation?
This was one area where men have historically been able to clearly demonstrate some value.
Empirical difficulties
I have no idea what the data looks like on either side of this question (grip strength or relationship formation), so I can't say much about specific data problems.
However, there is definitely going to be an issue with "the dreaded third thing". In particular, I'm concerned with how to isolate the impact of grip strength decline from other effects of testosterone decline. Ideally, we'd be able to do a longitudinal study of men, where their grip strengths and testosterone levels are recorded, as well as their relationship status over time.
Since there's no chance of doing that study, the best hope would be to put together some population level numbers over time and see if relationship formation rates still have a correlation with grip strength, after controlling for average testosterone levels.
I hope you enjoyed this half-baked idea. I mentioned to @denlillaapan that it might be fun to share ideas like this on SN. In all likelihood, no one will ever take these ideas any further, but they still might prompt fun discussions.
originally posted at https://stacker.news/items/886699
-
 @ 6e0ea5d6:0327f353
2025-02-27 22:40:23
@ 6e0ea5d6:0327f353
2025-02-27 22:40:23Ascolta bene, amico mio. Admiration is always better than mere understanding!
Simple understanding in a relationship is an easy, almost automatic gesture. Any woman can understand a man, tolerate his flaws, and accept his presence. But this often stems from pity, convenience, or merely the habit of having someone around. Understanding without admiration is not respect; it is resignation. A woman who only understands but does not admire may stay by your side, but she will never be truly loyal in her heart. And who wants to be merely tolerated out of pity when they could be followed with pride?
Admiration, on the other hand, is the pillar that upholds any worthy relationship. It’s not just about liking someone; it’s about recognizing the value in a man's daily battles, not just his victories. A woman who truly admires you takes pride in your strength, respects your struggles, and walks beside you with her head held high. She doesn’t just accept you—she follows you to the end because she sees greatness in what you build and what you represent.
Admiration is not just about affection; it’s about looking at the man beside you and feeling deep respect for who he is, what he builds, and what he stands for. Without that, what remains? Tolerance? Indifference? The woman who merely understands accepts your existence, but the one who admires follows you with pride because she sees value in your struggle, your strength, and your legacy.
So forget about being “understood” as a priority. Understanding can be a mere transaction, but admiration is the true foundation of any dignified relationship.
If your woman does not admire you for what you do, who you are, and what you build, she is either occupying a space she does not deserve, or you are too weak to be admired.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 5d4b6c8d:8a1c1ee3
2025-02-15 15:03:10
@ 5d4b6c8d:8a1c1ee3
2025-02-15 15:03:10Much to @realBitcoinDog's chagrin, we did eat out for Valentine's Day. Well, actually, we got some take out, but it definitely wasn't very healthy.
However, we did eat fairly early, so it didn't mess up my fasting.
Reflections
Even though I had been regularly fasting before February, this Fast February exercise has improved the habit and led to some noticeable outcomes.
The first couple of days, I was kind of snacky. Because of the fiscal fast element of Fast February, I had to snack on whatever was around the house already. That turned out to be the "wrong" type of applesauce that our daughter refuses to eat. After those first few days, though, I really haven't been very snacky.
In fact, my general appetite is noticeably lower.
The most pronounced non-appetite related effect has been more vivid dreams (or at least more memorable dreams).
On the con side, I have felt a little stiffer and have been stretching more often to alleviate muscle tension.
Score Card
Day 1: 14 hour fast (13 dry) Day 2: 15 hour fast (14 dry) Day 3: 17 hours (16 dry) Day 4: 18 hours (17 dry) Day 5: 18 hours (16 dry) Day 6: 19 hours (16 dry) Day 7: 16 hours (15 dry) Day 8: 18 hours (17 dry) Day 9: 17 hours (17 dry) Day 10: 15 hours (13 dry) Day 11: 20 hours (19 dry) Day 12: 20 hours (17 dry) Day 13: 16 hours (13 dry) Day 14: 17 hours (15 dry) Day 15: TBD (16 dry)
originally posted at https://stacker.news/items/886640
-
 @ 6389be64:ef439d32
2025-02-27 21:32:12
@ 6389be64:ef439d32
2025-02-27 21:32:12GA, plebs. The latest episode of Bitcoin And is out, and, as always, the chicanery is running rampant. Let’s break down the biggest topics I covered, and if you want the full, unfiltered rant, make sure to listen to the episode linked below.
House Democrats’ MEME Act: A Bad Joke?
House Democrats are proposing a bill to ban presidential meme coins, clearly aimed at Trump’s and Melania’s ill-advised token launches. While grifters launching meme coins is bad, this bill is just as ridiculous. If this legislation moves forward, expect a retaliatory strike exposing how politicians like Pelosi and Warren mysteriously amassed their fortunes. Will it pass? Doubtful. But it’s another sign of the government’s obsession with regulating everything except itself.
Senate Banking’s First Digital Asset Hearing: The Real Target Is You
Cynthia Lummis chaired the first digital asset hearing, and—surprise!—it was all about control. The discussion centered on stablecoins, AML, and KYC regulations, with witnesses suggesting Orwellian measures like freezing stablecoin transactions unless pre-approved by authorities. What was barely mentioned? Bitcoin. They want full oversight of stablecoins, which is really about controlling financial freedom. Expect more nonsense targeting self-custody wallets under the guise of stopping “bad actors.”
Bank of America and PayPal Want In on Stablecoins
Bank of America’s CEO openly stated they’ll launch a stablecoin as soon as regulation allows. Meanwhile, PayPal’s CEO paid for a hat using Bitcoin—not their own stablecoin, Pi USD. Why wouldn’t he use his own product? Maybe he knows stablecoins aren’t what they’re hyped up to be. Either way, the legacy financial system is gearing up to flood the market with stablecoins, not because they love crypto, but because it’s a tool to extend U.S. dollar dominance.
MetaPlanet Buys the Dip
Japan’s MetaPlanet issued $13.4M in bonds to buy more Bitcoin, proving once again that institutions see the writing on the wall. Unlike U.S. regulators who obsess over stablecoins, some companies are actually stacking sats.
UK Expands Crypto Seizure Powers
Across the pond, the UK government is pushing legislation to make it easier to seize and destroy crypto linked to criminal activity. While they frame it as going after the bad guys, it’s another move toward centralized control and financial surveillance.
Bitcoin Tools & Tech: Arc, SatoChip, and Nunchuk
Some bullish Bitcoin developments: ARC v0.5 is making Bitcoin’s second layer more efficient, SatoChip now supports Taproot and Nostr, and Nunchuk launched a group wallet with chat, making multisig collaboration easier.
The Bottom Line
The state is coming for financial privacy and control, and stablecoins are their weapon of choice. Bitcoiners need to stay focused, keep their coins in self-custody, and build out parallel systems. Expect more regulatory attacks, but don’t let them distract you—just keep stacking and transacting in ways they can’t control.
🎧 Listen to the full episode here: https://fountain.fm/episode/PYITCo18AJnsEkKLz2Ks
💰 Support the show by boosting sats on Podcasting 2.0! and I will see you on the other side.
-
 @ fd208ee8:0fd927c1
2025-02-15 07:37:01
@ fd208ee8:0fd927c1
2025-02-15 07:37:01E-cash are coupons or tokens for Bitcoin, or Bitcoin debt notes that the mint issues. The e-cash states, essentially, "IoU 2900 sats".
They're redeemable for Bitcoin on Lightning (hard money), and therefore can be used as cash (softer money), so long as the mint has a good reputation. That means that they're less fungible than Lightning because the e-cash from one mint can be more or less valuable than the e-cash from another. If a mint is buggy, offline, or disappears, then the e-cash is unreedemable.
It also means that e-cash is more anonymous than Lightning, and that the sender and receiver's wallets don't need to be online, to transact. Nutzaps now add the possibility of parking transactions one level farther out, on a relay. The same relays that cannot keep npub profiles and follow lists consistent will now do monetary transactions.
What we then have is * a transaction on a relay that triggers * a transaction on a mint that triggers * a transaction on Lightning that triggers * a transaction on Bitcoin.
Which means that every relay that stores the nuts is part of a wildcat banking system. Which is fine, but relay operators should consider whether they wish to carry the associated risks and liabilities. They should also be aware that they should implement the appropriate features in their relay, such as expiration tags (nuts rot after 2 weeks), and to make sure that only expired nuts are deleted.
There will be plenty of specialized relays for this, so don't feel pressured to join in, and research the topic carefully, for yourself.
https://github.com/nostr-protocol/nips/blob/master/60.md https://github.com/nostr-protocol/nips/blob/master/61.md
-
 @ c582af78:698069cc
2025-02-15 04:20:11
@ c582af78:698069cc
2025-02-15 04:20:111. The Battle of Cannae (216 BC) – Rome’s Darkest Hour, and Its Defining Moment
During the Second Punic War, Hannibal of Carthage faced a Roman army that outnumbered his forces 2-to-1. Instead of retreating, he met them head-on with a brilliant tactical maneuver. His army encircled and annihilated the Romans, slaughtering over 50,000 soldiers in a single day—one of the most devastating defeats in Roman history.
https://image.nostr.build/a2ccbcc267d3bc30d24d80873612ba70d8f69a00bdd6a90fc3682f91d87eb956.jpg
Any other nation would have surrendered. But Rome refused. Instead, it adapted, shifting to a war of attrition, avoiding direct confrontations, and gradually wearing down Hannibal’s forces.
Cannae became a paradox—it was Rome’s greatest defeat, yet it forged the Roman spirit of perseverance and relentless determination. Rome ultimately turned the tide, defeated Carthage, and emerged as the dominant power in the Mediterranean.
https://image.nostr.build/9c29ef6b6cebd916c105271927adaa5fe4e668a6078595390936cd7898464c31.jpg
Hannibal’s tactics at Cannae changed warfare forever. His use of battlefield deception and encirclement is still studied in military academies today, and no commander worth his salt is unfamiliar with Hannibal’s masterpiece at Cannae.
2. The Battle of Marathon (490 BC) – The Birth of Western Civilization
When King Darius I of Persia invaded Greece, he sought to crush Athens and expand Persian control. The Athenians, vastly outnumbered, faced what seemed like certain defeat. But instead of waiting for the Persians to march inland, they struck first.
Using superior tactics and their knowledge of the terrain, the Athenians routed the Persian army, sending them fleeing to their ships.
https://image.nostr.build/63c4bdba98f7a2a4ccb3e2a8edcd43596b595284245f3a3395a3c53f51124558.jpg
This stunning victory didn’t just preserve Greek independence—it safeguarded the nascent idea of democracy. Without it, the Golden Age of Greece—the era that produced Socrates, the Parthenon, and the foundations of Western philosophy and governance—might never have happened.
Marathon remains a symbol of strategy and courage overcoming overwhelming odds. Without it, the world might never have known Athenian democracy, Greek philosophy, or the cultural foundations of the West.
https://image.nostr.build/017a314c11238433545977e681801904b8b702e1b568ff6c9438e8577721a243.jpg
3. The Battle of Hastings (1066) – The Making of Modern England
In 1066, William of Normandy led his army across the English Channel to claim the throne of England. At the Battle of Hastings, he faced King Harold II’s Anglo-Saxon forces in a brutal fight that would decide the future of the island.
William’s forces employed innovative strategies, including a feigned retreat, which broke Harold’s defensive lines. Harold was killed, and with him, Anglo-Saxon rule in England.
https://image.nostr.build/110045a76be0577defc5d9b884e5d811235f1992941847ca8a1b1a7b80c9bf79.jpg
Hastings completely transformed England. The Normans introduced a new ruling elite, reshaped governance, and left an enduring mark on the English language. Old English fused with Norman French, laying the foundation for modern English.
Beyond language, the Norman conquest brought England closer to continental Europe, influencing its legal systems, architecture, and culture for centuries. Hastings wasn’t just a military victory—it was a cultural watershed that forever changed England and, by extension, the world.
https://image.nostr.build/2799f91505263370ffb3a899ea4c79a65894f56673b81a024b206e013f3e73a9.jpg
4. The Battle of Lepanto (1571) – Christendom Strikes Back
By the late 16th century, the Ottoman Empire had become a dominant naval power, threatening Christian trading colonies and the stability of Europe’s maritime trade routes.
In 1570, the Ottomans besieged the Venetian-held island of Cyprus. After an 11-month siege, the starving Venetian garrison surrendered under promises of safe passage—but the Ottomans betrayed them, imprisoned the soldiers, and flayed their commander alive.
In response, the Papal States, Spain, Venice, Genoa, and other Christian powers set aside their rivalries and formed the Holy League. In a climactic naval showdown, over 130,000 men engaged in a fierce battle that ultimately ended in a decisive Christian victory.
https://image.nostr.build/0f233ec50e817874e1e6711a1e035b436e206b032d8cac8b33a68230beb20e1b.jpg
Lepanto halted Ottoman expansion into the western Mediterranean and reestablished European control over crucial sea routes. Among the soldiers that day was Miguel de Cervantes, who was wounded and lost the use of his left arm. His experience shaped his literary masterpiece, Don Quixote, further embedding Lepanto’s legacy in European art and culture.
5. The Battle of Trafalgar (1805) – Britain Secures Global Supremacy
In 1805, Napoleon sought to break British naval dominance by uniting the French and Spanish fleets against Admiral Horatio Nelson. The Battle of Trafalgar would decide the fate of European power at sea.
Outnumbered, Nelson devised an unorthodox strategy, splitting his fleet into two perpendicular columns to punch through enemy lines. The result? A decisive British victory—22 enemy ships destroyed without a single British vessel lost.
Trafalgar didn’t just shatter Napoleon’s naval ambitions—it secured Britain’s command of the seas for over a century. This naval dominance paved the way for the Pax Britannica, allowing Britain to expand its empire and maintain global influence well into the 20th century.
https://image.nostr.build/bf5e00f020a0755ea50c1bf1def870cfb226cb5ad18a91445eddac8389b2f05f.jpg
But Trafalgar’s legacy is also bittersweet—Nelson was fatally shot in battle. As he lay dying, he was informed of the victory. His last words?
“Now I am satisfied. Thank God, I have done my duty.”
Nelson’s death turned him into a national hero, and Trafalgar became a defining moment in British history.
More Than Just Battles
These five battles weren’t just clashes of armies—they were turning points that shaped the world.
- Cannae forged Rome’s resilience.
- Marathon preserved Greek democracy.
- Hastings reshaped England’s culture and language.
- Lepanto altered the balance of power in the Mediterranean.
- Trafalgar secured British naval dominance for a century.
Each of these battles reshaped civilizations—proving that history isn’t just written in words, but also in blood, steel, and strategy.
-
 @ 2ed3596e:98b4cc78
2025-02-27 21:28:33
@ 2ed3596e:98b4cc78
2025-02-27 21:28:33Pay anyone in Canada with bitcoin! One step closer to replacing your bank with Bitcoin Well
Everyone who accepts e-Transfers, now accepts bitcoin! Canadians with a Bitcoin Well account can send money to anyone via e-Transfer using their bitcoin in self custody. Typical transactions, like rent payments, paying friends back for dinner, paying your cleaning lady or even to pay for that new (to you) boom box on Facebook marketplace, can now be paid quickly, securely and cheaper with your Bitcoin Well account. And best of all, it’s all done with bitcoin in self custody. Keep reading to learn more!
How to send an e-Transfer to anyone in Canada using bitcoin:
From the sell page in your Bitcoin Well account you can select the network (Bitcoin or Lightning Network) and how many dollars you’d like to send via e-Transfer. For more information on the Lightning Network click here.
Next you will see a new dropdown where you can choose the recipient for the e-Transfer. It will be the email on your Bitcoin Well account by default.

To add a new recipient, select the drop down and “Add recipient”. Here you will be asked to provide the recipient’s name, email and the security question/answer you’d like to provide for the e-Transfer.

You’ll be responsible for telling them the security question and answer, so don’t forget!

You can also invite your recipient to join Bitcoin Well with your ref link! You’ll earn Bitcoin Well points and sats when they use Bitcoin Well!
If you chose the Bitcoin network:
With all your information entered, you will be able to send bitcoin to the bitcoin address on screen and an e-Transfer will be sent to your recipient after 1 confirmation.
Note! This bitcoin address is permanently associated with your recipient. Any and all bitcoin received by this bitcoin address will be automatically converted into dollars and sent to your recipient; even if you do not login to your Bitcoin Well account!

If you chose the Lightning Network:
Select “Generate Invoice” to generate an LN-invoice which will be associated with your transaction. Once that invoice is paid an e-Transfer will be immediately sent to your desired recipient.
Of course, you can still send sats to your Bitcoin Well Payment Address any time to receive an e-Transfer yourself.

Banks out; Bitcoin Standard in
Bitcoin Well arms its customers with the knowledge and tools to fully live on a Bitcoin Standard and maximize their independence by keeping bitcoin in self custody instead of dollars in their bank.
Bitcoin Well now enables the same instant and fast transfer capabilities as a bank, but facilitated with bitcoin in self custody!
Replace your bank with Bitcoin Well!
Earn sats from your bitcoin transactions
Bitcoin Well is also the best place in the world to earn bitcoin. When you earn points in your Bitcoin Well account, you gain the opportunity to play the Bitcoin (Wishing) Well, where you win sats with every play.
The best part? We send bitcoin that you win straight to your personal wallet via the Lightning Network.
Oh yeah, did we mention you can win 1,000,000 sats? If you're an active Bitcoin Well customer, there is a chance you've earned a pile of points. The more you use your account for buying, selling or spending bitcoin - the more points you’ll earn! Log in to your Bitcoin Well account and check your point balance.
About Bitcoin Well
Bitcoin Well exists to enable independence. We do this by coupling the convenience of modern banking, with the benefits of bitcoin. In other words, we want to make it easy to use bitcoin in self-custody.
-
 @ 1c197b12:242e1642
2025-02-14 21:40:46
@ 1c197b12:242e1642
2025-02-14 21:40:46We the People of the United States, in Order to form a more perfect Union, establish Justice, insure domestic Tranquility, provide for the common defence, promote the general Welfare, and secure the Blessings of Liberty to ourselves and our Posterity, do ordain and establish this Constitution for the United States of America.
Article. I. Section. 1. All legislative Powers herein granted shall be vested in a Congress of the United States, which shall consist of a Senate and House of Representatives.
Section. 2. The House of Representatives shall be composed of Members chosen every second Year by the People of the several States, and the Electors in each State shall have the Qualifications requisite for Electors of the most numerous Branch of the State Legislature.
No Person shall be a Representative who shall not have attained to the Age of twenty five Years, and been seven Years a Citizen of the United States, and who shall not, when elected, be an Inhabitant of that State in which he shall be chosen.
Representatives and direct Taxes shall be apportioned among the several States which may be included within this Union, according to their respective Numbers, which shall be determined by adding to the whole Number of free Persons, including those bound to Service for a Term of Years, and excluding Indians not taxed, three fifths of all other Persons. The actual Enumeration shall be made within three Years after the first Meeting of the Congress of the United States, and within every subsequent Term of ten Years, in such Manner as they shall by Law direct. The Number of Representatives shall not exceed one for every thirty Thousand, but each State shall have at Least one Representative; and until such enumeration shall be made, the State of New Hampshire shall be entitled to chuse three, Massachusetts eight, Rhode-Island and Providence Plantations one, Connecticut five, New-York six, New Jersey four, Pennsylvania eight, Delaware one, Maryland six, Virginia ten, North Carolina five, South Carolina five, and Georgia three.
When vacancies happen in the Representation from any State, the Executive Authority thereof shall issue Writs of Election to fill such Vacancies.
The House of Representatives shall chuse their Speaker and other Officers; and shall have the sole Power of Impeachment.
Section. 3. The Senate of the United States shall be composed of two Senators from each State, chosen by the Legislature thereof, for six Years; and each Senator shall have one Vote.
Immediately after they shall be assembled in Consequence of the first Election, they shall be divided as equally as may be into three Classes. The Seats of the Senators of the first Class shall be vacated at the Expiration of the second Year, of the second Class at the Expiration of the fourth Year, and of the third Class at the Expiration of the sixth Year, so that one third may be chosen every second Year; and if Vacancies happen by Resignation, or otherwise, during the Recess of the Legislature of any State, the Executive thereof may make temporary Appointments until the next Meeting of the Legislature, which shall then fill such Vacancies.
No Person shall be a Senator who shall not have attained to the Age of thirty Years, and been nine Years a Citizen of the United States, and who shall not, when elected, be an Inhabitant of that State for which he shall be chosen.
The Vice President of the United States shall be President of the Senate, but shall have no Vote, unless they be equally divided.
The Senate shall chuse their other Officers, and also a President pro tempore, in the Absence of the Vice President, or when he shall exercise the Office of President of the United States.
The Senate shall have the sole Power to try all Impeachments. When sitting for that Purpose, they shall be on Oath or Affirmation. When the President of the United States is tried, the Chief Justice shall preside: And no Person shall be convicted without the Concurrence of two thirds of the Members present.
Judgment in Cases of Impeachment shall not extend further than to removal from Office, and disqualification to hold and enjoy any Office of honor, Trust or Profit under the United States: but the Party convicted shall nevertheless be liable and subject to Indictment, Trial, Judgment and Punishment, according to Law.
Section. 4. The Times, Places and Manner of holding Elections for Senators and Representatives, shall be prescribed in each State by the Legislature thereof; but the Congress may at any time by Law make or alter such Regulations, except as to the Places of chusing Senators.
The Congress shall assemble at least once in every Year, and such Meeting shall be on the first Monday in December, unless they shall by Law appoint a different Day.
Section. 5. Each House shall be the Judge of the Elections, Returns and Qualifications of its own Members, and a Majority of each shall constitute a Quorum to do Business; but a smaller Number may adjourn from day to day, and may be authorized to compel the Attendance of absent Members, in such Manner, and under such Penalties as each House may provide.
Each House may determine the Rules of its Proceedings, punish its Members for disorderly Behaviour, and, with the Concurrence of two thirds, expel a Member.
Each House shall keep a Journal of its Proceedings, and from time to time publish the same, excepting such Parts as may in their Judgment require Secrecy; and the Yeas and Nays of the Members of either House on any question shall, at the Desire of one fifth of those Present, be entered on the Journal.
Neither House, during the Session of Congress, shall, without the Consent of the other, adjourn for more than three days, nor to any other Place than that in which the two Houses shall be sitting.
Section. 6. The Senators and Representatives shall receive a Compensation for their Services, to be ascertained by Law, and paid out of the Treasury of the United States. They shall in all Cases, except Treason, Felony and Breach of the Peace, be privileged from Arrest during their Attendance at the Session of their respective Houses, and in going to and returning from the same; and for any Speech or Debate in either House, they shall not be questioned in any other Place.
No Senator or Representative shall, during the Time for which he was elected, be appointed to any civil Office under the Authority of the United States, which shall have been created, or the Emoluments whereof shall have been encreased during such time; and no Person holding any Office under the United States, shall be a Member of either House during his Continuance in Office.
Section. 7. All Bills for raising Revenue shall originate in the House of Representatives; but the Senate may propose or concur with Amendments as on other Bills.
Every Bill which shall have passed the House of Representatives and the Senate, shall, before it become a Law, be presented to the President of the United States; If he approve he shall sign it, but if not he shall return it, with his Objections to that House in which it shall have originated, who shall enter the Objections at large on their Journal, and proceed to reconsider it. If after such Reconsideration two thirds of that House shall agree to pass the Bill, it shall be sent, together with the Objections, to the other House, by which it shall likewise be reconsidered, and if approved by two thirds of that House, it shall become a Law. But in all such Cases the Votes of both Houses shall be determined by yeas and Nays, and the Names of the Persons voting for and against the Bill shall be entered on the Journal of each House respectively. If any Bill shall not be returned by the President within ten Days (Sundays excepted) after it shall have been presented to him, the Same shall be a Law, in like Manner as if he had signed it, unless the Congress by their Adjournment prevent its Return, in which Case it shall not be a Law.
Every Order, Resolution, or Vote to which the Concurrence of the Senate and House of Representatives may be necessary (except on a question of Adjournment) shall be presented to the President of the United States; and before the Same shall take Effect, shall be approved by him, or being disapproved by him, shall be repassed by two thirds of the Senate and House of Representatives, according to the Rules and Limitations prescribed in the Case of a Bill.
Section. 8. The Congress shall have Power To lay and collect Taxes, Duties, Imposts and Excises, to pay the Debts and provide for the common Defence and general Welfare of the United States; but all Duties, Imposts and Excises shall be uniform throughout the United States;
To borrow Money on the credit of the United States;
To regulate Commerce with foreign Nations, and among the several States, and with the Indian Tribes;
To establish an uniform Rule of Naturalization, and uniform Laws on the subject of Bankruptcies throughout the United States;
To coin Money, regulate the Value thereof, and of foreign Coin, and fix the Standard of Weights and Measures;
To provide for the Punishment of counterfeiting the Securities and current Coin of the United States;
To establish Post Offices and post Roads;
To promote the Progress of Science and useful Arts, by securing for limited Times to Authors and Inventors the exclusive Right to their respective Writings and Discoveries;
To constitute Tribunals inferior to the supreme Court;
To define and punish Piracies and Felonies committed on the high Seas, and Offences against the Law of Nations;
To declare War, grant Letters of Marque and Reprisal, and make Rules concerning Captures on Land and Water;
To raise and support Armies, but no Appropriation of Money to that Use shall be for a longer Term than two Years;
To provide and maintain a Navy;
To make Rules for the Government and Regulation of the land and naval Forces;
To provide for calling forth the Militia to execute the Laws of the Union, suppress Insurrections and repel Invasions;
To provide for organizing, arming, and disciplining, the Militia, and for governing such Part of them as may be employed in the Service of the United States, reserving to the States respectively, the Appointment of the Officers, and the Authority of training the Militia according to the discipline prescribed by Congress;
To exercise exclusive Legislation in all Cases whatsoever, over such District (not exceeding ten Miles square) as may, by Cession of particular States, and the Acceptance of Congress, become the Seat of the Government of the United States, and to exercise like Authority over all Places purchased by the Consent of the Legislature of the State in which the Same shall be, for the Erection of Forts, Magazines, Arsenals, dock-Yards, and other needful Buildings;—And
To make all Laws which shall be necessary and proper for carrying into Execution the foregoing Powers, and all other Powers vested by this Constitution in the Government of the United States, or in any Department or Officer thereof.
Section. 9. The Migration or Importation of such Persons as any of the States now existing shall think proper to admit, shall not be prohibited by the Congress prior to the Year one thousand eight hundred and eight, but a Tax or duty may be imposed on such Importation, not exceeding ten dollars for each Person.
The Privilege of the Writ of Habeas Corpus shall not be suspended, unless when in Cases of Rebellion or Invasion the public Safety may require it.
No Bill of Attainder or ex post facto Law shall be passed.
No Capitation, or other direct, Tax shall be laid, unless in Proportion to the Census or enumeration herein before directed to be taken.
No Tax or Duty shall be laid on Articles exported from any State.
No Preference shall be given by any Regulation of Commerce or Revenue to the Ports of one State over those of another: nor shall Vessels bound to, or from, one State, be obliged to enter, clear, or pay Duties in another.
No Money shall be drawn from the Treasury, but in Consequence of Appropriations made by Law; and a regular Statement and Account of the Receipts and Expenditures of all public Money shall be published from time to time.
No Title of Nobility shall be granted by the United States: And no Person holding any Office of Profit or Trust under them, shall, without the Consent of the Congress, accept of any present, Emolument, Office, or Title, of any kind whatever, from any King, Prince, or foreign State.
Section. 10. No State shall enter into any Treaty, Alliance, or Confederation; grant Letters of Marque and Reprisal; coin Money; emit Bills of Credit; make any Thing but gold and silver Coin a Tender in Payment of Debts; pass any Bill of Attainder, ex post facto Law, or Law impairing the Obligation of Contracts, or grant any Title of Nobility.
No State shall, without the Consent of the Congress, lay any Imposts or Duties on Imports or Exports, except what may be absolutely necessary for executing it's inspection Laws: and the net Produce of all Duties and Imposts, laid by any State on Imports or Exports, shall be for the Use of the Treasury of the United States; and all such Laws shall be subject to the Revision and Controul of the Congress.
No State shall, without the Consent of Congress, lay any Duty of Tonnage, keep Troops, or Ships of War in time of Peace, enter into any Agreement or Compact with another State, or with a foreign Power, or engage in War, unless actually invaded, or in such imminent Danger as will not admit of delay.
Article. II. Section. 1. The executive Power shall be vested in a President of the United States of America. He shall hold his Office during the Term of four Years, and, together with the Vice President, chosen for the same Term, be elected, as follows
Each State shall appoint, in such Manner as the Legislature thereof may direct, a Number of Electors, equal to the whole Number of Senators and Representatives to which the State may be entitled in the Congress: but no Senator or Representative, or Person holding an Office of Trust or Profit under the United States, shall be appointed an Elector.
The Electors shall meet in their respective States, and vote by Ballot for two Persons, of whom one at least shall not be an Inhabitant of the same State with themselves. And they shall make a List of all the Persons voted for, and of the Number of Votes for each; which List they shall sign and certify, and transmit sealed to the Seat of the Government of the United States, directed to the President of the Senate. The President of the Senate shall, in the Presence of the Senate and House of Representatives, open all the Certificates, and the Votes shall then be counted. The Person having the greatest Number of Votes shall be the President, if such Number be a Majority of the whole Number of Electors appointed; and if there be more than one who have such Majority, and have an equal Number of Votes, then the House of Representatives shall immediately chuse by Ballot one of them for President; and if no Person have a Majority, then from the five highest on the List the said House shall in like Manner chuse the President. But in chusing the President, the Votes shall be taken by States, the Representation from each State having one Vote; A quorum for this Purpose shall consist of a Member or Members from two thirds of the States, and a Majority of all the States shall be necessary to a Choice. In every Case, after the Choice of the President, the Person having the greatest Number of Votes of the Electors shall be the Vice President. But if there should remain two or more who have equal Votes, the Senate shall chuse from them by Ballot the Vice President.
The Congress may determine the Time of chusing the Electors, and the Day on which they shall give their Votes; which Day shall be the same throughout the United States.
No Person except a natural born Citizen, or a Citizen of the United States, at the time of the Adoption of this Constitution, shall be eligible to the Office of President; neither shall any Person be eligible to that Office who shall not have attained to the Age of thirty five Years, and been fourteen Years a Resident within the United States.
In Case of the Removal of the President from Office, or of his Death, Resignation, or Inability to discharge the Powers and Duties of the said Office, the Same shall devolve on the Vice President, and the Congress may by Law provide for the Case of Removal, Death, Resignation or Inability, both of the President and Vice President, declaring what Officer shall then act as President, and such Officer shall act accordingly, until the Disability be removed, or a President shall be elected.
The President shall, at stated Times, receive for his Services, a Compensation, which shall neither be encreased nor diminished during the Period for which he shall have been elected, and he shall not receive within that Period any other Emolument from the United States, or any of them.
Before he enter on the Execution of his Office, he shall take the following Oath or Affirmation:—"I do solemnly swear (or affirm) that I will faithfully execute the Office of President of the United States, and will to the best of my Ability, preserve, protect and defend the Constitution of the United States."
Section. 2. The President shall be Commander in Chief of the Army and Navy of the United States, and of the Militia of the several States, when called into the actual Service of the United States; he may require the Opinion, in writing, of the principal Officer in each of the executive Departments, upon any Subject relating to the Duties of their respective Offices, and he shall have Power to grant Reprieves and Pardons for Offences against the United States, except in Cases of Impeachment.
He shall have Power, by and with the Advice and Consent of the Senate, to make Treaties, provided two thirds of the Senators present concur; and he shall nominate, and by and with the Advice and Consent of the Senate, shall appoint Ambassadors, other public Ministers and Consuls, Judges of the supreme Court, and all other Officers of the United States, whose Appointments are not herein otherwise provided for, and which shall be established by Law: but the Congress may by Law vest the Appointment of such inferior Officers, as they think proper, in the President alone, in the Courts of Law, or in the Heads of Departments.
The President shall have Power to fill up all Vacancies that may happen during the Recess of the Senate, by granting Commissions which shall expire at the End of their next Session.
Section. 3. He shall from time to time give to the Congress Information of the State of the Union, and recommend to their Consideration such Measures as he shall judge necessary and expedient; he may, on extraordinary Occasions, convene both Houses, or either of them, and in Case of Disagreement between them, with Respect to the Time of Adjournment, he may adjourn them to such Time as he shall think proper; he shall receive Ambassadors and other public Ministers; he shall take Care that the Laws be faithfully executed, and shall Commission all the Officers of the United States.
Section. 4. The President, Vice President and all civil Officers of the United States, shall be removed from Office on Impeachment for, and Conviction of, Treason, Bribery, or other high Crimes and Misdemeanors.
Article. III. Section. 1. The judicial Power of the United States, shall be vested in one supreme Court, and in such inferior Courts as the Congress may from time to time ordain and establish. The Judges, both of the supreme and inferior Courts, shall hold their Offices during good Behaviour, and shall, at stated Times, receive for their Services, a Compensation, which shall not be diminished during their Continuance in Office.
Section. 2. The judicial Power shall extend to all Cases, in Law and Equity, arising under this Constitution, the Laws of the United States, and Treaties made, or which shall be made, under their Authority;—to all Cases affecting Ambassadors, other public Ministers and Consuls;—to all Cases of admiralty and maritime Jurisdiction;—to Controversies to which the United States shall be a Party;—to Controversies between two or more States;— between a State and Citizens of another State,—between Citizens of different States,—between Citizens of the same State claiming Lands under Grants of different States, and between a State, or the Citizens thereof, and foreign States, Citizens or Subjects.
In all Cases affecting Ambassadors, other public Ministers and Consuls, and those in which a State shall be Party, the supreme Court shall have original Jurisdiction. In all the other Cases before mentioned, the supreme Court shall have appellate Jurisdiction, both as to Law and Fact, with such Exceptions, and under such Regulations as the Congress shall make.
The Trial of all Crimes, except in Cases of Impeachment, shall be by Jury; and such Trial shall be held in the State where the said Crimes shall have been committed; but when not committed within any State, the Trial shall be at such Place or Places as the Congress may by Law have directed.
Section. 3. Treason against the United States, shall consist only in levying War against them, or in adhering to their Enemies, giving them Aid and Comfort. No Person shall be convicted of Treason unless on the Testimony of two Witnesses to the same overt Act, or on Confession in open Court.
The Congress shall have Power to declare the Punishment of Treason, but no Attainder of Treason shall work Corruption of Blood, or Forfeiture except during the Life of the Person attainted.
Article. IV. Section. 1. Full Faith and Credit shall be given in each State to the public Acts, Records, and judicial Proceedings of every other State. And the Congress may by general Laws prescribe the Manner in which such Acts, Records and Proceedings shall be proved, and the Effect thereof.
Section. 2. The Citizens of each State shall be entitled to all Privileges and Immunities of Citizens in the several States.
A Person charged in any State with Treason, Felony, or other Crime, who shall flee from Justice, and be found in another State, shall on Demand of the executive Authority of the State from which he fled, be delivered up, to be removed to the State having Jurisdiction of the Crime.
No Person held to Service or Labour in one State, under the Laws thereof, escaping into another, shall, in Consequence of any Law or Regulation therein, be discharged from such Service or Labour, but shall be delivered up on Claim of the Party to whom such Service or Labour may be due.
Section. 3. New States may be admitted by the Congress into this Union; but no new State shall be formed or erected within the Jurisdiction of any other State; nor any State be formed by the Junction of two or more States, or Parts of States, without the Consent of the Legislatures of the States concerned as well as of the Congress.
The Congress shall have Power to dispose of and make all needful Rules and Regulations respecting the Territory or other Property belonging to the United States; and nothing in this Constitution shall be so construed as to Prejudice any Claims of the United States, or of any particular State.
Section. 4. The United States shall guarantee to every State in this Union a Republican Form of Government, and shall protect each of them against Invasion; and on Application of the Legislature, or of the Executive (when the Legislature cannot be convened) against domestic Violence.
Article. V. The Congress, whenever two thirds of both Houses shall deem it necessary, shall propose Amendments to this Constitution, or, on the Application of the Legislatures of two thirds of the several States, shall call a Convention for proposing Amendments, which, in either Case, shall be valid to all Intents and Purposes, as Part of this Constitution, when ratified by the Legislatures of three fourths of the several States, or by Conventions in three fourths thereof, as the one or the other Mode of Ratification may be proposed by the Congress; Provided that no Amendment which may be made prior to the Year One thousand eight hundred and eight shall in any Manner affect the first and fourth Clauses in the Ninth Section of the first Article; and that no State, without its Consent, shall be deprived of its equal Suffrage in the Senate.
Article. VI. All Debts contracted and Engagements entered into, before the Adoption of this Constitution, shall be as valid against the United States under this Constitution, as under the Confederation.
This Constitution, and the Laws of the United States which shall be made in Pursuance thereof; and all Treaties made, or which shall be made, under the Authority of the United States, shall be the supreme Law of the Land; and the Judges in every State shall be bound thereby, any Thing in the Constitution or Laws of any State to the Contrary notwithstanding.
The Senators and Representatives before mentioned, and the Members of the several State Legislatures, and all executive and judicial Officers, both of the United States and of the several States, shall be bound by Oath or Affirmation, to support this Constitution; but no religious Test shall ever be required as a Qualification to any Office or public Trust under the United States.
Article. VII. The Ratification of the Conventions of nine States, shall be sufficient for the Establishment of this Constitution between the States so ratifying the Same.
The Word, "the," being interlined between the seventh and eighth Lines of the first Page, The Word "Thirty" being partly written on an Erazure in the fifteenth Line of the first Page, The Words "is tried" being interlined between the thirty second and thirty third Lines of the first Page and the Word "the" being interlined between the forty third and forty fourth Lines of the second Page.
Attest William Jackson Secretary
done in Convention by the Unanimous Consent of the States present the Seventeenth Day of September in the Year of our Lord one thousand seven hundred and Eighty seven and of the Independance of the United States of America the Twelfth In witness whereof We have hereunto subscribed our Names,
-
 @ dbb19ae0:c3f22d5a
2025-02-27 20:31:03
@ dbb19ae0:c3f22d5a
2025-02-27 20:31:03Using nostr_sdk 0.39 replace nsec_key with your secret key replace npub_to_follow by the npub to follow
``` python from nostr_sdk import Metadata, Client, Keys, Filter, Kind, KindStandard, Contact, PublicKey, EventBuilder from datetime import timedelta import asyncio
async def main(): keys = Keys.parse("nsec_key") client = Client() await client.add_relay("wss://relay.damus.io") await client.connect()
# Get current contact list f = Filter().author(keys.public_key()).kind(Kind.from_std(KindStandard.CONTACT_LIST)) events = await client.fetch_events(f, timedelta(seconds=10)) event = events.first() if event: # Get current contact public keys and add a new contact public_keys = event.tags().public_keys() new_public_key = PublicKey.parse("npub_to_follow") public_keys.append(new_public_key) # Create a new contact list event and send it to relays contacts = [Contact(public_key=pk, relay_url=None, alias=None) for pk in public_keys] event = EventBuilder.contact_list(contacts).sign_with_keys(keys) await client.send_event(event) print(f"Added follow to: {new_public_key}") else: print("No contact list found")if name == 'main': asyncio.run(main()) ```
https://github.com/ev3rst/nostr_sdk_examples/blob/main/ns-follow-npub.py
-
 @ 1c197b12:242e1642
2025-02-14 21:38:15
@ 1c197b12:242e1642
2025-02-14 21:38:15Today, I'm going to attempt to install Servus to my test server. I'll be using a raspberry Pi4 4GB version with a 16GB microSD card (because what I have laying around). And, as you know... if it'll run on a Pi, it'll run pretty much anywhere.
What is SERVUS?
From GitHub... "Servus is a CMS, personal Nostr relay and personal Blossom server fully self-contained within one executable file."
Here's what you'll need:
A spare server. It can be a VPS, old laptop, old computer, 3rd market server from a decommissioned datacenter that you got for cheap on Ebay, a NUC... something that can run Linux.
- An understanding of the Linux terminal.
- install git and cargo.
- A web browser (don't you side-eye me!).
Let Us Begin...
I'm assuming you're using a Debian-based system. Open your terminal and enter the following:
Go ahead and ssh into your server with something like: "ssh yourusername@ipaddress" or "ssh yourusername@domainname.tld" enter your password when prompted and hit enter.

If you plan to do other stuff with your server later on, you might even consider using "ssh-copy-id yourusername@ipaddress" in order to not have to enter you password, all-the-time.

(Without the quotes) "su", or "sudo su". Whatever means you use to get to superuser (root). Then, enter your password.

Once in root, type: apt install git cargo -y Then, hit enter. You'll see a wall text... yadda yadda.


Now, you'll type (without quotes): "git clone https://github.com/servuscms/servus.git" and hit enter. You'll see a progress bar.

If you type "ls" you should see a folder labeled, "servus". We now change directories by typing, "cd servus". Inside of the servus folder you'll see a few other folders and a few files by typing "ls" again.

According the the servus github, there are a few build options. I'm going to use the "release" version for this tutorial. We do this by typing, "cargo build --release". You'll see a fetch progress bar and a wall of text.


NOTE: I'm using a raspberry pi 4, in this tutorial. At the end of trying "cargo build --release" I got a version error for a package called "anstream v0.6.14" because it requires "rustc 1.65.0", or higher. The error message gives you a fix by typing "cargo update -p anstream@0.6.14 --precise ver"

BUT that won't work. Here's how to fix it:
Type the following (without quotations): "apt purge rustc -y && apt install curl -y && curl https://sh.rustup.rs -sSf | sh"
This will remove the outdated rustc. Then, you're installing curl so that you can install the latest version of rustc and cargo because they aren't in the distro repo. Restart your machine with: "sudo reboot". Once you're back into your servus directory, just run the "cargo build" command, again. Now back to the show!
Now that we have run the "cargo build" command, it's time to move on to setting up access and ssl. According to github, there are a few options. They are as follows:
-
./target/debug/servus - this starts Servus on port 4884, without SSL
-
sudo ./target/debug/servus --ssl-acme[-production] --contact-email youremail@example.com (this starts Servus on port 443 and obtains SSL certificates from Let's Encrypt using ACME by providing a contact email).
-
sudo ./target/debug/servus --ssl-cert
--ssl-key (this starts Servus on port 443 using the providedand ) I'll be using the command no calling for SSL. More information can be found here: https://github.com/servuscms/servus

So from the terminal we input (without quotes): "./target/release/servus" because, as you may recall, I used the "cargo build --release" version earlier.
It will ask a few questions. Here's what I put...
Domain: test.local
Admin pubkey: nostr:npub1rsvhkyk2nnsyzkmsuaq9h9ms7rkxhn8mtxejkca2l4pvkfpwzepql3vmtf

Then, you'll get a bit of output with your ip and port interface. In this case, it's http://localhost:4884 Now go to your browser and input that address, it's local, or the IP address of the server... something like, http://192.168.x.x:4884 and HUZZAH!!! Just like that, you should see your site. To get to the admin section of your site, just add "/.admin" (without quotes) to the IP address you just input into the browser.


CONGRATS! I hope this was helpful :-)
While Servus is extremely experimental, and it is advised to not run it in production. There are a number of features worth taking a look at. More information about what Servus can do can be found here: Servus Github
DONE.
-
 @ 1c197b12:242e1642
2025-02-14 21:27:28
@ 1c197b12:242e1642
2025-02-14 21:27:28This article will be basic instructions for extreme normies (I say that lovingly), or anyone looking to get started with using zap.stream and sharing to nostr.
EQUIPMENT Getting started is incredibly easy and your equipment needs are miniscule.
An old desktop or laptop running Linux, MacOs, or Windows made in the passed 15yrs should do. Im currently using and old Dell Latitude E5430 with an Intel i5-3210M with 32Gigs of ram and 250GB hard drive. Technically, you go as low as using a Raspberry Pi 4B+ running Owncast, but Ill save that so a future tutorial.
Let's get started.
ON YOUR COMPUTER You'll need to install OBS (open broaster software). OBS is the go-to for streaming to social media. There are tons of YouTube videos on it's function. WE, however, will only be doing the basics to get us up and running.
First, go to https://obsproject.com/

Once on the OBS site, choose the correct download for you system. Linux, MacOs or Windows. Download (remember where you downloaded the file to). Go there and install your download. You may have to enter your password to install on your particular operating system. This is normal.
Once you've installed OBS, open the application. It should look something like this...

For our purposes, we will be in studio mode. Locate the 'Studio Mode' button on the right lower-hand side of the screen, and click it.

You'll see the screen split like in the image above. The left-side is from your desktop, and the right-side is what your broadcast will look like.
Next, we go to settings. The 'Settings' button is located right below the 'Studio Mode" button.

Now we're in settings and you should see something like this...

Now locate stream in the right-hand menu. It should be the second in the list. Click it.

Once in the stream section, go to 'Service' and in the right-hand drop-down, find and select 'Custom...' from the drop-down menu.

Remeber where this is because we'll need to come back to it, shortly.
ZAPSTREAM We need our streamkey credentials from Zapstream. Go to https://zap.stream. Then, go to your dashboard.

Located on the lower right-hand side is the Server URL and Stream Key. You'll need to copy/paste this in OBS.

You may have to generate new keys, if they aren't already there. This is normal. If you're interested in multi-streaming (That's where you broadcast to multiple social media platforms all at once), youll need the server URL and streamkeys from each. You'll place them in their respective forms in Zapstream's 'Stream Forwarding" section.

Use the custom form, if the platform you want to stream to isn't listed.
*Side-Note: remember that you can use your nostr identity across multiple nostr client applications. So when your login for Amethyst, as an example, could be used when you login to zapstream. Also, i would suggest using Alby's browser extension. It makes it much easier to fund your stream, as well as receive zaps. *
Now, BACK TO OBS... With Stream URL and Key in hand, paste them in the 'Stream" section of OBS' settings. Service [Custom...] Server [Server URL] StreamKey [Your zapstream stream key]

After you've entered all your streaming credentials, click 'OK' at the bottom, on the right-hand side.
WHAT'S NEXT? Let's setup your first stream from OBS. First we need to choose a source. Your source is your input device. It can be your webcam, your mic, your monitor, or any particular window on your screen. assuming you're an absolute beginner, we're going to use the source 'Window Capture (Xcomposite)'.

Now, open your source file. We'll use a video source called 'grannyhiphop.mp4'. In your case it can be whatever you want to stream; Just be sure to select the proper source.

Double-click on 'Window Capture' in your sources list. In the pop-up window, select your file from the 'Window' drop-down menu.


You should see something like this...

Working in the left display of OBS, we will adjust the video by left-click, hold and drag the bottom corner, so that it takes up the whole display.

In order to adjust the right-side display ( the broadcast side), we need to manipulate the video source by changing it's size.

This may take some time to adjust the size. This is normal. What I've found to help is, after every adjustment, I click the 'Fade (300ms)' button. I have no idea why it helps, but it does, lol.

Finally, after getting everything to look the way you want, you click the 'Start Stream' button.

BACK TO ZAPSTREAM Now, we go back to zapstream to check to see if our stream is up. It may take a few moments to update. You may even need to refresh the page. This is normal.
 STREAMS UP!!!
STREAMS UP!!!A few things, in closing. You'll notice that your dashbooard has changed. It'll show current stream time, how much time you have left (according to your funding source), who's zapped you with how much theyve zapped, the ability to post a note about your stream (to both nostr and twitter), and it shows your chatbox with your listeners. There are also a raid feature, stream settings (where you can title & tag your stream). You can 'topup' your funding for your stream. As well as, see your current balance.
You did a great and If you ever need more help, just use the tag #asknostr in your note. There are alway nostriches willing to help.
STAY AWESOME!!!
-
 @ 78c90fc4:4bff983c
2025-02-27 20:19:08
@ 78c90fc4:4bff983c
2025-02-27 20:19:08Gerichtliche Beschwerde wg. Arbeitsverweigerung
Sehr geehrte Damen und Herren
\ Da meine Fragen zum Schutz der Bevölkerung an das kantonale Gesundheitsamt und die weiteren Verantwortungsträger bis heute nicht beantwortet wurden, habe ich mich mit einer Beschwerde an das Kantonsgericht Baselland gewandt.
Ignorieren und Wegschauen bei möglichen Offizialdelikten (schwere Körperverletzung) ist kein verantwortungsvolles Handeln. Bitte stellen Sie sich den Fragen und der Realität.
\ Freundliche Grüsse
Oliver Christen
https://x.com/RealWsiegrist/status/1895162279953367067
Verbrechen gegen die Menschlichkeit sind schwerwiegende Verstöße gegen das Völkerrecht, die durch systematische oder ausgedehnte Angriffe gegen die Zivilbevölkerung gekennzeichnet sind. Sie zählen zu den Kernverbrechen des Völkerstrafrechts und sind unabhängig von Kriegszuständen strafbar.
https://x.com/RealWsiegrist/status/1895162279953367067
Covid Dossier; Eine Aufzeichnung der militärischen und geheimdienstlichen Koordination des globalen Covid-Ereignisses
https://www.aletheialib.org/doc/809

-
 @ 6538925e:571e55c3
2025-02-13 16:05:42
@ 6538925e:571e55c3
2025-02-13 16:05:42 \
Nostr Live Streams (Beta)
\
Nostr Live Streams (Beta)If you follow shows like Rabbit Hole Recap, THE Bitcoin Podcast or Simply Bitcoin on Nostr, you can now watch the video in Fountain and hang out in the live chat as it’s being recorded. You'll find livestreams from people who follow on Nostr at the top of the home screen.
As well and live podcasts, you will also find live music events from PhantomPowerMedia, radio stations like NoGood and Noderunners, as well as channels dedicated to gaming, art, coding and much more.
Bringing creators and fans together through live experiences enables audience participation and creates a special feeling of community, so we’re really excited to get this into your hands.
Nostr livestreams are a beta feature - i.e. we still have a lot more work to do! We will continue to make improvements to livestreams over the coming months - so we would love to hear your feedback.
 \
Storage Manager
\
Storage ManagerWe’ve added a storage manager in the app’s settings so that you can view file storage size for audio downloads, video downloads, transcripts, image cache, feed cache, and temp files. You can delete all files in any of these folders to free up storage on your device so that Fountain continues to run optimally.
There are other performance and stability improvements that we are working on too. For example, in the next couple of weeks we will be rolling out an image proxy service, which should reduce mobile data usage and optimise storage.
Stay tuned for further updates and, as always, thanks for your support.
-
 @ 8412613c:df65608a
2025-02-27 19:35:22
@ 8412613c:df65608a
2025-02-27 19:35:22The book "Till We Have Faces" by C.S. Lewis had a profound spiritual impact on me, unlike most books that typically stay on an intellectual or entertainment level. I kept thinking, "Why didn't I read this sooner?" (It had been on my list for years). However, I believe I wouldn't have understood it as deeply as I did now, and I attribute that to my decision to fully embrace my Christian faith and accept Jesus as the Son of God who incarnated and resurrected—with no more questions or doubts, just faith. This choice has been truly liberating for me.
Although Till We Have Faces is not explicitly a Christian book, it beautifully reflects the themes of voluntary sacrifice, selfless love, suffering, and the mystery of the divine by retelling the myth of Psyche and Eros from the perspective of Psyche’s sister, Orual. Her journey through profound grief and blame toward the gods ultimately leads her to inner transformation and peace at the end of her life. C.S. Lewis’ personal faith undeniably influenced his writing, often exploring spiritual and philosophical themes through the lens of myth and allegory, as we see in this book.
I want to briefly mention a few topics that gave me pause:
The case against the gods
‘But, your eyes being open, you saw no such thing.’
‘You don’t think—not possibly—not as a mere hundredth chance—there might be things that are real though we can’t see them?’
‘Certainly I do. Such things as Justice, Equality, the Soul, or musical notes.’
‘Oh, grandfather, I don’t mean things like that. If there are souls, could there not be soul-houses? (p. 161).
It was clever of the author to make Psyche's palace invisible to mortal eyes, as this allows readers to relate to Orual's struggle with the nature of reality. Orual faces the abyss that humans encounter when witnessing the limits of reason.
If what I saw was real. I was in great fear. Perhaps it was not real. I looked and looked to see if it would not fade or change. Then as I rose (for all this time I was still kneeling where I had drunk), almost before I stood on my feet, the whole thing was vanished. (p. 150).
Even though Orual has a glimpse of the divine, she makes an important decision that will mark her for the rest of her life: she chooses to neglect recognizing her vision as the sign she had been asking for, and instead looks for other possible explanations. She thinks the gods are cruel and untrustworthy, and also blames them for their lack of clarity in their messaging. She expresses that if they wanted her to understand something, they are at fault for not being clear.
The gods never send us this invitation to delight so readily or so strongly as when they are preparing some new agony. We are their bubbles; they blow us big before they prick us. (p. 111).
Orual reached her breaking point when the gods twisted what she believed to be real: her experiences and her life story. She interpreted this event as a mockery by the gods, and so decided to write a book from her perspective—a case against them—without realizing that, in doing so, she was writing a case against herself:
Now, you who read, judge between the gods and me. They gave me nothing in the world to love but Psyche and then took her from me. But that was not enough. They then brought me to her at such a place and time that it hung on my word whether she should continue in bliss or be cast out into misery. They would not tell me whether she was the bride of a god, or mad, or a brute’s or villain’s spoil. They would give no clear sign, though I begged for it. I had to guess. And because I guessed wrong they punished me—what’s worse, punished me through her. And even that was not enough; they have now sent out a lying story in which I was given no riddle to guess, but knew and saw that she was the god’s bride, and of my own will destroyed her, and that for jealousy. As if I were another Redival. I say the gods deal very unrightly with us. For they will neither (which would be best of all) go away and leave us to live our own short days to ourselves, nor will they show themselves openly and tell us what they would have us do. For that too would be endurable. But to hint and hover, to draw near us in dreams and oracles, or in a waking vision that vanishes as soon as seen, to be dead silent when we question them and then glide back and whisper (words we cannot understand) in our ears when we most wish to be free of them, and to show to one what they hide from another; what is all this but cat-and-mouse play, blindman’s buff, and mere jugglery? Why must holy places be dark places? (pp. 283-284).
I have always believed in God as Jesus, yet I understand Orual's accusations. I have questioned "unfair" situations, victimized myself, and blamed God. I have also saddened the beautiful souls of believers when, in my state of rebellion, I harshly questioned their faith, even as they were showing me Christ's love. I saw myself in many of Orual's attitudes
With time, I have come to understand that humans can move between reason and faith, each requiring different skills. Dismissing either is dangerous. Reason protects us from deception but it can also blind us from truths. Faith is part of what gives us purpose in life, it comes with uncertainty but also with a blessing:
Then Jesus told him, “Because you have seen me, you have believed; blessed are those who have not seen and yet have believed. -John 20:39.
Dying before dying
This part of the book was truly inspiring to me because I have been obsessed with these words for a long time [^1]:
If you die before you die, you won't die when you die. -Inscription at St. Paul's Monastery on Mt. Athos.
So I recognized them in the text:
Die before you die. There is no chance after. (p. 318).
Orual explains what the gods meant by “dying before dying”:
Then I remembered that conversation which his friends had with Socrates before he drank the hemlock, and how he said that true wisdom is the skill and practise of death... But by the death which is wisdom I supposed he meant the death of our passions and desires and vain opinions. And immediately (it is terrible to be a fool) I thought I saw my way clear and not impossible. To say that I was Ungit meant that I was as ugly in soul as she; greedy, blood-gorged. But if I practised true philosophy, as Socrates meant it, I should change my ugly soul into a fair one. And this, the gods helping me, I would do. I would set about it at once. (pp. 321-322).
These words brought me to the central Christian teaching of "dying to self" or "crucifying the old self”, which is only achieved through divine intervention. The idea of dying before dying is described by Paul as follows:
I have been crucified with Christ. It is no longer I who live, but Christ who lives in me. And the life I now live in the flesh I live by faith in the Son of God, who loved me and gave himself for me. -Galatians 2:20
Dreams
Orual was stubborn and tried to fix her sorrow by another form of dying: completely changing her identity and true nature by neglecting herself and becoming someone else. This might seem similar to “dying before dying”, but the latter just comes through an act of humility and surrender by recognizing that only divine mercy can prevent us from going astray and truly heal. Orual, however, relied on her own strength and pride to endure her suffering. She hid behind a veil and metaphorically killed herself.
I had worn a veil because I wished to be secret. I now determined that I would go always veiled. I have kept this rule, within doors and without, ever since. It is a sort of treaty made with my ugliness. There had been a time in childhood when I didn’t yet know I was ugly. Then there was a time (for in this book I must hide none of my shames or follies) when I believed, as girls do—and as Batta was always telling me—that I could make it more tolerable by this or that done to my clothes or my hair. Now, I chose to be veiled. The Fox, that night, was the last man who ever saw my face; and not many women have seen it either. (p. 205).
I am the Queen; I’ll kill Orual too. (p. 256).
By writing her book, Orual finally reaches a state where she is ready for divine intervention. Ultimately, she removes her veil. The following is one of the most important paragraphs:
Not many days have passed since I wrote those words no answer, but I must unroll my book again. It would be better to rewrite it from the beginning, but I think there’s no time for that. Weakness comes on me fast... Since I cannot mend the book, I must add to it. To leave it as it was would be to die perjured; I know so much more than I did about the woman who wrote it. What began the change was the very writing itself. Let no one lightly set about such a work. Memory, once waked, will play the tyrant. I found I must set down (for I was speaking as before judges and must not lie) passions and thoughts of my own which I had clean forgotten. The past which I wrote down was not the past that I thought I had (all these years) been remembering. I did not, even when I had finished the book, see clearly many things that I see now. The change which the writing wrought in me (and of which I did not write) was only a beginning—only to prepare me for the gods’ surgery. They used my own pen to probe my wound. (p. 287).
Through random encounters, dreams, and visions, the gods showed Orual what she had been missing her whole life. One specific dream (or vision) caught my attention and made me think that C.S. Lewis had a profound insight while writing this masterpiece: Orual had a vision in which she presented her case against the gods in a courtroom before a judge. The assembly was made up of gods and ghosts, some of whom she knew. When the judge asked her to read her complaint, she had a scroll that was not the book she had written while recounting the story of her life. But she read it anyway until the judge said "enough," and she understood that she had read it over and over. The judge asked if she had her answer, and she replied "yes."
The complaint was the answer. To have heard myself making it was to be answered. (p. 335).
This was incredible, and I could relate. I have had similar dreams in which I have a book in my hands—a book I know I wrote. Suddenly, I become lucid and tell myself, "Here is the answer; when I read it, I will know." This has been a recurring dream, and it's interesting because there are insights we only have access to on a deeper inner level. I have also dreamed of conversing with Jesus, repeating certain words, some of which I do not even remember. I interpret these kinds of dreams as follows:
In the same way, the Spirit helps us in our weakness. We do not know what we ought to pray for, but the Spirit himself intercedes for us through wordless groans. -Romans 8:26
I think that C.S. Lewis, speaking through Orual and the Fox, understands this and writes:
Lightly men talk of saying what they mean. Often when he was teaching me to write in Greek the Fox would say, ‘Child, to say the very thing you really mean, the whole of it, nothing more or less or other than what you really mean; that’s the whole art and joy of words.’ A glib saying. When the time comes to you at which you will be forced at last to utter the speech which has lain at the centre of your soul for years, which you have, all that time, idiot-like, been saying over and over, you’ll not talk about joy of words. I saw well why the gods do not speak to us openly, nor let us answer. Till that word can be dug out of us, why should they hear the babble that we think we mean? How can they meet us face to face till we have faces? (p. 335).
I am very impressed with how the author explored Orual's life through her own eyes, enabling the reader to understand her transformation once she finally confronted her shortcomings and humbly accepted divine wisdom. With this new knowledge, she could finally see her path from a different perspective. Furthermore, the reader was able to appreciate the role of the gods: they weren’t meant to alleviate Orual’s suffering, but rather to lead her to see that it had a purpose—to transcend. This story made me reflect on my own journey and acknowledge Jesus's presence and mercy in my life and His selfless love as the key to transformation.
This book resonated so deeply with me. I absolutely recommend it. To C.S. Lewis, thank you—your words truly touched my heart.
References:
Lewis, C. S.. Till We Have Faces: A Myth Retold. Kindle Edition.
[^1]: See: https://habla.news/u/nancyqa@mynostr.space/1691458659942
-
 @ f1989a96:bcaaf2c1
2025-02-13 14:24:32
@ f1989a96:bcaaf2c1
2025-02-13 14:24:32Good morning, readers!
This week, we highlight how authoritarian regimes are manipulating digital assets. The Central African Republic launched a government-backed meme coin that crashed spectacularly within a day of launch as regime insiders cashed out for profits, leaving the public with worthless tokens.
Meanwhile, the Nigerian regime introduced its first official stablecoin, cNGN. It is issued by the African Stablecoin Consortium and is backed 1:1 with the naira. Still, it operates under the direct oversight of the Nigerian Securities and Exchange Commission, allowing further surveillance of Nigerians’ financial activity alongside the struggling eNaira CBDC.
On the freedom tech front, Mullad VPN now supports Bitcoin payments via the Lightning Network, offering activists, journalists, and individuals under oppressive regimes a censorship-resistant and permissionless way to pay for their privacy. Additionally, SeedSigner, an open-source hardware wallet for Bitcoin self-custody, rolled out multilingual support, expanding accessibility to Spanish-speaking activists and human rights defenders.\ \ Finally, journalist Frank Corva explores Africa’s grassroots Bitcoin movement, where open-source tools and circular economies are empowering communities inside authoritarian regimes with financial freedom. For those who doubt Bitcoin’s real-world impact, this article is a must-read.
Now, let’s get right to it!
Subscribe Here
GLOBAL NEWS
Central African Republic | Launches Meme Coin Experiment
The Central African Republic (CAR) debuted a government-backed meme coin, $CAR, which President Faustin-Archange Touadéra claims will “unite people” and “support national development.” In reality, meme coins are speculative assets that often serve as vehicles for insider profit. This scheme follows CAR’s failed Sango Coin project, which promised citizenship and land in exchange for locked investments but sold only 7.5% of its supply. Those who did “buy in” did not receive what was promised. In 2022, CAR briefly made Bitcoin legal tender, calling it a path to sovereignty — only to abandon it shortly after. Instead of supporting open and neutral money like Bitcoin, the government has turned to dubious crypto schemes. The real beneficiaries of $CAR appear to be regime insiders who reportedly cashed out $40 million while the public holds worthless tokens.
Nigeria | Debuts Naira Stablecoin
The Nigerian state launched its first regulated stablecoin, cNGN. Similar to US dollar-pegged stablecoins like USDT and USDC, cNGN is pegged 1:1 to its local currency (the naira). It is issued by the African Stablecoin Consortium (ASC), a private coalition of Nigerian financial institutions and blockchain companies. Positioned as a bridge between fiat and digital assets, cNGN aims to facilitate remittances and trade but comes with strict verification requirements that limit financial privacy. The Nigerian SEC also tightly regulates the stablecoin and it is only available on government-approved exchanges, Busha and Quidax. As Nigeria expands its control over digital transactions — through both cNGN and its struggling eNaira CBDC — more and more Nigerians are turning to Bitcoin as a censorship-resistant alternative.
Russia | Proposes Registry to Track Bitcoin Mining Hardware
Russia’s deputy energy minister, Yevgeny Grabchak, has proposed a centralized registry of Bitcoin mining equipment and wallet addresses to “identify mining activities and ensure stricter enforcement of bans in restricted regions,” such as Russian-occupied Ukraine territories. Meanwhile, the Chairman of the State Duma Committee on Energy, Nikolai Shulginov, warned that last year’s mining ban in several Russian and occupied regions may not be enough to eliminate mining fully. As an authoritarian state with an egregious human rights record and a long history of financial repression, Russia appears intent on tightening surveillance of economic activity — especially that of Bitcoin. By registering, tracking, and restricting mining, the Kremlin expands its financial control, undermines economic autonomy, and limits access to permissionless money.
Turkey | Erdoğan Targets Opposition as Inflation Forecast Rises
Turkish President Recep Tayyip Erdoğan sentenced Istanbul Mayor Ekrem Imamoglu — a key political rival — to seven years in prison on charges widely seen as politically motivated. If upheld, the conviction will bar Imamoglu from office, further clearing Erdoğan’s path to dominance ahead of the 2028 elections. At the same time, Turkey’s economic crisis is worsening. Accelerating inflation forced the central bank to raise its 2025 forecast from 21% to 24%, exacerbating the lira’s decline and eroding purchasing power. As both political and financial repression deepen, more Turks are turning to alternatives to sidestep Erdoğan’s expanding control over the economic and political sphere.
Georgia | Regime to Pass Censorship Law
Georgia’s ruling Georgian Dream party is set to introduce a media censorship law aimed at enforcing government-defined standards for journalistic objectivity and ethics, while also restricting foreign funding for media outlets. MP Mamuka Mdinaradze claims the law will establish monitoring mechanisms and is modeled after UK regulations, though critics compare it to Belarusian-style repression. Georgian Dream Prime Minister Irakli Kobakhidze defended the move as necessary to close legislative “loopholes” and strengthen state control. Journalists and activists warn that the law is part of a broader crackdown on press freedom and dissent. Decentralized social networks like Nostr will become increasingly vital for journalists and activists to communicate freely, resist censorship, and ensure the flow of independent information.
____________
Webinar Series for Nonprofits: Become Unstoppable
HRF will host a free, three-day webinar from March 17-19, teaching human rights defenders and nonprofits how to use Bitcoin to counter state censorship and confiscation. Sessions run daily from 10:30 a.m. to 12:00 p.m. EDT and are beginner-friendly. The webinar will be led by Anna Chekhovich, HRF’s Bitcoin nonprofit adoption lead and financial manager at Alexei Navalny’s Anti-Corruption Foundation.
Register Here
SXSW | The Human Rights Risks of Central Bank Digital Currencies (CBDCs)
Join HRF at SXSW 2025 in Austin from March 9-12 to explore how CBDCs threaten financial freedom. Experts Roger Huang, Charlene Fadirepo, and Nick Anthony will discuss how authoritarian regimes use CBDCs for surveillance and control on March 9. Attendees can also visit HRF’s CBDC Tracker booth to explore an interactive map of CBDC developments worldwide.
Get Tickets
____________
BITCOIN AND FREEDOM TECH NEWS
Mullvad VPN | Testing Lightning Network Payments
Mullvad VPN is experimenting with Bitcoin for payments via the Lightning Network, a second-layer payment protocol built on Bitcoin that enables faster, cheaper, and more private transactions. This integration lets Mullvad VPN users pay for their services in bitcoin while enhancing their privacy and bypassing payment networks that track or censor financial activity. VPNs protect users by masking IP addresses and encrypting traffic. Accepting Bitcoin over Lightning strengthens this protection with a censorship-resistant payment option. For activists, journalists, and individuals in authoritarian regimes, this combination provides a shield against surveillance.
SeedSigner | Releases Multilingual Support
SeedSigner, an open-source and customizable Bitcoin hardware wallet and HRF grantee, introduced multilingual support for Spanish. This update makes secure Bitcoin self-custody more accessible to Spanish-speaking activists and human rights defenders who may rely on Bitcoin for transactional freedom. By expanding access to secure self-custody, SeedSigner helps reduce dependence on restrictive financial systems and allows more people in Nicaragua, Venezuela, Cuba, and beyond to “be their own bank.”
Iris | Implements Private Bitcoin Payments with Cashu
Iris, a Nostr client, has added support for a Cashu wallet to allow users to send and receive ecash. Cashu is an open-source Chaumian ecash protocol built for Bitcoin and integrated with the Lightning Network. It lets users make fast, low-cost, and extremely private transactions using Bitcoin-backed ecash. While it requires a trusted custodian, it helps users spend Bitcoin anonymously without revealing their identity or transaction activity. This ability provides activists and nonprofits a different way to make private Bitcoin payments alongside nostr’s censorship-resistant communications.
Sparrow Wallet | Supports Lark for USB Hardware Wallets
Sparrow Wallet, a popular open-source Bitcoin wallet, has added support for Lark, a new tool for USB hardware wallet communication. Lark works alongside the existing Hardware Wallet Interface (HWI), giving users an alternative way to connect their hardware wallets via USB. This update improves reliability, reduces dependence on a single software interface, and strengthens Bitcoin self-custody.
Bitcoin Dada | Opens Applications for Second Cohort of Dada Devs
Bitcoin Dada, an HRF-supported nonprofit initiative empowering African women through Bitcoin and financial education, is now accepting applications for the second cohort of Dada Devs. This developer program provides hands-on training, mentorship, and a collaborative community to help African women under authoritarian regimes contribute to Bitcoin development. If you’re an aspiring female developer, apply now to join a network of African women shaping the future of finance. Applications close Feb. 13.
Summer of Bitcoin | Applications for Summer 2025 Cohort Now Open
Summer of Bitcoin, an HRF-supported Bitcoin internship program, is now accepting applications for its summer 2025 cohort. This program introduces students from anywhere, including from authoritarian regimes, to Bitcoin open-source development and design, giving interns the option to choose between a developer or designer track based on their interests. Participants will gain hands-on work experience, contribute to real-world Bitcoin projects, and receive mentorship from industry leaders. You can learn more and apply here.
Spiral | Announces Grant Renewals for the Bitcoin Design Community and BDK
Spiral, a Bitcoin company building and funding open-source projects, announced renewed grants for critical initiatives, including the Bitcoin Design Community and Bitcoin Dev Kit (BDK). The Bitcoin Design Community is a free and open-source resource for designers, developers, and others working on non-custodial Bitcoin products. This grant will support designers who push the user experience and adoption of Bitcoin forward. Meanwhile, BDK is a software library that helps developers in building cross-platform Bitcoin wallets. Its grant will support the project’s continued refinement and development.
RECOMMENDED CONTENT
The Bitcoin and Cypherpunk Spirit Is Alive and Well in Africa by Frank Corva
In this article for Bitcoin Magazine, journalist Frank Corva spotlights Bitcoin's growing presence across Africa. Across the continent, people are building Bitcoin circular economies, open-source financial tools, and educational initiatives. From Bitcoin Ekasi in South Africa to AfriBit Kibera in Kenya and Bitcoin Dua in Ghana, these grassroots initiatives drive financial inclusion and education for individuals and communities. Meanwhile, tools like Tando and Machankura are expanding access to transactional freedom, and conferences like Adopting Bitcoin Captetown and the Africa Bitcoin Conference nurture ongoing collaboration between individuals, developers, and activists to advance financial freedom on a continent that otherwise has very little liberal democracy. Read the full article here.
Using Bitcoin Without Internet! Here’s How Machankura Makes It Happen with Anita Posch
In this short interview, Bitcoin educator and host of the Bitcoin for Fairness channel, Anita Posch, speaks with Mary Imasuen, a Machankura team member, about how this technology makes Bitcoin accessible to Africans without Internet access. Machankura is an app that allows feature phones to send and receive Bitcoin using the Unstructured Supplementary Service Data (USSD) protocol, a mobile communications system similar to SMS. This means people can transact in Bitcoin without needing a smartphone or data connection, a situation common to many living under autocratic regimes in sub-Saharan Africa. By removing Internet barriers, Machankura helps millions of Africans overcome high data costs and unreliable networks, offering a practical solution to financial inclusion.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ 3b7fc823:e194354f
2025-02-13 02:25:42
@ 3b7fc823:e194354f
2025-02-13 02:25:42site:example.com intitle:"index of" inurl:admin intext:"password"
site:example.com site:.gov site:.edu site:*.mil
inurl:login inurl:admin inurl:dashboard inurl:portal intitle:"admin login"
intitle:"index of /" intitle:"index of" "parent directory" intitle:"index of" "backup"
filetype:pdf "confidential" filetype:xls "username | password" filetype:doc "top secret" filetype:sql "database"
intext:"username" intext:"password" intext:"login" intext:"password" filetype:txt "passwords"
inurl:"viewerframe?mode=" inurl:"/view.shtml" inurl:"/view/index.shtml"
intitle:"index of" "wp-config.php" inurl:".git"
filetype:xls intext:"email" filetype:csv intext:"email"
inurl:"/setup.cgi?next_file=netgear.cfg" inurl:"/wificonf.html"